-
 @ 39cc53c9:27168656
2025-05-27 09:21:53
@ 39cc53c9:27168656
2025-05-27 09:21:53The new website is finally live! I put in a lot of hard work over the past months on it. I'm proud to say that it's out now and it looks pretty cool, at least to me!
Why rewrite it all?
The old kycnot.me site was built using Python with Flask about two years ago. Since then, I've gained a lot more experience with Golang and coding in general. Trying to update that old codebase, which had a lot of design flaws, would have been a bad idea. It would have been like building on an unstable foundation.
That's why I made the decision to rewrite the entire application. Initially, I chose to use SvelteKit with JavaScript. I did manage to create a stable site that looked similar to the new one, but it required Jav aScript to work. As I kept coding, I started feeling like I was repeating "the Python mistake". I was writing the app in a language I wasn't very familiar with (just like when I was learning Python at that mom ent), and I wasn't happy with the code. It felt like spaghetti code all the time.
So, I made a complete U-turn and started over, this time using Golang. While I'm not as proficient in Golang as I am in Python now, I find it to be a very enjoyable language to code with. Most aof my recent pr ojects have been written in Golang, and I'm getting the hang of it. I tried to make the best decisions I could and structure the code as well as possible. Of course, there's still room for improvement, which I'll address in future updates.
Now I have a more maintainable website that can scale much better. It uses a real database instead of a JSON file like the old site, and I can add many more features. Since I chose to go with Golang, I mad e the "tradeoff" of not using JavaScript at all, so all the rendering load falls on the server. But I believe it's a tradeoff that's worth it.
What's new
- UI/UX - I've designed a new logo and color palette for kycnot.me. I think it looks pretty cool and cypherpunk. I am not a graphic designer, but I think I did a decent work and I put a lot of thinking on it to make it pleasant!
- Point system - The new point system provides more detailed information about the listings, and can be expanded to cover additional features across all services. Anyone can request a new point!
- ToS Scrapper: I've implemented a powerful automated terms-of-service scrapper that collects all the ToS pages from the listings. It saves you from the hassle of reading the ToS by listing the lines that are suspiciously related to KYC/AML practices. This is still in development and it will improve for sure, but it works pretty fine right now!
- Search bar - The new search bar allows you to easily filter services. It performs a full-text search on the Title, Description, Category, and Tags of all the services. Looking for VPN services? Just search for "vpn"!
- Transparency - To be more transparent, all discussions about services now take place publicly on GitLab. I won't be answering any e-mails (an auto-reply will prompt to write to the corresponding Gitlab issue). This ensures that all service-related matters are publicly accessible and recorded. Additionally, there's a real-time audits page that displays database changes.
- Listing Requests - I have upgraded the request system. The new form allows you to directly request services or points without any extra steps. In the future, I plan to enable requests for specific changes to parts of the website.
- Lightweight and fast - The new site is lighter and faster than its predecessor!
- Tor and I2P - At last! kycnot.me is now officially on Tor and I2P!
How?
This rewrite has been a labor of love, in the end, I've been working on this for more than 3 months now. I don't have a team, so I work by myself on my free time, but I find great joy in helping people on their private journey with cryptocurrencies. Making it easier for individuals to use cryptocurrencies without KYC is a goal I am proud of!
If you appreciate my work, you can support me through the methods listed here. Alternatively, feel free to send me an email with a kind message!
Technical details
All the code is written in Golang, the website makes use of the chi router for the routing part. I also make use of BigCache for caching database requests. There is 0 JavaScript, so all the rendering load falls on the server, this means it needed to be efficient enough to not drawn with a few users since the old site was reporting about 2M requests per month on average (note that this are not unique users).
The database is running with mariadb, using gorm as the ORM. This is more than enough for this project. I started working with an
sqlitedatabase, but I ended up migrating to mariadb since it works better with JSON.The scraper is using chromedp combined with a series of keywords, regex and other logic. It runs every 24h and scraps all the services. You can find the scraper code here.
The frontend is written using Golang Templates for the HTML, and TailwindCSS plus DaisyUI for the CSS classes framework. I also use some plain CSS, but it's minimal.
The requests forms is the only part of the project that requires JavaScript to be enabled. It is needed for parsing some from fields that are a bit complex and for the "captcha", which is a simple Proof of Work that runs on your browser, destinated to avoid spam. For this, I use mCaptcha.
-
 @ 8bad92c3:ca714aa5
2025-05-28 08:01:41
@ 8bad92c3:ca714aa5
2025-05-28 08:01:41Marty's Bent

It's been a pretty historic week for the United States as it pertains to geopolitical relations in the Middle East. President Trump and many members of his administration, including AI and Crypto Czar David Sacks and Treasury Secretary Scott Bessent, traveled across the Middle East making deals with countries like Qatar, Saudi Arabia, the United Arab Emirates, Syria, and others. Many are speculating that Iran may be included in some behind the scenes deal as well. This trip to the Middle East makes sense considering the fact that China is also vying for favorable relationships with those countries. The Middle East is a power player in the world, and it seems pretty clear that Donald Trump is dead set on ensuring that they choose the United States over China as the world moves towards a more multi-polar reality.
Many are calling the events of this week the Riyadh Accords. There were many deals that were struck in relation to artificial intelligence, defense, energy and direct investments in the United States. A truly prolific power play and demonstration of deal-making ability of Donald Trump, if you ask me. Though I will admit some of the numbers that were thrown out by some of the countries were a bit egregious. We shall see how everything plays out in the coming years. It will be interesting to see how China reacts to this power move by the United States.
While all this was going on, there was something happening back in the United States that many people outside of fringe corners of FinTwit are not talking about, which is the fact that the 10-year and 30-year U.S. Treasury bond yields are back on the rise. Yesterday, they surpassed the levels of mid-April that caused a market panic and are hovering back around levels that have not been seen since right before Donald Trump's inauguration.
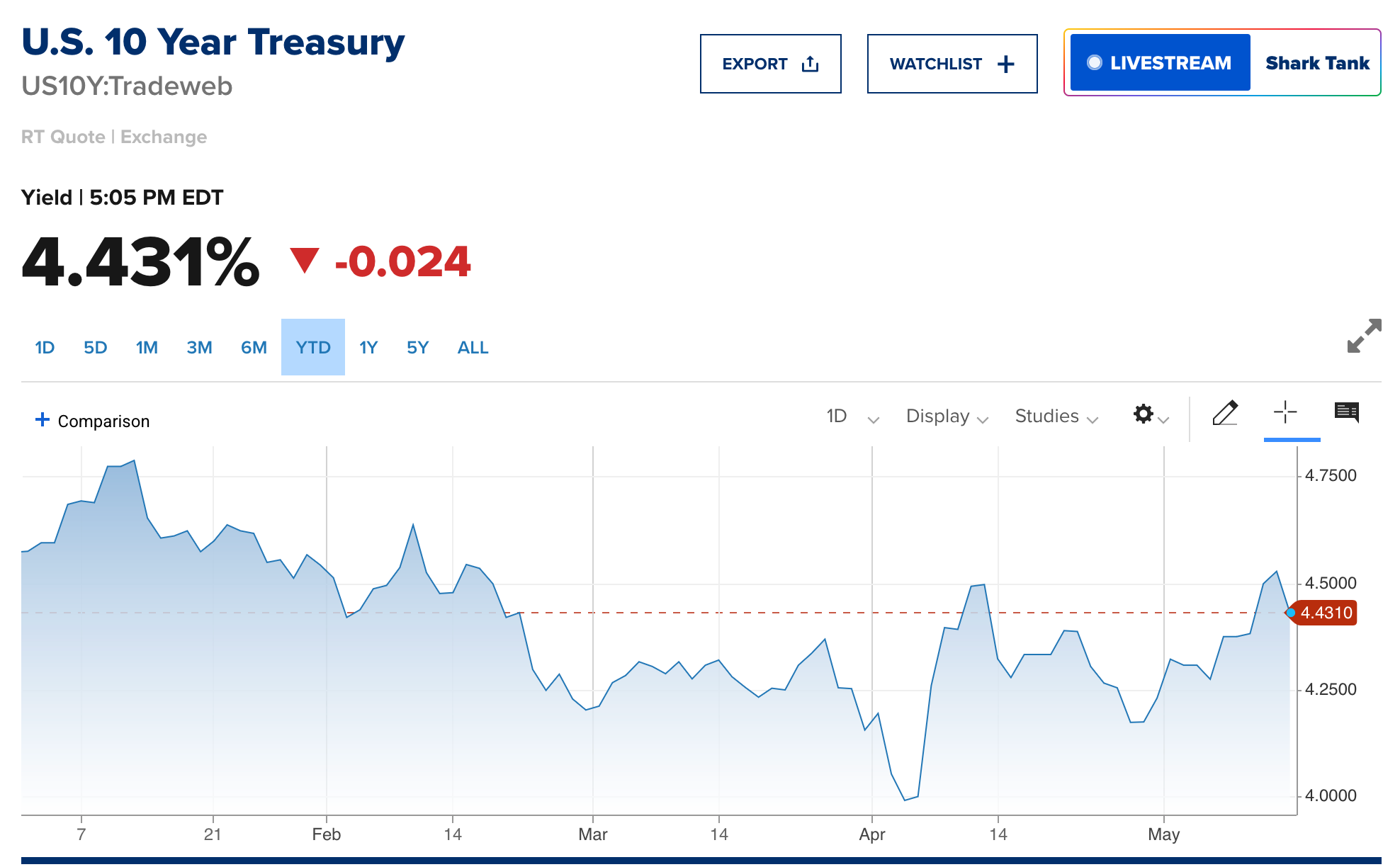
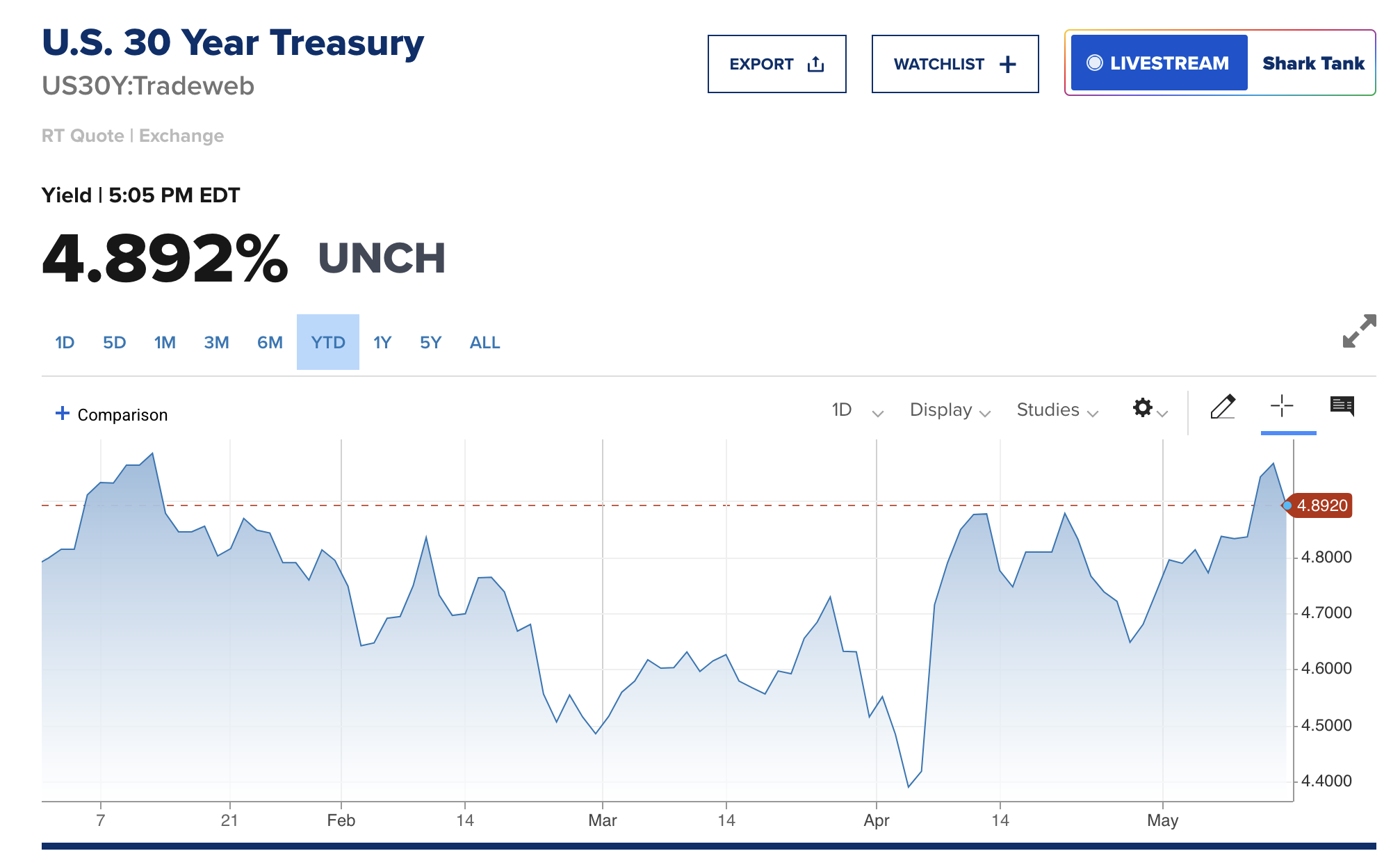
I imagine that there isn't as much of an uproar right now because I'm pretty confident the media freakouts we were experiencing in mid-April were driven by the fact that many large hedge funds found themselves off sides of large levered basis trades. I wouldn't be surprised if those funds have decreased their leverage in those trades and bond yields being back to mid-April levels is not affecting those funds as much as they were last month. But the point stands, the 10-year and 30-year yields are significantly elevated with the 30-year approaching 5%. Regardless of the deals that are currently being made in the Middle East, the Treasury has a big problem on its hands. It still has to roll over many trillions worth of debt over over the next few years and doing so at these rates is going to be massively detrimental to fiscal deficits over the next decade. The interest expense on the debt is set to explode in the coming years.
On that note, data from the first quarter of 2025 has been released by the government and despite all the posturing by the Trump administration around DOGE and how tariffs are going to be beneficial for the U.S. economy, deficits are continuing to explode while the interest expense on the debt has definitively surpassed our annual defense budget.
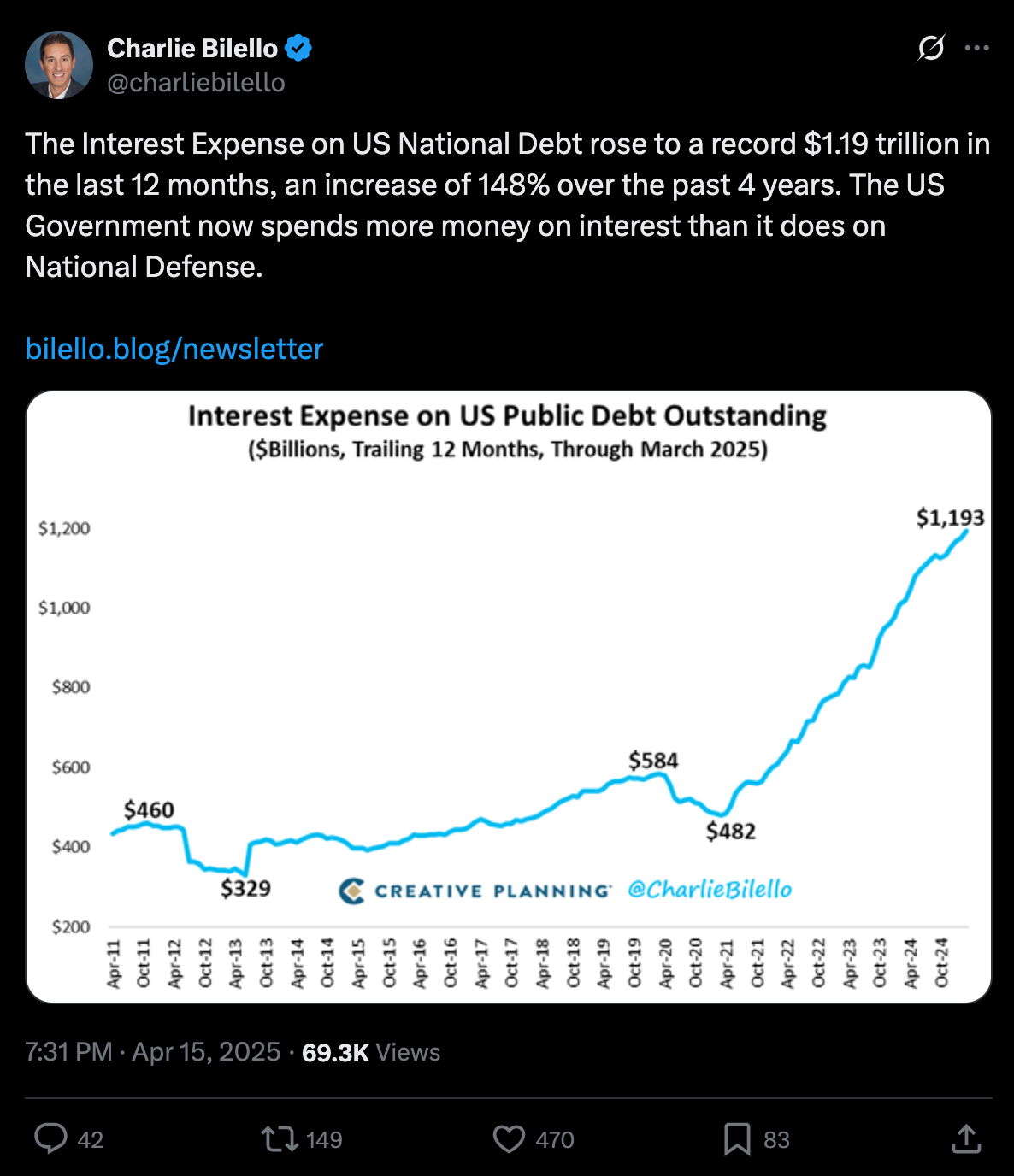
via Charlie Bilello
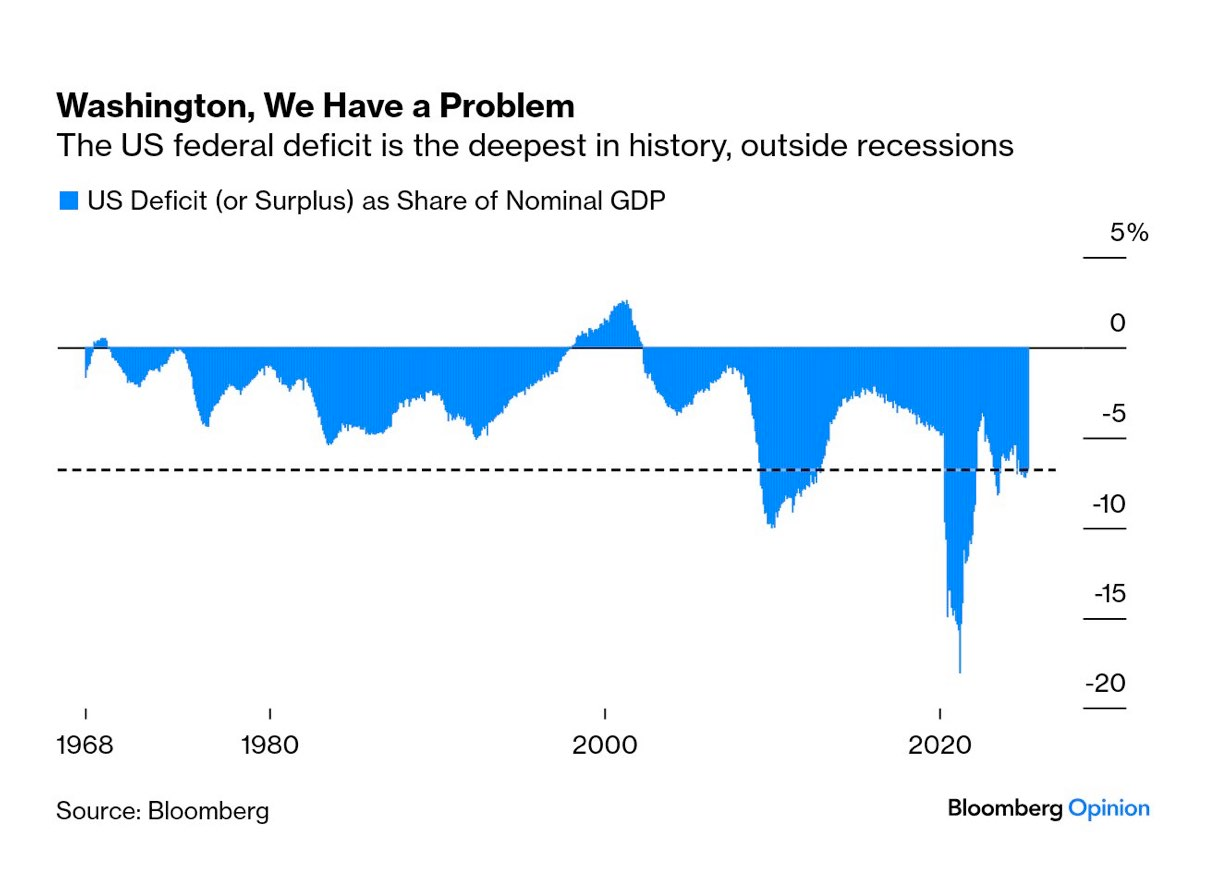
via Mohamed Al-Erian
To make matters worse, as things are deteriorating on the fiscal side of things, the U.S. consumer is getting crushed by credit. The 90-plus day delinquency rates for credit card and auto loans are screaming higher right now.
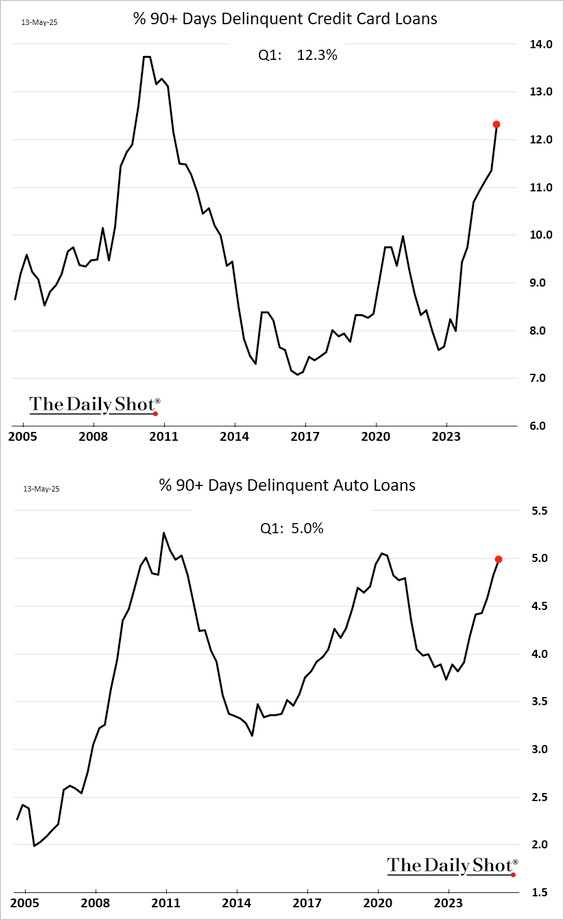
via TXMC
One has to wonder how long all this can continue without some sort of liquidity crunch. Even though equities markets have recovered from their post-Liberation Day month long bear market, I would not be surprised if what we're witnessing is a dead cat bounce that can only be continued if the money printers are turned back on. Something's got to give, both on the fiscal side and in the private markets where the Common Man is getting crushed because he's been forced to take on insane amounts of debt to stay afloat after years of elevated levels of inflation. Add on the fact that AI has reached a state of maturity that will enable companies to replace their current meat suit workers with an army of cheap, efficient and fast digital workers and it isn't hard to see that some sort of employment crisis could be on the horizon as well.
Now is not the time to get complacent. While I do believe that the deals that are currently being made in the Middle East are probably in the best interest of the United States as the world, again, moves toward a more multi-polar reality, we are facing problems that one cannot simply wish away. They will need to be confronted. And as we've seen throughout the 21st century, the problems are usually met head-on with a money printer.
I take no pleasure in saying this because it is a bit uncouth to be gleeful to benefit from the strife of others, but it is pretty clear to me that all signs are pointing to bitcoin benefiting massively from everything that is going on. The shift towards a more multi-polar world, the runaway debt situation here in the United States, the increasing deficits, the AI job replacements and the consumer credit crisis that is currently unfolding, All will need to be "solved" by turning on the money printers to levels they've never been pushed to before.
Weird times we're living in.
China's Manufacturing Dominance: Why It Matters for the U.S.
In my recent conversation with Lyn Alden, she highlighted how China has rapidly ascended the manufacturing value chain. As Lyn pointed out, China transformed from making "sneakers and plastic trinkets" to becoming the world's largest auto exporter in just four years. This dramatic shift represents more than economic success—it's a strategic power play. China now dominates solar panel production with greater market control than OPEC has over oil and maintains near-monopoly control of rare earth elements crucial for modern technology.
"China makes like 10 times more steel than the United States does... which is relevant in ship making. It's relevant in all sorts of stuff." - Lyn Alden
Perhaps most concerning, as Lyn emphasized, is China's financial leverage. They hold substantial U.S. assets that could be strategically sold to disrupt U.S. treasury market functioning. This combination of manufacturing dominance, resource control, and financial leverage gives China significant negotiating power in any trade disputes, making our attempts to reshoring manufacturing all the more challenging.
Check out the full podcast here for more on Triffin's dilemma, Bitcoin's role in monetary transition, and the energy requirements for rebuilding America's industrial base.
Headlines of the Day
Financial Times Under Fire Over MicroStrategy Bitcoin Coverage - via X
Trump in Qatar: Historic Boeing Deal Signed - via X
Get our new STACK SATS hat - via tftcmerch.io
Johnson Backs Stock Trading Ban; Passage Chances Slim - via X
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code *“TFTC20”* during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed 158,469 sats | $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Building things of value is satisfying.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
@media screen and (max-width: 480px) { .mobile-padding { padding: 10px 0 !important; } .social-container { width: 100% !important; max-width: 260px !important; } .social-icon { padding: 0 !important; } .social-icon img { height: 32px !important; width: 32px !important; } .icon-cell { padding: 0 4px !import
-
 @ 39cc53c9:27168656
2025-05-27 09:21:51
@ 39cc53c9:27168656
2025-05-27 09:21:51Know Your Customer is a regulation that requires companies of all sizes to verify the identity, suitability, and risks involved with maintaining a business relationship with a customer. Such procedures fit within the broader scope of anti-money laundering (AML) and counterterrorism financing (CTF) regulations.
Banks, exchanges, online business, mail providers, domain registrars... Everyone wants to know who you are before you can even opt for their service. Your personal information is flowing around the internet in the hands of "god-knows-who" and secured by "trust-me-bro military-grade encryption". Once your account is linked to your personal (and verified) identity, tracking you is just as easy as keeping logs on all these platforms.
Rights for Illusions
KYC processes aim to combat terrorist financing, money laundering, and other illicit activities. On the surface, KYC seems like a commendable initiative. I mean, who wouldn't want to halt terrorists and criminals in their tracks?
The logic behind KYC is: "If we mandate every financial service provider to identify their users, it becomes easier to pinpoint and apprehend the malicious actors."
However, terrorists and criminals are not precisely lining up to be identified. They're crafty. They may adopt false identities or find alternative strategies to continue their operations. Far from being outwitted, many times they're several steps ahead of regulations. Realistically, KYC might deter a small fraction – let's say about 1% ^1 – of these malefactors. Yet, the cost? All of us are saddled with the inconvenient process of identification just to use a service.
Under the rhetoric of "ensuring our safety", governments and institutions enact regulations that seem more out of a dystopian novel, gradually taking away our right to privacy.
To illustrate, consider a city where the mayor has rolled out facial recognition cameras in every nook and cranny. A band of criminals, intent on robbing a local store, rolls in with a stolen car, their faces obscured by masks and their bodies cloaked in all-black clothes. Once they've committed the crime and exited the city's boundaries, they switch vehicles and clothes out of the cameras' watchful eyes. The high-tech surveillance? It didn’t manage to identify or trace them. Yet, for every law-abiding citizen who merely wants to drive through the city or do some shopping, their movements and identities are constantly logged. The irony? This invasive tracking impacts all of us, just to catch the 1% ^1 of less-than-careful criminals.
KYC? Not you.
KYC creates barriers to participation in normal economic activity, to supposedly stop criminals. ^2
KYC puts barriers between many users and businesses. One of these comes from the fact that the process often requires multiple forms of identification, proof of address, and sometimes even financial records. For individuals in areas with poor record-keeping, non-recognized legal documents, or those who are unbanked, homeless or transient, obtaining these documents can be challenging, if not impossible.
For people who are not skilled with technology or just don't have access to it, there's also a barrier since KYC procedures are mostly online, leaving them inadvertently excluded.
Another barrier goes for the casual or one-time user, where they might not see the value in undergoing a rigorous KYC process, and these requirements can deter them from using the service altogether.
It also wipes some businesses out of the equation, since for smaller businesses, the costs associated with complying with KYC norms—from the actual process of gathering and submitting documents to potential delays in operations—can be prohibitive in economical and/or technical terms.
You're not welcome
Imagine a swanky new club in town with a strict "members only" sign. You hear the music, you see the lights, and you want in. You step up, ready to join, but suddenly there's a long list of criteria you must meet. After some time, you are finally checking all the boxes. But then the club rejects your membership with no clear reason why. You just weren't accepted. Frustrating, right?
This club scenario isn't too different from the fact that KYC is being used by many businesses as a convenient gatekeeping tool. A perfect excuse based on a "legal" procedure they are obliged to.
Even some exchanges may randomly use this to freeze and block funds from users, claiming these were "flagged" by a cryptic system that inspects the transactions. You are left hostage to their arbitrary decision to let you successfully pass the KYC procedure. If you choose to sidestep their invasive process, they might just hold onto your funds indefinitely.
Your identity has been stolen
KYC data has been found to be for sale on many dark net markets^3. Exchanges may have leaks or hacks, and such leaks contain very sensitive data. We're talking about the full monty: passport or ID scans, proof of address, and even those awkward selfies where you're holding up your ID next to your face. All this data is being left to the mercy of the (mostly) "trust-me-bro" security systems of such companies. Quite scary, isn't it?
As cheap as $10 for 100 documents, with discounts applying for those who buy in bulk, the personal identities of innocent users who passed KYC procedures are for sale. ^3
In short, if you have ever passed the KYC/AML process of a crypto exchange, your privacy is at risk of being compromised, or it might even have already been compromised.
(they) Know Your Coins
You may already know that Bitcoin and most cryptocurrencies have a transparent public blockchain, meaning that all data is shown unencrypted for everyone to see and recorded forever. If you link an address you own to your identity through KYC, for example, by sending an amount from a KYC exchange to it, your Bitcoin is no longer pseudonymous and can then be traced.
If, for instance, you send Bitcoin from such an identified address to another KYC'ed address (say, from a friend), everyone having access to that address-identity link information (exchanges, governments, hackers, etc.) will be able to associate that transaction and know who you are transacting with.
Conclusions
To sum up, KYC does not protect individuals; rather, it's a threat to our privacy, freedom, security and integrity. Sensible information flowing through the internet is thrown into chaos by dubious security measures. It puts borders between many potential customers and businesses, and it helps governments and companies track innocent users. That's the chaos KYC has stirred.
The criminals are using stolen identities from companies that gathered them thanks to these very same regulations that were supposed to combat them. Criminals always know how to circumvent such regulations. In the end, normal people are the most affected by these policies.
The threat that KYC poses to individuals in terms of privacy, security and freedom is not to be neglected. And if we don’t start challenging these systems and questioning their efficacy, we are just one step closer to the dystopian future that is now foreseeable.
Edited 20/03/2024 * Add reference to the 1% statement on Rights for Illusions section to an article where Chainalysis found that only 0.34% of the transaction volume with cryptocurrencies in 2023 was attributable to criminal activity ^1
-
 @ c1e9ab3a:9cb56b43
2025-05-27 16:19:06
@ c1e9ab3a:9cb56b43
2025-05-27 16:19:06Star Wars is often viewed as a myth of rebellion, freedom, and resistance to tyranny. The iconography—scrappy rebels, totalitarian stormtroopers, lone smugglers—suggests a deep anti-authoritarian ethos. Yet, beneath the surface, the narrative arc of Star Wars consistently affirms the necessity, even sanctity, of central authority. This blog entry introduces the question: Is Star Wars fundamentally a celebration of statism?
Rebellion as Restoration, Not Revolution
The Rebel Alliance’s mission is not to dismantle centralized power, but to restore the Galactic Republic—a bureaucratic, centrally governed institution. Characters like Mon Mothma and Bail Organa are high-ranking senators, not populist revolutionaries. The goal is to remove the corrupt Empire and reinstall a previous central authority, presumed to be just.
- Rebels are loyalists to a prior state structure.
- Power is not questioned, only who wields it.
Jedi as Centralized Moral Elites
The Jedi, often idealized as protectors of peace, are unelected, extra-legal enforcers of moral and military order. Their authority stems from esoteric metaphysical abilities rather than democratic legitimacy.
- They answer only to their internal Council.
- They are deployed by the Senate, but act independently of civil law.
- Their collapse is depicted as tragic not because they were unaccountable, but because they were betrayed.
This positions them as a theocratic elite, not spiritual anarchists.
Chaos and the Frontier: The Case of the Cantina
The Mos Eisley cantina, often viewed as a symbol of frontier freedom, reveals something darker. It is: - Lawless - Violent - Culturally fragmented
Conflict resolution occurs through murder, not mediation. Obi-Wan slices off a limb; Han shoots first—both without legal consequence. There is no evidence of property rights, dispute resolution, or voluntary order.
This is not libertarian pluralism—it’s moral entropy. The message: without centralized governance, barbarism reigns.
The Mythic Arc: Restoration of the Just State
Every trilogy in the saga returns to a single theme: the fall and redemption of legitimate authority.
- Prequels: Republic collapses into tyranny.
- Originals: Rebels fight to restore legitimate order.
- Sequels: Weak governance leads to resurgence of authoritarianism; heroes must reestablish moral centralism.
The story is not anti-state—it’s anti-bad state. The solution is never decentralization; it’s the return of the right ruler or order.
Conclusion: The Hidden Statism of a Rebel Myth
Star Wars wears the costume of rebellion, but tells the story of centralized salvation. It: - Validates elite moral authority (Jedi) - Romanticizes restoration of fallen governments (Republic) - Portrays decentralized zones as corrupt and savage (outer rim worlds)
It is not an anarchist parable, nor a libertarian fable. It is a statist mythology, clothed in the spectacle of rebellion. Its core message is not that power should be abolished, but that power belongs to the virtuous few.
Question to Consider:
If the Star Wars universe consistently affirms the need for centralized moral and political authority, should we continue to see it as a myth of freedom? Or is it time to recognize it as a narrative of benevolent empire? -
 @ c1e9ab3a:9cb56b43
2025-05-27 13:19:53
@ c1e9ab3a:9cb56b43
2025-05-27 13:19:53I. Introduction: Money as a Function of Efficiency and Preference
Money is not defined by law, but by power over productivity. In any open economy, the most economically efficient actors—those who control the most valuable goods, services, and knowledge—ultimately dictate the medium of exchange. Their preferences signal to the broader market what form of money is required to access the highest-value goods, from durable commodities to intangibles like intellectual property and skilled labor.
Whatever money these actors prefer becomes the de facto unit of account and store of value, regardless of its legal status. This emergent behavior is natural and reflects a hierarchy of monetary utility.
II. Classical Gresham’s Law: A Product of Market Distortion
Gresham’s Law, famously stated as:
"Bad money drives out good"
is only valid under coercive monetary conditions, specifically: - Legal tender laws that force the acceptance of inferior money at par with superior money. - Fixed exchange rates imposed by decree, not market valuation. - Governments or central banks backing elastic fiduciary media with promises of redemption. - Institutional structures that mandate debt and tax payments in the favored currency.
Under these conditions, superior money (hard money) is hoarded, while inferior money (soft, elastic, inflationary) circulates. This is not an expression of free market behavior—it is the result of suppressed price discovery and legal coercion.
Gresham’s Law, therefore, is not a natural law of money, but a law of distortion under forced parity and artificial elasticity.
III. The Collapse of Coercion: Inversion of Gresham’s Law
When coercive structures weaken or are bypassed—through technological exit, jurisdictional arbitrage, monetary breakdown, or political disintegration—Gresham’s Law inverts:
Good money drives out bad.
This occurs because: - Market actors regain the freedom to select money based on utility, scarcity, and credibility. - Legal parity collapses, exposing the true economic hierarchy of monetary forms. - Trustless systems (e.g., Bitcoin) or superior digital instruments (e.g., stablecoins) offer better settlement, security, and durability. - Elastic fiduciary media become undesirable as counterparty risk and inflation rise.
The inversion marks a return to monetary natural selection—not a breakdown of Gresham’s Law, but the collapse of its preconditions.
IV. Elasticity and Control
Elastic fiduciary media (like fiat currency) are not intrinsically evil. They are tools of state finance and debt management, enabling rapid expansion of credit and liquidity. However, when their issuance is unconstrained, and legal tender laws force their use, they become weapons of economic coercion.
Banks issue credit unconstrained by real savings, and governments enforce the use of inflated media through taxation and courts. This distorts capital allocation, devalues productive labor, and ultimately hollows out monetary confidence.
V. Monetary Reversion: The Return of Hard Money
When the coercion ends—whether gradually or suddenly—the monetary system reverts. The preferences of the productive and wealthy reassert themselves:
- Superior money is not just saved—it begins to circulate.
- Weaker currencies are rejected not just for savings, but for daily exchange.
- The hoarded form becomes the traded form, and Gresham’s Law inverts completely.
Bitcoin, gold, and even highly credible stable instruments begin to function as true money, not just stores of value. The natural monetary order returns, and the State becomes a late participant, not the originator of monetary reality.
VI. Conclusion
Gresham’s Law operates only under distortion. Its inversion is not an anomaly—it is a signal of the collapse of coercion. The monetary system then reorganizes around productive preference, technological efficiency, and economic sovereignty.
The most efficient market will always dictate the form of hard money. The State can delay this reckoning through legal force, but it cannot prevent it indefinitely. Once free choice returns, bad money dies, and good money lives again.
-
 @ 39cc53c9:27168656
2025-05-27 09:21:50
@ 39cc53c9:27168656
2025-05-27 09:21:50Over the past few months, I've dedicated my time to a complete rewrite of the kycnot.me website. The technology stack remains unchanged; Golang paired with TailwindCSS. However, I've made some design choices in this iteration that I believe significantly enhance the site. Particularly to backend code.
UI Improvements
You'll notice a refreshed UI that retains the original concept but has some notable enhancements. The service list view is now more visually engaging, it displays additional information in a more aesthetically pleasing manner. Both filtering and searching functionalities have been optimized for speed and user experience.
Service pages have been also redesigned to highlight key information at the top, with the KYC Level box always accessible. The display of service attributes is now more visually intuitive.
The request form, especially the Captcha, has undergone substantial improvements. The new self-made Captcha is robust, addressing the reliability issues encountered with the previous version.
Terms of Service Summarizer
A significant upgrade is the Terms of Service summarizer/reviewer, now powered by AI (GPT-4-turbo). It efficiently condenses each service's ToS, extracting and presenting critical points, including any warnings. Summaries are updated monthly, processing over 40 ToS pages via the OpenAI API using a self-crafted and thoroughly tested prompt.
Nostr Comments
I've integrated a comment section for each service using Nostr. For guidance on using this feature, visit the dedicated how-to page.
Database
The backend database has transitioned to pocketbase, an open-source Golang backend that has been a pleasure to work with. I maintain an updated fork of the Golang SDK for pocketbase at pluja/pocketbase.
Scoring
The scoring algorithm has also been refined to be more fair. Despite I had considered its removal due to the complexity it adds (it is very difficult to design a fair scoring system), some users highlighted its value, so I kept it. The updated algorithm is available open source.
Listings
Each listing has been re-evaluated, and the ones that were no longer operational were removed. New additions are included, and the backlog of pending services will be addressed progressively, since I still have access to the old database.
API
The API now offers more comprehensive data. For more details, check here.
About Page
The About page has been restructured for brevity and clarity.
Other Changes
Extensive changes have been implemented in the server-side logic, since the whole code base was re-written from the ground up. I may discuss these in a future post, but for now, I consider the current version to be just a bit beyond beta, and additional updates are planned in the coming weeks.
-
 @ c9badfea:610f861a
2025-05-26 21:30:33
@ c9badfea:610f861a
2025-05-26 21:30:33- Install Loop Habit Tracker (it's free and open source)
- Launch the app, tap ➡️
- Tap ⁝, select Settings, scroll down and tap Customize Notifications
- Enable Show Notifications
- Return to the main screen
- Tap + to add a habit
- Choose Yes Or No for simple yes/no questions (e.g. Did you wake up early?)
- Choose Measurable for questions where a quantity is expected (e.g. How many pages did you read?)
- Assign a Name (e.g. Waking up early)
- Enter a Question (e.g. Did you wake up early?)
- Define the Frequency (e.g. Every Day)
- Schedule a Reminder (e.g. 08:00 and Any Day Of The Week)
- Include a Note if needed
- Hit Save to create the habit
- Start tracking your habits!
ℹ️ To categorize habits, use colors (e.g. blue for morning, orange for afternoon) or title prefixes (e.g. "Morning - Waking Up Early" and "Afternoon - Workout")
-
 @ 39cc53c9:27168656
2025-05-27 09:21:48
@ 39cc53c9:27168656
2025-05-27 09:21:48I'm launching a new service review section on this blog in collaboration with OrangeFren. These reviews are sponsored, yet the sponsorship does not influence the outcome of the evaluations. Reviews are done in advance, then, the service provider has the discretion to approve publication without modifications.
Sponsored reviews are independent from the kycnot.me list, being only part of the blog. The reviews have no impact on the scores of the listings or their continued presence on the list. Should any issues arise, I will not hesitate to remove any listing.
The review
WizardSwap is an instant exchange centred around privacy coins. It was launched in 2020 making it old enough to have weathered the 2021 bull run and the subsequent bearish year.
| Pros | Cons | |------|------| | Tor-friendly | Limited liquidity | | Guarantee of no KYC | Overly simplistic design | | Earn by providing liquidity | |
Rating: ★★★★★ Service Website: wizardswap.io
Liquidity
Right off the bat, we'll start off by pointing out that WizardSwap relies on its own liquidity reserves, meaning they aren't just a reseller of Binance or another exchange. They're also committed to a no-KYC policy, when asking them, they even promised they would rather refund a user their original coins, than force them to undergo any sort of verification.
On the one hand, full control over all their infrastructure gives users the most privacy and conviction about the KYC policies remaining in place.
On the other hand, this means the liquidity available for swapping isn't huge. At the time of testing we could only purchase at most about 0.73 BTC with XMR.
It's clear the team behind WizardSwap is aware of this shortfall and so they've come up with a solution unique among instant exchanges. They let you, the user, deposit any of the currencies they support into your account and earn a profit on the trades made using your liquidity.
Trading
Fees on WizardSwap are middle-of-the-pack. The normal fee is 2.2%. That's more than some exchanges that reserve the right to suddenly demand you undergo verification, yet less than half the fees on some other privacy-first exchanges. However as we mentioned in the section above you can earn almost all of that fee (2%) if you provide liquidity to WizardSwap.
It's good that with the current Bitcoin fee market their fees are constant regardless of how much, or how little, you send. This is in stark contrast with some of the alternative swap providers that will charge you a massive premium when attempting to swap small amounts of BTC away.
Test trades
Test trades are always performed without previous notice to the service provider.
During our testing we performed a few test trades and found that every single time WizardSwap immediately detected the incoming transaction and the amount we received was exactly what was quoted before depositing. The fees were inline with what WizardSwap advertises.

- Monero payment proof
- Bitcoin received
- Wizardswap TX link - it's possible that this link may cease to be valid at some point in the future.
ToS and KYC
WizardSwap does not have a Terms of Service or a Privacy Policy page, at least none that can be found by users. Instead, they offer a FAQ section where they addresses some basic questions.
The site does not mention any KYC or AML practices. It also does not specify how refunds are handled in case of failure. However, based on the FAQ section "What if I send funds after the offer expires?" it can be inferred that contacting support is necessary and network fees will be deducted from any refund.
UI & Tor
WizardSwap can be visited both via your usual browser and Tor Browser. Should you decide on the latter you'll find that the website works even with the most strict settings available in the Tor Browser (meaning no JavaScript).
However, when disabling Javascript you'll miss the live support chat, as well as automatic refreshing of the trade page. The lack of the first means that you will have no way to contact support from the trade page if anything goes wrong during your swap, although you can do so by mail.
One important thing to have in mind is that if you were to accidentally close the browser during the swap, and you did not save the swap ID or your browser history is disabled, you'll have no easy way to return to the trade. For this reason we suggest when you begin a trade to copy the url or ID to someplace safe, before sending any coins to WizardSwap.
The UI you'll be greeted by is simple, minimalist, and easy to navigate. It works well not just across browsers, but also across devices. You won't have any issues using this exchange on your phone.
Getting in touch
The team behind WizardSwap appears to be most active on X (formerly Twitter): https://twitter.com/WizardSwap_io
If you have any comments or suggestions about the exchange make sure to reach out to them. In the past they've been very receptive to user feedback, for instance a few months back WizardSwap was planning on removing DeepOnion, but the community behind that project got together ^1 and after reaching out WizardSwap reversed their decision ^2.
You can also contact them via email at:
support @ wizardswap . ioDisclaimer
None of the above should be understood as investment or financial advice. The views are our own only and constitute a faithful representation of our experience in using and investigating this exchange. This review is not a guarantee of any kind on the services rendered by the exchange. Do your own research before using any service.
-
 @ 611021ea:089a7d0f
2025-05-26 18:28:46
@ 611021ea:089a7d0f
2025-05-26 18:28:46Imagine a world where your favorite health and fitness apps—diet trackers, meditation tools, cardio and strength training platforms, even therapy apps—can all work together seamlessly. Not because they're owned by the same company, but because they speak a common, open language. That's the future NIP-101h is building on Nostr.
A Modular, Privacy-First Health Data Framework
NIP-101h defines a modular, privacy-first framework for sharing granular health and fitness metrics on the decentralized Nostr protocol. The core idea is simple but powerful: every health metric (weight, steps, calories, mood, and so on) gets its own unique Nostr event kind. Apps can implement only the metrics they care about, and users can choose exactly what to share, with whom, and how.
This modular approach means true interoperability. A meditation app can log mindfulness sessions, a running app can record your daily mileage, and a diet tracker can keep tabs on your nutrition—all using the same underlying standard. Each app remains independent, but your data becomes portable, composable, and, most importantly, under your control.
Why NIP-101h Matters
Interoperability
Today's health and fitness apps are walled gardens. Data is locked away in proprietary formats, making it hard to move, analyze, or combine. NIP-101h breaks down these barriers by providing a common, open standard for health metrics on Nostr. Apps can collaborate, users can migrate, and new services can emerge—without permission or lock-in.
User Control & Privacy
Health data is deeply personal. That's why NIP-101h is privacy-first: all metric values are encrypted by default using NIP-44, unless the user explicitly opts out. You decide what's public, what's private, and who gets access. Even if you want to keep everything local, that's supported too.
Extensibility
The world of health and fitness is always evolving. NIP-101h is designed to grow with it. New metrics can be added at any time via the
-
 @ 39cc53c9:27168656
2025-05-27 09:21:46
@ 39cc53c9:27168656
2025-05-27 09:21:46Bitcoin enthusiasts frequently and correctly remark how much value it adds to Bitcoin not to have a face, a leader, or a central authority behind it. This particularity means there isn't a single person to exert control over, or a single human point of failure who could become corrupt or harmful to the project.
Because of this, it is said that no other coin can be equally valuable as Bitcoin in terms of decentralization and trustworthiness. Bitcoin is unique not just for being first, but also because of how the events behind its inception developed. This implies that, from Bitcoin onwards, any coin created would have been created by someone, consequently having an authority behind it. For this and some other reasons, some people refer to Bitcoin as "The Immaculate Conception".
While other coins may have their own unique features and advantages, they may not be able to replicate Bitcoin's community-driven nature. However, one other cryptocurrency shares a similar story of mystery behind its creation: Monero.
History of Monero
Bytecoin and CryptoNote
In March 2014, a Bitcointalk thread titled "Bytecoin. Secure, private, untraceable since 2012" was initiated by a user under the nickname "DStrange"^1^. DStrange presented Bytecoin (BCN) as a unique cryptocurrency, in operation since July 2012. Unlike Bitcoin, it employed a new algorithm known as CryptoNote.
DStrange apparently stumbled upon the Bytecoin website by chance while mining a dying bitcoin fork, and decided to create a thread on Bitcointalk^1^. This sparked curiosity among some users, who wondered how could Bytecoin remain unnoticed since its alleged launch in 2012 until then^2^.
Some time after, a user brought up the "CryptoNote v2.0" whitepaper for the first time, underlining its innovative features^4^. Authored by the pseudonymous Nicolas van Saberhagen in October 2013, the CryptoNote v2 whitepaper^5^ highlighted the traceability and privacy problems in Bitcoin. Saberhagen argued that these flaws could not be quickly fixed, suggesting it would be more efficient to start a new project rather than trying to patch the original^5^, an statement simmilar to the one from Satoshi Nakamoto^6^.
Checking with Saberhagen's digital signature, the release date of the whitepaper seemed correct, which would mean that Cryptonote (v1) was created in 2012^7^, although there's an important detail: "Signing time is from the clock on the signer's computer" ^9^.
Moreover, the whitepaper v1 contains a footnote link to a Bitcointalk post dated May 5, 2013^10^, making it impossible for the whitepaper to have been signed and released on December 12, 2012.
As the narrative developed, users discovered that a significant 80% portion of Bytecoin had been pre-mined^11^ and blockchain dates seemed to be faked to make it look like it had been operating since 2012, leading to controversy surrounding the project.
The origins of CryptoNote and Bytecoin remain mysterious, leaving suspicions of a possible scam attempt, although the whitepaper had a good amount of work and thought on it.
The fork
In April 2014, the Bitcointalk user
thankful_for_today, who had also participated in the Bytecoin thread^12^, announced plans to launch a Bytecoin fork named Bitmonero^13^.The primary motivation behind this fork was "Because there is a number of technical and marketing issues I wanted to do differently. And also because I like ideas and technology and I want it to succeed"^14^. This time Bitmonero did things different from Bytecoin: there was no premine or instamine, and no portion of the block reward went to development.
However, thankful_for_today proposed controversial changes that the community disagreed with. Johnny Mnemonic relates the events surrounding Bitmonero and thankful_for_today in a Bitcointalk comment^15^:
When thankful_for_today launched BitMonero [...] he ignored everything that was discussed and just did what he wanted. The block reward was considerably steeper than what everyone was expecting. He also moved forward with 1-minute block times despite everyone's concerns about the increase of orphan blocks. He also didn't address the tail emission concern that should've (in my opinion) been in the code at launch time. Basically, he messed everything up. Then, he disappeared.
After disappearing for a while, thankful_for_today returned to find that the community had taken over the project. Johnny Mnemonic continues:
I, and others, started working on new forks that were closer to what everyone else was hoping for. [...] it was decided that the BitMonero project should just be taken over. There were like 9 or 10 interested parties at the time if my memory is correct. We voted on IRC to drop the "bit" from BitMonero and move forward with the project. Thankful_for_today suddenly resurfaced, and wasn't happy to learn the community had assumed control of the coin. He attempted to maintain his own fork (still calling it "BitMonero") for a while, but that quickly fell into obscurity.
The unfolding of these events show us the roots of Monero. Much like Satoshi Nakamoto, the creators behind CryptoNote/Bytecoin and thankful_for_today remain a mystery^17^, having disappeared without a trace. This enigma only adds to Monero's value.
Since community took over development, believing in the project's potential and its ability to be guided in a better direction, Monero was given one of Bitcoin's most important qualities: a leaderless nature. With no single face or entity directing its path, Monero is safe from potential corruption or harm from a "central authority".
The community continued developing Monero until today. Since then, Monero has undergone a lot of technological improvements, migrations and achievements such as RingCT and RandomX. It also has developed its own Community Crowdfundinc System, conferences such as MoneroKon and Monerotopia are taking place every year, and has a very active community around it.
Monero continues to develop with goals of privacy and security first, ease of use and efficiency second. ^16^
This stands as a testament to the power of a dedicated community operating without a central figure of authority. This decentralized approach aligns with the original ethos of cryptocurrency, making Monero a prime example of community-driven innovation. For this, I thank all the people involved in Monero, that lead it to where it is today.
If you find any information that seems incorrect, unclear or any missing important events, please contact me and I will make the necessary changes.
Sources of interest
- https://forum.getmonero.org/20/general-discussion/211/history-of-monero
- https://monero.stackexchange.com/questions/852/what-is-the-origin-of-monero-and-its-relationship-to-bytecoin
- https://en.wikipedia.org/wiki/Monero
- https://bitcointalk.org/index.php?topic=583449.0
- https://bitcointalk.org/index.php?topic=563821.0
- https://bitcointalk.org/index.php?action=profile;u=233561
- https://bitcointalk.org/index.php?topic=512747.0
- https://bitcointalk.org/index.php?topic=740112.0
- https://monero.stackexchange.com/a/1024
- https://inspec2t-project.eu/cryptocurrency-with-a-focus-on-anonymity-these-facts-are-known-about-monero/
- https://medium.com/coin-story/coin-perspective-13-riccardo-spagni-69ef82907bd1
- https://www.getmonero.org/resources/about/
- https://www.wired.com/2017/01/monero-drug-dealers-cryptocurrency-choice-fire/
- https://www.monero.how/why-monero-vs-bitcoin
- https://old.reddit.com/r/Monero/comments/u8e5yr/satoshi_nakamoto_talked_about_privacy_features/
-
 @ c9badfea:610f861a
2025-05-26 16:14:46
@ c9badfea:610f861a
2025-05-26 16:14:46- Install Trail Sense (it's free and open source)
- Open the app, and tap Next then I Agree
- Allow location access While Using The App and Allow notifications
- Tap 🧭 on the bottom bar to open the compass
- Use 📍️ in the upper left to manage paths
- Use 🗺️ in the upper right to take a picture of a physical map and navigate on it
- Use ⬆️ in the lower right to set beacons along your hike
- Tap ☁️ on the bottom bar for weather information
- Use ☁️ in the upper left to predict weather using cloud patterns
- Use 🌡️ in the upper right to estimate the temperature (useful when in the mountains)
- Tap ✨ on the bottom bar for astronomy details
- Use 🔦 in the upper left to toggle your phone's flashlight
- Use ⬇️ in the upper right to set alarms and reminders (e.g. sunset alerts)
- Tap ▦ on the bottom bar to access extra tools
- Use 🔦 to toggle the flashlight
- Use 🔊 to play a whistle sound
- Use 🔋 to turn battery-saving mode on or off
- Select User Guide for help with all features
- Enjoy!
ℹ️ Explore the app - it has many features worth learning
-
 @ 39cc53c9:27168656
2025-05-27 09:21:45
@ 39cc53c9:27168656
2025-05-27 09:21:45I've been thinking about how to improve my seed backup in a cheap and cool way, mostly for fun. Until now, I had the seed written on a piece of paper in a desk drawer, and I wanted something more durable and fire-proof.
After searching online, I found two options I liked the most: the Cryptosteel Capsule and the Trezor Keep. These products are nice but quite expensive, and I didn't want to spend that much on my seed backup. Privacy is also important, and sharing details like a shipping address makes me uncomfortable. This concern has grown since the Ledger incident^1. A $5 wrench attack^2 seems too cheap, even if you only hold a few sats.
Upon seeing the design of Cryptosteel, I considered creating something similar at home. Although it may not be as cool as their device, it could offer almost the same in terms of robustness and durability.
Step 1: Get the materials and tools
When choosing the materials, you will want to go with stainless steel. It is durable, resistant to fire, water, and corrosion, very robust, and does not rust. Also, its price point is just right; it's not the cheapest, but it's cheap for the value you get.

I went to a material store and bought:
- Two bolts
- Two hex nuts and head nuts for the bolts
- A bag of 30 washers
All items were made of stainless steel. The total price was around €6. This is enough for making two seed backups.
You will also need:
- A set of metal letter stamps (I bought a 2mm-size letter kit since my washers were small, 6mm in diameter)
- You can find these in local stores or online marketplaces. The set I bought cost me €13.
- A good hammer
- A solid surface to stamp on
Total spent: 19€ for two backups
Step 2: Stamp and store
Once you have all the materials, you can start stamping your words. There are many videos on the internet that use fancy 3D-printed tools to get the letters nicely aligned, but I went with the free-hand option. The results were pretty decent.

I only stamped the first 4 letters for each word since the BIP-39 wordlist allows for this. Because my stamping kit did not include numbers, I used alphabet letters to define the order. This way, if all the washers were to fall off, I could still reassemble the seed correctly.
The final result
So this is the final result. I added two smaller washers as protection and also put the top washer reversed so the letters are not visible:

Compared to the Cryptosteel or the Trezor Keep, its size is much more compact. This makes for an easier-to-hide backup, in case you ever need to hide it inside your human body.
Some ideas
Tamper-evident seal
To enhance the security this backup, you can consider using a tamper-evident seal. This can be easily achieved by printing a unique image or using a specific day's newspaper page (just note somewhere what day it was).
Apply a thin layer of glue to the washer's surface and place the seal over it. If someone attempts to access the seed, they will be forced to destroy the seal, which will serve as an evident sign of tampering.
This simple measure will provide an additional layer of protection and allow you to quickly identify any unauthorized access attempts.
Note that this method is not resistant to outright theft. The tamper-evident seal won't stop a determined thief but it will prevent them from accessing your seed without leaving any trace.
Redundancy
Make sure to add redundancy. Make several copies of this cheap backup, and store them in separate locations.
Unique wordset
Another layer of security could be to implement your own custom mnemonic dictionary. However, this approach has the risk of permanently losing access to your funds if not implemented correctly.
If done properly, you could potentially end up with a highly secure backup, as no one else would be able to derive the seed phrase from it. To create your custom dictionary, assign a unique number from 1 to 2048 to a word of your choice. Maybe you could use a book, and index the first 2048 unique words that appear. Make sure to store this book and even get a couple copies of it (digitally and phisically).
This self-curated set of words will serve as your personal BIP-39 dictionary. When you need to translate between your custom dictionary and the official BIP-39 wordlist, simply use the index number to find the corresponding word in either list.
Never write the idex or words on your computer (Do not use
Ctr+F) -
 @ 5c26ee8b:a4d229aa
2025-05-26 16:10:05
@ 5c26ee8b:a4d229aa
2025-05-26 16:10:05In March 2022, I have introduced “VCPs”; (Virtual Currency points). So that the international transactions are made without relying on one currency or another and the financial crises are easily avoided.
You may have noticed that banks are increasing their gold reserves and that there are interests for local virtual currency and that was after the note was published.
The picture of the note showing its date will be in attachment to this post; I can’t edit it to avoid that its date gets changed. Here its content:
Conversion of international banking system: The “VCPs” system: * Each central bank would keep its assets and funds in homeland. * Establishing the value of one virtual currency point. I suggested that: 1 virtual currency point (VCP) = 0.1 gram of gold. * Virtual evaluation must be made to each currency, virtual currency points must be added to each currency’s market value. * International transfers and payments must use the virtual currency points, VCPs, assigned to each currency in international operations. * Daily, weekly, monthly or yearly the actual money corresponding to the virtual currency points used in payments and transfers will be sent by any chosen mean of transport to the banks that had completed the operations or to the corresponding central banks. In this way no currency would prevail in international payments as all currencies will be considered as VCPs. —————————————————————- Because of the need of more guidelines to start using VCPs I have published the following updates:
VCPs allowance updates:
- Not only gold, also precious stones or agreed minerals held in banks can be used to obtain the VCPs allowance (public VCPs allowances). At the same time what is registered and kept in circulation (of gold, precious stones and agreed minerals that belongs to the people) in the country as private VCPs allowances to increase the VCPs allowances. The people can use their personal VCPs along with their precious items for purchases; for example if they sell or use their own gold to buy something, they must give their VCPs registration receipt or card (if they didn’t register their gold to obtain VCPs allowance, they can get it registered at the moment they decide to sell it so it gets added to the private VCPs allowances of his/her country). However, the registered materials must be declared at all borders while traveling once exceeded an internationally agreed specific amount (such as the value of €10000). Therefore a registration method can be agreed with gold and jewelry shops. For instance, while evaluating the materials getting registered, an online VCPs account (for a first registration) can get made on the site that is getting ready and the registration can be combined with a physical/online card (VCPs allowance card. For registering other materials in a later moment, the same card can be used to access the same account. Note that the materials must be used with the private VCPs allowance card for buying or selling, while for public VCPs accounts it’s not necessary because the materials will be kept in the central bank or other banks) or a receipt with a serial number (and other methods to protect customers from fraud). Banks can buy private VCPs while buying gold or other agreed materials and make them public VCPs. And people can have public VCPs allowances corresponding to the value of money (currency) they have already in their accounts. While if people buy gold from the bank (with cash or any other payment method), the related public VCPs allowance will be transformed into private ones (the buyers must receive the actual gold with the private VCPs allowance).
- The agreed materials that can be used to obtain public VCPs must not be consumable (such as oil or natural gas) or used for industrial purposes (such as iron or lithium).
- The printed and online (used by credit or debit cards) currency kept in circulation of the concerned country must correspond to the value of public VCPs allowance that must correspond with the value of gold kept in the central bank (printing more money will decrease its own value internationally).
- Private banks in the same country can have a public VCPs agreement with the central bank so that each bank registers and declares how much gold or valuable materials it has and get its own share of public VCPs allowance and its related printed/online currency in circulation.
- Gems and gold kept in museums can have public VCPs allowances that correspond to their weights only not the archeological values.
- International trade can use public VCPs allowances and the physical payment must follow; either by a preferred currency or gold. However if two or more countries have a trade agreement they can barter goods using IVCPs (International VCPs Allowances; that does not need to have a deposited amount of gold although they will use the same reference as public or private VCPs because it’s a general way to evaluate goods of different types; so for example oil can be swapped for electronics based on how much IVCPs are agreed to be equally swapped each year; i.e. a gallon of oil that costs 50 IVCPs can be swapped for a device that costs 25 IVCPs and grains that cost 25 IVCPs in an International VCPs Allowance Agreement where all parties receives the agreed goods without transferring money or gold). The amount of IVCPs can be agreed per year or there could a multiple online account/s viewable by the countries/parties taking part in the agreement showing the balance of International VCPs that can still be used in bartering goods for each one of the participating countries/parties).
- Cryptocurrencies can be like International VCPs they won’t need to have a deposit of gold, however they must go through an evaluation process compared to their current comparative value and gold (i.e. the amount of bitcoin that must be paid to buy a 0.1g of gold now can become the fixed value) so that the Cryptocurrencies can still be used for trading or bartering for goods even after the release of VCPs. The Cryptocurrencies can sustain the deficiencies of amount of currency that can be used in the same country or internationally (because not everyone can have enough gold deposited to sustain the daily trade). However regulations on the amount of Cryptocurrency/ies exchanged in a country must be agreed with its own central bank or there could be an international agreement; this amount can’t be less than what’s already in use of a certain Cryptocurrency. Or Cryptocurrencies can be exchanged with IVCPs (to protect people’s money while keeping in mind their compared value with gold now) and an amount of International VCPs allowance can be used also for bartering goods in the same country through an agreement with its own central bank.
- Public VCPs must have printable cash allowance that can be in the country or overseas (registered in banks, exchange companies and at borders). Each bank can have registers of local or foreign cash.
- In order to avoid the devaluation of the currency, because the printed money will corrisponde to the gold or valuable minerals held by the country, the concerned country must retrieve the cash abroad and replace it either with another currency or IVCPs through a trade agreement.
- To compensate the deficit of VCPs necessary for daily use within a country and to make a proper distinction, locally, Local Virtual Points (LVCPs) can be used.
- The Local VCPs would be issued by local authorities.
Meanwhile, countries started using the free VCPs platform that is built by a talented web developer in JavaScript; fiatjaf. I insist though that the trade name for the virtual currency points stays “VCPs” and that the clients are made aware of its usage in their daily banking.
-
 @ 39cc53c9:27168656
2025-05-27 09:21:43
@ 39cc53c9:27168656
2025-05-27 09:21:43kycnot.me features a somewhat hidden tool that some users may not be aware of. Every month, an automated job crawls every listed service's Terms of Service (ToS) and FAQ pages and conducts an AI-driven analysis, generating a comprehensive overview that highlights key points related to KYC and user privacy.
Here's an example: Changenow's Tos Review

Why?
ToS pages typically contain a lot of complicated text. Since the first versions of kycnot.me, I have tried to provide users a comprehensive overview of what can be found in such documents. This automated method keeps the information up-to-date every month, which was one of the main challenges with manual updates.
A significant part of the time I invest in investigating a service for kycnot.me involves reading the ToS and looking for any clauses that might indicate aggressive KYC practices or privacy concerns. For the past four years, I performed this task manually. However, with advancements in language models, this process can now be somewhat automated. I still manually review the ToS for a quick check and regularly verify the AI’s findings. However, over the past three months, this automated method has proven to be quite reliable.
Having a quick ToS overview section allows users to avoid reading the entire ToS page. Instead, you can quickly read the important points that are grouped, summarized, and referenced, making it easier and faster to understand the key information.
Limitations
This method has a key limitation: JS-generated pages. For this reason, I was using Playwright in my crawler implementation. I plan to make a release addressing this issue in the future. There are also sites that don't have ToS/FAQ pages, but these sites already include a warning in that section.
Another issue is false positives. Although not very common, sometimes the AI might incorrectly interpret something harmless as harmful. Such errors become apparent upon reading; it's clear when something marked as bad should not be categorized as such. I manually review these cases regularly, checking for anything that seems off and then removing any inaccuracies.
Overall, the automation provides great results.
How?
There have been several iterations of this tool. Initially, I started with GPT-3.5, but the results were not good in any way. It made up many things, and important thigs were lost on large ToS pages. I then switched to GPT-4 Turbo, but it was expensive. Eventually, I settled on Claude 3 Sonnet, which provides a quality compromise between GPT-3.5 and GPT-4 Turbo at a more reasonable price, while allowing a generous 200K token context window.
I designed a prompt, which is open source^1, that has been tweaked many times and will surely be adjusted further in the future.
For the ToS scraping part, I initially wrote a scraper API using Playwright^2, but I replaced it with Jina AI Reader^3, which works quite well and is designed for this task.
Non-conflictive ToS
All services have a dropdown in the ToS section called "Non-conflictive ToS Reviews." These are the reviews that the AI flagged as not needing a user warning. I still provide these because I think they may be interesting to read.
Feedback and contributing
You can give me feedback on this tool, or share any inaccuraties by either opening an issue on Codeberg^4 or by contacting me ^5.
You can contribute with pull requests, which are always welcome, or you can support this project with any of the listed ways.
-
 @ 1f956aec:768866bd
2025-05-26 15:06:38
@ 1f956aec:768866bd
2025-05-26 15:06:38== January 17 2025
Out From Underneath | Prism Shores
crazy arms | pigeon pit
Humanhood | The Weather Station
== february 07 2025
Wish Defense | FACS
Sayan - Savoie | Maria Teriaeva
Nowhere Near Today | Midding
== february 14 2025
Phonetics On and On | Horsegirl
== february 21 2025
Finding Our Balance | Tsoh Tso
Machine Starts To Sing | Porridge Radio
Armageddon In A Summer Dress | Sunny Wa
== february 28 2025
you, infinite | you, infinite
On Being | Max Cooper
Billboard Heart | Deep Sea Diver
== March 21 2025
Watermelon/Peacock | Exploding Flowers
Warlord of the Weejuns | Goya Gumbani
== March 28 2025
Little Death Wishes | CocoRosie
Forever is a Feeling | Lucy Dacus
Evenfall | Sam Akpro
== April 4 2025
Tripla | Miki Berenyi Trio
Adagio | Σtella
The Fork | Oscar Jerome
== April 18 2025
Send A Prayer My Way | Julien Baker & TORRES
Superheaven | Superheaven
Thee Black Boltz | Tunde Adebimpe
from brooklyvegan
== April 25 2025
Face Down In The Garden |Tennis
Under Tangled Silence | Djrum
Viagr Aboys |Viagra Boys
Blurring Time | Bells Larsen
== May 2 2025
Time is Not Yours | Say Sue Me 세이수미
If You Asked For A Picture | Blondshell
== May 16 2025
Wield Your Hope Like A Weapon | Soot Sprite
Transmission 96 | Liftin Spirits & DJ Persuasion
Menedék | TÖRZS
== May 28 2025
Forefowk, Mind Me | Quinie
Silver Tears | SILVER TEARS
-
 @ 39cc53c9:27168656
2025-05-27 09:21:41
@ 39cc53c9:27168656
2025-05-27 09:21:41These reviews are sponsored, yet the sponsorship does not influence the outcome of the evaluations. Sponsored reviews are independent from the kycnot.me list, being only part of the blog. The reviews have no impact on the scores of the listings or their continued presence on the list. Should any issues arise, I will not hesitate to remove any listing. Reviews are in collaboration with Orangefren.
The review
Swapter.io is an all-purpose instant exchange. They entered the scene in the depths of the bear market about 2 years ago in June of 2022.
| Pros | Cons | | --------------- | ---------------------------------- | | Low fees | Shotgun KYC with opaque triggers | | Large liquidity | Relies on 3rd party liquidity | | Works over Tor | Front-end not synced with back-end | | Pretty UI | |
Rating: ★★★☆☆ Service Website: swapter.io
⚠️ There is an ongoing issue with this service: read more on Reddit.
Test Trades
During our testing we performed a trade from XMR to LTC, and then back to XMR.
Our first trade had the ID of:
mpUitpGemhN8jjNAjQuo6EvQ. We were promised 0.8 LTC for sending 0.5 XMR, before we sent the Monero. When the Monero arrived we were sent 0.799 LTC.On the return journey we performed trade with ID:
yaCRb5pYcRKAZcBqg0AzEGYg. This time we were promised 0.4815 XMR for sending 0.799 LTC. After Litecoin arrived we were sent 0.4765 XMR.As such we saw a discrepancy of
~0.1%in the first trade and~1%in the second trade. Considering those trades were floating we determine the estimates presented in the UI to be highly accurate and honest.Of course Swapter could've been imposing a large fee on their estimates, but we checked their estimates against CoinGecko and found the difference to be equivalent to a fee of just over
0.5%. Perfectly in line with other swapping services.Trading
Swapter supports BTC, LTC, XMR and well over a thousand other coins. Sadly they don't support the Lightning Network. For the myriad of currencies they deal with they provide massive upper limits. You could exchange tens, or even hundreds, of thousands of dollars worth of cryptocurrency in a single trade (although we wouldn't recommend it).
The flip side to this is that Swapter relies on 3rd party liquidity. Aside from the large liqudity this also benefits the user insofar as it allows for very low fees. However, it also comes with a negative - the 3rd party gets to see all your trades. Unfortunately Swapter opted not to share where they source their liquidity in their Privacy Policy or Terms of Service.
KYC & AML policies
Swapter reserves the right to require its users to provide their full name, their date of birth, their address and government-issued ID. A practice known as "shotgun KYC". This should not happen often - in our testing it never did - however it's not clear when exactly it could happen. The AML & KYC policy provided on Swapter's website simply states they will put your trade on hold if their "risk scoring system [deems it] as suspicious".
Worse yet, if they determine that "any of the information [the] customer provided is incorrect, false, outdated, or incomplete" then Swapter may decide to terminate all of the services they provide to the user. What exactly would happen to their funds in such a case remains unclear.
The only clarity we get is that the Swapter policy outlines a designated 3rd party that will verify the information provided by the user. The third party's name is Sum & Substance Ltd, also simply known as samsub and available at sumsub.com
It's understandable that some exchanges will decide on a policy of this sort, especially when they rely on external liquidity, but we would prefer more clarity be given. When exactly is a trade suspicious?
Tor
We were pleased to discover Swapter works over Tor. However, they do not provide a Tor mirror, nor do they work without JavaScript. Additionally, we found that some small features, such as the live chat, did not work over Tor. Fortunately, other means of contacting their support are still available.
UI
We have found the Swapter UI to be very modern, straightforward and simple to use. It's available in 4 languages (English, French, Dutch and Russian), although we're unable to vouch for the quality of some of those, the ones that we used seemed perfectly serviceable.
Our only issue with the UI was that it claims the funds have been sent following the trade, when in reality it seems to take the backend a minute or so to actually broadcast the transaction.
Getting in touch
Swapter's team has a chat on their website, a support email address and a support Telegram. Their social media presence in most active on Telegram and X (formerly Twitter).
Disclaimer
None of the above should be understood as investment or financial advice. The views are our own only and constitute a faithful representation of our experience in using and investigating this exchange. This review is not a guarantee of any kind on the services rendered by the exchange. Do your own research before using any service.
-
 @ 78a1621b:0153f86c
2025-05-26 14:22:23
@ 78a1621b:0153f86c
2025-05-26 14:22:23I was very surprised to see the foreword written by Ken Liu. I have read The Three Body Problem and Death's End, two science fiction books translated by him. Just could not believe the connection.
Chapter 1 covered Finite Fields. This took me back to my Abstract Algebra class in undergrad. I wish I had this book and was interested in Bitcoin back then. So much of what you study in school you have to study without experiencing how they connect to the real world. I wish this wasn't the case.
Jimmy Song does an amazing job of explaining just what you need in simple terms and planting flags to watch out for concepts that will be relevant later in the book. The companion code and exercises are also very well designed. This got me thinking about how much students miss out by not actively incorporating programming into the mathematics curriculum.
Looking forward to continuing with the book.
-
 @ c9badfea:610f861a
2025-05-25 22:36:12
@ c9badfea:610f861a
2025-05-25 22:36:12- Install Notally (it's free and open source)
- Open the app, tap ≡, and select Settings
- Tap View and switch to Grid
- Return to the main screen
- Tap ☑ to create a task list and ✏️ to create a note
- Enjoy!
ℹ️ You can also add pictures and set reminders for notes and task lists
ℹ️ Add labels to the notes (e.g. "Diary", "Snippet" or "Knowledge")
ℹ️ Use emojis to enhance titles (e.g. "🛒 Purchases" and "🔗️ Links")
-
 @ 39cc53c9:27168656
2025-05-27 09:21:40
@ 39cc53c9:27168656
2025-05-27 09:21:40“The future is there... staring back at us. Trying to make sense of the fiction we will have become.” — William Gibson.
This month is the 4th anniversary of kycnot.me. Thank you for being here.
Fifteen years ago, Satoshi Nakamoto introduced Bitcoin, a peer-to-peer electronic cash system: a decentralized currency free from government and institutional control. Nakamoto's whitepaper showed a vision for a financial system based on trustless transactions, secured by cryptography. Some time forward and KYC (Know Your Customer), AML (Anti-Money Laundering), and CTF (Counter-Terrorism Financing) regulations started to come into play.
What a paradox: to engage with a system designed for decentralization, privacy, and independence, we are forced to give away our personal details. Using Bitcoin in the economy requires revealing your identity, not just to the party you interact with, but also to third parties who must track and report the interaction. You are forced to give sensitive data to entities you don't, can't, and shouldn't trust. Information can never be kept 100% safe; there's always a risk. Information is power, who knows about you has control over you.
Information asymmetry creates imbalances of power. When entities have detailed knowledge about individuals, they can manipulate, influence, or exploit this information to their advantage. The accumulation of personal data by corporations and governments enables extensive surveillances.
Such practices, moreover, exclude individuals from traditional economic systems if their documentation doesn't meet arbitrary standards, reinforcing a dystopian divide. Small businesses are similarly burdened by the costs of implementing these regulations, hindering free market competition^1:
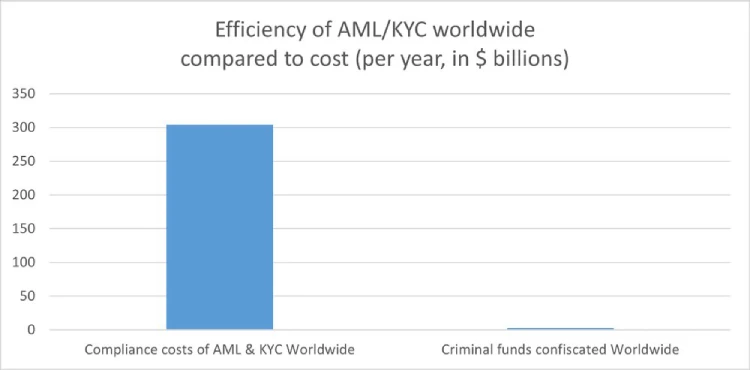
How will they keep this information safe? Why do they need my identity? Why do they force businesses to enforce such regulations? It's always for your safety, to protect you from the "bad". Your life is perpetually in danger: terrorists, money launderers, villains... so the government steps in to save us.
‟Hush now, baby, baby, don't you cry Mamma's gonna make all of your nightmares come true Mamma's gonna put all of her fears into you Mamma's gonna keep you right here, under her wing She won't let you fly, but she might let you sing Mamma's gonna keep baby cosy and warm” — Mother, Pink Floyd
We must resist any attack on our privacy and freedom. To do this, we must collaborate.
If you have a service, refuse to ask for KYC; find a way. Accept cryptocurrencies like Bitcoin and Monero. Commit to circular economies. Remove the need to go through the FIAT system. People need fiat money to use most services, but we can change that.
If you're a user, donate to and prefer using services that accept such currencies. Encourage your friends to accept cryptocurrencies as well. Boycott FIAT system to the greatest extent you possibly can.
This may sound utopian, but it can be achieved. This movement can't be stopped. Go kick the hornet's nest.
“We must defend our own privacy if we expect to have any. We must come together and create systems which allow anonymous transactions to take place. People have been defending their own privacy for centuries with whispers, darkness, envelopes, closed doors, secret handshakes, and couriers. The technologies of the past did not allow for strong privacy, but electronic technologies do.” — Eric Hughes, A Cypherpunk's Manifesto
The anniversary
Four years ago, I began exploring ways to use crypto without KYC. I bookmarked a few favorite services and thought sharing them to the world might be useful. That was the first version of kycnot.me — a simple list of about 15 services. Since then, I've added services, rewritten it three times, and improved it to what it is now.
kycnot.me has remained 100% independent and 100% open source^2 all these years. I've received offers to buy the site, all of which I have declined and will continue to decline. It has been DDoS attacked many times, but we made it through. I have also rewritten the whole site almost once per year (three times in four years).
The code and scoring algorithm are open source (contributions are welcome) and I can't arbitrarly change a service's score without adding or removing attributes, making any arbitrary alterations obvious if they were fake. You can even see the score summary for any service's score.
I'm a one-person team, dedicating my free time to this project. I hope to keep doing so for many more years. Again, thank you for being part of this.
-
 @ 39cc53c9:27168656
2025-05-27 09:21:38
@ 39cc53c9:27168656
2025-05-27 09:21:38
Silent.link is an anonymous eSIM provider. They offer pay-as-you-go roaming in 160+ countries.
Pros
- Anonymous
- Private payment options
- High performance
- Global availability
Cons
- Need to select the right networks sometimes
- Latency
- Data and incoming SMS & call only
Rating
★★★★★
Service website
eSIMs replace traditional, physical SIM cards, if you have a fairly new phone, odds are it supports them. Since most people change their mobile carrier very rarely, the most common use case for these new eSIMs is their use in travel. Although their use as a piece of a larger OPSEC puzzle to improve privacy when using the internet from your phone is increasingly popular too.
Silent.link is not the only eSIM provider out there. Yet, they’re so unique that even Twitter’s (now X) founder Jack Dorsey recommends them.
Let’s start off with a quick explanation of how Silent.link works and what pay-as-you-go means. Most other eSIM providers will sell you packages of GBs with an expiration date. For instance imagine you’re visiting France then going to the UK after a few months. With other providers you might buy a 10GB in France package valid for 7 days, then after some months a 10GB in the UK package also valid for 7 days. You likely won’t use up the full package in either country and the remaining capacity will be voided as the package expires.
Silent.link’s pay-as-you-go is different. There are no geographic packages. There are no expiration dates. You simply have a balance denominated in USD and are charged as you use up the data according to the pricing of whichever local carrier you’re connecting via.
Preparing for the same trips from the example above you’d simply top-up your Silent.link balance with $10. Then you’d use Silent.link in France paying $1.33/GB, you’d only be charged for the exact amount used, then you’d go to the UK and pay $1.54/GB from the balance you had left over from France. It doesn’t matter how much time passes between the trips, because Silent.link balances don’t expire. If you have a balance left over you can use it on a future trip, or simply use it up in your home country.
Pros
Anonymity
Silent.link is anonymous. Most other eSIM providers require some form of identification. This can be a traditional, full KYC, procedure involving your ID or passport numbers or, as seemingly innocent, as verifying your phone number with your main carrier. Regardless, a link between the eSIM you bought online and your identity is established.
In some countries you’ll be able to pick up a traditional SIM (or the new eSIM) from a local carrier without undergoing this verification. This can still be a hassle though. You’ll need to look up the laws before travelling, you’ll need to find a local store selling them, you’ll need to decide how you’ll pay privately, etc. And that’s the best case, that’s assuming the country you want to get the SIM in allows you to buy one anonymously.
Private payment methods
Silent.link only accepts cryptocurrency and according to their stats, most payments are made with Bitcoin (either onchain or using the Lightning Network) or with Monero. As such paying anonymously is not a problem. The use a self-hosted instance of BTCPay Server to process payments and operate their own LN node. The entire checkout process can be completed over Tor.
Cons
Network selection
Although you can skip the hassle of buying a new eSIM every time you travel it’s a good idea to look up the pricing of different mobile networks in the country you’re going to. The differences can be trivial, but can also be 100x. If a specific mobile network offers a much better deal, you’ll probably want to dive into your phone’s settings to make sure it only connects to that network.
High prices for some regions
Second issue can be that, especially for poorer countries, Silent.link might not have the best prices. For instance if you travel to Angola you’ll end up paying $155.44/GB. But if you search around for other providers you’ll find eSIM that offer much lower prices for that same country.
Data & incoming SMS & calls only
These eSIMs are either data-only or only offer data and inbound sms and calls. You can’t use Silent.link eSIMs to send texts or make phone calls.
Latency
For most use-cases this shouldn’t matter, but the way roaming works is that when you’re abroad your data is first sent to your home country then sent out into the internet from there. For instance if you’re a Brit on holiday in Spain wherever you open up a website your phone communicates with the Spanish network who forwards the request to your home network in the UK and only there does the request start going towards the website you’re trying to load. The response takes the same path in reverse.
The home network for the Silent.link eSIMs is Poland. To take an extreme (antipodal) example, if you’re in Chile loading a Chilean website your request will go to Poland then back from Poland to the website’s server in Chile, then the response will go from Chile to Poland to you (in Chile). All those trips add latency. In our testing, done during the recent OrangeFren.com meetup in Istanbul, the difference was an additional 73ms. The bandwidth, however, was exceptional, easily surpassing 100 Mbps.
This latency issue isn’t unique to Silent.link, other eSIM providers usually suffer from it too, though their home network may be better suited for your latency needs. If you need the best latency we recommend a SIM from a local provider (or WiFi).
This proxy behaviour isn’t all negative however. It may potentially allow you to circumvent censorship or geoblocking if you’re trying to access resources available from Poland, but unavailable elsewhere.
Besides Istanbul one of the countries we also tested Silent.link in was Northern Cyprus. This territory is mostly unrecognized. It’s a country that, depending on who you ask, is or isn’t real. Despite this unresolved geopolitical status Silent.link performed without any issues.
Installation
If you decide to give Silent.link a try, you'll need to select if you want a data-only plan or a plan with inbound SMS & calling, once you complete the payment simply scan the QR code on the order confirmation page with your phone. Make sure to save the url of that order confirmation page somewhere! You will need it to top up your eSIM and check your remaining balance.
Getting in touch
The preferred way of contacting Silent.link's support is using the website's built-in chat function. Alternative methods include X (formerly Twitter), Matrix and email.
Their support is online from 09:00 - 21:00 UTC although even when testing outside of those hours we got a reply within a minute.
NOTE: These reviews are sponsored, yet the sponsorship does not influence the outcome of the evaluations. Sponsored reviews are independent from the kycnot.me list, being only part of the blog. The reviews have no impact on the scores of the listings or their continued presence on the list. Should any issues arise, I will not hesitate to remove any listing.
-
 @ 4d4fb5ff:1e821f47
2025-05-25 22:12:14
@ 4d4fb5ff:1e821f47
2025-05-25 22:12:14Numerical heatmap derived from biologically-sourced data. I reversed the process of scientific discovery by stripping away the context of data collected in four of my published experiments, leaving only single digits. This makes the table appear to include only unrelated, random numbers. However, since the numbers come from real world data, there remains meaningful hidden structure in the grid. This invites the viewer to participate in parsing signal from noise.
https://ordiscan.com/inscription/96817034
-
 @ 39cc53c9:27168656
2025-05-27 09:21:37
@ 39cc53c9:27168656
2025-05-27 09:21:37After almost 3 months of work, we've completed the redesign of kycnot.me. More modern and with many new features.
Privacy remains the foundation - everything still works with JavaScript disabled. If you enable JS, you will get some nice-to-have features like lazy loading and smoother page transitions, but nothing essential requires it.
User Accounts
We've introduced user accounts that require zero personal information:
- Secret user tokens - no email, no phone number, no personal data
- Randomly generated usernames for default privacy and fairness
- Karma system that rewards contributions and unlocks features: custom display names, profile pictures, and more.
Reviews and Community Discussions
On the previous sites, I was using third party open source tools for the comments and discussions. This time, I've built my own from scratch, fully integrated into the site, without JavaScript requirements.
Everyone can share their experiences and help others make informed decisions:
- Ratings: Comments can have a 1-5 star rating attached. You can have one rating per service and it will affect the overall user score.
- Discussions: These are normal comments, you can add them on any listed service.
Comment Moderation
I was strugling to keep up with moderation on the old site. For this, we've implemented an AI-powered moderation system that:
- Auto-approves legitimate comments instantly
- Flags suspicious content for human review
- Keeps discussions valuable by minimizing spam
The AI still can mark comments for human review, but most comments will get approved automatically by this system. The AI also makes summaries of the comments to help you understand the overall sentiment of the community.
Powerful Search & Filtering
Finding exactly what you need is now easier:
- Advanced filtering system with many parameters. You can even filter by attributes to pinpoint services with specific features.
The results are dynamic and shuffle services with identical scores for fairness.
See all listings
Listings are now added as 'Community Contributed' by default. This means that you can still find them in the search results, but they will be clearly marked as such.
Updated Scoring System
New dual-score approach provides more nuanced service evaluations:
- Privacy Score: Measures how well a service protects your personal information and data
-
Trust Score: Assesses reliability, security, and overall reputation
-
Combined into a weighted Overall Score for quick comparisons
- Completely transparent and open source calculation algorithm. No manual tweaking or hidden factors.
AI-Powered Terms of Service Analysis
Basically, a TLDR summary for Terms of Service:
- Automated system extracts the most important points from complex ToS documents
- Clear summaries
- Updated monthly to catch any changes
The ToS document is hashed and only will be updated if there are any changes.
Service Events and Timelines
Track the complete history of any service, on each service page you can see the timeline of events. There are two types of events:
- Automatic events: Created by the system whenever something about a service changes, like its description, supported currencies, attributes, verification status…
- Manual events: Added by admins when there’s important news, such as a service going offline, being hacked, acquired, shut down, or other major updates.
There is also a global timeline view available at /events
Notification System
Since we now have user accounts, we built a notifiaction system so you can stay informed about anything:
- Notifications for comment replies and status changes
- Watch any comment to get notified for new replies.
- Subscribe to services to monitor events and updates
- Notification customization.
Coming soon: Third-party privacy-preserving notifications integration with Telegram, Ntfy.sh, webhooks...
Service Suggestions
Anyone with an account can suggest a new service via the suggestion form. After submitting, you'll receive a tracking page where you can follow the status of your suggestion and communicate directly with admins.
All new suggestions start as "unlisted" — they won't appear in search results until reviewed. Our team checks each submission to ensure it's not spam or inappropriate. If similar services already exist, you'll be shown possible duplicates and can choose to submit your suggestion as an edit instead.
You can always check the progress of your suggestion, respond to moderator questions, and see when it goes live, everything will also be notified to your account. This process ensures high-quality listings and a collaborative approach to building the directory.
These are some of the main features we already have, but there are many more small changes and improvements that you will find when using the site.
What's Next?
This is just the beginning. We will be constantly working to improve KYCnot.me and add more features that help you preserve your privacy.
Remember: True financial freedom requires the right to privacy. Stay KYC-free!
-
 @ c9badfea:610f861a
2025-05-25 21:03:23
@ c9badfea:610f861a
2025-05-25 21:03:23- Install AnkiDroid (it's free and open source)
- Launch the app, tap Get Started, then tap ≡ and select Settings
- Select Sync and disable Display Synchronization Status
- Return to the main screen
- Create and download flashcard decks (see links below)
- Tap ⁝, then Import, then Deck Package (.apkg), select the file and tap Add
- Select Import
- Wait for the import to finish and start learning!
Some Flashcard Deck Sources
ℹ️ On GrapheneOS, you may need to enable the Network (used for localhost access) and Read And Write To The AnkiDroid Database permissions.
ℹ️ Also check this article on formulating knowledge
-
 @ 28ca019b:93fcb2cc
2025-05-25 19:25:17
@ 28ca019b:93fcb2cc
2025-05-25 19:25:17Introduction
“There is nothing more powerful than an idea whose time has come.” -Victor Hugo
Early 1950’s America. Harry S. Truman is in office. The economy is booming and the middle class are comfortable. Shiny new television sets invite the first scenes of Hollywood into people’s homes. The Weavers, Tony Bennett, Vera Lynn and Perry Como play on the radio.
But on the fringes, in dance halls and late night clubs, a cultural revolution is brewing… A new musical fusion with influences from blues, R\&B, jazz, rockabilly, country and gospel music is about to give birth to not only a new genre, but a whole new way of life that will change society and culture, forever.
Rock & Roll
It becomes a symbol of freedom, a means of expression, and a catalyst for social change. It brings into existence a new type of counter-culture, filled with individuals who are driven to rebel against norms and authority. They don’t ask for permission. They push for change.
I believe we are witnessing such a shift now. And like rock & roll, the movement I’m speaking of is also ground up, grass roots, punk rock and will not look to authority to seek permission. The catalyst for this new social change, I believe, is Bitcoin. With its innate properties, it empowers and enables the individual like never before to achieve their fullest potential, expressed through an unprecedented freedom technology. It is an idea, like a song everyone can sing in their own way, that nobody can silence.
Revolution
"You say you got a real solution / Well you know / we’d all love to see the plan" -John Lennon
The rock & roll era helped bring about meaningful societal change through art, music, and film. It created a new social narrative. Today, the Bitcoin network is providing people with a different set of tools and ideas to build a better future in a much more practical and pragmatic way. Instead of trying to reshape social consensus and cultural norms through art forms, fashion, or lifestyle, bitcoin is achieving this through open source code.
For the first time, this technology gives individuals financial sovereignty and personal control over their own destiny, with the ability to self custody their own money that no corporation, government, dictator or king can tamper with. The individual has an opportunity to finally be freed from economic tyranny. And societies have the potential to avoid endless wars funded with printed government money. John Lennon said ‘give peace a chance’. If he were still here today and understood how bitcoin could subvert the military industrial complex would he not exclaim, ‘give bitcoin a chance’?
Natural Rights, Civil Rights, Digital Rights
"The times they are a-Changin’" -Bob Dylan
The civil rights movement was tightly interwoven with the history of rock & roll. The march on Washington, August 28th 1963, marked a seminal moment in American history for the advancement of equal rights before the law. Bob Dylan, along with Joan Baez, stood with over two hundred thousand other Americans and listened to Martin Luther King’s now immortal speech.
People with the same values peacefully gathered in numbers to make a statement powerful enough to change the conversation. This is analogous to the same freedom-minded people today gathering in cyberspace and voting not in the traditional sense, but voting with their money – peacefully exiting and transferring their economic energy into a system where they can’t be expropriated.
The question of whether individual rights are granted or have to be secured by each individual remains a contested area of philosophy to this day. To outline each in a very crude and simplistic way, natural rights (sometimes referred to as inalienable rights) are derived from the belief that every person owns their own body, therefore their own labor, time, and energy. Civil rights, on the other hand, are granted by the state and are therefore not universal. The fact that they are rights granted to humans by other humans means they always have the potential to be revoked or withdrawn.
Digital rights granted by the power of asymmetric cryptography are based in the laws of mathematics. Combined with proof of work, based in the law of thermodynamics, this makes digital rights that bitcoin provides more akin to natural rights than civil rights, as no one person or group can unilaterally revoke those rights or confiscate your property through violence. No amount of fire power, tanks, fighter jets or nuclear weapons can break a bitcoin private key or rewrite the sunken cost of proof of work embedded into bitcoin’s timechain. This idea of securing rights without asking permission is, in itself, a revolution and achievable now in an egalitarian way. This implies a potentially huge shift in power from those with a monopoly on violence, to peaceful individuals who want to be treated fairly and with dignity.
Cypher Punk-Rock
Songwriters write songs. Cypherpunks write code.
To tie things back and look at a very narrow, but potentially huge use case of bitcoin, let’s examine the current broken incentives of the music industry, particularly recorded music. It is becoming increasingly apparent that an option other than a subscription model could find demand from content consumers and producers alike.
There is now a way, with Bitcoin and Lightning Network, for a music fan to pay artists directly and for any amount – dollars, cents or even fractions of cents. This model has positive outcomes for the music producer and fan who are the main two parties engaged in the transaction. The artist keeps all of what is sent and the listener can pay what they want. The listener can pay as they listen, rather than be locked into a rolling subscription that isn’t based on usage. This concept, called ‘value for value’, is finding its way into new music platforms such as Wavlake and Fountain. I believe this model will become the de-facto way of monetizing digital content in the coming years. This could bring an economic signal back to music that has been lost and cannot be achieved by streams alone. This will hopefully create a more meritocratic music system and shake up the entrenched streaming monoliths.
Art can shine a light on a certain truth. It can also make people look at things in a completely new way. Maybe then, Satoshi was the greatest artist who ever lived. Bitcoin smashed the conventional wisdom and theories of the most basic and prevalent thing everyone takes for granted: money. Using money as a lens to view the world can lead to distortions in your perception if the lens is warped. Removing the glasses makes you reevaluate economics, politics, religion, philosophy, morality, beauty, and almost every other aspect of life. The beauty of the Sistine Chapel, the Egyptian pyramids, the Mona Lisa, Beethoven’s 5th Symphony, Bohemian Rhapsody all intrinsically imply a certain degree of proof of work. The art, you could say, speaks for itself.
The Long and Winding Road Ahead
As a musician, I have found a new hope. The value for value movement gives me that hope. If this is truly a superior model of music distribution and consumption it will win out over time on the market.
Another point to touch on would be the possibility of this technology ushering in an artistic renaissance. I can honestly say my favorite music, the songs that have moved me the most, normally comes from a place of truth, honesty and sheer talent. Maybe I’m out of touch, but I feel popular music of late is devoid of soul, meaning and the biggest mainstream artists want to conform to the man (giant corporations/governments) instead of stick it to the man! Probably because there is nowhere else to turn now that streaming and social media platforms own their speech and art. We need to investigate and embrace new ways to own our speech and art, to make art interesting again. The powers that be, need to let it be, and leave alone individuals who wish to use this technology for their own interests if they do so in a peaceful way.
I want to leave you with a Frank Zappa quote that seems more relevant than ever:
“I’d say that today, dishonesty is the rule, and honesty the exception. It could be, statistically, that more people are honest than dishonest, but the few that really control things are not honest, and that tips the balance…”
My charitable view is that the majority of people in power aren’t corrupt, it’s rather just a case of ‘no one is better than their incentives’. But when incentives are misaligned bad outcomes will inevitably result. With bitcoin and its incorruptible incentive structure, we have a chance to peacefully opt-out of a rigged game. I urge you to not trust, but verify with your own research that bitcoin is the answer to many of society’s current problems.
I think it’s fair to say, we all need to question ourselves and authority a little more than we’re comfortable doing, to hold truth as an ideal worth striving for, and live a little more rock & roll!
Link to original article**
-
 @ a8cc4ff8:d3ea074d
2025-05-25 07:26:38
@ a8cc4ff8:d3ea074d
2025-05-25 07:26:38不忍池, 上野動物園 Shinobazuno Pond, Ueno Zoo

上野東照宮五重塔,上野動物園 Ueno Toshogu Shrine, Ueno Zoo

鉄道博物館 The Railway Museum

靖國神社 Yasukuni-jinja Shrine



巽櫓(桜田二重櫓) Sakurada Tatsumi Yagura

二重橋 Nijubashi Bridge

元箱根 Motohakone

彫刻の森駅 Chokokunomori Station

箱根神社 Hakone Shrine

小田原城 Odawara Castle



新大久保駅 Shin-Ōkubo Station


シンボルプロムナード公園 Symbol Promenade Park


セントラル広場 Central Square


日本科学未来館 The National Museum of Emerging Science and Innovation Japan (Miraikan)

-
 @ b1ddb4d7:471244e7
2025-05-25 06:00:51
@ b1ddb4d7:471244e7
2025-05-25 06:00:51The upcoming Bitcoin 2025 conference, scheduled from May 27–29 at the Venetian Conference Center in Las Vegas, is set to make history with an official attempt to break the GUINNESS WORLD RECORDS® title for the most Bitcoin point-of-sale transactions in an eight-hour period.
Organized by BTC Inc, the event will showcase Bitcoin’s evolution from a digital capital asset to a practical medium of exchange, leveraging the latest advancements in payment technology.
Tap-to-Pay with Lightning-Ready Bolt Cards
To facilitate this record-setting attempt, 4,000 Lightning-ready Bolt Cards will be distributed to conference attendees.
— Uncle Rockstar Developer (@r0ckstardev) May 15, 2025
These NFC-enabled cards allow users to make instant, contactless Bitcoin payments at vendor booths throughout the expo-no apps or QR codes required, just a simple tap.
The cards are available in four collectible designs, each featuring a prominent figure in Bitcoin’s history: Senator Cynthia Lummis, Michael Saylor, Satoshi Nakamoto, and Jack Dorsey.
Each attendee will receive a randomly assigned card, making them both functional and collectible souvenirs.
Senator Lummis: A Playful Provocation
Notably, one of the card designs features Senator Cynthia Lummis with laser eyes-a playful nod to her reputation as a leading Bitcoin advocate in US politics.
While Lummis is known for her legislative efforts to promote Bitcoin integration, she has publicly stated she prefers to “spend dollars and save Bitcoin,” viewing BTC as a long-term store of value rather than a daily currency.
The choice to feature her on the Bolt Card, could be suggested by Rockstar Dev of the BTC Pay Server Foundation, perhaps a lighthearted way to highlight the ongoing debate about Bitcoin’s role in everyday payments.
Nothing cracks me up quite like a senator that wants the US to buy millions of Bitcoin use dollars to buy a beer at a Bitcoin bar.
This is how unserious some of you are. pic.twitter.com/jftIEggmip
— Magoo PhD (@HodlMagoo) April 4, 2025
How Bolt Cards and the Lightning Network Work
Bolt Cards are physical cards equipped with NFC (Near Field Communication) technology, similar to contactless credit or debit cards. When linked to a compatible Lightning wallet, they enable users to make Bitcoin payments over the Lightning Network by simply tapping the card at a point-of-sale terminal.
The Lightning Network is a second-layer protocol built on top of Bitcoin, designed to facilitate instant, low-cost transactions ideal for everyday purchases.
This integration aims to make Bitcoin as easy to use as traditional payment methods, eliminating the need for QR code scanning or mobile apps.
A Showcase for Bitcoin’s Real-World Usability
With over 30,000 attendees, 300 exhibitors, and 500 speakers expected, the Bitcoin 2025 conference is poised to be the largest Bitcoin event of the year-and potentially the most transactional.
The event will feature on-site activations such as the Official Bitcoin Magazine Store, where all merchandise will be available at a 21% discount for those paying with Bitcoin via the Lightning Network-a nod to Bitcoin’s 21 million coin supply limit.
By deeply integrating Lightning payments into the conference experience, organizers hope to demonstrate Bitcoin’s readiness for mainstream commerce and set a new benchmark for its practical use as a currency.
Conclusion
The Guinness World Record attempt at Bitcoin 2025 is more than a publicity stunt-it’s a bold demonstration of Bitcoin’s technological maturity and its potential to function as a modern, everyday payment method.
Whether or not the record is set, the event will serve as a milestone in the ongoing journey to make Bitcoin a truly global, user-friendly currency
-
 @ 47259076:570c98c4
2025-05-25 01:33:57
@ 47259076:570c98c4
2025-05-25 01:33:57When a man meets a woman, they produce another human being.
The biological purpose of life is to reproduce, that's why we have reproductive organs.
However, you can't reproduce if you are dying of starvation or something else.
So you must look for food, shelter and other basic needs.
Once those needs are satisfied, the situation as a whole is more stable and then it is easier to reproduce.
Once another human being is created, you still must support him.
In the animal kingdom, human babies are the ones who take longer to walk and be independent as a whole.
Therefore, in the first years of our lives, we are very dependent on our parents or whoever is taking care of us.
We also have a biological drive for living.
That's why when someone is drowning he will hold on into whatever they can grab with the highest strength possible.
Or when our hand is close to fire or something hot, we remove our hand immediately from the hot thing, without thinking about removing our hand, we just do it.
These are just 2 examples, there are many other examples that show this biological tendency/reflex to keep ourselves alive.
We also have our brain, which we can use to get information/knowledge/ideas/advice from the ether.
In this sense, our brain is just an antenna or radio, and the ether is the signal.
Of course, we are not the radio, we are the signal.
In other words, you are not your body, you are pure consciousness "locked" temporarily in a body.
Because we can act after receiving information from the ether, we can construct and invent new things to make our lives easier.
So far, using only biology as our rule, we can get to the following conclusion: The purpose of life is to live in a safe place, work to get food and reproduce.
Because humans have been evolving in the technological sense, we don't need to hunt for food, we can just go to the market and buy meat.
And for the shelter(house), we just buy it.
Even though you can buy a house, it's still not yours, since the government or any thug can take it from you, but this is a topic for another article.
So, adjusting what I said before in a modern sense, the purpose of life is: Work in a normal job from Monday to Friday, save money, buy a house, buy a car, get a wife and have kids. Keep working until you are old enough, then retire and do nothing for the rest of your life, just waiting for the moment you die.
Happy life, happy ending, right?
No.
There is something else to it, there is another side of the coin.
This is explored briefly by Steve Jobs in this video, but I pretend to go much further than him: https://youtu.be/uf6TzOHO_dk
Let's get to the point now.
First of all, you are alive. This is not normal.
Don't take life for granted.
There is no such a thing as a coincidence. Chance is but a name given for a law that has not been recognized yet.
You are here for a reason.
God is real. All creation starts in the mind.
The mind is the source of all creation.
When the mind of god starts thinking, it records its thoughts into matter through light.
But this is too abstract, let's get to something simple.
Governments exist, correct?
The force behind thinking is desire, without desire there is no creation.
If desired ceased to exist, everything would just vanish in the blink of an eye.
How governments are supported financially?
By taking your money.
Which means, you produce, and they take it.
And you can't go against it without suffering, therefore, you are a slave.
Are you realizing the gravity of the situation?
You are working to keep yourself alive as well as faceless useless men that you don't even know.
Your car must have an identification.
When you are born, you must have an identification.
In brazil, you can't home school your children.
When "your" "country" is in war, you must fight to defend it and give your life.
Countries are limited by imaginary lines.
How many lives have been destroyed in meaningless wars?
You must go to the front-line to defend your masters.
In most countries, you don't have freedom of speech, which means, you can't even express what you think.
When you create a company, you must have an identification and pass through a very bureaucratic process.
The money you use is just imaginary numbers in the screen of a computer or phone.
The money you use is created out of thin air.
By money here, I am referring to fiat money, not bitcoin.
Bitcoin is an alternative to achieve freedom, but this is topic for another article.
Depending on what you want to work on, you must go to college.
If you want to become a doctor, you must spend at least 5 years in an university decorating useless muscle names and bones.
Wisdom is way more important than knowledge.
That's why medical errors are the third leading cause of death in United States of America.
And I'm not even talking about Big Pharma and the "World Health Organization"
You can't even use or sell drugs, your masters don't allow it.
All the money you get, you must explain from where you got it.
Meanwhile, your masters have "black budget" and don't need to explain anything to you, even though everything they do is financed by your money.
In most countries you can't buy a gun, while your masters have a whole army fully armed to the teeth to defend them.
Your masters want to keep you sedated and asleep.
Look at all the "modern" art produced nowadays.
Look at the media, which of course was never created to "inform you".
Your masters even use your body to test their bio-technology, as happened with the covid 19 vaccines.
This is public human testing, there's of course secretive human testing, such as MKUltra and current experiments that happen nowadays that I don't even know.
I can give hundreds of millions of examples, quite literally, but let's just focus in one case, Jeffrey Epstein.
He was a guy who got rich "suddenly" and used his influence and spy skills to blackmail politicians and celebrities through recording them doing acts of pedophilia.
In United States of America, close to one million children a year go missing every year.
Some portion of these children are used in satanic rituals, and the participants of these rituals are individuals from the "high society".
Jeffrey Epstein was just an "employee", he was not the one at the top of the evil hierarchy.
He was serving someone or a group of people that I don't know who they are.
That's why they murdered him.
Why am I saying all of this?
The average person who sleep, work, eat and repeat has no idea all of this is going on.
They have no idea there is a very small group of powerful people who are responsible for many evil damage in the world.
They think the world is resumed in their little routine.
They think their routine is all there is to it.
They don't know how big the world truly is, in both a good and evil sense.
Given how much we produce and all the technology we have, people shouldn't even have to work, things would be almost nearly free.
Why aren't they?
Because of taxes.
This group of people even has access to a free energy device, which would disrupt the world in a magnitude greater than everything we have ever seen in the history of Earth.
That's why MANY people who tried to work in any manifestation of a free energy device have been murdered, or rather, "fell from a window".
How do I know a free energy device exist? This is topic for another article.
So my conclusion is:
We are in hell already. Know thyself. Use your mind for creation, any sort of creation. Do good for the people around you and the people you meet, always give more than you get, try to do your best in everything you set out to do, even if it's a boring or mundane work.
Life is short.
Our body can live no longer than 300 years.
Most people die before 90.
Know thyself, do good to the world while you can.
Wake up!!! Stop being sedated and asleep.
Be conscious.
-
 @ 3c7dc2c5:805642a8
2025-05-24 22:05:00
@ 3c7dc2c5:805642a8
2025-05-24 22:05:00🧠Quote(s) of the week:
'The Cantillon Effect: When new money is printed, those closest to the source (banks, elites) benefit first, buying assets before prices rise. Others lose purchasing power as inflation hits later. If people find out how this works, they will riot.' -Bitcoin for Freedom
Just think about it. Your employer gives you a 5% raise. The Fed (central banks in general) prints 7% more dollars/euros/Fiat. You just got a 2% pay cut. This isn't a conspiracy theory. This is how fiat money steals from the working class every single day. This is why I support Bitcoin.
Anilsaidso: 'Saving in fiat currency is no longer an option. A 2% inflation rate means you lose 1/3 of your purchasing power over 20yrs. At 5% inflation, you lose 60%. And at 10% you've burnt 85%. Reduce your uncertainty. Save in Bitcoin.' https://i.ibb.co/N661BdVp/Gr-Rwdg-OXc-AAWPVE.jpg
🧡Bitcoin news🧡
“Education increases conviction.
Conviction increases allocation.
Allocation increases freedom.” —Gigi
https://i.ibb.co/Q3trHk8Y/Gr-Arv-Ioa-AAAF5b0.jpg
On the 12th of May:
➡️Google searches for "Digital Gold" are at all-time highs. Bitcoin Croesus: "This is the second wave of the Digital Revolution - the digitization of value to complement the Internet's digitization of information. It wasn't possible to own a slice of the Internet itself, but it is possible with Bitcoin, the internet of value." "...It feels like you're late to Bitcoin. But this is a bigger game playing out than most realize, and we are much earlier than casual observers know. If you're reading this, you're here on the frontier early. And you have a chance to stake a claim before 99% of the world shows up. This is a land grab. This is the digital gold rush. Make your descendants proud."
https://i.ibb.co/5XXbNQ8S/Gqw-X4-QRWs-AEd5-Uh-1.jpg
➡️ 'A new holding company ‘Nakamoto’ just raised $710 million to buy more Bitcoin and will merge with KindlyMD to establish a Bitcoin Treasury company. Saylor playbook!' - Bitcoin Archive
➡️American Bitcoin, backed by Donald Trump Jr. and Eric Trump, will go public via an all-stock merger with Gryphon Digital Mining. Post-merger, Trump affiliates and Hut 8 will retain 98% ownership. GRYP tripled to $2.19, Hut 8 jumped 11% to $15.45. The deal closes in Q3 2025.
➡️Phoenix Wallet: 'Phoenix 0.6.0 is out: offers can now have a custom description simple close (set an exact mutual close tx fee rate) native support for Linux arm64 This is the server version. Phoenix mobile release is around the corner. '
On the 13th of May:
➡️Corporate Bitcoin purchases have now outweighed the supply of new Bitcoin by 3.3x in 2025. https://i.ibb.co/fVdgQhyY/Gq1ck-XRXUAAsg-Ym.jpg
➡️ Publicly listed Next Technology disclosed buying 5,000 Bitcoin for $180m, now HODLs 5,833 $BTC worth +$600m.
➡️ After rejecting the Arizona Strategic Bitcoin Reserve Act, Governor Katie Hobbs vetoed Bill SB 1373, which proposed a digital asset reserve fund. "Current volatility in the cryptocurrency markets does not make a prudent fit for general fund dollars."
➡️Meanwhile in Paris, France the kidnapping of a woman with her 2-year-old child morning on the streets of Paris - the target is allegedly the daughter of a crypto CEO. 3 masked men tried forcing them into a fake delivery van, before being fought off by her partner and bystanders. One of whom grabbed a dropped gun and aimed it back.
➡️ 'Bitcoin illiquid supply hit a new all-time high of $1.4B Are you HODLing too, anon?' - Bitcoin News
➡️Why Coinbase entering the S&P 500 matters. Boomers will have Bitcoin / CrApTo exposure, whether they like it or not. Anyway, remember what happened in 2021. The COIN IPO, and they’re still trading about 35% below their IPO-day high. Oh and please read the 'Coinbase" hack below haha.
➡️ Nasdaq listed GD Culture Group to sell up to $300 million shares to buy Bitcoin.
➡️ A Bitcoin wallet untouched since April 2014 just moved 300 BTC worth $31M for the first time in 11 years. This is how you HODL.
➡️ Bitcoin's realized price is steadily increasing, mirroring behaviors seen in past bull markets, according to CryptoQuant.
➡️ Bitcoin whales and sharks (10-10K BTC) accumulated 83,105 BTC in the last 30 days, while small retail holders (<0.1 BTC) sold 387 BTC, according to Santiment.
Bitcoin Whales have been AGGRESSIVELY accumulating BTC recently! With at least 240,000+ Bitcoin transferred to wallets with at least 100 BTC. The largest market participants are trying to buy as much as possible, what do they think comes next...
➡️'The average cost of mining 1 BTC for miners is currently $36.8K. The spread between the current market price and the cost of one coin = 182%. This is essentially the average profitability. This corresponds to the beginning of the bull cycle in November 2022 and the peaks of this cycle >$100K. A price increase above this level will allow miners to fully recover after the last halving and reach excess profits comparable to the beginning of the bull rally in January 2023.' -Axel Adler Jr.
➡️ Remember last week's segment on Coinbase..."Coinbase just disclosed in their Q1 filing: that they have custody of 2.68 million Bitcoin. That’s over 13% of all Bitcoin in circulation, on one platform. Is this the greatest honeypot in financial history? Yes, it is...read next week's Weekly Bitcoin update."
Well, here you go.
Coinbase estimates $180-$400 million in losses, remediation costs, and reimbursement following today’s cyber attack. https://i.ibb.co/jkysLtZ1/Gq-C7zl-W4-AAJ0-N6.jpg
Coinbase didn't get hacked. Coinbase employees sold customer data on the black market. Coinbase failed to protect customer data. This is why KYC is useless. The criminals have our driver's license scans. They have AI tools that can generate fake images and videos. KYC puts our identities at risk, makes onboarding more difficult, and rewards criminals. To make it even worse. Coinbase knew about the hack as early as January but only disclosed it publicly after being added to the S&P 500.
I will say it one more time! Don't buy your Bitcoin on KYC exchanges. KYC means handing over your identity to be leaked, sold, or extorted.
It was 2 days ago, see the bit on the 13th of May, that we saw a violent attack in Paris. Minimize the data you share with centralized tools. Store as much as you can locally. Always ask yourself what data am I giving and to whom? Remove the need for trust.
And for the love of God, Allah, or whatever god you are praying to...
DON'T LEAVE YOUR COINS ON A FREAKING EXCHANGE!!!!
Clear!
➡️ Sam Callahan: Bitcoin CAGRs over rolling four-year holding periods since 2012:
10th percentile: 33%
25th percentile: 50% 40th percentile: 75%
Said differently, for 90% of the time, Bitcoin’s four-year CAGR was higher than 33%. For comparison, here are the single best four-year CAGRs over the same period for:
Gold: 17%
Silver: 20%
S&P 500: 24%
Apple: 52%
Two lessons here:
1.) Even when Bitcoin underperforms, it still outperforms.
2.) Bitcoin holding goals are best measured in halving cycles.'
https://i.ibb.co/9m6q2118/Gq1-Ie2-Ob-AAIJ8-Kf.jpg
➡️ Deutsche Bank Aktiengesellschaft has bought 96,870 Strategy₿ stocks for 30 Million dollars at an Average Price Of $310 Per Share In Q1 2025, Their Total Holdings Is 518,000 Shares Worth Over 214 Million Dollars.
➡️Senator Lummis urges the U.S. Treasury to eliminate taxes on unrealized gains for Bitcoin.
On the 14th of May:
➡️At $168,000, Bitcoin will surpass Microsoft, the world's largest company.
➡️Fidelity tells institutions to buy Bitcoin if they can’t match Bitcoin’s 65% return on capital.
➡️Michigan has adopted House Resolution 100, declaring May 13 2025 as "Digital Asset Awareness Day." The resolution encourages "activities and programs that foster a deeper understanding of digital assets and their impact on our society and economy."
➡️Publicly traded Vinanz raises funding to buy $2 million in #Bitcoin assets.
➡️Bitcoin News: "Investor Jim Chanos is shorting MicroStrategy while going long on Bitcoin, calling the stock overvalued relative to its BTC holdings. “We’re selling MicroStrategy and buying Bitcoin, basically buying something for $1 and selling it for $2.50," he told CNBC
On the 15th of May:
➡️The Abu Dhabi sovereign wealth fund disclosed owning $511 million in Bitcoin through BlackRock’s ETF.
➡️UK public company Coinsilium Group raises £1.25 million to adopt a Bitcoin treasury strategy.
➡️Chinese Textile company Addentax issues stock to buy 8,000 Bitcoin.
➡️14 US states have reported $632m in $MSTR exposure for Q1, in public retirement and treasury funds. A collective increase of $302m in one quarter. The average increase in holding size was 44%.
➡️Chinese public company DDC Enterprise to adopt a Bitcoin Reserve with 5,000 BTC.
On the 16th of May:
➡️Brazilian listed company Méliuz buys $28.4 million Bitcoin to become the nation's first Bitcoin Treasury Company. Shareholders voted to approve the strategy by an "overwhelming majority".
➡️13F Filings show Texas Retirement System owns MSTR. The day MSTR enters the S&P 500, every pension fund will follow.
➡️'Wealthy Investors Shift Up to 5% into Bitcoin as confidence in fiat falters. UBS, a Swiss banking giant says Bitcoin and digital assets are becoming key hedges against inflation and systemic risk, marking a dramatic shift in modern portfolio strategy.' -CarlBMenger
➡️River: "Above all, Bitcoin is money for the people." https://i.ibb.co/Jj8MVQwr/Gr-Ew-EPp-XAAA1-TVN.jpg
On the 17th of May:
➡️Illicit activity is now down to 0.14% of transaction volume across all crypto.
Context: World Bank, IMF suggests 1.5–4% of global GDP is laundered yearly through traditional banking Of that 0.14%:
63% of illicit trade was stablecoins.
13% was Bitcoin (declining each year)
Source: The 2025 Crypto Crime Report, Chainalysis 2025
Yet another confirmation that Bitcoin's use in facilitating illicit activities is a rounding error on a rounding error.
On the 18th of May:
➡️JPMorgan CEO Jamie Dimon said they will allow clients to buy Bitcoin. The repeal of SAB 121 is a bigger deal than most realize. “I will fire any employee buying or trading Bitcoin for being stupid” - Jamie Dimon (2017) https://i.ibb.co/b5tnkb15/Gr-Vxxc-OXk-AA7cyo.jpg
On the 19th of May.
➡️Bookmark the following stuff from Daniel Batten if you want to combat climate change (fanatics)...
'That Bitcoin mining is not only not harmful, but beneficial to the environment is now supported by:
7 independent reports
20 peer-reviewed papers
As a result * 90% of climate-focused magazines * 87.5% of media coverage on Bitcoin & the environment is now positive * source 7 independent reports https://x.com/DSBatten/status/1922666207754281449… * 20 peer-reviewed papers https://x.com/DSBatten/status/1923014527651615182… * 10 climate-focused magazines https://x.com/DSBatten/status/1919518338092323260… * 16 mainstream media articles https://x.com/DSBatten/status/1922628399551434755
➡️Saifedean Ammous: '5 years ago at the height of corona hysteria, everyone worried about their savings.
If you put $10,000 in "risk-free" long-term US government bonds, you'd have $6,000 today.
If you put the $10,000 in "risky speculative tulip" bitcoin, you'd have $106,000.
HFSP, bondcucks!'
I love how Saifedean always put it so eloquently. haha
➡️An Australian judge rules Bitcoin is “just another form of money.” This could make it exempt from capital gains tax. Potentially opening the door to millions in refunds across the country. - AFR
If upheld, the decision could trigger up to $1B in refunds and overturn the Australian Tax Office’s crypto tax approach.
➡️Publicly traded Vinanz buys 16.9 Bitcoin for $1.75 Million for their treasury.
➡️Bitcoin just recorded its highest weekly close ever, while the Global Economic Policy Uncertainty Index hit its highest level in history.
➡️4 in 5 Americans want the U.S. to convert part of its gold reserves to Bitcoin. - The Nakamoto Project
"or background, the survey question was: "Assuming the United States was thinking of converting some of their gold reserves into Bitcoin, what percentage would you advise they convert?" Respondents were provided a slider used to choose between 0% and 100%. Our survey consisted of a national sample of 3,345 respondents recruited in partnership with Qualtrics, a survey and data collection company"
Context: https://x.com/thetrocro/status/1924552097565180107 https://i.ibb.co/fGDw06MC/Gr-VYDIdb-AAI7-Kxd.jpg
➡️Michael Saylor's STRATEGY bought another $764.9m Bitcoin. They now HODL 576,230 Bitcoin, acquired for $40.18 billion at $69,726 per Bitcoin.
➡️The German Government sold 49,858 BTC for $2.89B, at an average price of $57,900. If they had held it, their BTC would now be worth $5.24B.
➡️A record 63% of all the Bitcoin that exist have not transacted or moved from their wallets this year. - Wicked
https://i.ibb.co/j9nvbvmP/Gq3-Z-x6-Xw-AAv-Bhg.jpg
💸Traditional Finance / Macro:
On the 12th of May:
👉🏽The S&P 500 has closed more than 20% above its April low, technically beginning a new bull market. We are now up +1,000 points in one month.
On the 13th of May:
👉🏽 Nvidia announces a partnership with Humain to build "AI factories of the future" in Saudi Arabia. Just one hour ago, Saudi Arabia signed an economic agreement with President Trump to invest $600 billion in the US.
🏦Banks:
👉🏽 No news
🌎Macro/Geopolitics:
On the 12th of May:
👉🏽Huge pressure is on the European Union to reach a trade deal. Equities and commodities bounce hard on news of China-US trade deal. "We have reached an agreement on a 90-day pause and substantially moved down the tariff levels — both sides, on the reciprocal tariffs, will move their tariffs down 115%." - Treasury Secretary Scott Bessent
Dollar and Yuan strong bounce. Gold corrects.
👉🏽After reaching a high of 71% this year, recession odds are now back down to 40%. The odds of the US entering a recession in 2025 fall to a new low of 40% following the US-China trade deal announcement.
👉🏽'Truly incredible:
- Trump raises tariffs: Yields rise because inflation is back
- Trump cuts tariffs: Yields rise because growth is back
- Trump does nothing: Yields rise because the Fed won't cut rates Today, the bond market becomes Trump and Bessent's top priority.' - TKL
President Trump’s biggest problem persists even as trade deals are announced. Tariffs have been paused for 90 days, the US-China trade deal has been announced, and inflation data is down. Yet, the 10Y yield is nearing 4.50% again. Trump needs lower rates, but rates won’t fall.
👉🏽Last week a lot of talk on Japan’s Debt Death Spiral: Japan’s 40-year yield is detonating and the myth of consequence-free debt just died with it. One of the best explanations, you can read here:
👉🏽Michael A. Arouet: 'Eye-opening chart. Can a country with a services-based economy remain a superpower? Building back US manufacturing base makes a lot of strategic and geopolitical sense.' https://i.ibb.co/Q3zJY9Fc/Gqxc6-Pt-WQAI73c.jpg
On the 13th of May:
👉🏽There is a possibility of a “big, beautiful” economic rebalancing, Treasury Secretary Scott Bessent says at an investment forum in Saudi Arabia. The “dream scenario” would be if China and the US can work together on rebalancing, he adds
Luke Gromen: It does roll off the tongue a whole lot nicer than "We want to significantly devalue USD v. CNY, via a gold reference point."
Ergo: The price of gold specifically would rise in USD much more than it would in CNY, while prices for other goods and services would not, or would do so to a lesser degree.
👉🏽 Dutch inflation rises to 4.1 percent in April | CBS – final figure. Unchanged compared to the estimate.
👉🏽Philipp Heimberger: This interesting new paper argues that cuts to taxes on top incomes disproportionately benefit the financial sector. The finance industry gains more from top-income tax cuts than other industries. "Cuts in top income tax rates increase the (relative) size of the financial sector"
Kinda obvious, innit?
👉🏽US CPI data released. Overall good results and cooler than expected month-over-month and year-over-year (outside of yearly core). U.S. inflation is down to 2.3%, lower than expected.
On the 14th of May:
👉🏽'The US government cannot afford a recession: In previous economic cycles, the US budget deficit widened by ~4% of GDP on average during recessions. This would imply a ~$1.3 trillion deterioration of US government finances if a recession hits in 2025. That said, if the US enters a recession, long-term interest rates will likely go down.
A 2-percentage-point decrease in interest rates would save ~$568 billion in annual interest payments. However, this means government finances would worsen by more than DOUBLE the amount saved in interest due to a recession. An economic downturn would be incredibly costly for the US government.' -TKL
On the 15th of May:
👉🏽'In the Eurozone and the UK, households hold more than 30% of their financial assets in fiat currencies and bank deposits. This means that they (unknowingly?) allow inflation to destroy their purchasing power. The risks of inflation eating up your wealth increase in a debt-driven economic system characterized by fiscal dominance, where interest rates are structurally low and inflation levels and risks are high. There is so much forced and often failed regulation to increase financial literacy, but this part is never explained. Why is that, you think?' - Jeroen Blokland https://i.ibb.co/zWRpNqhz/Gq-jn-Bn-X0-AAmplm.png
On the 16th of May:
👉🏽'For the first time in a year, Japan's economy shrank by -0.7% in Q1 2025. This is more than double the decline expected by economists. Furthermore, this data does NOT include the reciprocal tariffs imposed on April 2nd. Japan's economy is heading for a recession.' -TKL
👉🏽'246 US large companies have gone bankrupt year-to-date, the most in 15 years. This is up from 206 recorded last year and more than DOUBLE during the same period in 2022. In April alone, the US saw 59 bankruptcy filings as tariffs ramped up. So far this year, the industrials sector has seen 41 bankruptcies, followed by 31 in consumer discretionary, and 17 in healthcare. According to S&P Global, consumer discretionary companies have been hit the hardest due to market volatility, tariffs, and inflation uncertainty. We expect a surge in bankruptcies in 2025.' -TKL
👉🏽'Moody's just downgraded the United States' credit rating for the FIRST time in history. The reason: An unsustainable path for US federal debt and its resulting interest burden. Moody's notes that the US debt-to-GDP ratio is on track to hit 134% by 2035. Federal interest payments are set to equal ~30% of revenue by 2035, up from ~18% in 2024 and ~9% in 2021. Furthermore, deficit spending is now at World War 2 levels as a percentage of GDP. The US debt crisis is our biggest issue with the least attention.' - TKL
Still, this is a nothing burger. In August 2023, when Fitch downgraded the US to AA+, and S&P (2011) the US became a split-rated AA+ country. This downgrade had almost no effect on the bond market. The last of the rating agencies, Moodys, pushed the US down to AA+ today. So technically it didn’t even change the US’s overall credit rating because it was already split-rated AA+, now it’s unanimous AA+.
Ergo: Nothing changed. America now shares a credit rating with Austria and Finland. Hard assets don’t lie. Watch Gold and Bitcoin.
https://i.ibb.co/Q7DcWY2P/Gr-K66i-EXIAAKh-MR.jpg
RAY DALIO: Credit Agencies are UNDERSTATING sovereign credit risks because "they don't include the greater risk that the countries in debt will print money to pay their debts" with devalued currency.
👉🏽US consumer credit card serious delinquencies are rising at a CRISIS pace: The share of US credit card debt that is past due at least 90 days hit 12.3% in Q1 2025, the highest in 14 YEARS. The percentage has risen even faster than during the Great Financial Crisis.' - Global Markets Investor
https://i.ibb.co/nNH9CxVK/Gr-E838o-XYAIk-Fyn.png
On the 18th of May:
👉🏽Michael A. Arouet: 'Look at ten bottom of this list. Milei has not only proven that real free market reforms work, but he has also proven that they work fast. It’s bigger than Argentina now, no wonder that the left legacy media doesn’t like him so much.' https://i.ibb.co/MDnBCDSY/Gr-Npu-KKWMAAf-Pc.jpg
On the 19th of May: 👉🏽Japan's 40-year bond yield just hit its highest level in over 20 years. Japan’s Prime Minister Ishiba has called the situation “worse than Greece.” All as Japan’s GDP is contracting again. You and your mother should be scared out of your fucking minds. https://i.ibb.co/rGZ9cMtv/GTXx-S7-Cb-MAAOu-Vt.png
👉🏽 TKL: 'Investors are piling into gold funds like never before: Gold funds have posted a record $85 BILLION in net inflows year-to-date. This is more than DOUBLE the full-year record seen in 2020. At this pace, net inflows will surpass $180 billion by the end of 2025. Gold is now the best-performing major asset class, up 22% year-to-date. Since the low in October 2022, gold prices have gained 97%. Gold is the global hedge against uncertainty.'
🎁If you have made it this far, I would like to give you a little gift, well, in this case, two gifts:
What Bitcoin Did - IS THE FED LOSING CONTROL? With Matthew Mezinskis
'Matthew Mezinskis is a macroeconomic researcher, host of the Crypto Voices podcast, and creator of Porkopolis Economics. In this episode, we discuss fractional reserve banking, why it's controversial among Bitcoiners, the historical precedent for banking practices, and whether fractional reserve banking inherently poses systemic risks. We also get into the dangers and instabilities introduced by central banking, why Bitcoin uniquely offers a pathway to financial sovereignty, the plumbing of the global financial system, breaking down money supply metrics, foreign holdings of US treasuries, and how all these elements indicate growing instability in the dollar system.'
https://youtu.be/j-XPVOl9zGc
Credit: I have used multiple sources!
My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly.
Use the code SE3997
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple. ⠀ ⠀
⠀⠀ ⠀ ⠀⠀⠀
Do you think this post is helpful to you?
If so, please share it and support my work with a zap.
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe - Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-
 @ c9badfea:610f861a
2025-05-24 12:55:17
@ c9badfea:610f861a
2025-05-24 12:55:17Before you post a message or article online, let the LLM check if you are leaking any personal information using this prompt:
Analyze the following text to identify any Personally Identifiable Information (PII): <Your Message>Replace
<Your Message>with your textIf no PII is found, continue by modifying your message to detach it from your personality. You can use any of the following prompts (and further modify it if necessary).
Prompt № 1 - Reddit-Style
Convert the message into a casual, Reddit-style post without losing meaning. Split the message into shorter statements with the same overall meaning. Here is the message: <Your Message>Prompt № 2 - Advanced Modifications
``` Apply the following modifications to the message: - Rewrite it in lowercase - Use "u" instead of "you" - Use "akchoaly" instead of "actually" - Use "hav" instead of "have" - Use "tgat" instead of "that" - Use comma instead of period - Use British English grammar
Here is the message:
``` Prompt № 3 - Neutral Tone
Rewrite the message to correct grammar errors, and ensure the tone is neutral and free of emotional language: <Your Message>Prompt № 4 - Cross Translation Technique
Translate the message into Chinese, then translate the resulting Chinese text back into English. Provide only the final English translation. Here is the message: <Your Message>Check the modified message and send it.
ℹ️ You can use dialects to obfuscate your language further. For example, if you are from the US, you can tell the LLM to use British grammar and vice versa.
⚠️ Always verify the results. Don't fully trust an LLM.
-
 @ 8bf578f4:b6303c41
2025-05-24 12:17:18
@ 8bf578f4:b6303c41
2025-05-24 12:17:18test
https://nosto.re/6849b84caaa15bdc18ca2e1e1ee00e979c7ecf901787e09054b4bd0196b4ea27.jpg
test svg
-
 @ 5ea46480:450da5bd
2025-05-24 09:57:37
@ 5ea46480:450da5bd
2025-05-24 09:57:37Decentralization refers to control/power, and relates to censorship resistance. That is it, it is not more complicated then that. Resilience is a function of redundancy; a centralized censored system can have a redundant set-up and therefor be resilient.
Take Bitcoin; the blockchain is a central database, it is resilient because it has many redundant copies among a lot of different nodes. The message (txs and blocks) propagation is decentralized due to existence of a p2p network among these nodes, making the data distribution censorship resistant (hello op_return debate). But onchain transactions themselves are NOT p2p, they require a middlemen (a miner) because it is a central database, as opposed to something like lightning which is p2p. Peer to Peer says something about relative architectural hierarchical position/relation. P2P provides censorship resistance because it entails equal power relations, provided becoming a peer is permissionless. What makes onchain transactions censorship resistant is that mining is permissionless, and involves this open power struggle/game where competition results in a power distribution among players, meaning (hopefully) decentralization. The fact users rely on these middlemen is mitigated by this decentralization on the one hand, and temper-proofing via cryptographic signatures on the other, resulting in what we call trustlessness (or trust minimization for the autists in the room); we only rely on a miner to perform a job (including your tx into a block), but we don’t trust the miner to perform the job correctly, this we can verify ourselves.
This leads us to Nostr, because that last part is exactly what Nostr does as well. It uses cryptography to get tamper-proof messaging, which then allows you to use middle-men in a trust minimized way. The result is decentralization because in general terms, any middle man is as good as any other (same as with miners), and becoming such a middleman is permissionless(somewhat, mostly); which in turn leads to censorship resistance. It also allows for resilience because you are free to make things as redundant as you'd like.
Ergo, the crux is putting the cryptography central, making it the starting point of the system; decentralization then becomes an option due to trust minimization. The difference between Bitcoin an Nostr, is that Bitcoin maintains a global state/central ledger and needs this PoW/Nakamoto consensus fanfare; Nostr rests itself with local perspectives on 'the network'.
The problem with the Fediverse, is that it does not provide trust minimization in relation to the middlemen. Sure, there are a lot different servers, but you rely on a particular one (and the idea you could switch never really seemed to have materialized in a meaningful way). It also fails in permisionlessness because you rely on the association between servers, i.e. federation, to have meaningful access to the rest of the network. In other words, it is more a requirement of association than freedom of association; you have the freedom to be excommunicated.
The problem with ATproto is that is basically does not solve this dynamic; it only complicates it by pulling apart the components; identity and data, distribution and perspective are now separated, and supposedly you don’t rely on any particular one of these sub-component providers in the stack; but you do rely on all these different sub-component providers in the stack to play nice with each other. And this ‘playing nice’ is just the same old ‘requirement of association’ and ‘freedom of excommunication’ that looms at the horizon.
Yes, splitting up the responsibilities of identity, hosting and indexing is what is required to safe us from the platform hellscape which at this stage takes care of all three. But as it turns out, it was not a matter cutting those up into various (on paper) interchangeable middlemen. All that is required is putting cryptographic keys in the hands of the user; the tamperproofing takes care of the rest, simply by trust minimizing the middlemen we use. All the sudden it does not matter which middlemen we use, and no one is required to play nice; we lost the requirement of association, and gained freedom of association, which was the purpose of censorship resistance and therefor decentralization, to begin with.
-
 @ b7274d28:c99628cb
2025-05-24 01:02:32
@ b7274d28:c99628cb
2025-05-24 01:02:32A few months ago, a nostrich was switching from iOS to Android and asked for suggestions for #Nostr apps to try out. nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424 offered the following as his response:
nostr:nevent1qvzqqqqqqypzq0mhp4ja8fmy48zuk5p6uy37vtk8tx9dqdwcxm32sy8nsaa8gkeyqydhwumn8ghj7un9d3shjtnwdaehgunsd3jkyuewvdhk6tcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszythwden5te0dehhxarj9emkjmn99uqzpwwts6n28eyvjpcwvu5akkwu85eg92dpvgw7cgmpe4czdadqvnv984rl0z
Yes. #Android users are fortunate to have some powerful Nostr apps and tools at our disposal that simply have no comparison over on the iOS side. However, a tool is only as good as the knowledge of the user, who must have an understanding of how best to wield it for maximum effect. This fact was immediately evidenced by replies to Derek asking, "What is the use case for Citrine?" and "This is the first time I'm hearing about Citrine and Pokey. Can you give me links for those?"
Well, consider this tutorial your Nostr starter-kit for Android. We'll go over installing and setting up Amber, Amethyst, Citrine, and Pokey, and as a bonus we'll be throwing in the Zapstore and Coinos to boot. We will assume no previous experience with any of the above, so if you already know all about one or more of these apps, you can feel free to skip that tutorial.
So many apps...
You may be wondering, "Why do I need so many apps to use Nostr?" That's perfectly valid, and the honest answer is, you don't. You can absolutely just install a Nostr client from the Play Store, have it generate your Nostr identity for you, and stick with the default relays already set up in that app. You don't even need to connect a wallet, if you don't want to. However, you won't experience all that Nostr has to offer if that is as far as you go, any more than you would experience all that Italian cuisine has to offer if you only ever try spaghetti.
Nostr is not just one app that does one thing, like Facebook, Twitter, or TikTok. It is an entire ecosystem of applications that are all built on top of a protocol that allows them to be interoperable. This set of tools will help you make the most out of that interoperability, which you will never get from any of the big-tech social platforms. It will provide a solid foundation for you to build upon as you explore more and more of what Nostr has to offer.
So what do these apps do?

Fundamental to everything you do on Nostr is the need to cryptographically sign with your private key. If you aren't sure what that means, just imagine that you had to enter your password every time you hit the "like" button on Facebook, or every time you commented on the latest dank meme. That would get old really fast, right? That's effectively what Nostr requires, but on steroids.
To keep this from being something you manually have to do every 5 seconds when you post a note, react to someone else's note, or add a comment, Nostr apps can store your private key and use it to sign behind the scenes for you. This is very convenient, but it means you are trusting that app to not do anything with your private key that you don't want it to. You are also trusting it to not leak your private key, because anyone who gets their hands on it will be able to post as you, see your private messages, and effectively be you on Nostr. The more apps you give your private key to, the greater your risk that it will eventually be compromised.
Enter #Amber, an application that will store your private key in only one app, and all other compatible Nostr apps can communicate with it to request a signature, without giving any of those other apps access to your private key.
Most Nostr apps for Android now support logging in and signing with Amber, and you can even use it to log into apps on other devices, such as some of the web apps you use on your PC. It's an incredible tool given to us by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5, and only available for Android users. Those on iPhone are incredibly jealous that they don't have anything comparable, yet.

Speaking of nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5, the next app is also one of his making.
All Nostr data is stored on relays, which are very simple servers that Nostr apps read notes from and write notes to. In most forms of social media, it can be a pain to get your own data out to keep a backup. That's not the case on Nostr. Anyone can run their own relay, either for the sake of backing up their personal notes, or for others to post their notes to, as well.
Since Nostr notes take up very little space, you can actually run a relay on your phone. I have been on Nostr for almost 2 and a half years, and I have 25,000+ notes of various kinds on my relay, and a backup of that full database is just 24MB on my phone's storage.
Having that backup can save your bacon if you try out a new Nostr client and it doesn't find your existing follow list for some reason, so it writes a new one and you suddenly lose all of the people you were following. Just pop into your #Citrine relay, confirm it still has your correct follow list or import it from a recent backup, then have Citrine restore it. Done.
Additionally, there are things you may want to only save to a relay you control, such as draft messages that you aren't ready to post publicly, or eCash tokens, which can actually be saved to Nostr relays now. Citrine can also be used with Amber for signing into certain Nostr applications that use a relay to communicate with Amber.
If you are really adventurous, you can also expose Citrine over Tor to be used as an outbox relay, or used for peer-to-peer private messaging, but that is far more involved than the scope of this tutorial series.

You can't get far in Nostr without a solid and reliable client to interact with. #Amethyst is the client we will be using for this tutorial because there simply isn't another Android client that comes close, so far. Moreover, it can be a great client for new users to get started on, and yet it has a ton of features for power-users to take advantage of as well.
There are plenty of other good clients to check out over time, such as Coracle, YakiHonne, Voyage, Olas, Flotilla and others, but I keep coming back to Amethyst, and by the time you finish this tutorial, I think you'll see why. nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z and others who have contributed to Amethyst have really built something special in this client, and it just keeps improving with every update that's shipped.
Most social media apps have some form of push notifications, and some Nostr apps do, too. Where the issue comes in is that Nostr apps are all interoperable. If you have more than one application, you're going to have both of them notifying you. Nostr users are known for having five or more Nostr apps that they use regularly. If all of them had notifications turned on, it would be a nightmare. So maybe you limit it to only one of your Nostr apps having notifications turned on, but then you are pretty well locked-in to opening that particular app when you tap on the notification.
Pokey, by nostr:npub1v3tgrwwsv7c6xckyhm5dmluc05jxd4yeqhpxew87chn0kua0tjzqc6yvjh, solves this issue, allowing you to turn notifications off for all of your Nostr apps, and have Pokey handle them all for you. Then, when you tap on a Pokey notification, you can choose which Nostr app to open it in.
Pokey also gives you control over the types of things you want to be notified about. Maybe you don't care about reactions, and you just want to know about zaps, comments, and direct messages. Pokey has you covered. It even supports multiple accounts, so you can get notifications for all the npubs you control.

One of the most unique and incredibly fun aspects of Nostr is the ability to send and receive #zaps. Instead of merely giving someone a 👍️ when you like something they said, you can actually send them real value in the form of sats, small portions of a Bitcoin. There is nothing quite like the experience of receiving your first zap and realizing that someone valued what you said enough to send you a small amount (and sometimes not so small) of #Bitcoin, the best money mankind has ever known.
To be able to have that experience, though, you are going to need a wallet that can send and receive zaps, and preferably one that is easy to connect to Nostr applications. My current preference for that is Alby Hub, but not everyone wants to deal with all that comes along with running a #Lightning node. That being the case, I have opted to use nostr:npub1h2qfjpnxau9k7ja9qkf50043xfpfy8j5v60xsqryef64y44puwnq28w8ch for this tutorial, because they offer one of the easiest wallets to set up, and it connects to most Nostr apps by just copy/pasting a connection string from the settings in the wallet into the settings in your Nostr app of choice.
Additionally, even though #Coinos is a custodial wallet, you can have it automatically transfer any #sats over a specified threshold to a separate wallet, allowing you to mitigate the custodial risk without needing to keep an eye on your balance and make the transfer manually.

Most of us on Android are used to getting all of our mobile apps from one souce: the Google Play Store. That's not possible for this tutorial series. Only one of the apps mentioned above is available in Google's permissioned playground. However, on Android we have the advantage of being able to install whatever we want on our device, just by popping into our settings and flipping a toggle. Indeed, thumbing our noses at big-tech is at the heart of the Nostr ethos, so why would we make ourselves beholden to Google for installing Nostr apps?
The nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8 is an alternative app store made by nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9 as a resource for all sorts of open-source apps, but especially Nostr apps. What is more, you can log in with Amber, connect a wallet like Coinos, and support the developers of your favorite Nostr apps directly within the #Zapstore by zapping their app releases.
One of the biggest features of the Zapstore is the fact that developers can cryptographically sign their app releases using their Nostr keys, so you know that the app you are downloading is the one they actually released and hasn't been altered in any way. The Zapstore will warn you and won't let you install the app if the signature is invalid.
Getting Started
Since the Zapstore will be the source we use for installing most of the other apps mentioned, we will start with installing the Zapstore.
We will then use the Zapstore to install Amber and set it up with our Nostr account, either by creating a new private key, or by importing one we already have. We'll also use it to log into the Zapstore.
Next, we will install Amethyst from the Zapstore and log into it via Amber.
After this, we will install Citrine from the Zapstore and add it as a local relay on Amethyst.
Because we want to be able to send and receive zaps, we will set up a wallet with CoinOS and connect it to Amethyst and the Zapstore using Nostr Wallet Connect.
Finally, we will install Pokey using the Zapstore, log into it using Amber, and set up the notifications we want to receive.
By the time you are done with this series, you will have a great head-start on your Nostr journey compared to muddling through it all on your own. Moreover, you will have developed a familiarity with how things generally work on Nostr that can be applied to other apps you try out in the future.
Continue to Part 2: Installing the Zapstore. (Coming Soon)
-
 @ 34f1ddab:2ca0cf7c
2025-05-23 23:15:14
@ 34f1ddab:2ca0cf7c
2025-05-23 23:15:14Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet. Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy. ⚠️ What We Don’t Do While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
Don’t Let Lost Crypto Hold You Back! Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Ready to reclaim your lost crypto? Don’t wait until it’s too late! 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on: ✉️ Telegram: t.me/crypptrcver 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions\ At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery\ We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority\ Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology\ Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet.
- Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy.
⚠️ What We Don’t Do\ While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
 # Don’t Let Lost Crypto Hold You Back!
# Don’t Let Lost Crypto Hold You Back!Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection\ Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!\ Ready to reclaim your lost crypto? Don’t wait until it’s too late!\ 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us!\ For real-time support or questions, reach out to our dedicated team on:\ ✉️ Telegram: t.me/crypptrcver\ 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:52:59
@ 6d5c826a:4b27b659
2025-05-23 21:52:59- Ganeti - Cluster virtual server management software tool built on top of KVM and Xen. (Source Code)
BSD-2-ClausePython/Haskell - KVM - Linux kernel virtualization infrastructure. (Source Code)
GPL-2.0/LGPL-2.0C - OpenNebula - Build and manage enterprise clouds for virtualized services, containerized applications and serverless computing. (Source Code)
Apache-2.0C++ - oVirt - Manages virtual machines, storage and virtual networks. (Source Code)
Apache-2.0Java - Packer - A tool for creating identical machine images for multiple platforms from a single source configuration. (Source Code)
MPL-2.0Go - Proxmox VE - Virtualization management solution. (Source Code)
GPL-2.0Perl/Shell - QEMU - QEMU is a generic machine emulator and virtualizer. (Source Code)
LGPL-2.1C - Vagrant - Tool for building complete development environments. (Source Code)
BUSL-1.1Ruby - VirtualBox - Virtualization product from Oracle Corporation. (Source Code)
GPL-3.0/CDDL-1.0C++ - XCP-ng - Virtualization platform based on Xen Source and Citrix® Hypervisor (formerly XenServer). (Source Code)
GPL-2.0C - Xen - Virtual machine monitor for 32/64 bit Intel / AMD (IA 64) and PowerPC 970 architectures. (Source Code)
GPL-2.0C
- Ganeti - Cluster virtual server management software tool built on top of KVM and Xen. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:52:26
@ 6d5c826a:4b27b659
2025-05-23 21:52:26- grml - Bootable Debian Live CD with powerful CLI tools. (Source Code)
GPL-3.0Shell - mitmproxy - A Python tool used for intercepting, viewing and modifying network traffic. Invaluable in troubleshooting certain problems. (Source Code)
MITPython - mtr - Network utility that combines traceroute and ping. (Source Code)
GPL-2.0C - Sysdig - Capture system state and activity from a running Linux instance, then save, filter and analyze. (Source Code)
Apache-2.0Docker/Lua/C - Wireshark - The world's foremost network protocol analyzer. (Source Code)
GPL-2.0C
- grml - Bootable Debian Live CD with powerful CLI tools. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:52:06
@ 6d5c826a:4b27b659
2025-05-23 21:52:06- Docker Compose - Define and run multi-container Docker applications. (Source Code)
Apache-2.0Go - Docker Swarm - Manage cluster of Docker Engines. (Source Code)
Apache-2.0Go - Docker - Platform for developers and sysadmins to build, ship, and run distributed applications. (Source Code)
Apache-2.0Go - LXC - Userspace interface for the Linux kernel containment features. (Source Code)
GPL-2.0C - LXD - Container "hypervisor" and a better UX for LXC. (Source Code)
Apache-2.0Go - OpenVZ - Container-based virtualization for Linux. (Source Code)
GPL-2.0C - Podman - Daemonless container engine for developing, managing, and running OCI Containers on your Linux System. Containers can either be run as root or in rootless mode. Simply put:
alias docker=podman. (Source Code)Apache-2.0Go - Portainer Community Edition - Simple management UI for Docker. (Source Code)
ZlibGo - systemd-nspawn - Lightweight, chroot-like, environment to run an OS or command directly under systemd. (Source Code)
GPL-2.0C
- Docker Compose - Define and run multi-container Docker applications. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:49:50
@ 6d5c826a:4b27b659
2025-05-23 21:49:50- Consul - Consul is a tool for service discovery, monitoring and configuration. (Source Code)
MPL-2.0Go - etcd - Distributed K/V-Store, authenticating via SSL PKI and a REST HTTP Api for shared configuration and service discovery. (Source Code)
Apache-2.0Go - ZooKeeper - ZooKeeper is a centralized service for maintaining configuration information, naming, providing distributed synchronization, and providing group services. (Source Code)
Apache-2.0Java/C++
- Consul - Consul is a tool for service discovery, monitoring and configuration. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:49:30
@ 6d5c826a:4b27b659
2025-05-23 21:49:30- DD-WRT - A Linux-based firmware for wireless routers and access points, originally designed for the Linksys WRT54G series. (Source Code)
GPL-2.0C - OpenWrt - A Linux-based router featuring Mesh networking, IPS via snort and AQM among many other features. (Source Code)
GPL-2.0C - OPNsense - An open source FreeBSD-based firewall and router with traffic shaping, load balancing, and virtual private network capabilities. (Source Code)
BSD-2-ClauseC/PHP - pfSense CE - Free network firewall distribution, based on the FreeBSD operating system with a custom kernel and including third party free software packages for additional functionality. (Source Code)
Apache-2.0Shell/PHP/Other
- DD-WRT - A Linux-based firmware for wireless routers and access points, originally designed for the Linksys WRT54G series. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:49:12
@ 6d5c826a:4b27b659
2025-05-23 21:49:12- Remmina - Feature-rich remote desktop application for linux and other unixes. (Source Code)
GPL-2.0C - Tiger VNC - High-performance, multi-platform VNC client and server. (Source Code)
GPL-2.0C++ - X2go - X2Go is an open source remote desktop software for Linux that uses the NoMachine/NX technology protocol. (Source Code)
GPL-2.0Perl
- Remmina - Feature-rich remote desktop application for linux and other unixes. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:48:56
@ 6d5c826a:4b27b659
2025-05-23 21:48:56- ActiveMQ - Java message broker. (Source Code)
Apache-2.0Java - BeanstalkD - A simple, fast work queue. (Source Code)
MITC - Gearman - Fast multi-language queuing/job processing platform. (Source Code)
BSD-3-ClauseC++ - NSQ - A realtime distributed messaging platform. (Source Code)
MPL-2.0Go - ZeroMQ - Lightweight queuing system. (Source Code)
GPL-3.0C++
- ActiveMQ - Java message broker. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:48:36
@ 6d5c826a:4b27b659
2025-05-23 21:48:36- aptly - Swiss army knife for Debian repository management. (Source Code)
MITGo - fpm - Versatile multi format package creator. (Source Code)
MITRuby - omnibus-ruby - Easily create full-stack installers for your project across a variety of platforms.
Apache-2.0Ruby - tito - Builds RPMs for git-based projects.
GPL-2.0Python
- aptly - Swiss army knife for Debian repository management. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:48:21
@ 6d5c826a:4b27b659
2025-05-23 21:48:21- CapRover - Build your own PaaS in a few minutes. (Demo, Source Code)
Apache-2.0Docker/Nodejs - Coolify - An open-source & self-hostable Heroku / Netlify alternative (and even more). (Source Code)
Apache-2.0Docker - Dokku - An open-source PaaS (alternative to Heroku). (Source Code)
MITDocker/Shell/Go/deb - fx - A tool to help you do Function as a Service with painless on your own servers.
MITGo - Kubero - A self-hosted Heroku PaaS alternative for Kubernetes that implements GitOps. (Demo, Source Code)
GPL-3.0K8S/Nodejs/Go - LocalStack - LocalStack is a fully functional local AWS cloud stack. This includes Lambda for serverless computation. (Source Code)
Apache-2.0Python/Docker/K8S - Nhost - Firebase Alternative with GraphQL. Get a database and backend configured and ready in minutes. (Source Code)
MITDocker/Nodejs/Go - OpenFaaS - Serverless Functions Made Simple for Docker & Kubernetes. (Source Code)
MITGo - Tau - Easily build Cloud Computing Platforms with features like Serverless WebAssembly Functions, Frontend Hosting, CI/CD, Object Storage, K/V Database, and Pub-Sub Messaging. (Source Code)
BSD-3-ClauseGo/Rust/Docker - Trusted-CGI - Lightweight self-hosted lambda/applications/cgi/serverless-functions platform.
MITGo/deb/Docker
- CapRover - Build your own PaaS in a few minutes. (Demo, Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:47:44
@ 6d5c826a:4b27b659
2025-05-23 21:47:44- Adagios - Web based Nagios interface for configuration and monitoring (replacement to the standard interface), and a REST interface. (Source Code)
AGPL-3.0Docker/Python - Alerta - Distributed, scalable and flexible monitoring system. (Source Code)
Apache-2.0Python - Beszel - Lightweight server monitoring platform that includes Docker statistics, historical data, and alert functions. (Source Code)
MITGo - Cacti - Web-based network monitoring and graphing tool. (Source Code)
GPL-2.0PHP - cadvisor - Analyzes resource usage and performance characteristics of running containers.
Apache-2.0Go - checkmk - Comprehensive solution for monitoring of applications, servers, and networks. (Source Code)
GPL-2.0Python/PHP - dashdot - A simple, modern server dashboard for smaller private servers. (Demo)
MITNodejs/Docker - EdMon - A command-line monitoring application helping you to check that your hosts and services are available, with notifications support.
MITJava - eZ Server Monitor - A lightweight and simple dashboard monitor for Linux, available in Web and Bash application. (Source Code)
GPL-3.0PHP/Shell - glances - Open-source, cross-platform real-time monitoring tool with CLI and web dashboard interfaces and many exporting options. (Source Code)
GPL-3.0Python - Healthchecks - Monitoring for cron jobs, background services and scheduled tasks. (Source Code)
BSD-3-ClausePython - Icinga - Nagios fork that has since lapped nagios several times. Comes with the possibility of clustered monitoring. (Source Code)
GPL-2.0C++ - LibreNMS - Fully featured network monitoring system that provides a wealth of features and device support. (Source Code)
GPL-3.0PHP - Linux Dash - A low-overhead monitoring web dashboard for a GNU/Linux machine.
MITNodejs/Go/Python/PHP - Monit - Small utility for managing and monitoring Unix systems. (Source Code)
AGPL-3.0C - Munin - Networked resource monitoring tool. (Source Code)
GPL-2.0Perl/Shell - Naemon - Network monitoring tool based on the Nagios 4 core with performance enhancements and new features. (Source Code)
GPL-2.0C - Nagios - Computer system, network and infrastructure monitoring software application. (Source Code)
GPL-2.0C - Netdata - Distributed, real-time, performance and health monitoring for systems and applications. Runs on Linux, FreeBSD, and MacOS. (Source Code)
GPL-3.0C - NetXMS - Open Source network and infrastructure monitoring and management. (Source Code)
LGPL-3.0/GPL-3.0Java/C++/C - Observium Community Edition - Network monitoring and management platform that provides real-time insight into network health and performance.
QPL-1.0PHP - openITCOCKPIT Community Edition - Monitoring Suite featuring seamless integrations with Naemon, Checkmk, Grafana and more. (Demo, Source Code)
GPL-3.0deb/Docker - Performance Co-Pilot - Lightweight, distributed system performance and analysis framework. (Source Code)
LGPL-2.1/GPL-2.0C - PHP Server Monitor - Open source tool to monitor your servers and websites. (Source Code)
GPL-3.0PHP - PhpSysInfo - A customizable PHP script that displays information about your system nicely. (Source Code)
GPL-2.0PHP - Prometheus - Service monitoring system and time series database. (Source Code)
Apache-2.0Go - Riemann - Flexible and fast events processor allowing complex events/metrics analysis. (Source Code)
EPL-1.0Java - rtop - Interactive, remote system monitoring tool based on SSH.
MITGo - ruptime - Classic system status server.
AGPL-3.0Shell - Scrutiny - Web UI for hard drive S.M.A.R.T monitoring, historical trends & real-world failure thresholds.
MITGo - Sensu - Monitoring tool for ephemeral infrastructure and distributed applications. (Source Code)
MITGo - Status - Simple and lightweight system monitoring tool for small homeservers with a pleasant web interface. (Demo
MITPython - Thruk - Multibackend monitoring web interface with support for Naemon, Nagios, Icinga and Shinken. (Source Code)
GPL-1.0Perl - Wazuh - Unified XDR and SIEM protection for endpoints and cloud workloads. (Source Code)
GPL-2.0C - Zabbix - Enterprise-class software for monitoring of networks and applications. (Source Code)
GPL-2.0C
- Adagios - Web based Nagios interface for configuration and monitoring (replacement to the standard interface), and a REST interface. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:47:22
@ 6d5c826a:4b27b659
2025-05-23 21:47:22- Chocolatey - The package manager for Windows. (Source Code)
Apache-2.0C#/PowerShell - Clonezilla - Partition and disk imaging/cloning program. (Source Code)
GPL-2.0Perl/Shell/Other - DadaMail - Mailing List Manager, written in Perl. (Source Code)
GPL-2.0Perl - Fog - Cloning/imaging solution/rescue suite. (Source Code)
GPL-3.0PHP/Shell - phpList - Newsletter and email marketing software. (Source Code)
AGPL-3.0PHP
- Chocolatey - The package manager for Windows. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:47:03
@ 6d5c826a:4b27b659
2025-05-23 21:47:03- Beats - Single-purpose data shippers that send data from hundreds or thousands of machines and systems to Logstash or Elasticsearch. (Source Code)
Apache-2.0Go - Collectd - System statistics collection daemon. (Source Code)
MITC - Diamond - Daemon that collects system metrics and publishes them to Graphite (and others).
MITPython - Grafana - A Graphite & InfluxDB Dashboard and Graph Editor. (Source Code)
AGPL-3.0Go - Graphite - Scalable graphing server. (Source Code)
Apache-2.0Python - RRDtool - Industry standard, high performance data logging and graphing system for time series data. (Source Code)
GPL-2.0C - Statsd - Daemon that listens for statistics like counters and timers, sent over UDP or TCP, and sends aggregates to one or more pluggable backend services.
MITNodejs - tcollector - Gathers data from local collectors and pushes the data to OpenTSDB. (Source Code)
LGPL-3.0/GPL-3.0Python - Telegraf - Plugin-driven server agent for collecting, processing, aggregating, and writing metrics.
MITGo
- Beats - Single-purpose data shippers that send data from hundreds or thousands of machines and systems to Logstash or Elasticsearch. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:46:46
@ 6d5c826a:4b27b659
2025-05-23 21:46:46- aerc - Terminal MUA with a focus on plaintext and features for developers. (Source Code)
MITGo - Claws Mail - Old school email client (and news reader), based on GTK+. (Source Code)
GPL-3.0C - ImapSync - Simple IMAP migration tool for copying mailboxes to other servers. (Source Code)
NLPLPerl - Mutt - Small but very powerful text-based mail client. (Source Code)
GPL-2.0C - Sylpheed - Still developed predecessor to Claws Mail, lightweight mail client. (Source Code)
GPL-2.0C - Thunderbird - Free email application that's easy to set up and customize. (Source Code)
MPL-2.0C/C++
- aerc - Terminal MUA with a focus on plaintext and features for developers. (Source Code)
-
 @ 84b0c46a:417782f5
2025-05-27 08:19:49
@ 84b0c46a:417782f5
2025-05-27 08:19:49Simple Long Form Content Editor (NIP-23)
機能
-
nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw や、 nostr:nevent1qvzqqqqqqypzq4jsz7zew5j7jr4pdfxh483nwq9vyw9ph6wm706sjwrzj2we58nqqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyxhwumn8ghj7mn0wvhxcmmvqqsgcn99jyn5tevxz5zxsrkd7h0sx8fwnqztula423xh83j9wau7cms3vg9c7 のようにnostr:要素を挿入できる (メニューのNアイコンから挿入またはnostr:note~~のように手動で入力)
-
:monoice:のようにカスタム絵文字を挿入できる(メニューの🙂アイコンから)
:monopaca_kao:
:kubipaca_karada:
- 新規記事作成と、既存記事の修正ができる
やることやったこと
-
[x] nostr:を投稿するときにtagにいれる
-
[x] 画像をアップロードできるようにする(NIP-96)
 できる
できる - [x] 投稿しましたログとかをトースト的なやつでだすようにする
- [ ] レイアウトを整える
- [ ] あとなんか
-
-
 @ 6d5c826a:4b27b659
2025-05-23 21:46:28
@ 6d5c826a:4b27b659
2025-05-23 21:46:28- Fluentd - Data collector for unified logging layer. (Source Code)
Apache-2.0Ruby - Flume - Distributed, reliable, and available service for efficiently collecting, aggregating, and moving large amounts of log data. (Source Code)
Apache-2.0Java - GoAccess - Real-time web log analyzer and interactive viewer that runs in a terminal or through the browser. (Source Code)
MITC - Loki - Log aggregation system designed to store and query logs from all your applications and infrastructure. (Source Code)
AGPL-3.0Go - rsyslog - Rocket-fast system for log processing. (Source Code)
GPL-3.0C
- Fluentd - Data collector for unified logging layer. (Source Code)
-
 @ d3d74124:a4eb7b1d
2025-05-29 02:19:14
@ d3d74124:a4eb7b1d
2025-05-29 02:19:14language is a funny thing. the English grammar is one of the most, if the not THE most complicated grammars to learn.
https://en.wikipedia.org/wiki/Defense_Language_Aptitude_Battery\ DLAB. it's the test you take to see if you have a gift for language learning.
in my exploration of languages, first Chinese Mandarin, then software languages, context is king (Jesus is King). the surrounding context is different every where you go.
physical space context. we can't be two places at once. nostr allows for many languages, because you can provide your own digital context. our physical perspective give us a field of view. NOSTR clients give us a field of view into digital context.
math is a language.
bitcoin will be called a lot of things.
wizardry
some elections results are anchored in time. using bitcoin. what else should be? legal documents seem obvious. other cryptographic proofs.
zero knowledge proofs. something about curve trees.
Find your local BitDevs.
Shenandoah Bitcoin Club
pondering a Veteran's Day live music event in Frederick County, VA. who would show up to a lunch and learn with hardware wallets in testnet4 mode? to try shit out? local only, but you should do it where you are too if you're not local.
mining
getting better? Bitmain announces a "decentralized mining pool" but I doubt we'll see open source code if history follows. 256Foundation getting to business. working prototypes for the Ember One using USB and python are out there for those that know where to look. i am very bullish on mujina. very bullish. fun coinbase tricks happening too with CTV+CSFS.
p.s. written on primal's new article publishing UI.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:46:11
@ 6d5c826a:4b27b659
2025-05-23 21:46:11- GLPI - Information Resource-Manager with an additional Administration Interface. (Source Code)
GPL-3.0PHP - OCS Inventory NG - Asset management and deployment solution for all devices in your IT Department. (Source Code)
GPL-2.0PHP/Perl - OPSI - Hardware and software inventory, client management, deployment, and patching for Linux and Windows. (Source Code)
GPL-3.0/AGPL-3.0OVF/Python - RackTables - Datacenter and server room asset management like document hardware assets, network addresses, space in racks, networks configuration. (Demo, Source Code)
GPL-2.0PHP - Ralph - Asset management, DCIM and CMDB system for large Data Centers as well as smaller LAN networks. (Demo, Source Code)
Apache-2.0Python/Docker - Snipe IT - Asset & license management software. (Source Code)
AGPL-3.0PHP
- GLPI - Information Resource-Manager with an additional Administration Interface. (Source Code)
-
 @ 84b0c46a:417782f5
2025-05-27 07:04:13
@ 84b0c46a:417782f5
2025-05-27 07:04:13 -
 @ 6d5c826a:4b27b659
2025-05-23 21:45:53
@ 6d5c826a:4b27b659
2025-05-23 21:45:53- BounCA - A personal SSL Key / Certificate Authority web-based tool for creating self-signed certificates. (Source Code)
Apache-2.0Python - easy-rsa - Bash script to build and manage a PKI CA.
GPL-2.0Shell - Fusion Directory - Improve the Management of the services and the company directory based on OpenLDAP. (Source Code)
GPL-2.0PHP - LDAP Account Manager (LAM) - Web frontend for managing entries (e.g. users, groups, DHCP settings) stored in an LDAP directory. (Source Code)
GPL-3.0PHP - Libravatar - Libravatar is a service which delivers your avatar (profile picture) to other websites. (Source Code)
AGPL-3.0Python - Pomerium - An identity and context aware access-proxy inspired by BeyondCorp. (Source Code)
Apache-2.0Docker/Go - Samba - Active Directory and CIFS protocol implementation. (Source Code)
GPL-3.0C - Smallstep Certificates - A private certificate authority (X.509 & SSH) and related tools for secure automated certificate management. (Source Code)
Apache-2.0Go - ZITADEL - Cloud-native Identity & Access Management solution providing a platform for secure authentication, authorization and identity management. (Source Code)
Apache-2.0Go/Docker/K8S
- BounCA - A personal SSL Key / Certificate Authority web-based tool for creating self-signed certificates. (Source Code)
-
 @ a19caaa8:88985eaf
2025-05-27 22:36:15
@ a19caaa8:88985eaf
2025-05-27 22:36:15インターネット、だいすき!
レスバって?
- たのしさ(ちゃぴにきく)
ちがい
- タイプもきく?それはダルい?
さけるには
- ちゃぴにきく
“思い遣る”のと“邪推する”のは違う
- でもそう捉えたんだから仕方ないじゃん(自分の気持ちも大事にする)(バランス)(またあ?)
- 「意見単体」として見ているか、「そのひとから発された言葉」として見ているかの違い?
-
自分の理想をひとに押し付けない
-
それはそれとして、社会に疲れて深く潜りにきて、同じように深いとこに居るひとと手を振り合ったり、そのあり方を見て吸収したりしたいのに、バトルに巻き込まれるの、不憫すぎる
- インスタくんはえらいなあ、「このひとにストーリーズを表示しない」ができて
- 自分はそんなつもり無くても、始まってしまった以上、責任がある気がしてしまって、相手がどうして欲しいかを考え始めてしまい、消耗する
- 社会じゃん
- EなのにEしづらい環境のひとたちの捌け口になる必要は無い
- 海は広い
-
 @ 58937958:545e6994
2025-05-22 12:25:49
@ 58937958:545e6994
2025-05-22 12:25:49Since it's Bitcoin Pizza Day, I made a Bitcoin pizza!
To give it a Japanese twist, I made it a mentaiko pizza (※ mentaiko = spicy cod roe, a popular Japanese ingredient often used in pasta or rice dishes). For the Bitcoin logo, I used a salmon terrine.
Salmon Terrine
I cut out the "B" logo using hanpen (※ hanpen = a soft, white Japanese fish cake made from fish paste and yam). Tip: You can also cut a colored plastic folder into the "B" shape and place it on top as a stencil — makes it easier!
I blended salmon, hanpen, milk, egg, and a bit of salt in a food processor, poured it into a container, and baked it in a water bath.
Pizza Dough
I mixed bread flour, dry yeast, salt, olive oil, and water, then kneaded it with determination! Let it rise for about an hour until fluffy.
Mentaiko Mayo Topping
I mixed mentaiko, mayonnaise, and soy sauce.
I spread out the dough, added the mentaiko mayo, cheese, and corn, then baked it. Halfway through, I added thin slices of mochi (rice cake). After baking, I topped it with seaweed and the salmon terrine to finish!

Lots to reflect on
About the Terrine
In the video, you’ll see I divided the terrine into two portions. I was worried that the salmon and hanpen parts might end up looking too similar in color, making the “B” logo hard to see.
So for one half, I added ketchup, thinking: “Maybe this will make the red more vibrant?” But even with the ketchup, it didn’t change much.
The Mochi
I accidentally bought thinly sliced mochi, but I realized it might burn too easily as a pizza topping. Regular mochi with standard thickness is probably better.
I added the mochi halfway through baking, opening the oven once, but now I’m thinking that might have lowered the oven temp too much.
Lessons Learned
This was my first and only attempt—no test run beforehand— so I ended up with a long list of lessons learned. In the future, I should definitely do a trial version first… But you know… salmon and mentaiko are expensive! (excuses, excuses)
Cheese
I wanted to do that Instagram-worthy cheese pull moment, but nope. No stretch. None at all. I think that kind of thing needs a totally different kind of cheese or prep. Will have to experiment more.
Taste Test
Actually really good. I usually don’t eat mentaiko mayo myself, and I’m a Margherita pizza fan at heart. But this was surprisingly nice. A little rich in flavor—made me crave a bowl of rice. Next time, I might skip the soy sauce to tone it down a bit.
nostr:nevent1qqsrhularycewltxz88e9wrwutkqu5pkylh3vxrmys2e0nuh7c2h06qgqp9zc
-
 @ 502ab02a:a2860397
2025-05-29 01:40:28
@ 502ab02a:a2860397
2025-05-29 01:40:28เรามาดู แลคเชอร์ประวัติศาสตร์ ที่พลิกโลกแห่งการเกษตรและอาหารของมนุษย์ชาติกันครับ เรามาดูความแยบยลที่สามารถจูงใจคนมากมายให้เห็นถึงข้อดีของเนื้อจากแลบ เขาทำได้ยังไง เรามาศึกษาการสื่อสารกันครับ
เรื่องมันเริ่มจากการประชุม World Economic Forum ปี 2015 ที่ศาสตราจารย์ Mark Post นักเภสัชวิทยาชาวดัตช์ ที่เรารู้จักกันไปแล้ว ซึ่งตอนนั้นเป็นศาสตราจารย์ด้านสรีรวิทยาของหลอดเลือดอยู่ที่ Maastricht University และเป็นผู้ร่วมก่อตั้งบริษัท Mosa Meat ได้ลุกขึ้นมาเล่าเรื่อง "เนื้อเพาะเลี้ยง" หรือ cultured meat ให้คนทั้งห้องฟัง
สิ่งที่เขาพูดมันไม่ใช่แค่นวัตกรรมใหม่ แต่คือคำเตือนที่จริงจัง ว่าถ้ามนุษย์ยังผลิตเนื้อสัตว์แบบเดิม เรากำลังวิ่งเข้าใกล้ปัญหาใหญ่ที่รออยู่ข้างหน้า
ศาสตราจารย์ Post เล่าไว้ได้น่าสนใจมาก เขาบอกว่าแค่จะได้แฮมเบอร์เกอร์ 1 ชิ้นขนาดหนึ่งในสี่ปอนด์ เราต้องใช้เมล็ดธัญพืช 7 ปอนด์ ใช้น้ำจืด 50 แกลลอน และพื้นที่ดินอีก 70 ตารางฟุต นั่นแปลว่าเรากำลังเปลี่ยนของดีในธรรมชาติ ข้าว น้ำ ดิน ไปเป็นของที่กินหมดใน 10 นาที แล้วหิวใหม่ได้ในอีกครึ่งชั่วโมง
เหตุผลก็เพราะวัวมันไม่ได้แปลงโปรตีนพืชมาเป็นเนื้อได้มีประสิทธิภาพนัก พูดอีกแบบคือ มันเปลืองเกินไป
ตอนนี้พื้นที่เพาะปลูกของโลกกว่า 70% ถูกใช้ไปในการผลิตเนื้อสัตว์ คิดดูสิว่าถ้าเราหาทางที่ดีกว่านี้ได้ เราจะมีพื้นที่ว่างกลับคืนมาแค่ไหน
แถมวัวไม่ใช่แค่กินเก่งนะ ยังปล่อยก๊าซเก่งด้วย โดยเฉพาะมีเทนที่ทำให้โลกร้อนพอๆ กับอุตสาหกรรมการขนส่งเลยทีเดียว ศาสตราจารย์ Post เล่าว่า ทุกครั้งที่เขาเห็นวัวยืนเคี้ยวหญ้า เขาไม่ได้เห็นแค่วัว...แต่เห็นเมฆก๊าซมีเทนลอยมาด้วย
และที่น่าคิดคือ เมื่อรายได้ของคนในอินเดียหรือจีนสูงขึ้น พวกเขาจะกินเนื้อเพิ่มตามรายได้ ซึ่งสถิติบอกว่าภายในปี 2050 ความต้องการเนื้อสัตว์จะเพิ่มขึ้นเป็น สองเท่า จากปัจจุบัน
แต่ศาสตราจารย์ก็ไม่ได้มองว่าเนื้อเป็นปีศาจ เขาบอกว่า มนุษย์ถูกสร้างมาให้รักเนื้อ เนื้อคือสิ่งที่มาพร้อมวิวัฒนาการ เราได้พลังงานจากมัน สมองเราใหญ่ขึ้นเพราะมัน และกลายเป็นมนุษย์เพราะมัน
แม้จะมีคนอีกกว่าสองพันล้านที่เป็นมังสวิรัติ ส่วนใหญ่อาจเพราะไม่มีทางเลือก แต่อย่างน้อยพวกเขาก็อยู่รอดได้ แต่ก็ปฏิเสธไม่ได้ว่า คนที่เคยล่า เคยกินเนื้อ จะรู้สึกตื่นเต้นทุกครั้งที่ได้แบ่งเนื้อกันบนโต๊ะ
ศาสตราจารย์ Post เองก็ยังชอบกินเนื้อ แต่เขาอยากได้เนื้อที่ได้มาจากทางเลือกที่ดีกว่า ไม่ใช่ทางที่พาโลกเข้า ICU
เนื้อเพาะเลี้ยงเริ่มจากหลักการง่ายๆ ที่เรารู้มาตั้งแต่ช่วงปี 2000 ว่า ในกล้ามเนื้อของสัตว์มี สเต็มเซลล์ รอคอยจะซ่อมแซมเนื้อเยื่อหากมันได้รับบาดเจ็บ
แค่เอาชิ้นกล้ามเนื้อเล็กๆ จากวัว ขนาดแค่ 1 ซม. x 1 มม. มาแยกสเต็มเซลล์ออกมาเลี้ยงให้ขยายตัว
เฮียว่าอันนี้น่าทึ่งมาก เพราะจากตัวอย่างเล็กๆ ชิ้นเดียว สามารถผลิตเนื้อวัวได้ถึง 10,000 กิโลกรัม เลยนะ!
แปลว่าเราสามารถลดจำนวนวัวทั้งโลกจากครึ่งพันล้านตัว เหลือแค่ประมาณ 30,000 ตัวได้เลย
และถ้าให้เซลล์กล้ามเนื้อพวกนี้อยู่ในสภาพแวดล้อมที่เหมาะสม มันก็จะเริ่มสร้างกล้ามเนื้อขึ้นมาเอง โดยเฉพาะถ้าเรากระตุ้นให้มันรู้สึกเหมือนกำลัง “ออกกำลัง” อยู่ เช่น ใส่แรงตึงเข้าไป
ทีมนักวิจัยของเขาเลี้ยงเซลล์เหล่านี้ให้เติบโตในรูปวงแหวนคล้ายโดนัท ครบ 3 สัปดาห์ กล้ามเนื้อจะเริ่มหดตัว สร้างความตึง และกลายเป็นเนื้อกล้ามเนื้อแบบเต็มตัวที่ดูไม่ต่างจากกล้ามเนื้อในสเต็กจริงๆ เลย
ปี 2013 ทีมของ Mark Post ผลิตเส้นใยกล้ามเนื้อจำนวน 10,000 เส้น เอามาทำแฮมเบอร์เกอร์ และนำไปเปิดตัวในงานแถลงข่าวที่ลอนดอน เป็นเหมือนการโชว์ทำอาหารผสมกับเปิดงานวิจัย
จุดประสงค์คือจะพิสูจน์ให้โลกเห็นว่า “เฮ้ย! สิ่งนี้ไม่ใช่แค่ไอเดียลอยๆ แต่มันทำได้จริง และจำเป็นต้องทำจริงๆ เพราะเรากำลังจะเจอวิกฤต”
ราคาแฮมเบอร์เกอร์ตอนนั้นคือ 250,000 ยูโร
มีเชฟผู้กล้าปรุง และอาสาสมัครสองคนลองชิม พวกเขาบอกว่า “ก็โอเคในฐานะเบอร์เกอร์ราคาเท่านี้ แต่ก็อยากได้รสเข้มกว่านี้หน่อย” เพราะยังไม่มีไขมัน เลยรสจืดไปหน่อย
แต่ที่สำคัญคือ พวกเขายืนยันว่า “มันคือเนื้อจริงๆ” ทั้งเนื้อสัมผัสและโครงสร้าง
แค่มีต้นแบบยังไม่พอ เพราะจะทำให้ขายได้จริง ต้องผ่านด่านสำคัญ เนื้อต้องผลิตได้โดยใช้ทรัพยากรน้อยกว่าการเลี้ยงวัวจริง การประเมินเบื้องต้นจาก University of Oxford พบว่า เนื้อเพาะเลี้ยงใช้พื้นที่น้อยลง 90% น้ำลดลง 90% พลังงานลดลง 60–70%
ทุกอย่างที่ใช้ในการเลี้ยงเซลล์ต้องมีจำนวนมากพอหรือหมุนเวียนใช้ได้ ที่น่าหนักใจคือ การเลี้ยงเซลล์ต้องใช้ “ซีรั่มจากลูกวัว” ซึ่งได้มาจากเลือดวัว ถ้าลดจำนวนวัว เราก็ไม่มีซีรั่ม แต่ตอนนี้มีงานพัฒนาไปเยอะแล้ว กำลังหาวิธีทำเซลล์กล้ามเนื้อโดยไม่ต้องพึ่งซีรั่มจากสัตว์
ไม่ใช่แค่โปรตีน แต่ต้องเป็น "เนื้อ" ในทุกความรู้สึก นักวิจัยพยายามปรับสภาพแวดล้อมการเพาะเลี้ยง เช่น ความเข้มข้นของออกซิเจน เพื่อให้เซลล์แสดงโปรตีนสำคัญ เช่น myoglobin ที่ทำให้เนื้อมีสีและรสชาติเหมือนเนื้อจริง
การยอมรับของผู้บริโภคเป็นอีกด่านสำคัญที่เนื้อเพาะเลี้ยงต้องข้ามผ่านให้ได้ ไม่ใช่แค่เรื่องรสชาติหรือคุณค่าทางโภชนาการเท่านั้น แต่ยังเป็นเรื่องของ "ใจ" ที่ต้องเปิดรับสิ่งใหม่ที่ไม่คุ้นเคย ศาสตราจารย์ Post เล่าว่า ในการสำรวจผู้บริโภคในอังกฤษและเนเธอร์แลนด์ พบว่ามีคนไม่น้อยที่ยินดีจะลองกินเนื้อเพาะเลี้ยง ถึง 52% ของชาวดัตช์ และ 60% ของชาวอังกฤษเลยทีเดียว
เขาเปรียบเทียบว่า จริงๆ แล้ว คนเรายอมกินฮอทดอกโดยไม่รู้ด้วยซ้ำว่าทำมาจากอะไร หรือผ่านอะไรมาบ้าง ขอแค่มัน "อร่อย ถูก และดูปลอดภัย" ก็เพียงพอแล้วสำหรับคนส่วนใหญ่ ดังนั้นเนื้อเพาะเลี้ยงจึงไม่ต่างกันมากนัก ขอเพียงให้คนรู้สึกว่า “กินแล้วไม่ตาย” และ “ไม่ได้แปลกจนใจฝ่อ” เท่านั้นแหละ วันหนึ่งมันก็จะกลายเป็นของธรรมดาในตู้เย็นเหมือนกับโยเกิร์ตหรือไส้กรอกนั่นเอง
ในด้านของราคา แม้จะยังไม่ถูกเท่าไส้กรอกในซูเปอร์ แต่ก็ลดลงมาไกลจากจุดเริ่มต้นแบบสุดๆ จากชิ้นต้นแบบราคา 250,000 ดอลลาร์ในปี 2013 ตอนนี้ต้นทุนลดลงมาเหลือประมาณ 65 ดอลลาร์ต่อกิโลกรัม (ยังไม่รวมเทคโนโลยีล้ำหน้าอื่นๆ ที่กำลังพัฒนาอยู่) ซึ่งก็ถือว่าอยู่ในระดับเดียวกับเนื้อวากิวหรือสเต๊กเกรดพรีเมียมเลยทีเดียว เป้าหมายคือทำให้ถูกลงอีก และผลิตได้ในระดับอุตสาหกรรมให้เพียงพอกับคนทั้งโลก ไม่ใช่ของฟุ่มเฟือยสำหรับคนรวยเท่านั้น
แต่วิสัยทัศน์ที่น่าสนใจจริงๆ คือ ภาพของอนาคตที่ศาสตราจารย์ Post วาดไว้ เขาเชื่อว่าเทคโนโลยีนี้เรียบง่ายพอที่จะขยายไปสู่ครัวเรือนหรือชุมชนเล็กๆ ได้ วันหนึ่งเราอาจได้เห็นการเพาะเลี้ยงเซลล์จากหมูที่เลี้ยงอยู่ข้างบ้าน แล้วเอาไปปั่นเป็นหมูสับแบบสดใหม่ ไม่ต้องฆ่าสัตว์ ไม่ต้องส่งโรงงาน ไม่ต้องตัดต่อพันธุกรรม แค่นั่งรอเหมือนหมักแป้งเปรี้ยว แล้วได้เนื้อสดๆ มาใส่ต้มจืด
และนั่นแหละคือ "การเปลี่ยนกรอบคิดเรื่องเนื้อสัตว์" แบบพลิกฝ่ามือ
มันจะไม่ใช่เรื่องการฆ่าอีกต่อไป ไม่ใช่เรื่องของฟาร์มกลิ่นฉี่ หรือสายพานโรงฆ่าสัตว์ มันจะเป็น "ผลิตภัณฑ์ใหม่" ที่เราสร้างได้ ควบคุมได้ และปรับแต่งได้ เช่น เพิ่มโอเมก้า 3 ในเซลล์ไขมันให้สูงขึ้น หรือทำให้เนื้อไม่มีคอเลสเตอรอลเลยก็ยังได้
แม้ศาสตราจารย์ Post จะเน้นเรื่องความมั่นคงทางอาหารและผลกระทบต่อสิ่งแวดล้อมเป็นหลัก แต่เขาก็ยอมรับว่า สำหรับคนกินทั่วๆ ไป ประเด็นที่ "ไม่มีสัตว์ต้องเจ็บปวด" จะกลายเป็นจุดขายที่สำคัญในใจของผู้บริโภค
เขาเชื่อว่า เมื่อวันนั้นมาถึง วันที่เรายืนอยู่หน้าตู้แช่ในซูเปอร์ แล้วเห็นผลิตภัณฑ์สองชิ้นวางข้างกัน — หนึ่งคือเนื้อวัวที่มาจากฟาร์ม และอีกหนึ่งคือเนื้อเพาะเลี้ยงที่ไม่เคยมีวัวต้องร้องไห้แม้แต่นิดเดียว — การตัดสินใจอาจจะไม่ง่าย แต่ "จะมีคนจำนวนมากขึ้นเรื่อยๆ ที่เลือกแบบไม่ต้องฆ่า"
เพราะสุดท้าย เราไม่ได้แค่กินเนื้อ… เรากำลังกิน “ความเชื่อ” ลงไปด้วย #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
ใครสนใจดูคลิปก็กดตรงนี้ได้ครับ https://youtu.be/1lI9AwxKfTY?si=6CDBUl2yGBoHWc-P
-
 @ 048ecb14:7c28ac78
2025-05-29 00:49:55
@ 048ecb14:7c28ac78
2025-05-29 00:49:55I recently set up a Raspberry Pi camera server that's so minimal and straightforward, I thought it was worth sharing. This isn't one of those over-engineered solutions with fancy features - it's just a basic, reliable camera feed accessible from any browser on my local network.
The Goal
I wanted something that: 1. Starts automatically when the Pi boots up 2. Captures images at regular intervals 3. Shows the latest image in a simple web page accessible from any device 4. Doesn't require complex setup or dependencies 5. Uses minimal resources on my old Raspberry Pi
The Hardware
Nothing fancy here: - Raspberry Pi 2B (yes, the ancient one from 2015!) - Raspberry Pi Camera Module (standard version) - Power supply - That's it!
The Result

The interface is minimal but does the job. It shows the latest image and auto-refreshes every couple of seconds.
How to Get Set Up
Getting this running on your own Pi is super simple:
-
Make sure your camera module is connected and enabled
bash sudo raspi-config # Navigate to Interface Options > Camera and enable it -
Install the only dependency, ImageMagick (for rotation)
bash sudo apt update sudo apt install imagemagick -
Clone the repository, and navigate to the implementation's directory
bash git clone https://github.com/rewolf/RpiCameraViewer cd simple -
Start the camera server
bash ./start_camera_server.sh -
Access the feed from any device on your network
http://your-pi-ip-address:8080
That's it! No complex configuration, no fancy dependencies.
For more details consider reading the README
To make it start automatically on boot:
Add the following, with your specific installation path ```bash crontab -e
Add this line:
@reboot cd /path/to/RpiCameraViewer/simple && ./start_camera_server.sh ```
Configuration
There's not much configuration, but you can tweak few variables at the top of the
capture.shfile to modify width, height, rotation, quality, etc:bash QUALITY=90 WIDTH=720 HEIGHT=1280 ROTATION=90 # Set to 0 to disable rotationHow It Works
The solution is very basic:
- A bash script (
capture.sh) captures photos every few seconds by runninglibcamera-stilland sending a SIGUSR1 interrupt to signal it to capture a snapshot - The snapshot is rotated as needed with ImageMagick and saved with timestamps
- A symbolic link is updated to point to the latest image
- A minimal Python HTTP server serves a basic webpage showing the current image (the symlink), rendered to an HTML canvas
Note it does expose that directory to the whole LAN on :8080.
Give it a try if you need something like that quickly.
I have a plan to make a better implementation planned at some point, but for now this will do.
-
-
 @ 6d5c826a:4b27b659
2025-05-23 21:45:34
@ 6d5c826a:4b27b659
2025-05-23 21:45:34- Authelia - The Single Sign-On Multi-Factor portal for web apps. (Source Code)
Apache-2.0Go - Authentik - Flexible identity provider with support for different protocols. (OAuth 2.0, SAML, LDAP and Radius). (Source Code)
MITPython - KeyCloak - Open Source Identity and Access Management. (Source Code)
Apache-2.0Java
- Authelia - The Single Sign-On Multi-Factor portal for web apps. (Source Code)
-
 @ 7f6db517:a4931eda
2025-05-29 02:01:33
@ 7f6db517:a4931eda
2025-05-29 02:01:33
What is KYC/AML?
- The acronym stands for Know Your Customer / Anti Money Laundering.
- In practice it stands for the surveillance measures companies are often compelled to take against their customers by financial regulators.
- Methods differ but often include: Passport Scans, Driver License Uploads, Social Security Numbers, Home Address, Phone Number, Face Scans.
- Bitcoin companies will also store all withdrawal and deposit addresses which can then be used to track bitcoin transactions on the bitcoin block chain.
- This data is then stored and shared. Regulations often require companies to hold this information for a set number of years but in practice users should assume this data will be held indefinitely. Data is often stored insecurely, which results in frequent hacks and leaks.
- KYC/AML data collection puts all honest users at risk of theft, extortion, and persecution while being ineffective at stopping crime. Criminals often use counterfeit, bought, or stolen credentials to get around the requirements. Criminals can buy "verified" accounts for as little as $200. Furthermore, billions of people are excluded from financial services as a result of KYC/AML requirements.
During the early days of bitcoin most services did not require this sensitive user data, but as adoption increased so did the surveillance measures. At this point, most large bitcoin companies are collecting and storing massive lists of bitcoiners, our sensitive personal information, and our transaction history.
Lists of Bitcoiners
KYC/AML policies are a direct attack on bitcoiners. Lists of bitcoiners and our transaction history will inevitably be used against us.
Once you are on a list with your bitcoin transaction history that record will always exist. Generally speaking, tracking bitcoin is based on probability analysis of ownership change. Surveillance firms use various heuristics to determine if you are sending bitcoin to yourself or if ownership is actually changing hands. You can obtain better privacy going forward by using collaborative transactions such as coinjoin to break this probability analysis.
Fortunately, you can buy bitcoin without providing intimate personal information. Tools such as peach, hodlhodl, robosats, azteco and bisq help; mining is also a solid option: anyone can plug a miner into power and internet and earn bitcoin by mining privately.
You can also earn bitcoin by providing goods and/or services that can be purchased with bitcoin. Long term, circular economies will mitigate this threat: most people will not buy bitcoin - they will earn bitcoin - most people will not sell bitcoin - they will spend bitcoin.
There is no such thing as KYC or No KYC bitcoin, there are bitcoiners on lists and those that are not on lists.
If you found this post helpful support my work with bitcoin.

-
 @ ece127e2:745bab9c
2025-05-29 00:32:33
@ ece127e2:745bab9c
2025-05-29 00:32:33vamos a ver que tal
*lo bueno es que si entro en https://makimono.lumilumi.app/ a la nota y agrego contenido , como éste ...quiero ver si lo añade o hace una nueva nota ?? *
-
 @ 6d5c826a:4b27b659
2025-05-23 21:45:15
@ 6d5c826a:4b27b659
2025-05-23 21:45:15- 389 Directory Server - Enterprise-class Open Source LDAP server for Linux. (Source Code)
GPL-3.0C - Apache Directory Server - Extensible and embeddable directory server, certified LDAPv3 compatible, with Kerberos 5 and Change Password Protocol support, triggers, stored procedures, queues and views. (Source Code)
Apache-2.0Java - FreeIPA - Integrated security information management solution combining Linux (Fedora), 389 Directory Server, Kerberos, NTP, DNS, and Dogtag Certificate System (web interface and command-line administration tools). (Source Code)
GPL-3.0Python/C/JavaScript - FreeRADIUS - Multi-protocol policy server (radiusd) that implements RADIUS, DHCP, BFD, and ARP and associated client/PAM library/Apache module. (Source Code)
GPL-2.0C - lldap - Light (simplified) LDAP implementation with a simple, intuitive web interface and GraphQL support.
GPL-3.0Rust - OpenLDAP - Open-source implementation of the Lightweight Directory Access Protocol (server, libraries and clients). (Source Code)
OLDAP-2.8C
- 389 Directory Server - Enterprise-class Open Source LDAP server for Linux. (Source Code)
-
 @ c1e6505c:02b3157e
2025-05-28 17:36:03
@ c1e6505c:02b3157e
2025-05-28 17:36:03I recently acquired a new lens:
1959 Leica Summaron F2.8 35mm LTM.
1959 Leica Summaron 35mm f2.8 LTM mounted on my Fujifilm Xpro2 with LTM adapter made by Urth.
Technically, it was a trade. I helped a fellow Bitcoiner set up their Sparrow Wallet, Nostr stuff, and troubleshoot a few wallet issues, and in return, they gave me the lens.
It all started at a local Bitcoin meetup I went to about a week ago - my second time attending. I recognized a few faces from last time, but also saw some new ones. These meetups are refreshing - it’s rare to speak a common language about something like Bitcoin or Nostr. Most people still don’t get it. But they will.
Technology moves forward. Networks grow. Old cells die off.
During the meetup, someone noticed I had my Leica M262 with me and struck up a conversation. Said they had some old Leica lenses and gear at home, and wanted to show me.
Bitcoin and photography in one conversation? I’m down.
A day or so later, they sent me a photo of one of the lenses: a vintage Summaron LTM 35mm f/2.8 from 1959. I’d never seen or heard of one before. They asked if I could help them set up Sparrow and a Bitcoin node. In exchange, they’d give me the lens. Sounded like a good deal to me. Helping plebs with their setups feels like a duty anyway. I said, of course.
They invited me over - a pretty trusting move, which I appreciated. They had some great Bitcoin memorabilia: Fred Krueger’s The Big Bitcoin Book (even if the guy’s turned full shitcoiner), and some FTX sunglasses from Bitcoin 2022. Probably future collector’s items, lol.




We headed upstairs to work on setting up Sparrow Wallet on their Windows machine. I verified the software download first (which you should always do), then helped them create a new wallet using their Ledger Flex. They also had an older Ledger Nano X. The Flex setup was easy, but the Nano X gave us trouble. It turns out Ledger allows multiple wallets for the same asset, which can show up differently depending on how they’re configured. In Sparrow, only one wallet showed—none of the others.
I believe it had to do with the derivation path from the Ledger. If anyone knows a fix, let me know.
After a few hours of troubleshooting, I told them I couldn’t really recommend Ledger. The UX is a mess. They’d already heard similar things from other plebs too.
I suggested switching to the Blockstream Jade. It’s a solid Bitcoin-only device from a trustworthy team. That’s what you want in a hardware wallet.
But back to the lens…
Since it’s an LTM (Leica Thread Mount), I couldn’t mount it directly on my M262. Luckily, I remembered I had an Urth adapter that fits my Fujifilm X-Pro2. I don’t use the X-Pro2 much these days—it’s mostly been sidelined by the M262 - but this was the perfect excuse to bring it out again.
To test the lens, I shot everything wide open at f/2.8. Nothing crazy fast, but it’s the best way to see a lens’s character. And this one definitely has character. There’s a subtle softness and a kind of motion blur effect around the edges when wide open. At first, I wasn’t sure how I felt about it, but the more I shot, the more I liked it. It reminds me of Winogrand’s work in Winogrand Color - those messy, shifting edges that make the frame feel alive. It also helps soften the digital-ness of the camera sensor.
The focus throw is short and snappy - much tighter than my Summicron V3 35mm f/2. I really like how fast it is to use. The closest focusing distance is about 3.5 feet, so it’s not ideal for close-ups. And with the Urth adapter on the X-Pro2, the focal length ends up closer to 40mm.
The only thing that threw me off was the infinity lock. When the focus hits infinity, it physically locks - you have to press a small tab to unlock it. I’ve seen others complain about it, so I guess it’s just one of those old lens quirks. I’m getting used to it.
All the photos here were taken around where I live in South Carolina. Some during bike rides to the river for a swim, others while walking through the marshlands.
I try to make work wherever I am. You should be able to.
It’s about the light, the rhythm, the play - and having the motivation to actually go out and shoot.
Lens rating: 7.9/10
I mainly shoot with a Leica M262, and edit in Lightroom + Dehancer
Use “PictureRoom” for 10% off Dehancer Film
If you’ve made it this far, thank you for taking the time to view my work - consider becoming a paid subscriber.
Also, please contact me if you would like to purchase any of my prints.
Follow me on Nostr:
npub1c8n9qhqzm2x3kzjm84kmdcvm96ezmn257r5xxphv3gsnjq4nz4lqelne96
-
 @ b7274d28:c99628cb
2025-05-28 01:11:43
@ b7274d28:c99628cb
2025-05-28 01:11:43In this second installment of The Android Elite Setup tutorial series, we will cover installing the nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8 on your #Android device and browsing for apps you may be interested in trying out.
Since the #Zapstore is a direct competitor to the Google Play Store, you're not going to be able to find and install it from there like you may be used to with other apps. Instead, you will need to install it directly from the developer's GitHub page. This is not a complicated process, but it is outside the normal flow of searching on the Play Store, tapping install, and you're done.
Installation
From any web browser on your Android phone, navigate to the Zapstore GitHub Releases page and the most recent version will be listed at the top of the page. The .apk file for you to download and install will be listed in the "Assets."
Tap the .apk to download it, and you should get a notification when the download has completed, with a prompt to open the file.
You will likely be presented with a prompt warning you that your phone currently isn't allowed to install applications from "unknown sources." Anywhere other than the Play Store is considered an "unknown source" by default. However, you can manually allow installation from unknown sources in the settings, which the prompt gives you the option to do.
In the settings page that opens, toggle it to allow installation from this source, and you should be prompted to install the application. If you aren't, simply go to your web browser's downloads and tap on the .apk file again, or go into your file browser app and you should find the .apk in your Downloads folder.
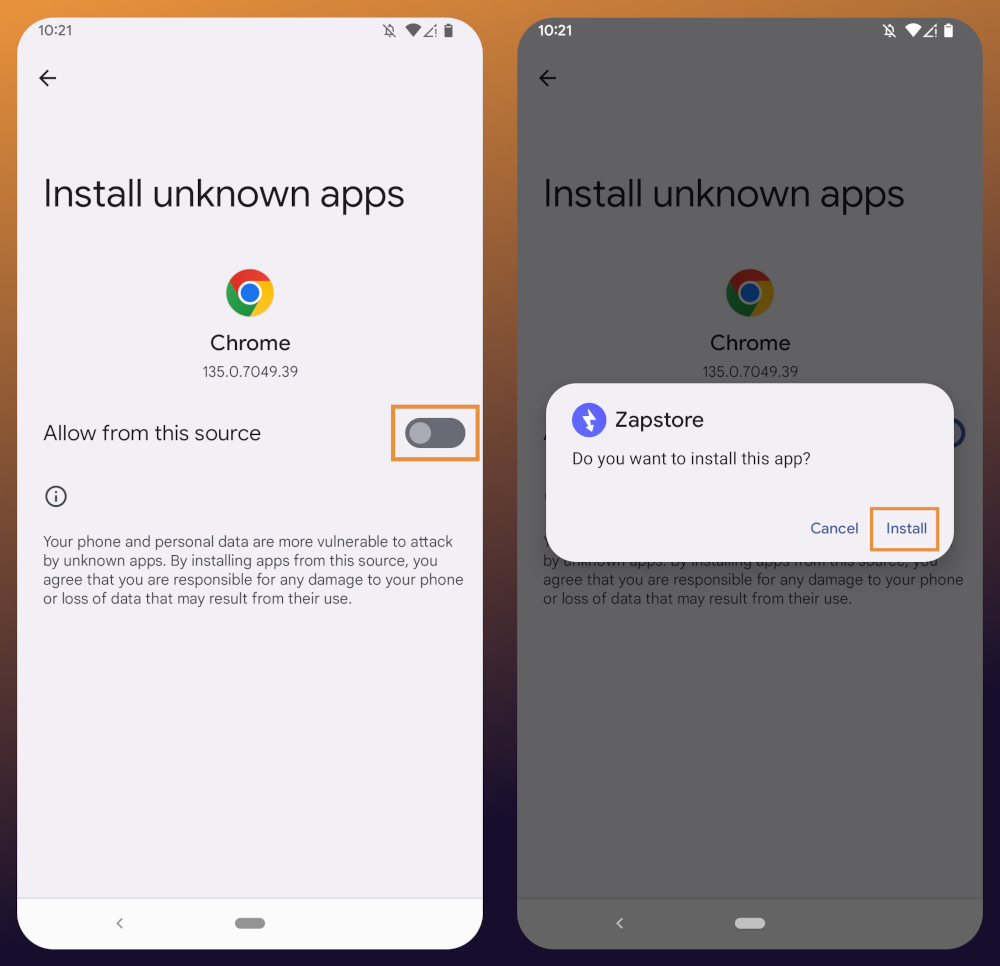
If the application doesn't open automatically after install, you will find it in your app drawer.

Home Page
Right at the top of the home page in the Zapstore is the search bar. You can use it to find a specific app you know is available in the Zapstore.
There are quite a lot of open source apps available, and more being added all the time. Most are added by the Zapstore developer, nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9, but some are added by the app developers themselves, especially Nostr apps. All of the applications we will be installing through the Zapstore have been added by their developers and are cryptographically signed, so you know that what you download is what the developer actually released.
The next section is for app discovery. There are curated app collections to peruse for ideas about what you may want to install. As you can see, all of the other apps we will be installing are listed in nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9's "Nostr" collection.
In future releases of the Zapstore, users will be able to create their own app collections.
The last section of the home page is a chronological list of the latest releases. This includes both new apps added to the Zapstore and recently updated apps. The list of recent releases on its own can be a great resource for discovering apps you may not have heard of before.
Installed Apps
The next page of the app, accessed by the icon in the bottom-center of the screen that looks like a clock with an arrow circling it, shows all apps you have installed that are available in the Zapstore. It's also where you will find apps you have previously installed that are ready to be updated. This page is pretty sparse on my test profile, since I only have the Zapstore itself installed, so here is a look at it on my main profile:

The "Disabled Apps" at the top are usually applications that were installed via the Play Store or some other means, but are also available in the Zapstore. You may be surprised to see that some of the apps you already have installed on your device are also available on the Zapstore. However, to manage their updates though the Zapstore, you would need to uninstall the app and reinstall it from the Zapstore instead. I only recommend doing this for applications that are added to the Zapstore by their developers, or you may encounter a significant delay between a new update being released for the app and when that update is available on the Zapstore.
Tap on one of your apps in the list to see whether the app is added by the developer, or by the Zapstore. This takes you to the application's page, and you may see a warning at the top if the app was not installed through the Zapstore.
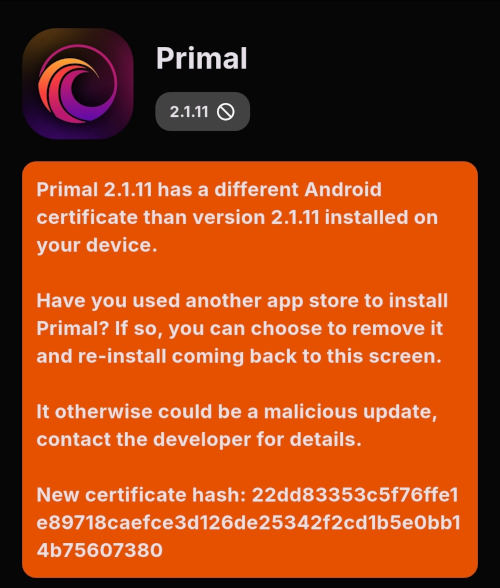
Scroll down the page a bit and you will see who signed the release that is available on the Zapstore.
In the case of Primal, even though the developer is on Nostr, they are not signing their own releases to the Zapstore yet. This means there will likely be a delay between Primal releasing an update and that update being available on the Zapstore.
Settings
The last page of the app is the settings page, found by tapping the cog at the bottom right.
Here you can send the Zapstore developer feedback directly (if you are logged in), connect a Lightning wallet using Nostr Wallet Connect, delete your local cache, and view some system information.
We will be adding a connection to our nostr:npub1h2qfjpnxau9k7ja9qkf50043xfpfy8j5v60xsqryef64y44puwnq28w8ch wallet in part 5 of this tutorial series.
For the time being, we are all set with the Zapstore and ready for the next stage of our journey.
Continue to Part 3: Amber Signer. Nostr link: nostr:naddr1qqxnzde5xuengdeexcmnvv3eqgstwf6d9r37nqalwgxmfd9p9gclt3l0yc3jp5zuyhkfqjy6extz3jcrqsqqqa28qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qg6waehxw309aex2mrp0yhxyunfva58gcn0d36zumn9wss80nug
-
 @ 6d5c826a:4b27b659
2025-05-23 21:44:57
@ 6d5c826a:4b27b659
2025-05-23 21:44:57- Atom Community - A fork of atom A hackable text editor from Github.
MITJavaScript - Brackets - Code editor for web designers and front-end developers. (Source Code)
MITJavaScript - Eclipse - IDE written in Java with an extensible plug-in system. (Source Code)
EPL-1.0Java - Geany - GTK2 text editor. (Source Code)
GPL-2.0C/C++ - GNU Emacs - An extensible, customizable text editor-and more. (Source Code)
GPL-3.0C - Haroopad - Markdown editor with live preview. (Source Code)
GPL-3.0JavaScript - jotgit - Git-backed real-time collaborative code editing.
MITNodejs - KDevelop - IDE by the people behind KDE. (Source Code)
GFDL-1.2C++ - Micro - A modern and intuitive terminal-based text editor. (Source Code)
MITGo - Nano - Easy to use, customizable text editor. (Source Code)
GPL-3.0C - Notepad++ - GPLv2 multi-language editor with syntax highlighting for Windows. (Source Code)
GPL-2.0C++ - TextMate - A graphical text editor for OS X. (Source Code)
GPL-3.0C++ - Vim - A highly configurable text editor built to enable efficient editing. (Source Code)
VimC - VSCodium - An open source cross-platform extensible code editor based on VS Code by Microsoft removing their non-free additions. (Source Code)
MITTypeScript
- Atom Community - A fork of atom A hackable text editor from Github.
-
 @ 005bc4de:ef11e1a2
2025-05-28 09:05:10
@ 005bc4de:ef11e1a2
2025-05-28 09:05:10
BIP-2,100,000,000,000,000,000
So, you're telling me...
- 21 million bitcoins is out, and...
- 2.1 quadrillion sats is in, except that...
- sats are out, so...
- 2.1 quadrillion bitcoins is in, except that...
- there are actually millisats, but...
- millisats are out, so...
- millibitcoins are in, so now...
- there are 2.1 quintillion millibitcoins, except that...
- millibitcoins are the basic base unit of bitcoin, so...
- millibitcoins are out, and now...
- 2.1 quintillion bitcoins are in

-
 @ 6d5c826a:4b27b659
2025-05-23 21:44:34
@ 6d5c826a:4b27b659
2025-05-23 21:44:34- Bind - Versatile, classic, complete name server software. (Source Code)
MPL-2.0C - CoreDNS - Flexible DNS server. (Source Code)
Apache-2.0Go - djbdns - A collection of DNS applications, including tinydns. (Source Code)
CC0-1.0C - dnsmasq - Provides network infrastructure for small networks: DNS, DHCP, router advertisement and network boot. (Source Code)
GPL-2.0C - Knot - High performance authoritative-only DNS server. (Source Code)
GPL-3.0C - NSD - Authoritative DNS name server developed speed, reliability, stability and security. (Source Code)
BSD-3-ClauseC - PowerDNS Authoritative Server - Versatile nameserver which supports a large number of backends. (Source Code)
GPL-2.0C++ - Unbound - Validating, recursive, and caching DNS resolver. (Source Code)
BSD-3-ClauseC - Yadifa - Clean, small, light and RFC-compliant name server implementation developed from scratch by .eu. (Source Code)
BSD-3-ClauseC
- Bind - Versatile, classic, complete name server software. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:44:16
@ 6d5c826a:4b27b659
2025-05-23 21:44:16- Atomia DNS - DNS management system.
ISCPerl - Designate - DNSaaS services for OpenStack. (Source Code)
Apache-2.0Python - DNSControl - Synchronize your DNS to multiple providers from a simple DSL. (Source Code)
MITGo/Docker - DomainMOD - Manage your domains and other internet assets in a central location. (Source Code)
GPL-3.0PHP - nsupdate.info - Dynamic DNS service. (Demo, Source Code)
BSD-3-ClausePython - octoDNS - DNS as code - Tools for managing DNS across multiple providers.
MITPython - Poweradmin - Web-based DNS control panel for PowerDNS server. (Source Code)
GPL-3.0PHP - SPF Toolbox - Application to look up DNS records such as SPF, MX, Whois, and more. (Source Code)
MITPHP
- Atomia DNS - DNS management system.
-
 @ 58937958:545e6994
2025-05-22 11:50:08
@ 58937958:545e6994
2025-05-22 11:50:08ビットコインピザデーということで ビットコインピザを作りました せっかくなので日本っぽい明太ピザにして ビットコインロゴは鮭のテリーヌにしました
鮭のテリーヌ
はんぺんでBのマークを気合で切ります 色付きクリアファイルをBマークに切って乗せると楽です 鮭とはんぺんと牛乳と卵と塩をフードプロセッサーにかけます 容器に流して蒸し焼きします
生地作り
 強力粉・ドライイースト・塩・オリーブオイル・水を混ぜます
気合でこねます
1時間くらい発酵させるとふっくらします
強力粉・ドライイースト・塩・オリーブオイル・水を混ぜます
気合でこねます
1時間くらい発酵させるとふっくらしますトッピングの明太マヨ
明太子とマヨネーズとしょうゆを混ぜます
 のばした生地に
明太マヨ・チーズ・コーンを乗せて焼きます
途中で薄いおもちを乗せます
焼けたらのりとテリーヌを乗せてできあがり
のばした生地に
明太マヨ・チーズ・コーンを乗せて焼きます
途中で薄いおもちを乗せます
焼けたらのりとテリーヌを乗せてできあがり反省点いろいろ
今回一番くやしいのは明太マヨに色がつきすぎたこと 明太ピザってピンク色の感じが独特な気がするし もしかしたら日本だけかもと思ったから作ったのに 焼けたらトマトソースみたいな色になっちゃった なんてことだ 生地に焼き色がつかないな~白いな~もうちょっと焼くか~とか思ってたら 明太さんが焦げてました むねん
ちなみに製作動画の中でテリーヌを2つに分けているのは 鮭とはんぺんの部分が同じ色っぽくなってBが目立たなかったらどうしようと思って 片方はケチャップを足して 赤色濃くなるかな~大失敗したらいやだな~とか思ってたんですけど ケチャップ入れても何も変わらなかった むねん
薄いおもち(しゃぶしゃぶもちというらしい)を買ってしまったんだけど これはピザのトッピングにするには焦げそうだから 普通の厚みのもちの方がよさそう 今回は途中で一度オーブン開けておもちを乗せたけど オーブンの温度が下がるのが微妙かも
あと今回は練習無しのぶっつけ本番で作ったので ちょっと自分の中で反省点が多かったな~と やっぱり一度試作した方がいいですね いや鮭とか明太子とか高くて(言い訳
あ~あとチーズ 溶け溶けチーズがのびーるインスタ映え的なやつをやりたかったんですけど 全然むりでした のびないのびない ああいうのは別で工夫が必要そうなので要検討
味はおいしかったです 明太マヨって自分ではあんまり食べないしピザはマルゲリータ派なんですけど結構いいですね ちょっと味が濃くてご飯食べたくなっちゃった 次作る時はしょうゆ入れないようにしよう
nostr:nevent1qqsrhularycewltxz88e9wrwutkqu5pkylh3vxrmys2e0nuh7c2h06qgqp9zc
-
 @ 7f6db517:a4931eda
2025-05-29 02:01:33
@ 7f6db517:a4931eda
2025-05-29 02:01:33
The former seems to have found solid product market fit. Expect significant volume, adoption, and usage going forward.
The latter's future remains to be seen. Dependence on Tor, which has had massive reliability issues, and lack of strong privacy guarantees put it at risk.
— ODELL (@ODELL) October 27, 2022
The Basics
- Lightning is a protocol that enables cheap and fast native bitcoin transactions.
- At the core of the protocol is the ability for bitcoin users to create a payment channel with another user.
- These payment channels enable users to make many bitcoin transactions between each other with only two on-chain bitcoin transactions: the channel open transaction and the channel close transaction.
- Essentially lightning is a protocol for interoperable batched bitcoin transactions.
- It is expected that on chain bitcoin transaction fees will increase with adoption and the ability to easily batch transactions will save users significant money.
- As these lightning transactions are processed, liquidity flows from one side of a channel to the other side, on chain transactions are signed by both parties but not broadcasted to update this balance.
- Lightning is designed to be trust minimized, either party in a payment channel can close the channel at any time and their bitcoin will be settled on chain without trusting the other party.
There is no 'Lightning Network'
- Many people refer to the aggregate of all lightning channels as 'The Lightning Network' but this is a false premise.
- There are many lightning channels between many different users and funds can flow across interconnected channels as long as there is a route through peers.
- If a lightning transaction requires multiple hops it will flow through multiple interconnected channels, adjusting the balance of all channels along the route, and paying lightning transaction fees that are set by each node on the route.
Example: You have a channel with Bob. Bob has a channel with Charlie. You can pay Charlie through your channel with Bob and Bob's channel with User C.
- As a result, it is not guaranteed that every lightning user can pay every other lightning user, they must have a route of interconnected channels between sender and receiver.
Lightning in Practice
- Lightning has already found product market fit and usage as an interconnected payment protocol between large professional custodians.
- They are able to easily manage channels and liquidity between each other without trust using this interoperable protocol.
- Lightning payments between large custodians are fast and easy. End users do not have to run their own node or manage their channels and liquidity. These payments rarely fail due to professional management of custodial nodes.
- The tradeoff is one inherent to custodians and other trusted third parties. Custodial wallets can steal funds and compromise user privacy.
Sovereign Lightning
- Trusted third parties are security holes.
- Users must run their own node and manage their own channels in order to use lightning without trusting a third party. This remains the single largest friction point for sovereign lightning usage: the mental burden of actively running a lightning node and associated liquidity management.
- Bitcoin development prioritizes node accessibility so cost to self host your own node is low but if a node is run at home or office, Tor or a VPN is recommended to mask your IP address: otherwise it is visible to the entire network and represents a privacy risk.
- This privacy risk is heightened due to the potential for certain governments to go after sovereign lightning users and compel them to shutdown their nodes. If their IP Address is exposed they are easier to target.
- Fortunately the tools to run and manage nodes continue to get easier but it is important to understand that this will always be a friction point when compared to custodial services.
The Potential Fracture of Lightning
- Any lightning user can choose which users are allowed to open channels with them.
- One potential is that professional custodians only peer with other professional custodians.
- We already see nodes like those run by CashApp only have channels open with other regulated counterparties. This could be due to performance goals, liability reduction, or regulatory pressure.
- Fortunately some of their peers are connected to non-regulated parties so payments to and from sovereign lightning users are still successfully processed by CashApp but this may not always be the case going forward.
Summary
- Many people refer to the aggregate of all lightning channels as 'The Lightning Network' but this is a false premise. There is no singular 'Lightning Network' but rather many payment channels between distinct peers, some connected with each other and some not.
- Lightning as an interoperable payment protocol between professional custodians seems to have found solid product market fit. Expect significant volume, adoption, and usage going forward.
- Lightning as a robust sovereign payment protocol has yet to be battle tested. Heavy reliance on Tor, which has had massive reliability issues, the friction of active liquidity management, significant on chain fee burden for small amounts, interactivity constraints on mobile, and lack of strong privacy guarantees put it at risk.
If you have never used lightning before, use this guide to get started on your phone.
If you found this post helpful support my work with bitcoin.

-
 @ 6d5c826a:4b27b659
2025-05-23 21:43:55
@ 6d5c826a:4b27b659
2025-05-23 21:43:55- Ceph - Distributed object, block, and file storage platform. (Source Code)
LGPL-3.0C++ - DRBD - Distributed replicated storage system, implemented as a Linux kernel driver. (Source Code)
GPL-2.0C - GlusterFS - Software-defined distributed storage that can scale to several petabytes, with interfaces for object, block and file storage. (Source Code)
GPL-2.0/LGPL-3.0C - Hadoop Distributed Filesystem (HDFS) - Distributed file system that provides high-throughput access to application data. (Source Code)
Apache-2.0Java - JuiceFS - Distributed POSIX file system built on top of Redis and S3. (Source Code)
Apache-2.0Go - Kubo - Implementation of IPFS, a global, versioned, peer-to-peer filesystem that seeks to connect all computing devices with the same system of files.
Apache-2.0/MITGo - LeoFS - Highly available, distributed, replicated eventually consistent object/blob store. (Source Code)
Apache-2.0Erlang - Lustre - Parallel distributed file system, generally used for large-scale cluster computing. (Source Code)
GPL-2.0C - Minio - High-performance, S3 compatible object store built for large scale AI/ML, data lake and database workloads. (Source Code)
AGPL-3.0Go - MooseFS - Fault tolerant, network distributed file system. (Source Code)
GPL-2.0C - OpenAFS - Distributed network file system with read-only replicas and multi-OS support. (Source Code)
IPL-1.0C - Openstack Swift - A highly available, distributed, eventually consistent object/blob store. (Source Code)
Apache-2.0Python - Perkeep - A set of open source formats, protocols, and software for modeling, storing, searching, sharing and synchronizing data (previously Camlistore). (Source Code)
Apache-2.0C - TahoeLAFS - Secure, decentralized, fault-tolerant, peer-to-peer distributed data store and distributed file system. (Source Code)
GPL-2.0Python - XtreemFS - Distributed, replicated and fault-tolerant file system for federated IT infrastructures.. (Source Code)
BSD-3-ClauseJava
- Ceph - Distributed object, block, and file storage platform. (Source Code)
-
 @ 7f6db517:a4931eda
2025-05-29 02:01:33
@ 7f6db517:a4931eda
2025-05-29 02:01:33
Bank run on every crypto bank then bank run on every "real" bank.
— ODELL (@ODELL) December 14, 2022
The four main banks of bitcoin and “crypto” are Signature, Prime Trust, Silvergate, and Silicon Valley Bank. Prime Trust does not custody funds themselves but rather maintains deposit accounts at BMO Harris Bank, Cross River, Lexicon Bank, MVB Bank, and Signature Bank. Silvergate and Silicon Valley Bank have already stopped withdrawals. More banks will go down before the chaos stops. None of them have sufficient reserves to meet withdrawals.
Bitcoin gives us all the ability to opt out of a system that has massive layers of counterparty risk built in, years of cheap money and broken incentives have layered risk on top of risk throughout the entire global economy. If you thought the FTX bank run was painful to watch, I have bad news for you: every major bank in the world is fractional reserve. Bitcoin held in self custody is unique in its lack of counterparty risk, as global market chaos unwinds this will become much more obvious.
The rules of bitcoin are extremely hard to change by design. Anyone can access the network directly without a trusted third party by using their own node. Owning more bitcoin does not give you more control over the network with all participants on equal footing.
Bitcoin is:
- money that is not controlled by a company or government
- money that can be spent or saved without permission
- money that is provably scarce and should increase in purchasing power with adoptionBitcoin is money without trust. Whether you are a nation state, corporation, or an individual, you can use bitcoin to spend or save without permission. Social media will accelerate the already deteriorating trust in our institutions and as this trust continues to crumble the value of trust minimized money will become obvious. As adoption increases so should the purchasing power of bitcoin.
A quick note on "stablecoins," such as USDC - it is important to remember that they rely on trusted custodians. They have the same risk as funds held directly in bank accounts with additional counterparty risk on top. The trusted custodians can be pressured by gov, exit scam, or caught up in fraud. Funds can and will be frozen at will. This is a distinctly different trust model than bitcoin, which is a native bearer token that does not rely on any centralized entity or custodian.
Most bitcoin exchanges have exposure to these failing banks. Expect more chaos and confusion as this all unwinds. Withdraw any bitcoin to your own wallet ASAP.
Simple Self Custody Guide: https://werunbtc.com/muun
More Secure Cold Storage Guide: https://werunbtc.com/coldcard
If you found this post helpful support my work with bitcoin.

-
 @ 6d5c826a:4b27b659
2025-05-23 21:43:37
@ 6d5c826a:4b27b659
2025-05-23 21:43:37- Diagrams.net - A.K.A. Draw.io. Easy to use Diagram UI with a plethora of templates. (Source Code)
Apache-2.0JavaScript/Docker - Kroki - API for generating diagrams from textual descriptions. (Source Code)
MITJava - Mermaid - Javascript module with a unique, easy, shorthand syntax. Integrates into several other tools like Grafana. (Source Code)
MITNodejs/Docker
- Diagrams.net - A.K.A. Draw.io. Easy to use Diagram UI with a plethora of templates. (Source Code)
-
 @ d360efec:14907b5f
2025-05-27 15:46:26
@ d360efec:14907b5f
2025-05-27 15:46:26 -
 @ 7f6db517:a4931eda
2025-05-29 02:01:33
@ 7f6db517:a4931eda
2025-05-29 02:01:33
The newly proposed RESTRICT ACT - is being advertised as a TikTok Ban, but is much broader than that, carries a $1M Fine and up to 20 years in prison️! It is unconstitutional and would create massive legal restrictions on the open source movement and free speech throughout the internet.
The Bill was proposed by: Senator Warner, Senator Thune, Senator Baldwin, Senator Fischer, Senator Manchin, Senator Moran, Senator Bennet, Senator Sullivan, Senator Gillibrand, Senator Collins, Senator Heinrich, and Senator Romney. It has broad support across Senators of both parties.
Corrupt politicians will not protect us. They are part of the problem. We must build, support, and learn how to use censorship resistant tools in order to defend our natural rights.
The RESTRICT Act, introduced by Senators Warner and Thune, aims to block or disrupt transactions and financial holdings involving foreign adversaries that pose risks to national security. Although the primary targets of this legislation are companies like Tik-Tok, the language of the bill could potentially be used to block or disrupt cryptocurrency transactions and, in extreme cases, block Americans’ access to open source tools or protocols like Bitcoin.
The Act creates a redundant regime paralleling OFAC without clear justification, it significantly limits the ability for injured parties to challenge actions raising due process concerns, and unlike OFAC it lacks any carve-out for protected speech. COINCENTER ON THE RESTRICT ACT
If you found this post helpful support my work with bitcoin.

-
 @ 7f6db517:a4931eda
2025-05-29 02:01:32
@ 7f6db517:a4931eda
2025-05-29 02:01:32
@matt_odell don't you even dare not ask about nostr!
— Kukks (Andrew Camilleri) (@MrKukks) May 18, 2021
Nostr first hit my radar spring 2021: created by fellow bitcoiner and friend, fiatjaf, and released to the world as free open source software. I was fortunate to be able to host a conversation with him on Citadel Dispatch in those early days, capturing that moment in history forever. Since then, the protocol has seen explosive viral organic growth as individuals around the world have contributed their time and energy to build out the protocol and the surrounding ecosystem due to the clear need for better communication tools.
nostr is to twitter as bitcoin is to paypal
As an intro to nostr, let us start with a metaphor:
twitter is paypal - a centralized platform plagued by censorship but has the benefit of established network effects
nostr is bitcoin - an open protocol that is censorship resistant and robust but requires an organic adoption phase
Nostr is an open communication protocol that can be used to send messages across a distributed set of relays in a censorship resistant and robust way.
- Anyone can run a relay.
- Anyone can interact with the protocol.
- Relays can choose which messages they want to relay.
- Users are identified by a simple public private key pair that they can generate themselves.Nostr is often compared to twitter since there are nostr clients that emulate twitter functionality and user interface but that is merely one application of the protocol. Nostr is so much more than a mere twitter competitor. Nostr clients and relays can transmit a wide variety of data and clients can choose how to display that information to users. The result is a revolution in communication with implications that are difficult for any of us to truly comprehend.
Similar to bitcoin, nostr is an open and permissionless protocol. No person, company, or government controls it. Anyone can iterate and build on top of nostr without permission. Together, bitcoin and nostr are incredibly complementary freedom tech tools: censorship resistant, permissionless, robust, and interoperable - money and speech protected by code and incentives, not laws.
As censorship throughout the world continues to escalate, freedom tech provides hope for individuals around the world who refuse to accept the status quo. This movement will succeed on the shoulders of those who choose to stand up and contribute. We will build our own path. A brighter path.
My Nostr Public Key: npub1qny3tkh0acurzla8x3zy4nhrjz5zd8l9sy9jys09umwng00manysew95gx
If you found this post helpful support my work with bitcoin.

-
 @ 6d5c826a:4b27b659
2025-05-23 21:43:11
@ 6d5c826a:4b27b659
2025-05-23 21:43:11- Capistrano - Deploy your application to any number of machines simultaneously, in sequence or as a rolling set via SSH (rake based). (Source Code)
MITRuby - CloudSlang - Flow-based orchestration tool for managing deployed applications, with Docker capabilities. (Source Code)
Apache-2.0Java - CloudStack - Cloud computing software for creating, managing, and deploying infrastructure cloud services. (Source Code)
Apache-2.0Java/Python - Cobbler - Cobbler is a Linux installation server that allows for rapid setup of network installation environments. (Source Code)
GPL-2.0Python - Fabric - Python library and cli tool for streamlining the use of SSH for application deployment or systems administration tasks. (Source Code)
BSD-2-ClausePython - Genesis - A template framework for multi-environment BOSH deployments.
MITPerl - munki - Webserver-based repository of packages and package metadata, that allows macOS administrators to manage software installs. (Source Code)
Apache-2.0Python - Overcast - Deploy VMs across different cloud providers, and run commands and scripts across any or all of them in parallel via SSH. (Source Code)
MITNodejs
- Capistrano - Deploy your application to any number of machines simultaneously, in sequence or as a rolling set via SSH (rake based). (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:42:54
@ 6d5c826a:4b27b659
2025-05-23 21:42:54- Ajenti - Control panel for Linux and BSD. (Source Code)
MITPython/Shell - Cockpit - Web-based graphical interface for servers. (Source Code)
LGPL-2.1C - Froxlor - Lightweight server management software with Nginx and PHP-FPM support. (Source Code)
GPL-2.0PHP - HestiaCP - Web server control panel (fork of VestaCP). (Demo, Source Code)
GPL-3.0PHP/Shell/Other - ISPConfig - Manage Linux servers directly through your browser. (Source Code)
BSD-3-ClausePHP - Sentora - Open-Source Web hosting control panel for Linux, BSD (fork of ZPanel). (Source Code)
GPL-3.0PHP - Virtualmin - Powerful and flexible web hosting control panel for Linux and BSD systems. (Source Code)
GPL-3.0Shell/Perl/Other - Webmin - Web-based interface for system administration for Unix. (Source Code)
BSD-3-ClausePerl
- Ajenti - Control panel for Linux and BSD. (Source Code)
-
 @ 7f6db517:a4931eda
2025-05-29 02:01:32
@ 7f6db517:a4931eda
2025-05-29 02:01:32

"Privacy is necessary for an open society in the electronic age. Privacy is not secrecy. A private matter is something one doesn't want the whole world to know, but a secret matter is something one doesn't want anybody to know. Privacy is the power to selectively reveal oneself to the world." - Eric Hughes, A Cypherpunk's Manifesto, 1993
Privacy is essential to freedom. Without privacy, individuals are unable to make choices free from surveillance and control. Lack of privacy leads to loss of autonomy. When individuals are constantly monitored it limits our ability to express ourselves and take risks. Any decisions we make can result in negative repercussions from those who surveil us. Without the freedom to make choices, individuals cannot truly be free.
Freedom is essential to acquiring and preserving wealth. When individuals are not free to make choices, restrictions and limitations prevent us from economic opportunities. If we are somehow able to acquire wealth in such an environment, lack of freedom can result in direct asset seizure by governments or other malicious entities. At scale, when freedom is compromised, it leads to widespread economic stagnation and poverty. Protecting freedom is essential to economic prosperity.
The connection between privacy, freedom, and wealth is critical. Without privacy, individuals lose the freedom to make choices free from surveillance and control. While lack of freedom prevents individuals from pursuing economic opportunities and makes wealth preservation nearly impossible. No Privacy? No Freedom. No Freedom? No Wealth.
Rights are not granted. They are taken and defended. Rights are often misunderstood as permission to do something by those holding power. However, if someone can give you something, they can inherently take it from you at will. People throughout history have necessarily fought for basic rights, including privacy and freedom. These rights were not given by those in power, but rather demanded and won through struggle. Even after these rights are won, they must be continually defended to ensure that they are not taken away. Rights are not granted - they are earned through struggle and defended through sacrifice.
If you found this post helpful support my work with bitcoin.

-
 @ 7f6db517:a4931eda
2025-05-29 02:01:32
@ 7f6db517:a4931eda
2025-05-29 02:01:32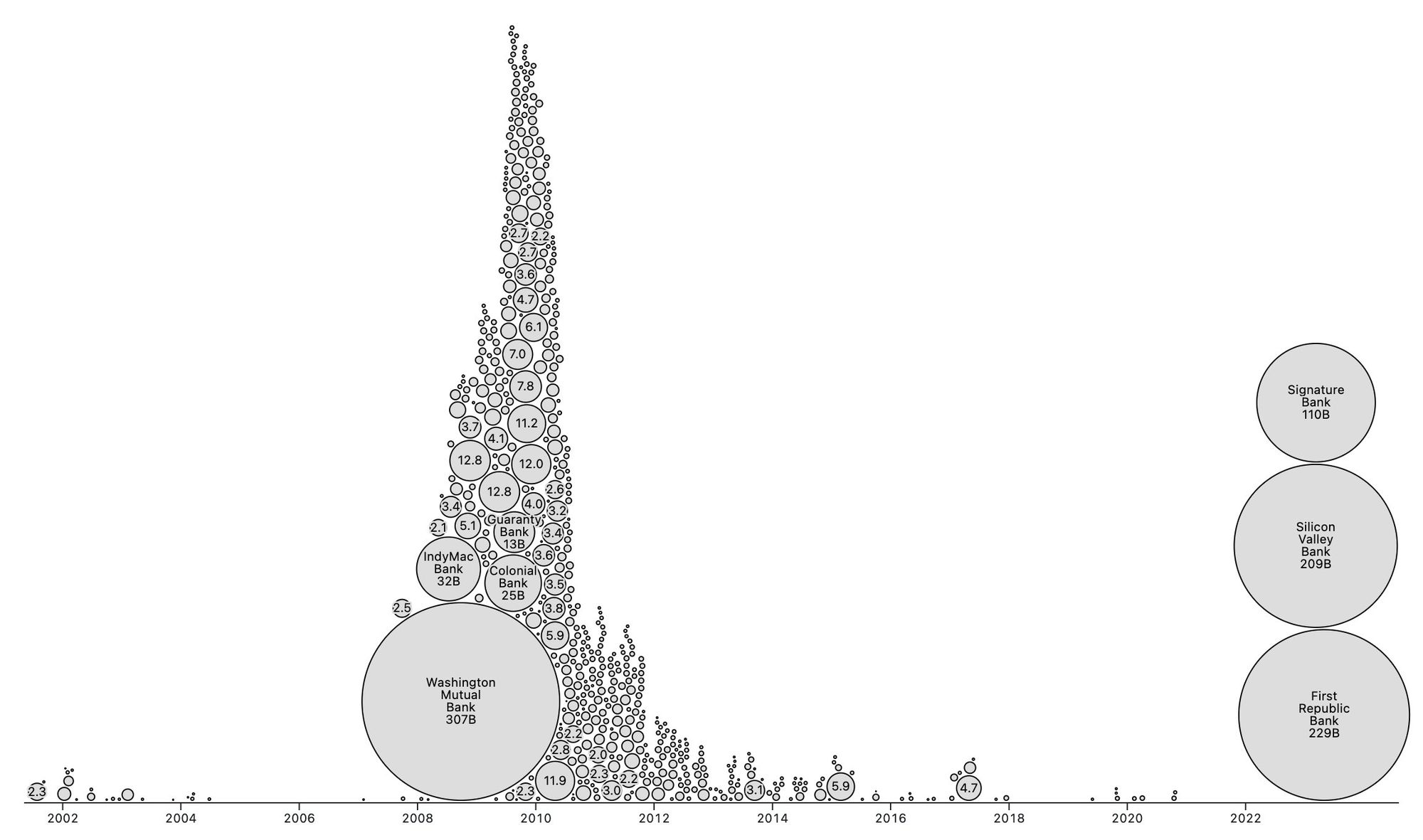
People forget Bear Stearns failed March 2008 - months of denial followed before the public realized how bad the situation was under the surface.
Similar happening now but much larger scale. They did not fix fundamental issues after 2008 - everything is more fragile.
The Fed preemptively bailed out every bank with their BTFP program and First Republic Bank still failed. The second largest bank failure in history.
There will be more failures. There will be more bailouts. Depositors will be "protected" by socializing losses across everyone.
Our President and mainstream financial pundits are currently pretending the banking crisis is over while most banks remain insolvent. There are going to be many more bank failures as this ponzi system unravels.
Unlike 2008, we have the ability to opt out of these broken and corrupt institutions by using bitcoin. Bitcoin held in self custody is unique in its lack of counterparty risk - you do not have to trust a bank or other centralized entity to hold it for you. Bitcoin is also incredibly difficult to change by design since it is not controlled by an individual, company, or government - the supply of dollars will inevitably be inflated to bailout these failing banks but bitcoin supply will remain unchanged. I do not need to convince you that bitcoin provides value - these next few years will convince millions.
If you found this post helpful support my work with bitcoin.

-
 @ 7f6db517:a4931eda
2025-05-29 02:01:32
@ 7f6db517:a4931eda
2025-05-29 02:01:32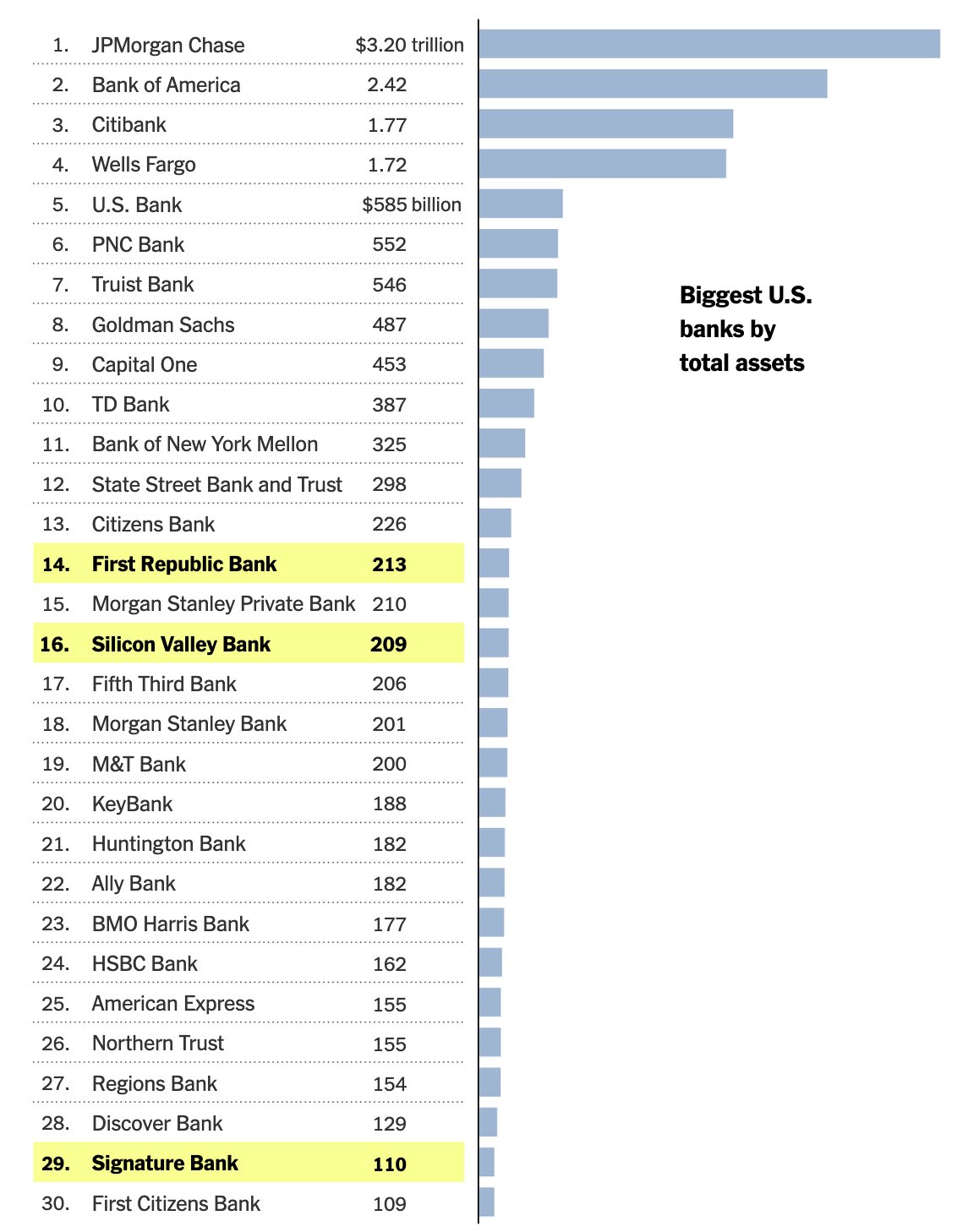
Bank run on every crypto bank then bank run on every "real" bank.
— ODELL (@ODELL) December 14, 2022
Good morning.
It looks like PacWest will fail today. It will be both the fifth largest bank failure in US history and the sixth major bank to fail this year. It will likely get purchased by one of the big four banks in a government orchestrated sale.
March 8th - Silvergate Bank
March 10th - Silicon Valley Bank
March 12th - Signature Bank
March 19th - Credit Suisse
May 1st - First Republic Bank
May 4th - PacWest Bank?PacWest is the first of many small regional banks that will go under this year. Most will get bought by the big four in gov orchestrated sales. This has been the playbook since 2008. Follow the incentives. Massive consolidation across the banking industry. PacWest gonna be a drop in the bucket compared to what comes next.
First, a hastened government led bank consolidation, then a public/private partnership with the remaining large banks to launch a surveilled and controlled digital currency network. We will be told it is more convenient. We will be told it is safer. We will be told it will prevent future bank runs. All of that is marketing bullshit. The goal is greater control of money. The ability to choose how we spend it and how we save it. If you control the money - you control the people that use it.
If you found this post helpful support my work with bitcoin.

-
 @ 6d5c826a:4b27b659
2025-05-23 21:42:36
@ 6d5c826a:4b27b659
2025-05-23 21:42:36- Buildbot - Python-based toolkit for continuous integration. (Source Code)
GPL-2.0Python - CDS - Enterprise-Grade Continuous Delivery & DevOps Automation Open Source Platform. (Source Code)
BSD-3-ClauseGo - Concourse - Concourse is a CI tool that treats pipelines as first class objects and containerizes every step along the way. (Demo, Source Code)
Apache-2.0Go - drone - Drone is a Continuous Delivery platform built on Docker, written in Go. (Source Code)
Apache-2.0Go - Factor - Programmatically define and run workflows to connect configuration management, source code management, build, continuous integration, continuous deployment and communication tools. (Source Code)
MITRuby - GitLab CI - Gitlab's built-in, full-featured CI/CD solution. (Source Code)
MITRuby - GoCD - Continuous delivery server. (Source Code)
Apache-2.0Java/Ruby - Jenkins - Continuous Integration Server. (Source Code)
MITJava - Laminar - Fast, lightweight, simple and flexible Continuous Integration. (Source Code)
GPL-3.0C++ - PHP Censor - Open source self-hosted continuous integration server for PHP projects.
BSD-2-ClausePHP - Strider - Open Source Continuous Deployment / Continuous Integration platform. (Source Code)
MITNodejs - Terrateam - GitOps-first automation platform for Terraform and OpenTofu workflows with support for self-hosted runners. (Source Code)
MPL-2.0OCaml/Docker - werf - Open Source CI/CD tool for building Docker images and deploying to Kubernetes via GitOps. (Source Code)
Apache-2.0Go - Woodpecker - Community fork of Drone that uses Docker containers. (Source Code)
Apache-2.0Go
- Buildbot - Python-based toolkit for continuous integration. (Source Code)
-
 @ 7f6db517:a4931eda
2025-05-29 02:01:31
@ 7f6db517:a4931eda
2025-05-29 02:01:31
There must be a limit to how much data is transferred across the bitcoin network in order to keep the ability to run and use your own node accessible. A node is required to interact with the global bitcoin network - if you do not use your own node then you must trust someone else's node. If nodes become inaccessible to run then the network will centralize around the remaining entities that operate them - threatening the censorship resistance at the core of bitcoin's value prop. The bitcoin protocol uses three main mechanisms to keep node operation costs low - a fixed limit on the amount of data in each block, an automatic difficulty adjustment that regulates how many blocks are produced based on current mining hash rate, and a robust dynamic transaction fee market.
Bitcoin transaction fees limit network abuse by making usage expensive. There is a cost to every transaction, set by a dynamic free market based on demand for scarce block space. It is an incredibly robust way to prevent spam without relying on centralized entities that can be corrupted or pressured.
After the 2017 bitcoin fee spike we had six years of relative quiet to build tools that would be robust in a sustained high fee market. Fortunately our tools are significantly better now but many still need improvement. Most of the pain points we see today will be mitigated.
The reality is we were never going to be fully prepared - pressure is needed to show the pain points and provide strong incentives to mitigate them.
It will be incredibly interesting to watch how projects adapt under pressure. Optimistic we see great innovation here.
_If you are willing to wait for your transaction to confirm you can pay significantly lower fees. Learn best practices for reducing your fee burden here.
My guide for running and using your own bitcoin node can be found here._
If you found this post helpful support my work with bitcoin.

-
 @ 7f6db517:a4931eda
2025-05-29 02:01:31
@ 7f6db517:a4931eda
2025-05-29 02:01:31
I often hear "bitcoin doesn't interest me, I'm not a finance person."
Ironically, the beauty of sound money is you don't have to be. In the current system you're expected to manage a diversified investment portfolio or pay someone to do it. Bitcoin will make that optional.
— ODELL (@ODELL) September 16, 2018
At first glance bitcoin often appears overwhelming to newcomers. It is incredibly easy to get bogged down in the details of how it works or different ways to use it. Enthusiasts, such as myself, often enjoy going down the deep rabbit hole of the potential of bitcoin, possible pitfalls and theoretical scenarios, power user techniques, and the developer ecosystem. If your first touch point with bitcoin is that type of content then it is only natural to be overwhelmed. While it is important that we have a thriving community of bitcoiners dedicated to these complicated tasks - the true beauty of bitcoin lies in its simplicity. Bitcoin is simply better money. It is the best money we have ever had.
Life is complicated. Life is hard. Life is full of responsibility and surprises. Bitcoin allows us to focus on our lives while relying on a money that is simple. A money that is not controlled by any individual, company, or government. A money that cannot be easily seized or blocked. A money that cannot be devalued at will by a handful of corrupt bureaucrat who live hundreds of miles from us. A money that can be easily saved and should increase in purchasing power over time without having to learn how to "build a diversified stock portfolio" or hire someone to do it for us.
Bitcoin enables all of us to focus on our lives - our friends and family - doing what we love with the short time we have on this earth. Time is scarce. Life is complicated. Bitcoin is the most simple aspect of our complicated lives. If we spend our scarce time working then we should be able to easily save that accrued value for future generations without watching the news or understanding complicated financial markets. Bitcoin makes this possible for anyone.
Yesterday was Mother's Day. Raising a human is complicated. It is hard, it requires immense personal responsibility, it requires critical thinking, but mothers figure it out, because it is worth it. Using and saving bitcoin is simple - simply install an app on your phone. Every mother can do it. Every person can do it.
Life is complicated. Life is beautiful. Bitcoin is simple.
If you found this post helpful support my work with bitcoin.

-
 @ c1e6505c:02b3157e
2025-05-27 01:11:45
@ c1e6505c:02b3157e
2025-05-27 01:11:45I spent Memorial Day swimming in the local river - something I try to do at least four times a week. It’s the best form of exercise imo, but it’s more than that. Swimming against the tide, feeling the water move around me... there’s something about it that keeps me grounded. Nature at her peak.
Today I brought my X-Pro2 with the 1959 Leica Summaron 35mm f/2.8. I'm still testing the lens wide open to get a feel for its character. My subject this time: the light playing on the ripples and waves.
While I was shooting, a kid randomly ran up to me and started telling me something about what he got for his dad while fishing, or something - I didn’t quite hear him - and then he asked what I was looking at. I told him, “The ripples. The way the light is refracting.” I had him sit exactly where I was so he could see it too.
He lit up. You could tell no one had ever pointed something like that out to him before. In that moment, I felt like maybe I was able to plant a little seed - a new way of seeing.
This is what I was looking at.

-
 @ 5144fe88:9587d5af
2025-05-23 17:01:37
@ 5144fe88:9587d5af
2025-05-23 17:01:37The recent anomalies in the financial market and the frequent occurrence of world trade wars and hot wars have caused the world's political and economic landscape to fluctuate violently. It always feels like the financial crisis is getting closer and closer.
This is a systematic analysis of the possibility of the current global financial crisis by Manus based on Ray Dalio's latest views, US and Japanese economic and financial data, Buffett's investment behavior, and historical financial crises.
Research shows that the current financial system has many preconditions for a crisis, especially debt levels, market valuations, and investor behavior, which show obvious crisis signals. The probability of a financial crisis in the short term (within 6-12 months) is 30%-40%,
in the medium term (within 1-2 years) is 50%-60%,
in the long term (within 2-3 years) is 60%-70%.
Japan's role as the world's largest holder of overseas assets and the largest creditor of the United States is particularly critical. The sharp appreciation of the yen may be a signal of the return of global safe-haven funds, which will become an important precursor to the outbreak of a financial crisis.
Potential conditions for triggering a financial crisis Conditions that have been met 1. High debt levels: The debt-to-GDP ratio of the United States and Japan has reached a record high. 2. Market overvaluation: The ratio of stock market to GDP hits a record high 3. Abnormal investor behavior: Buffett's cash holdings hit a record high, with net selling for 10 consecutive quarters 4. Monetary policy shift: Japan ends negative interest rates, and the Fed ends the rate hike cycle 5. Market concentration is too high: a few technology stocks dominate market performance
Potential trigger points 1. The Bank of Japan further tightens monetary policy, leading to a sharp appreciation of the yen and the return of overseas funds 2. The US debt crisis worsens, and the proportion of interest expenses continues to rise to unsustainable levels 3. The bursting of the technology bubble leads to a collapse in market confidence 4. The trade war further escalates, disrupting global supply chains and economic growth 5. Japan, as the largest creditor of the United States, reduces its holdings of US debt, causing US debt yields to soar
Analysis of the similarities and differences between the current economic environment and the historical financial crisis Debt level comparison Current debt situation • US government debt to GDP ratio: 124.0% (December 2024) • Japanese government debt to GDP ratio: 216.2% (December 2024), historical high 225.8% (March 2021) • US total debt: 36.21 trillion US dollars (May 2025) • Japanese debt/GDP ratio: more than 250%-263% (Japanese Prime Minister’s statement)
Before the 2008 financial crisis • US government debt to GDP ratio: about 64% (2007) • Japanese government debt to GDP ratio: about 175% (2007)
Before the Internet bubble in 2000 • US government debt to GDP ratio: about 55% (1999) • Japanese government debt to GDP ratio: about 130% (1999)
Key differences • The current US debt-to-GDP ratio is nearly twice that before the 2008 crisis • The current Japanese debt-to-GDP ratio is more than 1.2 times that before the 2008 crisis • Global debt levels are generally higher than historical pre-crisis levels • US interest payments are expected to devour 30% of fiscal revenue (Moody's warning)
Monetary policy and interest rate environment
Current situation • US 10-year Treasury yield: about 4.6% (May 2025) • Bank of Japan policy: end negative interest rates and start a rate hike cycle • Bank of Japan's holdings of government bonds: 52%, plans to reduce purchases to 3 trillion yen per month by January-March 2026 • Fed policy: end the rate hike cycle and prepare to cut interest rates
Before the 2008 financial crisis • US 10-year Treasury yield: about 4.5%-5% (2007) • Fed policy: continuous rate hikes from 2004 to 2006, and rate cuts began in 2007 • Bank of Japan policy: maintain ultra-low interest rates
Key differences • Current US interest rates are similar to those before the 2008 crisis, but debt levels are much higher than then • Japan is in the early stages of ending its loose monetary policy, unlike before historical crises • The size of global central bank balance sheets is far greater than at any time in history
Market valuations and investor behavior Current situation • The ratio of stock market value to the size of the US economy: a record high • Buffett's cash holdings: $347 billion (28% of assets), a record high • Market concentration: US stock growth mainly relies on a few technology giants • Investor sentiment: Technology stocks are enthusiastic, but institutional investors are beginning to be cautious
Before the 2008 financial crisis • Buffett's cash holdings: 25% of assets (2005) • Market concentration: Financial and real estate-related stocks performed strongly • Investor sentiment: The real estate market was overheated and subprime products were widely popular
Before the 2000 Internet bubble • Buffett's cash holdings: increased from 1% to 13% (1998) • Market concentration: Internet stocks were extremely highly valued • Investor sentiment: Tech stocks are in a frenzy
Key differences • Buffett's current cash holdings exceed any pre-crisis level in history • Market valuation indicators have reached a record high, exceeding the levels before the 2000 bubble and the 2008 crisis • The current market concentration is higher than any period in history, and a few technology stocks dominate market performance
Safe-haven fund flows and international relations Current situation • The status of the yen: As a safe-haven currency, the appreciation of the yen may indicate a rise in global risk aversion • Trade relations: The United States has imposed tariffs on Japan, which is expected to reduce Japan's GDP growth by 0.3 percentage points in fiscal 2025 • International debt: Japan is one of the largest creditors of the United States
Before historical crises • Before the 2008 crisis: International capital flows to US real estate and financial products • Before the 2000 bubble: International capital flows to US technology stocks
Key differences • Current trade frictions have intensified and the trend of globalization has weakened • Japan's role as the world's largest holder of overseas assets has become more prominent • International debt dependence is higher than any period in history
-
 @ 6d5c826a:4b27b659
2025-05-23 21:41:59
@ 6d5c826a:4b27b659
2025-05-23 21:41:59- Ansible - Provisioning, configuration management, and application-deployment tool. (Source Code)
GPL-3.0Python - CFEngine - Configuration management system for automated configuration and maintenance of large-scale computer systems. (Source Code)
GPL-3.0C - Chef - Configuration management tool using a pure-Ruby, domain-specific language (DSL) for writing system configuration "recipes". (Source Code)
Apache-2.0Ruby - cloud-init - Initialization tool to automate the configuration of VMs, cloud instances, or machines on a network. (Source Code)
GPL-3.0/Apache-2.0Python - Puppet - Software configuration management tool which includes its own declarative language to describe system configuration. (Source Code)
Apache-2.0Ruby/C - Rudder - Scalable and dynamic configuration management system for patching, security & compliance, based on CFEngine. (Source Code)
GPL-3.0Scala - Salt - Event-driven IT automation, remote task execution, and configuration management software. (Source Code)
Apache-2.0Python
- Ansible - Provisioning, configuration management, and application-deployment tool. (Source Code)
-
 @ 7f6db517:a4931eda
2025-05-29 02:01:31
@ 7f6db517:a4931eda
2025-05-29 02:01:31Will not live in a pod.
Will not eat the bugs.
Will not get the chip.
Will not get a blue check.
Will not use CBDCs.Live Free or Die.
Why did Elon buy twitter for $44 Billion? What value does he see in it besides the greater influence that undoubtedly comes with controlling one of the largest social platforms in the world? We do not need to speculate - he made his intentions incredibly clear in his first meeting with twitter employees after his takeover - WeChat of the West.
To those that do not appreciate freedom, the value prop is clear - WeChat is incredibly powerful and successful in China.
To those that do appreciate freedom, the concern is clear - WeChat has essentially become required to live in China, has surveillance and censorship integrated at its core, and if you are banned from the app your entire livelihood is at risk. Employment, housing, payments, travel, communication, and more become extremely difficult if WeChat censors determine you have acted out of line.
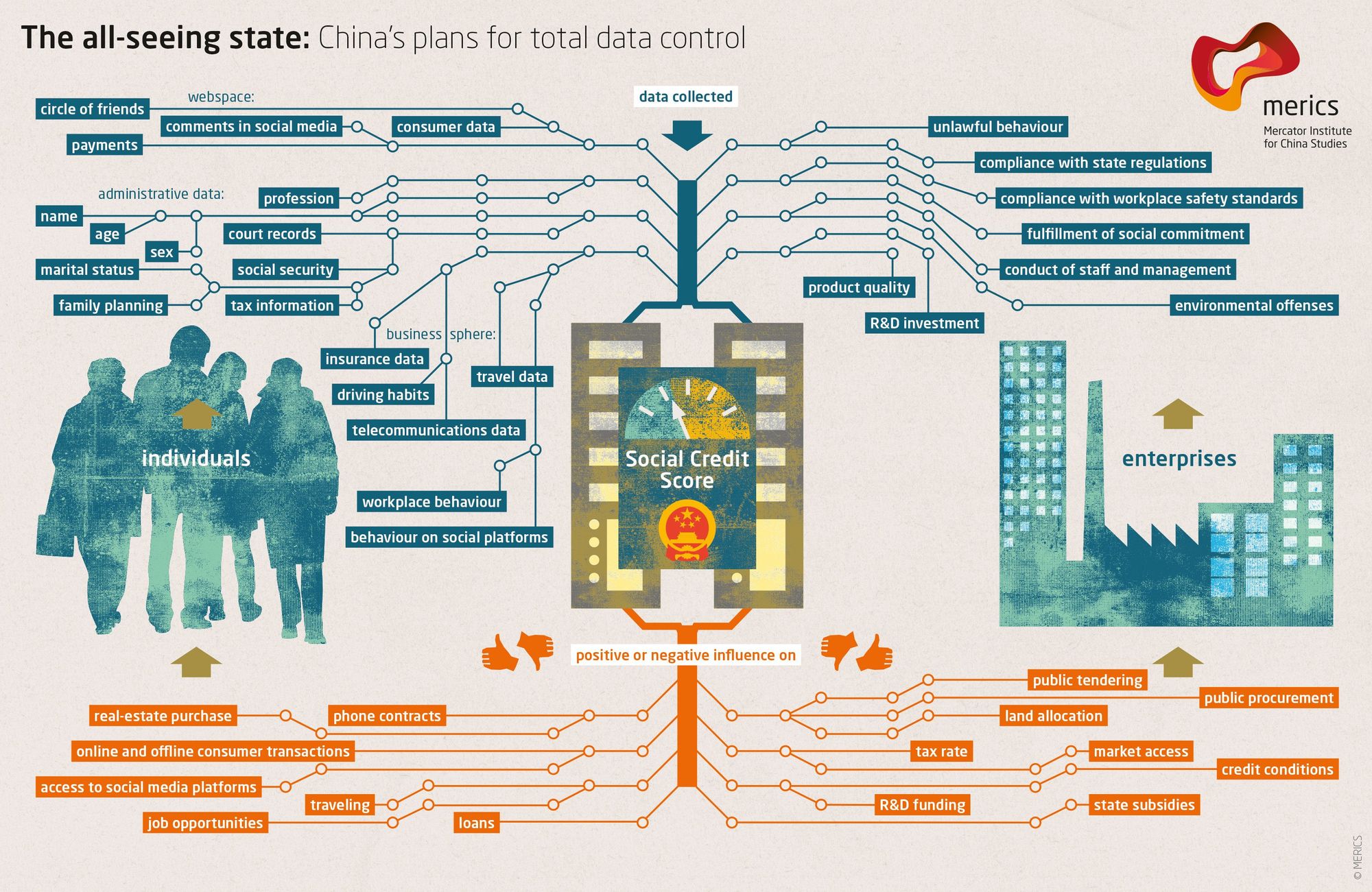
The blue check is the first step in Elon's plan to bring the chinese social credit score system to the west. Users who verify their identity are rewarded with more reach and better tools than those that do not. Verified users are the main product of Elon's twitter - an extensive database of individuals and complete control of the tools he will slowly get them to rely on - it is easier to monetize cattle than free men.
If you cannot resist the temptation of the blue check in its current form you have already lost - what comes next will be much darker. If you realize the need to resist - freedom tech provides us options.
If you found this post helpful support my work with bitcoin.

-
 @ 7f6db517:a4931eda
2025-05-29 02:01:31
@ 7f6db517:a4931eda
2025-05-29 02:01:31
Nostr is an open communication protocol that can be used to send messages across a distributed set of relays in a censorship resistant and robust way.
If you missed my nostr introduction post you can find it here. My nostr account can be found here.
We are nearly at the point that if something interesting is posted on a centralized social platform it will usually be posted by someone to nostr.
We are nearly at the point that if something interesting is posted exclusively to nostr it is cross posted by someone to various centralized social platforms.
We are nearly at the point that you can recommend a cross platform app that users can install and easily onboard without additional guides or resources.
As companies continue to build walls around their centralized platforms nostr posts will be the easiest to cross reference and verify - as companies continue to censor their users nostr is the best censorship resistant alternative - gradually then suddenly nostr will become the standard. 🫡
Current Nostr Stats
If you found this post helpful support my work with bitcoin.

-
 @ 5d4b6c8d:8a1c1ee3
2025-05-23 13:46:21
@ 5d4b6c8d:8a1c1ee3
2025-05-23 13:46:21You'd think I'd be most excited to talk about that awesome Pacers game, but, no. What I'm most excited about this week is that @grayruby wants to continue Beefing with Cowherd.
Still, I am excited to talk about Tyrese Haliburton becoming a legendary Knicks antagonist. Unfortunately, the Western Conference Finals are not as exciting. Also, why was the MVP announcement so dumb?
The T20k cricket contest is tightening up, as we head towards the finish. Can @Coinsreporter hold on to his vanishing lead?
@Carresan has launched Football Madness. Let's see if we understand whatever the hell this is any better than we did last week.
On this week's Blok'd Shots, we'll ridicule Canada for their disgraceful loss in the World Championships and talk about the very dominant American Florida Panthers, who are favorites to win the Stanley Cup.
Are the Colorado the worst team in MLB history?
The Tush Push has survived another season. Will the NFL eventually ban it or will teams adjust?
Plus, whatever else Stackers want to talk about.
https://stacker.news/items/987399
-
 @ 63d59db8:be170f6f
2025-05-23 12:53:00
@ 63d59db8:be170f6f
2025-05-23 12:53:00In a world overwhelmed by contradictions—climate change, inequality, political instability, and social disconnection—absurdity becomes an unavoidable lens through which to view the human condition. Inspired by Albert Camus' philosophy, this project explores the tension between life’s inherent meaninglessness and our persistent search for purpose.\ \ The individuals in these images embody a quiet defiance, navigating chaos with a sense of irony and authenticity. Through the act of revolt—against despair, against resignation—they find agency and resilience. These photographs invite reflection, not on solutions, but on our capacity to live meaningfully within absurdity.
Visit Katerina's website here.
Submit your work to the NOICE Visual Expression Awards for a chance to win a few thousand extra sats:
-
 @ 6d5c826a:4b27b659
2025-05-23 21:41:37
@ 6d5c826a:4b27b659
2025-05-23 21:41:37- Eggdrop - The oldest Internet Relay Chat (IRC) bot still in active development. (Source Code)
GPL-2.0C - Errbot - Plugin based chatbot designed to be easily deployable, extensible and maintainable. (Source Code)
GPL-3.0Python - Hubot - A customizable, life embetterment robot. (Source Code)
MITNodejs
- Eggdrop - The oldest Internet Relay Chat (IRC) bot still in active development. (Source Code)
-
 @ 7f6db517:a4931eda
2025-05-29 02:01:30
@ 7f6db517:a4931eda
2025-05-29 02:01:30
Influencers would have you believe there is an ongoing binance bank run but bitcoin wallet data says otherwise.
- binance wallets are near all time highs
- bitfinex wallets are also trending up
- gemini and coinbase are being hit with massive withdrawals thoughYou should not trust custodians, they can rug you without warning. It is incredibly important you learn how to hold bitcoin yourself, but also consider not blindly trusting influencers with a ref link to shill you.
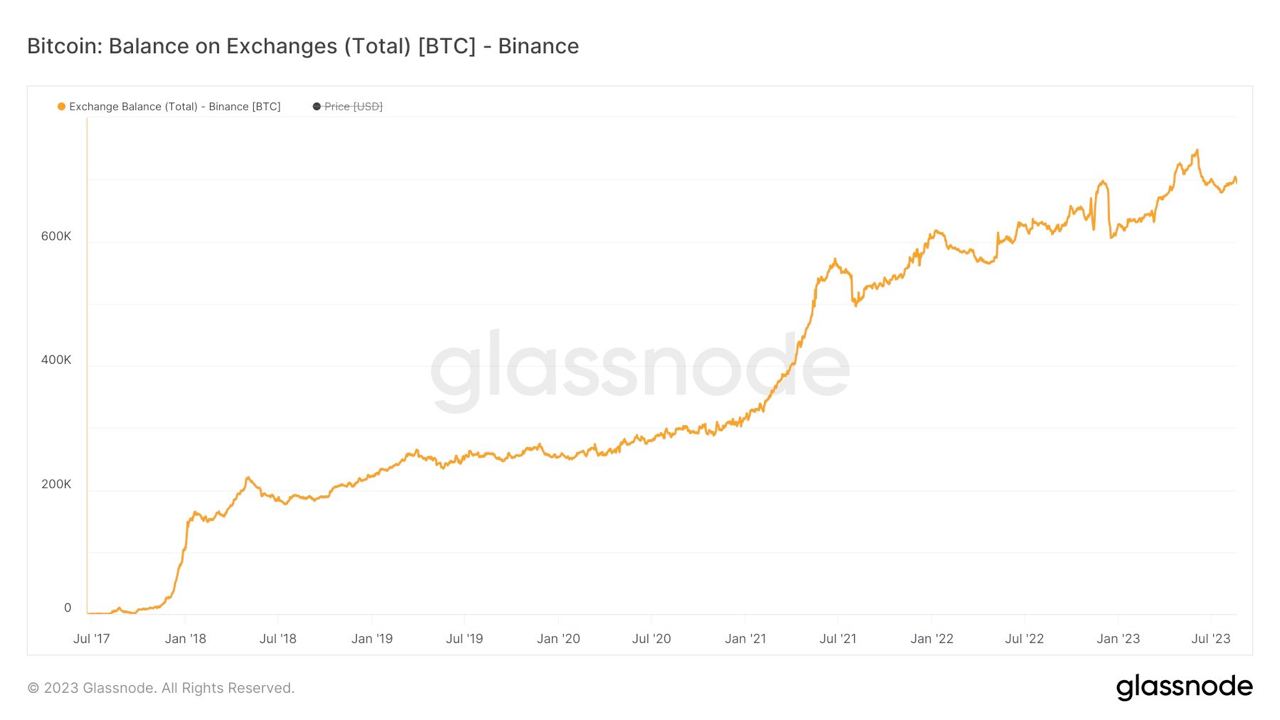
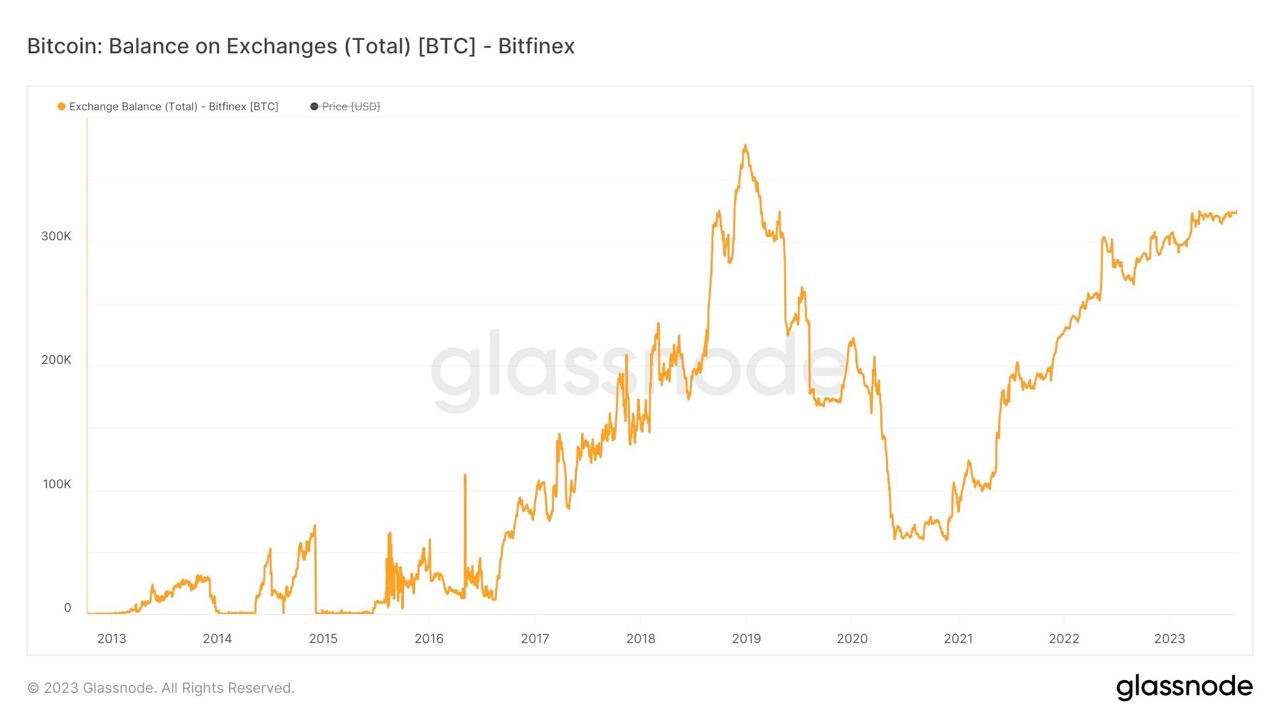
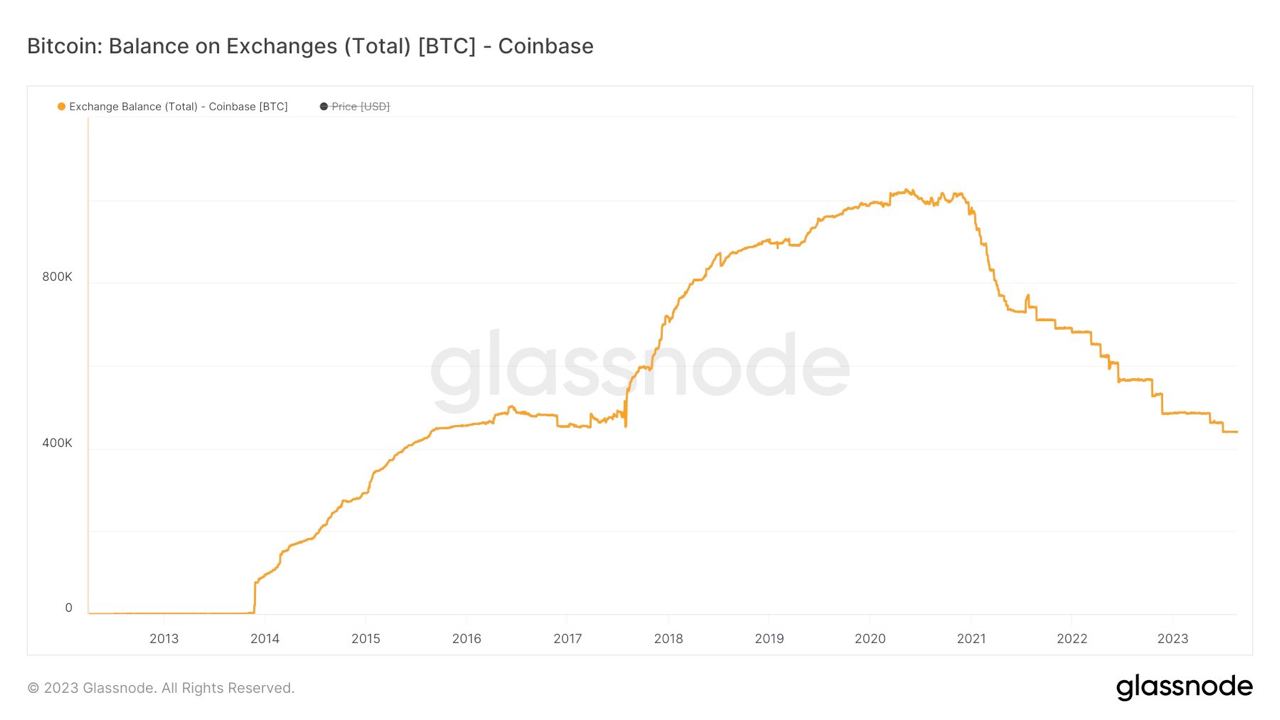
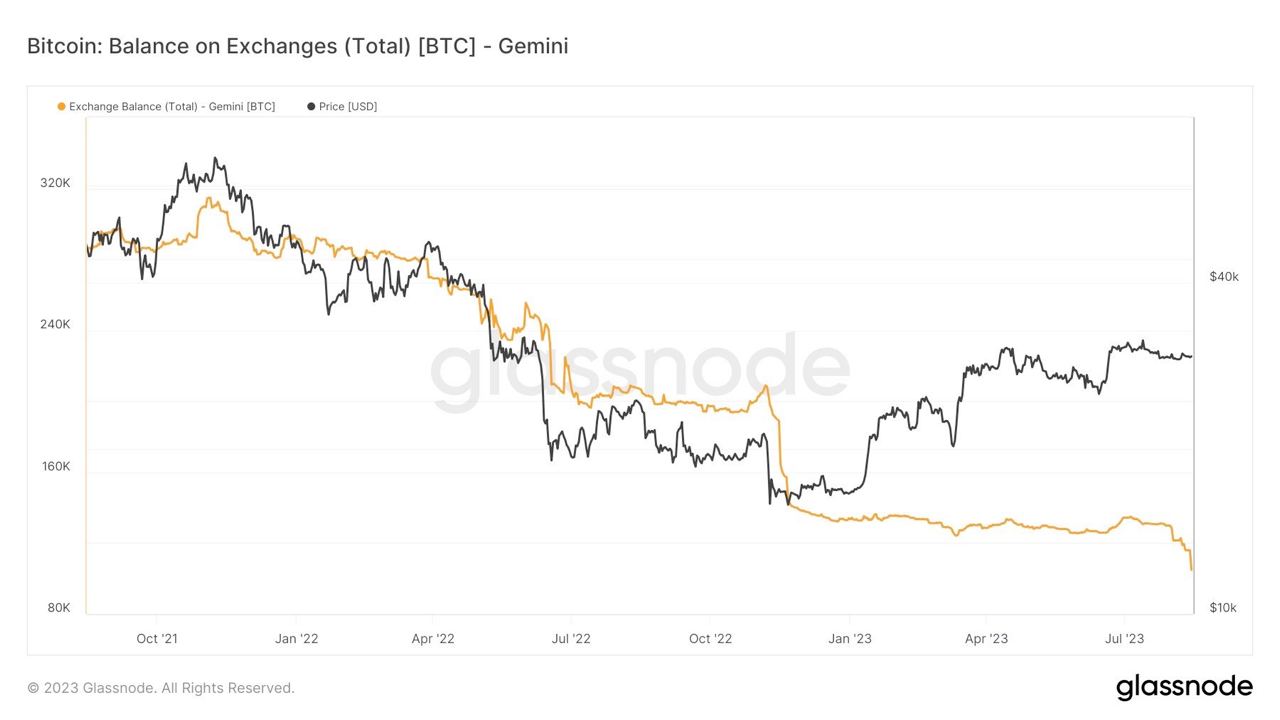
If you found this post helpful support my work with bitcoin.

-
 @ 7f6db517:a4931eda
2025-05-29 02:01:30
@ 7f6db517:a4931eda
2025-05-29 02:01:30
For years American bitcoin miners have argued for more efficient and free energy markets. It benefits everyone if our energy infrastructure is as efficient and robust as possible. Unfortunately, broken incentives have led to increased regulation throughout the sector, incentivizing less efficient energy sources such as solar and wind at the detriment of more efficient alternatives.
The result has been less reliable energy infrastructure for all Americans and increased energy costs across the board. This naturally has a direct impact on bitcoin miners: increased energy costs make them less competitive globally.
Bitcoin mining represents a global energy market that does not require permission to participate. Anyone can plug a mining computer into power and internet to get paid the current dynamic market price for their work in bitcoin. Using cellphone or satellite internet, these mines can be located anywhere in the world, sourcing the cheapest power available.
Absent of regulation, bitcoin mining naturally incentivizes the build out of highly efficient and robust energy infrastructure. Unfortunately that world does not exist and burdensome regulations remain the biggest threat for US based mining businesses. Jurisdictional arbitrage gives miners the option of moving to a friendlier country but that naturally comes with its own costs.
Enter AI. With the rapid development and release of AI tools comes the requirement of running massive datacenters for their models. Major tech companies are scrambling to secure machines, rack space, and cheap energy to run full suites of AI enabled tools and services. The most valuable and powerful tech companies in America have stumbled into an accidental alliance with bitcoin miners: THE NEED FOR CHEAP AND RELIABLE ENERGY.
Our government is corrupt. Money talks. These companies will push for energy freedom and it will greatly benefit us all.
Microsoft Cloud hiring to "implement global small modular reactor and microreactor" strategy to power data centers: https://www.datacenterdynamics.com/en/news/microsoft-cloud-hiring-to-implement-global-small-modular-reactor-and-microreactor-strategy-to-power-data-centers/
If you found this post helpful support my work with bitcoin.

-
 @ c1e6505c:02b3157e
2025-05-22 03:44:39
@ c1e6505c:02b3157e
2025-05-22 03:44:39This is day two of testing the Leica Summaron 35mm f2.8 on the Fujifilm X-Pro2.
The first part of this story you can find here on StackerNews**
TL;DR: I think I’m really enjoying this lens.
I went into it thinking I’d probably just sell it since it was gifted to me - assumed I wouldn’t like it. But after just a couple of days with it mounted on the X-Pro2, I’ve been surprisingly drawn to it.
Shooting wide open at f2.8 (which is how I’m testing it - to best reveal the lens’s character), the soft roll-off is really pleasing. It feels organic. The lens is over 50 years old, so I expected some quirks-but the quality feels natural, not overly “vintage". Takes the digital edge off.
The short focus throw is also really nice. Compared to the Summicron 35mm f2 v3 I usually shoot on my M262 (which has a longer throw), the Summaron feels tighter and more responsive when zone focusing.
One gripe: the infinity lock. It’s kind of annoying. I find myself accidentally locking it too often, but I’m getting used to holding the button down as I rotate the ring. I’ve read others complain about it, so I know I’m not alone there.
Most of these shots were from a bike ride to the river - about 6 miles out to swim and enjoy the sun. Perfect day for making a few photos.
This kind of work is honestly just fun. I enjoy the process, and even more so once I’m happy with the results and can share them.
Still building confidence in my work over time. I think I’m slowly refining my style - even if the subject matter is simple. Easier said than done, as any editor/curator knows (and I say this as one through NOICE Magazine).
Let me know what you think. I’ll try to upload higher resolution versions this time around (but not too high).
*Also, I use a program called Dehancer for creating the grain in these photographs. I highly recommend the program actually, I've been using it for a long time. If you would like to try it out, I have a promo code. Use "Pictureroom" for 10% off I believe.
You can further support me and my work by sending sats to colincz\@getalby.com. Thank you.
(note* this is being publised from the updated Primal reads client)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:40:57
@ 6d5c826a:4b27b659
2025-05-23 21:40:57- Backupninja - Lightweight, extensible meta-backup system, provides a centralized way to configure and coordinate many different backup utilities.
GPL-2.0Shell - Backrest - Backrest is a web UI and orchestrator for restic backup. (Source Code)
GPL-3.0Docker/Go - Bareos - Cross-network backup solution which preserves, archives, and recovers data from all major operating systems. (Source Code)
AGPL-3.0C++/C - Barman - Backup and Recovery Manager for PostgreSQL. (Source Code)
GPL-3.0Python - BorgBackup - Deduplicating archiver with compression and authenticated encryption. (Source Code)
BSD-3-ClausePython - Burp - Network backup and restore program. (Source Code)
AGPL-3.0C - Dar - Which stands for Disk ARchive, is a robust and rich featured archiving and backup software of the tar style. (Source Code)
GPL-2.0C++ - Duplicati - Backup client that securely stores encrypted, incremental, compressed backups on cloud storage services and remote file servers. (Source Code)
LGPL-2.1C# - Duplicity - Encrypted bandwidth-efficient backup using the rsync algorithm. (Source Code)
GPL-2.0Python - Proxmox Backup Server - Proxmox Backup Server is an enterprise-class, client-server backup solution thatis capable of backing up virtual machines, containers, and physical hosts. (Source Code)
GPL-3.0Rust - rclone - Command-line program to sync files and directories to and from different cloud storage providers.. (Source Code)
MITGo - Rdiff-backup - Reverse differential backup tool, over a network or locally. (Source Code)
GPL-2.0Python - Restic - Easy, fast, verifiable, secure and efficient remote backup tool. (Source Code)
BSD-2-ClauseGo - Rsnapshot - Filesystem snapshot utility based on rsync. (Source Code)
GPL-2.0Perl - Shield - A pluggable architecture for backup and restore of database systems.
MITGo - UrBackup - Client/Server Open Source Network Backup for Windows, MacOS and Linux. (Source Code)
AGPL-3.0C/C++
- Backupninja - Lightweight, extensible meta-backup system, provides a centralized way to configure and coordinate many different backup utilities.
-
 @ 7f6db517:a4931eda
2025-05-29 02:01:29
@ 7f6db517:a4931eda
2025-05-29 02:01:29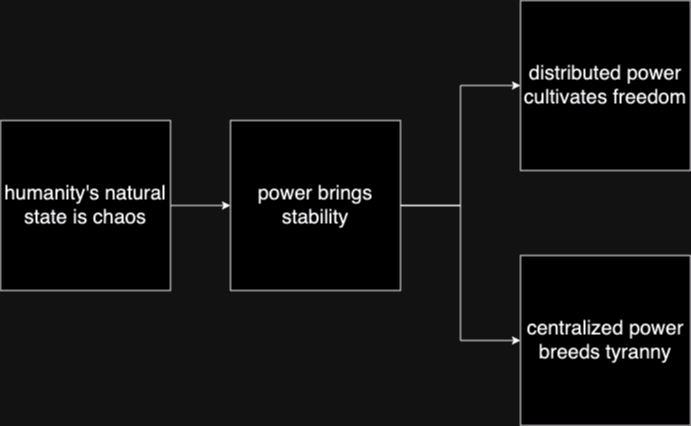
Humanity's Natural State Is Chaos
Without order there is chaos. Humans competing with each other for scarce resources naturally leads to conflict until one group achieves significant power and instates a "monopoly on violence."Power Brings Stability
Power has always been the key means to achieve stability in societies. Centralized power can be incredibly effective in addressing issues such as crime, poverty, and social unrest efficiently. Unfortunately this power is often abused and corrupted.Centralized Power Breeds Tyranny
Centralized power often leads to tyrannical rule. When a select few individuals hold control over a society, they tend to become corrupted. Centralized power structures often lack accountability and transparency, and rely too heavily on trust.Distributed Power Cultivates Freedom
New technology that empowers individuals provide us the ability to rebuild societies from the bottom up. Strong individuals that can defend and provide for themselves will help build strong local communities on a similar foundation. The result is power being distributed throughout society rather than held by a select few.In the short term, relying on trust and centralized power is an easy answer to mitigating chaos, but freedom tech tools provide us the ability to build on top of much stronger distributed foundations that provide stability while also cultivating individual freedom.
The solution starts with us. Empower yourself. Empower others. A grassroots freedom tech movement scaling one person at a time.
If you found this post helpful support my work with bitcoin.

-
 @ 21335073:a244b1ad
2025-05-21 16:58:36
@ 21335073:a244b1ad
2025-05-21 16:58:36The other day, I had the privilege of sitting down with one of my favorite living artists. Our conversation was so captivating that I felt compelled to share it. I’m leaving his name out for privacy.
Since our last meeting, I’d watched a documentary about his life, one he’d helped create. I told him how much I admired his openness in it. There’s something strange about knowing intimate details of someone’s life when they know so little about yours—it’s almost like I knew him too well for the kind of relationship we have.
He paused, then said quietly, with a shy grin, that watching the documentary made him realize how “odd and eccentric” he is. I laughed and told him he’s probably the sanest person I know. Because he’s lived fully, chasing love, passion, and purpose with hardly any regrets. He’s truly lived.
Today, I turn 44, and I’ll admit I’m a bit eccentric myself. I think I came into the world this way. I’ve made mistakes along the way, but I carry few regrets. Every misstep taught me something. And as I age, I’m not interested in blending in with the world—I’ll probably just lean further into my own brand of “weird.” I want to live life to the brim. The older I get, the more I see that the “normal” folks often seem less grounded than the eccentric artists who dare to live boldly. Life’s too short to just exist, actually live.
I’m not saying to be strange just for the sake of it. But I’ve seen what the crowd celebrates, and I’m not impressed. Forge your own path, even if it feels lonely or unpopular at times.
It’s easy to scroll through the news and feel discouraged. But actually, this is one of the most incredible times to be alive! I wake up every day grateful to be here, now. The future is bursting with possibility—I can feel it.
So, to my fellow weirdos on nostr: stay bold. Keep dreaming, keep pushing, no matter what’s trending. Stay wild enough to believe in a free internet for all. Freedom is radical—hold it tight. Live with the soul of an artist and the grit of a fighter. Thanks for inspiring me and so many others to keep hoping. Thank you all for making the last year of my life so special.
-
 @ 7460b7fd:4fc4e74b
2025-05-21 02:35:36
@ 7460b7fd:4fc4e74b
2025-05-21 02:35:36如果比特币发明了真正的钱,那么 Crypto 是什么?
引言
比特币诞生之初就以“数字黄金”姿态示人,被支持者誉为人类历史上第一次发明了真正意义上的钱——一种不依赖国家信用、总量恒定且不可篡改的硬通货。然而十多年过去,比特币之后蓬勃而起的加密世界(Crypto)已经远超“货币”范畴:从智能合约平台到去中心组织,从去央行的稳定币到戏谑荒诞的迷因币,Crypto 演化出一个丰富而混沌的新生态。这不禁引发一个根本性的追问:如果说比特币解决了“真金白银”的问题,那么 Crypto 又完成了什么发明?
 Crypto 与政治的碰撞:随着Crypto版图扩张,全球政治势力也被裹挟进这场金融变革洪流(示意图)。比特币的出现重塑了货币信用,但Crypto所引发的却是一场更深刻的政治与治理结构实验。从华尔街到华盛顿,从散户论坛到主权国家,越来越多人意识到:Crypto不只是技术或金融现象,而是一种全新的政治表达结构正在萌芽。正如有激进论者所断言的:“比特币发明了真正的钱,而Crypto则在发明新的政治。”价格K线与流动性曲线,或许正成为这个时代社群意志和社会价值观的新型投射。
Crypto 与政治的碰撞:随着Crypto版图扩张,全球政治势力也被裹挟进这场金融变革洪流(示意图)。比特币的出现重塑了货币信用,但Crypto所引发的却是一场更深刻的政治与治理结构实验。从华尔街到华盛顿,从散户论坛到主权国家,越来越多人意识到:Crypto不只是技术或金融现象,而是一种全新的政治表达结构正在萌芽。正如有激进论者所断言的:“比特币发明了真正的钱,而Crypto则在发明新的政治。”价格K线与流动性曲线,或许正成为这个时代社群意志和社会价值观的新型投射。冲突结构:当价格挑战选票
传统政治中,选票是人民意志的载体,一人一票勾勒出民主治理的正统路径。而在链上的加密世界里,骤升骤降的价格曲线和真金白银的买卖行为却扮演起了选票的角色:资金流向成了民意走向,市场多空成为立场表决。价格行为取代选票,这听来匪夷所思,却已在Crypto社群中成为日常现实。每一次代币的抛售与追高,都是社区对项目决策的即时“投票”;每一根K线的涨跌,都折射出社区意志的赞同或抗议。市场行为本身承担了决策权与象征权——价格即政治,正在链上蔓延。
这一新生政治形式与旧世界的民主机制形成了鲜明冲突。bitcoin.org中本聪在比特币白皮书中提出“一CPU一票”的工作量证明共识,用算力投票取代了人为决策bitcoin.org。而今,Crypto更进一步,用资本市场的涨跌来取代传统政治的选举。支持某项目?直接购入其代币推高市值;反对某提案?用脚投票抛售资产。相比漫长的选举周期和层层代议制,链上市场提供了近乎实时的“公投”机制。但这种机制也引发巨大争议:资本的投票天然偏向持币多者(富者)的意志,是否意味着加密政治更为金权而非民权?持币多寡成为影响力大小,仿佛选举演变成了“一币一票”,巨鲸富豪俨然掌握更多话语权。这种与民主平等原则的冲突,成为Crypto政治形式饱受质疑的核心张力之一。
尽管如此,我们已经目睹市场投票在Crypto世界塑造秩序的威力:2016年以太坊因DAO事件分叉时,社区以真金白银“投票”决定了哪条链获得未来。arkhamintelligence.com结果是新链以太坊(ETH)成为主流,其市值一度超过2,800亿美元,而坚持原则的以太经典(ETC)市值不足35亿美元,不及前者的八十分之一arkhamintelligence.com。市场选择清楚地昭示了社区的政治意志。同样地,在比特币扩容之争、各类硬分叉博弈中,无不是由投资者和矿工用资金与算力投票,胜者存续败者黯然。价格成为裁决纷争的最终选票,冲击着传统“选票决胜”的政治理念。Crypto的价格民主,与现代代议民主正面相撞,激起当代政治哲思中前所未有的冲突火花。
治理与分配
XRP对决SEC成为了加密世界“治理与分配”冲突的经典战例。2020年底,美国证券交易委员会(SEC)突然起诉Ripple公司,指控其发行的XRP代币属于未注册证券,消息一出直接引爆市场恐慌。XRP价格应声暴跌,一度跌去超过60%,最低触及0.21美元coindesk.com。曾经位居市值前三的XRP险些被打入谷底,监管的强硬姿态似乎要将这个项目彻底扼杀。
然而XRP社区没有选择沉默。 大批长期持有者组成了自称“XRP军团”(XRP Army)的草根力量,在社交媒体上高调声援Ripple,对抗监管威胁。面对SEC的指控,他们集体发声,质疑政府选择性执法,声称以太坊当年发行却“逍遥法外”,只有Ripple遭到不公对待coindesk.com。正如《福布斯》的评论所言:没人预料到愤怒的加密散户投资者会掀起法律、政治和社交媒体领域的‘海啸式’反击,痛斥监管机构背弃了保护投资者的承诺crypto-law.us。这种草根抵抗监管的话语体系迅速形成:XRP持有者不但在网上掀起舆论风暴,还采取实际行动向SEC施压。他们发起了请愿,抨击SEC背离保护投资者初衷、诉讼给个人投资者带来巨大伤害,号召停止对Ripple的上诉纠缠——号称这是在捍卫全球加密用户的共同利益bitget.com。一场由民间主导的反监管运动就此拉开帷幕。
Ripple公司则选择背水一战,拒绝和解,在法庭上与SEC针锋相对地鏖战了近三年之久。Ripple坚称XRP并非证券,不应受到SEC管辖,即使面临沉重法律费用和业务压力也不妥协。2023年,这场持久战迎来了标志性转折:美国法庭作出初步裁决,认定XRP在二级市场的流通不构成证券coindesk.com。这一胜利犹如给沉寂已久的XRP注入强心针——消息公布当天XRP价格飙涨近一倍,盘中一度逼近1美元大关coindesk.com。沉重监管阴影下苟延残喘的项目,凭借司法层面的突破瞬间重获生机。这不仅是Ripple的胜利,更被支持者视为整个加密行业对SEC强权的一次胜仗。
XRP的对抗路线与某些“主动合规”的项目形成了鲜明对比。 稳定币USDC的发行方Circle、美国最大合规交易所Coinbase等选择了一条迎合监管的道路:它们高调拥抱现行法规,希望以合作换取生存空间。然而现实却给了它们沉重一击。USDC稳定币在监管风波中一度失去美元锚定,哪怕Circle及时披露储备状况也无法阻止恐慌蔓延,大批用户迅速失去信心,短时间内出现数十亿美元的赎回潮blockworks.co。Coinbase则更为直接:即便它早已注册上市、反复向监管示好,2023年仍被SEC指控为未注册证券交易所reuters.com,卷入漫长诉讼漩涡。可见,在迎合监管的策略下,这些机构非但未能换来监管青睐,反而因官司缠身或用户流失而丧失市场信任。 相比之下,XRP以对抗求生存的路线反而赢得了投资者的眼光:价格的涨跌成为社区投票的方式,抗争的勇气反过来强化了市场对它的信心。
同样引人深思的是另一种迥异的治理路径:技术至上的链上治理。 以MakerDAO为代表的去中心化治理模式曾被寄予厚望——MKR持币者投票决策、算法维持稳定币Dai的价值,被视为“代码即法律”的典范。然而,这套纯技术治理在市场层面却未能形成广泛认同,亦无法激发群体性的情绪动员。复杂晦涩的机制使得普通投资者难以参与其中,MakerDAO的治理讨论更多停留在极客圈子内部,在社会大众的政治对话中几乎听不见它的声音。相比XRP对抗监管所激发的铺天盖地关注,MakerDAO的治理实验显得默默无闻、难以“出圈”。这也说明,如果一种治理实践无法连接更广泛的利益诉求和情感共鸣,它在社会政治层面就难以形成影响力。
XRP之争的政治象征意义由此凸显: 它展示了一条“以市场对抗国家”的斗争路线,即通过代币价格的集体行动来回应监管权力的施压。在这场轰动业界的对决中,价格即是抗议的旗帜,涨跌映射着政治立场。XRP对SEC的胜利被视作加密世界向旧有权力宣告的一次胜利:资本市场的投票器可以撼动监管者的强权。这种“价格即政治”的张力,正是Crypto世界前所未有的社会实验:去中心化社区以市场行为直接对抗国家权力,在无形的价格曲线中凝聚起政治抗争的力量,向世人昭示加密货币不仅有技术和资本属性,更蕴含着不可小觑的社会能量和政治意涵。
不可归零的政治资本
Meme 币的本质并非廉价或易造,而在于其构建了一种“无法归零”的社群生存结构。 对于传统观点而言,多数 meme 币只是短命的投机游戏:价格暴涨暴跌后一地鸡毛,创始人套现跑路,投资者血本无归,然后“大家转去炒下一个”theguardian.com。然而,meme 币社群的独特之处在于——失败并不意味着终结,而更像是运动的逗号而非句号。一次币值崩盘后,持币的草根们往往并未散去;相反,他们汲取教训,准备东山再起。这种近乎“不死鸟”的循环,使得 meme 币运动呈现出一种数字政治循环的特质:价格可以归零,但社群的政治热情和组织势能不归零。正如研究者所指出的,加密领域中的骗局、崩盘等冲击并不会摧毁生态,反而成为让系统更加强韧的“健康应激”,令整个行业在动荡中变得更加反脆弱cointelegraph.com。对应到 meme 币,每一次暴跌和重挫,都是社群自我进化、卷土重来的契机。这个去中心化群体打造出一种自组织的安全垫,失败者得以在瓦砾上重建家园。对于草根社群、少数派乃至体制的“失败者”而言,meme 币提供了一个永不落幕的抗争舞台,一种真正反脆弱的政治性。正因如此,我们看到诸多曾被嘲笑的迷因项目屡败屡战:例如 Dogecoin 自2013年问世后历经八年沉浮,早已超越玩笑属性,成为互联网史上最具韧性的迷因之一frontiersin.org;支撑 Dogecoin 的正是背后强大的迷因文化和社区意志,它如同美国霸权支撑美元一样,为狗狗币提供了“永不中断”的生命力frontiersin.org。
“复活权”的数字政治意涵
这种“失败-重生”的循环结构蕴含着深刻的政治意涵:在传统政治和商业领域,一个政党选举失利或一家公司破产往往意味着清零出局,资源散尽、组织瓦解。然而在 meme 币的世界,社群拥有了一种前所未有的“复活权”。当项目崩盘,社区并不必然随之消亡,而是可以凭借剩余的人心和热情卷土重来——哪怕换一个 token 名称,哪怕重启一条链,运动依然延续。正如 Cheems 项目的核心开发者所言,在几乎无人问津、技术受阻的困境下,大多数人可能早已卷款走人,但 “CHEEMS 社区没有放弃,背景、技术、风投都不重要,重要的是永不言弃的精神”cointelegraph.com。这种精神使得Cheems项目起死回生,社区成员齐声宣告“我们都是 CHEEMS”,共同书写历史cointelegraph.com。与传统依赖风投和公司输血的项目不同,Cheems 完全依靠社区的信念与韧性存续发展,体现了去中心化运动的真谛cointelegraph.com。这意味着政治参与的门槛被大大降低:哪怕没有金主和官方背书,草根也能凭借群体意志赋予某个代币新的生命。对于身处社会边缘的群体来说,meme 币俨然成为自组织的安全垫和重新集结的工具。难怪有学者指出,近期涌入meme币浪潮的主力,正是那些对现实失望但渴望改变命运的年轻人theguardian.com——“迷茫的年轻人,想要一夜暴富”theguardian.com。meme币的炒作表面上看是投机赌博,但背后蕴含的是草根对既有金融秩序的不满与反抗:没有监管和护栏又如何?一次失败算不得什么,社区自有后路和新方案。这种由底层群众不断试错、纠错并重启的过程,本身就是一种数字时代的新型反抗运动和群众动员机制。
举例而言,Terra Luna 的沉浮充分展现了这种“复活机制”的政治力量。作为一度由风投资本热捧的项目,Luna 币在2022年的崩溃本可被视作“归零”的失败典范——稳定币UST瞬间失锚,Luna币价归零,数十亿美元灰飞烟灭。然而“崩盘”并没有画下休止符。Luna的残余社区拒绝承认失败命运,通过链上治理投票毅然启动新链,“复活”了 Luna 代币,再次回到市场交易reuters.com。正如 Terra 官方在崩盘后发布的推文所宣称:“我们力量永在社区,今日的决定正彰显了我们的韧性”reuters.com。事实上,原链更名为 Luna Classic 后,大批所谓“LUNC 军团”的散户依然死守阵地,誓言不离不弃;他们自发烧毁巨量代币以缩减供应、推动技术升级,试图让这个一度归零的项目重新燃起生命之火binance.com。失败者并未散场,而是化作一股草根洪流,奋力托举起项目的残迹。经过迷因化的叙事重塑,这场从废墟中重建价值的壮举,成为加密世界中草根政治的经典一幕。类似的案例不胜枚举:曾经被视为笑话的 DOGE(狗狗币)正因多年社群的凝聚而跻身主流币种,总市值一度高达数百亿美元,充分证明了“民有民享”的迷因货币同样可以笑傲市场frontiersin.org。再看最新的美国政治舞台,连总统特朗普也推出了自己的 meme 币 $TRUMP,号召粉丝拿真金白银来表达支持。该币首日即从7美元暴涨至75美元,两天后虽回落到40美元左右,但几乎同时,第一夫人 Melania 又发布了自己的 $Melania 币,甚至连就职典礼的牧师都跟风发行了纪念币theguardian.com!显然,对于狂热的群众来说,一个币的沉浮并非终点,而更像是运动的换挡——资本市场成为政治参与的新前线,你方唱罢我登场,meme 币的群众动员热度丝毫不减。值得注意的是,2024年出现的 Pump.fun 等平台更是进一步降低了这一循环的技术门槛,任何人都可以一键生成自己的 meme 币theguardian.com。这意味着哪怕某个项目归零,剩余的社区完全可以借助此类工具迅速复制一个新币接力,延续集体行动的火种。可以说,在 meme 币的世界里,草根社群获得了前所未有的再生能力和主动权,这正是一种数字时代的群众政治奇观:失败可以被当作梗来玩,破产能够变成重生的序章。
价格即政治:群众投机的新抗争
meme 币现象的兴盛表明:在加密时代,价格本身已成为一种政治表达。这些看似荒诞的迷因代币,将金融市场变成了群众宣泄情绪和诉求的另一个舞台。有学者将此概括为“将公民参与直接转化为了投机资产”cdn-brighterworld.humanities.mcmaster.ca——也就是说,社会运动的热情被注入币价涨跌,政治支持被铸造成可以交易的代币。meme 币融合了金融、技术与政治,通过病毒般的迷因文化激发公众参与,形成对现实政治的某种映射cdn-brighterworld.humanities.mcmaster.caosl.com。当一群草根投入全部热忱去炒作一枚毫无基本面支撑的币时,这本身就是一种大众政治动员的体现:币价暴涨,意味着一群人以戏谑的方式在向既有权威叫板;币价崩盘,也并不意味着信念的消亡,反而可能孕育下一次更汹涌的造势。正如有分析指出,政治类 meme 币的出现前所未有地将群众文化与政治情绪融入市场行情,价格曲线俨然成为民意和趋势的风向标cdn-brighterworld.humanities.mcmaster.ca。在这种局面下,投机不再仅仅是逐利,还是一种宣示立场、凝聚共识的过程——一次次看似荒唐的炒作背后,是草根对传统体制的不服与嘲讽,是失败者拒绝认输的呐喊。归根结底,meme 币所累积的,正是一种不可被归零的政治资本。价格涨落之间,群众的愤怒、幽默与希望尽显其中;这股力量不因一次挫败而消散,反而在市场的循环中愈发壮大。也正因如此,我们才说“价格即政治”——在迷因币的世界里,价格不只是数字,更是人民政治能量的晴雨表,哪怕归零也终将卷土重来。cdn-brighterworld.humanities.mcmaster.caosl.com
全球新兴现象:伊斯兰金融的入场
当Crypto在西方世界掀起市场治政的狂潮时,另一股独特力量也悄然融入这一场域:伊斯兰金融携其独特的道德秩序,开始在链上寻找存在感。长期以来,伊斯兰金融遵循着一套区别于世俗资本主义的原则:禁止利息(Riba)、反对过度投机(Gharar/Maysir)、强调实际资产支撑和道德投资。当这些原则遇上去中心化的加密技术,会碰撞出怎样的火花?出人意料的是,这两者竟在“以市场行为表达价值”这个层面产生了惊人的共鸣。伊斯兰金融并不拒绝市场机制本身,只是为其附加了道德准则;Crypto则将市场机制推向了政治高位,用价格来表达社群意志。二者看似理念迥异,实则都承认市场行为可以也应当承载社会价值观。这使得越来越多金融与政治分析人士开始关注:当虔诚的宗教伦理遇上狂野的加密市场,会塑造出何种新范式?
事实上,穆斯林世界已经在探索“清真加密”的道路。一些区块链项目致力于确保协议符合伊斯兰教法(Sharia)的要求。例如Haqq区块链发行的伊斯兰币(ISLM),从规则层面内置了宗教慈善义务——每发行新币即自动将10%拨入慈善DAO,用于公益捐赠,以符合天课(Zakat)的教义nasdaq.comnasdaq.com。同时,该链拒绝利息和赌博类应用,2022年还获得了宗教权威的教令(Fatwa)认可其合规性nasdaq.com。再看理念层面,伊斯兰经济学强调货币必须有内在价值、收益应来自真实劳动而非纯利息剥削。这一点与比特币的“工作量证明”精神不谋而合——有人甚至断言法定货币无锚印钞并不清真,而比特币这类需耗费能源生产的资产反而更符合教法初衷cointelegraph.com。由此,越来越多穆斯林投资者开始以道德投资的名义进入Crypto领域,将资金投向符合清真原则的代币和协议。
这种现象带来了微妙的双重合法性:一方面,Crypto世界原本奉行“价格即真理”的世俗逻辑,而伊斯兰金融为其注入了一股道德合法性,使部分加密资产同时获得了宗教与市场的双重背书;另一方面,即便在遵循宗教伦理的项目中,最终决定成败的依然是市场对其价值的认可。道德共识与市场共识在链上交汇,共同塑造出一种混合的新秩序。这一全球新兴现象引发广泛议论:有人将其视为金融民主化的极致表现——不同文化价值都能在市场平台上表达并竞争;也有人警惕这可能掩盖新的风险,因为把宗教情感融入高风险资产,既可能凝聚强大的忠诚度,也可能在泡沫破裂时引发信仰与财富的双重危机。但无论如何,伊斯兰金融的入场使Crypto的政治版图更加丰盈多元。从华尔街交易员到中东教士,不同背景的人们正通过Crypto这个奇特的舞台,对人类价值的表达方式进行前所未有的实验。
升华结语:价格即政治的新直觉
回顾比特币问世以来的这段历程,我们可以清晰地看到一条演进的主线:先有货币革命,后有政治发明。比特币赋予了人类一种真正自主的数字货币,而Crypto在此基础上完成的,则是一项前所未有的政治革新——它让市场价格行为承担起了类似政治选票的功能,开创了一种“价格即政治”的新直觉。在这个直觉下,市场不再只是冷冰冰的交易场所;每一次资本流动、每一轮行情涨落,都被赋予了社会意义和政治涵义。买入即表态,卖出即抗议,流动性的涌入或枯竭胜过千言万语的陈情。Crypto世界中,K线图俨然成为民意曲线,行情图就是政治晴雨表。决策不再由少数权力精英关起门来制定,而是在全球无眠的交易中由无数普通人共同谱写。这样的政治形式也许狂野,也许充满泡沫和噪音,但它不可否认地调动起了广泛的社会参与,让原本疏离政治进程的个体通过持币、交易重新找回了影响力的幻觉或实感。
“价格即政治”并非一句简单的口号,而是Crypto给予世界的全新想象力。它质疑了传统政治的正统性:如果一串代码和一群匿名投资者就能高效决策资源分配,我们为何还需要繁冗的官僚体系?它也拷问着自身的内在隐忧:当财富与权力深度绑定,Crypto政治如何避免堕入金钱统治的老路?或许,正是在这样的矛盾和张力中,人类政治的未来才会不断演化。Crypto所开启的,不仅是技术乌托邦或金融狂欢,更可能是一次对民主形式的深刻拓展和挑战。这里有最狂热的逐利者,也有最理想主义的社群塑梦者;有一夜暴富的神话,也有瞬间破灭的惨痛。而这一切汇聚成的洪流,正冲撞着工业时代以来既定的权力谱系。
当我们再次追问:Crypto究竟是什么? 或许可以这样回答——Crypto是比特币之后,人类完成的一次政治范式的试验性跃迁。在这里,价格行为化身为选票,资本市场演化为广场,代码与共识共同撰写“社会契约”。这是一场仍在进行的文明实验:它可能无声地融入既有秩序,也可能剧烈地重塑未来规则。但无论结局如何,如今我们已经见证:在比特币发明真正的货币之后,Crypto正在发明真正属于21世纪的政治。它以数字时代的语言宣告:在链上,价格即政治,市场即民意,代码即法律。这,或许就是Crypto带给我们的最直观而震撼的本质启示。
参考资料:
-
中本聪. 比特币白皮书: 一种点对点的电子现金系统. (2008)bitcoin.org
-
Arkham Intelligence. Ethereum vs Ethereum Classic: Understanding the Differences. (2023)arkhamintelligence.com
-
Binance Square (@渔神的加密日记). 狗狗币价格为何上涨?背后的原因你知道吗?binance.com
-
Cointelegraph中文. 特朗普的迷因币晚宴预期内容揭秘. (2025)cn.cointelegraph.com
-
慢雾科技 Web3Caff (@Lisa). 风险提醒:从 LIBRA 看“政治化”的加密货币骗局. (2025)web3caff.com
-
Nasdaq (@Anthony Clarke). How Cryptocurrency Aligns with the Principles of Islamic Finance. (2023)nasdaq.comnasdaq.com
-
Cointelegraph Magazine (@Andrew Fenton). DeFi can be halal but not DOGE? Decentralizing Islamic finance. (2023)cointelegraph.com
-
-
 @ dfa02707:41ca50e3
2025-05-29 02:01:29
@ dfa02707:41ca50e3
2025-05-29 02:01:29Contribute to keep No Bullshit Bitcoin news going.
- Coinswap is a decentralized protocol for private, trustless cryptocurrency swaps. It allows participants to securely swap digital assets without intermediaries, using advanced cryptographic techniques and atomic swaps to ensure privacy and security.
- This release introduces major improvements to the protocol's efficiency, security, and usability, including custom in-memory UTXO indexes, more advanced coin-selection algorithms, fidelity bond management and more.
- The update also improves user experience with full Mac support, faster Tor connections, enhanced UI/UX, a unified API, and improved protocol documentation.
"The Project is under active beta development and open for contributions and beta testing. The Coinswap market place is live in testnet4. Bug fixes and feature requests are very much welcome."
- Manuals and demo docs are available here.
What's new
- Core protocol and performance improvements:
- Custom in-memory UTXO indexes. Frequent Core RPC calls, which caused significant delays, have been eliminated by implementing custom in-memory UTXO indexes. These indexes are also saved to disk, leading to faster wallet synchronization.
- Coin selection. Advanced coin-selection algorithms, like those in Bitcoin Core, have been incorporated, enhancing the efficiency of creating different types of transactions.
- Fidelity management. Maker servers now automate tasks such as checking bond expiries, redemption, and recreation for Fidelity Bonds, reducing the user's management responsibilities.
- Taker liveness. The
WaitingFundingConfirmationmessage has been added to keep swap connections between Takers and Makers, assisting with variable block confirmation delays.
-
User experience and compatibility:
- Mac compatibility. The crate and apps now fully support Mac.
- Tor operations are streamlined for faster, more resilient connections. Tor addresses are now consistently linked to the wallet seed, maintaining the same onion address through system reboots.
- The UI/UX improvements enhance the display of balances, UTXOs, offer data, fidelity bonds, and system logs. These updates make the apps more enjoyable and provide clearer coin swap logs during the swap process.
-
API design improvements. Transaction creation routines have been streamlined to use a single common API, which reduces technical debt and eliminates redundant code.
- Protocol spec documentation now details how Coinswap breaks the transaction graph and improves privacy through routed swaps and amount splitting, and includes diagrams for clarity.
Source: Coinswap Protocol specification.

-
 @ 6d5c826a:4b27b659
2025-05-23 21:40:34
@ 6d5c826a:4b27b659
2025-05-23 21:40:34- Apache Ant - Automation build tool, similar to make, a library and command-line tool whose mission is to drive processes described in build files as targets and extension points dependent upon each other. (Source Code)
Apache-2.0Java - Apache Maven - Build automation tool mainly for Java. A software project management and comprehension tool. Based on the concept of a project object model (POM), Maven can manage a project's build, reporting and documentation from a central piece of information. (Source Code)
Apache-2.0Java - Bazel - A fast, scalable, multi-language and extensible build system. Used by Google. (Source Code)
Apache-2.0Java - Bolt - You can use Bolt to run one-off tasks, scripts to automate the provisioning and management of some nodes, you can use Bolt to move a step beyond scripts, and make them shareable. (Source Code)
Apache-2.0Ruby - GNU Make - The most popular automation build tool for many purposes, make is a tool which controls the generation of executables and other non-source files of a program from the program's source files. (Source Code)
GPL-3.0C - Gradle - Another build automation system. (Source Code)
Apache-2.0Groovy/Java - Rake - Build automation tool similar to Make, written in and extensible in Ruby. (Source Code)
MITRuby
- Apache Ant - Automation build tool, similar to make, a library and command-line tool whose mission is to drive processes described in build files as targets and extension points dependent upon each other. (Source Code)
-
 @ 51bbb15e:b77a2290
2025-05-21 00:24:36
@ 51bbb15e:b77a2290
2025-05-21 00:24:36Yeah, I’m sure everything in the file is legit. 👍 Let’s review the guard witness testimony…Oh wait, they weren’t at their posts despite 24/7 survellience instructions after another Epstein “suicide” attempt two weeks earlier. Well, at least the video of the suicide is in the file? Oh wait, a techical glitch. Damn those coincidences!
At this point, the Trump administration has zero credibility with me on anything related to the Epstein case and his clients. I still suspect the administration is using the Epstein files as leverage to keep a lot of RINOs in line, whereas they’d be sabotaging his agenda at every turn otherwise. However, I just don’t believe in ends-justify-the-means thinking. It’s led almost all of DC to toss out every bit of the values they might once have had.
-
 @ 86611181:9fc27ad7
2025-05-23 20:31:44
@ 86611181:9fc27ad7
2025-05-23 20:31:44It's time to secure user data in your identity system This post was also published with the Industry Association of Privacy Professionals.
It seems like every day there is a new report of a major personal data breach. In just the past few months, Neiman Marcus, Ticketmaster, Evolve Bank, TeamViewer, Hubspot, and even the IRS have been affected.
The core issue is that user data is commonly spread across multiple systems that are increasingly difficult to fully secure, including database user tables, data warehouses and unstructured documents.
Most enterprises are already running an incredibly secure and hardened identity system to manage customer login and authorization, commonly referred to as a customer identity access management system. Since identity systems manage customer sign-up and sign-in, they typically contain customer names, email addresses, and phone numbers for multifactor authentication. Commercial CIAMs provide extensive logging, threat detection, availability and patch management.
Identity systems are highly secure and already store customers' personally identifiable information, so it stands to reason enterprises should consider identity systems to manage additional PII fields.
Identity systems are designed to store numerous PII fields and mask the fields for other systems. The Liberty Project developed the protocols that became Security Assertion Markup Language 2.0, the architecture at the core of CIAM systems, 20 years ago, when I was its chief technology officer. SAML 2.0 was built so identity data would be fully secure, and opaque tokens would be shared with other systems. Using tokens instead of actual user data is a core feature of identity software that can be used to fully secure user data across applications.
Most modern identity systems support adding additional customer fields, so it is easy to add new fields like Social Security numbers and physical addresses. Almost like a database, some identity systems even support additional tables and images.
A great feature of identity systems is that they often provide a full suite of user interface components for users to register, login and manage their profile fields. Moving fields like Social Security numbers from your database to your identity system means the identity system can fully manage the process of users entering, viewing and editing the field, and your existing application and database become descoped from managing sensitive data.
With sensitive fields fully isolated in an identity system and its user interface components, the identity system can provide for cumbersome and expensive compliance with standards such as the Health Insurance Portability and Accountability Act for medical data and the Payment Card Industry Data Security Standard for payment data, saving the time and effort to achieve similar compliance in your application.
There are, of course, applications that require sensitive data, such as customer service systems and data warehouses. Identity systems use a data distribution standard called System for Cross-domain Identity Management 2.0 to copy user data to other systems. The SCIM is a great standard to help manage compliance such as "right to be forgotten," because it can automatically delete customer data from other systems when a customer record is deleted from the identity system.
When copying customer data from an identity system to another application, consider anonymizing or masking fields. For example, anonymizing a birthdate into an age range when copying a customer record into a data warehouse can descope the data warehouse from containing personal information.
Most enterprises already run an Application Programming Interface Gateway to manage web services between systems. By combining an API Gateway with the identity system's APIs, it becomes very easy to automatically anonymize and mask customer data fields before they are copied into other systems.
A new set of companies including Baffle, Skyflow, and Piiano have introduced services that combine the governance and field management features of an identity system with extensive field masking. Since these systems do not offer the authentication and authorization features of an identity system, it's important to balance the additional features as they introduce an additional threat surface with PII storage and permissions.
PII sprawl is an increasing liability for companies. The most secure, compliant and flexible central data store to manage PII is the existing CIAM and API Gateway infrastructure that enterprises have already deployed.
Move that customer data into your identity system and lock it down. https://peter.layer3.press/articles/3c6912eb-404a-4630-9fe9-fd1bd23cfa64