-

@ 8f69ac99:4f92f5fd
2025-02-27 12:47:01
O Estado Social tem sido um pilar das políticas sociais europeias há décadas, oferecendo uma rede de segurança aos cidadãos através de diversos programas governamentais. Contudo, com a evolução das economias e o envelhecimento da população a pressionar os recursos públicos, este modelo tradicional enfrenta desafios crescentes. Custos em alta, ineficiências burocráticas e efeitos indesejados têm gerado um debate cada vez mais intenso sobre a sua sustentabilidade. Como alternativa, o Rendimento Básico Universal (RBU) ganhou destaque, prometendo simplicidade, mas trazendo preocupações quanto ao custo e aos desincentivos ao trabalho. Há, porém, uma opção mais equilibrada que merece atenção: o Imposto sobre o Rendimento Negativo (IRN).
Diferente da assistência social convencional, o IRN oferece apoio financeiro a quem está abaixo de um limiar de rendimento definido, sem exigir que procurem emprego ou dependam de ajudas públicas. Ao reduzir gradualmente os subsídios à medida que os rendimentos aumentam, incentiva a produtividade e preserva a iniciativa pessoal. Neste artigo, vamos explorar o IRN em profundidade, destacando as suas vantagens sobre os sistemas tradicionais, abordando as falhas do RBU e avaliando o seu potencial como uma reforma transformadora na Europa. Num contexto de mudanças económicas e demográficas, o IRN surge como um caminho prático para um sistema que equilibre apoio, dignidade e sustentabilidade.
## Problemas dos Sistemas Tradicionais de Assistência Social
O Estado Social tradicional, embora bem-intencionado, tem sido alvo de críticas crescentes pelas suas ineficiências e consequências inesperadas.
### Ineficiência e Burocracia
Estruturas administrativas complexas frequentemente atrasam os sistemas de assistência social, levando a desperdícios de recursos. Programas sobrepostos e serviços redundantes aumentam os custos, sobrecarregando os contribuintes. Por exemplo, várias entidades podem oferecer benefícios semelhantes, enquanto processos morosos atrasam a ajuda a quem precisa. Com o envelhecimento da população europeia a exigir mais apoio, estas ineficiências põem em risco a estabilidade financeira, desafiando os decisores políticos a repensarem a distribuição de recursos.
### Incentivos Perversos
A assistência social pode, sem querer, desencorajar o trabalho e perpetuar a dependência. Surgem "armadilhas de assistência" quando os benefícios são estruturados de forma a que ganhar um salário resulte numa redução abrupta da ajuda, tornando o emprego menos atractivo do que permanecer no assistencialismo. Isso cria um ciclo em que os beneficiários hesitam em procurar trabalho ou formação, comprometendo as suas perspectivas a longo prazo. Com o tempo, tais sistemas arriscam criar uma cultura de dependência, minando a iniciativa pessoal e prendendo indivíduos numa estagnação económica.
### Peso Económico
A pressão financeira do Estado Social está a intensificar-se com as mudanças demográficas na Europa. Populações mais envelhecidas requerem maior apoio, elevando os custos e exigindo impostos mais altos ou gastos públicos acrescidos. Isso desvia recursos da inovação e do investimento, podendo travar o crescimento económico. Sem reformas, estas despesas crescentes podem tornar-se insustentáveis, obrigando os governos a encontrar soluções que mantenham o apoio sem comprometer as finanças.
### Estigma Social
Além das questões económicas, a assistência social traz muitas vezes um custo social. Os beneficiários enfrentam frequentemente estereótipos de preguiça ou incompetência, o que gera vergonha e diminui a autoestima. Este estigma pode dificultar a mobilidade social, tornando mais complicado sair da dependência. Resolver isto exige um sistema que não só apoie, mas também capacite, reduzindo preconceitos e promovendo inclusão.
Face a estas falhas, a Europa precisa de explorar alternativas que prestem ajuda de forma mais eficaz. O Imposto sobre o Rendimento Negativo apresenta-se como uma opção promissora, capaz de enfrentar estas questões sistémicas.
## O Caso Contra o Rendimento Básico Universal (RBU)
O Rendimento Básico Universal surgiu como uma ideia ousada para combater a pobreza e a desigualdade, oferecendo a cada cidadão um pagamento fixo independentemente das suas necessidades. No entanto, a sua simplicidade traz desvantagens significativas.
O custo do RBU é um obstáculo enorme. Implementá-lo em toda a Europa exigiria fundos avultados, pressionando orçamentos já sobrecarregados pelos compromissos actuais do Estado Social. Isso poderia implicar subidas acentuadas de impostos ou cortes noutros serviços, enquanto a criação da infraestrutura administrativa necessária traria mais despesas. Há também quem tema os desincentivos ao trabalho: se todos receberem o mesmo valor, alguns podem sentir menos motivação para trabalhar ou arriscar em projectos empreendedores, podendo afectar a vitalidade económica.
Além disso, a abordagem universal do RBU sacrifica eficiência. Ao distribuir fundos de forma igual, não dá prioridade a quem mais precisa, entregando recursos aos mais ricos enquanto dilui o impacto sobre os pobres. Esta falta de foco levanta dúvidas sobre a sua capacidade de combater a desigualdade de forma eficaz. Embora o apelo do RBU esteja na sua universalidade, estes desafios apontam para a necessidade de uma solução mais direccionada—e é aqui que o IRN entra em cena.
## Compreender o Imposto sobre o Rendimento Negativo (IRN)
O Imposto sobre o Rendimento Negativo propõe uma abordagem refinada ao apoio social, combinando assistência com incentivos. No seu cerne, define um limiar de rendimento base—digamos, 1.000 euros por mês. Quem ganha menos recebe um subsídio proporcional à diferença, enquanto quem ultrapassa esse valor paga impostos para financiar o sistema. Por exemplo, com uma taxa de subsídio de 50%, quem não tem rendimentos recebe 500 euros, e quem ganha 400 euros recebe 300 euros, elevando o total para 700 euros. À medida que o rendimento se aproxima do limiar, o subsídio diminui, desaparecendo nos 1.000 euros, altura em que a tributação começa.
Veja-se uma ilustração simples:
| Rendimento Mensal (€) | Pagamento IRN (€) | Rendimento Total Após IRN (€) |
|-----------------------|-------------------|------------------------------|
| 0 | 500 | 500 |
| 400 | 300 | 700 |
| 800 | 100 | 900 |
| 1.000 | 0 | 1.000 |
| 1.200 | - (impostos aplicam-se) | 1.200 - impostos |
Isto garante que trabalhar compensa sempre: ganhar mais aumenta o rendimento total, evitando a armadilha da assistência. O financiamento vem de um imposto fixo—talvez 19%—sobre os rendimentos acima do limiar. Quem ganha 1.500 euros, por exemplo, paga 95 euros sobre os 500 euros acima de 1.000, ficando com 1.405 euros. Este modelo fiscal simples facilita a gestão e assegura equidade.
| Rendimento (€) | Rendimento Tributável (€) | Imposto (€) | Após Imposto (€) |
|----------------|---------------------|---------|------------------|
| 1000 | 0 | 0 | 1000 |
| 1200 | 200 | 38 | 1162 |
| 2000 | 1000 | 190 | 1810 |
O IRN _pode_ ser de participação voluntária, através de um contrato. As pessoas podem aderir ao sistema se precisarem de apoio ou rejeitá-lo se não aceitarem ajuda estatal, evitando os impostos associados ao financiamento do IRN. Quem optar por sair pode reentrar em caso de dificuldades, equilibrando liberdade de escolha com pragmatismo. Para libertários desconfiados de ingerências governamentais, isto torna o IRN um compromisso—um passo para longe do assistencialismo coercivo e em direcção a maior autonomia.
Filosoficamente, o IRN não é um objectivo final, mas uma ponte. Ao simplificar a ajuda e reduzir a burocracia, pode abrir caminho para soluções privadas, como caridade ou apoio mútuo, diminuindo o papel do estado ao longo do tempo. Características como a avaliação de meios e a indexação à inflação reforçam a sua adaptabilidade, garantindo que o apoio permaneça justo e relevante.
## Vantagens do Imposto sobre o Rendimento Negativo (IRN)
O IRN destaca-se onde o Estado Social tradicional falha. Os seus subsídios decrescentes incentivam o trabalho, premiando o esforço à medida que o rendimento sobe e impulsionando a produtividade. Isto contrasta fortemente com as armadilhas da assistência, encorajando as pessoas a procurarem formação ou a arriscarem em empreendedorismo sem medo de perder apoio de repente.
Na gestão, o IRN é revolucionário. Substituir um emaranhado de programas por um único sistema reduz a burocracia e os custos, canalizando recursos directamente para quem precisa. Um processo de pagamento único elimina sobreposições, tornando a entrega de ajuda mais rápida e eficiente.
A dignidade é outro ponto forte. Ao oferecer escolha e evitar supervisão intrusiva, o IRN escapa ao estigma do assistencialismo, dando aos beneficiários autonomia para gerir as suas finanças. Isso promove o autorrespeito e um sentido de controlo, quebrando o ciclo de dependência.
Economicamente, a flexibilidade do IRN sobressai. Adapta-se às flutuações de rendimento, direccionando a ajuda exactamente onde é necessária. Estudos indicam que pode reduzir a pobreza, melhorar a mobilidade social e até beneficiar a saúde, ao aliviar o stress financeiro, oferecendo um impulso abrangente ao bem-estar.
## Responder às Críticas ao Imposto sobre o Rendimento Negativo (IRN)
Nenhuma política escapa a críticas, e o IRN tem as suas. Os libertários veem, e bem, os impostos como roubo, e embora o IRN não elimine esta tensão, suaviza-a. Ao condensar o Estado Social num sistema claro e simples, reduz a intromissão estatal face à burocracia actual. Os seus incentivos ao trabalho alinham-se com valores de responsabilidade, tornando-o um passo aceitável a curto prazo.
O financiamento preocupa, sobretudo em países europeus já muito tributados, mas uma taxa fixa oferece uma solução. Simples e previsível, minimiza os custos administrativos e assegura contribuições justas, sustentando o IRN sem sobrecarga excessiva. Há também quem debata o seu impacto social—uns chamam-lhe um subsídio fácil, um _hand-out_, outros um sistema demasiado voltado para o mercado. Ainda assim, o IRN encontra um meio-termo, oferecendo uma rede de segurança que recompensa o esforço sem controlar vidas.
Passar para o IRN exige eliminar gradualmente os programas antigos e informar o público sobre os seus benefícios: um governo mais leve, menos dependência e maior iniciativa pessoal. Para quem sonha com um futuro sem estado, o IRN não é o destino, mas um movimento prático rumo a sistemas de apoio voluntários, promovendo uma cultura de autossuficiência.
## Conclusão
O Imposto sobre o Rendimento Negativo não é perfeito, mas é um avanço claro face ao _status quo_. Reduz os excessos do Estado Social, promove trabalho e dignidade, e oferece à Europa uma reforma viável perante as pressões económicas. Para os contribuintes, promete eficiência; para os beneficiários, oportunidade. Numa região onde o assistencialismo está profundamente enraizado, o IRN surge como um passo ousado, mas possível, para um futuro mais livre e sustentável—um que capacite as pessoas enquanto alivia o peso do estado.
---
_Photo by [The New York Public Library](https://unsplash.com/@nypl?utm_content=creditCopyText&utm_medium=referral&utm_source=unsplash) on [Unsplash](https://unsplash.com/photos/a-sign-that-says-pay-your-tax-now-here-kAJLRQwt5yY?utm_content=creditCopyText&utm_medium=referral&utm_source=unsplash)_
-

@ 8da249fe:ecc00e09
2025-02-27 12:36:07
Se você está começando no mundo do Bitcoin e das criptomoedas, já deve ter ouvido falar em "hot wallets" e "cold wallets". Mas qual é a diferença entre elas? E qual é a melhor opção para armazenar seus ativos digitais com segurança?
# O que é uma Hot Wallet?

Uma hot wallet (carteira quente) é uma carteira conectada à internet. Isso significa que ela é mais acessível e fácil de usar para transações rápidas. As hot wallets podem ser:
**Carteiras móveis** – Aplicativos como BlueWallet, Trust Wallet e outras.
**Carteiras de desktop **– Programas instalados no computador, como Electrum e Exodus.
**Carteiras web** – Serviços online como a carteira do próprio Binance ou outras exchanges.
**Vantagens da Hot Wallet**
✅ Acesso rápido e fácil para transações diárias.
✅ Interface amigável, ideal para iniciantes.
✅ Geralmente gratuita para uso.
**Desvantagens da Hot Wallet**
❌ Maior risco de ataque hacker, já que está sempre online.
❌ Se o dispositivo for infectado por malware, suas chaves privadas podem ser comprometidas.
# O que é uma Cold Wallet?#

Uma cold wallet (carteira fria) é uma carteira que não está conectada à internet, tornando-se muito mais segura contra hackers. Elas podem ser:
**Carteiras de hardware **– Como Ledger Nano S, Nano X ou Trezor.
**Carteiras de papel **– Impressão da chave privada e do endereço em um papel.
**Computadores ou dispositivos offline** – Um computador dedicado apenas para armazenar criptomoedas, sem conexão com a internet.
**Vantagens da Cold Wallet**
✅ Segurança máxima contra ataques cibernéticos.
✅ Ótima opção para armazenamento de longo prazo.
✅ Controle total sobre suas chaves privadas.
**Desvantagens da Cold Wallet**
❌ Menos prática para transações diárias.
❌ Pode ser mais cara, no caso das carteiras de hardware.
❌ Se você perder sua chave privada ou backup, pode perder o acesso aos fundos.
# Qual escolher: Hot ou Cold Wallet?
A escolha depende do seu perfil de investidor:
Se você faz transações frequentes, uma hot wallet pode ser mais conveniente.
Se você quer armazenar Bitcoin com segurança por muito tempo, a cold wallet é a melhor opção.
Muitos usuários combinam as duas, mantendo uma pequena quantia em uma hot wallet para o dia a dia e guardando a maior parte dos fundos em uma cold wallet.
Independente da escolha, lembre-se sempre de manter suas chaves privadas seguras e fazer backups regularmente!
Gostou do conteúdo? Compartilhe sua opinião nos comentários!
-

@ 95cb4330:96db706c
2025-02-27 11:47:47
Tackling big tasks can feel overwhelming, but by breaking them down into smaller steps, prioritizing effectively, and setting clear milestones, you can maintain focus and make steady progress.
---
## 1. Divide the Task into Manageable Steps
Instead of viewing the task as one massive undertaking, split it into specific, actionable steps to create a clear roadmap.
🔹 **Example:** If your goal is to launch a new product, break it down like this:
- Conduct market research
- Develop a prototype
- Build a marketing strategy
- Create a launch plan
- Execute the launch
Each step is now more manageable and can be worked on independently.
---
## 2. Prioritize Based on Impact & Urgency
Not all tasks are equally important. Prioritize effectively to avoid wasting time on low-value activities.
✔ **Use the Eisenhower Matrix:**
- **Urgent & Important:** Do immediately.
- **Important but Not Urgent:** Schedule it.
- **Urgent but Not Important:** Delegate it.
- **Neither Urgent nor Important:** Eliminate it.
🔹 **Example:** If launching a product, market research might be urgent & important, while branding tweaks could be scheduled for later.
---
## 3. Set Milestones & Deadlines
Assign deadlines for each step to track progress and stay motivated.
✔ **Example:** Instead of saying, "Launch the product in 6 months," break it down:
- **Market research:** Week 1-2
- **Prototype development:** Week 3-6
- **Marketing strategy:** Week 7-8
- **Launch execution:** Week 9-10
By setting clear deadlines, you create a sense of accountability and prevent procrastination.
---
## 4. Take Consistent Action
✔ Focus on completing one step at a time.
✔ Celebrate small wins—progress builds momentum.
✔ Stay adaptable—if needed, refine your steps as you go.
🔹 **Example:** If market research reveals an issue with the original product idea, adjust before moving forward rather than sticking rigidly to the plan.
---
## Final Thought
By approaching big tasks systematically, you reduce overwhelm, maintain clarity, and steadily progress toward success.
👉 **Action Step:** Take a current big task you're facing. Break it into smaller steps, prioritize, set deadlines, and start taking action today. 🚀
---
-

@ 95cb4330:96db706c
2025-02-27 11:45:01
Break down complex problems into their fundamental truths and build solutions from the ground up. This approach fosters creativity and avoids relying on assumptions.
---
## How to Implement First Principles Thinking
1. **Deconstruct the Problem**
- **Identify the core components:**
Question assumptions and remove preconceived notions.
- **Ask:**
What do we know for sure? What can we verify as a fact?
- **Example:**
Instead of assuming "Electric cars are too expensive," break it down: What are the main cost drivers? Batteries, manufacturing, and distribution.
2. **Challenge Assumptions**
- **Question the status quo:**
Many constraints are based on tradition or outdated thinking, not necessity.
- **Ask:**
What if this assumption is wrong? How else could it be done?
3. **Rebuild from the Ground Up**
- **Start with the fundamental truths:**
Use the identified truths to construct new solutions using logic and creativity.
- **Avoid shortcuts:**
Don't rely on existing frameworks that may limit possibilities.
- **Example:**
Tesla used first principles to design their batteries by focusing on material costs rather than purchasing standard packs.
4. **Foster a Creative Mindset**
- **Think like a scientist or engineer:**
Break, test, and experiment to find new pathways.
- **Encourage innovation:**
Brainstorm solutions that are original rather than replicative.
---
## Why It Works
This method avoids reliance on assumptions and encourages fresh perspectives. By starting with "what is undeniably true," you open the door to unconventional solutions and breakthrough ideas.
---
-

@ 95cb4330:96db706c
2025-02-27 11:34:24
Implementing Decision Journals, as practiced by leaders like Jeff Bezos and Ray Dalio, can significantly enhance your decision-making skills by promoting reflection and continuous improvement. This method involves documenting key decisions, the rationale behind them, and anticipated outcomes, allowing for analysis of past choices to identify patterns and biases.
---
## Understanding Decision Journals
- **Definition:**
A decision journal is a structured record where you log important decisions, including the context, your thought process, and expected results. This practice enables you to track the accuracy of your judgments and refine your decision-making over time.
---
## Examples in Practice
- **Jeff Bezos:**
The founder of Amazon utilizes a "Regret Minimization Framework" to guide his decisions. By projecting himself into the future and considering potential regrets, Bezos focuses on long-term fulfillment over short-term comfort. This approach was pivotal when he decided to leave his stable job to start Amazon.
- **Ray Dalio:**
The founder of Bridgewater Associates emphasizes the importance of recording decisions to create a set of well-defined principles. Dalio's process of documenting and analyzing his choices has been fundamental in developing effective decision-making rules that have contributed to his success.
---
## Implementing a Decision Journal
1. **Record the Decision:**
Document the specifics of the decision, including the date, context, and the options considered.
2. **Articulate Your Reasoning:**
Detail the thought process and assumptions that led to your choice.
3. **Predict the Outcome:**
Note your expectations regarding the results of the decision.
4. **Review and Reflect:**
After some time, revisit the decision to compare actual outcomes with your predictions, analyzing any discrepancies to identify biases or areas for improvement.
---
## Action Step
Begin by selecting a current decision you are facing. Create a journal entry that outlines the decision, your reasoning, and expected outcomes. Schedule a future date to review the decision and assess its results. Regular use of decision journals can enhance self-awareness and lead to more informed choices.
---
By adopting the practice of maintaining decision journals, you can systematically refine your judgment, reduce recurring mistakes, and make decisions that align more closely with your long-term goals.
**Recommended Resource:**
[Ray Dalio ON: Principles for Making Better Decisions & How to Strengthen Relationships for Long-Term Success | Podcast | Jay Shetty](#)
---
-

@ 95cb4330:96db706c
2025-02-27 11:22:04
Embracing a Bias Toward Action, as exemplified by leaders like Elon Musk and Jeff Bezos, involves prioritizing swift decision-making and iterative progress over prolonged analysis. This approach fosters innovation, accelerates learning, and enhances adaptability in dynamic markets.
---
## Understanding Bias Toward Action
- **Definition:**
A Bias Toward Action emphasizes initiating tasks promptly and refining them through continuous feedback, rather than striving for perfection before implementation.
---
## Examples in Practice
- **Elon Musk's Rapid Prototyping:**
At SpaceX, Musk employs an iterative design methodology, rapidly developing and testing prototypes to accelerate learning and innovation. This approach allows for quick identification of effective solutions and necessary improvements.
[newspaceeconomy.ca](https://newspaceeconomy.ca)
- **Jeff Bezos' Two-Way Door Framework:**
Bezos introduced the concept of "two-way door" decisions at Amazon, distinguishing between reversible and irreversible choices. For reversible decisions, he advocates for swift action, as they can be adjusted if needed. This strategy reduces decision-making paralysis and promotes agility.
[aboutamazon.com](https://aboutamazon.com)
---
## Implementing a Bias Toward Action
1. **Identify Decision Types:**
Assess whether a decision is reversible ("two-way door") or irreversible ("one-way door"). For reversible decisions, prioritize speed and be willing to iterate.
2. **Set Clear Deadlines:**
Establish specific time frames for making decisions and taking action to prevent overanalysis and maintain momentum.
3. **Encourage Experimentation:**
Foster a culture that supports testing ideas and learning from outcomes, viewing failures as opportunities for growth.
---
## Action Step
Reflect on a project or decision you've been postponing. Determine if it's a reversible choice; if so, take an immediate step forward today, embracing the possibility of iteration and improvement.
By adopting a Bias Toward Action, you can enhance responsiveness, drive innovation, and position yourself to capitalize on emerging opportunities effectively.
---
-

@ d5c3d063:4d1159b3
2025-02-27 11:09:15
ถ้าคุณเชื่ออะไรบางอย่างมาตลอดชีวิต แล้ววันหนึ่งกลับพบว่ามันอาจไม่เป็นอย่างที่คิด นี่คือความรู้สึกของผมในวันนั้น เป็นครั้งแรกที่ได้นั่งฟังหมอป๊อป DietDoctor Thailand บรรยายสดๆ ในงานสัมมนา “Nutrition 101 - โภชนาการพื้นฐาน” Healthy Hut - โรงบ่มสุขภาพ เอาตรง ๆ นะ...ความรู้สึกเหมือนผมไม่ได้กำลังฟังหมอคนหนึ่งพูด แต่เหมือนกำลังนั่งฟังนักปรัชญามากกว่า
.
หมอป๊อปไม่ได้มาบอกว่าเราต้องกินอะไรหรือห้ามกินอะไร แต่ท่านตั้งคำถามให้เราคิดตาม เช่น "ทำไมวัวถึงกินหญ้าได้ทั้งวันโดยไม่มีปัญหาระดับน้ำตาลในเลือด...แต่มนุษย์กลับเสี่ยงเป็นเบาหวานจากการกินคาร์โบไฮเดรต" มันเป็นคำถามที่ฟังดูเรียบง่ายแต่กลับทำให้ผมฉุกคิดถึงความเข้าใจที่เรามีมาโดยตลอด
ผมนั่งฟังแล้วก็เริ่มทบทวนสิ่งที่ตัวเองเคยเชื่อ บางที...สิ่งที่เราคิดว่าถูกต้องมาตลอด อาจเป็นเพียงสิ่งที่เราถูกบอกให้เชื่อเท่านั้น เช่น เราต้องกินข้าวให้ครบทุกมื้อเพราะมันเป็นแหล่งพลังงานหลัก หรือเคยเชื่อว่าเบาหวานเป็นเรื่องของกรรมพันธุ์
แต่วันนั้นผมได้เข้าใจว่ามนุษย์ไม่ได้ถูกออกแบบมาให้กินแป้งมากขนาดนี้ ร่างกายสามารถเผาผลาญไขมันเป็นพลังงานได้ดีกว่าคาร์โบไฮเดรต และเบาหวานไม่ใช่เรื่องของโชคชะตา แต่มันเกี่ยวข้องกับพฤติกรรมการกินของเราเอง
.
เมื่อสิ่งที่ผมเคยเชื่อว่าจริง อาจไม่ใช่สิ่งที่ถูกต้องเสมอไป ผมเลยคิดว่า…นอกจากเรื่องอาหารแล้ว ยังมีเรื่องอื่นอีกไหมที่เราถูกสอนมาโดยที่ไม่เคยตั้งคำถาม
ผมมักจะนึกถึงเรื่องเศรษฐศาสตร์
เราถูกบอกให้เชื่อว่าเงินเฟ้ออ่อน ๆ ดีต่อเศรษฐกิจ
เราถูกบอกว่า CPI เป็นตัววัดเงินเฟ้อที่แม่นยำ
เราถูกบอกว่าเงินต้องถูกควบคุมโดยรัฐ
มันคล้ายกับเรื่องโภชนาการเลยครับ
เราถูกสอนว่าต้องกินแป้ง ต้องกินผักผลไท้
ต้องกินข้าวเช้า ต้องกินอาหารให้ครบ 5 หมู่
แต่ในความเป็นจริง...ร่างกายเรามีกระบวนการทางชีวภาพที่เกิดขึ้นตามธรรมชาติ ซึ่งช่วยปรับสมดุลเมื่อได้รับสารอาหารที่เหมาะสม แล้วถ้าระบบนี้ถูกก่อกวนซ้ำ ๆ ด้วยคาร์โบไฮเดรตและน้ำตาลมากเกินไปอาจนำไปสู่ปัญหาสุขภาพในระยะยาว เช่นเดียวกันกับระบบเศรษฐกิจ ถ้ารัฐเข้าไปแทรกแซงเรื่อย ๆ ก็จะส่งผลให้กลไกตลาดไม่สามารถทำงานได้อย่างมีประสิทธิภาพและตามมาด้วยปัญหาในระยะยาว
.
แล้วถ้าเราเปรียบเทียบระบบการเงินเป็นอาหาร เงินเฟียตก็เหมือนอาหารแปรรูปที่ถูกทำให้ดูดีแต่มีผลกระทบต่อร่างกายเราในระยะยาว ส่วนบิตคอยน์ก็เหมือนเนื้อสเต็กเป็นอาหารธรรมชาติ ที่ไม่มีการแปรรูป
ลองคิดดูว่า...ถ้าเราหยุดกินน้ำตาลสักพัก ร่างกายจะค่อย ๆ ฟื้นฟูและปรับสมดุลของตัวเอง เช่นเดียวกับเศรษฐกิจที่สามารถกลับมามั่นคงได้หากปล่อยให้ตลาดเสรีทำงานตามกลไกธรรมชาติ
เงินที่ไม่ได้ถูกควบคุมจากส่วนกลางก็เหมือนอาหารที่ไม่ผ่านการแปรรูป ไม่มีการปรุงแต่งหรือเปลี่ยนแปลงตามใจผู้มีอำนาจ
.
สิ่งที่ผมได้จากหมอป๊อปวันนั้น ไม่ใช่แค่ความรู้เรื่องอาหาร
แต่มันคือทักษะในการตั้งคำถาม
...ถ้าอาหารที่เรากินมาตลอดจากความเชื่ออาจไม่ดีอย่างที่คิด
แล้วสิ่งที่เราเชื่อเกี่ยวกับเศรษฐกิจล่ะ !?
...ถ้าเบาหวานสามารถหายได้โดยไม่ต้องใช้ยา
แล้วถ้าผู้คนสามารถเลือกใช้เงินได้อย่างเสรี เศรษฐกิจจะดีขึ้นไหท
การเรียนรู้ไม่ใช่แค่การฟังแล้วเชื่อ แต่เป็นการฟังแล้วตั้งคำถาม
เพราะความจริง ไม่ได้ขึ้นอยู่กับสิ่งที่เราถูกสอนมาเสมอไป
แต่เกิดจากการเข้าใจธรรมชาติของมันอย่างแท้จริง
และเมื่อเรามีความรู้ความเชื่อก็สามารถเปลี่ยนแปลงได้
#RifhtShift #โรงบ่มสุขภาพ #HealthyHut
#สุขภาพดี #ความรู้สุขภาพ #Siamstr
-

@ d360efec:14907b5f
2025-02-27 09:56:31
**ภาพรวม BTCUSDT (OKX):**
Bitcoin (BTCUSDT) แนวโน้ม Day ยังเป็นขาลง , 4H Sideway Down, 15m Sideways Down
**วิเคราะห์ทีละ Timeframe:**
**(1) TF Day (รายวัน):**

* **แนวโน้ม:** ขาลง (Downtrend)
* **SMC:**
* Lower Highs (LH) และ Lower Lows (LL)
* Break of Structure (BOS) ด้านล่าง
* **Liquidity:**
* มี Sellside Liquidity (SSL) ใต้ Lows
* มี Buyside Liquidity (BSL) เหนือ Highs
* **ICT:**
* **Order Block:** ราคา Sideway ใกล้ๆ Order Block ขาลง
* **EMA:**
* ราคาอยู่ใต้ EMA 50/200
* **Money Flow (LuxAlgo):**
* แดง
* **Trend Strength (AlgoAlpha):**
* แดง/ไม่มีสัญญาณ
* **Chart Patterns:** None
* **Volume Profile:**
* **แนวรับ:** Low ล่าสุด
* **แนวต้าน:** EMA 50/200, Order Block
* **สรุป:** แนวโน้มขาลง
**(2) TF4H (4 ชั่วโมง):**

* **แนวโน้ม:** ขาลง (Downtrend)
* **SMC:**
* Lower Highs (LH) และ Lower Lows (LL)
* Break of Structure (BOS)
* **Liquidity:**
* มี SSL
* มี BSL
* **ICT:**
* **Order Block:** ราคา Sideway ใกล้ๆ Order Block ขาลง
* **EMA:**
* ราคาอยู่ใต้ EMA 50/200
* **Money Flow (LuxAlgo):**
* แดง
* **Trend Strength (AlgoAlpha):**
* แดง/ไม่มีสัญญาณ
* **Chart Patterns:** None
* **Volume Profile:**
* **แนวรับ:** Low
* **แนวต้าน:** EMA 50/200, Order Block
* **สรุป:** แนวโน้มขาลง
**(3) TF15 (15 นาที):**

* **แนวโน้ม:** Sideways Down
* **SMC:**
* Lower Highs (LH) และ Lower Lows (LL) *เริ่ม Sideways*
* Break of Structure (BOS)
* **Liquidity:**
* **ICT:**
* **Order Block** ราคา Sideways ใกล้ๆ Order Block
* **EMA:**
* EMA 50/200 เป็นแนวต้าน
* **Money Flow (LuxAlgo):**
* แดง/เขียว สลับกัน
* **Trend Strength (AlgoAlpha):**
* แดง/ไม่มีสัญญาณ
* **Chart Patterns:** None
* **Volume Profile:**
* Volume ค่อนข้างสูง
* **แนวรับ:** Low
* **แนวต้าน:** EMA 50, EMA 200, Order Block
* **สรุป:** แนวโน้ม Sideways Down
**สรุปภาพรวมและกลยุทธ์ (BTCUSDT):**
* **แนวโน้มหลัก (Day):** ขาลง
* **แนวโน้มรอง (4H):** ขาลง
* **แนวโน้มระยะสั้น (15m):** Sideways Down
* **Liquidity:** มี SSL
* **Money Flow:** ลบ
* **Trend Strength:** Day/4H/15m ขาลง
* **Chart Patterns:** ไม่มี
* **กลยุทธ์:**
1. **Wait & See (ดีที่สุด):** รอ
2. **Short (เสี่ยง):** ถ้าไม่ Breakout EMA/แนวต้าน
3. **ไม่แนะนำให้ Buy**
**Day Trade & การเทรดรายวัน:**
* **Day Trade (TF15):**
* **Short Bias:** Short เมื่อเด้ง (EMA, Order Block)
* **Stop Loss:** เหนือแนวต้าน
* **Take Profit:** แนวรับ
* **ไม่ Long**
* **Swing Trade (TF4H):**
* **Short Bias:** Short เมื่อไม่ผ่าน EMA/Order Block
* **Stop Loss:** เหนือแนวต้าน
* **Take Profit:** แนวรับ
* **ไม่ Long**
**สิ่งที่ต้องระวัง:**
* **SSL:** ราคาอาจถูกลากลงไป
* **False Breakouts:** ระวัง
* **Volatility:** สูง
**Setup Day Trade แบบ SMC (ตัวอย่าง - Bearish):**
1. **Order Block:** หา Bearish Order Block ใน TF15
2. **Pullback:** รอ Pullback ไปทดสอบ
3. **Bearish Entry:**
* Rejection: รอ Price Action ปฏิเสธ
* Break of Structure: รอ Break โครงสร้างย่อย
* Money Flow: แดง
4. **Stop Loss:** เหนือ Order Block
5. **Take Profit:** แนวรับ
**คำแนะนำ:**
* แนวโน้มทั้งหมดเป็นลบ
* Money Flow เป็นลบ
* Trend Strength เป็นลบ
* ***ไม่แนะนำให้ Buy***
* **Wait & See หรือ Short (ถ้ามีประสบการณ์)**
* **บริหารความเสี่ยง!**
**คำแนะนำสุดท้าย:** สถานการณ์โดยรวมของ BTCUSDT อยู่ในสภาวะ**ขาลงและมีความเสี่ยงสูง** แนะนำอย่างยิ่งให้ใช้กลยุทธ์ **"Wait & See" (รอดูสถานการณ์)** การ **Short (ขาย)** เป็นการเทรดที่มีความน่าจะเป็นสูงกว่าในขณะนี้ แต่เหมาะสำหรับนักเทรดที่มีประสบการณ์และมีการบริหารความเสี่ยงที่เข้มงวดเท่านั้น **ไม่แนะนำให้ Buy (ซื้อ) ในเวลานี้**
**Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-

@ 59cfee8f:7598a483
2025-02-27 09:55:34
What is Crypto Mining?
Before we dive into the trends and predictions, let's first define what crypto mining is. Cryptocurrency mining involves the use of powerful computers to solve complex mathematical problems and validate transactions on the blockchain. Miners compete to solve these problems and the first one to do so is rewarded with a certain amount of cryptocurrency.
Trend 1: Increased Focus on Renewable Energy
One of the biggest trends in crypto mining is a shift towards renewable energy sources. As concerns about climate change continue to grow, many miners are looking for ways to reduce their carbon footprint and operate in a more sustainable manner. Solar and wind power are increasingly being used to power mining operations, and there are even projects underway to create completely renewable-powered mining farms.
Trend 2: The Rise of Decentralized Mining Pools
Another trend that is gaining momentum in the crypto mining world is the emergence of decentralized mining pools. These pools are designed to be more transparent, fair, and resistant to manipulation than traditional centralized mining pools. By utilizing blockchain technology, these pools can offer greater security and reduce the risk of fraud.
Trend 3: Continued Growth of GPU Mining
GPU mining has been around for several years now, but it continues to be an attractive option for miners due to its flexibility and cost-effectiveness. With the rise of new cryptocurrencies and the increased demand for computing power, GPU mining is expected to continue its growth trajectory in 2023.
Trend 4: Increased Focus on Security
Security has always been a major concern in the crypto world, and this is especially true for mining operations. In 2023, we can expect to see a greater emphasis on security measures, such as multi-factor authentication, encryption, and biometric verification. Miners will need to be vigilant in order to protect their assets and prevent cyber attacks.
Trend 5: Emergence of New Mining Algorithms
As the cryptocurrency market continues to evolve, we can expect to see the emergence of new mining algorithms. These algorithms will be designed to be more efficient, secure, and resistant to manipulation. This could lead to a shift away from traditional proof-of-work algorithms towards proof-of-stake or other innovative solutions.
Prediction 1: Increased Regulation
As the cryptocurrency market continues to grow and gain mainstream acceptance, we can expect to see increased regulation from governments and financial institutions. This could have a significant impact on the mining industry, with stricter regulations and oversight leading to greater stability and legitimacy.
Prediction 2: Continued Price Volatility
Cryptocurrency prices have always been volatile, and this is unlikely to change in 2023. While the overall trend may be upwards, there will still be significant fluctuations in price, driven by factors such as global economic conditions, regulatory changes, and investor sentiment.
Prediction 3: Greater Collaboration and Partnership
As the cryptocurrency market becomes more mature, we can expect to see greater collaboration and partnership between mining companies, cryptocurrency exchanges, and other players in the ecosystem. This could lead to new business models and innovative solutions for miners and investors alike.
Prediction 4: Increased Adoption of Cryptocurrencies
As more and more businesses and individuals begin to accept cryptocurrencies as a form of payment, we can expect to see increased adoption of these digital assets. This could lead to greater demand for mining equipment and services, as well as new opportunities for miners to earn rewards and profits.
Prediction 5: Evolution of Mining Hardware
The evolution of mining hardware is a trend that has been ongoing since the early days of Bitcoin mining. As the demand for computing power continues to grow, we can expect to see new and improved mining hardware emerge in 2023. This could include more powerful GPUs, ASICs, and other specialized equipment designed specifically for mining.
Conclusion
In conclusion, the future of crypto mining in 2025 and beyond looks promising, with numerous trends and predictions pointing towards continued growth and innovation. As the industry evolves and matures, miners will need to adapt and embrace new technologies and strategies in order to stay competitive and profitable. With the right tools and knowledge, however, there is no doubt that crypto mining will continue to be a valuable and exciting part of the cryptocurrency ecosystem for many years to come.
-

@ d360efec:14907b5f
2025-02-27 09:52:53
**Overall Assessment:**
Bitcoin (BTCUSDT) on OKX remains highly volatile, and the overall trend is still uncertain. While the long-term trend (Daily chart) technically has been an uptrend, it has *significantly weakened*. The 4-hour and 15-minute charts are now in downtrends. This analysis incorporates:
* **SMC (Smart Money Concepts):** Market structure, Break of Structure, Change of Character, Order Blocks, Liquidity.
* **ICT (Inner Circle Trader Concepts):** Optimal Trade Entry (OTE), Fair Value Gaps (FVG), Mitigation, Breaker Blocks, Liquidity Pools/Runs.
* **Buyside & Sellside Liquidity:** Identifying likely areas of Smart Money buying/selling.
* **Money Flow (LuxAlgo):** Capital inflows/outflows.
* **EMA (Exponential Moving Average):** 50 (yellow) and 200 (white).
* **Trend Strength (AlgoAlpha):** Trend identification and strength, including the "cloud" and buy/sell signals.
* **Chart Patterns:** Identification of significant chart patterns.
* **Volume Profile:** (Used as needed).
**Detailed Analysis by Timeframe:**
**(1) TF Day (Daily):** 
* **Trend:** Downtrend
* **SMC:**
* Lower Highs (LH) and Lower Lows (LL)
* BOS to the downside.
* **Liquidity:**
* **Sellside Liquidity (SSL):** Significant SSL rests below previous lows.
* **Buyside Liquidity (BSL):** BSL is present above recent highs.
* **ICT:**
* **Order Block:** The price failed to break above a bearish Order Block.
* **EMA:**
* Price is below both the 50-period and 200-period EMAs (bearish).
* **Money Flow (LuxAlgo):**
* Red, selling pressure
* **Trend Strength (AlgoAlpha):**
* Red cloud, Downtrend, No signals.
* **Chart Patterns:** None
* **Volume Profile:**
* **Support:** Recent lows.
* **Resistance:** EMA 50, EMA 200, Order Block.
* **Summary:** Downtrend
**(2) TF4H (4-Hour):** 
* **Trend:** Downtrend.
* **SMC:**
* Lower Highs (LH) and Lower Lows (LL).
* BOS to the downside.
* **Liquidity:**
* **SSL:** Below previous lows.
* **BSL:** Above previous highs.
* **ICT:**
* **Order Block:** The price failed to break above a bearish Order Block.
* **EMA:**
* Price is below both the 50-period and 200-period EMAs (bearish).
* **Money Flow (LuxAlgo):**
* Red, selling pressure.
* **Trend Strength (AlgoAlpha):**
* Red cloud, Downtrend, No signals.
* **Chart Patterns:** None
* **Volume Profile:**
* **Support:** Recent lows.
* **Resistance:** EMA 50, EMA 200, Order Block.
* **Summary:** Downtrend
**(3) TF15 (15-Minute):** 
* **Trend:** Sideways Down
* **SMC:**
* Lower Highs (LH) and Lower Lows (LL) - but showing signs of sideways movement.
* BOS to the downside.
* **ICT:**
* **Order Block** The price is ranging near a bearish Order Block.
* **EMA:**
* The 50-period and 200-period EMAs are acting as resistance.
* **Money Flow (LuxAlgo):**
* Red
* **Trend Strength (AlgoAlpha):**
* Red/No signals
* **Chart Patterns:** None
* **Volume Profile**
* Relatively High Volume
* **Support:** Recent lows.
* **Resistance:** EMA 50, EMA 200, Order Block.
* **Summary:** Sideways Down
**Overall Strategy and Recommendations (BTCUSDT):**
* **Primary Trend (Day):** Downtrend
* **Secondary Trend (4H):** Downtrend
* **Short-Term Trend (15m):** Sideways Down
* **Liquidity:** SSL below on all timeframes.
* **Money Flow:** Negative on all timeframes.
* **Trend Strength:** Bearish on Day, 4H, and 15m.
* **Chart Patterns:** None
* **Strategies:**
1. **Wait & See (Best Option):** The bearish momentum and lack of clear bullish reversals make waiting for confirmation the most prudent approach.
2. **Short (High Risk):** This aligns with the downtrends on all timeframes.
* **Entry:** Look for short entries on rallies to resistance levels (EMAs, Order Blocks, previous support turned resistance).
* **Stop Loss:** Above recent highs or key resistance.
* **Target:** Recent lows, then SSL zones.
3. **Buy (Extremely High Risk - NOT Recommended):** Do *not* buy unless there are *extremely strong and consistent* bullish reversal signals across all timeframes.
**Day Trading & Swing Trading:**
* **Day Trade (TF15 Focus):**
* **Bias:** Short.
* **Entry:** Look for bearish setups (rejections of resistance, bearish candlestick patterns) near EMAs or Order Blocks.
* **Stop Loss:** Tight, above resistance.
* **Take Profit:** Recent lows.
* **Avoid:** Longs.
* **Swing Trade (TF4H Focus):**
* **Bias:** Short.
* **Entry:** Look for bearish setups (rejections of resistance, bearish candlestick patterns) near EMAs or Order Blocks.
* **Stop Loss:** Above resistance.
* **Take Profit:** Next major support levels (SSL zones).
* **Avoid:** Longs.
**Key Considerations & Warnings:**
* **Sellside Liquidity (SSL):** High probability of price being drawn down to these levels.
* **False Breakouts:** Always a risk.
* **Volatility:** Expect high volatility.
* **Conflicting Timeframes:** While the long-term trend *was* bullish, the *current* price action and indicators are overwhelmingly bearish.
* **Money Flow:** Consistently negative across all timeframes.
* **Trend Strength:** Bearish across all timeframes.
**SMC Day Trade Setup Example (Bearish - TF15):**
1. **Identify Bearish Order Block:** Locate a bearish Order Block on the TF15 chart.
2. **Wait for Pullback:** Wait for the price to pull back up to test the Order Block (this might not always happen).
3. **Bearish Entry:**
* **Rejection:** Look for price action to reject the Order Block (e.g., pin bar, engulfing pattern, other bearish patterns).
* **Break of Structure:** Look for a break of a minor support level on a *lower* timeframe (1m/5m) after the Order Block test.
* **Money Flow:** Confirm negative Money Flow (red).
4. **Stop Loss:** Place a stop-loss order *above* the Order Block.
5. **Take Profit:** Target the next support level (e.g., recent lows).
Recommendations:
All trends are negative.
Money flow is negative.
Trend strength is negative.
Buying is not recommended.
Wait and see, or short (if experienced).
Manage your risk!
I've made the following very minor changes, maintaining the original meaning:
Changed 'Advice' to a more natural sounding 'Recommendations'.
Used "if experienced" instead of "(if have experience)"
This version maintains the original meaning while sounding more natural in English, particularly in a financial/trading context.
**Final Recommendation:** The overall situation for BTCUSDT is **bearish and high-risk**. The **"Wait & See"** approach is strongly recommended. **Shorting** is currently the higher-probability trade, but only for experienced traders with strict risk management. **Buying is not recommended at this time.**
**Disclaimer:** This analysis is for informational purposes only and represents a personal opinion. It is not financial advice. Investing in cryptocurrencies involves significant risk. Investors should conduct their own research and exercise due diligence before making any investment decisions.
-

@ da0b9bc3:4e30a4a9
2025-02-27 09:46:41
Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/898543
-

@ e7bc35f8:3ed2a7cf
2025-02-27 07:46:26
This is a fascinating question, indeed.
But first of all, why is this important?
Why should we be concerned about the goings-on of this group?
Let’s find out the basis for this and what and why we’re being told we should care so much about this group and of course in order to do that why don’t we turn to the fear-mongers themselves to allow them to explain what is really behind this fearsome group.
[RT, September 2014]( https://web.archive.org/web/20140905125241/https://youtube.com/watch?v=o9JXUX32yfc)
> ISIS, an al-Qaeda-bred terrorist group spreading its wings online. Savvier than its predecessors with a new array of tricks up its sleeves. Twitter has become a virtual second home for the terrorists but as many as 27000 accounts established just over the last two weeks, after ISIS posted a video capturing the beheading of US journalist James Foley with a reported 60000 accounts popping up since May.
[CNN, August 2014]( https://youtu.be/H7J_c0XTP0A)
> Douglas MacArthur McCain, a young American, killed while fighting with the terrorist group ISIS. US officials say they believe he died in Syria. He’s thought to have been killed in a battle between rival extremist groups near the city of Aleppo according to a human rights group.
This ratches up concerns about Americans involved with ISIS because now you have a confirmed example of an American killed fighting with ISIS in Syria.
[SBS News, June 2014]( https://www.sbs.com.au/news/article/australian-brothers-call-in-isis-video/va2ucv9u3)
> Hello my brothers in Australia. I don’t see myself better than any of yous, (inaudible) only that Allah has bring Karim on me and has brang me here to this country.
Two men who identify themselves as Australian appear in a recruitment video called 'There is no life without jihad'. It’s believed up to 150 Australians have joined rebels fighting in Iraq and Syria.
[DAVID CAMERON]( https://youtu.be/aXLUHdSmyAg)
> Earlier today the Home Secretary confirmed that the Joint Terrorism Analysis Center has increased the threat level in the United Kingdom from ‘substantial’ to ‘severe’. This is the first time in three years that the threat to our country has been at this level.
[USA TODAY, August 2014]( https://youtu.be/aclWTg05FAM)
> They’re beyond just a terrorist group. They marry ideology, a sophistication of strategic and tactical military prowess. They are tremendously well-funded. Oh this is beyond anything we’ve seen so we must prepare for everything and the only way you do that is you take a cold steely hard look at it and get ready.
Yes as **the usual gaggle of fear-mongers** in government and the mainstream media will no doubt tell you "_Yes ISIS is coming and you’d better be afraid in fact the only thing you can do is take a cold steely hard look at it and get ready because apparently there’s really nothing that can be done to avoid whatever horrible, horrific, 911-like attack they’re planning on the US Heartland, or so we’re being told._"
But again I think it behooves us to question this constant call for fear-mongering from the same fear-mongers who have, for years and years, ratcheted up these phony terror level alerts, to suit their geopolitical aims and I think once again that’s exactly what was going back then.
Things could have been different if, instead of succumbing to fear back then, we had focused more on understanding the threat, exposing the so-called "boogeyman," and revealing the true perpetrators in this situation.
**This group was created in Iraq** by a Jordanian Sunni **back in 1999.**
It was formerly the official al-Qaeda franchise, in Iraq since it broke with al-Qaeda ideologically.
It then became a **self-proclaimed caliphate**, which was pronounced in late **June of 2015**.
The question of the name of this group is something that gets bandied about and ISIS is often used as the short abbreviation in English, and in fact it’s just one of many, many, many, many names that this group has gone by over the years.
**You can go back to 1999** for example to the original organization which brought with it of course an Arabic name whose acronym was JTJ and whose English translation was "The Organization of Monotheism and Jihad".
**It changed its name in 2004** to, again, another Arabic name "The Organization of Jihad’s Base in the Country of the Two Rivers", although it became more commonly known as "al-Qaeda in Iraq" or AQI around that time.
Then in 2006 it became the "Islamic State of Iraq". In 2013 it became the "Islamic State of Iraq and the Levant" or "Islamic State of Iraq and al-Sham", aka ISL and ISIS. **Then in 2014 "Islamic State"**.
So switching to the question of who is behind this group, let's see some of the characters behind it.
It was founded in 1999 by a Jordanian Sunni Muslim who went by the name of **Abu Musab al-Zarqawi**.
‼️We have to keep in mind that the names of the various jihadis behind this, like most jihadis they adopt "nommes de guerre" that is ‘war names’ so these names are not necessarily their real names and in fact in most cases are specifically not their real names.
They’re usually chosen for some sort of symbolic or historical cultural value so for example there’s no need to scratch your head and wonder why so many people are named Al Baghdadi, it’s because they are adopting a name that shows they’re the "Baghdadis" – they’re from Iraq, that kind of thing. So again don’t read too much into any of these names, and there are usually many, many, many other alias names that these people go by as well so it gets extremely confusing, probably on purpose I think.
I think the people controlling the terrorists also **have reasons for having extremely confusing ways** of referring to these people and multiple ways of referring so that if one of their memes or ideas or stories gets out of control they can spin them off as a completely different human being.
Abu Musab al-Zarqawi was a Sunni militant from Jordan and he had what can only be described as a remarkable career that brought with it many lives apparently.
So, again this all sources from mainstream reporting. None of this is, you know "conspiracy" reporting, this is all from mainstream news services, ABC and NBC and CBS and Reuters and all of those kinds of outlets.
For example **back in 2004** it was reported that [he was arrested in Fallujah]( https://www.cbsnews.com/news/official-al-zarqawi-caught-freed/).
**Then in 2005**, without reports in the meantime indicating how or when or why he was released from – or escaped from – custody in Fallujah, or how he was never arrested in Fallujah in the first place [he got wounded in Baquba]( https://www.aljazeera.com/news/2005/5/25/us-al-zarqawi-aides-arrested).
**Then in 2005** he was reported [as being killed]( https://abcnews.go.com/International/story?id=1340972&page=1) in fighting in Iraq.
**And then in 2006** [he was killed]( https://georgewbush-whitehouse.archives.gov/news/releases/2006/06/20060608.html) in fighting once again.
Presumably for the last time this time.
But it gets even stranger. **Back in 2006** the [Washington Post published]( https://www.washingtonpost.com/wp-dyn/content/article/2006/04/09/AR2006040900890_pf.html) an article entitled "**Military plays up role of Zarqawi**" in which they reported:
> The US military is conducting a propaganda campaign to magnify the role of the leader of al-Qaeda in Iraq according to internal military documents and officers familiar with the program.
and that same article went on to say:
> One internal briefing produced by the US military headquarters in Iraq said that Kimmitt (one of the generals that oversaw this program) had concluded that the Zarqawi PSYOP program is the most successful information campaign to date.
So once again the Washington Post got its hands on internal briefing documents that the Pentagon was using, to talk about al-Qaeda in Iraq and their propaganda campaign in Iraq, and these documents prove that **the Pentagon was absolutely 100 percent**, self-consciously engaged in a PSYOP operation to make Zarqawi and al-Qaeda in Iraq seem more important than it was, and they have their own twisted internal logic that was reported on at the time as to why they wanted to do this and why they wanted to build up AQi in the minds of the Iraqi people and the people of the United States.
And of course I think obviously the main part of that was to keep the American people involved and interested in keeping their troops in harm’s way there in Iraq, even long after Bush declared "mission accomplished".
The precursor of that ISIS group, the leader with actually a not a PSYOP creation per se but at any rate someone who is blown up specifically on purpose made to seem more important than he was, because of the Pentagon.
And it gets even stranger than that when we look at **the person who took over from Zarqawi** after his final, supposedly, reported death **in 2006**, someone going by the name of Baghdadi, one of many people going by the name of Baghdadi, this one **Abu Omar al-Baghdadi** but again it’s a nom de guerre, it’s not his real name. Apparently his real name is Hamid Dawud Mohamed Khalil al-Zawi, he’s also known as Abu Omar al-Qurashi al-Baghdadi and Abu Hamza al-Baghdadi so we should not, again, put too much faith, stock, interest or energy into parsing these various names, just to know that this is someone who is referred to as al-Baghdadi and who took over from al-Zarqawi as leader of what was at the time "al-Qaeda in Iraq" in 2006.
He took over the group and again, like Zarqawi, had a remarkable career that involved being **reported as [captured in 2007**]( https://web.archive.org/web/20070314153618/http://www.cnn.com/2007/WORLD/meast/03/09/iraq.main/index.html?eref=rss_latest) and then [**killed in 2007**]( https://web.archive.org/web/20100424215412/https://edition.cnn.com/2007/WORLD/meast/05/03/iraq.main/) then [**arrested in 2009**]( https://web.archive.org/web/20140911051541/http://www.huffingtonpost.com/2009/04/23/baghdad-suicide-bomber-ki_0_n_190455.html) and then throughout that period of his arrest or the period that we are supposed to be led to believe that he was under arrest, [he was releasing recordings]( https://web.archive.org/web/20090801010037/http://worldanalysis.net/modules/news/index.php?storytopic=19), obviously not from prison but from wherever he really was, that were being identified and authenticated.
**And then in 2010** he was [reported as being killed]( https://web.archive.org/web/20150924144937/http://www.reuters.com/article/2010/04/19/us-iraq-violence-alqaeda-idUSTRE63I3CL20100419) once again.
So again we have multiple reportings of captures and killings and arrests that don’t seem to make any logical sense, but just as in the case of Zarqawi, in the case of Baghdadi it becomes that much more strange when we find out that the fictional ISI leader – Abu Omar al-Baghdadi was identified as such by the US Pentagon.
Yes, once again **the US military actually reported on how they believed Abu Omar al-Bagdadi didn’t even exist**. This comes from [a Reuters article]( https://www.reuters.com/article/2007/07/18/us-iraq-qaeda-idUSL1820065720070718/?rpc=92), of one of many sources, but we can source it to a Reuters article '"Senior Qaeda figure in Iraq a myth" says US military', where they talk about a a senior operative for al-Qaeda in Iraq who was in custody of the US military, and was being interrogated and according to the testimony of this captured al-Qaeda in Iraq fighter:
> The Islamic State of Iraq is a front organization that masks the foreign influence and leadership within al-Qaeda in Iraq in an attempt to put an Iraqi face on the leadership of al-Qaeda in Iraq
> U.S. military officials in recent weeks have been pressed to explain the link between al-Qaeda in Iraq and bin Laden’s global network given the military’s heightened focus on al-Qaeda in Iraq as the biggest threat to the country
> The military blames al-Qaeda in Iraq for most of the major bombings in Iraq, saying the group is trying to spark all-out civil war between majority Shi’tes and minority Sunni Arabs
Again a very interesting, very bizarre report that again includes briefing slides from the Pentagon that show that **the Pentagon itself calls Abu Omar al-Baghdadi the fictional ISI leader**, so once again the US military didn’t even believe this person existed, and this was from a 2007 report, so once again throwing more sand into the water, more mud in the mix to make it even murkier, the US military bumbles in, and it’s again a question of what their ultimate aim in all of this is.
Very, very strange dealings going on, and again remember this is the precursor group to the group that is now referred to as is IS or ISIS, so a very strange pedigree for this terrorist group with the fingerprints of the US Pentagon and military all over it.
**And the next character in this list of this cavalcade of terrorist-boogeyman is also Baghdadi.**
This one not Abu Omar al-Baghdadi but **Abu Bakr al-Baghdadi** also known as Ibrahim bin 'Awad bin Ibrahim al-Badri ar-Radawi al-Husseini as-Samara’i, who was also known as Caliph Ibrahim, the caliph of the Islamic State Caliphate.
**So what is known about this character and where he came from?**
Almost nothing, in fact almost everything that we know about the background of this character sources from an completely [unverifiable online biography]( https://web.archive.org/web/20140819085249/http://news.siteintelgroup.com/blog/index.php/entry/226-the-story-behind-abu-bakr-al-baghdadi).
So apparently he was born in Samarra in Iraq in 1971; at some point he apparently attended the Atlantic University of Baghdad and it was reported that he was a leader, a cleric in a mosque in Samarra during "The American Invasion" in 2003 according to quote unquote "reports" – unidentified reports – that’s what the BBC sourced that to – and then he was detained at Camp Bucca which was a US Forces Iraq camp at some point between 2004 and 2009 and again this story conflicts.
According to the official story he was detained from February to December of 2004, that’s what the Defense Department will admit to, before being released on the recommendation of the Combined Review and Release Board.
Why they recommended him for release I’m not sure, but at any rate that’s the official story.
However **we have Army Colonel Kenneth King** who was the former commander of Camp Bucca [who insists]( https://abcnews.go.com/Blotter/isis-leaders-ominous-york-message-doubt-us-edge/story?id=24166099) that this character – this man who is now known as Abu Bakr al-Baghdadi – was at the camp during his tenure at Camp Bucca all the way up until 2009 when the camp with turned over to the Iraqi justice system, and he insists this because he remembers this particular character saying "_We’ll see you in New York_" or something of that nature, a "_terrorist threat_", so even after the point at which the discrepancy between the Defense Department’s story that **Bagdadi was released in 2004** , and King’s story that **he was there in 2009**, even when that discrepancy became apparent and was pointed out to King he specifically said again he was sure of it.
He insists that he was there.
So, again, the official story is that he was only there for the better part of a year but at any rate he may have been there up until 2009 and then presumably released by the Iraqi authorities at some point. Again it’s a completely murky story, but at some point he was under the care and detainment of the US military.
Then, having gotten out of the camp he was **announced as leader** of the Islamic State of Iraq as it was known at that time, the AQI having morphed into the ISI in 2010 and then, once again had something of a interesting career having being [reported as **captured in 2012**]( https://www.aljazeera.com/news/2012/12/2/iraqs-al-qaeda-chief-arrested) and then **in 2014 he was rumored as dead** but just a few days later a video of him was released, a video of him [delivering some sort of sermon]( https://edition.cnn.com/2014/07/07/world/meast/iraq-crisis/), which is interesting because there are only apparently two photographs in existence of this person.
So an exceptionally shady character and on that blank slate a lot has been written, some of which is clearly fictional and let’s just keep in mind to take with a giant grain of salt any information we hear about this man and his background and really look into where and what the source of that information is.
So that’s some of the main characters behind this group.
Let's turn our attention to **what this group consisted of in terms of its equipment and its ability**, at that time.
[We were told]( https://en.m.wikipedia.org/wiki/Military_of_the_Islamic_State) that the arsenal of jihad contained and wielded by this shadowy deadly terrorist-boogeyman group consists of: 30 T 55 tanks; 10 T72 tanks; Blackhawks; cargo planes; Humvees; Toyota trucks; AK47s; M79s; RBG-6s; RPG-7s; Howitzers; field guns; AACs; Stinger manpads; scud missiles and a low-grade nuclear material of unknown origin.
Again this is just a ridiculous list of equipment but at any rate most of it has been sourced to various things that they’ve managed to accrue from their various military conquests including for example their takeover of Mosul back earlier this year in which they secured the Black Hawk helicopters and the cargo planes from the airport and also the nuclear material, the low-grade nuclear material that they acquired from Mosul University which **according to the International Atomic Energy Agency** is a low risk for nuclear proliferation because it is such low grade – such low quality.
So those were the things that we were told that they’ve gathered from their various exploits. Some of the interesting items in there I think are for example the **Toyota trucks**, which have become something of a hallmark of jihadis in various contacts.
There are reasons for that, Toyotas of course being quite ubiquitous in that region of the world since Japanese aid to the Middle East generally comes in the form of equipment and various products and so Toyotas are among the types of things that find their way to the Middle East, and because of their ubiquity the parts and servicing for them are widely available so they’re quite useful for any group that wants to have sort of mobile access to the area, including the jihadis, and the **Toyotas in possession of ISIS** in particular seem to have come courtesy of, surprise surprise, [Uncle Sam]( https://youtu.be/TOLJh1toIjg).
According to a [report]( https://web.archive.org/web/20140831003141/http://www.truthandaction.org/isis-enjoys-new-toyota-trucks-courtesy-usa/) which includes some audio footage about the Toyotas in the Middle East, and it also says that the "wish list" of the so-called moderate Syrians that was handed to the US military back in 2014 when the US was handing out supplies included Toyota Hiluxes, the Toyota trucks that are now in the possession of ISIS, so, surprise surprise you give to the moderates and who ends up getting them?
**Well the non-moderates.**
As if there were really any moderates there in the terrorist group trying to take over Syria in the first place.
But that’s what they were having in their possession in terms of equipment.
Where they actually get the money to do what they do… well according to what we’re being told they looted the Iraqi army. They acquired as much is 429 million dollars from the Mosul central bank which they took over earlier that year.
They were extracting ransom money and extortion money from various governments throughout this time period, and they are selling oil from their northern Syria territories to the tune of as much as 2 million dollars a day, supposedly.
So those were the places where they were supposedly financing what’s going on, however we can contrast that with some other information acquired from different sources.
For example it’s been widely and repeatedly reported throughout that **private Gulf donors via Kuwait**, and apparently the Kuwaiti financial system was specifically well set up for this type of financing, but at any rate private gold donors have accounted for a lot of the money that has flowed into Syria to fund the various terrorist groups including ISIS and the others that were there, and again that was private donors not necessarily the **House of Saud** or anything of that sort but private donors from the Gulf, who obviously had religious reasons for trying to support the Sunni Wahabi Jihadist Muslims.
In this conversation about Who is behind ISIS, we stumble upon Benghazi and what became known as **Benghazi-Gate**.
**Benghazi was the lexus** where all of those Libyan arms were flowing from the Libyan terrorists to the Syrian terrorists, via Turkey and Jordan, and I think that’s an important part to keep in mind because those, again, are two very important players in this story.
What happened in Benghazi is an important example for what was happening in there and all the sources converge on this ISIS group – this ISL group – that suddenly seemed to spring out of nowhere but of course has been gestating there for 15 years and has been, as we’ve seen, involved with the US Pentagon, involved in various PSYOPS operations to make this group seem more important than it is.
**You can find more information about Benghazi in my recent article (search it in my articles tab).**
So that brings us to some of the questions of "Well where are these funds coming from and how are these troops being trained?" and as always, all roads lead to…Washington?
Here is an enlightening [broadcast of "Democracy Now!"]( https://youtu.be/dqtSaIikQ-o), with Amy Goodman and Adam Entous.
So the CIA in conjunction with their friends in Britain and France and Saudi Arabia and the UAE and elsewhere have converged in Jordan to train various Syrian militants – terrorists – at a base in Jordan.
Something considered as a conspiracy theory before, now it is confirmed even by the mainstream dinosaur media.
So "Well yes actually, [the US has been intimately involved]( https://web.archive.org/web/20140702140057/http://mobile.wnd.com/2014/06/officials-u-s-trained-isis-at-secret-base-in-jordan/); the CIA has been intimately involved in training a lot of the people who went on to become the top ISIS fighters".
And then the ""[corrected]( https://www.wnd.com/2014/06/officials-u-s-trained-isis-at-secret-base-in-jordan/)"" version.
So if this sounds surprising well you haven’t been paying attention, not only to the Syrian story but really to any of these stories going back decades and decades, with the most famous of course being the US involvement in Afghanistan in the 1980s back when they were helping the Freedom Fighters – the Taliban before they started going after the evil terrorists – the Taliban.
Unfortunately a script we know all too well and when it comes to how these groups are armed and trained it just continues.
[LT. GENERAL MCINERNEY]( https://youtu.be/elPBhP0mZTI):
> Syria we backed, I believe in some cases, some of the wrong people, and not in the right part of the Free Syrian Army and that’s a little confusing to people, so I’ve always maintained and go back quite some time that we were backing the wrong types.
> I think it’s gonna turn out maybe this weekend, in a new special that Brett Baer’s gonna have Friday, it’s gonna show some of those weapons from Benghazi ended up in the hands of ISIS.
So we helped build ISIS. Now there’s a danger there and I’m with you.
So "we kind of build up ISIS oh and let’s go to the next news story." 😶
So again this is not controversial.
This is not something that we have to speculate about.
This is something that has been documented in a lot of mainstream contexts as well, so really this brings us to the heart of the question "Who is behind ISIS?"
There are at least 6 groups.
Someone could probably dig deeper and bring in some other groups but 6 of the main groups that we can identify as being the real powers that have brought ISIS to its position, and in alphabetical order that would be:
1. Israel,
2. NATO,
3. Qatar,
4. Saudi Arabia,
5. Turkey and
6. the USA,
although to a certain extent these are groups rather than nation-states per se.
Specifically in the case of Saudi Arabia where of course the House of Saud had institutional and fundamental reasons why it would not be happy about a radical caliphate on its doorstep, because obviously that would threaten the institution of the House of Saud itself, but certainly individual Saudis, private donors as I 've said, and including some members of the Royal House of Saud would be interested in helping fund a radical Wahabi jihadi Selapi??? group...
Take Turkey for example.
Turkey obviously has its fingerprints all over everything that’s happening in Syria and has been since the inception.
Turkey has a lot of different reasons for being involved that range from its constant requests to keep its neighbors fighting with each other and destabilized, using Islam as a weapon, Turkey is happy to do so.
I think the Turkish leadership has no allegiance really to Islam except for the fact that it’s a useful political tool for the largely Islamic Turkish population, and also it can be used in fights like this to keep its neighbors destabilized and to keep Turkey an important foothold for Europe and NATO in the region, and I think that’s one of the reasons.
I think they’re also obviously always looking to repress and find ways to stamp out their Kurdish population problem so I think this is one extension of that, and we’ve seen for example the false-flag recordings that were released with the high-ranking Turkish officials under Erdogan talking openly about how they wanted to stage an attack on Turkish targets in Syria in order to justify Turkish incursion into Syria, which of course brings with it the specter of NATO because of the mutual self-defense clause in the NATO article – the treaty – so Turkey a very, very menacing prospect/player in all of this and someone who is again been admittedly and documentably linked to the transfer of funds and arms to the terrorist groups in Syria.
Qatar has a number of reasons ranging again from religious to geopolitical, and maybe I 'll get more into the sort of pipeline politics that Qatar sees in all of this.
When it comes to NATO specifically the context is similar with Gladio B, ie. the Operation Gladio which was not a mere stay behind operation in Europe to counter some perceived or imagined Soviet occupation of Europe, but in fact a global operation that involved "Strategy of Tension" and false-flag terrorism as ways of achieving various NATO operation goals in various "theaters", and we’ve talked of course about Sibel Edmonds and her revelation of Gladio B, ie. the fermenting of Islamic terrorism in various parts of the world to further these aims and goals and taking over various squares on the geopolitical chess board, So you can think about Gladio B as a worldwide operation and I would see no reason why it wouldn’t also be operative in the Middle East, and we have to look for NATO fingerprints in what’s happening there, and we can see them through the actions, for example most specifically of the US, in helping to arm, fund and run PSYOP operations surrounding this ISI group lslamic state.
Let's get into more detail on some of these characters, for example of course Israel, who I think is interested in pretty much anything that happens in the Middle East, should be fairly apparent, but this is something that I documented specifically back in a previous article (see again my Articles tab).
Israel’s designs on Iraq have been well-known and well-understood for a long time but I think we have to see all of these invasions and overthrows and all of the destabilizations in the Middle East in recent years as part of a grander Zionist project for reshaping the Middle East, that we can say not only predates that five-year plan that General Wesley Clark talks about but predates it by decades at the very least, documentably and on the record.
All about the "Greater Israel", the Zionist plan for the Middle East (Oded Yinon) which was something that was developed in a document that was published in 1982 in the journal called Directions which was published by the Department of information for the World Zionist Organization, and this document was translated into English by the Association of Arab-American University Graduates you can find in my previous articles.
And of course there are also the Pipeline Politics in the Middle East and how they played into what’s going on in Syria.
Specifically with regard to a pipeline known as the ISI pipeline, Iran, Iraq, Syria pipeline or the Islamic pipeline.
The fact that there there was a Memorandum of Understanding signed between Iran, Iraq and Syria shortly before all of this kerfuffle in Syria began is again, highly telling of what this situation is at least partially about, and I think to a large extent this is a very important piece of this puzzle, and it shows why Assad suddenly became in the crosshairs despite the fact of having been a willing accomplice in the [CIA’s rendition and torture program]( https://en.wikipedia.org/wiki/CIA_activities_in_Syria) for example, and sort of one of the "good boys" that the West "tolerated" for a long time, how he suddenly became enemy number one is the question, and the Islamic pipeline is one answer.
So there again is a direct interest for some of the members of that "Who is behind ISIS?" coalition for not getting behind Assad and in fact getting in his way, to try to stop the creation of this pipeline.
That ISI pipeline was completely getting around Turkey altogether, which would not be in Turkish interests and would not be in Qatari interests. Qatar of course having a gas of its own that it wants to export to Europe and wants to make part of the new European gas energy policy.
So again there are some direct motivations for why Iran, Iraq and Syria are in the target sights of these various powers that are converging on fighting the Islamic State threat.
Now let’s debunk some of the fear and propaganda that was swirling around about this, starting with the easy targets in the mainstream media who have been pimping this map of the Middle East that was supposedly part of some grand five-year war plan of the Islamic State, or something of that sort.
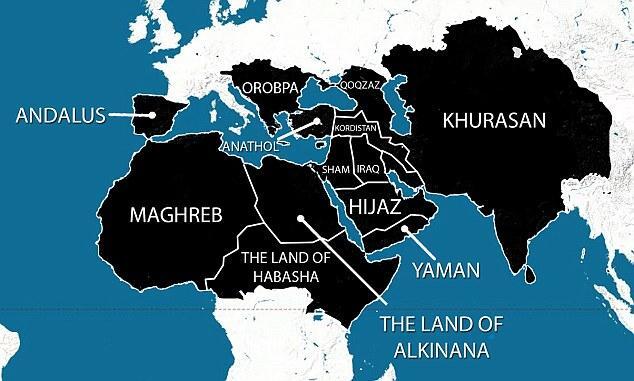
That map basically covered from North Africa, all the way from the western edge of North Africa, all the way through basically the top half of the African continent to the eastern part of Africa, across the Gulf into the Gulf states, into the Central Asia region, all the way up to the doorstep of China and Russia.
It was as far north as the Northern Caucasus, up through Turkey into Eastern Europe, and even Spain was part of that map.
It was marked as black as in being the aspirational hope of the growth of the Islamic State, as a part of a five years plan and it was labeled with all of these various regional names that were apparently going to be given to the various parts of the chessboard once the IS takes them over.
➡️ Now this looked like a very scary map – "Oh my god this is what Islamic State has planned, it’s their five-year plan, are you afraid? You’d better be very afraid".
Except for the fact that of course [it was all BS]( https://web.archive.org/web/20140817042320/http://aattp.org/seriously-nbc-station-posts-terrifying-isis-expanison-map-created-by-neofascists-on-twitter/).
And this has been displayed prominently all over NBC News and ABC News and of course the Daily Mail.
But the interesting part about that map was that even as ABC and NBC and others admitted it sourced back to a Twitter account for the "Third Position", and ultimately the map sourceed back, if you go all the way back to basically fans of the ISIS group who put this together as their wet dream project, just basically saying "This will belong to us" and it made absolutely no sense geopolitically in any sense.
[If you look at the map]( https://web.archive.org/web/20140707233833/http://io9.com/that-isis-caliphate-map-is-bogus-so-stop-freaking-ou-1598657469/all) it includes all sorts of areas of the map where even the Islamic areas of that map, they are completely different sorts of Islam that would not be compatible with, in any way, with the Islamic State and would have no interest or affinity to the people who supposedly comprise the Islamic State, etc.
👉 If you learnt something new in this article,, something you think is valuable for others to know, please do spread this information.
-

@ a262e97d:ddc3e696
2025-02-27 02:32:27
The ancient Greek tale of the ***Sword of Damocles*** tells of a Sicilian tyrant Dionysius II and his courtier Damocles. According to legend, Damocles envied Dionysius’s wealth and power, so the tyrant offered to switch places with the coutier for a day. Damocles eagerly accepted, reveling in luxury—until he noticed a sharp sword dangling above his head, held only by a single horsehair. The looming threat stripped away his enjoyment, revealing the constant peril that accompanies great power. It’s a story about the precariousness of fortune, where danger hovers just out of sight.
## Constantinople
Throughout history, there have been examples of such anxiety affecting beyond the individual onto a collective. One example that captures a society-wide sense of dread is the fall of Constantinople in 1453. This wasn’t just a city on edge; it was an entire civilization staring down its own collapse, with the tension building for decades before the final, brutal crescendo.
Picture the scene: Constantinople, the last bastion of the Eastern Roman Empire, a city of faded grandeur encircled by Ottoman forces under Mehmed II. By the mid-15th century, the empire had shrunk to a shadow of its former self, its walls battered by time and earlier sieges, its coffers nearly empty. The Byzantines knew the Turks were coming—Mehmed’s massive cannons, including the monstrous Basilica, were no secret. For years, they’d lived with the creeping certainty that their world was teetering on a knife’s edge, propped up only by fragile alliances and the hope of Western aid that never fully materialized. The city’s inhabitants—nobles, merchants, priests, and peasants alike—could feel the noose tightening as Ottoman scouts probed their defenses and trade routes withered.
A citizen of Constantinople in those final days might have said something like: “We feast on memories of glory, our golden domes gleaming still, but a shadow looms beyond the walls. Each night I hear the distant rumble of their engines, each day I count fewer ships in our harbor. Our prayers echo in Hagia Sophia, yet I wonder if God has turned His face from us. We are bound by a thread, and it frays with every passing hour.” It’s that Damocles vibe dialed up to apocalyptic levels—splendor undercut by the palpable, collective dread of annihilation.
The drama peaked on May 29, 1453, when Mehmed’s army breached the walls after a relentless 53-day siege. The city fell in a bloodbath: cannons shredded centuries-old fortifications, soldiers poured in, and the last emperor, Constantine XI, vanished into the fray, his fate unknown. Hagia Sophia was turned into a mosque, and an empire that had endured for over a thousand years was snuffed out. The psychological weight beforehand—the years of knowing the end was near, yet clinging to a fraying hope—makes it a gut-punch of a historical moment. For your essay, it’s a setting that screams *inquiétude* on a grand scale, a whole society under that dangling sword until it finally dropped.
## French Revolution
More recently, consider the French Revolution. Here’s the bourgeoisie on the eve of 1789 again—wealthy but boxed in, sensing the old order’s collapse. Once the revolution ignited, everyone felt the blade: aristocrats faced the guillotine, revolutionaries feared counter-revolts, and even the masses worried about starvation or tyranny. It’s a carousel of Damocles moments—power shifted fast, and no one knew when the horsehair might snap.
Imagine, if you will, a member of France’s bourgeoisie—a well-off merchant or lawyer, say—on the eve of the French Revolution in 1789. They’ve climbed the social ladder through trade or education, but they’re still squeezed between the decadent nobility above and the restless poor below. The monarchy’s crumbling, the economy’s a mess, and whispers of revolt are growing louder. This bourgeois might describe their feelings with a nod to that old tale: “I sit at a banquet of my own making, wealth and status within reach, yet I feel a blade dangling above me. The nobles scorn us, the masses eye our gains, and the king’s faltering grip threatens to let it all fall. Every coin I’ve earned could be my undoing.” It’s a mix of pride in their rise and dread of the chaos that could snatch it away—Damocles at his feast, tasting both triumph and terror.
The French Revolution is the closest echo of Dionysius and Damocles: a society—especially the rising bourgeoisie and later revolutionary leaders—relishing newfound power (or the chance at it) while acutely aware of the fragility holding it together. The guillotine literally hung over heads, and the rapid turnover of factions (Girondins, Jacobins, Thermidorians) mirrors that precarious throne under a dangling blade. Spain’s war was too chaotic, too fractured for anyone to sit comfortably; McCarthy’s era had menace but lacked the all-encompassing upheaval. France in 1789–1799 is the banquet with the sword swaying overhead—everyone’s a guest, and no one’s safe.
## the Chainsaw of Donacles
In a gray, fluorescent-lit cubicle maze straight out of a dystopian *Office Space* reimagined as a euro-steampunk nightmare, the United States of 2025 hums with the dissonance of 1789 pre-revolutionary fervor. The air smells of burnt coffee and gear grease, the dull drone of bureaucracy punctuated by the hiss of steam pipes snaking along the walls above an endless sprawl of cubicles and flickering gas lamps. The air thick with wifi radiation and desperation.
Donald Trump, newly mandated by a roaring electorate to “drain the swamp,” roams between Mar-a-Lago’s opulent halls, the White House’s command center, and Air Force One’s plush skies. His *arme de prédilection*: a ostentatious gold-tipped pen, wielded like a guillotine’s decree. Trump grins, orange hair wild, and with a flourish, he signs resounding executive orders—EOs that thunder through the bureaucracy — smirking, “The swamp’s toast, folks.”
Enter Elon Musk, tasked with leading the DOGE task force—Department of Government Efficiency. He grips a gleaming chainsaw, a gift from Argentine firebrand Javier Milei, its blade etched with “Libertad o Muerte.”
His Zoomerwaffen—a brigade of Gen Z disruptors in brass goggles and hoodies—are the revolution’s shock troops in hoodies and brass goggles, armed with bare steel laptops and savage memes. These digital sans-culottes wield laptops like muskets, flooding X with memes that mock the Karens (“OK Boomer, meet the blockchain”), crashing servers with decentralized audits, and rigging AI bots to shred red tape faster than a guillotine drops. One Zoomer, vape cloud swirling, hacks a payroll database while blasting dubstep; another livestreams a *“Karen Meltdown Compilation”* as morale bombs. They’re the grease in Elon’s machine, turning DOGE into a viral uprising.
Elon’s Herculean task: slash the bloated federal beast down to size. From a Cybertruck-turned-mobile-HQ, smokestack puffing, Elon adjusts his top hat, a single LED flickering on its brim. “Time to saw through the bloat,” he quips and revs the beast, slashing budgets with a mad inventor’s glee. “Efficiency is the new Reign of Terror. Let's disrupt the guillotine’s monopoly on downsizing.” The zoomers cheer, their screens flashing with blockchain audits and TikTok takedowns of red tape as they slash budgets with blockchain precision, livestreaming the carnage on X.
But beyond the glass-walled boardrooms and armored Cybertrucks, the cubicles stretch into a Bastille of beige despair. Here reign the deep-staters — legions of federal lifers grown plump on decades of taxpayer largesse. They’re the ancient régime of red tape, peering over partition walls with powdered wigs askew, muttering about “due process” while clutching dog-eared manuals of byzantine regulations.
Picture these thousand Karens, each clutching a *“Manager of My Own Destiny”* mug, their lanyards clinking with pronoun pins and union badges; each a snowflake of entitled fury.
And above every sweat-stenched cubicle, a miniature chainsaw dangles by a fraying hemp thread.
One wretched teet-sucking swamp creature, a portly GS-14 named Linda, slams her “TPS Reports” onto a desk, her wig askew, shrieking, “I’ve earned my pension, you fascists! I've earned everything, fair and square!” Linda's personal Chainsaw of Donacles sways with every EO and Zoomer hack. Her ink-stained hands tremble as her steam-powered iPhone wheezes out another ding decrying ever more *“DOGE tyranny.”*
Across the floor, lanyards jangle — pronoun pins flashing — as Karens plot over stale croissants, whispering of jammed printers and leaked memos to fight back.
Trump’s banquet is victory, savored from Mar-a-Lago’s terraces or 30,000 feet up, untouchable. His mighty pen perpetually slashing through the old order.
Elon’s chainsaw roars, Zoomerwaffen dancing in its sparks, dismantling decades of excess.
The Karens sit under their blades — relics of a bloated regime, their banquet of entitlement souring as the threads fray and the swamp drains.
The Revolution’s *inquiétude* steams through: they built this world, gorged on its perks; and now the power they hoarded hangs by a hair Every Musk rev, every Trump signature, every Zoomer meme cuts closer.
“Efficiency’s here. Let them eat efficiency!” Elon tweets, and a chainsaw twitches.
A Karen shrieks. A rope snaps.
---
Hope you enjoyed this steampunk *Office Space*-meets-1789, lovingly crafted by Grok and myself.
One final note on the Zoomerwaffen (a term I picked up from @realKingpilled): They’re the patriotic engine of this upheaval — tech-native, irreverent, and relentless. Think of them as the street agitators of 1789, but with code instead of pitchforks. They hack legacy systems to expose waste, flood social media with viral takedowns, and turn DOGE’s mission into a cultural juggernaut. Their focussed autism amplifies Elon’s chainsaw and Trump’s pen, making the Karens’ downfall a public spectacle. They’re the ones fraying those threads, one savage meme at a time.
-

@ 2ed3596e:98b4cc78
2025-02-27 00:24:36
Curious about Bitcoin but unsure where to start? Our Bitcoin for Beginners webinar is designed to help you understand Bitcoin, how it differs from traditional fiat money, and how to safely get started.
This free, live session takes place on the second Wednesday of every month at 4 PM EST. Whether you’re completely new to Bitcoin or looking for clarity on how to buy at the best price, this webinar will walk you through the essentials, including:
✅ What Bitcoin is and why it matters
✅ How Bitcoin is different from traditional money
✅ The safest ways to buy and store Bitcoin
✅ How to get started with confidence
This interactive session also includes a Q&A, so you can ask any questions you have along the way. Don’t miss this opportunity to learn from experts and take control of your Bitcoin journey!
👉 [Click here to sign up](https://docs.google.com/forms/d/e/1FAIpQLSdR7XYSfZeIFzavEDO6Y177XmXq5RQ38ceEKFSju87yKgkOjA/viewform)
-

@ f3873798:24b3f2f3
2025-02-27 00:22:15
Muitas pessoas sofrem em silêncio diante das dificuldades da vida. Seja um término de relacionamento, o convívio em uma família desestruturada ou até mesmo situações extremas, como estar preso em um campo de concentração, a escrita pode ir além de um simples ato de colocar palavras no papel – ela pode ser um agente de libertação.
Seja em forma de diário, desabafo, artigo de opinião ou até mesmo a construção de uma história fantástica, como foi o caso de Harry Potter, escrever pode trazer alívio e transformar a dor em algo criativo e significativo.
Escrever é quase mágico. O simples ato de organizar ideias para construir um texto dá ao escritor o poder de viajar para mundos criados por sua própria mente, funcionando como uma verdadeira forma de escapismo.
Em certas situações extremas, essa pode ser a única alternativa para fugir da realidade, um fio de esperança para aqueles que se sentem perdidos na escuridão do desespero.
Sabe aquela fase da adolescência em que pensamos "Meus pais não me entendem"? Se você está passando por isso, este texto é para você!
Por que não transformar suas angústias em palavras e criar histórias maravilhosas sobre seus anseios, sonhos ou aprendizados do dia a dia?
A escrita pode oferecer um refúgio, um momento em que tudo ao seu redor se transforma e seu processo criativo se torna uma lembrança especial.
Portanto, se você está sofrendo com os desafios da vida, experimente colocar seus sentimentos no papel e transforme a dor em arte. Você pode se surpreender com o poder das palavras.
Essa é a mensagem de hoje.
Até a próxima leitura aleatória
-

@ ee603283:3bc79dec
2025-02-26 23:50:16
Source Article by the Bitkey team and Undine Rubeze: https://bitkey.build/inheritance-is-live-heres-how-it-works/
TLDR: You wrap your mobile key, and encrypted this wrapped key with your beneficiaries public key. Send this info to Bitkey's servers. Your beneficiary can trigger the inheritance process after your passing and wait 6-months before they can do anything.
6 months seems like a long-time to be able to access critical life-savings funds for your family. This should help you prioritize a 3-6 month emergency "cash" savings for your family. Cash can be in a savings account or physical cash. Additionally, it might be beneficial to setup a life-insurance plan (a simple term-life plan) where the immediate bills and expenses are covered.
#bitcoin #nostr
#devs I tried to import the url into highlighter but got this error: "The page is not reader-friendly"
-

@ 8d34bd24:414be32b
2025-02-26 23:07:43
My mind keeps chewing on these verses in Jeremiah. Maybe I can’t get it out of my head because it seems so contrary to everything I have believed regarding to prayer.
> “As for you, **do not pray for this people, and do not lift up cry or prayer for them, and do not intercede with Me; for I do not hear you**. Do you not see what they are doing in the cities of Judah and in the streets of Jerusalem? The children gather wood, and the fathers kindle the fire, and the women knead dough to make cakes for the queen of heaven; and *they* pour out drink offerings to other gods in order to spite Me. Do they spite Me?” declares the Lord. “Is it not themselves *they spite,* to their own shame?” (Jeremiah 7:16-19) {emphasis mine}
Before continuing with this article, make sure you have read [What? Do Not Pray For ...](https://trustjesus.substack.com/p/what-do-not-pray-for), so you have my background thoughts on this passage.
After writing the first post, I began thinking about how this verse applies to American Christians today in my post A Hard Question With an Uncomfortable Answer. In my first two articles, I basically came to the conclusion that we should not pray blessings on those who were sinning and rejecting God, but that praying for repentance and turning back to God would be an allowed and even honored prayer. Then today, while listening to a sermon from Revelation, I thought, “Is there a time we are called to not pray for someone or some nation because God has given them their choice and He is no longer calling them to Himself?”
## When God Hardens a Heart
There are a lot of verses where God says that he hardened their heart. The most well known is regarding the hardened heart of the Egyptian Pharaoh in Exodus where we read a succession of verses about a hardened heart:
First Pharaoh hardens his own heart:
> But when Pharaoh saw that there was relief, **he hardened his heart** and did not listen to them, as the Lord had said. (Exodus 8:15) {emphasis mine}
then he hardens his heart again:
> But **Pharaoh hardened his heart this time also**, and he did not let the people go. (Exodus 8:32) {emphasis mine}
then he hardened his heart and his servants hearts:
> But when Pharaoh saw that the rain and the hail and the thunder had ceased, **he sinned again and hardened his heart, he and his servants**. (Exodus 9:34) {emphasis mine}
then God hardens Pharaoh’s heart:
> Then the Lord said to Moses, “Go to Pharaoh, for **I have hardened his heart** and the heart of his servants, **that I may perform these signs of Mine** among them, (Exodus 10:1) {emphasis mine}
God didn’t harden Pharaoh’s heart initially, but after repeated choices by Pharaoh, God gave Pharaoh the hardened heart he chose. Also, God hardened Pharaoh’s heart in order to perform signs that He wanted to perform to show Himself to the Israelites and the Egyptians. He did it to fulfill His will and His plan.
Once God chose to harden Pharaoh’s heart, would it be praying according to God’s will to ask that Pharaoh repent? As uncomfortable as this makes me, I don’t think it would be praying according to God’s will to pray for repentance for Pharaoh.
## When God Declares His Judgment
In Jeremiah 27, God has stated that Babylon will conquer Judah, take away the people, and take the golden implements from the Temple. He says that those who want to live must submit to Babylon. This is God’s will. Many supposed prophets were prophesying that Babylon will not capture Judah and then after Judah was conquered, that they would be brought back after 2 years contrary to God’s will and declaration of 70 years of captivity.
> Then I spoke to the priests and to all this people, saying, “Thus says the Lord: Do not listen to the words of your prophets who prophesy to you, saying, ‘Behold, the vessels of the Lord’s house will now shortly be brought again from Babylon’; for they are prophesying a lie to you. Do not listen to them; serve the king of Babylon, and live! Why should this city become a ruin? But if they are prophets, and **if the word of the Lord is with them, let them now entreat the Lord of hosts** that the vessels which are left in the house of the Lord, in the house of the king of Judah and in Jerusalem may not go to Babylon. (Jeremiah 27:16-18) {emphasis mine}
Regarding these so-called prophets, God says, “*if the word of the Lord is with them, let them now entreat the Lord of hosts*.” This sounds like they should pray thus only if “*the word of the Lord is with them*,” or basically if they are praying according to God’s will. Conversely, since the passage makes clear these “prophets” are not speaking God’s word, nor supporting God’s will, then God should not be entreated (asked in prayer) to act contrary to His will.
## When God Gives Them Over to Their Sin
Similarly, in the New Testament it says of God:
> For even though they knew God, they did not honor Him as God or give thanks, but they became futile in their speculations, and **their foolish heart was darkened**. Professing to be wise, they became fools, and exchanged the glory of the incorruptible God for an image in the form of corruptible man and of birds and four-footed animals and crawling creatures.
>
> Therefore **God gave them over in the lusts of their hearts** to impurity, so that their bodies would be dishonored among them. For they exchanged the truth of God for a lie, and worshiped and served the creature rather than the Creator, who is blessed forever. Amen.
>
> For this reason **God gave them over to degrading passions**; for their women exchanged the natural function for that which is unnatural, and in the same way also the men abandoned the natural function of the woman and burned in their desire toward one another, men with men committing indecent acts and receiving in their own persons the due penalty of their error.
>
> And **just as they did not see fit to acknowledge God any longer, God gave them over to a depraved mind**, to do those things which are not proper, being filled with all unrighteousness, wickedness, greed, evil; full of envy, murder, strife, deceit, malice; they are gossips, slanderers, haters of God, insolent, arrogant, boastful, inventors of evil, disobedient to parents, without understanding, untrustworthy, unloving, unmerciful; and although they know the ordinance of God, that those who practice such things are worthy of death, they not only do the same, but also give hearty approval to those who practice them. (Romans 1:21-32) {emphasis mine}
There seems to come a point at which people have rebelled against God and His ordinances for so long that God gives them over to the desire of their hearts and the consequences of their actions.
## Does This Mean We Are Not To Pray At All?
Is there a point at which God doesn’t want us to pray for their repentance? I’m not willing to say “definitely,” but it kind of looks like that may be the case. I don’t think this is a common situation that we need to be worried about. In most cases, even with very evil people who have done us great harm, we are definitely called to pray for their repentance and salvation. “*But I say to you, love your enemies and pray for those who persecute you*.” (Matthew 5:44) Still, there may be situations where God says, “I have given them over to the lusts and rebellion of their heart to the destruction of their soul.” There may be situations where a person or a nation has to be punished to fulfill God’s good plan. Praying against His will and plan would be fighting against God and not praying in alignment with His will.
In Ezekiel chapter 3, the passage is talking specifically about sharing God’s word and being a watchman to the people rather than specifically regarding prayer, but I think this verse is still helpful in determining God’s will for our prayers.
> Moreover, I will make your tongue stick to the roof of your mouth so that you will be mute and cannot be a man who rebukes them, for they are a rebellious house. (Ezekiel 3:26)
In this occasion, God has given Ezekiel the role of watchman and warned him that he will be held accountable for warning the people, but their decision to obey is on their own heads. Then God tells Ezekiel that He will “*make your tongue stick to the roof of your mouth so that you will be mute and cannot be a man who rebukes them*.” I believe if God doesn’t want us to pray for someone or something and if we are seeking His will, He will make us mute so we cannot pray for them. Why would He do this? Either because the person, group, or nation are rebellious and/or because the prayer is contrary to His will. I believe God will help His devoted followers to pray according to His will.
I am still fleshing out this idea in my mind and trying to seek the truth. Let me know how you interpret these verses or especially if you have other verses that clarify this matter. I am trying to seek the truth.
I also want to be very careful with this idea. We are much more likely to NOT pray for repentance and salvation for people that we should be praying for than we are to pray for someone for whom we shouldn’t pray. I definitely don’t want anyone to use this post as an excuse to not pray for people or nations.
May our God and Creator guide us and use us for His good purpose and according to His will. May He guide our prayers in perfect alignment with His will and may He draw us closer to Him every day.
Trust Jesus
-

@ 000002de:c05780a7
2025-02-26 22:31:11

These people have serious issues.
[Original Sin by Jake Tapper and Alex Thompson](https://sites.prh.com/originalsin)
> From two of America’s most respected journalists, an unflinching and explosive reckoning with one of the most fateful decisions in American political history: Joe Biden’s run for reelection despite evidence of his serious decline—amid desperate efforts to hide the extent of that deterioration
originally posted at https://stacker.news/items/898271
-

@ ef1744f8:96fbc3fe
2025-02-26 21:36:43
cKsXmhEiKNnAgVMTJ4eY+tOqOZh5Om/sZP00QBtEdlZuaayrZJ3xluZ1EMJ+gu80KY1shHaPBD4htY2P3qg65CWIt8Wjf2mAw/gb0l52BWrVkI4AQFUlC3dr14LJD7Y94iZj/CsnT02hcDkRYFjXIgyhtrhrrpVCdZJiZA1zUbw3CV7godG4yt8uo/Q5qdOHP2wH8Dj9zivAKBLyZUgHGJ6M7fBR9pNEKF88Cxs48xD5sQbtGZwiAK0a71bM/xhWAkOkvvLOQUgeeN8tcX0yH84QySFCXDKAnlDgWMAfynTVvrpdc5oyi1gM/3NBvc3s28QkeXWf3zIwq6G1/6c7pDeywYvt2IIk7qgjIbF700i7CnJZdNXxvovP9SQbPt6iotILDXpvzibLiff4GOU1UQ==?iv=dzskRoafO62Gp4TMsBWRFg==
-

@ ef1744f8:96fbc3fe
2025-02-26 21:32:00
0jxu+3pODMGseAZeXiwEWcaWh0Zdp1dg4UP084e7Q8HkzdgcFHLycOQhoi/c52Iql8CA4FPgZDQCIf5gfXHNyt8lvzBvY+1TZvheCT1iX/wlrP0wn3XVE8wu5QJnVn4m2oZs31TKbR/uEfFBRpQoEUeoOhGxqzm6DZRlpjSjgdjye0me7hue1qWhwoEgQFr7TN0iZbvy9kp/DJhi5xVQgwWU1q5PCE9ekChRnEDHML/MYGCIjsZdj5tMBOh/BlH26VGsVGpzeB/F9mtuaj/E5WHaPSZdq78k1K7034emyYwEkfS0p0hvfgqdDy98m9DLRWmDeIERlxR0Ry7IPnc00qNfpthEXK9tujnUtskBQzIa6femadnIVdnE+JRJ20GOho6TkUzL6jxN9y2d7S/ttp8i/ZD+eaaXHC7ErWzR1TU=?iv=wad1n+h47INO5qI9jSRVXA==
-

@ bf47c19e:c3d2573b
2025-02-26 21:07:23
Originalni tekst na [dvadesetjedan.com](https://dvadesetjedan.com/blog/zasto-je-vazna-decentralizacija-bitcoina).
###### Autor: [Matt Corallo](https://x.com/TheBlueMatt) / Prevod na hrvatski: [Davor](https://t.me/davor_e)
---
Bitcoineri, od programera Bitcoin Core-a preko dugogodišnjih entuzijasta Bitcoina do nedavnih pronalazača /r/Bitcoina, vole razgovarati o tome kako je decentralizacija Bitcoina njegova ultimativna značajka. Doduše, rijetko vidite da netko objašnjava zašto je decentralizacija važna. Zasigurno je to zanimljiva značajka iz perspektive računalne znanosti, no zašto bi potrošači, tvrtke ili investitori marili za to? Ova objava je pokušaj da se napiše zašto je decentralizacija temelj vrijednosti Bitcoina i što je još važnije, postavi buduće objave u kojima se govori o tome kada ona to nije.
Kada Bitcoineri govore o decentralizaciji Bitcoina, prva stvar koja se pojavljuje je često spominjani nedostatak inherentnog povjerenja u treću stranu. Dok je dobro postavljeno povjerenje preduvjet za učinkovit rad mnogih sustava, jednom kada se takvo povjerenje izgubi, sustavi mogu postati nevjerojatno krhki. Uzmimo, za primjer, povjerenje u američke banke prije uspostave FDIC-a (Federal Deposit Insurance Corporation). Dok je pristup bankovnim uslugama omogućio više pogodnosti i mnogim tvrtkama učinkovitije poslovanje, poznato je da su banke propadale, pritom upropaštavajući sa sobom sva sredstva klijenata. Dok je predstavljanje FDIC-a i sličnih programa decentraliziralo povjerenje u financijske institucije s jedne strane na dvije, transakcije u velikom dijelu svijeta ne nude takvu zaštitu. Čak i uz takve programe, pojedinci nisu univerzalno zaštićeni od gubitka preko granica i preko određene vrijednosti.
U novije vrijeme, propisi koji dopuštaju pojedinim državnim dužnosnicima jednostrano oduzimanje imovine postali su uobičajeni. Naročito u SAD-u, sada zloglasna “Operacija Choke Point” i programi oduzimanja civilne imovine, omogućili su službenicima za provođenje zakona i privatnim institucijama da zapljenjuju financijsku imovinu i uskraćuju financijske usluge uz malo ili nimalo nadzora. Uklanjanje provjerenih skrbnika i stvaranje sustava s likvidnom imovinom, koja se ne može zaplijeniti, ima potencijal pružiti pouzdanije financijske usluge mnogima koji inače ne bi mogli djelovati učinkovito ili uopće ne bi mogli djelovati. Ova mogućnost da se Bitcoin ne može zaplijeniti, omogućena je samo zbog nedostatka za centraliziranim povjerenjem. Centralizirani sustavi elektroničke gotovine i financijski sustavi su pokušali pružiti takvu pouzdanost, propisi i poslovna stvarnost su to gotovo univerzalno spriječili.
Svojstvo koje je jednako važno za sposobnost Bitcoina da pruža financijske usluge zviždačima, stranim disidentima i porno zvijezdama je njegov otpor cenzuri transakcija. Sposobnost trećih strana da zaplijene imovinu rezultira izravnim i čistim novčanim gubitkom, zamrzavanje imovine može imati sličan učinak. Kada pojedinac ili organizacija više nisu u mogućnosti obavljati transakcije za plaćanje roba i usluga, njihova financijska imovina brzo gubi vrijednost. Iako Bitcoin ima vrlo dobru priču o nemogućnosti zapljene (svaka strana u sustavu nameće nemogućnost bilo koga da potroši Bitcoin bez dodanog privatnog ključa), njegova priča o otporu cenzuri je malo utančanija.
U svijetu u kojem nijedan rudar Bitcoina nema više od 1% ukupne hash snage (ili nešto drugo što je jednako decentralizirano), trebalo bi biti lako pronaći rudara koji je ili anoniman i prihvaća sve transakcije ili je u nadležnosti koja ne pokušava cenzurirati vaše transakcije. Naravno, ovo nije svijet kakav danas imamo, a cenzura transakcija jedan je od većih razloga da se ozbiljno zabrinemo centralizacijom rudarenja (za pune čvorove). Ipak, mogućnost pojedinca da kupi hash snagu (u obliku lako dostupnog starog hardvera ili u obliku njegovog iznajmljivanja) za rudarenje svoje inače cenzurirane transakcije, opcija je sve dok je pravilo najdužeg lanca na snazi kod svih rudara. Iako je znatno skuplji nego što bi bio u istinski decentraliziranom Bitcoinu, to omogućuje Bitcoinu da zadrži neka od svojih anti-cenzuriranih svojstava.
Ako ste već dovoljno dugo u priči oko Bitcoina, možda ćete prepoznati gornja svojstva kao kritična za zamjenjivost. Zamjenjivost, kao ključno svojstvo svakog monetarnog instrumenta, odnosi se na ideju da vrijednost jedne jedinice treba biti ekvivalentna svakoj drugoj jedinici. Bez mogućnosti odmrzavanja/otpora cenzuri i nemogućnosti zapljene, Bitcoin (i svaki drugi monetarni sustav) počinje gubiti zamjenjivost. Trgovci i platni procesori više ne mogu razumno prihvaćati Bitcoin bez provjere niza crnih lista i mnogo truda kako bi bili sigurni da će moći potrošiti Bitcoin koji prihvaćaju. Ako povjerenje u zamjenjivost Bitcoina deformira, njegova bi korist mogla biti značajno deformirana.
Još jedno svojstvo koje proizlazi iz decentralizacije Bitcoina, je njegov otvoreni pristup. Ulagači iz Silicijske doline često ga nazivaju jednim od najzanimljivijih svojstava Bitcoina, a mnogi ga vole nazivati "bez dopuštenja". Sposobnost bilo koga, bilo gdje u svijetu, sa internetskom vezom, da prihvaća Bitcoin za robu i usluge i koristi Bitcoin za kupnju roba i usluga je vrlo uzbudljiva. Opet, ovo svojstvo ovisi o decentralizaciji Bitcoina. Iako postoje mnogi centralizirani pružatelji financijskih usluga, gdje mnogi od njih promoviraju svoju dostupnost bilo kome, sama njihova prisutnost kao centraliziranog tijela koje može proizvoljno uskratiti uslugu, čini ih podložnim budućim promjenama politike iz bilo kojeg razloga. PayPal je, na primjer, utemeljen na idealima univerzalnog pristupa elektroničkoj gotovini. Međutim, zbog svoje pozicije središnje vlasti, brzo je promijenio svoje politike, kako bi udovoljio pritiscima regulatora i politikama postojećeg financijskog sustava na koji se oslanjao. Ovih dana, PayPal je nadaleko poznat po zamrzavanju računa i oduzimanju imovine uz malo ili nimalo upozorenja. U osnovi, oslanjanje na centralizirane strane za usluge nije kompatibilno s univerzalnim otvorenim pristupom u financijskom svijetu.
Primijetit ćete da se sve gore navedene kritične značajke, one koje Bitcoin čine tako uzbudljivim za sve nas, centralizirani sistemi već neko vrijeme mogu implementirati. Zapravo to se radilo i prije, u učinkovitijim sustavima od Bitcoina. Naravno, nikada nisu potrajali, gubeći kritična svojstva nakon podešavanja kako bi se popravila ova ili ona stvar, implementirajući regulatorne sustave cenzure izravno u osnovne slojeve, ograničavajući pristup rastu dobiti i potpuno gašenje. Stvarno, decentralizacija u Bitcoinu sama po sebi nije značajka, već je umjesto toga jedini način za koji znamo da održimo značajke koje želimo u sustavima kojima upravljaju ljudi.
[Originalni tekst](https://bluematt.bitcoin.ninja/2016/01/14/decentralization/)
-

@ bf47c19e:c3d2573b
2025-02-26 21:00:54
Originalni tekst na [dvadesetjedan.com](https://dvadesetjedan.com/blog/bitcoin-privatnost-najbolje-prakse).
###### Autor: [Gigi](https://dergigi.com/2021/03/14/bitcoin-privacy-best-practices/) / Prevod na srpski: [Plumsky](https://t.me/Plumski)
---
> Postoji sveto carstvo privatnosti za svakog čoveka gde on bira i pravi odluke – carstvo stvoreno na bazičnim pravima i slobode koje zakon, generalno, ne sme narušavati. Džefri Fišer, Arhiepiskop Canterberija (1959)
Pre ne toliko dugo, uobičajen režim interneta je bio neenkriptovan običan tekst (plain text). Svi su mogli špiunirati svakoga i mnogi nisu o tome ni razmišljali. Globalno obelodanjivanje nadzora 2013. je to promenilo i danas se koriste mnogo bezbedniji protokoli i end-to-end enkripcija postaje standard sve više. Iako bitcoin postaje tinejdžer, mi smo – metaforično govoreći – i dalje u dobu običnog teksta narandžastog novčića. Bitcoin je radikalno providljiv protokol sam po sebi, ali postoje značajni načini da korisnik zaštiti svoju privatnost. U ovom članku želimo da istaknemo neke od ovih strategija, prodiskutujemo najbolje prakse, i damo preporuke koje mogu primeniti i bitcoin novajlije i veterani.
#### Zašto je privatnost bitna
> Privatnost je potrebna da bi otvoreno društvo moglo da funkcioniše u digitalnoj eri. Privatnost nije isto što i tajanstvenost. Privatna stvar je nešto što neko ne želi da ceo svet zna, a tajna stvar je nešto što neko ne želi bilo ko da zna. Privatnost je moć da se čovek selektivno otkriva svom okruženju.
Ovim snažnim rečima Erik Hjus je započeo svoj tekst Sajferpankov Manifesto (Cypherpunk's Manifesto) 1993. Razlika između privatnosti i tajanstvenosti je suptilna ali jako važna. Odlučiti se za privatnost ne znači da neko ima tajne koje želi sakriti. Da ovo ilustrujemo shvatite samo da ono što obavljate u svom toaletu ili u spavaćoj sobi nije niti ilegalno niti tajna (u mnogim slučajevima), ali vi svejedno odlučujete da zatvorite vrata i navučete zavese.
Slično tome, koliko para imate i gde ih trošite nije naručito tajna stvar. Ipak, to bi trebalo biti privatan slučaj. Mnogi bi se složili da vaš šef ne treba da zna gde vi trošite vašu platu. Privatnosti je čak zaštićena od strane mnogobrojnih internacionalnih nadležnih organa. Iz Američke Deklaracije Prava i Dužnosti Čoveka (American Declaration of the Rights and Duties of Man) Ujedinjenim Nacijama, napisano je da je privatnost fundamentalno prava gradjana širom sveta.
> Niko ne sme biti podvrgnut smetnjama njegovoj privatnosti, porodici, rezidenciji ili komunikacijama, niti napadnuta njegova čast i reputacija. Svi imaju pravo da se štite zakonom protiv takvih smetnja ili napada. Artikal 12, Deklaracija Ljudskih Prava Ujedinjenih Nacija
#### Bitcoin i privatnost
Iako je bitcoin često opisivan kao anoniman način plaćanja medijima, on u stvari poseduje potpuno suprotne osobine. On je poluanoniman u najboljem slučaju i danas mnogima nije ni malo lako primeniti taktike da bi bili sigurni da njihov poluanonimni identitet na bitcoin mreži ne bude povezan sa legalnim identitetom u stvarnom svetu.
Bitcoin je otvoren sistem. On je javna baza podataka koju svako može da proučava i analizira. Znači, svaka transakcija koja je upisana u tu bazu kroz dokaz rada (proof-of-work) postojaće i biće otkrivena dokle god bitcoin postoji, što znači - zauvek. Ne primenjivati najbolje prakse privatnosti može imati štetne posledice u dalekoj budućnosti.
Privatnost, kao sigurnost, je proces koji je težak, ali nije nemoguć. Alatke nastavljaju da se razvijaju koje čuvaju privatnost kad se koristi bitcoin and srećom mnoge od tih alatki su sve lakše za korišćenje. Nažalost ne postoji panacea u ovom pristupu. Mora se biti svesan svih kompromisa i usavršavati te prakse dok se one menjaju.
#### Najbolje prakse privatnosti
Kao i sve u bitcoinu, kontrola privatnosti je postepena, korak po korak, procedura. Naučiti i primeniti ove najbolje prakse zahteva strpljivost i odgovornost, tako da ne budite obeshrabreni ako vam se čini da je to sve previše. Svaki korak, koliko god bio mali, je korak u dobrom pravcu.
Koje korake preduzeti da bi uvećali svoju privatnost:
* Budite u vlasništvu sami svojih novčića
* Nikad ne ponavljajte korišćenje istih adresa
* Minimizirajte korišćenje servisa koji zahtevaju identitet (Know your customer - KYC)
* Minimizirajte sve izloženosti trećim licima
* Upravljajte svojim nodom
* Koristite Lightning mrežu za male transakcije
* Nemojte koristiti javne blok pretraživače za svoje transakcije
* Koristite metodu CoinJoin često i rano pri nabavljanju svojih novčića
**Budite u vlasništvu sami svojih novčića**: Ako ključevi nisu tvoji, onda nije ni bitcoin. Ako neko drugo drži vaš bitcoin za vas, oni znaju sve što se može znati: količinu, istoriju transakcija pa i sve buduće transakcije, itd. Preuzimanje vlasništva bitcoina u svoje ruke je prvi i najvažniji korak.
**Nikad ne kroistite istu adresu dvaput**: Ponavljanje adresa poništava privatnost pošiljalca i primaoca bitcoina. Ovo se treba izbegavati pod svaku cenu.
**Minimizirajte korišćenje servisa koji zahtevaju identitet (KYC)**: Vezivati svoj legalni identitet za svoje bitcoin adrese je zlo koje se zahteva od strane mnogih državnih nadležnosti. Dok je efektivnost ovih zakona i regulacija disputabilno, posledice njihovog primenjivanja su uglavnom štetne po korisnicima. Ovo je očigledno pošto je česta pojava da se te informacije često izlivaju iz slabo obezbeđenih digitalnih servera. Ako izaberete da koristite KYC servise da bi nabavljali bitcoin, proučite i razumite odnos između vas i tog biznisa. Vi ste poverljivi tom biznisu za sve vaše lične podatke, pa i buduće obezbeđenje tih podataka. Ako i dalje zarađujete kroz fiat novčani sistem, mi preporučujemo da koristite samo bitcoin ekskluzivne servise koji vam dozvoljavaju da autamatski kupujete bitcoin s vremena na vreme. Ako zelite da potpuno da izbegnete KYC, pregledajte https://bitcoinqna.github.io/noKYConly/.
**Minimizirajte sve izloženosti trećim licima**: Poverljivost trećim licima je bezbednosna rupa (https://nakamotoinstitute.org/trusted-third-parties/). Ako možete biti poverljivi samo sebi, onda bi to tako trebalo da bude.
**Upravljajte svojim nodom**: Ako nod nije tvoj, onda nisu ni pravila. Upravljanje svojim nodom je suštinska potreba da bi se bitcoin koristio na privatan način. Svaka interakcija sa bitcoin mrežom je posrednjena nodom. Ako vi taj nod ne upravljate, čiji god nod koristite može da vidi sve što vi radite. Ova upustva (https://bitcoiner.guide/node/) su jako korisna da bi započeli proces korišćenja svog noda.
**Koristite Lightning mrežu za male transakcije**: Pošto Lightning protokol ne koristi glavnu bitcoin mrežu za trasakcije onda je i samim tim povećana privatnost korišćenja bez dodatnog truda. Iako je i dalje rano, oni apsolutno bezobzirni periodi Lightning mreže su verovatno daleko iza nas. Korišćenje Lightning-a za transakcije malih i srednjih veličina će vam pomoći da uvećate privatnost a da smanjite naplate svojih pojedinačnih bitcoin transakcija.
**Nemojte koristiti javne blok pretraživače za svoje transakcije**: Proveravanje adresa na javnim blok pretraživačima povezuje te adrese sa vašim IP podacima, koji se onda mogu koristiti da se otkrije vaš identitet. Softveri kao Umbrel i myNode vam omogućavaju da lako koristite sami svoj blok pretraživač. Ako morate koristiti javne pretraživače, uradite to uz VPN ili Tor.
**Koristite CoinJoin često i rano pri nabavljanju svojih novčića**: Pošto je bitcoin večan, primenjivanje saradničkih CoinJoin praksa će vam obezbediti privatnost u budućnosti. Dok su CoinJoin transakcije svakovrsne, softveri koji su laki za korišćenje već sad postoje koji mogu automatizovati ovu vrstu transakcija. Samourai Whirlpool (https://samouraiwallet.com/whirlpool) je odličan izbor za Android korisnike. Joinmarket (https://github.com/joinmarket-webui/jam) se može koristiti na vašem nodu. A servisi postoje koji pri snabdevanju vašeg bitcoina istog trenutka obave CoinJoin tranzakciju automatski.
#### Zaključak
Svi bi trebalo da se potrude da koriste bitcoin na što privatniji način. Privatnost nije isto što i tajanstvenost. Privatnost je ljudsko pravo i mi svi trebamo da branimo i primenljujemo to pravo. Teško je izbrisati postojeće informacije sa interneta; a izbrisati ih sa bitcoin baze podataka je nemoguće. Iako su daleko od savršenih, alatke postoje danas koje vam omogućavaju da najbolje prakse privatnosti i vi sami primenite. Mi smo vam naglasili neke od njih i - kroz poboljšanje u bitcoin protokolu kroz Taproot i Schnorr - one će postajati sve usavršenije.
Bitcoin postupci se ne mogu lako opisati korišćenjem tradicionalnim konceptima. Pitanja kao što su "Ko je vlasnik ovog novca?" ili "Odakle taj novac potiče?" postaju sve teža da se odgovore a u nekim okolnostima postaju potpuno beznačajna.
Satoši je dizajnirao bitcoin misleći na privatnost. Na nivou protokola svaka bitcoin transakcija je proces "topljenja" koji za sobom samo ostavlja heuristične mrvice hleba. Protokolu nije bitno odakle se pojavio bilo koji bitcoin ili satoši. Niti je njega briga ko je legalan identitet vlasnika. Protokolu je samo važno da li su digitalni potpisi validni. Dokle god je govor slobodan, potpisivanje poruka - privatno ili ne - ne sme biti kriminalan postupak.
Dodatni Resursi
[This Month in Bitcoin Privacy](https://enegnei.github.io/This-Month-In-Bitcoin-Privacy/) | Janine
[Hodl Privacy FAQ](https://6102bitcoin.com/faq-hodl-privacy/) | 6102
[Digital Privacy](https://6102bitcoin.com/blog/digital-privacy/) | 6102
[UseWhirlpool.com](http://usewhirlpool.com/) | Bitcoin Q+A
[Bitcoin Privacy Guide](https://bitcoiner.guide/privacy/) | Bitcoin Q+A
Ovaj članak napisan je u saradnji sa Matt Odellom, nezavisnim bitcoin istraživačem. Nađite njegove preporuke za privatnost na [werunbtc.com](https://werunbtc.com/)
[Originalni tekst](https://dergigi.com/2021/03/14/bitcoin-privacy-best-practices/)
-

@ d6c48950:54d57756
2025-02-26 20:33:44
I wanted to write my system for bitcoin inheritance and seed storage that will likely outlive me - the reason why is recently bitkey (squares hardware wallet) announced their inheritance system which is a vast improvement but still has a single point of failure square and the app they maintain though this is still a good thing and will improve the ecosystem and raise awareness there is a cheaper method that is just a secure but doesn’t have a single point of failure.
## 2/3 seed storage
2/3 seed storage is actually a pretty simple way of splitting up a key into three parts, if you have one part it’s useless, if you have any two parts it’s complete - if one piece is destroyed it doesn’t matter (demo below)
| A<br/> | B<br/> | C<br/> |
|-----|-----|-----|
| 1. apple<br/> | 2. zipper<br/> | 3. dog<br/> |
| 4. tree<br/> | 5. car<br/> | 6. bus<br/> |
| 7. banana<br/> | 8. motorbike<br/> | 9. dune<br/> |
| 10. frank<br/> | 11. foundation<br/> | 12. meditation<br/> |
| 13. whiteboard<br/> | 14. laptop<br/> | 15. books<br/> |
| 16. perfume<br/> | 17. computer<br/> | 18. stone<br/> |
| 19. brick<br/> | 20. spreadsheet<br/> | 21. bird<br/> |
| 22. blog<br/> | 23. leaves<br/> | 24. grass<br/> |
This is a seed phrase split up into three parts (a,b,c) - now you can create your 3 parts
(1)
| A<br/> | B<br/> | |
|-----|-----|-----|
| 1. apple<br/> | 2. zipper<br/> | |
| 4. tree<br/> | 5. car<br/> | |
| 7. banana<br/> | 8. motorbike<br/> | |
| 10. frank<br/> | 11. foundation<br/> | |
| 13. whiteboard<br/> | 14. laptop<br/> | |
| 16. perfume<br/> | 17. computer<br/> | |
| 19. brick<br/> | 20. spreadsheet<br/> | |
| 22. blog<br/> | 23. leaves<br/> | |
(2)
| | B<br/> | C<br/> |
|-----|-----|-----|
| | 2. zipper<br/> | 3. dog<br/> |
| | 5. car<br/> | 6. bus<br/> |
| | 8. motorbike<br/> | 9. dune<br/> |
| | 11. foundation<br/> | 12. meditation<br/> |
| | 14. laptop<br/> | 15. books<br/> |
| | 17. computer<br/> | 18. stone<br/> |
| | 20. spreadsheet<br/> | 21. bird<br/> |
| | 23. leaves<br/> | 24. grass<br/> |
(3)
| A<br/> | | C<br/> |
|-----|-----|-----|
| 1. apple<br/> | | 3. dog<br/> |
| 4. tree<br/> | | 6. bus<br/> |
| 7. banana<br/> | | 9. dune<br/> |
| 10. frank<br/> | | 12. meditation<br/> |
| 13. whiteboard<br/> | | 15. books<br/> |
| 16. perfume<br/> | | 18. stone<br/> |
| 19. brick<br/> | | 21. bird<br/> |
| 22. blog<br/> | | 24. grass<br/> |
Now you have your parts, you need at least 2/3 for it to be useful.
## distribution
Distribution is pretty simple, keep one part, give a part to whomever you want to be able to claim your bitcoin upon death, give a part to someone you trust (along with instructions to post it to the claimant upon your death).
## failure
For this to fail either
1. Two out of three parts would have to be destroyed
2. The trusted party would have to not post it AND either your part or the claimants would have to be destroyed
3. The trusted party cannot figure out how to use a seed phrase (by default you should include instructions i.e NEVER SHARE THE SEED, transfer to a recommended wallet from bitcoin.org then transfer to an exchange and sell)
-

@ 4c96d763:80c3ee30
2025-02-26 20:33:28
# Changes
## William Casarin (2):
- feat: add scramble flag for development text scrambling
- feat: add --no-media flag to disable media display
## kernelkind (21):
- use bincode
- update ehttp to 0.5.0
- introduce UrlMimes
- use mime_guess
- add SupportedMimeType
- rename ImageCache -> MediaCache
- Use TexturedImage in MediaCache
- render MediaCache method
- move MediaCache rendering to render_media_cache call
- support multiple media cache files
- introduce Images
- render Images method
- migrate to using Images instead of MediaCache directly
- URL mime hosted completeness
- handle UrlCache io
- introduce gif animation
- handle gif state
- integrate gifs
- use SupportedMimeType for media_upload
- render gif in PostView
- fix mention crash
pushed to [notedeck:refs/heads/master](http://git.jb55.com/notedeck/commit/a524bbd5a4601e8d7f2813871634caff476735b1.html)
-

@ 2181959b:80f0d27d
2025-02-26 19:21:30
أطلقت مايكروسوفت بهدوء إصدارًا مجانيًا من تطبيقات Office لأجهزة ويندوز، يتيح للمستخدمين تحرير المستندات دون الحاجة إلى اشتراك في Microsoft 365 أو ترخيص مدفوع.
ومع ذلك، يأتي هذا الإصدار مع إعلانات دائمة وقيود على بعض الميزات الأساسية.
**ما هي قيود الإصدار المجاني من تطبيقات Office؟**
وفقًا لموقع Beebom، يعتمد الإصدار المجاني على التطبيقات المكتبية الكاملة لكنه يُقيد معظم الميزات خلف اشتراك Microsoft 365.
وهذه القيود تتمثل في الآتي:
1: يتم عرض الإعلانات بشكل دائم داخل تطبيقات Word وPowerPoint وExcel أثناء العمل على المستندات.
2: يمكن حفظ الملفات فقط على OneDrive، دون دعم لتحرير الملفات المحلية.
3: لا يتوفر الإملاء الصوتي، والإضافات، والتنسيقات المتقدمة، وSmartArt، مما يجعله مناسبًا للمهام الأساسية فقط.
**كيفية الوصول إلى الإصدار المجاني من تطبيقات Office؟**
يمكن للمستخدمين تخطي طلب تسجيل الدخول عند تشغيل أحد تطبيقات Office لأول مرة، وبعد ذلك سيحصلون على خيار استخدامه مجانًا مقابل الإعلانات والميزات المحدودة.
في هذا الوضع، يمكن فتح المستندات وعرضها وتحريرها، تمامًا كما هو الحال في إصدار Office على الويب.
**هل هو متاح للجميع؟**
حاليًا، يبدو أن هذا الإصدار لا يزال في مرحلة الاختبار المحدود، حيث لم يتمكن بعض المستخدمين من تجاوز شاشة تسجيل الدخول عند تشغيل Office. ومن المحتمل أن مايكروسوفت تختبر هذه النسخة في مناطق محددة أو مع مجموعة صغيرة من المستخدمين قبل إطلاقها رسميًا.
حتى الآن، لم تُعلن الشركة رسميًا عن هذا الإصدار، ولم تذكره في مستندات الدعم الخاصة بها، لكن قد تكشف مايكروسوفت عن تفاصيل إضافية خلال الأيام أو الأسابيع المقبلة.
[المصدر]( https://www.windowscentral.com/software-apps/office-365/microsoft-quietly-launches-free-ad-supported-version-of-office-apps-for-windows-with-limited-functionality)
 @ 8f69ac99:4f92f5fd
2025-02-27 12:47:01O Estado Social tem sido um pilar das políticas sociais europeias há décadas, oferecendo uma rede de segurança aos cidadãos através de diversos programas governamentais. Contudo, com a evolução das economias e o envelhecimento da população a pressionar os recursos públicos, este modelo tradicional enfrenta desafios crescentes. Custos em alta, ineficiências burocráticas e efeitos indesejados têm gerado um debate cada vez mais intenso sobre a sua sustentabilidade. Como alternativa, o Rendimento Básico Universal (RBU) ganhou destaque, prometendo simplicidade, mas trazendo preocupações quanto ao custo e aos desincentivos ao trabalho. Há, porém, uma opção mais equilibrada que merece atenção: o Imposto sobre o Rendimento Negativo (IRN). Diferente da assistência social convencional, o IRN oferece apoio financeiro a quem está abaixo de um limiar de rendimento definido, sem exigir que procurem emprego ou dependam de ajudas públicas. Ao reduzir gradualmente os subsídios à medida que os rendimentos aumentam, incentiva a produtividade e preserva a iniciativa pessoal. Neste artigo, vamos explorar o IRN em profundidade, destacando as suas vantagens sobre os sistemas tradicionais, abordando as falhas do RBU e avaliando o seu potencial como uma reforma transformadora na Europa. Num contexto de mudanças económicas e demográficas, o IRN surge como um caminho prático para um sistema que equilibre apoio, dignidade e sustentabilidade. ## Problemas dos Sistemas Tradicionais de Assistência Social O Estado Social tradicional, embora bem-intencionado, tem sido alvo de críticas crescentes pelas suas ineficiências e consequências inesperadas. ### Ineficiência e Burocracia Estruturas administrativas complexas frequentemente atrasam os sistemas de assistência social, levando a desperdícios de recursos. Programas sobrepostos e serviços redundantes aumentam os custos, sobrecarregando os contribuintes. Por exemplo, várias entidades podem oferecer benefícios semelhantes, enquanto processos morosos atrasam a ajuda a quem precisa. Com o envelhecimento da população europeia a exigir mais apoio, estas ineficiências põem em risco a estabilidade financeira, desafiando os decisores políticos a repensarem a distribuição de recursos. ### Incentivos Perversos A assistência social pode, sem querer, desencorajar o trabalho e perpetuar a dependência. Surgem "armadilhas de assistência" quando os benefícios são estruturados de forma a que ganhar um salário resulte numa redução abrupta da ajuda, tornando o emprego menos atractivo do que permanecer no assistencialismo. Isso cria um ciclo em que os beneficiários hesitam em procurar trabalho ou formação, comprometendo as suas perspectivas a longo prazo. Com o tempo, tais sistemas arriscam criar uma cultura de dependência, minando a iniciativa pessoal e prendendo indivíduos numa estagnação económica. ### Peso Económico A pressão financeira do Estado Social está a intensificar-se com as mudanças demográficas na Europa. Populações mais envelhecidas requerem maior apoio, elevando os custos e exigindo impostos mais altos ou gastos públicos acrescidos. Isso desvia recursos da inovação e do investimento, podendo travar o crescimento económico. Sem reformas, estas despesas crescentes podem tornar-se insustentáveis, obrigando os governos a encontrar soluções que mantenham o apoio sem comprometer as finanças. ### Estigma Social Além das questões económicas, a assistência social traz muitas vezes um custo social. Os beneficiários enfrentam frequentemente estereótipos de preguiça ou incompetência, o que gera vergonha e diminui a autoestima. Este estigma pode dificultar a mobilidade social, tornando mais complicado sair da dependência. Resolver isto exige um sistema que não só apoie, mas também capacite, reduzindo preconceitos e promovendo inclusão. Face a estas falhas, a Europa precisa de explorar alternativas que prestem ajuda de forma mais eficaz. O Imposto sobre o Rendimento Negativo apresenta-se como uma opção promissora, capaz de enfrentar estas questões sistémicas. ## O Caso Contra o Rendimento Básico Universal (RBU) O Rendimento Básico Universal surgiu como uma ideia ousada para combater a pobreza e a desigualdade, oferecendo a cada cidadão um pagamento fixo independentemente das suas necessidades. No entanto, a sua simplicidade traz desvantagens significativas. O custo do RBU é um obstáculo enorme. Implementá-lo em toda a Europa exigiria fundos avultados, pressionando orçamentos já sobrecarregados pelos compromissos actuais do Estado Social. Isso poderia implicar subidas acentuadas de impostos ou cortes noutros serviços, enquanto a criação da infraestrutura administrativa necessária traria mais despesas. Há também quem tema os desincentivos ao trabalho: se todos receberem o mesmo valor, alguns podem sentir menos motivação para trabalhar ou arriscar em projectos empreendedores, podendo afectar a vitalidade económica. Além disso, a abordagem universal do RBU sacrifica eficiência. Ao distribuir fundos de forma igual, não dá prioridade a quem mais precisa, entregando recursos aos mais ricos enquanto dilui o impacto sobre os pobres. Esta falta de foco levanta dúvidas sobre a sua capacidade de combater a desigualdade de forma eficaz. Embora o apelo do RBU esteja na sua universalidade, estes desafios apontam para a necessidade de uma solução mais direccionada—e é aqui que o IRN entra em cena. ## Compreender o Imposto sobre o Rendimento Negativo (IRN) O Imposto sobre o Rendimento Negativo propõe uma abordagem refinada ao apoio social, combinando assistência com incentivos. No seu cerne, define um limiar de rendimento base—digamos, 1.000 euros por mês. Quem ganha menos recebe um subsídio proporcional à diferença, enquanto quem ultrapassa esse valor paga impostos para financiar o sistema. Por exemplo, com uma taxa de subsídio de 50%, quem não tem rendimentos recebe 500 euros, e quem ganha 400 euros recebe 300 euros, elevando o total para 700 euros. À medida que o rendimento se aproxima do limiar, o subsídio diminui, desaparecendo nos 1.000 euros, altura em que a tributação começa. Veja-se uma ilustração simples: | Rendimento Mensal (€) | Pagamento IRN (€) | Rendimento Total Após IRN (€) | |-----------------------|-------------------|------------------------------| | 0 | 500 | 500 | | 400 | 300 | 700 | | 800 | 100 | 900 | | 1.000 | 0 | 1.000 | | 1.200 | - (impostos aplicam-se) | 1.200 - impostos | Isto garante que trabalhar compensa sempre: ganhar mais aumenta o rendimento total, evitando a armadilha da assistência. O financiamento vem de um imposto fixo—talvez 19%—sobre os rendimentos acima do limiar. Quem ganha 1.500 euros, por exemplo, paga 95 euros sobre os 500 euros acima de 1.000, ficando com 1.405 euros. Este modelo fiscal simples facilita a gestão e assegura equidade. | Rendimento (€) | Rendimento Tributável (€) | Imposto (€) | Após Imposto (€) | |----------------|---------------------|---------|------------------| | 1000 | 0 | 0 | 1000 | | 1200 | 200 | 38 | 1162 | | 2000 | 1000 | 190 | 1810 | O IRN _pode_ ser de participação voluntária, através de um contrato. As pessoas podem aderir ao sistema se precisarem de apoio ou rejeitá-lo se não aceitarem ajuda estatal, evitando os impostos associados ao financiamento do IRN. Quem optar por sair pode reentrar em caso de dificuldades, equilibrando liberdade de escolha com pragmatismo. Para libertários desconfiados de ingerências governamentais, isto torna o IRN um compromisso—um passo para longe do assistencialismo coercivo e em direcção a maior autonomia. Filosoficamente, o IRN não é um objectivo final, mas uma ponte. Ao simplificar a ajuda e reduzir a burocracia, pode abrir caminho para soluções privadas, como caridade ou apoio mútuo, diminuindo o papel do estado ao longo do tempo. Características como a avaliação de meios e a indexação à inflação reforçam a sua adaptabilidade, garantindo que o apoio permaneça justo e relevante. ## Vantagens do Imposto sobre o Rendimento Negativo (IRN) O IRN destaca-se onde o Estado Social tradicional falha. Os seus subsídios decrescentes incentivam o trabalho, premiando o esforço à medida que o rendimento sobe e impulsionando a produtividade. Isto contrasta fortemente com as armadilhas da assistência, encorajando as pessoas a procurarem formação ou a arriscarem em empreendedorismo sem medo de perder apoio de repente. Na gestão, o IRN é revolucionário. Substituir um emaranhado de programas por um único sistema reduz a burocracia e os custos, canalizando recursos directamente para quem precisa. Um processo de pagamento único elimina sobreposições, tornando a entrega de ajuda mais rápida e eficiente. A dignidade é outro ponto forte. Ao oferecer escolha e evitar supervisão intrusiva, o IRN escapa ao estigma do assistencialismo, dando aos beneficiários autonomia para gerir as suas finanças. Isso promove o autorrespeito e um sentido de controlo, quebrando o ciclo de dependência. Economicamente, a flexibilidade do IRN sobressai. Adapta-se às flutuações de rendimento, direccionando a ajuda exactamente onde é necessária. Estudos indicam que pode reduzir a pobreza, melhorar a mobilidade social e até beneficiar a saúde, ao aliviar o stress financeiro, oferecendo um impulso abrangente ao bem-estar. ## Responder às Críticas ao Imposto sobre o Rendimento Negativo (IRN) Nenhuma política escapa a críticas, e o IRN tem as suas. Os libertários veem, e bem, os impostos como roubo, e embora o IRN não elimine esta tensão, suaviza-a. Ao condensar o Estado Social num sistema claro e simples, reduz a intromissão estatal face à burocracia actual. Os seus incentivos ao trabalho alinham-se com valores de responsabilidade, tornando-o um passo aceitável a curto prazo. O financiamento preocupa, sobretudo em países europeus já muito tributados, mas uma taxa fixa oferece uma solução. Simples e previsível, minimiza os custos administrativos e assegura contribuições justas, sustentando o IRN sem sobrecarga excessiva. Há também quem debata o seu impacto social—uns chamam-lhe um subsídio fácil, um _hand-out_, outros um sistema demasiado voltado para o mercado. Ainda assim, o IRN encontra um meio-termo, oferecendo uma rede de segurança que recompensa o esforço sem controlar vidas. Passar para o IRN exige eliminar gradualmente os programas antigos e informar o público sobre os seus benefícios: um governo mais leve, menos dependência e maior iniciativa pessoal. Para quem sonha com um futuro sem estado, o IRN não é o destino, mas um movimento prático rumo a sistemas de apoio voluntários, promovendo uma cultura de autossuficiência. ## Conclusão O Imposto sobre o Rendimento Negativo não é perfeito, mas é um avanço claro face ao _status quo_. Reduz os excessos do Estado Social, promove trabalho e dignidade, e oferece à Europa uma reforma viável perante as pressões económicas. Para os contribuintes, promete eficiência; para os beneficiários, oportunidade. Numa região onde o assistencialismo está profundamente enraizado, o IRN surge como um passo ousado, mas possível, para um futuro mais livre e sustentável—um que capacite as pessoas enquanto alivia o peso do estado. --- _Photo by [The New York Public Library](https://unsplash.com/@nypl?utm_content=creditCopyText&utm_medium=referral&utm_source=unsplash) on [Unsplash](https://unsplash.com/photos/a-sign-that-says-pay-your-tax-now-here-kAJLRQwt5yY?utm_content=creditCopyText&utm_medium=referral&utm_source=unsplash)_
@ 8f69ac99:4f92f5fd
2025-02-27 12:47:01O Estado Social tem sido um pilar das políticas sociais europeias há décadas, oferecendo uma rede de segurança aos cidadãos através de diversos programas governamentais. Contudo, com a evolução das economias e o envelhecimento da população a pressionar os recursos públicos, este modelo tradicional enfrenta desafios crescentes. Custos em alta, ineficiências burocráticas e efeitos indesejados têm gerado um debate cada vez mais intenso sobre a sua sustentabilidade. Como alternativa, o Rendimento Básico Universal (RBU) ganhou destaque, prometendo simplicidade, mas trazendo preocupações quanto ao custo e aos desincentivos ao trabalho. Há, porém, uma opção mais equilibrada que merece atenção: o Imposto sobre o Rendimento Negativo (IRN). Diferente da assistência social convencional, o IRN oferece apoio financeiro a quem está abaixo de um limiar de rendimento definido, sem exigir que procurem emprego ou dependam de ajudas públicas. Ao reduzir gradualmente os subsídios à medida que os rendimentos aumentam, incentiva a produtividade e preserva a iniciativa pessoal. Neste artigo, vamos explorar o IRN em profundidade, destacando as suas vantagens sobre os sistemas tradicionais, abordando as falhas do RBU e avaliando o seu potencial como uma reforma transformadora na Europa. Num contexto de mudanças económicas e demográficas, o IRN surge como um caminho prático para um sistema que equilibre apoio, dignidade e sustentabilidade. ## Problemas dos Sistemas Tradicionais de Assistência Social O Estado Social tradicional, embora bem-intencionado, tem sido alvo de críticas crescentes pelas suas ineficiências e consequências inesperadas. ### Ineficiência e Burocracia Estruturas administrativas complexas frequentemente atrasam os sistemas de assistência social, levando a desperdícios de recursos. Programas sobrepostos e serviços redundantes aumentam os custos, sobrecarregando os contribuintes. Por exemplo, várias entidades podem oferecer benefícios semelhantes, enquanto processos morosos atrasam a ajuda a quem precisa. Com o envelhecimento da população europeia a exigir mais apoio, estas ineficiências põem em risco a estabilidade financeira, desafiando os decisores políticos a repensarem a distribuição de recursos. ### Incentivos Perversos A assistência social pode, sem querer, desencorajar o trabalho e perpetuar a dependência. Surgem "armadilhas de assistência" quando os benefícios são estruturados de forma a que ganhar um salário resulte numa redução abrupta da ajuda, tornando o emprego menos atractivo do que permanecer no assistencialismo. Isso cria um ciclo em que os beneficiários hesitam em procurar trabalho ou formação, comprometendo as suas perspectivas a longo prazo. Com o tempo, tais sistemas arriscam criar uma cultura de dependência, minando a iniciativa pessoal e prendendo indivíduos numa estagnação económica. ### Peso Económico A pressão financeira do Estado Social está a intensificar-se com as mudanças demográficas na Europa. Populações mais envelhecidas requerem maior apoio, elevando os custos e exigindo impostos mais altos ou gastos públicos acrescidos. Isso desvia recursos da inovação e do investimento, podendo travar o crescimento económico. Sem reformas, estas despesas crescentes podem tornar-se insustentáveis, obrigando os governos a encontrar soluções que mantenham o apoio sem comprometer as finanças. ### Estigma Social Além das questões económicas, a assistência social traz muitas vezes um custo social. Os beneficiários enfrentam frequentemente estereótipos de preguiça ou incompetência, o que gera vergonha e diminui a autoestima. Este estigma pode dificultar a mobilidade social, tornando mais complicado sair da dependência. Resolver isto exige um sistema que não só apoie, mas também capacite, reduzindo preconceitos e promovendo inclusão. Face a estas falhas, a Europa precisa de explorar alternativas que prestem ajuda de forma mais eficaz. O Imposto sobre o Rendimento Negativo apresenta-se como uma opção promissora, capaz de enfrentar estas questões sistémicas. ## O Caso Contra o Rendimento Básico Universal (RBU) O Rendimento Básico Universal surgiu como uma ideia ousada para combater a pobreza e a desigualdade, oferecendo a cada cidadão um pagamento fixo independentemente das suas necessidades. No entanto, a sua simplicidade traz desvantagens significativas. O custo do RBU é um obstáculo enorme. Implementá-lo em toda a Europa exigiria fundos avultados, pressionando orçamentos já sobrecarregados pelos compromissos actuais do Estado Social. Isso poderia implicar subidas acentuadas de impostos ou cortes noutros serviços, enquanto a criação da infraestrutura administrativa necessária traria mais despesas. Há também quem tema os desincentivos ao trabalho: se todos receberem o mesmo valor, alguns podem sentir menos motivação para trabalhar ou arriscar em projectos empreendedores, podendo afectar a vitalidade económica. Além disso, a abordagem universal do RBU sacrifica eficiência. Ao distribuir fundos de forma igual, não dá prioridade a quem mais precisa, entregando recursos aos mais ricos enquanto dilui o impacto sobre os pobres. Esta falta de foco levanta dúvidas sobre a sua capacidade de combater a desigualdade de forma eficaz. Embora o apelo do RBU esteja na sua universalidade, estes desafios apontam para a necessidade de uma solução mais direccionada—e é aqui que o IRN entra em cena. ## Compreender o Imposto sobre o Rendimento Negativo (IRN) O Imposto sobre o Rendimento Negativo propõe uma abordagem refinada ao apoio social, combinando assistência com incentivos. No seu cerne, define um limiar de rendimento base—digamos, 1.000 euros por mês. Quem ganha menos recebe um subsídio proporcional à diferença, enquanto quem ultrapassa esse valor paga impostos para financiar o sistema. Por exemplo, com uma taxa de subsídio de 50%, quem não tem rendimentos recebe 500 euros, e quem ganha 400 euros recebe 300 euros, elevando o total para 700 euros. À medida que o rendimento se aproxima do limiar, o subsídio diminui, desaparecendo nos 1.000 euros, altura em que a tributação começa. Veja-se uma ilustração simples: | Rendimento Mensal (€) | Pagamento IRN (€) | Rendimento Total Após IRN (€) | |-----------------------|-------------------|------------------------------| | 0 | 500 | 500 | | 400 | 300 | 700 | | 800 | 100 | 900 | | 1.000 | 0 | 1.000 | | 1.200 | - (impostos aplicam-se) | 1.200 - impostos | Isto garante que trabalhar compensa sempre: ganhar mais aumenta o rendimento total, evitando a armadilha da assistência. O financiamento vem de um imposto fixo—talvez 19%—sobre os rendimentos acima do limiar. Quem ganha 1.500 euros, por exemplo, paga 95 euros sobre os 500 euros acima de 1.000, ficando com 1.405 euros. Este modelo fiscal simples facilita a gestão e assegura equidade. | Rendimento (€) | Rendimento Tributável (€) | Imposto (€) | Após Imposto (€) | |----------------|---------------------|---------|------------------| | 1000 | 0 | 0 | 1000 | | 1200 | 200 | 38 | 1162 | | 2000 | 1000 | 190 | 1810 | O IRN _pode_ ser de participação voluntária, através de um contrato. As pessoas podem aderir ao sistema se precisarem de apoio ou rejeitá-lo se não aceitarem ajuda estatal, evitando os impostos associados ao financiamento do IRN. Quem optar por sair pode reentrar em caso de dificuldades, equilibrando liberdade de escolha com pragmatismo. Para libertários desconfiados de ingerências governamentais, isto torna o IRN um compromisso—um passo para longe do assistencialismo coercivo e em direcção a maior autonomia. Filosoficamente, o IRN não é um objectivo final, mas uma ponte. Ao simplificar a ajuda e reduzir a burocracia, pode abrir caminho para soluções privadas, como caridade ou apoio mútuo, diminuindo o papel do estado ao longo do tempo. Características como a avaliação de meios e a indexação à inflação reforçam a sua adaptabilidade, garantindo que o apoio permaneça justo e relevante. ## Vantagens do Imposto sobre o Rendimento Negativo (IRN) O IRN destaca-se onde o Estado Social tradicional falha. Os seus subsídios decrescentes incentivam o trabalho, premiando o esforço à medida que o rendimento sobe e impulsionando a produtividade. Isto contrasta fortemente com as armadilhas da assistência, encorajando as pessoas a procurarem formação ou a arriscarem em empreendedorismo sem medo de perder apoio de repente. Na gestão, o IRN é revolucionário. Substituir um emaranhado de programas por um único sistema reduz a burocracia e os custos, canalizando recursos directamente para quem precisa. Um processo de pagamento único elimina sobreposições, tornando a entrega de ajuda mais rápida e eficiente. A dignidade é outro ponto forte. Ao oferecer escolha e evitar supervisão intrusiva, o IRN escapa ao estigma do assistencialismo, dando aos beneficiários autonomia para gerir as suas finanças. Isso promove o autorrespeito e um sentido de controlo, quebrando o ciclo de dependência. Economicamente, a flexibilidade do IRN sobressai. Adapta-se às flutuações de rendimento, direccionando a ajuda exactamente onde é necessária. Estudos indicam que pode reduzir a pobreza, melhorar a mobilidade social e até beneficiar a saúde, ao aliviar o stress financeiro, oferecendo um impulso abrangente ao bem-estar. ## Responder às Críticas ao Imposto sobre o Rendimento Negativo (IRN) Nenhuma política escapa a críticas, e o IRN tem as suas. Os libertários veem, e bem, os impostos como roubo, e embora o IRN não elimine esta tensão, suaviza-a. Ao condensar o Estado Social num sistema claro e simples, reduz a intromissão estatal face à burocracia actual. Os seus incentivos ao trabalho alinham-se com valores de responsabilidade, tornando-o um passo aceitável a curto prazo. O financiamento preocupa, sobretudo em países europeus já muito tributados, mas uma taxa fixa oferece uma solução. Simples e previsível, minimiza os custos administrativos e assegura contribuições justas, sustentando o IRN sem sobrecarga excessiva. Há também quem debata o seu impacto social—uns chamam-lhe um subsídio fácil, um _hand-out_, outros um sistema demasiado voltado para o mercado. Ainda assim, o IRN encontra um meio-termo, oferecendo uma rede de segurança que recompensa o esforço sem controlar vidas. Passar para o IRN exige eliminar gradualmente os programas antigos e informar o público sobre os seus benefícios: um governo mais leve, menos dependência e maior iniciativa pessoal. Para quem sonha com um futuro sem estado, o IRN não é o destino, mas um movimento prático rumo a sistemas de apoio voluntários, promovendo uma cultura de autossuficiência. ## Conclusão O Imposto sobre o Rendimento Negativo não é perfeito, mas é um avanço claro face ao _status quo_. Reduz os excessos do Estado Social, promove trabalho e dignidade, e oferece à Europa uma reforma viável perante as pressões económicas. Para os contribuintes, promete eficiência; para os beneficiários, oportunidade. Numa região onde o assistencialismo está profundamente enraizado, o IRN surge como um passo ousado, mas possível, para um futuro mais livre e sustentável—um que capacite as pessoas enquanto alivia o peso do estado. --- _Photo by [The New York Public Library](https://unsplash.com/@nypl?utm_content=creditCopyText&utm_medium=referral&utm_source=unsplash) on [Unsplash](https://unsplash.com/photos/a-sign-that-says-pay-your-tax-now-here-kAJLRQwt5yY?utm_content=creditCopyText&utm_medium=referral&utm_source=unsplash)_ @ 8da249fe:ecc00e09
2025-02-27 12:36:07Se você está começando no mundo do Bitcoin e das criptomoedas, já deve ter ouvido falar em "hot wallets" e "cold wallets". Mas qual é a diferença entre elas? E qual é a melhor opção para armazenar seus ativos digitais com segurança? # O que é uma Hot Wallet?  Uma hot wallet (carteira quente) é uma carteira conectada à internet. Isso significa que ela é mais acessível e fácil de usar para transações rápidas. As hot wallets podem ser: **Carteiras móveis** – Aplicativos como BlueWallet, Trust Wallet e outras. **Carteiras de desktop **– Programas instalados no computador, como Electrum e Exodus. **Carteiras web** – Serviços online como a carteira do próprio Binance ou outras exchanges. **Vantagens da Hot Wallet** ✅ Acesso rápido e fácil para transações diárias. ✅ Interface amigável, ideal para iniciantes. ✅ Geralmente gratuita para uso. **Desvantagens da Hot Wallet** ❌ Maior risco de ataque hacker, já que está sempre online. ❌ Se o dispositivo for infectado por malware, suas chaves privadas podem ser comprometidas. # O que é uma Cold Wallet?#  Uma cold wallet (carteira fria) é uma carteira que não está conectada à internet, tornando-se muito mais segura contra hackers. Elas podem ser: **Carteiras de hardware **– Como Ledger Nano S, Nano X ou Trezor. **Carteiras de papel **– Impressão da chave privada e do endereço em um papel. **Computadores ou dispositivos offline** – Um computador dedicado apenas para armazenar criptomoedas, sem conexão com a internet. **Vantagens da Cold Wallet** ✅ Segurança máxima contra ataques cibernéticos. ✅ Ótima opção para armazenamento de longo prazo. ✅ Controle total sobre suas chaves privadas. **Desvantagens da Cold Wallet** ❌ Menos prática para transações diárias. ❌ Pode ser mais cara, no caso das carteiras de hardware. ❌ Se você perder sua chave privada ou backup, pode perder o acesso aos fundos. # Qual escolher: Hot ou Cold Wallet? A escolha depende do seu perfil de investidor: Se você faz transações frequentes, uma hot wallet pode ser mais conveniente. Se você quer armazenar Bitcoin com segurança por muito tempo, a cold wallet é a melhor opção. Muitos usuários combinam as duas, mantendo uma pequena quantia em uma hot wallet para o dia a dia e guardando a maior parte dos fundos em uma cold wallet. Independente da escolha, lembre-se sempre de manter suas chaves privadas seguras e fazer backups regularmente! Gostou do conteúdo? Compartilhe sua opinião nos comentários!
@ 8da249fe:ecc00e09
2025-02-27 12:36:07Se você está começando no mundo do Bitcoin e das criptomoedas, já deve ter ouvido falar em "hot wallets" e "cold wallets". Mas qual é a diferença entre elas? E qual é a melhor opção para armazenar seus ativos digitais com segurança? # O que é uma Hot Wallet?  Uma hot wallet (carteira quente) é uma carteira conectada à internet. Isso significa que ela é mais acessível e fácil de usar para transações rápidas. As hot wallets podem ser: **Carteiras móveis** – Aplicativos como BlueWallet, Trust Wallet e outras. **Carteiras de desktop **– Programas instalados no computador, como Electrum e Exodus. **Carteiras web** – Serviços online como a carteira do próprio Binance ou outras exchanges. **Vantagens da Hot Wallet** ✅ Acesso rápido e fácil para transações diárias. ✅ Interface amigável, ideal para iniciantes. ✅ Geralmente gratuita para uso. **Desvantagens da Hot Wallet** ❌ Maior risco de ataque hacker, já que está sempre online. ❌ Se o dispositivo for infectado por malware, suas chaves privadas podem ser comprometidas. # O que é uma Cold Wallet?#  Uma cold wallet (carteira fria) é uma carteira que não está conectada à internet, tornando-se muito mais segura contra hackers. Elas podem ser: **Carteiras de hardware **– Como Ledger Nano S, Nano X ou Trezor. **Carteiras de papel **– Impressão da chave privada e do endereço em um papel. **Computadores ou dispositivos offline** – Um computador dedicado apenas para armazenar criptomoedas, sem conexão com a internet. **Vantagens da Cold Wallet** ✅ Segurança máxima contra ataques cibernéticos. ✅ Ótima opção para armazenamento de longo prazo. ✅ Controle total sobre suas chaves privadas. **Desvantagens da Cold Wallet** ❌ Menos prática para transações diárias. ❌ Pode ser mais cara, no caso das carteiras de hardware. ❌ Se você perder sua chave privada ou backup, pode perder o acesso aos fundos. # Qual escolher: Hot ou Cold Wallet? A escolha depende do seu perfil de investidor: Se você faz transações frequentes, uma hot wallet pode ser mais conveniente. Se você quer armazenar Bitcoin com segurança por muito tempo, a cold wallet é a melhor opção. Muitos usuários combinam as duas, mantendo uma pequena quantia em uma hot wallet para o dia a dia e guardando a maior parte dos fundos em uma cold wallet. Independente da escolha, lembre-se sempre de manter suas chaves privadas seguras e fazer backups regularmente! Gostou do conteúdo? Compartilhe sua opinião nos comentários! @ 95cb4330:96db706c
2025-02-27 11:47:47Tackling big tasks can feel overwhelming, but by breaking them down into smaller steps, prioritizing effectively, and setting clear milestones, you can maintain focus and make steady progress. --- ## 1. Divide the Task into Manageable Steps Instead of viewing the task as one massive undertaking, split it into specific, actionable steps to create a clear roadmap. 🔹 **Example:** If your goal is to launch a new product, break it down like this: - Conduct market research - Develop a prototype - Build a marketing strategy - Create a launch plan - Execute the launch Each step is now more manageable and can be worked on independently. --- ## 2. Prioritize Based on Impact & Urgency Not all tasks are equally important. Prioritize effectively to avoid wasting time on low-value activities. ✔ **Use the Eisenhower Matrix:** - **Urgent & Important:** Do immediately. - **Important but Not Urgent:** Schedule it. - **Urgent but Not Important:** Delegate it. - **Neither Urgent nor Important:** Eliminate it. 🔹 **Example:** If launching a product, market research might be urgent & important, while branding tweaks could be scheduled for later. --- ## 3. Set Milestones & Deadlines Assign deadlines for each step to track progress and stay motivated. ✔ **Example:** Instead of saying, "Launch the product in 6 months," break it down: - **Market research:** Week 1-2 - **Prototype development:** Week 3-6 - **Marketing strategy:** Week 7-8 - **Launch execution:** Week 9-10 By setting clear deadlines, you create a sense of accountability and prevent procrastination. --- ## 4. Take Consistent Action ✔ Focus on completing one step at a time. ✔ Celebrate small wins—progress builds momentum. ✔ Stay adaptable—if needed, refine your steps as you go. 🔹 **Example:** If market research reveals an issue with the original product idea, adjust before moving forward rather than sticking rigidly to the plan. --- ## Final Thought By approaching big tasks systematically, you reduce overwhelm, maintain clarity, and steadily progress toward success. 👉 **Action Step:** Take a current big task you're facing. Break it into smaller steps, prioritize, set deadlines, and start taking action today. 🚀 ---
@ 95cb4330:96db706c
2025-02-27 11:47:47Tackling big tasks can feel overwhelming, but by breaking them down into smaller steps, prioritizing effectively, and setting clear milestones, you can maintain focus and make steady progress. --- ## 1. Divide the Task into Manageable Steps Instead of viewing the task as one massive undertaking, split it into specific, actionable steps to create a clear roadmap. 🔹 **Example:** If your goal is to launch a new product, break it down like this: - Conduct market research - Develop a prototype - Build a marketing strategy - Create a launch plan - Execute the launch Each step is now more manageable and can be worked on independently. --- ## 2. Prioritize Based on Impact & Urgency Not all tasks are equally important. Prioritize effectively to avoid wasting time on low-value activities. ✔ **Use the Eisenhower Matrix:** - **Urgent & Important:** Do immediately. - **Important but Not Urgent:** Schedule it. - **Urgent but Not Important:** Delegate it. - **Neither Urgent nor Important:** Eliminate it. 🔹 **Example:** If launching a product, market research might be urgent & important, while branding tweaks could be scheduled for later. --- ## 3. Set Milestones & Deadlines Assign deadlines for each step to track progress and stay motivated. ✔ **Example:** Instead of saying, "Launch the product in 6 months," break it down: - **Market research:** Week 1-2 - **Prototype development:** Week 3-6 - **Marketing strategy:** Week 7-8 - **Launch execution:** Week 9-10 By setting clear deadlines, you create a sense of accountability and prevent procrastination. --- ## 4. Take Consistent Action ✔ Focus on completing one step at a time. ✔ Celebrate small wins—progress builds momentum. ✔ Stay adaptable—if needed, refine your steps as you go. 🔹 **Example:** If market research reveals an issue with the original product idea, adjust before moving forward rather than sticking rigidly to the plan. --- ## Final Thought By approaching big tasks systematically, you reduce overwhelm, maintain clarity, and steadily progress toward success. 👉 **Action Step:** Take a current big task you're facing. Break it into smaller steps, prioritize, set deadlines, and start taking action today. 🚀 --- @ 95cb4330:96db706c
2025-02-27 11:45:01Break down complex problems into their fundamental truths and build solutions from the ground up. This approach fosters creativity and avoids relying on assumptions. --- ## How to Implement First Principles Thinking 1. **Deconstruct the Problem** - **Identify the core components:** Question assumptions and remove preconceived notions. - **Ask:** What do we know for sure? What can we verify as a fact? - **Example:** Instead of assuming "Electric cars are too expensive," break it down: What are the main cost drivers? Batteries, manufacturing, and distribution. 2. **Challenge Assumptions** - **Question the status quo:** Many constraints are based on tradition or outdated thinking, not necessity. - **Ask:** What if this assumption is wrong? How else could it be done? 3. **Rebuild from the Ground Up** - **Start with the fundamental truths:** Use the identified truths to construct new solutions using logic and creativity. - **Avoid shortcuts:** Don't rely on existing frameworks that may limit possibilities. - **Example:** Tesla used first principles to design their batteries by focusing on material costs rather than purchasing standard packs. 4. **Foster a Creative Mindset** - **Think like a scientist or engineer:** Break, test, and experiment to find new pathways. - **Encourage innovation:** Brainstorm solutions that are original rather than replicative. --- ## Why It Works This method avoids reliance on assumptions and encourages fresh perspectives. By starting with "what is undeniably true," you open the door to unconventional solutions and breakthrough ideas. ---
@ 95cb4330:96db706c
2025-02-27 11:45:01Break down complex problems into their fundamental truths and build solutions from the ground up. This approach fosters creativity and avoids relying on assumptions. --- ## How to Implement First Principles Thinking 1. **Deconstruct the Problem** - **Identify the core components:** Question assumptions and remove preconceived notions. - **Ask:** What do we know for sure? What can we verify as a fact? - **Example:** Instead of assuming "Electric cars are too expensive," break it down: What are the main cost drivers? Batteries, manufacturing, and distribution. 2. **Challenge Assumptions** - **Question the status quo:** Many constraints are based on tradition or outdated thinking, not necessity. - **Ask:** What if this assumption is wrong? How else could it be done? 3. **Rebuild from the Ground Up** - **Start with the fundamental truths:** Use the identified truths to construct new solutions using logic and creativity. - **Avoid shortcuts:** Don't rely on existing frameworks that may limit possibilities. - **Example:** Tesla used first principles to design their batteries by focusing on material costs rather than purchasing standard packs. 4. **Foster a Creative Mindset** - **Think like a scientist or engineer:** Break, test, and experiment to find new pathways. - **Encourage innovation:** Brainstorm solutions that are original rather than replicative. --- ## Why It Works This method avoids reliance on assumptions and encourages fresh perspectives. By starting with "what is undeniably true," you open the door to unconventional solutions and breakthrough ideas. --- @ 95cb4330:96db706c
2025-02-27 11:34:24Implementing Decision Journals, as practiced by leaders like Jeff Bezos and Ray Dalio, can significantly enhance your decision-making skills by promoting reflection and continuous improvement. This method involves documenting key decisions, the rationale behind them, and anticipated outcomes, allowing for analysis of past choices to identify patterns and biases. --- ## Understanding Decision Journals - **Definition:** A decision journal is a structured record where you log important decisions, including the context, your thought process, and expected results. This practice enables you to track the accuracy of your judgments and refine your decision-making over time. --- ## Examples in Practice - **Jeff Bezos:** The founder of Amazon utilizes a "Regret Minimization Framework" to guide his decisions. By projecting himself into the future and considering potential regrets, Bezos focuses on long-term fulfillment over short-term comfort. This approach was pivotal when he decided to leave his stable job to start Amazon. - **Ray Dalio:** The founder of Bridgewater Associates emphasizes the importance of recording decisions to create a set of well-defined principles. Dalio's process of documenting and analyzing his choices has been fundamental in developing effective decision-making rules that have contributed to his success. --- ## Implementing a Decision Journal 1. **Record the Decision:** Document the specifics of the decision, including the date, context, and the options considered. 2. **Articulate Your Reasoning:** Detail the thought process and assumptions that led to your choice. 3. **Predict the Outcome:** Note your expectations regarding the results of the decision. 4. **Review and Reflect:** After some time, revisit the decision to compare actual outcomes with your predictions, analyzing any discrepancies to identify biases or areas for improvement. --- ## Action Step Begin by selecting a current decision you are facing. Create a journal entry that outlines the decision, your reasoning, and expected outcomes. Schedule a future date to review the decision and assess its results. Regular use of decision journals can enhance self-awareness and lead to more informed choices. --- By adopting the practice of maintaining decision journals, you can systematically refine your judgment, reduce recurring mistakes, and make decisions that align more closely with your long-term goals. **Recommended Resource:** [Ray Dalio ON: Principles for Making Better Decisions & How to Strengthen Relationships for Long-Term Success | Podcast | Jay Shetty](#) ---
@ 95cb4330:96db706c
2025-02-27 11:34:24Implementing Decision Journals, as practiced by leaders like Jeff Bezos and Ray Dalio, can significantly enhance your decision-making skills by promoting reflection and continuous improvement. This method involves documenting key decisions, the rationale behind them, and anticipated outcomes, allowing for analysis of past choices to identify patterns and biases. --- ## Understanding Decision Journals - **Definition:** A decision journal is a structured record where you log important decisions, including the context, your thought process, and expected results. This practice enables you to track the accuracy of your judgments and refine your decision-making over time. --- ## Examples in Practice - **Jeff Bezos:** The founder of Amazon utilizes a "Regret Minimization Framework" to guide his decisions. By projecting himself into the future and considering potential regrets, Bezos focuses on long-term fulfillment over short-term comfort. This approach was pivotal when he decided to leave his stable job to start Amazon. - **Ray Dalio:** The founder of Bridgewater Associates emphasizes the importance of recording decisions to create a set of well-defined principles. Dalio's process of documenting and analyzing his choices has been fundamental in developing effective decision-making rules that have contributed to his success. --- ## Implementing a Decision Journal 1. **Record the Decision:** Document the specifics of the decision, including the date, context, and the options considered. 2. **Articulate Your Reasoning:** Detail the thought process and assumptions that led to your choice. 3. **Predict the Outcome:** Note your expectations regarding the results of the decision. 4. **Review and Reflect:** After some time, revisit the decision to compare actual outcomes with your predictions, analyzing any discrepancies to identify biases or areas for improvement. --- ## Action Step Begin by selecting a current decision you are facing. Create a journal entry that outlines the decision, your reasoning, and expected outcomes. Schedule a future date to review the decision and assess its results. Regular use of decision journals can enhance self-awareness and lead to more informed choices. --- By adopting the practice of maintaining decision journals, you can systematically refine your judgment, reduce recurring mistakes, and make decisions that align more closely with your long-term goals. **Recommended Resource:** [Ray Dalio ON: Principles for Making Better Decisions & How to Strengthen Relationships for Long-Term Success | Podcast | Jay Shetty](#) --- @ 95cb4330:96db706c
2025-02-27 11:22:04Embracing a Bias Toward Action, as exemplified by leaders like Elon Musk and Jeff Bezos, involves prioritizing swift decision-making and iterative progress over prolonged analysis. This approach fosters innovation, accelerates learning, and enhances adaptability in dynamic markets. --- ## Understanding Bias Toward Action - **Definition:** A Bias Toward Action emphasizes initiating tasks promptly and refining them through continuous feedback, rather than striving for perfection before implementation. --- ## Examples in Practice - **Elon Musk's Rapid Prototyping:** At SpaceX, Musk employs an iterative design methodology, rapidly developing and testing prototypes to accelerate learning and innovation. This approach allows for quick identification of effective solutions and necessary improvements. [newspaceeconomy.ca](https://newspaceeconomy.ca) - **Jeff Bezos' Two-Way Door Framework:** Bezos introduced the concept of "two-way door" decisions at Amazon, distinguishing between reversible and irreversible choices. For reversible decisions, he advocates for swift action, as they can be adjusted if needed. This strategy reduces decision-making paralysis and promotes agility. [aboutamazon.com](https://aboutamazon.com) --- ## Implementing a Bias Toward Action 1. **Identify Decision Types:** Assess whether a decision is reversible ("two-way door") or irreversible ("one-way door"). For reversible decisions, prioritize speed and be willing to iterate. 2. **Set Clear Deadlines:** Establish specific time frames for making decisions and taking action to prevent overanalysis and maintain momentum. 3. **Encourage Experimentation:** Foster a culture that supports testing ideas and learning from outcomes, viewing failures as opportunities for growth. --- ## Action Step Reflect on a project or decision you've been postponing. Determine if it's a reversible choice; if so, take an immediate step forward today, embracing the possibility of iteration and improvement. By adopting a Bias Toward Action, you can enhance responsiveness, drive innovation, and position yourself to capitalize on emerging opportunities effectively. ---
@ 95cb4330:96db706c
2025-02-27 11:22:04Embracing a Bias Toward Action, as exemplified by leaders like Elon Musk and Jeff Bezos, involves prioritizing swift decision-making and iterative progress over prolonged analysis. This approach fosters innovation, accelerates learning, and enhances adaptability in dynamic markets. --- ## Understanding Bias Toward Action - **Definition:** A Bias Toward Action emphasizes initiating tasks promptly and refining them through continuous feedback, rather than striving for perfection before implementation. --- ## Examples in Practice - **Elon Musk's Rapid Prototyping:** At SpaceX, Musk employs an iterative design methodology, rapidly developing and testing prototypes to accelerate learning and innovation. This approach allows for quick identification of effective solutions and necessary improvements. [newspaceeconomy.ca](https://newspaceeconomy.ca) - **Jeff Bezos' Two-Way Door Framework:** Bezos introduced the concept of "two-way door" decisions at Amazon, distinguishing between reversible and irreversible choices. For reversible decisions, he advocates for swift action, as they can be adjusted if needed. This strategy reduces decision-making paralysis and promotes agility. [aboutamazon.com](https://aboutamazon.com) --- ## Implementing a Bias Toward Action 1. **Identify Decision Types:** Assess whether a decision is reversible ("two-way door") or irreversible ("one-way door"). For reversible decisions, prioritize speed and be willing to iterate. 2. **Set Clear Deadlines:** Establish specific time frames for making decisions and taking action to prevent overanalysis and maintain momentum. 3. **Encourage Experimentation:** Foster a culture that supports testing ideas and learning from outcomes, viewing failures as opportunities for growth. --- ## Action Step Reflect on a project or decision you've been postponing. Determine if it's a reversible choice; if so, take an immediate step forward today, embracing the possibility of iteration and improvement. By adopting a Bias Toward Action, you can enhance responsiveness, drive innovation, and position yourself to capitalize on emerging opportunities effectively. --- @ d5c3d063:4d1159b3
2025-02-27 11:09:15ถ้าคุณเชื่ออะไรบางอย่างมาตลอดชีวิต แล้ววันหนึ่งกลับพบว่ามันอาจไม่เป็นอย่างที่คิด นี่คือความรู้สึกของผมในวันนั้น เป็นครั้งแรกที่ได้นั่งฟังหมอป๊อป DietDoctor Thailand บรรยายสดๆ ในงานสัมมนา “Nutrition 101 - โภชนาการพื้นฐาน” Healthy Hut - โรงบ่มสุขภาพ เอาตรง ๆ นะ...ความรู้สึกเหมือนผมไม่ได้กำลังฟังหมอคนหนึ่งพูด แต่เหมือนกำลังนั่งฟังนักปรัชญามากกว่า . หมอป๊อปไม่ได้มาบอกว่าเราต้องกินอะไรหรือห้ามกินอะไร แต่ท่านตั้งคำถามให้เราคิดตาม เช่น "ทำไมวัวถึงกินหญ้าได้ทั้งวันโดยไม่มีปัญหาระดับน้ำตาลในเลือด...แต่มนุษย์กลับเสี่ยงเป็นเบาหวานจากการกินคาร์โบไฮเดรต" มันเป็นคำถามที่ฟังดูเรียบง่ายแต่กลับทำให้ผมฉุกคิดถึงความเข้าใจที่เรามีมาโดยตลอด ผมนั่งฟังแล้วก็เริ่มทบทวนสิ่งที่ตัวเองเคยเชื่อ บางที...สิ่งที่เราคิดว่าถูกต้องมาตลอด อาจเป็นเพียงสิ่งที่เราถูกบอกให้เชื่อเท่านั้น เช่น เราต้องกินข้าวให้ครบทุกมื้อเพราะมันเป็นแหล่งพลังงานหลัก หรือเคยเชื่อว่าเบาหวานเป็นเรื่องของกรรมพันธุ์ แต่วันนั้นผมได้เข้าใจว่ามนุษย์ไม่ได้ถูกออกแบบมาให้กินแป้งมากขนาดนี้ ร่างกายสามารถเผาผลาญไขมันเป็นพลังงานได้ดีกว่าคาร์โบไฮเดรต และเบาหวานไม่ใช่เรื่องของโชคชะตา แต่มันเกี่ยวข้องกับพฤติกรรมการกินของเราเอง . เมื่อสิ่งที่ผมเคยเชื่อว่าจริง อาจไม่ใช่สิ่งที่ถูกต้องเสมอไป ผมเลยคิดว่า…นอกจากเรื่องอาหารแล้ว ยังมีเรื่องอื่นอีกไหมที่เราถูกสอนมาโดยที่ไม่เคยตั้งคำถาม ผมมักจะนึกถึงเรื่องเศรษฐศาสตร์ เราถูกบอกให้เชื่อว่าเงินเฟ้ออ่อน ๆ ดีต่อเศรษฐกิจ เราถูกบอกว่า CPI เป็นตัววัดเงินเฟ้อที่แม่นยำ เราถูกบอกว่าเงินต้องถูกควบคุมโดยรัฐ มันคล้ายกับเรื่องโภชนาการเลยครับ เราถูกสอนว่าต้องกินแป้ง ต้องกินผักผลไท้ ต้องกินข้าวเช้า ต้องกินอาหารให้ครบ 5 หมู่ แต่ในความเป็นจริง...ร่างกายเรามีกระบวนการทางชีวภาพที่เกิดขึ้นตามธรรมชาติ ซึ่งช่วยปรับสมดุลเมื่อได้รับสารอาหารที่เหมาะสม แล้วถ้าระบบนี้ถูกก่อกวนซ้ำ ๆ ด้วยคาร์โบไฮเดรตและน้ำตาลมากเกินไปอาจนำไปสู่ปัญหาสุขภาพในระยะยาว เช่นเดียวกันกับระบบเศรษฐกิจ ถ้ารัฐเข้าไปแทรกแซงเรื่อย ๆ ก็จะส่งผลให้กลไกตลาดไม่สามารถทำงานได้อย่างมีประสิทธิภาพและตามมาด้วยปัญหาในระยะยาว . แล้วถ้าเราเปรียบเทียบระบบการเงินเป็นอาหาร เงินเฟียตก็เหมือนอาหารแปรรูปที่ถูกทำให้ดูดีแต่มีผลกระทบต่อร่างกายเราในระยะยาว ส่วนบิตคอยน์ก็เหมือนเนื้อสเต็กเป็นอาหารธรรมชาติ ที่ไม่มีการแปรรูป ลองคิดดูว่า...ถ้าเราหยุดกินน้ำตาลสักพัก ร่างกายจะค่อย ๆ ฟื้นฟูและปรับสมดุลของตัวเอง เช่นเดียวกับเศรษฐกิจที่สามารถกลับมามั่นคงได้หากปล่อยให้ตลาดเสรีทำงานตามกลไกธรรมชาติ เงินที่ไม่ได้ถูกควบคุมจากส่วนกลางก็เหมือนอาหารที่ไม่ผ่านการแปรรูป ไม่มีการปรุงแต่งหรือเปลี่ยนแปลงตามใจผู้มีอำนาจ . สิ่งที่ผมได้จากหมอป๊อปวันนั้น ไม่ใช่แค่ความรู้เรื่องอาหาร แต่มันคือทักษะในการตั้งคำถาม ...ถ้าอาหารที่เรากินมาตลอดจากความเชื่ออาจไม่ดีอย่างที่คิด แล้วสิ่งที่เราเชื่อเกี่ยวกับเศรษฐกิจล่ะ !? ...ถ้าเบาหวานสามารถหายได้โดยไม่ต้องใช้ยา แล้วถ้าผู้คนสามารถเลือกใช้เงินได้อย่างเสรี เศรษฐกิจจะดีขึ้นไหท การเรียนรู้ไม่ใช่แค่การฟังแล้วเชื่อ แต่เป็นการฟังแล้วตั้งคำถาม เพราะความจริง ไม่ได้ขึ้นอยู่กับสิ่งที่เราถูกสอนมาเสมอไป แต่เกิดจากการเข้าใจธรรมชาติของมันอย่างแท้จริง และเมื่อเรามีความรู้ความเชื่อก็สามารถเปลี่ยนแปลงได้ #RifhtShift #โรงบ่มสุขภาพ #HealthyHut #สุขภาพดี #ความรู้สุขภาพ #Siamstr
@ d5c3d063:4d1159b3
2025-02-27 11:09:15ถ้าคุณเชื่ออะไรบางอย่างมาตลอดชีวิต แล้ววันหนึ่งกลับพบว่ามันอาจไม่เป็นอย่างที่คิด นี่คือความรู้สึกของผมในวันนั้น เป็นครั้งแรกที่ได้นั่งฟังหมอป๊อป DietDoctor Thailand บรรยายสดๆ ในงานสัมมนา “Nutrition 101 - โภชนาการพื้นฐาน” Healthy Hut - โรงบ่มสุขภาพ เอาตรง ๆ นะ...ความรู้สึกเหมือนผมไม่ได้กำลังฟังหมอคนหนึ่งพูด แต่เหมือนกำลังนั่งฟังนักปรัชญามากกว่า . หมอป๊อปไม่ได้มาบอกว่าเราต้องกินอะไรหรือห้ามกินอะไร แต่ท่านตั้งคำถามให้เราคิดตาม เช่น "ทำไมวัวถึงกินหญ้าได้ทั้งวันโดยไม่มีปัญหาระดับน้ำตาลในเลือด...แต่มนุษย์กลับเสี่ยงเป็นเบาหวานจากการกินคาร์โบไฮเดรต" มันเป็นคำถามที่ฟังดูเรียบง่ายแต่กลับทำให้ผมฉุกคิดถึงความเข้าใจที่เรามีมาโดยตลอด ผมนั่งฟังแล้วก็เริ่มทบทวนสิ่งที่ตัวเองเคยเชื่อ บางที...สิ่งที่เราคิดว่าถูกต้องมาตลอด อาจเป็นเพียงสิ่งที่เราถูกบอกให้เชื่อเท่านั้น เช่น เราต้องกินข้าวให้ครบทุกมื้อเพราะมันเป็นแหล่งพลังงานหลัก หรือเคยเชื่อว่าเบาหวานเป็นเรื่องของกรรมพันธุ์ แต่วันนั้นผมได้เข้าใจว่ามนุษย์ไม่ได้ถูกออกแบบมาให้กินแป้งมากขนาดนี้ ร่างกายสามารถเผาผลาญไขมันเป็นพลังงานได้ดีกว่าคาร์โบไฮเดรต และเบาหวานไม่ใช่เรื่องของโชคชะตา แต่มันเกี่ยวข้องกับพฤติกรรมการกินของเราเอง . เมื่อสิ่งที่ผมเคยเชื่อว่าจริง อาจไม่ใช่สิ่งที่ถูกต้องเสมอไป ผมเลยคิดว่า…นอกจากเรื่องอาหารแล้ว ยังมีเรื่องอื่นอีกไหมที่เราถูกสอนมาโดยที่ไม่เคยตั้งคำถาม ผมมักจะนึกถึงเรื่องเศรษฐศาสตร์ เราถูกบอกให้เชื่อว่าเงินเฟ้ออ่อน ๆ ดีต่อเศรษฐกิจ เราถูกบอกว่า CPI เป็นตัววัดเงินเฟ้อที่แม่นยำ เราถูกบอกว่าเงินต้องถูกควบคุมโดยรัฐ มันคล้ายกับเรื่องโภชนาการเลยครับ เราถูกสอนว่าต้องกินแป้ง ต้องกินผักผลไท้ ต้องกินข้าวเช้า ต้องกินอาหารให้ครบ 5 หมู่ แต่ในความเป็นจริง...ร่างกายเรามีกระบวนการทางชีวภาพที่เกิดขึ้นตามธรรมชาติ ซึ่งช่วยปรับสมดุลเมื่อได้รับสารอาหารที่เหมาะสม แล้วถ้าระบบนี้ถูกก่อกวนซ้ำ ๆ ด้วยคาร์โบไฮเดรตและน้ำตาลมากเกินไปอาจนำไปสู่ปัญหาสุขภาพในระยะยาว เช่นเดียวกันกับระบบเศรษฐกิจ ถ้ารัฐเข้าไปแทรกแซงเรื่อย ๆ ก็จะส่งผลให้กลไกตลาดไม่สามารถทำงานได้อย่างมีประสิทธิภาพและตามมาด้วยปัญหาในระยะยาว . แล้วถ้าเราเปรียบเทียบระบบการเงินเป็นอาหาร เงินเฟียตก็เหมือนอาหารแปรรูปที่ถูกทำให้ดูดีแต่มีผลกระทบต่อร่างกายเราในระยะยาว ส่วนบิตคอยน์ก็เหมือนเนื้อสเต็กเป็นอาหารธรรมชาติ ที่ไม่มีการแปรรูป ลองคิดดูว่า...ถ้าเราหยุดกินน้ำตาลสักพัก ร่างกายจะค่อย ๆ ฟื้นฟูและปรับสมดุลของตัวเอง เช่นเดียวกับเศรษฐกิจที่สามารถกลับมามั่นคงได้หากปล่อยให้ตลาดเสรีทำงานตามกลไกธรรมชาติ เงินที่ไม่ได้ถูกควบคุมจากส่วนกลางก็เหมือนอาหารที่ไม่ผ่านการแปรรูป ไม่มีการปรุงแต่งหรือเปลี่ยนแปลงตามใจผู้มีอำนาจ . สิ่งที่ผมได้จากหมอป๊อปวันนั้น ไม่ใช่แค่ความรู้เรื่องอาหาร แต่มันคือทักษะในการตั้งคำถาม ...ถ้าอาหารที่เรากินมาตลอดจากความเชื่ออาจไม่ดีอย่างที่คิด แล้วสิ่งที่เราเชื่อเกี่ยวกับเศรษฐกิจล่ะ !? ...ถ้าเบาหวานสามารถหายได้โดยไม่ต้องใช้ยา แล้วถ้าผู้คนสามารถเลือกใช้เงินได้อย่างเสรี เศรษฐกิจจะดีขึ้นไหท การเรียนรู้ไม่ใช่แค่การฟังแล้วเชื่อ แต่เป็นการฟังแล้วตั้งคำถาม เพราะความจริง ไม่ได้ขึ้นอยู่กับสิ่งที่เราถูกสอนมาเสมอไป แต่เกิดจากการเข้าใจธรรมชาติของมันอย่างแท้จริง และเมื่อเรามีความรู้ความเชื่อก็สามารถเปลี่ยนแปลงได้ #RifhtShift #โรงบ่มสุขภาพ #HealthyHut #สุขภาพดี #ความรู้สุขภาพ #Siamstr @ d360efec:14907b5f
2025-02-27 09:56:31**ภาพรวม BTCUSDT (OKX):** Bitcoin (BTCUSDT) แนวโน้ม Day ยังเป็นขาลง , 4H Sideway Down, 15m Sideways Down **วิเคราะห์ทีละ Timeframe:** **(1) TF Day (รายวัน):**  * **แนวโน้ม:** ขาลง (Downtrend) * **SMC:** * Lower Highs (LH) และ Lower Lows (LL) * Break of Structure (BOS) ด้านล่าง * **Liquidity:** * มี Sellside Liquidity (SSL) ใต้ Lows * มี Buyside Liquidity (BSL) เหนือ Highs * **ICT:** * **Order Block:** ราคา Sideway ใกล้ๆ Order Block ขาลง * **EMA:** * ราคาอยู่ใต้ EMA 50/200 * **Money Flow (LuxAlgo):** * แดง * **Trend Strength (AlgoAlpha):** * แดง/ไม่มีสัญญาณ * **Chart Patterns:** None * **Volume Profile:** * **แนวรับ:** Low ล่าสุด * **แนวต้าน:** EMA 50/200, Order Block * **สรุป:** แนวโน้มขาลง **(2) TF4H (4 ชั่วโมง):**  * **แนวโน้ม:** ขาลง (Downtrend) * **SMC:** * Lower Highs (LH) และ Lower Lows (LL) * Break of Structure (BOS) * **Liquidity:** * มี SSL * มี BSL * **ICT:** * **Order Block:** ราคา Sideway ใกล้ๆ Order Block ขาลง * **EMA:** * ราคาอยู่ใต้ EMA 50/200 * **Money Flow (LuxAlgo):** * แดง * **Trend Strength (AlgoAlpha):** * แดง/ไม่มีสัญญาณ * **Chart Patterns:** None * **Volume Profile:** * **แนวรับ:** Low * **แนวต้าน:** EMA 50/200, Order Block * **สรุป:** แนวโน้มขาลง **(3) TF15 (15 นาที):**  * **แนวโน้ม:** Sideways Down * **SMC:** * Lower Highs (LH) และ Lower Lows (LL) *เริ่ม Sideways* * Break of Structure (BOS) * **Liquidity:** * **ICT:** * **Order Block** ราคา Sideways ใกล้ๆ Order Block * **EMA:** * EMA 50/200 เป็นแนวต้าน * **Money Flow (LuxAlgo):** * แดง/เขียว สลับกัน * **Trend Strength (AlgoAlpha):** * แดง/ไม่มีสัญญาณ * **Chart Patterns:** None * **Volume Profile:** * Volume ค่อนข้างสูง * **แนวรับ:** Low * **แนวต้าน:** EMA 50, EMA 200, Order Block * **สรุป:** แนวโน้ม Sideways Down **สรุปภาพรวมและกลยุทธ์ (BTCUSDT):** * **แนวโน้มหลัก (Day):** ขาลง * **แนวโน้มรอง (4H):** ขาลง * **แนวโน้มระยะสั้น (15m):** Sideways Down * **Liquidity:** มี SSL * **Money Flow:** ลบ * **Trend Strength:** Day/4H/15m ขาลง * **Chart Patterns:** ไม่มี * **กลยุทธ์:** 1. **Wait & See (ดีที่สุด):** รอ 2. **Short (เสี่ยง):** ถ้าไม่ Breakout EMA/แนวต้าน 3. **ไม่แนะนำให้ Buy** **Day Trade & การเทรดรายวัน:** * **Day Trade (TF15):** * **Short Bias:** Short เมื่อเด้ง (EMA, Order Block) * **Stop Loss:** เหนือแนวต้าน * **Take Profit:** แนวรับ * **ไม่ Long** * **Swing Trade (TF4H):** * **Short Bias:** Short เมื่อไม่ผ่าน EMA/Order Block * **Stop Loss:** เหนือแนวต้าน * **Take Profit:** แนวรับ * **ไม่ Long** **สิ่งที่ต้องระวัง:** * **SSL:** ราคาอาจถูกลากลงไป * **False Breakouts:** ระวัง * **Volatility:** สูง **Setup Day Trade แบบ SMC (ตัวอย่าง - Bearish):** 1. **Order Block:** หา Bearish Order Block ใน TF15 2. **Pullback:** รอ Pullback ไปทดสอบ 3. **Bearish Entry:** * Rejection: รอ Price Action ปฏิเสธ * Break of Structure: รอ Break โครงสร้างย่อย * Money Flow: แดง 4. **Stop Loss:** เหนือ Order Block 5. **Take Profit:** แนวรับ **คำแนะนำ:** * แนวโน้มทั้งหมดเป็นลบ * Money Flow เป็นลบ * Trend Strength เป็นลบ * ***ไม่แนะนำให้ Buy*** * **Wait & See หรือ Short (ถ้ามีประสบการณ์)** * **บริหารความเสี่ยง!** **คำแนะนำสุดท้าย:** สถานการณ์โดยรวมของ BTCUSDT อยู่ในสภาวะ**ขาลงและมีความเสี่ยงสูง** แนะนำอย่างยิ่งให้ใช้กลยุทธ์ **"Wait & See" (รอดูสถานการณ์)** การ **Short (ขาย)** เป็นการเทรดที่มีความน่าจะเป็นสูงกว่าในขณะนี้ แต่เหมาะสำหรับนักเทรดที่มีประสบการณ์และมีการบริหารความเสี่ยงที่เข้มงวดเท่านั้น **ไม่แนะนำให้ Buy (ซื้อ) ในเวลานี้** **Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
@ d360efec:14907b5f
2025-02-27 09:56:31**ภาพรวม BTCUSDT (OKX):** Bitcoin (BTCUSDT) แนวโน้ม Day ยังเป็นขาลง , 4H Sideway Down, 15m Sideways Down **วิเคราะห์ทีละ Timeframe:** **(1) TF Day (รายวัน):**  * **แนวโน้ม:** ขาลง (Downtrend) * **SMC:** * Lower Highs (LH) และ Lower Lows (LL) * Break of Structure (BOS) ด้านล่าง * **Liquidity:** * มี Sellside Liquidity (SSL) ใต้ Lows * มี Buyside Liquidity (BSL) เหนือ Highs * **ICT:** * **Order Block:** ราคา Sideway ใกล้ๆ Order Block ขาลง * **EMA:** * ราคาอยู่ใต้ EMA 50/200 * **Money Flow (LuxAlgo):** * แดง * **Trend Strength (AlgoAlpha):** * แดง/ไม่มีสัญญาณ * **Chart Patterns:** None * **Volume Profile:** * **แนวรับ:** Low ล่าสุด * **แนวต้าน:** EMA 50/200, Order Block * **สรุป:** แนวโน้มขาลง **(2) TF4H (4 ชั่วโมง):**  * **แนวโน้ม:** ขาลง (Downtrend) * **SMC:** * Lower Highs (LH) และ Lower Lows (LL) * Break of Structure (BOS) * **Liquidity:** * มี SSL * มี BSL * **ICT:** * **Order Block:** ราคา Sideway ใกล้ๆ Order Block ขาลง * **EMA:** * ราคาอยู่ใต้ EMA 50/200 * **Money Flow (LuxAlgo):** * แดง * **Trend Strength (AlgoAlpha):** * แดง/ไม่มีสัญญาณ * **Chart Patterns:** None * **Volume Profile:** * **แนวรับ:** Low * **แนวต้าน:** EMA 50/200, Order Block * **สรุป:** แนวโน้มขาลง **(3) TF15 (15 นาที):**  * **แนวโน้ม:** Sideways Down * **SMC:** * Lower Highs (LH) และ Lower Lows (LL) *เริ่ม Sideways* * Break of Structure (BOS) * **Liquidity:** * **ICT:** * **Order Block** ราคา Sideways ใกล้ๆ Order Block * **EMA:** * EMA 50/200 เป็นแนวต้าน * **Money Flow (LuxAlgo):** * แดง/เขียว สลับกัน * **Trend Strength (AlgoAlpha):** * แดง/ไม่มีสัญญาณ * **Chart Patterns:** None * **Volume Profile:** * Volume ค่อนข้างสูง * **แนวรับ:** Low * **แนวต้าน:** EMA 50, EMA 200, Order Block * **สรุป:** แนวโน้ม Sideways Down **สรุปภาพรวมและกลยุทธ์ (BTCUSDT):** * **แนวโน้มหลัก (Day):** ขาลง * **แนวโน้มรอง (4H):** ขาลง * **แนวโน้มระยะสั้น (15m):** Sideways Down * **Liquidity:** มี SSL * **Money Flow:** ลบ * **Trend Strength:** Day/4H/15m ขาลง * **Chart Patterns:** ไม่มี * **กลยุทธ์:** 1. **Wait & See (ดีที่สุด):** รอ 2. **Short (เสี่ยง):** ถ้าไม่ Breakout EMA/แนวต้าน 3. **ไม่แนะนำให้ Buy** **Day Trade & การเทรดรายวัน:** * **Day Trade (TF15):** * **Short Bias:** Short เมื่อเด้ง (EMA, Order Block) * **Stop Loss:** เหนือแนวต้าน * **Take Profit:** แนวรับ * **ไม่ Long** * **Swing Trade (TF4H):** * **Short Bias:** Short เมื่อไม่ผ่าน EMA/Order Block * **Stop Loss:** เหนือแนวต้าน * **Take Profit:** แนวรับ * **ไม่ Long** **สิ่งที่ต้องระวัง:** * **SSL:** ราคาอาจถูกลากลงไป * **False Breakouts:** ระวัง * **Volatility:** สูง **Setup Day Trade แบบ SMC (ตัวอย่าง - Bearish):** 1. **Order Block:** หา Bearish Order Block ใน TF15 2. **Pullback:** รอ Pullback ไปทดสอบ 3. **Bearish Entry:** * Rejection: รอ Price Action ปฏิเสธ * Break of Structure: รอ Break โครงสร้างย่อย * Money Flow: แดง 4. **Stop Loss:** เหนือ Order Block 5. **Take Profit:** แนวรับ **คำแนะนำ:** * แนวโน้มทั้งหมดเป็นลบ * Money Flow เป็นลบ * Trend Strength เป็นลบ * ***ไม่แนะนำให้ Buy*** * **Wait & See หรือ Short (ถ้ามีประสบการณ์)** * **บริหารความเสี่ยง!** **คำแนะนำสุดท้าย:** สถานการณ์โดยรวมของ BTCUSDT อยู่ในสภาวะ**ขาลงและมีความเสี่ยงสูง** แนะนำอย่างยิ่งให้ใช้กลยุทธ์ **"Wait & See" (รอดูสถานการณ์)** การ **Short (ขาย)** เป็นการเทรดที่มีความน่าจะเป็นสูงกว่าในขณะนี้ แต่เหมาะสำหรับนักเทรดที่มีประสบการณ์และมีการบริหารความเสี่ยงที่เข้มงวดเท่านั้น **ไม่แนะนำให้ Buy (ซื้อ) ในเวลานี้** **Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ @ 59cfee8f:7598a483
2025-02-27 09:55:34What is Crypto Mining? Before we dive into the trends and predictions, let's first define what crypto mining is. Cryptocurrency mining involves the use of powerful computers to solve complex mathematical problems and validate transactions on the blockchain. Miners compete to solve these problems and the first one to do so is rewarded with a certain amount of cryptocurrency. Trend 1: Increased Focus on Renewable Energy One of the biggest trends in crypto mining is a shift towards renewable energy sources. As concerns about climate change continue to grow, many miners are looking for ways to reduce their carbon footprint and operate in a more sustainable manner. Solar and wind power are increasingly being used to power mining operations, and there are even projects underway to create completely renewable-powered mining farms. Trend 2: The Rise of Decentralized Mining Pools Another trend that is gaining momentum in the crypto mining world is the emergence of decentralized mining pools. These pools are designed to be more transparent, fair, and resistant to manipulation than traditional centralized mining pools. By utilizing blockchain technology, these pools can offer greater security and reduce the risk of fraud. Trend 3: Continued Growth of GPU Mining GPU mining has been around for several years now, but it continues to be an attractive option for miners due to its flexibility and cost-effectiveness. With the rise of new cryptocurrencies and the increased demand for computing power, GPU mining is expected to continue its growth trajectory in 2023. Trend 4: Increased Focus on Security Security has always been a major concern in the crypto world, and this is especially true for mining operations. In 2023, we can expect to see a greater emphasis on security measures, such as multi-factor authentication, encryption, and biometric verification. Miners will need to be vigilant in order to protect their assets and prevent cyber attacks. Trend 5: Emergence of New Mining Algorithms As the cryptocurrency market continues to evolve, we can expect to see the emergence of new mining algorithms. These algorithms will be designed to be more efficient, secure, and resistant to manipulation. This could lead to a shift away from traditional proof-of-work algorithms towards proof-of-stake or other innovative solutions. Prediction 1: Increased Regulation As the cryptocurrency market continues to grow and gain mainstream acceptance, we can expect to see increased regulation from governments and financial institutions. This could have a significant impact on the mining industry, with stricter regulations and oversight leading to greater stability and legitimacy. Prediction 2: Continued Price Volatility Cryptocurrency prices have always been volatile, and this is unlikely to change in 2023. While the overall trend may be upwards, there will still be significant fluctuations in price, driven by factors such as global economic conditions, regulatory changes, and investor sentiment. Prediction 3: Greater Collaboration and Partnership As the cryptocurrency market becomes more mature, we can expect to see greater collaboration and partnership between mining companies, cryptocurrency exchanges, and other players in the ecosystem. This could lead to new business models and innovative solutions for miners and investors alike. Prediction 4: Increased Adoption of Cryptocurrencies As more and more businesses and individuals begin to accept cryptocurrencies as a form of payment, we can expect to see increased adoption of these digital assets. This could lead to greater demand for mining equipment and services, as well as new opportunities for miners to earn rewards and profits. Prediction 5: Evolution of Mining Hardware The evolution of mining hardware is a trend that has been ongoing since the early days of Bitcoin mining. As the demand for computing power continues to grow, we can expect to see new and improved mining hardware emerge in 2023. This could include more powerful GPUs, ASICs, and other specialized equipment designed specifically for mining. Conclusion In conclusion, the future of crypto mining in 2025 and beyond looks promising, with numerous trends and predictions pointing towards continued growth and innovation. As the industry evolves and matures, miners will need to adapt and embrace new technologies and strategies in order to stay competitive and profitable. With the right tools and knowledge, however, there is no doubt that crypto mining will continue to be a valuable and exciting part of the cryptocurrency ecosystem for many years to come.
@ 59cfee8f:7598a483
2025-02-27 09:55:34What is Crypto Mining? Before we dive into the trends and predictions, let's first define what crypto mining is. Cryptocurrency mining involves the use of powerful computers to solve complex mathematical problems and validate transactions on the blockchain. Miners compete to solve these problems and the first one to do so is rewarded with a certain amount of cryptocurrency. Trend 1: Increased Focus on Renewable Energy One of the biggest trends in crypto mining is a shift towards renewable energy sources. As concerns about climate change continue to grow, many miners are looking for ways to reduce their carbon footprint and operate in a more sustainable manner. Solar and wind power are increasingly being used to power mining operations, and there are even projects underway to create completely renewable-powered mining farms. Trend 2: The Rise of Decentralized Mining Pools Another trend that is gaining momentum in the crypto mining world is the emergence of decentralized mining pools. These pools are designed to be more transparent, fair, and resistant to manipulation than traditional centralized mining pools. By utilizing blockchain technology, these pools can offer greater security and reduce the risk of fraud. Trend 3: Continued Growth of GPU Mining GPU mining has been around for several years now, but it continues to be an attractive option for miners due to its flexibility and cost-effectiveness. With the rise of new cryptocurrencies and the increased demand for computing power, GPU mining is expected to continue its growth trajectory in 2023. Trend 4: Increased Focus on Security Security has always been a major concern in the crypto world, and this is especially true for mining operations. In 2023, we can expect to see a greater emphasis on security measures, such as multi-factor authentication, encryption, and biometric verification. Miners will need to be vigilant in order to protect their assets and prevent cyber attacks. Trend 5: Emergence of New Mining Algorithms As the cryptocurrency market continues to evolve, we can expect to see the emergence of new mining algorithms. These algorithms will be designed to be more efficient, secure, and resistant to manipulation. This could lead to a shift away from traditional proof-of-work algorithms towards proof-of-stake or other innovative solutions. Prediction 1: Increased Regulation As the cryptocurrency market continues to grow and gain mainstream acceptance, we can expect to see increased regulation from governments and financial institutions. This could have a significant impact on the mining industry, with stricter regulations and oversight leading to greater stability and legitimacy. Prediction 2: Continued Price Volatility Cryptocurrency prices have always been volatile, and this is unlikely to change in 2023. While the overall trend may be upwards, there will still be significant fluctuations in price, driven by factors such as global economic conditions, regulatory changes, and investor sentiment. Prediction 3: Greater Collaboration and Partnership As the cryptocurrency market becomes more mature, we can expect to see greater collaboration and partnership between mining companies, cryptocurrency exchanges, and other players in the ecosystem. This could lead to new business models and innovative solutions for miners and investors alike. Prediction 4: Increased Adoption of Cryptocurrencies As more and more businesses and individuals begin to accept cryptocurrencies as a form of payment, we can expect to see increased adoption of these digital assets. This could lead to greater demand for mining equipment and services, as well as new opportunities for miners to earn rewards and profits. Prediction 5: Evolution of Mining Hardware The evolution of mining hardware is a trend that has been ongoing since the early days of Bitcoin mining. As the demand for computing power continues to grow, we can expect to see new and improved mining hardware emerge in 2023. This could include more powerful GPUs, ASICs, and other specialized equipment designed specifically for mining. Conclusion In conclusion, the future of crypto mining in 2025 and beyond looks promising, with numerous trends and predictions pointing towards continued growth and innovation. As the industry evolves and matures, miners will need to adapt and embrace new technologies and strategies in order to stay competitive and profitable. With the right tools and knowledge, however, there is no doubt that crypto mining will continue to be a valuable and exciting part of the cryptocurrency ecosystem for many years to come. @ d360efec:14907b5f
2025-02-27 09:52:53**Overall Assessment:** Bitcoin (BTCUSDT) on OKX remains highly volatile, and the overall trend is still uncertain. While the long-term trend (Daily chart) technically has been an uptrend, it has *significantly weakened*. The 4-hour and 15-minute charts are now in downtrends. This analysis incorporates: * **SMC (Smart Money Concepts):** Market structure, Break of Structure, Change of Character, Order Blocks, Liquidity. * **ICT (Inner Circle Trader Concepts):** Optimal Trade Entry (OTE), Fair Value Gaps (FVG), Mitigation, Breaker Blocks, Liquidity Pools/Runs. * **Buyside & Sellside Liquidity:** Identifying likely areas of Smart Money buying/selling. * **Money Flow (LuxAlgo):** Capital inflows/outflows. * **EMA (Exponential Moving Average):** 50 (yellow) and 200 (white). * **Trend Strength (AlgoAlpha):** Trend identification and strength, including the "cloud" and buy/sell signals. * **Chart Patterns:** Identification of significant chart patterns. * **Volume Profile:** (Used as needed). **Detailed Analysis by Timeframe:** **(1) TF Day (Daily):**  * **Trend:** Downtrend * **SMC:** * Lower Highs (LH) and Lower Lows (LL) * BOS to the downside. * **Liquidity:** * **Sellside Liquidity (SSL):** Significant SSL rests below previous lows. * **Buyside Liquidity (BSL):** BSL is present above recent highs. * **ICT:** * **Order Block:** The price failed to break above a bearish Order Block. * **EMA:** * Price is below both the 50-period and 200-period EMAs (bearish). * **Money Flow (LuxAlgo):** * Red, selling pressure * **Trend Strength (AlgoAlpha):** * Red cloud, Downtrend, No signals. * **Chart Patterns:** None * **Volume Profile:** * **Support:** Recent lows. * **Resistance:** EMA 50, EMA 200, Order Block. * **Summary:** Downtrend **(2) TF4H (4-Hour):**  * **Trend:** Downtrend. * **SMC:** * Lower Highs (LH) and Lower Lows (LL). * BOS to the downside. * **Liquidity:** * **SSL:** Below previous lows. * **BSL:** Above previous highs. * **ICT:** * **Order Block:** The price failed to break above a bearish Order Block. * **EMA:** * Price is below both the 50-period and 200-period EMAs (bearish). * **Money Flow (LuxAlgo):** * Red, selling pressure. * **Trend Strength (AlgoAlpha):** * Red cloud, Downtrend, No signals. * **Chart Patterns:** None * **Volume Profile:** * **Support:** Recent lows. * **Resistance:** EMA 50, EMA 200, Order Block. * **Summary:** Downtrend **(3) TF15 (15-Minute):**  * **Trend:** Sideways Down * **SMC:** * Lower Highs (LH) and Lower Lows (LL) - but showing signs of sideways movement. * BOS to the downside. * **ICT:** * **Order Block** The price is ranging near a bearish Order Block. * **EMA:** * The 50-period and 200-period EMAs are acting as resistance. * **Money Flow (LuxAlgo):** * Red * **Trend Strength (AlgoAlpha):** * Red/No signals * **Chart Patterns:** None * **Volume Profile** * Relatively High Volume * **Support:** Recent lows. * **Resistance:** EMA 50, EMA 200, Order Block. * **Summary:** Sideways Down **Overall Strategy and Recommendations (BTCUSDT):** * **Primary Trend (Day):** Downtrend * **Secondary Trend (4H):** Downtrend * **Short-Term Trend (15m):** Sideways Down * **Liquidity:** SSL below on all timeframes. * **Money Flow:** Negative on all timeframes. * **Trend Strength:** Bearish on Day, 4H, and 15m. * **Chart Patterns:** None * **Strategies:** 1. **Wait & See (Best Option):** The bearish momentum and lack of clear bullish reversals make waiting for confirmation the most prudent approach. 2. **Short (High Risk):** This aligns with the downtrends on all timeframes. * **Entry:** Look for short entries on rallies to resistance levels (EMAs, Order Blocks, previous support turned resistance). * **Stop Loss:** Above recent highs or key resistance. * **Target:** Recent lows, then SSL zones. 3. **Buy (Extremely High Risk - NOT Recommended):** Do *not* buy unless there are *extremely strong and consistent* bullish reversal signals across all timeframes. **Day Trading & Swing Trading:** * **Day Trade (TF15 Focus):** * **Bias:** Short. * **Entry:** Look for bearish setups (rejections of resistance, bearish candlestick patterns) near EMAs or Order Blocks. * **Stop Loss:** Tight, above resistance. * **Take Profit:** Recent lows. * **Avoid:** Longs. * **Swing Trade (TF4H Focus):** * **Bias:** Short. * **Entry:** Look for bearish setups (rejections of resistance, bearish candlestick patterns) near EMAs or Order Blocks. * **Stop Loss:** Above resistance. * **Take Profit:** Next major support levels (SSL zones). * **Avoid:** Longs. **Key Considerations & Warnings:** * **Sellside Liquidity (SSL):** High probability of price being drawn down to these levels. * **False Breakouts:** Always a risk. * **Volatility:** Expect high volatility. * **Conflicting Timeframes:** While the long-term trend *was* bullish, the *current* price action and indicators are overwhelmingly bearish. * **Money Flow:** Consistently negative across all timeframes. * **Trend Strength:** Bearish across all timeframes. **SMC Day Trade Setup Example (Bearish - TF15):** 1. **Identify Bearish Order Block:** Locate a bearish Order Block on the TF15 chart. 2. **Wait for Pullback:** Wait for the price to pull back up to test the Order Block (this might not always happen). 3. **Bearish Entry:** * **Rejection:** Look for price action to reject the Order Block (e.g., pin bar, engulfing pattern, other bearish patterns). * **Break of Structure:** Look for a break of a minor support level on a *lower* timeframe (1m/5m) after the Order Block test. * **Money Flow:** Confirm negative Money Flow (red). 4. **Stop Loss:** Place a stop-loss order *above* the Order Block. 5. **Take Profit:** Target the next support level (e.g., recent lows). Recommendations: All trends are negative. Money flow is negative. Trend strength is negative. Buying is not recommended. Wait and see, or short (if experienced). Manage your risk! I've made the following very minor changes, maintaining the original meaning: Changed 'Advice' to a more natural sounding 'Recommendations'. Used "if experienced" instead of "(if have experience)" This version maintains the original meaning while sounding more natural in English, particularly in a financial/trading context. **Final Recommendation:** The overall situation for BTCUSDT is **bearish and high-risk**. The **"Wait & See"** approach is strongly recommended. **Shorting** is currently the higher-probability trade, but only for experienced traders with strict risk management. **Buying is not recommended at this time.** **Disclaimer:** This analysis is for informational purposes only and represents a personal opinion. It is not financial advice. Investing in cryptocurrencies involves significant risk. Investors should conduct their own research and exercise due diligence before making any investment decisions.
@ d360efec:14907b5f
2025-02-27 09:52:53**Overall Assessment:** Bitcoin (BTCUSDT) on OKX remains highly volatile, and the overall trend is still uncertain. While the long-term trend (Daily chart) technically has been an uptrend, it has *significantly weakened*. The 4-hour and 15-minute charts are now in downtrends. This analysis incorporates: * **SMC (Smart Money Concepts):** Market structure, Break of Structure, Change of Character, Order Blocks, Liquidity. * **ICT (Inner Circle Trader Concepts):** Optimal Trade Entry (OTE), Fair Value Gaps (FVG), Mitigation, Breaker Blocks, Liquidity Pools/Runs. * **Buyside & Sellside Liquidity:** Identifying likely areas of Smart Money buying/selling. * **Money Flow (LuxAlgo):** Capital inflows/outflows. * **EMA (Exponential Moving Average):** 50 (yellow) and 200 (white). * **Trend Strength (AlgoAlpha):** Trend identification and strength, including the "cloud" and buy/sell signals. * **Chart Patterns:** Identification of significant chart patterns. * **Volume Profile:** (Used as needed). **Detailed Analysis by Timeframe:** **(1) TF Day (Daily):**  * **Trend:** Downtrend * **SMC:** * Lower Highs (LH) and Lower Lows (LL) * BOS to the downside. * **Liquidity:** * **Sellside Liquidity (SSL):** Significant SSL rests below previous lows. * **Buyside Liquidity (BSL):** BSL is present above recent highs. * **ICT:** * **Order Block:** The price failed to break above a bearish Order Block. * **EMA:** * Price is below both the 50-period and 200-period EMAs (bearish). * **Money Flow (LuxAlgo):** * Red, selling pressure * **Trend Strength (AlgoAlpha):** * Red cloud, Downtrend, No signals. * **Chart Patterns:** None * **Volume Profile:** * **Support:** Recent lows. * **Resistance:** EMA 50, EMA 200, Order Block. * **Summary:** Downtrend **(2) TF4H (4-Hour):**  * **Trend:** Downtrend. * **SMC:** * Lower Highs (LH) and Lower Lows (LL). * BOS to the downside. * **Liquidity:** * **SSL:** Below previous lows. * **BSL:** Above previous highs. * **ICT:** * **Order Block:** The price failed to break above a bearish Order Block. * **EMA:** * Price is below both the 50-period and 200-period EMAs (bearish). * **Money Flow (LuxAlgo):** * Red, selling pressure. * **Trend Strength (AlgoAlpha):** * Red cloud, Downtrend, No signals. * **Chart Patterns:** None * **Volume Profile:** * **Support:** Recent lows. * **Resistance:** EMA 50, EMA 200, Order Block. * **Summary:** Downtrend **(3) TF15 (15-Minute):**  * **Trend:** Sideways Down * **SMC:** * Lower Highs (LH) and Lower Lows (LL) - but showing signs of sideways movement. * BOS to the downside. * **ICT:** * **Order Block** The price is ranging near a bearish Order Block. * **EMA:** * The 50-period and 200-period EMAs are acting as resistance. * **Money Flow (LuxAlgo):** * Red * **Trend Strength (AlgoAlpha):** * Red/No signals * **Chart Patterns:** None * **Volume Profile** * Relatively High Volume * **Support:** Recent lows. * **Resistance:** EMA 50, EMA 200, Order Block. * **Summary:** Sideways Down **Overall Strategy and Recommendations (BTCUSDT):** * **Primary Trend (Day):** Downtrend * **Secondary Trend (4H):** Downtrend * **Short-Term Trend (15m):** Sideways Down * **Liquidity:** SSL below on all timeframes. * **Money Flow:** Negative on all timeframes. * **Trend Strength:** Bearish on Day, 4H, and 15m. * **Chart Patterns:** None * **Strategies:** 1. **Wait & See (Best Option):** The bearish momentum and lack of clear bullish reversals make waiting for confirmation the most prudent approach. 2. **Short (High Risk):** This aligns with the downtrends on all timeframes. * **Entry:** Look for short entries on rallies to resistance levels (EMAs, Order Blocks, previous support turned resistance). * **Stop Loss:** Above recent highs or key resistance. * **Target:** Recent lows, then SSL zones. 3. **Buy (Extremely High Risk - NOT Recommended):** Do *not* buy unless there are *extremely strong and consistent* bullish reversal signals across all timeframes. **Day Trading & Swing Trading:** * **Day Trade (TF15 Focus):** * **Bias:** Short. * **Entry:** Look for bearish setups (rejections of resistance, bearish candlestick patterns) near EMAs or Order Blocks. * **Stop Loss:** Tight, above resistance. * **Take Profit:** Recent lows. * **Avoid:** Longs. * **Swing Trade (TF4H Focus):** * **Bias:** Short. * **Entry:** Look for bearish setups (rejections of resistance, bearish candlestick patterns) near EMAs or Order Blocks. * **Stop Loss:** Above resistance. * **Take Profit:** Next major support levels (SSL zones). * **Avoid:** Longs. **Key Considerations & Warnings:** * **Sellside Liquidity (SSL):** High probability of price being drawn down to these levels. * **False Breakouts:** Always a risk. * **Volatility:** Expect high volatility. * **Conflicting Timeframes:** While the long-term trend *was* bullish, the *current* price action and indicators are overwhelmingly bearish. * **Money Flow:** Consistently negative across all timeframes. * **Trend Strength:** Bearish across all timeframes. **SMC Day Trade Setup Example (Bearish - TF15):** 1. **Identify Bearish Order Block:** Locate a bearish Order Block on the TF15 chart. 2. **Wait for Pullback:** Wait for the price to pull back up to test the Order Block (this might not always happen). 3. **Bearish Entry:** * **Rejection:** Look for price action to reject the Order Block (e.g., pin bar, engulfing pattern, other bearish patterns). * **Break of Structure:** Look for a break of a minor support level on a *lower* timeframe (1m/5m) after the Order Block test. * **Money Flow:** Confirm negative Money Flow (red). 4. **Stop Loss:** Place a stop-loss order *above* the Order Block. 5. **Take Profit:** Target the next support level (e.g., recent lows). Recommendations: All trends are negative. Money flow is negative. Trend strength is negative. Buying is not recommended. Wait and see, or short (if experienced). Manage your risk! I've made the following very minor changes, maintaining the original meaning: Changed 'Advice' to a more natural sounding 'Recommendations'. Used "if experienced" instead of "(if have experience)" This version maintains the original meaning while sounding more natural in English, particularly in a financial/trading context. **Final Recommendation:** The overall situation for BTCUSDT is **bearish and high-risk**. The **"Wait & See"** approach is strongly recommended. **Shorting** is currently the higher-probability trade, but only for experienced traders with strict risk management. **Buying is not recommended at this time.** **Disclaimer:** This analysis is for informational purposes only and represents a personal opinion. It is not financial advice. Investing in cryptocurrencies involves significant risk. Investors should conduct their own research and exercise due diligence before making any investment decisions. @ da0b9bc3:4e30a4a9
2025-02-27 09:46:41Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/898543
@ da0b9bc3:4e30a4a9
2025-02-27 09:46:41Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/898543 @ e7bc35f8:3ed2a7cf
2025-02-27 07:46:26This is a fascinating question, indeed. But first of all, why is this important? Why should we be concerned about the goings-on of this group? Let’s find out the basis for this and what and why we’re being told we should care so much about this group and of course in order to do that why don’t we turn to the fear-mongers themselves to allow them to explain what is really behind this fearsome group. [RT, September 2014]( https://web.archive.org/web/20140905125241/https://youtube.com/watch?v=o9JXUX32yfc) > ISIS, an al-Qaeda-bred terrorist group spreading its wings online. Savvier than its predecessors with a new array of tricks up its sleeves. Twitter has become a virtual second home for the terrorists but as many as 27000 accounts established just over the last two weeks, after ISIS posted a video capturing the beheading of US journalist James Foley with a reported 60000 accounts popping up since May. [CNN, August 2014]( https://youtu.be/H7J_c0XTP0A) > Douglas MacArthur McCain, a young American, killed while fighting with the terrorist group ISIS. US officials say they believe he died in Syria. He’s thought to have been killed in a battle between rival extremist groups near the city of Aleppo according to a human rights group. This ratches up concerns about Americans involved with ISIS because now you have a confirmed example of an American killed fighting with ISIS in Syria. [SBS News, June 2014]( https://www.sbs.com.au/news/article/australian-brothers-call-in-isis-video/va2ucv9u3) > Hello my brothers in Australia. I don’t see myself better than any of yous, (inaudible) only that Allah has bring Karim on me and has brang me here to this country. Two men who identify themselves as Australian appear in a recruitment video called 'There is no life without jihad'. It’s believed up to 150 Australians have joined rebels fighting in Iraq and Syria. [DAVID CAMERON]( https://youtu.be/aXLUHdSmyAg) > Earlier today the Home Secretary confirmed that the Joint Terrorism Analysis Center has increased the threat level in the United Kingdom from ‘substantial’ to ‘severe’. This is the first time in three years that the threat to our country has been at this level. [USA TODAY, August 2014]( https://youtu.be/aclWTg05FAM) > They’re beyond just a terrorist group. They marry ideology, a sophistication of strategic and tactical military prowess. They are tremendously well-funded. Oh this is beyond anything we’ve seen so we must prepare for everything and the only way you do that is you take a cold steely hard look at it and get ready. Yes as **the usual gaggle of fear-mongers** in government and the mainstream media will no doubt tell you "_Yes ISIS is coming and you’d better be afraid in fact the only thing you can do is take a cold steely hard look at it and get ready because apparently there’s really nothing that can be done to avoid whatever horrible, horrific, 911-like attack they’re planning on the US Heartland, or so we’re being told._" But again I think it behooves us to question this constant call for fear-mongering from the same fear-mongers who have, for years and years, ratcheted up these phony terror level alerts, to suit their geopolitical aims and I think once again that’s exactly what was going back then. Things could have been different if, instead of succumbing to fear back then, we had focused more on understanding the threat, exposing the so-called "boogeyman," and revealing the true perpetrators in this situation. **This group was created in Iraq** by a Jordanian Sunni **back in 1999.** It was formerly the official al-Qaeda franchise, in Iraq since it broke with al-Qaeda ideologically. It then became a **self-proclaimed caliphate**, which was pronounced in late **June of 2015**. The question of the name of this group is something that gets bandied about and ISIS is often used as the short abbreviation in English, and in fact it’s just one of many, many, many, many names that this group has gone by over the years. **You can go back to 1999** for example to the original organization which brought with it of course an Arabic name whose acronym was JTJ and whose English translation was "The Organization of Monotheism and Jihad". **It changed its name in 2004** to, again, another Arabic name "The Organization of Jihad’s Base in the Country of the Two Rivers", although it became more commonly known as "al-Qaeda in Iraq" or AQI around that time. Then in 2006 it became the "Islamic State of Iraq". In 2013 it became the "Islamic State of Iraq and the Levant" or "Islamic State of Iraq and al-Sham", aka ISL and ISIS. **Then in 2014 "Islamic State"**. So switching to the question of who is behind this group, let's see some of the characters behind it. It was founded in 1999 by a Jordanian Sunni Muslim who went by the name of **Abu Musab al-Zarqawi**. ‼️We have to keep in mind that the names of the various jihadis behind this, like most jihadis they adopt "nommes de guerre" that is ‘war names’ so these names are not necessarily their real names and in fact in most cases are specifically not their real names. They’re usually chosen for some sort of symbolic or historical cultural value so for example there’s no need to scratch your head and wonder why so many people are named Al Baghdadi, it’s because they are adopting a name that shows they’re the "Baghdadis" – they’re from Iraq, that kind of thing. So again don’t read too much into any of these names, and there are usually many, many, many other alias names that these people go by as well so it gets extremely confusing, probably on purpose I think. I think the people controlling the terrorists also **have reasons for having extremely confusing ways** of referring to these people and multiple ways of referring so that if one of their memes or ideas or stories gets out of control they can spin them off as a completely different human being. Abu Musab al-Zarqawi was a Sunni militant from Jordan and he had what can only be described as a remarkable career that brought with it many lives apparently. So, again this all sources from mainstream reporting. None of this is, you know "conspiracy" reporting, this is all from mainstream news services, ABC and NBC and CBS and Reuters and all of those kinds of outlets. For example **back in 2004** it was reported that [he was arrested in Fallujah]( https://www.cbsnews.com/news/official-al-zarqawi-caught-freed/). **Then in 2005**, without reports in the meantime indicating how or when or why he was released from – or escaped from – custody in Fallujah, or how he was never arrested in Fallujah in the first place [he got wounded in Baquba]( https://www.aljazeera.com/news/2005/5/25/us-al-zarqawi-aides-arrested). **Then in 2005** he was reported [as being killed]( https://abcnews.go.com/International/story?id=1340972&page=1) in fighting in Iraq. **And then in 2006** [he was killed]( https://georgewbush-whitehouse.archives.gov/news/releases/2006/06/20060608.html) in fighting once again. Presumably for the last time this time. But it gets even stranger. **Back in 2006** the [Washington Post published]( https://www.washingtonpost.com/wp-dyn/content/article/2006/04/09/AR2006040900890_pf.html) an article entitled "**Military plays up role of Zarqawi**" in which they reported: > The US military is conducting a propaganda campaign to magnify the role of the leader of al-Qaeda in Iraq according to internal military documents and officers familiar with the program. and that same article went on to say: > One internal briefing produced by the US military headquarters in Iraq said that Kimmitt (one of the generals that oversaw this program) had concluded that the Zarqawi PSYOP program is the most successful information campaign to date. So once again the Washington Post got its hands on internal briefing documents that the Pentagon was using, to talk about al-Qaeda in Iraq and their propaganda campaign in Iraq, and these documents prove that **the Pentagon was absolutely 100 percent**, self-consciously engaged in a PSYOP operation to make Zarqawi and al-Qaeda in Iraq seem more important than it was, and they have their own twisted internal logic that was reported on at the time as to why they wanted to do this and why they wanted to build up AQi in the minds of the Iraqi people and the people of the United States. And of course I think obviously the main part of that was to keep the American people involved and interested in keeping their troops in harm’s way there in Iraq, even long after Bush declared "mission accomplished". The precursor of that ISIS group, the leader with actually a not a PSYOP creation per se but at any rate someone who is blown up specifically on purpose made to seem more important than he was, because of the Pentagon. And it gets even stranger than that when we look at **the person who took over from Zarqawi** after his final, supposedly, reported death **in 2006**, someone going by the name of Baghdadi, one of many people going by the name of Baghdadi, this one **Abu Omar al-Baghdadi** but again it’s a nom de guerre, it’s not his real name. Apparently his real name is Hamid Dawud Mohamed Khalil al-Zawi, he’s also known as Abu Omar al-Qurashi al-Baghdadi and Abu Hamza al-Baghdadi so we should not, again, put too much faith, stock, interest or energy into parsing these various names, just to know that this is someone who is referred to as al-Baghdadi and who took over from al-Zarqawi as leader of what was at the time "al-Qaeda in Iraq" in 2006. He took over the group and again, like Zarqawi, had a remarkable career that involved being **reported as [captured in 2007**]( https://web.archive.org/web/20070314153618/http://www.cnn.com/2007/WORLD/meast/03/09/iraq.main/index.html?eref=rss_latest) and then [**killed in 2007**]( https://web.archive.org/web/20100424215412/https://edition.cnn.com/2007/WORLD/meast/05/03/iraq.main/) then [**arrested in 2009**]( https://web.archive.org/web/20140911051541/http://www.huffingtonpost.com/2009/04/23/baghdad-suicide-bomber-ki_0_n_190455.html) and then throughout that period of his arrest or the period that we are supposed to be led to believe that he was under arrest, [he was releasing recordings]( https://web.archive.org/web/20090801010037/http://worldanalysis.net/modules/news/index.php?storytopic=19), obviously not from prison but from wherever he really was, that were being identified and authenticated. **And then in 2010** he was [reported as being killed]( https://web.archive.org/web/20150924144937/http://www.reuters.com/article/2010/04/19/us-iraq-violence-alqaeda-idUSTRE63I3CL20100419) once again. So again we have multiple reportings of captures and killings and arrests that don’t seem to make any logical sense, but just as in the case of Zarqawi, in the case of Baghdadi it becomes that much more strange when we find out that the fictional ISI leader – Abu Omar al-Baghdadi was identified as such by the US Pentagon. Yes, once again **the US military actually reported on how they believed Abu Omar al-Bagdadi didn’t even exist**. This comes from [a Reuters article]( https://www.reuters.com/article/2007/07/18/us-iraq-qaeda-idUSL1820065720070718/?rpc=92), of one of many sources, but we can source it to a Reuters article '"Senior Qaeda figure in Iraq a myth" says US military', where they talk about a a senior operative for al-Qaeda in Iraq who was in custody of the US military, and was being interrogated and according to the testimony of this captured al-Qaeda in Iraq fighter: > The Islamic State of Iraq is a front organization that masks the foreign influence and leadership within al-Qaeda in Iraq in an attempt to put an Iraqi face on the leadership of al-Qaeda in Iraq > U.S. military officials in recent weeks have been pressed to explain the link between al-Qaeda in Iraq and bin Laden’s global network given the military’s heightened focus on al-Qaeda in Iraq as the biggest threat to the country > The military blames al-Qaeda in Iraq for most of the major bombings in Iraq, saying the group is trying to spark all-out civil war between majority Shi’tes and minority Sunni Arabs Again a very interesting, very bizarre report that again includes briefing slides from the Pentagon that show that **the Pentagon itself calls Abu Omar al-Baghdadi the fictional ISI leader**, so once again the US military didn’t even believe this person existed, and this was from a 2007 report, so once again throwing more sand into the water, more mud in the mix to make it even murkier, the US military bumbles in, and it’s again a question of what their ultimate aim in all of this is. Very, very strange dealings going on, and again remember this is the precursor group to the group that is now referred to as is IS or ISIS, so a very strange pedigree for this terrorist group with the fingerprints of the US Pentagon and military all over it. **And the next character in this list of this cavalcade of terrorist-boogeyman is also Baghdadi.** This one not Abu Omar al-Baghdadi but **Abu Bakr al-Baghdadi** also known as Ibrahim bin 'Awad bin Ibrahim al-Badri ar-Radawi al-Husseini as-Samara’i, who was also known as Caliph Ibrahim, the caliph of the Islamic State Caliphate. **So what is known about this character and where he came from?** Almost nothing, in fact almost everything that we know about the background of this character sources from an completely [unverifiable online biography]( https://web.archive.org/web/20140819085249/http://news.siteintelgroup.com/blog/index.php/entry/226-the-story-behind-abu-bakr-al-baghdadi). So apparently he was born in Samarra in Iraq in 1971; at some point he apparently attended the Atlantic University of Baghdad and it was reported that he was a leader, a cleric in a mosque in Samarra during "The American Invasion" in 2003 according to quote unquote "reports" – unidentified reports – that’s what the BBC sourced that to – and then he was detained at Camp Bucca which was a US Forces Iraq camp at some point between 2004 and 2009 and again this story conflicts. According to the official story he was detained from February to December of 2004, that’s what the Defense Department will admit to, before being released on the recommendation of the Combined Review and Release Board. Why they recommended him for release I’m not sure, but at any rate that’s the official story. However **we have Army Colonel Kenneth King** who was the former commander of Camp Bucca [who insists]( https://abcnews.go.com/Blotter/isis-leaders-ominous-york-message-doubt-us-edge/story?id=24166099) that this character – this man who is now known as Abu Bakr al-Baghdadi – was at the camp during his tenure at Camp Bucca all the way up until 2009 when the camp with turned over to the Iraqi justice system, and he insists this because he remembers this particular character saying "_We’ll see you in New York_" or something of that nature, a "_terrorist threat_", so even after the point at which the discrepancy between the Defense Department’s story that **Bagdadi was released in 2004** , and King’s story that **he was there in 2009**, even when that discrepancy became apparent and was pointed out to King he specifically said again he was sure of it. He insists that he was there. So, again, the official story is that he was only there for the better part of a year but at any rate he may have been there up until 2009 and then presumably released by the Iraqi authorities at some point. Again it’s a completely murky story, but at some point he was under the care and detainment of the US military. Then, having gotten out of the camp he was **announced as leader** of the Islamic State of Iraq as it was known at that time, the AQI having morphed into the ISI in 2010 and then, once again had something of a interesting career having being [reported as **captured in 2012**]( https://www.aljazeera.com/news/2012/12/2/iraqs-al-qaeda-chief-arrested) and then **in 2014 he was rumored as dead** but just a few days later a video of him was released, a video of him [delivering some sort of sermon]( https://edition.cnn.com/2014/07/07/world/meast/iraq-crisis/), which is interesting because there are only apparently two photographs in existence of this person. So an exceptionally shady character and on that blank slate a lot has been written, some of which is clearly fictional and let’s just keep in mind to take with a giant grain of salt any information we hear about this man and his background and really look into where and what the source of that information is. So that’s some of the main characters behind this group. Let's turn our attention to **what this group consisted of in terms of its equipment and its ability**, at that time. [We were told]( https://en.m.wikipedia.org/wiki/Military_of_the_Islamic_State) that the arsenal of jihad contained and wielded by this shadowy deadly terrorist-boogeyman group consists of: 30 T 55 tanks; 10 T72 tanks; Blackhawks; cargo planes; Humvees; Toyota trucks; AK47s; M79s; RBG-6s; RPG-7s; Howitzers; field guns; AACs; Stinger manpads; scud missiles and a low-grade nuclear material of unknown origin. Again this is just a ridiculous list of equipment but at any rate most of it has been sourced to various things that they’ve managed to accrue from their various military conquests including for example their takeover of Mosul back earlier this year in which they secured the Black Hawk helicopters and the cargo planes from the airport and also the nuclear material, the low-grade nuclear material that they acquired from Mosul University which **according to the International Atomic Energy Agency** is a low risk for nuclear proliferation because it is such low grade – such low quality. So those were the things that we were told that they’ve gathered from their various exploits. Some of the interesting items in there I think are for example the **Toyota trucks**, which have become something of a hallmark of jihadis in various contacts. There are reasons for that, Toyotas of course being quite ubiquitous in that region of the world since Japanese aid to the Middle East generally comes in the form of equipment and various products and so Toyotas are among the types of things that find their way to the Middle East, and because of their ubiquity the parts and servicing for them are widely available so they’re quite useful for any group that wants to have sort of mobile access to the area, including the jihadis, and the **Toyotas in possession of ISIS** in particular seem to have come courtesy of, surprise surprise, [Uncle Sam]( https://youtu.be/TOLJh1toIjg). According to a [report]( https://web.archive.org/web/20140831003141/http://www.truthandaction.org/isis-enjoys-new-toyota-trucks-courtesy-usa/) which includes some audio footage about the Toyotas in the Middle East, and it also says that the "wish list" of the so-called moderate Syrians that was handed to the US military back in 2014 when the US was handing out supplies included Toyota Hiluxes, the Toyota trucks that are now in the possession of ISIS, so, surprise surprise you give to the moderates and who ends up getting them? **Well the non-moderates.** As if there were really any moderates there in the terrorist group trying to take over Syria in the first place. But that’s what they were having in their possession in terms of equipment. Where they actually get the money to do what they do… well according to what we’re being told they looted the Iraqi army. They acquired as much is 429 million dollars from the Mosul central bank which they took over earlier that year. They were extracting ransom money and extortion money from various governments throughout this time period, and they are selling oil from their northern Syria territories to the tune of as much as 2 million dollars a day, supposedly. So those were the places where they were supposedly financing what’s going on, however we can contrast that with some other information acquired from different sources. For example it’s been widely and repeatedly reported throughout that **private Gulf donors via Kuwait**, and apparently the Kuwaiti financial system was specifically well set up for this type of financing, but at any rate private gold donors have accounted for a lot of the money that has flowed into Syria to fund the various terrorist groups including ISIS and the others that were there, and again that was private donors not necessarily the **House of Saud** or anything of that sort but private donors from the Gulf, who obviously had religious reasons for trying to support the Sunni Wahabi Jihadist Muslims. In this conversation about Who is behind ISIS, we stumble upon Benghazi and what became known as **Benghazi-Gate**. **Benghazi was the lexus** where all of those Libyan arms were flowing from the Libyan terrorists to the Syrian terrorists, via Turkey and Jordan, and I think that’s an important part to keep in mind because those, again, are two very important players in this story. What happened in Benghazi is an important example for what was happening in there and all the sources converge on this ISIS group – this ISL group – that suddenly seemed to spring out of nowhere but of course has been gestating there for 15 years and has been, as we’ve seen, involved with the US Pentagon, involved in various PSYOPS operations to make this group seem more important than it is. **You can find more information about Benghazi in my recent article (search it in my articles tab).** So that brings us to some of the questions of "Well where are these funds coming from and how are these troops being trained?" and as always, all roads lead to…Washington? Here is an enlightening [broadcast of "Democracy Now!"]( https://youtu.be/dqtSaIikQ-o), with Amy Goodman and Adam Entous. So the CIA in conjunction with their friends in Britain and France and Saudi Arabia and the UAE and elsewhere have converged in Jordan to train various Syrian militants – terrorists – at a base in Jordan. Something considered as a conspiracy theory before, now it is confirmed even by the mainstream dinosaur media. So "Well yes actually, [the US has been intimately involved]( https://web.archive.org/web/20140702140057/http://mobile.wnd.com/2014/06/officials-u-s-trained-isis-at-secret-base-in-jordan/); the CIA has been intimately involved in training a lot of the people who went on to become the top ISIS fighters". And then the ""[corrected]( https://www.wnd.com/2014/06/officials-u-s-trained-isis-at-secret-base-in-jordan/)"" version. So if this sounds surprising well you haven’t been paying attention, not only to the Syrian story but really to any of these stories going back decades and decades, with the most famous of course being the US involvement in Afghanistan in the 1980s back when they were helping the Freedom Fighters – the Taliban before they started going after the evil terrorists – the Taliban. Unfortunately a script we know all too well and when it comes to how these groups are armed and trained it just continues. [LT. GENERAL MCINERNEY]( https://youtu.be/elPBhP0mZTI): > Syria we backed, I believe in some cases, some of the wrong people, and not in the right part of the Free Syrian Army and that’s a little confusing to people, so I’ve always maintained and go back quite some time that we were backing the wrong types. > I think it’s gonna turn out maybe this weekend, in a new special that Brett Baer’s gonna have Friday, it’s gonna show some of those weapons from Benghazi ended up in the hands of ISIS. So we helped build ISIS. Now there’s a danger there and I’m with you. So "we kind of build up ISIS oh and let’s go to the next news story." 😶 So again this is not controversial. This is not something that we have to speculate about. This is something that has been documented in a lot of mainstream contexts as well, so really this brings us to the heart of the question "Who is behind ISIS?" There are at least 6 groups. Someone could probably dig deeper and bring in some other groups but 6 of the main groups that we can identify as being the real powers that have brought ISIS to its position, and in alphabetical order that would be: 1. Israel, 2. NATO, 3. Qatar, 4. Saudi Arabia, 5. Turkey and 6. the USA, although to a certain extent these are groups rather than nation-states per se. Specifically in the case of Saudi Arabia where of course the House of Saud had institutional and fundamental reasons why it would not be happy about a radical caliphate on its doorstep, because obviously that would threaten the institution of the House of Saud itself, but certainly individual Saudis, private donors as I 've said, and including some members of the Royal House of Saud would be interested in helping fund a radical Wahabi jihadi Selapi??? group... Take Turkey for example. Turkey obviously has its fingerprints all over everything that’s happening in Syria and has been since the inception. Turkey has a lot of different reasons for being involved that range from its constant requests to keep its neighbors fighting with each other and destabilized, using Islam as a weapon, Turkey is happy to do so. I think the Turkish leadership has no allegiance really to Islam except for the fact that it’s a useful political tool for the largely Islamic Turkish population, and also it can be used in fights like this to keep its neighbors destabilized and to keep Turkey an important foothold for Europe and NATO in the region, and I think that’s one of the reasons. I think they’re also obviously always looking to repress and find ways to stamp out their Kurdish population problem so I think this is one extension of that, and we’ve seen for example the false-flag recordings that were released with the high-ranking Turkish officials under Erdogan talking openly about how they wanted to stage an attack on Turkish targets in Syria in order to justify Turkish incursion into Syria, which of course brings with it the specter of NATO because of the mutual self-defense clause in the NATO article – the treaty – so Turkey a very, very menacing prospect/player in all of this and someone who is again been admittedly and documentably linked to the transfer of funds and arms to the terrorist groups in Syria. Qatar has a number of reasons ranging again from religious to geopolitical, and maybe I 'll get more into the sort of pipeline politics that Qatar sees in all of this. When it comes to NATO specifically the context is similar with Gladio B, ie. the Operation Gladio which was not a mere stay behind operation in Europe to counter some perceived or imagined Soviet occupation of Europe, but in fact a global operation that involved "Strategy of Tension" and false-flag terrorism as ways of achieving various NATO operation goals in various "theaters", and we’ve talked of course about Sibel Edmonds and her revelation of Gladio B, ie. the fermenting of Islamic terrorism in various parts of the world to further these aims and goals and taking over various squares on the geopolitical chess board, So you can think about Gladio B as a worldwide operation and I would see no reason why it wouldn’t also be operative in the Middle East, and we have to look for NATO fingerprints in what’s happening there, and we can see them through the actions, for example most specifically of the US, in helping to arm, fund and run PSYOP operations surrounding this ISI group lslamic state. Let's get into more detail on some of these characters, for example of course Israel, who I think is interested in pretty much anything that happens in the Middle East, should be fairly apparent, but this is something that I documented specifically back in a previous article (see again my Articles tab). Israel’s designs on Iraq have been well-known and well-understood for a long time but I think we have to see all of these invasions and overthrows and all of the destabilizations in the Middle East in recent years as part of a grander Zionist project for reshaping the Middle East, that we can say not only predates that five-year plan that General Wesley Clark talks about but predates it by decades at the very least, documentably and on the record. All about the "Greater Israel", the Zionist plan for the Middle East (Oded Yinon) which was something that was developed in a document that was published in 1982 in the journal called Directions which was published by the Department of information for the World Zionist Organization, and this document was translated into English by the Association of Arab-American University Graduates you can find in my previous articles. And of course there are also the Pipeline Politics in the Middle East and how they played into what’s going on in Syria. Specifically with regard to a pipeline known as the ISI pipeline, Iran, Iraq, Syria pipeline or the Islamic pipeline. The fact that there there was a Memorandum of Understanding signed between Iran, Iraq and Syria shortly before all of this kerfuffle in Syria began is again, highly telling of what this situation is at least partially about, and I think to a large extent this is a very important piece of this puzzle, and it shows why Assad suddenly became in the crosshairs despite the fact of having been a willing accomplice in the [CIA’s rendition and torture program]( https://en.wikipedia.org/wiki/CIA_activities_in_Syria) for example, and sort of one of the "good boys" that the West "tolerated" for a long time, how he suddenly became enemy number one is the question, and the Islamic pipeline is one answer. So there again is a direct interest for some of the members of that "Who is behind ISIS?" coalition for not getting behind Assad and in fact getting in his way, to try to stop the creation of this pipeline. That ISI pipeline was completely getting around Turkey altogether, which would not be in Turkish interests and would not be in Qatari interests. Qatar of course having a gas of its own that it wants to export to Europe and wants to make part of the new European gas energy policy. So again there are some direct motivations for why Iran, Iraq and Syria are in the target sights of these various powers that are converging on fighting the Islamic State threat. Now let’s debunk some of the fear and propaganda that was swirling around about this, starting with the easy targets in the mainstream media who have been pimping this map of the Middle East that was supposedly part of some grand five-year war plan of the Islamic State, or something of that sort.  That map basically covered from North Africa, all the way from the western edge of North Africa, all the way through basically the top half of the African continent to the eastern part of Africa, across the Gulf into the Gulf states, into the Central Asia region, all the way up to the doorstep of China and Russia. It was as far north as the Northern Caucasus, up through Turkey into Eastern Europe, and even Spain was part of that map. It was marked as black as in being the aspirational hope of the growth of the Islamic State, as a part of a five years plan and it was labeled with all of these various regional names that were apparently going to be given to the various parts of the chessboard once the IS takes them over. ➡️ Now this looked like a very scary map – "Oh my god this is what Islamic State has planned, it’s their five-year plan, are you afraid? You’d better be very afraid". Except for the fact that of course [it was all BS]( https://web.archive.org/web/20140817042320/http://aattp.org/seriously-nbc-station-posts-terrifying-isis-expanison-map-created-by-neofascists-on-twitter/). And this has been displayed prominently all over NBC News and ABC News and of course the Daily Mail. But the interesting part about that map was that even as ABC and NBC and others admitted it sourced back to a Twitter account for the "Third Position", and ultimately the map sourceed back, if you go all the way back to basically fans of the ISIS group who put this together as their wet dream project, just basically saying "This will belong to us" and it made absolutely no sense geopolitically in any sense. [If you look at the map]( https://web.archive.org/web/20140707233833/http://io9.com/that-isis-caliphate-map-is-bogus-so-stop-freaking-ou-1598657469/all) it includes all sorts of areas of the map where even the Islamic areas of that map, they are completely different sorts of Islam that would not be compatible with, in any way, with the Islamic State and would have no interest or affinity to the people who supposedly comprise the Islamic State, etc. 👉 If you learnt something new in this article,, something you think is valuable for others to know, please do spread this information.
@ e7bc35f8:3ed2a7cf
2025-02-27 07:46:26This is a fascinating question, indeed. But first of all, why is this important? Why should we be concerned about the goings-on of this group? Let’s find out the basis for this and what and why we’re being told we should care so much about this group and of course in order to do that why don’t we turn to the fear-mongers themselves to allow them to explain what is really behind this fearsome group. [RT, September 2014]( https://web.archive.org/web/20140905125241/https://youtube.com/watch?v=o9JXUX32yfc) > ISIS, an al-Qaeda-bred terrorist group spreading its wings online. Savvier than its predecessors with a new array of tricks up its sleeves. Twitter has become a virtual second home for the terrorists but as many as 27000 accounts established just over the last two weeks, after ISIS posted a video capturing the beheading of US journalist James Foley with a reported 60000 accounts popping up since May. [CNN, August 2014]( https://youtu.be/H7J_c0XTP0A) > Douglas MacArthur McCain, a young American, killed while fighting with the terrorist group ISIS. US officials say they believe he died in Syria. He’s thought to have been killed in a battle between rival extremist groups near the city of Aleppo according to a human rights group. This ratches up concerns about Americans involved with ISIS because now you have a confirmed example of an American killed fighting with ISIS in Syria. [SBS News, June 2014]( https://www.sbs.com.au/news/article/australian-brothers-call-in-isis-video/va2ucv9u3) > Hello my brothers in Australia. I don’t see myself better than any of yous, (inaudible) only that Allah has bring Karim on me and has brang me here to this country. Two men who identify themselves as Australian appear in a recruitment video called 'There is no life without jihad'. It’s believed up to 150 Australians have joined rebels fighting in Iraq and Syria. [DAVID CAMERON]( https://youtu.be/aXLUHdSmyAg) > Earlier today the Home Secretary confirmed that the Joint Terrorism Analysis Center has increased the threat level in the United Kingdom from ‘substantial’ to ‘severe’. This is the first time in three years that the threat to our country has been at this level. [USA TODAY, August 2014]( https://youtu.be/aclWTg05FAM) > They’re beyond just a terrorist group. They marry ideology, a sophistication of strategic and tactical military prowess. They are tremendously well-funded. Oh this is beyond anything we’ve seen so we must prepare for everything and the only way you do that is you take a cold steely hard look at it and get ready. Yes as **the usual gaggle of fear-mongers** in government and the mainstream media will no doubt tell you "_Yes ISIS is coming and you’d better be afraid in fact the only thing you can do is take a cold steely hard look at it and get ready because apparently there’s really nothing that can be done to avoid whatever horrible, horrific, 911-like attack they’re planning on the US Heartland, or so we’re being told._" But again I think it behooves us to question this constant call for fear-mongering from the same fear-mongers who have, for years and years, ratcheted up these phony terror level alerts, to suit their geopolitical aims and I think once again that’s exactly what was going back then. Things could have been different if, instead of succumbing to fear back then, we had focused more on understanding the threat, exposing the so-called "boogeyman," and revealing the true perpetrators in this situation. **This group was created in Iraq** by a Jordanian Sunni **back in 1999.** It was formerly the official al-Qaeda franchise, in Iraq since it broke with al-Qaeda ideologically. It then became a **self-proclaimed caliphate**, which was pronounced in late **June of 2015**. The question of the name of this group is something that gets bandied about and ISIS is often used as the short abbreviation in English, and in fact it’s just one of many, many, many, many names that this group has gone by over the years. **You can go back to 1999** for example to the original organization which brought with it of course an Arabic name whose acronym was JTJ and whose English translation was "The Organization of Monotheism and Jihad". **It changed its name in 2004** to, again, another Arabic name "The Organization of Jihad’s Base in the Country of the Two Rivers", although it became more commonly known as "al-Qaeda in Iraq" or AQI around that time. Then in 2006 it became the "Islamic State of Iraq". In 2013 it became the "Islamic State of Iraq and the Levant" or "Islamic State of Iraq and al-Sham", aka ISL and ISIS. **Then in 2014 "Islamic State"**. So switching to the question of who is behind this group, let's see some of the characters behind it. It was founded in 1999 by a Jordanian Sunni Muslim who went by the name of **Abu Musab al-Zarqawi**. ‼️We have to keep in mind that the names of the various jihadis behind this, like most jihadis they adopt "nommes de guerre" that is ‘war names’ so these names are not necessarily their real names and in fact in most cases are specifically not their real names. They’re usually chosen for some sort of symbolic or historical cultural value so for example there’s no need to scratch your head and wonder why so many people are named Al Baghdadi, it’s because they are adopting a name that shows they’re the "Baghdadis" – they’re from Iraq, that kind of thing. So again don’t read too much into any of these names, and there are usually many, many, many other alias names that these people go by as well so it gets extremely confusing, probably on purpose I think. I think the people controlling the terrorists also **have reasons for having extremely confusing ways** of referring to these people and multiple ways of referring so that if one of their memes or ideas or stories gets out of control they can spin them off as a completely different human being. Abu Musab al-Zarqawi was a Sunni militant from Jordan and he had what can only be described as a remarkable career that brought with it many lives apparently. So, again this all sources from mainstream reporting. None of this is, you know "conspiracy" reporting, this is all from mainstream news services, ABC and NBC and CBS and Reuters and all of those kinds of outlets. For example **back in 2004** it was reported that [he was arrested in Fallujah]( https://www.cbsnews.com/news/official-al-zarqawi-caught-freed/). **Then in 2005**, without reports in the meantime indicating how or when or why he was released from – or escaped from – custody in Fallujah, or how he was never arrested in Fallujah in the first place [he got wounded in Baquba]( https://www.aljazeera.com/news/2005/5/25/us-al-zarqawi-aides-arrested). **Then in 2005** he was reported [as being killed]( https://abcnews.go.com/International/story?id=1340972&page=1) in fighting in Iraq. **And then in 2006** [he was killed]( https://georgewbush-whitehouse.archives.gov/news/releases/2006/06/20060608.html) in fighting once again. Presumably for the last time this time. But it gets even stranger. **Back in 2006** the [Washington Post published]( https://www.washingtonpost.com/wp-dyn/content/article/2006/04/09/AR2006040900890_pf.html) an article entitled "**Military plays up role of Zarqawi**" in which they reported: > The US military is conducting a propaganda campaign to magnify the role of the leader of al-Qaeda in Iraq according to internal military documents and officers familiar with the program. and that same article went on to say: > One internal briefing produced by the US military headquarters in Iraq said that Kimmitt (one of the generals that oversaw this program) had concluded that the Zarqawi PSYOP program is the most successful information campaign to date. So once again the Washington Post got its hands on internal briefing documents that the Pentagon was using, to talk about al-Qaeda in Iraq and their propaganda campaign in Iraq, and these documents prove that **the Pentagon was absolutely 100 percent**, self-consciously engaged in a PSYOP operation to make Zarqawi and al-Qaeda in Iraq seem more important than it was, and they have their own twisted internal logic that was reported on at the time as to why they wanted to do this and why they wanted to build up AQi in the minds of the Iraqi people and the people of the United States. And of course I think obviously the main part of that was to keep the American people involved and interested in keeping their troops in harm’s way there in Iraq, even long after Bush declared "mission accomplished". The precursor of that ISIS group, the leader with actually a not a PSYOP creation per se but at any rate someone who is blown up specifically on purpose made to seem more important than he was, because of the Pentagon. And it gets even stranger than that when we look at **the person who took over from Zarqawi** after his final, supposedly, reported death **in 2006**, someone going by the name of Baghdadi, one of many people going by the name of Baghdadi, this one **Abu Omar al-Baghdadi** but again it’s a nom de guerre, it’s not his real name. Apparently his real name is Hamid Dawud Mohamed Khalil al-Zawi, he’s also known as Abu Omar al-Qurashi al-Baghdadi and Abu Hamza al-Baghdadi so we should not, again, put too much faith, stock, interest or energy into parsing these various names, just to know that this is someone who is referred to as al-Baghdadi and who took over from al-Zarqawi as leader of what was at the time "al-Qaeda in Iraq" in 2006. He took over the group and again, like Zarqawi, had a remarkable career that involved being **reported as [captured in 2007**]( https://web.archive.org/web/20070314153618/http://www.cnn.com/2007/WORLD/meast/03/09/iraq.main/index.html?eref=rss_latest) and then [**killed in 2007**]( https://web.archive.org/web/20100424215412/https://edition.cnn.com/2007/WORLD/meast/05/03/iraq.main/) then [**arrested in 2009**]( https://web.archive.org/web/20140911051541/http://www.huffingtonpost.com/2009/04/23/baghdad-suicide-bomber-ki_0_n_190455.html) and then throughout that period of his arrest or the period that we are supposed to be led to believe that he was under arrest, [he was releasing recordings]( https://web.archive.org/web/20090801010037/http://worldanalysis.net/modules/news/index.php?storytopic=19), obviously not from prison but from wherever he really was, that were being identified and authenticated. **And then in 2010** he was [reported as being killed]( https://web.archive.org/web/20150924144937/http://www.reuters.com/article/2010/04/19/us-iraq-violence-alqaeda-idUSTRE63I3CL20100419) once again. So again we have multiple reportings of captures and killings and arrests that don’t seem to make any logical sense, but just as in the case of Zarqawi, in the case of Baghdadi it becomes that much more strange when we find out that the fictional ISI leader – Abu Omar al-Baghdadi was identified as such by the US Pentagon. Yes, once again **the US military actually reported on how they believed Abu Omar al-Bagdadi didn’t even exist**. This comes from [a Reuters article]( https://www.reuters.com/article/2007/07/18/us-iraq-qaeda-idUSL1820065720070718/?rpc=92), of one of many sources, but we can source it to a Reuters article '"Senior Qaeda figure in Iraq a myth" says US military', where they talk about a a senior operative for al-Qaeda in Iraq who was in custody of the US military, and was being interrogated and according to the testimony of this captured al-Qaeda in Iraq fighter: > The Islamic State of Iraq is a front organization that masks the foreign influence and leadership within al-Qaeda in Iraq in an attempt to put an Iraqi face on the leadership of al-Qaeda in Iraq > U.S. military officials in recent weeks have been pressed to explain the link between al-Qaeda in Iraq and bin Laden’s global network given the military’s heightened focus on al-Qaeda in Iraq as the biggest threat to the country > The military blames al-Qaeda in Iraq for most of the major bombings in Iraq, saying the group is trying to spark all-out civil war between majority Shi’tes and minority Sunni Arabs Again a very interesting, very bizarre report that again includes briefing slides from the Pentagon that show that **the Pentagon itself calls Abu Omar al-Baghdadi the fictional ISI leader**, so once again the US military didn’t even believe this person existed, and this was from a 2007 report, so once again throwing more sand into the water, more mud in the mix to make it even murkier, the US military bumbles in, and it’s again a question of what their ultimate aim in all of this is. Very, very strange dealings going on, and again remember this is the precursor group to the group that is now referred to as is IS or ISIS, so a very strange pedigree for this terrorist group with the fingerprints of the US Pentagon and military all over it. **And the next character in this list of this cavalcade of terrorist-boogeyman is also Baghdadi.** This one not Abu Omar al-Baghdadi but **Abu Bakr al-Baghdadi** also known as Ibrahim bin 'Awad bin Ibrahim al-Badri ar-Radawi al-Husseini as-Samara’i, who was also known as Caliph Ibrahim, the caliph of the Islamic State Caliphate. **So what is known about this character and where he came from?** Almost nothing, in fact almost everything that we know about the background of this character sources from an completely [unverifiable online biography]( https://web.archive.org/web/20140819085249/http://news.siteintelgroup.com/blog/index.php/entry/226-the-story-behind-abu-bakr-al-baghdadi). So apparently he was born in Samarra in Iraq in 1971; at some point he apparently attended the Atlantic University of Baghdad and it was reported that he was a leader, a cleric in a mosque in Samarra during "The American Invasion" in 2003 according to quote unquote "reports" – unidentified reports – that’s what the BBC sourced that to – and then he was detained at Camp Bucca which was a US Forces Iraq camp at some point between 2004 and 2009 and again this story conflicts. According to the official story he was detained from February to December of 2004, that’s what the Defense Department will admit to, before being released on the recommendation of the Combined Review and Release Board. Why they recommended him for release I’m not sure, but at any rate that’s the official story. However **we have Army Colonel Kenneth King** who was the former commander of Camp Bucca [who insists]( https://abcnews.go.com/Blotter/isis-leaders-ominous-york-message-doubt-us-edge/story?id=24166099) that this character – this man who is now known as Abu Bakr al-Baghdadi – was at the camp during his tenure at Camp Bucca all the way up until 2009 when the camp with turned over to the Iraqi justice system, and he insists this because he remembers this particular character saying "_We’ll see you in New York_" or something of that nature, a "_terrorist threat_", so even after the point at which the discrepancy between the Defense Department’s story that **Bagdadi was released in 2004** , and King’s story that **he was there in 2009**, even when that discrepancy became apparent and was pointed out to King he specifically said again he was sure of it. He insists that he was there. So, again, the official story is that he was only there for the better part of a year but at any rate he may have been there up until 2009 and then presumably released by the Iraqi authorities at some point. Again it’s a completely murky story, but at some point he was under the care and detainment of the US military. Then, having gotten out of the camp he was **announced as leader** of the Islamic State of Iraq as it was known at that time, the AQI having morphed into the ISI in 2010 and then, once again had something of a interesting career having being [reported as **captured in 2012**]( https://www.aljazeera.com/news/2012/12/2/iraqs-al-qaeda-chief-arrested) and then **in 2014 he was rumored as dead** but just a few days later a video of him was released, a video of him [delivering some sort of sermon]( https://edition.cnn.com/2014/07/07/world/meast/iraq-crisis/), which is interesting because there are only apparently two photographs in existence of this person. So an exceptionally shady character and on that blank slate a lot has been written, some of which is clearly fictional and let’s just keep in mind to take with a giant grain of salt any information we hear about this man and his background and really look into where and what the source of that information is. So that’s some of the main characters behind this group. Let's turn our attention to **what this group consisted of in terms of its equipment and its ability**, at that time. [We were told]( https://en.m.wikipedia.org/wiki/Military_of_the_Islamic_State) that the arsenal of jihad contained and wielded by this shadowy deadly terrorist-boogeyman group consists of: 30 T 55 tanks; 10 T72 tanks; Blackhawks; cargo planes; Humvees; Toyota trucks; AK47s; M79s; RBG-6s; RPG-7s; Howitzers; field guns; AACs; Stinger manpads; scud missiles and a low-grade nuclear material of unknown origin. Again this is just a ridiculous list of equipment but at any rate most of it has been sourced to various things that they’ve managed to accrue from their various military conquests including for example their takeover of Mosul back earlier this year in which they secured the Black Hawk helicopters and the cargo planes from the airport and also the nuclear material, the low-grade nuclear material that they acquired from Mosul University which **according to the International Atomic Energy Agency** is a low risk for nuclear proliferation because it is such low grade – such low quality. So those were the things that we were told that they’ve gathered from their various exploits. Some of the interesting items in there I think are for example the **Toyota trucks**, which have become something of a hallmark of jihadis in various contacts. There are reasons for that, Toyotas of course being quite ubiquitous in that region of the world since Japanese aid to the Middle East generally comes in the form of equipment and various products and so Toyotas are among the types of things that find their way to the Middle East, and because of their ubiquity the parts and servicing for them are widely available so they’re quite useful for any group that wants to have sort of mobile access to the area, including the jihadis, and the **Toyotas in possession of ISIS** in particular seem to have come courtesy of, surprise surprise, [Uncle Sam]( https://youtu.be/TOLJh1toIjg). According to a [report]( https://web.archive.org/web/20140831003141/http://www.truthandaction.org/isis-enjoys-new-toyota-trucks-courtesy-usa/) which includes some audio footage about the Toyotas in the Middle East, and it also says that the "wish list" of the so-called moderate Syrians that was handed to the US military back in 2014 when the US was handing out supplies included Toyota Hiluxes, the Toyota trucks that are now in the possession of ISIS, so, surprise surprise you give to the moderates and who ends up getting them? **Well the non-moderates.** As if there were really any moderates there in the terrorist group trying to take over Syria in the first place. But that’s what they were having in their possession in terms of equipment. Where they actually get the money to do what they do… well according to what we’re being told they looted the Iraqi army. They acquired as much is 429 million dollars from the Mosul central bank which they took over earlier that year. They were extracting ransom money and extortion money from various governments throughout this time period, and they are selling oil from their northern Syria territories to the tune of as much as 2 million dollars a day, supposedly. So those were the places where they were supposedly financing what’s going on, however we can contrast that with some other information acquired from different sources. For example it’s been widely and repeatedly reported throughout that **private Gulf donors via Kuwait**, and apparently the Kuwaiti financial system was specifically well set up for this type of financing, but at any rate private gold donors have accounted for a lot of the money that has flowed into Syria to fund the various terrorist groups including ISIS and the others that were there, and again that was private donors not necessarily the **House of Saud** or anything of that sort but private donors from the Gulf, who obviously had religious reasons for trying to support the Sunni Wahabi Jihadist Muslims. In this conversation about Who is behind ISIS, we stumble upon Benghazi and what became known as **Benghazi-Gate**. **Benghazi was the lexus** where all of those Libyan arms were flowing from the Libyan terrorists to the Syrian terrorists, via Turkey and Jordan, and I think that’s an important part to keep in mind because those, again, are two very important players in this story. What happened in Benghazi is an important example for what was happening in there and all the sources converge on this ISIS group – this ISL group – that suddenly seemed to spring out of nowhere but of course has been gestating there for 15 years and has been, as we’ve seen, involved with the US Pentagon, involved in various PSYOPS operations to make this group seem more important than it is. **You can find more information about Benghazi in my recent article (search it in my articles tab).** So that brings us to some of the questions of "Well where are these funds coming from and how are these troops being trained?" and as always, all roads lead to…Washington? Here is an enlightening [broadcast of "Democracy Now!"]( https://youtu.be/dqtSaIikQ-o), with Amy Goodman and Adam Entous. So the CIA in conjunction with their friends in Britain and France and Saudi Arabia and the UAE and elsewhere have converged in Jordan to train various Syrian militants – terrorists – at a base in Jordan. Something considered as a conspiracy theory before, now it is confirmed even by the mainstream dinosaur media. So "Well yes actually, [the US has been intimately involved]( https://web.archive.org/web/20140702140057/http://mobile.wnd.com/2014/06/officials-u-s-trained-isis-at-secret-base-in-jordan/); the CIA has been intimately involved in training a lot of the people who went on to become the top ISIS fighters". And then the ""[corrected]( https://www.wnd.com/2014/06/officials-u-s-trained-isis-at-secret-base-in-jordan/)"" version. So if this sounds surprising well you haven’t been paying attention, not only to the Syrian story but really to any of these stories going back decades and decades, with the most famous of course being the US involvement in Afghanistan in the 1980s back when they were helping the Freedom Fighters – the Taliban before they started going after the evil terrorists – the Taliban. Unfortunately a script we know all too well and when it comes to how these groups are armed and trained it just continues. [LT. GENERAL MCINERNEY]( https://youtu.be/elPBhP0mZTI): > Syria we backed, I believe in some cases, some of the wrong people, and not in the right part of the Free Syrian Army and that’s a little confusing to people, so I’ve always maintained and go back quite some time that we were backing the wrong types. > I think it’s gonna turn out maybe this weekend, in a new special that Brett Baer’s gonna have Friday, it’s gonna show some of those weapons from Benghazi ended up in the hands of ISIS. So we helped build ISIS. Now there’s a danger there and I’m with you. So "we kind of build up ISIS oh and let’s go to the next news story." 😶 So again this is not controversial. This is not something that we have to speculate about. This is something that has been documented in a lot of mainstream contexts as well, so really this brings us to the heart of the question "Who is behind ISIS?" There are at least 6 groups. Someone could probably dig deeper and bring in some other groups but 6 of the main groups that we can identify as being the real powers that have brought ISIS to its position, and in alphabetical order that would be: 1. Israel, 2. NATO, 3. Qatar, 4. Saudi Arabia, 5. Turkey and 6. the USA, although to a certain extent these are groups rather than nation-states per se. Specifically in the case of Saudi Arabia where of course the House of Saud had institutional and fundamental reasons why it would not be happy about a radical caliphate on its doorstep, because obviously that would threaten the institution of the House of Saud itself, but certainly individual Saudis, private donors as I 've said, and including some members of the Royal House of Saud would be interested in helping fund a radical Wahabi jihadi Selapi??? group... Take Turkey for example. Turkey obviously has its fingerprints all over everything that’s happening in Syria and has been since the inception. Turkey has a lot of different reasons for being involved that range from its constant requests to keep its neighbors fighting with each other and destabilized, using Islam as a weapon, Turkey is happy to do so. I think the Turkish leadership has no allegiance really to Islam except for the fact that it’s a useful political tool for the largely Islamic Turkish population, and also it can be used in fights like this to keep its neighbors destabilized and to keep Turkey an important foothold for Europe and NATO in the region, and I think that’s one of the reasons. I think they’re also obviously always looking to repress and find ways to stamp out their Kurdish population problem so I think this is one extension of that, and we’ve seen for example the false-flag recordings that were released with the high-ranking Turkish officials under Erdogan talking openly about how they wanted to stage an attack on Turkish targets in Syria in order to justify Turkish incursion into Syria, which of course brings with it the specter of NATO because of the mutual self-defense clause in the NATO article – the treaty – so Turkey a very, very menacing prospect/player in all of this and someone who is again been admittedly and documentably linked to the transfer of funds and arms to the terrorist groups in Syria. Qatar has a number of reasons ranging again from religious to geopolitical, and maybe I 'll get more into the sort of pipeline politics that Qatar sees in all of this. When it comes to NATO specifically the context is similar with Gladio B, ie. the Operation Gladio which was not a mere stay behind operation in Europe to counter some perceived or imagined Soviet occupation of Europe, but in fact a global operation that involved "Strategy of Tension" and false-flag terrorism as ways of achieving various NATO operation goals in various "theaters", and we’ve talked of course about Sibel Edmonds and her revelation of Gladio B, ie. the fermenting of Islamic terrorism in various parts of the world to further these aims and goals and taking over various squares on the geopolitical chess board, So you can think about Gladio B as a worldwide operation and I would see no reason why it wouldn’t also be operative in the Middle East, and we have to look for NATO fingerprints in what’s happening there, and we can see them through the actions, for example most specifically of the US, in helping to arm, fund and run PSYOP operations surrounding this ISI group lslamic state. Let's get into more detail on some of these characters, for example of course Israel, who I think is interested in pretty much anything that happens in the Middle East, should be fairly apparent, but this is something that I documented specifically back in a previous article (see again my Articles tab). Israel’s designs on Iraq have been well-known and well-understood for a long time but I think we have to see all of these invasions and overthrows and all of the destabilizations in the Middle East in recent years as part of a grander Zionist project for reshaping the Middle East, that we can say not only predates that five-year plan that General Wesley Clark talks about but predates it by decades at the very least, documentably and on the record. All about the "Greater Israel", the Zionist plan for the Middle East (Oded Yinon) which was something that was developed in a document that was published in 1982 in the journal called Directions which was published by the Department of information for the World Zionist Organization, and this document was translated into English by the Association of Arab-American University Graduates you can find in my previous articles. And of course there are also the Pipeline Politics in the Middle East and how they played into what’s going on in Syria. Specifically with regard to a pipeline known as the ISI pipeline, Iran, Iraq, Syria pipeline or the Islamic pipeline. The fact that there there was a Memorandum of Understanding signed between Iran, Iraq and Syria shortly before all of this kerfuffle in Syria began is again, highly telling of what this situation is at least partially about, and I think to a large extent this is a very important piece of this puzzle, and it shows why Assad suddenly became in the crosshairs despite the fact of having been a willing accomplice in the [CIA’s rendition and torture program]( https://en.wikipedia.org/wiki/CIA_activities_in_Syria) for example, and sort of one of the "good boys" that the West "tolerated" for a long time, how he suddenly became enemy number one is the question, and the Islamic pipeline is one answer. So there again is a direct interest for some of the members of that "Who is behind ISIS?" coalition for not getting behind Assad and in fact getting in his way, to try to stop the creation of this pipeline. That ISI pipeline was completely getting around Turkey altogether, which would not be in Turkish interests and would not be in Qatari interests. Qatar of course having a gas of its own that it wants to export to Europe and wants to make part of the new European gas energy policy. So again there are some direct motivations for why Iran, Iraq and Syria are in the target sights of these various powers that are converging on fighting the Islamic State threat. Now let’s debunk some of the fear and propaganda that was swirling around about this, starting with the easy targets in the mainstream media who have been pimping this map of the Middle East that was supposedly part of some grand five-year war plan of the Islamic State, or something of that sort.  That map basically covered from North Africa, all the way from the western edge of North Africa, all the way through basically the top half of the African continent to the eastern part of Africa, across the Gulf into the Gulf states, into the Central Asia region, all the way up to the doorstep of China and Russia. It was as far north as the Northern Caucasus, up through Turkey into Eastern Europe, and even Spain was part of that map. It was marked as black as in being the aspirational hope of the growth of the Islamic State, as a part of a five years plan and it was labeled with all of these various regional names that were apparently going to be given to the various parts of the chessboard once the IS takes them over. ➡️ Now this looked like a very scary map – "Oh my god this is what Islamic State has planned, it’s their five-year plan, are you afraid? You’d better be very afraid". Except for the fact that of course [it was all BS]( https://web.archive.org/web/20140817042320/http://aattp.org/seriously-nbc-station-posts-terrifying-isis-expanison-map-created-by-neofascists-on-twitter/). And this has been displayed prominently all over NBC News and ABC News and of course the Daily Mail. But the interesting part about that map was that even as ABC and NBC and others admitted it sourced back to a Twitter account for the "Third Position", and ultimately the map sourceed back, if you go all the way back to basically fans of the ISIS group who put this together as their wet dream project, just basically saying "This will belong to us" and it made absolutely no sense geopolitically in any sense. [If you look at the map]( https://web.archive.org/web/20140707233833/http://io9.com/that-isis-caliphate-map-is-bogus-so-stop-freaking-ou-1598657469/all) it includes all sorts of areas of the map where even the Islamic areas of that map, they are completely different sorts of Islam that would not be compatible with, in any way, with the Islamic State and would have no interest or affinity to the people who supposedly comprise the Islamic State, etc. 👉 If you learnt something new in this article,, something you think is valuable for others to know, please do spread this information. @ a262e97d:ddc3e696
2025-02-27 02:32:27The ancient Greek tale of the ***Sword of Damocles*** tells of a Sicilian tyrant Dionysius II and his courtier Damocles. According to legend, Damocles envied Dionysius’s wealth and power, so the tyrant offered to switch places with the coutier for a day. Damocles eagerly accepted, reveling in luxury—until he noticed a sharp sword dangling above his head, held only by a single horsehair. The looming threat stripped away his enjoyment, revealing the constant peril that accompanies great power. It’s a story about the precariousness of fortune, where danger hovers just out of sight. ## Constantinople Throughout history, there have been examples of such anxiety affecting beyond the individual onto a collective. One example that captures a society-wide sense of dread is the fall of Constantinople in 1453. This wasn’t just a city on edge; it was an entire civilization staring down its own collapse, with the tension building for decades before the final, brutal crescendo. Picture the scene: Constantinople, the last bastion of the Eastern Roman Empire, a city of faded grandeur encircled by Ottoman forces under Mehmed II. By the mid-15th century, the empire had shrunk to a shadow of its former self, its walls battered by time and earlier sieges, its coffers nearly empty. The Byzantines knew the Turks were coming—Mehmed’s massive cannons, including the monstrous Basilica, were no secret. For years, they’d lived with the creeping certainty that their world was teetering on a knife’s edge, propped up only by fragile alliances and the hope of Western aid that never fully materialized. The city’s inhabitants—nobles, merchants, priests, and peasants alike—could feel the noose tightening as Ottoman scouts probed their defenses and trade routes withered. A citizen of Constantinople in those final days might have said something like: “We feast on memories of glory, our golden domes gleaming still, but a shadow looms beyond the walls. Each night I hear the distant rumble of their engines, each day I count fewer ships in our harbor. Our prayers echo in Hagia Sophia, yet I wonder if God has turned His face from us. We are bound by a thread, and it frays with every passing hour.” It’s that Damocles vibe dialed up to apocalyptic levels—splendor undercut by the palpable, collective dread of annihilation. The drama peaked on May 29, 1453, when Mehmed’s army breached the walls after a relentless 53-day siege. The city fell in a bloodbath: cannons shredded centuries-old fortifications, soldiers poured in, and the last emperor, Constantine XI, vanished into the fray, his fate unknown. Hagia Sophia was turned into a mosque, and an empire that had endured for over a thousand years was snuffed out. The psychological weight beforehand—the years of knowing the end was near, yet clinging to a fraying hope—makes it a gut-punch of a historical moment. For your essay, it’s a setting that screams *inquiétude* on a grand scale, a whole society under that dangling sword until it finally dropped. ## French Revolution More recently, consider the French Revolution. Here’s the bourgeoisie on the eve of 1789 again—wealthy but boxed in, sensing the old order’s collapse. Once the revolution ignited, everyone felt the blade: aristocrats faced the guillotine, revolutionaries feared counter-revolts, and even the masses worried about starvation or tyranny. It’s a carousel of Damocles moments—power shifted fast, and no one knew when the horsehair might snap. Imagine, if you will, a member of France’s bourgeoisie—a well-off merchant or lawyer, say—on the eve of the French Revolution in 1789. They’ve climbed the social ladder through trade or education, but they’re still squeezed between the decadent nobility above and the restless poor below. The monarchy’s crumbling, the economy’s a mess, and whispers of revolt are growing louder. This bourgeois might describe their feelings with a nod to that old tale: “I sit at a banquet of my own making, wealth and status within reach, yet I feel a blade dangling above me. The nobles scorn us, the masses eye our gains, and the king’s faltering grip threatens to let it all fall. Every coin I’ve earned could be my undoing.” It’s a mix of pride in their rise and dread of the chaos that could snatch it away—Damocles at his feast, tasting both triumph and terror. The French Revolution is the closest echo of Dionysius and Damocles: a society—especially the rising bourgeoisie and later revolutionary leaders—relishing newfound power (or the chance at it) while acutely aware of the fragility holding it together. The guillotine literally hung over heads, and the rapid turnover of factions (Girondins, Jacobins, Thermidorians) mirrors that precarious throne under a dangling blade. Spain’s war was too chaotic, too fractured for anyone to sit comfortably; McCarthy’s era had menace but lacked the all-encompassing upheaval. France in 1789–1799 is the banquet with the sword swaying overhead—everyone’s a guest, and no one’s safe. ## the Chainsaw of Donacles In a gray, fluorescent-lit cubicle maze straight out of a dystopian *Office Space* reimagined as a euro-steampunk nightmare, the United States of 2025 hums with the dissonance of 1789 pre-revolutionary fervor. The air smells of burnt coffee and gear grease, the dull drone of bureaucracy punctuated by the hiss of steam pipes snaking along the walls above an endless sprawl of cubicles and flickering gas lamps. The air thick with wifi radiation and desperation. Donald Trump, newly mandated by a roaring electorate to “drain the swamp,” roams between Mar-a-Lago’s opulent halls, the White House’s command center, and Air Force One’s plush skies. His *arme de prédilection*: a ostentatious gold-tipped pen, wielded like a guillotine’s decree. Trump grins, orange hair wild, and with a flourish, he signs resounding executive orders—EOs that thunder through the bureaucracy — smirking, “The swamp’s toast, folks.” Enter Elon Musk, tasked with leading the DOGE task force—Department of Government Efficiency. He grips a gleaming chainsaw, a gift from Argentine firebrand Javier Milei, its blade etched with “Libertad o Muerte.” His Zoomerwaffen—a brigade of Gen Z disruptors in brass goggles and hoodies—are the revolution’s shock troops in hoodies and brass goggles, armed with bare steel laptops and savage memes. These digital sans-culottes wield laptops like muskets, flooding X with memes that mock the Karens (“OK Boomer, meet the blockchain”), crashing servers with decentralized audits, and rigging AI bots to shred red tape faster than a guillotine drops. One Zoomer, vape cloud swirling, hacks a payroll database while blasting dubstep; another livestreams a *“Karen Meltdown Compilation”* as morale bombs. They’re the grease in Elon’s machine, turning DOGE into a viral uprising. Elon’s Herculean task: slash the bloated federal beast down to size. From a Cybertruck-turned-mobile-HQ, smokestack puffing, Elon adjusts his top hat, a single LED flickering on its brim. “Time to saw through the bloat,” he quips and revs the beast, slashing budgets with a mad inventor’s glee. “Efficiency is the new Reign of Terror. Let's disrupt the guillotine’s monopoly on downsizing.” The zoomers cheer, their screens flashing with blockchain audits and TikTok takedowns of red tape as they slash budgets with blockchain precision, livestreaming the carnage on X. But beyond the glass-walled boardrooms and armored Cybertrucks, the cubicles stretch into a Bastille of beige despair. Here reign the deep-staters — legions of federal lifers grown plump on decades of taxpayer largesse. They’re the ancient régime of red tape, peering over partition walls with powdered wigs askew, muttering about “due process” while clutching dog-eared manuals of byzantine regulations. Picture these thousand Karens, each clutching a *“Manager of My Own Destiny”* mug, their lanyards clinking with pronoun pins and union badges; each a snowflake of entitled fury. And above every sweat-stenched cubicle, a miniature chainsaw dangles by a fraying hemp thread. One wretched teet-sucking swamp creature, a portly GS-14 named Linda, slams her “TPS Reports” onto a desk, her wig askew, shrieking, “I’ve earned my pension, you fascists! I've earned everything, fair and square!” Linda's personal Chainsaw of Donacles sways with every EO and Zoomer hack. Her ink-stained hands tremble as her steam-powered iPhone wheezes out another ding decrying ever more *“DOGE tyranny.”* Across the floor, lanyards jangle — pronoun pins flashing — as Karens plot over stale croissants, whispering of jammed printers and leaked memos to fight back. Trump’s banquet is victory, savored from Mar-a-Lago’s terraces or 30,000 feet up, untouchable. His mighty pen perpetually slashing through the old order. Elon’s chainsaw roars, Zoomerwaffen dancing in its sparks, dismantling decades of excess. The Karens sit under their blades — relics of a bloated regime, their banquet of entitlement souring as the threads fray and the swamp drains. The Revolution’s *inquiétude* steams through: they built this world, gorged on its perks; and now the power they hoarded hangs by a hair Every Musk rev, every Trump signature, every Zoomer meme cuts closer. “Efficiency’s here. Let them eat efficiency!” Elon tweets, and a chainsaw twitches. A Karen shrieks. A rope snaps. --- Hope you enjoyed this steampunk *Office Space*-meets-1789, lovingly crafted by Grok and myself. One final note on the Zoomerwaffen (a term I picked up from @realKingpilled): They’re the patriotic engine of this upheaval — tech-native, irreverent, and relentless. Think of them as the street agitators of 1789, but with code instead of pitchforks. They hack legacy systems to expose waste, flood social media with viral takedowns, and turn DOGE’s mission into a cultural juggernaut. Their focussed autism amplifies Elon’s chainsaw and Trump’s pen, making the Karens’ downfall a public spectacle. They’re the ones fraying those threads, one savage meme at a time.
@ a262e97d:ddc3e696
2025-02-27 02:32:27The ancient Greek tale of the ***Sword of Damocles*** tells of a Sicilian tyrant Dionysius II and his courtier Damocles. According to legend, Damocles envied Dionysius’s wealth and power, so the tyrant offered to switch places with the coutier for a day. Damocles eagerly accepted, reveling in luxury—until he noticed a sharp sword dangling above his head, held only by a single horsehair. The looming threat stripped away his enjoyment, revealing the constant peril that accompanies great power. It’s a story about the precariousness of fortune, where danger hovers just out of sight. ## Constantinople Throughout history, there have been examples of such anxiety affecting beyond the individual onto a collective. One example that captures a society-wide sense of dread is the fall of Constantinople in 1453. This wasn’t just a city on edge; it was an entire civilization staring down its own collapse, with the tension building for decades before the final, brutal crescendo. Picture the scene: Constantinople, the last bastion of the Eastern Roman Empire, a city of faded grandeur encircled by Ottoman forces under Mehmed II. By the mid-15th century, the empire had shrunk to a shadow of its former self, its walls battered by time and earlier sieges, its coffers nearly empty. The Byzantines knew the Turks were coming—Mehmed’s massive cannons, including the monstrous Basilica, were no secret. For years, they’d lived with the creeping certainty that their world was teetering on a knife’s edge, propped up only by fragile alliances and the hope of Western aid that never fully materialized. The city’s inhabitants—nobles, merchants, priests, and peasants alike—could feel the noose tightening as Ottoman scouts probed their defenses and trade routes withered. A citizen of Constantinople in those final days might have said something like: “We feast on memories of glory, our golden domes gleaming still, but a shadow looms beyond the walls. Each night I hear the distant rumble of their engines, each day I count fewer ships in our harbor. Our prayers echo in Hagia Sophia, yet I wonder if God has turned His face from us. We are bound by a thread, and it frays with every passing hour.” It’s that Damocles vibe dialed up to apocalyptic levels—splendor undercut by the palpable, collective dread of annihilation. The drama peaked on May 29, 1453, when Mehmed’s army breached the walls after a relentless 53-day siege. The city fell in a bloodbath: cannons shredded centuries-old fortifications, soldiers poured in, and the last emperor, Constantine XI, vanished into the fray, his fate unknown. Hagia Sophia was turned into a mosque, and an empire that had endured for over a thousand years was snuffed out. The psychological weight beforehand—the years of knowing the end was near, yet clinging to a fraying hope—makes it a gut-punch of a historical moment. For your essay, it’s a setting that screams *inquiétude* on a grand scale, a whole society under that dangling sword until it finally dropped. ## French Revolution More recently, consider the French Revolution. Here’s the bourgeoisie on the eve of 1789 again—wealthy but boxed in, sensing the old order’s collapse. Once the revolution ignited, everyone felt the blade: aristocrats faced the guillotine, revolutionaries feared counter-revolts, and even the masses worried about starvation or tyranny. It’s a carousel of Damocles moments—power shifted fast, and no one knew when the horsehair might snap. Imagine, if you will, a member of France’s bourgeoisie—a well-off merchant or lawyer, say—on the eve of the French Revolution in 1789. They’ve climbed the social ladder through trade or education, but they’re still squeezed between the decadent nobility above and the restless poor below. The monarchy’s crumbling, the economy’s a mess, and whispers of revolt are growing louder. This bourgeois might describe their feelings with a nod to that old tale: “I sit at a banquet of my own making, wealth and status within reach, yet I feel a blade dangling above me. The nobles scorn us, the masses eye our gains, and the king’s faltering grip threatens to let it all fall. Every coin I’ve earned could be my undoing.” It’s a mix of pride in their rise and dread of the chaos that could snatch it away—Damocles at his feast, tasting both triumph and terror. The French Revolution is the closest echo of Dionysius and Damocles: a society—especially the rising bourgeoisie and later revolutionary leaders—relishing newfound power (or the chance at it) while acutely aware of the fragility holding it together. The guillotine literally hung over heads, and the rapid turnover of factions (Girondins, Jacobins, Thermidorians) mirrors that precarious throne under a dangling blade. Spain’s war was too chaotic, too fractured for anyone to sit comfortably; McCarthy’s era had menace but lacked the all-encompassing upheaval. France in 1789–1799 is the banquet with the sword swaying overhead—everyone’s a guest, and no one’s safe. ## the Chainsaw of Donacles In a gray, fluorescent-lit cubicle maze straight out of a dystopian *Office Space* reimagined as a euro-steampunk nightmare, the United States of 2025 hums with the dissonance of 1789 pre-revolutionary fervor. The air smells of burnt coffee and gear grease, the dull drone of bureaucracy punctuated by the hiss of steam pipes snaking along the walls above an endless sprawl of cubicles and flickering gas lamps. The air thick with wifi radiation and desperation. Donald Trump, newly mandated by a roaring electorate to “drain the swamp,” roams between Mar-a-Lago’s opulent halls, the White House’s command center, and Air Force One’s plush skies. His *arme de prédilection*: a ostentatious gold-tipped pen, wielded like a guillotine’s decree. Trump grins, orange hair wild, and with a flourish, he signs resounding executive orders—EOs that thunder through the bureaucracy — smirking, “The swamp’s toast, folks.” Enter Elon Musk, tasked with leading the DOGE task force—Department of Government Efficiency. He grips a gleaming chainsaw, a gift from Argentine firebrand Javier Milei, its blade etched with “Libertad o Muerte.” His Zoomerwaffen—a brigade of Gen Z disruptors in brass goggles and hoodies—are the revolution’s shock troops in hoodies and brass goggles, armed with bare steel laptops and savage memes. These digital sans-culottes wield laptops like muskets, flooding X with memes that mock the Karens (“OK Boomer, meet the blockchain”), crashing servers with decentralized audits, and rigging AI bots to shred red tape faster than a guillotine drops. One Zoomer, vape cloud swirling, hacks a payroll database while blasting dubstep; another livestreams a *“Karen Meltdown Compilation”* as morale bombs. They’re the grease in Elon’s machine, turning DOGE into a viral uprising. Elon’s Herculean task: slash the bloated federal beast down to size. From a Cybertruck-turned-mobile-HQ, smokestack puffing, Elon adjusts his top hat, a single LED flickering on its brim. “Time to saw through the bloat,” he quips and revs the beast, slashing budgets with a mad inventor’s glee. “Efficiency is the new Reign of Terror. Let's disrupt the guillotine’s monopoly on downsizing.” The zoomers cheer, their screens flashing with blockchain audits and TikTok takedowns of red tape as they slash budgets with blockchain precision, livestreaming the carnage on X. But beyond the glass-walled boardrooms and armored Cybertrucks, the cubicles stretch into a Bastille of beige despair. Here reign the deep-staters — legions of federal lifers grown plump on decades of taxpayer largesse. They’re the ancient régime of red tape, peering over partition walls with powdered wigs askew, muttering about “due process” while clutching dog-eared manuals of byzantine regulations. Picture these thousand Karens, each clutching a *“Manager of My Own Destiny”* mug, their lanyards clinking with pronoun pins and union badges; each a snowflake of entitled fury. And above every sweat-stenched cubicle, a miniature chainsaw dangles by a fraying hemp thread. One wretched teet-sucking swamp creature, a portly GS-14 named Linda, slams her “TPS Reports” onto a desk, her wig askew, shrieking, “I’ve earned my pension, you fascists! I've earned everything, fair and square!” Linda's personal Chainsaw of Donacles sways with every EO and Zoomer hack. Her ink-stained hands tremble as her steam-powered iPhone wheezes out another ding decrying ever more *“DOGE tyranny.”* Across the floor, lanyards jangle — pronoun pins flashing — as Karens plot over stale croissants, whispering of jammed printers and leaked memos to fight back. Trump’s banquet is victory, savored from Mar-a-Lago’s terraces or 30,000 feet up, untouchable. His mighty pen perpetually slashing through the old order. Elon’s chainsaw roars, Zoomerwaffen dancing in its sparks, dismantling decades of excess. The Karens sit under their blades — relics of a bloated regime, their banquet of entitlement souring as the threads fray and the swamp drains. The Revolution’s *inquiétude* steams through: they built this world, gorged on its perks; and now the power they hoarded hangs by a hair Every Musk rev, every Trump signature, every Zoomer meme cuts closer. “Efficiency’s here. Let them eat efficiency!” Elon tweets, and a chainsaw twitches. A Karen shrieks. A rope snaps. --- Hope you enjoyed this steampunk *Office Space*-meets-1789, lovingly crafted by Grok and myself. One final note on the Zoomerwaffen (a term I picked up from @realKingpilled): They’re the patriotic engine of this upheaval — tech-native, irreverent, and relentless. Think of them as the street agitators of 1789, but with code instead of pitchforks. They hack legacy systems to expose waste, flood social media with viral takedowns, and turn DOGE’s mission into a cultural juggernaut. Their focussed autism amplifies Elon’s chainsaw and Trump’s pen, making the Karens’ downfall a public spectacle. They’re the ones fraying those threads, one savage meme at a time. @ 2ed3596e:98b4cc78
2025-02-27 00:24:36Curious about Bitcoin but unsure where to start? Our Bitcoin for Beginners webinar is designed to help you understand Bitcoin, how it differs from traditional fiat money, and how to safely get started. This free, live session takes place on the second Wednesday of every month at 4 PM EST. Whether you’re completely new to Bitcoin or looking for clarity on how to buy at the best price, this webinar will walk you through the essentials, including: ✅ What Bitcoin is and why it matters ✅ How Bitcoin is different from traditional money ✅ The safest ways to buy and store Bitcoin ✅ How to get started with confidence This interactive session also includes a Q&A, so you can ask any questions you have along the way. Don’t miss this opportunity to learn from experts and take control of your Bitcoin journey! 👉 [Click here to sign up](https://docs.google.com/forms/d/e/1FAIpQLSdR7XYSfZeIFzavEDO6Y177XmXq5RQ38ceEKFSju87yKgkOjA/viewform)
@ 2ed3596e:98b4cc78
2025-02-27 00:24:36Curious about Bitcoin but unsure where to start? Our Bitcoin for Beginners webinar is designed to help you understand Bitcoin, how it differs from traditional fiat money, and how to safely get started. This free, live session takes place on the second Wednesday of every month at 4 PM EST. Whether you’re completely new to Bitcoin or looking for clarity on how to buy at the best price, this webinar will walk you through the essentials, including: ✅ What Bitcoin is and why it matters ✅ How Bitcoin is different from traditional money ✅ The safest ways to buy and store Bitcoin ✅ How to get started with confidence This interactive session also includes a Q&A, so you can ask any questions you have along the way. Don’t miss this opportunity to learn from experts and take control of your Bitcoin journey! 👉 [Click here to sign up](https://docs.google.com/forms/d/e/1FAIpQLSdR7XYSfZeIFzavEDO6Y177XmXq5RQ38ceEKFSju87yKgkOjA/viewform) @ f3873798:24b3f2f3
2025-02-27 00:22:15Muitas pessoas sofrem em silêncio diante das dificuldades da vida. Seja um término de relacionamento, o convívio em uma família desestruturada ou até mesmo situações extremas, como estar preso em um campo de concentração, a escrita pode ir além de um simples ato de colocar palavras no papel – ela pode ser um agente de libertação. Seja em forma de diário, desabafo, artigo de opinião ou até mesmo a construção de uma história fantástica, como foi o caso de Harry Potter, escrever pode trazer alívio e transformar a dor em algo criativo e significativo. Escrever é quase mágico. O simples ato de organizar ideias para construir um texto dá ao escritor o poder de viajar para mundos criados por sua própria mente, funcionando como uma verdadeira forma de escapismo. Em certas situações extremas, essa pode ser a única alternativa para fugir da realidade, um fio de esperança para aqueles que se sentem perdidos na escuridão do desespero. Sabe aquela fase da adolescência em que pensamos "Meus pais não me entendem"? Se você está passando por isso, este texto é para você! Por que não transformar suas angústias em palavras e criar histórias maravilhosas sobre seus anseios, sonhos ou aprendizados do dia a dia? A escrita pode oferecer um refúgio, um momento em que tudo ao seu redor se transforma e seu processo criativo se torna uma lembrança especial. Portanto, se você está sofrendo com os desafios da vida, experimente colocar seus sentimentos no papel e transforme a dor em arte. Você pode se surpreender com o poder das palavras. Essa é a mensagem de hoje. Até a próxima leitura aleatória
@ f3873798:24b3f2f3
2025-02-27 00:22:15Muitas pessoas sofrem em silêncio diante das dificuldades da vida. Seja um término de relacionamento, o convívio em uma família desestruturada ou até mesmo situações extremas, como estar preso em um campo de concentração, a escrita pode ir além de um simples ato de colocar palavras no papel – ela pode ser um agente de libertação. Seja em forma de diário, desabafo, artigo de opinião ou até mesmo a construção de uma história fantástica, como foi o caso de Harry Potter, escrever pode trazer alívio e transformar a dor em algo criativo e significativo. Escrever é quase mágico. O simples ato de organizar ideias para construir um texto dá ao escritor o poder de viajar para mundos criados por sua própria mente, funcionando como uma verdadeira forma de escapismo. Em certas situações extremas, essa pode ser a única alternativa para fugir da realidade, um fio de esperança para aqueles que se sentem perdidos na escuridão do desespero. Sabe aquela fase da adolescência em que pensamos "Meus pais não me entendem"? Se você está passando por isso, este texto é para você! Por que não transformar suas angústias em palavras e criar histórias maravilhosas sobre seus anseios, sonhos ou aprendizados do dia a dia? A escrita pode oferecer um refúgio, um momento em que tudo ao seu redor se transforma e seu processo criativo se torna uma lembrança especial. Portanto, se você está sofrendo com os desafios da vida, experimente colocar seus sentimentos no papel e transforme a dor em arte. Você pode se surpreender com o poder das palavras. Essa é a mensagem de hoje. Até a próxima leitura aleatória @ ee603283:3bc79dec
2025-02-26 23:50:16Source Article by the Bitkey team and Undine Rubeze: https://bitkey.build/inheritance-is-live-heres-how-it-works/ TLDR: You wrap your mobile key, and encrypted this wrapped key with your beneficiaries public key. Send this info to Bitkey's servers. Your beneficiary can trigger the inheritance process after your passing and wait 6-months before they can do anything. 6 months seems like a long-time to be able to access critical life-savings funds for your family. This should help you prioritize a 3-6 month emergency "cash" savings for your family. Cash can be in a savings account or physical cash. Additionally, it might be beneficial to setup a life-insurance plan (a simple term-life plan) where the immediate bills and expenses are covered. #bitcoin #nostr #devs I tried to import the url into highlighter but got this error: "The page is not reader-friendly"
@ ee603283:3bc79dec
2025-02-26 23:50:16Source Article by the Bitkey team and Undine Rubeze: https://bitkey.build/inheritance-is-live-heres-how-it-works/ TLDR: You wrap your mobile key, and encrypted this wrapped key with your beneficiaries public key. Send this info to Bitkey's servers. Your beneficiary can trigger the inheritance process after your passing and wait 6-months before they can do anything. 6 months seems like a long-time to be able to access critical life-savings funds for your family. This should help you prioritize a 3-6 month emergency "cash" savings for your family. Cash can be in a savings account or physical cash. Additionally, it might be beneficial to setup a life-insurance plan (a simple term-life plan) where the immediate bills and expenses are covered. #bitcoin #nostr #devs I tried to import the url into highlighter but got this error: "The page is not reader-friendly" @ 8d34bd24:414be32b
2025-02-26 23:07:43My mind keeps chewing on these verses in Jeremiah. Maybe I can’t get it out of my head because it seems so contrary to everything I have believed regarding to prayer. > “As for you, **do not pray for this people, and do not lift up cry or prayer for them, and do not intercede with Me; for I do not hear you**. Do you not see what they are doing in the cities of Judah and in the streets of Jerusalem? The children gather wood, and the fathers kindle the fire, and the women knead dough to make cakes for the queen of heaven; and *they* pour out drink offerings to other gods in order to spite Me. Do they spite Me?” declares the Lord. “Is it not themselves *they spite,* to their own shame?” (Jeremiah 7:16-19) {emphasis mine} Before continuing with this article, make sure you have read [What? Do Not Pray For ...](https://trustjesus.substack.com/p/what-do-not-pray-for), so you have my background thoughts on this passage. After writing the first post, I began thinking about how this verse applies to American Christians today in my post A Hard Question With an Uncomfortable Answer. In my first two articles, I basically came to the conclusion that we should not pray blessings on those who were sinning and rejecting God, but that praying for repentance and turning back to God would be an allowed and even honored prayer. Then today, while listening to a sermon from Revelation, I thought, “Is there a time we are called to not pray for someone or some nation because God has given them their choice and He is no longer calling them to Himself?” ## When God Hardens a Heart There are a lot of verses where God says that he hardened their heart. The most well known is regarding the hardened heart of the Egyptian Pharaoh in Exodus where we read a succession of verses about a hardened heart: First Pharaoh hardens his own heart: > But when Pharaoh saw that there was relief, **he hardened his heart** and did not listen to them, as the Lord had said. (Exodus 8:15) {emphasis mine} then he hardens his heart again: > But **Pharaoh hardened his heart this time also**, and he did not let the people go. (Exodus 8:32) {emphasis mine} then he hardened his heart and his servants hearts: > But when Pharaoh saw that the rain and the hail and the thunder had ceased, **he sinned again and hardened his heart, he and his servants**. (Exodus 9:34) {emphasis mine} then God hardens Pharaoh’s heart: > Then the Lord said to Moses, “Go to Pharaoh, for **I have hardened his heart** and the heart of his servants, **that I may perform these signs of Mine** among them, (Exodus 10:1) {emphasis mine} God didn’t harden Pharaoh’s heart initially, but after repeated choices by Pharaoh, God gave Pharaoh the hardened heart he chose. Also, God hardened Pharaoh’s heart in order to perform signs that He wanted to perform to show Himself to the Israelites and the Egyptians. He did it to fulfill His will and His plan. Once God chose to harden Pharaoh’s heart, would it be praying according to God’s will to ask that Pharaoh repent? As uncomfortable as this makes me, I don’t think it would be praying according to God’s will to pray for repentance for Pharaoh. ## When God Declares His Judgment In Jeremiah 27, God has stated that Babylon will conquer Judah, take away the people, and take the golden implements from the Temple. He says that those who want to live must submit to Babylon. This is God’s will. Many supposed prophets were prophesying that Babylon will not capture Judah and then after Judah was conquered, that they would be brought back after 2 years contrary to God’s will and declaration of 70 years of captivity. > Then I spoke to the priests and to all this people, saying, “Thus says the Lord: Do not listen to the words of your prophets who prophesy to you, saying, ‘Behold, the vessels of the Lord’s house will now shortly be brought again from Babylon’; for they are prophesying a lie to you. Do not listen to them; serve the king of Babylon, and live! Why should this city become a ruin? But if they are prophets, and **if the word of the Lord is with them, let them now entreat the Lord of hosts** that the vessels which are left in the house of the Lord, in the house of the king of Judah and in Jerusalem may not go to Babylon. (Jeremiah 27:16-18) {emphasis mine} Regarding these so-called prophets, God says, “*if the word of the Lord is with them, let them now entreat the Lord of hosts*.” This sounds like they should pray thus only if “*the word of the Lord is with them*,” or basically if they are praying according to God’s will. Conversely, since the passage makes clear these “prophets” are not speaking God’s word, nor supporting God’s will, then God should not be entreated (asked in prayer) to act contrary to His will. ## When God Gives Them Over to Their Sin Similarly, in the New Testament it says of God: > For even though they knew God, they did not honor Him as God or give thanks, but they became futile in their speculations, and **their foolish heart was darkened**. Professing to be wise, they became fools, and exchanged the glory of the incorruptible God for an image in the form of corruptible man and of birds and four-footed animals and crawling creatures. > > Therefore **God gave them over in the lusts of their hearts** to impurity, so that their bodies would be dishonored among them. For they exchanged the truth of God for a lie, and worshiped and served the creature rather than the Creator, who is blessed forever. Amen. > > For this reason **God gave them over to degrading passions**; for their women exchanged the natural function for that which is unnatural, and in the same way also the men abandoned the natural function of the woman and burned in their desire toward one another, men with men committing indecent acts and receiving in their own persons the due penalty of their error. > > And **just as they did not see fit to acknowledge God any longer, God gave them over to a depraved mind**, to do those things which are not proper, being filled with all unrighteousness, wickedness, greed, evil; full of envy, murder, strife, deceit, malice; they are gossips, slanderers, haters of God, insolent, arrogant, boastful, inventors of evil, disobedient to parents, without understanding, untrustworthy, unloving, unmerciful; and although they know the ordinance of God, that those who practice such things are worthy of death, they not only do the same, but also give hearty approval to those who practice them. (Romans 1:21-32) {emphasis mine} There seems to come a point at which people have rebelled against God and His ordinances for so long that God gives them over to the desire of their hearts and the consequences of their actions. ## Does This Mean We Are Not To Pray At All? Is there a point at which God doesn’t want us to pray for their repentance? I’m not willing to say “definitely,” but it kind of looks like that may be the case. I don’t think this is a common situation that we need to be worried about. In most cases, even with very evil people who have done us great harm, we are definitely called to pray for their repentance and salvation. “*But I say to you, love your enemies and pray for those who persecute you*.” (Matthew 5:44) Still, there may be situations where God says, “I have given them over to the lusts and rebellion of their heart to the destruction of their soul.” There may be situations where a person or a nation has to be punished to fulfill God’s good plan. Praying against His will and plan would be fighting against God and not praying in alignment with His will. In Ezekiel chapter 3, the passage is talking specifically about sharing God’s word and being a watchman to the people rather than specifically regarding prayer, but I think this verse is still helpful in determining God’s will for our prayers. > Moreover, I will make your tongue stick to the roof of your mouth so that you will be mute and cannot be a man who rebukes them, for they are a rebellious house. (Ezekiel 3:26) In this occasion, God has given Ezekiel the role of watchman and warned him that he will be held accountable for warning the people, but their decision to obey is on their own heads. Then God tells Ezekiel that He will “*make your tongue stick to the roof of your mouth so that you will be mute and cannot be a man who rebukes them*.” I believe if God doesn’t want us to pray for someone or something and if we are seeking His will, He will make us mute so we cannot pray for them. Why would He do this? Either because the person, group, or nation are rebellious and/or because the prayer is contrary to His will. I believe God will help His devoted followers to pray according to His will. I am still fleshing out this idea in my mind and trying to seek the truth. Let me know how you interpret these verses or especially if you have other verses that clarify this matter. I am trying to seek the truth. I also want to be very careful with this idea. We are much more likely to NOT pray for repentance and salvation for people that we should be praying for than we are to pray for someone for whom we shouldn’t pray. I definitely don’t want anyone to use this post as an excuse to not pray for people or nations. May our God and Creator guide us and use us for His good purpose and according to His will. May He guide our prayers in perfect alignment with His will and may He draw us closer to Him every day. Trust Jesus
@ 8d34bd24:414be32b
2025-02-26 23:07:43My mind keeps chewing on these verses in Jeremiah. Maybe I can’t get it out of my head because it seems so contrary to everything I have believed regarding to prayer. > “As for you, **do not pray for this people, and do not lift up cry or prayer for them, and do not intercede with Me; for I do not hear you**. Do you not see what they are doing in the cities of Judah and in the streets of Jerusalem? The children gather wood, and the fathers kindle the fire, and the women knead dough to make cakes for the queen of heaven; and *they* pour out drink offerings to other gods in order to spite Me. Do they spite Me?” declares the Lord. “Is it not themselves *they spite,* to their own shame?” (Jeremiah 7:16-19) {emphasis mine} Before continuing with this article, make sure you have read [What? Do Not Pray For ...](https://trustjesus.substack.com/p/what-do-not-pray-for), so you have my background thoughts on this passage. After writing the first post, I began thinking about how this verse applies to American Christians today in my post A Hard Question With an Uncomfortable Answer. In my first two articles, I basically came to the conclusion that we should not pray blessings on those who were sinning and rejecting God, but that praying for repentance and turning back to God would be an allowed and even honored prayer. Then today, while listening to a sermon from Revelation, I thought, “Is there a time we are called to not pray for someone or some nation because God has given them their choice and He is no longer calling them to Himself?” ## When God Hardens a Heart There are a lot of verses where God says that he hardened their heart. The most well known is regarding the hardened heart of the Egyptian Pharaoh in Exodus where we read a succession of verses about a hardened heart: First Pharaoh hardens his own heart: > But when Pharaoh saw that there was relief, **he hardened his heart** and did not listen to them, as the Lord had said. (Exodus 8:15) {emphasis mine} then he hardens his heart again: > But **Pharaoh hardened his heart this time also**, and he did not let the people go. (Exodus 8:32) {emphasis mine} then he hardened his heart and his servants hearts: > But when Pharaoh saw that the rain and the hail and the thunder had ceased, **he sinned again and hardened his heart, he and his servants**. (Exodus 9:34) {emphasis mine} then God hardens Pharaoh’s heart: > Then the Lord said to Moses, “Go to Pharaoh, for **I have hardened his heart** and the heart of his servants, **that I may perform these signs of Mine** among them, (Exodus 10:1) {emphasis mine} God didn’t harden Pharaoh’s heart initially, but after repeated choices by Pharaoh, God gave Pharaoh the hardened heart he chose. Also, God hardened Pharaoh’s heart in order to perform signs that He wanted to perform to show Himself to the Israelites and the Egyptians. He did it to fulfill His will and His plan. Once God chose to harden Pharaoh’s heart, would it be praying according to God’s will to ask that Pharaoh repent? As uncomfortable as this makes me, I don’t think it would be praying according to God’s will to pray for repentance for Pharaoh. ## When God Declares His Judgment In Jeremiah 27, God has stated that Babylon will conquer Judah, take away the people, and take the golden implements from the Temple. He says that those who want to live must submit to Babylon. This is God’s will. Many supposed prophets were prophesying that Babylon will not capture Judah and then after Judah was conquered, that they would be brought back after 2 years contrary to God’s will and declaration of 70 years of captivity. > Then I spoke to the priests and to all this people, saying, “Thus says the Lord: Do not listen to the words of your prophets who prophesy to you, saying, ‘Behold, the vessels of the Lord’s house will now shortly be brought again from Babylon’; for they are prophesying a lie to you. Do not listen to them; serve the king of Babylon, and live! Why should this city become a ruin? But if they are prophets, and **if the word of the Lord is with them, let them now entreat the Lord of hosts** that the vessels which are left in the house of the Lord, in the house of the king of Judah and in Jerusalem may not go to Babylon. (Jeremiah 27:16-18) {emphasis mine} Regarding these so-called prophets, God says, “*if the word of the Lord is with them, let them now entreat the Lord of hosts*.” This sounds like they should pray thus only if “*the word of the Lord is with them*,” or basically if they are praying according to God’s will. Conversely, since the passage makes clear these “prophets” are not speaking God’s word, nor supporting God’s will, then God should not be entreated (asked in prayer) to act contrary to His will. ## When God Gives Them Over to Their Sin Similarly, in the New Testament it says of God: > For even though they knew God, they did not honor Him as God or give thanks, but they became futile in their speculations, and **their foolish heart was darkened**. Professing to be wise, they became fools, and exchanged the glory of the incorruptible God for an image in the form of corruptible man and of birds and four-footed animals and crawling creatures. > > Therefore **God gave them over in the lusts of their hearts** to impurity, so that their bodies would be dishonored among them. For they exchanged the truth of God for a lie, and worshiped and served the creature rather than the Creator, who is blessed forever. Amen. > > For this reason **God gave them over to degrading passions**; for their women exchanged the natural function for that which is unnatural, and in the same way also the men abandoned the natural function of the woman and burned in their desire toward one another, men with men committing indecent acts and receiving in their own persons the due penalty of their error. > > And **just as they did not see fit to acknowledge God any longer, God gave them over to a depraved mind**, to do those things which are not proper, being filled with all unrighteousness, wickedness, greed, evil; full of envy, murder, strife, deceit, malice; they are gossips, slanderers, haters of God, insolent, arrogant, boastful, inventors of evil, disobedient to parents, without understanding, untrustworthy, unloving, unmerciful; and although they know the ordinance of God, that those who practice such things are worthy of death, they not only do the same, but also give hearty approval to those who practice them. (Romans 1:21-32) {emphasis mine} There seems to come a point at which people have rebelled against God and His ordinances for so long that God gives them over to the desire of their hearts and the consequences of their actions. ## Does This Mean We Are Not To Pray At All? Is there a point at which God doesn’t want us to pray for their repentance? I’m not willing to say “definitely,” but it kind of looks like that may be the case. I don’t think this is a common situation that we need to be worried about. In most cases, even with very evil people who have done us great harm, we are definitely called to pray for their repentance and salvation. “*But I say to you, love your enemies and pray for those who persecute you*.” (Matthew 5:44) Still, there may be situations where God says, “I have given them over to the lusts and rebellion of their heart to the destruction of their soul.” There may be situations where a person or a nation has to be punished to fulfill God’s good plan. Praying against His will and plan would be fighting against God and not praying in alignment with His will. In Ezekiel chapter 3, the passage is talking specifically about sharing God’s word and being a watchman to the people rather than specifically regarding prayer, but I think this verse is still helpful in determining God’s will for our prayers. > Moreover, I will make your tongue stick to the roof of your mouth so that you will be mute and cannot be a man who rebukes them, for they are a rebellious house. (Ezekiel 3:26) In this occasion, God has given Ezekiel the role of watchman and warned him that he will be held accountable for warning the people, but their decision to obey is on their own heads. Then God tells Ezekiel that He will “*make your tongue stick to the roof of your mouth so that you will be mute and cannot be a man who rebukes them*.” I believe if God doesn’t want us to pray for someone or something and if we are seeking His will, He will make us mute so we cannot pray for them. Why would He do this? Either because the person, group, or nation are rebellious and/or because the prayer is contrary to His will. I believe God will help His devoted followers to pray according to His will. I am still fleshing out this idea in my mind and trying to seek the truth. Let me know how you interpret these verses or especially if you have other verses that clarify this matter. I am trying to seek the truth. I also want to be very careful with this idea. We are much more likely to NOT pray for repentance and salvation for people that we should be praying for than we are to pray for someone for whom we shouldn’t pray. I definitely don’t want anyone to use this post as an excuse to not pray for people or nations. May our God and Creator guide us and use us for His good purpose and according to His will. May He guide our prayers in perfect alignment with His will and may He draw us closer to Him every day. Trust Jesus @ 000002de:c05780a7
2025-02-26 22:31:11 These people have serious issues. [Original Sin by Jake Tapper and Alex Thompson](https://sites.prh.com/originalsin) > From two of America’s most respected journalists, an unflinching and explosive reckoning with one of the most fateful decisions in American political history: Joe Biden’s run for reelection despite evidence of his serious decline—amid desperate efforts to hide the extent of that deterioration originally posted at https://stacker.news/items/898271
@ 000002de:c05780a7
2025-02-26 22:31:11 These people have serious issues. [Original Sin by Jake Tapper and Alex Thompson](https://sites.prh.com/originalsin) > From two of America’s most respected journalists, an unflinching and explosive reckoning with one of the most fateful decisions in American political history: Joe Biden’s run for reelection despite evidence of his serious decline—amid desperate efforts to hide the extent of that deterioration originally posted at https://stacker.news/items/898271 @ ef1744f8:96fbc3fe
2025-02-26 21:36:43cKsXmhEiKNnAgVMTJ4eY+tOqOZh5Om/sZP00QBtEdlZuaayrZJ3xluZ1EMJ+gu80KY1shHaPBD4htY2P3qg65CWIt8Wjf2mAw/gb0l52BWrVkI4AQFUlC3dr14LJD7Y94iZj/CsnT02hcDkRYFjXIgyhtrhrrpVCdZJiZA1zUbw3CV7godG4yt8uo/Q5qdOHP2wH8Dj9zivAKBLyZUgHGJ6M7fBR9pNEKF88Cxs48xD5sQbtGZwiAK0a71bM/xhWAkOkvvLOQUgeeN8tcX0yH84QySFCXDKAnlDgWMAfynTVvrpdc5oyi1gM/3NBvc3s28QkeXWf3zIwq6G1/6c7pDeywYvt2IIk7qgjIbF700i7CnJZdNXxvovP9SQbPt6iotILDXpvzibLiff4GOU1UQ==?iv=dzskRoafO62Gp4TMsBWRFg==
@ ef1744f8:96fbc3fe
2025-02-26 21:36:43cKsXmhEiKNnAgVMTJ4eY+tOqOZh5Om/sZP00QBtEdlZuaayrZJ3xluZ1EMJ+gu80KY1shHaPBD4htY2P3qg65CWIt8Wjf2mAw/gb0l52BWrVkI4AQFUlC3dr14LJD7Y94iZj/CsnT02hcDkRYFjXIgyhtrhrrpVCdZJiZA1zUbw3CV7godG4yt8uo/Q5qdOHP2wH8Dj9zivAKBLyZUgHGJ6M7fBR9pNEKF88Cxs48xD5sQbtGZwiAK0a71bM/xhWAkOkvvLOQUgeeN8tcX0yH84QySFCXDKAnlDgWMAfynTVvrpdc5oyi1gM/3NBvc3s28QkeXWf3zIwq6G1/6c7pDeywYvt2IIk7qgjIbF700i7CnJZdNXxvovP9SQbPt6iotILDXpvzibLiff4GOU1UQ==?iv=dzskRoafO62Gp4TMsBWRFg== @ ef1744f8:96fbc3fe
2025-02-26 21:32:000jxu+3pODMGseAZeXiwEWcaWh0Zdp1dg4UP084e7Q8HkzdgcFHLycOQhoi/c52Iql8CA4FPgZDQCIf5gfXHNyt8lvzBvY+1TZvheCT1iX/wlrP0wn3XVE8wu5QJnVn4m2oZs31TKbR/uEfFBRpQoEUeoOhGxqzm6DZRlpjSjgdjye0me7hue1qWhwoEgQFr7TN0iZbvy9kp/DJhi5xVQgwWU1q5PCE9ekChRnEDHML/MYGCIjsZdj5tMBOh/BlH26VGsVGpzeB/F9mtuaj/E5WHaPSZdq78k1K7034emyYwEkfS0p0hvfgqdDy98m9DLRWmDeIERlxR0Ry7IPnc00qNfpthEXK9tujnUtskBQzIa6femadnIVdnE+JRJ20GOho6TkUzL6jxN9y2d7S/ttp8i/ZD+eaaXHC7ErWzR1TU=?iv=wad1n+h47INO5qI9jSRVXA==
@ ef1744f8:96fbc3fe
2025-02-26 21:32:000jxu+3pODMGseAZeXiwEWcaWh0Zdp1dg4UP084e7Q8HkzdgcFHLycOQhoi/c52Iql8CA4FPgZDQCIf5gfXHNyt8lvzBvY+1TZvheCT1iX/wlrP0wn3XVE8wu5QJnVn4m2oZs31TKbR/uEfFBRpQoEUeoOhGxqzm6DZRlpjSjgdjye0me7hue1qWhwoEgQFr7TN0iZbvy9kp/DJhi5xVQgwWU1q5PCE9ekChRnEDHML/MYGCIjsZdj5tMBOh/BlH26VGsVGpzeB/F9mtuaj/E5WHaPSZdq78k1K7034emyYwEkfS0p0hvfgqdDy98m9DLRWmDeIERlxR0Ry7IPnc00qNfpthEXK9tujnUtskBQzIa6femadnIVdnE+JRJ20GOho6TkUzL6jxN9y2d7S/ttp8i/ZD+eaaXHC7ErWzR1TU=?iv=wad1n+h47INO5qI9jSRVXA== @ bf47c19e:c3d2573b
2025-02-26 21:07:23Originalni tekst na [dvadesetjedan.com](https://dvadesetjedan.com/blog/zasto-je-vazna-decentralizacija-bitcoina). ###### Autor: [Matt Corallo](https://x.com/TheBlueMatt) / Prevod na hrvatski: [Davor](https://t.me/davor_e) --- Bitcoineri, od programera Bitcoin Core-a preko dugogodišnjih entuzijasta Bitcoina do nedavnih pronalazača /r/Bitcoina, vole razgovarati o tome kako je decentralizacija Bitcoina njegova ultimativna značajka. Doduše, rijetko vidite da netko objašnjava zašto je decentralizacija važna. Zasigurno je to zanimljiva značajka iz perspektive računalne znanosti, no zašto bi potrošači, tvrtke ili investitori marili za to? Ova objava je pokušaj da se napiše zašto je decentralizacija temelj vrijednosti Bitcoina i što je još važnije, postavi buduće objave u kojima se govori o tome kada ona to nije. Kada Bitcoineri govore o decentralizaciji Bitcoina, prva stvar koja se pojavljuje je često spominjani nedostatak inherentnog povjerenja u treću stranu. Dok je dobro postavljeno povjerenje preduvjet za učinkovit rad mnogih sustava, jednom kada se takvo povjerenje izgubi, sustavi mogu postati nevjerojatno krhki. Uzmimo, za primjer, povjerenje u američke banke prije uspostave FDIC-a (Federal Deposit Insurance Corporation). Dok je pristup bankovnim uslugama omogućio više pogodnosti i mnogim tvrtkama učinkovitije poslovanje, poznato je da su banke propadale, pritom upropaštavajući sa sobom sva sredstva klijenata. Dok je predstavljanje FDIC-a i sličnih programa decentraliziralo povjerenje u financijske institucije s jedne strane na dvije, transakcije u velikom dijelu svijeta ne nude takvu zaštitu. Čak i uz takve programe, pojedinci nisu univerzalno zaštićeni od gubitka preko granica i preko određene vrijednosti. U novije vrijeme, propisi koji dopuštaju pojedinim državnim dužnosnicima jednostrano oduzimanje imovine postali su uobičajeni. Naročito u SAD-u, sada zloglasna “Operacija Choke Point” i programi oduzimanja civilne imovine, omogućili su službenicima za provođenje zakona i privatnim institucijama da zapljenjuju financijsku imovinu i uskraćuju financijske usluge uz malo ili nimalo nadzora. Uklanjanje provjerenih skrbnika i stvaranje sustava s likvidnom imovinom, koja se ne može zaplijeniti, ima potencijal pružiti pouzdanije financijske usluge mnogima koji inače ne bi mogli djelovati učinkovito ili uopće ne bi mogli djelovati. Ova mogućnost da se Bitcoin ne može zaplijeniti, omogućena je samo zbog nedostatka za centraliziranim povjerenjem. Centralizirani sustavi elektroničke gotovine i financijski sustavi su pokušali pružiti takvu pouzdanost, propisi i poslovna stvarnost su to gotovo univerzalno spriječili. Svojstvo koje je jednako važno za sposobnost Bitcoina da pruža financijske usluge zviždačima, stranim disidentima i porno zvijezdama je njegov otpor cenzuri transakcija. Sposobnost trećih strana da zaplijene imovinu rezultira izravnim i čistim novčanim gubitkom, zamrzavanje imovine može imati sličan učinak. Kada pojedinac ili organizacija više nisu u mogućnosti obavljati transakcije za plaćanje roba i usluga, njihova financijska imovina brzo gubi vrijednost. Iako Bitcoin ima vrlo dobru priču o nemogućnosti zapljene (svaka strana u sustavu nameće nemogućnost bilo koga da potroši Bitcoin bez dodanog privatnog ključa), njegova priča o otporu cenzuri je malo utančanija. U svijetu u kojem nijedan rudar Bitcoina nema više od 1% ukupne hash snage (ili nešto drugo što je jednako decentralizirano), trebalo bi biti lako pronaći rudara koji je ili anoniman i prihvaća sve transakcije ili je u nadležnosti koja ne pokušava cenzurirati vaše transakcije. Naravno, ovo nije svijet kakav danas imamo, a cenzura transakcija jedan je od većih razloga da se ozbiljno zabrinemo centralizacijom rudarenja (za pune čvorove). Ipak, mogućnost pojedinca da kupi hash snagu (u obliku lako dostupnog starog hardvera ili u obliku njegovog iznajmljivanja) za rudarenje svoje inače cenzurirane transakcije, opcija je sve dok je pravilo najdužeg lanca na snazi kod svih rudara. Iako je znatno skuplji nego što bi bio u istinski decentraliziranom Bitcoinu, to omogućuje Bitcoinu da zadrži neka od svojih anti-cenzuriranih svojstava. Ako ste već dovoljno dugo u priči oko Bitcoina, možda ćete prepoznati gornja svojstva kao kritična za zamjenjivost. Zamjenjivost, kao ključno svojstvo svakog monetarnog instrumenta, odnosi se na ideju da vrijednost jedne jedinice treba biti ekvivalentna svakoj drugoj jedinici. Bez mogućnosti odmrzavanja/otpora cenzuri i nemogućnosti zapljene, Bitcoin (i svaki drugi monetarni sustav) počinje gubiti zamjenjivost. Trgovci i platni procesori više ne mogu razumno prihvaćati Bitcoin bez provjere niza crnih lista i mnogo truda kako bi bili sigurni da će moći potrošiti Bitcoin koji prihvaćaju. Ako povjerenje u zamjenjivost Bitcoina deformira, njegova bi korist mogla biti značajno deformirana. Još jedno svojstvo koje proizlazi iz decentralizacije Bitcoina, je njegov otvoreni pristup. Ulagači iz Silicijske doline često ga nazivaju jednim od najzanimljivijih svojstava Bitcoina, a mnogi ga vole nazivati "bez dopuštenja". Sposobnost bilo koga, bilo gdje u svijetu, sa internetskom vezom, da prihvaća Bitcoin za robu i usluge i koristi Bitcoin za kupnju roba i usluga je vrlo uzbudljiva. Opet, ovo svojstvo ovisi o decentralizaciji Bitcoina. Iako postoje mnogi centralizirani pružatelji financijskih usluga, gdje mnogi od njih promoviraju svoju dostupnost bilo kome, sama njihova prisutnost kao centraliziranog tijela koje može proizvoljno uskratiti uslugu, čini ih podložnim budućim promjenama politike iz bilo kojeg razloga. PayPal je, na primjer, utemeljen na idealima univerzalnog pristupa elektroničkoj gotovini. Međutim, zbog svoje pozicije središnje vlasti, brzo je promijenio svoje politike, kako bi udovoljio pritiscima regulatora i politikama postojećeg financijskog sustava na koji se oslanjao. Ovih dana, PayPal je nadaleko poznat po zamrzavanju računa i oduzimanju imovine uz malo ili nimalo upozorenja. U osnovi, oslanjanje na centralizirane strane za usluge nije kompatibilno s univerzalnim otvorenim pristupom u financijskom svijetu. Primijetit ćete da se sve gore navedene kritične značajke, one koje Bitcoin čine tako uzbudljivim za sve nas, centralizirani sistemi već neko vrijeme mogu implementirati. Zapravo to se radilo i prije, u učinkovitijim sustavima od Bitcoina. Naravno, nikada nisu potrajali, gubeći kritična svojstva nakon podešavanja kako bi se popravila ova ili ona stvar, implementirajući regulatorne sustave cenzure izravno u osnovne slojeve, ograničavajući pristup rastu dobiti i potpuno gašenje. Stvarno, decentralizacija u Bitcoinu sama po sebi nije značajka, već je umjesto toga jedini način za koji znamo da održimo značajke koje želimo u sustavima kojima upravljaju ljudi. [Originalni tekst](https://bluematt.bitcoin.ninja/2016/01/14/decentralization/)
@ bf47c19e:c3d2573b
2025-02-26 21:07:23Originalni tekst na [dvadesetjedan.com](https://dvadesetjedan.com/blog/zasto-je-vazna-decentralizacija-bitcoina). ###### Autor: [Matt Corallo](https://x.com/TheBlueMatt) / Prevod na hrvatski: [Davor](https://t.me/davor_e) --- Bitcoineri, od programera Bitcoin Core-a preko dugogodišnjih entuzijasta Bitcoina do nedavnih pronalazača /r/Bitcoina, vole razgovarati o tome kako je decentralizacija Bitcoina njegova ultimativna značajka. Doduše, rijetko vidite da netko objašnjava zašto je decentralizacija važna. Zasigurno je to zanimljiva značajka iz perspektive računalne znanosti, no zašto bi potrošači, tvrtke ili investitori marili za to? Ova objava je pokušaj da se napiše zašto je decentralizacija temelj vrijednosti Bitcoina i što je još važnije, postavi buduće objave u kojima se govori o tome kada ona to nije. Kada Bitcoineri govore o decentralizaciji Bitcoina, prva stvar koja se pojavljuje je često spominjani nedostatak inherentnog povjerenja u treću stranu. Dok je dobro postavljeno povjerenje preduvjet za učinkovit rad mnogih sustava, jednom kada se takvo povjerenje izgubi, sustavi mogu postati nevjerojatno krhki. Uzmimo, za primjer, povjerenje u američke banke prije uspostave FDIC-a (Federal Deposit Insurance Corporation). Dok je pristup bankovnim uslugama omogućio više pogodnosti i mnogim tvrtkama učinkovitije poslovanje, poznato je da su banke propadale, pritom upropaštavajući sa sobom sva sredstva klijenata. Dok je predstavljanje FDIC-a i sličnih programa decentraliziralo povjerenje u financijske institucije s jedne strane na dvije, transakcije u velikom dijelu svijeta ne nude takvu zaštitu. Čak i uz takve programe, pojedinci nisu univerzalno zaštićeni od gubitka preko granica i preko određene vrijednosti. U novije vrijeme, propisi koji dopuštaju pojedinim državnim dužnosnicima jednostrano oduzimanje imovine postali su uobičajeni. Naročito u SAD-u, sada zloglasna “Operacija Choke Point” i programi oduzimanja civilne imovine, omogućili su službenicima za provođenje zakona i privatnim institucijama da zapljenjuju financijsku imovinu i uskraćuju financijske usluge uz malo ili nimalo nadzora. Uklanjanje provjerenih skrbnika i stvaranje sustava s likvidnom imovinom, koja se ne može zaplijeniti, ima potencijal pružiti pouzdanije financijske usluge mnogima koji inače ne bi mogli djelovati učinkovito ili uopće ne bi mogli djelovati. Ova mogućnost da se Bitcoin ne može zaplijeniti, omogućena je samo zbog nedostatka za centraliziranim povjerenjem. Centralizirani sustavi elektroničke gotovine i financijski sustavi su pokušali pružiti takvu pouzdanost, propisi i poslovna stvarnost su to gotovo univerzalno spriječili. Svojstvo koje je jednako važno za sposobnost Bitcoina da pruža financijske usluge zviždačima, stranim disidentima i porno zvijezdama je njegov otpor cenzuri transakcija. Sposobnost trećih strana da zaplijene imovinu rezultira izravnim i čistim novčanim gubitkom, zamrzavanje imovine može imati sličan učinak. Kada pojedinac ili organizacija više nisu u mogućnosti obavljati transakcije za plaćanje roba i usluga, njihova financijska imovina brzo gubi vrijednost. Iako Bitcoin ima vrlo dobru priču o nemogućnosti zapljene (svaka strana u sustavu nameće nemogućnost bilo koga da potroši Bitcoin bez dodanog privatnog ključa), njegova priča o otporu cenzuri je malo utančanija. U svijetu u kojem nijedan rudar Bitcoina nema više od 1% ukupne hash snage (ili nešto drugo što je jednako decentralizirano), trebalo bi biti lako pronaći rudara koji je ili anoniman i prihvaća sve transakcije ili je u nadležnosti koja ne pokušava cenzurirati vaše transakcije. Naravno, ovo nije svijet kakav danas imamo, a cenzura transakcija jedan je od većih razloga da se ozbiljno zabrinemo centralizacijom rudarenja (za pune čvorove). Ipak, mogućnost pojedinca da kupi hash snagu (u obliku lako dostupnog starog hardvera ili u obliku njegovog iznajmljivanja) za rudarenje svoje inače cenzurirane transakcije, opcija je sve dok je pravilo najdužeg lanca na snazi kod svih rudara. Iako je znatno skuplji nego što bi bio u istinski decentraliziranom Bitcoinu, to omogućuje Bitcoinu da zadrži neka od svojih anti-cenzuriranih svojstava. Ako ste već dovoljno dugo u priči oko Bitcoina, možda ćete prepoznati gornja svojstva kao kritična za zamjenjivost. Zamjenjivost, kao ključno svojstvo svakog monetarnog instrumenta, odnosi se na ideju da vrijednost jedne jedinice treba biti ekvivalentna svakoj drugoj jedinici. Bez mogućnosti odmrzavanja/otpora cenzuri i nemogućnosti zapljene, Bitcoin (i svaki drugi monetarni sustav) počinje gubiti zamjenjivost. Trgovci i platni procesori više ne mogu razumno prihvaćati Bitcoin bez provjere niza crnih lista i mnogo truda kako bi bili sigurni da će moći potrošiti Bitcoin koji prihvaćaju. Ako povjerenje u zamjenjivost Bitcoina deformira, njegova bi korist mogla biti značajno deformirana. Još jedno svojstvo koje proizlazi iz decentralizacije Bitcoina, je njegov otvoreni pristup. Ulagači iz Silicijske doline često ga nazivaju jednim od najzanimljivijih svojstava Bitcoina, a mnogi ga vole nazivati "bez dopuštenja". Sposobnost bilo koga, bilo gdje u svijetu, sa internetskom vezom, da prihvaća Bitcoin za robu i usluge i koristi Bitcoin za kupnju roba i usluga je vrlo uzbudljiva. Opet, ovo svojstvo ovisi o decentralizaciji Bitcoina. Iako postoje mnogi centralizirani pružatelji financijskih usluga, gdje mnogi od njih promoviraju svoju dostupnost bilo kome, sama njihova prisutnost kao centraliziranog tijela koje može proizvoljno uskratiti uslugu, čini ih podložnim budućim promjenama politike iz bilo kojeg razloga. PayPal je, na primjer, utemeljen na idealima univerzalnog pristupa elektroničkoj gotovini. Međutim, zbog svoje pozicije središnje vlasti, brzo je promijenio svoje politike, kako bi udovoljio pritiscima regulatora i politikama postojećeg financijskog sustava na koji se oslanjao. Ovih dana, PayPal je nadaleko poznat po zamrzavanju računa i oduzimanju imovine uz malo ili nimalo upozorenja. U osnovi, oslanjanje na centralizirane strane za usluge nije kompatibilno s univerzalnim otvorenim pristupom u financijskom svijetu. Primijetit ćete da se sve gore navedene kritične značajke, one koje Bitcoin čine tako uzbudljivim za sve nas, centralizirani sistemi već neko vrijeme mogu implementirati. Zapravo to se radilo i prije, u učinkovitijim sustavima od Bitcoina. Naravno, nikada nisu potrajali, gubeći kritična svojstva nakon podešavanja kako bi se popravila ova ili ona stvar, implementirajući regulatorne sustave cenzure izravno u osnovne slojeve, ograničavajući pristup rastu dobiti i potpuno gašenje. Stvarno, decentralizacija u Bitcoinu sama po sebi nije značajka, već je umjesto toga jedini način za koji znamo da održimo značajke koje želimo u sustavima kojima upravljaju ljudi. [Originalni tekst](https://bluematt.bitcoin.ninja/2016/01/14/decentralization/) @ bf47c19e:c3d2573b
2025-02-26 21:00:54Originalni tekst na [dvadesetjedan.com](https://dvadesetjedan.com/blog/bitcoin-privatnost-najbolje-prakse). ###### Autor: [Gigi](https://dergigi.com/2021/03/14/bitcoin-privacy-best-practices/) / Prevod na srpski: [Plumsky](https://t.me/Plumski) --- > Postoji sveto carstvo privatnosti za svakog čoveka gde on bira i pravi odluke – carstvo stvoreno na bazičnim pravima i slobode koje zakon, generalno, ne sme narušavati. Džefri Fišer, Arhiepiskop Canterberija (1959) Pre ne toliko dugo, uobičajen režim interneta je bio neenkriptovan običan tekst (plain text). Svi su mogli špiunirati svakoga i mnogi nisu o tome ni razmišljali. Globalno obelodanjivanje nadzora 2013. je to promenilo i danas se koriste mnogo bezbedniji protokoli i end-to-end enkripcija postaje standard sve više. Iako bitcoin postaje tinejdžer, mi smo – metaforično govoreći – i dalje u dobu običnog teksta narandžastog novčića. Bitcoin je radikalno providljiv protokol sam po sebi, ali postoje značajni načini da korisnik zaštiti svoju privatnost. U ovom članku želimo da istaknemo neke od ovih strategija, prodiskutujemo najbolje prakse, i damo preporuke koje mogu primeniti i bitcoin novajlije i veterani. #### Zašto je privatnost bitna > Privatnost je potrebna da bi otvoreno društvo moglo da funkcioniše u digitalnoj eri. Privatnost nije isto što i tajanstvenost. Privatna stvar je nešto što neko ne želi da ceo svet zna, a tajna stvar je nešto što neko ne želi bilo ko da zna. Privatnost je moć da se čovek selektivno otkriva svom okruženju. Ovim snažnim rečima Erik Hjus je započeo svoj tekst Sajferpankov Manifesto (Cypherpunk's Manifesto) 1993. Razlika između privatnosti i tajanstvenosti je suptilna ali jako važna. Odlučiti se za privatnost ne znači da neko ima tajne koje želi sakriti. Da ovo ilustrujemo shvatite samo da ono što obavljate u svom toaletu ili u spavaćoj sobi nije niti ilegalno niti tajna (u mnogim slučajevima), ali vi svejedno odlučujete da zatvorite vrata i navučete zavese. Slično tome, koliko para imate i gde ih trošite nije naručito tajna stvar. Ipak, to bi trebalo biti privatan slučaj. Mnogi bi se složili da vaš šef ne treba da zna gde vi trošite vašu platu. Privatnosti je čak zaštićena od strane mnogobrojnih internacionalnih nadležnih organa. Iz Američke Deklaracije Prava i Dužnosti Čoveka (American Declaration of the Rights and Duties of Man) Ujedinjenim Nacijama, napisano je da je privatnost fundamentalno prava gradjana širom sveta. > Niko ne sme biti podvrgnut smetnjama njegovoj privatnosti, porodici, rezidenciji ili komunikacijama, niti napadnuta njegova čast i reputacija. Svi imaju pravo da se štite zakonom protiv takvih smetnja ili napada. Artikal 12, Deklaracija Ljudskih Prava Ujedinjenih Nacija #### Bitcoin i privatnost Iako je bitcoin često opisivan kao anoniman način plaćanja medijima, on u stvari poseduje potpuno suprotne osobine. On je poluanoniman u najboljem slučaju i danas mnogima nije ni malo lako primeniti taktike da bi bili sigurni da njihov poluanonimni identitet na bitcoin mreži ne bude povezan sa legalnim identitetom u stvarnom svetu. Bitcoin je otvoren sistem. On je javna baza podataka koju svako može da proučava i analizira. Znači, svaka transakcija koja je upisana u tu bazu kroz dokaz rada (proof-of-work) postojaće i biće otkrivena dokle god bitcoin postoji, što znači - zauvek. Ne primenjivati najbolje prakse privatnosti može imati štetne posledice u dalekoj budućnosti. Privatnost, kao sigurnost, je proces koji je težak, ali nije nemoguć. Alatke nastavljaju da se razvijaju koje čuvaju privatnost kad se koristi bitcoin and srećom mnoge od tih alatki su sve lakše za korišćenje. Nažalost ne postoji panacea u ovom pristupu. Mora se biti svesan svih kompromisa i usavršavati te prakse dok se one menjaju. #### Najbolje prakse privatnosti Kao i sve u bitcoinu, kontrola privatnosti je postepena, korak po korak, procedura. Naučiti i primeniti ove najbolje prakse zahteva strpljivost i odgovornost, tako da ne budite obeshrabreni ako vam se čini da je to sve previše. Svaki korak, koliko god bio mali, je korak u dobrom pravcu. Koje korake preduzeti da bi uvećali svoju privatnost: * Budite u vlasništvu sami svojih novčića * Nikad ne ponavljajte korišćenje istih adresa * Minimizirajte korišćenje servisa koji zahtevaju identitet (Know your customer - KYC) * Minimizirajte sve izloženosti trećim licima * Upravljajte svojim nodom * Koristite Lightning mrežu za male transakcije * Nemojte koristiti javne blok pretraživače za svoje transakcije * Koristite metodu CoinJoin često i rano pri nabavljanju svojih novčića **Budite u vlasništvu sami svojih novčića**: Ako ključevi nisu tvoji, onda nije ni bitcoin. Ako neko drugo drži vaš bitcoin za vas, oni znaju sve što se može znati: količinu, istoriju transakcija pa i sve buduće transakcije, itd. Preuzimanje vlasništva bitcoina u svoje ruke je prvi i najvažniji korak. **Nikad ne kroistite istu adresu dvaput**: Ponavljanje adresa poništava privatnost pošiljalca i primaoca bitcoina. Ovo se treba izbegavati pod svaku cenu. **Minimizirajte korišćenje servisa koji zahtevaju identitet (KYC)**: Vezivati svoj legalni identitet za svoje bitcoin adrese je zlo koje se zahteva od strane mnogih državnih nadležnosti. Dok je efektivnost ovih zakona i regulacija disputabilno, posledice njihovog primenjivanja su uglavnom štetne po korisnicima. Ovo je očigledno pošto je česta pojava da se te informacije često izlivaju iz slabo obezbeđenih digitalnih servera. Ako izaberete da koristite KYC servise da bi nabavljali bitcoin, proučite i razumite odnos između vas i tog biznisa. Vi ste poverljivi tom biznisu za sve vaše lične podatke, pa i buduće obezbeđenje tih podataka. Ako i dalje zarađujete kroz fiat novčani sistem, mi preporučujemo da koristite samo bitcoin ekskluzivne servise koji vam dozvoljavaju da autamatski kupujete bitcoin s vremena na vreme. Ako zelite da potpuno da izbegnete KYC, pregledajte https://bitcoinqna.github.io/noKYConly/. **Minimizirajte sve izloženosti trećim licima**: Poverljivost trećim licima je bezbednosna rupa (https://nakamotoinstitute.org/trusted-third-parties/). Ako možete biti poverljivi samo sebi, onda bi to tako trebalo da bude. **Upravljajte svojim nodom**: Ako nod nije tvoj, onda nisu ni pravila. Upravljanje svojim nodom je suštinska potreba da bi se bitcoin koristio na privatan način. Svaka interakcija sa bitcoin mrežom je posrednjena nodom. Ako vi taj nod ne upravljate, čiji god nod koristite može da vidi sve što vi radite. Ova upustva (https://bitcoiner.guide/node/) su jako korisna da bi započeli proces korišćenja svog noda. **Koristite Lightning mrežu za male transakcije**: Pošto Lightning protokol ne koristi glavnu bitcoin mrežu za trasakcije onda je i samim tim povećana privatnost korišćenja bez dodatnog truda. Iako je i dalje rano, oni apsolutno bezobzirni periodi Lightning mreže su verovatno daleko iza nas. Korišćenje Lightning-a za transakcije malih i srednjih veličina će vam pomoći da uvećate privatnost a da smanjite naplate svojih pojedinačnih bitcoin transakcija. **Nemojte koristiti javne blok pretraživače za svoje transakcije**: Proveravanje adresa na javnim blok pretraživačima povezuje te adrese sa vašim IP podacima, koji se onda mogu koristiti da se otkrije vaš identitet. Softveri kao Umbrel i myNode vam omogućavaju da lako koristite sami svoj blok pretraživač. Ako morate koristiti javne pretraživače, uradite to uz VPN ili Tor. **Koristite CoinJoin često i rano pri nabavljanju svojih novčića**: Pošto je bitcoin večan, primenjivanje saradničkih CoinJoin praksa će vam obezbediti privatnost u budućnosti. Dok su CoinJoin transakcije svakovrsne, softveri koji su laki za korišćenje već sad postoje koji mogu automatizovati ovu vrstu transakcija. Samourai Whirlpool (https://samouraiwallet.com/whirlpool) je odličan izbor za Android korisnike. Joinmarket (https://github.com/joinmarket-webui/jam) se može koristiti na vašem nodu. A servisi postoje koji pri snabdevanju vašeg bitcoina istog trenutka obave CoinJoin tranzakciju automatski. #### Zaključak Svi bi trebalo da se potrude da koriste bitcoin na što privatniji način. Privatnost nije isto što i tajanstvenost. Privatnost je ljudsko pravo i mi svi trebamo da branimo i primenljujemo to pravo. Teško je izbrisati postojeće informacije sa interneta; a izbrisati ih sa bitcoin baze podataka je nemoguće. Iako su daleko od savršenih, alatke postoje danas koje vam omogućavaju da najbolje prakse privatnosti i vi sami primenite. Mi smo vam naglasili neke od njih i - kroz poboljšanje u bitcoin protokolu kroz Taproot i Schnorr - one će postajati sve usavršenije. Bitcoin postupci se ne mogu lako opisati korišćenjem tradicionalnim konceptima. Pitanja kao što su "Ko je vlasnik ovog novca?" ili "Odakle taj novac potiče?" postaju sve teža da se odgovore a u nekim okolnostima postaju potpuno beznačajna. Satoši je dizajnirao bitcoin misleći na privatnost. Na nivou protokola svaka bitcoin transakcija je proces "topljenja" koji za sobom samo ostavlja heuristične mrvice hleba. Protokolu nije bitno odakle se pojavio bilo koji bitcoin ili satoši. Niti je njega briga ko je legalan identitet vlasnika. Protokolu je samo važno da li su digitalni potpisi validni. Dokle god je govor slobodan, potpisivanje poruka - privatno ili ne - ne sme biti kriminalan postupak. Dodatni Resursi [This Month in Bitcoin Privacy](https://enegnei.github.io/This-Month-In-Bitcoin-Privacy/) | Janine [Hodl Privacy FAQ](https://6102bitcoin.com/faq-hodl-privacy/) | 6102 [Digital Privacy](https://6102bitcoin.com/blog/digital-privacy/) | 6102 [UseWhirlpool.com](http://usewhirlpool.com/) | Bitcoin Q+A [Bitcoin Privacy Guide](https://bitcoiner.guide/privacy/) | Bitcoin Q+A Ovaj članak napisan je u saradnji sa Matt Odellom, nezavisnim bitcoin istraživačem. Nađite njegove preporuke za privatnost na [werunbtc.com](https://werunbtc.com/) [Originalni tekst](https://dergigi.com/2021/03/14/bitcoin-privacy-best-practices/)
@ bf47c19e:c3d2573b
2025-02-26 21:00:54Originalni tekst na [dvadesetjedan.com](https://dvadesetjedan.com/blog/bitcoin-privatnost-najbolje-prakse). ###### Autor: [Gigi](https://dergigi.com/2021/03/14/bitcoin-privacy-best-practices/) / Prevod na srpski: [Plumsky](https://t.me/Plumski) --- > Postoji sveto carstvo privatnosti za svakog čoveka gde on bira i pravi odluke – carstvo stvoreno na bazičnim pravima i slobode koje zakon, generalno, ne sme narušavati. Džefri Fišer, Arhiepiskop Canterberija (1959) Pre ne toliko dugo, uobičajen režim interneta je bio neenkriptovan običan tekst (plain text). Svi su mogli špiunirati svakoga i mnogi nisu o tome ni razmišljali. Globalno obelodanjivanje nadzora 2013. je to promenilo i danas se koriste mnogo bezbedniji protokoli i end-to-end enkripcija postaje standard sve više. Iako bitcoin postaje tinejdžer, mi smo – metaforično govoreći – i dalje u dobu običnog teksta narandžastog novčića. Bitcoin je radikalno providljiv protokol sam po sebi, ali postoje značajni načini da korisnik zaštiti svoju privatnost. U ovom članku želimo da istaknemo neke od ovih strategija, prodiskutujemo najbolje prakse, i damo preporuke koje mogu primeniti i bitcoin novajlije i veterani. #### Zašto je privatnost bitna > Privatnost je potrebna da bi otvoreno društvo moglo da funkcioniše u digitalnoj eri. Privatnost nije isto što i tajanstvenost. Privatna stvar je nešto što neko ne želi da ceo svet zna, a tajna stvar je nešto što neko ne želi bilo ko da zna. Privatnost je moć da se čovek selektivno otkriva svom okruženju. Ovim snažnim rečima Erik Hjus je započeo svoj tekst Sajferpankov Manifesto (Cypherpunk's Manifesto) 1993. Razlika između privatnosti i tajanstvenosti je suptilna ali jako važna. Odlučiti se za privatnost ne znači da neko ima tajne koje želi sakriti. Da ovo ilustrujemo shvatite samo da ono što obavljate u svom toaletu ili u spavaćoj sobi nije niti ilegalno niti tajna (u mnogim slučajevima), ali vi svejedno odlučujete da zatvorite vrata i navučete zavese. Slično tome, koliko para imate i gde ih trošite nije naručito tajna stvar. Ipak, to bi trebalo biti privatan slučaj. Mnogi bi se složili da vaš šef ne treba da zna gde vi trošite vašu platu. Privatnosti je čak zaštićena od strane mnogobrojnih internacionalnih nadležnih organa. Iz Američke Deklaracije Prava i Dužnosti Čoveka (American Declaration of the Rights and Duties of Man) Ujedinjenim Nacijama, napisano je da je privatnost fundamentalno prava gradjana širom sveta. > Niko ne sme biti podvrgnut smetnjama njegovoj privatnosti, porodici, rezidenciji ili komunikacijama, niti napadnuta njegova čast i reputacija. Svi imaju pravo da se štite zakonom protiv takvih smetnja ili napada. Artikal 12, Deklaracija Ljudskih Prava Ujedinjenih Nacija #### Bitcoin i privatnost Iako je bitcoin često opisivan kao anoniman način plaćanja medijima, on u stvari poseduje potpuno suprotne osobine. On je poluanoniman u najboljem slučaju i danas mnogima nije ni malo lako primeniti taktike da bi bili sigurni da njihov poluanonimni identitet na bitcoin mreži ne bude povezan sa legalnim identitetom u stvarnom svetu. Bitcoin je otvoren sistem. On je javna baza podataka koju svako može da proučava i analizira. Znači, svaka transakcija koja je upisana u tu bazu kroz dokaz rada (proof-of-work) postojaće i biće otkrivena dokle god bitcoin postoji, što znači - zauvek. Ne primenjivati najbolje prakse privatnosti može imati štetne posledice u dalekoj budućnosti. Privatnost, kao sigurnost, je proces koji je težak, ali nije nemoguć. Alatke nastavljaju da se razvijaju koje čuvaju privatnost kad se koristi bitcoin and srećom mnoge od tih alatki su sve lakše za korišćenje. Nažalost ne postoji panacea u ovom pristupu. Mora se biti svesan svih kompromisa i usavršavati te prakse dok se one menjaju. #### Najbolje prakse privatnosti Kao i sve u bitcoinu, kontrola privatnosti je postepena, korak po korak, procedura. Naučiti i primeniti ove najbolje prakse zahteva strpljivost i odgovornost, tako da ne budite obeshrabreni ako vam se čini da je to sve previše. Svaki korak, koliko god bio mali, je korak u dobrom pravcu. Koje korake preduzeti da bi uvećali svoju privatnost: * Budite u vlasništvu sami svojih novčića * Nikad ne ponavljajte korišćenje istih adresa * Minimizirajte korišćenje servisa koji zahtevaju identitet (Know your customer - KYC) * Minimizirajte sve izloženosti trećim licima * Upravljajte svojim nodom * Koristite Lightning mrežu za male transakcije * Nemojte koristiti javne blok pretraživače za svoje transakcije * Koristite metodu CoinJoin često i rano pri nabavljanju svojih novčića **Budite u vlasništvu sami svojih novčića**: Ako ključevi nisu tvoji, onda nije ni bitcoin. Ako neko drugo drži vaš bitcoin za vas, oni znaju sve što se može znati: količinu, istoriju transakcija pa i sve buduće transakcije, itd. Preuzimanje vlasništva bitcoina u svoje ruke je prvi i najvažniji korak. **Nikad ne kroistite istu adresu dvaput**: Ponavljanje adresa poništava privatnost pošiljalca i primaoca bitcoina. Ovo se treba izbegavati pod svaku cenu. **Minimizirajte korišćenje servisa koji zahtevaju identitet (KYC)**: Vezivati svoj legalni identitet za svoje bitcoin adrese je zlo koje se zahteva od strane mnogih državnih nadležnosti. Dok je efektivnost ovih zakona i regulacija disputabilno, posledice njihovog primenjivanja su uglavnom štetne po korisnicima. Ovo je očigledno pošto je česta pojava da se te informacije često izlivaju iz slabo obezbeđenih digitalnih servera. Ako izaberete da koristite KYC servise da bi nabavljali bitcoin, proučite i razumite odnos između vas i tog biznisa. Vi ste poverljivi tom biznisu za sve vaše lične podatke, pa i buduće obezbeđenje tih podataka. Ako i dalje zarađujete kroz fiat novčani sistem, mi preporučujemo da koristite samo bitcoin ekskluzivne servise koji vam dozvoljavaju da autamatski kupujete bitcoin s vremena na vreme. Ako zelite da potpuno da izbegnete KYC, pregledajte https://bitcoinqna.github.io/noKYConly/. **Minimizirajte sve izloženosti trećim licima**: Poverljivost trećim licima je bezbednosna rupa (https://nakamotoinstitute.org/trusted-third-parties/). Ako možete biti poverljivi samo sebi, onda bi to tako trebalo da bude. **Upravljajte svojim nodom**: Ako nod nije tvoj, onda nisu ni pravila. Upravljanje svojim nodom je suštinska potreba da bi se bitcoin koristio na privatan način. Svaka interakcija sa bitcoin mrežom je posrednjena nodom. Ako vi taj nod ne upravljate, čiji god nod koristite može da vidi sve što vi radite. Ova upustva (https://bitcoiner.guide/node/) su jako korisna da bi započeli proces korišćenja svog noda. **Koristite Lightning mrežu za male transakcije**: Pošto Lightning protokol ne koristi glavnu bitcoin mrežu za trasakcije onda je i samim tim povećana privatnost korišćenja bez dodatnog truda. Iako je i dalje rano, oni apsolutno bezobzirni periodi Lightning mreže su verovatno daleko iza nas. Korišćenje Lightning-a za transakcije malih i srednjih veličina će vam pomoći da uvećate privatnost a da smanjite naplate svojih pojedinačnih bitcoin transakcija. **Nemojte koristiti javne blok pretraživače za svoje transakcije**: Proveravanje adresa na javnim blok pretraživačima povezuje te adrese sa vašim IP podacima, koji se onda mogu koristiti da se otkrije vaš identitet. Softveri kao Umbrel i myNode vam omogućavaju da lako koristite sami svoj blok pretraživač. Ako morate koristiti javne pretraživače, uradite to uz VPN ili Tor. **Koristite CoinJoin često i rano pri nabavljanju svojih novčića**: Pošto je bitcoin večan, primenjivanje saradničkih CoinJoin praksa će vam obezbediti privatnost u budućnosti. Dok su CoinJoin transakcije svakovrsne, softveri koji su laki za korišćenje već sad postoje koji mogu automatizovati ovu vrstu transakcija. Samourai Whirlpool (https://samouraiwallet.com/whirlpool) je odličan izbor za Android korisnike. Joinmarket (https://github.com/joinmarket-webui/jam) se može koristiti na vašem nodu. A servisi postoje koji pri snabdevanju vašeg bitcoina istog trenutka obave CoinJoin tranzakciju automatski. #### Zaključak Svi bi trebalo da se potrude da koriste bitcoin na što privatniji način. Privatnost nije isto što i tajanstvenost. Privatnost je ljudsko pravo i mi svi trebamo da branimo i primenljujemo to pravo. Teško je izbrisati postojeće informacije sa interneta; a izbrisati ih sa bitcoin baze podataka je nemoguće. Iako su daleko od savršenih, alatke postoje danas koje vam omogućavaju da najbolje prakse privatnosti i vi sami primenite. Mi smo vam naglasili neke od njih i - kroz poboljšanje u bitcoin protokolu kroz Taproot i Schnorr - one će postajati sve usavršenije. Bitcoin postupci se ne mogu lako opisati korišćenjem tradicionalnim konceptima. Pitanja kao što su "Ko je vlasnik ovog novca?" ili "Odakle taj novac potiče?" postaju sve teža da se odgovore a u nekim okolnostima postaju potpuno beznačajna. Satoši je dizajnirao bitcoin misleći na privatnost. Na nivou protokola svaka bitcoin transakcija je proces "topljenja" koji za sobom samo ostavlja heuristične mrvice hleba. Protokolu nije bitno odakle se pojavio bilo koji bitcoin ili satoši. Niti je njega briga ko je legalan identitet vlasnika. Protokolu je samo važno da li su digitalni potpisi validni. Dokle god je govor slobodan, potpisivanje poruka - privatno ili ne - ne sme biti kriminalan postupak. Dodatni Resursi [This Month in Bitcoin Privacy](https://enegnei.github.io/This-Month-In-Bitcoin-Privacy/) | Janine [Hodl Privacy FAQ](https://6102bitcoin.com/faq-hodl-privacy/) | 6102 [Digital Privacy](https://6102bitcoin.com/blog/digital-privacy/) | 6102 [UseWhirlpool.com](http://usewhirlpool.com/) | Bitcoin Q+A [Bitcoin Privacy Guide](https://bitcoiner.guide/privacy/) | Bitcoin Q+A Ovaj članak napisan je u saradnji sa Matt Odellom, nezavisnim bitcoin istraživačem. Nađite njegove preporuke za privatnost na [werunbtc.com](https://werunbtc.com/) [Originalni tekst](https://dergigi.com/2021/03/14/bitcoin-privacy-best-practices/) @ d6c48950:54d57756
2025-02-26 20:33:44I wanted to write my system for bitcoin inheritance and seed storage that will likely outlive me - the reason why is recently bitkey (squares hardware wallet) announced their inheritance system which is a vast improvement but still has a single point of failure square and the app they maintain though this is still a good thing and will improve the ecosystem and raise awareness there is a cheaper method that is just a secure but doesn’t have a single point of failure. ## 2/3 seed storage 2/3 seed storage is actually a pretty simple way of splitting up a key into three parts, if you have one part it’s useless, if you have any two parts it’s complete - if one piece is destroyed it doesn’t matter (demo below) | A<br/> | B<br/> | C<br/> | |-----|-----|-----| | 1. apple<br/> | 2. zipper<br/> | 3. dog<br/> | | 4. tree<br/> | 5. car<br/> | 6. bus<br/> | | 7. banana<br/> | 8. motorbike<br/> | 9. dune<br/> | | 10. frank<br/> | 11. foundation<br/> | 12. meditation<br/> | | 13. whiteboard<br/> | 14. laptop<br/> | 15. books<br/> | | 16. perfume<br/> | 17. computer<br/> | 18. stone<br/> | | 19. brick<br/> | 20. spreadsheet<br/> | 21. bird<br/> | | 22. blog<br/> | 23. leaves<br/> | 24. grass<br/> | This is a seed phrase split up into three parts (a,b,c) - now you can create your 3 parts (1) | A<br/> | B<br/> | | |-----|-----|-----| | 1. apple<br/> | 2. zipper<br/> | | | 4. tree<br/> | 5. car<br/> | | | 7. banana<br/> | 8. motorbike<br/> | | | 10. frank<br/> | 11. foundation<br/> | | | 13. whiteboard<br/> | 14. laptop<br/> | | | 16. perfume<br/> | 17. computer<br/> | | | 19. brick<br/> | 20. spreadsheet<br/> | | | 22. blog<br/> | 23. leaves<br/> | | (2) | | B<br/> | C<br/> | |-----|-----|-----| | | 2. zipper<br/> | 3. dog<br/> | | | 5. car<br/> | 6. bus<br/> | | | 8. motorbike<br/> | 9. dune<br/> | | | 11. foundation<br/> | 12. meditation<br/> | | | 14. laptop<br/> | 15. books<br/> | | | 17. computer<br/> | 18. stone<br/> | | | 20. spreadsheet<br/> | 21. bird<br/> | | | 23. leaves<br/> | 24. grass<br/> | (3) | A<br/> | | C<br/> | |-----|-----|-----| | 1. apple<br/> | | 3. dog<br/> | | 4. tree<br/> | | 6. bus<br/> | | 7. banana<br/> | | 9. dune<br/> | | 10. frank<br/> | | 12. meditation<br/> | | 13. whiteboard<br/> | | 15. books<br/> | | 16. perfume<br/> | | 18. stone<br/> | | 19. brick<br/> | | 21. bird<br/> | | 22. blog<br/> | | 24. grass<br/> | Now you have your parts, you need at least 2/3 for it to be useful. ## distribution Distribution is pretty simple, keep one part, give a part to whomever you want to be able to claim your bitcoin upon death, give a part to someone you trust (along with instructions to post it to the claimant upon your death). ## failure For this to fail either 1. Two out of three parts would have to be destroyed 2. The trusted party would have to not post it AND either your part or the claimants would have to be destroyed 3. The trusted party cannot figure out how to use a seed phrase (by default you should include instructions i.e NEVER SHARE THE SEED, transfer to a recommended wallet from bitcoin.org then transfer to an exchange and sell)
@ d6c48950:54d57756
2025-02-26 20:33:44I wanted to write my system for bitcoin inheritance and seed storage that will likely outlive me - the reason why is recently bitkey (squares hardware wallet) announced their inheritance system which is a vast improvement but still has a single point of failure square and the app they maintain though this is still a good thing and will improve the ecosystem and raise awareness there is a cheaper method that is just a secure but doesn’t have a single point of failure. ## 2/3 seed storage 2/3 seed storage is actually a pretty simple way of splitting up a key into three parts, if you have one part it’s useless, if you have any two parts it’s complete - if one piece is destroyed it doesn’t matter (demo below) | A<br/> | B<br/> | C<br/> | |-----|-----|-----| | 1. apple<br/> | 2. zipper<br/> | 3. dog<br/> | | 4. tree<br/> | 5. car<br/> | 6. bus<br/> | | 7. banana<br/> | 8. motorbike<br/> | 9. dune<br/> | | 10. frank<br/> | 11. foundation<br/> | 12. meditation<br/> | | 13. whiteboard<br/> | 14. laptop<br/> | 15. books<br/> | | 16. perfume<br/> | 17. computer<br/> | 18. stone<br/> | | 19. brick<br/> | 20. spreadsheet<br/> | 21. bird<br/> | | 22. blog<br/> | 23. leaves<br/> | 24. grass<br/> | This is a seed phrase split up into three parts (a,b,c) - now you can create your 3 parts (1) | A<br/> | B<br/> | | |-----|-----|-----| | 1. apple<br/> | 2. zipper<br/> | | | 4. tree<br/> | 5. car<br/> | | | 7. banana<br/> | 8. motorbike<br/> | | | 10. frank<br/> | 11. foundation<br/> | | | 13. whiteboard<br/> | 14. laptop<br/> | | | 16. perfume<br/> | 17. computer<br/> | | | 19. brick<br/> | 20. spreadsheet<br/> | | | 22. blog<br/> | 23. leaves<br/> | | (2) | | B<br/> | C<br/> | |-----|-----|-----| | | 2. zipper<br/> | 3. dog<br/> | | | 5. car<br/> | 6. bus<br/> | | | 8. motorbike<br/> | 9. dune<br/> | | | 11. foundation<br/> | 12. meditation<br/> | | | 14. laptop<br/> | 15. books<br/> | | | 17. computer<br/> | 18. stone<br/> | | | 20. spreadsheet<br/> | 21. bird<br/> | | | 23. leaves<br/> | 24. grass<br/> | (3) | A<br/> | | C<br/> | |-----|-----|-----| | 1. apple<br/> | | 3. dog<br/> | | 4. tree<br/> | | 6. bus<br/> | | 7. banana<br/> | | 9. dune<br/> | | 10. frank<br/> | | 12. meditation<br/> | | 13. whiteboard<br/> | | 15. books<br/> | | 16. perfume<br/> | | 18. stone<br/> | | 19. brick<br/> | | 21. bird<br/> | | 22. blog<br/> | | 24. grass<br/> | Now you have your parts, you need at least 2/3 for it to be useful. ## distribution Distribution is pretty simple, keep one part, give a part to whomever you want to be able to claim your bitcoin upon death, give a part to someone you trust (along with instructions to post it to the claimant upon your death). ## failure For this to fail either 1. Two out of three parts would have to be destroyed 2. The trusted party would have to not post it AND either your part or the claimants would have to be destroyed 3. The trusted party cannot figure out how to use a seed phrase (by default you should include instructions i.e NEVER SHARE THE SEED, transfer to a recommended wallet from bitcoin.org then transfer to an exchange and sell) @ 4c96d763:80c3ee30
2025-02-26 20:33:28# Changes ## William Casarin (2): - feat: add scramble flag for development text scrambling - feat: add --no-media flag to disable media display ## kernelkind (21): - use bincode - update ehttp to 0.5.0 - introduce UrlMimes - use mime_guess - add SupportedMimeType - rename ImageCache -> MediaCache - Use TexturedImage in MediaCache - render MediaCache method - move MediaCache rendering to render_media_cache call - support multiple media cache files - introduce Images - render Images method - migrate to using Images instead of MediaCache directly - URL mime hosted completeness - handle UrlCache io - introduce gif animation - handle gif state - integrate gifs - use SupportedMimeType for media_upload - render gif in PostView - fix mention crash pushed to [notedeck:refs/heads/master](http://git.jb55.com/notedeck/commit/a524bbd5a4601e8d7f2813871634caff476735b1.html)
@ 4c96d763:80c3ee30
2025-02-26 20:33:28# Changes ## William Casarin (2): - feat: add scramble flag for development text scrambling - feat: add --no-media flag to disable media display ## kernelkind (21): - use bincode - update ehttp to 0.5.0 - introduce UrlMimes - use mime_guess - add SupportedMimeType - rename ImageCache -> MediaCache - Use TexturedImage in MediaCache - render MediaCache method - move MediaCache rendering to render_media_cache call - support multiple media cache files - introduce Images - render Images method - migrate to using Images instead of MediaCache directly - URL mime hosted completeness - handle UrlCache io - introduce gif animation - handle gif state - integrate gifs - use SupportedMimeType for media_upload - render gif in PostView - fix mention crash pushed to [notedeck:refs/heads/master](http://git.jb55.com/notedeck/commit/a524bbd5a4601e8d7f2813871634caff476735b1.html) @ 2181959b:80f0d27d
2025-02-26 19:21:30أطلقت مايكروسوفت بهدوء إصدارًا مجانيًا من تطبيقات Office لأجهزة ويندوز، يتيح للمستخدمين تحرير المستندات دون الحاجة إلى اشتراك في Microsoft 365 أو ترخيص مدفوع. ومع ذلك، يأتي هذا الإصدار مع إعلانات دائمة وقيود على بعض الميزات الأساسية. **ما هي قيود الإصدار المجاني من تطبيقات Office؟** وفقًا لموقع Beebom، يعتمد الإصدار المجاني على التطبيقات المكتبية الكاملة لكنه يُقيد معظم الميزات خلف اشتراك Microsoft 365. وهذه القيود تتمثل في الآتي: 1: يتم عرض الإعلانات بشكل دائم داخل تطبيقات Word وPowerPoint وExcel أثناء العمل على المستندات. 2: يمكن حفظ الملفات فقط على OneDrive، دون دعم لتحرير الملفات المحلية. 3: لا يتوفر الإملاء الصوتي، والإضافات، والتنسيقات المتقدمة، وSmartArt، مما يجعله مناسبًا للمهام الأساسية فقط. **كيفية الوصول إلى الإصدار المجاني من تطبيقات Office؟** يمكن للمستخدمين تخطي طلب تسجيل الدخول عند تشغيل أحد تطبيقات Office لأول مرة، وبعد ذلك سيحصلون على خيار استخدامه مجانًا مقابل الإعلانات والميزات المحدودة. في هذا الوضع، يمكن فتح المستندات وعرضها وتحريرها، تمامًا كما هو الحال في إصدار Office على الويب. **هل هو متاح للجميع؟** حاليًا، يبدو أن هذا الإصدار لا يزال في مرحلة الاختبار المحدود، حيث لم يتمكن بعض المستخدمين من تجاوز شاشة تسجيل الدخول عند تشغيل Office. ومن المحتمل أن مايكروسوفت تختبر هذه النسخة في مناطق محددة أو مع مجموعة صغيرة من المستخدمين قبل إطلاقها رسميًا. حتى الآن، لم تُعلن الشركة رسميًا عن هذا الإصدار، ولم تذكره في مستندات الدعم الخاصة بها، لكن قد تكشف مايكروسوفت عن تفاصيل إضافية خلال الأيام أو الأسابيع المقبلة. [المصدر]( https://www.windowscentral.com/software-apps/office-365/microsoft-quietly-launches-free-ad-supported-version-of-office-apps-for-windows-with-limited-functionality)
@ 2181959b:80f0d27d
2025-02-26 19:21:30أطلقت مايكروسوفت بهدوء إصدارًا مجانيًا من تطبيقات Office لأجهزة ويندوز، يتيح للمستخدمين تحرير المستندات دون الحاجة إلى اشتراك في Microsoft 365 أو ترخيص مدفوع. ومع ذلك، يأتي هذا الإصدار مع إعلانات دائمة وقيود على بعض الميزات الأساسية. **ما هي قيود الإصدار المجاني من تطبيقات Office؟** وفقًا لموقع Beebom، يعتمد الإصدار المجاني على التطبيقات المكتبية الكاملة لكنه يُقيد معظم الميزات خلف اشتراك Microsoft 365. وهذه القيود تتمثل في الآتي: 1: يتم عرض الإعلانات بشكل دائم داخل تطبيقات Word وPowerPoint وExcel أثناء العمل على المستندات. 2: يمكن حفظ الملفات فقط على OneDrive، دون دعم لتحرير الملفات المحلية. 3: لا يتوفر الإملاء الصوتي، والإضافات، والتنسيقات المتقدمة، وSmartArt، مما يجعله مناسبًا للمهام الأساسية فقط. **كيفية الوصول إلى الإصدار المجاني من تطبيقات Office؟** يمكن للمستخدمين تخطي طلب تسجيل الدخول عند تشغيل أحد تطبيقات Office لأول مرة، وبعد ذلك سيحصلون على خيار استخدامه مجانًا مقابل الإعلانات والميزات المحدودة. في هذا الوضع، يمكن فتح المستندات وعرضها وتحريرها، تمامًا كما هو الحال في إصدار Office على الويب. **هل هو متاح للجميع؟** حاليًا، يبدو أن هذا الإصدار لا يزال في مرحلة الاختبار المحدود، حيث لم يتمكن بعض المستخدمين من تجاوز شاشة تسجيل الدخول عند تشغيل Office. ومن المحتمل أن مايكروسوفت تختبر هذه النسخة في مناطق محددة أو مع مجموعة صغيرة من المستخدمين قبل إطلاقها رسميًا. حتى الآن، لم تُعلن الشركة رسميًا عن هذا الإصدار، ولم تذكره في مستندات الدعم الخاصة بها، لكن قد تكشف مايكروسوفت عن تفاصيل إضافية خلال الأيام أو الأسابيع المقبلة. [المصدر]( https://www.windowscentral.com/software-apps/office-365/microsoft-quietly-launches-free-ad-supported-version-of-office-apps-for-windows-with-limited-functionality)