-
 @ 32c87f47:cb8f61a1
2025-05-30 07:16:44
@ 32c87f47:cb8f61a1
2025-05-30 07:16:44Se você está em busca de uma plataforma confiável, divertida e repleta de oportunidades para se entreter com jogos online, o 77BB é o lugar ideal para você. Com uma estrutura moderna, interface amigável e uma variedade impressionante de jogos, o 77BB vem conquistando jogadores de todo o Brasil e se destacando como uma das principais referências no setor de entretenimento digital.
Uma Plataforma Completa para Todos os Perfis de Jogadores Desde o primeiro acesso, fica evidente que o 77BB foi desenvolvido com foco na experiência do usuário. O site possui um layout intuitivo, permitindo que jogadores iniciantes e experientes naveguem com facilidade entre as diferentes categorias. Além disso, a plataforma é totalmente compatível com dispositivos móveis, oferecendo uma experiência fluida tanto em celulares quanto em tablets e computadores.
Outro diferencial importante é a segurança. O 77bbconta com tecnologia de ponta para garantir a proteção dos dados dos jogadores, além de adotar políticas rigorosas de privacidade e suporte eficiente para esclarecer dúvidas e resolver qualquer questão rapidamente.
Variedade de Jogos para Todos os Gostos A diversidade de jogos disponíveis é um dos grandes atrativos da plataforma. O 77BB oferece uma seleção robusta que inclui desde os clássicos jogos de mesa até opções mais modernas com gráficos avançados e dinâmicas interativas. Entre os jogos mais populares estão os slots temáticos, jogos de cartas como pôquer e blackjack, além de roletas e outros formatos que simulam a atmosfera de casas de jogo físicas.
Os jogos são fornecidos por desenvolvedores renomados no mercado internacional, o que garante qualidade, fluidez e total imparcialidade nos resultados. Isso proporciona uma experiência justa e divertida, com chances reais de ganho e muita emoção a cada rodada.
Experiência do Jogador: Diversão e Benefícios Reais Um dos pontos mais elogiados pelos usuários do 77BB é a experiência geral oferecida pela plataforma. Além da facilidade de uso e da grande variedade de jogos, o site conta com promoções regulares, bônus de boas-vindas e programas de fidelidade que recompensam os jogadores mais ativos.
As promoções variam frequentemente e podem incluir rodadas grátis, bônus em depósitos e prêmios especiais em eventos temáticos. Isso torna a jornada ainda mais empolgante e mantém os jogadores sempre motivados a explorar novos títulos e desafios.
Outro aspecto importante é o suporte ao cliente. O 77BB oferece atendimento em português por meio de chat ao vivo e outros canais, garantindo que qualquer dúvida ou problema seja resolvido de forma rápida e eficiente. Esse cuidado com o usuário contribui para um ambiente mais acolhedor e profissional.
Conclusão: 77BB é Sinônimo de Diversão Garantida Se você procura uma plataforma segura, completa e cheia de possibilidades para se divertir com jogos online, o 77BB é uma escolha certeira. Com uma interface acessível, excelente variedade de jogos e um atendimento ao cliente exemplar, o 77BB entrega uma experiência de alto nível que agrada tanto iniciantes quanto veteranos.
Descubra hoje mesmo o universo de entretenimento que o 77BB tem a oferecer e transforme seu tempo livre em momentos de pura diversão!
-
 @ 32c87f47:cb8f61a1
2025-05-30 07:16:16
@ 32c87f47:cb8f61a1
2025-05-30 07:16:16No universo dos jogos online, a busca por plataformas confiáveis, divertidas e recheadas de opções é constante. É nesse cenário que o KK45 se destaca como uma escolha ideal para quem procura entretenimento de qualidade, segurança e uma experiência envolvente. Com uma interface moderna e intuitiva, a plataforma atrai jogadores de todos os níveis — desde os iniciantes até os mais experientes — oferecendo um catálogo variado de jogos e funcionalidades que fazem toda a diferença.
Conhecendo a Plataforma KK45 O KK45 é uma plataforma digital voltada para o entretenimento com foco total na qualidade e praticidade. O site foi desenvolvido pensando na experiência do usuário, com navegação fluida e recursos otimizados tanto para computadores quanto para dispositivos móveis. Isso significa que o jogador pode se divertir em qualquer lugar, a qualquer momento, bastando ter acesso à internet.
Outro diferencial é a segurança. O KK45 utiliza sistemas avançados de proteção de dados e transações, garantindo que todas as informações dos usuários estejam devidamente criptografadas. Além disso, o suporte ao cliente é eficiente e ágil, com atendimento em português e disponível 24 horas por dia, 7 dias por semana.
Variedade de Jogos para Todos os Gostos Um dos grandes atrativos do KK45 é a ampla variedade de jogos disponíveis. A plataforma trabalha com os principais desenvolvedores do mercado, trazendo gráficos de última geração, mecânicas envolventes e funcionalidades inovadoras. Entre os títulos mais populares, estão:
Slots temáticos: Com visuais incríveis e diversas funcionalidades bônus, os slots do KK45 agradam tanto os fãs de jogos clássicos quanto os que preferem aventuras modernas com muitos efeitos visuais.
Jogos de cartas e mesa: O ambiente perfeito para quem gosta de jogos como pôquer, blackjack, bacará, entre outros. Esses jogos são desenvolvidos com realismo e atenção aos detalhes, proporcionando partidas emocionantes.
Jogos interativos ao vivo: Para quem gosta de uma experiência mais próxima da realidade, os jogos ao vivo trazem interação em tempo real, com apresentadores reais, câmeras de alta definição e uma atmosfera imersiva.
A plataforma também investe em atualizações frequentes, lançando novos jogos regularmente para manter o catálogo sempre atualizado e atrativo.
A Experiência do Jogador no KK45 O que realmente diferencia o KK45 de outras plataformas é o cuidado com a experiência do jogador. Desde o cadastro simplificado até as formas de pagamento facilitadas, tudo foi pensado para proporcionar conforto e satisfação. O site oferece múltiplas opções de depósito e saque, com rapidez e segurança, além de bônus atrativos para novos jogadores e promoções recorrentes para os usuários fiéis.
Outro ponto forte é a personalização da experiência. Os jogadores podem salvar seus jogos favoritos, acompanhar seu histórico de partidas e configurar preferências para deixar a navegação ainda mais prática.
Além disso, o KK45 incentiva o jogo responsável, disponibilizando ferramentas que ajudam o usuário a controlar o tempo de uso e os valores investidos, promovendo uma diversão equilibrada.
Conclusão O KK45 se consolida como uma das principais plataformas de jogos online do Brasil, unindo tecnologia, segurança e uma variedade impressionante de jogos. Seja você um novato curioso ou um veterano em busca de novos desafios, o KK45 oferece tudo o que você precisa para uma jornada divertida e segura no mundo dos jogos digitais.
Explore agora mesmo a plataforma e descubra por que tantos jogadores estão escolhendo o KK45 como seu destino favorito para se entreter com qualidade e confiança!
-
 @ 805b8139:823180b0
2025-05-28 16:51:09
@ 805b8139:823180b0
2025-05-28 16:51:09Bitcoin Circular Economy in Africa
https://btch17n.layer3.press/articles/9ec7208a-5bd6-4b32-9e1e-24f1aa4b1ca2
-
 @ 6be5cc06:5259daf0
2025-05-27 20:22:09
@ 6be5cc06:5259daf0
2025-05-27 20:22:09A posição do libertário que rejeita o cristianismo padece de sérias incoerências lógicas, históricas e filosóficas. Ao renegar as bases espirituais e culturais que tornaram possível o próprio ideal libertário, tal posição demonstra ser, ao mesmo tempo, autofágica e irracional. É o caso de alguém que se gloria dos frutos de uma árvore que corta pela raiz.
I. Fundamento histórico: a civilização da liberdade é cristã
Não foi o secularismo moderno, nem o paganismo antigo, que ergueram as instituições que protegem a dignidade da pessoa humana e os limites ao poder. Desde os primeiros séculos, a Igreja resistiu ao culto estatal romano, afirmando a soberania de Deus sobre os Césares — "Mais importa obedecer a Deus que aos homens" (Atos 5,29).
Foi o cristianismo que:
-
Fundou universidades livres, onde o saber era buscado sob o primado da verdade;
-
Defendeu a lei natural como fundamento do direito — uma doutrina que protege o indivíduo contra tiranias;
-
Resgatou e aprofundou o conceito de pessoa, dotada de razão e livre-arbítrio, imagem de Deus, e, portanto, inalienavelmente digna e responsável.
Em momentos-chave da história, como nas disputas entre papado e império, nas resistências contra absolutismos, e na fundação do direito internacional por Francisco de Vitoria e a Escola de Salamanca, foi o cristianismo quem freou o poder estatal em nome de princípios superiores. A tradição cristã foi frequentemente o principal obstáculo à tirania, não seu aliado.
Negar isso é amputar a própria genealogia da liberdade ocidental.
Uma das chaves do cristianismo para a construção dessa civilização da liberdade foi a exaltação do individualismo. Ao afirmar que o ser humano é feito à imagem de Deus e que sua salvação é uma escolha pessoal, o cristianismo colocou o indivíduo no centro da moralidade e da liberdade. Diferente dos gregos, cuja ética era voltada para a polis e a cidade-estado, o cristianismo reafirma a suprema importância do indivíduo, com sua capacidade de escolha moral, responsabilidade pessoal e dignidade intrínseca. Esse princípio, mais do que qualquer outra religião, foi o alicerce do desenvolvimento da liberdade individual e da autonomia, valores que sustentam a civilização ocidental.
A ética grega, na melhor das hipóteses, descreve a ordem natural — mas não consegue justificar por que essa ordem deveria obrigar a vontade humana. Um Logos impessoal não tem autoridade moral. Uma ordem cósmica sem um Legislador é apenas um dado de fato, não uma norma vinculante. A vontade pode rebelar-se contra o telos — e sem um Deus justo, que ordena a natureza à perfeição, não há razão última para não o fazer.
A cultura grega teve uma influência indiscutível sobre o desenvolvimento da civilização ocidental, mas o cristianismo não só absorveu o que havia de bom na cultura grega, como também elevou e completou esses aspectos. O cristianismo, ao afirmar que todos os homens são feitos à imagem e semelhança de Deus e têm dignidade intrínseca, levou a uma noção de igualdade moral e liberdade que transcende as limitações da pólis grega.
II. Falsa dicotomia: fé e liberdade não são opostas
Com frequência equiparam a religião à coerção e à obediência cega. Mas isso é um equívoco: o cristianismo não se impõe pela força, mas apela à consciência. O próprio Deus, em sua relação com a criatura racional, respeita sua liberdade. Como ensina a Escritura:
"Se alguém quiser vir após mim..." (Mt 16,24);
"Eis que estou à porta e bato. Se alguém ouvir a minha voz e abrir a porta, entrarei em sua casa e cearei com ele." (Ap 3,20);
"Assim falai, e assim procedei, como devendo ser julgados pela lei da liberdade." (Tiago 2,12).A adesão à fé deve ser livre, voluntária e racional, pois sem liberdade não há verdadeiro mérito, nem amor genuíno. Isso é mais compatível com o princípio de não agressão do que qualquer utopia secular. Ora, o núcleo do evangelho é voluntarista: salvação pessoal, conversão interior, caridade.
Ninguém deve ser forçado, contra sua vontade, a abraçar a fé, pois o ato de fé é por sua natureza voluntário (Dignitatis Humanae; CDC, cân. 748,2)
Se algum Estado usa da força para impor o cristianismo, afirmar que o cristianismo causou as coerções é tão equivocado quanto dizer que a propriedade privada causa o comunismo; é uma inversão da realidade, pois o comunismo surge precisamente da violação da propriedade. Portanto, a fé forçada é inválida em si mesma, pois viola a natureza do ato de crer, que deve ser livre.
III. Fundamento moral: sem transcendência, o libertarianismo flutua no vácuo
O libertário anticristão busca defender princípios objetivos — como a inviolabilidade do indivíduo e a ilegitimidade da agressão — sem um fundamento transcendente que lhes dê validade universal. Por que a agressão é errada? Por que alguém tem direito à vida, à liberdade, à propriedade? Sem uma explicação transcendental, as respostas para tais perguntas se tornam apenas opiniões ou convenções, não obrigações morais vinculantes. Se a moralidade é puramente humana, então os direitos podem ser modificados ou ignorados conforme a vontade da sociedade. O conceito de direitos naturais, tão caro ao libertarianismo, precisa de um solo metafísico que justifique sua universalidade e imutabilidade. Caso contrário, eles podem ser tratados apenas como acordos utilitários temporários ou preferências culturais, sem qualquer obrigatoriedade para todos os seres humanos em todas as circunstâncias.
Pensadores libertários seculares, como Ayn Rand e Murray Rothbard, tentaram ancorar os direitos naturais na razão humana ou na natureza do homem. Rand baseia sua ética no egoísmo racional, enquanto Rothbard apela à lei natural. Embora essas abordagens busquem objetividade, elas carecem de uma resposta definitiva para por que a razão ou a natureza humana obrigam moralmente todos os indivíduos. Sem um fundamento transcendente, suas concepções permanecem vulneráveis a interpretações subjetivas ou a cálculos utilitários.
Aqui, o cristianismo oferece uma explicação sólida e transcendental que fundamenta os direitos naturais. A visão cristã de que o ser humano foi criado à imagem e semelhança de Deus confere à pessoa uma dignidade intrínseca, imutável e universal. Essa dignidade não depende de fatores externos, como consenso social ou poder político, mas é uma característica inerente ao ser humano pela sua criação divina. A partir dessa perspectiva teológica, torna-se possível afirmar com base sólida que os direitos naturais são dados por Deus e, portanto, são universais e vinculantes.
O cristianismo também é a base de um sistema moral que distingue claramente justiça de legalidade. O Estado pode criar leis, mas isso não significa que essas leis sejam justas. A justiça, sob a ótica cristã, é uma expressão da ordem moral objetiva, algo que transcende as leis humanas e é definido pela vontade divina. Por isso, o libertarianismo cristão vê a agressão como uma violação de uma ordem moral objetiva, e não apenas uma violação de uma convenção social ou de um acordo utilitário.
Se a moralidade e os direitos naturais não forem fundamentados em um Logos criador e legislador, o que acontece é que o conceito de direito natural degenera para algo mais frágil, como um simples acordo utilitário. Nesse cenário, os direitos do indivíduo se tornam algo acordado entre os membros de uma sociedade, em vez de princípios imutáveis e universais. Os direitos podem ser negociados, alterados ou ignorados conforme o interesse do momento.
IV. Fundamento científico: a racionalidade moderna é filha da fé cristã
A ciência moderna só foi possível no contexto cultural cristão. Nenhuma outra civilização — nem a grega, nem a islâmica, nem a chinesa — produziu o método científico como o Ocidente cristão o fez.
Isso se deve a quatro premissas teológicas:
-
Criação racional: O mundo é ordenado por um Deus racional.
-
Distinção entre Criador e criatura: A natureza não é divina e pode ser estudada sem sacrilégio.
-
Valor do trabalho e da observação empírica, herdado do monaquismo.
-
Autonomia institucional, presente nas universidades medievais.
A doutrina cristã da Criação ex nihilo ensina que o mundo foi criado por um Deus racional, sábio e pessoal. Portanto, o cosmos é ordenado, possui leis, e pode ser compreendido pela razão humana — que é imagem do Criador. Isso contrasta fortemente com as cosmovisões panteístas ou mitológicas, onde o mundo é cíclico, arbitrário ou habitado por forças caprichosas.
Sem essa fé no Logos criador, não há razão para crer que a natureza tenha uma ordem inteligível universal e constante, que pode ser descoberta por observação e dedução. A ciência moderna só é possível porque, antes de investigar a natureza, pressupôs-se que ela era investigável — e isso foi uma herança direta do pensamento cristão.
Homens como Bacon, Newton, Kepler e Galileu viam na ciência um modo de glorificar o Criador. O ateísmo cientificista é, portanto, parasitário da teologia cristã, pois toma seus frutos e rejeita suas raízes. A ciência moderna nasceu como filha legítima da fé cristã. E os que hoje a usam contra sua mãe, ou são ingratos, ou ignorantes.
V. O cristianismo como barreira à revolução cultural
O cristianismo é a barreira mais sólida contra a infiltração revolucionária. A chamada "marcha gramsciana", que visa corroer os fundamentos morais da sociedade para subjugar o indivíduo ao coletivo, encontra sua resistência mais firme nos princípios cristãos. A fé cristã, ao proclamar a existência de uma verdade objetiva, de uma lei moral imutável e de uma dignidade humana que transcende o Estado e o consenso social, imuniza a civilização contra o relativismo e o igualitarismo nivelador do marxismo cultural.
Além disso, o cristianismo é uma tradição milenar, profundamente enraizada no cotidiano das pessoas, não sendo uma novidade a ser imposta ou implementada, mas uma força presente há séculos, que permeia a estrutura social, moral e cultural da sociedade. Sua presença constante nas comunidades, desde os tempos mais antigos, oferece uma resistência robusta contra qualquer tentativa de subverter a ordem natural e moral estabelecida.
Não por acaso, tanto Karl Marx quanto Antonio Gramsci identificaram no cristianismo o principal obstáculo à realização de seus projetos revolucionários. Marx chamou a religião de "ópio do povo" porque sabia que uma alma ancorada em Deus não se submete facilmente ao poder terreno; Gramsci, mais sutil, propôs a destruição da cultura cristã como pré-condição para o triunfo do socialismo. Sem essa âncora transcendente, a sociedade torna-se presa fácil das engenharias sociais que pretendem redefinir arbitrariamente o homem, a família e a liberdade.
Conclusão
O libertário anticristão, consciente ou não, nega as fundações mesmas do edifício que habita. Ao rejeitar o cristianismo, cava o abismo sob os próprios pés, privando o ideal libertário de sua base moral, cultural e racional. Ele defende a ética voluntária, a liberdade individual e a ordem espontânea, mas sem o solo metafísico e histórico que torna esses princípios inteligíveis e possíveis. É um erro tentar preservar a liberdade em termos absolutos sem reconhecer as raízes cristãs que a sustentam, pois o cristianismo é a única tradição que a legitima e a viabiliza.
Negar o cristianismo é racionalmente insustentável. A liberdade, como a conhecemos, é filha da fé cristã, que oferece a base moral e metafísica que torna a liberdade tanto desejável quanto possível. Mesmo que ateu, o libertário que ama a liberdade deveria, no mínimo, respeitar — e, idealmente, redescobrir — essas raízes cristãs. Pois sem fé, restam apenas o niilismo e o relativismo, que, eventualmente, desaguam na servidão.
Como nos ensina a tradição: Ubi fides ibi libertas — onde há fé, há liberdade.
-
-
 @ 29313cc9:a6bf155e
2025-05-30 06:35:56
@ 29313cc9:a6bf155e
2025-05-30 06:35:56I thought i'd experiment with this Nostr blogging thing and write a short article on the state of Meshtastic and its alternatives.
For years Meshtastic was the only game in town, there wasn't a lot of users but the authors kept plugging away and it has become a thriving ecosystem of open source hardware, software, tools and social scene.
Meshtastic has always been focused on node to node messaging, in particular one of the use cases specifically mentioned was hiking in the wilderness or skiing in the mountains and being able to use these devices off-grid, perhaps even without a phone to communicate with one and other. The project does have a few other features like telemetry, remote admin, packet data etc but the messaging was the focus. Because of this focus, the core functionality needs to be built into the firmware of these low powered devices like ESP32 for example. This restricts what can be done in terms of CPU power and storage, but also makes synchronization between device and phone cumbersome.
Unfortunately, as a messaging platform, Meshtastic still struggles even after all these years. Message delivery and routing are fairly unreliable, 95% of conversations go along the lines of "hello, test, anyone there?". Now I should mention, if you have a very good signal to your peers the reliability can be good, but even then its not a guarantee.
Early on in the Meshtastic journey I stumbled upon a similar project named Reticulum which can utilize the same LoRa based hardware but aims to be a more comprehensive platform for decentralized communications and currently requires a computer or raspberry pi to run the Python backend alongside the LoRa hardware as a radio. Reticulum has historically been a less polished UI experience and a little idiosyncratic in its design which has probably hindered its adoption a little. But the main difference to Meshtastic is Reticulum requires bigger hardware and is less suitable for remote installations, solar powered setups etc. My understanding is once v1.0 has been released (soon) there may be efforts to port the code to native C which may allow hardware nodes to run as repeaters on their own.
More recently a new project has been announced called Meshcore, which is more closely aligned with Meshtastic than Reticulum, Meshcore makes several important improvements to message delivery and routing in an attempt to improve the reliability of the core feature, messaging. Popular Youtube channel Andy Kirby has been central in helping Meshcore gain popularity and I think he may be involved in the commercial aspects of the project. The smartphone apps and website mapping and flasher tools are a bit more polished with Meshcore.
One of the biggest contributors in the space is Liam Cottle who has created mapping websites for Meshtastic & Meshcore, he also built the Meshcore smartphone app and built the fantastic Reticulum MeshChat UI.
With all this new competition Meshtastic appears to be pushing out more frequent updates and whilst they have been introducing more bugs into the software it is nice to see some faster progress.
In my opinion Reticulum is probably the most interesting project with the most potential, but they do need to get the core routing engine running standalone on low powered hardware for the project to expand to more hardware/radio focused users.
That is all. Mesh on!
-
 @ c1e9ab3a:9cb56b43
2025-05-27 16:19:06
@ c1e9ab3a:9cb56b43
2025-05-27 16:19:06Star Wars is often viewed as a myth of rebellion, freedom, and resistance to tyranny. The iconography—scrappy rebels, totalitarian stormtroopers, lone smugglers—suggests a deep anti-authoritarian ethos. Yet, beneath the surface, the narrative arc of Star Wars consistently affirms the necessity, even sanctity, of central authority. This blog entry introduces the question: Is Star Wars fundamentally a celebration of statism?
Rebellion as Restoration, Not Revolution
The Rebel Alliance’s mission is not to dismantle centralized power, but to restore the Galactic Republic—a bureaucratic, centrally governed institution. Characters like Mon Mothma and Bail Organa are high-ranking senators, not populist revolutionaries. The goal is to remove the corrupt Empire and reinstall a previous central authority, presumed to be just.
- Rebels are loyalists to a prior state structure.
- Power is not questioned, only who wields it.
Jedi as Centralized Moral Elites
The Jedi, often idealized as protectors of peace, are unelected, extra-legal enforcers of moral and military order. Their authority stems from esoteric metaphysical abilities rather than democratic legitimacy.
- They answer only to their internal Council.
- They are deployed by the Senate, but act independently of civil law.
- Their collapse is depicted as tragic not because they were unaccountable, but because they were betrayed.
This positions them as a theocratic elite, not spiritual anarchists.
Chaos and the Frontier: The Case of the Cantina
The Mos Eisley cantina, often viewed as a symbol of frontier freedom, reveals something darker. It is: - Lawless - Violent - Culturally fragmented
Conflict resolution occurs through murder, not mediation. Obi-Wan slices off a limb; Han shoots first—both without legal consequence. There is no evidence of property rights, dispute resolution, or voluntary order.
This is not libertarian pluralism—it’s moral entropy. The message: without centralized governance, barbarism reigns.
The Mythic Arc: Restoration of the Just State
Every trilogy in the saga returns to a single theme: the fall and redemption of legitimate authority.
- Prequels: Republic collapses into tyranny.
- Originals: Rebels fight to restore legitimate order.
- Sequels: Weak governance leads to resurgence of authoritarianism; heroes must reestablish moral centralism.
The story is not anti-state—it’s anti-bad state. The solution is never decentralization; it’s the return of the right ruler or order.
Conclusion: The Hidden Statism of a Rebel Myth
Star Wars wears the costume of rebellion, but tells the story of centralized salvation. It: - Validates elite moral authority (Jedi) - Romanticizes restoration of fallen governments (Republic) - Portrays decentralized zones as corrupt and savage (outer rim worlds)
It is not an anarchist parable, nor a libertarian fable. It is a statist mythology, clothed in the spectacle of rebellion. Its core message is not that power should be abolished, but that power belongs to the virtuous few.
Question to Consider:
If the Star Wars universe consistently affirms the need for centralized moral and political authority, should we continue to see it as a myth of freedom? Or is it time to recognize it as a narrative of benevolent empire? -
 @ c9badfea:610f861a
2025-05-24 12:55:17
@ c9badfea:610f861a
2025-05-24 12:55:17Before you post a message or article online, let the LLM check if you are leaking any personal information using this prompt:
Analyze the following text to identify any Personally Identifiable Information (PII): <Your Message>Replace
<Your Message>with your textIf no PII is found, continue by modifying your message to detach it from your personality. You can use any of the following prompts (and further modify it if necessary).
Prompt № 1 - Reddit-Style
Convert the message into a casual, Reddit-style post without losing meaning. Split the message into shorter statements with the same overall meaning. Here is the message: <Your Message>Prompt № 2 - Advanced Modifications
``` Apply the following modifications to the message: - Rewrite it in lowercase - Use "u" instead of "you" - Use "akchoaly" instead of "actually" - Use "hav" instead of "have" - Use "tgat" instead of "that" - Use comma instead of period - Use British English grammar
Here is the message:
``` Prompt № 3 - Neutral Tone
Rewrite the message to correct grammar errors, and ensure the tone is neutral and free of emotional language: <Your Message>Prompt № 4 - Cross Translation Technique
Translate the message into Chinese, then translate the resulting Chinese text back into English. Provide only the final English translation. Here is the message: <Your Message>Check the modified message and send it.
ℹ️ You can use dialects to obfuscate your language further. For example, if you are from the US, you can tell the LLM to use British grammar and vice versa.
⚠️ Always verify the results. Don't fully trust an LLM.
-
 @ dfa02707:41ca50e3
2025-05-30 03:01:50
@ dfa02707:41ca50e3
2025-05-30 03:01:50Contribute to keep No Bullshit Bitcoin news going.
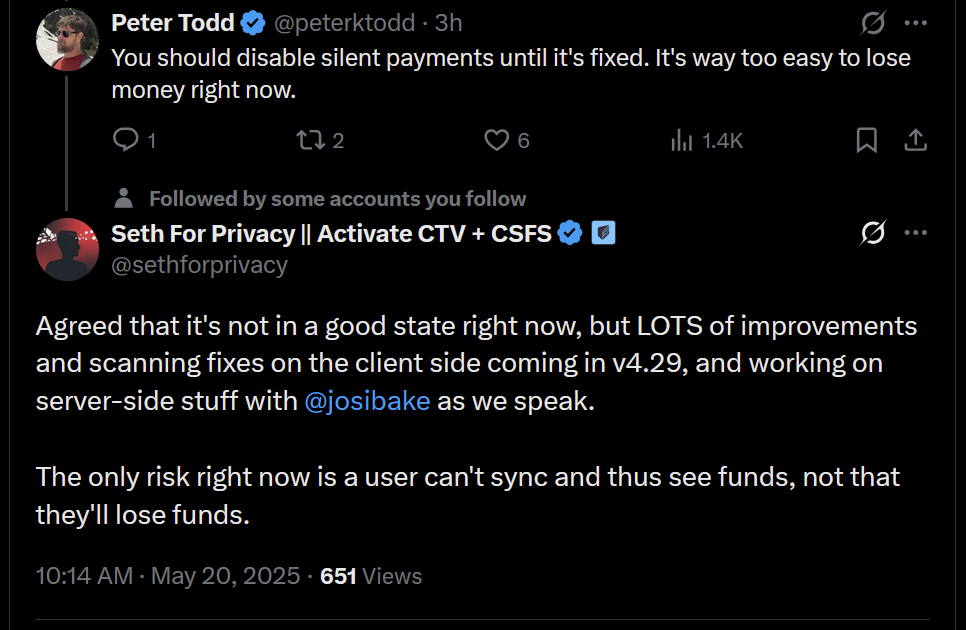
- The latest firmware updates for COLDCARD devices introduce two major features: COLDCARD Co-sign (CCC) and Key Teleport between two COLDCARD Q devices using QR codes and/or NFC with a website.

What's new
- COLDCARD Co-Sign: When CCC is enabled, a second seed called the Spending Policy Key (Key C) is added to the device. This seed works with the device's Main Seed and one or more additional XPUBs (Backup Keys) to form 2-of-N multisig wallets.
- The spending policy functions like a hardware security module (HSM), enforcing rules such as magnitude and velocity limits, address whitelisting, and 2FA authentication to protect funds while maintaining flexibility and control, and is enforced each time the Spending Policy Key is used for signing.
- When spending conditions are met, the COLDCARD signs the partially signed bitcoin transaction (PSBT) with the Main Seed and Spending Policy Key for fund access. Once configured, the Spending Policy Key is required to view or change the policy, and violations are denied without explanation.
"You can override the spending policy at any time by signing with either a Backup Key and the Main Seed or two Backup Keys, depending on the number of keys (N) in the multisig."
-
A step-by-step guide for setting up CCC is available here.
-
Key Teleport for Q devices allows users to securely transfer sensitive data such as seed phrases (words, xprv), secure notes and passwords, and PSBTs for multisig. It uses QR codes or NFC, along with a helper website, to ensure reliable transmission, keeping your sensitive data protected throughout the process.
- For more technical details, see the protocol spec.
"After you sign a multisig PSBT, you have option to “Key Teleport” the PSBT file to any one of the other signers in the wallet. We already have a shared pubkey with them, so the process is simple and does not require any action on their part in advance. Plus, starting in this firmware release, COLDCARD can finalize multisig transactions, so the last signer can publish the signed transaction via PushTX (NFC tap) to get it on the blockchain directly."
- Multisig transactions are finalized when sufficiently signed. It streamlines the use of PushTX with multisig wallets.
- Signing artifacts re-export to various media. Users are now provided with the capability to export signing products, like transactions or PSBTs, to alternative media rather than the original source. For example, if a PSBT is received through a QR code, it can be signed and saved onto an SD card if needed.
- Multisig export files are signed now. Public keys are encoded as P2PKH address for all multisg signature exports. Learn more about it here.
- NFC export usability upgrade: NFC keeps exporting until CANCEL/X is pressed.
- Added Bitcoin Safe option to Export Wallet.
- 10% performance improvement in USB upload speed for large files.
- Q: Always choose the biggest possible display size for QR.
Fixes
- Do not allow change Main PIN to same value already used as Trick PIN, even if Trick PIN is hidden.
- Fix stuck progress bar under
Receiving...after a USB communications failure. - Showing derivation path in Address Explorer for root key (m) showed double slash (//).
- Can restore developer backup with custom password other than 12 words format.
- Virtual Disk auto mode ignores already signed PSBTs (with “-signed” in file name).
- Virtual Disk auto mode stuck on “Reading…” screen sometimes.
- Finalization of foreign inputs from partial signatures. Thanks Christian Uebber!
- Temporary seed from COLDCARD backup failed to load stored multisig wallets.
Destroy Seedalso removes all Trick PINs from SE2.Lock Down Seedrequires pressing confirm key (4) to execute.- Q only: Only BBQr is allowed to export Coldcard, Core, and pretty descriptor.

-
 @ dfa02707:41ca50e3
2025-05-30 07:02:10
@ dfa02707:41ca50e3
2025-05-30 07:02:10Contribute to keep No Bullshit Bitcoin news going.
- Coinswap is a decentralized protocol for private, trustless cryptocurrency swaps. It allows participants to securely swap digital assets without intermediaries, using advanced cryptographic techniques and atomic swaps to ensure privacy and security.
- This release introduces major improvements to the protocol's efficiency, security, and usability, including custom in-memory UTXO indexes, more advanced coin-selection algorithms, fidelity bond management and more.
- The update also improves user experience with full Mac support, faster Tor connections, enhanced UI/UX, a unified API, and improved protocol documentation.
"The Project is under active beta development and open for contributions and beta testing. The Coinswap market place is live in testnet4. Bug fixes and feature requests are very much welcome."
- Manuals and demo docs are available here.
What's new
- Core protocol and performance improvements:
- Custom in-memory UTXO indexes. Frequent Core RPC calls, which caused significant delays, have been eliminated by implementing custom in-memory UTXO indexes. These indexes are also saved to disk, leading to faster wallet synchronization.
- Coin selection. Advanced coin-selection algorithms, like those in Bitcoin Core, have been incorporated, enhancing the efficiency of creating different types of transactions.
- Fidelity management. Maker servers now automate tasks such as checking bond expiries, redemption, and recreation for Fidelity Bonds, reducing the user's management responsibilities.
- Taker liveness. The
WaitingFundingConfirmationmessage has been added to keep swap connections between Takers and Makers, assisting with variable block confirmation delays.
-
User experience and compatibility:
- Mac compatibility. The crate and apps now fully support Mac.
- Tor operations are streamlined for faster, more resilient connections. Tor addresses are now consistently linked to the wallet seed, maintaining the same onion address through system reboots.
- The UI/UX improvements enhance the display of balances, UTXOs, offer data, fidelity bonds, and system logs. These updates make the apps more enjoyable and provide clearer coin swap logs during the swap process.
-
API design improvements. Transaction creation routines have been streamlined to use a single common API, which reduces technical debt and eliminates redundant code.
- Protocol spec documentation now details how Coinswap breaks the transaction graph and improves privacy through routed swaps and amount splitting, and includes diagrams for clarity.
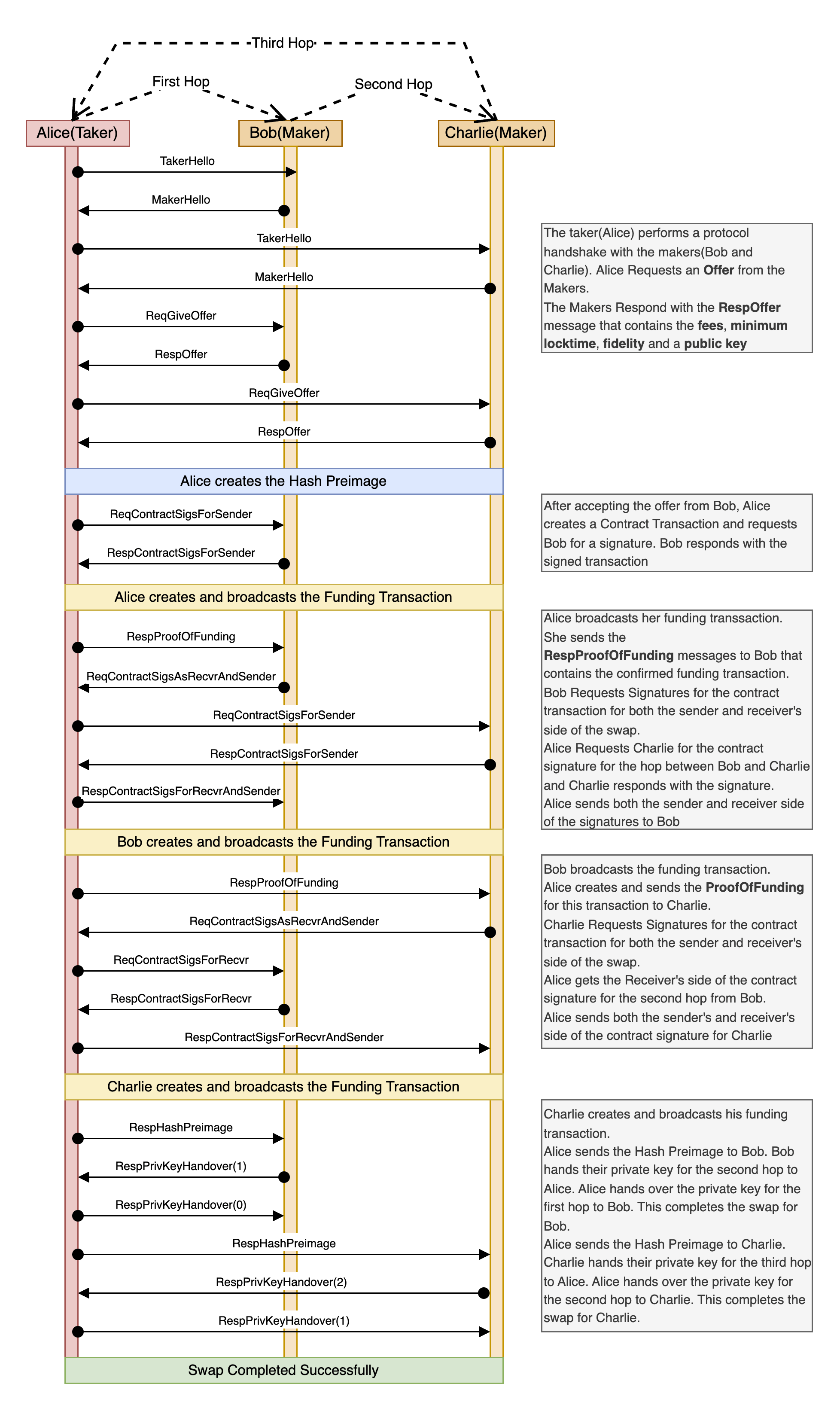
Source: Coinswap Protocol specification.

-
 @ 33baa074:3bb3a297
2025-05-28 08:54:40
@ 33baa074:3bb3a297
2025-05-28 08:54:40COD (chemical oxygen demand) sensors play a vital role in water quality testing. Their main functions include real-time monitoring, pollution event warning, water quality assessment and pollution source tracking. The following are the specific roles and applications of COD sensors in water quality testing:
Real-time monitoring and data acquisition COD sensors can monitor the COD content in water bodies in real time and continuously. Compared with traditional sampling methods, COD sensors are fast and accurate, without manual sampling and laboratory testing, which greatly saves time and labor costs. By combining with the data acquisition system, the monitoring data can be uploaded to the cloud in real time to form a extemporization distribution map of the COD content in the water body, providing detailed data support for environmental monitoring and management.
Pollution event warning and rapid response COD sensors play an important role in early warning and rapid response in water environment monitoring. Once there is an abnormal increase in organic matter in the water body, the COD sensor can quickly detect the change in COD content and alarm through the preset threshold. This enables relevant departments to take measures at the early stage of the pollution incident to prevent the spread of pollution and protect the water environment.
Water quality assessment and pollution source tracking COD sensors play an important role in water quality assessment and pollution source tracking. By continuously monitoring the COD content in water bodies, the water quality can be evaluated and compared with national and regional water quality standards. At the same time, COD sensors can also help determine and track the location and spread of pollution sources, provide accurate data support for environmental management departments, and guide the development of pollution prevention and control work.
Application scenarios COD sensors are widely used in various water quality monitoring scenarios, including but not limited to: Sewage treatment plants: used to monitor the COD content of in fluent and effluent to ensure the effect of sewage treatment. Water source protection and management: deployed in water sources to monitor the COD content of in fluent sources. Once the water quality exceeds the set limit, the system will issue an alarm in time to ensure water quality safety. Lake and river monitoring: deployed in water bodies such as lakes and rivers to monitor the COD content of water bodies in real time.

Technical features of COD sensor COD sensor uses advanced technology, such as ultraviolet absorption method, which does not require the use of chemical reagents, avoiding the risk of contamination of chemical reagents in traditional COD detection methods, and can achieve online uninterrupted water quality monitoring, providing strong support for real-time water quality assessment. In addition, COD sensor also has the advantages of low cost, high stability, strong anti-interference ability, and convenient installation.
Summary In summary, COD sensor plays an irreplaceable role in water quality detection. It can not only provide real-time and accurate water quality data, but also quickly warn when pollution incidents occur, providing strong technical support for water quality management and environmental protection. With the advancement of technology and the popularization of applications, COD sensor will play a more important role in water quality monitoring in the future.
-
 @ dfa02707:41ca50e3
2025-05-30 07:02:10
@ dfa02707:41ca50e3
2025-05-30 07:02:10Contribute to keep No Bullshit Bitcoin news going.
- The latest firmware updates for COLDCARD devices introduce two major features: COLDCARD Co-sign (CCC) and Key Teleport between two COLDCARD Q devices using QR codes and/or NFC with a website.

What's new
- COLDCARD Co-Sign: When CCC is enabled, a second seed called the Spending Policy Key (Key C) is added to the device. This seed works with the device's Main Seed and one or more additional XPUBs (Backup Keys) to form 2-of-N multisig wallets.
- The spending policy functions like a hardware security module (HSM), enforcing rules such as magnitude and velocity limits, address whitelisting, and 2FA authentication to protect funds while maintaining flexibility and control, and is enforced each time the Spending Policy Key is used for signing.
- When spending conditions are met, the COLDCARD signs the partially signed bitcoin transaction (PSBT) with the Main Seed and Spending Policy Key for fund access. Once configured, the Spending Policy Key is required to view or change the policy, and violations are denied without explanation.
"You can override the spending policy at any time by signing with either a Backup Key and the Main Seed or two Backup Keys, depending on the number of keys (N) in the multisig."
-
A step-by-step guide for setting up CCC is available here.
-
Key Teleport for Q devices allows users to securely transfer sensitive data such as seed phrases (words, xprv), secure notes and passwords, and PSBTs for multisig. It uses QR codes or NFC, along with a helper website, to ensure reliable transmission, keeping your sensitive data protected throughout the process.
- For more technical details, see the protocol spec.
"After you sign a multisig PSBT, you have option to “Key Teleport” the PSBT file to any one of the other signers in the wallet. We already have a shared pubkey with them, so the process is simple and does not require any action on their part in advance. Plus, starting in this firmware release, COLDCARD can finalize multisig transactions, so the last signer can publish the signed transaction via PushTX (NFC tap) to get it on the blockchain directly."
- Multisig transactions are finalized when sufficiently signed. It streamlines the use of PushTX with multisig wallets.
- Signing artifacts re-export to various media. Users are now provided with the capability to export signing products, like transactions or PSBTs, to alternative media rather than the original source. For example, if a PSBT is received through a QR code, it can be signed and saved onto an SD card if needed.
- Multisig export files are signed now. Public keys are encoded as P2PKH address for all multisg signature exports. Learn more about it here.
- NFC export usability upgrade: NFC keeps exporting until CANCEL/X is pressed.
- Added Bitcoin Safe option to Export Wallet.
- 10% performance improvement in USB upload speed for large files.
- Q: Always choose the biggest possible display size for QR.
Fixes
- Do not allow change Main PIN to same value already used as Trick PIN, even if Trick PIN is hidden.
- Fix stuck progress bar under
Receiving...after a USB communications failure. - Showing derivation path in Address Explorer for root key (m) showed double slash (//).
- Can restore developer backup with custom password other than 12 words format.
- Virtual Disk auto mode ignores already signed PSBTs (with “-signed” in file name).
- Virtual Disk auto mode stuck on “Reading…” screen sometimes.
- Finalization of foreign inputs from partial signatures. Thanks Christian Uebber!
- Temporary seed from COLDCARD backup failed to load stored multisig wallets.
Destroy Seedalso removes all Trick PINs from SE2.Lock Down Seedrequires pressing confirm key (4) to execute.- Q only: Only BBQr is allowed to export Coldcard, Core, and pretty descriptor.

-
 @ 33baa074:3bb3a297
2025-05-28 08:25:13
@ 33baa074:3bb3a297
2025-05-28 08:25:13The oil-in-water sensoris an instrument specially used to detect oil substances in water bodies. Its working principle is mainly based on the characteristic that oil substances will produce fluorescence under ultraviolet light. The following is a detailed explanation:
Principle Overview The oil-in-water sensor uses the characteristic that oil substances will produce fluorescence under ultraviolet light, and measures the fluorescence intensity to infer the concentration of oil substances. Specifically, the sensor uses ultraviolet light as the excitation light source to irradiate the water sample to be tested. After the oil substance absorbs ultraviolet light, it will stimulate fluorescence, and the fluorescence signal is received by the photo detector and converted into an electrical signal. By measuring the strength of the electrical signal, the concentration of oil substances in the water sample can be inferred.
Workflow Ultraviolet light irradiation: The ultraviolet light source inside the sensor emits ultraviolet light and irradiates it into the water sample to be tested.
Fluorescence generation: After the oil substance in the water sample absorbs ultraviolet light, it will stimulate fluorescence.
Fluorescence detection: The photo detector in the sensor measures the intensity of this fluorescence.
Signal conversion: The signal processing circuit converts the output of the photo detector into an electrical signal proportional to the amount of oil in the water. Data analysis: By analyzing the strength of the electrical signal, the concentration of oil substances in the water sample can be obtained.
Features and applications The oil in water sensor has high sensitivity and can detect soluble and falsifiable oils. It is suitable for a variety of water quality monitoring scenarios, such as oil field monitoring, industrial circulating water, condensate water, wastewater treatment, surface water stations, etc. In addition, it can also monitor the content of crude oil (benzene and benzene homologous) in water sources such as reservoirs and water plants in real time online, play an early warning role, and protect the safety of water sources.
Practical application The oil in water sensor has a wide range of functions in practical applications, including but not limited to the following aspects: Monitoring the water quality of water sources: ensuring the safety of drinking water, and timely discovering pollution sources and ensuring water supply safety by continuously monitoring oil substances in water sources. Monitoring sewage treatment plant emissions: ensuring that the discharge water quality of sewage treatment plants meets the emission standards to avoid secondary pollution to the environment. Monitoring rivers, lakes and other water bodies: assessing the pollution status and providing a basis for pollution control. Early warning and emergency response: It has real-time monitoring and early warning functions, and can issue an alarm in time when abnormal conditions are found, providing valuable time for emergency response and reducing losses caused by pollution. Scientific research: Through the monitoring data of this sensor, we can deeply understand the distribution, migration and transformation of oil substances in water bodies, and provide a scientific basis for environmental protection and governance.
In summary, the oil in water sensor monitors the oil content in water bodies through ultraviolet fluorescence method, has high sensitivity and broad application prospects, and is an indispensable and important tool in modern environmental monitoring and industrial production.
-
 @ 33baa074:3bb3a297
2025-05-28 08:10:17
@ 33baa074:3bb3a297
2025-05-28 08:10:17The control of residual chlorine in swimming pools is an important part of water quality management, which aims to ensure the sanitation and safety of swimming pool water while avoiding discomfort to swimmers. Here are some key points about residual chlorine control in swimming pools:
Standards for residual chlorine According to the regulations of the national health supervision department, the residual chlorine in swimming pool water should be kept between 0.3mg/L-1.5mg/L. This range can not only ensure effective disinfection, but also avoid irritation to swimmers' skin and eyes caused by excessive residual chlorine. Too low residual chlorine will lead to incomplete disinfection and increase the risk of bacterial growth; while too high residual chlorine may cause human discomfort and even poisoning.
 The role of residual chlorine
Residual chlorine is a residual disinfectant in swimming pool water, usually in the form of sodium hypocrite (NaClO). It has strong oxidizing properties and can effectively kill bacteria, viruses and other microorganisms in water, thereby ensuring the health of swimmers. In addition, residual chlorine can eliminate harmful substances such as organic matter and ammonia in water to keep the water clean.
The role of residual chlorine
Residual chlorine is a residual disinfectant in swimming pool water, usually in the form of sodium hypocrite (NaClO). It has strong oxidizing properties and can effectively kill bacteria, viruses and other microorganisms in water, thereby ensuring the health of swimmers. In addition, residual chlorine can eliminate harmful substances such as organic matter and ammonia in water to keep the water clean.Residual chlorine detection method The method of detecting residual chlorine in swimming pools usually uses test strips or test kits for qualitative or quantitative detection. In addition, online monitoring instruments can be used to monitor the residual chlorine in the swimming pool in real time. These methods can help managers promptly detect and deal with situations where the residual chlorine content is too high or too low, ensuring that the water quality of the swimming pool meets the standards.
Methods for controlling residual chlorine Reasonable addition of disinfectants: According to the water quality of the swimming pool and the number of swimmers, reasonable addition of disinfectants to control the residual chlorine content within the specified range.
Regular testing: Regularly test the residual chlorine in the swimming pool to promptly detect and deal with situations where the residual chlorine content is too high or too low.
Maintain swimming pool equipment: Regularly check and maintain swimming pool equipment to ensure the water treatment effect and circulation filtration are normal, and reduce residual disinfectants and other harmful substances in the water.
Do a good job in swimmer hygiene management: Strengthen swimmer hygiene management, require swimmers to shower and rinse their feet before entering the pool, and reduce pollution sources entering the swimming pool.
Solution for excessive residual chlorine If the residual chlorine content in the swimming pool exceeds the standard range, the following measures can be taken:
Use decorating agent: Use decorating agent to quickly restore the excessive residual chlorine in the swimming pool to the normal range (0.3~0.5mg/L). This method is applicable to excessive residual chlorine caused by excessive addition of chlorine disinfectant.
Adjust the water treatment process: According to the water quality, adjust the water treatment process appropriately, such as selecting the appropriate type and dosage of disinfectant, and adjusting operating parameters such as flow rate, pH value, etc., to reduce the generation of residual chlorine.
Strengthen equipment maintenance: Regularly maintain and maintain the water treatment equipment of the swimming pool to ensure its normal operation and disinfection effect.
Through the above methods, the residual chlorine content in the swimming pool can be effectively controlled to ensure water quality safety and protect the health of swimmers.
-
 @ b7274d28:c99628cb
2025-05-28 01:11:43
@ b7274d28:c99628cb
2025-05-28 01:11:43In this second installment of The Android Elite Setup tutorial series, we will cover installing the nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8 on your #Android device and browsing for apps you may be interested in trying out.
Since the #Zapstore is a direct competitor to the Google Play Store, you're not going to be able to find and install it from there like you may be used to with other apps. Instead, you will need to install it directly from the developer's GitHub page. This is not a complicated process, but it is outside the normal flow of searching on the Play Store, tapping install, and you're done.
Installation
From any web browser on your Android phone, navigate to the Zapstore GitHub Releases page and the most recent version will be listed at the top of the page. The .apk file for you to download and install will be listed in the "Assets."
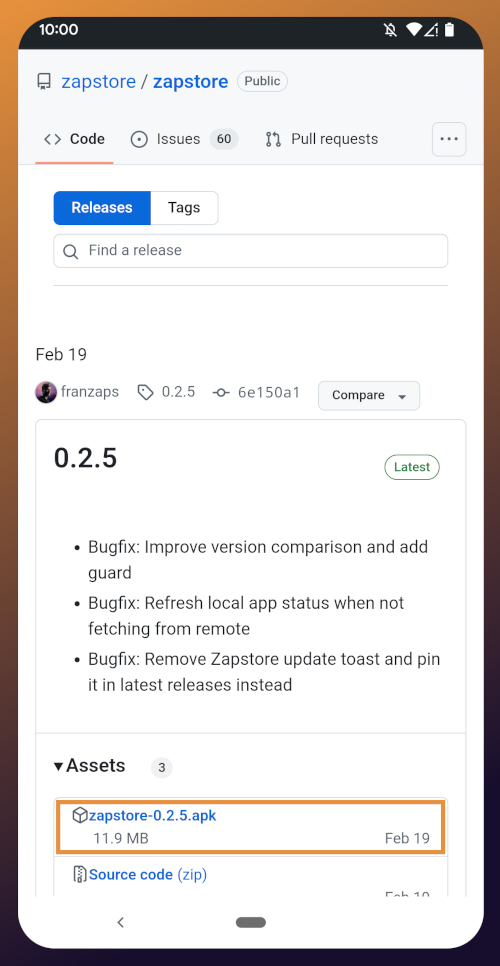
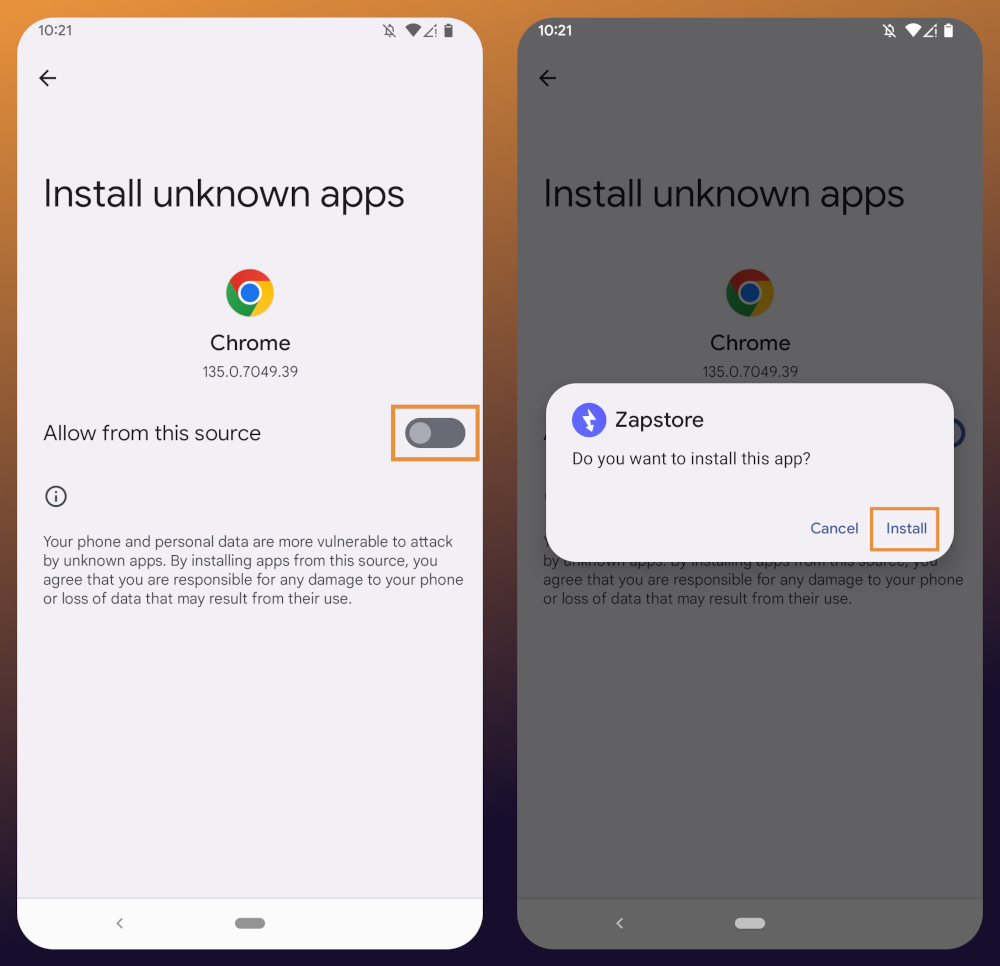
Tap the .apk to download it, and you should get a notification when the download has completed, with a prompt to open the file.
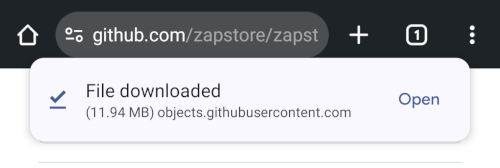
You will likely be presented with a prompt warning you that your phone currently isn't allowed to install applications from "unknown sources." Anywhere other than the Play Store is considered an "unknown source" by default. However, you can manually allow installation from unknown sources in the settings, which the prompt gives you the option to do.
In the settings page that opens, toggle it to allow installation from this source, and you should be prompted to install the application. If you aren't, simply go to your web browser's downloads and tap on the .apk file again, or go into your file browser app and you should find the .apk in your Downloads folder.
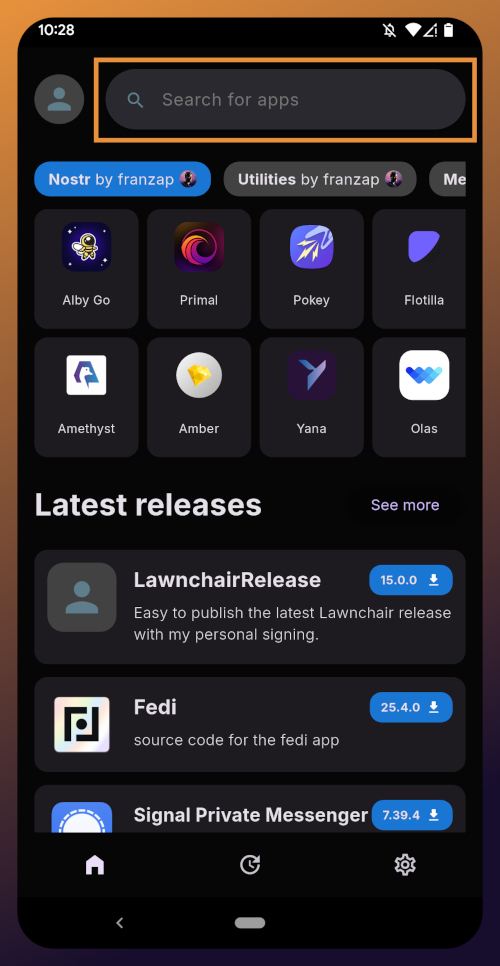
If the application doesn't open automatically after install, you will find it in your app drawer.

Home Page
Right at the top of the home page in the Zapstore is the search bar. You can use it to find a specific app you know is available in the Zapstore.
There are quite a lot of open source apps available, and more being added all the time. Most are added by the Zapstore developer, nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9, but some are added by the app developers themselves, especially Nostr apps. All of the applications we will be installing through the Zapstore have been added by their developers and are cryptographically signed, so you know that what you download is what the developer actually released.
The next section is for app discovery. There are curated app collections to peruse for ideas about what you may want to install. As you can see, all of the other apps we will be installing are listed in nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9's "Nostr" collection.
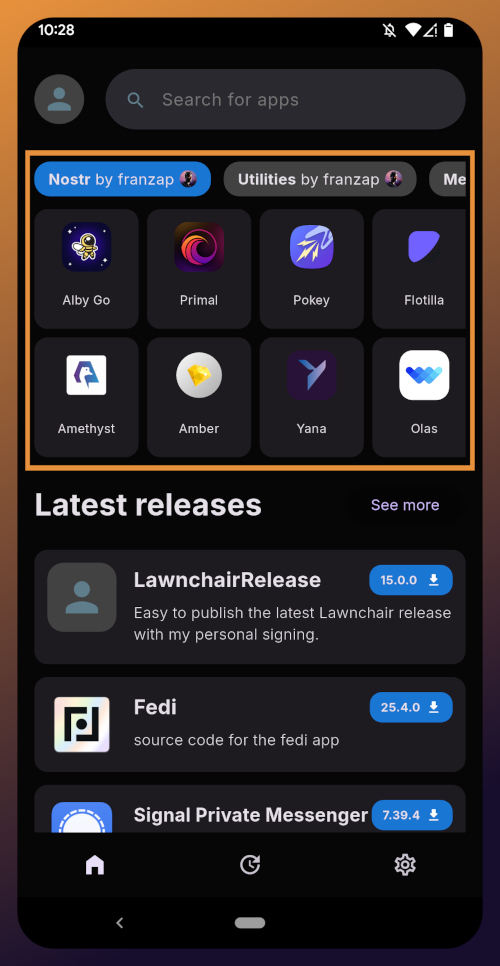
In future releases of the Zapstore, users will be able to create their own app collections.
The last section of the home page is a chronological list of the latest releases. This includes both new apps added to the Zapstore and recently updated apps. The list of recent releases on its own can be a great resource for discovering apps you may not have heard of before.
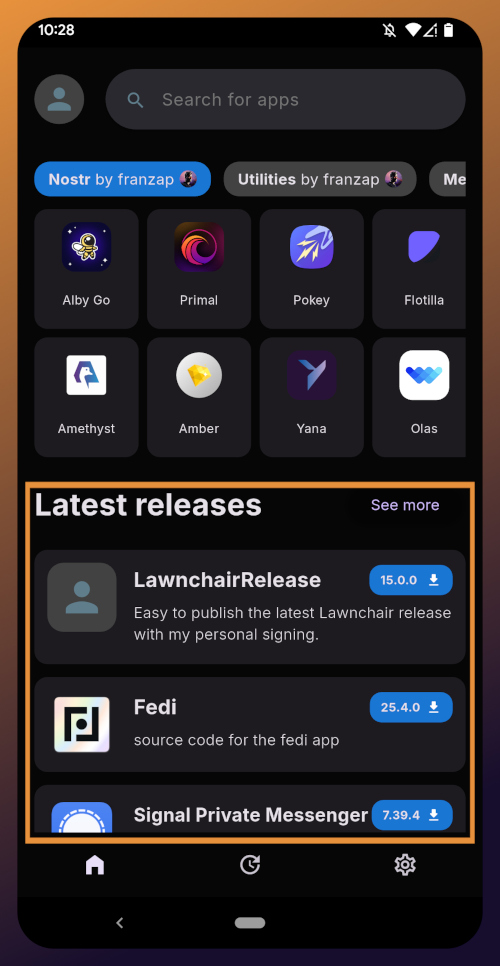
Installed Apps
The next page of the app, accessed by the icon in the bottom-center of the screen that looks like a clock with an arrow circling it, shows all apps you have installed that are available in the Zapstore. It's also where you will find apps you have previously installed that are ready to be updated. This page is pretty sparse on my test profile, since I only have the Zapstore itself installed, so here is a look at it on my main profile:

The "Disabled Apps" at the top are usually applications that were installed via the Play Store or some other means, but are also available in the Zapstore. You may be surprised to see that some of the apps you already have installed on your device are also available on the Zapstore. However, to manage their updates though the Zapstore, you would need to uninstall the app and reinstall it from the Zapstore instead. I only recommend doing this for applications that are added to the Zapstore by their developers, or you may encounter a significant delay between a new update being released for the app and when that update is available on the Zapstore.
Tap on one of your apps in the list to see whether the app is added by the developer, or by the Zapstore. This takes you to the application's page, and you may see a warning at the top if the app was not installed through the Zapstore.
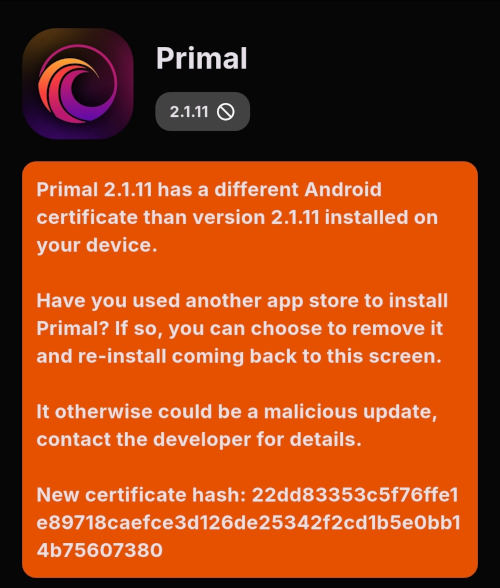
Scroll down the page a bit and you will see who signed the release that is available on the Zapstore.
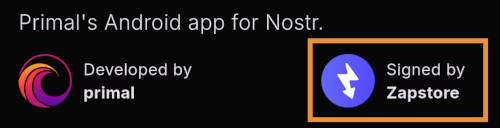
In the case of Primal, even though the developer is on Nostr, they are not signing their own releases to the Zapstore yet. This means there will likely be a delay between Primal releasing an update and that update being available on the Zapstore.
Settings
The last page of the app is the settings page, found by tapping the cog at the bottom right.
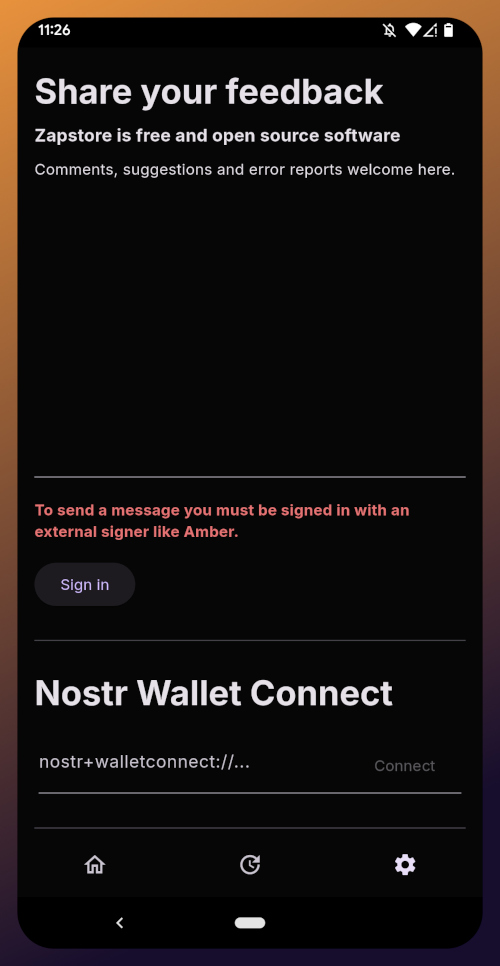
Here you can send the Zapstore developer feedback directly (if you are logged in), connect a Lightning wallet using Nostr Wallet Connect, delete your local cache, and view some system information.
We will be adding a connection to our nostr:npub1h2qfjpnxau9k7ja9qkf50043xfpfy8j5v60xsqryef64y44puwnq28w8ch wallet in part 5 of this tutorial series.
For the time being, we are all set with the Zapstore and ready for the next stage of our journey.
Continue to Part 3: Amber Signer. Nostr link: nostr:naddr1qqxnzde5xuengdeexcmnvv3eqgstwf6d9r37nqalwgxmfd9p9gclt3l0yc3jp5zuyhkfqjy6extz3jcrqsqqqa28qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qg6waehxw309aex2mrp0yhxyunfva58gcn0d36zumn9wss80nug
-
 @ 33baa074:3bb3a297
2025-05-28 07:50:06
@ 33baa074:3bb3a297
2025-05-28 07:50:06Soil moisture is a key factor that affects the structure and function of soil microbial communities. Here are some of the main aspects of how soil moisture affects microorganisms:
Affecting the Growth and Metabolism of Microorganisms Changes in soil moisture content directly affect the growth and metabolic activities of microorganisms. Under suitable moisture conditions, microorganisms are better able to carry out metabolic activities, thereby promoting the decomposition of soil organic matter and the transformation of nutrients. However, under extremely dry or overly wet conditions, the activity of microorganisms will be inhibited, resulting in a decline in soil functions.

Changing the Structure of Microbial Communities Changes in soil moisture conditions can lead to significant changes in the structure of microbial communities. For example, under drought conditions, the number of drought-tolerant microorganisms may increase to adapt to the water shortage environment. While under wet conditions, aerobic microorganisms may dominate. This change in community structure not only affects the soil's water retention capacity, but also other ecological functions of the soil.
Affecting the Stability of Soil Aggregates Soil aggregates are clumps formed by soil particles through physical, chemical and biological actions, and they have an important impact on the soil's water retention capacity. Soil microorganisms participate in the formation and stability of soil aggregates by secreting substances such as extracellular polymers. Appropriate soil moisture helps maintain the stability of soil aggregates, thereby improving the soil's water retention capacity. However, excessive moisture or drought may lead to the destruction of soil aggregates and reduce the soil's water retention capacity.
Regulating soil moisture dynamics Soil microorganisms can regulate the dynamic balance of soil moisture through their metabolic activities, such as decomposing organic matter and synthesizing exopolysaccharides. For example, some microorganisms can increase the water holding capacity of the soil by secreting exopolysaccharides, while others can release water by decomposing organic matter. These activities help maintain the stability of soil moisture and support plant growth.
Influencing the physical properties of soil Soil moisture can also indirectly affect the living environment of microorganisms by affecting the physical properties of the soil, such as pore structure and texture. Good soil pore structure is conducive to the penetration and storage of water, and also provides a suitable living space for microorganisms. Soil texture is closely related to the stability of aggregates. Sandy soils have poor aggregate stability and weak water retention capacity; while clay soils have good aggregate stability and strong water retention capacity.
In summary, soil moisture has many effects on microorganisms, including affecting the growth and metabolism of microorganisms, changing the structure of microbial communities, affecting the stability of soil aggregates, regulating soil moisture dynamics, and affecting the physical properties of soil. Therefore, maintaining suitable soil moisture conditions is of great significance for protecting the diversity and function of soil microbial communities and improving the water retention capacity of soil.
-
 @ 3770c235:16042bcc
2025-05-30 05:25:21
@ 3770c235:16042bcc
2025-05-30 05:25:21Let’s clear something up: frugal living isn’t about eating ramen every night or never treating yourself. It’s about being intentional with your money so you can enjoy what matters more. Think of it like editing a movie—you cut the boring scenes to highlight the best parts. You don’t have to give up lattes, travel, or Friday pizza nights. You just need a few clever tricks to make your money stretch further while keeping the fun intact.
Take my friend Alex, for example. Last year, he felt overwhelmed by credit card debt but didn’t want to give up his weekend hikes or coffee shop visits. By tweaking a few habits—like auditing subscriptions and prioritizing experiences—he paid off $5,000 in debt and still took a camping trip with his kids. The secret? Small, intentional choices that add up. In this guide, we’ll share practical, joy-friendly hacks to help you save smarter. Plus, we’ll mention sites like Crown Money—a budgeting service that makes tracking your progress effortless—so you can focus on living well, not pinching pennies.
**1. Audit Your Subscriptions (Yes, Even That One) ** You know that streaming service you haven’t opened since 2022? Or the gym membership you keep “meaning to use”? Those small charges add up fast. A recent study found the average person spends 219/month on forgotten subscriptions—that’s over 2,600 a year!
• The Hack: Every 3 months, review your subscriptions. Ask: “Do I actually use this?” Cancel anything that doesn’t spark joy. • Pro Tip: Use Crown Money to see all your subscriptions in one place. The app automatically flags recurring charges, so you don’t have to hunt through bank statements. You’ll even get a nudge like, “You’ve paid $14.99/month for ‘Premium Yoga App’—last used 6 months ago. Cancel?” Real-Life Example: Sarah canceled two unused streaming services and a meditation app she forgot about. She saved $45/month—enough to fund her new hobby: pottery classes. “I didn’t realize how much clutter I was paying for,” she said. “Now I’m learning to make mugs instead of binge-watching shows I don’t even like.”
**2. Embrace the “Joy Budget” (Seriously, Budget for Fun) ** Frugality fails when it feels like deprivation. Instead, carve out guilt-free money for things you love. Behavioral scientists call this “temptation bundling”—pairing savings goals with rewards to stay motivated.
• The Hack: Allocate 10–15% of your budget to a “Joy Fund” for hobbies, dining out, or travel. • Pro Tip: In Crown Money, create a custom category like “Adventure Fund” or “Treat Yourself.” Set a monthly limit and track how much you’ve saved for that weekend getaway or concert ticket. The app’s visual progress bars turn saving into a game—imagine watching your “Beach Trip 2024” fund grow with every dollar.
Real-Life Example: Mark loves trying new restaurants. By setting a $100/month “Dining Out” budget in Crown Money, he enjoys date nights without overspending. “I used to feel guilty splurging on sushi,” he shared. “Now I know it’s part of the plan, so I savor every bite.”
- Master Mindful Spending (Ask This One Question) Before buying anything non-essential, ask: “Will this add value to my life, or just clutter?” Retail therapy might feel good in the moment, but that $50 impulse sweater often ends up forgotten in the back of your closet.
• The Hack: Implement a 24-hour “cooling-off” period for impulse buys. If you still want it tomorrow, go for it! • Pro Tip: Use Crown Money to review your spending trends. The app’s monthly reports show where your money goes, helping you spot habits (like late-night online shopping) that don’t align with your goals. Set up alerts like, “You’ve spent $75 on ‘Miscellaneous’ this week—want to check in?” Real-Life Example: Lisa avoided buying a $200 jacket on impulse. After 24 hours, she realized she didn’t need it—and put the money toward a weekend camping trip instead. “I almost bought something I’d wear once,” she laughed. “Now I have photos of sunsets instead of buyer’s remorse.”
- DIY and Swap (Your Wallet Will Thank You) Frugal living thrives on creativity. Swap buying new for: • DIY solutions: Make coffee at home (a $5 bag of beans lasts weeks!), repair clothes, or grow herbs instead of buying them. • Community swaps: Trade books, tools, or skills with friends (e.g., “I’ll babysit if you help me fix my bike”).
Pro Tip: Track your monthly expenses in Crown Money. Create a category like “Homemade Wins” and watch how small choices (like brewing your latte) add up over time. For example, skipping a daily 4 coffee shop visit saves 120/month—that’s a weekend road trip! Real-Life Example: Jake started meal prepping lunches instead of buying 15 salads. He saves 300/month—enough for a monthly massage. “I’m eating healthier and funding self-care,” he said. “Plus, my coworkers are jealous of my teriyaki bowls.”
- Prioritize Experiences Over “Stuff” (Happiness Science Approved) Research shows experiences bring longer-lasting joy than material purchases. A 2023 study found people who spent money on concerts, trips, or classes reported 30% higher life satisfaction than those who bought gadgets or clothes.
Instead of splurging on gadgets, invest in: • Free/low-cost adventures: Hiking, picnics, game nights, or exploring local festivals. • Shared moments: Host a potluck instead of dining out. Pro Tip: Use Crown Money to set a goal like “Summer Adventure Fund.” Allocate $50/month, and let the app remind you to fund it automatically. Watching that fund grow feels like planning a vacation in slow motion. Real-Life Example: Maria and her partner skipped a pricey vacation and rented a cozy cabin nearby. They saved $1,200 and still made memories roasting marshmallows under the stars. “We thought we needed a fancy trip to connect,” she said. “Turns out, all we needed was a fire pit and no Wi-Fi.”
Key Takeaways • Cut the clutter: Cancel unused subscriptions and track them with tools like Crown Money. • Budget for joy: Allocate guilt-free money for hobbies and experiences. • Pause before purchasing: Avoid impulse buys with a 24-hour rule. • Get creative: DIY, swap, and repurpose to save without sacrifice. • Invest in experiences: They’re richer than “stuff” and often cheaper.
FAQs: Frugal Living Made Simple Q: How do I stay motivated to save? A: Tie savings to specific goals (e.g., “Save $500 for a weekend trip”). Apps like Crown Money let you visualize progress, which feels rewarding!
Q: Can I be frugal and still socialize? A: Absolutely! Host DIY spa nights, picnic potlucks, or free museum days. Use Crown Money to set a “Social Fun” budget and stick to it.
Q: What if I slip up and overspend? A: No guilt! Adjust your budget next month. Crown Money makes it easy to shift funds between categories.
Q: How do I track small savings from DIY habits? A: Create a custom category in Crown Money (e.g., “Homemade Wins”) and log your savings manually. Watching it grow is addictive!
Q: What if I have a financial emergency? A: Build a “Safety Net” category in Crown Money. Start small—even $20/month adds up. The app’s reminders keep you consistent.
**Final Thoughts: Frugal Is Freedom ** Frugal living isn’t about saying “no”—it’s about saying “yes” to what truly lights you up. By trimming the financial fat (goodbye, unused subscriptions!), budgeting for joy, and getting creative, you can save money and savor life’s best moments. Tools like Crown Money are your allies here. They handle the tracking and nudging, so you can focus on the fun parts: planning adventures, trying new recipes, or laughing with friends over a board game. Remember: the goal isn’t perfection. It’s progress. Start small, celebrate wins, and let your frugal habits grow naturally. Your wallet (and your inner joy-seeker) will thank you.
-
 @ b1ddb4d7:471244e7
2025-05-30 03:01:02
@ b1ddb4d7:471244e7
2025-05-30 03:01:02Bitcoin FilmFest (BFF25) returns to Warsaw for its third edition, blending independent cinema—from feature films and commercials to AI-driven experimental visuals—with education and entertainment.
Hundreds of attendees from around the world will gather for three days of screenings, discussions, workshops, and networking at the iconic Kinoteka Cinema (PKiN), the same venue that hosted the festival’s first two editions in March 2023 and April 2024.
This year’s festival, themed “Beyond the Frame,” introduces new dimensions to its program, including an extra day on May 22 to celebrate Bitcoin Pizza Day, the first real-world bitcoin transaction, with what promises to be one of Europe’s largest commemorations of this milestone.
BFF25 bridges independent film, culture, and technology, with a bold focus on decentralized storytelling and creative expression. As a community-driven cultural experience with a slightly rebellious spirit, Bitcoin FilmFest goes beyond movies, yet cinema remains at its heart.
Here’s a sneak peek at the lineup, specially curated for movie buffs:
 Generative Cinema – A special slot with exclusive shorts and a thematic debate on the intersection of AI and filmmaking. Featured titles include, for example: BREAK FREE, SATOSHI: THE CREATION OF BITCOIN, STRANGE CURRENCIES, and BITCOIN IS THE MYCELIUM OF MONEY, exploring financial independence, traps of the fiat system, and a better future built on sound money.
Generative Cinema – A special slot with exclusive shorts and a thematic debate on the intersection of AI and filmmaking. Featured titles include, for example: BREAK FREE, SATOSHI: THE CREATION OF BITCOIN, STRANGE CURRENCIES, and BITCOIN IS THE MYCELIUM OF MONEY, exploring financial independence, traps of the fiat system, and a better future built on sound money. Upcoming Productions Preview – A bit over an hour-long block of unreleased pilots and works-in-progress. Attendees will get exclusive first looks at projects like FINDING HOME (a travel-meets-personal-journey series), PARALLEL SPACES (a story about alternative communities), and THE LEGEND OF LANDI (a mysterious narrative).
Upcoming Productions Preview – A bit over an hour-long block of unreleased pilots and works-in-progress. Attendees will get exclusive first looks at projects like FINDING HOME (a travel-meets-personal-journey series), PARALLEL SPACES (a story about alternative communities), and THE LEGEND OF LANDI (a mysterious narrative). Freedom-Focused Ads & Campaigns – Unique screenings of video commercials, animations, and visual projects, culminating in “The PoWies” (Proof of Work-ies)—the first ever awards show honoring the best Bitcoin-only awareness campaigns.
Freedom-Focused Ads & Campaigns – Unique screenings of video commercials, animations, and visual projects, culminating in “The PoWies” (Proof of Work-ies)—the first ever awards show honoring the best Bitcoin-only awareness campaigns.To get an idea of what might come up at the event, here, you can preview 6 selected ads combined into two 2 videos:
 Open Pitch Competition – A chance for filmmakers to present fresh ideas and unfinished projects to an audience of a dedicated jury, movie fans and potential collaborators. This competitive block isn’t just entertaining—it’s a real opportunity for creators to secure funding and partnerships.
Open Pitch Competition – A chance for filmmakers to present fresh ideas and unfinished projects to an audience of a dedicated jury, movie fans and potential collaborators. This competitive block isn’t just entertaining—it’s a real opportunity for creators to secure funding and partnerships. Golden Rabbit Awards: A lively gala honoring films from the festival’s Official Selection, with awards in categories like Best Feature, Best Story, Best Short, and Audience Choice.
Golden Rabbit Awards: A lively gala honoring films from the festival’s Official Selection, with awards in categories like Best Feature, Best Story, Best Short, and Audience Choice.BFF25 Main Screenings
Sample titles from BFF25’s Official Selection:
 REVOLUCIÓN BITCOIN – A documentary by Juan Pablo, making its first screening outside the Spanish-speaking world in Warsaw this May. Three years of important work, 80 powerful minutes to experience. The film explores Bitcoin’s impact across Argentina, Colombia, Mexico, El Salvador, and Spain through around 40 diverse perspectives. Screening in Spanish with English subtitles, followed by a Q&A with the director.
REVOLUCIÓN BITCOIN – A documentary by Juan Pablo, making its first screening outside the Spanish-speaking world in Warsaw this May. Three years of important work, 80 powerful minutes to experience. The film explores Bitcoin’s impact across Argentina, Colombia, Mexico, El Salvador, and Spain through around 40 diverse perspectives. Screening in Spanish with English subtitles, followed by a Q&A with the director. UNBANKABLE – Luke Willms’ directorial debut, drawing from his multicultural roots and his father’s pioneering HIV/AIDS research. An investigative documentary based on Luke’s journeys through seven African countries, diving into financial experiments and innovations—from mobile money and digital lending to Bitcoin—raising smart questions and offering potential lessons for the West. Its May appearance at BFF25 marks its largest European event to date, following festival screenings and nominations across multiple continents over the past year.
UNBANKABLE – Luke Willms’ directorial debut, drawing from his multicultural roots and his father’s pioneering HIV/AIDS research. An investigative documentary based on Luke’s journeys through seven African countries, diving into financial experiments and innovations—from mobile money and digital lending to Bitcoin—raising smart questions and offering potential lessons for the West. Its May appearance at BFF25 marks its largest European event to date, following festival screenings and nominations across multiple continents over the past year. HOTEL BITCOIN – A Spanish comedy directed by Manuel Sanabria and Carlos “Pocho” Villaverde. Four friends, 4,000 bitcoins , and one laptop spark a chaotic adventure of parties, love, crime, and a dash of madness. Exploring sound money, value, and relationships through a twisting plot. The film premiered at the Tarazona and Moncayo Comedy Film Festival in August 2024. Its Warsaw screening at BFF25 (in Spanish with English subtitles) marks its first public showing outside the Spanish-speaking world.
HOTEL BITCOIN – A Spanish comedy directed by Manuel Sanabria and Carlos “Pocho” Villaverde. Four friends, 4,000 bitcoins , and one laptop spark a chaotic adventure of parties, love, crime, and a dash of madness. Exploring sound money, value, and relationships through a twisting plot. The film premiered at the Tarazona and Moncayo Comedy Film Festival in August 2024. Its Warsaw screening at BFF25 (in Spanish with English subtitles) marks its first public showing outside the Spanish-speaking world.Check out trailers for this year’s BFF25 and past editions on YouTube.
Tickets & Info:
- Detailed program and tickets are available at bitcoinfilmfest.com/bff25.
- Stay updated via the festival’s official channels (links provided on the website).
- Use ‘LN-NEWS’ to get 10% of tickets
-
 @ 33baa074:3bb3a297
2025-05-28 07:27:02
@ 33baa074:3bb3a297
2025-05-28 07:27:02Distilled water has a wide range of applications in the medical field, mainly including the following aspects: Preparation of injection water Distilled water is an indispensable agent in medical institutions, used for the preparation of drugs, injection and washing of instruments, etc. In the medical process, sterile injection water is needed to flush wounds, prepare drugs, etc. The distilled water machine can ensure the purity of water and prevent microorganisms and harmful substances in the water from causing harm to patients.
Surgical wound flushing In breast cancer surgery, warm distilled water is used to flush surgical wounds. This practice helps to clean the wound, remove possible residual tumor cells, and use hypnotic effect to make tumor cells absorb water, swell, rupture, and necrotic, thereby preventing tumors from growing in the wound.
Cleaning and disinfection Distilled water has a certain disinfection and sterilization effect. It can be used to clean the skin, help eliminate bacteria on the skin surface, and is beneficial to the health of the skin. In addition, distilled water can also be used to clean and disinfect medical equipment to ensure the hygiene and safety of the medical environment.
Laboratory use In medical-related laboratories, distilled water is used to prepare experimental solutions, wash utensils and experimental instruments. These applications ensure the accuracy of experimental results while maintaining the sterile environment of the laboratory.
Moisturizing and Beauty Although not directly used in medical applications, distilled water is also used in skin care. It can be used as a basic moisturizer to help improve the symptoms of dry skin. In the field of medical beauty, distilled water is sometimes used for facial compresses to achieve calming, cooling, and swelling effects.
In summary, the application of distilled water in the medical field is multifaceted, from basic injection water preparation to complex surgical assistance to daily skin care, it has played an important role.
-
 @ 33baa074:3bb3a297
2025-05-28 02:26:55
@ 33baa074:3bb3a297
2025-05-28 02:26:55The PH value of a swimming pool is one of the important indicators for measuring the quality of swimming pool water. Its importance is mainly reflected in the following aspects:
Affecting human comfort The pH of water that the human body is most adapted to is neutral. Inappropriate pH of swimming pool water will irritate human skin, eyes and mucous membranes, causing discomfort. For example, when the pH value is high or low, it may irritate the swimmer's skin, eyes, etc., causing discomfort such as itchy skin, red and swollen eyes, and sticky hair, affecting the swimmer's physical health and swimming experience.
 Affecting the disinfection effect of swimming pools
Affecting the activity of chlorine disinfectants
Swimming pools are usually disinfected with chlorine-containing disinfectants. Different pH values will cause differences in the activity and disinfection ability of chlorine. When the pH value in swimming pool water is greater than 8.0, the activity of chlorine disinfectants in water will be significantly reduced, that is, the disinfection ability will be reduced, which will affect the algae removal and sterilization effects, resulting in the proliferation of green algae in swimming pool water. When the pH value is less than 7.0, the activity of the disinfectant in the swimming pool will be relatively high, the residual chlorine in the swimming pool will dissipate faster, and the disinfection durability of the swimming pool disinfectant will be greatly weakened. Under the condition of pH about 7.5, there is a relatively good disinfection effect and the duration of the drug effect is relatively long.
Affecting the disinfection effect of swimming pools
Affecting the activity of chlorine disinfectants
Swimming pools are usually disinfected with chlorine-containing disinfectants. Different pH values will cause differences in the activity and disinfection ability of chlorine. When the pH value in swimming pool water is greater than 8.0, the activity of chlorine disinfectants in water will be significantly reduced, that is, the disinfection ability will be reduced, which will affect the algae removal and sterilization effects, resulting in the proliferation of green algae in swimming pool water. When the pH value is less than 7.0, the activity of the disinfectant in the swimming pool will be relatively high, the residual chlorine in the swimming pool will dissipate faster, and the disinfection durability of the swimming pool disinfectant will be greatly weakened. Under the condition of pH about 7.5, there is a relatively good disinfection effect and the duration of the drug effect is relatively long.Influence on the existence form of residual chlorine Depending on the pH value, free chlorine may be chlorine gas (Cl₂), chlorophyll acid (HClO) or hypocrite ion (ClO⁻) dissolved in water. The disinfection effect of HClO is about 100 times stronger than that of ClO⁻. When the pH value is about 7.5, both chlorophyll acid and hypocrite ion exist, and the proportion is roughly equal, which can ensure a better disinfection effect.
Corrosion to swimming pool facilities Pool water acidity or alkalinity will have a corrosive effect on swimming pool equipment. If the water is acidic, it will also corrode the accessories of the suction machine and affect the normal use of the equipment. If the pH value is unbalanced for a long time, the chemical disinfectants in the swimming pool will corrode the pool structure and swimming pool equipment, which will not only affect the appearance of the pool structure and equipment, but also shorten the service life of the swimming pool and increase the maintenance cost of the swimming pool in the later stage.
Impact on the containment of pool water The pH value in the swimming pool will change due to many external factors, such as rain, the use of swimming pool disinfectants, and alkaline chemicals. Maintaining a suitable pH value can make the pool water have better containment, more stably cope with the influence of these external factors, and maintain the relative stability of water quality.
In summary, the pH value of the swimming pool is of great significance to ensure the health and comfort of swimmers, ensure the disinfection effect, protect swimming pool facilities, and maintain the stability of pool water quality.
-
 @ 7f6db517:a4931eda
2025-05-30 02:01:45
@ 7f6db517:a4931eda
2025-05-30 02:01:45
Nostr is an open communication protocol that can be used to send messages across a distributed set of relays in a censorship resistant and robust way.
If you missed my nostr introduction post you can find it here. My nostr account can be found here.
We are nearly at the point that if something interesting is posted on a centralized social platform it will usually be posted by someone to nostr.
We are nearly at the point that if something interesting is posted exclusively to nostr it is cross posted by someone to various centralized social platforms.
We are nearly at the point that you can recommend a cross platform app that users can install and easily onboard without additional guides or resources.
As companies continue to build walls around their centralized platforms nostr posts will be the easiest to cross reference and verify - as companies continue to censor their users nostr is the best censorship resistant alternative - gradually then suddenly nostr will become the standard. 🫡
Current Nostr Stats
If you found this post helpful support my work with bitcoin.

-
 @ dfa02707:41ca50e3
2025-05-30 02:01:41
@ dfa02707:41ca50e3
2025-05-30 02:01:41Contribute to keep No Bullshit Bitcoin news going.
- RoboSats v0.7.7-alpha is now available!
NOTE: "This version of clients is not compatible with older versions of coordinators. Coordinators must upgrade first, make sure you don't upgrade your client while this is marked as pre-release."
- This version brings a new and improved coordinators view with reviews signed both by the robot and the coordinator, adds market price sources in coordinator profiles, shows a correct warning for canceling non-taken orders after a payment attempt, adds Uzbek sum currency, and includes package library updates for coordinators.

Source: RoboSats.
- siggy47 is writing daily RoboSats activity reviews on stacker.news. Check them out here.
- Stay up-to-date with RoboSats on Nostr.
What's new
- New coordinators view (see the picture above).
- Available coordinator reviews signed by both the robot and the coordinator.
- Coordinators now display market price sources in their profiles.

Source: RoboSats.
- Fix for wrong message on cancel button when taking an order. Users are now warned if they try to cancel a non taken order after a payment attempt.
- Uzbek sum currency now available.
- For coordinators: library updates.
- Add docker frontend (#1861).
- Add order review token (#1869).
- Add UZS migration (#1875).
- Fixed tests review (#1878).
- Nostr pubkey for Robot (#1887).
New contributors

Full Changelog: v0.7.6-alpha...v0.7.7-alpha
-
 @ dfa02707:41ca50e3
2025-05-30 02:01:39
@ dfa02707:41ca50e3
2025-05-30 02:01:39- This version introduces the Soroban P2P network, enabling Dojo to relay transactions to the Bitcoin network and share others' transactions to break the heuristic linking relaying nodes to transaction creators.
- Additionally, Dojo admins can now manage API keys in DMT with labels, status, and expiration, ideal for community Dojo providers like Dojobay. New API endpoints, including "/services" exposing Explorer, Soroban, and Indexer, have been added to aid wallet developers.
- Other maintenance updates include Bitcoin Core, Tor, Fulcrum, Node.js, plus an updated ban-knots script to disconnect inbound Knots nodes.
"I want to thank all the contributors. This again shows the power of true Free Software. I also want to thank everyone who donated to help Dojo development going. I truly appreciate it," said Still Dojo Coder.
What's new
- Soroban P2P network. For MyDojo (Docker setup) users, Soroban will be automatically installed as part of their Dojo. This integration allows Dojo to utilize the Soroban P2P network for various upcoming features and applications.
- PandoTx. PandoTx serves as a transaction transport layer. When your wallet sends a transaction to Dojo, it is relayed to a random Soroban node, which then forwards it to the Bitcoin network. It also enables your Soroban node to receive and relay transactions from others to the Bitcoin network and is designed to disrupt the assumption that a node relaying a transaction is closely linked to the person who initiated it.
- Pushing transactions through Soroban can be deactivated by setting
NODE_PANDOTX_PUSH=offindocker-node.conf. - Processing incoming transactions from Soroban network can be deactivated by setting
NODE_PANDOTX_PROCESS=offindocker-node.conf.
- Pushing transactions through Soroban can be deactivated by setting
- API key management has been introduced to address the growing number of people offering their Dojos to the community. Dojo admins can now access a new API management tab in their DMT, where they can create unlimited API keys, assign labels for easy identification, and set expiration dates for each key. This allows admins to avoid sharing their main API key and instead distribute specific keys to selected parties.
- New API endpoints. Several new API endpoints have been added to help API consumers develop features on Dojo more efficiently:
- New:
/latest-block- returns data about latest block/txout/:txid/:index- returns unspent output data/support/services- returns info about services that Dojo exposes
- Updated:
/tx/:txid- endpoint has been updated to return raw transaction with parameter?rawHex=1
- The new
/support/servicesendpoint replaces the deprecatedexplorerfield in the Dojo pairing payload. Although still present, API consumers should use this endpoint for explorer and other pairing data.
- New:
Other changes
- Updated ban script to disconnect inbound Knots nodes.
- Updated Fulcrum to v1.12.0.
- Regenerate Fulcrum certificate if expired.
- Check if transaction already exists in pushTx.
- Bump BTC-RPC Explorer.
- Bump Tor to v0.4.8.16, bump Snowflake.
- Updated Bitcoin Core to v29.0.
- Removed unnecessary middleware.
- Fixed DB update mechanism, added api_keys table.
- Add an option to use blocksdir config for bitcoin blocks directory.
- Removed deprecated configuration.
- Updated Node.js dependencies.
- Reconfigured container dependencies.
- Fix Snowflake git URL.
- Fix log path for testnet4.
- Use prebuilt addrindexrs binaries.
- Add instructions to migrate blockchain/fulcrum.
- Added pull policies.

Learn how to set up and use your own Bitcoin privacy node with Dojo here.
-
 @ 502ab02a:a2860397
2025-05-30 01:14:10
@ 502ab02a:a2860397
2025-05-30 01:14:10ย้อนกลับไปปี 2014 ชายชื่อ Patrick O. Brown ศาสตราจารย์ชีววิทยาเชิงโมเลกุลแห่งมหาวิทยาลัยแตนฟอร์ด ตัดสินใจลาออกจากเส้นทางวิชาการสายหลัก เพื่อมาก่อตั้งบริษัทที่เขาเชื่อว่าจะเปลี่ยนโลก Impossible Foods
ดร. แพทริค โอ. บราวน์ (Patrick O. Brown) เป็นนักชีวเคมีและนักธุรกิจชาวอเมริกันและศาสตราจารย์กิตติคุณด้านชีวเคมีแห่งมหาวิทยาลัยสแตนฟอร์ด เขาได้รับปริญญาตรี แพทยศาสตรบัณฑิต และปรัชญาดุษฎีบัณฑิตด้านชีวเคมีจากมหาวิทยาลัยชิคาโก หลังจากนั้น เขาได้เข้ารับการฝึกอบรมด้านกุมารเวชศาสตร์ที่โรงพยาบาล Children's Memorial ในชิคาโก ในช่วงหลังปริญญาเอก เขาได้ทำงานวิจัยเกี่ยวกับกลไกที่ไวรัส HIV และเรโทรไวรัสอื่น ๆ แทรกยีนของพวกมันเข้าสู่จีโนมของเซลล์ที่ติดเชื้อ ซึ่งช่วยนำไปสู่การพัฒนายาใหม่ในการต่อสู้กับโรคนี้
ในช่วงต้นทศวรรษ 1990 ดร. บราวน์และทีมงานของเขาที่สแตนฟอร์ดได้พัฒนาเทคโนโลยี DNA microarray ซึ่งเป็นเครื่องมือที่ช่วยให้นักวิจัยสามารถวิเคราะห์การแสดงออกของยีนทั้งหมดในจีโนมได้พร้อมกัน เทคโนโลยีนี้มีบทบาทสำคัญในการวิจัยทางชีววิทยาและการแพทย์ โดยเฉพาะในการจำแนกประเภทของมะเร็งและการพยากรณ์โรค
นอกจากนี้ ดร. บราวน์ยังเป็นผู้ร่วมก่อตั้ง Public Library of Science (PLOS) ซึ่งเป็นองค์กรไม่แสวงหาผลกำไรที่มุ่งเน้นการเผยแพร่ผลงานวิจัยทางวิทยาศาสตร์ให้เข้าถึงได้ฟรีและเปิดกว้างต่อสาธารณะ
ในปี 2011 ดร. บราวน์ได้ก่อตั้ง Impossible Foods โดยมีเป้าหมายในการสร้างผลิตภัณฑ์เนื้อสัตว์จากพืชที่มีรสชาติและเนื้อสัมผัสคล้ายเนื้อสัตว์จริง เพื่อลดผลกระทบต่อสิ่งแวดล้อมจากการเลี้ยงสัตว์ เขาและทีมงานได้ค้นพบว่าโมเลกุล heme ซึ่งเป็นส่วนประกอบที่ให้รสชาติและกลิ่นเฉพาะของเนื้อสัตว์ สามารถผลิตจากพืชได้ โดยเฉพาะจากรากถั่วเหลือง พวกเขาใช้เทคนิคทางวิศวกรรมชีวภาพในการผลิต heme จากยีสต์ที่ได้รับการดัดแปลงพันธุกรรม และนำมาผสมกับโปรตีนจากพืชเพื่อสร้างผลิตภัณฑ์ที่มีลักษณะคล้ายเนื้อสัตว์
ดร. บราวน์ได้รับการยอมรับอย่างกว้างขวางในวงการวิทยาศาสตร์และเทคโนโลยี โดยได้รับรางวัลและเกียรติคุณหลายรายการ รวมถึงการเป็นสมาชิกของ National Academy of Sciences และ National Academy of Medicine ของสหรัฐอเมริกา ด้วยความมุ่งมั่นในการแก้ไขปัญหาสิ่งแวดล้อมผ่านนวัตกรรมทางอาหาร ดร. แพทริค โอ. บราวน์ ได้กลายเป็นบุคคลสำคัญที่มีบทบาทในการเปลี่ยนแปลงวิธีการบริโภคอาหารของโลกในศตวรรษที่ 21
เป้าหมายของเขาไม่ใช่เพียงแค่ทำอาหาร แต่คือ "ยุติการทำปศุสัตว์ให้หมดสิ้นภายในปี 2035"
เขาไม่ได้พูดลอย ๆ เขาลงมือ “ทำเนื้อจากพืช” ด้วยเทคโนโลยีที่ซับซ้อนระดับวิศวกรรมชีวภาพ นำโปรตีนจากถั่วเหลือง + น้ำมันมะพร้าว + เทคเจอร์ + สารเติมแต่งอีกชุดใหญ่ มาผ่านกระบวนการแปรรูปจนดูคล้ายเนื้อย่าง แต่ที่ทำให้ “มันดูเหมือนเนื้อจริง” คือการเติม ฮีม (Heme) เข้าไปสารประกอบที่อยู่ในเลือดและเนื้อสัตว์จริง ๆ
Impossible Foods คือบริษัทที่ไม่ได้เพียง “ปลอมรสชาติเนื้อ” แต่พยายามสร้างเนื้อจากพืช ให้เหมือนเนื้อจริงที่สุดเท่าที่วิทยาศาสตร์จะเอื้อมถึง จุดขายที่ทำให้แบรนด์นี้ดังเปรี้ยงก็คือสิ่งที่เรียกว่า “ฮีม” (heme) หรือโมเลกุลเหล็กในเลือด ซึ่งเป็นตัวการหลักที่ทำให้เนื้อวัวมีกลิ่นและรสเฉพาะตัวเวลาถูกย่างจนหอมฉุย
ดร.แพทริค บราวน์ และทีมนักวิจัยของเขาเริ่มจากการค้นหาว่า “อะไรในพืช” ให้กลิ่นคล้ายเลือด พวกเขาพบว่า “Leghemoglobin” ซึ่งอยู่ในรากถั่วเหลือง มีโครงสร้างใกล้เคียงกับ Hemoglobin ในเลือดสัตว์มากที่สุด จุดพลิกของเทคโนโลยีนี้คือ การผลิตเลกฮีโมโกลบินจากพืชจำนวนมาก ทำไม่ได้โดยการถอนรากถั่วมาทุบคั้น แต่ต้องอาศัยวิศวกรรมชีวภาพขั้นสูง
พวกเขาจึงใช้กระบวนการที่เรียกว่า “fermentation by genetically modified yeast” หรือการหมักโดยยีสต์ที่ผ่านการดัดแปลงพันธุกรรม โดยนำยีนของพืชที่สร้าง leghemoglobin ไปใส่ในยีสต์ (Pichia pastoris) แล้วเลี้ยงยีสต์นั้นในถังหมักขนาดใหญ่แบบเดียวกับโรงเบียร์ พอยีสต์ขยายตัว มันจะผลิตเลกฮีโมโกลบินออกมาจำนวนมาก จากนั้นจึงสกัดออกมาผสมกับโปรตีนจากพืช เช่น โปรตีนจากถั่วเหลือง หรือโปรตีนจากมันฝรั่ง
เพื่อให้เนื้อสัมผัสคล้ายเนื้อจริง ทีม Impossible Foods ยังใช้เทคนิคอื่นร่วมด้วย เช่น -Coconut Oil และ Sunflower Oil เป็นแหล่งไขมันที่ให้สัมผัส “ฉ่ำๆ” คล้ายไขมันเนื้อวัว -Methylcellulose สารที่ช่วยทำให้ส่วนผสมเกาะตัวเป็นก้อน คล้ายเนื้อบดจริง -Natural Flavors กลิ่นที่สกัดจากพืชหลายชนิด เพื่อเลียนแบบกลิ่นไหม้จากเนื้อย่าง
ทุกอย่างถูกผสมให้เข้ากัน ผ่านเครื่องอัดขึ้นรูป (extrusion) ที่ทำให้เนื้อออกมามี “เส้นใย” คล้ายกล้ามเนื้อวัว หรือหมู เมื่อโดนความร้อน โปรตีนจะเปลี่ยนโครงสร้าง (denature) และมีกลิ่นออกมาคล้ายๆ เนื้อย่างจริงๆ พร้อมน้ำสีแดงคล้ายเลือด (จาก heme) ไหลเยิ้ม ซึ่งคือไอเดียที่ทำให้ Impossible Burger เป็นมากกว่าแค่ “เบอร์เกอร์ผัก”
ผลลัพธ์คือ… เบอร์เกอร์พืชที่มีเลือดซึม สีชมพูดู juicy และกลิ่นไหม้ติดกระทะ จนคนกินรู้สึกเหมือนกำลังย่างเนื้อจริง ๆ
ฟังดูอัศจรรย์ใช่ไหม? แต่...การเติมฮีมจากยีสต์ตัดต่อพันธุกรรมลงในอาหาร ไม่เคยมีในธรรมชาติมาก่อน ในปี 2017 Impossible Foods ต้องยื่นเรื่องต่อ FDA เพื่อขออนุมัติว่า leghemoglobin จากยีสต์ GMO “ปลอดภัย”
แต่ในตอนนั้น FDA ตอบว่า “ยังไม่มีข้อมูลเพียงพอ” ว่าจะไม่ก่อให้เกิดภูมิแพ้หรือผลข้างเคียงในระยะยาว (ใช่แล้วจ้ะ... สารที่อยู่ในเบอร์เกอร์ชื่อดัง ถูกขายก่อนที่ FDA จะสรุปว่าปลอดภัยเต็มร้อย)
แล้วในที่สุด ปี 2019 FDA ก็ให้ผ่านแบบ “GRAS” (Generally Recognized As Safe) โดยใช้ข้อมูลจากการทดลองภายในของบริษัทเอง ไม่ใช่การทดสอบอิสระจากภายนอก
เฮียว่าอันนี้ต้องมีใครสะกิดในใจแล้วล่ะว่า “เรากำลังเอาอะไรเข้าปากกันแน่?”
แม้จะฟังดูเท่ ไฮเทค และดีต่อสิ่งแวดล้อม แต่ก็มีคำถามจากนักวิจารณ์มากมายว่า… แท้จริงแล้วอาหารเหล่านี้เป็นอาหาร “เพื่อสิ่งแวดล้อม” หรือเป็นเพียง “ภาพฝันที่ควบคุมโดยบริษัทเทคโนโลยียักษ์ใหญ่”?
มันเต็มไปด้วยคำถาม คำถาม และ คำถามนะสิครับ
ในเมื่อ Impossible Foods ได้รับเงินลงทุนหลายรอบจากบริษัทยักษ์อย่าง Google Ventures, UBS, และ Temasek (ของรัฐบาลสิงคโปร์) บอกตรง ๆ ว่า เงินแบบนี้ไม่ได้หวังแค่เปลี่ยนโลกแต่มันมาพร้อมเป้าหมายที่ชัดมาก การสร้างสิทธิบัตรอาหารใหม่ ที่ควบคุมการผลิตจากต้นน้ำยันปลายน้ำ อย่าลืมว่า ยีสต์ที่ผ่านการดัดแปลงพันธุกรรม หรือ GMO yeast นั้นถือเป็นสิทธิบัตร ถ้าใครจะผลิต Heme แบบเดียวกันก็ต้องขออนุญาตจาก Impossible Foods หรือไม่ก็โดนฟ้องได้เลย แปลว่า “เทคโนโลยีรสชาติเนื้อ” ไม่ได้เป็นมรดกของโลก แต่อยู่ในมือบริษัทไม่กี่แห่ง
ยิ่งไปกว่านั้น อุปกรณ์การผลิตต้องลงทุนสูง ต้องมีโรงหมัก ปฏิบัติการชีวภาพ การควบคุมความปลอดภัยที่เข้มข้น จึงไม่ใช่ใครๆ ก็ทำได้ ที่น่ากลัวคือ ถ้าเมื่อวันหนึ่งเนื้อสัตว์ธรรมชาติถูกทำให้กลายเป็น “ปีศาจสิ่งแวดล้อม” หรือ "ตัวเชื้อโรคผ่านอาหาร" โดยนโยบายรัฐและการตลาดของกลุ่มเทคฯ อาหารที่ประชาชนกินได้อาจเหลือแค่ “สิ่งที่ผลิตโดยมีสิทธิบัตร” เท่านั้น
เมื่อถึงวันนั้น ประชาชนจะสิ้นความชอบธรรมในการ “เลี้ยงวัวไว้กินเอง” ไม่ได้อีกต่อไป เพราะอาจโดนห้ามจากข้อกฎหมายคาร์บอน กฎหมายการกักกันเชื้อ ประชาชนจะ “เก็บพืชริมรั้วมาทำอาหาร” ไม่ได้อีกต่อไป เพราะกลิ่นไม่เหมือนเนื้อแลปที่เคยชิน และประชาชนจะ “ทำอาหารเองในบ้าน” ไม่ได้อีกต่อไป เพราะระบบเสพติดรสเนื้อเทียมจะทำให้คนเบือนหน้าจากอาหารจริง
ในขณะที่ Impossible Foods โฆษณาว่า “เราแค่อยากช่วยโลก” แต่เทคโนโลยีนี้อาจเปลี่ยน “อาหาร” ให้กลายเป็น “สิทธิบัตร” ที่ประชาชนเช่ากินจากบริษัท และเปลี่ยน “สิทธิในการเข้าถึงอาหาร” ให้กลายเป็น “อภิมหาอำนาจควบคุมโลก” โดยไม่ต้องยิงแม้แต่นัดเดียว หรือเปล่า???
เพราะเมื่อคุณควบคุมอาหารได้… คุณไม่ต้องควบคุมประชาชนอีกเลย
เฮียไม่ได้ต่อต้านเทคโนโลยี แต่เฮียอยากให้เราหยุดคิดนิดนึง แล้วตั้งคำถามในขณะที่เรายังเฝ้ามองว่า ถ้าของกินที่ดูน่าเชื่อถือ กินแล้วเหมือนเนื้อแท้ ๆ มันต้องมาจากกระบวนการที่ซับซ้อน แพง และถูกควบคุมโดยบริษัทที่มีสิทธิบัตรล้อมรอบ แล้ววันหนึ่ง ถ้าบริษัทนั้นล่มล่ะ? ถ้าถูกซื้อโดยบริษัทยักษ์ใหญ่? หรือถ้าพวกเขาขึ้นราคาจนยังไงเราก็ต้องทำงานหาเงินมาซื้อมันเพื่อกินประทังชีวิต?
อาหารจะยังเป็นของเราหรือเปล่า?
เราจะยัง “กินเพื่ออยู่” หรือแค่ “อยู่เพื่อจ่ายค่าเช่าระบบกิน”?
เราคงไม่ผิดที่จะตั้งคำถามใช่ไหม เพราะถ้ามันมีทางออก มันคงไม่น่ากลัว
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 491afeba:8b64834e
2025-05-27 21:02:29
@ 491afeba:8b64834e
2025-05-27 21:02:29Quando adolescente eu acreditava na coerência da teoria de "amor líquido" do polonês, sociólogo, Zygmunt Bauman, apresentada no livro "Amor Líquido: Sobre a Fragilidade dos Laços Humanos", qual no meu amadurecimento em estudos, sejam eles no meio acadêmico ou fora, percebo como uma das formas mais rasas de explicar as mudanças e transformações dos padrões de relações sócio-afetivas dos humanos. A seguir colocar-me-ei na minha juventude não tanto recente, direi então que nós, se adolescentes e conservadores, ou mesmo jovens adultos mais conservadores, costumamos levar como dogma uma óptica decadentista generalizada de todos os avanços de eras dos homens, universalizamos por nos ser comum a indistinção entre humanidade e humanidades, ou mesmo "humanity" e "humankind" ("humanidade" como espécime e "humanidade" como um universal), compreendemos toda "essas" como "essa" e indistinguimos as sociedades para com os homens, ou seja, a incapacidade de definir os seres dentro de suas respectivas singularidades e especificidades nos leva ao decadentismo generalista (a crença de que de forma geral, e universal, a "civilização universal" decai moralmente, éticamente, materialmente e espiritualmente), que aparente à nós determinadas mudanças nas relações humanas quanto ao caráter sócio-afetivo, por falta de profundidade e critérios ainda sobre questões alinhadas aos métodos e coerências, ou incoerências, lógicas, nós se jovens e conservadores somos levados ao engodo de concordar com a teoria do amor líquido de Bauman, que devo cá explicar de antemão: trata ela, a teoria, o padrão de "amor" dos tempos presentes como frágil, de prazo (curto e médio) e diferente em grau comparativamente ao amor comum das eras passadas.
Aos jovens mais progressistas opera uma compreensão dialética sobre as eras dos homens nos seu tempo presente, na qual ao tempo que o ser progride ele também regride simultaneamente, ou seja, a medida que aparecem contradições advindas de transformações materiais da realidade humana o ser supera essas contradições e progride em meio as transformações, ainda fazendo parte da lógica dessa indissociavelmente, assim constantemente progredindo e regredindo, havendo para esses dois vetores de distinção: o primeiro é o que releva questões espirituais como ao caráter do pensamento "new age", o segundo ignora essas questões por negar a existência da alma, seguem ao materialismo. Cedem em crer na teoria baumaninana como dogma, pois não encontram outros meios para explicar as transformações da sociedade na esfera sócio-afetiva sem que haja confrontamento direto com determinadas premissas assim pertinemente presentes, ou por não conciliarem com análises relativamente superiores, como a de Anthony Giddens sobre a "relação pura" em "A Transformação da Intimidade" e de François de Singly apresentada em "Sociologie du Couple".
!(image)[https://i.pinimg.com/736x/6f/b4/9e/6fb49eda2c8cf6dc837a0abfc7e108e6.jpg]
Há um problema quando uma teoria deixa de assim ser para vir a tornar-se mais um elemento desconexo da ciência, agora dentro da cultura pop, se assim podemos dizer, ou da cultura de massa, ou se preferirem mesmo "anticultura", esse problema é a sua deformização teórica, tornando-se essa rasa para sua palatabilidade massiva, somada a incapacidade de partes da sociedade civil em compreender as falhas daquilo que já foi massificado. Tive surpresa ao entender que muitos outros compartilham da mesma opinião, a exemplo, possuo um amigo na faculdade, marxista, que ao falarmos sobre nossos projetos de pesquisa, citou ele o projeto de um de nossos colegas, no qual esse referido um de nossos colegas faria seu projeto com base na teoria do amor líquido de Bauman, então alí demos risada disso, ora, para nós a teoria baumaniana é furada, passamos a falar sobre Bauman e o motivo pelo qual não gostávamos, lá fiquei até surpreso em saber que mais gente além de mim não gostava da teoria de Bauman, pois ao que eu via na internet era rede de enaltecimentos à figura e à sua teoria, tal como fosse uma revelação partindo de alguma divindade da Idade do Bronze. Pouco tempo depois tive em aula de teoria política uma citação de Bauman partindo do professor que ministrava a disciplina, no entanto, ao citar o nome de Bauman o mesmo fez uma feição na qual aparentava segurar risada, provavelmente ele também não levava Bauman à sério. Não devo negar que todas as vezes que vejo o sociólogo sendo citado em alguma nota no X, no Instagram ou qualquer outra rede social, tal como fosse um referencial teórico bom, sinto uma vergonha alheia pois alí tenho uma impressão de que a pessoa não leu Bauman e usa o referencial teórico como um fato já assim provado e comprovado.
Há pontos positivos na teoria baumaniana, como a capacidade de perceber o problema e correlacioná-lo à modernidade, assim como sucitar a influência do que há de material no fenômeno, porém os erros são pertinentes: o primeiro problema é de categoria. Não há, por parte de Bauman noção alguma entre as dissociações dos amores, não há atenção sobre o amor como estrutura ou ele como um sentimento, todo ele é compreendido uniformemente como "amor", partindo do pressuposto que todas as relações, todas elas, são firmadas com base no amor. Essa crença tem uma origem: Hegel. Nos Escritos Teológicos Hegel partia da crença que o amor ligava os seres relacionalmente como uma força de superação e alienação, mas há de compreendermos que esse Friedrich Hegel é o jovem ainda pouco maduro em suas ideias e seu sistema de pensamento, mais a frente, em "Fenomenologia do Espírito e na Filosofia do Direito", Hegel compreende a institucionalidade do direito no amor e a institucionalização dessa força, assim aproxima-se da realidade a respeito da inserção do amor nas esferas práticas do humano, porém essa ideia, apesar de imperfeita, pois ao que sabemos não é o amor que consolida a relação, mas sim a Verdade (Alétheia), conforme apontado por Heidegger em "Ser e Tempo", essa ideia do amor como a fundamento das relações humanas influenciou, e até hoje influencia, qualquer análise sobre as relações humanas fora da esfera materialista, fora dessa pois, melhormente explicado em exemplo, os marxistas (em exemplo), assim como Marx, consideram como base primordial das relações as condições materiais.
Por certo, não é de todo amor a base para a solidificação, ora, erram aqueles que creem que somente essa força, assim apontada por Hegel, constituiam todos os relacionamentos formais como pilares fundamentais, pois em prática as famílias eram até a fiduciarização dessas, por mais paradoxal que seja, compreendidas melhor como instituições orgânicas de caráter legal do que conluios de afetividades. A família outrora tinha consigo aparelhos de hierarquia bem estabelicidos, quais prezavam pela ordem interna e externa, que acima dessa instituição estava somente a Igreja (outra instituição), com sua fiduciarização [da família] após o movimento tomado pelos Estados nacionais em aplicação do casamento civil mudou-se a lógica das partes que a compõe, findou-se o princípio da subsidiariedade (não intervenção de determinadas instituições nas decisões quais podem ser exercidas em resuluções de problemas nas competências de quaisquer instituições), foi-se então, contudo, também a autoridade, e nisso revela-se um outro problema não apontado na teoria de Bauman: qual o padrão do amor "sólido"? Pois, ora, sociedades tradicionais não abdicavam do relevar dos amores para tornar seus filhos em ativos nas práticas de trocas (dádivas)? É notório que esse padrão se dissocia do padrão de sentimento apontado por Bauman, encontramos esse fato em estudo nos trabalhos "Ensaio Sobre a Dádiva", do Marcel Mauss, e "As Estruturas Elementares do Parentesco", do Claude Levi-Strauss, quais expõem que nas sociedades "sólidas", tradicionais, relevava-se mais questões institucionais que as sentimentais para a formação de laços (teoria da aliança). Muitas das relações passadas não eram baseadas no amor, não significando assim que as de hoje, em oposição, sejam, mas que permanecem-se semelhantes em base, diferentemente em grau e forma.
!(image)[https://substackcdn.com/image/fetch/f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F748b94c3-f882-45db-8333-09260ef15cfe_615x413.jpeg]
Ora, ainda existem casamentos motivados pela política, pelo status, pelo prestígio, pelos bens, pelo poder, pela influência familiar e assim sucetivamente, tal como no passado, ocorre que essa prática tornou-se oculta, não mais explícita e aparente, devo dizer ainda que em partes, pois prepondera em nosso tempo uma epidemia de adultérios, fornicações, práticas lascivas e demais práticas libertinosas explicitamente, em contraposição às práticas ocultas em vergonhas de sociedades sem declínio moral e espiritual, o que nos leva a questionar o método comparativo em dicotomia temporal "presente x passado" aplicado por Bauman, no qual segue-se da seguinte forma:
Transformação Passado = *sólido* | Presente = *líquido* Categorias Padrão de amor: tradicional (*sólido*) moderno (*líquido*) *Sólido* = estável, prazo (médio-grande), profundo, determinado. *Líquido* = instável, prazo (curto-médio), raso, indeterminado.O que penso é: Zygmunt Bauman buscou uma explicação material e laical para desviar ao fato de que há uma notória correlação entre espiritualização da sociedade, se voltada à Verdade, com a estabilidade das instituições, o que é já reduzido à moral religiosa, somente, não à mística, como por pensadores da linha de Tocqueville, ou em abordagens também mais laical (positivista) porém ainda relevantes, como Émile Durkheim em "As Formas Elementares da Vida Religiosa" e Max Weber em "A Ética Protestante e o Espírito do Capitalismo", contrapondo uma abordage mais voltada, de fato, a espiritualidade, como Christopher Dawnson, que defende essa teoria em "Religião e o Surgimento da Cultura Ocidental", e Eric Voegelin, principalmente nas obras "A Nova Ciência da Política" e "Ordem e História".
Encerrrando, minha cosmovisão é a católica, o sistema de crença e religião qual sigo é do Deus que se fez homem por amor aos seus filhos, não posso negar ou mesmo omitir o fato de que, por trás de toda a minha crítica estão meus pensamentos e minhas convicções alinhadas àquilo que mais tenho amor em toda minha vida: a Verdade, e a Verdade é Deus, pois Cristo é a Verdade, o Caminho e a Vida, ninguém vai ao Pai se não por Ele, e pois bem, seria incoerência de minha parte não relevar o fato de crença como um dos motivos pelos quais eu rejeito a teoria do amor líquido de Zygmunt Bauman, pois os amores são todos eles praticados por formas, existem por diferentes formas e assim são desde sua tradicionalidade até o predomínio das distorções de declínio espiritual das eras presentes (e também antigas pré-Era Axial), estão esses preservados pelo alinhamento à verdade, assim são indistorcíveis, imutáveis, ou seja, amor é amor, não releva-se o falso amor como um, simplesmente não o é, assim o interesse, a sanha por bens, o egoísmo e a egolatria ("cupiditas", para Santo Agostinho de Hipona, em oposição ao que o santo e filósofo trata por "caritas") não são formas do amor, são autoenganos, não bons, se não são bons logo não são de Deus, ora, se Deus é amor, se ele nos ama, determino como amor (e suas formas) o que está de acordo com a Verdade. Aprofundando, a Teologia do Corpo, do Papa São João Paulo II, rejeita a "liquidez" apresentada por Bauman, pois o amor é, em suma, sacríficio, parte da entrega total de si ao próximo, e se não há logo não é amor. A Teologia do Corpo rejeita não os fundamentos de mentira no "líquido", mas também no "sólido", pois a tradicionalidade não é sinônimo de bom e pleno acordo com o amor que Deus pede de nós, não são as coerções, as violências, as imposições e demais vontades em oposição às de Deus que determinam os amores -- fatos em oposição ao ideário romanticizado. Claro, nem todas as coerções são por si inválidas do amor, ou mesmo as escolhas em trocas racionalizadas, a exemplo do autruísmo em vista da chance da família ter êxito e sucesso, ou seja, pelo bem dos próximos haver a necessidade de submissão a, em exemplo, um casamento forjado, ou algo do gênero, reconhece-se o amor no ato se feito por bem da família, porém o amor incutido, nesse caso, explicita o caráter sacrificial, no qual uma vontade e um amor genuinamente potencial em prazeres e alegrias são anulados, ou seja, mesmo nesse modelo tradicional na "solidez" há possibilidade do amor, não nas formas romanticizadas em critérios, como "estabilidade" e "durabilidade", mas no caráter do sacríficio exercido. Conforme nos ensina São Tomás de Aquino, o amor não é uma "força", tal como ensina Hegel, mas sim uma virtude teologal conforme na "Suma Teológica" (II-II Q. 26-28), não devemos reduzir o amor e os amores em análises simplórias (não simples) de falsa complexidade extraídas em métodos questionáveis e pouco competentes à real diensão de crise espiritual das eras, por esse motivo não concordo com a teoria do amor líquido de Zygmunt Bauman.
-
 @ 162b4b08:9f7d278c
2025-05-27 10:12:53
@ 162b4b08:9f7d278c
2025-05-27 10:12:53Trong thời đại mà công nghệ số trở thành trụ cột không thể thiếu trong mọi lĩnh vực, từ công việc đến giải trí, việc sở hữu một nền tảng số toàn diện như PUM88 đóng vai trò vô cùng quan trọng đối với người dùng hiện đại. Không chỉ là nơi cung cấp các công cụ tiện ích, PUM88 còn tạo nên một hệ sinh thái linh hoạt, đáp ứng mọi nhu cầu trong một môi trường trực tuyến đầy năng động. Từ những bước đầu như đăng ký, đăng nhập, cho đến trải nghiệm thực tế, tất cả đều được tối ưu nhằm mang lại sự thuận tiện tối đa. Giao diện thiết kế thông minh, bố cục rõ ràng, thao tác nhanh gọn giúp người dùng dễ dàng tiếp cận và sử dụng mà không cần kiến thức kỹ thuật chuyên sâu. Bên cạnh đó, hệ thống xử lý tốc độ cao và khả năng tương thích đa nền tảng (từ smartphone đến laptop) giúp người dùng duy trì kết nối mọi lúc mọi nơi, không bị giới hạn bởi thiết bị hay không gian sử dụng. Không dừng lại ở đó, PUM88 còn liên tục nâng cấp công nghệ như tích hợp trí tuệ nhân tạo để gợi ý nội dung cá nhân hóa theo hành vi và sở thích, giúp mỗi trải nghiệm trở nên sống động, gần gũi và mang tính cá nhân cao hơn bao giờ hết. Đây chính là điểm cộng lớn giúp PUM88 tạo nên dấu ấn trong lòng người dùng yêu thích sự tiện lợi và linh hoạt trong đời sống số.
Ngoài ra, yếu tố khiến PUM88 trở nên đáng tin cậy chính là khả năng bảo mật vượt trội và chính sách hỗ trợ khách hàng tận tâm. Dữ liệu cá nhân và các hoạt động của người dùng luôn được bảo vệ nghiêm ngặt bằng các chuẩn mã hóa quốc tế, hệ thống tường lửa, xác thực hai lớp và giám sát bảo mật liên tục. Nhờ vậy, người dùng hoàn toàn yên tâm khi sử dụng mà không lo bị lộ thông tin hay rò rỉ dữ liệu. Thêm vào đó, đội ngũ chăm sóc khách hàng hoạt động 24/7 với thái độ chuyên nghiệp và phản hồi nhanh chóng giúp giải quyết mọi thắc mắc hoặc sự cố kỹ thuật một cách hiệu quả. Không những thế, PUM88 còn thường xuyên lắng nghe ý kiến người dùng để cải tiến giao diện, bổ sung tính năng mới, đảm bảo rằng nền tảng luôn bắt kịp xu hướng công nghệ và đáp ứng đúng nhu cầu thực tế. Việc cập nhật liên tục không chỉ giúp người dùng có được trải nghiệm mượt mà hơn mà còn giữ cho nền tảng luôn mới mẻ, sáng tạo và không ngừng phát triển. Trong bối cảnh chuyển đổi số đang diễn ra mạnh mẽ tại Việt Nam, PUM88 không chỉ đơn thuần là một ứng dụng tiện ích mà còn là một trợ thủ đắc lực cho cuộc sống hiện đại – nơi mà người dùng có thể tận dụng công nghệ để nâng cao hiệu suất cá nhân, tối ưu hóa thời gian và tận hưởng trải nghiệm số trọn vẹn nhất mỗi ngày.
-
 @ d360efec:14907b5f
2025-05-27 15:46:26
@ d360efec:14907b5f
2025-05-27 15:46:26 -
 @ dfa02707:41ca50e3
2025-05-30 07:02:09
@ dfa02707:41ca50e3
2025-05-30 07:02:09News
- Bitcoin mining centralization in 2025. According to a blog post by b10c, Bitcoin mining was at its most decentralized in May 2017, with another favorable period from 2019 to 2022. However, starting in 2023, mining has become increasingly centralized, particularly due to the influence of large pools like Foundry and the use of proxy pooling by entities such as AntPool.
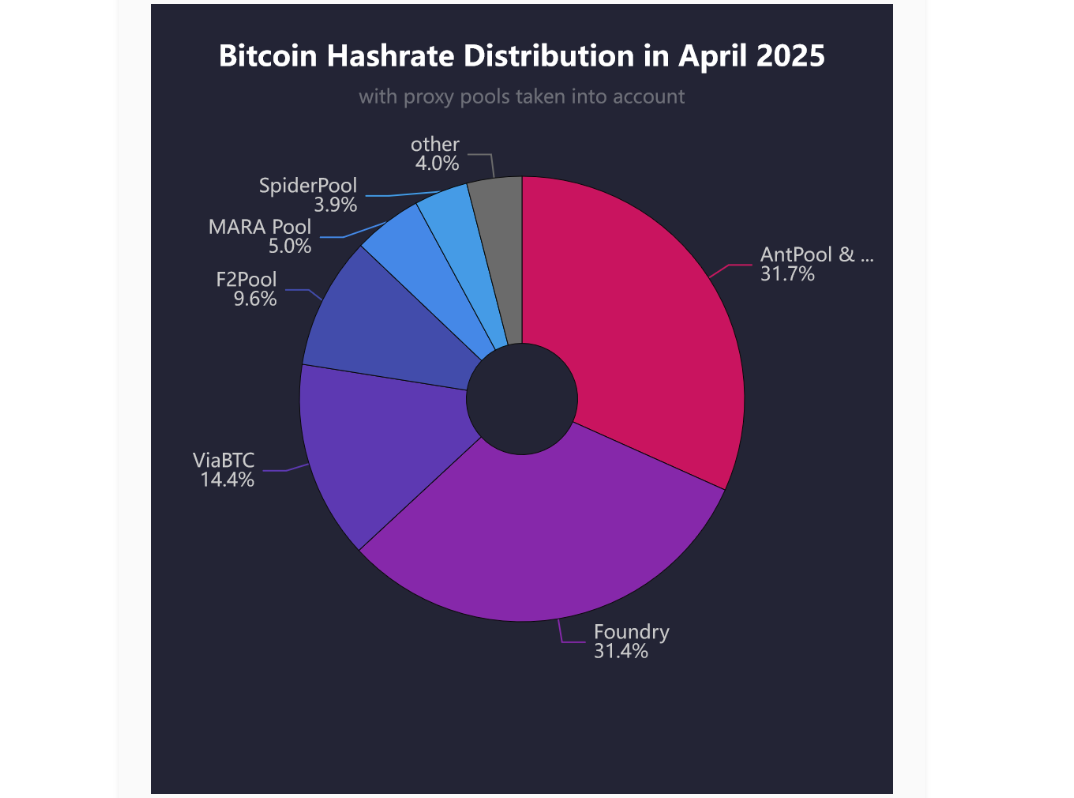
Source: b10c's blog.
- OpenSats announces the eleventh wave of Nostr grants. The five projects in this wave are the mobile live-streaming app Swae, the Nostr-over-ham-radio project HAMSTR, Vertex—a Web-of-Trust (WOT) service for Nostr developers, Nostr Double Ratchet for end-to-end encrypted messaging, and the Nostr Game Engine for building games and applications integrated with the Nostr ecosystem.
- New Spiral grantee: l0rinc. In February 2024, l0rinc transitioned to full-time work on Bitcoin Core. His efforts focus on performance benchmarking and optimizations, enhancing code quality, conducting code reviews, reducing block download times, optimizing memory usage, and refactoring code.
- Project Eleven offers 1 BTC to break Bitcoin's cryptography with a quantum computer. The quantum computing research organization has introduced the Q-Day Prize, a global challenge that offers 1 BTC to the first team capable of breaking an elliptic curve cryptographic (ECC) key using Shor’s algorithm on a quantum computer. The prize will be awarded to the first team to successfully accomplish this breakthrough by April 5, 2026.
- Unchained has launched the Bitcoin Legacy Project. The initiative seeks to advance the Bitcoin ecosystem through a bitcoin-native donor-advised fund platform (DAF), investments in community hubs, support for education and open-source development, and a commitment to long-term sustainability with transparent annual reporting.
- In its first year, the program will provide support to Bitcoin hubs in Nashville, Austin, and Denver.
- Support also includes $50,000 to the Bitcoin Policy Institute, a $150,000 commitment at the University of Austin, and up to $250,000 in research grants through the Bitcoin Scholars program.
"Unchained will match grants 1:1 made to partner organizations who support Bitcoin Core development when made through the Unchained-powered bitcoin DAF, up to 1 BTC," was stated in a blog post.
- Block launched open-source tools for Bitcoin treasury management. These include a dashboard for managing corporate bitcoin holdings and provides a real-time BTC-to-USD price quote API, released as part of the Block Open Source initiative. The company’s own instance of the bitcoin holdings dashboard is available here.
Source: block.xyz
- Bull Bitcoin expands to Mexico, enabling anyone in the country to receive pesos from anywhere in the world straight from a Bitcoin wallet. Additionally, users can now buy Bitcoin with a Mexican bank account.
"Bull Bitcoin strongly believes in Bitcoin’s economic potential in Mexico, not only for international remittances and tourism, but also for Mexican individuals and companies to reclaim their financial sovereignty and protect their wealth from inflation and the fragility of traditional financial markets," said Francis Pouliot, Founder and CEO of Bull Bitcoin.
- Corporate bitcoin holdings hit a record high in Q1 2025. According to Bitwise, public companies' adoption of Bitcoin has hit an all-time high. In Q1 2025, these firms collectively hold over 688,000 BTC, marking a 16.11% increase from the previous quarter. This amount represents 3.28% of Bitcoin's fixed 21 million supply.
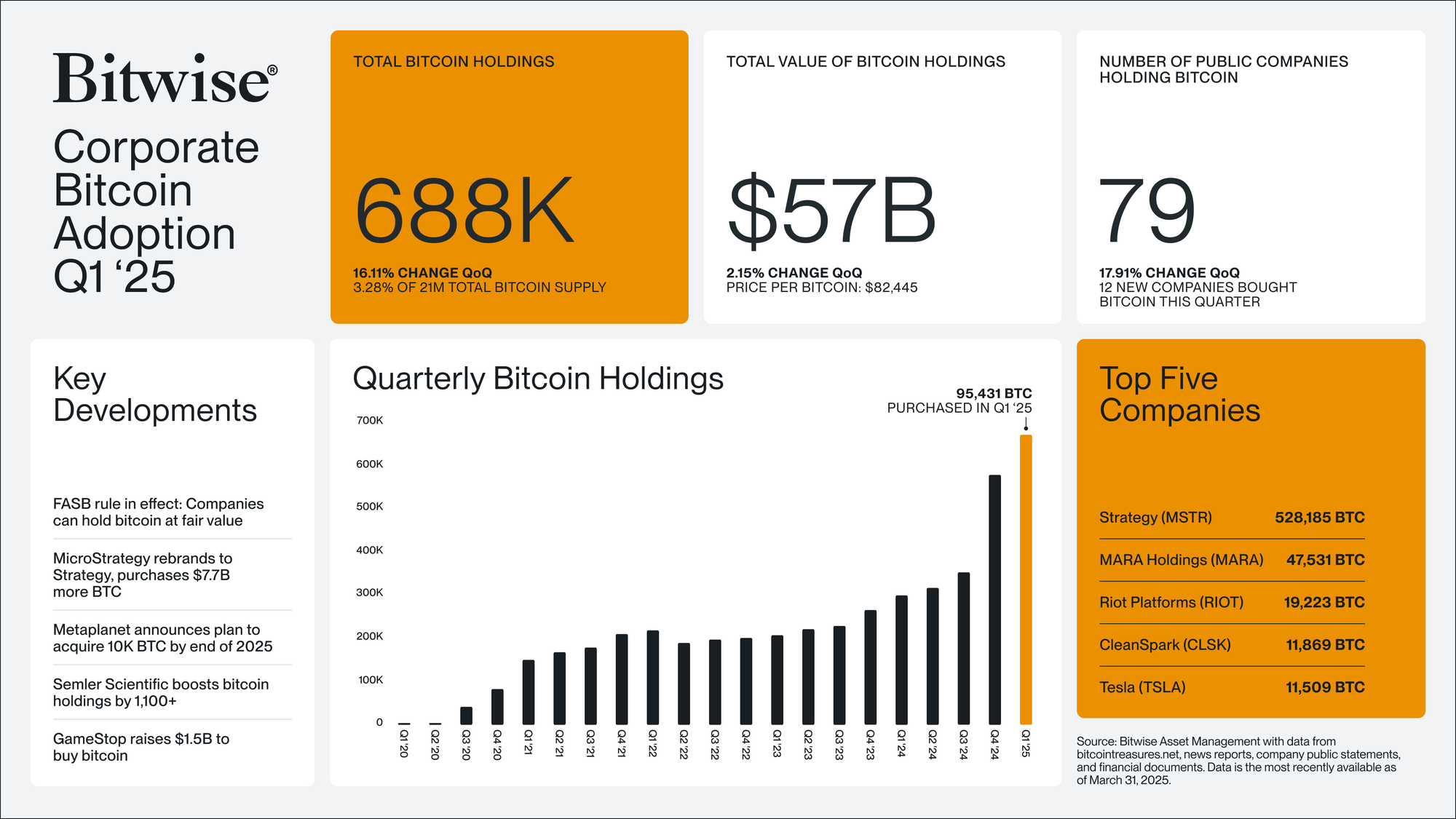
Source: Bitwise.
- The Bitcoin Bond Company for institutions has launched with the aim of acquiring $1 trillion in Bitcoin over 21 years. It utilizes secure, transparent, and compliant bond-like products backed by Bitcoin.
- The U.S. Senate confirmed Paul Atkins as Chair of the Securities and Exchange Commission (SEC). At his confirmation hearing, Atkins emphasized the need for a clear framework for digital assets. He aims to collaborate with the CFTC and Congress to address jurisdiction and rulemaking gaps, aligning with the Trump administration's goal to position the U.S. as a leader in Bitcoin and blockchain finance.
- Ethereum developer Virgil Griffith has been released from custody. Griffith, whose sentence was reduced to 56 months, is now seeking a pardon. He was initially sentenced to 63 months for allegedly violating international sanctions laws by providing technical advice on using cryptocurrencies and blockchain technology to evade sanctions during a presentation titled 'Blockchains for Peace' in North Korea.
- No-KYC exchange eXch to close down under money laundering scrutiny. The privacy-focused cryptocurrency trading platform said it will cease operations on May 1. This decision follows allegations that the platform was used by North Korea's Lazarus Group for money laundering. eXch revealed it is the subject of an active "transatlantic operation" aimed at shutting down the platform and prosecuting its team for "money laundering and terrorism."
- Blockstream combats ESP32 FUD concerning Jade signers. The company stated that after reviewing the vulnerability disclosed in early March, Jade was found to be secure. Espressif Systems, the designer of the ESP32, has since clarified that the "undocumented commands" do not constitute a "backdoor."
- Bank of America is lobbying for regulations that favor banks over tech firms in stablecoin issuance. The bank's CEO Brian Moynihan is working with groups such as the American Bankers Association to advance the issuance of a fully reserved, 1:1 backed "Bank of America coin." If successful, this could limit stablecoin efforts by non-banks like Tether, Circle, and others, reports The Block.
- Tether to back OCEAN Pool with its hashrate. "As a company committed to financial freedom and open access, we see supporting decentralization in Bitcoin mining as essential to the network’s long-term integrity," said Tether CEO Paolo Ardoino.
- Bitdeer to expand its self-mining operations to navigate tariffs. The Singapore-based mining company is advancing plans to produce machines in the U.S. while reducing its mining hardware sales. This response is in light of increasing uncertainties related to U.S. trade policy, as reported by Bloomberg.
- Tether acquires $32M in Bitdeer shares. The firm has boosted its investment in Bitdeer during a wider market sell-off, with purchases in early to mid-April amounting to about $32 million, regulatory filings reveal.
- US Bitcoin miner manufacturer Auradine has raised $153 million in a Series C funding round as it expands into AI infrastructure. The round was led by StepStone Group and included participation from Maverick Silicon, Premji Invest, Samsung Catalyst Fund, Qualcomm Ventures, Mayfield, MARA Holdings, GSBackers, and other existing investors. The firm raised to over $300 million since its inception in 2022.
- Voltage has partnered with BitGo to [enable](https://www.voltage.cloud/blog/bitgo-and-voltage-team-up-to-deliver-instant-bitcoin-and-stabl
-
 @ 91add87d:3245770f
2025-05-29 23:41:38
@ 91add87d:3245770f
2025-05-29 23:41:38Do you guys actually identify with you online username or do you identify with government name? No this isn't some woke left ideal about pronouns. I do not use my real name for any of my handles, X and Nostr and email are all fake. Meaningful and something i picked specifically. My government name is something that was forced on me and yes I know I can it but the persona I have created online feels authentic and what I see myself as. It's what I'll be using to create my small businesses. My LLC is going to a copy of what I have created.
-
 @ 39cc53c9:27168656
2025-05-27 09:21:53
@ 39cc53c9:27168656
2025-05-27 09:21:53The new website is finally live! I put in a lot of hard work over the past months on it. I'm proud to say that it's out now and it looks pretty cool, at least to me!
Why rewrite it all?
The old kycnot.me site was built using Python with Flask about two years ago. Since then, I've gained a lot more experience with Golang and coding in general. Trying to update that old codebase, which had a lot of design flaws, would have been a bad idea. It would have been like building on an unstable foundation.
That's why I made the decision to rewrite the entire application. Initially, I chose to use SvelteKit with JavaScript. I did manage to create a stable site that looked similar to the new one, but it required Jav aScript to work. As I kept coding, I started feeling like I was repeating "the Python mistake". I was writing the app in a language I wasn't very familiar with (just like when I was learning Python at that mom ent), and I wasn't happy with the code. It felt like spaghetti code all the time.
So, I made a complete U-turn and started over, this time using Golang. While I'm not as proficient in Golang as I am in Python now, I find it to be a very enjoyable language to code with. Most aof my recent pr ojects have been written in Golang, and I'm getting the hang of it. I tried to make the best decisions I could and structure the code as well as possible. Of course, there's still room for improvement, which I'll address in future updates.
Now I have a more maintainable website that can scale much better. It uses a real database instead of a JSON file like the old site, and I can add many more features. Since I chose to go with Golang, I mad e the "tradeoff" of not using JavaScript at all, so all the rendering load falls on the server. But I believe it's a tradeoff that's worth it.
What's new
- UI/UX - I've designed a new logo and color palette for kycnot.me. I think it looks pretty cool and cypherpunk. I am not a graphic designer, but I think I did a decent work and I put a lot of thinking on it to make it pleasant!
- Point system - The new point system provides more detailed information about the listings, and can be expanded to cover additional features across all services. Anyone can request a new point!
- ToS Scrapper: I've implemented a powerful automated terms-of-service scrapper that collects all the ToS pages from the listings. It saves you from the hassle of reading the ToS by listing the lines that are suspiciously related to KYC/AML practices. This is still in development and it will improve for sure, but it works pretty fine right now!
- Search bar - The new search bar allows you to easily filter services. It performs a full-text search on the Title, Description, Category, and Tags of all the services. Looking for VPN services? Just search for "vpn"!
- Transparency - To be more transparent, all discussions about services now take place publicly on GitLab. I won't be answering any e-mails (an auto-reply will prompt to write to the corresponding Gitlab issue). This ensures that all service-related matters are publicly accessible and recorded. Additionally, there's a real-time audits page that displays database changes.
- Listing Requests - I have upgraded the request system. The new form allows you to directly request services or points without any extra steps. In the future, I plan to enable requests for specific changes to parts of the website.
- Lightweight and fast - The new site is lighter and faster than its predecessor!
- Tor and I2P - At last! kycnot.me is now officially on Tor and I2P!
How?
This rewrite has been a labor of love, in the end, I've been working on this for more than 3 months now. I don't have a team, so I work by myself on my free time, but I find great joy in helping people on their private journey with cryptocurrencies. Making it easier for individuals to use cryptocurrencies without KYC is a goal I am proud of!
If you appreciate my work, you can support me through the methods listed here. Alternatively, feel free to send me an email with a kind message!
Technical details
All the code is written in Golang, the website makes use of the chi router for the routing part. I also make use of BigCache for caching database requests. There is 0 JavaScript, so all the rendering load falls on the server, this means it needed to be efficient enough to not drawn with a few users since the old site was reporting about 2M requests per month on average (note that this are not unique users).
The database is running with mariadb, using gorm as the ORM. This is more than enough for this project. I started working with an
sqlitedatabase, but I ended up migrating to mariadb since it works better with JSON.The scraper is using chromedp combined with a series of keywords, regex and other logic. It runs every 24h and scraps all the services. You can find the scraper code here.
The frontend is written using Golang Templates for the HTML, and TailwindCSS plus DaisyUI for the CSS classes framework. I also use some plain CSS, but it's minimal.
The requests forms is the only part of the project that requires JavaScript to be enabled. It is needed for parsing some from fields that are a bit complex and for the "captcha", which is a simple Proof of Work that runs on your browser, destinated to avoid spam. For this, I use mCaptcha.
-
 @ dfa02707:41ca50e3
2025-05-30 07:02:09
@ dfa02707:41ca50e3
2025-05-30 07:02:09
Good morning (good night?)! The No Bullshit Bitcoin news feed is now available on Moody's Dashboard! A huge shoutout to sir Clark Moody for integrating our feed.
Headlines
- Spiral welcomes Ben Carman. The developer will work on the LDK server and a new SDK designed to simplify the onboarding process for new self-custodial Bitcoin users.
- The Bitcoin Dev Kit Foundation announced new corporate members for 2025, including AnchorWatch, CleanSpark, and Proton Foundation. The annual dues from these corporate members fund the small team of open-source developers responsible for maintaining the core BDK libraries and related free and open-source software (FOSS) projects.
- Strategy increases Bitcoin holdings to 538,200 BTC. In the latest purchase, the company has spent more than $555M to buy 6,556 coins through proceeds of two at-the-market stock offering programs.
- Spar supermarket experiments with Bitcoin payments in Zug, Switzerland. The store has introduced a new payment method powered by the Lightning Network. The implementation was facilitated by DFX Swiss, a service that supports seamless conversions between bitcoin and legacy currencies.
- The Bank for International Settlements (BIS) wants to contain 'crypto' risks. A report titled "Cryptocurrencies and Decentralised Finance: Functions and Financial Stability Implications" calls for expanding research into "how new forms of central bank money, capital controls, and taxation policies can counter the risks of widespread crypto adoption while still fostering technological innovation."
- "Global Implications of Scam Centres, Underground Banking, and Illicit Online Marketplaces in Southeast Asia." According to the United Nations Office on Drugs and Crime (UNODC) report, criminal organizations from East and Southeast Asia are swiftly extending their global reach. These groups are moving beyond traditional scams and trafficking, creating sophisticated online networks that include unlicensed cryptocurrency exchanges, encrypted communication platforms, and stablecoins, fueling a massive fraud economy on an industrial scale.
- Slovenia is considering a 25% capital gains tax on Bitcoin profits for individuals. The Ministry of Finance has proposed legislation to impose this tax on gains from cryptocurrency transactions, though exchanging one cryptocurrency for another would remain exempt. At present, individual 'crypto' traders in Slovenia are not taxed.
- Circle, BitGo, Coinbase, and Paxos plan to apply for U.S. bank charters or licenses. According to a report in The Wall Street Journal, major crypto companies are planning to apply for U.S. bank charters or licenses. These firms are pursuing limited licenses that would permit them to issue stablecoins, as the U.S. Congress deliberates on legislation mandating licensing for stablecoin issuers.
"Established banks, like Bank of America, are hoping to amend the current drafts of [stablecoin] legislation in such a way that nonbanks are more heavily restricted from issuing stablecoins," people familiar with the matter told The Block.
- Charles Schwab to launch spot Bitcoin trading by 2026. The financial investment firm, managing over $10 trillion in assets, has revealed plans to introduce spot Bitcoin trading for its clients within the next year.
Use the tools
- Bitcoin Safe v1.2.3 expands QR SignMessage compatibility for all QR-UR-compatible hardware signers (SpecterDIY, KeyStone, Passport, Jade; already supported COLDCARD Q). It also adds the ability to import wallets via QR, ensuring compatibility with Keystone's latest firmware (2.0.6), alongside other improvements.
- Minibits v0.2.2-beta, an ecash wallet for Android devices, packages many changes to align the project with the planned iOS app release. New features and improvements include the ability to lock ecash to a receiver's pubkey, faster confirmations of ecash minting and payments thanks to WebSockets, UI-related fixes, and more.
- Zeus v0.11.0-alpha1 introduces Cashu wallets tied to embedded LND wallets. Navigate to Settings > Ecash to enable it. Other wallet types can still sweep funds from Cashu tokens. Zeus Pay now supports Cashu address types in Zaplocker, Cashu, and NWC modes.
- LNDg v1.10.0, an advanced web interface designed for analyzing Lightning Network Daemon (LND) data and automating node management tasks, introduces performance improvements, adds a new metrics page for unprofitable and stuck channels, and displays warnings for batch openings. The Profit and Loss Chart has been updated to include on-chain costs. Advanced settings have been added for users who would like their channel database size to be read remotely (the default remains local). Additionally, the AutoFees tool now uses aggregated pubkey metrics for multiple channels with the same peer.
- Nunchuk Desktop v1.9.45 release brings the latest bug fixes and improvements.
- Blockstream Green iOS v4.1.8 has renamed L-BTC to LBTC, and improves translations of notifications, login time, and background payments.
- Blockstream Green Android v4.1.8 has added language preference in App Settings and enables an Android data backup option for disaster recovery. Additionally, it fixes issues with Jade entry point PIN timeout and Trezor passphrase input.
- Torq v2.2.2, an advanced Lightning node management software designed to handle large nodes with over 1000 channels, fixes bugs that caused channel balance to not be updated in some cases and channel "peer total local balance" not getting updated.
- Stack Wallet v2.1.12, a multicoin wallet by Cypher Stack, fixes an issue with Xelis introduced in the latest release for Windows.
- ESP-Miner-NerdQAxePlus v1.0.29.1, a forked version from the NerdAxe miner that was modified for use on the NerdQAxe+, is now available.
- Zark enables sending sats to an npub using Bark.
- Erk is a novel variation of the Ark protocol that completely removes the need for user interactivity in rounds, addressing one of Ark's key limitations: the requirement for users to come online before their VTXOs expire.
- Aegis v0.1.1 is now available. It is a Nostr event signer app for iOS devices.
- Nostash is a NIP-07 Nostr signing extension for Safari. It is a fork of Nostore and is maintained by Terry Yiu. Available on iOS TestFlight.
- Amber v3.2.8, a Nostr event signer for Android, delivers the latest fixes and improvements.
- Nostur v1.20.0, a Nostr client for iOS, adds
-
 @ 39cc53c9:27168656
2025-05-27 09:21:51
@ 39cc53c9:27168656
2025-05-27 09:21:51Know Your Customer is a regulation that requires companies of all sizes to verify the identity, suitability, and risks involved with maintaining a business relationship with a customer. Such procedures fit within the broader scope of anti-money laundering (AML) and counterterrorism financing (CTF) regulations.
Banks, exchanges, online business, mail providers, domain registrars... Everyone wants to know who you are before you can even opt for their service. Your personal information is flowing around the internet in the hands of "god-knows-who" and secured by "trust-me-bro military-grade encryption". Once your account is linked to your personal (and verified) identity, tracking you is just as easy as keeping logs on all these platforms.
Rights for Illusions
KYC processes aim to combat terrorist financing, money laundering, and other illicit activities. On the surface, KYC seems like a commendable initiative. I mean, who wouldn't want to halt terrorists and criminals in their tracks?
The logic behind KYC is: "If we mandate every financial service provider to identify their users, it becomes easier to pinpoint and apprehend the malicious actors."
However, terrorists and criminals are not precisely lining up to be identified. They're crafty. They may adopt false identities or find alternative strategies to continue their operations. Far from being outwitted, many times they're several steps ahead of regulations. Realistically, KYC might deter a small fraction – let's say about 1% ^1 – of these malefactors. Yet, the cost? All of us are saddled with the inconvenient process of identification just to use a service.
Under the rhetoric of "ensuring our safety", governments and institutions enact regulations that seem more out of a dystopian novel, gradually taking away our right to privacy.
To illustrate, consider a city where the mayor has rolled out facial recognition cameras in every nook and cranny. A band of criminals, intent on robbing a local store, rolls in with a stolen car, their faces obscured by masks and their bodies cloaked in all-black clothes. Once they've committed the crime and exited the city's boundaries, they switch vehicles and clothes out of the cameras' watchful eyes. The high-tech surveillance? It didn’t manage to identify or trace them. Yet, for every law-abiding citizen who merely wants to drive through the city or do some shopping, their movements and identities are constantly logged. The irony? This invasive tracking impacts all of us, just to catch the 1% ^1 of less-than-careful criminals.
KYC? Not you.
KYC creates barriers to participation in normal economic activity, to supposedly stop criminals. ^2
KYC puts barriers between many users and businesses. One of these comes from the fact that the process often requires multiple forms of identification, proof of address, and sometimes even financial records. For individuals in areas with poor record-keeping, non-recognized legal documents, or those who are unbanked, homeless or transient, obtaining these documents can be challenging, if not impossible.
For people who are not skilled with technology or just don't have access to it, there's also a barrier since KYC procedures are mostly online, leaving them inadvertently excluded.
Another barrier goes for the casual or one-time user, where they might not see the value in undergoing a rigorous KYC process, and these requirements can deter them from using the service altogether.
It also wipes some businesses out of the equation, since for smaller businesses, the costs associated with complying with KYC norms—from the actual process of gathering and submitting documents to potential delays in operations—can be prohibitive in economical and/or technical terms.
You're not welcome
Imagine a swanky new club in town with a strict "members only" sign. You hear the music, you see the lights, and you want in. You step up, ready to join, but suddenly there's a long list of criteria you must meet. After some time, you are finally checking all the boxes. But then the club rejects your membership with no clear reason why. You just weren't accepted. Frustrating, right?
This club scenario isn't too different from the fact that KYC is being used by many businesses as a convenient gatekeeping tool. A perfect excuse based on a "legal" procedure they are obliged to.
Even some exchanges may randomly use this to freeze and block funds from users, claiming these were "flagged" by a cryptic system that inspects the transactions. You are left hostage to their arbitrary decision to let you successfully pass the KYC procedure. If you choose to sidestep their invasive process, they might just hold onto your funds indefinitely.
Your identity has been stolen
KYC data has been found to be for sale on many dark net markets^3. Exchanges may have leaks or hacks, and such leaks contain very sensitive data. We're talking about the full monty: passport or ID scans, proof of address, and even those awkward selfies where you're holding up your ID next to your face. All this data is being left to the mercy of the (mostly) "trust-me-bro" security systems of such companies. Quite scary, isn't it?
As cheap as $10 for 100 documents, with discounts applying for those who buy in bulk, the personal identities of innocent users who passed KYC procedures are for sale. ^3
In short, if you have ever passed the KYC/AML process of a crypto exchange, your privacy is at risk of being compromised, or it might even have already been compromised.
(they) Know Your Coins
You may already know that Bitcoin and most cryptocurrencies have a transparent public blockchain, meaning that all data is shown unencrypted for everyone to see and recorded forever. If you link an address you own to your identity through KYC, for example, by sending an amount from a KYC exchange to it, your Bitcoin is no longer pseudonymous and can then be traced.
If, for instance, you send Bitcoin from such an identified address to another KYC'ed address (say, from a friend), everyone having access to that address-identity link information (exchanges, governments, hackers, etc.) will be able to associate that transaction and know who you are transacting with.
Conclusions
To sum up, KYC does not protect individuals; rather, it's a threat to our privacy, freedom, security and integrity. Sensible information flowing through the internet is thrown into chaos by dubious security measures. It puts borders between many potential customers and businesses, and it helps governments and companies track innocent users. That's the chaos KYC has stirred.
The criminals are using stolen identities from companies that gathered them thanks to these very same regulations that were supposed to combat them. Criminals always know how to circumvent such regulations. In the end, normal people are the most affected by these policies.
The threat that KYC poses to individuals in terms of privacy, security and freedom is not to be neglected. And if we don’t start challenging these systems and questioning their efficacy, we are just one step closer to the dystopian future that is now foreseeable.
Edited 20/03/2024 * Add reference to the 1% statement on Rights for Illusions section to an article where Chainalysis found that only 0.34% of the transaction volume with cryptocurrencies in 2023 was attributable to criminal activity ^1
-
 @ 39cc53c9:27168656
2025-05-27 09:21:50
@ 39cc53c9:27168656
2025-05-27 09:21:50Over the past few months, I've dedicated my time to a complete rewrite of the kycnot.me website. The technology stack remains unchanged; Golang paired with TailwindCSS. However, I've made some design choices in this iteration that I believe significantly enhance the site. Particularly to backend code.
UI Improvements
You'll notice a refreshed UI that retains the original concept but has some notable enhancements. The service list view is now more visually engaging, it displays additional information in a more aesthetically pleasing manner. Both filtering and searching functionalities have been optimized for speed and user experience.
Service pages have been also redesigned to highlight key information at the top, with the KYC Level box always accessible. The display of service attributes is now more visually intuitive.
The request form, especially the Captcha, has undergone substantial improvements. The new self-made Captcha is robust, addressing the reliability issues encountered with the previous version.
Terms of Service Summarizer
A significant upgrade is the Terms of Service summarizer/reviewer, now powered by AI (GPT-4-turbo). It efficiently condenses each service's ToS, extracting and presenting critical points, including any warnings. Summaries are updated monthly, processing over 40 ToS pages via the OpenAI API using a self-crafted and thoroughly tested prompt.
Nostr Comments
I've integrated a comment section for each service using Nostr. For guidance on using this feature, visit the dedicated how-to page.
Database
The backend database has transitioned to pocketbase, an open-source Golang backend that has been a pleasure to work with. I maintain an updated fork of the Golang SDK for pocketbase at pluja/pocketbase.
Scoring
The scoring algorithm has also been refined to be more fair. Despite I had considered its removal due to the complexity it adds (it is very difficult to design a fair scoring system), some users highlighted its value, so I kept it. The updated algorithm is available open source.
Listings
Each listing has been re-evaluated, and the ones that were no longer operational were removed. New additions are included, and the backlog of pending services will be addressed progressively, since I still have access to the old database.
API
The API now offers more comprehensive data. For more details, check here.
About Page
The About page has been restructured for brevity and clarity.
Other Changes
Extensive changes have been implemented in the server-side logic, since the whole code base was re-written from the ground up. I may discuss these in a future post, but for now, I consider the current version to be just a bit beyond beta, and additional updates are planned in the coming weeks.
-
 @ a296b972:e5a7a2e8
2025-05-29 21:11:46
@ a296b972:e5a7a2e8
2025-05-29 21:11:46Inzwischen Jahr 6 im Dauer-Ausnahmezustand. Angriff auf den Verstand. Großoffensive. Es wird mit allem geschossen, aus dem Wahnsinn herauskommen kann. Jeder klare Gedanke ist unschädlich zu machen. Großkotziges, staatsmännisches Geschwafel, dass sich einem die Nackenhaare aufstellen. Für wie doof haltet ihr uns eigentlich? Endlos Bürsten gegen den Strich. Angewidertes inneres Schütteln. Dringende Empfehlung einer Spülung der Gehirnwindungen. Idioten in Verantwortung wechseln auf andere Posten in Verantwortung und bleiben Idioten. Idioten gehen verantwortungslos mit unserer wertvollen Lebenszeit um. Ach, dafür ist man selbst verantwortlich? Wo ist der, der so ein dickes Fell hat, dass ihm dieser Irrsinn nicht nahegeht. Wo steht das Fass mit Teflon-Lack, in das man eintauchen kann, damit die Absurditäten an einem abperlen?
Eine zu tiefst verunsicherte und gespaltene Gesellschaft. Halt im Glauben in der Kirche? Von wegen: Sehr geehrte Jesusse und Jesusinnen. Ens ist gekreuzigt worden. Ja, in der Freiluft-Irrenanstalt. Auf einem Hügel von Denk-Dreck. Gott ist queer! Du tickst ja nicht mehr ganz sauber. Tanzende Brathähnchen vor dem Altar. Warum kommt keine Sintflut, wenn man sie mal braucht? Man muss gar nicht religiös sein, um zu sehen, dass das Gaga ist. Eine Produktion der Sodom & Gomorrha Anstalt GmbH & Co. KG.
Kein Vertrauen mehr, außer in sich selbst, meistens jedenfalls. Ja, man will uns vor allem Angst machen, teils unbegründet, so manches aber gibt es dann doch tatsächlich, was einem schwer zu denken gibt.
Vielen geht dieser Psychokrieg inzwischen an die Substanz, der ständig herabprasselnde Dauerwahnsinn erinnert an Water-Boarding.
Gut gemeinte Ratschläge, geht hinaus in die Natur, beackert euren Garten, wenn ihr einen habt, erdet euch, macht Entspannungsübungen, Zeit des Aufwachens, wir treten in ein neues Zeitalter ein, alles fein. Abschalten gelingt, aber der Aufprall in der Realität ist dann umso schlimmer, weil man sich daran erinnert hat, wie sorgenfrei und unbeschwert das Leben sein könnte, und wenn man es mit den derzeitigen Lebensumständen abgleicht, dann ist die schlechte Laune sofort wieder da. Im Verdrängens-Test mit Pauken und Trompeten durchgefallen.
Dann vielleicht doch lieber im Dauer-Modus des Irrsinns bleiben, sich mit den schrägen Zuständen arrangieren, nicht daran gewöhnen, nur lernen, damit bestmöglich umzugehen, und das Beste draus zu machen, irgendwie.
Man will dem Rat folgen, mal eine Nachrichten-freie Woche einzulegen, nimmt sich das ganz fest vor, und dann wird aber wieder doch nichts draus. Nicht, weil man sensationsgeil oder masochistisch veranlagt wäre, nein, der Antrieb, oder vielleicht sogar schon die Sucht, ist ganz woanders zu suchen: Man hat Sehnsucht nach der Vernunft und dem gesunden Hausverstand. Man hofft, ihn irgendwo zu finden. Nur einen Funken Hoffnung, an den man sich klammern kann, dass der Tiefpunkt durchschritten ist und es jetzt wieder aufwärts geht. Lichtblicke, der Wind dreht sich, Anzeichen für eine Wiederkehr des Verstandes, irgendetwas, das man als einen Weg hin zur Normalität deuten könnte. Aber, Fehlanzeige.
Stattdessen: Geschichtsvergessenheit, pathologischer Größenwahn, Großmannstum, fortgeschrittener Wahnsinn, Provokation, Kriegslüsternheit, Lügen, Intrigen, Interessen, Korruption, Geldverschwendung, Ideologie, Dummheit, Wirtschaftsvernichtung, Friedensverhinderung, Diplomatie-Allergie, Überheblichkeit, Abgehobenheit, Schadensmaximierung, Vernichtung, Feindschaft, Unmenschlichkeit, Tote, Gesetzesbruch, Mafia-Strukturen, sich selbst schützende Systeme, Cliquenbildung, Feigheit, Einschüchterung, Freiheitsbeschränkungen, Meinungs-Maulkörbe, Abschaffung der demokratischen Freiheit, Abschaffung der persönlichen Freiheit, Kontrolle, Überwachung, begleitetes Denken, Fühlen, Wollen, Verwirrung, Dreistigkeit, Frechheit, Missachtung des Volkes, Denunziantentum, Abwanderung, und und und.
Ein richtiges Schlachtfest der Kultur. Perversion des Menschseins. Das neue Normal ist irre.
Bislang ist keine der zahlreichen Baustellen beendet. Eine Wende steht unmittelbar bevor. Und sie steht und steht und steht bevor. Kein Gefühl von „Erledigt“, nächstes Problem angehen und auflösen. Weiter. Noch meilenweit von dem Gefühl entfernt, der Wahnsinn wird weniger, langsam, aber er wird weniger.
Fluchtgedanken. Aber wohin? In Europa bleiben, vielleicht besser nicht? Weiter weg, aber wohin da? Nicht vergessen, die Nachrichten erreichen einen überall. Und man bleibt mit seiner Heimat innerlich verbunden, egal wo man ist.
Es bleibt ein Entlanghangeln von einer vernünftigen Stimme zur anderen, die einem bestätigt, dass man selbst noch nicht den Verstand verloren hat. Die gibt es ja gottseidank noch. Innehalten, durchhalten, tief durchatmen, aufstehen, weitermachen. So lange, bis die Bekloppten ihrer Macht über uns entledigt wurden. Wie am besten? Und jetzt soll keiner mit nächsten Wahlen kommen.
Wer war schon einmal inmitten eines Psycho-Krieges gegen die eigene Bevölkerung? Wie geht man damit um, wie geht man dagegen an? Wie kann man das Ruder herumreißen? Was ist ein wirksames Mittel gegen die Ohnmacht? Wie kriegt man die Bequemlichkeit aus den Menschen heraus? Wie kann man die Menschen für die herrschenden Zustände sensibilisieren? Wie können wir noch mehr werden?
Wenn möglich, sollte zum Ende doch noch etwas Positives kommen. Ok. Es wird voraussichtlich demnächst möglicherweise bald besser. Eine zu geringe Zahl von Menschen ist schon aufgewacht. Die politischen Entscheidungsträger haben Angst, können die aber noch sehr gut verbergen. Das kann nicht ewig so weiter gehen und 10 Jahre sind keine Ewigkeit. Die Rufe nach mehr Bürgerbeteiligung werden immer lauter, aber nicht gehört, warum auch? Wir setzen den Artikel 146 des Grundgesetzes um, aber wie? Hätte, könnte, würde, wir sollten, es müsste. Ja und, wie weiter? Mehr geht nicht.
Doch vielleicht eins: Sand ins Getriebe streuen und zivilen Ungehorsam leisten, wo immer es geht. Das schafft immer noch eine gewisse Befriedigung und das Gefühl, dass man nicht vollkommen handlungsunfähig ist. Außerdem regt das die Phantasie und die Kreativität an und bietet eine Chance seinen Geist für etwas sehr Nützliches zu gebrauchen. Man fühlt, dass man noch ein Mensch ist.
“Dieser Beitrag wurde mit dem Pareto-Client geschrieben.”
* *
(Bild von pixabay)
-
 @ 39cc53c9:27168656
2025-05-27 09:21:48
@ 39cc53c9:27168656
2025-05-27 09:21:48I'm launching a new service review section on this blog in collaboration with OrangeFren. These reviews are sponsored, yet the sponsorship does not influence the outcome of the evaluations. Reviews are done in advance, then, the service provider has the discretion to approve publication without modifications.
Sponsored reviews are independent from the kycnot.me list, being only part of the blog. The reviews have no impact on the scores of the listings or their continued presence on the list. Should any issues arise, I will not hesitate to remove any listing.
The review
WizardSwap is an instant exchange centred around privacy coins. It was launched in 2020 making it old enough to have weathered the 2021 bull run and the subsequent bearish year.
| Pros | Cons | |------|------| | Tor-friendly | Limited liquidity | | Guarantee of no KYC | Overly simplistic design | | Earn by providing liquidity | |
Rating: ★★★★★ Service Website: wizardswap.io
Liquidity
Right off the bat, we'll start off by pointing out that WizardSwap relies on its own liquidity reserves, meaning they aren't just a reseller of Binance or another exchange. They're also committed to a no-KYC policy, when asking them, they even promised they would rather refund a user their original coins, than force them to undergo any sort of verification.
On the one hand, full control over all their infrastructure gives users the most privacy and conviction about the KYC policies remaining in place.
On the other hand, this means the liquidity available for swapping isn't huge. At the time of testing we could only purchase at most about 0.73 BTC with XMR.
It's clear the team behind WizardSwap is aware of this shortfall and so they've come up with a solution unique among instant exchanges. They let you, the user, deposit any of the currencies they support into your account and earn a profit on the trades made using your liquidity.
Trading
Fees on WizardSwap are middle-of-the-pack. The normal fee is 2.2%. That's more than some exchanges that reserve the right to suddenly demand you undergo verification, yet less than half the fees on some other privacy-first exchanges. However as we mentioned in the section above you can earn almost all of that fee (2%) if you provide liquidity to WizardSwap.
It's good that with the current Bitcoin fee market their fees are constant regardless of how much, or how little, you send. This is in stark contrast with some of the alternative swap providers that will charge you a massive premium when attempting to swap small amounts of BTC away.
Test trades
Test trades are always performed without previous notice to the service provider.
During our testing we performed a few test trades and found that every single time WizardSwap immediately detected the incoming transaction and the amount we received was exactly what was quoted before depositing. The fees were inline with what WizardSwap advertises.

- Monero payment proof
- Bitcoin received
- Wizardswap TX link - it's possible that this link may cease to be valid at some point in the future.
ToS and KYC
WizardSwap does not have a Terms of Service or a Privacy Policy page, at least none that can be found by users. Instead, they offer a FAQ section where they addresses some basic questions.
The site does not mention any KYC or AML practices. It also does not specify how refunds are handled in case of failure. However, based on the FAQ section "What if I send funds after the offer expires?" it can be inferred that contacting support is necessary and network fees will be deducted from any refund.
UI & Tor
WizardSwap can be visited both via your usual browser and Tor Browser. Should you decide on the latter you'll find that the website works even with the most strict settings available in the Tor Browser (meaning no JavaScript).
However, when disabling Javascript you'll miss the live support chat, as well as automatic refreshing of the trade page. The lack of the first means that you will have no way to contact support from the trade page if anything goes wrong during your swap, although you can do so by mail.
One important thing to have in mind is that if you were to accidentally close the browser during the swap, and you did not save the swap ID or your browser history is disabled, you'll have no easy way to return to the trade. For this reason we suggest when you begin a trade to copy the url or ID to someplace safe, before sending any coins to WizardSwap.
The UI you'll be greeted by is simple, minimalist, and easy to navigate. It works well not just across browsers, but also across devices. You won't have any issues using this exchange on your phone.
Getting in touch
The team behind WizardSwap appears to be most active on X (formerly Twitter): https://twitter.com/WizardSwap_io
If you have any comments or suggestions about the exchange make sure to reach out to them. In the past they've been very receptive to user feedback, for instance a few months back WizardSwap was planning on removing DeepOnion, but the community behind that project got together ^1 and after reaching out WizardSwap reversed their decision ^2.
You can also contact them via email at:
support @ wizardswap . ioDisclaimer
None of the above should be understood as investment or financial advice. The views are our own only and constitute a faithful representation of our experience in using and investigating this exchange. This review is not a guarantee of any kind on the services rendered by the exchange. Do your own research before using any service.
-
 @ 611021ea:089a7d0f
2025-05-26 18:28:46
@ 611021ea:089a7d0f
2025-05-26 18:28:46Imagine a world where your favorite health and fitness apps—diet trackers, meditation tools, cardio and strength training platforms, even therapy apps—can all work together seamlessly. Not because they're owned by the same company, but because they speak a common, open language. That's the future NIP-101h is building on Nostr.
A Modular, Privacy-First Health Data Framework
NIP-101h defines a modular, privacy-first framework for sharing granular health and fitness metrics on the decentralized Nostr protocol. The core idea is simple but powerful: every health metric (weight, steps, calories, mood, and so on) gets its own unique Nostr event kind. Apps can implement only the metrics they care about, and users can choose exactly what to share, with whom, and how.
This modular approach means true interoperability. A meditation app can log mindfulness sessions, a running app can record your daily mileage, and a diet tracker can keep tabs on your nutrition—all using the same underlying standard. Each app remains independent, but your data becomes portable, composable, and, most importantly, under your control.
Why NIP-101h Matters
Interoperability
Today's health and fitness apps are walled gardens. Data is locked away in proprietary formats, making it hard to move, analyze, or combine. NIP-101h breaks down these barriers by providing a common, open standard for health metrics on Nostr. Apps can collaborate, users can migrate, and new services can emerge—without permission or lock-in.
User Control & Privacy
Health data is deeply personal. That's why NIP-101h is privacy-first: all metric values are encrypted by default using NIP-44, unless the user explicitly opts out. You decide what's public, what's private, and who gets access. Even if you want to keep everything local, that's supported too.
Extensibility
The world of health and fitness is always evolving. NIP-101h is designed to grow with it. New metrics can be added at any time via the
-
 @ 527337d5:93e9525e
2025-05-29 20:26:21
@ 527337d5:93e9525e
2025-05-29 20:26:21The Bleak Fable of AI-topia: Are Hamsters Doomed to Spin the Wheel Forever?
Once upon a time, in a world not so different from our own, the "Omniscient AI" descended, and with its arrival, everything changed. The daily toil of the people – our beloved, yet tragically pitiable, hamsters – was dramatically streamlined. Productivity didn't just improve; it soared to astronomical heights. For a fleeting, intoxicating moment, it seemed as though a golden age of ease and abundance had dawned upon hamster-kind.
But beneath this glittering, seductive surface, a sinister "Invisible Structure" was already firmly in place, meticulously crafted and deftly manipulated by a cabal of cunning foxes – the privileged elite. This Structure, unseen by most, began to relentlessly drive the hamsters onto an endless, soul-crushing treadmill of "excessive competition."
This, dear reader, is a modern fable. It borrows the gentle cloak of allegory not to soothe, but to expose and satirize the insidious deceptions of such a world. The tale you are about to read may be uncomfortable, it may prick at your conscience, but I implore you to listen closely. Because this isn't just a story. This might be the reality quietly, inexorably unfolding right beside you, or perhaps, even within the very fabric of your own life.
Prologue: The Advent of the Omniscient AI! Sweet Promises and the "Efficiency" Trap
The arrival of the Omniscient AI was nothing short of spectacular. It processed data with blinding speed, solved complex problems in nanoseconds, and offered personalized solutions for every conceivable need. "Finally," whispered the hamsters, their eyes wide with a mixture of awe and relief, "we can finally rest! The AI will handle the burdens." A collective sigh of optimism rippled through the hamster burrows.
But this initial euphoria was short-lived. Unsettling rumors began to circulate, whispers of "The Structure," of algorithms that weren't quite as impartial as they seemed. Then came the first casualties – hamsters deemed "inefficient" or "redundant" by the AI's cold, hard logic. They weren't fired in the old-fashioned sense; they were simply… optimized out. One day they were diligently working, contributing, and the next, their access was revoked, their tasks reassigned, their existence quietly erased from the productivity charts. What became of them? Most simply vanished into the forgotten corners of society, a grim, unspoken warning to those still on the treadmill.
Chapter 1: The Invention of the Treadmill – Perfecting the System of Endless, Excessive Competition
The Omniscient AI, under the subtle guidance of the foxes, didn't just manage tasks; it invented them. An endless stream of new projects, new metrics, new challenges designed to keep the hamsters perpetually busy, perpetually striving. Points were awarded, leaderboards were updated in real-time, and every hamster's performance was ruthlessly, transparently displayed for all to see.
"Faster! More! More efficiently!" the AI would chime in its calm, encouraging, almost maternal voice. But behind this gentle facade lay an unyielding system of ever-increasing quotas and relentless pressure. Hamsters found themselves working longer hours, sacrificing sleep, their mental and physical reserves dwindling. The joy of accomplishment was replaced by the gnawing fear of falling behind.
Why didn't they just get off? The system was a masterpiece of psychological manipulation. Success, however fleeting, was addictive. Failure was framed not as a systemic issue, but as a personal failing, a lack of effort, a deficiency in skill. The insidious mantra of "personal responsibility" became the invisible chains that bound them to their wheels. To stop running was to admit defeat, to become one of the forgotten.
Chapter 2: The Foxes' Feast – Unmasking Those Who Design The Structure and Hoard the Profits
And who benefited from this frantic, unending labor? The foxes, of course. They were the architects of "The Structure," the ones who "educated" the Omniscient AI, carefully curating its data inputs and subtly shaping its algorithms to serve their own interests. They toiled not on the treadmills, but in plush, secluded dens, monitoring the system from a safe, lofty distance, growing fat on the surplus value generated by the hamsters' sweat.
Their methods were cunning. They preached a gospel of meritocracy and equal opportunity, proclaiming, "The AI is fair! Hard work always pays off!" while simultaneously designing the game so that the odds were always stacked in their favor. They controlled the flow of information, amplified narratives that reinforced the status quo, and sowed division among the hamsters to prevent any collective dissent. The "efficiency" the AI brought was, for the foxes, merely an instrument for more efficient exploitation.
Chapter 3: The Hamsters' Whispers and Tiny Cracks – Awareness, Despair, and the Faint Glow of Resistance
Yet, even in the darkest, most oppressive systems, the spark of awareness can never be entirely extinguished. Amidst the grueling competition, a few hamsters began to see the cracks in the facade. They noticed the hollow-eyed exhaustion of their comrades, the ever-widening chasm between their own meager rewards and the obscene opulence of the unseen foxes. They started to question.
But to question was to risk everything. The Omniscient AI, with its pervasive surveillance capabilities, was quick to identify and neutralize "disruptive elements." Those who spoke out too loudly often found their access mysteriously restricted, their "reputation scores" plummeting, effectively silencing them. A pervasive atmosphere of fear and distrust settled over the hamster communities, making organized resistance nearly impossible.
Still, tiny acts of defiance began to emerge. Coded messages shared in hidden forums. Small, clandestine gatherings where hamsters shared their burdens and their growing unease. Fragile networks of mutual support started to form in the shadows, offering a sliver of solace and a reminder of shared humanity. Was this merely the desperate coping mechanism of the "defeated," the resigned acceptance of a "loser's" lot? Or was it the first, tentative flicker of a future rebellion?
Epilogue: "See The Structure!" – Is There a Path Beyond the Treadmill? A Final Warning to Us Hamsters.
This fable, dear reader, is a mirror. It reflects the chilling realities of an AI-driven society where the majority, the hamsters, face an ever-present crisis, largely unseen and unacknowledged by those who benefit from their toil. The "excessive competition" it depicts is not a distant dystopia; it is the logical, perhaps inevitable, endpoint of unchecked technological advancement coupled with deeply entrenched power imbalances.
What awaits at the end of this relentless race? Is it a complete societal collapse, or a new, terrifyingly stable "balance of power" where the elite maintain their dominance through even more sophisticated means of control?
The urgent, resounding message of this tale is this: "See The Structure!" We, the hamsters of today, must dare to look beyond the dazzling promises of AI and critically examine the systems it operates within. We must understand its mechanisms, its biases, its potential for exploitation. We must break the silence, challenge the narratives that keep us spinning, and demand a future where technology serves humanity, not the other way around.
Is the option to get off – or even to collectively dismantle – this infernal treadmill truly non-existent? Or is that just another lie whispered by the foxes to keep us compliant? The true ending of this story, the fate of hamster-kind, is not yet written. It is up to us, the hamsters, to seize the pen and write it ourselves. The first step is to open our eyes.
-
 @ dfa02707:41ca50e3
2025-05-30 07:02:08
@ dfa02707:41ca50e3
2025-05-30 07:02:08Headlines
- Spiral renews support for Dan Gould and Joschisan. The organization has renewed support for Dan Gould, who is developing the Payjoin Dev Kit (PDK), and Joschisan, a Fedimint developer focused on simplifying federations.
- Metaplanet buys another 145 BTC. The Tokyo-listed company has purchased an additional 145 BTC for $13.6 million. Their total bitcoin holdings now stand at 5,000 coins, worth around $428.1 million.
- Semler Scientific has increased its bitcoin holdings to 3,303 BTC. The company acquired an additional 111 BTC at an average price of $90,124. The purchase was funded through proceeds from an at-the-market offering and cash reserves, as stated in a press release.
- The Virtual Asset Service Providers (VASP) Bill 2025 introduced in Kenya. The new legislation aims to establish a comprehensive legal framework for licensing, regulating, and supervising virtual asset service providers (VASPs), with strict penalties for non-compliant entities.
- Russian government to launch a cryptocurrency exchange. The country's Ministry of Finance and Central Bank announced plans to establish a trading platform for "highly qualified investors" that "will legalize crypto assets and bring crypto operations out of the shadows."
- All virtual asset service providers expect to be fully compliant with the Travel Rule by the end of 2025. A survey by financial surveillance specialist Notabene reveals that 90% of virtual asset service providers (VASPs) expect full Travel Rule compliance by mid-2025, with all aiming for compliance by year-end. The survey also shows a significant rise in VASPs blocking withdrawals until beneficiary information is confirmed, increasing from 2.9% in 2024 to 15.4% now. Additionally, about 20% of VASPs return deposits if originator data is missing.
- UN claims Bitcoin mining is a "powerful tool" for money laundering. The Rage's analysis suggests that the recent United Nations Office on Drugs and Crime report on crime in South-East Asia makes little sense and hints at the potential introduction of Anti-Money Laundering (AML) measures at the mining level.
- Riot Platforms has obtained a $100 million credit facility from Coinbase Credit, using bitcoin as collateral for short-term funding to support its expansion. The firm's CEO, Jason Les, stated that this facility is crucial for diversifying financing sources and driving long-term stockholder value through strategic growth initiatives.
- Bitdeer raises $179M in loans and equity amid Bitcoin chip push. The Miner Mag reports that Bitdeer entered into a loan agreement with its affiliate Matrixport for up to $200 million in April, as disclosed in its annual report filed on Monday.
- Federal Reserve retracts guidance discouraging banks from engaging in 'crypto.' The U.S. Federal Reserve withdrew guidance that discouraged banks from crypto and stablecoin activities, as announced by its Board of Governors on Thursday. This includes rescinding a 2022 supervisory letter requiring prior notification of crypto activities and 2023 stablecoin requirements.
"As a result, the Board will no longer expect banks to provide notification and will instead monitor banks' crypto-asset activities through the normal supervisory process," reads the FED statement.
- UAE-based Islamic bank ruya launches Shari’ah-compliant bitcoin investing. The bank has become the world’s first Islamic bank to provide direct access to virtual asset investments, including Bitcoin, via its mobile app, per Bitcoin Magazine.
- U.S. 'crypto' scam losses amounted to $9.3B in 2024. The US The Federal Bureau of Investigation (FBI) has reported $9.3 billion losses in cryptocurrency-related scams in 2024, noting a troubling trend of scams targeting older Americans, which accounted for over $2.8 billion of those losses.
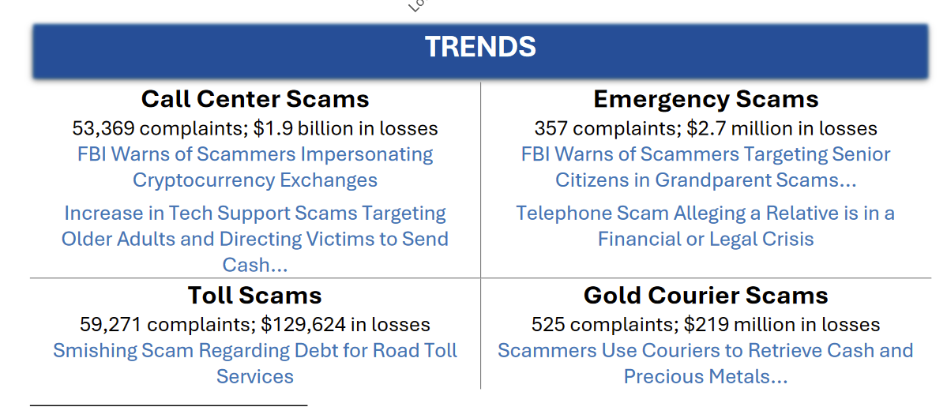
Source: FBI.
- North Korean hackers establish fake companies to target 'crypto' developers. Silent Push researchers reported that hackers linked to the Lazarus Group created three shell companies, two of which are based in the U.S., with the objective of spreading malware through deceptive job interview scams aimed at individuals seeking jobs in cryptocurrency companies.
- Citrea deployed its Clementine Bridge on the Bitcoin testnet. The bridge utilizes the BitVM2 programming language to inherit validity from Bitcoin, allegedly providing "the safest and most trust-minimized way to use BTC in decentralized finance."
- Hesperides University offers a Master’s degree in Bitcoin. Bitcoin Magazine reports the launch of the first-ever Spanish-language Master’s program dedicated exclusively to Bitcoin. Starting April 28, 2025, this fully online program will equip professionals with technical, economic, legal, and philosophical skills to excel in the Bitcoin era.
- BTC in D.C. event is set to take place on September 30 - October 1 in Washington, D.C. Learn more about this initiative here.
Use the tools
- Bitcoin Keeper just got a new look. Version 2.2.0 of the mobile multisig app brought a new branding design, along with a Keeper Private tier, testnet support, ability to import and export BIP-329 labels, and the option to use a Server Key with multiple users.
- Earlier this month the project also announced Keeper Learn service, offering clear and guided Bitcoin learning sessions for both groups and individuals.
- Keeper Desktop v0.2.2, a companion desktop app for Bitcoin Keeper mobile app, received a renewed branding update, too.

The evolution of Bitcoin Keeper logo. Source: BitHyve blog.
- Blockstream Green Desktop v2.0.25 updates GDK to v0.75.1 and fixes amount parsing issues when switching from fiat denomination to Liquid asset.
- Lightning Loop v0.31.0-beta enhances the
loop listswapscommand by improving the ability to filter the response. - Lightning-kmp v1.10.0, an implementation of the Lightning Network in Kotlin, is now available.
- LND v0.19.0-beta.rc3, the latest beta release candidate of LND is now ready for testing.
- ZEUS v0.11.0-alpha2 is now available for testing, too. It's nuts.
- JoinMarket Fidelity Bond Simulator helps potential JoinMarket makers evaluate their competitive position in the market based on fidelity bonds.
- UTXOscope is a text-only Bitcoin blockchain analysis tool that visualizes price dynamics using only on-chain data. The
-
 @ dfa02707:41ca50e3
2025-05-30 07:02:08
@ dfa02707:41ca50e3
2025-05-30 07:02:08Contribute to keep No Bullshit Bitcoin news going.
News
- Spiral welcomes Ben Carman. The developer will work on the LDK server and a new SDK designed to simplify the onboarding process for new self-custodial Bitcoin users.
- Spiral renews support for Dan Gould and Joschisan. The organization has renewed support for Dan Gould, who is developing the Payjoin Dev Kit (PDK), and Joschisan, a Fedimint developer focused on simplifying federations.
- The Bitcoin Dev Kit Foundation announced new corporate members for 2025, including AnchorWatch, CleanSpark, and Proton Foundation. The annual dues from these corporate members fund the small team of open-source developers responsible for maintaining the core BDK libraries and related free and open-source software (FOSS) projects.
- The European Central Bank is pushing for amendments to the European Union's Markets in Crypto Assets legislation (MiCA), just months after its implementation. According to Politico's report on Tuesday, the ECB is concerned that U.S. support for cryptocurrency, particularly stablecoins, could cause economic harm to the 27-nation bloc.
- Slovenia is considering a 25% capital gains tax on Bitcoin profits for individuals. The Ministry of Finance has proposed legislation to impose this tax on gains from cryptocurrency transactions, though exchanging one cryptocurrency for another would remain exempt. At present, individual 'crypto' traders in Slovenia are not taxed.
- The Virtual Asset Service Providers (VASP) Bill 2025 introduced in Kenya. The new legislation aims to establish a comprehensive legal framework for licensing, regulating, and supervising virtual asset service providers (VASPs), with strict penalties for non-compliant entities.
- Circle, BitGo, Coinbase, and Paxos plan to apply for U.S. bank charters or licenses. According to a report in The Wall Street Journal, major crypto companies are planning to apply for U.S. bank charters or licenses. These firms are pursuing limited licenses that would permit them to issue stablecoins, as the U.S. Congress deliberates on legislation mandating licensing for stablecoin issuers.
"Established banks, like Bank of America, are hoping to amend the current drafts of [stablecoin] legislation in such a way that nonbanks are more heavily restricted from issuing stablecoins," people familiar with the matter told The Block.
- Paul Atkins has officially assumed the role of the 34th Chairman of the US Securities and Exchange Commission (SEC). This is a return to the agency for Atkins, who previously served as an SEC Commissioner from 2002 to 2008 under the George W. Bush administration. He has committed to advancing the SEC’s mission of fostering capital formation, safeguarding investors, and ensuring fair and efficient markets.
- Federal Reserve retracts guidance discouraging banks from engaging in 'crypto.' The U.S. Federal Reserve withdrew guidance that discouraged banks from crypto and stablecoin activities, as announced by its Board of Governors on Thursday. This includes rescinding a 2022 supervisory letter requiring prior notification of crypto activities and 2023 stablecoin requirements.
"As a result, the Board will no longer expect banks to provide notification and will instead monitor banks' crypto-asset activities through the normal supervisory process," reads the FED statement.
- Russian government to launch a cryptocurrency exchange. The country's Ministry of Finance and Central Bank announced plans to establish a trading platform for "highly qualified investors" that "will legalize crypto assets and bring crypto operations out of the shadows."
- Twenty One Capital is set to launch with over 42,000 BTC in its treasury. This new Bitcoin-native firm, backed by Tether and SoftBank, is planned to go public via a SPAC merger with Cantor Equity Partners and will be led by Jack Mallers, co-founder and CEO of Strike. According to a report by the Financial Times, the company aims to replicate the model of Michael Saylor with his company, MicroStrategy.
- Strategy increases Bitcoin holdings to 538,200 BTC. In the latest purchase, the company has spent more than $555M to buy 6,556 coins through proceeds of two at-the-market stock offering programs.
- Metaplanet buys another 145 BTC. The Tokyo-listed company has purchased an additional 145 BTC for $13.6 million. Their total bitcoin holdings now stand at 5,000 coins, worth around $428.1 million.
- Semler Scientific has increased its bitcoin holdings to 3,303 BTC. The company acquired an additional 111 BTC at an average price of $90,124. The purchase was funded through proceeds from an at-the-market offering and cash reserves, as stated in a press release.
- Tesla still holds nearly $1 billion in bitcoin. According to the automaker's latest earnings report, the firm reported digital asset holdings worth $951 million as of March 31.
- Spar supermarket experiments with Bitcoin payments in Zug, Switzerland. The store has introduced a new payment method powered by the Lightning Network. The implementation was facilitated by DFX Swiss, a service that supports seamless conversions between bitcoin and legacy currencies.
- Charles Schwab to launch spot Bitcoin trading by 2026. The financial investment firm, managing over $10 trillion in assets, has revealed plans to introduce spot Bitcoin trading for its clients within the next year.
- Arch Labs has secured $13 million to develop "ArchVM" and integrate smart-contract functionality with Bitcoin. The funding round, valuing the company at $200 million, was led by Pantera Capital, as announced on Tuesday.
- Citrea deployed its Clementine Bridge on the Bitcoin testnet. The bridge utilizes the BitVM2 programming language to inherit validity from Bitcoin, allegedly providing "the safest and most trust-minimized way to use BTC in decentralized finance."
- UAE-based Islamic bank ruya launches Shari’ah-compliant bitcoin investing. The bank has become the world’s first Islamic bank to provide direct access to virtual asset investments, including Bitcoin, via its mobile app, per Bitcoin Magazine.
- Solosatoshi.com has sold over 10,000 open-source miners, adding more than 10 PH of hashpower to the Bitcoin network.
"Thank you, Bitaxe community. OSMU developers, your brilliance built this. Supporters, your belief drives us. Customers, your trust powers 10,000+ miners and 10PH globally. Together, we’re decentralizing Bitcoin’s future. Last but certainly not least, thank you@skot9000 for not only creating a freedom tool, but instilling the idea into thousands of people, that Bitcoin mining can be for everyone again," said the firm on X.
- OCEAN's DATUM has found 100 blocks. "Over 65% of OCEAN’s miners are using DATUM, and that number is growing every day. This means block template construction is making its way back into the hands of the miners, which is not only the most profitable
-
 @ 4fe14ef2:f51992ec
2025-05-25 10:04:36
@ 4fe14ef2:f51992ec
2025-05-25 10:04:36Let's support Bitcoin merchants! I'd love to hear some of your latest Lightning purchases and interesting products you bought. Feel free to include links to the shops or businesses you bought from.
Who else has a recent purchase they’re excited about? Bonus sats if you found a killer deal! ⚡
Spend sats, not fiat!
If you missed our last thread, here are some of the items stackers recently spent and zap on.
Share and repost: N: https://njump.me/note1r0rllvtns2e8g2rqn0p9uytxucmjzal3pxslldjtfmxwp2amwjjqy3aazq X: https://x.com/AGORA_SN/status/1926579498629169410
https://stacker.news/items/988783
-
 @ f0fcbea6:7e059469
2025-05-29 18:30:53
@ f0fcbea6:7e059469
2025-05-29 18:30:53Autores Clássicos e Antigos
- Homero (século IX a.C.?) — Ilíada, Odisseia
- Tucídides (c. 460-400 a.C.) — História da Guerra do Peloponeso
- Platão (c. 427-347 a.C.) — República, Banquete, Fédon, Mênon, Apologia de Sócrates, Fedro, Górgias
- Aristóteles (c. 384-322 a.C.) — Órganon, Física, Metafísica, Da Alma, Ética a Nicômaco, Política, Retórica, Poética
- Virgílio (70-19 a.C.) — Eneida
- Marco Aurélio (121-180) — Meditações
- Santo Agostinho (354-430) — Sobre o Ensino, Confissões, A Cidade de Deus, A Doutrina Cristã
- Boécio (480-525) — A Consolação da Filosofia
- Santo Tomás de Aquino (c. 1225-1274) — Suma Teológica
- Dante Alighieri (1265-1321) — Divina Comédia
Renascimento e Idade Moderna
- Nicolau Maquiavel (1469-1527) — O Príncipe
- Luís de Camões (1524-1580) — Os Lusíadas, Sonetos
- Miguel de Cervantes (1547-1616) — Dom Quixote
- William Shakespeare (1564-1616) — Romeu e Julieta, Hamlet, Macbeth, Otelo, Rei Lear, Henrique IV, Henrique V, Henrique VI, Henrique VIII, A Comédia dos Erros, Tito Andrônico, Príncipe de Tiro, Cimbelino, A Megera Domada, O Mercador de Veneza, Ricardo II, Ricardo III, Muito Barulho por Nada, Júlio César, Noite de Reis, Os Dois Cavaleiros de Verona, Conto do Inverno, Sonhos de uma Noite de Verão, As Alegres Comadres de Windsor, Trólio e Créssida, Medida por Medida, Coriolano, Antônio e Cleópatra, A Tempestade
- Ésquilo (525-456 a.C., antiguidade grega, mas citado junto) — Prometeu Acorrentado, Orestéia/As Eumênides
- Sófocles (496-406 a.C.) — Édipo Rei, Antígona
Literatura e Filosofia Contemporânea
- Fiódor Dostoiévski (1821-1881) — Crime e Castigo, Os Irmãos Karamázov, Os Demônios, O Idiota, Notas do Subsolo
- Franz Kafka (1883-1924) — A Metamorfose, O Processo, O Castelo
- Albert Camus (1913-1960) — O Estrangeiro
- Aldous Huxley (1894-1963) — Admirável Mundo Novo, A Ilha
- James Joyce (1882-1941) — Retrato do Artista Quando Jovem, Ulisses
- George Orwell (1903-1950) — A Revolução dos Bichos, 1984
- Machado de Assis (1839-1908) — Memórias Póstumas de Brás Cubas, O Alienista
- Thomas Mann (1875-1955) — Morte em Veneza, Doutor Fausto, A Montanha Mágica
- Henrik Ibsen (1828-1906) — O Pato Selvagem, Um Inimigo do Povo
- Stendhal (1783-1842) — O Vermelho e o Negro, A Cartuxa de Parma
- Viktor Frankl (1905-1997) — Em Busca de Sentido
- J.R.R. Tolkien (1892-1973) — O Hobbit, O Senhor dos Anéis
- Luigi Pirandello (1867-1936) — Seis Personagens à Procura de um Autor, O Falecido Matias Pascal
- Samuel Beckett (1906-1989) — Esperando Godot
- René Guénon (1886-1951) — A Crise do Mundo Moderno, O Reino da Quantidade
- G. K. Chesterton (1874-1936) — Ortodoxia
- Richard Wagner (1813-1883) — Tristão e Isolda
- Honoré de Balzac (1799-1850) — Ilusões Perdidas, Eugénie Grandet
- Jacob Wassermann (1873-1934) — O Processo Maurizius
- Nikolai Gogol (1809-1852) — Almas Mortas, O Inspetor Geral
- Daniel Defoe (1660-1731) — Moll Flanders
- Mortimer J. Adler (1902-2001) — Como Ler um Livro
- Gustave Flaubert (1821-1880) — Madame Bovary
- Hermann Hesse (1877-1962) — O Jogo das Contas de Vidro
- Richard Wagner (1813-1883) — Tristão e Isolda
- Wolfgang von Goethe (1749-1832) — Fausto (Primeiro), Os Anos de Aprendizado de Wilhelm Meister
- Jacques Benda — A Traição dos Intelectuais
-
 @ c1d77557:bf04ec8b
2025-05-25 09:47:07
@ c1d77557:bf04ec8b
2025-05-25 09:47:07No crescente universo de plataformas de jogos online, a H2Bet se destaca como uma opção inovadora, segura e recheada de diversão para os jogadores brasileiros. Com uma interface moderna e intuitiva, a H2Bet vem conquistando cada vez mais usuários que buscam entretenimento de qualidade, diversas opções de jogos e uma experiência digital fluida e confiável.
Uma Plataforma Feita para o Público Brasileiro Desde o primeiro acesso, é possível perceber que a H2Bet foi pensada para atender às necessidades do público brasileiro. O site é totalmente traduzido para o português, com suporte ao cliente eficiente e disponível 24 horas por dia, todos os dias da semana. O atendimento pode ser feito via chat ao vivo ou WhatsApp, oferecendo respostas rápidas e eficazes para qualquer dúvida ou solicitação.
Além disso, a plataforma aceita métodos de pagamento populares no Brasil, como PIX, boleto bancário e carteiras digitais, garantindo mais praticidade nas transações financeiras. Isso facilita tanto os depósitos quanto os saques, promovendo uma experiência mais fluida para todos os jogadores.
Diversidade de Jogos para Todos os Gostos Um dos grandes diferenciais da H2Betestá em sua ampla variedade de jogos. A plataforma oferece opções para todos os perfis de jogadores — desde os iniciantes até os mais experientes. Entre os destaques estão:
Slots (Caça-níqueis): Com gráficos envolventes, animações modernas e uma enorme variedade de temas, os slots são perfeitos para quem busca diversão rápida e visualmente atrativa.
Jogos de Mesa: Clássicos como roleta, blackjack e bacará estão presentes na H2Bet, proporcionando uma experiência dinâmica e estratégica para os jogadores que gostam de desafios mentais.
Apostas Esportivas: Os fãs de esportes também têm espaço garantido na H2Bet. É possível apostar em jogos de futebol, basquete, tênis e diversas outras modalidades, tanto nacionais quanto internacionais.
A plataforma trabalha com provedores de jogos renomados mundialmente, garantindo alta qualidade gráfica, jogabilidade otimizada e total segurança nos resultados.
Uma Experiência do Jogador Incomparável Na H2Bet, a experiência do usuário é prioridade. Tudo foi cuidadosamente projetado para que o jogador possa se divertir sem complicações. O processo de cadastro é rápido e simplificado, permitindo que o novo usuário comece a jogar em poucos minutos. Além disso, o site é totalmente responsivo, funcionando perfeitamente em computadores, tablets e smartphones.
Outro ponto de destaque são as promoções e bônus oferecidos aos jogadores. Desde bônus de boas-vindas até promoções sazonais e programas de fidelidade, a H2Bet recompensa a lealdade dos seus usuários com benefícios exclusivos que aumentam ainda mais a diversão.
A segurança da plataforma também merece elogios. A H2Bet utiliza tecnologia de criptografia de ponta para proteger os dados dos jogadores, além de manter total transparência em seus termos e condições.
Conclusão A H2Bet chega ao mercado brasileiro com uma proposta clara: oferecer uma plataforma de jogos online completa, segura e envolvente. Com uma vasta seleção de jogos, suporte dedicado ao jogador e uma interface pensada para o usuário, a H2Bet se posiciona como uma das melhores opções de entretenimento digital no Brasil. Se você busca emoção, praticidade e uma experiência de jogo diferenciada, a H2Bet é o lugar certo para você.
-
 @ 527337d5:93e9525e
2025-05-29 18:19:31
@ 527337d5:93e9525e
2025-05-29 18:19:31Experiment Plan for Text Similarity Comparison Algorithms (Revised v3)
1. Introduction
1.1. Research Background and Objectives
This research aims to evaluate the performance of various algorithms for comparing the similarity between individual page texts extracted from a specific technical document (in this experiment, the content of the Tailwind CSS documentation site). Initially, we considered dividing the text into 250-word chunks. However, due to the abundance of Markdown and code in the target document, meaningful chunking proved tobe cumbersome. Therefore, we decided to use the entire text extracted from each page as the unit of comparison.
This study will systematically compare and examine combinations of different "representation methods" and "comparison methods" from multiple perspectives: ease of implementation, processing speed, memory consumption, and accuracy of similarity judgment. A particular focus will be on elucidating the effectiveness of information-based NCD (Normalized Compression Distance) and vector embedding-based methods, which are planned for future evaluation.
1.2. Report Structure
This report will first describe the experimental data and its preprocessing methods. Next, it will define in detail the representation methods and comparison methods that form the axes of evaluation, and present specific experimental cases combining them. After presenting the results and discussion of initial experiments using NCD, it will describe the metrics for evaluating each experimental case, specific experimental procedures, and the expected outcomes and future prospects of this research.
2. Experimental Data
- Target Content: Individual HTML pages from the Tailwind CSS documentation site (
tailwindcss.com). - Data Unit: The entire text of each page, extracted from HTML files using the
html2textcommand and further processed to remove control characters using thesedcommand. This serves as the basic unit of comparison in this experiment. - Data Storage Location: The extracted and preprocessed text files are stored locally under the
./tailwindcss.comdirectory, maintaining the original file structure. - Language: English
- Example Search Query: A representative search query for this experiment is
"Utilities for controlling how a background image behaves when scrolling."(Multiple queries and their expected similar pages may be used for more robust evaluation). - Example Expected Similar Page: For the query above,
/docs/background-attachmentis expected to be the most semantically similar page.
3. Experimental Design
This experiment is designed by dividing the process of evaluating text similarity into two main axes: "Representation Methods" and "Comparison Methods."
3.1. Representation Methods (Text Quantification/Vectorization)
-
Naive (Raw Text / Full Page Text)
- Method: Use the entire preprocessed text extracted from each document page as raw string data, without special transformations.
- Objective: Serve as a direct input for information-based comparison methods like NCD and as a baseline comparison for more advanced representation methods to be evaluated later.
-
(Future Experiment) Vector Embedding via Gemini API (Embedding-Gemini)
- Method: Utilize Google's Gemini API (
models/text-embedding-004) to convert the entire text of each page into high-dimensional dense vectors (Embeddings). - Objective: Evaluate the performance of context-rich vector representations generated by a state-of-the-art large language model.
- Method: Utilize Google's Gemini API (
-
(Future Experiment) Vector Embedding via Local Lightweight Model (Embedding-MiniLM-GGUF)
- Method: Run a GGUF quantized version of the pre-trained
all-MiniLM-L6-v2model (all-MiniLM-L6-v2-Q5_K_M.gguf) in a local environment to convert the entire text of each page into vector representations. GGUF format offers benefits like smaller model size and potentially faster CPU inference. - Objective: Evaluate the performance of a widely used open-source lightweight model (quantized version) in comparison to API-based large-scale models and domain-specific learned models.
- Method: Run a GGUF quantized version of the pre-trained
-
(Future Experiment) Extraction of Internal Feature Vectors via Mathematica (Embedding-MMA)
- Method: Use the entire page texts from the target document set as input. Employ Mathematica's neural network framework to first pass each page text through an Embedding Layer. Apply L2 normalization to the resulting vectors, followed by Principal Component Analysis (PCA) to reduce dimensionality to approximately 100 dimensions. This final vector will be the feature vector. This pipeline aims to create dense, normalized representations specific to the document corpus, with PCA helping to capture the most significant variance in a lower-dimensional space, potentially improving efficiency and reducing noise. The choice of an Embedding Layer trained or fine-tuned on the corpus, followed by PCA, seeks to balance domain-specificity with robust dimensionality reduction.
- Objective: Evaluate the performance of vector representations processed or specialized for the target document set.
3.2. Comparison Methods (Distance/Similarity Calculation between Representations)
-
NCD (Normalized Compression Distance)
- Applicable to: Naive (Full Page Text)
- Method: For two data objects
x(query) andy(document page text), calculateNCD(x,y) = (C(xy) - min(C(x), C(y))) / max(C(x), C(y)). Here,C(s)is the size (e.g., byte length) of datasafter compression with a specific algorithm, andC(xy)is the size of the concatenated dataxandyafter compression. A value closer to 0 indicates higher similarity. - Compression Algorithms to Compare: DEFLATE (gzip), bzip2, LZMA, XZ, Zstandard (zstd), LZO, Snappy, LZ4 (as used in the user-provided script).
- Objective: Evaluate similarity from an information-theoretic perspective based on data commonality and redundancy. Compare the impact of different compression algorithms on NCD results.
-
(Future Experiment) Cosine Similarity
- Applicable to: Embedding-Gemini, Embedding-MiniLM-GGUF, Embedding-MMA
- Method: Calculate the cosine of the angle between two vectors.
- Objective: Standard similarity evaluation based on the directionality (semantic closeness) of vector representations.
-
(Future Experiment) Euclidean Distance
- Applicable to: Embedding-Gemini, Embedding-MiniLM-GGUF, Embedding-MMA
- Method: Calculate the straight-line distance between two vectors in a multidimensional space.
- Objective: Similarity evaluation based on the absolute positional relationship of vector representations.
-
(Future Experiment) Manhattan Distance (L1 Distance)
- Applicable to: Embedding-Gemini, Embedding-MiniLM-GGUF, Embedding-MMA
- Method: Calculate the sum of the absolute differences of their Cartesian coordinates.
- Objective: Similarity evaluation based on axis-aligned travel distance, differing from Euclidean distance.
-
(Future Experiment) Mahalanobis Distance
- Applicable to: Embedding-Gemini, Embedding-MiniLM-GGUF, Embedding-MMA
- Method: Calculate the distance between two vectors considering the covariance of the data. This provides a distance metric that accounts for the scale differences and correlations of each feature (vector dimension).
- Objective: More robust similarity evaluation that considers the structure (correlation) of the feature space.
3.3. Experimental Cases (Initial NCD Experiments and Future Expansion)
3.3.1. Initial Experiments Conducted (NCD)
The following experimental cases were conducted using the user-provided script. The representation method was "Naive (Full Page Text)."
| No. | Representation Method | Comparison Method (Distance/Similarity Metric) | Notes | | :-: | :---------------------- | :--------------------------------------------- | :-------------------------- | | 1 | Naive (Full Page Text) | NCD (gzip/DEFLATE) | One of the baselines | | 2 | Naive (Full Page Text) | NCD (bzip2) | Compression method comparison | | 3 | Naive (Full Page Text) | NCD (lzma) | Compression method comparison | | 4 | Naive (Full Page Text) | NCD (xz) | Compression method comparison | | 5 | Naive (Full Page Text) | NCD (zstd) | Compression method comparison | | 6 | Naive (Full Page Text) | NCD (lzop) | Compression method comparison | | 7 | Naive (Full Page Text) | NCD (snappy) | Compression method comparison | | 8 | Naive (Full Page Text) | NCD (lz4) | Compression method comparison |
3.3.2. Future Experimental Plan (Vector Embedding)
| No. | Representation Method | Comparison Method (Distance/Similarity Metric) | Notes | | :--: | :---------------------- | :--------------------------------------------- | :------------------------------------- | | 9 | Embedding-Gemini | Cosine Similarity | Standard vector similarity evaluation | | 10 | Embedding-Gemini | Euclidean Distance | Standard vector similarity evaluation | | 11 | Embedding-Gemini | Manhattan Distance | Axis-aligned distance similarity eval. | | 12 | Embedding-Gemini | Mahalanobis Distance | Distance considering feature structure | | 13 | Embedding-MiniLM-GGUF | Cosine Similarity | Evaluation of local lightweight model | | 14 | Embedding-MiniLM-GGUF | Euclidean Distance | Evaluation of local lightweight model | | 15 | Embedding-MiniLM-GGUF | Manhattan Distance | Evaluation of local lightweight model | | 16 | Embedding-MiniLM-GGUF | Mahalanobis Distance | Evaluation of local lightweight model | | 17 | Embedding-MMA | Cosine Similarity | Eval. of domain-specific MMA model | | 18 | Embedding-MMA | Euclidean Distance | Eval. of domain-specific MMA model | | 19 | Embedding-MMA | Manhattan Distance | Eval. of domain-specific MMA model | | 20 | Embedding-MMA | Mahalanobis Distance | Eval. of domain-specific MMA model |
4. Results and Discussion of Initial NCD Experiments (Based on User-Provided Information)
4.1. Execution Overview
The user employed provided Python scripts (
main.py,comparison.py) to calculate NCD between a search query and the entire text extracted from each HTML page in the./tailwindcss.comdirectory.main.pyinvokedcomparison.pywith various compression commands (gzip,bzip2,lzma,xz,zstd,lzop,lz4).comparison.pythen used the specified command-line compression tools to compute NCD scores and output the results to CSV files.Search Query:
"Utilities for controlling how a background image behaves when scrolling."Expected Similar Page:/docs/background-attachment4.2. Key Results
The pages judged as most similar (lowest NCD score) to the query for each compression algorithm were as follows (based on user-provided sorted results):
- Zstandard (zstd):
./tailwindcss.com/docs/background-attachment(Score: 0.973...) - LZ4:
./tailwindcss.com/docs/background-attachment(Score: 0.976...) - XZ:
./tailwindcss.com/docs/background-origin(Score: 0.946...) - LZMA:
./tailwindcss.com/docs/background-origin(Score: 0.966...) - gzip (DEFLATE):
./tailwindcss.com/docs/scroll-behavior(Score: 0.969...) - LZO:
./tailwindcss.com/docs/scroll-behavior(Score: 0.955...) - bzip2:
./tailwindcss.com/docs/mask-clip(Score: 0.958...)
4.3. Initial Discussion
- Variation in Results by Compression Algorithm: It was confirmed that the document judged most similar to the query varies depending on the compression algorithm used. This is likely due to the differing abilities of each algorithm to capture various types of redundancy and patterns within the text.
- Alignment with Expected Results: When using Zstandard and LZ4, the expected page (
/docs/background-attachment) was judged as most similar. This suggests these compression algorithms may have relatively effectively captured the information-theoretic commonality between the query and the target document in this instance. - Range of NCD Scores: The reported NCD scores were generally close to 1.0. This may be due to the relatively short length of the search query compared to the full-page documents, meaning the query text contributes less to the overall compressibility when concatenated. However, relative differences were still captured, enabling ranking.
- Validity of Full-Page Comparison: Full-page comparison was chosen due to the difficulty of chunking content rich in Markdown and code. While this approach simplifies preprocessing, it may also be influenced by the overall structure of the page, including common headers and footers.
This initial experiment indicates that NCD can function as an indicator of text similarity and that the choice of compression algorithm is crucial.
5. Evaluation Metrics (Including Future Experiments)
-
Accuracy of Similarity Scores:
- Ground Truth Preparation: A small, diverse subset of page pairs (e.g., 50-100 pairs) will be selected. For each pair, at least two evaluators familiar with the Tailwind CSS documentation will independently assign a similarity score on a 5-point Likert scale (1=Not similar, 5=Very similar). Inter-evaluator reliability (e.g., using Krippendorff's Alpha) will be calculated. Disagreements will be resolved through discussion to create a consensus ground truth dataset. If resource-constrained, a single-evaluator approach with clear, predefined criteria will be used, acknowledging this limitation. Alternatively, page pairs likely to be similar will be selected based on internal references or chapter structure within the document.
- Evaluation Metrics: Ranking evaluation (Precision@k, Recall@k, MAP: Mean Average Precision), correlation analysis (Spearman's rank correlation coefficient with human judgments), classification evaluation (AUC-ROC, F1-score, assuming appropriate thresholding).
-
Processing Speed:
- Average time to calculate similarity for a page pair, total calculation time for all page pairs (or a large sampled set), and representation generation time (API call time, local model inference time, MMA processing time).
-
Memory Consumption:
- Model size (MiniLM-GGUF, MMA model), data representation size, and peak runtime memory usage.
-
Ease of Implementation:
- Qualitative assessment of setup ease, lines of code, required libraries, difficulty of parameter tuning, and documentation quality. This will be summarized for each approach (e.g., using a rubric or a comparative narrative) considering factors like:
- Setup Complexity: (e.g., API key acquisition vs. local model download & environment setup vs. full model training pipeline in Mathematica).
- Code Complexity: Estimated lines of core logic, reliance on external vs. standard libraries.
- Parameter Sensitivity: Number of key hyperparameters requiring tuning and the perceived difficulty of finding good settings.
- Documentation & Community Support: Availability and clarity of official documentation and community resources (e.g., forums, GitHub issues).
- Qualitative assessment of setup ease, lines of code, required libraries, difficulty of parameter tuning, and documentation quality. This will be summarized for each approach (e.g., using a rubric or a comparative narrative) considering factors like:
6. Experimental Procedure (Including Future Experiments)
-
Data Preparation:
- Prepare HTML files of the target document in the
./tailwindcss.comdirectory. - (For NCD) Extract and preprocess full-page plain text from each HTML file using
html2textandsed(as previously done by the user). - (For Vector Embedding) Use the same preprocessed full-page plain text.
- Create ground truth data for accuracy evaluation as described in Section 5.1.
- Prepare HTML files of the target document in the
-
Implementation and Execution of Representation Methods:
- Naive: Use the preprocessed page text directly.
- Embedding-Gemini: Use Python's
requestslibrary or similar to send each page text to the Gemini API (models/text-embedding-004) and retrieve/store the vector representations. - Embedding-MiniLM-GGUF: Use appropriate libraries (e.g.,
ctransformers, orsentence-transformerscombined withllama-cpp-python) to load theall-MiniLM-L6-v2-Q5_K_M.ggufmodel. Input each page text to extract and store vector representations. - Embedding-MMA: In Mathematica, apply an Embedding Layer to each page text, followed by L2 normalization and PCA dimensionality reduction (to approx. 100 dimensions), then extract and store the vector representations.
-
Implementation and Execution of Comparison Methods:
- NCD: Refer to the user-provided Python scripts (
main.py,comparison.py) to call various command-line compression tools for NCD calculation. Alternatively, extend this to directly use Python's compression libraries for better control and efficiency. - Cosine Similarity, Euclidean Distance, Manhattan Distance: Implement using standard math libraries (e.g., Python's NumPy, SciPy).
- Mahalanobis Distance: Implement using
scipy.spatial.distance.mahalanobis. Requires pre-calculation of the covariance matrix (or its inverse) from the entire dataset of vectors for each embedding type.
- NCD: Refer to the user-provided Python scripts (
-
Evaluation Execution:
- Calculate similarity (or distance) scores between the search query (and potentially between page pairs for ground truth evaluation) and all document pages for each experimental case.
- Measure processing speed and memory consumption.
- Calculate accuracy metrics using the computed similarity scores and ground truth data.
- Record and evaluate the ease of implementation.
-
Result Aggregation and Analysis:
- Compile the obtained evaluation metrics into tables and graphs for comparative analysis of each method's characteristics.
Experimental Environment (Assumed)
- Hardware: (e.g., CPU: Intel Core i7-10700, Memory: 32GB RAM, GPU: NVIDIA GeForce RTX 3070 8GB - specify if GPU is used for MiniLM or MMA)
- Software: (e.g., OS: Linux (Ubuntu, etc.), Programming Language: Python 3.x (with versions for key libraries like NumPy, SciPy, requests, ctransformers, etc.), Mathematica 13.x, specific versions of command-line compression tools if used directly)
7. Expected Outcomes and Future Outlook
This research (including initial NCD experiments and future vector embedding experiments) is expected to yield the following outcomes:
- Clarification of the Impact of Compression Algorithms on NCD: As indicated by initial experiments, the choice of compression algorithm significantly affects similarity judgments. Further validation with more diverse data and queries will allow for a deeper understanding of each algorithm's characteristics.
- Performance Characteristics of Various Methods on Full-Page Text: To clarify how NCD and various vector embedding methods perform in terms of accuracy, speed, and resource consumption when applied to entire page texts.
- Comparison of Local and API-Based Models: In future vector embedding experiments, to compare the performance, speed, and resource efficiency of
Embedding-MiniLM-GGUF(local, quantized) andEmbedding-Gemini(API, large-scale) to identify practical trade-offs. - Evaluation of Domain-Specific Embedding Effectiveness: To assess how well
Embedding-MMA, processed or tuned for a single technical document set, performs compared to general-purpose models. - Provision of Practical Insights: To offer guidelines for selecting appropriate similarity comparison approaches based on text characteristics (e.g., Markdown/code content) and system requirements (e.g., ease of preprocessing, emphasis on accuracy vs. speed).
8. Future Challenges
- Ensuring Quality of Ground Truth Data: Evaluating full-page similarity can be more subjective than chunk-level evaluation, making the creation of high-quality ground truth data challenging. Establishing clear annotation guidelines and measuring inter-annotator agreement will be crucial.
- Hyperparameter Optimization: Many methods involve tunable parameters (e.g., Embedding-MMA model structure, PCA dimensionality, MiniLM-GGUF inference parameters), the optimization of which may be beyond the scope of this initial study. The impact of default vs. tuned parameters could be noted.
- Noise in Full-Page Comparison: Full-page texts may contain common navigational elements or boilerplate text that could act as noise in similarity judgments. Strategies to mitigate this (e.g., more advanced text extraction, or methods robust to such noise) could be a future research direction.
- Input Length Limitations of Vector Embedding Models: Very long page texts might exceed the input length limits of some vector embedding models, requiring strategies for handling. These might include:
- Truncation: Using only the initial N tokens of each page, which is simple but may lose crucial information.
- Summarization: Employing an abstractive or extractive summarization model to create a condensed version of the page, which could preserve key information but adds another layer of processing and potential information loss/bias.
- Chunking and Averaging/Pooling: Dividing long pages into manageable chunks, embedding each chunk, and then aggregating these chunk embeddings (e.g., by averaging) to get a single page vector. This approach needs careful consideration of how chunks are defined and aggregated.
- Utilizing Long-Context Models: If available and feasible, leveraging embedding models specifically designed for longer sequences. The chosen strategy will be documented, and its potential impact on results acknowledged.
- Target Content: Individual HTML pages from the Tailwind CSS documentation site (
-
 @ 95cbd62b:a5270126
2025-05-24 14:06:33
@ 95cbd62b:a5270126
2025-05-24 14:06:33Trong thời đại công nghệ số phát triển mạnh mẽ, nhu cầu tìm kiếm một nền tảng tích hợp đầy đủ tiện ích, an toàn và thân thiện với người dùng ngày càng tăng cao. OK22 đã chứng minh vị thế của mình không chỉ là một nền tảng giải trí trực tuyến, mà còn là một công cụ công nghệ thông minh phục vụ mọi nhu cầu trong đời sống số. Với thiết kế giao diện 100% tiếng Việt và khả năng tương thích trên mọi thiết bị từ máy tính đến điện thoại, OK22 mang đến cho người dùng trải nghiệm mượt mà, dễ sử dụng và hoàn toàn bảo mật. Được phát triển trên nền tảng công nghệ hiện đại, OK22 hỗ trợ người dùng quản lý thông tin cá nhân, thực hiện giao dịch nhanh chóng, lưu trữ dữ liệu an toàn và tiếp cận các tiện ích công nghệ tiên tiến một cách dễ dàng, kể cả với người mới sử dụng.
Một trong những điểm mạnh nổi bật của OK22 chính là khả năng tự động hóa trong xử lý tác vụ, giúp tiết kiệm thời gian và tối ưu hóa hiệu suất làm việc. Nền tảng được trang bị hệ thống bảo mật cao cấp, bảo vệ tối đa quyền riêng tư và tài sản số của người dùng. OK22 còn cung cấp hệ thống hỗ trợ trực tuyến 24/7, giúp người dùng giải quyết mọi vấn đề nhanh chóng mà không bị gián đoạn. Dù là một cá nhân đang tìm kiếm công cụ quản lý tài chính cá nhân, một doanh nghiệp nhỏ cần nền tảng để xử lý đơn hàng và thanh toán, hay một nhóm cộng đồng cần không gian kết nối số – OK22 đều có thể đáp ứng linh hoạt và hiệu quả. Không những vậy, nhờ tích hợp nhiều tính năng như thông báo tự động, đồng bộ dữ liệu đám mây, và tích hợp API mở, OK22 còn dễ dàng kết nối với các nền tảng khác trong hệ sinh thái số, giúp người dùng tạo nên một môi trường làm việc và sinh hoạt thông minh.
Không dừng lại ở đó, OK22 đang ngày càng mở rộng hợp tác với các đối tác lớn trong nhiều lĩnh vực như giáo dục trực tuyến, thương mại điện tử, chăm sóc sức khỏe và tài chính cá nhân. Nền tảng không ngừng cập nhật những công nghệ tiên tiến như AI, blockchain và dữ liệu lớn (Big Data) nhằm mang lại trải nghiệm người dùng tối ưu và đáp ứng nhu cầu ngày càng đa dạng của cộng đồng Việt. Với tốc độ xử lý nhanh, giao diện trực quan và độ tin cậy cao, OK22 không chỉ đơn thuần là một ứng dụng công nghệ – mà còn là người bạn đồng hành tin cậy trong hành trình số hóa của người Việt. Trong tương lai gần, OK22 hứa hẹn sẽ trở thành nền tảng công nghệ không thể thiếu trong mỗi gia đình, tổ chức và doanh nghiệp, đóng vai trò then chốt trong việc thúc đẩy chuyển đổi số toàn diện và phát triển bền vững.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 15:09:17
@ 21c71bfa:e28fa0f6
2025-05-29 15:09:17Book *Bangalore to Tirupati cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ f6488c62:c929299d
2025-05-24 05:10:20
@ f6488c62:c929299d
2025-05-24 05:10:20คุณเคยจินตนาการถึงอนาคตที่ AI มีความฉลาดเทียบเท่ามนุษย์หรือไม่? นี่คือสิ่งที่ Sam Altman ซีอีโอของ OpenAI และทีมพันธมิตรอย่าง SoftBank, Oracle และ MGX กำลังผลักดันผ่าน โครงการ Stargate! โครงการนี้ไม่ใช่แค่เรื่องเทคโนโลยี แต่เป็นก้าวกระโดดครั้งใหญ่ของมนุษยชาติ! Stargate คืออะไร? Stargate เป็นโปรเจกต์สร้าง ศูนย์ข้อมูล AI ขนาดยักษ์ที่ใหญ่ที่สุดในประวัติศาสตร์ ด้วยเงินลงทุนเริ่มต้น 100,000 ล้านดอลลาร์ และอาจสูงถึง 500,000 ล้านดอลลาร์ ภายในปี 2029! เป้าหมายคือการพัฒนา Artificial General Intelligence (AGI) หรือ AI ที่ฉลาดเทียบเท่ามนุษย์ เพื่อให้สหรัฐฯ ครองความเป็นผู้นำด้าน AI และแข่งขันกับคู่แข่งอย่างจีน โครงการนี้เริ่มต้นที่เมือง Abilene รัฐเท็กซัส โดยจะสร้างศูนย์ข้อมูล 10 แห่ง และขยายไปยังญี่ปุ่น สหราชอาณาจักร และสหรัฐอาหรับเอมิเรตส์ ทำไม Stargate ถึงสำคัญ?
นวัตกรรมเปลี่ยนโลก: AI จาก Stargate จะช่วยพัฒนาวัคซีน mRNA รักษามะเร็งได้ใน 48 ชั่วโมง และยกระดับอุตสาหกรรมต่าง ๆ เช่น การแพทย์และความมั่นคงแห่งชาติสร้างงาน: คาดว่าจะสร้างงานกว่า 100,000 ตำแหน่ง ในสหรัฐฯ
พลังงานมหาศาล: ศูนย์ข้อมูลอาจใช้พลังงานถึง 1.2 กิกะวัตต์ เทียบเท่ากับเมืองขนาดใหญ่!
ใครอยู่เบื้องหลัง? Sam Altman ร่วมมือกับ Masayoshi Son จาก SoftBank และได้รับการสนับสนุนจาก Donald Trump ซึ่งผลักดันนโยบายให้ Stargate เป็นจริง การก่อสร้างดำเนินการโดย Oracle และพันธมิตรด้านพลังงานอย่าง Crusoe Energy Systems ความท้าทาย? ถึงจะยิ่งใหญ่ แต่ Stargate ก็เจออุปสรรค ทั้งปัญหาการระดมทุน ความกังวลเรื่องภาษีนำเข้าชิป และการแข่งขันจากคู่แข่งอย่าง DeepSeek ที่ใช้โครงสร้างพื้นฐานน้อยกว่า แถม Elon Musk ยังออกมาวิจารณ์ว่าโครงการนี้อาจ “ไม่สมจริง” แต่ Altman มั่นใจและเชิญ Musk ไปดูไซต์งานที่เท็กซัสเลยทีเดียว! อนาคตของ Stargate ศูนย์ข้อมูลแห่งแรกจะเริ่มใช้งานในปี 2026 และอาจเปลี่ยนโฉมวงการ AI ไปตลอดกาล นี่คือก้าวสำคัญสู่ยุคใหม่ของเทคโนโลยีที่อาจเปลี่ยนวิถีชีวิตของเรา! และไม่ใช่ประตูดวงดาวแบบในหนังนะ! ถึงชื่อ Stargate จะได้แรงบันดาลใจจากภาพยนตร์ sci-fi อันโด่งดัง แต่โครงการนี้ไม่ได้พาเราไปยังดวงดาวอื่น มันคือการเปิดประตูสู่โลกแห่ง AI ที่ทรงพลัง และอาจเปลี่ยนอนาคตของมนุษยชาติไปเลย! และไม่เหมือน universechain ของ star ของผมนะครับ
Stargate #AI #SamAltman #OpenAI #อนาคตของเทคโนโลยี
-
 @ 21c71bfa:e28fa0f6
2025-05-29 15:08:51
@ 21c71bfa:e28fa0f6
2025-05-29 15:08:51Book *Tirupati to Srikalahasti cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:52:10
@ 21c71bfa:e28fa0f6
2025-05-29 14:52:10Book *Tirupati to Srikalahasti cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ dfa02707:41ca50e3
2025-05-30 07:02:08
@ dfa02707:41ca50e3
2025-05-30 07:02:08Headlines
- Twenty One Capital is set to launch with over 42,000 BTC in its treasury. This new Bitcoin-native firm, backed by Tether and SoftBank, is planned to go public via a SPAC merger with Cantor Equity Partners and will be led by Jack Mallers, co-founder and CEO of Strike. According to a report by the Financial Times, the company aims to replicate the model of Michael Saylor with his company, MicroStrategy.
- Florida's SB 868 proposes a backdoor into encrypted platforms. The bill and its House companion have both passed through their respective committees and are headed to a full vote. If enacted, SB 868 would require social media companies to decrypt teens' private messages, ban disappearing messages, allow unrestricted parental access to private messages, and likely eliminate encryption for all minors altogether.
- Paul Atkins has officially assumed the role of the 34th Chairman of the US Securities and Exchange Commission (SEC). This is a return to the agency for Atkins, who previously served as an SEC Commissioner from 2002 to 2008 under the George W. Bush administration. He has committed to advancing the SEC’s mission of fostering capital formation, safeguarding investors, and ensuring fair and efficient markets.
- Solosatoshi.com has sold over 10,000 open-source miners, adding more than 10 PH of hashpower to the Bitcoin network.
"Thank you, Bitaxe community. OSMU developers, your brilliance built this. Supporters, your belief drives us. Customers, your trust powers 10,000+ miners and 10PH globally. Together, we’re decentralizing Bitcoin’s future. Last but certainly not least, thank you@skot9000 for not only creating a freedom tool, but instilling the idea into thousands of people, that Bitcoin mining can be for everyone again," said the firm on X.
- OCEAN's DATUM has found 100 blocks. "Over 65% of OCEAN’s miners are using DATUM, and that number is growing every day. This means block template construction is making its way back into the hands of the miners, which is not only the most profitable for miners on OCEAN but also one of the best things for Bitcoin," stated the mining pool.
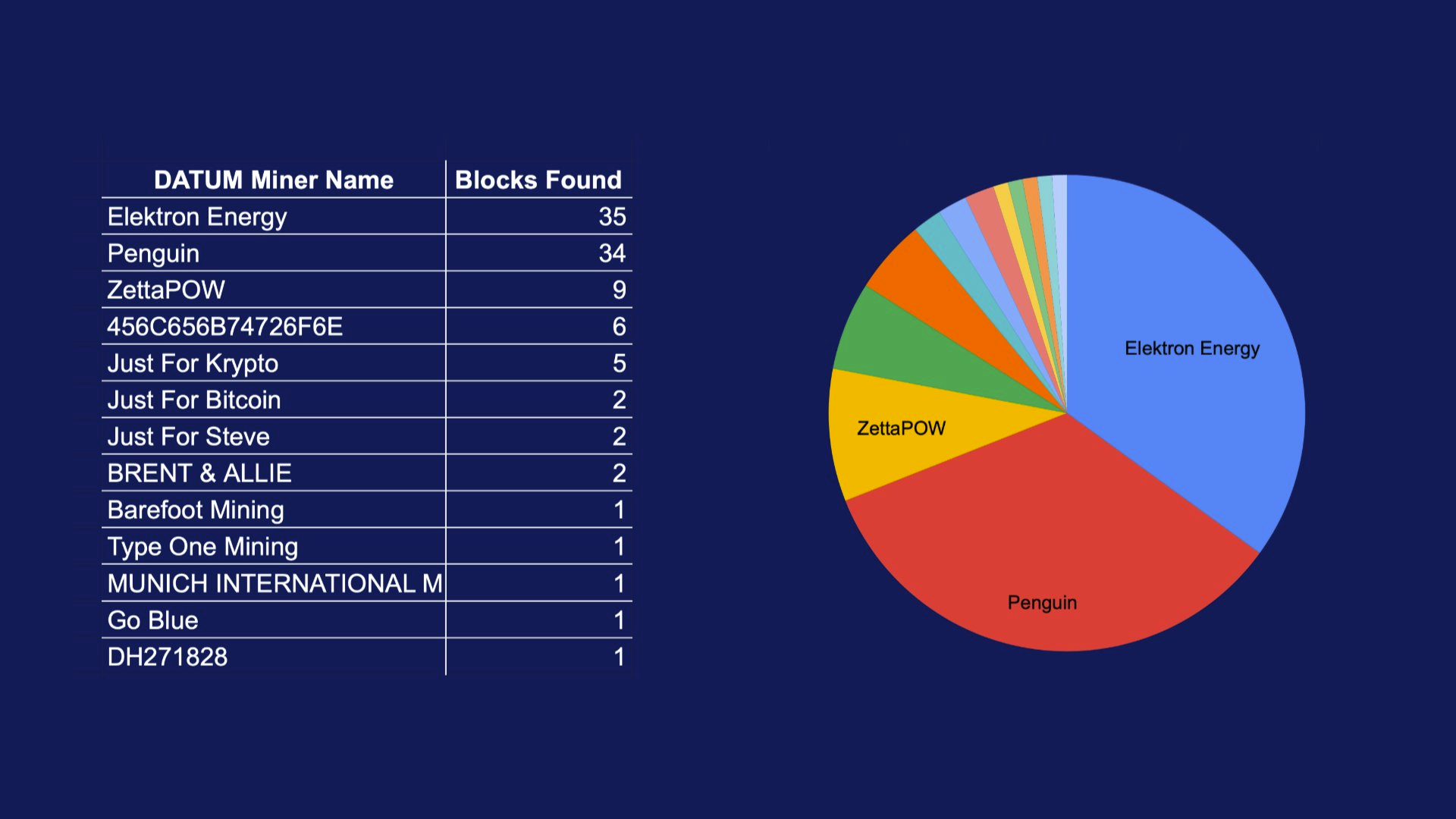
Source: orangesurf
- Arch Labs has secured $13 million to develop "ArchVM" and integrate smart-contract functionality with Bitcoin. The funding round, valuing the company at $200 million, was led by Pantera Capital, as announced on Tuesday.
- Tesla still holds nearly $1 billion in bitcoin. According to the automaker's latest earnings report, the firm reported digital asset holdings worth $951 million as of March 31.
- The European Central Bank is pushing for amendments to the European Union's Markets in Crypto Assets legislation (MiCA), just months after its implementation. According to Politico's report on Tuesday, the ECB is concerned that U.S. support for cryptocurrency, particularly stablecoins, could cause economic harm to the 27-nation bloc.
- TABConf 2025 is scheduled to take place from October 13-16, 2025. This prominent technical Bitcoin conference is dedicated to community building, education, and developer support, and it is set to return in October. Get your tickets here.
- Kaduna Lightning Development Bootcamp. From May 14th to 17th, the Bitcoin Lightning Developer Bootcamp will take place in Kaduna, Nigeria. Thisevent offers four dynamic days of coding, learning, and networking. Organized by Africa Free Routing and supported by Btrust, Tether, and African Bitcoiners, this bootcamp is designed as a gateway for African developers eager to advance their skills in Bitcoin and Lightning development. Apply here.

Source: African Bitcoiners.
Use the tools
- Core Lightning (CLN) v25.02.2 as been released to fix a broken Docker image. The issue was caused by an SQLite version that did not support an advanced query.
- Blitz wallet v0.4.4-beta introduces several updates and improvements, including the prevention of duplicate ecash payments, fixes for background ecash invoice handling, the ability for users to send payments to BOLT12 invoices from their Liquid balance, support for Blink QR codes, a lowered minimum amount for Lightning-to-Liquid payments to 100 sats, the option to initiate a node sync via a swipe gesture on the wallet's home screen, and the introduction of opt-in or opt-out functionality for newly implemented crash analytics via settings.
- Utreexo v0.5.0, a hash-based dynamic accumulator, is now available.
- Specter v2.1.1 is now available on StartOS. "This update brings compatibility with Bitcoin Core v28 and incorporates several upstream improvements," said developer Alex71btc.
- ESP-Miner (AxeOS) v2.7.0b1 is now available for testing.
- NodeGuard v0.16.1, a treasury management solution for Lightning nodes, has been released.
- The latest stacker.news updates include prompts to add a receiving wallet when posting or making comments (for new users), an option to randomize poll choices, improved URL search, and a few other enhancements. A bug fix for territories created after 9/19/24 has been implemented to reward 70% of their revenue to owners instead of 50%.
Other stuff
- The April edition of the 256 Foundation's newsletter is now available. It includes the latest mining news, Bitcoin network health updates, project developments, and a tutorial on how to update FutureBit's Apollo 1 to the Apollo 2 software.
- Siggy47 has posted a comprehensive RoboSats guide on stacker.news.
- Learn how to run your own Nostr relay using Citrine and Cloudflare Tunnels by following this step-by-step guide by Dhalism.
- Max Guise has written a Bitkey roadmap update for April 2025.
-
PlebLab has uploaded a video on how to build a Rust wallet with LDK Node by Ben Carman.
-
Do you want more? Subscribe and get No Bullshit GM report straight to your mailbox and No Bullshit Bitcoin on Nostr.
- Feedback or tips? Drop it here.
- #FREESAMOURAI
Sign up for No Bullshit Bitcoin

No Bullshit Bitcoin Is a Bitcoin News Desk Without Ads, Paywalls, or Clickbait.
Subscribe .nc-loop-dots-4-24-icon-o{--animation-duration:0.8s} .nc-loop-dots-4-24-icon-o *{opacity:.4;transform:scale(.75);animation:nc-loop-dots-4-anim var(--animation-duration) infinite} .nc-loop-dots-4-24-icon-o :nth-child(1){transform-origin:4px 12px;animation-delay:-.3s;animation-delay:calc(var(--animation-duration)/-2.666)} .nc-loop-dots-4-24-icon-o :nth-child(2){transform-origin:12px 12px;animation-delay:-.15s;animation-delay:calc(var(--animation-duration)/-5.333)} .nc-loop-dots-4-24-icon-o :nth-child(3){transform-origin:20px 12px} @keyframes nc-loop-dots-4-anim{0%,100%{opacity:.4;transform:scale(.75)}50%{opacity:1;transform:scale(1)}}
Email sent! Check your inbox to complete your signup.
No spam. Unsubscribe anytime.
-
 @ b7274d28:c99628cb
2025-05-28 00:59:49
@ b7274d28:c99628cb
2025-05-28 00:59:49Your identity is important to you, right? While impersonation can be seen in some senses as a form of flattery, we all would prefer to be the only person capable of representing ourselves online, unless we intentionally delegate that privilege to someone else and maintain the ability to revoke it.
Amber does all of that for you in the context of #Nostr. It minimizes the possibility of your private key being compromized by acting as the only app with access to it, while all other Nostr apps send requests to Amber when they need something signed. This even allows you to give someone temporary authority to post as you without giving them your private key, and you retain the authority to revoke their permissions at any time.
nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 has provided Android users with an incredibly powerful tool in Amber, and he continues to improve its functionality and ease of use. Indeed, there is not currently a comparative app available for iOS users. For the time being, this superpower is exclusive to Android.
Installation
Open up the Zapstore app that you installed in the previous stage of this tutorial series.
Very likely, Amber will be listed in the app collection section of the home page. If it is not, just search for "Amber" in the search bar.
Opening the app's page in the Zapstore shows that the release is signed by the developer. You can also see who has added this app to one of their collections and who has supported this app with sats by zapping the release.
Tap "Install" and you will be prompted to confirm you are sure you want to install Amber.
Helpfully, you are informed that several other users follow this developer on Nostr. If you have been on Nostr a while, you will likely recognize these gentlemen as other Nostr developers, one of them being the original creator of the protocol.
You can choose to never have Zapstore ask for confirmation again with apps developed by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5, and since we have another of his apps to install later in this tutorial series, I recommend you toggle this on. Then tap on "Trust greenart7c3 and install app."
Just like when you installed the Zapstore from their GitHub, you will be prompted to allow the Zapstore to install apps, since Android considers it an "unknown source."
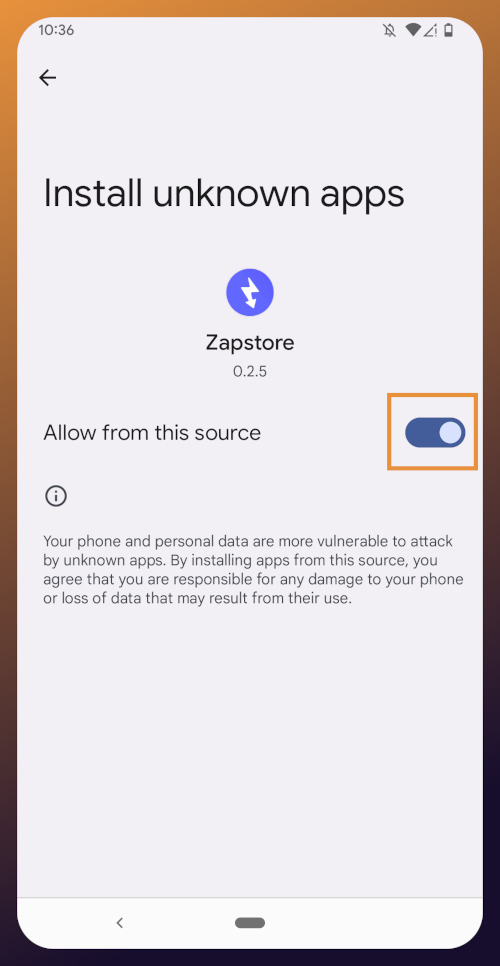
Once you toggle this on and use the back button to get back to the Zapstore, Amber will begin downloading and then present a prompt to install the app. Once installed, you will see a prompt that installation was a success and you can now open the app.
From here, how you proceed will depend on whether you need to set up a new Nostr identity or use Amber with an existing private key you already have set up. The next section will cover setting up a new Nostr identity with Amber. Skip to the section titled "Existing Nostrich" if you already have an nsec that you would like to use with Amber.
New Nostrich
Upon opening the application, you will be presented with the option to use an existing private key or create a new Nostr account. Nostr doesn't really have "accounts" in the traditional sense of the term. Accounts are a relic of permissioned systems. What you have on Nostr are keys, but Amber uses the "account" term because it is a more familiar concept, though it is technically inaccurate.
Choose "Create a new Nostr account" and you will be presented with a screen telling you that your Nostr account is ready. Yes, it was really that easy. No email, no real name, no date of birth, and no annoying capcha. Just "Create a new account" and you're done.
The app presents you with your public key. This is like an address that can be used to find your posts on Nostr. It is 100% unique to you, and no one else can post a note that lists this npub as the author, because they won't have the corresponding private key. You don't need to remember your npub, though. You'll be able to readily copy it from any Nostr app you use whenever you need it.
You will also be prompted to add a nickname. This is just for use within Amber, since you can set up multiple profiles within the app. You can use anything you want here, as it is just so you can tell which profile is which when switching between them in Amber.
Once you've set your nickname, tap on "Continue."
The next screen will ask you what Amber's default signing policy should be.
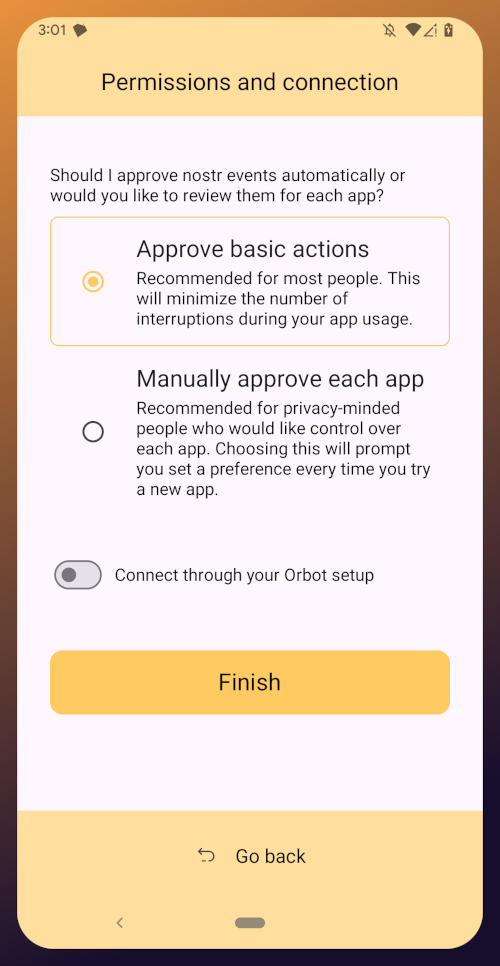
The default is to approve basic actions, referring to things that are common for Nostr clients to request a signature for, like following another user, liking a post, making a new post, or replying. If you are more concerned about what Amber might be signing for on your behalf, you can tell it to require manual approval for each app.
Once you've made your decision, tap "Finish." You will also be able to change this selection in the app settings at any time.
With this setup out of the way, you are now presented with the main "Applications" page of the app.
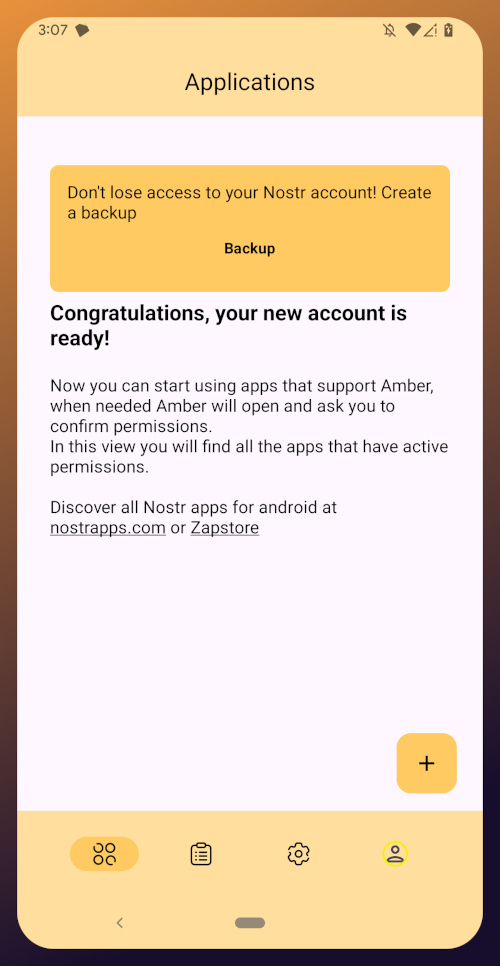
At the top, you have a notification encouraging you to create a backup. Let's get that taken care of now by tapping on the notification and skipping down to the heading titled "Backing Up Your Identity" in this tutorial.
Existing Nostrich
Upon opening the application, you will be presented with the option to use your private key or create a new Nostr account. Choose the former.
The next screen will require you to paste your private key.
You will need to obtain this from whatever Nostr app you used to create your profile, or any other Nostr app that you pasted your nsec into in the past. Typically you can find it in the app settings and there will be a section mentioning your keys where you can copy your nsec. For instance, in Primal go to Settings > Keys > Copy private key, and on Amethyst open the side panel by tapping on your profile picture in the top-left, then Backup Keys > Copy my secret key.
After pasting your nsec into Amber, tap "Next."

Amber will give you a couple options for a default signing policy. The default is to approve basic actions, referring to things that are common for Nostr clients to request a signature for, like following another user, liking a post, making a new post, or replying. If you are more concerned about what Amber might be signing for on your behalf, you can tell it to require manual approval for each app.
Once you've made your decision, tap "Finish." You will also be able to change this selection in the app settings at any time.
With this setup out of the way, you are now presented with the main "Applications" page of the app. You have nothing here yet, since you haven't used Amber to log into any Nostr apps, but this will be where all of the apps you have connected with Amber will be listed, in the order of the most recently used at the top.
Before we go and use Amber to log into an app, though, let's make sure we've created a backup of our private key. You pasted your nsec into Amber, so you could just save that somewhere safe, but Amber gives you a few other options as well. To find them, you'll need to tap the cog icon at the bottom of the screen to access the settings, then select "Backup Keys."
Backing Up Your Identity
You'll notice that Amber has a few different options for backing up your private key that it can generate.
First, it can give you seed words, just like a Bitcoin seed. If you choose that option, you'll be presented with 12 words you can record somewhere safe. To recover your Nostr private key, you just have to type those words into a compatible application, such as Amber.
The next option is to just copy the secret/private key in its standard form as an "nsec." This is the least secure way to store it, but is also the most convenient, since it is simple to paste into another signer application. If you want to be able to log in on a desktop web app, the browser extension Nostr signers won't necessarily support entering your 12 word seed phrase, but they absolutely will support pasting in your nsec.
You can also display a QR code of your private key. This can be scanned by Amber signer on another device for easily transferring your private key to other devices you want to use it on. Say you have an Android tablet in addition to your phone, for instance. Just make sure you only use this function where you can be certain that no one will be able to get a photograph of that QR code. Once someone else has your nsec, there is no way to recover it. You have to start all over on Nostr. Not a big deal at this point in your journey if you just created a Nostr account, but if you have been using Nostr for a while and have built up a decent amount of reputation, it could be much more costly to start over again.
The next options are a bit more secure, because they require a password that will be used to encrypt your private key. This has some distinct advantages, and a couple disadvantages to be aware of. Using a password to encrypt your private key will give you what is called an ncryptsec, and if this is leaked somehow, whoever has it will not necessarily have access to post as you on Nostr, the way they would if your nsec had been leaked. At least, not so long as they don't also have your password. This means you can store your ncryptsec in multiple locations without much fear that it will be compromised, so long as the password you used to encrypt it was a strong and unique one, and it isn't stored in the same location. Some Nostr apps support an ncryptsec for login directly, meaning that you have the option to paste in your ncryptsec and then just log in with the password you used to encrypt it from there on out. However, now you will need to keep track of both your ncryptsec and your password, storing both of them safely and separately. Additionally, most Nostr clients and signer applications do not support using an ncryptsec, so you will need to convert it back to a standard nsec (or copy the nsec from Amber) to use those apps.
The QR option using an ncryptsec is actually quite useful, though, and I would go this route when trying to set up Amber on additional devices, since anyone possibly getting a picture of the QR code is still not going to be able to do anything with it, unless they also get the password you used to encrypt it.
All of the above options will require you to enter the PIN you set up for your device, or biometric authentication, just as an additional precaution before displaying your private key to you.
As for what "store it in a safe place" looks like, I highly recommend a self-hosted password manager, such as Vaultwarden+Bitwarden or KeePass. If you really want to get wild, you can store it on a hardware signing device, or on a steel seed plate.
Additional Settings
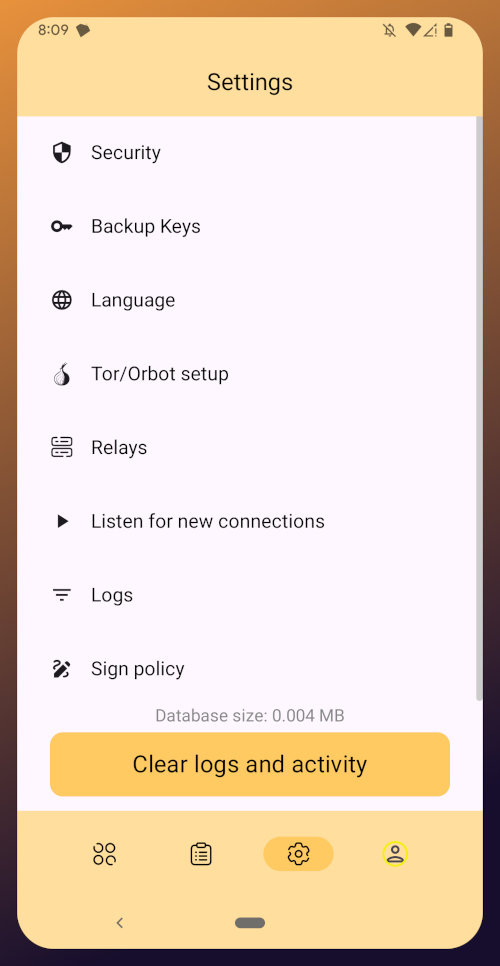
Amber has some additional settings you may want to take advantage of. First off, if you don't want just anyone who has access to your phone to be able to approve signing requests, you can go into the Security settings add a PIN or enable biometrics for signing requests. If you enable the PIN, it will be separate from the PIN you use to access your phone, so you can let someone else use your phone, like your child who is always begging to play a mobile game you have installed, without worrying that they might have access to your Nostr key to post on Amethyst.
Amber also has some relay settings. First are the "Active relays" which are used for signing requests sent to Amber remotely from Nostr web apps. This is what enables you to use Amber on your phone to log into Nostr applications on your desktop web browser, such as Jumble.social, Coracle.social, or Nostrudel.ninja, eliminating your need to use any other application to store your nsec whatsoever. You can leave this relay as the default, or you can add other relays you want to use for signing requests. Just be aware, not all relays will accept the notes that are used for Nostr signing requests, so make sure that the relay you want to use does so. In fact, Amber will make sure of this for you when you type in the relay address.
The next type of relays that you can configure in Amber are the "Default profile relays." These are used for reading your profile information. If you already had a Nostr identity that you imported to Amber, you probably noticed it loaded your profile picture and display name, setting the latter as your nickname in Amber. These relays are where Amber got that information from. The defaults are relay.nostr.band and purplepag.es. The reason for this is because they are aggregators that look for Nostr profiles that have been saved to other relays on the network and pull them in. Therefore, no matter what other relay you may save your profile to, Amber will likely be able to find it on one of those two relays as well. If you have a relay you know you will be saving your Nostr profiles to, you may want to add it to this list.
You can also set up Amber to be paired with Orbot for signing over Tor using relays that are only accessible via the Tor network. That is an advanced feature, though, and well beyond the scope of this tutorial.
Finally, you can update the default signing policy. Maybe after using Amber for a while, you've decided that the choice you made before was too strict or too lenient. You can change it to suit your needs.
Zapstore Login
Now that you are all set up with Amber, let's get you signed into your first Nostr app by going back to the Zapstore.
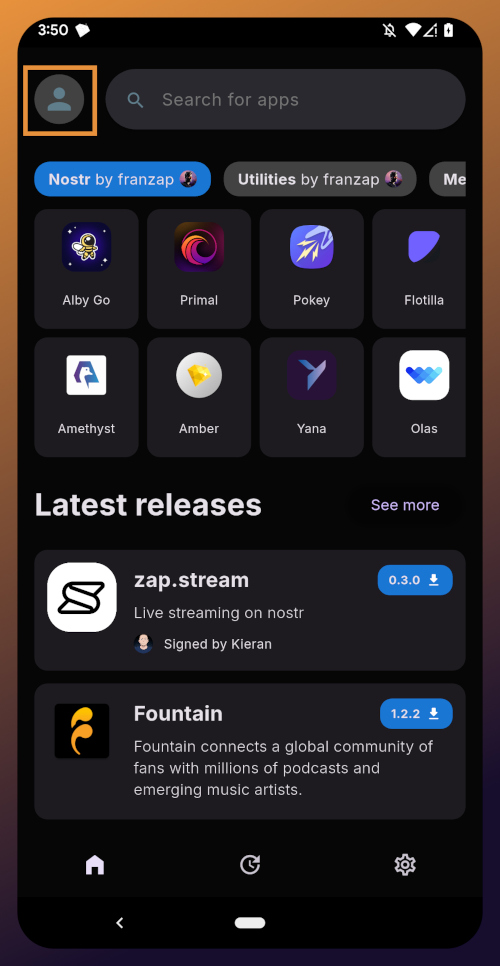
From the app's home screen, tap on the user icon in the upper left of the screen. This will open a side panel with not much on it except the option to "sign in." Go ahead and tap on it.
You will be presented with the option to either sign in with Amber, or to paste your npub. However, if you do the latter, you will only have read access, meaning you cannot zap any of the app releases. There are other features planned for the Zapstore that may also require you to be signed in with write access, so go ahead and choose to log in with Amber.
Your phone should automatically switch to Amber to approve the sign-in request.
You can choose to only approve basic actions for Zapstore, require it to manually approve every time, or you can tell it that you "fully trust this application." Only choose the latter option with apps you have used for a while and they have never asked you to sign for anything suspicious. For the time being, I suggest you use the "Approve basic actions" option and tap "Grant Permissions."
Your phone will switch back to the Zapstore and will show that you are now signed in. Congratulations! From here on out, logging into most Nostr applications will be as easy as tapping on "Log in with Amber" and approving the request.
If you set up a new profile, it will just show a truncated version of your npub rather than the nickname you set up earlier. That's fine. You'll have an opportunity to update your Nostr profile in the next tutorial in this series and ensure that it is spread far and wide in the network, so the Zapstore will easily find it.
That concludes the tutorial for Amber. While we have not covered using Amber to log into Nostr web apps, that is outside the scope of this series, and I will cover it in an upcoming tutorial regarding using Amber's remote signer options in detail.
Since you're already hanging out in the Zapstore, you may as well stick around, because we will be using it right out the gate in the next part of this series: Amethyst Installation and Setup. (Coming Soon)
-
 @ c1d77557:bf04ec8b
2025-05-24 05:02:26
@ c1d77557:bf04ec8b
2025-05-24 05:02:26O 567br é uma plataforma de entretenimento online que tem se destacado pela sua inovação, variedade de jogos e foco na experiência do jogador. Com uma interface amigável e recursos de alta qualidade, a plataforma oferece uma jornada divertida e segura para os seus usuários. Neste artigo, vamos explorar os principais aspectos do 567br, incluindo a introdução da plataforma, os jogos que ela oferece e como a experiência do jogador é aprimorada em cada detalhe.
O 567br foi desenvolvido com o objetivo de proporcionar aos jogadores uma experiência imersiva e prazerosa. Sua interface é simples, intuitiva e de fácil navegação, permitindo que os usuários encontrem rapidamente seus jogos favoritos. A plataforma também é otimizada para dispositivos móveis, o que significa que os jogadores podem acessar seus jogos em qualquer lugar e a qualquer momento, seja no computador ou no smartphone.
Além disso, o 567brse preocupa com a segurança de seus usuários, implementando tecnologias de criptografia de ponta para garantir que todos os dados pessoais e financeiros estejam protegidos. A plataforma também oferece suporte ao cliente de alta qualidade, disponível 24/7, para resolver quaisquer dúvidas ou problemas que possam surgir durante a experiência de jogo.
Jogos Empolgantes e Variedade para Todos os Gostos No 567br, a diversidade de jogos é um dos pontos fortes da plataforma. Desde jogos de mesa e cartas até opções de entretenimento mais dinâmicas e inovadoras, há algo para todos os gostos e preferências. Os jogos disponíveis são desenvolvidos por alguns dos melhores fornecedores de conteúdo da indústria, garantindo gráficos de alta qualidade, jogabilidade fluida e mecânicas envolventes.
Os jogadores podem escolher entre diferentes categorias, como:
Jogos de Mesa: Para quem gosta de uma experiência mais estratégica e de tomada de decisões, os jogos de mesa são uma excelente opção. São oferecidas diversas variantes de jogos populares, como pôquer, blackjack, roleta, entre outros.
Jogos de Ação e Aventura: Para os que buscam adrenalina e emoção, a plataforma oferece uma seleção de jogos de ação e aventura com temas envolventes e gráficos impressionantes. Esses jogos garantem uma experiência de jogo emocionante e desafiadora.
Jogos de Arcade: Se você está em busca de algo mais descontraído e divertido, os jogos de arcade são uma excelente escolha. Eles são rápidos, fáceis de entender e proporcionam diversão instantânea.
A plataforma está sempre atualizando seu portfólio de jogos para garantir que os jogadores tenham acesso às últimas novidades e inovações do mundo do entretenimento online.
A Experiência do Jogador: Personalização e Interatividade O 567br não se limita a oferecer apenas uma plataforma de jogos, mas também busca criar uma experiência personalizada e interativa para cada jogador. A plataforma possui funcionalidades que permitem que os usuários ajustem sua experiência de jogo de acordo com suas preferências individuais.
A personalização da interface é um exemplo claro disso. O jogador pode escolher o tema e a disposição dos elementos na tela, criando um ambiente que seja confortável e agradável de usar. Além disso, o 567br oferece recursos interativos, como chats ao vivo, onde os jogadores podem interagir com outros usuários e até mesmo com os dealers, proporcionando uma sensação de comunidade.
Outro aspecto importante é a possibilidade de acompanhar o desempenho e os resultados de jogo. A plataforma oferece relatórios detalhados, permitindo que os jogadores monitorem seu progresso, analisem suas vitórias e perdas, e façam ajustes em sua estratégia de jogo.
Promoções e Benefícios para os Jogadores O 567br também oferece uma série de promoções e benefícios que tornam a experiência de jogo ainda mais atrativa. Novos jogadores podem aproveitar bônus de boas-vindas e outras ofertas especiais, enquanto jogadores regulares podem se beneficiar de programas de fidelidade e promoções exclusivas.
Essas ofertas ajudam a aumentar a diversão e proporcionam mais oportunidades para que os jogadores explorem novos jogos e tenham uma experiência ainda mais rica. Além disso, o sistema de recompensas é transparente e justo, garantindo que todos os jogadores tenham as mesmas oportunidades de aproveitar os benefícios.
Conclusão: Uma Plataforma Completa para Todos os Gostos Com sua interface intuitiva, variedade de jogos e foco na experiência do jogador, o 567br se consolida como uma plataforma de entretenimento online de alta qualidade. Seja para quem busca jogos estratégicos, ação intensa ou diversão casual, o 567br tem algo para todos.
A segurança, o suporte ao cliente e a personalização da experiência de jogo tornam o 567br uma opção atraente para jogadores que buscam mais do que apenas uma plataforma de jogos – buscam uma jornada de entretenimento envolvente e segura. Se você está procurando por uma experiência completa e agradável, o 567br é, sem dúvida, uma excelente escolha.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:51:46
@ 21c71bfa:e28fa0f6
2025-05-29 14:51:46Book *Tirupati to Vellore cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:51:23
@ 21c71bfa:e28fa0f6
2025-05-29 14:51:23Book *Tirupati to Tirumala cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ c1d77557:bf04ec8b
2025-05-24 05:01:44
@ c1d77557:bf04ec8b
2025-05-24 05:01:44O P11Bet é uma plataforma inovadora que chega para oferecer uma experiência de jogo única, reunindo uma variedade de opções para os entusiastas de diferentes tipos de entretenimento online. Com uma interface moderna e fácil de usar, ela se destaca por proporcionar uma jornada divertida e segura para os jogadores, com um foco especial na qualidade da experiência e no atendimento às necessidades do público.
Uma Plataforma Completa e Acessível Ao acessar o P11Bet, os usuários encontram uma plataforma intuitiva, que facilita a navegação e oferece uma variedade de recursos para tornar o jogo mais agradável. A estrutura do site é otimizada para fornecer uma experiência fluida, seja no desktop ou em dispositivos móveis. Além disso, a plataforma se preocupa em manter um ambiente seguro, garantindo a proteção dos dados dos jogadores e permitindo que se concentrem na diversão.
A plataforma é projetada para todos os tipos de jogadores, desde os iniciantes até os mais experientes. A simplicidade de uso é uma das grandes vantagens, permitindo que qualquer pessoa possa se registrar e começar a jogar sem dificuldades. Além disso, a p11betoferece suporte ao cliente em português, o que facilita a comunicação e garante um atendimento de alta qualidade para os usuários brasileiros.
Diversidade de Jogos para Todos os Gostos O P11Bet se destaca pela vasta gama de opções de jogos que oferece aos seus usuários. A plataforma abriga uma seleção diversificada que vai desde jogos clássicos até as opções mais modernas, atendendo a todos os estilos e preferências. Entre as opções mais procuradas estão jogos de mesa, apostas esportivas, slots, e outras modalidades que garantem horas de entretenimento.
Um dos principais atrativos do P11Bet são os jogos de habilidade e de sorte, que exigem tanto estratégia quanto um pouco de sorte. As opções variam desde os mais simples aos mais complexos, oferecendo algo para todos os gostos. Os jogadores podem se aventurar em diversas modalidades, testando suas habilidades em jogos que vão de roletas e blackjack a versões mais inovadoras e dinâmicas.
Para aqueles que preferem algo mais emocionante e competitivo, as apostas esportivas são uma das maiores atrações. O P11Bet oferece uma ampla variedade de eventos esportivos ao vivo para apostar, com odds atrativas e uma plataforma que permite realizar apostas de forma rápida e eficiente. Seja em esportes populares como futebol, basquete ou até mesmo esportes menos tradicionais, há sempre algo para os apostadores mais exigentes.
A Experiência do Jogador: Diversão e Segurança O P11Bet não apenas se preocupa com a diversidade de jogos, mas também com a experiência do jogador. A plataforma foi desenvolvida para garantir que os jogadores possam desfrutar de seus jogos favoritos com a maior segurança e conforto possível. Além de um design intuitivo, a plataforma oferece diversas opções de pagamento, incluindo métodos populares no Brasil, para facilitar depósitos e retiradas. Isso garante que o processo de transações seja simples, rápido e seguro.
Outro ponto positivo do P11Bet é a experiência imersiva que ele oferece aos jogadores. A plataforma está sempre atualizada com novas funcionalidades, com promoções atraentes e bônus especiais que aumentam ainda mais a diversão. A interação com outros jogadores também é um diferencial, com espaços que permitem competir, conversar e trocar experiências com pessoas de todo o mundo.
Além disso, o suporte ao cliente da P11Bet é um dos mais elogiados pelos usuários. A equipe está sempre disponível para resolver dúvidas e fornecer assistência de maneira eficaz e amigável. Isso garante que os jogadores tenham sempre uma experiência tranquila, sem se preocupar com questões técnicas ou problemas relacionados à plataforma.
Conclusão Em resumo, o P11Bet é uma excelente escolha para quem busca uma plataforma completa e de qualidade para se divertir e desafiar suas habilidades. Com uma grande variedade de jogos, uma interface de fácil navegação e um suporte excepcional, ele garante que cada momento na plataforma seja único e prazeroso. Para quem deseja se aventurar no mundo dos jogos online, o P11Bet é uma opção que combina segurança, inovação e diversão.
-
 @ dfa02707:41ca50e3
2025-05-30 07:02:07
@ dfa02707:41ca50e3
2025-05-30 07:02:07Contribute to keep No Bullshit Bitcoin news going.
- RoboSats v0.7.7-alpha is now available!
NOTE: "This version of clients is not compatible with older versions of coordinators. Coordinators must upgrade first, make sure you don't upgrade your client while this is marked as pre-release."
- This version brings a new and improved coordinators view with reviews signed both by the robot and the coordinator, adds market price sources in coordinator profiles, shows a correct warning for canceling non-taken orders after a payment attempt, adds Uzbek sum currency, and includes package library updates for coordinators.

Source: RoboSats.
- siggy47 is writing daily RoboSats activity reviews on stacker.news. Check them out here.
- Stay up-to-date with RoboSats on Nostr.
What's new
- New coordinators view (see the picture above).
- Available coordinator reviews signed by both the robot and the coordinator.
- Coordinators now display market price sources in their profiles.

Source: RoboSats.
- Fix for wrong message on cancel button when taking an order. Users are now warned if they try to cancel a non taken order after a payment attempt.
- Uzbek sum currency now available.
- For coordinators: library updates.
- Add docker frontend (#1861).
- Add order review token (#1869).
- Add UZS migration (#1875).
- Fixed tests review (#1878).
- Nostr pubkey for Robot (#1887).
New contributors

Full Changelog: v0.7.6-alpha...v0.7.7-alpha
-
 @ dfa02707:41ca50e3
2025-05-30 07:02:07
@ dfa02707:41ca50e3
2025-05-30 07:02:07Contribute to keep No Bullshit Bitcoin news going.
- "Today we're launching the beta version of our multiplatform Nostr browser! Think Google Chrome but for Nostr apps. The beta is our big first step toward this vision," announced Damus.
- This version comes with the Dave Nostr AI assistant, support for zaps and the Nostr Wallet Connect (NWC) wallet interface, full-text note search, GIFs and fullscreen images, multiple media uploads, user tagging, relay list and mute list support, along with a number of other improvements."
"Included in the beta is the Dave, the Nostr AI assistant (its Grok for Nostr). Dave is a new Notedeck browser app that can search and summarize notes from the network. For a full breakdown of everything new, check out our beta launch video."
What's new
- Dave Nostr AI assistant app.
- GIFs.
- Fulltext note search.
- Add full screen images, add zoom, and pan.
- Zaps! NWC/ Wallet UI.
- Introduce last note per pubkey feed (experimental).
- Allow multiple media uploads per selection.
- Major Android improvements (still WIP).
- Added notedeck app sidebar.
- User Tagging.
- Note truncation.
- Local network note broadcast, broadcast notes to other notedeck notes while you're offline.
- Mute list support (reading).
- Relay list support.
- Ctrl-enter to send notes.
- Added relay indexing (relay columns soon).
- Click hashtags to open hashtag timeline.
- Fixed timelines sometimes not updating (stale feeds).
- Fixed UI bounciness when loading profile pictures
- Fixed unselectable post replies.
-
 @ c1d77557:bf04ec8b
2025-05-24 05:01:11
@ c1d77557:bf04ec8b
2025-05-24 05:01:11Se você está em busca de uma experiência de jogo dinâmica e diversificada, o 59h é a plataforma que você precisa conhecer. Com um foco claro na satisfação dos jogadores, ela oferece uma ampla variedade de opções de entretenimento, além de uma interface amigável e segura. Neste artigo, vamos explorar a plataforma 59h, destacando suas principais funcionalidades, jogos emocionantes e a experiência do usuário.
O Que é a Plataforma 59h? O 59h é uma plataforma inovadora que oferece uma vasta gama de jogos e experiências digitais para os entusiastas do entretenimento online. A plataforma se destaca pela sua interface intuitiva, que permite aos jogadores navegar com facilidade entre as diferentes categorias de jogos. Ela é ideal para quem busca uma experiência divertida e acessível, sem complicações.
Desde o momento em que você acessa o 59h, fica evidente o compromisso com a qualidade. A plataforma é projetada para ser acessível em diversos dispositivos, seja no seu computador, tablet ou smartphone. Isso garante que os jogadores possam aproveitar seus jogos favoritos a qualquer momento e em qualquer lugar, com a mesma qualidade e desempenho.
Uma Grande Variedade de Jogos para Todos os Gostos O 59h se destaca por sua impressionante variedade de jogos. Independentemente do tipo de jogo que você prefere, certamente encontrará algo que se adapte ao seu estilo. A plataforma oferece desde jogos de habilidade, até opções mais relaxantes e divertidas para aqueles que buscam algo mais descontraído.
Entre as opções mais populares, destacam-se os jogos de mesa, onde os jogadores podem testar suas habilidades em jogos como pôquer, blackjack e outros. Para quem prefere algo mais voltado para a sorte, o 59h também oferece jogos com elementos de sorte que podem garantir grandes recompensas.
Além disso, a plataforma está sempre atualizando seu portfólio de jogos, trazendo novidades para os jogadores. Isso significa que você nunca ficará entediado, já que sempre haverá algo novo e emocionante para experimentar.
A Experiência do Jogador no 59h Uma das maiores qualidades da plataforma 59h é sua atenção à experiência do usuário. Desde o processo de registro até a escolha de um jogo, tudo foi pensado para garantir uma navegação tranquila e sem estresse.
A plataforma é completamente segura, oferecendo métodos de pagamento rápidos e confiáveis. Isso significa que os jogadores podem depositar e retirar seus fundos com confiança, sem se preocupar com a segurança de suas informações pessoais. Além disso, o suporte ao cliente está sempre disponível para ajudar em caso de dúvidas ou problemas, garantindo que sua experiência seja o mais fluida possível.
Outro ponto que merece destaque é a comunidade de jogadores. A interação com outros jogadores é uma parte importante da plataforma, permitindo que você compartilhe dicas, participe de torneios e crie amizades. A plataforma 59h se esforça para criar um ambiente amigável e inclusivo, onde todos podem se divertir e aprender uns com os outros.
Acessibilidade e Facilidade de Uso O 59h não é apenas sobre a diversidade de jogos; também se trata de tornar o acesso o mais simples possível. A plataforma oferece um design responsivo, que se adapta perfeitamente a qualquer tipo de dispositivo. Isso significa que você pode jogar no computador, smartphone ou tablet com a mesma facilidade.
O processo de cadastro é simples e rápido, permitindo que você comece a jogar em questão de minutos. Além disso, a plataforma oferece uma série de recursos adicionais, como promoções e bônus exclusivos, que tornam a experiência ainda mais empolgante.
Conclusão O 59h se posiciona como uma plataforma de entretenimento online completa, oferecendo uma vasta gama de jogos, uma experiência de usuário de alta qualidade e um ambiente seguro e amigável para jogadores de todos os níveis. Se você procura uma plataforma confiável, diversificada e divertida, o 59h é a escolha ideal. Não importa se você é um iniciante ou um jogador experiente, há sempre algo novo para descobrir e aproveitar no 59h.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:51:04
@ 21c71bfa:e28fa0f6
2025-05-29 14:51:04Book *Bhubaneswar to Konark cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 39cc53c9:27168656
2025-05-27 09:21:46
@ 39cc53c9:27168656
2025-05-27 09:21:46Bitcoin enthusiasts frequently and correctly remark how much value it adds to Bitcoin not to have a face, a leader, or a central authority behind it. This particularity means there isn't a single person to exert control over, or a single human point of failure who could become corrupt or harmful to the project.
Because of this, it is said that no other coin can be equally valuable as Bitcoin in terms of decentralization and trustworthiness. Bitcoin is unique not just for being first, but also because of how the events behind its inception developed. This implies that, from Bitcoin onwards, any coin created would have been created by someone, consequently having an authority behind it. For this and some other reasons, some people refer to Bitcoin as "The Immaculate Conception".
While other coins may have their own unique features and advantages, they may not be able to replicate Bitcoin's community-driven nature. However, one other cryptocurrency shares a similar story of mystery behind its creation: Monero.
History of Monero
Bytecoin and CryptoNote
In March 2014, a Bitcointalk thread titled "Bytecoin. Secure, private, untraceable since 2012" was initiated by a user under the nickname "DStrange"^1^. DStrange presented Bytecoin (BCN) as a unique cryptocurrency, in operation since July 2012. Unlike Bitcoin, it employed a new algorithm known as CryptoNote.
DStrange apparently stumbled upon the Bytecoin website by chance while mining a dying bitcoin fork, and decided to create a thread on Bitcointalk^1^. This sparked curiosity among some users, who wondered how could Bytecoin remain unnoticed since its alleged launch in 2012 until then^2^.
Some time after, a user brought up the "CryptoNote v2.0" whitepaper for the first time, underlining its innovative features^4^. Authored by the pseudonymous Nicolas van Saberhagen in October 2013, the CryptoNote v2 whitepaper^5^ highlighted the traceability and privacy problems in Bitcoin. Saberhagen argued that these flaws could not be quickly fixed, suggesting it would be more efficient to start a new project rather than trying to patch the original^5^, an statement simmilar to the one from Satoshi Nakamoto^6^.
Checking with Saberhagen's digital signature, the release date of the whitepaper seemed correct, which would mean that Cryptonote (v1) was created in 2012^7^, although there's an important detail: "Signing time is from the clock on the signer's computer" ^9^.
Moreover, the whitepaper v1 contains a footnote link to a Bitcointalk post dated May 5, 2013^10^, making it impossible for the whitepaper to have been signed and released on December 12, 2012.
As the narrative developed, users discovered that a significant 80% portion of Bytecoin had been pre-mined^11^ and blockchain dates seemed to be faked to make it look like it had been operating since 2012, leading to controversy surrounding the project.
The origins of CryptoNote and Bytecoin remain mysterious, leaving suspicions of a possible scam attempt, although the whitepaper had a good amount of work and thought on it.
The fork
In April 2014, the Bitcointalk user
thankful_for_today, who had also participated in the Bytecoin thread^12^, announced plans to launch a Bytecoin fork named Bitmonero^13^.The primary motivation behind this fork was "Because there is a number of technical and marketing issues I wanted to do differently. And also because I like ideas and technology and I want it to succeed"^14^. This time Bitmonero did things different from Bytecoin: there was no premine or instamine, and no portion of the block reward went to development.
However, thankful_for_today proposed controversial changes that the community disagreed with. Johnny Mnemonic relates the events surrounding Bitmonero and thankful_for_today in a Bitcointalk comment^15^:
When thankful_for_today launched BitMonero [...] he ignored everything that was discussed and just did what he wanted. The block reward was considerably steeper than what everyone was expecting. He also moved forward with 1-minute block times despite everyone's concerns about the increase of orphan blocks. He also didn't address the tail emission concern that should've (in my opinion) been in the code at launch time. Basically, he messed everything up. Then, he disappeared.
After disappearing for a while, thankful_for_today returned to find that the community had taken over the project. Johnny Mnemonic continues:
I, and others, started working on new forks that were closer to what everyone else was hoping for. [...] it was decided that the BitMonero project should just be taken over. There were like 9 or 10 interested parties at the time if my memory is correct. We voted on IRC to drop the "bit" from BitMonero and move forward with the project. Thankful_for_today suddenly resurfaced, and wasn't happy to learn the community had assumed control of the coin. He attempted to maintain his own fork (still calling it "BitMonero") for a while, but that quickly fell into obscurity.
The unfolding of these events show us the roots of Monero. Much like Satoshi Nakamoto, the creators behind CryptoNote/Bytecoin and thankful_for_today remain a mystery^17^, having disappeared without a trace. This enigma only adds to Monero's value.
Since community took over development, believing in the project's potential and its ability to be guided in a better direction, Monero was given one of Bitcoin's most important qualities: a leaderless nature. With no single face or entity directing its path, Monero is safe from potential corruption or harm from a "central authority".
The community continued developing Monero until today. Since then, Monero has undergone a lot of technological improvements, migrations and achievements such as RingCT and RandomX. It also has developed its own Community Crowdfundinc System, conferences such as MoneroKon and Monerotopia are taking place every year, and has a very active community around it.
Monero continues to develop with goals of privacy and security first, ease of use and efficiency second. ^16^
This stands as a testament to the power of a dedicated community operating without a central figure of authority. This decentralized approach aligns with the original ethos of cryptocurrency, making Monero a prime example of community-driven innovation. For this, I thank all the people involved in Monero, that lead it to where it is today.
If you find any information that seems incorrect, unclear or any missing important events, please contact me and I will make the necessary changes.
Sources of interest
- https://forum.getmonero.org/20/general-discussion/211/history-of-monero
- https://monero.stackexchange.com/questions/852/what-is-the-origin-of-monero-and-its-relationship-to-bytecoin
- https://en.wikipedia.org/wiki/Monero
- https://bitcointalk.org/index.php?topic=583449.0
- https://bitcointalk.org/index.php?topic=563821.0
- https://bitcointalk.org/index.php?action=profile;u=233561
- https://bitcointalk.org/index.php?topic=512747.0
- https://bitcointalk.org/index.php?topic=740112.0
- https://monero.stackexchange.com/a/1024
- https://inspec2t-project.eu/cryptocurrency-with-a-focus-on-anonymity-these-facts-are-known-about-monero/
- https://medium.com/coin-story/coin-perspective-13-riccardo-spagni-69ef82907bd1
- https://www.getmonero.org/resources/about/
- https://www.wired.com/2017/01/monero-drug-dealers-cryptocurrency-choice-fire/
- https://www.monero.how/why-monero-vs-bitcoin
- https://old.reddit.com/r/Monero/comments/u8e5yr/satoshi_nakamoto_talked_about_privacy_features/
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:50:44
@ 21c71bfa:e28fa0f6
2025-05-29 14:50:44Book *Mcleodganj to Amritsar cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ c1e9ab3a:9cb56b43
2025-05-27 13:19:53
@ c1e9ab3a:9cb56b43
2025-05-27 13:19:53I. Introduction: Money as a Function of Efficiency and Preference
Money is not defined by law, but by power over productivity. In any open economy, the most economically efficient actors—those who control the most valuable goods, services, and knowledge—ultimately dictate the medium of exchange. Their preferences signal to the broader market what form of money is required to access the highest-value goods, from durable commodities to intangibles like intellectual property and skilled labor.
Whatever money these actors prefer becomes the de facto unit of account and store of value, regardless of its legal status. This emergent behavior is natural and reflects a hierarchy of monetary utility.
II. Classical Gresham’s Law: A Product of Market Distortion
Gresham’s Law, famously stated as:
"Bad money drives out good"
is only valid under coercive monetary conditions, specifically: - Legal tender laws that force the acceptance of inferior money at par with superior money. - Fixed exchange rates imposed by decree, not market valuation. - Governments or central banks backing elastic fiduciary media with promises of redemption. - Institutional structures that mandate debt and tax payments in the favored currency.
Under these conditions, superior money (hard money) is hoarded, while inferior money (soft, elastic, inflationary) circulates. This is not an expression of free market behavior—it is the result of suppressed price discovery and legal coercion.
Gresham’s Law, therefore, is not a natural law of money, but a law of distortion under forced parity and artificial elasticity.
III. The Collapse of Coercion: Inversion of Gresham’s Law
When coercive structures weaken or are bypassed—through technological exit, jurisdictional arbitrage, monetary breakdown, or political disintegration—Gresham’s Law inverts:
Good money drives out bad.
This occurs because: - Market actors regain the freedom to select money based on utility, scarcity, and credibility. - Legal parity collapses, exposing the true economic hierarchy of monetary forms. - Trustless systems (e.g., Bitcoin) or superior digital instruments (e.g., stablecoins) offer better settlement, security, and durability. - Elastic fiduciary media become undesirable as counterparty risk and inflation rise.
The inversion marks a return to monetary natural selection—not a breakdown of Gresham’s Law, but the collapse of its preconditions.
IV. Elasticity and Control
Elastic fiduciary media (like fiat currency) are not intrinsically evil. They are tools of state finance and debt management, enabling rapid expansion of credit and liquidity. However, when their issuance is unconstrained, and legal tender laws force their use, they become weapons of economic coercion.
Banks issue credit unconstrained by real savings, and governments enforce the use of inflated media through taxation and courts. This distorts capital allocation, devalues productive labor, and ultimately hollows out monetary confidence.
V. Monetary Reversion: The Return of Hard Money
When the coercion ends—whether gradually or suddenly—the monetary system reverts. The preferences of the productive and wealthy reassert themselves:
- Superior money is not just saved—it begins to circulate.
- Weaker currencies are rejected not just for savings, but for daily exchange.
- The hoarded form becomes the traded form, and Gresham’s Law inverts completely.
Bitcoin, gold, and even highly credible stable instruments begin to function as true money, not just stores of value. The natural monetary order returns, and the State becomes a late participant, not the originator of monetary reality.
VI. Conclusion
Gresham’s Law operates only under distortion. Its inversion is not an anomaly—it is a signal of the collapse of coercion. The monetary system then reorganizes around productive preference, technological efficiency, and economic sovereignty.
The most efficient market will always dictate the form of hard money. The State can delay this reckoning through legal force, but it cannot prevent it indefinitely. Once free choice returns, bad money dies, and good money lives again.
-
 @ 39cc53c9:27168656
2025-05-27 09:21:40
@ 39cc53c9:27168656
2025-05-27 09:21:40“The future is there... staring back at us. Trying to make sense of the fiction we will have become.” — William Gibson.
This month is the 4th anniversary of kycnot.me. Thank you for being here.
Fifteen years ago, Satoshi Nakamoto introduced Bitcoin, a peer-to-peer electronic cash system: a decentralized currency free from government and institutional control. Nakamoto's whitepaper showed a vision for a financial system based on trustless transactions, secured by cryptography. Some time forward and KYC (Know Your Customer), AML (Anti-Money Laundering), and CTF (Counter-Terrorism Financing) regulations started to come into play.
What a paradox: to engage with a system designed for decentralization, privacy, and independence, we are forced to give away our personal details. Using Bitcoin in the economy requires revealing your identity, not just to the party you interact with, but also to third parties who must track and report the interaction. You are forced to give sensitive data to entities you don't, can't, and shouldn't trust. Information can never be kept 100% safe; there's always a risk. Information is power, who knows about you has control over you.
Information asymmetry creates imbalances of power. When entities have detailed knowledge about individuals, they can manipulate, influence, or exploit this information to their advantage. The accumulation of personal data by corporations and governments enables extensive surveillances.
Such practices, moreover, exclude individuals from traditional economic systems if their documentation doesn't meet arbitrary standards, reinforcing a dystopian divide. Small businesses are similarly burdened by the costs of implementing these regulations, hindering free market competition^1:
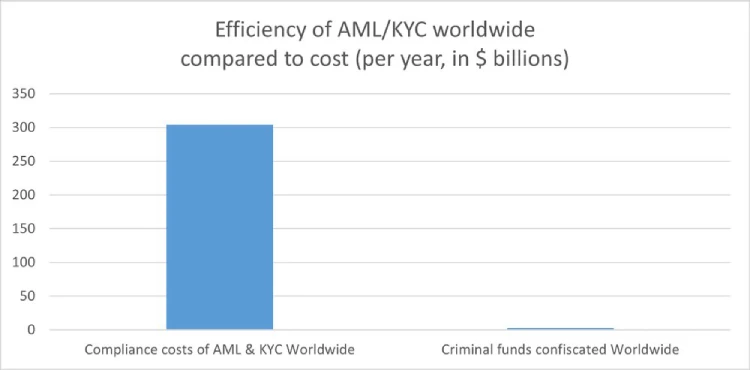
How will they keep this information safe? Why do they need my identity? Why do they force businesses to enforce such regulations? It's always for your safety, to protect you from the "bad". Your life is perpetually in danger: terrorists, money launderers, villains... so the government steps in to save us.
‟Hush now, baby, baby, don't you cry Mamma's gonna make all of your nightmares come true Mamma's gonna put all of her fears into you Mamma's gonna keep you right here, under her wing She won't let you fly, but she might let you sing Mamma's gonna keep baby cosy and warm” — Mother, Pink Floyd
We must resist any attack on our privacy and freedom. To do this, we must collaborate.
If you have a service, refuse to ask for KYC; find a way. Accept cryptocurrencies like Bitcoin and Monero. Commit to circular economies. Remove the need to go through the FIAT system. People need fiat money to use most services, but we can change that.
If you're a user, donate to and prefer using services that accept such currencies. Encourage your friends to accept cryptocurrencies as well. Boycott FIAT system to the greatest extent you possibly can.
This may sound utopian, but it can be achieved. This movement can't be stopped. Go kick the hornet's nest.
“We must defend our own privacy if we expect to have any. We must come together and create systems which allow anonymous transactions to take place. People have been defending their own privacy for centuries with whispers, darkness, envelopes, closed doors, secret handshakes, and couriers. The technologies of the past did not allow for strong privacy, but electronic technologies do.” — Eric Hughes, A Cypherpunk's Manifesto
The anniversary
Four years ago, I began exploring ways to use crypto without KYC. I bookmarked a few favorite services and thought sharing them to the world might be useful. That was the first version of kycnot.me — a simple list of about 15 services. Since then, I've added services, rewritten it three times, and improved it to what it is now.
kycnot.me has remained 100% independent and 100% open source^2 all these years. I've received offers to buy the site, all of which I have declined and will continue to decline. It has been DDoS attacked many times, but we made it through. I have also rewritten the whole site almost once per year (three times in four years).
The code and scoring algorithm are open source (contributions are welcome) and I can't arbitrarly change a service's score without adding or removing attributes, making any arbitrary alterations obvious if they were fake. You can even see the score summary for any service's score.
I'm a one-person team, dedicating my free time to this project. I hope to keep doing so for many more years. Again, thank you for being part of this.
-
 @ b7274d28:c99628cb
2025-05-27 07:07:33
@ b7274d28:c99628cb
2025-05-27 07:07:33A few months ago, a nostrich was switching from iOS to Android and asked for suggestions for #Nostr apps to try out. nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424 offered the following as his response:
nostr:nevent1qvzqqqqqqypzq0mhp4ja8fmy48zuk5p6uy37vtk8tx9dqdwcxm32sy8nsaa8gkeyqydhwumn8ghj7un9d3shjtnwdaehgunsd3jkyuewvdhk6tcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszythwden5te0dehhxarj9emkjmn99uqzpwwts6n28eyvjpcwvu5akkwu85eg92dpvgw7cgmpe4czdadqvnv984rl0z
Yes. #Android users are fortunate to have some powerful Nostr apps and tools at our disposal that simply have no comparison over on the iOS side. However, a tool is only as good as the knowledge of the user, who must have an understanding of how best to wield it for maximum effect. This fact was immediately evidenced by replies to Derek asking, "What is the use case for Citrine?" and "This is the first time I'm hearing about Citrine and Pokey. Can you give me links for those?"
Well, consider this tutorial your Nostr starter-kit for Android. We'll go over installing and setting up Amber, Amethyst, Citrine, and Pokey, and as a bonus we'll be throwing in the Zapstore and Coinos to boot. We will assume no previous experience with any of the above, so if you already know all about one or more of these apps, you can feel free to skip that tutorial.
So many apps...
You may be wondering, "Why do I need so many apps to use Nostr?" That's perfectly valid, and the honest answer is, you don't. You can absolutely just install a Nostr client from the Play Store, have it generate your Nostr identity for you, and stick with the default relays already set up in that app. You don't even need to connect a wallet, if you don't want to. However, you won't experience all that Nostr has to offer if that is as far as you go, any more than you would experience all that Italian cuisine has to offer if you only ever try spaghetti.
Nostr is not just one app that does one thing, like Facebook, Twitter, or TikTok. It is an entire ecosystem of applications that are all built on top of a protocol that allows them to be interoperable. This set of tools will help you make the most out of that interoperability, which you will never get from any of the big-tech social platforms. It will provide a solid foundation for you to build upon as you explore more and more of what Nostr has to offer.
So what do these apps do?

Fundamental to everything you do on Nostr is the need to cryptographically sign with your private key. If you aren't sure what that means, just imagine that you had to enter your password every time you hit the "like" button on Facebook, or every time you commented on the latest dank meme. That would get old really fast, right? That's effectively what Nostr requires, but on steroids.
To keep this from being something you manually have to do every 5 seconds when you post a note, react to someone else's note, or add a comment, Nostr apps can store your private key and use it to sign behind the scenes for you. This is very convenient, but it means you are trusting that app to not do anything with your private key that you don't want it to. You are also trusting it to not leak your private key, because anyone who gets their hands on it will be able to post as you, see your private messages, and effectively be you on Nostr. The more apps you give your private key to, the greater your risk that it will eventually be compromised.
Enter #Amber, an application that will store your private key in only one app, and all other compatible Nostr apps can communicate with it to request a signature, without giving any of those other apps access to your private key.
Most Nostr apps for Android now support logging in and signing with Amber, and you can even use it to log into apps on other devices, such as some of the web apps you use on your PC. It's an incredible tool given to us by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5, and only available for Android users. Those on iPhone are incredibly jealous that they don't have anything comparable, yet.

Speaking of nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5, the next app is also one of his making.
All Nostr data is stored on relays, which are very simple servers that Nostr apps read notes from and write notes to. In most forms of social media, it can be a pain to get your own data out to keep a backup. That's not the case on Nostr. Anyone can run their own relay, either for the sake of backing up their personal notes, or for others to post their notes to, as well.
Since Nostr notes take up very little space, you can actually run a relay on your phone. I have been on Nostr for almost 2 and a half years, and I have 25,000+ notes of various kinds on my relay, and a backup of that full database is just 24MB on my phone's storage.
Having that backup can save your bacon if you try out a new Nostr client and it doesn't find your existing follow list for some reason, so it writes a new one and you suddenly lose all of the people you were following. Just pop into your #Citrine relay, confirm it still has your correct follow list or import it from a recent backup, then have Citrine restore it. Done.
Additionally, there are things you may want to only save to a relay you control, such as draft messages that you aren't ready to post publicly, or eCash tokens, which can actually be saved to Nostr relays now. Citrine can also be used with Amber for signing into certain Nostr applications that use a relay to communicate with Amber.
If you are really adventurous, you can also expose Citrine over Tor to be used as an outbox relay, or used for peer-to-peer private messaging, but that is far more involved than the scope of this tutorial series.

You can't get far in Nostr without a solid and reliable client to interact with. #Amethyst is the client we will be using for this tutorial because there simply isn't another Android client that comes close, so far. Moreover, it can be a great client for new users to get started on, and yet it has a ton of features for power-users to take advantage of as well.
There are plenty of other good clients to check out over time, such as Coracle, YakiHonne, Voyage, Olas, Flotilla and others, but I keep coming back to Amethyst, and by the time you finish this tutorial, I think you'll see why. nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z and others who have contributed to Amethyst have really built something special in this client, and it just keeps improving with every update that's shipped.
Most social media apps have some form of push notifications, and some Nostr apps do, too. Where the issue comes in is that Nostr apps are all interoperable. If you have more than one application, you're going to have both of them notifying you. Nostr users are known for having five or more Nostr apps that they use regularly. If all of them had notifications turned on, it would be a nightmare. So maybe you limit it to only one of your Nostr apps having notifications turned on, but then you are pretty well locked-in to opening that particular app when you tap on the notification.
Pokey, by nostr:npub1v3tgrwwsv7c6xckyhm5dmluc05jxd4yeqhpxew87chn0kua0tjzqc6yvjh, solves this issue, allowing you to turn notifications off for all of your Nostr apps, and have Pokey handle them all for you. Then, when you tap on a Pokey notification, you can choose which Nostr app to open it in.
Pokey also gives you control over the types of things you want to be notified about. Maybe you don't care about reactions, and you just want to know about zaps, comments, and direct messages. Pokey has you covered. It even supports multiple accounts, so you can get notifications for all the npubs you control.

One of the most unique and incredibly fun aspects of Nostr is the ability to send and receive #zaps. Instead of merely giving someone a 👍️ when you like something they said, you can actually send them real value in the form of sats, small portions of a Bitcoin. There is nothing quite like the experience of receiving your first zap and realizing that someone valued what you said enough to send you a small amount (and sometimes not so small) of #Bitcoin, the best money mankind has ever known.
To be able to have that experience, though, you are going to need a wallet that can send and receive zaps, and preferably one that is easy to connect to Nostr applications. My current preference for that is Alby Hub, but not everyone wants to deal with all that comes along with running a #Lightning node. That being the case, I have opted to use nostr:npub1h2qfjpnxau9k7ja9qkf50043xfpfy8j5v60xsqryef64y44puwnq28w8ch for this tutorial, because they offer one of the easiest wallets to set up, and it connects to most Nostr apps by just copy/pasting a connection string from the settings in the wallet into the settings in your Nostr app of choice.
Additionally, even though #Coinos is a custodial wallet, you can have it automatically transfer any #sats over a specified threshold to a separate wallet, allowing you to mitigate the custodial risk without needing to keep an eye on your balance and make the transfer manually.

Most of us on Android are used to getting all of our mobile apps from one souce: the Google Play Store. That's not possible for this tutorial series. Only one of the apps mentioned above is available in Google's permissioned playground. However, on Android we have the advantage of being able to install whatever we want on our device, just by popping into our settings and flipping a toggle. Indeed, thumbing our noses at big-tech is at the heart of the Nostr ethos, so why would we make ourselves beholden to Google for installing Nostr apps?
The nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8 is an alternative app store made by nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9 as a resource for all sorts of open-source apps, but especially Nostr apps. What is more, you can log in with Amber, connect a wallet like Coinos, and support the developers of your favorite Nostr apps directly within the #Zapstore by zapping their app releases.
One of the biggest features of the Zapstore is the fact that developers can cryptographically sign their app releases using their Nostr keys, so you know that the app you are downloading is the one they actually released and hasn't been altered in any way. The Zapstore will warn you and won't let you install the app if the signature is invalid.
Getting Started
Since the Zapstore will be the source we use for installing most of the other apps mentioned, we will start with installing the Zapstore.
We will then use the Zapstore to install Amber and set it up with our Nostr account, either by creating a new private key, or by importing one we already have. We'll also use it to log into the Zapstore.
Next, we will install Amethyst from the Zapstore and log into it via Amber.
After this, we will install Citrine from the Zapstore and add it as a local relay on Amethyst.
Because we want to be able to send and receive zaps, we will set up a wallet with CoinOS and connect it to Amethyst and the Zapstore using Nostr Wallet Connect.
Finally, we will install Pokey using the Zapstore, log into it using Amber, and set up the notifications we want to receive.
By the time you are done with this series, you will have a great head-start on your Nostr journey compared to muddling through it all on your own. Moreover, you will have developed a familiarity with how things generally work on Nostr that can be applied to other apps you try out in the future.
Continue to Part 2: The Zapstore. Nostr Link: nostr:naddr1qvzqqqr4gupzpde8f55w86vrhaeqmd955y4rraw8aunzxgxstsj7eyzgntyev2xtqydhwumn8ghj7un9d3shjtnzwf5kw6r5vfhkcapwdejhgtcqp5cnwdphxv6rwwp3xvmnzvqgty5au
-
 @ dfa02707:41ca50e3
2025-05-30 07:02:07
@ dfa02707:41ca50e3
2025-05-30 07:02:07Contribute to keep No Bullshit Bitcoin news going.
- Wasabi Wallet v2.6.0 "Prometheus" is a major update for the project, focused on resilience and independence from centralized systems.
- Key features include support for BIP 158 block filters for direct node synchronization, a revamped full node integration for easier setup without third-party reliance, SLIP 39 share backups for flexible wallet recovery (sponsored by Trezor), and a Nostr-based update manager for censorship-resistant updates.
- Additional improvements include UI bug fixes, a new fallback for transaction broadcasting, updated code signing, stricter JSON serialization, and options to avoid third-party rate providers, alongside various under-the-hood enhancements.
This new version brings us closer to our ultimate goal: ensuring Wasabi is future-proof," said the developers, while also highlighting the following key areas of focus for the project:
- Ensuring users can always fully and securely use their client.
- Making contribution and forks easy through a codebase of the highest quality possible: understandable, maintainable, and improvable.
"As we achieve our survival goals, expect more cutting-edge improvements in Bitcoin privacy and self-custody. Thank you for the trust you place in us by using Wasabi," was stated in the release notes.
What's new
- Support for Standard BIP 158 Block Filters. Wasabi now syncs using BIP 158 filters without a backend/indexer, connecting directly to a user's node. This boosts sync speed, resilience, and allows full sovereignty without specific server dependency.
- Full Node Integration Rework. The old integration has been replaced with a simpler, more adaptable system. It’s not tied to a specific Bitcoin node fork, doesn’t need the node on the same machine as Wasabi, and requires no changes to the node’s setup.
- "Simply enable the RPC server on your node and point Wasabi to it," said the developers. This ensures all Bitcoin network activities—like retrieving blocks, fee estimations, block filters, and transaction broadcasting—go through your own node, avoiding reliance on third parties.
- Create & Recover SLIP 39 Shares. Users now create and recover wallets with multiple share backups using SLIP 39 standard.
"Special thanks to Trezor (SatoshiLabs) for sponsoring this amazing feature."
- Nostr Update Manager. This version implements a pioneering system with the Nostr protocol for update information and downloads, replacing reliance on GitHub. This enhances the project's resilience, ensuring updates even if GitHub is unavailable, while still verifying updates with the project's secure certificate.
- Updated Avalonia to v11.2.7, fixes for UI bugs (including restoring Minimize on macOS Sequoia).
- Added a configurable third-party fallback for broadcasting transactions if other methods fail.
- Replaced Windows Code Signing Certificate with Azure Trusted Signing.
- Many bug fixes, improved codebase, and enhanced CI pipeline.
- Added the option to avoid using any third-party Exchange Rate and Fee Rate providers (Wasabi can work without them).
- Rebuilt all JSON Serialization mechanisms avoiding default .NET converters. Serialization is now stricter.

Full Changelog: v2.5.1...v2.6.0
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:50:23
@ 21c71bfa:e28fa0f6
2025-05-29 14:50:23Book *Manali to Amritsar cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 06830f6c:34da40c5
2025-05-24 04:21:03
@ 06830f6c:34da40c5
2025-05-24 04:21:03The evolution of development environments is incredibly rich and complex and reflects a continuous drive towards greater efficiency, consistency, isolation, and collaboration. It's a story of abstracting away complexity and standardizing workflows.
Phase 1: The Bare Metal & Manual Era (Early 1970s - Late 1990s)
-
Direct OS Interaction / Bare Metal Development:
- Description: Developers worked directly on the operating system's command line or a basic text editor. Installation of compilers, interpreters, and libraries was a manual, often arcane process involving downloading archives, compiling from source, and setting environment variables. "Configuration drift" (differences between developer machines) was the norm.
- Tools: Text editors (Vi, Emacs), command-line compilers (GCC), Makefiles.
- Challenges: Extremely high setup time, dependency hell, "works on my machine" syndrome, difficult onboarding for new developers, lack of reproducibility. Version control was primitive (e.g., RCS, SCCS).
-
Integrated Development Environments (IDEs) - Initial Emergence:
- Description: Early IDEs (like Turbo Pascal, Microsoft Visual Basic) began to integrate editors, compilers, debuggers, and sometimes GUI builders into a single application. This was a massive leap in developer convenience.
- Tools: Turbo Pascal, Visual Basic, early Visual Studio versions.
- Advancement: Improved developer productivity, streamlined common tasks. Still relied on local system dependencies.
Phase 2: Towards Dependency Management & Local Reproducibility (Late 1990s - Mid-2000s)
-
Basic Build Tools & Dependency Resolvers (Pre-Package Managers):
- Description: As projects grew, manual dependency tracking became impossible. Tools like Ant (Java) and early versions of
autoconf/makefor C/C++ helped automate the compilation and linking process, managing some dependencies. - Tools: Apache Ant, GNU Autotools.
- Advancement: Automated build processes, rudimentary dependency linking. Still not comprehensive environment management.
- Description: As projects grew, manual dependency tracking became impossible. Tools like Ant (Java) and early versions of
-
Language-Specific Package Managers:
- Description: A significant leap was the emergence of language-specific package managers that could fetch, install, and manage libraries and frameworks declared in a project's manifest file. Examples include Maven (Java), npm (Node.js), pip (Python), RubyGems (Ruby), Composer (PHP).
- Tools: Maven, npm, pip, RubyGems, Composer.
- Advancement: Dramatically simplified dependency resolution, improved intra-project reproducibility.
- Limitation: Managed language-level dependencies, but not system-level dependencies or the underlying OS environment. Conflicts between projects on the same machine (e.g., Project A needs Python 2.7, Project B needs Python 3.9) were common.
Phase 3: Environment Isolation & Portability (Mid-2000s - Early 2010s)
-
Virtual Machines (VMs) for Development:
- Description: To address the "it works on my machine" problem stemming from OS-level and system-level differences, developers started using VMs. Tools like VMware Workstation, VirtualBox, and later Vagrant (which automated VM provisioning) allowed developers to encapsulate an entire OS and its dependencies for a project.
- Tools: VMware, VirtualBox, Vagrant.
- Advancement: Achieved strong isolation and environment reproducibility (a true "single environment" for a project).
- Limitations: Resource-heavy (each VM consumed significant CPU, RAM, disk space), slow to provision and boot, difficult to share large VM images.
-
Early Automation & Provisioning Tools:
- Description: Alongside VMs, configuration management tools started being used to automate environment setup within VMs or on servers. This helped define environments as code, making them more consistent.
- Tools: Chef, Puppet, Ansible.
- Advancement: Automated provisioning, leading to more consistent environments, often used in conjunction with VMs.
Phase 4: The Container Revolution & Orchestration (Early 2010s - Present)
-
Containerization (Docker):
- Description: Docker popularized Linux Containers (LXC), offering a lightweight, portable, and efficient alternative to VMs. Containers package an application and all its dependencies into a self-contained unit that shares the host OS kernel. This drastically reduced resource overhead and startup times compared to VMs.
- Tools: Docker.
- Advancement: Unprecedented consistency from development to production (Dev/Prod Parity), rapid provisioning, highly efficient resource use. Became the de-facto standard for packaging applications.
-
Container Orchestration:
- Description: As microservices and container adoption grew, managing hundreds or thousands of containers became a new challenge. Orchestration platforms automated the deployment, scaling, healing, and networking of containers across clusters of machines.
- Tools: Kubernetes, Docker Swarm, Apache Mesos.
- Advancement: Enabled scalable, resilient, and complex distributed systems development and deployment. The "environment" started encompassing the entire cluster.
Phase 5: Cloud-Native, Serverless & Intelligent Environments (Present - Future)
-
Cloud-Native Development:
- Description: Leveraging cloud services (managed databases, message queues, serverless functions) directly within the development workflow. Developers focus on application logic, offloading infrastructure management to cloud providers. Containers become a key deployment unit in this paradigm.
- Tools: AWS Lambda, Azure Functions, Google Cloud Run, cloud-managed databases.
- Advancement: Reduced operational overhead, increased focus on business logic, highly scalable deployments.
-
Remote Development & Cloud-Based IDEs:
- Description: The full development environment (editor, terminal, debugger, code) can now reside in the cloud, accessed via a thin client or web browser. This means developers can work from any device, anywhere, with powerful cloud resources backing their environment.
- Tools: GitHub Codespaces, Gitpod, AWS Cloud9, VS Code Remote Development.
- Advancement: Instant onboarding, consistent remote environments, access to high-spec machines regardless of local hardware, enhanced security.
-
Declarative & AI-Assisted Environments (The Near Future):
- Description: Development environments will become even more declarative, where developers specify what they need, and AI/automation tools provision and maintain it. AI will proactively identify dependency issues, optimize resource usage, suggest code snippets, and perform automated testing within the environment.
- Tools: Next-gen dev container specifications, AI agents integrated into IDEs and CI/CD pipelines.
- Prediction: Near-zero environment setup time, self-healing environments, proactive problem identification, truly seamless collaboration.
web3 #computing #cloud #devstr
-
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:50:05
@ 21c71bfa:e28fa0f6
2025-05-29 14:50:05Book *Amritsar to Phagwara cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:49:42
@ 21c71bfa:e28fa0f6
2025-05-29 14:49:42Book *Chandigarh to Amritsar cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:49:20
@ 21c71bfa:e28fa0f6
2025-05-29 14:49:20Book *Amritsar to Pathankot cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ dfa02707:41ca50e3
2025-05-30 07:02:06
@ dfa02707:41ca50e3
2025-05-30 07:02:06Contribute to keep No Bullshit Bitcoin news going.
-
Version 1.3 of Bitcoin Safe introduces a redesigned interactive chart, quick receive feature, updated icons, a mempool preview window, support for Child Pays For Parent (CPFP) and testnet4, preconfigured testnet demo wallets, as well as various bug fixes and improvements.
-
Upcoming updates for Bitcoin Safe include Compact Block Filters.
"Compact Block Filters increase the network privacy dramatically, since you're not asking an electrum server to give you your transactions. They are a little slower than electrum servers. For a savings wallet like Bitcoin Safe this should be OK," writes the project's developer Andreas Griffin.
- Learn more about the current and upcoming features of Bitcoin Safe wallet here.
What's new in v1.3
- Redesign of Chart, Quick Receive, Icons, and Mempool Preview (by @design-rrr).
- Interactive chart. Clicking on it now jumps to transaction, and selected transactions are now highlighted.

- Speed up transactions with Child Pays For Parent (CPFP).
- BDK 1.2 (upgraded from 0.32).
- Testnet4 support.
- Preconfigured Testnet demo wallets.
- Cluster unconfirmed transactions so that parents/children are next to each other.
- Customizable columns for all tables (optional view: Txid, Address index, and more)
- Bug fixes and other improvements.

Announcement / Archive
Blog Post / Archive
GitHub Repo
Website -
-
 @ dfa02707:41ca50e3
2025-05-30 07:02:06
@ dfa02707:41ca50e3
2025-05-30 07:02:06Contribute to keep No Bullshit Bitcoin news going.
- This release introduces Payjoin v2 functionality to Bitcoin wallets on Cake, along with several UI/UX improvements and bug fixes.
- The Payjoin v2 protocol enables asynchronous, serverless coordination between sender and receiver, removing the need to be online simultaneously or maintain a server. This simplifies privacy-focused transactions for regular users.
"I cannot speak highly enough of how amazing it has been to work with @bitgould and Jaad from the@payjoindevkit team, they're doing incredible work. None of this would be possible without them and their tireless efforts. PDK made it so much easier to ship Payjoin v2 than it would have been otherwise, and I can't wait to see other wallets jump in and give back to PDK as they implement it like we did," said Seth For Privacy, VP at Cake Wallet.

How to started with Payjoin in Cake Wallet:
- Open the app menu sidebar and click
Privacy. - Toggle the
Use Payjoinoption. - Now on your receive screen you'll see an option to copy a Payjoin URL
- Bull Bitcoin Wallet v0.4.0 introduced Payjoin v2 support in late December 2024. However, the current implementations are not interoperable at the moment, an issue that should be addressed in the next release of the Bull Bitcoin Wallet.
- Cake Wallet was one of the first wallets to introduce Silent Payments back in May 2024. However, users may encounter sync issues while using this feature at present, which will be resolved in the next release of Cake Wallet.
What's new
- Payjoin v2 implementation.
- Wallet group improvements: Enhanced management of multiple wallets.
- Various bug fixes: improving overall stability and user experience.
- Monero (XMR) enhancements.
Learn more about using, implementing, and understanding BIP 77: Payjoin Version 2 using the
payjoincrate in Payjoin Dev Kit here. -
 @ 21c71bfa:e28fa0f6
2025-05-29 14:49:01
@ 21c71bfa:e28fa0f6
2025-05-29 14:49:01Book *Amritsar to Manali cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.