-
 @ 5fd693e6:bf6061bb
2023-07-22 22:18:17
@ 5fd693e6:bf6061bb
2023-07-22 22:18:17WHAT IS NOSTR ADDRESS
Nostr Address = NIP 05 identifier NIP = a Nostr Implementation Possible
“Mapping Nostr keys to DNS-based internet identifiers”
it Maps your PubKey to URLYou should first read the actual NIP 05 spec, hopefully the following can make sense of that for end users.
a Nostr Address is how you create a readable unique handle. anyone can be @dave and there can be multiple @dave's on nostr, only one person can be dave@dave.com
In some cases, it’s an added layer of verification. If your Nostr Address ID is @stephenasmith@espn.com that’s a pretty strong indicator that this is the real Stephen A Smith, the only way to accomplish this is to have access to edit espn.com.
Personally, I use a similar handle across the web, and wanted to vanity my nip in the same fashion, just like on legacy new media, I am the only one who will have this name.
My philosophy here is, you own your own private key for NOSTR, so why have an address that’s a po box?
If you aren’t ready to pay for a domain or hosting, github offers you the chance to learn how to do this without spending money. BenGWeeks has written this guide Using GitHub Pages for NIP-05 Identifiers.
This results in his nostr address being Ben@BenGWeeks.github.io This is a great free way to set up a nostr address if you are ok with having github.io in your identifier. (Don’t miss steps 3-6 in his guide, you have to Deploy it as Static HTML.)
There is nothing wrong with supporting a NIP 05 provider services, or choosing someone kind enough to add you to theirs for free. This might serve your purposes just fine. Since we are all here learning this new protocol, I think it’s nice to learn or revisit publishing with the Hypertext Transfer Protocol (HTTP).
LET’S GET STARTED
You are going to create a webpage with a file path that looks like this: https://example.com/.well-known/nostr.json https://bengweeks.gihub.io/.well-known/nostr.json
STEP 1: Create /.well-know/nostr.json/
on github:
add file > create new file > name it /.well-know/nostr.json/ this will create both a folder and a file named nostr.json
on a self hosted server:
your hosting provider most likely has a file editor that can accomplish creating folders and files and provides a text editor. If you did this on github first, you can download these files and upload them to your new host.
Copy the following to the newly create nostr.json file
{ "names": { "bob": "b0635d6a9851d3aed0cd6c495b282167acf761729078d975fc341b22650b07b9" } }Replace “bob” with your name and replace the long string of characters with the hex version of your pubkey (convert your npub key at damus.io/key)
DOMAIN AS AN IDENTIFIER
My username is yunginternet and my domain is yunginter.net and I wanted my Nostr Address to be @yunginter.net not zach@yunginter.net so you replace the name with an underscore.
My nostr.json file looks like:
{ "names": { "_": "5fd693e61a7969ecf5c11dbf5ce20aedac1cea71721755b037955994bf6061bb" } }This results in my Nostr Address identifier being: _@yunginter.net
When I go to metadata.nostr.com/ or another client that allows me to edit my Nostr Address (they might still call it NIP 05 identifer) I will enter: _@yunginter.net
However, one should “expect Nostr clients to show and treat that as just @yunginter.net for all purposes.”
I like this because as on legacy new media, it just has one at sign in the identifier, instead of users having to type @bob@bob.com which looks like an email, both to human readers and operating systems, not a handle like @yunginter.net
STEP 2: CORS
You have to turn on CORS for your site. CORS stands for Cross-Origin Resource Sharing. This makes the json “get”-able.
CORS ON GITHUB PAGES
If you are following this tutorial from ben, Github.io pages have CORS enabled by default.
CORS ON A SELF-HOSTED WEBSITE
I tried to set up github with a custom domain pointing at github, and that seemed to not pass the allow access file. I still wanted my custom domain so I went to move my github page to a hosting provider.
In addition to registering a domain, you will also have to rent or set up web hosting, and maintain an SSL cert.
Fundamentally you need to add this to a .htaccess file: I didn’t have a .htaccess file, so my hosting provider had me create one in their file browser in the root directory of my site.
Header set Access-Control-Allow-Origin "*"It needs to be formatted based on the type of web server.
It’s easier to just ask your hosting provider “how do i properly add CORS to a .htaccess file” than to figure out how their server software wants it formatted. You can search their documentation or simply reach out to their customer support.
How this is formatted depends on the type of web server software your hosting provider is running, mine suggested i do it like the following because they are running apache:
<IfModule mod_headers.c> Header set Access-Control-Allow-Origin "*" </IfModule>But yours might suggest you do it like the following because they are running jetty:
This is why it’s just easier to reach out to them.
<filter> <filter-name>cross-origin</filter-name> <filter-class>org.eclipse.jetty.servlets.CrossOriginFilter</filter-class> </filter> <filter-mapping> <filter-name>cross-origin</filter-name> <url-pattern>/*</url-pattern> </filter-mapping>Once you save your .htaccess file you should be good to go.
STEP 3: UPDATE METADATA
Visit your https://example.com/.well-known/nostr.json page If you see this CORS json viewer like on this page you are all set.
Head to a client that allows you to input your Nostr Address (NIP 05 identifier) in your profile and you’re all set.
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 4bda8a0e:f0aaec7e
2023-07-22 13:07:31
@ 4bda8a0e:f0aaec7e
2023-07-22 13:07:31Benefit of Self-Recording 2: Small victories
In the real world, people don't radically change overnight. Most changes occur gradually. By all means, aim high in the long-term. In the short-term, you need to think in terms of incremental improvement. Quantitative records of your behavior will allow you to better articulate what a small step forward would actually look like. If the records say you smoke 20 cigarettes per day, you know that reducing smoking to 19 cigarettes per day is progress. If you exercise 10 minutes a day, you know that 10 minutes and 20 seconds constitutes an improvement.
Keeping records of the specific situations in which your target behavior occurs (or fails to occur) facilitates another kind of incremental improvement. Behavior can be changed one environment at the time. Furthermore, some environments will be more hostile to your desired behavior than others. Try ranking them by difficulty and start with the easier ones. For instance, it may be easier to avoid smoking when socializing with non-smokers than smokers. Or, it may be easier to start exercising on the weekends when you're not exhausted from work.
Every change in amount or specific environment constitutes a small victory. These are a great way of building confidence in your own ability and help you stay on track when the final goal is situated far into the future.
-
 @ d2e97f73:ea9a4d1b
2023-04-11 19:36:53
@ d2e97f73:ea9a4d1b
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 4bda8a0e:f0aaec7e
2023-07-22 12:59:06
@ 4bda8a0e:f0aaec7e
2023-07-22 12:59:06We all have behaviors that we struggle to add or subtract from our lives. One of the most basic techniques for doing so is to start recording how frequently the behavior in question occurs, and in what situations. If you want to add a behavior that currently has a frequency of zero, you should record the situations where you want it to occur, and what you were doing instead.
I've noticed that few people take this advice seriously. Maybe because of some notion that psychology is supposed to involve arcane mental wizardry and this just seems too simple. Well, solutions should be simple. Another set of reasons have to do with misconceptions about what can be recorded or how much work it would entail. Most importantly, however, is perhaps the lack of awareness around the many empirically verified benefits of self-recording. I'll be doing a short series on that, summarizing my thoughts around each benefit. One post. One benefit. Here's the first.
Benefit of Self-Recording 1: Change in the direction of your values
A common effect of observing our own behavior is that the behavior changes. This is known in the literature as "reactivity". There is nothing mystical about reactivity. If your primary concern is practical results, don't get hung up on "mind-over-matter" questions. Instead, let's look at the conditions under which reactivity tends to occur. It seems to happen if the self-observer assigns a negative or positive value to the behavior. Negative associations tend to decrease the frequency of the observed behavior, while positive associations tend to increase it. The key point is that you need both. Merely convincing yourself that a behavior is desirable or undesirable is not enough. You also need to become an observer of your own actions. Likewise, if you start self-recording and notice no change for weeks – examine your values. Try to articulate to yourself in writing why this behavior is good or bad for you. Reactivity will not always be enough to induce the change you want. But in many cases, it will, and it is an excellent place to start.
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ f4db5270:3c74e0d0
2023-07-22 16:32:18
@ f4db5270:3c74e0d0
2023-07-22 16:32:18 \n\n# "Ponti sotto la pioggia" (2023)\n40x60cm, oil on panel canvas\n\n(Available)\n\n\n-----------\n\n\nHere a moment work in progress...\n\n
\n\n# "Ponti sotto la pioggia" (2023)\n40x60cm, oil on panel canvas\n\n(Available)\n\n\n-----------\n\n\nHere a moment work in progress...\n\n \n\n\n-----------\n\n\nThe beginning...\n\n
\n\n\n-----------\n\n\nThe beginning...\n\n \n\n\n-----------\n\nThe original photo\n\n
\n\n\n-----------\n\nThe original photo\n\n
-
 @ b12b632c:d9e1ff79
2023-07-21 19:45:20
@ b12b632c:d9e1ff79
2023-07-21 19:45:20I love testing every new self hosted app and I can say that Nostr "world" is really good regarding self hosting stuff.
Today I tested a Nostr relay named Strfry.
Strfry is really simple to setup and support a lot's of Nostr NIPs.
Here is the list of what it is able to do :
- Supports most applicable NIPs: 1, 2, 4, 9, 11, 12, 15, 16, 20, 22, 28, 33, 40
- No external database required: All data is stored locally on the filesystem in LMDB
- Hot reloading of config file: No server restart needed for many config param changes
- Zero downtime restarts, for upgrading binary without impacting users
- Websocket compression: permessage-deflate with optional sliding window, when supported by clients
- Built-in support for real-time streaming (up/down/both) events from remote relays, and bulk import/export of events from/to jsonl files
- negentropy-based set reconcilliation for efficient syncing with remote relays
Installation with docker compose (v2)
Spoiler : you need to have a computer with more than 1 (v)Core / 2GB of RAM to build the docker image locally. If not, this below might crash your computer during docker image build. You may need to use a prebuilt strfry docker image.
I assume you've read my first article on Managing domain with Nginx Proxy Manager because I will use the NPM docker compose stack to publish strfry Nostr relay. Without the initial NPM configuration done, it may not work as expected. I'll use the same docker-compose.yml file and folder.
Get back in the "npm-stack" folder :
cd npm-stackCloning the strfry github repo locally :
git clone https://github.com/hoytech/strfry.gitModify the docker-compose file to locate the strfry configuration data outside of the folder repo directory to avoid mistake during futures upgrades (CTRL + X, S & ENTER to quit and save modifications) :
nano docker-compose.ymlYou don't have to insert the Nginx Proxy Manager part, you should already have it into the file. If not, check here. You should only have to add the strfry part.
``` version: '3.8' services: # should already be present into the docker-compose.yml app: image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: # These ports are in format
: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port # Add any other Stream port you want to expose # - '21:21' # FTP # Uncomment the next line if you uncomment anything in the section # environment: # Uncomment this if you want to change the location of # the SQLite DB file within the container # DB_SQLITE_FILE: "/data/database.sqlite" # Uncomment this if IPv6 is not enabled on your host # DISABLE_IPV6: 'true' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencryptstrfry-nostr-relay: container_name: strfry build: ./strfry volumes: - ./strfry-data/strfry.conf:/etc/strfry.conf - ./strfry-data/strfry-db:/app/strfry-db
ports is commented by NPM will access through docker internal network
no need to expose strfry port directly to the internet
ports:
- "7777:7777"
```
Before starting the container, we need to customize the strfry configuration file "strfry.conf". We'll copy the strfry configuration file and place it into the "strfry-data" folder to modify it with our own settings :
mkdir strfry-data && cp strfry/strfry.conf strfry-data/And modify the strfry.conf file with your own settings :
nano strfry-data/strfry.confYou can modify all the settings you need but the basics settings are :
- bind = "127.0.0.1" --> bind = "0.0.0.0" --> otherwise NPM won't be able to contact the strfry service
-
name = "strfry default" --> name of your nostr relay
-
description = "This is a strfry instance." --> your nostr relay description
-
pubkey = "" --> your pubkey in hex format. You can use the Damu's tool to generate your hex key from your npub key : https://damus.io/key/
-
contact = "" --> your email
``` relay { # Interface to listen on. Use 0.0.0.0 to listen on all interfaces (restart required) bind = "127.0.0.1"
# Port to open for the nostr websocket protocol (restart required) port = 7777 # Set OS-limit on maximum number of open files/sockets (if 0, don't attempt to set) (restart required) nofiles = 1000000 # HTTP header that contains the client's real IP, before reverse proxying (ie x-real-ip) (MUST be all lower-case) realIpHeader = "" info { # NIP-11: Name of this server. Short/descriptive (< 30 characters) name = "strfry default" # NIP-11: Detailed information about relay, free-form description = "This is a strfry instance." # NIP-11: Administrative nostr pubkey, for contact purposes pubkey = "" # NIP-11: Alternative administrative contact (email, website, etc) contact = "" }```
You can now start the docker strfry docker container :
docker compose up -dThis command will take a bit of time because it will build the strfry docker image locally before starting the container. If your VPS doesn't have lot's of (v)CPU/RAM, it could fail (nothing happening during the docker image build). My VPS has 1 vCore / 2GB of RAM and died few seconds after the build beginning.
If it's the case, you can use prebuilt strfry docker image available on the Docker hub : https://hub.docker.com/search?q=strfry&sort=updated_at&order=desc
That said, otherwise, you should see this :
``` user@vps:~/npm-stack$ docker compose up -d [+] Building 202.4s (15/15) FINISHED
=> [internal] load build definition from Dockerfile 0.2s => => transferring dockerfile: 724B 0.0s => [internal] load .dockerignore 0.3s => => transferring context: 2B 0.0s => [internal] load metadata for docker.io/library/ubuntu:jammy 0.0s => [build 1/7] FROM docker.io/library/ubuntu:jammy 0.4s => [internal] load build context 0.9s => => transferring context: 825.64kB 0.2s => [runner 2/4] WORKDIR /app 1.3s => [build 2/7] WORKDIR /build 1.5s => [runner 3/4] RUN apt update && apt install -y --no-install-recommends liblmdb0 libflatbuffers1 libsecp256k1-0 libb2-1 libzstd1 && rm -rf /var/lib/apt/lists/* 12.4s => [build 3/7] RUN apt update && apt install -y --no-install-recommends git g++ make pkg-config libtool ca-certificates libyaml-perl libtemplate-perl libregexp-grammars-perl libssl-dev zlib1g-dev l 55.5s => [build 4/7] COPY . . 0.9s => [build 5/7] RUN git submodule update --init 2.6s => [build 6/7] RUN make setup-golpe 10.8s => [build 7/7] RUN make -j4 126.8s => [runner 4/4] COPY --from=build /build/strfry strfry 1.3s => exporting to image 0.8s => => exporting layers 0.8s => => writing image sha256:1d346bf343e3bb63da2e4c70521a8350b35a02742dd52b12b131557e96ca7d05 0.0s => => naming to docker.io/library/docker-compose_strfry-nostr-relay 0.0sUse 'docker scan' to run Snyk tests against images to find vulnerabilities and learn how to fix them
[+] Running 02/02
⠿ Container strfry Started 11.0s ⠿ Container npm-stack-app-1 Running ```You can check if everything is OK with strfry container by checking the container logs :
user@vps:~/npm-stack$ docker logs strfry date time ( uptime ) [ thread name/id ] v| 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| arguments: /app/strfry relay 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| Current dir: /app 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| stderr verbosity: 0 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| ----------------------------------- 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| CONFIG: Loading config from file: /etc/strfry.conf 2023-07-21 19:26:58.529 ( 0.054s) [main thread ]INFO| CONFIG: successfully installed 2023-07-21 19:26:58.533 ( 0.058s) [Websocket ]INFO| Started websocket server on 0.0.0.0:7777Now, we have to create the subdomain where strfry Nostr relay will be accessible. You need to connect to your Nginx Proxy Manager admin UI and create a new proxy host with these settings :
"Details" tab (Websockets support is mandatory!, you can replace "strfry" by whatever you like, for instance : mybeautifulrelay.yourdomain.tld)
"Details" tab:

"SSL" tab:

And click on "Save"
If everything is OK, when you go to https://strfry.yourdomain.tld you should see :

To verify if strfry is working properly, you can test it with the (really useful!) website https://nostr.watch. You have to insert your relay URL into the nostr.watch URL like this : https://nostr.watch/relay/strfry.yourdomain.tld
You should see this :

If you are seeing your server as online, readable and writable, you made it ! You can add your Nostr strfry server to your Nostr prefered relay and begin to publish notes ! 🎇
Future work:
Once done, strfry will work like a charm but you may need to have more work to update strfry in the near future. I'm currently working on a bash script that will :
- Updatethe "strfry" folder,
- Backup the "strfry.conf" file,
- Download the latest "strfry.conf" from strfry github repo,
- Inject old configuration settings into the new "strfry.conf" file,
- Compose again the stack (rebuilding the image to get the latest code updates),
- etc.
Tell me if you need the script!
Voilààààà
See you soon in another Fractalized story!
-
 @ 53df7d8d:0995b599
2023-07-21 19:06:02
@ 53df7d8d:0995b599
2023-07-21 19:06:02Welcome you might be reading this on one of many content serving platform. New articles appear every Friday on the AOS website and broadcasted on Nostr. You can find the main Nostr publications on YakiHonne.
Classical Definition
Decentralised Autonomous organisations are classically defined as organisations that are governed and operated through smart contracts on a blockchain, typically utilising a decentralised network such as Ethereum. They are designed to be autonomous and self-executing, with decisions made based on predefined rules and consensus mechanisms.
DAOs aim to eliminate the need for traditional hierarchical structures and central authorities by enabling participants to collectively make decisions and manage the organisations resources. These resources can include funds, intellectual property, or other assets. DAOs often have their own native tokens, which can represent ownership, voting rights, or other forms of participation within the organisation.
Participants in a DAO can propose and vote on decisions, such as allocating funds, changing organisational rules, or implementing new projects. Voting power is typically determined by the number of tokens held by each participant. The execution of decisions is carried out automatically through smart contracts, ensuring transparency and removing the need for intermediaries.
DAOs have gained popularity due to their potential for increased transparency, inclusivity, and community-driven governance. However, it's worth noting that the concept is still evolving, and there have been challenges and risks associated with DAOs, such as potential vulnerabilities in smart contracts and the need to address legal and regulatory considerations.
Tldr: In summary, a classical definition of a DAO would emphasise its decentralised nature , self-governance through consensus, and the use of smart contracts to automate decision-making and operations .
Exploring the Problem Space
Now the previous classical notion was crafted in the light of the emergence of cryptocurrency's smart contract consensus protocols. What we will be doing is crafting a new deviation or expansion from this definition into a new concept and pair it with a development stack to create and explore some of these idea's.
The Governance Problem: The problem with this classical definition is that it mostly carries the autonomous aspect into a consensus mechanism operated by a human voting mechanism. In the new structure we focus on four models:
- No Governance
- AI Governance
- AI / Human Hybrid Governance
- Human Consensus Governance
The Sustainability Problem: Every organisation needs certain elements to survive these can be money, labor, devotion... that translate to innovation, maintenance and grit... This ties back into the governance model by having to make a decision in the consensus structure to provide the direction of the organisations future. The problem lies in balancing the monetary components in a more complex system with these future directions.
Now there is one structure that stands out, the one were innovation and maintenance are not required and this is usually set as a LTS version or just simple being compatible with some mainstream component like a browser. This might sound a little confusing since the only example we've been able to come up with in this space is uses a No Governance model.
The other Governance models support are more applicable to test structures with: - Value for Value propositions ( with or without initial funding ) - User generated development ( the users drive the innovation ) These are just two common examples to showcase structures that can grow on their own. The list is very long of models that can be used and will be more refined during testing.
The Smart Contract Problem: This is a little misleading since the new structure will still and can use smart contract structures. However we look to minimise the friction and complexity of these contract by shifting to more standerd layer 2 crypto currency transactions.
The Decentralised Problem: Since most of this is based on smart contract structures the idea of including Nostr in this equation seems like a new way forward. By making a client open and able to select it's own relay you can provide a long term front-end back-end decoupling that would just require you to understand on how to setup a private relay at home.
Compressing the extended Concept
To try and be as clear as possible in the outline of this exploration the concepts are build according to rules promoting ( Community Growing, Long Term Support, Autonomy ).
1) 🌱 Seeding Costs
The structure should be able to exist without the need of monetary fuel. It can however be provided a seed amount to start operating on layer 2 crypto.
2) 🖖 Client / Relay decoupling
Build a client organisation that uses Nostr as a decentralised backend. Providing you the option of running a relay at home for your own use cases.
3) 🏛️ Extending Governance
The structure should be able to support and explore these government models to its fullest extend. While sharing easy deployable builds with our community.
Now this is our first public note on this project and topic and we'll be diving deep and expanding more on this in the coming months while we develop some examples and add more rules to try and clearly define the directions we explore and build towards.
🫶 M371554
-
 @ a1c65c8a:24548ccb
2023-07-21 18:40:08
@ a1c65c8a:24548ccb
2023-07-21 18:40:08Welcome to my experiment
Recently, I stood up a relay at nostr.sixteensixtyone.com (nostr 1661) as an experiment of sorts. I have questions about the future of decentralized social media. Has bitcoin found a use case beyond investment? How do all the parts fit together? How much does it cost to run this stuff? How do we defray those costs? Show me the money.
**I am also a bitcoin skeptic. ** Wasn't always that way. I mined about a quarter's worth. Bought some in the run up to 1k. Sold some, bought some, no great profits or losses. Fast forward to the run up to 68k, I thought it was clear the rise was unsustainable. My True Believing friends were as undaunted then as they remain today. I sold all my crypto investments several years ago and, except what I may have earned since this writing, I have no crypto investments at this time.
So, I posit the HODL and stack sats communities have it wrong. The current theme of "grab all you can, as fast as you can, before it goes the the moon!" is detrimental to bitcoin adoption. This behavior is exactly the opposite of what is need to make a bitcoin a viable financial vehicle as it reduces the incentive to spend it. Why would you spend your btc, if you think it will be more valuable tomorrow?
I suggest that building bitcoin technologies and earning bitcoin in the process is furthering adoption than more any laser-eyed social media personality begging you to HODL because it's going to the moon.
Welcome to my experiment.
-Sean
-
 @ f4db5270:3c74e0d0
2023-07-22 16:28:30
@ f4db5270:3c74e0d0
2023-07-22 16:28:30 \n\n# "Sunset at Playa Hermosa, Uvita" (2023)\n40x30cm, oil on panel canvas\n\n(Available)**\n\n-----------\n\n\nHere a moment work in progress...\n\n
\n\n# "Sunset at Playa Hermosa, Uvita" (2023)\n40x30cm, oil on panel canvas\n\n(Available)**\n\n-----------\n\n\nHere a moment work in progress...\n\n \n\n-----------\n\n\nThe beginning...\n\n
\n\n-----------\n\n\nThe beginning...\n\n \n\n-----------\n\n\nThe original photo\n
\n\n-----------\n\n\nThe original photo\n
-
 @ b12b632c:d9e1ff79
2023-07-21 14:19:38
@ b12b632c:d9e1ff79
2023-07-21 14:19:38Self hosting web applications comes quickly with the need to deal with HTTPS protocol and SSL certificates. The time where web applications was published over the 80/TCP port without any encryption is totally over. Now we have Let's Encrypt and other free certification authority that lets us play web applications with, at least, the basic minimum security required.
Second part of web self hosting stuff that is really useful is the web proxifycation.
It's possible to have multiple web applications accessible through HTTPS but as we can't use the some port (spoiler: we can) we are forced to have ugly URL as https://mybeautifudomain.tld:8443.
This is where Nginx Proxy Manager (NPM) comes to help us.
NPM, as gateway, will listen on the 443 https port and based on the subdomain you want to reach, it will redirect the network flow to the NPM differents declared backend ports. NPM will also request HTTPS cert for you and let you know when the certificate expires, really useful.
We'll now install NPM with docker compose (v2) and you'll see, it's very easy.
You can find the official NPM setup instructions here.
But before we absolutely need to do something. You need to connect to the registrar where you bought your domain name and go into the zone DNS section.You have to create a A record poing to your VPS IP. That will allow NPM to request SSL certificates for your domain and subdomains.
Create a new folder for the NPM docker stack :
mkdir npm-stack && cd npm-stackCreate a new docker-compose.yml :
nano docker-compose.ymlPaste this content into it (CTRL + X ; Y & ENTER to save/quit) :
``` version: '3.8' services: app: image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: # These ports are in format
: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port # Add any other Stream port you want to expose # - '21:21' # FTP # Uncomment the next line if you uncomment anything in the section # environment: # Uncomment this if you want to change the location of # the SQLite DB file within the container # DB_SQLITE_FILE: "/data/database.sqlite" # Uncomment this if IPv6 is not enabled on your host # DISABLE_IPV6: 'true' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt```
You'll not believe but it's done. NPM docker compose configuration is done.
To start Nginx Proxy Manager with docker compose, you just have to :
docker compose up -dYou'll see :
user@vps:~/tutorials/npm-stack$ docker compose up -d [+] Running 2/2 ✔ Network npm-stack_default Created ✔ Container npm-stack-app-1 StartedYou can check if NPM container is started by doing this command :
docker psYou'll see :
user@vps:~/tutorials/npm-stack$ docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 7bc5ea8ac9c8 jc21/nginx-proxy-manager:latest "/init" About a minute ago Up About a minute 0.0.0.0:80-81->80-81/tcp, :::80-81->80-81/tcp, 0.0.0.0:443->443/tcp, :::443->443/tcp npm-stack-app-1If the command show "Up X minutes" for the npm-stack-app-1, you're good to go! You can access to the NPM admin UI by going to http://YourIPAddress:81.You shoud see :

The default NPM login/password are : admin@example.com/changeme .If the login succeed, you should see a popup asking to edit your user by changing your email password :
 And your password :
And your password :
 Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
 Followed by "Add Proxy Host"
Followed by "Add Proxy Host"
 If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :
If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :Details tab :
 SSL tab :
SSL tab :
 And click on "Save".
And click on "Save".NPM will request the SSL certificate "admin.yourdomain.tld" for you.
If you have an erreor message "Internal Error" it's probably because your domaine DNS zone is not configured with an A DNS record pointing to your VPS IP.
Otherwise you should see (my domain is hidden) :

Clicking on the "Source" URL link "admin.yourdomain.tld" will open a pop-up and, surprise, you should see the NPM admin UI with the URL "https://admin.yourdomain.tld" !
If yes, bravo, everything is OK ! 🎇
You know now how to have a subdomain of your domain redirecting to a container web app. In the next blog post, you'll see how to setup a Nostr relay with NPM ;)
Voilààààà
See you soon in another Fractalized story!
-
 @ 75656740:dbc8f92a
2023-07-21 18:18:41
@ 75656740:dbc8f92a
2023-07-21 18:18:41\n> "Who do you say that I am?" \n\nIn Matthew 16 Jesus cut to the heart of what defines identity. First he asked what other people said about him, then he asked what the disciples thought, finally he gave his own take by agreeing with the disciples. In trying to understand who someone is, we have three and only three possible sources of information.\n\n1. Who they tell us they are.\n2. Who others say about them.\n3. What we observe for ourselves.\n\nPutting these three together constitutes identity. Identity is always unique for each connection in the social graph. Who you are to me is always different than who you are to anyone else. As such identity is largely out of our direct control. We can influence others perception of ourselves by comporting ourselves in a certain way, but we cannot compel it.\n\nWith this in mind, it is imperative to build protocols that mirror this reality as closely as possible. The problem is largely one of UI. How can we simultaneously display all three aspects of identity in a clear and uncluttered way? \n\nThe default has always been to just display an individual's claim to identity. Each user gets to choose a name and an avatar. This generally works in small communities with low rates of change both in who the members are and in how they present themselves. In these cases, each user can keep a mental map of what to expect from each name and avatar. "Oh that is just keyHammer24 doing his thing." Note that even if KeyHammer24 decides to change their nickname the mental map in the other users won't change instantly, if ever.\n\nThis falls apart in larger communities, where each user cannot maintain a mental model of who is who. Impersonation and collisions become a problem, so we add some "What others say about them" information such as blue check-marks or what "what we observe for ourselves" information like pet-names in a phone contact list or a note that we follow that account.\n\nI don't personally have a final solution for this, I only know that we should be collecting and displaying all three sources of information from the outset. Perhaps we could do something like...\n Default to showing a users preferred identifiers, but switch to the avatar and handle we self-assign them on hover.\n Display a percentage of confidence that we know who the person is and that they are presenting themselves as who we expect them to be. You probably aren't the Elon Musk that I expect if you recently had different names / aren't the one I follow / none of my network follows / have been reported as misleading.\n Reserve check-marks for keys that each user has signed in person. Only we can be the arbiter of who gets a check-mark in our own feed.\n Maintain a list of past aliases along with a "Community Notes" like description of an account brought up by clicking on a ⓘ icon.\n Have a full pet-names override.\n\nI think Nostr already have much of this built into the protocol, it just needs to be standardized into the interface of various application. This is something on which I am very interested in hearing other ideas.\n\n### A note on anonymity\nReal world identities should always be preferred. It allows for building real relationships and treating each other with real world respect. The real you is far more fascinating than a curated persona. Real identities should also never* be enforced at a protocol level. Some people will be in real circumstances that preclude honest engagement without threat to their safety. \n\nIf you found this engaging I also wrote about why Social Network companies have an unsolvable problem here. and why we have to design for finite reach here
-
 @ 1bc70a01:24f6a411
2023-07-21 12:03:38
@ 1bc70a01:24f6a411
2023-07-21 12:03:38The concept of value of value is one where information yearns to flow freely, transactions should be voluntary, unlimited and direct. In V4V model, people pay what something is worth to them.
Sounds great. On paper. There are some issues…
Free sucks
At least, that’s the perception. People don’t assign much value to free. Ask anyone who has ever ran any business and has not suggested a value for a product or service and they’ll tell you that they earned far less than when charging for the thing.
It’s true, some people will give a lot, some a little, and most none. Most - none. None.
Pricing is Signal
Pricing is a signal of desirability and quality. Of course, it is often incorrect and people manipulate pricing all the time. But for the most part, people don’t see much value in free. Unless a recommended price is offered, people will usually pay nothing. This is not a great model to thrive on if you spend years of your life acquiring knowledge and turning it into products that nobody ultimately buys. I have very personal experience with free. I’ve created and sold digital products and ran many pricing experiments myself. The highest priced products usually generated the most revenue. Surprise! The middle cost product (same product, just priced less) decimated the revenue stream. When set to 0 (even with a suggested minimum price), I generated almost no revenue at all.
None of this is surprising. Pricing acts as a psychological anchor. “You get what you pay for” is ingrained in our brains whether we think about it or not.
People are clueless
The issue with price is that most people don’t have a clue what anything is worth. The only time people have any rough idea of what they should pay for something is when they have already purchased that thing in the past. But, introduce something they have never before purchased and they won’t have a single clue about what to pay. Take for example a set of professional photos of you and your family. Unless you’ve been to a photo studio in the last 5 years, you probably won’t have a single clue what that package of photos is worth. Does that mean the product is worthless? Of course not, but people don’t know what to pay.
In a value for value model, the absence of price makes it super difficult to determine the value of anything. You may take some social cues from previous payments from other people, but this could backfire for the content creator.
Suppose I created a UI framework that saved developers hundreds of hours. In theory, I should be able to charge at least a few hours’ worth of value for this product. If the developer’s time is valued at $100/hour, a $200 price for a product that saves you $2000 worth of time seems very justifiable. Not only do you get to use it once, but you can re-use the product for ALL future projects and employment.
Now, remove the price and see what people pay. Absolutely nothing. You may have a few people who pay $200 voluntarily, but it’s highly unlikely The vast majority will pay nothing, and some may “tip” in the 5-$60 range. Anything that approaches a $100 mark is seen as a purchase. Hey, I don’t make the rules, I just see what other founders have figured out long ago and combine with my own observations. Don’t kill the messenger.
Free is Expensive
If I am accurate in my assessment and recall my personal experiences accurately, then the majority of people who consume your value will do so for free. When that content is a product, you may end up spending a lot of time on supporting the thing that is not generating any revenue. You don’t want to be rude and ignore people so you’ll probably spend your valuable time answering questions and helping them troubleshoot issues. All of that time adds up. Startup founders who offer free tiers or near free tiers of services learn very quickly that free customers are the most painful and demanding. You are basically forced to charge just to avoid dealing with demanding people who expect everything for nothing.
Free is Noise
Price is not just a request for value, but it acts as a feedback signal for future content. If you have no idea what people are paying for, it’s difficult to know if what you create is worth anything. A situation where the vast majority of your content is consumed for free yield a lot of noise.
Well, why not focus on the people who pay? You certainly could, but it ends up being a tiny fraction of the sample size you could have had if you actually charged something up front.
Lack of forecasting
Businesses rely on predictible revenue. Forecasting is necessary for all sorts of decisions if you work with anyone but yourself. It helps with purchasing decision (expenses) and with planning of future products. Value for value makes it impossible to know what your revenue will be next month as you just have no idea if everyone pays nothing or a lot.
V4V could make you uncompetitive
In a model where one person charges a fixed price and the other is relying on the good will of the people to "see the value" in their work, the person with predictible revenue will most likely win out in a competitive environment - enabling them to get ahead of you and your business. They will have an easier time planning further content / products and hiring people to scale the business even further.
It’s not all hopeless
That’s not to say that I don’t like the idea of value for value. Of course I only want people to pay if they find the thing useful. The issue is that people may not know the thing is useful until they’ve already acquired it. At that point who is going back to pay for the thing they already got for free? Few to none.
Value for value may work. For some.
I’m not saying value for value doesn’t work sometimes, for some people. It is entirely possible that a person earns a living on v4v transactions. However, I think for that to be true there may be other factors at play such as social standing, personal brand, influence, likability, status within a community. The vast majority of creators do not fall into this category and will just struggle.
I’m cautiously optimistic about V4V and hope it works out at scale. But as it stands, I have not seen much evidence that it actually pays the bills. Yes, there has been some support for podcasts on Fountain, but it is unclear whether it is just as or more significant than traditional transaction model.
“Information is not scarce” is irrelevant
There’s some notion that information yearns to be free and cannot be scarce by nature. I think this may be a false argument from the start. When we purchase digital things, we are not paying for scarcity - it’s totally irrelevant. We pay for the experience and the feeling we get from that thing. In fact, the same is probably true for physical products (with the added benefit of personal sustenance). I don’t go into the grocery store to buy a dinner and fork over the money because it’s scarce. I pay because I’m hungry. There’s utility and there’s pleasure and fulfillment. If I’m having a dinner with friends, there’s also fun. Unless I am totally misunderstanding the argument, I’m not sure how it applies.
In Summary
- Value 4 value may work at scale, but remains to be seen
- It could be great fun money but not serious enough to pay the bills (for most of us)
- Sounds good on paper but we humans have our own ways of thinking about value and what it's worth
- May work well for people who build a personal brand or have status in a community
As always I look forward to your thoughts. Let me know if I’m overlooking something or should consider some point of view in more depth.
-
 @ 97c70a44:ad98e322
2023-06-29 15:33:30
@ 97c70a44:ad98e322
2023-06-29 15:33:30First, a product announcement.\n\nCoracle now supports connection multiplexing, which can reduce bandwidth usage by over 90% depending on how many relays you use. It's opt-in for now, but you can set it up by going to Settings and entering
wss://multiplextr.coracle.socialas your "Multiplextr URL".\n\nYou can check out the source code and self-host the library using this link. If you're a dev and want to add client support for multiplextr, the library I built to support this use case might be of use.\n\nNow, on to your regularly scheduled blog post.\n\n \n\nThe above announcement isn't irrelevant to what I want to talk about in this post, which is (broadly) the question of "how can Nostr remain decentralized and still support advanced functionality?"\n\nThis is probably the most common question articulated among devs and enthusiasts - is search centralizing? What about recommendation engines? COUNT? Analytics? The answer is yes, and responses range from "it'll be fine" to "nostr is already captured".\n\nFor my part, I'm not sure if this problem can be solved. Already we have a browser wars dynamic emerging among clients, and business models based on proprietary services and advertising have been publicly considered. For the record, I don't think conventional business models are necessarily bad. The world works this way for a reason and Nostr isn't going to change that by default.\n\nNevertheless, I want to see a new internet emerge where my attention belongs to me, and I'm not beholden to massive companies who don't give a rip about me. As a result, much of the work I've put into Coracle hasn't gone into fun features, but into things I think will help realize the vision of Nostr. This gives me FOMO as I watch others' progress, but if I don't stay focused on my vision for Nostr, what am I even doing?\n\nI should be clear that this is not a judgment on the motivations of others, building for fun and profit is just as legitimate as building to idealistically realize the best of all Nostrs. However, I would say that it is every developer's duty to keep in mind that what we're trying to accomplish here is not a web2 clone.\n\n# Two, and only two options\n\nWith all that said, let's get into the meat of the problem. There's a false dichotomy floating around out there that we have two options for adding server-side functionality to the nostr ecosystem. Option 1: pack all required functionality into relays, eliminating the "dumb relay" model, and making it extremely difficult to run a relay. Option 2: keep relays dumb and the protocol minimal, allowing indexers, search engines, and recommendation services (which I'll collectively call "extensions" here) to profit by solving advanced use cases.\n\nBoth alternatives are obviously deficient. Relays need to be something hobbyists can run; requiring relays to fold in a recommendation engine or search index makes that much harder, and for every feature required, proprietary solutions will be able to build a bigger moat.\n\nOn the other hand, proprietary extensions will not bother to interoperate. This will result in an app-store-like landscape of competing extensions, which will redirect developer and user attention away from relays to extensions. If nostr is to succeed, relays must remain an important first-class concept. Aggregators and indexers that gloss over the differences between relays destroy much of the value an individual relay has to offer.\n\nIn either case, some components of the network will become too sophisticated for a layman to deploy. The only alternative is for a few professionals to take up the slack and grow their service as a business. But I think there's a way to squeeze between the horns of the dilemma.\n\n# It's all about routing\n\nIt seems to me that most people prefer the "extension" model of scaling functionality of Nostr as a pragmatic, market-driven alternative to the impossibility of requiring all relays to support all possible features. And I agree, the folks developing and operating more sophisticated tools should be compensated for their hard work.\n\nThe real problem with this approach is that not that extensions are competitive and specialized, but that they obscure the importance of relays by becoming gatekeepers for data by providing additional functionality. If a client or user has to select a search engine and ask it to return results for a given relay, they have given that search engine control over their results, when their trust really should be placed in the relay itself.\n\n(I will say as an aside, that there are scenarios when the gatekeeper approach does make sense, like when a user wants to "bring his own algorithm". But this should be something a user can opt-in to, not a default requirement for accessing the underlying protocol.)\n\nHere's my proposal: instead of requiring users to trust some non-standard extension to make decisions for them, flip the script and make relays the gatekeepers instead. With this approach, the addition of a single feature can open the door for relays to support any extension at no additional cost.\n\nOne of the most exciting aspects of Nostr is the redundancy relays provide. With Nostr, you don't need to trust a single entity to store your data for you! Why should you trust a single gatekeeper to route you to that data? Relays don't need to provide search or recommendations or indexing functionality directly, they can simply send you to a third-party extension they deem trustworthy.\n\nThis approach allows extensions to piggy-back on the trust already endowed in relays by end users. By allowing relays that are already aligned with end users to broker connections with extensions, they form a circuit breaker for delegated trust. This is more convenient for end users, and makes it easier to switch extensions if needed, since relay operators are more likely to have their finger on the pulse than end users.\n\nIt also enables cleaner business relationships. Instead of asking clients to create custom integrations with particular extensions leading to vendor lock-in, an extension provider can implement a common interface and sell to relays instead by offering to index their particular data set.\n\nWith this model, relays have the flexibility to either provide their own advanced functionality or delegate it to someone else, reducing the functionality gap that would otherwise emerge with thick relays without removing the ability for extension service providers to run a business, all the while keeping users and clients focused on interacting with relay operators rather than non-standard extensions.\n\n# Making it happen\n\nThe difficulty with this of course is that add-on services need to be identifiable based on functionality, and they must be interoperable. This means that their functionality must be described by some protocol (whether the core Nostr protocol or an addition to it), rather than by proprietary extensions. There will be extensions that are too complex or special-purpose to fit into this model, or for whom interoperability doesn't matter. That's ok. But for the rest, the work of specifying extensions will pay off in the long run.\n\nThis routing layer might take a variety of forms - I've already proposed an addition to to NIP 11 for service recommendations. Clients would look up what add-ons their relays recommend, then follow those recommendations to find a service that supports their requirements.\n\nIt also occurs to me having written my multiplexer relay this week (and here we come full circle) that it would be trivially easy for relays to proxy certain types of requests. So for example, a relay might fulfill REQs itself, but pass SEARCH requests on to a third-party extension and relay the result to the end user.\n\nIn either case though, a well-behaved client could get all the functionality desired, for all of the data required, without compomising the brilliant trust model fiatjaf came up with.\n\n# Conclusion\n\nI think this is a very important problem to solve, and I think relay-sponsored extension recommendations/routing is a very good way to do it. So, please comment with criticisms! And if you agree with me, and want to see something like this become the standard, comment on my pull request.\n
\n\nThe above announcement isn't irrelevant to what I want to talk about in this post, which is (broadly) the question of "how can Nostr remain decentralized and still support advanced functionality?"\n\nThis is probably the most common question articulated among devs and enthusiasts - is search centralizing? What about recommendation engines? COUNT? Analytics? The answer is yes, and responses range from "it'll be fine" to "nostr is already captured".\n\nFor my part, I'm not sure if this problem can be solved. Already we have a browser wars dynamic emerging among clients, and business models based on proprietary services and advertising have been publicly considered. For the record, I don't think conventional business models are necessarily bad. The world works this way for a reason and Nostr isn't going to change that by default.\n\nNevertheless, I want to see a new internet emerge where my attention belongs to me, and I'm not beholden to massive companies who don't give a rip about me. As a result, much of the work I've put into Coracle hasn't gone into fun features, but into things I think will help realize the vision of Nostr. This gives me FOMO as I watch others' progress, but if I don't stay focused on my vision for Nostr, what am I even doing?\n\nI should be clear that this is not a judgment on the motivations of others, building for fun and profit is just as legitimate as building to idealistically realize the best of all Nostrs. However, I would say that it is every developer's duty to keep in mind that what we're trying to accomplish here is not a web2 clone.\n\n# Two, and only two options\n\nWith all that said, let's get into the meat of the problem. There's a false dichotomy floating around out there that we have two options for adding server-side functionality to the nostr ecosystem. Option 1: pack all required functionality into relays, eliminating the "dumb relay" model, and making it extremely difficult to run a relay. Option 2: keep relays dumb and the protocol minimal, allowing indexers, search engines, and recommendation services (which I'll collectively call "extensions" here) to profit by solving advanced use cases.\n\nBoth alternatives are obviously deficient. Relays need to be something hobbyists can run; requiring relays to fold in a recommendation engine or search index makes that much harder, and for every feature required, proprietary solutions will be able to build a bigger moat.\n\nOn the other hand, proprietary extensions will not bother to interoperate. This will result in an app-store-like landscape of competing extensions, which will redirect developer and user attention away from relays to extensions. If nostr is to succeed, relays must remain an important first-class concept. Aggregators and indexers that gloss over the differences between relays destroy much of the value an individual relay has to offer.\n\nIn either case, some components of the network will become too sophisticated for a layman to deploy. The only alternative is for a few professionals to take up the slack and grow their service as a business. But I think there's a way to squeeze between the horns of the dilemma.\n\n# It's all about routing\n\nIt seems to me that most people prefer the "extension" model of scaling functionality of Nostr as a pragmatic, market-driven alternative to the impossibility of requiring all relays to support all possible features. And I agree, the folks developing and operating more sophisticated tools should be compensated for their hard work.\n\nThe real problem with this approach is that not that extensions are competitive and specialized, but that they obscure the importance of relays by becoming gatekeepers for data by providing additional functionality. If a client or user has to select a search engine and ask it to return results for a given relay, they have given that search engine control over their results, when their trust really should be placed in the relay itself.\n\n(I will say as an aside, that there are scenarios when the gatekeeper approach does make sense, like when a user wants to "bring his own algorithm". But this should be something a user can opt-in to, not a default requirement for accessing the underlying protocol.)\n\nHere's my proposal: instead of requiring users to trust some non-standard extension to make decisions for them, flip the script and make relays the gatekeepers instead. With this approach, the addition of a single feature can open the door for relays to support any extension at no additional cost.\n\nOne of the most exciting aspects of Nostr is the redundancy relays provide. With Nostr, you don't need to trust a single entity to store your data for you! Why should you trust a single gatekeeper to route you to that data? Relays don't need to provide search or recommendations or indexing functionality directly, they can simply send you to a third-party extension they deem trustworthy.\n\nThis approach allows extensions to piggy-back on the trust already endowed in relays by end users. By allowing relays that are already aligned with end users to broker connections with extensions, they form a circuit breaker for delegated trust. This is more convenient for end users, and makes it easier to switch extensions if needed, since relay operators are more likely to have their finger on the pulse than end users.\n\nIt also enables cleaner business relationships. Instead of asking clients to create custom integrations with particular extensions leading to vendor lock-in, an extension provider can implement a common interface and sell to relays instead by offering to index their particular data set.\n\nWith this model, relays have the flexibility to either provide their own advanced functionality or delegate it to someone else, reducing the functionality gap that would otherwise emerge with thick relays without removing the ability for extension service providers to run a business, all the while keeping users and clients focused on interacting with relay operators rather than non-standard extensions.\n\n# Making it happen\n\nThe difficulty with this of course is that add-on services need to be identifiable based on functionality, and they must be interoperable. This means that their functionality must be described by some protocol (whether the core Nostr protocol or an addition to it), rather than by proprietary extensions. There will be extensions that are too complex or special-purpose to fit into this model, or for whom interoperability doesn't matter. That's ok. But for the rest, the work of specifying extensions will pay off in the long run.\n\nThis routing layer might take a variety of forms - I've already proposed an addition to to NIP 11 for service recommendations. Clients would look up what add-ons their relays recommend, then follow those recommendations to find a service that supports their requirements.\n\nIt also occurs to me having written my multiplexer relay this week (and here we come full circle) that it would be trivially easy for relays to proxy certain types of requests. So for example, a relay might fulfill REQs itself, but pass SEARCH requests on to a third-party extension and relay the result to the end user.\n\nIn either case though, a well-behaved client could get all the functionality desired, for all of the data required, without compomising the brilliant trust model fiatjaf came up with.\n\n# Conclusion\n\nI think this is a very important problem to solve, and I think relay-sponsored extension recommendations/routing is a very good way to do it. So, please comment with criticisms! And if you agree with me, and want to see something like this become the standard, comment on my pull request.\n -
 @ 82b30d30:40c6c003
2023-07-22 08:31:22
@ 82b30d30:40c6c003
2023-07-22 08:31:22[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
-
 @ 72f97555:e0870ff3
2023-07-21 04:20:44
@ 72f97555:e0870ff3
2023-07-21 04:20:44We’ve watched them come and go: social networking attempts like Mastodon (Activity Pub), Blue Sky, and recently, Threads. They’ve begun to follow what feels very much like a pattern. First basic functionality is built out, then there’s a crisis of some sort on mainstream social media, then there’s a population explosion on the new social network, people quickly become disillusioned, then a population collapse. It can be very tempting, while watching these networks explode their user bases into the millions overnight, to wish for that for ourselves on Nostr. I do not. In fact, I believe this sudden explosive growth is partially responsible for the inevitable decline and collapse of these attempted “replacements” for any of the big corporately owned networks. Social networks don’t fail due to technology issues - they fail because of social issues.
Culture Matters
When people exodus a media platform en masse, they bring their culture with them. Their expectations of the types of content they want to interact with, the ways they intend to behave, and the ways they engage with others. These patterns are influenced by two factors in mainstream social: moderation, and tradition. - Moderation forms the culture in a top-down way, by establishing the limits of what kind of content will be acceptable on the platform. Platforms with relatively loose moderation policies will tend to attract people that diverge from established norms of behavior, more than those who typically conform. - Tradition also informs culture in unique ways for each platform - the things that are easiest to find, provoke an emotional response, and are easy to share tend to dominate. - Functionality also plays a role, albeit a lesser one, but one that tends to form the unique humor of a platform. Reddit is a fine example of this with its long threads of puns, each one building on the previous post. Hell threads on other platforms are another example. The problem arises because new platforms rarely meet the expectations of another culture formed on another platform. Functionality will be different in subtle but important ways, and the early adopters of the new platform will be interested in different topics. This is very true on Nostr, where posts are rewarded specifically for quality - a metric that is very difficult to quantify, but any long-time user can identify - and an overabundant quantity of posts is more likely to get you muted than followed.
Assimilation Matters
When users slowly trickle their way into a new platform, they are more inclined to ask questions, and attempt to understand the existing culture. They are the “new kid on the block” and will be more apt to seek feedback if they truly desire to achieve any sort of success. They then add the unique qualities of their personality to this information, and contribute something new to the culture, while still being a part of it. When a large group of users joins all at once, they bring their own connections with them. When the group joining dwarfs the existing user base, they have less motivation to seek advice on how to best utilize the platform to its fullest potential, expecting that they will be able to continue connecting and communicating with their existing contacts in the same way they always have. This will inevitably lead to frustration when the new platform does not provide them with the same success that they had on the former platform - leading to the inevitable conclusion that the “new Twitter (or Facebook, Instagram, et al.)” is not as good as the old one. And so we watch the tides of users go in and out, leaving old platforms in frustration for new ones, only to become equally frustrated with their inability to communicate and reach an audience as effectively as they used to, and returning to the old platform, or seeking yet greener pastures.
Stability Matters
Sudden growth causes sudden problems. Both Mastodon and Blue Sky encountered major issues that they were not prepared to handle, and handled badly. Mastodon operators found themselves facing enormous hosting bills, and Blue Sky faces serious obstacles in keeping their promises to provide a “safe” environment with the influx of new users. A slow, steady growth model allows the operators of services to face problems in a more measured way, and to build out both infrastructure and content tools to allow users to have a pleasant experience. It is less likely to take an otherwise major contributor to a project, and make them “tap out” due to rising costs, frustrated users, and a constant crisis mindset. Nostr is a distributed network, and has amazing potential for horizontal scaling. Even if one in ten-thousand users who onboards onto Nostr decides to run a relay, the network will be in good shape. Content distribution can be handled in a large number of ways - it isn’t tied fundamentally to the protocol itself - which allows many different providers to be used, and new ways of handling content to be built. But creating those relay operators and content hosts out of newbies takes time. A truly educated relay admin capable of handling the job of maintaining a secure and reliable relay takes weeks or days at best, assuming they are already familiar with similar tasks. Adding 10 million users overnight - the way Threads did - is likely to swamp existing providers before new providers have time to step in a fill the gap. Which would also have the effect of chilling user experience. There is a lot of new terminology and capability to take in when joining Nostr. For the mainstream person, they are going to have to learn about: cryptographic keys, Nostr Addresses (NIP-05), Lightning Wallets, Zaps and by proxy Bitcoin, and eventually Lists, Relay Management, Paid Relays, how to find content, moderate their own feed, and more. Right now, Nostr is doing an excellent job of answering those questions and educating users on the new terminology and techniques because the flow is small and steady with a few bursts.
The Tortoise and The Hare
I truly believe that the success of Nostr will be in no small part because it is growing steadily instead of all at once. Every user onboarded correctly adds to the army of people ready to help welcome the next little wave of people who learn about the decentralized and censorship resistant qualities of Nostr. These individuals are also given the time to become part of a kinder social group than is typically found on social media, and learn to truly become productive and successful as true Nostriches rather than just transplants from another place.
And that is truly the magic isn’t it? People don’t just move to Nostr, they become Nostriches. They become part of a real community, and they belong with us. We take refugees from other social media sites, and don’t leave them refugees. I think that’s beautiful and worth slowing down to do.
I don’t look to the short term for Nostr - I’m bullish for Nostr in the long haul. We are building to still be here after the others have already burnt themselves away. It reminds me of my home country:
“Give me your tired, your poor, your huddled masses yearning to breathe free, the wretched refuse of your teeming shore. Send these, the homeless, tempest-tossed to me, I lift my lamp beside the golden door!”
-
 @ 72f97555:e0870ff3
2023-07-21 04:18:38
@ 72f97555:e0870ff3
2023-07-21 04:18:38We’ve watched them come and go: social networking attempts like Mastodon (Activity Pub), Blue Sky, and recently, Threads. They’ve begun to follow what feels very much like a pattern. First basic functionality is built out, then there’s a crisis of some sort on mainstream social media, then there’s a population explosion on the new social network, people quickly become disillusioned, then a population collapse. It can be very tempting, while watching these networks explode their user bases into the millions overnight, to wish for that for ourselves on Nostr. I do not. In fact, I believe this sudden explosive growth is partially responsible for the inevitable decline and collapse of these attempted “replacements” for any of the big corporately owned networks. Social networks don’t fail due to technology issues - they fail because of social issues.
Culture Matters
When people exodus a media platform en masse, they bring their culture with them. Their expectations of the types of content they want to interact with, the ways they intend to behave, and the ways they engage with others. These patterns are influenced by two factors in mainstream social: moderation, and tradition. - Moderation forms the culture in a top-down way, by establishing the limits of what kind of content will be acceptable on the platform. Platforms with relatively loose moderation policies will tend to attract people that diverge from established norms of behavior, more than those who typically conform. - Tradition also informs culture in unique ways for each platform - the things that are easiest to find, provoke an emotional response, and are easy to share tend to dominate. - Functionality also plays a role, albeit a lesser one, but one that tends to form the unique humor of a platform. Reddit is a fine example of this with its long threads of puns, each one building on the previous post. Hell threads on other platforms are another example. The problem arises because new platforms rarely meet the expectations of another culture formed on another platform. Functionality will be different in subtle but important ways, and the early adopters of the new platform will be interested in different topics. This is very true on Nostr, where posts are rewarded specifically for quality - a metric that is very difficult to quantify, but any long-time user can identify - and an overabundant quantity of posts is more likely to get you muted than followed.
Assimilation Matters
When users slowly trickle their way into a new platform, they are more inclined to ask questions, and attempt to understand the existing culture. They are the “new kid on the block” and will be more apt to seek feedback if they truly desire to achieve any sort of success. They then add the unique qualities of their personality to this information, and contribute something new to the culture, while still being a part of it. When a large group of users joins all at once, they bring their own connections with them. When the group joining dwarfs the existing user base, they have less motivation to seek advice on how to best utilize the platform to its fullest potential, expecting that they will be able to continue connecting and communicating with their existing contacts in the same way they always have. This will inevitably lead to frustration when the new platform does not provide them with the same success that they had on the former platform - leading to the inevitable conclusion that the “new Twitter (or Facebook, Instagram, et al.)” is not as good as the old one. And so we watch the tides of users go in and out, leaving old platforms in frustration for new ones, only to become equally frustrated with their inability to communicate and reach an audience as effectively as they used to, and returning to the old platform, or seeking yet greener pastures.
Stability Matters
Sudden growth causes sudden problems. Both Mastodon and Blue Sky encountered major issues that they were not prepared to handle, and handled badly. Mastodon operators found themselves facing enormous hosting bills, and Blue Sky faces serious obstacles in keeping their promises to provide a “safe” environment with the influx of new users. A slow, steady growth model allows the operators of services to face problems in a more measured way, and to build out both infrastructure and content tools to allow users to have a pleasant experience. It is less likely to take an otherwise major contributor to a project, and make them “tap out” due to rising costs, frustrated users, and a constant crisis mindset. Nostr is a distributed network, and has amazing potential for horizontal scaling. Even if one in ten-thousand users who onboards onto Nostr decides to run a relay, the network will be in good shape. Content distribution can be handled in a large number of ways - it isn’t tied fundamentally to the protocol itself - which allows many different providers to be used, and new ways of handling content to be built. But creating those relay operators and content hosts out of newbies takes time. A truly educated relay admin capable of handling the job of maintaining a secure and reliable relay takes weeks or days at best, assuming they are already familiar with similar tasks. Adding 10 million users overnight - the way Threads did - is likely to swamp existing providers before new providers have time to step in a fill the gap. Which would also have the effect of chilling user experience. There is a lot of new terminology and capability to take in when joining Nostr. For the mainstream person, they are going to have to learn about: cryptographic keys, Nostr Addresses (NIP-05), Lightning Wallets, Zaps and by proxy Bitcoin, and eventually Lists, Relay Management, Paid Relays, how to find content, moderate their own feed, and more. Right now, Nostr is doing an excellent job of answering those questions and educating users on the new terminology and techniques because the flow is small and steady with a few bursts.
The Tortoise and The Hare
I truly believe that the success of Nostr will be in no small part because it is growing steadily instead of all at once. Every user onboarded correctly adds to the army of people ready to help welcome the next little wave of people who learn about the decentralized and censorship resistant qualities of Nostr. These individuals are also given the time to become part of a kinder social group than is typically found on social media, and learn to truly become productive and successful as true Nostriches rather than just transplants from another place.
And that is truly the magic isn’t it? People don’t just move to Nostr, they become Nostriches. They become part of a real community, and they belong with us. We take refugees from other social media sites, and don’t leave them refugees. I think that’s beautiful and worth slowing down to do.
I don’t look to the short term for Nostr - I’m bullish for Nostr in the long haul. We are building to still be here after the others have already burnt themselves away. It reminds me of my home country:
“Give me your tired, your poor, your huddled masses yearning to breathe free, the wretched refuse of your teeming shore. Send these, the homeless, tempest-tossed to me, I lift my lamp beside the golden door!”
~ TheSameCat
-
 @ 75da9402:77a65b5c
2023-07-17 17:48:42
@ 75da9402:77a65b5c
2023-07-17 17:48:42
### BIENVENID@ A NOSTR
Queridos amigos que desean unirse a Nostr, sé que para todos ustedes es nuevo este camino, pero créanme que vale la pena experimentar y conocer una nueva forma de conectar y comunicarse con personas en otras partes del mundo. Varias de las mentes mas brillantes y apasionadas por dejar una huella diferente en las comunicaciones humanas han puesto alma, mente, corazón y hasta sus propios fondos para desarrollar y aportar a nostr.
QUE ES NOSTR? ¿COMO EMPIEZO?
Nostr es un protocolo de comunicación que está diseñado para que las personas se conecten entre si de forma rápida, segura y divertida. No es una empresa de RRSS como Twitter, FB u otras, tampoco existe un dueño, CEO o accionistas ni moderadores ni administradores de contenido, tampoco pertenece algún país en específico. Dicho esto, si aún no sabes cómo empezar aquí vamos. Para conectarte a Nostr vas a usar aplicaciones llamadas también clientes, te sugiero empieces en tu móvil y estas son algunas de las que puedes descargar y probar para empezar, luego puedes buscar otros clientes de tu agrado:
Damus para usuarios de IPhone https://apps.apple.com/app/damus/id1628663131
Amethyst para usuarios de Android https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst
PASOS IMPORTANTES A SEGUIR
Vamos a realizar estos pasos con el cliente Damus pero en Amethyst funciona igual:
1.- Una vez que instalaste la aplicación cliente ábrela y vas a ir a la opción Crear Cuenta

2.- Te aparecera una pantalla que dice EULA, dale aceptar sin miedo como en todas tus RRSS jaja, tranquil@ no pasa nada.
3.- En la siguiente pantalla deberás: Subir foto de perfil (si lo deseas), Nombre de usuario (nick que te guste el mio jp ), Mostrar nombre (como quieres llamarte el mio johnny ), Informacion (una breve biografía tuya ) presiona Crear y listo ya puedes usar Nostr como un Sayayin :-P

4.- Antes de empezar a escribir tu primer post vamos a dar 2 pasos más que son fundamentales y algún día me lo agradecerás (pero si a ti nadie te dice que hacer jajaja, ya puedes empezar a usar Nostr y saltarte estos pasos). Ve a la parte superior izquierda de Damus y presiona en la foto de tu perfil, deberá aparecer un menú que dice Configuración presiónalo y debe llevarte a algunas opciones, entre ellas escoges la que dice Keys

5.- Este es el último paso y es EXTREMADAMENTE IMPORTANTE que lo sigas al pie de la letra por que vamos a guardar tus llaves (usuario y contraseña) de forma segura. Aquí debo informarte que en Nostr no usaras ni correo ni número de móvil ni otro dato personal que te identifique para poder acceder a tu cuenta y por lo tanto debes guardar tú mismo las llaves de acceso ya que si las pierdes NO HAY FORMA DE RECUPERAR, las perderás para siempre y deberás volver a iniciar de nuevo.
Dentro de la opción Keys encontraras dos identificadores el primero que empieza por npub... es tu clave publica (tu usuario) que todos ven en la red y más abajo encontraras tu llave secreta (tu contraseña) esta es la más importante y al activar el botón Mostrar aparecerá y empieza con nsec.... estas dos claves debes copiarlas y guardarlas con total seguridad NO LAS PIERDAS de preferencia para guardarlas usa un administrador de contraseña como Bitwarden o tu propio llavero de ICloud en tu IPhone.

Bien si ya hiciste estos 5 pasos en menos de 5 minutos ya estarás listo para navegar e interactuar con otras personas en #nostr. Existen otros conceptos dentro de la red que ya te explicare en otra guía, por ejemplo, los relés que son los que se encargan de trasmitir tus posts (en forma de notas) a todo el mundo, pero con los que vienen preconfigurados los clientes es suficiente por ahora.
DIVIERTETE NUEVO NOSTRICH
Es momento de lanzarte al universo de Nostr, publica tu primer post Hola Mundo y empieza hacer amigos y te aseguro que muchas buenas personas te responderán para darte la bienvenida, como sugerencia si hablas español o quieres conocer gente de este idioma: ve a la opción UNIVERSO (lupa de buscar) de tu cliente, aquí encontraras el feed global donde aparece todos los posts a nivel mundial donde también puedes conocer gente. Ahí escribes Seguidor Hispano le das seguir a todos los que sigue esa cuenta y puedes empezar a seguir a otros en tu idioma.
Si te ha gustado y servido este minitutorial, compártelo a otros y si quieres puedes también seguirme a veces comparto buenos memes :-) Copia mi usuario en el buscador y me sigues:
npub1whdfgqn66sytcta0l6c7vlt3h2lg67xcnsmzpk3pyvpmsaaxtdwqr8vs60
By Johnny
-
 @ b12b632c:d9e1ff79
2023-07-20 20:12:39
@ b12b632c:d9e1ff79
2023-07-20 20:12:39Self hosting web applications comes quickly with the need to deal with HTTPS protocol and SSL certificates. The time where web applications was published over the 80/TCP port without any encryption is totally over. Now we have Let's Encrypt and other free certification authority that lets us play web applications with, at least, the basic minimum security required.
Second part of web self hosting stuff that is really useful is the web proxifycation.
It's possible to have multiple web applications accessible through HTTPS but as we can't use the some port (spoiler: we can) we are forced to have ugly URL as https://mybeautifudomain.tld:8443.
This is where Nginx Proxy Manager (NPM) comes to help us.
NPM, as gateway, will listen on the 443 https port and based on the subdomain you want to reach, it will redirect the network flow to the NPM differents declared backend ports. NPM will also request HTTPS cert for you and let you know when the certificate expires, really useful.
We'll now install NPM with docker compose (v2) and you'll see, it's very easy.
You can find the official NPM setup instructions here.
But before we absolutely need to do something. You need to connect to the registrar where you bought your domain name and go into the zone DNS section.You have to create a A record poing to your VPS IP. That will allow NPM to request SSL certificates for your domain and subdomains.
Create a new folder for the NPM docker stack :
mkdir npm-stack && cd npm-stackCreate a new docker-compose.yml :
nano docker-compose.ymlPaste this content into it (CTRL + X ; Y & ENTER to save/quit) :
``` version: '3.8' services: app: image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: # These ports are in format
: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port # Add any other Stream port you want to expose # - '21:21' # FTP # Uncomment the next line if you uncomment anything in the section # environment: # Uncomment this if you want to change the location of # the SQLite DB file within the container # DB_SQLITE_FILE: "/data/database.sqlite" # Uncomment this if IPv6 is not enabled on your host # DISABLE_IPV6: 'true' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt```
You'll not believe but it's done. NPM docker compose configuration is done.
To start Nginx Proxy Manager with docker compose, you just have to :
docker compose up -dYou'll see :
user@vps:~/tutorials/npm-stack$ docker compose up -d [+] Running 2/2 ✔ Network npm-stack_default Created ✔ Container npm-stack-app-1 StartedYou can check if NPM container is started by doing this command :
docker psYou'll see :
user@vps:~/tutorials/npm-stack$ docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 7bc5ea8ac9c8 jc21/nginx-proxy-manager:latest "/init" About a minute ago Up About a minute 0.0.0.0:80-81->80-81/tcp, :::80-81->80-81/tcp, 0.0.0.0:443->443/tcp, :::443->443/tcp npm-stack-app-1If the command show "Up X minutes" for the npm-stack-app-1, you're good to go! You can access to the NPM admin UI by going to http://YourIPAddress:81.You shoud see :

The default NPM login/password are : admin@example.com/changeme .If the login succeed, you should see a popup asking to edit your user by changing your email password :
 And your password :
And your password :
 Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
 Followed by "Add Proxy Host"
Followed by "Add Proxy Host"
 If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :
If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :Details tab :
 SSL tab :
SSL tab :
 And click on "Save".
And click on "Save".NPM will request the SSL certificate "admin.yourdomain.tld" for you.
If you have an erreor message "Internal Error" it's probably because your domaine DNS zone is not configured with an A DNS record pointing to your VPS IP.
Otherwise you should see (my domain is hidden) :

Clicking on the "Source" URL link "admin.yourdomain.tld" will open a pop-up and, surprise, you should see the NPM admin UI with the URL "https://admin.yourdomain.tld" !
If yes, bravo, everything is OK ! 🎇
You know now how to have a subdomain of your domain redirecting to a container web app. In the next blog post, you'll see how to setup a Nostr relay with NPM ;)
Voilààààà
See you soon in another Fractalized story!
-
 @ 97c70a44:ad98e322
2023-06-26 19:17:23
@ 97c70a44:ad98e322
2023-06-26 19:17:23Metadata Leakage\n\nIt's a well-known fact that Nostr's NIP 04 DMs leak metadata. This seems like an obvious flaw, and has been pointed out as such many times. After all, if anyone can see who you're messaging and how frequently, what time of the day, how large your messages are, who else is mentioned, and correlate multiple separate conversations with one another, how private are your communications really?\n\nA common retort repeated among those who "get" Nostr (myself included) is "it's not a bug, it's a feature". This hearkens back to the early days of the internet, when internet security was less than an afterthought, and social platforms throve on various permutations of the anonymous confessions-type app. How interesting to be able to flex to your friends about whom you're DMing and how often! Most conversations don't really need to be private anyway, so we might as well gamify them. Nostr is nothing if not fun.\n\nIn all seriousness though, metadata leakage is a problem. In one sense, Nostr's DMs are a huge improvement over legacy direct messages (the platform can no longer rat you out to the FBI), but they are also a massive step backward (literally anyone can rat you out to the FBI). I'm completely confident we'll be able to solve this issue for DMs, but solving it for other data types within Nostr might pose a bigger problem.\n\n# Social Content\n\nA use case for Nostr I've had on my mind these last few months is web-of-trust reviews and recommendations. The same sybil attack that allows bots to threaten social networks has also been used as a marketing tool for unscrupulous sellers. NPS surveys, purchased reviews, and platform complicity have destroyed the credibility of product reviews online, just like keyword-stuffed content has ruined Google's search results.\n\nProof-of-work would do nothing to defend against this attack, because the problem is not volume, it's false credibility. The correct tool to employ against false credibility is web-of-trust — verifiable trustworthiness relative to the end user's own social graph.\n\nThis is a huge opportunity for Nostr, and one I'm very excited about. Imagine you want to know whether the vibro-recombinant-shake-faker (VRSF) will result in visible abs in under 6 days. Well, it has over 4 thousand 5-star reviews on Amazon, and all the 1-star reviews are riddled with typos and non sequiturs. So it must work, and make you smarter into the deal! Well, sadly no, visible abs are actually a lie sold to you by "big gym".\n\nNow imagine you could find your three friends who fell for this gyp and ask them what they thought — you might just end up with a lower average rating, and you'd certainly have a higher level of certainty that the VRSF is not worth the vibra-foam it's molded from.\n\nThis same query could be performed for any product, service, or cultural experience. And you wouldn't be limited to asking for opinions from your entire social graph, it would be easy to curate a list of epicureans to help you choose a restaurant, or trusted bookworms to help you decide what to read next.\n\nCurrently, big tech is unable to pull this off, because Facebook won't share its social graph with Google, and Google won't share its business data with Facebook. But if an open database of people and businesses exists on Nostr, anyone can re-combine these silos in new and interesting ways.\n\n# Notes and other Spies\n\nSo that's the pitch, but let's consider the downsides.\n\nAn open social graph coupled with recommendations means that not only can you ask what your friends think about a given product, you can ask:\n\n- What a given person's friends think about a product\n- What kind of person likes a given product\n- How products and people cluster\n\nThat last one in particular is interesting, since it means you could find reasonable answers to some interesting questions:\n\n- Does a given region have fertility problems?\n- What are the political leanings of a given group?\n- How effective was a particular advertisement with a given group?\n\nThis is the kind of social experiment that has historically earned Facebook so much heat. Democratizing this data does not prevent its correlation from being a violation of personal privacy, especially since it will be computationally expensive to do sophisticated analysis on it — and the results of that analysis can be kept private. And to be clear, this is a problem well beyond the combination of social information and public reviews. This is just one example of many similar things that could go wrong with an open database of user behavior.\n\nNot to put too fine a point on it, we are at risk of handing the surveillance panopticon over to our would-be overlords on a silver platter. Just as walled gardens have managed us in the past to sway political opinion or pump the bags of Big X, an open, interoperable content graph will make building a repressive administrative state almost too easy.\n\n# Let's not give up just yet\n\nSo what can we do about it? I want a ratings system based on my social graph, but not at the expense of our collective privacy. We need to keep this threat in mind as we build out Nostr to address novel use cases. Zero-knowledge proofs might be relevant here, or we might be able to get by with a simple re-configuration of data custody.\n\nIn the future users might publish to a small number of relays they trust not to relay their data, similar to @fiatjaf's NIP-29 chat proposal. These relays might then support a more sophisticated query interface so that they can answer questions without revealing too much information. One interesting thing about this approach is that it might push relays towards the PWN model BlueSky uses.\n\nNot all data needs to be treated the same way either, which would give us flexibility when implementing these heuristics. Just as a note might be either broadcast or sent to a single person or group, certain reviews or other activity might only be revealed to people who authenticate themselves in some way.\n\nLike so many other questions with Nostr, this requires our concentrated attention. If all we're doing is building a convenient system for Klaus Schwab to make sure we ate our breakfast bugs, what are we even doing?\n\n
-
 @ 0d97beae:c5274a14
2023-07-20 11:36:34
@ 0d97beae:c5274a14
2023-07-20 11:36:34testing
-
 @ cc8d072e:a6a026cb
2023-06-04 13:15:43
@ cc8d072e:a6a026cb
2023-06-04 13:15:43欢迎来到Nostr\n\n以下是使您的 Nostr 之旅更顺畅的几个步骤 \n\n---\n_本指南适用于: \n 英语 原作者 nostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7\n 法语 感谢 nostr:npub1nftkhktqglvcsj5n4wetkpzxpy4e5x78wwj9y9p70ar9u5u8wh6qsxmzqs \n 俄语 \n\n--- \n你好,Nostrich同胞!\n\nNostr 是一种全新的模式,有几个步骤可以让您的加入流程更加顺畅,体验更加丰富。 \n\n## 👋欢迎 \n\n由于您正在阅读本文,因此可以安全地假设您已经通过下载应用程序加入了 Nostr 您可能正在使用移动设备(例如 Damus、Amethyst,Plebstr) 或Nostr网络客户端(例如 snort.social、Nostrgram、Iris)。 对于新手来说,按照您选择的应用程序建议的步骤进行操作非常重要——欢迎程序提供了所有基础知识,您不必做更多的调整除非您真的很需要。 如果您偶然发现这篇文章,但还没有 Nostr“帐户”,您可以按照这个简单的分步指南 作者是nostr:npub1cly0v30agkcfq40mdsndzjrn0tt76ykaan0q6ny80wy034qedpjsqwamhz -- \n
npub1cly0v30agk cfq40mdsndzjrn0tt76ykaan0q6ny80wy034qedpjsqwamhz。 \n\n--- \n\n## 🤙玩得开心 \nNostr 的建立是为了确保人们可以在此过程中建立联系、被听到发声并从中获得乐趣。 这就是重点(很明显,有很多严肃的用例,例如作为自由斗士和告密者的工具,但这值得单独写一篇文章),所以如果你觉得使用过程有任何负担,请联系更有经验的Nostriches,我们很乐意提供帮助。 与Nostr互动一点也不难,但与传统平台相比它有一些特点,所以你完全被允许(并鼓励)提出问题。 \n这是一份 非官方 的 Nostr 大使名单,他们很乐意帮助您加入: \nnostr:naddr1qqg5ummnw3ezqstdvfshxumpv3hhyuczypl4c26wfzswnlk2vwjxky7dhqjgnaqzqwvdvz3qwz5k3j4grrt46qcyqqq82vgwv96yu \n_名单上的所有nostriches都获得了 Nostr Ambassador 徽章,方便您查找、验证和关注它们_ \n\n---\n ## ⚡️ 启用 Zaps \nZaps 是加入 Nostr 后人们可能会注意到的第一个区别。 它们允许 Nostr 用户立即发送价值并支持创建有用和有趣的内容。 这要归功于比特币和闪电网络。 这些去中心化的支付协议让你可以立即发送一些 sats(比特币网络上的最小单位),就像在传统社交媒体平台上给某人的帖子点赞一样容易。 我们称此模型为 Value-4-Value,您可以在此处找到有关此最终货币化模型的更多信息:https://dergigi.com/value/ \n查看由nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424创建的这篇笔记,nostr:note154j3vn6eqaz43va0v99fclhkdp8xf0c7l07ye9aapgl29a6dusfslg8g7g 这是对 zaps 的一个很好的介绍: \n即使您不认为自己是内容创建者,您也应该启用 Zaps——人们会发现您的一些笔记很有价值,并且可能想给您发送一些 sats。 开始在 Nostr onley 上获得价值的最简单方法需要几个步骤: \n\n0 为您的移动设备下载 Wallet of Santoshi[^1](可能是比特币和闪电网络新手的最佳选择)[^2]\n1 点击“接收” \n2 点击您在屏幕上看到的 Lightning 地址(看起来像电子邮件地址的字符串)将其复制到剪贴板。 \n3 将复制的地址粘贴到您的 Nostr 客户端的相应字段中(该字段可能会显示“比特币闪电地址”、“LN 地址”或任何类似内容,具体取决于您使用的应用程序)。
\n3 将复制的地址粘贴到您的 Nostr 客户端的相应字段中(该字段可能会显示“比特币闪电地址”、“LN 地址”或任何类似内容,具体取决于您使用的应用程序)。  \n\n--- \n\n## 📫 获取 Nostr 地址\nNostr 地址,通常被 Nostr OG 称为“NIP-05 标识符”,看起来像一封电子邮件,并且: \n🔍 帮助您使您的帐户易于发现和分享 \n✔️ 证明您是人类 --- 这是 Nostr 地址的示例:Tony@nostr.21ideas.org
\n\n--- \n\n## 📫 获取 Nostr 地址\nNostr 地址,通常被 Nostr OG 称为“NIP-05 标识符”,看起来像一封电子邮件,并且: \n🔍 帮助您使您的帐户易于发现和分享 \n✔️ 证明您是人类 --- 这是 Nostr 地址的示例:Tony@nostr.21ideas.org  它很容易记住并随后粘贴到任何 Nostr 应用程序中以找到相应的用户。\n\n--- \n要获得 Nostr 地址,您可以使用免费服务,例如 Nostr Check(由 nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624)或付费服务,例如 Nostr Plebs 了解有关此方法的更多信息。 \n\n--- \n\n## 🙇♀️ 学习基础知识 \n\n在后台,Nostr 与传统社交平台有很大不同,因此对它的内容有一个基本的了解对任何新手来说都是有益的。 请不要误会,我并不是建议您学习编程语言或协议的技术细节。 我的意思是看到更大的图景并理解 Nostr 和 Twitter / Medium / Reddit 之间的区别会有很大帮助。 例如,没有密码和登录名,取而代之的是私钥和公钥。 我不会深入探讨,因为有一些详尽的资源可以帮助您理解 Nostr。 由 nostr:npub12gu8c6uee3p243gez6cgk76362admlqe72aq3kp2fppjsjwmm7eqj9fle6 和 💜 准备的在这个组织整齐的登陆页面 收集了所有值得您关注的内容 \n
它很容易记住并随后粘贴到任何 Nostr 应用程序中以找到相应的用户。\n\n--- \n要获得 Nostr 地址,您可以使用免费服务,例如 Nostr Check(由 nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624)或付费服务,例如 Nostr Plebs 了解有关此方法的更多信息。 \n\n--- \n\n## 🙇♀️ 学习基础知识 \n\n在后台,Nostr 与传统社交平台有很大不同,因此对它的内容有一个基本的了解对任何新手来说都是有益的。 请不要误会,我并不是建议您学习编程语言或协议的技术细节。 我的意思是看到更大的图景并理解 Nostr 和 Twitter / Medium / Reddit 之间的区别会有很大帮助。 例如,没有密码和登录名,取而代之的是私钥和公钥。 我不会深入探讨,因为有一些详尽的资源可以帮助您理解 Nostr。 由 nostr:npub12gu8c6uee3p243gez6cgk76362admlqe72aq3kp2fppjsjwmm7eqj9fle6 和 💜 准备的在这个组织整齐的登陆页面 收集了所有值得您关注的内容 \n \n_上述资源提供的信息也将帮助您保护您的 Nostr 密钥(即您的帐户),因此请务必查看。_ \n\n--- \n## 🤝 建立连接 \n与才华横溢的[^3]人建立联系的能力使 Nostr 与众不同。 \n在这里,每个人都可以发表意见,没有人会被排除在外。 有几种简单的方法可以在 Nostr 上找到有趣的人: \n 查找您在 Twitter 上关注的人:https://www.nostr.directory/ 是一个很好的工具。 \n 关注您信任的人:访问与您有共同兴趣的人的个人资料,查看他们关注的人的列表并与他们联系。 \n
\n_上述资源提供的信息也将帮助您保护您的 Nostr 密钥(即您的帐户),因此请务必查看。_ \n\n--- \n## 🤝 建立连接 \n与才华横溢的[^3]人建立联系的能力使 Nostr 与众不同。 \n在这里,每个人都可以发表意见,没有人会被排除在外。 有几种简单的方法可以在 Nostr 上找到有趣的人: \n 查找您在 Twitter 上关注的人:https://www.nostr.directory/ 是一个很好的工具。 \n 关注您信任的人:访问与您有共同兴趣的人的个人资料,查看他们关注的人的列表并与他们联系。 \n * 访问全球订阅源:每个 Nostr 客户端(一个 Nostr 应用程序,如果你愿意这样说的话)都有一个选项卡,可以让你切换到全球订阅源,它汇总了所有 Nostr 用户的所有笔记。 只需关注您感兴趣的人(不过请耐心等待——您可能会遇到大量垃圾邮件)。\n
* 访问全球订阅源:每个 Nostr 客户端(一个 Nostr 应用程序,如果你愿意这样说的话)都有一个选项卡,可以让你切换到全球订阅源,它汇总了所有 Nostr 用户的所有笔记。 只需关注您感兴趣的人(不过请耐心等待——您可能会遇到大量垃圾邮件)。\n  \n--- \n## 🗺️探索 \n上面提到的 5 个步骤是一个很好的开始,它将极大地改善您的体验,但还有更多的东西有待发现和享受! Nostr 不是 Twitter 的替代品,它的可能性仅受想象力的限制。
\n--- \n## 🗺️探索 \n上面提到的 5 个步骤是一个很好的开始,它将极大地改善您的体验,但还有更多的东西有待发现和享受! Nostr 不是 Twitter 的替代品,它的可能性仅受想象力的限制。  \n查看有趣且有用的 Nostr 项目列表: \n https://nostrapps.com/ Nostr 应用列表 * https://nostrplebs.com/ – 获取您的 NIP-05 和其他 Nostr 功能(付费) \n https://nostrcheck.me/ – Nostr 地址、媒体上传、中继 \n https://nostr.build/ – 上传和管理媒体(以及更多) \n https://nostr.band/ – Nostr 网络和用户信息 \n https://zaplife.lol/ – zapping统计 \n https://nostrit.com/ – 定时发送帖子\n https://nostrnests.com/ – Twitter 空间 2.0\n https://nostryfied.online/ - 备份您的 Nostr 信息 \n https://www.wavman.app/ Nostr 音乐播放器 --- \n## 📻 中继\n熟悉 Nostr 后,请务必查看我关于 Nostr 中继的快速指南:https://lnshort.it/nostr-relays。 这不是您旅程开始时要担心的话题,但在以后深入研究绝对重要。 \n\n## 📱 手机上的 Nostr \n在移动设备上流畅的 Nostr 体验是可行的。 本指南将帮助您在智能手机上的 Nostr Web 应用程序中无缝登录、发帖、zap 等:https://lnshort.it/nostr-mobile \n \n感谢阅读,我们在兔子洞的另一边见\nnostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7 \n \n_发现这篇文章有价值吗_\n_Zap_⚡ 21ideas@getalby.com \n关注:
\n查看有趣且有用的 Nostr 项目列表: \n https://nostrapps.com/ Nostr 应用列表 * https://nostrplebs.com/ – 获取您的 NIP-05 和其他 Nostr 功能(付费) \n https://nostrcheck.me/ – Nostr 地址、媒体上传、中继 \n https://nostr.build/ – 上传和管理媒体(以及更多) \n https://nostr.band/ – Nostr 网络和用户信息 \n https://zaplife.lol/ – zapping统计 \n https://nostrit.com/ – 定时发送帖子\n https://nostrnests.com/ – Twitter 空间 2.0\n https://nostryfied.online/ - 备份您的 Nostr 信息 \n https://www.wavman.app/ Nostr 音乐播放器 --- \n## 📻 中继\n熟悉 Nostr 后,请务必查看我关于 Nostr 中继的快速指南:https://lnshort.it/nostr-relays。 这不是您旅程开始时要担心的话题,但在以后深入研究绝对重要。 \n\n## 📱 手机上的 Nostr \n在移动设备上流畅的 Nostr 体验是可行的。 本指南将帮助您在智能手机上的 Nostr Web 应用程序中无缝登录、发帖、zap 等:https://lnshort.it/nostr-mobile \n \n感谢阅读,我们在兔子洞的另一边见\nnostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7 \n \n_发现这篇文章有价值吗_\n_Zap_⚡ 21ideas@getalby.com \n关注:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7查看我的项目 https://bitcal.21ideas.org/about/\n\n \n\n[^1]:还有更多支持闪电地址的钱包,您可以自由选择您喜欢的 \n[^2]:不要忘记返回钱包并备份你的账户\n[^3]:nostr:npub1fl7pr0azlpgk469u034lsgn46dvwguz9g339p03dpetp9cs5pq5qxzeknp 是其中一个Nostrich,他设计了本指南的封面上使用的徽标\n\n\n译者: Sherry, 数据科学|软件工程|nossence|nostr.hk|组织过一些nostr meetup|写一些文章来将nostr带到每个人身边\n\n_Zap⚡ spang@getalby.com \n关注:npub1ejxswthae3nkljavznmv66p9ahp4wmj4adux525htmsrff4qym9sz2t3tv\n\n\n\n\n\n -
 @ 07e83368:9587bdec
2023-07-20 07:41:38
@ 07e83368:9587bdec
2023-07-20 07:41:38Just thinking aloud about how I'd attack Nostr blogs and clients if I were an authoritarian government. I'd appreciate comments from people with technical experience on how states like China and Russia would do it!
Fear
As a dictator, the danger I'm afraid of is a popular platform to - spread criticism freely to the masses of normal people (non-IT folk) - organise protest, civil resistance, non-compliance - interact freely which creates a feeling of community
Crackdown
So how would I stop Nostr blogs and clients?
1️⃣ Make Nostr mobile apps illegal & ban them from app stores 2️⃣ Block URLs of popular blog webapps like Yakihonne or Habla 3️⃣ Block relays 4️⃣ Spam relays with disinfo 5️⃣ Arrest popular opposition figures, confiscate their computers, steal private key if possible to then spread disinfo
Are there ways to make those more resilient? 🤔
Counter 2️⃣ (my only new idea so far)
I've heard of the idea of Nostr-based DNS here: a Nostr Name System (NNS). With this in mind, clients like Yakihonne and Primal could implement a cached functionality to resolve their own URL via NNS rather than DNS. If that worked, as long as you have the cache, I think you'd be fine. And you can wipe your cache pretty quickly if you need to hand over your device.
But what if you don't have the cached functionality because it was wiped or you're new user? Thinking about this problem I came up with the following: What about a single HTML file with vanilla JS, no dependencies, that does the following: - tries to connect to many Nostr relays & gets relay recommendations of even more relays - pulls a note from Nostr with updated list of most popular Nostr clients - resolves their IPs via NNS - displays them in a list with links
The functionality should be kept basic so that the file needs little to no updating. That way the file could be spread by any means, over multiple channels and provide a fairly censorship-resistent entry-point to popular Nostr clients.
Anyway, just a few thoughts. Tell me what you think! ❤️
-
 @ c80b5248:6b30d720
2023-07-20 04:06:46
@ c80b5248:6b30d720
2023-07-20 04:06:46Why this isn't a PR
I didn't know exactly where to post this... I have been thinking a lot the past few days about how we can use nostr and moderated communities NIP-172 to free the power of git from it's centralized overlord, GitHub.
I know there are already a few open pull requests that inspired this. PR #223 has lots of great discussion about the benefits of leaning on existing git servers for a nostr-git implementation. PR #324 establishes the usage of a
"c"tag to make commits available for queries on relays. I think this aspect will be critical for fast and effecient git content discovery over nostr.Given that I have limited experience with submitting PRs to open project on GitHub and was not sure where to share these ideas. I took it as an opportunity to write a sample NIP! I would love to get feedback from others, especially folks like nostr:npub1melv683fw6n2mvhl5h6dhqd8mqfv3wmxnz4qph83ua4dk4006ezsrt5c24 and nostr:npub160t5zfxalddaccdc7xx30sentwa5lrr3rq4rtm38x99ynf8t0vwsvzyjc9, who have both been working on their PRs longer than I have been thinking about this.
A few highlights
- Git remotes get their own kind and they are replaceable. This allows events that reference the remote repository to use a static address (just like a longform article) that will continue to work if the author changes the location of the remote - especially important to maintain censorship resistance.
- The git remote kind can provide indexed
"c"tags that allow remote discovery via relays. If multiple servers have instances of the Nostr git repository then all of those relays can quickly be surfaced by querying on the correct commit hash. - Because these coordination events effectively suggest changes that a user might pull into their existing git repositories it makes sense to use these events within moderated communities NIP-172 to establish approval mechanisms that indicate when a git-enabled client should merge a PR or whether or not a commit should be trusted.
The last thing I will note is that I have framed the usage of the new event kinds assuming that only key commits will be posted to Nostr. This should reduce data usage on relays if only commits that require discussion or action need to be posted and referenced. Git-enabled clients will still be able to access all other commits from individual remote git servers. However, there is nothing outside of data size stopping this framework from being used to track every single commit on a repository if that ended up being desirable.
Enough of the preamble...
NIP-XXX
Git Remote Index and Commit Checkpoints
draftoptionalauthor:armstrysGit Kinds
The goal of this nip is to introduce mechanisms for git remote repository discovery and commit checkpointing into the Nostr protocol. Git is already decentralized by nature. Centralized clients like GitHub serve two primary purposes. - They establish one central remote repository as the source of truth. - They provide a platform for non-git metadata tracking including issues and comments.
A decentralized implementation on Nostr should replace the central remote repository with discovery mechanisms that take advantage of the already decentralized nature of git and also provide Nostr-native representations of commits that need to be referenced by external metadata not handled by git.
This nip introduces two new kinds to achieve this: - A "git repository" parameterized replaceable event (
kind:34617) to provide undateable connection points to existing git servers that are easily discoverable and referenced by the second new kind... - A "git checkpoint" event (kind:4617) which has the sole purpose of providing a coordination reference point for key commits in a git repository and should follow a reply structure similar to the chain of commits in git.With these two kinds it is possible to represent censorship resistant personal repositories, forked repositories, and even moderated repositories by integrating these kinds with NIP-172.
Note: This implementation assumes nothing about how the client will interact with git because it only aims to coordinate a layer above git to track metadata and discover existing git server locations. Clients would need to integrate authentication via other providers until git server implementations with Nostr authentication are available.
Git Tags
Additionally, we introduce two application-specific tags that should be used in conjunction with the new git event kinds: 1. A
"c"tag that takes a commit, a branch name, and a marker ('',"head","compare","output") like so:["c", "<commit hash>", "<branch name>","<marker>"]. 2. A"git-history"tag that provides a plain text history of commands that a user ran to generate a merge output (e.g.“git checkout <base hash>\ngit merge <compare hash> —no-ff”). 3. An"auth-required"tag that allows an author to publicize whether a remote requires authentication to access. Clients SHOULD assume that remotes with no"auth-required"default totrue- the equivalent of["auth-required", true]Git Remote Definition
Kind:34617defines a replaceable event (NIP-33) that provides a url to a remote repository as it's.content. Using a replaceable event allows other events (like commit checkpoints) to reference this remote via"a"tag without concern that the links will break should the author need to change the location of the remote repository. The event SHOULD contain one or more"c"tags for any commit that define the"head"commit of each branch that the user author wants to make discoverable in the repository. The author can include other commits on each branch for key commits like releases.json { "id": "<32-bytes lowercase hex-encoded SHA-256 of the the serialized event data>", "pubkey": "<32-bytes lowercase hex-encoded public key of the event creator>", "created_at": "<Unix timestamp in seconds>", "kind": 34617, "tags": [ ["auth-required", false], ["a", "34550:<Community event author pubkey>:<d-identifier of the community>", "<Optional relay url>"], ["d", "<git remote name>"], ["c", "<commit hash>", "<branch name>","head"], ["c", "<commit hash>", "<branch name>",""], ["c", "<commit hash>", "<other branch name>","head"], ], "content": "<address to remote>" }Git Checkpoint Definition
The usage of
"c"marked tags help reference different git-related events, all usingkind:34617: 1. An event with a two"c"tags marked"head"and"output"should be interpreted as a standard commit checkpoint. 2. An event with three"c"tags marked"head","compare", and"output"should be interpreted as a merge checkpoint 3. An event with a"c"tag marked"compare", but with no"output"commit should be interpreted as a pull/merge request 4. An event with at least one"c"tag but without a"compare"or"output"marker should be interpreted as a release/tag and should reply to the appropriate commit. 5. An barekind:34617event with no"c"tag should be interpreted as a comment if it is a reply to another event or as an issue if it is not.A commit checkpoint SHOULD include at least one
"a"tag to akind:34617remote repository where the tagged git commit in question can be found. Clients may also query for matching"c"tags to discover other relevant remotes as needed.Clients should interpret any
"a"tag that includes"34617:*"as the first place to search for commits referenced in akind:4617event.Clients MUST use marked event tags (NIP-10) to chain checkpoints by onto the last availably commit checkpoint on the same branch. Identifying the proper
"root"and"reply"events allow other clients to follow and discover events in the same chain and forks.Both
kind:34617andkind:4617events MAY include a NIP-172 style"a"tag to establish a moderated repository. This may also help with repository remote discovery and organization as thekind:34550community event could suggest default remotes for the community.An example of a standard commit checkpoint:
json { "id": "<32-bytes lowercase hex-encoded SHA-256 of the the serialized event data>", "pubkey": "<32-bytes lowercase hex-encoded public key of the event creator>", "created_at": "<Unix timestamp in seconds>", "kind": 4617, "tags": [ ["c", "<current head hash>", "<optional branch name>","head"], ["c", "<expected output hash>", "<branch name>", "output"], ["a", "34617:<compare remote event author pubkey>:<compare remote name>"], ["e", "<event id of first checkpoint with output on checkpoint chain>", "<optional relay url>", "root id"], ["e", "<event id of previous checkpoint with output on checkpoint chain>", "<optional relay url>", "reply"], ["a", "34550:<Community event author pubkey>:<d-identifier of the community>", "<Optional relay url>"] ], "content": "<description of commit>" }An example of a merge/pull request checkpoint:
json { "id": "<32-bytes lowercase hex-encoded SHA-256 of the the serialized event data>", "pubkey": "<32-bytes lowercase hex-encoded public key of the event creator>", "created_at": "<Unix timestamp in seconds>", "kind": 4617, "tags": [ ["c", "<current head hash>", "<branch name>","head"], ["c", "<compare output hash>", "<branch name>", "compare"], ["a", "34617:<compare remote event author pubkey>:<compare remote name>"], ["e", "<event id of first checkpoint with output on checkpoint chain>", "<optional relay url>", "root id"], ["e", "<event id of previous checkpoint with output on checkpoint chain>", "<optional relay url>", "reply"], ["a", "34550:<Community event author pubkey>:<d-identifier of the community>", "<Optional relay url>"] ], "content": "<description of merge/pull request>" }An example of a merge checkpoint:
json { "id": "<32-bytes lowercase hex-encoded SHA-256 of the the serialized event data>", "pubkey": "<32-bytes lowercase hex-encoded public key of the event creator>", "created_at": "<Unix timestamp in seconds>", "kind": 4617, "tags": [ ["git-history", "<plain text commands used to execute merge>"], ["c", "<current head hash>", "<branch name>","head"], ["c", "<compare hash>", "<optional branch name>", "compare"], ["c", "<expected output hash>", "<branch name>", "output"], ["a", "34617:<compare remote event author pubkey>:<compare remote name>"], ["e", "<event id of first checkpoint with output on checkpoint chain>", "<optional relay url>", "root id"], ["e", "<event id of previous checkpoint with output on checkpoint chain>", "<optional relay url>", "reply"], ["e", "<event id of merge/pull request>", "<optional relay url>", "mention"], ["a", "34550:<Community event author pubkey>:<d-identifier of the community>", "<Optional relay url>"], ["p", "<hex pubkey of merge/pull request author>"] ], "content": "<description of changes since last checkpoint>" }When establishing a merge checkpoint that references a merge/pull request the client should include the merge/pull request author as a"p"tag similar to the usage of replies in NIP-10 -
 @ 97c70a44:ad98e322
2023-06-01 13:46:54
@ 97c70a44:ad98e322
2023-06-01 13:46:54I think I cracked the code on private groups.\n\nInstead of relying on relays to implement access control as in this PR, we could combine the Gift Wrap proposal with @PABLOF7z's nsec bunker to create private groups with easy administration and moderation!\n\nGift wrap fixes DM metadata leakage by using a temporary private key to send a DM to a recipient. The recipient decrypts the wrapper to find a regular nostr event inside. This could be another kind 4 as in the proposal, or anything else. Which means you can send kind 1's or anything else in a wrapped event.\n\nNow suppose you had a pubkey that you wanted to represent a group instead of a person. Put its nsec in a (modified) nsec bunker, and now you can allow other people than yourself to request signatures. A shared private key! Anyone who has access to this nsec bunker could also de-crypt any gift wrapped note sent to it. Relay-free read access control!\n\nThere are lots of ways you could manage this access list, but I think a compelling one would be to create a NIP 51 list (public or private!) of group members and set up the nsec bunker to authenticate using that list. Boom, dynamic member lists!\n\nYou could also create a NIP 51 list for admins, and pre-configure which event kinds each list is allowed to post using the group's nsec. So maybe members could only publish wrapped kind-1's, but admins could publish wrapped kind-0's (you can now zap a group!), kind 9's for moderation, updated member and moderator lists, normal kind 1's for public information about the group, etc.\n\nGift wrap would support:\n\n- Leak-free DMs\n- Fully private groups\n- Public-read groups (nsec bunker would allow for admin, but everyone would publish regular instead of wrapped events).\n- Organizations and other shared accounts, with role-based authorization (list/kind mappings)!\n\nOf course, no clients currently support this kind of thing, but support would not be hard to add, and it creates an entirely new set of affordances with two very simple applications of the core protocol.\n\nThere are a few drawbacks I can think of, of course. Gift wrap makes it harder to search notes by tag. You could:\n\n- Leave all tags off (other than for DM recipient as in the proposal)\n- Selectively keep tags that aren't revealing of identity\n- Encrypt tag values. When a client wants to query a tag, it must encrypt the value using the same pubkey and include that in the filter. This, I think, is ok for the group use case above.\n\nThere are also a number of proposals in the works to fix NIP 04 DMs which are apparently broken from a cryptographic standpoint, so implementing this should probably wait until that stuff is sorted out. But it should be possible however that ends up materializing.\n\nSo am I nuts? Or is this a galaxy brain solution?
-
 @ 92294577:49af776d
2023-07-19 23:40:11
@ 92294577:49af776d
2023-07-19 23:40:11Growing evidence suggests, however, there is no ‘one size fits all’ approach but rather many complementary protocols, each addressing different problems and catering to specific use cases and markets.
In this edition of Layer-2 Roundup, we look at some of these second-layer protocols in detail. Among other things, we will explore their interoperability (or lack thereof) and the projects using these solutions to promote mass adoption. We will also look at some of the various growing pains experienced so far, as seen recently as a result of May’s high-fee market environment.
Choosing the Right Tool for the Job
Each second layer addresses a unique set of limitations inherent in the mainchain, such as the lack of high transaction throughput, privacy, or the ability to issue assets. For example, if you want to send a friend a small amount of sats and value affordability and speed, Lightning is likely the best option. Whereas if you are a financial institution wanting to issue an asset like a bond or digital security, it makes more sense to use Liquid.
https://cdn.nostr.build/i/5fdbca0ff4cd19d5cccd049387d495812a91b45fafd5e9a4c899eb7478611378.png
There are also varying tradeoffs when using each solution that may affect a user’s decision to opt in, like Lightning’s liquidity constraints or the trust requirements (albeit distributed) seen with federated models, such as Liquid and Fedimint. As creator Burak has openly shared, even the newest addition to the layer-2 landscape, Ark, has tradeoffs with the mainchain and other L2s.
Like the old analogy of 'choosing the right tool for the job,' in a hyperbitcoinized world, users can expect to have a toolkit of L2s at their disposal, with different capabilities and tradeoffs.
Increasing Interoperability
Often overlooked is the importance of interoperability between not only the second-layer protocol and Bitcoin but the layer-2 protocols themselves. A second layer, where end-users can leverage several protocols together and move seamlessly between them, creates a healthier, more resilient financial system and an overall better user experience—both essential for mass adoption. For example, by running Lightning on top of Liquid, users gain greater privacy, additional liquidity, and cheaper fees (and much more, as we will explore later).
While both Liquid and Lightning networks operate independently, they are complementary and interoperable, offering a secure, alternative method to stacking sats or a more cost-effective option to Lightning channel rebalancing, especially when fees are high on the mainchain.
Elements, the open-source codebase that Liquid is built on, is designed to be as close to parity with Bitcoin Core as possible. This not only offers some nice security guarantees (since any bug fix or performance improvement upstream in Bitcoin can be merged into Elements) but also greater interoperability with other L2s, given that its design functions very similarly to Bitcoin.
Connecting the Second Layer with Lightning
The basis of Lightning is its network of payment channels, which are fundamentally made possible through Bitcoin's Unspent Transaction Outputs (UTXOs) in conjunction with Lightning's Hashed Timelock Contracts (HTLCs). The UTXO model allows certain script conditions, and hash puzzles and time constraints to be encoded in the transaction for payment to be securely routed across Lightning.
One of the many design features that Liquid inherits from Bitcoin is its UTXO model. This compatibility allows Lightning's HTLCs to function with Liquid Bitcoin (L-BTC) in a manner similar to how they function with Bitcoin, enabling the payment network to operate on top of Liquid. Note that this Lightning Network on Liquid would run as a separate network but with all the advantages of Liquid as its underlying chain (e.g., Confidential Transactions and deterministic blocks). You could even bridge the two networks if you ran both—one on top of Bitcoin, the other on Liquid—for greater cross-platform compatibility. The payments remain end-to-end secure since both use the HTLC construction. The bridge, however, gets to dictate a dynamic exchange rate if the two assets being transferred are different, which is not an issue when transferring BTC and L-BTC since they are pegged.
Lightning's inherent decentralization, wide adoption, and compatibility with UTXO-based technologies could position it as the connective tissue between each L2. It could act as a primary hub for new protocols seeking to bridge to existing ones, helping to avoid the chicken-and-egg problem of adoption that has plagued new protocols in the past.
This thesis has begun to play out more recently, with several big-name exchanges adding Lightning and swap platforms incorporating Liquid with Lightning to leverage the benefits of both protocols.
Unfairly Cheap with Lightning and Liquid
In early May, on-chain Bitcoin transaction costs surged due to network congestion, resulting in the highest fees seen in nearly two years. This affected major exchanges like Binance and Coinbase, and even some Lightning-compatible wallets like Muun, pricing some users out of the market entirely. This week-long episode underscored the importance of hardening scalability solutions like Lightning, which have so far relied on mainchain transactions to keep liquidity balanced. The event also raised awareness of the powerful benefits of using layer-2 technologies together, especially when fees on Bitcoin's mainchain are not only high but also volatile.
One of the new products in-market driven by this episode is the use of Liquid submarine swaps by Boltz to offer cheap Lightning channel liquidity to its users. As opening a Lightning channel requires an on-chain transaction and many users rely on the mainchain to add liquidity to their Lightning node, costs can quickly add up in high-fee conditions. By using the Liquid sidechain instead of the Bitcoin mainchain as the underlying liquidity source, users can rebalance their Lightning channels independently from the congested mainchain mempool—and do so without losing self-custody of their funds, thanks to the atomic nature of the swap.
In a high-fee scenario, users can expect upwards of 99% savings using the Liquid swap feature. Boltz intends to expand the scope of their Liquid integration by building an L-BTC <> BTC chain-to-chain atomic swap for trustless peg-outs—the first of its kind.
You can read more about Boltz's decision to add Liquid and why in their write-up here.
📺 Lightning Channel Rebalancing with Liquid Bitcoin on boltz.exchange
Another option for users is the self-hosted rebalancing protocol PeerSwap, which allows Lightning node operators to rebalance their channels with peers directly using BTC and L-BTC atomic swaps. This setup eliminates the need for a third-party coordinator for even greater savings and allows smaller nodes to better compete with larger ones. PeerSwap is currently available for both CLN and LND implementations.
The story does not end there, though. In addition to provisioning Lightning liquidity with Liquid, users turned to Lightning <> Liquid swaps to stack sats (and humbly, I might add). Many used a cheap starting point like Strike, Cash App, or some other fiat on-ramp to buy Lightning Bitcoin (LN-BTC) directly and then moved to one of the growing number of Lightning to Liquid swap services like Boltz, SideShift, or Classic CoinOs to convert to L-BTC to HODL for the mid-term. So, why would anyone HODL in L-BTC rather than LN-BTC? Unlike with Lightning, Liquid assets can be self-custodied offline in cold storage, like on a hardware device such as Jade. This setup is better for HODLing over a longer time frame—another difference to consider when deciding what layer-2 solution is best for you and your specific use case.
The Emergence of the Bitcoin Superapp
Some builders are already working on improving the Bitcoin layer-2 user experience by directly integrating swaps and multi-protocol support into their app offerings.
For example, the Blockstream Green team is in the final stages of adding Lightning capability via Greenlight, giving Bitcoiners the ability to self-custody mainchain, Liquid, and Lightning all in one app. Green, SideSwap, and the soon-to-be rereleased version of the AQUA wallet also plan to incorporate in-app Lightning <> Liquid swaps using the Boltz API.
Wallby, a newly anointed Bitcoin ‘superapp,’ supports the custody of mainchain, Liquid, and Rootstock, with further plans to add Lightning and RGB. The Wallby team is also placing emphasis on features. For instance, users can already add bitcoin and other digital assets to liquidity pools and earn interest through an automated market maker (AMM), with the ability to lend and borrow peer-to-peer and perform cross-chain swaps also on the way.
The emergence of these Bitcoin superapps and new features like in-app swaps prioritizes improving user experience, something the Bitcoin space is notoriously bad at (to the point it has become a running meme). This pivot and Lightning's maturation as a sort of lingua franca of Bitcoin will be a crucial part of the strategy for increasing layer-2 interoperability and facilitating mass adoption. Each protocol will have a unique place in the hyperbitcoinization story, ending in a second layer that is stronger than each individual protocol on its own.
-
 @ 32e18276:5c68e245
2023-06-01 04:17:00
@ 32e18276:5c68e245
2023-06-01 04:17:00Double-entry accounting is a tried and true method for tracking the flow of money using a principle from physics: the conservation of energy. If we account for all the inflows and outflows of money, then we know that we can build an accurate picture of all of the money we've made and spent.\n\nBitcoin is particularly good at accounting in this sense, since transaction inflows and outflows are checked by code, with the latest state of the ledger stored in the UTXO set.\n\nWhat about lightning? Every transaction is not stored on the blockchain, so we need same way to account for all the incoming and outgoing lightning transactions. Luckily for us, core-lightning (CLN) comes with a plugin that describes these transactions in detail!\n\nFor every transaction, CLN stores the amount credited and debited from your node: routed payments, invoices, etc. To access this, you just need to run the
lightning-cli bkpr-listaccounteventscommand:\n\n\nlightning-cli bkpr-listaccountevents | jq -cr '.events[] | [.type,.tag,.credit_msat,.debit_msat,.timestamp,.description] | @tsv' > events.txt\n\n\nThis will save a tab-separated file with some basic information about each credit and debit event on your node.\n\n\nchannel invoice 232000000 0 1662187126 Havana\nchannel invoice 2050000 0 1662242391 coinos voucher\nchannel invoice 0 1002203 1662463949 lightningpicturebot\nchannel invoice 300000 0 1663110636 [["text/plain","jb55's lightning address"],["text/identifier","jb55@sendsats.lol"]]\nchannel invoice 0 102626 1663483583 Mile high lightning club \n\n\nNow here's comes the cool part, we can take this data and build a ledger-cli file. ledger is a very powerful command-line accounting tool built on a plaintext transaction format. Using the tab-separated file we got from CLN, we can build a ledger file with a chart-of-accounts that we can use for detailed reporting. To do this, I wrote a script for convertingbkptreports to ledger:\n\nhttp://git.jb55.com/cln-ledger\n\nThe ledger file looks like so:\n\n\n2023-05-31 f10074c748917a2ecd8c5ffb5c3067114e2677fa6152d5b5fd89c0aec7fd81c5\n expenses:zap:1971 1971000 msat\n assets:cln -1971000 msat\n\n2023-05-31 damus donations\n income:lnurl:damus@sendsats.lol -111000 msat\n assets:cln 111000 msat\n\n2023-05-31 Zap\n income:zap:event:f8dd1e7eafa18add4aa8ff78c63f17bdb2fab3ade44f8980f094bdf3fb72d512 -10000000 msat\n assets:cln 10000000 msat\n\n\nEach transaction has multiple postings which track the flow of money from one account to another. Once we have this file we can quickly build reports:\n\n## Balance report\n\nHere's the command for "account balance report since 2023-05 in CAD"\n\n$ ledger -b 2023-05-01 -S amount -X CAD -f cln.ledger bal\n\n\n CAD5290 assets:cln\n CAD2202 expenses\n CAD525 routed\n CAD1677 unknown\nCAD-7492 income\n CAD-587 unknown\n CAD-526 routed\nCAD-1515 lnurl\n CAD-614 jb55@sendsats.lol\n CAD-1 tipjar\n CAD-537 damus@sendsats.lol\n CAD-364 gpt3@sendsats.lol\nCAD-4012 merch\nCAD-2571 tshirt\nCAD-1441 hat\n CAD-852 zap\n CAD-847 event\n CAD-66 30e763a1206774753da01ba4ce95852a37841e1a1777076ba82e068f6730b75d\n CAD-60 f9cda1d7b6792e5320a52909dcd98d20e7f95003de7a813fa18aa8c43ea66710\n CAD-49 5ae0087aa6245365a6d357befa9a59b587c01cf30bd8580cd4f79dc67fc30aef\n CAD-43 a4d44469dd3db920257e0bca0b6ee063dfbf6622514a55e2d222f321744a2a0e\n ...\n------------\n 0\n\n\nAs we can see it shows a breakdown of all the sats we've earned (in this case converted to fiat). We can have a higher-level summary using the depth argument:\n\n$ ledger -M -S amount -X sat -f cln.ledger bal\n\n\n sat14694904 assets:cln\n sat6116712 expenses\n sat1457926 routed\n sat4658786 unknown\nsat-20811616 income\n sat-1630529 unknown\n sat-1461610 routed\n sat-4207647 lnurl\nsat-11144666 merch\n sat-2367164 zap\n------------\n 0\n\n\nAs we can see we made 14 million sats this month, not bad! The number at the bottom balances to zero which means we've properly accounted for all income and expenses.\n\n## Daily Damus Donation Earnings\n\nTo support damus, some users have turned on a feature that sends zaps to support damus development. This simply sends a payment to the damus@sendsats.lol lightning address. Since we record these we can build a daily report of damus donations:\n\n$ ledger -D -V -f cln.ledger reg damus\n\n\n23-May-15 - 23-May-15 ..damus@sendsats.lol CAD-46 CAD-46\n23-May-16 - 23-May-16 ..damus@sendsats.lol CAD-73 CAD-120\n23-May-17 - 23-May-17 ..damus@sendsats.lol CAD-41 CAD-161\n23-May-18 - 23-May-18 ..damus@sendsats.lol CAD-37 CAD-197\n23-May-19 - 23-May-19 ..damus@sendsats.lol CAD-35 CAD-233\n23-May-20 - 23-May-20 ..damus@sendsats.lol CAD-28 CAD-261\n23-May-21 - 23-May-21 ..damus@sendsats.lol CAD-19 CAD-280\n23-May-22 - 23-May-22 ..damus@sendsats.lol CAD-29 CAD-309\n23-May-23 - 23-May-23 ..damus@sendsats.lol CAD-19 CAD-328\n23-May-24 - 23-May-24 ..damus@sendsats.lol CAD-25 CAD-353\n23-May-25 - 23-May-25 ..damus@sendsats.lol CAD-36 CAD-390\n23-May-26 - 23-May-26 ..damus@sendsats.lol CAD-37 CAD-426\n23-May-27 - 23-May-27 ..damus@sendsats.lol CAD-25 CAD-451\n23-May-28 - 23-May-28 ..damus@sendsats.lol CAD-25 CAD-476\n23-May-29 - 23-May-29 ..damus@sendsats.lol CAD-12 CAD-488\n23-May-30 - 23-May-30 ..damus@sendsats.lol CAD-29 CAD-517\n23-May-31 - 23-May-31 ..damus@sendsats.lol CAD-21 CAD-537\n\n\nNot making bank or anything but this covered the relay server costs this month!\n\nHopefully ya'll found this useful, feel free to fork the script and try it out! -
 @ aa55a479:f7598935
2023-07-19 17:54:44
@ aa55a479:f7598935
2023-07-19 17:54:44Test
-
 @ 2d5b6404:d4b500b0
2023-07-08 00:56:26
@ 2d5b6404:d4b500b0
2023-07-08 00:56:26nostr streamからzap streamにタイトルも変更し大幅なアップデートがされました。 今までは自分でcloudflare streamに月額課金してマニュアル設定しなければなりませんでしたが、zap streamとOBSを紐づけてSATS(21 sats/min)を支払うだけで簡単にlive配信を開始することができるようになりました。
必要なものは3つだけです。zap streamとalby(アルビー)とOBSです。
はじめにzap streamにログインするためalbyのアカウント作成が必要になります。別の記事でalbyの登録方法をまとめたのでそちらを参考にしてみてください。
→primalが作成したalby(アルビー)の使い方ショート動画
OBSに関しては多くの解説動画がでていますのでそちらを参考に設定してみてください。 ぼくが参考にした動画です。→ https://youtu.be/ZQjsPJpMLiQ
最後にzap streamとOBSを紐づけるだけです。 zap streamのページを開いてalbyでログインします。 ログインしたら右上のアイコンの横のStreamを押します。

Stream Providers
API.ZAP.STREAM
Stream Url
rtmp://in.zap.stream/liveをコピーして、OBSの設定→配信のサーバーの欄に貼り付けます。
Stream Key
・・・・・・・・・をコピーして、OBSの設定→配信のストリームキーに貼り付けます。

次にBalanceのTOPUPを押してSATSを支払います。21 sats/min 1分21satsなので1時間だと1260satsを先に支払います。長時間配信する場合は多めに入金しておきましょう。
あとはEdit Streamでタイトルやサムネイルを設定してSAVEします。 アダルトコンテンツの場合NSFW Contentにチェックをいれてください。

zap streamとOBSの設定が完了したら、OBSで配信開始すれば勝手にzap streamでlive配信が開始されます。
以上がzap streamでlive配信する方法です。
ライブコーディングやゲーム配信をしているユーザーがすでにいますのでVtuderの方などどんどん配信してみてください。
-
 @ 76c71aae:3e29cafa
2023-05-30 21:59:50
@ 76c71aae:3e29cafa
2023-05-30 21:59:50Joining a new digital community can be an exhilarating and empowering experience. This has been observed on numerous occasions when people join new platforms such as Nostr, BlueSky, Farcaster, Post.news, Tribel, and many others, as well as older social media platforms such as blogs, Usenet, LiveJournal, Xanga, AOL, Flickr, Facebook, Instagram, and TikTok.\n\nInitially, these spaces create an idealistic environment where individuals are eager to connect, share, and participate in a virtual gathering that resembles a festival. However, it is worth examining what it is about these new social spaces that generates such a euphoric atmosphere, and whether it is feasible to sustain this utopian sentiment as communities expand and develop.\n\nThe Magic of Connection:\n\n\nJoining a new digital community can be a transformative experience. In her book "Paradise Built in Hell," Rebecca Solnit argues that when people are taken out of their familiar routines and confronted with real human needs, the best aspects of human nature come to the forefront. This disproves the negative assumption that humans are inherently selfish and demonstrates our natural ability to empathize and connect with one another. The sense of community and collaboration that we feel in emerging social spaces, patticipatory festivals such as 'Burningman', are a great example of this phenomenon.\n\nUtopias Form Where They Shouldn’t Exist:\n\n\nThe concept of "Paradise Built in Hell" becomes evident during natural and economic disasters. I personally witnessed this idea during Argentina's economic crisis in the early 2000s. Despite the difficulties, people came together and collaborated in new ways to support each other, as the collapsing economy demanded it. This same phenomenon is observed following earthquakes and other natural disasters, where people often speak of those days with a magical, almost reverential tone.\n\nRebecca Solnit argues that "Disaster is when the shackles of conventional belief and role fall away and the possibilities open up; people rise to the occasion or sink to the level of their fears and prejudices." In these challenging moments, we see the true nature of humanity: our ability to show compassion, resilience, and unity in the face of adversity.\n\nSocial Media and All Digital Spaces Have Physical Analogues:\n\n\nThe similarities between digital and physical communities are rooted in the fact that each has its own distinct set of unspoken rules and social norms. Just as we know to be quiet in a library, loud at a concert, social at a cocktail party, and anti-social on the subway, we also understand the unique dynamics of different digital platforms. Twitter resembles a bustling dive bar, Instagram an art gallery, TikTok an amusement park hall of mirrors, and Facebook a community hall rented for a retirement party. Every new digital space has its analogues in the physical world because human interaction remains consistent, even if the medium differs. As we navigate the ever-changing landscape of digital communities, we are reminded of our innate ability to adapt, connect, and thrive in the face of adversity. This adaptability empowers us to form new connections and rediscover the power of community, whether in the digital or physical realm.\n\nThe Small Community Paradox:\n\n\nTo maintain the utopian atmosphere of new digital communities, one effective approach is to keep them small or create numerous smaller sub-communities. In these sub-communities, people can engage in the social labor of connection and conflict resolution.\n\nIt is important to note, however, that this approach may conflict with the network effect principle. This principle states that each new member joining the community increases its overall value for all participants. As communities grow and the network effect takes hold, the utopian feeling may often fade, giving way to sub-tribes and conflict.\n\nNevertheless, with a confident approach, the community can adapt and navigate these challenges to foster a positive environment for all members.\n\nThe Fleeting Nature of Utopia:\n\n\nThe fleeting utopian sensation experienced within new digital communities is inevitable. Although it is not the design or coding of platforms such as BlueSky, Nostr, Mastodon, or Scuttlebutt that generates this feeling of euphoria, it is instead the human dynamics of joining something novel and building a community that cultivates this enchanting ambiance. Hakim Bey's concept of Temporary Autonomous Zones (TAZs) endorses this notion, demonstrating how short-lived spaces of freedom and interaction can emerge within established social structures. As communities expand and progress, the real challenge lies in sustaining the initial energy and sense of connection that made them so desirable in the first place.\n\nParallel to Protests and Uprisings:\n\n\nThis utopian sentiment is not limited to digital communities; it is also present during times of revolution, protests, and uprisings. There is a profoundly human element to the sense of love, connection, solidarity, and community that arises during these moments.\n\nThe most impactful moments of my life have been when I participated in protests that were met with repression. These protests ranged from tree-sits to protect old-growth redwoods in the forests where I grew up, to large convergences of the anti-globalization and anti-war movements, to Occupy's reclamation of public spaces, and to recent Black Lives Matter protests. All of these protests were scenes of anguish, repression, and, in some cases, violence, especially from the police. However, they were also places where I experienced the most love, connection, humanity, and common purpose. We were all individuals, together, living and breathing solidarity.\n\nCultivating and Sustaining Utopian Energy:\n\n\nTo preserve the utopian essence of new digital communities as they grow, one approach is to foster a culture of empathy, connection, and inclusiveness from the very beginning. Prioritizing these values and actively engaging in conflict resolution can help communities maintain that special feeling.\n\nAnother way to preserve the utopian essence of digital communities is to focus on building tools for the construction and maintenance of these digital public spaces. Unlike corporate social media platforms that only provide an illusion of public space while actually being privately owned, like a shopping mall, we need to create spaces that are community-controlled and collectively owned as a commons with confidence.\n\nUnderstanding the Commons:\n\n\nThe concept of the commons offers a compelling alternative to traditional models of state or private ownership. Elinor Ostrom, the first woman to win the Nobel Prize in Economics, conducted extensive research on this topic, and her findings are truly remarkable. Through her work, she proved that commons can be effectively managed and maintained, debunking the misguided belief that these resources are doomed to fail and end in tragedy.\n\nDesigning for Digital Commons:\n\n\nTo design digital commons, we must prioritize transparency, decentralization, and participatory governance. By empowering users to make decisions about the direction and rules of their digital communities, we ensure that the spaces remain truly public and that the needs and desires of the community are at the forefront.\n\nOpen-source technology and decentralized protocols can play a vital role in the development of these digital commons. By allowing users to maintain control over their data and ensuring that no single entity has a monopoly over the platform, we create an environment that fosters collaboration, creativity, and innovation.\n\nThe Characteristics of a Well-Functioning Digital Commons:\n\n\n1. Clearly defined boundaries: Members and their rights are easily identifiable, and access to the shared digital resources is well-regulated.\n2. Proportional equivalence between benefits and costs: Users contribute to the commons according to their capabilities, and benefits are distributed fairly among members.\n3. Collective decision-making: Users have a say in shaping the rules and policies that govern their digital communities, promoting a sense of ownership and accountability.\n4. Monitoring: Transparent systems are in place to track the usage and management of shared resources, ensuring that members adhere to established rules.\n5. Graduated sanctions: Penalties for rule violations are proportional and escalate based on the severity and frequency of the transgressions.\n6. Conflict resolution mechanisms: Efficient and fair processes are in place to address disputes among members, promoting harmony and trust within the community.\n7. Minimal recognition of rights to organize: Users have the autonomy to self-organize and make decisions about their digital commons without excessive interference from external authorities.\n8. Nested enterprises: Digital commons are organized into multiple, interconnected layers of governance, with smaller communities operating within the context of larger ones, fostering collaboration and coordination.\n\nBy incorporating these principles into the design of digital commons, we can create spaces that are robust, sustainable, and equitable. This, in turn, fosters innovation, collaboration, and genuine community engagement.\n\nDeveloping Community-Driven Tools:\n\n\nTo create and maintain digital public spaces, we need tools that empower communities to effectively manage their digital commons. These tools should facilitate communication, conflict resolution, and decision-making while promoting inclusiveness, empathy, and shared values. By empowering communities to shape their digital spaces and collaboratively resolve issues, we can help preserve the utopian essence that initially attracted people to these platforms.\n\nAdapting to Growth and Change:\n\n\nAs digital communities continue to grow, it's crucial to acknowledge that their needs and challenges will inevitably change over time. To maintain a utopian atmosphere, we must be willing to adapt and consistently improve the tools and processes that sustain these digital public spaces. By promoting continuous feedback and collaboration among community members, we can ensure that the platform remains responsive to the needs of its users, fostering an environment of connection and belonging with conviction.\n\nConclusion:\n\n\nJoining a new digital community can be a thrilling experience, but maintaining that sense of euphoria as the community grows can be difficult. To achieve this, we must design and construct digital commons that prioritize community control, collective ownership, and participatory governance. With the appropriate tools and a dedication to adapting to the evolving needs of the community, we can create spaces that continue to foster the magic of connection even as they transform. In doing so, we can nurture and sustain the utopian energy that makes these digital spaces so unique.\n\n\nPost Script:\n\nSince the completion of this essay, Bluesky has evolved from its initial utopian stage to a phase grappling with context, norms, and scalability. With an increasing user base, the once agreed-upon behavioral norms began to crumble. The initial playfulness, while staying within the community's value constraints, took a disturbing turn when individuals started posting racist and homophobic content. The situation deteriorated rapidly, escalating to the point of issuing death threats. Inspired by the "Nazi bar" parable, the community demanded urgent action to outline acceptable behavior and remove those who couldn't comply.\n\nBluesky, currently hosted on a single server, possesses the capability to enforce a unified set of community guidelines and terms of service. The creators of Bluesky, much like any other social media platform's developers, aimed for a laissez-faire approach. However, they eventually had to revise the terms of service and ban the trolls. This action was chaotic and resulted in significant loss of trust and goodwill.\n\nAdditionally, this did not aid the community in establishing governance for the burgeoning social media commons. Protocols such as Bluesky, Nostr, DSNP, Scuttlebutt, Farcaster, and Lens are not designed to operate in isolation. Among these, only ActivityPub and Mastodon have successfully implemented a model to manage abuse and community moderation at scale. Nonetheless, potential solutions are under development. I've personally contributed to proposals for specifications, codes, and norms on Nostr and know that Bluesky's team is making similar strides.\n\nIt is essential that the user community actively participate in this process. The Design Justice movement provides a valuable blueprint and strategies for achieving this. By applying principles of co-design and design justice, we can collaboratively build solutions. The stakes are too high to leave this endeavor to a small group of technologists alone. \n
-
 @ deba271e:36005655
2023-05-06 18:50:59
@ deba271e:36005655
2023-05-06 18:50:59(This is a repost from my original article for Stacker News)\n\nIs some specific website, like Twitter, bringing you joy or is it bringing you the opposite? Do you have a hard time stopping? Here's a quick tutorial recommended by 9 out 10 dentists. \n\nFirst rule: Never run random bash scripts you find online without reading the scripts yourself! \n\n---\n\n## Blocking with /etc/hosts\nIf you understand the first rule, then read, copypaste and run following script in your terminal. \n\nOn Linux or MacOS\n
shell\nsudo bash -c "cat >> /etc/hosts << EOF\n\n0.0.0.0 twitter.com\n0.0.0.0 reddit.com\nEOF\n"\n\nAnd that's it. This should apply the rule immediately. \nIf you want to check how does your/etc/hostslook like, then just runnano /etc/hosts.\n\nOn Windows\nbatch\necho 0.0.0.0 twitter.com >> %WINDIR%\\System32\\Drivers\\Etc\\Hosts\necho 0.0.0.0 reddit.com >> %WINDIR%\\System32\\Drivers\\Etc\\Hosts\n\n\n--- \n\n## Blocking with pi-hole\nEven better option is if you have pi-hole set up on your network to proxy all your DNS requests. If you didn't know pi-hole is also available on Umbrel or Citadel.\n\nSimple steps:\n1. Sign in to your your pi-hole admin interface, e.g. https://pi.hole/admin/index.php\n2. Navigate to Blacklist\n3. Addtwitter.comin the Domain input box and click on Add to Blacklist\n4. You are all set. -
 @ 0b963191:fc5e7ffd
2023-07-19 16:53:34
@ 0b963191:fc5e7ffd
2023-07-19 16:53:34https://zap.stream is a live streaming site powered by nostr. It easily and permissionlessly allows anyone to set up a stream via their nostr identity and have a Twitch\Youtube style experience. Did I mention that like most things in the nostr universe, it's also powered by zaps? Viewers are able to zap the streamers and other chat participants!
Here is the TL;DR

I wrote this guide, which will probably change a lot, to provide quick start steps on how to set up your own stream and start receiving zaps.
Ingredients
The first things you will need to make sure you have set up are as follows: * Nostr npub you're going to be using as your "streaming channel" identity * Some sats on a lightning wallet (start with 5000 to play around). Also make sure you link lightning to your profile * NIP-07 browser extension for the npub\nsec * Streamer software, we will use OBS (https://obsproject.com) * Creativity
Zap.Stream website

When you head over to zap.stream you will see a very clean site with a list of streams that are active, pending, and ended. As of right now you can see how mean people are viewing a stream, although this may be on a bit of a delay from accurate count as of today.
After you Login with your nostr identity via NIP-07, you will see a stream button. If you made it this far, we're in good shape and can move on to setting up OBS.
Streaming software
I used OBS because that's what was recommended and it is very easy to get set up. Any streaming software that can send to a rmtp URL should work and I heard others using more sophisticated setups.
Download and run OBS. Review the documentation if needed. The main settings we need to look at are under Stream.
We will need to set the service to "Custom" and we will see input boxes for Server and Stream Key. Let's go back to the zap.stream site to get those.

If we go to the Stream dialog we will see a two Stream Providers up time "API.ZAP.STREAM" and "MANUAL". When you become an expert and want to stream directly from your servers or another service you can select Manual. For our quick start we will be using API.ZAP.STREAM.

Copy the Stream URL and Stream Key and paste them into OBS.
Sats ⚡️ for streaming
As of this writing zap.stream charges 10 sats/minute for streaming to their service. This may change in the future and we will need to load sats up to stream. Use whichever lighting wallet you have and send at least 5000 sats over.

Note: When you get below 500 sats a bot will kindly remind you to top up your balance. Your stream will stop when you run out of sats.
Metadata
Add in the metadata for your stream including a Title, Summary, Splashpage. When you save this all that's left is firing up OBS.

Start Streaming
Now that everything is in place, you should be able to start streaming to zap.stream. I recommend doing a few tests beforehand. When you are ready tell all your friends on "kind 1" and beyond and start making content.
Please contribute to Kieran via v0l@getalby.com to help keep development moving.
Disclaimer: Zap.stream is very new. Things are subject to change and move fast. I will try to update the documentation as frequently as possible. I am not responsible for any bad outcomes. Have fun!
Change Log
- 7.19.2023 - Changed sats per minute to 10
-
 @ c9dccd5f:dce00d9a
2023-05-02 07:16:55
@ c9dccd5f:dce00d9a
2023-05-02 07:16:55Every fundamental particle carries an intrinsic angular momentum, which we call 'spin'. It is important to remember that this is an intrinsic quantum mechanical property of particles. There is no such thing as a spinning sphere in the classical sense. Nevertheless, the image of a spinning sphere is often a good analogue to understand what is going on.\n\n## Helicity\n\nThe helicity of a particle is the projection of its spin vector onto its linear momentum. In the spinning analogy, it is the relation of its spin direction to its direction of motion. The particle helicity is called either right-handed or left-handed. We say that the particle has right-handed helicity if the spin is aligned with the direction of motion, and left-handed helicity if the spin and motion have opposite orientations. In the spinning analogy, we can immediately understand where the names come from and what they mean. We look at your hands, make a fist and spread the thumbs. The thumbs indicate the direction of motion and the curled fingers indicate the direction of spin. We point our thumbs in the direction of motion and compare the fingers with the direction of spinning we see: If they are in the same direction as the right hand, we call it right-handed helicity, and conversely.\n\nSince massless particles (e.g. photons) travel at the speed of light, we will never find a reference frame in which this particle is at rest, i.e. we cannot find a rest frame. Therefore, the helicity will never change, since the spin is fixed and the direction of motion is the same in all reference frames.\n\nOn the other hand, massive particles travel at a speed less than that of light, so in principle we can find a rest frame. In fact, we can even find a reference frame in which the particle appears to be moving in the opposite direction. Yet the spin of a particle never changes. This leads to the fact that for massive particles the helicity can change because the direction of motion can be reversed, resulting in the opposite helicity. Note that this is not possible for massless particles, because we cannot move faster than them. \n\nThus we see that the mass of a particle tells us whether the helicity of a particle is an intrinsic property of the particle. For a massless particle, the helicity is fixed in all reference frames, whereas for a massive particle this is not the case, because different observers can infer different helicities for the same particle. \n\nAs physicists, we like to find fundamental properties of a particle. We therefore ask whether there is a related property to helicity that is intrinsic to particles. We call this fundamental property chirality.\n\n## Chirality\n\nChirality and helicity are closely related. Just as we say a particle has right-handed or left-handed helicity, we say a particle has right-handed or left-handed chirality. Sometimes we can drop the '-handed' and just say right-/left-helicity or right-/left-chirality. For massless particles, helicity and chirality are the same thing, so a right-chiral particle will also have right-helicity. For massive particles, however, helicity and chirality are different. A massive particle has a certain chirality but can have both helicity states, e.g. a right-chiral particle can have right or left helicity depending on the frame of reference. \n\nChirality is an abstract concept that refers to a fundamental intrinsic quantum mechanical property of a particle. However, a useful and nice visualisation can be made by looking at our hands. We hold our hand in front of us. The left and right hands are mirror images of each other. No matter how we rotate, flip or move one hand, it will never look exactly like the other hand. Our hands have different chirality.\n\nIn physics, particles with different chirality can be considered as completely different particles. It refers to how a particle's quantum mechanical wave function behaves under rotation. The quantum wave functions of left- and right-chiral particles behave differently under rotation.\n\nThe measurable physical effect of a particle's chirality can be seen in the theory of the weak interaction. The weak interaction only affects left-chiral particles and not right-chiral ones. As a result, neutrinos, which are weakly interacting particles, are only observed in left-handed chiral states.\n\n---\n\n_I hope this post has helped you understand the concept of helicity and chirality in physics. If anything is still unclear, or if an explanation could be improved to make it easier to understand, please comment or write to me. I am happy to answer. I'm looking forward to your feedback. PV_ 🤙\n\n---\n\n
v0 @ 785591; v1 @ 785712: fixed typos and added a missing sentence; v2 @ 787922: slight changes to the layout -
 @ 5e5fc143:393d5a2c
2023-04-15 17:18:11
@ 5e5fc143:393d5a2c
2023-04-15 17:18:11\nJust revisiting some quick tips for #newbies #pow #public #blockchain users only.\n\nif you just getting started with bitcoin or any pow crypto coins or been using or storing them for a while, you not must forget the roots and fundamentals.\n\nHot Wallet — It gets connected to live internet at some point in time essentially to sign / send a tx i.e. spending transaction — exposes the private key of the address from in the process\n\nCold Wallet — It never ever gets connected or online and can always keep receiving inbound amounts\nPaper wallets are best n cheapest form of cold wallet that can used once n thrown away.\n\n#Cold wallets need to either “import”ed or “sweep”ed in order to used or spend — https://coinsutra.com/private-key-import-vs-sweep-difference/\n\n\n
 \n\nAny thin #wallet is always dependent on connectivity to live up2date node server where-as self-sufficient qt / cli wallet takes a while to sync up to latest block height in order to be usable.\n\nBeginners should always resist the attraction of quick and fast — thin n 3rd party wallets and always start a long learning journey of core wallets of any coin — either “qt” GUI wallet or command line “coin-cli” wallet\n\nAlmost all #proofofwork #blockchains i.e. #POW has #node #wallet - everyone who use support he #public #blockchain secures own you coin value\n\nYou can run fullnode either on clearnet or over onion 🧅 #BTC has >55% of nodes running in onion out of total 15000+ live fullnodes and 50000+ bitcoincore wallets around blockheight 777000 . Other notable pow chains are #LTC #RVN and rest are babychains for now !\n\nAlways delete hot wallet to test practice restoration before sending any large refunds to it to be safe. \n\nLarge funds are always best to keep in self custody node wallets rare n occasional use\n\nFinal word — Cannot see private key 🔑 or seed 🌱 in any wallet means not your coin. 😲\n\nThat’s all for now n Thank you 🙏 ! ⚡️ https://getalby.com/p/captjack ⚡️\n\n\nSome Cold wallet nostr posts\nnostr:note1p6ke5wqshgxtfzj5de3u04hejl2c5ygj8xk8ex6fqdsg29jmt33qnx57y2\nnostr:note1rse0l220quur6vfx0htje94ezecjj03y6j7lguwl09fmvmpt6g3q0cg7yw\nnostr:note1q5w8dyjuqc7sz7ygl97y0ztv6sal2hm4yrf5nmur2tkz9lq2wx9qcjw90q\n\nsome nostr specific lightning ⚡️ Layer2 wallets with blockchain mainnet option\nnostr:naddr1qqsky6t5vdhkjm3qd35kw6r5de5kueeqf38zqampd3kx2apqdehhxarjqyv8wue69uhkummnw3e8qun00puju6t08genxven9uqkvamnwvaz7tmxd9k8getj9ehx7um5wgh8w6twv5hkuur4vgchgefsw4a8xdnkdgerjatddfshsmr3w93hgwpjdgu8zdnswpuk2enj0pcnqdnydpersepkwpm8wenpw3nkkut2d44xwams8a38ymmpv33kzum58468yat9qyt8wumn8ghj7un9d3shjtngv9kkuet59e5k7tczyqvq5m2zcltylrpetrvazrw45sgha24va288lxq8s8562vfkeatfxqcyqqq823ckqlhc8\nrelated blog post \nnostr:naddr1qqxnzd3cxyenjv3c8qmr2v34qy88wumn8ghj7mn0wvhxcmmv9uq3zamnwvaz7tmwdaehgu3wwa5kuef0qydhwumn8ghj7mn0wd68ytn4wdjkcetnwdeks6t59e3k7tczyp6x5fz66g2wd9ffu4zwlzjzwek9t7mqk7w0qzksvsys2qm63k9ngqcyqqq823cpdfq87\n\n
\n\nAny thin #wallet is always dependent on connectivity to live up2date node server where-as self-sufficient qt / cli wallet takes a while to sync up to latest block height in order to be usable.\n\nBeginners should always resist the attraction of quick and fast — thin n 3rd party wallets and always start a long learning journey of core wallets of any coin — either “qt” GUI wallet or command line “coin-cli” wallet\n\nAlmost all #proofofwork #blockchains i.e. #POW has #node #wallet - everyone who use support he #public #blockchain secures own you coin value\n\nYou can run fullnode either on clearnet or over onion 🧅 #BTC has >55% of nodes running in onion out of total 15000+ live fullnodes and 50000+ bitcoincore wallets around blockheight 777000 . Other notable pow chains are #LTC #RVN and rest are babychains for now !\n\nAlways delete hot wallet to test practice restoration before sending any large refunds to it to be safe. \n\nLarge funds are always best to keep in self custody node wallets rare n occasional use\n\nFinal word — Cannot see private key 🔑 or seed 🌱 in any wallet means not your coin. 😲\n\nThat’s all for now n Thank you 🙏 ! ⚡️ https://getalby.com/p/captjack ⚡️\n\n\nSome Cold wallet nostr posts\nnostr:note1p6ke5wqshgxtfzj5de3u04hejl2c5ygj8xk8ex6fqdsg29jmt33qnx57y2\nnostr:note1rse0l220quur6vfx0htje94ezecjj03y6j7lguwl09fmvmpt6g3q0cg7yw\nnostr:note1q5w8dyjuqc7sz7ygl97y0ztv6sal2hm4yrf5nmur2tkz9lq2wx9qcjw90q\n\nsome nostr specific lightning ⚡️ Layer2 wallets with blockchain mainnet option\nnostr:naddr1qqsky6t5vdhkjm3qd35kw6r5de5kueeqf38zqampd3kx2apqdehhxarjqyv8wue69uhkummnw3e8qun00puju6t08genxven9uqkvamnwvaz7tmxd9k8getj9ehx7um5wgh8w6twv5hkuur4vgchgefsw4a8xdnkdgerjatddfshsmr3w93hgwpjdgu8zdnswpuk2enj0pcnqdnydpersepkwpm8wenpw3nkkut2d44xwams8a38ymmpv33kzum58468yat9qyt8wumn8ghj7un9d3shjtngv9kkuet59e5k7tczyqvq5m2zcltylrpetrvazrw45sgha24va288lxq8s8562vfkeatfxqcyqqq823ckqlhc8\nrelated blog post \nnostr:naddr1qqxnzd3cxyenjv3c8qmr2v34qy88wumn8ghj7mn0wvhxcmmv9uq3zamnwvaz7tmwdaehgu3wwa5kuef0qydhwumn8ghj7mn0wd68ytn4wdjkcetnwdeks6t59e3k7tczyp6x5fz66g2wd9ffu4zwlzjzwek9t7mqk7w0qzksvsys2qm63k9ngqcyqqq823cpdfq87\n\n -
 @ 9be0be0e:c3cbb81e
2023-07-19 11:05:48
@ 9be0be0e:c3cbb81e
2023-07-19 11:05:48Enable the freedom to communicate.
Reach should be the result of how many people want or don’t want to listen to your message, there is no reason for a third party or algorithm to be required in this equation.
You should be in control of what you can or cannot see. Who you block should be up to you.
Ideally Nostur tries to reduce the need to require or trust any third party in order to communicate, unless there is no other way.
BUT
Nostur is built for iPhone, iPad and Mac users. In one way this is a limitation, (e.g., zap restrictions by Apple) but if we are using the Apple ecosystem already, we might as well use it to our advantage.
Nostur's target audience already trusts Apple with their data, their messages, photos, calendar, reminders, security cameras, etc.
We don’t need to store our data on random relays, and hope our contact list doesn’t get lost, or leak metadata to the public. We can store everything on our device, and sync using iCloud, it is reliable, and we already use it for far more important data anyway. Converting Apple users to Android or GrapheneOS is an uphill battle, I applaud people who take that route, but it’s not for Nostur users, we have people saying don't trust the media, don't use twitter, don't use iPhone, if we keep going, we end up sending smoke signals in a circle. As for interoperability, we can still publish or export using nostr native formats so you can use your data in another nostr app.
Nostur will publish to relays, but our data is on our device first, iCloud second, and third-party relays third. And you can still use a personal private relay for yourself if you want.
With this in mind, Nostur tries to let relays just be relays, not personal storage. Using relays for storage might end up centralising nostr, in the same way email, which used to be decentralised, is now mostly hosted by google and microsoft.
If you disagree with this mission or direction, Nostur's source is released under GPL-3.0 license, so feel free to fork and create a different version.
Ultimately, the goal of Nostur is not to get more people to use Nostur, but to get more people to use nostr.
-
 @ 92294577:49af776d
2023-07-19 05:41:30
@ 92294577:49af776d
2023-07-19 05:41:30Here is the simplest Simplicity program:
main := idenThis program takes an empty input and produces an empty output. Let’s do something more interesting, taking a bit and inverting it:
``` bit0 := injl unit : 1 * 1 -> 2 bit1 := injr unit : 1 * 1 -> 2
padR := pair iden unit : 2 -> 2 * 1 bitflip := case bit1 bit0 : 2 * 1 -> 2 main := comp padR bitflip : 2 -> 2 ```
Here the final Simplicity expression is our
mainfunction. By reading from bottom to top, we can see that it is the composition of several smaller functions, eventually grounding out in unit combinators. Unit combinators produce an empty output. Along withiden, which takes an arbitrary input and returns it unchanged, andwitness, which outputs an externally-provided value, unit combinators form the basis for every Simplicity expression.In this code snippet, we’ve provided type annotations to help indicate what data is flowing from each part of the expression to the next. Here “1” represents the unit type, which is what we’ve been referring to as an “empty output”. “2” represents a bit, which may take the value 0 or 1.
Don’t worry if you didn’t follow this snippet in any detail. It’s only here to show visually what Simplicity code looks like. Later in this post, we’ll analyze a more interesting program more carefully.
A Specification Language
Ultimately, all programming languages express the idea of combining computations to build larger ones. Bitcoin Script (like Forth, or PostScript) does this by means of a stack machine, in which each computation manipulates a list of data objects in turn. Ethereum’s EVM uses a function call architecture where code can call other blocks of code (possibly in other contracts), which take data as input and return data as output. This is also the model used by pretty-much all mainstream programming languages today.
Programming languages use side effects to interact with the outside world, such as the transaction being spent. In EVM, contracts also have access to key-value data stores, which allow them to maintain state across transactions without explicitly passing it.
In both Bitcoin Script and EVM, bit inversion can be done with a single opcode (though the Bitcoin version can take many different inputs, most of which do not resemble bits, while the EVM version acts bitwise but always on 256 bits at once). It’s reasonable to ask why the Simplicity model leads to such verbosity for such simple things.
Our goal with Simplicity is to formally specify the semantics of programs, both in terms of what functions they represent, and what computational resources are involved in evaluating them. It would be possible, in principle, to formally specify a language which operates like Bitcoin Script or EVM, but the task would be extremely difficult, and the result would be nearly as difficult for anybody to verify. Instead, with Simplicity, we defined a small set of basic combinators, each of which reflects a mathematically fundamental way of combining functions. The resulting language’s semantics are so small that they fit on a T-shirt.
In practice, for things like bit inversion, this code will only be written once, then reused. In fact, we’ve done the writing for you and built it into the language. When writing your own code, you can simply use the shortcut
jet_notin place of the above code. We will talk more about jets in the next section.Eventually, in practice, almost nobody will be writing Simplicity code at all. Simplicity provides a well-defined foundation for blockchain programs, but it is just that: a foundation. The real work will be done in higher-level languages, which compile down to Simplicity code alongside proofs of their correct operation.
Programs Versus Expressions
Expressions that have trivial input and output values have a special name. We call these expressions programs. Mathematically speaking, only one function exists mapping a trivial input to a trivial output, so it’s not obvious that such Simplicity expressions would be useful at all. But not only are they useful, they’re the only such expressions allowed on the blockchain!
So, what is the strategy? There are actually two: one is that the Simplicity programs committed in addresses have holes in them, which are only filled in when coins are actually spent; the other is that Simplicity programs have side effects, which allow them to access blockchain data or abort early, thereby stepping outside the bounds of pure mathematical functions.
There are two ways to specify holes in Simplicity programs: the
disconnectandwitnesscombinators.disconnectis a bit subtle, and we have talked about it in the past. But witnesses are very simple: thewitnesscombinator returns a value of a given type, called a witness, (such as a digital signature, hash preimage, or specific choice of signing keys).There are also two ways that Simplicity supports side effects: one is by introspecting transaction data (which we will also discuss more in a later post), and the other is by assertions. Assertions halt the program execution. In Bitcoin Script, the VERIFY opcode is used for assertions, and allows the program to fail if it encounters an invalid signature or other data. EVM uses the STOP opcode for the same purpose.
We can now see how a program whose input and output types are nominally trivial, can actually effect a useful computation: witnesses serve the purpose of program inputs, while assertions provide a “pass/fail” program output.
Let’s consider another example. Here is a program that takes two witnesses and checks them for equality:
``` -- Witnesses wit1 := witness : 1 -> 2^32 wit2 := witness : 1 -> 2^32
-- Program code pr1 := pair wit1 wit2 : 1 -> 2^64 jt2 := jet_eq_32 : 2^64 -> 2 cp3 := comp pr1 jt2 : 1 -> 2 jt4 := jet_verify : 2 -> 1
main := comp cp3 jt4 : 1 -> 1 ```
We can read this program from bottom to top: the program itself is a single expression called main, of type 1->1. Here the “type” of an expression indicates what kind of values it takes as input and output. The 1 type has only a single value, so describes no information. The 2 type has two possible values, so it can represent a single bit, 2^32 is a 32-bit string, and so on.
From the bottom equality, we see main is the composition of the expressions with names cp3 and jt4. Then cp3 is itself the composition of pr1 and jt2, and so on. There are five combinators used in this program:
-
comp, or composition, takes two expressions and evaluates the second with the first’s output as input.
-
pair takes two expressions and produces a new expression whose output is a pair of values: the left part is the output of the first expression, and the right part the output of the second.
-
witness takes no input but has a polymorphic type as its output: whatever type is needed for the program to make sense, that’s its type. And the value it yields is one provided at evaluation time.
-
jet_eq_32 is a jet, which means it is a single combinator that replaces a larger Simplicity expression. The replaced expression is called its specification, and a Simplicity interpreter can evaluate the jet either by evaluating the specification, or by using optimized machine code which has the same effect. This particular jet takes two 32-bit values and outputs a single bit, indicating whether the two values were equal (1) or unequal (0).
-
jet_verify is also a jet. This one takes a single bit as input, and if that bit is 0, it aborts the program. It has no output.
Conclusion
This was a dense blog post in which we saw what Simplicity code looks like, and observed that even simple-seeming functionality can look pretty complex when it’s written out explicitly. But this complexity reflects what’s actually going on inside. As a specification language, Simplicity allows us to make everything explicit, so that we can mathematically model it, prove the essential properties that we need for our applications, and then encapsulate it, confident that we have a rock-solid foundation for the things we believe about our code.
Simplicity has several more combinators and many jets, which we’ll talk about in future posts. As we build up the language, we’ll explore more practical examples and look at what it means to “prove” properties of programs.
My next post will introduce the concept of sharing, which allows two identical expressions to be merged into one, and introduces some subtleties related to what it means to be “identical”.
Join the Simplicity discussions on GitHub to ask questions, connect with the community, and share your insights. And follow us at @blksresearch on Twitter to stay up to date with the latest in Simplicity blog post releases.
-
-
 @ 0d119c15:6d7b1b39
2023-07-19 04:10:57
@ 0d119c15:6d7b1b39
2023-07-19 04:10:57在這篇文章中,我將向大家介紹如何自行架設 nostr relay。在這裡,我們將使用 strfry 作為我們的 nostr relay server,並透過 nginx 作為反向代理(reverse proxy),最後利用 letsencrypt 來進行 SSL 簽章。
參考資源: - strfry GitHub repo - strfry relay installation guide
步驟一:建立使用者
首先,我們需要創建一個新的系統使用者
strfry。這樣可以確保運行 strfry 的過程中,如果發生問題,不會影響到系統的其他部分。bash adduser --gecos "" --disabled-password strfry su - strfry步驟二:建置 strfry
接著,我們需要安裝必要的套件並且編譯 strfry。這些套件包含 git、build-essential、libyaml-perl、libtemplate-perl、libregexp-grammars-perl、libssl-dev、zlib1g-dev、liblmdb-dev、libflatbuffers-dev、libsecp256k1-dev、libzstd-dev。
bash sudo apt install -y git build-essential libyaml-perl libtemplate-perl libregexp-grammars-perl libssl-dev zlib1g-dev liblmdb-dev libflatbuffers-dev libsecp256k1-dev libzstd-dev git submodule update --init make setup-golpe make -j4步驟三:設定 strfry 工作空間
我將 strfry 的工作空間放置在
/home/strfry底下,因此首先需要創建一個strfry-db資料夾,然後將範例的配置文件複製到/home/strfry底下。bash mkdir /home/strfry/strfry-db cp /home/strfry/strfry/strfry.conf ./步驟四:修改配置文件
接著我們需要修改配置文件,特別是
info部分的內容,包括伺服器名稱、描述、公鑰,以及聯絡方式。```yaml info { # NIP-11: Name of this server. Short/descriptive (< 30 characters) name = "strfry default"
# NIP-11: Detailed information about relay, free-form description = "This is a strfry instance." # NIP-11: Administrative nostr pubkey, for contact purposes pubkey = "unset" # NIP-11: Alternative administrative contact (email, website, etc) contact = "unset"} ```
步驟五:設定 nginx
首先,我們需要以 root 使用者身分來運行以下命令。接著,我們需要安裝 nginx、certbot 以及 python3-certbot-nginx。然後刪除預設的 nginx 設定檔,並貼上新的設定檔。最後重啟 nginx。
```bash
run as root
su root
Install nginx
apt install nginx certbot python3-certbot-nginx
Delete the default nginx settings file
rm -rf /etc/nginx/sites-available/default
Paste in new settings file.
sudo vim /etc/nginx/sites-available/default
Restart nginx
sudo service nginx restart
set DNS A Record
Request SSL cert from letsencrypt/certbot
sudo certbot --nginx -d subdomain.yourdomain.org ```
nginx 設定檔內容如下:
nginx server { server_name subdomain.yourdomain.org; location / { proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header Host $host; proxy_pass http://127.0.0.1:7777; proxy_http_version 1.1; proxy_set_header Upgrade $http_upgrade; proxy_set_header Connection "upgrade"; } }步驟六:設定 systemd
接著,我們需要建立一個 systemd 服務單元檔案,讓我們的 strfry 可以作為一個服務來運行。
bash vim /etc/systemd/system/strfry.service內容如下:
```ini [Unit] Description=Strfry Relay After=network.target
[Service] WorkingDirectory=/home/strfry ExecStart=/home/strfry/strfry/strfry relay KillSignal=SIGINT
Type=simple Restart=always RestartSec=30 TimeoutSec=240 LimitNOFILE=1000000
User=strfry
[Install] WantedBy=multi-user.target ```
接著我們需要啟用並啟動 strfry 服務,並確認其運行狀態。
```bash
Enable strfry service
systemctl enable strfry
Start strfry
systemctl start strfry
Check status
systemctl status strfry ```
至此,你已經完成了 nostr relay 的設定。你可以透過 Websocket King 確認你的 nostr relay 是否正常運作。
-
 @ de7ecd1e:55efd645
2023-02-20 16:41:11
@ de7ecd1e:55efd645
2023-02-20 16:41:11Web 1.0\n\nThe web was proposed in 1989, by Tim Berners-Lee but had been conceived decades earlier. The proposal was not read for a full year, and, after that, allowed as a side-project with the infamous words, "vague, but exciting".\n\nThe first version added hyperlinks to existing browser technology. Bundled together were:\n\n- HTTP and the first server\n- the first web browser, which was also an editor\n- HTML which was based on SGML\n\nImportantly a new type of variable was created, the hyperlink, originally the UDI (Universal Document Identifier). This was later standardized as the URI, with an intent to go beyond just documents to describe Things as well.\n\nWeb 1.0 was in competition with Gopher at the time, and Gopher was winning. However, there was a rumour that Gopher might charge some royalties on their protocol, say, to enterprise customers, and with that, the people flocked to the web and made it take off as a grass roots movement.\n\nHTTP was a formal specification in 1997 a full 8 years later, and the architecture of the world wide web was published in 2004, 7 years after that.\n\n
 \n\n\n## Web 2.0\n\nAs the web grew as a system, businesses started to spring up around it. A product was a browser called Mosaic, made by Marc Andreessen. While Mosiac added multi media, it also removed the editing functionality in the original browser, a tragic loss.\n\nWithout editing built in, the web needed central servers to allow user generated content. These servers grew in time to become giants. A technology added on this was AJAX, which allowed browsers to interact with servers asynchronously to generate richer applications and realtime updates. \n\nThis system of greater usability was branded "Web 2.0", popularized by Tim O'Reilly. It was not a formal upgrade of the web, so considered somewhat cheeky by some, the inventor of the web calling the term "jargon". Jargon it is, but the term stuck, and the web did go to a next level, adding important things like search, commerce, and the social web.\n\nWith the increased centralization of servers came other problems, such as pervasive tracking, monopolistic effects, censorship and information engineering.\n\n
\n\n\n## Web 2.0\n\nAs the web grew as a system, businesses started to spring up around it. A product was a browser called Mosaic, made by Marc Andreessen. While Mosiac added multi media, it also removed the editing functionality in the original browser, a tragic loss.\n\nWithout editing built in, the web needed central servers to allow user generated content. These servers grew in time to become giants. A technology added on this was AJAX, which allowed browsers to interact with servers asynchronously to generate richer applications and realtime updates. \n\nThis system of greater usability was branded "Web 2.0", popularized by Tim O'Reilly. It was not a formal upgrade of the web, so considered somewhat cheeky by some, the inventor of the web calling the term "jargon". Jargon it is, but the term stuck, and the web did go to a next level, adding important things like search, commerce, and the social web.\n\nWith the increased centralization of servers came other problems, such as pervasive tracking, monopolistic effects, censorship and information engineering.\n\n\n\n## Web 3.0\n\nWeb 3.0 was a term coined by Tim Berners-Lee, to represent a radical new idea, which allowed both data and documents to be denoted, on the web. This is of course a radical old idea which was in the web 1.0 proposal, a so-called "semantic web", but with the name 2.0 already co-opted, Tim decided to call it web 3.0.\n\nThe was formalized in the RDF (resource definition framework) which made extensive use of XML. Later it was renamed Linked Data, sometimes called the web of data. This has been popularized by schema.org which allows commonly used terms to be put in web pages, allowing easier search, and link previews.\n\nBerners-Lee continues to work on a project called Solid, which stands for "Social Linked Data" (a term I coined in 2012), with the aim of making Linked Data more social, and benefiting from same usability upgrades and lessons learned from "Web 2.0"\n\nThe full web 3.0 stack is standardized at the w3c, though has grown over time, leading to a somewhat complex system, and steep learning curve for new developers.\n\nA note on the deceptively named web3. This was an attempt by VCs (including Marc Andreessen again) and others to co-opt the web brand. The main aim was an affinity scam to sell tokens to the unsuspecting public. The issue is that it is not the web at all. In this case Berners-Lee did speak out against it:\n\nhttps://www.cnbc.com/2022/11/04/web-inventor-tim-berners-lee-wants-us-to-ignore-web3.html\n\n
 \n\n## Towards Web 4.0\n\nThe first 3 "versions" of the web work well enough. However, the web itself is ephemeral. The average age of a link is 100 days. And there is no good mechanism at web scale to ensure the integrity or version control of information on the web. A possible approach to the next version of the web would be towards a Temporal Web. I wrote a post about this here:\n\nhttps://lists.w3.org/Archives/Public/public-rww/2021May/0006.html\n\nA significant innovation in recent times is that of Bitcoin, which is a web scale timestamp server. It orders records (blocks) in time, robustly and securely, creating a permanent record. It also, for the first time in history, creates a global currency that is strongly resistant to money printing by fiat.\n\nThese two systems working together could create a robust temporal backbone to the web, allowing commerce without rent seeking, and creating whole new business models that are more decentralized, and act in the interests of the users, competing with each other with better services, rather than, serving privacy intrusive monopolies.\n\n
\n\n## Towards Web 4.0\n\nThe first 3 "versions" of the web work well enough. However, the web itself is ephemeral. The average age of a link is 100 days. And there is no good mechanism at web scale to ensure the integrity or version control of information on the web. A possible approach to the next version of the web would be towards a Temporal Web. I wrote a post about this here:\n\nhttps://lists.w3.org/Archives/Public/public-rww/2021May/0006.html\n\nA significant innovation in recent times is that of Bitcoin, which is a web scale timestamp server. It orders records (blocks) in time, robustly and securely, creating a permanent record. It also, for the first time in history, creates a global currency that is strongly resistant to money printing by fiat.\n\nThese two systems working together could create a robust temporal backbone to the web, allowing commerce without rent seeking, and creating whole new business models that are more decentralized, and act in the interests of the users, competing with each other with better services, rather than, serving privacy intrusive monopolies.\n\n \n\n## Web 5.0\n\nWhat web 5.0 will look like, nobody knows. However the aim of the original proposal was to have both humans and machines working together. A semantic web was needed for that, to make it easier for machines to participate. Although machines are often censored or blocked on the large platforms, or, even worse, act with perverse incentives to spam users with adverts, noisy information and propaganda.\n\nOne guess about web 5.0 could be a web of machine agents, virtual assistants, working together with people to act in the interests of people. This builds on a Temporal web as machines can then evolve over time and the best ones will emerge, in an evolutionary way. Artificial Intelligence can further be folded into the system to optimize its utility to humanity.\n\nA note on web5: This was an earnest attempt to push back on web3 and remove some of the more corrupt aspects, such as copious use of money printing. It has some alignment with the web, but it is not web 5.0, however, I hope it produces something interesting. Never fight an affinity scam with an affinity scam.\n\nIMHO a promising project in this area is Nostr. It reuses the websockets standard to relay information from one user to another which is signed. Importantly, it is grass roots, as the original web was, has already integrated fast cheap payments, with bitcoin and the lightning network in many apps. Unlike the semantic web, it has a very easy developer experience which has seen high uptake from developers. Additionally, the tagging system allows integration with time chains paving a cow path for a temporal web, and then perhaps humans and agents co existing for mutual benefit. We are still early, but time will tell how the web evolves.\n\n
\n\n## Web 5.0\n\nWhat web 5.0 will look like, nobody knows. However the aim of the original proposal was to have both humans and machines working together. A semantic web was needed for that, to make it easier for machines to participate. Although machines are often censored or blocked on the large platforms, or, even worse, act with perverse incentives to spam users with adverts, noisy information and propaganda.\n\nOne guess about web 5.0 could be a web of machine agents, virtual assistants, working together with people to act in the interests of people. This builds on a Temporal web as machines can then evolve over time and the best ones will emerge, in an evolutionary way. Artificial Intelligence can further be folded into the system to optimize its utility to humanity.\n\nA note on web5: This was an earnest attempt to push back on web3 and remove some of the more corrupt aspects, such as copious use of money printing. It has some alignment with the web, but it is not web 5.0, however, I hope it produces something interesting. Never fight an affinity scam with an affinity scam.\n\nIMHO a promising project in this area is Nostr. It reuses the websockets standard to relay information from one user to another which is signed. Importantly, it is grass roots, as the original web was, has already integrated fast cheap payments, with bitcoin and the lightning network in many apps. Unlike the semantic web, it has a very easy developer experience which has seen high uptake from developers. Additionally, the tagging system allows integration with time chains paving a cow path for a temporal web, and then perhaps humans and agents co existing for mutual benefit. We are still early, but time will tell how the web evolves.\n\n \n\nOpinions are the views of the author
\n\nOpinions are the views of the author -
 @ 32e18276:5c68e245
2023-07-19 02:56:47
@ 32e18276:5c68e245
2023-07-19 02:56:47I’m so lazy I’m thinking of running the damus merch store via stateless and serverless lightning payment links. All data is collected and stored in the lightning invoice descriptions which are fetched from your node. You can do this without having to run any server code except a lightning node!
This is the same tech we used when selling merch as at bitcoin Miami. It was extremely reliable. I love these things, they are so easy. Integrating with the legacy fiat system is such a pita, It may just be a lightning-only store for now because of how simple this is. Here's what a lightning payment link looks like:
http://lnlink.org/?d=ASED88EIzNU2uFJoQfClxYISu55lhKHrSTCA58HMNPgtrXECMjQuODQuMTUyLjE4Nzo4MzI0AANgB6Cj2QCeZAFOZ1nS6qGuRe4Vf6qzwJyQ5Qo3b0HRt_w9MTIwJm1ldGhvZD1pbnZvaWNlfG1ldGhvZD13YWl0aW52b2ljZSZwbmFtZWxhYmVsXmxubGluay0mcmF0ZT04BERlYXRoIFN0YXIABQAAAGQGQW4gb2JqZWN0IG9mIHVuZmF0aG9tYWJsZSBwb3dlcgAHEwhodHRwczovL3VwbG9hZC53aWtpbWVkaWEub3JnL3dpa2lwZWRpYS9lbi9mL2Y5L0RlYXRoX3N0YXIxLnBuZwA=
How it works
The entire product page is stored as data in the url. When a customer click the link, the product info is decoded and rendered as a webpage. The data in the url includes
- The product name
- Description
- Price in sats
- Product image url
- Fields to collect data from the user
- Lightning node address
- Lightning node rune for fetching and waiting for invoice payments
This works thanks to a javascript library I created called "lnsocket". It allows you to connect to your CLN node over websockets. Once the user fills out all of the info, a new lightning invoice is fetched with this information in the description, by connecting directly to your node. This connection is end-to-end encrypted thanks to the lightning protocol itself.
To your lightning node, it looks like another lightning node is connecting to it, but in reality it's just a dumb client asking for things.
At this point, custom lightning packets called "commando" packets are sent to your node which asks your node to run certain commands. CLN authenticates these packets using the rune and then returns a response. This is pretty much the same as calling these commands directly on your lightning node, except now someone is doing it from a browser in a secure way!
Why not just run btcpayserver?
btcpayserver is cool and is more powerful, but I like exploring simpler ways to do things that don't require running lots of software which can be challenging for many non-technical people. You shouldn't have to become a server administrator to start accepting payments. It should be as simple as running a bitcoin and lightning node, pushing all of the application logic to the clients.
This is a similar philosophy to what we have in the nostr space. Let's make it easier for people to use self-sovereign tools. Everyone deserves freedom tech.
Anyways, I'm still working on https://lnlink.org. I just added images and nostr address support! You can make your own payment links here! Try it out:
http://lnlink.org/?d=ASED88EIzNU2uFJoQfClxYISu55lhKHrSTCA58HMNPgtrXECMjQuODQuMTUyLjE4Nzo4MzI0AANgB6Cj2QCeZAFOZ1nS6qGuRe4Vf6qzwJyQ5Qo3b0HRt_w9MTIwJm1ldGhvZD1pbnZvaWNlfG1ldGhvZD13YWl0aW52b2ljZSZwbmFtZWxhYmVsXmxubGluay0mcmF0ZT04BERlYXRoIFN0YXIABQAAAGQGQW4gb2JqZWN0IG9mIHVuZmF0aG9tYWJsZSBwb3dlcgAHEwhodHRwczovL3VwbG9hZC53aWtpbWVkaWEub3JnL3dpa2lwZWRpYS9lbi9mL2Y5L0RlYXRoX3N0YXIxLnBuZwA=&edit=1
-
 @ 49edd28f:90fb6d51
2021-11-07 16:58:53
@ 49edd28f:90fb6d51
2021-11-07 16:58:53We Went Back #1\n\n\n\nhttps://www.youtube.com/watch?v=sxj1H86J88U
-
 @ 3bf0c63f:aefa459d
2020-10-23 12:55:00
@ 3bf0c63f:aefa459d
2020-10-23 12:55:00\n# Parallel Chains\n\nWe want merged-mined blockchains. We want them because it is possible to do things in them that aren't doable in the normal Bitcoin blockchain because it is rightfully too expensive, but there are other things beside the world money that could benefit from a "distributed ledger" -- just like people believed in 2013 --, like issued assets and domain names (just the most obvious examples).\n\nOn the other hand we can't have -- like people believed in 2013 -- a copy of Bitcoin for every little idea with its own native token that is mined by proof-of-work and must get off the ground from being completely valueless into having some value by way of a miracle that operated only once with Bitcoin.\n\nIt's also not a good idea to have blockchains with custom merged-mining protocol (like Namecoin and Rootstock) that require Bitcoin miners to run their software and be an active participant and miner for that other network besides Bitcoin, because it's too cumbersome for everybody.\n\nLuckily Ruben Somsen invented this protocol for blind merged-mining that solves the issue above. Although it doesn't solve the fact that each parallel chain still needs some form of "native" token to pay miners -- or it must use another method that doesn't use a native token, such as trusted payments outside the chain.\n\n## How does it work\n\nWith the
SIGHASH_NOINPUT/SIGHASH_ANYPREVOUTsoft-fork[^eltoo] it becomes possible to create presigned transactions that aren't related to any previous UTXO.\n\nThen you create a long sequence of transactions (sufficient to last for many many years), each with annLockTimeof 1 and each spending the next (you create them from the last to the first). Since theirscriptSig(the unlocking script) will useSIGHASH_ANYPREVOUTyou can obtain a transaction id/hash that doesn't include the previous TXO, you can, for example, in a sequence of transactionsA0-->B(B spends output 0 from A), include the signature for "spending A0 on B" inside thescriptPubKey(the locking script) of "A0".\n\nWith the contraption described above it is possible to make that long string of transactions everybody will know (and know how to generate) but each transaction can only be spent by the next previously decided transaction, no matter what anyone does, and there always must be at least one block of difference between them.\n\nThen you combine it withRBF,SIGHASH_SINGLEandSIGHASH_ANYONECANPAYso parallel chain miners can add inputs and outputs to be able to compete on fees by including their own outputs and getting change back while at the same time writing a hash of the parallel block in the change output and you get everything working perfectly: everybody trying to spend the same output from the long string, each with a different parallel block hash, only the highest bidder will get the transaction included on the Bitcoin chain and thus only one parallel block will be mined.\n\n## See also\n\n- Drivechain\n\n[^eltoo]: The same thing used in Eltoo.\n -
 @ b12b632c:d9e1ff79
2023-07-19 00:17:02
@ b12b632c:d9e1ff79
2023-07-19 00:17:02Welcome to a new Fractalized episode of "it works but I can do better"!
Original blog post from : https://fractalized.ovh/use-ghost-blog-to-serve-your-nostr-nip05-and-lnurl/
Few day ago, I wanted to set my Ghost blog (this one) as root domain for Fractalized instead of the old basic Nginx container that served my NIP05. I succeed to do it with Nginx Proxy Manager (I need to create a blog post because NPM is really awesome) but my NIP05 was down.
Having a bad NIP05 on Amethyst is now in the top tier list of my worst nightmares.
As a reminder, to have a valid NIP05 on your prefered Nostr client, you need to have a file named "nostr.json" in a folder ".well-known" located in the web server root path (subdomain or domain). The URL shoud look like this http://domain.tld/.well-known/nostr.json
PS : this doesn't work with Ghost as explained later. If you are here for Ghost, skip this and go directly to 1).
You should have these info inside the nostr.json file (JSON format) :
{ "names": { "YourUsername": "YourNPUBkey" } }You can test it directly by going to the nostr.json URL, it should show you the JSON.
It was working like a charm on my previous Nginx and I needed to do it on my new Ghost. I saw on Google that I need to have the .well-known folder into the Ghost theme root folder (In my case I choosed the Solo theme). I created the folder, put my nostr.json file inside it and crossed my fingers. Result : 404 error.
I had to search a lot but it seems that Ghost forbid to server json file from its theme folders. Maybe for security reasons, I don't know. Nevertheless Ghost provide a method to do it (but it requires more than copy/paste some files in some folders) => routes
In the same time that configuring your NIP05, I also wanted to setup an LNURL to be zapped to pastagringo@fractalized.ovh (configured into my Amethyst profile). If you want more infromation on LNURL, it's very well explained here.
Because I want to use my Wallet of Satoshi sats wallet "behind" my LNURL, you'll have to read carefuly the EzoFox's blog post that explains how to retrieve your infos from Alby or WoS.
1) Configuring Ghost routes
Add the new route into the routes.yaml (accessible from "Settings" > "Labs" > "Beta features" > "Routes" ; you need to download the file, modify it and upload it again) to let him know where to look for the nostr.json file.
Here is the content of my routes.yaml file :
``` routes: /.well-known/nostr.json/: template: _nostr-json content_type: application/json /.well-known/lnurlp/YourUsername/: template: _lnurlp-YourUsername content_type: application/json collections: /: permalink: /{slug}/ template: index
taxonomies: tag: /tag/{slug}/ author: /author/{slug}/ ```
=> template : name of the file that ghost will search localy
=> content_type : file type (JSON is required for the NIP05)
The first route is about my NIP05 and the second route is about my LNURL.
2) Creating Ghost route .hbs files
To let Ghost serve our JSON content, I needed to create the two .hbs file filled into the routes.yaml file. These files need to be located into the root directory of the Ghost theme used. For me, it was Solo.
Here is there content of both files :
"_nostr-json.hbs"
{ "names": { "YourUsername": "YourNPUBkey" } }"_lnurlp-pastagringo.hbs" (in your case, _lnurlp-YourUsername.hbs)
{ "callback":"https://livingroomofsatoshi.com/api/v1/lnurl/payreq/XXXXX", "maxSendable":100000000000, "minSendable":1000, "metadata":"[[\"text/plain\",\"Pay to Wallet of Satoshi user: burlyring39\"],[\"text/identifier\",\"YourUsername@walletofsatoshi.com\"]]", "commentAllowed":32, "tag":"payRequest", "allowsNostr":true, "nostrPubkey":"YourNPUBkey" }After doing that, you almost finished, you just have to restart your Ghost blog. As I use Ghost from docker container, I just had to restart the container.
To verify if everything is working, you have to go in the routes URL created earlier:
https://YourDomain.tld/.well-known/nostr.jsonand
https://YourDomain.tld/.well-known/lnurlp/YourUsernameBoth URL should display JSON files from .hbs created ealier.
If it's the case, you can add your NIP05 and LNURL into your Nostr profile client and you should be able to see a valid tick from your domain and to be zapped on your LNURL (sending zaps to your WoS or Alby backend wallet).
Voilààààà
See you soon in another Fractalized story!
-
 @ 7e7224cf:d8febb7d
2023-07-18 20:19:29
@ 7e7224cf:d8febb7d
2023-07-18 20:19:29Hey bitcoiner!

This week, 13 years ago Bitcoin was first mentioned on Slashdot, which led to a major influx of new users.
nostr:note1pkcyqa7j0tld94ff435zdatyr9cr569d3xu5l7quaqc3hn9wwq6ssc8xuz
Hot Off the Press:
🚀 Bitcoin ETF Gets the Green Light for Applications from SEC
⚡️ Binance Brings Lightning Network Onboard
👁️ Big Brother Alert in Brazil
🤑 Funding Bitcoin Projects
🇪🇺 Europe Gears Up for Its First Spot Bitcoin ETF This Month
💖 A Bitcoin Tale That Will Melt Your Heart
🎬 Spotlight on Nostr: The Documentary
⚡️ Matching Zaps
🤐 EU's Crackdown on Free Speech?
👨💻 Fresh Releases
Mempool:

Lightning:

Mining:


🚀 Bitcoin ETF Gets the Green Light for Applications from SEC
The SEC is now taking Bitcoin ETF applications!

Guess what? The SEC just gave the thumbs up to Blackrock's Bitcoin ETF application, hinting at a broader acceptance of Bitcoin. Now, it's time for the review process and some public chit-chat about the proposal. With Blackrock, the world's biggest asset manager, in the game, it's clear that Bitcoin-based investment goodies are on the horizon in the U.S.
This exciting news comes amidst the SEC playing the tough cop with platforms for alleged securities law no-nos. Blackrock has picked Coinbase as the babysitter for its Ishares Bitcoin Trust, adding a dash of surveillance-sharing agreement to its filing.
Despite past rejections due to worries about market manipulation and investor protection, the Bitcoin world is buzzing with hope as more ETF applications, including one from Bitwise, are getting the nod.
Remember, folks! Not your keys - not your coins. Self-custody is the key to truly owning and controlling your Bitcoin. Without it, we can't fully embrace the decentralized spirit of Bitcoin and the financial freedom it promises.
⚡️ Binance Brings Lightning Network Onboard
Binance says "Hello!" to the lightning network
https://twitter.com/binance/status/1680777249090576385
Binance has rolled out the red carpet for the Lightning Network for BTC withdrawals and deposits, offering users a speedy and wallet-friendly transaction experience. Users can now pick "LIGHTNING" from the menu for Bitcoin transactions, along with other options. This move comes hot on the heels of the recent spike in BTC network fees, and Binance is joining the Lightning Network party along with other exchanges.
The biggest exchange integrating the Lightning Network could be a game-changer for Lightning Network adoption. As more users get a taste of faster and cheaper transactions, they might be tempted to dive deeper into this layer-2 scaling solution. Bringing the Lightning Network to the masses through such exchanges is a giant leap towards wider adoption and unlocking Bitcoin's scalability and efficiency potential. Find out more about Lightning here.
🇪🇺 Europe Gears Up for Its First Spot Bitcoin ETF This Month
Europe is all set to roll out its first spot Bitcoin ETF this month

Europe's maiden Bitcoin exchange-traded fund (ETF), which was scheduled to take off last year but got held up due to market weather, is now ready for takeoff this month, thanks to Jacobi Asset Management. This isn't your regular digital assets exchange-traded product that's structured as exchange-traded notes (ETNs). Nope, this ETF gives you direct ownership of the underlying assets and says "No, thank you!" to counterparty risks that come with derivatives.
Even with the handy-dandy ETFs, folks, don't forget to keep a tight grip on your private keys. Self-custody is the golden ticket to truly owning and securing your digital assets, keeping in step with the decentralized beat of Bitcoin. As we welcome regulated financial products like ETFs, let's not lose sight of the importance of holding our own keys. More on self-custody can be found here.
👁️ Big Brother Alert in Brazil
Brazilian CBDC might give the government the keys to its citizens' funds.

Brazil's central bank has unveiled the source code for its Central Bank Digital Currency (CBDC) pilot on GitHub, inviting the public to take a peek under the hood. But, developers stumbled upon some eyebrow-raising functions that could give the central bank the reins to individual wallets and their funds. These functions include the power to freeze and unfreeze wallets, shuffle funds around, and hit the pause button on transfers.
The central bank has admitted that these functions are part of the test drive, but it's still a mystery if they'll make it to the final cut. Some folks in the Bitcoin community are getting the jitters that CBDCs could put a damper on financial freedom and privacy. Critics, including Edward Snowden, are branding CBDCs as "crypto fascist currencies" that pose a threat to financial sovereignty and savings.
Bitcoin was born to offer an alternative to the traditional monetary system, with a big emphasis on financial sovereignty and privacy (see Satoshi's original post on p2p foundation here). CBDCs with such a high level of centralized control are setting off alarm bells about individual rights and privacy. While governments make the case that these measures are needed to tackle illicit activities, we need to keep our eyes wide open to safeguard our financial independence and protect our privacy in the digital era.
🤑 Funding Bitcoin Projects
OpenSats funds independent Bitcoin projects

OpenSats aims to fulfill Hal Finney's vision of using computers as tools to liberate and protect people instead of controlling them. OpenSats announced grants for numerous projects in the Bitcoin and Lightning ecosystem. These open-source projects, including Payjoin Dev Kit, Raspiblitz, BTCPay Server, and more, will receive funding to develop and improve tools that empower individuals and promote financial autonomy.
Thanks to Bitcoin's decentralized nature, anyone can sponsor and support projects they believe in without restrictions. This democratized funding approach allows innovative tools to flourish, fostering a community-driven ecosystem that prioritizes individual empowerment and privacy. The projects chosen by OpenSats exemplify the potential of creating a future where technology truly serves the people and enhances their freedom.
💖 A Bitcoin Tale That Will Melt Your Heart
Bitcoiners rally to raise $8k+ in just 6 hours for a woman in need
nostr:note1y2wjvxafyfevj7urlzyrfklszju7g6fc5sus257g89ymjh9efxmsntwlcd
In a heartwarming display of unity, Bitcoiners from every corner of the globe pulled together over 300 donations in just 6 hours, amassing a whopping $8k+ US. The recipient was Estela, a vendor in a market, who was left speechless by the generous Bitcoin gift that landed in her wallet. She was deeply moved by the wave of support that came flooding in from strangers worldwide.
Bitcoin's magic isn't just about making money; it's about making a difference. It gives people the power to back the causes they believe in and bring about positive change in their communities. This touching story is a reminder that at the heart of Bitcoin is the ability to foster a sense of community and goodwill, enriching the lives of people from all walks of life. It's a shining example of the true power of Bitcoin and the united spirit of bitcoiners around the world.
Byte-size buzz
-
Bitcoin mining difficulty reached a new ATH of 53.91T.
-
Lightning Network capacity dropped by a whopping 580 BTC due to River’s planned channel housekeeping.

Nostr Recap by Primal
nostr:note1vh2lekw94xvudjrhv7cmgmk43ssr4kdsz39vcx5ererxwaue4mfshm2h00
🎬 Spotlight on Nostr: The Documentary
The curtain rises on the first Nostr documentary.
Max DeMarco, a well-known YouTuber, Bitcoiner, and Nostr fan, has unveiled the first-ever Nostr documentary, featuring star appearances from Jack Dorsey, Rabble, and other notable nostriches. This documentary is a must-watch for newcomers and those who are just dipping their toes into the world of Nostr.
“Most people agree that Social Media is broken and that we need to find new solutions. I embarked on a journey to find out more about a new invention called NOSTR. Join me and see how I was able to understand more about that technology.” - Max DeMarco
What's even more fascinating is that while Twitter has rolled out its program to back content creators, Max hasn't seen a dime from his film there. Meanwhile, Nostr users have showered him with a cool 7M sats in appreciation for the value he delivered. All voluntarily, without any reliance on algorithms or middlemen. If this isn't the future of online interactions, then what is?
nostr:note1480zn0uz8g82varzf5mfjleqerqk86xqgwhpdrhut873s8jsar2ss5p9mf
Content like this is priceless, especially at this early stage, when most people are still in the dark about Nostr's existence, and some haven't even spotted any cracks in traditional social media platforms. Sure, Nostr is much more than just social media, but let's take it one step at a time and bring people onboard.
⚡️ Matching Zaps
ZapplePay Amps Up FOSS Support with Matching Zaps
nostr:note14esxgcj9us8ax5v92n8vte9uxgv4ry88rhrnzvh6f3gtlf49w64q4923vr
ZapplePay, the savvy solution to Apple's restrictions, has unveiled an exciting new feature - the ability to send a matching zap to Damus and/or OpenSats. This brilliant initiative is aimed at championing open source software and boosting awareness of both value-4-value and lightning.
While you are waiting for the arrival of more matching zap options, we encourage you to have a look at Tony's guide on ZapplePay here.
🤐 EU's Crackdown on Free Speech?
Social media platforms could face shutdowns for not removing government-unapproved content.

The EU's top brass might soon be pulling the plug on social media giants like TikTok and Snapchat for not being strict enough on troublesome content during riots. This startling revelation came from the EU's Internal Commissioner, Thierry Breton.
Under the upcoming Digital Services Act, social media platforms will be walking a tightrope. If they fail to promptly delete content that stokes violence or promotes harmful activities, they could face immediate sanctions, including potential bans.
Nineteen major online platforms, including TikTok, Snapchat, Instagram, and Twitter, will have to up their game to limit the spread of illegal and harmful content. If they fail, they could be hit with fines of up to a whopping 6 percent of their global revenue.
These guys are the best marketing team Nostr could ever dream of. Given the current global circumstances, people will naturally understand the significance of Nostr. They'll start seeking out platforms where they can communicate and express their thoughts freely. Given that there's no second-best, it's inevitable that everyone and everything will gravitate towards Nostr. Our primary task now is to gear up to manage the incoming surge.
Byte-size Buzz:
- Nostr.build increased free video uploads size to 25MB.
nostr:note1w4k3c0atweqa92rsk420pemjkqca9qcmaekm2ttfxjmdyl8d4ghsyh8f58

Bitcoin
-
Mutiny Wallet has made its beta publicly available. Check out the announcement and get the lowdown on the wallet here.
-
Zeus will no longer require users to run a Lightning Node to use the wallet.
nostr:note1zjzmg39ltv4j4tvcx5hez4fyph4ad4djznp55kt6mjef6w68fegqgs0q7v
-
Phoenix has introduced the 3rd generation of its self-custodial Lightning wallet.
-
With Bisq's latest update v1.9.12, you can now clone existing offers while sharing its maker fee and security deposit.
-
Peach Bitcoin's latest update allows users to change discount/premium after funding the escrow and now supports Liquid.
Nostr
-
Primal for iOS has roared into action and is now available on TestFlight. Get a sneak peek at the app by DOC of Nostr Report: https://habla.news/nostreport/primal-testflight-review
-
Damus' TestFlight update has introduced support for long-form notes, banner editing, multi-lingual hashtags, and more!
-
Nostr Band's Embed widget now displays user’s follows in a profile view:
-
Nostr Wallet Connect is now available on the Umbrel App Store.

Halving 101
A quick look at Bitcoin halving by nostr:npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u:

-
*“AgoraDesk overview. A Peer-to-Peer Cryptocurrency Marketplace.” Follow this link for a guide.
-
*“ZapplePay: Zap Even if They Say It’s Forbidden.” A guide on going around Apple’s note zaps restrictions by Tony.
-
*“A vision for content discovery and relay usage for basic social-networking in Nostr” by Fiatjaf: https://fiatjaf.com/3f106d31.html

-
Capital in the 21st Century [Allen Farrington] read by Guy Swan. Listen on Fountain.
-
Plebchain Radio - Max DeMarco discusses his Nostr Documentary. Listen on Fountain.
New to Fountain? Support Herald by downloading the app via this referral link.

Ostrich Work
The first and best Nostr Jobs board on the internet by nostr:npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc
“Ostrich Work is the first Nostr-native job board. Both for people looking to hire or work on Nostr projects but also because the jobs themselves are Nostr events (a new kind: 30402 event, in fact).”
The best place to find a Nostr-related job, or to search for a specialist to power your project.
Website: https://ostrich.work/
Obtainium
“Obtainium allows you to install and update Open-Source apps directly from their releases pages, and receive notifications when new releases are made available” – Derek Ross
GitHub repo: https://github.com/ImranR98/Obtainium
-
-
 @ 9a576bd9:538775f4
2023-07-18 15:11:38
@ 9a576bd9:538775f4
2023-07-18 15:11:38We are proud to announce that No Trust Verify now offers a Whoogle instance. search.notrustverify.ch is hosted in Switzerland and provides easy, privacy-friendly access to Google search engine results.
Why Woogle ?
-
No ads or sponsored content
-
No JavaScript
-
No cookies
-
No tracking/linking of your personal IP address
-
No AMP links
-
No URL tracking tags (i.e. utm=%s)
-
No referrer header
-
Tor and HTTP/SOCKS proxy support
-
Autocomplete/search suggestions
-
POST request search and suggestion queries (when possible)
-
View images at full res without site redirect (currently mobile only)
-
Light/Dark/System theme modes (with support for custom CSS theming)
-
Randomly generated User Agent
-
Duckduckgo-style bang (i.e.
!<tag> <query>) searches -
Optional location-based searching (i.e. results near <city>)
-
Optional NoJS mode to view search results in a separate window with JavaScript blocked
Firefox
To use search.notrustverify.ch as a search engine, simply go to search.notrustverify.ch and right-click on the address bar, then "Add Whoogle Search".
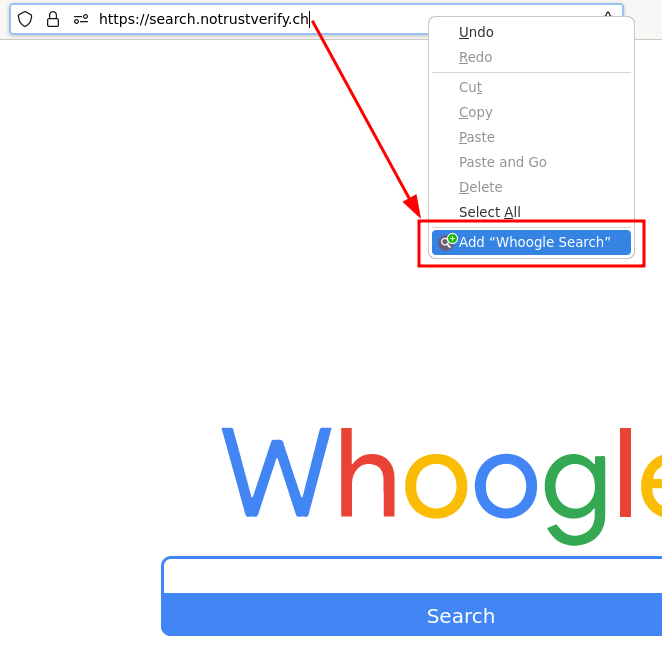
To use search.notrustverify.ch as your default search engine, go to Settings, "Search" and under "Default search engine", select "Whoogle".
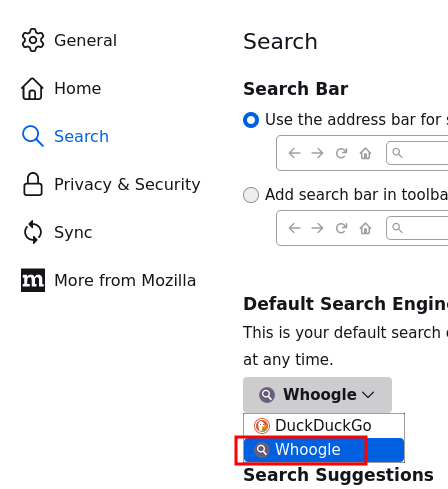
Chromium
For Chromium-based browsers such as Brave or Chrome, go to search.notrustverify.ch and in the URL bar, right-click and select "Manage search engines and site search".
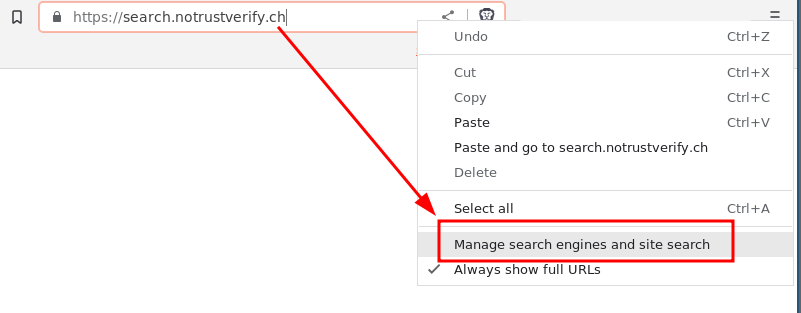
Then under "Search site" select "Add".
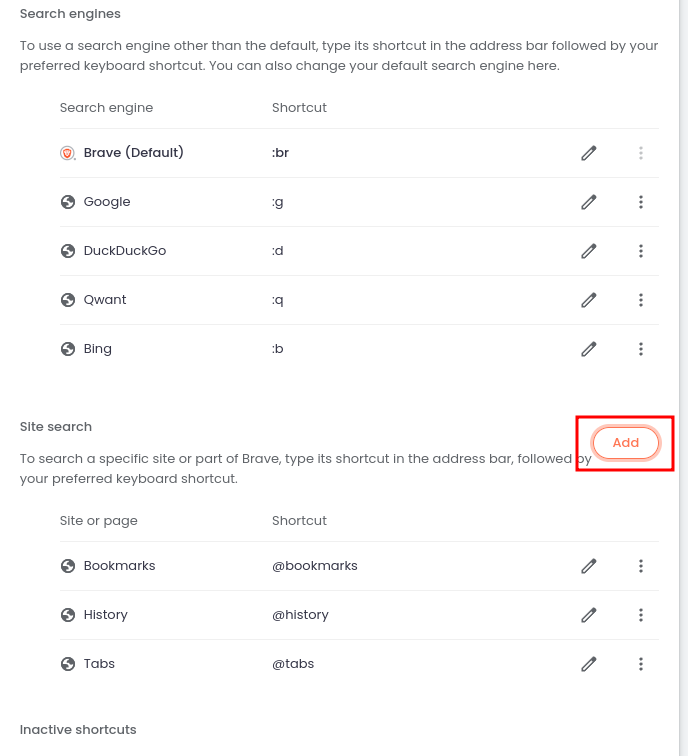
And enter the following values
-
Search engine: Whoogle
-
Shortcut: :wo:
-
URL with %s...: https://search.notrustverify.ch/search?q=%
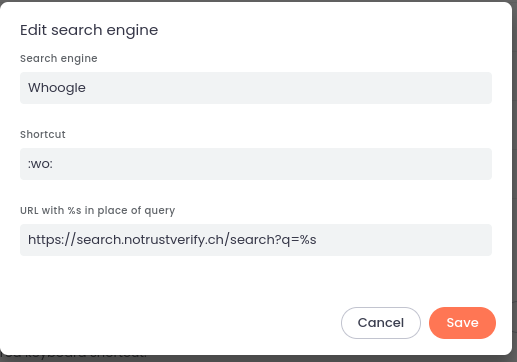
And finally, set Whoogle as the default search engine
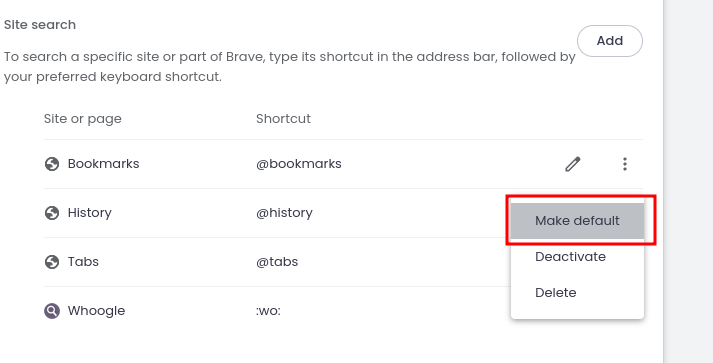
About No Trust Verify
We are members of the #VerifyValley. We support the Nym Technologies network and contribute to it since the testnet. We are happy to strengthen the mixnet with our mixnodes and our gateways.
Developer of pastenym.ch and isnymup.com
✅ Hosted in Switzerland
✅ Guaranteed commission: 5%.
✅ Bandwidth: 10 Gbit/sIdentity keys:
NTV1 : APxUbCmGp4K9qDzvwVADJFNu8S3JV1AJBw7q6bS5KN9E
NTV2 : 4yRfauFzZnejJhG2FACTVQ7UnYEcFUYw3HzXrmuwLMaR
NTV3 : ESPa5xnwZ7BebSX9SGmUbeYgNtkUeJo8PtbBx7JhzEHA
Do not hesitate to contact us:
-
-
 @ 3f770d65:7a745b24
2023-07-18 14:24:15
@ 3f770d65:7a745b24
2023-07-18 14:24:15We say that Stackchain is the gamification of buying bitcoin, however it’s much larger than that. It’s about building. It’s more than just Bitcoiners having fun in a bear market, stacking sats, doing what they were going to be doing anyway. It’s about building a community. Who would have known that the simple act of buying bitcoin, creating memes, and having laughs would have grown into the phenomena that it is today? No one could have foreseen the community and the relationships that have been built, all because of Stackchain.
This is the story of two Bitcoiners that met through Stackchain and ended up building a Nostr business together.
Last year during the early days of Stackchain, I met a fellow Stackchainer who just seemed to click with me. His name was Semisol. We seemed to get along great, have lots of laughs, and we both wanted to build with Stackchain. We wanted to take our Stackchain passion and technical skills to grow Stackchain, to help it flourish. Together, we brainstormed about how to build a website for Stackchain, we wanted to build an application so that Stackchain could survive off of Twitter, to make Stackchain its own platform. As a former entrepreneur, this truly excited me. While our hearts and our minds were in the right place, Stackchain wasn’t ready for this.
In the beginning, we saw Stackchain’s potential to grow and we tried to steer Stackchain with growth plans and business proposals. It took us a while to realize that no one can control Stackchain and especially in the early days, it was way too hard to even suggest moving forward with anything. That is, except for our beloved Stackjoin proposal. Everything else flopped.
In the end, Semisol, as a talented developer, moved on to other areas of interest, where he could contribute, and grow a platform. He reached out to me several times and told me to try something called Nostr. I gave Nostr a try and laughed at him. I told him that Nostr was barely usable, had a horrible user experience, and just was not worth my time. I didn’t realize that we just didn’t need to build it.
Fast forward a few months later and I noticed several Bitcoin developers were talking about Nostr, which even managed to gain the attention of Jack Dorsey. In mid-December 2022, I tried Nostr again. This time it clicked with me. Nostr was to social communication what Bitcoin was to money. Decentralized. Censorship resistant. Open source. People were building.
After reading and studying the protocol, I quickly realized that I was able to provide a service for not only myself to utilize, but also for many of my Stackchain friends that were starting to get curious about Nostr. I bought the domain name nostrplebs.com and started Nostr Plebs, a Nostr service provider. Nostr Plebs was filling a need for both myself and the Nostr ecosystem. I was able to build, to feel like I was contributing to the space and through this, provide a service that was wanted and needed by others. My entrepreneurial thirst was quenched. I finally had my Bitcoin adjacent business.
Nostr Plebs was an instant and overwhelming success. I clearly needed help. I immediately thought about my old Stackchainer friend, Semisol. Based on our previous conversations, I knew that he not only had the drive to build a service, but also had the technical skills needed. Together, we built the first NIP-05 ID service provider for Nostr. Together, we continue to grow our Nostr services, providing microservices to help grow the Nostr ecosystem. From ID services, to email, to Lightning addresses, to directory services, to audio communications, Nostr Plebs is a prominent name in the Nostr ecosystem.
Stackchain allowed two like minded Bitcoiners to find one another, discuss their passions and skills for building, and to ultimately build a service provider together. Due to all of this, I say Stackchain is beautiful. It’s beautiful because we’re not the only ones building. Stackchain embodies builders. Whether you’re building Stackchain content, building your bitcoin stack, building the community, or branching out and building new businesses, it all started with a simple $5 bitcoin purchase. That’s the beauty of it.
This article is featured in Stackchain Magazine Volume One, launching on July 18, 2023. You can order your copy today at Proof of Ink.
-
 @ 75bf2353:e1bfa895
2023-07-17 23:34:04
@ 75bf2353:e1bfa895
2023-07-17 23:34:04The Orange Pill App is an app that helps you meet bitcoiners. It started off being marketed as a dating app, but there are not a lot of women on it so it's morphed into more of bitcoin friend meeting app in my opinion. This is great for me since I am married with children. I even have a grandchild. I bought a yearly membership for 100k sats. They offer a lifetime membership for 500k sats. This is essentially a paywall. I have written about paywalls in the context of blogs. TL;DR: Paywalls suck. They require you to pay a fee before you even know if the article or product has any value. The reason why I feel a bit different about the OPA Paywall is more of a classified ad. I could make a post on Craigslist asking to meet bitcoiner friends, but this probably won't work. I could sign up for a meetup.com account but they don't accept my simplelogin address. I need a whitelisted email, so it's not very censorship resistant. Besides, I have found that many of these meetups attract memecoiners, yam-swappers, and blockchain, not bitcoin bros. Maybe an orange pill app secretly holds Monero or evangelizes Ethereum, but they are told that this app is for bitcoiners and bitcoiners only. It's like an online country club for Holders.
At first, I had some trouble meeting people because it was awkward. Here's how it went. WOW! There's a guy who lives ten miles away from me that is really into bitcoin. I should talk to him and ask him out for coffee. Then I thought that sounds kinda gay. I felt like I was asking a dude out on a date. I'm no homophobe, and I'm rooting for Anita Posh. but I'm not interested in dating dudes. I'm also not interested in dating women because I'm married, but I do want to make local bitcoin friends.

The Good
Since Meetup-dot-com blacklisted my email service provider, I got the idea to use the Orange Pill App to start my own meetup.
-
I made a website
-
Hosted it over nostrsites.com/riversidebtc
-
Hosted it over TOR
-
Created a vanity nostr key.
-
Created a nostr chat.
-
I created a matrix room
-
I created a "keet up"
I hosted my first meetup by adding it to the nostrchat. Someone showed up. I listed the next meetup on the Orange Pill App. More people are interested in attending the next meetup. These people are ride-or-die freaks willing to pay for a service that connects them to other bitcoiners. That's great. Most of us have friends and family that are exhausted of us talking about bitcoin so much. I know my wife is. For these reasons, I have come to love the orange pill app.
The Bad

By the way, they are not a sponsor of this blog. I don't want them to be because I want my writing to be free from undue influence. This way I can also tell you about some of the risks involved with using an app that uses your location data. To be fair, they do not give your exact location. According to the website, it only gives your location within a 1/8 of a mile.
That's a little concerning. I would rather it tell other people the city I live in instead of my approximate location. Physical Bitcoin attacks are rare, but Jameson Lopp has a list on GitHub that keeps on growing.
https://github.com/jlopp/physical-bitcoin-attacks/blob/master/README.md
Mitigate risk
If you use the orange pill app, it's best to meet people at a public place and be careful what information you reveal. Don't drive flashy cars or wear a fancy watch. Wear humble clothes that don't say THIS DUDE LOVES BITCOIN, ASK HIM WHERE HE KEEPS HIS KEYS.
Keep your actual location secret, I am an avid bicyclist. I'm not doing the Tour De Dope anytime soon, but ride about 5 days a week. I give location permission to the app only when I use the app. Therefore the app shows the approximate location of 5-10 miles away from my house. It's not perfect and I am not paranoid. It's just that bitcoin has taught me to think adversely and increased my game theoretical awareness of the world. I know a physical attack is unlikely. I also use multisig so I don't even have access to more than a few million sats at a time.
Of course, it should be obvious that you should meet at a public place and not dox your address. That's why I think starting a meetup is a good way to accomplish this. I almost had two people attend my last meetup, but the other person got there after we already left. If you do start a meetup, it makes sense to add a start and end time. I had to learn this the hard way because I'm really just winging it. Bitcvoiners are the smartest people I know so I'm sure you'll learn from my mistakes.
Build A Bitcoin Community

I urge you to join the orange pill app. One guy going around town putting tipcards from tipcard.io into tip jars around town is crazy. If 15 or 20 people do it, we are a movement. I am in this as an opposition to fiat and draconian central banks more concerned with printing money to fight wars, hand out free money to businesses, peanuts and lock-downs for plebs. We now see the cost of these government actions via high inflation. It's time to promote a decentralized alternative to central banking. After writing about bitcoin for over a year, I have learned that one man cannot do it alone. We need a group of principled men and women fighting for a new system that cannot be manipulated by political whim.
I'm no lefty. I came into bitcoin from a libertarian perspective, but there are millions of people in the United States that feel like something is wrong. I started reading the Progressive Case For Bitcoin and realized Jason talks about many of the same things Libertarians talk about. We say the Cantillon effect, and the progressives say wealth inequality. These are the same thing.
We analogize bitcoin to The Matrix so often because that movie has a great motif. The money is manipulated, but Adam Smith's description of the invisible hand is scapegoated. The Federal Reserve, Bank of England, or Bank of Venezuela are not invisible. They are big, fat visible hands. In a world where wealth inequality, un-affordable housing, and higher grocery bills, we can't just wait for our politicians to fix these things.
We need to build strong communities to address these issues on a local level. Elizabeth Warren talks a lot about Wealth Inequality, but she's funded by the banksters. We need to promote bitcoin as the solution to wealth inequality. You will not receive permission to launch an IPO. The Catillionaire politicians will not save you. The government cannot help you. We can only help ourselves.
Bitcoin fixes this. We don't need to tell people to pick themselves up by their bootstraps. We need to teach people how to circumvent the invisible theft of the visible hand that rules us all. We can offer an alternative to the fiat fuckery. We can save our peanuts in bitcoin until those peanuts become real wealth after a decade or two. You don't need permission to do this. Your wealth does not need to be based on your credit score, how much your family has saved for you to buy a house, or pay for college. You are not wasting your money on rent if you stack sats. Let's build communities to teach people how to do this.
Find Bitcoiners in your own community and build.
Blogging Bitcoin
Block Height: 799145
This blog is ad free and is written using the Value4Value model. Zaps and website bookmarks are appreciated. Check out my store
-
-
 @ b12b632c:d9e1ff79
2023-07-17 22:09:53
@ b12b632c:d9e1ff79
2023-07-17 22:09:53Today I created a new item (NIP05) to sell into my BTCpayserver store and everything was OK. The only thing that annoyed me a bit is that when a user pay the invoice to get his NIP on my Nostr Paid Relay, I need to warn him that he needs to fill his npub in the email info required by BTCpayserver before paying. Was not so user friendly. Not at all.
So I checked if BTCpayserver is able to create custom input before paying the invoice and at my big surprise, it's possible ! => release version v1.8
They even use as example my need from Nostr to get the user npub.
So it's possible, yes, but with at least the version 1.8.0. I checked immediately my BTCpayserver version on my Umbrel node and... damn... I'm in 1.7.2. I need to update my local BTCpayserver through Umbrel to access my so wanted BTCpayserver feature. I checked the local App Store but I can't see any "Update" button or something. I can see that the version installed is well the v1.7.2 but when I check the latest version available from the online Umbrel App Store. I can see v1.9.2. Damn bis.
I searched into the Umbrel Community forum, Telegram group, Google posts, asked the question on Nostr and didn't have any clue.
I finally found the answer from the Umbrel App Framework documention :
sudo ./scripts/repo checkout https://github.com/getumbrel/umbrel-apps.gitSo I did it and it updated my local Umbrel App Store to the latest version available and my BTCpayserver.
After few seconds, the BTCpaysever local URL is available and I'm allowed to login => everything is OK! \o/
See you soon in another Fractalized story!
-
 @ 32e18276:5c68e245
2023-07-17 21:55:39
@ 32e18276:5c68e245
2023-07-17 21:55:39Hey guys!
Another day, another TestFlight build. This fixes many mention bugs and includes bandwidth improvements.
During nostrica, jack told everyone to open their phones and say GM to fiatjaf. This actually brought down nostrica's wifi! Damus is really dumb when it first opens and makes many requests. Sometimes hundreds (nip05 validation, etc). This build fixes all those issues. Damus will no longer:
- Make hundreds of nostr address validation requests.
- Make tons of duplicate lnurl requests when validating zaps
nostr address validation only happens when you open someones profile now.
This build also fixes some annoying mention issues. If you forget a space when mentioning someone, it will automatically add it.
I've also removed the restriction where you were not allowed to login to "deleted" accounts. This was way too confusing for people, and logging into a deleted account will allow you to reset the profile information and get it going again. You're welcome NVK.
Another thing that was added in this build is support for
_usernames in nostr addresses. This will hide your full nostr address username when used. Damus will also hide your username if it matches your profile username. Damus always did this before but it was incorrect. Now it will show your full nostr address (nip05) with its proper username. You can stop bugging me about this now Semisol.Last but not least there are some small tweaks to longform note padding. Nothing too crazy but it does make notes like this look less cramped.
Until next time!
Added
- Show nostr address username and support abbreviated _ usernames (William Casarin)
- Re-add nip05 badges to profiles (William Casarin)
- Add space when tagging users in posts if needed (William Casarin)
- Added padding under word count on longform account (William Casarin)
Fixed
- Don't spam lnurls when validating zaps (William Casarin)
- Eliminate nostr address validation bandwidth on startup (William Casarin)
- Allow user to login to deleted profile (William Casarin)
- Fix issue where typing cc@bob would produce brokenb ccnostr:bob mention (William Casarin)
-
 @ 619af6a6:6d3bdf23
2023-07-23 01:20:10
@ 619af6a6:6d3bdf23
2023-07-23 01:20:10Neste artigo irei mencionar os motivos pelos quais eu abri uma conta no Xapo Bank e porque eu acho que todos os bitcoiners que gostariam de se desfazer das moedas fiat fracas, para viver de dólar/bitcoin deveriam fazer o mesmo.
Algumas características do Xapo Bank?
O Xapo Bank recentemente converteu seu produto em um Banco regulado em Gibraltar e que possui algumas características interessantes, por ex:
-
O Banco faz parte do "Fundo Garantidor de Crédito" de Gibraltar, que tem um seguro que garante o recebimento do valor equivalente a 100k euros nos depósitos em dólar no caso por ex de falência do Banco. Obs. Os depósitos em Bitcoin não possuem essa garantia.
-
Stablecoins de USDC e USDT são aceitas e são automaticamente convertidas para USD com a garantia do "Fundo Garantidor de Crédito". É possível também enviar o saldo de USD para endereços externos de USDC e USDT.
https://nostr.build/i/nostr.build_ec9ec721369c4fa2eaa77ea99825b6b25d97dc76e57b053490da8783fbdbb875.jpg
- Os juros recebidos dos depósitos USD são pagos em bitcoin (Sats), o que demonstra o propósito do Xapo Bank de estimular o usuário a poupar em Bitcoin e gastar em Dólar. Obs. Você pode a qualquer momento, caso deseje, converter os sats recebidos dos juros para USD.
https://nostr.build/i/nostr.build_fb9049e6bfc0e27705f82295bf341b59e72dda08ac5e8fc43465d18015717fe6.jpeg
- O Xapo Bank tem integração com a rede relâmpago (lightning network), permitindo enviar o saldo em BTC para pagar faturas lightning, limitado a um valor de 100 dólares por fatura. Em entrevistas recentes eles afirmaram que pretendem permitir pagar faturas lightning não somente com o saldo em BTC mas também com o saldo em US. Obs. Atualmente não é permitido depositar na conta Xapo usando a lightning.
https://nostr.build/i/nostr.build_1187cdd8fbff0d868672b71f203868ce5fe0622cf1480ed08081443aa6bd4bb8.jpg
-
Se você possuir tanto USD e Bitcoin na conta Xapo e usar o cartão fornecido por eles, o valor sempre irá sair da conta de USD, o que demonstra o propósito do Xapo Bank de estimular o usuário a poupar em Bitcoin e gastar em Dólar. Obs. Caso você possua somente saldo em BTC e usar o cartão, o valor será automaticamente convertido do saldo em BTC para USD e a compra será realizada sem problemas.
-
Tenho usado o cartão do Xapo aqui no Brasil e tem funcionado perfeitamente, existe um spread mínimo de aproximadamente 1% na conversão de dólar ou bitcoin mas que é compensado pelo cashback em bitcoin de 1.1%. Obs. No Brasil o cartão do Xapo só funciona no crédito, apesar de ser um cartão de débito, acredito que todos cartões emitidos no exterior funcionam dessa forma.
https://nostr.build/i/nostr.build_2d8999c09b34b27dd2aaa399a23342baabdb007ed879f3d2e932e6eeda882b61.jpeg
-
O Xapo Bank não usa os recursos dos usuários para emprestar para outros usuários. Eles investem os dólares em títulos de curta duração e repassam até 80% dos juros recebidos para os clientes.
-
A conta Xapo cobra uma anuidade de 150 dólares, que acho justa pela qualidade e pelos serviços prestados. Os três primeiros meses não tem taxa e você pode inclusive solicitar o cartão físico sem taxa.
-
Mesmo o Banco funcionando em Gibraltar, onde a moeda oficial é a Libra, eles aceitam depósito em GBP e EUR mas ambas as moedas são automaticamente convertidas para USD.
O Xapo Bank é um banco pró-bitcoin?
Tenho razões para acreditar que o Xapo Bank prepara seus produtos com a visão de tornar o bitcoin uma moeda amplamente usada no futuro, exemplo disso são os juros pagos em bitcoin, o cashback em bitcoin também, a integração com a rede relâmpago (lightning network) e o estímulo para usar atualmente USD ao invés de bitcoin nos gastos do cartão, incentivando o uso da moeda fraca (USD) para gastos do dia dia e o bitcoin como reserva de valor. Recentemente o CEO do Xapo publicou um artigo listando motivos pelos quais ele acredita que o dólar continuará sendo a moeda de reserva do mundo, que pode ser lido aqui: https://www.xapobank.com/blog/the-us-dollar-versus-emerging-market-currencies. Eu especulo que a intenção do Xapo Bank é focar em Dólar e Bitcoin e não fornecer nenhuma outra moeda no serviço deles e, caso forneçam, seriam somente como forma de depósito, com conversão automática para Dólar, como já ocorre no caso das moedas GBP e EUR. Talvez no futuro eles aceitem outras altcoins que seriam automaticamente convertidas para Bitcoin. Mais razões pelos quais o Xapo Bank é um serviço pró-bitcoin:
-
O fundador e chairman do Xapo Bank é o empreendedor e investidor argentino Wences Casares, que é um bitcoiner antigo na comunidade e que acredita bastante no bitcoin.
-
O Xapo Bank possui uma reserva de aproximadamente 30 mil bitcoins que eles compraram quando o bitcoin tinha um valor irrisório. Fonte: https://youtu.be/PMbN8cd_jBY?t=1455
-
-
 @ 0dde8796:14799cec
2023-07-17 14:18:05
@ 0dde8796:14799cec
2023-07-17 14:18:05
Studying bitcoin involves learning something about damn near everything. For me, I was introduced to computer science, coding, and cryptography, none of which I knew much about before falling down the rabbit hole. You will also learn about history, law, monetary theory and economics, all stuff I was interested in since the 1970s. My purpose here is to briefly explain a few economic concepts you may have never heard of before. If you start reading articles about bitcoin or listening to podcasts these terms will be thrown around as if they’re common knowledge.
I hope this short guide helps to flatten the learning curve.
Fiat Currency
Merriam Webster’s Dictionary defines fiat money as “money (such as paper currency) not convertible into coin or specie of equivalent value.” This is another way of saying that it is money not backed by an asset. Fiat money is money that is created by “fiat”, or decree of a governmental entity. The word fiat is defined as “an authoritative or arbitrary order.” I like to think of it as Joe Biden, or whichever grasping, ambitious insect has fought its way to the top of the dung heap when you’re reading this, standing at the peak with a crumpled dollar bill displayed in its outstretched hands shouting, “This is money!”
So, the next time some wiseass says to you “bitcoin isn’t backed by anything”, you can respond: “neither is [fill in the blank with your favorite government money]”.
The conversation will not likely end there.
The fiat fan will say: “that’s not true, it’s backed by the full faith and credit of the [United States] government.”
You then stare at him open mouthed and ask if he’s serious.
This points out the peculiar nature of the current fiat based system. There was a time not so long ago when the U.S. was considered creditworthy. Every nation in the world wanted to buy U.S. treasury bonds, which are really just fancy IOUs. Not any more. Guess who buys U.S. debt now? The U.S. government buys back its own debt. That’s a little oversimplified. U.S. pension funds and various mutual funds and ETFs also have to buy U.S. debt pursuant to their mandate. Here’s the interesting thing, though. For years, and probably even now in some circles, a U.S. treasury bond has been considered the world’s “risk free asset.” Check out this quote from the Smart Asset web site:
A risk-free asset is an investment with a guaranteed future value and virtually no potential for loss. Debt issued by the U.S. government (bonds, notes and Treasurys) is one of the most well-known risk-free assets. While these assets are no longer backed by gold assets, they are backed by the “full faith and credit” of the United States. Investors shift their portfolios into risk-free assets during periods of uncertainty. U.S. Treasury bills are generally regarded as the safest investment in the world, which is why domestic and foreign investors buy so many during a downturn.
Ponder, if you will, the insanity of this quote. In the upside down, crazy world fiat money creates, the IOUs of a government that has shown no constraint in debasing its currency is considered a risk free asset?
That’s probably why all those banks and insurance companies loaded up on U.S. treasuries these past few years. It never occurred to them that Jay Powell might start jacking up interest rates in a futile attempt to tame inflation. The value of those “risk free assets” plummeted as interest rates climbed.
We won’t know how this all ends for a while, but it won’t be pretty.
To sum up, fiat money is debt.
Seigniorage
Seigniorage is another word you should learn. It is defined as:
the difference between the face value of money, such as a $10 bill or a quarter coin, and the cost to produce it. In other words, the cost of producing a currency within a given economy or country is lower than the actual exchange value, which generally accrues to governments that mint the money.
The goal of all governments is to maintain positive seigniorage, that is, making sure the cost to produce the money is less than the face value of the money. The difference is pure profit.
Have you picked up a U.S. penny recently? It’s lighter than air. Compare one to a 1950s penny, if you can find one (see Gresham’s Law). They are light as a feather. As the government debases the U.S. dollar, it’s nearly impossible to keep the costs of producing a penny below its face value, but they try. The government isn’t too worried, though, because it more than makes up for it in the switch to digital dollars. Hardly anyone uses coins in the United States anymore. They don’t even need to spend much on ink and paper for the old one dollar bill. Everyone uses credit cards or debit cards or paypal or venmo to pay for even the smallest items. There is negligible cost in mouse clicking billions of dollars into existence.
Governments love seigniorage.

Cantillon Effect
Richard Cantillon was an 18th century banker and philosopher. He articulated the principle that “the flow of new money through the economy is beneficial to parties that receive the funds first, and less beneficial to those that receive it later on. The individuals and institutions closest to the central bank – banks and asset owners – are granted financial advantages at the cost of those least connected to the financial system.”
What this means, in essence, is that it’s good to be close friends with the guys printing the money. That’s because, in a fiat system, money can and will be created whenever the government feels like it. Since there’s no real cost involved to make this money, there is no reason for the government to stop issuing it.
When more money is pumped into the system, the price of goods and services eventually rises, since each unit of fiat is worth less, so you need more of them to buy that bagel or new car. But, the guys who get the new money first get to use it and spend it BEFORE the inflation sets in.

A good example of this is the U.S. banking system. Nowadays, new money doesn’t really get printed by the government. What happens is that the big banks with the political power get to borrow money from the federal reserve at what’s called a “discount rate.” So, if you want to get a new mortgage, these banks don’t pull money out of their vaults and lend it to you. Instead, they borrow it from the federal reserve at, let’s say 4 percent interest, and then they lend it out to you at, say 7 percent interest. So, the banks get all that profit, when they have really done nothing but create this money you use to buy your house out of thin air. They literally borrowed the money into existence. The consumer has to pay the retail interest rate set by the banks while the banks get the special, insider discount.
Another example of this was on display during the “Covid Crisis”. The U.S. government decided it needed to create more money to stimulate the economy it destroyed by shutting down businesses. But, the government didn’t shut down all businesses. Some could remain open. It’s good to be friends with the king. So, churches were closed down, but liquor stores could remain open, because they provided a vital service. The government next began to issue covid loans to help the businesses it just destroyed. Makes sense. Big, powerful corporations with lots of employees got PPP loans for each employee on the payroll. This was free money because the loans were all forgiven. The businesses got this money even if they were allowed to remain open, as many large businesses (like Amazon) were. Lots of politically connected businesses with powerful connections in Washington D.C. got this free money. Unfortunately, little mom and pop businesses were forced to shut their doors, and their PPP loans didn’t help much, since they only had a few employees. Too bad. They should have made friends with the king before the “pandemic” hit.
Rent Seeker
You hear this term a lot when learning about bitcoin. It is always spoken with derision, which really confused me at the beginning. I was a landlord for many years, and I was always seeking rent. Hey, I had to pay my bills too! What are we, communists? Why was this a bad thing?
Investopedia has a nice definition of rent seeking:
The concept of rent seeking was established in 1967 by Gordon Tullock and popularized by Anne Krueger in 1974. It evolved from the studies of Adam Smith, who is often regarded as the father of economics. The concept is based on an economic definition of “rent,” defined as economic wealth obtained through shrewd or potentially manipulative use of resources.
So in this context, rent seeking means that a business entity seeks to gain wealth without having to do any actual work. This is a lot different than the rent I collect, since I have to pay mortgages, taxes, repair expenses, etc. There’s nothing free about that rent.
Rent seekers gain this wealth by seeking favor from the government. Lobbyists spend most of their time “rent seeking” for their clients. The bigger the business, the more lobbying power it has.
Here are some examples of rent seeking:
-
A bank getting a lower discount interest rate to then turn around and lend to borrowers (see Cantillon Effect Above)
-
Government subsidies
-
Grants
-
Tariffs
-
Good old fashioned political bribes
-
Manipulating the legal system to create barriers to entry and limit competition (law licenses, CPA licenses, barber licenses, taxi licenses, real estate broker licenses)
Tullock noticed that rent seekers usually get a great deal. In other words, they get an enormous financial gain at a proportionately very low cost. This is known as Tullock’s Paradox.
I always wind up thinking about proof of stake(POS) shitcoins as being analogous to rent seeking. The stakers seek to earn money solely due to their advantageous position as holders of a large quantity of coins. They may likely have obtained this hoard as a result of an unfair pre-mine, where insiders got a special low price. Their financial rewards are not related to any productive work being done. They merely benefit from having a large stake.
This is the opposite of bitcoin, where proof of work (POW) is always required to gain more bitcoin. It requires time, effort, and energy.

Gresham’s Law
Sir Thomas Gresham was a British merchant and financier who lived from 1519 to 1579. He wrote about the value and minting of coins. Gresham's law is a principle that states that "bad money drives out good."
When I was a kid in the 1960s I used to help my father out in his pharmacy after school. One of my chores was to go through the cash register at the end of the day and take out all of the pre 1964 silver coins. In 1964 the U.S. government removed all the silver from dimes, quarters, and half dollars. I would look for the telltale brown ring along the edge of the coin. If there was no ring, I would take that coin out of the register and place it in a brown paper bag. We stored those bags in the attic. This is what Gresham’s Law is all about. My dad knew the silver coins were “better money” than the crappy alloy slugs the U.S. mint began issuing after 1964. So, he would save the good money, and get rid of the bad money by using it as change for his customers. Now, governments aren’t completely ignorant of Gresham’s Law. They combat this by forcing their citizens to use their fiat money. That’s why taxes usually must be paid with “official” money. This theory also played a role in the U.S. courting Saudi Arabia in the 1970s, agreeing to financially and militarily support the kingdom in exchange for establishing the U.S. dollar as the currency for all international oil trade. In essence, governments use force to protect their officially approved currency. Every time I see an article about bitcoin adoption that laments long term hodlers refusing to spend their bitcoin, I think of Gresham’s Law. There are many articles marveling about how the percentage of bitcoin that hasn’t been spent in years keeps growing. Why would anyone spend good money when they can trade depreciating fiat for the goods and services they need? It’s a struggle for me too. I would much rather spend and rid myself of the depreciating U.S. dollars I own than my precious bitcoin. I have to force myself to load up my bit refill Dunkin Donuts gift cards. This is a factor to consider when evaluating the pace of bitcoin adoption.
Conclusion
I hope some of you found this article useful. If it whet your appetite to learn more about Economics, I recommend a book called Economics In One Lesson, by Henry Hazlitt. This is a good introduction to the Austrian School Of Economics. We have been force fed Keynsian Krap in the west for too long.
You will discover Ludwig Von Mises and Friedrich Hayek if you are interested in learning more. Saifedean Ammous wrote a book called The Bitcoin Standard, which is widely considered the best introduction to bitcoin. Recently he wrote another book called Principles Of Economics. It is a university level textbook that teaches economic theory from an Austrian perspective. You might also want to give this book a read if you’re really interested, but be prepared to work hard. It can be a bit overwhelming.First Published On Stacker News On July17, 2023
-
-
 @ 81870f53:29bef6a6
2023-07-23 00:20:25
@ 81870f53:29bef6a6
2023-07-23 00:20:25暗号通貨市場とビットコインに対するブラックロックの本当の計画を探ってみましょう。 金融大手は最近ビットコインETFの申請を提出したが、この動きには深い意図が隠されている。 ブラックロックは、存在するすべてのビットコインを所有することで市場を支配しようとする可能性があり、権力の集中化に対する懸念が高まっている。
ブラックロック、SEC、米国民主党の緊密な関係は、政治的影響の可能性についての疑問を引き起こしている。 彼らの戦略には、暗号通貨の匿名性を排除し、すでに導入されているものに代わる競合製品を作成することも含まれます。
この状況は、私たちが知っている暗号通貨の世界を根本的に変える可能性があります。 こうした懸念にもかかわらず、ビットコインETFに関するSECの決定を注意深く監視し、将来に向けて有望な仮想通貨を蓄積することで、この状況を利用する機会はある。
-
 @ 18e3af1e:1d42e5df
2023-07-17 01:14:53
@ 18e3af1e:1d42e5df
2023-07-17 01:14:53AVISO: Este artículo se centra en el punto de vista moral del protocolo, exponiendo los problemas y soluciones que existen y cómo Nostr puede presentar una transición al sistema actual.
Empecemos con:
El protocolo abierto más sencillo que es capaz de crear una red "social" global resistente a la censura de una vez por todas.
No se basa en ningún servidor central de confianza, por lo tanto, es resistente; se basa en claves y firmas criptográficas, por lo que es a prueba de manipulaciones; no se basa en técnicas P2P, por lo tanto, funciona.
Eso es lo que dijo nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 , el creador de Nostr. Si quieres profundizar más, visita Github.
El (Los) problema(s):
Notas y Otras Cosas Transmitidas por Relés (Nostr). Primero abordemos los problemas que intenta resolver:
-
Como quizás sepas o no, LOS HUMANOS somos muy codiciosos por naturaleza. ¿Poder? Lo queremos todo, nunca es demasiado. Las empresas de tecnología están dirigidas por humanos, y si las matemáticas te dicen algo, es que esas empresas siempre querrán tener más control sobre ti (las matemáticas no mienten). Las empresas quieren poseerte, saber lo que haces, lo que dices y eventualmente intentarán saber lo que harás en el futuro antes de que siquiera lo pienses, basándose en tu comportamiento. Así que los humanos no son buenos teniendo tanto control masivo. Poder.
-
La publicidad como modelo de ingresos ha tenido un largo recorrido, pero solo en la era de la información podemos ver realmente lo molestos que son. Pero no se detiene con los anuncios que aparecen aquí y allá de vez en cuando, te rastrearán y rastrearán tu comportamiento para mostrar esos anuncios en cualquier parte de la web en la que te encuentres. Privacidad.
-
¿Crees que posees algo? Incorrecto. Echa un vistazo rápido a los términos y políticas de cualquiera de los grandes perros de las redes sociales. ¡Pertenecen a ellos! tus fotos, tus publicaciones, tu música, tus videos; porque al final, todo lo que publicas se guarda en sus servidores, ¿y qué es un servidor sino la computadora de otra persona? Los derechos de propiedad fueron muy difíciles de preservar en la era digital. Propiedad.
Si te falta alguna de las 3 P's (Poder, Privacidad, Propiedad) definitivamente no eres libre. Privacidad para el pasado para proteger tu bienestar y el de tus seres queridos (la privacidad no significa secreto, no te dejes engañar). Poder para el presente para hacer lo que esté a tu alcance.Propiedad para el futuro para preservar tu riqueza a lo largo del tiempo. Pasado, presente y futuro están intrínsecamente vinculados entre sí.
Soluciones que Nostr trae:
Desglosemos estos 3 componentes (Poder, Privacidad y Propiedad) de la libertad y presentemos algunas soluciones que ofrece el protocolo:
-
Poder: Nostr es una forma de poner el control de tus datos en tus propias manos, y con control me refiero a que podrías ser dueño de tus datos. Cada fragmento de información, desde unas pocas frases hasta una película completa, se puede almacenar en tu relé. La parte interesante es que tu relé también puede interactuar con otros, creando un nuevo nivel completo de redes sociales y, sinceramente, puede ir más allá de eso. No hay forma de censurarte, bloquearte o shadowbanear. Cuando tienes el control, estás libre de las cadenas de aquellos que están por encima de ti. Es importante enfatizar lo fácil y conveniente que es deshacerse de la responsabilidad de administrar tus propios datos... Eso es el queso dentro de la trampa para ratones.
-
Privacidad:
-
Privacidad se refiere al derecho de un individuo o grupo de mantener su información, comportamiento o pensamientos para sí mismos, lejos del escrutinio público y del acceso no autorizado. Implica establecer límites para proteger el espacio personal y controlar quién puede acceder a cierta información sobre ti. La privacidad es un derecho fundamental en muchos países y se considera esencial para la protección de la libertad y autonomía individuales.
-
Secreto, por otro lado, implica ocultar activamente información a otros, a menudo con un propósito específico. El secreto puede usarse para proteger la privacidad, pero también puede usarse con fines poco éticos o ilegales, como ocultar información a las autoridades o encubrir actos ilícitos. A diferencia de la privacidad, el secreto no es un derecho reconocido universalmente y, en muchos casos, la necesidad de secreto puede verse superada por otros intereses públicos, como la seguridad nacional o la necesidad de prevenir delitos.
En Nostr, ninguna entidad tiene control sobre el flujo de información o acceso a los datos del usuario. Esto reduce el riesgo de violaciones de datos o censura, ya que no hay un punto central que pueda ser objetivo. Utiliza la encriptación para asegurar la transmisión y el almacenamiento de datos, lo que dificulta el acceso de terceros a la información del usuario. Esto proporciona un nivel más alto de protección de la privacidad en comparación con las redes centralizadas, donde los datos a menudo se recopilan y almacenan por una entidad única, creando puntos de enfoque que pueden ser objetivo de ataques de los estados nacionales o de hackers individuales con fines personales.
- Propiedad: Los pares de claves públicas y privadas permiten a las personas poseer cosas en la era digital al proporcionar una forma segura y descentralizada de almacenar y transferir la propiedad de la información digital. Una clave pública es un identificador criptográfico único que se puede compartir públicamente. Se utiliza para recibir y almacenar datos, similar a un número de cuenta bancaria. Una clave privada, por otro lado, es un identificador criptográfico secreto que se utiliza para firmar transacciones y transferir la propiedad. Solo el propietario de una clave privada tiene la capacidad de transferir la propiedad de los activos (datos) asociados con su clave pública correspondiente.
Este conjunto de datos firmados se transmite a otros relés y se verifica en el lado del cliente. Este sistema proporciona una forma segura y descentralizada de almacenar y transferir la propiedad de la información, ya que no hay una autoridad central o un tercero de confianza involucrado como intermediario. Esto brinda a las personas un mayor control sobre sus datos.
En conclusión, los pares de claves públicas y privadas son una innovación importante en la era digital, que permite a las personas poseer y controlar su información digital de manera segura y descentralizada, y tiene el potencial de transformar muchas otras industrias en el futuro.
¡RECUPEREMOS NUESTRO PODER, RECUPEREMOS NUESTRA PRIVACIDAD, RECUPEREMOS NUESTRA PROPIEDAD, RECUPEREMOS NUESTRA LIBERTAD! -
-
 @ 18e3af1e:1d42e5df
2023-07-17 01:02:55
@ 18e3af1e:1d42e5df
2023-07-17 01:02:55Introducción
En la era digital, hay más formas que nunca de ser autosuficiente. La auto custodia es una idea que ofrece a las personas una libertad sin precedentes y un control total sobre su dinero y su información personal.
¿Cómo la auto custodia te protege de los abusos del gobierno?
La auto custodia es una forma de protegerte de los abusos del gobierno, porque significa que tú controlas toda la información que obra en tu poder. Esto puede incluir todo, desde los registros fiscales a los registros médicos e incluso las contraseñas de cuentas como el correo electrónico y las redes sociales.
Si tienes la custodia de tus datos, en el momento en que surja un problema con uno de estos elementos, como un robo de identidad o un pirateo informático, no habrá nadie más que pueda hacerse cargo de ellos, a menos que estén dispuestos a pasar por el mismo proceso que si te los compraran a ti (lo que sería muy caro).
Por primera vez en la historia, el individuo tiene más poder que el colectivo. La custodia propia se trata de concederte a ti mismo el derecho a tomar decisiones en nombre de aquellas personas de tu vida que aún no pueden tomarlas por sí mismas.
Estamos entrando en una nueva fase de la historia de la humanidad.
Estamos entrando en una nueva fase de la historia humana, en la que los individuos serán dueños de su propio destino. Esta es la promesa de la auto custodia.
La revolución digital nos ha proporcionado un acceso sin precedentes a la información y los servicios, pero también trae consigo nuevos retos que deben abordarse si queremos prosperar como especie.
También es un requisito previo para utilizar e interactuar con Bitcoin tal y como lo concibieron sus creadores. Sin esta propiedad, sería imposible crear valor de la nada, porque no se puede hacer algo de la nada.
Es difícil para quienes nunca han experimentado la libertad monetaria imaginar cómo sería operar sin una autoridad central que controle todo, desde la emisión de su moneda hasta los tipos de interés y todo lo demás.
Además, como el dinero es digital y la información es prácticamente libre (y por tanto puede transmitirse fácilmente por todo el mundo), nuestra actual infraestructura financiera no puede soportar este nivel de privacidad o seguridad. El resultado es que ya no vivimos en una época en la que las personas controlan su propia identidad o sus finanzas, sino que se ven obligadas a adoptar una identidad (es decir, "tú" cuando compras cosas), con todos los demás aspectos de su vida mediados por proveedores de servicios que recopilan datos sobre ellas para vender más cosas.
Bitcoin no es sólo un sistema de dinero
Bitcoin no es sólo un sistema monetario, sino una red que nos permite realizar transacciones de punto a punto preservando nuestra privacidad y autonomía monetaria. Un sistema que aprovecha la velocidad, descentralización y estabilidad que nos brinda el protocolo de la Internet, adicionándole capaz extras de pseudo-anonimato, permitiéndonos así auditar cualquier transacción generada desde cualquier llave publica dejando un rastro desde su Genesis, sin saber la identidad del o los individuos involucrados con susodicha dirección.
Conclusión
Como sabes, vivimos en una era digital, y es importante recordar que la información contenida en nuestros teléfonos es más valiosa que nunca. El problema es que tendemos a olvidar este hecho cuando se trata de nuestra propia privacidad y seguridad. Debemos aferrarnos a estos valores o, de lo contrario, corremos el riesgo de perder nuestra libertad individual para siempre.
La auto custodia es una tendencia que ganará impulso a medida que avancen las tecnologías. Es un primer paso axiomático hacia la construcción de un mundo mejor. También permite a los individuos evitar ser controlados por gobiernos e instituciones heredadas como bancos, empresas de tarjetas de crédito e incluso plataformas de redes sociales. La autogestión no solo tiene que ver con la libertad individual o la independencia financiera; se trata de reclamar nuestra capacidad de controlar nuestras propias vidas frente a la creciente interferencia gubernamental desde todos los frentes.
Nota: La mayoría de este artículo fue escrito por una inteligencia artificial, por eso la brevedad. Créditos para el avance en tecnología.
-
 @ 18e3af1e:1d42e5df
2023-07-17 01:01:36
@ 18e3af1e:1d42e5df
2023-07-17 01:01:36Nota: Este articulo fue originalmente creado por nostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7 , yo solo ayude a traducirlo al espanol
Una nueva herramienta
Fue lanzada una nueva herramienta de Nostr por el invisible guerrero Nostr nostr:npub1xdtducdnjerex88gkg2qk2atsdlqsyxqaag4h05jmcpyspqt30wscmntxy, el hombre detrás de nostr.band. Nostr Band potencia a reconocidos clientes de Nostr como Snort, Amethyst y Iris con sus herramientas backend. Además, Nostr Band sirve como una navaja suiza versátil para los usuarios finales, ofreciendo una amplia gama de servicios y características que incluyen búsqueda, estadísticas, direcciones de Nostr y más. Cabe destacar que la herramienta incorpora un sistema de relé robusto, previamente discutido en una de mis guías completas. Te invito a explorar las posibilidades que presenta este servicio visitando https://nostr.band/. Pero hoy, estoy emocionado de compartir el último desarrollo en el ecosistema de Nostr Band: Feeds.
Curación de contenido en Nostr
Nostr, al ser un protocolo relativamente joven, se ha centrado principalmente en sentar las bases y garantizar la funcionalidad básica. Como resultado, la implementación de ciertas características y posibilidades ha llevado tiempo. Un área en la que se ha estado careciendo es la curación de contenido. Hasta ahora, los usuarios finales han tenido opciones limitadas para dar forma al contenido que consumen, confiando en ajustar paquetes de relés o utilizando clientes específicos que ofrecen más flexibilidad para ajustar los feeds, como Primal.
Entre las herramientas disponibles se encuentra la potente microaplicación de nostr:npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc, conocida como listr.lol. Permite a los usuarios crear y gestionar listas para curar contenido de fuentes participantes. Sin embargo, su integración en clientes populares de Nostr aún está en progreso, lo que dificulta su uso en cierta medida. Además, las implementaciones actuales se centran principalmente en listas de perfiles, lo que limita la capacidad de realizar curación basada en temas. Otra opción es Zapddit, un cliente similar a Reddit desarrollado por nostr:npub1ltx67888tz7lqnxlrg06x234vjnq349tcfyp52r0lstclp548mcqnuz40t. Zapddit permite a los usuarios seguir temas deseados suscribiéndose a hashtags y evitar algunas conversaciones silenciando hashtags no deseados. Sin embargo, la dependencia de los hashtags presenta limitaciones, ya que no todos los usuarios los utilizan de manera consistente, lo que podría resultar en contenido perdido o exposición a contenido no deseado. Enfoque único
Feeds de Nostr.Band ofrecen una forma completamente nueva de curar contenido de Nostr, brindando a los lectores el poder de personalizar su consumo de información y permitiendo a los curadores crear flujos de información únicos mientras obtienen reconocimiento por sus esfuerzos. ¿Recuerdas cuando mencioné que no hay muchas herramientas que te permitan dar forma a tus feeds? ¡Pues es verdad! Todos tenemos gustos diferentes cuando se trata del contenido que queremos ver. Solo piensa en la variedad de plataformas tradicionales que tenemos: Twitter para actualizaciones rápidas y concisas, Instagram para contenido visual ligero, y así sucesivamente. Pero, ¿realmente necesitamos una aplicación separada para cada estado de ánimo? No lo creo. https://nostr.build/p/nb9416.jpg
Ingresa a Nostr Feeds, la solución que te permite curar tu propia experiencia de contenido sin la necesidad de múltiples aplicaciones. Personaliza tu feed según tus preferencias, ya sea que desees actualizaciones breves, notas populares o contenido visual cautivador. Di adiós a los feeds de talla única y dale la bienvenida a un nuevo nivel de curación de contenido. Suscríbete a los feeds que te interesen y recibe contenido curado adaptado a tus preferencias. ¡Haz que tu feed sea verdaderamente tuyo! ¿Suena interesante? ¡Sumergámonos en cómo funciona esto!
El consumidor
Como consumidor de contenido, todo lo que tienes que hacer es agregar un feed a tu lista de relés y comenzar a recibir contenido correspondiente en tu feed global, también conocido como "El Universo". ¿No quieres seguir el feed al que te suscribiste? Eres libre de eliminar el relé del paquete que utilizas. Explora una colección en constante crecimiento de feeds en esta página dedicada. Más creadores se están uniendo para proporcionar su propio contenido curado, ampliando tus opciones.
El curador
Imagina las posibilidades de crear tu propio feed. Ya sea para un círculo íntimo de amigos o aspirando a ser un curador global en el Universo Nostr, el poder está en tus manos. ¿Eres un conocedor del arte, un entusiasta de los autos o un educador? Crea tu propio feed y guía a tu comunidad hacia un mundo de contenido seleccionado y de alta calidad. En un mundo inundado de información, separar la señal del ruido es una habilidad invaluable. Con herramientas limitadas disponibles para los usuarios finales, poder ofrecer contenido verdaderamente valioso te convierte en un verdadero campeón en tu campo. Al curar tu feed, te conviertes en un faro de conocimiento, guiando a otros hacia el contenido más valioso y selecto. Es hora de redefinir el consumo de contenido y elevar la experiencia en Nostr. Únete a las filas de los curadores de contenido y marca la diferencia en el mar de información excesiva. 1. Crear un feed Visita https://feeds.nostr.band/index.html?create=true 2. Completa los campos requeridos. https://nostr.build/i/9fab5f04510b4b77b2be9dc29feea8e95372d07d65e8991fc8c78ed30c94c48b.jpg
- Para obtener acceso a tu propio relé, debes pagar la factura.
Desbloquear un feed conlleva una suscripción mensual, que te otorga acceso a una poderosa herramienta respaldada por el relé de nostr.band y herramientas de interfaz de usuario fáciles de usar. Esta infraestructura garantiza una curación sin problemas y sin esfuerzo al alcance de tus manos.
Siendo una etapa temprana, el potencial de mejora de los feeds es ilimitado. Al unirte desde el principio, te posicionas para alcanzar nuevas alturas antes que los demás. 4. ¡Listo! Ahora tienes tu feed listo para recopilar y compartir el mejor contenido. ¡Disfruta de la experiencia de curación y comparte tus descubrimientos con otros!
Gestionar un feed
Si bien se están desarrollando herramientas para simplificar el proceso de curación, aquí están los pasos actualmente necesarios para gestionar tu feed: 1. Copia el noteId de un evento que te gustaría agregar a tu feed (o búscalo en nostr.band). 2. Visita nostr.band y pega el noteId en el campo de búsqueda. 3. Haz clic en la nota que deseas agregar al feed. 4. Presiona el botón "Label" debajo de la nota y selecciona la etiqueta que corresponda al feed al que deseas agregar la nota. Estos pasos te permitirán administrar tu feed y agregar notas específicas a él. Recuerda que a medida que se desarrollen nuevas herramientas, el proceso de gestión del feed puede simplificarse aún más. https://nostr.build/i/a88c8138b0497a074945dee9430b075c6241da2715e5869eff490909b05c6f47.jpg
Todas las notas etiquetadas por ti se resaltarán en verde para tu comodidad. ¡Felicitaciones! Ahora tienes tu propio feed en Nostr que puedes curar. Comparte tu feed en los comentarios a continuación, veamos quién crea los feeds más creativos y útiles.
Beneficios de administrar tu propio feed
Además de ser un buen tío Jim ayudando a que tu círculo cercano de amigos y familiares reciba contenido seleccionado, puedes beneficiarte potencialmente de una mayor exposición en la comunidad e incluso ganar sats al administrar tu propio feed de calidad. Ya existen algunas opciones en este sentido (ten en cuenta que hay muchas más por venir): 1. Al crear tu propio feed, automáticamente te conviertes en un operador de relé de Nostr y te vuelves descubrible en la pestaña de información de relés. Esto ayuda a aumentar tu visibilidad y permite a los usuarios que valoran tu aporte interactuar contigo. https://nostr.build/i/7856a8a7bfad2d98f04fa3e8baaa3698ea79125a23fb1b5c9424f784a4a8a080.jpg 2. Algunos clientes, como Snort, admiten un "Zap Pool" que permite a los usuarios asignar un porcentaje deseado de zaps a los contribuyentes de infraestructura favoritos. Al crear un feed y convertirte en operador de relé, es posible que te vuelvas descubrible en el Zap Pool de Snort y comiences a recibir sats con cada zap enviado por los usuarios de Snort que hayan habilitado esta función. Esto brinda la oportunidad de recibir recompensas por tu contribución a la infraestructura y el ecosistema de Nostr.
https://nostr.build/i/ef98d1e4c8679df6c489dd5a3f5dcc13c75db17afd00a1bd65e7ca99a27a3088.jpg
—- Para mas contenido en español anidar este rele en configuraciones: wss://feeds.nostr.band/nostrhispano
- Para obtener acceso a tu propio relé, debes pagar la factura.
-
 @ 180a6d42:36cf5693
2023-07-11 15:56:07
@ 180a6d42:36cf5693
2023-07-11 15:56:07
This mini-guide aims to help you choose between a selection of Bitcoin lightning network (LN) wallets with an additional focus on working toward becoming unruggable through self-custody. No need to overthink, self-custody means: writing down and safely storing 12/24 words (aka 'seedphrase') offline, on paper/metal.
TL;DR. use WoS/LN.tips (transact📱) x Phoenix (save📱, self-custodial)
LN wallets (a selection)
Self-custodial LN wallets:
a. Phoenix app (📱, acts as a LN node*)
b. Breez (📱, acts as a LN node*)
c. Muun (📱, acts as a LN node*)
d. Zeus (📱, LN url)**
Custodial (by default) LN wallets:
a. Alby (browser extension, LN url)**
b. LN.tips (Telegram bot, LN url)**
c. Wallet of Satoshi (📱, LN url, use fresh email to sign-up)
d. ZBD (📱💻, LN url, kyc-free up to 500k sats)
sats= satoshi's (fractions of a bitcoin, e.g. 21.000 sats is 0.00021 BTC) LN url = Lightning address to add to your Nostr account to enable >receiving< Zaps
uses e.g. a big company LN node or submarine swaps *lightning node remote control apps: can also connect to self-hosted LN node
So to be clear, you have lightning wallets that act as (a) a wallet, (b) a self-custodial lightning wallet AND a lightning node on your phone, (c) a lightning node remote control app (if you run and self-host a LN node on a dedicated device).
Why choose custodial? It is only a temporary solution showing the power of LN where channels are already established and robust, is my conclusion. Be aware that there are major security/privacy trade-offs when using custodial wallets. However, if you're someone who's new to Nostr and/or bitcoin, and you e.g. want to enable receiving Zaps, it's obvious you play around with a custodial one with a smaller amount of sats first (let's say, up to ~ 21k sats/ 50$). I don't think it's realistic to expect someone new to this network to magically and instantly know how to spin up a LN node and manage channels. This is something that takes time to learn.
Unless you only use self-custodial LN wallets, it is advised to have your sats divided on more than one custodial wallet in case one of the hosted LN nodes temporarily goes down (not often) and you still want to transact at that moment.
Why choose self-custodial? When you're looking to learn more and/or if you plan to send/receive more substantial amounts of sats (e.g. for business) then you're ultimately going to want to learn to run a self-hosted node, preferably through Tor. Find trustworthy tutorials here.
A self-hosted node allows you to save on transaction fees; truly be in control of your bitcoin; and, protect yourself wrt third-party privacy violations. Know that you'll have to invest some time in learning and money in gear/gadgets in order to run your own (LN) node (~$200-$400).
What other choices do I have? If you're not ready to run a LN node just yet, you can also choose to go for one of the self-custodial wallets listed that act as a LN node on your mobile (e.g. Phoenix). The transaction fees are a bit higher than with custodial wallets but this is related to the wallet acting as a lightning node on your phone (e.g. with Phoenix you have to top-up the wallet with a minimum of 10.000 sats initially of which 3000 sats will be deducted in order to have the system open up lightning channels for you). A small price to pay for not having to have to run your own, self-hosted Bitcoin Lightning Node and managing it. Know that running your own lightning node has similar costs.
Tip: You can now deposit funds to self-custody on Lightning with Phoenix wallet for less than 500 sats when conditions are optimal* (compared to the previous 3000 sat/1%). They also made the LN<->onchain swaps trustless.
Summary
Here's a recommended Bitcoin wallet setup focussed on self-custody without having to have to run your own, self-hosted Bitcoin LN node:
Transacting bitcoin LN/L2 (active📱): Wallet of Satoshi and LN.tips
only use temporary, small amount of sats; custodial, but supports LN url
↕
Saving bitcoin, LN/L2 (passive📱): Phoenix wallet
self-custodial, easy, can swap LN↔on-chain, supports Tor
watch and learn: https://youtu.be/cbtAmevYpdM?t=223
↕
Saving bitcoin, Layer 1 aka on-chain (passive💻):
deep, air-gapped, cold storage (e.g. Seedsigner, Coldcard)
For a more extensive LN wallets comparison guide outside the scope of only Nostr, click here (would not recommend if you're new to all this; can be overwhelming).
Link to this blog: https://lnshort.it/lnwalletguidenostr
Find me on Nostr: matata@nostrplebs.com
-
 @ 18e3af1e:1d42e5df
2023-07-17 01:00:08
@ 18e3af1e:1d42e5df
2023-07-17 01:00:08Caveats:
-
No será GRATIS (nada lo es) te tomará un par de minutos de tu tiempo y algunos te harán caminar por ello.
-
No te hará rico, pero se acumulará y eventualmente quien sabe, tal vez tengas suficiente para ser…
-
En el momento de escribir esto, todos estos sitios están activos. Si ya no funcionan o los enlaces están rotos cuando estés leyendo esto... No me culpes.
Camina con sMiles sats por caminar:
Muy sencillo. Gana sats por caminar. También puedes girar la rueda y usar Fort Nakamoto para obtener sats adicionales.
https://nostr.build/i/3de92762bc722e7a531f8ceca21e43cd83ac6b00c4b436310777393a712e62cb.gif
Lotería de Bitcoin con LNscratch:
También muy autoexplicativo. Raspa un papel digital para tener la oportunidad de ganar sats cuando obtengas 4 marcas de verificación en línea recta. Normalmente obtengo 21 sats cada vez. Solo necesitas una billetera Lightning como GetAlby, Wallet of Satoshi (estas son las más populares, puedes echarles un vistazo más detallado) y estás listo.
https://nostr.build/i/021d0fcc9d11a75fdc3dfbee0b56ee39f7945e59346b38417c050d78cce1b1d1.jpg
Gana dinero por tareas fáciles en sats4likes:
Las tareas suelen ser: seguir, repostear, comentar, dar like y/o suscribirte. Eso es todo. Te pagan una cierta cantidad de sats establecida por el propietario de la tarea. La única desventaja es que necesitas una cuenta de Twitter (malo, malo, deberías estar usando Nostr) para iniciar sesión. Pero si no te importa, aquí está.
https://nostr.build/i/bdfe843adeb1a93bf227836d8ca5a347384dc643be328801044b94dddc470ac0.jpg
Nostr:
La mejor manera de acumular hasta ahora, únete a la fuerza y recibe un impacto (sats) por cualquier nota (publicación) que las personas consideren valiosa. En este momento se está construyendo todo un ecosistema sobre la capa de protocolo. Todos estos clientes (sitios web o aplicaciones construidas sobre Nostr) serán interoperables, lo que significa que con un par de claves (cuenta) podrás acceder a todos ellos.
El punto es que Nostr utiliza Lightning Network (Bitcoin) como una forma de transacción de valor, lo que impulsa enormemente el modelo de valor por valor.
Imagina recibir sats por publicar un meme divertido, o recibir sats por escribir un artículo (como este), o por hacer canciones y usar stemstr, zapstr.live... Los clientes pueden ser tantos como queramos, y pueden hacer cualquier cosa que queramos. Las posibilidades son infinitas.
Aquí tienes una introducción intuitiva y breve Hey Nostr.
Si conoces otras formas de ganar sats, por favor avísame. Las agregaré a este artículo. ¡Gracias por leer!
Recibe dinero compartiendo contenido en Stacker.news:
Es una excelente manera de acumular no solo más sats, sino también conocimiento y estar al tanto de las últimas noticias sobre Bitcoin, Nostr, Finanzas, Tecnología, etc. Simplemente crea una cuenta con cualquiera de sus métodos, aunque se recomienda Lightning. Luego deposita algunos sats si ya los tienes (se necesitan 10 sats para publicar o comentar), y observa cómo crece tu billetera. Cuanto más interesante y bien ejecutado sea tu enlace/discusión, más sats recibirás.
https://nostr.build/i/01db1dfcb9e13e1dc21098de6bf518605f1085e7319a53dfe8f358eca80c5b06.jpg
Acumula cuando uses tu DINERO FIAT para comprar cosas: The Bitcoin Company, Fold app, Lolli
Los agrupé porque son esencialmente muy similares. Cuando compras una tarjeta de regalo, obtienes Satsback (en lugar de cashback), funcionan o no en diferentes lugares; así que investiga por tu cuenta en ese asunto.
Fold es una opción más popular (actualmente solo funciona en Estados Unidos) porque tienen una tarjeta que puedes usar y obtener satsback de manera aún más fácil.
https://i.imgflip.com/7qenj8.jpg
Gana sats escuchando o haciendo podcasts: Fountain.fm
Si eres amante de los podcasts, definitivamente debes echarle un vistazo a este. Solo por escuchar puedes ganar sats. Puedes encontrar podcasts que tengan habilitada esta función, sea cual sea el tema (no necesariamente tiene que ser estrictamente sobre Bitcoin o Nostr, o incluso relacionado con la tecnología).
Si tienes o quieres tener un podcast, te recomiendo considerar esta opción. No necesitas patrocinadores para que tu podcast sea rentable. Los "Boosts" (como una donación en sats) o los "Sat Streams" (que te dan una cierta cantidad de satoshis por cada minuto que las personas escuchen tu podcast) son formas de monetización. Cuanto mejor sea tu contenido, más personas te darán dinero (literalmente).
Usa Lightning Faucets como este:
Simplemente sigue los pasos y canjea tus sats.
Si vives en un país donde la inflación no es estúpidamente alta (como Estados Unidos), considera hacer una donación a la causa..
https://nostr.build/i/e530ea35ea3d8dcf930a56cd0a8e8a998eb08d2c3c4be6311ab6a9f457b407a6.jpg
Lee por sats en la Bitcoin Magazine App:
No estaba seguro de agregar esta, pero funciona si lo único que quieres hacer es acumular y no te importan mucho los artículos.
¡Simplemente lee los artículos hasta el final (tus dedos pueden hacerlo más rápido que tus ojos guiño guiño) y obtén sats por ello! También puedes canjear flashcodes de BM Twitter (puaj), ¡son muy activos con esos códigos!
https://nostr.build/i/26b013f9820170d2316a77430acc4f4dea064fc52ca8c033a053be4e208a6c92.jpg
-
-
 @ 18e3af1e:1d42e5df
2023-07-17 00:45:07
@ 18e3af1e:1d42e5df
2023-07-17 00:45:07Primero y ante todo, debes evaluar las cosas que te gustan como ser humano en un panorama amplio, para poder comenzar a apuntar a temas y perfiles más específicos. Puedes comenzar determinando en qué categorías te encuentras dentro del espectro: deportes, arte, noticias, finanzas, manualidades, etc. Una vez que sepas qué buscar, podemos adentrarnos en secciones más detalladas dentro de cada categoría con las herramientas que verás en este artículo.
1. Encuentra, comparte y crea una lista de las personas que más te gustan
Encontrar listas de personas a seguir y marcadores de sus publicaciones es fácil con esta webapp. No solo eso, sino que también puedes crear la tuya propia para ayudar a otros a encontrar contenido que se alinee con sus likes o hobbies.
https://Listr.lol (nostr:npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc)
https://nostr.build/i/a97a849413949763bdb9d5f401f9ea499d8263fe9f6caca05086857e240794b2.jpg
Después de terminar de curar tu lista, puedes easialy compartirla en la esquina superior derecha. Te dará diferentes opciones, pero aquí tienes un enlace como ejemplo:
nostr:naddr1qqz8getnwspzp2lxh6sn20fh8anms0g44gk0pqdq307gsphm6tdc3zlyn026vzn3qvzqqqr4xqwgl5nl
Ten en mente que esta lista ES en realidad un evento de Nostr, así que puede interactuar con el Nostrverse. Aquí en Habla.news, la lista se mostrará en el artículo y es posible interactuar con ella si estás logueado con tu nsec.
2. Los hashtags son una excelente manera de encontrar temas que te gusten
El problema con el estado actual de Nostr es que la mayoría de los clientes se centran en un formato de contenido similar a "twitter". Encontrar #hashtags con personas en ellos no es fácil. Los hashtags populares como #coffeechain #Nostr etc, son geniales pero no muy específicos. A veces puedes crear uno pero hay casi nadie usándolos.
Por eso herramientas como zapddit.com (nostr:npub1ltx67888tz7lqnxlrg06x234vjnq349tcfyp52r0lstclp548mcqnuz40t) están actualmente desarrollando. Básicamente es un curador de hashtags donde puedes encontrar y seguir temas dentro del ecosistema Nostr. También puedes visitar Nostr.band y luego la sección de hashtags para ver los más populares.
https://nostr.build/i/0007e6d845c813b08378b267d3cdb7f958fe8f8212bda76ab57b6fe1bf90ee9a.jpg
Otra gran herramienta es un webclient llamado primal.net (nostr:npub12vkcxr0luzwp8e673v29eqjhrr7p9vqq8asav85swaepclllj09sylpugg), están haciendo algo similar a twitter donde puedes encontrar a los trending users. Pero también puedes buscar hashtags y luego añadirlos a tu feed. Dentro de esas "sub-comunidades" puedes encontrar más personas para seguir y expandirte desde ahí.
https://nostr.build/i/725b99fd10c1f0821577440aeb752481319252fad071c1714a811ac5f361deb2.jpg
3. ¡Comparte tus hobbies con hashtags!
Digamos que tocas el piano y te gustaría mostrarles a tus seguidores un video. ¡Eso es genial! Pero como nuevo usuario de Nostr, tu contenido puede estar muy oculto en el mar de otros usuarios. Podrías añadir el #piano a tu post, y hacerlo mucho más fácil para que nuevas personas encuentren tus cosas. Funciona en ambos sentidos (seguidor y seguido) para bien.
4. Contenido de formato largo combinado con resaltadores
Puedes descubrir nuevos temas en clientes como Habla.news o Blogstack.io de personas alrededor del mundo en muchos idiomas diferentes, pero una forma de descubrir un artículo de un contenido específico que puedas estar buscando o interesado en es usando Zapworthy (https://gotnostr.com/pablo@f7z.io) o highlighter.com. Permiten señalar específicamente una frase que te haya movido de alguna manera o que hayas encontrado interesante. Luego, esa misma frase puede ser exportada como un evento de Nostr y publicada en zapworthy/Highlighter y en tu perfil personal de Nostr.
Tienes un par de opciones aquí, dependiendo de cuánto utilices clientes basados en Nostr de formato largo. La primera opción y la más fácil para hacer esto es usarlo dentro de Habla.news en sí. Solo necesitas encontrar un artículo o post que te guste y luego HIGHLIGHT IT.
https://nostr.build/i/65234a7bdca356f5aceb8303121ef5e7d94ff4fa212dd6a19bec953b7c8d9d12.jpg
Luego puedes buscar en zapworthy.com y ver todos los highlights. Esto ayuda a las personas a buscar algo que te haya llamado la atención y que consideres digno de un buen "zap". Puedes hacer esto con cualquier otro artículo en Internet, pero en cambio debes ir a la página de zapworthy y usar su consola.
https://nostr.build/i/09c765169bba41a7fe69c25db5ef053d4a81cc5a4af56d2ad3f10b17a58c3ee0.jpg
Para ver un tutorial mas a fondo revisa la guia de nostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7 en ingles.
5.Seguir bots que busquen contenido por ti
Esto se explica por sí solo. Simplemente usa https://sb.nostr.band/ y busca el bot npub, síguelo con tu perfil y deja que el bot haga el resto. Obtendrá contenido de todo lo que tenga la palabra que el bot está destinado a buscar; y también de palabras con hashtag.
¡Espero que esto les haya sido útil a todos! <3
Agradecimientos especiales a nostr:npub1a6k75m9m2qv2ry8sz9u90hj38np8r5jvj374dnvzc49xke9wg7jqhnmu4x por señalar las herramientas que necesitaba para este artículo. Y a nostr:npub107jk7htfv243u0x5ynn43scq9wrxtaasmrwwa8lfu2ydwag6cx2quqncxg por esta increíble página!
-
 @ 18e3af1e:1d42e5df
2023-07-17 00:22:01
@ 18e3af1e:1d42e5df
2023-07-17 00:22:01Empecemos desde la iglesia
La manera en que la información es adquirida juega un papel esencial en la forma en que la especie humana en su totalidad evoluciona.
Antes del invento de la imprenta, leer y escribir era considerado un prestigio que solo los más poderosos podían darse el lujo de aprender. La creación de archivos de texto era un arduo trabajo, la mayoría de estos libros eran creados por monjes pertenecientes a la iglesia.
Veras, aparte de lo costoso que era hacer un libro por los materiales que se usaban (pieles de corderos y vacunos curtidos) también había que sumarle el precio del tiempo que el monje tardaba en escribirlo o, copiarlo. No existía un método de copiado de texto antes de la imprenta, el monje debía recrearlo lo mas parecido posible al escrito original. Un verdadero arte. Por lo que, el precio de un libro era en aproximado al de una yunta (par) de bueyes.
La scriptoria de los monasterios benedictinos puede entenderse como una tecnología alternativa a las imprentas, que todavía no existían. A pesar de lo costosas e ineficientes que eran las scriptoria, eran prácticamente el único mecanismo para reproducir y preservar el conocimiento escrito en el período feudal.
James Dale Davidson and William Rees-Mogg, The Sovereign Individual, 1994
https://substackcdn.com/image/fetch/w_1456,c_limit,f_webp,q_auto:good,fl_progressive:steep/https%3A%2F%2Fbucketeer-e05bbc84-baa3-437e-9518-adb32be77984.s3.amazonaws.com%2Fpublic%2Fimages%2Fbbe9651e-7fc8-455d-8921-a5a5734219ae_1144x707.png
Johannes Gutenberg al crear la imprenta de caracteres móviles dio una solución al sistema de copiado de la época. La información que antes era acaparada por la iglesia y altos mandos del estado medieval, información estancada en status quo por definición… Adquirió un nuevo riel de disipación, como un virus salido de control; inspiro a miles de millones de personas alrededor del mundo y abrió el camino para el pensamiento racional, que fue el catalizador que inicio la desintegración de los vínculos entre la iglesia y el estado.
https://substackcdn.com/image/fetch/w_1456,c_limit,f_webp,q_auto:good,fl_progressive:steep/https%3A%2F%2Fbucketeer-e05bbc84-baa3-437e-9518-adb32be77984.s3.amazonaws.com%2Fpublic%2Fimages%2F01245986-011b-4a8d-a3a7-dadd91855ac8_600x400.jpeg
Alguno de los logros más importantes propagados por la imprenta de Gutenberg:
-
Permitió la producción masiva de manuscritos y libros a bajo precio
-
La alfabetización de la población
-
Hizo posible (o anticipo) la llegada del Renacimiento que empezó en Europa Occidental durante los siglos XV y XVI. Es decir, la transición entre la Edad Media y los comienzos de la Edad Moderna.
-
El cambio cultural causado por la difusión de la información es inimaginable, el avance en ciencias naturales y humanas, arte, literatura, entre otros… Abrió los caminos para mentes racionales a difundir sus ideas y llegar a mano de la población que ahora podía adquirir estos libros. La iglesia ya no podía acaparar la información, no pudo detener la liberación de la población ante el yugo que suponía la religión corrupta en ese periodo histórico.
Recuerda: la información (no adulterada) en todas sus formas es verdad, y la verdad nos hace libres.
El Internet y Gobierno
Desde la creación del Internet hace más de 20 años y su expansión por el mundo; ha quedado claro que la manera en que consumimos información ha dado un paso gigantesco. Ya no solo usamos la imaginación para recrear escenarios descritos por los escritores, ahora podemos literalmente ver y oír lo que otras personas quieren expresar con sus creaciones, a través de los distintos formatos multimedia que ofrecen las diferentes capas del protocolo base de Internet.
Los gobiernos de todo el mundo han tenido que usar distintas marañas para ocultar la información que no desea ser divulgada, tal como las Iglesias medievales.
La era digital, un mundo donde todos estamos interconectados y la velocidad de la información viaja a la velocidad del rayo, donde todo y todos aprendemos por la retroalimentación constante de nuestros dispositivos móviles. El Internet de las cosas ya no es solo una visión, es una realidad.
Los Estados en el poder por su parte, pretenden hacernos tontos, ignorantes y dóciles con espejismos culturales totalmente alineados a una agenda idealista: propaganda. Esta es la manera en que los gobiernos han podido manipular a sus ciudadanos por cientos de años, y con el Internet se ha creado un arma masiva de verdades alteradas y guiones releídos. Los incentivos están mal, la honestidad no se paga porque la deuda es el pilar de todo. La deuda como sistema monetario carece de verdadero trabajo (al menos para aquellos que pueden crear más deuda con una entrada en la base de datos).
https://substackcdn.com/image/fetch/w_1456,c_limit,f_webp,q_auto:good,fl_progressive:steep/https%3A%2F%2Fbucketeer-e05bbc84-baa3-437e-9518-adb32be77984.s3.amazonaws.com%2Fpublic%2Fimages%2F8e5666be-95b2-43ce-af9c-32988076e199_1200x1600.jpeg
Criptografía, descentralización y escasez digital
Tal como Gutenberg, un(os) inventor(es) anónimo(s) bajo el seudónimo Satoshi Nakamoto descubrió la manera de poner en marcha un proyecto que permite separar el sistema monetario del Estado-Nación.
Bitcoin es un descubrimiento que se encontró uniendo varias piezas de un rompecabezas. Así como Gutenberg con la imprenta de tipos móviles mejoró invenciones ya existentes y lanzó su adopción por los cielos.
https://substackcdn.com/image/fetch/w_1456,c_limit,f_webp,q_auto:good,fl_progressive:steep/https%3A%2F%2Fbucketeer-e05bbc84-baa3-437e-9518-adb32be77984.s3.amazonaws.com%2Fpublic%2Fimages%2Fdfb5b8e5-fcdb-437a-a7db-92bc09484afd_1200x675.png
https://substackcdn.com/image/fetch/w_1456,c_limit,f_webp,q_auto:good,fl_progressive:steep/https%3A%2F%2Fbucketeer-e05bbc84-baa3-437e-9518-adb32be77984.s3.amazonaws.com%2Fpublic%2Fimages%2F270f0cd2-7b13-46cf-9d32-6da10044f46b_1200x675.png
https://substackcdn.com/image/fetch/w_1456,c_limit,f_webp,q_auto:good,fl_progressive:steep/https%3A%2F%2Fbucketeer-e05bbc84-baa3-437e-9518-adb32be77984.s3.amazonaws.com%2Fpublic%2Fimages%2F183df638-b064-4cbe-8ee1-cafaa5964ca4_711x514.png
nota: para mas info sobre este tema visita bitcoinmagazine. De aqui fueron tomadas las dos imagenes anteriores https://bitcoinmagazine.com/culture/bitcoin-and-the-printing-press
Bitcoin un proyecto que había sido lanzado una y otra vez bajo distintos nombres pero sin ningún momentum; hizo posible la adopción de un dinero sin entidad central o tercero que pudiese manipular las reglas del protocolo, pavimentando las calles para el transporte de dinero honesto criptográficamente verificable por cada nodo en la red.
Así como la tecnología de la impresión redujo el poder de los gremios medievales y alteró la estructura de poder de su tiempo, los métodos criptográficos cambiarán la naturaleza de las corporaciones y limitarán la intervención de los gobiernos en las transacciones económicas.
Timothy May, 1988
Dicen que la historia no se repite, pero si que rima. Si bien los gobiernos tratarán de aferrarse al poder, así como la iglesia en tiempos medievales trató de hacer ilegal el uso de la imprenta de Gutenberg y la difusión de información a través de los libros… Los gobiernos a través de los grandes bancos y gigantes pseudo -monopolios informáticos como Google, Meta, entre otros; intentarán desequilibrar la señal y balance del libre mercado para elegir el dinero honesto. En esto fallarán extraordinariamente, debido a la naturaleza del protocolo de Bitcoin, no existe un solo punto de fallo. No existe un CEO, un jefe, alguien a cargo. Es un ente que parece tener vida propia, parecido al sistema del reino fungi (familia a la que pertenecen los hongos).
La revolución comienza con la custodia propia
Si entiendes cómo funciona Bitcoin, entenderás que la única forma de tenerlo es conociendo tus llaves. Aquí, la información es propiedad en el nivel más explícito y literal de la oración.
Si la llave privada de tu llave pública está en tu poder, nadie más que tú y solo tú pueden tener acceso al envío de energía informática a través del Internet. Eres tú quien decide cuándo y cómo gastar tu dinero. La escasez del protocolo está escrita desde que el bloque Génesis fue minado y jamás podrá ser cambiada de nuevo. No hay entidad que devalúe su valor, tanto la tecnología como el sistema monetario de Bitcoin es deflacionario.
La naturaleza de Bitcoin es tal que una vez que se lanzó la versión 0.1, el diseño central se puso en piedra durante el resto de su vida útil.
Satoshi Nakamoto
Ya sea en cold storage (carteras que guardan tu llave privada dentro del dispositivo y nunca tocan el Internet) o una cartera en forma de app en tu dispositivo móvil, la custodia propia de tu bitcoin es la única forma de separarse de las rampas controladas por el sistema de legado.
Las casas de intercambio son un método conveniente de compra, pero no dejan de ser un punto de fallo debido a que pueden fácilmente capturadas por regulaciones del Estado.
Conclusión
La historia nos enseña que el poder se encuentra en la información. La descentralización informática está ocurriendo nuevamente en la era digital. Apple, Google, Twitter, Meta; solo por nombrar alguna de las más conocidas, son como la iglesia y, Bitcoin es la imprenta… Los libros provenientes de esa imprenta cambiarán el mundo.
Recuerda: Sino son tus llaves, no es tu casa.
-
-
 @ 18e3af1e:1d42e5df
2023-07-17 00:08:34
@ 18e3af1e:1d42e5df
2023-07-17 00:08:34Estos pasos que di (y que muchos como yo han dado) no son estrictamente literales, ni por numeración, o cualidades; pero si representan en su mayoría el dolor que algunos han tenido que soportar financiera, mental y físicamente, en todo el camino. Muchos, incluyéndome, vinieron por el dinero, por dar un salto rápido hacia las riquezas prometidas por escorias y charlatanes… Pero se quedaron por algo más noble: cambiar el sistema, cambiar el mundo.
“Crypto”
Curiosidad
Con una nueva generación, vienen nuevas tecnologías. Desde un punto de vista humano, cada uno busca su propia felicidad, aunque egoísta es lo que nos permite como especie optimizar el tiempo limitado que tenemos.
Existen otros tipos de humanos, a los que yo llamo “escorias y charlatanes” quienes persiguen el interés propio, pero a costa del limitado tiempo de los demás, pero gracias a ellos indirectamente llegamos a la convergencia.
Seguramente entraste en este mundo de las criptomonedas por Xcoin o Ycoin (o algunos de los más de 20 mil tokens que existen hoy), no fue casualidad… Fue marketing.
Escepticismo
Seguramente escuchaste por amistades o redes sociales de alguien que perdió mucho dinero jugando con estos tokens en el casino de las casas de intercambio. O quizás pensaste que era algo tonto y de moda, que no duraría más de un par de meses en desaparecer. Como un pensador lógico que eres, desististe de la idea de tan siquiera intentarlo.
Iniciación
Un día, escuchas sobre una palabra que ha retumbado en tu mente; ya sea porque vienes de un país con muchos recursos pero malos administradores, o porque simplemente conoces a alguien que habla sobre el tema: “Inflación”. Te dices a ti mismo “Si guardo mi dinero en el banco, todos mis ahorros se pueden ir en menos de una década” y decides meterte al mercado de stocks. Duraste un tiempo allí, pero te diste cuenta que no es lo tuyo, tienes que estudiar e invertir mucho tiempo que podrías usar en algo más productivo, o haciendo algo que te gusta.
Tu canal de YouTube o tu muro en Twitter, Facebook, Instagram o Tiktok está lleno de personas que dicen tener la llave para un mundo mejor:
“Solo invierte tu dinero aquí con esta nueva tecnología, nos vamos pa’ la luna” “El siguiente dinero del mundo” “Todos lo van a usar” “Es descentralizado” “Blockchain” “El siguiente Bitcoin”… Ya me entiendes.
Decides darle un vistazo y te sorprende lo fácil que es. Felicidades, ahora eres uno de los muchos como yo.
Especulación
En esta etapa ya eres a lo que llaman un “trader”. Pasas parte de tu tiempo revisando artículos, escuchando podcast o viendo videos sobre los últimos tokens que han salido al mercado. Revisas tu teléfono compulsivamente viendo como el precio de los tokens que compraste se mueve con volatilidad.
Es en este punto en el que ya probablemente hayas leído Tweets de algún “Bitcoin maxi”, llamando al token que compraste “shitcoin” y diciendo con total seguridad de que no resuelve ningún problema que una base de datos centralizada no pueda resolver, que lo que tú crees que va a revolucionar la industria es solo una falacia, un espejismo. Ignorando el comentario o respondiendo con un “Los Bitcoin Maxis son unos ortodoxos”, entre otros peyorativos que puedas encontrar.
Vives en tu burbuja, eres feliz allí (o eso crees) hasta el siguiente paso.
Primeras ganancias o perdidas
Aquí pongo un camino en Y. Si obtuviste ganancias de tus inversiones, donde todo es bonito y color de rosa; todas esas barritas verdes, donde crees que todo va a seguir subiendo hasta el infinitum, creeras que eres un genio. Seguiras apostando tu dinero (y si eres sensato dejaras tus ganancias a un lado), hasta que ocurra el desastre.
El Xcoin en el que habías invertido parte de tu portafolio empieza a caer, y cae rápido. Empiezas a preguntarte si venderlo ahora o esperar a que suba otro poco… Pasas 5 horas y vuelve a caer aún más. Felicidades, perdiste el 90% del dinero invertido. Razón? Xcoin era controlado por un grupo de personas que decidieron llevarse todo el dinero y dejar al Token sin liquidez ni uso aparente.
Si estas en el grupo de ganancias repetirás especulación hasta que entres al grupo de los perdedores, sino, caminaras un paso más.
Negación
No puede estar pasando. El dinero que has invertido, el tiempo… 90% solo se fue, sin más. Tratas de buscar culpables. Vas a Twitter, o canal de YouTube a demandar que se te devuelva tu dinero. Nadie te hace caso, y solo ves muchas personas más haciendo lo mismo de las cuales todas son ignoradas. No hay respuesta del creador o creadores de Xcoin.
Al final, todo fue tu culpa, aceptas que perdiste tu dinero. Jugaste un juego estúpido… Ganaste un premio estúpido.
Desinterés
Una vez en este paso, ya no hay más vuelta atrás. No hay shitcoin que te atraiga, tampoco lo hace Bitcoin. Para muchos, este es un momento de total nihilismo cibernético (hablando de Bitcoin y “Crypto”). Dependiendo de cuanto hayas perdido en uno de estos casinos de la nueva generación, eres más o menos resiliente a tan siquiera estar interesado en esta tecnología.
Repulsión
Muchas personas se quedan en este punto. No están abiertas a ningún tipo de idea que tenga que ver con “dinero mágico de internet”; Todo parece un fraude, una estafa. Es una pena que por culpa de unos cuantas escorias y charlatanes, se le quiten oportunidades a personas que tan desesperadamente buscan una salida al sistema monetario actual.
Si vives en un país beneficiado, donde puedes darte el lujo de perder un par de miles de dólares, pasar una rabieta de unos días y después olvidarlo… Tienes suerte.
Muchas personas ponen incluso sus ahorros de toda la vida, con tal de jugarse la lotería y tratar de hacer dinero rápido. Esas personas, como lo vimos con el infame TerraUSD y Luna, pierden no solo su dinero pero también su sanidad mental.
Lo que sigue
Hay una salida, si eres optimista sobre el futuro. Vivir recordando tus errores es lo más fácil; aprender de ellos y seguir adelante es lo que te llevara a encontrar la respuesta correcta.
Ser millonario no está mal, pero incluso ser millonario sin un propósito te dejara descubierto y desprotegido ante los pensamientos existencialistas que esta vida tiene para ti. No quieres ser millonario, quieres ser un millonario con propósito.
Bitcoin
Probablemente oíste de el por primera vez en una de las oleadas de Bitcoiners, por allá en el 2012-2015. O quizás, en alguna de las redes sociales pero decidiste no prestar atención porque no entendías lo que estabas leyendo o escuchando.
Curiosidad y escepticismo fueron parte de este camino también. Si este camino se cruzó con tu viaje por el mundo de “Crypto” posiblemente seas aún más cerrado para tomarte el tiempo de entender Bitcoin y lo que representa.
Aprendizaje
Esta para mí fue y sigue siendo uno de los pasos más interesantes sobre todo porque en teoría nunca dejas de aprender cosas dentro de todo el ecosistema de un protocolo mundial. La tecnología que rodea a Bitcoin siempre está en constante evolución.
Desde que haces tu primera compra en alguna casa de intercambio centralizada, comienzas un proceso de investigación bastante arduo (si eres un buen inversor) para saber qué es lo que estas comprando. Es en este punto en el que te das cuenta, que Bitcoin es más que solo una manera de invertir a futuro; es una manera de salir del sistema actual. Viniste por los retornos en tu inversión y te quedaste por algo que esta escalones y escalones más arriba: redistribución de riquezas mundial.
Evangelización
Cuando sabes de algo muy importante quieres contárselo a todos. Muchos te toman por tonto, otros solo ignoran lo que dices; pero siempre existirá alguien que entienda lo que dices o al menos intente entenderlo. Esas personas entraran por un proceso parecido al tuyo, o quizás, se salten de lleno toda la mala yerba que es “Crypto”, gracias a ti.
Gracias a ti, existirán muchas personas que no tengan que pasar por el dolor de perder su dinero y tiempo en estos casinos. Date una palmada de felicitaciones, porque en este último paso estas ayudando a construir un mundo mejor.
En conclusión
Cree este escrito no como un manual, sino más bien, como un diario de mis propias experiencias. Espero que de alguna manera te inspire a realizar algo que ayude a expandir los horizontes y esperanzas de muchos otros.
21 Millones es un número muy interesante.
Recuerda: Sino son tus llaves, no es tu casa.
-
 @ b5b75e66:3bc172e4
2023-07-16 23:48:32
@ b5b75e66:3bc172e4
2023-07-16 23:48:32Testing
-
 @ b5b75e66:3bc172e4
2023-07-16 23:45:59
@ b5b75e66:3bc172e4
2023-07-16 23:45:59Testing
-
 @ 32e18276:5c68e245
2023-07-16 22:47:17
@ 32e18276:5c68e245
2023-07-16 22:47:17Hey guys, I just pushed a new Damus update TestFlight. This should drastically improve longform event rendering. Let me know if you find any bugs!
Full Changelog
Added
- New markdown renderer (William Casarin)
- Added feedback when user adds a relay that is already on the list (Daniel D'Aquino)
Changed
- Hide nsec when logging in (cr0bar)
- Remove nip05 on events (William Casarin)
- Rename NIP05 to "nostr address" (William Casarin)
Fixed
- Fixed issue where hashtags were leaking in DMs (William Casarin)
- Fix issue with emojis next to hashtags and urls (William Casarin)
- relay detail view is not immediately available after adding new relay (Bryan Montz)
- Fix nostr:nostr:... bugs (William Casarin)
-
 @ 7f5c2b4e:a818d75d
2023-07-11 13:05:57
@ 7f5c2b4e:a818d75d
2023-07-11 13:05:57The Problem
Key delegation has been a hot topic in the Nostr community for ages now. Even though Nostr is a new protocol, things are moving so fast that it feels like it's been years since it was launched. If you think about it in terms of regular social media, it's easy to see why this feature is so important. It's like being able to give someone the keys to your house but still being the one who's in charge. A good example of this is how nsecBunker is helping nostr:npub10eezfnlq4ad2lyf3478na8f5las4l7guuf55vs8378lwtk87hd7slf6zka run a shared Nostr account. But that's just one use case. There are a lot more possibilities, and we're going to discuss some of them in this post.
Legacy solutions
The centralized nature of many platforms simplifies the problem of key management. Social media platforms like Facebook Business Manager, Twitter Business, and LinkedIn Pages offer built-in tools for delegating roles to team members without divulging original login credentials. Third-party platforms like Hootsuite, Buffer, and Sprout Social further streamline this process, enabling management of multiple accounts, scheduling posts, and assigning roles, all without compromising the security of original credentials.
For more technical solutions there are services like Amazon Key Management Service (KMS). KMS helps generate, control, and manage cryptographic keys used for data encryption. With KMS, you can create Customer Master Keys (CMKs), define usage policies, and set up automatic yearly rotation. When data is encrypted, KMS generates a data key, encrypts it with the CMK, and provides you with both plaintext and encrypted versions of the data key. The plaintext key is used for data encryption, then discarded, leaving only the encrypted data key. To decrypt, the encrypted data key is sent back to KMS, which decrypts it into plaintext, given the necessary permissions. This system is employed by many businesses and media outlets to ensure secure access and compliance.
However, while these traditional systems are robust, they leave the end-user dependent on the service provider, who retains the ability to revoke access at their discretion. And this is precisely the problem Nostr is trying to fix.
The Nostr Way
The First Attempt
The first attempt that received serious attention in this direction was NIP-26. It introduced a new 'delegation' tag that enables events to be delegated and signed by other keypairs. This proposal is meant to abstract the use of 'root' keypairs when interacting with clients, with the idea that a user could generate new keypairs for each client they wish to use and authorize those keypairs to generate events on behalf of their root public key, where the root keypair is stored in cold storage.
However, NIP-26 has been critiqued for its implications on key management. Arguably, the best explanation of the corresponding problems was layed out by nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 in his "Why I don't like NIP-26 as a solution for key management" post here. Initially, NIP-26 was praised for its optional nature. However, as NIP-26 began to be seen as a universal solution for key management on Nostr, it started to raise concerns. The concept entailed users generating a secure, offline key to sign delegation tags for each Nostr app, potentially rotating them periodically. This approach would make these keys "faceless entities" only identifiable by their master key, significantly changing the user experience and expectations from NIP-26.
This shift in approach would effectively render NIP-26 mandatory for usability, turning it from an optional enhancement to a necessary implementation for clients. This would remove the flexibility of choice and potentially complicate the protocol. Furthermore, while NIP-26 could provide some solutions in the realm of key management, it's not seen as a comprehensive solution. It's suggested that a multitude of key management methods could be more effective, maintaining the optional nature and possibly presenting a more elegant solution. There's an argument that if a mandatory key delegation method is indeed necessary for Nostr, an alternative design might be more optimized and easier to implement than NIP-26.
The Promising Alternative
NIP-26, while a noteworthy attempt, seemed to diverge from the core philosophy of Nostr. This discrepancy highlighted the need for an alternative solution that would respect this foundational principle and avoid precipitating Nostr down a slippery slope of mandatory adherence.
This is where nsecBunker, introduced by nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft, provides a compelling proposition. As the name suggests, nsecBunker enables users to establish and self-host their own bunker allowing them to manage Nostr keys. This Bunker can communicate with the user interface on your device, facilitating the creation of target keys, sharing them with corresponding Nostr users, and offering granular control over their interactions with the protocol.
Crucially, the implementation of nsecBunker does not necessitate significant changes in the builds of existing clients, preserving the opt-in nature of Nostr. Beyond adhering to Nostr's core principles, nsecBunker also holds potential to enhance user experiences and provide improved functionality, aspects I will elaborate on shortly.
How Does This Work?
nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft elaborates on the core concept behind nsecBunker:
nostr:note1uxjpstcw5ldxrlfzqvqs3nqqpvyumajz4r5elmaf8ffmjyu342qqwsn0yd
At a high level, this model bears similarities to the traditional Amazon KMS approach, albeit with certain distinct nuances. For a deep dive into the technical intricacies of this model, I recommend checking out nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft's work-in-progress SECURITY-MODEL.md on GitHub.
To put it simply, nsecBunker is a daemon that facilitates remote event signing. It operates with two types of keys: user keys and nsecBunker keys. The bunker key interacts with the admin UI and only communicates with the pre-defined (admin)
npub. Notably, this key doesn't store sensitive information or hold specific power -- it poses no threat to key material even if compromised.The user key, on the other hand, is used for signing purposes. These keys are encrypted with a passphrase following the same approach as LND. This passphrase is mandatory every time nsecBunker is initiated, and losing it equates to losing access to the keys.
During setup, the administrator pre-approves a key (or a set of keys) for communication with the nsecBunker. The administrator(s) then create target keys to distribute to the intended users. These users can interact with the Nostr infrastructure without ever accessing the private keys of the account they're using. Let's walk through the process of setting up a Bunker.
Running nsecBunker
Paid Subscription
The easiest way to run nsecBunker is to purchase a paid subscription. The process is very easy and intuitive and, thanks to Lightning Network, it does not require you to share any sensitive data, such as IDs or bank card details. Scan a lightning invoice and get access to your own bunker in seconds:
- Navigate to https://app.nsecbunker.com/ and press “Buy one here”:

- Click “Next”

- Paste your public key (or a few keys) you’d like to be in control of the target keys. The keys you’ll specify will be able to grant full or granular permission to target keys which, in turn, will be able to post on behalf of the admin account. The admin key will be able to, but have to be the same key that you’ll be signing as later on. This means that you will be able to create a target key to interact with Nostr and have it look like your account is the one that is logging in / posting / liking / etc., or a totally separate target key, which will be like a child account of yours, and won’t be linked to you for the outside world.

- Specify how many users you’d like to be able to sign Nostr events with the Bunker you are creating. The number of end users directly affects the yearly fee rate.

- Pay the lightning invoice

- That’s it – your keys management fortress is ready to be utilized.

Here's a quick demo on setting up and using your nsecBunker by nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft:
Alternatively, if you are confident in your tech skills, you can build your own nsecBunker. It’s an open source project, meaning that anyone can spin up their own version.
Docker setup
To quickly install nsecBunker via Docker run:
``` docker run -d --name nsecbunkerd pablof7z/nsecbunkerd start --admin
```
nsecBunker will give you a connection string like:
``` bunker://npub1tj2dmc4udvgafxxxxxxxrtgne8j8l6rgrnaykzc8sys9mzfcz@relay.nsecbunker.com
```
Visit https://app.nsecbunker.com/ to administrate your nsecBunker remotely. For details see the GitHub repository here.
Setting up your Connection
After procuring the string, navigate to https://app.nsecbunker.com/. Log in using your preferred NIP-07 browser extension. Ensure the Nostr account (nsec) you're using is the same one that is designated as the administrator. The bunker is designed in such a way that it will not reply or even recognize if anyone other than the administrator
npubis trying to communicate with it.
Input the connection string into the required field and hit 'Login'.
As you can see, I left my connection string visible in the screenshot above. This is to showcase that it doesn't require protection and is simply a way of connecting to your bunker. The security model here relies on your
npubbeing the only entity with an administrative account.You'll land on the following screen:
https://nostr.build/p/nb10013.png
Click the "Keys'' tab. If you see a "Loading" message under the "Keys" title, simply refresh the page, and you should see the "No keys created yet" message.
If after clicking the "Keys" tab button you do not see the "No keys created yet" message, that means there is some problem with the setup. It could be the mismatch of the pubs or the bunker could be offline.
You are now set to create and manage target keys (the npubs you will be able to share).
Creating a Key
Click on "Add Key". This will reveal a pop-up prompting for information necessary to create a new target access key.
https://nostr.build/p/nb10015.png
The Key name is self-explanatory: it helps distinguish your target keys.
The need to fill up the Nsec field depends on how you plan to use nsecBunker. If you leave the 'Nsec' field empty, a new Nostr account will be created. This lets you manage how the target key owner interacts with Nostr. But if you already have an account and want to give someone else access, you can do that by entering the private key for that account into the bunker. It's a similar result, but uses an existing account instead of creating a new one.
The Passphrase is crucial for encrypting your keys and securing communications. Every time your bunker restarts you will need a passphrase to enter the admin panel. Treat it with the same caution you'd exercise with your private key - without it, access to your managed keys is lost.
With these steps completed, you can now share the public key with the owner of the target account.
Activating the Target Account
To start posting with a target key, users should visit https://coracle.social/ and click the "Advanced Login" button, followed by "Log in with Nsec Bunker".
https://nostr.build/i/c493ee745080ad4fd58a5c796792cadb491a0f194adc478bc7735399fb386c04.png
Enter the
npubor a token received from the Bunker administrator.https://nostr.build/i/7106719c873683c21a970662ecf3ebf95149b774efd0f36b8c1efcc16c8dbb99.png
The standard account setup process applies here (in case of a new account), but stay in touch with the Bunker administrator, as they must approve all new interactions.
The nsecBunker Admin UI displays the authorization request for 30 seconds, implying the need for synchronous coordination with the person requesting permission.
While tokens do not require any authorization (more on this below), if you first log in to https://coracle.social/ with the
npub, the administrator will receive an authorization request...https://nostr.build/p/nb10017.png
...and will be prompted to name this session.
https://nostr.build/p/nb10018.png
Each subsequent interaction will also generate a request in the admin UI. You can either authorize interactions by event kind - Always allow - or bulk-authorize all future interactions - Always allow signing all kinds - (yet to be enabled).
The "Always allow" feature signifies that the administrator is required to authorize each event type just a single time. For instance, if a user wishes to post a note, which is kind 1 event, the administrator's authorization is needed only once for this specific event type. Subsequently, the user can post additional notes without requiring further permissions. Please be aware that as the tool progresses, the precision of access permissions will be further refined.
https://nostr.build/p/nb10019.png
Introduction of Policies (see below) streamlines the system by allowing the issuance of an authorization token for the receiver, making administrators' lives much easier.
That's it. The target account owner can now interact with Nostr users without ever touching private keys. See the note below, which was posted by a co-author of nostr:npub10eezfnlq4ad2lyf3478na8f5las4l7guuf55vs8378lwtk87hd7slf6zka, who does not have access to the Herald's private key:
nostr:note1hmz72mg8d2hegpj0npungypqsv3wqtffjq3q3duwmk5zcha860uqnx0mx0
For the video tutorial on setting up the nsecBunker check out this video by Pablo:
If you opt for the "Always allow all kinds" option, the setup process will only need to be performed once. Target account owners can then interact with other Nostr users without further assistance. However, if the managed account owner logs out of Coracle and logs back in, the setup process needs to be repeated for security reasons.
Tokens
Tokens allow you to issue permissions to users, which they apply to an npub of their choosing without requiring interactivity. Creating tokens is super simple:
- Head over to the Keys tab;
- Click on the Tokens button;
https://nostr.build/i/c190e60cb125dd418f7db649678b1f083b314df3bf898caecff59291b0e6a85f.png
- Click Add Token
https://nostr.build/i/be1c2d723d7f9e4c0849634cdeed037e3b3f0e0db728eafac270edd392097234.png
-
Fill up required fields
-
Client name is required for your own reference
- Policy lets you choose which rights you'd like to grant to the token holder
- Set an expiry date if you'd like
- Hit Create Token
https://nostr.build/i/a046336915eba2bd6748188e86aa6eb3d387fb7d0dc48dc8645772f1fdd5cfc1.png
Policies
The latest update to nsecBunker has introduced the "Policies" tab, a feature that enhances the authorization process and gives administrators more detailed control over permissions. This addition enables the creation of access tokens to distribute to account holders. Each token can be customized to permit certain event types, set an expiration date for the token holder's privileges, and even define the number of times user's interactions can be authorized.
To leverage this new feature, navigate to the "Policies" tab and select "New Policy":
https://nostr.build/p/nb10298.png
Give your new policy a name and a short description...
https://nostr.build/p/nb10299.png
-
The "Method" dropdown menu provides a way to refine the assigned permissions. While the default "Sign Event" option will suit most users, if you want to restrict the user to only engage with Direct Messages or the Highlighter, select the appropriate option. For instance, using the "Encrypt" method provides the user with permissions to send Direct Messages (DMs) and to generate Highlighter events, such as private notes. Conversely, the "Decrypt" option enables the user to access and read Direct Messages and other encrypted data that is specifically intended for the private key owner.
-
Within the "Permission" menu, you have the flexibility to either permit all actions or, as demonstrated in the above screenshot, restrict the user to only publishing long-form posts. This functionality could be beneficial, for instance, if you are delegating your blogging responsibilities and prefer the copywriter to not have access to other areas of your account.
-
The "Usage count" setting allows you to control the number of interactions the target account can perform.
Select "Add Policy" followed by "Save Policy". As illustrated below, your chosen settings will generate various types of access tokens, each with distinct rights and descriptions. The token at the top of the screenshot, for example, restricts the holder to only publishing long-form posts, while the token at the bottom grants the holder full access:
https://nostr.build/p/nb10300.png
Navigate to the "Keys" tab and select the key to which you wish to assign rights, as outlined by the policy you created. Note that you'll need to unlock the key first by pressing the corresponding button and entering your nsecBunker passphrase. Click on "Tokens"
https://nostr.build/p/nb10301.png
Select the policy you wish to assign to the key and, if desired, set an expiration time:
https://nostr.build/p/nb10302.png
Click on "Create Token". A token, which takes the form of a Nostr public key, will be generated. You can now share this token with the intended user:
https://nostr.build/p/nb10303.png
For a live demonstration of this feature, check out Pablo's video:
Use Cases
"The possibilities of nsec bunker are endless." - nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn
The pace of development in the Nostr ecosystem is impressive. Just a day after the release of nsecBunker, nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft integrated Bunker support into another one of his creations - the Highlighter.
nostr:note1u8x403llme28vpnsz83las60rgfuw2ht9hcf5tsscl3lnfgdlvkqu3096n
You can find out more about this super efficient productivity tool in my earlier guide here: nostr:naddr1qqxnzd3cxg6rxdfkxyerzv3nqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa28mg64kz. As the Highlighter was recently redesigned, my guide needs some updates, but it's still a great resource to understand what Highlighter is and how it functions.
The revamped Highlighter is loaded with new features, such as Lists, Highlights, Private Notes, and of course, the nsecBunker login option. With this feature, you can log into the app without ever disclosing your private key to either the app or the NIP-07 extension provider.
The integration of Highlighter with nsecBunker paves the way to nostr applications that work seamlessly with browsers that don't have a NIP-07 extension, as is the case in most cases on mobile, massively lowering the adoption of Nostr among a general, less tech-savvy, audience.
To use this feature, click on "Sign in" instead of logging in with your browser extension...
https://nostr.build/p/nb10150.png
...and enter the
npubyou got with the nsecBunker:https://nostr.build/p/nb10154.png
As the administrator approves your connection you get logged in. The process here is identical to the one I described for Coracle.
https://nostr.build/p/nb10155.png
Take note, with the introduction of Policies, the Highlighter - fully integrated with nsecBunker - also supports the fine-tuning of corresponding permissions:
https://nostr.build/p/nb10304.png
Highlighter showcases just one of many use cases of nsecBunker. Here are some more, but keep in mind that I'm only giving you a brief overview of the tool's potential:
-
Separate Accounts for Different Use Cases: nsecBunker enhances your security model by allowing you to retain your private key while using different Nostr clients.
-
Collective Social Media Account Management: nsecBunker can be used by journalist teams or companies to collectively run social media accounts, increasing user awareness of their products or services.
-
Child Control: Parents can utilize nsecBunker to set up accounts for their children, ensuring they adhere to family practices.
-
Burner Accounts: nsecBunker enables you to create specific accounts for specific use cases, all under your control.
-
Corporate Accounts: Businesses can generate keys for their employees, allotting rights specific to their positions.
However, the applications of nsecBunker are not limited to these. For example, one exciting possibility that emerged shortly after nsecBunker's release was the potential solution to creating private groups within the Nostr community. As nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn astutely observed, the possibilities with nsecBunker are indeed endless. Have a look at his long form post here: nostr:naddr1qqwkzttswfhhqmmnv9kz6en0wgkhqunfweshgefdvaex7atswvq3jamnwvaz7tmjv4kxz7fwdehhxarjd93kstnvv9hxgqgewaehxw309ac82unpwe5kgcfwdehhxarj9ekxzmnyqy2hwumn8ghj7mn0wd68ytnfdehhxarp9e3kxqg4waehxw309ahx7um5wghx66tvda6jumr0dsq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqyg8wumn8ghj7mn0wd68ytnhd9hx2qtxwaehxw309anxjmr5v4ezumn0wd68ytnhd9hx2tmwwp6kyvfsv9mh56mwdfnn2u34d3sk5mnjx5engvecdejxx7t209kxwutnwfh8yar3x4nhyue58y6hvdpjw93nvcthwd4rgdtewvmn7cnjdaskgcmpwd6r6arjw4jsz9nhwden5te0vf5hgcm0d9hx2u3wwdhkx6tpdsq35amnwvaz7tmjv4kxz7fwdaexzmn8v4cxjmrv9ejx2asprfmhxue69uhhyetvv9ujumn0wd68yurvv438xtnrdaksz8rhwden5te0w4hxjan9wfek2tnwdaehgunfvd5zumrpdejqz8rhwden5te0dehhxarj9ekh2arfdeuhwctvd3jhgtnrdaksz9thwden5te0v4jx2m3wdehhxarj9ekxzmnyqyv8wumn8ghj7un9d3shjtnwdaehgunpw35jucm0d5pzp978pfzrv6n9xhq5tvenl9e74pklmskh4xw6vxxyp3j8qkke3cezqvzqqqr4guzz40fz
Supported clients
Here's a list of Nostr clients supporting nsecBunker (keep in mind that new clients are actively adding support of this tool, so the list may not always be extensive, feel free to leave comments if you see that some clients are missing):
Note that every client that offers you to login with a so-called "NIP-46" supports nsecBunker login.
Nostr = Everything × Freedom
Harnessing the unparalleled power of the most advanced currency humanity has ever seen, Nostr is an open and censorship-resistant protocol that promotes freedom of expression and allows you to stay anonymous. Its very foundation is rooted in open-source principles, making the collective knowledge and experience gathered through its development accessible to all. The protocol itself, along with most Nostr applications, are open-source. This allows anyone to contribute, adapt, or even build upon existing developments to create something uniquely their own. This is where the true power of censorship-resistant, open-source software resides - it's unstoppable.
Legacy systems, bound by their proprietary constraints, simply cannot compete with the collective intellectual power of what began as a cypherpunk movement and has now blossomed into a vibrant community of dedicated individuals. These individuals are committed to bettering the world, rather than merely filling their pockets with others' hard-earned money. Together, we are paving the way towards a future where freedom of speech and self-sovereignty are the norm, and the fruits of our labor contribute to societal progress. This collective effort fosters the creation of tools that empower us to build better, move faster, and grow stronger. More on this in my post here: nostr:naddr1qqxnzd3cxs6rxv3hxsensv3nqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa28z78gua.
We invite you to join this peaceful revolution. Participate in the growth of permissionless protocols, contribute to open-source software, and share your ideas to further enhance this vibrant ecosystem. Together, we are not just evolving technology - we are shaping a more open, inclusive, and equitable future.
Like what nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft is building? Make sure to support him!
-
Pablo's Nostr account: nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft
-
Pablo's site: https://pablof7z.com/
-
 @ 7f5c2b4e:a818d75d
2023-07-05 13:45:17
@ 7f5c2b4e:a818d75d
2023-07-05 13:45:17This FAQ is also available in Spanish: nostr:naddr1qqx9zat994jhxttgv93xccgpr9mhxue69uhhyetvv9ujumn0wd68y6trdqhxcctwvsq3jamnwvaz7tmsw4exzanfv3sjumn0wd68ytnvv9hxgqg4waehxw309ahx7um5wghxjmn0wd6xztnrvvq32amnwvaz7tmwdaehgu3wd45kcmm49ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgswaehxw309ahx7um5wgh8w6twv5qkvamnwvaz7tmxd9k8getj9ehx7um5wgh8w6twv5hkuur4vgcnqcth0f4ku6n8x4er2mrpdfh8ydfnxsensmnyvduk57tvvachxunwwf68zdt8wfengwf4wc6ryutrxeshwum2xs6hjueh8a38ymmpv33kzum58468yat9qyt8wumn8ghj7cnfw33k76twv4ezuum0vd5kzmqprfmhxue69uhhyetvv9ujummjv9hxwetsd9kxctnyv4mqzxnhwden5te0wfjkccte9ehx7um5wfcxcetzwvhxxmmdqyw8wumn8ghj7atwd9mx2unnv5hxummnw3exjcmg9ekxzmnyqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdqy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqgcwaehxw309aex2mrp0yhxummnw3exzarf9e3k7mgzypl4c26wfzswnlk2vwjxky7dhqjgnaqzqwvdvz3qwz5k3j4grrt46qcyqqq823crwnvag thanks to nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624
What is Habla News?
Habla is a Nostr-based platform that allows you to create and manage long-form posts. You could compare it to Medium, yet Habla is so much more than that. Habla is superior to traditional blogging platforms because it is built on top of Nostr. It is interoperable with a plethora of other Nostr apps, which makes the user experience seamless and more engaging. Moreover, thanks to the Lightning Network, your input – if found valuable by the readers – can and will be instantly rewarded with the best money humanity has ever witnessed: bitcoin.
What is Nostr?
Nostr is a new way to communicate online that provides a ton of benefits for its users. It is free for everyone; you do not require an ID or any other third party verification to start connecting, mingling with like-minded people, and growing the community around you. Nostr is often mistaken for a social media platform, but it is much more than that. We encourage you to check out the Nostr resources gathered here to realize the potential magnitude of this tool.
How do I sign into Habla?
To start writing on Habla, simply create an Habla/Nostr account and log in. Follow these few simple steps to register, start sharing value, and receive value back.
How do I earn with Habla?
Habla allows you to receive value directly from your readers. No bank account or ID is required. Simply connect your Lightning address to your Habla / Nostr account and receive funds directly to your wallet – no third parties, no waiting for withdrawals, no sweat. Follow these simple steps to do so.
Why is posting on Habla different?
The Nostr protocol is super lightweight, which introduces some peculiarities into how the Nostr-based apps must behave. We won't go into technical details, but the most obvious difference you will notice as a content creator is that you'll have to use a different and, possibly, unusual format of text while composing your posts. But fear not; Habla provides tools that make this process easy and intuitive. Here's a quick video by nostr:npub1wkljx5c6a8uccc5etws8ry0y3r4dgavh2dcav0tal4rtmcdl4z2sfu5u0t explaining the basics of posting with Habla (the guide was made prior to the redesign, yet remains useful):
https://nostr.build/p/nb9474.mp4
Habla (and many other Nostr apps) uses the well-established format, which is called Markdown. It has been around for almost a decade now and is supported by most apps you use every day. The reason you might not have heard about Markdown is because traditional apps usually hide it from the user, and we are working on doing so as well. You can find out more about Markdown here.
Where is my content stored?
Traditional blogging platforms store your content on their own servers. It is a convenient and (used to be) solid approach, but it bears critical risks. Leaving the fruits of your labor with a single party means they have full control over your content. Nostr fixes this. Every time you post something, your content is broadcast to numerous relays for further storage and redistribution. If any relay operator blocks your post or refuses to redistribute it, your readers can turn to other relays and access your content (do not worry if this sounds complicated; everything happens under the hood). This ensures you never get silenced. That said, Habla does not run its own relay; we've decided to concentrate on what we do best – build an intuitive, efficient, and easy-to-use blogging platform that rewards – and leave the content storage and distribution to the pros in that field.
How do I post?
Habla provides all the necessary tools to produce rich posts that stand out. Prepare your article, format your text with the help of designated tools, add media, and preview the results prior to publishing. All you need is at your fingertips, and the platform is only getting better and friendlier day by day.
Who can read my posts on Habla?
Anyone on the Internet can read your posts. However, if your readers would like to interact with your work – be it by following you / commenting / giving value back – they should create a Nostr account. We encourage you to onboard your followers to grow a thriving community and reach new heights. This quick guide will help you and your peers get started.
This FAQ is a work in progress, and it will evolve as both Habla and Nostr develop into even more powerful tools. Please provide feedback so that I can make it better.
-
 @ 7f5c2b4e:a818d75d
2023-07-16 14:45:19
@ 7f5c2b4e:a818d75d
2023-07-16 14:45:19There's been a fair share of complaints about Habla's links and those lengthy naddr strings 😅. These strings are part of the Nostr protocol and are used to identify unique published events. It's not just Habla, other long-form post platforms use them too. But I understand, they can be a bit much. Take a look at this behemoth of a link:
nostr:naddr1qqxnzd3cxy6rjv3hx5cnyde5qyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa28qxmz8jIt's not surprising that people might be asking, "Is this spam?" or "Is there a virus hidden in there?"
You might be wondering, "Why not just use 'normal links' from the start?" Well, it's not as simple as it seems. Every app based on Nostr needs to be compatible with the protocol and other clients. If we cut corners, we'd end up with a regular app, not much different from the big centralized platforms. But the good news is, people are starting to see the downsides of traditional platforms like Facebook and Twitter: they hoard your data, hold your content hostage, and they lack interoperability.
The Habla team has been focused on building on Nostr's solid foundation. This ensures Habla follows the same rules as other Nostr-native apps, making it interoperable and resilient. Now, that the foundation is laid, the time has come to make things more user-friendly and less intimidating for newcomers.
User-friendly URLs
User-friendly URLs are often taken for granted. But as I mentioned earlier, they're not so easy to implement in a decentralized environment. Yet, they are already here!

Now you can publish a post on Habla and give it a URL you like. Plus, it'll have a preview, making it look just like traditional posts, like the ones you see on Medium or Substack. But don't worry, Habla posts still have all the advantages Nostr provides: you're still in control of your content, you've got access to peer-to-peer permissionless payments, and you can't be censored.
nostr:note1wecyc8ahzyr3hgn5m7ztrp73kg7vtenca4ph82rsp0hl30lmh0ksk07sqy
Here's what Habla post links look like on popular clients now:

The link format will show the platform's domain (habla.news), your account name (tony), and an ID that you get to pick. This applies to every user who has received a Nostr address with Habla. If you're interested in getting one, don't hesitate to reach out to nostr:npub107jk7htfv243u0x5ynn43scq9wrxtaasmrwwa8lfu2ydwag6cx2quqncxg (this process will be automated soon™). If your nostr address is anything other than
your-name@habla.news, your full nostr address will be displayed in the URL between the domain and the identifier, like so:https://habla.news/u/satoshi@bitcoin.org/article.To choose the ID, just change the string of numbers in the last field on your creator dashboard while you're composing a post:

Remember, this is a unique identifier. So, if you decide to change it after saving a draft or posting your article, you'll end up with a new post and a new identifier. So, double-check everything before you hit save.
All Habla posts will now show the human readable URLs in the search bar of your browser, making it easy for you to copy, paste and share the articles. However, some users may still want to get a hold of that
naddrlink I’ve mentioned earlier. This can be done by clicking the Share button right next to the article’s title:Still Early
This is a big step forward, but we've still got a long road ahead. There are loads of new features and improvements coming your way, so hang tight and let us know if you run into any bumps along the road. Feel free to reach out to nostr:npub107jk7htfv243u0x5ynn43scq9wrxtaasmrwwa8lfu2ydwag6cx2quqncxg or me at nostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7.
Nostriches are building something that we hope will stand the test of time. Nostr and the tools built on it are all about making sure our kids don't grow up to be digital slaves. That's why we're taking things slow and steady, rather than rushing for quick wins.
I want to give a big shout-out to everyone who's joining us in this peaceful revolution - developers, content creators, testers, and shitposters 😄. We're all in this together, even when things don't work as expected or aren't quite ready for prime time. We keep pushing forward. This will pay off - being a pioneer always does! LFG!
-
 @ c8df6ae8:22293a06
2023-07-16 06:48:03
@ c8df6ae8:22293a06
2023-07-16 06:48:03Celsius lied to investors by presenting itself as a safe investment opportunity and a chance to gain financial freedom, but, behind the scenes, the company operated a failed business model and took significant risks with investors' crypto assets.
— Gurbir S. Grewal, Director, Division of Enforcement, SEC
Aloha! The latest issue of the Bitcoin For Families newsletter comes to you all the way from Maui 🤿🏖️☀️ and it will help you avoid the next Celsius.
Bitcoin is not an investment tool. It's a savings tool
This week the Securities and Exchange Commission (SEC) charged Celsius and its founder Alex Mashinsky with the unregistered offer and sale of crypto asset securities through Celsius’s lending program, making false and misleading statements, and engaging in market manipulation
If you invested your money there, that money is gone and I'm sorry for you.
If you’re new to Bitcoin and you are considering buying Bitcoin, you’re probably wondering:
How do I avoid the next Celsius?
How do I make sure that I’m working with a company that won’t pull the rug out from under me?
There is no such thing as 100% certainty, but based on my experience, the companies that meet the following criteria are unlikely to rug pull you: * Bitcoin only - Does not offer yield - Encourages you to self-custody
Bitcoin only
There is Bitcoin, and then there is everything else.
The SEC itself classifies Bitcoin as a commodity and all other crypto currency tokens as securities (and most of them operating as unregistered securities).
Companies that focus exclusively on Bitcoin are driven by their desire to expand the adoption of Bitcoin.
These companies won’t try to sell you other tokens (shitcoins) and promise you that you’re going to catch the next wave, the next token to go to the moon, just to take your money.
Does not offer yield
Bitcoin is like digital gold. Bitcoin on its own does not produce anything and therefore it offers no yield.
A company that offers you certain return on your Bitcoin deposits can only do so by giving your deposits to speculators and hoping that they will deliver a return equal or higher than what this company offered you.
They also really hope that the speculators don’t lose your money because that’s when they start doing the funny accounting to hide the loses.
You want to avoid that. Don’t chase yield.
Just save with Bitcoin and be happy that your savings are stored in the soundest money in the world.
Encourages you to self-custody
Bitcoin was built so that no one can rug pull you. If you self-custody your Bitcoin, as opposed to letting others custody it for you, It has no counterparty risk.
When you self-custody your Bitcoin, nobody can take it away from you. There is no rug to pull.
You want to self-custody and therefore you want to work with companies that encourage you and make it easy for you to move your Bitcoin from their custody to yours.
My recommendations
These are the companies that I feel comfortable recommending.
Swan
I buy Bitcoin with Swan. Their CEO is extremely vocal in calling out crypto companies that he believes are doing the wrong thing: he called out FTX and Celsius way before they collapsed and he has also called out Binance (which hasn’t collapsed, so far).
If you want to open an account with them, use the referral link at the bottom of the newsletter and you will get $10 worth of Bitcoin free.
Just watch the latest episode of their Swan Signal episode to get an idea of how they operate:
Unchained
Unchained offers storage, inheritance and retirement Bitcoin products. I have not worked with them but I have heard very good feedback from people I trust.
Notable notes
Recommendations
Cory Klippsten
Cory is on a mission to onboard 10 million people to Bitcoin and help them self-custody.
Follow him on Twitter if you want to stay clear of unethical operators in the industry. He has no qualms calling them out.
Bitcoin Breakdown
Bitcoin Breakdown gives you the TLDR summaries of the biggest events in Bitcoin. A fantastic way to stay up to date with the industry.
Check it out here.
What did you think of today's newsletter?
Your feedback helps me create the best newsletter possible for you.
Please leave a comment and checkout comments from other subscribers and readers. I love hearing from the Bitcoin For Families community ❤️ 🙏🏻
Buy Bitcoin with Swan
If you want to buy Bitcoin, I highly recommend using Swan. They are a Bitcoin only business that is focused on self-custody and educating their users. It's where I buy my Bitcoin.
Use this link to receive $10 free to get you started.
See you again next week! — Alejandro
This newsletter is for educational purposes. It does not represent financial advice. Do your own research before buying Bitcoin.
-
 @ 32dc4f25:f95ddcce
2023-06-30 02:52:42
@ 32dc4f25:f95ddcce
2023-06-30 02:52:42Nostr, short for “Notes and other stuff transmitted through relays,” is a new communication protocol developed in 2021 by Lightning Network developer fiatjaf, which evolved out of LNBits developer Ben Arc’s attempt at a fully-decentralized marketplace called Diagon Alley. As opposed to other communication solutions, which mostly function via dumb clients and smart servers, Nostr offers smart clients and dumb servers, which heightens censorship resistance for users.
In Nostr, all data is stored locally with users and merely distributed via relays, rather than stored on central servers, such as via Twitter. In the case of social media, Nostr increases censorship resistance, as users are enabled to fully own their own content and profiles. In light of recent controversies around Twitter’s censorship policies, users began migrating toward the federated communications solution Mastodon. However, in Mastodon, ownership over content and profiles lies with those running the Mastodon servers users signed up with. While federations such as Mastodon offer more censorship resistance than centralized servers — as users are able to simply sign up to another server when censored — criticism has arisen around potential censorship on Mastodon through server owners.
In December 2022, the Nostr community received a 14 BTC grant from Twitter Founder Jack Dorsey, which brought unprecedented attention to the protocol. As applications built on Nostr evolved, the mobile client Damus jumped to number one in social networking on the iOS app store in China, resulting in its ban. In an apparent effort to contain the #MarchOffTwitter, Twitter CEO Elon Musk shortly banned the publication of Nostr-related content, along with bans on other third-party platforms such as Instagram, but to no avail.
While Nostr is by no means a privacy protocol, it could bring potential improvements to Bitcoin privacy.

A Nostr public key shared via Twitter, 2022
While Nostr is not a privacy protocol per se — among other issues, clients by default leak users’ IP addresses to relays — the Nostr protocol could bring improvements to Bitcoin privacy.
Improving Privacy And Scalability Of BIP47
BIP47 is a Bitcoin Improvement Proposal to create reusable payment codes while protecting the privacy of users for recurring payments. Without BIP47, users need to tediously generate new addresses by hand to avoid address reuse. When a user reuses an address for transactions, the user enables anyone watching the blockchain to easily cluster all transactions belonging to the address reused and form a graph of the user’s payment history and net worth. The prevention of address reuse is therefore a privacy best practice in Bitcoin and already implemented in many Bitcoin wallets by default. However, when a user aims to establish recurring payments with another party, such as in a merchant-customer relationship, a frequent generation of new addresses can be inconvenient.
With BIP47, a customer can generate a set of addresses to use for payments for the merchant. If a customer purchases products monthly, the merchant would need to send the customer an address each month. With BIP47, the customer creates a dedicated payment code for the merchant, which functions similarly to an extended public key. This allows the customer to automatically generate new addresses for the merchant, instead of the merchant needing to create addresses for the customer.
BIP47 makes use of notification addresses, which are monitored by HD wallets for outputs. In a notification transaction, the merchant sends the customer a blinded public key and chain code via the OP_RETURN field, together with a shared secret to keep the shared addresses private on the public blockchain. This exchange creates several issues due to the architecture of the Bitcoin network. The first two are economic: A notification transaction consists of 80 bytes, which can become expensive for users when fees on the Bitcoin network are high. Notification transactions, in addition, create unsendable outputs, which bloat the UTXO set over time. This increases the computing load on Bitcoin nodes who, at the time*, need to store the entire UTXO set, meaning every Bitcoin output that has not been used as a new input to ensure the validity of transactions.
A notification transaction creates so-called toxic change. When a user receives change from a notification transaction and spends the change to a third party, anyone watching the blockchain is able to correlate the user’s recurring payments to their non-recurring payments, even when addresses are not reused. A notification address also only exists once for each wallet. If a merchant wanted to establish recurring payments with 10 customers, anyone watching the blockchain is able to gain insight into the merchant’s customer base, as all 10 customers would need to create notification transactions for the merchant to the same notification address.
Instead of using notification transactions to exchange payment codes between merchants and customers, payment codes could be exchanged via Nostr. As opposed to other communication methods, Nostr is suitable for the exchange of BIP47 payment codes as no central authority exists to potentially censor the exchange of messages. At the same time, all direct messages on Nostr are encrypted by default, eliminating the need to compute shared secrets. By making use of BIP47 via Nostr, users can avoid the creation of UTXO set bloat via unspendable outputs and eliminate the correlation of recurring versus non-recurring payments as well as the publication of customer bases through the avoidance of toxic change and the re-use of notification addresses.
*Note: Storing the entire current UTXO set for Bitcoin nodes may potentially be eliminated in the future via the implementation of UTreeXO, which shifts the burden of proving that a transaction spends a valid UTXO to the owner of the UTXO, reducing the storage requirements from gigabytes to kilobytes.
Nostr Pay-To-EndPoint
In Bitcoin, blockchain analysis services operate the heuristic of “common input ownership” to map transactions to identities. Within this heuristic, a transaction containing different public keys used as inputs is classified as belonging to one person. Due to its UTXO-based architecture, through which inputs and outputs of transactions are linked, the Bitcoin protocol is also prone to subset sum analysis. In subset sum analysis, adversaries are able to calculate the probability of inputs and outputs belonging to the same entity, even when different public keys are used as inputs to one transaction. For example, if a transaction has inputs of 1, 4, 7, 23 and 6, and outputs of 5 and 36, it can be deduced that input 1 and 4 and inputs 7, 23 and 6 belong to the same entity.
 Source: “Knowledge Discovery In Cryptocurrency Transactions: A Survey” by Xia Fan Lu and Xin-Jiang Jang, 2021
Source: “Knowledge Discovery In Cryptocurrency Transactions: A Survey” by Xia Fan Lu and Xin-Jiang Jang, 2021Pay-to-EndPoint (P2EP) is a privacy-preserving reinvention of Satoshi Nakamoto’s Pay-to-IP (P2IP) coded into the original Bitcoin client. One form of a P2EP transaction are PayJoins, which are transactions designed to break the common input ownership heuristic. In a PayJoin transaction, both the sender and the receiver contribute inputs to a transaction to break the common input heuristic. With PayJoins, users exchange information about what UTXOs will be used as inputs via any communication channel, such as a Tor Onion, which functions as the end point, to construct a partially-signed bitcoin transaction (PSBT). Once both parties have agreed to the terms and signed the transaction, a PayJoin transaction looks just like any other Bitcoin transaction on chain. Because involved parties act as both sender and receiver, a PayJoin transaction breaks the common ownership heuristic as well as subset sum analysis: parties may contribute inputs of 3 and 5, while the transaction generates outputs of 6 and 2.
 *Source: “Pay To EndPoint” by Adam Fiscor, 2018 *
*Source: “Pay To EndPoint” by Adam Fiscor, 2018 *The problem: PayJoin transactions are complicated to coordinate, as participants have to be online at the same time when using a clearnet domain or Tor Onion endpoints. If a user initiates a P2EP transaction and, for example, closes their computer or otherwise disturbs network connectivity, the transaction cannot be communicated. In Nostr, communication is asynchronous: users fetch information from relays once network connectivity is restored. By using Nostr keys instead of Tor Onions as endpoints for P2EP transactions, P2EP transactions could be coordinated more easily.
Another implementation of P2EP is the much-debated LNURL. With LNURL, instead of tediously needing to generate new invoices for each transaction, users are able to receive a static endpoint pointing at a web server to automatically generate new invoices. However, because web servers are reliant on the global Domain Name Service (DNS), users of LNURL inevitably reveal their identity to the hosting provider, as well as their IP address to payees if no proper precautions are taken. Wide adoption of LNURL would therefore be a detriment to the pseudonymity of the Lightning Network. Instead of using a web server as the endpoint for LNURL, users could use Nostr keys as endpoints for LNURL transactions to conceal their identities.
Nostr For CoinJoins
While a PayJoin is great to break the common ownership heuristic as well as subset sum analysis, PayJoins are unable to offer privacy to both sender and receiver toward the cooperating party. PayJoins are essentially two-party CoinJoins, limited to two participants — this means that both sender and receiver are aware of their own inputs and outputs, leaving the inputs and outputs of their partner identifiable. Unless a PayJoin is facilitated with CoinJoined transactions, users risk revealing their wallet balances as well as past and future transactions to their PayJoin partners.
In anonymous-amount credential systems such as Wasabi Wallet’s protocol for CoinJoin coordination, WabiSabi, Nostr keys can function as communication endpoints for the coordination of a CoinJoin transaction. This enables the sender and receiver of a CoinJoin transaction to exchange the credentials needed to participate in CoinJoin rounds, essentially enabling a form of discreet payments within a CoinJoin. With the use of Nostr keys as endpoints in CoinJoins, cooperating parties remain unaware of their counterparties’ balances and transactions by hiding in the crowd. At the same time, using Nostr keys as endpoints for CoinJoin transactions helps PayJoin users save on fees by facilitating payments directly within the CoinJoin, rather than CoinJoining to facilitate the payment after.
Another use for Nostr in CoinJoins lies in the discovery of coordinators. While most CoinJoin coordinators run behind Tor to obscure the identity of CoinJoin participants, users are currently unable to easily discover new coordinators to join with the exception of JoinMarket, a CoinJoin marketplace targeted toward more advanced CoinJoin users. While CoinJoin users are able to add custom coordinators to Wasabi Wallet — a trivial task as easy as exchanging a URL in the backend — no way exists to automate the process of updating coordinators due to the lack of a platform for publication. Instead, to discover new coordinators, users must search social media and forums, such as Reddit or Twitter, to add coordinators manually. However, the publication of a coordinator service via social media or forums may pose a risk to coordination providers depending on the policies applied to the service, as certain pages may easily be shut down.
If Tor is an anonymous remailer, meaning a protocol facilitating the anonymous forwarding and receiving of messages between peers, Nostr can function as an anonymous bulletin board. CoinJoin coordinators can publish their services via a Nostr event type, and CoinJoin wallets can be enabled to automatically pull from those relays to display within their clients. The broadcasting of coordinator servers via Nostr, such as facilitated via BTCPay’ Servers CoinJoin plugin and proposed in the Lightning-enabled CoinJoin software Vortex, can eliminate the need to manually search for and add CoinJoin coordinators in CoinJoin clients, helping to further decentralize the CoinJoin coordination landscape.
Circumventing IP Requirements With NOSTR
As touched upon previously, the Nostr protocol was originally conceptualized to realize a fully-decentralized marketplace called Diagon Alley. As the Nostr protocol evolved, Diagon Alley became the LNbits extension NostrMarkets: a Nostr-native marketplace which enables merchants and customers to run and interact with online shops via relays. In NostrMarkets, customers can subscribe to a merchant's public key to fetch products from relays instead of accessing a merchant’s site via a webshop. This increases the censorship resistance of online shops, as merchants are not dependent on seizable websites — rather, a merchant’s shop is hosted with all relays the shop sets up to communicate with. Even if the merchant's server were to be seized, its shop could easily be set up at a different location, as all products are stored with relays on the Nostr network. NostrMarkets handles order and payment coordination via encrypted Nostr direct messages, while payments are facilitated through the Lightning Network.
In addition to its censorship resistance, the LNbits extension NostrMarkets enables fully-anonymous marketplaces. Instead of exposing a merchant’s IP to the whole world, both merchants and customers only reveal their IPs to the relays they connect to, which can easily be mitigated by running a client or shop behind Tor. As an upside to fully running a shop behind Tor, which makes a shop only accessible via the Tor browser and .onion web pages, NostrMarkets can run in any web browser or smartphone, improving the user experience of privacy-preserving, client-server communications. Because payments are negotiated via encrypted Nostr direct messages and facilitated via the Lightning Network, payments in NostrMarkets remain comparatively private as long as the shop’s Lightning node runs behind Tor, as a payment coordination direct message is indistinguishable from other direct messages in Nostr.
Another way to circumvent the requirement of IP addresses in server client communication is NOSTREST. REST, short for “representational state transfer,” is part of the software architecture of the world wide web, used to facilitate communication between servers and clients via GET, POST, PUT, DELETE and PATCH requests. But, when a client sends a REST request to a server, IP addresses are revealed, potentially revealing personally-identifiable information. On GitHub, escapee proposed a REST API bridge built on Nostr, called NOSTREST. By using Nostr keys without identification headers, both users and server operators do not need to know the IP addresses of their counterparts. A NOSTREST implementation can therefore improve the privacy of Bitcoin applications using REST as servers do not need the clients’ IP addresses.
One such example could be the running of custodial Chaumian e-cash mints, a form of anonymous-amount credential systems. In an e-cash mint, the mint operator does not know the balances or value exchanged by its users. However, due to the current architecture of REST, it does learn the user’s IP address unless running behind Tor by default, such as in the e-cash system Cashu. But implementing and managing Tor support is tedious. With the NOSTREST bridge, projects can easily preserve the privacy of their users. By running an e-cash mint behind Tor using NOSTREST to communicate between server and clients, communication can be facilitated asynchronously, while both server operator and user only learn each other’s public keys, eliminating the risk of identification via IP.
*The original author of this article is L0la L33tz. It was initially published in Bitcoin Magazine. Original article link: https://bitcoinmagazine.com/technical/how-nostr-can-improve-bitcoin-privacy
*
-
 @ c5fb6ecc:e58c38bb
2023-05-12 00:59:58
@ c5fb6ecc:e58c38bb
2023-05-12 00:59:58https://ln.tips is a great wallet. It's an extremely easy to use, custodial Lightning wallet for the masses. Each telegram account has it's own
@ln.tipsLN Address, but sometimes you want to use your own domain.In this guide I will teach you how to setup LN Address redirection with your own domain using Cloudflare's Redirection Rules.
Prerequisites
- A Web Domain that's has Cloudflare setup on it.
- https://ln.tips setup and ready to go.
- Using ln.tips is optional. This guide will work with any other custodial wallet that provides you with an LN Address will work too.
Setup
Getting your destructured LN Address
ln.tips
Since ln.tips provides two LN addresses to everybody, you have two options. 1. Use your Telegram username LN address (Not Recommended) 1. This isn't recommended because anyone can see your Telegram username with this method and use it to message you. It's the best choice for anonymity from other users. 2. ex:
nym@ln.tips2. Use your anonymous LN address (Recommended) 1. This is recommended because the address is random, nobody can look this up back to your Telegram account. 2. Can be obtained by running/advancedto the bot, and finding it under "Anonymous Lightning address" 3. ex:0x84e6b3ea699ab309@ln.tipsWhat option you pick doesn't matter to your next step, you're going to want to take the username portion of the address (everything before the @, like an email address) add
https://ln.tips/.well-known/lnurlp/<username>username goes at the end.The final url should look something like
https://ln.tips/.well-known/lnurlp/0x84e6b3ea699ab309(depending on the method you chose)Other platforms
Custodial Wallets that provide you with a Lightning address work similarly to this. Apps like Wallet of Satoshi provide you with a completely random address when you sign up, so a Wallet of Satoshi destructured address would look like:
https://walletofsatoshi.com/.well-known/lnurlp/LawyerCicanery69Setting up Cloudflare Redirects
Assuming that you have Cloudflare hooked up and ready to go, you're going to want to follow a few steps. 1. Open your site on the panel 2. On the sidebar, click the dropdown arrow next to Rules 3. Click "Redirect Rules" 4. Press the button that says "Create Rule" 5. Configure your new rule 1. Give it a name. ex: "lnaddr" 2. Configure the first condition 1. Set "Field" to
URI Path2. Set "Operator" tostarts with3. Set "Value" to/.well-known/lnurlp/3. Configure the "then" 1. Set "Type" toStatic2. Set "URL" to your destructured Lightning address from earlier 3. Set "Status Code" to3074. Check "Preserve query string" 6. Click SaveAll done! Now whenever someone goes to pay your new Lightning address, it should automatically redirect to your custodial wallet. Have fun!
-
 @ e8ed3798:67dd345a
2023-07-16 02:58:24
@ e8ed3798:67dd345a
2023-07-16 02:58:24Dans cet article, nous allons explorer les origines conceptuelles du métaverse original appelé « cyberespace » et voir comment le protocole Nostr lui permet d'exister comme il a été prédit dans la littérature de science-fiction primitive. Ensuite, nous explorerons ce que le cyberespace pourrait faire pour l'humanité et comment vous pouvez contribuer à ce nouveau projet passionnant de métaverse open source.
Un concept obscurci par le temps
Qu'est-ce qu'un "métavers" ? Demandez à 10 personnes différentes et vous obtiendrez 10 réponses différentes. Certains diront qu'il s'agit d'un jeu en ligne où vous pouvez utiliser et transférer des actifs cryptographiques. Certains diront que c'est une expérience de réalité virtuelle avec une entrée extrasensorielle pour des choses comme l'odorat et le toucher. Certains diront qu'un métavers est n'importe quel endroit où vous pouvez vous connecter et vous exprimer numériquement. Et d’autres enfin peuvent vous dire que le métavers n'existe pas encore parce que nous n'avons pas la technologie pour le réaliser.
Il est difficile de définir ce qu'est un métavers parce que personne ne l'a encore construit de manière convaincante. Ceci est démontrable en demandant simplement à n'importe qui de vous montrer un métavers. Ils peuvent vous montrer VR Chat, ou Meta (Facebook), ou HoloLens ou Apple Vision, ou le serveur Discord ou l'écosystème NFT de quelqu'un, ou dire "ce n'est pas réel, et si c'est le cas, c'est probablement stupide".
Mais comment en sommes-nous arrivés là ? Pourquoi connaissons-nous tous le métavers mais nous ne pouvons pas le définir et nous ne savons même pas à quoi il ressemble ? D'où vient l'idée du métavers ? Cette réponse nous donnera le contexte conceptuel dont nous avons besoin pour démêler la question de "qu'est-ce qu'un métavers" et voir comment le cyberespace peut exister aujourd'hui.
Le mot "métavers" a été popularisé pour la première fois dans le livre "Snow Crash" de Neal Stephenson en 1992, et il s'est lui même inspiré du livre "Neuromancer" de William Gibson publié en 1984 (et de 2 autres livres d'une trilogie intitulée "The Sprawl"), qui a popularisé le mot « cyberespace » et « matrice » en référence aux espaces numériques 3D.
Ainsi, le cyberespace a précédé « le métavers » de 8 ans et sert de socle à notre exploration. Le cyberespace de Gibson était un monde numérique en 3D auquel on pouvait se connecter via une plate-forme de cyberespace - une interface machine/cerveau - et interagir avec toutes les données du monde entier. Les intelligences artificielles protégeaient les constructions de données et éloignait les intrus avec des programmes de rétroaction mortels qui feraient frire le cerveau de l'opérateur humain. Dans les livres, le cyberespace est décrit comme étant utilisé pour à peu près tout : divertissement, éducation, communication, commerce, stockage de données et crime, et il est utilisé quotidiennement par des milliards de personnes à travers le monde, y compris des millions de personnes dans des colonies orbitales.
Propriétés mystérieuses
Dans l'œuvre de Gibson, le cyberespace possède de nombreuses qualités fascinantes qui, jusqu'à ce jour, restaient très mystérieuses et semblaient impossibles. Voici quelques exemples.
1. Le cyberespace est sans autorisation
Tout le monde peut utiliser le cyberespace, mais personne n'en a le contrôle total ; le cyberespace semble exister en dehors de toute juridiction et de tout système. Il ne tombe jamais en panne pour maintenance, n'a pas de problèmes de connexion ou ne subit pas de failles de sécurité. Il semble exister partout à la fois, même s'il est explicitement affirmé que le cyberespace a été créé par l'humanité. Comment l'humanité peut-elle créer un système numérique ininterrompu et omniprésent que personne ne peut contrôler mais que tout le monde peut utiliser ?
2. Le pouvoir est exercé sans privilège
Certaines personnes, entreprises et IA disposent de niveaux de pouvoir plus élevés dans le cyberespace que d'autres, mais le mécanisme de ce pouvoir ne découle pas d'autorisations, de niveaux d'accès ou de capacités d'administrateur privilégié ; au contraire, le pouvoir provient d'une autre source mystérieuse qui ne peut être accordée, régie ou révoquée par aucune loi, système ou autorité. Ce pouvoir semble aussi fortement influencé par...
3. Matériel et compétence
Le matériel que les gens utilisent pour se connecter au cyberespace ont un impact direct sur leurs capacités dans le cyberespace. Il existe un exemple spécifique où un personnage utilise un deck cyberespace premium et décrit la grande vitesse et la fluidité de sa capacité à voler dans le cyberespace. Peu de temps après, cet opérateur est capturé et immobilisé par un autre opérateur dangereusement qualifié, démontrant que si le matériel du cyberespace est de premier plan, le niveau de compétence de l'opérateur est également un facteur important régissant les interactions dans le cyberespace. Cela démontre également que le conflit est possible dans le cyberespace. Comment est-il possible que le matériel soit directement corrélé à votre capacité d'action virtuelle ? Comment quelqu'un d'autre peut-il influencer vos actions contre votre volonté dans cette réalité numérique ?
4. L'espace est rare
Bitcoin a été la première ressource numérique rare à avoir jamais existé, et ayant été créée il y a seulement 14 ans, les ressources numériques rares sont encore un concept nouveau pour l'humanité en 2023. Dans le cyberespace de Gibson, le territoire a été conquis, capturé et combattu, indiquant que le l'espace dans le cyberespace peut être rare ou précieux d'une certaine manière. Comment pourrait-il être possible de se battre pour un territoire numérique ou de l'acquérir sans qu'aucun intermédiaire au pouvoir ne sache qui possède quoi ?
5. La construction a un coût
Les constructions, ou "bâtiments" du cyberespace, nécessitaient une sorte d'effort ou de coût pour être créées, mais il n'était pas clair dans cette littérature à qui ce coût était payé ou comment l'effort était dépensé.
Le métavers de "Snow Crash" de Stephenson partage de nombreuses propriétés avec le cyberespace de Gibson, bien que Stephenson ait une certaine opinion sur la forme littérale du métavers. Il le décrit comme une rue qui s'enroule autour d'une planète noire, et la terre de la rue est l'endroit où les gens construisent des choses et revendiquent un territoire.
De même, ce métavers ne semble pas appartenir ou être contrôlé par une seule entité, mais il est accessible à tous dans le monde pour se connecter, interagir et construire 24h/24 et 7j/7. Il n'est pas décrit comme une application ou un logiciel, mais plutôt comme un lieu qui est la somme d'autres logiciels créés par de nombreuses parties différentes avec des intérêts et des motivations différents.
Voici quelques traits mystérieux du métavers de Stephenson:
6. Règles sans règles
Les règles du métavers n'ont jamais été enfreintes, pas même par des pirates ou des méchants. Comment les règles sont-elles appliquées par un système que personne ne contrôle ?
7. Pas de téléportation, règles localisées
Le métavers a des règles sur où vous pouvez apparaître et comment vous vous déplacez. La téléportation n'est pas une option. Un logiciel de véhicule spécialisé pourrait faciliter les déplacements. Les règles de voyage sont appliquées par le métavers lui-même. Les expériences dans le métavers ont été localisées dans des constructions qui implémentent leurs propres règles. Par exemple, le combat à l'épée est autorisé dans le paradis des hackers The Black Sun parce qu'il est programmé pour y exister; d'autres endroits n’ont pas de telles activités. Comment certains endroits du cyberespace peuvent-ils avoir des règles uniques distinctes du reste du cyberespace ? Comment la localité est-elle appliquée dans un système numérique contrôlé par personne ?
8. Personnalisez sans tout compromettre
Les gens ont pu personnaliser l'apparence de leurs avatars et constructions. Comment gérez-vous cela pour que les gens n'en abusent pas? Sans règles applicables, une personne pourrait faire en sorte que son avatar soit de la taille de l'univers et ruiner le métavers pour tout le monde.
9. Tout est connecté
Les systèmes numériques du monde réel sont également présents dans le métavers, bien qu'ils soient loin des zones généralement peuplées. Comment les systèmes du monde réel sont-ils liés au métavers ?
J'énumère ces nombreux points afin de fournir un contexte où l'idée du "métavers" a commencé. Ces deux livres ont contribué à définir à l'origine ce qu'était le métavers, même s'il soulevait de nombreuses questions spécifiques qui, naturellement, n'ont jamais été abordées. Comme je l'ai dit : si les auteurs savaient comment construire les choses sur lesquelles ils écrivaient, ils n'auraient peut-être pas besoin de vendre de livres du tout ! C'est de la fiction après tout. Les détails ne sont pas nécessaires, mais je me suis concentré sur la découverte de ces détails dans le contexte des nouvelles technologies telles que Bitcoin et Nostr et je pense qu'ils peuvent maintenant être définis.
Pour résumer, voici les mystérieuses propriétés du cyberespace/métavers :
- Tout le monde peut l'utiliser
- Personne ne le contrôle
- Il existe partout
- Le pouvoir d'un individu n'est accordé par aucun système ou autorité, mais provient de son matériel et de ses compétences
- Les individus peuvent opposer leur pouvoir les uns aux autres
- Le territoire est rare et peut être capturé
- Les constructions peuvent être construites sur le territoire mais ont un certain coût
- Le système applique des règles à tout le monde, ou incite d'une manière ou d'une autre tout le monde à suivre les règles - même les mauvais acteurs
- la localité est imposée et le voyage demande du temps
- certaines localités ont des règles uniques
- la liberté de personnaliser votre avatar et vos constructions est limitée d'une manière ou d'une autre pour empêcher la corruption totale et l'abus de l'espace numérique
- il existe une certaine forme de connexion entre les systèmes numériques du monde réel et le cyberespace
Rien de tel
Je tiens à préciser qu'aucun métavers existant aujourd'hui ne présente toutes les propriétés ci-dessus ou même quelques-unes d'entre elles, et très peu de systèmes numériques présentent ne serait-ce qu'une seule de ces propriétés.
Avant de découvrir Neuromancer il y a plusieurs mois, ma perception du "cyberespace" était celle d'un concept étrange et naïf de ce que deviendraient les systèmes informatiques interconnectés qui ne se sont jamais concrétisés. J'avais l'habitude de qualifier ironiquement Internet de "cyberespace" lorsque je parlais avec d'autres développeurs comme une sorte d'exagération humoristique. Je pensais que le cyberespace était une relique culturelle et une prédiction ratée de ce que serait Internet. Le fameux monde construit en néon filaire 3D brillant ne s'est jamais matérialisé, et pour cela, j'ai toujours ressenti un sentiment de perte de ce qui aurait pu être.
Pourquoi le cyberespace n'a-t-il jamais vu le jour ? Au fur et à mesure que les ordinateurs devenaient plus avancés et axés sur le consommateur, ils n'ont pas tenté d'émuler un espace 3D, mais ont plutôt fait la chose pratique et sensée d'émuler des documents papier afin que les gens puissent travailler numériquement.
Alors qu'Internet devenait un utilitaire domestique, les systèmes et applications centralisés étaient le premier et le seul moyen que l'humanité connaissait pour développer ses capacités collectives en ligne. Les sites Web se sont développés au fur et à mesure qu'ils rassemblaient des utilisateurs et sont devenus des mastodontes. eBay, Google, Amazon, Paypal. Bien qu'Internet lui-même soit techniquement décentralisé, les systèmes et applications décentralisés viendront plus tard lorsque les problèmes de centralisation deviendront évidents lorsque ces géants de l'Internet commenceront à abuser de leur pouvoir.
Alors qu'Internet continuait de croître et ressemblait de moins en moins aux mondes fictifs du cyberespace et du métavers, ces nobles idées de mondes numériques 3D se sont transformées en jouets pour la plupart des gens - des peluches inutiles mais divertissantes. La notion de cyberespace s'est estompée dans la culture rétro des années 80 et le mot “cyberespace” a été douloureusement réutilisé pour simplement désigner collectivement Internet ou les systèmes en réseau. Ceci, cependant, est une utilisation terriblement inexacte du mot. Il n'y a pas d'espace à proprement parler sur Internet.
Mais, malheureusement, Internet était la chose la plus proche que nous ayons jamais eue de la vision de Gibson du cyberespace, et , malheureusement, ce n'était vraiment pas vraiment proche, sauf que les gens du monde entier l'utilisent pour à peu près tout. Toutes les autres propriétés magiques du cyberespace ont été simplement oubliées. C'était de la fiction. Ils n'étaient pas nécessaires. Ce n'était pas possible. Il n'y avait aucun moyen de le faire fonctionner et aucune raison de le faire.
Cependant, lors de la lecture de ces livres de près de 4 décennies, il y a quelque chose d'émouvant pour moi dans le fait qu'à travers ces divers travaux de divers auteurs, le métavers (ou cyberespace) possède des propriétés cohérentes qu'aucun auteur n'est disposé à modifier. Qu'y a-t-il de si inviolable dans un concept fictif qui le rendrait si cohérent d'une œuvre à l'autre ? Peut-être y a-t-il un noyau de vérité dans ce qui est imaginé, et cette vérité est si convaincante qu'elle doit être répétée jusqu'à ce qu'elle franchisse le voile entre l'idée et la réalité.
Réalité et cyberespace
J'ai toujours été fasciné par la capacité de la technologie à améliorer nos vies, et je me suis efforcé de créer des logiciels conséquents toute ma vie, comme des jeux vidéo joués via des montres de fitness et des applications Web de navigation en réalité augmentée, mais ce n'est que lorsque j'ai lu Softwar que j'ai réalisé quelque chose de profond:
En réalité, je suis capable de faire tout ce que je veux tant que j'ai l'énergie thermodynamique pour le faire.
Ce n'est peut-être pas légal ou socialement acceptable, mais si j'ai l'énergie de faire quelque chose, je peux. De même, si quelqu'un veut m'empêcher de faire quelque chose, il ne peut pas le faire à moins qu'il ne dépense suffisamment d'énergie pour m'arrêter.
Cela signifie que la réalité fonctionne sans permission , car personne ne peut interdire mes actions. Cela signifie également que la réalité est thermodynamique , car chaque action a un coût qui doit être payé à l'univers sous forme d'entropie.
Inversement, dans les systèmes numériques, la quantité d'énergie dont vous disposez n'a pas d'importance. Les choses que vous pouvez faire ne sont que les choses que vous êtes autorisé à faire par le système autorisé. Cela signifie que dans un système numérique, vous avez toujours un sous-ensemble très limité d'actions disponibles, et votre capacité à exécuter ces actions n'a rien à voir avec votre potentiel thermodynamique mais tout à voir avec les autorisations qui vous sont accordées par d'autres. Peu importe la force de mes muscles ou mon intelligence, je ne peux pas faire plus que ce qu'un système numérique me permet de faire, et même si je le pirate, je ne peux toujours pas faire ce que je veux . Juste un peu plus que ce que je suis censé faire.
Presque tous les systèmes et logiciels numériques sont arbitraires et non thermodynamiques.
C'est pourquoi, fondamentalement, aucun métavers qui n'a jamais été construit n'a vraiment d'importance. C'est pourquoi aucun jeu vidéo ne vous intéresse éternellement, car les actions que vous pouvez faire et la mesure dans laquelle vous pouvez les faire sont arbitrairement déconnectées de votre capacité à agir dans la réalité. C'est “juste un jeu” , un sous-ensemble limité de la réalité.
Ce n'est pas fondamentalement une mauvaise chose. De toute évidence, le logiciel a beaucoup fait pour l'humanité. Et des règles basées sur des logiciels ont été utilisées dans de nombreux contextes pour que les choses restent équitables pour tout le monde. Sauf que, malheureusement, les systèmes numériques ne sont jamais vraiment équitables. Il y a toujours un programmeur qui a écrit les règles. Il y a toujours un administrateur au-dessus de vous. Il y a toujours un hacker. Et il y a toujours quelqu'un avec plus de permissions que vous qui peut limiter votre potentiel. Comparé à la réalité, cela semble arbitraire et capricieux. Pourtant, dans la réalité, l'univers auquel vous payez vos coûts d'entropie est vraiment, terriblement impartial. C'est pourquoi les systèmes thermodynamiques sont fondamentalement justes ; même si cela ne vous semble pas juste , c'est vraiment les mêmes règles pour tout le monde, sans exception .
La réalité est un protocole thermodynamique sans autorisation, et presque rien dans le monde numérique ne ressemble à cela.
Nostr, cependant, est sans autorisation. Jusqu'à présent, vous ne considériez peut être pas cela comme une propriété fondamentale de notre univers, mais c'est le cas, et le fait que nostr présente cette même propriété est assez convaincant. En fait, tout système véritablement sans autorisation (il y en a très peu) semble avoir la capacité magique de capter l'imagination des gens d'une manière qu'aucun autre système numérique ne peut. Des choses telles que le bitcoin, le système numérique sans autorisation le plus célèbre, ont des effets si larges et profonds sur les personnes qui le saisissent qu'ils ont été publiés et décrits dans certains cas , comme celui d'Andreas M. Antonopoulos, un ambassadeur de Bitcoin émérite, qui a carrément arrêté de manger, d'arrêté de dormir, pour faire de la recherche de façon obsessionnelle. Ils changent complètement leur mode de vie. Comme Bitcoin, Nostr peut également être thermodynamique via une preuve de travail (NIP-13). Et avec la combinaison de ces deux propriétés, qui sont partagées avec la réalité, nous sommes soudainement capables de dissiper tous les mystères que nous avons rencontrés concernant le cyberespace.
La preuve de travail est l'ingrédient secret pour dissoudre la fiction dans la science- fiction du cyberespace.
Un mystère résolu à propos du cyberespace et du Bitcoin
La raison pour laquelle les propriétés du cyberespace et du métavers sont si mystérieuses est qu'elles sont en fait des propriétés de la réalité, mais à l'intérieur d'un système numérique.
En réalité, il n'est pas surprenant que votre matériel et vos compétences affectent votre capacité. Pas étonnant que votre travail détermine votre pouvoir. Pas étonnant que vous ne puissiez pas vous téléporter et que vous deviez voyager en utilisant de l'énergie. Il n'est pas surprenant que la construction de constructions ou la personnalisation demande des efforts et des coûts. Pas étonnant que le territoire soit rare et doive être défendu. Pas étonnant que des conflits se produisent entre les gens. Tout cela est tellement normal qu'il est facile de l'oublier.
La raison pour laquelle ces choses dans Neuromancer et Snow Crash et d'autres travaux sur le métavers semblaient si mystérieuses est qu'elles n'étaient pas possibles à modéliser dans un espace numérique . Ces auteurs ont pris des propriétés de la réalité et les ont placées dans un espace numérique, et cela semblait incroyable parce que personne ne savait comment cela pouvait réellement fonctionner.
C'est ainsi que c'est possible : vous concevez un système numérique qui a les mêmes propriétés fondamentales que la réalité. Il doit être sans autorisation.Il doit être thermodynamique. Ensuite, vous avez un système dans lequel le cyberespace peut exister.
Nostr est la réalisation de ces exigences. Comme Bitcoin, Nostr a captivé l'imagination de milliers d'utilisateurs et de développeurs précoces. La magie est là. Mais peu de gens peuvent comprendre pourquoi c'est si magique. La réponse est que lorsque vous créez un système numérique capable de modéliser les mêmes propriétés de la réalité, vous créez une extension de la réalité elle-même . Il s'agit de l'une des découvertes les plus importantes de l'histoire de l'humanité, car une extension numérique de la réalité peut permettre à l'humanité de se connecter, de collaborer et de grandir dans un endroit où sa distance physique n'a pas d'importance. À moins d'avancées majeures dans la technologie spatiale, le cyberespace sera le départ le plus important de la Terre que vous puissiez vivre au cours de votre vie.
Je postule qu'une action virtuelle sans autorisation et thermodynamique est aussi réelle qu'une action physique réelle, sauf que les conséquences de cette action se produisent dans l'espace numérique plutôt que dans l'espace physique. Ce n'est pas tout à fait la réalité, mais c'est comme un miroir. C'est une véritable extension de la réalité. Rien n'y est déconnecté du monde réel. Et donc, contrairement à tout autre système numérique, il peut être véritablement conséquent.
Scepticisme sain
Attendez une minute, me direz-vous. Le cyberespace n'est encore qu'un moyen de communication numérique. Les e-mails, les SMS et le chat vidéo ne suffisent-ils pas ? Pourquoi avons-nous besoin du cyberespace ? Comment pourrait-il être si important pour l'humanité?
C'est une excellente question.
On peut se poser des questions similaires sur le bitcoin. N'avons-nous pas déjà de l'argent numérique ? Pourquoi avons-nous besoin d'argent absolument rare, décentralisé et résistant à la censure ?
Ou à propos de nostr : pourquoi avons-nous besoin d'un autre moyen de transmettre du texte ? A quoi bon être décentralisé et résistant à la censure ?
Comme le bitcoin, le cyberespace transforme quelque chose de numérique en une ressource rare, mais au lieu de permettre la capture du temps (sur une chaîne temporelle), le cyberespace permet la capture d'un espace rare (dans une construction ou votre chaîne de mouvement).
Dans le monde physique, nos mouvements peuvent facilement être censurés. Notre expression du pouvoir est censurée. Notre capture de l'espace est censurée. Ce n'est pas le cas dans le cyberespace. La seule chose qui compte dans le cyberespace est l'énergie thermodynamique que vous exercez - tout comme dans la réalité, mais moins les structures de pouvoir autorisées (artificielles) des gouvernements et des lois.
Tout comme le bitcoin ne se soucie pas de qui vous êtes ou à qui vous transmettez de la valeur, le cyberespace ne se soucie pas de qui vous êtes, de l'endroit où vous vous déplacez ou de l'endroit où vous revendiquez de l'espace.
Conséquences de la preuve de travail en détail
J'aimerais énumérer les manières spécifiques dont la preuve de travail dans Nostr démystifie les propriétés mystérieuses du cyberespace mentionnées précédemment.
- Tout le monde peut utiliser le cyberespace mais personne n'en a le contrôle total.
Remplacez simplement "cyberspace" par "nostr" et la déclaration ci-dessus est déjà vraie. Si nous construisons le cyberespace sur nostr, alors le cyberespace héritera de ces propriétés.
- Certaines personnes, entreprises et IA exercent des niveaux de pouvoir plus élevés dans le cyberespace que d'autres
Si nous basons la puissance d'une entité sur sa production thermodynamique via une preuve de travail, nous avons alors un moyen sans autorisation pour les participants du cyberespace de mettre en œuvre leur potentiel thermodynamique réel dans le cyberespace, quel que soit le degré qu'ils choisissent.
- Le matériel que les gens utilisent pour se connecter au cyberespace ont un impact direct sur leurs capacités dans le cyberespace.
Si toutes les actions dans le cyberespace sont thermodynamiques comme dans la réalité, alors le matériel capable de plus grandes quantités de preuves de travail permettra des actions plus puissantes. Téléphone mobile, ordinateur de bureau ou ferme ASIC : faites votre choix.
- Le territoire dans le cyberespace a été conquis, capturé et disputé, ce qui indique qu'il peut être rare ou précieux d'une manière ou d'une autre. Construire a un coût.
Le territoire dans le cyberespace est l'espace de coordonnées tridimensionnel maximum qui peut être représenté par 256 bits. En cryptographie, nostr et bitcoin, les nombres de 256 bits sont très couramment utilisés avec des fonctions mathématiques comme SHA-256 qui traitent les données par blocs de 256, c'est donc une bonne quantité "ronde" d'informations avec lesquelles travailler.
Vous pouvez diviser un nombre de 256 bits en coordonnées X, Y et Z de 85 bits chacune. Cela laisse 1 bit supplémentaire le moins significatif parmi les 256 bits qui est ignoré (pour l’instant). Cela signifie que chaque axe du cyberespace mesure 2^85 unités de long.
L'espace peut être réclamé en publiant un événement de construction dont l'ID d'événement est la coordonnée. L'ID d'événement est obtenu à partir du hachage de l'événement (processus standard pour tous les événements du protocole nostr). Cela signifie que l'ID d'événement peut être extrait pour obtenir les coordonnées que vous désirez (ou au moins quelque chose à proximité).
Si deux constructions se chevauchent, celle qui a le plus de preuve de travail l'emporte. C'est ainsi que le territoire peut être contesté sans autorisation dans le cyberespace, comme le suggèrent les travaux de Gibson.
Le coût de la construction est la preuve de travail, et l'entretien de ce territoire par la preuve de travail est l'analogie numérique soit de payer des impôts à un gouvernement qui protégera votre terrain, soit de protéger votre terrain avec votre propre énergie thermodynamique. Remarquez comment l'argent, également connu sous le nom de temps, est inextricablement lié à la propriété d'un bien dans la réalité et maintenant aussi dans le cyberespace. Si la propriété était libre de posséder et d'entretenir, vaudrait-elle quelque chose ?
On m'a présenté l'argument selon lequel il ne vous coûte rien de détenir des bitcoins, donc les constructions ou l'immobilier du cyberespace ne devraient pas être différents. À cela, je dis que pour que vous déteniez votre bitcoin, un coût énorme est dépensé par tous les mineurs du monde. Sans eux, votre bitcoin serait dépensé deux fois ou volé par des transactions invalides. La validité de votre bitcoin immobile nécessite le fonctionnement continu et perpétuel du plus grand réseau informatique au monde. Ainsi, la dépense énergétique continue pour sécuriser votre propriété est vraie avec le bitcoin, le cyberespace et toutes vos affaires en réalité également.
Contrairement au bitcoin, dont la valeur réside dans l'ensemble du réseau, les constructions n'ont de valeur que pour leur propriétaire. Par conséquent, il est de la responsabilité du propriétaire de la construction de la défendre.
Des relations symbiotiques plus complexes dans la défense des constructions peuvent découler de la lutte perpétuelle pour la survie inhérente à tout système thermodynamique. Mais ce n'est que spéculation.
Application universelle des règles
Comme pour tout protocole, la déviation vous en exclut et la soumission accorde une part de sa valeur. Changer le méta-protocole du cyberespace, que ce soit en désobéissant à ses règles ou en les réécrivant, aboutit à une bifurcation irréconciliable de la réalité numérique. La valeur du cyberespace en tant que protocole dépend des effets de réseau comme n'importe quel protocole, et le premier arrivé a un fort avantage dans toute guerre de protocole. De plus, comme toutes les actions nécessitent une preuve de travail et doivent être enchaînées, la somme de votre historique dans le cyberespace risque d'être invalidée si vous vous écartez du protocole que tout le monde suit.
En fin de compte, je crois que le but du cyberespace devrait être d'imprégner l'humanité de nouvelles capacités et opportunités, et je pense que ce sera le cas, simplement en vertu du fait qu'il est construit sur un protocole et interagit avec des protocoles qui imprègnent également l'humanité de nouvelles capacités. et opportunités (Nostr, bitcoin et TCP-IP). Je souhaite que le cyberespace soit suffisamment flexible et capable de prendre en charge autant de cas d'utilisation que possible tant que les propriétés fondamentales sont préservées en tant qu'axiomatiques non négociables. Le cyberespace lui-même doit être à la fois sans autorisation et thermodynamique. Sans ces propriétés, le cyberespace devient juste une autre illusion numérique en dehors de la réalité.
Flexibilité, localité et personnalisation
Avec ces axiomes à l'esprit, je pense qu'il serait très intelligent de créer une méthode pour définir des règles au niveau de la construction qui n'existent que dans certains espaces. Cela permettrait à des interactions et à des systèmes personnalisés d'exister dans le tissu du cyberespace, ce qui le rendrait très flexible et local. Tout système ou personnalisation de ce type, même cosmétique, doit imposer un coût thermodynamique fondamental. Les détails de la façon dont cela pourrait fonctionner restent à développer, mais les plans de la fiction, nos axiomes et notre ingéniosité nous y mèneront.
Le métaverse des choses
Parce que nostr est un protocole compatible avec le Web, il est trivial de connecter tout ce qu’on veut au cyberespace. J'adore raconter comment j'ai été témoin d'une conversation au début de 2022 entre une personne et (si je me souviens bien) le lave vaisselle intelligent de Will Casarin qui publiait des mises à jour de statut de type 1 sur nostr. Si quelqu'un peut parler à un lave-vaisselle intelligent via nostr, alors le métaverse des choses existe déjà. Cependant, la mesure dans laquelle ces choses s'exposent au métaverse devrait suivre le même modèle de sécurité que pour Internet dans son ensemble. Contrairement à la fiction, je doute que quiconque permette qu'une preuve de travail suffisante soit la seule condition préalable pour réquisitionner un système du monde réel. C'est OK. En fin de compte, la relation entre la réalité et le cyberespace n'est pas censée être une carte 1:1. Les systèmes numériques ne devraient vraiment participer au cyberespace que s'ils partagent les mêmes propriétés que le cyberespace. La plupart des systèmes numériques sont autorisés et non thermodynamiques, et n'ont donc pas de raison impérieuse d'exister dans le cyberespace. Mais tout est effectivement possible.
Chasser un fantôme ou suivre un plan ?
J'aimerais faire la distinction que le but d'une construction (et de la plupart des choses) dans le cyberespace du monde réel n'est pas nécessairement le même que dans le cyberespace littéraire de Gibson ni dans le métavers littéraire de Stephenson. Mais les propriétés fondamentales telles que décrites restent les mêmes, et cela est activé par la preuve de travail.
N'oubliez pas que la chose remarquable à propos du cyberespace de Gibson est qu'il s'agit d'un monde numérique qui fonctionne comme la réalité - il y a une résolution égalitaire des conflits, un espace rare et des règles universellement appliquées. Le méta-protocole du cyberespace permet également à un système numérique de fonctionner comme un espace dans la réalité. Les motivations et les raisons derrière ce système numérique peuvent être complètement différentes de celles des livres, mais cela ne signifie pas que les mécanismes sont moins précis.
Mon but n'est pas de reproduire le travail de Gibson et Stephenson dans la réalité. Les propriétés de cette fiction sont convaincantes, et la mise en œuvre et l'utilisation du cyberespace dépendront entièrement des forces du marché libre - exactement comme il se doit. Ce n'est pas à moi de décider. Ces travaux ont ouvert la voie conceptuelle pour créer cette nouvelle réalité numérique thermodynamique. Les motivations et les actions humaines qui façonnent le cyberespace lui donneront sans aucun doute un aspect très différent de celui décrit dans les livres, tandis que les propriétés fondamentales restent identiques.
Tout au long du processus de conception du méta-protocole du cyberespace, j'ai essayé de le garder aussi simple et fondamental que possible, en utilisant ces livres comme guide. Que ces auteurs l'aient réalisé ou non, leurs représentations du cyberespace et du métaverse étaient extrêmement cohérentes, ce qui en fait non seulement une grande fiction crédible, mais aussi un excellent guide à suivre pour développer un système réel.
Entrez dans le cyberespace
J'aimerais donner quelques exemples concrets du fonctionnement du cyberespace afin que les concepts présentés ici ne soient pas sans application.
NOSTR en 3 minutes
Pour interagir avec le cyberespace, il suffit de publier certains "types" d'événements nostr. Si vous n'êtes pas familier avec nostr, voici une courte explication. Nostr est composé de personnes exécutant des clients, qui ne sont que des applications comme sur votre téléphone ou votre ordinateur, et de personnes exécutant des relais, qui sont comme des serveurs qui stockent des événements. Les clients téléchargent des flux d'événements à partir des relais en temps réel. Les clients peuvent également publier des événements sur des relais. Publier un événement, c'est comme envoyer un tweet. Les clients publient normalement le même événement sur plusieurs relais à la fois. Tant que vous envoyez le tweet à au moins un relais auquel votre ami est connecté, il verra votre tweet. N'importe qui peut exécuter un relais ou créer un client et se connecter aux relais de son choix. De cette façon, nostr est sans autorisation et décentralisé.
Un événement de "type 1" est essentiellement un tweet, mais il existe d'autres types d'événements, chacun représenté par un nombre. Un événement de type 0 est ce que vous publiez lorsque vous mettez à jour votre profil avec une nouvelle biographie ou un nouveau nom d'utilisateur. N'importe qui peut créer un nouveau type d'événement et lui attribuer n'importe quel numéro, sauf qu'il serait mal pris en charge si vous utilisiez un numéro qui est déjà accepté dans le cadre du protocole nostr à une autre fin que celle pour laquelle vous l'utilisez. Heureusement, il y a beaucoup de chiffres à faire circuler.
Une paire de clés privée/publique est une identité cryptographique anonyme, et elle peut être utilisée pour une communication sécurisée, le stockage de bitcoin et d'autres choses diverses. Les clés elles-mêmes ne sont que des nombres insondables et inimaginables représentés dans le système de nombres hexadécimaux qui comprend les nombres 0-9 et a-f (base 16 au lieu de base 10). Lorsque vous publiez un événement sur nostr, il est signé par votre clé privée et l'événement contient votre clé publique. Cela permet à quiconque de vérifier que l'événement provient légitimement de cette clé publique, que seule une certaine personne contrôle vraisemblablement. De cette façon, personne ne peut falsifier des événements sans les invalider, car la signature ne correspondrait pas à la clé publique.
Méta-protocole
C'est pourquoi j'appelle le cyberespace un méta-protocole, car il s'agit simplement d'une manière spécifique de publier et d'interpréter des types d'événements spéciaux sur Nostr et de les visualiser dans un espace 3D.
Dérive
Pour vous déplacer dans le cyberespace, vous devez publier un événement de type 333, appelé événement Drift. Cet événement contient vos coordonnées cyberespace 3D, votre direction, votre vitesse existante, une référence à votre événement Drift précédent et une preuve de travail pour ajouter de la vitesse selon votre direction. La quantité de preuve de travail sur l'événement de dérive détermine votre accélération. La preuve de travail peut être ajoutée à n'importe quel événement nostr en choisissant une quantité de travail, représentée par le nombre de zéros binaires en tête sur l'ID de l'événement, et en hachant l'événement avec un nonce différent jusqu'à ce que la quantité de travail cible soit atteinte. Ce processus est spécifié dans NIP-13 .
Chaque événement de dérive peut être validé en exécutant les coordonnées et la vitesse à travers un algorithme de cyberespace normalisé (en cours de développement) pour vérifier que les changements de valeur d'un événement de dérive à l'autre se situent dans une plage d'erreur tolérable. Il s'agit en effet d'une manière de simuler le mouvement au sein d'un système physique afin de valider que les mouvements n'ont pas enfreint les règles de la physique du cyberespace. De cette façon, chaque participant au cyberespace est un validateur de tous ceux dont il est physiquement proche. Lorsqu'un événement de dérive est signé, la référence à l'événement de dérive précédent est incluse dans la signature. Cela crée, en effet, un historique de chaîne de hachage personnel vérifiable de vos mouvements et actions dans le cyberespace que n'importe qui d'autre peut vérifier.
Malhonnêteté et punition
Afin d'encourager les gens à être honnêtes à propos de leurs chaînes de mouvement, toute personne qui trouve une chaîne de mouvement invalide - ou "cassé" - peut punir son propriétaire en publiant un événement Derezz dessus, ce qui invalidera toutes les chaînes de mouvement et les preuves de travail. appartenant à la victime et les téléporter vers leurs coordonnées d'origine où ils sont apparus à l'origine lorsqu'ils ont utilisé le cyberespace pour la première fois. Il s'agit effectivement d'un respawn. Vous partez de zéro, mais vous pouvez conserver vos constructions.
On peut facilement mentir sur ses chaînes de mouvement et se téléporter n'importe où et n'importe quand. Mais sur Nostr, pour la plupart, les événements ne peuvent pas être supprimés. Par conséquent, un tricheur laissera une trace lumineuse par laquelle d'autres pourront le cyber-tuer via Derezz. Une chaîne de mouvement brisée est comme une copie fantôme du tricheur qui ne peut pas bouger. Pour des raisons de protocole plus profondes que les aventuriers peuvent explorer dans la spécification, cela rend la copie fantôme plus vulnérable à Derezz.
Un tricheur peut choisir d'ignorer l'attaque Derezz et de continuer à se téléporter là où il le souhaite. Rien dans Nostr ou dans le cyberespace ne peut arrêter cela. Mais pour tous ceux qui suivent le protocole, ce type de comportement peut facilement être ignoré. Le tricheur habituel peut aussi bien être un fantôme, car ses actions thermodynamiques seront ignorées par tous ceux qui ont choisi d'obéir au protocole. Le tricheur peut se racheter en publiant une très longue chaîne d'événements valides, mais cette période probatoire peut être trop exigeante pour les briseurs de protocole habituels. D'autres actions agressives peuvent être dirigées contre les tricheurs, rendant leur opération dans le cyberespace improductive, difficile et dangereuse.
Un tricheur dans le cyberespace est une cible facile. Comme la punition des tricheurs est un noble acte de justice plutôt qu'un acte pervers de prédation, je m'attends à ce que les tricheurs dans le cyberespace soient punis avec une grande rapidité et gaieté.
Les incitations à la circulation honnête légitiment l'aspect spatial du cyberespace. Dans le cyberespace, l'espace est réel et conséquent. Le parcourir a un coût. Il n'y a pas deux endroits fondamentalement identiques car il y a un coût réel pour les visiter. Et tout l'espace est rare, en raison de la limite stricte du système de coordonnées 2 ^ 85, qui a été choisi pour être compatible avec l'algorithme minier le plus populaire au monde, SHA-256.
D'autres actions
Pour tout savoir sur les différents types d'événements que l'on peut publier pour interagir avec le cyberespace, consultez (et contribuez !) à la spécification oficielle du cyberespace ici : https://github.com/arkin0x/cyberspace Dans cette spécification, vous trouverez des détails techniques de mise en œuvre permettant aux clients d'interagir avec le méta-protocole du cyberespace, y compris des définitions d'autres actions pouvant être entreprises par les opérateurs, notamment :
- manipuler la "gravité" pour affecter d'autres opérateurs
- créer une armure de preuve de travail contre Derezz
- dissimuler son emplacement avec furtivité
- et plus!
Ubiquité et omniprésence du cyberespace
Un développement récent très intéressant est un projet open source appelé
nostrmeshlnbits qui permet à quiconque d'héberger un relais nostr sur un petit appareil en réseau maillé, tel qu'un Arduino. Imaginez un réseau de milliards de ces appareils, dispersés à travers le monde, fonctionnant sur des batteries et des panneaux solaires, chacun contribuant à l'infrastructure du cyberespace - un cosmos numérique décentralisé et omniprésent, accessible de pratiquement n'importe où. Ce niveau d'ubiquité nous rapproche un peu plus de la vision du travail de Gibson, où le cyberespace devient une partie intégrante de notre vie quotidienne et peut être trouvé partout , même dans l'espace extra-atmosphérique !Avec un réseau aussi omniprésent, les limites spatiales du cyberespace s'étendent bien au-delà des frontières numériques conventionnelles, s'entrelaçant avec notre monde physique d'une manière qui était autrefois le domaine de la science-fiction. Les implications de ce développement sont énormes et jettent les bases des utilisations potentielles et de l'influence du cyberespace, que nous explorerons dans la section suivante.
Conséquences du cyberespace
Il est difficile de prédire si le cyberespace trouvera sa place dans la vie quotidienne de milliards de personnes ou sera à nouveau oublié. Cependant, les fondements du cyberespace sont inextricablement liés aux technologies qui ont été développées et adoptées au nom de la liberté humaine et des droits de la personne : cryptographie à clé publique, hachage, preuve de travail, bitcoin et nostr.
En tant que personne qui prend la science-fiction suffisamment au sérieux pour en supprimer entièrement la fiction, je trouve que la spéculation est inestimable. On ne peut pas aller là où l'imagination ne mène pas d'abord. Toute notre perception du monde est analysée à partir d'une abstraction créée par notre esprit. Nous attribuons automatiquement un sens à des choses intrinsèquement dépourvues de sens - symboles, modèles, etc. La fiction est notre réalité, et notre perception du monde est la somme des modèles logiques au sein de cette fiction. Par conséquent, faisons ce que nous faisons le mieux et créons de la fiction, ou spéculons, sans hésitation.
Personnellement, j'envisage le cyberespace comme un lieu de commerce et d'organisation sociale. Les constructions permettent aux gens de revendiquer des cyber terres. Ils peuvent utiliser ce terrain pour concevoir des expériences interactives régies par des règles localisées et la thermodynamique. Le réseau Lightning permet un transfert instantané de valeur à travers le cyberespace, facilitant la transaction d'informations, de services, d'expériences cybernétiques, de biens numériques et physiques.
Les cas d'utilisation incluent les achats, les jeux, les jeux d'argent, les compétitions, les cyber événements en direct, les rassemblements sociaux à présence virtuelle, les manifestations virtuelles, les espaces collaboratifs, la publicité, l'éducation, le tourisme, le développement d'applications basées sur le cyberespace, la visualisation de données, la recherche, les réseaux sociaux et même plus que nous n'avons pas encore imaginé.
Conclusion
Alors que nous nous aventurons dans les vastes paysages numériques du cyberespace, nous ne traversons pas simplement des données sans vie, mais nous nous immergeons dans un monde qui reflète l'ordre et la complexité de notre réalité physique. Cette approche révolutionnaire du cyberespace n'est pas simplement un mirage de science-fiction, mais une exploration tangible de ses principes clés, construits sur le socle de la cryptographie à clé publique, du hachage, de la preuve de travail, du bitcoin et de Nostr.
Grâce à la mise en œuvre d'un méta-protocole superposé à Nostr, le cyberespace ouvre une myriade d'opportunités - dériver à travers les étendues illimitées du cosmos numérique, créer des domaines personnels ou s'engager dans des interactions sociales dynamiques. Tout comme les actions dans le monde physique entraînent des coûts et des conséquences, le cyberespace impose également son propre ensemble unique de règles et de répercussions, favorisant un sentiment de responsabilité partagée, d'équité et de coopération entre ses habitants.
Considéré comme un terrain de jeu pour la créativité, le commerce et l'organisation sociale, le cyberespace, dans son état de formation actuel, montre déjà un énorme potentiel pour un large éventail de cas d'utilisation. Ses propriétés thermodynamiques inhérentes et sa nature sans autorisation offrent une fusion révolutionnaire de réalités numériques et physiques, prête à augmenter profondément nos capacités, nos expériences et nos opportunités dans un domaine dynamique, inclusif, global et conséquent.
Cependant, l'aspect le plus excitant du cyberespace n'est pas seulement ce qu'il offre actuellement, mais son potentiel d'évolution et de redéfinition continu. Au fur et à mesure de l’engagement de plus en plus de personnes, il est appelé à se développer et à se transformer d'une manière que nous pouvons difficilement imaginer aujourd'hui.
Alors que nous nous tenons à l'aube de cette frontière numérique, nous ne poursuivons pas les fantômes de la fiction. Au lieu de cela, nous sommes les architectes et les pionniers d'un nouveau domaine révolutionnaire, où l'existence numérique converge avec les principes physiques. Ce mélange remarquable de technologie et d'imagination humaine ouvre la voie à une ère sans précédent d'exploration et d'innovation, signalant un avenir aussi excitant qu'imprévisible.
Rejoignez-moi dans cette grande entreprise pour façonner le cyberespace, pour transformer cette nouvelle frontière en un monde numérique partagé et diversifié qui reflète le meilleur de l'esprit et de l'ingéniosité humains. Ensemble, entrons dans le cyberespace, la frontière du futur.
Construis avec moi
Le cyberespace est pour l'humanité, et donc je souhaite qu'autant d'humains que possible soient impliqués dans sa construction.
J'ai créé les ressources suivantes pour tous ceux qui souhaitent en savoir plus ou s'impliquer :
Rejoignez le groupe ONOSENDAI Telegram : https://t.me/ONOSENDAITECH J'adore répondre aux questions ! Venez et demandez ( en anglais only) !
Les Pull request sont les bienvenues sur la spécification : https://github.com/arkin0x/cyberspace
Découvrez le premier client du cyberespace, ONOSENDAI : https//onosendai.tech (thermodynamique encore en développement)
LesPull Request sont également les bienvenues sur ONOSENDAI : https://github.com/arkin0x/ONOSENDAI
Qui suis je
Mon nom est Nick. Mon ID: arkinox. Je crée des sites Web depuis l'âge de 11 ans et je conçois des jeux depuis l'âge de 4 ans. J'ai été directeur du Web pour une société de marketing du Midwest pendant 10 ans et co-fondateur et vice-président senior d'une société de réalité augmentée, innovatar .io, depuis 4 ans.
Soutenir les logiciels libres
Si vous souhaitez soutenir le développement de ce protocole, j'aimerais que vous vous impliquiez. De plus, j'accepte les dons et je recherche des occasions de le poursuivre à plein temps.
Suivez moi sur nostr : npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w
Zap moi avec Bitcoin Lightning : arkinox@getalby.com
Traduction Française
Cryptoclay Suivez moi sur nostr : npub10v2cn47qfuw92hn0mpqzgcm6e9wwkjznu870hvdmsg7gkt8avn7q29r43s
Zap (Je compte développer activement et faire des conférences en FR) : theunhosted@getalby.com
Soli Deo gloria
-
 @ e8ed3798:67dd345a
2023-07-16 02:49:48
@ e8ed3798:67dd345a
2023-07-16 02:49:48This article has been translated into Japanese here: https://yakihonne.com/article/naddr1qq257w2t8qeksc6tdg6njnekdc6x55j0w56nvq3qarkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqxpqqqp65wu2llgg
This article has been translated into French here: https://yakihonne.com/article/naddr1qq2h23jjwck4zajsv4485h68f5mj6c66vfmxuq3qarkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqxpqqqp65wvsexdg
In this article we are going to explore the conceptual origins of the original metaverse called "cyberspace" and see how nostr finally enables it to exist as it was predicted in early science fiction. Then we will explore what cyberspace might be able to do for humanity and how you can contribute to this exciting new open-source metaverse project.
A Concept Obscured by Time
What is a "metaverse"? Ask 10 different people and you will get 10 different answers. Some will say that it is an online game where you can use and transfer crypto assets. Some will say it's a virtual reality experience with extrasensory input for things like smell and touch. Some will say that a metaverse is anywhere you can connect and express yourself digitally. And some may tell you the metaverse doesn't exist yet because we don't have the technology to make it happen.
It's hard to define what a metaverse is because nobody has convincingly built it yet. This is demonstrable by simply asking anyone to show you a metaverse. They may show you VR Chat, or Meta (Facebook), or the HoloLens or Apple Vision, or someone's Discord server or NFT ecosystem, or say "it's not real, and if it is it's probably stupid."
But how did we get here? Why do we all know about the metaverse but we can't define it and we don't even know what it looks like? Where did the idea of the metaverse come from? This answer will give us the conceptual background we need to untangle the question of "what is a metaverse" and see how cyberspace can exist today.
The word "metaverse" was first popularized in Neal Stephenson's 1992 book "Snow Crash", and he was in turn inspired by William Gibson's earlier 1984 book "Neuromancer" (and 2 other books in a trilogy called "The Sprawl"), which popularized the word "cyberspace" and "matrix" in reference to digital 3D spaces.
Accordingly, cyberspace preceded "the metaverse" by 8 years and serves as the foundation for our exploration. Gibson's cyberspace was a digital 3D world one could connect to via a cyberspace deck — a machine/brain interface — and interact with all the data in the entire world. Artificial Intelligences guarded data constructs and kept out intruders with lethal feedback programs that would fry human operator's brains. In the books, cyberspace is described as being used for pretty much everything: entertainment, education, communication, commerce, data storage, and crime, and it is used daily by billions of people throughout the world, including millions of people in orbital colonies.
Mysterious Properties
In Gibson's work, cyberspace has many fascinating qualities that, until nostr, remained very mysterious and seemed to be impossible. Here are some examples.
1. Cyberspace is Permissionless
Everyone can use cyberspace but nobody has full control over it; cyberspace seems to exist outside of every jurisdiction and system. It never goes down for maintenance or has connection issues or suffers security breaches. It seems to exist everywhere at once, even though it is explicitly stated that cyberspace was created by humanity. How can humanity create an uninterruptable, omnipresent digital system that nobody can control but everyone can use?
2. Power is Wielded Without Privilege
Certain people, corporations, and AI weilded greater levels of power in cyberspace than others, but the mechanism of that power was not derived from permissions or access levels or privileged administrator capabilities; rather, the power came from some mysterious other source that could not be granted, governed, or revoked by any law or system or authority. This power seemed also to be heavily influenced by...
3. Hardware and Skill
The hardware that people used to connect to cyberspace had a direct impact on their capabilities in cyberspace. There is a a specific example where a character uses a premium cyberspace deck and describes the speed and smoothness of their ability to fly through cyberspace. A short while later, this operator is captured and immobilized by another dangerously skilled operator, demonstrating that while the cyberspace hardware was top-tier, the operator's skill level was also a big factor governing interactions in cyberspace. This also demonstrates that conflict is possible in cyberspace. How is it possible that hardware directly correlates to your capacity for virtual action? How can someone else influence your actions against your will in this digital reality?
4. Space is Scarce
Bitcoin was the first scarce digital resource to ever exist, and having only been created 14 years ago, scarce digital resources are still a novel concept to humanity in 2023. In Gibson's cyberspace, territory was conquered, captured, and fought over, indicating that the space in cyberspace may be scarce or valuable in some way. How could it be possible to fight for digital territory or acquire it without any governing intermediary took keep track of who owns what?
5. Construction Has a Cost
Constructs, or cyberspace "buildings", required some kind of effort or cost to create, but it was not clear to whom this cost was paid or how the effort was expended.
The metaverse of Stephenson's "Snow Crash" shares many properties with Gibson's cyberspace, although Stephenson is somewhat opinionated with the literal shape of the metaverse. He depicts it as a street that wraps around a black planet, and the land off the street is where people build things and claim territory.
This metaverse similarly does not seem to be owned or controlled by any single entity, yet it is available to everyone in the world to connect, interact, and build in 24/7. It is not described as an application or piece of software, but rather a place that is the sum of other software created by many different parties with different interests and motivations.
Here are some mysterious traits of Stephenson's metaverse:
6. Rules without Rulers
The rules of the metaverse were never broken — not even by hackers or bad guys. How are rules enforced by a system nobody controls?
7. No Teleportation, Localized Rules
The metaverse had rules about where you could spawn in and how you move. Teleportation was not an option. Specialized vehicle software could make traveling easier. Rules for travel were enforced by the metaverse itself. Experiences in the metaverse were localized to constructs that implemented their own rules. For example, sword fighting was allowed in The Black Sun hacker haven because it was programmed to exist there; other places did not have such activities. How can certain places in cyberspace have unique rules separate from the rest of cyberspace? How is locality enforced in a digital system controlled by noone?
8. Customize Without Compromising Everything
People were able to customize how their avatars and constructs looked. How do you govern this so people don't abuse it? Without enforceable rules, one person could make their avatar be the size of the universe and ruin the metaverse for everyone.
9. Everything is Connected
Digital systems in the real world had a presence in the metaverse too, although they were far from commonly populated areas. How do real world systems relate to the metaverse?
I enumerate these points in order to provide some context for where the idea for "the metaverse" began. These two books were instrumental in originally defining what the metaverse was even though it raised many specific questions that naturally were never addressed. As I have said: if the authors knew how to build the things they wrote about, they might not need to sell any books at all! This is fiction after all. Specifics are not required, but I have been focused on uncovering these specifics in the context of new technologies such as bitcoin and nostr and I believe they may now be defined.
To summarize, here are the mysterious properties of cyberspace/the metaverse:
- Everyone can use it
- Nobody controls it
- It exists everywhere
- An individual's power is not granted by any system or authority but comes from their hardware and skill
- Individuals can weild their power against each other
- Territory is scarce and may be captured
- Constructs may be build on territory but have some kind of cost
- The system enforces rules on everyone, or somehow incentivises everyone to follow the rules — even bad actors
- locality is enforced and travel requires time
- certain localities have unique rules
- freedom to customize your avatar and constructs are bounded in some way to prevent total corruption and abuse of digital space
- there is some form of connection between real world digital systems and cyberspace
Nothing Like It
I want to make it very clear that no metaverse in existence today exhibits all of the above properties or even a few of them, and very few digital systems exhibit even one of these properties.
Before I discovered Neuromancer several months ago, my perception of "cyberspace" was that of a quaint, naive concept of what interconnected computer systems would become that never came to pass. I used to ironically refer to the internet as "cyberspace" when talking with other developers as a kind of humorous or self-important overemphasis. I thought that cyberspace was a cultural relic and a failed prediction of what the internet would be. The glossy, 3D wireframe neon world never materialized, and for this I've always felt a sense of loss of what could have been.
Why didn't cyberspace ever come into existence? As computers became more advanced and consumer-focused, they did not attempt to emulate a 3D space, but rather did the practical and sensible thing of emulating paper documents so people could get work done digitally.
As the internet became a household utility, centralized systems and applications were the first and only way that humanity knew to grow our collective capabilities online. Websites grew as they collected users and became behemoths. Ebay, Google, Amazon, PayPal. Although the internet itself was technically decentralized, decentralized systems and applications would come later when the problems with centralization became obvious as these internet giants started abusing their power.
As the internet continued to grow and resemble less and less the fictional worlds of cyberspace and the metaverse, these lofty ideas of digital 3D worlds turned into toys for most people — unnecessary but entertaining fluff. The notion of cyberspace faded into 80's retro culture and the word cyberspace was painfully repurposed to simply refer to the internet or networked systems collectively. This, however, is a terribly inaccurate use of the word. There is no space to speak of on the internet. But, sadly, the interet was the closest thing we have ever had to Gibson's vision of cyberspace, and it really wasn't close by any measure except that people all over the world use it for pretty much everything. All the other magical properties of cyberspace were simply forgotten. They were fiction. They weren't necessary. They weren't possible. There was no way to make it work and no reason to do so.
However, when reading these books from nearly 4 decades past, there is something poignant to me in the fact that across these various works by various authors, the metaverse (or cyberspace) posesses consistent properties that no author is willing to alter. What is so inviolate about a fictional concept that would make it so consistent across works? Perhaps there is a kernel of truth in what is imagined, and that truth is so compelling that it must be repeated until it crosses the veil between idea and reality.
Reality And Cyberspace
I have always been fascinated by technology's ability to improve our lives, and I have strived to create consequential software my entire life, like video games played via fitness watches and augmented reality navigation web apps, but it wasn't until I read Softwar that I realized something profound.
In reality, I am able to do anything I want as long as I have the thermodynamic energy to do it.
It may not be legal or socially acceptable, but if I have the energy to do something, I can. Likewise, if someone wants to stop me from doing something, they can't unless they also expend enough energy to stop me.
This means that reality is permissionless, because nobody can disallow my actions. It also means reality is thermodynamic, because every action has a cost that must be paid to the universe in the form of entropy.
Conversely, in digital systems, the amount of energy you have is irrelevant. The things you can do are only the things you are allowed to do by the permissioned system, or, the things you can trick the system into letting you do. This means that within a digital system, you always have a severely limited subset of available actions, and your ability to execute those actions has nothing to do with your thermodynamic potential and everything to do with the permissions you are granted by others. No matter how strong my muscles are or how clever I am, I can't do more than a digital system allows me to do, and even if I hack it, I still can't do anything I want — only more than I'm supposed to.
Almost all digital systems and software are permissioned and non-thermodynamic.
This is why, fundamentally, no metaverse that has ever been built actually matters. This is why no video game keeps you interested in it forever, because the actions that you can do and the extent to which you can do them are arbitrarily disconnected from your ability to act in reality. It's "just a game" — a limited subset of reality.
This isn't fundamentally a bad thing. Obviously, software has done a lot for humanity. And software-based rules have been used in many contexts to keep things fair for everybody. Except, unfortunately, digital systems are never truly fair. There's always a programmer who wrote the rules. There's always an admin above you. There's always a hacker. And there's always someone with more permissions than you who can restrict your potential. Compared to reality, this seems arbitrary and capricious. At least in reality, the universe to which you pay your entropy costs is truly, terribly impartial and unbiased. This is why thermodynamic systems are fundamentally fair; even though it may not seem fair to you it is truly fair to everyone.
Reality is a permissionless, thermodynamic protocol, and almost nothing in the digital world resembles this whatsoever.
Nostr, however, is permissionless. Until now you may not have considered this to be a fundamental property of our universe, but it is, and the fact that nostr exhibits this same property is quite compelling. In fact, any system that is truly permissionless (of which there are very few) seems to have the magic ability to capture people's imaginations in ways that no other digital system can. Things such as bitcoin, perhaps the most famous permissionless digital system, has such broad and profound effects on people who grasp it that they have been known in some cases (such as Andreas M. Antonopoulos') to stop eating, stop sleeping, research it obsessively, and completely change their entire way of life. How's that for consequential software?
Like bitcoin, nostr can also be thermodynamic via proof-of-work (NIP-13). And with the combination of these two properties, which are shared with reality, we are suddenly able to dispell every single mystery we've encountered regarding cyberspace.
Proof-of-work is the secret ingredient to dissolve the fiction in the science fiction of cyberspace.
A Mystery Solved About Cyberspace and Bitcoin
The reason that the properties of cyberspace and the metaverse are so mysterious is because they are actually properties of reality, but inside a digital system.
In reality, it is no surprise that your hardware and skill affects your ability. No surprise that your work determines your power. No surprise that you can't teleport and must travel using energy. No surprise that building constructs or customizing yourself takes effort and cost. No surprise that territory is scarce and must be defended. No surprise that conflict happens between people. All of this is so completely normal that it's easy to overlook.
The reason these things in Neuromancer and Snow Crash and other works about the metaverse seemed so mysterious is because they weren't possible to model in a digital space. These authors took properties of reality and put them in a digital space, and it seemed amazing because nobody knew how it could actually work.
This is how it is possible: you design a digital system that has the same fundamental properties as reality. It must be permissionless. It must be thermodynamic. Then you have a system wherein cyberspace can exist.
Nostr is the fulfillment of these requirements. Like bitcoin, nostr has captured the imaginations of thousands of early adopters and developers. The magic is there. But few may realize why it is feels so magical. The answer is that when you make a digital system that can model reality's own properties, you have created an extension of reality itself. This is one of the most significant discoveries in human history, because a digital extension of reality can allow humanity to connect, collaborate, and grow in a place where their physical diatance does not matter. Barring any major advancements in spacefaring technology, cyberspace will be the most significant departure from earth you may experience in your lifetime.
I posit that a virtual action which is permissionless and thermodynamic is as real as a physical action, except the consequences of that action happen in the digital space rather than the physical one. It's not quite reality, but it is like a mirror. It is a true extension of reality. Nothing in it is disconnected from the real world. And therefore, unlike any other digital system, it can be truly consequential.
Healthy Skepticism
Wait a minute, you may say. Cyberspace is still just a digital way of communicating. Isn't email and texting and video chat good enough? Why do we need cyberspace? How could it possibly be so important to humanity?
This is a great question.
One may ask similar questions about bitcoin. Don't we already have digital money? Why do we need absolutely scarce, decentralized censorship-resistant money?
Or about nostr: why do we need another way to transmit text? What good is it to be decentralized and censorship resistant?
Like bitcoin, cyberspace makes something digital into a scarce resource, but instead of enabling the capture of time (on a timechain) cyberspace enables the capture of scarce space (in a construct or your movement chain).
In the physical world, our movement can easily be censored. Our expression of power is censored. Our capture of space is censored. Not so in cyberspace. The only thing that matters in cyberspace is the thermodynamic energy you exert — just like in reality, but minus the permissioned (artificial) power structures of governments and laws.
Just as bitcoin doesn't care who you are or who you are transmitting value to, cyberspace doesn't care who you are or where you are moving to or where you are claiming space.
Consequences of Proof-of-Work in Detail
I'd like to enumerate the specific ways in which proof-of-work in nostr demystifies the mysterious properties of cyberspace mentioned earlier.
- Everyone can use cyberspace but nobody has full control over it.
Just replace "cyberspace" with "nostr" and the above statement is already true. If we build cyberspace on nostr, then cyberspace will inherit these properties.
- Certain people, corporations, and AI weilded greater levels of power in cyberspace than others
If we base an entity's power on their thermodynamic output via proof-of-work, then we have a permissionless way for cyberspace participants to enact their real thermodynamic potential in cyberspace to whatever degree they choose.
- The hardware that people used to connect to cyberspace had a direct impact on their capabilities in cyberspace.
If all actions in cyberspace are thermodynamic like in reality, then hardware capable of greater amounts of proof-of-work will enable more powerful actions. Mobile phone, desktop computer, or ASIC farm: take your pick.
- Territory in cyberspace was conquered, captured, and fought over, indicating that it may be scarce or valuable in some way. Constructing had a cost.
The territory in cyberspace is the maximum 3-dimensional coordinate space that can be represented by 256 bits. In cryptography, nostr, and bitcoin, 256-bit numbers are very commonly used along with mathematical functions like SHA-256 that process data in blocks of 256, so it is a good "round" amount of information to work with.
You can divide a 256-bit number into X, Y, and Z coordinates that are each 85 bits long. This leaves 1 extra least-significant bit from the 256 bits that is ignored.
This means that each axis of cyberspace is 2^85 units long.
Space can be claimed by publishing a construct event whose event ID is the coordinate. The event ID is obtained from hashing the event (standard process for all events in the nostr protocol). This means the event ID can be mined to obtain the coordinates you desire (or at least something close by).
If two constructs overlap, the one with the most proof-of-work wins. This is how territory can be contested in a permissionless way in cyberspace, as alluded to in Gibson's works.
The cost of construction is the proof-of-work, and the maintenance of that territory by proof-of-work is the digital analogy of either paying taxes to a government who will protect your land, or, protecting your land with your own thermodynamic energy. Notice how money, also known as time, is inextricably linked to the ownership of property in reality and now also in cyberspace. If property were free to own and maintain, would it be worth anything at all?
I have been presented with the argument that it does not cost you anything to hold bitcoin, so constructs or cyberspace real estate should be no different. To this I say that for you to hold your bitcoin, a tremendous amount of cost is expended by all the miners in the world. If not for them, your bitcoin would be double-spent or stolen by invalid transactions. The validity of your unmoving bitcoin requires the continual, perpetual operation of the largest computer network in the world. So, continual energy expenditure to secure your property is true with bitcoin, cyberspace, and all of your things in reality as well.
Unlike bitcoin, whose value lies in the entire network, constructs are valuable only to their owner. Therefore, it is the responsibility of the construct's owner to defend it.
More complex symbiotic relationships in construct defense may be borne out of the perpetual fight for survival inherent in any thermodynamic system. But this is only speculation.
Enforcing rules universally
As with any protocol, deviation excludes you from it and submission grants a share in its value. Forking the cyberspace meta-protocol, whether by disobeying its rules or rewriting them, results in an irreconcilable forking of digital reality. The value of cyberspace as a protocol depends on network effects like any protocol, and the first-mover has a strong advantage in any protocol war. Additionally, as all actions require proof-of-work and must be chained together, the sum of your history in cyberspace is put at risk of invalidation should you deviate from the protocol everyone else is following.
Ultimately I believe that the purpose of cyberspace should be to imbue humanity with new capabilities and opportunities, and I think that it will, simply by virtue of the fact that it is built on a protocol and interoperates with protocols that likewise imbue humanity with new capabilities and opportunities (notsr, bitcoin, and TCP-IP). I desire that cyberspace will be flexible and capable enough to support as many use-cases as possible as long as the fundamental properties are preserved as axiomatic non-negotiables. Cyberspace itself must be both permissionless and thermodynamic. Without these properties, cyberspace becomes just another digital illusion apart from reality.
Flexibility, locality, and customzation
With these axioms in mind, I think it would be very smart to create a method of defining construct-level rules that exist only within certain spaces. This would allow for custom interactions and systems to exist in the fabric of cyberspace, making it very flexible and local. Any such system or customization, even if cosmetic, must impose a fundamental thermodynamic cost. The details of how this could work are yet to be developed, but the blueprints of fiction, our axioms, and our ingenuity will lead us to it.
The metaverse of things
Because nostr is a web-friendly protocol, it is trivial to connect anything to cyberspace. I love to tell the tale of how I witnessed an early 2022 conversation between someone and (if I remember correctly) Will Casarin's smart dishwasher that was posting kind 1 status updates to nostr. If someone can talk to a smart dishwasher over nostr, then the Metaverse of Things already exists. However, the degree to which these things expose themselves to the metaverse should follow the same security model as for the internet at large. Unlike in fiction, I doubt anyone will allow sufficient proof-of-work be the only prequisite for commandeering a real-world system. That's ok. Ultimately, the relationship between reality and cyberspace isn't meant to be a 1:1 map. Digital systems only really ought to participate in cyberspace if they share the same properties as cyberspace. Most digital systems are permissioned and non-thermodynamic, and therefore do not have a compelling reason to exist in cyberspace. But anything is indeed possible.
Chasing a Ghost or Following a Blueprint?
I'd like to make the distinction that the purpose of a construct (and of most things) in the real-world cyberspace is not necessarily the same as in Gibson's literary cyberspace nor in Stephenson's literary metaverse. But the fundamental properties as depicted remain the same, and it is enabled by proof-of-work.
Remember, the remarkable thing about Gibson's cyberspace is that it is a digital world that functions like reality — there is egalitarian conflict resolution, scarce space, and universally enforced rules. The cyberspace meta-protocol likewise enables a digital system to function like space in reality. The motivations and reasons behind this digital system may be completely different than in the books, but that doesn't mean the mechanisms are any less accurate.
My goal is not to reproduce Gibson's and Stephenson's work in reality. The properties of this fiction are compelling, and the implementation and usage of cyberspace will completely depend on free market forces — exactly as it should be. It is not for me to decide. These works opened the conceptual pathway to creating this new thermodynamic digital reality. The human motivations and actions that shape cyberspace will undoubtedly cause it to look plenty different than depicted in the books, while the funamental properties remain identical.
Throughout the process of designing the cyberspace meta-protocol I have tried to keep it as simple and fundamental as possible, using these books as my guidepost. Whether these authors realized it or not, their depictions of cyberspace and the metaverse were extremely consistent and coherent, which makes not only for great fiction and believability but also for a great guide to follow in developing a real system.
Step Into Cyberspace
I'd like to provide some concrete examples of how cyberspace works so that the concepts presented herein are not without application.
NOSTR in 3 minutes
To interact with cyberspace, one must simply publish certain "kinds" of nostr events. If you are not familiar with nostr, here is a short explanation. Nostr is made up of people running clients, which are just apps like on your phone or desktop, and people running relays, which are like servers that store events. Clients download streams of events from relays in real time. Clients can also publish events to relays. Publishing an event is like sending a tweet. Clients normally publish the same event to many relays at once. As long as you send the tweet to at least one relay that your friend is connected to, they will see your tweet. Anyone can run a relay or build a client and connect to whichever relays they want. In this way, nostr is permissionless and decentralized.
A "kind 1" event is essentially a tweet, but there are other kinds of events, each represented by a number. A kind 0 event is what you publish when you update your profile with a new bio or screen name. Anyone may make up a new kind of event and assign it any number, except it would be poorly supported if you used a number that is already accepted as part of the nostr protocol for another purpose than you are using it for. Luckily, there are a lot of numbers to go around.
A private/public keypair is an anonymous cryptographic identity, and it can be used for secure communication, storage of bitcoin, and other various things. The keys themselves are just unfathomly large unguessable numbers represented in the hexadecimal number system which includes numbers 0-9 and a-f (base 16 instead of base 10). When you publish an event on nostr, it is signed by your private key, and the event contains your public key. This allows anyone to verify that the event is legitimately from that public key, which presumably only a certain person controls. In this way, nobody can forge or tamper with events without invalidating them, because the signature would not match the public key.
Meta-protocol
This is why I refer to cyberspace as a meta-protocol because it is simply a specific way of publishing and interpreting specific event kinds over nostr and visualizing them in a 3D space.
Drift
To move in cyberspace, you must publish a kind 333 event, referred to as a Drift event. This event contains your 3D cyberspace coordinates, your direction, your existing velocity, a reference to your previous Drift event, and proof-of-work to add velocity by your direction. The amount of proof-of-work on the drift event determines your acceleration. Proof-of-work can be added to any nostr event by choosing an amount of work, represented by the number of leading binary zeroes on the event's ID, and hashing the event with a different nonce until the target amount of work is reached. This process is specified in NIP-13.
Each Drift event may be validated by running the coordinates and velocity through a standardized cyberspace algorithm (currently being developed) to verify that the value changes from one drift event to the next are within a tolerable range of error. It is in effect a way of simulating the movement within a physics system in order to validate that the movements did not break the rules of cyberspace physics. In this way, every participant in cyberspace is a validator of everyone else they are physically near.
When a drift event is signed, the reference to the previous drift event is included in the signature. This creates, in effect, a personal verifiable hash chain history of your movements and actions in cyberspace that anyone else can verify.
Dishonesty and Punishment
In order to encourage people to be honest about their movement chains, anyone who finds an invalid — or "broken" — movement chain may punish its owner by publishing a Derezz event on it, which will invalidate all movement chains and proof-of-work owned by the victim and teleport them back to their home coordinate where they originally spawned when they first used cyberspace. This is effectively a respawn. You start from scratch, but you can keep your constructs.
One can easily lie about their movement chains and teleport anywhere at any time. But on nostr, for the most part, events cannot be deleted. Therefore, a cheater will leave a bright trail by which others may cyber-kill them via Derezz. A broken movement chain is like a ghost copy of the cheater that can't move. For deeper protocol reasons that the adventurous may explore in the spec, this makes the ghost copy extra vulnerable to Derezz.
A cheater may choose to ignore the Derezz attack and continue to teleport where desired. Nothing in nostr or cyberspace can stop this. But to everyone else who follows the protocol, this type of behavior can easily be ignored. The habitual cheater may as well be a ghost, as their thermodynamic actions will be ignored by everyone else who has chosen to obey the protocol. The cheater might redeem themselves by publishing a very long valid chain of events, but this probationary period may be too demanding for habitual protocol breakers. Other aggressive actions may be leveled against cheaters, making their operation in cyberspace unproductive, difficult, and dangerous.
A cheater in cyberspace is an easy target. As the punishment of cheaters is a noble act of justice rather than an evil act of predation, I expect cheaters in cyberspace to be punished with great swiftness and mirth.
Incentives for honest movement legitimize the spatial aspect of cyberspace. In cyberspace, space is real and consequential. Traversing it has a cost. No two places are funamentally the same because there is a real cost to visit them. And all space is scarce, because of the hard limit of the 2^85 coordinate system, which was chosen to be compatible with the most popular mining agorithm in the world, SHA-256.
Other actions
To read all about the different kinds of events one can publish to interact with cyberspace, check out (and contribute!) to the official cyberspace specification here: https://github.com/arkin0x/cyberspace
In this specification you will find technical implementation details for clients to interact with the cyberspace meta-protocol, including definitions of other actions that may be taken by operators, including:
- manipulating "gravity" to affect other operators
- creating proof-of-work armor against Derezz
- cloaking one's location with stealth
- and more!
Ubiquity and Omnipresence of Cyberspace
A very interesting recent development is an open-source project called
nostrmeshby lnbits that enables anyone to host a nostr relay on a small mesh-networked device, such as an Arduino. Imagine a network of billions of these devices, scattered across the globe, running on battieries and solar panels, each contributing to the infrastructure of cyberspace — a decentralized, omnipresent digital cosmos, accessible from virtually anywhere. This level of ubiquity brings us one step closer to the vision of Gibson's work, where cyberspace becomes an integral part of our daily lives and can be found everywhere — even in outer space!With such a ubiquitous and omnipresent network, the spatial limitations of cyberspace extend far beyond conventional digital boundaries, intertwining with our physical world in a way that was once the domain of science fiction. The implications of this development are enormous and lay the foundation for the potential uses and influence of cyberspace, which we will explore in the following section.
Consequences of Cyberspace
It is difficult to predict whether cyberspace will find its place in the daily lives of billions or be forgotten once again. However, the foundations of cyberspace are inextricably linked to technologies that have been developed and adopted for the sake of human freedom and personal rights: public key cryptography, hashing, proof-of-work, bitcoin, and nostr.
As one who takes science fiction seriously enough to remove the fiction from it entirely, I find speculation to be invaluable. One cannot go where the imagination does not first lead. Our entire perception of the world is parsed from an abstraction created by our minds. We automatically assign meaning to inherently meaningless things — symbols, patterns, etc. Fiction is our reality, and our perception of the world is the sum of logical patterns within this fiction. Therefore, let us do what we do best and create fiction, or speculate, without hesitation.
I personally envision cyberspace to be a place of commerce and social organization. Constructs enable people to claim cyber land. They can use this land to design interactive experiences that are governed by localized rules and thernodynamics. The Lightning network enables instant transfer of value through cyberspace, facilitating the transaction of information, services, cyber experiences, digital and physical goods.
Use cases include shopping, gaming, gambling, competitions, live cyber events, virtual-presence social gatherings, virtual protests, collaborative spaces, advertising, education, tourism, development of cyberspace-based applications, data visualization, research, social networking, and even more that we haven't imagined yet.
Conclusion
As we venture into the vast digital landscapes of cyberspace, we are not simply traversing through lifeless data, but immersing ourselves in a consequential world that reflects the order and complexity of our physical reality. This revolutionary approach to cyberspace isn't merely a mirage of science fiction, but a tangible exploration of its key principles, built on the bedrock of public key cryptography, hashing, proof-of-work, bitcoin, and nostr.
Through the implementation of a meta-protocol layered over nostr, cyberspace opens a myriad of opportunities – drifting through the boundless expanses of the digital cosmos, crafting personal domains, or engaging in vibrant social interactions. Just as actions in the physical world carry costs and consequences, so too does cyberspace enforce its own unique set of rules and repercussions, fostering a sense of shared responsibility, fairness, and cooperation among its denizens.
Envisioned as a playground for creativity, commerce, and social organization, cyberspace, in its current formative state, already shows tremendous potential for an expansive array of use cases. Its inherent thermodynamic properties and permissionless nature offer a groundbreaking amalgamation of digital and physical realities, poised to profoundly augment our capabilities, experiences, and opportunities in a dynamic, inclusive, global, and consequential realm.
However, the most exciting aspect of cyberspace is not merely what it currently offers, but its potential to continuously evolve and redefine itself. As more people engage with and contribute to its development, it's bound to expand and morph in ways we can hardly fathom today.
As we stand on the cusp of this digital frontier, we are not chasing after phantoms of fiction. Instead, we are architects and pioneers of a revolutionary new realm, where digital existence converges with physical principles. This remarkable blend of technology and human imagination sets the stage for an unprecedented era of exploration and innovation, signaling a future that is as exciting as it is unpredictable.
Join me on this grand endeavor to shape cyberspace, to mold this new frontier into a shared and diverse digital world that reflects the best of human spirit and ingenuity. Together, let's step into cyberspace, the frontier of the future.
Build with me
Cyberspace is for humanity, and therefore I desire as many humans to be involved in its construction as possible. I have created the following resources for anyone who wants to learn more or get involved:
Join the ONOSENDAI Telegram group: https://t.me/ONOSENDAITECH
I love answering questions! Please hop in and ask away!
Pull requests welcome on the spec: https://github.com/arkin0x/cyberspace
Check out the first cyberspace client, ONOSENDAI: https//onosendai.tech (thermodynamics still in development)
Pull requests welcome on ONOSENDAI: https://github.com/arkin0x/ONOSENDAI
whoami
My name is Nick. I go by arkinox. I have been making websites since I was 11 and designing games since I was 4. I've been the director of web for a midwest marketing firm for 10 years and the co-founder and senior vice president of an augmented reality company, innovatar.io, for 4 years.
Support FOSS
If you would like to support development of this protocol I would love for you to get involved. Also, I am accepting donations and looking for opportunities to pursue it full time.
Follow me on nostr: npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w
Zap me with Bitcoin Lightning: arkinox@getalby.com
Soli Deo gloria
-
 @ d5b41074:156978f1
2023-05-07 21:38:01
@ d5b41074:156978f1
2023-05-07 21:38:01Hyper-Nostr: Bringing P2P to relays
People suggested me to write a detailed post blog about my project, explaining how to use it, what it is, what to expect, and how it works. This post is the attempt of doing that.
What is it?
Hyper-Nostr is a decentralized nostr relay. It is a distributed relay, where everyone can have its own local node. Then, they behave as a single relay, sending and keeping the events on the network.
Right now, to use it you need to have
npm, which requiresnodejs. I may add plain executables on the future. You install it asnpm install -g hyper-nostrand then you can start your own node ashyper-nostr [<port> [<topics>...]]. Last step is to add the relay on your client asws://localhost:[port]/[topic]for each topic you want to have on that client. I am still working on havingwssinstead ofws, but looks like clients accept the connection because it is onlocalhost. UPDATE: you can use some reverse proxy to havewss. I personally use caddy so I can docaddy reverse-proxy --to localhost:3000.Right, the topics. The topic is how we find each other, to send the events and have an unified database. Think of it as the address of the hyper-nostr relay, or a specific instance of it.
Having all configured, you can now expect it to work just as a standard relay: it will receive events that was send to these, you will be able to send and receive events, and it will save the events on it.
How it even works?
This project is Powered by Holepunch.
The connections and event streamings happen on Hyperswarm, Autobase linearized the underlying files, and uses a Hyperbeedee database (loosely based on MongoDB).
The hyperswarm and cores management was highly abstracted thanks to Hyper SDK.
Want to know more? Okay, lemme try to explain: - Hyper SDK creates a unified swarm instance that is used by the entirety of the relay; - Each topic creates two underlying hypercores: one that is the same for everyone in the topic, used to connect the peers, and the other is local, for your own local database; - Then, the discovery core has two extensions: the event broadcasting extension, to relay to the connected users the real-time events, and the syncing extension, to share the local databases to the peers; - Then, with the help of Autobase, all the local databases are linearized, giving an unified database shared across all peers. - With that, it is as if every peer has the same database when querying, and every peer receives the broadcasted events on real-time too (filtering by the subscriptions, as specified on NIP-01).
What to expect? (or, what are these logs)
The first message the relay prints is
your key is <key>. This key is the hyperswarm public key, which for now I am doing nothing with it, but maybe in the future I will implement private relays that you connect specific peers on it. Still thinking on it.If you have passed initial topics, they will log here too. When you see
listening on <port>, the relay is now open to receive websocket connections (aka it is ready for your client to connect).During the database indexing it generates a warning of
(node:<PID>) MaxListenersExceededWarning: Possible EventEmitter memory leak detected. 11 append listeners added to [LinearizedCoreSession]. Use emitter.setMaxListeners() to increase limit (Usenode --trace-warnings ...to show where the warning was created). This warning is expected, dont panic.To each websocket connection, the relay will also log 2 messages:
ws connection startedandws connection stablished. They were first there to detect silent crashes during the topic initialization, that happens between these two logs if it didnt happen yet.To each topic initialized, it logs
swarm hyper-nostr-<topic> created with hyper!. The prefix is to mitigate the risk of topic crashing on the hyperswarm.Finally, there is one last thing to expect: peers connections. It logs a count of peers on topics on each connection, in the format of
<count> peers on <topic>!every time the connections update.What do you think? Do you liked this project?
Consider sharing your thoughts with me, I would love to know. Do you think the explanation was superficial? What could I have explained better? Do you have some suggestion for the project?
Consider supporting me, I have no formal job currently, and I am spending a lot of time and energy on this project.
-
 @ c8383d81:f9139549
2023-07-14 18:40:14
@ c8383d81:f9139549
2023-07-14 18:40:14I listened today to the Nostrovia podcast with Stewart Mackenzie about Named Data Networking and I agree that because Nostr is still relying on the TCP/IP stack that in and of itself can be easily censored by a nation state. ( so it is not very resistant in that way) I would like to add that the censorship resistant is more of a having no extra central middel men corporation and an idea that as long as some parts of the network are open and relaying there will always be an option for decentralised communications and reseeding of the network. Together we can build multiple communication protocols making it more difficult to shut them all down so maybe some of the answer lies in multiple protocols ... however if they all rely on TCP/IP and DNS magic we'll always be in the same boat.
Maybe someday relays will operate on Named Data Networking but until that day.

This made me think of what Nostr than really is to me and here is the answer:
In the last months i've been talking to people from all over the world from China to Venezuela and some of these places still experience censorship, financial disruption that all have implications on people's daily lives. Nostr offers a great parring with lightning to create decentralised applications. View it as a free backend relay network to build structures that allow all elements of a normall application but without all the extra costs and overhead associated with it. This enables more users to participate and lower the adoption curve. Allowing all Nostriches to be able to experience equal opportunities. I'm definitely still making big plans for this protocol!
-
 @ 50c59a1c:6b0a027e
2023-07-14 17:37:59
@ 50c59a1c:6b0a027e
2023-07-14 17:37:59"Kill every buffalo you can! Every dead buffalo is an Indian gone."
Near the end of the 19th century, this was the stated goal of the US government. At the time large swaths of Texas, Oklahoma, and Colorado were still controlled by the Comanche, the last great Indian nation of the American Plains. The Comanche were brutal in their methods of war, and had absorbed many of their enemies well before the Europeans arrived. They had been successful at beating back the Mexican and Spanish armies and were confident they could do it again.
They were decentralized. They could navigate their territory more effectively, and could survive longer in the inhospitable areas of the high plains. They knew where to find water and where to hide. The Comanche owned and controlled thousands of horses, which made them wealthy. They were better horsemen than their enemies and could hit a target from 50 yards while riding at full speed. They had ways of fighting and terrorizing the encroaching frontiersmen that instilled fear in their enemy. No other nation had been able to defeat them, but they failed to recognize their greatest weakness. Their dependence on the buffalo.
The buffalo's value among the Plains tribes, was priceless. Experts estimate that 60 million Buffalo freely grazed and cultivated the land. For centuries, they provided the people with everything from fly swatters to shelters. The native tribes followed the herds and only killed what they needed. Since the Buffalo were life-givers, the people carefully maintained a balance, never overkilling for sport, and only hunted for sustenance.
Generals William T. Sherman and Philip Sheridan believed that if the government could eradicate the Buffalo, the Indians would have no choice but to give up. He was quoted as saying, "Take away anything essential for the survival of a people, and they will surrender. As long as the Buffalo roamed the Plains, so did the Indians." In a fifty-five-year period, from 1830-1885, soldiers, hunters, and settlers killed more than 40 million Buffalo.
The annihiliation of the buffalo led to the subjugation of the Comanche. They became wards and dependants of the state. They were moved onto reserves and their ways of living were not permitted. They were not allowed to hunt, and were forced to farm. They could not leave their reserve without permission, and were often provided with food that was not edible. The nations were broken and defeated, but this was still not enough. The government needed to destroy a generation. They needed to kill the Indian in every child.
"Kill the Indian in every child"
Residential schools were the means by which this task was undertaken. Children were taken from their homes and were taught that their beliefs were evil. That they were savages. They were meant to feel worthless, and were taught to hate who they once were. Through an instutional system of abuse and "re-education" the goal was to eradicate a culture of freedom, so that it could be replaced with one of servitude and obedience. The last of these schools in Canada was closed in 1996.
"Kill the liberty, control the man"
Like the first nations of the Great Plains, we are in a battle for the right to choose what kind of life we want to live. Our battle is not one that will be fought out in the open. We will not see the faces of our enemies. Today, our warriors are developers. Their horses are their hardware, their minds are their bows, and their code are their arrows. The protocols they build are the ancient paths that have always existed in the physical world. The paths that connect individuals, who freely transact in ideas and value, where their reputations are the most important currency. Reputations built upon their ideas, rather than their identities.
These paths are used to connect and protect our community. These paths guide us towards shelter, sustenance, and community. They enlighten, entertain, and enrich. Our communities are built on the values we share. Freedom, openness, critical thought, and the inherent right to challenge the ideas of others. It is our job as individuals to protect these paths, to promote these paths, and to welcome newcomers and refugees from the old system.
Like the Comanche, the protocols and networks we build have weaknesses. They have points of failure that can be exploited. We have dependencies, just as the Comanche were dependent on the buffalo. Those in power have been relentless in their attempts to starve us into submission. They have attacked our networks through policies related to energy, self custody, KYC, and privacy. Great technical minds and efforts have been devoted to protecting our "buffalo". Bitcoin has been tested many times and has proven itself to be resilient, but they will continue to poke and prod until they find our "buffalo".
Luckily, I don't believe our children will have to undergo the same overt physical and mental abuse of residential schools. However, we need to ask ourselves what values are being instilled in our children? Are they being taught to value privacy? Are they being taught to value freedom of expression, without fears of being canceled? Are they being taught how economies function, or the misery communism has caused throughout the world? Are they being taught to demand control over their data, to be free, and sovereign, or are they being indoctrinated into a state where they are passive participants in a system predicated on dependency? Are they being taught to put in the work to create and build things of value, or are they being taught to sell themselves in the most "clickable" way to garner attention and eyeballs. The more extreme and abhorrant the act, the more successful one can be.
If you want to know what the goals of those in power are, observe how they treat their children. Listen to what they are being taught. Dictators and the purveyors of tyranny know that if they want to control the future, they need to control the children. We are just begining to wake up to the fight for control over the values and beliefs that are taught to our children. The values and beliefs that will be fought over, well after we are dead.
We can not underestimate what those in power are prepared to do, and we can not ignore their ability to convince others to do the same. 60 million buffalo once roamed the great plains of North America, which were followed and hunted by a nation of warrios, who were resilient and self sufficient. They were sovereign, they land and weapons, but their enemies had bigger weapons.
Our warriors are stronger, our protocols are better, our communities are fortified by a system of truth, but we need to be ready for the battles that lay ahead. It is our stories, our ideas, and our ability to communicate that will win this war, because we are all on the reserve now.
-
 @ 0c9b1e9f:3f6db0e0
2023-05-06 01:08:43
@ 0c9b1e9f:3f6db0e0
2023-05-06 01:08:43[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
[19]
[20]
[21]
[22]
[23]
[24]
[25]
[26]
[27]
[28]
[29]
[30]
[31]
[32]
[33]
[34]
[35]
[36]
[37]
[38]
[39]
[40]
[41]
[42]
[43]
[44]
[45]
[46]
[47]
[48]
[49]
[50]
[51]
-
 @ c8383d81:f9139549
2023-07-14 17:22:22
@ c8383d81:f9139549
2023-07-14 17:22:22Today we setup the software prerequisites & clone the Famewerk template. Once you have the following installed on your system you can repeat the Flamewerk setup instructions for anything project you want to build. This will be the most difficult and heavy part of the setup process so take your time to setup your tools properly !
- NodeJS 14.19.2
- Github Account & Github Desktop App
- Yarn
- VS Code or any other code editor
Installing NodeJS
[
Node.js
Node.js® is a JavaScript runtime built on Chrome’s V8 JavaScript engine.
 Node.jsNode.js
Node.jsNode.js ](https://nodejs.org/en/)
Before we can start using the template, we need to have NodeJS installed on our system. NodeJS is a JavaScript runtime built on Chrome's V8 JavaScript engine. It allows us to run JavaScript code on the server-side, making it possible to build scalable and efficient applications.
](https://nodejs.org/en/)
Before we can start using the template, we need to have NodeJS installed on our system. NodeJS is a JavaScript runtime built on Chrome's V8 JavaScript engine. It allows us to run JavaScript code on the server-side, making it possible to build scalable and efficient applications.To install NodeJS, follow these steps:
- Go to the NodeJS website.
- Click on the "Download" button for the recommended version.
- Run the installer and follow the prompts to complete the installation.
Once NodeJS is installed, you can check if it's installed correctly by running the following command in your terminal:
node -vIf NodeJS is installed correctly, you should see the version number.
node -vExpected output: 14.19.2
Setting Up a GitHub Account
To start, head over to GitHub and create an account. Once you have created an account, you can start setting up your profile. Your profile is where you can showcase your coding skills, share your projects, and connect with other developers. You can add a profile picture, a bio, and links to your social media profiles.
Setting Up GitHub Desktop
GitHub Desktop is a tool that allows you to manage your repositories on GitHub. It is a user-friendly interface that makes it easy to manage your code. To install GitHub Desktop, head over to the GitHub Desktop website and download the version for your operating system. Once you have downloaded the software, install it on your computer.
Once you have installed GitHub Desktop, you can sign in with your GitHub account details. Once you have signed in, you can clone a repository from GitHub. Cloning a repository creates a local copy of the code on your computer. You can then make changes to the code and push those changes back to GitHub.
Installing Yarn through npm
[
Yarn
Fast, reliable, and secure dependency management.
Yarn
 ](https://classic.yarnpkg.com/lang/en/docs/install/#mac-stable)
Yarn is a package manager for JavaScript. It allows you to manage your dependencies and install packages easily. To install Yarn, you first need to have Node.js and npm installed on your computer. You can download Node.js from the official website.
](https://classic.yarnpkg.com/lang/en/docs/install/#mac-stable)
Yarn is a package manager for JavaScript. It allows you to manage your dependencies and install packages easily. To install Yarn, you first need to have Node.js and npm installed on your computer. You can download Node.js from the official website.Once you have Node.js and npm installed, open up your terminal or command prompt and run the following command:
npm install -g yarnThis command installs Yarn globally on your computer. You can now use Yarn to manage your dependencies in your projects.
yarn -vExpected output: >1.22.18
Downloading Visual Studio Code
[
Download Visual Studio Code - Mac, Linux, Windows
Visual Studio Code is free and available on your favorite platform - Linux, macOS, and Windows. Download Visual Studio Code to experience a redefined code editor, optimized for building and debugging modern web and cloud applications.
MicrosoftMicrosoft
 ](https://code.visualstudio.com/download)
The first step in installing Visual Studio Code is to download the installer for your operating system. You can download the installer from the official Visual Studio Code website. Once you've reached the download page, select the version of Visual Studio Code that is compatible with your operating system. Next, click on the download button to start the download process. The installer file size is relatively small, so the download should complete quickly.
](https://code.visualstudio.com/download)
The first step in installing Visual Studio Code is to download the installer for your operating system. You can download the installer from the official Visual Studio Code website. Once you've reached the download page, select the version of Visual Studio Code that is compatible with your operating system. Next, click on the download button to start the download process. The installer file size is relatively small, so the download should complete quickly.Installing Visual Studio Code
Once the download is complete, locate the installer file and double-click on it to start the installation process. Follow the on-screen instructions to install Visual Studio Code on your device. During the installation process, you'll be prompted to select the installation location and choose the features you want to install. You can leave these settings as default or customize them as per your requirement.
🔥 Setup Flamewerk
Cloning the Flamewerk Template with Github Desktop
You can get started by cloning the Github template using Github Desktop. We will be using the "startup" template, which can be found at https://github.com/flamewerk/startup. Follow these steps to clone the repository:
- Open Github Desktop and click on the “File” menu.
- Select “Clone Repository” from the dropdown menu.
- In the “Clone a Repository” window, select the “URL” tab.
- Copy the URL of the “startup” Github template from the Github repository.
- Paste the URL into the “Repository URL” field in Github Desktop.
- Choose the location on your computer where you want to save the repository.
- Click on the “Clone” button.
Github Desktop will clone the repository to your computer.
Opening the Folder with Visual Studio Code
After cloning the repository, you can proceed to open the folder in Visual Studio Code. Here are the steps:
- Open Visual Studio Code.
- Click on the “File” menu.
- Select “Open Folder” from the dropdown menu.
- Navigate to the location where you saved the repository and select the folder.
- Click on the “Open” button.
Visual Studio Code will open the folder containing the cloned repository.
Installing Packages with Yarn and Running the Dev Command
Before running the development command, you need to install the necessary packages using yarn. Here are the steps:
- Open the integrated terminal in Visual Studio Code by clicking on the “Terminal” menu and selecting “New Terminal”.
- In the terminal, type the following command:
yarn install
Yarn will install the necessary packages.
Once the packages are installed, you can run the dev command. Here are the steps:
- In the terminal, type the following command:
yarn dev
The dev command will start the development server.
-
 @ c8383d81:f9139549
2023-07-14 17:19:00
@ c8383d81:f9139549
2023-07-14 17:19:00So for the last year and a half I've been using the GPT-3 to help with write ups.I looked trough some of the AI tools on AppSumo and settled on https://rytr.me/
It was an interesting experience and but sometimes felt a bit limited on the sentiment. Now looking back after some Chat-GPT3 experience what seemed most limiting was the start prompt and the understanding on how to give a good base.
This base can be written or bought: [
PromptBase | Prompt Marketplace: DALL·E, Midjourney, ChatGPT, Stable Diffusion & GPT
A marketplace for quality DALL·E, Midjourney, ChatGPT, Stable Diffusion & GPT Prompts. Find the best prompts, produce better results, save on API costs, make money selling prompts.
 Prompt Marketplace: DALL·E, Midjourney, ChatGPT, Stable Diffusion & GPT
Prompt Marketplace: DALL·E, Midjourney, ChatGPT, Stable Diffusion & GPT ](https://promptbase.com/)
Now we have image generation and multi-modal access to these language models the accessibility and opportunities have grown exponentially.
](https://promptbase.com/)
Now we have image generation and multi-modal access to these language models the accessibility and opportunities have grown exponentially.Currently most images for blog posts are generated by Dall-E.
So how does this process work in production ?
🏞️ Images Basic Prompt Gen:
- Define a specific Graphic Styles like: Digital Art, Rendering, Cyberpunk, Pixel art, Isometric, Oil Painting
- Combined with a one sentence image request.
- Select the best matching one and extend the canvas
- Replace parts, generate variations.
🖋️ Writing Content Prompt Gen:
Now this will be a work in progress. For good base prompts you can expect a setup of about one A4 worth of setup.
Setup the roll:
- You will act as a professional journalist/content writer
- Tasked to write blogpost.
Define the answer format:
- Your answers will always be formatted in markdown.
- Each topic wil be eleborated on in minimum 200 words and maximum 400.
Injection Parameters
- You are provided with the following summary:
- You are provided with the following summary topics list:
- Convey the following sentiment: (Ex. Commercial, Casuall reading,... )
- Define the overal goal: The goal of this blogpost is to: (Ex. Convince the reader of purchasing X )
Examples of this approach will show up on this website and examples of the prompts used will also follow in this series to explore AI tool assistance.
-
 @ 52b4a076:e7fad8bd
2023-05-01 19:37:20
@ 52b4a076:e7fad8bd
2023-05-01 19:37:20What is NIP-05 really?
If you look at the spec, it's a way to map Nostr public keys to DNS-based internet identifiers, such as
name@example.com.If you look at Nostr Plebs:
It's a human readable identifier for your public key. It makes finding your profile on Nostr easier. It makes identifying your account easier.
If you look at basically any client, you see a checkmark, which you assume means verification.
If you ask someone, they probably will call it verification.
How did we get here?
Initially, there was only one client, which was (kind of) the reference implementation: Branle.
When it added support for NIP-05 identifiers, it used to replace the display name with the NIP-05 identifier, and it had to distinguish a NIP-05 from someone setting their display name to a NIP-05. So they added a checkmark...
Then there was astral.ninja and Damus: The former was a fork of Branle, and therefore inherited the checkmark. Damus didn't implement NIP-05 until a while later, and they added a checkmark because Astral and other clients were doing it.
And then came new clients, all copying what the previous ones did... (Snort originally did not have a checkmark, but that changed later.)
The first NIP-05 provider
Long story short, people were wondering what NIP-05 is and wanted it, and that's how Nostr Plebs came to be.
They initially called their service verification. Somewhere between January and February, they removed all mentions to verification except one (because people were searching for it), and publicly said that NIP-05 is not verification. But that didn't work.
Then, there were the new NIP-05 providers, some understood perfectly what a NIP-05 identifier is and applied the correct nomenclature. Others misnamed it as verification, adding confusion to users. This made the problem worse on top of the popular clients showing checkmarks.
(from this point in the article we'll refer to it as a Nostr address)
And so, the scams begin
Spammers and scammers started to abuse Nostr addresses to scam people: - Some providers has been used by fake crypto airdrop bots. - A few Nostr address providers have terminated multitude of impersonating and scam identifiers over the past weeks.
This goes to show that Nostr addresses don't verify anything, they are just providers of human readable handles.
Nostr addresses can be proof of association
Nostr addresses can be a proof of association. The easiest analogy to understand is email:
jack@cash.app -> You could assume this is the Jack that works at Cash App.
jack@nostr-address-provider.example.com -> This could be any Jack.
What now?
We urge that clients stop showing a checkmark for all Nostr addresses, as they are not useful for verification.
We also urge that clients hide checkmarks for all domain names, without exception in the same way we do not show checkmarks for emails.
Lastly, NIP-05 is a nostr address and that is why we urge all clients to use the proper nomenclature.
Signed:
- Semisol, Nostr Plebs (semisol@nostrplebs.com)
- Quentin, nostrcheck.me (quentin@nostrcheck.me)
- Derek Ross, Nostr Plebs (derekross@nostrplebs.com)
- Bitcoin Nostrich, Bitcoin Nostr (BitcoinNostrich@BitcoinNostr.com)
- Remina, zaps.lol (remina@zaps.lol)
- Harry Hodler, nostr-check.com (harryhodler@nostr-check.com)
-
 @ 46fcbe30:6bd8ce4d
2023-04-22 18:36:28
@ 46fcbe30:6bd8ce4d
2023-04-22 18:36:28Due to a bug you might have to scroll down a LOT to find the main content.
With more than 4000 products listed, it's time to extract some numbers.
The following is a breakdown of how many products fall into each verdict and meta-verdict:
| Meta / Verdict | ok | stale obsolete
defunct discontinued | Comment | | --- | --- | --- | --- | | fewusers | 194 | 1229 | Once stale or obsolete, these products have little chance to ever make an impact in the Bitcoin ecosystem. We don't look deeper into these. We started tracking them just in case. Only few were defunct when we first added them. | | custodial | 671 | 310 | This is what the bulk of Bitcoiners use apparently. The most popular mobile Bitcoin "wallets" are custodial (or the rather similar no-send-receive). | | wip | 202 | 639 | For some products we do archaeology and assign verdicts even after they are defunct but that's rather low priority. 202 to go ... for now. | | nosource | 235 | 151 | Most of these are defending their closed-source-ness with prevention of fake copy apps. Either way, nobody can check if they are playing by the rules. | | nowallet | 146 | 119 | Products that look like they might be wallets get looked into and we keep them around to not look into these again and again. Should we hide them somehow? | | nobtc | 105 | 69 | We currently don't analyze products that don't also manage BTC. | | nosendreceive | 84 | 30 | MercadoPago and PayPal have more than 100 million users each - and usually users cannot cash their bitcoins in or out to a self-custodial wallet. | | vapor | 77 | 2 | Most of these are hardware products. | | noita | 32 | 12 | "no interface to authorize a transaction" - No screen. No buttons. Mostly NFC tags that can sign transactions to avoid leaking the key but they sign whatever. | | ftbfs | 19 | 22 | "failed to build from source" - these products share source but we failed to build them in the latest version. | | unreleased | 34 | 6 | Mostly hardware products that were announced and maybe even do a pre-sale already but haven't delivered yet. Once defunct, these are the "vapor ware". | | fake | 4 | 34 | Luckily most of these are available only for a short time after being classified as "fake" but some blatant fakes survive longer than others. | | nonverifiable | 20 | 16 | These are self-custodial, share code and many are working on reproducibility. We track these closely. | | diy | 18 | 13 | Mostly hardware products. When you do it yourself, it is on you to be transparent. | | prefilled | 12 | 11 | Yep. These exist. And people use them. When funds move, it might have been the provider or the client. Both have plausible deniability. | | plainkey | 13 | 7 | These are mostly NFC tags in varying form factors that surrender the private keys to a companion app to do whatever with them. | | obfuscated | 8 | 9 | If we had more resources, we probably would find more products for this verdict. | | reproducible | 9 | 2 | Few verdicts contain fewer products than this - most transparent - verdict. But there is a backlog of hardware wallet projects and later desktop wallets but the latter is a hard problem to solve. | | sealed-plainkey | 6 | 3 | A verdict exclusive to bearer tokens. | | sealed-noita | 3 | 0 | A verdict exclusive to bearer tokens and until some open source "secure element" comes around, the top verdict there. | -
 @ c8383d81:f9139549
2023-07-14 17:18:21
@ c8383d81:f9139549
2023-07-14 17:18:21Create applications that stand out but are reliable and with a modern UI in 2 min. Choose what back-end provider you want to use to store your data.
As for every build we start with a fresh copy of the Flamewerk Template.
For everybody new, you are one blog post away of learning to build Flamewerk apps read our setup of NodeJS, Yarn, Github and VS code. [
Flamewerk: Nuxt3 Startup Theme
🔥 Build Modern Webapps for Free Forever with one easy config, Deploy in less then 5min on any cloudprovider. Create a website, application, shop or community with super documentation and our community.
 Flamewerk
Flamewerk ](https://flamewerk.com/news/setup-installation)
More documentation can be found at https://flamewerk.com/docs/setup
](https://flamewerk.com/news/setup-installation)
More documentation can be found at https://flamewerk.com/docs/setupOkay that out of the way let's start.
Today's focus is on the project.js file. Make sure you have the following project.js settings defined.
layout: 'app', // (default, web, app ) headertype: 'Application', // Options: Tiny, Maximum, Application footertype: 'Tiny', // Options: Tiny, Minimal, Maximum, Ecommerce
Setting up auth
Example of a page: content/en/login.md
--- title: 'Flamewerk' description: 'meta description of the page' --- :BlockAuthFullSimpleHooking your provider up to one of the Flamewerk blocks follows in a latter post! So stay tuned and learn how to create a standard multi tenant solution.
-
 @ c8383d81:f9139549
2023-07-14 17:17:27
@ c8383d81:f9139549
2023-07-14 17:17:27Making your own components
To make a component make a file in the components folder for this example it will be called YourComponentName.vue .
<template> <p> This is a new component </p> </template> <script setup> </script>From now on you can reference this component in your markdown files or pages.
MDC Page Usage
--- title: 'Flamewerk' description: 'meta description of the page' --- :ComponentsYourComponentNameHow to wrap Content in a component:
<template> <slot /> </template> <script setup> </script> --- title: 'Flamewerk' description: 'meta description of the page' --- ::ComponentsYourComponentName This Text will be loaded in de slot component ::Blocks
Prebuild Flamewerk Components ( Do Not Edit in this folder )
-
 @ 6e468422:15deee93
2023-04-04 13:23:19
@ 6e468422:15deee93
2023-04-04 13:23:19Not too long ago, I tried to paint a picture of what a vision for a value-enabled web could look like. Now, only a couple of months later, all this stuff is being built. On nostr, and on lightning. Orange and purple, a match made in heaven.
It goes without saying that I'm beyond delighted. What a time to be alive!
nostr
Here's the thing that nostr got right, and it's the same thing that Bitcoin got right: information is easy to spread and hard to stifle.[^fn-stifle] Information can be copied quickly and perfectly, which is, I believe, the underlying reason for its desire to be free.
[^fn-stifle]: That's a Satoshi quote, of course: "Bitcoin's solution is to use a peer-to-peer network to check for double-spending. In a nutshell, the network works like a distributed timestamp server, stamping the first transaction to spend a coin. It takes advantage of the nature of information being easy to spread but hard to stifle."
Easy to spread, hard to stifle. That's the base reality of the nature of information. As always, the smart thing is to work with nature, not against it.[^1] That's what's beautiful about the orange coin and the purple ostrich: both manage to work with the peculiarities of information, not against them. Both realize that information can and should be copied, as it can be perfectly read and easily spread, always. Both understand that resistance to censorship comes from writing to many places, making the cost of deletion prohibitive.
Information does not just want to be free, it longs to be free. Information expands to fill the available storage space. Information is Rumor's younger, stronger cousin; Information is fleeter of foot, has more eyes, knows more, and understands less than Rumor.
Eric Hughes, A Cypherpunk's Manifesto
Nostr is quickly establishing itself as a base layer for information exchange, one that is identity-native and value-enabled. It is distinctly different from systems that came before it, just like Bitcoin is distinctly different from monies that came before it.
As of today, the focus of nostr is mostly on short text notes, the so-called "type 1" events more commonly known as tweets.[^fn-kinds] However, as you should be aware by now, nostr is way more than just an alternative to twitter. It is a new paradigm. Change the note kind from
1to30023and you don't have an alternative to Twitter, but a replacement for Medium, Substack, and all the other long-form platforms. I believe that special-purpose clients that focus on certain content types will emerge over time, just like we have seen the emergence of special-purpose platforms in the Web 2.0 era. This time, however, the network effects are cumulative, not separate. A new paradigm.Let me now turn to one such special-purpose client, a nostr-based reading app.
[^fn-kinds]: Refer to the various NIPs to discover the multitude of event kinds defined by the protocol.
Reading
I'm constantly surprised that, even though most people do read a lot online, very few people seem to have a reading workflow or reading tools.
Why that is is anyone's guess, but maybe the added value of such tools is not readily apparent. You can just read the stuff right there, on the ad-ridden, dead-ugly site, right? Why should you sign up for another site, use another app, or bind yourself to another closed platform?
That's a fair point, but the success of Medium and Substack shows that there is an appetite for clean reading and writing, as well as providing avenues for authors to get paid for their writing (and a willingness of readers to support said authors, just because).
The problem is, of course, that all of these platforms are platforms, which is to say, walled gardens that imprison readers and writers alike. Worse than that: they are fiat platforms, which means that permissionless value-flows are not only absent from their DNA, they are outright impossible.[^2]
Nostr fixes this.

The beauty of nostr is that it is not a platform. It's a protocol, which means that you don't have to sign up for it---you can create an identity yourself. You don't have to ask for permission; you just do, without having to rely on the benevolence of whatever dictator is in charge of the platform right now.
Nostr is not a platform, and yet, powerful tools and services can be built and monetized on top of it. This is good for users, good for service providers, and good for the network(s) at large. Win-win-win.
So what am I talking about, exactly? How can nostr improve everyone's reading (and writing) experience?
Allow me to paint a (rough) picture of what I have in mind. Nostr already supports private and public bookmarks, so let's start from there.
Imagine a special-purpose client that scans all your bookmarks for long-form content.[^fn-urls] Everything that you marked to be read later is shown in an orderly fashion, which is to say searchable, sortable, filterable, and displayed without distractions. Voilà, you have yourself a reading app. That's, in essence, how Pocket, Readwise, and other reading apps work. But all these apps are walled gardens without much interoperability and without direct monetization.
[^fn-urls]: In the nostr world long-form content is simply markdown as defined in NIP-23, but it could also be a link to an article or PDF, which in turn could get converted into markdown and posted as an event to a special relay.
Bitcoin fixes the direct monetization part.[^fn-v4v] Nostr fixes the interoperability part.
[^fn-v4v]: ...because Bitcoin makes V4V practical. (Paywalls are not the way.)
Alright, we got ourselves a boring reading app. Great. Now, imagine that users are able to highlight passages. These highlights, just like bookmarks now, could be private or public. When shared publicly, something interesting emerges: an overlay on existing content, a lens on the written Web. In other words: swarm highlights.
Imagine a visual overlay of all public highlights, automatically shining a light on what the swarm of readers found most useful, insightful, funny, etc.
Further, imagine the possibility of sharing these highlights as a "type 1" event with one click, automatically tagging the highlighter(s)---as well as the author, of course---so that eventual sat-flows can be split and forwarded automatically.
Voilà, you have a system that allows for value to flow back to those who provide it, be it authors, editors, curators, or readers that willingly slog through the information jungle to share and highlight the best stuff (which is a form of curation, of course).
Zaps make nostr a defacto address book[^fn-pp] of payment information, which is to say lightning addresses, as of now. Thanks to nostr wallet connect (among other developments), sending sats ~~will soon be~~ is already as frictionless as leaving a like.
[^fn-pp]: The Yellow Pages are dead, long live The Purple Pages!
Value-for-value and participatory payment flows are something that traditional reading apps desperately lack, be it Pocket, Instapaper, Readwise, or the simple reading mode that is part of every browser.
A neat side-effect of a more structured way to share passages of text is that it enables semi-structured discussions around said passages---which could be another useful overlay inside special-purpose clients, providing context and further insights.[^5]
Further, imagine the option of seamlessly switching from text-on-screen to text-to-speech, allowing the user to stream sats if desired, as Podcasting 2.0 clients already do.[^3]
Imagine user-built curations of the best articles of the week, bundled neatly for your reading pleasure, incentivized by a small value split that allows the curator to participate in the flow of sats.
You get the idea.
I'm sure that the various implementation details will be hashed out, but as I see it, 90% of the stuff is already there. Maybe we'll need another NIP or two, but I don't see a reason why this can't be built---and, more importantly: I don't see a reason why it wouldn't be sustainable for everyone involved.
Most puzzle pieces are already there, and the rest of them can probably be implemented by custom event types. From the point of view of nostr, most everything is an event: bookmarks are events, highlights are events, marking something as read is an event, and sharing an excerpt or a highlight is an event. Public actions are out in the open, private actions are encrypted, the data is not in a silo, and everyone wins. Especially the users, those who are at the edge of the network and usually lose out on the value generated.
In this case, the reading case, the users are mostly "consumers" of content. What changes from the producing perspective, the perspective of the writer?
Writing
Back to the one thing that nostr got right: information is easy to spread but hard to stifle. In addition to that, digital information can be copied perfectly, which is why it shouldn't matter where stuff is published in the first place.
Allow me to repeat this point in all caps, for emphasis: IT SHOULD NOT MATTER WHERE INFORMATION IS PUBLISHED, and, maybe even more importantly, it shouldn't matter if it is published in a hundred different places at once.[^fn-torrents]
What matters is trust and accuracy, which is to say, digital signatures and reputation. To translate this to nostr speak: because every event is signed by default, as long as you trust the person behind the signature, it doesn't matter from which relay the information is fetched.
This is already true (or mostly true) on the regular web. Whether you read the internet archive version of an article or the version that is published by an online magazine, the version on the author's website, or the version read by some guy that has read more about Bitcoin than anyone else you know[^fn-guy]---it's all the same, essentially. What matters is the information itself.
[^fn-guy]: There is only one such guy, as we all know, and it's this Guy: nostr:npub1h8nk2346qezka5cpm8jjh3yl5j88pf4ly2ptu7s6uu55wcfqy0wq36rpev
Practically speaking, the source of truth in a hypernostrized world is---you guessed it---an event. An event signed by the author, which allows for the information to be wrapped in a tamper-proof manner, which in turn allows the information to spread far and wide---without it being hosted in one place.
The first clients that focus on long-form content already exist, and I expect more clients to pop up over time.[^4] As mentioned before, one could easily imagine prism-like value splits seamlessly integrated into these clients, splitting zaps automatically to compensate writers, editors, proofreaders, and illustrators in a V4V fashion. Further, one could imagine various compute-intensive services built into these special-purpose clients, such as GPT Ghostwriters, or writing aids such as Grammarly and the like. All these services could be seamlessly paid for in sats, without the requirement of any sign-ups or the gathering of any user data. That's the beauty of money proper.
Plagiarism is one issue that needs to be dealt with, of course. Humans are greedy, and some humans are assholes. Neither bitcoin nor nostr fixes this. However, while plagiarism detection is not necessarily trivial, it is also not impossible, especially if most texts are published on nostr first. Nostr-based publishing tools allow for OpenTimestamp attestations thanks to NIP-03, which in turn allows for plagiarism detection based on "first seen" lookups.
That's just one way to deal with the problem, of course. In any case, I'm confident that we'll figure it out.
Value
I believe that in the open ~~attention~~ information economy we find ourselves in, value will mostly derive from effective curation, dissemination, and transmission of information, not the exclusive ownership of it.
Although it is still early days, the statistics around Podcasting 2.0 and nostr zaps clearly show that (a) people are willing to monetarily reward content they care about, and (b) the willingness to send sats increases as friction decreases.
The ingenious thing about boostagrams and zaps is that they are direct and visible, which is to say, public and interactive. They are neither regular transactions nor simple donations---they are something else entirely. An unforgable value signal, a special form of gratitude and appreciation.
Contrast that with a link to Paypal or Patreon: impersonal, slow, indirect, and friction-laden. It's the opposite of a super-charged interaction.
While today's information jungle increasingly presents itself in the form of (short) videos and (long-form) audio, I believe that we will see a renaissance of the written word, especially if we manage to move away from an economy built around attention, towards an economy built upon value and insight.
The orange future now has a purple hue, and I believe that it will be as bright as ever. We just have a lot of building to do.
Further Reading
NIPs and Resources
- Nostr Resources
- value4value.info
- nips.be
- NIP-23: Long-form content
- NIP-57: Event-specific zap markers
- NIP-47: Nostr Wallet Connect
- NIP-03: OpenTimestamps attestations for events
Originally published on dergigi.com
[^1]: Paywalls work against this nature, which is why I consider them misguided at best and incredibly retarded at worst.
[^2]: Fiat doesn't work for the value-enabled web, as fiat rails can never be open and permissionless. Digital fiat is never money. It is---and always will be---credit.
[^3]: Whether the recipient is a text-to-speech service provider or a human narrator doesn't even matter too much, sats will flow just the same.
[^4]: BlogStack and Habla being two of them.
[^5]: Use a URI as the discussion base (instead of a highlight), and you got yourself a Disqus in purple feathers!
[^fn-torrents]: That's what torrents got right, and ipfs for that matter.
-
 @ c8383d81:f9139549
2023-07-14 17:17:04
@ c8383d81:f9139549
2023-07-14 17:17:04Flamewerk utilities 3 methods of providing language agnostic components and content.
CURRENTLY THE FOLLOWING LANGUAGES ARE SUPPORTED ( but are easily extended )
ENGLISH, DANISH, GERMAN, DUTCH, FRENCH, SPANISH
1# The Global language files
Outside of the Flamewerk folder you will find a folder called locales. This folder contains files referencing the supported language.
{ "homepage": { "title": "Hej og velkommen til ", "subtitle": "Opret en hjemmeside." }, "footer":{ "rights":"Alle rettigheder forbeholdes." } } <p> {{ $t("homepage.subtitle") }} </p>2# The content directory
In the flamewerk folder you find the content folder this contains subfolders: en, da, de, es, nl, fr
When you set in the project.js file
language: "en",All default content should be stored in the en folder.
Example: if you have a translated file in the de folder if will load the translated version if no translation is present it defaults to the standard language folder.
3# In Component Translation
In an effort to create components that are language agnostic out of the box, it is also possible to add the translation in the component using the local scope:
<template> <div> <h2> {{ t('hello') }} </h2> </div> </template> <script setup> const { t } = useI18n({ useScope: "local" }); </script> <i18n lang="json"> { "da": { "hello": "Hej og velkommen til " }, "de": { "hello": "Hallo und willkommen bei " }, "en": { "hello": "Hello and welcome at " }, "es": { "hello": "Hola y bienvenidos a " }, "fr": { "hello": "Bonjour et bienvenue chez " }, "nl": { "hello": "Ahoy en welkom bij " } } </i18n>4# Automated translation tools
Some of these online solution suport i18n vue formatting allowing you to upload the files from the locales directory and get a clean fast translation. [
Translate your i18n Locales | Get Instant Results
Internationalize your Software and Documentation. Simply copy/paste your file to translate i18n locales - fast and customized.
 simpleen
simpleen](https://simpleen.io/)[
Content & Software localization on autopilot
Software & content localization on autopilot. Productive software developers choose Localazy for automated SW i18n and content localization. Start for free now!
localazy.comLocalazy
 ](https://localazy.com/)[
](https://localazy.com/)[Translation Management for software projects
Try out the most user-friendly software for managing translations. Help your dev and management team to cooperate better thanks to SimpleLocalize
SimpleLocalizeJakub
 ](https://simplelocalize.io/)
](https://simplelocalize.io/) -
 @ c8383d81:f9139549
2023-07-14 17:16:43
@ c8383d81:f9139549
2023-07-14 17:16:43Alright! lets get down to building a Resume to share your skills and idea's with fellow humans on the world wide web!
For everybody new, you are one blog post away of learning to build Flamewerk apps read our setup of NodeJS, Yarn, Github and VS code. [
Flamewerk: Nuxt3 Startup Theme
🔥 Build Modern Webapps for Free Forever with one easy config, Deploy in less then 5min on any cloudprovider. Create a website, application, shop or community with super documentation and our community.
 Flamewerk
Flamewerk ](https://flamewerk.com/news/setup-installation)
More documentation can be found at https://flamewerk.com/docs/setup
](https://flamewerk.com/news/setup-installation)
More documentation can be found at https://flamewerk.com/docs/setupOkay that out of the way let's start.
First we will open the index.md file in the content/en/ directory. Remove all the content here and replace it with the following code:
--- title: 'Resume Page' description: 'Resume Meta Description of the Page' --- ::BlockProseContent #🌎 Hello World ::Now for our first trick we will use Flamewerk blocks to set the basic layout.
Replace the code in the index.md with the following, you can save the file in between adding a block to see the page grow, in the end you will end up with for example a page like this.
--- title: 'Resume Page' description: 'Resume Meta Description of the Page' --- :BlockResumePrintblock :::BlockResumePage :BlockResumeHeader ::BlockResumeColumn :BlockResumeLinks :BlockResumeSummary :BlockResumeExperience :BlockResumeSkills :BlockResumeProjects :BlockResumeEducation :: :::This trick uses the data stored in the page.js to populate the basic blocks with its content.
You should now have this result:

 To understand the syntactic sugar used here in the markdown works it is important to undestand that the ::: and :: represent opening and closing tags so the block :BlockResumeLinks is rendered with the ::BlockResumeColumn.
This basicly boils down to if you forget a : or add : to the wrong place your layout might shift.
To understand the syntactic sugar used here in the markdown works it is important to undestand that the ::: and :: represent opening and closing tags so the block :BlockResumeLinks is rendered with the ::BlockResumeColumn.
This basicly boils down to if you forget a : or add : to the wrong place your layout might shift.To modify and customize the data for your own resume: Open Page.js
Thats it for today, feel free to reach out our join or follow our socials: [
Discord - A New Way to Chat with Friends & Communities
Discord is the easiest way to communicate over voice, video, and text. Chat, hang out, and stay close with your friends and communities.
Discord
 ](https://discord.gg/flamewerk)[
](https://discord.gg/flamewerk)[Flamewerk
Nuxt3 Startup Template. Flamewerk has 3 repositories available. Follow their code on GitHub.
 GitHub
GitHub](https://github.com/flamewerk)
-
 @ 434f9799:2d548c15
2022-07-24 03:49:30
@ 434f9799:2d548c15
2022-07-24 03:49:30看了较多的插画, 对于内容级别模糊认知是一个在整理过程中很大的问题, 频道最常用 R18 来作为情色已否的一个最重要的分界点, 但是这个界限对于我来说依旧是模糊不清的, 现在会考虑的因素包括裸露及接近裸露的程度 / 裸露的内容占比 / 暗示程度.
于是我还是得好好学习一下关于内容分级的一些常识, 这里我能找到的写得最清晰明了的介绍关于内容分级的是 Google Play 的帮助文档和维基百科词条, 不同的国家地区都有不同的分级制度, 因此如果要面向当地的观众(?)那么就得考虑当地的内容分级... 有意思的是现在中国目前游戏(如原神)中使用的内容标识分级神似欧洲的 PEGI. 常用的 "R18" 是来源于日本的内容分级制度, 但目前为止正式的内容分级依旧是经过人工核验, 对于现在机器审查只是为了降低人力成本而使用算法模型构建的一种 "筛子" 毫无人类灵活可变的优点, 但是人类又没有机器那样完全固定的认知, 一张色图看一遍觉得一点都不色情, 但是看了三遍就会觉得很色, 就很神奇. 认知偏差不断地修正我的审美甚至XP.
在 Pixiv 的全年龄向排行榜里面有遇见过那种对于一些刻画特别细致, 形状和颜色都已经在画中了, 但是它依旧是 "全年龄", 在 Pixiv 提供的帮助 "什么是浏览限制" 中囊括了从投稿到用户浏览的内容分级概念 (对于插画这一个特殊的门类 Pixiv 可谓是很具有代表性了), 在里面提到关于 "R18" 的定义是 "与性有关的内容、性行为的刻画、性器官的接触与接合等,使人联想起性行为的事物", 我只想说一句: "那我看什么都有冲动怎么办?" 实在是还不够详细;
往下一级的有 "轻度的性描写" 是介于全年龄和 R18 之间的说大不大说小也不小的一块奇怪区域, 描述也最为详细: "无论年龄、性别,任何会勾起性联想的表现、接吻、拥抱、露出内衣等; 使人联想起性行为前后的表现、表情以及其他隐晦表现; 强调胸部、乳沟、乳头、臀部、两腿间等部位、以及隐约可见这些部位的构图及表现; 穿着极为暴露的服装或泳衣的人物、极为裸露的人物、穿着透明材质服装的人物、让人联想起裸体的人物表现等."
这个区域中作品是所有分级制度中对于情色划分争议最大的地方, 有不少国家和地区的分级制度和观众认识会将它打上 R18 的标签, 况且 Pixiv 这里还仅仅是针对于 "插画" 这一个很小的艺术门类... 很详细, 且这类作品不能用 R18 来形容, 且 Pixiv 也没有单独为这类区分对待, 那种 "三眼色"(?) 的作品也被划进全年龄榜单了...
~~色情真是个可怕的东西~~
-
 @ c75622fd:a9b66e1d
2023-03-18 15:09:42
@ c75622fd:a9b66e1d
2023-03-18 15:09:42[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
[19]
[20]
[21]
[22]
[23]
[24]
[25]
[26]
[27]
[28]
[29]
[30]
[31]
[32]
[33]
[34]
[35]
[36]
[37]
[38]
[39]
[40]
[41]
[42]
[43]
[44]
[45]
[46]
[47]
[48]
[49]
[50]
[51]
[52]
[53]
[54]
[55]
[56]
[57]
[58]
[59]
[60]
[61]
[62]
[63]
[64]
[65]
[66]
[67]
[68]
[69]
[70]
[71]
[72]
[73]
[74]
[75]
[76]
[77]
[78]
[79]
[80]
[81]
[82]
[83]
[84]
-
 @ c8383d81:f9139549
2023-07-14 17:16:20
@ c8383d81:f9139549
2023-07-14 17:16:20On today's chopping block, Search Engine Optimization, the easy way ! Set Project Global defaults or page specific descriptions to optimize your targets bookmarks!
SETTING PROJECT META DATA:
Providing accurate meta-data per page follows this hierarchical overwriting setup: By default all pages score 100% on Google Lighthouse Meta.
💡
Currently it requires the Global and App Level Meta data to be set to have a full SEO Project coverage. In the near future we will work for this to be fully set from the Project Config.
- Global Level
( Project Default SEO Meta Data )
- App Level
( Currently contains the Twitter Meta Data )
- Layout Level
( Website, Application, Ecommerce, Community )
- Page Level
( Page Specific )
- Component Level
( Example is a Product Component )
1. The Global Level
- Nuxt Config
This project makes use of Kevin Marrec's Nuxt Pwa Module a Nuxt3 version of the Nuxt2 PWA module, until official and upstream monitored closely.
The Module uses most of the same documentation as the Nuxt V2 Module.
pwa: { meta: { title: "Flamewerk: Nuxt3 Startup Theme ", name: "Flamewerk", description: "🔥 Build Modern Webapps for Free Forever with one easy.", ogImage: { path: "https://flamewerk.com/Thumbnail.png", width: 1200, height: 627, type: "image/png", }, twitterSite: "https://twitter.com/flamewerk", twitterCard: "summary_large_image", twitterCreator: "@flamewerk", ogUrl: "https://flamewerk.com/", }, },
[
Meta Module
Meta easily adds common meta tags into your project with zero-config needed
 Nuxt PWA
Nuxt PWA ](https://pwa.nuxtjs.org/meta)
](https://pwa.nuxtjs.org/meta)2. The App Level
- App.vue
meta: [ { property: "twitter:title", content: "Flamewerk: Startup Theme"}, { property: "twitter:image", content: "/Thumbnail.png" }, { property: "twitter:description", content: "Build Modern Webapps for Free Forever with one easy config."}, ],
It is very important to note that the Thumbnail picture should have at least dimensions of ( 1200 x 1200 px ) and not exceed 250kb !
3. The Layout Level
useHead({ meta: [ { title: "New Layout Title." }, { description: "Build Modern Webapps for Free." }, { property: "twitter:title", content: "Flamewerk: Theme" }, { property: "twitter:image", content: "/Thumbnail.png" }, { property: "twitter:description", content: "Build Modern Webapps for Free Forever with one easy config.", }, ], });4. The Page Level
--- layout: post title: Blogging Like a Hacker desciption: Metadata page ---Note that YAML front matter is not parsed by the Markdown parser, but is removed prior to parsing by Jekyll (or whatever tool you're using) and could actually be used to request a different parser than the default Markdown parser for that page (I don't recall if Jekyll does that, but I have seen some tools which do).
It is also possible to define custom meta data using a page route by using vuehead. Example: layout & component level.
5. The Component Level
Dynamic component rendering: Examples: Product list or blogposts
useHead({ meta: [ { title: ContstantTitle }, { description: ConstantName }, ], }); -
 @ 3bf0c63f:aefa459d
2022-10-29 19:19:00
@ 3bf0c63f:aefa459d
2022-10-29 19:19:00What is better than bounties and grants?
The experience with bounties from HRF wasn't great. No one has answered to the calls for implementing what they wanted because the work was too much and the risk of not getting paid very real. The experience with grants in general from Spiral is also not great: many random developers making cool but useless projects, wasted money.
The two kinds of open-source financial support that have worked so far are:
- Paying people who are already doing useful work so they can continue doing that. That is the experience of some people who are "maintaining" Bitcoin Core, for example, or other open-source projects. You're doing a thing, you've proven yourself valuable and you definitely seem to be interested in that personally such that you don't need a boss telling you what to do, so take the money and just keep doing that.
- Structured open-source initiatives, like the LDK effort. Although LDK is arguably useless, it has a stated goal and that goal is being delivered. I don't have any knowledge about how its development process works, but they have people being paid and "bosses" that direct the work to be done, as any team needs. So it is not the same as an open grant.
The thing that is missing is a way to provide these open loose grants to people that don't require bosses, but also that don't just pick a winner and let them do whatever stupid idea they might have (Spiral grants), and also do not mandate that they do something big before being paid and offers no guarantee of that they will be paid whatsoever.
The solution: smaller flexible bounties in large quantities
My suggestions is: instead of giving 1 bitcoin for a huge very specific project, state some "principles", or "problems", in a loose manner, that you want to see solved. For example, "we, the organization X, wants to see projects that use zero-knowledge proofs to help Bitcoin somehow, because we love zero-knowledge proofs".
Then state that you're going to give 20 grants of 0.05 bitcoins each, at random times, for projects that you see being done that may be on the right track.
That will tilt people that may had a small inclination to work on these problems to actually start doing something, and if they see that what they're doing is being appreciated and awarded with a payment, they will be more incentivized to finish it. There could even be a conditional bounty (like HRF did with Cashu) for finishing the project with certain requirements, but this only works after some structure is already in place for a certain project.
-
 @ c8383d81:f9139549
2023-07-14 17:15:51
@ c8383d81:f9139549
2023-07-14 17:15:51Still with us, Ready to setup Shop? Let's start introducing some commerce into the mix ! On todays menu setting up points of sale in your project.
As for every build we start with a fresh copy of the Flamewerk Template.
For everybody new, you are one blog post away of learning to build Flamewerk apps read our setup of NodeJS, Yarn, Github and VS code. [
Flamewerk: Nuxt3 Startup Theme
🔥 Build Modern Webapps for Free Forever with one easy config, Deploy in less then 5min on any cloudprovider. Create a website, application, shop or community with super documentation and our community.
 Flamewerk
Flamewerk ](https://flamewerk.com/news/setup-installation)
More documentation can be found at https://flamewerk.com/docs/setup
](https://flamewerk.com/news/setup-installation)
More documentation can be found at https://flamewerk.com/docs/setupOkay that out of the way let's start.
For our e-commerce integration we will use Snipcart to povide us with a shopping cart. Signup for a free API key to start recieving payments. [
Add a Shopping Cart to Any Website in Minutes
Add a shopping cart to your site in minutes. Works with any site builder, CMS, and framework. 20 000+ merchants trust our e-commerce solution for their website. Join them!
 Snipcart
Snipcart ](https://snipcart.com/)
Today's focus is on the project.js file and products.js file.
Make sure you have the following project.js settings defined.
](https://snipcart.com/)
Today's focus is on the project.js file and products.js file.
Make sure you have the following project.js settings defined.layout: 'web', // (default, web, app ) headertype: 'Maximum', // Options: Tiny, Maximum, Application footertype: 'Ecommerce', // Options: Tiny, Minimal, Maximum, Ecommerce shop: true, // Enable Ecommerce shopcurrency: 'eur', // Default Currenty ( Should be an object) snipcartid: 'CopyApiKeyHere', // Snipcart API
Setting up shop
Example of a page: content/en/shop.md
--- title: 'Webshop' description: 'meta description of the page' --- :BlockShopProductsCategory{type="Product" category="New" max=4 title="Fresh Products" icon="👑" subtitle="Newest product releases and most popular items."} :BlockShopProductsShippingblockCustomizing a product in the Project.js inventory List:
{ id: 1, identity: "1", type: "Product", //Options Product, Digital, Subscription category: "New", title: "Hoody with zipper", description: "Simple Black with logo", stock: "low", //Options: Low & Out By default products are stocked price: { usd: 40, eur: 35, }, image: "https://production.flamewerk.com/stock/product1.jpg", imagelocal: "/stock/product1.jpg", features: [ "100% Extra hacker power", "Can be used as a Emo/Hardcore hoody", "Makes you look badass", ], },That's it for the basics around adding products and a storefront to your project ! See you tomorrow for our final build example.
-
 @ 3bf0c63f:aefa459d
2022-10-29 13:24:00
@ 3bf0c63f:aefa459d
2022-10-29 13:24:00On Bitcoin Bounties
The HRF has awarded two bounties yesterday. The episode exposes some of the problems of the bounties and grants culture that exists on Bitcoin.
First, when the bounties were announced, almost an year ago, I felt they were very hard to achieve (and also very useless, but let's set that aside).
The first, "a wallet that integrates bolt12 so it can receive tips noncustodially", could be understood as a bounty for mobile wallets only, in which case the implementation would be hacky, hard and take a lot of time; or it could be understood as being valid for any wallet, in which case it was already implemented in CLN (at the time called "c-lightning"), so the bounty didn't make sense.
The second, a wallet with a noncustodial US dollar balance, is arguably impossible, since there is no way to achieve it without trusted oracles, therefore it is probably invalid. If one assumed that trust was fine, then it was already implemented by StandardSats at the time. It felt it was designed to use some weird construct like DLCs -- and Chris Steward did publish a guide on how to implement a wallet that would be eligible for the bounty using DLCs, therefore the path seemed to be set there, but this would be a very hard and time-intensive thing.
The third, a noncustodial wallet with optional custodial ecash functionality, seemed to be targeting Fedimint directly, which already existed at the time and was about to release exactly these features.
Time passed and apparently no one tried to claim any of these bounties. My explanation is that, at least for 1 and 2, it was so hard to get it done that no one would risk trying and getting rejected. It is better for a programmer to work on something that interests them directly if they're working for free.
For 3 I believe no one even tried anything because the bounty was already set to be given to Fedimint.
Fast-forward to today and bounties 1 and 3 were awarded to two projects that were created by the sole interest of the developers with no attempt to actually claim these bounties -- and indeed, the two winners strictly do not qualify according to the descriptions from last year.
What if someone was working for months on trying to actually fulfill the criteria? That person would be in a very bad shape now, having thrown away all the work. Considering this it was a very good choice for everyone involved to not try to claim any of the bounties.
The winners have merit only in having pursued their own interests and in creating useful programs as the result. I'm sure the bounties do not feel to them like a deserved payment for the specific work they did, but more like a token of recognition for having worked on Bitcoin-related stuff at all, and an incentive to continue to work.
-
 @ c8383d81:f9139549
2023-07-14 17:15:08
@ c8383d81:f9139549
2023-07-14 17:15:08More fancy tricks for fast website building today brings the most used and usefull example, the best way to spread your message !
As for every build we start with a fresh copy of the Flamewerk Template.
For everybody new, you are one blog post away of learning to build Flamewerk apps read our setup of NodeJS, Yarn, Github and VS code. [
Flamewerk: Nuxt3 Startup Theme
🔥 Build Modern Webapps for Free Forever with one easy config, Deploy in less then 5min on any cloudprovider. Create a website, application, shop or community with super documentation and our community.
 Flamewerk
Flamewerk ](https://flamewerk.com/news/setup-installation)
More documentation can be found at https://flamewerk.com/docs/setup
](https://flamewerk.com/news/setup-installation)
More documentation can be found at https://flamewerk.com/docs/setupOkay that out of the way let's start.
Todays analogy comes in thinking of building a project like a 🌴 Coconuts 🥥. The shell of the coconut will be the JavaScript files: Project, Api and Products and to some extend Page files. the coconut meat is consistent of your content and custom functionality.
Today's focus is on the project.js file, this contains the basic shell of your project. For setting up a website layout we will customize the following layout parameter. You can customize the headertype and footertype with the options provided;
layout: 'web', // (default, web, app ) headertype: 'Maximum', // Options: Tiny, Maximum, Application footertype: 'Tiny', // Options: Tiny, Minimal, Maximum, Ecommerce Once you have this setup you can experiment with various settings in this file.
Once you have this setup you can experiment with various settings in this file.Adding content
The extra section today is about adding extra pages and start the basics around translations.
Every markdown page you add in the content/en/ folder wil be rendered as a page that will be accessable trough every language enless a translated content file is present.
Example of a page: content/en/test.md
--- title: 'Test Page' description: 'Test Meta Description of the Page' --- ::BlockProseContent #🌎 Hello World ::You can visit this page on the route: localhost:3000/test
Currently the following languages are supported and you can use this functionality by simple adding a folder in the content directory:
- da ( Danish )
- de ( German )
- es ( Spanish )
- fr ( French )
- nl ( Dutch )
You set the default directory to load content from in the project.js file:
language: "en",More Details about indept translation can be found here: https://flamewerk.com/docs/translation
-
 @ 3bf0c63f:aefa459d
2022-09-12 02:28:00
@ 3bf0c63f:aefa459d
2022-09-12 02:28:00A prediction market as a distributed set of oracle federations
See also: Truthcoin as a spacechain.
This is not Truthcoin, but hopefully the essence of what makes it good is present here: permissionless, uncensorable prediction markets for fun, profit, making cheap talk expensive and revolutionizing the emergence and diffusion of knowledge in society.
The idea
The idea is just to reuse Fedimint's codebase to implement federated oracle corporations that will host individual prediction markets inside them.
Pegging in and out of a federation can be done through Lightning gateways, and once inside the federation users can buy and sell shares of individual markets using a native LMSR market-maker.
Then we make a decentralized directory of these bets using something simple like Nostr so everybody can just join any market very easily.
Why?
The premise of this idea is that we can't have a centralized prediction market platform because governments will shut it down, but we can instead have a pseudonymous oracle corporation that also holds the funds being gambled at each time in a multisig Bitcoin wallet and hope for the best.
Each corporation may exist to host a single market and then vanish afterwards -- its members returning later to form a new corporation and host a new market before leaving again.
There is custodial risk, but the fact that the members may accrue reputation as the time passes and that this is not one big giant multisig holding all the funds of everybody but one multisig for each market makes it so this is slightly better.
In any case, no massive amounts are expected to be used in this scheme, which defeats some of the use cases of prediction markets (funding public goods, for example), but since these are so advanced and society is not yet ready for them, we can leave them for later and first just try to get some sports betting working.
This proto-truthcoin implementation should work just well enough to increase the appetite of bitcoiners and society in general for more powerful prediction markets.
Why is this better than DLCs?
Because DLCs have no liquidity. In their current implementations and in all future plans from DLC enthusiasts they don't even have order books. They're not seen very much as general-purpose prediction markets, but mostly as a way to create monetary instruments and derivatives.
They could work as prediction markets, but then they would need order books and order books are terrible for liquidity. LMSR market makers are much better.
But it is custodial!
If you make a public order book tied to known oracles using a DLC the oracle may also be considered custodial since it becomes really easy for him to join multiple trades as a counterpart then lie and steal the money. The bets only really "discreet" if they're illiquid meaningless bets between two guys. If they're happening in a well-known public place they're not discreet anymore.
DLC proponents may say this can be improved by users using multiple oracles and forming effectively a federation between them, but that is hardly different from choosing a reputable oracle corporation in this scheme and trusting that for the life of the bet.
But Hivemind is better!
Yes.
-
 @ c8383d81:f9139549
2023-07-14 17:14:39
@ c8383d81:f9139549
2023-07-14 17:14:39If you are reading this release archive post:
Currently Flamewerk has reached EOL and will be rearchitected in a new DAO structure follow and recieve new content starting from 21/07/23 !
❤️🔥 HaveHeart
Flamewerk:Start Date:Completion Date: Version 1.0 Description: Flamewerk Cleanup and Demo Configs Goals and Community Setup ( AI, Crypto, Back-End, Logging )
🛒 Snipcart
Flamewerk: Start Date:Completion Date: Version 0.927/01/2023DescriptionCommercial integration: Snipcart integrationsShop and App Layouts
💣 Bombardi
Flamewerk:Start Date:Completion Date:Version 0.719/11/202210/01/2023DescriptionBase Nuxt2 Migrations completedSingle Repo 90% Completed ( Nuxt Content )
🎠 Stables
Flamewerk:Start Date:Completion Date:Version 0.616/11/202218/11/2022DescriptionUpgrading to Nuxt3 Stable Release Candidate
🦾 AutoNation
Flamewerk:Start Date:Completion Date:Version 0.501/11/202215/11/2022DescriptionMigrating Nuxt2 and Fast Language Agnostic Model ExpantionSEO & PWA Integrations
🍍 PiniaColada
Flamewerk:Start Date:Completion Date:Version 0.425/10/202231/10/2022DescriptionPinia integration
👻 SelfGhost
Flamewerk:Start Date:Completion Date:Version 0.320/09/202230/09/2022DescriptionCommercial integrations: of Ghost & Fathom analytics
🍓 JAMing
Flamewerk:Start Date:Completion Date:Version 0.225/08/202220/09/2022DescriptionTailwind, Dark/Light, HeadlessUI
🍟 UniFried
Flamewerk:Start Date:Completion Date:Version 0.112/08/202225/08/2022DescriptionNUXT 3.0.0-rc.8 starting with a clear projectMigration strategy and define folder structures
-
 @ c8383d81:f9139549
2023-07-14 17:13:48
@ c8383d81:f9139549
2023-07-14 17:13:48THE ARCHIVE
Today we Archive the flamewerk project to embark on a rewrite of the underlaying archicture and structure to support DAO development.
This showcases basics around Flamewerk and building.
Since the flamewerk project is being archived these logs are purely educational and for archiving.
This Nuxt3 Template is the ultimate starter for building web projects. The Series is comprised out of 5 Chapters all free all with Zero Costs:
Setup ( #1 ) Build ( #2, #3, #4, #5 ) Tools ( #6, #7 ) Blocks ( #8, #9, #10 ) Extend ( #11, #12, #13, #14 )SETUP
The first chapter we setup the tools you will need for the building days We will be using NodeJS, Yarn, Github and VS code and Flamewerk. Every Build starts from a fresh clone of the Flamewerk template so once you have the tools up and running on your local machine you are ready for building.
BUILD
Here we build a project a day from a Resume & Whitepaper, Website, Shop, Application & Documentation. The idea is to get you to understand the project, api, products files.
TOOLS
Once you have a grip on the code basics we will explore adding AI tools to make your work more automated. With some free tools we will look into how to create these files without having to code.
BLOCKS
The Flamewerk template uses blocks that are ready to be used if you can write a little bit of syntactic markdown. Allowing you to take full control of the design with a simple iterative process. Here we explore some cool things like:
Use ChatGPT3 in your application Building a Nostr AppEXTEND
If you have made it this far the end of this series focuses on extending the template with more languages, blocks and deployment.
So grab a beverage and feel free to reach out and extend some feedback ! Happy building !
-
 @ 3bf0c63f:aefa459d
2022-05-27 14:34:00
@ 3bf0c63f:aefa459d
2022-05-27 14:34:00Formula for making games with satoshis
I think the only way to do in-game sats and make the game more interesting instead of breaking the mechanics is by doing something like
- Asking everybody to pay the same amount to join;
- They get that same amount inside the game as balances;
- They must use these balances to buy items to win the game;
- The money they used becomes available as in-game rewards for other players;
- They must spend some money otherwise they just lose all the time;
- They can't use too much because if they run out of money they are eliminated.
If you think about it, that's how poker mostly works, and it's one of the few games in which paying money to play makes the game more interesting and not less.
In Poker:
- Everybody pays the same amount to join.
- Everybody gets that amount in tokens or whatever, I don't know, this varies;
- Everybody must pay money to bet on each hand;
- The money used on each round is taken by the round winner;
- If you don't bet you can't play the rounds, you're just eliminated;
- If you go all-in all the time like a mad person you'll lose.
In a game like Worms, for example, this could be something like:
- Idem;
- Idem;
- You must use money to buy guns and ammunitions;
- Whatever you spent goes to a pot for the winners or each round -- or maybe it goes to the people that contributed in killing you;
- If you don't buy any guns you're useless;
- If you spend everything on a single gun that's probably unwise.
You can also apply this to games like Counter-Strike or Dota or even Starcraft or Bolo and probably to most games as long as they have a fixed duration with a fixed set of players.
The formula is not static nor a panacea. There is room for creativity on what each player can spend their money in and how the spent money is distributed during the game. Some hard task of balancing and incentivizing is still necessary so the player that starts winning doesn't automatically win for having more money as the game goes on.
-
 @ c8383d81:f9139549
2023-07-14 15:06:55
@ c8383d81:f9139549
2023-07-14 15:06:55💡 Idea
The best idea's create connections, provide real world solutions and communities.
🌟 Domain
After going trough numerous of domain registrars in the last couple years the search for a registrar that could offer a stable home to register and bring domains to from aftermarkets grew after having to deal with numerous of accounts and payment followup.
Eventually Dynadot came out to be my choice however Cloudflare also shared first place.
This Evaluation took into account the following platform aspects.
- Cheap / Stable Price for Standard LTD's ( .com, .org, .net, .xyz )
- Whois Privacy enabled by default with no extra cost
- Number of extra domain supported LTD's
- A normall UI without upselling and vendor lock in
Domain Hunting Tips and Tricks
Finding the right domain can be challenging most .com's have been registered and parked for reselling way before the modern internet came into existence. As a solution new LTDs offer a way to get the right keyword however SEO can be an issue and for general consumers understanding new LTDs is far from common knowledge. Preferably finding an available .com, .org and .net is recommended since these are generally well know in the consumer space.
1. Domain Competition Grid.
Once you settled on the name or keyword you would like to build the project under. Visit the keyword .com .net .org in a browser and check if a competitor is already using this brandname to build something similar. if the domains are parked and for sale there might be a landing page provided by some of the big aftermarkets for you to get an idea of the offering price or a way to submit a bid to the domain owner.
2. Synonyms and Slang
If the domain competition grid comes up empty or a competitor already is running a service finding a synonym can be useful and repeat the competition grid avoid changing one letter in the word since this can confuse the consumer again. Slang can also be difficult to use properly but the upside can be huge, if the slang becomes popular and integrated in the common vocabulary.
3. Aftermarket and Expired Domains
Most dictionary keywords will be parked as they were the first to fall victim to dictionary scraping
To look for a great domain that will cost you an extra buck the following aftermarkets should be checked for parked domains Sedo, Dan, Namecheap, Dynadot and Gandi
A great source to check for dropped domains and expired domains also a "complete" after market database is * expireddomains .net * also a great source to get inspired for new brands.
4. Exotic LTDs
In general i would definitely suggest avoiding these enless it makes sense with the targeted consumers location. From a Global LTD perspective .xyz and .io are still common to have a look at registering.
5. General Avoidance Tips
- Plural or 's domain
- +15 characters
- Hypens
- IDN's
- Generally avoid new TLD's
- Single character changes
🚀 Launch
🧱 BUILDING
This is where Flamewerk comes in a Fast Language Agnostic Multipurpose startup template with zero cost in mind.
🧑💻 HOSTING
A-OS supports multiple hosts as of writing Cloudflare, Digital Ocean, Netlify, Amazon WebServices and Google Cloud are supported however every static host provider can be used.
No more vender lockin since migrating to a new host doesn't take longer than 10 minutes.
I enjoyed partaking in the cloudflare beta and found the UI most intuitive and the grab a repository and build to work flawless a small speed shootout also showed that Cloudflare's hosting is most reliable at serving pages at lightning speed.
The factors that make choosing the right static host:
- Price factoring number of Builds, Sites, Seats
- Page Load Speed
- Ease of Github Build integration
- Concurrent builds
- Number of sites
- Requests
- Bandwidth
Cloudflare claims and these are verified:
- Fastest network: run your site on the Cloudflare edge, milliseconds from end users – up to 115% faster than competing platforms.
- Incredibly scalable: with one of the world’s largest networks, Cloudflare can absorb traffic from the most visited sites.
- Always secure: SSL works out of the box, so you never have to worry about provisioning certificates.
- Stay ahead of the curve: support for the latest web standards with HTTP/3, QUIC, image compression out of the box, and more.
- With deep Git integration, Cloudflare Pages works the way developers work. Just tell us your build command (e.g. npm run build) and we’ll take care of the rest, logs included.
🧪 TESTING
Webpage performance is one of the most important factors when it comes to website optimization. A slow-loading website can leave visitors frustrated and may even cause them to leave your site before it has loaded completely.
There are many different ways to test how quickly a webpage loads on your browser, but the Lighthouse page speed testing tool is one of the simplest ways to get an overview of how well your site is performing.
The best way to improve webpage loading time is by reducing the number of requests that are made per page view, minifying assets that are included in each request, and unblocking any JavaScript libraries that may be blocked by default in older browsers.
🤹 PERFORMANCE
Since all pages will be hosted as SSR, the performance is out of the box very fast. The other focus points on Lighthouse testing include accessibility, best practices and SEO. Again out the box these score near perfect but can be improved using extra modules like, Robot for creating a custom Robot.txt and Sitemap for including or excluding pages with a custom sitemap.
Mobile Optimization still in the works Performance varies between 10 to 15 points.For future optimization testing i will be looking into Googles Core Web Vitals report for fixing poor user experiences on your site.
Why page performance matters
Longer page load times have a severe effect on bounce rates. For example:
- If page load time increases from 1 second to 3 seconds, bounce rate increases 32%
- If page load time increases from 1 second to 6 seconds, bounce rate increases by 106%
-
 @ c8383d81:f9139549
2023-07-14 15:06:02
@ c8383d81:f9139549
2023-07-14 15:06:02The Process of UI Design in Product Engineering
The user interface (UI) is a critical part of any product engineering process. It is the interface through which users interact with the product, and it is important for it to be designed with usability and user experience in mind. The process of UI design in product engineering involves several steps, from gathering requirements to prototyping and testing.
Gather Requirements
The first step in the UI design process is to gather requirements. This involves understanding the product’s purpose, the goals of the user, and the context in which the product will be used. This information should be collected through user research, interviews, and surveys.
Design
Once the requirements have been gathered, the next step is to design the UI. This involves creating a wireframe or mockup of the interface, which should include the layout, elements, and interactions. The design should be based on the user requirements and should be tested with users to ensure it meets their needs.
Prototype
Once the design is complete, the next step is to create a prototype. This is a working version of the UI, which can be tested and iterated on. Prototyping is an important part of the design process, as it allows for feedback and refinement before the UI is implemented.
Test
Once the prototype is complete, the next step is to test the UI. This involves testing the usability and user experience of the interface. Testing should be done with real users, and the results should be used to refine the design.
Implement
Once the design is complete and tested, the next step is to implement the UI. This involves turning the design into a working product. This may involve coding or using a UI framework.
Iterate
Once the UI is implemented, the process is not over. UI design is an iterative process, and it should be tested and refined over time. This is necessary to ensure the UI continues to meet the needs of users.
The process of UI design in product engineering is a complex one, and it requires knowledge of user experience and usability. However, by following the steps outlined above, it is possible to create a UI that meets the needs of users and is easy to use.


-
 @ 3bf0c63f:aefa459d
2022-05-10 21:57:00
@ 3bf0c63f:aefa459d
2022-05-10 21:57:00Doing automatic payouts to users on the Lightning Network
No service wants to keep users balances forever or "become a custodian", as that may have some complications dependending on who is doing it.
But the sad truth is that there is no way to do automatic payouts to users on the Lightning Network. So if you're running a marketplace or a game of some kind that takes sats from some users, does something, then sends sats out to other users, you must keep a table with balances for each user.
-- But I can ask for a Lightning Address!
No, you can't, because mobile users of noncustodial wallets do not have those things generally, and that's not the purpose of Lightning Addresses anyway. Well, of course you can, but what I'm trying to say is that you shouldn't, as that is an anti-practice that will cause people to not want to use your service or force them into custodial providers -- which may be ok for them, but may not be.
-- So if I ignore the concerns above I can do this with Lightning Addresses, right?
Not really, because payments can fail. The user might input an invalid Lightning Address, or the Lightning Address may stop working after a while. Or even if it is working and online your payout can still fail for many reason inherent to Lightning.
That means you need to keep a table of balances for your users anyway. It doesn't matter.
Since you are already keeping a table of balances, now it's your chance to bring back the mobile noncustodial wallet users into a greater standard that accomodates everybody: LUD-14.
Wallets can implement LUD-14 support and then be made to withdraw balances from your service automatically every time they're turned on or periodically or upon manual request from the user. That limits the amount of user balance you'll have to keep on your service (but you can also add more rules around that, for example, automatically confiscating balances that stay parked too long, or putting a hard limit on the balance size for each user).
-- But with Lightning Addresses I can do instant payouts!
Yes, you can, but that's why LUD-15 exists: for all custodial providers, noncustodial wallets that rely on some kind of friendly server or coordinator (like Breez, Blixt or Phoenix) or even noncustodial providers running some kind of homemade server, you can dispatch these requests that cause them to withdraw the money automatically, which makes the experience similar to instant payouts -- and better, since then the payment requests can be more meaningful and say they are withdrawals from your service instead of saying that you're donating money to them (which is what most Lightning Address payments really mean).
-
 @ 44dc1c2d:31c74f0b
2023-07-13 19:53:19
@ 44dc1c2d:31c74f0b
2023-07-13 19:53:19When most people think of the “Dark Web” or “DarkNet” the first thing that comes to mind is probably Tor. Tor is basically a household name now; love it or hate it most people have heard of it.
As you may or may not know there are a small handful of different privacy focused networks out there. Each one with different ideas on how privacy on the internet should work. I2P or The Invisible Internet Project’s approach is to act as a fully encrypted and private layer of the internet.
This post is not going to be a “why one is better than the other” type post. Each network has its own use cases with their own set of pluses and minuses. This post is simply going to try and explain what I2P is in a broad sense with some comparison to Tor.
I’ll cover things like how to host a site and set up an Outproxy in another post. As with most of my posts this will assume that you do have some basic networking knowledge but I do try and keep it as accessible as I can.
A brief history
I2P was initially released in 2003 and started as a fork of freenet. Its is an anonymous peer-to-peer distributed communication layer designed to run any traditional internet service (Email, HTTP, File Sharing, Web hosting), as well as more traditional distributed applications such as DNS.
It is designed so that other software can use it for anonymous communication, due to this you can get pretty much anything to communicate Via I2P. There are already a fair number of applications working on I2P such as Email, Chat, and File sharing, crypto currency and more.
Routing
I2P uses what they call “Garlic routing” which is a variation on onion routing. There is a long list of technical differences that you can read about here if you want to get into the nuts and bolts of things, I’m only going to give a broad overview here.
As we know, Onion routing is a technique for building paths (Circuits in Tor terms, Tunnels in I2P terms.) through a series of peers and then using the tunnel to pass data. A message is encrypted by the sender and decrypted every hop until it reaches its destination. With each hop stripping a layer of encryption to get the directions to reach its next peer.
In this way both Garlic and Onion routing are conceptually identical but this is where that stops, where Tor does a single message at a time and a single reply, I2P bundles messages together in what Michael Freedman coined as a “Bulb” (Or a Clove on the official site). All messages have their own delivery instructions that get bundled and delivererd allowing for more efficient routing inside the network. This helps to increase overall network speed. This is a primary advantage in I2P, it's optimized in a way that is generally faster than Tor.
Another key difference is that traffic is unidirectional not bidirectional like in Tor, this allows for more flexibility in the protocol for more reliable delivery. Each router creates a series of in-bound and out-bound tunnels. This setup allows for things like UDP and P2P connections. Tor by design will probably never support UDP and while P2P connections are technically possible with Tor, they are highly discouraged and damaging to the network. P2P is the meat and potatoes of I2P making it ideal for file sharing and other forms of p2p communication.
I think it’s also worth pointing out that with I2P "Exit nodes" or OutProxies are not a focus. While a major use case for Tor is to help people in countries with heavily censored internet to reach sites on the “clear net” that might be blocked by a government. I2P does not officially “exit” traffic from the network.
Exit nodes (OutProxies) in I2P are run by volunteers which are, essentially, centralized services. OutProxying is also not officially advised as the privacy benefits you get from I2P come from remaining in the network. But it can be done and is. Nowadays people even use Tor Exit Nodes in conjunction with I2P. This a perfect segway to talk a bit about the network structure of I2P as this varies quite a bit from Tor.
Tor Network Structure Refresh
I’ll start off with a refresher on Tor. There are enough similarities between the networks that without diving too deep it helps with some comparisons. Tor has various elements to its network. A basic Tor connection takes a minimum of three different kinds of nodes. An entry node, a relay, and an exit. The first node is your entry node. Keep in mind any relay node can act as an entry node, the only difference being that the entry is the only node that knows who you really are.
Relay nodes are the ones that pass your traffic along to exit nodes after a few hops. The exit node communicates with your destination and can forward traffic out of the network. Exit nodes serve as a source for your destination server. This is part of how Tor keeps your traffic anonymous. Exit nodes also send the traffic back to you.
Directory servers are critical for maintaining Tor network. They store the identity of the nodes on the network. The directory servers are hard-coded into the Tor browser and when you fire up the Tor browser these directory servers choose your entry, relay, and exit to form a circuit. At the time of writing there are only 10 directory servers. You can see them here. The other purpose of these servers is to maintain the health of the network by monitoring the activity of nodes and replacing unhealthy nodes with healthy ones to maintain the stability of the network.
It’s also worth noting that relay servers technically have two categories: the “advertised relay nodes” ; these are the relays that are publicly available in the list that the directory servers maintain. Then there are “Bridge nodes”. These are private relays as they are not listed in directory servers. They exist purely for government blocks. In theory you can block the nodes on the public list, but you can’t block what you can’t find so therefore bridge nodes exist. It’s hard to gauge the number of bridges out there but it's estimated to be in the 2k range. You can see that here.
That's Tor in a nutshell. On to I2P
I2P Software
When you install I2P you get software that has everything with it you need to connect to the network and host with. Every “node” in I2P is also a router so there is no distinct difference from a server and pure client like with Tor.
This leads to I2P to be almost completely decentralized. I have to say “almost” due to the need of what they call “Reseed Servers” this is how you make your first connections and join the network. These servers help with what’s called the DHT ( Distributed hash table ) bootstrap problem. There is no reliable method ( yet! ) to get out of running at least one permanent bootstrap node that non-network users can find to get their foothold in the network. Once you're connected to the network you only discover peers by making “exploratory” tunnels. But to make your initial connections you need to get your peers from somewhere. This model contrasts with Tors directory servers a great deal.
Floodfill routers or peers are I2P’s directory servers that store the directory or the Network Database (netDB for short). Floodfill servers are untrusted and varying. Any router can be set to act as a floodfill router. To increase reliability of the netDB floodfill is automatically turned on only on high bandwidth routers (this has to be manually configured). In addition to having high bandwidth a router must also pass health checks like outbound message queue time and job lag before floodfill is automatically turned on. It is estimated that only 6% of the network are floodfill routers.
The netDB that I2P uses is a specialized distributed database. It only contains a few types of data. The big two being Router contact info (RouterInfos) and Destination contact info (LeaseSets). Each bit of data is signed by the host and is verified by anyone who chooses to store the site in their own local copy of the netDB. It also stores liveliness data of a site, this allows bad entries to be dropped, and newer entries to replace older ones.
Tunnels (or circuits on the Tor network) are how routers communicate and route traffic. I2P builds virtual “Tunnels” between routers for communication; they are temporary and unidirectional. For a basic connection you need at least four tunnels two outbound two inbound. Each tunnel has a set amount of hops that is set in router settings with a maximum of seven hops. The amount of hops per tunnel of course affects things like latency, throughput, reliability. and anonymity and a user can fine tune the amount of hops based on need. Three hops is recommended for most users as its a fair balance of anonymity and speed. Peers are selected by a continuous polling and ranking performance rather than trusting claimed capacity.
I could spend several more pages covering the specifics of I2P but I’ll leave you with a link to the main documentation if you want to take a deeper look at the network and how it works.
To Sum up
In conclusion I would say that I2P has a lot of potential. While Tor is designed to act as an anonymizing proxy for the Vanilla Internet, I2P is specifically designed to make an anonymous layer on top of the TCP/IP stack for hidden services and P2P applications. It's not perfect (Name a solution that is though… I’ll wait) but it's a good attempt at an anonymized network layer. (Yes TOR can do this as well but its main use case IMO is circumventing government blocks to clear net sites.)
I think it's far more flexible than Tor and while it currently is more technically involved to use than Tor at the moment, I hope that will be eventually overcome by working it into the background of more apps etc....The need to install something plus configuring a proxy on a separate browser from your primary browser can be daunting to some vs Tor’s just installing a browser and off you go. Although Firefox plugins like “I2P In Private Browsing” does a good job managing I2P via tab containers in Firefox eliminating the need to have a separate browser or do any extra configuration, it still has a ways to go.
The I2P project has a fair amount of self awareness when it comes down to what the network could be vulnerable to. Outside of unforeseen software vulnerabilities that could jeopardize the network a few of the attacks they talk about and try to mitigate include: Brute force, Timing attacks, DOS attacks, Intersection attacks and syble attacks to name a few. If you want to learn more about these potential issues and how they try and mitigate them here is the official page.
I2P is a smaller network that's not as battle tested as Tor but its optimization for hidden services and its more P2P nature is very appealing. Also Monero and Bitcoin support I2P now for node communication. Along with a few other privacy focused cyptos joining the network. I personally hope to see more Bitcoin and Monero users to enable I2P on their nodes.
I hope this helps answer some questions about I2P and encourages you to learn more and start exploring how you can use I2P to help you maintain at least a modicum of privacy in an ever surveilled world. I'll leave some links below to get you started. Have fun exploring and tinkering!
Until next time.
-
 @ 1e52c554:21771908
2023-07-23 00:18:01
@ 1e52c554:21771908
2023-07-23 00:18:01``` New Music
I wait for a new rain of melodies To erase these old echoes of sadness Left after losing strands of happiness That did not last but left some memories.
Thinking stars live as well their agonies Meandering through glorious madness I breath blue velvets and skies' gladness Used in their past to clothe their ecstasies.
Still carrying your smile within my heart I delve into dreams where nothing has changed And dress with those passions that are alive. But my new days are somehow hard to chart And this is why I have also arranged Other musics on which I will survive. *** ```
Analysis "New Music"
Sonnet 75 by Francisco Luis Arroyave Tabares, titled "New Music," is a beautifully crafted poem that explores themes of loss, memory, hope, and resilience. The sonnet form, traditionally composed of 14 lines with a specific rhyme scheme, is used here to convey a deeply personal narrative.
The first quatrain introduces the theme of longing for a "new rain of melodies" to wash away the "old echoes of sadness." The speaker is yearning for a fresh start, a new beginning that will help him forget the pain of the past. The "strands of happiness" that were lost have left behind memories, suggesting a past relationship or experience that brought joy but is now a source of sorrow.
In the second quatrain, the speaker finds solace and inspiration in the natural world, specifically the stars and the sky. The "Thinking stars" and "blue velvets and skies' gladness" serve as metaphors for the speaker's own emotional journey. The stars, despite their "agonies," continue to shine, reflecting the speaker's resilience in the face of adversity.
The first tercet delves deeper into the speaker's emotional state. He carries the memory of a loved one's smile in his heart, and he finds comfort in dreams where "nothing has changed." This suggests a longing for the past, a desire to return to happier times.
The final tercet reveals the speaker's struggle to navigate his "new days," which are "hard to chart." Despite this, he has arranged "other musics" on which he will survive, indicating his determination to move forward and find new sources of joy and inspiration.
Overall, "New Music" is a poignant exploration of the human capacity to endure loss and change. It emphasizes the power of memory and the natural world as sources of comfort and inspiration, and it ultimately affirms the resilience of the human spirit.
Themes
The poem delves into the following themes: - Loss and longing for a fresh start - The power of memory and the natural world - Resilience and the ability to find new sources of joy
Structure and Rhyme Scheme
Sonnet 75 by Francisco Luis Arroyave Tabares follows the structure of a Shakespearean sonnet, which is composed of three quatrains (four-line stanzas) and a final couplet (two-line stanza). The rhyme scheme of a Shakespearean sonnet is ABAB CDCD EFEF GG.
Let's break down the rhyme scheme of Sonnet 75:
- I wait for a new rain of melodies (A)
- To erase these old echoes of sadness (B)
- Left after losing strands of happiness (A)
-
That did not last but left some memories. (B)
-
Thinking stars live as well their agonies (C)
- Meandering through glorious madness (D)
- I breath blue velvets and skies' gladness (C)
-
Used in their past to clothe their ecstasies. (D)
-
Still carrying your smile within my heart (E)
- I delve into dreams where nothing has changed (F)
- And dress with those passions that are alive. (E)
-
But my new days are somehow hard to chart (F)
-
And this is why I have also arranged (G)
- Other musics on which I will survive. (G)
So, the rhyme scheme of Sonnet 75 is ABAB CDCD EFEF GG, which is consistent with the structure of a Shakespearean sonnet. This structure allows the poet to develop three distinct but interrelated ideas (one in each quatrain) before presenting a final summarizing or concluding thought in the couplet.
Analysis of Aspects
While we've discussed the themes, rhyme scheme, and structure of Sonnet 75, there are still several aspects that can be further analyzed, including its use of imagery, metaphor, and tone.
Imagery: The sonnet is rich in vivid and evocative imagery. Phrases like "new rain of melodies," "blue velvets and skies' gladness," and "Thinking stars" create a sensory experience for the reader, painting a picture of the speaker's emotional landscape. This imagery serves to heighten the emotional resonance of the poem and draw the reader into the speaker's experience.
Metaphor: The sonnet uses metaphor to convey complex emotions and ideas. For example, the "new rain of melodies" can be seen as a metaphor for hope and renewal, while the "Thinking stars" could represent the speaker's introspection and resilience. The "other musics" in the final line can be interpreted as new experiences or opportunities that will help the speaker move forward.
Tone: The tone of the sonnet is introspective and melancholic, but ultimately hopeful. The speaker expresses sadness and longing, particularly in the first two quatrains, but also demonstrates a determination to overcome his struggles and find new sources of joy. This shift in tone is particularly evident in the final couplet, which ends the sonnet on a note of resilience and optimism.
Meter: Like traditional sonnets, Sonnet 75 is written in iambic pentameter, which means each line consists of five pairs of unstressed and stressed syllables. This rhythmic pattern gives the poem a musical quality, reinforcing the theme of "new music" and contributing to the overall mood and flow of the sonnet.
Symbolism: The sonnet also employs symbolism. The "rain of melodies" symbolizes a cleansing or renewal, the "stars" symbolize guidance and resilience, and the "blue velvets and skies' gladness" symbolize tranquility and hope. These symbols add depth to the poem, allowing the speaker to express complex emotions and ideas in a nuanced way.
In conclusion, Sonnet 75 is a complex and layered poem that uses a variety of poetic techniques to convey a deeply personal narrative of loss, memory, and resilience.
(GPT4)
Count the syllables of each line of the poem
(www.howmanysyllables.com)
New Music
10 I wait for a new rain of melodies
10 To erase these old echoes of sadness
10 Left after losing strands of happiness
10 That did not last but left some memories.
10 Thinking stars live as well their agonies
10 Meandering through glorious madness
9 I breath blue velvets and skies' gladness
10 Used in their past to clothe their ecstasies.
10 Still carrying your smile within my heart
10 I delve into dreams where nothing has
changed
10 And dress with those passions that are alive.
10 But my new days are somehow hard to chart
10 And this is why I have also arranged
10 Other musics on which I will survive.



