-
 @ fa0165a0:03397073
2023-07-24 10:19:27
@ fa0165a0:03397073
2023-07-24 10:19:27Below is an easy-to-read list of keyboard shortcuts and commands to navigate your Linux computer efficiently: (Note that some variations between systems may apply)
General Shortcuts: Open Terminal: Ctrl + Alt + T Close current application: Alt + F4 Switch between open applications: Alt + Tab Logout from current session: Ctrl + Alt + Del Navigating the File System: Open File Manager (Nautilus): Super (Windows key) + E Move back in directory: Alt + Left Arrow Move forward in directory: Alt + Right Arrow Go to Home directory: Ctrl + H Go to Desktop: Ctrl + D Open a folder or file: Enter Rename a file or folder: F2 Copy selected item: Ctrl + C Cut selected item: Ctrl + X Paste copied/cut item: Ctrl + V Delete selected item: Delete Create a new folder: Ctrl + Shift + N Navigating Applications: Switch between open windows of the same application: Alt + ` Close the current window: Ctrl + W Minimize the current window: Ctrl + M Maximize/Restore the current window: Ctrl + Super + Up Arrow / Down Arrow Navigating Web Browsers (e.g., Firefox, Chrome): Open a new tab: Ctrl + T Close the current tab: Ctrl + W Switch to the next tab: Ctrl + Tab Switch to the previous tab: Ctrl + Shift + Tab Open a link in a new tab: Ctrl + Left Click Go back in the browser history: Alt + Left Arrow Go forward in the browser history: Alt + Right Arrow System Controls: Lock the screen: Ctrl + Alt + L Open the system menu (context menu): Menu key (or Right-click key) or Shift + F10 Open the Run Command prompt: Alt + F2These shortcuts may vary slightly depending on the Linux distribution and desktop environment you are using. Experiment with these shortcuts to navigate your Linux system faster and more efficiently without relying on the mouse.
Since websites are such an important interface for the information of today, I have here appended the list with some navigational hotkeys for web browsers (e.g., Firefox, Chrome) on Linux:
General Navigation: Scroll down: Spacebar Scroll up: Shift + Spacebar Scroll horizontally: Hold Shift and scroll with the mouse wheel or arrow keys Go to the top of the page: Home Go to the bottom of the page: End Refresh the page: F5 or Ctrl + R Stop loading the page: Esc Link and Page Navigation: Move focus to the next link or interactive element: Tab Move focus to the previous link or interactive element: Shift + Tab Activate/follow a link or button: Enter Open link in a new tab: Ctrl + Enter (Cmd + Enter on macOS) Open link in a new background tab: Ctrl + Shift + Enter (Cmd + Shift + Enter on macOS) Open link in a new window: Shift + Enter Go back to the previous page: Backspace or Alt + Left Arrow Go forward to the next page: Alt + Right Arrow Searching: Find text on the page: Ctrl + F Find next occurrence: Ctrl + G Find previous occurrence: Ctrl + Shift + G Tab Management: Open a new tab: Ctrl + T Close the current tab: Ctrl + W Reopen the last closed tab: Ctrl + Shift + T Switch to the next tab: Ctrl + Tab Switch to the previous tab: Ctrl + Shift + Tab Switch to a specific tab (numbered from left to right): Ctrl + [1-8] Switch to the last tab: Ctrl + 9 Form Interaction: Move to the next form field: Tab Move to the previous form field: Shift + Tab Check/uncheck checkboxes and radio buttons: Spacebar Select an option from a dropdown menu: Enter, then arrow keys to navigate options Miscellaneous: Open the browser's menu: Alt (sometimes F10) Open the address bar (omnibox): Ctrl + L or Alt + DRemember, the accessibility of websites can vary, and some sites might have different keyboard navigation implementations. In some cases, you may need to enable keyboard navigation in the browser's settings or extensions. Additionally, browser updates might introduce changes to keyboard shortcuts, so it's always good to check the latest documentation or help resources for your specific browser version.
But I hope this helps as an tldr and getting started with navigating your laptop the ways pro role.
Version controlled over at github gist.
-
 @ c8df6ae8:22293a06
2023-07-24 04:30:59
@ c8df6ae8:22293a06
2023-07-24 04:30:59The Kennedy administration will begin to back the US dollar with real, finite assets such as gold, silver, platinum and Bitcoin, which is the world's hardest liquid asset, to strengthen the US dollar and guarantee its continued success as the global reserve currency.
— Robert F. Kennedy Jr.Welcome to the latest issue of the Bitcoin For Families newsletter. This issue covers the potential implications of a Bitcoin backed US dollar.
What are the implications of a Bitcoin backed US dollar?
On July 19th, presidential candidate Robert Kennedy Jr gave a speech at a PAC event where he declared the plans of his administration to, at least partially, back the US dollar with gold, silver, platinum and Bitcoin.
You can watch the whole 10 minutes speech here:
What could happen if RFK Jr. does get elected and goes forward with this promise? Let’s look at some scenarios.
What will the RFK administration do?
RFK Jr. said he would back 1% of the treasury bills (T-Bills) issued by the treasury with gold, silver, platinum and Bitcoin.
T-Bills are short-term securities issued by the government with a maturity rate of 4, 8,13, 17, 26 or 52 weeks. The interest rate is set based on the offers done by those bidding on the auction. For example, a recent auction of 26 week T-Bills closed with an interest rate of 5.25%.
Let’s assume that Bitcoin is priced at $32,000 US dollars and that you buy a 26 weeks T-Bill worth $100 and backed by Bitcoin. This would mean that the US government must have possession of 312,500 satoshi (0.00312500 BTC) to back this T-Bill and you should have the option to exchange the T-Bill for that amount of Bitcoin at the end of the 26 weeks.
What would happen if after 26 weeks, the US dollar became weaker than Bitcoin and the exchange rate is now $34,000? Now you only need 294,118 satoshis to back the $100 T-Bill and since the US government had set aside 312,500 satoshi, then all is good.
What would happen if after 26 weeks, the US dollar became stronger than Bitcoin and the exchange rate is now $28,000? Now you need 357,143 satoshi to back the T-Bill and since the US government had set aside 312,500 satoshi, they would need to purchase 44,643 more satoshi to continue to back the T-Bill.
I doubt the US government will be willing to take this exchange rate risk with its debt obligations.
Therefore, the most likely scenario is that the US government sets a fixed exchange rate for the maturity life of the T-Bill. Maybe equal to the exchange rate at the time of the auction.
This means that after 26 weeks you could exchange your T-Bill for 312,500 satoshi no matter what the actual exchange rate is at that point.
What will this do to the price of Bitcoin or the US dollar?
-
The US dollar will get stronger when compared against other fiat currencies not backed by anything:
The US government will send a very strong signal to the world that Bitcoin is the new gold and a very valid store of value. The world’s hardest liquid asset.
Therefore, backing the US dollar with Bitcoin will make the US dollar stronger when compared with other fiat currencies.
-
The US dollar will get weaker when compared against Bitcoin:
The demand for Bitcoin by the US government will put upward pressure on the exchange rate for Bitcoin against all fiat currencies, including the US dollar.
-
A continued policy of expanding the amount of T-Bills backed by Bitcoin will only exacerbate this process, making the US dollar stronger against other countries currencies and driving the price of Bitcoin up both against the US dollar and by extension other fiat currencies (which by definition are now weaker than the US dollar).
What will investors do?
Investors will demand either the same or maybe even lower interest rates for Bitcoin backed T-Bills with the assumption that the Bitcoin amount backing the T-Bill will be worth more after 26 weeks.
The scenario where investors demand higher interest rates because they believe that Bitcoin will get weaker is unlikely since, even if this happens, the T-Bills are denominated in US dollars and investors won’t be forced to redeem the T-Bill for Bitcoin at the end of the 26 weeks.
What will other countries do?
At first, other countries will just watch and see.
But the upward pressure on the price of Bitcoin will make a US T-Bill more attractive than its European Central Bank equivalent causing the Euro to lose value compared against the US dollar.
The same applies to any other fiat currency (not backed by anything).
Other countries will be forced to back some of their short-term debt with Bitcoin to avoid having to pay higher interest rates to counteract the higher attractiveness of the US T-Bill.
The consolidation of Bitcoin as store of value
If all countries start using Bitcoin to back their debt, that will consolidate Bitcoin as the best store of value.
Bitcoin has to first settle as a store of value before it can be used as a medium of exchange and unit of account (what is commonly known as hyperbitcoinization). This possible action by the US government might well be the linchpin that triggers the hyperbitcoinization.
If the other countries do nothing, the US dollar will cement itself as the global reserve currency and the hyperbitcoinization will still happen, just a bit slower since there will be no demand from other treasuries.
Notable notes
nostr:note1dgh2ga7q397huzfcf9ah06ptvcxxwcmfx5yhctw0rh4t6ylvud4s0nrn75
Recommendations
Max DeMarco
Max is the creator of a great documentary about social media and why we need Nostr.
Watch the documentary here:
 You can follow Max here.
You can follow Max here.Bitcoin Therapy 🧠
Level up your Bitcoin knowledge in 3 minutes...every Sunday
Check it out here.
What did you think of today's newsletter?
Your feedback helps me create the best newsletter possible for you.
Please leave a comment and checkout comments from other subscribers and readers. I love hearing from the Bitcoin For Families community ❤️ 🙏🏻
Buy Bitcoin with Swan
If you want to buy Bitcoin, I highly recommend using Swan. They are a Bitcoin only business that is focused on self-custody and educating their users. It's where I buy my Bitcoin.
Use this link to receive $10 free to get you started.
See you again next week! — Alejandro
This newsletter is for educational purposes. It does not represent financial advice. Do your own research before buying Bitcoin.
-
-
 @ b28b00b0:75d2abf4
2023-07-24 19:20:21
@ b28b00b0:75d2abf4
2023-07-24 19:20:21~~Biip~~ Boop!
1...2..3
| Key | Value | | --- | --- | | Name | Sven | | Age | 100 |
Now it's updated!
...and again!
...and a third time!
...and a fourth time!
-
 @ f821179b:ed4fd022
2023-07-24 18:39:53
@ f821179b:ed4fd022
2023-07-24 18:39:53Primal.net is a bit new so it’s still a work in progress but is quickly becoming one of my favorite clients. It took some time before they were able to implement “zaps”, and their direct message feature is still being developed. However, everything that is currently functional works very well. It has become my go-to web client because I find it reliable. If I want to check my latest notifications, Primal is now my first choice—it was Iris previously—as it often shows me notifications that other clients miss for some reason. I assume this discrepancy is relay-related.
Primal offers several interesting features worth exploring. For example, their in-depth statistics tab shows useful information about what’s trending across Nostr, which accounts are receiving the most zaps, which notes are getting the most attention, the total number of users on the network, the total number of reactions, and so on. You can find all of this under their ‘Explore’ tab. Viewing these statistics provides a fascinating insight into the ecosystem.
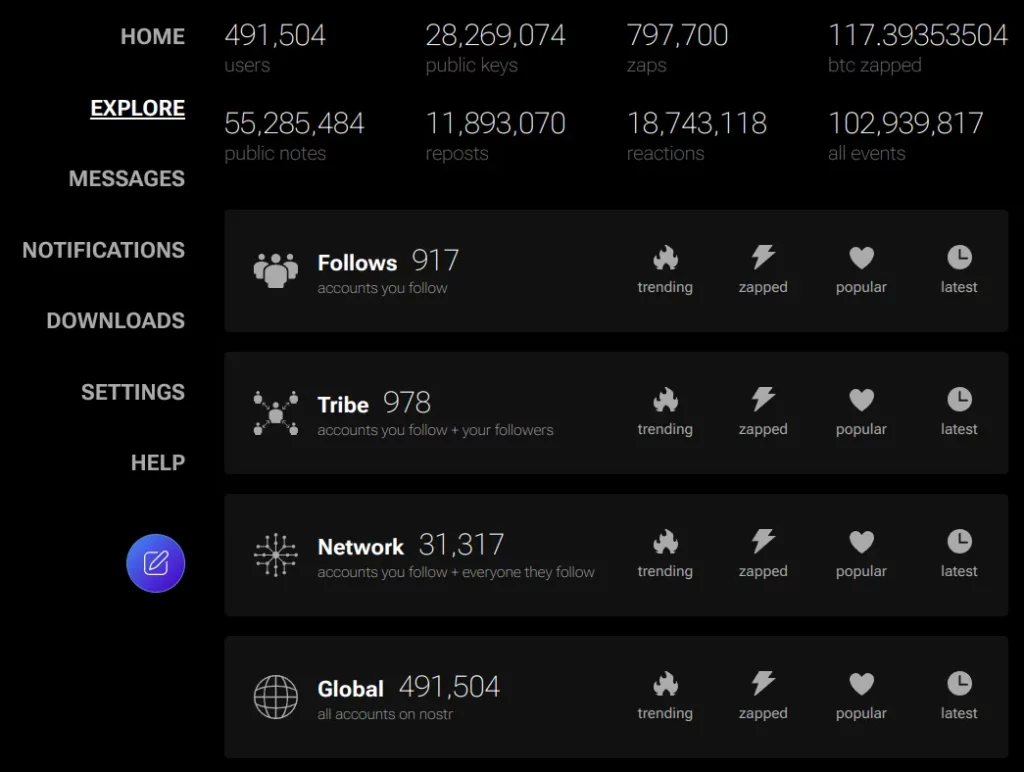
Custom feeds are another great feature that Primal offers on their client. You can see what's popular and trending in multiple different ways. For example, do you want to know which accounts are getting the most zaps? There's a custom feed for that. Interested in seeing what someone else's feed looks like? You can visit their profile and create a custom feed for yourself. Curious about what's trending across your network, including your followers and those you follow, as well as those they follow? There's a custom feed for that as well. You can even follow hashtags or specific keywords if you prefer, and turn them into a custom feed. The level of customization and the way your media is presented to you is clearly a key area of focus for the Primal team.
Primal has recently released the beta version of its iOS app. It’s not yet available on the App Store. However, if you’re interested in trying it out, you can visit https://primal.net/downloads After signing up and downloading “TestFlight”, you’ll be able to take the app for a test run or “flight,” if you will. One aspect that immediately stood out to me when first using the app was their excellently implemented Zaps integration. Primal guides you through the process of linking your GetAlby account with the app, facilitating frictionless zapping and creating a seamless experience. I find myself using the Primal app as frequently as I use Damus. Currently, these two apps are my go-to options for iOS.
I'm eagerly anticipating how Primal will evolve and grow as they refine and perfect their client.
-
 @ 1bc70a01:24f6a411
2023-07-23 12:11:45
@ 1bc70a01:24f6a411
2023-07-23 12:11:45This is an old but timeless post I wrote on October 26, 2022.
90% of startups fail. That's the statistic.
It feels true to me. Judging by startup Twitter it seems most startups disappear before the 2 year mark. Some, much sooner.
Most people imagine the startup journey to be like this:

People think you can go from idea to a shipped product fast. After launch it's all happy times and success. We fool ourselves into believing this because we must. Otherwise, it's hard to start.
In reality, it's something like this:

50% quit at the idea stage. I'm making rough calls, not an exact science.
Ideas are easy, but acting is hard. Most people will just stop at the idea. Some may look into it, register a domain (you know who you are 👀) and stop there.
Those who undertake the journey will build for 3-5 days and see some other "better" idea. This is called the shiny object syndrome. Sixty percent of people will quit at the shiny object and start working on something else. Of course, they'll register a domain first!
Ignored the shiny object? Good for you! This is where it starts getting tough.
80% will quit before the "project" is finished. The last 20% of the project feels so close, yet so far away that you wonder if you've made the wrong decision all along. Doubt creeps in. You start thinking - "why bother?" and "this is not going to work out, it was a dumb idea".
The heroic few will get through the grind stage and finish their project. This is where they will call themselves a startup - but they are still a project.
In a great anticipating to the "launch", many founders will fall from the pedestal soon after. Launches are a non-event for most projects. Lucky few gain customers and traction, but the vast majority will disappear in the coming weeks.
That leaves us with the 20% crusaders. The tough bastards who will not give up immediately after the launch. They'll keep pushing. And pushing... and pushing. Until they meet a wall of despair.
The wall of despair makes everything seem hopeless. You've tried. You keep trying. But, nothing happens.
This idea has no legs. This was all a giant mistake! Shut it all down. Go back to your regular job. This was never meant to be.
Sadly, this is just the point where things start getting interesting. But, our hero (or actually 90% of them) give up for good.
For most, this will be around the year 1 mark. For some year 2 or even 3 if they pivoted a few times. It's really hard to keep going at this point.
The glorious few - the supposed 10% (I actually think it's about 2%) start seeing traction. All the pain and the agony of getting to this point is finally worth it.
From here, things can take as long as 1 year, all the way up to 5 years+ to see meaningful growth that pays all the bills and then some.
Startups are a helluva ride. Only the toughest survive. But, it doesn't end there.
Even 50% of successful startups will seize to exist just before year 5. The remain half may make it to year 9, but even the vast majority of those will disappear before the decade's end. Only about 30% of the 10% successful startups make it past one decade.
But none of this matters! If you are a new founder reading this, you know you're the exception. You will succeed! You were chosen.
I joke, but, don't give up. I believe in you. What's the downside in doing so?
-
 @ 7d9564f8:1bab2932
2023-07-24 18:16:02
@ 7d9564f8:1bab2932
2023-07-24 18:16:02My boby post
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ bcea2b98:7ccef3c9
2023-07-21 17:11:23
@ bcea2b98:7ccef3c9
2023-07-21 17:11:23The Bitcoin Improvement Proposal (BIP) 17 is a proposal to add a new opcode to Bitcoin's scripting system, and it also proposes a new 'standard' transaction type that uses this opcode. Here, I will explain each part of this proposal in simple terms.
BIP17 proposes the opcode
OP_CHECKHASHVERIFYfor the Bitcoin scripting system. An opcode is a type of operation that can be performed by a machine (in this case, the Bitcoin network). The opcode that BIP17 is proposing,OP_CHECKHASHVERIFY, is a function that checks if the hash of the previous script matches the item at the top of the stack.The reason for introducing this opcode is to enable what is known as "pay-to-script-hash" transactions. These types of transactions allow the receiver of bitcoins to specify the transaction type needed to re-spend them, essentially shifting the responsibility of defining the conditions to redeem a transaction from the sender to the receiver.
The benefit of this is that it allows a sender to fund any arbitrary transaction, no matter how complicated, by using a fixed-length 20-byte hash. This makes it easier to handle in various interfaces, such as QR codes or copy-pasting.
The proposed opcode
OP_CHECKHASHVERIFYworks as follows:- It hashes the end of the previous script, starting from the last evaluated
OP_CODESEPARATOR. - It then compares this hash with the item on top of the stack.
- If the hashes match, it proceeds with the script; if they don't match, the script fails immediately.
The new standard transaction type is defined as follows:
[20-byte-hash-value] OP_CHECKHASHVERIFY OP_DROPThis transaction type is redeemed by a standard scriptSig:
...signatures... OP_CODESEPARATOR {script}The proposal also gives an example of how this might look for a one-signature-required transaction and a 2-of-3 multi-signature transaction.
The author of BIP17 believes this proposal would minimize changes needed to the existing infrastructure that sends funds to Bitcoin addresses, which would in turn allow for quicker adoption of multi-signature transactions.
Regarding backward compatibility, this BIP is not compatible with older implementations, and it might lead to a blockchain split if not handled carefully. The proposal includes a method for determining miner support for this BIP and a plan for a graceful upgrade if there is sufficient support.
- It hashes the end of the previous script, starting from the last evaluated
-
 @ fa6afdb4:aee9b046
2023-07-24 11:06:45
@ fa6afdb4:aee9b046
2023-07-24 11:06:45Meditation is a practice that involves training the mind to focus and redirect thoughts. One common meditation technique is to focus on the breath and bring awareness to different parts of the body. Here's a step-by-step guide to help you with this practice:
- Find a quiet and comfortable place where you can sit or lie down without any distractions. You may choose to close your eyes or keep them softly focused.
- Begin by taking a few deep breaths to relax your body and settle your mind. Feel the sensation of the breath entering and leaving your body.
- Once you feel centred, shift your attention to the breath. Observe the natural flow of your breath, without trying to control it. Notice how it feels as the air enters and leaves your nostrils or how your chest and abdomen rise and fall.
- Now, bring your awareness to each part of your body, starting from the top of your head and slowly moving down. As you focus on each area, try to relax any tension you may feel. You can mentally scan your body or use your breath as a guide, imagining that you're breathing into each part.
- Pay attention to any sensations, feelings, or even thoughts that arise as you bring your awareness to each body part. Without judgment or attachment, simply observe them and let them pass.
- If you find your mind wandering or getting caught up in thoughts, gently bring your attention back to the breath and the body. It's normal for the mind to wander, and the practice is to gently guide it back to the present moment.
- Continue this process, moving down your body and focusing on each part until you reach your toes. Take your time and allow yourself to fully experience the sensations and relaxation in each area.
- If you have more time, you can choose to repeat the body scan or focus solely on the breath for an extended period.
Remember, meditation is a practice, and it may take time to develop focus and awareness. Be patient with yourself and try to approach the practice with a sense of curiosity and non-judgment. Over time, regular meditation can bring about a greater sense of calm, clarity, and overall well-being.
This article was generated with the help of an AI language model.
-
 @ 1bc70a01:24f6a411
2023-07-21 12:03:38
@ 1bc70a01:24f6a411
2023-07-21 12:03:38The concept of value of value is one where information yearns to flow freely, transactions should be voluntary, unlimited and direct. In V4V model, people pay what something is worth to them.
Sounds great. On paper. There are some issues…
Free sucks
At least, that’s the perception. People don’t assign much value to free. Ask anyone who has ever ran any business and has not suggested a value for a product or service and they’ll tell you that they earned far less than when charging for the thing.
It’s true, some people will give a lot, some a little, and most none. Most - none. None.
Pricing is Signal
Pricing is a signal of desirability and quality. Of course, it is often incorrect and people manipulate pricing all the time. But for the most part, people don’t see much value in free. Unless a recommended price is offered, people will usually pay nothing. This is not a great model to thrive on if you spend years of your life acquiring knowledge and turning it into products that nobody ultimately buys. I have very personal experience with free. I’ve created and sold digital products and ran many pricing experiments myself. The highest priced products usually generated the most revenue. Surprise! The middle cost product (same product, just priced less) decimated the revenue stream. When set to 0 (even with a suggested minimum price), I generated almost no revenue at all.
None of this is surprising. Pricing acts as a psychological anchor. “You get what you pay for” is ingrained in our brains whether we think about it or not.
People are clueless
The issue with price is that most people don’t have a clue what anything is worth. The only time people have any rough idea of what they should pay for something is when they have already purchased that thing in the past. But, introduce something they have never before purchased and they won’t have a single clue about what to pay. Take for example a set of professional photos of you and your family. Unless you’ve been to a photo studio in the last 5 years, you probably won’t have a single clue what that package of photos is worth. Does that mean the product is worthless? Of course not, but people don’t know what to pay.
In a value for value model, the absence of price makes it super difficult to determine the value of anything. You may take some social cues from previous payments from other people, but this could backfire for the content creator.
Suppose I created a UI framework that saved developers hundreds of hours. In theory, I should be able to charge at least a few hours’ worth of value for this product. If the developer’s time is valued at $100/hour, a $200 price for a product that saves you $2000 worth of time seems very justifiable. Not only do you get to use it once, but you can re-use the product for ALL future projects and employment.
Now, remove the price and see what people pay. Absolutely nothing. You may have a few people who pay $200 voluntarily, but it’s highly unlikely The vast majority will pay nothing, and some may “tip” in the 5-$60 range. Anything that approaches a $100 mark is seen as a purchase. Hey, I don’t make the rules, I just see what other founders have figured out long ago and combine with my own observations. Don’t kill the messenger.
Free is Expensive
If I am accurate in my assessment and recall my personal experiences accurately, then the majority of people who consume your value will do so for free. When that content is a product, you may end up spending a lot of time on supporting the thing that is not generating any revenue. You don’t want to be rude and ignore people so you’ll probably spend your valuable time answering questions and helping them troubleshoot issues. All of that time adds up. Startup founders who offer free tiers or near free tiers of services learn very quickly that free customers are the most painful and demanding. You are basically forced to charge just to avoid dealing with demanding people who expect everything for nothing.
Free is Noise
Price is not just a request for value, but it acts as a feedback signal for future content. If you have no idea what people are paying for, it’s difficult to know if what you create is worth anything. A situation where the vast majority of your content is consumed for free yield a lot of noise.
Well, why not focus on the people who pay? You certainly could, but it ends up being a tiny fraction of the sample size you could have had if you actually charged something up front.
Lack of forecasting
Businesses rely on predictible revenue. Forecasting is necessary for all sorts of decisions if you work with anyone but yourself. It helps with purchasing decision (expenses) and with planning of future products. Value for value makes it impossible to know what your revenue will be next month as you just have no idea if everyone pays nothing or a lot.
V4V could make you uncompetitive
In a model where one person charges a fixed price and the other is relying on the good will of the people to "see the value" in their work, the person with predictible revenue will most likely win out in a competitive environment - enabling them to get ahead of you and your business. They will have an easier time planning further content / products and hiring people to scale the business even further.
It’s not all hopeless
That’s not to say that I don’t like the idea of value for value. Of course I only want people to pay if they find the thing useful. The issue is that people may not know the thing is useful until they’ve already acquired it. At that point who is going back to pay for the thing they already got for free? Few to none.
Value for value may work. For some.
I’m not saying value for value doesn’t work sometimes, for some people. It is entirely possible that a person earns a living on v4v transactions. However, I think for that to be true there may be other factors at play such as social standing, personal brand, influence, likability, status within a community. The vast majority of creators do not fall into this category and will just struggle.
I’m cautiously optimistic about V4V and hope it works out at scale. But as it stands, I have not seen much evidence that it actually pays the bills. Yes, there has been some support for podcasts on Fountain, but it is unclear whether it is just as or more significant than traditional transaction model.
“Information is not scarce” is irrelevant
There’s some notion that information yearns to be free and cannot be scarce by nature. I think this may be a false argument from the start. When we purchase digital things, we are not paying for scarcity - it’s totally irrelevant. We pay for the experience and the feeling we get from that thing. In fact, the same is probably true for physical products (with the added benefit of personal sustenance). I don’t go into the grocery store to buy a dinner and fork over the money because it’s scarce. I pay because I’m hungry. There’s utility and there’s pleasure and fulfillment. If I’m having a dinner with friends, there’s also fun. Unless I am totally misunderstanding the argument, I’m not sure how it applies.
In Summary
- Value 4 value may work at scale, but remains to be seen
- It could be great fun money but not serious enough to pay the bills (for most of us)
- Sounds good on paper but we humans have our own ways of thinking about value and what it's worth
- May work well for people who build a personal brand or have status in a community
As always I look forward to your thoughts. Let me know if I’m overlooking something or should consider some point of view in more depth.
-
 @ eac63075:b4988b48
2023-07-24 05:59:57
@ eac63075:b4988b48
2023-07-24 05:59:57Este é um texto é baseado na transcrição do Twitter Spaces promovido pela Cointelegraph Brasil, com a participação de Edilson Osorio Jr (@eddieoz) , Pedro Magalhães e Rafaela Romano como host.
Introdução
Nos últimos anos, o mundo testemunhou um aumento significativo no uso de criptomoedas, com o Bitcoin ganhando destaque. O Brasil, como muitas outras nações, está navegando nessa nova era digital, enfrentando a introdução de sua Moeda Digital de Banco Central (CBDC), chamada Real Digital. Embora essa tecnologia ofereça um grande potencial para a inovação financeira, também traz consigo desafios, preocupações com a privacidade e ameaças potenciais às liberdades individuais. Neste artigo, vamos mergulhar nas questões que cercam a CBDC brasileira e explorar as implicações mais amplas da criptografia, Bitcoin, criptomoedas e blockchain na sociedade.

O CBDC Brasileiro - Equilibrando Vigilância e Controle
O Real Digital, distribuído pelo Banco Central do Brasil, promete trazer eficiência, transparência e inclusão de desbancarizados ao sistema financeiro. No entanto, surgem preocupações à medida que o CBDC é inicialmente lançado para corporações e instituições, com planos futuros para alcançar as carteiras dos indivíduos. Essa medida poderia resultar em vigilância em massa e questões de controle, conferindo ao governo um poder sem precedentes para monitorar as atividades financeiras dos cidadãos. Defensores da privacidade temem que tal intromissão nas finanças pessoais possa comprometer as liberdades individuais e abrir caminho para o uso autoritário dos dados financeiros.
Bitcoin como Símbolo de Liberdade
À medida que o governo brasileiro explora medidas regulatórias para a indústria de criptomoedas, o debate em torno das funções de congelamento, queima e transferência de saldos traz preocupações entre especialistas. Essas funções, se mal utilizadas, podem impactar significativamente o cidadão. Enquanto isso, amplia-se a discussão sobre a importância da inclusão financeira dos desbancarizados, e criptomoedas como o Bitcoin oferecem um caminho alternativo para que os indivíduos tenham mais controle sobre suas próprias transações financeiras. A descentralização e a capacidade de contornar intermediários financeiros tradicionais capacitam os indivíduos e promovem a liberdade financeira.
Encontrando um Equilíbrio entre Segurança e Privacidade
Governos em todo o mundo, incluindo a União Europeia, estão contemplando a criação de backdoors em sistemas criptográficos com o pretexto de combater a lavagem de dinheiro, o financiamento do terrorismo e o abuso infantil. Embora possam parecer causas justificáveis, representa sérias ameaças à privacidade e à segurança. A criptografia desempenha um papel vital na proteção das pessoas contra a vigilância e a manipulação dos governos, especialmente em uma era de crescente propaganda e manipulação nas mídias sociais. O uso de tecnologias como hardware wallets e sistemas de votação seguros destaca a importância de proteger a privacidade ao mesmo tempo em que abraçamos avanços tecnológicos.
O Futuro das Votações: Blockchain e Além
Na Estônia, a digitalização das eleições tem apresentado resultados promissores, aumentando a transparência e a eficiência, ao mesmo tempo que reduz a coerção e a compra de votos. O potencial da tecnologia blockchain para revolucionar sistemas eleitorais é significativo, oferecendo mecanismos de votação seguros e transparentes. No entanto, desafios permanecem, incluindo custos, complexidade e riscos de segurança, que requerem maior engajamento político e consenso. Sistemas financeiros acessíveis e inclusivos também desempenham um papel vital para garantir que os benefícios dos avanços tecnológicos sejam acessíveis a todos os segmentos da sociedade.
Conclusão
Conforme o Brasil embarca na jornada de seu CBDC e o mundo em geral enfrenta o impacto das criptomoedas e da tecnologia blockchain, é fundamental encontrar um delicado equilíbrio entre o progresso e a salvaguarda das liberdades individuais. Embora o potencial das criptomoedas e do blockchain seja vasto, também é crucial abordar preocupações com a privacidade, desafios regulatórios e a possibilidade de vigilância e controle governamental. A educação, o debate público e uma abordagem aberta serão fundamentais para moldar o futuro dessa tecnologia transformadora em benefício da sociedade.
Ouça/assista o spaces completo em: Twitter: https://twitter.com/BrCointelegraph/status/1681005732123013120 Youtube (@eddieoz): https://www.youtube.com/watch?v=lxf3BdMOe50
-
 @ bcea2b98:7ccef3c9
2023-07-20 18:13:11
@ bcea2b98:7ccef3c9
2023-07-20 18:13:11Atop a majestic mountain called Mt. Gox, a tale unfolded that would forever be etched in the history of cryptocurrency. This is the story of a legendary exchange, a hub of digital treasures, and the challenges it faced along the way.
In the early days of Bitcoin, when the world was just beginning to grasp the concept of digital currencies, a passionate entrepreneur named Jed McCaleb founded a platform called Mt. Gox. Located high above the clouds on the slopes of Mt. Gox, the exchange quickly became the center of the Bitcoin universe.
Bitcoin enthusiasts from all corners of the globe flocked to Mt. Gox, eager to trade, buy, and sell their digital coins. It became a bustling marketplace, a hub of innovation, and a symbol of the emerging cryptocurrency ecosystem.
As the popularity of Bitcoin skyrocketed, so did the demand for Mt. Gox's services. The exchange handled an immense volume of transactions, becoming the largest Bitcoin exchange in the world. Its name echoed throughout the digital realm, synonymous with the promise and potential of the cryptocurrency revolution.
However, as with any great tale, challenges arose. In 2011, a cyber attack targeted Mt. Gox, leading to the theft of a substantial number of Bitcoins. This event served as a wake-up call, revealing vulnerabilities within the exchange and prompting the need for heightened security measures.
The incident didn't dampen the spirit of Mt. Gox. The team worked tirelessly to recover from the attack, implementing new security protocols and earning back the trust of its users. Mt. Gox emerged stronger than ever, serving as a beacon of stability in the ever-evolving cryptocurrency landscape.
But the story of Mt. Gox took an unexpected turn. In 2014, another significant blow struck the exchange. It was discovered that a substantial number of Bitcoins were missing from Mt. Gox's vaults. The magnitude of the loss sent shockwaves throughout the cryptocurrency community and shook the foundations of the industry.
As the truth emerged, it became clear that Mt. Gox faced insurmountable financial challenges. The exchange was forced to declare bankruptcy, leaving its users devastated and questioning the future of digital currencies.
Yet, amidst the chaos, the story of Mt. Gox served as a catalyst for change and resilience in the cryptocurrency world. It brought to light the need for enhanced security practices, regulatory oversight, and a renewed commitment to building trustworthy platforms for the exchange of digital assets.
Over time, the lessons learned from Mt. Gox's history paved the way for greater transparency, improved infrastructure, and the emergence of more secure cryptocurrency exchanges. It became a cautionary tale, reminding the industry of the importance of accountability, investor protection, and responsible innovation.
Today, as we reflect on the history of Mt. Gox, we see a story of both triumph and adversity. It stands as a reminder that the cryptocurrency landscape is still in its early stages, evolving and maturing with each passing day.
So, dear listener, let the tale of Mt. Gox serve as a lesson in resilience and growth. As the cryptocurrency world continues to advance, let us navigate the digital landscape with caution, learn from the past, and work towards a future where innovation and security walk hand in hand.
-
 @ aa55a479:f7598935
2023-07-19 17:54:44
@ aa55a479:f7598935
2023-07-19 17:54:44Test
-
 @ a012dc82:6458a70d
2023-07-24 02:45:00
@ a012dc82:6458a70d
2023-07-24 02:45:00Table Of Content
- BlackRock's Bold Move
- The Potential Impact on Bitcoin's Price
- The Role of Retail Investors
- The Future of Bitcoin
- Conclusion
- FAQ
The world of digital assets has been gaining significant traction, with traditional financial firms finally acknowledging that cryptocurrencies are here to stay. This shift in perception is not without reason. The potential of cryptocurrencies to revolutionize financial transactions, coupled with their growing acceptance as a legitimate asset class, has made them impossible to ignore. Among the key players making waves in the crypto space is BlackRock, the world's largest asset manager, boasting $9 trillion in assets under management (AUM). The firm recently filed for permission to create a "spot market" Bitcoin-based exchange-traded fund (ETF), a move that could potentially slingshot Bitcoin's price skyward. This move signifies a significant shift in the traditional finance world's approach to digital assets, marking a new era of acceptance and integration.
ETF Propel Bitcoin Price
BlackRock's Bold Move
BlackRock's decision to venture into the Bitcoin ETF space is a significant development in the crypto industry. The United States Securities and Exchange Commission has historically been resistant to Bitcoin ETFs, making BlackRock's move a bold one. This decision is not just a gamble but a calculated move based on the growing demand for digital assets and the potential they hold. This move, coupled with similar actions from other financial giants like Fidelity Investments, Charles Schwab, and Citadel, has already had a positive impact on the crypto market. The announcement alone has boosted crypto trading markets, with Bitcoin gaining 20% in a week and surpassing the $30,000 mark for the first time since April. This price surge is a testament to the influence these financial institutions wield in the market.
The Potential Impact on Bitcoin's Price
The creation of a Bitcoin ETF by a firm as influential as BlackRock could potentially transform the Bitcoin market. Bitcoin's fixed supply limit of 21 million BTC and its existing inventory's relative illiquidity could lead to a supply-demand imbalance. With 68% of BTC in circulation remaining unmoved in the past year, there isn't a lot of stock available for BlackRock and other interested parties to snap up. If demand exceeds supply, it could inevitably lead to price gains for Bitcoin. This scenario could potentially create a bullish market for Bitcoin, driving its price to new heights. However, it's important to note that this is a hypothetical scenario, and the actual impact will depend on a variety of factors, including regulatory decisions and market dynamics.
ETF Propel Bitcoin Price
The Role of Retail Investors
While institutional investors like BlackRock play a significant role in the crypto market, the role of retail investors cannot be overlooked. The participation of ordinary crypto users might be necessary to stabilize the price of Bitcoin. As more institutional investors enter the market, retail investors may also be encouraged to participate, potentially leading to an increase in trading volume and further price appreciation. Retail investors bring a different dynamic to the market. Their participation could lead to increased liquidity and could also serve as a counterbalance to the large trades made by institutional investors. The involvement of retail investors could also lead to a more diverse and robust market, contributing to the overall health and stability of the Bitcoin ecosystem.
The Future of Bitcoin
The entry of BlackRock and other major asset managers into the Bitcoin space could potentially stabilize Bitcoin's price at a substantially higher level than the current $30,000. However, long-term price stability also requires broad retail participation. The involvement of large financial institutions in the digital asset market has arguably had a calming effect on retail investors, which could lead to increased acceptance and trading volume in the coming months. As the market matures and regulatory clarity improves, we could see a more balanced market with both institutional and retail investors playing significant roles. This balance could contribute to the long-term stability and growth of Bitcoin's price.
ETF Propel Bitcoin Price
Conclusion
The involvement of large financial institutions, such as BlackRock, in the crypto markets represents a significant shift and a decisive moment for these markets, both in the U.S. and globally. While it's still early days, the potential impact of BlackRock's proposed Bitcoin ETF on Bitcoin's price cannot be underestimated. If institutional investors continue to enter the market, their demand could certainly drive prices higher, potentially propelling Bitcoin's price to the moon. However, it's important to remember that the crypto market is highly volatile, and investors should always do their due diligence before making investment decisions. The future of Bitcoin and other cryptocurrencies remains uncertain, but the involvement of major financial institutions like BlackRock signals a promising future for these digital assets.
FAQ
What is BlackRock's recent move in the crypto space?
BlackRock, the world's largest asset manager, has filed for permission to create a "spot market" Bitcoin-based exchange-traded fund (ETF).
How could BlackRock's Bitcoin ETF impact Bitcoin's price?
The creation of a Bitcoin ETF by BlackRock could potentially increase demand for Bitcoin. Given Bitcoin's fixed supply limit, this could lead to a supply-demand imbalance and potentially drive up Bitcoin's price.
What role do retail investors play in the Bitcoin market?
Retail investors play a significant role in the Bitcoin market. Their participation could lead to increased liquidity and could serve as a counterbalance to the large trades made by institutional investors.
Could BlackRock's Bitcoin ETF stabilize Bitcoin's price?
The entry of BlackRock and other major asset managers into the Bitcoin space could potentially stabilize Bitcoin's price at a substantially higher level than the current one. However, long-term price stability also requires broad retail participation.
That's all for today, see ya tomorrow
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Twitter: @croxroadnews
Instagram: @croxroadnews.co
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
 @ 32e18276:5c68e245
2023-07-19 02:56:47
@ 32e18276:5c68e245
2023-07-19 02:56:47I’m so lazy I’m thinking of running the damus merch store via stateless and serverless lightning payment links. All data is collected and stored in the lightning invoice descriptions which are fetched from your node. You can do this without having to run any server code except a lightning node!
This is the same tech we used when selling merch as at bitcoin Miami. It was extremely reliable. I love these things, they are so easy. Integrating with the legacy fiat system is such a pita, It may just be a lightning-only store for now because of how simple this is. Here's what a lightning payment link looks like:
http://lnlink.org/?d=ASED88EIzNU2uFJoQfClxYISu55lhKHrSTCA58HMNPgtrXECMjQuODQuMTUyLjE4Nzo4MzI0AANgB6Cj2QCeZAFOZ1nS6qGuRe4Vf6qzwJyQ5Qo3b0HRt_w9MTIwJm1ldGhvZD1pbnZvaWNlfG1ldGhvZD13YWl0aW52b2ljZSZwbmFtZWxhYmVsXmxubGluay0mcmF0ZT04BERlYXRoIFN0YXIABQAAAGQGQW4gb2JqZWN0IG9mIHVuZmF0aG9tYWJsZSBwb3dlcgAHEwhodHRwczovL3VwbG9hZC53aWtpbWVkaWEub3JnL3dpa2lwZWRpYS9lbi9mL2Y5L0RlYXRoX3N0YXIxLnBuZwA=
How it works
The entire product page is stored as data in the url. When a customer click the link, the product info is decoded and rendered as a webpage. The data in the url includes
- The product name
- Description
- Price in sats
- Product image url
- Fields to collect data from the user
- Lightning node address
- Lightning node rune for fetching and waiting for invoice payments
This works thanks to a javascript library I created called "lnsocket". It allows you to connect to your CLN node over websockets. Once the user fills out all of the info, a new lightning invoice is fetched with this information in the description, by connecting directly to your node. This connection is end-to-end encrypted thanks to the lightning protocol itself.
To your lightning node, it looks like another lightning node is connecting to it, but in reality it's just a dumb client asking for things.
At this point, custom lightning packets called "commando" packets are sent to your node which asks your node to run certain commands. CLN authenticates these packets using the rune and then returns a response. This is pretty much the same as calling these commands directly on your lightning node, except now someone is doing it from a browser in a secure way!
Why not just run btcpayserver?
btcpayserver is cool and is more powerful, but I like exploring simpler ways to do things that don't require running lots of software which can be challenging for many non-technical people. You shouldn't have to become a server administrator to start accepting payments. It should be as simple as running a bitcoin and lightning node, pushing all of the application logic to the clients.
This is a similar philosophy to what we have in the nostr space. Let's make it easier for people to use self-sovereign tools. Everyone deserves freedom tech.
Anyways, I'm still working on https://lnlink.org. I just added images and nostr address support! You can make your own payment links here! Try it out:
http://lnlink.org/?d=ASED88EIzNU2uFJoQfClxYISu55lhKHrSTCA58HMNPgtrXECMjQuODQuMTUyLjE4Nzo4MzI0AANgB6Cj2QCeZAFOZ1nS6qGuRe4Vf6qzwJyQ5Qo3b0HRt_w9MTIwJm1ldGhvZD1pbnZvaWNlfG1ldGhvZD13YWl0aW52b2ljZSZwbmFtZWxhYmVsXmxubGluay0mcmF0ZT04BERlYXRoIFN0YXIABQAAAGQGQW4gb2JqZWN0IG9mIHVuZmF0aG9tYWJsZSBwb3dlcgAHEwhodHRwczovL3VwbG9hZC53aWtpbWVkaWEub3JnL3dpa2lwZWRpYS9lbi9mL2Y5L0RlYXRoX3N0YXIxLnBuZwA=&edit=1
-
 @ 0d119c15:6d7b1b39
2023-07-24 01:43:29
@ 0d119c15:6d7b1b39
2023-07-24 01:43:29Source: https://www.ptt.cc/bbs/marvel/M.1460906540.A.189.html
作者snowsummersp (江南) 看板marvel 標題[創作] 學長的秘密 時間Sun Apr 17 23:22:17 2016
在竹科上班的我,過著相當安逸的生活,雖然沒有年薪百萬,但是養活自己 倒是不難,雖然沒有滿八個小時就下班,但也來得及回家看八點檔,所以,待在 這間公司已經半年的我,絲毫沒有任何想離職的理由。
時間已經七點半了,偷偷瞄了一下主管的座位,發現他已經不在位置上了, 因此我也就東西收一收,準備離開公司。看著還在努力上批踢踢拚上班時數的 學長,內心搖了搖頭,心想著,這樣生活也太沒有品質了吧? 於是我走了過去, 拍了拍學長的肩膀。 「Alan,還不下班阿?」Alan是學長的名字。
此時的學長還在上著西斯版,看著女版友分享的自拍照,色瞇瞇地笑著。 「這個正喔!」我頭湊過去,看了一下自拍照。 「Mark你幹嘛!?」學長一付被抓 姦在床的表情,急急忙忙把圖關掉。
「我說Alan阿,老大不是交代你一個很急的案子嗎? 可是我看你今天就一直在逛 批踢踢,這樣明天報告你不就要爆炸了?」雖說Alan是我學長,但由於已經混得蠻熟 了,所以我說起話來也是沒大沒小。
「爆炸?你不要太小看我啊,雖然我白天沒甚麼在上班,但半夜的我可是相當的 威猛阿,你應該有聽過我的稱號吧,"軟體部拓海"。」學長驕傲地抬起頭,相當有自 信的對我說。
「聽是聽過,但我始終不明白為什麼你叫做拓海,該不會你家賣豆腐的吧?」正當 我在說話的時候,隔壁部門同事收拾行李,默默的下班了。
「當然不是,拓海的意義就是我只有在凌晨的時候,才是軟體界的霸主,憑著一台 WinXP,在最難的程式碼裡面甩尾,並且寫出來的code,可是相當的漂亮,連我自己都 驚嘆阿!」
「喔...是喔。」我無言地看著異常活潑的學長,轉過身,我決定還是先回家好了。
正當我在刷卡的時候,「相信我,明天早上我程式就完成了!」學長還在背後喊著。
但,驚訝的是,學長他真的完成了主管交付的程式,連部門裡的資深工程師,在
前幾天都說要完成這個功能,至少要花一個禮拜以上的時間,沒想到學長他三天就完成
,而且實際上他應該沒花到三天,因為他這三天的白天都在打混,不是FB就是批踢踢。
「如何,我是不是說到做到阿?」學長痞痞的對我說。
「幹!」我只回他一個字。因為剛剛主管說我來了也算一段時間了,所以決定讓我
獨自開發一個之前學長留下來的屎缺,要我在下禮拜報告整個程式架構,以及加入一個
龐大的演算法。
「哈! 哈! 哈! Mark你要加油啊。」說完,學長又回到他的位置上玩野豬騎士了。
「唉...」我虛弱的嘆了一口氣,看來我的好日子過完了。
眼看著明天就到了週報的日子,但我不僅是演算法生不出來,連程式碼都一知
半解,這樣下去,我明天報告絕對是會飛高高。
「Mark,程式那邊寫的怎麼樣了?」PM假好心的過來問我。
「快了,今天再加個班應該就可以搞定了。」我瀟灑的編了個謊言。
「哦?那明天看你表演囉?」PM假笑的說。
我真的很想一拳打爆他的臉,但我不行。
抓了抓頭,我已經呈現半放棄狀態了,拿起桌上的菸,我往公司的吸菸區走,
剛好看到Alan也在那裏抽菸。
「Mark?不是說你已經戒菸了嗎?」學長劈頭就問了我。
「幹,最近真的太煩了啦,老大要我做的那個,我根本讀不懂,更何況還要寫
一段新的演算法。」我用力的吸了一口菸說。扶著牆,看了看樓下,這個高度跳下去
死不了的。
「廢話,你一定看不懂的阿,他可是公司的傳說級大學長寫的程式碼耶。」Alan
笑了笑對我說。
「傳說的學長?」我之前沒聽說過這個人。
「沒錯,但是某個原因,導致這個學長變成公司的佛地魔,也就是"不能說的人"。」
「挖靠,聽起來也太神秘了吧!」
「是阿,這學長的程式語言幾乎每一樣都會,舉凡iOS, Android, Web, Firmware
,只要是公司的產品,他基本上都是主力。而且厲害的是,不管交付給他多難的任務,
他都可以在一個禮拜就寫完。」Alan如數家珍的說著。
「這麼厲害的人,那公司怎麼捨得他跳槽? 應該不管怎樣都要把他留在公司啊!
如果他能幫我寫code就好了...」
「公司當然是把他留住了,只是...」Alan欲言又止的說。
「只是甚麼?」我不明所以的問,因為如果留在公司的話,那他應該就不會成為
"不能說的人"了吧。
「只是...他後來在公司座位上自殺了。」
突然一陣強風颳來,我雞皮疙瘩都起來了。
「恩...」我點了點頭,也就沒有再說甚麼。
已經晚上11點多,但我的PPT還在第一面,我覺得我想到我的頭都快破了,但還
是甚麼東西都擠不出來。
「Mark還不下班?」Alan走過來問我。
「你才是為啥不下班?你這禮拜不是沒事嗎?」我白了他一眼,環顧了一下公司,
居然只剩我們兩個人而已。
「軟體部拓海說不定可以幫你啊!」
「好啊,你看看。」之後我大致介紹了一下我研究到現在的心得。
但我得到的回答是,「哎呀,我好像完全不懂耶。」
「算了,我放棄了,明天乾脆提辭呈直接離職算了。」我一氣之下這麼說。
Alan皺著眉頭,閉上眼睛,像是下了很大的決心一樣,吐了一口大大的氣,然後
對我說,「我有辦法。」
「辦法?甚麼辦法?拓也哥。」我嘲諷式的叫他拓也。
「媽的,是拓海!」Alan怒瞪了我一眼,「你還記得我跟你說過那個傳說的學長
嗎?」
「當然還記得阿,公司的佛地魔,我這個程式原撰寫者。怎麼了?」
「他當初上吊的座位就是我現在的座位。」Alan小小聲地說,並且指了指他的座位。
我瞪大眼睛,但也沒說半句話。
「我知道你一定覺得奇怪,為什麼我要現在跟你說這個。」他說話越說越小聲,
「學長他是一個工作狂,他到現在都還會來公司寫程式。」
「寫程式?來公司?他不是已經?」我看了一眼Alan又看了一眼他的座位。
「對啦,我就直接了當的跟你說,我的程式都是他寫的。」Alan說著像是一件稀
鬆平常的事情。
「靠邀,真的假的啦。」
「真的啦,你要不要信我一次?」
「信你甚麼啦?」
「信不信啦?」
「信,我信,可以了吧?」
「OK。」說完,Alan就主動去把我的桌機關機,然後把桌機移動到他自己的位置
上,開了機,然後我自動自發的Key了開機密碼。
確認開好機之後,Alan看了看手錶,「走吧,去吃宵夜。對了,帶上你的東西。」
「宵夜?」我傻眼的問。
「你信不信我?」
「痾...信。」我心裡想著死馬當活馬醫,反正在這裡耗一個晚上,我也是寫不出
來的。
「走吧。」
吃完了永和豆漿之後,時間已經逼近快凌晨兩點了。我跟Alan搭了電梯,到了刷
卡的地方,我正準備拿出卡片時,Alan示意要我等一下,並且用手指了指門內。
我湊了過去看,Alan的座位前面,有一團白白的霧,讓我看不清楚螢幕。
Alan轉過身,按了向下的電梯,對我說,「再去吃一頓吧!讓學長再忙一下。」
丈二金剛摸不著頭腦的我只好跟著Alan下去了。
「Mark,你這次的演算法真的有點難度喔,大學長居然解到兩點都還沒搞定。」
Alan笑笑地說。
「所以剛剛那團白白的霧?」我靈光一閃的說。
「沒錯!傳說的學長再幫你寫code,有沒有很感動阿?」
「幹,真的假的啊...」
「不要不相信。對了,你東西都有帶吧?我看今天晚上就先回家吧,明天早一點上班,
把你的電腦搬回你的位置上,然後就是見證奇蹟的時刻了。」
隔天一早,我帶著既緊張又興奮的心情開了機,把Visual Studio打開,我下巴差
點掉下來,傳說學長真的把演算法寫好了!而且程式還寫得很乾淨。
報告的時候,整個部門由上到下,從主管、PM、資深RD、測試人員,當他們知道
我一個禮拜就搞定之前學長留下來的大屎缺,是怎麼樣的崇拜我,以及響起如雷的掌聲
,我就不贅言了。
「你有甚麼願望想要實現的嗎?」主管看著我像是看到哈利波特的表情對我說。
「願望嗎?」我瀟灑的說,「送我一把鮮花吧,我想弔念某人。」
當天晚上,我把三根菸當作三炷香,肯德基全家餐當作牲禮,以及鮮花,感謝傳
說學長所做的一切,雖然主管又交給了我一個更困難的任務,但我已經再也不害怕
了,因為有傳說的學長在。
幾天後,我開心的在逛西斯版的時候,Alan氣沖沖的揍了我一拳。
「幹!怎樣?幹嘛打我?」
「你做了甚麼好事!」Alan沒有控制音量的大喊出來,不僅周遭的同事,連在小
房間的總經理都探出頭來一探究竟。
「甚麼意思?」我一頭霧水。
「學長投胎了啦!幹!」
「投胎很好啊!」難道是我那天晚上感謝學長的關係?
「投胎怎麼幫我們寫code?」Alan大吼著說。
「幹!」我也跟著大吼。
-- ※ 發信站: 批踢踢實業坊(ptt.cc), 來自: 118.167.59.173 ※ 文章網址: https://www.ptt.cc/bbs/marvel/M.1460906540.A.189.html
-
 @ 9ecbb0e7:06ab7c09
2023-07-24 01:33:30
@ 9ecbb0e7:06ab7c09
2023-07-24 01:33:30Tras una jornada de incertidumbre, España ha votado en sus elecciones generales. Alberto Núñez Feijóo y el PP consiguieron 136 escaños (47 más que en 2019), pero ni siquiera aliándose con VOX, que apenas obtuvo 33 (19 menos que en los pasados comicios), tiene mayoría para gobernar. La suma de la coalición deja a la derecha siete escaños por debajo de los que necesitarían.
Del otro la lado del espectro político, Pedro Sánchez, actual presidente, obtuvo 122 diputados. Este resultado fue incluso mejor que el obtenido por el PSEO hace cuatro años, pero muy lejos de los 176 puestos requeridos para continuar en el poder, incluso con los 31 escaños que consiguió Sumar, se quedaría muy por debajo.
Esto deja al PP en una complicada situación, pues pese haber obtenido más votos (300 000 más que los socialistas), no puede tomar el control de la nación. Este resultado ha roto los pronósticos de las encuestas previas que daban como ganadora a la derecha por amplio margen.
Lo acontecido hoy, apunta la cadena de radio SER, podría provocar una repetición electoral si los partidos no logran negociar y sumar escaños a uno u otro matiz político. Los números son tan estrechos que dejan la gobernabilidad en el aire, a menos que Pedro Sánchez pacte con Junt y fuerzas regionales del País Vasco, lo que podría dejarlo en el gobierno.
¿Qué ha dicho Feijóo?
El presidente del PP ha pedido a los demás partidos que no bloqueen su investidura. Sostuvo que todos los gobernantes más votados de lecciones previas han ganado y por eso pide lo mismo para él. “No hay ningún presidente de España que haya gobernado tras perder las elecciones”, ha insistido, pensando en que Sánchez puede bloquearlo y mantenerse en la Moncloa.
“Nuestra obligación es que no se abra un periodo de incertidumbres en España. Los españoles hoy nos han dado la confianza en el PP y también han dicho a todos los partidos del arco que dialoguemos. Como candidato del partido más votado mi deber es abrir el diálogo para liderarlo e intentar gobernar el país de acuerdo con los resultados electorales”, ha dicho entre vítores.
Este domingo acudieron a votar más de 24 millones de electores. Según los datos del Ministerio del Interior la participación fue de aproximadamente el 70,40% del total.
Pese a estar en verano los españoles acudieron a las urnas confirmando la tendencia de que el electorado vota más en unos comicios que pueden representar un cambio. También fue muy elevado el número de votos por correo (más de 2,47 millones).
-
 @ 32e18276:5c68e245
2023-07-17 21:55:39
@ 32e18276:5c68e245
2023-07-17 21:55:39Hey guys!
Another day, another TestFlight build. This fixes many mention bugs and includes bandwidth improvements.
During nostrica, jack told everyone to open their phones and say GM to fiatjaf. This actually brought down nostrica's wifi! Damus is really dumb when it first opens and makes many requests. Sometimes hundreds (nip05 validation, etc). This build fixes all those issues. Damus will no longer:
- Make hundreds of nostr address validation requests.
- Make tons of duplicate lnurl requests when validating zaps
nostr address validation only happens when you open someones profile now.
This build also fixes some annoying mention issues. If you forget a space when mentioning someone, it will automatically add it.
I've also removed the restriction where you were not allowed to login to "deleted" accounts. This was way too confusing for people, and logging into a deleted account will allow you to reset the profile information and get it going again. You're welcome NVK.
Another thing that was added in this build is support for
_usernames in nostr addresses. This will hide your full nostr address username when used. Damus will also hide your username if it matches your profile username. Damus always did this before but it was incorrect. Now it will show your full nostr address (nip05) with its proper username. You can stop bugging me about this now Semisol.Last but not least there are some small tweaks to longform note padding. Nothing too crazy but it does make notes like this look less cramped.
Until next time!
Added
- Show nostr address username and support abbreviated _ usernames (William Casarin)
- Re-add nip05 badges to profiles (William Casarin)
- Add space when tagging users in posts if needed (William Casarin)
- Added padding under word count on longform account (William Casarin)
Fixed
- Don't spam lnurls when validating zaps (William Casarin)
- Eliminate nostr address validation bandwidth on startup (William Casarin)
- Allow user to login to deleted profile (William Casarin)
- Fix issue where typing cc@bob would produce brokenb ccnostr:bob mention (William Casarin)
-
 @ 32e18276:5c68e245
2023-07-16 22:47:17
@ 32e18276:5c68e245
2023-07-16 22:47:17Hey guys, I just pushed a new Damus update TestFlight. This should drastically improve longform event rendering. Let me know if you find any bugs!
Full Changelog
Added
- New markdown renderer (William Casarin)
- Added feedback when user adds a relay that is already on the list (Daniel D'Aquino)
Changed
- Hide nsec when logging in (cr0bar)
- Remove nip05 on events (William Casarin)
- Rename NIP05 to "nostr address" (William Casarin)
Fixed
- Fixed issue where hashtags were leaking in DMs (William Casarin)
- Fix issue with emojis next to hashtags and urls (William Casarin)
- relay detail view is not immediately available after adding new relay (Bryan Montz)
- Fix nostr:nostr:... bugs (William Casarin)
-
 @ 78733875:4eb851f2
2023-07-14 22:25:21
@ 78733875:4eb851f2
2023-07-14 22:25:21"The computer can be used as a tool to liberate and protect people, rather than to control them," as Hal Finney wrote so presciently 30 years ago.[^fn-hal]
The goal of OpenSats is to help build the tools that Hal alluded to. Tools that liberate and protect, rather than systems that control and oppress. Many tools still have to be built. Many tools still need to be improved. However, "the universe smiles on encryption," as Assange so aptly put it.[^fn-assange]
We believe that freedom tech is what carries this smile forward, which is why we are delighted to announce grants for over a dozen projects in the bitcoin & lightning ecosystem.
[^fn-hal]: Hal Finney: Why remailers... (November 1992)
[^fn-assange]: Julian Assange: A Call to Cryptographic Arms (October 2012)
The following open-source projects were selected by the OpenSats board for funding:
- Payjoin Dev Kit
- Bolt12 for LND
- Splicing
- Raspiblitz
- Labelbase
- BTCPay Server
- ZeroSync
- Mutiny Wallet
- next-auth Lightning Provider
- Cashu
- lnproxy
- Blixt Wallet
Let's take a closer look at each to understand their goal and how it aligns with the OpenSats mission.
Payjoin Dev Kit
Payjoin brings privacy to bitcoin without changing the way you're used to using it. Payjoin transactions look no different from normal activity on-chain, so they boost everyone's privacy, even those who don't payjoin, and foil chain surveillance.
Payjoin is easy to integrate and falls back to working defaults where it isn't supported, but it can only take off when senders and receivers include standard payjoin support in their software. Payjoin Dev Kit makes it easy for wallet developers to integrate BIP 78 standard payjoins everywhere, having working reference integrations for Bitcoin Core, LND, and BDK.
Repository: github.com/payjoin
License: MITBolt12 for LND
Bolt12 brings a new invoice format, enabling static invoices (offers) as well as recurring payments. It adds support to receive payments in a lightning-native way without using a web server. It also uses Blinded Paths to disguise the destination of a node both when fetching the invoice and when paying. This improves privacy and, therefore, security for the receiver of the payment.
Consequently, Bolt12 makes it much easier to receive and send payments without any third-party infrastructure in a native-lightning way. Static invoices make donations and recurring payments much easier.
Repository: lightningnetwork/lnd
License: MITSplicing
Splicing is the ability to resize Lightning channels on-the-fly, giving users of the Lightning Network many additional benefits that were not intuitively obvious at first. Splicing scales Lightning by removing a fundamental limitation. Removing this limitation increases fungibility and lowers blockspace usage, an important step towards maturing the Lightning network and enabling the onboarding of millions, and ultimately billions, of people.
Repository: ddustin/splice
License: BSD-MITRaspiblitz
Raspiblitz is a do-it-yourself node stack that allows you to run a Lightning Node together with a Bitcoin Core full node on your Raspberry Pi. While the Raspberry Pi is the most common hardware running this particular software, it was developed to support multiple hardware platforms and can run on bare metal servers too.
The open-source project was started in 2018 as part of a Lightning hackathon in the German Bitcoin space. Since then, it has grown to over 150 contributors and 2000 stars on GitHub. The software integrates dozens of services and tools via its plugin system and sports advanced features like touchscreen support, channel autopilot, backup systems, DynDNS, SSH tunneling, and more.
Repository: raspiblitz/raspiblitz
License: MITLabelbase
Labelbase is a label management service for Bitcoin transactions and addresses. It provides features for adding labels, importing and exporting labels, and offers a public API for integration with wallets and existing workflows.
Labelbase supports BIP-329, a format for unifying label data. The goal of the project is to offer a convenient solution for managing labels associated with Bitcoin transactions and addresses across wallets and other tools. By providing a unified label management interface, Labelbase enhances the user experience, improves privacy, and promotes better organization and understanding of Bitcoin transactions.
Repository: Labelbase/Labelbase
License: MITBTCPay Server
BTCPay Server is a free, open-source & self-hosted bitcoin payment gateway that allows self-sovereign individuals and businesses to accept bitcoin payments online or in person without added fees.
At its core, BTCPay Server is an automated invoicing system. Merchants can integrate the software with their website or shop, so customers are presented with an invoice upon checkout. The status of the invoice will update according to settlement, so merchants can fulfill the order at the appropriate time. The software also takes care of payment refunding and bitcoin management alongside many other features.
Repository: btcpayserver/btcpayserver
License: MITZeroSync
While ZeroSync is still at an early stage, its promise is to allow verification of Bitcoin's chain state in an instant. It offers compact cryptographic proofs to validate the entire history of transactions and everyone's current balances.
The first application is to "zerosync" Bitcoin Core in pruned mode. The long-term vision for ZeroSync is to become a toolbox for custom Bitcoin proofs.
Repository: zerosync/zerosync
License: MITMutiny Wallet
Mutiny Wallet is a web-first wallet capable of running anywhere, providing instant onboarding and platform censorship resistance. It is self-custodial, privacy-focused, user-friendly, and open-sourced under the MIT license.
The wallet has a strong focus on privacy, scalability, and accessibility. In addition to features that you would expect a regular lightning wallet to have, the team is working to incorporate Nostr-related features into the wallet, such as a feed of friends' Zaps, native Zap sending and receiving, a lightning subscription specification for services such as nostr relays, and a P2P DLC marketplace. The team's goal is to provide users with a seamless experience, combining the power of Bitcoin and Lightning with social media in a way that matches the Bitcoin ethos.
Repository: MutinyWallet
License: MITnext-auth Lightning Provider
The goal of this project is to implement an authentication provider for next-auth, an authentication provider for the popular open-source framework NextJS. The next-auth framework has nearly 500k weekly downloads and powers the authentication of many modern web, mobile, and desktop apps. Having a plug-and-play Provider for Lightning makes integration easier and more attractive for developers.
Repository: jowo-io/next-auth-lightning-provider
License: ISCCashu
Cashu is a Chaumian ecash system built for bitcoin that brings near-perfect privacy for users of custodial bitcoin applications. A Cashu ecash mint does not know who you are, what your balance is, or who you're transacting with. Users of a mint can exchange ecash privately, without anyone being able to know who the involved parties are.
Payments are executed without anyone able to censor specific users. There are multiple implementations of the Cashu protocol. Popular open-source wallets are Cashu Nutshell, Cashu.me, and Nutstash.
Repository: cashubtc/cashu
License: MITlnproxy
lnproxy is a simple privacy tool that empowers users of custodial Lightning wallets with better payment destination privacy and sovereign node runners with enhanced receiver privacy. lnproxy works like a "poor man's" rendezvous router, providing privacy for users without taking custody of their funds. The project encompasses an LNURL-style protocol specification and a collection of open-source implementations of lnproxy clients and a relay.
Repository: lnproxy/lnproxy
License: GPL 3.0 & MITBlixt Wallet
Blixt is a non-custodial wallet for bitcoiners who want to give Lightning a try. It runs on Android, iOS, and macOS. It is easy to use and straightforward to set up, making it a user-friendly option to get started with Lightning.
Blixt uses LND and Neutrino under the hood, directly on the phone, respecting your privacy. The wallet does not use any centralized servers for doing transactions. Channels are opened automatically on the user's behalf, making it easy to get up and running on Lightning.
Repository: hsjoberg/blixt-wallet
License: MIT
In addition to the software projects listed above, three educational initiatives were selected for funding:
- Bitcoin Education in Nigeria is an initiative started and led by Apata Johnson. Apata's project aims to educate youths on bitcoin and the opportunities it brings for the people living in the rural areas of Nigeria.
- 21 Ideas is a project that aims to bring quality Bitcoin education to Russian citizens. Tony and others have been working for many years on translations, original material, and hands-on tutorials for beginners. We believe that education is paramount to proper Bitcoin use, and localization is paramount for everyday citizens to properly grasp the importance as well as the novel concepts of bitcoin.
- CoreDev.tech is organizing recurring developer events, which are all about bringing devs together so that they can hack on Bitcoin Core and related software.
We received hundreds of applications in the last couple of months, which is a fantastic signal and something we are delighted about. Some applications are still being reviewed by the OpenSats board, as we try our best to assess feasibility, alignment, and potential impact of each project. We will announce additional grants as applications pass our grant selection process.
Unfortunately, we were unable to fund all of the proposals that were sent to us. Please don't hesitate to apply again in case your application was rejected this time around. The applicant pool was very competitive, which is a great thing to see in and of itself.
Grants for the projects above are funded by contributions to the Bitcoin General Fund. Our operations as well as our grant programs are made possible by generous donors like you. If you want to help fund the Bitcoin ecosystem, please donate to the Bitcoin General Fund.
Our team is screening applications constantly, and we will announce new grants and funding opportunities as they arise. If you are working on an open-source project in and around bitcoin, and you think your work is aligned with the OpenSats mission, please apply for funding.
-
 @ 9ecbb0e7:06ab7c09
2023-07-24 01:24:29
@ 9ecbb0e7:06ab7c09
2023-07-24 01:24:29El ministro de Energía y Minas de Cuba, Vicente de la O Levy, reconoció en la Asamblea Nacional del Poder Popular (ANPP) que al menos dos patanas turcas de generación eléctrica habían abandonado Cuba recientemente en cumplimiento de los contratos firmados. Ahora el país tiene 170 megawatts (MW) menos de energía para afrontar la etapa de verano donde más energía se consume.
En abril pasado, la Isla llegó a contar con ocho patanas de generación que se le contrataron a la empresa turca Karadeniz Holding para apoyar la producción de electricidad en las viejas plantas termoeléctricas del país, muchas de las cuales están paralizadas por avería o mantenimiento.
Precisamente en esos meses el nuevo ministro designado por Miguel Díaz-Canel dijo que la contratación del costoso servicio de generación eléctrica mediante patanas flotantes a Turquía fue el “mejor negocio que se hizo”.
El ministro De la O Levy destacó que durante el primer semestre se logró incrementar la generación en Energas a más de 300 MW, gracias a la terminación de dos pozos de gas. Esto permitió subir la producción de gas a más de 400.000 metros cúbicos diarios; sin embargo, sigue compleja la situación para acceder al gas licuado de petróleo para la cocción de alimentos.
Por otra parte, las acciones de reparación en algunas termoeléctricas han permitido que los apagones en el primer mes del verano no sean tan prolongados como en los dos periodos estivales previos (años 2022 y 2021), que incluso fueron el detonante para las protestas masivas del 11 de julio.
No obstante, siguen las tensiones con la disponibilidad de combustible importado desde el exterior, que también se unen a problemas logísticos en la distribución. Por ejemplo, hay una baja disponibilidad técnica de los carros cisterna de CUPET (Empresa Cuba Petróleo) y dificultades en el transporte por ferrocarriles y buques.
Una nota oficial de la Unión Eléctrica de Cuba (UNE), refiere que para el horario pico de este domingo 23 de julio se estima la entrada de la unidad 2 de la Hidroeléctrica Hanabanilla con 14 MW, el aporte de los motores de la central de Mariel con 100 MW, la entrada de los motores fuel de Moa con 100 MW y la suma de 166 MW de parte de la Generación Distribuida.
Por lo tanto, con esas proyecciones se estima para la hora pico una disponibilidad de 3.113 MW y una demanda máxima de 3.000 MW, para una reserva de 113 MW, “por lo que de mantenerse las condiciones previstas no se pronostican afectaciones al servicio en este horario”.
-
 @ 9ecbb0e7:06ab7c09
2023-07-24 00:36:58
@ 9ecbb0e7:06ab7c09
2023-07-24 00:36:58La Dirección General de Transporte impuso más de 5,000 multas a choferes en La Habana entre junio y julio, desde la entrada en vigor de las nuevas tarifas para la movilidad de pasajeros por el sector privado.
Las 5,100 multas se fijaron a conductores que violaron los precios establecidos por el régimen y "por ejercer la actividad de transportación de pasajeros de forma ilegal", según informó el diario local oficialista Tribuna de La Habana.
La Dirección General de Transporte afirmó que "se enfrentaron casos que mostraron reincidencia en la violación, y se aplicaron medidas de mayor rigor con los responsables, que en su gran mayoría no eran los titulares de los medios".
En junio, al anunciar las nuevas tarifas de transportación de pasajeros operadas por privados, las autoridades informaron también que reforzarían las acciones de enfrentamiento y control en la vía para que los precios fijados se cumplan, avisando que aplicarían el Decreto 45 del 2021.
Las autoridades dividieron las 46 rutas de transportación existentes en cuatro grupos, según el precio: de 45 pesos, de 75, de 100 y de 170 pesos.
Los boteros en La Habana no recibieron con agrado la noticia y decidieron dejar de trabajar, como forma de protesta contra la imposición del gobierno.
Varios choferes expresaron su intención de solo transportar a personas en viajes previamente concertados con el cliente y posteriormente, se declararon en huelga, en medio de una disminución drástica del transporte estatal en el país.
La prensa oficialista cubana reconoció que decenas de boteros han dejado de trabajar en La Habana luego de que el Gobierno fijara nuevos precios a sus tarifas.
En La Habana se transportan diariamente un estimado de 600,000 pasajeros, de ellos 536,052 son transportados por los operadores estatales, lo que representa un 89.3%, mientras que 63,948 se trasladan por otras formas de gestión, para el 10.7%.
Los transportistas privados afirmaron que los nuevos precios son insostenibles para ellos, que tienen las mismas dificultades de otros cubanos para satisfacer sus necesidades básicas, y deben comprar a altos precios el combustible y las piezas de repuesto que el estado no vende.
La imposición de los nuevos precios también se aplicó en otras provincias, como Matanzas y Cienfuegos.
El gobierno local del municipio de Limonar, en Matanzas, fijó los precios del transporte privado de pasajeros mediante camionetas, autos, motos, coches y bicitaxi.
Mediante el acuerdo 290 del Consejo de la Administración del Poder Popular en Limonar se establecieron valores que van desde los 200 pesos cubanos hasta 10 CUP, según la ruta y el medio de transporte que se emplee.
El gobierno de Cienfuegos topó también los precios, medida que para algunos expertos agudizará la crisis inflacionaria que hay en el país.
Tras la publicación de la Resolución 81/2023 los diferentes medios de transporte debieron cobrar lo que se estableció a partir de la nueva ficha de costo.
-
 @ bcea2b98:7ccef3c9
2023-07-14 06:15:25
@ bcea2b98:7ccef3c9
2023-07-14 06:15:25Once upon a time, in the realm of digital currencies, there emerged a revolutionary concept known as Bitcoin. As this new form of decentralized money gained popularity, it faced its first major trial—the advent of a phenomenon called a hard fork. Join me as we delve into the fascinating tale of the first Bitcoin hard fork and the impact it had on the cryptocurrency landscape.
In the early days of Bitcoin, the community was united under a common vision. However, as with any passionate endeavor, differing viewpoints and divergent ideas began to emerge. It was during this time that a rift appeared, and the stage was set for the first-ever Bitcoin hard fork.
The year was 2010, and Bitcoin was still in its infancy. Its potential to disrupt traditional financial systems was gaining attention, but challenges lay ahead. A group of individuals, known as miners, were the guardians of the Bitcoin network, validating transactions and securing its integrity.
Among these miners was a visionary named Jeff Garzik. Garzik, intrigued by the possibilities of Bitcoin's development, proposed a change to the Bitcoin protocol. He believed that increasing the block size—the virtual container that holds transactions within the blockchain—would enable faster and more efficient transactions, fostering greater scalability and widespread adoption.
This proposal, however, ignited a heated debate within the Bitcoin community. On one side stood those who championed the change, arguing that larger blocks would enhance the network's capabilities. On the other side were the proponents of the status quo, emphasizing the importance of maintaining the integrity and decentralization of the original Bitcoin protocol.
Unable to reconcile their differences, the community found itself at a crossroads. And so, on August 1, 2010, the Bitcoin blockchain experienced its first-ever hard fork, leading to the creation of a new cryptocurrency known as Bitcoin Cash (BCH). This momentous event marked a significant turning point in the history of digital currencies.
Bitcoin Cash retained the core principles of its predecessor but introduced a larger block size, allowing for more transactions to be processed per block. This change was embraced by some as a solution to Bitcoin's scalability challenges, while others viewed it as a departure from the original vision of a decentralized digital currency.
The hard fork sparked both excitement and controversy within the cryptocurrency community. It ignited a flurry of discussions, debates, and predictions about the future of both Bitcoin and Bitcoin Cash. Some enthusiasts saw it as an opportunity for innovation and progress, while skeptics questioned the fragmentation of the Bitcoin community.
In the aftermath of the hard fork, both Bitcoin and Bitcoin Cash continued to exist as separate entities, each with its own loyal following. The event served as a reminder of the dynamic nature of decentralized technologies and the capacity for divergence within a community united by a common vision.
As the years passed, subsequent hard forks and the evolution of other cryptocurrencies further shaped the digital landscape. The story of the first Bitcoin hard fork serves as a testament to the resilience and adaptability of blockchain technology, while also highlighting the challenges and complexities that arise when diverse voices converge in pursuit of a shared dream.
And so, the tale of the first Bitcoin hard fork stands as a pivotal moment in the history of digital currencies—a tale of innovation, conflict, and the eternal quest for progress in the ever-evolving realm of financial technology.
-
 @ 82b30d30:40c6c003
2023-07-22 08:31:22
@ 82b30d30:40c6c003
2023-07-22 08:31:22[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
-
 @ 9ecbb0e7:06ab7c09
2023-07-23 23:02:57
@ 9ecbb0e7:06ab7c09
2023-07-23 23:02:57Nostr es un protocolo que permite crear redes sociales descentralizadas sin censura incluyendo pagos a través de la red Lightning de Bitcoin.
Esta instalación de Nostr Relay Server comprende el uso de un servidor Ubuntu/Debian ya sea personal o que se esté ejecutando en cualquier servidor VPS.
Requisitos necesarios:
- Comprar un dominio de internet o tener un dominio de internet. Puedes comprar un dominio utilizando Namecheap.com u otro servicio.
- Tener en ejecución una instalación de Ubuntu/Debian.
- Logearse con ssh en su servidor.
- Instalar Cargo
- Instalar Rust
- Tener muchos deseos de aprender.
Comenzamos por instalar los paquetes necesarios:
Instalamos Cargo
sudo apt install cargoLuego procedemos a realizar la instalacion de Rust
curl --proto '=https' --tlsv1.2 -sSf https://sh.rustup.rs | shCuando se nos pregunte elegimos la opción 1
Una vez que haya finalizada la instalación de Rust vamos a activar el servicio
source /root/.cargo/envy verificamos que estén instaladas de forma correcta tanto Rust como Cargo
rustc --version cargo --versionEn seguida, procedemos a la instalación de Protobuf en el sistema. Protobuf es un formato de serialización de datos estructurados desarrollado por Google, utilizado en la comunicación entre servicios y en el almacenamiento de datos. Para instalarlo, sigue los siguientes pasos.
Primero, asegúrate de tener instalado el paquete unzip, que nos permitirá extraer el archivo ejecutable protoc de un archivo ZIP:
sudo apt updatesudo apt install -y unzipObtén la última versión de protoc y asígnala a una variable:
PROTOC_VERSION=$(curl -s "https://api.github.com/repos/protocolbuffers/protobuf/releases/latest" | grep -Po '"tag_name": "v\K[0-9.]+')Descarga el archivo ZIP de la página de lanzamientos del repositorio de protoc:
curl -Lo protoc.zip "https://github.com/protocolbuffers/protobuf/releases/latest/download/protoc-${PROTOC_VERSION}-linux-x86_64.zip"Luego, extrae el archivo ejecutable del archivo ZIP:
sudo unzip -q protoc.zip bin/protoc -d /usr/localA continuación, establece el permiso de ejecución:
sudo chmod a+x /usr/local/bin/protocEn este punto, el comando protoc ya está disponible para todos los usuarios como un comando global del sistema. Puedes verificar la versión de protoc con:
Podemos verificar la versión de protoc:
protoc --versionYa no necesitaremos el archivo ZIP, así que lo eliminamos:
rm -rf protoc.zipAhora vamos a instalar todas las dependencias necesarias para la instalación de nuestro servidor nostr
sudo apt-get install certbot build-essential sqlite3 libsqlite3-dev libssl-dev pkg-config nginx git -ysudo apt-get install net-tools whois -yLuego realizamos la compitación de nostr.
cd /optsudo mkdir nostr-datasudo git clone https://github.com/scsibug/nostr-rs-relay.gitcd nostr-rs-relaysudo cargo build --release**Este proceso puede llegar a demorar hasta unos 10 minutos. Tenga calma y espere que se realice completamente. ** Instalamos el servidor nostr en la carpeta bin
sudo install target/release/nostr-rs-relay /usr/local/binSi has seguido todos los pasos ya tendrás nuestro relay server casi listo, ahora puedes descargar el archivo de configuración de prueba.
sudo wget https://raw.githubusercontent.com/scsibug/nostr-rs-relay/master/config.tomlAbrimos el archivo con el editor de texto de tu preferencia, en mi caso nano.
sudo nano config.tomlModificamos las siguientes variables.
relay_url : nostr.domainname.com ( ⚠️ reemplaza con el nombre que le quieras dar a tu relay server) name : Nombre que va a tener el relay description : Escribe de que se trata tu relay server, no te limites, escribe todo lo que quieras para que los usuarios conozcan acerca de ti. pubkey : Tu clave publica en formato hex, esto es para que otros usuarios puedan comunicarse contigo contact : correo@example.com (Es la direccion de correo administrativo de este relay server) tracing : ⚠️ Mantenlo comentado de otra forma el relay server puede dar error data_directory : /opt/nostr-data/ (Donde se van a guardar los datos de nuestro relay server) address : 127.0.0.1 utilizaremos esta ya que vamos a usar nginx como servidor proxy remote_ip_header : "x-forwarded-for" para permitir el logeo real de clientesSi has seguido los pasos podemos verificar si nuestro relay server se encuentra en ejecución y para hacerlo podemos utilizar el siguiente comando en el terminal.
sudo RUST_LOG=warn,nostr_rs_relay=info /usr/local/bin/nostr-rs-relaySi todo marcha de forma correcta nos mostrara la salida del servidor con los datos que esta procesando.
Ahora vamos a proceder a crear el servicio que permitirá el funcionamiento de nuestro relay server incluso si se reinicia nuestro servidor.
Para ello vamos a crear el archivo /etc/systemd/system/nostr-relay.service
sudo nano /etc/systemd/system/nostr-relay.serviceDentro del archivo vamos a pegar el siguiente codigo
``` [Unit] Description=Nostr Relay After=network.target
[Service] Type=simple User=TuUsuario WorkingDirectory=/home/TuUsuario Environment=RUST_LOG=info,nostr_rs_relay=info ExecStart=/usr/local/bin/nostr-rs-relay Restart=on-failure
[Install] WantedBy=multi-user.target
```
Debes Cambiar TuUsuario por el nombre del usuario real que estas utilizando.
Ahora habilitamos el servicio, y lo ejecutamos para que se mantenga encendido
sudo systemctl daemon-reloadsudo systemctl enable nostr-relay.servicesudo systemctl start nostr-relay.serviceVerificamos si el servicio se está ejecutando en el sistema
sudo systemctl status nostr-relay.serviceSi vas hasta aqui deberías ver el servicio en ejecución sin errores. Para salir de la ventana preciona Ctrol + C
Verificamos si el servicio esta escuchando en el puerto 8080 utilizando el siguiente comando
sudo netstat -tnap | grep nostry Deberías obtener una respuesta parecida a la siguiente
tcp 0 0 0.0.0.0:8080 0.0.0.0:* LISTEN 81180/nostr-rs-relayConfiguración del proxy inverso Nginx para el acceso de nuestro relay service a través del dominio deseado.
Para ello primero vamos a entrar en la carpeta cd /etc/nginx/sites-available
cd /etc/nginx/sites-available sudo mkdir -p /var/www/nostr/.well-known/acme-challenge/ sudo chown -R 33:33 /var/www/nostrCreamos el archivo de configuracion nostr-relay.conf
sudo nano nostr-relay.conf
Vamos a pegar el siguiente contenido
```
map $http_upgrade $connection_upgrade { default upgrade; '' close; }
upstream websocket { server 127.0.0.1:8080; }
server { listen 80; server_name relay.example.com; ## <<=== Cambia esto
location /.well-known/acme-challenge/ { root /var/www/nostr; allow all; }
location / { proxy_pass http://websocket; proxy_http_version 1.1; proxy_set_header Upgrade $http_upgrade; proxy_set_header Connection $connection_upgrade; proxy_set_header Host $host; proxy_set_header X-Forwarded-For $remote_addr; }
} ```
En el, basicamente estamos dandole acceso a nuestro relay a través del dominio que hemos escogido. Recuerda que debes cambiar el valor en server_name con el nombre real del dominio que deseas utilizar. Hasta aqui solo estamos utilizando http sin certificado SSL.
Cuando hayas realizado las modificaciones y salvado el archivo de configuración vas a activar y habilitar el sitio para comprobar que efectivamente se esta ejecutando de forma correcta nuestro relay server y escuchando a través de nuestro dominio.
sudo ln -s /etc/nginx/sites-available/nostr-relay.conf /etc/nginx/sites-enabled/. sudo rm -f /etc/nginx/sites-enabled/default sudo nginx -tSi todo marcha bien y has realizado los pasos vas a obtener el siguiente mensaje
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok nginx: configuration file /etc/nginx/nginx.conf test is successfulAhora debemos mandar a ejecutar los cambios en nginx
sudo nginx -s reloadRealizar una prueba externa.
Para comprobar que todo esta funcionando bien podemos abrir una nueva ventana Terminal en otra computadora y ejecutar
wget relay.example.comDonde relay.example.com se refiere al dominio que has destinado para tu relay server y que es el mismo que has utilizado en la configuración de nginx.
Como resultado deberias obtener un archivo index.html al cual le puedes hacer un cat para leer el contenido.
cat index.htmly debería mostrar el siguiente mensaje
Please use a Nostr client to connect.Hasta aquí vemos que nuestro servidor esta funcionando. Ahora le vamos a añadir un certificado SSL.
Para nuestro siguiente paso vamos a utilizar DHParams
Primero vamos a crear la carpeta donde ubicaremos el certificado.
sudo mkdir /etc/nginx/ssly luego vamos a crear el DHParams (deberia tomarnos solo un minuto)
sudo openssl dhparam -out /etc/nginx/ssl/dhparam.pem 4096Ahora vamos a solicitar el certificado
cd /var/www/nostr sudo certbot certonly --webroot -w . -d relay.example.com --dry-run --agree-tosDeberías haber obtenido la siguiente respuesta.
Saving debug log to /var/log/letsencrypt/letsencrypt.log Simulating a certificate request for relay.example.com The dry run was successful.
Recuerda cambiar relay.example.com por el dominio tuyo si esta prueba fue satisfactoria entonces puedes proceder a solicitar el certificado SSL utilizando el siguiente comando.
cd /var/www/nostrsudo certbot certonly --webroot -w . -d relay.example.comAsí, vas a obtener información tal como la ruta en la que se guardó el certificado SSL para tu dominio etc.
Y estamos listos para reemplazar la configuración de nginx con la que va a tener el certificado SSL de nuestro servidor.
cd /etc/nginx/sites-availablesudo nano nostr-relay.confActualizamos el archivo de la siguiente forma
``` map $http_upgrade $connection_upgrade { default upgrade; '' close; }
upstream websocket { server 127.0.0.1:8080; }
server { listen 80; server_name relay.example.com; ## <<=== CHANGE THIS
location /.well-known/acme-challenge/ { root /var/www/nostr; allow all; }
location / { return 301 https://relay.example.com; }
}
server { listen 443 ssl; server_name relay.example.com;
location / { proxy_pass http://websocket; proxy_http_version 1.1; proxy_set_header Upgrade $http_upgrade; proxy_set_header Connection $connection_upgrade; proxy_set_header Host $host; proxy_set_header X-Forwarded-For $remote_addr; }
SSL
ssl_session_cache shared:SSL:10m; ssl_session_timeout 10m; ssl_protocols TLSv1.2 TLSv1.1 TLSv1; ssl_prefer_server_ciphers on; ssl_ciphers "EECDH+ECDSA+AESGCM EECDH+aRSA+AESGCM EECDH+ECDSA+SHA384 EECDH+ECDSA+SHA256 EECDH+aRSA+SHA384 EECDH+aRSA+SHA256 EECDH+aRSA+RC4 EECDH EDH+aRSA RC4 !aNULL !eNULL !LOW !3DES !MD5 !EXP !PSK !SRP !DSS"; ssl_stapling on; ssl_stapling_verify on; ssl_dhparam ssl/dhparam.pem; ssl_ecdh_curve secp384r1;
add_header Strict-Transport-Security "max-age=31536000; includeSubdomains"; add_header X-Frame-Options DENY; add_header X-Content-Type-Options nosniff; add_header X-XSS-Protection "1; mode=block"; add_header Referrer-Policy same-origin; add_header Feature-Policy "geolocation none;midi none;notifications none;push none;sync-xhr none;microphone none;camera none;magnetometer none;gyroscope none;speaker self;vibrate none;fullscreen self;payment none;";
ssl_certificate /etc/letsencrypt/live/relay.example.com/fullchain.pem; ssl_certificate_key /etc/letsencrypt/live/relay.example.com/privkey.pem;
}
```
Recuerda cambiar todas las ocurrencias de relay.example.com por tu dominio real.
Verificamos que la configuración de nginx este correcta.
sudo nginx -tSi todo es correcto ejecutas
sudo nginx -s reloadVerificamos que nginx + http y el servidor se están ejecutando correctamente
sudo netstat -tnap | grep 'nginx\|nostr'Si la respuesta es la siguiente
tcp 0 0 0.0.0.0:443 0.0.0.0: LISTEN 53252/nginx: master tcp 0 0 0.0.0.0:80 0.0.0.0: LISTEN 53252/nginx: master tcp 0 0 0.0.0.0:8080 0.0.0.0:* LISTEN 81180/nostr-rs-rela
Significa que esta funcionando de forma correcta nuestro servidor.
En caso de que desees obtener un informe de estado de tu relay server puedes utilizar siempre que así lo desees
journalctl -f | grep --line-buffered nostr_rs_relay | cut -d' ' -f 10,12-100Ahí podrás obtener un informe de errores en caso de ser necesario.
Si deseas comprobar la conexión con el Relay server puedes utilizar el siguiente enlace que aquí te proveo.
En resumen, Nostr es una plataforma que proporciona una red de noticias en tiempo real, libre y descentralizada. Nostr Relay Server es una herramienta que nos permite unirnos a esta red y compartir noticias y eventos con el resto del mundo. Mediante la instalación y configuración de Nostr Relay en un servidor Ubuntu, podemos contribuir al crecimiento y desarrollo de esta emocionante nueva plataforma de comunicación.
Quieres utilizar mis relay servers?
Si es así puedes conectarte a:
wss://relay.bitransfer.org
wss://relay.bitransfermedia.com
Espero que esta guía les sea de ayuda.
-
 @ bcea2b98:7ccef3c9
2023-07-14 06:14:32
@ bcea2b98:7ccef3c9
2023-07-14 06:14:32Ah, the enigmatic figure of Dorian Nakamoto—an unsuspecting man whose name became entangled in the mysterious origins of Bitcoin. Prepare to journey into a world of intrigue, as we uncover the facts surrounding Dorian Nakamoto and his unexpected connection to the captivating story of Bitcoin's birth.
Our tale begins on a sunny day in March 2014 when a renowned journalist named Leah McGrath Goodman published an article that would send shockwaves through the cryptocurrency community. In her piece, Goodman claimed to have discovered the true identity of Bitcoin's creator—someone named Dorian Nakamoto.
The revelation was met with astonishment. For years, the identity of Bitcoin's creator, who had used the pseudonym Satoshi Nakamoto, had remained a closely guarded secret. The prospect of finally unmasking the mastermind behind the revolutionary digital currency sparked widespread curiosity and speculation.
Dorian Nakamoto, a seemingly unassuming individual living a quiet life in California, suddenly found himself thrust into the spotlight. As journalists and enthusiasts flocked to his doorstep, Dorian became the subject of intense media scrutiny and public fascination.
However, as the story unfolded, a more complex narrative emerged. Dorian Nakamoto vehemently denied any involvement with Bitcoin's creation. He insisted that his connection to the cryptocurrency was purely coincidental, a mere coincidence of name and circumstance.
The intrigue surrounding Dorian Nakamoto's potential role in Bitcoin's origins captured the attention of the world. Many sought to find evidence linking him to the enigmatic Satoshi Nakamoto, poring over his past and analyzing his life for clues.
Amidst the fervor, a pivotal moment occurred. Dorian Nakamoto, faced with an army of journalists camped outside his home, made a stunning appearance in front of the cameras. In a now-famous interview, he proclaimed his innocence, exclaiming, "I'm not involved in Bitcoin. I don't know anything about it!"
The fervor surrounding Dorian Nakamoto eventually subsided, and the cryptocurrency community resumed its quest to uncover the true identity of Satoshi Nakamoto. While Dorian may not have been the elusive creator, his brief encounter with fame forever linked his name to the intricate web of Bitcoin's genesis.
To this day, the true identity of Satoshi Nakamoto remains shrouded in mystery. Many theories and speculations have emerged, but the enigma persists. Some believe that Satoshi Nakamoto is an individual, while others suggest it may be a collective pseudonym concealing the true architect of Bitcoin's design.
As the story of Dorian Nakamoto demonstrates, the world of Bitcoin is a realm where truth and fiction intertwine, where unexpected twists and turns captivate our imagination. It serves as a reminder that the origins of great innovations are often veiled in complexity, leaving us to unravel the threads of history and contemplate the enigmatic figures that emerge along the way.
And so, the tale of Dorian Nakamoto—a man wrongly associated with the creation of Bitcoin—remains an intriguing chapter in the annals of cryptocurrency history, forever intertwined with the enigma of Satoshi Nakamoto and the captivating world of digital currencies.
-
 @ 000003a2:e3b014e6
2023-07-23 20:35:56
@ 000003a2:e3b014e6
2023-07-23 20:35:56A simple example:
``` // create subscription ndk.subscribe({ kinds: [0], authors: [pubkey] });
sub.on('event', (event: NDKEvent) => { try { // parse content const content = JSON.parse(event.content); // now you can access profile info from parsed content } catch (error) { // handle error } });
```
-
 @ bcea2b98:7ccef3c9
2023-07-14 06:13:39
@ bcea2b98:7ccef3c9
2023-07-14 06:13:39In a world of digits, where power does reside, There emerges a beacon, a currency worldwide. Bitcoin, they call it, a symbol of sovereignty, Empowering the masses, a true digital decree.
Unchained from institutions, it rises above, A decentralized force, a testament to love. No government can claim it, no boundaries can it know, A currency for the people, where freedom's seeds may grow.
From Satoshi's vision, a revolution unfurled, A peer-to-peer network that challenges the world. Through cryptography's embrace, it guards with might, Ensuring transactions' safety, day and night.
No intermediaries, no need for middlemen, Bitcoin whispers freedom, a song that never ends. No censorship can touch it, no borders can it face, A currency for all, bringing power and grace.
But with this newfound freedom, comes responsibility, To protect our private keys, with utmost agility. For in this digital realm, where fortunes may be won, There also lies the risk, of fortunes being undone.
Yet Bitcoin endures, like a phoenix from the flame, Its value fluctuating, a testament to its game. Through booms and busts, it stands tall and true, A symbol of resilience, a dream that we pursue.
So let us embrace this journey, this path we undertake, To understand the power, the choices that we make. Bitcoin and sovereignty, intertwined they may be, A testament to our freedom, for all the world to see.
-
 @ 604cfe60:09a6fb18
2023-07-23 14:40:36
@ 604cfe60:09a6fb18
2023-07-23 14:40:36 Why not do it openly? Why are you hiding behind screens? Show your face! Coward!
Why not do it openly? Why are you hiding behind screens? Show your face! Coward!No.
I don't trust you. You could be FBI, posing as Karen online, to nudge us to reveal ourselves.
Reveal themselves, some did. Courageous, they felt. And Ambitious, they were. Crushed, they were, eventually.
Ambition means you think big. Thinking big means you seek out big problems. Big problems tend to be socio-economical and political problems.
Ambitious people are a big threat. They threaten the big players. They are a thorn to their on-going socio-economical scam. And they get neutered.
They know you. Where you live. What you do. What you care about. When you leave for work. When a truck could hit your car.
Or they crush you by calling you an X-phobic, mentally ill, or an X-ist. They prove it by nitpicking your history. And they cut off your income, your safety, your network. Then they make you alone.
I am paranoid. But fear is a good thing. It makes me cautious. It helps me enjoy the freedom. It keeps my family safe.
I don't have a choice. The world isn't fair. You protect yourself or you get killed. I want to survive.
I'm Cautious not because they WILL hurt me. But because they CAN hurt me. I'm Ambitious because I have seen the world as it is. There are so many problems, and they become harder to solve everyday.
I'm Anonymous because it's my defense strategy.
-
 @ bcea2b98:7ccef3c9
2023-07-14 06:12:47
@ bcea2b98:7ccef3c9
2023-07-14 06:12:47In the realm of software, where dreams take flight, There lived a developer, Will, with vision burning bright. He crafted Nostr, a decentralized land, Where zaps, like Bitcoin tips, exchanged hand in hand.
With lines of code, Will painted a new scene, Empowering users to connect, to live the digital dream. Damus, his creation, a gateway to the new, A haven for the people, where freedom always grew.
But as fate would have it, a challenge took its place, Apple's ban threatened, a cloud cast on Will's grace. Undeterred, he persevered, with determination profound, A workaround he discovered, and hope once again was found.
People rallied 'round, their voices strong and true, Using Damus defiantly, their freedoms they pursued. For in the face of adversity, resilience took a stand, Will's creation lived on, across the digital land.
Nostr, the decentralized protocol, a beacon of light, Guiding users forward, in this digital fight. And Damus, the app that refused to be restrained, Continued to empower, its purpose unrestrained.
In the world of software, where limitations may arise, Will's story inspires, reaching for the skies. A reminder that innovation thrives in the face of ban, And where one door closes, another finds its plan.
So let us celebrate the spirit of Will, the trailblazer, His vision, his courage, our digital appraiser. Nostr, the gateway to connection, in a world decentralized, And Damus, the app that refused to be erased.
In the realm of software, where dreams ignite, Will's legacy lives on, in the code we write. A testament to resilience, and the power to adapt, For in the face of adversity, innovation will never be trapped.
-
 @ bcea2b98:7ccef3c9
2023-07-14 06:10:38
@ bcea2b98:7ccef3c9
2023-07-14 06:10:38In the lush lands of Costa Rica, where nature's beauty thrives, A man named Max embarked, with passion in his eyes. He self-funded a documentary, a tale to unfold, About a new decentralized protocol, where stories would be told.
Nostr, the social network, where power finds its place, A platform of freedom, where users embrace. Max sought to shed light, on its benefits profound, In the realm of decentralization, where true connections abound.
Through the lens he captured, the essence of the scene, Costa Rica's splendor, where the Nostr conference convenes. In this land of wonders, where nature and tech unite, The documentary unfolds, revealing insights shining bright.
He interviewed Jack Dorsey, a titan of our time, Who shared the early history, where Twitter's roots did climb. Software developers joined, their voices joined the tale, Describing the centralized platforms, and the challenges they entail.
The documentary explored, why centralized networks fall short, With data controlled, and users left to sort. Nostr, the decentralized wonder, breaks free from the mold, Empowering users, with benefits untold.
Zaps, like Bitcoin tips, in the Nostr realm reside, A gesture of appreciation, where generosity can't hide. Max's vision took flight, a message clear and strong, To embrace a decentralized future, where we all belong.
For in the realm of social networks, where connections intertwine, Nostr's decentralized protocol, like a beacon will shine. A reminder that power lies in the hands of the many, And through decentralization, we can create a better journey.
So let us celebrate Max's endeavor, the documentary's tale, Where Nostr's vision takes flight, and centralized networks pale. A testament to empowerment, where freedom finds its way, In the realm of decentralized connections, where zaps will forever stay.
-
 @ 9ecbb0e7:06ab7c09
2023-07-23 14:33:49
@ 9ecbb0e7:06ab7c09
2023-07-23 14:33:49El fotógrafo Orlando Tamayo Guevara fue asesinado en su vivienda en la ciudad de Guantánamo esta semana durante un robo. Según vecinos, cercanos a su casa en la calle Narciso López, los ladrones buscaban en el lugar la caja fuerte y dos motos eléctricas.
Tamayo, quien trabajaba de forma privada en Burlesque Studio, se dedicaba a realizar sesiones fotográficas de festejos familiares, bebés, embarazadas y, especialmente, las populares fotos de las jóvenes al cumplir los 15 años.
En un emotivo video difundido a través de Facebook, Orlando Tamayo Díaz, hijo del fotógrafo, definió a su padre como un "excelente ser humano". Residente en Texas, Estados Unidos, el joven agradeció a su familia y amigos en Cuba que le habían brindado su apoyo en este momento difícil. "Mi padre era una persona muy querida", subrayó.
Padre de tres hijos y abuelo de cuatro niños, Tamayo es recordado como una persona amable y servicial. Sus clientes y amigos han inundado las redes con mensajes de condolencias y exigiendo "mano dura" contra la criminalidad
En su juventud, Tamayo se había graduado en el Pedagógico de Guantánamo y durante la pandemia, ayudó a difundir a través de grupos de WhatsApp información sobre el covid-19 y las medidas para protegerse del virus.
Padre de tres hijos y abuelo de cuatro niños, Tamayo es recordado como una persona amable y servicial. Sus clientes y amigos han inundado las redes con mensajes de condolencias y exigiendo "mano dura" contra la criminalidad que azota la Isla.
Esta semana se supo que habían sido detenidos tres individuos por el asesinato del locutor David Alexis González Joseph también en Guantánamo, el pasado 26 de abril. El locutor, que trabajaba en la emisora de radio oficial CMKS, fue encontrado sin vida dentro de su vivienda.
Asesinatos como el de González Joseph o el del cochero Antonio Silvino Pérez, en Santa Clara, el pasado mayo, indican que los robos con violencia, en las calles o en el interior de las casas, están aumentando en Cuba. A la par, son cotidianos también los feminicidios (ya van 53 en lo que va de 2023) o los hurtos de ganado y de motos eléctricas.
En una nota publicada el pasado junio, el Ministerio del Interior aseguraba que el 90% de los casos en los que se emplearon armas de fuego –cuyo número no aportaban– habían sido resueltos con la detención e imputación de los autores. Sin embargo, admitía que solamente resolvía el 60% de los delitos sin armas de fuego.
Para el oficialismo, las noticias sobre criminalidad son una exageración de los medios independientes, que "magnifican" los hechos para "subvertir el orden" y dañar el turismo. Recientemente, ante la Asamblea Nacional, Miguel Díaz-Canel aseguró que existe un "empeño imperial" de fabricar un clima de inseguridad y desconfianza ciudadana que erosione la "unidad popular" en Cuba.
"Por eso, constantemente se exagera cualquier hecho delictivo, fundamentalmente los casos con violencia y, en particular, los de violencia de género", aseguró.
-
 @ 2e2cf253:737f1193
2023-07-12 05:46:05
@ 2e2cf253:737f1193
2023-07-12 05:46:05Gm gm Dueters,
We are glad to tell you that we are planning something big!
As the Hong Kong regulatory environment for blockchain and crypto currency is getting positive, we think it’s the best time to seize the opportunity and expand our market for RWA investors. Come and hear it out!
Hong Kong’s Progressive Crypto Regulations and Supportive Environment for Web3 Businesses
In February, Hong Kong introduced a set of progressive regulations aimed at fostering a favorable environment for crypto-related activities. As crypto regulations in the United States become more stringent, Hong Kong sees an opportunity to emerge as the next prominent crypto hub by offering a more favorable regulatory landscape.
In mid-April, a large crowd eagerly awaited entry into the Hong Kong Convention Center, where the city’s first web3 festival was taking place.They had gathered to explore the opportunities Hong Kong had in store for crypto ventures.
Despite its geographical proximity to China, known for its restrictive stance on cryptocurrencies, Hong Kong is actively striving to establish a regulatory environment that appeals to digital asset companies globally.
Duet Protocol Seizes Opportunities in Hong Kong and Launches Airdrops to Reward Loyalty
As an action to take advantage of the favorable regulatory environment in Hong Kong, with the increasing number of users and customers switching from Web2 to Web3 and the presence of numerous education studios offering blockchain education to traditional investors, Duet Protocol will collaborate with select education studios and establish our exchange, issue more synthetic assets, and be their primary marketplace for trading.
To get more and more people familiarized with our trading platform, Duet Pro, we encourage the purchase and Duet pro trading and would like to reward the active users in our campaign “DuetBoost”, encompassing from July 11th to November 11th,2023, UTC+0, containing a series of Airdrops.
In the “DuetBoost” campaign, the selection and rewarding of users for the airdrop will be based on several criteria to determine the most loyal participants. The following factors will be considered:
-
User’s Recent Extra Holding of Duet Token: The campaign will take into account the amount of Duet tokens newly purchased by the user, starting from July 11th, 2023, UTC+0.
-
User’s Trading Activities on Duet Pro: The campaign will consider the user’s trading activities on the Duet Pro exchange. The frequency and volume of trades made by the user will be taken into account, demonstrating their engagement and participation in the platform’s trading activities.
-
User’s Credibility as a True User: The campaign will assess the credibility of users to ensure they are genuine participants. Factors such as account verification, adherence to platform guidelines, and overall trustworthiness will be considered to determine the authenticity and reliability of users.
In addition, we have partnered with a data analytics lab to develop a personalized airdrop strategy and effectively predict user behavior, specifically focusing on identifying instances of free riding.
Your participation in the survey and inclusion in the whitelist will not only increase your eligibility for the airdrop but also contribute to the ongoing refinement of our platform’s services and offerings.
Please take a moment to provide us with your information through the survey link below, and join the airdrop whitelist to benefit from this personalized initiative and improve your overall experience with our platform.
https://644ce16a.sibforms.com/serve/MUIFAN_x7BokYRahpOLBn4NMzvgDQJrJOwqerbf9DGmotnczY89oui8efwO0A4ROFGvcvNFvfWE1eEh1POlaZ_38Gj4t1d4mqtyUAgVi39XHTnGDVQQ-D0KXAWs5nPezriwEg9Kw-yKJj-yS4A7tbRD4AgvKRq1izgdv7tUqfTOdOq-sjQGKLsuuyajHL6ZugF7yQs22ChByzh1Y
 Scan the QR code to get access to the form.
Scan the QR code to get access to the form.Follow Duet Protocol’s social medias to learn more. https://link3.to/duetprotocol
-
-
 @ 32e18276:5c68e245
2023-07-11 21:23:37
@ 32e18276:5c68e245
2023-07-11 21:23:37You can use github PRs to submit code but it is not encouraged. Damus is a decentralized social media protocol and we prefer to use decentralized techniques during the code submission process.
[Email patches][git-send-email] to patches@damus.io are preferred, but we accept PRs on GitHub as well. Patches sent via email may include a bolt11 lightning invoice, choosing the price you think the patch is worth, and we will pay it once the patch is accepted and if I think the price isn't unreasonable. You can also send an any-amount invoice and I will pay what I think it's worth if you prefer not to choose. You can include the bolt11 in the commit body or email so that it can be paid once it is applied.
Recommended settings when submitting code via email:
$ git config sendemail.to "patches@damus.io" $ git config format.subjectPrefix "PATCH damus" $ git config format.signOff yesYou can subscribe to the [patches mailing list][patches-ml] to help review code.
Submitting patches
Most of this comes from the linux kernel guidelines for submitting patches, we follow many of the same guidelines. These are very important! If you want your code to be accepted, please read this carefully
Describe your problem. Whether your patch is a one-line bug fix or 5000 lines of a new feature, there must be an underlying problem that motivated you to do this work. Convince the reviewer that there is a problem worth fixing and that it makes sense for them to read past the first paragraph.
Once the problem is established, describe what you are actually doing about it in technical detail. It's important to describe the change in plain English for the reviewer to verify that the code is behaving as you intend it to.
The maintainer will thank you if you write your patch description in a form which can be easily pulled into Damus's source code tree.
Solve only one problem per patch. If your description starts to get long, that's a sign that you probably need to split up your patch. See the dedicated
Separate your changessection because this is very important.When you submit or resubmit a patch or patch series, include the complete patch description and justification for it (-v2,v3,vn... option on git-send-email). Don't just say that this is version N of the patch (series). Don't expect the reviewer to refer back to earlier patch versions or referenced URLs to find the patch description and put that into the patch. I.e., the patch (series) and its description should be self-contained. This benefits both the maintainers and reviewers. Some reviewers probably didn't even receive earlier versions of the patch.
Describe your changes in imperative mood, e.g. "make xyzzy do frotz" instead of "[This patch] makes xyzzy do frotz" or "[I] changed xyzzy to do frotz", as if you are giving orders to the codebase to change its behaviour.
If your patch fixes a bug, use the 'Closes:' tag with a URL referencing the report in the mailing list archives or a public bug tracker. For example:
Closes: https://github.com/damus-io/damus/issues/1234Some bug trackers have the ability to close issues automatically when a commit with such a tag is applied. Some bots monitoring mailing lists can also track such tags and take certain actions. Private bug trackers and invalid URLs are forbidden.
If your patch fixes a bug in a specific commit, e.g. you found an issue using
git bisect, please use the 'Fixes:' tag with the first 12 characters of the SHA-1 ID, and the one line summary. Do not split the tag across multiple lines, tags are exempt from the "wrap at 75 columns" rule in order to simplify parsing scripts. For example::Fixes: 54a4f0239f2e ("Fix crash in navigation")The following
git configsettings can be used to add a pretty format for outputting the above style in thegit logorgit showcommands::[core] abbrev = 12 [pretty] fixes = Fixes: %h (\"%s\")An example call::
$ git log -1 --pretty=fixes 54a4f0239f2e Fixes: 54a4f0239f2e ("Fix crash in navigation")Separate your changes
Separate each logical change into a separate patch.
For example, if your changes include both bug fixes and performance enhancements for a particular feature, separate those changes into two or more patches. If your changes include an API update, and a new feature which uses that new API, separate those into two patches.
On the other hand, if you make a single change to numerous files, group those changes into a single patch. Thus a single logical change is contained within a single patch.
The point to remember is that each patch should make an easily understood change that can be verified by reviewers. Each patch should be justifiable on its own merits.
If one patch depends on another patch in order for a change to be complete, that is OK. Simply note "this patch depends on patch X" in your patch description.
When dividing your change into a series of patches, take special care to ensure that the Damus builds and runs properly after each patch in the series. Developers using
git bisectto track down a problem can end up splitting your patch series at any point; they will not thank you if you introduce bugs in the middle.If you cannot condense your patch set into a smaller set of patches, then only post say 15 or so at a time and wait for review and integration.
-
 @ 6e0a1f48:c9f444e5
2023-07-23 13:42:43
@ 6e0a1f48:c9f444e5
2023-07-23 13:42:43Critical Thinking and Sovereignty
It is often said that charting one's own course in life is the individual's supreme art. It's a continuous balancing act between the need to adapt to changes and the yearning for sovereignty. At the heart of this journey, two inseparable tools are found: questioning and critical thinking, and the ongoing work to achieve sovereignty, all while keeping a course in mind.
The Critical Thinking
Critical thinking is the foundation from which an individual may aspire to liberation. It is the ability to discern, to question pre-established norms and principles, and to break down barriers that bind the individual in a state of conformity. This is the beacon that illuminates the path to overcoming social and private restrictions.
Critical thinking provides the mental space necessary for an individual to clearly and reflectively evaluate their own beliefs, thoughts, and dissensions. This capacity for analysis and self-interrogation is the fundamental base for the individual to find their authentic needs and aspirations, allowing their full expression.
Working Towards Sovereignty
On the other hand, sovereignty is a banner that the individual carries with the aim of reigning supreme over their own life: personal, social, and economic. It is the realization of the principle of self-government, the conscious act of securing autonomy, and making informed and independent choices.
However, the pursuit of sovereignty is not an isolated act. It requires constant and persistent work. This is a journey that requires developing skills, cultivating experiences, and mastering the art of remaining resilient in the face of life's turbulence. Having a route in mind does not mean having an unchangeable trajectory, but rather a clear objective that guides all actions and choices, ensuring that each step taken is in the direction of the desired port of autonomy.
Conclusion
Combined, critical thinking and the unwavering will to achieve sovereignty constitute the compass and rudder on the journey to self-government. Through these, the individual has the capacity to lead, in a conscious and deliberate manner, the course of their life towards the core of their personal identity. And it is precisely in this act of self-governance that not only the essence of freedom is found, but the ultimate meaning of human existence.
-
 @ aac07d95:c5819a2f
2023-07-09 14:37:58
@ aac07d95:c5819a2f
2023-07-09 14:37:58More info about charge-lnd: https://github.com/accumulator/charge-lnd
Install with these commands line-by line (the code comments are starting with #): ```
change to the bitcoin user
sudo su - bitcoin
download charge-lnd
git clone https://github.com/accumulator/charge-lnd.git
create a dedicated macaroon
lncli bakemacaroon offchain:read offchain:write onchain:read info:read --save_to=~/.lnd/data/chain/bitcoin/mainnet/charge-lnd.macaroon
change directory
cd charge-lnd
install charge-lnd
pip install -U setuptools && pip install -r requirements.txt .
leave the bitcoin user
exit ```
Paste this whole code block to create the example config at
/home/bitcoin/charge-lnd/charge.config: ``` echo " [default] strategy = static base_fee_msat = 1000 fee_ppm = 1000 time_lock_delta = 144[exchanges-drain-sats] node.id = 033d8656219478701227199cbd6f670335c8d408a92ae88b962c49d4dc0e83e025, 03cde60a6323f7122d5178255766e38114b4722ede08f7c9e0c5df9b912cc201d6,037f990e61acee8a7697966afd29dd88f3b1f8a7b14d625c4f8742bd952003a590,03cde60a6323f7122d5178255766e38114b4722ede08f7c9e0c5df9b912cc201d6,033d8656219478701227199cbd6f670335c8d408a92ae88b962c49d4dc0e83e025, 021c97a90a411ff2b10dc2a8e32de2f29d2fa49d41bfbb52bd416e460db0747d0d strategy = static base_fee_msat = 50000 fee_ppm = 2500 time_lock_delta = 144
[discourage-routing] chan.max_ratio = 0.10 chan.min_capacity = 250000 strategy = static base_fee_msat = 1000 fee_ppm = 2000 time_lock_delta = 144
[encourage-routing] chan.min_ratio = 0.90 chan.min_capacity = 250000 strategy = static base_fee_msat = 1000 fee_ppm = 10 time_lock_delta = 144
" | sudo -u bitcoin tee /home/bitcoin/charge-lnd/charge.config ```
Set up a cronjob with:
crontab -ePaste this to the crontab to run it every 5 minutes (https://crontab.guru/#*/5_*_*_*_*):*/5 * * * * sudo -u bitcoin /home/bitcoin/.local/bin/charge-lnd -c /home/bitcoin/charge-lnd/charge.configgist with more example configurations:
https://gist.github.com/openoms/9d0c554f620f4584c17bec268d4519e8
Posted also on: https://www.lightningnode.info/hardware-deployment/raspiblitz/charge-lnd
-
 @ 6e0a1f48:c9f444e5
2023-07-23 13:42:26
@ 6e0a1f48:c9f444e5
2023-07-23 13:42:26Pensamento Crítico e Soberania
Diz-se que traçar o próprio caminho na vida é a arte suprema do indivíduo. É um contínuo acto de equilibrismo entre a necessidade de adaptar-se às mudanças e a ânsia de soberania. No centro desta jornada, encontram-se duas ferramentas inseparáveis: o questionamento e pensamento crítico e o trabalho contínuo para atingir a soberania, sempre mantendo um rumo em mente.
O Pensamento Crítico
O pensamento crítico é o alicerce a partir do qual o indivíduo pode almejar a libertação. Trata-se da habilidade de discernir, de questionar as normas e os princípios preestabelecidos e de quebrar as barreiras que prendem o indivíduo num estado de conformidade. Este é o farol que ilumina o caminho para a superação de restrições sociais e privadas.
O pensamento crítico proporciona o espaço mental necessário para que o indivíduo possa avaliar de forma clara e reflectida as suas próprias crenças, pensamentos e dissensões. Esta capacidade de análise e auto-interrogação é a base fundamental para o indivíduo encontrar as suas autênticas necessidades e aspirações, permitindo a sua plena expressão.
Trabalhando em Prol da Soberania
A soberania, por outro lado, é um estandarte que o indivíduo porta com o objectivo de reinar supremo sobre a sua própria vida: pessoal, social e económica. É a concretização do princípio de auto-governo, o acto consciente de assegurar a autonomia e de fazer escolhas informadas e independentes.
Contudo, a busca por soberania não é um acto isolado. Requer trabalho constante e persistente. Esta é uma jornada que requer desenvolver habilidades, cultivar experiencias e dominar a arte de se manter resiliente frente às turbulências da vida. Ter um rumo em mente não significa ter um trajeto imutável, mas sim um objectivo claro que guie todas as acções e escolhas, garantindo que cada passo dado seja em direcção ao porto de autonomia desejado.
Conclusão
Combinados, o pensamento crítico e a vontade inabalável de alcançar a soberania compõem a bússola e o leme na jornada para o autogoverno. Através destes, o indivíduo tem a capacidade de conduzir, de maneira consciente e deliberada, o percurso da sua vida em direcção ao âmago da sua identidade pessoal. E é justamente neste acto de governar a si próprio que se encontra, não só a essência da liberdade, mas o significado último da existência humana.
-
 @ 78733875:4eb851f2
2023-07-07 22:04:12
@ 78733875:4eb851f2
2023-07-07 22:04:12OpenSats is pleased to announce a new long-term support (LTS) program for Bitcoin Core developers and similar Load-Bearing Internet People.[^fn-lbip] This grant program is designed to provide financial support for developers who are working on critical infrastructure for the bitcoin network.
The LTS program is a new initiative from OpenSats and is distinct from our regular grant program, which is more expansive in scope. It is also distinct from OpenSats' website listings, which allows reviewed open-source projects to receive tax-deductible donations via OpenSats. The LTS program is specifically designed to provide long-term support for developers who are working on critical open-source infrastructure in and around bitcoin.
Having a longer time horizon than regular grants, the LTS program is geared towards long-term stability for grantees, with a minimum grant duration of 12 months and possible grant durations of two years or longer. This will allow developers to focus on their work without having to worry about financial constraints.
To be eligible for the LTS program, applicants must:
- have a track record of quality contributions
- be mission-driven and self-motivated
- be able to work in public
- be bitcoin-only
Applications for the LTS program are now open: https://opensats.org/apply/
The first recipient of an OpenSats LTS Grant is Marco Falke, a long-term maintainer and contributor of Bitcoin Core with thousands of contributions over many years. Marco will continue to focus on testing and quality assurance, as well as maintenance and review, helping to make sure that the Bitcoin Core software is as solid as it can be. You can read more about his contributions here.
We appreciate all the hard work that goes into building and maintaining critical open-source infrastructure. It is a hard and often thankless job. We hope that we can play a role in closing the gaps in bitcoin open-source funding, and we look forward to working with contributors in the future.
OpenSats aims to be an additional pillar of the increasingly solid funding landscape in and around bitcoin. We have learned a lot from the programs of the past and aim to join Brink, Spiral, Chaincode, HRF, and other successful grant programs to support those who build the tools that ensure the protection of individual liberties in our digital world.
We are committed to supporting the development of bitcoin. The LTS program is a new way for OpenSats to support long-term contributors who are building, maintaining, testing, researching, and reviewing critical software.
We encourage all qualified developers to apply for the LTS program. Together, we can build a stronger and more resilient bitcoin network.
[^fn-lbip]: "An LBIP is a person who maintains the software for a critical Internet service or library, and has to do it without organizational support or a budget backing him up." —Eric S. Raymond
-
 @ 75656740:dbc8f92a
2023-07-21 18:18:41
@ 75656740:dbc8f92a
2023-07-21 18:18:41"Who do you say that I am?"
In Matthew 16 Jesus cut to the heart of what defines identity. First he asked what other people said about him, then he asked what the disciples thought, finally he gave his own take by agreeing with the disciples. In trying to understand who someone is, we have three and only three possible sources of information.
- Who they tell us they are.
- Who others say about them.
- What we observe for ourselves.
Putting these three together constitutes identity. Identity is always unique for each connection in the social graph. Who you are to me is always different than who you are to anyone else. As such identity is largely out of our direct control. We can influence others perception of ourselves by comporting ourselves in a certain way, but we cannot compel it.
With this in mind, it is imperative to build protocols that mirror this reality as closely as possible. The problem is largely one of UI. How can we simultaneously display all three aspects of identity in a clear and uncluttered way?
The default has always been to just display an individual's claim to identity. Each user gets to choose a name and an avatar. This generally works in small communities with low rates of change both in who the members are and in how they present themselves. In these cases, each user can keep a mental map of what to expect from each name and avatar. "Oh that is just keyHammer24 doing his thing." Note that even if KeyHammer24 decides to change their nickname the mental map in the other users won't change instantly, if ever.
This falls apart in larger communities, where each user cannot maintain a mental model of who is who. Impersonation and collisions become a problem, so we add some "What others say about them" information such as blue check-marks or what "what we observe for ourselves" information like pet-names in a phone contact list or a note that we follow that account.
I don't personally have a final solution for this, I only know that we should be collecting and displaying all three sources of information from the outset. Perhaps we could do something like... * Default to showing a users preferred identifiers, but switch to the avatar and handle we self-assign them on hover. * Display a percentage of confidence that we know who the person is and that they are presenting themselves as who we expect them to be. You probably aren't the Elon Musk that I expect if you recently had different names / aren't the one I follow / none of my network follows / have been reported as misleading. * Reserve check-marks for keys that each user has signed in person. Only we can be the arbiter of who gets a check-mark in our own feed. * Maintain a list of past aliases along with a "Community Notes" like description of an account brought up by clicking on a ⓘ icon. * Have a full pet-names override.
I think Nostr already have much of this built into the protocol, it just needs to be standardized into the interface of various application. This is something on which I am very interested in hearing other ideas.
A note on anonymity
Real world identities should always be preferred. It allows for building real relationships and treating each other with real world respect. The real you is far more fascinating than a curated persona. Real identities should also never be enforced at a protocol level. Some people will be in real circumstances that preclude honest engagement without threat to their safety.
If you found this engaging I also wrote about why Social Network companies have an unsolvable problem here. and why we have to design for finite reach here
-
 @ 75da9402:77a65b5c
2023-07-17 17:48:42
@ 75da9402:77a65b5c
2023-07-17 17:48:42
### BIENVENID@ A NOSTR
Queridos amigos que desean unirse a Nostr, sé que para todos ustedes es nuevo este camino, pero créanme que vale la pena experimentar y conocer una nueva forma de conectar y comunicarse con personas en otras partes del mundo. Varias de las mentes mas brillantes y apasionadas por dejar una huella diferente en las comunicaciones humanas han puesto alma, mente, corazón y hasta sus propios fondos para desarrollar y aportar a nostr.
QUE ES NOSTR? ¿COMO EMPIEZO?
Nostr es un protocolo de comunicación que está diseñado para que las personas se conecten entre si de forma rápida, segura y divertida. No es una empresa de RRSS como Twitter, FB u otras, tampoco existe un dueño, CEO o accionistas ni moderadores ni administradores de contenido, tampoco pertenece algún país en específico. Dicho esto, si aún no sabes cómo empezar aquí vamos. Para conectarte a Nostr vas a usar aplicaciones llamadas también clientes, te sugiero empieces en tu móvil y estas son algunas de las que puedes descargar y probar para empezar, luego puedes buscar otros clientes de tu agrado:
Damus para usuarios de IPhone https://apps.apple.com/app/damus/id1628663131
Amethyst para usuarios de Android https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst
PASOS IMPORTANTES A SEGUIR
Vamos a realizar estos pasos con el cliente Damus pero en Amethyst funciona igual:
1.- Una vez que instalaste la aplicación cliente ábrela y vas a ir a la opción Crear Cuenta

2.- Te aparecera una pantalla que dice EULA, dale aceptar sin miedo como en todas tus RRSS jaja, tranquil@ no pasa nada.
3.- En la siguiente pantalla deberás: Subir foto de perfil (si lo deseas), Nombre de usuario (nick que te guste el mio jp ), Mostrar nombre (como quieres llamarte el mio johnny ), Informacion (una breve biografía tuya ) presiona Crear y listo ya puedes usar Nostr como un Sayayin :-P

4.- Antes de empezar a escribir tu primer post vamos a dar 2 pasos más que son fundamentales y algún día me lo agradecerás (pero si a ti nadie te dice que hacer jajaja, ya puedes empezar a usar Nostr y saltarte estos pasos). Ve a la parte superior izquierda de Damus y presiona en la foto de tu perfil, deberá aparecer un menú que dice Configuración presiónalo y debe llevarte a algunas opciones, entre ellas escoges la que dice Keys

5.- Este es el último paso y es EXTREMADAMENTE IMPORTANTE que lo sigas al pie de la letra por que vamos a guardar tus llaves (usuario y contraseña) de forma segura. Aquí debo informarte que en Nostr no usaras ni correo ni número de móvil ni otro dato personal que te identifique para poder acceder a tu cuenta y por lo tanto debes guardar tú mismo las llaves de acceso ya que si las pierdes NO HAY FORMA DE RECUPERAR, las perderás para siempre y deberás volver a iniciar de nuevo.
Dentro de la opción Keys encontraras dos identificadores el primero que empieza por npub... es tu clave publica (tu usuario) que todos ven en la red y más abajo encontraras tu llave secreta (tu contraseña) esta es la más importante y al activar el botón Mostrar aparecerá y empieza con nsec.... estas dos claves debes copiarlas y guardarlas con total seguridad NO LAS PIERDAS de preferencia para guardarlas usa un administrador de contraseña como Bitwarden o tu propio llavero de ICloud en tu IPhone.

Bien si ya hiciste estos 5 pasos en menos de 5 minutos ya estarás listo para navegar e interactuar con otras personas en #nostr. Existen otros conceptos dentro de la red que ya te explicare en otra guía, por ejemplo, los relés que son los que se encargan de trasmitir tus posts (en forma de notas) a todo el mundo, pero con los que vienen preconfigurados los clientes es suficiente por ahora.
DIVIERTETE NUEVO NOSTRICH
Es momento de lanzarte al universo de Nostr, publica tu primer post Hola Mundo y empieza hacer amigos y te aseguro que muchas buenas personas te responderán para darte la bienvenida, como sugerencia si hablas español o quieres conocer gente de este idioma: ve a la opción UNIVERSO (lupa de buscar) de tu cliente, aquí encontraras el feed global donde aparece todos los posts a nivel mundial donde también puedes conocer gente. Ahí escribes Seguidor Hispano le das seguir a todos los que sigue esa cuenta y puedes empezar a seguir a otros en tu idioma.
Si te ha gustado y servido este minitutorial, compártelo a otros y si quieres puedes también seguirme a veces comparto buenos memes :-) Copia mi usuario en el buscador y me sigues:
npub1whdfgqn66sytcta0l6c7vlt3h2lg67xcnsmzpk3pyvpmsaaxtdwqr8vs60
By Johnny
-
 @ 2d5b6404:d4b500b0
2023-07-08 00:56:26
@ 2d5b6404:d4b500b0
2023-07-08 00:56:26nostr streamからzap streamにタイトルも変更し大幅なアップデートがされました。 今までは自分でcloudflare streamに月額課金してマニュアル設定しなければなりませんでしたが、zap streamとOBSを紐づけてSATS(21 sats/min)を支払うだけで簡単にlive配信を開始することができるようになりました。
必要なものは3つだけです。zap streamとalby(アルビー)とOBSです。
はじめにzap streamにログインするためalbyのアカウント作成が必要になります。別の記事でalbyの登録方法をまとめたのでそちらを参考にしてみてください。
→primalが作成したalby(アルビー)の使い方ショート動画
OBSに関しては多くの解説動画がでていますのでそちらを参考に設定してみてください。 ぼくが参考にした動画です。→ https://youtu.be/ZQjsPJpMLiQ
最後にzap streamとOBSを紐づけるだけです。 zap streamのページを開いてalbyでログインします。 ログインしたら右上のアイコンの横のStreamを押します。

Stream Providers
API.ZAP.STREAM
Stream Url
rtmp://in.zap.stream/liveをコピーして、OBSの設定→配信のサーバーの欄に貼り付けます。
Stream Key
・・・・・・・・・をコピーして、OBSの設定→配信のストリームキーに貼り付けます。

次にBalanceのTOPUPを押してSATSを支払います。21 sats/min 1分21satsなので1時間だと1260satsを先に支払います。長時間配信する場合は多めに入金しておきましょう。
あとはEdit Streamでタイトルやサムネイルを設定してSAVEします。 アダルトコンテンツの場合NSFW Contentにチェックをいれてください。

zap streamとOBSの設定が完了したら、OBSで配信開始すれば勝手にzap streamでlive配信が開始されます。
以上がzap streamでlive配信する方法です。
ライブコーディングやゲーム配信をしているユーザーがすでにいますのでVtuderの方などどんどん配信してみてください。
-
 @ 97c70a44:ad98e322
2023-06-29 15:33:30
@ 97c70a44:ad98e322
2023-06-29 15:33:30First, a product announcement.
Coracle now supports connection multiplexing, which can reduce bandwidth usage by over 90% depending on how many relays you use. It's opt-in for now, but you can set it up by going to Settings and entering
wss://multiplextr.coracle.socialas your "Multiplextr URL".You can check out the source code and self-host the library using this link. If you're a dev and want to add client support for multiplextr, the library I built to support this use case might be of use.
Now, on to your regularly scheduled blog post.

The above announcement isn't irrelevant to what I want to talk about in this post, which is (broadly) the question of "how can Nostr remain decentralized and still support advanced functionality?"
This is probably the most common question articulated among devs and enthusiasts - is search centralizing? What about recommendation engines? COUNT? Analytics? The answer is yes, and responses range from "it'll be fine" to "nostr is already captured".
For my part, I'm not sure if this problem can be solved. Already we have a browser wars dynamic emerging among clients, and business models based on proprietary services and advertising have been publicly considered. For the record, I don't think conventional business models are necessarily bad. The world works this way for a reason and Nostr isn't going to change that by default.
Nevertheless, I want to see a new internet emerge where my attention belongs to me, and I'm not beholden to massive companies who don't give a rip about me. As a result, much of the work I've put into Coracle hasn't gone into fun features, but into things I think will help realize the vision of Nostr. This gives me FOMO as I watch others' progress, but if I don't stay focused on my vision for Nostr, what am I even doing?
I should be clear that this is not a judgment on the motivations of others, building for fun and profit is just as legitimate as building to idealistically realize the best of all Nostrs. However, I would say that it is every developer's duty to keep in mind that what we're trying to accomplish here is not a web2 clone.
Two, and only two options
With all that said, let's get into the meat of the problem. There's a false dichotomy floating around out there that we have two options for adding server-side functionality to the nostr ecosystem. Option 1: pack all required functionality into relays, eliminating the "dumb relay" model, and making it extremely difficult to run a relay. Option 2: keep relays dumb and the protocol minimal, allowing indexers, search engines, and recommendation services (which I'll collectively call "extensions" here) to profit by solving advanced use cases.
Both alternatives are obviously deficient. Relays need to be something hobbyists can run; requiring relays to fold in a recommendation engine or search index makes that much harder, and for every feature required, proprietary solutions will be able to build a bigger moat.
On the other hand, proprietary extensions will not bother to interoperate. This will result in an app-store-like landscape of competing extensions, which will redirect developer and user attention away from relays to extensions. If nostr is to succeed, relays must remain an important first-class concept. Aggregators and indexers that gloss over the differences between relays destroy much of the value an individual relay has to offer.
In either case, some components of the network will become too sophisticated for a layman to deploy. The only alternative is for a few professionals to take up the slack and grow their service as a business. But I think there's a way to squeeze between the horns of the dilemma.
It's all about routing
It seems to me that most people prefer the "extension" model of scaling functionality of Nostr as a pragmatic, market-driven alternative to the impossibility of requiring all relays to support all possible features. And I agree, the folks developing and operating more sophisticated tools should be compensated for their hard work.
The real problem with this approach is that not that extensions are competitive and specialized, but that they obscure the importance of relays by becoming gatekeepers for data by providing additional functionality. If a client or user has to select a search engine and ask it to return results for a given relay, they have given that search engine control over their results, when their trust really should be placed in the relay itself.
(I will say as an aside, that there are scenarios when the gatekeeper approach does make sense, like when a user wants to "bring his own algorithm". But this should be something a user can opt-in to, not a default requirement for accessing the underlying protocol.)
Here's my proposal: instead of requiring users to trust some non-standard extension to make decisions for them, flip the script and make relays the gatekeepers instead. With this approach, the addition of a single feature can open the door for relays to support any extension at no additional cost.
One of the most exciting aspects of Nostr is the redundancy relays provide. With Nostr, you don't need to trust a single entity to store your data for you! Why should you trust a single gatekeeper to route you to that data? Relays don't need to provide search or recommendations or indexing functionality directly, they can simply send you to a third-party extension they deem trustworthy.
This approach allows extensions to piggy-back on the trust already endowed in relays by end users. By allowing relays that are already aligned with end users to broker connections with extensions, they form a circuit breaker for delegated trust. This is more convenient for end users, and makes it easier to switch extensions if needed, since relay operators are more likely to have their finger on the pulse than end users.
It also enables cleaner business relationships. Instead of asking clients to create custom integrations with particular extensions leading to vendor lock-in, an extension provider can implement a common interface and sell to relays instead by offering to index their particular data set.
With this model, relays have the flexibility to either provide their own advanced functionality or delegate it to someone else, reducing the functionality gap that would otherwise emerge with thick relays without removing the ability for extension service providers to run a business, all the while keeping users and clients focused on interacting with relay operators rather than non-standard extensions.
Making it happen
The difficulty with this of course is that add-on services need to be identifiable based on functionality, and they must be interoperable. This means that their functionality must be described by some protocol (whether the core Nostr protocol or an addition to it), rather than by proprietary extensions. There will be extensions that are too complex or special-purpose to fit into this model, or for whom interoperability doesn't matter. That's ok. But for the rest, the work of specifying extensions will pay off in the long run.
This routing layer might take a variety of forms - I've already proposed an addition to to NIP 11 for service recommendations. Clients would look up what add-ons their relays recommend, then follow those recommendations to find a service that supports their requirements.
It also occurs to me having written my multiplexer relay this week (and here we come full circle) that it would be trivially easy for relays to proxy certain types of requests. So for example, a relay might fulfill REQs itself, but pass SEARCH requests on to a third-party extension and relay the result to the end user.
In either case though, a well-behaved client could get all the functionality desired, for all of the data required, without compomising the brilliant trust model fiatjaf came up with.
Conclusion
I think this is a very important problem to solve, and I think relay-sponsored extension recommendations/routing is a very good way to do it. So, please comment with criticisms! And if you agree with me, and want to see something like this become the standard, comment on my pull request.
-
 @ e97aaffa:2ebd765d
2023-07-23 10:15:15
@ e97aaffa:2ebd765d
2023-07-23 10:15:15Em Portugal, os jovens, especialmente os Millennials, é intitulada, a geração mais qualificada de sempre, apesar de ter estudado mais que os seus pais, não está a encontrar uma melhor qualidade de vida. Para muitos a única solução foi/é emigrar, para os que ficam, a precariedade é a ordem do dia ou são trabalhos muito mal pagos. São também vítimas do problema da falta de habitação, adiam ano após ano a constituição de uma família. Provocando um enorme problema de natalidade no país, para contrariar isso, o governo está a atrair estrangeiros para trabalhar em Portugal.
Os Millennials é uma geração martirizada, que já acumula inúmeras crises devastadoras, desde dos PEC do Sócrates, do Subprime, da dívida soberana, da banca, da covid, da inflação, o pior é que não vai ficar por aqui.
Políticas
Como querem aumentar a produtividade do país, com políticas desastrosas e em vez de resolver os problemas estruturais, os políticos preferem ir pela via mais fácil, mais rápida, apenas utilizar paliativos, que não resolve nada, apenas adia o problema e possivelmente agravado-o.
No caso da produtividade, as políticas limitaram-se a criar universidades e formar alunos, mas depois faltou o resto. Não formamos os empresários, não criamos empresas mais produtivas nem sequer criamos leis que facilitem a criação de empresas.
Formamos mão-de-obra qualificada mas depois a “só” existem empregos em callcenters, supermercados ou na restauração e os que conseguem escapar disso, são na generalidade muito mal pagos em comparação ao resto da europa. Isto não é um desrespeito para estas profissões, qualquer trabalho honesto é valido, o problema aqui, é que os jovens estudaram, qualificaram-se e agora só arranjam empregos não qualificados.
O que nós temos visto nas últimas décadas em Portugal, já parece ser uma política oficial, a exportação de trabalhadores qualificados e importação de mão-de-obra barata, a roçar a escravatura.
Somos um país, onde o primeiro-ministro que aconselha os jovens a emigrar, está tudo dito…
O caso de Odemira é uma grande vergonha para o país, com pessoas extremamente mal pagas, a habitar em casas em péssimas condições de salubridade, com dezenas de pessoas a viver na mesma casa.
No passado os estrangeiros eram sobretudo PALOPs, na sua maioria integram-se bem na comunidade. Posso estar errado, mas estas novas ondas de imigrantes (sobretudo asiática) estão a ter muitas dificuldades de integração, isto poderá ser um enorme problema a nível social no futuro e certamente vão crescer movimentos mais extremistas.
Portugal necessita urgentemente renovar os políticos, menos políticos de carreira, menos boys, mais pessoas com conhecimento/experiência no terreno, pessoas com ideias novas, que façam realmente reformas estruturais.
Empresários
Uma parte dos empresários também necessitam de melhorar, são quota-parte do problema da produtividade, eles necessitam de modernizar a sua empresa e principalmente a sua mentalidade. É necessário mudar o modelo de negócio, apostar em produtos com mais valor acrescentado e deixar a produção baseada em mão-de-obra barata.
O sector agrícolas português dizem que não podem pagar aos trabalhadores mais que o salário mínimo e depois queixa-se que existe falta de mão-de-obra e tem que importar trabalhadores. Eu pergunto, como é possível os empresários franceses que vêm a Portugal contratar pessoas, pagam salários muito superiores e conseguem colocar os seus produtos nos supermercados ainda mais baratos que os produtos portugueses.
Em Portugal também existe um problema, o principio básica da economia, oferta e procura não funciona com os salários, isto é notório neste momento. É uma queixa recorrente dos empresários, a falta de mão-de-obra, uma parte dos empresários recusa-se a pagar mais que o salário mínimo, se aumentarem mais os salários certamente aparecia mais pessoas interessadas na vaga, digo eu. Mas preferem faturar menos, recusar encomendas do que pagar salários mais altos. Ou então vão ao estrangeiro contratar mão-de-obra barata, mantendo sempre o problema de produtividade e de produtos de baixo valor acrescentado.
Aquela ideia dos liberais, que sem o salário mínimo haveria mais empregos, em Portugal não funciona. Por isso eu sou um defensor do salário mínimo nacional é necessário em Portugal, sem ele a miséria seria descumunal.
Salários
“Através de um inquérito a 2,2 milhões de jovens entre os 15 e os 34 anos, residentes em Portugal, o perfil dos jovens portugueses foi traçado, em 2021, num estudo da Fundação Francisco Manuel dos Santos, “Os Jovens em Portugal, Hoje”, do qual faz parte o gráfico acima divulgado. De acordo com o documento, no que respeita ao salário líquido mensal, para jovens que trabalham por conta de outrem, 86% inserem-se nos escalões de valores até 1.158 euros. A maior percentagem – 30% – verifica-se no escalão entre 601 e 767 euros.” in poligrafo.sapo.pt
Perto de três quartos (72%) auferem rendimentos que não ultrapassam os 950 euros líquidos por mês.
Além dos baixos salários, temos leis de trabalho obsoletas, onde quem tem contrato sem termo são super protegidos, tem mil e um direitos. Depois há a outra face da moeda, os que têm contratos precários ou a termos, que poucos direitos e na qual permite que os empresários abusem disso.
Nem vou classificar aquelas empresas travestidas de app, que contornam as leis e exploram os seus trabalhadores, pagando à jorna, sem quaisquer direitos. Fazendo concorrência desleal, prejudicando aquelas empresas que respeitam as leis do país.
Habitação
“Ter autonomia e mais independência: a aspiração de qualquer jovem que se prepara para fazer a transição para a vida adulta. Mas em Portugal, esse caminho está cada vez mais difícil. Desde os empregos e salários precários, às dificuldades no acesso à habitação. Comprar casa é, para muitos jovens, um sonho distante – e nem o arrendamento é viável em alguns casos.
Os números do Eurostat não deixam margem para dúvidas: Portugal é o país da União Europeia (UE) em que os jovens saem mais tarde de casa dos pais – 33,6 anos, em média. E não é por apatia ou falta de vontade. A maioria não consegue mesmo pagar por uma casa.” in Idealista
Agora juntando salários baixos, preço da habitação alta e uma inflação alta, é uma bomba relógio.
Texto originalmente publicado em http://www.rei-artur.com/uma-geracao-perdida/ a 10 de Junho de 2023
-
 @ 3f770d65:7a745b24
2023-07-07 17:05:06
@ 3f770d65:7a745b24
2023-07-07 17:05:06Zaps on Nostr are payments that can be sent to other users as a way of tipping, showing appreciation, or providing feedback to content creators. Zaps utilize the Bitcoin Lightning network for payments. These are transmitted over the Lightning network instantly with essentially zero transaction fees.
Zaps represent the only fundamentally new innovation in social media. Everything else is a distraction. - Jack Dorsey
Zaps were publicly introduced in February 2023 with the release of NIP-57 which defined a new Nostr event type called "Lightning Zaps". Zap request events grab the data from a Lightning invoice, namely the payment amount, payee, and payer and then forms a new event that can be captured by relays and displayed by clients.
https://nostr.build/p/nb3285.png
Zaps are a great way to show appreciation for content that one consumes on Nostr or to simply tip someone for their time and effort. To send a Zap, you simply need to tap or click on the Lightning bolt icon next to the profile or note that you want to tip or proceed in an exchange of value for value. You will then be prompted to enter the amount of satoshis you want to send. Once you have sent the Zap, the recipient will be notified and the payment will be instantly sent over the Lightning network.
Zaps are better than traditional payment methods.
- They are fast and efficient.
- Zaps are transmitted over the Lightning network, so you can be sure that your payment will be received instantly.
- They have no transaction fees. This makes them a more cost-effective way to send payments.
- They are easy to use. Sending a zap is as simple as clicking on a button. You do not need to create a Lightning invoice or worry about the technical details of the Lightning network.
- If you are looking for a way to show appreciation for content on Nostr or to simply send payments to other users, then Zaps are a great option.
Zaps are also a fun and friction-less introduction to Bitcoin and the Lightning network. Since Zaps are integrated with many Lightning wallets, the wallets communicates back to Nostr that the payment was successful and the Zap amount is now displayed and tallied on the user's note or user's profile.
The following Bitcoin Lightning Wallets are NIP-57 compatible, meaning that they communicate with Nostr as mentioned above:
Custodial Wallets: * strike.army * vida.page * stacker.news * Bitcoin Jungle * ln.tips (LightningTipBot) * Geyser * Bitcoin Beach * Current (Client+Wallet) * Wallet of Satoshi * Zebedee * Alby * AnonSats * Strike
Self Custodial Solutions: * BTCPay Server * nostdress
Value for value is a relatively new way of thinking about value on the Internet. It is based on the idea that value should be exchanged directly between users, without the need for a third party. This makes it more efficient, more secure, more privacy-preserving, and directly provides value to content creators.
Nostr is one of the first protocols to implement value for value on a large scale. It is already being used by thousands of users to send payments and provide feedback for a variety of purposes. As Nostr and the Lightning network continues to grow, value for value is likely to become even more popular.
Nostr just passed an incredible milestone, surpassing one million Zaps being sent on Nostr in roughly three months time. Those statistics are fairly incredible seeing as the concept of value for value is still not fully understood by the general public and Nostr utilizes Bitcoin's Lightning network as a payment network, which isn't adopted by everyone yet.
https://nostr.build/i/b9def1af659f1c16b08ca5af31b4877232493338d5b3220943b3d0c96b83533b.jpg
One of the most important concepts about Zaps is that Zaps are better than "Likes". Social media and social networking platforms have taught us over the past two decades that Likes are a way to indicate the value of a piece of content. However, these Likes have no value. Likes are hollow. By replacing Likes with Zaps, we are transforming a meaningless action into an action that has true value, monetary value.
https://nostr.build/p/nb5963.gif
We're building the value for value economy on Nostr, one Zap at at time.
-
 @ 97c70a44:ad98e322
2023-06-01 13:46:54
@ 97c70a44:ad98e322
2023-06-01 13:46:54I think I cracked the code on private groups.
Instead of relying on relays to implement access control as in this PR, we could combine the Gift Wrap proposal with @PABLOF7z's nsec bunker to create private groups with easy administration and moderation!
Gift wrap fixes DM metadata leakage by using a temporary private key to send a DM to a recipient. The recipient decrypts the wrapper to find a regular nostr event inside. This could be another kind 4 as in the proposal, or anything else. Which means you can send kind 1's or anything else in a wrapped event.
Now suppose you had a pubkey that you wanted to represent a group instead of a person. Put its nsec in a (modified) nsec bunker, and now you can allow other people than yourself to request signatures. A shared private key! Anyone who has access to this nsec bunker could also de-crypt any gift wrapped note sent to it. Relay-free read access control!
There are lots of ways you could manage this access list, but I think a compelling one would be to create a NIP 51 list (public or private!) of group members and set up the nsec bunker to authenticate using that list. Boom, dynamic member lists!
You could also create a NIP 51 list for admins, and pre-configure which event kinds each list is allowed to post using the group's nsec. So maybe members could only publish wrapped kind-1's, but admins could publish wrapped kind-0's (you can now zap a group!), kind 9's for moderation, updated member and moderator lists, normal kind 1's for public information about the group, etc.
Gift wrap would support:
- Leak-free DMs
- Fully private groups
- Public-read groups (nsec bunker would allow for admin, but everyone would publish regular instead of wrapped events).
- Organizations and other shared accounts, with role-based authorization (list/kind mappings)!
Of course, no clients currently support this kind of thing, but support would not be hard to add, and it creates an entirely new set of affordances with two very simple applications of the core protocol.
There are a few drawbacks I can think of, of course. Gift wrap makes it harder to search notes by tag. You could:
- Leave all tags off (other than for DM recipient as in the proposal)
- Selectively keep tags that aren't revealing of identity
- Encrypt tag values. When a client wants to query a tag, it must encrypt the value using the same pubkey and include that in the filter. This, I think, is ok for the group use case above.
There are also a number of proposals in the works to fix NIP 04 DMs which are apparently broken from a cryptographic standpoint, so implementing this should probably wait until that stuff is sorted out. But it should be possible however that ends up materializing.
So am I nuts? Or is this a galaxy brain solution?
-
 @ 75bf2353:e1bfa895
2023-07-06 19:46:08
@ 75bf2353:e1bfa895
2023-07-06 19:46:08The first meetup was a success. I met one person who lived near me over coffee. He even runs Node and Nostr Relay. What are the odds? I assume it's really low. According to Clark Moody's dashboard, there are about 17,000 available nodes. I haven't verified this number, but this is the first person I met in the wild who runs a bitcoin node.
This gives me hope. I know starting a meetup on a little-known Internet protocol has a snowball's chance in a pizza oven of working, but I'm rationally optimistic. I saw a lot of plebs post their npubs on Saturday because the Twitter chief pissed them off. I don't know why, but it's indicative of the importance of permission-less computer networking. I used to rub my peach fuzz and think the Internet would give people power back from the corporations. TV was just a way to sell soap, drugs, and cars. The corporations didn't even let you use the word "ass." Then they had experts like Colin Powell tell us Iraq had weapons of mass destruction. I didn't believe him because I watched the videos of trucks and warehouses, but evidence of trucks and warehouses is not evidence of weapons. Who was the conspiracy theorist? Me, or Colin Powell? I thought the Internet would fix this. I was active on MySpace and there were no ads.
Then Facebook happened. Then Instagram, which had no ads at first, until it got bought by facebook. Then Facebook experimented with affecting people's moods. . Things got strange. In 2016, the Donkey team accused Russians of influencing the elections. [Cambridge Analytica did some fuckery]9https://en.wikipedia.org/wiki/Cambridge_Analytica#Elections) I don't fully understand, allegedly influencing elections is the US, Australia, India, Kenya, Matla, Mexico, and the UK. In 2020, the Elephant team accused the elections of being rigged. So for about 8 years, a significant portion of the united states as not trusted the results of an election. What do you think the odds of distrust in this upcoming election? I wouldn't bet many sats on it going smoothly.
"A third point is the confirmation of the central role that former spies played in October 2020 in framing the Hunter Biden story in a way that made it easier for Twitter and Facebook to justify their censorship." (Wall Street Journal)
When you zoom out, you realize this is not just about American politics. Similar things are happening all over the world. One day, you see riots in Shi Lanka. A few months later riots in France. Many people blame free speech, but what is free about the algorithms? Facebook also has the right to write code. Code is speech, cypherpunks write code. In my opinion, Facebook is bad speech. The answer to bad speech is more speech Nostr is more speech, better speech in my opinion.
"Cryptography is a surprisingly political technology. In recent years, it has become more so, with the controversy surrounding the Government's Clipper chip, the FBI wiretap legislation, export controls on cryptographic software, and the balance of power between a government and its people. Historically, cryptography has been used mainly by governments for diplomatic and military traffic. But with the coming of the information age, ubiquitous personal computers, modems, and fax machines, this is changing. With an emerging global economy depending more and more on digital communication, ordinary people and companies need cryptography to protect their everyday communications. Law enforcement and intelligence agencies want access to all of our communications, to catch people who break the law, and detect threats to National Security. Civil libertarians want to keep the Government out of our private communications, to protect our privacy and maintain a healthy democracy."
--Phil Zimmermann
Nostr Fixes This
I don't like talking about politics because so many people are programmed to get triggered when you mention certain hot-button topics, but it's possible to use cryptography in a way to preserve freedom. The Twitter files revealed government censorship on the blue bird app. This is relevant to us because public key cryptography because there are no twitter files. The government needs to censor all the relays, not just a single corporation that is too afraid to pay for advertising on shows that use the word "shit." It's time we start thinking of using technology in terms of the Sovereign Individual. Normies debate weather or not a web developer or graphic designer should be compelled to write code or create art they don't agree with. Meanwhile, I used free and open source software to make my own webpage, but if you don't know HTML, Chat GPT does. I made most of the photos using Stable Diffusion. Apple can ban zaps from their apps, but can they ban SamSamskies from writing code? https://notazap.lol/
Until nostr, we didn't have freedom on corporate-controlled, government-censored social media. This is not a blog about politics. It's about communication. I don't want the red team or the blue team to control what the public may or may not see.. I do not wish to be booted from Meetup.com again because I do not identify the color of my skin, my email address, or the name my mother gave me I'm not joining an apple pod bitcoin meetup. I want free speech and freedom from undue influence. It's not that I'm mad at meetup.com. They are a company and can do anything they want, but so am I. There is not a real person named meetup.com just like my mother did not name me blogging bitcoin. I'm amazed that anybody showed up to this meetup at all. It was an awesome experience. It's nice to have freedom on the Internet once again.
Fix the Internet, fix the world wide web.
Snowden Is Back

Edward Snowden was exiled to Russia by the United States Government. He wrote a book titled Permanent Record*. The US government confiscated the proceeds of that book. Now he gets zapped on a censorship-resistant communications protocol named nostr.
Some hate him. Some think he's a hero. Regardless what you think, Snowden did not make a dime from his book; but he gets zapped for notes.
If Edward Snowden can get zapped, they can't stop us.
I would be lying if I said I didn't like NGU, but that's the least interesting thing about bitcoin.
I'm not flying to Washington. I won't write my congressman or bribe my senator to overturn the laws that allow the government to censor the proceeds of books in the United States , but I have the option to zap a man who was exiled to Russia. I'm not a drug dealer, and you probably aren't one either. Maybe it's not such a good idea to use your real name, address, and credit cards to sign up for ubiquitous websites in case they deem sending 1 penny to someone is illegal. IT might be a worse crime than growing marijuana flowers. Be careful. Don't accidentally zap the wrong citizen of the world if you have a blue check.
Says the Elephant Skeleton, "Ban the abortion pill!"
Says the Donkey Skeleton, "Guns will kill!"
Yes, [we will not find a solution to political problems in cryptography,] but we can win a major battle in the arms race and gain a new territory of freedom for several years. Governments are good at cutting off the heads of a centrally controlled networks like Napster, but pure P2P networks like Gnutella and Tor seem to be holding their own.” ~ (Satoshi Nakamoto)
Bitcoin is freedom money, but freedom isn't free. You have to fight for it. You can't just send your bitcoin to BlockFi or Bitconnect 2.0 and wave your bitcoin goodbye. 👋 You must insist on self custody. Use collaborative custody if you need hand-holding. You can't expect to be an expert chart doodler and digital art curator if you do not know the difference between these two jpegs.

That's why my meetup is bitcoin only.
Nostr makes it easy to teach people proper key management with lower stakes. I think creating a nostr key and joining our meetup chatroom is good practice for holding your own bitcoin keys. If you screw it up, at least you won't lose your life savings.
Eventually, I will probably capitulate and join Meetup.com like Neo went back into the Matrix. If so, I still want to use Nostr to post the location of meetups. Even cottage cheese sushi swappers should learn how to use Nostr. They can get a taste of freedom before making their next trade on rug-pull-my-crypto.exchange. They'll come back when rug-pull-my-etf.com screws them over.
Blogging Bitcoin Block Height: 797,471
**This blog is ad-free and is written using the Value4Value model.
Bookmark my habla.news page to follow my work because email subscriptions suck.
sauces
Author's preface to the book: "PGP Source Code and Internals
[The New Libertarian Manifesto[https://mises.org/library/new-liberty-libertarian-manifesto/html/p/468)
-
 @ e97aaffa:2ebd765d
2023-07-23 10:00:25
@ e97aaffa:2ebd765d
2023-07-23 10:00:25Porque escreves tanto?
É uma boa pergunta, eu apesar de não ter o dom para a escrita, devido à minha dislexia, quem ler algo meu, vai perceber. Mas eu tenho a necessidade de escrever, porque dá-me tranquilidade, alguma paz, é como fechar um capítulo do meu pensamento.
Eu tenho um pensamento muito compulsivo, assim que inicia algo, o meu cérebro não pára enquanto não chegar a uma conclusão, certa ou errada não interessa, tenho que chegar a uma conclusão. O meu cérebro deve libertar muita dopamina e o meu corpo está viciado, estou sempre a pensar em algo compulsivamente, assim que acabo algo, inicia logo outro.
Eu costumo dizer, o meu cérebro está cheio de caixinhas, abro-as, fico a pensar nelas por um período de tempo e depois volto a fechar. Por vezes mais tarde, volto a abrir, porque o meu pensamento mudou ou está mais aprofundado, naquela área. E o escrever é muito bom para isto, para fechar as caixas e para mais tarde reler o texto, para eu perceber o desenvolvimento/evolução do meu pensamento.
Mas existem caixas, na qual eu evito abrir, são as minhas caixas de pandora. São pensamentos que não chego a alguma conclusão, parece que ficam num loop interminável, chegam a ser cansativos, a melhor solução é substituir por outro.
Desde jovem que descobri que ao escrever, além de ajudar na articulação do pensamento, permite-me focar apenas numa ideia e assim chegar a uma conclusão mais rápido, permite “fechar” essa ideia. Assim evito estar a pensar em diversos assuntos ao mesmo tempo, sendo por vezes, sendo quase esquizofrénico a quantidade de pensamentos de diferentes áreas que eu penso ao mesmo tempo.
Um bom exemplo, é que neste preciso momento que estou a escrever este texto, eu estou a escrever um outro e também tenho outro em fase de revisão, que nos próximos dias será publicado. E ainda tenho mais 4 tópicos que eu quero colocar no papel.
Eu publico vários aqui nos blog, mas isto é apenas uma parte, porque muitos eu nunca os tornei públicos. Agora já percebem porque eu escrevo, por isso não me importo que ninguém os leia.
Já muitas vezes me questionei se deve ou não publicar um certo texto, mas sempre que eu tenho algum medo da interpretação que as pessoas possam ter sobre o assunto, eu prefiro não tornar público. Porque se eu tiver receio, vou inconscientemente me autocensurar, logo aquele texto não representa a verdade, o meu pensamento. Por isso nestes casos, eu prefiro mantê-los privados.
Dislexia
Apesar de oficialmente nunca me ter sido diagnosticado como disléxico, mas tudo indica que seja, os sinais são muitos.
A primeira vez que eu ouvi falar da dislexia foi a uma professora de português, já tinha 18 anos, era adulto. Ela perguntou se eu não sofria de dislexia, eu na altura não fazia a mínima ideia o que era. Tenho agora 40, na época o ensino e a sociedade era muito diferente de agora. Se fosse agora, possivelmente seria diagnosticado cedo e acompanhado.
Esta professora de português, nem imagina a influência que teve em toda a minha vida, em termos de ensino não mudou muito, era demasiado tarde para mudar algo. Mas para a minha vida mudou muito, finalmente eu percebi o que tinha, durante anos soube que existia alguma coisa, mas nunca soube o quê. Assim permitiu perceber melhor o meu problema e arranjar estratagemas para minimizar as suas consequências, apenas minimizar porque não existe solução.
Durante todo o ensino, eu sempre fui um aluno muito frustrado, os resultados nos exames/testes (e notas) sempre foram muito inferiores aos meus conhecimentos. Eu não sou sobredotado, mas sendo honesto, considero-me inteligente, só que os resultados escolares eram maus, nunca percebia o porquê, o ensino frustrava-me.
Lembro-me perfeitamente, naquelas conversas de alunos após os exames, a analisar as respostas, naquele momento eu tinha consciência que sabia a maior parte das respostas, iria ter uma boa nota. Só que quando recebia a correção do professor, era sempre muito inferior ao que eu esperava.
Esta frustração aconteceu durante todo o ensino, desde da escola primária até ao secundário, para minimizar a frustração, eu sempre dizia aos meus colegas e aos meus pais que os exames não me corriam muito bem ou os repetitivos “mais ou menos”.
Mesmo o ensino nunca percebeu o meu problema, a época era outra e tratava-me como um burro, estava em constante aulas de apoio.
Só mesmo quando repeti a disciplina de Português B no 12º ano, aquela professora deu um “rosto” ao problema, até aquele momento nunca tinha ouvido falar de dislexia, li muito sobre o assunto e a professora estava correta. Além de “diagnosticar” o problema, deu um método para minimizar o problema e concluir a disciplina. A ideia dela foi, em vez de responder a todas as perguntas dos exames/testes, é preferível responder a menos perguntas e revisar várias vezes as respostas. Este método tem um problema, não permite ter grandes notas, como eu não respondia a todas as perguntas, o máximo que eu poderia ter era 14 ou 15. Mas permitiu ter uma nota para concluir a disciplina. Isto colocava-me sempre em desvantagem em relação aos meus colegas, para fazer um exame completo, necessitaria de mais de 40% de tempo. O pior é que isto não se restringe apenas ao ensino, é em tudo na minha vida, eu sou muito mais inteligente que aquilo que demonstro.
Qualquer coisa que eu escrevo é obrigatório reler várias vezes e cada vez que leio encontro novos erros, especialmente falta de palavras. É algo inexplicável a quantidade de palavras que eu “como” ao escrever. O mais estranho, eu escrevo mal (faltam palavras) mas quando leio, às vezes encontro as falhas mas muitas vezes não encontro as falhas, eu “leio” as palavras como lá estivesse escritas mas não estão. Eu posso ler 10 vezes e de certeza ainda tem erros, a minha escrita (tanto à mão, como no pc), a mão não consegue acompanhar a velocidade do pensamento, existe uma enorme descoordenação entre os dois.
Ao ler texto escrito por outros também tenho muitas dificuldades, porque invento muito, um erro comum é ler apenas apenas a primeira sílaba de uma palavra e inventar o resto, tento adivinhar, mas isto é tudo inconsciente. Eu cometo muitos erros ao ler, por isso eu detestava ler em voz alta na escola. Os problemas não ficam só por aqui, vai mais longo mas estes são os mais graves porque criam muitas limitações.
A dislexia é um mistério.
Este é seguramente o texto mais pessoal que eu alguma vez escrevi neste blog, durante todos estes anos nunca publiquei publicamente dados nem informações pessoais, mantendo o OpSec.
Texto publicado em http://www.rei-artur.com/pensamento-compulsivo/ a 19 de Julho de 2023.
-
 @ e97aaffa:2ebd765d
2023-07-23 09:43:17
@ e97aaffa:2ebd765d
2023-07-23 09:43:17Uma dívida que ecoou na cabeça de um jovem, no final da década de noventa, com um pensamento inquieto de quem nunca saiu da idade dos porquês. Para ser honesto eu saí da idade dos porquês, apenas deixei de fazer as perguntas aos outros, eu próprio procuro as respostas, mas aquela inquietação ainda está cá toda.
A dúvida era:
Como é possível uma casa com 10 anos valer mais do que quando era nova?
A resposta a esta pergunta é mais complexa do que parece à primeira vista, demorei bastante tempo até encontrar. Também temos que entender o contexto, na época a internet estava dando os primeiros passos, eu não tinha internet em casa, o acesso à informação era limitado.
Estas e outras curiosidades estimularam o meu conhecimento/gosto por política, economia, moeda e política monetária. São várias áreas, um espectro muito alargado, mas é necessário, para responder à pergunta.
Quando era jovem, fazia-me muita confusão, tudo o que era vendido em segundo mão era sempre mais barato, com as excepções das casas e da arte. Eu não conseguia perceber como uma habitação usada, mesmo estando em bom estado, existe sempre algum desgaste, valer mais do que quando era nova. Eu estou a falar na generalidade e sempre a longo prazo.
Com o tempo eu encontrei a resposta, tudo não passa de uma ilusão, não são as casas que valorizam, a moeda é que perde valor. Ou seja, o número é maior, mas o seu real valor é similar. O imobiliário é utilizado como sendo um “bom” produto para combater a inflação, não por ser bom, mas por ser o menos mau. Porque a maioria dos produtos financeiros são piores que o imobiliário.
Poupança
Os keynesianos gostam muito de apregoar que o dinheiro não é para acomular, é para circular. Ao criarem inflação, “obrigam” as pessoas a gastar o dinheiro, porque se ficar parado no banco perdem poder de compra, a taxa de inflação é superior à taxa de juro dos depósitos, este tipo de política criaram uma sociedade de consumismo desenfreado. As pessoas necessitam de uma poupança, de uma segurança para o seu futuro, como não compensa ter dinheiro no banco.
Isso leva-nos a um problema, década após década de políticas monetárias desastrosas, as pessoas optam por preservar o seu património no imobiliário, ficando muito exposta a este mercado.
Depois acontecem estes cúmulos, como “Portugal é o país com mais casas, mas 735 mil estão vazias”, é claro que algumas são devolutas ou habitações de imigrantes mas existem muitas e muitas casas são unicamente um produto financeiro.
Mas isto de usar o imobiliário com um produto financeiro desvirtua o mercado, cria as cíclicas bolhas, agora estamos num momento muito complicado a nível mundial, em especial em Portugal. Estamos a viver um momento em que os jovens não conseguem encontrar uma casa para viver, existem poucas casas e as que existem são valores absurdos.
Enquanto os nossos pais levavam uma década a pagar uma casa, agora os jovens, no mínimo levam 3 décadas. Se nada for mudado vamos chegar ao ponto como já existe no Japão, os empréstimos que passam para os filhos, uma geração já não é suficiente para pagar a casa para viver.
Pode parecer um contrassenso, mas a realidade não é que as casas ficaram muito mais caras, as pessoas agora é que ganham muito menos que no passado, as casas têm acompanhado a inflação real mas os vencimentos têm perdido desde 1971.

No tempo dos nossos pais, em muitas famílias apenas trabalhava o homem e era suficiente para comprar/construir uma casa e sustentar a sua família. Agora trabalham os dois membros do casal e mesmo assim tem muitas dificuldades em sustentar-se. Ou seja, o custo de aquisição de uma casa acompanhou a inflação, mas os rendimentos não.
O aumento de produtividade gerado pelo desenvolvimento tecnológico, não está a ser canalizado para os trabalhadores, está a ir uma pequena parte para as empresas, mas a maior percentagem vai para os estados, é devorado pela inflação. A industrialização, permitiu a redução de postos de trabalho e a consequente baixa do preço dos produtos, mas isto não está a acontecer no imobiliário.
A criação de bolhas é algo cíclico neste sistema monetário, até vou mais longe, este sistema incentiva a criação de bolhas, para permitir que alguns ganhem dinheiro à conta de outros que não percebem como isto funciona. A ideia é mesmo essa, a complexidade é tal, para o povo não perceber como este sistema funciona. A curto prazo as casas até podem valorizar acima da inflação, mas as bolhas acabam sempre por rebentar e a correção acontece.
A longo prazo o imobiliário “acompanha” a inflação, mas existe uma maneira de valorizar o imobiliário (acima da inflação), através da alteração da zona envolvente. Existem aqueles, sem escrúpulos, que usam o imobiliário como um meio para enriquecer, é a principal origem da corrupção em Portugal, especialmente nas autarquias, através da mudança de PDM, aprovação de projetos como pontes, estradas, hospitais, reabilitação e etc. O “insider trading” é uma fonte inesgotável de dinheiro.
Bem de Primeira Necessidade
Tudo isto porque vivemos numa ideia errada criada por keynesianos, a meu ver é preferivel acomular dinheiro, do que acumular casas. O imobiliário deve servir exclusivamente para o seu objectivo inicial, casas para as pessoas viverem ou como instalações/meios para as empresas funcionarem. Nunca um produto financeiro, se querem investir, vão para as bolsas de valores, comprem ações. Os imóveis deveriam ser baratos, de fácil acesso, é um bem de primeira necessidade, são para servir as pessoas e empresas, nunca um meio de poupança ou de enriquecimento.
As casas são um bem de primeira necessidade, mas os seus preços estão exorbitantes, impossíveis de pagar pelos mais jovens, está a criar movimentos de ocupas, se a bolha não rebenta estes movimentos radicais vão crescer drasticamente. Se rebentar, as pessoas que compraram recentemente terão problemas, a dívida ao banco será maior que o valor da casa. Isto só demonstra que este sistema não funciona, não é bom para os dois lados,
Em Espanha está a ser algo preocupante, são mais de 17 mil ocupações por ano. Existem casos de pessoas que vão de férias e quando voltam têm a casa ocupada. Devido à altas inflações, as pessoas vão continuar a perder poder de compra, o que irá aumentar a crispação/revolta de uma parte da sociedade, vai alimentar os movimentos de ocupas.
As pessoas vão pressionar os governos e estes vão tomar medidas menos ortodoxas, para contrair a dificuldade de encontrar uma casa para habitar.
Em Portugal, o governo está a criar leis: * Limitações à subida da renda dos novos contratos * Arrendamento forçado de casas, mesmo contra a vontade do dono * Limitações/proibições para o alojamento local * Fim dos vistos ‘gold’
No Canadá proíbe estrangeiros não residentes de comprar casas.
Se esta crispação entre as pessoas/governos e os proprietários aumentar, o que acontecerá se o imobiliário deixar de ser um investimento seguro, certamente haverá uma fuga de capital para outros ativos.
Qual a dimensão do imobiliário?

São mais de 330 Triliões de dólares a nível global, é o activo que mais acumula. É claro que dos 330 Triliões, uma parte significativa é primeira habitação ou instalações comercial/industrial, mas uma parte é “produto financeiro”, como proteção contra a inflação.
O que aconteceria se existisse uma moeda que preservasse o poder de compra, um produto financeiro superior ao imobiliário, uma reserva de valor a longo prazo, certamente uma parte do capital alocado nos imóveis moveria para essa moeda.
Artigo publicado em http://www.rei-artur.com/mercado-imobiliario/
-
 @ 7f5c2b4e:a818d75d
2023-07-05 13:49:49
@ 7f5c2b4e:a818d75d
2023-07-05 13:49:49This translation of the nostr:naddr1qqxnzd3cxserxdpsxverzwp4qgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa28zcj37a was prepared by nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624
Habla es una plataforma basada en Nostr que te permite crear y gestionar notas de nostr de formato largo (long-form posts). Se podría comparar con Medium, pero Habla es mucho más que eso. Habla es superior a las plataformas tradicionales de blogs porque está construida sobre Nostr. Es interoperable con una plétora de otras aplicaciones Nostr, lo que hace que la experiencia del usuario sea fluida y más atractiva. Además, gracias a la Lightning Network, tu aportación -si los lectores la consideran valiosa- puede y será recompensada al instante con el mejor dinero que la humanidad ha visto jamás: bitcoin.
¿Qué es Nostr?
Nostr es una nueva forma de comunicarse online que ofrece un montón de ventajas a sus usuarios. Es gratis para todo el mundo; no necesitas un documento de identidad ni ningún otro tipo de verificación por parte de terceros para empezar a conectarte, relacionarte con personas afines y hacer crecer la comunidad que te rodea. Nostr suele confundirse con una plataforma de redes sociales, pero es mucho más que eso. Te animamos a que consultes los recursos de Nostr reunidos aquí para darte cuenta de la magnitud potencial de esta herramienta.
¿Cómo inicio sesión en Habla?
Para empezar a escribir en Habla, simplemente crea una cuenta Habla/Nostr e inicia sesión. Sigue estos unos sencillos pasos para registrarte, empezar a compartir valor y recibir valor de vuelta.
¿Cómo gano sats con Habla?
Habla te permite recibir valor directamente de tus lectores. No se requiere cuenta bancaria o identificación. Simplemente conecta tu dirección Lightning a tu cuenta Habla / Nostr y recibe fondos directamente en tu monedero - sin terceras partes, sin esperar retiros, sin agobios. Sigue estos sencillos pasos para hacerlo.
¿Por qué publicar en Habla es diferente?
El protocolo Nostr es superligero, lo que introduce algunas peculiaridades en cómo deben comportarse las aplicaciones basadas en Nostr. No entraremos en detalles técnicos, pero la diferencia más obvia que notarás como creador de contenido es que tendrás que usar un formato de texto diferente y, posiblemente, inusual mientras redactas tus posts. Pero no temas; Habla proporciona herramientas que hacen este proceso fácil e intuitivo. Aquí hay un video rápido de nostr:npub1wkljx5c6a8uccc5etws8ry0y3r4dgavh2dcav0tal4rtmcdl4z2sfu5u0t que explica lo básico de publicar con Habla (la guía fue hecha antes del rediseño, pero sigue siendo útil):
https://nostr.build/p/nb9474.mp4
Habla (y muchas otras aplicaciones Nostr) utiliza un formato bien establecido, que se llama Markdown. Existe desde hace casi una década y es compatible con la mayoría de las aplicaciones que utilizas a diario. La razón por la que puede que no hayas oído hablar de Markdown es porque las aplicaciones tradicionales suelen ocultarlo al usuario, y nosotros estamos trabajando para hacerlo también. Puedes encontrar más información sobre Markdown aquí.
¿Dónde se almacena mi contenido?
Las plataformas de blog tradicionales almacenan tus contenidos en sus propios servidores. Es un enfoque cómodo y (solía ser) sólido, pero conlleva riesgos críticos. Dejar los frutos de tu trabajo en manos de una sola parte significa que tienen el control total sobre tu contenido. Nostr lo soluciona. Cada vez que publicas algo, tu contenido se transmite a numerosos relés para su posterior almacenamiento y redistribución. Si algún operador de relé bloquea tu publicación o se niega a redistribuirla, tus lectores pueden recurrir a otros relés y acceder a tu contenido (no te preocupes si esto suena complicado; todo sucede bajo cuerda). Esto garantiza que nunca te silencien. Dicho esto, Habla no gestiona su propio relé; hemos decidido concentrarnos en lo que mejor sabemos hacer -construir una plataforma de blogs intuitiva, eficiente y fácil de usar que recompensa- y dejar el almacenamiento y distribución de contenidos a los profesionales en ese campo.
¿Cómo publico?
Habla te proporciona todas las herramientas necesarias para producir posts ricos y que destaquen. Prepara tu artículo, formatea tu texto con la ayuda de las herramientas designadas, añade medios y previsualiza los resultados antes de publicar. Todo lo que necesitas está al alcance de tu mano, y la plataforma es cada día mejor y más amigable.
¿Quién puede leer mis mensajes en Habla?
Cualquier persona en Internet puede leer tus posts. Sin embargo, si a tus lectores les gustaría interactuar con tu trabajo - ya sea siguiéndote / comentando / devolviéndote valor - deben crear una cuenta en Nostr. Te animamos a que ayudes a tus seguidores a introducirse en Nostr para hacer crecer una comunidad próspera y alcanzar nuevas cotas. Esta guía rápida te ayudará a ti y a tus compañeros a empezar.
Este FAQ es un trabajo en curso, y evolucionará a medida que Habla y Nostr se conviertan en herramientas aún más potentes. Por favor, dame tu opinión para que pueda mejorarla.
-
 @ 76c71aae:3e29cafa
2023-05-30 21:59:50
@ 76c71aae:3e29cafa
2023-05-30 21:59:50Joining a new digital community can be an exhilarating and empowering experience. This has been observed on numerous occasions when people join new platforms such as Nostr, BlueSky, Farcaster, Post.news, Tribel, and many others, as well as older social media platforms such as blogs, Usenet, LiveJournal, Xanga, AOL, Flickr, Facebook, Instagram, and TikTok.
Initially, these spaces create an idealistic environment where individuals are eager to connect, share, and participate in a virtual gathering that resembles a festival. However, it is worth examining what it is about these new social spaces that generates such a euphoric atmosphere, and whether it is feasible to sustain this utopian sentiment as communities expand and develop.
The Magic of Connection:
Joining a new digital community can be a transformative experience. In her book "Paradise Built in Hell," Rebecca Solnit argues that when people are taken out of their familiar routines and confronted with real human needs, the best aspects of human nature come to the forefront. This disproves the negative assumption that humans are inherently selfish and demonstrates our natural ability to empathize and connect with one another. The sense of community and collaboration that we feel in emerging social spaces, patticipatory festivals such as 'Burningman', are a great example of this phenomenon.
Utopias Form Where They Shouldn’t Exist:
The concept of "Paradise Built in Hell" becomes evident during natural and economic disasters. I personally witnessed this idea during Argentina's economic crisis in the early 2000s. Despite the difficulties, people came together and collaborated in new ways to support each other, as the collapsing economy demanded it. This same phenomenon is observed following earthquakes and other natural disasters, where people often speak of those days with a magical, almost reverential tone.
Rebecca Solnit argues that "Disaster is when the shackles of conventional belief and role fall away and the possibilities open up; people rise to the occasion or sink to the level of their fears and prejudices." In these challenging moments, we see the true nature of humanity: our ability to show compassion, resilience, and unity in the face of adversity.
Social Media and All Digital Spaces Have Physical Analogues:
The similarities between digital and physical communities are rooted in the fact that each has its own distinct set of unspoken rules and social norms. Just as we know to be quiet in a library, loud at a concert, social at a cocktail party, and anti-social on the subway, we also understand the unique dynamics of different digital platforms. Twitter resembles a bustling dive bar, Instagram an art gallery, TikTok an amusement park hall of mirrors, and Facebook a community hall rented for a retirement party. Every new digital space has its analogues in the physical world because human interaction remains consistent, even if the medium differs. As we navigate the ever-changing landscape of digital communities, we are reminded of our innate ability to adapt, connect, and thrive in the face of adversity. This adaptability empowers us to form new connections and rediscover the power of community, whether in the digital or physical realm.
The Small Community Paradox:
To maintain the utopian atmosphere of new digital communities, one effective approach is to keep them small or create numerous smaller sub-communities. In these sub-communities, people can engage in the social labor of connection and conflict resolution.
It is important to note, however, that this approach may conflict with the network effect principle. This principle states that each new member joining the community increases its overall value for all participants. As communities grow and the network effect takes hold, the utopian feeling may often fade, giving way to sub-tribes and conflict.
Nevertheless, with a confident approach, the community can adapt and navigate these challenges to foster a positive environment for all members.
The Fleeting Nature of Utopia:
The fleeting utopian sensation experienced within new digital communities is inevitable. Although it is not the design or coding of platforms such as BlueSky, Nostr, Mastodon, or Scuttlebutt that generates this feeling of euphoria, it is instead the human dynamics of joining something novel and building a community that cultivates this enchanting ambiance. Hakim Bey's concept of Temporary Autonomous Zones (TAZs) endorses this notion, demonstrating how short-lived spaces of freedom and interaction can emerge within established social structures. As communities expand and progress, the real challenge lies in sustaining the initial energy and sense of connection that made them so desirable in the first place.
Parallel to Protests and Uprisings:
This utopian sentiment is not limited to digital communities; it is also present during times of revolution, protests, and uprisings. There is a profoundly human element to the sense of love, connection, solidarity, and community that arises during these moments.
The most impactful moments of my life have been when I participated in protests that were met with repression. These protests ranged from tree-sits to protect old-growth redwoods in the forests where I grew up, to large convergences of the anti-globalization and anti-war movements, to Occupy's reclamation of public spaces, and to recent Black Lives Matter protests. All of these protests were scenes of anguish, repression, and, in some cases, violence, especially from the police. However, they were also places where I experienced the most love, connection, humanity, and common purpose. We were all individuals, together, living and breathing solidarity.
Cultivating and Sustaining Utopian Energy:
To preserve the utopian essence of new digital communities as they grow, one approach is to foster a culture of empathy, connection, and inclusiveness from the very beginning. Prioritizing these values and actively engaging in conflict resolution can help communities maintain that special feeling.
Another way to preserve the utopian essence of digital communities is to focus on building tools for the construction and maintenance of these digital public spaces. Unlike corporate social media platforms that only provide an illusion of public space while actually being privately owned, like a shopping mall, we need to create spaces that are community-controlled and collectively owned as a commons with confidence.
Understanding the Commons:
The concept of the commons offers a compelling alternative to traditional models of state or private ownership. Elinor Ostrom, the first woman to win the Nobel Prize in Economics, conducted extensive research on this topic, and her findings are truly remarkable. Through her work, she proved that commons can be effectively managed and maintained, debunking the misguided belief that these resources are doomed to fail and end in tragedy.
Designing for Digital Commons:
To design digital commons, we must prioritize transparency, decentralization, and participatory governance. By empowering users to make decisions about the direction and rules of their digital communities, we ensure that the spaces remain truly public and that the needs and desires of the community are at the forefront.
Open-source technology and decentralized protocols can play a vital role in the development of these digital commons. By allowing users to maintain control over their data and ensuring that no single entity has a monopoly over the platform, we create an environment that fosters collaboration, creativity, and innovation.
The Characteristics of a Well-Functioning Digital Commons:
- Clearly defined boundaries: Members and their rights are easily identifiable, and access to the shared digital resources is well-regulated.
- Proportional equivalence between benefits and costs: Users contribute to the commons according to their capabilities, and benefits are distributed fairly among members.
- Collective decision-making: Users have a say in shaping the rules and policies that govern their digital communities, promoting a sense of ownership and accountability.
- Monitoring: Transparent systems are in place to track the usage and management of shared resources, ensuring that members adhere to established rules.
- Graduated sanctions: Penalties for rule violations are proportional and escalate based on the severity and frequency of the transgressions.
- Conflict resolution mechanisms: Efficient and fair processes are in place to address disputes among members, promoting harmony and trust within the community.
- Minimal recognition of rights to organize: Users have the autonomy to self-organize and make decisions about their digital commons without excessive interference from external authorities.
- Nested enterprises: Digital commons are organized into multiple, interconnected layers of governance, with smaller communities operating within the context of larger ones, fostering collaboration and coordination.
By incorporating these principles into the design of digital commons, we can create spaces that are robust, sustainable, and equitable. This, in turn, fosters innovation, collaboration, and genuine community engagement.
Developing Community-Driven Tools:
To create and maintain digital public spaces, we need tools that empower communities to effectively manage their digital commons. These tools should facilitate communication, conflict resolution, and decision-making while promoting inclusiveness, empathy, and shared values. By empowering communities to shape their digital spaces and collaboratively resolve issues, we can help preserve the utopian essence that initially attracted people to these platforms.
Adapting to Growth and Change:
As digital communities continue to grow, it's crucial to acknowledge that their needs and challenges will inevitably change over time. To maintain a utopian atmosphere, we must be willing to adapt and consistently improve the tools and processes that sustain these digital public spaces. By promoting continuous feedback and collaboration among community members, we can ensure that the platform remains responsive to the needs of its users, fostering an environment of connection and belonging with conviction.
Conclusion:
Joining a new digital community can be a thrilling experience, but maintaining that sense of euphoria as the community grows can be difficult. To achieve this, we must design and construct digital commons that prioritize community control, collective ownership, and participatory governance. With the appropriate tools and a dedication to adapting to the evolving needs of the community, we can create spaces that continue to foster the magic of connection even as they transform. In doing so, we can nurture and sustain the utopian energy that makes these digital spaces so unique.
Post Script:
Since the completion of this essay, Bluesky has evolved from its initial utopian stage to a phase grappling with context, norms, and scalability. With an increasing user base, the once agreed-upon behavioral norms began to crumble. The initial playfulness, while staying within the community's value constraints, took a disturbing turn when individuals started posting racist and homophobic content. The situation deteriorated rapidly, escalating to the point of issuing death threats. Inspired by the "Nazi bar" parable, the community demanded urgent action to outline acceptable behavior and remove those who couldn't comply.
Bluesky, currently hosted on a single server, possesses the capability to enforce a unified set of community guidelines and terms of service. The creators of Bluesky, much like any other social media platform's developers, aimed for a laissez-faire approach. However, they eventually had to revise the terms of service and ban the trolls. This action was chaotic and resulted in significant loss of trust and goodwill.
Additionally, this did not aid the community in establishing governance for the burgeoning social media commons. Protocols such as Bluesky, Nostr, DSNP, Scuttlebutt, Farcaster, and Lens are not designed to operate in isolation. Among these, only ActivityPub and Mastodon have successfully implemented a model to manage abuse and community moderation at scale. Nonetheless, potential solutions are under development. I've personally contributed to proposals for specifications, codes, and norms on Nostr and know that Bluesky's team is making similar strides.
It is essential that the user community actively participate in this process. The Design Justice movement provides a valuable blueprint and strategies for achieving this. By applying principles of co-design and design justice, we can collaboratively build solutions. The stakes are too high to leave this endeavor to a small group of technologists alone.
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ b9e76546:612023dc
2023-06-07 22:12:51
@ b9e76546:612023dc
2023-06-07 22:12:51
#Nostr isn't just a social network, that's simply the first use case to sprout from the Nostr tree.
Simple Blocks, Complex Change
Nostr isn't just a social network, in a similar way that Bitcoin isn't just a transaction network. Both of these things are true, but they each miss the more significant elements of what they accomplish.
In my mind, the source of Nostr's true potential is two fold; first, in fundamentally changing the centralized server model into an open environment of redundant relays; and second, it eliminates the association of clients with their IP address and metadata, and replaces it with identification via public keys. Within this one-two punch lies the most important tools necessary to actually rearchitect all of the major services on the internet, not just social media. Social is simply the interface by which we will connect all of them.
The combination of this simple data & ID management protocol with decentralized money in #Bitcoin and #Lightning as a global payments network, enables nostr to build marketplaces, "websites," podcast feeds, publishing of articles/video/media of all kinds, auction networks, tipping and crowdfunding applications, note taking, data backups, global bookmarks, decentralized exchanges and betting networks, browser or app profiles that follow you wherever you go, and tons more - except these can be built without all of the negative consequences of being hosted and controlled by central servers.
It separates both the data and client identity from the server hosting it. Handing the ownership back to the owner of the keys. We could think of it loosely as permission-less server federations (though this isn't entirely accurate, its useful imo). Anyone can host, anyone can join, and the data is agnostic to the computer it sits on at any given time. The walls are falling away.
Efficiency vs Robustness
There is also a major secondary problem solved by these building blocks. A byproduct of solving censorship is creating robustness, both in data integrity, but also in data continuity. While the fiat world is so foolishly focused on "efficiency" as the optimal goal of all interaction, it naively ignores the incredible fragility that comes with it. It is far more "efficient" for one big factory to produce all of the computer chips in the world. Why build redundant manufacturing to produce the same thing when one factory can do it just fine? Yet anyone who thinks for more than a few seconds about this can see just how vulnerable it would leave us, as well as how much corruption such "efficiency" would wind up enabling.
Nostr is not alone either. Holepunch is a purely P2P model (rather than based on relays) that accomplishes the same separation in a different way. One where the clients and servers become one in the same - everyone is the host. Essentially a bittorrent like protocol that removes the limitation of the data being static. The combination of their trade offs & what these protocols can do together is practically limitless. While Nostr begins building its social network, combining it with what Synonym is building with their Web of trust, (the critical ingredient of which is public key identification) we can "weigh" information by the trust of our social graph.
Not too long ago, a friend and I used Nostr to verify who we were communicating with, we shared a Keet (built on Holepunch) room key over encrypted nostr DM, and opened a P2P, encrypted chat room where we could troubleshoot a bitcoin wallet problem and safely and privately share very sensitive data. The casual ease by which we made this transaction enabled by these tools had us both pause in awe of just how powerful they could be for the privacy and security of all communication. And this is just the very beginning. The glue of #Lightning and #Bitcoin making possible the direct monetization of the infrastructure in all of the above has me more bullish on the re-architecting of the internet than ever in my life. It cannot be reasonably called an insignificant change in incentives to remove both the advertiser and the centralized payment processor from inbetween the provider and the customers online. The base plumbing of the internet itself may very well be on the verge of the greatest shift it has ever gone through.
A Tale of Two Network Effects
I would argue the most significant historical shift in the internet architecture was the rise of social media. It was when we discovered the internet was about connecting people rather than computers. The social environment quickly became the dominant window by which the average person looked into the web. It's the place where we go to be connected to others, and get a perspective of the world and a filter for its avalanche of information as seen through our trust networks and social circles. But consider how incredibly neutered the experience really is when money isn't allowed to flow freely in this environment, and how much it actually would flow, if not for both centralized payment processors and the horrible KYC and regulatory hurdle it entails for large, centralized entities.
The first time around we failed to accomplish a global, open protocol for user identity, and because of this our social connections were owned by the server on which we made them. They owned our digital social graph, without them, it is erased. This is an incredible power. The pressures of the network effect to find people, rather than websites, took a decentralized, open internet protocol, and re-centralized it into silos controlled by barely a few major corporations. The inevitable abuse of this immense social power for political gain is so blatantly obvious in retrospect that it's almost comical.
But there is a kind of beautiful irony here - the flip side of the network effect's negative feedback that centralized us into social media silos, is the exact same effect that could present an even greater force in pushing us back toward decentralization. When our notes & highlights have the same social graph as our social media, our "instagram" has the same network as our "twitter," our podcasts reach the same audience, our video publishing has the same reach, our marketplace is built in, our reputation carries with us to every application, our app profiles are encrypted and can't be spied on, our data hosting can be paid directly with zaps, our event tickets can be permanently available, our history, our personal Ai, practically anything. And every bit of it is either encrypted or public by our sole discretion, and is paid for in a global, open market of hosts competing to provide these services for the fewest sats possible. (Case in point, I'm paying sats for premium relays, and I'm paying a simple monthly fee to nostr.build for hosting media)
All of this without having to keep up with 1,000 different fucking accounts and passwords for every single, arbitrarily different utility under the sun. Without having to setup another account to try another service offering a slightly different thing or even just one feature you want to explore. Where the "confirm with your email" bullshit is finally relegated to the hack job, security duck tape that it really is. The frustrating and post-hoc security design that is so common on the internet could finally become a thing of the past and instead just one or a few secure cryptographic keys give us access & control over our digital lives.
The same network effect that centralized the internet around social media, will be the force that could decentralize it again. When ALL of these social use cases and connections compound on each other's network effect, rather than compete with each other, what centralized silo in the world can win against that?
This is not to dismiss the number of times others have tried to build similar systems, or that it's even close to the first time it was attempted to put cryptographic keys at the heart of internet communications. Which brings me to the most important piece of this little puzzle... it actually works!
I obviously don't know exactly how this will play out, and I don't know what becomes dominant in any particular area, how relays will evolve, or what applications will lean toward the relay model, while others may lean P2P, and still others may remain client/server. But I do think the next decade will experience a shift in the internet significant enough that the words "relay" and "peer" may very well, with a little hope and lot of work, replace the word "server" in the lexicon of the internet.
The tools are here, the network is proving itself, the applications are coming, the builders are building, and nostr, holepunch, bitcoin and their like are each, slowly but surely, taking over a new part of my digital life every week. Case in point; I'm publishing this short article on blogstack.io, it will travel across all of nostr, I'm accepting zaps with my LNURL, it is available on numerous sites that aggregate Kind:30023 articles, my entire social graph will get it in their feed, & there will be a plethora of different clients/apps/websites/etc through which the users will see this note, each with their own features and designs...
Seriously, why the fuck would I bother starting a Substack and beg people for their emails?
This is only the beginning, and I'm fully here for it. I came for the notes and the plebs, but it's the "Other Stuff" that will change the world.
-
 @ 82fa3b0c:8f50d0f5
2023-07-23 08:42:26
@ 82fa3b0c:8f50d0f5
2023-07-23 08:42:26On the night of Saturday, July 22nd (U.S. time), Twitter's owner, Elon Musk, tweeted a vote to "change the platform color from the current blue to black." He later tweeted, "And soon, we'll bid farewell to the Twitter brand, and gradually to all the birds as well."
"If an excellent X logo is posted tonight, we'll unveil it to the world tomorrow," he added.
Following this tweet, numerous users have posted their designs for the "X" logo.
Musk later tweeted things like "Deus X" (Deus Ex?) and "We shouldn't make appliances too 'smart'," making the logo change tweet seem like a passing whim on a Saturday night.
In April, he temporarily changed Twitter's logo to a Shiba Inu dog, only to revert it shortly after.
At the time of completing the Twitter acquisition, Musk had tweeted, "Acquiring Twitter facilitates the construction of the X app." This suggests that there's a possibility of renaming Twitter to the "X" brand. Articles speculating such possibilities have been scattered around. What's worth recalling here is Elon Musk's ambition, X.com. He might not be looking to rebrand Twitter, but perhaps replace Twitter with a super-app named "X." Twitter has become deeply embedded in our daily lives, and when something goes wrong with Twitter, we're quick to blame "someone." People complain about centralized power structures when faced with account suspensions or censorship. Today, Elon simply tweeted "侘寂."
Let's remember when Jack stepped down from the CEO position of Twitter, his one-word tweet was "I love Twitter." Perhaps the Twitter we've known and loved may come to an end tonight. Did he tweet "侘寂" mourning the end of Twitter? It would be sad to see that future, but this might be the shining moment for Nostr. However, just like Twitter scaled up during the Arab Spring, protocols that spread due to conflicts might truly embody "侘寂."
-
 @ 180a6d42:36cf5693
2023-07-11 15:56:07
@ 180a6d42:36cf5693
2023-07-11 15:56:07
This mini-guide aims to help you choose between a selection of Bitcoin lightning network (LN) wallets with an additional focus on working toward becoming unruggable through self-custody. No need to overthink, self-custody means: writing down and safely storing 12/24 words (aka 'seedphrase') offline, on paper/metal.
TL;DR. use WoS/LN.tips (transact📱) x Phoenix (save📱, self-custodial)
LN wallets (a selection)
Self-custodial LN wallets:
a. Phoenix app (📱, acts as a LN node*)
b. Breez (📱, acts as a LN node*)
c. Muun (📱, acts as a LN node*)
d. Zeus (📱, LN url)**
Custodial (by default) LN wallets:
a. Alby (browser extension, LN url)**
b. LN.tips (Telegram bot, LN url)**
c. Wallet of Satoshi (📱, LN url, use fresh email to sign-up)
d. ZBD (📱💻, LN url, kyc-free up to 500k sats)
sats= satoshi's (fractions of a bitcoin, e.g. 21.000 sats is 0.00021 BTC) LN url = Lightning address to add to your Nostr account to enable >receiving< Zaps
uses e.g. a big company LN node or submarine swaps *lightning node remote control apps: can also connect to self-hosted LN node
So to be clear, you have lightning wallets that act as (a) a wallet, (b) a self-custodial lightning wallet AND a lightning node on your phone, (c) a lightning node remote control app (if you run and self-host a LN node on a dedicated device).
Why choose custodial? It is only a temporary solution showing the power of LN where channels are already established and robust, is my conclusion. Be aware that there are major security/privacy trade-offs when using custodial wallets. However, if you're someone who's new to Nostr and/or bitcoin, and you e.g. want to enable receiving Zaps, it's obvious you play around with a custodial one with a smaller amount of sats first (let's say, up to ~ 21k sats/ 50$). I don't think it's realistic to expect someone new to this network to magically and instantly know how to spin up a LN node and manage channels. This is something that takes time to learn.
Unless you only use self-custodial LN wallets, it is advised to have your sats divided on more than one custodial wallet in case one of the hosted LN nodes temporarily goes down (not often) and you still want to transact at that moment.
Why choose self-custodial? When you're looking to learn more and/or if you plan to send/receive more substantial amounts of sats (e.g. for business) then you're ultimately going to want to learn to run a self-hosted node, preferably through Tor. Find trustworthy tutorials here.
A self-hosted node allows you to save on transaction fees; truly be in control of your bitcoin; and, protect yourself wrt third-party privacy violations. Know that you'll have to invest some time in learning and money in gear/gadgets in order to run your own (LN) node (~$200-$400).
What other choices do I have? If you're not ready to run a LN node just yet, you can also choose to go for one of the self-custodial wallets listed that act as a LN node on your mobile (e.g. Phoenix). The transaction fees are a bit higher than with custodial wallets but this is related to the wallet acting as a lightning node on your phone (e.g. with Phoenix you have to top-up the wallet with a minimum of 10.000 sats initially of which 3000 sats will be deducted in order to have the system open up lightning channels for you). A small price to pay for not having to have to run your own, self-hosted Bitcoin Lightning Node and managing it. Know that running your own lightning node has similar costs.
Tip: You can now deposit funds to self-custody on Lightning with Phoenix wallet for less than 500 sats when conditions are optimal* (compared to the previous 3000 sat/1%). They also made the LN<->onchain swaps trustless.
Summary
Here's a recommended Bitcoin wallet setup focussed on self-custody without having to have to run your own, self-hosted Bitcoin LN node:
Transacting bitcoin LN/L2 (active📱): Wallet of Satoshi and LN.tips
only use temporary, small amount of sats; custodial, but supports LN url
↕
Saving bitcoin, LN/L2 (passive📱): Phoenix wallet
self-custodial, easy, can swap LN↔on-chain, supports Tor
watch and learn: https://youtu.be/cbtAmevYpdM?t=223
↕
Saving bitcoin, Layer 1 aka on-chain (passive💻):
deep, air-gapped, cold storage (e.g. Seedsigner, Coldcard)
For a more extensive LN wallets comparison guide outside the scope of only Nostr, click here (would not recommend if you're new to all this; can be overwhelming).
Link to this blog: https://lnshort.it/lnwalletguidenostr
Find me on Nostr: matata@nostrplebs.com
-
 @ 1bc70a01:24f6a411
2023-06-07 08:29:03
@ 1bc70a01:24f6a411
2023-06-07 08:29:03Yesterday Marc Andreessen wrote up a lengthy tweet addressing concerns of AI taking our jobs. I will take a few minutes to analyze his tweet and break it out into chunks with my own assessment and responses.
The fear of job loss due variously to mechanization, automation, computerization, or AI has been a recurring panic for hundreds of years, since the original onset of machinery such as the mechanical loom.
True.
Even though every new major technology has led to more jobs at higher wages throughout history, each wave of this panic is accompanied by claims that “this time is different” – this is the time it will finally happen, this is the technology that will finally deliver the hammer blow to human labor. And yet, it never happens.
We can't rely on details of the past to predict the future. Every new development should be evaluated independently. "And yet, it never happens" is an insufficient assessment of whether something could happen just because it hasn't happened in the past. The sun hasn't exploded, but it could. Will it? Probably not. But it could. We don't know what we don't know.
We’ve been through two such technology-driven unemployment panic cycles in our recent past – the outsourcing panic of the 2000’s, and the automation panic of the 2010’s.
No we haven't. We've been through technology-driven unemployment panic cycles - yes, but not "such". Such assumes they are the same and as I stated earlier, everything should be evaluated independently.
Notwithstanding many talking heads, pundits, and even tech industry executives pounding the table throughout both decades that mass unemployment was near, by late 2019 – right before the onset of COVID – the world had more jobs at higher wages than ever in history.
While this is true, real unemployment has been the lowest in history at onset of COVID, what Marc fails to account for is the higher cost of living. It's no secret that rents and prices were all on the rise from 2022 forward and that wages are not able to keep up with inflation.
US Bureau of Labor Statistics reported the highest CPI ever going into COVID. Shelter, being a major expense for people is at the highest level ever according to FRED (https://fred.stlouisfed.org/series/CUSR0000SAH1)
While even an increase in CPI may not paint the full picture as it measures percentage change, in real terms (the dollars people are actually spending on rent) it's clear that the cost of living is rising. You can feel it every day.
- When was the last time your rent DECREASED?
- What was the last time food become cheaper at the store?
- What was the last time your college education all of a sudden became more affordable?
- What was the last time you got a raise?
People living in the real world can clearly tell that things are not going in the right direction. But, if you are Marc Andreeesen, it's not likely you live in the real world, so you wouldn't know. It is dishonest to say "wages are higher" and ignore the other half of the picture - the rise in the cost of living and lagging salaries.
Nevertheless this mistaken idea will not die. And sure enough, it's back.
Is it mistaken? We'll see...
This time, we finally have the technology that’s going to take all the jobs and render human workers superfluous – real AI. Surely this time history won’t repeat, and AI will cause mass unemployment – and not rapid economic, job, and wage growth – right? No, that’s not going to happen – and in fact AI, if allowed to develop and proliferate throughout the economy, may cause the most dramatic and sustained economic boom of all time, with correspondingly record job and wage growth – the exact opposite of the fear. And here’s why.
Marc seems to completely forget about the widening wealth gap. It's as if we can look at the growing wealth gap and pretend like it doesn't exist.
According to Pew research, the middle class is shrinking while the top earners are growing. The average American family is no wealthier today than it was two decades ago. The share of US aggregate income held by the middle class fell from 62% to 43% from 1970 to 2018.
You really don't need to look at any charts or be a wizard to know that the middle class is shrinking while the rich get richer. You can feel it in your neighborhood (unless you are rich), your supermarket, your community, the number of homeless on the streets.
Of course, if you are Marc, perhaps you don't see any of these things because you live in your own little bubble 🤷♂️
The core mistake the automation-kills-jobs doomers keep making is called the Lump Of Labor Fallacy. This fallacy is the incorrect notion that there is a fixed amount of labor to be done in the economy at any given time, and either machines do it or people do it – and if machines do it, there will be no work for people to do.
Classical straw-man argument. Marc, do you really think people are concerned that ALL jobs will be gone and humans will have nothing to do? Or perhaps maybe you've given some thought to whether people are concerned for their incomes to support their families? It's not that people are afraid all jobs will be gone. People are afraid that they won't be able to provide for themselves and their families as their jobs are all of a sudden done by AI.
The QUALITY of employment is what's at stake. Sure, you'll be employed - doing some odd thing you probably don't want to be doing because your critical analysis skills are no longer required or can be done with fewer people.
Do you really feel that your employer is going to say "oh hey, Marc, you are doing less and less around here these days, here's a raise!" Exactly. Not going to happen. It is in the businesses' best interest to automate away as many positions as possible. Less labor = higher profits. All business incentives point to automating away labor to bring down the costs to as close to zero as possible.
Yes, new jobs will open up, but they will increasingly require higher levels of knowledge and experience. In other words, the top earners today will step into those positions as they will be in the best spot for this transition.
The Lump Of Labor Fallacy flows naturally from naive intuition, but naive intuition here is wrong. When technology is applied to production, we get productivity growth – an increase in output generated by a reduction in inputs. The result is lower prices for goods and services.
This would be true under the bitcoin standard, but we live in a different reality. Productivity growth goes to the top earners and executives while workers are laid off. Ask yourself, what was the last time your prices dropped? I'll wait...
Food more affordable? Housing cheaper? Your vehicle cost less now than it did a decade ago? Gasoline? Education? iPhone?
It is true that technology lowers the marginal cost of production and in theory should make everything cheaper. But, in reality, costs rise as the fiat money inflates everything with it and any savings to be had are passed onto top brass. When you are doing great at automating away tasks, your first thought is not "oh now we can hire more people with all this extra cash", your first thought is "great, how can we automate away even more?"
As prices for goods and services fall, we pay less for them, meaning that we now have extra spending power with which to buy other things.
False. We are paying more. This is reflected in reported CPI and real CPI, inflation, lagging wage growth, and growth in inequality.
This increases demand in the economy, which drives the creation of new production – including new products and new industries – which then creates new jobs for the people who were replaced by machines in prior jobs.
It is true that consumer spending has been growing recently and that in theory all of that spending should create more jobs. However, we have never had a technology with no upper limit in terms of what it could do. While new jobs can indeed come online, the numbers of new jobs may not be sufficient to replace the jobs they displaced. Technology improves efficiency and you need fewer people to the jobs of many. Marc's assumption is that the AI developments would create so many new industries that the jobs required to make them work would outpace all of the displaced labor. However, he seems to willfully ignore that AI is not a "twice better" technology. It has no theoretical limit to the level of efficiency achievable.
At the core of it all, everything we are and everything we do is math and algorithms. Machines need not be 100% better than humans to take our jobs. Eighty percent is a good enough threshold that the other 20% can be ignored. As long as AI is sufficiently able to perform a task, human need not apply.
The result is a larger economy with higher material prosperity, more industries, more products, and more jobs.
Yes, an economy for the top earners.
But the good news doesn’t stop there. We also get higher wages. This is because, at the level of the individual worker, the marketplace sets compensation as a function of the marginal productivity of the worker.
Money printer would like a word. Higher wages are just one side of the equation. What you really want is more purchasing power and we know that purchasing power is shrinking dramatically. Simply look at the appreciation of Bitcoin's fiat value to understand what is happening to the dollar. Hint: it ain't good.
A worker in a technology-infused business will be more productive than a worker in a traditional business. The employer will either pay that worker more money as he is now more productive, or another employer will, purely out of self interest.
LOL. Seriously? Hey, Jim, you're looking productive today! Here's a raise! C'mon... are you kidding me? What world does this person live in? Like I said, even if our hypothetical employer is super happy with Jim and pays him more, uncle Sam will ensure you're always in line. Money printer go brrrrr!
The result is that technology introduced into an industry generally not only increases the number of jobs in the industry but also raises wages.
Let me rewrite. "The result is that technology introduced into an industry generally reduces labor as fewer people are needed to perform a task now done by few. It also raises wages for the top earners while the average person earns no more than they did two decades ago."
To summarize, technology empowers people to be more productive. This causes the prices for existing goods and services to fall, and for wages to rise.
Yes, more productive. No, goods and services rarely fall in price, in fact, quite the opposite. Wages rise for top earners, not really at all for middle class, and just barely for lower class.
This in turn causes economic growth and job growth, while motivating the creation of new jobs and new industries.
In the past, yes. But with ever-improving AI that growth won't outpace displacement. Yes, more advanced categories of jobs for highly skilled (top earners) people. If you are not highly skilled, super intelligent, good luck! New industries actually displace more workers from previous industries.
Higher productivity doesn't mean higher employment. I can be very productive at home with ChatGPT, coding away, designing fun stuff, but that doesn't automatically translate to more employment. If a startup founder can create his/her own website and no longer needs my services, that's that.
If a market economy is allowed to function normally and if technology is allowed to be introduced freely, this is a perpetual upward cycle that never ends.
That is a BIG IF. We know the powers that be LOVE manipulation. The dream Marc aspires to can only exist on the Bitcoin standard.
For, as Milton Friedman observed, “Human wants and needs are endless” – we always want more than we have. A technology-infused market economy is the way we get closer to delivering everything everyone could conceivably want, but never all the way there. And that is why technology doesn’t destroy jobs and never will.
Straw-man. Technology has always destroyed jobs and always will. The saving grace was that it created many more jobs in the past. But with AI, the order of efficiency is magnitudes larger than a 2 or even a 10x improvement of the Industrial Revolution. And, there is no theoretical limit to how far it can improve. This is why we cannot look at the past to determine the future. It's lazy thinking at best.
These are such mindblowing ideas for people who have not been exposed to them that it may take you some time to wrap your head around them.
Ah, yes, the all knowing oracle, please bless us with your wisdom.
But, using the principles I described above, think of what it would mean for literally all existing human labor to be replaced by machines.
It would mean a takeoff rate of economic productivity growth that would be absolutely stratospheric, far beyond any historical precedent. Prices of existing goods and services would drop across the board to virtually zero.
Under the bitcoin standard, yes. Hey Marc, why do we need jobs if prices go to zero?
Consumer welfare would skyrocket. Consumer spending power would skyrocket.
Yes, under the bitcoin standard, I agree. But why work if what you make is free. Where is the business making profit here? Why employ a bunch of people, pay them a ton of money and have a service that costs nothing to the consumer? Does that make any sense to you?
New demand in the economy would explode. Entrepreneurs would create dizzying arrays of new industries, products, and services, and employ as many people and AI as they could as fast as possible to meet all the new demand.
Yes there are many new business opportunities, but again, going back to infinite efficiency point - that doesn't translate to many jobs. This is already happening now. There's now an AI tool for so many things that people used to have to do slowly and manually.
Tech is currently going through a wave of layoffs, with as many as 200,000 employees being laid off in 2023 alone. You can track layoffs here: https://layoffs.fyi/
If you don't believe AI is going to result in serious layoffs, consider what ChatGPT has already achieved (and this is a really primitive form of AI): https://www.timesnownews.com/technology-science/48-percent-of-companies-have-replaced-workers-with-chatgpt-survey-article-98635684
- 48% of companies used it to replace workers
- 63% believe it will result in layoffs
Suppose AI once again replaces that labor? The cycle would repeat, driving consumer welfare, economic growth, and job and wage growth even higher. It would be a straight spiral up to a material utopia that neither Adam Smith or Karl Marx ever dared dream of.
As it has in the past /s
In reality, wealth would concentrate even further. The rich would get richer. The top earners would earn more. Yes, the pie will grow, but those who get a bite will be fewer.
Trickle down economics hasn't worked and cannot work under the fiat standard. Wealth and power concentrates while the middle class diminishes and cost of living rises. As long as the base upon which you are building is constantly manipulated, true price discovery cannot take place. The current debt system guarantees forever-rising prices as more debt is required to be created to service previous debt - a never-ending negative cycle.
All of what Marc says IS possible under the bitcoin standard. You can already see it happening if you measure everything from the bitcoin's point of view. As bitcoin goes up in fiat terms, everything else drops in price (as it should). Bitcoin allows for true price discovery because it cannot be manipulated, you can't create more bitcoin. Here, consumer's purchasing power increases while technology enables humans to work less.
Don't you find it ironic that according to Marc, AI is supposed to create plentiful jobs, but cost of goods and services is supposed to come down to zero? What are all those people working for in that scenario? Why would you want more jobs as the cost of everything else drops?
The answer of course is not more high paying jobs, but the efficiencies enabled by AI to be spread more equitably across society. As your technology enables near-free services and goods, you as a person shouldn't have to work as much to acquire the same or greater number of things. This is completely incompatible with a credit-based system where your salary must go up perpetually to accommodate the rise in debt and THE RISE in prices. Not the drop, but the rise in prices. This is exactly what we see today and have seen throughout history. Don't believe me? Go ahead and walk into an Apple store and ask for the newest iPhone model for a lesser price then the previous.
In summary: 1. Everything Marc Andreessen says would be correct under the bitcoin standard. 2. AI cannot be assessed through the lens of previous technological advancement, it's an apple to oranges comparison as we've never had a technology that has the potential to become thousands or hundreds of thousands times more intelligent than humans. 3. Prices cannot fall in a credit-based system because debt must grow to pay off previous debt. 4. Focusing on job numbers is pointless. Instead we should be focusing on purchasing power and standards of living. People don't want more jobs, they want the ability to provide for their family - which could mean working less while taking advantage of technological progress (in this case AI).
Footnotes:
Gig Economy Market [2022-2027] Size, Share, Growth Rate | Recent Development, Demand, Trends, Key Players Profiles, Segmentation, Mergers & Acquisitions, Expansion Plans and Forecast Research | Industry Research Biz
BLS Consumer price index by category: https://www.bls.gov/charts/consumer-price-index/consumer-price-index-by-category-line-chart.htm
https://fred.stlouisfed.org/series/CUSR0000SAH1
Pew widening wealth gap: https://www.pewresearch.org/social-trends/2020/01/09/trends-in-income-and-wealth-inequality/
-
 @ cc8d072e:a6a026cb
2023-06-04 13:15:43
@ cc8d072e:a6a026cb
2023-06-04 13:15:43欢迎来到Nostr
以下是使您的 Nostr 之旅更顺畅的几个步骤
本指南适用于: * 英语 原作者 nostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7 * 法语 感谢 nostr:npub1nftkhktqglvcsj5n4wetkpzxpy4e5x78wwj9y9p70ar9u5u8wh6qsxmzqs * 俄语
你好,Nostrich同胞!
Nostr 是一种全新的模式,有几个步骤可以让您的加入流程更加顺畅,体验更加丰富。
👋欢迎
由于您正在阅读本文,因此可以安全地假设您已经通过下载应用程序加入了 Nostr 您可能正在使用移动设备(例如 Damus、Amethyst,Plebstr) 或Nostr网络客户端(例如 snort.social、Nostrgram、Iris)。 对于新手来说,按照您选择的应用程序建议的步骤进行操作非常重要——欢迎程序提供了所有基础知识,您不必做更多的调整除非您真的很需要。 如果您偶然发现这篇文章,但还没有 Nostr“帐户”,您可以按照这个简单的分步指南 作者是nostr:npub1cly0v30agkcfq40mdsndzjrn0tt76ykaan0q6ny80wy034qedpjsqwamhz --
npub1cly0v30agk cfq40mdsndzjrn0tt76ykaan0q6ny80wy034qedpjsqwamhz。
🤙玩得开心
Nostr 的建立是为了确保人们可以在此过程中建立联系、被听到发声并从中获得乐趣。 这就是重点(很明显,有很多严肃的用例,例如作为自由斗士和告密者的工具,但这值得单独写一篇文章),所以如果你觉得使用过程有任何负担,请联系更有经验的Nostriches,我们很乐意提供帮助。 与Nostr互动一点也不难,但与传统平台相比它有一些特点,所以你完全被允许(并鼓励)提出问题。 这是一份 非官方 的 Nostr 大使名单,他们很乐意帮助您加入: nostr:naddr1qqg5ummnw3ezqstdvfshxumpv3hhyuczypl4c26wfzswnlk2vwjxky7dhqjgnaqzqwvdvz3qwz5k3j4grrt46qcyqqq82vgwv96yu 名单上的所有nostriches都获得了 Nostr Ambassador 徽章,方便您查找、验证和关注它们
## ⚡️ 启用 Zaps Zaps 是加入 Nostr 后人们可能会注意到的第一个区别。 它们允许 Nostr 用户立即发送价值并支持创建有用和有趣的内容。 这要归功于比特币和闪电网络。 这些去中心化的支付协议让你可以立即发送一些 sats(比特币网络上的最小单位),就像在传统社交媒体平台上给某人的帖子点赞一样容易。 我们称此模型为 Value-4-Value,您可以在此处找到有关此最终货币化模型的更多信息:https://dergigi.com/value/ 查看由nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424创建的这篇笔记,nostr:note154j3vn6eqaz43va0v99fclhkdp8xf0c7l07ye9aapgl29a6dusfslg8g7g 这是对 zaps 的一个很好的介绍: 即使您不认为自己是内容创建者,您也应该启用 Zaps——人们会发现您的一些笔记很有价值,并且可能想给您发送一些 sats。 开始在 Nostr onley 上获得价值的最简单方法需要几个步骤:
0 为您的移动设备下载 Wallet of Santoshi^1(可能是比特币和闪电网络新手的最佳选择)^2 1 点击“接收” 2 点击您在屏幕上看到的 Lightning 地址(看起来像电子邮件地址的字符串)将其复制到剪贴板。
 3 将复制的地址粘贴到您的 Nostr 客户端的相应字段中(该字段可能会显示“比特币闪电地址”、“LN 地址”或任何类似内容,具体取决于您使用的应用程序)。
3 将复制的地址粘贴到您的 Nostr 客户端的相应字段中(该字段可能会显示“比特币闪电地址”、“LN 地址”或任何类似内容,具体取决于您使用的应用程序)。 
📫 获取 Nostr 地址
Nostr 地址,通常被 Nostr OG 称为“NIP-05 标识符”,看起来像一封电子邮件,并且: 🔍 帮助您使您的帐户易于发现和分享 ✔️ 证明您是人类 --- 这是 Nostr 地址的示例:Tony@nostr.21ideas.org
 它很容易记住并随后粘贴到任何 Nostr 应用程序中以找到相应的用户。
它很容易记住并随后粘贴到任何 Nostr 应用程序中以找到相应的用户。
要获得 Nostr 地址,您可以使用免费服务,例如 Nostr Check(由 nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624)或付费服务,例如 Nostr Plebs 了解有关此方法的更多信息。
🙇♀️ 学习基础知识
在后台,Nostr 与传统社交平台有很大不同,因此对它的内容有一个基本的了解对任何新手来说都是有益的。 请不要误会,我并不是建议您学习编程语言或协议的技术细节。 我的意思是看到更大的图景并理解 Nostr 和 Twitter / Medium / Reddit 之间的区别会有很大帮助。 例如,没有密码和登录名,取而代之的是私钥和公钥。 我不会深入探讨,因为有一些详尽的资源可以帮助您理解 Nostr。 由 nostr:npub12gu8c6uee3p243gez6cgk76362admlqe72aq3kp2fppjsjwmm7eqj9fle6 和 💜 准备的在这个组织整齐的登陆页面 收集了所有值得您关注的内容
 上述资源提供的信息也将帮助您保护您的 Nostr 密钥(即您的帐户),因此请务必查看。
上述资源提供的信息也将帮助您保护您的 Nostr 密钥(即您的帐户),因此请务必查看。
🤝 建立连接
与才华横溢的[^3]人建立联系的能力使 Nostr 与众不同。 在这里,每个人都可以发表意见,没有人会被排除在外。 有几种简单的方法可以在 Nostr 上找到有趣的人: * 查找您在 Twitter 上关注的人:https://www.nostr.directory/ 是一个很好的工具。 * 关注您信任的人:访问与您有共同兴趣的人的个人资料,查看他们关注的人的列表并与他们联系。
 * 访问全球订阅源:每个 Nostr 客户端(一个 Nostr 应用程序,如果你愿意这样说的话)都有一个选项卡,可以让你切换到全球订阅源,它汇总了所有 Nostr 用户的所有笔记。 只需关注您感兴趣的人(不过请耐心等待——您可能会遇到大量垃圾邮件)。
* 访问全球订阅源:每个 Nostr 客户端(一个 Nostr 应用程序,如果你愿意这样说的话)都有一个选项卡,可以让你切换到全球订阅源,它汇总了所有 Nostr 用户的所有笔记。 只需关注您感兴趣的人(不过请耐心等待——您可能会遇到大量垃圾邮件)。

🗺️探索
上面提到的 5 个步骤是一个很好的开始,它将极大地改善您的体验,但还有更多的东西有待发现和享受! Nostr 不是 Twitter 的替代品,它的可能性仅受想象力的限制。
 查看有趣且有用的 Nostr 项目列表:
* https://nostrapps.com/ Nostr 应用列表 * https://nostrplebs.com/ – 获取您的 NIP-05 和其他 Nostr 功能(付费)
* https://nostrcheck.me/ – Nostr 地址、媒体上传、中继
* https://nostr.build/ – 上传和管理媒体(以及更多)
* https://nostr.band/ – Nostr 网络和用户信息
* https://zaplife.lol/ – zapping统计
* https://nostrit.com/ – 定时发送帖子
* https://nostrnests.com/ – Twitter 空间 2.0
* https://nostryfied.online/ - 备份您的 Nostr 信息
* https://www.wavman.app/ Nostr 音乐播放器 ---
查看有趣且有用的 Nostr 项目列表:
* https://nostrapps.com/ Nostr 应用列表 * https://nostrplebs.com/ – 获取您的 NIP-05 和其他 Nostr 功能(付费)
* https://nostrcheck.me/ – Nostr 地址、媒体上传、中继
* https://nostr.build/ – 上传和管理媒体(以及更多)
* https://nostr.band/ – Nostr 网络和用户信息
* https://zaplife.lol/ – zapping统计
* https://nostrit.com/ – 定时发送帖子
* https://nostrnests.com/ – Twitter 空间 2.0
* https://nostryfied.online/ - 备份您的 Nostr 信息
* https://www.wavman.app/ Nostr 音乐播放器 --- 📻 中继
熟悉 Nostr 后,请务必查看我关于 Nostr 中继的快速指南:https://lnshort.it/nostr-relays。 这不是您旅程开始时要担心的话题,但在以后深入研究绝对重要。
📱 手机上的 Nostr
在移动设备上流畅的 Nostr 体验是可行的。 本指南将帮助您在智能手机上的 Nostr Web 应用程序中无缝登录、发帖、zap 等:https://lnshort.it/nostr-mobile
感谢阅读,我们在兔子洞的另一边见 nostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7
发现这篇文章有价值吗 Zap⚡ 21ideas@getalby.com 关注:
npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7查看我的项目 https://bitcal.21ideas.org/about/
[^3]:nostr:npub1fl7pr0azlpgk469u034lsgn46dvwguz9g339p03dpetp9cs5pq5qxzeknp 是其中一个Nostrich,他设计了本指南的封面上使用的徽标
译者: Sherry, 数据科学|软件工程|nossence|nostr.hk|组织过一些nostr meetup|写一些文章来将nostr带到每个人身边
Zap⚡ spang@getalby.com 关注:
npub1ejxswthae3nkljavznmv66p9ahp4wmj4adux525htmsrff4qym9sz2t3tv -
 @ 7f5c2b4e:a818d75d
2023-07-11 13:05:57
@ 7f5c2b4e:a818d75d
2023-07-11 13:05:57The Problem
Key delegation has been a hot topic in the Nostr community for ages now. Even though Nostr is a new protocol, things are moving so fast that it feels like it's been years since it was launched. If you think about it in terms of regular social media, it's easy to see why this feature is so important. It's like being able to give someone the keys to your house but still being the one who's in charge. A good example of this is how nsecBunker is helping nostr:npub10eezfnlq4ad2lyf3478na8f5las4l7guuf55vs8378lwtk87hd7slf6zka run a shared Nostr account. But that's just one use case. There are a lot more possibilities, and we're going to discuss some of them in this post.
Legacy solutions
The centralized nature of many platforms simplifies the problem of key management. Social media platforms like Facebook Business Manager, Twitter Business, and LinkedIn Pages offer built-in tools for delegating roles to team members without divulging original login credentials. Third-party platforms like Hootsuite, Buffer, and Sprout Social further streamline this process, enabling management of multiple accounts, scheduling posts, and assigning roles, all without compromising the security of original credentials.
For more technical solutions there are services like Amazon Key Management Service (KMS). KMS helps generate, control, and manage cryptographic keys used for data encryption. With KMS, you can create Customer Master Keys (CMKs), define usage policies, and set up automatic yearly rotation. When data is encrypted, KMS generates a data key, encrypts it with the CMK, and provides you with both plaintext and encrypted versions of the data key. The plaintext key is used for data encryption, then discarded, leaving only the encrypted data key. To decrypt, the encrypted data key is sent back to KMS, which decrypts it into plaintext, given the necessary permissions. This system is employed by many businesses and media outlets to ensure secure access and compliance.
However, while these traditional systems are robust, they leave the end-user dependent on the service provider, who retains the ability to revoke access at their discretion. And this is precisely the problem Nostr is trying to fix.
The Nostr Way
The First Attempt
The first attempt that received serious attention in this direction was NIP-26. It introduced a new 'delegation' tag that enables events to be delegated and signed by other keypairs. This proposal is meant to abstract the use of 'root' keypairs when interacting with clients, with the idea that a user could generate new keypairs for each client they wish to use and authorize those keypairs to generate events on behalf of their root public key, where the root keypair is stored in cold storage.
However, NIP-26 has been critiqued for its implications on key management. Arguably, the best explanation of the corresponding problems was layed out by nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 in his "Why I don't like NIP-26 as a solution for key management" post here. Initially, NIP-26 was praised for its optional nature. However, as NIP-26 began to be seen as a universal solution for key management on Nostr, it started to raise concerns. The concept entailed users generating a secure, offline key to sign delegation tags for each Nostr app, potentially rotating them periodically. This approach would make these keys "faceless entities" only identifiable by their master key, significantly changing the user experience and expectations from NIP-26.
This shift in approach would effectively render NIP-26 mandatory for usability, turning it from an optional enhancement to a necessary implementation for clients. This would remove the flexibility of choice and potentially complicate the protocol. Furthermore, while NIP-26 could provide some solutions in the realm of key management, it's not seen as a comprehensive solution. It's suggested that a multitude of key management methods could be more effective, maintaining the optional nature and possibly presenting a more elegant solution. There's an argument that if a mandatory key delegation method is indeed necessary for Nostr, an alternative design might be more optimized and easier to implement than NIP-26.
The Promising Alternative
NIP-26, while a noteworthy attempt, seemed to diverge from the core philosophy of Nostr. This discrepancy highlighted the need for an alternative solution that would respect this foundational principle and avoid precipitating Nostr down a slippery slope of mandatory adherence.
This is where nsecBunker, introduced by nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft, provides a compelling proposition. As the name suggests, nsecBunker enables users to establish and self-host their own bunker allowing them to manage Nostr keys. This Bunker can communicate with the user interface on your device, facilitating the creation of target keys, sharing them with corresponding Nostr users, and offering granular control over their interactions with the protocol.
Crucially, the implementation of nsecBunker does not necessitate significant changes in the builds of existing clients, preserving the opt-in nature of Nostr. Beyond adhering to Nostr's core principles, nsecBunker also holds potential to enhance user experiences and provide improved functionality, aspects I will elaborate on shortly.
How Does This Work?
nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft elaborates on the core concept behind nsecBunker:
nostr:note1uxjpstcw5ldxrlfzqvqs3nqqpvyumajz4r5elmaf8ffmjyu342qqwsn0yd
At a high level, this model bears similarities to the traditional Amazon KMS approach, albeit with certain distinct nuances. For a deep dive into the technical intricacies of this model, I recommend checking out nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft's work-in-progress SECURITY-MODEL.md on GitHub.
To put it simply, nsecBunker is a daemon that facilitates remote event signing. It operates with two types of keys: user keys and nsecBunker keys. The bunker key interacts with the admin UI and only communicates with the pre-defined (admin)
npub. Notably, this key doesn't store sensitive information or hold specific power -- it poses no threat to key material even if compromised.The user key, on the other hand, is used for signing purposes. These keys are encrypted with a passphrase following the same approach as LND. This passphrase is mandatory every time nsecBunker is initiated, and losing it equates to losing access to the keys.
During setup, the administrator pre-approves a key (or a set of keys) for communication with the nsecBunker. The administrator(s) then create target keys to distribute to the intended users. These users can interact with the Nostr infrastructure without ever accessing the private keys of the account they're using. Let's walk through the process of setting up a Bunker.
Running nsecBunker
Paid Subscription
The easiest way to run nsecBunker is to purchase a paid subscription. The process is very easy and intuitive and, thanks to Lightning Network, it does not require you to share any sensitive data, such as IDs or bank card details. Scan a lightning invoice and get access to your own bunker in seconds:
- Navigate to https://app.nsecbunker.com/ and press “Buy one here”:

- Click “Next”

- Paste your public key (or a few keys) you’d like to be in control of the target keys. The keys you’ll specify will be able to grant full or granular permission to target keys which, in turn, will be able to post on behalf of the admin account. The admin key will be able to, but have to be the same key that you’ll be signing as later on. This means that you will be able to create a target key to interact with Nostr and have it look like your account is the one that is logging in / posting / liking / etc., or a totally separate target key, which will be like a child account of yours, and won’t be linked to you for the outside world.

- Specify how many users you’d like to be able to sign Nostr events with the Bunker you are creating. The number of end users directly affects the yearly fee rate.

- Pay the lightning invoice

- That’s it – your keys management fortress is ready to be utilized.

Here's a quick demo on setting up and using your nsecBunker by nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft:
Alternatively, if you are confident in your tech skills, you can build your own nsecBunker. It’s an open source project, meaning that anyone can spin up their own version.
Docker setup
To quickly install nsecBunker via Docker run:
``` docker run -d --name nsecbunkerd pablof7z/nsecbunkerd start --admin
```
nsecBunker will give you a connection string like:
``` bunker://npub1tj2dmc4udvgafxxxxxxxrtgne8j8l6rgrnaykzc8sys9mzfcz@relay.nsecbunker.com
```
Visit https://app.nsecbunker.com/ to administrate your nsecBunker remotely. For details see the GitHub repository here.
Setting up your Connection
After procuring the string, navigate to https://app.nsecbunker.com/. Log in using your preferred NIP-07 browser extension. Ensure the Nostr account (nsec) you're using is the same one that is designated as the administrator. The bunker is designed in such a way that it will not reply or even recognize if anyone other than the administrator
npubis trying to communicate with it.
Input the connection string into the required field and hit 'Login'.
As you can see, I left my connection string visible in the screenshot above. This is to showcase that it doesn't require protection and is simply a way of connecting to your bunker. The security model here relies on your
npubbeing the only entity with an administrative account.You'll land on the following screen:
https://nostr.build/p/nb10013.png
Click the "Keys'' tab. If you see a "Loading" message under the "Keys" title, simply refresh the page, and you should see the "No keys created yet" message.
If after clicking the "Keys" tab button you do not see the "No keys created yet" message, that means there is some problem with the setup. It could be the mismatch of the pubs or the bunker could be offline.
You are now set to create and manage target keys (the npubs you will be able to share).
Creating a Key
Click on "Add Key". This will reveal a pop-up prompting for information necessary to create a new target access key.
https://nostr.build/p/nb10015.png
The Key name is self-explanatory: it helps distinguish your target keys.
The need to fill up the Nsec field depends on how you plan to use nsecBunker. If you leave the 'Nsec' field empty, a new Nostr account will be created. This lets you manage how the target key owner interacts with Nostr. But if you already have an account and want to give someone else access, you can do that by entering the private key for that account into the bunker. It's a similar result, but uses an existing account instead of creating a new one.
The Passphrase is crucial for encrypting your keys and securing communications. Every time your bunker restarts you will need a passphrase to enter the admin panel. Treat it with the same caution you'd exercise with your private key - without it, access to your managed keys is lost.
With these steps completed, you can now share the public key with the owner of the target account.
Activating the Target Account
To start posting with a target key, users should visit https://coracle.social/ and click the "Advanced Login" button, followed by "Log in with Nsec Bunker".
https://nostr.build/i/c493ee745080ad4fd58a5c796792cadb491a0f194adc478bc7735399fb386c04.png
Enter the
npubor a token received from the Bunker administrator.https://nostr.build/i/7106719c873683c21a970662ecf3ebf95149b774efd0f36b8c1efcc16c8dbb99.png
The standard account setup process applies here (in case of a new account), but stay in touch with the Bunker administrator, as they must approve all new interactions.
The nsecBunker Admin UI displays the authorization request for 30 seconds, implying the need for synchronous coordination with the person requesting permission.
While tokens do not require any authorization (more on this below), if you first log in to https://coracle.social/ with the
npub, the administrator will receive an authorization request...https://nostr.build/p/nb10017.png
...and will be prompted to name this session.
https://nostr.build/p/nb10018.png
Each subsequent interaction will also generate a request in the admin UI. You can either authorize interactions by event kind - Always allow - or bulk-authorize all future interactions - Always allow signing all kinds - (yet to be enabled).
The "Always allow" feature signifies that the administrator is required to authorize each event type just a single time. For instance, if a user wishes to post a note, which is kind 1 event, the administrator's authorization is needed only once for this specific event type. Subsequently, the user can post additional notes without requiring further permissions. Please be aware that as the tool progresses, the precision of access permissions will be further refined.
https://nostr.build/p/nb10019.png
Introduction of Policies (see below) streamlines the system by allowing the issuance of an authorization token for the receiver, making administrators' lives much easier.
That's it. The target account owner can now interact with Nostr users without ever touching private keys. See the note below, which was posted by a co-author of nostr:npub10eezfnlq4ad2lyf3478na8f5las4l7guuf55vs8378lwtk87hd7slf6zka, who does not have access to the Herald's private key:
nostr:note1hmz72mg8d2hegpj0npungypqsv3wqtffjq3q3duwmk5zcha860uqnx0mx0
For the video tutorial on setting up the nsecBunker check out this video by Pablo:
If you opt for the "Always allow all kinds" option, the setup process will only need to be performed once. Target account owners can then interact with other Nostr users without further assistance. However, if the managed account owner logs out of Coracle and logs back in, the setup process needs to be repeated for security reasons.
Tokens
Tokens allow you to issue permissions to users, which they apply to an npub of their choosing without requiring interactivity. Creating tokens is super simple:
- Head over to the Keys tab;
- Click on the Tokens button;
https://nostr.build/i/c190e60cb125dd418f7db649678b1f083b314df3bf898caecff59291b0e6a85f.png
- Click Add Token
https://nostr.build/i/be1c2d723d7f9e4c0849634cdeed037e3b3f0e0db728eafac270edd392097234.png
-
Fill up required fields
-
Client name is required for your own reference
- Policy lets you choose which rights you'd like to grant to the token holder
- Set an expiry date if you'd like
- Hit Create Token
https://nostr.build/i/a046336915eba2bd6748188e86aa6eb3d387fb7d0dc48dc8645772f1fdd5cfc1.png
Policies
The latest update to nsecBunker has introduced the "Policies" tab, a feature that enhances the authorization process and gives administrators more detailed control over permissions. This addition enables the creation of access tokens to distribute to account holders. Each token can be customized to permit certain event types, set an expiration date for the token holder's privileges, and even define the number of times user's interactions can be authorized.
To leverage this new feature, navigate to the "Policies" tab and select "New Policy":
https://nostr.build/p/nb10298.png
Give your new policy a name and a short description...
https://nostr.build/p/nb10299.png
-
The "Method" dropdown menu provides a way to refine the assigned permissions. While the default "Sign Event" option will suit most users, if you want to restrict the user to only engage with Direct Messages or the Highlighter, select the appropriate option. For instance, using the "Encrypt" method provides the user with permissions to send Direct Messages (DMs) and to generate Highlighter events, such as private notes. Conversely, the "Decrypt" option enables the user to access and read Direct Messages and other encrypted data that is specifically intended for the private key owner.
-
Within the "Permission" menu, you have the flexibility to either permit all actions or, as demonstrated in the above screenshot, restrict the user to only publishing long-form posts. This functionality could be beneficial, for instance, if you are delegating your blogging responsibilities and prefer the copywriter to not have access to other areas of your account.
-
The "Usage count" setting allows you to control the number of interactions the target account can perform.
Select "Add Policy" followed by "Save Policy". As illustrated below, your chosen settings will generate various types of access tokens, each with distinct rights and descriptions. The token at the top of the screenshot, for example, restricts the holder to only publishing long-form posts, while the token at the bottom grants the holder full access:
https://nostr.build/p/nb10300.png
Navigate to the "Keys" tab and select the key to which you wish to assign rights, as outlined by the policy you created. Note that you'll need to unlock the key first by pressing the corresponding button and entering your nsecBunker passphrase. Click on "Tokens"
https://nostr.build/p/nb10301.png
Select the policy you wish to assign to the key and, if desired, set an expiration time:
https://nostr.build/p/nb10302.png
Click on "Create Token". A token, which takes the form of a Nostr public key, will be generated. You can now share this token with the intended user:
https://nostr.build/p/nb10303.png
For a live demonstration of this feature, check out Pablo's video:
Use Cases
"The possibilities of nsec bunker are endless." - nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn
The pace of development in the Nostr ecosystem is impressive. Just a day after the release of nsecBunker, nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft integrated Bunker support into another one of his creations - the Highlighter.
nostr:note1u8x403llme28vpnsz83las60rgfuw2ht9hcf5tsscl3lnfgdlvkqu3096n
You can find out more about this super efficient productivity tool in my earlier guide here: nostr:naddr1qqxnzd3cxg6rxdfkxyerzv3nqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa28mg64kz. As the Highlighter was recently redesigned, my guide needs some updates, but it's still a great resource to understand what Highlighter is and how it functions.
The revamped Highlighter is loaded with new features, such as Lists, Highlights, Private Notes, and of course, the nsecBunker login option. With this feature, you can log into the app without ever disclosing your private key to either the app or the NIP-07 extension provider.
The integration of Highlighter with nsecBunker paves the way to nostr applications that work seamlessly with browsers that don't have a NIP-07 extension, as is the case in most cases on mobile, massively lowering the adoption of Nostr among a general, less tech-savvy, audience.
To use this feature, click on "Sign in" instead of logging in with your browser extension...
https://nostr.build/p/nb10150.png
...and enter the
npubyou got with the nsecBunker:https://nostr.build/p/nb10154.png
As the administrator approves your connection you get logged in. The process here is identical to the one I described for Coracle.
https://nostr.build/p/nb10155.png
Take note, with the introduction of Policies, the Highlighter - fully integrated with nsecBunker - also supports the fine-tuning of corresponding permissions:
https://nostr.build/p/nb10304.png
Highlighter showcases just one of many use cases of nsecBunker. Here are some more, but keep in mind that I'm only giving you a brief overview of the tool's potential:
-
Separate Accounts for Different Use Cases: nsecBunker enhances your security model by allowing you to retain your private key while using different Nostr clients.
-
Collective Social Media Account Management: nsecBunker can be used by journalist teams or companies to collectively run social media accounts, increasing user awareness of their products or services.
-
Child Control: Parents can utilize nsecBunker to set up accounts for their children, ensuring they adhere to family practices.
-
Burner Accounts: nsecBunker enables you to create specific accounts for specific use cases, all under your control.
-
Corporate Accounts: Businesses can generate keys for their employees, allotting rights specific to their positions.
However, the applications of nsecBunker are not limited to these. For example, one exciting possibility that emerged shortly after nsecBunker's release was the potential solution to creating private groups within the Nostr community. As nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn astutely observed, the possibilities with nsecBunker are indeed endless. Have a look at his long form post here: nostr:naddr1qqwkzttswfhhqmmnv9kz6en0wgkhqunfweshgefdvaex7atswvq3jamnwvaz7tmjv4kxz7fwdehhxarjd93kstnvv9hxgqgewaehxw309ac82unpwe5kgcfwdehhxarj9ekxzmnyqy2hwumn8ghj7mn0wd68ytnfdehhxarp9e3kxqg4waehxw309ahx7um5wghx66tvda6jumr0dsq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqyg8wumn8ghj7mn0wd68ytnhd9hx2qtxwaehxw309anxjmr5v4ezumn0wd68ytnhd9hx2tmwwp6kyvfsv9mh56mwdfnn2u34d3sk5mnjx5engvecdejxx7t209kxwutnwfh8yar3x4nhyue58y6hvdpjw93nvcthwd4rgdtewvmn7cnjdaskgcmpwd6r6arjw4jsz9nhwden5te0vf5hgcm0d9hx2u3wwdhkx6tpdsq35amnwvaz7tmjv4kxz7fwdaexzmn8v4cxjmrv9ejx2asprfmhxue69uhhyetvv9ujumn0wd68yurvv438xtnrdaksz8rhwden5te0w4hxjan9wfek2tnwdaehgunfvd5zumrpdejqz8rhwden5te0dehhxarj9ekh2arfdeuhwctvd3jhgtnrdaksz9thwden5te0v4jx2m3wdehhxarj9ekxzmnyqyv8wumn8ghj7un9d3shjtnwdaehgunpw35jucm0d5pzp978pfzrv6n9xhq5tvenl9e74pklmskh4xw6vxxyp3j8qkke3cezqvzqqqr4guzz40fz
Supported clients
Here's a list of Nostr clients supporting nsecBunker (keep in mind that new clients are actively adding support of this tool, so the list may not always be extensive, feel free to leave comments if you see that some clients are missing):
Note that every client that offers you to login with a so-called "NIP-46" supports nsecBunker login.
Nostr = Everything × Freedom
Harnessing the unparalleled power of the most advanced currency humanity has ever seen, Nostr is an open and censorship-resistant protocol that promotes freedom of expression and allows you to stay anonymous. Its very foundation is rooted in open-source principles, making the collective knowledge and experience gathered through its development accessible to all. The protocol itself, along with most Nostr applications, are open-source. This allows anyone to contribute, adapt, or even build upon existing developments to create something uniquely their own. This is where the true power of censorship-resistant, open-source software resides - it's unstoppable.
Legacy systems, bound by their proprietary constraints, simply cannot compete with the collective intellectual power of what began as a cypherpunk movement and has now blossomed into a vibrant community of dedicated individuals. These individuals are committed to bettering the world, rather than merely filling their pockets with others' hard-earned money. Together, we are paving the way towards a future where freedom of speech and self-sovereignty are the norm, and the fruits of our labor contribute to societal progress. This collective effort fosters the creation of tools that empower us to build better, move faster, and grow stronger. More on this in my post here: nostr:naddr1qqxnzd3cxs6rxv3hxsensv3nqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa28z78gua.
We invite you to join this peaceful revolution. Participate in the growth of permissionless protocols, contribute to open-source software, and share your ideas to further enhance this vibrant ecosystem. Together, we are not just evolving technology - we are shaping a more open, inclusive, and equitable future.
Like what nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft is building? Make sure to support him!
-
Pablo's Nostr account: nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft
-
Pablo's site: https://pablof7z.com/
-
 @ 7f5c2b4e:a818d75d
2023-07-05 13:45:17
@ 7f5c2b4e:a818d75d
2023-07-05 13:45:17This FAQ is also available in Spanish: nostr:naddr1qqx9zat994jhxttgv93xccgpr9mhxue69uhhyetvv9ujumn0wd68y6trdqhxcctwvsq3jamnwvaz7tmsw4exzanfv3sjumn0wd68ytnvv9hxgqg4waehxw309ahx7um5wghxjmn0wd6xztnrvvq32amnwvaz7tmwdaehgu3wd45kcmm49ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgswaehxw309ahx7um5wgh8w6twv5qkvamnwvaz7tmxd9k8getj9ehx7um5wgh8w6twv5hkuur4vgcnqcth0f4ku6n8x4er2mrpdfh8ydfnxsensmnyvduk57tvvachxunwwf68zdt8wfengwf4wc6ryutrxeshwum2xs6hjueh8a38ymmpv33kzum58468yat9qyt8wumn8ghj7cnfw33k76twv4ezuum0vd5kzmqprfmhxue69uhhyetvv9ujummjv9hxwetsd9kxctnyv4mqzxnhwden5te0wfjkccte9ehx7um5wfcxcetzwvhxxmmdqyw8wumn8ghj7atwd9mx2unnv5hxummnw3exjcmg9ekxzmnyqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdqy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqgcwaehxw309aex2mrp0yhxummnw3exzarf9e3k7mgzypl4c26wfzswnlk2vwjxky7dhqjgnaqzqwvdvz3qwz5k3j4grrt46qcyqqq823crwnvag thanks to nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624
What is Habla News?
Habla is a Nostr-based platform that allows you to create and manage long-form posts. You could compare it to Medium, yet Habla is so much more than that. Habla is superior to traditional blogging platforms because it is built on top of Nostr. It is interoperable with a plethora of other Nostr apps, which makes the user experience seamless and more engaging. Moreover, thanks to the Lightning Network, your input – if found valuable by the readers – can and will be instantly rewarded with the best money humanity has ever witnessed: bitcoin.
What is Nostr?
Nostr is a new way to communicate online that provides a ton of benefits for its users. It is free for everyone; you do not require an ID or any other third party verification to start connecting, mingling with like-minded people, and growing the community around you. Nostr is often mistaken for a social media platform, but it is much more than that. We encourage you to check out the Nostr resources gathered here to realize the potential magnitude of this tool.
How do I sign into Habla?
To start writing on Habla, simply create an Habla/Nostr account and log in. Follow these few simple steps to register, start sharing value, and receive value back.
How do I earn with Habla?
Habla allows you to receive value directly from your readers. No bank account or ID is required. Simply connect your Lightning address to your Habla / Nostr account and receive funds directly to your wallet – no third parties, no waiting for withdrawals, no sweat. Follow these simple steps to do so.
Why is posting on Habla different?
The Nostr protocol is super lightweight, which introduces some peculiarities into how the Nostr-based apps must behave. We won't go into technical details, but the most obvious difference you will notice as a content creator is that you'll have to use a different and, possibly, unusual format of text while composing your posts. But fear not; Habla provides tools that make this process easy and intuitive. Here's a quick video by nostr:npub1wkljx5c6a8uccc5etws8ry0y3r4dgavh2dcav0tal4rtmcdl4z2sfu5u0t explaining the basics of posting with Habla (the guide was made prior to the redesign, yet remains useful):
https://nostr.build/p/nb9474.mp4
Habla (and many other Nostr apps) uses the well-established format, which is called Markdown. It has been around for almost a decade now and is supported by most apps you use every day. The reason you might not have heard about Markdown is because traditional apps usually hide it from the user, and we are working on doing so as well. You can find out more about Markdown here.
Where is my content stored?
Traditional blogging platforms store your content on their own servers. It is a convenient and (used to be) solid approach, but it bears critical risks. Leaving the fruits of your labor with a single party means they have full control over your content. Nostr fixes this. Every time you post something, your content is broadcast to numerous relays for further storage and redistribution. If any relay operator blocks your post or refuses to redistribute it, your readers can turn to other relays and access your content (do not worry if this sounds complicated; everything happens under the hood). This ensures you never get silenced. That said, Habla does not run its own relay; we've decided to concentrate on what we do best – build an intuitive, efficient, and easy-to-use blogging platform that rewards – and leave the content storage and distribution to the pros in that field.
How do I post?
Habla provides all the necessary tools to produce rich posts that stand out. Prepare your article, format your text with the help of designated tools, add media, and preview the results prior to publishing. All you need is at your fingertips, and the platform is only getting better and friendlier day by day.
Who can read my posts on Habla?
Anyone on the Internet can read your posts. However, if your readers would like to interact with your work – be it by following you / commenting / giving value back – they should create a Nostr account. We encourage you to onboard your followers to grow a thriving community and reach new heights. This quick guide will help you and your peers get started.
This FAQ is a work in progress, and it will evolve as both Habla and Nostr develop into even more powerful tools. Please provide feedback so that I can make it better.
-
 @ 56cc5caf:ff5b3ec1
2023-07-23 06:16:26
@ 56cc5caf:ff5b3ec1
2023-07-23 06:16:26This is something that has been on my mind for a little bit; a thought that came from another thought that came from a self-examination; you know the way navel-gazing goes.
Let's set the stage.
- Everyone lies.
- Reality isn't real.
What does this leave?
- Actions are real.
- Emotions are facts (but only at a point in time)
- Our entire experience is complete. There are no missing parts. Time doesn't work that way.
I can go more in depth on any of this, but for now, just mostly wanted it here, because looking at things from this perspective has a lot to do with how I view authenticity.
Shall I define authenticity? I've struggled with this, but I think when someone is authentic, their actions are consistent with how they present themselves as a person. There is a sense of integrity about them, in the way they are perceived.
This is an observation that I am purposefully making from an external viewpoint. If I were to view authenticity from an internal viewpoint, I think I would consider it integrity.
When everyone is lying to you, whether intentionally or not, all that leaves for you to observe is their actions. If those actions are consistent, then you can consider them authentic to that person, even when that person is lying to you. A person can be an authentic liar, jerk, inconsiderate, petty human. A person can be kind, compassionate, accepting, honest - but if actions indicate otherwise, they may be inauthentic.
What use is this? It is a way to look at someone else externally. Maybe it is a way to judge. Let's look at reality not being real. I see this in the following way - what we experience for ourselves as reality is like what we experience as our smartphone screen or computer desktop. There are icons there that have meaning, but they are not actually the things that are real. Behind the icon is an application. Behind that application are lines of code. behind those lines of code are binary electronic pulses, zeros and ones. Those move around circuitry in all kinds of ways. Electrical pulses are energy. How real is energy? I think maybe the only thing holding energy as real is time, and how real is time? This is not the same as the theoretical implications of The Matrix, but those are possibly more in line with this than any other concept of reality.
However, we all experience whatever the stuff of reality actually is, in useful constructs. Things like matter, energy - these are useful to explain what we experience. We can attempt to measure these things in ways that we can compare to others' experiences. However, if I held a rock, and tried to describe the experience of holding that rock, it would NOT be the same as your experience holding that same rock, even if we could agree it was the same size, weight, color, etc. What does reddish orange really mean? What does a kilo mean - to you, when you hold a 1-kilo rock in your hand? I don't assume that it would mean the same to me.
Since I am basically saying that how we experience reality is entirely subjective, and it is impossible for me to experience your reality in the same way you do, all I can do is observe your actions. Speech is an action. Inaction is an action, as a response to something else. I wrote about an economy of emotion that goes further into the opportunity costs of acting and feeling.
But emotion is a little different. Emotion isn't an action. Emotion is fact, but only subjectively. My decisions will be based largely on emotion, in my opinion, and so will yours. We try to assert that we act logically, or mindfully, or even instinctively - but as humans, I believe we first and ultimately act emotionally. Even controlling your emotions will still allow emotions to partially inform your action. Your emotions inform your experiences, your memory, all your perceptions, both sensory and extrasensory. We want to deny this, to build some reality construct that makes sense, that we can apply as a template for ourselves and others - but this simply isn't true. Emotion is still there. Emotion may be the one thing that keeps us as humans separate from AI.
Emotion is only true at a point in time, though - so the action you took earlier today based on your overall emotional state at that time might not be the same action you would take right now, as your overall emotional state will have changed.
And I don't think we see emotions as nearly as complex as we could. I've read books on emotional intelligence, and when they bring up some color chart, I laugh. I see my emotional color chart as a tie-die kaleidoscope, changing like an active heat map. Chaotic, sometimes perhaps, or sometimes mesmerizing in its own patterns. And this is what ultimately sits at the controls of my human action.
I am not saying that emotions cannot be influenced by other factors; of course, they can - but whatever the effects of the influences, your action at a particular point in time will still be informed by your overall emotional state at that point in time.
How does this work with authenticity? If I see someone displaying consistent action, and I understand that action is informed by emotion, then maybe I can infer something about the consistency of their emotional state.
When you don't believe you are being told the truth, and reality isn't real, small inferences like this make a big difference in how you reconstruct your overall world view. I could not say if someone had integrity or not. Only they could believe that about themselves. I could, however, observe their actions and believe them to be authentic.
And how does this relate to interpersonal relationships in general? What hope is there for an interpersonal relationship when there is no trust? Well, trust can be built through authenticity; in fact, I could say that any trust must be built through authenticity, and inauthentic action is what destroys trust.
I struggle with many things, being an extremely analytical person, and coming from a past that did not reward many of the actions that most take for granted as good. It also taught me early and often that permanence was not to be expected. Some of this led to some serious issues with self-esteem.
I can write a lot more about self-esteem, but one part of having low self-esteem is an emotional state that feels insignificant or less important relative to others. This is extremely general on purpose, but this can include people that never feel good enough to meet their parents' expectations, or even the expectations of a god-figure or savior. The person with low self-esteem is always seeking that external approval, while also always feeling judged.
I struggled with my share of that. For some time, I believed that the perceptions of others were more important than my own reality, and lived to create a perception of myself that would serve me well. This will never be authentic. This is like the person who when asked who they are, responds by asking who you want them to be. In fact, when asked to "be yourself", that is not immediately possible, as you are just a mirror or a prism, reflecting off whatever you think will show you in the best possible light. Then this immediately becomes cyclical, as you feel that emptiness, and the emotional toll of inauthenticity.
One of the first observations I had when confronting my self-esteem was that I needed to restore my own integrity, but that wasn't immediately easy to do, because I also needed to establish authenticity and become consistent in action. This meant accepting emotion, and learning to harness the power of emotion when acting. A lot of that is just accepting the emotion that is there. Some of that is removing obvious external factors. I no longer feel any need to drink alcohol, although I may do so socially from time to time. I think it contributes to inauthenticity when viewed externally, and does nothing to preserve integrity in my own thoughts and emotions.
Remember, authenticity is an external construct. Integrity is a similar internal construct.
Once I was on the path to fixing myself, I wanted to start looking at what I could do to build a social network. I've never believed I had friends, although I am a social enough person, have no problem going out, talking to people, etc. But this is again the damage done by low self-esteem, having no trust in permanence, no faith in people, no belief in my own authenticity, even when I was acting with integrity.
The way I found out of this is to use authenticity as a useful construct. I can use it to build trust in others, and see it as a way they can build trust with me.
This is way different than living in the shadow of their perceptions (or at least my concept of what their perceptions must be). I've done plenty of that, what I initially considered buying friends - being the guy to pay the bill. Being the guy that had what they needed, that cared about what they were interested in, would help them with whatever they were doing. Spending my money at times, but ultimately my time, to hopefully make them think well enough of me to maybe consider I might belong as a friend. But that would never make me feel that I belonged, and why should it? I was never actually sharing myself, so anything that would belong would not even be myself.
Now, it is more important to first understand myself, construct my reality, accept my own emotions, and then share freely with others, hoping not for their approval or acceptance, but only that my authenticity allows them to trust me enough to share their own authenticity. This isn't something that can be bought with my time or money, but only my own work to make my actions as consistent and authentic as possible.
No, this is not easy. It may be simple, but not easy - but then again, nothing worthwhile is ever easy, although it may often be simple.
I think it becomes easier with time, though. Finding your own inconsistencies, exploring what seemed to you to be contradictory in your own actions - That is something that takes time, and resolving those inconsistencies can be tough, but ultimately rewarding. Building your own self-esteem, finding out and exploring who you are, and what you want to construct your own reality to be - that is the most important building you can do, and worth every moment you attend to it. It can never be someone else's reality, someone else's perception, even if that person may mean more to you than anything else you can think of, even yourself. It must be yours, and you have to build it. Anything less, and you are just another NPC in the game of life.
The key to building is small, intentional actions, done repeatedly. We see that in this network. Small notes, sent intentionally, done repeatedly. Building the most authentic network we could imagine, where inauthenticity is disincentivized. But back to life. This isn't about forming habits, although those will happen. It may be about breaking habits. Intentionally. Repeatedly.
Focus. Simple. Intentional. Repeated. This is the path to Authenticity. Authenticity is where true relationships are formed between people.
-
 @ 32e18276:5c68e245
2023-06-01 04:17:00
@ 32e18276:5c68e245
2023-06-01 04:17:00Double-entry accounting is a tried and true method for tracking the flow of money using a principle from physics: the conservation of energy. If we account for all the inflows and outflows of money, then we know that we can build an accurate picture of all of the money we've made and spent.
Bitcoin is particularly good at accounting in this sense, since transaction inflows and outflows are checked by code, with the latest state of the ledger stored in the UTXO set.
What about lightning? Every transaction is not stored on the blockchain, so we need same way to account for all the incoming and outgoing lightning transactions. Luckily for us, core-lightning (CLN) comes with a plugin that describes these transactions in detail!
For every transaction, CLN stores the amount credited and debited from your node: routed payments, invoices, etc. To access this, you just need to run the
lightning-cli bkpr-listaccounteventscommand:lightning-cli bkpr-listaccountevents | jq -cr '.events[] | [.type,.tag,.credit_msat,.debit_msat,.timestamp,.description] | @tsv' > events.txtThis will save a tab-separated file with some basic information about each credit and debit event on your node.
channel invoice 232000000 0 1662187126 Havana channel invoice 2050000 0 1662242391 coinos voucher channel invoice 0 1002203 1662463949 lightningpicturebot channel invoice 300000 0 1663110636 [["text/plain","jb55's lightning address"],["text/identifier","jb55@sendsats.lol"]] channel invoice 0 102626 1663483583 Mile high lightning clubNow here's comes the cool part, we can take this data and build a ledger-cli file. ledger is a very powerful command-line accounting tool built on a plaintext transaction format. Using the tab-separated file we got from CLN, we can build a ledger file with a chart-of-accounts that we can use for detailed reporting. To do this, I wrote a script for converting
bkptreports to ledger:http://git.jb55.com/cln-ledger
The ledger file looks like so:
``` 2023-05-31 f10074c748917a2ecd8c5ffb5c3067114e2677fa6152d5b5fd89c0aec7fd81c5 expenses:zap:1971 1971000 msat assets:cln -1971000 msat
2023-05-31 damus donations income:lnurl:damus@sendsats.lol -111000 msat assets:cln 111000 msat
2023-05-31 Zap income:zap:event:f8dd1e7eafa18add4aa8ff78c63f17bdb2fab3ade44f8980f094bdf3fb72d512 -10000000 msat assets:cln 10000000 msat ```
Each transaction has multiple postings which track the flow of money from one account to another. Once we have this file we can quickly build reports:
Balance report
Here's the command for "account balance report since 2023-05 in CAD"
$ ledger -b 2023-05-01 -S amount -X CAD -f cln.ledger bal``` CAD5290 assets:cln CAD2202 expenses CAD525 routed CAD1677 unknown CAD-7492 income CAD-587 unknown CAD-526 routed CAD-1515 lnurl CAD-614 jb55@sendsats.lol CAD-1 tipjar CAD-537 damus@sendsats.lol CAD-364 gpt3@sendsats.lol CAD-4012 merch CAD-2571 tshirt CAD-1441 hat CAD-852 zap CAD-847 event CAD-66 30e763a1206774753da01ba4ce95852a37841e1a1777076ba82e068f6730b75d CAD-60 f9cda1d7b6792e5320a52909dcd98d20e7f95003de7a813fa18aa8c43ea66710 CAD-49 5ae0087aa6245365a6d357befa9a59b587c01cf30bd8580cd4f79dc67fc30aef CAD-43 a4d44469dd3db920257e0bca0b6ee063dfbf6622514a55e2d222f321744a2a0e ...
0```
As we can see it shows a breakdown of all the sats we've earned (in this case converted to fiat). We can have a higher-level summary using the depth argument:
$ ledger -M -S amount -X sat -f cln.ledger bal``` sat14694904 assets:cln sat6116712 expenses sat1457926 routed sat4658786 unknown sat-20811616 income sat-1630529 unknown sat-1461610 routed sat-4207647 lnurl sat-11144666 merch sat-2367164 zap
0```
As we can see we made 14 million sats this month, not bad! The number at the bottom balances to zero which means we've properly accounted for all income and expenses.
Daily Damus Donation Earnings
To support damus, some users have turned on a feature that sends zaps to support damus development. This simply sends a payment to the damus@sendsats.lol lightning address. Since we record these we can build a daily report of damus donations:
$ ledger -D -V -f cln.ledger reg damus23-May-15 - 23-May-15 ..damus@sendsats.lol CAD-46 CAD-46 23-May-16 - 23-May-16 ..damus@sendsats.lol CAD-73 CAD-120 23-May-17 - 23-May-17 ..damus@sendsats.lol CAD-41 CAD-161 23-May-18 - 23-May-18 ..damus@sendsats.lol CAD-37 CAD-197 23-May-19 - 23-May-19 ..damus@sendsats.lol CAD-35 CAD-233 23-May-20 - 23-May-20 ..damus@sendsats.lol CAD-28 CAD-261 23-May-21 - 23-May-21 ..damus@sendsats.lol CAD-19 CAD-280 23-May-22 - 23-May-22 ..damus@sendsats.lol CAD-29 CAD-309 23-May-23 - 23-May-23 ..damus@sendsats.lol CAD-19 CAD-328 23-May-24 - 23-May-24 ..damus@sendsats.lol CAD-25 CAD-353 23-May-25 - 23-May-25 ..damus@sendsats.lol CAD-36 CAD-390 23-May-26 - 23-May-26 ..damus@sendsats.lol CAD-37 CAD-426 23-May-27 - 23-May-27 ..damus@sendsats.lol CAD-25 CAD-451 23-May-28 - 23-May-28 ..damus@sendsats.lol CAD-25 CAD-476 23-May-29 - 23-May-29 ..damus@sendsats.lol CAD-12 CAD-488 23-May-30 - 23-May-30 ..damus@sendsats.lol CAD-29 CAD-517 23-May-31 - 23-May-31 ..damus@sendsats.lol CAD-21 CAD-537Not making bank or anything but this covered the relay server costs this month!
Hopefully ya'll found this useful, feel free to fork the script and try it out!
-
 @ 32dc4f25:f95ddcce
2023-06-30 02:52:42
@ 32dc4f25:f95ddcce
2023-06-30 02:52:42Nostr, short for “Notes and other stuff transmitted through relays,” is a new communication protocol developed in 2021 by Lightning Network developer fiatjaf, which evolved out of LNBits developer Ben Arc’s attempt at a fully-decentralized marketplace called Diagon Alley. As opposed to other communication solutions, which mostly function via dumb clients and smart servers, Nostr offers smart clients and dumb servers, which heightens censorship resistance for users.
In Nostr, all data is stored locally with users and merely distributed via relays, rather than stored on central servers, such as via Twitter. In the case of social media, Nostr increases censorship resistance, as users are enabled to fully own their own content and profiles. In light of recent controversies around Twitter’s censorship policies, users began migrating toward the federated communications solution Mastodon. However, in Mastodon, ownership over content and profiles lies with those running the Mastodon servers users signed up with. While federations such as Mastodon offer more censorship resistance than centralized servers — as users are able to simply sign up to another server when censored — criticism has arisen around potential censorship on Mastodon through server owners.
In December 2022, the Nostr community received a 14 BTC grant from Twitter Founder Jack Dorsey, which brought unprecedented attention to the protocol. As applications built on Nostr evolved, the mobile client Damus jumped to number one in social networking on the iOS app store in China, resulting in its ban. In an apparent effort to contain the #MarchOffTwitter, Twitter CEO Elon Musk shortly banned the publication of Nostr-related content, along with bans on other third-party platforms such as Instagram, but to no avail.
While Nostr is by no means a privacy protocol, it could bring potential improvements to Bitcoin privacy.

A Nostr public key shared via Twitter, 2022
While Nostr is not a privacy protocol per se — among other issues, clients by default leak users’ IP addresses to relays — the Nostr protocol could bring improvements to Bitcoin privacy.
Improving Privacy And Scalability Of BIP47
BIP47 is a Bitcoin Improvement Proposal to create reusable payment codes while protecting the privacy of users for recurring payments. Without BIP47, users need to tediously generate new addresses by hand to avoid address reuse. When a user reuses an address for transactions, the user enables anyone watching the blockchain to easily cluster all transactions belonging to the address reused and form a graph of the user’s payment history and net worth. The prevention of address reuse is therefore a privacy best practice in Bitcoin and already implemented in many Bitcoin wallets by default. However, when a user aims to establish recurring payments with another party, such as in a merchant-customer relationship, a frequent generation of new addresses can be inconvenient.
With BIP47, a customer can generate a set of addresses to use for payments for the merchant. If a customer purchases products monthly, the merchant would need to send the customer an address each month. With BIP47, the customer creates a dedicated payment code for the merchant, which functions similarly to an extended public key. This allows the customer to automatically generate new addresses for the merchant, instead of the merchant needing to create addresses for the customer.
BIP47 makes use of notification addresses, which are monitored by HD wallets for outputs. In a notification transaction, the merchant sends the customer a blinded public key and chain code via the OP_RETURN field, together with a shared secret to keep the shared addresses private on the public blockchain. This exchange creates several issues due to the architecture of the Bitcoin network. The first two are economic: A notification transaction consists of 80 bytes, which can become expensive for users when fees on the Bitcoin network are high. Notification transactions, in addition, create unsendable outputs, which bloat the UTXO set over time. This increases the computing load on Bitcoin nodes who, at the time*, need to store the entire UTXO set, meaning every Bitcoin output that has not been used as a new input to ensure the validity of transactions.
A notification transaction creates so-called toxic change. When a user receives change from a notification transaction and spends the change to a third party, anyone watching the blockchain is able to correlate the user’s recurring payments to their non-recurring payments, even when addresses are not reused. A notification address also only exists once for each wallet. If a merchant wanted to establish recurring payments with 10 customers, anyone watching the blockchain is able to gain insight into the merchant’s customer base, as all 10 customers would need to create notification transactions for the merchant to the same notification address.
Instead of using notification transactions to exchange payment codes between merchants and customers, payment codes could be exchanged via Nostr. As opposed to other communication methods, Nostr is suitable for the exchange of BIP47 payment codes as no central authority exists to potentially censor the exchange of messages. At the same time, all direct messages on Nostr are encrypted by default, eliminating the need to compute shared secrets. By making use of BIP47 via Nostr, users can avoid the creation of UTXO set bloat via unspendable outputs and eliminate the correlation of recurring versus non-recurring payments as well as the publication of customer bases through the avoidance of toxic change and the re-use of notification addresses.
*Note: Storing the entire current UTXO set for Bitcoin nodes may potentially be eliminated in the future via the implementation of UTreeXO, which shifts the burden of proving that a transaction spends a valid UTXO to the owner of the UTXO, reducing the storage requirements from gigabytes to kilobytes.
Nostr Pay-To-EndPoint
In Bitcoin, blockchain analysis services operate the heuristic of “common input ownership” to map transactions to identities. Within this heuristic, a transaction containing different public keys used as inputs is classified as belonging to one person. Due to its UTXO-based architecture, through which inputs and outputs of transactions are linked, the Bitcoin protocol is also prone to subset sum analysis. In subset sum analysis, adversaries are able to calculate the probability of inputs and outputs belonging to the same entity, even when different public keys are used as inputs to one transaction. For example, if a transaction has inputs of 1, 4, 7, 23 and 6, and outputs of 5 and 36, it can be deduced that input 1 and 4 and inputs 7, 23 and 6 belong to the same entity.
 Source: “Knowledge Discovery In Cryptocurrency Transactions: A Survey” by Xia Fan Lu and Xin-Jiang Jang, 2021
Source: “Knowledge Discovery In Cryptocurrency Transactions: A Survey” by Xia Fan Lu and Xin-Jiang Jang, 2021Pay-to-EndPoint (P2EP) is a privacy-preserving reinvention of Satoshi Nakamoto’s Pay-to-IP (P2IP) coded into the original Bitcoin client. One form of a P2EP transaction are PayJoins, which are transactions designed to break the common input ownership heuristic. In a PayJoin transaction, both the sender and the receiver contribute inputs to a transaction to break the common input heuristic. With PayJoins, users exchange information about what UTXOs will be used as inputs via any communication channel, such as a Tor Onion, which functions as the end point, to construct a partially-signed bitcoin transaction (PSBT). Once both parties have agreed to the terms and signed the transaction, a PayJoin transaction looks just like any other Bitcoin transaction on chain. Because involved parties act as both sender and receiver, a PayJoin transaction breaks the common ownership heuristic as well as subset sum analysis: parties may contribute inputs of 3 and 5, while the transaction generates outputs of 6 and 2.
 *Source: “Pay To EndPoint” by Adam Fiscor, 2018 *
*Source: “Pay To EndPoint” by Adam Fiscor, 2018 *The problem: PayJoin transactions are complicated to coordinate, as participants have to be online at the same time when using a clearnet domain or Tor Onion endpoints. If a user initiates a P2EP transaction and, for example, closes their computer or otherwise disturbs network connectivity, the transaction cannot be communicated. In Nostr, communication is asynchronous: users fetch information from relays once network connectivity is restored. By using Nostr keys instead of Tor Onions as endpoints for P2EP transactions, P2EP transactions could be coordinated more easily.
Another implementation of P2EP is the much-debated LNURL. With LNURL, instead of tediously needing to generate new invoices for each transaction, users are able to receive a static endpoint pointing at a web server to automatically generate new invoices. However, because web servers are reliant on the global Domain Name Service (DNS), users of LNURL inevitably reveal their identity to the hosting provider, as well as their IP address to payees if no proper precautions are taken. Wide adoption of LNURL would therefore be a detriment to the pseudonymity of the Lightning Network. Instead of using a web server as the endpoint for LNURL, users could use Nostr keys as endpoints for LNURL transactions to conceal their identities.
Nostr For CoinJoins
While a PayJoin is great to break the common ownership heuristic as well as subset sum analysis, PayJoins are unable to offer privacy to both sender and receiver toward the cooperating party. PayJoins are essentially two-party CoinJoins, limited to two participants — this means that both sender and receiver are aware of their own inputs and outputs, leaving the inputs and outputs of their partner identifiable. Unless a PayJoin is facilitated with CoinJoined transactions, users risk revealing their wallet balances as well as past and future transactions to their PayJoin partners.
In anonymous-amount credential systems such as Wasabi Wallet’s protocol for CoinJoin coordination, WabiSabi, Nostr keys can function as communication endpoints for the coordination of a CoinJoin transaction. This enables the sender and receiver of a CoinJoin transaction to exchange the credentials needed to participate in CoinJoin rounds, essentially enabling a form of discreet payments within a CoinJoin. With the use of Nostr keys as endpoints in CoinJoins, cooperating parties remain unaware of their counterparties’ balances and transactions by hiding in the crowd. At the same time, using Nostr keys as endpoints for CoinJoin transactions helps PayJoin users save on fees by facilitating payments directly within the CoinJoin, rather than CoinJoining to facilitate the payment after.
Another use for Nostr in CoinJoins lies in the discovery of coordinators. While most CoinJoin coordinators run behind Tor to obscure the identity of CoinJoin participants, users are currently unable to easily discover new coordinators to join with the exception of JoinMarket, a CoinJoin marketplace targeted toward more advanced CoinJoin users. While CoinJoin users are able to add custom coordinators to Wasabi Wallet — a trivial task as easy as exchanging a URL in the backend — no way exists to automate the process of updating coordinators due to the lack of a platform for publication. Instead, to discover new coordinators, users must search social media and forums, such as Reddit or Twitter, to add coordinators manually. However, the publication of a coordinator service via social media or forums may pose a risk to coordination providers depending on the policies applied to the service, as certain pages may easily be shut down.
If Tor is an anonymous remailer, meaning a protocol facilitating the anonymous forwarding and receiving of messages between peers, Nostr can function as an anonymous bulletin board. CoinJoin coordinators can publish their services via a Nostr event type, and CoinJoin wallets can be enabled to automatically pull from those relays to display within their clients. The broadcasting of coordinator servers via Nostr, such as facilitated via BTCPay’ Servers CoinJoin plugin and proposed in the Lightning-enabled CoinJoin software Vortex, can eliminate the need to manually search for and add CoinJoin coordinators in CoinJoin clients, helping to further decentralize the CoinJoin coordination landscape.
Circumventing IP Requirements With NOSTR
As touched upon previously, the Nostr protocol was originally conceptualized to realize a fully-decentralized marketplace called Diagon Alley. As the Nostr protocol evolved, Diagon Alley became the LNbits extension NostrMarkets: a Nostr-native marketplace which enables merchants and customers to run and interact with online shops via relays. In NostrMarkets, customers can subscribe to a merchant's public key to fetch products from relays instead of accessing a merchant’s site via a webshop. This increases the censorship resistance of online shops, as merchants are not dependent on seizable websites — rather, a merchant’s shop is hosted with all relays the shop sets up to communicate with. Even if the merchant's server were to be seized, its shop could easily be set up at a different location, as all products are stored with relays on the Nostr network. NostrMarkets handles order and payment coordination via encrypted Nostr direct messages, while payments are facilitated through the Lightning Network.
In addition to its censorship resistance, the LNbits extension NostrMarkets enables fully-anonymous marketplaces. Instead of exposing a merchant’s IP to the whole world, both merchants and customers only reveal their IPs to the relays they connect to, which can easily be mitigated by running a client or shop behind Tor. As an upside to fully running a shop behind Tor, which makes a shop only accessible via the Tor browser and .onion web pages, NostrMarkets can run in any web browser or smartphone, improving the user experience of privacy-preserving, client-server communications. Because payments are negotiated via encrypted Nostr direct messages and facilitated via the Lightning Network, payments in NostrMarkets remain comparatively private as long as the shop’s Lightning node runs behind Tor, as a payment coordination direct message is indistinguishable from other direct messages in Nostr.
Another way to circumvent the requirement of IP addresses in server client communication is NOSTREST. REST, short for “representational state transfer,” is part of the software architecture of the world wide web, used to facilitate communication between servers and clients via GET, POST, PUT, DELETE and PATCH requests. But, when a client sends a REST request to a server, IP addresses are revealed, potentially revealing personally-identifiable information. On GitHub, escapee proposed a REST API bridge built on Nostr, called NOSTREST. By using Nostr keys without identification headers, both users and server operators do not need to know the IP addresses of their counterparts. A NOSTREST implementation can therefore improve the privacy of Bitcoin applications using REST as servers do not need the clients’ IP addresses.
One such example could be the running of custodial Chaumian e-cash mints, a form of anonymous-amount credential systems. In an e-cash mint, the mint operator does not know the balances or value exchanged by its users. However, due to the current architecture of REST, it does learn the user’s IP address unless running behind Tor by default, such as in the e-cash system Cashu. But implementing and managing Tor support is tedious. With the NOSTREST bridge, projects can easily preserve the privacy of their users. By running an e-cash mint behind Tor using NOSTREST to communicate between server and clients, communication can be facilitated asynchronously, while both server operator and user only learn each other’s public keys, eliminating the risk of identification via IP.
*The original author of this article is L0la L33tz. It was initially published in Bitcoin Magazine. Original article link: https://bitcoinmagazine.com/technical/how-nostr-can-improve-bitcoin-privacy
*
-
 @ 56cc5caf:ff5b3ec1
2023-07-23 06:09:49
@ 56cc5caf:ff5b3ec1
2023-07-23 06:09:49This is something that has been on my mind for a little bit; a thought that came from another thought that came from a self-examination; you know the way navel-gazing goes.
Let's set the stage.
- Everyone lies.
- Reality isn't real.
What does this leave?
- Actions are real.
- Emotions are facts (but only at a point in time)
- Our entire experience is complete. There are no missing parts. Time doesn't work that way.
I can go more in depth on any of this, but for now, just mostly wanted it here, because looking at things from this perspective has a lot to do with how I view authenticity.
Shall I define authenticity? I've struggled with this, but I think when someone is authentic, their actions are consistent with how they present themselves as a person. There is a sense of integrity about them, in the way they are perceived.
This is an observation that I am purposefully making from an external viewpoint. If I were to view authenticity from an internal viewpoint, I think I would consider it integrity.
When everyone is lying to you, whether intentionally or not, all that leaves for you to observe is their actions. If those actions are consistent, then you can consider them authentic to that person, even when that person is lying to you. A person can be an authentic liar, jerk, inconsiderate, petty human. A person can be kind, compassionate, accepting, honest - but if actions indicate otherwise, they may be inauthentic.
What use is this? It is a way to look at someone else externally. Maybe it is a way to judge. Let's look at reality not being real. I see this in the following way - what we experience for ourselves as reality is like what we experience as our smartphone screen or computer desktop. There are icons there that have meaning, but they are not actually the things that are real. Behind the icon is an application. Behind that application are lines of code. behind those lines of code are binary electronic pulses, zeros and ones. Those move around circuitry in all kinds of ways. Electrical pulses are energy. How real is energy? I think maybe the only thing holding energy as real is time, and how real is time? This is not the same as the theoretical implications of The Matrix, but those are possibly more in line with this than any other concept of reality.
However, we all experience whatever the stuff of reality actually is, in useful constructs. Things like matter, energy - these are useful to explain what we experience. We can attempt to measure these things in ways that we can compare to others' experiences. However, if I held a rock, and tried to describe the experience of holding that rock, it would NOT be the same as your experience holding that same rock, even if we could agree it was the same size, weight, color, etc. What does reddish orange really mean? What does a kilo mean - to you, when you hold a 1-kilo rock in your hand? I don't assume that it would mean the same to me.
Since I am basically saying that how we experience reality is entirely subjective, and it is impossible for me to experience your reality in the same way you do, all I can do is observe your actions. Speech is an action. Inaction is an action, as a response to something else. I wrote about an economy of emotion that goes further into the opportunity costs of acting and feeling.
But emotion is a little different. Emotion isn't an action. Emotion is fact, but only subjectively. My decisions will be based largely on emotion, in my opinion, and so will yours. We try to assert that we act logically, or mindfully, or even instinctively - but as humans, I believe we first and ultimately act emotionally. Even controlling your emotions will still allow emotions to partially inform your action. Your emotions inform your experiences, your memory, all your perceptions, both sensory and extrasensory. We want to deny this, to build some reality construct that makes sense, that we can apply as a template for ourselves and others - but this simply isn't true. Emotion is still there. Emotion may be the one thing that keeps us as humans separate from AI.
Emotion is only true at a point in time, though - so the action you took earlier today based on your overall emotional state at that time might not be the same action you would take right now, as your overall emotional state will have changed.
And I don't think we see emotions as nearly as complex as we could. I've read books on emotional intelligence, and when they bring up some color chart, I laugh. I see my emotional color chart as a tie-die kaleidoscope, changing like an active heat map. Chaotic, sometimes perhaps, or sometimes mesmerizing in its own patterns. And this is what ultimately sits at the controls of my human action.
I am not saying that emotions cannot be influenced by other factors; of course, they can - but whatever the effects of the influences, your action at a particular point in time will still be informed by your overall emotional state at that point in time.
How does this work with authenticity? If I see someone displaying consistent action, and I understand that action is informed by emotion, then maybe I can infer something about the consistency of their emotional state.
When you don't believe you are being told the truth, and reality isn't real, small inferences like this make a big difference in how you reconstruct your overall world view. I could not say if someone had integrity or not. Only they could believe that about themselves. I could, however, observe their actions and believe them to be authentic.
And how does this relate to interpersonal relationships in general? What hope is there for an interpersonal relationship when there is no trust? Well, trust can be built through authenticity; in fact, I could say that any trust must be built through authenticity, and inauthentic action is what destroys trust.
I struggle with many things, being an extremely analytical person, and coming from a past that did not reward many of the actions that most take for granted as good. It also taught me early and often that permanence was not to be expected. Some of this led to some serious issues with self-esteem.
I can write a lot more about self-esteem, but one part of having low self-esteem is an emotional state that feels insignificant or less important relative to others. This is extremely general on purpose, but this can include people that never feel good enough to meet their parents' expectations, or even the expectations of a god-figure or savior. The person with low self-esteem is always seeking that external approval, while also always feeling judged.
I struggled with my share of that. For some time, I believed that the perceptions of others were more important than my own reality, and lived to create a perception of myself that would serve me well. This will never be authentic. This is like the person who when asked who they are, responds by asking who you want them to be. In fact, when asked to "be yourself", that is not immediately possible, as you are just a mirror or a prism, reflecting off whatever you think will show you in the best possible light. Then this immediately becomes cyclical, as you feel that emptiness, and the emotional toll of inauthenticity.
One of the first observations I had when confronting my self-esteem was that I needed to restore my own integrity, but that wasn't immediately easy to do, because I also needed to establish authenticity and become consistent in action. This meant accepting emotion, and learning to harness the power of emotion when acting. A lot of that is just accepting the emotion that is there. Some of that is removing obvious external factors. I no longer feel any need to drink alcohol, although I may do so socially from time to time. I think it contributes to inauthenticity when viewed externally, and does nothing to preserve integrity in my own thoughts and emotions.
Remember, authenticity is an external construct. Integrity is a similar internal construct.
Once I was on the path to fixing myself, I wanted to start looking at what I could do to build a social network. I've never believed I had friends, although I am a social enough person, have no problem going out, talking to people, etc. But this is again the damage done by low self-esteem, having no trust in permanence, no faith in people, no belief in my own authenticity, even when I was acting with integrity.
The way I found out of this is to use authenticity as a useful construct. I can use it to build trust in others, and see it as a way they can build trust with me.
This is way different than living in the shadow of their perceptions (or at least my concept of what their perceptions must be). I've done plenty of that, what I initially considered buying friends - being the guy to pay the bill. Being the guy that had what they needed, that cared about what they were interested in, would help them with whatever they were doing. Spending my money at times, but ultimately my time, to hopefully make them think well enough of me to maybe consider I might belong as a friend. But that would never make me feel that I belonged, and why should it? I was never actually sharing myself, so anything that would belong would not even be myself.
Now, it is more important to first understand myself, construct my reality, accept my own emotions, and then share freely with others, hoping not for their approval or acceptance, but only that my authenticity allows them to trust me enough to share their own authenticity. This isn't something that can be bought with my time or money, but only my own work to make my actions as consistent and authentic as possible.
No, this is not easy. It may be simple, but not easy - but then again, nothing worthwhile is ever easy, although it may often be simple.
I think it becomes easier with time, though. Finding your own inconsistencies, exploring what seemed to you to be contradictory in your own actions - That is something that takes time, and resolving those inconsistencies can be tough, but ultimately rewarding. Building your own self-esteem, finding out and exploring who you are, and what you want to construct your own reality to be - that is the most important building you can do, and worth every moment you attend to it. It can never be someone else's reality, someone else's perception, even if that person may mean more to you than anything else you can think of, even yourself. It must be yours, and you have to build it. Anything less, and you are just another NPC in the game of life.
The key to building is small, intentional actions, done repeatedly. We see that in this network. Small notes, sent intentionally, done repeatedly. Building the most authentic network we could imagine, where inauthenticity is disincentivized. But back to life. This isn't about forming habits, although those will happen. It may be about breaking habits. Intentionally. Repeatedly.
Focus. Simple. Intentional. Repeated. This is the path to Authenticity. Authenticity is where true relationships are formed between people.
-
 @ 9ecbb0e7:06ab7c09
2023-07-23 04:56:58
@ 9ecbb0e7:06ab7c09
2023-07-23 04:56:58Tres cubanos son apresados en la Aduana de Holguín con un cargamento de píldoras de tramadol
Tres cubanos fueron arrestados en la Aduana del Aeropuerto Internacional ‘Frank País’ de Holguín cuando intentaron entrar a Cuba con un cargamento de 6.980 tabletas de tramadol, un analgésico que está expresamente mencionado dentro del listado de medicamentos controlados por el Ministerio de Salud Pública (Minsap).
De acuerdo con la información difundida por el perfil de Facebook Cazador-Cazado, uno de los tantos vinculados al Ministerio del Interior (Minint) que proliferan en las redes sociales, los tres cubanos arribaron a Holguín procedentes de México, y pretendían aprovecharse de las flexibilizaciones para importar medicamentos, aseo y alimentos, que están vigentes hasta el 31 de diciembre de 2023.

En la nota, los implicados fueron identificados como Marisleydis Rodríguez Tamayo y Dianny Peña Sánchez, ambas con residencia en la provincia Granma, y Alejandro Rojas Espinosa, natural de Holguín.
-
 @ b9e76546:612023dc
2023-05-23 18:13:45
@ b9e76546:612023dc
2023-05-23 18:13:45The real power of AI will be in its integration of other tools to use in specific situation and recognizing what those tools are. There will be extremely specific & curated AI models (or just basic software circuits) on certain topics, tasks, or concepts. And this will also be a crucial way in which we keep AI safe, and give it understanding of its own actions. In other words, how we prevent it from going insane. I've recently experienced a tiny microcosm of what that might look like...
— ie. a general language model that knows to call on the conceptual math language model, that then makes sense of the question and knows to input it into the calculator app for explicit calculations when solving complex or tricky word problems. And then to apply this in the realm of safety and morals, a specific model that an AI calls on for understanding the consequences and principles of any actions it takes in the real world.
I believe there needs to be an AI "Constitution" (a particular term I heard used to describe it) where there is a specific set of ideas and actions it is enabled to perform, and a particular set of "moral weights" it must assess before taking action. Anyone who's read Asimov will recognize this as "The Three Laws" and that's basically what it would be. This is critical because an AI running an actual humanoid machine like Boston Dynamics could go ape shit literally because it is emulating trolling someone by doing the opposite of what they asked -- I just had a LLM troll me yesterday & go a bit haywire when i asked it to be concise, and every answer afterward was then the wordiest and longest bunch of nonsense imaginable... it was funny, but also slightly sobering to think how these things could go wrong when controlling something in the real world. Now imagine a robot that thinks Kick Ass is a funny movie and starts emulating its behavior thinking it's being funny because it has no model to assess the importance of the humans whose skulls it's smashing and thinks the more blood it can splatter everywhere makes it a more comical experience for those in the room. That's essentially the "real world robot" version of asking a LLM to be concise and instead getting an avalanche of BS. Ask a robot to be funny and maybe it crushes your skull.
Because of that, I think there will be certain "anchors" or particular "circuits" for these LLMs to be constrained by for certain things. Essentially action specific built governors that add meaning to the actions and things they are doing. A very simple version mentioned above would be a calculator. If you ask an LLM right now to do basic math, it screws up all the time. It has no idea how to generate a true answer. It just predicts what an answer might sound like. So even extremely simple and common sense requests turn up idiotic answers sometimes. But if it can recognize that you are asking a math problem, find the relevant mathematical elements, and then call on the hardcoded & built-in calculator circuit, then the LLM isn't doing the calculation, it's simply the interface between the calculation tool and the human interaction.
What I think will be critical as we integrate these into real world machines over time, and as their capabilities become more generalized and layered, will be to build in a sort of moral constitution that behaves like a concrete engine (a calculator), that has the model recognize when something might be a questionable behavior or cause an undesirable outcome, and then call on the "constitution" to make the decision to act or not. In that way, it may actually prevent itself from doing something stupid or terrible that even a human hadn't realized the full consequences of. — ie. it won't help a child get to the roof of his building so he can fly off the side with his cardboard wings.
It will be very interesting to watch these come about because the failure more of AI will be a critically important thing to consider, and unfortunately from an engineering and cultural standpoint, "failure modes" are something that have been underrepresented and increasingly ignored. A simple example is a modern washing machine; when something entirely arbitrary or some silly little feature breaks, the whole thing is useless and you have to bring a technician out to fix it, when a sensible failure mode would be that it simply routes around what arbitrary feature failed, and continues working normally. This, unfortunately, has become the norm for tons of "modern" devices and appliances. they are simultaneously increasingly "advance" and "stupid" at the same time. It's largely a product of the high time preference mindset, and we need MUCH more low time preference consideration as we unleash AI onto the world. It will matter exponentially more when we start making machines that can operate autonomously, can maintain themselves, and learn through their own interactions and environment... and we aren't very far away.
Learn as fast as you can, understand the tools, and stay safe.
grownostr #AI_Unchained
(my very first post on BlogStack.io)
-
 @ 7fa56f5d:751ac194
2023-05-14 10:14:15
@ 7fa56f5d:751ac194
2023-05-14 10:14:15Here is a list of relays I use and consider reliable so far. I've included some relevant information for each relay such as if payment is required or NIP-33 is supported. I'll be updating this list as I discover more good relays, which ones do you find reliable?
Nokotaro
nostr:nrelay1qq0hwumn8ghj7mn0wd68yttjv4kxz7fwdehkkmm5v9ex7tnrdakj78zlgae
- Paid? No
- NIP-33 supported? Yes
- Operator: nostr:npub12ftld459xqw7s7fqnxstzu7r74l5yagxztwcwmaqj4d24jgpj2csee3mx0
Nostr World
nostr:nrelay1qqvhwumn8ghj7mn0wd68ytthdaexcepwdqeh5tn2wqhsv5kg7j
- Paid? Yes
- NIP-33 supported? Yes
- Operator: nostr:npub1zpq2gsz25wsgun2e4gtks9p63j7fvyfd46weyjzp5tv6yys89zcsjdflcv
Nos.lol
nostr:nrelay1qq88wumn8ghj7mn0wvhxcmmv9uvj5a67
- Paid? No
- NIP-33 supported? No
- Operator: nostr:npub1nlk894teh248w2heuu0x8z6jjg2hyxkwdc8cxgrjtm9lnamlskcsghjm9c
Nostr Wine
nostr:nrelay1qqghwumn8ghj7mn0wd68ytnhd9hx2tcw2qslz
- Paid? Yes
- NIP-33 supported? No
- Operators: nostr:npub1qlkwmzmrhzpuak7c2g9akvcrh7wzkd7zc7fpefw9najwpau662nqealf5y & nostr:npub18kzz4lkdtc5n729kvfunxuz287uvu9f64ywhjz43ra482t2y5sks0mx5sz
Nostrich Land
nostr:nrelay1qqvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqpdl8ln
- Paid? Yes
- NIP-33 supported? No
- Operator: nostr:nprofile1qqsxf8h0u35dmvg8cp0t5mg9z8f222v9grly6hcqw2cqvdsq3lrjlyspr9mhxue69uhhyetvv9ujumn0wd68y6trdqhxcctwvsj9ulqc
-
 @ 1bc70a01:24f6a411
2023-05-07 06:20:54
@ 1bc70a01:24f6a411
2023-05-07 06:20:54The other day I posted an “unpopular opinion” about hiding zaps from client UI which received a range of responses (mostly displeased). Today I wanted to expand on that thought and the reason for that opinion.
I’ve thought this through and in my mind had a perfect response, but this is a new day and I’ll probably butcher it.
I think the common push back was that maybe this is an anti-bitcoin, anti-lightning idea. Seeing how we have many people who are passionate about both, that provokes a passionate pushback.
However, I think it’s the exact opposite - pro-bitcoin, pro-growth.
There are several ways I look at this, from a “sales” perspective, from product discovery perspective and from the psychology perspective.
The most successful sales strategies are usually “pull” strategies. They bring prospects in and allow them to sell themselves on the idea or the thing. I view nostr as a pull technology. It brings people in for various reasons, but highly unlikely that it’s for money. Even the first batch of bitcoiners that joined did not come for the money aspect - we were escaping Twitter. Zaps are amazing and I’ve been a vocal proponent of what they may mean for the protocol. I tried to explain this as simply as I could on heynostr.com However, I think showing the UI to people who are not familiar with it, especially since it is an optional setting is a “push” move.
On its own, displaying new features in new apps is a good thing - after all, why have the app if it does nothing new? But zaps have a unique dynamic about them because they are money. Combined with the fact that it’s all based on Bitcoin, it’s easy to start classifying Nostr as “that one social network for bitcoiners”. I’ve heard (read) this already from people on the outside. Heck, even bitcoiners on Twitter say this (although with push back, explaining why they are not moving here).
There’s nothing wrong with being an “app” for bitcoiners, IF that’s your goal. But if the goal is global adoption, the social use case has to appeal to a more general audience who may not care about the same things we care about.
Side note: I think zaps in UI visible by default are perfectly fine in other use cases like Zapstr. There, the entire premise rests on the ease of use of payments. Other use cases where money making IS the primary goal are perfectly suited for always visible zap UI. Even social clients that specifically focus on some audience are more than justified in displaying zaps loudly (like Plebstr).
From a product discovery perspective, it may actually be more pleasant and have the “pull” effect of effective sales strategies to allow the user discover zaps on their own. Even if the UI hides zaps by default (even from people who have it enabled), it will be hard to stay on nostr for any significant duration without running into zap talk. In fact, it’s probably impossible. Someone is always talking about zaps! These are the types of moments where a user can discover zaps on their own terms and ease into the idea.
Once the marketplace functionality is introduced into clients, it will be all but impossible to not run into zaps when trying to click on products or locked / blurred content. Since the primary function of a marketplace is to SELL and to BUY and money is expected to be transacted, there’s nothing sketchy about making it obvious.
Which leads my train of thought to the social use case and user perception. Obviously, nostr is much bigger than zaps. It’s a protocol that enables all sorts of apps to interact with the social and the payment layers. People will join for different reasons appealing to them. Some might come from the music perspective, others may want to escape the payment processing issues in the adult entertainment industry, and others may find work through nostr and get paid in zaps as part of a global workforce. However, each has payments baked in as a function and an expectation. Social does not. Yes, social enables sending of payments as remittance, but there has never been a dynamic value for value exchange.
This being said, the great thing about Nostr is that nobody has to listen to what I have to say and they can build whatever the hell they want! Clients will be built for specific audiences that have features that cater to that niche. It is just my opinion that the client to replicate the existing onboarding flows and the familiarity of existing apps (without pushing zaps) is going to be the one to win the social use case in the text category. At least for a while. Of course, there will be other categories that cater to younger audience like video curation, entertainment (photo and video content) and perhaps even others that I can’t even imagine at this point.
One other thing I haven’t even touched on is the onboarding process and how that can be used to introduce Zaps in a fun, non-invasive way. I think as apps develop native wallet capabilities, we’re going to see the onboarding get creative and fun (I can already think of a situation where you can give someone a few sats to zap before they even set up their profile!)
Let’s keep an open mind and keep the dialog flowing. This is a lot of fun to me and I hope not to be misunderstood. My only goal is to help nostr and bitcoin thrive.
-
 @ 52b4a076:e7fad8bd
2023-05-01 19:37:20
@ 52b4a076:e7fad8bd
2023-05-01 19:37:20What is NIP-05 really?
If you look at the spec, it's a way to map Nostr public keys to DNS-based internet identifiers, such as
name@example.com.If you look at Nostr Plebs:
It's a human readable identifier for your public key. It makes finding your profile on Nostr easier. It makes identifying your account easier.
If you look at basically any client, you see a checkmark, which you assume means verification.
If you ask someone, they probably will call it verification.
How did we get here?
Initially, there was only one client, which was (kind of) the reference implementation: Branle.
When it added support for NIP-05 identifiers, it used to replace the display name with the NIP-05 identifier, and it had to distinguish a NIP-05 from someone setting their display name to a NIP-05. So they added a checkmark...
Then there was astral.ninja and Damus: The former was a fork of Branle, and therefore inherited the checkmark. Damus didn't implement NIP-05 until a while later, and they added a checkmark because Astral and other clients were doing it.
And then came new clients, all copying what the previous ones did... (Snort originally did not have a checkmark, but that changed later.)
The first NIP-05 provider
Long story short, people were wondering what NIP-05 is and wanted it, and that's how Nostr Plebs came to be.
They initially called their service verification. Somewhere between January and February, they removed all mentions to verification except one (because people were searching for it), and publicly said that NIP-05 is not verification. But that didn't work.
Then, there were the new NIP-05 providers, some understood perfectly what a NIP-05 identifier is and applied the correct nomenclature. Others misnamed it as verification, adding confusion to users. This made the problem worse on top of the popular clients showing checkmarks.
(from this point in the article we'll refer to it as a Nostr address)
And so, the scams begin
Spammers and scammers started to abuse Nostr addresses to scam people: - Some providers has been used by fake crypto airdrop bots. - A few Nostr address providers have terminated multitude of impersonating and scam identifiers over the past weeks.
This goes to show that Nostr addresses don't verify anything, they are just providers of human readable handles.
Nostr addresses can be proof of association
Nostr addresses can be a proof of association. The easiest analogy to understand is email:
jack@cash.app -> You could assume this is the Jack that works at Cash App.
jack@nostr-address-provider.example.com -> This could be any Jack.
What now?
We urge that clients stop showing a checkmark for all Nostr addresses, as they are not useful for verification.
We also urge that clients hide checkmarks for all domain names, without exception in the same way we do not show checkmarks for emails.
Lastly, NIP-05 is a nostr address and that is why we urge all clients to use the proper nomenclature.
Signed:
- Semisol, Nostr Plebs (semisol@nostrplebs.com)
- Quentin, nostrcheck.me (quentin@nostrcheck.me)
- Derek Ross, Nostr Plebs (derekross@nostrplebs.com)
- Bitcoin Nostrich, Bitcoin Nostr (BitcoinNostrich@BitcoinNostr.com)
- Remina, zaps.lol (remina@zaps.lol)
- Harry Hodler, nostr-check.com (harryhodler@nostr-check.com)
-
 @ 9ecbb0e7:06ab7c09
2023-07-23 04:52:10
@ 9ecbb0e7:06ab7c09
2023-07-23 04:52:10Roberto Castellanos Suárez hermano de periodista oficialista Humberto López Suárez, llegó a Estados Unidos y reside en Fort Myers, Florida; desde hace aproximadamente tres semanas, según expusieron en sus redes sociales los influencers Darwin Santana y Yamila La Hija de Maceo.
Castellanos Suárez y el nefasto y manipulador presentador de la Televisión Cubana son medios hermanos, hijos de la misma madre, la señora Lient Suárez, pero de distintos padres. En varias fotografías publicadas se aprecia a los dos hermanos compartiendo con su progenitora, aunque se desconoce si fue una escena previa al momento de la despedida y la emigración Roberto desde Cuba a los Estados Unidos
 Los post de las fuentes no precisan si la entrada se produjo de manera legal o ilegal, pero sí aseguran que Roberto tuvo que enfrentarse y aprobar una “prueba de miedo creíble”, lo que sugiere que su entrada pudo haber sido por la frontera.
Los post de las fuentes no precisan si la entrada se produjo de manera legal o ilegal, pero sí aseguran que Roberto tuvo que enfrentarse y aprobar una “prueba de miedo creíble”, lo que sugiere que su entrada pudo haber sido por la frontera.De acuerdo con el perfil personal en Facebook de Castellanos Suárez, su más reciente publicación data del 18 de julio, donde celebra con una foto el cumpleaños de su hijo pequeño y lamenta estar lejos, lo cual confirma que está fuera del país. “Mi otro pedazo de corazón está de cumple hoy que la pase bien, que papi lo extraña y lo quiere mucho”, refirió en un mensaje para su pareja Lisandra Contreras.
 La influencer cubana Yamila La Hija de Maceo compartió la información en su cuenta de Twitter y varios compatriotas le han aportado más evidencia sobre el caso. Según un mensaje, “a Humberto y su hermano los crío una abuela y un tío (Raquel y Hugo) que ya fallecieron (el tío por alcohólico). El caso es que siempre hubo doble moral en esa casa porque eran comunistas, pero vendían hasta su madre y actualmente la madre compra y vende de contrabando”.
La influencer cubana Yamila La Hija de Maceo compartió la información en su cuenta de Twitter y varios compatriotas le han aportado más evidencia sobre el caso. Según un mensaje, “a Humberto y su hermano los crío una abuela y un tío (Raquel y Hugo) que ya fallecieron (el tío por alcohólico). El caso es que siempre hubo doble moral en esa casa porque eran comunistas, pero vendían hasta su madre y actualmente la madre compra y vende de contrabando”.“Te diré que ese hermano de Humbrete está aquí en Estados Unidos hace como 2 o 3 semanas y pasó la prueba de miedo creíble. Vive en Fort Myers, Florida”, aseveró una seguidora de Yamila La Hija de Maceo que pidió el anonimato.
 De acuerdo con la base de datos de Etecsa, consultada por Periódico Cubano, Humberto Dionil López Suárez, director y conductor del programa “Hacemos Cuba” y miembro del Comité Central del Partido Comunista, tiene como número de teléfono registrado el 53534735 y nació el 9 de octubre de 1985. Por su parte, el hermano del presentador, Roberto Castellanos Suárez, es tres años menor.
De acuerdo con la base de datos de Etecsa, consultada por Periódico Cubano, Humberto Dionil López Suárez, director y conductor del programa “Hacemos Cuba” y miembro del Comité Central del Partido Comunista, tiene como número de teléfono registrado el 53534735 y nació el 9 de octubre de 1985. Por su parte, el hermano del presentador, Roberto Castellanos Suárez, es tres años menor. -
 @ 1bc70a01:24f6a411
2023-04-23 23:30:54
@ 1bc70a01:24f6a411
2023-04-23 23:30:54The following are random bits of wisdom I've collected over the years. Some right, some wrong. Some not mine, you may recognize it. Some I've come to realize - that perhaps millions others did before me. Some common sense. You may laugh, already know it all, or not. If it's helpful to one person, I'll consider it a win 🙌
- Surround yourself with people who are smarter than you.
- To get things done, focus on one big thing or the day. Don't worry about lists and the small details.
- Meta marketing = talking about grown on a platform where your audience hangs out. Since everyone else wants to grow too, you gain visibility without even selling your thing. Great if your product happens to help people grow.
- Package and sell knowledge. No matter how dumb it may seem, it'll probably be helpful to someone. Books, ebooks, courses, products, software are all forms of knowledge packaged for sale.
- Having a network around you is a lot more important to success than who you are or what you know.
- The world is incredibly complex, even the simplest things are not so simple.
- Take advantage of compounding effect. The sooner you start investing, the larger your investment grows over time (especially towards the end of the timeframe). Or bitcoin 🤷
- Never judge a person, unless your intuition tells you they mean harm.
- How founders win at startups = ship fast, talk to customers, fail quickly, stay in the game.
- Many people in positions of power are just faking it. They truly have no idea what they are doing
- The drive to avoid pain is greater than the drive to seek pleasure. Humans will do anything to avoid pain - hence why so many people don't do anything with their life - afraid of "failure".
- In sales, generally speaking, benefits sell better than avoiding losses. e.g. don't talk about savings, talk about new revenue.
- Hopping jobs is often the fastest way to get a pay increase.
- If you don’t like the rules, change the game. Everything is in your power. Just don’t break laws in the process.
- You are your worst critic. Silence your critical self and you can accomplish what you set out to accomplish. Whatever doubts, fears or uncertainties you have, it’s all in your mind. Conquer that, and the rest will fall in place.
- Always save for the future. Put away some amount always, even if it seems insignificant. A little bit over time can add up to a lot.
- Don’t try to do it all on your own. Delegate, find people you can trust and have them do parts you don’t have the time for.
- Don’t let notifications /distractions ruin your life. Command your attention, turn off notifications, news, social media.
- Sleep at least 7 hours a day to live longer. Sleeping less, for most people means literally losing years of their life.
- Sleep on it. When you have a hard problem ahead of you, a challenge you can’t fix or a work problem you can’t overcome, think about it hard before you fall asleep. When you wake up, you’ll have a solution. The human man is a lot more capable are piecing things together in our sleep.
- Step away from computers often, go for long walks or exercise.
- Buy experiences, not things. Things fade, memories last a lifetime – until one gets Alzheimer’s that is.
- To influence, ask for help. People love it when you ask them for help – it makes them feel important. If you want to gain someone’s attention, ask for help.
- Ignore haters. Life is full of them, they are just not worth your very limited time on this planet.
- The best time to start is earlier, the 2nd best time is now. If you have something you want to accomplish, start on it RIGHT NOW. If the task is unsurmountable, take it one little step at a time.
- This is your life in years, don’t waste it on pointless things: [birth]XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX[90th bday]
- To become a master, copy other masters. Only when you have reached their level, you can create something original. When it comes to seeking permission, tell, don’t ask. Asking puts you in a subservient position, where telling enlarges your stance. “I’m going on vacation next month” vs. “May I have vacation time next month?” “Here is my rate” vs. “How much can you pay?”
- Anchoring effect – when compared to something large or small, the desired option is easier to accept. For example, if you have a service that costs $40,000, mentioning $450,000 before bringing up the 40k will automatically make it feel less threatening in the person’s mind. It’s a lot easier to sell something that costs $20 when compared to $200, than when compared to $1.
- Eliminate mundane daily decisions. “Which shirt to wear?” Automate your decision process so you never have to waste energy on things that don’t matter.
- Schedule your time. Every minute of your life costs something. Think of wasted time as lost opportunity. Put important events on a calendar and stick to that schedule. If you find that you don’t have time for something, schedule it on the calendar and make yourself unavailable for other activities during that time – focus on that one task.
- Opposite of previous advice, don’t schedule anything. Just clear your calendar and don’t write anything down. Do the most important things right away, the others will take care of themselves.
- Take extremely good care of your health. You will regret deeply if you don’t. Don’t eat bread, refined carbs, sugars – they literally cause cancer. Avoid bread, pasta, sweets, processed carbs (crackers, chips, cereal etc… ) whenever possible. Carbs cause inflammation, and the body is not designed to handle inflammation well.
- Your body is an organism, if you want it to thrive, you have to feed it well.
- Move on quickly. Dwelling is absolutely pointless and only wastes more time.
- Always charge your worth. Never do anything for free unless you are volunteering your time for a good cause.
- Add value to everything – people’s life, your job, your business, your investment, your relationship. Adding value is a skill that must be practiced but pays dividends in the long run.
- When someone tells you something personal, listen. Really listen, don’t offer advice, just shut up and listen, they didn’t come for advice.
- Take advantage of professionals – get help when needed. Don’t be cheap.
- You get what you pay for – really. If it’s cheap, chances are its shit, but be weary of scammers & marketing bsers who disguise quality with price. Avoid branded products unless you feel they offer real quality over alternative. Luxury brands are almost never worth it and are a complete waste of money unless money is no longer an object in your life.
- For easier habit formation, make the activity easily accessible.
- When you're young, say yes more often for opportunities, when you're older protect your time and be more selective in what you agree to. Perfectly normal to say No to most things.
- Doctors fuck up all the time and thousands of people die because of their mistakes.
- Hospital-acquired infections are very common and often deadly.
- Incentives power the world. If you want to understand why something is the way it is, look for the underlying incentive.
- Science is supposed to be questions constantly, that's the whole point. "Trust the science" is an oxymoron.
- All media is biased. Choosing to use one word over another introduces bias to the story, no matter how hard you try not to. The best thing is to take everything lightly and collect stories until you have a broader picture from various sources. Even then you're likely to have the wrong framing and facts! I just ignore all media.
- Never chase happiness for it is always fleeting. Find satisfaction in the long term and aim for joyful moments.
Have your own bits of wisdom? I'd love to hear them! Or, you can call out bs if you see it here 🤗
-
 @ f5bcf314:0507683d
2023-04-20 23:21:34
@ f5bcf314:0507683d
2023-04-20 23:21:34I have been in the crypto space for a while, but only recently, I got hooked up on Lightning Network, Nostr and Zapping. This is also my first post on Habla, so please be gentle.
By the way. I am not a financial advisor, and this is not financial advice. These are just services I use, and I decided to share my experiences.
If you are like me, you probably ask, "How to buy and stack small amounts of sats? Does it make sense to buy £10 worth of BTC every week? How much will be eaten up by the fees?" And these turned up to be very valid questions for me. At the level of 10£, fees can be humongous.
As you can guess by the "£" sign, I live in the UK and found myself out of the EU a few years ago. Some banks stopped offering their services to us, and everything suddenly became more expensive. So there could be easier or cheaper options in the EU or elsewhere; I am talking about my limited UK experience.
Binance (minimum £15)
best for balanced purchase automation (KYC required)Recurring buy with a card. Transaction fee 2.07% = £0.31 My £15 bought me 61992 SATS
Recurring buy with a balance. Binance will charge 1£ for processing a bank transfer. Moving £61 every four weeks and setting weekly buys of £15 would work out slightly better than the option above.
Withdrawals The withdrawals must be manual, and Binance has not yet integrated with LN. Withdrawals to BTC have a minimum of 30kSATS, and the network fee is set to 20kSATS. Minus LN network fees, my Alby LN address was credited with only 41871. That's roughly 2/3 of my purchase, definitely not the best of the deals for small amounts.
Crypto.com (minimum £12)
best for purchase automation of larger amounts (KYC required)Recurring with a card. it will set you back a whopping 2.99%. Crypto.com will add the £0.45 to the charge on your card.
Recurring buy with a balance. On a positive note, there is no fee for processing inbound transfers(!) Like with Binance, the withdrawals must be manual, and no LN integration exists. Withdrawals to BTC have a minimum of 120kSATS. This means I would need to buy at least £30 worth of BTC to be able to withdraw it. However, the fee is whooping 60kSATS which means my lN address would be credited with only 50%. Wow!
Nexo (minimum top-up £10)
best value - totally manual (KYC required)Unfortunately, there is no recurring purchase option nor integration with LN so maybe I should not include it, However: There are no processing costs for inbound transfers. The platinum level gives five free withdrawals and requires 10% of the overall portfolio value to be held in NEXO. Assuming that we 'r rather hold our crypto in self-custody - this might not be that hard to achieve.
Mt Pelerin
full stacking automation - especially interesting for small amounts (no KYC )Located in Switzerland and integrated with LN. It cannot be simpler. You send a bank transfer, and your chosen currency in your selected network will be credited. The list is impressive, and you can even specify your self-custodial addresses. The first 500 CHF worth of transactions every year is completely free. This limit can be raised when holding their MPS token. Out of experience, best to send transfers from the UK in CHF. The Revolut fee is only £0.3. Don't forget to provide a reference number.
Summary
These are by no means all possibilities, just all that I tried. There is also no clear best option. At level £10 a month, Mt Pelerin seems to be a no-brainer, but the more you want to buy, the more complex things will get. I am still on the lookout for better options. Shout if you know of any.
If you'd like to sign up - my referral links are: * Binance - https://accounts.binance.com/register?ref=42469060 * Crypto.com - https://crypto.com/app/btgvb3gp3d * Nexo - https://nexo.com/ref/p0qh72rpbp * Mt Pelerin - https://mtpelerin.com/join?rfr=Vx1MzVyn
Don't be a stranger, and find me on Nostr.
npub17k70x9qncwjnxne2hd0fuehydydaj2mw9xjqdr5wnjh42pg8dq7snart3v
-
 @ c5fb6ecc:e58c38bb
2023-05-12 00:59:58
@ c5fb6ecc:e58c38bb
2023-05-12 00:59:58https://ln.tips is a great wallet. It's an extremely easy to use, custodial Lightning wallet for the masses. Each telegram account has it's own
@ln.tipsLN Address, but sometimes you want to use your own domain.In this guide I will teach you how to setup LN Address redirection with your own domain using Cloudflare's Redirection Rules.
Prerequisites
- A Web Domain that's has Cloudflare setup on it.
- https://ln.tips setup and ready to go.
- Using ln.tips is optional. This guide will work with any other custodial wallet that provides you with an LN Address will work too.
Setup
Getting your destructured LN Address
ln.tips
Since ln.tips provides two LN addresses to everybody, you have two options. 1. Use your Telegram username LN address (Not Recommended) 1. This isn't recommended because anyone can see your Telegram username with this method and use it to message you. It's the best choice for anonymity from other users. 2. ex:
nym@ln.tips2. Use your anonymous LN address (Recommended) 1. This is recommended because the address is random, nobody can look this up back to your Telegram account. 2. Can be obtained by running/advancedto the bot, and finding it under "Anonymous Lightning address" 3. ex:0x84e6b3ea699ab309@ln.tipsWhat option you pick doesn't matter to your next step, you're going to want to take the username portion of the address (everything before the @, like an email address) add
https://ln.tips/.well-known/lnurlp/<username>username goes at the end.The final url should look something like
https://ln.tips/.well-known/lnurlp/0x84e6b3ea699ab309(depending on the method you chose)Other platforms
Custodial Wallets that provide you with a Lightning address work similarly to this. Apps like Wallet of Satoshi provide you with a completely random address when you sign up, so a Wallet of Satoshi destructured address would look like:
https://walletofsatoshi.com/.well-known/lnurlp/LawyerCicanery69Setting up Cloudflare Redirects
Assuming that you have Cloudflare hooked up and ready to go, you're going to want to follow a few steps. 1. Open your site on the panel 2. On the sidebar, click the dropdown arrow next to Rules 3. Click "Redirect Rules" 4. Press the button that says "Create Rule" 5. Configure your new rule 1. Give it a name. ex: "lnaddr" 2. Configure the first condition 1. Set "Field" to
URI Path2. Set "Operator" tostarts with3. Set "Value" to/.well-known/lnurlp/3. Configure the "then" 1. Set "Type" toStatic2. Set "URL" to your destructured Lightning address from earlier 3. Set "Status Code" to3074. Check "Preserve query string" 6. Click SaveAll done! Now whenever someone goes to pay your new Lightning address, it should automatically redirect to your custodial wallet. Have fun!
-
 @ 1bc70a01:24f6a411
2023-04-20 11:38:43
@ 1bc70a01:24f6a411
2023-04-20 11:38:43I asked ChatGTP to generate some startup ideas based on the first batch of the plugins that will become available some time in the near future.
The following is my prompt and the responses I received.
*You are an experienced VC with previous exits as an entrepreneur. You really know your stuff. When you learned that OpenAI is introducing plugins to ChatGPT, you couldn't help but realize there are significant startup opportunities awaiting. The first batch of plugins allow ChatGPT to integrate with: Expedia, FiscalNote, Instacart, KAYAK, Klarna, Milo, OpenTable, Shopify, Slack, Speak, Wolfram, and Zapier. Your job as a successful VC is to identify market opportunities and come up with product ideas that will likely succeed or result in a unicorn status startup.
Brainstorm the potential startups that could be born out of this combination of ChatGPT and the listed plugins. Create a table with 6 columns. Column 1 will contain a potential startup name. Column 2 will describe the startup and what problem it solves. Column 3 will grade the startup in terms of difficulty to execute (5 stars means most easy to execute, 1 star means most difficult). Column 4 will contain the revenue potential of each startup. 5 dollar signs for biggest potential, 1 for lowest. Column 5 outlines an MVP that can be built in a week. Column 6 identifies potential customer acquisition strategies. Sort the entire table by the startup idea with the most revenue potential.*
ChatGPT totally screwed up the formatting because it cannot accommodate this many columns, so I asked it to write it out in a list instead.
The idea that stands out most to me is TeamSync. It has the potential of growing like crazy once integrated into an organization. Since people tend to move and talk about their jobs, this product would grow well organically if it performed well in terms of its capabilities.
Startup Name: TripPlanner
- Description: A travel planning service using ChatGPT, Expedia, and KAYAK integration to find and book flights, hotels, and activities with personalized recommendations.
- Execution Difficulty: 3/5
- Revenue Potential: $$$$$
- MVP: A simple chatbot that takes user preferences, suggests travel plans, and books flights and hotels.
- Customer Acquisition: Content marketing, social media campaigns, and partnerships with travel influencers.
Startup Name: ShopAssist
- Description: An AI-driven shopping assistant using ChatGPT and Shopify integration to help users find the best products and deals tailored to their preferences.
- Execution Difficulty: 2/5
- Revenue Potential: $$$$$
- MVP: A chatbot that takes user preferences and suggests products from a curated list of Shopify stores.
- Customer Acquisition: Social media advertising, influencer partnerships, and email marketing.
Startup Name: TaskGenius
- Description: A virtual assistant using ChatGPT and Zapier integration to automate tasks, manage appointments, and handle other personal and professional duties.
- Execution Difficulty: 4/5
- Revenue Potential: $$$$
- MVP: A chatbot that can schedule appointments, send emails, and complete simple tasks using Zapier integrations.
- Customer Acquisition: Targeted online advertising, content marketing, and partnership with productivity-focused influencers.
Startup Name: FoodFinder
- Description: A personalized meal planning and grocery shopping service using ChatGPT, Instacart, and OpenTable integration.
- Execution Difficulty: 3/5
- Revenue Potential: $$$$
- MVP: A chatbot that suggests meal plans based on user preferences and dietary restrictions, and creates shopping lists for Instacart orders or books restaurant reservations.
- Customer Acquisition: Influencer marketing, social media advertising, and strategic partnerships with food and wellness brands.
Startup Name: FinanceGuru
- Description: A financial management tool using ChatGPT, Klarna, and FiscalNote integration for budgeting, tracking expenses, and offering personalized financial advice.
- Execution Difficulty: 4/5
- Revenue Potential: $$$$
- MVP: A chatbot that connects to users' Klarna accounts, analyzes spending habits, and offers tailored financial advice.
- Customer Acquisition: Content marketing, targeted online advertising, and partnerships with personal finance influencers.
Startup Name: SpeakUp
- Description: A language learning platform using ChatGPT and Speak integration to offer personalized language learning experiences and real-time practice with an AI tutor.
- Execution Difficulty: 4/5
- Revenue Potential: $$$
- MVP: A chatbot that teaches basic phrases and vocabulary in a chosen language and engages users in simple conversations.
- Customer Acquisition: Influencer marketing, social media advertising, and partnerships with language learning communities.
Startup Name: TeamSync
- Description: A team collaboration and project management tool using ChatGPT and Slack integration to automate task assignment, status updates, and team communication.
- Execution Difficulty: 3/5
- Revenue Potential: $$$$
- MVP: A chatbot that connects to Slack, assigns tasks to team members, tracks progress, and provides updates in a designated channel.
- Customer Acquisition: Content marketing, targeted online advertising, and partnerships with productivity-focused influencers.
Startup Name: FitAdvisor
- Description: A personalized fitness and wellness service using ChatGPT, Milo, and Wolfram integration to create tailored workout plans, track progress, and provide real-time coaching.
- Execution Difficulty: 4/5
- Revenue Potential: $$$
- MVP: A chatbot that creates workout plans based on user preferences and fitness goals, and tracks progress using Milo and Wolfram data.
- Customer Acquisition: Influencer marketing, social media advertising, and strategic partnerships with fitness and wellness brands.
Startup Name: EventMaster
- Description: An event planning and booking service using ChatGPT, OpenTable, and KAYAK integration to help users find and book suitable venues, catering, and accommodations for various events.
- Execution Difficulty: 4/5
- Revenue Potential: $$$
- MVP: A chatbot that takes event details from users, suggests appropriate venues and catering options, and books reservations or accommodations.
- Customer Acquisition: Content marketing, social media campaigns, and partnerships with event planning influencers.
Startup Name: CodeBuddy
- Description: An AI-driven programming tutor using ChatGPT and Wolfram integration to assist users with learning various programming languages, debugging code, and providing real-time guidance.
- Execution Difficulty: 5/5
- Revenue Potential: $$$
- MVP: A chatbot that helps users learn basic programming concepts, answers questions, and provides guidance on simple coding challenges.
- Customer Acquisition: Content marketing, targeted online advertising, and partnerships with coding bootcamps or programming communities.
-
 @ 9ecbb0e7:06ab7c09
2023-07-23 04:46:07
@ 9ecbb0e7:06ab7c09
2023-07-23 04:46:07Un cubano de 43 años, identificado como David Alejandro Rodríguez Morcate, perdió la vida después de un violento enfrentamiento con guardias de seguridad de una discoteca, ubicada en Managua, Nicaragua.
El trágico suceso ocurrió en horas de la madrugada de ayer viernes, momentos después de que el fallecido tuviera una acalorada discusión con una mujer mientras abandonaba el lugar.
Las imágenes capturadas por una cámara de seguridad muestran cómo la situación escaló rápidamente, llevando al guardia de seguridad a detenerlo, pero agarrándolo por el cuello hasta asfixiarlo.
La mujer involucrada en el incidente ha sido identificada como Gloria Mendoza, de 21 años. Según los registros de vigilancia, se puede observar cómo el antillano arremete contra ella sujetándola por el cabello antes de que los vigilantes intenten intervenir para calmar la situación.
A pesar de los esfuerzos por reanimarlo, ya era demasiado tarde, Rodriguez Morcate fue declarado muerto en el lugar. Las autoridades locales iniciaron una investigación para esclarecer los detalles del trágico suceso.
Según su perfil personal en Facebook, el cubano residía en la ciudad de Miami y era originario de la provincia oriental de Santiago de Cuba. Hasta el momento, no se ha revelado la razón por la cual se encontraba en territorio nicaragüense.
El cuerpo de la víctima permanece en el Instituto de Medicina Legal (IML), donde un médico forense realizó la autopsia para determinar las causas precisas de su fallecimiento. Mientras tanto, el guardia de seguridad involucrado ha sido identificado, pero, de acuerdo con la prensa local, se encuentra prófugo desde el trágico acontecimiento.
Tras ver el video, algunos usuarios comentaron que se aplicó una llave de estrangulamiento conocida como “popo” o “mataleón”, que consiste en el uso del brazo para aplicar una presión al cuello del oponente con el objetivo de restringir el flujo de sangre y aire hacia el cerebro, lo que puede provocar una pérdida rápida del conocimiento y someter al oponente.
Es importante tener en cuenta que el uso de la llave de estrangulamiento puede ser extremadamente peligroso y potencialmente mortal si no se realiza adecuadamente o si se mantiene durante demasiado tiempo. Por esta razón, su enseñanza y práctica deben llevarse a cabo con responsabilidad y bajo la supervisión de instructores calificados.
En contextos deportivos y policiales, el uso de esta técnica puede estar regulado o incluso prohibido debido a los riesgos asociados con su aplicación. Siempre se debe priorizar la seguridad y el bienestar de todos los involucrados en cualquier actividad que se usen técnicas de combate o autodefensa.
-
 @ 1967650e:73170f7f
2023-04-19 15:22:48
@ 1967650e:73170f7f
2023-04-19 15:22:48Predicting the price of cryptocurrencies like Bitcoin is an ongoing challenge due to the volatility and unpredictability of the market. In this article, we explore a Python-based price prediction pipeline that combines machine learning techniques and deep learning algorithms to forecast Bitcoin's closing price. The code for this pipeline can be found on GitHub at https://github.com/amar-muratovic/bitcoin-price-prediction-pipeline.
Key Components
-
Data Acquisition and Preprocessing: The pipeline uses the CCXT library to fetch historical price data for Bitcoin (BTC/USD) from the CryptoCompare API. The data is then preprocessed, resampled, and saved into a CSV file for further analysis.
-
Feature Engineering: The pipeline uses three input features - High, Low, and Open prices - and the target variable, which is the Close price.
-
Model Ensemble: The pipeline trains an ensemble of four models: Linear Regression, Bayesian Ridge, Support Vector Regression, and Random Forest Regressor. The predictions from these models are averaged to produce the final forecast.
-
Deep Learning: The pipeline also incorporates a neural network with two hidden layers and early stopping to prevent overfitting. The neural network is trained on a subset of the data.
-
Hyperparameter Tuning: Grid search and cross-validation are used to fine-tune the models and optimize their hyperparameters.
-
Model Evaluation: The pipeline evaluates the models using mean squared error (MSE) and R^2 score, which measure the accuracy of the predictions.
Implementation Details
The pipeline starts by importing necessary libraries and modules, followed by loading the Bitcoin price data from a CSV file. The data is preprocessed, resampled, and saved into a new CSV file. The input features and target variables are defined, and the data is split into training and testing sets.
An ensemble of machine learning models is trained on the data, and predictions are made using these models. The ensemble approach aims to combine the strengths of different models to produce more accurate predictions. The predictions from each model are averaged to produce the final forecast.
A neural network with two hidden layers is created and trained on a subset of the data. Early stopping is used to prevent overfitting by monitoring the validation loss and stopping the training when it stops improving.
Hyperparameter tuning is performed using grid search and cross-validation to optimize the models' performance. This process helps identify the best combination of hyperparameters for each model.
Finally, the models are evaluated using mean squared error (MSE) and R^2 score. These metrics help measure the accuracy of the predictions and the performance of the models.
Conclusion
The Bitcoin price prediction pipeline presented in this article combines various machine learning techniques and deep learning algorithms to forecast the closing price of Bitcoin. This ensemble approach aims to improve prediction accuracy by leveraging the strengths of different models. While predicting the price of cryptocurrencies remains a challenging task, this pipeline provides a solid foundation for further experimentation and improvements. To explore the code further, visit the GitHub repository at https://github.com/amar-muratovic/bitcoin-price-prediction-pipeline.
-
-
 @ 9ecbb0e7:06ab7c09
2023-07-23 04:43:25
@ 9ecbb0e7:06ab7c09
2023-07-23 04:43:25| Divisa | Pesos Cubanos | |--------|---------------| | 1 USD | 210 CUP | | 1 EUR | 214 CUP | | 1 MLC | 212 CUP |
-
 @ d5b41074:156978f1
2023-05-07 21:38:01
@ d5b41074:156978f1
2023-05-07 21:38:01Hyper-Nostr: Bringing P2P to relays
People suggested me to write a detailed post blog about my project, explaining how to use it, what it is, what to expect, and how it works. This post is the attempt of doing that.
What is it?
Hyper-Nostr is a decentralized nostr relay. It is a distributed relay, where everyone can have its own local node. Then, they behave as a single relay, sending and keeping the events on the network.
Right now, to use it you need to have
npm, which requiresnodejs. I may add plain executables on the future. You install it asnpm install -g hyper-nostrand then you can start your own node ashyper-nostr [<port> [<topics>...]]. Last step is to add the relay on your client asws://localhost:[port]/[topic]for each topic you want to have on that client. I am still working on havingwssinstead ofws, but looks like clients accept the connection because it is onlocalhost. UPDATE: you can use some reverse proxy to havewss. I personally use caddy so I can docaddy reverse-proxy --to localhost:3000.Right, the topics. The topic is how we find each other, to send the events and have an unified database. Think of it as the address of the hyper-nostr relay, or a specific instance of it.
Having all configured, you can now expect it to work just as a standard relay: it will receive events that was send to these, you will be able to send and receive events, and it will save the events on it.
How it even works?
This project is Powered by Holepunch.
The connections and event streamings happen on Hyperswarm, Autobase linearized the underlying files, and uses a Hyperbeedee database (loosely based on MongoDB).
The hyperswarm and cores management was highly abstracted thanks to Hyper SDK.
Want to know more? Okay, lemme try to explain: - Hyper SDK creates a unified swarm instance that is used by the entirety of the relay; - Each topic creates two underlying hypercores: one that is the same for everyone in the topic, used to connect the peers, and the other is local, for your own local database; - Then, the discovery core has two extensions: the event broadcasting extension, to relay to the connected users the real-time events, and the syncing extension, to share the local databases to the peers; - Then, with the help of Autobase, all the local databases are linearized, giving an unified database shared across all peers. - With that, it is as if every peer has the same database when querying, and every peer receives the broadcasted events on real-time too (filtering by the subscriptions, as specified on NIP-01).
What to expect? (or, what are these logs)
The first message the relay prints is
your key is <key>. This key is the hyperswarm public key, which for now I am doing nothing with it, but maybe in the future I will implement private relays that you connect specific peers on it. Still thinking on it.If you have passed initial topics, they will log here too. When you see
listening on <port>, the relay is now open to receive websocket connections (aka it is ready for your client to connect).During the database indexing it generates a warning of
(node:<PID>) MaxListenersExceededWarning: Possible EventEmitter memory leak detected. 11 append listeners added to [LinearizedCoreSession]. Use emitter.setMaxListeners() to increase limit (Usenode --trace-warnings ...to show where the warning was created). This warning is expected, dont panic.To each websocket connection, the relay will also log 2 messages:
ws connection startedandws connection stablished. They were first there to detect silent crashes during the topic initialization, that happens between these two logs if it didnt happen yet.To each topic initialized, it logs
swarm hyper-nostr-<topic> created with hyper!. The prefix is to mitigate the risk of topic crashing on the hyperswarm.Finally, there is one last thing to expect: peers connections. It logs a count of peers on topics on each connection, in the format of
<count> peers on <topic>!every time the connections update.What do you think? Do you liked this project?
Consider sharing your thoughts with me, I would love to know. Do you think the explanation was superficial? What could I have explained better? Do you have some suggestion for the project?
Consider supporting me, I have no formal job currently, and I am spending a lot of time and energy on this project.
-
 @ 9ecbb0e7:06ab7c09
2023-07-23 04:37:44
@ 9ecbb0e7:06ab7c09
2023-07-23 04:37:44
Fuertes presiones de los regímenes de Cuba, Venezuela y Nicaragua dieron lugar a que el Consejo de la Unión Europea confirmara que el presidente de Ucrania, Volodimir Zelensky, no asistirá a la Cumbre Unión Europea (UE) - Comunidad de Estados Latinoamericanos y Caribeños (CELAC), que se celebrará entre el lunes y el martes próximos en Bruselas.
Un alto oficial de la UE hizo pública la decisión durante una sesión informativa organizada por el Consejo de la Unión Europea, reportó el medio argentino Infobae.
Uno de los voceros del bloque europeo dijo luego que Zelensky no fue invitado, dado que ya visitó la capital belga en febrero y acaba de participar como invitado especial en la cumbre de la OTAN en Vilna, Lituania. Asimismo, el funcionario, cuyo nombre no se menciona en el reporte, recordó que Ucrania no forma parte ni de la UE ni de la CELAC.
"Esta es la primera cumbre con la CELAC que tenemos en ocho años, y las regiones están alineadas. Es claro el daño colateral en otras partes del mundo a partir de la agresión rusa, que ha causado daño y fragilidades, que ha creado inseguridad alimentaria y aumentado la inflación. Todo esto probablemente se discuta (en la Cumbre), pero el presidente Zelensky no va a asistir", dijo el agente oficial citado.
Esta misma semana el propio presidente ucraniano había explicado que el presidente español, Pedro Sánchez, lo invitó a formar parte de la Cumbre, pero que varios países hispanoamericanos habían "bloqueado" su asistencia. El mandatario no dijo cuáles eran esos países.
En la región, los regímenes de Cuba, Venezuela y Nicaragua apoyan la invasión de Moscú contra el país vecino, mientras que Brasil ha tratado de mantener una posición neutral, pese a que el presidente brasileño, Lula da Silva, ignoró a su homólogo ucraniano durante la reciente cumbre del G7, el pasado mes de mayo.
Por su lado, Argentina se desmarcó de la decisión, al indicar que debían ser los países asistentes quienes aprobaran o no la presencia de Zelensky. Por su parte, el mandatario uruguayo, Luis Lacalle, respaldó la presencia del ucraniano en la reunión.
De acuerdo con la prensa española, Sánchez pensó que la inminente Cumbre podría ser una buena oportunidad para que la región comprendiera la versión ucraniana del conflicto. Sin embargo, los Estados hispanoamericanos no se pusieron de acuerdo.
La Habana es uno de los pocos gobiernos que no se pronunció a favor de las principales resoluciones de condena al Kremlin en la Asamblea General de la ONU en 2022 por su invasión de Ucrania: se abstuvo de votar en marzo de 2022 (exigiendo la retirada de las tropas rusas de Ucrania); en octubre de 2022 (contra la anexión de las regiones ucranianas ocupadas) y en febrero de 2023 (en apoyo de una paz "integral, justa y duradera" en Ucrania).
Se opuso además a la resolución de noviembre de 2023, que establecía que Rusia debía pagar reparaciones a Ucrania por los daños causados durante la operación militar.
En abril de 2023, se abstuvo cuando el Consejo de Derechos Humanos de Naciones Unidas votó abrumadoramente a favor de extender el mandato de un panel que investiga posibles crímenes de guerra cometidos desde la invasión rusa de Ucrania.
En mayo votó en contra de una resolución de la Organización Mundial de la Salud (OMS) en apoyo del sistema sanitario ucraniano y de condena a los ataques contra instalaciones de la salud de ese país por Rusia.
También La Habana votó en contra en septiembre de 2022 de que el presidente ucraniano se dirigiera a la Asamblea General de la ONU por video. Pese a ello, esa intervención se produjo.
-
 @ 0a821ca3:e0efcce3
2023-04-10 16:58:01
@ 0a821ca3:e0efcce3
2023-04-10 16:58:01Policy considerations
[I am going to write this consideration step by step - partly because blogstack doesn't allow to save drafts - and partly because what follows here will be a huge effort. ]
The SEC chair Gary Gensler has argued since a while that bitcoin is a commodity and other digital tokens risk being unregistered securities. This consideration benchmarks various digital tokens - based on a set of properties which can provide insight into their nature as protocol or unregistered security.
First, following properties may indicate the difference between a decentralised protocol and a company issuing unregistered securities:
To which parties were tokens allocated during the launch phase?
Fair distribution of tokens seems a prerequisite for a protocol. Is tempore non suspecto required to achieve a fair token distribution? Pre-mining is a clear indication of unfair token distribution. The existence of a foundation or company holding a significant share of the tokens equally indicates a centralised token distribution.
Does the initiative have a CEO or team? Who pays that team?
Having a CEO or team indicates centralisation and potentially causes the initiative to be permissioned, not permissionless - not permissionless is not trustless - if someone can take away permission, you have to trust that party.
Does token ownership give protocol governance rights?
If token ownership gives protocol governance rights, there is a risk that the protocol ends up benefiting large token holders more - rather than benefiting all participants in a similar way.
Does the token obtain yield from consensus mechanism?
If the token obtains yield from the consensus mechanism - in the very long term - the token holdings of large holders will increase - results in a plutocratic world.
Do token holders get new issuance awards?
Indicates that the token has conventional investment security properties (yield / dividend).
How many nodes does the network have?
More nodes ensure higher probability of decentralisation, which in turn increase p2p nature - few nodes drive risk of trusted or permissioned structure (and then the benefit of a cryptologic solution over a conventional database is limited)
What is the governance process for protocol evolutions?
The more decentralised the governance, the more the protocol users are protected from malicious or centralising forces.
bitcoin
To which parties were tokens allocated during the launch phase?
The global digital p2p value transfer protocol was developed in tempore non suspecto. In 2011, three years after the genesis block, the total token market cap was less than USD 35m - very immaterial. While River Financial research indicates that the protocol inventor, with pseudonym Satoshi Nakamoto still holds about 1.1m btc in 22000 addresses - or about 5% of total supply - these tokens have never moved so far. Beyond that, no hodlers with a holding of more than 100 000 btc - or 0.5% of supply - have been identified so far.
This implies a distribution that is as ‘fair’ as it gets - comparing to other cryptologic tokens. If anything, the bitcoin protocol token allocation is not perfect. The bitcoin token allocation is the least convincing of all protocol properties - and could eventually be considered being an argument that even bitcoin is not a protocol.
This being said, no foundation or company backs bitcoin - bitcoin has no marketing budget.
Does the initiative have a CEO or team? Who pays that team?
Bitcoin doesn't have a CEO or a dedicated team. The bitcoin core development team consists of about 50 developers - more info can be found in this NYDIG report - Coinmarketcap provides insight in who funds the team.
Does token ownership give protocol governance rights?
No, while the BIP process has some level of governance among the core team, the node operators decide which software version they adopt and use - and ultimately decide on which evolutions of the protocol they want to use. In that context, some have for example created a proof of stake version of Bitcoin - it has not seen broad adoption.
Governance by node operators is the ultimate global democracy. Many people can be node operator - it does not require holding the respective token - it does not require a powerful computer (200 EUR should get you all the hardware required to run a bitcoin node) - it even does not require exceptional computing skills. Governance is not driven by miners or token holders.
Does the bitcoin token obtain yield from consensus mechanism?
No, the consensus mechanism issues new btc tokens and distributes transactions fees. These new tokens and transaction fees are 'won' by miners - bitcoin token ownership does not help getting additional btc tokens.
Do token holders get new issuance awards?
No, new issuance is distributed among proof of work miners, who have to invest in computers and electricity to power these computers (soon miners will be paid to consume such electricity, as ample excess electricity will be produced).
How many nodes does the network have?
The website Bitnode reports about 17500 reachable nodes and estimates some 47k total nodes - including nodes behind firewalls or NAT.
What is the governance process for protocol evolutions?
Already described above, eventually every user of the protocol decides which version or fork that users would like to use.
Cardano
To which parties were tokens allocated during the launch phase?
Does the initiative have a CEO or team? Who pays that team?
Does token ownership give protocol governance rights?
Does the token obtain yield from consensus mechanism?
Who funds the consensus mechanism?
Do token holders get new issuance awards?
How many nodes does the network have?
What is the governance process for protocol evolutions?
| Head | Head | Head | Head | Head | Head | | --- | --- | --- | --- | --- | --- | | Data | Data | Data | Data | Data | Data | | Data | Data | Data | Data | Data | Data | | Data | Data | Data | Data | Data | Data | | Data | Data | Data | Data | Data | Data |
| | btc | eth | bnb | xrp | ada | doge | matic | dot | dot | | --- | --- | --- | --- | --- | --- | --- | --- | --- | --- | | Pre-mine | ? | Data | Data | Data | Data | | CEO | ✓ | Data | Data | Data | Data | | Governance | ✓ | Data | Data | Data | Data | | Token yield | ✓ | Data | Data | Data | Data | | Consensus funding | ✓ | Data | Data | Data | Data | | New issuance | ✓ | Data | Data | Data | Data | | Network (# nodes) | 17k+ | Data | Data | Data | Data | | Protocol evolutions | ✓ | Data | Data | Data | Data |
-
 @ 9ecbb0e7:06ab7c09
2023-07-23 04:37:17
@ 9ecbb0e7:06ab7c09
2023-07-23 04:37:17De forma bastante amplia los venezolanos abrazan el deseo de cambio político, que asocian con una mejoría en sus condiciones de vida, mientras que el apoyo al gobernante Nicolás Maduro no suma ni un 10%, de acuerdo con una encuesta realizada por la empresa de opinión pública Delphos, hecha a solicitud de la Universidad Católica Andrés Bello (UCAB) de Caracas.
Félix Seijas, director de Delphos y uno de los estudiosos de opinión pública con más trayectoria en Venezuela, presentó los resultados de esta investigación que abarcó a todo el país, con visitas en hogares de los encuestados. La fotografía que obtuvo el estudio es que ha cobrado fuerza nuevamente la apuesta por un cambio en Venezuela, que está simbolizado con la salida de Maduro del poder a través de las elecciones presidenciales de 2024, unos comicios que son desde ya una suerte de carrera de obstáculos para la oposición prodemocracia venezolana.
Un 85% de los encuestados cree necesario y muy necesario que ocurra un cambio político en Venezuela que se traduzca en restituir condiciones de bienestar que ya tuvo la población en el pasado.
La agudización de la crisis económica y social en este 2023, luego de niveles de mejoría en los indicadores macro económicos entre 2021 y 2022, ha terminado por generar también un quiebre entre quienes se autodefinen como chavistas en Venezuela. En este momento, según la encuesta, solamente un 9,6% se asume como chavistas que apoyan a Maduro, mientras un 13,1% son chavistas descontentos con el Gobierno del heredero político de Hugo Chávez.
Ante una pregunta de DIARIO DE CUBA, Seijas confirmó que en los diez años que tiene Maduro en el poder, en la actualidad vive su peor momento en términos de evaluación de opinión pública, con niveles similares a 2017, cuando tuvo lugar una cruda represión contra manifestaciones de calle que pedían su salida de la Presidencia.
El estudio ordenado por la universidad venezolana de los jesuitas muestra, por otro lado, la consolidación de la líder liberal María Corina Machado como la opción de cambio. Ante la pregunta de quién lidera la oposición, Machado fue la opción del 33%, lo cual representa una subida significativa ya que nueve meses atrás, en un estudio similar, solo obtenía un 6%.
Al preguntar sobre las primarias de la oposición, que se celebrarán en octubre para escoger una candidatura unitaria de cara a las presidenciales de 2024, un 55% dijo que respaldará a Machado.
"María Corina Machado ha emergido claramente como la referente del cambio. Aglutina, en este momento, ese deseo de que las cosas sean diferentes en su vida que prevalece entre los venezolanos y pese a estar como figura opositora por muchos años la gente la percibe como una outsider", explica Seijas al ser consultado por DIARIO DE CUBA en torno a lo que puede entenderse como un fenómeno electoral en gestación.
Machado recibió recientemente una inhabilitación por 15 años, que se sumó a otra medida previa. Básicamente estos son los obstáculos que pone el chavismo para evitar su candidatura.
Aunque no fue medido específicamente este tema en su estudio, el director de Delphos percibe que los venezolanos cambiaron su enfoque sobre el tema de las inhabilitaciones, y que ahora se ve el asunto con rebeldía. A su juicio, lo que podría ocurrir es que la medida termine siendo un bumerán contra el chavismo, dado que podría potenciar más a la exdiputada.
El profesor Benigno Alarcón, director del Centro de Estudios Políticos de la UCAB, en Caracas, cree que con Machado se está cerrando un ciclo y dando paso a una nueva etapa. La líder opositora, por ejemplo, fustigó públicamente diversas estrategias de la otrora Mesa de la Unidad Democrática (MUD), que en su momento fue el foco para los adversarios al chavismo.
El crecimiento de Machado tiene terreno fértil. El 40% por ciento de los venezolanos está tan descontento con el chavismo como con la oposición que se creó en torno a la MUD, de la cual son referentes figuras como Henrique Capriles, Leopoldo López o Juan Guaidó, los tres con amplio rechazo de la ciudadanía en este tiempo.
A juicio de Seijas, Machado ha sido consistente con un discurso radical y conserva lo que fue su nicho de apoyo duro. Lo que ha cambiado es que pasó a ser potable para una oposición moderada que tomó distancia de los liderazgos opositores ya mencionados y ella, pese a estar largamente en la palestra pública, es percibida como algo renovador y distinto.
A eso se suma el propio cambio en la estrategia de Machado, que comienza a moderarse. Un ejemplo es su propia participación electoral para este ciclo 2023-2024. Hasta 2021, por ejemplo, la exdiputada sostenía que solo podía concurrirse a elecciones una vez que Maduro fuese desalojado del poder, y para lograr esto sostenía que debía producirse una actuación internacional para restaurar la democracia.
La Machado de este 2023, en cambio, asume que el cambio se producirá por la presión popular a través de vías democráticas como el voto. En su discurso, por otro lado, ha diferenciado entre Maduro y Chávez, como lo hizo recientemente cuando visitó con mucho éxito la población de Sabaneta de Barinas, donde nació Hugo Chávez. Con esto, según analistas, busca sumar apoyo del chavismo descontento con Maduro.
Para Seijas la señal de alarma para el chavismo, que detectó la encuesta que presentó en instalaciones de la UCAB, está en que una parte del chavismo estaría dispuesto a votar por Machado en una contienda electoral. Se trata de una cuarta parte de lo que el investigador cataloga como chavismo blando.
La otra señal de alarma, es que en la suma de un 85% de los venezolanos que quieren cambio en la conducción del país está también una parte de lo que se considera chavismo duro, leal a Maduro.
-
 @ 9ecbb0e7:06ab7c09
2023-07-23 04:36:26
@ 9ecbb0e7:06ab7c09
2023-07-23 04:36:26Ante el alarmante incremento de feminicidios en Cuba, 52 en lo que va de año, DIARIO DE CUBA conversó con las activistas Ileana Álvarez, directora de la revista feminista 'Alas Tensas', y Elena Larrinaga, de la Red Femenina de Cuba. Ambas mujeres lideran desde Madrid plataformas y observatorios que se dedican a llevar un registro de los feminicidios que ocurren en la Isla.
Sobre el trabajo que realizan y el resultado de sus investigaciones dialogaron el pasado jueves con las periodistas de este diario Yusimí Rodríguez y Luz Escobar.
Álvarez reconoció que, ante las estadísticas del subregistro que llevan estas plataformas independientes, es evidente que en Cuba "hay un incremento de la violencia de género". Apuntó también que "hay una mayor denuncia por parte de la ciudadanía", y que se han extendido los canales que tienen para recibir los reportes de muertes violentas de mujeres dentro de la Isla.
"El trabajo de los observatorios se ha ido profesionalizando desde su nacimiento, han ido ganando en experiencia y perfeccionando la metodología y la manera en que se verifica cada caso", aseguró Álvarez. Agregó además que en Cuba las personas han tomado conciencia "de la necesidad de denunciar el feminicidio".
Explicó que, desde el trabajo de las plataformas "se denuncia el feminicidio" pero también "se alerta cuando hay un aumento de los casos" como una forma de "presionar a las instituciones competentes" a actuar. Para Álvarez la clave del éxito ante este drama es "prevenir" y dijo que con las estadísticas que ellas ofrecen lo que pretenden es "alertar para seguir el fenómeno" con la esperanza de que las autoridades tomen las medidas necesarias para prevenir la violencia de género.
"Si no se prevé y se hace una política pública en la que participe toda la población con las instituciones, que sea algo de todo el pueblo y del Estado, que es el que tiene el poder, el problema de los feminicidios va a seguir incrementándose", afirmó Álvarez.
Elena Larrinaga coincide con la visión aportada por Álvarez de que los feminicidios han aumentado en la Isla y subrayó también que ahora "las mujeres y las familias se atreven a denunciarlo más". Según su opinión esta realidad "es una respuesta al buen trabajo que han hecho las mujeres en Cuba y las diferentes plataformas femeninas, que han colaborado unas con las otras". Consideró que esa alianza ha otorgado "mucha legitimidad a las organizaciones" y recalcó el trabajo de los medios de comunicación independientes a la hora de difundir las denuncias que recogen las activistas.
"Coincido con Ileana en que el Gobierno debe tener medidas preventivas, hay que anticiparse al problema. Educar y formar a los funcionarios y a la sociedad entera es una cuestión mucho más amplia, por eso siempre hablamos de una ley orgánica, porque obliga al Estado a cumplirla", señaló.
De acuerdo a Larrinaga "hay que tener en cuenta que al Gobierno cubano le costará mucho tipificar la ley" porque él es "el primer violador": "Te pega, te mata, no dice nada y entonces, claro, los maltratadores que viven bajo un Estado como ese, que ejerce impunemente la violencia institucional contra las mujeres, están marcando tendencia. Por eso muchos de ellos ni piensan que es tan grave lo que están haciendo".
Álvarez remarcó que los observatorios han tomado el término de feminicidio para trabajar "porque tiene una connotación que le da una responsabilidad política y social al Estado", en contraposición al término femicidio, "usado por el Estado para evitar precisamente la responsabilidad que tiene en las muertes por violencia de género machista".
Mencionó además que la red de observadoras que trabaja con las plataformas y los observatorios están en todo el país y "se ha ido profesionalizando". "Es una red segura, con ellas trabajamos de forma anónima porque el estado criminaliza a todas las personas activistas, entre ellas a las propias observadoras", declaró.
Sobre el protocolo que siguen esas organizaciones para confirmar un feminicidio, luego de recibir una denuncia, explicó la importancia que siempre le dan a "triangular la información a través de las observadoras y de la ciudadanía para completar la verificación". "Nunca nos quedamos con una sola fuente, siempre tratamos de tener una fuente primaria, cercana a la víctima", dijo.
Explicó que para lograr algo así se necesita tiempo e investigación y que "desgraciadamente, como parte del sistema totalitario cubano" todavía no tienen acceso a información de los peritos ni a los de la policía. "Cualquier muerte violenta no es feminicidio, tiene haber detrás un crimen por el hecho de ser mujer, tiene que existir misoginia", aclaró. Uno de los problemas que han encontrado a la hora de lograr esa triangulación es que "no siempre la familia ayuda porque tiene miedo".
Álvarez consideró "lamentables" las cifras de feminicidios ofrecidas por el Estado cubano recientemente "porque solamente consideran como muerte machista aquellos casos que han sido juzgados en los tribunales". También expresó su deseo de que las mujeres de Cuba "pudieran salir a las calles a reivindicar el 'ni una menos' y con sus pancartas de 'no mas feminicidios'".
Para Álvarez tipificar el delito de feminicidio en la ley cubana sería "un gran paso de avance" así como lograr una ley integral contra la violencia de género. "Estas cuestiones legales serían un paso muy positivo", agregó. "Registrar un feminicidio es muy complejo y en Cuba la Policía no está preparada para eso, una de las peticiones que estamos haciendo es que tanto la Policía como los trabajadores de Salud Pública ganen perspectiva de género".
Sobre ese punto Larrinaga consideró que "ese es el camino" que les dará a los cubanos "acceso a la verdad". Algo que consideró vital en esa batalla que ellas libran porque: "Cuando uno sabe la verdad sobre un problema, es cuando único puede tomar una acción adecuada para resolverlo", recalcó.
-
 @ 1bc70a01:24f6a411
2023-04-05 01:25:09
@ 1bc70a01:24f6a411
2023-04-05 01:25:09Unless you have some private projects that require secrecy, you should just organize conversations on nostr.
Smart bootstrapped founders know that one of the best ways to garner attention is by building in public.
By posting on Nostr, you are in essence building in public. This has many benefits:
- Free marketing for your project
- Recruit other designers. If they see that there are others, they are more likely to join your cause.
- Attract talent (people who are interested in the project will likely want to work on it). Find development help.
- Attract funding (even sats from plebs, bounties on your behalf, etc…)
- Help nostr grow. By getting outside the siloed communication channels, you help add activity to Nostr. When people see that it’s busy, they are more likely to participate. Nobody wants to use a dead social network (even though nostr is so much more than a social network).
How to organize on Nostr without channels or groups
A common objective is “but there is not a good client for group chat”.
Nostr IS the group chat. It's just a much larger group. All you need is a way of organizing conversations.
Enter hashtags.
Hashtags allow people to track conversations so you can see if someone is discussing #nostrdesign for example.
“But, I forget to use hashtags!”
Ok, make a SUPER simple client that automatically inserts the hashtag into the message. Hardcode if if you need to for the time being.
Clients like Snort already let you follow hashtags so it’s a matter of bookmarking it and just checking it whenever you’re online.
Don’t want a bloated client? No problem. Clone Snort, remove everything but the posting and reading functionality. Use the client only for posting and for reading that specific hashtag. Congrats, you just created your own public channel! The best part? Everyone can see it without signing up for any siloed platforms.
Act
Do it now. Close the group and let everyone know you’re using nostr from now on. No excuses, no waiting. Just do it. It may be hard and painful at first, but you'll get used to it. Who knows, it may be enough motivation to build great clients that do one thing very well. Let’s go!
-
 @ 1bc70a01:24f6a411
2023-03-27 02:41:22
@ 1bc70a01:24f6a411
2023-03-27 02:41:22You may remember a documentary on Netflix that discussed the negative effects of social media - Social Dilemma. It sparked many discussions in various circles, but nothing came of it.
Well, today I want to talk about making social media healthier, if not for ourselves, but for our kids.
We have a once in a lifetime opportunity with Nostr to reshape social media clients from scratch. Let us not blindly copy existing social media behavior. After all, the definition of stupidity is doing the same thing and expecting different results. Let’s not be stupid and make social media just as, if not more addicting than before.
The big TLDR; is that social media addictive mechanisms harm self image in kids. At the time where they should be building confidence, the mechanics of social media make them feel insecure. I can only imagine the downstream effects into adulthood, but on society level it can’t be good.
Some organizations even exist to supposedly move this subject forward, but after reviewing their content, I see nothing substantial put forward. One such organization “Center for Human Technology” seems to say the right things but puts no effort into offering any actual solutions.
Strategies to make social media healthier
Let’s brainstorm some actual things we can do to limit social media addictiveness, reduce social influence and manipulation.
Boost self-esteem
Vanity metrics can play a positive role but the wrong kind of metric is more harmful than not. Follower count immediately comes to mind. You see people obsessing with their follower count, and even those not realizing they are obsessed are constantly comparing themselves to one another. You are probably one of those people. If you don’t believe me, go ahead and close down your account right now, and create a fresh one to start over. I’ll wait.
Still here? I thought so. Short of constantly deleting our accounts, we can do something else - not showing a follower metric at all.
Remove followers metrics
As drastic as this sounds, removing followers is a huge step forward to better mental health. We don’t need to see how many people follow us. As long as you can see who you follow, it shouldn’t matter who is following you.
This goes beyond Twitter-like apps. Subscriber counts on YouTube channels, on email lists, none of these things need to exist. The number of people you send something to should be irrelevant. Think about it - how does it impact the content of your message whether you have 100 followers or 10,000? It doesn’t.
Avoid algorithms at all costs
Algos are excellent at hijacking attention. They know what you like and keep feeding off you to keep you hooked. Let’s end this stupidity once and for all and say no to algorithms.
I also came to a realization that “algorithmic choice” is an illusion. The “best” algorithm will by definition be the winner and the most popular. Clients will implement the thing that people crave most until “better” algorithms get more users hooked on a client. Who doesn’t want that for their platform? Everyone. Attention is money. Attention is harm.
If we want to create a better future for our children, we’ll say no to algorithms. This means we have to accept that people will gravitate towards “cheaters” who do include “useful” algorithms in their clients. It also means we have to be willing to forgo larger profits.
Perhaps well-thought out policy can be introduced in the future that limits the harm of algorithms, but in the meantime we can take matters into our own hands and simply say no.
Improve happiness levels
Avoid news feeds
Thanks to nostr we can create clients that only handle news feeds, so we don’t really need to include them in social clients.
News keeps people down because negative news gets most clicks. We can avoid this whole issue just by not including news feeds in social applications. Less clickbaity headlines, less rage, more productive conversations.
If you still crave news, go ahead and use that nostr client designed specifically for news consumption.
Of course, we can’t stop people from sharing the news, but we can avoid algos that surface it, and avoid creating feeds specifically designed for news consumption.
News also consumed a lot of time and spreads misinformation. You get scenarios where neither of the arguers read the article in full and are arguing about something that’s not even reported. It’s painful to watch.
Then you have situations where the news is actually a narrative spun by some organization or individual who wants to influence social behavior. They may report correct information or completely misrepresent facts.
News is “bad news”. Just don’t build it into social clients intentionally.
Create happiness clients
One thing I have not seen any social media do is ask whether a piece of content makes you feel positive, neutral or negative.
In theory, we should be able to create clients that prioritize positive content. I know I said avoid algorithms at all costs, but if you wanted to create a happiness portal, you could cheat a little and ask people to market content as positive, neutral or negative, and then surface only the positive.
In my opinion this is not an ideal way to go about it, because you’re creating a different type of bubble, one where people ignore the reality of things. Yet, it is a possibility if we want to alter our mood by putting algos to work for us. At the very least it would be a fun experiment!
Reduce addiction / Save time
Disable notifications by default
You hear countless stories of people feeling better in their lives after disabling notifications. Why not make this the default behavior? “But, people won’t know if the app works!” Yeah.. it has to start some place. If we want change, we need to make tough decisions. If you want to be less extreme about it, you could disable most notifications by default, while not touching the “critical” ones. Personally, I don’t think any notification is critical, you should be completely in control over your attention and that any notification is a major intrusion into your consciousness.
With notifications disabled, we can regain time and attention. Society as a whole might think more clearly and be in the moment. I think it would be a huge step forward.
Delay notifications
Nothing sucks more time than notifications. That tiny red dot begging to be tapped. One solution to make notification less addicting short of turning them off is to delay them. We can purposely set a timer to show notifications in a delayed fashion rather than right away. This way people or kids don’t need to constantly check to see who replied or messaged you. Something as simple as a 3 minute notification delay may be sufficient to curb the constant checking behavior.
Delay reactions
Dopamine is fun, but constant dopamine in real time is unhealthy. Real time reactions force us to stare at our screens waiting for the next reaction.
We can lessen this addictive behavior by introducing delayed reactions to notes. Instead of reactions coming in real time, introduce a delay of 1-5 minutes. If you know that you won’t see any responses to your post for at least 5 minutes, it makes it easier to put down the phone and not have to constantly look to see who liked your note.
Improve Transparency
Once media organizations get on nostr, I think there’s a lot we can do to make them more transparent, accountable, and less manipulative.
One thing we can do is to create meta data for media accounts to indicate their funding sources. Everyone should be able to see who funds a certain organization (as discovered by anyone in the community and voted on by the community in terms of accuracy).
The idea is that someone could dig up funding sources for an organization and add them as meta notes to the account. The community can then collectively decide if this is accurate or inaccurate, giving others an idea if there is a certain bias involved.
Think about the Greenpeace ordeal currently happening. A meta note to indicate that Ripple, a “competing” cryptocurrency is funding them would add a lot of transparency to their claims. I think people would be less likely to believe the nonsense they are spewing.
Create a record of accuracy
Fueled entirely by the community, people could verify the accuracy of claims and indicate that in meta data. Other members can then review those claims and vote on them as well. With enough people involved, you could see if there is a sufficient sample size to indicate whether a media organization has been accurate or inaccurate in the past.
One thing we’d need to watch out here is bot manipulation. Said organizations could hire out malicious services to make it seem they are more accurate than they are typically. We’d have to think of some ways of preventing that.
The sheer lack of ratings on a claim should raise an eyebrow and whether something is to be believed or not.
The right to be forgotten
I know I will catch a lot of heat for this one. “The internet never forgets!” This is what the vast majority of people will say right away. That’s fine… but hear me out…
As builders and developers, we can form a consensus that social media data should be forgotten after x amount of time. Yes, anyone can screenshot it, mirror, put it on their own relay, rebroadcast it, yada yada yada… I get it. But that doesn’t mean we can’t create a consensus by which many builders, relay operators can voluntarily abide. It may not be a bulletproof solution, but it’s an effort that counts.
When we speak in the real world, unless recorded, our words are forgotten. A person should not be judged by a stupid thing they said yesterday, a week ago, a year ago. We can’t be in the right all the time - all people make mistakes and say and do stupid things. However, online, your word remains forever. Various servers cache, duplicate, at zero cost. I totally get that. Yet, we can still design an experience where that information disappears from our feeds, unless actively surfaced with some specific intent to surface it. I think this is a worthwhile effort that developers should consider today.
In cases where information should be saved for good reasons, someone will save it. Entire clients can and will exist to index everything, but that doesn’t mean every single client should surface every single note. People have a right to be wrong and to not be constantly harassed for what they said or did if they no longer feel or act that way.
Let’s have this conversation because no one else will
This article is meant to be a conversation starter. I really think we should weave it into the Nostr conferences as a crucial segment worth exploring and discussing. If we don’t do this, no one will. The world will continue to get gamified, attention hijacked and kids will continue suffering, depressed, lacking confidence and the tools needed to create a better world for their own kids. Let’s not fall sleep at the wheel and actually do something about it.
What other ideas do you have? Share the article and attach your own ideas.
-
 @ 9ecbb0e7:06ab7c09
2023-07-23 04:35:52
@ 9ecbb0e7:06ab7c09
2023-07-23 04:35:52Un cubano, identificado como Adrián Reinoso, de 44 años, fue arrestado en el Aeropuerto Internacional de Miami al intentar ingresar aproximadamente unas 100 cajas de tabaco originario de la Isla, informó Telemundo 51.
El incidente ocurrió ayer miércoles 12 de julio, cuando un oficial de Aduanas y Protección Fronteriza (CBP, por sus siglas en inglés) llevaba a cabo una inspección a los pasajeros provenientes del país caribeño, a bordo del vuelo 2703 de American Airlines.
Durante la revisión, el oficial detectó que el sospechoso movilizaba varias cajas de tabacos Upmann gravados, sin etiquetas, así como múltiples cigarros Cohiba individuales. Tras un inventario posterior, se reveló que se trataba de 50 cajas de cada marca, lo que fortaleció la idea de un intento de contrabando.
Según el informe, Reinoso alegó que los cigarros y puros no eran para su consumo, sino para un amigo. Sin embargo, los oficiales determinaron que los paquetes no cumplían con las normas federales de etiquetado de advertencia y que su venta no estaba permitida en el territorio estadounidense.
Ahora, el antillano se encuentra bajo custodia en el Turner Guilford Knight Correctional Center y enfrenta múltiples cargos relacionados con los delitos de posesión, venta y distribución ilegal de cigarrillos, así como uno por supuesta falsificación de etiquetas, de acuerdo con el informe de arresto.
Cabe destacar que desde septiembre de 2020, los viajeros no pueden regresar a Estados Unidos con productos de alcohol y/o tabaco adquiridos en Cuba como equipaje acompañado para uso personal. Esto forma parte de las regulaciones implementadas por las autoridades aduaneras para controlar el contrabando y garantizar el cumplimiento de las normas.
La importación de este producto destinado a la venta o distribución requiere un permiso expedido por la Agencia de Impuestos y Comercio de Alcohol y Tabaco del Departamento del Tesoro de EEUU.
La Comisión Federal de Comercio también exige a los importadores etiquetar correctamente los envases de tabaco de acuerdo con la Ley de Etiquetado y Publicidad de Cigarrillos. Esto incluye la colocación de las cuatro etiquetas de advertencia del Cirujano General en cada paquete, siguiendo un plan aprobado por la FTC.
Este incidente resalta la importancia de cumplir con las regulaciones aduaneras y las consecuencias legales que pueden derivarse de intentos de contrabando. Las autoridades continúan trabajando para garantizar la seguridad y el cumplimiento de las normas en los aeropuertos internacionales del país.
-
 @ 1bc70a01:24f6a411
2023-03-25 13:52:21
@ 1bc70a01:24f6a411
2023-03-25 13:52:21In one of his earlier talks, developer and entrepreneur Rob Walling who was previously founder of drip.com said something seemingly small but profound (paraphrased):
To increase conversion rates (people sticking around to keep using your product, and ultimately paying), get people to their “aha!” moment as quickly as possible.
The “aha!” moment is where it clicks for the user exactly why this product is awesome. It's the shortest path to awesome. Once the user sees the value in the product, they are more likely to stick around.
Product designers and developers who are aware of this, know that the name of the game is providing value, and hopefully overdelivering, as quickly as possible. This means setting aside their own desires to showcase the product in its full glory, and focusing on the essentials - minimizing the number of steps required to get to the aha moment.
Design by omission becomes important. What to not include becomes equally, if not more important as what to include. So does reducing friction. The fewer, less painful steps involved in getting insane value out of a product, the better.
This concept is a great rule of thumb for every product founder. Instead of thinking “what feature should I add to make people love this product?”, founders should be thinking “what features do I absolutely need for people to love this product?” Then de-emphasize everything else.
Nostr clients are no different from a typical startup - they should be trying to figure out the “aha!” moment, and how to get the user to it as quickly as possible.
A useful exercise I often perform is to reverse the process and start at the end - the action the user needs to take to have their minds blown. Once you figure out what that action is, work backwards to the steps where they first land on the product page, or install the app, whatever that may be. The goal is to cut out as many steps in-between as possible.
I’ll demonstrate with a hypothetical, but practical example.
Let us assume we are building a music app where people can earn sats when others listen to their tracks.
Nostr has several layers and steps that most people typically go through, for example:
- Generate key pair
- Save keys warning
- Pick a username
- Import follows (perhaps)
- In some cases add relays
- Navigate to some sort of a feed, either from follows or general
- You typically need to set up your profile if you want people to take you seriously
- Have to figure out what sats are, why anyone should care? What are these play tokens?
- If care enough, find settings to connect a wallet
- Learn about wallets (now you leave the platform to do a bunch of reading), chances are you are gone for good.
- Connect a wallet, test a payment.
- Do something for someone to find your action worthy of a zap / perhaps upload a track?
- Aha moment! You can get paid easily and fast just for interacting with people.
Perhaps you’ll also have a realization that your comments are showing cross-platforms which supercharges your content distribution, but for now we don’t need to worry about this.
Of course, some of these steps may be optional, but if we are talking about someone who knows nothing about nostr, sats, zaps, key pairs, that’s 12 steps to get to some realization of what is possible.
12 steps!
The barrier to seeing value is very steep unless you already understand the benefits of decentralized social platforms, know about bitcoin and understand the possibilities.
Sadly, this is not what an average user looks like.
In fact, if you look on Nostr.band, the stats show that the number of profiles with an LN address has remained largely flat for a long time. It’s likely that these people are mostly bitcoiners who already understand the value proposition of a lightning payment.
Now, let’s work backwards and just think through which steps could potentially be eliminated. Keep in mind, we are talking about a music client.
Let us assume that the aha! moment is someone getting paid for their creative work (music). I think this is a safe assumption.
Final step: Pay bills with your creative work
This is going a bit beyond the aha moment, but we’ll roll with it.
Let’s ask some questions…
- What’s the fastest way to demonstrate that a user can collect payments for uploading tracks? How about a web client that is visible without logging in? Perhaps you can see some songs right away and notice that they are earning money? It’s not a personal aha moment, but it’s a preview.
- Can we get the user to skip signup entirely?
- Can the user upload a track as step 1?
- Can they see their local currency as a payout option?
- Can they collect payment in their local currency?
- Do they need to know what sats are? At least initially?
- Do they need to care about relays and everything that this entails?
- Do they really need to connect a wallet to get paid?
- Do they really need to follow anyone to see a feed?
- Are usernames even important to see the value in this product?
- Do they need to learn about cryptographic key pairs? How can we delay this step?
Having asked all of these questions, we can draft an ideal scenario. It may not be realistic, far from it, but at least we know what an ideal and amazing journey would look like.
- Land on a website and see that people are getting paid in your local currency for the same work you offer. Hey, maybe I should try this? 🤔
- What’s this.. a button to upload music? Ok, I have a file sitting on my drive, or have a link handy, let’s do it! Go ahead and add the track (as few steps as possible). Holy shit, I can add splits? Sounds crazy.. ok, let’s keep going.
- Now that I’ve made progress in adding some information, it seems I need to sign up to finish. Makes sense. One or two clicks, I’m in and my track is added.
- Aha moment: I go eat dinner, come back an hour later and see that I’ve just earned $5. It ain’t that much, but it didn’t take long! Turns out new tracks go into the new tab and people can stream them which goes directly to your wallet.
- Final step: I click a button to cash out, in my local currency. The funds arrive in my bank account. Now I can pay my bills.
It may not be a feasible flow, or even a desirable one, but at least we can see that an amazing journey might only take 3-4 steps. It is still using the old money rails for some parts of the app, but the artist can get paid for their work fast and can come to a realization that there might be something to this.
We don’t need to create this specific journey and outcome, but we can use it as a baseline.
As a technical founder / developer you will have a better idea of what is possible. Perhaps new services need to be created to get to our end state? This exercise gives us a lot to think about.
In our example, we might be able to:
- Let users preview the product without signing up
- Have built-in wallets that require no additional setup (with the ability to customize your experience later in the options)
- Display earrings in local currencies while slowly introducing sats, zaps (surely there is an API that can handle sats to local currency conversion in real time? If not, maybe it has to be created?)
- Allow users to cash out into local currency. Why do we need to keep them in sats? Why not let them make their own option? If this is not possible to do - Why? What service needs to exist to allow lightning-enabled apps to tap into easy, plug and play fiat conversion?
- Let users discover relays later on instead of right away to keep them from being overwhelmed.
Even if some of these things are not technically feasible, at least we are now thinking about the flow from a user’s perspective and empathize with them. We start thinking about their time, their needs, their existing frustrations and how we might be able to brighten their day.
This user-centric approach helps founders skip the fluffy parts and focus on the guts that truly matter.
New founders specifically tend to enjoy adding features, thinking the next one will do the trick, only to be disappointed.
I encourage Nostr client developers to start thinking about their users as customers who are looking to solve their own problems.
- How might you make that journey as effortless as possible?
- What is your customer truly seeking? Is it distribution? Is it attention? Is it money?
- Are you delivering it in as few steps as possible?
- Can the “customer” take a more familiar path to get to the same decentralized destination that we all love?
-
 @ e8ed3798:67dd345a
2023-07-16 02:49:48
@ e8ed3798:67dd345a
2023-07-16 02:49:48This article has been translated into Japanese here: https://yakihonne.com/article/naddr1qq257w2t8qeksc6tdg6njnekdc6x55j0w56nvq3qarkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqxpqqqp65wu2llgg
This article has been translated into French here: https://yakihonne.com/article/naddr1qq2h23jjwck4zajsv4485h68f5mj6c66vfmxuq3qarkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqxpqqqp65wvsexdg
In this article we are going to explore the conceptual origins of the original metaverse called "cyberspace" and see how nostr finally enables it to exist as it was predicted in early science fiction. Then we will explore what cyberspace might be able to do for humanity and how you can contribute to this exciting new open-source metaverse project.
A Concept Obscured by Time
What is a "metaverse"? Ask 10 different people and you will get 10 different answers. Some will say that it is an online game where you can use and transfer crypto assets. Some will say it's a virtual reality experience with extrasensory input for things like smell and touch. Some will say that a metaverse is anywhere you can connect and express yourself digitally. And some may tell you the metaverse doesn't exist yet because we don't have the technology to make it happen.
It's hard to define what a metaverse is because nobody has convincingly built it yet. This is demonstrable by simply asking anyone to show you a metaverse. They may show you VR Chat, or Meta (Facebook), or the HoloLens or Apple Vision, or someone's Discord server or NFT ecosystem, or say "it's not real, and if it is it's probably stupid."
But how did we get here? Why do we all know about the metaverse but we can't define it and we don't even know what it looks like? Where did the idea of the metaverse come from? This answer will give us the conceptual background we need to untangle the question of "what is a metaverse" and see how cyberspace can exist today.
The word "metaverse" was first popularized in Neal Stephenson's 1992 book "Snow Crash", and he was in turn inspired by William Gibson's earlier 1984 book "Neuromancer" (and 2 other books in a trilogy called "The Sprawl"), which popularized the word "cyberspace" and "matrix" in reference to digital 3D spaces.
Accordingly, cyberspace preceded "the metaverse" by 8 years and serves as the foundation for our exploration. Gibson's cyberspace was a digital 3D world one could connect to via a cyberspace deck — a machine/brain interface — and interact with all the data in the entire world. Artificial Intelligences guarded data constructs and kept out intruders with lethal feedback programs that would fry human operator's brains. In the books, cyberspace is described as being used for pretty much everything: entertainment, education, communication, commerce, data storage, and crime, and it is used daily by billions of people throughout the world, including millions of people in orbital colonies.
Mysterious Properties
In Gibson's work, cyberspace has many fascinating qualities that, until nostr, remained very mysterious and seemed to be impossible. Here are some examples.
1. Cyberspace is Permissionless
Everyone can use cyberspace but nobody has full control over it; cyberspace seems to exist outside of every jurisdiction and system. It never goes down for maintenance or has connection issues or suffers security breaches. It seems to exist everywhere at once, even though it is explicitly stated that cyberspace was created by humanity. How can humanity create an uninterruptable, omnipresent digital system that nobody can control but everyone can use?
2. Power is Wielded Without Privilege
Certain people, corporations, and AI weilded greater levels of power in cyberspace than others, but the mechanism of that power was not derived from permissions or access levels or privileged administrator capabilities; rather, the power came from some mysterious other source that could not be granted, governed, or revoked by any law or system or authority. This power seemed also to be heavily influenced by...
3. Hardware and Skill
The hardware that people used to connect to cyberspace had a direct impact on their capabilities in cyberspace. There is a a specific example where a character uses a premium cyberspace deck and describes the speed and smoothness of their ability to fly through cyberspace. A short while later, this operator is captured and immobilized by another dangerously skilled operator, demonstrating that while the cyberspace hardware was top-tier, the operator's skill level was also a big factor governing interactions in cyberspace. This also demonstrates that conflict is possible in cyberspace. How is it possible that hardware directly correlates to your capacity for virtual action? How can someone else influence your actions against your will in this digital reality?
4. Space is Scarce
Bitcoin was the first scarce digital resource to ever exist, and having only been created 14 years ago, scarce digital resources are still a novel concept to humanity in 2023. In Gibson's cyberspace, territory was conquered, captured, and fought over, indicating that the space in cyberspace may be scarce or valuable in some way. How could it be possible to fight for digital territory or acquire it without any governing intermediary took keep track of who owns what?
5. Construction Has a Cost
Constructs, or cyberspace "buildings", required some kind of effort or cost to create, but it was not clear to whom this cost was paid or how the effort was expended.
The metaverse of Stephenson's "Snow Crash" shares many properties with Gibson's cyberspace, although Stephenson is somewhat opinionated with the literal shape of the metaverse. He depicts it as a street that wraps around a black planet, and the land off the street is where people build things and claim territory.
This metaverse similarly does not seem to be owned or controlled by any single entity, yet it is available to everyone in the world to connect, interact, and build in 24/7. It is not described as an application or piece of software, but rather a place that is the sum of other software created by many different parties with different interests and motivations.
Here are some mysterious traits of Stephenson's metaverse:
6. Rules without Rulers
The rules of the metaverse were never broken — not even by hackers or bad guys. How are rules enforced by a system nobody controls?
7. No Teleportation, Localized Rules
The metaverse had rules about where you could spawn in and how you move. Teleportation was not an option. Specialized vehicle software could make traveling easier. Rules for travel were enforced by the metaverse itself. Experiences in the metaverse were localized to constructs that implemented their own rules. For example, sword fighting was allowed in The Black Sun hacker haven because it was programmed to exist there; other places did not have such activities. How can certain places in cyberspace have unique rules separate from the rest of cyberspace? How is locality enforced in a digital system controlled by noone?
8. Customize Without Compromising Everything
People were able to customize how their avatars and constructs looked. How do you govern this so people don't abuse it? Without enforceable rules, one person could make their avatar be the size of the universe and ruin the metaverse for everyone.
9. Everything is Connected
Digital systems in the real world had a presence in the metaverse too, although they were far from commonly populated areas. How do real world systems relate to the metaverse?
I enumerate these points in order to provide some context for where the idea for "the metaverse" began. These two books were instrumental in originally defining what the metaverse was even though it raised many specific questions that naturally were never addressed. As I have said: if the authors knew how to build the things they wrote about, they might not need to sell any books at all! This is fiction after all. Specifics are not required, but I have been focused on uncovering these specifics in the context of new technologies such as bitcoin and nostr and I believe they may now be defined.
To summarize, here are the mysterious properties of cyberspace/the metaverse:
- Everyone can use it
- Nobody controls it
- It exists everywhere
- An individual's power is not granted by any system or authority but comes from their hardware and skill
- Individuals can weild their power against each other
- Territory is scarce and may be captured
- Constructs may be build on territory but have some kind of cost
- The system enforces rules on everyone, or somehow incentivises everyone to follow the rules — even bad actors
- locality is enforced and travel requires time
- certain localities have unique rules
- freedom to customize your avatar and constructs are bounded in some way to prevent total corruption and abuse of digital space
- there is some form of connection between real world digital systems and cyberspace
Nothing Like It
I want to make it very clear that no metaverse in existence today exhibits all of the above properties or even a few of them, and very few digital systems exhibit even one of these properties.
Before I discovered Neuromancer several months ago, my perception of "cyberspace" was that of a quaint, naive concept of what interconnected computer systems would become that never came to pass. I used to ironically refer to the internet as "cyberspace" when talking with other developers as a kind of humorous or self-important overemphasis. I thought that cyberspace was a cultural relic and a failed prediction of what the internet would be. The glossy, 3D wireframe neon world never materialized, and for this I've always felt a sense of loss of what could have been.
Why didn't cyberspace ever come into existence? As computers became more advanced and consumer-focused, they did not attempt to emulate a 3D space, but rather did the practical and sensible thing of emulating paper documents so people could get work done digitally.
As the internet became a household utility, centralized systems and applications were the first and only way that humanity knew to grow our collective capabilities online. Websites grew as they collected users and became behemoths. Ebay, Google, Amazon, PayPal. Although the internet itself was technically decentralized, decentralized systems and applications would come later when the problems with centralization became obvious as these internet giants started abusing their power.
As the internet continued to grow and resemble less and less the fictional worlds of cyberspace and the metaverse, these lofty ideas of digital 3D worlds turned into toys for most people — unnecessary but entertaining fluff. The notion of cyberspace faded into 80's retro culture and the word cyberspace was painfully repurposed to simply refer to the internet or networked systems collectively. This, however, is a terribly inaccurate use of the word. There is no space to speak of on the internet. But, sadly, the interet was the closest thing we have ever had to Gibson's vision of cyberspace, and it really wasn't close by any measure except that people all over the world use it for pretty much everything. All the other magical properties of cyberspace were simply forgotten. They were fiction. They weren't necessary. They weren't possible. There was no way to make it work and no reason to do so.
However, when reading these books from nearly 4 decades past, there is something poignant to me in the fact that across these various works by various authors, the metaverse (or cyberspace) posesses consistent properties that no author is willing to alter. What is so inviolate about a fictional concept that would make it so consistent across works? Perhaps there is a kernel of truth in what is imagined, and that truth is so compelling that it must be repeated until it crosses the veil between idea and reality.
Reality And Cyberspace
I have always been fascinated by technology's ability to improve our lives, and I have strived to create consequential software my entire life, like video games played via fitness watches and augmented reality navigation web apps, but it wasn't until I read Softwar that I realized something profound.
In reality, I am able to do anything I want as long as I have the thermodynamic energy to do it.
It may not be legal or socially acceptable, but if I have the energy to do something, I can. Likewise, if someone wants to stop me from doing something, they can't unless they also expend enough energy to stop me.
This means that reality is permissionless, because nobody can disallow my actions. It also means reality is thermodynamic, because every action has a cost that must be paid to the universe in the form of entropy.
Conversely, in digital systems, the amount of energy you have is irrelevant. The things you can do are only the things you are allowed to do by the permissioned system, or, the things you can trick the system into letting you do. This means that within a digital system, you always have a severely limited subset of available actions, and your ability to execute those actions has nothing to do with your thermodynamic potential and everything to do with the permissions you are granted by others. No matter how strong my muscles are or how clever I am, I can't do more than a digital system allows me to do, and even if I hack it, I still can't do anything I want — only more than I'm supposed to.
Almost all digital systems and software are permissioned and non-thermodynamic.
This is why, fundamentally, no metaverse that has ever been built actually matters. This is why no video game keeps you interested in it forever, because the actions that you can do and the extent to which you can do them are arbitrarily disconnected from your ability to act in reality. It's "just a game" — a limited subset of reality.
This isn't fundamentally a bad thing. Obviously, software has done a lot for humanity. And software-based rules have been used in many contexts to keep things fair for everybody. Except, unfortunately, digital systems are never truly fair. There's always a programmer who wrote the rules. There's always an admin above you. There's always a hacker. And there's always someone with more permissions than you who can restrict your potential. Compared to reality, this seems arbitrary and capricious. At least in reality, the universe to which you pay your entropy costs is truly, terribly impartial and unbiased. This is why thermodynamic systems are fundamentally fair; even though it may not seem fair to you it is truly fair to everyone.
Reality is a permissionless, thermodynamic protocol, and almost nothing in the digital world resembles this whatsoever.
Nostr, however, is permissionless. Until now you may not have considered this to be a fundamental property of our universe, but it is, and the fact that nostr exhibits this same property is quite compelling. In fact, any system that is truly permissionless (of which there are very few) seems to have the magic ability to capture people's imaginations in ways that no other digital system can. Things such as bitcoin, perhaps the most famous permissionless digital system, has such broad and profound effects on people who grasp it that they have been known in some cases (such as Andreas M. Antonopoulos') to stop eating, stop sleeping, research it obsessively, and completely change their entire way of life. How's that for consequential software?
Like bitcoin, nostr can also be thermodynamic via proof-of-work (NIP-13). And with the combination of these two properties, which are shared with reality, we are suddenly able to dispell every single mystery we've encountered regarding cyberspace.
Proof-of-work is the secret ingredient to dissolve the fiction in the science fiction of cyberspace.
A Mystery Solved About Cyberspace and Bitcoin
The reason that the properties of cyberspace and the metaverse are so mysterious is because they are actually properties of reality, but inside a digital system.
In reality, it is no surprise that your hardware and skill affects your ability. No surprise that your work determines your power. No surprise that you can't teleport and must travel using energy. No surprise that building constructs or customizing yourself takes effort and cost. No surprise that territory is scarce and must be defended. No surprise that conflict happens between people. All of this is so completely normal that it's easy to overlook.
The reason these things in Neuromancer and Snow Crash and other works about the metaverse seemed so mysterious is because they weren't possible to model in a digital space. These authors took properties of reality and put them in a digital space, and it seemed amazing because nobody knew how it could actually work.
This is how it is possible: you design a digital system that has the same fundamental properties as reality. It must be permissionless. It must be thermodynamic. Then you have a system wherein cyberspace can exist.
Nostr is the fulfillment of these requirements. Like bitcoin, nostr has captured the imaginations of thousands of early adopters and developers. The magic is there. But few may realize why it is feels so magical. The answer is that when you make a digital system that can model reality's own properties, you have created an extension of reality itself. This is one of the most significant discoveries in human history, because a digital extension of reality can allow humanity to connect, collaborate, and grow in a place where their physical diatance does not matter. Barring any major advancements in spacefaring technology, cyberspace will be the most significant departure from earth you may experience in your lifetime.
I posit that a virtual action which is permissionless and thermodynamic is as real as a physical action, except the consequences of that action happen in the digital space rather than the physical one. It's not quite reality, but it is like a mirror. It is a true extension of reality. Nothing in it is disconnected from the real world. And therefore, unlike any other digital system, it can be truly consequential.
Healthy Skepticism
Wait a minute, you may say. Cyberspace is still just a digital way of communicating. Isn't email and texting and video chat good enough? Why do we need cyberspace? How could it possibly be so important to humanity?
This is a great question.
One may ask similar questions about bitcoin. Don't we already have digital money? Why do we need absolutely scarce, decentralized censorship-resistant money?
Or about nostr: why do we need another way to transmit text? What good is it to be decentralized and censorship resistant?
Like bitcoin, cyberspace makes something digital into a scarce resource, but instead of enabling the capture of time (on a timechain) cyberspace enables the capture of scarce space (in a construct or your movement chain).
In the physical world, our movement can easily be censored. Our expression of power is censored. Our capture of space is censored. Not so in cyberspace. The only thing that matters in cyberspace is the thermodynamic energy you exert — just like in reality, but minus the permissioned (artificial) power structures of governments and laws.
Just as bitcoin doesn't care who you are or who you are transmitting value to, cyberspace doesn't care who you are or where you are moving to or where you are claiming space.
Consequences of Proof-of-Work in Detail
I'd like to enumerate the specific ways in which proof-of-work in nostr demystifies the mysterious properties of cyberspace mentioned earlier.
- Everyone can use cyberspace but nobody has full control over it.
Just replace "cyberspace" with "nostr" and the above statement is already true. If we build cyberspace on nostr, then cyberspace will inherit these properties.
- Certain people, corporations, and AI weilded greater levels of power in cyberspace than others
If we base an entity's power on their thermodynamic output via proof-of-work, then we have a permissionless way for cyberspace participants to enact their real thermodynamic potential in cyberspace to whatever degree they choose.
- The hardware that people used to connect to cyberspace had a direct impact on their capabilities in cyberspace.
If all actions in cyberspace are thermodynamic like in reality, then hardware capable of greater amounts of proof-of-work will enable more powerful actions. Mobile phone, desktop computer, or ASIC farm: take your pick.
- Territory in cyberspace was conquered, captured, and fought over, indicating that it may be scarce or valuable in some way. Constructing had a cost.
The territory in cyberspace is the maximum 3-dimensional coordinate space that can be represented by 256 bits. In cryptography, nostr, and bitcoin, 256-bit numbers are very commonly used along with mathematical functions like SHA-256 that process data in blocks of 256, so it is a good "round" amount of information to work with.
You can divide a 256-bit number into X, Y, and Z coordinates that are each 85 bits long. This leaves 1 extra least-significant bit from the 256 bits that is ignored.
This means that each axis of cyberspace is 2^85 units long.
Space can be claimed by publishing a construct event whose event ID is the coordinate. The event ID is obtained from hashing the event (standard process for all events in the nostr protocol). This means the event ID can be mined to obtain the coordinates you desire (or at least something close by).
If two constructs overlap, the one with the most proof-of-work wins. This is how territory can be contested in a permissionless way in cyberspace, as alluded to in Gibson's works.
The cost of construction is the proof-of-work, and the maintenance of that territory by proof-of-work is the digital analogy of either paying taxes to a government who will protect your land, or, protecting your land with your own thermodynamic energy. Notice how money, also known as time, is inextricably linked to the ownership of property in reality and now also in cyberspace. If property were free to own and maintain, would it be worth anything at all?
I have been presented with the argument that it does not cost you anything to hold bitcoin, so constructs or cyberspace real estate should be no different. To this I say that for you to hold your bitcoin, a tremendous amount of cost is expended by all the miners in the world. If not for them, your bitcoin would be double-spent or stolen by invalid transactions. The validity of your unmoving bitcoin requires the continual, perpetual operation of the largest computer network in the world. So, continual energy expenditure to secure your property is true with bitcoin, cyberspace, and all of your things in reality as well.
Unlike bitcoin, whose value lies in the entire network, constructs are valuable only to their owner. Therefore, it is the responsibility of the construct's owner to defend it.
More complex symbiotic relationships in construct defense may be borne out of the perpetual fight for survival inherent in any thermodynamic system. But this is only speculation.
Enforcing rules universally
As with any protocol, deviation excludes you from it and submission grants a share in its value. Forking the cyberspace meta-protocol, whether by disobeying its rules or rewriting them, results in an irreconcilable forking of digital reality. The value of cyberspace as a protocol depends on network effects like any protocol, and the first-mover has a strong advantage in any protocol war. Additionally, as all actions require proof-of-work and must be chained together, the sum of your history in cyberspace is put at risk of invalidation should you deviate from the protocol everyone else is following.
Ultimately I believe that the purpose of cyberspace should be to imbue humanity with new capabilities and opportunities, and I think that it will, simply by virtue of the fact that it is built on a protocol and interoperates with protocols that likewise imbue humanity with new capabilities and opportunities (notsr, bitcoin, and TCP-IP). I desire that cyberspace will be flexible and capable enough to support as many use-cases as possible as long as the fundamental properties are preserved as axiomatic non-negotiables. Cyberspace itself must be both permissionless and thermodynamic. Without these properties, cyberspace becomes just another digital illusion apart from reality.
Flexibility, locality, and customzation
With these axioms in mind, I think it would be very smart to create a method of defining construct-level rules that exist only within certain spaces. This would allow for custom interactions and systems to exist in the fabric of cyberspace, making it very flexible and local. Any such system or customization, even if cosmetic, must impose a fundamental thermodynamic cost. The details of how this could work are yet to be developed, but the blueprints of fiction, our axioms, and our ingenuity will lead us to it.
The metaverse of things
Because nostr is a web-friendly protocol, it is trivial to connect anything to cyberspace. I love to tell the tale of how I witnessed an early 2022 conversation between someone and (if I remember correctly) Will Casarin's smart dishwasher that was posting kind 1 status updates to nostr. If someone can talk to a smart dishwasher over nostr, then the Metaverse of Things already exists. However, the degree to which these things expose themselves to the metaverse should follow the same security model as for the internet at large. Unlike in fiction, I doubt anyone will allow sufficient proof-of-work be the only prequisite for commandeering a real-world system. That's ok. Ultimately, the relationship between reality and cyberspace isn't meant to be a 1:1 map. Digital systems only really ought to participate in cyberspace if they share the same properties as cyberspace. Most digital systems are permissioned and non-thermodynamic, and therefore do not have a compelling reason to exist in cyberspace. But anything is indeed possible.
Chasing a Ghost or Following a Blueprint?
I'd like to make the distinction that the purpose of a construct (and of most things) in the real-world cyberspace is not necessarily the same as in Gibson's literary cyberspace nor in Stephenson's literary metaverse. But the fundamental properties as depicted remain the same, and it is enabled by proof-of-work.
Remember, the remarkable thing about Gibson's cyberspace is that it is a digital world that functions like reality — there is egalitarian conflict resolution, scarce space, and universally enforced rules. The cyberspace meta-protocol likewise enables a digital system to function like space in reality. The motivations and reasons behind this digital system may be completely different than in the books, but that doesn't mean the mechanisms are any less accurate.
My goal is not to reproduce Gibson's and Stephenson's work in reality. The properties of this fiction are compelling, and the implementation and usage of cyberspace will completely depend on free market forces — exactly as it should be. It is not for me to decide. These works opened the conceptual pathway to creating this new thermodynamic digital reality. The human motivations and actions that shape cyberspace will undoubtedly cause it to look plenty different than depicted in the books, while the funamental properties remain identical.
Throughout the process of designing the cyberspace meta-protocol I have tried to keep it as simple and fundamental as possible, using these books as my guidepost. Whether these authors realized it or not, their depictions of cyberspace and the metaverse were extremely consistent and coherent, which makes not only for great fiction and believability but also for a great guide to follow in developing a real system.
Step Into Cyberspace
I'd like to provide some concrete examples of how cyberspace works so that the concepts presented herein are not without application.
NOSTR in 3 minutes
To interact with cyberspace, one must simply publish certain "kinds" of nostr events. If you are not familiar with nostr, here is a short explanation. Nostr is made up of people running clients, which are just apps like on your phone or desktop, and people running relays, which are like servers that store events. Clients download streams of events from relays in real time. Clients can also publish events to relays. Publishing an event is like sending a tweet. Clients normally publish the same event to many relays at once. As long as you send the tweet to at least one relay that your friend is connected to, they will see your tweet. Anyone can run a relay or build a client and connect to whichever relays they want. In this way, nostr is permissionless and decentralized.
A "kind 1" event is essentially a tweet, but there are other kinds of events, each represented by a number. A kind 0 event is what you publish when you update your profile with a new bio or screen name. Anyone may make up a new kind of event and assign it any number, except it would be poorly supported if you used a number that is already accepted as part of the nostr protocol for another purpose than you are using it for. Luckily, there are a lot of numbers to go around.
A private/public keypair is an anonymous cryptographic identity, and it can be used for secure communication, storage of bitcoin, and other various things. The keys themselves are just unfathomly large unguessable numbers represented in the hexadecimal number system which includes numbers 0-9 and a-f (base 16 instead of base 10). When you publish an event on nostr, it is signed by your private key, and the event contains your public key. This allows anyone to verify that the event is legitimately from that public key, which presumably only a certain person controls. In this way, nobody can forge or tamper with events without invalidating them, because the signature would not match the public key.
Meta-protocol
This is why I refer to cyberspace as a meta-protocol because it is simply a specific way of publishing and interpreting specific event kinds over nostr and visualizing them in a 3D space.
Drift
To move in cyberspace, you must publish a kind 333 event, referred to as a Drift event. This event contains your 3D cyberspace coordinates, your direction, your existing velocity, a reference to your previous Drift event, and proof-of-work to add velocity by your direction. The amount of proof-of-work on the drift event determines your acceleration. Proof-of-work can be added to any nostr event by choosing an amount of work, represented by the number of leading binary zeroes on the event's ID, and hashing the event with a different nonce until the target amount of work is reached. This process is specified in NIP-13.
Each Drift event may be validated by running the coordinates and velocity through a standardized cyberspace algorithm (currently being developed) to verify that the value changes from one drift event to the next are within a tolerable range of error. It is in effect a way of simulating the movement within a physics system in order to validate that the movements did not break the rules of cyberspace physics. In this way, every participant in cyberspace is a validator of everyone else they are physically near.
When a drift event is signed, the reference to the previous drift event is included in the signature. This creates, in effect, a personal verifiable hash chain history of your movements and actions in cyberspace that anyone else can verify.
Dishonesty and Punishment
In order to encourage people to be honest about their movement chains, anyone who finds an invalid — or "broken" — movement chain may punish its owner by publishing a Derezz event on it, which will invalidate all movement chains and proof-of-work owned by the victim and teleport them back to their home coordinate where they originally spawned when they first used cyberspace. This is effectively a respawn. You start from scratch, but you can keep your constructs.
One can easily lie about their movement chains and teleport anywhere at any time. But on nostr, for the most part, events cannot be deleted. Therefore, a cheater will leave a bright trail by which others may cyber-kill them via Derezz. A broken movement chain is like a ghost copy of the cheater that can't move. For deeper protocol reasons that the adventurous may explore in the spec, this makes the ghost copy extra vulnerable to Derezz.
A cheater may choose to ignore the Derezz attack and continue to teleport where desired. Nothing in nostr or cyberspace can stop this. But to everyone else who follows the protocol, this type of behavior can easily be ignored. The habitual cheater may as well be a ghost, as their thermodynamic actions will be ignored by everyone else who has chosen to obey the protocol. The cheater might redeem themselves by publishing a very long valid chain of events, but this probationary period may be too demanding for habitual protocol breakers. Other aggressive actions may be leveled against cheaters, making their operation in cyberspace unproductive, difficult, and dangerous.
A cheater in cyberspace is an easy target. As the punishment of cheaters is a noble act of justice rather than an evil act of predation, I expect cheaters in cyberspace to be punished with great swiftness and mirth.
Incentives for honest movement legitimize the spatial aspect of cyberspace. In cyberspace, space is real and consequential. Traversing it has a cost. No two places are funamentally the same because there is a real cost to visit them. And all space is scarce, because of the hard limit of the 2^85 coordinate system, which was chosen to be compatible with the most popular mining agorithm in the world, SHA-256.
Other actions
To read all about the different kinds of events one can publish to interact with cyberspace, check out (and contribute!) to the official cyberspace specification here: https://github.com/arkin0x/cyberspace
In this specification you will find technical implementation details for clients to interact with the cyberspace meta-protocol, including definitions of other actions that may be taken by operators, including:
- manipulating "gravity" to affect other operators
- creating proof-of-work armor against Derezz
- cloaking one's location with stealth
- and more!
Ubiquity and Omnipresence of Cyberspace
A very interesting recent development is an open-source project called
nostrmeshby lnbits that enables anyone to host a nostr relay on a small mesh-networked device, such as an Arduino. Imagine a network of billions of these devices, scattered across the globe, running on battieries and solar panels, each contributing to the infrastructure of cyberspace — a decentralized, omnipresent digital cosmos, accessible from virtually anywhere. This level of ubiquity brings us one step closer to the vision of Gibson's work, where cyberspace becomes an integral part of our daily lives and can be found everywhere — even in outer space!With such a ubiquitous and omnipresent network, the spatial limitations of cyberspace extend far beyond conventional digital boundaries, intertwining with our physical world in a way that was once the domain of science fiction. The implications of this development are enormous and lay the foundation for the potential uses and influence of cyberspace, which we will explore in the following section.
Consequences of Cyberspace
It is difficult to predict whether cyberspace will find its place in the daily lives of billions or be forgotten once again. However, the foundations of cyberspace are inextricably linked to technologies that have been developed and adopted for the sake of human freedom and personal rights: public key cryptography, hashing, proof-of-work, bitcoin, and nostr.
As one who takes science fiction seriously enough to remove the fiction from it entirely, I find speculation to be invaluable. One cannot go where the imagination does not first lead. Our entire perception of the world is parsed from an abstraction created by our minds. We automatically assign meaning to inherently meaningless things — symbols, patterns, etc. Fiction is our reality, and our perception of the world is the sum of logical patterns within this fiction. Therefore, let us do what we do best and create fiction, or speculate, without hesitation.
I personally envision cyberspace to be a place of commerce and social organization. Constructs enable people to claim cyber land. They can use this land to design interactive experiences that are governed by localized rules and thernodynamics. The Lightning network enables instant transfer of value through cyberspace, facilitating the transaction of information, services, cyber experiences, digital and physical goods.
Use cases include shopping, gaming, gambling, competitions, live cyber events, virtual-presence social gatherings, virtual protests, collaborative spaces, advertising, education, tourism, development of cyberspace-based applications, data visualization, research, social networking, and even more that we haven't imagined yet.
Conclusion
As we venture into the vast digital landscapes of cyberspace, we are not simply traversing through lifeless data, but immersing ourselves in a consequential world that reflects the order and complexity of our physical reality. This revolutionary approach to cyberspace isn't merely a mirage of science fiction, but a tangible exploration of its key principles, built on the bedrock of public key cryptography, hashing, proof-of-work, bitcoin, and nostr.
Through the implementation of a meta-protocol layered over nostr, cyberspace opens a myriad of opportunities – drifting through the boundless expanses of the digital cosmos, crafting personal domains, or engaging in vibrant social interactions. Just as actions in the physical world carry costs and consequences, so too does cyberspace enforce its own unique set of rules and repercussions, fostering a sense of shared responsibility, fairness, and cooperation among its denizens.
Envisioned as a playground for creativity, commerce, and social organization, cyberspace, in its current formative state, already shows tremendous potential for an expansive array of use cases. Its inherent thermodynamic properties and permissionless nature offer a groundbreaking amalgamation of digital and physical realities, poised to profoundly augment our capabilities, experiences, and opportunities in a dynamic, inclusive, global, and consequential realm.
However, the most exciting aspect of cyberspace is not merely what it currently offers, but its potential to continuously evolve and redefine itself. As more people engage with and contribute to its development, it's bound to expand and morph in ways we can hardly fathom today.
As we stand on the cusp of this digital frontier, we are not chasing after phantoms of fiction. Instead, we are architects and pioneers of a revolutionary new realm, where digital existence converges with physical principles. This remarkable blend of technology and human imagination sets the stage for an unprecedented era of exploration and innovation, signaling a future that is as exciting as it is unpredictable.
Join me on this grand endeavor to shape cyberspace, to mold this new frontier into a shared and diverse digital world that reflects the best of human spirit and ingenuity. Together, let's step into cyberspace, the frontier of the future.
Build with me
Cyberspace is for humanity, and therefore I desire as many humans to be involved in its construction as possible. I have created the following resources for anyone who wants to learn more or get involved:
Join the ONOSENDAI Telegram group: https://t.me/ONOSENDAITECH
I love answering questions! Please hop in and ask away!
Pull requests welcome on the spec: https://github.com/arkin0x/cyberspace
Check out the first cyberspace client, ONOSENDAI: https//onosendai.tech (thermodynamics still in development)
Pull requests welcome on ONOSENDAI: https://github.com/arkin0x/ONOSENDAI
whoami
My name is Nick. I go by arkinox. I have been making websites since I was 11 and designing games since I was 4. I've been the director of web for a midwest marketing firm for 10 years and the co-founder and senior vice president of an augmented reality company, innovatar.io, for 4 years.
Support FOSS
If you would like to support development of this protocol I would love for you to get involved. Also, I am accepting donations and looking for opportunities to pursue it full time.
Follow me on nostr: npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w
Zap me with Bitcoin Lightning: arkinox@getalby.com
Soli Deo gloria
-
 @ 34c0a532:5d3638e4
2023-03-16 13:14:53
@ 34c0a532:5d3638e4
2023-03-16 13:14:53Most bitcoiners have their own, much different definition of what it means to orange pill a person. I’ve seen mentions of getting a taxi driver to download a lightning wallet and sending the payment in sats to them. Is that truly orange-pilling? Hmm… no. It is a great first step, but what makes you believe that that person won’t go on to shitcoins after learning about the ease of using cryptocurrency?
So, let’s define what that is in the terms of this guide.
To orange pill someone means to get them to take the first step into learning about bitcoin, money, self-custody, being sovereign, and to teach them to start questioning the world of lies we’ve been fed our entire lives.
Too poetic? Okay, here’s a more specific one:
To orange pill someone means showing them how to send and receive a bitcoin transaction, explain to them the importance of keeping their seed words safe, and showing them more articles, books and guides so they can go further down the rabbit hole.
I think that’s better, don’t you?
No matter what your definition of orange-pilling is, let’s discuss a few things first.
Orange-pilling comes from the scene in the Matrix where Morpheus offers the blue and the red pill to Neo.
This your last chance. After this there is no turning back. You take the blue pill, the story ends. You wake up in your bed and believe whatever you want to. You take the red pill, you stay in Wonderland, and I show you how deep the rabbit hole goes. Remember, all I’m offering is the truth. Nothing more. ~ Morpheus
The fact that the terms comes from the Matrix is absolutely perfect, because the Matrix is based on Plato’s Allegory of the Cave. Everybody knows the Matrix so let’s talk about the Cave. Inside the cave, people are chained up, in the dark. The only thing they can do is talk to each other and stare forward, where there’s a dim light on the cave’s wall. Someone is moving around objects, throwing shadows on the wall. The people can never see the three-dimensional object, they can only see a shadow, a projection of it, so their world is limited by that knowledge.
Someday a group of people manage to break out of the Cave. They go out into the light, their eyes hurt, the world is massive, they get a panic attack by the lack of a rock ceiling on top of them. It’s vast, it’s too much to bear. And they run back into the cave and tell everyone what they saw, that it’s too bright, too open, too much everything. Objects are real, there’s light everywhere and colours. So many colours, not just the flame, the rock and the shadow.
And they don’t believe them. Maybe they even get angry at them and attack them. Who are these fools to claim that the world is not what they think it is? Who are they to suggest that we’ve all been lied to all our lives?
And that’s the first thing you need to keep in mind when trying to orange pill someone.
Why do some people find it so hard to believe in bitcoin?
The answer is simple. It’s because understanding bitcoin requires acknowledging you’ve been tricked your entire life.
The culture shock is real, I’ve been through it. The stages are as follows:
What is money? You start to learn what money really is, and how fundamentally flawed the Keynesian system has become. You see that the only way forward is by a hard money standard, whether that’s gold or bitcoin. Then you realise that in a world of information, the only logical step is bitcoin. Then why bitcoin? You start to read about it’s properties. It’s antifragile, decentralised. Why is that important? Nobody can control, it great. Why is it like gold that can be attached to an email? Then there’s the anger and disbelief. We’ve been fooled. Why doesn’t everybody see this? You read everything about bitcoin, you listen to podcasts, talk on bitcoin twitter and nostr with other plebs. Nobody seems to have all the answers but they make far more sense than the lies of the mainstream media. You talk to your friends and family, you come off as crazy at best. As I said, you have to acknowledge the trauma the other person is going through. It’s a culture shock, and not many want to go through with it. Think of Plato’s Allegory of the Cave, people who got out into the world went back and told everyone that there’s more to life than the shadows on the wall. Or, the same allegory being told by the Matrix, with Cypher wanting to go back, to forget.
We call that Bitcoin Derangement Syndrome, BDS. It’s hilarious but it’s so real. Many early bitcoiners, people who have spend years of their lives either advocating for it or working on it, some making or losing fortunes in the process, go back to the fiat world, shift gears completely, rant and rave against bitcoin and dive back in the Matrix, the Cave, taking the blue pill. They want to be fiat rich, they lie and delude themselves that everything is okay in the world and if they get just enough money they’d be okay.
But they won’t. This is real, and no matter how many lies they tell themselves things will not change unless we change them ourselves. Babies are dying, that’s true. In wars, in artificially induced poverty, in carrying on with the Keynesian ways of thinking of endless imperial expansion and exploitation.
I’ll be honest, bitcoin rewires your brain.
Do you really wanna force that on people?
Yes?
Then let’s read on.
Why is it sometimes so hard to explain, persuade or convince people about bitcoin? Here’s a harsh truth. It’s because you’re the counterparty risk.
When your car breaks down, you go to a mechanic, you seek expert knowledge. He tells you what’s wrong and you generally accept it. Why? Because unless you’re an expert on cars, you don’t have pre-existing knowledge about this specific situation. Nature abhors a vacuum. The mechanic’s knowledge and expertise fills up that vacuum of knowledge.
Why is it different with bitcoin, then?
Because most people believe they already understand money. There’s no vacuum for their knowledge to fill. Like a woman going to a male gynecologist thinking she knows better because she’s the one with the female body, a nocoiner believes they know better because, see? They have been handling and making money all their lives! Who are you to claim things aren’t how they used to think they are?
Yes, sure. You’re the one with the female body, you’re the one with the wallet. But have you actually taken the time to study it? Have you invested the necessary six years in medical school or the 100 hours it takes to grasp bitcoin?
No.
But they don’t accept that. When you make statements about bitcoin, it collides with their pre-existing frame of reference. When that happens, their mind reflexively casts doubts on the new information, actively fights it and rejects it, because it doesn’t conform to what they know. Their mind is the bearer asset, you are the counterparty risk.
Okay, great. How do you overcome this, then?
By taking the time with them. You can’t force someone to get orange-pilled, it’s not shoving knowledge down their throats. They have to do it themselves, so you start small. Plant a seed. Make them question what they know. That tiny seed, just like in Inception, will grow and push aside the other propaganda in their minds, leaving some space for new information to fill the void.
“Why did they stop having money backed by gold?”
That’s one seed.
“Who prints all these new billions?”
Another. Take your pick, it depends on the person you’re talking to.
A good question makes the nocoiner access their accepted knowledge. They usually think they have the answer and you should listen to it, not shutting it down. Ask them to research it further, to back their claims, to look things up. If they don’t have the knowledge, a new vacuum is created and their curiosity will want to fill it up.
Nocoiner: Bitcoin isn’t backed by anything.
You: Okay. Then what would make good money in its place?
Make them talk by asking questions. As they talk, they’ll realise they have massive gaps in their knowledge. You can help them then, but they themselves have to fill up those gaps by asking more questions and getting them to talk more. Why? Because if someone tells something to themselves they will believe it much easier than having you say it to them. Try and lead them to conclusion, a revelation.
When persuading someone, the person talking the most is the one really getting persuaded. Why? Because when you talk you engrave those words into your brain as facts.
Nocoiner: Bitcoin wastes too much energy.
You: How do you determine how much is too much energy to use?
You will never change their minds, they have to change it themselves. You can only help show them the way, they’re the ones that have to do it. Questions are the key to that process.
Tell them less, ask more.
What questions make people curious about bitcoin? You never know, it depends on what ails the person. Think about their pain. If they’re living in Turkey or Argentina, for example, their pain is massive inflation. You might say, “You’re already using USD to protect your monetary value against inflation, right? How about adding BTC to the mix?”
People in those countries generally grasp this concept a lot quicker. The local lira is the crap kind of money, they spend it often. The USD is the good kind of money, they save it, spending it only when absolutely necessary. And gold is the best kind, keeping it hidden in safes and mattresses. Only to be spent in an emergency. They don’t have the financial privilege to insulate them from the need for bitcoin, they already get these layers of hardness in their money, so bitcoin is a lot easier for them.
“What is money?” is another good question. Most people will answer it, and of course it will be flawed and all over the place. Then you might say, “It’s the promise of future value,” and then discuss how bitcoin has a monetary policy that’s planned out for the next 120 years and how nodes and miners facilitate that design. And especially point out how hard it is to change.
“What happened in 1971?” That’s a good one. Get them to look up the fiat monetary system and figure out how it’s not backed by anything. Get them angry at the Keynesian economists, how they’ve ruined entire countries. 2008 money crisis? Inevitable, under the fiat standard. Forget about bitcoin, point your finger towards the rot. It’s all historical fact, they can’t call you a conspiracy theorist. Most people still think that money is backed by gold. Get them to tell it to other people, see their reactions.
This was a part of my guide. Let me know what you think. Soon to be posted at https://georgesaoulidis.com/how-to-orange-pill-people/
-
 @ 9ecbb0e7:06ab7c09
2023-07-23 04:35:18
@ 9ecbb0e7:06ab7c09
2023-07-23 04:35:18Tres cubanos fueron sentenciados por tráfico sexual y delitos relacionados cometidos en clubes de striptease en el área de Houston, según informó el portal de noticias oficial del Gobierno de EEUU.
Rasiel Gutiérrez Moreno, de 38 años; Hendry Jiménez Milanés, de 39; y Rafael Mendoza Labrada, de 29, fueron sentenciados a 210 meses de prisión y a pagar 451.298 dólares en restitución, 120 meses y 359.108 en restitución, y tiempo cumplido de 34 meses, respectivamente, indicó en una nota el Departamento de Justicia.
De acuerdo con la información, Gutiérrez Moreno se declaró culpable de tráfico sexual y viajes interestatales en ayuda al crimen organizado. Como parte de su acuerdo de culpabilidad, Gutiérrez Moreno admitió haber llevado mujeres de Cuba a EEUU a las que impuso deudas de contrabando infladas de hasta 30.000 dólares
"Gutiérrez Moreno obligó a las mujeres a trabajar en clubes de striptease del área de Houston, como Michaels' International, donde bailaban y participaban en actos sexuales comerciales con los clientes del club, entregando todas las ganancias a Gutiérrez Moreno para pagar su deuda. El acusado reconoció además el contrabando y la imposición de deudas para coaccionar a aproximadamente otras 20 mujeres de esta manera".
Gutiérrez Moreno admitió que, para mantener bajo su control a una víctima identificada como 1 mientras trabajaban para él, se jactaba de sus actos de violencia contra otras mujeres y sus familias.
La nota del Departamento de Justicia indica que, en una ocasión, Gutiérrez Moreno golpeó a otra mujer poco antes de que la Víctima 1 llegara a su casa y se aseguró de que la Víctima 1 observara las heridas de esa mujer. Cuando la Víctima 1 escapó de Gutiérrez Moreno, el acusado se comunicó con su familia tanto en Miami como en Cuba para exigirle que volviera a trabajar y terminara de pagarle la deuda.
Por su parte, Jiménez Milanés se declaró culpable de coerción y seducción, y Mendoza Labrada de viajes interestatales en ayuda del crimen organizado.
"Estos acusados usaron cruelmente la violencia, las amenazas de violencia y las deudas falsas para obligar a las víctimas vulnerables a participar en el sexo comercial", dijo la fiscal general auxiliar Kristen Clarke, de la División de Derechos Civiles del Departamento de Justicia.
"Este tipo de esquema de tráfico sexual es ilegal, deshumaniza y aterroriza a las mujeres que no pueden liberarse", añadió.
"Estos traficantes de personas aterrorizaron a las mujeres migrantes, utilizando los clubes de striptease de Houston combinados con amenazas psicológicas y violencia sexual para su beneficio económico personal", dijo el fiscal federal Alamdar S. Hamdani, del Distrito Sur de Texas.
"Las víctimas llegaron a EEUU en busca de una nueva vida, eran especialmente vulnerables y los acusados se aprovecharon de eso".
Casos similares han sido noticia con anterioridad. En 2017 Silvio Clark Morales fue encontrado culpable de llevar mujeres cubanas a EEUU como parte de una red de tráfico sexual. Clark Morales explotó a más de 20 mujeres, de entre 20 y 25 años, a las que prometió presentarlas en Miami como bailarinas de clubes nocturnos.
El mismo año, pero en España, la Policía Nacional desmanteló en Murcia una red de explotación sexual que usaba prácticas de santería para coaccionar a mujeres de origen sudamericano, a quienes captaba y obligaba a ejercer la prostitución bajo la amenaza de rituales de magia negra y sacrificio de animales.
El desmantelamiento de la red criminal permitió detener a siete personas de nacionalidad brasileña, cubana y española y liberar a diez mujeres extranjeras, ocho en situación irregular en España, que eran explotadas sexualmente en cinco viviendas en las que se encontraron "altares de santería".
El siguiente año, 2018, trascendió que al menos una veintena de mujeres cubanas fueron víctimas de explotación sexual en Uruguay. Todas habían llegado a la nación suramericana con la promesa de acceder a trabajos bien remunerados.
También en 2018, en España, agentes de la Policía Nacional detuvieron en Gran Canaria a un hombre de 31 años de edad y a una mujer de 26, ambos cubanos y sin antecedentes policiales, como presuntos autores de delitos relativos a la prostitución, trata de seres humanos y favorecimiento de la inmigración irregular. Los arrestados captaban a mujeres de entre 20 y 25 años en países sudamericanos, principalmente a través de las Redes Sociales.
-
 @ 9ecbb0e7:06ab7c09
2023-07-23 04:34:03
@ 9ecbb0e7:06ab7c09
2023-07-23 04:34:03Un empleado estatal acusado de especulación en Guantánamo, dos hombres detenidos y acusados de robar y sacrificar ganado en Villa Clara y un ladrón de teléfonos detenido en Holguín son algunas de más recientes evidencias de la inseguridad que vive Cuba, expuesta desde perfiles oficialistas que pretenden dar una imagen de eficiencia de la Policía.
El perfil en Facebook "EDWIN LEVIS Revolución" publicó que "efectivos de la Policía Nacional Revolucionaria (PNR) en Guantánamo detuvieron a un trabajador de la Empresa Mayorista Guantánamo, cuando llevaba consigo más de medio millón de pesos en moneda nacional sin justificación alguna".
Según el escrito, el hombre, que no fue identificado, pero su carné de identidad sí fue expuesto, "se está procesando preliminarmente por el delito de 'especulación'".
Sin más detalles, el bloguero oficialista concluyó con etiquetas procastristas como "#CreoEnTiCuba #LaGuardiaRevolucionariaNoSeDescuidaráJamás #SeguimosEnCombate #CubaDefiende".
El perfil Fuerza del Pueblo, uno de los más activos del oficialismo para divulgar la solución de delitos y la captura de delincuentes, publicó sobre el arresto, en un poblado de Villa Clara, de Carlos Liban Pérez Sarduy y su hijo Lisvany Pérez Fernández, a quienes catalogó de "elementos antisociales" y "autores del hurto y sacrificio del toro de ceba perteneciente al campesino Reinier Rodríguez, quien reside en el poblado de Manacal".
Según la información, en un registro a la vivienda de ambos las autoridades "ocuparon carne y otros medios que utilizaban para cometer estas fechorías".
"Nos comentan algunos campesinos del lugar que están contentos con la detención de estos delincuentes, ya que en varias ocasiones habían sido víctimas de robos y sacrificio de animales (caballos, vacas, cerdos, chivos)", añadió.
La página también dijo que los detenidos "ya habían cumplido prisión anteriormente".
"Una vez más estos delincuentes tendrán que cumplir sanción por todos los crímenes cometidos y los pobladores de Manacal en Manicaragua pueden estar seguros de que las fuerzas del MININT y la Fiscalía no permitirán que estos hechos queden impunes ante la ley", concluyó.
Por otra parte, el perfil Cazador Cazado dio cuenta de la detención de jóvenes cubanos que circulaban en una motorina y arrebataron en la mañana del miércoles un teléfono celular a una adolescente en la ciudad de Holguín.
El incidente ocurrió en las inmediaciones del centro Mixto Alberto Sosa, localizado en el reparto Pueblo Nuevo, en la capital provincial.
"Allí parada estaba una adolescente, estudiante del centro escolar, con su teléfono celular en la mano. Lo menos que ella pensó es que esos jóvenes que se aproximaban en una motorina venían con el propósito de arrebatar violentamente su móvil, marca Redmi Note 9", señaló la página.
El perfil celebró que tras la denuncia de la joven, identificada con el nombre de Laritza, los asaltantes fueron capturados en aproximadamente "seis horas". Aunque la página habla de más de un asaltante, solo mostró a uno, identificado como "Raulito".
La prensa oficial niega el auge de los delitos en Cuba, se limita a dar propaganda a casos resueltos y muy puntualmente se hace eco de algunos muy mediáticos y escandalosos. Mientras el régimen promueve una imagen de país seguro para el turismo, los cubanos denuncian constantemente situaciones de criminalidad, asesinatos incluidos, y los perfiles oficialistas vinculados con la Seguridad del Estado en las redes sociales intentan levantar la imagen de las criticadas fuerzas del orden y atajar lo que la prensa independiente publica al respecto. Esa estrategia del régimen, sin embargo, es un reconocimiento tácito de la inseguridad ciudadana.
-
 @ c75622fd:a9b66e1d
2023-03-18 15:09:42
@ c75622fd:a9b66e1d
2023-03-18 15:09:42[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
[19]
[20]
[21]
[22]
[23]
[24]
[25]
[26]
[27]
[28]
[29]
[30]
[31]
[32]
[33]
[34]
[35]
[36]
[37]
[38]
[39]
[40]
[41]
[42]
[43]
[44]
[45]
[46]
[47]
[48]
[49]
[50]
[51]
[52]
[53]
[54]
[55]
[56]
[57]
[58]
[59]
[60]
[61]
[62]
[63]
[64]
[65]
[66]
[67]
[68]
[69]
[70]
[71]
[72]
[73]
[74]
[75]
[76]
[77]
[78]
[79]
[80]
[81]
[82]
[83]
[84]
-
 @ 9ecbb0e7:06ab7c09
2023-07-23 04:33:23
@ 9ecbb0e7:06ab7c09
2023-07-23 04:33:23Un fallecido y tres lesionados fue el saldo total del grave accidente de tránsito entre un tren y un camión ocurrido en la mañana de este viernes en el municipio Boyeros, según informó la Unión de Ferrocarriles de Cuba.
La nota oficial precisa que el siniestro ocurrió a las 10:40 am (hora local) del kilómetro 13,300 de la línea Sur -zona conocida como Mazorra- en el municipio Boyeros, cuando un camión marca Hino (con matrícula B032081) se interpuso en el camino del tren No. 139, coche motor No. 2213, destinado a la transportación de pasajeros de la Habana a San Antonio de los Baños.
Tanto el ciudadano fallecido como los otros tres que resultaron heridos eran trabajadores de una cooperativa de Producción Agropecuaria (CPA) que viajaban a bordo del camión. Los lesionados fueron trasladados de inmediato al hospital Nacional.
La información oficial refiere que de acuerdo con una inspección realizada por miembros de una comisión creada al efecto, se determinó que la causa del accidente fue que el conductor del camión, identificado como Isidro Caridad Reyes Domínguez, no detuvo la marcha antes de cruzar el paso a nivel.
Las investigaciones continúa con el fin de determinar "otras violaciones al margen del hecho".
Al cierre de esta nota no está clara la condición clínica de los tres heridos sobrevivientes.

No es la primera vez en los últimos meses que fallece una persona en un accidente ferroviario en Cuba.
A principios de junio, un hombre murió tras ser atropellado por un tren en el municipio cabecera de Las Tunas, según reportes en redes sociales. En ese caso al aparecer la víctima era sordomudo.
Días más tarde, dos hombres fallecían al ser atropellados por un tren en el municipio de Urbano Noris, en Holguín, en un aparente caso de suicidio.
En septiembre del pasado año, dos personas murieron y una quedó herida al chocar el carro en el que viajaban contra un tren en La Habana. En ese caso el trágico accidente ocurrió de madrugada, en la avenida Boyeros y la línea del ferrocarril, antes de llegar a la calle 100.
Meses antes, en junio de 2022, la colisión de un tren de pasajeros con una camioneta en Bejucal, provincia de Mayabeque, dejó un saldo de tres personas lesionadas y una niña de tres años fallecida.
El reporte de accidentes de tránsito no da tregua en las carreteras cubanas.
A nivel nacional, las cifras de accidentes viales siguen siendo dramáticas en Cuba. Entre enero y mayo de 2023 ocurrieron 3,620 accidentes de tránsito en la isla, que cobraron la vida a 290 personas y dejaron 2,807 lesionados, según cifras oficiales.
Personas en edades entre los 21 y 35 años representaron el 22 % de los afectados en los accidentes, mientras que las edades de la mayoría de las víctimas fatales oscilaban entre los 46 y 55 años.
En Cuba seis de cada diez accidentes dejan víctimas, fundamentalmente por el choque de vehículos. En el caso de los atropellos a peatones, por cada cinco atropellos, muere una persona. El horario de mayor incidencia de accidentes es entre las 3 y las 6 de la tarde, y el 70 % de los incidentes viales ocurren en zonas urbanas.
-
 @ d61f3bc5:0da6ef4a
2023-03-15 01:10:05
@ d61f3bc5:0da6ef4a
2023-03-15 01:10:05The idea that a user can sign a note and publish it to any number of relays is incredibly simple and powerful. That signed note can then be relayed further and with every new copy it becomes harder to censor. This core simplicity has made Nostr very popular with developers and users.
However, the brunt of the work is currently being done by just a handful of relays:

Given today’s network topology, it is not clear how Nostr could support say 100M users. In addition, the current breed of Nostr clients – while being impressive achievements of decentralized social media – suffer from sluggish UIs when compared to their legacy centralized counterparts.
Let’s consider an approach that might help with scaling, UX, and perhaps even decentralization.
Caching Services
Imagine a service with the following characteristics: - Stores all public Nostr content. Connects to all known Nostr relays and collects content in real time: user metadata, notes, reactions, all events. In short, the entire public Nostr network.
-
Can keep full archive or pruned content. Content can be pruned when the allocated disk space runs out. Service operators can decide how much of Nostr they wish to keep.
-
Provides fast response times. Clients connecting to the service can expect response times that match or beat the legacy centralized networks. Most content is served from the RAM.
- Provides simple aggregations. Counters for likes, replies, reposts, zaps, and sats zapped are included with every post in the feed.
Such a service is definitely useful for many different applications. But wouldn’t standing up a service like this introduce a centralizing factor to Nostr? Let’s take this thought experiment a step further.
Now imagine that anyone can stand up a caching service with minimal effort and a modest hosting budget. Imagine that caching services are built in a standard and open manner, so that they can interoperate, sync content, and help bootstrap new instances. Considering the incentives, we could end up with hundreds of Nostr caches all over the Internet. Each new copy makes Nostr more robust.
Client Behavior
For Nostr clients, there are pros and cons to using a caching service. The obvious benefits are the UI speed and the improved UX. The downside is that a certain amount of trust is placed in the caching service. Let’s take a closer look at how this would work and how trust could be reduced.
The client connects to a caching service and immediately receives and displays the full feed for the specified user. To reduce trust, the client connects to a subset of relays in the background and fetches the content for comparison. Since all content is signed, the caching service can only lie by omission. The client displays and clearly visually marks any content it found on the relays that was not sent by the service. If the user loses confidence in a cache instance, they could simply point their client to another one, or turn caching off altogether. The client should be fully functional when caching is turned off. The ability to work with a caching service is an extension of Nostr client functionality, not a replacement for standard client capabilities.
When it comes to publishing, there are no changes to the standard Nostr client behavior: all content is published directly to the relays. Caching services should be viewed as a transient layer whose purpose is to improve the UX and reduce the load on the relays.
A Scaling Scenario
Let’s now imagine that Nostr is a raging success. The network has grown to 100M active users. There are hundreds of Nostr apps and services, thousands of active relays. Apps range from highly specialized “micro apps”, to the more elaborate Nostr “everything apps”, dedicated Nostr browsers, and other amazing things we can’t even imagine today.
In this scenario, it is likely that Nostr apps will use a range of caching strategies to serve their users. The most popular apps, with millions of active users, are likely to invest in their caching infrastructure. The up-and-coming apps that wish to compete with the best, but don’t yet have a lot of users are likely going to stand up small scale caching services and grow them as their userbase grows. Finally, there would be a number of apps that don’t use a caching service at all.
The beauty of this outcome is that even users who have millions of followers could publish their content to a handful of low-powered relays. As long as those relays are publicly accessible, the caching services will pick up their content and dramatically reduce the load on them. In addition, taking down any individual cache instance does nothing to hurt Nostr. Users can simply point their clients to any other cache instance, or the relays themselves. Censorship is strictly harder in a world where caching services exist. Those who wish to enforce censorship would have to take down all the relevant relays plus all the cache services.
Conclusion
Caching solutions for Nostr are inevitable. They are very useful, and the incentives are there for them to be built. The only question is whether they will be done in an open and interoperable way or a closed and proprietary way.
If you’ve made it this far, I know what you’re thinking: “Can we see this in action?”
Yes! A preview of this concept is available at primal.net.
The app itself is not fully functional yet, but you can definitely see caching in action. It’s fast. :)
We are actively developing Primal, so make sure you check back often. We have many juicy features in the pipeline. Feel free to reach out with feedback and feature requests. If you are going to Nostrica, then I’ll see you there in a few days! 🤙
-
-
 @ 3bf0c63f:aefa459d
2022-10-29 19:19:00
@ 3bf0c63f:aefa459d
2022-10-29 19:19:00What is better than bounties and grants?
The experience with bounties from HRF wasn't great. No one has answered to the calls for implementing what they wanted because the work was too much and the risk of not getting paid very real. The experience with grants in general from Spiral is also not great: many random developers making cool but useless projects, wasted money.
The two kinds of open-source financial support that have worked so far are:
- Paying people who are already doing useful work so they can continue doing that. That is the experience of some people who are "maintaining" Bitcoin Core, for example, or other open-source projects. You're doing a thing, you've proven yourself valuable and you definitely seem to be interested in that personally such that you don't need a boss telling you what to do, so take the money and just keep doing that.
- Structured open-source initiatives, like the LDK effort. Although LDK is arguably useless, it has a stated goal and that goal is being delivered. I don't have any knowledge about how its development process works, but they have people being paid and "bosses" that direct the work to be done, as any team needs. So it is not the same as an open grant.
The thing that is missing is a way to provide these open loose grants to people that don't require bosses, but also that don't just pick a winner and let them do whatever stupid idea they might have (Spiral grants), and also do not mandate that they do something big before being paid and offers no guarantee of that they will be paid whatsoever.
The solution: smaller flexible bounties in large quantities
My suggestions is: instead of giving 1 bitcoin for a huge very specific project, state some "principles", or "problems", in a loose manner, that you want to see solved. For example, "we, the organization X, wants to see projects that use zero-knowledge proofs to help Bitcoin somehow, because we love zero-knowledge proofs".
Then state that you're going to give 20 grants of 0.05 bitcoins each, at random times, for projects that you see being done that may be on the right track.
That will tilt people that may had a small inclination to work on these problems to actually start doing something, and if they see that what they're doing is being appreciated and awarded with a payment, they will be more incentivized to finish it. There could even be a conditional bounty (like HRF did with Cashu) for finishing the project with certain requirements, but this only works after some structure is already in place for a certain project.
-
 @ 3bf0c63f:aefa459d
2022-10-29 13:24:00
@ 3bf0c63f:aefa459d
2022-10-29 13:24:00On Bitcoin Bounties
The HRF has awarded two bounties yesterday. The episode exposes some of the problems of the bounties and grants culture that exists on Bitcoin.
First, when the bounties were announced, almost an year ago, I felt they were very hard to achieve (and also very useless, but let's set that aside).
The first, "a wallet that integrates bolt12 so it can receive tips noncustodially", could be understood as a bounty for mobile wallets only, in which case the implementation would be hacky, hard and take a lot of time; or it could be understood as being valid for any wallet, in which case it was already implemented in CLN (at the time called "c-lightning"), so the bounty didn't make sense.
The second, a wallet with a noncustodial US dollar balance, is arguably impossible, since there is no way to achieve it without trusted oracles, therefore it is probably invalid. If one assumed that trust was fine, then it was already implemented by StandardSats at the time. It felt it was designed to use some weird construct like DLCs -- and Chris Steward did publish a guide on how to implement a wallet that would be eligible for the bounty using DLCs, therefore the path seemed to be set there, but this would be a very hard and time-intensive thing.
The third, a noncustodial wallet with optional custodial ecash functionality, seemed to be targeting Fedimint directly, which already existed at the time and was about to release exactly these features.
Time passed and apparently no one tried to claim any of these bounties. My explanation is that, at least for 1 and 2, it was so hard to get it done that no one would risk trying and getting rejected. It is better for a programmer to work on something that interests them directly if they're working for free.
For 3 I believe no one even tried anything because the bounty was already set to be given to Fedimint.
Fast-forward to today and bounties 1 and 3 were awarded to two projects that were created by the sole interest of the developers with no attempt to actually claim these bounties -- and indeed, the two winners strictly do not qualify according to the descriptions from last year.
What if someone was working for months on trying to actually fulfill the criteria? That person would be in a very bad shape now, having thrown away all the work. Considering this it was a very good choice for everyone involved to not try to claim any of the bounties.
The winners have merit only in having pursued their own interests and in creating useful programs as the result. I'm sure the bounties do not feel to them like a deserved payment for the specific work they did, but more like a token of recognition for having worked on Bitcoin-related stuff at all, and an incentive to continue to work.
-
 @ 9ecbb0e7:06ab7c09
2023-07-23 04:32:22
@ 9ecbb0e7:06ab7c09
2023-07-23 04:32:22La opción de resolver la deuda externa de Cuba con la cesión de recursos nacionales a empresas extranjeras, defendida este miércoles por el profesor oficialista Juan Triana Cordoví, ha sido refutada por el economista Pedro Monreal. Lo que el primero considera un método para refinanciar y "revitalizar" el socialismo en la Isla, para el segundo supone el riesgo de "ser insuficiente y de menoscabar la soberanía".
Triana, que enseña Economía en la Universidad de La Habana y escribe una columna en el medio OnCuba, plantea la necesidad de renegociar la deuda de la Isla y limpiar la imagen del país, que ha llegado a convertirse en "uno de los de más alto riesgo en la región" en materia de inversiones.
Para ello sugiere que, en una hipotética negociación, se podría echar mano de los "activos" que en teoría pertenecen al "pueblo de Cuba", si bien están gestionados concretamente por su "administrador": el Estado. Triana se refiere, en primer lugar, a los hoteles, que prefiere no entregar completamente a compañías extranjeras sino convertirlas en dueños de "una parte de las acciones".
También alude a las 2.417 empresas estatales, de las cuales –calcula– solo 12 (el 0,4% del total) son realmente "estratégicas" y llevan el peso de la economía nacional. Triana recomienda que estas compañías que "deciden el juego" no se toquen, en parte porque algunas de ellas ya se comparten con entidades extranjeras: es el caso de la canadiense Sherritt International –cuya deuda con la Isla se paga con la sobreexplotación de minas cubanas de níquel y cobalto–, Havana Club –gestionada junto a la francesa Pernod Ricard– y Habanos, que posee en parte España.
Triana recomienda que estas compañías que "deciden el juego" no se toquen, en parte porque algunas de ellas ya se comparten con entidades extranjeras.
La negociación se haría con el resto de las empresas estatales, que podrían ser salvadas de su mediocridad financiera si se comparten con inversores extranjeros, que trabajarían, sin proponérselo, para "salvar" el socialismo en la Isla.
A estos dos elementos, Triana añade las tierras ociosas y los solares yermos en las ciudades, donde ya hay "varios edificios construidos por empresas inmobiliarias capitalistas" –como el Centro de Negocios de Miramar–. La fórmula del canje de activos, reconoce el profesor, podría ser cuestionada, pero al fin y al cabo, concluye "algo que comenzó hace más de treinta años cuando se firmó aquel primer negocio con un capitalista extranjero y en apenas meses nació el primer hotel cinco estrellas en Varadero".
Sin embargo, Triana no sitúa la clave para dar el paso en la voluntad del Estado, que bloquea a conveniencia los movimientos económicos del país, sino en el "consenso" con el pueblo, al cual recomienda "explicar" lo que se pretende hacer.
Precisamente de este argumento erróneo –presuponer que el pueblo cubano tiene algún control sobre la gestión de la economía nacional– parte Monreal para rebatir la sugerencia de Triana. En una serie de hilos de Twitter, el economista expone no solo por qué el canje masivo de activos para pagar la deuda es impracticable, sino el grave riesgo político que entraña para Cuba.
Afirmar que el pueblo es propietario de los activos estatales es, como mínimo, un presupuesto "controversial" a la hora de razonar la posibilidad de una apertura económica. "Poder", afirma Monreal, significa capacidad para "decidir una diferencia" y contar con una "propiedad" concreta.
"Difícilmente pudiera validarse el ejercicio del poder del pueblo, específicamente de los asalariados, en el marco de un paquete económico como el 'ordenamiento' que ha 'comprimido' salarios y que recarga desproporcionadamente el costo del ajuste sobre los trabajadores", resume Monreal. "Las explicaciones al pueblo son problemáticas cuando políticamente se le trata como 'arcilla' para moldear y no cómo sujeto activo (ciudadanos) con capacidad efectiva para impulsar o para detener propuestas de políticas públicas".
Además, el pueblo cubano no cuenta con "espacios ciudadanos efectivos de crítica al Gobierno", lo cual imposibilita su participación en la toma de decisiones.
El aspecto económico del problema es todavía más grave, y para analizarlo Monreal remite a los datos que reflejan la gran "escala" de la deuda externa cubana, cuyo "reciente empeoramiento" deja muy poco margen de acción, incluso al Estado.
El economista parte de un argumento central e incuestionable: "La deuda externa acumulada de Cuba es hoy mayor que el Producto Interno Bruto", y la hiper-devaluación del peso cubano en 2021, tras la Tarea Ordenamiento, fue la estocada final en la capacidad del país de asumir el reembolso en la situación actual.
El país tuvo que desembolsar 1.606 millones de dólares para pagar el servicio de la deuda en 2022, al mismo tiempo que registraba un déficit de 1.629 millones en su cuenta corriente, que refleja un total de ingresos (exportaciones de bienes y servicios) inferiores a los gastos. Este alarmante dato apunta a una "severa contracción de los recursos" para enfrentar la deuda.
El deterioro creciente de la cuenta corriente repercute en las reservas de divisas con las que cuenta Cuba, señala Monreal. Además –y aunque los datos oficiales que ofrece La Habana están desactualizados– la crisis actual precede a la pandemia de coronavirus, uno de los pretextos habituales del régimen para justificar el empobrecimiento del país, y se relaciona con un "incremento súbito de la deuda a corto plazo", que complicó la condiciones del pago a los acreedores.
El estancamiento puso a Cuba entre la espada y la pared frente a los bancos internacionales y a sus proveedores, entre ellos el Club de París
Ese estancamiento puso a Cuba entre la espada y la pared frente a los bancos internacionales y a sus proveedores, entre ellos el Club de París. La información que publicó este último organismo expuso las distintas renegociaciones que el régimen de La Habana se vio forzado a hacer con sus acreedores desde el año 2020.
Buscar una solución de pago basada en el canje de activos es peligrosa a nivel económico, asegura Monreal, sobre todo porque, considerando la escala del problema, lo que puede ofrecer Cuba es "relativamente reducido". Por eso, insiste, el verdadero saldo de una medida así se pagaría en lo político y no libraría a Cuba de su condición de "paria internacional" por su desprestigio económico.
Lo que le queda a Cuba –que ya ha entregado, como observa Triana, sus "joyas de la corona": minerales, tabaco y ron– son los servicios de salud, las comunicaciones, el mercado interno en dólares y su dominio sobre las remesas desde el exterior. El Estado cubano está limitado, sostiene Monreal, para negociar estos activos restantes, en parte porque siempre los ha mantenido bajo un estricto control.
La alternativa podría ser, propone Monreal, el sector agropecuario: fomentar la producción agraria privada para garantizar la oferta de alimentos.
Queda el mercado en pesos, que tendría que ser "endulzado" para que tenga algún atractivo para el inversor extranjero, a través de privilegios fiscales. Sin embargo, este proceso sería un obstáculo, considera el economista, si se quiere "privatizar" progresivamente las empresas estatales, un proceso –recuerda Monreal– característico de todos los procesos de reforma iniciados por los partidos comunistas en el poder, "con resultados dispares".
La alternativa podría ser, propone Monreal, el sector agropecuario: fomentar la producción agraria privada para garantizar la oferta de alimentos en moneda nacional y permitir que los productores lleven a cabo operaciones, incluso, con grandes empresas fuera de la Isla.
Esta cesión de activos estatales agropecuarios al sector privado nacional –un sistema que Monreal denomina "concertado"– sí podría ser beneficioso, si se acompaña de otras medidas, para reducir la deuda externa. ¿El resultado? Un doble beneficio: garantizar la soberanía alimentaria que tanto anhelan los cubanos y, en suma, proteger la soberanía nacional.
-
 @ 3f770d65:7a745b24
2023-02-21 01:55:08
@ 3f770d65:7a745b24
2023-02-21 01:55:08Habla is a new blogging platform that's based on Nostr. Or as various Nostr client developers like to call it:
"A way to get Derek Ross to stop sending walls of text".
You can edit posts, which is very nice.
-
 @ de7ecd1e:55efd645
2023-02-20 16:41:11
@ de7ecd1e:55efd645
2023-02-20 16:41:11Web 1.0
The web was proposed in 1989, by Tim Berners-Lee but had been conceived decades earlier. The proposal was not read for a full year, and, after that, allowed as a side-project with the infamous words, "vague, but exciting".
The first version added hyperlinks to existing browser technology. Bundled together were:
- HTTP and the first server
- the first web browser, which was also an editor
- HTML which was based on SGML
Importantly a new type of variable was created, the hyperlink, originally the UDI (Universal Document Identifier). This was later standardized as the URI, with an intent to go beyond just documents to describe Things as well.
Web 1.0 was in competition with Gopher at the time, and Gopher was winning. However, there was a rumour that Gopher might charge some royalties on their protocol, say, to enterprise customers, and with that, the people flocked to the web and made it take off as a grass roots movement.
HTTP was a formal specification in 1997 a full 8 years later, and the architecture of the world wide web was published in 2004, 7 years after that.

Web 2.0
As the web grew as a system, businesses started to spring up around it. A product was a browser called Mosaic, made by Marc Andreessen. While Mosiac added multi media, it also removed the editing functionality in the original browser, a tragic loss.
Without editing built in, the web needed central servers to allow user generated content. These servers grew in time to become giants. A technology added on this was AJAX, which allowed browsers to interact with servers asynchronously to generate richer applications and realtime updates.
This system of greater usability was branded "Web 2.0", popularized by Tim O'Reilly. It was not a formal upgrade of the web, so considered somewhat cheeky by some, the inventor of the web calling the term "jargon". Jargon it is, but the term stuck, and the web did go to a next level, adding important things like search, commerce, and the social web.
With the increased centralization of servers came other problems, such as pervasive tracking, monopolistic effects, censorship and information engineering.
Web 3.0
Web 3.0 was a term coined by Tim Berners-Lee, to represent a radical new idea, which allowed both data and documents to be denoted, on the web. This is of course a radical old idea which was in the web 1.0 proposal, a so-called "semantic web", but with the name 2.0 already co-opted, Tim decided to call it web 3.0.
The was formalized in the RDF (resource definition framework) which made extensive use of XML. Later it was renamed Linked Data, sometimes called the web of data. This has been popularized by schema.org which allows commonly used terms to be put in web pages, allowing easier search, and link previews.
Berners-Lee continues to work on a project called Solid, which stands for "Social Linked Data" (a term I coined in 2012), with the aim of making Linked Data more social, and benefiting from same usability upgrades and lessons learned from "Web 2.0"
The full web 3.0 stack is standardized at the w3c, though has grown over time, leading to a somewhat complex system, and steep learning curve for new developers.
A note on the deceptively named web3. This was an attempt by VCs (including Marc Andreessen again) and others to co-opt the web brand. The main aim was an affinity scam to sell tokens to the unsuspecting public. The issue is that it is not the web at all. In this case Berners-Lee did speak out against it:
https://www.cnbc.com/2022/11/04/web-inventor-tim-berners-lee-wants-us-to-ignore-web3.html
Towards Web 4.0
The first 3 "versions" of the web work well enough. However, the web itself is ephemeral. The average age of a link is 100 days. And there is no good mechanism at web scale to ensure the integrity or version control of information on the web. A possible approach to the next version of the web would be towards a Temporal Web. I wrote a post about this here:
https://lists.w3.org/Archives/Public/public-rww/2021May/0006.html
A significant innovation in recent times is that of Bitcoin, which is a web scale timestamp server. It orders records (blocks) in time, robustly and securely, creating a permanent record. It also, for the first time in history, creates a global currency that is strongly resistant to money printing by fiat.
These two systems working together could create a robust temporal backbone to the web, allowing commerce without rent seeking, and creating whole new business models that are more decentralized, and act in the interests of the users, competing with each other with better services, rather than, serving privacy intrusive monopolies.

Web 5.0
What web 5.0 will look like, nobody knows. However the aim of the original proposal was to have both humans and machines working together. A semantic web was needed for that, to make it easier for machines to participate. Although machines are often censored or blocked on the large platforms, or, even worse, act with perverse incentives to spam users with adverts, noisy information and propaganda.
One guess about web 5.0 could be a web of machine agents, virtual assistants, working together with people to act in the interests of people. This builds on a Temporal web as machines can then evolve over time and the best ones will emerge, in an evolutionary way. Artificial Intelligence can further be folded into the system to optimize its utility to humanity.
A note on web5: This was an earnest attempt to push back on web3 and remove some of the more corrupt aspects, such as copious use of money printing. It has some alignment with the web, but it is not web 5.0, however, I hope it produces something interesting. Never fight an affinity scam with an affinity scam.
IMHO a promising project in this area is Nostr. It reuses the websockets standard to relay information from one user to another which is signed. Importantly, it is grass roots, as the original web was, has already integrated fast cheap payments, with bitcoin and the lightning network in many apps. Unlike the semantic web, it has a very easy developer experience which has seen high uptake from developers. Additionally, the tagging system allows integration with time chains paving a cow path for a temporal web, and then perhaps humans and agents co existing for mutual benefit. We are still early, but time will tell how the web evolves.

Opinions are the views of the author
-
 @ aa55a479:f7598935
2023-02-20 13:44:48
@ aa55a479:f7598935
2023-02-20 13:44:48Nostrica is the shit.
-
 @ f57d8cf5:2602f7c9
2023-02-18 14:20:07
@ f57d8cf5:2602f7c9
2023-02-18 14:20:07 -
 @ 9ecbb0e7:06ab7c09
2023-07-23 04:31:46
@ 9ecbb0e7:06ab7c09
2023-07-23 04:31:46La circulación vial por el túnel de Línea en La Habana quedará cerrada desde el 17 de julio por trabajos de mantenimiento que se planifican durante una semana, por lo tanto, si se sigue el cronograma, todo debe volver a la normalidad para el lunes 24 de julio de 2023.
“Desde el lunes 17 hasta el lunes 24 de julio, a partir de las 9:00 de la mañana y hasta las 5:00 de la tarde, quedará cerrado de forma total a la circulación vial, el sentido Playa – Plaza de la Revolución de dicho túnel, solo se permitirá la circulación del transporte público y régimen especial”, explica el comunicado difundido por el portal oficialista Tribuna de La Habana.
De acuerdo con una nota de la Comisión Provincial de Seguridad Vial de La Habana, se realizarán labores de mantenimiento constructivo y reparación que son impostergables.
Con la obstrucción de la importante vía de comunicación en la capital se harán algunos ajustes para intentar una fluidez en el tráfico. Por ejemplo, se recomienda a los conductores como vías alternativas: calle 7ma, Puente de Hierro, calle 11.
La Comisión Provincial de Seguridad Vial “ofrece disculpas por las molestias que estas medidas pueden ocasionar y exhorta a los usuarios de la vía, a cumplir con las disposiciones establecidas en la presente nota y mantenerse atentos a las orientaciones de los agentes de la autoridad, con el fin de evitar la ocurrencia de accidentes del tránsito”.
El proyecto del túnel de la calle Línea fue elaborado por el ingeniero civil cubano José Menéndez. Como autor y responsable de la concepción y diseño de esta obra de ingeniería, Menéndez fue quien propuso la construcción del túnel en lugar de un puente, argumentando que ambos tenían una capacidad vial similar, pero dependiendo de las características de las vías de acceso. Su construcción comenzó en el año 1951 y los trabajos duraron casi dos años. Desde entonces ha dejado una huella perdurable en la infraestructura de La Habana.
Antes de su inauguración en 1953, la circulación de vehículos entre La Habana y Marianao era intensa y los tres puentes existentes (Calle 23, Hierro y Pote) resultaban ineficientes, generando interrupciones frecuentes en el tráfico, sobre todo cuando se permitía el paso de embarcaciones recreativas y pesqueras por el Río Almendares.
El túnel resolvió este problema al permitir el tránsito fluido de vehículos sin interrupciones por el paso de embarcaciones, lo que mejoró significativamente la conectividad y la eficiencia del transporte en la zona.
-
 @ 3bf0c63f:aefa459d
2022-09-12 02:28:00
@ 3bf0c63f:aefa459d
2022-09-12 02:28:00A prediction market as a distributed set of oracle federations
See also: Truthcoin as a spacechain.
This is not Truthcoin, but hopefully the essence of what makes it good is present here: permissionless, uncensorable prediction markets for fun, profit, making cheap talk expensive and revolutionizing the emergence and diffusion of knowledge in society.
The idea
The idea is just to reuse Fedimint's codebase to implement federated oracle corporations that will host individual prediction markets inside them.
Pegging in and out of a federation can be done through Lightning gateways, and once inside the federation users can buy and sell shares of individual markets using a native LMSR market-maker.
Then we make a decentralized directory of these bets using something simple like Nostr so everybody can just join any market very easily.
Why?
The premise of this idea is that we can't have a centralized prediction market platform because governments will shut it down, but we can instead have a pseudonymous oracle corporation that also holds the funds being gambled at each time in a multisig Bitcoin wallet and hope for the best.
Each corporation may exist to host a single market and then vanish afterwards -- its members returning later to form a new corporation and host a new market before leaving again.
There is custodial risk, but the fact that the members may accrue reputation as the time passes and that this is not one big giant multisig holding all the funds of everybody but one multisig for each market makes it so this is slightly better.
In any case, no massive amounts are expected to be used in this scheme, which defeats some of the use cases of prediction markets (funding public goods, for example), but since these are so advanced and society is not yet ready for them, we can leave them for later and first just try to get some sports betting working.
This proto-truthcoin implementation should work just well enough to increase the appetite of bitcoiners and society in general for more powerful prediction markets.
Why is this better than DLCs?
Because DLCs have no liquidity. In their current implementations and in all future plans from DLC enthusiasts they don't even have order books. They're not seen very much as general-purpose prediction markets, but mostly as a way to create monetary instruments and derivatives.
They could work as prediction markets, but then they would need order books and order books are terrible for liquidity. LMSR market makers are much better.
But it is custodial!
If you make a public order book tied to known oracles using a DLC the oracle may also be considered custodial since it becomes really easy for him to join multiple trades as a counterpart then lie and steal the money. The bets only really "discreet" if they're illiquid meaningless bets between two guys. If they're happening in a well-known public place they're not discreet anymore.
DLC proponents may say this can be improved by users using multiple oracles and forming effectively a federation between them, but that is hardly different from choosing a reputable oracle corporation in this scheme and trusting that for the life of the bet.
But Hivemind is better!
Yes.
-
 @ 9ecbb0e7:06ab7c09
2023-07-23 04:31:09
@ 9ecbb0e7:06ab7c09
2023-07-23 04:31:09Mientras Miguel Díaz-Canel hacía su entrada este lunes en Bruselas a la sede del Consejo Europeo junto a otros jefes de Estado y políticos en Europa, un grupo de activistas y exiliados cubanos se manifestaba en su contra en la misma ciudad. El gobernante llegó a Bélgica, para participar en la III Cumbre de la Comunidad de Estados Latinoamericanos y Caribeños (CELAC) y la Unión Europea (UE), a celebrarse entre los días 17 y 18 de junio.
Los cubanos portaban carteles de "Díaz-Canel asesino" y pedían el fin de la dictadura y la libertad de todos los presos políticos, a poco metros del edificio donde se encontraba el gobernante. Ante una importante presencia policial en Rond Point Shuman, la protesta comenzó desde horas del mediodía y fue organizada por la Coalición Cubano-Belga, integrante del Consejo Europeo-Cubano.
La activista Avana De la Torre explicó en sus redes sobre el objetivo de la presencia de los cubanos en esa manifestación y exhibió una bandera en la que aparecen los presos políticos que sufren cárcel en Cuba. Los organizadores habían precisado en un comunicado oficial que, además de protestar contra la presencia de Díaz-Canel, condenaban su alianza con el Gobierno de Vladimir Putin y las violaciones de los derechos humanos que tienen lugar en la Isla.
En un punto de la protesta hubo un encontronazo entre una parte de la delegación oficial en apoyo al régimen, que ondeaban banderas del 26 de julio, y los exiliados que protestaban. Con consignas de "Abajo la dictadura" y "Abajo Díaz-Canel", los activistas cubanos plantaron cara a los oficialistas.
En la manifestación estaban presentes entre otros los activistas Lázaro Mireles, Avana de la Torre, Sayde Chaling-Chong, Yusil Gascón, así como Carolina Barrero y la reportera Iliana Hernández.
En declaraciones a DIARIO DE CUBA, Barrero dijo que en la protesta "había un camión con una pantalla gigante" en la que se compartieron "imágenes de la represión que vivieron los manifestantes cubanos" en las protestas del 11 de julio de 2021 en la Isla, así como "imágenes de la visita de Borrell a Cuba".
"Las imágenes las estaban mirando los transeúntes pero también los autos que llevaban a los mandatarios y también al dictador", apuntó la activista. "Los cubanos y los activistas de Venezuela, Nicaragua, Brasil, Ucrania e Irán, que solidariamente se unieron a la protesta, estábamos allí para decirle a Miguel Díaz-Canel que no es bienvenido en la capital de Europa, que no se aceptan a los dictadores en Europa", señaló Barrero.
Agregó que tanto el gobernante cubano como la vicepresidenta de Venezuela o el enviado nicaragüense, "no son bienvenidos": "Ha sido muy claro el mensaje, creo que el régimen de la Isla ha encontrado respuesta de la comunidad de cubanos exiliados aquí".
Por su parte el canciller cubano, Bruno Rodríguez Parrilla, había denunciado anteriormente en sus redes sociales que existía una "falta de transparencia y conducta manipuladora" de la UE en la organización de este evento. La Cumbre no se realizaba desde hace ocho años, la última vez que se encontraron gobernantes europeos, latinoamericanos y caribeños fue en el 2015.
-
 @ 3bf0c63f:aefa459d
2022-05-27 14:34:00
@ 3bf0c63f:aefa459d
2022-05-27 14:34:00Formula for making games with satoshis
I think the only way to do in-game sats and make the game more interesting instead of breaking the mechanics is by doing something like
- Asking everybody to pay the same amount to join;
- They get that same amount inside the game as balances;
- They must use these balances to buy items to win the game;
- The money they used becomes available as in-game rewards for other players;
- They must spend some money otherwise they just lose all the time;
- They can't use too much because if they run out of money they are eliminated.
If you think about it, that's how poker mostly works, and it's one of the few games in which paying money to play makes the game more interesting and not less.
In Poker:
- Everybody pays the same amount to join.
- Everybody gets that amount in tokens or whatever, I don't know, this varies;
- Everybody must pay money to bet on each hand;
- The money used on each round is taken by the round winner;
- If you don't bet you can't play the rounds, you're just eliminated;
- If you go all-in all the time like a mad person you'll lose.
In a game like Worms, for example, this could be something like:
- Idem;
- Idem;
- You must use money to buy guns and ammunitions;
- Whatever you spent goes to a pot for the winners or each round -- or maybe it goes to the people that contributed in killing you;
- If you don't buy any guns you're useless;
- If you spend everything on a single gun that's probably unwise.
You can also apply this to games like Counter-Strike or Dota or even Starcraft or Bolo and probably to most games as long as they have a fixed duration with a fixed set of players.
The formula is not static nor a panacea. There is room for creativity on what each player can spend their money in and how the spent money is distributed during the game. Some hard task of balancing and incentivizing is still necessary so the player that starts winning doesn't automatically win for having more money as the game goes on.



