-
 @ 5d1d83de:d0db5aa0
2025-06-01 06:04:32
@ 5d1d83de:d0db5aa0
2025-06-01 06:04:32As long as the base unit of the trading system can be manipulated a free trading system cannot emerge.
The trading system will either be manipulated by printed subsidies or will be manipulated by artificial exchange rates.
Free trading was available during a gold standard and free trading will become available again during a future bitcoin standard.
https://stacker.news/items/989491
-
 @ 7f6db517:a4931eda
2025-06-01 06:01:32
@ 7f6db517:a4931eda
2025-06-01 06:01:32
I often hear "bitcoin doesn't interest me, I'm not a finance person."
Ironically, the beauty of sound money is you don't have to be. In the current system you're expected to manage a diversified investment portfolio or pay someone to do it. Bitcoin will make that optional.
— ODELL (@ODELL) September 16, 2018
At first glance bitcoin often appears overwhelming to newcomers. It is incredibly easy to get bogged down in the details of how it works or different ways to use it. Enthusiasts, such as myself, often enjoy going down the deep rabbit hole of the potential of bitcoin, possible pitfalls and theoretical scenarios, power user techniques, and the developer ecosystem. If your first touch point with bitcoin is that type of content then it is only natural to be overwhelmed. While it is important that we have a thriving community of bitcoiners dedicated to these complicated tasks - the true beauty of bitcoin lies in its simplicity. Bitcoin is simply better money. It is the best money we have ever had.
Life is complicated. Life is hard. Life is full of responsibility and surprises. Bitcoin allows us to focus on our lives while relying on a money that is simple. A money that is not controlled by any individual, company, or government. A money that cannot be easily seized or blocked. A money that cannot be devalued at will by a handful of corrupt bureaucrat who live hundreds of miles from us. A money that can be easily saved and should increase in purchasing power over time without having to learn how to "build a diversified stock portfolio" or hire someone to do it for us.
Bitcoin enables all of us to focus on our lives - our friends and family - doing what we love with the short time we have on this earth. Time is scarce. Life is complicated. Bitcoin is the most simple aspect of our complicated lives. If we spend our scarce time working then we should be able to easily save that accrued value for future generations without watching the news or understanding complicated financial markets. Bitcoin makes this possible for anyone.
Yesterday was Mother's Day. Raising a human is complicated. It is hard, it requires immense personal responsibility, it requires critical thinking, but mothers figure it out, because it is worth it. Using and saving bitcoin is simple - simply install an app on your phone. Every mother can do it. Every person can do it.
Life is complicated. Life is beautiful. Bitcoin is simple.
If you found this post helpful support my work with bitcoin.

-
 @ eb0157af:77ab6c55
2025-06-01 06:01:12
@ eb0157af:77ab6c55
2025-06-01 06:01:12The blockchain analytics firm claims to have identified the Bitcoin addresses held by the company led by Saylor.
Arkham Intelligence announced it had identified addresses linked to Strategy. According to Arkham’s statements, an additional 70,816 BTC connected to the company have been identified, with an estimated value of around $7.6 billion at current prices. This discovery would bring the total amount of Strategy’s identified holdings to $54.5 billion.
SAYLOR SAID HE WOULD NEVER REVEAL HIS ADDRESSES … SO WE DID
We have identified an additional 70,816 BTC belonging to Strategy, bringing our total identified MSTR BTC holdings to $54.5 Billion. We are the first to publicly identify these holdings.
This represents 87.5% of… pic.twitter.com/P3OVdVrhQL
— Arkham (@arkham) May 28, 2025
The analytics firm claims to have mapped 87.5% of Strategy’s total holdings. In a provocative post on X, Arkham wrote:
“Saylor said he would never reveal his addresses. So, we did it for him.
Previously, we tagged:
– 107,000 BTC sent to MSTR’s Fidelity deposits (Fidelity does not segregate custody, so these BTC do not appear in the MSTR entity)
– Over 327,000 BTC held in segregated custody, including Coinbase Prime, in our MSTR entity.”Arkham’s revelations directly clash with Michael Saylor’s public statements on wallet security. During the Bitcoin 2025 conference in Las Vegas, the Strategy chairman explicitly warned against publishing corporate wallet addresses.
“No institutional or enterprise security analyst would ever think it’s a good idea to publish all the wallet addresses so you can be tracked back and forth,” Saylor said during the event.
The executive chairman of Strategy added:
“The current, conventional way to publish proof-of-reserves is an insecure proof of reserves… It’s not a good idea, it’s a bad idea.”
He compared publishing wallet addresses to “publishing the addresses, bank accounts, and phone numbers of your kids hoping it will protect them — when in fact it makes them more vulnerable.”
Finally, the executive chairman suggested using artificial intelligence to explore the security implications of such a practice, claiming that in-depth research could produce “50 pages” of potential security risks.
The post Arkham reveals 87% of Strategy’s Bitcoin addresses appeared first on Atlas21.
-
 @ 9ca447d2:fbf5a36d
2025-06-01 06:00:52
@ 9ca447d2:fbf5a36d
2025-06-01 06:00:52The third annual Bitcoin FilmFest (aka BFF25) proved once again that sovereign minds and decentralized culture thrive together.
For four electrifying days in Poland’s capital, the festival’s rallying call—’Fix the money, fix the culture‘—wasn’t just a slogan but a living, breathing movement.
From May 22-25, 2025, Warsaw buzzed with cinematic innovation, Bitcoin philosophy, and artistic vibe marking this gathering as truly incomparable.
Rebel Tribe with Unfiltered Creativity
With 200+ attendees from 20+ countries – primarily Poland, Czech Republic, the UK and Germany (~70% combined), plus representation from Spain, Italy, USA, Turkey and 15+ other nations including Thailand, Israel, Dubai and Latin America—BFF25 became a true global hub of freedom-fighters at heart.
The European Pizza Day opener (May 22), celebrating Bitcoin’s first real-world transaction, saw rainy evening weather that couldn’t dampen the energy.
With concerts by Roger9000 and ABBE plus DJ sets from MadMunky, 2140 collective w/Airklipz and G.O.L.D., all early arrivals had a memorable start.
Dual Focus on Film and Bitcoin Culture
-
Seven film workshops and seven hands-on sessions running parallel across Friday and Saturday at Amondo Cinema Club. Film: Martin Piga, Oswald Horowitz, Psyfer, Juan Pablo Mejía, Kristina Weiserova, Rare Passenger, Noa Gruman & Lahav Levi (Scardust). Bitcoin/Nostr: Aleks Svetski, Ioni Appelberg, Flash, CryptoSteel, Bitrefill, Polish Bitcoin Association, Bitvocation.
-
The Community Stage (Friday to Sunday afternoon) gave important space for both projects and individuals discussing their work and passions.
Everything from music, art, fiction, Nostr, personal sovereignty to Polish-language debates on Bitcoin’s state and its possible future. -
Onscreen, 9 cinematic blocks from Friday to Sunday featured titles like UNBAKABLE, REVOLUCIÓN BITCOIN, HOTEL BITCOIN, PLANDEMIC: THE MUSICAL, plus shorts on new media (AI/experimental cinema), parallel communities (outcast cinema), and newly released pilots.
-
Cinematic shark-tank with a €3,000 bounty: 8 contestants
- Martin Piga: “PARALLEL SPACES”
- Kristina Weiserova: “PUZZLE”
- Aaron Koenig : “SATOSHI’S LAST WILL”
- Philip Charter: “21 FUTURES”
- Jenna Reid: “WHERE DO WE GO FROM HERE?”
- Mr Black: “A LODGING OF WAYFARING MEN”
- Oswald Horowitz: “THE LEGEND OF LANDI”
The event ended with Jenna winning.
-
Official Gala: Golden Rabbits 2025 crowned:
- HOTEL BITCOIN by Manuel Sanabria & Carlos “Pocho” Villaverde (Best Story)
- SATOSHI: THE CREATION OF BITCOIN by Arthur Machado (Best Short)
- REVOLUCIÓN BITCOIN by Juan Pablo Mejía (Audience Choice)
- NO MORE INFLATION by Maiku Tsukai’s aka Bitcoin Shooter (Best Film)
Nights Charged with Music and Unscripted Surprise
The festival’s legendary afterparties kept the energy high—Friday’s underground gathering at Morph Club (ex-Barbazaar) featured Aaron Koening’s live concert and 2140 DJs (Akme + Andy Princz).
The weekend’s unforgettable moment came when Noa Gruman took the stage with “MY HEAVEN” (Scardust original) and “40HPW” — her powerful tribute to Bitcoin podcasts and Bugle.News.
Lightning-Powered Innovation, and Extras
-
Lightning in Action: Flash enabled instant Bitcoin payments across both main venues (Amondo + Samo Centrum, merch stations, and online shop)
-
IndeeHub Backstage Pass: Attendees unlocked exclusive access to Lightning-powered VOD featuring selected films from BFF23-25
-
BFF TV: Kiki (El Salvador) broadcasting live interviews, event clips, and trailers. Day One, and Day Two to rewatch online.
-
Comedy Strike: Robert Le Ricain’s Gala stand-up proved Bitcoiners pack brains and humor—in equal measure.
A Community-Driven Cultural Experience
Bitcoin FilmFest wasn’t just an event—it was proof that culture shifts when money gets fixed. Mark your calendars for June 2026 and the next edition. More info and tickets going on sale soon.
-
-
 @ cae03c48:2a7d6671
2025-06-01 06:00:31
@ cae03c48:2a7d6671
2025-06-01 06:00:31Bitcoin Magazine

Panama City Mayor Mizrachi: “Bitcoin Is Not Just Safe, It’s Prosperous”At the 2025 Bitcoin Conference in Las Vegas, the Director of Bitcoin Beach Mike Peterson, the Presidential Advisors of Building Bitcoin Country El Salvador Max & Stacy and the Mayor City of Panama Mayer Mizrachi discussed Bitcoins future in Panama.
At the beginning of the panel, Is Panama Next? El Salvador Leading The Region For Bitcoin Adoption, Mayor Mizrachi started by mentioning, “We accept Bitcoin. The city gets paid in Bitcoin, but it receives in dollars through an intermediary processing, payments processor. Bitcoin is not just safe. It’s prosperous.”
Max commented about the scammers in crypto and how El Salvador is managing it.
“We did a couple of things early on, one was to create The Bitcoin Office which will be directly reporting to the President, and then also we passed a law which will say bitcoin is money and everything else is an unregistered security,” said Max.
Mike Peterson stated, “the access of Bitcoin in Central America to do battle against the globalists that have always looked at the regionist back yard. This is intolerable and this is going to change right now.” After Mizrachi commented, “Imagine yourself in an economic block powered by El Salvador, supported by Panama and the rest will come.”
Stacy reminded everybody about El Salvador’s School system.
“El Salvador is the first country in the world to have a comprehensive public school financial literacy education program from 7 years old,” mentioned Stacy. “These are little kids, learning financial literacy.”
Max ended the panel by saying, “the US game theory right? Because the US wants to buy a lot of Bitcoin, so if Panama wants to buy a lot of bitcoin then it helps everybody in the US. This is the beautiful expression of game theory perfectly aligned in the protocol that is changing the world that we live in. And on the street level what bitcoin does to the population is to go from a spending mentality to a saving mentality.”
You can watch the full panel discussion and the rest of the Bitcoin 2025 Conference Day 3 below:
This post Panama City Mayor Mizrachi: “Bitcoin Is Not Just Safe, It’s Prosperous” first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ cae03c48:2a7d6671
2025-06-01 06:00:30
@ cae03c48:2a7d6671
2025-06-01 06:00:30Bitcoin Magazine

The Debt Train Has No Brakes: Lyn Alden Makes the Case for BTC at Bitcoin 2025“Nothing stops this train,” Lyn Alden initially stated at Bitcoin 2025, walking the audience through a data-rich presentation that made one thing clear: the U.S. fiscal system is out of control—and Bitcoin is more necessary than ever.
Her first chart, sourced from the Federal Reserve’s FRED database, displayed a stark decoupling: the unemployment rate is down, yet the fiscal deficit has surged past 7% of GDP. “This started around 2017, went into overdrive during the pandemic, and hasn’t corrected,” Alden said. “That’s not normal. We’re in a new era.”
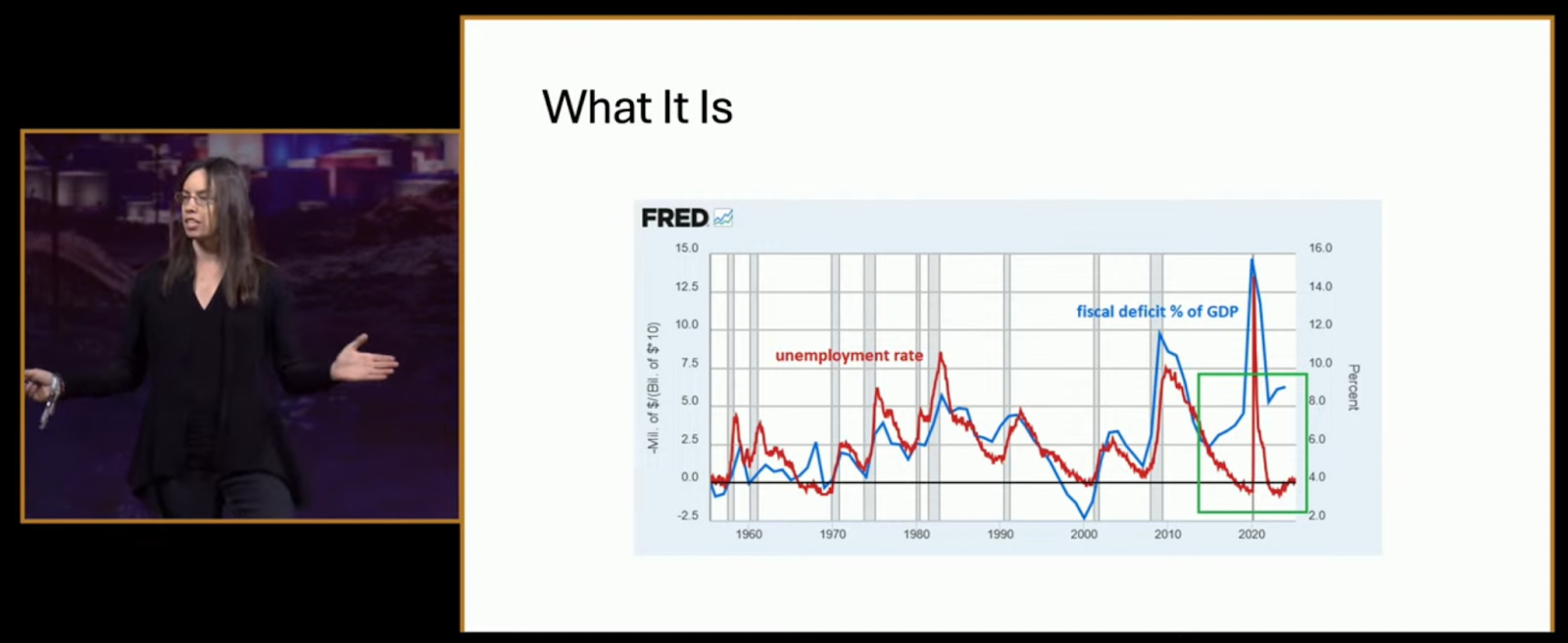
She didn’t mince words. “Nothing stops this train because there are no brakes attached to it anymore. The brakes are heavily impaired.
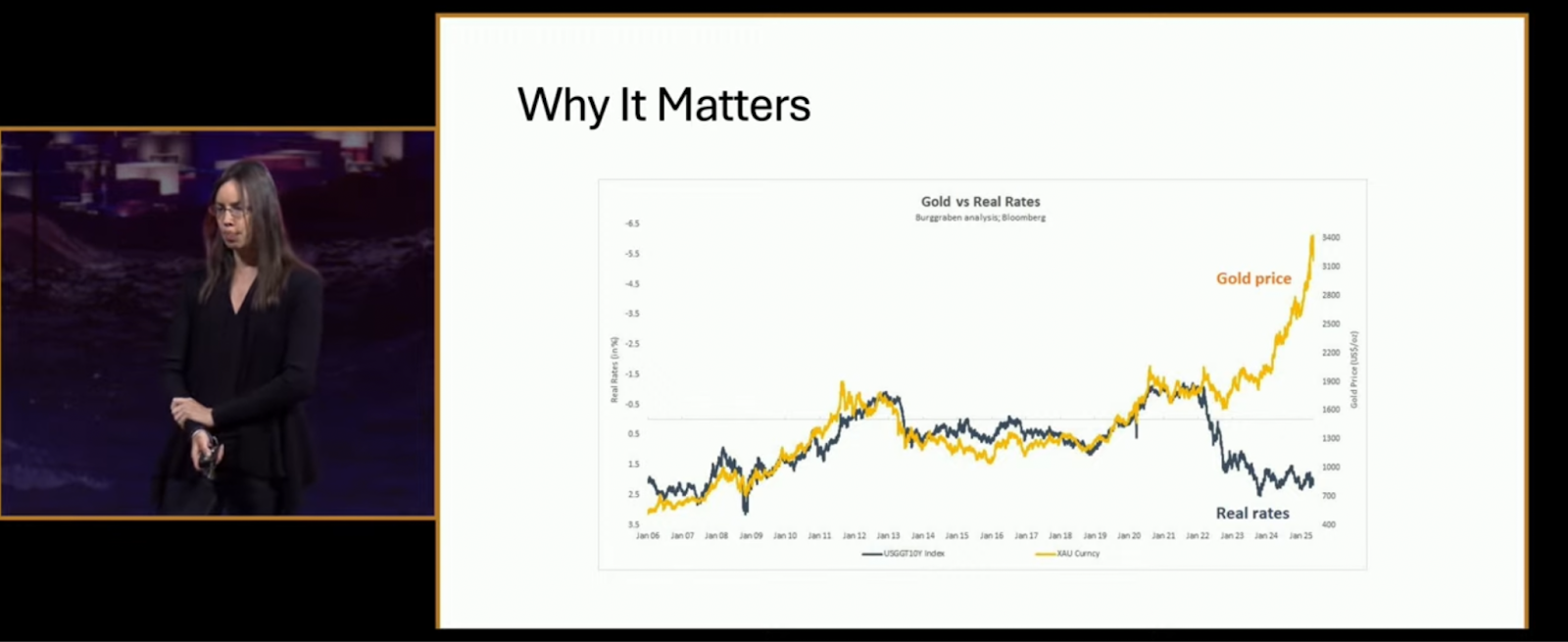
Why should Bitcoiners care? Because, as Alden explained, “it matters for asset prices—especially anything scarce.” She displayed a gold vs. real rates chart that showed gold soaring as real interest rates plunged. “Five years ago, most would have said Bitcoin couldn’t thrive in a high-rate environment. Yet here we are—Bitcoin over $100K, gold at new highs, and banks breaking under pressure.”
Next came what she called “The Turning Point”—a side-by-side showing how public debt growth overtook private sector debt post-2008, flipping a decades-long norm. “This is inflationary, persistent, and it means the Fed can’t slow things down anymore.”
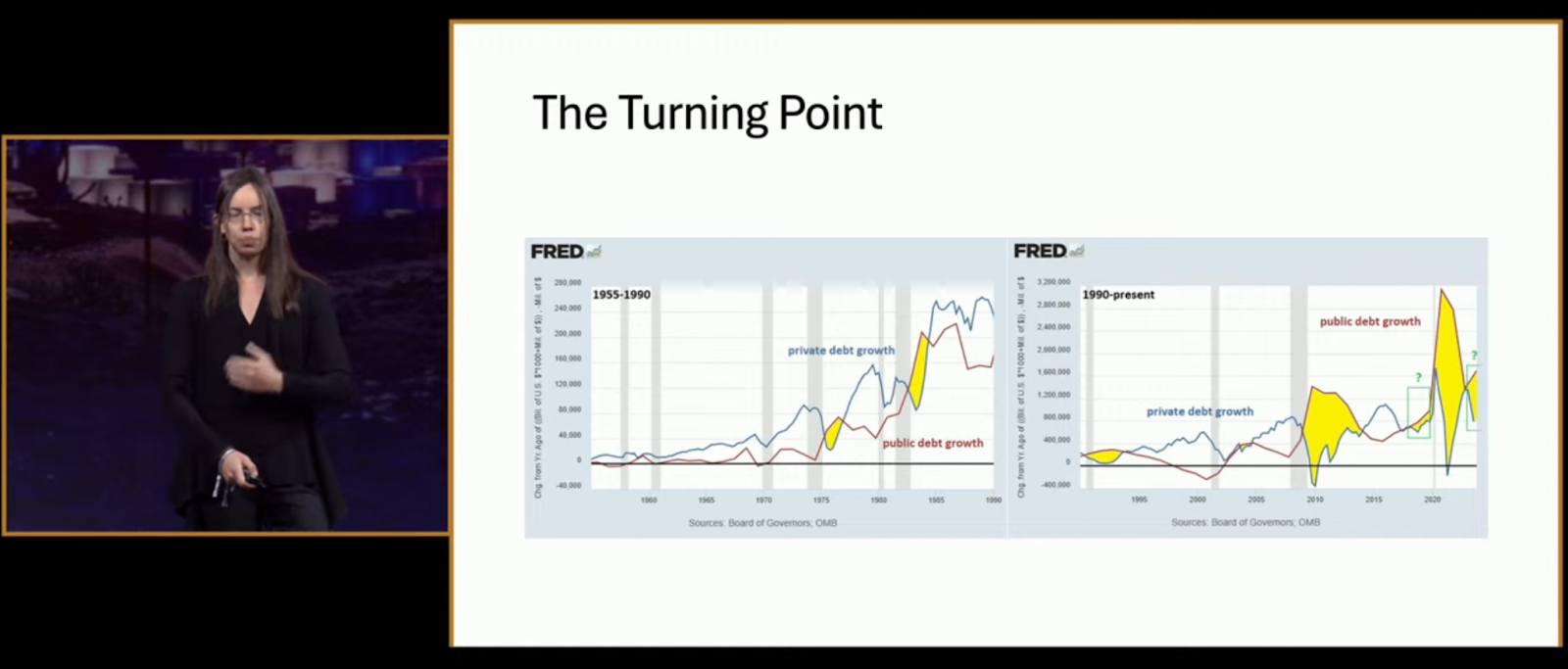
Another chart revealed why rising interest rates are now accelerating the deficit. “They’ve lost their brakes. Raising rates just makes the federal interest bill explode faster than it slows bank lending.”
Alden called it a ponzi: “The system is built on constant growth. Like a shark, it dies if it stops swimming.”
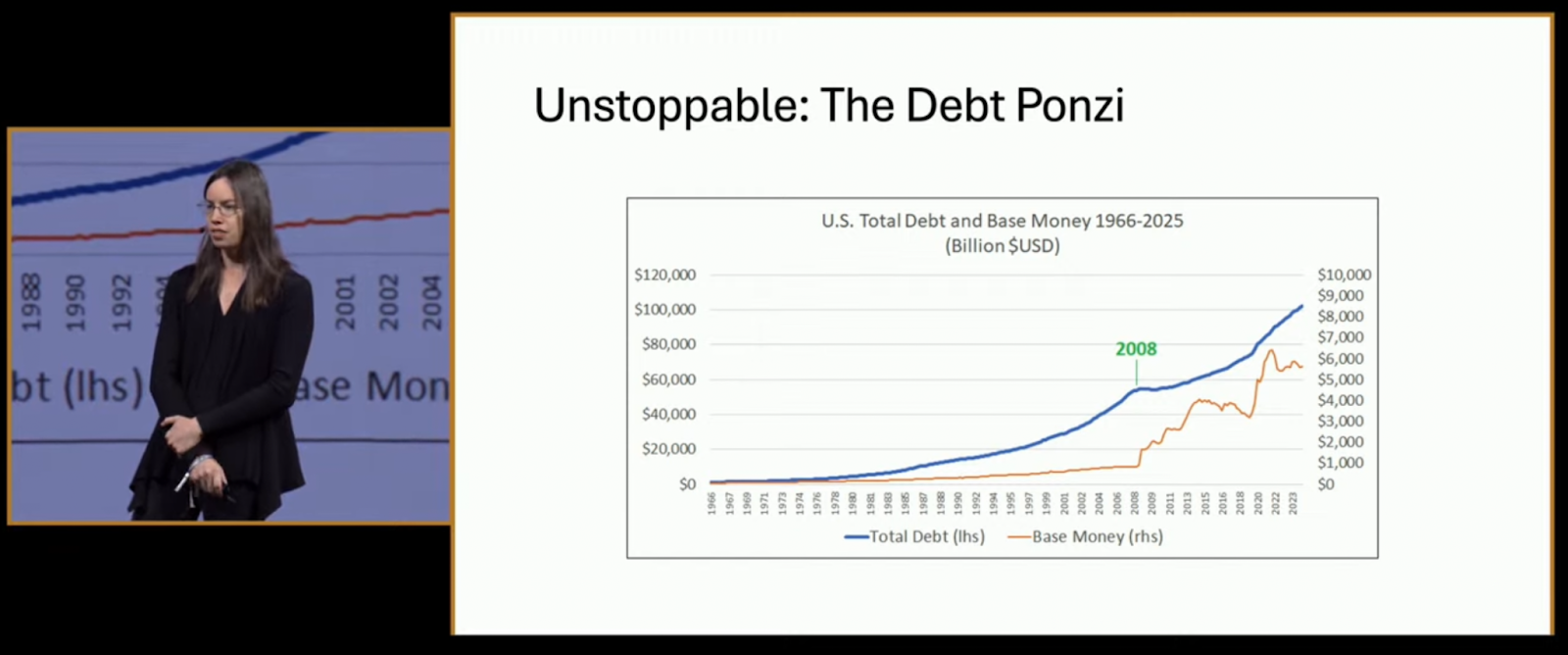
Her slide showed a relentless rise in total debt versus base money—except for a jolt in 2008, and again after 2020. “This isn’t going backward. Ever.”
So why Bitcoin? “Because it’s the opposite. Scarce, decentralized, and mathematically capped,” Alden concluded. “There are two reasons nothing stops this train: math and human nature. Bitcoin is the mirror of this system—and the best protection from it.”
You can watch the full panel discussion and the rest of the Bitcoin 2025 Conference Day 3 below:
This post The Debt Train Has No Brakes: Lyn Alden Makes the Case for BTC at Bitcoin 2025 first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ cae03c48:2a7d6671
2025-06-01 06:00:30
@ cae03c48:2a7d6671
2025-06-01 06:00:30Bitcoin Magazine

Jack Mallers Announced A New System of Bitcoin Backed Loans at StrikeThe Founder and CEO of Strike, Jack Mallers, at the 2025 Bitcoin Conference in Las Vegas, announced a new system of Bitcoin backed loans at Strike with one digit interest rate.
Jack Mallers began his keynote by pointing at the biggest problem. Fiat currency.
“The best time to go to Whole Foods and buy eggs with your dollars was 1913,” said Mallers. “Every other time after, you are getting screwed.”
What’s the solution?
“The solution is Bitcoin,” stated Mallers. “Bitcoin is the money that we coincide that nobody can print. You can’t print, you can’t debase my time and energy, you cannot deprive me of owning assets, of getting out of debt, of living sovereignly and protecting my future, my family, my priced possessions. Bitcoin is what we invented to do that.”
Mallers gave a power message to the audience by explaining that people should HODL every dollar they have in Bitcoin. People should also spend a little of it to have a nice life.
“You can’t HODL forever,” said Jack.
While talking about loans that people borrow against their Bitcoin. He explained why he thinks banks putting 20% in interest for loans backed with Bitcoin is outrageous.
“All these professional economists, they are like Bitcoin is risky and volatile,” stated Mallers. “No it’s not. This is the magnificent 7 one year volatility and the orange one in the middle is Bitcoin. It’s no more risky and volatile. It’s a little bit more volatile than Apple, but is far less more volatile than Tesla.”
“As Bitcoin matures, its volatility goes down,” continued Jack. “Bitcoin volatility is at a point where it is no more risky than a Tesla Stock. We should not be paying double digits rates for a loan.”
Mallers announced his new system of loans at Strike of 9-13% in interest rates. It will allow people to get loans from $10,000 to $1 billion.
Mallers closed by saying, “please be responsible. This is debt. Debt is like fire in my opinion. It can heat a civilization. It can warm your home, but if you go too crazy it can burn your house down.”
“Life is short,” said Jack. “Take the trip, but with bitcoin you just get to take a better one.”
This post Jack Mallers Announced A New System of Bitcoin Backed Loans at Strike first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ cae03c48:2a7d6671
2025-06-01 06:00:29
@ cae03c48:2a7d6671
2025-06-01 06:00:29Bitcoin Magazine

Michael Saylor Presents The 21 Ways to Wealth at Bitcoin 2025Michael Saylor, Executive Chairman of Strategy, took the stage at Bitcoin 2025 delivering a keynote titled “21 Ways to Wealth.” He stated: “This speech is for you. I’ve traveled the world and told countries, institutional investors, and even the disembodied spirits of our children’s children why they need Bitcoin. This is for every individual, every family, every small business. It’s for everybody.”
He began with clarity. “The first way to wealth is clarity,” he said. “Clarity comes the moment you realize Bitcoin is capital—perfected capital, programmable capital, incorruptible capital.” For Saylor, every thoughtful individual on Earth will ultimately seek such pristine capital, and every AI system will prefer it as well.
The second path is conviction. Bitcoin, he said, will appreciate faster than every other asset, because it’s engineered for performance. “It’s going to grow faster than real estate or collectibles. It is the most efficient store of value in human history.”
The third way is courage. “If you’re going to get rich on Bitcoin, you need courage,” he warned. “Wealth favors those who embrace intelligent monetary risk. Some people will get left behind. Others will juggle it. But the bold will feed the fire—sell your bonds, buy Bitcoin. An extraordinary explosion of value is coming.”
Fourth comes cooperation. “You are more powerful if you have the full support of your family. Your children have time and potential. The secret is transferring capital into their hands. Families that move in unity are unstoppable.”
The fifth is capability. “Master AI,” he said. “In 2025, everything you can imagine is at your fingertips—wisdom, analysis, creativity. Ask AI, argue with it, use it. You can become a super genius. Don’t put your ego first—put your interests first. Your family will thank you.”
Saylor’s sixth way to wealth is composition: construct legal entities that scale your strategy and protect your assets. “Ask the AI and figure it out. You can work hard, or you can work smart. This year, everyone should be operating like the most sophisticated millionaire family office.”
The seventh is citizenship. Choose your economic nexus carefully—“domicile where sovereignty respects your freedom,” he said. “This isn’t just about this year—it’s about this century.”
Eighth is civility. “Respect the natural power structures of the world. Respect the force of nature,” he explained. “If you want to generate wealth in the Bitcoin universe, don’t fight unnecessarily. Find common ground. Inflation and distraction are your enemies.”
Ninth is corporation. “A well-structured corporation is the most powerful wealth engine on Earth. Families are powerful. Partnerships are even more powerful. But corporations can scale globally. What is your vehicle? What is your path?”
The tenth way is focus. “Just because you can do a thing doesn’t mean you should,” he warned. “If you invest in Bitcoin, there’s a 90% chance it will succeed over five years. Don’t confuse ambition with accomplishment. Come up with a strategy—and stick to it.”
The eleventh is equity. “Share your opportunities with investors who will share your risk,” he said, pointing to MicroStrategy’s own rise from $10 million to a $5 billion market cap by aligning with equity partners who believed in the Bitcoin mission.
The twelfth is credit. “There are people in the world who are afraid of the future—they want small yield, certainty. Offer that. Give creditors security in return for capital. Convert their fear into fuel and turn risk into yield by investing in Bitcoin.”
The thirteenth is compliance. “Create the best company you can within the rules of your market. Learn the rules of the road. If you know them, you can drive faster. You can scale legally and sustainably.”
The fourteenth way is capitalization. “Velocity compounds wealth,” Saylor said. “Raise and reinvest capital as fast and as often as you can. The faster your money moves into productive Bitcoin strategies, the more it multiplies.”
Fifteenth is communication. “Speak with candor. Act with transparency. And repeat your message often,” he urged. “Creating wealth with Bitcoin is simple—but only if people understand what you’re doing and why you’re doing it.”
Sixteenth is commitment. “Don’t allow yourself to be distracted,” he said. “Don’t chase your own ideas. Don’t feed the trolls. Stay committed to Bitcoin. It’s the greatest idea in the world. The world probably doesn’t care what you think—but it will care when you win.”
The Seventeenth way is competence. “You’re not competing with noise—you’re competing with someone who is laser-focused, who executes flawlessly,” he said. “You must deliver consistent, precise, and reliable performance. That’s how you win.”
The Eighteenth is adaptation. “Circumstances change. Every structure you trust today will eventually fail. A wise person is prepared to abandon their baggage and adjust plans when needed. Rigidity is ruin.”
Nineteenth is evolution. “Build on your core strengths. You don’t need to start over—you need to level up. Leverage what you already do best, and expand it through Bitcoin and advanced technologies.”
Twentieth is advocacy. “Inspire others to walk the Bitcoin path,” he said. “Become an evangelist for economic freedom. Show others what this revolution really means. Show them the way.”
Finally, the twenty-first way is generosity. “When you’re successful—and you will be successful—spread happiness. Share security. Deliver hope. That light inside you will shine. And others will be drawn to it.”
As he ended, Saylor smiled and quoted the very origin of it all:
“It might make sense to get some, in case it catches on.” – Satoshi.
In Michael Saylor’s worldview, Bitcoin is not a get-rich-quick scheme—it’s the ultimate long-term play. It is the foundation of generational wealth, the engine of personal and institutional freedom, and the tool for those bold enough to lead humanity into a more sovereign, secure future.
You can watch the full panel discussion and the rest of the Bitcoin 2025 Conference Day 3 below:
This post Michael Saylor Presents The 21 Ways to Wealth at Bitcoin 2025 first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ cae03c48:2a7d6671
2025-06-01 06:00:28
@ cae03c48:2a7d6671
2025-06-01 06:00:28Bitcoin Magazine

Bitcoin Builders Exist Because Of UsersBuilder: Nicholas Gregory
Language(s): C++, Rust
Contribute(s/ed) To: Ocean Sidechain, Mainstay, Mercury Wallet, Mercury Layer
Work(s/ed) At: CommerceBlock (formerly)
Prior to Bitcoin, Nicholas was a software developer working in the financial system for banking firms developing trading and derivatives platforms. After the 2008 financial crisis he began to consider alternatives to the legacy financial system in the fallout.
Like many from that time, he completely ignored the original Slashdot article featuring the Bitcoin whitepaper due to the apparent focus on Windows as an application platform (Nicholas was a UNIX/Linux developer). Thankfully someone he knew introduced him to Bitcoin later on.
The thing that captured his interest about Bitcoin rather than other alternatives at the time was its specific architecture as a distributed computer network.
“The fact that it was like an alternative way. It was all based around [a] kind of […] network. And what I mean by that, building financial systems, people always wanted a system that was 24-7.
And how do you deal with someone interacting [with] it in different geographical parts of the world without it being centralized?
And I’d seen various ways of people solving that problem, but it never had been done, you know, in a kind of […] scalable solution. And using […] cryptography and proof of work to solve that issue was just weird, to be honest. It was totally weird for me.”
All of the other systems he had designed, and some that he built, were systems distributed across multiple parts of the world. Unlike Bitcoin however, these systems were permissioned and restricted who could update the relevant database(s) despite that fact that copies of them were redundantly distributed globally.
“The fact that in Bitcoin you had everyone kind of doing this proof of work game, which is what it is. And whoever wins does the [database] write. That mess[ed] with my head. That was […] very unique.”
Beginning To Build
Nicholas’s path to building in the space was an organic one. At the time he was living in New York City, and being a developer he of course found the original Bitdevs founded in NYC. Back then meetups were incredibly small, sometimes even less than a dozen people, so the environment was much more conducive to in-depth conversations than some larger meetups these days.
He first began building a “hobbyist” Over The Counter (OTC) trading software stack for some people (back then a very significant volume of bitcoin was traded OTC for cash or other fiat mediums). From here Nicholas and Omar Shibli, whom he met at Bitdevs, worked together on Pay To Contract (BIP 175).
BIP 175 specifies a scheme where a customer purchasing a good participates in generating the address the merchant provides. This is done by the two first agreeing on a contract describing what is being paid for, afterwards the merchant sends a master public key to the consumer, who uses the hash of that description of the item or service to generate an individual address using the hash and master public key.
This allows the customer to prove what the merchant agreed to sell them, and that the payment for the good or service has been made. Simply publishing the master public key and contract allows any third party to generate the address that was paid, and verify that the appropriate amount of funds were sent there.
Ocean and Mainstay
Nicholas and Omar went on to found CommerceBlock, a Bitcoin infrastructure company. Commerceblock took a similar approach to business as Blockstream, building technological platforms to facilitate the use of Bitcoin and blockchains in general in commerce and finance. Shortly afterwards Nicholas met Tom Trevethan who came on board.
“I met Tom via, yeah, a mutual friend, happy to say who it is. There’s a guy called, who, new people probably don’t know who he is, but OGs do, John Matonis. John Matonis was a good friend of mine, [I’d] known him for a while. He introduced me to Tom, who was, you know, kind of more on the cryptography side. And it kind of went from there.”
The first major project they worked on was Ocean, a fork of the Elements sidechain platform developed by Blockstream that the Liquid sidechain was based on. The companies CoinShares and Blockchain in partnership with others launched an Ocean based sidechain in 2019 to issue DGLD, a gold backed digital token.
“So we, you know, we were working on forks of Elements, doing bespoke sidechains. […] Tom had some ideas around cryptography. And I think one of our first ideas was about how to bolt on these forks of Elements onto […] the Bitcoin main chain. […] We thought the cleanest way to do that was […] using some sort of, I can’t remember, but it was something [based on] single-use sealed sets, which was an invention by Peter Todd. And I think we implemented that fairly well with Mainstay.”
The main distinction between Ocean and Liquid as a sidechain platform is Ocean’s use of a protocol designed at Commerceblock called Mainstay. Mainstay is a timestamping protocol that, unlike Opentimestamps, strictly orders the merkle tree it builds instead of randomly adding items in whatever order they are submitted in. This allows each sidechain to timestamp its current blockheight into the Bitcoin blockchain everytime mainchain miners find a block.
While this is useless for any bitcoin pegged into the sidechain, for regulated real world assets (RWA), this provides a singular history of ownership that even the federation operating the sidechain cannot change. This removes ambiguity of ownership during legal disputes.
When asked about the eventually shuttering of the project, Nicholas had this to say:
“I don’t know if we were early, but we had a few clients. But it was, yeah, there wasn’t much adoption. I mean, Liquid wasn’t doing amazing. And, you know, being based in London/Europe, whenever we met clients to do POCs, we were competing against other well-funded projects.
It shows how many years ago they’d either received money from people like IBM or some of the big consultancies and were promoting Hyperledger. Or it was the days when we would be competing against EOS and Tezos. So because we were like a company that needed money to build prototypes or build sidechains, it kind of made it very hard. And back then there wasn’t much adoption.”
Mercury Wallet and Mercury Layer
After shutting down Ocean, Nicholas and Tom eventually began working on a statechain implementation, though the path to this was not straightforward.
“[T]here were a few things happening at the same time that led to it. So the two things were we were involved in a [proof of concept], a very small […]POC for like a potential client. But this rolled around Discreet Log Contracts. And one of the challenges of Discreet Log Contracts, they’re very capital inefficient. So we wanted a way to novate those contracts. And it just so happened that Ruben Sampson, you know, wrote this kind of white paper/Medium post about statechains. And […] those two ideas, that kind of solved potentially that issue around DLCs.”
In the end they did not wind up deploying a statechain solution for managing DLCs, but went in a different direction.
Well, there was another thing happening at the same time, coinswaps. And, yeah, bear in mind, in those days, everyone worried that by […] 2024/2025 […] network fees could be pretty high. And to do […] coin swaps, you kind of want to do multiple rounds. So […] state chains felt perfect because […] you basically take a UTXO, you put it off the chain, and then you can swap it as much as you want.”
Mercury Wallet was fully built out and functional, but sadly never gained any user adoption. Samourai Wallet and Wasabi Wallet at the time dominated the privacy tool ecosystem, and Mercury Wallet was never able to successfully take a bite out of the market.
Rather than completely give up, they went back to the drawing board to build a statechain variant using Schnorr with the coordinator server blind signing, meaning it could not see what it was signing. When asked why those changes were made, he had this to say: “That would give us a lot more flexibility to do other things in Bitcoin with L2s. You know, the moment you have a blinded solution, we thought, well, this could start having interoperability with Lightning.”
Rather than building a user facing wallet this time, they built out a Software Development Kit (SDK) that could be integrated with other wallets.
“{…] I guess with Mercury Layer, it was very much building a kind of […] full-fledged Layer 2 that anyone could use. So we [built] it as an SDK. We did have a default wallet that people could run. But we were hoping that other people would integrate it.”
The End of CommerceBlock
In the end, CommerceBlock shuttered its doors after many years of brilliant engineering work. Nicholas and the rest of the team built numerous systems and protocols that were very well engineered, but at the end of the day they seemed to always be one step ahead of the curve. That’s not necessarily a good thing when it comes to building systems for end users.
If your work is too far ahead of the demand from users, then in the end that isn’t a sustainable strategy.
“…being in the UK, which is not doing that well from a regulatory point of view, played into it. If I
-
 @ 35f80bda:406855c0
2025-06-01 04:36:56
@ 35f80bda:406855c0
2025-06-01 04:36:56Privacy is necessary for an open society in the electronic age. Privacy is not secrecy. A private matter is something one doesn't want the whole world to know, but a secret matter is something one doesn't want anybody to know. Privacy is the power to selectively reveal oneself to the world.
If two parties have some sort of dealings, then each has a memory of their interaction. Each party can speak about their own memory of this; how could anyone prevent it? One could pass laws against it, but the freedom of speech, even more than privacy, is fundamental to an open society; we seek not to restrict any speech at all. If many parties speak together in the same forum, each can speak to all the others and aggregate together knowledge about individuals and other parties. The power of electronic communications has enabled such group speech, and it will not go away merely because we might want it to.
Since we desire privacy, we must ensure that each party to a transaction have knowledge only of that which is directly necessary for that transaction. Since any information can be spoken of, we must ensure that we reveal as little as possible. In most cases personal identity is not salient. When I purchase a magazine at a store and hand cash to the clerk, there is no need to know who I am. When I ask my electronic mail provider to send and receive messages, my provider need not know to whom I am speaking or what I am saying or what others are saying to me; my provider only need know how to get the message there and how much I owe them in fees. When my identity is revealed by the underlying mechanism of the transaction, I have no privacy. I cannot here selectively reveal myself; I must always reveal myself.
Therefore, privacy in an open society requires anonymous transaction systems. Until now, cash has been the primary such system. An anonymous transaction system is not a secret transaction system. An anonymous system empowers individuals to reveal their identity when desired and only when desired; this is the essence of privacy.
Privacy in an open society also requires cryptography. If I say something, I want it heard only by those for whom I intend it. If the content of my speech is available to the world, I have no privacy. To encrypt is to indicate the desire for privacy, and to encrypt with weak cryptography is to indicate not too much desire for privacy. Furthermore, to reveal one's identity with assurance when the default is anonymity requires the cryptographic signature.
We cannot expect governments, corporations, or other large, faceless organizations to grant us privacy out of their beneficence. It is to their advantage to speak of us, and we should expect that they will speak. To try to prevent their speech is to fight against the realities of information. Information does not just want to be free, it longs to be free. Information expands to fill the available storage space. Information is Rumor's younger, stronger cousin; Information is fleeter of foot, has more eyes, knows more, and understands less than Rumor.
We must defend our own privacy if we expect to have any. We must come together and create systems which allow anonymous transactions to take place. People have been defending their own privacy for centuries with whispers, darkness, envelopes, closed doors, secret handshakes, and couriers. The technologies of the past did not allow for strong privacy, but electronic technologies do.
We the Cypherpunks are dedicated to building anonymous systems. We are defending our privacy with cryptography, with anonymous mail forwarding systems, with digital signatures, and with electronic money.
Cypherpunks write code. We know that someone has to write software to defend privacy, and since we can't get privacy unless we all do, we're going to write it. We publish our code so that our fellow Cypherpunks may practice and play with it. Our code is free for all to use, worldwide. We don't much care if you don't approve of the software we write. We know that software can't be destroyed and that a widely dispersed system can't be shut down.
Cypherpunks deplore regulations on cryptography, for encryption is fundamentally a private act. The act of encryption, in fact, removes information from the public realm. Even laws against cryptography reach only so far as a nation's border and the arm of its violence. Cryptography will ineluctably spread over the whole globe, and with it the anonymous transactions systems that it makes possible.
For privacy to be widespread it must be part of a social contract. People must come and together deploy these systems for the common good. Privacy only extends so far as the cooperation of one's fellows in society. We the Cypherpunks seek your questions and your concerns and hope we may engage you so that we do not deceive ourselves. We will not, however, be moved out of our course because some may disagree with our goals.
The Cypherpunks are actively engaged in making the networks safer for privacy. Let us proceed together apace.
Onward.
Eric Hughes hughes@soda.berkeley.edu
9 March 1993
-
 @ cae03c48:2a7d6671
2025-06-01 06:00:27
@ cae03c48:2a7d6671
2025-06-01 06:00:27Bitcoin Magazine

Amboss Launches Rails, a Self-Custodial Bitcoin Yield ServiceAmboss, a leader in AI-driven solutions for the Bitcoin Lightning Network, today announced Rails, a groundbreaking self-custodial Bitcoin yield service. According to a press release sent to Bitcoin Magazine, it’s designed to empower companies, custodians, and high net worth individuals. This allows participants to earn a yield on their Bitcoin.
Big news from @TheBitcoinConf !
We’re thrilled to announce Rails—a self-custodial Bitcoin yield service that empowers you to earn on your BTC while supercharging the Lightning Network.Let’s bring Bitcoin to the World.https://t.co/3WYYvB95hP
— AMBOSS
 (@ambosstech) May 29, 2025
(@ambosstech) May 29, 2025Rails also launched a secure way for Liquidity Providers (LPs) to hold all custody of their Bitcoin while generating returns from liquidity leases and payment routing, although they are not guaranteed. The implementation of Amboss’ AI technology, Rails strengthened their Lighting Network with more dependable transactions and larger payment volumes.
“Rails is a transformative force for the Lightning Network,” said the CEO and Co-Founder of Amboss Jesse Shrader. “It’s not just about yield—it’s about enabling businesses to strengthen the network while earning on their Bitcoin. This is a critical step in Bitcoin’s evolution as a global medium of exchange.”
The service offers two options:
- Rails LP is designed for high net worth individuals, custodians, and companies with Bitcoin treasuries, requiring a minimum commitment of 1 BTC for one year.
- Liquidity subscriptions are designed for businesses that receive Bitcoin payments, with fees starting at 0.5%.
Amboss partnered with CoinCorner and Flux (a joint venture between Axiom and CoinCorner), to bring Rails to the market. CoinCorner has incorporated it into both its exchange platform and daily payment services in the Isle of Man. Flux is jointly focused on advancing the Lightning Network’s presence in global payments. Their participation highlights growing industry trust in Rails as a tool to scale Bitcoin effectively.
“Rails offers a practical way for businesses like ours to participate in the Lightning Network’s growth,” said the CFO of CoinCorner David Boylan. “We’ve been using the Lightning Network for years, and Rails provides a structured approach to engaging with its economy, particularly through liquidity leasing and payment routing. This aligns with our goal of making Bitcoin more accessible and practical for everyday use.”
This post Amboss Launches Rails, a Self-Custodial Bitcoin Yield Service first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 7f6db517:a4931eda
2025-06-01 05:01:49
@ 7f6db517:a4931eda
2025-06-01 05:01:49
Bank run on every crypto bank then bank run on every "real" bank.
— ODELL (@ODELL) December 14, 2022
The four main banks of bitcoin and “crypto” are Signature, Prime Trust, Silvergate, and Silicon Valley Bank. Prime Trust does not custody funds themselves but rather maintains deposit accounts at BMO Harris Bank, Cross River, Lexicon Bank, MVB Bank, and Signature Bank. Silvergate and Silicon Valley Bank have already stopped withdrawals. More banks will go down before the chaos stops. None of them have sufficient reserves to meet withdrawals.
Bitcoin gives us all the ability to opt out of a system that has massive layers of counterparty risk built in, years of cheap money and broken incentives have layered risk on top of risk throughout the entire global economy. If you thought the FTX bank run was painful to watch, I have bad news for you: every major bank in the world is fractional reserve. Bitcoin held in self custody is unique in its lack of counterparty risk, as global market chaos unwinds this will become much more obvious.
The rules of bitcoin are extremely hard to change by design. Anyone can access the network directly without a trusted third party by using their own node. Owning more bitcoin does not give you more control over the network with all participants on equal footing.
Bitcoin is:
- money that is not controlled by a company or government
- money that can be spent or saved without permission
- money that is provably scarce and should increase in purchasing power with adoptionBitcoin is money without trust. Whether you are a nation state, corporation, or an individual, you can use bitcoin to spend or save without permission. Social media will accelerate the already deteriorating trust in our institutions and as this trust continues to crumble the value of trust minimized money will become obvious. As adoption increases so should the purchasing power of bitcoin.
A quick note on "stablecoins," such as USDC - it is important to remember that they rely on trusted custodians. They have the same risk as funds held directly in bank accounts with additional counterparty risk on top. The trusted custodians can be pressured by gov, exit scam, or caught up in fraud. Funds can and will be frozen at will. This is a distinctly different trust model than bitcoin, which is a native bearer token that does not rely on any centralized entity or custodian.
Most bitcoin exchanges have exposure to these failing banks. Expect more chaos and confusion as this all unwinds. Withdraw any bitcoin to your own wallet ASAP.
Simple Self Custody Guide: https://werunbtc.com/muun
More Secure Cold Storage Guide: https://werunbtc.com/coldcard
If you found this post helpful support my work with bitcoin.

-
 @ a10260a2:caa23e3e
2025-06-01 04:26:33
@ a10260a2:caa23e3e
2025-06-01 04:26:33In this post, you’ll see how easy it is to consolidate some UTXOs. Hopefully this’ll give you the confidence to try it out whenever fees are low. It’s super simple and can be done in two steps!
Step 1
Go to your wallet and grab a receive address. As you can see, this wallet has two UTXOs.

Step 2
Once you have a receive address, send the max amount in your wallet to it (i.e. you’ll be sending to yourself). What you’ll receive is your all your bitcoin back minus the network fee. In this case, the cost was 900 sats.

That’s it.
Next time, when you go to Send > Coin Control, you’ll see that you have one large UTXO instead of one large and one small.


-
 @ 8d34bd24:414be32b
2025-06-01 04:04:10
@ 8d34bd24:414be32b
2025-06-01 04:04:10Many people today believe that the church has replaced Israel and that the promises given to Israel now apply to the church. When we say this, we are calling God a liar.
Can you imagine a groom promising to love and cherish his wife until death do they part and then saying, “I’m keeping my promise by loving and cherishing a new and different wife.”? We would never consider that man to be honest, faithful, and good. If God promised to protect and guide Israel, to have a descendant of David on the throne, and to give them the land, we can only trust Him if He fulfills these promises.
When we say the church has replaced Israel, we make two mistakes. We raise up the church beyond what is right and we put down Israel. We need to be careful because God promised Abraham:
“And I will bless those who bless you, And the one who curses you I will curse. And in you all the families of the earth will be blessed.” (Genesis 12:3)
and He reiterated this promise to Israel during the Exodus:
“He couches, he lies down as a lion,\ And as a lion, who dares rouse him?\ Blessed is everyone who blesses you [Israel],\ And cursed is everyone who curses you [Israel].” (Numbers 24:9) {clarification mine}
When we curse Israel or the Jews, we will be under God’s curse. Now this does not mean that every criticism of a particular action by Israel’s leaders brings a curse. Today’s nation of Israel is led by fallible men like every other nation, so there are mistakes made or corruption by particular leaders. It does, however, mean that generalizations against Israel and the Jews are wrong and of Satan.
Paul specifically warned the church against thinking they had replaced Israel in God’s blessing and love.
If the first piece of dough is holy, the lump is also; and if the root is holy, the branches are too.
But if some of the branches were broken off, and you, being a wild olive, were grafted in among them and became partaker with them of the rich root of the olive tree, do not be arrogant toward the branches; but if you are arrogant, remember that it is not you who supports the root, but the root supports you. You will say then, “Branches were broken off so that I might be grafted in.” Quite right, they were broken off for their unbelief, but you stand by your faith. Do not be conceited, but fear; for if God did not spare the natural branches, He will not spare you, either. Behold then the kindness and severity of God; to those who fell, severity, but to you, God’s kindness, if you continue in His kindness; otherwise you also will be cut off. And they also, if they do not continue in their unbelief, will be grafted in, for God is able to graft them in again. For if you were cut off from what is by nature a wild olive tree, and were grafted contrary to nature into a cultivated olive tree, how much more will these who are the natural branches be grafted into their own olive tree?
For I do not want you, brethren, to be uninformed of this mystery—so that you will not be wise in your own estimation—that a partial hardening has happened to Israel until the fullness of the Gentiles has come in; and so all Israel will be saved; just as it is written,
“The Deliverer will come from Zion,\ He will remove ungodliness from Jacob.”\ “This is My covenant with them,\ When I take away their sins.” *From the standpoint of the gospel they are enemies for your sake, but from the standpoint of God’s choice they are beloved for the sake of the fathers*; for the gifts and the calling of God are irrevocable**. For just as you once were disobedient to God, but now have been shown mercy because of their disobedience, so these also now have been disobedient, that because of the mercy shown to you they also may now be shown mercy. For God has shut up all in disobedience so that He may show mercy to all. (Romans 11:16-32) {emphasis mine}
Paul warns that although the Jews were pruned away due to rejection of Him and gentiles were grafted into Him by faith, if we reject God’s word, we can be pruned away and if the Jews return to Jesus, they can be grafted back in. He predicts that the Jews will return. “…that a partial hardening has happened to Israel until the fullness of the Gentiles has come in; and so all Israel will be saved.” He also says regarding Israel that “the gifts and the calling of God are irrevocable.” Yes, Israel rejected Jesus and was punished for doing so, but they will be called back to God and trust in their Messiah, Jesus. In the end, all the promises of God to Abraham, Jacob, David, and others regarding Israel, will be brought to complete fulfillment.
Both the Old and New Testaments talk about Israel being punished for rejecting God and their Messiah, but that, after the time of the Gentiles, they will be called back to Him.
and they will fall by the edge of the sword, and will be led captive into all the nations; and Jerusalem will be trampled under foot by the Gentiles until the times of the Gentiles are fulfilled. (Luke 21:24)
After Daniel had been in prayer and repentance for the sins of Israel, the angel Gabriel came with this prophecy about Israel.
“Seventy weeks have been decreed for your people and your holy city, to finish the transgression, to make an end of sin, to make atonement for iniquity, to bring in everlasting righteousness, to seal up vision and prophecy and to anoint the most holy place. So you are to know and discern that from the issuing of a decree to restore and rebuild Jerusalem until Messiah the Prince there will be seven weeks and sixty-two weeks; it will be built again, with plaza and moat, even in times of distress. Then after the sixty-two weeks the Messiah will be cut off and have nothing, and the people of the prince who is to come will destroy the city and the sanctuary. And its end will come with a flood; even to the end there will be war; desolations are determined. (Daniel 9:24-26)
In this prophecy, the prediction of 69 weeks (literally sevens, but meaning groups of 7 years) from the decree to rebuild Jerusalem (by Artaxerxes) to the Messiah was fulfilled to the day when Jesus rode into Jerusalem on a donkey on Palm Sunday.
I always thought it strange that the prophecy predicted 70 sevens and that there was the first 69 sevens (483 years), then \~2,000 years where nothing happens, and then comes the final seven — the Great Tribulation. It didn’t make sense until I realized, the 70 sevens referred to the years of Israel. The time of the gentiles intervenes between the 69th and 70th sevens. This delay happened due to Israel rejecting their Messiah.
When He approached Jerusalem, He saw the city and wept over it, saying, “If you had known in this day, even you, the things which make for peace! But now they have been hidden from your eyes. For the days will come upon you when your enemies will throw up a barricade against you, and surround you and hem you in on every side, and they will level you to the ground and your children within you, and they will not leave in you one stone upon another, because you did not recognize the time of your visitation.” (Luke 19:41-44)
We are now in the time of the Gentiles, the church age, the intermission in the story of Israel. After the church is raptured, the story will return to Israel. The Jews (at least many of them) will finally accept their Messiah. They will suffer through the Tribulation while witnessing to the world and then God will finally fully fulfill His promises to Israel through the Millennial kingdom.
Alas! for that day is great,\ There is none like it;\ And it is the time of Jacob’s distress,\ But he will be saved from it.
‘It shall come about on that day,’ declares the Lord of hosts, ‘that I will break his yoke from off their neck and will tear off their bonds; and strangers will no longer make them their slaves. But they shall serve the Lord their God and David their king, whom I will raise up for them.
Fear not, O Jacob My servant,’ declares the Lord,\ ‘And do not be dismayed, O Israel;\ For behold, I will save you from afar\ And your offspring from the land of their captivity.\ And Jacob will return and will be quiet and at ease,\ And no one will make him afraid.\ For I am with you,’ declares the Lord, ‘to save you;\ For I will destroy completely all the nations where I have scattered you,\ Only I will not destroy you completely.\ But I will chasten you justly\ And will by no means leave you unpunished.’ \ (Jeremiah 30:7-11) {emphasis mine}
Jacob’s distress is the final Tribulation. The 144,000 Jewish witnesses will be saved through the whole Tribulation. Others may become saved and die a martyrs death, but they will then be brought into the millennial kingdom where the Messiah will fill the throne of David and Israel will reach from the River to the Sea.
The Jews have already been saved “from afar, and your offspring from the land of their captivity” with the recreation of Israel in 1947 and the continual return of Jews to their homeland.
God is working to fulfill His promises to Israel and His work is nearly complete.
“O Jacob My servant, do not fear,” declares the Lord, “For I am with you. For I will make a full end of all the nations where I have driven you, Yet I will not make a full end of you; But I will correct you properly And by no means leave you unpunished.” (Jeremiah 46:28)
God promises a “full end of all the nations where I have driven you.” Those nations and people who try to destroy Israel will be destroyed. As Christians we should love what God loves, and despite Israel’s repeated betrayals, God still loves Israel, so we should, too.
May the God of heaven give us a right view of Israel. May we see them as God sees them. May God use us to share the Gospel in such a way as to lead to a harvest of Jews for the Kingdom of God. To God be the glory!
Trust Jesus
-
 @ 8bad92c3:ca714aa5
2025-06-01 04:01:17
@ 8bad92c3:ca714aa5
2025-06-01 04:01:17Key Takeaways

Dr. Jack Kruse returns in this fiery episode to expose what he alleges is a coordinated campaign by Big Pharma, technocrats, and global elites to control public health narratives and financial systems through manipulated health policies and propaganda. He accuses figures like Calli and Casey Means of fronting a compromised "Maha Movement," backed by A16Z, Big Tech, and the World Economic Forum, with ambitions to embed themselves into U.S. health policy and bioweapons programs. Kruse details his covert efforts to expose these connections, claiming they led to the withdrawal of Casey Means' Surgeon General nomination, and warns of a looming biotechnocratic surveillance state where mRNA vaccines act as bioweapons to enforce compliance. Urging Bitcoiners to expand their fight for sovereignty beyond finance into healthcare and biology, Kruse argues that the true war is over time sovereignty—not just monetary freedom—and that protecting children from vaccine harms is now the most urgent front in this escalating battle.
Best Quotes
"Bitcoin is worthless if you have no time."
"We’re not playing games here. This is to the death."
"Big Pharma is just the drug dealer. The real boss is the Department of Defense and DARPA."
"The real battle in D.C. isn’t left vs. right, it’s Rothschilds and Rockefellers vs. the technocrats."
"First principle Bitcoiners need to become first principle decentralizers of life itself."
Conclusion
This episode delivers a provocative call to action from Dr. Jack Kruse, who warns that the fight for sovereignty must go beyond finance to confront what he sees as the immediate threat of centralized bio-surveillance through mRNA vaccines. Blending insider claims with health activism, Kruse urges Bitcoiners and the public to recognize that true freedom requires decentralizing not only money but also healthcare and information systems, arguing that without protecting biological sovereignty, Bitcoin’s promise of liberty will be meaningless if people are left physically, mentally, or politically compromised.
Timestamps
0:00 - Intro
0:47 - Outlining MAHA infiltration
22:59 - Fold & Bitkey
24:35- Danger to children
28:27 - Political shell game
35:40 - Unchained
36:09 - Time theft
41:07 - Vax data
46:32 - Bioweapon and control system
58:29 - Game plan - Decentralized yourself
1:15:16 - Priorities
1:24:30 - Support Mary Talley BowdenTranscript
(00:00) me, Larry Leard, those kind of Bitcoiners, the people that are out there that have money, like they're looking to take us out. You need to know a little bit about the back history that I don't think I've talked about anywhere on any other podcast. Rick Callie is linked to the current administration is through Susie Watts.
(00:17) They both were working at Mercury PR basically is the frontman for propaganda for Big Farm. Basically, who pays you? You become their [ __ ] We're not playing games here. This is to the death. This is the biggest issue facing Maha now. It's not Froot Loops. It's not red dye. But the messenger RA job can drop you like Demar Handler.
(00:40) Can end your career like JJ Watt. Dr. Jack Cruz, welcome back to the show. Thank you, sir, for having me. Well, thank you for being here. I mean, you're making a lot of noise around a topic that I wasn't well aware of. I'm not going to lie. I think I got duped by or we'll find out if I actually got duped by the meanses. Cali means was coming in last year talking big about Maja getting the food correct.
(01:15) Um, basically telling the story of him being a lobbyist and understanding how corrupt the food system is. And we talked about it last time we were on two months ago. this sort of maha movement has shifted towards focusing on preventative care particularly in diets and you were on the Danny Danny Jones show late last year with Cali means uh sort of pressuring him to admit that the vaccine should be pulled off the market and he did not did not bite and would not budge on that and now his sister Casey has been appointed to surgeon general and
(01:50) this is something Let me let me tell you a little bit about that because you need to know a little bit about the back history that I don't think I've talked about anywhere on any other podcast. She was going to be named surgeon general uh back then. Just so you know that I knew it and I knew quite a bit of other things.
(02:16) So what was my goal? I knew um that Cali and Casey were tied to big tech. They were tied specifically, which you'll be interested in, A16Z, the shitcoiners extraordinaire, and they were also tied to the World Economic Forum through the book deal. Um, so my goal at that time as part of the person that was big in the mob like, and Marty, I don't know if you know this back part of the story.
(02:46) Maha begins not with Casey and Cali and Bobby Kennedy. It began with me, Bobby, and Rick Rubin on Rick's podcast the day that I told RFK Jr. that SV40 was in the Fiser Jabs. Mhm. And that's when Bobby found out that I wrote the law for Blly for a constitutional amendment for medical freedom. And he asked me to use four pages of the law.
(03:13) And Blly cleared me to do that. And then Aaron Siri, who was Bobby's attorney and working with a lot of the stuff that Bobby does with vaccines and I can Aaron contacted me. So just so you're clear, this is two and a half years ago. This is before this is a year previous to Casey and Cali coming on the scene. And I was always behind the scenes.
(03:37) I was not really interested in getting involved um in the [ __ ] show. But when I saw these two show up, the way they showed up and when I heard Cali actually say on a podcast that, you know, he was the modus operande of the Maha movement and he's the one that brought Bobby and Trump together.
(04:02) I said, "That's where I draw a [ __ ] line." I'm like, "Uh-uh. These guys, I know exactly what they're going to do. I see the game plan. they're going to use a shell game and I needed to have proof before you can come out and be a savage. You got to have proof. So, I hired three former Secret Service agents to actually do a very deep dive.
(04:24) We're talking about the kind of dive that you would get uh if you were going for a Supreme Court nomination. Okay? It cost me a lot of money. And why did I think it was important? Because as you know, you know, as a Bitcoiner, you just saw the big scam that happened with Maya Paribu down in Cerninam that happened after.
(04:49) Well, when I hired these guys, when all of my research that I had done was confirmed by them, I said, "Okay, now we need to go on a podcast very publicly and we need to put Cali's feet to the fire." Why? because I knew and he did not know that I knew this prior to the podcast. Uh that his sister was going to be nominated for surgeon general then.
(05:14) And because he didn't know and you you'll be able to confirm this or the savages in your audience can confirm this with Danny Jones. Do you know that Cali cancelled the podcast to do it into uh February? Yeah. Well, I think it was April of 25 because he didn't want to give anybody the time and day.
(05:37) So, what did I start doing? I started posting some of the information back in November that I found and the links to the Wjikis and the links to Bin, the links to A16Z. I didn't didn't give a ton of the information, but let's just put it this way. enough to make Callie and Cassie scream a little bit that people in DC started to read all my tweets.
(06:04) And then he called Danny up and said, "Danny, I want to do this podcast immediately." And I knew the reason why. Cuz I was baiting him to come so I could hit him with the big stuff. Why? Because you have to understand these two kids, you know, tied to the Rockefellers. They're tied to the banking elite.
(06:26) They're tied to the World Economics Form. Rick Callie is linked to the current administration is through Susie Watts. They both were working at Mercury PR and uh Mercury PR uh basically is the frontman for propaganda for Big Farm and everybody knows that, but not everybody knew that Cali worked for them.
(06:50) And you know the story that he sold all you guys, how he fooled you. And I consider you a smart guy, a savage, it's not shocking how he fooled you because he said as a um a lobbyist basically who pays you, you become their [ __ ] to to be quite honest and you'll say things that will make sense. Everybody in creation who's going to watch your podcast knows that all the things that Casey and Cali have said have been said literally for 30, 40, 50 years going all the way back to probably Anel Peas about diet and exercise.
(07:25) Everybody [ __ ] knows that. It's not new. They just decided to repackage it up and then they actually got in Bobby's ear about it. And when I released all this stuff, did Bobby know what I had? Yeah, he knew. And did the people in DC all what all their antennas up about this issue? Who was most pissed off with Uncle Jack back then? Susie [ __ ] Walls.
(07:56) Why? because those two are her babies that were going to be the amber that Susie Cassidy Cassidy Big Farmer were going to place around um Bobby Kennedy once he got confirmed. And that's why for the savages that are listening to this podcast, you go back and look at Nicole's tweet from, you know, I guess it was about four or five days ago that this didn't make sense.
(08:20) Why? because I gave the data directly to the people in DC behind the scenes of what was really going on and because it was so explosive. That's the reason Susie had to not give the job to Casey Means. She had to wait till the heat died down. So they elevated Janette and Janette bas -
 @ 8bad92c3:ca714aa5
2025-06-01 04:01:15
@ 8bad92c3:ca714aa5
2025-06-01 04:01:15Key Takeaways

In this episode, Bram Kanstein delivers a powerful exploration of how studying money for thousands of hours led him to a single, life-changing conclusion: Bitcoin is the key to preserving value and reclaiming personal agency in an increasingly unstable world. Through the lens of a disillusioned millennial generation—raised with technological optimism but betrayed by economic reality—Bram exposes the fiat system as one built on illusion, debt, and diminishing returns. He explains how Bitcoin’s transparent, rule-based design offers a principled alternative, especially for those wired to question systems and seek truth. Describing the fiat economy as a “high-velocity trash system” that undermines innovation and long-term planning, he argues Bitcoin creates the time and space to think, build, and live freely. As AI reshapes the labor market, Bram sees Bitcoin as a vital foundation for individuals to adapt, maintain sovereignty, and thrive in a future defined by rapid technological disruption.
Best Quotes
“Anything that you would want to fix in the world is broken because the money is broken.”
“You’re stacking nothing. Literal paper.”
“You have to red pill before you orange pill.”
“The only thing you need to do is move to the other money that they cannot mess with.”
“One Bitcoin is one Bitcoin. That’s the whole point.”
“Millennials are primed to understand Bitcoin.”
“Bitcoin lets you get out of the rat race and start walking your own path.”
“The fiat mindset is a zero-sum game. In Bitcoin, value is created.”
“We should stop asking how to value Bitcoin—and start asking how to value everything else in Bitcoin.”
“Even with a master’s in economics, people still don’t understand what money is.”
Conclusion
This episode delivers a powerful call to rethink everything we assume about money, arguing that understanding Bitcoin is less about profit and more about reclaiming personal agency in a world defined by uncertainty. Bram Kanstein shows how asking fundamental questions—like “What is money?”—can lead to a deeper sense of purpose and autonomy. As AI and systemic instability accelerate, Bitcoin emerges not just as sound money, but as a life tool for intentional living, long-term thinking, and individual sovereignty.
Timestamps
0:00 - Intro
0:36 - INTJ bitcoiners
4:58 - The millennial headspace is primed for bitcoin
7:25 - Bitcoin gives time and space to build
15:29 - Fold & Bitkey
17:05 - Seeing systemic problems
26:25 - Bitcoin’s positive feedback loop
33:55 - Recognize your agency
37:58 - Unchained
38:27 - Fiat money creates uncertainty
44:41 - What is money?
54:04 - Money and energy
1:03:43 - Bitcoin allows growth
1:09:02 - Bitcoin/AI
1:31:34 - Optimistic noteTranscript
(00:00) Let's say you're a millennial and mid-30s and you want to retire in 30 years. If you calculate the amount of dollar, pound the euro, yen units. You need way more units of that money than you think right now. They are funding pension funds, but the pension funds are using that money for the people that are actually retiring.
(00:17) No one knows about money. They don't know how debt works, how finance works. But that's kind of how it's designed, right? Like that's what eventually keeps the Ponzi alive. And I just started with the question, what do you think happens if you call the bank and say like, hey, can I get 100 or 200k in cash? Man, you got an editor like in house.
(00:39) That's That's pro. That's uh it's because this setup I'm so far away from the computer. I just need somebody to hit the button. Okay. Okay. the extent the extent of of Logan's job extends far beyond just hitting the button. But yeah, INTJ I think uh I think it was as we rear into what looks to be another bull market.
(01:05) I think getting back to first principles and discussing the challenges of studying and understanding Bitcoin, it's important to to highlight the archetype of individuals who have studied fallen down the rabbit hole and really dedicated their lives to Bitcoin. And this INTJ cohort that exists within Bitcoin seems pretty material apparently. Yeah.
(01:35) I mean, I have many moments where I just realize that I'm lucky that my brain is wired in a certain way, you know. I feel like crazy blessed that I figured out this Bitcoin thing, you know, and that when I ran into certain realizations along the way in my Bitcoin journey that I was like, hm, you know, how does this actually work? you know, do I actually understand the systems I'm participating in, the things that I believe, you know, the the the the people that I abstracted um or or outsourced certain responsibilities to to take care of, for example, my money
(02:10) in the bank. You know, I I think um being wired in a certain way definitely helps in grasping Bitcoin to a degree where you're like, okay, this is the only thing I need to pay attention to, you know, in my life. And yeah, we we jokingly started talking about this because I have the hat here, but there was this um I think it was like like a Twitter poll actually or someone shared it on Twitter and this is already like two or three years old where where someone investigated these MyersBriggs um personality types and I think there's
(02:42) only like 2% of people that have INTJ but like 20% of Bitcoiners have that personality type. So it um it apparently helps. So yeah, I just I just quickly Googled it actually. It says uh the INTJ is the architect. It's a personality type with the introverted intuitive thinking and judging traits. These thoughtful tacticians love perfecting the details of life, applying creativity and rationality to everything they do.
(03:09) I think the rationality part here is what um what uh I think helps you to to gro Bitcoin eventually. Yeah, it reminds me of I forget what the study was, but postco it was a similar distribution of just like 2% of people were highly skeptical of what was going on with the lockdowns and the attack on bodily autonomy.
(03:38) And there was a study that was done about I forget it was bees or some type of fly that they they have like the horde of um the horde of the particular fly I think it was bees has like 2% act as these sort of alarm bells that are on the outside the outskirts of the community and they'll start communicating like hey something's wrong here and people the other flies or bees will be skeptical at first but then eventually uh the alarm bells will be proven to be right that there was some sort of danger around the corner. That's fascinating.
(04:09) Yeah. Yeah, that's fascinating. I I think we're not that special eventually, you know, like we think we have all this autonomy, but but um yeah, we're we're just wired in a certain way. And I think I don't know where you want to take this conversation, but I think, you know, part of growing up and being an adult is figuring out, you know, how do I actually work and how do I work with how I work, you know? Yeah. No, it is.
(04:36) And as I get older, creep into my mid-30s, which is hard hard to come to grips with, it is uh really falling back on like, all right, I I feel like I have a good perspective on the world and my place in it, and how do I just optimize to make sure I'm aligning my my work and my career, I guess, if you call it that, with what I'm passionate about. Yeah.
(05:00) Well, I also think that is actually why our generation, you know, my my podcast is Bitcoin for millennials. I think uh the millennials are primed to understand Bitcoin. You know, we are in this life phase where big things happen, you know, starting a family or settling somewhere or or making big career moves or decide Yeah.
(05:25) like deciding what am I going to spend like the next 10 20 years on and uh I think it's an interesting phase actually I I don't know how that was for you but but for me like the the 30s were really where I dove more and more into Bitcoin like got got that stronger conviction and also yeah kind of was invited to go further down that that rabbit hole you know and like how I see it now is that that Bitcoin is really the foundation for the rest of my life, you know, like it it gives me time and space to look forward and enthusiasm, you know, like I sometimes lurk on the
(06:01) millennial subreddit, you know, or the finance sub subreddit. And many people in our generation are very nihilistic, you know, they're very unsure about the future. Like some people aren't even having kids because they think they cannot afford it, you know. And uh whenever I read that, I just think like, yeah, I I don't really have those things.
(06:22) But I know it's because of Bitcoin, you know. I I know that Bitcoin gives me, yeah, like I said, the time and space to figure out what's next, like what should I focus on? Like it gives time and space to to try out stuff, to build something, you know, to to to really attempt at at doing something. Where I see many people that don't see that, they are more in the consumer type, you know, like they they just spend the money that's worth the most today, you know, like that's what they're incentivized to do. Yeah.
(06:49) And is is that why you started Bitcoin for millennials is to number one put the put the message out there. Millennials come listen to this. One of you Yes. that is trying to educate you about this. But because this is something I think about a lot is somebody's like dead smack in the middle of the millennial generation and has observed many of the things you just described in my own life, my own network.
(07:13) And that's part of the reason why this podcast exists. And um what I'm trying to do at TFTC is just try to figure out a way to reach into the minds of millennials, hopefully c -
 @ 8bad92c3:ca714aa5
2025-06-01 04:01:15
@ 8bad92c3:ca714aa5
2025-06-01 04:01:15Key Takeaways

In this episode of TFTC, energy economist Anas Alhajji outlines a profound shift in U.S. foreign policy under Trump—away from military intervention and toward transactional diplomacy focused on trade, reconstruction, and curbing Chinese and Russian influence in the Middle East. He highlights Trump’s quiet outreach to Syria as emblematic of the U.S.'s strategic flexibility in legitimizing former adversaries when economically beneficial. Alhajji dismisses BRICS as a fractured bloc incapable of rivaling the U.S.-led order and insists the dollar and petrodollar remain dominant. On energy, he warns that despite favorable fundamentals, prices are suppressed by political confusion, underinvestment, and an aging power grid ill-prepared for the AI and urbanization boom. He also contends that Iran is stalling negotiations to buy time for nuclear advancement and that any deal will be superficial. Finally, Alhajji debunks the myth of Trump being pro-oil, noting his long-standing hostility toward the industry and explaining why a repeat of his past energy boom is implausible given today’s financial and structural constraints.
Best Quotes
- “BRICS is a paper tiger. Everything about BRICS is what China does—and that’s it.”
- “The dollar is here to stay. The petrodollar is here to stay. End of story.”
- “Trump hates the oil industry. He always classified it as an enemy.”
- “Energy projects are 30- to 40-year investments, but politicians think in 4-year cycles. That’s where the disconnect lies.”
- “People think shale will boom again. It won’t. The model changed from ‘drill baby drill’ to ‘control baby control.’”
- “The real story of Trump’s trip wasn’t about politics—it was investment, investment, investment.”
- “Without massive investment in the grid and gas turbines, blackouts will become the norm—even in rich countries like Kuwait.”
- “Iran and China have perfected the game of oil exports. Sanctions are just theater at this point.”
Conclusion
Anas Alhajji’s conclusion challenges conventional narratives, arguing that global power is shifting from military dominance to economic leverage, infrastructure investment, and energy control. He presents a nuanced view of U.S. foreign policy under Trump, emphasizing the strategic importance of trade and reconstruction over regime change. As energy demand soars and geopolitical risks mount, Alhajji warns that the real dangers lie not in foreign adversaries, but in policy confusion, infrastructural lag, and complacency—making this episode a crucial listen for anyone seeking to understand the high-stakes intersection of energy, economics, and diplomacy.
Timestamps
0:00 - Intro
0:48 - Syria and US diplomacy in Middle East
12:50 - Trump in the Middle East
18:12 - Fold & Bitkey
19:48 - Iran - Nuclear program and PR
33:53 - Unchained
34:22 - Crude markets, trade war and US debt
54:28 - Trump's energy stance
1:05:46 - Energy sector challanges
1:14:44 - Policy recommendations
1:21:18 - AI and bitcoinTranscript
(00:00) oil prices market fundamentals support higher price than where we are today. But because of this confusion, everyone is scared of low economic growth and that is a serious problem. The US media ignored part of Trump's speech when he said we are not about nation building and they refer to Afghanistan and Iraq.
(00:15) Look at them. This is a criticism of George W. Bush. We have groups that are talking about the demise of the dollar, the rise of bricks. Bricks is a paper tiger. Everything about bricks is what China does and that's it. The dollar is here to stay and the petro dollar is here to stay.
(00:31) The perception is that the Trump administration is cold but the reality Trump hates the oil [Music] indust. How are you? Very good. Very good. Thank you. As you were telling me, you've been a bit sleepd deprived this week trying to keep up with what's going on. Oh, absolutely. I mean, Trump keeps us on our toes uh all the time.
(01:06) In fact, I plan certain things for the weekend and Trump will say something or he will do something and all of a sudden we get busy again. Uh so clients are not going to wait for you until you finish your work. Basically, they want to know what's going on. So what is going on? What what how profound were the events in the Middle East? These are very uh very profound changes basically because it is very clear that if you look at the last 15 years uh and you look at the growth uh in the Middle East, you look at the growth of Saudi Arabia and uh the
(01:41) role of Turkey for example in the region uh it just just amazing be beyond any uh any thoughts. Uh in fact both of them Turkey and Saudi Arabia are part of the G20. Uh so they have economic influence and they have political influence. And of course the icing on the cake for those who are familiar with the region is to recognize the Syrian government and meet with the Syrian uh president.
(02:11) Uh this is a major a major change in economics and politics uh of the Middle East. Let's touch on that Syria uh topic for a while because I think a lot of people here in the United States were a bit shocked at how sort of welcoming President Trump was towards the new Syrian president considering the fact that uh he was considered an enemy not too long ago here in the United States.
(02:42) What first of all it's a fact of life for those who would like to check the history of politics. There were many people around the world who were classified or they were on the terrorism list and then they became friends of the United States or they were became heroes. I mean Nelson Mandela is one of them. You look at Latin America, there are presidents in Latin America who were uh the enemy of the United States and then they became uh uh cooperative with the United States and the United States recognized their governments and the result of their uh elections. Uh so
(03:15) we've seen this historically uh several uh several times around the world and as they say freedom fighters for some basically are the enemies and the terrorists for for others etc. So uh what we've seen that's why the the visit is very important that the recognition of this government is very important. uh the fact on the ground that uh the president of Syria had the power on the ground uh he had the the the people on the ground and he had the control on the ground and whatever he's been he's been doing since he came into power until now
(03:52) he done all the right steps u and people loved him I mean everyone who went to Syria whether the Syrians who left Syria 40 years ago or uh the visitors who are coming to Syria, they will tell you, "We have never seen the Syrian people as happy as we've seen them today, despite the fact that they they live in misery.
(04:17) They don't have um 8 million people without housing. Uh there is barely any electricity in most of the country. There is no internet. There is barely any food. The uh inflation is rampant, etc. But people are happy because they lived in fear for a very long time. And uh the steps they have taken. For example, the uh ministers in the previous government uh are still there and they are still in the housing of the government.
(04:49) They still have the drivers. They still have the cars from the previous government. They still have it until today. So uh they they were classified as enemies before. But all of a sudden now you have a new government that is uh accepting them. Uh so we we see some changes on the ground that are positive and we'll see how these things will go given that the area around them basically has been unstable for a very long time.
(05:17) how because I don't the the news when I was actually it was surreal for me because my first trip to the Middle East was last December when it was literally f flying over Syria to Abu Dhabi when uh um Assad was getting thrown out and it was pretty surreal to be in that region of the world.
(05:43) How as it pertains to like religious minorities within Syria moving forward is there protractions protections there? Um well let me just uh I want to emphasize one point that is very important. What did the interest of Turkey, Saudi Arabia and the United States in Syria if remember Syria was controlled by Iran and was controlled by the Russians.
(06:09) So in a sense it becomes uh kind of an imperative that taking it away from Iran and Russia and not bringing Iran or Russia back is extremely important. Now the Russians are still there and they have their own base but at least they are not bombing the Syrians and not killing them anymore. But the idea here is taking Syria out of Iran and Russia and probably later on if they kick the Russians out, Russians will not have access to the Mediterranean.
(06:37) Uh so there is an interest uh of all parties basically to take Russia out of Iran and um out of uh Syria regardless the country is uh devastated and it creates massive opportunities for US companies on all levels and uh we've seen a contract uh done recently with you mentioned Abu Dhabi uh uh a contract uh uh with the UA a basically to revamp all the Syrian ports and work on the Syrian ports.
(07:13) Uh so such contracts basically uh when you have a country that has nothing and it's completely devastated the whole infrastructure is devastated. Who is going to build it? If the uh what the Chinese, the Russians, so who who are going to build it? So, uh I think there is a a big room for US companies and others basically to come in and uh literally help on one side and make money on the other.
(07:38) Yeah, I think that that's what I'm trying to discern. What was this convoy from the United States to the Middle East this week signali -
 @ 8bad92c3:ca714aa5
2025-06-01 04:01:14
@ 8bad92c3:ca714aa5
2025-06-01 04:01:14Key Takeaways

In this episode of TFTC, Jessy Gilger, Managing Partner at Sound Advisory and architect of Ganet Trust, unpacks the complexities of retiring on Bitcoin, emphasizing that the “right” amount depends on spending habits, age, and minimizing withdrawal pressure. He introduces Ganet Trust as a Bitcoin-native fiduciary solution that leverages multisig custody to meet institutional compliance standards without sacrificing decentralization. Jessy also critiques high-yield derivative products like MSTY, warning of systemic risks and advocating for safer alternatives like SMAs. The conversation broadens into the emotional pitfalls of financial decision-making, the importance of aligning wealth with values, and the evolving macro landscape where Bitcoin’s intersection with traditional finance and tax policy will shape how individuals and institutions protect and grow their holdings across generations.
Best Quotes
"The most comfort comes from putting as little pressure as possible against that stack."
"Multisig is the upgrade from a honeypot to a distributed key setup."
"If a whale pees in the pool, everyone is affected."
"Everyone feels late to Bitcoin because they know someone who got in earlier."
"Stacking Saturdays is my new stack sats."
"Bitcoin doesn’t know about trust, it knows private keys."
"The money is there to serve your values—not the other way around."
"Some financial products will help, some will hurt, and some will fail. Our job is to help clients navigate them safely."
Conclusion
This episode offers a powerful blend of practical insight and philosophical reflection on long-term Bitcoin strategy, emphasizing the need for sound custody, inheritance planning, and emotional discipline in a volatile, financialized world. Jessy Gilger introduces Ganet Trust as a vital solution for secure, compliant Bitcoin ownership, while his “stacking Saturdays” mantra reframes wealth as a pursuit of time, freedom, and meaningful priorities. As Bitcoin moves further into the mainstream, the conversation urges listeners to stay grounded, think generationally, and build resilient systems for both assets and life.
Timestamps
00:00 - Intro
0:33 - Bitcoin Retirement Planning at New All-Time Highs
5:22 - How Gannett Trust Works
10:05 - High Net Worth Bitcoin Storage and Estate Planning Solutions
16:48 - MSTY Derivatives: Understanding MicroStrategy Product Risks
19:53 - Bitkey
20:56 - How MSTY Works and the Whale in the Pool Problem
30:16 - Unchained
30:37 - Bitcoin Financialization and Corporate Treasury Strategy
39:35 - Avoiding Ego-Driven Bitcoin Mistakes and Building Bridges
47:33 - Stack Saturdays
53:15 - Tax Policy Changes and Wild Times Ahead
57:18 - Where to Find Gannett Trust and ClosingTranscript
(00:00) We have people retiring with hundreds of Bitcoin. Do you need to be on a yacht every week or are you staying humble and keeping those stats? 10 of the 12 ETFs are at Coinbase means all the keys are at Coinbase and with the news of the last week like, hey, there could be cracks. Micro Strategy is built on Bitcoin.
(00:18) It's got all of the risks of Bitcoin, right? But then it's got its own set of risks. Let's call them Sailor and Profitability. Then you have derivatives which are on top of Micro Strategy and they retain the risks of everything underneath. meeting on a on a day when we hit new all-time highs. Bitcoin approached $110,000.
(00:43) Got Jesse back on the show to talk about many things, not just the price ripping. A lot of good things happening on the unch unchained side of things. Watching Ganet Trust. We'll get into it. Yeah, lot lots of stuff happening. I think um the price likes Ganet. I I think that's the uh the mover. What uh I mean that's been a big discussion in in the space right now is uh are we heading to new all-time highs? How should Bitcoiners be preparing? How much Bitcoin do people need to retire? How how are you thinking about all this as we approach what seems
(01:22) to be another bull cycle? Yeah, that's a common question, right? How much Bitcoin do I need to retire? I get it a lot and there's so many other questions I want to ask like, well, how much money are you spending, right? Do you do you need to be on a yacht every week or are you staying humble and keeping those stats? And so, the amount of Bitcoin can vary because the spending pressure you're putting against your Bitcoin stack is the the biggest factor, right? And age is probably the second.
(01:54) a 30-year-old retiring on Bitcoin is different than a 75year-old retiring on Bitcoin just because of the horizon. So, stacks vary. We've got people retiring with um less than seven figures of Bitcoin because they have other assets and then we have people retiring with hundreds of Bitcoin um and putting very little pressure against that portfolio.
(02:16) So, can go in a lot of different ways. Um but it is a question of the day as you're poking new all-time highs. Everyone's like, "Well, how high is it going to get?" And then huge question is do we have cycles again right if countries are buying what what would a downside look like and that's the big question in the retirees mind is how do I protect and not ride that downside all the way down if we do have another 70 80% drawback. Yeah. No.
(02:42) And I think particularly for younger people having in their mind like the perspective of 21 million Bitcoin, 8 billion people, what's the stat? 60 million millionaires in the world. Mhm. How much how many stats do I need to get to to feel comfortable that I have a sufficient slice of the Bitcoin pie? That feel comfortable concept is just so different, right? because Bitcoin is moving and shaking and all-time highs or down 30% and that's still within a bull market.
(03:15) Is that comfortable, right? Can you actually hang it up and like, all right, not going into work and I'm just going to continue to ride these adoption cycles. I don't know if it ever gets comfortable. The most comfort comes from putting as little pressure as possible against that stack, right? that you're not pushing these withdrawal rates of like 5 10 20% of my Bitcoin stack.
(03:38) I'm needing to live on every because then you're requiring Bitcoin to do something for you in the short term which is just not great at, right? What what's Bitcoin price going to be in a year? Far less reliable than what's Bitcoin price going to be in 30 years. Yeah. Yeah. Yeah. Well, I I think one of the holdups too is the ability for people to get into Bitcoin and know where to put it and not only have certainty of what it will be valued at in 30 years, but will they have access to it? That's one thing that you guys
(04:10) have been very much focused. I know sound advisory is separate from Unchained technically but within the Unchained umbrella but Unchained focused on helping secure individuals and businesses and trust uh Bitcoin and I think today's announcement of Ganet Trust is a massive step in a direction towards more certainty for long-term holdings for particular entities.
(04:36) Yes, the unchained umbrella or or family of companies is growing and the intention will be for sound advisory to tuck under or be merged into folded into Ganet Trust Company as it gets stood up. But it is the most robust uh compliance offering that um is out there in the fiduciary space. And so that in my opinion was the one thing missing as people want to live on a Bitcoin standard.
(05:04) Sometimes they're in an entity or an organization or have a structure that requires a fiduciary standard. And these two coming together is solved by Ganet Trust Company. So it's going to be the most robust way to hold Bitcoin and have like true inheritance that can be um administered through generations. So how how does this work mechanically via Ganet? Mechanically.
(05:28) So as the first Bitcoin native trust company, other other trust companies do exist, right? but they don't build upon Bitcoin in the way that Unchained has. So Ganet in its um in its Unchained roots and using Unchained technology is going to be able to use multi-IG to achieve um trust company goals.
(05:50) And what that likely will mean is Ganet holding a key, Unchained holding a key, third party holding a key. Those three keys together ensure that the Bitcoin is not being held at any one spot, right? We could get into the Coinbase honeypot. We actually talked about this on our last episode like, "Hey, what do you think is the uh the risk out there that the industry might disagree with?" Said, "I'm launching a new segment.
(06:15) I'm going to ask you a prediction of what what's out there that the uh the industry doesn't see eye to eye with you at." And I was at conferences and they're saying, "Hey, Coinbase is the best. That's where we put all the cut." That means all the keys are at Coinbase and with the news of the last week like, hey, there could be cracks, right? If you've got exposure to Coinbase now, you could be questioning. I was on the list.
(06:37) I got the email. You were affected. That's not great. It doesn't feel good knowing that information that information could have been a lot worse. That headline could have been private keys being mismanaged. When you overlay what Ganet is going to offer to the custody space, it means that not all of the keys are going to be at any one entity.
(07:00) And so that gives the Bitcoiner who understands multisig the confidence that okay, I'm upgrading from a honeypot to a distributed key setup. But it has to be done in a fiduciary and compliant way to satisfy the the institutional and big money of the world, right? family offices, uh, Bitcoin treasury companies, they're going to need a structure that the CIO, the -
 @ 8bad92c3:ca714aa5
2025-06-01 04:01:13
@ 8bad92c3:ca714aa5
2025-06-01 04:01:13Key Takeaways

In this landmark episode of TFTC, Adam Back and Sean Bill explore Bitcoin’s path to $1 million, focusing on its growing role as pristine collateral in a faltering financial system. Back highlights Blockstream’s infrastructure efforts, from mining operations to tokenized securities, designed to support this transformation, while Bill shares how he navigated institutional skepticism to bring Bitcoin exposure to a U.S. pension fund. Together, they unpack how institutions are entering the space through structured products and Bitcoin-backed credit, with Blockstream’s mining notes offering a glimpse of this new financial architecture. Amid rising debt, inflation, and fiat fragility, the duo presents Bitcoin not just as sound money, but as a strategic reserve asset gaining traction from El Salvador to Wall Street.
Best Quotes
"It's not a stretch to say that Bitcoin could reach parity with gold. That would imply something closer to a million dollars a coin."
"Digital gold vastly understates Bitcoin’s potential, but it’s where the conversation had to start."
"We’re not just building software, we’re solving financial market gaps, one at a time."
"You can wipe out an entire pension fund’s unfunded liability with a 2% allocation to Bitcoin, if it performs as we expect."
"ETF buyers are the new hodlers. They’re not day traders; they’re five-year pocket investors."
"Bitcoin is becoming super collateral, its role in structured credit could help engineer the soft landing everyone hopes for."
"In a world of financial repression, Bitcoin is how the have-nots finally access property rights and savings."
"Emerging markets will be the early adopters of Bitcoin finance because they need it the most."
"You worked for your money. To systematically steal it through hidden inflation is perverse."
"Bitcoin could be the story that saves public pensions, and the people relying on them."
Conclusion
This episode presents a bold vision of Bitcoin as more than sound money, it’s the foundation of a new global financial system. Adam Back and Sean Bill argue that Bitcoin’s role as “super collateral” is reshaping credit, pensions, and sovereign reserves, while a robust infrastructure of financial tools quietly prepares it to absorb institutional capital. As fiat trust erodes, Bitcoin’s adoption will be driven not by hype, but by necessity, and when the shift becomes undeniable, $1 million per coin will mark the start of a new financial era.
Timestamps
00:00:00 - Intro
00:00:38 - New ATH
00:02:06 - Sean's Journey Getting Bitcoin Into Pensions
00:03:15 - Blockstream's Evolution Into Finance
00:08:30 - Building Bitcoin Financial Infrastructure
00:14:30 - The Challenge of Conservative Pension Boards
00:17:02 - Bitkey
00:18:10 - Bitcoin's Current Price and Market Cycle
00:24:05 - Bitcoin as Super Collateral
00:27:24 - Unchained
00:30:09 - Cypherpunk Ideals vs Financial Reality
00:34:55 - Pension Fund Crisis and Bitcoin Solution
00:42:29 - The Cypherpunk Banking Stack
00:49:54 - Digital Cash and Free Banking
00:57:06 - Liquid Network and Institutional Rails
01:07:49 - Sean At CBOT
01:22:16 - Bitcoin Futures and Market Structure
01:25:53 - 2025 Bitcoin Price PredictionsTranscript
(00:00) I'm uh permeable, so I'm always astounded that it's not, you know, 10 or 100 times higher. If everybody saw it, the addressable mark, I mean, it would already be 100 200 trillion asset class, right? That's not a stretch to say that Bitcoin could reach parody with gold. That would imply something closer to a million dollars a coin.
(00:18) You see some established public market companies in different countries saying, "Oh, we're going to buy a billion of Bitcoin. We're going to raise and buy 500." Black Rockck ETF. They're even talking about recommended allocations to portfolio managers in the 2% range. Obviously, digital gold would vastly understate the potential of Bitcoin.
(00:38) Gentlemen, thank you for joining me. Of course. Thanks for having us on. Uh Adam, I was just saying I'm woefully embarrassed. This podcast is almost 8 years old and this is your first time on the show. Oh, okay. This is uh but it's an exciting time. Yeah. And you uh really dedicated to podcast. It's been a lot of years, a lot of episodes, right? It has been. Cool.
(00:59) I think we're approaching 700, which is crazy to think. Wow, that is impressive. The uh No, we're talking hit a new alltime high today. Yeah, Bitcoin doing Bitcoin things just as we were on stage uh at the talking hedge kind of asset manager conference uh trying to explain to them why they should put Bitcoin in their uh fund allocations.
(01:23) Yeah, we were discussing it before we hit record and I saw Tur's tweet looked like Tur was at the event, too. Yeah, he was. M so 50% held up they have Bitcoin in their personal account but only 2% or 4% of the funds very few that actually had allocated to Bitcoin. So a lot of them are believers at a personal level but they haven't been able to sell it within their institution you know so they own it themselves uh but they haven't quite gotten the boards to agree yet.
(01:53) So which was a similar situation I was in in 2019 when I first proposed it. You know, I had my experience with Bitcoin. I had a very good experience and was trying to convince uh the pensions in California that they should be looking at adding Bitcoin to the portfolio. Yeah. And it was great to hear some of your background last night, Sean.
(02:11) So, Sean, for those of you watching, uh is the CIO at Blockstream now. Yeah. I am really excited to have both of you here because I've got into Bitcoin in 2013 and nerded out uh on the tech side of Bitcoin distributed system mining full nodes the layered stack that's been built out and so I followed probably all the work that you guys have done at Blockstream since you've been around and it's been really cool to see everything you've done from the Blockstream satellite.
(02:42) I've broadcast some transactions through that before. It's a Jade um uh CLN or excuse me, Core Lightning now. Um the uh liquid and now over the last few years really sort of leaning into the financialization of finance as I like to um to reference it. And so Adam, like how's that transition from being hypert focused towards a more financial perspective on Bitcoin been? Well, actually in our 2014 uh kickoff meeting, you know, with the founders sitting around big whiteboard, we were trying to forward cast what we'd have to do to get
(03:28) a Bitcoin layer 2 for, you know, settlement of assets and Bitcoin working. And one of the risk you know so we thought we'll build the tech and other people issue the assets but like well they might be lazy they might not do it if that happens we'll have to do it ourselves. So there was a lot of situations like that actually where you know you would think there would be lots of people building applications but many people are really just more in business development and a technology is basically a website and a database and
(03:55) you know Bitcoin core wallet on a server or something like that right so we actually ended up building a lot of middleware and getting into asset management a couple earlier steps one was the mining note so we're doing hosting and mining in our own account and what we did when when it was public that we were hosting initially Fidelity was the uh launch customer.
(04:16) They kept coming back to us and saying, "No, we need we need some hosting." And you know, uh, they'd looked around and decided that we were the best. We were we were like, "No, no, we're prop mining. We don't do hosting." But they persuaded us to host them. And then we're like, "Okay, maybe we should expand and host for other people.
(04:31) " And then that became news. And so then a lot of Bitcoiners contacted us and says, you know, I've got like a dozen miners. Can you host them for me? And of course, if you're if you're hosting for thousands of customers, that's a whole you need need a support team. Somebody has got two miners and one of them's crashed or failed, they're very upset, right? It's half the revenue.
(04:52) Whereas somebody's got, you know, 10,000 per client, it's just part of the, you know, maintenance cycle like a big data center. Discs fail 1% a year, you replace them when they die, they raid, it doesn't matter, right? So, it's kind of that phenomena. So we try to figure out well how can we help you know how can we help people do this without creating a you know that painoint and so we designed this mining note concept where it's kind of socialized so that collectively they look like one of the enterprise customers and then we put a 10% buffer in it so that we would eat
(05:22) the first 10% of equipment failure so they wouldn't get you know the drooping hash rate as miners like failed due to age uh for the for the onset And we also figured out how to try and make them a unified market. So, you know, we're selling more tranches into the market. This started in 2021, a three-year product.
(05:45) And um you know, there was some people on the launch branch and then some people 3 months later. So, what we do is look at how many Bitcoin it had mined in the first three months. We buy that and then match it with a 33month contract for the next one. And so the economically equivalent neither dilutive or anti-dilutive for the buyer and therefore they could trade in a unified market even though there were eight sales tranches over the first I don't know like 12 months or something like that and that that market you know it was using initially using uh liquid
(06:17) security tokens uh with uh stalker a European company that does the securitization I mean the legal p -
 @ eb0157af:77ab6c55
2025-06-01 04:01:08
@ eb0157af:77ab6c55
2025-06-01 04:01:08The revelation by Miles Suter, Product Lead at Block, at the Bitcoin Conference 2025 confirms the economic potential of LN for professional operators, but the yield comes mainly from routing fees
During the Bitcoin 2025 conference in Las Vegas, Miles Suter, Bitcoin Product Lead at Block Inc., revealed data that could change the economic perception of the Lightning Network: the company’s routing node is generating annual returns of 9.7% on invested liquidity.

During his presentation, Suter confirmed what many experts suspected but no one had ever quantified precisely: Lightning payment routing can be not only technically effective, but also economically profitable on a large scale. With an estimated public capacity of 184 BTC (approximately $20 million), Block is demonstrating that Lightning infrastructure can generate significant returns through the use of bitcoin as a payment method.
Non-custodial yield, with a doubt
Lightning routing represents what experts define as “true non-custodial yield” – returns generated from the pure economic utility of bitcoin as a means of payment, without having to entrust one’s funds to third parties.
“We are earning almost 10% returns on Bitcoin by effectively routing real payments on the Lightning network,” Suter declared.
Riccardo Masutti — researcher and founder of Baited — has, however, observed that the double-digit yields advertised by Block are closely tied to an exceptionally aggressive fee structure that markedly deviates from the median parameters of the Lightning Network. In particular, the Cash App nodes apply a fee rate of 2,147,483,647 ppm, resulting in fees up to 2 million times higher than the average cost of standard channel transactions. Block’s own node also enforces significant fees: to route a million satoshis, it requires 1,053 sats in outgoing fees and 2,955 sats in incoming fees, compared to a network median base fee of approximately 0.999839 sat and a median fee rate of 0.000063 sat/sat. This discrepancy suggests that the yield is generated more by a surcharge imposed on intermediated payments than by any real efficiency in liquidity allocation.
In 2024 Cash App recorded an increase in Lightning payment volume equal to 7 times that of the previous year: one in four outgoing payments now occurs via LN, Suter stated.
According to Block’s Product Lead “if Bitcoin becomes only digital gold, we have failed the mission. If we don’t use bitcoin for payments, we risk losing one of the most important promises permissionless money. If we don’t preserve the qualities of cash in the digital world, human liberty is seriously in trouble.”
The company aims to incentivize practical and daily use of bitcoin, seeing Lightning payments as the key to realizing Satoshi Nakamoto’s original vision of a “peer-to-peer electronic payment system.”
The post According to Block, routing on Lightning yields 10% annually: but the yield comes from fees appeared first on Atlas21.
-
 @ f4a890ce:af88c4aa
2025-06-01 03:52:49
@ f4a890ce:af88c4aa
2025-06-01 03:52:49執行摘要
隨著比特幣再創歷史新高,市場總市值攀升至 3.39 兆美元,成交量顯著回溫至 704 億美元,顯示多頭氣氛延續。然而,鏈上與衍生品數據釋出警訊,操作上應更加謹慎。 本週需關注三大數據變化:
清算與槓桿風險:永續合約持倉升至 159.7B,多空雙邊爆倉規模擴大。若價格劇烈波動,將可能引發連鎖平倉與資金撤離。 鏈上結構是否轉弱:雖鯨魚持續吸籌,NUPL 指標尚未突破歷史高點,市場情緒未到亢奮,但並不代表市場毫無壓力。 ETF 資金動能是否續強:BTC 與 ETH ETF 雖持續流入,但增幅放緩,若出現流出,將影響市場對主流資產的風險偏好。
此外,Coinbase 與 Korea溢價指數維持正值,代表現貨買盤尚有支撐。整體結構仍偏多,但需持續追蹤資金是否轉趨保守,以應對高位震盪風險。
加密市場
本週加密貨幣市場總市值下降至 3.24 兆美元,較前週略有回落,顯示市場資金流入動能稍微減弱。交易活動方面,當週總成交量達到 591.66 億美元,較上週減少,反映市場活躍度有所下降,投資者情緒轉趨保守。
https://coinmarketcap.com/charts/
市場情緒指標顯示,恐懼與貪婪指數為 55,處於中性區間,代表市場情緒較為平穩,但貪婪情緒較前週下降,投資者對市場前景的信心稍微減弱。
https://www.coinglass.com/zh-TW/pro/i/FearGreedIndex
此外,相對強弱指標處於中性至超賣區間,顯示部分標地短期內可能存在修正壓力,市場仍需消化部分參與者獲利籌碼。
https://www.coinglass.com/zh-TW/pro/i/RsiHeatMap
山寨幣季節指數降至 14,顯示市場資金仍主要流向比特幣及主流加密貨幣,投資者對高風險資產的配置仍較為保守,中小型代幣尚未獲得市場關注。
https://www.blockchaincenter.net/en/altcoin-season-index/
穩定幣市值上升至 2,475.81 億美元,顯示部分資金正在尋求避險,或為市場修正後的潛在買盤做準備。
https://defillama.com/stablecoins
小結
本週加密市場總市值與成交量同步下降,顯示市場資金流動性稍微減弱,交易活躍度下降。恐懼與貪婪指數落在中性區間,市場情緒較為平穩,但投資人信心略有減弱。相對強弱指標顯示市場仍存在修正壓力,短線上漲動能有限。山寨幣季節指數低迷,市場資金仍集中於主流幣種,而穩定幣市值增長,顯示投資者維持謹慎態度,靜待市場更明朗的機會。未來市場走勢仍將受到宏觀經濟因素及市場資金流動影響,需密切關注相關變化。
衍生性商品
槓桿交易持續活躍,本週永續合約持倉規模達 144.18B,顯示市場仍具有強勁的槓桿需求。
https://www.coinglass.com/zh-TW/pro/futures/Cryptofutures
資金費率維持 0.01%,大部分交易所仍為 正費率,市場情緒偏向多頭。
https://www.coinglass.com/zh-TW/FundingRate
爆倉數據方面,本週整體空單爆倉達 826.391M,而多單爆倉則達 1148.547M,顯示市場波動仍造成大規模強制平倉。其中 5月30日 空單爆倉 84.91M,多單爆倉 796.623M,顯示當日市場波動較為劇烈。
https://www.coinglass.com/zh-TW/LiquidationData
清算熱力圖顯示,$93,000 附近 的清算金額達 211.54M,此區間可能成為市場交易的重要風險區域。
https://www.coinglass.com/zh-TW/pro/futures/LiquidationHeatMap
期權市場保持穩定交易量,投資者在不同價格區間進行配置: * $100,000 行權價的看跌期權合約數量達 7.6K,總金額達 $28.16M,顯示市場對該區間的風險防禦仍較為明顯。 * $110,000 行權價的看漲期權合約數量為 10.62K,總金額 $47.56M,顯示市場對上行潛力仍有較高期待。
https://www.coinglass.com/zh-TW/pro/options/OIStrike
最大痛點出現在 2025/06/27 的 $100,000,名義金額 11.97B,以及 2025/06/06 的 $105,000,名義金額 2.85B,顯示市場對未來走勢的佈局仍存在分歧。
https://www.coinglass.com/zh-TW/pro/options/max-pain
小結
加密市場槓桿交易活躍,爆倉情況顯示市場波動仍帶來顯著風險。永續合約與期權市場的數據反映出投資者對市場未來走勢的不同看法,多空資金配置仍在競爭中。隨著市場價格熱區逐漸明朗,投資者需密切關注資金流向與槓桿風險,調整交易策略,以降低市場劇烈變動帶來的影響。
ETF
本週,加密貨幣衍生性商品市場依舊保持穩定,ETF資金流入顯示市場情緒良好。比特幣(BTC)ETF流入2.117億美元。
而以太坊(ETH)ETF則流入5,860萬美元,相比前週的資金流向,ETH的流入幅度顯著提升,可能反映市場對其關注度增強。
https://coinmarketcap.com/zh-tw/etf/
小結
比特幣 ETF 的資金流入雖略低於上週,但仍保持穩健。市場近期受到宏觀經濟變數影響,包括貨幣政策調整與投資者風險偏好的轉變,使得資金配置較為謹慎。此外,以太坊 ETF 的資金流入大幅提升,顯示出投資者可能對 ETH 的技術發展與未來潛力更為樂觀。特別是近期市場對去中心化金融(DeFi)與以太坊網絡升級的關注,也可能促使資金流入提升。
整體而言,本週 ETF 市場仍然展現穩健資金流入,尤其 ETH 的流入幅度增加值得關注。投資者對市場的信心維持穩定,但仍需密切關注宏觀經濟環境以及技術面因素對衍生性商品市場的影響,以評估後續市場動能。
鏈上分析 | BTC
近期鏈上數據顯示,比特幣在二級交易所的儲備量再度創下新低,反映出市場上流通的 BTC 數量持續減少,整體壓力趨緩。
地址分佈方面延續上週趨勢,10–100 顆持倉的中小戶數量持續下降,而 100–1k、1k–10k 及 10k 以上的大型地址則全面增加,尤其是 10k+ 地址出現明顯跳升,顯示有特大型機構或長期資金加速進場。
https://cryptoquant.com/community/dashboard/67e2481ba2a7203afd437b31
鯨魚活躍地址持續上升,代表主力資金在當前價位仍具操作意願與信心。
https://cryptoquant.com/community/dashboard/67e2481ba2a7203afd437b31
從 Exchange Netflow 觀察,目前市場仍處於穩定的淨流出狀態,表明投資者傾向將 BTC 移出交易所、進行長期儲存,進一步減少潛在賣壓。
根據 URPD(UTXO Realized Price Distribution)指標觀察,目前市場中多數比特幣地址的持倉成本集中於 9 萬美元附近,顯示該價格區間具備顯著的籌碼密集度與潛在支撐力,若價格回落至此區間,預期將有較強的買盤介入,形成穩定支撐。
https://charts.bgeometrics.com/distribution_realized_price.html
另一方面,從 NRPL(Net Realized Profit/Loss)指標來看,過去兩次關鍵價格突破均伴隨著大量已實現的盈虧,顯示投資者在獲利後傾向了結部分持倉。然而本次上漲過程中,NRPL 數據顯示已實現盈虧尚處於初步上升階段,暗示市場中仍有大量潛在利潤尚未兌現,市場動能尚未充分釋放。
https://charts.bgeometrics.com/nrpl.html
溢價指數方面,Coinbase Premium Index 持續位於 0 以上,顯示美國市場對 BTC 需求穩健;而 Korea Premium Index 則攀升至 3,反映亞洲市場對 BTC 價格有更高追價意願,顯示整體市場情緒偏向樂觀。
Coinbase Premium Index:https://cryptoquant.com/asset/btc/chart/market-data/coinbase-premium-index?window=DAY&priceScale=log&metricScale=linear&chartStyle=line&sma=0&ema=0
Korea Premium Index:https://cryptoquant.com/asset/btc/chart/market-data/korea-premium-index?window=DAY&sma=0&ema=0&priceScale=log&metricScale=linear&chartStyle=line
小結
近期比特幣鏈上數據持續展現強勁表現。首先,二級交易所的比特幣儲備量再度創下新低,反映出整體市場供給持續減少,為價格提供中長期支撐。 在地址分布方面,10–100 顆地址數量延續下跌趨勢,而 100–1k、1k–10k 以及 10k 顆以上的地址數量皆呈現上升,尤其 10k 顆以上的大型地址數量突然明顯增加,顯示超級大戶進場布局意圖明確。 鯨魚活躍地址也持續上升,顯示主力資金開始進一步參與市場;交易所的 Exchange Netflow 指標則持續顯示資金處於淨流出狀態,佐證了比特幣正由交易所流向冷錢包持有,偏多氛圍濃厚。 同時,Coinbase 溢價指數仍維持在 0 以上,代表美國買盤持續存在,而韓國溢價指數更顯強勁,已升至 3,反映亞洲市場情緒火熱。 從 URPD 指標來看,多數比特幣地址的購入價格集中於 9 萬美元,意味此區具備紮實支撐;而 NRPL 指標顯示,與前兩次價格突破相比,目前的已實現盈虧尚處初升階段,代表仍有大量潛在利潤未被釋放,後續若市場進一步上漲,可能會引發更大規模的獲利了結,總之整體來看鏈上結構穩健,上行動能仍未停止。
總體經濟
本週加密貨幣市場繼續受到總體經濟環境的影響,資金流動性仍受限,價格波動性加大。聯邦基金有效利率維持在 4.33%,顯示市場依然處於高利率環境。
https://fred.stlouisfed.org/series/FEDFUNDS
隨著 6 月 18 日即將召開的 FOMC 會議,市場對利率決策的預期進一步集中,4.25%-4.50% 區間的機率已從 94.4% 上升至 97.8%,而 4.00%-4.25% 的預測則下降至 2.2%,顯示市場對維持較高利率的預期持續增強,這可能抑制風險資產的表現,包括加密貨幣。
https://www.cmegroup.com/cn-t/markets/interest-rates/cme-fedwatch-tool.html
消費者物價指數 (CPI) 為 2.33%,與前期持平,顯示通膨壓力維持穩定。另一方面,失業率仍保持在 4.2%,顯示勞動市場仍然穩健,企業對人力需求依然穩定。由於市場流動性仍受抑制,加密貨幣投資者仍需面對波動風險,尤其是高槓桿交易,風險控制將成為投資策略的重要考量。
失業率:https://www.macromicro.me/series/37/unemployment-rate
消費者物價指數(CPI):https://www.macromicro.me/series/128/consumer-price-index-sa-yoy
值得關注的是,美國 M2 貨幣供給量已連續數月呈現上升趨勢,顯示市場資金逐步回流、流動性環境有所寬鬆。從歷史走勢來看,M2 的變化與比特幣價格具有高度正相關性,特別是在寬鬆週期中,比特幣常伴隨著資金充裕而出現顯著上漲。若當前趨勢延續,M2 持續上升將可能為加密資產市場提供有力支撐,未來比特幣行情表現值得期待。然而,仍需觀察美聯儲政策走向,以確認這波資金釋放是否具備延續性。
https://charts.bgeometrics.com/m2.html
小結
隨著 FOMC 會議臨近,市場對於短期內貨幣政策的變動趨於保守,預期高利率環境將延續一段時間。若會議結果符合市場預期並維持較高利率,加密市場可能會進一步受到流動性受限的影響。然而,若後續經濟數據顯示通膨持續降溫或就業市場開始走弱,市場對未來貨幣政策轉向的預期可能升高,進而帶動風險資產回暖。 美國 M2 貨幣供給量近幾個月持續上升,顯示市場資金正逐步回籠。從歷史數據來看,M2 走勢與比特幣價格具有正相關性,在流動性大量回升的背景下,長期而言對加密市場構成潛在利多。若資金供給趨勢延續,有望為未來行情提供結構性支撐。 整體而言,加密貨幣市場仍受總體經濟環境影響,高利率政策持續壓制資金流動性,短期內價格波動風險較高。投資者應密切關注即將召開的 FOMC 會議及後續政策動向,以評估市場走勢並調整交易策略。
新聞
比特幣序數現在可以透過 BitVMX 橋接到 Cardano
美國法院判定川普關稅無效,白宮顧問:對上訴有信心,將敲定三項貿易協議
巴基斯坦將建立比特幣戰略儲備,為加密貨幣挖礦分配2000兆瓦能源
巴拿馬城市長表示,船舶可以使用比特幣支付巴拿馬運河過境費並免於排隊
美國眾議院共和黨正式提出加密貨幣市場結構法案
美國證券交易委員會稱加密貨幣質押並不違反美國證券法
-
 @ 502ab02a:a2860397
2025-06-01 01:22:46
@ 502ab02a:a2860397
2025-06-01 01:22:46ไม่ต้องคาดหวังวิชาการมากๆในวันอาทิตย์ก็ได้นะครับ วันนี้เรามาคุยเรื่องแดดในอีกแบบกันบ้าง เพราะเห็นว่าช่วงนี้ฝนตกบ่อยจนบางทีก็มีแดดมาให้ตากแค่แว๊บเดียวจริงๆ แต่มันเป็นแว๊บที่ทำให้นึกอะไรขึ้นมาได้ครับ
เฮียชอบมองฟ้าเวลาฝนหยุดตกใหม่ๆ ฟ้ายังไม่ใสสนิท แต่มีแสงอ่อนๆ ทะลุเมฆบางๆ แดดแบบนี้แหละที่มักจะพา “รุ้งกินน้ำ” มาวิ่งเล่นกลางท้องฟ้า
สมัยก่อนเคยสงสัยว่า แค่แสงผ่านหยดน้ำในอากาศ ทำไมถึงแยกสีได้เจ็ดเฉดแบบนั้น จนวันหนึ่งเฮียได้รู้ว่า หยดน้ำเล็กๆ เหล่านั้น ไม่ใช่แค่ “ใส” แต่ทำหน้าที่เหมือน “เลนส์” อย่างดีของธรรมชาติ เป็นเลนส์ที่รวมแสง กระจายแสง หักเหแสง แล้วเปลี่ยนพลังธรรมดาให้กลายเป็นภาพมหัศจรรย์บนฟ้า
และนั่นแหละที่ทำให้เฮียเริ่มสงสัยต่อว่า...มันจะเป็นไปได้ไหม ที่หยดน้ำจะสร้าง “ไฟ” จากแสงแดดได้จริงๆ? คำตอบคือ ได้จ้ะ 55555
ในฟิสิกส์ เราเรียกปรากฏการณ์นี้ว่า focusing of light หรือการรวมแสง ซึ่งสามารถเกิดขึ้นได้จริงแม้ผ่านเลนส์ธรรมชาติอย่างหยดน้ำ หรือแม้แต่ไอน้ำบางๆ ที่ล่องลอยอยู่ในอากาศ พลังงานแสงที่รวมผ่านเลนส์แบบนี้ อาจมีความร้อนพอจุดไฟติดได้เลยทีเดียว เช่น ไฟไหม้ที่เริ่มจากแว่นขยาย หรือจากกระจกเว้าสะท้อนแดด ก็ล้วนใช้หลักเดียวกัน
สมัยก่อนก็มีตำนานว่าอาร์คีมีดีส นักคณิตแห่งกรีก เคยใช้กระจกสะท้อนแดดเผาเรือข้าศึก โชว์พลังแสงจากฟ้าจนกลายเป็นเรื่องเล่าในตำนาน แม้จะถกเถียงกันว่าเวอร์ไปหรือเปล่า แต่หลักการมันจริงจังนะครับ
เพราะในโลกของความเป็นจริงพลังงานเกือบทั้งหมดที่โลกใช้ได้ในวันนี้...มาจากแดด
-ลมที่พัดเกิดจากอุณหภูมิบนพื้นดินที่แดดอุ่นไม่เท่ากัน -ฝนที่ตกก็เพราะแดดระเหยน้ำขึ้นไปเป็นไอ -พืชเติบโตได้เพราะแดดกระตุ้นให้เกิดกระบวนการสังเคราะห์แสง -แม้แต่ไฟฟ้าที่มนุษย์ใช้ ก็เริ่มต้นจากโฟตอนเล็กๆ ที่ปล่อยตัวเองออกมาจากดวงอาทิตย์
โลกของเรา คือเครื่องจักรแปรแสงเป็นชีวิต หยดน้ำ เป็นเพียงหนึ่งในฟันเฟืองใสๆ ที่เปลี่ยนแสงนั้นให้เกิดรูปร่าง เกิดพลัง เกิดไฟ และสุดท้ายกลายเป็น "ความรุ่งเรืองของชีวิต"
ย้อนกลับไปในประวัติศาสตร์ มนุษย์รู้เรื่องนี้มาก่อนเราจะมีไฟฟ้าเสียอีก อียิปต์โบราณบูชาเทพ “รา” เทพแห่งดวงอาทิตย์ ชาวอินคาและมายา วัดจังหวะชีวิตจากการเคลื่อนของแดด ในจีนยุคโบราณ เชื่อว่าไฟฟ้าบนฟ้า ไอน้ำบนดิน ต้องสมดุล ไม่งั้นจะเกิดโรคระบาด ทั้งหมดบอกเราว่า แดดไม่ใช่แค่แสง แต่เป็นครูของชีวิต
แต่ที่เฮียชอบที่สุดคือ แม้จะเป็นเพียงหยดน้ำหนึ่งหยด ถ้าอยู่ในที่ที่เหมาะ เจอกับแสงที่ใช่ มันสามารถจุด “ไฟ” ขึ้นมาได้จริงๆ
เฮียว่านี่แหละคือสัญลักษณ์ของมนุษย์ เราก็เหมือนหยดเล็กๆ ใสๆ ธรรมดาแต่ถ้าได้พบแดดของตัวเอง ไม่ว่าแดดนั้นจะเป็นแรงบันดาลใจ ความรัก งานที่ทำ หรือความฝันในใจ และถ้าเรายอมเป็น “เลนส์” ให้พลังนั้นลอดผ่าน ไฟบางอย่างก็จะลุกขึ้นในตัวเราและทำให้โลกรอบข้างอุ่นขึ้นด้วย
เฮียเลยอยากชวนให้ลองหันหน้าเข้าหาแดด ไม่ต้องถึงขั้นจ้องตากับพระอาทิตย์ แค่ยอมให้แสงนั้นผ่านใจเรา เพราะแม้แดดจะเหมือนเดิมทุกวัน แต่ใจเราต่างหากที่เปลี่ยนไปในทุกครั้งและบางที แค่แสงหนึ่งหยด ก็อาจเป็นไฟสำหรับทั้งชีวิต
#SundaySpecialเราจะไปเป็นหมูแดดเดียว #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ f4a890ce:af88c4aa
2025-06-01 03:33:35
@ f4a890ce:af88c4aa
2025-06-01 03:33:35執行摘要
市場持續上探新高,總市值達3.26兆美 元,ETF資金穩定流入,鏈上鯨魚持續吸籌,讓 人忍不住想問,是不是該追?然而,數據提醒 我們需保持冷靜。 我們這週需觀察: • 衍生品爆倉與槓桿是否過熱,清算風險升溫, 短線資金可能因波動而退場。 • 觀察鏈上數據是否延續偏多結構。交易所比 特幣儲備持續下滑、大型地址增加,若鯨魚 活躍度持續上升,將有利於中期支撐力道。 同時觀察穩定幣市值變化,以判斷資金 是否持續布局。整體而言,市場結構偏多,但 上行須有資金支持,操作上宜保留彈性,避免 追高。
加密市場
本週加密貨幣市場總市值攀升至3.39 兆美 元,顯示市場持續向上,資本流入動能仍然強勁。交 易量方面,當週總成交量達到704 億美元,相較前週 有所提升,買賣雙方均展現較高的參與度。
https://coinmarketcap.com/charts/
市場情緒指標顯示,恐懼與貪婪指數為67, 仍屬「貪婪」區間,表明投資人對市場前景仍保持樂 觀,但貪婪情緒略有下降,顯示部分投資者可能開始 謹慎調整持倉策略。
https://www.coinglass.com/zh-TW/pro/i/FearGreedIndex
同時,相對強弱指標處於中性至超賣區間, 部分資產短期內面臨修正壓力,但市場尚未進入明顯 弱勢。
https://www.coinglass.com/zh-TW/pro/i/RsiHeatMap
值得注意的是,山寨幣季節指數下降至18, 表明市場資金仍主要流向比特幣及主流加密貨幣,投 資者對風險資產的偏好仍相對保守,中小型代幣尚未 獲得明顯關注。
https://www.blockchaincenter.net/en/altcoin-season-index/
此外,穩定幣市值增至2,462.75 億美元,反 映部分資金尋求避險,或為市場調整後的潛在買盤做 準備。
https://defillama.com/stablecoins
小結
本週加密市場總市值持續上升,而成交量顯 著提高,顯示市場活躍度增加,資金流入動能仍在延 續。恐懼與貪婪指數仍處於貪婪區間,市場情緒樂觀, 但投資者開始謹慎調整。相對強弱指標顯示市場尚未 進入弱勢,但需關注短期修正壓力。山寨幣季節指數 低迷,資金仍集中於主流幣種,而穩定幣市值增長, 可能顯示市場內部資金配置仍較為謹慎。
衍生性商品
市場槓桿交易持續增長,本週永續合約市場 的持倉規模達159.68B,顯示投資者對槓桿交易的需 求仍然強勁。
https://www.coinglass.com/zh-TW/pro/futures/Cryptofutures
資金費率方面,市場維持正費率,主要交易 所的資金費率保持在0.01%左右,表明市場仍偏多。
https://www.coinglass.com/zh-TW/FundingRate
爆倉數據顯示,空單爆倉金額達826.391M, 而多單爆倉金額達1148.547M,近期市場波動導致大 量強制平倉,尤其是多頭受壓較為明顯。
https://www.coinglass.com/zh-TW/LiquidationData
清算熱力圖顯示,$105,000 附近的清算金額 達166.41M,這一價格區間成為市場交易的重要關注 點,投資者需留意可能的風險變化。
https://www.coinglass.com/zh-TW/pro/futures/LiquidationHeatMap
期權市場交易活躍,投資者在不同價格區間 展開佈局: • $100,000行權價的看跌期權合約數量為6.93K,總 金額達$18.34M,顯示市場對該區間的下行風險仍 保持一定的防禦。 • $110,000行權價的看漲期權合約數量為13.32K,總 金額達$76.11M,顯示市場對上行的預期依然較為 強烈。
https://www.coinglass.com/zh-TW/pro/options/OIStrike
此外,最大痛點分別出現在2025/05/30 的 $98,000(名義金額9.7B)以及2025/06/27 的 $95,000(名義金額11.14B),顯示市場對不同價位的 佈局仍然存在分歧,但相較於上週有所收斂。
https://www.coinglass.com/zh-TW/pro/options/max-pain
小結
本週加密市場仍處於高度波動的環境,槓桿 交易與清算熱點區域成為市場關注的焦點。多頭與空 頭的資金配置存在競爭,爆倉規模顯示槓桿風險仍然 不可忽視。期權市場則呈現不同價格區間的佈局策略, 投資者對短期與中期的市場走勢保持不同看法。建議 投資者密切關注市場資金流向與槓桿風險,調整交易 策略,以降低市場波動帶來的潛在影響。
ETF
本週,加密貨幣衍生性商品市場保持活躍, 其中比特幣(BTC)與以太坊(ETH)ETF的資金流入 顯示投資人對市場的信心仍然穩定。比特幣ETF本週 流入2.602億美元。
而以太坊ETF則流入2,220萬美元,儘管流入 規模較上週略有下降,但仍顯示機構與散戶投資人對 市場的參與度不減。
https://coinmarketcap.com/zh-tw/etf/
小結
整體而言,本週加密貨幣衍生性商品市場保 持資金流入趨勢,雖然比特幣ETF流入金額略低於前 週,但以太坊ETF呈現穩定增長。市場投資情緒仍然 良好,未來需持續關注技術發展與宏觀經濟環境對 ETF與衍生性商品市場的影響,以掌握市場動能變化。
鏈上分析 | BTC
二級交易所的比特幣儲備量再次創下新低, 顯示市場上的比特幣供給持續減少,潛在拋壓進一步 降低。這一現象通常反映出投資者傾向於將資產移至 自有錢包,展現長期持有的傾向。
即使比特幣價格已創下歷史新高,地址分佈 方面仍延續與上週相同的趨勢。
https://cryptoquant.com/community/dashboard/67e2481ba2a7203afd437b31
鯨魚活躍地址仍延續上週,無論是新鯨魚或 老鯨魚,近期均明顯提升鏈上活動頻率,顯示其對市 場後市表現持續看好。整體而言,資金與籌碼正在流 向鯨魚,為比特幣後續表現提供強勁支撐。
https://cryptoquant.com/community/dashboard/67e2481ba2a7203afd437b31
然而值得關注的是,即便比特幣價格已創下 歷史新高,NUPL 指標卻未能超越前兩次牛市的高點。 這代表市場雖然整體仍處於盈利狀態,但尚未進入過 度亢奮或泡沫化階段,投資人情緒相對理性。這樣的 結構可能為後續漲勢留下空間。
目前觀察CoinbasePremium Index 與 Korea Premium Index 皆位於0 以上,顯示美國與韓 國市場的現貨買盤相對活躍,市場需求強勁。這也反 映出在全球主要市場中,投資者對比特幣仍具有高度 興趣與買入力道,尤其是來自機構或散戶資金較多的 交易平台表現出溢價狀態,通常代表有資金持續流入 並推升現貨價格,對中短期價格走勢構成支撐。未來 若兩大溢價指數持續維持正值,將有助於延續市場的 多頭氣氛。
CoinbasePremium Index:https://cryptoquant.com/asset/btc/chart/market-data/coinbase-premium-index?window=DAY&sma=0&ema=0&priceScale=log&metricScale=linear&chartStyle=line
Korea Premium Index:https://cryptoquant.com/asset/btc/chart/market-data/korea-premium-index?window=DAY&sma=0&ema=0&priceScale=log&metricScale=linear&chartStyle=line
小結
即便比特幣價格已創下歷史新高,鏈上數據 顯示市場仍存在結構性變化與短期潛在風險。從地址 分布來看,10–100 顆持倉的中小戶數量持續創下新低, 而100–1k、1k–10k 乃至於 10k 以上的地址數量則穩定 上升,顯示資金持續集中於大戶與機構手中。與此同 時,鯨魚活躍地址全面上升,顯示大資金正在積極參 與市場。 值得注意的是,雖然價格已突破新高, NUPL 指標雖來到相對高點,卻尚未超越過去兩次牛 市的峰值,代表市場情緒尚未達到極度貪婪或全面樂 觀的階段,潛在上行空間仍待觀察。 此外,CoinbasePremium Index 與 Korea Premium Index 雙雙維持在正值,代表現貨買盤動能 仍強,有助於支撐價格表現。整體而言,鏈上結構健 康,但需密切關注中小持倉賣壓與市場情緒是否過熱, 避免短線波動風險。
總體經濟
本週總體經濟數據顯示,聯邦基金有效利率 仍維持在4.33%,反映市場依然處於高利率環境。
https://fred.stlouisfed.org/series/FEDFUNDS
隨著6 月18 日即將召開的聯邦公開市場委 員會(FOMC) 會議,市場對利率決策的預期更加集中, 其中4.25%-4.50% 區間的機率已從91.7% 上升至 94.4%,而4.00%-4.25% 的預測則下降至5.6%,顯示 市場對維持較高利率的預期仍在強化,這可能會抑制 風險資產的表現,包括加密貨幣。
https://www.cmegroup.com/cn-t/markets/interest-rates/cme-fedwatch-tool.html
消費者物價指數(CPI) 為2.33%,和上週一 致,失業率保持在4.2%,顯示勞動市場仍然穩定,企 業對人力需求的支撐作用持續發揮。當前情勢意味著 聯準會在利率決策上將維持謹慎,避免過度調整對經 濟產生負面影響。
失業率:https://www.macromicro.me/series/37/unemployment-rate
消費者物價指數(CPI) :https://www.macromicro.me/series/128/consumer-price-index-sa-yoy
小結
加密貨幣市場仍受總體經濟環境影響,高利 率政策使得資金流動性受限,價格波動性加大。投資 者應密切關注即將召開的FOMC 會議及後續政策動向, 以評估市場短期內的走勢與投資機會。
新聞
參議院推進穩定幣法案,為最終通過掃清道路
Crypto.com 收購 Allnew Investments,取得 MiFID 執照,可在歐洲提供衍生性商品交易
德州眾議院通過法案,距離建立戰略比特幣儲備更近一步
香港通過新穩定幣許可法案加入全球競爭
讓外國人更容易買美股!Kraken 將推出蘋果、 Nvidia 等代幣化股票交易
https://blockcast.it/2025/05/23/kraken-to-launch-tokenized-stock-trading-for-non-u-s-customers/
-
 @ 7f6db517:a4931eda
2025-06-01 03:01:36
@ 7f6db517:a4931eda
2025-06-01 03:01:36
The newly proposed RESTRICT ACT - is being advertised as a TikTok Ban, but is much broader than that, carries a $1M Fine and up to 20 years in prison️! It is unconstitutional and would create massive legal restrictions on the open source movement and free speech throughout the internet.
The Bill was proposed by: Senator Warner, Senator Thune, Senator Baldwin, Senator Fischer, Senator Manchin, Senator Moran, Senator Bennet, Senator Sullivan, Senator Gillibrand, Senator Collins, Senator Heinrich, and Senator Romney. It has broad support across Senators of both parties.
Corrupt politicians will not protect us. They are part of the problem. We must build, support, and learn how to use censorship resistant tools in order to defend our natural rights.
The RESTRICT Act, introduced by Senators Warner and Thune, aims to block or disrupt transactions and financial holdings involving foreign adversaries that pose risks to national security. Although the primary targets of this legislation are companies like Tik-Tok, the language of the bill could potentially be used to block or disrupt cryptocurrency transactions and, in extreme cases, block Americans’ access to open source tools or protocols like Bitcoin.
The Act creates a redundant regime paralleling OFAC without clear justification, it significantly limits the ability for injured parties to challenge actions raising due process concerns, and unlike OFAC it lacks any carve-out for protected speech. COINCENTER ON THE RESTRICT ACT
If you found this post helpful support my work with bitcoin.

-
 @ dfa02707:41ca50e3
2025-06-01 03:01:33
@ dfa02707:41ca50e3
2025-06-01 03:01:33Contribute to keep No Bullshit Bitcoin news going.
- The latest firmware updates for COLDCARD devices introduce two major features: COLDCARD Co-sign (CCC) and Key Teleport between two COLDCARD Q devices using QR codes and/or NFC with a website.

What's new
- COLDCARD Co-Sign: When CCC is enabled, a second seed called the Spending Policy Key (Key C) is added to the device. This seed works with the device's Main Seed and one or more additional XPUBs (Backup Keys) to form 2-of-N multisig wallets.
- The spending policy functions like a hardware security module (HSM), enforcing rules such as magnitude and velocity limits, address whitelisting, and 2FA authentication to protect funds while maintaining flexibility and control, and is enforced each time the Spending Policy Key is used for signing.
- When spending conditions are met, the COLDCARD signs the partially signed bitcoin transaction (PSBT) with the Main Seed and Spending Policy Key for fund access. Once configured, the Spending Policy Key is required to view or change the policy, and violations are denied without explanation.
"You can override the spending policy at any time by signing with either a Backup Key and the Main Seed or two Backup Keys, depending on the number of keys (N) in the multisig."
-
A step-by-step guide for setting up CCC is available here.
-
Key Teleport for Q devices allows users to securely transfer sensitive data such as seed phrases (words, xprv), secure notes and passwords, and PSBTs for multisig. It uses QR codes or NFC, along with a helper website, to ensure reliable transmission, keeping your sensitive data protected throughout the process.
- For more technical details, see the protocol spec.
"After you sign a multisig PSBT, you have option to “Key Teleport” the PSBT file to any one of the other signers in the wallet. We already have a shared pubkey with them, so the process is simple and does not require any action on their part in advance. Plus, starting in this firmware release, COLDCARD can finalize multisig transactions, so the last signer can publish the signed transaction via PushTX (NFC tap) to get it on the blockchain directly."
- Multisig transactions are finalized when sufficiently signed. It streamlines the use of PushTX with multisig wallets.
- Signing artifacts re-export to various media. Users are now provided with the capability to export signing products, like transactions or PSBTs, to alternative media rather than the original source. For example, if a PSBT is received through a QR code, it can be signed and saved onto an SD card if needed.
- Multisig export files are signed now. Public keys are encoded as P2PKH address for all multisg signature exports. Learn more about it here.
- NFC export usability upgrade: NFC keeps exporting until CANCEL/X is pressed.
- Added Bitcoin Safe option to Export Wallet.
- 10% performance improvement in USB upload speed for large files.
- Q: Always choose the biggest possible display size for QR.
Fixes
- Do not allow change Main PIN to same value already used as Trick PIN, even if Trick PIN is hidden.
- Fix stuck progress bar under
Receiving...after a USB communications failure. - Showing derivation path in Address Explorer for root key (m) showed double slash (//).
- Can restore developer backup with custom password other than 12 words format.
- Virtual Disk auto mode ignores already signed PSBTs (with “-signed” in file name).
- Virtual Disk auto mode stuck on “Reading…” screen sometimes.
- Finalization of foreign inputs from partial signatures. Thanks Christian Uebber!
- Temporary seed from COLDCARD backup failed to load stored multisig wallets.
Destroy Seedalso removes all Trick PINs from SE2.Lock Down Seedrequires pressing confirm key (4) to execute.- Q only: Only BBQr is allowed to export Coldcard, Core, and pretty descriptor.

-
 @ dfa02707:41ca50e3
2025-06-01 03:01:33
@ dfa02707:41ca50e3
2025-06-01 03:01:33News
- Bitcoin mining centralization in 2025. According to a blog post by b10c, Bitcoin mining was at its most decentralized in May 2017, with another favorable period from 2019 to 2022. However, starting in 2023, mining has become increasingly centralized, particularly due to the influence of large pools like Foundry and the use of proxy pooling by entities such as AntPool.
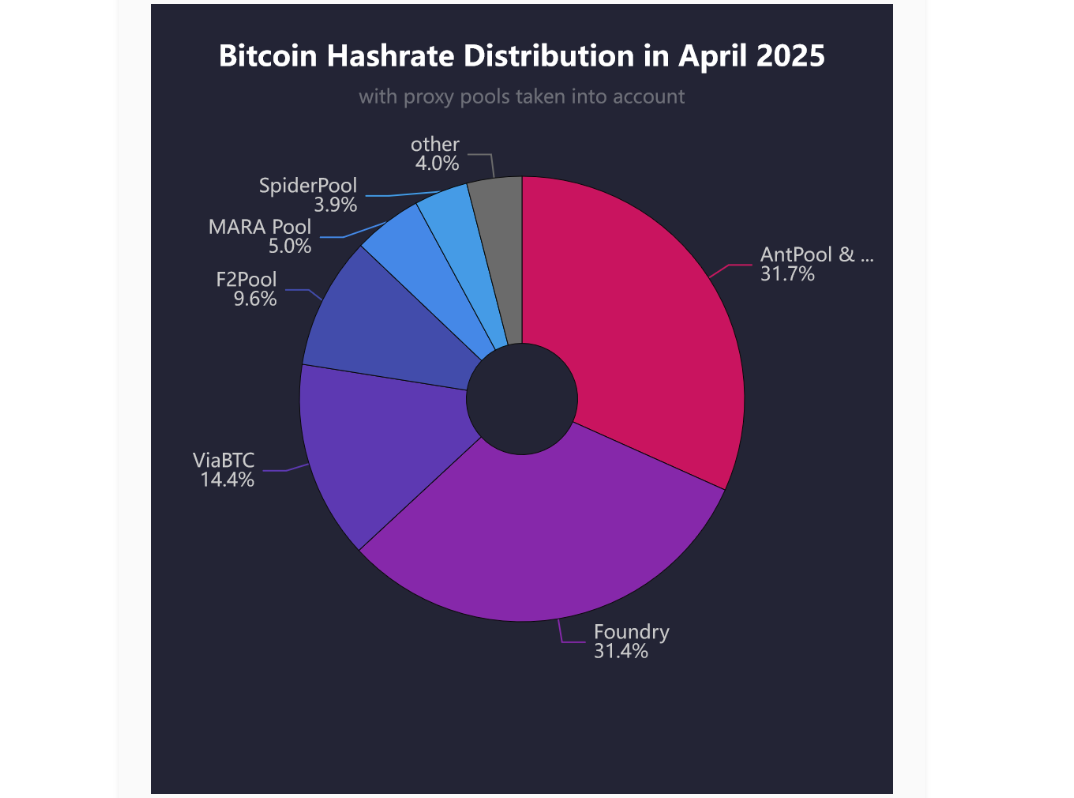
Source: b10c's blog.
- OpenSats announces the eleventh wave of Nostr grants. The five projects in this wave are the mobile live-streaming app Swae, the Nostr-over-ham-radio project HAMSTR, Vertex—a Web-of-Trust (WOT) service for Nostr developers, Nostr Double Ratchet for end-to-end encrypted messaging, and the Nostr Game Engine for building games and applications integrated with the Nostr ecosystem.
- New Spiral grantee: l0rinc. In February 2024, l0rinc transitioned to full-time work on Bitcoin Core. His efforts focus on performance benchmarking and optimizations, enhancing code quality, conducting code reviews, reducing block download times, optimizing memory usage, and refactoring code.
- Project Eleven offers 1 BTC to break Bitcoin's cryptography with a quantum computer. The quantum computing research organization has introduced the Q-Day Prize, a global challenge that offers 1 BTC to the first team capable of breaking an elliptic curve cryptographic (ECC) key using Shor’s algorithm on a quantum computer. The prize will be awarded to the first team to successfully accomplish this breakthrough by April 5, 2026.
- Unchained has launched the Bitcoin Legacy Project. The initiative seeks to advance the Bitcoin ecosystem through a bitcoin-native donor-advised fund platform (DAF), investments in community hubs, support for education and open-source development, and a commitment to long-term sustainability with transparent annual reporting.
- In its first year, the program will provide support to Bitcoin hubs in Nashville, Austin, and Denver.
- Support also includes $50,000 to the Bitcoin Policy Institute, a $150,000 commitment at the University of Austin, and up to $250,000 in research grants through the Bitcoin Scholars program.
"Unchained will match grants 1:1 made to partner organizations who support Bitcoin Core development when made through the Unchained-powered bitcoin DAF, up to 1 BTC," was stated in a blog post.
- Block launched open-source tools for Bitcoin treasury management. These include a dashboard for managing corporate bitcoin holdings and provides a real-time BTC-to-USD price quote API, released as part of the Block Open Source initiative. The company’s own instance of the bitcoin holdings dashboard is available here.
Source: block.xyz
- Bull Bitcoin expands to Mexico, enabling anyone in the country to receive pesos from anywhere in the world straight from a Bitcoin wallet. Additionally, users can now buy Bitcoin with a Mexican bank account.
"Bull Bitcoin strongly believes in Bitcoin’s economic potential in Mexico, not only for international remittances and tourism, but also for Mexican individuals and companies to reclaim their financial sovereignty and protect their wealth from inflation and the fragility of traditional financial markets," said Francis Pouliot, Founder and CEO of Bull Bitcoin.
- Corporate bitcoin holdings hit a record high in Q1 2025. According to Bitwise, public companies' adoption of Bitcoin has hit an all-time high. In Q1 2025, these firms collectively hold over 688,000 BTC, marking a 16.11% increase from the previous quarter. This amount represents 3.28% of Bitcoin's fixed 21 million supply.
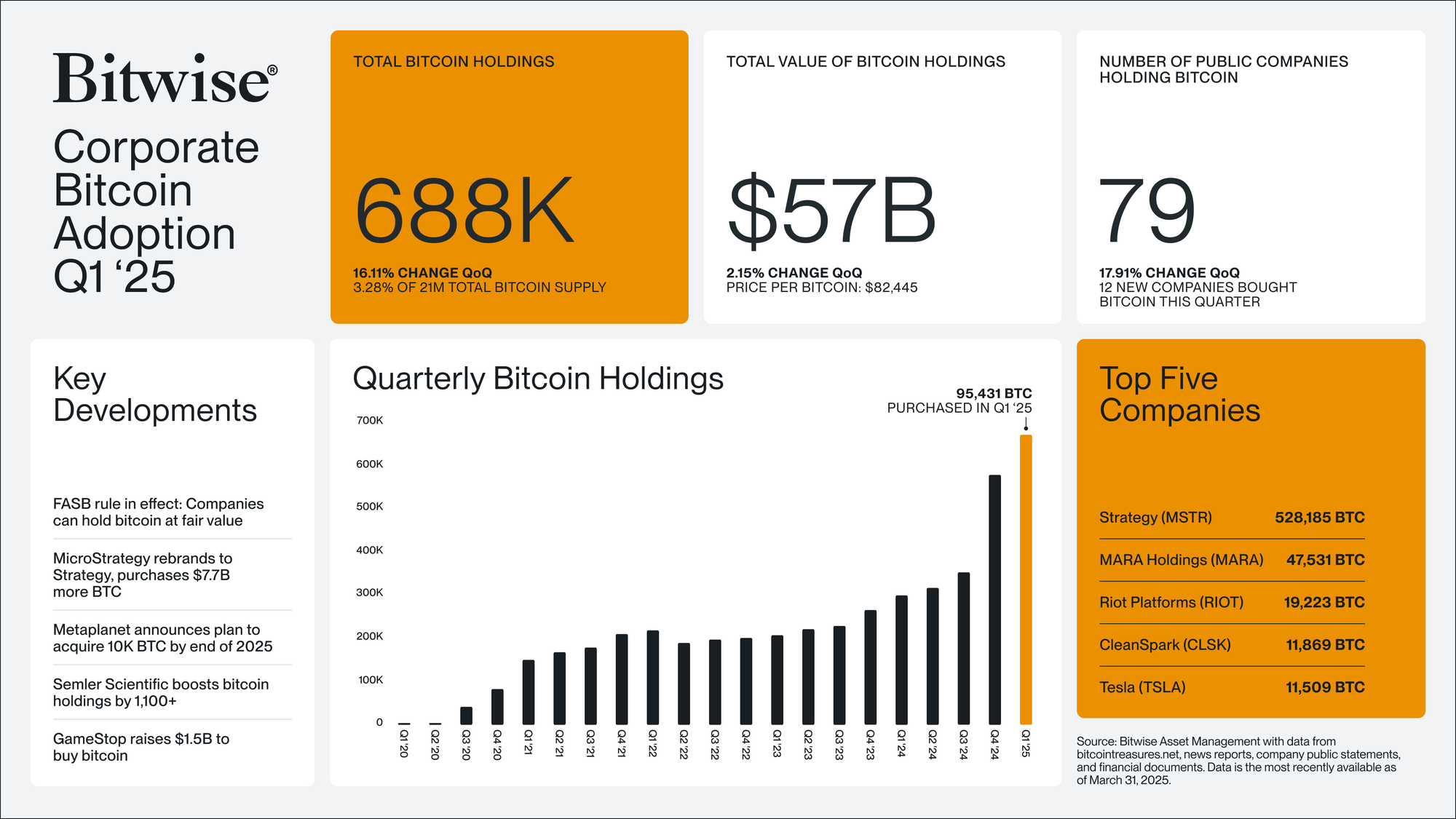
Source: Bitwise.
- The Bitcoin Bond Company for institutions has launched with the aim of acquiring $1 trillion in Bitcoin over 21 years. It utilizes secure, transparent, and compliant bond-like products backed by Bitcoin.
- The U.S. Senate confirmed Paul Atkins as Chair of the Securities and Exchange Commission (SEC). At his confirmation hearing, Atkins emphasized the need for a clear framework for digital assets. He aims to collaborate with the CFTC and Congress to address jurisdiction and rulemaking gaps, aligning with the Trump administration's goal to position the U.S. as a leader in Bitcoin and blockchain finance.
- Ethereum developer Virgil Griffith has been released from custody. Griffith, whose sentence was reduced to 56 months, is now seeking a pardon. He was initially sentenced to 63 months for allegedly violating international sanctions laws by providing technical advice on using cryptocurrencies and blockchain technology to evade sanctions during a presentation titled 'Blockchains for Peace' in North Korea.
- No-KYC exchange eXch to close down under money laundering scrutiny. The privacy-focused cryptocurrency trading platform said it will cease operations on May 1. This decision follows allegations that the platform was used by North Korea's Lazarus Group for money laundering. eXch revealed it is the subject of an active "transatlantic operation" aimed at shutting down the platform and prosecuting its team for "money laundering and terrorism."
- Blockstream combats ESP32 FUD concerning Jade signers. The company stated that after reviewing the vulnerability disclosed in early March, Jade was found to be secure. Espressif Systems, the designer of the ESP32, has since clarified that the "undocumented commands" do not constitute a "backdoor."
- Bank of America is lobbying for regulations that favor banks over tech firms in stablecoin issuance. The bank's CEO Brian Moynihan is working with groups such as the American Bankers Association to advance the issuance of a fully reserved, 1:1 backed "Bank of America coin." If successful, this could limit stablecoin efforts by non-banks like Tether, Circle, and others, reports The Block.
- Tether to back OCEAN Pool with its hashrate. "As a company committed to financial freedom and open access, we see supporting decentralization in Bitcoin mining as essential to the network’s long-term integrity," said Tether CEO Paolo Ardoino.
- Bitdeer to expand its self-mining operations to navigate tariffs. The Singapore-based mining company is advancing plans to produce machines in the U.S. while reducing its mining hardware sales. This response is in light of increasing uncertainties related to U.S. trade policy, as reported by Bloomberg.
- Tether acquires $32M in Bitdeer shares. The firm has boosted its investment in Bitdeer during a wider market sell-off, with purchases in early to mid-April amounting to about $32 million, regulatory filings reveal.
- US Bitcoin miner manufacturer Auradine has raised $153 million in a Series C funding round as it expands into AI infrastructure. The round was led by StepStone Group and included participation from Maverick Silicon, Premji Invest, Samsung Catalyst Fund, Qualcomm Ventures, Mayfield, MARA Holdings, GSBackers, and other existing investors. The firm raised to over $300 million since its inception in 2022.
- Voltage has partnered with BitGo to [enable](https://www.voltage.cloud/blog/bitgo-and-voltage-team-up-to-deliver-instant-bitcoin-and-stabl
-
 @ dfa02707:41ca50e3
2025-06-01 03:01:33
@ dfa02707:41ca50e3
2025-06-01 03:01:33Contribute to keep No Bullshit Bitcoin news going.
- Coinswap is a decentralized protocol for private, trustless cryptocurrency swaps. It allows participants to securely swap digital assets without intermediaries, using advanced cryptographic techniques and atomic swaps to ensure privacy and security.
- This release introduces major improvements to the protocol's efficiency, security, and usability, including custom in-memory UTXO indexes, more advanced coin-selection algorithms, fidelity bond management and more.
- The update also improves user experience with full Mac support, faster Tor connections, enhanced UI/UX, a unified API, and improved protocol documentation.
"The Project is under active beta development and open for contributions and beta testing. The Coinswap market place is live in testnet4. Bug fixes and feature requests are very much welcome."
- Manuals and demo docs are available here.
What's new
- Core protocol and performance improvements:
- Custom in-memory UTXO indexes. Frequent Core RPC calls, which caused significant delays, have been eliminated by implementing custom in-memory UTXO indexes. These indexes are also saved to disk, leading to faster wallet synchronization.
- Coin selection. Advanced coin-selection algorithms, like those in Bitcoin Core, have been incorporated, enhancing the efficiency of creating different types of transactions.
- Fidelity management. Maker servers now automate tasks such as checking bond expiries, redemption, and recreation for Fidelity Bonds, reducing the user's management responsibilities.
- Taker liveness. The
WaitingFundingConfirmationmessage has been added to keep swap connections between Takers and Makers, assisting with variable block confirmation delays.
-
User experience and compatibility:
- Mac compatibility. The crate and apps now fully support Mac.
- Tor operations are streamlined for faster, more resilient connections. Tor addresses are now consistently linked to the wallet seed, maintaining the same onion address through system reboots.
- The UI/UX improvements enhance the display of balances, UTXOs, offer data, fidelity bonds, and system logs. These updates make the apps more enjoyable and provide clearer coin swap logs during the swap process.
-
API design improvements. Transaction creation routines have been streamlined to use a single common API, which reduces technical debt and eliminates redundant code.
- Protocol spec documentation now details how Coinswap breaks the transaction graph and improves privacy through routed swaps and amount splitting, and includes diagrams for clarity.
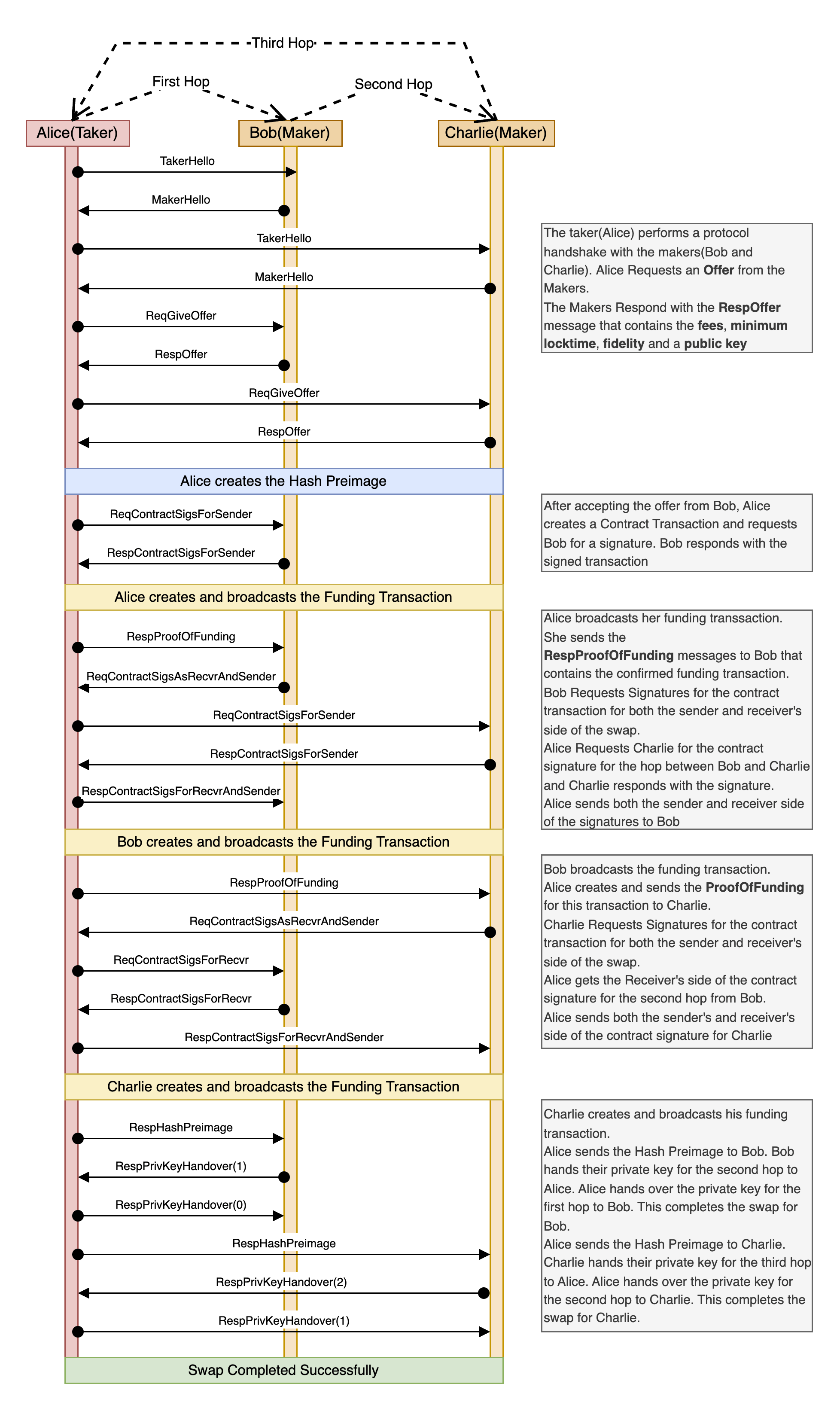
Source: Coinswap Protocol specification.

-
 @ dfa02707:41ca50e3
2025-06-01 03:01:31
@ dfa02707:41ca50e3
2025-06-01 03:01:31Contribute to keep No Bullshit Bitcoin news going.
News
- Spiral welcomes Ben Carman. The developer will work on the LDK server and a new SDK designed to simplify the onboarding process for new self-custodial Bitcoin users.
- Spiral renews support for Dan Gould and Joschisan. The organization has renewed support for Dan Gould, who is developing the Payjoin Dev Kit (PDK), and Joschisan, a Fedimint developer focused on simplifying federations.
- The Bitcoin Dev Kit Foundation announced new corporate members for 2025, including AnchorWatch, CleanSpark, and Proton Foundation. The annual dues from these corporate members fund the small team of open-source developers responsible for maintaining the core BDK libraries and related free and open-source software (FOSS) projects.
- The European Central Bank is pushing for amendments to the European Union's Markets in Crypto Assets legislation (MiCA), just months after its implementation. According to Politico's report on Tuesday, the ECB is concerned that U.S. support for cryptocurrency, particularly stablecoins, could cause economic harm to the 27-nation bloc.
- Slovenia is considering a 25% capital gains tax on Bitcoin profits for individuals. The Ministry of Finance has proposed legislation to impose this tax on gains from cryptocurrency transactions, though exchanging one cryptocurrency for another would remain exempt. At present, individual 'crypto' traders in Slovenia are not taxed.
- The Virtual Asset Service Providers (VASP) Bill 2025 introduced in Kenya. The new legislation aims to establish a comprehensive legal framework for licensing, regulating, and supervising virtual asset service providers (VASPs), with strict penalties for non-compliant entities.
- Circle, BitGo, Coinbase, and Paxos plan to apply for U.S. bank charters or licenses. According to a report in The Wall Street Journal, major crypto companies are planning to apply for U.S. bank charters or licenses. These firms are pursuing limited licenses that would permit them to issue stablecoins, as the U.S. Congress deliberates on legislation mandating licensing for stablecoin issuers.
"Established banks, like Bank of America, are hoping to amend the current drafts of [stablecoin] legislation in such a way that nonbanks are more heavily restricted from issuing stablecoins," people familiar with the matter told The Block.
- Paul Atkins has officially assumed the role of the 34th Chairman of the US Securities and Exchange Commission (SEC). This is a return to the agency for Atkins, who previously served as an SEC Commissioner from 2002 to 2008 under the George W. Bush administration. He has committed to advancing the SEC’s mission of fostering capital formation, safeguarding investors, and ensuring fair and efficient markets.
- Federal Reserve retracts guidance discouraging banks from engaging in 'crypto.' The U.S. Federal Reserve withdrew guidance that discouraged banks from crypto and stablecoin activities, as announced by its Board of Governors on Thursday. This includes rescinding a 2022 supervisory letter requiring prior notification of crypto activities and 2023 stablecoin requirements.
"As a result, the Board will no longer expect banks to provide notification and will instead monitor banks' crypto-asset activities through the normal supervisory process," reads the FED statement.
- Russian government to launch a cryptocurrency exchange. The country's Ministry of Finance and Central Bank announced plans to establish a trading platform for "highly qualified investors" that "will legalize crypto assets and bring crypto operations out of the shadows."
- Twenty One Capital is set to launch with over 42,000 BTC in its treasury. This new Bitcoin-native firm, backed by Tether and SoftBank, is planned to go public via a SPAC merger with Cantor Equity Partners and will be led by Jack Mallers, co-founder and CEO of Strike. According to a report by the Financial Times, the company aims to replicate the model of Michael Saylor with his company, MicroStrategy.
- Strategy increases Bitcoin holdings to 538,200 BTC. In the latest purchase, the company has spent more than $555M to buy 6,556 coins through proceeds of two at-the-market stock offering programs.
- Metaplanet buys another 145 BTC. The Tokyo-listed company has purchased an additional 145 BTC for $13.6 million. Their total bitcoin holdings now stand at 5,000 coins, worth around $428.1 million.
- Semler Scientific has increased its bitcoin holdings to 3,303 BTC. The company acquired an additional 111 BTC at an average price of $90,124. The purchase was funded through proceeds from an at-the-market offering and cash reserves, as stated in a press release.
- Tesla still holds nearly $1 billion in bitcoin. According to the automaker's latest earnings report, the firm reported digital asset holdings worth $951 million as of March 31.
- Spar supermarket experiments with Bitcoin payments in Zug, Switzerland. The store has introduced a new payment method powered by the Lightning Network. The implementation was facilitated by DFX Swiss, a service that supports seamless conversions between bitcoin and legacy currencies.
- Charles Schwab to launch spot Bitcoin trading by 2026. The financial investment firm, managing over $10 trillion in assets, has revealed plans to introduce spot Bitcoin trading for its clients within the next year.
- Arch Labs has secured $13 million to develop "ArchVM" and integrate smart-contract functionality with Bitcoin. The funding round, valuing the company at $200 million, was led by Pantera Capital, as announced on Tuesday.
- Citrea deployed its Clementine Bridge on the Bitcoin testnet. The bridge utilizes the BitVM2 programming language to inherit validity from Bitcoin, allegedly providing "the safest and most trust-minimized way to use BTC in decentralized finance."
- UAE-based Islamic bank ruya launches Shari’ah-compliant bitcoin investing. The bank has become the world’s first Islamic bank to provide direct access to virtual asset investments, including Bitcoin, via its mobile app, per Bitcoin Magazine.
- Solosatoshi.com has sold over 10,000 open-source miners, adding more than 10 PH of hashpower to the Bitcoin network.
"Thank you, Bitaxe community. OSMU developers, your brilliance built this. Supporters, your belief drives us. Customers, your trust powers 10,000+ miners and 10PH globally. Together, we’re decentralizing Bitcoin’s future. Last but certainly not least, thank you@skot9000 for not only creating a freedom tool, but instilling the idea into thousands of people, that Bitcoin mining can be for everyone again," said the firm on X.
- OCEAN's DATUM has found 100 blocks. "Over 65% of OCEAN’s miners are using DATUM, and that number is growing every day. This means block template construction is making its way back into the hands of the miners, which is not only the most profitable
-
 @ dfa02707:41ca50e3
2025-06-01 03:01:30
@ dfa02707:41ca50e3
2025-06-01 03:01:30Contribute to keep No Bullshit Bitcoin news going.
- Wasabi Wallet v2.6.0 "Prometheus" is a major update for the project, focused on resilience and independence from centralized systems.
- Key features include support for BIP 158 block filters for direct node synchronization, a revamped full node integration for easier setup without third-party reliance, SLIP 39 share backups for flexible wallet recovery (sponsored by Trezor), and a Nostr-based update manager for censorship-resistant updates.
- Additional improvements include UI bug fixes, a new fallback for transaction broadcasting, updated code signing, stricter JSON serialization, and options to avoid third-party rate providers, alongside various under-the-hood enhancements.
This new version brings us closer to our ultimate goal: ensuring Wasabi is future-proof," said the developers, while also highlighting the following key areas of focus for the project:
- Ensuring users can always fully and securely use their client.
- Making contribution and forks easy through a codebase of the highest quality possible: understandable, maintainable, and improvable.
"As we achieve our survival goals, expect more cutting-edge improvements in Bitcoin privacy and self-custody. Thank you for the trust you place in us by using Wasabi," was stated in the release notes.
What's new
- Support for Standard BIP 158 Block Filters. Wasabi now syncs using BIP 158 filters without a backend/indexer, connecting directly to a user's node. This boosts sync speed, resilience, and allows full sovereignty without specific server dependency.
- Full Node Integration Rework. The old integration has been replaced with a simpler, more adaptable system. It’s not tied to a specific Bitcoin node fork, doesn’t need the node on the same machine as Wasabi, and requires no changes to the node’s setup.
- "Simply enable the RPC server on your node and point Wasabi to it," said the developers. This ensures all Bitcoin network activities—like retrieving blocks, fee estimations, block filters, and transaction broadcasting—go through your own node, avoiding reliance on third parties.
- Create & Recover SLIP 39 Shares. Users now create and recover wallets with multiple share backups using SLIP 39 standard.
"Special thanks to Trezor (SatoshiLabs) for sponsoring this amazing feature."
- Nostr Update Manager. This version implements a pioneering system with the Nostr protocol for update information and downloads, replacing reliance on GitHub. This enhances the project's resilience, ensuring updates even if GitHub is unavailable, while still verifying updates with the project's secure certificate.
- Updated Avalonia to v11.2.7, fixes for UI bugs (including restoring Minimize on macOS Sequoia).
- Added a configurable third-party fallback for broadcasting transactions if other methods fail.
- Replaced Windows Code Signing Certificate with Azure Trusted Signing.
- Many bug fixes, improved codebase, and enhanced CI pipeline.
- Added the option to avoid using any third-party Exchange Rate and Fee Rate providers (Wasabi can work without them).
- Rebuilt all JSON Serialization mechanisms avoiding default .NET converters. Serialization is now stricter.

Full Changelog: v2.5.1...v2.6.0
-
 @ dfa02707:41ca50e3
2025-06-01 03:01:30
@ dfa02707:41ca50e3
2025-06-01 03:01:30Contribute to keep No Bullshit Bitcoin news going.
- RoboSats v0.7.7-alpha is now available!
NOTE: "This version of clients is not compatible with older versions of coordinators. Coordinators must upgrade first, make sure you don't upgrade your client while this is marked as pre-release."
- This version brings a new and improved coordinators view with reviews signed both by the robot and the coordinator, adds market price sources in coordinator profiles, shows a correct warning for canceling non-taken orders after a payment attempt, adds Uzbek sum currency, and includes package library updates for coordinators.

Source: RoboSats.
- siggy47 is writing daily RoboSats activity reviews on stacker.news. Check them out here.
- Stay up-to-date with RoboSats on Nostr.
What's new
- New coordinators view (see the picture above).
- Available coordinator reviews signed by both the robot and the coordinator.
- Coordinators now display market price sources in their profiles.

Source: RoboSats.
- Fix for wrong message on cancel button when taking an order. Users are now warned if they try to cancel a non taken order after a payment attempt.
- Uzbek sum currency now available.
- For coordinators: library updates.
- Add docker frontend (#1861).
- Add order review token (#1869).
- Add UZS migration (#1875).
- Fixed tests review (#1878).
- Nostr pubkey for Robot (#1887).
New contributors

Full Changelog: v0.7.6-alpha...v0.7.7-alpha
-
 @ 58537364:705b4b85
2025-06-01 01:05:37
@ 58537364:705b4b85
2025-06-01 01:05:37โลกเป็นอย่างไร เพราะใจเราเป็นอย่างนั้น
พระอาจารย์ไพศาล วิสาโล วัดป่าสุคะโต แสดงธรรม เย็นวันที่ ๓๑ กรกฎาคม ๒๕๖๕

คนเราทุกคนมีตา หู จมูก ลิ้น กาย แล้วก็ใจ ตา หู จมูก ลิ้น กาย มีไว้เพื่อรับรู้โลกภายนอก ตารับรู้รูป หูรับรู้เสียง จมูกรับรู้กลิ่น ลิ้นรับรู้รส และกายก็รับรู้สัมผัสที่เรียกว่าโผฏฐัพพะ และไม่ว่าจะรับรู้โลกภายนอกอะไร มันก็ส่งมาที่ใจ ใจทำหน้าที่คิด ทำหน้าที่รู้สึก
เราก็คงจะสังเกตได้ว่า เรารับรู้อะไร ใจก็มักจะเป็นอย่างนั้น เช่น ถ้าเกิดเราเห็นภาพคนกำลังอดอยากหิวโหย ก็เกิดความรู้สึกเศร้า สงสารในใจของเรา ถ้าเห็นภาพอุบัติเหตุรถยนต์ ก็เกิดความเสียวสยอง หรือว่าหวาดวิตกในใจ ถ้าเห็นเด็กกำลังร้องไห้ ก็เกิดความรู้สึกเศร้าในใจของเรา แต่ถ้าเกิดเห็นภาพคนกำลังสนุกสนานรื่นเริง มันก็มีความยินดีเกิดขึ้นในใจ
รับรู้อะไรก็มีผลต่อใจของเรา รับรู้สิ่งที่เป็นลบ ใจก็พลอยรู้สึกลบไปด้วย รับรู้สิ่งที่เป็นบวก ใจก็พลอยเป็นบวกไปด้วย เพราะฉะนั้นการรับรู้อะไร ก็เป็นสิ่งที่เราต้องใส่ใจ
ถ้าเราอยากจะให้ใจเราสงบ ใจเราเป็นสุข ไม่ถูกแผดเผาด้วยความโกรธ หรือว่าไม่ถูกกดกดดันด้วยความเศร้า หรือว่าถูกกระตุ้นเร้าด้วยความโลภ ความอยาก อันนี้ก็โยงไปถึงว่า เราเลือกที่จะอยู่ไหนด้วย ถ้าเราเลือกที่จะอยู่ในที่ที่สงบสงัด ใจก็พลอยสงบ หรือว่าสามารถจะเย็นได้ง่าย
เพราะฉะนั้นธรรมะข้อหนึ่งในโอวาทปาฏิโมกข์คือ พึงนอนและนั่งในที่สงัด ในที่ที่สงัดที่ที่เป็นรมณีย์ มันก็มีส่วนน้อมใจให้สงบไปด้วย
รวมทั้งการรู้จักใช้หู ใช้ตา ใช้จมูกให้เป็น ต้องรู้จักเลือกรับรู้สิ่งที่มันจะเกื้อกูล ต่อการสร้างกุศลธรรมขึ้นมาในใจ อย่างไรก็ตามเท่านั้นยังไม่พอ เพราะว่าการรับรู้ของเรา บ่อยครั้งเราไม่ได้รับรู้สิ่งที่เกิดขึ้นข้างหน้าเราอย่างที่มันเป็นจริง
บ่อยครั้งเราก็มีการตีความหรือปรุงแต่ง เราไม่ได้เห็นอย่างที่รูปปรากฏ เราไม่ได้ได้ยินอย่างที่เสียงมากระทบหูเรา เพราะว่ามีการตีความ หรือปรุงแต่งซ้อน แบบเรียกว่าสนิทแนบแน่นเลย อย่างเช่น เห็นคนกระซิบกระซาบต่อหน้าเรา เราก็อาจจะตีความไปว่า เขากำลังพูดถึงเรา หรืออาจจะถึงขั้นนินทาเรา แต่ความจริงอาจจะไม่ได้เป็นอย่างนั้น
หรือว่ามีคนบางคนมองหน้าเรา จ้องเรา เราก็อาจจะตีความว่า เขากำลังหาเรื่องเราก็ได้ หรือเขากำลังไม่พอใจเรา แต่ว่าความจริงอาจจะไม่ได้เป็นอย่างนั้นก็ได้ แต่ว่าเราตีความไปแล้ว แล้วส่วนใหญ่เราก็จะไม่ได้เห็น ไม่ได้รับรู้สด ๆ หรือว่าอย่างที่มันเป็น
แต่ว่ามันมีการตีความ ตีความในทางบวกก็มี ตีความในทางลบก็มี ซึ่งตรงนี้บ่อยครั้งก็สร้างปัญหา หรือสร้างความทุกข์ให้กับเรา เพราะการที่เราไม่ได้เห็นอะไรอย่างที่มันเป็นจริงๆ มันมีการตีความในใจของเราหรือด้วยใจของเรา และเราก็เผลอไปคิดว่า สิ่งที่จิตตีความ มันคือความจริง แต่บ่อยครั้งมันก็เป็นแค่การปรุงแต่ง หรือความคิดของเราเอง
มีพระทิเบตท่านหนึ่งเล่าว่า มีคราวหนึ่งจะเดินทางขึ้นเครื่องบิน ที่สนามบินมีการตรวจเอกซเรย์ข้าวของ โทรศัพท์ คอมพิวเตอร์ ระหว่างที่กำลังรอข้าวของของท่านที่กำลังผ่านการเอกซเรย์ ท่านก็เหลือบไปมองเห็นด่านรักษาความปลอดภัยอีกด่านหนึ่ง ที่เป็นด่านสุดท้าย
แล้วก็สังเกตว่ามีเจ้าหน้าที่รักษาความปลอดภัยคนหนึ่ง รูปร่างสูงใหญ่ มีหนวดเฟิ้มเลย จ้องมองมาที่ท่าน จ้องแบบเขม็งเลย ท่านเหลียวไปมองหลายครั้งก็เห็นว่าเขายังจ้องไม่เลิก ก็รู้สึกไม่ค่อยสู้ดีแล้ว เอ๊ะ หรือว่าเจ้าหน้าที่คนนี้กำลังสงสัยอะไรเราหรือเปล่า ถึงจ้องมองแบบนั้น แล้วยิ่งเห็นเจ้าหน้าที่คนนั้นจ้องมองมากเท่าไหร่ โดยที่ไม่มีรอยยิ้มเลยนะ ท่านก็เลยนึกในใจว่า เขาคงจะสงสัยเรา
ยิ่งมองเจ้าหน้าที่คนนั้น ก็ยิ่งรู้สึกว่าเจ้าหน้าที่คนนี้ หน้าเหี้ยม แล้วก็ดูหยาบกระด้าง หน้าตารูปร่างเหมือนมาเฟียเลย จู่ ๆ เจ้าหน้าที่คนนั้นก็วิทยุ พระทิเบตก็คิดสงสัยว่าคงต้องมีอะไรแน่ แล้วก็จริงด้วย มีเจ้าหน้าที่คนใหม่เดินมาที่ชายคนนี้ แล้วก็พูดคุยอะไรกันสักอย่าง แล้วเจ้าหน้าที่ที่มีหนวดก็ชี้มาที่ตัวท่าน
พระทิเบตใจเขาก็ไม่สู้ดีแล้ว เจ้าหน้าที่คนใหม่ก็มา พอมายืนแทนเจ้าหน้าที่คนแรกที่มีหนวด เจ้าหน้าที่ที่มีหนวดนั่นก็เดินตรงมาเลยที่ท่าน แล้วก็ถามว่า คุณคือมิสเตอร์ยงเกใช่ไหม ท่านก็ตอบว่าใช่ มีอะไรเหรอ เจ้าหน้าที่คนนั้นก็บอกว่า ผมอยากจะขอบคุณคุณเหลือเกินนะ เพราะว่าหนังสือคุณนี่ช่วยผมได้มากเลย อยากจะขอบคุณจริง ๆ เลย
เท่านี้แหละ พระทิเบตก็ยิ้มเลย แล้วเจ้าหน้าที่คนนั้นก็ยิ้มด้วย แล้วก็มาเขย่ามือกัน เป็นมิตรเลยนะ ก็รู้สึกโล่งอกขึ้นมาเลย นึกว่าจะมีเรื่องอะไร อ๋อ ที่แท้มาขอบคุณที่ได้อ่านหนังสือของเรา ทีแรกนึกว่าจะมาสงสัย มาค้นตัวอะไรสักอย่าง
แล้วท่านก็พบว่าภาพของชายคนนั้น ในสายตาของท่านเปลี่ยนไปเลย จากคนที่มีสีหน้าเหี้ยม กระด้างเหมือนมาเฟีย กลายเป็นคนที่อารมณ์ดี ใจดี สุภาพเรียบร้อย มีความเป็นมิตร และท่านก็มาเอะใจ ทำไมเรามองเจ้าหน้าที่คนนี้เปลี่ยนไป ทีแรกเห็นเป็นคนเหี้ยม คนหยาบ แต่เห็นตอนนี้กลายเป็นมิตร มีน้ำใจ แล้วก็มีความสุภาพ ก็คนคนเดียวกันแหละ แต่ทำไมเห็นต่างกันเลย แบบตรงข้ามกันเลย หลังจากที่เขามาทักทาย แล้วก็มาขอบคุณ
อันนี้ก็ชี้ให้เห็นว่าจิตของคนเรา มันส่งผลมากต่อการรับรู้ ทีแรกพอเห็นเจ้าหน้าที่คนนั้นจ้องมองเขม็งเลย ที่จริงเขาก็ไม่ได้มีอะไรในใจ แต่ว่าพระทิเบตท่านนี้ตีความไปแล้วว่า เขาคงไม่ชอบเราหรือคิดไม่ดีกับเรา ตีความไปในทางร้ายแล้ว ไม่ได้เห็นอย่างที่เป็น
พอตีความไปในทางร้ายเขาคิดไม่ดีกับเรา ท่านก็เลยรู้สึกไม่ดีกับเขา พอรู้สึกไม่ดีกับเขา ภาพของเขาที่เห็นในใจของท่าน ก็กลายเป็นคนที่ดูเหี้ยม กระด้าง เหมือนมาเฟีย เหมือนอันธพาล แต่ว่าพอเขามีอากัปกริยาในทางที่เป็นมิตร มาขอบคุณ มาขอบอกขอบใจ ความรู้สึกของท่านที่มีต่อเขาก็เปลี่ยนไป แทนที่จะเห็นว่าเขาคิดไม่ดีกับเรา ที่แท้เขาขอบคุณเรา พอรู้สึกดีกับเขา ภาพของเขาในสายตาของท่านก็เปลี่ยนไปเลย กลายเป็นคนที่สุภาพเรียบร้อย มีความเป็นมิตร
อันนี้เป็นสิ่งที่ชี้ให้เห็นเลยว่า คนเราบ่อยครั้งเรารับรู้อะไรก็ตาม เราไม่ได้รับรู้อย่างที่มันเป็น แต่ว่ามีการตีความ และถ้าเราตีความในทางลบ ว่าเขาคิดไม่ดีกับเรา จิตมันก็มีปฏิกิริยาตอบโต้ทันทีเลย พอคิดว่าเจ้าหน้าที่คนนี้เขาคิดไม่ดีกับเรา ท่านก็รู้สึกไม่ดีกับเขาโดยอัตโนมัติเลย
พอรู้สึกไม่ดีกับเขา ภาพของเขาที่ท่านเห็นก็กลายเป็นภาพของคนที่ดูดุร้าย ดูเหี้ยม มีการเติมแต่ง มีการใส่สี และนี่คือสิ่งที่เกิดขึ้นกับคนเรา เกิดขึ้นกับเราในชีวิตประจำวัน เรารับรู้อะไร เราก็ไม่เคยรับรู้อย่างที่มันเป็น แต่ว่ามีการตีความ
ถ้าตีความในทางบวกก็ดีไป ถ้าตีความในทางลบ ก็เกิดความวิตก เกิดความกลัว เกิดความเครียด เกิดความขุ่นมัว และพอใจมีความวิตก มีความขุ่นมัว มองอะไรออกไป ก็เห็นแต่ภาพในทางลบ คนๆหนึ่งก็ถูกมองว่ากลายเป็นคนที่เหี้ยม กลายเป็นคนที่กระด้าง แต่พอใจเปลี่ยนไป ความรู้สึกที่มีต่อคนคนนั้นเปลี่ยนไป ภาพที่เห็นหรือว่าภาพที่มองออกไป มันก็เป็นอีกแบบหนึ่ง ตรงข้ามกันเลย
พูดอีกอย่างหนึ่งก็คือว่า ไม่ใช่แค่ว่าเราเห็นอะไรใจก็เป็นอย่างนั้น ในทางกลับกัน ใจเราเป็นอย่างไรก็เห็นโลกไปในทางนั้น ถ้าใจเราขุ่นมัว ใจเรามีความเครียด หรือมีความรู้สึกเป็นลบ โลกที่อยู่รอบตัวเรา หรือคนที่อยู่ข้างหน้าเรา ก็ถูกเติมแต่งให้เป็นลบไปด้วย มีการใส่สี แต่ถ้าเรารู้สึกบวกกับเขา ภาพที่เห็นก็เปลี่ยนไป กลายเป็นบวกไปด้วย อันนี้คือสิ่งที่เกิดขึ้นกับเราตลอดเวลาเลยว่าก็ว่าได้
โลกเป็นอย่างไร มันก็อยู่ที่ใจของเราว่าเป็นอย่างไรด้วย ฉะนั้นบ่อยครั้ง เวลาเรารู้สึกว่าโลกมันหม่นหมอง ผู้คนไม่น่ารัก มันอาจจะเป็นเพราะว่าใจเราหม่นหมอง หรือว่าใจเรามีความรู้สึกที่เป็นลบก็ได้
ฉะนั้นก่อนที่เราจะไปตัดสิน ไปวิพากษ์วิจารณ์ หรือไปมองว่าโลกมันแย่ บางทีเราต้องกลับมาดูที่ใจของเรา ว่าใจเรามันมีการเติมแต่ง รูปที่ได้เห็น เสียงที่ได้ยินหรือเปล่า
ในปฏิจจสมุปบาท จะมีปัจจยาการตอนต้นเลยที่บอกว่า อวิชชาเป็นปัจจัยให้เกิดสังขาร สังขารเป็นปัจจัยให้กับวิญญาณ ที่พูดมาก็เป็นเรื่องที่ชี้ให้เห็นว่า สังขารปรุงแต่งวิญญาณอย่างไร
สังขารในที่นี้ก็คือการปรุงแต่ง หรือความรู้สึกนึกคิดในใจ อารมณ์ที่เกิดขึ้นในใจ มันก็ไปปรุงแต่งการรับรู้ ไม่ว่าจะเป็นการรับรู้ทางตา ทางหู ทางจมูก ทางลิ้น ทางกาย หรือแม้แต่ทางใจ ถ้าใจมีความรู้สึกในทางลบ เช่นคิดลบ หรือรู้สึกลบกับใคร ก็จะเห็นภาพคนๆ นั้นในทางลบไปด้วย เห็นเป็นคนที่กระด้าง เป็นคนที่เหี้ยม เป็นคนที่ไม่น่ารัก แต่ถ้าใจมีความรู้สึกเป็นบวก ก็จะเห็นเขาเป็นคนที่เป็นมิตร เห็นเขาสุภาพ
อันนี้ก็ไม่ต่างจากเรื่องของคนผู้ชายคนหนึ่งไปพักที่โรงแรม แล้วก็ถอดสร้อยคอที่คล้องพระสมเด็จราคาแพงด้วย ไว้ที่หัวนอน ออกไปทำธุระตอนเช้า ไปออกกำลังกาย กินข้าวเสร็จก็กลับเข้ามาในห้อง สร้อยหาย เอ๊ะ ใครเอาไป สงสัยพนักงานทำความสะอาด เพราะว่าในช่วงนั้น มีพนักงานทำความสะอาดเข้าไปจัดเตียง
เขาก็ตามหาว่าใครเป็นพนักงานทำความสะอาด พอพบเห็นเขา ก็ปักใจเชื่อเลยว่าเขาขโมยเอาสร้อยคอไป แล้วก็เฝ้าสังเกตผู้ชายคนนั้น ดูท่วงท่ามีพิรุธ แววตาก็มีพิรุธ ไม่กล้าสบตาเขา ใช่แน่ๆ เลย เอาสร้อยคอของเราไป แต่ปรากฏว่าตอนสายๆ หรือตอนบ่าย ปรากฏว่าเจอสร้อยมันตกอยู่หลังเตียง
พอรู้ว่าชายคนนั้น พนักงานทำความสะอาดไม่ได้ขโมยไป ก็เห็นเขาในภาพใหม่เลย น้ำเสียงเขาก็ไม่ได้มีพิรุธอะไร พูดจาก็ดี อากัปกริยาก็ไม่ได้ผิดปกติอะไร ภาพของพนักงานทำความสะอาดเปลี่ยนไปเลย
ที่จริงก็ไม่ได้เปลี่ยนไปหรอก เขาก็เหมือนเดิม ไม่ว่าตอนเช้า ตอนสาย หรือตอนบ่าย แต่ที่เปลี่ยนไปคือใจของผู้ชายคนนั้น ทีแรกปักใจเชื่อว่าพนักงานทำความสะอาดเป็นขโมย พอคิดแบบนั้นเข้า ก็เห็นแต่พิรุธ แต่พอรู้ว่าเขาไม่ได้ขโมยไป ภาพที่เห็นก็เปลี่ยนไป อันนี้เรียกว่าสังขารเป็นปัจจัยให้เกิดวิญญาณ
แล้วไม่ใช่เฉพาะกรณีแบบนี้เท่านั้น ในชีวิตประจำวันทั่วๆ ไป เวลาเรามีความทุกข์ ความเครียด แล้วเรารู้สึกว่าเป็นเพราะโลกภายนอก เป็นเพราะคนรอบตัว เช่นเราเห็นเขาไปในทางลบทางร้าย เราก็เลยเป็นทุกข์ ให้เราลองสังเกตดูก็ได้ว่า บ่อยครั้งความทุกข์ของเรา มันเกิดจากการที่เราตีความไปในทางลบ หรือว่าปรุงแต่งไปในทางร้ายหรือเปล่า
ฉะนั้นถ้าเรารู้จักหมั่นสังเกต หมั่นทบทวน เอาประสบการณ์ที่เคยเข้าใจผิดที่ตีความในทางลบ หรือว่าเติมแต่งในทางร้าย และทำให้เราเกิดความทุกข์ เกิดความวิตก เกิดความเครียด หรือว่าเกิดความไม่พอใจ เอามาเป็นบทเรียนสอนใจ มันจะช่วยทำให้เรารู้จักทักท้วง
ทักท้วงว่าสิ่งที่เราเห็น ที่จริงมันอาจจะไม่ใช่เป็นความจริงก็ได้ มันอาจจะมีการตีความไปแล้วในทางลบ หรือที่เรามองเห็น มองออกไปข้างนอก อาจจะมีการเติมแต่งไปในทางร้ายก็ได้ ไม่ว่ารับเข้ามาจะเป็นรูป รส กลิ่น เสียงที่ได้ยิน หรือมองออกไป มันมักจะมีการตีความหรือเติมแต่ง
แล้วมันก็ไม่จำเป็นต้องเป็นทางลบ อาจจะเป็นไปในทางบวกก็ได้ อันนี้ที่เขาเรียกว่าอคติ ฉันทาคติก็คือลำเอียงเพราะชอบ อันนี้ก็หมายถึงว่า มองเห็นคลาดเคลื่อนจากความเป็นจริง เพราะว่ามีความชอบ เขาทำอะไรก็ดูดีไปหมด เขาทำอะไรก็ดูถูกต้องไปหมด ทั้งๆ ที่ที่ผิดก็มี ที่พลาดก็มี แต่ว่าไม่เห็นเพราะว่ามองเห็นแต่ด้านดี อันนี้เพราะว่าลำเอียงเพราะชอบ หรือมิฉะนั้นก็ตรงข้าม โทสาคติ ลำเอียงเพราะโกรธ หรือลำเอียงเพราะกลัว ภยาคติ หรือว่าลำเอียงเพราะหลง
อย่างกรณีของพระทิเบต ท่านก็เกิดโทสาคติ ทีแรกเกิดโทสาคติ ก็เลยเห็นเจ้าหน้าที่รักษาความปลอดภัยคนนั้น เหี้ยม ดุ เหมือนผู้ร้าย เหมือนมาเฟีย แต่พอเขามาขอบคุณ เขามาแสดงความเป็นมิตร ก็เปลี่ยนไปเลย ฉันทาคติมาแทนโทสาคติ ก็เห็นเขาเป็นคนที่เป็นมิตร สุภาพเรียบร้อย อันนี้ก็เป็นสิ่งที่เราควรจะสังเกตได้ กับประสบการณ์ของตัวเราเอง ว่ามันเป็นอย่างนั้นบ้างหรือเปล่า จะได้เป็นเครื่องเตือนใจเรา เพื่อไม่ให้เราทุกข์ ที่สร้างขึ้นมาเอง
บางครั้งความทุกข์เราไปมองว่าเป็นเพราะคนนู้นคนนี้ แต่ที่จริงเป็นเพราะการปรุงแต่ง การตีความในทางลบ หรือว่าการเติมแต่งในทางร้ายของเรา
ที่พระพุทธเจ้าตรัสว่า ธรรมทั้งหลายมีใจเป็นใหญ่ มีใจเป็นหัวหน้า สำเร็จได้ด้วยใจ อันนี้ก็เป็นตัวอย่างหนึ่งว่า โลกภายนอกที่เราเห็นผ่าน ตา หู จมูก ลิ้น กาย หรือแม้กระทั่งความคิด มันล้วนแล้วแต่เกิดหรือถูกกำหนดด้วยใจของเรา ถ้าใจเราเป็นลบก็เห็นเป็นลบ ถ้าใจเราเป็นบวกก็เห็นเป็นบวก
ฉะนั้นการกลับมาดูใจของเรา จึงเป็นเรื่องที่สำคัญมาก ถ้าไม่อยากให้เกิดไฟเผาในใจของเรา ก็ต้องกลับมาสำรวจตรวจตา หรือสอดส่องใจของเราว่า มันมีอคติ โทสาคติ ภยาคติหรือเปล่า หรือมันมีการเติมแต่งไปในทางลบทางร้ายหรือเปล่า ไม่อย่างนั้นเราก็จะสร้างหรือก่อทุกข์ขึ้นมาในใจของเรา ทั้งที่ความจริงไม่ได้เป็นอย่างนั้น.
พระอาจารย์ไพศาล วิสาโล
ขอขอบคุณ Visalo.org
-
 @ c9badfea:610f861a
2025-06-01 00:32:13
@ c9badfea:610f861a
2025-06-01 00:32:13- Install Feeder (it's free and open source)
- Discover RSS feeds from various sources (see links below)
- Copy the Feed URL
- Open Feeder, tap the ⁞ icon, and choose Add Feed
- Paste the Feed URL and tap Search
- Select the found RSS feed item
- Scroll down and tap OK
Some Sources
ℹ️ You can also use YouTube channel URLs as feeds
-
 @ dfa02707:41ca50e3
2025-06-01 03:01:29
@ dfa02707:41ca50e3
2025-06-01 03:01:29Contribute to keep No Bullshit Bitcoin news going.
-
Version 1.3 of Bitcoin Safe introduces a redesigned interactive chart, quick receive feature, updated icons, a mempool preview window, support for Child Pays For Parent (CPFP) and testnet4, preconfigured testnet demo wallets, as well as various bug fixes and improvements.
-
Upcoming updates for Bitcoin Safe include Compact Block Filters.
"Compact Block Filters increase the network privacy dramatically, since you're not asking an electrum server to give you your transactions. They are a little slower than electrum servers. For a savings wallet like Bitcoin Safe this should be OK," writes the project's developer Andreas Griffin.
- Learn more about the current and upcoming features of Bitcoin Safe wallet here.
What's new in v1.3
- Redesign of Chart, Quick Receive, Icons, and Mempool Preview (by @design-rrr).
- Interactive chart. Clicking on it now jumps to transaction, and selected transactions are now highlighted.

- Speed up transactions with Child Pays For Parent (CPFP).
- BDK 1.2 (upgraded from 0.32).
- Testnet4 support.
- Preconfigured Testnet demo wallets.
- Cluster unconfirmed transactions so that parents/children are next to each other.
- Customizable columns for all tables (optional view: Txid, Address index, and more)
- Bug fixes and other improvements.

Announcement / Archive
Blog Post / Archive
GitHub Repo
Website -
-
 @ 8bad92c3:ca714aa5
2025-06-01 03:01:27
@ 8bad92c3:ca714aa5
2025-06-01 03:01:27Marty's Bent

It's been a pretty historic week for the United States as it pertains to geopolitical relations in the Middle East. President Trump and many members of his administration, including AI and Crypto Czar David Sacks and Treasury Secretary Scott Bessent, traveled across the Middle East making deals with countries like Qatar, Saudi Arabia, the United Arab Emirates, Syria, and others. Many are speculating that Iran may be included in some behind the scenes deal as well. This trip to the Middle East makes sense considering the fact that China is also vying for favorable relationships with those countries. The Middle East is a power player in the world, and it seems pretty clear that Donald Trump is dead set on ensuring that they choose the United States over China as the world moves towards a more multi-polar reality.
Many are calling the events of this week the Riyadh Accords. There were many deals that were struck in relation to artificial intelligence, defense, energy and direct investments in the United States. A truly prolific power play and demonstration of deal-making ability of Donald Trump, if you ask me. Though I will admit some of the numbers that were thrown out by some of the countries were a bit egregious. We shall see how everything plays out in the coming years. It will be interesting to see how China reacts to this power move by the United States.
While all this was going on, there was something happening back in the United States that many people outside of fringe corners of FinTwit are not talking about, which is the fact that the 10-year and 30-year U.S. Treasury bond yields are back on the rise. Yesterday, they surpassed the levels of mid-April that caused a market panic and are hovering back around levels that have not been seen since right before Donald Trump's inauguration.
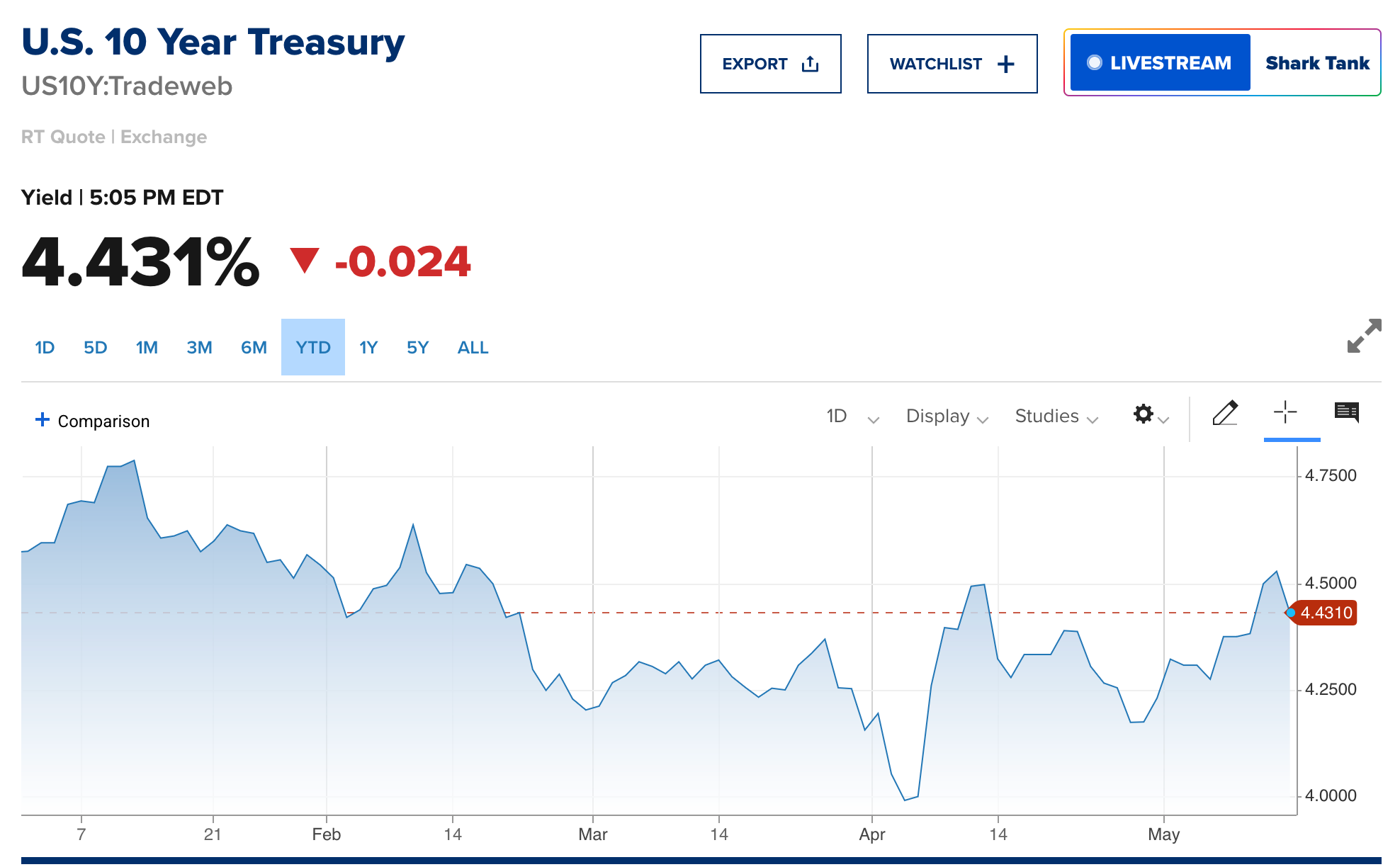
I imagine that there isn't as much of an uproar right now because I'm pretty confident the media freakouts we were experiencing in mid-April were driven by the fact that many large hedge funds found themselves off sides of large levered basis trades. I wouldn't be surprised if those funds have decreased their leverage in those trades and bond yields being back to mid-April levels is not affecting those funds as much as they were last month. But the point stands, the 10-year and 30-year yields are significantly elevated with the 30-year approaching 5%. Regardless of the deals that are currently being made in the Middle East, the Treasury has a big problem on its hands. It still has to roll over many trillions worth of debt over over the next few years and doing so at these rates is going to be massively detrimental to fiscal deficits over the next decade. The interest expense on the debt is set to explode in the coming years.
On that note, data from the first quarter of 2025 has been released by the government and despite all the posturing by the Trump administration around DOGE and how tariffs are going to be beneficial for the U.S. economy, deficits are continuing to explode while the interest expense on the debt has definitively surpassed our annual defense budget.
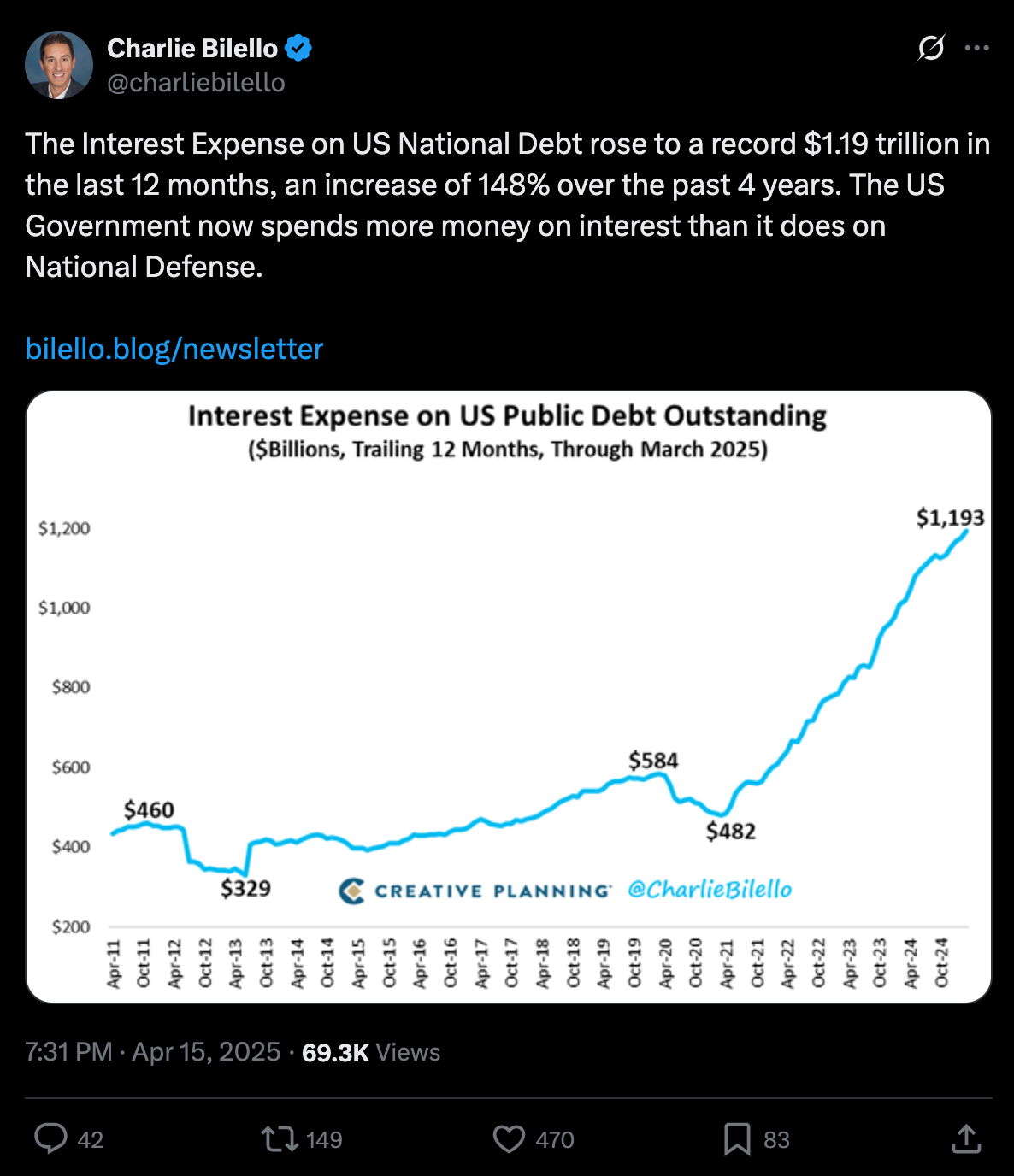
via Charlie Bilello
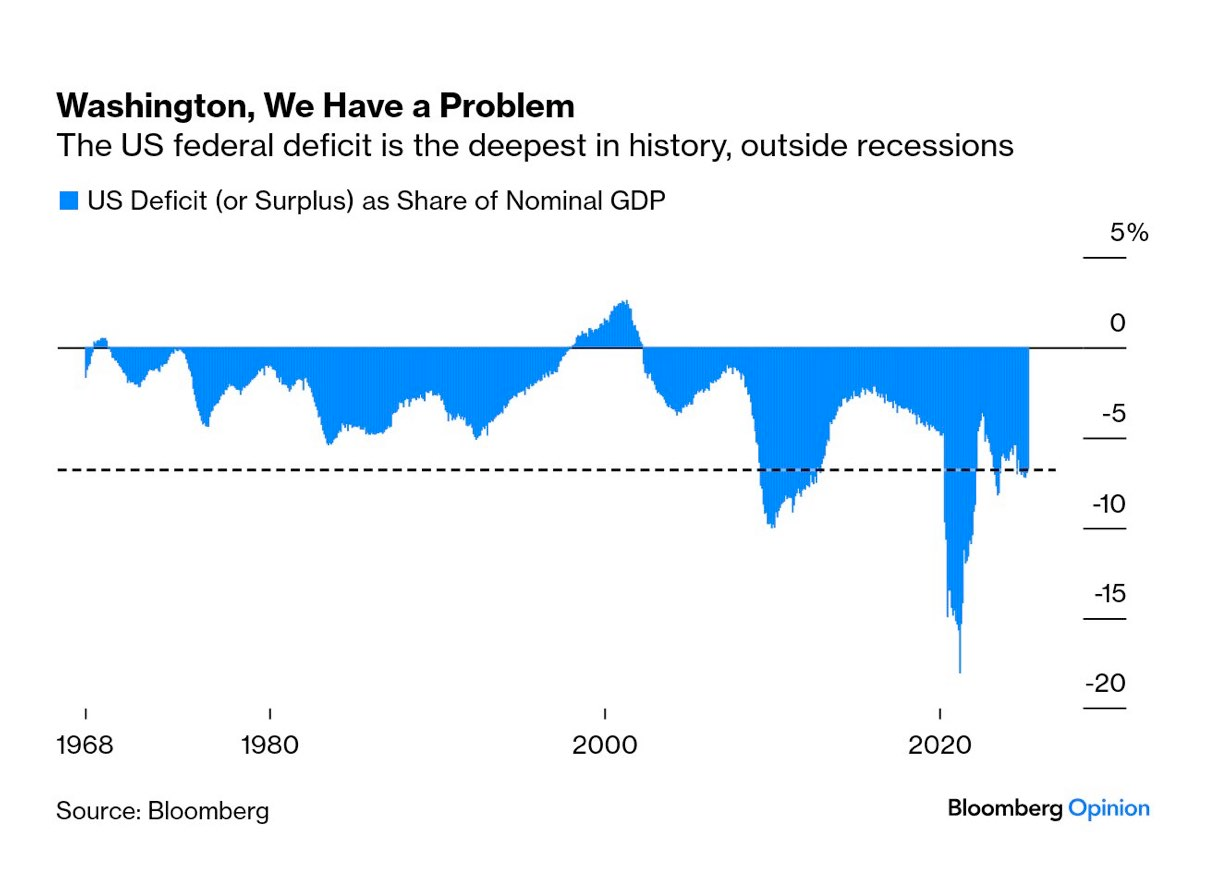
via Mohamed Al-Erian
To make matters worse, as things are deteriorating on the fiscal side of things, the U.S. consumer is getting crushed by credit. The 90-plus day delinquency rates for credit card and auto loans are screaming higher right now.
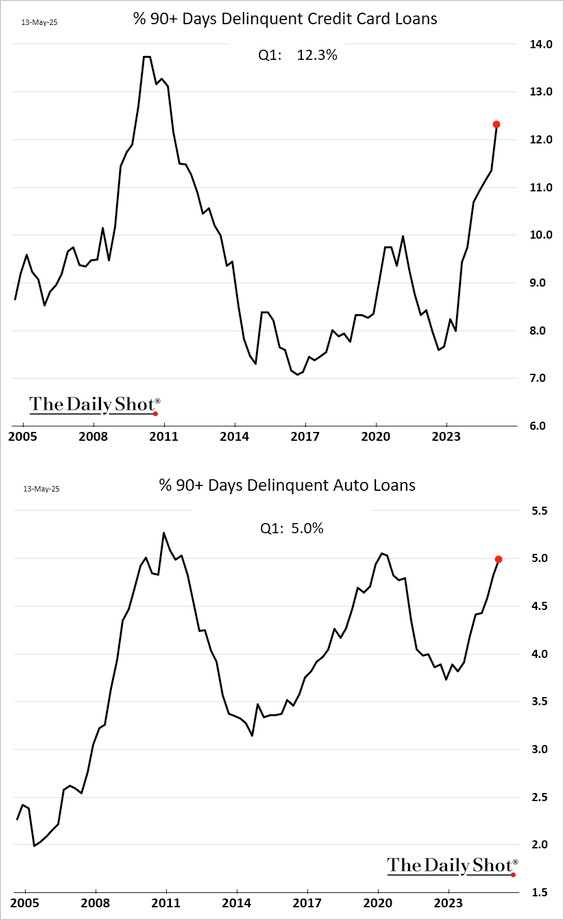
via TXMC
One has to wonder how long all this can continue without some sort of liquidity crunch. Even though equities markets have recovered from their post-Liberation Day month long bear market, I would not be surprised if what we're witnessing is a dead cat bounce that can only be continued if the money printers are turned back on. Something's got to give, both on the fiscal side and in the private markets where the Common Man is getting crushed because he's been forced to take on insane amounts of debt to stay afloat after years of elevated levels of inflation. Add on the fact that AI has reached a state of maturity that will enable companies to replace their current meat suit workers with an army of cheap, efficient and fast digital workers and it isn't hard to see that some sort of employment crisis could be on the horizon as well.
Now is not the time to get complacent. While I do believe that the deals that are currently being made in the Middle East are probably in the best interest of the United States as the world, again, moves toward a more multi-polar reality, we are facing problems that one cannot simply wish away. They will need to be confronted. And as we've seen throughout the 21st century, the problems are usually met head-on with a money printer.
I take no pleasure in saying this because it is a bit uncouth to be gleeful to benefit from the strife of others, but it is pretty clear to me that all signs are pointing to bitcoin benefiting massively from everything that is going on. The shift towards a more multi-polar world, the runaway debt situation here in the United States, the increasing deficits, the AI job replacements and the consumer credit crisis that is currently unfolding, All will need to be "solved" by turning on the money printers to levels they've never been pushed to before.
Weird times we're living in.
China's Manufacturing Dominance: Why It Matters for the U.S.
In my recent conversation with Lyn Alden, she highlighted how China has rapidly ascended the manufacturing value chain. As Lyn pointed out, China transformed from making "sneakers and plastic trinkets" to becoming the world's largest auto exporter in just four years. This dramatic shift represents more than economic success—it's a strategic power play. China now dominates solar panel production with greater market control than OPEC has over oil and maintains near-monopoly control of rare earth elements crucial for modern technology.
"China makes like 10 times more steel than the United States does... which is relevant in ship making. It's relevant in all sorts of stuff." - Lyn Alden
Perhaps most concerning, as Lyn emphasized, is China's financial leverage. They hold substantial U.S. assets that could be strategically sold to disrupt U.S. treasury market functioning. This combination of manufacturing dominance, resource control, and financial leverage gives China significant negotiating power in any trade disputes, making our attempts to reshoring manufacturing all the more challenging.
Check out the full podcast here for more on Triffin's dilemma, Bitcoin's role in monetary transition, and the energy requirements for rebuilding America's industrial base.
Headlines of the Day
Financial Times Under Fire Over MicroStrategy Bitcoin Coverage - via X
Trump in Qatar: Historic Boeing Deal Signed - via X
Get our new STACK SATS hat - via tftcmerch.io
Johnson Backs Stock Trading Ban; Passage Chances Slim - via X
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code *“TFTC20”* during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed 158,469 sats | $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Building things of value is satisfying.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
@media screen and (max-width: 480px) { .mobile-padding { padding: 10px 0 !important; } .social-container { width: 100% !important; max-width: 260px !important; } .social-icon { padding: 0 !important; } .social-icon img { height: 32px !important; width: 32px !important; } .icon-cell { padding: 0 4px !import
-
 @ 9b12847f:9a3ee831
2025-05-31 23:42:09
@ 9b12847f:9a3ee831
2025-05-31 23:42:09What is the CGT loan trap?
The Capital Gains Tax (CGT) loan trap, is where you take a bitcoin-backed loan, expecting that providing the collateral does not trigger CGT, only to find that it does trigger CGT.
Oof.
It's a particularly dangerous trap for plebs because bitcoin collateralised lending typically requires over-collateralisation which is often 2x the amount being borrowed. This means if CGT is triggered on the provision of the collateral, your CGT is 2x the CGT bill had you just sold down the bitcoin for the amount you borrowed.
That's without adding the additional cost of the interest on the loan; more oof.
Why it's important to pay attention to this
Firstly because if you're caught in the trap, you're the one who is liable and not the Lender.
Secondly, because all bitcoin transactions are permanent records and you can reasonably assume that future tax collection sleuths will backtrack through yesterday's transactions. Lenders who KYC their customers provide an easy data collection point for tax collectors, and that data doesn't go away.
And lastly, because there is no emerging signs of fiscal responsibility at the sovereign level, so it's reasonable to assume tax agencies are being directed to increase collections .. and bitcoiners aren't going to get any sort of pass there.
And of course, the bigger the Bitcoin network grows, the more attractive bitcoin collateralised lending will be, and the the more attention it will garner .. and some of that will be from tax collectors.
So, what determines if CGT is applicable?
The concept of beneficial ownership is the relevant term to understand and pay attention to. A change in beneficial ownership is what tax authorities use as the trigger to determine if a CGT event has occurred. This isn't a term or concept isolated to my country (Australia) or the US or the UK or Europe - it's one that's been actively harmonised across the G20. It applies to all asset classes.
The beneficial owner is the one who enjoys the benefits of the asset. It's slightly different to the concept of legal owner which is the person or entity on a government register as the "owner" of the asset.
And if you're a bitcoiner reading this, you're probably already aware that there is no government register of the "ownership of bitcoin" - that's very literally what the timechain, and your bitcoin private keys, are .. but we digress.
Where there is a change in the beneficial owner of an asset, that triggers a CGT liability. This isn't new, it's not related to bitcoin specifically but to all asset classes, and it is consistent over a wide group of countries. The way that each jurisdiction legislates, enforces and applies it will vary somewhat.
So let's explore how that relates to providing collateral in bitcoin-backed loans.
Types of bitcoin backed loans
Bitcoin represents pristine and unimpeachable collateral, so any dollar lender should be happily accepting it as collateral from their perspective. But let's focus on the issue of changing beneficial ownership and how that ties into the borrower's CGT liabilities.
There are loans available from platforms that provide the dollar liquidity, and there are loans from peers.
Loans from platforms
Loans from platforms are going to require KYC information because there is a centralised lender and that will come with a legal construct. The three things to pay attention to are:
- Legal terms and conditions
Ideally, the platform terms should have a statement that acknowledges the unchanged beneficial ownership of the collateral by the borrower, as long as the borrower does not default on the loan.
There may not be such a statement, and if there is not, then the next point on how the collateral is managed needs some careful attention.
The immediate red-flag is if the terms categorically state that there is a change of beneficial ownership of the collateral; being a party to such a contract would legally acknowledge that you transferred beneficial ownership, triggering CGT.
NB: The legal terms and conditions should be generally accessible. If they aren't available then request them from support. If they're not forthcoming, then it's a giant red flag and I'd recommend you exit stage left.
- How the collateral is custodied
A key test that is used to determine if beneficial ownership has changed is the custody of the asset(s). If bitcoin as collateral is kept in a discrete location, and is not pooled with other collateral, then there is a strong case to maintain the chain of unbroken beneficial ownership.
By contrast, collateral that is sent into a "pool" can be deemed to be disposed of, since it's not the same bitcoin that is being returned on successful completion of the loan. I am personally aware of plebs who have been "bitten" by using lending services who "pool" collateral from multiple loans into a pool, and consequently receive different bitcoin on loan completion. The safe assumption is that collateral that is pooled, will be deemed a disposal for CGT events.
- Whether collateral can be re-hypothecated
Ignoring the very dubious issues around re-hypothecation more generally, (who remembers BlockFi, Celsius, Genesis, 3Arrows Capital etc), from a CGT trigger event perspective, if collateral can be re-hypothecated, it will likely be deemed a disposal for CGT purposes.
Loans that are peer-to-peer
There are other borrowing mechanisms that are based on enabling borrowing interaction directly between peers. These typically do not need to introduce the privacy and security risks of KYC, and so consequently do not require a specific legal contract between the peers.
The "terms" of the agreement are defined in the code that implements the contract between the parties, with the collateral held in a multi-party escrow, and returned to the Borrower should they successfully repay their loan. Only if the loan is NOT repaid, or needs to be liquidated, does the collateral change ownership.
In an ideal world, the usage terms for such platforms would acknowledge that the collateral provided by the Borrower remains their unchanged beneficial ownership unless the contract is liquidated, or the loan is not repaid.
Examples of platforms that allow peers to connect and create contracts for borrowing between themselves include Debifi, Lend at HodlHodl, Firefish and Lendasat.
How did I end up down this rabbit hole?
I narrowly avoided falling into precisely this trap recently when I was considering a loan from https://ledn.io I was curious that the Loan terms weren't available to review on their site, or from the customer dashboard after I signed up.
They happily provided them on request (https://www.ledn.io/legal/usd-loan-agreement), and once I got to Section 7 (b), it became clear this wasn't a product I wanted to use because every supply of collateral to Ledn, for any loan, would automatically trigger a CGT event.
Ledn, like every other lending platform, do not offer tax advice, and are clear to state the tax implications of using their products are up to the borrower to assess with their appropriate advisors.
Like many things in Bitcoin, this then made me curious about how widespread this practice was, what the underlying legal definitions were, how widely and harmoniously they were applied .. and here we are .. writing (and reading) blog posts!
So why borrow against your bitcoin at all?
Bitcoin-backed loans can potentially provide a mechanism to access dollars, without selling your bitcoin, and thereby deferring CGT on the sale of bitcoin.
For bitcoiners who've humbly stacked sats for several cycles, borrowing against your bitcoin, may provide a mechanism to further delay spending or selling sats, thereby increasing your purchasing power further.
When you borrow against your bitcoin, you are expecting bitcoin to continue to increase in purchasing power, and at a higher rate than the cost of the interest on the loan. Based on 16 years of bitcoin price history, this is a pretty safe assumption.
Don't however, make assumptions on CGT events that can potentially undermine the entire financial logic of going down this route in the first place; check carefully.
What will definitely trigger a CGT event?
Firstly and most obviously, if you take a bitcoin collateralised loan, and fail to repay the loan or are margin called and liquidated, then that portion of the collateral required to extinguish your loan will be sold. That's clearly a change of beneficial ownership, and that transaction will trigger a CGT liability.
Next, any service or product which explicitly requires you to acknowledge a change of beneficial ownership of the collateral on lodgement, will also trigger a CGT event.
After that, as we outlined earlier, pay close attention to collateral custody mechanisms and transparency and clarity on re-hypothecation - both of which are potential CGT trigger events.
So what's worth checking out?
Currently these are the lending offers that I'm aware of that are worth considering and I understand don't fall foul of the three key aspects outlined above.
As always, do your own checking, and validate with your accounting/legal advisors; the consequences of getting this wrong are potentially significant.
To be clear, I've no financial interest in any of these platforms, nor have I been paid to write this article, nor do I use referral codes. I have used some of these platforms, and believe them all to be operated by reputable teams with high integrity.
Final thoughts
Lastly, for those coming to the @bitcoinbushbash at the end of July in Palm Cove Queensland, I'll be presenting a session on this topic.
-
 @ eb0157af:77ab6c55
2025-06-01 03:01:16
@ eb0157af:77ab6c55
2025-06-01 03:01:16At Bitcoin 2025, the company unveils the Blockstream App and a strategic roadmap to accelerate adoption.
During the Bitcoin 2025 conference held in Las Vegas, Blockstream announced several updates, including a new non-custodial application and a corporate strategy structured around three operational divisions.
Introducing the Blockstream App: a new Bitcoin wallet that grows with you.
From first sats to advanced custody, it brings self-sovereignty into reach no matter where you start. Available now on Android, coming soon to iOS.
 pic.twitter.com/UBiNHKh8bO
pic.twitter.com/UBiNHKh8bO— Blockstream (@Blockstream) May 29, 2025
The new Blockstream App allows users to purchase Bitcoin directly and store it in their own wallet, eliminating the need to rely on external custodians for fund management. This technological solution is built on the infrastructure of the Blockstream Green wallet. The app supports Bitcoin, Lightning, and Liquid.
The app’s design has been conceived to meet the needs of a diverse audience, the company stated. Its interface is accessible for beginners while retaining advanced functionalities for more experienced users.
It also remains compatible with advanced security features such as hardware wallet signing and air-gapped transactions via Blockstream Jade.
Corporate strategy: consumer, enterprise, and BAM
During the event, Blockstream revealed a strategic restructuring organized into three distinct operational units. This new framework aims to strengthen the company’s position within the Bitcoin economy through tailored approaches for specific markets.
The Consumer division will focus on developing products for retail users, while the Enterprise division will manage relationships with corporate clients. Blockstream Asset Management (BAM) will serve as the company’s institutional arm, specializing in Bitcoin investment products for institutional customers.
Adam Back, CEO of Blockstream, commented:
“The past year has shown clearly that Bitcoin no longer sits on the margins of the global financial system—it is rapidly becoming the foundation. Our vision is simple: the future of finance runs on Bitcoin.”
The post Blockstream launches a non-custodial app to buy Bitcoin appeared first on Atlas21.
-
 @ b1ddb4d7:471244e7
2025-06-01 03:00:53
@ b1ddb4d7:471244e7
2025-06-01 03:00:53Custodial Lightning wallets allow users to transact without managing private keys or channel liquidity. The provider handles technical complexities, but this convenience comes with critical trade-offs:
- You don’t control your keys: The custodian holds your bitcoin.
- Centralized points of failure: Servers can be hacked or shut down.
- Surveillance risks: Providers track transaction metadata.
Key Risks of Custodial Lightning Wallets
*1. Hacks and Exit Scams*
Custodians centralize large amounts of bitcoin, attracting hackers:
- Nearly $2.2 billion worth of funds were stolen from hacks in 2024.
- Lightning custodians suffered breaches, losing user funds.
Unlike non-custodial wallets, victims have no recourse since they don’t hold keys.
*2. Censorship and Account Freezes*
Custodians comply with regulators, risking fund seizures:
- Strike (a custodial Lightning app) froze accounts of users in sanctioned regions.
- A U.K. court in 2020 ordered Bitfinex to freeze bitcoin worth $860,000 after the exchange and blockchain sleuthing firm Chainalysis traced the funds to a ransomware payment.
*3. Privacy Erosion*
Custodians log user activity, exposing sensitive data:
- Transaction amounts, receiver addresses, and IPs are recorded.
*4. Service Downtime*
Centralized infrastructure risks outages.
*5. Inflation of Lightning Network Centralization*
Custodians dominate liquidity, weakening network resilience:
- At the moment, 10% of the nodes on Lightning control 80% of the liquidity.
- This centralization contradicts bitcoin’s decentralized ethos.
How to Switch to Self-Custodial Lightning Wallets
Migrating from custodial services is straightforward:
*1. Choose a Non-Custodial Wallet*
Opt for wallets that let you control keys and channels:
- Flash: The self-custodial tool that lets you own your keys, control your coins, and transact instantly.
- Breez Wallet : Non-custodial, POS integrations.
- Core Lightning : Advanced, for self-hosted node operators.
*2. Transfer Funds Securely*
- Withdraw funds from your custodial wallet to a bitcoin on-chain address.
- Send bitcoin to your non-custodial Lightning wallet.
*3. Set Up Channel Backups*
Use tools like Static Channel Backups (SCB) to recover channels if needed.
*4. Best Practices*
- Enable Tor: Mask your IP (e.g., Breez’s built-in Tor support).
- Verify Receiving Addresses: Avoid phishing scams.
- Regularly Rebalance Channels: Use tools like Lightning Pool for liquidity.
Why Self-Custodial Lightning Matters
- Self-custody: Control your keys and funds.
- Censorship resistance: No third party can block transactions.
- Network health: Decentralized liquidity strengthens Lightning.
Self-custodial wallets now rival custodial ease.
Custodial Lightning wallets sacrifice security for convenience, putting users at risk of hacks, surveillance, and frozen funds. As bitcoin adoption grows, so does the urgency to embrace self-custodial solutions.
Take action today:
- Withdraw custodial funds to a hardware wallet.
- Migrate to a self-custodial Lightning wallet.
- Educate others on the risks of custodial control.
The Lightning Network’s potential hinges on decentralization—don’t let custodians become its Achilles’ heel.
-
 @ a10260a2:caa23e3e
2025-05-31 23:39:05
@ a10260a2:caa23e3e
2025-05-31 23:39:05Last Updated: May 31, 2025
First off, big shoutout to Coinos for having support for adding a memo to BOLT12 offers. This provides a solid alternative for the pleb who wants to support mining decentralization but doesn’t want to set up a CLN node and pay thousands of sats for a channel only to get little rewards. This is the case for most of us who only have a miner or two (e.g. a Bitaxe and/or an S9).
Before we get into setting up Lightning payouts, you’ll want to have your miner configured to mine with OCEAN of course. You’ll also want to make sure that the bitcoin address you use is from a wallet that supports signing messages.
These are the ones listed in the OCEAN docs:
- Bitcoin Knots/Bitcoin Core
- Coldcard
- Electrum
- LND (Command Line)
- Seedsigner
- Sparrow
- Specter
- Trezor
I checked one of my favorite, user-friendly wallets — Blue Wallet — and it happens to support signing messages as well.
Just tap the three dots on the upper right and you’ll see the “Sign/Verify Message” button at the bottom.
Update [January 18]: You can now use Coinos to sign by going to https://coinos.io/sign
The trick here is to not refresh the page. In other words, when you're logged in to your Coinos account, go to the URL and use the legacy address (starts with a "1") that's displayed to configure your miner(s). If you refresh the page, you're going to get a new address which will cause the signing to fail later on. Remember, keep the tab open and don't refresh the page.

Whichever wallet you choose, generate a receive address to use when configuring your miner (it’ll also be your OCEAN username).
Here’s how it looks on the Bitaxe (AxeOS)…
And the Antminer S9 (Braiins OS).
NOTE: There’s a slight difference in the URL format between the two apps. Other than that, the username will be your bitcoin address followed by the optional “.” + the nickname for your machine.
You can find more details on OCEAN’s get started page.
Alright, now that your miner is pointed at OCEAN. Let’s configure Lightning payouts!
Generating the BOLT12 Offer
In the Coinos app, go to Receive > Bolt 12. This should be opened in another tab from the one we're using to sign the the configuration message.
Tap “Set memo” and set it to “OCEAN Payouts for [insert your bitcoin address]” (this text is case-sensitive). Use the same bitcoin address you used above to configure your miner(s).
After tapping OK, copy the BOLT12 offer (it should start with “lno”) and proceed to the next step.
Generating the Configuration Message
Navigate to the My Stats page by searching for your OCEAN Bitcoin address.
The click the Configuration link next to Next Block to access the configuration form.
Paste the BOLT12 offer here, update the block height to latest, click GENERATE, and copy the generated unsigned message.
Signing the Configuration Message
To sign the generated message, go back to Blue Wallet and use the signing function. Paste the configuration message in the Message field, tap Sign, and copy the signed message that’s generated.
If you're using Coinos to sign, return to the page that you kept open (and didn't refresh) and do the same. Paste the configuration message, click submit, and copy the signed message.
Submitting the Signed Message
Once signed, copy the signature, paste it in the OCEAN configuration form, and click CONFIRM.
If all goes well, you should see a confirmation that the configuration was successful. Congrats! 🎉
All you gotta do now is sit back, relax, and wait for a block to be found…
Or you can look into setting up DATUM. 😎
-
 @ 4c96d763:80c3ee30
2025-05-31 23:33:02
@ 4c96d763:80c3ee30
2025-05-31 23:33:02Changes
Fernando López Guevara (2):
- feat(column): add tooltip on remove column button
- feat(hashtag-column): handle new hashtag on Enter key press
pushed to notedeck:refs/heads/master
-
 @ b1ddb4d7:471244e7
2025-06-01 03:00:51
@ b1ddb4d7:471244e7
2025-06-01 03:00:51The upcoming Bitcoin 2025 conference, scheduled from May 27–29 at the Venetian Conference Center in Las Vegas, is set to make history with an official attempt to break the GUINNESS WORLD RECORDS® title for the most Bitcoin point-of-sale transactions in an eight-hour period.
Organized by BTC Inc, the event will showcase Bitcoin’s evolution from a digital capital asset to a practical medium of exchange, leveraging the latest advancements in payment technology.
Tap-to-Pay with Lightning-Ready Bolt Cards
To facilitate this record-setting attempt, 4,000 Lightning-ready Bolt Cards will be distributed to conference attendees.
— Uncle Rockstar Developer (@r0ckstardev) May 15, 2025
These NFC-enabled cards allow users to make instant, contactless Bitcoin payments at vendor booths throughout the expo-no apps or QR codes required, just a simple tap.
The cards are available in four collectible designs, each featuring a prominent figure in Bitcoin’s history: Senator Cynthia Lummis, Michael Saylor, Satoshi Nakamoto, and Jack Dorsey.
Each attendee will receive a randomly assigned card, making them both functional and collectible souvenirs.
Senator Lummis: A Playful Provocation
Notably, one of the card designs features Senator Cynthia Lummis with laser eyes-a playful nod to her reputation as a leading Bitcoin advocate in US politics.
While Lummis is known for her legislative efforts to promote Bitcoin integration, she has publicly stated she prefers to “spend dollars and save Bitcoin,” viewing BTC as a long-term store of value rather than a daily currency.
The choice to feature her on the Bolt Card, could be suggested by Rockstar Dev of the BTC Pay Server Foundation, perhaps a lighthearted way to highlight the ongoing debate about Bitcoin’s role in everyday payments.
Nothing cracks me up quite like a senator that wants the US to buy millions of Bitcoin use dollars to buy a beer at a Bitcoin bar.
This is how unserious some of you are. pic.twitter.com/jftIEggmip
— Magoo PhD (@HodlMagoo) April 4, 2025
How Bolt Cards and the Lightning Network Work
Bolt Cards are physical cards equipped with NFC (Near Field Communication) technology, similar to contactless credit or debit cards. When linked to a compatible Lightning wallet, they enable users to make Bitcoin payments over the Lightning Network by simply tapping the card at a point-of-sale terminal.
The Lightning Network is a second-layer protocol built on top of Bitcoin, designed to facilitate instant, low-cost transactions ideal for everyday purchases.
This integration aims to make Bitcoin as easy to use as traditional payment methods, eliminating the need for QR code scanning or mobile apps.
A Showcase for Bitcoin’s Real-World Usability
With over 30,000 attendees, 300 exhibitors, and 500 speakers expected, the Bitcoin 2025 conference is poised to be the largest Bitcoin event of the year-and potentially the most transactional.
The event will feature on-site activations such as the Official Bitcoin Magazine Store, where all merchandise will be available at a 21% discount for those paying with Bitcoin via the Lightning Network-a nod to Bitcoin’s 21 million coin supply limit.
By deeply integrating Lightning payments into the conference experience, organizers hope to demonstrate Bitcoin’s readiness for mainstream commerce and set a new benchmark for its practical use as a currency.
Conclusion
The Guinness World Record attempt at Bitcoin 2025 is more than a publicity stunt-it’s a bold demonstration of Bitcoin’s technological maturity and its potential to function as a modern, everyday payment method.
Whether or not the record is set, the event will serve as a milestone in the ongoing journey to make Bitcoin a truly global, user-friendly currency
-
 @ c2865f41:eaff678a
2025-05-31 20:09:44
@ c2865f41:eaff678a
2025-05-31 20:09:44Unwilling to investigate. No interpellation of neighbors, witnesses, experts. No report emitted commenting on the petition, but just ignoring to answer. As such O.S.R. calls upon the justice system to address the wrongs. The analog drawing of geometer at the time of entree in the register of the O.S.R property
See the map attached, it is annotated and self-explaining, could not be clearer. O.S.R challenges the court to convoke when still alive), and any explanation he can give as to his drawing, now ignored by the same instance(Plav Cadastre) that mandated him in the first place. The example record
See attachment: the example record is out of a Swiss register, note the precise identity and details, address etc. of the owner of said parcel. That is what the constitution of Montenegro subscribes to: to have similar practices respected. The trail into the forest See attachment, another supporting map, as an example of the practices that are pertinent to justify an immediate injunction by the court, of all activities on the contested parcels.
-
 @ b1ddb4d7:471244e7
2025-06-01 03:00:48
@ b1ddb4d7:471244e7
2025-06-01 03:00:48Bitcoin FilmFest (BFF25) returns to Warsaw for its third edition, blending independent cinema—from feature films and commercials to AI-driven experimental visuals—with education and entertainment.
Hundreds of attendees from around the world will gather for three days of screenings, discussions, workshops, and networking at the iconic Kinoteka Cinema (PKiN), the same venue that hosted the festival’s first two editions in March 2023 and April 2024.
This year’s festival, themed “Beyond the Frame,” introduces new dimensions to its program, including an extra day on May 22 to celebrate Bitcoin Pizza Day, the first real-world bitcoin transaction, with what promises to be one of Europe’s largest commemorations of this milestone.
BFF25 bridges independent film, culture, and technology, with a bold focus on decentralized storytelling and creative expression. As a community-driven cultural experience with a slightly rebellious spirit, Bitcoin FilmFest goes beyond movies, yet cinema remains at its heart.
Here’s a sneak peek at the lineup, specially curated for movie buffs:
 Generative Cinema – A special slot with exclusive shorts and a thematic debate on the intersection of AI and filmmaking. Featured titles include, for example: BREAK FREE, SATOSHI: THE CREATION OF BITCOIN, STRANGE CURRENCIES, and BITCOIN IS THE MYCELIUM OF MONEY, exploring financial independence, traps of the fiat system, and a better future built on sound money.
Generative Cinema – A special slot with exclusive shorts and a thematic debate on the intersection of AI and filmmaking. Featured titles include, for example: BREAK FREE, SATOSHI: THE CREATION OF BITCOIN, STRANGE CURRENCIES, and BITCOIN IS THE MYCELIUM OF MONEY, exploring financial independence, traps of the fiat system, and a better future built on sound money. Upcoming Productions Preview – A bit over an hour-long block of unreleased pilots and works-in-progress. Attendees will get exclusive first looks at projects like FINDING HOME (a travel-meets-personal-journey series), PARALLEL SPACES (a story about alternative communities), and THE LEGEND OF LANDI (a mysterious narrative).
Upcoming Productions Preview – A bit over an hour-long block of unreleased pilots and works-in-progress. Attendees will get exclusive first looks at projects like FINDING HOME (a travel-meets-personal-journey series), PARALLEL SPACES (a story about alternative communities), and THE LEGEND OF LANDI (a mysterious narrative). Freedom-Focused Ads & Campaigns – Unique screenings of video commercials, animations, and visual projects, culminating in “The PoWies” (Proof of Work-ies)—the first ever awards show honoring the best Bitcoin-only awareness campaigns.
Freedom-Focused Ads & Campaigns – Unique screenings of video commercials, animations, and visual projects, culminating in “The PoWies” (Proof of Work-ies)—the first ever awards show honoring the best Bitcoin-only awareness campaigns.To get an idea of what might come up at the event, here, you can preview 6 selected ads combined into two 2 videos:
 Open Pitch Competition – A chance for filmmakers to present fresh ideas and unfinished projects to an audience of a dedicated jury, movie fans and potential collaborators. This competitive block isn’t just entertaining—it’s a real opportunity for creators to secure funding and partnerships.
Open Pitch Competition – A chance for filmmakers to present fresh ideas and unfinished projects to an audience of a dedicated jury, movie fans and potential collaborators. This competitive block isn’t just entertaining—it’s a real opportunity for creators to secure funding and partnerships. Golden Rabbit Awards: A lively gala honoring films from the festival’s Official Selection, with awards in categories like Best Feature, Best Story, Best Short, and Audience Choice.
Golden Rabbit Awards: A lively gala honoring films from the festival’s Official Selection, with awards in categories like Best Feature, Best Story, Best Short, and Audience Choice.BFF25 Main Screenings
Sample titles from BFF25’s Official Selection:
 REVOLUCIÓN BITCOIN – A documentary by Juan Pablo, making its first screening outside the Spanish-speaking world in Warsaw this May. Three years of important work, 80 powerful minutes to experience. The film explores Bitcoin’s impact across Argentina, Colombia, Mexico, El Salvador, and Spain through around 40 diverse perspectives. Screening in Spanish with English subtitles, followed by a Q&A with the director.
REVOLUCIÓN BITCOIN – A documentary by Juan Pablo, making its first screening outside the Spanish-speaking world in Warsaw this May. Three years of important work, 80 powerful minutes to experience. The film explores Bitcoin’s impact across Argentina, Colombia, Mexico, El Salvador, and Spain through around 40 diverse perspectives. Screening in Spanish with English subtitles, followed by a Q&A with the director. UNBANKABLE – Luke Willms’ directorial debut, drawing from his multicultural roots and his father’s pioneering HIV/AIDS research. An investigative documentary based on Luke’s journeys through seven African countries, diving into financial experiments and innovations—from mobile money and digital lending to Bitcoin—raising smart questions and offering potential lessons for the West. Its May appearance at BFF25 marks its largest European event to date, following festival screenings and nominations across multiple continents over the past year.
UNBANKABLE – Luke Willms’ directorial debut, drawing from his multicultural roots and his father’s pioneering HIV/AIDS research. An investigative documentary based on Luke’s journeys through seven African countries, diving into financial experiments and innovations—from mobile money and digital lending to Bitcoin—raising smart questions and offering potential lessons for the West. Its May appearance at BFF25 marks its largest European event to date, following festival screenings and nominations across multiple continents over the past year. HOTEL BITCOIN – A Spanish comedy directed by Manuel Sanabria and Carlos “Pocho” Villaverde. Four friends, 4,000 bitcoins , and one laptop spark a chaotic adventure of parties, love, crime, and a dash of madness. Exploring sound money, value, and relationships through a twisting plot. The film premiered at the Tarazona and Moncayo Comedy Film Festival in August 2024. Its Warsaw screening at BFF25 (in Spanish with English subtitles) marks its first public showing outside the Spanish-speaking world.
HOTEL BITCOIN – A Spanish comedy directed by Manuel Sanabria and Carlos “Pocho” Villaverde. Four friends, 4,000 bitcoins , and one laptop spark a chaotic adventure of parties, love, crime, and a dash of madness. Exploring sound money, value, and relationships through a twisting plot. The film premiered at the Tarazona and Moncayo Comedy Film Festival in August 2024. Its Warsaw screening at BFF25 (in Spanish with English subtitles) marks its first public showing outside the Spanish-speaking world.Check out trailers for this year’s BFF25 and past editions on YouTube.
Tickets & Info:
- Detailed program and tickets are available at bitcoinfilmfest.com/bff25.
- Stay updated via the festival’s official channels (links provided on the website).
- Use ‘LN-NEWS’ to get 10% of tickets
-
 @ 2e8970de:63345c7a
2025-05-31 19:51:28
@ 2e8970de:63345c7a
2025-05-31 19:51:28Enfortumab Vedotin and Pembrolizumab doubled survival rates, with fewer serious side effects in advanced bladder cancer.
https://www.nejm.org/doi/full/10.1056/NEJMoa2312117
https://stacker.news/items/993799
-
 @ 0970cf17:135aa040
2025-05-31 18:32:00
@ 0970cf17:135aa040
2025-05-31 18:32:00{"pattern":{"kick":[true,false,true,false,true,false,true,false,true,false,true,false,true,false,true,false],"snare":[false,true,false,true,false,true,false,true,false,true,false,true,false,true,false,true],"hihat":[true,false,true,true,false,false,true,true,false,false,true,true,false,false,true,true],"openhat":[true,false,false,true,false,false,false,false,true,false,false,true,false,false,true,false],"crash":[false,false,true,false,false,false,true,false,false,false,false,true,false,false,true,false],"ride":[false,false,true,false,false,false,false,true,false,false,false,true,false,false,true,false],"tom1":[false,true,false,false,true,false,false,true,false,false,true,false,true,false,true,false],"tom2":[true,false,false,false,true,false,false,false,false,true,false,true,false,false,true,false]},"bpm":220,"swing":0,"timeSignature":"4/4","drumKit":"standard","timestamp":1748716320785}
-
 @ b1ddb4d7:471244e7
2025-06-01 03:00:47
@ b1ddb4d7:471244e7
2025-06-01 03:00:47Starting January 1, 2026, the United Kingdom will impose some of the world’s most stringent reporting requirements on cryptocurrency firms.
All platforms operating in or serving UK customers-domestic and foreign alike-must collect and disclose extensive personal and transactional data for every user, including individuals, companies, trusts, and charities.
This regulatory drive marks the UK’s formal adoption of the OECD’s Crypto-Asset Reporting Framework (CARF), a global initiative designed to bring crypto oversight in line with traditional banking and to curb tax evasion in the rapidly expanding digital asset sector.
What Will Be Reported?
Crypto firms must gather and submit the following for each transaction:
- User’s full legal name, home address, and taxpayer identification number
- Detailed data on every trade or transfer: type of cryptocurrency, amount, and nature of the transaction
- Identifying information for corporate, trust, and charitable clients
The obligation extends to all digital asset activities, including crypto-to-crypto and crypto-to-fiat trades, and applies to both UK residents and non-residents using UK-based platforms. The first annual reports covering 2026 activity are due by May 31, 2027.
Enforcement and Penalties
Non-compliance will carry stiff financial penalties, with fines of up to £300 per user account for inaccurate or missing data-a potentially enormous liability for large exchanges. The UK government has urged crypto firms to begin collecting this information immediately to ensure operational readiness.
Regulatory Context and Market Impact
This move is part of a broader UK strategy to position itself as a global fintech hub while clamping down on fraud and illicit finance. UK Chancellor Rachel Reeves has championed these measures, stating, “Britain is open for business – but closed to fraud, abuse, and instability”. The regulatory expansion comes amid a surge in crypto adoption: the UK’s Financial Conduct Authority reported that 12% of UK adults owned crypto in 2024, up from just 4% in 2021.
Enormous Risks for Consumers: Lessons from the Coinbase Data Breach
While the new framework aims to enhance transparency and protect consumers, it also dramatically increases the volume of sensitive personal data held by crypto firms-raising the stakes for cybersecurity.
The risks are underscored by the recent high-profile breach at Coinbase, one of the world’s largest exchanges.
In May 2025, Coinbase disclosed that cybercriminals, aided by bribed offshore contractors, accessed and exfiltrated customer data including names, addresses, government IDs, and partial bank details.
The attackers then used this information for sophisticated phishing campaigns, successfully deceiving some customers into surrendering account credentials and funds.
“While private encryption keys remained secure, sufficient customer information was exposed to enable sophisticated phishing attacks by criminals posing as Coinbase personnel.”
Coinbase now faces up to $400 million in compensation costs and has pledged to reimburse affected users, but the incident highlights the systemic vulnerability created when large troves of personal data are centralized-even if passwords and private keys are not directly compromised. The breach also triggered a notable drop in Coinbase’s share price and prompted a $20 million bounty for information leading to the attackers’ capture.
The Bottom Line
The UK’s forthcoming crypto reporting regime represents a landmark in financial regulation, promising greater transparency and tax compliance. However, as the Coinbase episode demonstrates, the aggregation of sensitive user data at scale poses a significant cybersecurity risk.
As regulators push for more oversight, the challenge will be ensuring that consumer protection does not become a double-edged sword-exposing users to new threats even as it seeks to shield them from old ones.
-
 @ b1ddb4d7:471244e7
2025-06-01 03:00:46
@ b1ddb4d7:471244e7
2025-06-01 03:00:46This article was originally published on aier.org
Even after eleven years experience, and a per Bitcoin price of nearly $20,000, the incredulous are still with us. I understand why. Bitcoin is not like other traditional financial assets.
Even describing it as an asset is misleading. It is not the same as a stock, as a payment system, or a money. It has features of all these but it is not identical to them.
What Bitcoin is depends on its use as a means of storing and porting value, which in turn rests of secure titles to ownership of a scarce good. Those without experience in the sector look at all of this and get frustrated that understanding why it is valuable is not so easy to grasp.
In this article, I’m updating an analysis I wrote six years ago. It still holds up. For those who don’t want to slog through the entire article, my thesis is that Bitcoin’s value obtains from its underlying technology, which is an open-source ledger that keeps track of ownership rights and permits the transfer of these rights. Bitcoin managed to bundle its unit of account with a payment system that lives on the ledger. That’s its innovation and why it obtained a value and that value continues to rise.
Consider the criticism offered by traditional gold advocates, who have, for decades, pushed the idea that sound money must be backed by something real, hard, and independently valuable. Bitcoin doesn’t qualify, right? Maybe it does.
Bitcoin first emerged as a possible competitor to national, government-managed money in 2009. Satoshi Nakamoto’s white paper was released October 31, 2008. The structure and language of this paper sent the message: This currency is for computer technicians, not economists nor political pundits. The paper’s circulation was limited; novices who read it were mystified.
But the lack of interest didn’t stop history from moving forward. Two months later, those who were paying attention saw the emergence of the “Genesis Block,” the first group of bitcoins generated through Nakamoto’s concept of a distributed ledger that lived on any computer node in the world that wanted to host it.
Here we are all these years later and a single bitcoin trades at $18,500. The currency is held and accepted by many thousands of institutions, both online and offline. Its payment system is very popular in poor countries without vast banking infrastructures but also in developed countries. And major institutions—including the Federal Reserve, the OECD, the World Bank, and major investment houses—are paying respectful attention and weaving blockchain technology into their operations.
Enthusiasts, who are found in every country, say that its exchange value will soar even more in the future because its supply is strictly limited and it provides a system vastly superior to government money. Bitcoin is transferred between individuals without a third party. It is relatively low-cost to exchange. It has a predictable supply. It is durable, fungible, and divisible: all crucial features of money. It creates a monetary system that doesn’t depend on trust and identity, much less on central banks and government. It is a new system for the digital age.
Hard lessons for hard money
To those educated in the “hard money” tradition, the whole idea has been a serious challenge. Speaking for myself, I had been reading about bitcoin for two years before I came anywhere close to understanding it. There was just something about the whole idea that bugged me. You can’t make money out of nothing, much less out of computer code. Why does it have value then? There must be something amiss. This is not how we expected money to be reformed.
There’s the problem: our expectations. We should have been paying closer attention to Ludwig von Mises’ theory of money’s origins—not to what we think he wrote, but to what he actually did write.
In 1912, Mises released The Theory of Money and Credit. It was a huge hit in Europe when it came out in German, and it was translated into English. While covering every aspect of money, his core contribution was in tracing the value and price of money—and not just money itself—to its origins. That is, he explained how money gets its price in terms of the goods and services it obtains. He later called this process the “regression theorem,” and as it turns out, bitcoin satisfies the conditions of the theorem.
Mises’ teacher, Carl Menger, demonstrated that money itself originates from the market—not from the State and not from social contract. It emerges gradually as monetary entrepreneurs seek out an ideal form of commodity for indirect exchange. Instead of merely bartering with each other, people acquire a good not to consume, but to trade. That good becomes money, the most marketable commodity.
But Mises added that the value of money traces backward in time to its value as a bartered commodity. Mises said that this is the only way money can have value.
The theory of the value of money as such can trace back the objective exchange value of money only to that point where it ceases to be the value of money and becomes merely the value of a commodity…. If in this way we continually go farther and farther back we must eventually arrive at a point where we no longer find any component in the objective exchange value of money that arises from valuations based on the function of money as a common medium of exchange; where the value of money is nothing other than the value of an object that is useful in some other way than as money…. Before it was usual to acquire goods in the market, not for personal consumption, but simply in order to exchange them again for the goods that were really wanted, each individual commodity was only accredited with that value given by the subjective valuations based on its direct utility.
Mises’ explanation solved a major problem that had long mystified economists. It is a narrative of conjectural history, and yet it makes perfect sense. Would salt have become money had it otherwise been completely useless? Would beaver pelts have obtained monetary value had they not been useful for clothing? Would silver or gold have had money value if they had no value as commodities first? The answer in all cases of monetary history is clearly no. The initial value of money, before it becomes widely traded as money, originates in its direct utility. It’s an explanation that is demonstrated through historical reconstruction. That’s Mises’ regression theorem.
Bitcoin’s Use Value
At first glance, bitcoin would seem to be an exception. You can’t use a bitcoin for anything other than money. It can’t be worn as jewelry. You can’t make a machine out of it. You can’t eat it or even decorate with it. Its value is only realized as a unit that facilitates indirect exchange. And yet, bitcoin already is money. It’s used every day. You can see the exchanges in real time. It’s not a myth. It’s the real deal.
It might seem like we have to choose. Is Mises wrong? Maybe we have to toss out his whole theory. Or maybe his point was purely historical and doesn’t apply in the future of a digital age. Or maybe his regression theorem is proof that bitcoin is just an empty mania with no staying power, because it can’t be reduced to its value as a useful commodity.
And yet, you don’t have to resort to complicated monetary theory in order to understand the sense of alarm surrounding bitcoin. Many people, as I did, just have a feeling of uneasiness about a money that has no basis in anything physical. Sure, you can print out a bitcoin on a piece of paper, but having a paper with a QR code or a public key is not enough to relieve that sense of unease.
How can we resolve this problem? In my own mind, I toyed with the issue for more than a year. It puzzled me. I wondered if Mises’ insight applied only in a pre-digital age. I followed the speculations online that the value of bitcoin would be zero but for the national currencies into which it is converted. Perhaps the demand for bitcoin overcame the demands of Mises’ scenario because of a desperate need for something other than the dollar.
As time passed—and I read the work of Konrad Graf, Peter Surda, and Daniel Krawisz—finally the resolution came. Bitcoin is both a payment system and a money. The payment system is the source of value, while the accounting unit merely expresses that value in terms of price. The unity of money and payment is its most unusual feature, and the one that most commentators have had trouble wrapping their heads around.
We are all used to thinking of currency as separate from payment systems. This thinking is a reflection of the technological limitations of history. There is the dollar and there are credit cards. There is the euro and there is PayPal. There is the yen and there are wire services. In each case, money transfer relies on third-party service providers. In order to use them, you need to establish what is called a “trust relationship” with them, which is to say that the institution arranging the deal has to believe that you are going to pay.
This wedge between money and payment has always been with us, except for the case of physical proximity.
If I give you a dollar for your pizza slice, there is no third party. But payment systems, third parties, and trust relationships become necessary once you leave geographic proximity. That’s when companies like Visa and institutions like banks become indispensable. They are the application that makes the monetary software do what you want it to do.
The hitch is that
-
 @ 90c656ff:9383fd4e
2025-05-31 18:09:27
@ 90c656ff:9383fd4e
2025-05-31 18:09:27Since its emergence in 2009, Bitcoin has generated a wide range of success and failure stories. Some of these stories feature people who invested early and reaped the rewards of their foresight, while others highlight the ups and downs that define Bitcoin’s highly volatile market. Over the years, many of these cases have become iconic—serving as both inspiration and cautionary tales for newcomers.
Success stories
01 - Laszlo Hanyecz – The 10,000 Bitcoin Pizza
One of the most legendary stories in Bitcoin’s history involves Laszlo Hanyecz, a programmer from Florida. In 2010, he paid 10,000 bitcoins for two pizzas. At the time, the value was negligible, and the transaction went largely unnoticed. In retrospect, however, those 10,000 bitcoins would be worth hundreds of millions of dollars today.
Though Hanyecz didn’t become rich from this transaction, the story of the “10,000 bitcoin pizza” has become a symbol of Bitcoin’s extraordinary rise in value—and a reminder of how even small holdings in the early days could have been life-changing.
02 - Michael Saylor and MicroStrategy
Michael Saylor, CEO of MicroStrategy, made headlines in 2020 by transforming his company into the first major corporation to invest heavily in Bitcoin. Purchasing over 100,000 bitcoins as a treasury reserve, Saylor positioned Bitcoin as a strategic hedge against inflation and fiat currency devaluation.
Initially met with skepticism, Saylor’s decision turned out to be highly profitable as Bitcoin’s price soared. His bold move inspired other corporations and institutional investors to consider Bitcoin, and he remains one of the cryptocurrency’s most vocal advocates in the business world.
Failure Stories
01 - James Howells – The Lost 8,000 Bitcoins
James Howells, an IT professional from Wales, accidentally discarded a hard drive in 2013 containing the private keys to 8,000 mined bitcoins—worth only a few thousand pounds at the time. As Bitcoin's value skyrocketed, he attempted to recover the drive from a landfill, but was denied permission by local authorities.
This story has become a powerful lesson in crypto security and the consequences of lost private keys. Despite multiple campaigns to dig up the landfill, the bitcoins remain unrecovered.
02 - Mt. Gox Collapse – The Fall of a Giant
At its peak, Mt. Gox was the largest Bitcoin exchange in the world. In 2014, it collapsed after losing about 850,000 bitcoins—worth over $450 million at the time—due to hacking, internal security failures, and poor management.
The exchange’s failure devastated thousands of investors and highlighted the vulnerabilities in early crypto infrastructure. Though some funds were later recovered, the Mt. Gox disaster remains one of Bitcoin’s darkest moments and a turning point for the push toward greater security and transparency in the crypto industry.
- The impact of volatility and adoption
These stories reflect the unpredictable and high-risk nature of the Bitcoin market. The same volatility that has made millionaires has also led to substantial losses. While some view Bitcoin as a path to financial freedom and a hedge against inflation, others have suffered from poor planning, mismanagement, or unfortunate timing.
Bitcoin’s growing adoption, especially in emerging markets and among institutional players and shows its increasing legitimacy, as an alternative to traditional finance. However, exchange failures and lost fortunes underscore the need for robust infrastructure, personal responsibility, and long-term thinking.
In summary, success and failure are two sides of the same coin in the world of Bitcoin. From life-changing gains to heartbreaking losses, these stories illustrate the risks and rewards of participating in a young and volatile market. Whether as a cautionary tale or a source of inspiration, they emphasize the importance of education, security, and strategy for anyone engaging with this revolutionary form of money.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ b1ddb4d7:471244e7
2025-06-01 03:00:43
@ b1ddb4d7:471244e7
2025-06-01 03:00:43When Sergei talks about bitcoin, he doesn’t sound like someone chasing profits or followers. He sounds like someone about to build a monastery in the ruins.
While the mainstream world chases headlines and hype, Sergei shows up in local meetups from Sacramento to Cleveland, mentors curious minds, and shares what he knows is true – hoping that, with the right spark, someone will light their own way forward.
We interviewed Sergei to trace his steps: where he started, what keeps him going, and why teaching bitcoin is far more than explaining how to set up a node – it’s about reaching the right minds before the noise consumes them. So we began where most journeys start: at the beginning.

First Steps
- So, where did it all begin for you and what made you stay curious?
I first heard about bitcoin from a friend’s book recommendation, American Kingpin, the book about Silk Road (online drug marketplace). He is still not a true bitcoiner, although I helped him secure private keys with some bitcoin.
I was really busy at the time – focused on my school curriculum, running a 7-bedroom Airbnb, and working for a standardized test prep company. Bitcoin seemed too technical for me to explore, and the pace of my work left no time for it.
After graduating, while pursuing more training, I started playing around with stocks and maximizing my savings. Passive income seemed like the path to early retirement, as per the promise of the FIRE movement (Financial Independence, Retire Early). I mostly followed the mainstream news and my mentor’s advice – he liked preferred stocks at the time.
I had some Coinbase IOUs and remember sending bitcoin within the Coinbase ledger to a couple friends. I also recall the 2018 crash; I actually saw the legendary price spike live but couldn’t benefit because my funds were stuck amidst the frenzy. I withdrew from that investment completely for some time. Thankfully, my mentor advised to keep en eye on bitcoin.
Around late 2019, I started DCA-ing cautiously. Additionally, my friend and I were discussing famous billionaires, and how there was no curriculum for becoming a billionaire. So, I typed “billionaires” into my podcast app, and landed on We Study Billionaires podcast.
That’s where I kept hearing Preston Pysh mention bitcoin, before splitting into his own podcast series, Bitcoin Fundamentals. I didn’t understand most of the terminology of stocks, bonds, etc, yet I kept listening and trying to absorb it thru repetition. Today, I realize all that financial talk was mostly noise.
When people ask me for a technical explanation of fiat, I say: it’s all made up, just like the fiat price of bitcoin! Starting in 2020, during the so-called pandemic, I dove deeper. I religiously read Bitcoin Magazine, scrolled thru Bitcoin Twitter, and joined Simply Bitcoin Telegram group back when DarthCoin was an admin.
DarthCoin was my favorite bitcoiner – experienced, knowledgeable, and unapologetic. Watching him shift from rage to kindness, from passion to despair, gave me a glimpse at what a true educator’s journey would look like.
The struggle isn’t about adoption at scale anymore. It’s about reaching the few who are willing to study, take risks, and stay out of fiat traps. The vast majority won’t follow that example – not yet at least… if I start telling others the requirements for true freedom and prosperity, they would certainly say “Hell no!”
- At what point did you start teaching others, and why?
After college, I helped teach at a standardized test preparation company, and mentored some students one-on-one. I even tried working at a kindergarten briefly, but left quickly; Babysitting is not teaching.
What I discovered is that those who will succeed don’t really need my help – they would succeed with or without me, because they already have the inner drive.
Once you realize your people are perishing for lack of knowledge, the only rational thing to do is help raise their level of knowledge and understanding. That’s the Great Work.
I sometimes imagine myself as a political prisoner. If that were to happen, I’d probably start teaching fellow prisoners, doctors, janitors, even guards. In a way we already live in an open-air prison, So what else is there to do but teach, organize, and conspire to dismantle the Matrix?

Building on Bitcoin
- You hosted some in-person meetups in Sacramento. What did you learn from those?
My first presentation was on MultiSig storage with SeedSigner, and submarine swaps through Boltz.exchange.
I realized quickly that I had overestimated the group’s technical background. Even the meetup organizer, a financial advisor, asked, “How is anyone supposed to follow these steps?” I responded that reading was required… He decided that Unchained is an easier way.
At a crypto meetup, I gave a much simpler talk, outlining how bitcoin will save the world, based on a DarthCoin’s guide. Only one person stuck around to ask questions – a man who seemed a little out there, and did not really seem to get the message beyond the strength of cryptographic security of bitcoin.
Again, I overestimated the audience’s readiness. That forced me to rethink my strategy. People are extremely early and reluctant to study.
- Now in Ohio, you hold sessions via the Orange Pill App. What’s changed?
My new motto is: educate the educators. The corollary is: don’t orange-pill stupid normies (as DarthCoin puts it).
I’ve shifted to small, technical sessions in order to raise a few solid guardians of this esoteric knowledge who really get it and can carry it forward.
The youngest attendee at one of my sessions is a newborn baby – he mostly sleeps, but maybe he still absorbs some of the educational vibes.
- How do local groups like Sactown and Cleveland Bitcoiners influence your work?
Every meetup reflects its local culture. Sacramento and Bay Area Bitcoiners, for example, do camping trips – once we camped through a desert storm, shielding our burgers from sand while others went to shoot guns.
Cleveland Bitcoiners are different. They amass large gatherings. They recently threw a 100k party. They do a bit more community outreach. Some are curious about the esoteric topics such as jurisdiction, spirituality, and healthful living.
I have no permanent allegiance to any state, race, or group. I go where I can teach and learn. I anticipate that in my next phase, I’ll meet Bitcoiners so advanced that I’ll have to give up my fiat job and focus full-time on serious projects where real health and wealth are on the line.
Hopefully, I’ll be ready. I believe the universe always challenges you exactly to your limit – no less, no more.
- What do people struggle with the most when it comes to technical education?
The biggest struggle isn’t technical – it’s a lack of deep curiosity. People ask “how” and “what” – how do I set up a node, what should one do with the lightning channels? But very few ask “why?”
Why does on-chain bitcoin not contribute to the circular economy? Why is it essential to run Lightning? Why did humanity fall into mental enslavement in the first place?
I’d rather teach two-year-olds who constantly ask “why” than adults who ask how to flip a profit. What worries me most is that most two-year-olds will grow up asking state-funded AI bots for answers and live according to its recommendations.
- One Cleveland Bitcoiner shows up at gold bug meetups. How valuable is face-to-face education?
I don’t think the older generation is going to reverse the current human condition. Most of them have been under mind control for too long, and they just don’t have the attention span to study and change their ways.
They’re better off stacking gold and helping fund their grandkids’ education. If I were to focus on a demographic, I’d go for teenagers – high school age – because by college, the indoctrination is usually too strong, and they’re chasing fiat mastery.
As for the gold bug meetup? Perhaps one day I will show up with a ukulele to sing some bitcoin-themed songs. Seniors love such entertainment.
- How do you choose what to focus on in your sessions, especially for different types of learners?
I don’t come in with a rigid agenda. I’ve collected a massive library of resources over the years and never stopped reading. My browser tab and folder count are exploding.
At the meetup, people share questions or topics they’re curious about, then I take that home, do my homework, and bring back a session based on those themes. I give them the key takeaways, plus where to dive deeper.
Most people won’t – or can’t – study the way I do, and I expect attendees to put in the work. I suspect that it’s more important to reach those who want to learn but don’t know how, the so-called nescient (not knowing), rather than the ignorant.
There are way too many ignorant bitcoiners, so my mission is to find those who are curious what’s beyond the facade of fake reality and superficial promises.
That naturally means that fewer people show up, and that’s fine. I’m not here for the crowds; I’m here to educate the educators. One bitcoiner who came decided to branch off into self-custody sessions and that’s awesome. Personally, I’m much more focused on Lightning.
I want to see broader adoption of tools like auth, sign-message, NWC, and LSPs. Next month, I’m going deep into eCash solutions, because let’s face it – most newcomers won’t be able to afford their own UTXO or open a lightning channel; additionally, it has to be fun and easy for them to transact sats, otherwise they won’t do it. Additionally, they’ll need to rely on
-
 @ 7f6db517:a4931eda
2025-06-01 02:01:31
@ 7f6db517:a4931eda
2025-06-01 02:01:31
Nostr is an open communication protocol that can be used to send messages across a distributed set of relays in a censorship resistant and robust way.
If you missed my nostr introduction post you can find it here. My nostr account can be found here.
We are nearly at the point that if something interesting is posted on a centralized social platform it will usually be posted by someone to nostr.
We are nearly at the point that if something interesting is posted exclusively to nostr it is cross posted by someone to various centralized social platforms.
We are nearly at the point that you can recommend a cross platform app that users can install and easily onboard without additional guides or resources.
As companies continue to build walls around their centralized platforms nostr posts will be the easiest to cross reference and verify - as companies continue to censor their users nostr is the best censorship resistant alternative - gradually then suddenly nostr will become the standard. 🫡
Current Nostr Stats
If you found this post helpful support my work with bitcoin.

-
 @ 8bad92c3:ca714aa5
2025-06-01 02:01:25
@ 8bad92c3:ca714aa5
2025-06-01 02:01:25Marty's Bent
via me

It seems like every other day there's another company announced that is going public with the intent of competing with Strategy by leveraging capital markets to create financial instruments to acquire Bitcoin in a way that is accretive for shareholders. This is certainly a very interesting trend, very bullish for bitcoin in the short-term, and undoubtedly making it so bitcoin is top of mind in the mainstream. I won't pretend to know whether or not these strategies will ultimately be successful or fail in the short, medium or long term. However, one thing I do know is that the themes that interest me, both here at TFTC and in my role as Managing Partner at Ten31, are companies that are building good businesses that are efficient, have product-market-fit, generate revenues and profits and roll those profits into bitcoin.
While it seems pretty clear that Strategy has tapped into an arbitrage that exists in capital markets, it's not really that exciting. From a business perspective, it's actually pretty straightforward and simple; find where potential arbitrage opportunities exists between pools of capital looking for exposure to spot bitcoin or bitcoin's volatility but can't buy the actual asset, and provide them with products that give them access to exposure while simultaneously creating a cult-like retail following. Rinse and repeat. To the extent that this strategy is repeatable is yet to be seen. I imagine it can expand pretty rapidly. Particularly if we have a speculative fervor around companies that do this. But in the long run, I think the signal is falling back to first principles, looking for businesses that are actually providing goods and services to the broader economy - not focused on the hyper-financialized part of the economy - to provide value and create efficiencies that enable higher margins and profitability.
With this in mind, I think it's important to highlight the combined leverage that entrepreneurs have by utilizing bitcoin treasuries and AI tools that are emerging and becoming more advanced by the week. As I said in the tweet above, there's never been a better time to start a business that finds product-market fit and cash flows quickly with a team of two to three people. If you've been reading this rag over the last few weeks, you know that I've been experimenting with these AI tools and using them to make our business processes more efficient here at TFTC. I've also been using them at Ten31 to do deep research and analysis.
It has become abundantly clear to me that any founder or entrepreneur that is not utilizing the AI tools that are emerging is going to get left behind. As it stands today, all anyone has to do to get an idea from a thought in your head to the prototype stage to a minimum viable product is to hop into something like Claude or ChatGPT, have a brief conversation with an AI model that can do deep research about a particular niche that you want to provide a good service to and begin building.
Later this week, I will launch an app called Opportunity Cost in the Chrome and Firefox stores. It took me a few hours of work over the span of a week to ideate and iterate on the concept to the point where I had a working prototype that I handed off to a developer who is solving the last mile problem I have as an "idea guy" of getting the product to market. Only six months ago, accomplishing something like this would have been impossible for me. I've never written a line of code that's actually worked outside of the modded MySpace page I made back in middle school. I've always had a lot of ideas but have never been able to effectively communicate them to developers who can actually build them. With a combination of ChatGPT-03 and Replit, I was able to build an actual product that works. I'm using it in my browser today. It's pretty insane.
There are thousands of people coming to the same realization at the same time right now and going out there and building niche products very cheaply, with small teams, they are getting to market very quickly, and are amassing five figures, six figures, sometimes seven figures of MRR with extremely high profit margins. What most of these entrepreneurs have not really caught on to yet is that they should be cycling a portion - in my opinion, a large portion - of those profits into bitcoin. The combination of building a company utilizing these AI tools, getting it to market, getting revenue and profits, and turning those profits into bitcoin cannot be understated. You're going to begin seeing teams of one to ten people building businesses worth billions of dollars and they're going to need to store the value they create, any money that cannot be debased.
Grant Gilliam, one of the co-founders of Ten31, wrote about this in early 2024, bitcoin being the fourth lever of equity value growth for companies.
[
Bitcoin Treasury - The Fourth Lever to Equity Value Growth
Most companies do not hold enough bitcoin There is a saying you often hear in bitcoin circles that “you can never have enough bitcoin.” This is typically expressed by those who have spent the time to both understand bitcoin’s unique and superior monetary properties and also to appreciate why tho
Ten31 - Investors in bitcoin infrastructure and freedom techGrant Gilliam
](https://ten31.vc/insights/treasury?ref=tftc.io)
We already see this theme playing out at Ten31 with some of our portfolio companies, most notably Strike, which recently released some of their financials, highlighting the fact that they're extremely profitable with high margins and a relatively small team (~75). This is extremely impressive, especially when you consider the fact that they're a global company competing with the likes of Coinbase and Block, which have each thousands of employees.
Even those who are paying attention to the developments in the AI space and how the tools can enable entrepreneurs to build faster aren't really grasping the gravity of what's at play here. Many are simply thinking of consumer apps that can be built and distributed quickly to market, but the ways in which AI can be implemented extend far beyond the digital world. Here's a great example of a company a fellow freak is building with the mindset of keeping the team small, utilizing AI tools to automate processes and quickly push profits into bitcoin.
via Cormac
Again, this is where the exciting things are happening in my mind. People leveraging new tools to solve real problems to drive real value that ultimately produce profits for entrepreneurs. The entrepreneurs who decide to save those profits in bitcoin will find that the equity value growth of their companies accelerates exponentially as they provide more value, gain more traction, and increase their profits while also riding the bitcoin as it continues on its monetization phase. The compounded leverage of building a company that leverages AI tools and sweeps profits into bitcoin is going to be the biggest asymmetric play of the next decade. Personally, I also see it as something that's much more fulfilling than the pure play bitcoin treasury companies that are coming to market because consumers and entrepreneurs are able to recive and provide a ton of value in the real economy.
If you're looking to stay on top of the developments in the AI space and how you can apply the tools to help build your business or create a new business, I highly recommend you follow somebody like Greg Isenberg, whose Startup Ideas Podcast has been incredibly valuable for me as I attempt to get a lay of the land of how to implement AI into my businesses.
America's Two Economies
In my recent podcast with Lyn Alden, she outlined how our trade deficits create a cycle that's reshaping America's economic geography. As Alden explained, US trade deficits pump dollars into international markets, but these dollars don't disappear - they return as investments in US financial assets. This cycle gradually depletes industrial heartlands while enriching financial centers on the coasts, creating what amounts to two separate American economies.
"We're basically constantly taking economic vibrancy out of Michigan and Ohio and rural Pennsylvania where the steel mills were... and stuffing it back into financial assets in New York and Silicon Valley." - Lyn Alden
This pattern has persisted for over four decades, accelerating significantly since the early 1980s. Alden emphasized that while economists may argue there's still room before reaching a crisis point, the political consequences are already here. The growing divide between these two Americas has fueled populist sentiment as voters who feel left behind seek economic rebalancing, even if they can't articulate the exact mechanisms causing their hardship.
Check out the full podcast here for more on China's man
-
 @ 90c656ff:9383fd4e
2025-05-31 18:01:32
@ 90c656ff:9383fd4e
2025-05-31 18:01:32Since its launch in 2009, Bitcoin has attracted the attention of a wide range of investors and visionaries who believe in its potential to revolutionize the global financial system. Over the years, several figures have stood out within the movement—either as pioneers who helped build it or as investors who bet on its future. These individuals have played crucial roles in Bitcoin's development, its growing adoption, and its legitimacy in financial markets.
- Satoshi Nakamoto
The most significant Bitcoin pioneer is undoubtedly its creator, Satoshi Nakamoto. Although the name is a pseudonym, Nakamoto's contribution to the creation and launch of Bitcoin was foundational. In 2008, Nakamoto published the famous whitepaper "Bitcoin: A Peer-to-Peer Electronic Cash System," outlining the concept of a decentralized digital currency that could operate without the need for a central authority like a bank. In 2009, he released the Bitcoin software and mined the first block of the blockchain—the “genesis block.”
Nakamoto remained a mysterious figure and gradually withdrew from public involvement around 2011, leaving the project in the hands of a growing community of developers. Though his identity remains unknown, his impact on ushering in a new digital era is undeniable.
- Hal Finney
Hal Finney was one of Nakamoto’s earliest collaborators and is widely known as the first person to receive a Bitcoin transaction. In January 2009, he received 10 bitcoins from Nakamoto as part of an early test, becoming one of the first believers in the project. Finney, a respected programmer and cryptography expert, played a vital role in Bitcoin’s early technical development and helped promote it within the digital privacy community.
He was a dedicated advocate for decentralized technologies and supported Bitcoin until his death in 2014. Finney is remembered as a key pioneer of digital currency.
- Roger Ver
Known as “Bitcoin Jesus,” Roger Ver was one of the first investors and outspoken advocates for Bitcoin. Captivated by the idea of decentralized money, Ver made early investments in various Bitcoin-related startups and projects. He quickly recognized Bitcoin’s disruptive potential and became a leading voice promoting its adoption as a payment method and financial tool.
Ver was instrumental in creating companies and initiatives that supported Bitcoin's early ecosystem. Although he later became a controversial figure—due to his advocacy for Bitcoin Cash as an alternative to the original Bitcoin blockchain—his contributions to Bitcoin's early popularity remain significant.
- Tim Draper
Tim Draper is one of the most prominent venture capitalists in the Bitcoin space. In 2014, he famously purchased nearly 30,000 bitcoins from a U.S. government auction, following the shutdown of the Silk Road marketplace. Draper paid approximately $19 million for the coins and has since become a public advocate for Bitcoin as a viable alternative to fiat currencies.
As the founder of Draper Associates, he is known for his long-term vision and conviction in the potential of cryptocurrencies. Draper frequently promotes Bitcoin as a tool for democratizing finance and anticipates its mass adoption in the coming years.
- Michael Saylor
Michael Saylor, CEO of MicroStrategy, is a leading figure in institutional Bitcoin adoption. In 2020, he made headlines by purchasing over 100,000 bitcoins for his company—making MicroStrategy the first publicly traded company to adopt Bitcoin as a treasury reserve asset. Saylor has since become a vocal proponent of Bitcoin as a hedge against inflation and a superior store of value compared to fiat money.
His bold move has helped legitimize Bitcoin in the corporate world and inspired other companies to follow suit. Saylor continues to assert that Bitcoin is the future of finance and that MicroStrategy’s strategy serves as a model for corporate treasury management in the digital age.
In summary, the pioneers and investors who helped grow and promote Bitcoin have played essential roles in the evolution of this disruptive technology. From the enigmatic Satoshi Nakamoto to key figures like Hal Finney, Roger Ver, Tim Draper, and Michael Saylor, Bitcoin has been shaped by individuals with a unique vision for the future of money and financial freedom. Through their belief and perseverance, they helped lay the foundation for Bitcoin’s global adoption—transforming it from a radical idea into a revolutionary force in the financial system. While Bitcoin’s future will depend on its continued innovation and broader adoption, the contributions of these early leaders are undeniable.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 90c656ff:9383fd4e
2025-05-31 17:54:42
@ 90c656ff:9383fd4e
2025-05-31 17:54:42Since its creation, Bitcoin has been one of the most hotly debated assets in the financial world—both by passionate supporters and skeptics. Its extreme volatility and the impact it has had on the traditional financial system have made it a constant subject of speculation. Over time, Bitcoin’s adoption has grown, sparking ongoing discussions about its future—both in terms of price and integration into the global financial system. In this context, multiple scenarios have been proposed, ranging from optimistic to cautious, depending on factors like regulation, institutional adoption, and technological innovation.
Bitcoin’s price: forecasts and influencing factors
01 - Institutional Adoption: The growing use of Bitcoin by major companies and institutional investors has been seen as a bullish driver. Companies like Tesla, MicroStrategy, and Square have added Bitcoin to their balance sheets, boosting confidence in it as a store of value. As more businesses follow suit, demand for Bitcoin could increase, pushing the price upward.
02 - Government Regulation: How governments respond to Bitcoin is one of the biggest sources of uncertainty. Heavy-handed regulation could restrict access and dampen interest, while a more favorable approach could boost adoption and support price growth. Countries like El Salvador have shown positive trends by adopting Bitcoin as legal tender, though in many others, regulation remains a significant challenge.
03 - Limited Supply: With a maximum supply of 21 million coins, Bitcoin is immune to inflationary money printing. This scarcity makes it especially attractive as a store of value, particularly during times of global economic uncertainty, potentially supporting long-term price appreciation.
04 - Technology and Scalability: Innovations like the Lightning Network and Taproot, aimed at improving scalability and transaction efficiency, could help increase Bitcoin's utility—making it more accessible for daily use and positively impacting its market value.
Global adoption of Bitcoin: The path toward financial inclusion
Bitcoin adoption is rising globally, especially in regions where traditional financial systems are inefficient or inaccessible. Countries facing economic instability, such as those plagued by high inflation or currency crises, are increasingly viewing Bitcoin as a viable alternative. Financial inclusion is a key driver of this adoption, as Bitcoin offers financial services to people excluded from the traditional banking sector.
01 - Emerging Markets: In countries like Brazil, Argentina, Nigeria, and others, demand for Bitcoin has grown as people seek to protect their assets from the devaluation of local currencies. In these regions, Bitcoin functions as both a store of value and a medium of exchange free from central authority control.
02 - Adoption by Governments and Businesses: As more companies and even governments embrace Bitcoin, its integration into the global economy could accelerate. El Salvador, for example, has shown it’s possible to adopt Bitcoin as an official currency, while more businesses are accepting it as a payment method—further legitimizing its role in global commerce.
03 - Education and Accessibility: As more people understand how Bitcoin works and appreciate its advantages—such as security, privacy, and financial freedom—adoption is likely to grow. Easier-to-use exchanges and improved wallet interfaces are making it simpler for everyday users to access and use Bitcoin.
Future scenarios: Optimism or caution?
Bitcoin's future remains uncertain, but several possible outcomes are taking shape. The optimistic scenario foresees greater price appreciation and widespread global adoption, driven by technological innovation, increased institutional trust, and the search for a decentralized alternative to the traditional financial system. In this case, Bitcoin could become a widely accepted form of payment and a global store of value, with prices reaching new all-time highs.
On the other hand, the more cautious scenario suggests that obstacles like government regulation, competition from other digital currencies, and potential technical shortcomings could prevent Bitcoin from becoming central to the financial system. Furthermore, price volatility could deter those seeking stability and security.
In summary, predictions about Bitcoin’s price and global adoption are undeniably complex and influenced by a wide range of factors. Bitcoin’s future will depend on how society, governments, and businesses respond to this new form of money. While the potential for appreciation is significant, the risks and volatility involved cannot be ignored. As global adoption increases and technology continues to evolve, it will be essential to closely monitor the developments shaping Bitcoin’s role in the global financial landscape.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ eb0157af:77ab6c55
2025-06-01 02:01:11
@ eb0157af:77ab6c55
2025-06-01 02:01:11The company unveils a service to generate returns from the Lightning Network while maintaining full control over one’s bitcoin.
Amboss, a company dedicated to developing the Lightning Network ecosystem, has announced the launch of Rails, a platform that enables users to earn yields on their bitcoin while retaining complete custody.
Rails stands out as the first fully self-custodial yield-generation service built specifically for the Lightning Network. Users can act as Liquidity Providers (LPs) while maintaining full control over their funds, contributing at the same time to improving the performance and scalability of the Lightning Network.
The service leverages Amboss’ AI infrastructure to optimize the speed, reliability, and capacity of Lightning transactions.
How it works
Rails’ yield-generation mechanism is based on two main activities:
- Payment routing: users earn fees by facilitating payment routing through the Lightning Network;
- Liquidity leasing: by providing liquidity to other participants in the LN network.
Although returns are not guaranteed, the performance demonstrated by companies like Block is notable. During the Bitcoin 2025 conference in Las Vegas, Miles Suter of Block revealed that their routing node is generating a 9.7% APR on deposited bitcoin while maintaining control over private keys.
Strategic partnerships
Amboss has entered into partnerships with CoinCorner and Flux to launch Rails. CoinCorner has integrated the service into its exchange and payment platforms, while Flux aims to expand the Lightning Network’s role in global payments.
David Boylan, CFO of CoinCorner, stated:
“Rails offers a practical way for businesses like ours to participate in the Lightning Network’s growth. We’ve been using the Lightning Network for years, and Rails provides a structured approach to engaging with its economy, particularly through liquidity leasing and payment routing.”
Two complementary solutions
Rails offers two distinct services:
- Rails LP: designed for businesses with bitcoin treasuries, custodians, and high-net-worth individuals, with a minimum commitment of 1 BTC for one year;
- Liquidity subscriptions: aimed at businesses accepting bitcoin payments, with fees starting from 0.5%.
Jesse Shrader, co-founder and CEO of Amboss, commented:
“Rails is a transformative force for the Lightning Network. It’s not just about yield — it’s about enabling businesses to strengthen the network while earning on their bitcoins. This is a critical step in bitcoin’s evolution as a global medium of exchange.”
The post Amboss launches Rails: a service to earn yields from the Lightning Network appeared first on Atlas21.
-
 @ eb0157af:77ab6c55
2025-06-01 02:01:09
@ eb0157af:77ab6c55
2025-06-01 02:01:09A new investment vehicle combines exposure to Bitcoin with downside protection based on the price of gold.
On May 29, Cantor Fitzgerald Asset Management announced the launch of an investment product that merges direct exposure to Bitcoin with a bearish hedge linked to gold.
According to the financial institution, the new fund offers a solution for investors seeking to benefit from the growth potential of the leading cryptocurrency while maintaining a safety net tied to the precious metal.
Fund features
The fund is structured with a five-year term and no cap on potential upside, allowing investors to fully capture Bitcoin’s growth. The “1-to-1” protection mechanism means that any losses on Bitcoin would be offset by corresponding gains from gold.
Brandon Lutnick, Chairman of Cantor and son of former CEO Howard Lutnick (now Commerce Secretary in the Trump administration), called the product “a truly revolutionary investment vehicle” that helps investors access Bitcoin’s potential while providing downside protection. “There are still people on the Earth that are still scared of Bitcoin, and we want to bring them into this ecosystem,” Lutnick added.
The fund marks Cantor Fitzgerald’s first BTC-focused investment product. The firm, with 79 years of history and $14.8 billion in assets under management, is making its first significant move into the Bitcoin market.
The announcement follows the closing of its first round of financing agreements with Maple Finance and FalconX. Through its “Bitcoin Financing Business” division, Cantor plans to initially make up to $2 billion in financing available to institutional clients.
The post Cantor Fitzgerald launches Bitcoin fund with gold hedge appeared first on Atlas21.
-
 @ 90c656ff:9383fd4e
2025-05-31 17:49:25
@ 90c656ff:9383fd4e
2025-05-31 17:49:25With the growing digitalization of money, governments around the world have begun developing Central Bank Digital Currencies (CBDCs) in response to the rising popularity of Bitcoin. While Bitcoin represents a decentralized and censorship-resistant financial system, CBDCs are digital versions of fiat currencies, directly controlled by central banks. This emerging competition could shape the future of money and define the balance between financial freedom and state control.
Key differences between Bitcoin and CBDCs
Bitcoin and CBDCs differ in nearly every fundamental aspect:
01 - Centralization vs Decentralization: Bitcoin operates on a decentralized network where no government or entity can change the rules or censor transactions. CBDCs, on the other hand, are issued and managed by central banks, enabling greater control over the circulation and use of money.
02 - Fixed Supply vs Controlled Inflation: Bitcoin has a fixed supply of 21 million units, making it a scarce and deflationary asset. CBDCs can be issued without limits, much like traditional fiat currencies, and are subject to inflationary monetary policies.
03 - Privacy vs Surveillance: Bitcoin allows pseudonymous transactions, ensuring a certain degree of financial privacy. CBDCs may be designed to track every transaction, enabling full governmental oversight—and potentially, control over how citizens spend their money.
04 - Censorship Resistance vs State Control: Bitcoin enables anyone to transact without needing third-party approval. CBDCs, being centralized, could be used by governments to restrict undesirable transactions or even freeze funds at the press of a button.
What are governments aiming for with CBDCs?
The introduction of CBDCs is often promoted with benefits such as:
01 - Greater efficiency in financial transactions by removing intermediaries and reducing banking costs.
02 - Easier implementation of economic policies, such as direct stimulus payments or automated taxation.
03 - Enhanced ability to combat illegal activities through real-time transaction tracking.
However, these justifications raise serious concerns about the erosion of financial privacy and the expansion of government power over the monetary system.
Bitcoin as an alternative to CBDCs
The rise of CBDCs may, in fact, reinforce Bitcoin’s position as the true alternative to state-controlled money. As citizens become aware of the risks associated with a fully centralized financial system, demand for a decentralized, censorship-resistant asset like Bitcoin may increase.
01 - Protection from state control: Bitcoin empowers users with full sovereignty over their money, free from arbitrary freezes or confiscations.
02 - Preservation of financial privacy: Unlike CBDCs, which may monitor every transaction, Bitcoin offers a level of anonymity that shields individuals from excessive surveillance.
03 - Store of value against inflation: While governments can endlessly issue CBDCs, Bitcoin’s guaranteed scarcity positions it as a hedge against irresponsible monetary policy.
In summary, the competition between Bitcoin and CBDCs is set to become one of the defining financial battles of the future. As governments seek to reinforce their control through centralized digital currencies, Bitcoin remains the leading option for those who value financial independence and protection from state surveillance. The choice between a free, decentralized financial system and a monitored, government-controlled one may determine the course of the digital economy for decades to come.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 9ca447d2:fbf5a36d
2025-06-01 02:01:04
@ 9ca447d2:fbf5a36d
2025-06-01 02:01:04Mac users who use Ledger hardware wallets to manage their digital assets are being warned about a new scam that uses fake apps to steal funds.
Cybercriminals have launched multiple phishing campaigns using malware that targets macOS systems, replacing the real Ledger Live app with a fake version that asks users to enter their recovery phrase.
These fake apps look almost identical to the real Ledger Live, but instead of helping users manage their bitcoin, they steal the 24-word recovery phrase—the master key to the user’s digital assets.
According to a detailed analysis by Moonlock, the attacks start when users’ computers get infected with Atomic macOS Stealer malware from one of over 2,800 hacked websites. Once installed, the malware removes the legitimate Ledger Live app and installs a malicious version in its place.
The fake app then shows a pop-up message saying it has detected “suspicious activity”, and asks the user to enter their recovery phrase to fix the issue. Once entered, the seed phrase is sent to a server controlled by the attacker.
2,800 websites discovered infected with Atomic Stealer — Moonlock
“Once entered, the seed phrase is sent to an attacker-controlled server, exposing the user’s assets in seconds,” Moonlock said in their May 22 report.
With the recovery phrase, the scammers can drain the user’s wallet of all digital assets—bitcoin and other tokens.
This isn’t an isolated incident. Moonlock has been tracking this malware since August 2024 and has found at least four active campaigns targeting Mac users. They believe the attackers are getting more sophisticated and are refining their methods.
“This isn’t just a theft. It’s a high-stakes effort to outsmart one of the most trusted tools in the crypto world. And the thieves are not backing down,” Moonlock researchers said.
Initially, the fake Ledger Live apps could only steal passwords and view wallet details. This gave attackers some insight into victims’ assets but no way to steal funds directly.
However, over time, hackers have improved their tactics and are now harvesting recovery phrases, so they can take full control of wallets and move funds freely.
One strain of malware, called Odyssey, was spotted in March and was linked to a hacker using the alias “Rodrigo”.
Odyssey replaces Ledger Live with a trojanized app and displays a phishing page asking users to enter their recovery phrases after showing a fake “critical error” message. Another copycat campaign using AMOS (Atomic macOS Stealer) followed soon after.
The fake Ledger Live app asks for user’s seed phrase — Moonlock
In one case, a fake app even displayed an “App corrupted” error after stealing the seed phrase to lower the victim’s suspicion and buy time to transfer the funds.
For years, computers running MacOS were considered safer than their Windows counterparts, because the operating system is less prone to malware. This advanced malware shows that users can never be too careful.
Attackers aren’t just relying on infected apps to steal from users. Other scam tactics include:
- Discord attacks: In May, a moderator account in Ledger’s official Discord server was compromised. Attackers used it to post fake verification links.
- Reddit phishing: In January, a user reported losing $15,000 after unknowingly entering their recovery phrase into a fake app.
- Physical mail scams: In April, some Ledger users received letters claiming to be from the company. These letters included QR codes leading to phishing sites that asked for seed phrases under the guise of a “critical security update”.
Attackers are increasingly targeting users holding hardware wallets, because they might be holding larger amounts.
Earlier this month, a Trezor One user reported being contacted by Coinbase impersonators, who tricked him into entering his seed phrase into a fake website, resulting in loss of 17.5 BTC.
The final goal for all these attacks is similar: the attackers are looking for users’ seed phrases, and they are getting creative in finding new ways to acquire them.
One sure way of staying safe is to learn more. The golden standard rule is to NEVER enter your seed phrase into a computer or a website, no matter how urgent or convincing it looks.
If you are a hardware wallet user, make sure you purchase the wallet from official sources. And the ONLY electronic place you can enter your seed phrases is on the hardware wallet itself.
If a process requires you to enter your seed phrase anywhere on a computer itself, it is definitely a scam.
Related: Bitcoin Hardware Wallet Hacks | What You Need to Know
-
 @ 9ca447d2:fbf5a36d
2025-06-01 02:01:03
@ 9ca447d2:fbf5a36d
2025-06-01 02:01:03When making critical decisions about investments, company acquisitions, or capital deployment, organizations rely on a fundamental tool: the hurdle rate. This is the minimum rate of return that a project or investment must achieve to be considered viable by managers or investors.
The hurdle rate is not just a number — it’s a filter that separates promising opportunities from those that don’t justify the risk.
It acts as a crucial benchmark. If the expected return on an investment falls below the hurdle rate, that opportunity is typically rejected.
Setting this rate involves a careful consideration of several factors, including the company’s cost of capital, specific risk profile, inflation rates, and opportunity cost of allocating resources elsewhere.
In essence, the hurdle rate ensures that only projects with the potential to create real value move forward.
Bitcoin has emerged as a disruptive and compelling candidate for a new kind of hurdle rate in capital allocation. Its unique properties challenge the conventions of traditional finance and invite a new thought pattern of what’s considered an appropriate benchmark.
Bitcoin’s fixed supply (capped at 21 million), and its decentralized, borderless nature makes it fundamentally resistant to inflation and debasement, unlike fiat currencies that can be printed at will by central banks.
Here’s the real question for investors and fund managers: if your portfolio or fund consistently fails to outperform bitcoin, at what point do you simply start allocating to bitcoin instead?
This isn’t rocket science. Over the past decade, bitcoin has not only outperformed traditional assets, but has also redefined what investors should expect as a minimum acceptable rate.
Asset classes comparison since 2013 — Seeking Alpha
The numbers speak for themselves.
From 2013-2023, bitcoin delivered the highest annual return in 8 out of those 11 years. This is not a fluke or a bubble, it’s a decade-long trend that demands attention from anyone serious about capital growth.
Typically, most investment managers use the S&P 500 as their benchmark hurdle rate. Will their potential investment generate more return than the S&P? If not, it’s usually dismissed.
Since 1970, the S&P 500 has provided an average annual return of 10.66%. Investment managers routinely reject ideas that can’t beat this average, recognizing that anything less is not worth the risk or effort.
But what happens when we compare this to bitcoin?
Over the last 10 years, bitcoin’s average annual return has been an astonishing 49%. While it’s unlikely that this rate will persist forever, it’s impossible to ignore the magnitude and consistency of bitcoin’s outperformance.
Bitcoin hasn’t just beat the S&P—it’s outperformed every major asset class, including gold, treasuries, real estate, commodities, and equities.
Of course, past performance isn’t a guarantee of future results. So the question becomes: can bitcoin continue to deliver, and are we ready to use it as a benchmark for investment decisions?
To answer this, it’s essential to understand the underlying forces driving bitcoin’s price appreciation.
Several macroeconomic factors contribute to bitcoin’s rise, including money printing, economic uncertainty, and the ongoing debasement of fiat currencies.
When governments print money or run deficits, confidence in traditional currencies erodes. In such environments, investors naturally seek scarce assets, historically gold, and now increasingly bitcoin.
Consider the current fiscal reality: the United States is burdened with over $36 trillion in national debt, and there’s little indication that the money printing will stop.
This environment only strengthens the case for bitcoin as a store of value and as a benchmark for capital allocation. Bitcoin’s staying power is becoming undeniable.
Those who fail to adapt, risk being left behind. We’re already witnessing the early stages of institutional and corporate adoption, and it’s only a matter of time before bitcoin becomes a standard reference point for hurdle rates across the investment world.
Visionary leaders like Michael Saylor of Strategy, have openly discussed the challenges of outperforming the world’s top companies.
Saylor recognized that if your investment, company, or project cannot reasonably be expected to outperform bitcoin, it may be more rational to simply hold bitcoin itself.
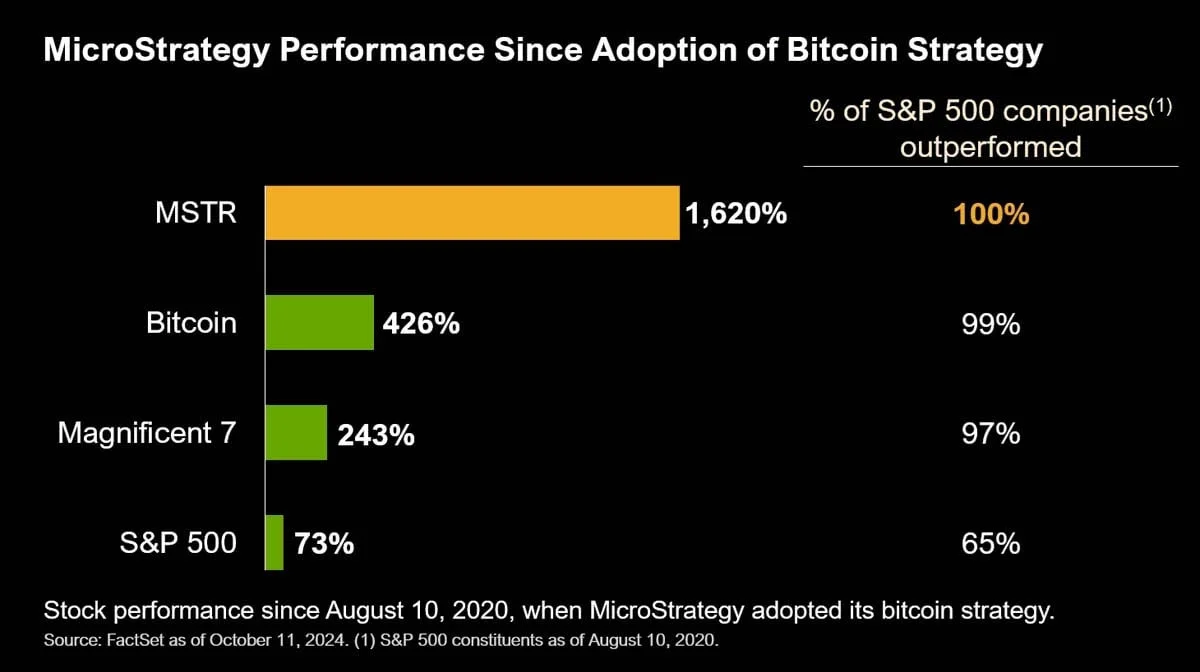
MSTR performance compared to bitcoin, Magnificent 7 and S&P500 — aicoin
In a world where bitcoin has established itself as the premier performing asset, the message is clear: if you can’t beat bitcoin, why not join it?
Just buy bitcoin.
-
 @ b1ddb4d7:471244e7
2025-06-01 02:00:38
@ b1ddb4d7:471244e7
2025-06-01 02:00:38Sati, a Bitcoin payments app and Lightning infrastructure provider, announced the launch of its Lightning integration with Xverse wallet.
Launched in 2025 with investors of the likes as Draper Associates and Ricardo Salinas, Sati powers Bitcoin payments on applications such as WhatsApp to fuel the next wave of adoption.
The Whatsapp bot allows users to send bitcoin via the messaging app through a special bot. After verifying their identity, the user selects the “send” option, chooses to pay to a Lightning address, enters the amount (1,000 sats), confirms with a PIN, and the transaction is completed, with the funds appearing instantly in the recipient wallet.
The new integration will now bring Lightning functionality to over 1.5 million people worldwide. Users can send and receive sats (Bitcoin’s smallest denomination) instantly over the Lightning Network all within the Xverse app,
Further, every xverse wallet user gets a Lightning Address instantly. That means they can receive tips, pay invoices, and use Bitcoin for microtransactions—all without having to manage channels or switch between different apps.
While Xverse adds support for Lightning, users should be cautious in using the wallet as it’s mostly known for enabling access to rug pull projects.
Initially designed in 2017, the Lightning Network has grown to become Bitcoin’s leading layer-2, with a current BTC capacity of over $465M.
“Bitcoin was not meant to be an asset for Wall Street—it was built for peer-to-peer money, borderless and accessible,” said Felipe Servin, Founder and CEO of Sati. “Integrating Lightning natively into Xverse brings that vision back to life, making Bitcoin usable at scale for billions.”
Sati expects USDT on Lightning to be supported as early as July 2025 for users accessing Sati through WhatsApp.
This integration positions Sati’s role as a Lightning infrastructure provider, not just a consumer app. By leveraging its API-based solution, the company provides plug-and-play backend services to wallets and platforms looking to add Bitcoin payments without compromising on security or UX.
Sati recently closed a $600K pre-seed round. The funding is used to support global expansion, stablecoin integration, Lightning infrastructure growth, and broader access to Bitcoin in emerging markets.
The Sati team is attending Bitcoin2025 in Las Vegas this week and looking forward to connect with bitcoin enthusiasts.
-
 @ bf47c19e:c3d2573b
2025-05-31 17:12:24
@ bf47c19e:c3d2573b
2025-05-31 17:12:24Originalni tekst na bitcoin-balkan.com.
Pregled sadržaja
- Koji Bitcoin Novčanici su Dostupni?
- Šta je Mnemonic Oporavak ili Seed Fraza sa 12 ili 24 Reči?
- Kako Čuvati Seed Frazu
- Saveti za Osiguravanje Vaše Seed Fraze
- Šta će se Desiti sa Vašim Bitcoin-om Nakon što Umrete?
- Kako Koristite Seed Frazu za Oporavak Vašeg Novčanika?
- Ako je Vaša Seed Fraza Sigurna, Biće i Vaša Sredstava!
Za one koji tek ulaze u igru sa kriptovalutama, šansa da vaša Bitcoin sredstva ne budu sigurna i zaštićena može biti pomalo zastrašujuća. Srećom, postoji mnogo user-friendly Bitcoin novčanika, i svaki od njih ima izvrsnu funkciju rezervne kopije, koja vam omogućava trenutan povraćaj Bitcoin sredstava, ako vaš uređaj na kome se nalazi novčanik ikada bude zagubljen ili izgubljen. Ova funkcija, poznata kao „seed fraza“, ili seed fraza za oporavak, predstavlja jedinstveni niz reči koje će vaš novčanik generisati, i koje deluju kao password za vaše lične Bitcoin podatke. Ovaj skup reči omogućava trenutni povraćaj vaših bitcoin sredstava.
Iako možete lako zapostaviti svoju seed frazu, misleći da ćete se kasnije pozabaviti sa njom, uvek je najbolje biti proaktivan kada je reč o osiguranju zaštite vaše fraze za oporavak. Fraza za oporavak je vaša rezervna kopija – pa iako vam neće trebati svaki dan, biće kritična u slučaju da vam se novčanik pokvari. Takođe, fraza za oporavak može da omogući svima pristup vašem bitcoin-u, pa je zato veoma važno da se ona čuva na sigurnom.
U ovom članku, prikazaću vam:
- Spisak glavnih Bitcoin hardware novčanika koje možete koristiti za skladištenje vaših Bitcoin-a.
- Sveobuhvatan pregled mnogih metoda koje možete koristiti za čuvanje vaše seed fraze
- Razne prednosti i mane za svaku od njih
- Saveti koje možete da koristite da biste maksimizirali ukupnu sigurnost svoje seed fraze
- Kako sigurno čuvati vašu seed frazu
- Kako proslediti svoj Bitcoin u slučaju vaše smrti
Kada završite sa čitanjem, trebalo bi da ste na dobrom putu da čuvate svoju seed frazu koristeći najsigurnija i najpouzdanija dostupna sredstva, obezbeđujući najveću zaštitu svojih Bitcoin sredstava bez obzira na to šta se sa vama ili vašim digitalnim uređajima dogodi u budućnosti. Za početak ćemo dati brzi pregled hardware novčanika i šta tačno predstavlja fraza za oporavak.
Koji Bitcoin Novčanici su Dostupni?
Ispod ćete pronaći listu od nekoliko najpopularnijih novčanika koji su dostupni danas. Softverski novčanici rade na vašem telefonu ili računaru, dok su hardware novčanici namenski delovi hardvera (poput specijalizovanog fleš diska) koji omogućavaju lak i siguran pristup vašem bitcoin-u uz jaku sigurnost.
- Coldcard (hardverski novčanik)
- Blockstream Jade (hardverski novčanik)
- Electrum (softverski novčanik)
- Sparrow (softverski novčanik)
Svaki od ovih novčanika će vam dati seed frazu, koja se sastoji od 12 ili 24 reči, što će vam omogućiti pristup svim bitcoin adresama povezanim sa vašim novčanikom – a samim tim i svim vašim sredstvima.
Šta je Mnemonic Oporavak ili Seed Fraza sa 12 ili 24 Reči?
Najjednostavnije rečeno, seed fraza je niz određenih reči u kojima se nalaze sve potrebne informacije kako bi se u potpunosti povratila vaša Bitcoin sredstva. Koji god novčanik odlučite da koristite, generisaće jedinstvenu seed frazu, posebno za vas, a taj softver će vas uputiti da čuvate seed frazu na neki način, gde će biti dostupna u slučaju nužde. Seed fraza će biti jedinstvena i obično sadrži od 12 ili 24 reči, od kojih se neke mogu ponoviti. Pre nego što sačuvate seed frazu, pročitajte odeljak 4) sa našim savetima!
Seed fraza omogućava pristup vašim bitcoin sredstvima svima koji je poseduju- omogućavajući vam da povratite sredstava ako vam se novčanik pokvari, ili omogućavajući lopovu da dobije pristup vašim bitcoin-ima.
To čini vašu seed frazu vrednom poput zlatne poluge. Zbog toga je pravilno čuvanje vaše seed fraze veoma važno – morate uravnotežiti lak način oporavka i sigurnost protiv krađe i hakovanja. Međutim, s obzirom da je vaša seed fraza samo niz reči, ona se može snimati i skladištiti na mnogo jednostavniji način (i mnogo jeftinije!) od zlatne poluge – čineći je potencijalno mnogo sigurnijom.
Primarna svrha seed fraze je da ima neku vrstu fizičkog sredstva za povraćaj Bitcoin sredstava ako vas izneveri novčanik. To uključuje ako vam se sruši sistem na računaru, ako vam se ošteti hard disk, izgubite telefon ili razbijete hardware novčanik – u svakom slučaju gde vaš novčanik postane nepristupačan.
Seed fraze zasnivaju se na specifikacijama otvorenog koda kompatibilnim sa Bitcoin protokolom, što znači da dok god imate svoju seed frazu, možete koristiti mnoge druge vrste novčanika da biste povratili pristup svom bitcoin-u. Recimo da danas posedujete Trezor, ali za 10 godina vam se uređaj pokvari ili Trezor prestane da posluje – možete jednostavno kupiti drugačiji hardware novčanik ili skinuti novčanik na svoj telefon, i pomoću svoje seed fraze povratiti pristup svojim bitcoin-ima.
Kako seed fraza funkcioniše?
Seed fraze funkcionišu slično kao i bilo koji drugi oblik koda, pri čemu svaka reč predstavlja numeričku vrednost koju novčanik razume. Fraze se generišu nasumično na osnovu unapred određene baze reči. Iako ponekad imate mogućnost da smislite sopstvenu seed frazu, omogućavanje novčaniku da generiše seed frazu je najbolja opcija za vašu sigurnost.
Jedna od prednosti koja je svojstvena prirodi seed fraza je ta što se u njima koriste stvarne prepoznatljive reči na engleskom jeziku koje se mogu izvesti i upamtiti bez obzira na male greške kao rezultat ružnog rukopisa. Ovo je suprotno od mnogih drugih nasumično generisanih passworda, gde svaki karakter mora biti jasno čitljiv da bi se password mogao pravilno kreirati, jer su oni jednostavno niz slučajnih karaktera. Stoga seed fraze imaju i prednosti randomizacije, kao i prednosti lako prepoznatljivih i uobičajenih reči.
Zašto Niko Ne Može da Predpostavi Seed Frazu?
Mogli biste da pomislite da bi niz od 24 reči možda bio lak nekome da ga pretpostavi, ili da bi nekome bilo isplativo da napravi računarski ciklus mogućih kombinacija, dok ne pronadje novčanik koji sadrži neke bitcoin-e kako bi mogao da ih ukrade.
Reči za frazu za oporavak ili seed frazu dolaze sa liste koja se sastoji od 2048 reči – pa čak i seed od 12 reči za Bitcoin novčanik ima 2048^12 kombinacija ili 2^132. Procenjuje se da u univerzumu postoji 10^21 zvezda, pa je nepotrebno reći da ovo predstavlja mnogo mogućih kombinacija. Čak i kada bi svaki čovek na Zemlji danas imao 1.000.000 novčanika (čak i bez adresa), to bi iznosilo samo 7.800.000.000.000.000 novčanika – što je oko 2^53. Ovo čini negde oko polovine mogućih kombinacija, ali to bi sakrilo snagu eksponencijalnog rasta.
Kada bi svi na svetu imali po 1.000.000 bitcoin novčanika, mi bismo i dalje koristili samo 0.000000000000000000000001654% od svih mogućih novčanika. To je neuporedivo teže nego pronaći jedno određeno zrno peska u celokupnom pesku koji se nalazi na Zemlji.

Čak i taj pronalazak određenog zrna peska na ovoj plaži bila bi kao šetnja parkom nasuprot pogađanju bilo koje random seed fraze.
Dakle, prilično je sigurno reći da niko uskoro neće pokušati da pogadja bitcoin novčanike. Bila bi potrebna vojska računara i veoma dugačak vremenski period da se pronadje samo jedan novčanik sa sredstvima u tom prostranstvu.
Kako Čuvati Seed Frazu
Neverovatno je važno kako zapisujete i skladištite svoju seed frazu, s obzirom na ogromnu količinu moći koju će oni koji je poseduju imati nad vašim Bitcoin sredstvima. Takođe, budući da je poenta seed fraze da bude lako dostupna gde i kada vam zatreba, čuvanje na nekom sigurnom, ali i pristupačnom mestu, je neophodno. Specifična metoda koju koristite za transkripciju vaše seed fraze je takođe važna, bez obzira na to kako se čuva, jer se neke metode transkripcije pokazale mnogo sigurnijim od drugih.
Pogledajte naš odeljak sa savetima, pre nego što zapišete svoju seed frazu!
Preporučujemo vam da fizički sačuvate svoju seed frazu nakon što vam je softver ili hardware novčanik isporuči. Fizičko skladištenje čini vašu seed frazu manje otvorenom za hakere koji bi mogli da vam ukradu frazu za oporavak iz digitalne memorije vašeg računara ili pametnog telefona.. Međutim, mnogi ljudi će i dalje odabrati neki oblik digitalnih sredstava za čuvanje svojih seed fraza, bilo zato što je to dominantno sredstvo ili jednostavno kao dodatni oblik rezervne kopije. Hajde da pogledajmo kako fizička, a tako i digitalna sredstva koja možete koristiti za čuvanje vaše seed fraze, kako se ona koriste, i specifične prednosti i nedostatke svake od njih.
Zapisivanje Vaše Seed fraze – na Papiru ili Digitalno
Zapisivanje Vaše Seed Fraze na Papir
Naravno, najočigledniji metod unošenja vaše digitalne seed fraze u fizički svet je isti onaj metod koji biste obično koristili za unošenje bilo kog drugog oblika pisanja u fizički svet – olovkom i papirom. Jednostavno zapisivanje vaše seed fraze na papir u potpunosti može biti dovoljno da vam pruži sigurnost koju želite. Međutim, postoje neka upozorenja oko upotrebe olovke i papira koja ovu najjednostavniju metodu čine ne baš tako idealnom za čuvanje nečega toliko važnog kao što je seed fraza.
Kao prvo, sam papir je lako uništiv, a o mastilu da i ne govorimo. U slučaju poplave ili požara, papir će biti uništen, što znači da će i vaša seed fraza biti uništena zajedno sa njim. Naravno, ovo su loše vesti i za svakoga ko verovatno gubi i sav svoj hardver i opremu u požaru ili poplavi. Kao drugu stvar, papir je neverovatno lako zagubiti. Može se oduvati, pomešati sa otpadom ili jednostavno pomešati sa nečim drugim i negde izgubiti, i nikada ga više nećete videti. Iz ovih i više drugih razloga, oni koji žele da zapišu svoju seed frazu u fizički svet, često traže sredstva koja su izdržljivija i trajnija od papira.
Graviranje Vaše Seed Fraze na Čeličnoj Back-Up Ploči
Back-up ploče od nerđajućeg čelika su stvorene kako bi korisnici Bitcoin-a imali način da trajnije urežu svoje seed fraze u fizički svet od puke olovke i papira. Napravljene su od nerđajućeg čelika, na koje se vaša seed fraza može trajno urezati. Budući da je gravura napravljena na čeliku, ona će u slučaju požara ili poplave moći da traje mnogo duže od papira. Ploča može biti bilo šta, od male kartice koju možete držati u novčaniku do većeg komada koji se može trajno čuvati kod kuće ili u sefu.
Bilo koju veličinu pločice da izaberete, možete je kupiti zajedno sa alatima za samograviranje (koji nisu uvek u kompletu), što znači da korisnik ne mora da deli svoju seed frazu sa onima od kojih je kupio ploču. Budući da su ove ploče stvorene posebno za potrebe izdržavanja katastrofe, obično sadrže brojne garancije o njihovoj trajnosti, otporne su na bilo koje elemenate koje možete baciti na njih, od vode do vatre, kao i od prekomernog korišćenja i habanja.
Što se tiče back-up ploča od nerđajućeg čelika, svaki proizvođač nudi svoj jedinstveni spin. Pogledajmo 5 najboljih proizvođača back-up ploča od nerđajućeg čelika na tržištu i da vidimo kako su se pokazali:
Cryptosteel
Sa sedištem u Velikoj Britaniji, Cryptosteel nudi čelične „Kapsule“ i „Kasete“ sa cenom u eurima, s tim da je kapsula približno veličine laserskog pokazivača, a kaseta je veličine, pa, kasete. Kapsula košta 74 eura, a kaseta 108 eura, mada se nude popusti za velike narudžbine. Umesto da zahtevaju gravuru, svaka Kaseta ili Kapsula dolazi sa odredjenom količinom čeličnih pločica koje se mogu staviti prema redosledu vaše seed fraze.
Blockplate
Blockplate nudi čelične back-up ploče po ceni od 69 USD za dve – svaka ploča sadrži 12 reči. Njihove verzija jedne ploče, koja izgleda identično, košta 49 USD po paru. Potpuno četvrtaste i malo manje od podmetača, ove ploče vam omogućavaju da svoju seed frazu sačuvate na mreži koristeći samo prosti udarac u sredinu, nisu potrebne pločice sa slovima.
Coldbit
Coldbit nudi heavy-duty kartice sa futrolama po ceni od 69 eura i setove za graviranje za dodatnih 20 eura. Takođe se možete odlučiti da sami uradite graviranje pomoću alata koji imate kod kuće, a koji može urezati čelik, poput dijamantske Dremel burgije. Oslanjajući se na čistu doslovnu transkripciju sličnu Hodlinox pločama, ove ploče ipak nude malo veću zaštitu i neke sjajne dizajne.
Billfold by Privacy Pros
Preimenovan u Privacy Pros, brend Billfold je i dalje dostupan po ceni od 89 USD. Koristi dizajn kartice vrlo sličan Cryptosteel Kaseti, sa malim pločicama koje slažete da biste formirali svoju seed frazu.
Kriptovanje Vaše Seed Fraze i Njeno Digitalno Skladištenje
Iako se generalno preporučuje da svoju seed frazu ne skladištite digitalno, oni koji su bolje upućeni u digitalnu bezbednost, ovo mogu videti kao floskulu koja se može ignorisati. Iako laici sigurno ne bi smeli da šalju i primaju svoje seed fraze e-mailom, pravilno digitalno kriptovanje i skladištenje sredstvima poput cloud-a ili USB fleš memorije mogu biti jednako sigurna i bezbedna sredstva za skladištenje, kao i fizička sredstva, poput čeličnih back-up ploča. Takođe, kada se oba sredstva koriste zajedno, to vam pruža krajnju mrežu rezervnih kopija u slučaju bilo kakvih hitnih slučajeva.
Kriptovanje možda nije nešto što je lako za svakoga, ali postoje mnoge treće strane koji će se pobrinuti da odrade kriptovanje za vas. Obavezno diskonektujte računar sa Interneta dok unosite seed u računar i izvodite kriptovanje – ne verujte online uslugama kriptovanja!
Odatle, na vama ostaje da odlučite kako ćete da je čuvate, bilo na cloud-u ili na USB fleš memoriji. Prednost čuvanja na cloud-u je u tome što podaci nisu povezani ni sa jednim fizičkim uređajem i može im se pristupiti sa bilo kog mesta pomoću passworda na cloud-u. Međutim, to takođe znači da su podaci nešto pristupačniji nego da se čuvaju na USB fleš memoriji. Zapamtite da ako se odlučite za USB fleš memoriju, ona možda neće moći da se izdrži protiv požara i vode, baš kao što to mogu prosti nefizički podaci na cloud-u. Fleš memorija koja se koristi na USB-u takođe nije dizajnirana da traje duže od 10 godina, pa imajte i to na umu.
Digitalno čuvanje seed fraze preporučujem isključivo informatičarima tj ljudima sa dosta iskustva u kriptiranju informacija. Za 99% nas čekič i čelična pločica koju čuvamo na 2 ili 3 mesta + dodatna 13. ili 25. reč je najbolje rešenje.
Gde i Kako Čuvati Svoju Seed Frazu
Bez obzira da li ste odlučili da svoju seed frazu sačuvate na čeličnoj ploči, USB-u ili jednostavno na parčetu papira, moraćete da je stavite negde – a idealno bi bilo da je stavite na više mesta u slučaju da se jedna uništi ili izgubi.
Najbolji savet koji mogu da vam dam je gde ne trebate da čuvate svoju seed frazu. Na kraju, mesto na koje stavite svoju seed frazu najbolje je da sačuvate za sebe, i zato evo nekoliko mesta na koja definitivno ne želite da stavite seed frazu, ako želite da izbegnete da upadne u pogrešne ruke.
Ne Čuvajte Svoju Seed Frazu u…
- Sef u Banci: Izgleda kao odlično mesto, zar ne? Pogrešno – banke prave greške, a kako sefovi postaju sve manje popularni, one prave još više grešaka!
- Sef u Kući: Opet se čini kao odlično mesto – međutim, ovo je prvo mesto koje će provalnik potražiti. Čak i ako ne mogu da otvore sef, većinu malih kućnih sefova moguće je lako premestiti i odneti u kolicima, i kasnije ih razbiti.
- Ispod Kreveta ili Dušeka: Klasično mesto za skrivanje novca, takođe je jedno od prvih mesta koje će provalnik pogledati.
- U Frižideru: Možda mislite da maskiranje vašeg seed-a u posudi za hranu izgleda kao dobar način zabune, ali ovo je uobičajena taktika za skrivanje dragocenosti, pa bi provalnici mogli potražiti i ovde.
- Ormarić za Nakit ili Fioke za Veš: To su uobičajena mesta za čuvanje drugih vrsta dragocenosti, pa će ih provalnik brzo pokrasti.
Budite kreativni, ali ne toliko kreativni da izgubite seed frazu, jer ne možete da se setite gde ste je sakrili.
Takođe je važno razmotriti i mogućnost pravljenja rezervnih kopija vašeg seed-a na više lokacija. Na taj način, čak i ako je jedno mesto potpuno uništeno (recimo da vam oluja odnese kuću), i dalje ćete da imate vaš seed na drugoj lokaciji.
Shamir-ovo Tajno Deljenje – Širite Vašu Frazu za Oporavak
Shamir-ovo Tajno Deljenje (eng. Shamir Secret Sharing), je algoritam koji vam omogućava da svoj seed podelite na više seed-ova koji su sami po sebi beskorisni. Međutim, njihovim rekombinovanjem vratićete vaš seed za oporavak.
Ovo je dobar korak ukoliko želite da podelite vaš seed sa vašim advokatom, računovođom, članovima porodice itd. – jer obezbeđuje da niko od njih nema pristup vašem celom seed-u.
Način na koji Shamir deluje je to što deli vaš seed na više manjih seed-ova koje možete predati pouzdanim pojedincima. Kada postavite Shamir-ov backup, odlučujete koliko ‘deljenja’ želite da kreirate i koliko delova je potrebno za oporavak vašeg celog seeda – na primer, možete da napravite 5 deljenja i kažete da su bilo koja 3 dela potrebna za oporavak vašeg seed-a.
Neki hardware novčanici, poput Trezor Model T, podržavaju Shamir Backups na user-friendly način.
Saveti za Osiguravanje Vaše Seed Fraze
Postoji mnogo opštih stvari koje morate imati na umu kada je reč o držanju vaše seed fraze na sigurnom. Neke od ovih stvari su samo zdrav razum, dok većini ljudi možda ništa neće pasti na pamet bez nečije pomoći. Neće sve metode biti praktične za sve čitaoce, ali imajte na umu da što više bezbednosnih metoda vežbate, vaša seed fraza će biti sigurnija. Učinite koliko god možete da vaša seed fraza bude sigurna i ona će vam biti pri ruci kada vam zatreba.
Ne Pravite Slike ili Screenshotove Vaše Seed Fraze
Ne slikanje vaše seed fraze je dovoljno jednostavno. Svaka slika koju napravite stvara dodatnu spoljnu datoteku koja se može duplirati, izgubiti ili ukrasti. Što je manji digitalni otisak vaše seed fraze, to je bolje. Međutim, postoji mnogo različitih načina na koje se mogu ukrasti fotografije vaše seed fraze, što može iznenaditi prosečnog čitaoca. Prvo, hakeri i ostale treće strane mogu da preuzmu sliku vaše seed fraze putem sigurnosnih kamera, poput onih na bankomatima. Takođe, kamere na računaru, telefonu i drugim ličnim uređajima mogu predstavljati još veći rizik. Iz ovih razloga, umanjivanje ukupne vidljivosti i izloženosti vaše seed fraze, i pre i posle dokumentovanja u fizičkom svetu, je apsolutna potreba.
Ne Izgovarajte Svoju Seed Frazu Naglas – Nikad!
Ako ste ikada razgovarali telefonom i Google Assistant vas je prekinuo, onda znate da vas stalno slušaju. Bilo da ste napolju u javnosti ili ste sami kod kuće, treće strane slušaju. Ako su te treće strane zainteresovane, možda će moći da dobiju pristup vašim ličnim podacima. Iz tog razloga, uzdržavanje od izgovaranja naglas vaše seed fraze treba smatrati vitalnim delom zaštite vaše seed fraze. Lakše je špijunirati nekoga preko zvuka, nego što je to slučaj sa vizuelnim elementima, pa izgovaranje naglas vaše seed fraze čini je mnogo podložnijom presretanju od strane onih koji je mogu zloupotrebiti.
Ne Čuvajte Svoju Seed Frazu u Password Menadžeru
Čuvanje vaše seed fraze u password menadžeru može se činiti sigurnim i prikladnim načinom izrade rezervnih kopija, ali to nosi velike rizike. Seed fraza se mnogo razlikuje od password za recimo vaš Facebook nalog. To je zato što su passwordi samo alati za potvrdu identiteta za centralizovane usluge – što znači da ako izgubite pristup računu ili budete hakovani, možete kontaktirati broj podrške i proći kroz neke korake da biste povratili kontrolu nad svojim nalogom.
Kod Bitcoin-a, prema njegovom dizajnu, ne postoji broj podrške. Ne postoji centralna stranka koja kontroliše Bitcoin transakcije, čineći ga neverovatno slobodnim i otvorenim – ali to takođe znači da morate vrlo ozbiljno da preuzmete odgovornost za svoju seed frazu. Ako padne u pogrešne ruke jer je vaš password menadžer hakovan, možete izgubiti svoje bitcoin-e.
Ne Koristite Online Usluge Oporavka Seed-a
Ako vam neki website traži da unesete svoju seed frazu – čak i ako vam se čini kao pouzdan – dobro razmislite pre nego što to učinite. Većina „usluga online oporavka“ su maskirane prevare, usresredjene samo na kradju seed fraza nevinih ljudi! Ne budi jedan od njih.
Koristite Pristupnu Frazu(dodatnu reč) da Biste Dodali još Sigurnosti
Trezor podešavanje pristupne fraze | Ledger podešavanje pristupne fraze
Ako vaš novčanik podržava dodavanje pristupne fraze, trebalo bi da je koristite. Pristupna fraza je password koji dodate svom seed-u i funkcioniše kao 13. ili 25. reč u vašoj seed frazi. Zbog toga je vaš novčanik mnogo teže ukrasti. Ako se pristupna fraza čuva na drugačijoj lokaciji od vašeg seed-a, vaši bitcoin-i su sigurni čak i ako neko dobije pristup vašoj seed frazi.
Zaštitite Svoju Seed Frazu
Bez obzira da li svoju seed frazu čuvate u digitalnom oblaku ili na čeličnoj ploči, postojanje nekog načina čuvanja koji štiti seed frazu od elemenata kao što su požar i poplava, mora se smatrati obaveznim. Kao što je već rečeno, čelične ploče mogu se napraviti da izdrže većinu katastrofa, a skladištenje na cloud-u pruža nefizička sredstva koja mogu biti jednako sigurna kao i druga sredstva ako koristite pravu enkripciju. Upotreba jednog ili oba ova sredstva može vam pomoći da vam garantuje maksimalnu zaštitu bez obzira na to šta se dogodi.
Koristite Više Metoda za Pravljenje Rezervnih Kopija Kad God Možete
Korišćenje nekoliko različitih metoda za čuvanje vaše seed fraze ima puno prednosti, ali ima i neke nedostatke ako im ne pristupite sa dovoljno pažnje. Iako vam više načina za skladištenje pruža veću zaštitu, to takođe proširuje vaš celokupni profil, što znači da postoji više područja koja su otvorena za napad. Ipak, korišćenje najmanje dve odvojene metode za pravljenje rezervnih kopija obično se smatra dobrom idejom, jer imate rezervne kopije za slučaj da vam se nešto desi! Nikad ne znate šta će se dogoditi, a u tome i jeste poenta seed fraza.
Ograničite Pristup Vašoj Seed Frazi što je Više Moguće
Naravno, neki ljudi mogu da se odluče da svoju seed frazu podele sa pouzdanom trećom stranom, kao sredstvo radi osiguranja njene zaštite, ali, generalno, što je manji broj ljudi sa kojima delite svoju seed frazu, time bolje. Vaša je lična odluka s kim ćete deliti svoju seed frazu, i u vašem je najboljem interesu da to pravo mudro koristite.
Ne Pričajte o Količini Bitcoin-a Koje Posedujete
Nekima je ovo možda najteži savet, ali možda i najvažniji. Ako niko ne zna da imate bitcoin, i koliko ga imate, smanjujete verovatnoću da će neko pokušati da dodje do vaše seed fraze ili novčanika. Zato držite jezik za zubima!
Šta će se Desiti sa Vašim Bitcoin-om Nakon što Umrete?
Kao i sa bilo kojim drugim sredstvom, trebalo bi da imate predstavu o tome kako će se postupati sa vašim Bitcoin-om nakon što umrete. S obzirom da je ovo relativno nova tema, nema puno presedana kada je reč o prenošenju i nasleđivanju Bitcoin-a. Iako mnogi mogu da pomisle da moraju da angažuju advokata, prenošenje Bitcoin-a zaista podrazumeva samo puko prenošenje vaše seed fraze, zajedno sa nekim vašim konkretnim srestvima.
Prilikom pripreme za prosleđivanje vaše seed fraze u slučaju vaše smrti, važno je zapamtiti da prosledite i detaljan zapis o svojoj digitalnoj imovini. Za razliku od fizičkih materijala, digitalna sredstva se ne mogu lako kvantifikovati fizičkom procenom. Ukoliko nije svesna da postoji, ta osoba možda neće znati šta tačno prima. Stoga, ona možda neće zaista primiti ono što ste joj namenili da nasledi. To je takođe razlog zašto bi svi trebali da drže svu svoju imovinu sažetom i što organizovanijom, u slučaju nužde.
Ako razumete engleski jezik preporučujem da pročitate knjigu: Cryptoasset Inheritance Planning od Pamela Morgan
Kako Koristite Seed Frazu za Oporavak Vašeg Novčanika?
Za većinu novčanika, upotreba seed fraze jednostavna je poput pritiskanja pravih tipki i kucanja iste. Odatle, seed fraza će vratiti sav sadržaj i podatke novčanika na bilo koji uređaj koji koristite. Na ovaj način, korišćenje seed fraze znači da možete imati novčanik kod sebe gde god da krenete, bez obzira na sve, čak i ako se novčanik izgubi ili uništi – sve što vam zaista treba je vaša seed fraza.
Opet, ne koristite nikakve online usluge za seed frazu! U najvećem broju slučajeva to su prevare.
Bez obzira da li koristite mobilni novčanik kao što je Muun ili hardware novčanik kao što su Trezor ili Ledger, sredstva za upotrebu vaše seed fraze su u osnovi ista – jedina razlika je hardver koji koristite za to. Kod aplikacija poput Muun jednostavno pokrenete aplikaciju i ona vam daje mogućnost oporavka prethodnog novčanika. Zatim ćete odabrati dužinu svoje seed fraze i uneti je tačno onako kako je prikazana.
Uz hardware novčanike poput onih koje je izradio Trezor, dobićete istu opciju za povratak kada pokrenete uređaj i instalirate firmware. Dobićete isti izbor da odredite dužinu svoje seed fraze, a zatim će zatražiti od vas da je unesete potpuno isto.
Ako je moguče uvjek koristite isti hardware/software wallet prilikom oporavka vaše seed fraze kao što ste koristili kad ste je pravili.
Ako je Vaša Seed Fraza Sigurna, Biće i Vaša Sredstava!
Na kraju dana, važno je da zapamtite da što više brige ulažete u pravilno skladištenje i zaštitu svoje seed fraze, to će vaša sredstva biti sigurnija i za vas i za vaše voljene. Digitalno doba predstavlja širok spektar novih opasnosti, a svet kriptovaluta je leglo za većinu njih.
Ako želite da preduzmete proaktivne mere u obezbeđivanju najveće zaštite vašeg bitcoin-a, čuvanje vaše seed fraze na sigurnom i pristupačnom mestu je neophodno. Vaša seed fraza možda sada ne izgleda kao velika stvar, ali će izgledati kao velika stvar kada dođe vreme da je upotrebite. Ukoliko želite da vi i vaša Bitcoin sredstva budete zaštićeni u slučaju nužde ili čak u slučaju vaše smrti, preduzimanje odgovarajućih sredstava za čuvanje i zaštitu vaše seed fraze je osnovni prvi korak.
-
 @ 2dd9250b:6e928072
2025-05-31 16:23:22
@ 2dd9250b:6e928072
2025-05-31 16:23:22Durante a década de 1990, houve o aumento da globalização da economia, determinando a adição do fluxo internacional de capitais, de produtos e serviços. Este fenômeno levou a uma interdependência maior entre as economias dos países. Justamente por causa da possibilidade de que um eventual colapso econômico em um país resulte no contágio dos demais. Diante disso, aumentou a preocupação com os riscos incentivando a utilização de sofisticados modelos e estratégias de avaliação de gestão de risco.
Na década, ganharam destaque ainda os graves problemas financeiros enfrentados, entre outros, pelo banco inglês Barings Bank, e pelo fundo de investimento norte-americano Long Term Capital Management.
Outro grande destaque foi a fraude superior a US$ 7 bilhões sofrida pelo banco Société Generale em Janeiro de 2008.
O Barings Bank é um banco inglês que faliu em 1995 em razão de operações financeiras irregulares e mal-sucedidas realizadas pelo seu principal operador de mercado. O rombo da instituição foi superior à US$ 1,3 Bilhão e causado por uma aposta equivocada no desempenho futuro no índice de ações no Japão. Na realidade, o mercado acionário japonês caiu mais de 15% na época, determinando a falência do banco. O Baring Bank foi vendido a um grupo financeiro holandês (ING) pelo valor simbólico de uma libra esterlina.
O Long Term Capital Management era um fundo de investimento de que perdeu em 1998 mais de US$ 4,6 bilhões em operações nos mercados financeiros internacionais. O LTCM foi socorrido pelo Banco Central dos Estados Unidos (Federal Reserve ), que coordenou uma operação de socorro financeiro à instituição. A justificativa do Banco Central para esta decisão era "o receio das possíveis consequências mundiais da falência do fundo de investimento".
O banco francês Société Generale informou, em janeiro de 2008, uma perda de US$ 7,16 bilhões determinadas por fraudes efetuadas por um operador do mercado financeiro. Segundo revelou a instituição, o operador assumiu posições no mercado sem o conhecimento da direção do banco. A instituição teve que recorrer a uma urgente captação de recursos no mercado próxima a US$ 5,0 bilhões.
E finalmente chegamos ao caso mais problemático da era das finanças modernas anterior ao Bitcoin, o caso Lehman Brothers.
O Lehman Brothers era o 4° maior de investimentos dos EUA quando pediu concordata em 15/09/2008 com dívidas que superavam inacreditáveis US$ 600 bilhões.
Não se tinha contas correntes ou talão de cheques do Lehman Brothers. Era um banco especializado em investimentos e complexas operações financeiras. Havia feito pesados investimentos em empréstimos a juros fixos no famigerado mercado subprime, e o crédito imobiliário voltado a pessoas consideradas de forte risco de inadimplência.
Com essa carteira de investimentos que valia bem menos que o estimado e o acúmulo de projetos financeiros, minou a confiança dos investidores na instituição de 158 anos. Suas ações passaram de US$ 80 a menos de US$ 4. Acumulando fracassos nas negociações para levantar fundos; a instituição de cerca de 25 mil funcionários entrou em concordata.
O Federal Reserve resgatou algumas instituições financeiras grandes e tradicionais norte-americanas como a seguradora AIG no meio da crise. O Fed injetou um capital de US$ 182, 3 bilhões no American International Group (AIG).
Foi exatamente essa decisão do Fed em salvar alguns bancos e deixar quebrar outros, que causou insegurança por parte dos clientes. E os clientes ficaram insatisfeitos tanto com os bancos de investimentos quanto com as agências de classificação de risco, como a Standard & Poor's que tinha dado uma nota alta para o Lehman Brothers no mesmo dia em que ele quebrou.
E essa foi uma das razões pelo qual o Bitcoin foi criado. Satoshi Nakamoto entendeu que as pessoas não estavam mais confiando nem no Governo, nem nos Bancos Privados que o Governo federal restagatava quando eles quebravam e isso prejudicou muita gente. Tanto que o “hash” do Genesis Block contém o título do artigo “Chancellor on brink of second bailout for banks” (Chanceler à beira de segundo resgate para bancos, em português) da edição britânica do The Times.
Esse texto foi parcialmente editado do texto de ASSAF Neto, CAF (2014).
-
 @ 6c05c73e:c4356f17
2025-05-31 16:14:38
@ 6c05c73e:c4356f17
2025-05-31 16:14:38Análise Detalhada das Melhores Ações para Junho 2025
O mercado financeiro está em constante movimento, e identificar oportunidades de investimento é crucial para o sucesso. Exploraremos uma seleção de ações promissoras para junho de 2025. Analisaremos cada ativo individualmente, destacando seus pontos fortes e fracos para auxiliar investidores na tomada de decisões informadas. As ações a seguir foram selecionadas com base em análises de mercado e potencial de crescimento, e incluem nomes como ALOS3, RECV3, AZUL4, USO, USDBRL, BIDU, REXR, PR, GPN e CIVI.
Análise Individual das Ações
ALOS3
Essa é uma empresa que já falei aqui e está sempre voltando ao radar. Vou deixar ela em primeiro lugar, porque para mim é. Não existe empresa imobiliária tão saudável quanto ela.
Ponto Forte: ALOS3 tem demonstrado um crescimento consistente no setor de tecnologia, com inovações e expansão de mercado. A empresa possui uma forte base de clientes e uma estratégia sólida para o futuro.
Ponto Fraco: A alta volatilidade do setor tecnológico pode impactar o desempenho de ALOS3, tornando-o um investimento de maior risco em comparação com setores mais estáveis.
RECV3
Essa empresa apareceu no meu radar esse mês. Nem sabia da sua existência. Mas, isso porque seu IPO foi em 2021. E sua especialidade está em otimização de produção e revitalização de campos de petróleo.
Ponto Forte: RECV3 se destaca no setor de varejo, com uma rede de distribuição bem estabelecida e uma marca reconhecida. A empresa tem apresentado resultados financeiros positivos e um plano de expansão ambicioso.
Ponto Fraco: A concorrência acirrada no varejo e as flutuações na economia podem afetar as margens de lucro de RECV3.
AZUL4
A empresa anunciou essa semana que entrou em recuperação judicial. Contudo, o setor aéreo é sempre uma incógnita. Na minha visão, a operação de crédito da empresa é o diamante escondido.
Ponto Forte: AZUL4 é uma das principais companhias aéreas do Brasil, com uma vasta rede de rotas e uma frota moderna. A empresa tem se beneficiado da recuperação do setor de viagens e do aumento da demanda.
Ponto Fraco: O setor aéreo é altamente sensível a fatores externos como preços de combustível e crises econômicas, o que pode gerar instabilidade para AZUL4.
USO
Com os preços do petróleo em queda, devido ao aumento de produção divulgado pela OPEC. Enxergamos uma oportunidade de médio prazo. Pois, se faz muitos produtos com petróleo. Da um Google e pesquisa aí.
Ponto Forte: USO é um fundo de investimento ligado ao petróleo, que pode se beneficiar do aumento dos preços do petróleo devido a tensões geopolíticas ou aumento da demanda global.
Ponto Fraco: O preço do petróleo é extremamente volátil e sujeito a eventos imprevisíveis, tornando o USO um investimento de alto risco.
USDBRL
Não é novidade para ninguém que o dólar está previsto em R$6 para logo menos. A julgar pela impressão monetária, juros e inflação. Não vai ser difícil chegar lá. O P O R T U N I D A D E !
Ponto Forte: USDBRL representa a taxa de câmbio entre o dólar americano e o real brasileiro. Investir nesse ativo pode ser uma forma de se proteger contra a desvalorização do real e diversificar a carteira.
Ponto Fraco: A taxa de câmbio é influenciada por inúmeros fatores econômicos e políticos, tornando-a altamente volátil e difícil de prever.
BIDU
O maior motor de busca na China está derretendo. Em partes pelos avanços das IA. Que agora são amplamente usadas para pesquisas.
Ponto Forte: BIDU é uma das maiores empresas de tecnologia da China, com forte presença no mercado de buscas e inteligência artificial. A empresa tem um grande potencial de crescimento no mercado asiático.
Ponto Fraco: As regulamentações governamentais na China e a concorrência com outras gigantes da tecnologia podem limitar o crescimento de BIDU.
REXR
Empresa californiana focada em desenvolvimento imobiliário. Com excelentes resultados e fundamentos.
Ponto Forte: REXR é uma empresa do setor imobiliário com um portfólio diversificado e um histórico de crescimento constante. A empresa tem se beneficiado do aquecimento do mercado imobiliário em algumas regiões.
Ponto Fraco: O mercado imobiliário é sensível a taxas de juros e ciclos econômicos, o que pode impactar o desempenho de REXR em momentos de crise.
PR
Cara, essa empresa chama muito a atenção. Pelos números robustos. A empresa administra petróleo e campos de gás.
Ponto Forte: A empresa PR atua no setor de recursos naturais e tem se beneficiado do aumento da demanda por commodities. A empresa possui ativos valiosos e uma operação eficiente.
Ponto Fraco: A volatilidade dos preços das commodities e questões ambientais podem afetar negativamente o desempenho de PR.
GPN
A empresa tem excelentes fundamentos e está sentada sobre uma pilha de dinheiro em caixa que excede e muito a real necessidade da empresa. Olho nela!
Ponto Forte: GPN é uma empresa do setor financeiro, com destaque para serviços de pagamento e tecnologia financeira. A empresa tem apresentado crescimento consistente e inovação em seus produtos.
Ponto Fraco: A concorrência no setor financeiro e as regulamentações podem impactar as margens de lucro de GPN.
CIVI
Para concluir nossa lista. Temos essa empresa de construção civil que derreteu caixa. Mas, tem seu valor patrimonial bem abaixo do esperado.
Ponto Forte: CIVI é uma empresa do setor de construção civil, com projetos de infraestrutura e desenvolvimento urbano. A empresa tem se beneficiado de investimentos governamentais e crescimento populacional.
Ponto Fraco: O setor de construção civil é sensível a crises econômicas e atrasos em projetos, o que pode gerar instabilidade para CIVI.
Resumo da ópera:
Investir em ações requer pesquisa e análise cuidadosa. Cada uma das empresas listadas apresenta pontos fortes e fracos que devem ser considerados. ALOS3 se destaca pela sua excelente gestão nos shoppings e imóveis. BIDU se destaca no setor de tecnologia, enquanto RECV3 e AZUL4 oferecem oportunidades nos setores de varejo e aviação. USO e USDBRL são investimentos mais voláteis, ligados ao petróleo e câmbio, respectivamente. REXR e CIVI representam o setor imobiliário e construção civil, enquanto PR e GPN atuam nos setores de recursos naturais e financeiro. Esperamos que esta análise tenha sido útil. Boa sorte em seus investimentos!
Disclaimer
Lembre-se: este não é um conselho de investimento. Faça sua própria pesquisa antes de investir. Resultados passados não garantem lucros futuros. Cuide do seu dinheiro!
Bio
Apaixonado por investimentos e pela transformação que eles podem trazer, a equipe threedolar dedica-se a desmistificar o mundo financeiro e guiar seus leitores rumo à independência financeira. Acreditamos que o conhecimento é a chave para o sucesso nos investimentos.
Links
-
 @ f85b9c2c:d190bcff
2025-06-01 00:43:38
@ f85b9c2c:d190bcff
2025-06-01 00:43:38Avoid it if you’re sensitive.

Haha 😂, just wanted to get your attention.
If you’re reading this, congrats your amongst those who survived to see this message. It doesn’t matter if you’re depressed, sad, angry at someone or you missed something. Come on man, being alive is already a win for you.
Smile, You deserve it.
Yes, I know the world is cruel and very unfair. But remember, you can’t fight all those battles alone. That’s why we ask God to take care of it. But hey, today is Sunday.A blessed day for the Christians. Go ahead smile 😊, you deserve it. You managed to wake up today while some didn’t. You should be grateful for that. It’s a blessing to see tomorrow. You don’t know what today holds.
I just want to remind you that, you deserve the whole world. Go out there, chase your dreams, don’t let them die in your comfort zone. And remember, always wear a smile on that pretty face of yours. You deserve the world.
-
 @ f85b9c2c:d190bcff
2025-06-01 00:37:22
@ f85b9c2c:d190bcff
2025-06-01 00:37:22Fully devoted to Jesus: Mark 10:28 (NIV) Then Peter spoke up, “We have left everything to follow you!”
As a Christian, you received Jesus into your life because the Holy Spirit revealed to you the glory of God in Jesus and your heart melted at His sight.

You became aware of your lostness, wickedness, and hopelessness without a savior so you surrendered to Him and asked him to save you. You asked Him to become the lord of your life. The first apostles were clear about something, they had to surrender everything in order to follow Jesus. When they yielded to Jesus as Lord it meant He was Lord of all.
Yes, everything. Yes, all.
They surrendered work, possessions, essentially their lives — Mark 1:18 (NIV) At once they left their nets and followed him. They were literally fully devoted to Jesus.
They modeled 1 Kings 8:61 Let your heart therefore be wholly devoted to the Lord our God, to walk in His statutes and to keep His commandments, as at this day.”It might not look identical to the apostles calling but it should have the same motive behind it. When Jesus becomes your Lord, He should have complete control over your, . Relationship
.Money
.Possessions
.Career
.Kids
.Time
.Mouth
.Mind
.Body
.Everything
Have a blissful Sunday 🙏.
-
 @ 2e8970de:63345c7a
2025-05-31 11:54:55
@ 2e8970de:63345c7a
2025-05-31 11:54:55https://evidence.nejm.org/doi/full/10.1056/EVIDoa2300311
The solution to peanut allergy? Import Bamba!
https://stacker.news/items/993440
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-01 00:08:04
@ 5d4b6c8d:8a1c1ee3
2025-06-01 00:08:04How'd everyone do on their ~HealthAndFitness goals today?
I got pretty good sleep, stuck to my fast pretty well, didn't eat much junk food, and was pretty active with chores and errands. Not a particularly strong day, but not a weak on, either.
https://stacker.news/items/994000
-
 @ 005bc4de:ef11e1a2
2025-05-31 10:55:47
@ 005bc4de:ef11e1a2
2025-05-31 10:55:47LUV and Hivebits/HBIT/Wusang pause tl;dr LUV and HBIT (aka, Hivebits and the Wusang game) are on a pause at the moment, taking a break. https://files.peakd.com/file/peakd-hive/crrdlx/23x1SY8Vx8j1mVGnDFtq7ebuzKNGd8K9Ssex51AEerxks1VYikxGPShM7bjNhmSrEZ2wf.png Image from pixabay.com Why? There are odd things going on. I have a theory, but here's what is known... May 28, 2025, at about 1:30 pm GMT (8:30 AM EDT), a second attack (for lack of better term) hit HBIT in about a week. It seemed to start with @tyler45 with this comment https://peakd.com/blog/@tyler45/comment-20250528125108033 tx: https://he.dtools.dev/tx/7e7d4126196ca5b6dbe0a04dcded0e25d3bcc7f4 See tyler45's activity at https://he.dtools.dev/@tyler45 Notice the reply and WUSANG command is to a post by @olivia897 and how many of the other WUSANG comments on the explorer are in reply to olivia897. It seems these are all auto-generated accounts. The names and "birthdates" and interactions all point to automation. Once initiated, things happened very fast on the back end, clearly not being done manually. In this way, this seems rather sophisticated technically. I estimate just over 400 HBIT were pilfered the other day from the @Hivebits account before I noticed and was able to shut things down. Just for a little background, after the first attack May 21, 2025. I wrote a small bit of info: https://peakd.com/hivebits/@crrdlx/hbit-resource-credits A couple of days ago this post by @holoz0r was interesting: https://peakd.com/hive-133987/@holoz0r/text-analytics-reveal-thirty-two-percent-of-comments-on-hive-are-not-unique-and-at-least-ten-percent-add-no-value-to-discussion The thing that caught my eye was that the WUSANG comment was the largest by far, along with BBH (hello @bradleyarrow), because the attackers used both commands. Then, a few days later, things happened again: sudden start, repetitive bot attack, until I shut things down. So, a pause This is a period in my personal calendar where I simply don't have time to sit down at a computer for an extended period and try fiddle with this stuff. So, for now @Luvshares and @Hivebits (HBIT) and the @Wusang game are on hold. Plus, there's other fun stuff to do. https://files.peakd.com/file/peakd-hive/crrdlx/AJL43SREA1EuyqPXhydmqaq1RHhRVoYd12PfiBN5vDMu2WSKUtGeYWgKJyuRwV8.jpg I go by @crrdlx or "CR" for short. See all my links or contact info at https://linktr.ee/crrdlx.
Originally posted on Hive at https://peakd.com/@crrdlx/luv-and-hivebitshbitwusang-pause
Auto cross-post via Hostr v0.1.48 (br) at https://hostr-home.vercel.app
-
 @ 866e0139:6a9334e5
2025-05-31 10:45:03
@ 866e0139:6a9334e5
2025-05-31 10:45:03Autor: Marcel Bühler. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
In einem Artikel in der NZZ vom 27. Mai mit dem Titel "Trump nennt Putin verrückt" wird über den laut Kiew grössten russischen Drohnenangriff seit Beginn des Krieges auf ukrainische Städte berichtet. Dabei sollen am vergangenen Wochenende 355 Drohnen und 69 Raketen auf Kiew, Odessa, Ternipol (Westukraine) und andere Städte gesteuert bzw. abgefeuert worden sein. 288 Drohnen und 9 Raketen konnten laut Kiew von der ukrainischen Luftverteidigung abgeschossen werden. Was der Artikel verschweigt: bereits in der Woche davor, am 20. - 22. Mai hatte die Ukraine 485 Drohnen gegen russische Städte wie Kursk, Belgorod oder Brijansk geflogen, 63 davon erreichten die Region Moskau. Auch am Wochenende schickten die Ukrainer 205 Drohnen gegen russische Städte, 13 davon erreichten Moskau. Auch hier konnte die Luftverteidigung die meisten Drohnen unschädlich machen, eine davon hatte gar den Helikopter von Präsident Putin (!) im Visier. Als Reaktion darauf erklärte Präsident Putin, dass in der ukrainischen Region Sumy bzw. Tschernihiw im Norden eine Sicherheitszoneeingerichtet werden soll da die meisten Drohnen von hier aus gestartet wurden. Auch am 27./28. Mai schickte die Ukraine wieder 296 Drohnen Richtung Moskau, offenbar soll die russische Luftverteidigung damit überlastet werden um später westliche Cruise Missiles wie "Storm shadows", "Skalp" oder die umstrittenen deutschen "Taurus" effektiver einsetzen zu können. Der neue Bundeskanzler Friedrich Merz hat dafür rund 5 Milliarden Euro in Aussicht gestellt um solche Waffensysteme in der Ukraine selber zusammenbauen zu können.
Diese Gewaltspirale hat eine lange Geschichte: diese begann 2007 mit der 43. Münchner Sicherheitskonferenz, in der Präsident Putin sich gegen die unilaterale Weltordnung der USA und ihrer Verbündeten aussprach. Auch erteilte er den NATO-Osterweiterungen seit 1991 eine deutliche Absage, da diese entgegen (mündlich) gemachten Zusicherungen vollzogen wurden (siehe im Anhang die Rede im Wortlaut). Bei anderer Gelegenheit bezeichnete er vor allem einen möglichen NATO-Beitritt der (ehemals russischen) Ukraine als die "rote Linie", da es hier im Osten eine gemeinsame Grenze zu Russland über weit mehr als tausend Kilometer gebe und zudem Millionen von russischstämmigen Bürgern in der Ukraine lebten welche durch die Unabhängigkeit des Landes von ihrem Mutterland getrennt seinen. Im mittlerweile umstrittenen Budapester Memorandum von 5.12.1994 hatten zudem die Signatarmächte USA, GB und die Russische Föderation in getrennten Dokumenten die Unabhängigkeit und territoriale Integrität der Ukraine garantiert, wenn diese ein neutraler Pufferstaat zwischen der NATO und der Russischen Föderation sei und auf ihre Atomwaffen aus der sowjetischen Zeit verzichte (die Neutralität war in der ukrainischen Verfassung verankert). Trotzdem erklärten am darauffolgenden NATO-Gipfel in Bukarest im April 2008 die versammelten Staats- und Regierungschefs der 26 NATO-Staaten: "Die NATO begrüßt die euro-atlantischen Bestrebungen der Ukraine und Georgiens, die dem Bündnis beitreten wollen. Wir kamen heute überein, dass diese Länder NATO-Mitglieder werden." Zudem wurde die Unabhängigkeitserklärung des Kosowo vorbehaltlos anerkannt, dies nach einer völkerrechtswidrigen militärischen Intervention (d.h. ohne eine entsprechende UN-Resolution) der NATO gegen die Republik Serbien im Jahr 1999 (Staatsgrenzen dürfen also unter Umständen verändert werden).
Die Gewalt begann schon wenige Monate danach, als der durch die "Rosenrevolution" 2003 mit Unterstützung der USA in Tiflis an die Macht gekommene Exil-Georgier, Michail Saakaschwili, in der Nacht auf den 8.8.2008 einen militärischen Angriff auf die seit 1992/93 abtrünnigen Südosseten bzw. deren Hauptstadt Zchinwali befahl und dabei auch russische Friedenstruppen (als Schutzmacht der Osseten) unter Beschuss gerieten. Dies nachdem die Regierung Bush jr. die georgische Armee durch NATO-Offiziere ausgebildet und aufgerüstet hatte. Laut einem NZZ-Artikel vom 1.10.2009 kam eine von der EU eingesetzte Untersuchungskommission unter der Schweizer Diplomatin Heidi Tagliavini 2009 zum Schluss, dass zuvor von beiden Seiten Provokationen in Form von Terroranschlägen, Entführungen und Morde begangen worden waren. Zudem hatte Russland jahrelang an willige Osseten und Abchasen russische Pässe ausgegeben, was völkerrechtswidrig sei, da dies die Staatlichkeit Georgiens untergrabe (Abchasien ist eine weitere abtrünnige Region Georgiens am schwarzen Meer). Saakaschwili wollte offenkundig mit dem überraschenden Angriff auf die Osseten die volle Kontrolle der Zentralregierung über das Gebiet wieder erlangen, da die Satzungen der NATO nur die Aufnahme von Ländern erlauben in denen keine ungelösten territorialen Konflikte vorhanden sind. Den Abchasen hätte also das gleiche Schicksal gedroht wenn die Aktion erfolgreich gewesen wäre. Da die Russen aber aufgepasst hatten, lief innert 24 Stunden eine russische Gegenoffensive welche die georgischen Verbände und ihre amerikanischen Berater innert wenigen Tagen bis nach Gori (Geburtsort von Stalin) zurückwarf. Präsident Saakaschwili verlor bald darauf in Tiflis die Macht und setzte sich in die Ukraine ab. Die heutige georgische Regierung unterhält wieder politische und wirtschaftliche Beziehungen zu Russland und verzichtet auf einen NATO-Beitritt. Siehe dazu das Interview von Roger Köppel mit dem aktuellen georgischen Regierungschef Kobachidse (auf englisch mit deutschen Untertiteln):
https://www.youtube.com/watch?v=xWh6bAfLdhw
In der Ukraine begann die Gewalt mit dem rechtswidrigen Sturz des 2010 legal gewählten Präsidenten Wiktor Janukowitsch, der zwischen der EU und Russland hin und her gerissen war und daher die Unterzeichnung eines EU-Assoziierungsabkommens auf unbestimmte Zeit vertagte. Nach den folgenden wochenlangen Protesten und Krawallen auf dem Maidan in Kiew ("Euromaidan") unterschrieb er unter Vermittlung Deutschlands, Frankreichs und Polens am 21.2.2014 einen Vertrag mit der Opposition und versprach baldige Neuwahlen. Trotzdem wurde er am Tag darauf durch einen regelrechten Putsch gestürzt und in die Flucht getrieben, indem unbekannte Heckenschützen aus verschiedenen Positionen zuerst auf die "Berkut"-Polizei und anschliessend auf militante Demonstranten schossen, welche die "Institutskaja" hinauf das durch eine Strassensperre der Polizei geschützte Regierungsviertel stürmen wollten.
Dabei kamen insgesamt 104 Menschen ums Leben, darunter 34 Polizisten und Vertreter der Regierung. Nach dem Putsch wurde der zuvor völlig unbekannte Exil-Ukrainer Arsenij Jazenjuk Chef der neuen Übergangsregierung, von dem die Europagesandte des US-Statedepartements, Victoria Nuland, bereits einige Tage davor in einem abgehörten Telefongespräch mit dem amerikanischen Botschafter in Kiew, Geoffrey Pyatt, gesprochen hatte ("Jaz is our man"). Die mit rund 600 Mann unter Führung von Andrij Parubi während Wochen auf dem Maidan präsenten militanten und teilweise bewaffneten Kräfte des "Prawi sektor" ("Rechter Sektor") und der "Swoboda" ("Freiheit") weigerten sich zuerst, der neuen Regierung ihre Waffen auszuhändigen. Mitglieder der "Swoboda" unter Oleh Tjahibok besetzten aber anfangs im Kabinett das Aussen-, Innen-, Verteidigungs- sowie das Ministerium für Kultur und "strategische" Kommunikation (Propaganda), während die Mitglieder des "Prawi sektor" unter Dmitro Jarosch eine Zusammenarbeit mit der neuen Regierung verweigerten. Als eine der ersten Amtshandlungen nach dem Putsch wurde in der ganzen Ukraine die russische Sprache als offizielle Amtssprache und als Unterrichtssprache in den Schulen verboten (auch in den mehrheitlich von russischstämmigen Menschen bewohnten Regionen im Osten und Süden des Landes).
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Als erste Reaktion auf den rechtswidrigen Umsturz wurde in Simferopol auf der Krim das lokale Parlament von prorussischen Aktivisten besetzt und russische Soldaten verliessen illegal den Flottenstützpunkt in Sewastopol und besetzten strategische Positionen auf der ganzen Krim bzw. blockierten die ukrainischen Kasernen. Unter dem Schutz dieser "grünen Männchen" konnte dann am 16.3.2014 ein Referendum über den zukünftigen Status der Krim durchgeführt werden. Rund 70% der Bevölkerung stimmten für eine Wiedervereinigung mit Russland, was ungefähr dem Anteil der ethnischen Russen auf der Krim entspricht. Der Kommandant der ukrainischen Flotte in Sewastopol lief mit dem Grossteil der Matrosen zu den Russen über, so dass fast die gesamte Flotte im Kriegshafen verblieb (die Schwarzmeerflotte war anfang der 90er Jahre zwischen Russland und der Ukraine aufgeteilt worden). Die restlichen Matrosen und Soldaten durften später in die Ukraine heimkehren. Angesichts der klaren Machtverhältnisse auf der Krim verzichteten die ukrainischen Ultra-Nationalisten auf die angedrohte Entsendung von "Zügen der Freundschaft" (mit bewaffneten Schlägern) nach Simferopol.
Auch in den Städten Lugansk, Donezk und Mariupol in der Ostukraine besetzten prorussische Aktivisten analog den Vorgängen einige Monate zuvor in der Westukraine Regierungs- und Verwaltungsgebäude und hissten russische Fahnen auf vielen Gebäuden. Auch hier gab es am 11. bzw. 12.5.2014 Referenden über die zukünftige Zugehörigkeit dieser Gebiete, doch konnten dabei nur ungefähr die Hälfte der Bevölkerungen überhaupt darüber abstimmen, weil die Separatisten nicht die volle Kontrolle über die jeweiligen Bezirke hatten. Auch in anderen ukrainischen Städten wie Odessa und Charkow gab es prorussische Demonstrationen, doch wurden diese von den ukrainischen Behörden unterdrückt. In Odessa kam es am 2.5.2014 zu einem Massaker, als prorussische Aktivisten von mit Zügen aus Kiew angereisten Rechtsradikalen und Hooligans in ein Gewerkschaftshaus abgedrängt wurden welches dann kurzerhand abgefackelt und mit Handfeuerwaffen beschossen wurde. Rund 50 Menschen verloren dabei ihr Leben während die ukrainische Polizei untätig herumstand.
Die am 12.4.2014 von der neuen Regierung in Kiew verkündete "Antiterror-Operation" gegen die Separatisten im Osten wurde anfangs nur zaghaft umgesetzt, da viele russischstämmige Soldaten auch hier mit den Aufständischen sympathisierten und teilweise mitsamt dem Material überliefen. Erst nachdem sich der "Spreu vom Weizen" getrennt hatte und nach der Bildung von Freiwilligenverbänden wie "Donbas","Asow" oder "Aidar" - welche in der ukrainischen Nationalgarde (dem Innen- und nicht dem Verteidigungsministerium unterstellt) zusammengefasst wurden - gewann die ukrainische Offensive an Kraft, so dass bereits im Mai/Juni 2014 die Hafenstadt Mariupol vom Asow'schen Bataillon (später ein Regiment bzw. neu die 12. Brigade für spezielle Aufgaben) und einer Marinebrigade zurückerobert und bis zur vollständigen Kapitulation im berühmten Stahlwerk "Asowstal" nach der russischen Intervention vom 24.2.2022 besetzt werden konnte. Bei den heftigen Kämpfen im Frühjahr 2022 mussten die Zivilisten wochenlang im Keller ausharren, da die Stadtverwaltung die rechtzeitige Evakuierung der Zivilbevölkerung versäumt hatte). Nach den Kesselschlachten von Ilowaisk im Juli/Aug. 2014 bzw. von Debaltsewoim Jan./Feb. 2015, bei denen weit über tausend ukrainische Soldaten und hunderte von Kämpfern der neu aufgestellten Donezker- und Lugansker Volksmilizen sowie vermutlich rund 100 russische Soldaten ihr Leben verloren (laut Kiew beteiligten sich mehrere russische Bataillone an den Kämpfen), wurde am 12.2.2015 das Minsker Abkommen (Minsk II) unter Vermittlung von Weissrussland, Deutschland und Frankreich unterzeichnet. Vertragspartner als Unterzeichnende waren: der frühere Präsident der Ukraine Leonid Kutschma, der Botschafter der Russischen Föderation in der Ukraine Michail Surabow, die Milizenführer der selbstproklamierten Volksrepubliken Igor Plotnizki und Alexander Sachartschenko sowie die OSZE-Beauftragte Heidi Tagliavini. Der Waffenstillstand und die vertrauensbildenden Massnahmen (wie z.B. der Rückzug der schweren Waffen von der Frontlinie) wurden dabei von beiden Seiten wiederholt verletzt. Am 18.2.2017 unterzeichnete der russische Präsident Wladimir Putin ein Dekret, nach dem Pässe und andere Papiere der Volksrepubliken Donezk und Lugansk von Russland offiziell als gültig anerkannt wurden, was wiederum die Staatlichkeit der Ukraine untergrub und daher dem Minsker Abkommen widersprach, wonach die abtrünnigen Gebiete weiterhin zur Ukraine gehörten. Insgesamt verloren in dem jahrelangen Konflikt bis 2022 rund 14'000 Menschen ihr Leben, darunter ca. 3'500 Zivilisten inkl. 200 Kinder, besonders in der Stadt Donezk und Umgebung welche von der ukrainischen Armee immer wieder mit Artillerie (Granaten und Raketen) oder durch Scharfschützen beschossen wurde.
Nachdem eine von NATO-Offizieren jahrelang gut ausgebildete und mit modernen Waffen aufgerüstete ukrainische Elitearmee von rund 130'000 Mann ab Sommer 2021 vor dem Donbas aufmarschiert war um den Konflikt offenkundig gewaltsam zu lösen und seit Anfang 2022 auch der ukrainische Beschuss von Donezk und dessen Umland wieder verstärkt wurde, unterzeichnete Präsident Putin am 21.2.2022 ein Freundschafts- und Beistandsabkommen mit den ostukrainischen Volksrepubliken und anerkannte ausdrücklich deren Unabhängigkeitvon Kiew. Das Minsker Abkommen habe keine Zukunft mehr. Am 24.2.2022 intervenierte die russische Armee mit anfangs "nur" rund 190'000 Mann in der Ukraine da die rund 40'000 Mann der Donezker- und Lugansker Volksmilizen einem Angriff der ukrainischen Elitearmee nicht mehr hätten standhalten können. Zuvor hatte die Russische Föderation im Dez. 2021 den USA noch einmal Verhandlungen über den Abschluss eines gesamteuropäischen Sicherheitsabkommen unter Berücksichtigung des Konflikts in der Ukraine vorgeschlagen, was aber von der Regierung Biden abgelehnt wurde. Bei Beginn der "speziellen Militäroperation" erklärte Joe Biden öffentlich, das politische Ziel sei der Sturz des Regimes in Moskau.
Mit dem Beginn der russischen Sommeroffensive an allen Frontabschnitten dürften die ukrainischen Kräfte endgültig überdehnt werden. Da der Oberbefehlshaber der Ukraine, Alexander Syrskij, aus der Region Sumy und Charkow verschiedene Verbände wie die 36. Marinebrigade, die 43. Artilleriebrigade, die 44. mechanisierte Brigade, die 82. Air Assault Brigade sowie die berüchtigte 12. Brigade "Asow" nach Südosten verlegen musste, um die Lage um den wichtigen Logistikpunkt Pokrowsk bzw. die Stadt Konstantinowka zu stabilisieren, dürften die Russen auch bei der oben erwähnten Einrichtung einer Sicherheitszone im Norden rasche Fortschritte machen. Rund 50'000 russische Soldaten werden dort eingesetzt um die zukünftige Bedrohung durch ukrainische Drohnen zu minimieren.
Zusammenfassend kann gesagt werden, dass in dem jahrelangen Konflikt alle Seiten das Völkerrecht missachtetoder zum eigenen Vorteil interpretiert haben. Angefangen damit hat aber klar der Westen (NATO und EU), der mit der finanziellen und politischen Unterstützung des rechtswidrigen Putsches in Kiew 2014 die Gewaltspirale in der Ukraine in Gang setzte und mit den anhaltenden Waffenlieferungen und Geheimdienstinformationen für den Tod von weit mehr als einer Million Soldaten auf beiden Seiten und unzähligen Zivilisten entscheidend mitverantwortlichist. Zudem wurde zumindest im Falle der Ukraine mit der NATO-Erklärung von 2008 zu deren Aufnahme als Beitrittskandidat der Geist des Budapester Memorandums von 1994 verletzt. In einem erstaunlich offenen, zweiseitigen Interview in der NZZ vom 6. Mai hat der amerikanische Politikwissenschaftler Prof. John Mearsheimervon der Universität Chicago erklärt, er hätte anstelle von Präsident Putin "die Ukraine schon viel früher überfallen". Und: "Der Westen ist der Bösewicht. Aber das wollen die USA und die Europäer natürlich nicht hören". Er glaube, dass dieser Krieg auf dem Schlachtfeld entschieden werde und dass wir am Ende einen eingefrorenen Konflikt haben werden (ähnlich wie in Georgien).
Über das Problem des ukrainischen Faschismus und Ultra-Nationalismus, der letztlich die multiethnische Ukraine in ihren Grenzen von 1991 zerstört hat, äusserte er sich nicht. Stattdessen hat die EU gerade die ersten 150 Milliarden Euro zum Aufbau einer eigenen Rüstungsindustrie beschlossen. Der neue Vorsteher des Schweizer Verteidigungsdepartementes, Bundesrat Martin Pfister, hat in einem NZZ-Artikel vom 27. Mai erklärt, die Kooperation mit der EU und der NATO müsse intensiviert werden, "stets in Vereinbarkeit mit der Neutralität". In der gleichen NZZ-Ausgabe wurde auch berichtet, dass die Schweiz den Spitzendiplomaten Gabriel Lüchinger nach Moskau schicke um für Friedensgespräche in der Schweiz zu sondieren (Bürgenstock II).
Ob der während Jahren provozierte und stigmatisierte "russische Bär" darauf noch eingeht?
(Der Beitrag folgt der Schweizer Rechtschreibung)
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
In Kürze folgt eine Mail an alle Genossenschafter, danke für die Geduld!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ a4043831:3b64ac02
2025-05-31 10:20:02
@ a4043831:3b64ac02
2025-05-31 10:20:02Money can be complicated. You work hard, save diligently, and try to make smart choices. But when it comes to long-term financial security, is that enough? That’s where wealth management services come in. They help you plan, invest, and secure your financial future. But are they the right fit for you?
Let’s find out.
What Is Wealth Management?
Wealth management isn’t just about investing. It’s about creating a strategy that covers all aspects of your financial life—retirement, taxes, healthcare, and even the legacy you want to leave behind.
At Passive Capital Management, wealth management is designed to help you navigate life’s financial twists and turns with confidence. Whether you’re planning for retirement, growing your assets, or protecting what you’ve built, a structured approach can make all the difference.
Do You Need Wealth Management?
Not everyone needs a wealth manager. But if you answer “yes” to any of these questions, it might be time to consider it:
- Do you worry about outliving your retirement savings?
- Are you unsure how to structure your investments for long-term security?
- Do you want a plan that adapts as your life changes?
- Are tax implications of your income and investments confusing?
- Do you want to leave behind a financial legacy for your family?
If any of these concerns sound familiar, a wealth management service could help you create a roadmap for financial success.
The Key Benefits of Wealth Management
1. Retirement Planning: More Than Just Saving
Retirement isn’t just about putting money aside. It’s about ensuring you can live comfortably once your regular income stops. Passive Capital Management helps clients create a sustainable retirement strategy, ensuring they have enough to cover daily expenses, healthcare, and even the fun things—like travel or hobbies.
By assessing income sources like pensions, social security, and investments, they build a tailored plan that matches your lifestyle and long-term goals.
2. Investment Strategies: Making Your Money Work for You
Investing can feel overwhelming. Stocks, bonds, real estate—where do you even begin? Wealth management helps you make informed choices based on your risk tolerance, time horizon, and financial objectives.
Rather than chasing trends, a well-planned investment strategy focuses on steady, long-term growth while minimizing unnecessary risks.
3. Tax Planning: Keeping More of What You Earn
No one likes to pay more taxes than necessary. But without a strategy, you might be doing just that.
Wealth managers help structure your income, retirement withdrawals, and investments in a tax-efficient way. Whether it's maximizing tax-free accounts or minimizing liabilities, they ensure you keep more of what you’ve earned.
4. Healthcare and Long-Term Care Planning
As you age, healthcare becomes a bigger concern—and a bigger expense. Without proper planning, medical costs can quickly eat into your savings.
A solid financial plan includes strategies to manage these costs, whether through insurance, savings, or investment strategies. This way, you get the care you need without financial stress.
5. Estate and Legacy Planning
Do you want to leave something behind for your loved ones? Wealth management ensures your assets are distributed according to your wishes, minimizing tax burdens and avoiding unnecessary legal complications.
Whether you’re thinking about passing on wealth to family or contributing to a cause you care about, having a plan in place ensures your money makes the impact you want.
When Should You Start?
The best time to start planning? Yesterday. The second-best time? Today.
Wealth management isn’t just for retirees or the ultra-rich. It’s for anyone who wants financial security and a clear plan for the future. Whether you’re in your 30s and just starting to build wealth or in your 50s preparing for retirement, having expert guidance can help you make smarter financial decisions.
Final Thoughts: Is It Right for You?
If you want peace of mind about your financial future, wealth management might be a great fit. It helps you grow your money, protect your assets, and ensure a comfortable life—now and in the years to come.
At Passive Capital Management, the goal is simple: to help you achieve financial freedom with confidence. If that sounds like something you want, it might be time to explore how wealth management can work for you.
Ready to take the next step? Let’s talk.
-
 @ 7f6db517:a4931eda
2025-05-31 22:01:46
@ 7f6db517:a4931eda
2025-05-31 22:01:46
What is KYC/AML?
- The acronym stands for Know Your Customer / Anti Money Laundering.
- In practice it stands for the surveillance measures companies are often compelled to take against their customers by financial regulators.
- Methods differ but often include: Passport Scans, Driver License Uploads, Social Security Numbers, Home Address, Phone Number, Face Scans.
- Bitcoin companies will also store all withdrawal and deposit addresses which can then be used to track bitcoin transactions on the bitcoin block chain.
- This data is then stored and shared. Regulations often require companies to hold this information for a set number of years but in practice users should assume this data will be held indefinitely. Data is often stored insecurely, which results in frequent hacks and leaks.
- KYC/AML data collection puts all honest users at risk of theft, extortion, and persecution while being ineffective at stopping crime. Criminals often use counterfeit, bought, or stolen credentials to get around the requirements. Criminals can buy "verified" accounts for as little as $200. Furthermore, billions of people are excluded from financial services as a result of KYC/AML requirements.
During the early days of bitcoin most services did not require this sensitive user data, but as adoption increased so did the surveillance measures. At this point, most large bitcoin companies are collecting and storing massive lists of bitcoiners, our sensitive personal information, and our transaction history.
Lists of Bitcoiners
KYC/AML policies are a direct attack on bitcoiners. Lists of bitcoiners and our transaction history will inevitably be used against us.
Once you are on a list with your bitcoin transaction history that record will always exist. Generally speaking, tracking bitcoin is based on probability analysis of ownership change. Surveillance firms use various heuristics to determine if you are sending bitcoin to yourself or if ownership is actually changing hands. You can obtain better privacy going forward by using collaborative transactions such as coinjoin to break this probability analysis.
Fortunately, you can buy bitcoin without providing intimate personal information. Tools such as peach, hodlhodl, robosats, azteco and bisq help; mining is also a solid option: anyone can plug a miner into power and internet and earn bitcoin by mining privately.
You can also earn bitcoin by providing goods and/or services that can be purchased with bitcoin. Long term, circular economies will mitigate this threat: most people will not buy bitcoin - they will earn bitcoin - most people will not sell bitcoin - they will spend bitcoin.
There is no such thing as KYC or No KYC bitcoin, there are bitcoiners on lists and those that are not on lists.
If you found this post helpful support my work with bitcoin.

-
 @ 17e2889f:a8fbe515
2025-05-31 09:14:33
@ 17e2889f:a8fbe515
2025-05-31 09:14:33More content will come soon!
Headline
-
 @ dfa02707:41ca50e3
2025-05-31 22:01:41
@ dfa02707:41ca50e3
2025-05-31 22:01:41
Good morning (good night?)! The No Bullshit Bitcoin news feed is now available on Moody's Dashboard! A huge shoutout to sir Clark Moody for integrating our feed.
Headlines
- Spiral welcomes Ben Carman. The developer will work on the LDK server and a new SDK designed to simplify the onboarding process for new self-custodial Bitcoin users.
- The Bitcoin Dev Kit Foundation announced new corporate members for 2025, including AnchorWatch, CleanSpark, and Proton Foundation. The annual dues from these corporate members fund the small team of open-source developers responsible for maintaining the core BDK libraries and related free and open-source software (FOSS) projects.
- Strategy increases Bitcoin holdings to 538,200 BTC. In the latest purchase, the company has spent more than $555M to buy 6,556 coins through proceeds of two at-the-market stock offering programs.
- Spar supermarket experiments with Bitcoin payments in Zug, Switzerland. The store has introduced a new payment method powered by the Lightning Network. The implementation was facilitated by DFX Swiss, a service that supports seamless conversions between bitcoin and legacy currencies.
- The Bank for International Settlements (BIS) wants to contain 'crypto' risks. A report titled "Cryptocurrencies and Decentralised Finance: Functions and Financial Stability Implications" calls for expanding research into "how new forms of central bank money, capital controls, and taxation policies can counter the risks of widespread crypto adoption while still fostering technological innovation."
- "Global Implications of Scam Centres, Underground Banking, and Illicit Online Marketplaces in Southeast Asia." According to the United Nations Office on Drugs and Crime (UNODC) report, criminal organizations from East and Southeast Asia are swiftly extending their global reach. These groups are moving beyond traditional scams and trafficking, creating sophisticated online networks that include unlicensed cryptocurrency exchanges, encrypted communication platforms, and stablecoins, fueling a massive fraud economy on an industrial scale.
- Slovenia is considering a 25% capital gains tax on Bitcoin profits for individuals. The Ministry of Finance has proposed legislation to impose this tax on gains from cryptocurrency transactions, though exchanging one cryptocurrency for another would remain exempt. At present, individual 'crypto' traders in Slovenia are not taxed.
- Circle, BitGo, Coinbase, and Paxos plan to apply for U.S. bank charters or licenses. According to a report in The Wall Street Journal, major crypto companies are planning to apply for U.S. bank charters or licenses. These firms are pursuing limited licenses that would permit them to issue stablecoins, as the U.S. Congress deliberates on legislation mandating licensing for stablecoin issuers.
"Established banks, like Bank of America, are hoping to amend the current drafts of [stablecoin] legislation in such a way that nonbanks are more heavily restricted from issuing stablecoins," people familiar with the matter told The Block.
- Charles Schwab to launch spot Bitcoin trading by 2026. The financial investment firm, managing over $10 trillion in assets, has revealed plans to introduce spot Bitcoin trading for its clients within the next year.
Use the tools
- Bitcoin Safe v1.2.3 expands QR SignMessage compatibility for all QR-UR-compatible hardware signers (SpecterDIY, KeyStone, Passport, Jade; already supported COLDCARD Q). It also adds the ability to import wallets via QR, ensuring compatibility with Keystone's latest firmware (2.0.6), alongside other improvements.
- Minibits v0.2.2-beta, an ecash wallet for Android devices, packages many changes to align the project with the planned iOS app release. New features and improvements include the ability to lock ecash to a receiver's pubkey, faster confirmations of ecash minting and payments thanks to WebSockets, UI-related fixes, and more.
- Zeus v0.11.0-alpha1 introduces Cashu wallets tied to embedded LND wallets. Navigate to Settings > Ecash to enable it. Other wallet types can still sweep funds from Cashu tokens. Zeus Pay now supports Cashu address types in Zaplocker, Cashu, and NWC modes.
- LNDg v1.10.0, an advanced web interface designed for analyzing Lightning Network Daemon (LND) data and automating node management tasks, introduces performance improvements, adds a new metrics page for unprofitable and stuck channels, and displays warnings for batch openings. The Profit and Loss Chart has been updated to include on-chain costs. Advanced settings have been added for users who would like their channel database size to be read remotely (the default remains local). Additionally, the AutoFees tool now uses aggregated pubkey metrics for multiple channels with the same peer.
- Nunchuk Desktop v1.9.45 release brings the latest bug fixes and improvements.
- Blockstream Green iOS v4.1.8 has renamed L-BTC to LBTC, and improves translations of notifications, login time, and background payments.
- Blockstream Green Android v4.1.8 has added language preference in App Settings and enables an Android data backup option for disaster recovery. Additionally, it fixes issues with Jade entry point PIN timeout and Trezor passphrase input.
- Torq v2.2.2, an advanced Lightning node management software designed to handle large nodes with over 1000 channels, fixes bugs that caused channel balance to not be updated in some cases and channel "peer total local balance" not getting updated.
- Stack Wallet v2.1.12, a multicoin wallet by Cypher Stack, fixes an issue with Xelis introduced in the latest release for Windows.
- ESP-Miner-NerdQAxePlus v1.0.29.1, a forked version from the NerdAxe miner that was modified for use on the NerdQAxe+, is now available.
- Zark enables sending sats to an npub using Bark.
- Erk is a novel variation of the Ark protocol that completely removes the need for user interactivity in rounds, addressing one of Ark's key limitations: the requirement for users to come online before their VTXOs expire.
- Aegis v0.1.1 is now available. It is a Nostr event signer app for iOS devices.
- Nostash is a NIP-07 Nostr signing extension for Safari. It is a fork of Nostore and is maintained by Terry Yiu. Available on iOS TestFlight.
- Amber v3.2.8, a Nostr event signer for Android, delivers the latest fixes and improvements.
- Nostur v1.20.0, a Nostr client for iOS, adds
-
 @ 84b0c46a:417782f5
2025-05-31 09:11:23
@ 84b0c46a:417782f5
2025-05-31 09:11:23Simple Long Form Content Editor (NIP-23)
機能
-
nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw や、 nostr:nevent1qvzqqqqqqypzq4jsz7zew5j7jr4pdfxh483nwq9vyw9ph6wm706sjwrzj2we58nqqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyxhwumn8ghj7mn0wvhxcmmvqqsgcn99jyn5tevxz5zxsrkd7h0sx8fwnqztula423xh83j9wau7cms3vg9c7 のようにnostr:要素を挿入できる (メニューのNアイコンから挿入またはnostr:note~~のように手動で入力)
-
:monoice:のようにカスタム絵文字を挿入できる(メニューの🙂アイコンから)
:monopaca_kao:
:kubipaca_karada:
- 新規記事作成と、既存記事の修正ができる
やることやったこと
-
[x] nostr:を投稿するときにtagにいれる
-
[x] 画像をアップロードできるようにする(NIP-96)
 できる
できる - [x] 投稿しましたログとかをトースト的なやつでだすようにする
- [ ] レイアウトを整える
- [ ] あとなんか
test
nostr:naddr1qvzqqqr4gupzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qqxnzde58q6njvpkxqersv3ejxw9x9
-
-
 @ dfa02707:41ca50e3
2025-05-31 22:01:38
@ dfa02707:41ca50e3
2025-05-31 22:01:38- This version introduces the Soroban P2P network, enabling Dojo to relay transactions to the Bitcoin network and share others' transactions to break the heuristic linking relaying nodes to transaction creators.
- Additionally, Dojo admins can now manage API keys in DMT with labels, status, and expiration, ideal for community Dojo providers like Dojobay. New API endpoints, including "/services" exposing Explorer, Soroban, and Indexer, have been added to aid wallet developers.
- Other maintenance updates include Bitcoin Core, Tor, Fulcrum, Node.js, plus an updated ban-knots script to disconnect inbound Knots nodes.
"I want to thank all the contributors. This again shows the power of true Free Software. I also want to thank everyone who donated to help Dojo development going. I truly appreciate it," said Still Dojo Coder.
What's new
- Soroban P2P network. For MyDojo (Docker setup) users, Soroban will be automatically installed as part of their Dojo. This integration allows Dojo to utilize the Soroban P2P network for various upcoming features and applications.
- PandoTx. PandoTx serves as a transaction transport layer. When your wallet sends a transaction to Dojo, it is relayed to a random Soroban node, which then forwards it to the Bitcoin network. It also enables your Soroban node to receive and relay transactions from others to the Bitcoin network and is designed to disrupt the assumption that a node relaying a transaction is closely linked to the person who initiated it.
- Pushing transactions through Soroban can be deactivated by setting
NODE_PANDOTX_PUSH=offindocker-node.conf. - Processing incoming transactions from Soroban network can be deactivated by setting
NODE_PANDOTX_PROCESS=offindocker-node.conf.
- Pushing transactions through Soroban can be deactivated by setting
- API key management has been introduced to address the growing number of people offering their Dojos to the community. Dojo admins can now access a new API management tab in their DMT, where they can create unlimited API keys, assign labels for easy identification, and set expiration dates for each key. This allows admins to avoid sharing their main API key and instead distribute specific keys to selected parties.
- New API endpoints. Several new API endpoints have been added to help API consumers develop features on Dojo more efficiently:
- New:
/latest-block- returns data about latest block/txout/:txid/:index- returns unspent output data/support/services- returns info about services that Dojo exposes
- Updated:
/tx/:txid- endpoint has been updated to return raw transaction with parameter?rawHex=1
- The new
/support/servicesendpoint replaces the deprecatedexplorerfield in the Dojo pairing payload. Although still present, API consumers should use this endpoint for explorer and other pairing data.
- New:
Other changes
- Updated ban script to disconnect inbound Knots nodes.
- Updated Fulcrum to v1.12.0.
- Regenerate Fulcrum certificate if expired.
- Check if transaction already exists in pushTx.
- Bump BTC-RPC Explorer.
- Bump Tor to v0.4.8.16, bump Snowflake.
- Updated Bitcoin Core to v29.0.
- Removed unnecessary middleware.
- Fixed DB update mechanism, added api_keys table.
- Add an option to use blocksdir config for bitcoin blocks directory.
- Removed deprecated configuration.
- Updated Node.js dependencies.
- Reconfigured container dependencies.
- Fix Snowflake git URL.
- Fix log path for testnet4.
- Use prebuilt addrindexrs binaries.
- Add instructions to migrate blockchain/fulcrum.
- Added pull policies.
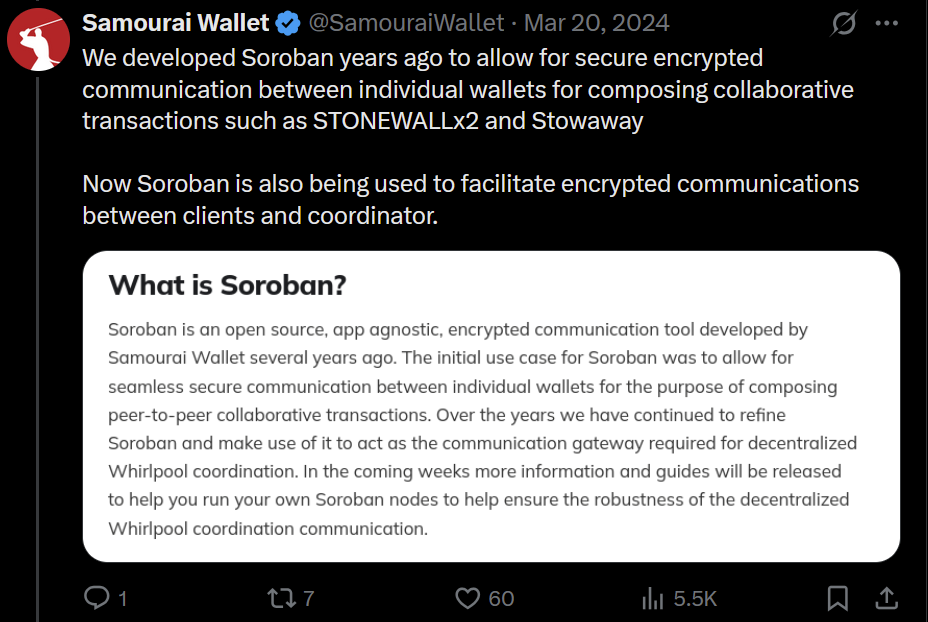

Learn how to set up and use your own Bitcoin privacy node with Dojo here.
-
 @ 57d1a264:69f1fee1
2025-05-31 06:19:55
@ 57d1a264:69f1fee1
2025-05-31 06:19:55Knowledge- Pattern knowledge- Trend knowledge- A desire to learn more- A desire to explore good designExperience- A sense of where to start/what will work- Good taste- Good judge of your own design and others’- Comfortable working in many styles- Willing to have a strong opinionCreativity- Novel ideas- Exhaustive exploration of options/approaches- Exhaustive iterationQuality- A preference for quality- A preference to test designs- Open to feedback- Able to balance classical and expressive aesthetics- Able to balance aesthetics and usability- Obsessed with details- RigorousTechnical skills- Good typography- Good composition/layout- Good colour choices- Good at some associated skills (e.g. prototyping, animation, imagery, writing)- Tool expertiseWider picture- Informed by understanding of the product (e.g. research)- System thinking (how the work is connected to other things)- Product thinking (what makes a successful product)- Development thinking (how a design might be implemented)- Practical mindset when necessary- Believes in importance of accessibilityCommunication- Able to articulate your design “feelings”- Able to explain design principles to others- Can clearly document/explain the design (e.g. specifications, mockups)- Good relationship-building, especially with developers- Able to “sell” a design idea
Read more aboutAnthony Hobday.https://stacker.news/items/993319
-
 @ 3770c235:16042bcc
2025-05-31 05:30:22
@ 3770c235:16042bcc
2025-05-31 05:30:22In a world full of constant stimulation, overflowing schedules, and ever-growing to-do lists, our physical spaces often bear the brunt of our busy lives. The clutter in our homes and workplaces can slowly pile up until it becomes overwhelming, contributing not only to a chaotic environment but also to increased levels of stress and anxiety.
But what if the simple act of removing junk and organizing your space could bring clarity to your mind, lift your mood, and create a lasting positive impact on your mental health? Decluttering isn't just about aesthetics—it’s about mental wellness. Junk removal can be a powerful tool to help you take control of your space and, in turn, your mindset. Let’s explore how clearing the clutter can boost mental health and transform your daily life.
The Psychological Impact of Clutter Clutter isn’t just stuff—it’s unmade decisions and postponed actions. Psychologists have long understood the connection between our environment and our emotional well-being. Clutter bombards our minds with excessive stimuli, making it difficult to focus or relax. It sends a signal that work is never done, which can lead to chronic stress.
A study published in the Personality and Social Psychology Bulletin found that women who described their homes as cluttered or full of unfinished projects were more likely to be fatigued and depressed than those who described their homes as restorative and restful. The same study found that cortisol levels—the body’s main stress hormone—were significantly higher in women living in cluttered environments.
Additionally, according to a UCLA study, families living in homes with a high density of household objects experienced increased levels of anxiety. The psychological toll of clutter isn’t minor; it has real, measurable effects on our mental health.
Junk Removal as an Act of Self-Care Self-care isn't just about spa days or bubble baths—it's about creating systems and habits that support your well-being. Removing clutter and excess junk from your living or working space can be an essential act of self-care, sending your brain a clear message: you deserve a clean, peaceful environment.
The physical act of junk removal creates a sense of accomplishment. Whether it’s donating unused clothing, throwing away broken items, or clearing out the garage, every bag removed is a step toward emotional relief. The process can be surprisingly cathartic, especially for those dealing with stress, grief, or major life transitions.
Why Clutter Creates Mental Clutter Clutter and disorganization can reduce our ability to process information. Researchers at Princeton University Neuroscience Institute found that physical clutter competes for your attention, resulting in decreased performance and increased stress. When your environment is chaotic, your mind tends to mimic that chaos.
Every time you walk past a cluttered desk or disorganized closet, your brain registers it as a task you haven't completed. Over time, this leads to mental fatigue. You might find yourself feeling constantly behind, overwhelmed, or unable to concentrate—even when you're not consciously thinking about the mess.
On the flip side, a tidy, clutter-free environment can promote mental clarity, boost productivity, and help foster a greater sense of control and calm.
How Junk Removal Enhances Mood There’s a distinct emotional payoff to junk removal. Many people report feeling lighter, freer, and happier after decluttering a space. Here's why: 1. Reduces Anxiety and Stress Too much clutter can create a constant low-grade stress that gnaws away at your peace of mind. By physically removing items that no longer serve a purpose, you're also removing sources of tension. 2. Improves Focus and Productivity When your environment is clear, your mind follows suit. A cleaner space supports sharper thinking and better decision-making. Whether you're working from home or studying, a decluttered area can significantly enhance your ability to concentrate. 3. Boosts Self-Esteem Clutter can carry feelings of guilt or shame—reminders of undone tasks, unused purchases, or poor organizational habits. Taking the step to clean up can restore confidence and create a sense of achievement.
- Encourages Mindfulness Decluttering forces you to be present. You have to examine each item, reflect on its usefulness, and make a conscious decision about its place in your life. This process promotes mindfulness and intentional living.
The Decluttering Process: Step-by-Step for Mental Clarity If the idea of decluttering your entire home feels overwhelming, start small. Begin with one drawer, one shelf, or one room. Here's a practical approach to get started:
Step 1: Set a Clear Intention Know why you're decluttering. Is it to feel less stressed? To improve your focus? Having a specific goal will keep you motivated. Step 2: Sort Items into Categories Use the classic “keep, donate, toss” system. Be honest with yourself about what adds value to your life. Step 3: Focus on One Area at a Time Avoid jumping from room to room. Focus your energy on one space to see progress quickly and stay motivated.
Step 4: Remove the Junk Promptly Once you've sorted items for removal, don’t let them linger. Hire a junk removal service or take them to a donation center right away. Step 5: Maintain Your Space Set a monthly reminder to reassess clutter. Make it a habit, not a one-time task.
Professional Help: The Role of Junk Removal Services For some people, the physical and emotional burden of clearing out clutter is too overwhelming to tackle alone. This is where professional junk removal services come in. These services not only handle the heavy lifting but also offer a judgment-free way to transform your space quickly and efficiently. By outsourcing the task, you reduce stress and avoid decision fatigue. It’s a practical solution for busy professionals, seniors downsizing, or those recovering from emotional trauma like the loss of a loved one.
The mental relief from seeing a room go from chaotic to clean in just a few hours is worth the investment. Plus, many services are eco-friendly and donate reusable items to charities, adding another layer of purpose to the process.
Real-Life Impacts: Statistics that Speak Decluttering doesn’t just feel good—it’s backed by data. Consider this: • According to a study by the National Association of Professional Organizers, 54% of Americans are overwhelmed by clutter, and 78% have no idea what to do with it [source]. • A report from the Journal of Environmental Psychology found that people with clean homes are happier and more relaxed, with higher activity levels and lower levels of cortisol [source]. These statistics highlight how deeply our environment influences our emotional health—and how important it is to reclaim control of your space.
Decluttering in the Digital Age While physical clutter is the most obvious, digital clutter can also affect your mental state. Overflowing email inboxes, unorganized files, and constant notifications can leave you feeling scattered and distracted. Take time to regularly clean up your digital life by: • Unsubscribing from unwanted emails • Deleting unused apps • Organizing desktop files and folders • Turning off non-essential notifications Just like physical spaces, a clean digital environment supports a clearer, more focused mind.
When Clutter Signals Something Deeper While decluttering is beneficial, it’s important to recognize when excessive clutter or hoarding behavior may be a sign of deeper mental health issues. Conditions such as depression, anxiety, and obsessive-compulsive disorder (OCD) can manifest in the inability to discard items or maintain an organized space. If clutter feels insurmountable or leads to distress and dysfunction, it may be time to seek support from a mental health professional. Therapy can help address the root causes and develop strategies for long-term change.
Final Thoughts: Clearing the Path to Mental Well-Being Junk removal and decluttering may seem like simple tasks, but their effects on your mental health can be profound. By reducing chaos in your environment, you invite peace, focus, and emotional clarity into your life. Whether you choose to tackle the clutter yourself or enlist the help of professionals, taking the first step is often the hardest—and the most transformative. Your environment is a mirror of your mind. Clear the clutter, and you’ll often find that clarity, joy, and calm aren’t far behind.
-
 @ dfa02707:41ca50e3
2025-05-31 22:01:38
@ dfa02707:41ca50e3
2025-05-31 22:01:38Contribute to keep No Bullshit Bitcoin news going.
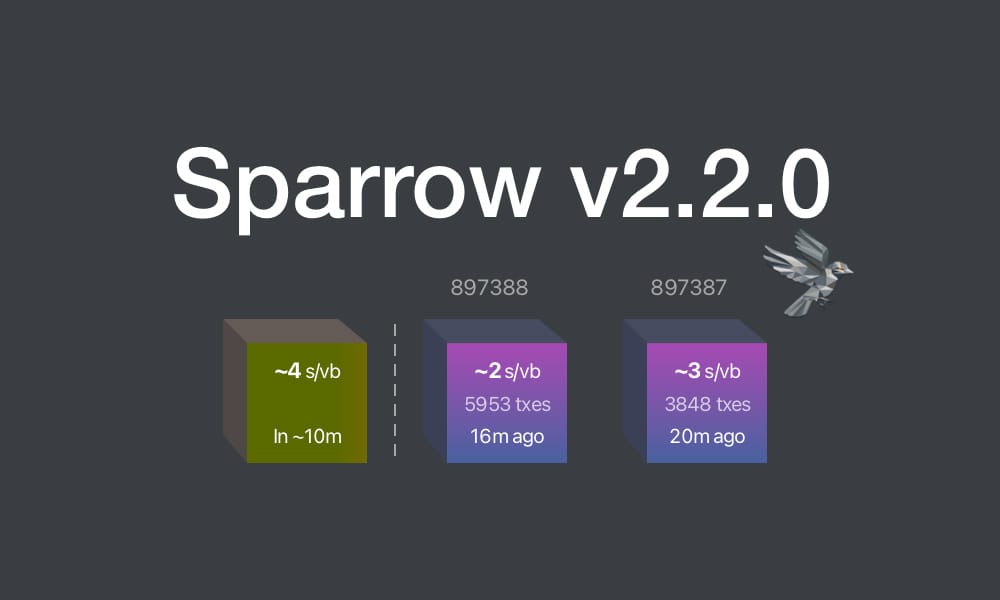
This update brings key enhancements for clarity and usability:
- Recent Blocks View: Added to the Send tab and inspired by Mempool's visualization, it displays the last 2 blocks and the estimated next block to help choose fee rates.
- Camera System Overhaul: Features a new library for higher resolution detection and mouse-scroll zoom support when available.
- Vector-Based Images: All app images are now vectorized and theme-aware, enhancing contrast, especially in dark mode.
- Tor & P2A Updates: Upgraded internal Tor and improved support for pay-to-anchor (P2A) outputs.
- Linux Package Rename: For Linux users, Sparrow has been renamed to sparrowwallet (or sparrowserver); in some cases, the original sparrow package may need manual removal.
- Additional updates include showing total payments in multi-payment transaction diagrams, better handling of long labels, and other UI enhancements.
- Sparrow v2.2.1 is a bug fix release that addresses missing UUID issue when starting Tor on recent macOS versions, icons for external sources in Settings and Recent Blocks view, repackaged
.debinstalls to use older gzip instead of zstd compression, and removed display of median fee rate where fee rates source is set to Server.
Learn how to get started with Sparrow wallet:
Release notes (v2.2.0)
- Added Recent Blocks view to Send tab.
- Converted all bitmapped images to theme aware SVG format for all wallet models and dialogs.
- Support send and display of pay to anchor (P2A) outputs.
- Renamed
sparrowpackage tosparrowwalletandsparrowserveron Linux. - Switched camera library to openpnp-capture.
- Support FHD (1920 x 1080) and UHD4k (3840 x 2160) capture resolutions.
- Support camera zoom with mouse scroll where possible.
- In the Download Verifier, prefer verifying the dropped file over the default file where the file is not in the manifest.
- Show a warning (with an option to disable the check) when importing a wallet with a derivation path matching another script type.
- In Cormorant, avoid calling the
listwalletdirRPC on initialization due to a potentially slow response on Windows. - Avoid server address resolution for public servers.
- Assume server address is non local for resolution failures where a proxy is configured.
- Added a tooltip to indicate truncated labels in table cells.
- Dynamically truncate input and output labels in the tree on a transaction tab, and add tooltips if necessary.
- Improved tooltips for wallet tabs and transaction diagrams with long labels.
- Show the address where available on input and output tooltips in transaction tab tree.
- Show the total amount sent in payments in the transaction diagram when constructing multiple payment transactions.
- Reset preferred table column widths on adjustment to improve handling after window resizing.
- Added accessible text to improve screen reader navigation on seed entry.
- Made Wallet Summary table grow horizontally with dialog sizing.
- Reduced tooltip show delay to 200ms.
- Show transaction diagram fee percentage as less than 0.01% rather than 0.00%.
- Optimized and reduced Electrum server RPC calls.
- Upgraded Bouncy Castle, PGPainless and Logback libraries.
- Upgraded internal Tor to v0.4.8.16.
- Bug fix: Fixed issue with random ordering of keystore origins on labels import.
- Bug fix: Fixed non-zero account script type detection when signing a message on Trezor devices.
- Bug fix: Fixed issue parsing remote Coldcard xpub encoded on a different network.
- Bug fix: Fixed inclusion of fees on wallet label exports.
- Bug fix: Increase Trezor device libusb timeout.
Linux users: Note that the
sparrowpackage has been renamed tosparrowwalletorsparrowserver, and in some cases you may need to manually uninstall the originalsparrowpackage. Look in the/optfolder to ensure you have the new name, and the original is removed.What's new in v2.2.1
- Updated Tor library to fix missing UUID issue when starting Tor on recent macOS versions.
- Repackaged
.debinstalls to use older gzip instead of zstd compression. - Removed display of median fee rate where fee rates source is set to Server.
- Added icons for external sources in Settings and Recent Blocks view
- Bug fix: Fixed issue in Recent Blocks view when switching fee rates source
- Bug fix: Fixed NPE on null fee returned from server
-
 @ c230edd3:8ad4a712
2025-05-31 01:51:38
@ c230edd3:8ad4a712
2025-05-31 01:51:38Chef's notes
Most Santa Maria tri tip roast recipes call for red wine vinegar and dijon mustard. I prefer other ingredients in place of those, but should you like those flavors and textures, they are more traditional.
Keep in mind when cooking and slicing, that the grain of tri-tip runs in 3 directions and the meat is unevenly thick. Pulling the roast when the thin end achieves well done, the thicker end will be a nice medium rare. When slicing, change direction to cut against the grain as you transition through for the most tender outcome.
Details
- ⏲️ Prep time: 10 minutes
- 🍳 Cook time: 1 hour ( with grill heating time)
- 🍽️ Servings: 4-6
Ingredients
- 1.5 - 2 lb Tri-Tip Roast
- 1 Tbsp Kosher Salt
- 1 tsp Black Pepper
- 1 tsp Cayanne Pepper ( substitute all or some with smoked paprika for a milder taste)
- 1 tsp Garlic Powder
- 1 tsp Onion Powder
- 1 Tbsp Rosemary
- 2 Tbsp Stone Ground Mustard
- 1 Tbsp Rice Vinegar
- 2-3 Cloves Garlic, Minced
Directions
- Mix all dry spices.
- Pat the roast dry and coat on all sides with seasdoning mix.
- Cover loosely and allow to sit in fridge for 8-12 hours.
- Preheat grill to 475 degrees F, allow meat to sit at room temp during this process.
- Mix vinegar, mustard, and minced garlic.
- Place meat on hot grill, fat side down and coat the upward side with mustard mix
- Grill approximately 7-10 minutes.
- Flip meat, repeat coating and grilling.
- Flip once more and grill for 2-3 minutes to caramelize the glaze and until the fat begins to render.
- Remove from grill and let the roast rest for 5 minutes before slicing,
- Serve with grilled veggies or any side of your choice. This is a bit spicy so it goes well with a salsa fresca and tortillas, too.
-
 @ 9ca447d2:fbf5a36d
2025-05-31 22:01:20
@ 9ca447d2:fbf5a36d
2025-05-31 22:01:20Adam O’Brien, Founder and CEO of Bitcoin Well, discovered Bitcoin in 2013 during its early days as what he describes as “hilarious internet money.”
Today, he leads a publicly traded Canadian company that’s redefining how people interact with this magic internet money, all while navigating a financial system that has personally debanked him and even his uninvolved loved ones.
“I had a terrible experience trying to buy bitcoin in 2013,” O’Brien explains. “Now of course today there are platforms like Bitcoin Well and many others that allow you to buy bitcoin with ease online, but in 2013 that wasn’t the case.”
This frustrating experience sparked the entrepreneurial question that would shape his future: “There must be a better way.”
With a background in restaurant management and customer service, O’Brien started small, meeting people locally in Edmonton, Canada to sell them bitcoin.
Soon after, he purchased and deployed Alberta’s first bitcoin ATM. The business grew organically, with a second machine following, then a third. Before long, Bitcoin Well had become one of Canada’s largest bitcoin ATM operators.
Today, Bitcoin Well operates approximately 160 bitcoin ATMs across Canada. While they’re no longer deploying new machines, these ATMs provide a crucial service that O’Brien is particularly proud of:
“In Canada, you can actually buy bitcoin up to $1,000 without giving your identity to Bitcoin Well. We’re the only platform in the country that is able to offer that service, which is fully legal, fully above board.”
Bitcoin Well has a fleet of over 170 bitcoin ATMs across Canada
The Pivot to Freedom
In 2020, O’Brien’s vision for the company evolved. What began as a mission for Bitcoin accessibility transformed into something deeper: a quest for financial freedom.
“I’m debanked across Canada. I don’t have my bank, even my wife has lost her bank accounts because of my work,” O’Brien revealed. “She’s not involved with the business at all. She’s a stay-at-home mother to our four kids, and she’s unbanked from the majority of the banks in Canada.”
This personal experience crystallized a troubling reality: “It became very clear to me that my money in the banking system was always going to be subject to how much I play by the rules.”
For someone self-described as “freedom-focused” and “freedom-minded,” this realization prompted a strategic shift. Bitcoin Well began developing its online platform, the Bitcoin portal, allowing users to buy, sell, and actually use bitcoin to replace traditional banking functions. O’Brien explains:
“The goal here is that we can be a conduit between the legacy financial system you know, and how you pay your bills, your rent, your power, credit card and phone bills and all that stuff without having to have money in what I would call a captured fiat account.”
He summarizes the company’s North Star simply: “Allow people to replace their bank with bitcoin in self-custody.”
Living the Mission
O’Brien doesn’t just preach Bitcoin independence, he lives it. Debanked across Canada, he relies on Bitcoin Well’s services for his daily financial needs.
“I’ve got a normal American Express, but I pay that off with Bitcoin at the end of the month,” he shares. “In Canada, we’ve got the equivalent of Venmo, it’s called Interac e-Transfer. I can send an Interac e-Transfer to anyone in the country from bitcoin in self-custody.”
This allows him to navigate everyday situations where merchants don’t accept bitcoin directly.
“It’s spring right now. I’ve got a little property. The guy comes and picks up our rakes and trims the trees and all this stuff, and I pay him. He doesn’t want to accept bitcoin, but I’m able to pay in bitcoin, and he gets the money that he wants.”
In the U.S., Bitcoin Well customers can have their paychecks deposited with a designated portion automatically converted to sats and sent directly to self-custody, allowing clients to stack sats sovereignly without having to think much about it.
With Bitcoin Well you can set up automatic DCA
Building the Right Team
The journey hasn’t been without challenges. O’Brien candidly describes how rapid growth in 2021 led to hiring missteps.
“We scaled so fast I kind of lost control of hiring practice and culture, and we ended up with people that I felt like we had to almost convince of the mission,” he admits.
“Some of them weren’t convinced…they were just there because of the job, or they didn’t really understand the need for the freedom that I speak about every single day.”
After scaling back from that hiring spree, the company refocused on building a team aligned with its core values, emphasizing “hiring Bitcoiners really.”
The result has been transformative: “It’s so much fun having a team that is mission-focused and aligned on our mission to enable independence. Having everyone aligned and kind of running towards that mission is pretty special.”
This alignment creates a powerful filter for decision-making: “When we have a decision to make, it’s like, well, which one enables more independence? And usually there’s a pretty obvious answer. So we’re able to make very fast decisions that help the business and help the mission.”
Raising the Next Generation
Beyond building Bitcoin Well, O’Brien and his wife are raising four children with intention. The family is transitioning to homeschooling next year, allowing them to travel to Bitcoin conferences together while teaching their children to question everything.
“If you don’t indoctrinate your kids, the state will do it for you,” O’Brien states firmly. It’s a fair point, as indoctrination usually comes with a negative connotation, but it should not, since everyone gets indoctrinated with something.
It’s up to parents to decide what their kids are going to be indoctrinated with, and as parents, the O’Briens have chosen to actively shape their children’s worldview rather than defaulting to institutional influences.
Their approach combines Bitcoin principles with biblical values, with a heavy emphasis on lowering time preference. Something O’Brien notes is “10, 20, 30, 50 times more important” with children, though admittedly “way harder.”
“I think Bitcoiners more than anyone understand the need for generational thinking,” he observes.
“I’m so bullish on the amount of Bitcoiners that have more kids or that want to have more kids and that are actually excited to have kids compared to some of my fiat friends that are like, ‘Oh, it’s too expensive and I want to party.’ It’s like, man, you’re just missing the point.”
A Call to Support Bitcoin-Only Businesses
One of O’Brien’s most passionate messages is a call to action for fellow Bitcoiners: support businesses that align with your values.
“I want to call people to support businesses that are actually making steps towards the change they want to see in the world,” he urges. “If I hear one more Bitcoin maxi tell me that they’re using Kraken or Coinbase because it’s cheaper — why do you support the casinos?”
He expresses concern about the future if Bitcoin-only companies struggle to survive: “It would be very sad if all the Bitcoin-only and non-custodial businesses went out of business. That would make it very hard for me to feel comfortable onboarding my no-coiner friends.”
His message to Bitcoiners is clear: “A call out to all my fellow Bitcoiners to support and use the platform that they want to see their kids use.”
Bitcoin Well (TSX.V: BTCW, OTCQB: BCNWF) continues to build infrastructure for those who want to use Bitcoin daily while maintaining self-custody. For O’Brien, the mission is simple but powerful: enable independence and give people the freedom to control their own financial destiny.
-
 @ 812cff5a:5c40aeeb
2025-05-31 01:12:55
@ 812cff5a:5c40aeeb
2025-05-31 01:12:55NIP-02 — أنماط المفاتيح العامة
رقم التعريف (NIP): 02
العنوان: أنماط المفاتيح العامة
الحالة: نهائي
المؤلف: fiatjaf
التاريخ: 2020-12-10
الملخص
يقترح هذا المستند نمطًا معياريًا لطريقة تمثيل المفاتيح العامة (public keys) في نُستر — يُعرف باسم
npub— لتسهيل مشاركتها وقراءتها من قبل البشر، تمامًا كما يتم تمثيل عناوين البيتكوين بـ bech32.
التنسيق المقترح
نقترح استخدام bech32 لترميز المفاتيح العامة، حيث يكون التنسيق كالتالي:
npub1<سلسلة bech32>على سبيل المثال:
npub1qqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqzv9sxهذا الشكل يمكن نسخه بسهولة، والتعرف عليه بصريًا، والتعامل معه دون الوقوع في أخطاء النسخ الشائعة للمفاتيح بصيغ hex.
السبب
- الشكل hex التقليدي للمفاتيح العامة (مثل
32e...af1) صعب القراءة. - bech32 أسهل للمشاركة عبر الرسائل أو الوسائط الاجتماعية.
- وجود بادئة
npub1يوضح فورًا أن السلسلة تمثل مفتاحًا عامًا في نظام نُستر.
ملاحظات إضافية
- نفس المبدأ يُستخدم أيضًا مع أنواع أخرى مثل
note(لتمثيل معرفات الأحداث) وnsec(للمفاتيح الخاصة). - هذه الصيغ لا تغيّر البيانات الأصلية، بل فقط تمثلها بطريقة أسهل وأكثر أمانًا للبشر.
الخلاصة
npubهو معيار لتنسيق المفاتيح العامة باستخدام bech32، مما يجعلها أكثر قابلية للقراءة والاستخدام من قبل البشر.
يُوصى بأن تستخدم جميع تطبيقات نُستر هذا النمط عند عرض أو مشاركة المفاتيح العامة. - الشكل hex التقليدي للمفاتيح العامة (مثل
-
 @ b1ddb4d7:471244e7
2025-05-31 22:01:00
@ b1ddb4d7:471244e7
2025-05-31 22:01:00Flash, an all-in-one Bitcoin payment platform, has announced the launch of Flash 2.0, the most intuitive and powerful Bitcoin payment solution to date.
With a completely redesigned interface, expanded e-commerce integrations, and a frictionless onboarding process, Flash 2.0 makes accepting Bitcoin easier than ever for businesses worldwide.
 We did the unthinkable!
We did the unthinkable! Website monetization used to be super complicated.
"Buy me a coffee" — But only if we both have a bank account.
WHAT IF WE DON'T?
Thanks to @paywflash and bitcoin, it's just 5 CLICKS – and no banks!
 Start accepting donations on your website… pic.twitter.com/uwZUrvmEZ1
Start accepting donations on your website… pic.twitter.com/uwZUrvmEZ1— Flash • The Bitcoin Payment Gateway (@paywflash) May 13, 2025
Accept Bitcoin in Three Minutes
Setting up Bitcoin payments has long been a challenge for merchants, requiring technical expertise, third-party processors, and lengthy verification procedures. Flash 2.0 eliminates these barriers, allowing any business to start accepting Bitcoin in just three minutes, with no technical set-up and full control over their funds.
The Bitcoin Payment Revolution
The world is witnessing a seismic shift in finance. Governments are backing Bitcoin funds, major companies are adding Bitcoin to their balance sheets, and political figures are embracing it as the future of money. Just as Stripe revolutionized internet payments, Flash is now doing the same for Bitcoin. Businesses that adapt today will gain a competitive edge in a rapidly evolving financial landscape.
With Bitcoin adoption accelerating, consumers are looking for places to spend it. Flash 2.0 ensures businesses of all sizes can seamlessly accept Bitcoin and position themselves at the forefront of this financial revolution.
All-in-One Monetization Platform
More than just a payment gateway, Flash 2.0 is a complete Bitcoin monetization suite, providing multiple ways for businesses to integrate Bitcoin into their operations. Merchants can accept payments online and in-store, content creators can monetize with donations and paywalls, and freelancers can send instant invoices via payment links.
For example, a jewelry designer selling products on WooCommerce can now integrate Flash for online payments, use Flash’s Point-of-Sale system at trade shows, enable Bitcoin donations for her digital artwork, and lock premium content behind Flash Paywalls. The possibilities are endless.
E-Commerce for Everyone
With built-in integrations for Shopify, WooCommerce, and soon Wix and OpenCart, Flash 2.0 enables Bitcoin payments on 95% of e-commerce stores worldwide. Businesses can now add Bitcoin as a payment option in just a few clicks—without needing developers or external payment processors.
And for those looking to start selling, Flash’s built-in e-commerce features allow users to create online stores, showcase products, and manage payments seamlessly.
No Middlemen, No Chargebacks, No Limits
Unlike traditional payment platforms, Flash does not hold or process funds. Businesses receive Bitcoin directly, instantly, and securely. There are no chargebacks, giving merchants full control over refunds and eliminating fraud. Flash also remains KYC-free, ensuring a seamless experience for businesses and customers alike.
A Completely Redesigned Experience
“The world is waking up to Bitcoin. Just like the internet revolutionized commerce, Bitcoin is reshaping finance. Businesses need solutions that are simple, efficient, and truly decentralized. Flash 2.0 is more than just a payment processor—it’s a gateway to the future of digital transactions, putting financial power back into the hands of businesses.”
— Pierre Corbin, CEO at Flash.
Flash 2.0 introduces a brand-new user interface, making it easier than ever to navigate, set up payments, and manage transactions. With an intuitive dashboard, streamlined checkout, and enhanced mobile compatibility, the platform is built for both new and experienced Bitcoin users.
About Flash
Flash is an all-in-one Bitcoin payment platform that empowers businesses, creators, and freelancers to accept, manage, and grow with Bitcoin. With a mission to make Bitcoin payments accessible to everyone, Flash eliminates complexity and gives users full control over their funds.
To learn more or get started, visit www.paywithflash.com.
Press Contact:
Julien Bouvier
Head of Marketing
+3360941039 -
 @ 14206a66:689725cf
2025-05-31 00:54:40
@ 14206a66:689725cf
2025-05-31 00:54:40We’ve all been there, you’re locked in, desperately fighting with spreadsheets, the dishwasher’s going, and a banana cake is in the oven. Suddenly, all goes quiet, lights are off, oven’s off, PC dead as a doorknob. You check the fusebox, it’s fine. Must be a blackout. Usually, the power comes back on after 30 minutes to an hour, but you’re left standing there wondering what happened.
We’ve just seen a country-wide scale event like this, which was much more extreme. On 28th April, the Iberian Peninsula experienced a catastrophic breakdown of the grid (see here).
Power was off for several days. I won’t dig into the details of this particular event; doing so is way beyond my pay grade. Suffice it to say it follows the ideas I want to introduce in this article.
We’ll begin with the simplest model I can think of, getting to grips with the issue from first principles. Then I’ll walk through how the basic premise scales up the Australian grid (or at least the east coast, the NEM), before introducing the shadowy supergeniuses in control of it all (AEMO) and one of the most important market mechanisms they use - Frequency Control Ancillary Services (FCAS).
Part one: First principles
Imagine a way-over-simplified system with a single source of power and a single load. Our source of power is just a battery that produces 10MW of power at an assumed 1000V. The battery has no rotating components. It is connected to a very basic inverter. The inverter is designed to produce 50 Hz AC power; however, let's imagine it has no sophisticated voltage controls or protections (unlike real inverters). All that our inverter comprises is a basic switching and timing circuit.
This specific frequency of 50 Hz is a fundamental design standard for almost all AC electrical equipment. Just like a clock needs to tick at a precise rate to tell accurate time, electrical devices like motors rely on the AC power cycling exactly 50 times per second. If the frequency deviates too much, it can cause motors to speed up or slow down incorrectly, or sensitive electronics to malfunction. Our simple inverter, despite its limitations, is designed to produce 50 Hz because that's what the heater and any other AC device expect.
Our load is a large but mechanically simple industrial heater. It has a large coil that produces heat by running a current through it. Importantly, the heater has a dial to adjust temperature (which can change its power consumption). The heater is currently set to draw 10MW of power.
That’s the start, with a simplified system in equilibrium, all is well. The heater is producing heat, and you can make up your own story about what the heat is used for. The important point is that the voltage, current, and frequency are all stable.
Next, the foreman operating the heater turns the dial up to increase the heat output. Assume the heater now wants to draw 20MW of power. We’re simplifying, so also assume that in this instant, the voltage remains at 1000V.
To draw this much power, the heater now has to draw more current (because power = voltage x current, it’s the rules). Since we assumed the voltage remains at 1000V, there is an instantaneous demand for more power from the battery than it was previously supplying.
The battery now attempts to supply this current, which means the current must flow through the battery’s components, the inverter’s components, and the wire connecting the battery to the heater. All of these physical components have resistance. This means the actual voltage the heater receives will be lower than 1000V.
Now that the heater is receiving voltage lower than 1000V, things start to go wrong. The power consumed by the heater is proportional to the square of the voltage across it (rules are rules), so power = voltage^2 / resistance. Following this rule, since the voltage has decreased, then that means the actual power the heater draws will be less than the 20MW desired. For example, it might only draw 15MW, but it depends on the resistances in all the components, which we haven’t set.
Things just get uglier. The battery and inverter are operating under extreme stress, trying to deliver the higher current demanded, but at reduced voltage. Inside the inverter and the battery, the components start getting hot (rules, again). Since we assumed the battery and inverter are super simple, the inverter can't adjust its power output based on actual grid conditions (like a sophisticated one would); it can only fail. Then the heater goes out, and the foreman gets mad; it’s just a bad day all around.
The fix: add a spinny thing.
Reimagine the situation just as before, but now, instead of a battery, imagine the source of power is a contemporary synchronous generator system. Say it’s a hydro plant, where the spinning turbine is directly connected to the grid. This generator, unlike the battery-inverter, inherently uses its large rotating mass to move a metal rod up and down inside a magnetic coil and produces AC power. Importantly, it synchronises with our system’s required 50 Hz rhythm.
In this case, the story proceeds as before. When the foreman turns the heater dial up the heater wants to draw 20MW. In this case, the increased current flows through the impedance of the generator’s internal components and the wire. Just as before, this causes an immediate, rapid voltage drop at the heater’s terminals. In that instant, the heater will not get its desired 20MW because the voltage is too low.
Since the generator’s power output is less than the load demand, the lack of energy causes the rotating mass of the generator to decelerate (energy is conserved), and the frequency of the AC power in the system drops below 50 HZ. Because the generator’s turbine is a large mass, it has substantial inertia (pesky rules again), so the drop in frequency happens much more slowly than in our first story, and there is no catastrophic failure of the system. Instea,d this inertia buys time for the system to react.
The reaction comes from the manager of the generator. In the real world, this is a piece of software called a governor, but it’s useful to imagine it’s a person. The manager sees the drop in frequency and presses some buttons to let more water flow to the turbine, the frequency climbs back to 50 HZ and the power output of the generator increases.
Then the heater gets its required 20MW of power at 1000V and 50Hz, and the foreman is happy, everyone’s happy, it’s just a good time.
Frequency, in this simple system, indicates power imbalances and triggers the manager of the generator to respond. Equally, we could have assumed the foreman can be notified that he shouldn’t increase the heater’s dial - we can manage the imbalance either on the supply (generator) or demand (heater) side, or a mix of both.
This hints at a crucial question: how the hell do we coordinate this? Even with just a single load and a single generator, what sort of contracts would the foreman and generator manager need to keep everything running?
Part deux: AEMO, the not-so-invisible hand coordinating the market
Above is a story of a system with one load and one generator, without protections for the management of voltage or frequency. I walked through how this simple system could suffer a catastrophic breakdown as a result of the load increasing. Followed by a slight added complexity, which solves the issue.
Everything that applies in the simplified model also applies in the real world; the basic principles scale up and create complex incentives, coordination, and knowledge problems.
In my simple story, there was a manager in charge of the generator and a foreman in charge of the heater. In the much more complex National Electricity Market (NEM), there’s a third main actor: Australian Energy Market Operator (AEMO, because it operates the energy market, perfect naming convention). Among a host of competing priorities, AEMO has one role we’re particularly interested in: making sure we have a good time, i.e making sure the grid is stable. How it does so is the economics bit.
The NEM covers a huge geographic area (all the way up the East Coast from South Australia up to North Port Douglas). Within the vast area it covers are around 10 million customer connections (source). AEMO provides an interactive map that shows you how many substations there are - lots!
here's a map from AEMO
With all those connections and interconnections, the only constant is change. Strong winds can suddenly break connections, generators can trip for a host of reasons, and sometimes physics just says “no”.
On the flip side, sometimes large loads connect unpredictably and want instant power to be available. The physics says supply must equal demand or things get bad, so how does AEMO make sure supply equals demand?
In short, dispatch instructions. AEMO coordinates the supply-side market participants using signals to their control rooms. The economics of it could be summed up as: AEMO is a visible hand trying to approximate the role of Smith’s invisible hand in the market*.
Though not the focus of my current article, dispatch can be (over)simplified as follows: Every five minutes, generators send an offer to AEMO containing a price-quantity pair for power output. AEMO sorts the offer from lowest price to highest and matches supply to forecasted demand, starting from the lowest offer to create a dispatch interval/dispatch window, within system constraints. Importantly, generators all receive the highest marginal price (spot price) of all offers within the dispatch interval. Then, all generators included in the dispatch interval receive revenue equal to their power dispatched times the spot price.
So, assuming the system is in balance. This plays out, and everyone’s happy. But that’s not guaranteed in such a complex interconnected system like the NEM. So, what happens if, after offers are placed and power is scheduled, a generator suddenly trips off (cutting supply) or a large load connects unexpectedly (rapidly ramping up demand)?
AEMO needs some sort of backup power supply or backup demand as a contingency for when imbalances happen. One of such contingencies is what we call this service provision Frequency Control Ancillary Services (FCAS). So named because AEMO uses system frequency to understand where, when, and how much extra supply or demand (load) is required to return the system to the normal stable operation.
But AEMO doesn’t own any generators, batteries, or large loads itself. So, how does it get them? Someone came up with the idea that you can sell backup supply or demand (load) to AEMO, for a fee. This idea implies that AEMO has to find the right incentives to bring backup supply or backup demand (load) online in a flash.
There’s a market for that!
Actually, there are eight markets, but we’re simplifying.
To procure FCAS, AEMO runs a similar auction process to the market for power. Participants submit bids to AEMO every five minutes, containing a service type and availability across up to 10 price bands. The service type is one of: increase/decrease frequency in one of the three time intervals.
AEMO then considers all bids and finds the least-cost solution that meets all system requirements, matching the supply of FCAS to the demand for FCAS. Just like in the market for power, AEMO orders the FCAS bids into a “merit order” based on price for each service type (lowest price to highest price). It then decides which bids it will accept and pays all accepted bids the highest marginal price of all accepted bids. This creates a price signal for FCAS in the market.
The design has obvious intentions: FCAS suppliers win big if they can be super low cost while their competitors are high cost.
Just like in the market for power, once bids are accepted, AEMO sends a signal to the control panels of the FCAS participants.
You can see how , by following this process, AEMO acts to approximate the emergent order (or invisible hand) of a market by creating price signals for both power supply as well as FCAS. Then, physically matching those price signals with the actual power flows using a (pretty amazing, honestly) control scheme.
The idea that AEMO is only approximating the invisible hand is important; I’ll explore that more deeply in future articles.
That’s the physics and market mechanisms in a nutshell. But who sells FCAS to AEMO, and what about the mullah, dollars, buckerinos, fat stacks?
Part tres: How big is the market
Firstly, who can participate in the FCAS market? As far as I understand, it’s quite open; if you invent a device that meets the standards and go through the application process, then you can participate. AEMO’s concern is system stability, so from their POV, any particular device is fair game as long as you meet the engineering standards.
One common example is certain electricity retailers who use their customers’ hot water cylinders as a demand response. By sending an electrical signal to your hot water cylinder, the company can turn it off for a short period, reducing demand (load). There’s a complex “annoyance cost” paid by the consumer of their hot water cylinder being turned off, but then that’s balanced against potentially lower bills as the electricity retailer can substitute FCAS revenue.
Another example is grid-scale batteries; these can build or release charge on a whim. For batteries, the incentives are about whether their charge is worth more in the spot market or in the supply response FCAS market. If the battery is connected to a facility like a solar plant, then the incentives get more complex; is it worth selling power instantly or building charge in the battery for potential spot market or FCAS later? Add in a futures market and you just get more complexity.
A final, still emerging, example is bitcoin miners, these are basically just computers. These machines can be powered up or down relatively quickly and easily with little ill physical effects, and no ill effects to the Bitcoin network or protocol. When they are powered up, they earn a stream of income for the owners in the form of bitcoin.
This creates an interesting dynamic when bitcoin miners participate in the FCAS market; their FCAS bid, all else equal, should be at least the value of the opportunity cost of not mining bitcoin.
A completely unanswered question is what happens if bitcoin mining becomes a large proportion of FCAS? Consider a case where the FCAS from bitcoin miners drops out of the market because bitcoin fees spike and miners find it more profitable to mine rather than provide FCAS.
Alright, but the money! Surely FCAS is lucrative?
AEMO publishes data on FCAS. The most readily understandable data is the payment data. This is, as the name suggests, how much AEMO paid to FCAS participants over the eight service types (and in each State/Territory in the NEM) each month. This is the raw revenue of FCAS market participants. One way to think of it is as the cost of stability.
In total, FCAS payments have been about $39 million this year (up to week 20, which ended May 18).
AEMO has also provided total revenue for FCAS from batteries in the NEM, specifically in its Quarterly Energy Dynamics - Q1 2025, covering 1 January to 31 March 2025 report. This data suggests that batteries in the NEM have earned $69 million in 2024, which is 42.9 percent of all FCAS costs. This is remarkable to me, because grid-scale batteries are relatively new to the market as compared to other generation and storage technologies.
The cause lies in the fact that batteries can* *have a low marginal cost to charge and discharge, so the fact that they captured such market share this fast highlights the idea that he who produces FCAS cheapest wins.
This data release also contains aggregate FCAS costs for all states. The data tells us that in 2024, total FCAS costs were $161 million.
The fact that there is such a healthy pot up for grabs speaks to the fragility of our grid, but also to the resilience; it's a strange duality.
With continued investment in solar generation, because such systems have little to no inertia, we could see increased frequency excursions (technical term for being out of range). Engineers are busy solving this using inverters, which simulate inertia. These are genius, but such innovations take time (and standards) to be adopted.
Then there’s the question of critical infrastructure risk - how tolerant can we be of instability when datacenters mining Bitcoin and running AI models are on the line
At the risk of repeating myself, the whole construction is very much a visible hand trying to approximate what Adam Smith’s invisible hand might do.
Fin
Full disclosure, I do use AI (Gemini specifically) to help me research, learn, and write my articles, but I go over everything multiple times to make it my own voice and reflect my own ideas.
*Adam Smith described the idea of an invisible hand, which directs the market, coordinating people's desires, as a metaphor to explain how people in a market somehow end up serving each other's best interests even without directly communicating.
-
 @ 81022b27:2b8d0644
2025-05-31 00:47:43
@ 81022b27:2b8d0644
2025-05-31 00:47:43Today some clients and I were talking and they asked me about my recent seminar where I attended the “Unleash The Power Within” seminar with Tony Robbins. I explained that the firewalk I performed was not the highlight of the seminar, It was all the junk I got rid of mentally. We talked some more and then someone said something a little derogatory about Scientology.
I said, “wait a second, Scientology changed my life!”
It’s true. Some of the things I learned through Dianetics and Scientology were catalysts in me changing my entire life around.
It started one evening in Coral Gables, FL when I was walking down the street going to meet someone for dinner. I was stopped by a lady holding a clipboard outside of a 50’s-looking building.
“Would you like to take personality test?”
I asked: “What’s that?”
She explained and since I’m always early to things, I had plenty of time to kill. I said: “Sure! let’s do it!”
I took the test and the results seemed spot on. Then they asked if I would like to learn more about the mind , I could sign up for a course for a modest amount and I was genuinely curious about the whole deal and I agreed.
The Class I came back like a week later to start the class. I’m remembering that building had a distinct smell. It wasn’t bad. I can’t really describe it, but if I ever smell something similar, I’d recognize it instantly.
I walked in and they took me to a big room, a classroom with lots of tables and chairs. Every table had a small box with objects in it. There were people reading, there were people in groups studying, lots of chatter.
It seemed exciting!
I don’t remember if it was my first lesson or not, but we had to do TR’s (Training Routines) and I was asked to sit across from some guy and just stare at him. Look him in the eyes and not laugh, not blink excessively, just keep your composure.
Bah! Stupid! But I can do this!
We started the exercise and it seemed silly at first, but then my heart started racing and started freaking out. It felt like I was in a tunnel, but somehow his eyes were attacking me.
Then all of a sudden I’m hovering 8 feet above myself and I’m looking at the situation from above.
Next thing I know, I’m back in my body and the exercise is over.
The teacher, or facilitator came by to ask me how everything went. I started to tell her exactly what happened and she was writing very matter-of-fact-ly.
“And then I left my body!,” I emphasized.
“So you exteriorized?” She asked.
“I guess.”, I mumbled.
What really made me curious is these people are just nonchalantly just writing down stuff like it’s no big deal.
They got me. I was hooked.
Auditing
I started doing some courses whenever I had some free time: maybe once or twice a week. I learned that there is something that they call the “reactive mind” and that past traumas can affect someone in the present time.
We did this exercise that when my “Auditor” would snap her fingers, I would repeat the first word that popped into my mind, until we got a string of words. I would the repeat this string of words until they “lost their charge” and had no effect.
During one of these sessions, I
felt like I was choking.
No, not choking !
I could taste salt water!
I was drowning!
This shook me up because I had no recollection of almost drowning like that.
I asked my mother if I ever almost drowned and I was surprised by her answer.
She said; “Yes. We were at the beach-you were a baby and in the water with your father. A wave got both of you and your dad had to throw you towards me like a football, because he couldn’t fight the riptide.”
Wow.
Study Tech
before you start the “heavy” course, you must learn how to study. So they have designed a way to teach people “How.”
I thought, “wow, no one ever really taught me how to study.”
In high school, I kind of just skated by, with no need to ever read or do much. I didn’t make valedictorian, but I was discovering my social life and that was top priority for me at the time.
They showed me if you read something and can’t remember what you just read, t means you read past a misunderstood word. You never skip a word you don’t understand. There are always dictionaries at every study table.
If you get woozy and want to bail on the material being studied, then you have skipped a gradient, so you should go back to a point you understand and work back up.
If you get a headache while, studying, that means you have a “lack of mass” and the topic is abstract and you need to make it more physical to be able to understand it.
That is why they had those baskets with modeling clay and stuff in it, so you could model out concepts.
I still use this knowledge.
Basic Study Manual
The Purification Program
At some point one of the coaches pointed out that if I wanted to make quicker progress, I should do The Purification Program. The Program is designed to get rid of environmental toxins and medications and other materials that are stuck in your physical body and is interfering with your progress “up the bridge”
So of course, I am fascinated by this idea and sign up for the course, This time, it;s a lot of books and it’s going to cost be some serious cash. I didn’t have that kind of money, because I was scraping by on an assistant manager at Wendy’s salary.
No worries, take out a new credit card to pay for it. And one of the members drove out to my work to get the signature (and $$) to pay for the course. I think It was the end of the month and they got a bonus if I signed up before then.
The Program
The program basically consists of sitting in a sauna for 5 hours a day, Taking supplements: cal-mag, megadoses of niacin, and oils
It was perfectly organized: we were taken to a different part of the building to an area with a eucalyptus smell. We were shown the sauna-it was a large sauna , It could hold like 10 people.
We were given our supplements and then told to jog for few blocks around the building and then come into the sauna.
By the time you are done with the run, the niacin has kicked in and given you a nice “flush” skin is red and blood vessels have dilated. Now you’re ready for the sauna.
Everything done here is monitored. The guy supervising us was a Medical Doctor and he recorded weight going in and was always available supervising and answering any questions.
Five hours a day in a sauna is a LONG time- especially with someone like me who is not crazy about sweating constantly.
You were free to come in and out to prevent from getting overheated and get in the shower to cool off.
I brought reading material, I was doing this!
Reactions
X Ray Radiation
For the first couple of days, nothing significant happened except my skin started getting better.
One day as I am leaving the sauna to cool off, I take a look in the mirror and it looks like I’d been in a fight. Both my eyes had black rings like bruises around them.
I asked the attendant what this was and he looked at them and asked me if I had been exposed to many x-rays. I said that yes, I had been a sick kid and had tons of diagnostic procedures and medicines and stuff.
He said : “Ok, get back in there! You’re just running out x-ray radiation”
Came back out about 20 minutes later and the rings were gone.
Medications
I’m sitting in the sauna and I start getting sleepy. More like “anesthesia count down to ten sleepy”
Again, I was concerned, so I asked attendant what the deal was and he said I was likely detoxing from medicines and drugs I’d taken.
Went back in until it cleared up.
Chlorine
One day there were about 5 of us in the sauna and all of a sudden a strong smell of chlorine started. It keeps getting worse until it was so bad it was burning our eyes. We all exited the sauna thinking there was some sort of chlorine spill or something like that.
The attendant asked: “Has any of you worked as a pool maintenance tech?”
We looked around and one guy raised his hand.
The attendant said “Ok! Everyone dismissed for today except for you!” as he pointed to the Pool Tech guy. “Get back in there!”
I was doing this in the mornings when I had the evening shifts at the restaurant and when I worked days, Id try to make it to the sauna in the evenings.
After about 3 weeks, everything started to taper off and I was done.
I was feeling great and there was something different about everything, I felt like I was more awake and aware. And my skin and complexion were fabulous!
Clear Body, Clear Mind
The Sea Org
At some point, the people in charge routed me to talk to someone one in the Sea Org.
It was a small glass office, like the one you are led into when you are buying a car. I was greeted by a man in an impressive looking uniform like Captain Steubing from the “Love Boat”.
He said they had been watching me and my progress and were impressed with my IQ score. He said I stood out among the other people and compared me to this woman we could see through the glass.
He basically ripped her to shreds in front of me, telling me how her life was in chaos and how she had created all of her chaos and that somehow I was different from her.
They basically offered me a job.
One catch:
I had to sign a contract for a “billion years” and I couldn’t be in debt.
Seeing I was already in debt from some of the previous courses, I didn’t qualify. Also a billion years seemed a bit long.
I thanked him and said I would consider it- I was pretty sure it was a solid no, but I didn’t want to tell him that. I was probably intimidated by the uniform.
Healing with Vitamins
This was not an official class or anything, but during my time there, I saw whenever someone was having issues with their body, they would consult with one of the counselors and they would look into a little book: “Earl Mindell’s Vitamin Bible” or see a chiropractor down the road who was apparently a Scientologist.
I used what little I learned and suggested home remedies to my Wendy’s employees and their families and developed a little side gig offering supplements to anyone willing to listen.
The Bottom Line
I know there is a lot of negative press and negativity in general about Scientology, but be clear about this: Scientology changed my life!
I’m not an active Scientologist, and don’t feel like I want to go back. But it definitely shaped me into the person that I am today.
If there is bias against the church in this article, it’s just the way that it’s run. Running an organization like an MLM encourages bad behavior.
I have moved countless times since those days, and the first piece of forwarded mail is usually from a Scientology Org.
I’m not sure I would have taken the steps to make a drastic change and decide to attend chiropractic school had it not been for my brief time in Scientology,
Love,
-Dan
-
 @ d360efec:14907b5f
2025-05-31 00:36:48
@ d360efec:14907b5f
2025-05-31 00:36:48 -
 @ 81022b27:2b8d0644
2025-05-31 00:25:44
@ 81022b27:2b8d0644
2025-05-31 00:25:44I did my chiropractic studies at Life University in Georgia. When I picked schools, I had no idea about chiropractic philosophies or the politics in chiropractic.
I picked Life for two reasons: It was the closest to home (Miami at the time), and it was the first one to get back to me and tell me I was accepted.
My chiropractor in Miami wanted me to attend Palmer College, but that was in Iowa, and it sounded remote and cold. So, hell no.
I was so excited to start my new life that I crammed a U-Haul with all my junk and headed to Marietta.
Once classes started, someone suggested I join clubs to make friends.
I asked around, and there was this club having an upcoming party. It was Spizz Club. Spizz was short for Spizzerinctum, which meant “chiropractic enthusiasm.”
Well, I had a lot of that—plus, there were some attractive girls in that club.
I showed up at the party, which was at a student’s apartment, and got greeted with a long, uncomfortable hug. Do you remember the old cartoon of Pepe Le Pew and the cat? Well, I was the cat.
I grabbed a beer and started mingling. It was one uncomfortably long hug after another. Some made moaning sounds!
Fucking weirdos.
I got invited to a philosophy class while I was at the party. My social calendar wasn’t exactly overflowing, so I went.
Wow! These people were explaining concepts I’d known deep down my entire life, but I was hearing them out loud for the first time.
Deciding to move 700 miles away and change careers was a rash and selfish decision because I was running away.
Running from:
Failure
A failed marriage
Failure at real estate
Failure at finding something I was good at
Failure at being happy
Failure as a student, ten years after high school with no degree.
Here I am, listening to the speakers, and I realized this was different.
Maybe this was MY thing.
Maybe I could be a chiropractor.
Maybe I could help people.
Maybe I could be proud of myself.
Maybe someone could be proud of me.
That night changed me. The weirdos seemed less weird. I made friends, I found my footing.
Chiropractic college was tough, much tougher than I expected. I had always kind of “skated by,” but now I had to put in hard work because I hadn’t been in school full-time for ten years.
I also had never lived the college life, and apparently I was partying too much. We hit the bars to blow off steam after midterms and finals—turns out, there were a lot midterms and finals.
I almost flunked out one quarter, but there was a lot going on. My 85-year-old dad came to visit and was going to stay with me for a bit, then he passed away suddenly.
I had a lot of guilt from that, thinking that I could have done something different and could have stayed around a little longer. That guilt would resurface years later in a Craniosacral therapy session.
I couldn’t fail at this. This was too important. I went to a Hypnotherapist to see if maybe I could get “programmed” to not flunk out. Apparently, it worked.
Funny thing, I worked hard and time passed. We did it. We graduated and made it through.
Look, those brutal study sessions weren’t easy, and almost flunking out scared the hell out of me. I am thankful that Chiropractic passion stuck with me. That Spizz still gets me through some days.
Live Long and Prosper,
-Danny
-
 @ a3c6f928:d45494fb
2025-05-31 18:52:24
@ a3c6f928:d45494fb
2025-05-31 18:52:24Fear is one of the most powerful forces that shapes our decisions, limits our growth, and holds us back from living fully. Yet, freedom from fear is not about becoming fearless—it's about no longer allowing fear to control us. In uncertain times, reclaiming our power means learning how to face fear, understand it, and ultimately rise above it.
Understanding Fear’s Grip
Fear thrives in the unknown. It whispers worst-case scenarios, paralyzes action, and magnifies our sense of powerlessness. But fear is also a signal. It tells us where growth lies, where change is needed, and where courage must rise.
What Freedom from Fear Looks Like
Taking Action Despite Anxiety: You feel the fear, but you move forward anyway.
Letting Go of Control: You stop trying to predict or perfect every outcome.
Trusting Yourself: You believe in your ability to adapt and respond.
Embracing Uncertainty: You understand that discomfort is part of transformation.
Steps Toward Reclaiming Power
-
Name the Fear: Clarity shrinks fear. When you name what you're afraid of, it loses some of its grip.
-
Breathe Through It: Deep breathing brings you back to the present, where fear often has less power.
-
Challenge the Narrative: Ask: "Is this true? Is this fear protecting me or limiting me?"
-
Take Small Steps: Fear often dissolves when met with action. Start small, but start.
-
Build a Resilient Mindset: Remind yourself of what you've overcome before. You are stronger than your fear.
Why It Matters Now
In a world filled with rapid change, fear can become a default state. But freedom is a choice. A daily one. When you stop letting fear steer your life, you open the door to possibilities, growth, and deeper peace.
“Fear does not stop death. It stops life.”
Choose courage. Claim your power. Walk freely—even through fear.
-
-
 @ 81022b27:2b8d0644
2025-05-30 23:46:46
@ 81022b27:2b8d0644
2025-05-30 23:46:46How the birth of my grandson is making me re-think my own future
I just became a grandfather. My youngest daughter had a baby boy.
I’m thrilled.
And
I’m scared.
Babies are pure potential Infinite possibilities, all sorts of different paths they could take.
They haven’t drank the Kool-Aid, or in fact any Kool-Aid at all, lol
Will he be gregarious and outgoing?
Will he be shy and introverted?
Will he want to be an artist?
An engineer?
Will he be brave or scared?
Will he be like his grandfather, trying to overcompensate in his later life for being afraid of nearly everything in the early part of his life?
I am thrilled. All the grandparents that I have ever met said to me:
Just wait until you have grandkids, its different
And yes, it is different.
I’m not so worried about the how to take care of the baby-all I have to do is love him.
The other day, I was just holding him and was able to stay in “the love state” for the longest time ever.
(The love state is the goal of a meditation that I do-The goal is to stay “in love” feeling for as long as you can.)
I was able to get to this place so easily with him!
He has also taught me to slow down even more. He is not in a hurry to do anything. His job is to eat, poop and grow.
I feel like I get to savor the time I get with him even more than with my own kids.
I’m Scared His mom has had her share of issues.
She is now a single mom trying to navigate all the responsibilities of being a parent.
I didn’t think she was ready, but here we are.
She doesn’t have her mom to help guide her, but I thank god that she has Christi-my girlfriend. She has been such an incredible support for both Audrey and me.
I’m scared mostly because now my own future is uncertain.
I had my future planned out like where i wanted to retire-the things I wanted to do and now this little guy has me re-thinking all my plans about the future.
Here’s to uncertainty!!
Live Long and Prosper 🖖,
-Dan
Links | The Natural Life | The Intuitive Chiropractor
-
 @ 7f6db517:a4931eda
2025-05-31 18:01:26
@ 7f6db517:a4931eda
2025-05-31 18:01:26

"Privacy is necessary for an open society in the electronic age. Privacy is not secrecy. A private matter is something one doesn't want the whole world to know, but a secret matter is something one doesn't want anybody to know. Privacy is the power to selectively reveal oneself to the world." - Eric Hughes, A Cypherpunk's Manifesto, 1993
Privacy is essential to freedom. Without privacy, individuals are unable to make choices free from surveillance and control. Lack of privacy leads to loss of autonomy. When individuals are constantly monitored it limits our ability to express ourselves and take risks. Any decisions we make can result in negative repercussions from those who surveil us. Without the freedom to make choices, individuals cannot truly be free.
Freedom is essential to acquiring and preserving wealth. When individuals are not free to make choices, restrictions and limitations prevent us from economic opportunities. If we are somehow able to acquire wealth in such an environment, lack of freedom can result in direct asset seizure by governments or other malicious entities. At scale, when freedom is compromised, it leads to widespread economic stagnation and poverty. Protecting freedom is essential to economic prosperity.
The connection between privacy, freedom, and wealth is critical. Without privacy, individuals lose the freedom to make choices free from surveillance and control. While lack of freedom prevents individuals from pursuing economic opportunities and makes wealth preservation nearly impossible. No Privacy? No Freedom. No Freedom? No Wealth.
Rights are not granted. They are taken and defended. Rights are often misunderstood as permission to do something by those holding power. However, if someone can give you something, they can inherently take it from you at will. People throughout history have necessarily fought for basic rights, including privacy and freedom. These rights were not given by those in power, but rather demanded and won through struggle. Even after these rights are won, they must be continually defended to ensure that they are not taken away. Rights are not granted - they are earned through struggle and defended through sacrifice.
If you found this post helpful support my work with bitcoin.

-
 @ 81022b27:2b8d0644
2025-05-30 23:11:38
@ 81022b27:2b8d0644
2025-05-30 23:11:38Today is Mother’s Day and throughout the day I’ve been texting my friends who are moms and wishing them well on their day.
A buddy of mine sent me a text and said “Happy Mother’s Day, lol!”
Immediately replied back “same to you!”
Then I started thinking: Did he mean that because I am both father and mother to my daughters? Or was it just typical guy behavior (from my era) joking around calling me gay.
Then I got to thinking about how today is tough for my daughters because they lost their mom to cancer over 4 years ago.
I was driving when i got the text and next thing I know tears are streaming down my face. Maybe it has been tough for me too.
These girls have NEEDED their mom on so many occasions! I could never fill those shoes!
I could have really used her help with our youngest daughter. Maybe she could have said ONE thing to her to make her thing twice about un-aliving herself.
Maybe she could’ve shared my grief, or maybe we could’ve just talked about the situation and how we can get our tortured little girl back from her uncomfortable reality.
Full disclosure: My daughters are all adults, and their mother and I were no longer together. We had been divorced for about 8 years when she passed.
When she passed away, I felt like I couldn’t grieve-after all, I was just the ex-husband.
Took me a while to realize that I had lost a family member too. I don’t think I have completely gotten over it, at least not well. There was a lot of anger and resentment in the divorce and over the years we had tried to be civil, and even had holiday celebrations with EVERYONE attending. Come to find out, the new husband hated that arrangement.
Before she passed, we said we still loved each other and said our goodbyes. I told her I would look after our daughters and made sure her mom was ok. Maybe i’m feeling so emotional because I feel like I’ve made a mess of things here or I’m simply not over it yet.
Happy Mother’s Day!
-
 @ eb0157af:77ab6c55
2025-05-31 18:01:10
@ eb0157af:77ab6c55
2025-05-31 18:01:10The Wall Street financial institution has signed strategic agreements for bitcoin-backed loans with Maple Finance and FalconX.
According to Bloomberg, on May 27 Cantor Fitzgerald officially launched its new division dedicated to Bitcoin lending, announcing the completion of the first transactions of its Bitcoin Financing Business. The Wall Street firm confirmed it has finalized a first round of deals with two crypto sector players: Maple Finance and FalconX.
The company initially plans to make up to $2 billion in financing available to institutional clients.
Brandon Lutnick, President of Cantor Fitzgerald, commented:
“From the start, Cantor recognized the transformative impact that financial services for digital assets would have on the global economy. This milestone highlights how the combination of Cantor’s deep expertise and entrepreneurial spirit creates a distinctive advantage on Wall Street.”
The partnership with Maple Finance is part of Cantor’s broader expansion strategy. Sidney Powell, Co-Founder and CEO of Maple Finance, emphasized how the deal will expand his company’s ability to serve clients looking to access the digital asset market:
“We’re seeing strong and growing demand from institutions seeking to enter the crypto market through trusted and regulated channels.”
Josh Barkhordar, Head of U.S. Sales at FalconX, stated:
“Digital assets have lacked the institutional-grade credit infrastructure essential for healthy capital markets. This collaboration between Cantor and a crypto-native firm is a meaningful step toward building that framework.”
To ensure the security and reliability of its bitcoin-backed financing services, Cantor Fitzgerald has selected Anchorage Digital and Copper.co for custody solutions.
The post Cantor Fitzgerald launches first bitcoin-backed loans appeared first on Atlas21.
-
 @ eb0157af:77ab6c55
2025-05-31 18:01:03
@ eb0157af:77ab6c55
2025-05-31 18:01:03Bitmain’s new device raises the bar for energy efficiency.
During the World Digital Mining Summit, Bitmain introduced its latest bitcoin mining device: the Antminer S23 Hydro. The new miner promises an energy efficiency of 9.5 joules per terahash (J/TH), setting new industry standards.
 ANTMINER S23 Hyd. Newly Launched at WDMS 2025!
ANTMINER S23 Hyd. Newly Launched at WDMS 2025!
 580T 9.5J/T
580T 9.5J/T
Sales Start from May 28th, 9:00AM (EST)
Shipping from Q1, 2026 pic.twitter.com/Kg3VJTt7Rg— BITMAIN (@BITMAINtech) May 27, 2025
According to Bitmain’s presentation, the Antminer S23 Hydro delivers up to 580 TH/s with a power consumption of 5,510 watts.
Scheduled for release in early 2026, the Antminer S23 Hydro marks a major leap forward compared to the first ASIC devices dedicated to mining. To put it in perspective, the first specialized miners launched in 2013 consumed around 1,200 J/TH. Bitmain’s latest device therefore represents a more than 99% improvement in efficiency.
Hashprice and economic challenges
In recent months, the hashprice — the metric measuring mining profitability — has remained relatively low, dropping below $39 per petahash per second during the year. As of now, the hashprice stands at around $55 per petahash per second, according to data from Hashrate Index.
This scenario has pushed several companies in the sector to rethink their expansion strategies. Instead of increasing hashing capacity, many are choosing to upgrade their existing fleets, focusing on efficiency rather than sheer scale.
The introduction of the Antminer S23 Hydro could catalyze a transformation within the mining ecosystem. The gradual replacement of outdated devices with more efficient technology could lead to a significant reduction in the Bitcoin network’s overall energy consumption.
The post Bitmain unveils the Antminer S23 Hydro: unprecedented efficiency appeared first on Atlas21.
-
 @ 81022b27:2b8d0644
2025-05-30 23:02:22
@ 81022b27:2b8d0644
2025-05-30 23:02:22I love my job, I really do. Helping people feel better, getting their bodies back in line-it’s why I show up every day.
But some of my clients?
Some of them act like I’m a magician who can fix years of you ignoring their body in one session.
So, here’s the unfiltered truth—what I’d really like to say when they’re sitting there, complaining, not listening, and interfering with their own healing process. Buckle up, because I’m not holding back.
- There’s nothing wrong with you! Just keep getting adjusted regularly, and for God’s sake, stop going to the medical doctor.
- Stop saying you don’t know what happened.
- You didn’t even try it out before; you’re saying it still hurts. Move around a little!
- No, I’m not doing the fucking ring-dinger that you saw someone do on TikTok.
- No, it’s not because you’re old. It’s because you don’t take care of yourself.
- You’re only 35; you’re not allowed to say you’re old.
- No wonder you don’t listen to your body—you can’t shut up for five seconds to listen to anything!
- Yes, like I’ve told you countless times before-the nervous system controls everything, that’s why you feel great after an adjustment.
- No, I don’t really know why that other chiropractor does the “Flying 7” on all their clients
- You’re the problem.
- No, I’m not making it hurt. It hurts already. I’m trying to fix this.
- Your attitude sucks. No wonder everything hurts.
- You’ve been coming to see me for years, but only when something hurts. The best I can do when you’re hurting is get you out of pain. Imagine if you came in when you’re not in pain—maybe we could really accomplish something then! (Oh, yeah—I do tell them this already!)
- You hate your (job/wife/kids) and you wonder why you’re having health issues?
- It’s not arthritis. Your doctor just wants you to shut up about that pain.
- Tell your doctor that I said he doesn’t know what the hell he is talking about!
- You’d be better off if you flushed all those medications down the toilet and started over.
- How’s that surgery worked out for you? What number surgery is that?
- A little bit of exercise isn’t going to kill you.
I know that makes me sound like i’m grumpy all the time, but that’s just not true. Most of my clients think that I’m just there to fix the pain, but I am freeing, directing life force-allowing it to flow freely throughout the body.
“I suffer for my art”
a client said this quote explains what I feel. I think it’s a bit harsh.
What would you say to YOUR people?
Live Long and prosper!
_Dan from http://theintuitivechiropractor.com
-
 @ 9ca447d2:fbf5a36d
2025-05-31 18:00:47
@ 9ca447d2:fbf5a36d
2025-05-31 18:00:47Trump Media & Technology Group (TMTG), the company behind Truth Social and other Trump-branded digital platforms, is planning to raise $2.5 billion to build one of the largest bitcoin treasuries among public companies.
The deal involves the sale of approximately $1.5 billion in common stock and $1.0 billion in convertible senior secured notes.
According to the company, the offering is expected to close by the end of May, pending standard closing conditions.
Devin Nunes, CEO of Trump Media, said the investment in bitcoin is a big part of the company’s long-term plan.
“We view Bitcoin as an apex instrument of financial freedom,” Nunes said.
“This investment will help defend our Company against harassment and discrimination by financial institutions, which plague many Americans and U.S. firms.”
He added that the bitcoin treasury will be used to create new synergies across the company’s platforms including Truth Social, Truth+, and the upcoming financial tech brand Truth.Fi.
“It’s a big step forward in the company’s plans to evolve into a holding company by acquiring additional profit-generating, crown jewel assets consistent with America First principles,” Nunes said.
The $2.5 billion raise will come from about 50 institutional investors. The $1 billion in convertible notes will have 0% interest and be convertible into shares at a 35% premium.
TMTG’s current liquid assets, including cash and short-term investments, are $759 million as of the end of the first quarter of 2025. With this new funding, the company’s liquid assets will be over $3 billion.
Custody of the bitcoin treasury will be handled by Crypto.com and Anchorage Digital. They will manage and store the digital assets.
Earlier this week The Financial Times reported Trump Media was planning to raise $3 billion for digital assets acquisitions.
The article said the funds would be used to buy bitcoin and other digital assets, and an announcement could come before a major related event in Las Vegas.
Related: Bitcoin 2025 Conference Kicks off in Las Vegas Today
Trump Media denied the FT report. In a statement, the company said, “Apparently the Financial Times has dumb writers listening to even dumber sources.”
There was no further comment. However, the official $2.5 billion figure, which was announced shortly after by Trump Media through a press release, aligns with its actual filing and investor communication.
Trump Media’s official announcement
This comes at a time when the Trump family and political allies are showing renewed interest in Bitcoin.
President Donald Trump who is now back in office since the 2025 election, has said he wants to make the U.S. the “crypto capital of the world.”
Trump Media is also working on retail bitcoin investment products including ETFs aligned with America First policies.
These products will make bitcoin more accessible to retail investors and support pro-Trump financial initiatives.
But not everyone is happy.
Democratic Senator Elizabeth Warren recently expressed concerns about Trump Media’s Bitcoin plans. She asked U.S. regulators to clarify their oversight of digital-asset ETFs, warning of investor risk.
Industry insiders are comparing Trump Media’s plans to Strategy (MSTR) which has built a multi-billion dollar bitcoin treasury over the last year. They used stock and bond sales to fund their bitcoin purchases.
-
 @ c9badfea:610f861a
2025-05-30 22:47:09
@ c9badfea:610f861a
2025-05-30 22:47:09- Install Saber (it's free and open source)
- Open the app
- Tap + and select New Note
- Explore the tools in the upper toolbar:
- Tap ⬅️ to go back to the main screen
- Tap ⋮ to change the background (e.g. grid, college-ruled, lined, or custom image/PDF)
- Tap 📄 to insert a new page
- Tap 🪟 to view all pages
- Explore the tools in the bottom toolbar:
- Tap the selected pen tool ✒️ to adjust its settings (e.g. size and behavior)
- Tap ✏️ to use the pencil tool
- Tap 🖊️ to use the highlighter
- Tap ⚪️ to change the current color
- Tap 👆 to enter move mode
- Tap ⬅️ to undo, or ➡️ to redo
- Tap ⠪ to export your drawing as a PDF
- Start creating handwritten notes and drawings!
-
 @ 84b0c46a:417782f5
2025-05-30 22:17:19
@ 84b0c46a:417782f5
2025-05-30 22:17:195/24 nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsq3wamnwvaz7tmwdaehgu3wd968gctwd4hjumt9dcqs6amnwvaz7tmev9382tndv5qjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3zamnwvaz7tmwveex2mrp0yhxzursqyfhwumn8ghj7am0wshxummnw3ezumn9wsqzqxk47yl7vwqu0yrv4fljymp4m2vf0gtesmel4cgg638h82rt4hdn6yyejn
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqs8msrjypjuvhwaarkq72739wl5rewl49vx0ku6s3u3y03anmau5dscqjj0l
nostr:nevent1qvzqqqqqqypzqnza2du6qe3nnjy0dcgpu0kmr7awunk78m4rtl7x78rxfvay8qlwqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqs0fzqwr2xt044zglcwcj3dnnxuk0vlcmwcw0sdzw7yhzfsn009ttss5pv6k
こていたんさんのアイコン

5/25 nostr:nevent1qvzqqqqqqypzqnza2du6qe3nnjy0dcgpu0kmr7awunk78m4rtl7x78rxfvay8qlwqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqs0ku3qs4zskmclvtqm0lt707jwn2ylz9v2xj2qakznyp86j4p7fzqd85kfq
nostr:nevent1qvzqqqqqqypzqnza2du6qe3nnjy0dcgpu0kmr7awunk78m4rtl7x78rxfvay8qlwqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqs8054fh3l8qtngdfpdwxfl84r36ju3f65zmhjvjy67y7gjj0mhjks2c7w80
nostr:nevent1qvzqqqqqqypzqnza2du6qe3nnjy0dcgpu0kmr7awunk78m4rtl7x78rxfvay8qlwqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqsr8nycy3gvjfdn3rqjc49j2gwhwjdhu6d5ms6uxx7y44kzf0u2ftsc8r3c3
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsq3wamnwvaz7tmwdaehgu3wd968gctwd4hjumt9dcqs6amnwvaz7tmev9382tndv5qjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3zamnwvaz7tmwveex2mrp0yhxzursqyfhwumn8ghj7am0wshxummnw3ezumn9wsqzpmcs4xzsusg9s6cn2acasjsam2pwmf6m8h0z08kfca56f8aqwyf2fjwv7w
nostr:nevent1qvzqqqqqqypzphu0pfjqc0lap83f8xv6e73en5zhfjzsrlx6hnk22pewugzhmpa9qqsvh305tpg0xesw6n4eu2kmumgx0mcv0cn64zznyydzpezzsazdugcyrfqm0
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsq3wamnwvaz7tmwdaehgu3wd968gctwd4hjumt9dcqs6amnwvaz7tmev9382tndv5qjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3zamnwvaz7tmwveex2mrp0yhxzursqyfhwumn8ghj7am0wshxummnw3ezumn9wsqzq2aq2l9cq04ygjjk4tq8zfjmuezvckcav8cfqv6z745744nfd2nqlxpq04
nostr:nevent1qvzqqqqqqypzphu0pfjqc0lap83f8xv6e73en5zhfjzsrlx6hnk22pewugzhmpa9qqs05f8xz5uahsdzceq9d0mp860hck3ash8s3ssp3paxxu620tw4ufssk6ntz
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsq3wamnwvaz7tmwdaehgu3wd968gctwd4hjumt9dcqs6amnwvaz7tmev9382tndv5qjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3zamnwvaz7tmwveex2mrp0yhxzursqyfhwumn8ghj7am0wshxummnw3ezumn9wsqzppyeyt0xt0fps85hxv4evdhgy35m9zfzhsqtnq93rsy4arnw3n853sc0u7
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsq3wamnwvaz7tmwdaehgu3wd968gctwd4hjumt9dcqs6amnwvaz7tmev9382tndv5qjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3zamnwvaz7tmwveex2mrp0yhxzursqyfhwumn8ghj7am0wshxummnw3ezumn9wsqzq7emnt7e67h5cygnyvz922x2m4f3x30hpvns3yxls2v4t2uy0vrc6060ek
nostr:nevent1qvzqqqqqqypzplnr7nuypscwtkhtmqaakpyw4cqgtqm5klcyc6qqcmzf6296zrcfqqspu5ny2laxuqtrryffsf455fldpnluw5ladrq32cfveu6mjjgmuxsynheu3
nostr:nevent1qvzqqqqqqypzphla8l7r42mzjvdgevy0pg4y3rd8gupaprgaa7fcdzhrpaddu7lpqqsyhjuxzjkgzp5d8xt8wg8vzekcnaw6ud7htrnqppy2xmpeajrhqncs0rv4c
nostr:nevent1qvzqqqqqqypzphu0pfjqc0lap83f8xv6e73en5zhfjzsrlx6hnk22pewugzhmpa9qqswm6wxhc3h426py80vjm9jj03j8vhvrnhwmalunlxm0pq5xvxqs5qpr2kq7
nostr:nevent1qvzqqqqqqypzplnr7nuypscwtkhtmqaakpyw4cqgtqm5klcyc6qqcmzf6296zrcfqqsgehqf8cl5sp0wfw0fzl982lvhmy9j23vpus70wddtytkr4qygxlchprwv6
nostr:nevent1qvzqqqqqqypzqnza2du6qe3nnjy0dcgpu0kmr7awunk78m4rtl7x78rxfvay8qlwqqsvkrvnh8lzw4rfx87278rwxp2uymej2alputzn2nl525p85c3703cmrgkfn
nostr:nevent1qvzqqqqqqypzqnza2du6qe3nnjy0dcgpu0kmr7awunk78m4rtl7x78rxfvay8qlwqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpz9mhxue69uhkuenjv4kxz7fwv9c8qqgawaehxw309aex2mrp0yhxummnw3ezuamfwfjkgmn9wshx5uqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqsf2u5larth503yh236mhssn2tes4shvawnv4kufzh3889cr9dt4wculcv6w
nostr:nevent1qvzqqqqqqypzqnza2du6qe3nnjy0dcgpu0kmr7awunk78m4rtl7x78rxfvay8qlwqqspnfvau4ylywwk2f7nrm68ue6c86j9p4y0cu4parfwapun0nsw97sad9jwf
nostr:nevent1qvzqqqqqqypzplnr7nuypscwtkhtmqaakpyw4cqgtqm5klcyc6qqcmzf6296zrcfqqs2y7lha9uy30wwdt9yn47s6krqv3e8duj6nqrl27e2s6dl465xssg5gt4ue
nostr:nevent1qvzqqqqqqypzplnr7nuypscwtkhtmqaakpyw4cqgtqm5klcyc6qqcmzf6296zrcfqqsyf8peg4zggp858zfha6dt4mjxss4nhc3k4szqynh0u53j22asx6sdhpfwc
nostr:nevent1qvzqqqqqqypzphla8l7r42mzjvdgevy0pg4y3rd8gupaprgaa7fcdzhrpaddu7lpqqsr0s5ger5l8aapw63yyve5sne5rge0ractks4v4l0yn3ezcvq3f4s8wthq8
nostr:nevent1qvzqqqqqqypzphu0pfjqc0lap83f8xv6e73en5zhfjzsrlx6hnk22pewugzhmpa9qqs93gfz3kskw2lcxadwu3dvanyq7xstaj39vfqmppnng0nvz5gjm8syq9p8p
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsq3wamnwvaz7tmwdaehgu3wd968gctwd4hjumt9dcqs6amnwvaz7tmev9382tndv5qjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3zamnwvaz7tmwveex2mrp0yhxzursqyfhwumn8ghj7am0wshxummnw3ezumn9wsqzp5tlgnw663dswldulvnvgczfr08aflg35cu2syaaddmppvjytvn09tc679
nostr:nevent1qvzqqqqqqypzpe30ylfgzj39zuwyvmfdwcf26xsxdkcnv26wykwmtsrkl8nty89hqqswq489vn7h9hz2q0w60m05wn5xuqd0vvnqcxwxkewmh7h72yjtrrc6yulf2
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsq3wamnwvaz7tmwdaehgu3wd968gctwd4hjumt9dcqs6amnwvaz7tmev9382tndv5qjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3zamnwvaz7tmwveex2mrp0yhxzursqyfhwumn8ghj7am0wshxummnw3ezumn9wsqzqzcyhx8d350shzfczewxkhxemqknfeu5z8kj0arrur9wn726k5hjayfwl6
nostr:nevent1qvzqqqqqqypzplnr7nuypscwtkhtmqaakpyw4cqgtqm5klcyc6qqcmzf6296zrcfqqsrnvmc5r2rs6jx7z8v3gvnzpkfsc3vqqxg0ygnk8wn3jmulzq887q07smq2
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsq3wamnwvaz7tmwdaehgu3wd968gctwd4hjumt9dcqs6amnwvaz7tmev9382tndv5qjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3zamnwvaz7tmwveex2mrp0yhxzursqyfhwumn8ghj7am0wshxummnw3ezumn9wsqzqzk0lg9aq8yzg0m4dcqp5a0a468c3jmtcw058hvckt6yj0nlnl0mqfgav7
nostr:nevent1qvzqqqqqqypzpu89j3vdtkj0cec9mzs4hcmetfq5a9d6fw5smezlpyqhme90uq27qqsf4js8wu9zlp74kj5erkwsq9rvhj0d6xmynevt4tsa766nsvja04gsrfaz5
nostr:nevent1qvzqqqqqqypzpu89j3vdtkj0cec9mzs4hcmetfq5a9d6fw5smezlpyqhme90uq27qqsqky2uqkzu60f3tkcttx59q675sxmd9ypyppnd50ukmhlx3qwrqfgmmxmjh
nostr:nevent1qvzqqqqqqypzq6lj6gusf8gqyqgj2s0vzjyw3fgj9ufhqdefn8fsvljn6vdjq69hqqsvtkn6rkgmttjzzm3nn58d85eve5834pnamzhy0u4p584jger8uvgttcqhe
nostr:nevent1qvzqqqqqqypzq6mwr88y02ghe0sn5elwkszn4xesreuwexg5z0n42j2npz8dvtfmqqstua4ssqq9wejs4kjvjjs0azlzjftt6qgh8l80msn2zd8k0nxw5ccnv7p2w
nostr:nevent1qvzqqqqqqypzq6lj6gusf8gqyqgj2s0vzjyw3fgj9ufhqdefn8fsvljn6vdjq69hqqsywfl8gfpxkynq54ju27aa5rqd0mjz9lx2haqzaszelm3vhlfa5mc3n0hkj
nostr:nevent1qvzqqqqqqypzq6mwr88y02ghe0sn5elwkszn4xesreuwexg5z0n42j2npz8dvtfmqqs86az8q8zd9wevcnnw6rcrg6edc3jfzff6sza572a25yywr477s9g4yfrq0
nostr:nevent1qvzqqqqqqypzprzeywf3jcmljlsq0kks66q7vh8rtvdvuvemv20z6vlegewpxfsgqqsq47mwcs7kpylrqwkyec76839nwrk09cx33s3lwdv88e34fkx4hdqf2sa8r
nostr:nevent1qvzqqqqqqypzq6mwr88y02ghe0sn5elwkszn4xesreuwexg5z0n42j2npz8dvtfmqqsxykjsdzg9nnaweajftl4g33amcdh4wjmdq3y30w6fu555e3xpm2c2n4wah
nostr:nevent1qvzqqqqqqypzprzeywf3jcmljlsq0kks66q7vh8rtvdvuvemv20z6vlegewpxfsgqqs9cgpau6l4rfmhkwav4jsjhxjwpgehyhuw3c39q46v23q75qdjfssp3jr0k
nostr:nevent1qvzqqqqqqypzq6mwr88y02ghe0sn5elwkszn4xesreuwexg5z0n42j2npz8dvtfmqqsxrzydard7yz0cp79uk30u9g7wv0nq9sfw36e7f5tefd7z7vfezvsq7kqy4
nostr:nevent1qvzqqqqqqypzpvgsp0c85zgh8rcf2683v7s058fzspcqt0em5ednf8z9c3q5qy5fqqsghpetrx0lkxd4d79vk90h66vln5pd9lklh64sk8qa75a453g20jc3j3q9y
nostr:nevent1qvzqqqqqqypzpvgsp0c85zgh8rcf2683v7s058fzspcqt0em5ednf8z9c3q5qy5fqqsxrmm05rgdzdpthuh9zmk7jf9jmhu0jfty6kf5v8s2f8252683drgf6m79g
nostr:nevent1qvzqqqqqqypzpdc866l8lkwvncdwaqlgrsueg9tvlnm5mm2mpyg3jv8aam445rpqqqswcp6exyy0f9sgpypzlc4dx40equyxeyhwskzgeks78r9rp54w7hc05v93n
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqstvk6q4xwtd7evpzggkcngqhlk5gktme0sj6235nuf0axxxngktpc88gqd7
nostr:nevent1qvzqqqqqqypzq6lj6gusf8gqyqgj2s0vzjyw3fgj9ufhqdefn8fsvljn6vdjq69hqqswfythwf02x6ekjpfdrucd6cx6su2t3uq3td45d4v0xrucfphy38cn0mmw2
nostr:nevent1qvzqqqqqqypzqu3j6ujahw4eezqm9gn2lz8av5waj9ek9fcwclfsrq5kc63zla2wqqsxpddg7lf4yqmpeg9z82flqa8fzpfcwmn4qfluvy95p03l8pjud2cfjx43u
nostr:nevent1qvzqqqqqqypzpq4np5cygstsu65vsx0ggphrv23kj4z553sh39xwyur08pqvdsqrqqsxzm8fx8aaprn533e0c44edf60lw73a6z5vzzumzd6edttgl0uawgn4kgp2
nostr:nevent1qvzqqqqqqypzpq4np5cygstsu65vsx0ggphrv23kj4z553sh39xwyur08pqvdsqrqqs88tvfyn6h8ls3h2994nmpykj2zc2l90vqwj8epzwfjnz2dy0mcjqyhsms5
nostr:nevent1qvzqqqqqqypzqt7zjsv2gxscw5l9d6k8j5agctlm6rr3rz3c6mar4eqmn69uu6c2qqsdavnxvhtlnkamt8cap09aan7mu2z364ltmeh8u747nvvj60h5jcsyf3hjz
nostr:nevent1qvzqqqqqqypzq6mwr88y02ghe0sn5elwkszn4xesreuwexg5z0n42j2npz8dvtfmqqsq86a0sr2h0p4qfesv00ztyqpdw545rsnq2nmq9quafahwxp8elhckws7wh
nostr:nevent1qvzqqqqqqypzqf4m96ldd32j6ecvsp9s6e2jv7euvc4jrcpx6mjg4jf6vpc9xz2cqqsqp3ugj5y8epkjyh62cfnm4gen27nhq055668glhgzjm87p64ep5sgqgawl
nostr:nevent1qvzqqqqqqypzqcmflwpta32zy6lsnwektdhs6ud3d3ql2mn7ml20jl0z87wr9qw6qqsfagdtz0ldem963wwelh2lc8d4qkuxlmfq0j62qwt6lrkvd8v36squ8d4k8
nostr:nevent1qvzqqqqqqypzpvj726mjcemd4uhpyutaykvsm0y54n5fzte5mhgtv46vhg8lunhfqqsgrrj849xmqpvdx6h9554gnetguxzz2ad8fqvpmvhm0zy85m4pl8swnyg5s
nostr:nevent1qvzqqqqqqypzq6lj6gusf8gqyqgj2s0vzjyw3fgj9ufhqdefn8fsvljn6vdjq69hqqs2n5mz6j5yft327mld352hazjwfrla3w92gpzuvmpgffjttsqyq6qgu5dwe
nostr:nevent1qvzqqqqqqypzq6mwr88y02ghe0sn5elwkszn4xesreuwexg5z0n42j2npz8dvtfmqqsz6wr7cnewt7t7vt4t2c28jtmppu832vs2syacv0sy8lcn28075ss277lty
nostr:nevent1qvzqqqqqqypzplnr7nuypscwtkhtmqaakpyw4cqgtqm5klcyc6qqcmzf6296zrcfqqsdrt35drfatmhl795f36em4yy7gsaasr3xkvgmdwswr7f87rcrmuc7z7kf8
nostr:nevent1qvzqqqqqqypzpvj726mjcemd4uhpyutaykvsm0y54n5fzte5mhgtv46vhg8lunhfqqsrl6c8gu74vkwa5ahlsycxjx40a3gzrx6uxm0qmpa35nrnd7ntysc4d6llh
nostr:nevent1qvzqqqqqqypzqwyu5j2hjyd3ycyn7s4q4yrcv52mtyc3m3dfg26qf4lpdutjs7pgqqsq945chuafedqk95uglwl3xumcuvjcdgz66ykd840hfsa4xpp6dgqa9vsft
nostr:nevent1qvzqqqqqqypzqf4m96ldd32j6ecvsp9s6e2jv7euvc4jrcpx6mjg4jf6vpc9xz2cqqsynxwgyy8nsu2r3dx8f37hww6keemkhh962ghq45umlxz2khemytgzv08n4
nostr:nevent1qvzqqqqqqypzqyrx5pw3ga88uye6jusg5h93w75uq8jts8c0zsms44vlfg9yw45pqyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqqsdex6xy8kq8l64c0gq606yguaqn8fxrsyl67m6ld5cctxxwe79jpcsmxhh6
nostr:nevent1qvzqqqqqqypzpj7tpc9kqtkr4xklc62kh7lru27pydu7uyals5zuu303eqca9ef2qyt8wumn8ghj7um9v9exx6pwdehhxtn5dajxz7gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqpq7gkdqqukguh3r79yfxcy9tsxpx348wqys6q8v3njfyqj4vga727sh9cfpt
5/26 nostr:nevent1qvzqqqqqqypzpq4np5cygstsu65vsx0ggphrv23kj4z553sh39xwyur08pqvdsqrqyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqqspk6e9e9wph23lt7xumuuu90rayzcswp3gz96c3w25raq9r9agw5cnfgve5
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqqsfnspcp9yqu989mnnpwj9tphrrj05268vjkwwmx7jcus4mn7erqngl94f9y
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqqs84x0ws9myccv29kf99jkuwqh8rj9ws23kn5s9yyl0scz67m97z2g7rq7z5
nostr:nevent1qvzqqqqqqypzphu0pfjqc0lap83f8xv6e73en5zhfjzsrlx6hnk22pewugzhmpa9qyg8wumn8ghj7mn0wd68ytnhd9hx2qgkwaehxw309aek2ctjvd5zumn0wvh8gmmyv9usz9nhwden5te0wfjkccte9ehx7um5wghxyctwvsqzqk76agahvd3t5lutvkuj69pccwrurey3fws0kjnrsemwlx9ntvwukkjfk6
nostr:nevent1qvzqqqqqqypzqrqykrtju88xhdq0an0vdnccdfvrmqr8da0n8p5fs8reaczhxmpeqyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqqyz3twtpw08v554hph0j6wpk598rd677pfa460y2pcdd2064aaevjwe74erq
nostr:nevent1qvzqqqqqqypzqx34k480waf274x2e0hd7re5nceq7z3wu5q59zp3xnp7uvv8nnn3qyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqqyp59rw9n380w5kvdth9qefc28xsrt99l33tmfgvq02kut3dnepk6zr7ng2t
nostr:nevent1qvzqqqqqqypzplnr7nuypscwtkhtmqaakpyw4cqgtqm5klcyc6qqcmzf6296zrcfqyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqqyq8q2qcfne76j4c9y794xz9g5unuxhf98deh3mupmnwpn33mwlxhzmxuefq
nostr:nevent1qvzqqqqqqypzpmzzcaj5rzeah8y940ln4z855wa72af4a6aac4zjypql55egcpsqqyt8wumn8ghj7um9v9exx6pwdehhxtn5dajxz7gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqpqscswkz2s03r6yhz0yz40h634nkf2j2vpkvqd3vk5rl7lgaj9unns7qz3ms
nostr:nevent1qvzqqqqqqypzprfe5ru6zvakym6hq5eycwdr2vx2q8awzaaw8wu9mq4wlek8yhenqyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqqyqr5njtg8f5xdm52p3k9mugfqk3zuc0ycsxaj6j5uf4amkrdt3ymq8kuyhj
nostr:nevent1qvzqqqqqqypzq0363fpyt2sgytq9p3pduzch6rlrp4z8e6swvzr72km83pg76qmnqyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqqyrj0xgrrwr2meuurst5lsqn744wt6uxhfmyralknm7cl57lsapcrkunqcnn
nostr:nevent1qvzqqqqqqypzqf57dat64x3qpjq5u6ucwgvpnh0q8r9xpspepwrmvkxnqz4k6rgyqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqqyq2yn3cjlmns8ttaam8ev2rn3csm26wnwhe3ccvk8s5e8x6ejyykql8em9d
nostr:nevent1qvzqqqqqqypzqx34k480waf274x2e0hd7re5nceq7z3wu5q59zp3xnp7uvv8nnn3qyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqqyqu2p8vtuwvxmzqh7mlq2lp3xel8z9l0xg5e3hyxjlwamsm0p3pvq9qh4d0
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqsr9tpqqfeke4qt9xlg6m34446dpd844myrw9cc4tmqcrf3xfp9yqsxa05hf
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqqypyaj8uyahtgwf5evyk5deqx90udyrmxff99gqskfcl3eqh0mgmw6nlnlud
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqsdpy08r0758lz0js2zpk5fe5mpqxd349mdqxg2vk3y7azlme2ysqqm8uy75
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqs8s0r7c908mmhxk090zvmlajfgswwcnmwxj34dtqjpyxry0tmumagcmm29s
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqs0x6pgm96r70y8836l0d5ajj6nrlq6p5fz06wdu26fkpg3gznctscf5ggxn
5/27 nostr:nevent1qvzqqqqqqypzqxlwemj4760tc2ysgqmqdu5tt68th2er6gn8xrsjkjlhvtff6gtzqyt8wumn8ghj7um9v9exx6pwdehhxtn5dajxz7gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqpqlq0lp52xg7uv4wwzuqy9yhtmcpy5v8ad8v7ft9xcwkdncd97h66q0wmawu
nostr:nevent1qvzqqqqqqypzpq4np5cygstsu65vsx0ggphrv23kj4z553sh39xwyur08pqvdsqrqyt8wumn8ghj7um9v9exx6pwdehhxtn5dajxz7gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqpqpt2wncdxkptxyhj025vd53vjpxz3hjs452px7y8g6gzsxmnfw2fsp2rv0k
KAZもさん nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsq3wamnwvaz7tmwdaehgu3wd968gctwd4hjumt9dcqs6amnwvaz7tmev9382tndv5qjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3zamnwvaz7tmwveex2mrp0yhxzursqyfhwumn8ghj7am0wshxummnw3ezumn9wsqzpk3nll8rr3sj6adsrfrlgjpj4cyn2sg9rmlz9m2djwk5zp2ku80czfr460
5/28 kaijiさん nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsqjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3zamnwvaz7tmwveex2mrp0yhxzursqythwumn8ghj7mn0wd68ytnfw36xzmndduhx6etwqyfhwumn8ghj7am0wshxummnw3ezumn9wsqzpt7w33qv7tlywj0wphremkdft6dpnv3z8mvw0t2pdxcgvlzw6sathjmz0v
マルフォイ nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqyw8wumn8ghj7umjw3ex2mrp0yhxxttnw3jkcmrpwghxuet5qyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqs8r0frcfwqkgpefhd0knjurekna8ztnq69432f3k00wccd0vcrl5c6qr3gh
5/29 nostr:nevent1qvzqqqqqqypzqrec47eremps2u8wvnu6f2sfjg5njhkrxuw9l6r8uzwfzy2gqq2aqyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqqsp2c6xh22lfj2ccy95lqu584hfpfz0ds7w2llnf4sv2qs445yqcgqmgwq57
nostr:nevent1qvzqqqqqqypzphu0pfjqc0lap83f8xv6e73en5zhfjzsrlx6hnk22pewugzhmpa9qyt8wumn8ghj7um9v9exx6pwdehhxtn5dajxz7gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqpqt43r3wtjkr5ezxay6dh7jq94nelduvsk07w5ufxrver5f6jfggksakz9e8
nostr:nevent1qvzqqqqqqypzqyqmxrhg3sn6z00x30mu3srrdr4ru05rweq4jhqcvat805v2g6j9qyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqqjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qzymhwden5te0wahhgtnwdaehgu3wdejhgqpqn6n7xrrmk40ucmh9m5ktae58xjqz6h7epj6mcffpcmuhgpysvv6snh5vf5
nostr:nevent1qvzqqqqqqypzpk28l9nyyf4av8f8j8jhh8k60mt2sc643ux2td3n547kvk4lrsglqyt8wumn8ghj7um9v9exx6pwdehhxtn5dajxz7gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqpq6gv8avhe93ypvypd66rmn34760s3sldj3x2cz5w4yu2xy9z8tt2qadd7kl
nostr:nevent1qvzqqqqqqypzpk28l9nyyf4av8f8j8jhh8k60mt2sc643ux2td3n547kvk4lrsglqyt8wumn8ghj7um9v9exx6pwdehhxtn5dajxz7gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqpqn2pfqkgcfk3cdhtvkqqlfycsy2j2xe6c6jz8gzfxlnddnq8jq6vqecuvwy
nostr:nevent1qvzqqqqqqypzpug7j8zm7jr0hjunpkpgz8gzdvgn5h8mw77g4wg58xnmsav6pvz2qqspds662qvcpz995r5rx39wzncyzcx3q5zfpe8ztgx4zdwy9znvu9cv28mya
5/30 nostr:nevent1qvzqqqqqqypzp54kkqfyshkxm078mpzygmfxpqfq6fwu2njry424strce6dmvhwyqqstc5jak2vax4uejyrmu2td3w0spv6k4mds9sfwqtvmh0hwaa3eststwmtzt
nostr:nevent1qvzqqqqqqypzp54kkqfyshkxm078mpzygmfxpqfq6fwu2njry424strce6dmvhwyqqs9v75spmgrxngfn805q5d9fsqa562a8240xkr6z3kvkszkra9plvsgm2qw4
nostr:nevent1qvzqqqqqqypzp62ezs5gz04adyt8xmyghw2ej3yk7eradlnknmuysd5ha2udqnfdqyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqqjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqswy0smsrukck33hfhavscvs68pg9m4d859np8pkgvrc49kwjzr4ac0cwhea
nostr:nevent1qvzqqqqqqypzpc9ge0t4a0lya7a63fjl749mgdv9ssz0dhqt5jnytz3y6lmy9525qyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqqjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qzymhwden5te0wahhgtnwdaehgu3wdejhgqpqeunx8pj5hc255wqu4ea9cgz6cptjvcx6jk8yfd8u55smjl6y8z9sepz5xt
nostr:nevent1qvzqqqqqqypzp62ezs5gz04adyt8xmyghw2ej3yk7eradlnknmuysd5ha2udqnfdqyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqqjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqst07pk8637lvs5vjnp00quzhcsx8ghran90nsm6sycnm3a626lnqqw0py8w
nostr:nevent1qvzqqqqqqypzp62ezs5gz04adyt8xmyghw2ej3yk7eradlnknmuysd5ha2udqnfdqyxhwumn8ghj77tpvf6jumt9qyw8wumn8ghj7umjw3ex2mrp0yhxxttnw3jkcmrpwghxuet5qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqsya6zp38496uetw83txlr294nttk6myuc0n7hxrl2d7jma2rvvcesnz2naf
nostr:nevent1qvzqqqqqqypzqlwpvac39uz74ay4g7qx2sa3cqrvuvjhy7899vwf40lkxfcw6uz0qyxhwumn8ghj77tpvf6jumt9qyghwumn8ghj7mnxwfjkccte9eshquqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqsz6zj33hmynuhq20nscntjc3lhx4hl5azhf0cx38g5nmhpjezuttqpdr0ht
nostr:nevent1qvzqqqqqqypzqhh27290rxjexusv8as357lpxy423nnznzfh4fjkq22k94tvqcpaqyxhwumn8ghj77tpvf6jumt9qyghwumn8ghj7u3wddhk56tjvyhxjmcqyrfpj9ym2apvgjpmcy4qjq2ks89uzuwm27d9jpj9flk7438sm23kqjetapu
nostr:nevent1qvzqqqqqqypzpuy2jdcyy3vqr4l9ucmhlpuwnsl29h7lwsvaez00eu4467jlvf7eqythwumn8ghj7mn0wd68ytnfw36xzmndduhx6etwqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqsphe28h7t6jmwlvpd90q38xkde87hmy9q24u90sgeaz6hu6nfsazqxkfw56
-
 @ a8d1560d:3fec7a08
2025-05-30 22:16:48
@ a8d1560d:3fec7a08
2025-05-30 22:16:48NIP-XX
Documentation and Wikis with Spaces and Format Declaration
draftoptionalSummary
This NIP introduces a system for collaborative documentation and wikis on Nostr. It improves upon earlier efforts by adding namespace-like Spaces, explicit content format declaration, and clearer separation of article types, including redirects and merge requests.
Motivation
Previous approaches to wiki-style collaborative content on Nostr had two key limitations:
- Format instability – No declared format per event led to breaking changes (e.g. a shift from Markdown to Asciidoc).
- Lack of namespace separation – All articles existed in a global space, causing confusion and collision between unrelated projects.
This NIP addresses both by introducing:
- Spaces – individually defined wikis or documentation sets.
- Explicit per-article format declaration.
- Dedicated event kinds for articles, redirects, merge requests, and space metadata.
Specification
kind: 31055– Space DefinitionDefines a project namespace for articles.
Tags: -
["name", "<space title>"]-["slug", "<short identifier>"]-["description", "<optional description>"]-["language", "<ISO language code>"]-["license", "<license text or SPDX ID>"]Content: (optional) full description or README for the space.
kind: 31056– ArticleAn article in a specific format belonging to a defined space.
Tags: -
["space", "<slug>"]-["title", "<article title>"]-["format", "markdown" | "asciidoc" | "wikitext" | "html"]-["format-version", "<format version>"](optional) -["prev", "<event-id>"](optional) -["summary", "<short change summary>"](optional)Content: full body of the article in the declared format.
kind: 31057– RedirectRedirects from one article title to another within the same space.
Tags: -
["space", "<slug>"]-["from", "<old title>"]-["to", "<new title>"]Content: empty.
kind: 31058– Merge RequestProposes a revision to an article without directly altering the original.
Tags: -
["space", "<slug>"]-["title", "<article title>"]-["base", "<event-id>"]-["format", "<format>"]-["comment", "<short summary>"](optional)Content: proposed article content.
Format Guidelines
Currently allowed formats: -
markdown-asciidoc-wikitext-htmlClients MUST ignore formats they do not support. Clients MAY apply stricter formatting rules.
Client Behavior
Clients: - MUST render only supported formats. - MUST treat
spaceas a case-sensitive namespace. - SHOULD allow filtering, browsing and searching within Spaces. - SHOULD support revision tracking viaprev. - MAY support diff/merge tooling forkind: 31058.
Examples
Space Definition
json { "kind": 31055, "tags": [ ["name", "Bitcoin Docs"], ["slug", "btc-docs"], ["description", "Developer documentation for Bitcoin tools"], ["language", "en"], ["license", "MIT"] ], "content": "Welcome to the Bitcoin Docs Space." }Markdown Article
json { "kind": 31056, "tags": [ ["space", "btc-docs"], ["title", "Installation Guide"], ["format", "markdown"] ], "content": "# Installation\n\nFollow these steps to install the software..." }Asciidoc Article
json { "kind": 31056, "tags": [ ["space", "btc-docs"], ["title", "RPC Reference"], ["format", "asciidoc"] ], "content": "= RPC Reference\n\nThis section describes JSON-RPC calls." }Wikitext Article
json { "kind": 31056, "tags": [ ["space", "btc-docs"], ["title", "Block Structure"], ["format", "wikitext"] ], "content": "== Block Structure ==\n\nThe structure of a Bitcoin block is..." }Redirect
json { "kind": 31057, "tags": [ ["space", "btc-docs"], ["from", "Getting Started"], ["to", "Installation Guide"] ], "content": "" }Merge Request
json { "kind": 31058, "tags": [ ["space", "btc-docs"], ["title", "Installation Guide"], ["base", "d72fa1..."], ["format", "markdown"], ["comment", "Added step for testnet"] ], "content": "# Installation\n\nNow includes setup instructions for testnet users." }
Acknowledgements
This proposal builds on earlier ideas for decentralized wikis and documentation within Nostr, while solving common issues related to format instability and lack of project separation.
-
 @ bf47c19e:c3d2573b
2025-05-30 21:48:21
@ bf47c19e:c3d2573b
2025-05-30 21:48:21Originalni tekst na novimagazin.rs. / Autor: Mijat Lakićević

Razgovarao: Mijat Lakićević
Do januara ove godine Lazar Stojković je radio na UC Berkeley School of Information na poziciji asistenta Mortena Hansena, jednog od najistaknutijih profesora menadžmenta u svetu. U martu se, međutim, odlučuje da napusti akademsku karijeru i zauzima poziciju glavnog dizajnera proizvoda u jednom novom start-apu u San Francisku. Ono što za sada o tome može da kaže jeste da je okupljen “fantastičan tim” (o čemu, recimo, govori podatak da je “prethodna kompanija koju je osnovao naš CEO 2013. godine prodata za preko 200 miliona dolara”) u koji su investirale neke od najznačajnijih američkih “venture capital” firmi: Founder Collective (investirali u Uber, BuzzFeed, Periscope, IFTTT, Venmo, Vimeo, itd), General Catalyst (investirali u Airbnb, Snapchat, itd.); Formation 8 (investirali u Oculus). Pored toga, međutim, naš sagovornik nije izgubio sve veze sa Srbijom, naprotiv; trenutno kao mentor u beogradskom ICT Habu, ali i na druge načine, pomaže razvoj start-ap kompanija i povezivanje naše tehnološke zajednice sa Silicijumskom dolinom.
U SAD ima mnogo naših ljudi, naročito u oblasti visokih tehnologija, ali povratne sprege nema. Dačić je pre dve godine bio u SAD na investicionoj konferenciji, kakvi su efekti?
Efekti su svakako dobri za Dačića i pripadnike državne delegacije koja je turistički obišla Zapadnu obalu. Ni Majkrosoft nije loše prošao, jer mu je tadašnji predsednik Vlade usput ostavio još novca srpskih poreskih obveznika. Sve u svemu, ceo taj put mogao bi da se okvalifikuje više kao “shopping trip” za trošenje novca, nego kao investiciona konferencija za njegovo privlačenje. Osim toga, sam događaj u San Francisku bio je amaterski organizovan – niti je imao bilo kakav publicitet u lokalnim medijima, niti je postojala vidljivost u ovdašnjoj tehnološkoj zajednici.
Veću korist od toga donela je majska poseta mojih prijatelja iz 500 Start-ups, drugog najboljeg start-ap akceleratora u svetu, zvezdarskom ICT Habu. Osim predavanja koje su održali start-apima u Beogradu i Novom Sadu, njih trojica su tom prilikom odlučili da 500 Start-ups investira u TruckTrack Vuka Nikolića. Kasnije se jedan od njih odlučio i da kupi stan u Beogradu, jer se potpuno zaljubio u atmosferu srpske prestonice. To su direktne strane investicije, a ne politički marketing.
Što se povratne sprege između tehnološke dijaspore i Srbije tiče, ne bih se složio da ona uopšte ne postoji, ona je samo u skladu sa opštim privrednim okruženjem u zemlji.
Kakva je na osnovu vašeg iskustva ta poslovna klima?
Poslovnu klimu u Srbiji karakterišu: neefikasnost javne uprave i gomila nepotrebne birokratije; arhaičan sistem obrazovanja, uglavnom neprilagođen potrebama tržišta, koji ne proizvodi dovoljno kvalifikovane radne snage; sporost sudova i proizvoljno tumačenje čak i onih relativno savremenih zakona. Uvek se setim onih momaka koji su završili u zatvoru zbog affiliate sajta i dečka kome je tržišni inspektor uručio pozamašnu kaznu za obavljanje delatnosti za koju nije registrovan zbog 10 evra koje je dotični zaradio za godinu dana od specijalizovanog bloga o parfemima. Ako postoji nerazumevanje za bilo kakvo tehnološko preduzetništvo, čak i na tom najnižem nivou, šta onda reći za ozbiljnije poslove?
Kad ste već pomenuli visoke tehnologije, u Srbiji se mnogo govori da je to naša šansa, primer koji ste pomenuli to demantuje.
I ne samo to. U Srbiji nema propisa koji bi potpomogli dalji razvoj tehnološke industrije. Na primer, Srbija još uvek nema pravni ekvivalent “safe harbor” stavki iz američkog Digital milenijum kopirajt akta (Digital Millenium Copyright Act – DMCA), koji je na snazi još od 1998. godine, a predstavlja zakonski mehanizam zaštite za kreatore digitalnih proizvoda od pokušaja drugih da zloupotrebe njihove mobilne aplikacije.
Sa druge strane, ima mnogo propisa koji sprečavaju bilo kakav napredak u određenim oblastima, u čemu ubedljivo prednjači Narodna banka Srbije. Moj omiljeni primer čak nije ni ceo onaj višegodišnji cirkus sa PayPalom koji je nastao zbog zakona o deviznom poslovanju, već zabrana NBS da domaća pravna lica imaju bilo kakve veze sa bitkoinom. Čisto da stavimo stvari u perspektivu, dotična tehnološka inovacija koju po značaju mnogi ovde upoređuju sa World Wide Webom, počinje polako da menja kompletan dosadašnji finansijski sistem i, sa investicijama od blizu 360 miliona dolara, samo od početka ove godine predstavlja ubedljivo najbrže rastuću tehnološku oblast u svetu kada je reč o investiranje u start-apove. Naravno, od toga ni dinar neće završiti u Srbiji.
Posledice?
Nerazumevanje da u današnjem globalizovanom svetu niko ko se bavi tehnologijom jednostavno ne mora da trpi sve ovo gore pobrojano. Zahvaljujući poslovanju koje nije vezano za fizičku lokaciju, svako ima slobodu da bilo kada želi izmesti svoj biznis gde god poželi, a sa njim i kompletne poreske i druge prihode za zemlju u kojoj je biznis registrovan. I ljudi to i rade. Čim se pojave bilo kakvi prihodi, gotovo svi koji imaju veze sa tehnologijom – od frilensera do preduzetnika – Srbiji se zahvale na saradnji, zatvore firmu tu i otvore preko Interneta kompaniju u Delaveru, Singapuru ili negde drugde, jer im jednostavno ne pada na pamet da finansiraju postojeći sistem u Srbiji. Ubrzo nakon što se biznis izmesti iz Srbije, dobar deo shvati da ni oni ne moraju baš da budu tu, nakon čega sledi emigracija.
Najalarmantnija stvar u vezi sa ovim poslednjim je što se uopšte ne radi o običnim inženjerima, koji ionako odlaze u ogromnom broju već skoro 25 godina i čija svaka kupljena karta u jednom pravcu, bar u slučaju IT stručnjaka, Srbiju košta između 50 i 100 hiljada evra, jer je to cena njihovog obrazovanja. Ne, ovde je reč o preduzetnicima koji pokreću nove poslove, stvaraju vrednost, otvaraju nova radna mesta. A svako radno mesto u tehnološkoj industriji u proseku kreira još 4,3 druga radna mesta u privredi, dok, na primer, svako radno mesto u proizvodnji kreira samo 1,4 druga mesta. Njihov egzodus – koji se, bar sudeći po krugu ljudi koje poznajem, samo ubrzava poslednjih godina – ne samo da dugoročno znači ogroman finansijski gubitak za zemlju, već predstavlja i svojevrsnu nacionalnu katastrofu.
Dakle, povratne sprege nema, jer se oni ne vraćaju u Srbiju?
Zbog svih ovih stvari o kojima sam govorio retko kome ko je iole profesionalno ostvaren u inostranstvu uopšte pada na pamet da se vraća i pokreće bilo kakav biznis iz Srbije. Umesto toga, ljudi se odlučuju za nešto drugo: osnivaju kompanije tamo gde je poslovna klima dobra, što znači ne u Srbiji, a onda Srbiju koriste kao neku vrstu domaće autsorsing destinacije. Odnos cena-kvalitet tu je zaista odličan. Na primer, za godišnju platu jednog dobrog softverskog inženjera u San Francisku, u Beogradu se može zaposliti ceo tim.
Naravno, američke kompanije koje su osnovali naši ljudi koriste to kao “tajno oružje”, pa se tako, na primer, ceo razvojni tim veoma uspešnog start-apa Frejm iz Silicijumske doline nalazi u Nišu, jer je odatle njegov osnivač Nikola Božinović, koji inače već gotovo 20 godina živi u Americi. Takvih primera ima mnogo. Poznajem nekolicinu ljudi koji su potrošili bukvalno milione dolara na autsorsing u Srbiji tokom poslednjih desetak godina. Oni bi vrlo rado investirali u srpske start-apove, i ne samo oni, ali je ponuda još uvek jako tanka, poslovna klima nikome ne uliva poverenje, a start-ap ekosistem je u ranoj fazi razvoja, pa do tih transakcija još uvek ne dolazi u nekom značajnijem broju.
Start-ap eko sistem. Šta pod tim podrazumevate?
To znači, prvo, konačan prestanak maštanja o reindustrijalizaciji koju će doneti neki krupni investitori iz inostranstva. Oni se ionako, bar u novijoj istoriji Srbije, nikada nisu pojavljivali bez debelih subvencija i ekspresnog proglašavanja njihovih ugovora državnom tajnom. Drugo, to znači prepoznavanje resursa kojima raspolažemo, dakle pametnih mladih ljudi koji se bave tehnologijom, s jedne strane, i pružanje tim ljudima najboljih uslova za život i rad, sa druge, umesto da im se i jedno i drugo na svakom koraku otežava.
Na primer, šta bi se desilo kada bismo u Novom Sadu umesto brojnih postojećih firmi koje se bave autsorsing uslugama imali stotinjak kompanija fokusiranih na proizvode kao što je Eipix? Odgovor: imali bismo oko 15.000 novih radnih mesta, veoma bogatu prestonicu Pokrajine, visok rast životnog standarda u tom delu zemlje i mnogo naplaćenog poreza.
Ta prilika neće trajati večito. Procenat mladih preduzetnika kojima je jedini cilj da odu iz zemlje, jer u njoj ne vide nikakvu perspektivu, iz godine u godinu raste. Strani investicioni fondovi bukvalno otimaju najperspektivnije nove srpske start-apove. Na primer, bugarski Eleven raspolaže sa desetak miliona evra kapitala, mahom iz evropskih fondova. U okruženju koje im ne nudi baš ništa osim problema, tridesetak najzanimljivijih srpskih start-apova prodalo je svoje vlasničke udele Elevenu uz obavezu preseljenja u Sofiju, ruku na srce, uglavnom privremenog. Ko zna koliko će novih kompanija, koje bi mogle da budu novi Nordeusi, Srbija zbog toga izgubiti u korist svog istočnog suseda?
I vi spadate u grupu mladih ljudi koje opisujete. Opisali ste i razloge zbog kojih se odlazi. Ipak, konkretno, zašto ste vi otišli iz Srbije?
Kao što ste rekli, otišao sam iz svih onih na početku ovog razgovora navedenih razloga, plus opšta društvena klima koja je, nažalost, izuzetno nezdrava. Iako ima solidan potencijal da bude lepo mesto za život i posao, zemlja u kojoj sam rođen postala je udžbenički primer negativne društvene selekcije i jednostavno nije zemlja u kojoj želim da živim i u kojoj bih jednog dana trebalo da odgajam svoju decu.
Šta ste pronašli u Americi?
U Zalivskoj oblasti San Franciska pronašao sam jedno napredno, stimulativno, kosmopolitsko okruženje, zagledano u budućnost. To je neki jedinstveni koktel globalizacije, hakerskog idealizma, hipi etike, mešavine vrednosti koje kreira tehnološka industrija sa starim kapitalizmom Zapadne obale, umetničke ekscentričnosti San Franciska, tipično kalifornijske opuštenosti i vere u to da ovde svojim znanjem svet možemo da učinimo boljim mestom. Osim toga, Zalivska oblast, tj. Silicijumska dolina, ima ubedljivo najveću koncentraciju pametnih ljudi na jednom mestu u celom svetu.
Filozofija razvoja u SAD, u poređenju sa Srbijom, ako to uopšte ima smisla?
Poređenje nema previše smisla, jer su filozofije poslovanja i poslovna klima dijametralno suprotni između ove dve zemlje. Biznis je u Americi nacionalni sport broj jedan. Čak i ljudi koji rade relativno slabo plaćene poslove, trude se da imaju svoj mali investicioni portfelj hartija od vrednosti i svi prate kretanje cene akcija na berzi. Kada govorimo o preduzetništvu, kapital je dostupan za bilo koju dobru ideju. Start-apovi se ne fokusiraju toliko na profit na kraće staze, već teže brzom rastu. Tako nije ništa neobično da investitori u neki neprofitabilni biznis investiraju i po stotinjak miliona dolara. A desi se i, recimo, čak 1,2 milijarde kao u slučaju Snapchata, iako ta firma do sada nije napravila nijedan cent prihoda, jer znaju da će novac sam po sebi kasnije doći ako se napravi proizvod koji ima vrednost za veliki broj ljudi.
U Srbiji ništa od gore nabrojanog nije slučaj. Korporativizacija praktično ne postoji, što je posledica skandalozno visokih troškova osnivanja i vođenja akcionarskog preduzeća kao forme privrednog društva. Poređenja radi, u Americi osnivanje korporacije košta 150-300 dolara, završava se brzo preko Interneta, ne postoje tekući troškovi ako nema prihoda i zato maltene svi imaju registrovanu neku firmu. Pošto su korporacije u Srbiji za domaće privrednike skupa egzotika, većina ekonomske aktivnosti ide kroz preduzetnike – “sole proprietorship” – i društva sa ograničenom odgovornošću. Posledica toga je da je Beogradska berza danas potpuno irelevantan faktor, tako da je i interesovanje građana za investiranje tim putem praktično nepostojeće. To dalje vodi ka tome da se imućniji ljudi uglavnom odlučuju za investiranje u nekretnine, što je jedan od najkonzervativnijih pristupa investicijama i donosi najmanju dobit. Što se pokretanja novog posla tiče, u Srbiji to u većini slučajeva znači pozajmljivanje novca od PRP – porodica, rodbina i prijatelji – ili odlazak u banku po kredit. “Venture capital” ne postoji, što srpske firme onda stavlja pred izazov da moraju što pre da budu profitabilne, jer jednom kada početni kapital nestane – “game over”. Niko ne razmišlja o agresivnom rastu koji se kasnije može pretvoriti u masivne prihode i tržišnu dominaciju, jer su fokusirani na to kako da plate PDV sledećeg meseca za prodatu robu ili usluge koje još uvek nisu ni naplatili. Zbog toga svi otvaraju pekare, kafiće i kioske brze hrane: promet kreće odmah i “cash flow” se brzo stabilizuje. Zbog svega toga Srbija ima primitivnu ekonomiju koja je u proseku oko pola veka iza razvijenog sveta.
Predlagali ste pre dve godine da se Srbija orijentiše ka razvoju robotike, civilnih bespilotnih letelica i 3D štampe. Niko vas nije čuo. Šta se desilo u međuvremenu u tim sferama, da li je sad kasno za to, šta su nove prilike, ako ih ima?
Sva tri i dalje stoje kao ogromne prilike za razvoj, jer će potražnja u srednjem roku biti toliko veća od ponude da je i dalje u pitanju fantastična biznis prilika. Druge dve nove prilike su Bitcoin i Virtual Reality.
Bitcoin i kriptovalute – koje, kao što rekoh na početku, nijedno pravno lice u Srbiji ne sme ni da takne, zahvaljujući uobičajenoj kratkovidosti Narodne banke Srbije. Blockchain kao “open source” projekat već obećava da postane osnova svih finansijskih transakcija u budućnosti, i ne samo njih, a već sada počinje polako da ubija praistorijske biznise koji se oslanjaju na skupe informacione transakcije, kao što je na primer Vestern union.
Virtual Reality je drugi veliki talas tehnološke inovacije koji nama kao čovečanstvu, nakon tridesetak godina iščekivanja i razočaranja, konačno stiže zahvaljujući tehnologijama kao što su Oculus, u vlasništvu Facebooka; Magic Leap, glavni investitor Gugl; HoloLens, Majkrosoftovo čedo, pa čak i Cardboard, Guglov genijalni projekat za upotrebu pametnih telefona kao VR naočara. Ovaj mega trend će dugoročno potpuno promeniti gotovo celokupnu ljudsku interakciju sa mašinama, od toga kako radimo do toga kako se zabavljamo u slobodno vreme. Rekao bih da su startne pozicije što se platformi tiče već zauzete – bar za prvo vreme, jer su pomenute korporacije potrošile milijarde dolara na istraživanje i razvoj tih tehnologija – ali postoji ogroman prazan prostor što se tiče kreiranja sadržaja za njih. Narednih godina će se na tome praviti imperije.
-
 @ b1ddb4d7:471244e7
2025-05-31 16:00:51
@ b1ddb4d7:471244e7
2025-05-31 16:00:51In the heart of East Africa, where M-Pesa reigns supreme and innovation pulses through bustling markets, a quiet revolution is brewing—one that could redefine how millions interact with money.
Enter Bitika, the Kenyan startup turning bitcoin’s complexity into a three-step dance, merging the lightning speed of sats with the trusted rhythm of mobile money.
At the helm is a founder whose “aha” moment came not in a boardroom, but at his kitchen table, watching his father grapple with the gap between understanding bitcoin and actually using it.
Bitika was born from that friction—a bridge between M-Pesa’s ubiquity and bitcoin’s borderless promise, wrapped in a name as playful as the Swahili slang that inspired it.
But this isn’t just a story about simplifying transactions. It’s about liquidity battles, regulatory tightropes, and a vision to turn Bitika into the invisible rails powering Africa’s Bitcoin future.
Building on Bitcoin
- Tell us a bit about yourself and how you got into bitcoin/fintech, and what keeps you passionate about this space?
I first came across bitcoin in 2020, but like many at that time, I didn’t fully grasp what it really was. It sounded too complicated, probably with the heavy terminologies. Over time, I kept digging deeper and became more curious.
I started digging into finance and how money works and realised this was what I needed to understand bitcoin’s objectives. I realized that bitcoin wasn’t just a new type of money—it was a breakthrough in how we think about freedom, ownership, and global finance.
What keeps me passionate is how bitcoin can empower people—especially in Africa—to take control of their wealth, without relying on unstable systems or middlemen.
- What pivotal moment or experience inspired you to create Bitika? Was there a specific gap in Kenya’s financial ecosystem that sparked the idea?
Yes, this idea was actually born right in my own home. I’ve always been an advocate for bitcoin, sharing it with friends, family, and even strangers. My dad and I had countless conversations about it. Eventually, he understood the concept. But when he asked, “How do I even buy bitcoin?” or “Can you just buy it for me?” and after taking him through binance—that hit me.
If someone I’d educated still found the buying process difficult, how many others were feeling the same way? That was the lightbulb moment. I saw a clear gap: the process of buying bitcoin was too technical for the average Kenyan. That’s the problem Bitika set out to solve.
- How did you identify the synergy between bitcoin and M-Pesa as a solution for accessibility?
M-Pesa is at the center of daily life in Kenya. Everyone uses it—from buying groceries to paying rent. Instead of forcing people to learn new tools, I decided to meet them where they already are. That synergy between M-Pesa and bitcoin felt natural. It’s about bridging what people already trust with something powerful and new.
- Share the story behind the name “Bitika” – does it hold a cultural or symbolic meaning?
Funny enough, Bitika isn’t a deeply planned name. It came while I was thinking about bitcoin and the type of transformation it brings to individuals. In Swahili, we often add “-ka” to words for flair—like “bambika” from “bamba.”
So, I just coined Bitika as a playful and catchy way to reflect something bitcoin-related, but also uniquely local. I stuck with it because thinking of an ideal brand name is the toughest challenge for me.
- Walk us through the user journey – how does buying bitcoin via M-Pesa in “3 simple steps” work under the hood?
It’s beautifully simple.
1. The user enters the amount they want to spend in KES—starting from as little as 50 KES (about $0.30).
2. They input their Lightning wallet address.
3. They enter their M-Pesa number, which triggers an STK push (payment prompt) on their phone. Once confirmed—pap!—they receive bitcoin almost instantly.
Under the hood, we fetch the live BTC price, validate wallet addresses, check available liquidity, process the mobile payment, and send sats via the Lightning Network—all streamlined into a smooth experience for the user.
- Who’s Bitika’s primary audience? Are you focusing on unbanked populations, tech enthusiasts, or both?
Both. Bitika is designed for everyday people—especially the unbanked and underbanked who are excluded from traditional finance. But we also attract bitcoiners who just want a faster, easier way to buy sats. What unites them is the desire for a seamless and low-barrier bitcoin experience.
Community and Overcoming Challenges
- What challenges has Bitika faced navigating Kenya’s bitcoin regulations, and how do you build trust with regulators?
Regulation is still evolving here. Parliament has drafted bills, but none have been passed into law yet. We’re currently in a revision phase where policymakers are trying to strike a balance between encouraging innovation and protecting the public.
We focus on transparency and open dialogue—we believe that building trust with regulators starts with showing how bitcoin can serve the public good.
- What was the toughest obstacle in building Bitika, and how did you overcome it?
Liquidity. Since we don’t have deep capital reserves, we often run into situations where we have to pause operations often to manually restock our bitcoin supply. It’s frustrating—for us and for users. We’re working on automating this process and securing funding to maintain consistent liquidity so users can access bitcoin at any time, without disruption.
This remains our most critical issue—and the primary reason we’re seeking support.
- Are you eyeing new African markets? What’s next for Bitika’s product?
Absolutely. The long-term vision is to expand Bitika into other African countries facing similar financial challenges. But first, we want to turn Bitika into a developer-first tool—infrastructure that others can build on. Imagine local apps, savings products, or financial tools built using Bitika’s simple bitcoin rails. That’s where we’re heading.
- What would you tell other African entrepreneurs aiming to disrupt traditional finance?
Disrupting finance sounds exciting—but the reality is messy. People fear what they don’t understand. That’s why simplicity is everything. Build tools that hide the complexity, and focus on making the user’s life easier. Most importantly, stay rooted in local context—solve problems people actually face.
What’s Next?
- What’s your message to Kenyans hesitant to try bitcoin, and to enthusiasts watching Bitika?
To my fellow Kenyans: bitcoin isn’t just an investment—it’s a sovereign tool. It’s money you truly own. Start small, learn, and ask questions.
To the bitcoin community: Bitika is proof that bitcoin is working in Africa. Let’s keep pushing. Let’s build tools that matter.
- How can the bitcoin community, both locally and globally, support Bitika’s mission?
We’re currently fundraising on Geyser. Support—whether it’s financial, technical, or simply sharing our story—goes a long way. Every sat you contribute helps us stay live, grow our liquidity, and continue building a tool that brings bitcoin closer to the everyday person in Africa.
Support here: https://geyser.fund/project/bitika
-
 @ c9badfea:610f861a
2025-05-30 21:42:40
@ c9badfea:610f861a
2025-05-30 21:42:40Separators
- ▰▱▰▱▰▱▰▱
- ░░▒▒▓▓██▓▓▒▒░░
- ▁▃▅▇▅▃▅▇▅▃▁
- ◇◆◇◆◇◆◇
- ◥◤◢◣◥◤◢◣
- ▪▫▪▫▪▫▪▫▪▫▪▫▪▫▪▫
- ▮▯▮▯▮▯▮▯▮▯▮▯▮▯▮▯
Nametags
- ⚞Name⚟
- ⫍Name⫎
- 〚Name〛
- 〘Name〙
- 〖Name〗
- 〔Name〕
- 【Name】
- 《Name》
- 「Name」
- 〈Name〉
- ⦗Name⦘
- ⦇Name⦈
- ⦍Name⦐
- ⦋Name⦌
- ⦅Name⦆
- ⟬Name⟭
- ❨Name❩
Checklists
- ◇ Item
- ◆ Item
- ◈ Item
- ☐ Item
- ☑ Item
- ☒ Item
- ▢ Item
Bulletpoints
- •
- ∙
- ☛
- ☞
- ❧
- ⦾
- ⦿
- ◦
- ⊳
- ►
- ▸
- ▹
-
 @ bf47c19e:c3d2573b
2025-05-30 20:58:03
@ bf47c19e:c3d2573b
2025-05-30 20:58:03Originalni tekst na bitcoin-balkan.com.
Pregled sadržaja
- Šta je blockchain?
- Kako mogu da saznam više o Bitcoin-u?
Ukoliko niste pročitali naš uvodni tekst o Bitcoin-u, i zašto vam je važno da to učinite, onda prvo pročitajte: Šta je Bitcoin i kako on može da nam pomogne?
Bitcoin, sa velikim B na početku, odnosi se na mrežu računara koji održavaju knjigu stanja na akauntima bitcoin digitalne valute, slično kao što banke održavaju knjigu stanja na računima dolara, eura ili neke druge valute. Bitcoin softver, odnosno protokol, takođe omogućava korisnicima da putem interneta pošalju bitcoin-e sa svog akaunta na drugi akaunt, slično PayPal-u ili Venmo-u, ali bez kompanije koja pruža uslugu prenosa. Bitcoin softver je otvorenog koda, tako da svako može da ga pokrene na svom računaru i da se pridružiti mreži.
Najbolji način da se razume kako Bitcoin funkcioniše “iznutra” je da ga zamislimo kao finansijski sistem.
Centralne banke i vlade proizvode i distribuiraju novac pozajmljujući ga ljudima, i trošeći ga na oružje, puteve i socijalne programe. Ovaj sistem se naziva sistemom zasnovanom na dugovima, jer svaki put kada banka da zajam, stvara se nova valuta koja ranije nije postojala. Ova valuta ima vrednost jer dug koji ju je stvorio ima vrednost: primalac zajma obećava da će otplatiti svoj dug banci, plus kamate.
Kad god banka odobri kredit, ona stvara novu valutu. Ovo takodje važi i kada podignete hipoteku ili kredit za auto. Takođe se primenjuje i kada Američke Federalne Rezerve kupuju državne obveznice od vlade Sjedinjenih Država. U svakom od ovih slučajeva, banka šalje novonastalu valutu primaocu zajma. Primaoc zajma obećava banci da će u budućnosti vratiti tu valutu, plus kamate. Međutim, ulaz nove valute u sistem znači i da opada vrednost postojeće valute koja je u opticaju. To se dešava kroz proces koji se obično naziva inflacija.
Da bi imali koristi od pogodnih usluga koje nude banke, poput kreditnih kartica i digitalnih transfera novca, normalni ljudi i preduzeća obično novac drže na bankovnim računima. Svaka banka poseduje svoju knjigu sa računima svih svojih klijenata.
Banke su neophodne da bi omogućile digitalna plaćanja koja vršimo svakodnevno, jer su nam potrebne pouzdane strane koje bi proverile da li se sav računovodstveni sistem sabira. U suprotnom, bilo bi lako da neko uradi “copy-paste“ jednog dela digitalnog novca i da ga potroši dva puta, ili da doda par nula na stanje svog računa.
Sada razumemo nekoliko ključnih tačaka o trenutnom sistemu zasnovanom na dugu: banke proizvode novu valutu svaki put kad pozajmljuju novac, a većina ljudi svoj novac čuva u bankama koje im nude pogodnosti.
Bitcoin je malo drugačiji. Hajde da započnemo ovo putovanje sa pitanjem.
Šta ako bi svi posedovali knjigu stanja na računima, baš kao i banka?
Umesto da banke poseduju po jednu knjigu depozita svojih klijenata, šta ako svi poseduju istu knjigu, sa detaljnim opisima svih stanja na računima svih učesnika u ekonomiji? O privatnosti ne morate da brinete ni na trenutak – to ćemo objasniti kasnije.
Hajde da vidimo kako bi transakcija mogla da se izvrši koristeći ovakav bankarski sistem. Recimo da Ana želi da plati Davidu 10 digitalnih „novčića“. Ona tu transakciju zapisuje u e-mail, potpisuje je digitalno kako bi svi bili sigurni da e-mail dolazi od stvarne Ane, i šalje ga svima ostalima. Kada ostali prime taj e-mail, oni ažuriraju svoje knjige, tako što skinu 10 novčića sa Aninog računa i dodaju 10 novčića na Davidov račun.
Zašto bi se neko trudio da evidentira transakciju u svojoj knjizi?
Recimo da će prva osoba koja izvrši sledeće korake dobiti 5 novčića:
- Proverom da li je prava Ana potpisala transakciju
- Proverom da li Ana ima dovoljno sredstava na svom računu da plati Davidu 10 novčića
- Zapisivanje transakcije ukoliko ispunjava uslove 1) i 2)
Primetićete da se ovo mnogo razlikuje od trenutnog monetarnog sistema. U novom sistemu morate da imate novčiće da biste mogli da ih date nekom drugom. Ne postoje banke sa posebnim privilegijama koje mogu da stvore valutu davanjem zajma.
Umesto da dozvoljava samo maloj grupi bankara da prave nove valute, novi sistem omogućava svima da kreiraju novu valutu ako pružaju korisnu uslugu mreži: verifikovanje i evidentiranje transakcija između ljudi. Nazvaćemo ovo nagradom za potvrđivanje.
Kako se svi slože oko pravila sistema? Ona su kodirana u softverskom protokolu otvorenog koda. To znači da svako može besplatno da preuzme pravila sistema sa interneta i da počne da ih koristi za zaradu valute u sistemu. Ako svi koriste isti skup pravila, njihove knjige će se sinhronizovati, jer će prihvatiti i odbiti potpuno iste transakcije.
- Otvoreni kod = svako može da preuzme kod i da ga pročita
- Softverski protokol = skup pravila napisanih u kodu
Kako zaustaviti ljude koji pokušavaju da prevare sistem da bi zaradili “nagradu za potvrdu”?
Recimo da Boris i Marko žele da se obogate – oni bi mogli jedan drugom da plaćaju po jedan novčić u krug, vodeći računa da neko od njih prvi zabeleži transakciju kako bi mogli da zahtevaju nagradu za potvrdu. Pomoću ove šeme oni bi u osnovi mogli da stvore (odštampaju) novu valutu, kad god oni to požele!
Softverski protokol to zaustavlja zahtevajući da osoba koja validira transakciju uradi neki „posao“ sa računarom kako bi je zabeležila. Ovo osigurava da računari moraju da troše energiju za zabeležavanje transakcija, pa bi u tom slučaju varanje sistema bilo veoma skupo. Borisova i Markova šema varanja sistema više nema finansijskog smisla. Da bismo demonstrirali ovaj proces, pogledajmo Filipa i njegov C-Bot računar. Filip je na svoj računar instalirao Bitcoin protokol, koji predstavlja Bitcoin-ov softverski protokol otvorenog koda koji sadrži pravila Bitcoin sistema.
Kako C-Bot Verifikuje Transakcije
Korak 1: Slušanje transakcija
Prvo, C-Bot sluša transakcije (skraćeno “txn”) koje Ana, Boris, Marko i David emituju putem interneta.
Korak 2: Stvara “Heš”
Drugo, C-Bot će prikupiti sledeće delove podataka:
- Sve Bitcoin transakcije koje ljudi šalju
- Tajni broj (objasnićemo kasnije)
- Nonce – neki slučajan broj
C-Bot sve ovo stavlja u heš mašinu. Mašina za heširanje uzima sve ove podatke i proizvodi 256 bitova (bitovi su 1 i 0) koji se jedinstveno uklapaju u te podatke, nazvane ‘heš’. To heširanje je poput otiska prsta podataka. Uvek ćete dobiti isti heš sa istim ulaznim podacima. Mašina za heširanje je takođe jednosmerna: lako je stvoriti heš od nekih podataka, ali ne možete da stavite heš u mašinu i da vratite ulazne podatke.
C-Bot će iznova isprobavati svoju heš mašinu sa drugim nonce-om (slučajnim brojem). Svaki put, on će proveriti da li je mašina proizvela heš za koji Bitcoin softverski protokol kaže da je tačan.
Ovaj proces pronalaženja heša troši puno vremena i energije. Mašina za heširanje je jednosmerna, tako da C-Bot ne može tek tako da stavi ‘tačan’ heš u mašinu i otkrije ulazne podatke. Svaki računar na Bitcoin mreži takođe prolazi kroz ovaj proces pokušavajući da pronađe ‘ispravan’ heš.
Ukoliko bi ovi računari uspeli da pronađu ‘ispravan’ heš bez velikog trošenja energije, mogli bi da prevare sistem. Dva računara bi mogla da prosleđuju transakcije u krug, zarađujući bitcoin-e svaki put kada bi potvrdili transakciju.
Korak 3: Pronalaženje Ispravnog Heša
C-Bot konačno pronalazi heš koji zadovoljava pravila Bitcoin protokola koristeći sve nedavne transakcije. Sada ovaj blok podataka šalje na druge računare. Blok se sastoji od nedavnih transakcija, nonce-a i tajnog broja. Ti drugi računari stavljaju sve ove podatke kroz istu heš mašinu za sebe, da bi proverili da li je heširanje tog C-Bota tačno. S obzirom da znamo da računari ne mogu da varaju u ovoj igri, znamo da je C-Bot morao da izvrši neka izračunavanja sa svojom heš mašinom da bi pronašao ispravan heš.
Heš bloka C-Bota koji je poslat, sada postaje tajni broj koji ulazi u izračunavanje sledećeg bloka. Budući da heš svakog bloka u ‘blockchain-u’ bitcoin-a koristi heš poslednjeg bloka kao ulaz, bila bi potrebna apsurdna količina energije da se prepiše istorija transakcija (lanac blokova, eng. the blockchain)
Budući da se svačija stanja bitcoin-a zasnivaju na transakcijama na i sa njihovih računa, to takođe onemogućava izmenu bilo čijih stanja bitcoin-a.
Čitav ovaj proces poznat je pod nazivom rudarenje bitcoin-a. Svaki računar na mreži pokušava da proba nove podatke kroz heš mašinu, bilione puta u sekundi.
Šta je blockchain?
Blockchain predstavlja istoriju Bitcoin transakcija, koja omogućava bilo kome da utvrdi svoje Bitcoin stanje.
- ‘Block – Blok’ = Grupa Bitcoin transakcija, nonce-a i heša prethodnog bloka
- ‘Chain – Lanac’ = Heš svakog bloka takođe koristi heš prethodnog bloka kao ulaz. Ovo povezuje podatke svakog bloka sa svakim drugim blokom, stvarajući chain – lanac.
Na blockchain-u, prava imena nisu povezana sa bitcoin-ima. Bitcoin-i su povezani samo sa slučajnim nizom brojeva i slova poznatim kao ‘javni ključ’. Ovo korisnike Bitcoin-a i njihova stanja čini poprilično anonimnima za sve koji vode knjigu.
Kada posedujete bitcoin-e, vi imate password za otključavanje vaših bitcoin bankovnih računa. Ovi računi postoje na hiljadama računara širom sveta koji pokreću Bitcoin protokol.
Kako mogu da saznam više o Bitcoin-u?
Ovaj članak vam je dao razumevanje o tome kako funkcioniše Bitcoin protokol i kako se osiguravaju njegova neverovatna svojstva.
Ako želite da saznate više, preporučujem vam ove izvore:
Ako vam se sviđa moj rad, molim vas da ga podelite sa svojim prijateljima i porodicom. Cilj mi je da svima pružim pogled u ekonomiju i na to kako ona utiče na njihov život.
-
 @ 2cde0e02:180a96b9
2025-05-31 15:06:26
@ 2cde0e02:180a96b9
2025-05-31 15:06:26https://stacker.news/items/993562
-
 @ 7f6db517:a4931eda
2025-05-31 15:01:42
@ 7f6db517:a4931eda
2025-05-31 15:01:42
People forget Bear Stearns failed March 2008 - months of denial followed before the public realized how bad the situation was under the surface.
Similar happening now but much larger scale. They did not fix fundamental issues after 2008 - everything is more fragile.
The Fed preemptively bailed out every bank with their BTFP program and First Republic Bank still failed. The second largest bank failure in history.
There will be more failures. There will be more bailouts. Depositors will be "protected" by socializing losses across everyone.
Our President and mainstream financial pundits are currently pretending the banking crisis is over while most banks remain insolvent. There are going to be many more bank failures as this ponzi system unravels.
Unlike 2008, we have the ability to opt out of these broken and corrupt institutions by using bitcoin. Bitcoin held in self custody is unique in its lack of counterparty risk - you do not have to trust a bank or other centralized entity to hold it for you. Bitcoin is also incredibly difficult to change by design since it is not controlled by an individual, company, or government - the supply of dollars will inevitably be inflated to bailout these failing banks but bitcoin supply will remain unchanged. I do not need to convince you that bitcoin provides value - these next few years will convince millions.
If you found this post helpful support my work with bitcoin.