-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 04222fa1:634e9de5
2024-03-07 10:02:06
@ 04222fa1:634e9de5
2024-03-07 10:02:06As the price of Bitcoin hits the headlines once again, the normies get interested
At my sauna last night we got on to the subject
I stayed pretty quiet, then one guy in the corner says...
It's the currency of the dark web, only criminals use it. OK pretty standard response
Next guy says...
You need two accounts, one for the hackers to find and a secret one
Then another interjected....
Do I go to the bank and ask them to put it in my account? Like, how do I buy it
And another....
You have to open your account abroad to be 100% safe
Safe to say we are early
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 06a5736d:9993b167
2024-03-07 09:44:42
@ 06a5736d:9993b167
2024-03-07 09:44:42Chef's notes
I found the recipe on BBC recipes, should be the first one to pop up if you google easy banana bread recipe.
Details
- ⏲️ Prep time: 15-20min
- 🍳 Cook time: 40-50min
- 🍽️ Servings: 4-8 (depending on portion size). I also didn’t bake this in the usual bread tin, I used a semi deep oven dish as that’s all I had.
Ingredients
- 140g unsalted butter
- 140g caster sugar (I only put 90g as it was for the kids but you can tweak it to your liking)
- 2large eggs
- 1tsp baking soda
- 140g self raising flour
- 1tbs cinnamon powder
- 1tsp vanilla extract
- 1 cup fresh blueberries
- 3 ripe bananas
Directions
- Beat the butter and sugar until a paste is formed
- Add in 2 beaten eggs and mix together
- Gently add the flour and baking soda bit by bit whilst mixing it all well
- Once combined, add in your cinnamon and vanilla
- Add in your washed blueberries
- Mash the bananas well and add to mixture.
- Fold the mixture until well mixed together and set aside
- Preheat oven to 180c
- Butter your dish and line with parchment paper ( I didn’t have this available so I covered it with butter and then added flour all around to prevent it from sticking. Works just the same)
- Once oven is heated up, carefully place the dish into the middle and bake for 40-50min. Make sure to check after 30min as every oven is different.
- Once cooked, remove from oven and let it cool for 10mins before removing from dish (this is to prevent it from falling apart)
- Last step. Cut a slice and enjoy on it’s own or how I did, with some yummy custard
-
 @ fa984bd7:58018f52
2024-02-28 22:15:25
@ fa984bd7:58018f52
2024-02-28 22:15:25I have recently launched Wikifreedia, which is a different take on how Wikipedia-style systems can work.
Yes, it's built on nostr, but that's not the most interesting part.
The fascinating aspect is that there is no "official" entry on any topic. Anyone can create or edit any entry and build their own take about what they care about.
Think the entry about Mao is missing something? Go ahead and edit it, you don't need to ask for permission from anyone.
Stuart Bowman put it best on a #SovEng hike:
The path to truth is in the integration of opposites.
Since launching Wikifreedia, less than a week ago, quite a few people asked me if it would be possible to import ALL of wikipedia into it.
Yes. Yes it would.
I initially started looking into it to make it happen as I am often quick to jump into action.
But, after thinking about it, I am not convinced importing all of Wikipedia is the way to go.
The magical thing about building an encyclopedia with no canonical entry on any topic is that each individual can bring to light the part they are interested the most about a certain topic, it can be dozens or hundreds, or perhaps more, entries that focus on the edges of a topic.
Whereas, Wikipedia, in their Quijotean approach to truth, have focused on the impossible path of seeking neutrality.
Humans can't be neutral, we have biases.
Show me an unbiased human and I'll show you a lifeless human.
Biases are good. Having an opinion is good. Seeking neutrality is seeking to devoid our views and opinions of humanity.
Importing Wikipedia would mean importing a massive amount of colorless trivia, a few interesting tidbits, but, more important than anything, a vast amount of watered-down useless information.
All edges of the truth having been neutered by a democratic process that searches for a single truth via consensus.
"What's the worst that could happen?"
Sure, importing wikipedia would simply be one more entry on each topic.
Yes.
But culture has incredibly strong momentum.
And if the culture that develops in this type of media is that of exclusively watered-down comfortable truths, then some magic could be lost.
If people who are passionate or have a unique perspective about a topic feel like the "right approach" is to use the wikipedia-based article then I would see this as an extremely negative action.
An alternative
An idea we discussed on the #SovEng hike was, what if the wikipedia entry is processed by different "AI agents" with different perspectives.
Perhaps instead of blankly importing the "Napoleon" article, an LLM trained to behave as a 1850s russian peasant could be asked to write a wiki about Napoleon. And then an agent tried to behave like Margaret Thatcher could write one.
Etc, etc.
Embrace the chaos. Embrace the bias.
-
 @ 57d1a264:69f1fee1
2024-03-07 08:11:40
@ 57d1a264:69f1fee1
2024-03-07 08:11:40Prompt: Dropdown ===============
Is it a menu dropdown? Or a tip that's dropped down during a tutorial? Or inside a software tool to show more features? What extra information is displayed? The current price of gold? A login/logout button? Menu selections? @SN territories?
Flex your design muscles and join in. Most of all, keep this exercise loose and keep it stress-free. The FUC is about growing our design skills, together, as a community. We can't wait to see what you create!
Happy designing, Stackers!
Share Your Results When you finish the challenge, post your work on this thread! If you also share it on
nostr, be sure to use the hashtag #FUCdesiger and tag Design_r@iris.to or @Design__r on X! We'll keep an eye out and repost good examples on a regular basis.
Curious to know WTF is a FUC? Read the ⚡️Flash Ui Challenges welcoming post.
Looking for more FUCs? Check the archive here!
-
 @ 57d1a264:69f1fee1
2024-03-07 07:49:34
@ 57d1a264:69f1fee1
2024-03-07 07:49:34What's got you buzzing with excitement, and which trends are you ready to cheers?
Share your insights and learnings!
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ 6871d8df:4a9396c1
2024-02-24 22:42:16
@ 6871d8df:4a9396c1
2024-02-24 22:42:16In an era where data seems to be as valuable as currency, the prevailing trend in AI starkly contrasts with the concept of personal data ownership. The explosion of AI and the ensuing race have made it easy to overlook where the data is coming from. The current model, dominated by big tech players, involves collecting vast amounts of user data and selling it to AI companies for training LLMs. Reddit recently penned a 60 million dollar deal, Google guards and mines Youtube, and more are going this direction. But is that their data to sell? Yes, it's on their platforms, but without the users to generate it, what would they monetize? To me, this practice raises significant ethical questions, as it assumes that user data is a commodity that companies can exploit at will.
The heart of the issue lies in the ownership of data. Why, in today's digital age, do we not retain ownership of our data? Why can't our data follow us, under our control, to wherever we want to go? These questions echo the broader sentiment that while some in the tech industry — such as the blockchain-first crypto bros — recognize the importance of data ownership, their "blockchain for everything solutions," to me, fall significantly short in execution.
Reddit further complicates this with its current move to IPO, which, on the heels of the large data deal, might reinforce the mistaken belief that user-generated data is a corporate asset. Others, no doubt, will follow suit. This underscores the urgent need for a paradigm shift towards recognizing and respecting user data as personal property.
In my perfect world, the digital landscape would undergo a revolutionary transformation centered around the empowerment and sovereignty of individual data ownership. Platforms like Twitter, Reddit, Yelp, YouTube, and Stack Overflow, integral to our digital lives, would operate on a fundamentally different premise: user-owned data.
In this envisioned future, data ownership would not just be a concept but a practice, with public and private keys ensuring the authenticity and privacy of individual identities. This model would eliminate the private data silos that currently dominate, where companies profit from selling user data without consent. Instead, data would traverse a decentralized protocol akin to the internet, prioritizing user control and transparency.
The cornerstone of this world would be a meritocratic digital ecosystem. Success for companies would hinge on their ability to leverage user-owned data to deliver unparalleled value rather than their capacity to gatekeep and monetize information. If a company breaks my trust, I can move to a competitor, and my data, connections, and followers will come with me. This shift would herald an era where consent, privacy, and utility define the digital experience, ensuring that the benefits of technology are equitably distributed and aligned with the users' interests and rights.
The conversation needs to shift fundamentally. We must challenge this trajectory and advocate for a future where data ownership and privacy are not just ideals but realities. If we continue on our current path without prioritizing individual data rights, the future of digital privacy and autonomy is bleak. Big tech's dominance allows them to treat user data as a commodity, potentially selling and exploiting it without consent. This imbalance has already led to users being cut off from their digital identities and connections when platforms terminate accounts, underscoring the need for a digital ecosystem that empowers user control over data. Without changing direction, we risk a future where our content — and our freedoms by consequence — are controlled by a few powerful entities, threatening our rights and the democratic essence of the digital realm. We must advocate for a shift towards data ownership by individuals to preserve our digital freedoms and democracy.
-
 @ dffd3ffc:5ade7be1
2024-03-07 04:00:29
@ dffd3ffc:5ade7be1
2024-03-07 04:00:29[3]
[4]
[5]
[6]
[7]
[8]
-
 @ e372d24b:e25df41f
2024-02-21 23:31:38
@ e372d24b:e25df41f
2024-02-21 23:31:38The evolution of Bitcoin and the spread of literacy are two revolutions that have reshaped society, challenging norms and democratizing access to power and knowledge. Both started as exclusive domains: literacy confined to the elite and Bitcoin, a niche technology understood by few. Yet, their journeys towards mass adoption share striking similarities and transformative impacts.
**Gutenberg Meets Satoshi: Catalysts of Change The printing press and Bitcoin technology both played pivotal roles in democratizing their respective domains. Gutenberg's press made knowledge accessible, just as Bitcoin exchanges made digital currency available to the masses. These innovations broke down barriers, spreading like wildfire and challenging centralized power.
**A Rebellion Against Centralization The essence of both literacy and Bitcoin is the fight against centralization. They shifted power from the few to the many, empowering individuals and fostering a more distributed, egalitarian society. This decentralization challenged established hierarchies, whether in the form of monarchs and religious leaders or modern financial institutions and governments.
**Bridging Divides: The Ongoing Struggle Despite their successes, both movements face challenges in achieving universal access. The digital divide for Bitcoin mirrors the literacy gap, highlighting the need for continued efforts in education and technology to ensure that the benefits of these revolutions reach all corners of the globe.
**Conclusion: A Compact Legacy of Empowerment Bitcoin and literacy are more than just about transactions or reading; they're about reshaping power dynamics and promoting freedom, knowledge, and autonomy. Their stories remind us of the power of innovation to drive societal progress and the ongoing quest for a more inclusive world. As we forge ahead, these parallel journeys continue to inspire a future where access to knowledge and financial empowerment is a right, not a privilege.
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ e968e50b:db2a803a
2024-03-06 19:30:42
@ e968e50b:db2a803a
2024-03-06 19:30:42I past these on display at an antique store recently. Here are a couple of thoughts. Alabama was issuing it's own currency. The cent was worth enough that it made sense to have paper money for significantly less than a dollar.
-
 @ c11cf5f8:4928464d
2024-03-06 16:54:51
@ c11cf5f8:4928464d
2024-03-06 16:54:51Trying to submit a post as usual, but getting this error when clicking on post:
submit error: Invalid
prisma.$queryRawUnsafe()invocation: Raw query failed. Code:23503. Message:insert or update on table "ItemUpload" violates foreign key constraint "ItemUpload_uploadId_fkey"What's next?
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ a4a6b584:1e05b95b
2024-03-07 03:04:17
@ a4a6b584:1e05b95b
2024-03-07 03:04:17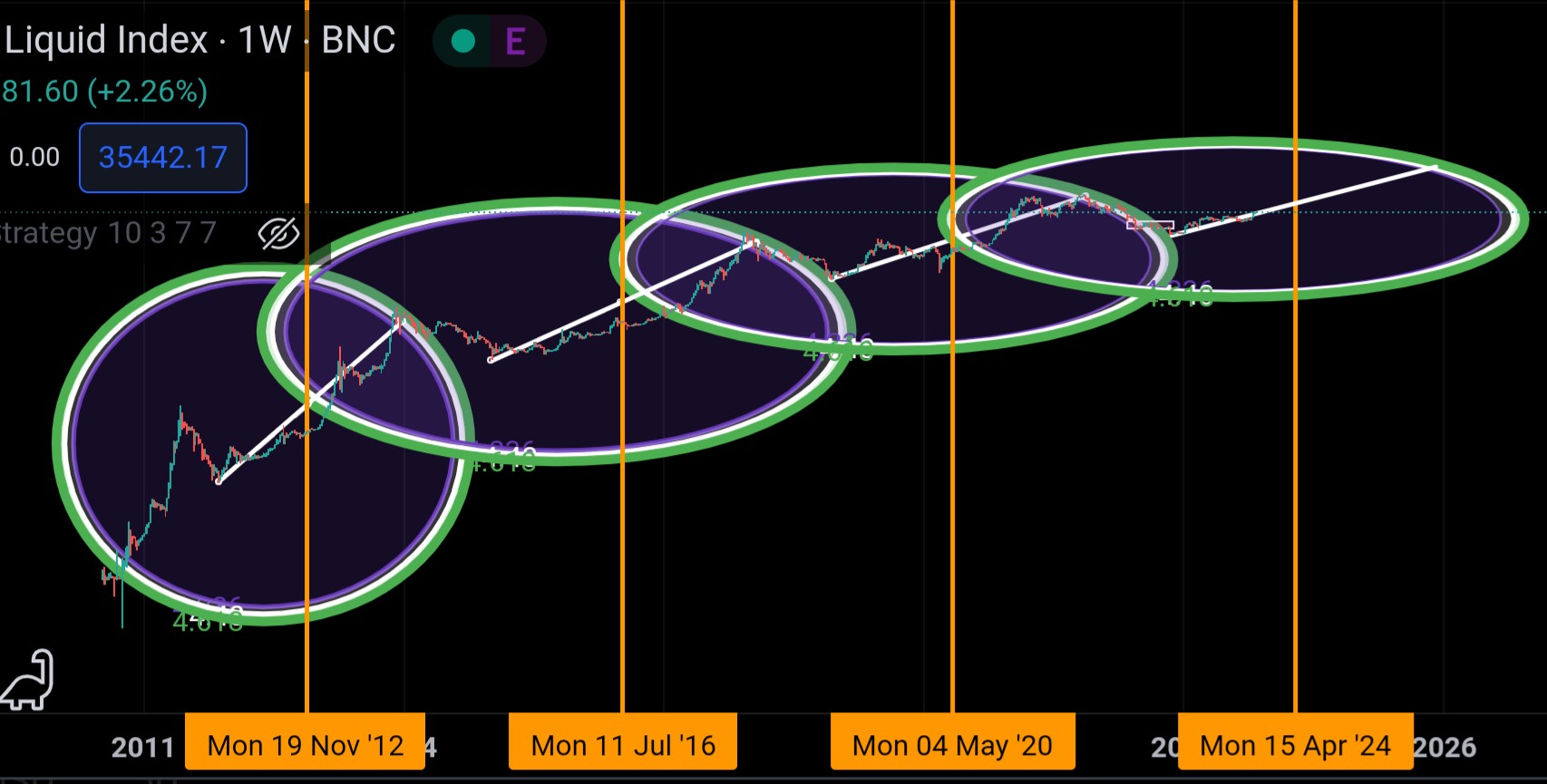
https://www.tradingview.com/chart/tKlgCet5/
Welcome to a novel approach to understanding Bitcoin's price action. As a staunch Bitcoin maximalist, I believe in the inherent value and transformative potential of this asset. As the world economy starts to wake up and reprice itself against this new asset, it helps to help a tool to keep you calm and know how to plan accordingly. Let's delve into the "Satoshi Circles" method and how it might provide insights into Bitcoin's future price movements.
The Genesis of Satoshi Circles:
Drawing inspiration from the mysterious Bitcoin creator, Satoshi Nakamoto, the "Satoshi Circles" method integrates the application of Fibonacci circles with Bitcoin's halving events. Here's a brief step-by-step guide:
-
Identify Halving Events: Mark the date of each Bitcoin halving event with a vertical line on your chart.
-
Draw Trend Lines: From the low of each cycle, draw a trend line to the corresponding halving event.
-
Overlay Fibonacci Circles: Using the chart data from the trend line during the timeframe from the cycle's bottom to the halving, overlay a Fibonacci circle. If done accurately, this circle will offer insights into potential market tops.
Accuracy and Margin of Error:
No method, however ingenious, offers precise predictions every time. With the "Satoshi Circles" method, there's a margin of error to be mindful of:
-
Trend Line Precision: Ensuring accuracy when drawing the trend line is crucial. Small deviations can significantly alter predictions.
-
Bitcoin's Volatility: As an asset, Bitcoin is susceptible to global events, regulatory changes, and macroeconomic factors that may disrupt technical patterns.
-
Fibonacci Circle's Range: The actual top could materialize anywhere within the designated Fibonacci circle. Thus, it's not about pinpointing an exact price but identifying a probable range.
Looking Forward to April 2024:
It's worth noting that the true potential of the "Satoshi Circles" method can't be fully realized until after the April 2024 halving. Post this event, critical data points such as the bottom price and halving date will be solidified. Consequently, the Fibonacci circle can be appropriately placed, and the preceding trend line can be extended to intersect with the circle, unveiling the possible top range. This anticipation builds a compelling case for closely monitoring Bitcoin's journey post the forthcoming halving.
Conclusion:
While the "Satoshi Circles" approach offers a fresh perspective on predicting Bitcoin's price action, it's always vital to approach trading and investments with caution and diligence. Macroeconomics can change quickly and the world could see that Bitcoin's potential remains vast much faster than anticipated, but as HODLers of the hardest money on Earth, it's our responsibility to keep calm and spread the word.
We are all Satoshi.
Adam Malin
You can find me on Twitter or on Nostr at
npub15jnttpymeytm80hatjqcvhhqhzrhx6gxp8pq0wn93rhnu8s9h9dsha32lxYou can view and write comments on this or any other post by using the Satcom browser extention.
value4value Did you find any value from this article? Click here to send me a tip!
-
-
 @ e968e50b:db2a803a
2024-03-06 14:21:04
@ e968e50b:db2a803a
2024-03-06 14:21:04So I've got an Umbrel server that has it's own (seemingly plug and play) nostr relay. It does my SN crossposts fine and generally seems to work, but every client I log into gives it a big red dot or field. The server is definitely online when I'm looking at these settings. This may really expose my ignorance, but is the difference between ws and wss in the url significant? Any suggestions would be appreciated. Given the standard Umbrel user, I'm sure I'm not the only person curious about this.
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 3bf0c63f:aefa459d
2024-03-06 13:04:06
@ 3bf0c63f:aefa459d
2024-03-06 13:04:06início
"Vocês vêem? Vêem a história? Vêem alguma coisa? Me parece que estou tentando lhes contar um sonho -- fazendo uma tentativa inútil, porque nenhum relato de sonho pode transmitir a sensação de sonho, aquela mistura de absurdo, surpresa e espanto numa excitação de revolta tentando se impôr, aquela noção de ser tomado pelo incompreensível que é da própria essência dos sonhos..."
Ele ficou em silêncio por alguns instantes.
"... Não, é impossível; é impossível transmitir a sensação viva de qualquer época determinada de nossa existência -- aquela que constitui a sua verdade, o seu significado, a sua essência sutil e contundente. É impossível. Vivemos, como sonhamos -- sozinhos..."
- Livros mencionados por Olavo de Carvalho
- Antiga homepage Olavo de Carvalho
- Bitcoin explicado de um jeito correto e inteligível
- Reclamações
-
 @ d2e97f73:ea9a4d1b
2023-04-11 19:36:53
@ d2e97f73:ea9a4d1b
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ c11cf5f8:4928464d
2024-03-06 12:37:55
@ c11cf5f8:4928464d
2024-03-06 12:37:55Hey stackers, let’s lay down your unique and unusual offerings. Unveil the unexpected!
Need a hand? Check our tutorials… What hidden gems do y'all have up for sale? Let's rustle up some dusted serendipitous and it in the ~AGORA marketplace.
Click any link👇below to start! [⚖️ SELL] - [🛒 BUY] - [🧑💻 HIRE] - [🖇 OFFER] - [🧑⚖️ AUCTION] - [🤝 SWAP] - [🆓 FREE] - [⭐ REVIEW]
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 57d1a264:69f1fee1
2024-03-06 10:21:10
@ 57d1a264:69f1fee1
2024-03-06 10:21:10I thought it could be an interesting topic to discuss here, as designers we probably lack the tech knowledge necessary to make this happen.
The issue is also a BIP on the bitcoin repository https://github.com/bitcoin/bips/pull/1551
https://www.youtube.com/watch?v=gAmrqSaL5Mo
And here the issue opened on the Bitcoin design repository https://github.com/BitcoinDesign/Meta/issues/638
In reality, we already have it on the Lightning network, it would make sense to apply it to onchain addresses too? It would even possible to do?
-
 @ 57d1a264:69f1fee1
2024-03-06 07:27:16
@ 57d1a264:69f1fee1
2024-03-06 07:27:16Prompt: Nostr Subscription ===============
What is a person subscribing to? A nostr thread, a zapstream platform, or a private messaging group? Is it just a button or a widget?
What type of information are you looking to capture from the user? Their
nymandnpub? Their location? Age consent? Something else?Flex your design muscles and join in. Most of all, keep this exercise loose and keep it stress-free. The FUC is about growing our design skills, together, as a community. We can't wait to see what you create!
Happy designing, Stackers!
Share Your Results When you finish the challenge, post your work on this thread! If you also share it on
nostr, be sure to use the hashtag #FUCdesiger and tag Design_r@iris.to or @Design__r on X! We'll keep an eye out and repost good examples on a regular basis.
Curious to know WTF is a FUC? Read the ⚡️Flash Ui Challenges welcoming post.
Looking for more FUCs? Check the archive here!
-
 @ 57d1a264:69f1fee1
2024-03-06 07:16:55
@ 57d1a264:69f1fee1
2024-03-06 07:16:55An opportunity to share some bits of a process you embrace to achieve anything you aim to. What steps do you follow from concept to design completion? What’s your tricks? Any useful guide or tutorial to share? Where are you now?
-
 @ a4a6b584:1e05b95b
2024-03-07 02:57:07
@ a4a6b584:1e05b95b
2024-03-07 02:57:07Introduction
The double-slit experiment, initially executed with light by Thomas Young in the early 1800s and later with particles in the 20th century, signifies a cornerstone in our understanding of quantum mechanics. This experiment, featuring particles forming an interference pattern suggestive of wave-like behavior, which dissipates upon attempting to discern the particle's path, challenges our classical intuition and opens a plethora of questions about the quantum world.
The Orthodox QED View
QED, crystallized in the 1920s, furnishes a robust mathematical framework to elucidate interactions between light and matter, utilizing principles like wave-particle duality and probabilistic interactions, albeit without offering a physical causality for these quantum phenomena.
Insight into Quantum Phenomena: Zeeman Effect & Lamb Shift
The Zeeman Effect, which pertains to the splitting of a spectral line into several components in the presence of a magnetic field (( \Delta E = \mu B )), and the Lamb Shift, involving a minute difference in energy levels due to vacuum fluctuations, are both accurately predicted by QED, underscoring its predictive prowess, despite its abstract nature.
The Alternative SED View
SED, which surfaced in the 1960s, diverges from QED by proffering a physical explanation for quantum phenomena through particle interactions with a background field of quantum vacuum fluctuations, or the zero-point field (ZPF), though it is crucial to note that SED is not widely embraced in the scientific community due to inconsistencies with certain quantum predictions.
Probing into Quantum Vacuum: The Casimir Effect
The Casimir Effect, which involves a quantifiable force emerging between two parallel plates in a vacuum, attributed to ZPF, provides a tangible manifestation of vacuum fluctuations, potentially aligning with the mechanistic approach of SED.
SED vs QED: A Rigorous Analysis
Both SED and QED adeptly predict quantum phenomena but diverge significantly in their explanatory frameworks. While SED provides a mechanistic model involving interactions with the ZPF, QED leans heavily on abstract mathematical formulations, offering precise predictions without delving into the underlying physical causality.
Evolution and Challenges: Fine Structure Constant
SED and QED have evolved along disparate paths, with QED’s mathematical formalism and SED’s deterministic mechanisms offering different perspectives on quantum phenomena. Both theories adeptly address aspects like the Fine Structure Constant, which governs electron and electromagnetic interactions, yet challenges like explaining non-local quantum entanglement and the probabilistic nature of quantum mechanics remain.
Future Avenues and Experiments
The future trajectory of SED and its potential to diverge from QED predictions hinge upon experimental validation. Experiments probing variations in the Fine Structure Constant or exploring vacuum energy (as suggested by the Casimir Effect) might reveal nuanced insights into the physical reality of ZPF, thus enabling further differentiation between QED and SED predictions.
Conclusion
In conclusion, while SED offers an intuitive and deterministic framework to interpret quantum phenomena, it necessitates further refinement and experimental validation to be juxtaposed with the predictive precision of QED. As our understanding and experimental capabilities advance, SED may potentially unravel novel insights into the quantum domain, offering a mechanistic perspective to the enigmatic quantum world, thereby paving the path toward a deeper understanding of quantum mechanics.
References
-
Bethe, H. A., & Salpeter, E. E. (1957). Quantum Mechanics of One- and Two-Electron Atoms. Springer, Berlin; Academic Press, New York.
-
Condon, E. U., & Shortley, G. H. (1935). The Theory of Atomic Spectra. Cambridge University Press.
-
De la Peña, L., & Cetto, A. M. (1996). The Quantum Dice: An Introduction to Stochastic Electrodynamics (Fundamental Theories of Physics, Vol. 75). Dordrecht; Boston; London: Kluwer Academic Publishers.
-
De la Peña, L., & Cetto, A. M. (2006). The foundations of linear stochastic electrodynamics. Foundations of Physics, 36(3), 350-368. DOI: 10.1007/s10701-006-9046-0.
-
Feynman, R. P., Leighton, R. B., & Sands, M. (1965). The Feynman Lectures on Physics, Vol. III: Quantum Mechanics. Addison-Wesley.
-
Griffiths, D. J. (2005). Introduction to Quantum Mechanics (2nd ed.). Upper Saddle River, NJ: Pearson Prentice Hall.
-
Lamoreaux, S. K. (1997). Demonstration of the Casimir Force in the 0.6 to 6 μm Range. Physical Review Letters, 78(1), 5-8. DOI: Not Available.
-
Milonni, P. W. (1994). The Quantum Vacuum: An Introduction to Quantum Electrodynamics. San Diego: Academic Press.
-
Setterfield, B. (n.d.). Quantum Mechanics. Retrieved from https://barrysetterfield.org/Quantum_Mechanics.html.
-
Setterfield, B. (n.d.). Quantum Effects. Retrieved from https://barrysetterfield.org/Quantum_Effects/Quantum_Effects.html.
-
Setterfield, B. (2015). Quantum Effects and the Zero Point Energy. Retrieved from https://barrysetterfield.org/GSRresearchpapers.html.
Adam Malin
You can find me on Twitter or on Nostr at
npub15jnttpymeytm80hatjqcvhhqhzrhx6gxp8pq0wn93rhnu8s9h9dsha32lxYou can view and write comments on this or any other post by using the Satcom browser extention.
value4value Did you find any value from this article? Click here to send me a tip!
-
-
 @ ec965405:63996966
2024-03-06 04:36:27
@ ec965405:63996966
2024-03-06 04:36:27I'm finally getting around to sharing this note after Aaron Bushnell, a 25 year old united states service member streamed a video of his self immolation in front of an israeli embassy on Twitch last weekend in protest of the ongoing Palestinian genocide. He's the second in recent months to do so and the first to lose his life in the process. This note is for the martyrs.
Finalmente estoy compartiendo esta nota después de que Aaron Bushnell, un miembro de 25 años de las fuerzas armadas de Estados Unidos, transmitiera en vivo su autoinmolación frente a una embajada israelí en Twitch el fin de semana pasado en protesta por el genocidio palestino en curso. Es el segundo que lo hace en los últimos meses y el primero en perder la vida en el proceso. Esta nota es para los mártires.

I woke up feeling sick to my stomach in the middle of the night during my recent delgation to Cuba; probably a side effect of mixing 3 plates of Ropa Vieja at dinner with cigars and beer at La Fabrica the night before. Chastising myself for hitting my body with 3 things I normally avoid at home (tobacco, alcohol, and meat), I wasn't able to make it downstairs to the cafeteria for breakfast or the day trip with the group. I was allowed to stay and rest at the center in the morning while they checked out El Rincón de los Milagros,where they learned about the impact of the Haitian revolution on Cuban society. Everyone said I would have loved it. After looking through their pictures and videos of the drum sessions,I'm certain I would have. I'm going to prioritize visiting this spot next time I'm in Cuba.
Me desperté sintiéndome mal del estómago en medio de la noche, durante mi reciente delegación a Cuba; probablemente un efecto secundario de mezclar 3 platos de Ropa Vieja en la cena, con cigarros y cerveza en La Fábrica la noche anterior. Regañándome a mí mismo por someter mi cuerpo a 3 cosas que normalmente evito en casa (tabaco, alcohol y carne), no logré bajar a la cafetería para desayunar ni unirme al viaje del día con el grupo. Me permitieron quedarme a descansar en el centro durante la mañana mientras ellos visitaban El Rincón de los Milagros, donde aprendieron sobre el impacto de la revolución haitiana en la sociedad cubana. Todos dijeron que me hubiera encantado. Después de ver sus fotos y videos de las sesiones de tambores, estoy seguro de que así hubiera sido. Voy a hacer de visitar este lugar una prioridad la próxima vez que esté en Cuba.

On the flip side, I was deficient in sleep hours, so catching up on rest put me in a better position to participate in the evening social at El Sauce. El Sauce is a smaller venue that wasn't nearly as packed as La Fabrica the previous evening. I enjoyed down time with my fellow delegates, happy to get to know them in an intimate space and eventualy joining them on the dance floor for an electric slide.
Por otro lado, me faltaban horas de sueño, así que ponerme al día con el descanso me colocó en una mejor posición para participar en el evento social de la noche en El Sauce. El Sauce es un lugar más pequeño que no estaba tan lleno como La Fábrica la noche anterior. Disfruté del tiempo libre con mis compañeros delegados, contento de llegar a conocerlos en un espacio íntimo y finalmente uniéndome a ellos en la pista de baile para un electric slide.

I watched a man dressed in plain shorts and a red shirt dance enthusiastically with at least 5 separate partners of varying ages and genders throughout the night, radiating joy with each graceful spin as if he hadn't a care in the world. His magnetic energy drew everyone around him into his orbit despite coming to El Sauce alone that night. The circumstances of an inhumane blockade on his country did not seem to phase him as he laughed and sang along to the music, his humanity on full display for us to see.
Observé a un hombre vestido con shorts sencillos y una camisa roja bailar entusiasmado con al menos 5 parejas distintas de variadas edades y géneros a lo largo de la noche, irradiando alegría con cada giro elegante como si no tuviera ninguna preocupación en el mundo. Su energía magnética atraía a todos a su alrededor a pesar de haber llegado solo a El Sauce esa noche. Las circunstancias de un bloqueo inhumano sobre su país parecían no afectarle mientras reía y cantaba junto a la música, mostrando su humanidad para que todos la viéramos
Before dinner the next evening, the group gathered in the cafeteria for a reflection activity about our first few days in Cuba where we broke the ice by sharing an African word that we were familiar with and its significance to us. My mind instantly snapped to "Ubuntu", a word that represents the inception of my programming journey and my intentions with what comes from it. From the African Journal of Social Work,
Antes de la cena la siguiente noche, el grupo se reunió en la cafetería para una actividad reflexiva sobre nuestros primeros días en Cuba, donde rompimos el hielo compartiendo una palabra africana con la que estuviéramos familiarizados y su significado para nosotros. Mi mente se dirigió instantáneamente a 'Ubuntu', una palabra que representa el inicio de mi carrera en la programación y mis intenciones con lo que resulte de ello. Según el Journal Africano de Trabajo Social:
Ubuntu refers to a collection of values and practices that Black people of Africa or of African origin view as making people authentic human beings. While the nuances of these values and practices vary across different ethnic groups, they all point to one thing – an authentic individual human being is part of a larger and more significant relational, communal, societal, environmental and spiritual world. Ubuntu se refiere a un conjunto de valores y prácticas que las personas negras de África o de origen africano consideran que hacen a los seres humanos auténticos. Aunque los matices de estos valores y prácticas varían entre los distintos grupos étnicos, todos apuntan a lo mismo: un ser humano auténtico es parte de un mundo más amplio y significativo que incluye lo relacional, lo comunal, la sociedad, el medio ambiente y lo espiritual.
I explained my philosophy around the use of open sourced software and a healthier relationship with the Internet highlighting the need to boycot corporate tech platforms that inflict irreparable harm on the massses. The constant bombardment of corporate advertising guided by antagonizing algorithms fuel a dire behavioral health crisis that's actively destroying the fabric of our society and disconnecting us from our humanity. Open source software is my weapon in this war against the tech corporations that dominate our dystopic digital lives that I will leverage to center humanity and dignity in communications.
Expliqué mi filosofía sobre el uso de software de código abierto y una relación más saludable con internet, resaltando la necesidad de boicotear las plataformas tecnológicas corporativas que infligen un daño irreparable a las masas. El constante bombardeo de publicidad corporativa, guiado por algoritmos antagonistas, alimenta una grave crisis de salud conductual que está destruyendo activamente el tejido de nuestra sociedad y desconectándonos de nuestra humanidad. El software de código abierto es mi arma en esta guerra contra las corporaciones tecnológicas que dominan nuestras vidas digitales distópicas, el cual utilizaré para centrar la humanidad y la dignidad en nuestras comunicaciones.
I shared this with the group, happy to look over at a fellow delegate and see her point to the bracelet on her wrist with the letters U-B-U-N-T-U spelled out. I felt right at home with this crew.
Compartí esto con el grupo, contento de mirar a una compañera delegada y verla señalar hacia la pulsera en su muñeca con las letras U-B-U-N-T-U. Me sentí como en casa con este equipo.

-
 @ 18e3af1e:1d42e5df
2024-03-06 00:58:47
@ 18e3af1e:1d42e5df
2024-03-06 00:58:47Disclosure
Now, this is purely an opinion. I have not done research and I haven't even thought it throw for that long. Is more like an idea I have of the future, a hunch if you allow me. Just want to record this thought.
The term "mining hardware" will fade away from people's mind in generations to come. But why?
Is not because the term is used in an incorrect way, or have this bad connotations (like mining gold for example, bad for the planet), but rather the use of home appliances. Allow me to articulate it a bit more:
Home appliances are always use for an specific purpose, and that's make our life's easier A.K.A save time. Dishwasher help us with the dishes so we don't have wash them by hand, washer help us with cloth, and so on...
In this generation we don't even think about all the technology behind all this innovation, we only use them for the purpose they were built for. Bitcoin "mining" equipment is the same.
Virtually ANYTHING can have a "bitcoin miner" inside of it (I'm exaggerating, you get the idea). If somehow making an appliance that "mines" bitcoin, the idea that people in the future will call it "washer-miner" would be kind of far fetch. The word "mining" itself will fade in the background, just like all this other components domestic appliances use that most of us have no clue.
Share your thoughts please.
-
 @ 6ad3e2a3:c90b7740
2024-02-21 15:25:18
@ 6ad3e2a3:c90b7740
2024-02-21 15:25:18It’s really hard to beat an efficient market. It can be done, but only if you have the conviction of a visionary, and you see something most people miss. I would never argue you shouldn’t try, but at a minimum, you should pick your spots carefully.
What a contrast between an efficient market where everyone is weighing in with his valuation independently and one characterized by group-think, where only a few are truly looking at the landscape, and everyone else is following along blindly. In this kind of market, anyone able to follow his own obvious observations, not corrupted by groupthink, can clean up.
Let’s use the recent Super Bowl as an example. Imagine everyone thought the 49ers would win easily. All the pundits, the influencers, the “sharps”. In fact, let’s imagine even opining that the Chiefs would win made you look like an idiot, someone who understood nothing about the NFL. In fact, uttering such an opinion not only disqualified you in NFL-savvy circles but made you a social pariah, a person of low-status who could safely be dismissed out of hand not only on football matters but generally.
In such a scenario, what do you think the point spread in the Super Bowl would have been? I’ll say 49ers minus 20. In that case, the Chiefs would have been an awfully good bet — easy money.
Unfortunately for people like me betting the actual Super Bowl, the real NFL market is pretty efficient, and I got only two points with the Chiefs (It turned out to be enough, but the game, which went into overtime, surely could have gone either way.) In other words, I had no advantage over anyone else when placing this bet.
By contrast, it was trivially easy to be right about Russiagate being a fraud, the lab leak being obvious, the "safety and efficacy" of the mRNA shot being a lie, the "climate change" agenda being a power grab, January 6 as an “insurrection” being absurd, Bitcoin being a store of value and Joe Biden's obvious dementia because massive amounts of bribery go into keeping people in the dark about those things.
As the laptop class is incentivized to believe lies in order to get ahead socially and professionally, there is no longer a free market of ideas operating in those spheres. There is thus a giant information gap between those willing to think for themselves and those limited by the parameters of what's socially and professionally advantageous to believe.
If this gap closes, it's game over for the ruling class whose continued authority depends on it existentially. Is anyone going to vote for a plainly demented Joe Biden unless Trump were a fascist dictator hellbent on destroying democracy by fomenting insurrections? Will anyone sign up for vaccine passports if the medicines being mandated are ineffective and outright dangerous? What will be left of your overlords’ credibility should you dare to transgress the boundaries of this modern church?
It’s not surprising they resort to aggressive tactics, including illegal ones like censorship, to prevent these ideas from taking hold should social and professional incentives prove insufficient. (Censorship in the information age seems like a rather desperate strategy, but probably no more desperate than the Church imprisoning Galileo in the hopes of staving off the scientific enlightenment.)
In the meantime, the person who is not limited by what ideas are acceptable to his overlords will thrive relative to the one who is, and the information gap will also translate to gaps in real-world health and prosperity, offsetting the astro-turfed incentives offered to those on the impoverished side of the gap. Once this process persists long enough, and the incentives cease, the scope of the damage done to those who stayed within the prescribed limits will be apparent to everyone.
In fact, to many, it already is.
-
 @ 6ad3e2a3:c90b7740
2024-03-05 22:11:05
@ 6ad3e2a3:c90b7740
2024-03-05 22:11:05I got into it with a friend and fellow Jew about Israel the other day. It’s not a topic I talk about much, either here or on my podcast and not because I’m worried about offending anyone — that ship has long sailed. It’s because I’m not entirely clear on the facts, and I find the usual back and forth about who did what to whom when to be endlessly debatable, unresolvable and uninteresting. Same goes for the history.
My basic understanding is that Israel is killing a lot of innocent people, and that’s both bad strategic policy and also evil. Of course, the US killed a million Iraqis for less (nothing), and no one seems to mind much. I mean you mind, but if you don’t think George Bush (who gave Michelle Obama a candy once) and Dick Cheney should be prosecuted for war crimes because come on, that’s absurd, then you don’t really mind.
And I get it. The “Iraqis” are just a concept to you and me, as are the Palestinians, the Ukrainians, the Yemenis and the Congolese. Just a bunch of unfortunate, oppressed, murdered humans about whom we all feel terrible, but who also occupy less of our mindshare than that fucking parking ticket we got yesterday. I swear I read the sign three times!
It’s normal for people to care almost exclusively about themselves, their families and their friends. People who purport to care so much about “humanity”, to paraphrase Dostoevsky, often do so while despising and mistreating the individual human beings with whom they come into contact. I’d much more trust someone who risked his reputation and livelihood for a friend than someone going on about third-world oppressed peoples on social media, for example.
But this natural tendency to prioritize those nearest to us often seems to undergird how we see the world and the sides we take in these discussions. For example, my friend sees Israel as a potential homeland for his family should things get ugly for Jews in the US. He is therefore inclined to support them generally, even if he doesn’t always support their particular tactics or conduct.
I live in Europe which seems to me more antisemitic than the US, and I’d rather Israel not fuel more of that by killing a whole bunch of seemingly innocent people. That’s honestly what I think was framing the conversation, the initial biases we brought to it. I think of it as “talking your book,” a phrase used to describe when people talk up their own investments simply because they are invested. And there is no bigger investment than your family’s safety.
So you have people convinced Israel is a potential safe haven, and others who see it, rightly or wrongly, as a flashpoint for conflict and driver of antisemitism. The former will talk their books, say how Israel was savagely attacked and has terrorists right on its border, and the latter will point to the conditions under which the Palestinians live and the disproportionate response to the attack.
But as someone who lacks the appetite to sift through the propaganda and delve into what’s really happening and why, and who has never been and has no desire to go to the region, I don’t care to weigh in much about the truth on the ground. As I said, from what I can tell, Israel is doing something stupid and evil right now, but what I can tell from afar is neither definitive, nor especially important.
What I can say is even though my “book” is for Israel to stop killing innocent Palestinians, my real book, the thing that is most in my family’s interest is justice. That is, if in fact Israel were truly fighting terrorists and within its self-defense rights, then I would want it to defend itself as it is, even if it seems to make things harder for me. That’s because I have faith that justice is more in my interest than whatever appears to advantage me in the short run.
And I would also argue that the “book” of those who view Israel as a potential safe-haven for Jews is also for Israel to be harshly condemned and punished internationally if it’s in fact the case that they are committing war crimes. What’s true and just always trumps what’s apparently expeditious and advantageous in your real book. That is, if you are a person of faith, and by that I don’t mean nominally a Jew, a Muslim or a Christian, but someone with actual faith.
So rather than argue the facts on the ground with people talking their books (and often manipulated by powerful interests that shape what they see as their books), it’s better to understand what’s in our deeper interest, what’s more important than our fears, which incidentally might correspond less to reality than to someone’s cleverly incepted narrative about it.
Otherwise, I expect things will only get worse.
-
 @ a4a6b584:1e05b95b
2024-03-07 02:55:48
@ a4a6b584:1e05b95b
2024-03-07 02:55:481. Revisiting and Rekindling Stallman’s Vision
Dominating today's software funding environment are two formidable models: the subscription-based Software as a Service (SaaS) model and the Advertising-based revenue model. However, they emanate a disconcerting discord with user-centric principles.
-
SaaS: Criticized for its semblance to rent-seeking behaviors, this model often raises eyebrows for potentially prioritizing profits over users.
-
Ad-based Model: While user data becomes a commodity, this model can divert focus from genuine user needs, instead favoring revenue generation through targeted advertising.
Reflecting upon Richard Stallman's GNU General Public License—embodying a world where code is an open, collective pursuit—I implore us to ponder: Have our attempts at ensuring remuneration veered us away from community-driven innovation, burying its essence beneath the rent-seeking predilections of current software funding models?
2. AI: A Catalyst Transforming Software Creation and Funding
AI, with its capability to democratize software creation, is not merely a technological advancement; it's a seismic shift. Imagine a future where coding becomes a universally accessible skill, transforming complex programming into simple, English language-based tasks. This transcendence could not only dismantle traditional funding models but perhaps, reinvent the entire software creation and distribution ecosystem.
The profound implications of AI render the former conundrums of software funding potentially obsolete, prompting a pivotal query: How does one navigate through this newfound landscape of minimized manual intervention and maximized automated innovation?
3. Bitcoin: An Unwavering Anchor Amidst Economic Flux
If we indeed teeter on the brink of an AI-induced deflationary epoch—marked by job displacement and dwindling prices—Bitcoin emerges as a novel, stabilizing financial bastion.
-
A Deflationary Shield: Despite burgeoning product inventories and diminishing prices, Bitcoin’s scarcity (capped at 21 million coins) offers a hedge against deflation.
-
An Inflationary Bulwark: Unaffected by AI’s boundless productivity, Bitcoin’s inherent fixed supply also fortifies it against inflationary pressures.
-
Capital Allocation Power: Bitcoin holders, empowered by amplified capital allocation abilities, may steer funding towards community-aligned, innovative projects, reminiscent of the Stallman-inspired utopian visions.
In this sea of economic ambiguity fostered by AI advancements, Bitcoin potentially carves out a path, standing resolute against both inflation and deflation, enabling a sustainable channel for capital allocation and investment.
Navigating the Future with AI and Bitcoin
The intersection of technology, economics, and individual autonomy within this complex tapestry conjures a myriad of questions, beckoning explorers like us to dissect, debate, and delve into uncharted territories. How do we marry the equitable ethos of community-centric innovation with the disruptive dynamism of AI and the financial acumen embedded in Bitcoin?
Join me in this exploration, as we endeavor to chart a course through these entwining narratives, seeking to harmonize the ethos of collective innovation, the transformative potential of AI, and the prudent economic guardianship of Bitcoin.
Adam Malin
You can find me on Twitter or on Nostr at
npub15jnttpymeytm80hatjqcvhhqhzrhx6gxp8pq0wn93rhnu8s9h9dsha32lxYou can view and write comments on this or any other post by using the Satcom browser extention.
value4value Did you find any value from this article? Click here to send me a tip!
-
-
 @ 6ad3e2a3:c90b7740
2024-02-10 10:37:19
@ 6ad3e2a3:c90b7740
2024-02-10 10:37:19I tend to post what I think, and sometimes people don’t appreciate some of what I’m saying. That’s okay — they are free to unfollow, unsubscribe, mute or even block! But occasionally, they will go farther and try actually to deter me from posting, telling others in the public square what I’m saying is “dangerous” or “harmful”. I’ve even been accused of “killing people” and having a “body count!”
A recent example of this happened a couple months ago when I posted the following observation about the colonoscopy procedure:
Somepeopletook exception to this post, despite the risk/benefit disclaimer, arguing it was dangerous because it could deter people from getting this potentially life-saving procedure. In other words, let’s say colonoscopies save lives, and if 100 people who read my post were convinced not to get one, maybe one of them would get a preventable form of cancer.
I understand the argument, but it’s a terrible one. For starters, each adult human being reading that post has agency. Whether he does or does not do something is never solely because he heard me make an observation. Anyone who reads a tweet from someone neither claiming special expertise in the subject matter nor even purporting to give advice as to risk/benefit and decides not to do something was almost certainly not going to do it anyway for a variety of reasons. I am not a puppet-master of other people with special powers to command them to do things.
To conclude someone is responsible for another adult’s behavior simply because of an observation is to invite all kinds of absurdities. If I post about how crunchy, salty and tangy a particular Doritos flavor is (I do not eat Doritos!), and someone struggling with a junk food addiction reads it and falls off the wagon, am I therefore responsible for the deleterious health effects of his binge?
If posting negative (even though accurate) observations about a health-promoting procedure makes us responsible for someone who subsequently forgoes that procedure, surely posting positive observations about unhealthy behaviors should be viewed similarly. Posting a photo of yourself with a glass of scotch and a cigar in a swanky Vegas lounge with the caption “My happy place” might just be the image that sends an alcoholic reaching for the bottle! Only virtuous, healthful and wholesome messages are permitted!
But could even a picture of yourself in tip-top shape at the beach, surrounded by your healthy and beautiful family cause single people to feel lonely and depressed? Better not post on social media at all. Better not even go out in public if you’re well-dressed and have a healthy and beautiful family. Virtually anything you do could trigger a negative emotion in someone, and who knows where it could lead?
And what if Donald Trump were to say something positive about colonoscopies? Surely, there’s a cohort of people who would reflexively start to question them because everything he says is bad. So even someone posting ostensibly healthful information could be killing people by virtue of their reaction to the poster himself.
But let’s set the absurd implications aside and address the argument on its merits. Even if we concede getting the colonoscopy would have led to early detection and a successful removal of colon cancer (which is not always the case), not getting the colonoscopy is certainly not the proximate cause of the cancer. It might be a but-for cause, but the proximate cause would be some combination of diet, environmental toxins and genetics. Surely, my tweet, no matter how much it stuck with him, cannot be credited with the yeoman’s work of industrial pollution, a pesticide, hormone and antibiotic laden corporate food supply and any risk-augmenting personal behaviors (smoking, eating a poor diet, not exercising) from the person himself.
Further, anyone declining an often free preventative medical procedure probably lacks trust in the medical system generally, and my tweet surely did not cause the medical establishment to offer such consistently wrongheaded advice during the covid era and squander so much of the good will and esteem in which people once held it.
Put differently, my posting about Doritos’ crunch can’t be isolated from the hundreds of millions in marketing from Pepsi-co subsidiary Frito Lay that preceded it.
But even this is not the most pertinent objection to the notion it’s wrong to express earnest observations about medical procedures or lifestyle choices. The primary reason people should feel free to share what they believe or observe is that the science is never all in. Just as eggs were once considered harmful due to their cholesterol content and margarine healthful for its lack thereof, we might one day discover that colonoscopies (and the removal of polyps during the procedure) are themselves sometimes the trigger for colon cancer.
Set aside whether that particular hypothetical mechanism during that particular procedure sounds farfetched, it isn’t hard to imagine more generally that many of the treatments deemed “dangerous” to question might not in fact be net beneficial.
The implications of this are twofold: (1) if someone were on the hook for observations that might deter ostensibly net beneficial procedures, should those procedures later turn out to have been net harmful, those who recommended them would similarly have to be on the hook for those harms. (And I am not talking about the medical establishment that should very much on the hook were that the case, but the ordinary person encouraging his friends and social media followers to follow establishment medical advice.)
And (2) if it were verboten to share earnest observations that contradict the establishment dictum, we would disable the very error-correction mechanism that allows us to update our body of knowledge. Put differently, the examples of expert consensus being wrong and in need of correction span the millennia, from Galileo challenging the geocentric paradigm of the church to Einstein updating Newton’s theories on gravity. Without the ability to question openly the knowledge of the day, whether scientific, medical or political, our myriad errors in attending to human affairs would not merely cause acute harm — they would be permanent.
In short, anyone who discourages you from expressing earnest observations is himself engaging in the most harmful speech of which we can conceive, for though his perceived end might be prevention of local harm, it actually precludes the possibility of progress itself.
-
 @ 3bf0c63f:aefa459d
2024-01-29 02:19:25
@ 3bf0c63f:aefa459d
2024-01-29 02:19:25Nostr: a quick introduction, attempt #1
Nostr doesn't have a material existence, it is not a website or an app. Nostr is just a description what kind of messages each computer can send to the others and vice-versa. It's a very simple thing, but the fact that such description exists allows different apps to connect to different servers automatically, without people having to talk behind the scenes or sign contracts or anything like that.
When you use a Nostr client that is what happens, your client will connect to a bunch of servers, called relays, and all these relays will speak the same "language" so your client will be able to publish notes to them all and also download notes from other people.
That's basically what Nostr is: this communication layer between the client you run on your phone or desktop computer and the relay that someone else is running on some server somewhere. There is no central authority dictating who can connect to whom or even anyone who knows for sure where each note is stored.
If you think about it, Nostr is very much like the internet itself: there are millions of websites out there, and basically anyone can run a new one, and there are websites that allow you to store and publish your stuff on them.
The added benefit of Nostr is that this unified "language" that all Nostr clients speak allow them to switch very easily and cleanly between relays. So if one relay decides to ban someone that person can switch to publishing to others relays and their audience will quickly follow them there. Likewise, it becomes much easier for relays to impose any restrictions they want on their users: no relay has to uphold a moral ground of "absolute free speech": each relay can decide to delete notes or ban users for no reason, or even only store notes from a preselected set of people and no one will be entitled to complain about that.
There are some bad things about this design: on Nostr there are no guarantees that relays will have the notes you want to read or that they will store the notes you're sending to them. We can't just assume all relays will have everything — much to the contrary, as Nostr grows more relays will exist and people will tend to publishing to a small set of all the relays, so depending on the decisions each client takes when publishing and when fetching notes, users may see a different set of replies to a note, for example, and be confused.
Another problem with the idea of publishing to multiple servers is that they may be run by all sorts of malicious people that may edit your notes. Since no one wants to see garbage published under their name, Nostr fixes that by requiring notes to have a cryptographic signature. This signature is attached to the note and verified by everybody at all times, which ensures the notes weren't tampered (if any part of the note is changed even by a single character that would cause the signature to become invalid and then the note would be dropped). The fix is perfect, except for the fact that it introduces the requirement that each user must now hold this 63-character code that starts with "nsec1", which they must not reveal to anyone. Although annoying, this requirement brings another benefit: that users can automatically have the same identity in many different contexts and even use their Nostr identity to login to non-Nostr websites easily without having to rely on any third-party.
To conclude: Nostr is like the internet (or the internet of some decades ago): a little chaotic, but very open. It is better than the internet because it is structured and actions can be automated, but, like in the internet itself, nothing is guaranteed to work at all times and users many have to do some manual work from time to time to fix things. Plus, there is the cryptographic key stuff, which is painful, but cool.
-
 @ e968e50b:db2a803a
2024-03-05 20:24:11
@ e968e50b:db2a803a
2024-03-05 20:24:11Hey Math nerds! Do you like thinking about the philosophical implications of Conway's Game of Life, but really just fantasize about running around and messing with the board? Well I've got a treat for you!
-
 @ 3bf0c63f:aefa459d
2024-01-15 11:15:06
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06Pequenos problemas que o Estado cria para a sociedade e que não são sempre lembrados
- **vale-transporte**: transferir o custo com o transporte do funcionário para um terceiro o estimula a morar longe de onde trabalha, já que morar perto é normalmente mais caro e a economia com transporte é inexistente. - **atestado médico**: o direito a faltar o trabalho com atestado médico cria a exigência desse atestado para todas as situações, substituindo o livre acordo entre patrão e empregado e sobrecarregando os médicos e postos de saúde com visitas desnecessárias de assalariados resfriados. - **prisões**: com dinheiro mal-administrado, burocracia e péssima alocação de recursos -- problemas que empresas privadas em competição (ou mesmo sem qualquer competição) saberiam resolver muito melhor -- o Estado fica sem presídios, com os poucos existentes entupidos, muito acima de sua alocação máxima, e com isto, segundo a bizarra corrente de responsabilidades que culpa o juiz que condenou o criminoso por sua morte na cadeia, juízes deixam de condenar à prisão os bandidos, soltando-os na rua. - **justiça**: entrar com processos é grátis e isto faz proliferar a atividade dos advogados que se dedicam a criar problemas judiciais onde não seria necessário e a entupir os tribunais, impedindo-os de fazer o que mais deveriam fazer. - **justiça**: como a justiça só obedece às leis e ignora acordos pessoais, escritos ou não, as pessoas não fazem acordos, recorrem sempre à justiça estatal, e entopem-na de assuntos que seriam muito melhor resolvidos entre vizinhos. - **leis civis**: as leis criadas pelos parlamentares ignoram os costumes da sociedade e são um incentivo a que as pessoas não respeitem nem criem normas sociais -- que seriam maneiras mais rápidas, baratas e satisfatórias de resolver problemas. - **leis de trãnsito**: quanto mais leis de trânsito, mais serviço de fiscalização são delegados aos policiais, que deixam de combater crimes por isto (afinal de contas, eles não querem de fato arriscar suas vidas combatendo o crime, a fiscalização é uma excelente desculpa para se esquivarem a esta responsabilidade). - **financiamento educacional**: é uma espécie de subsídio às faculdades privadas que faz com que se criem cursos e mais cursos que são cada vez menos recheados de algum conhecimento ou técnica útil e cada vez mais inúteis. - **leis de tombamento**: são um incentivo a que o dono de qualquer área ou construção "histórica" destrua todo e qualquer vestígio de história que houver nele antes que as autoridades descubram, o que poderia não acontecer se ele pudesse, por exemplo, usar, mostrar e se beneficiar da história daquele local sem correr o risco de perder, de fato, a sua propriedade. - **zoneamento urbano**: torna as cidades mais espalhadas, criando uma necessidade gigantesca de carros, ônibus e outros meios de transporte para as pessoas se locomoverem das zonas de moradia para as zonas de trabalho. - **zoneamento urbano**: faz com que as pessoas percam horas no trânsito todos os dias, o que é, além de um desperdício, um atentado contra a sua saúde, que estaria muito melhor servida numa caminhada diária entre a casa e o trabalho. - **zoneamento urbano**: torna ruas e as casas menos seguras criando zonas enormes, tanto de residências quanto de indústrias, onde não há movimento de gente alguma. - **escola obrigatória + currículo escolar nacional**: emburrece todas as crianças. - **leis contra trabalho infantil**: tira das crianças a oportunidade de aprender ofícios úteis e levar um dinheiro para ajudar a família. - **licitações**: como não existem os critérios do mercado para decidir qual é o melhor prestador de serviço, criam-se comissões de pessoas que vão decidir coisas. isto incentiva os prestadores de serviço que estão concorrendo na licitação a tentar comprar os membros dessas comissões. isto, fora a corrupção, gera problemas reais: __(i)__ a escolha dos serviços acaba sendo a pior possível, já que a empresa prestadora que vence está claramente mais dedicada a comprar comissões do que a fazer um bom trabalho (este problema afeta tantas áreas, desde a construção de estradas até a qualidade da merenda escolar, que é impossível listar aqui); __(ii)__ o processo corruptor acaba, no longo prazo, eliminando as empresas que prestavam e deixando para competir apenas as corruptas, e a qualidade tende a piorar progressivamente. - **cartéis**: o Estado em geral cria e depois fica refém de vários grupos de interesse. o caso dos taxistas contra o Uber é o que está na moda hoje (e o que mostra como os Estados se comportam da mesma forma no mundo todo). - **multas**: quando algum indivíduo ou empresa comete uma fraude financeira, ou causa algum dano material involuntário, as vítimas do caso são as pessoas que sofreram o dano ou perderam dinheiro, mas o Estado tem sempre leis que prevêem multas para os responsáveis. A justiça estatal é sempre muito rígida e rápida na aplicação dessas multas, mas relapsa e vaga no que diz respeito à indenização das vítimas. O que em geral acontece é que o Estado aplica uma enorme multa ao responsável pelo mal, retirando deste os recursos que dispunha para indenizar as vítimas, e se retira do caso, deixando estas desamparadas. - **desapropriação**: o Estado pode pegar qualquer propriedade de qualquer pessoa mediante uma indenização que é necessariamente inferior ao valor da propriedade para o seu presente dono (caso contrário ele a teria vendido voluntariamente). - **seguro-desemprego**: se há, por exemplo, um prazo mínimo de 1 ano para o sujeito ter direito a receber seguro-desemprego, isto o incentiva a planejar ficar apenas 1 ano em cada emprego (ano este que será sucedido por um período de desemprego remunerado), matando todas as possibilidades de aprendizado ou aquisição de experiência naquela empresa específica ou ascensão hierárquica. - **previdência**: a previdência social tem todos os defeitos de cálculo do mundo, e não importa muito ela ser uma forma horrível de poupar dinheiro, porque ela tem garantias bizarras de longevidade fornecidas pelo Estado, além de ser compulsória. Isso serve para criar no imaginário geral a idéia da __aposentadoria__, uma época mágica em que todos os dias serão finais de semana. A idéia da aposentadoria influencia o sujeito a não se preocupar em ter um emprego que faça sentido, mas sim em ter um trabalho qualquer, que o permita se aposentar. - **regulamentação impossível**: milhares de coisas são proibidas, há regulamentações sobre os aspectos mais mínimos de cada empreendimento ou construção ou espaço. se todas essas regulamentações fossem exigidas não haveria condições de produção e todos morreriam. portanto, elas não são exigidas. porém, o Estado, ou um agente individual imbuído do poder estatal pode, se desejar, exigi-las todas de um cidadão inimigo seu. qualquer pessoa pode viver a vida inteira sem cumprir nem 10% das regulamentações estatais, mas viverá também todo esse tempo com medo de se tornar um alvo de sua exigência, num estado de terror psicológico. - **perversão de critérios**: para muitas coisas sobre as quais a sociedade normalmente chegaria a um valor ou comportamento "razoável" espontaneamente, o Estado dita regras. estas regras muitas vezes não são obrigatórias, são mais "sugestões" ou limites, como o salário mínimo, ou as 44 horas semanais de trabalho. a sociedade, porém, passa a usar esses valores como se fossem o normal. são raras, por exemplo, as ofertas de emprego que fogem à regra das 44h semanais. - **inflação**: subir os preços é difícil e constrangedor para as empresas, pedir aumento de salário é difícil e constrangedor para o funcionário. a inflação força as pessoas a fazer isso, mas o aumento não é automático, como alguns economistas podem pensar (enquanto alguns outros ficam muito satisfeitos de que esse processo seja demorado e difícil). - **inflação**: a inflação destrói a capacidade das pessoas de julgar preços entre concorrentes usando a própria memória. - **inflação**: a inflação destrói os cálculos de lucro/prejuízo das empresas e prejudica enormemente as decisões empresariais que seriam baseadas neles. - **inflação**: a inflação redistribui a riqueza dos mais pobres e mais afastados do sistema financeiro para os mais ricos, os bancos e as megaempresas. - **inflação**: a inflação estimula o endividamento e o consumismo. - **lixo:** ao prover coleta e armazenamento de lixo "grátis para todos" o Estado incentiva a criação de lixo. se tivessem que pagar para que recolhessem o seu lixo, as pessoas (e conseqüentemente as empresas) se empenhariam mais em produzir coisas usando menos plástico, menos embalagens, menos sacolas. - **leis contra crimes financeiros:** ao criar legislação para dificultar acesso ao sistema financeiro por parte de criminosos a dificuldade e os custos para acesso a esse mesmo sistema pelas pessoas de bem cresce absurdamente, levando a um percentual enorme de gente incapaz de usá-lo, para detrimento de todos -- e no final das contas os grandes criminosos ainda conseguem burlar tudo. -
 @ 3bf0c63f:aefa459d
2024-01-15 11:15:06
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06Anglicismos estúpidos no português contemporâneo
Palavras e expressões que ninguém deveria usar porque não têm o sentido que as pessoas acham que têm, são apenas aportuguesamentos de palavras inglesas que por nuances da história têm um sentido ligeiramente diferente em inglês.
Cada erro é acompanhado também de uma sugestão de como corrigi-lo.
Palavras que existem em português com sentido diferente
- submissão (de trabalhos): envio, apresentação
- disrupção: perturbação
- assumir: considerar, pressupor, presumir
- realizar: perceber
- endereçar: tratar de
- suporte (ao cliente): atendimento
- suportar (uma idéia, um projeto): apoiar, financiar
- suportar (uma função, recurso, característica): oferecer, ser compatível com
- literacia: instrução, alfabetização
- convoluto: complicado.
- acurácia: precisão.
- resiliência: resistência.
Aportuguesamentos desnecessários
- estartar: iniciar, começar
- treidar: negociar, especular
Expressões
- "não é sobre...": "não se trata de..."
Ver também
-
 @ eea716ed:ec1e1eda
2024-03-05 16:21:20
@ eea716ed:ec1e1eda
2024-03-05 16:21:20We're building a new version of Bitcoin Search.
We'd love your input on the product in the spirit of building out loud (and following good product practice). It's very easy!
Instructions
You'll notice two versions of a few sections: - Landing page above the scroll - Version A - Version B - Explore - Version A where everything is on the landing page - Version B is on the landing page. The "Explore more" button on the bottom goes to a separate page here (sources) or here (authors). - Benefits - Version A - Version B
There's a few elements - Footer - Search bar drop down
And the overall search page itself - Unfiltered - Filtered
Feedback Template
You can copy-paste this template with your feedback.
Above the scroll - I prefer version ... because ....
Explore section/ page - I prefer version .... because...
Benefits section - I prefer version ... because ...
Elements: - Footer: - One thing i like/ dislike about the footer is... - Searchbar dropdown - One thing i like/ dislike about the dropdown is...
Search page - One thing i like/dislike about the search page is...
Overall: My favorite part of what I saw was...
One thing I hope you change this one thing in the final product: ...
A question I still have is...
If you prefer to give verbal feedback
If instead you'd like to participate in a 30 min user interview (no video of you + not recorded), feel free to sign up here
Built with 💛 by the Bitcoin Dev Project
-
 @ 7f5c2b4e:a818d75d
2024-03-05 15:40:04
@ 7f5c2b4e:a818d75d
2024-03-05 15:40:04Nsec.app is a Nostr application which lets you share access to your account and login to Nostr apps seamlessly with numerous devices.
The app is super useful when collaboratively running a Nostr account. It lets you generate tokens to share with partners or colleagues and provide different levels of access to different individuals.
Another bonus feature of nsec.app is letting you forget about Nostr browser extensions. Extensions have their fair share of useful features, but using nsec.app (or other apps that support NIP-46 login, e.g. nsecBunker) is often more convenient, arguably more secure and offers some features, that extensions aren't able to deliver.
Let's walk through the process of starting the nsec.app and see what features it has to offer.
Installation
Nsec.app is a PWA (see my short blog post on PWAs and their benefits here), meaning that it can be saved to your device in a way that it feels and acts like a native app. Alternatively the app can be used in the browser.
Visit Nsec.app:
https://i.nostr.build/axlP.png
After pressing the "Get started" button you'll be welcomed by three main options: "Sign up", "Login" or "Import Key". Let's explore each of these options:
- Sign up: This option suits those, who do not have a Nostr account yet. I'd steer clear from this option for now and create an account in a more "conventional" way – via one of the popular Nostr clients or by utilizing a dedicated browser extension.
Stay tuned as the developers are working on wide implementation of NIP49. At the moment few Nostr clients support NIP49, so you won't have many options of using keys created with nsec.app. When most Nostr apps support NIP49 logins, signing up to Nostr via nsec.app will become a more convenient option.
If you decide to utilize nsec.app to create your Nostr account, the process is super simple:
1) Choose your Nostr address 2) Create and confirm your password 3) Enjoy your new Nostr account 💜
https://i.nostr.build/JqgP.png
- Import key: This approach assumes you would like to start using nsec.app with the existing Nostr account.
https://i.nostr.build/5e9y.png
In this case you'll need to choose your username, provide your private key and choose a password. This will create the nsec.app account (by setting a username and a password) while binding it with your original Nostr account (by providing your private key).
It is worth noting that your keys will be encrypted by your password and stored on nsec.app's server to sync to other devices in end-to-end encrypted manner.
- Login: This approach assumes you've already set up nsec.app and would like to enter your dashboard from a new device.
https://i.nostr.build/k6aa.png
Do not forget to click the "Enable background service" tile after setting up your account. This will ensure you receive a notification whenever the request to authorize a login is created.
https://i.nostr.build/Zrdx.png
Usage
After setting up nsec.app you're ready to start utilizing it to login to numerous Nostr apps.
The most powerful feature of nsec.app is that it lets you login to apps without having to use the browser extension or exposing your private key.
For example, I can now turn Coracle client into a PWA on my iPhone, which is otherwise impossible, because Apple does not allow you to utilize browser extensions with PWAs.
Another use case is delegating the rights to interact with Nostr on behalf of the account you created.
Regardless of wether you want to use the app single-handedly, or delegate the private key, the process is as follows:
- Use nsec.app to create a login string by pressing "Connect app".
- Copy the string by pressing the corresponding button.
https://i.nostr.build/rvVB.png
- Paste the string into the client that you'd like to login to.
- As you (or your companion) try to login to the Nostr app, nsec.app will display a notification asking you (the administrator) to approve the login.
https://i.nostr.build/7x53.png
As you can see, there are two options for you to choose from:
- Basic permissions: This will approve all potential future interactions.
- On demand: This will log the user in and ask for your approvals every time the user tries to interact with the protocol in a new way (like, zap, follow, etc.)
That's it. You can now interact with nostr without ever having to utilize the browser extension or share your private key with any app.
Features
Customization
Nsec.app lets you customize the way your connected apps look. You can name them, specify a website address and choose an icon of your choice. Very handy functionality for when you start actively using the app:
https://i.nostr.build/ej6X.png
As the stack of connected apps grows this will help you distinguish between them in order to introduce any necessary changes.
https://i.nostr.build/XEgW.png
Connected apps management
This leads us to the next important part of using nsec.app: revoking access to apps. This is especially important when it comes to sharing access to account with someone else. In case you no longer plan to collaborate on the account, or you simply do not need some app connection to function any longer, you can revoke access at any time.
Just open the app you need and: (a) press "Delete app" (this completely cuts connection between your app and nsec.app) or (b) press the three dots next to the existing approved permission followed by "Delete permission" (this cancels the given permission, so that the next time you (or other user) tries to interact with the protocol, you will receive a notification asking you to approve their action).
https://i.nostr.build/d3QD.png
NIP49 logins
Nsec.app allows you to utilize another way of logging into Nostr apps – NIP49. We touched on this approach earlier, so let's explore how it works.
Here's an example with Noogle:
- Choose the Login with NCryptSec option:
https://i.nostr.build/DzeV.png
- Enter the encrypted Nsec (to be retrieved from the nsec.app in Settings -> Export) and the nsec.app password:
https://i.nostr.build/R505.png
That's it. You're logged in.
https://i.nostr.build/moLR.png
At the moment few clients support this NIP, but given the benefits of this functionality, it shouldn't be long before we see more and more clients join in.
Outro
Just like with every other Nostr app, there's a lot of work to be done. Nevertheless, nsec.app already solves many important problems, and is definitely worth your attention. Give it a try and let us know if you find any bugs, or come up with some ideas worth implementing. Feel free to ping myself or, better yet, the app developer nostr:npub1xdtducdnjerex88gkg2qk2atsdlqsyxqaag4h05jmcpyspqt30wscmntxy
Hope this guide was useful! If so, don't forget to zap this post 😉
See you on the other side of the Nostr rabbit hole
Tony⚡️
-
 @ c11cf5f8:4928464d
2024-03-05 12:20:18
@ c11cf5f8:4928464d
2024-03-05 12:20:18Is callin'! Wrangle up your latest tech discoveries, reviews, and recommendations.
Found any gadgets or gizmos that blew your mind? Don't be shy—share the pros and cons and help your fellow stackers in the ~AGORA stay ahead of the tech curve!
-
 @ a012dc82:6458a70d
2024-03-07 02:23:30
@ a012dc82:6458a70d
2024-03-07 02:23:30Table Of Content
-
Content
-
Introduction
-
What is Bitcoin?
-
How do bitcoins enter circulation?
-
Bitcoin’s environmental impacts
-
Energy consumption and greenhouse gas emissions
-
Water issues and e-waste
-
NFTs
-
How can cryptocurrencies be more sustainable?
-
-
Conclusion
-
FAQ
-
External Links
In April of 2011, one bitcoin was worth exactly one dollar. In April, the price of one bitcoin hit an all-time high of about $65,000, and as of the time of this writing, the price of one bitcoin is roughly $48,000. The fact that some bitcoin investors have become billionaires overnight has piqued the interest of an increasing number of individuals in the prospect of becoming wealthy by investing in cryptocurrencies like Bitcoin. On the other hand, the expanding popularity of Bitcoin may make it difficult for the world to forestall the most severe effects of climate change. This cryptocurrency uses a lot of energy, and its effects on the environment are quite far-reaching.
Before we can begin to grasp Bitcoin's effects on the environment, we must first understand what Bitcoin is and how it operates.
What is Bitcoin?
A cryptocurrency is a digital means of exchange that only exists in digital form; it does not have a physical equivalent, such as a coin or a note, and there was no initial investment of money to get it started. "It's a marketplace, and as long as people are prepared to ascribe value to it, then that's it," said R.A. Farrokhnia, a professor at Columbia Business School and the executive director of the Columbia Fintech Initiative. Bitcoin is the world's most widely used cryptocurrency, accounting for more than half of all cryptocurrencies. It may be used to purchase a wide variety of goods and services, including automobiles, home furnishings, and even vacations. This month, the value of all the bitcoins in circulation was $903 billion.
Decentralized refers to the fact that no central authority, such as a bank or government, regulates cryptocurrencies such as bitcoin and ethereum. The benefits of doing business in this manner include the absence of transaction fees, the accessibility of the platform, and the simplification of complex financial dealings such as the transfer of funds across countries. Although transactions are recorded, the identities of the people carrying them out are not revealed. Because cryptocurrencies can't be tracked and there's no one in charge of how they're used, many bad people, like tax evaders, criminals, and terrorists, may use them for bad things.
Because cryptocurrencies don't exist in the form of actual money and they don't have a centralized authority, they had to devise a method to assure that their transactions are safe and that their tokens can only be used once. In 2008, an anonymous individual (or people) going by the name Satoshi Nakamoto (whose actual identity is still a mystery) came up with a solution to these problems, which led to the creation of bitcoin. The solution that Nakamoto came up with was a digital ledger system that generated confidence in the system via the use of mathematics and encryption, and it logged transactions in a distributed ledger called blockchain. A blockchain is a transparent database that is shared throughout a network. It records transactions in blocks that are connected together, and each block is linked to the one that came before it. Nodes are powerful computers that are linked to the other computers that make up the Bitcoin network. These nodes are responsible for running the Bitcoin software and validating transactions and blocks. Every node in the network has its own copy of the complete blockchain, which includes a record of each transaction that has been processed on it.
Nakamoto limited the total number of bitcoins that could ever be produced to 21 million. Although there is much conjecture about the mathematical theories that led to the selection of that number, the actual reason for its selection is unknown to anybody. As of this month, it is expected that there are now 18.8 million bitcoins in circulation, and it is expected that any remaining bitcoins will be issued by the year 2140.
How do bitcoins enter circulation?
Mining is essentially the process of verifying and recording new transactions on the blockchain, is how new bitcoins are created. Mining is also how new blocks are added to the network. New bitcoins are awarded to the miner who is the first to accomplish this goal.
Bitcoin miners are responsible for determining whether a collection of transactions that have been grouped together into a block are legitimate. This includes verifying anywhere from 20 to 30 different variables, such as addresses, names, timestamps, the amount of money that senders have in their accounts, whether or not they have previously spent it, etc. The miners then compete to see who can solve a conundrum or riddle the earliest to have their validation acknowledged first. To solve the puzzle, you will need to come up with a number that will only be used once. This number is referred to as the nonce, which stands for "number used once." When this number is combined with the data contained in the block and processed by a particular algorithm, it will produce a random 64-digit string of numbers and letters. This random number must be lower than or equal to the 64-digit goal specified by the system, also referred to as the target hash. Once the nonce that creates the desired hash has been located, the miner who won the competition will have their new block connected to the one that came before it. This will ensure that all blocks are connected in a chain. Because altering one block would affect all of the blocks that followed it, this makes it impossible to tamper with the network. The outcome is subsequently shared with the other blockchain network members, and all nodes update the version of the blockchain they are using. The term "proof of work" refers to either the process of validating work or the consensus method. The miner who wins gets new bitcoins and the transaction fees are paid for by the person who receives the bitcoins.
The higher the price of bitcoin is, the greater the number of miners fighting for it, making the puzzles more difficult. The Bitcoin protocol seeks to have blocks of transactions mined every 10 minutes; hence, the possibility of discovering the nonce in fewer than ten minutes grows if there are more miners on the network with greater computer power. The system then makes the target hash more difficult to locate by adding more zeroes to the front of it; the lower that number is, and the more difficult it is to produce a random number below it, the more zeroes that are added to the front of the target hash. The solution to the problem is simplified by the system whenever there is less computational power available to process it. The Bitcoin network will modify the difficulty of mining in order to maintain a block production rate of ten minutes.
The amount of bitcoin that miners are rewarded with is half every 210,000 blocks. According to the information provided by Investopedia, the mining of a single block back in 2009 resulted in the acquisition of fifty bitcoins. By November 2020, the reward for completing a block was 6.25 bitcoins, but the price of one bitcoin was around $17,900, so a miner would get $111,875 (6.25 times 17,900) for completing a block.
Miners with less computational capacity on their own may join mining pools, which do not need to reveal how many active miners they have. It is thought that there are one million bitcoin miners functioning and competing, but it is hard to be certain.
Farrokhnia said, "I have a sense that Nakamoto had the concept that everyone could be a miner—that you could mine with nothing more than your laptop." This was in reference to the idea that mining could be done with nothing more than a laptop. You started to witness the emergence of these mining pools as Bitcoin grew more popular and more people started using the system, and the rewards were genuinely worth money. This greatly raised the difficulty level. This spiraled into a vicious circle, an arms race for the most powerful computers; however, the more powerful the hardware miners have, the more difficult it is to find the nonce.
Because Bitcoin encourages strong competition, its effects on the environment directly result from this.
Bitcoin’s environmental impacts
Energy consumption and greenhouse gas emissions
The process of attempting to come up with the correct nonce that will yield the target hash is essentially a game of trial and error, similar to how a burglar could try several random passwords in order to get into your account. This process can take billions of attempts. It is estimated that each transaction using Bitcoin uses 707 kilowatt hours of electricity due to the large number of machines involved in the process. In addition, the computers soak up more energy due to the heat they produce and the necessity to keep them at a constant temperature. And although it is impossible to know exactly how much electricity Bitcoin uses because different computers and cooling systems have varying levels of energy efficiency, an analysis conducted by the University of Cambridge estimated that bitcoin mining consumes 121.36 terawatt hours each and every year. This is more than the total consumption of all of Argentina as well as greater than the consumption of Google, Apple, Facebook, and Microsoft combined.
And the situation will only worsen as miners are forced to continuously upgrade their computational power to remain competitive with one another. In addition, since incentives are consistently slashed in half, miners need to either process a greater volume of transactions or lower the amount of Bitcoin power they consume in order for mining to be financially feasible. Consequently, miners are required to search for the most affordable sources of electricity and upgrade to faster, more power-hungry machines. The amount of energy required to mine Bitcoin almost grew by 62 times between 2015 and March of 2021. According to Cambridge University research, only 39 percent of this energy comes from renewable sources, and most of it comes from hydropower, which may negatively affect ecosystems and biodiversity, according to Cambridge University research.
By 2020, China would control more than 65 percent of the global processing power used to run the Bitcoin network.Miners took advantage of China's inexpensive energy, which was generated either by hydropower or polluting coal power plants. However, China has recently tightened down on mining due to worries about the financial dangers associated with cryptocurrencies and the large energy consumption associated with mining, both of which go against China's carbon neutral objective by 2060. As a direct consequence of this, a significant number of Chinese bitcoin miners are exploring the possibility of relocating their operations to locations in other nations, such as the United States or Kazakhstan, both of which get the majority of their power from fossil fuels. To bolster their own economies, a number of states in the United States actively seek to recruit Chinese miners. However, if the miners cannot relocate, they plan to sell their equipment to various other miners throughout the world. Miners in the United States are now raising hundreds of millions of dollars to invest in bitcoin mining and turning old factories and power plants into large-scale bitcoin mining operations.
An example of this is the Greenidge Generation facility in Dresden, New York, which used to be a coal power plant but has now been converted to run on natural gas and has started mining bitcoin. As a result of becoming one of the biggest cryptocurrency miners in the United States between 2019 and 2020, the facility's emissions of greenhouse gases surged by nearly a factor of 10. Greenidge hopes to turn other power plants into mining operations by 2025 and has plans to quadruple its mining capacity by July, then double it again by 2022. Even while Greenidge committed back in June to becoming carbon neutral by buying carbon offsets, the reality is that if it weren't for bitcoin mining, the facility probably wouldn't be operational at all. Other polluting peaker plants, which are power plants that are normally only operated during peak demand for a few hours once a month, are being taken over for cryptocurrency mining so that they may run around the clock.
Earth Justice and the Sierra Club have sent a letter to the New York State Department of Environmental Conservation, requesting the department to refuse to renew Greenidge's permit, which would give the company permission to increase the amount of greenhouse gases it emits. They also cautioned that there are almost 30 power plants in upstate New York that have the potential to be converted into bitcoin mining operations. If this were to take place, it could undermine the efforts that the state of New York is making to eliminate almost all greenhouse gas emissions by the year 2050.
Because it translates into an estimated 22 to 22.9 million metric tons of CO2 emissions per year, Bitcoin's power consumption has serious consequences for climate change and the achievement of the objectives of the Paris Accord. This is because it is comparable to the CO2 emissions from the energy usage of 2.6 to 2.7 billion houses for one year. According to one analysis, Bitcoin might cause global warming to exceed 2 degrees Celsius. According to one estimate, bitcoin mining in China might be responsible for 130 million metric tons of CO2 emission by the year 2024. On the other hand, if more mining moved to the United States and other countries, this number would likely rise much more without more use of renewable energy.
Water issues and e-waste
Additionally, using significant quantities of water are power facilities such as Greenidge. Greenidge takes as much as 139 million gallons of fresh water from Seneca Lake every day to cool the plant. However, the water that is released back into the lake is between 30 and 50 degrees Fahrenheit hotter than the lake's average temperature, putting the wildlife and ecology of the lake in danger. Additionally, larvae, fish, and other forms of animals might be sucked in and killed by the massive intake pipes.
And even if it someday becomes feasible to do all bitcoin mining using renewable energy, the issue of electronic waste will always be a concern. In order to be successful, miners need to have access to the most advanced gear, which should be able to do the most number of calculations while using the least amount of power. This highly specialized hardware is rendered useless every one and a half years and cannot be rewritten to perform any other function. It is estimated that the Bitcoin network makes 11.5 kilotons of e-waste per year, which adds to the already large amount of e-waste we have a problem with.
NFTs
Since December, a new trend in the realm of art known as NFTs has added to the list of worries about the impact of cryptocurrencies on the environment. These are non-fungible tokens, digital files of images, music, films, or other types of artwork stamped with one-of-a-kind strings of code. People are able to read or duplicate NFTs, but there is only one unique NFT that belongs to the buyer. This unique NFT is recorded on the blockchain and safeguarded using the same energy-intensive proof of work procedure. NFTs are already selling for tens of thousands of dollars, and a digital artist by the name of Beeple just sold an NFT for more than 69 million dollars.
NFTs are generated on Ethereum, which is now the second most popular cryptocurrency after Bitcoin. The typical non-fungible token transaction causes the release of 440 pounds of carbon dioxide into the atmosphere, which is the same as traveling 500 miles in a vehicle fueled by gasoline. This results in emissions that are 10 times greater than the typical Ethereum transaction.
According to the calculations of one digital artist, the carbon footprint of a typical NFT is more than the amount of power used in a single month by a person living in the EU. Some artists, worried about the effects that NFTs have on the environment, are attempting to raise awareness and seek methods to create NFTs that are more environmentally friendly.
How can cryptocurrencies be more sustainable?
It would be difficult for the whole Bitcoin network to migrate to a more energy-efficient system because of the millions of dollars spent on hardware and infrastructure. This is particularly true given that there is no central oversight body to oversee the change. However, a number of efforts are underway that aim to lessen the impact that Bitcoin and cryptocurrencies in general have on the environment. Elon Musk, CEO of Tesla, recently discussed the energy consumption of leading crypto mining firms in North America with the CEOs of such companies. Because of this, a brand-new Bitcoin Mining Council has been set up to help make the energy industry more open.
The Crypto Climate Accord is another initiative that has the backing of 40 different projects. Its goal is for blockchains to run on energy derived from 100 percent renewable sources by 2025, and for the entire cryptocurrency industry to achieve net zero emissions by 2040.It intends to decarbonize blockchains by using more energy efficient validation methods; advocating for proof of work systems to be located in areas with abundant renewable energy that can be harnessed; and encouraging the purchase of certificates to support renewable energy generators in the same way that carbon offsets support environmentally friendly projects.
Ethereum has set a goal of reducing its energy consumption by 99.95% by 2022.This will be accomplished by moving to an alternative validation system known as proof of stake, which a few smaller cryptocurrencies have already implemented. Proof of stake is an alternative to proof of work that does not necessitate using computational power to solve puzzles to earn the right to verify transactions. Instead, the process is similar to that of a lottery. Potential validators have to risk some of their Ethereum currency (ETH) to be considered; the more coins they stake, the higher their chances of being chosen at random by the system to act as the validator. Participants in Ethereum 2.0 will be required to stake 32 ETH (each of which is worth approximately $3600 as of this writing), with multiples of 32 ETH required for additional validator opportunities. When a new block is validated and confirmed correct, validators will be compensated with coins and allowed to retain the coins they staked throughout the validation process.
Because validators would lose their stake and be kicked off the network if they cheated or allowed bogus transactions in the block, the system provides an extra layer of protection against fraudulent activity. Stakes grow more valuable as the price of ETH rises, which improves network security. However, energy requirements stay the same throughout this process. However, some individuals are concerned that proof of stake would give those who have the most ETH greater control, resulting in a less decentralized system.
According to Farrokhnia, "Blockchain is a very configurable and versatile technology." [Citation needed] You are free to construct it in any shape or form that is conducive to achieving your goal. Therefore, one example of a proof of consensus method is termed "proof of reputation." This mechanism works on the principle that "the more respectable you are, the more votes you have in verifying things." Blocks and transactions are verified by pre-approved participants who are required to reveal their true identities. The proof of authority system depends on its participants' reputation and trustworthiness. Some cryptocurrencies utilize a proof of coverage system that requires miners to offer a service, such as hosting a router in their house, so the network may grow. This is one of the requirements for mining these coins.
Moving bitcoin facilities next to oil fields would be another way to reduce the environmental impact of cryptocurrency mining. These operations would collect waste methane gas that is often burned off, pump it to generators, and utilize the electricity from the generators to mine bitcoin. In West Texas, where there is an abundance of wind power, there are plans to mine some bitcoin. Bitcoin mining operations close to wind farms can use the extra energy made by those farms. This is because the amount of power made by the wind can sometimes be more than what the transmission lines can handle.
According to Farrokhnia, even if these concepts are conceivable in a theoretical sense, it's feasible that they won't work in practice. He said that each of these concepts calls for a significant initial capital expenditure. "And we know that interest in mining is predicated on the price of bitcoin itself. As a result, you could have a wide variety of extremely pricey solutions that would aim to be more energy efficient. However, as soon as the price of bitcoin were to drop below a certain threshold, all of these projects would be [cancelled] because they are simply not financially feasible. Given the unpredictability of Bitcoin's price and the lack of clarity around its potential future, who would make those kinds of investments in their right mind?
The development of Farrokhnia is the best chance it has of becoming a more environmentally friendly cryptocurrency. He is of the opinion that cryptocurrencies must take environmental factors into account if they want to achieve widespread acceptance and that more recent cryptocurrencies that minimize their impact on the environment may one day surpass Bitcoin.
According to Farrokhnia, "A new generation of crypto is coming on board." [Cryptocurrency] "They are going to move away from proof of work for a variety of reasons, one of which is the environmental effect, since young programmers are generating the majority of these. This is one of the reasons why they are moving away from proof of work. They are definitely more aware of the environment, and we can only hope that they understand the importance of their work beyond what they are building and that they will take into account how complicated the world is today.
Conclusion
Alternative methods of reducing the environmental impact of cryptocurrency mining include relocating bitcoin mining operations to areas near oil fields and using the waste methane gas from flared flares to power generators. You might have a lot of very expensive solutions that attempt to be more energy efficient, but as soon as the price of bitcoin dropped below a certain level, all these initiatives would be [cancelled] because they are simply not financially possible. He thinks that Bitcoin will be replaced by a newer cryptocurrency that is better for the environment because the industry won't be able to ignore environmental concerns.
FAQ
Is the use of Bitcoin bad for the environment? According to the findings of the experts, the entire global climate damage caused by bitcoin between the years 2016 and 2021 is anticipated to amount to $12 billion, and within that time period, carbon emissions have climbed 126 times.
In what ways is the mining of bitcoins harmful to the environment? The digital currency's reliance on a computing process to verify transactions known as "proof-of-work mining" is to blame for the disproportionate amount of damage it causes to the environment. Participating in "proof-of-work mining" requires massive electricity expenditures, and those who do so are rewarded with the opportunity to win some new bitcoin.
Is the use of Bitcoin kind to the environment? According to environmentalists' assessments, the "mining" of bitcoin requires an alarmingly high quantity of fossil fuels. On the other hand, there are other cryptocurrencies that are better for the environment and do less harm to the world. Because of these, worries about the relationship between cryptocurrencies and the environment might be eased.
Why are NFTs detrimental to the health of the environment? Indeed, conventional approaches to minting and validating NFTs use significant amounts of energy. The vast majority of non-fungible tokens (NFTs) in existence today are hosted on OpenSea, a platform built on Ethereum that is notorious for its high level of energy consumption. Yes, the environment is being harmed when NFTs are used in these situations.
That's all for today, see ya tomorrow
If you want more, be sure to follow us on :
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 3cd2ea88:bafdaceb
2024-03-07 01:21:29
@ 3cd2ea88:bafdaceb
2024-03-07 01:21:29Event continues!
Trade futures, earn entries, and win:
1st draw: Guaranteed SHIB for all!
Bitget welcome bonus
Trading fee discount coupons
Don't miss out!
Sign up on Bitget and start trading!
-
 @ 57d1a264:69f1fee1
2024-03-05 07:47:20
@ 57d1a264:69f1fee1
2024-03-05 07:47:20Prompt: Nostalgia Design ===============
Your design prompt today is to create a design inspired by nostalgia — whatever nostalgia means to you. Who doesn't love revisiting the best parts of their childhood?
Whether it be a funky web design, a retro advertisement, pixel art or a Y2K inspired graphic, you have total creative freedom.
Flex your design muscles and join in. Most of all, keep this exercise loose and keep it stress-free. The FUC is about growing our design skills, together, as a community. We can't wait to see what you create!
Happy designing, Stackers!
Share Your Results When you finish the challenge, post your work on this thread! If you also share it on
nostr, be sure to use the hashtag #FUCdesiger and tag Design_r@iris.to or @Design__r on X! We'll keep an eye out and repost good examples on a regular basis.
Curious to know WTF is a FUC? Read the ⚡️Flash Ui Challenges welcoming post.
Looking for more FUCs? Check the archive here!
-
 @ 57d1a264:69f1fee1
2024-03-05 07:31:05
@ 57d1a264:69f1fee1
2024-03-05 07:31:05What's your favorite paraphernalia, and how has it improved your life? What it has helped you design or accomplish lately?
-
 @ 000002de:c05780a7
2024-03-04 22:09:47
@ 000002de:c05780a7
2024-03-04 22:09:47I started this as a comment on @felipe's post "What is your story with Linux? Me first:" but decided it was getting a bit long.
How it Began
It started on my first day at my first job in tech. I was working part time and being trained by a retired IT guy that had built the computers and set up the servers I was going to manage. He showed my my workstation which was running some Linux distro. I knew nothing about Linux at the time and I don't recall which distro it was. I am pretty sure it was using KDE though. He just called it Linux. At the time I was using OS X (now called Mac OS). I didn't dive into Linux at all. I only used it when I had to use it.
Fast forward a few years and our team was tasked with launching a set of web sites and I needed to set up servers for hosting them. I had never done this before. I hired a consultant to help me evaluate and do the work. He was a Linux guy, and also a Vim user and regularly encouraged me to dive into Vim. I'm still grateful for that. He was a Debian fan but due to my limited knowledge of Linux and upper management's desire for support we went with Red Hat Enterprise Linux (RHEL). What is funny is I now work at Red Hat. I started learning more and more about Linux servers as I ran them. I set up many Debian servers and have been using Linux on the server ever since. I still default to Debian when I need to set up a server. I know it best. Over the years hosting web sites for myself and others has taught me quite a bit about Linux but that is only the first part.
The Year of the Linux Desktop
In 2020 I started working at Red Hat. I stayed on MacOS but over the years I had started to tire of Apple's neglect of their operating system, their increased focus on iOS and making MacOS more like iOS. I wanted to do things that MacOS just couldn't do. My job required a lot of use of Docker and MacOS at the time was painfully bad at running Docker Desktop. In 2021 I'd finally had it with their hardware as well and decided to try to make a go all in using Linux on the desktop. After all I now worked at a Linux company and had many co-workers that used Linux as their main OS.
I did my research and decided to go with Fedora since I like the desktop environment. I later learned that DE is not a great reason to choose a distro. But, all and all Fedora has been solid and I haven't been tempted to go back to MacOS. I bought an early Framework laptops and soon after requested a company issued Thinkpad. I installed Fedora on both and haven't looked back.
I've tried Arch but its never stuck as my daily driver. I still use it on an old Thinkpad from time to time. I'm planning to try NixOS soon. I've also tried to use a couple tiling window managers but just haven't been able to make the jump yet. I think that's where I will land as I have used Tmux for my development work for 10+ years now and I like the UX. Linux has an amazing ecosystem and there's so much you can do with it. I now recommend anyone getting into programming or working in IT start using it as their main workstation. I wish I had done it much sooner. Thankfully there was a lot of knowledge I gained using MacOS that transferred to Linux since they share the same origin but there is no substitute for Linux.
-
 @ f3df9bc0:a95119eb
2024-03-07 00:29:47
@ f3df9bc0:a95119eb
2024-03-07 00:29:47 -
 @ 81870f53:29bef6a6
2024-03-06 20:23:17
@ 81870f53:29bef6a6
2024-03-06 20:23:17自動車産業の柱の一つであるメルセデス・ベンツは最近、完全電気自動車の廃止を発表し、開発戦略に大きな変更を加えた。この決定は、一部の人にとって驚くべきものではありますが、市場の現実と財政的要請が蔓延する複雑な経済状況の中で行われます。
メルセデス・ベンツの発表は、自動車業界全体の一連の挫折を受けて行われた。高い開発コストや製造コスト、収益性の問題など、電気自動車の生産における課題により、多くのメーカーは計画の再検討を余儀なくされています。メルセデス・ベンツにとって、この決定は電動モビリティへの移行に伴うコストと利点の実用的な評価を反映しています。
メルセデス・ベンツが全電気技術を放棄したのも、長期的な経済的考慮によるものだ。電気自動車の需要は依然として不確実であり、充電インフラはまだ開発中ですが、この技術への多額の投資はかなりの財務リスクを伴います。メルセデス・ベンツは、ハイブリッド パワートレインや改良された内燃エンジンなど、より多様なソリューションにリソースを集中することを選択することで、長期的な経済的存続を確保しようとしています。
この決定を、より持続可能なモビリティへの移行にとって後退とみなす人もいるかもしれない。しかし、より深く分析すると、問題はさらに微妙であることが明らかになります。実際には、経済的な持続可能性は環境の持続可能性と同じくらい重要です。企業は、環境上の責務と経済的現実の両方を考慮した情報に基づいた意思決定を行う必要があります。この文脈において、メルセデス・ベンツのアプローチは、現在の課題に対する賢明かつ責任ある対応であるように見えます。
自動車経済の観察者にとって、メルセデス・ベンツの発表は、エネルギー転換に関する政府政策の有効性についても疑問を投げかけている。多くの政府は電気自動車の導入を促進するために税制上の優遇措置や排出削減目標を実施していますが、これらの措置は必ずしも普及を促進することに成功しているわけではありません。市場の現実や消費者のニーズに合わせてこれらの政策を再考する時期が来ています。
結局のところ、メルセデス・ベンツの全電気自動車からの脱却は、経済的な決定は慎重かつ洞察力を持って行う必要があることを思い出させる重要なものだ。自動車産業のようなダイナミックで競争の激しい分野では、企業は市場の変化に適応し、長期的な生き残りを確実にするために戦略を常に再評価する必要があります。電動モビリティが進歩し続けるにつれて、環境への願望と経済的要請の間のバランスを維持することが不可欠です
この記事がお役に立てば幸いです。 もしそうなら、チップをおくるどうぞ https://getalby.com/p/bitcap
-
 @ 7dd04080:36f6813d
2024-03-04 18:49:56
@ 7dd04080:36f6813d
2024-03-04 18:49:56All filmmakers' and musicians' lightning address QR codes will now be displayed with their videos inside our Roku app. This should greatly enhance the ability to receive direct tips from television watchers worldwide. All they need to do is open their favorite Lightning wallet on their phone, point its camera at the QR code, and choose the number of Sats to send to an artist.
For more information, check out our site: https://versusmedia.com/
-
 @ 3bf0c63f:aefa459d
2024-01-14 14:52:16
@ 3bf0c63f:aefa459d
2024-01-14 14:52:16Drivechain
Understanding Drivechain requires a shift from the paradigm most bitcoiners are used to. It is not about "trustlessness" or "mathematical certainty", but game theory and incentives. (Well, Bitcoin in general is also that, but people prefer to ignore it and focus on some illusion of trustlessness provided by mathematics.)
Here we will describe the basic mechanism (simple) and incentives (complex) of "hashrate escrow" and how it enables a 2-way peg between the mainchain (Bitcoin) and various sidechains.
The full concept of "Drivechain" also involves blind merged mining (i.e., the sidechains mine themselves by publishing their block hashes to the mainchain without the miners having to run the sidechain software), but this is much easier to understand and can be accomplished either by the BIP-301 mechanism or by the Spacechains mechanism.
How does hashrate escrow work from the point of view of Bitcoin?
A new address type is created. Anything that goes in that is locked and can only be spent if all miners agree on the Withdrawal Transaction (
WT^) that will spend it for 6 months. There is one of these special addresses for each sidechain.To gather miners' agreement
bitcoindkeeps track of the "score" of all transactions that could possibly spend from that address. On every block mined, for each sidechain, the miner can use a portion of their coinbase to either increase the score of oneWT^by 1 while decreasing the score of all others by 1; or they can decrease the score of allWT^s by 1; or they can do nothing.Once a transaction has gotten a score high enough, it is published and funds are effectively transferred from the sidechain to the withdrawing users.
If a timeout of 6 months passes and the score doesn't meet the threshold, that
WT^is discarded.What does the above procedure mean?
It means that people can transfer coins from the mainchain to a sidechain by depositing to the special address. Then they can withdraw from the sidechain by making a special withdraw transaction in the sidechain.
The special transaction somehow freezes funds in the sidechain while a transaction that aggregates all withdrawals into a single mainchain
WT^, which is then submitted to the mainchain miners so they can start voting on it and finally after some months it is published.Now the crucial part: the validity of the
WT^is not verified by the Bitcoin mainchain rules, i.e., if Bob has requested a withdraw from the sidechain to his mainchain address, but someone publishes a wrongWT^that instead takes Bob's funds and sends them to Alice's main address there is no way the mainchain will know that. What determines the "validity" of theWT^is the miner vote score and only that. It is the job of miners to vote correctly -- and for that they may want to run the sidechain node in SPV mode so they can attest for the existence of a reference to theWT^transaction in the sidechain blockchain (which then ensures it is ok) or do these checks by some other means.What? 6 months to get my money back?
Yes. But no, in practice anyone who wants their money back will be able to use an atomic swap, submarine swap or other similar service to transfer funds from the sidechain to the mainchain and vice-versa. The long delayed withdraw costs would be incurred by few liquidity providers that would gain some small profit from it.
Why bother with this at all?
Drivechains solve many different problems:
It enables experimentation and new use cases for Bitcoin
Issued assets, fully private transactions, stateful blockchain contracts, turing-completeness, decentralized games, some "DeFi" aspects, prediction markets, futarchy, decentralized and yet meaningful human-readable names, big blocks with a ton of normal transactions on them, a chain optimized only for Lighting-style networks to be built on top of it.
These are some ideas that may have merit to them, but were never actually tried because they couldn't be tried with real Bitcoin or inferfacing with real bitcoins. They were either relegated to the shitcoin territory or to custodial solutions like Liquid or RSK that may have failed to gain network effect because of that.
It solves conflicts and infighting
Some people want fully private transactions in a UTXO model, others want "accounts" they can tie to their name and build reputation on top; some people want simple multisig solutions, others want complex code that reads a ton of variables; some people want to put all the transactions on a global chain in batches every 10 minutes, others want off-chain instant transactions backed by funds previously locked in channels; some want to spend, others want to just hold; some want to use blockchain technology to solve all the problems in the world, others just want to solve money.
With Drivechain-based sidechains all these groups can be happy simultaneously and don't fight. Meanwhile they will all be using the same money and contributing to each other's ecosystem even unwillingly, it's also easy and free for them to change their group affiliation later, which reduces cognitive dissonance.
It solves "scaling"
Multiple chains like the ones described above would certainly do a lot to accomodate many more transactions that the current Bitcoin chain can. One could have special Lightning Network chains, but even just big block chains or big-block-mimblewimble chains or whatnot could probably do a good job. Or even something less cool like 200 independent chains just like Bitcoin is today, no extra features (and you can call it "sharding"), just that would already multiply the current total capacity by 200.
Use your imagination.
It solves the blockchain security budget issue
The calculation is simple: you imagine what security budget is reasonable for each block in a world without block subsidy and divide that for the amount of bytes you can fit in a single block: that is the price to be paid in satoshis per byte. In reasonable estimative, the price necessary for every Bitcoin transaction goes to very large amounts, such that not only any day-to-day transaction has insanely prohibitive costs, but also Lightning channel opens and closes are impracticable.
So without a solution like Drivechain you'll be left with only one alternative: pushing Bitcoin usage to trusted services like Liquid and RSK or custodial Lightning wallets. With Drivechain, though, there could be thousands of transactions happening in sidechains and being all aggregated into a sidechain block that would then pay a very large fee to be published (via blind merged mining) to the mainchain. Bitcoin security guaranteed.
It keeps Bitcoin decentralized
Once we have sidechains to accomodate the normal transactions, the mainchain functionality can be reduced to be only a "hub" for the sidechains' comings and goings, and then the maximum block size for the mainchain can be reduced to, say, 100kb, which would make running a full node very very easy.
Can miners steal?
Yes. If a group of coordinated miners are able to secure the majority of the hashpower and keep their coordination for 6 months, they can publish a
WT^that takes the money from the sidechains and pays to themselves.Will miners steal?
No, because the incentives are such that they won't.
Although it may look at first that stealing is an obvious strategy for miners as it is free money, there are many costs involved:
- The cost of ceasing blind-merged mining returns -- as stealing will kill a sidechain, all the fees from it that miners would be expected to earn for the next years are gone;
- The cost of Bitcoin price going down: If a steal is successful that will mean Drivechains are not safe, therefore Bitcoin is less useful, and miner credibility will also be hurt, which are likely to cause the Bitcoin price to go down, which in turn may kill the miners' businesses and savings;
- The cost of coordination -- assuming miners are just normal businesses, they just want to do their work and get paid, but stealing from a Drivechain will require coordination with other miners to conduct an immoral act in a way that has many pitfalls and is likely to be broken over the months;
- The cost of miners leaving your mining pool: when we talked about "miners" above we were actually talking about mining pools operators, so they must also consider the risk of miners migrating from their mining pool to others as they begin the process of stealing;
- The cost of community goodwill -- when participating in a steal operation, a miner will suffer a ton of backlash from the community. Even if the attempt fails at the end, the fact that it was attempted will contribute to growing concerns over exaggerated miners power over the Bitcoin ecosystem, which may end up causing the community to agree on a hard-fork to change the mining algorithm in the future, or to do something to increase participation of more entities in the mining process (such as development or cheapment of new ASICs), which have a chance of decreasing the profits of current miners.
Another point to take in consideration is that one may be inclined to think a newly-created sidechain or a sidechain with relatively low usage may be more easily stolen from, since the blind merged mining returns from it (point 1 above) are going to be small -- but the fact is also that a sidechain with small usage will also have less money to be stolen from, and since the other costs besides 1 are less elastic at the end it will not be worth stealing from these too.
All of the above consideration are valid only if miners are stealing from good sidechains. If there is a sidechain that is doing things wrong, scamming people, not being used at all, or is full of bugs, for example, that will be perceived as a bad sidechain, and then miners can and will safely steal from it and kill it, which will be perceived as a good thing by everybody.
What do we do if miners steal?
Paul Sztorc has suggested in the past that a user-activated soft-fork could prevent miners from stealing, i.e., most Bitcoin users and nodes issue a rule similar to this one to invalidate the inclusion of a faulty
WT^and thus cause any miner that includes it in a block to be relegated to their own Bitcoin fork that other nodes won't accept.This suggestion has made people think Drivechain is a sidechain solution backed by user-actived soft-forks for safety, which is very far from the truth. Drivechains must not and will not rely on this kind of soft-fork, although they are possible, as the coordination costs are too high and no one should ever expect these things to happen.
If even with all the incentives against them (see above) miners do still steal from a good sidechain that will mean the failure of the Drivechain experiment. It will very likely also mean the failure of the Bitcoin experiment too, as it will be proven that miners can coordinate to act maliciously over a prolonged period of time regardless of economic and social incentives, meaning they are probably in it just for attacking Bitcoin, backed by nation-states or something else, and therefore no Bitcoin transaction in the mainchain is to be expected to be safe ever again.
Why use this and not a full-blown trustless and open sidechain technology?
Because it is impossible.
If you ever heard someone saying "just use a sidechain", "do this in a sidechain" or anything like that, be aware that these people are either talking about "federated" sidechains (i.e., funds are kept in custody by a group of entities) or they are talking about Drivechain, or they are disillusioned and think it is possible to do sidechains in any other manner.
No, I mean a trustless 2-way peg with correctness of the withdrawals verified by the Bitcoin protocol!
That is not possible unless Bitcoin verifies all transactions that happen in all the sidechains, which would be akin to drastically increasing the blocksize and expanding the Bitcoin rules in tons of ways, i.e., a terrible idea that no one wants.
What about the Blockstream sidechains whitepaper?
Yes, that was a way to do it. The Drivechain hashrate escrow is a conceptually simpler way to achieve the same thing with improved incentives, less junk in the chain, more safety.
Isn't the hashrate escrow a very complex soft-fork?
Yes, but it is much simpler than SegWit. And, unlike SegWit, it doesn't force anything on users, i.e., it isn't a mandatory blocksize increase.
Why should we expect miners to care enough to participate in the voting mechanism?
Because it's in their own self-interest to do it, and it costs very little. Today over half of the miners mine RSK. It's not blind merged mining, it's a very convoluted process that requires them to run a RSK full node. For the Drivechain sidechains, an SPV node would be enough, or maybe just getting data from a block explorer API, so much much simpler.
What if I still don't like Drivechain even after reading this?
That is the entire point! You don't have to like it or use it as long as you're fine with other people using it. The hashrate escrow special addresses will not impact you at all, validation cost is minimal, and you get the benefit of people who want to use Drivechain migrating to their own sidechains and freeing up space for you in the mainchain. See also the point above about infighting.
See also
-
 @ 7175188c:6382a72c
2024-03-04 17:54:15
@ 7175188c:6382a72c
2024-03-04 17:54:15Disclaimer: I know it's GNU/Linux but I'll be referring to it as Linux for short.
The first time I remember reading something about Linux was around 1998, while sitting on the toilet on my friend's house.
There was a pile of magazines near the loo and one caught my eyes. I can't recall exactly what it was but I think it was about the fusion of Mandrake Linux with Conectiva Linux forming the new (at the time) distro, Mandriva Linux. At that time, I knew nothing about Linux at the time but, as I flipped through pages and pages of blue screenshots, I was hooked.
From 99 to ~2002, I remember seeing my friend's brother installing Linux on his desktop a few times. I also remember playing around on KDE on his freshly installed Suse Linux and, maybe in 2003, I remember mindless typing my first apt get commands and breaking his installation of Kurumin Linux 'cause it messed with some dependencies or something. Good days :)
The first time I installed Linux on a machine I owned was in 2004, the same year I bought my first computer with my own money. It was the Kurumin Linux wich was huge in Brazil at that time. Kurumin was one of the first live distros (that I know of) so it was easy to play with without breaking (too much) stuff.
From 2005 to the present day, Linux (mostly Debian Stable with i3wm) remain my main operating system and I only used other OSs on work related tasks, like Windows on a work machine between 2010 and 2013 for .NET development and MacOS on a few old macs for iOS development between 2014 and today.
That's it for this post. There are more interesting stories like when Canonical was giving away free installation CDs and I ordered some to sell'em on Brazil's equivalent of Ebay 😅 or when in 2009 I made an unsolicited "port" of a DOS program of the softhouse I was working on to "work" on DOSEMU (or DOSBox, I don't remember exactly). It probably wouldn't work in production but, man, was it fast.
Now it's your turn.
PS: thanks @hodlme for creating the Linux territory!
-
 @ 5d4b6c8d:8a1c1ee3
2024-03-04 16:47:50
@ 5d4b6c8d:8a1c1ee3
2024-03-04 16:47:50I mentioned going to Dune part 2 in the saloon and promised to make a post about it. Without spoiling the main events of the plot, I'm going to discuss what's so amazing about Dune. I'll focus on the books, since this is ~BooksAndArticles, but I'll also give my impressions of the adaptation.
I'd love to hear other people's thoughts about book and/or movie.
Dune (the book)
First off, Dune is one of my favorite books of all time. I'm an economist with a background in atmospheric science who loves sci-fi, so Dune is very much up my alley. I've read all of the Frank Herbert books, and I recommend all of them, but the first one is really special. It's worth noting that Star Wars was heavily influenced by Dune (to the point where I've heard Star Wars referred to as a knock-off).
Dune is a planet that is the sole producer of an extremely valuable commodity, "spice", that is basically a combination of spices and petroleum in the context of Earth history. So, think about a substantially more extreme version of the spice trade. The planet is incredibly inhospitable: hotter and drier than any desert on Earth, plus there are enormous carnivorous worms in the desert. The native inhabitants of the planet are ferocious desert warriors who are in perpetual conflict with the oligarchs attempting to harvest spice.
@r3drun3 made a post about the economics of Dune. The political setting of this universe is very detailed. There's an empire, but also great houses, trade guilds, and professional societies. Each of those are described in great detail, which makes the world incredibly immersive. There are a ton of dynamics in play all the time, but it's written so well as to not be confusing or hard to keep track of.
There are many themes being explored in Dune (understatement alert), so I'll just discuss a couple of my favorites. The most striking element of the book to me was how intricately detailed the native culture of Dune (the Fremen) is described. The society is fundamentally shaped around water scarcity and there are a wide array of cultural practices, beliefs, and technologies that exist to help them survive this place. There is also a religious belief system that has been externally curated and manipulated to make the Fremen receptive to a messiah that one of the secret societies is trying to create. It's a fascinating exploration of propaganda and myth making.
As a slight aside, I've been reading The Wheel of Time (review here) and there's a lot of overlap with Dune. One is sci-fi and the other is fantasy, but there are a ton of parallels.
Dune Parts 1 and 2 (the movies)
The two recent movies are fairly faithful to the book they are adapting, but they have radically pared down the content. The first book describes many characters in great detail, which would have been very difficult to cover in a movie. As a result, the movies are largely told from Paul Atreides' perspective and many of the things that would have been explained in the book are seen without exposition in the movies.
The director does a phenomenal job of showing many of the complex elements of the books without needing to spend precious screen time on exposition. Dune is also a very alien universe, despite being mostly about humanity. It takes place in the far distant future and the technologies are supposed to be simultaneously understandable in function and unfamiliar in form. This is executed beautifully on screen: everything is grand and distinctive and foreign.
The performances are overwhelmingly excellent, with just a couple of exceptions (Jason Momoa cough, Christopher Walken cough). Timothée Chalamet, in particular, has some incredible scenes in part 2.
-
 @ b5035b7a:f170dae3
2024-03-06 17:04:45
@ b5035b7a:f170dae3
2024-03-06 17:04:45Initial post
codecodequote quotes
- list item
- second list item
Regular paragraph.
-
 @ 7175188c:6382a72c
2024-03-04 14:36:04
@ 7175188c:6382a72c
2024-03-04 14:36:04Hey, Stackers!
I'm planning to start posting long-form content regularly on a couple of user-created territories so I was wondering if there's a way to know if a territory is permanently funded. Is there?
Also, what happens to posts made on an archived territory? I know that Stackers can still see archived posts and comments but are they still discoverable?
@ek
-
 @ 3bf0c63f:aefa459d
2024-01-14 14:52:16
@ 3bf0c63f:aefa459d
2024-01-14 14:52:16bitcoinddecentralizationIt is better to have multiple curator teams, with different vetting processes and release schedules for
bitcoindthan a single one."More eyes on code", "Contribute to Core", "Everybody should audit the code".
All these points repeated again and again fell to Earth on the day it was discovered that Bitcoin Core developers merged a variable name change from "blacklist" to "blocklist" without even discussing or acknowledging the fact that that innocent pull request opened by a sybil account was a social attack.
After a big lot of people manifested their dissatisfaction with that event on Twitter and on GitHub, most Core developers simply ignored everybody's concerns or even personally attacked people who were complaining.
The event has shown that:
1) Bitcoin Core ultimately rests on the hands of a couple maintainers and they decide what goes on the GitHub repository[^pr-merged-very-quickly] and the binary releases that will be downloaded by thousands; 2) Bitcoin Core is susceptible to social attacks; 2) "More eyes on code" don't matter, as these extra eyes can be ignored and dismissed.
Solution:
bitcoinddecentralizationIf usage was spread across 10 different
bitcoindflavors, the network would be much more resistant to social attacks to a single team.This has nothing to do with the question on if it is better to have multiple different Bitcoin node implementations or not, because here we're basically talking about the same software.
Multiple teams, each with their own release process, their own logo, some subtle changes, or perhaps no changes at all, just a different name for their
bitcoindflavor, and that's it.Every day or week or month or year, each flavor merges all changes from Bitcoin Core on their own fork. If there's anything suspicious or too leftist (or perhaps too rightist, in case there's a leftist
bitcoindflavor), maybe they will spot it and not merge.This way we keep the best of both worlds: all software development, bugfixes, improvements goes on Bitcoin Core, other flavors just copy. If there's some non-consensus change whose efficacy is debatable, one of the flavors will merge on their fork and test, and later others -- including Core -- can copy that too. Plus, we get resistant to attacks: in case there is an attack on Bitcoin Core, only 10% of the network would be compromised. the other flavors would be safe.
Run Bitcoin Knots
The first example of a
bitcoindsoftware that follows Bitcoin Core closely, adds some small changes, but has an independent vetting and release process is Bitcoin Knots, maintained by the incorruptible Luke DashJr.Next time you decide to run
bitcoind, run Bitcoin Knots instead and contribute tobitcoinddecentralization!
See also:
[^pr-merged-very-quickly]: See PR 20624, for example, a very complicated change that could be introducing bugs or be a deliberate attack, merged in 3 days without time for discussion.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Splitpages
The simplest possible service: it splitted PDF pages in half.
Created specially to solve the problem of those scanned books that come with two pages side-by-side as if they were a single page and are much harder to read on Kindle because of that.

It required me to learn about Heroku Buildpacks though, and fork or contribute to a Heroku Buildpack that embedded a mupdf binary.
-
 @ b5035b7a:f170dae3
2024-03-06 16:54:14
@ b5035b7a:f170dae3
2024-03-06 16:54:14Interested in a larger time frame, a larger context.
My rabbit holes: - Finance, geo-politics, martial events(these days Ukraine, Gaza), energy - my weaknesses: malinois dogs, when sporting - fitness+health+diet+exercise - vast spaces, unspoiled nature - water and air - artificial intelligence - genetics(biology of) - Jewish proportionality as compared to malinois
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28OP_CHECKTEMPLATEVERIFYand the "covenants" dramaThere are many ideas for "covenants" (I don't think this concept helps in the specific case of examining proposals, but fine). Some people think "we" (it's not obvious who is included in this group) should somehow examine them and come up with the perfect synthesis.
It is not clear what form this magic gathering of ideas will take and who (or which ideas) will be allowed to speak, but suppose it happens and there is intense research and conversations and people (ideas) really enjoy themselves in the process.
What are we left with at the end? Someone has to actually commit the time and put the effort and come up with a concrete proposal to be implemented on Bitcoin, and whatever the result is it will have trade-offs. Some great features will not make into this proposal, others will make in a worsened form, and some will be contemplated very nicely, there will be some extra costs related to maintenance or code complexity that will have to be taken. Someone, a concreate person, will decide upon these things using their own personal preferences and biases, and many people will not be pleased with their choices.
That has already happened. Jeremy Rubin has already conjured all the covenant ideas in a magic gathering that lasted more than 3 years and came up with a synthesis that has the best trade-offs he could find. CTV is the result of that operation.
The fate of CTV in the popular opinion illustrated by the thoughtless responses it has evoked such as "can we do better?" and "we need more review and research and more consideration of other ideas for covenants" is a preview of what would probably happen if these suggestions were followed again and someone spent the next 3 years again considering ideas, talking to other researchers and came up with a new synthesis. Again, that person would be faced with "can we do better?" responses from people that were not happy enough with the choices.
And unless some famous Bitcoin Core or retired Bitcoin Core developers were personally attracted by this synthesis then they would take some time to review and give their blessing to this new synthesis.
To summarize the argument of this article, the actual question in the current CTV drama is that there exists hidden criteria for proposals to be accepted by the general community into Bitcoin, and no one has these criteria clear in their minds. It is not as simple not as straightforward as "do research" nor it is as humanly impossible as "get consensus", it has a much bigger social element into it, but I also do not know what is the exact form of these hidden criteria.
This is said not to blame anyone -- except the ignorant people who are not aware of the existence of these things and just keep repeating completely false and unhelpful advice for Jeremy Rubin and are not self-conscious enough to ever realize what they're doing.
-
 @ c11cf5f8:4928464d
2024-03-04 14:29:53
@ c11cf5f8:4928464d
2024-03-04 14:29:53Y'all ready for a week of thrilling opportunities? Time to brush off the spurs and saddle up for a ride into the exciting ad-ventures ahead! What innovative goods or services are y'all bringin' on the wagon this week? Give us a sneak peek and let that entrepreneurial spirit get out.
Take some pics and start posting your items now!
[⚖️ SELL] - [🛒 BUY] - [🧑💻 HIRE] - [🖇 OFFER] - [🧑⚖️ AUCTION] - [🤝 SWAP] - [🆓 FREE] - [⭐ REVIEW]
Stay humble, stack sats!
-
 @ 1e52c554:21771908
2024-03-06 16:33:20
@ 1e52c554:21771908
2024-03-06 16:33:20Posthumous work of the Colombian poet born in Don Matias on January 20, 1948.
Welcome to this blog dedicated to the Posthumous work of the Colombian poet Francisco Luis Arroyave Tabares (my father), born in Don Matias on January 20, 1948-2010. Where I will be publishing each of the 175 sonnets from his unpublished collection 'Sonnets For The Twenty-First Century And A Circadian Musical (1984-1987).' Analyzed with GPT4 artificial intelligence and illustrated with AI tools... I hope you enjoy this garden of words snatched from the solitude of a locked room.
Likewise, any enthusiast of the sonnet form is invited to conduct their personal studies of Arroyave Tabares' work, as it is a collection that, although registered since 1989, has not yet been published.
Frank Duna

Analysis "In Shandows I will wait"
Introduction
Sonnet 89 is a deeply emotional and introspective poem that explores themes of love, loss, longing, and hope. It uses vivid and evocative imagery to convey the speaker's emotional state and his complex relationship with love.
Thematic Analysis
First Quatrain: The speaker recalls a past love, which is now only an echo or a memory. The use of words like “emptiness”, “confines”, and “echoes” suggests a sense of loss and longing.
Second Quatrain: The speaker talks about the new experiences in life (symbolized by “new-sprung blooms”) but they do not bring the pleasure he seeks. The “pungent hill” surrounded by loneliness could symbolize the challenges or hardships he’s facing.
Third Quatrain: The speaker’s soul, described as “bleak”, calls out for its other half, suggesting a sense of incompleteness. The fleeting nature of happiness and the reference to Venus (the Roman goddess of love) leaving behind a cloud of dust could symbolize the transient nature of love.
Couplet: The speaker resolves to wait in the shadows until true love occurs again. This shows a sense of hope and patience.
Overall, the sonnet explores themes of love, loss, longing, and hope. The language is rich and evocative, painting a vivid picture of the speaker’s emotional landscape. The use of natural imagery (blooms, hill, forest, dust) adds a layer of depth to the poem, linking the speaker’s emotional state to the natural world. The sonnet ends on a hopeful note, suggesting the possibility of love rekindling in the future.
Rhyme Scheme
The sonnet follows the Shakespearean sonnet rhyme scheme, which is ABABCDCDEFEFGG. Let’s break it down:
The first quatrain (lines 1-4) has the rhyme scheme ABAB:
A: In Shandows I will wait B: Easily I recall the emptiness A: Dwelling in confines by which love went by B: As echoes still full with loftinessThe second quatrain (lines 5-8) follows the scheme CDCD:
C: New-sprung blooms through my life lucently rill D: Yet they do not fulfill pleasures I seek C: And loneliness surrounds that pungent hill D: Where my fervors became blameless an meek.The third quatrain (lines 9-12) follows the scheme EFEF:
E: My bleak soul with mellifluous accent F: Calls its other half in deep forest lost. E: For happines has been evanescent F: And Venus left behind a cloud of dust.Finally, the couplet (lines 13-14) follows the scheme GG:
G: In shadows I will wait with my murmurs G: Until the real love once again occurs.This rhyme scheme is typical of Shakespearean sonnets and helps to give the poem its rhythm and flow. It also serves to emphasize certain themes and ideas within the poem, creating a sense of unity and coherence. The final couplet often provides a resolution or commentary on the themes presented in the quatrains. In this case, it reaffirms the speaker’s resolution to wait for true love.
Additional Aspects
Let’s delve deeper into the sonnet’s language, imagery, themes, meter, and overall impact.
Language and Imagery: The sonnet uses rich and evocative language to create vivid imagery. Phrases like “In shadows I will wait”, “New-sprung blooms through my life lucently rill”, and “Venus left behind a cloud of dust” paint a picture in the reader’s mind and evoke strong emotions. The use of words like “emptiness”, “echoes”, “loneliness”, and “bleak” further emphasize the themes of longing and solitude.
Themes: The main themes of the sonnet are love, loss, loneliness, and hope. The speaker expresses a deep longing for a lost love and the pain of solitude, yet also holds onto hope for the future. The recurring image of waiting in the shadows suggests patience and resilience in the face of adversity.
Meter: The sonnet follows the traditional iambic pentameter of Shakespearean sonnets, which consists of five pairs of unstressed and stressed syllables per line. This gives the poem a rhythmic quality and helps to emphasize certain words and ideas.
Overall: the sonnet is a poignant exploration of the human experience of love and longing. The combination of vivid imagery, emotional language, and rhythmic meter creates a powerful and moving piece of poetry. The speaker’s journey from recalling past love, through experiencing loneliness, to holding onto hope for future love, resonates with readers and invites them to reflect on their own experiences of love and loss. The sonnet ends on a hopeful note, reaffirming the human capacity for resilience and the enduring power of love.
(GPT4)
Syllable count for each line.
``` In Shandows I will wait
10 Easily I recall the emptiness 10 Dwelling in confines by which love went by 9 As echoes still full with loftiness 10 I find for remembrance or alibi.
10 New-sprung blooms through my life lucently rill
10 Yet they do not fulfill pleasures I seek 10 And loneliness surrounds that pungent hill 10 Where my fervors became blameless an meek.10 My bleak soul with mellifluous accent 10 Calls its other half in deep forest lost. 10 For happines has been evanescent 10 And Venus left behind a cloud of dust.
10 In shadows I will wait with my murmurs 10 Until the real love once again occurs. *** ```
Sonnets For The Twenty First Century And A Circadian Musical Written By Francisco Luis Arroyave Tabares (1984-1987)
Analyzed by GPT4; Image by Frank Duna; First published on Nostr Protocol by franciscoarroyavet@nostrplebs.com
 *In Shandows I will wait
*In Shandows I will wait -
 @ 1e52c554:21771908
2024-03-06 16:14:14
@ 1e52c554:21771908
2024-03-06 16:14:14Posthumous work of the Colombian poet born in Don Matias on January 20, 1948.
Welcome to this blog dedicated to the Posthumous work of the Colombian poet Francisco Luis Arroyave Tabares (my father), born in Don Matias on January 20, 1948-2010. Where I will be publishing each of the 175 sonnets from his unpublished collection 'Sonnets For The Twenty-First Century And A Circadian Musical (1984-1987).' Analyzed with GPT4 artificial intelligence and illustrated with AI tools... I hope you enjoy this garden of words snatched from the solitude of a locked room.
Likewise, any enthusiast of the sonnet form is invited to conduct their personal studies of Arroyave Tabares' work, as it is a collection that, although registered since 1989, has not yet been published.
Frank Duna

Analysis "The Best 0f Her Enthroned In My Hours"
Introduction
Sonnet 88 by Francisco Luis Arroyave Tabares, titled "The Best 0f Her Enthroned In My Hours," is a complex and emotionally charged poem that explores themes of love, loss, longing, and the passage of time.
Thematic Analysis
** Octave:** The octave presents a conflict, a problem, or a question. In this case, the speaker is expressing his struggle with a heartache that is both constant and intense. He describes his heart as being “immured by hush and amour” and fading in a world that is constantly becoming darker. He’s been trying to find peace and encourage passion, but sometimes he longs for the “lost musics” that her eyes once asked for.
Sestet: The sestet usually provides a resolution or commentary on the problem presented in the octave. Here, the speaker talks about a recent change in his life - he now has a “queen of depths” who is the best part of his hours. His old ideas are put away to age like wine, suggesting that he’s moving on from the past and looking forward to future missions and dreams.
In summary, this sonnet explores themes of love, loss, and hope for the future. The octave sets up a problem of heartache and longing, while the sestet offers a resolution of moving on and embracing new love and dreams. It’s a beautiful expression of the human experience of love and loss.
Rhyme Scheme
Let’s analyze the rhyme scheme of the sonnet. The rhyme scheme is ABBA ABBA CDE CDE, which is a typical Italian or Petrarchan sonnet structure.
Here’s how it applies to the sonnet:
Octave:
Line 1 (A): Is there any other way of masking Line 2 (B): The incessant and maddening dolour Line 3 (B): Of a heart immured by hush and amour Line 4 (A): That fades in a world that keeps on dusking? Line 5 (A): Most of my forces I have been tasking Line 6 (B): To peace my soul and encourage ardour Line 7 (B): While some times I demand from my contour Line 8 (A): The lost musics that her eyes were asking.**Sestet: **
Line 9 (C): In recent days a queen of depths I have Line 10 (D): With the best of her enthroned in my hours Line 11 (E): As passions live and trot with dear visions. Line 12 (C): My old ideas I put in a cave Line 13 (D): To age with wìnes for other times of ours Line 14 (E): And dreams that look for our future missions.In the octave, the first and fourth lines rhyme, as do the second and third lines, creating an ABBA pattern. This pattern is repeated in the next four lines. In the sestet, the first, fourth lines rhyme ©, as do the second, fifth (D), and the third, sixth (E), creating a CDE CDE pattern. This rhyme scheme helps to emphasize the shift in tone between the octave and the sestet. It’s a beautiful structure that adds to the overall impact of the poem.
Additional Aspects
Let’s delve deeper into the analysis of “The Best 0f Her Enthroned In My Hours” by Francisco Luis Arroyave Tabares:
Language and Imagery: The sonnet uses rich and evocative language to convey its themes. The imagery of a heart “immured by hush and amour” and a world that is “dusking” paints a vivid picture of the speaker’s emotional state. The use of words like “masking”, “dolour”, and “ardour” add a layer of complexity and depth to the poem. The sonnet also uses metaphorical language, such as “queen of depths” and “old ideas I put in a cave”, which adds to the overall imagery and helps to convey the speaker’s feelings and experiences.
Themes: The main themes of the sonnet are love, loss, and hope. The speaker talks about a past love that has caused him pain and sorrow, but also about a new love that brings him joy and hope. The theme of time is also present, with the speaker putting his old ideas away to age like wine, suggesting a process of healing and moving on.
Meter: The sonnet appears to follow the iambic pentameter, which is a common meter in English poetry and is often used in sonnets. This means that each line of the poem has five metrical feet, each consisting of one unstressed syllable followed by one stressed syllable. This gives the poem a rhythmic quality and helps to guide the reader through the poem. ** Overall:** this sonnet is a beautiful exploration of the themes of love, loss, and hope. The use of rich language and vivid imagery, combined with the traditional sonnet structure and meter, creates a powerful and moving piece of poetry. The speaker’s journey from pain and longing to acceptance and hope is conveyed with depth and emotion, making this sonnet a poignant expression of the human experience.
(GPT4)
Syllable count for each line.
```
The Best 0f Her Enthroned In My Hours
10 Is there any other way of masking 10 The incessant and maddening dolour 10 Of a heart immured by hush and amour 10 That fades in a world that keeps on dusking?
10 Most of my forces I have been tasking 10 To peace my soul and encourage ardour 10 While some times I demand from my contour 10 The lost musics that her eyes were asking.
10 In recent days a queen of depths I have 10 With the best of her enthroned in my hours 10 As passions live and trot with dear visions. 10 My old ideas I put in a cave 10 To age with wìnes for other times of ours 10 And dreams that look for our future missions. ***
```
Sonnets For The Twenty First Century And A Circadian Musical Written By Francisco Luis Arroyave Tabares (1984-1987)
Analyzed by GPT4; Image by leonardo.ai; First published on Nostr Protocol by franciscoarroyavet@nostrplebs.com
 The Best 0f Her Enthroned In My Hours
The Best 0f Her Enthroned In My Hours -
 @ 599f67f7:21fb3ea9
2024-03-04 14:26:12
@ 599f67f7:21fb3ea9
2024-03-04 14:26:12Conectarse a muchos relays nostr puede agotar rápidamente la batería y el ancho de banda, especialmente si utilizas nostr en tu teléfono. Conectarse a los relays a través de un proxy nostr puede reducir el consumo de ancho de banda y de batería, además de ofrecer la ventaja adicional de ocultar tu dirección IP real a los relays.
¿Cómo funciona?
Un proxy nostr se conecta a un grupo de relays. Obtiene y publica eventos en esos relays. La aplicación cliente sólo necesita abrir una conexión websocket hacia el proxy para acceder a todos los relays a los que el proxy está conectado.
 Imagen por cortesía de Yonle 2023
Imagen por cortesía de Yonle 2023Como el cliente sólo abre una conexión en lugar de muchas, ahorra ancho de banda y batería.
Como el proxy se conecta a los relays en nombre del cliente, la dirección IP del proxy se expone a los relays en lugar de la del cliente. (Aunque sigue siendo necesario confiar en el proveedor del proxy).
Cómo utilizarlo
Un proxy nostr puede ser fácilmente autoalojado. Echa un vistazo a este repo por nostr:npub1x3azxuysp5vmfer4vgs4jn5tmfcx4ew8sh0qnev7gczljxsr7jwqa3g4el para instrucciones de auto-alojamiento.
Para los que no tenemos recursos para autoalojarnos, Bitcoin Txoko alberga una instancia comunitaria.
Como puedes ver, está conectado a algunos de los relays más populares.
Para utilizarlo, sólo tienes que añadir
wss://bostr.bitcointxoko.coma tu lista de relays.
También puedes eliminar los relays redundantes ahora que ya no necesitas conexiones directas con ellos.
Ya está. ¡Feliz zapping y nos vemos en nostr!
El servicio comunitario bostr.bitcointxoko.com se distribuye con el siguiente aviso de copyright.
Copyright 2023 Yonle yonle@lecturify.net
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met:
-
Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
-
Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution.
-
Neither the name of the copyright holder nor the names of its contributors may be used to endorse or promote products derived from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
La siguiente información no está actualizada. La instancia de la comunidad nproxy ya no se mantiene. Utilízala bajo tu propia responsabilidad. Muchas gracias a nostr:npub1gzuushllat7pet0ccv9yuhygvc8ldeyhrgxuwg744dn5khnpk3gs3ea5ds por su corrección.
Un proxy nostr puede ser fácilmente autoalojado. Echa un vistazo a este repo por nostr:npub1txukm7xckhnxkwu450sm59vh2znwm45mewaps4awkef2tvsgh4vsf7phrl para instrucciones de auto-alojamiento.
Para los que no tenemos recursos para autoalojarnos, Bitcoin Txoko alberga una instancia comunitaria.
Para utilizarlo, sólo tienes que añadir
wss://nproxy.bitcointxoko.coma tu lista de relays.
-
-
 @ 599f67f7:21fb3ea9
2024-03-04 14:25:25
@ 599f67f7:21fb3ea9
2024-03-04 14:25:25¿Qué es Cashu?
Cashu es un protocolo de ecash de código abierto para Bitcoin que ofrece transacciones instantáneas sin comisiones con una privacidad casi perfecta. Consulta nostr:naddr1qqxnzd3e8y6rvdpe8qur2v3cqgs9n8m87l0hd9xxqwndqcmwzh4uvyxmwlw0637kuhg98pkcy8ana2grqsqqqa28f238dz para obtener más detalles.
Nutstash
Nutstash es una increíble billetera web de Cashu desarrollada por nostr:npub1cj6ndx5akfazux7f0vjl4fyx9k0ulf682p437fe03a9ndwqjm0tqj886t6 que implementa la mayoría de los NUTs, así como el envío y recepción a través de Nostr. También puedes instalarla como una Progressive Web App (PWA) en tu teléfono.
⚠️ Tanto Nutstash como Cashu todavía están en fase beta. Existe la posibilidad de perder fondos. Lee sobre los riesgos antes de usar la aplicación. Haz pruebas con pequeñas cantidades con las que te sientas cómodo perdiendo.
Pruébalo
Vamos a explicar cómo interactuar con una mint, recibir y enviar ecash, hacer copias de seguridad, convertir a Lightning y hacer intercambios entre mints, y al final probaremos la funcionalidad de los contactos de Nostr.
Añadir un mint
Para interactuar con ecash, primero necesitas tener acceso a una mint, donde se crean y canjean tus tokens de ecash.
- Ve a Txoko Mint.
- Abre la mint en Nutstash.
💡 Puedes añadir mints adicionales en Nutstash yendo a
Mint, pegando la URL de la mint y presionandoAdd Mint("Añadir Mint"). Algunas mints públicas se pueden encontrar en MintIndex. Ten en cuenta que algunas mints reservarán una cierta cantidad de sats para pagar las tarifas de enrutamiento, lo que significa que no podrás retirar todos tus sats.
Crear tokens
Puedes financiar tu billetera de ecash tanto recibiendo ecash directamente como creando nuevos tokens de ecash pagando una factura de Lightning.
- En la pestaña
Mint, elige la mint en la que quieres crear nuevos tokens y presionaMint. - Elige una cantidad. Prueba con una cantidad pequeña, como 100 sats.
- Crea la factura y págala desde una billetera de Lightning. Una vez que se haya pagado la factura, deberías tener tokens de ecash.
Realizar transacciones con ecash
Realizar transacciones con ecash implica básicamente enviar y recibir bloques de datos. Por lo tanto, puedes probar estas funcionalidades enviando y recibiendo a ti mismo. 1. Para enviar ecash, ve a
Wallet>Send. 2. Selecciona la mint desde la que quieres enviar. 3. Elige una cantidad. Opcionalmente, utiliza la selección de monedas. 4. Haz clic en enviar tokens. 5. Copia el token. En este punto, puedes enviar el token a otra persona o canjearlo en tu propia billetera. Dado que solo estamos probando las cosas, haremos lo último.- Para recibir ecash, haz clic en
Wallet>Receive. - Pega el token de cashu.
- Haz clic en
Receive.
💡 Puedes verificar los tokens de ecash pendientes y reclamarlos si el destinatario aún no los ha canjeado. Para hacer esto, ve a la pestaña
Walletsy buscaTokens. Asegúrate de que la columnaPendingesté marcada. Debería haber una lista de tokens pendientes, haz clic en el botón de actualización para verificar su estado. Si no han sido reclamados, puedes copiar y canjear el token.Intercambio de múltiples mints
Es posible que te hayas preguntado si diferentes mints pueden enviar y recibir entre sí. La respuesta es sí. Bueno, más o menos. En lugar de enviar tokens de cashu entre sí, las transacciones entre mints se realizan a través de Lightning. Para probar esto, puedes agregar otra mint si aún no lo has hecho, por ejemplo, la mint de LNbits.
💡 Ten en cuenta que algunas mints reservarán una cierta cantidad de sats para pagar las tarifas de enrutamiento, lo que significa que no podrás retirar todos tus sats. Para evitar esto, también puedes crear tu propia mint con tu billetera Bitcoin Txoko LNbits activando la extensión de Cashu. Bitcoin Txoko no requiere reservas, por lo que puedes retirar todos tus sats.
- Ve a la pestaña
Minty agrega una nueva mint si aún no lo has hecho. - Una vez que tengas varias mints, tendrás la opción de
Inter-Mint Swap. Abre la opción y lee la advertencia. - Si deseas continuar, elige una mint de la que quieres hacer el intercambio y una mint a la que quieres hacer el intercambio.
- Elige una cantidad.
- Confirma la cantidad (
Confirm amount), verifica las tarifas estimadas de enrutamiento y procede con el intercambio (Swap). En segundo plano, la mint que envía está pagando una factura de Lightning a la mint que recibe. Una vez que se haya liquidado la factura, el token intercambiado debería aparecer en el saldo de tu billetera en la mint que recibe.
Convertir a lightning
Cuando quieras convertir tus sats de cashu de nuevo a sats de Lightning, puedes convertir o "derretir" tus tokens de cashu.
- Haz clic en
Payo toca el ícono de la cámara para escanear un código QR. - Ingresa o escanea una factura.
- Opcionalmente, utiliza la selección de monedas.
- Presiona
Pay. La mint funde los tokens de cashu y paga la factura de Lightning.
Copias de seguridad
Hacer copias de seguridad de los tokens de Cashu es probablemente diferente al proceso que estás acostumbrado a hacer para respaldar las billeteras de Bitcoin y Lightning. Dado que los fondos están representados por tokens que son simplemente bloques de datos, solo estás respaldando estos datos cuando haces una copia de seguridad de los tokens de Cashu. Esto también significa que tus copias de seguridad cambiarán cada vez que realices una transacción y necesitarás hacer una nueva copia de seguridad después de cada transacción.
Los diferentes clientes de billeteras han implementado las copias de seguridad de manera diferente y solo funcionarán con la misma billetera que ha creado la copia de seguridad. Nutstash utiliza un archivo JSON como copia de seguridad, que también incluye tu historial de transacciones junto con los tokens que has agregado.
- Para descargar la copia de seguridad en formato JSON, ve a
Settings("Configuración") >Backup Tokens("Copia de seguridad de tokens"), descarga el archivo JSON y guárdalo en un lugar seguro. - Para restaurar la copia de seguridad, ve a
Settings("Configuración") >Restore("Restaurar"). Lee la advertencia. Los datos actuales de tu billetera se sobrescribirán.
Nostr
Dado que puedes enviar tokens de Cashu a través de cualquier protocolo basado en texto, Nostr es una excelente opción para Cashu. Nutstash facilita el envío de tokens de Cashu a través de Nostr.
Primero, necesitas conectar un firmante externo de Nostr a Nutstash para que Nutstash pueda cifrar y firmar mensajes directos utilizados para enviar tokens de ecash. Para hacer esto,
- Ve a la pestaña
Settings("Configuración") y encuentra la secciónNostr. - Activa
Nostr. - Puedes configurar (
Configure) los retransmisores manualmente o permitir que Nutstash lea tu lista de retransmisores después de completar el siguiente paso. - Activa
Use external key("Usar clave externa"). Debes tener instalada una extensión de firmante de Nostr en tu navegador. Algunas buenas opciones son nos2x, Alby y Nostore (para Safari en iOS). - Una vez que Nutstash detecte tu extensión de firmante, permítele leer tu lista de retransmisores y clave pública.
- Si permites que Nutstash descifre los mensajes, buscará tokens de Cashu en tus mensajes directos. Una vez encontrados, aparecerán en la pestaña
Walleten la bandeja de entrada (Inbox). Allí podrás canjearlos en tu billetera.
Para enviar Cashu a través de Nostr,
- Ve a
Send("Enviar"). - Elige un mint.
- Elige una cantidad. Opcionalmente, utiliza la selección de monedas.
- Presiona
Send("Enviar"). - En
Send via Nostr("Enviar a través de Nostr"), ingresa una dirección de Nostr en formato npub, hexadecimal o NIP-05. Alternativamente, escanea el código QR del perfil de alguien. - Presiona
Send via Nostr("Enviar a través de Nostr") y firma el mensaje tipo 4 con tu firmante externo. - Informa al destinatario que revise su bandeja de entrada, ¡deberían tener algunos Cashu esperándolos allí!
Conclusión
¿Encontraste útil esta guía? ¡Intenta enviarnos algunos tokens de Cashu a través de Nostr!
-
 @ 82b30d30:40c6c003
2024-03-06 15:40:24
@ 82b30d30:40c6c003
2024-03-06 15:40:24[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
[19]
[20]
[21]
[22]
