
@ Cryptape
2025-03-14 01:00:24
## Crypto Insights
### Privacy-Preserving One-Click k-of-n Multisig Descriptor Backup and Recovery Solution
This [post](https://delvingbitcoin.org/t/multisigbackup-com-backup-and-recover-a-k-of-n-descriptor-using-only-n-seeds/1430) introduces an open-source project [multisigbackup.com](http://multisigbackup.com/), designed for the backup and recovery of multisig descriptors as simple as possible by requiring only the threshold number of seeds.
The challenge is, to recover a 2-of-3 multisig wallet, at least two seed phrases and an output descriptor are needed. Users often store descriptors on laptops or in the cloud, which, while cost-effective, have poor inheritance and are prone to being lost or accidentally deleted. Additionally, services like Unchained, Casa, and Nunchuk offer annual paid custodial services, where they keep a copy of the descriptors.
[MultisigBackup.com](https://multisigbackup.com/), however, encrypts the descriptor and inscribes the data on the Bitcoin blockchain. Users only need to input their descriptor, and the tool will encrypt it and generate a taproot address, permanently saving the encrypted data with a single payment.
### Preventing Potential MEVil on Bitcoin: A Private Mempool Approach
To address the potential surge in MEVil on Bitcoin, developers Matt Corallo and 7d5x9 [discussed](https://delvingbitcoin.org/t/best-worst-case-mevil-response/1465) the best and worst-case scenarios. This proposal can be seen as an extension of Ethereum's PBS (Proposer-Bidder Separation) model, where the proposer doesn't submit a full block template but only bids on individual or group transactions inclusion with constraints, such as "I want to be the first transaction included, and it interacts with a DEX containing the string X." This ensures that the public mempool remains a reliable way to include transactions (because miners will fill their blocks from both the public mempool and private orders), providing censorship resistance similar to today while still allowing MEVil-extraction experts to pay miners for the inclusion of specific transactions.
The authors acknowledge that this design is highly centralized. However, developers must consider what Bitcoin will look like if MEVil becomes a significant part of mining and should be prepared for this shift in case it happens.
They also provide a more detailed explanation in [MEVpool: A Private Mempool Marketplace Standard](https://github.com/mevpool/mevpool/blob/0550f5d85e4023ff8ac7da5193973355b855bcc8/mevpool-marketplace.md).
### Progress of BTC DeFi-Related Projects
* **Bitlayer:** Following the previous [announcement](https://blog.bitlayer.org/Bitlayer_Advances_the_First_BitVM_Implementation_Through_Major_Strategic_Partnerships/) about advancing the BitVM implementation in collaboration with five chains, including Base, Starknet, Arbitrum, Sonic, and Plume Network, Bitlayer has recently established partnerships with [Celestia](https://x.com/BitlayerLabs/status/1899195108853235850) and [StakeStone](https://x.com/BitlayerLabs/status/1899007317850341453), further enhancing Bitcoin's liquidity.
* **BOB (Build-on-Bitcoin):** Continuously [advancing a series of Hybrid BTC yield products](https://blog.gobob.xyz/posts/bob-launches-hybrid-btc-yield-products-ushering-in-a-new-era-of-bitcoin-defi), building a multi-chain BTC yield layer. Recently, they also started collaborations with institutional digital asset platform [Fireblocks](https://x.com/FireblocksHQ) and the ZK & BitVM-based DeFi platform [Fiamma](https://x.com/fiamma_labs), among other projects.
### Underrated Privacy Tools on the Lightning Network
The author [designed](https://stacker.news/items/909079) two different Lightning Network roles— as "Lightning Service Provider" (LnSP) and "Liquidity Service Provider" (LiSP)—and introduced often overlooked concepts (such as Wrapped invoices, Just-in-time channels) and privacy-friendly tools (such as [zero-conf channels](https://github.com/lightningnetwork/lnd/blob/master/docs/zero_conf_channels.md), [zaplocker](https://github.com/supertestnet/zaplocker)) in each context respectively.
### Core Lightning Releases v25.02 with Onion Packet Filler Accreditation
Core Lightning [announced](https://x.com/Core_LN?ref_src=twsrc%5Egoogle%7Ctwcamp%5Eserp%7Ctwgr%5Eauthor) the release of v25.02, which introduces Onion Packet Filler Accreditation, with key features including:
* For Users: Channel backup turns peers into watchtowers, allowing user nodes to generate penalty transactions.
* For Network: Stricter checks implemented using [Splicing](https://www.btcstudy.org/2023/11/02/lightning-channel-splicing-principal-explained/) for better interoperability with Eclair.
For more details, refer to the [release note](https://github.com/ElementsProject/lightning/releases).
### Frostr: Splitting Nostr Private Keys for Enhanced Security
[Frostr](https://www.frostr.org/) is a tool utilizing FROST to provide simple t-of-n remote signing and key rotation protocols for Nostr. It breaks a user's Nostr secret key into several shares and uses subsets of these shares to sign messages. The benefits include:
* Enhanced security: Even if one share is lost or stolen, the user’s complete key remains confidential and controlled by themselves.
* Flexible key rotation: Users can replace or update key shares without altering their digital identity, ensuring that their digital identity and security are no longer threatened by private key leakage.
### Breaking Down the Bybit Hack: Lessons From Crypto’s Largest Heist
In this article, Matt Gleason [provides a detailed analysis](https://a16zcrypto.com/posts/article/bybit-hack-lessons/) of how the Bybit exchange and Safe multi-signature interface were compromised in crypto’s largest heist. He also highlights measures Safe could have taken to prevent or mitigate such attacks, including:
* Advanced capabilities to detect and respond to asset modifications.
* Advanced capabilities to detect when a developer is compromised.
* Tight controls around code repositories, build environments, deployments, and more to keep them from being easily modified; and, if they do need to be modified, to ensure that the right people are using the right process
The author also discussed this major heist in [this podcast](https://a16zcrypto.com/posts/podcast/bybit-hack-security/).
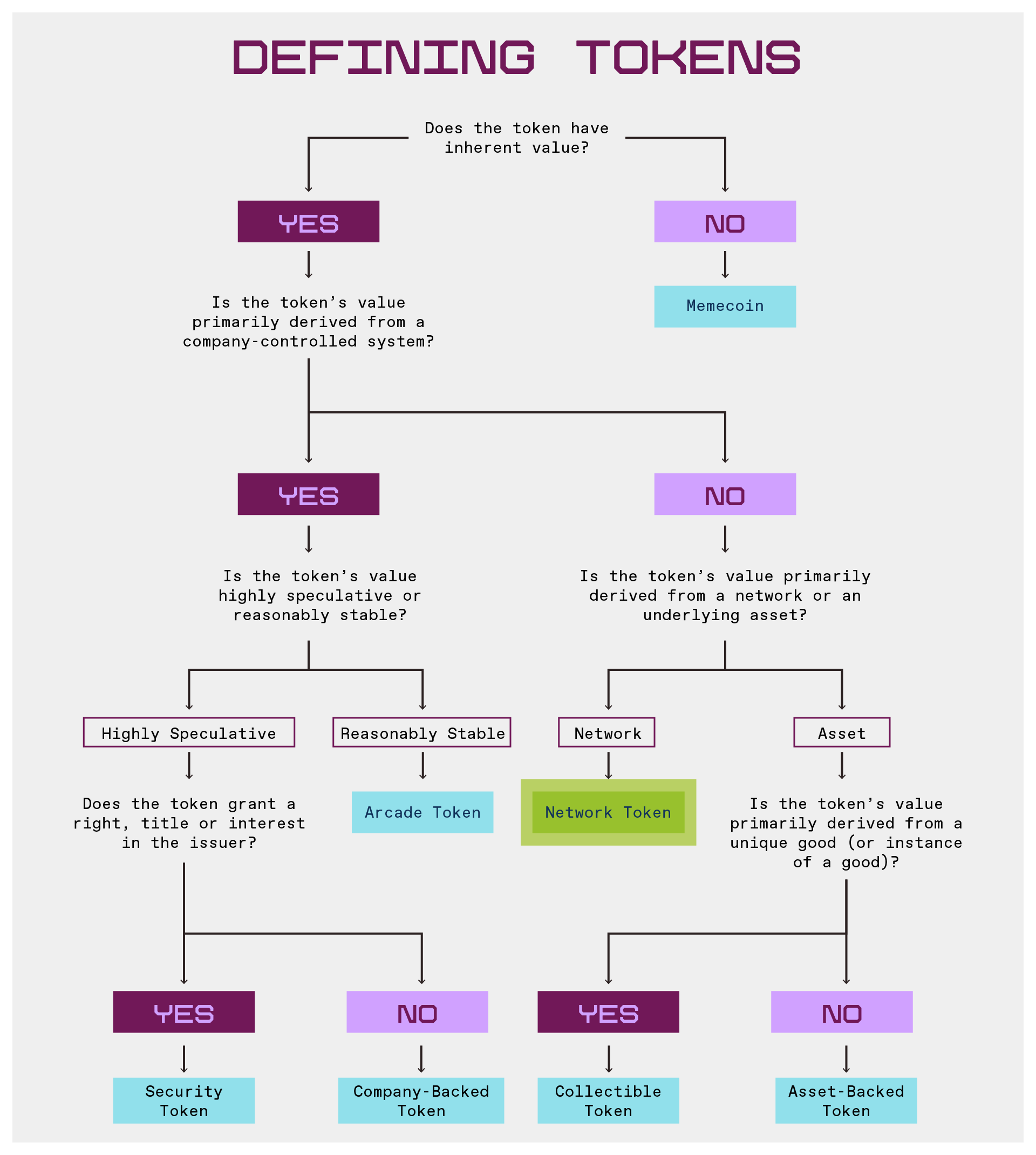
### Understanding Token Types and Their Design Implications
Any type of token fundamentally enables digital ownership. However, once tokens are embedded as part of software, they can be programmed to represent almost anything: Bitcoin as digital stores of value, Ethereum as productive and consumptive assets, collectibles like digital trading cards and game items, payment stablecoin like USDC, and digitized shares of stock, among others.

[This article](https://a16zcrypto.com/posts/article/defining-tokens/#section--8) points out that these design choices are important because different characteristics determine the applicable legal frameworks and defines various token types.
The author specifically mentions that meme coins are tokens with no inherent utility or value, and are only related to memes and community-driven initiatives, not related to networks, companies, or applications. The article also provides a flowchart to help quickly identify token types.
## Top Reads on Blockchain and Beyond
### BitVMX Efficiency Improvement with ESSPI Optimization
ESSPI is an optimized method that utilizes ECDSA / Schnorr signatures to sign the input of the BitVMX program, replacing the traditional inefficient one-time signature (OTS) scheme, like Lamport and Winternitz. Compared to the 1:200 ratio of Winternitz signatures, ESSPI achieves a 1:1 data expansion. The team also introduced 4 innovations to BitVMX, enabling it to verify uncompressed SPV proofs, STARKs, NOVAs, and Bulletproofs, expanding the applicability of BitVMX.
Full paper: [ESSPI: ECDSA/Schnorr Signed Program Input for BitVMX](https://bitvmx.org/files/esspi-ecdsa-input-bitvmx.pdf)
### Lattice-Based Privacy-Preserving Decentralized Multi-Party Payment Scheme
The problem addressed by this research is that existing privacy schemes that hide transaction amounts (such as the [MimbleWimble](https://www.elliptic.co/blog/explaining-mimblewimble-the-privacy-upgrade-to-litecoin) protocol) are only for one-to-one transactions between a payer and a payee, which have limited use cases and do not support multi-party transactions with multiple payers or payees.
The research introduces a new "privacy-preserving decentralized multi-party payment" (PDMP) scheme, which ensures that transaction amounts in multi-party transactions remain confidential to others. It defines the ideal functionality of this system, capturing the privacy and security properties of cryptocurrencies. The research instantiates a lattice-based PDMP protocol in a hybrid model, which can universally composable (UC) securely realize the functionality with a simulation-based security proof. To support this protocol, the team developed a lattice-based verifiable multi-secret sharing scheme and a lattice-based multi-prover non-interactive zero-knowledge argument, both of which are quantum-secure.
Full paper: [A lattice-based privacy-preserving decentralized multi-party payment scheme](https://www.sciencedirect.com/science/article/abs/pii/S1389128625000970)
 @ Cryptape
2025-03-14 01:00:24## Crypto Insights ### Privacy-Preserving One-Click k-of-n Multisig Descriptor Backup and Recovery Solution This [post](https://delvingbitcoin.org/t/multisigbackup-com-backup-and-recover-a-k-of-n-descriptor-using-only-n-seeds/1430) introduces an open-source project [multisigbackup.com](http://multisigbackup.com/), designed for the backup and recovery of multisig descriptors as simple as possible by requiring only the threshold number of seeds. The challenge is, to recover a 2-of-3 multisig wallet, at least two seed phrases and an output descriptor are needed. Users often store descriptors on laptops or in the cloud, which, while cost-effective, have poor inheritance and are prone to being lost or accidentally deleted. Additionally, services like Unchained, Casa, and Nunchuk offer annual paid custodial services, where they keep a copy of the descriptors. [MultisigBackup.com](https://multisigbackup.com/), however, encrypts the descriptor and inscribes the data on the Bitcoin blockchain. Users only need to input their descriptor, and the tool will encrypt it and generate a taproot address, permanently saving the encrypted data with a single payment. ### Preventing Potential MEVil on Bitcoin: A Private Mempool Approach To address the potential surge in MEVil on Bitcoin, developers Matt Corallo and 7d5x9 [discussed](https://delvingbitcoin.org/t/best-worst-case-mevil-response/1465) the best and worst-case scenarios. This proposal can be seen as an extension of Ethereum's PBS (Proposer-Bidder Separation) model, where the proposer doesn't submit a full block template but only bids on individual or group transactions inclusion with constraints, such as "I want to be the first transaction included, and it interacts with a DEX containing the string X." This ensures that the public mempool remains a reliable way to include transactions (because miners will fill their blocks from both the public mempool and private orders), providing censorship resistance similar to today while still allowing MEVil-extraction experts to pay miners for the inclusion of specific transactions. The authors acknowledge that this design is highly centralized. However, developers must consider what Bitcoin will look like if MEVil becomes a significant part of mining and should be prepared for this shift in case it happens. They also provide a more detailed explanation in [MEVpool: A Private Mempool Marketplace Standard](https://github.com/mevpool/mevpool/blob/0550f5d85e4023ff8ac7da5193973355b855bcc8/mevpool-marketplace.md). ### Progress of BTC DeFi-Related Projects * **Bitlayer:** Following the previous [announcement](https://blog.bitlayer.org/Bitlayer_Advances_the_First_BitVM_Implementation_Through_Major_Strategic_Partnerships/) about advancing the BitVM implementation in collaboration with five chains, including Base, Starknet, Arbitrum, Sonic, and Plume Network, Bitlayer has recently established partnerships with [Celestia](https://x.com/BitlayerLabs/status/1899195108853235850) and [StakeStone](https://x.com/BitlayerLabs/status/1899007317850341453), further enhancing Bitcoin's liquidity. * **BOB (Build-on-Bitcoin):** Continuously [advancing a series of Hybrid BTC yield products](https://blog.gobob.xyz/posts/bob-launches-hybrid-btc-yield-products-ushering-in-a-new-era-of-bitcoin-defi), building a multi-chain BTC yield layer. Recently, they also started collaborations with institutional digital asset platform [Fireblocks](https://x.com/FireblocksHQ) and the ZK & BitVM-based DeFi platform [Fiamma](https://x.com/fiamma_labs), among other projects. ### Underrated Privacy Tools on the Lightning Network The author [designed](https://stacker.news/items/909079) two different Lightning Network roles— as "Lightning Service Provider" (LnSP) and "Liquidity Service Provider" (LiSP)—and introduced often overlooked concepts (such as Wrapped invoices, Just-in-time channels) and privacy-friendly tools (such as [zero-conf channels](https://github.com/lightningnetwork/lnd/blob/master/docs/zero_conf_channels.md), [zaplocker](https://github.com/supertestnet/zaplocker)) in each context respectively. ### Core Lightning Releases v25.02 with Onion Packet Filler Accreditation Core Lightning [announced](https://x.com/Core_LN?ref_src=twsrc%5Egoogle%7Ctwcamp%5Eserp%7Ctwgr%5Eauthor) the release of v25.02, which introduces Onion Packet Filler Accreditation, with key features including: * For Users: Channel backup turns peers into watchtowers, allowing user nodes to generate penalty transactions. * For Network: Stricter checks implemented using [Splicing](https://www.btcstudy.org/2023/11/02/lightning-channel-splicing-principal-explained/) for better interoperability with Eclair. For more details, refer to the [release note](https://github.com/ElementsProject/lightning/releases). ### Frostr: Splitting Nostr Private Keys for Enhanced Security [Frostr](https://www.frostr.org/) is a tool utilizing FROST to provide simple t-of-n remote signing and key rotation protocols for Nostr. It breaks a user's Nostr secret key into several shares and uses subsets of these shares to sign messages. The benefits include: * Enhanced security: Even if one share is lost or stolen, the user’s complete key remains confidential and controlled by themselves. * Flexible key rotation: Users can replace or update key shares without altering their digital identity, ensuring that their digital identity and security are no longer threatened by private key leakage. ### Breaking Down the Bybit Hack: Lessons From Crypto’s Largest Heist In this article, Matt Gleason [provides a detailed analysis](https://a16zcrypto.com/posts/article/bybit-hack-lessons/) of how the Bybit exchange and Safe multi-signature interface were compromised in crypto’s largest heist. He also highlights measures Safe could have taken to prevent or mitigate such attacks, including: * Advanced capabilities to detect and respond to asset modifications. * Advanced capabilities to detect when a developer is compromised. * Tight controls around code repositories, build environments, deployments, and more to keep them from being easily modified; and, if they do need to be modified, to ensure that the right people are using the right process The author also discussed this major heist in [this podcast](https://a16zcrypto.com/posts/podcast/bybit-hack-security/). ### Understanding Token Types and Their Design Implications Any type of token fundamentally enables digital ownership. However, once tokens are embedded as part of software, they can be programmed to represent almost anything: Bitcoin as digital stores of value, Ethereum as productive and consumptive assets, collectibles like digital trading cards and game items, payment stablecoin like USDC, and digitized shares of stock, among others.  [This article](https://a16zcrypto.com/posts/article/defining-tokens/#section--8) points out that these design choices are important because different characteristics determine the applicable legal frameworks and defines various token types. The author specifically mentions that meme coins are tokens with no inherent utility or value, and are only related to memes and community-driven initiatives, not related to networks, companies, or applications. The article also provides a flowchart to help quickly identify token types.  ## Top Reads on Blockchain and Beyond ### BitVMX Efficiency Improvement with ESSPI Optimization ESSPI is an optimized method that utilizes ECDSA / Schnorr signatures to sign the input of the BitVMX program, replacing the traditional inefficient one-time signature (OTS) scheme, like Lamport and Winternitz. Compared to the 1:200 ratio of Winternitz signatures, ESSPI achieves a 1:1 data expansion. The team also introduced 4 innovations to BitVMX, enabling it to verify uncompressed SPV proofs, STARKs, NOVAs, and Bulletproofs, expanding the applicability of BitVMX. Full paper: [ESSPI: ECDSA/Schnorr Signed Program Input for BitVMX](https://bitvmx.org/files/esspi-ecdsa-input-bitvmx.pdf) ### Lattice-Based Privacy-Preserving Decentralized Multi-Party Payment Scheme The problem addressed by this research is that existing privacy schemes that hide transaction amounts (such as the [MimbleWimble](https://www.elliptic.co/blog/explaining-mimblewimble-the-privacy-upgrade-to-litecoin) protocol) are only for one-to-one transactions between a payer and a payee, which have limited use cases and do not support multi-party transactions with multiple payers or payees. The research introduces a new "privacy-preserving decentralized multi-party payment" (PDMP) scheme, which ensures that transaction amounts in multi-party transactions remain confidential to others. It defines the ideal functionality of this system, capturing the privacy and security properties of cryptocurrencies. The research instantiates a lattice-based PDMP protocol in a hybrid model, which can universally composable (UC) securely realize the functionality with a simulation-based security proof. To support this protocol, the team developed a lattice-based verifiable multi-secret sharing scheme and a lattice-based multi-prover non-interactive zero-knowledge argument, both of which are quantum-secure. Full paper: [A lattice-based privacy-preserving decentralized multi-party payment scheme](https://www.sciencedirect.com/science/article/abs/pii/S1389128625000970)
@ Cryptape
2025-03-14 01:00:24## Crypto Insights ### Privacy-Preserving One-Click k-of-n Multisig Descriptor Backup and Recovery Solution This [post](https://delvingbitcoin.org/t/multisigbackup-com-backup-and-recover-a-k-of-n-descriptor-using-only-n-seeds/1430) introduces an open-source project [multisigbackup.com](http://multisigbackup.com/), designed for the backup and recovery of multisig descriptors as simple as possible by requiring only the threshold number of seeds. The challenge is, to recover a 2-of-3 multisig wallet, at least two seed phrases and an output descriptor are needed. Users often store descriptors on laptops or in the cloud, which, while cost-effective, have poor inheritance and are prone to being lost or accidentally deleted. Additionally, services like Unchained, Casa, and Nunchuk offer annual paid custodial services, where they keep a copy of the descriptors. [MultisigBackup.com](https://multisigbackup.com/), however, encrypts the descriptor and inscribes the data on the Bitcoin blockchain. Users only need to input their descriptor, and the tool will encrypt it and generate a taproot address, permanently saving the encrypted data with a single payment. ### Preventing Potential MEVil on Bitcoin: A Private Mempool Approach To address the potential surge in MEVil on Bitcoin, developers Matt Corallo and 7d5x9 [discussed](https://delvingbitcoin.org/t/best-worst-case-mevil-response/1465) the best and worst-case scenarios. This proposal can be seen as an extension of Ethereum's PBS (Proposer-Bidder Separation) model, where the proposer doesn't submit a full block template but only bids on individual or group transactions inclusion with constraints, such as "I want to be the first transaction included, and it interacts with a DEX containing the string X." This ensures that the public mempool remains a reliable way to include transactions (because miners will fill their blocks from both the public mempool and private orders), providing censorship resistance similar to today while still allowing MEVil-extraction experts to pay miners for the inclusion of specific transactions. The authors acknowledge that this design is highly centralized. However, developers must consider what Bitcoin will look like if MEVil becomes a significant part of mining and should be prepared for this shift in case it happens. They also provide a more detailed explanation in [MEVpool: A Private Mempool Marketplace Standard](https://github.com/mevpool/mevpool/blob/0550f5d85e4023ff8ac7da5193973355b855bcc8/mevpool-marketplace.md). ### Progress of BTC DeFi-Related Projects * **Bitlayer:** Following the previous [announcement](https://blog.bitlayer.org/Bitlayer_Advances_the_First_BitVM_Implementation_Through_Major_Strategic_Partnerships/) about advancing the BitVM implementation in collaboration with five chains, including Base, Starknet, Arbitrum, Sonic, and Plume Network, Bitlayer has recently established partnerships with [Celestia](https://x.com/BitlayerLabs/status/1899195108853235850) and [StakeStone](https://x.com/BitlayerLabs/status/1899007317850341453), further enhancing Bitcoin's liquidity. * **BOB (Build-on-Bitcoin):** Continuously [advancing a series of Hybrid BTC yield products](https://blog.gobob.xyz/posts/bob-launches-hybrid-btc-yield-products-ushering-in-a-new-era-of-bitcoin-defi), building a multi-chain BTC yield layer. Recently, they also started collaborations with institutional digital asset platform [Fireblocks](https://x.com/FireblocksHQ) and the ZK & BitVM-based DeFi platform [Fiamma](https://x.com/fiamma_labs), among other projects. ### Underrated Privacy Tools on the Lightning Network The author [designed](https://stacker.news/items/909079) two different Lightning Network roles— as "Lightning Service Provider" (LnSP) and "Liquidity Service Provider" (LiSP)—and introduced often overlooked concepts (such as Wrapped invoices, Just-in-time channels) and privacy-friendly tools (such as [zero-conf channels](https://github.com/lightningnetwork/lnd/blob/master/docs/zero_conf_channels.md), [zaplocker](https://github.com/supertestnet/zaplocker)) in each context respectively. ### Core Lightning Releases v25.02 with Onion Packet Filler Accreditation Core Lightning [announced](https://x.com/Core_LN?ref_src=twsrc%5Egoogle%7Ctwcamp%5Eserp%7Ctwgr%5Eauthor) the release of v25.02, which introduces Onion Packet Filler Accreditation, with key features including: * For Users: Channel backup turns peers into watchtowers, allowing user nodes to generate penalty transactions. * For Network: Stricter checks implemented using [Splicing](https://www.btcstudy.org/2023/11/02/lightning-channel-splicing-principal-explained/) for better interoperability with Eclair. For more details, refer to the [release note](https://github.com/ElementsProject/lightning/releases). ### Frostr: Splitting Nostr Private Keys for Enhanced Security [Frostr](https://www.frostr.org/) is a tool utilizing FROST to provide simple t-of-n remote signing and key rotation protocols for Nostr. It breaks a user's Nostr secret key into several shares and uses subsets of these shares to sign messages. The benefits include: * Enhanced security: Even if one share is lost or stolen, the user’s complete key remains confidential and controlled by themselves. * Flexible key rotation: Users can replace or update key shares without altering their digital identity, ensuring that their digital identity and security are no longer threatened by private key leakage. ### Breaking Down the Bybit Hack: Lessons From Crypto’s Largest Heist In this article, Matt Gleason [provides a detailed analysis](https://a16zcrypto.com/posts/article/bybit-hack-lessons/) of how the Bybit exchange and Safe multi-signature interface were compromised in crypto’s largest heist. He also highlights measures Safe could have taken to prevent or mitigate such attacks, including: * Advanced capabilities to detect and respond to asset modifications. * Advanced capabilities to detect when a developer is compromised. * Tight controls around code repositories, build environments, deployments, and more to keep them from being easily modified; and, if they do need to be modified, to ensure that the right people are using the right process The author also discussed this major heist in [this podcast](https://a16zcrypto.com/posts/podcast/bybit-hack-security/). ### Understanding Token Types and Their Design Implications Any type of token fundamentally enables digital ownership. However, once tokens are embedded as part of software, they can be programmed to represent almost anything: Bitcoin as digital stores of value, Ethereum as productive and consumptive assets, collectibles like digital trading cards and game items, payment stablecoin like USDC, and digitized shares of stock, among others.  [This article](https://a16zcrypto.com/posts/article/defining-tokens/#section--8) points out that these design choices are important because different characteristics determine the applicable legal frameworks and defines various token types. The author specifically mentions that meme coins are tokens with no inherent utility or value, and are only related to memes and community-driven initiatives, not related to networks, companies, or applications. The article also provides a flowchart to help quickly identify token types.  ## Top Reads on Blockchain and Beyond ### BitVMX Efficiency Improvement with ESSPI Optimization ESSPI is an optimized method that utilizes ECDSA / Schnorr signatures to sign the input of the BitVMX program, replacing the traditional inefficient one-time signature (OTS) scheme, like Lamport and Winternitz. Compared to the 1:200 ratio of Winternitz signatures, ESSPI achieves a 1:1 data expansion. The team also introduced 4 innovations to BitVMX, enabling it to verify uncompressed SPV proofs, STARKs, NOVAs, and Bulletproofs, expanding the applicability of BitVMX. Full paper: [ESSPI: ECDSA/Schnorr Signed Program Input for BitVMX](https://bitvmx.org/files/esspi-ecdsa-input-bitvmx.pdf) ### Lattice-Based Privacy-Preserving Decentralized Multi-Party Payment Scheme The problem addressed by this research is that existing privacy schemes that hide transaction amounts (such as the [MimbleWimble](https://www.elliptic.co/blog/explaining-mimblewimble-the-privacy-upgrade-to-litecoin) protocol) are only for one-to-one transactions between a payer and a payee, which have limited use cases and do not support multi-party transactions with multiple payers or payees. The research introduces a new "privacy-preserving decentralized multi-party payment" (PDMP) scheme, which ensures that transaction amounts in multi-party transactions remain confidential to others. It defines the ideal functionality of this system, capturing the privacy and security properties of cryptocurrencies. The research instantiates a lattice-based PDMP protocol in a hybrid model, which can universally composable (UC) securely realize the functionality with a simulation-based security proof. To support this protocol, the team developed a lattice-based verifiable multi-secret sharing scheme and a lattice-based multi-prover non-interactive zero-knowledge argument, both of which are quantum-secure. Full paper: [A lattice-based privacy-preserving decentralized multi-party payment scheme](https://www.sciencedirect.com/science/article/abs/pii/S1389128625000970)