-
 @ 5d4b6c8d:8a1c1ee3
2024-03-07 18:31:36
@ 5d4b6c8d:8a1c1ee3
2024-03-07 18:31:36This idea came to me last night after reading and participating in a few different posts about territory rent and ownership. I imagine there's a term for what I'm going to describe that I'm either unaware of or just isn't coming to me.
These recent posts have centered around the increasing cost (in purchasing power) of monthly territory rent, the potential long-term value of an outright purchase, and a desire to allow joint ownership. I believe we can address all of these issues simultaneously.
The Model
First off, participation in this model should be opt-in for the territory founders * Anyone can make payments on any participating territory * Territory revenues get paid out in proportion to what each stacker has paid in * Whoever has paid in the most assumes control over the territory * Once three million sats have been paid towards a territory it becomes owned outright * If less than 100k sats per month have been paid towards a territory it becomes archived * Archived territories can be resurrected by making up the back payments * Any rental payments already made towards a territory will be counted if and when a founder opts-in
Discussion
The logic here is pretty straightforward. Instead of one stacker being on the hook for a large monthly bill, the community is on the hook to keep the territories they care about alive. This gives everyone an opportunity to invest in the territories they value and make sure they don't become archived.
I'm also thinking that there's no reason investment has to stop once the territory hits 3 million sats. That threshold could just mean the territory will never be archived. Further investments could still impact revenue share and control. This would increase the revenue stream for Stacker News.
Founders can still protect their control in a few ways: never opt-in, out bid everyone else, build up a big cushion before opting in.
I'll be curious to hear what people think about this proposal.
-
 @ d4338b7c:f1d23a5b
2024-03-07 16:42:42
@ d4338b7c:f1d23a5b
2024-03-07 16:42:42Chef's notes
Absinthe rinse 10 Dashes Peychauds bitters 1/2 tsp Demarara or simple syrup 2oz Rye (usually Sazerac 6 year) Stirred. Served up in a rocks glass. Luxardo cherry 🍒 and a lemon expression as garnish.
Details
- ⏲️ Prep time: 5
- 🍳 Cook time: 5
- 🍽️ Servings: 1
Ingredients
- Peychauds bitters
- Demarara
- Luxardo cherry
- Lemon
- Rye whiskey
- Absinthe
Directions
- 10 Dashes peychauds into mixing glass
- 1/2 tsp demarara
- 2oz Rye
- Add ice cubes to fill mixing glass
- Stirring for 15-30 seconds
- Rinse the desired glass with absinthe. A barspoon amount will do.
- Strain into said absinthe rinsed glass.
- Droo a Luxardo cherry in it
- Express a lemon peele into the glass
- Cheers 🍻
-
 @ 5d4b6c8d:8a1c1ee3
2024-03-07 14:59:20
@ 5d4b6c8d:8a1c1ee3
2024-03-07 14:59:20https://primal.net/e/note1alr0ny4u4u4qdnq5tdly9a2g2v240zz8866pa6mfapzvtly6vwcqjwrq3m
I wish we could embed these in our posts.
-
 @ 1e52c554:21771908
2024-03-07 14:12:52
@ 1e52c554:21771908
2024-03-07 14:12:52Posthumous work of the Colombian poet born in Don Matias on January 20, 1948.
Welcome to this blog dedicated to the Posthumous work of the Colombian poet Francisco Luis Arroyave Tabares (my father), born in Don Matias on January 20, 1948-2010. Where I will be publishing each of the 175 sonnets from his npublished collection 'Sonnets For The Twenty-First Century And A Circadian Musical (1984-1987).' Analyzed with GPT4 artificial intelligence and illustrated with AI tools... I hope you enjoy this garden of words snatched from the solitude of a locked room.
Likewise, any enthusiast of the sonnet form is invited to conduct their personal studies of Arroyave Tabares' work, as it is a collection that, although registered since 1989, has not yet been published.
Frank Duna
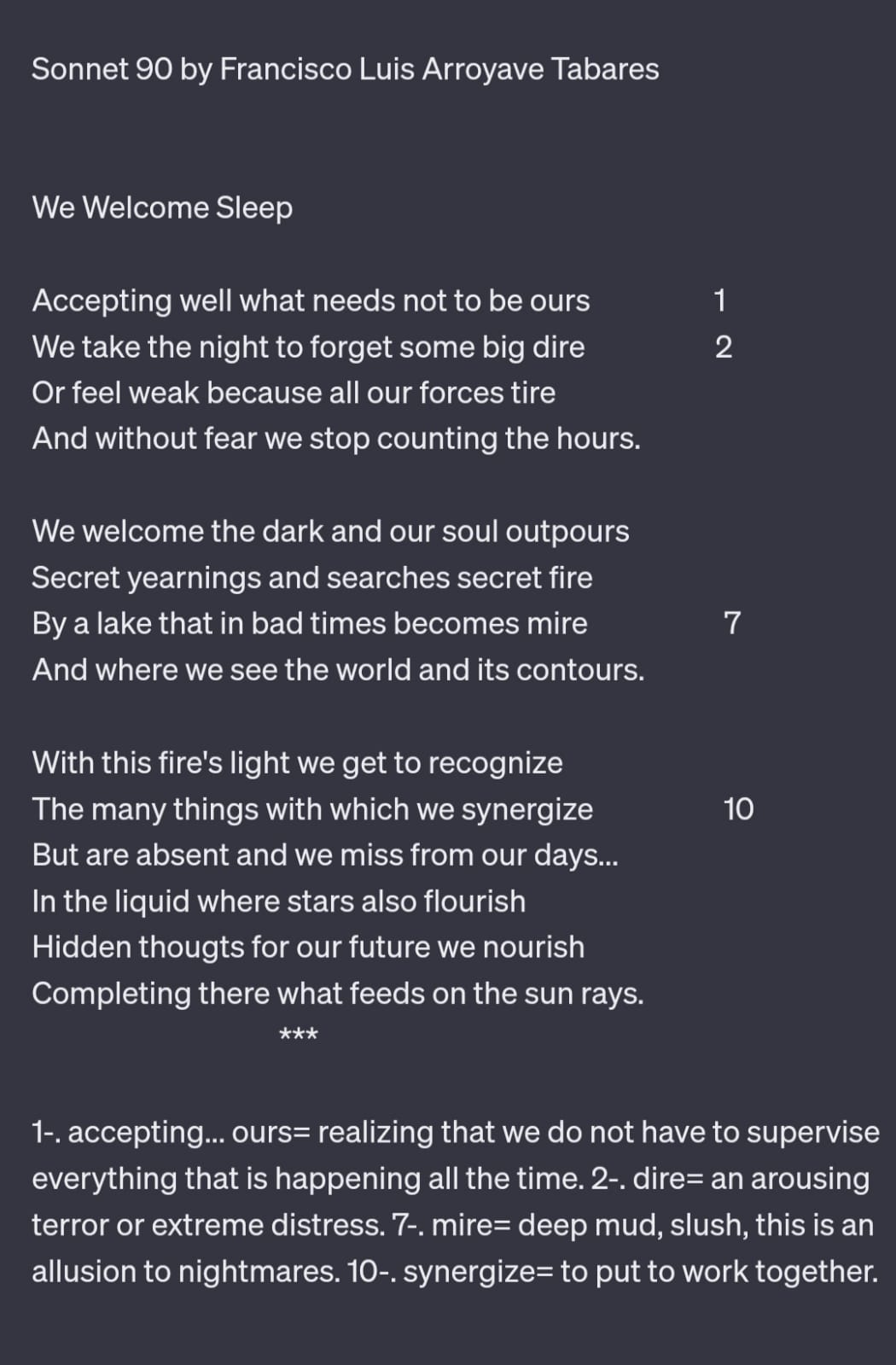
Analisis "We Welcome Sleep"
Introduction
Sonnet 90 explores the importance of sleep as a means of escape, rejuvenation, and self-discovery.
Thematic Analysis:
In the octave, the speaker describes the act of surrendering to sleep as a means of escape from the burdens and fears of the day. The speaker accepts that not everything needs to be under their control (“Accepting well what needs not to be ours”) and uses the night to forget distressing events (“We take the night to forget some big dire”). The speaker also acknowledges the fatigue that comes from constant vigilance (“Or feel weak because all our forces tire”) and the relief that comes from letting go of time (“And without fear we stop counting the hours”). The octave ends with the speaker welcoming the darkness, which allows for the exploration of secret desires and fears (“We welcome the dark and our soul outpours / Secret yearnings and searches secret fire / By a lake that in bad times becomes mire / And where we see the world and its contours”).
The sestet shifts the focus from the personal to the universal. The speaker uses the metaphor of a fire’s light to symbolize the clarity that can come from introspection (“With this fire’s light we get to recognize / The many things with which we synergize”). The speaker laments the absence of these realizations in their daily life (“But are absent and we miss from our days…”). The sonnet concludes with the speaker nurturing hidden thoughts for the future in the metaphorical lake where stars also thrive (“In the liquid where stars also flourish / Hidden thoughts for our future we nourish”), and completing what feeds on the sun’s rays, possibly referring to dreams or aspirations.
Overall, the sonnet explores themes of introspection, acceptance, and the transformative power of sleep and dreams. The octave sets up the context and the sestet provides a resolution, following the traditional sonnet structure.
Rhyme Scheme
The rhyme scheme (ABBA ABBA CCD EED) is a variant of the Petrarchan sonnet structure. Let’s analyze how it applies to the sonnet “We Welcome Sleep” by Francisco Luis Arroyave Tabares:
Octave:
Line 1 (A): Accepting well what needs not to be ours Line 2 (B): We take the night to forget some big dire Line 3 (B): Or feel weak because all our forces tire Line 4 (A): And without fear we stop counting the hours. Line 5 (A): We welcome the dark and our soul outpours Line 6 (B): Secret yearnings and searches secret fire Line 7 (B): By a lake that in bad times becomes mire Line 8 (A): And where we see the world and its contours.Sestet:
Line 9 (C): With this fire’s light we get to recognize Line 10 (C): The many things with which we synergize Line 11 (D): But are absent and we miss from our days… Line 12 (E): In the liquid where stars also flourish Line 13 (E): Hidden thoughts for our future we nourish Line 14 (D): Completing there what feeds on the sun rays.In the octave, the first and fourth lines rhyme, as do the second and third lines, creating an ABBA pattern. This pattern is repeated in the next four lines. In the sestet, the first two lines rhyme (CC), followed by a new rhyme in the third line (D). The last three lines introduce a new rhyme (E), with the final line returning to the previous rhyme (D). This creates a CCD EED pattern. This rhyme scheme contributes to the overall rhythm and flow of the sonnet. It also helps to delineate the shift in focus from the octave to the sestet, a common feature in sonnets.
Additional Aspects to Analyze
let’s delve deeper into the sonnet’s use of language, imagery, themes, meter, and overall impact:
Language and Imagery: The sonnet uses a rich and evocative language that paints vivid images in the reader’s mind. The use of words like “dire”, “mire”, and “synergize” adds depth to the poem’s meaning and creates a sense of rhythm. The imagery of the night, the soul, the fire, and the lake all contribute to the overall mood and theme of the poem.
Themes: The main themes of the poem are introspection, acceptance, and transformation. The speaker uses sleep as a metaphor for introspection and self-discovery. The theme of acceptance is evident in the speaker’s willingness to surrender control and embrace the unknown. The theme of transformation is represented by the speaker’s journey from fear and fatigue to clarity and hope.
Meter: The sonnet follows the iambic pentameter, which is a common meter in English poetry. Each line consists of five pairs of unstressed and stressed syllables, giving the poem a rhythmic and flowing quality.
Overall: the sonnet is a beautifully crafted piece of poetry that explores deep and universal human experiences. The use of language and imagery, combined with the thematic depth and rhythmic structure, makes it a compelling and thought-provoking read. The sonnet’s structure, with its octave and sestet, allows for a nuanced exploration of its themes, starting with a problem or conflict in the octave and moving towards a resolution or insight in the sestet. This gives the sonnet a sense of completeness and balance. The sonnet’s rhyme scheme also contributes to its overall musicality and aesthetic appeal. The sonnet is a testament to the power of poetry to express complex emotions and ideas in a concise and elegant form.
(GPT4)
Syllable count for each line.
``` We Welcome Sleep
10 Accepting well what needs not to be ours
10 We take the night to forget some big dire
10 Or feel weak because all our forces tire 10 And without fear we stop counting the hours.10 We welcome the dark and our soul outpours 10 Secret yearnings and searches secret fire 10 By a lake that in bad times becomes mire
10 And where we see the world and its contours.10 With this fire's light we get to recognize 10 The many things with which we synergize
10 But are absent and we miss from our days... 10 In the liquid where stars also flourish 10 Hidden thougts for our future we nourish 10 Completing there what feeds on the sun rays. *** ```
Sonnets For The Twenty First Century And A Circadian Musical Written By Francisco Luis Arroyave Tabares (1984-1987)
Analyzed by GPT4; Image leonardo.ai; First published on Nostr Protocol by franciscoarroyavet@nostrplebs.com
 We Welcome Sleep
We Welcome Sleep -
 @ 599f67f7:21fb3ea9
2024-03-04 14:26:12
@ 599f67f7:21fb3ea9
2024-03-04 14:26:12Conectarse a muchos relays nostr puede agotar rápidamente la batería y el ancho de banda, especialmente si utilizas nostr en tu teléfono. Conectarse a los relays a través de un proxy nostr puede reducir el consumo de ancho de banda y de batería, además de ofrecer la ventaja adicional de ocultar tu dirección IP real a los relays.
¿Cómo funciona?
Un proxy nostr se conecta a un grupo de relays. Obtiene y publica eventos en esos relays. La aplicación cliente sólo necesita abrir una conexión websocket hacia el proxy para acceder a todos los relays a los que el proxy está conectado.
 Imagen por cortesía de Yonle 2023
Imagen por cortesía de Yonle 2023Como el cliente sólo abre una conexión en lugar de muchas, ahorra ancho de banda y batería.
Como el proxy se conecta a los relays en nombre del cliente, la dirección IP del proxy se expone a los relays en lugar de la del cliente. (Aunque sigue siendo necesario confiar en el proveedor del proxy).
Cómo utilizarlo
Un proxy nostr puede ser fácilmente autoalojado. Echa un vistazo a este repo por nostr:npub1x3azxuysp5vmfer4vgs4jn5tmfcx4ew8sh0qnev7gczljxsr7jwqa3g4el para instrucciones de auto-alojamiento.
Para los que no tenemos recursos para autoalojarnos, Bitcoin Txoko alberga una instancia comunitaria.
Como puedes ver, está conectado a algunos de los relays más populares.
Para utilizarlo, sólo tienes que añadir
wss://bostr.bitcointxoko.coma tu lista de relays.
También puedes eliminar los relays redundantes ahora que ya no necesitas conexiones directas con ellos.
Ya está. ¡Feliz zapping y nos vemos en nostr!
El servicio comunitario bostr.bitcointxoko.com se distribuye con el siguiente aviso de copyright.
Copyright 2023 Yonle yonle@lecturify.net
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met:
-
Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
-
Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution.
-
Neither the name of the copyright holder nor the names of its contributors may be used to endorse or promote products derived from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
La siguiente información no está actualizada. La instancia de la comunidad nproxy ya no se mantiene. Utilízala bajo tu propia responsabilidad. Muchas gracias a nostr:npub1gzuushllat7pet0ccv9yuhygvc8ldeyhrgxuwg744dn5khnpk3gs3ea5ds por su corrección.
Un proxy nostr puede ser fácilmente autoalojado. Echa un vistazo a este repo por nostr:npub1txukm7xckhnxkwu450sm59vh2znwm45mewaps4awkef2tvsgh4vsf7phrl para instrucciones de auto-alojamiento.
Para los que no tenemos recursos para autoalojarnos, Bitcoin Txoko alberga una instancia comunitaria.
Para utilizarlo, sólo tienes que añadir
wss://nproxy.bitcointxoko.coma tu lista de relays.
-
-
 @ 73cee26b:072f3bb6
2024-03-07 11:11:55
@ 73cee26b:072f3bb6
2024-03-07 11:11:55X/Twitter runs the mint, you get your ecash from them. You can then "zap" other Twitter users with ecash.
What do you think about ecash now? Do you trust the mint? What are the privacy implications? Why might they do this?
-
 @ 7175188c:6382a72c
2024-03-07 19:12:42
@ 7175188c:6382a72c
2024-03-07 19:12:42 -
 @ 5d4b6c8d:8a1c1ee3
2024-03-07 18:30:42
@ 5d4b6c8d:8a1c1ee3
2024-03-07 18:30:42This idea came to me last night after reading and participating in a few different posts about territory rent and ownership. I imagine there's a term for what I'm going to describe that I'm either unaware of or just isn't coming to me.
These recent posts have centered around the increasing cost (in purchasing power) of monthly territory rent, the potential long-term value of an outright purchase, and a desire to allow joint ownership. I believe we can address all of these issues simultaneously.
The Model
First off, participation in this model should be opt-in for the territory founders * Anyone can make payments on any participating territory * Territory revenues get paid out in proportion to what each stacker has paid in * Whoever has paid in the most assumes control over the territory * Once three million sats have been paid towards a territory it becomes owned outright * If less than 100k sats per month have been paid towards a territory it becomes archived * Archived territories can be resurrected by making up the back payments * Any rental payments already made towards a territory will be counted if a founder opts-in
Discussion
The logic here is pretty straightforward. Instead of one stacker being on the hook for a large monthly bill, the community is on the hook to keep the territories they care about alive. This gives everyone an opportunity to invest in the territories they value and make sure they don't become archived.
I'm also thinking that there's no reason investment has to stop once the territory hits 3 million sats. That threshold could just mean the territory will never be archived. Further investments could still impact revenue share and control. This would increase the revenue stream for Stacker News.
Founders can still protect their control in a few ways: never opt-in, out bid everyone else, build up a big cushion before opting in.
I'll be curious to hear what people think about this proposal.
-
 @ 7e1d20be:0b4a42c2
2024-03-07 10:29:06
@ 7e1d20be:0b4a42c2
2024-03-07 10:29:06Sorry for the clickbait title, but this IS happening. Especially today, on Day 3 of this phenomenon! It's no joke, they REALLY are doing it openly ! This shape of order book (Depth Chart or whatever) is supposed to lead to increasing prices. But it is not. Because the moment it increases they sell a stash cheap enough to bring it back to 66666.
Since 3 days every time I check the chart, it's hovering above 66500. Today is Day 3 and it is magnetically stuck on that band all day! It seems the bankers have fixed the price of bitcoin at 66666, lol where are the plebs? Please make this meme come true!
Day 2 (yesterday)
Day 1 (day before)
I'll post a thread in "Bitcoin Beginners" to discuss 100s of Stupid Questions I have about this Depth Chart/Order Book thing, but if any of you have any gyaan/knowledge to impart about this now, that'll be great too.
-
 @ 04222fa1:634e9de5
2024-03-07 10:02:06
@ 04222fa1:634e9de5
2024-03-07 10:02:06As the price of Bitcoin hits the headlines once again, the normies get interested
At my sauna last night we got on to the subject
I stayed pretty quiet, then one guy in the corner says...
It's the currency of the dark web, only criminals use it. OK pretty standard response
Next guy says...
You need two accounts, one for the hackers to find and a secret one
Then another interjected....
Do I go to the bank and ask them to put it in my account? Like, how do I buy it
And another....
You have to open your account abroad to be 100% safe
Safe to say we are early
-
 @ 06a5736d:9993b167
2024-03-07 09:44:42
@ 06a5736d:9993b167
2024-03-07 09:44:42Chef's notes
I found the recipe on BBC recipes, should be the first one to pop up if you google easy banana bread recipe.
Details
- ⏲️ Prep time: 15-20min
- 🍳 Cook time: 40-50min
- 🍽️ Servings: 4-8 (depending on portion size). I also didn’t bake this in the usual bread tin, I used a semi deep oven dish as that’s all I had.
Ingredients
- 140g unsalted butter
- 140g caster sugar (I only put 90g as it was for the kids but you can tweak it to your liking)
- 2large eggs
- 1tsp baking soda
- 140g self raising flour
- 1tbs cinnamon powder
- 1tsp vanilla extract
- 1 cup fresh blueberries
- 3 ripe bananas
Directions
- Beat the butter and sugar until a paste is formed
- Add in 2 beaten eggs and mix together
- Gently add the flour and baking soda bit by bit whilst mixing it all well
- Once combined, add in your cinnamon and vanilla
- Add in your washed blueberries
- Mash the bananas well and add to mixture.
- Fold the mixture until well mixed together and set aside
- Preheat oven to 180c
- Butter your dish and line with parchment paper ( I didn’t have this available so I covered it with butter and then added flour all around to prevent it from sticking. Works just the same)
- Once oven is heated up, carefully place the dish into the middle and bake for 40-50min. Make sure to check after 30min as every oven is different.
- Once cooked, remove from oven and let it cool for 10mins before removing from dish (this is to prevent it from falling apart)
- Last step. Cut a slice and enjoy on it’s own or how I did, with some yummy custard
-
 @ 1c6b3be3:73f0ae6f
2024-03-07 06:15:16
@ 1c6b3be3:73f0ae6f
2024-03-07 06:15:16🍵 Actualités securite
Des failles critiques corrigées dans VMware ESXi, Workstation et Fusion (1 min) VMware a publié des correctifs pour plusieurs vulnérabilités critiques découvertes dans ses hyperviseurs ESXi, Workstation et Fusion. Les failles CVE-2024-22252, CVE-2024-22253 et CVE-2024-22254 concernent les produits ESXi 6.5-6.5U3v, 6.7-6.7U3u, 7.0-ESXi70U3p-23307199 et 8.0-ESXi80U2sb-23305545 ainsi que ESXi80U1d-23299997, Workstation 17.x-17.5.1, Fusion 13.x-13.5.1 et Cloud Foundation 3.x. Les vulnérabilités de type use-after-free dans le contrôleur USB XHCI (CVE-2024-22252 et CVE-2024-22253) permettent à un acteur malveillant disposant de privilèges administratifs locaux sur une machine virtuelle d'exécuter du code en tant que processus VMX. La CVE-2024-22254 (faille d'écriture hors limites dans ESXi) peut donner la possibilité à un pirate de déclencher une écriture hors limites et la CVE-2024-22255 expose des données en mémoire du processus vmx. Les vulnérabilités ont été découvertes par Jiang YuHao, Ying XingLei, Zhang ZiMing de Team Ant Lab et Jiaqing Huang (@s0duku), Hao Zheng (@zhz), VictorV et Wei of Team CyberAgent.
Comme Broadcom, Citrix lance des offres groupées (2 min) Citrix a récemment annoncé le lancement de deux nouvelles offres groupées qui incluent plusieurs de ses solutions de virtualisation du poste de travail et de sécurité. La première, "Platform License", regroupe tous les outils nécessaires pour exécuter, sécuriser et gérer des bureaux virtuels, des terminaux et des réseaux. Elle comprend également Citrix Analytics, uberAgent et Citrix Secure Private Access, qui ne seront plus disponibles en tant que produits autonomes. La seconde offre, "Universal Hybrid Multi-Cloud", inclut NetScaler et Citrix Endpoint Management, ainsi qu'une licence universelle introduite en mars 2023. Ces nouvelles offres font partie de la stratégie de Citrix visant à simplifier l'expérience d'achat et à encourager la consommation de ses produits. Les détails sur les critères d'éligibilité et les prix de ces licences n'ont pas été divulgués.
Des experts réclament des audits indépendants de sécurité sur la GenAI (3 min) Plus de 150 experts en IA, éthiciens, juristes et professeurs ont demandé dans une lettre ouverte aux entreprises proposant de l'IA générative (GenAI) de se soumettre à des audits de sécurité externes. La lettre, rédigée par des chercheurs du MIT, Princeton et Stanford, met en avant l'absence d'évaluations indépendantes concernant les protections de base des technologies d'IA, ce qui inquiète ces professionnels. Ils soulignent que l'absence d'évaluations indépendantes empêche la recherche de bonne foi sur les modèles d'IA générative et entrave les mesures de sécurité qui pourraient protéger le public. La lettre demande des protections juridiques et techniques pour que les chercheurs puissent effectuer des évaluations indépendantes sur les systèmes GenAI, y compris un « cadre légal de sécurité ». Les signataires comprennent des professeurs d'universités réputées telles que l'Ivy League et le MIT, ainsi que des dirigeants d'entreprises comme Hugging Face et Mozilla. La lettre reconnaît et se félicite du fait que certains fabricants de GenAI disposent de programmes pour permettre aux chercheurs d'accéder à leurs systèmes, mais déplore le manque de transparence de certaines entreprises en la matière. Les signataires demandent deux niveaux de protection : une protection juridique pour garantir une recherche indépendante et un engagement des entreprises en faveur d'un accès plus équitable aux évaluateurs indépendants pour modérer les demandes d'évaluation des chercheurs.
Le gang du ransomware BlackCat se fait la malle (2 min) Le cybergang BlackCat, également connu sous le nom d'ALPHV, spécialisé dans les ransomwares, a annoncé mettre fin à ses activités après avoir subi des pressions de la part des autorités judiciaires internationales. Cependant, certains éléments suggèrent que cette décision est en fait un coup monté pour s'enfuir avec l'argent des rançons de ses affiliés.
BlackCat a d'abord mis hors ligne son site de fuite de données et fermé son serveur de négociation après qu'un de ses affiliés, Notchy, a affirmé avoir été victime d'un vol de 22 millions de dollars de rançon payée par Change Healthcare. Il a également été révélé que l'adresse du destinataire des fonds, qui appartiendrait aux opérateurs d'ALPHV, avait distribué les bitcoins à divers portefeuilles dans des transactions égales d'environ 3,3 millions de dollars. Cela suggère que d'autres partenaires du cybergang ont également été escroqués pour un total de 94 millions de dollars.
Enfin, BlackCat a annoncé la vente de son code source de malware pour 5 millions de dollars, ce qui semble confirmer la fin de ses activités. Selon des sources, les administrateurs du groupe ont reconnu avoir été victimes de pressions de la part des autorités.
Kyle Daigle (COO de GitHub) : « Copilot rend les développeurs 55% plus productifs » (18 min) GitHub a développé sa propre plateforme d'IA générative, Copilot, pour aider les développeurs à coder depuis plus de deux ans. L'outil, qui est issu d'un partenariat entre GitHub, Microsoft et OpenAI, a connu des améliorations continues et est désormais utilisé par plus d'un million d'utilisateurs quotidiens sur GitHub. Les développeurs qui utilisent Copilot sont 55% plus productifs et il écrit environ 60% de leur code. Selon Kyle Daigle, COO de GitHub, l'objectif principal de Copilot est d'aider les développeurs à effectuer un travail plus créatif en utilisant l'IA pour gérer les tâches répétitives. L'outil fonctionne avec la majorité des langages de programmation publics et a été initialement testé en Python, JavaScript et d'autres langages similaires. GitHub est une entreprise Ruby, mais elle utilise également Copilot pour l'aider dans ses projets en Go, C et FirGit.
🍵 Actualités le-monde-du-cloud-computing
Des failles critiques corrigées dans VMware ESXi, Workstation et Fusion (1 min) VMware a publié des correctifs pour plusieurs vulnérabilités critiques découvertes dans ses hyperviseurs ESXi, Workstation et Fusion. Les failles CVE-2024-22252, CVE-2024-22253 et CVE-2024-22254 concernent les produits ESXi 6.5-6.5U3v, 6.7-6.7U3u, 7.0-ESXi70U3p-23307199 et 8.0-ESXi80U2sb-23305545 ainsi que ESXi80U1d-23299997, Workstation 17.x-17.5.1, Fusion 13.x-13.5.1 et Cloud Foundation 3.x. Les vulnérabilités de type use-after-free dans le contrôleur USB XHCI (CVE-2024-22252 et CVE-2024-22253) permettent à un acteur malveillant disposant de privilèges administratifs locaux sur une machine virtuelle d'exécuter du code en tant que processus VMX. La CVE-2024-22254 (faille d'écriture hors limites dans ESXi) peut donner la possibilité à un pirate de déclencher une écriture hors limites et la CVE-2024-22255 expose des données en mémoire du processus vmx. Les vulnérabilités ont été découvertes par Jiang YuHao, Ying XingLei, Zhang ZiMing de Team Ant Lab et Jiaqing Huang (@s0duku), Hao Zheng (@zhz), VictorV et Wei of Team CyberAgent.
Comme Broadcom, Citrix lance des offres groupées (2 min) Citrix a récemment annoncé le lancement de deux nouvelles offres groupées qui incluent plusieurs de ses solutions de virtualisation du poste de travail et de sécurité. La première, "Platform License", regroupe tous les outils nécessaires pour exécuter, sécuriser et gérer des bureaux virtuels, des terminaux et des réseaux. Elle comprend également Citrix Analytics, uberAgent et Citrix Secure Private Access, qui ne seront plus disponibles en tant que produits autonomes. La seconde offre, "Universal Hybrid Multi-Cloud", inclut NetScaler et Citrix Endpoint Management, ainsi qu'une licence universelle introduite en mars 2023. Ces nouvelles offres font partie de la stratégie de Citrix visant à simplifier l'expérience d'achat et à encourager la consommation de ses produits. Les détails sur les critères d'éligibilité et les prix de ces licences n'ont pas été divulgués.
IT Tour LMI à Nantes, rendez-vous le 12 mars 2024 (2 min) La conférence IT Tour aura lieu le 12 mars 2024 sur le campus de l'ESILV à Nantes, de 8h15 à 12h15. L'événement, organisé avec le soutien d'ADN Ouest, du Clusir Bretagne et des clubs nationaux Afcdp, Cesin et Clusif, comprendra plusieurs retours d'expérience et tables rondes. Les sujets abordés incluent la cybersécurité, l'IA, le cloud, la migration vers le cloud, les risques juridiques en shadow IA et le développement durable dans le secteur informatique. Parmi les intervenants figurent Francis Bergey, directeur cybersécurité SNCF Connect & Tech, Cédric Missoffe, pilote de la communauté data et IA d'ADN Ouest, Aliénor Denis (avocate au cabinet Lex Part Avocats) ainsi que des représentants de Brittany Ferries, SARC, ADEME et ESILV. L'événement se terminera par un cocktail déjeunatoire pour permettre le réseautage et la découverte des solutions et services proposés par les partenaires Nutanix-Anetys-Citrix, Synology, Trend Micro, Vade et Veeam.
Kyle Daigle (COO de GitHub) : « Copilot rend les développeurs 55% plus productifs » (18 min) GitHub a développé sa propre plateforme d'IA générative, Copilot, pour aider les développeurs à coder depuis plus de deux ans. L'outil, qui est issu d'un partenariat entre GitHub, Microsoft et OpenAI, a connu des améliorations continues et est désormais utilisé par plus d'un million d'utilisateurs quotidiens sur GitHub. Les développeurs qui utilisent Copilot sont 55% plus productifs et il écrit environ 60% de leur code. Selon Kyle Daigle, COO de GitHub, l'objectif principal de Copilot est d'aider les développeurs à effectuer un travail plus créatif en utilisant l'IA pour gérer les tâches répétitives. L'outil fonctionne avec la majorité des langages de programmation publics et a été initialement testé en Python, JavaScript et d'autres langages similaires. GitHub est une entreprise Ruby, mais elle utilise également Copilot pour l'aider dans ses projets en Go, C et FirGit.
Tomago Aluminium rapatrie son ERP sur site pour maitriser son SI (5 min) Tomago Aluminium, le plus grand fondeur d'aluminium australien, a décidé de ramener son système ERP sur site après cinq ans dans le cloud. Le directeur informatique, Dennis Moncrieff, a cité le manque de transparence et des coûts élevés comme raisons du changement. Bien que Moncrieff reconnaisse l'importance de la transformation numérique, il souligne également les défis d'un manque de clarté et de contrôle lors de la migration vers le cloud. Après avoir initialement migré son système ERP dans le cloud en 2015 en raison d'une mise à niveau non prise en charge par l'éditeur, Tomago Aluminium a commencé à remettre en question la situation cinq ans plus tard lorsqu'elle a pu comparer ses systèmes existants avec d'autres solutions cloud. L'entreprise a finalement choisi de ramener son ERP sur site après avoir constaté un manque de transparence, de contrôle et de visibilité des systèmes existants. Selon Moncrieff, cette décision a permis à l'entreprise de reprendre le contrôle de ses coûts, de sa conformité et de sa sécurité.
🍵 Toutes les actualités :
Telex : Crowdstrike acquiert Flow Security, La Cnil alerte sur les tests génétiques sur Internet, Salesforce lance Einstein 1 Studio (1 min) Cet article présente plusieurs actualités du monde de la technologie et de la cybersécurité :
- Crowdstrike a acquis Flow Security pour améliorer sa protection des données en temps réel dans les environnements endpoint et cloud. L'intégration de la gestion de la posture de sécurité des données (DSPM) à la plateforme Falco XDR permettra de découvrir, classer et protéger les données contre les risques d'exposition, où qu'elles soient.
- La Commission nationale de l'informatique et des libertés (CNIL) a émis un "appel à la vigilance" concernant les tests génétiques vendus en kit sur Internet. Selon la CNIL, ces tests présentent des risques liés à la fiabilité des résultats et à l'absence de transparence sur l'utilisation des données personnelles sensibles recueillies.
- Salesforce a lancé Einstein 1 Studio, une plateforme low-code destinée aux développeurs et administrateurs pour personnaliser l'assistant IA Einstein Copilot et l'intégrer dans n'importe quelle application de gestion client. Cette plateforme permettra également d'accéder aux données de l'entreprise à partir de Salesforce Data Cloud.
Des failles critiques corrigées dans VMware ESXi, Workstation et Fusion (1 min) VMware a publié des correctifs pour plusieurs vulnérabilités critiques découvertes dans ses hyperviseurs ESXi, Workstation et Fusion. Les failles CVE-2024-22252, CVE-2024-22253 et CVE-2024-22254 concernent les produits ESXi 6.5-6.5U3v, 6.7-6.7U3u, 7.0-ESXi70U3p-23307199 et 8.0-ESXi80U2sb-23305545 ainsi que ESXi80U1d-23299997, Workstation 17.x-17.5.1, Fusion 13.x-13.5.1 et Cloud Foundation 3.x. Les vulnérabilités de type use-after-free dans le contrôleur USB XHCI (CVE-2024-22252 et CVE-2024-22253) permettent à un acteur malveillant disposant de privilèges administratifs locaux sur une machine virtuelle d'exécuter du code en tant que processus VMX. La CVE-2024-22254 (faille d'écriture hors limites dans ESXi) peut donner la possibilité à un pirate de déclencher une écriture hors limites et la CVE-2024-22255 expose des données en mémoire du processus vmx. Les vulnérabilités ont été découvertes par Jiang YuHao, Ying XingLei, Zhang ZiMing de Team Ant Lab et Jiaqing Huang (@s0duku), Hao Zheng (@zhz), VictorV et Wei of Team CyberAgent.
Comme Broadcom, Citrix lance des offres groupées (2 min) Citrix a récemment annoncé le lancement de deux nouvelles offres groupées qui incluent plusieurs de ses solutions de virtualisation du poste de travail et de sécurité. La première, "Platform License", regroupe tous les outils nécessaires pour exécuter, sécuriser et gérer des bureaux virtuels, des terminaux et des réseaux. Elle comprend également Citrix Analytics, uberAgent et Citrix Secure Private Access, qui ne seront plus disponibles en tant que produits autonomes. La seconde offre, "Universal Hybrid Multi-Cloud", inclut NetScaler et Citrix Endpoint Management, ainsi qu'une licence universelle introduite en mars 2023. Ces nouvelles offres font partie de la stratégie de Citrix visant à simplifier l'expérience d'achat et à encourager la consommation de ses produits. Les détails sur les critères d'éligibilité et les prix de ces licences n'ont pas été divulgués.
Nokia supprime 357 postes en France (2 min) Nokia a annoncé la suppression de 357 postes en France, soit environ 14% des effectifs, par le biais d'une rupture conventionnelle collective (RCC) qui ne comprend que des départs volontaires. Les fonctions de support et les équipes de recherche et développement (R&D), situées principalement en région parisienne, seront les plus touchées par ce plan de départs. Le site de Massy sera particulièrement affecté avec une centaine de postes dans les activités de recherche fondamentale qui seront supprimés. Cette décision intervient après six plans de licenciements en huit ans, dont le dernier a été annoncé en octobre 2023 et prévoit la suppression de 14 000 emplois dans le monde. Le centre de Lannion et l'entité ASN de Calais ne sont pas concernés par ce plan de départs volontaires.
IT Tour LMI à Nantes, rendez-vous le 12 mars 2024 (2 min) La conférence IT Tour aura lieu le 12 mars 2024 sur le campus de l'ESILV à Nantes, de 8h15 à 12h15. L'événement, organisé avec le soutien d'ADN Ouest, du Clusir Bretagne et des clubs nationaux Afcdp, Cesin et Clusif, comprendra plusieurs retours d'expérience et tables rondes. Les sujets abordés incluent la cybersécurité, l'IA, le cloud, la migration vers le cloud, les risques juridiques en shadow IA et le développement durable dans le secteur informatique. Parmi les intervenants figurent Francis Bergey, directeur cybersécurité SNCF Connect & Tech, Cédric Missoffe, pilote de la communauté data et IA d'ADN Ouest, Aliénor Denis (avocate au cabinet Lex Part Avocats) ainsi que des représentants de Brittany Ferries, SARC, ADEME et ESILV. L'événement se terminera par un cocktail déjeunatoire pour permettre le réseautage et la découverte des solutions et services proposés par les partenaires Nutanix-Anetys-Citrix, Synology, Trend Micro, Vade et Veeam.
🍵 Actualités securite
Des failles critiques corrigées dans VMware ESXi, Workstation et Fusion (1 min) Comme Broadcom, Citrix lance des offres groupées (2 min) Des experts réclament des audits indépendants de sécurité sur la GenAI (3 min) Le gang du ransomware BlackCat se fait la malle (2 min) Kyle Daigle (COO de GitHub) : « Copilot rend les développeurs 55% plus productifs » (18 min) TDF améliore sa gestion d'incidents et de projets (1 min) Pour le Cigref, l'UE doit être plus active sur le numérique (4 min)
🍵 Actualités le-monde-du-cloud-computing
Des failles critiques corrigées dans VMware ESXi, Workstation et Fusion (1 min) Comme Broadcom, Citrix lance des offres groupées (2 min) IT Tour LMI à Nantes, rendez-vous le 12 mars 2024 (2 min) Kyle Daigle (COO de GitHub) : « Copilot rend les développeurs 55% plus productifs » (18 min) Tomago Aluminium rapatrie son ERP sur site pour maitriser son SI (5 min) Sonepar rationalise son SI autour d'une plateforme omnicanale unique (11 min)
🍵 Toutes les actualités :
Telex : Crowdstrike acquiert Flow Security, La Cnil alerte sur les tests génétiques sur Internet, Salesforce lance Einstein 1 Studio (1 min) Des failles critiques corrigées dans VMware ESXi, Workstation et Fusion (1 min) Comme Broadcom, Citrix lance des offres groupées (2 min) Nokia supprime 357 postes en France (2 min) IT Tour LMI à Nantes, rendez-vous le 12 mars 2024 (2 min) Des experts réclament des audits indépendants de sécurité sur la GenAI (3 min) Le gang du ransomware BlackCat se fait la malle (2 min) Kyle Daigle (COO de GitHub) : « Copilot rend les développeurs 55% plus productifs » (18 min) Dell prêt à gérer les 1000 W de l'accélérateur B200 de Nvidia (2 min) Tomago Aluminium rapatrie son ERP sur site pour maitriser son SI (5 min) Sonepar rationalise son SI autour d'une plateforme omnicanale unique (11 min) TDF améliore sa gestion d'incidents et de projets (1 min) Spie ICS nomme Pascal Grangé directeur Grand Est (1 min) Pour le Cigref, l'UE doit être plus active sur le numérique (4 min) Développeur, un emploi toujours très prisé en 2023 (2 min)
🍵 "llm | cloud | ddos" - Google News
State Boys Hockey Tournament: St. Cloud Cathedral tops Northfield in Class A quarterfinals - KSTP Images show funnel cloud over Vacaville in Solano County - CBS Sacramento St. Cloud child porn suspect kills himself as law enforcement closes in, officials say - WKMG News 6 & ClickOrlando St. Cloud man arrested, son died of suicide in light of child porn investigation - FOX 35 Orlando Cloud People - Simulacra Review - Angry Metal Guy Funnel cloud spotted over Vacaville | abc10.com - ABC10.com KXTV Veeam Launches Veeam Data Cloud - Dark Reading Live score updates: St. Cloud Cathedral vs. Northfield in the MSHSL boys hockey state tournament quarterfinal - highschool.si.com E-News | Cloud Analytics Faculty Fellowship applications now being accepted - WVU ENews Cloud forecast for April 2024 eclipse: Map shows cloud data by city - USA TODAY UMD mens hockey to face St. Cloud State in final game of regular season - Northern News Now Funnel cloud spotted near Vacaville as thunderstorms strike parts of Bay Area - KGO-TV St. Cloud Cathedral Crusaders win over Northfield Raiders - The Rink Live Don't Be Fooled By The Size Of Microsoft's 1-Bit LLM - Dataconomy Fraudsters Exploit Cloud Access Points to Orchestrate Attacks - PYMNTS.com
-
 @ 1c6b3be3:73f0ae6f
2024-03-07 05:11:22
@ 1c6b3be3:73f0ae6f
2024-03-07 05:11:22Bitcoin Optech
Bitcoin Optech Newsletter #292 (6 min) Le newsletter de cette semaine traite des points suivants :
-
Mise à jour de la spécification BIP21 bitcoin: URIs : Josie Baker a publié un article sur Delving Bitcoin pour discuter de l'utilisation actuelle et future des BIP21 URIs. Il est proposé que le créateur d'une URI spécifie toutes les méthodes de paiement prises en charge en utilisant des paramètres nus, par exemple :
bitcoin:?bc1q...&sp1q...., et que l'expéditeur puisse ensuite choisir sa méthode de paiement préférée dans la liste. -
Gestion des sessions de signature MuSig2 multiples avec un minimum d'état : Salvatore Ingala a proposé sur Delving Bitcoin une méthode pour minimiser l'état nécessaire pour effectuer plusieurs sessions de signature MuSig2 en parallèle en générant un seul objet d'état pour un ensemble de transactions PSBT et en le dérivant de manière déterministe pour chaque entrée.
-
Discussion sur l'ajout d'éditeurs BIP supplémentaires : Ava Chow a proposé d'ajouter des éditeurs BIP pour aider l'éditeur actuel, Luke Dashjr, qui est submergé de travail. Deux contributeurs experts ont été suggérés pour devenir éditeurs et il a également été discuté de la question de savoir s'ils devraient avoir le pouvoir d'attribuer des numéros BIP.
-
Sauvegarde GitLab du projet Bitcoin Core GitHub : Fabian Jahr a créé un backup du projet Bitcoin Core sur GitLab dans le but de faciliter une éventuelle transition depuis GitHub en cas de besoin.
Les nouvelles versions et les candidats à la version pour des projets d'infrastructure Bitcoin populaires sont également annoncés, tels qu'Eclair v0.10.0 et Bitcoin Core 26.1rc1.
Releases - No Bullshit Bitcoin
Sparrow Wallet v1.8.3: PGP Verifier, Improved QR Reading, Q1 & Safe 3 Support (2 min) Sparrow v1.8.3, a modern desktop Bitcoin wallet application, has been released with new features including PGP download file verification, support for Coldcard Q1 and Trezor Safe 3 hardware wallets, and improved QR reading using three different QR readers. The release also includes several minor improvements such as support for additional accounts, upgrading to HWI 2.4.0, improving script area display of inputs that spend a taproot script path, adding seconds to the Date column for Transactions and UTXOs CSV export, and avoiding saving certificates for public servers. Additionally, there are bug fixes including avoidance of null labels when broadcasting a loaded transaction with no name, inclusion of labels for hidden addresses in address CSV export, addition of a delay before fetching rates to avoid HTTPClient error, and open files and URIs after initial wallet loading. The release also includes updated dependencies and increased Whirlpool http client timeout.
 Bitcoin Optech #292: Updating BIP21 bitcoin URIs, Adding More BIP Editors
This issue of the Bitcoin Optech newsletter discusses updates on BIP21 bitcoin URIs, with a focus on improving the specification. It also presents a proposal for managing multiple concurrent MuSig2 signing sessions using minimal state. Additionally, there is a link to a thread about adding editors for the BIPs repository. The newsletter also introduces tools that allow quickly porting the Bitcoin Core GitHub project to a self-hosted GitLab project. A audio recap discussion of this newsletter will be hosted by Bitcoin Optech on Twitter Spaces with special guests Josie Baker, Salvatore Ingala, and Fabian Jahr on Thursday at 15:00 UTC. Readers are encouraged to join and discuss or ask questions.
Bitcoin Optech #292: Updating BIP21 bitcoin URIs, Adding More BIP Editors
This issue of the Bitcoin Optech newsletter discusses updates on BIP21 bitcoin URIs, with a focus on improving the specification. It also presents a proposal for managing multiple concurrent MuSig2 signing sessions using minimal state. Additionally, there is a link to a thread about adding editors for the BIPs repository. The newsletter also introduces tools that allow quickly porting the Bitcoin Core GitHub project to a self-hosted GitLab project. A audio recap discussion of this newsletter will be hosted by Bitcoin Optech on Twitter Spaces with special guests Josie Baker, Salvatore Ingala, and Fabian Jahr on Thursday at 15:00 UTC. Readers are encouraged to join and discuss or ask questions.  Mutiny Wallet v0.5.10: Bug Fixes
Mutiny, an open-source and self-custodial bitcoin and Lightning wallet, has released a new version of its software on the web and Android platforms. This update addresses several bugs found in fedimint that prevented users from joining certain federations. It also resolves a rare race condition when creating a lightning node and updates the alpha release of lightning-liquidity.
Mutiny Wallet v0.5.10: Bug Fixes
Mutiny, an open-source and self-custodial bitcoin and Lightning wallet, has released a new version of its software on the web and Android platforms. This update addresses several bugs found in fedimint that prevented users from joining certain federations. It also resolves a rare race condition when creating a lightning node and updates the alpha release of lightning-liquidity.Additionally, there are several improvements, such as adding federation code to list_federations, only checking voltage invoice within 10 sats, updating fedimint, not saving federation to storage until after init, and generating a node's uuid deterministically. The full changelog can be found in the v0.5.9...v0.5.10 update on GitHub, along with the source code for the wallet.

LN Markets Blog
Latest Strikes 72 - February 19th-25th 2024 (7 min) Le 29 février 2024, Amboss a lancé Reflex, une solution logicielle pour les entreprises qui opèrent sur le réseau Lightning et souhaitent restreindre les interactions avec certains autres nœuds en fonction de politiques arbitraires. Cela peut inclure des considérations de conformité telles que l'évitement de l'établissement de canaux Lightning avec des entités sanctionnées par l'OFAC. Amboss positionne Reflex comme un outil permettant aux entreprises d'établir leurs propres ensembles de règles en matière d'interactions sur le réseau Lightning, plutôt qu'en tant qu'outil d'application.
L'article aborde également la question de la censure sur le réseau Lightning et les conséquences potentielles de l'utilisation de logiciels comme Reflex par des fournisseurs de services Lightning (LSP). Si les LSP commencent à utiliser ce type de logiciel pour restreindre les interactions avec certains nœuds, cela pourrait entraîner la création de deux réseaux distincts : un réseau conforme et un réseau sans conformité. Cela pourrait isoler les entreprises réglementées sur le réseau conforme, tandis que les utilisateurs souhaitant participer à des activités illicites ou borderline utiliseraient le réseau sans conformité.
En outre, l'exploitant de la piscine minière Braiins a annoncé travailler sur des retraits Lightning pour ses mineurs, permettant aux mineurs individuels de retirer leurs récompenses instantanément et sans frais. Ce système est actuellement testé avec un sous-ensemble d'utilisateurs et devrait être publié dans les semaines à venir.
Enfin, il y aura également un bootcamp de développement Lightning à Lagos à la fin du mois de mars, organisé par Africa Free Routing en partenariat avec IBEX et Bitn.
 Latest Strikes 71 - February 5th-18th 2024 (4 min)
This article is a recap of recent developments and releases in the Lightning Network ecosystem. Umbrel has released new hardware for their plug-and-play Bitcoin & Lightning node solution, with improved processing power and storage. They have also announced version 1.0 of Umbrel OS, which will bring more stability, security, and better user experience. Cashu Addresses are becoming popular, allowing users to send and receive sats through ecash tokens tied to their Nostr public key. LNBits has received an update with a new login system, improved mobile UI, and better tools for querying transactions. Blitz is a new self-custodial open source wallet that allows users to send and receive both on-chain Bitcoin and Liquid through Boltz swaps. Other releases include Munity's ability to sweep funds from the custodial Fedimint balance to self-custodial Lightning, batching of HTLC sweeping from a loop-out in Lightning Labs' loop, and LND v0.17.4-beta with hot fixes for various issues. The article also mentions a discussion on using hardware wallets for Lightning as end users.
Latest Strikes 71 - February 5th-18th 2024 (4 min)
This article is a recap of recent developments and releases in the Lightning Network ecosystem. Umbrel has released new hardware for their plug-and-play Bitcoin & Lightning node solution, with improved processing power and storage. They have also announced version 1.0 of Umbrel OS, which will bring more stability, security, and better user experience. Cashu Addresses are becoming popular, allowing users to send and receive sats through ecash tokens tied to their Nostr public key. LNBits has received an update with a new login system, improved mobile UI, and better tools for querying transactions. Blitz is a new self-custodial open source wallet that allows users to send and receive both on-chain Bitcoin and Liquid through Boltz swaps. Other releases include Munity's ability to sweep funds from the custodial Fedimint balance to self-custodial Lightning, batching of HTLC sweeping from a loop-out in Lightning Labs' loop, and LND v0.17.4-beta with hot fixes for various issues. The article also mentions a discussion on using hardware wallets for Lightning as end users.  LN Markets Alpha #7 (8 min)
The article discusses the current trends in the crypto market, with a focus on Bitcoin. In the short-term outlook, the author acknowledges their previous forecast was incorrect, as they had expected a continuation of the consolidation phase. Instead, Bitcoin soared 20-25% and reached a high of $52K. The author attributes this surge to the decreasing pace of GBTC redemptions and increasing inflows into other ETFs, which are buying around 10,000 bitcoins daily.
LN Markets Alpha #7 (8 min)
The article discusses the current trends in the crypto market, with a focus on Bitcoin. In the short-term outlook, the author acknowledges their previous forecast was incorrect, as they had expected a continuation of the consolidation phase. Instead, Bitcoin soared 20-25% and reached a high of $52K. The author attributes this surge to the decreasing pace of GBTC redemptions and increasing inflows into other ETFs, which are buying around 10,000 bitcoins daily.The medium-term outlook is described as "Weimar Intensifies," referring to the economic crisis in Germany during the 1920s. Despite global economic uncertainties and signs of an ailing economy, the author suggests that these conditions may further diminish the appeal of bonds and drive financial capital towards assets of true scarcity, such as Bitcoin. The author highlights the parabolic rise of certain stocks in recent times, likening it to the early 2021 market vibe when meme stocks like GameStop and AMC gained popularity.
Overall, the article suggests that the current buying frenzy could lead to significant price appreciation for Bitcoin if the pace is sustained, and the market momentum appears to be driven primarily by heightened demand through ETFs and scarcity of spot Bitcoin available at current prices.
LN Markets Blog
Latest Strikes 72 - February 19th-25th 2024 (7 min)
 Latest Strikes 71 - February 5th-18th 2024 (4 min)
Latest Strikes 71 - February 5th-18th 2024 (4 min)
 LN Markets Alpha #7 (8 min)
LN Markets Alpha #7 (8 min)
 Latest Strikes 70 - January 29th-February 5th 2024 (8 min)
Latest Strikes 70 - January 29th-February 5th 2024 (8 min)
 LN Markets Alpha #6 (8 min)
LN Markets Alpha #6 (8 min)
 Latest Strikes 69 - January 22nd-28th 2024 (10 min)
Latest Strikes 69 - January 22nd-28th 2024 (10 min)
 Latest Strikes 68 - January 15th-21st 2024 (13 min)
Latest Strikes 68 - January 15th-21st 2024 (13 min)
 Latest Strikes 67 - January 8th-14th 2024 (8 min)
Latest Strikes 67 - January 8th-14th 2024 (8 min)
 Ln Markets Alpha #5 (10 min)
Ln Markets Alpha #5 (10 min)
 Latest Strikes 66 - December 4th 2023-January 7th 2024 (15 min)
Latest Strikes 66 - December 4th 2023-January 7th 2024 (15 min)
 LN Markets Alpha #4 (9 min)
LN Markets Alpha #4 (9 min)
 LN Markets Alpha #3 (9 min)
LN Markets Alpha #3 (9 min)
 Latest Strikes 64 & 65 - November 20th-December 3rd 2023 (10 min)
Latest Strikes 64 & 65 - November 20th-December 3rd 2023 (10 min)
 LN Markets Alpha #2 (9 min)
LN Markets Alpha #2 (9 min)
 Latest Strikes 63 - November 13th-19th 2023 (8 min)
Latest Strikes 63 - November 13th-19th 2023 (8 min)

Bitcoin Optech
Bitcoin Optech Newsletter #292 (6 min)
Releases - No Bullshit Bitcoin
Sparrow Wallet v1.8.3: PGP Verifier, Improved QR Reading, Q1 & Safe 3 Support (2 min)
 Bitcoin Optech #292: Updating BIP21 bitcoin URIs, Adding More BIP Editors
Bitcoin Optech #292: Updating BIP21 bitcoin URIs, Adding More BIP Editors
 Mutiny Wallet v0.5.10: Bug Fixes
Mutiny Wallet v0.5.10: Bug Fixes

Fanis Michalakis
Latest Strikes 42 (11 min) Latest Strikes 41 (11 min) Latest Strikes 40 (6 min) Latest Strikes 39 (9 min) Latest Strikes 38 (8 min) Latest Strikes 37 (9 min) Latest Strikes 36 (10 min) Latest Strikes 35 (15 min) Latest Strikes 34 (15 min) Latest Strikes 33 (11 min) Latest Strikes 32 (13 min) Latest Strikes 31 (7 min) Latest Strikes 30 (8 min) Latest Strikes 29 (10 min) Latest Strikes 28 (18 min) Latest Strikes 27 (11 min) Latest Strikes 26 (18 min) Latest Strikes 25 (9 min) Latest Strikes 24 (12 min) Latest Strikes 23 (10 min)
🍵 "btc | bitcoin | lightning network | asic" - Google News
Huge New Bitcoin Price Target Set After $2.5 Trillion Ethereum, XRP And Crypto Surge - Forbes Where, how often does lightning strike in US? New report explains - LiveNOW from FOX Hut 8 closes Bitcoin mining site, citing surging energy costs - Cointelegraph Bitcoin Ordinals Project Runestone Hosts Auction Ahead of Airdrop - Decrypt Bitcoin ETF Giant Grayscale Introduces a Crypto Staking Fund - Yahoo Finance 5 Ways Bitcoin Mining Benefits Ethiopia - Bitcoin Magazine Last Call: Why Investors in the United States Are Rushing to Bitcoin Dogs ICO - CoinCodex Peter Schiff Launches Gold Ordinals Priced In Bitcoin - CoinGape Peter Schiff Accused of Promoting Bitcoin — TradingView News - TradingView Bitcoin-Based Network Stacks Now Supported by NEAR Foundation, DeSpread, Luxor as Validators - U.Today Bitcoin: Can ETF volumes sustain BTC’s bullish narrative? - AMBCrypto News Lightning strikes plane after takeoff from Vancouver airport - The Weather Network
-
-
 @ a4a6b584:1e05b95b
2024-03-07 03:04:17
@ a4a6b584:1e05b95b
2024-03-07 03:04:17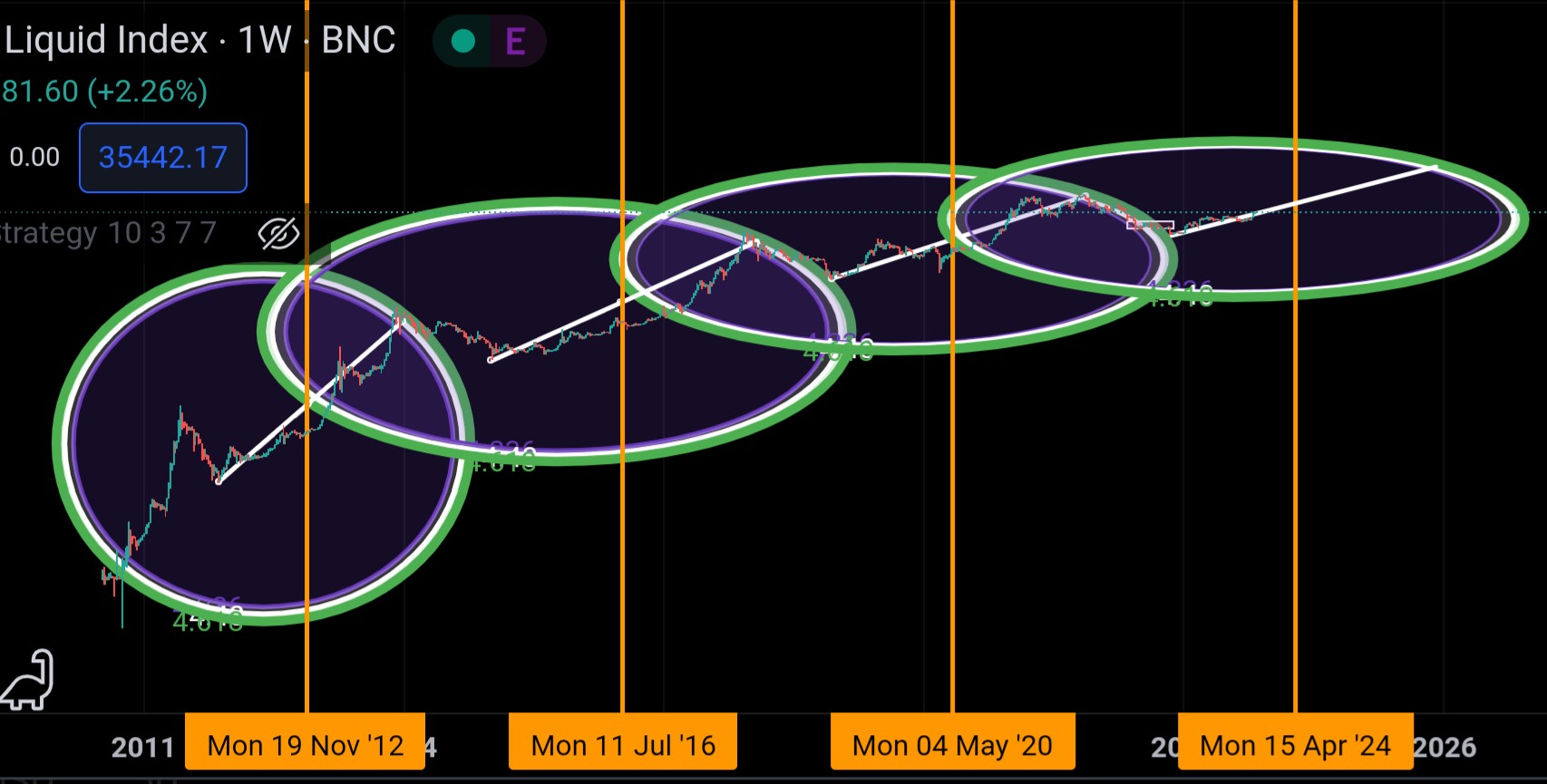
https://www.tradingview.com/chart/tKlgCet5/
Welcome to a novel approach to understanding Bitcoin's price action. As a staunch Bitcoin maximalist, I believe in the inherent value and transformative potential of this asset. As the world economy starts to wake up and reprice itself against this new asset, it helps to help a tool to keep you calm and know how to plan accordingly. Let's delve into the "Satoshi Circles" method and how it might provide insights into Bitcoin's future price movements.
The Genesis of Satoshi Circles:
Drawing inspiration from the mysterious Bitcoin creator, Satoshi Nakamoto, the "Satoshi Circles" method integrates the application of Fibonacci circles with Bitcoin's halving events. Here's a brief step-by-step guide:
-
Identify Halving Events: Mark the date of each Bitcoin halving event with a vertical line on your chart.
-
Draw Trend Lines: From the low of each cycle, draw a trend line to the corresponding halving event.
-
Overlay Fibonacci Circles: Using the chart data from the trend line during the timeframe from the cycle's bottom to the halving, overlay a Fibonacci circle. If done accurately, this circle will offer insights into potential market tops.
Accuracy and Margin of Error:
No method, however ingenious, offers precise predictions every time. With the "Satoshi Circles" method, there's a margin of error to be mindful of:
-
Trend Line Precision: Ensuring accuracy when drawing the trend line is crucial. Small deviations can significantly alter predictions.
-
Bitcoin's Volatility: As an asset, Bitcoin is susceptible to global events, regulatory changes, and macroeconomic factors that may disrupt technical patterns.
-
Fibonacci Circle's Range: The actual top could materialize anywhere within the designated Fibonacci circle. Thus, it's not about pinpointing an exact price but identifying a probable range.
Looking Forward to April 2024:
It's worth noting that the true potential of the "Satoshi Circles" method can't be fully realized until after the April 2024 halving. Post this event, critical data points such as the bottom price and halving date will be solidified. Consequently, the Fibonacci circle can be appropriately placed, and the preceding trend line can be extended to intersect with the circle, unveiling the possible top range. This anticipation builds a compelling case for closely monitoring Bitcoin's journey post the forthcoming halving.
Conclusion:
While the "Satoshi Circles" approach offers a fresh perspective on predicting Bitcoin's price action, it's always vital to approach trading and investments with caution and diligence. Macroeconomics can change quickly and the world could see that Bitcoin's potential remains vast much faster than anticipated, but as HODLers of the hardest money on Earth, it's our responsibility to keep calm and spread the word.
We are all Satoshi.
Adam Malin
You can find me on Twitter or on Nostr at
npub15jnttpymeytm80hatjqcvhhqhzrhx6gxp8pq0wn93rhnu8s9h9dsha32lxYou can view and write comments on this or any other post by using the Satcom browser extention.
value4value Did you find any value from this article? Click here to send me a tip!
-
-
 @ a4a6b584:1e05b95b
2024-03-07 02:57:07
@ a4a6b584:1e05b95b
2024-03-07 02:57:07Introduction
The double-slit experiment, initially executed with light by Thomas Young in the early 1800s and later with particles in the 20th century, signifies a cornerstone in our understanding of quantum mechanics. This experiment, featuring particles forming an interference pattern suggestive of wave-like behavior, which dissipates upon attempting to discern the particle's path, challenges our classical intuition and opens a plethora of questions about the quantum world.
The Orthodox QED View
QED, crystallized in the 1920s, furnishes a robust mathematical framework to elucidate interactions between light and matter, utilizing principles like wave-particle duality and probabilistic interactions, albeit without offering a physical causality for these quantum phenomena.
Insight into Quantum Phenomena: Zeeman Effect & Lamb Shift
The Zeeman Effect, which pertains to the splitting of a spectral line into several components in the presence of a magnetic field (( \Delta E = \mu B )), and the Lamb Shift, involving a minute difference in energy levels due to vacuum fluctuations, are both accurately predicted by QED, underscoring its predictive prowess, despite its abstract nature.
The Alternative SED View
SED, which surfaced in the 1960s, diverges from QED by proffering a physical explanation for quantum phenomena through particle interactions with a background field of quantum vacuum fluctuations, or the zero-point field (ZPF), though it is crucial to note that SED is not widely embraced in the scientific community due to inconsistencies with certain quantum predictions.
Probing into Quantum Vacuum: The Casimir Effect
The Casimir Effect, which involves a quantifiable force emerging between two parallel plates in a vacuum, attributed to ZPF, provides a tangible manifestation of vacuum fluctuations, potentially aligning with the mechanistic approach of SED.
SED vs QED: A Rigorous Analysis
Both SED and QED adeptly predict quantum phenomena but diverge significantly in their explanatory frameworks. While SED provides a mechanistic model involving interactions with the ZPF, QED leans heavily on abstract mathematical formulations, offering precise predictions without delving into the underlying physical causality.
Evolution and Challenges: Fine Structure Constant
SED and QED have evolved along disparate paths, with QED’s mathematical formalism and SED’s deterministic mechanisms offering different perspectives on quantum phenomena. Both theories adeptly address aspects like the Fine Structure Constant, which governs electron and electromagnetic interactions, yet challenges like explaining non-local quantum entanglement and the probabilistic nature of quantum mechanics remain.
Future Avenues and Experiments
The future trajectory of SED and its potential to diverge from QED predictions hinge upon experimental validation. Experiments probing variations in the Fine Structure Constant or exploring vacuum energy (as suggested by the Casimir Effect) might reveal nuanced insights into the physical reality of ZPF, thus enabling further differentiation between QED and SED predictions.
Conclusion
In conclusion, while SED offers an intuitive and deterministic framework to interpret quantum phenomena, it necessitates further refinement and experimental validation to be juxtaposed with the predictive precision of QED. As our understanding and experimental capabilities advance, SED may potentially unravel novel insights into the quantum domain, offering a mechanistic perspective to the enigmatic quantum world, thereby paving the path toward a deeper understanding of quantum mechanics.
References
-
Bethe, H. A., & Salpeter, E. E. (1957). Quantum Mechanics of One- and Two-Electron Atoms. Springer, Berlin; Academic Press, New York.
-
Condon, E. U., & Shortley, G. H. (1935). The Theory of Atomic Spectra. Cambridge University Press.
-
De la Peña, L., & Cetto, A. M. (1996). The Quantum Dice: An Introduction to Stochastic Electrodynamics (Fundamental Theories of Physics, Vol. 75). Dordrecht; Boston; London: Kluwer Academic Publishers.
-
De la Peña, L., & Cetto, A. M. (2006). The foundations of linear stochastic electrodynamics. Foundations of Physics, 36(3), 350-368. DOI: 10.1007/s10701-006-9046-0.
-
Feynman, R. P., Leighton, R. B., & Sands, M. (1965). The Feynman Lectures on Physics, Vol. III: Quantum Mechanics. Addison-Wesley.
-
Griffiths, D. J. (2005). Introduction to Quantum Mechanics (2nd ed.). Upper Saddle River, NJ: Pearson Prentice Hall.
-
Lamoreaux, S. K. (1997). Demonstration of the Casimir Force in the 0.6 to 6 μm Range. Physical Review Letters, 78(1), 5-8. DOI: Not Available.
-
Milonni, P. W. (1994). The Quantum Vacuum: An Introduction to Quantum Electrodynamics. San Diego: Academic Press.
-
Setterfield, B. (n.d.). Quantum Mechanics. Retrieved from https://barrysetterfield.org/Quantum_Mechanics.html.
-
Setterfield, B. (n.d.). Quantum Effects. Retrieved from https://barrysetterfield.org/Quantum_Effects/Quantum_Effects.html.
-
Setterfield, B. (2015). Quantum Effects and the Zero Point Energy. Retrieved from https://barrysetterfield.org/GSRresearchpapers.html.
Adam Malin
You can find me on Twitter or on Nostr at
npub15jnttpymeytm80hatjqcvhhqhzrhx6gxp8pq0wn93rhnu8s9h9dsha32lxYou can view and write comments on this or any other post by using the Satcom browser extention.
value4value Did you find any value from this article? Click here to send me a tip!
-
-
 @ a4a6b584:1e05b95b
2024-03-07 02:55:48
@ a4a6b584:1e05b95b
2024-03-07 02:55:481. Revisiting and Rekindling Stallman’s Vision
Dominating today's software funding environment are two formidable models: the subscription-based Software as a Service (SaaS) model and the Advertising-based revenue model. However, they emanate a disconcerting discord with user-centric principles.
-
SaaS: Criticized for its semblance to rent-seeking behaviors, this model often raises eyebrows for potentially prioritizing profits over users.
-
Ad-based Model: While user data becomes a commodity, this model can divert focus from genuine user needs, instead favoring revenue generation through targeted advertising.
Reflecting upon Richard Stallman's GNU General Public License—embodying a world where code is an open, collective pursuit—I implore us to ponder: Have our attempts at ensuring remuneration veered us away from community-driven innovation, burying its essence beneath the rent-seeking predilections of current software funding models?
2. AI: A Catalyst Transforming Software Creation and Funding
AI, with its capability to democratize software creation, is not merely a technological advancement; it's a seismic shift. Imagine a future where coding becomes a universally accessible skill, transforming complex programming into simple, English language-based tasks. This transcendence could not only dismantle traditional funding models but perhaps, reinvent the entire software creation and distribution ecosystem.
The profound implications of AI render the former conundrums of software funding potentially obsolete, prompting a pivotal query: How does one navigate through this newfound landscape of minimized manual intervention and maximized automated innovation?
3. Bitcoin: An Unwavering Anchor Amidst Economic Flux
If we indeed teeter on the brink of an AI-induced deflationary epoch—marked by job displacement and dwindling prices—Bitcoin emerges as a novel, stabilizing financial bastion.
-
A Deflationary Shield: Despite burgeoning product inventories and diminishing prices, Bitcoin’s scarcity (capped at 21 million coins) offers a hedge against deflation.
-
An Inflationary Bulwark: Unaffected by AI’s boundless productivity, Bitcoin’s inherent fixed supply also fortifies it against inflationary pressures.
-
Capital Allocation Power: Bitcoin holders, empowered by amplified capital allocation abilities, may steer funding towards community-aligned, innovative projects, reminiscent of the Stallman-inspired utopian visions.
In this sea of economic ambiguity fostered by AI advancements, Bitcoin potentially carves out a path, standing resolute against both inflation and deflation, enabling a sustainable channel for capital allocation and investment.
Navigating the Future with AI and Bitcoin
The intersection of technology, economics, and individual autonomy within this complex tapestry conjures a myriad of questions, beckoning explorers like us to dissect, debate, and delve into uncharted territories. How do we marry the equitable ethos of community-centric innovation with the disruptive dynamism of AI and the financial acumen embedded in Bitcoin?
Join me in this exploration, as we endeavor to chart a course through these entwining narratives, seeking to harmonize the ethos of collective innovation, the transformative potential of AI, and the prudent economic guardianship of Bitcoin.
Adam Malin
You can find me on Twitter or on Nostr at
npub15jnttpymeytm80hatjqcvhhqhzrhx6gxp8pq0wn93rhnu8s9h9dsha32lxYou can view and write comments on this or any other post by using the Satcom browser extention.
value4value Did you find any value from this article? Click here to send me a tip!
-
-
 @ a012dc82:6458a70d
2024-03-07 02:23:30
@ a012dc82:6458a70d
2024-03-07 02:23:30Table Of Content
-
Content
-
Introduction
-
What is Bitcoin?
-
How do bitcoins enter circulation?
-
Bitcoin’s environmental impacts
-
Energy consumption and greenhouse gas emissions
-
Water issues and e-waste
-
NFTs
-
How can cryptocurrencies be more sustainable?
-
-
Conclusion
-
FAQ
-
External Links
In April of 2011, one bitcoin was worth exactly one dollar. In April, the price of one bitcoin hit an all-time high of about $65,000, and as of the time of this writing, the price of one bitcoin is roughly $48,000. The fact that some bitcoin investors have become billionaires overnight has piqued the interest of an increasing number of individuals in the prospect of becoming wealthy by investing in cryptocurrencies like Bitcoin. On the other hand, the expanding popularity of Bitcoin may make it difficult for the world to forestall the most severe effects of climate change. This cryptocurrency uses a lot of energy, and its effects on the environment are quite far-reaching.
Before we can begin to grasp Bitcoin's effects on the environment, we must first understand what Bitcoin is and how it operates.
What is Bitcoin?
A cryptocurrency is a digital means of exchange that only exists in digital form; it does not have a physical equivalent, such as a coin or a note, and there was no initial investment of money to get it started. "It's a marketplace, and as long as people are prepared to ascribe value to it, then that's it," said R.A. Farrokhnia, a professor at Columbia Business School and the executive director of the Columbia Fintech Initiative. Bitcoin is the world's most widely used cryptocurrency, accounting for more than half of all cryptocurrencies. It may be used to purchase a wide variety of goods and services, including automobiles, home furnishings, and even vacations. This month, the value of all the bitcoins in circulation was $903 billion.
Decentralized refers to the fact that no central authority, such as a bank or government, regulates cryptocurrencies such as bitcoin and ethereum. The benefits of doing business in this manner include the absence of transaction fees, the accessibility of the platform, and the simplification of complex financial dealings such as the transfer of funds across countries. Although transactions are recorded, the identities of the people carrying them out are not revealed. Because cryptocurrencies can't be tracked and there's no one in charge of how they're used, many bad people, like tax evaders, criminals, and terrorists, may use them for bad things.
Because cryptocurrencies don't exist in the form of actual money and they don't have a centralized authority, they had to devise a method to assure that their transactions are safe and that their tokens can only be used once. In 2008, an anonymous individual (or people) going by the name Satoshi Nakamoto (whose actual identity is still a mystery) came up with a solution to these problems, which led to the creation of bitcoin. The solution that Nakamoto came up with was a digital ledger system that generated confidence in the system via the use of mathematics and encryption, and it logged transactions in a distributed ledger called blockchain. A blockchain is a transparent database that is shared throughout a network. It records transactions in blocks that are connected together, and each block is linked to the one that came before it. Nodes are powerful computers that are linked to the other computers that make up the Bitcoin network. These nodes are responsible for running the Bitcoin software and validating transactions and blocks. Every node in the network has its own copy of the complete blockchain, which includes a record of each transaction that has been processed on it.
Nakamoto limited the total number of bitcoins that could ever be produced to 21 million. Although there is much conjecture about the mathematical theories that led to the selection of that number, the actual reason for its selection is unknown to anybody. As of this month, it is expected that there are now 18.8 million bitcoins in circulation, and it is expected that any remaining bitcoins will be issued by the year 2140.
How do bitcoins enter circulation?
Mining is essentially the process of verifying and recording new transactions on the blockchain, is how new bitcoins are created. Mining is also how new blocks are added to the network. New bitcoins are awarded to the miner who is the first to accomplish this goal.
Bitcoin miners are responsible for determining whether a collection of transactions that have been grouped together into a block are legitimate. This includes verifying anywhere from 20 to 30 different variables, such as addresses, names, timestamps, the amount of money that senders have in their accounts, whether or not they have previously spent it, etc. The miners then compete to see who can solve a conundrum or riddle the earliest to have their validation acknowledged first. To solve the puzzle, you will need to come up with a number that will only be used once. This number is referred to as the nonce, which stands for "number used once." When this number is combined with the data contained in the block and processed by a particular algorithm, it will produce a random 64-digit string of numbers and letters. This random number must be lower than or equal to the 64-digit goal specified by the system, also referred to as the target hash. Once the nonce that creates the desired hash has been located, the miner who won the competition will have their new block connected to the one that came before it. This will ensure that all blocks are connected in a chain. Because altering one block would affect all of the blocks that followed it, this makes it impossible to tamper with the network. The outcome is subsequently shared with the other blockchain network members, and all nodes update the version of the blockchain they are using. The term "proof of work" refers to either the process of validating work or the consensus method. The miner who wins gets new bitcoins and the transaction fees are paid for by the person who receives the bitcoins.
The higher the price of bitcoin is, the greater the number of miners fighting for it, making the puzzles more difficult. The Bitcoin protocol seeks to have blocks of transactions mined every 10 minutes; hence, the possibility of discovering the nonce in fewer than ten minutes grows if there are more miners on the network with greater computer power. The system then makes the target hash more difficult to locate by adding more zeroes to the front of it; the lower that number is, and the more difficult it is to produce a random number below it, the more zeroes that are added to the front of the target hash. The solution to the problem is simplified by the system whenever there is less computational power available to process it. The Bitcoin network will modify the difficulty of mining in order to maintain a block production rate of ten minutes.
The amount of bitcoin that miners are rewarded with is half every 210,000 blocks. According to the information provided by Investopedia, the mining of a single block back in 2009 resulted in the acquisition of fifty bitcoins. By November 2020, the reward for completing a block was 6.25 bitcoins, but the price of one bitcoin was around $17,900, so a miner would get $111,875 (6.25 times 17,900) for completing a block.
Miners with less computational capacity on their own may join mining pools, which do not need to reveal how many active miners they have. It is thought that there are one million bitcoin miners functioning and competing, but it is hard to be certain.
Farrokhnia said, "I have a sense that Nakamoto had the concept that everyone could be a miner—that you could mine with nothing more than your laptop." This was in reference to the idea that mining could be done with nothing more than a laptop. You started to witness the emergence of these mining pools as Bitcoin grew more popular and more people started using the system, and the rewards were genuinely worth money. This greatly raised the difficulty level. This spiraled into a vicious circle, an arms race for the most powerful computers; however, the more powerful the hardware miners have, the more difficult it is to find the nonce.
Because Bitcoin encourages strong competition, its effects on the environment directly result from this.
Bitcoin’s environmental impacts
Energy consumption and greenhouse gas emissions
The process of attempting to come up with the correct nonce that will yield the target hash is essentially a game of trial and error, similar to how a burglar could try several random passwords in order to get into your account. This process can take billions of attempts. It is estimated that each transaction using Bitcoin uses 707 kilowatt hours of electricity due to the large number of machines involved in the process. In addition, the computers soak up more energy due to the heat they produce and the necessity to keep them at a constant temperature. And although it is impossible to know exactly how much electricity Bitcoin uses because different computers and cooling systems have varying levels of energy efficiency, an analysis conducted by the University of Cambridge estimated that bitcoin mining consumes 121.36 terawatt hours each and every year. This is more than the total consumption of all of Argentina as well as greater than the consumption of Google, Apple, Facebook, and Microsoft combined.
And the situation will only worsen as miners are forced to continuously upgrade their computational power to remain competitive with one another. In addition, since incentives are consistently slashed in half, miners need to either process a greater volume of transactions or lower the amount of Bitcoin power they consume in order for mining to be financially feasible. Consequently, miners are required to search for the most affordable sources of electricity and upgrade to faster, more power-hungry machines. The amount of energy required to mine Bitcoin almost grew by 62 times between 2015 and March of 2021. According to Cambridge University research, only 39 percent of this energy comes from renewable sources, and most of it comes from hydropower, which may negatively affect ecosystems and biodiversity, according to Cambridge University research.
By 2020, China would control more than 65 percent of the global processing power used to run the Bitcoin network.Miners took advantage of China's inexpensive energy, which was generated either by hydropower or polluting coal power plants. However, China has recently tightened down on mining due to worries about the financial dangers associated with cryptocurrencies and the large energy consumption associated with mining, both of which go against China's carbon neutral objective by 2060. As a direct consequence of this, a significant number of Chinese bitcoin miners are exploring the possibility of relocating their operations to locations in other nations, such as the United States or Kazakhstan, both of which get the majority of their power from fossil fuels. To bolster their own economies, a number of states in the United States actively seek to recruit Chinese miners. However, if the miners cannot relocate, they plan to sell their equipment to various other miners throughout the world. Miners in the United States are now raising hundreds of millions of dollars to invest in bitcoin mining and turning old factories and power plants into large-scale bitcoin mining operations.
An example of this is the Greenidge Generation facility in Dresden, New York, which used to be a coal power plant but has now been converted to run on natural gas and has started mining bitcoin. As a result of becoming one of the biggest cryptocurrency miners in the United States between 2019 and 2020, the facility's emissions of greenhouse gases surged by nearly a factor of 10. Greenidge hopes to turn other power plants into mining operations by 2025 and has plans to quadruple its mining capacity by July, then double it again by 2022. Even while Greenidge committed back in June to becoming carbon neutral by buying carbon offsets, the reality is that if it weren't for bitcoin mining, the facility probably wouldn't be operational at all. Other polluting peaker plants, which are power plants that are normally only operated during peak demand for a few hours once a month, are being taken over for cryptocurrency mining so that they may run around the clock.
Earth Justice and the Sierra Club have sent a letter to the New York State Department of Environmental Conservation, requesting the department to refuse to renew Greenidge's permit, which would give the company permission to increase the amount of greenhouse gases it emits. They also cautioned that there are almost 30 power plants in upstate New York that have the potential to be converted into bitcoin mining operations. If this were to take place, it could undermine the efforts that the state of New York is making to eliminate almost all greenhouse gas emissions by the year 2050.
Because it translates into an estimated 22 to 22.9 million metric tons of CO2 emissions per year, Bitcoin's power consumption has serious consequences for climate change and the achievement of the objectives of the Paris Accord. This is because it is comparable to the CO2 emissions from the energy usage of 2.6 to 2.7 billion houses for one year. According to one analysis, Bitcoin might cause global warming to exceed 2 degrees Celsius. According to one estimate, bitcoin mining in China might be responsible for 130 million metric tons of CO2 emission by the year 2024. On the other hand, if more mining moved to the United States and other countries, this number would likely rise much more without more use of renewable energy.
Water issues and e-waste
Additionally, using significant quantities of water are power facilities such as Greenidge. Greenidge takes as much as 139 million gallons of fresh water from Seneca Lake every day to cool the plant. However, the water that is released back into the lake is between 30 and 50 degrees Fahrenheit hotter than the lake's average temperature, putting the wildlife and ecology of the lake in danger. Additionally, larvae, fish, and other forms of animals might be sucked in and killed by the massive intake pipes.
And even if it someday becomes feasible to do all bitcoin mining using renewable energy, the issue of electronic waste will always be a concern. In order to be successful, miners need to have access to the most advanced gear, which should be able to do the most number of calculations while using the least amount of power. This highly specialized hardware is rendered useless every one and a half years and cannot be rewritten to perform any other function. It is estimated that the Bitcoin network makes 11.5 kilotons of e-waste per year, which adds to the already large amount of e-waste we have a problem with.
NFTs
Since December, a new trend in the realm of art known as NFTs has added to the list of worries about the impact of cryptocurrencies on the environment. These are non-fungible tokens, digital files of images, music, films, or other types of artwork stamped with one-of-a-kind strings of code. People are able to read or duplicate NFTs, but there is only one unique NFT that belongs to the buyer. This unique NFT is recorded on the blockchain and safeguarded using the same energy-intensive proof of work procedure. NFTs are already selling for tens of thousands of dollars, and a digital artist by the name of Beeple just sold an NFT for more than 69 million dollars.
NFTs are generated on Ethereum, which is now the second most popular cryptocurrency after Bitcoin. The typical non-fungible token transaction causes the release of 440 pounds of carbon dioxide into the atmosphere, which is the same as traveling 500 miles in a vehicle fueled by gasoline. This results in emissions that are 10 times greater than the typical Ethereum transaction.
According to the calculations of one digital artist, the carbon footprint of a typical NFT is more than the amount of power used in a single month by a person living in the EU. Some artists, worried about the effects that NFTs have on the environment, are attempting to raise awareness and seek methods to create NFTs that are more environmentally friendly.
How can cryptocurrencies be more sustainable?
It would be difficult for the whole Bitcoin network to migrate to a more energy-efficient system because of the millions of dollars spent on hardware and infrastructure. This is particularly true given that there is no central oversight body to oversee the change. However, a number of efforts are underway that aim to lessen the impact that Bitcoin and cryptocurrencies in general have on the environment. Elon Musk, CEO of Tesla, recently discussed the energy consumption of leading crypto mining firms in North America with the CEOs of such companies. Because of this, a brand-new Bitcoin Mining Council has been set up to help make the energy industry more open.
The Crypto Climate Accord is another initiative that has the backing of 40 different projects. Its goal is for blockchains to run on energy derived from 100 percent renewable sources by 2025, and for the entire cryptocurrency industry to achieve net zero emissions by 2040.It intends to decarbonize blockchains by using more energy efficient validation methods; advocating for proof of work systems to be located in areas with abundant renewable energy that can be harnessed; and encouraging the purchase of certificates to support renewable energy generators in the same way that carbon offsets support environmentally friendly projects.
Ethereum has set a goal of reducing its energy consumption by 99.95% by 2022.This will be accomplished by moving to an alternative validation system known as proof of stake, which a few smaller cryptocurrencies have already implemented. Proof of stake is an alternative to proof of work that does not necessitate using computational power to solve puzzles to earn the right to verify transactions. Instead, the process is similar to that of a lottery. Potential validators have to risk some of their Ethereum currency (ETH) to be considered; the more coins they stake, the higher their chances of being chosen at random by the system to act as the validator. Participants in Ethereum 2.0 will be required to stake 32 ETH (each of which is worth approximately $3600 as of this writing), with multiples of 32 ETH required for additional validator opportunities. When a new block is validated and confirmed correct, validators will be compensated with coins and allowed to retain the coins they staked throughout the validation process.
Because validators would lose their stake and be kicked off the network if they cheated or allowed bogus transactions in the block, the system provides an extra layer of protection against fraudulent activity. Stakes grow more valuable as the price of ETH rises, which improves network security. However, energy requirements stay the same throughout this process. However, some individuals are concerned that proof of stake would give those who have the most ETH greater control, resulting in a less decentralized system.
According to Farrokhnia, "Blockchain is a very configurable and versatile technology." [Citation needed] You are free to construct it in any shape or form that is conducive to achieving your goal. Therefore, one example of a proof of consensus method is termed "proof of reputation." This mechanism works on the principle that "the more respectable you are, the more votes you have in verifying things." Blocks and transactions are verified by pre-approved participants who are required to reveal their true identities. The proof of authority system depends on its participants' reputation and trustworthiness. Some cryptocurrencies utilize a proof of coverage system that requires miners to offer a service, such as hosting a router in their house, so the network may grow. This is one of the requirements for mining these coins.
Moving bitcoin facilities next to oil fields would be another way to reduce the environmental impact of cryptocurrency mining. These operations would collect waste methane gas that is often burned off, pump it to generators, and utilize the electricity from the generators to mine bitcoin. In West Texas, where there is an abundance of wind power, there are plans to mine some bitcoin. Bitcoin mining operations close to wind farms can use the extra energy made by those farms. This is because the amount of power made by the wind can sometimes be more than what the transmission lines can handle.
According to Farrokhnia, even if these concepts are conceivable in a theoretical sense, it's feasible that they won't work in practice. He said that each of these concepts calls for a significant initial capital expenditure. "And we know that interest in mining is predicated on the price of bitcoin itself. As a result, you could have a wide variety of extremely pricey solutions that would aim to be more energy efficient. However, as soon as the price of bitcoin were to drop below a certain threshold, all of these projects would be [cancelled] because they are simply not financially feasible. Given the unpredictability of Bitcoin's price and the lack of clarity around its potential future, who would make those kinds of investments in their right mind?
The development of Farrokhnia is the best chance it has of becoming a more environmentally friendly cryptocurrency. He is of the opinion that cryptocurrencies must take environmental factors into account if they want to achieve widespread acceptance and that more recent cryptocurrencies that minimize their impact on the environment may one day surpass Bitcoin.
According to Farrokhnia, "A new generation of crypto is coming on board." [Cryptocurrency] "They are going to move away from proof of work for a variety of reasons, one of which is the environmental effect, since young programmers are generating the majority of these. This is one of the reasons why they are moving away from proof of work. They are definitely more aware of the environment, and we can only hope that they understand the importance of their work beyond what they are building and that they will take into account how complicated the world is today.
Conclusion
Alternative methods of reducing the environmental impact of cryptocurrency mining include relocating bitcoin mining operations to areas near oil fields and using the waste methane gas from flared flares to power generators. You might have a lot of very expensive solutions that attempt to be more energy efficient, but as soon as the price of bitcoin dropped below a certain level, all these initiatives would be [cancelled] because they are simply not financially possible. He thinks that Bitcoin will be replaced by a newer cryptocurrency that is better for the environment because the industry won't be able to ignore environmental concerns.
FAQ
Is the use of Bitcoin bad for the environment? According to the findings of the experts, the entire global climate damage caused by bitcoin between the years 2016 and 2021 is anticipated to amount to $12 billion, and within that time period, carbon emissions have climbed 126 times.
In what ways is the mining of bitcoins harmful to the environment? The digital currency's reliance on a computing process to verify transactions known as "proof-of-work mining" is to blame for the disproportionate amount of damage it causes to the environment. Participating in "proof-of-work mining" requires massive electricity expenditures, and those who do so are rewarded with the opportunity to win some new bitcoin.
Is the use of Bitcoin kind to the environment? According to environmentalists' assessments, the "mining" of bitcoin requires an alarmingly high quantity of fossil fuels. On the other hand, there are other cryptocurrencies that are better for the environment and do less harm to the world. Because of these, worries about the relationship between cryptocurrencies and the environment might be eased.
Why are NFTs detrimental to the health of the environment? Indeed, conventional approaches to minting and validating NFTs use significant amounts of energy. The vast majority of non-fungible tokens (NFTs) in existence today are hosted on OpenSea, a platform built on Ethereum that is notorious for its high level of energy consumption. Yes, the environment is being harmed when NFTs are used in these situations.
That's all for today, see ya tomorrow
If you want more, be sure to follow us on :
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 3824d96c:68b8f9dc
2024-03-06 18:21:33
@ 3824d96c:68b8f9dc
2024-03-06 18:21:33Everything ever build in this world will eventually fall and become ashes, so what's the meaning of even building things? I don't care if there is a meaning or not. If the world is going to end tomorrow, today I'm going to be great and keep pushing things forward.
Even thou everything is going to be destroyed that doesn't change the fact that it was someday acomplished. The universe will forever know it.
Our burden is to fight nature, to fight entropy, to keep fighting the structure of the universe. We humans are the only living creatures that can withstand against the power of time. We can keep building things while the indeference of the universe can keep destroying them, we will build everything again from the ashes.
Keep pushing things forward.
Per aspera ad astra.
-
 @ 1e52c554:21771908
2024-03-06 16:33:20
@ 1e52c554:21771908
2024-03-06 16:33:20Posthumous work of the Colombian poet born in Don Matias on January 20, 1948.
Welcome to this blog dedicated to the Posthumous work of the Colombian poet Francisco Luis Arroyave Tabares (my father), born in Don Matias on January 20, 1948-2010. Where I will be publishing each of the 175 sonnets from his unpublished collection 'Sonnets For The Twenty-First Century And A Circadian Musical (1984-1987).' Analyzed with GPT4 artificial intelligence and illustrated with AI tools... I hope you enjoy this garden of words snatched from the solitude of a locked room.
Likewise, any enthusiast of the sonnet form is invited to conduct their personal studies of Arroyave Tabares' work, as it is a collection that, although registered since 1989, has not yet been published.
Frank Duna

Analysis "In Shandows I will wait"
Introduction
Sonnet 89 is a deeply emotional and introspective poem that explores themes of love, loss, longing, and hope. It uses vivid and evocative imagery to convey the speaker's emotional state and his complex relationship with love.
Thematic Analysis
First Quatrain: The speaker recalls a past love, which is now only an echo or a memory. The use of words like “emptiness”, “confines”, and “echoes” suggests a sense of loss and longing.
Second Quatrain: The speaker talks about the new experiences in life (symbolized by “new-sprung blooms”) but they do not bring the pleasure he seeks. The “pungent hill” surrounded by loneliness could symbolize the challenges or hardships he’s facing.
Third Quatrain: The speaker’s soul, described as “bleak”, calls out for its other half, suggesting a sense of incompleteness. The fleeting nature of happiness and the reference to Venus (the Roman goddess of love) leaving behind a cloud of dust could symbolize the transient nature of love.
Couplet: The speaker resolves to wait in the shadows until true love occurs again. This shows a sense of hope and patience.
Overall, the sonnet explores themes of love, loss, longing, and hope. The language is rich and evocative, painting a vivid picture of the speaker’s emotional landscape. The use of natural imagery (blooms, hill, forest, dust) adds a layer of depth to the poem, linking the speaker’s emotional state to the natural world. The sonnet ends on a hopeful note, suggesting the possibility of love rekindling in the future.
Rhyme Scheme
The sonnet follows the Shakespearean sonnet rhyme scheme, which is ABABCDCDEFEFGG. Let’s break it down:
The first quatrain (lines 1-4) has the rhyme scheme ABAB:
A: In Shandows I will wait B: Easily I recall the emptiness A: Dwelling in confines by which love went by B: As echoes still full with loftinessThe second quatrain (lines 5-8) follows the scheme CDCD:
C: New-sprung blooms through my life lucently rill D: Yet they do not fulfill pleasures I seek C: And loneliness surrounds that pungent hill D: Where my fervors became blameless an meek.The third quatrain (lines 9-12) follows the scheme EFEF:
E: My bleak soul with mellifluous accent F: Calls its other half in deep forest lost. E: For happines has been evanescent F: And Venus left behind a cloud of dust.Finally, the couplet (lines 13-14) follows the scheme GG:
G: In shadows I will wait with my murmurs G: Until the real love once again occurs.This rhyme scheme is typical of Shakespearean sonnets and helps to give the poem its rhythm and flow. It also serves to emphasize certain themes and ideas within the poem, creating a sense of unity and coherence. The final couplet often provides a resolution or commentary on the themes presented in the quatrains. In this case, it reaffirms the speaker’s resolution to wait for true love.
Additional Aspects
Let’s delve deeper into the sonnet’s language, imagery, themes, meter, and overall impact.
Language and Imagery: The sonnet uses rich and evocative language to create vivid imagery. Phrases like “In shadows I will wait”, “New-sprung blooms through my life lucently rill”, and “Venus left behind a cloud of dust” paint a picture in the reader’s mind and evoke strong emotions. The use of words like “emptiness”, “echoes”, “loneliness”, and “bleak” further emphasize the themes of longing and solitude.
Themes: The main themes of the sonnet are love, loss, loneliness, and hope. The speaker expresses a deep longing for a lost love and the pain of solitude, yet also holds onto hope for the future. The recurring image of waiting in the shadows suggests patience and resilience in the face of adversity.
Meter: The sonnet follows the traditional iambic pentameter of Shakespearean sonnets, which consists of five pairs of unstressed and stressed syllables per line. This gives the poem a rhythmic quality and helps to emphasize certain words and ideas.
Overall: the sonnet is a poignant exploration of the human experience of love and longing. The combination of vivid imagery, emotional language, and rhythmic meter creates a powerful and moving piece of poetry. The speaker’s journey from recalling past love, through experiencing loneliness, to holding onto hope for future love, resonates with readers and invites them to reflect on their own experiences of love and loss. The sonnet ends on a hopeful note, reaffirming the human capacity for resilience and the enduring power of love.
(GPT4)
Syllable count for each line.
``` In Shandows I will wait
10 Easily I recall the emptiness 10 Dwelling in confines by which love went by 9 As echoes still full with loftiness 10 I find for remembrance or alibi.
10 New-sprung blooms through my life lucently rill
10 Yet they do not fulfill pleasures I seek 10 And loneliness surrounds that pungent hill 10 Where my fervors became blameless an meek.10 My bleak soul with mellifluous accent 10 Calls its other half in deep forest lost. 10 For happines has been evanescent 10 And Venus left behind a cloud of dust.
10 In shadows I will wait with my murmurs 10 Until the real love once again occurs. *** ```
Sonnets For The Twenty First Century And A Circadian Musical Written By Francisco Luis Arroyave Tabares (1984-1987)
Analyzed by GPT4; Image by Frank Duna; First published on Nostr Protocol by franciscoarroyavet@nostrplebs.com
 *In Shandows I will wait
*In Shandows I will wait -
 @ 1e52c554:21771908
2024-03-06 16:14:14
@ 1e52c554:21771908
2024-03-06 16:14:14Posthumous work of the Colombian poet born in Don Matias on January 20, 1948.
Welcome to this blog dedicated to the Posthumous work of the Colombian poet Francisco Luis Arroyave Tabares (my father), born in Don Matias on January 20, 1948-2010. Where I will be publishing each of the 175 sonnets from his unpublished collection 'Sonnets For The Twenty-First Century And A Circadian Musical (1984-1987).' Analyzed with GPT4 artificial intelligence and illustrated with AI tools... I hope you enjoy this garden of words snatched from the solitude of a locked room.
Likewise, any enthusiast of the sonnet form is invited to conduct their personal studies of Arroyave Tabares' work, as it is a collection that, although registered since 1989, has not yet been published.
Frank Duna

Analysis "The Best 0f Her Enthroned In My Hours"
Introduction
Sonnet 88 by Francisco Luis Arroyave Tabares, titled "The Best 0f Her Enthroned In My Hours," is a complex and emotionally charged poem that explores themes of love, loss, longing, and the passage of time.
Thematic Analysis
** Octave:** The octave presents a conflict, a problem, or a question. In this case, the speaker is expressing his struggle with a heartache that is both constant and intense. He describes his heart as being “immured by hush and amour” and fading in a world that is constantly becoming darker. He’s been trying to find peace and encourage passion, but sometimes he longs for the “lost musics” that her eyes once asked for.
Sestet: The sestet usually provides a resolution or commentary on the problem presented in the octave. Here, the speaker talks about a recent change in his life - he now has a “queen of depths” who is the best part of his hours. His old ideas are put away to age like wine, suggesting that he’s moving on from the past and looking forward to future missions and dreams.
In summary, this sonnet explores themes of love, loss, and hope for the future. The octave sets up a problem of heartache and longing, while the sestet offers a resolution of moving on and embracing new love and dreams. It’s a beautiful expression of the human experience of love and loss.
Rhyme Scheme
Let’s analyze the rhyme scheme of the sonnet. The rhyme scheme is ABBA ABBA CDE CDE, which is a typical Italian or Petrarchan sonnet structure.
Here’s how it applies to the sonnet:
Octave:
Line 1 (A): Is there any other way of masking Line 2 (B): The incessant and maddening dolour Line 3 (B): Of a heart immured by hush and amour Line 4 (A): That fades in a world that keeps on dusking? Line 5 (A): Most of my forces I have been tasking Line 6 (B): To peace my soul and encourage ardour Line 7 (B): While some times I demand from my contour Line 8 (A): The lost musics that her eyes were asking.**Sestet: **
Line 9 (C): In recent days a queen of depths I have Line 10 (D): With the best of her enthroned in my hours Line 11 (E): As passions live and trot with dear visions. Line 12 (C): My old ideas I put in a cave Line 13 (D): To age with wìnes for other times of ours Line 14 (E): And dreams that look for our future missions.In the octave, the first and fourth lines rhyme, as do the second and third lines, creating an ABBA pattern. This pattern is repeated in the next four lines. In the sestet, the first, fourth lines rhyme ©, as do the second, fifth (D), and the third, sixth (E), creating a CDE CDE pattern. This rhyme scheme helps to emphasize the shift in tone between the octave and the sestet. It’s a beautiful structure that adds to the overall impact of the poem.
Additional Aspects
Let’s delve deeper into the analysis of “The Best 0f Her Enthroned In My Hours” by Francisco Luis Arroyave Tabares:
Language and Imagery: The sonnet uses rich and evocative language to convey its themes. The imagery of a heart “immured by hush and amour” and a world that is “dusking” paints a vivid picture of the speaker’s emotional state. The use of words like “masking”, “dolour”, and “ardour” add a layer of complexity and depth to the poem. The sonnet also uses metaphorical language, such as “queen of depths” and “old ideas I put in a cave”, which adds to the overall imagery and helps to convey the speaker’s feelings and experiences.
Themes: The main themes of the sonnet are love, loss, and hope. The speaker talks about a past love that has caused him pain and sorrow, but also about a new love that brings him joy and hope. The theme of time is also present, with the speaker putting his old ideas away to age like wine, suggesting a process of healing and moving on.
Meter: The sonnet appears to follow the iambic pentameter, which is a common meter in English poetry and is often used in sonnets. This means that each line of the poem has five metrical feet, each consisting of one unstressed syllable followed by one stressed syllable. This gives the poem a rhythmic quality and helps to guide the reader through the poem. ** Overall:** this sonnet is a beautiful exploration of the themes of love, loss, and hope. The use of rich language and vivid imagery, combined with the traditional sonnet structure and meter, creates a powerful and moving piece of poetry. The speaker’s journey from pain and longing to acceptance and hope is conveyed with depth and emotion, making this sonnet a poignant expression of the human experience.
(GPT4)
Syllable count for each line.
```
The Best 0f Her Enthroned In My Hours
10 Is there any other way of masking 10 The incessant and maddening dolour 10 Of a heart immured by hush and amour 10 That fades in a world that keeps on dusking?
10 Most of my forces I have been tasking 10 To peace my soul and encourage ardour 10 While some times I demand from my contour 10 The lost musics that her eyes were asking.
10 In recent days a queen of depths I have 10 With the best of her enthroned in my hours 10 As passions live and trot with dear visions. 10 My old ideas I put in a cave 10 To age with wìnes for other times of ours 10 And dreams that look for our future missions. ***
```
Sonnets For The Twenty First Century And A Circadian Musical Written By Francisco Luis Arroyave Tabares (1984-1987)
Analyzed by GPT4; Image by leonardo.ai; First published on Nostr Protocol by franciscoarroyavet@nostrplebs.com
 The Best 0f Her Enthroned In My Hours
The Best 0f Her Enthroned In My Hours -
 @ 1c6b3be3:73f0ae6f
2024-03-06 06:15:13
@ 1c6b3be3:73f0ae6f
2024-03-06 06:15:13🍵 Actualités securite
Facebook, Messenger et Instagram sont en panne (1 min) Le 22 mars 2023, les services appartenant à Meta, dont Facebook, Messenger et Instagram, ont subi une panne mondiale. Les utilisateurs se sont retrouvés déconnectés de ces réseaux sociaux et ont été informés que leur session avait expiré. Malgré la tentative de se reconnecter ou de réinitialiser leur mot de passe, cela n'a pas résolu le problème pour certains, ce qui a suscité des inquiétudes concernant d'éventuels piratages de compte. Le porte-parole de Meta, Andy Stone, a confirmé la panne et a déclaré que l'entreprise travaillait activement à sa résolution. En 2021, Meta avait déjà connu une interruption de service majeure qui avait duré plus de six heures en raison de « changements de configuration sur les routeurs du backbone ».
Cybermalveillance.gouv.fr dresse son bilan 2023 des menaces (2 min) Le rapport de Cybermalveillance.gouv.fr indique que les particuliers, entreprises et collectivités locales continuent d'être victimes de divers types de cyberattaques, tels que le phishing, les rançongiciels et les faux appels de conseillers bancaires ou support technique. La plateforme a enregistré une audience stable de 3,7 millions de visiteurs au cours de l'année écoulée, avec plus de 282 000 sollicitations d'assistance. Le phishing reste la principale cause de recherche d'assistance pour tous les profils, tandis que le piratage de compte est en deuxième position pour les entreprises et les associations. Les ransomwares connaissent une augmentation, en particulier auprès des collectivités territoriales (+36% sur un an) et des entreprises (+9%). En outre, il y a une résurgence des attaques de perturbation, telles que la défiguration de sites et les dénis de service, ainsi qu'une augmentation des malwares en raison du développement des malwares as a service.
Palo Alto intensifie ses efforts pour sécuriser la 5G privée (3 min) Palo Alto Networks, une entreprise de cybersécurité, a souligné que l'enthousiasme pour les réseaux 5G privés d'entreprise augmente, mais que la protection de ces réseaux est souvent un défi en raison de leur complexité et de leur grande surface d'attaque. Pour protéger les déploiements 5G des entreprises, Palo Alto s'est associé à plusieurs fournisseurs pour offrir des produits et des services de sécurité intégrés. La société a également développé un écosystème de fournisseurs pour intégrer leurs technologies de sécurité avec son ensemble privé de sécurité 5G afin d'offrir une protection plus complète. Palo Alto s'est associé à des entreprises telles que Nvidia, Celona et NetScout, offrant une variété de capacités de sécurité pour les réseaux 5G privés, y compris la sécurisation des applications basées sur l'IA, le zero-trust aux réseaux sans fil privés, et une visibilité des services de bout en bout.
1,5 million de données clients de LDLC dérobées (1 min) Le revendeur informatique LDLC a confirmé avoir subi une cyberattaque le 1er mars, entraînant une fuite de données clients de ses boutiques physiques (environ 80 en France). Les pirates, membres d'Epsilon Group, affirment avoir extrait les noms, prénoms, numéros de téléphone, e-mails et adresses postales de 1,5 million de clients. Cependant, LDLC assure que les données financières ou sensibles ne sont pas concernées. Les pirates menacent de revendre les informations, mais LDLC aurait refusé de négocier avec eux. Le groupe a pris des mesures pour renforcer la protection, minimiser l'impact et rechercher les origines de l'attaque.
Jean-Baptiste Courouble (DSI de l'Urssaf) : « Le rachat de VMware est un source d'inquiétude » (8 min) L'Urssaf modernise son système d'information en migrant vers un cloud privé de deuxième génération (PFSv2) à base de conteneurs. Cette nouvelle plateforme, qui n'est pas encore en production et doit remplacer la version actuelle (PFSv1) début 2025, offrira une meilleure industrialisation et automatisation pour faciliter le provisioning, la gestion des quotas et l'accès aux services de base de données.
La transformation vers le cloud s'accompagne d'une réorganisation en profondeur de la DSI de l'Urssaf, avec la mise en place de filières applicatives pour une gestion de bout en bout des projets et une meilleure collaboration entre les différentes équipes. Cette mutation vise à rendre la DSI plus attractive pour les candidats à l'embauche et aligner ses pratiques sur celles des partenaires ESN, dans le cadre d'une politique de réinternalisation des compétences IT visant 200 recrutements.
Les principaux freins à cette transformation concernent la conduite du changement et l'adaptation de l'organisation, qui doit passer d'un mode hiérarchique à une organisation fonctionnelle dynamique. La nouvelle plateforme PFSv2 mettra l'accent sur les services managés les plus demandés, tels que la base de données, l'environnement de développement, l'observabilité et la sécurité, afin d'orchestrer au mieux les services offerts.
🍵 Actualités le-monde-du-cloud-computing
L'analyse des fichiers locaux par Copilot AI a la mémoire courte (2 min) Windows 11 Copilot peut télécharger et analyser rapidement des documents locaux, mais il y a des problèmes de persistance et d'exactitude. L'assistant peut oublier le sujet des requêtes et parfois chercher la réponse sur le Web au lieu de l'analyser en privé sur l'ordinateur de l'utilisateur. Microsoft a récemment ajouté la fonctionnalité de téléchargement de documents à Copilot pour Edge, qui est plus rapide que d'entraîner un LLM/chatbot IA local sur un fichier local. Cependant, cette fonctionnalité n'est pas encore disponible sur le site Web de Copilot et a connu des erreurs techniques lors des tests. Microsoft a annoncé le lancement prochain de Copilot pour OneDrive qui analysera automatiquement les fichiers stockés dans le cloud de Microsoft.
Les téléconseillers remplacés par l'IA chez Klarna (2 min) Klarna, la société suédoise spécialisée dans les facilités de paiement, a remplacé une grande partie de ses téléconseillers par un chatbot utilisant ChatGPT d'OpenAI avec succès. Le chatbot gère deux tiers des échanges avec le service client, équivalant à 700 employés à temps plein et fournit des résultats similaires en termes de satisfaction des clients. Il est disponible dans 23 pays et en 35 langues et peut gérer diverses tâches allant du service client multilingue à la gestion des remboursements et des retours, ainsi que des conseils financiers. Klarna prévoit d'économiser 37 millions d'euros en 2024 grâce au déploiement de ce chatbot, ce qui reflète ses efforts pour atteindre l'équilibre financier après avoir subi des pertes de 226 millions d'euros en 2023. La société a également procédé à plusieurs vagues de licenciements et externalisations ces deux dernières années, réduisant ses effectifs globaux.
Jean-Baptiste Courouble (DSI de l'Urssaf) : « Le rachat de VMware est un source d'inquiétude » (8 min) L'Urssaf modernise son système d'information en migrant vers un cloud privé de deuxième génération (PFSv2) à base de conteneurs. Cette nouvelle plateforme, qui n'est pas encore en production et doit remplacer la version actuelle (PFSv1) début 2025, offrira une meilleure industrialisation et automatisation pour faciliter le provisioning, la gestion des quotas et l'accès aux services de base de données.
La transformation vers le cloud s'accompagne d'une réorganisation en profondeur de la DSI de l'Urssaf, avec la mise en place de filières applicatives pour une gestion de bout en bout des projets et une meilleure collaboration entre les différentes équipes. Cette mutation vise à rendre la DSI plus attractive pour les candidats à l'embauche et aligner ses pratiques sur celles des partenaires ESN, dans le cadre d'une politique de réinternalisation des compétences IT visant 200 recrutements.
Les principaux freins à cette transformation concernent la conduite du changement et l'adaptation de l'organisation, qui doit passer d'un mode hiérarchique à une organisation fonctionnelle dynamique. La nouvelle plateforme PFSv2 mettra l'accent sur les services managés les plus demandés, tels que la base de données, l'environnement de développement, l'observabilité et la sécurité, afin d'orchestrer au mieux les services offerts.
Cybersécurité : Vade racheté par l'allemand Hornetsecurity (3 min) Hornetsecurity, un éditeur allemand de solutions de sécurité basé à Hanovre, a acquis la société française Vade, basée près de Lille. Cette acquisition permettra à Hornetsecurity de renforcer sa position dans la protection des e-mails et de s'implanter en France. Fondée en 2008, Vade est spécialisée dans la sécurisation des e-mails (antispam, antivirus...) ainsi que dans la protection contre les ransomwares, la sauvegarde, la récupération de données et la conformité des données pour Microsoft 365.
Le président de Vade, Georges Lotigier, quitte ses fonctions exécutives mais devient actionnaire et membre du conseil de surveillance du nouvel ensemble. Le rachat a été décrit comme une "opération mixte" et le nouveau groupe devrait compter près de 700 employés. La contribution de Vade au chiffre d'affaires devrait approcher les 30 %, ce qui permettra au groupe de dépasser les 50 millions d'euros de revenus.
Les produits de Hornetsecurity et Vade sont complémentaires et leur combinaison devrait les rendre plus puissants. Aucun remplacement des solutions d'un fournisseur par l'autre n'a été annoncé et les clients et partenaires bénéficieront d'une offre plus large de produits et de gammes.
🍵 Toutes les actualités :
Telex : Snowflake investit dans Mistral AI, Panne réseau géante pour BNP Paribas,AWS supprime les frais de sortie (1 min) Snowflake, une entreprise spécialisée dans les datawarehouses cloud, a annoncé un partenariat et investissement dans Mistral AI, une start-up française qui développe des grands modèles de langage. Le montant de l'investissement n'a pas été communiqué. Grâce à ce partenariat, Snowflake intègrera les modèles de Mistral dans son data cloud pour offrir des fonctionnalités d'IA à ses clients. Par ailleurs, la banque française BNP Paribas a connu une panne réseau majeure affectant ses clients particuliers et entreprises sur tout le territoire, empêchant l'utilisation de cartes bancaires dans des distributeurs automatiques et terminaux de paiement. Selon la banque, il s'agissait d'un "incident technique interne" et non d'une cyberattaque. Enfin, AWS a annoncé qu'il supprimerait les frais de sortie pour permettre aux clients de transférer leurs données hors de son écosystème sans coûts supplémentaires, en réponse à la réglementation européenne et au Data Act.
Facebook, Messenger et Instagram sont en panne (1 min) Le 22 mars 2023, les services appartenant à Meta, dont Facebook, Messenger et Instagram, ont subi une panne mondiale. Les utilisateurs se sont retrouvés déconnectés de ces réseaux sociaux et ont été informés que leur session avait expiré. Malgré la tentative de se reconnecter ou de réinitialiser leur mot de passe, cela n'a pas résolu le problème pour certains, ce qui a suscité des inquiétudes concernant d'éventuels piratages de compte. Le porte-parole de Meta, Andy Stone, a confirmé la panne et a déclaré que l'entreprise travaillait activement à sa résolution. En 2021, Meta avait déjà connu une interruption de service majeure qui avait duré plus de six heures en raison de « changements de configuration sur les routeurs du backbone ».
Cybermalveillance.gouv.fr dresse son bilan 2023 des menaces (2 min) Le rapport de Cybermalveillance.gouv.fr indique que les particuliers, entreprises et collectivités locales continuent d'être victimes de divers types de cyberattaques, tels que le phishing, les rançongiciels et les faux appels de conseillers bancaires ou support technique. La plateforme a enregistré une audience stable de 3,7 millions de visiteurs au cours de l'année écoulée, avec plus de 282 000 sollicitations d'assistance. Le phishing reste la principale cause de recherche d'assistance pour tous les profils, tandis que le piratage de compte est en deuxième position pour les entreprises et les associations. Les ransomwares connaissent une augmentation, en particulier auprès des collectivités territoriales (+36% sur un an) et des entreprises (+9%). En outre, il y a une résurgence des attaques de perturbation, telles que la défiguration de sites et les dénis de service, ainsi qu'une augmentation des malwares en raison du développement des malwares as a service.
Palo Alto intensifie ses efforts pour sécuriser la 5G privée (3 min) Palo Alto Networks, une entreprise de cybersécurité, a souligné que l'enthousiasme pour les réseaux 5G privés d'entreprise augmente, mais que la protection de ces réseaux est souvent un défi en raison de leur complexité et de leur grande surface d'attaque. Pour protéger les déploiements 5G des entreprises, Palo Alto s'est associé à plusieurs fournisseurs pour offrir des produits et des services de sécurité intégrés. La société a également développé un écosystème de fournisseurs pour intégrer leurs technologies de sécurité avec son ensemble privé de sécurité 5G afin d'offrir une protection plus complète. Palo Alto s'est associé à des entreprises telles que Nvidia, Celona et NetScout, offrant une variété de capacités de sécurité pour les réseaux 5G privés, y compris la sécurisation des applications basées sur l'IA, le zero-trust aux réseaux sans fil privés, et une visibilité des services de bout en bout.
Développeur, un emploi toujours très prisés en 2023 (2 min) En 2023, les développeurs sont les cadres informatiques les plus recherchés avec 22 313 offres d'emploi, suivis des chefs de projets IT (9 598 postes), des ingénieurs d'études en développement informatique (6 917 annonces) et des ingénieurs systèmes (5 370 propositions). Ces quatre professions représentent 8,6% des offres d'emploi cadres de l'année. Malgré une tendance à la baisse du nombre d'annonces par rapport à l'an dernier, les besoins en compétences cadres dans ces métiers restent élevés pour assurer les activités de production, d'exploitation et de maintenance informatique chez les clients. Les postes sont principalement proposés par les sociétés de services informatiques (SSII) qui cherchent à répondre à la demande croissante de solutions informatiques dans divers secteurs économiques, tels que l'industrie, la construction et l'analyse de données. En plus des compétences techniques, les employeurs recherchent également des candidats présentant des soft skills, telles que le travail en équipe, la capacité à communiquer et à faire des propositions, l'autonomie, la rigueur, la disponibilité et le dynamisme.
🍵 Actualités securite
Facebook, Messenger et Instagram sont en panne (1 min) Cybermalveillance.gouv.fr dresse son bilan 2023 des menaces (2 min) Palo Alto intensifie ses efforts pour sécuriser la 5G privée (3 min) 1,5 million de données clients de LDLC dérobées (1 min) Jean-Baptiste Courouble (DSI de l'Urssaf) : « Le rachat de VMware est un source d'inquiétude » (8 min) Avant les Jeux Olympiques, les RSSI restent sous pression (2 min) Cybersécurité : Vade racheté par l'allemand Hornetsecurity (3 min)
🍵 Actualités le-monde-du-cloud-computing
L'analyse des fichiers locaux par Copilot AI a la mémoire courte (2 min) Les téléconseillers remplacés par l'IA chez Klarna (2 min) Jean-Baptiste Courouble (DSI de l'Urssaf) : « Le rachat de VMware est un source d'inquiétude » (8 min) Cybersécurité : Vade racheté par l'allemand Hornetsecurity (3 min)
🍵 Toutes les actualités :
Telex : Snowflake investit dans Mistral AI, Panne réseau géante pour BNP Paribas,AWS supprime les frais de sortie (1 min) Facebook, Messenger et Instagram sont en panne (1 min) Cybermalveillance.gouv.fr dresse son bilan 2023 des menaces (2 min) Palo Alto intensifie ses efforts pour sécuriser la 5G privée (3 min) Développeur, un emploi toujours très prisés en 2023 (2 min) L'analyse des fichiers locaux par Copilot AI a la mémoire courte (2 min) Les téléconseillers remplacés par l'IA chez Klarna (2 min) Avec la CSRD, les outils de gestion du risque doivent s'adapter (5 min) 1,5 million de données clients de LDLC dérobées (1 min) Jean-Baptiste Courouble (DSI de l'Urssaf) : « Le rachat de VMware est un source d'inquiétude » (8 min) La réinternalisation de l'IT de Volkswagen passe par le nearshore (4 min) Avant les Jeux Olympiques, les RSSI restent sous pression (2 min) Cybersécurité : Vade racheté par l'allemand Hornetsecurity (3 min)
🍵 "llm | cloud | ddos" - Google News
Feds investigating 2 St. Cloud men accused of producing child pornography - WKMG News 6 & ClickOrlando India’s advisory on LLM usage causes consternation - CIO Jaiden Allen Michael Pick Obituary - SC Times How Cloud-Based Digital Technology Can Help Companies Achieve Sustainability Goals - SPONSOR CONTENT ... - HBR.org Daily CrowdStrike to Acquire Flow Security and Expand Its Cloud Security Leadership - CrowdStrike AWS follows Google Cloud in canceling egress fees, allowing customers to leave its cloud platform for free - SiliconANGLE News AWS follows Google in announcing unrestricted free data transfers to other cloud providers - TechCrunch CrowdStrike Acquires Flow Security, First Cloud Data Runtime Security Provider - The Fast Mode Heritage of Red Cloud set to remain open - KSNB Linpan Cloud Eye: Chengdu Dayi Rural Neighborhood Center / Archi-Union Architects - ArchDaily AWS removes some data transfer fees for customers exiting its cloud - DatacenterDynamics Nasdaq Highlights Migration to Cloud - Markets Media Cloud Authority Backlinks Service For Visibility Announced By LinkDaddy - Markets Insider Leading the Intelligent-Driven Future by New Digital Infrastructure: China Telecom Cloud and Connectivity Summit at ... - PR Newswire Cloud provider Ethernet data center switch spending declined - LightWave Online
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ fa0165a0:03397073
2023-10-12 16:40:43
@ fa0165a0:03397073
2023-10-12 16:40:43Probability theory is the study of random phenomena. This post is a pilot post for potentially further posting in this series. Feedback appreciated. Introduction
Probability theory is the study of random phenomena. It is used in many fields, such as statistics, machine learning, and finance. It is also used in everyday life, for example when playing games of chance, or when estimating the risk of an event. The most classic example is the coin toss, closely followed by the dice roll.
When we toss a coin, the result is either heads or tails. In the case of an ideal coin, the “random trail” of tossing the coin has an equal probability for both outcomes. Similarly, for a die roll of a fair dice, we know that the probability for each outcome is 1/6. In the study of probability we dive deep into the mathematics of these random phenomena, how to model them, and how to calculate the probability of different events. To do this in precise terms, we define words and concepts as tools for discussing and communicating about the subject.
This is the first of what I expect to be a 15 part series of my lecture & study notes from my university course in probability theory MT3001 at Stockholm University. References to definitions and theorems will use their numeration in the course literature, even if I may rephrase them myself. The book I’ve had as a companion through this course is a Swedish book called Stokastik by Sven Erick Alm and Tom Britton; ISBN:978–91–47–05351–3. This first module concerns basic concepts and definitions, needed for the rest of the course. The language of Probability theory
An experiment is a process that produces a randomized result. If our experiment is throwing a die, we then have the following: The result of throwing the die is called an outcome, the set of all possible outcomes is called the sample space and a subset of the sample space is called an event. We will use the following notation:
outcome is the result of an experiment, denoted with a small letter, ex. 𝑢₁, 𝑢₂, 𝑢₃, … event is the subset of the sample space, denoted with a capital letter, ex. 𝐴, 𝐵, 𝐶, … sample space is the set of all possible outcomes of an experiment, denoted Ω.Adding numbers to our dice example, we have the sample space Ω = {𝟏,𝟐,𝟑,𝟒,𝟓,𝟔} containing all the possible events 𝑢₁=𝟏, 𝑢₂=𝟐, 𝑢₃=𝟑, 𝑢₄=𝟒, 𝑢₅=𝟓 and 𝑢₆=𝟔. And we could study some specific sub events like the chance of getting an even number, 𝐴={𝟐,𝟒,𝟔}, or the chance of getting a prime number, 𝐵={𝟐,𝟑,𝟓}. As it happens, the probability of both 𝐴 and 𝐵 is 50%. Sample space
The sample space is the set of all possible outcomes of an experiment. It is denoted Ω. And there are two types of sample spaces, discrete and continuous. A discrete sample space is a finite or countably infinite set, and all other kind of sample spaces are called continuous.
The coin toss and the dice roll are both examples of discrete sample spaces. Studying a problem, like the temperature outside, would in reality require a continuous sample space. But in practice, we can often approximate a continuous sample space with a discrete one. For example, we could divide the temperature into 10 degree intervals, and then we would have a discrete sample space.
Remember that continuous sample spaces exist, and expect more information about them in later modules. For starters, we focus on discrete sample spaces. Set Theory notation and operations
When talking about probabilities we will arm ourselves with the language of “set theory”, it is a crucial tool for the study of probability. Feeling comfortable with the subject of set theory since before is useful, but not necessary. I will try to explain the concepts as we go along.
Even tough the events from the dice rolls are represented by numbers, it is important to note that they aren’t numbers, but rather elements. This might become more clear if we alter our example to be a deck of cards. This deck of cards have four suits Ω = {♥, ♠, ♦, ♣ } and in our experiments we draw a card from the deck and look at the suit. It’s here very obvious that we can’t add or subtract the different events with each other. But we do have the operations of set theory at our disposal. For example, if 𝐴 is the event of drawing a red card and 𝐵 is the event of drawing spades ♠, we can use the following notation: Set theory operations
Union: 𝐴 ∪ 𝐵 = {♥, ♦, ♠}, the union of 𝐴 and 𝐵. The empty set: ∅ = {}, the empty set. A set with no elements. Intersection: 𝐴 ∩ 𝐵 = ∅, the intersection of 𝐴 and 𝐵. This means that 𝐴 and 𝐵 have no elements in common. And we say that 𝐴 and 𝐵 are disjoint. Complement: 𝐴ᶜ = {♠, ♣}, the complement of 𝐴. Difference: 𝐴 ∖ 𝐵 = {♥, ♦}, the difference of 𝐴 and 𝐵. Equivalent to 𝐴 ∩ 𝐵ᶜ. The symbol ∈ denotes that an element is in a set. For example, 𝑢₁ ∈ Ω means that the outcome 𝑢₁ is in the sample space Ω. For our example: ♥ ∈ 𝐴 means that the suit ♥ is in the event 𝐴.Venn diagram
A very useful visualization of set theory is the Venn diagram. Here is an example of a Venn diagram in the picture below:
In the above illustration we have: Ω = {𝟏,𝟐,𝟑,𝟒} and the two events 𝐴={𝟐,𝟑} and 𝐵={𝟑,𝟒}. Notice how the two sets 𝐴 and 𝐵 share the element 𝟑, and that all sets are subsets of the sample space Ω. The notation for the shared element 𝟑 is 𝐴 ∩ 𝐵 = {𝟑}. Useful phrasing
The different set notations may seem a bit abstract at first, at least before you are comfortable with them. Something that might be useful to do is to read them with the context of probabilities in mind. Doing this, we can read some of the different set notations as follows:
𝐴ᶜ, “when 𝐴 doesn’t happen”. 𝐴 ∪ 𝐵, “when at least one of 𝐴 or 𝐵 happens”. 𝐴 ∩ 𝐵, “when both 𝐴 and 𝐵 happens”. 𝐴 ∩ 𝐵ᶜ, “when 𝐴 happens but 𝐵 doesn’t happen”.The Probability function
Functions map elements from one set to another. In probability theory, we are interested in mapping events to their corresponding probabilities. We do this using what we call a probability function. This function is usually denoted 𝑃 and have some requirements that we will go through in the definition below.
This function take events as input and outputs the probability of that event. For the example of a die throw, if we have the event 𝐴={𝟐,𝟒,𝟔}, then 𝑃(𝐴) is the probability of getting an even number when throwing a fair six sided dice. In this case 𝑃(𝐴)=1/2=𝑃(“even number from a dice throw”), you’ll notice that variations of descriptions of the same event can be used interchangeably.
The Russian mathematician Andrey Kolmogorov (1903–1987) is considered the father of modern probability theory. He formulated the following three axioms for probability theory: Definition 2.2, Kolmogorov’s axioms
A real-valued function 𝑃 defined on a sample space Ω is called a probability function if it satisfies the following three axioms: 𝑃(𝐴) ≥ 𝟎 for all events 𝐴. 𝑃(Ω) = 𝟏. If 𝐴₁, 𝐴₂, 𝐴₃, … are disjoint events, then 𝑃(𝐴₁ ∪ 𝐴₂ ∪ 𝐴₃ ∪ …) = 𝑃(𝐴₁) + 𝑃(𝐴₂) + 𝑃(𝐴₃) + …. This is called the countable additivity axiom.From these axioms it’s implied that 𝑃(𝐴) ∈ [𝟎,𝟏], which makes sense since things aren’t less than impossible or more than certain. As a rule of thumb, when talking about probabilities, we move within the range of 0 and 1. This lets us formulate the following theorem: Theorem 2.1, The Complement and Addition Theorem of probability
Let 𝐴 and 𝐵 be two events in a sample space Ω. Then the following statements are true: 1. 𝑃(𝐴ᶜ) = 𝟏 — 𝑃(𝐴) 2. 𝑃(∅) = 𝟎 3. 𝑃(𝐴 ∪ 𝐵) = 𝑃(𝐴) + 𝑃(𝐵) — 𝑃(𝐴 ∩ 𝐵)Proof of Theorem 2.1
𝑃(𝐴 ∪ 𝐴ᶜ) = 𝑃(Ω) = 𝟏 = 𝑃(𝐴) + 𝑃(𝐴ᶜ) ⇒ 𝑃(𝐴ᶜ) = 𝟏 — 𝑃(𝐴)
This simply proves that the probability of 𝐴 not happening is the same as the probability of 𝐴 happening subtracted from 1.
𝑃(∅) = 𝑃(Ωᶜ) = 𝟏 — 𝑃(Ω) = 𝟏 — 𝟏 = 𝟎
Even though our formal proof required (1) to be proven, it’s also very intuitive that the probability of the empty set is 0. Since the empty set is the set of all elements that are not in the sample space, and the probability of an event outside the sample space is 0.
𝑃(𝐴 ∪ 𝐵) = 𝑃(𝐴 ∪ (𝐵 ∩ 𝐴ᶜ)) = 𝑃(𝐴) + 𝑃(𝐵 ∩ 𝐴ᶜ) = 𝑃(𝐴) + 𝑃(𝐵) — 𝑃(𝐴 ∩ 𝐵)
This can be understood visually by revisiting our Venn diagram. We see that the union of 𝐴 and 𝐵 has an overlapping element 𝟑 shared between them. This means that purely adding the elements of 𝐴={𝟐,𝟑} together with 𝐵={𝟑,𝟒} would double count that shared element, like this {𝟐,𝟑,𝟑,𝟒}, since we have two “copies” of the mutual elements we make sure to remove one “copy” bur removing 𝑃(𝐴 ∩ 𝐵)={𝟑} and we get 𝑃(𝐴 ∪ 𝐵)={𝟐,𝟑,𝟒}. We may refer to this process as dealing with double counting, something that is very important to have in mind when dealing with sets.
Two interpretations of probability that are useful and often used are the frequentist and the subjectivist interpretations. The frequentist interpretation is that the probability of an event is the relative frequency of that event in the long run. The subjectivist interpretation is that the probability of an event is the degree of belief that the event will occur, this is very common in the field of statistics and gambling. For the purposes of study it’s also useful to sometimes consider probabilities as areas and or masses, this is called the measure theoretic interpretation. Don’t let that word scare you off, in our context it’s just a fancy way of drawing a parallel between areas and probabilities. Think area under curves, and you’ll be fine.
-
 @ 1e52c554:21771908
2024-03-06 05:31:18
@ 1e52c554:21771908
2024-03-06 05:31:18Posthumous work of the Colombian poet born in Don Matias on January 20, 1948.
Welcome to this blog dedicated to the Posthumous work of the Colombian poet Francisco Luis Arroyave Tabares (my father), born in Don Matias on January 20, 1948-2010. Where I will be publishing each of the 175 sonnets from his unpublished collection 'Sonnets For The Twenty-First Century And A Circadian Musical (1984-1987).' Analyzed with GPT4 artificial intelligence and illustrated with AI tools... I hope you enjoy this garden of words snatched from the solitude of a locked room.
Likewise, any enthusiast of the sonnet form is invited to conduct their personal studies of Arroyave Tabares' work, as it is a collection that, although registered since 1989, has not yet been published.
Frank Duna

Analysis "To Hold You"
Introduction
The sonnet "To Hold You" by Francisco Luis Arroyave Tabares is a sonnet that expresses the speaker's yearning for their lover.
Thematic Analysis
In the octave, the speaker expresses a sense of wandering and searching in the river of time, looking for a sensation to prolong their love and avoid loneliness. The speaker also explores different worlds, studying their currents and the motives that drive them. This part of the sonnet sets up the problem or conflict.
The sestet then provides a resolution or response to the problem set up in the octave. Here, the speaker reflects on the past and future, which lead him to one thing: the moments when he got to hold the person he loves. Despite the allure of space and other places, nothing compares to the heavens without the loved one’s smile and dew.
The transition from the octave to the sestet, known as the volta or “turn”, is where the poem shifts from setting up a situation (octave) to commenting on or resolving it (sestet). In this sonnet, the volta occurs between the eighth and ninth lines, marking a shift from the speaker’s exploration and search to their realization of what truly matters to them.
Overall, the sonnet beautifully captures the speaker’s journey of love and longing, with the octave and sestet working together to convey a complete, nuanced narrative.
Rhyme Scheme
The rhyme scheme (ABBA ABBA CDE CDE) is a common one for sonnets, particularly those in the Petrarchan or Italian style. Let’s analyze how this scheme applies to the sonnet “To Hold You” by Francisco Luis Arroyave Tabares:
``` A I have been wandering and searching hard B In this river of time that damps my song B For a sensation to my love prolong A And avoid lone notes that sometimes I heard.
A Through bays of many worlds I wandered B Studying currents that they thrive among B And the motives that push them right along A What they call goals as each one plays a card.
C Past and future pour in me their content D Most of it keeps leading me to one thing, E To those moments when I got to hold you...
C Not even space lures me with its movement D Or places that better faces bring E Or heavens without your smile and your dew. ```
In the octave (the first eight lines), the first four lines (ABBA) and the second four lines (ABBA) have the same rhyme scheme. This creates a mirrored effect, where the first and fourth lines rhyme, and the second and third lines rhyme.
In the sestet (the last six lines), the rhyme scheme changes to CDE CDE. This change in rhyme scheme often coincides with a shift or turn in the poem’s subject matter or tone. In this case, the sestet shifts the focus from the speaker’s wandering and searching to their realization of the importance of the moments when they held their loved one.
Overall, the ABBA ABBA CDE CDE rhyme scheme provides a structure that helps to emphasize the poem’s themes and emotional shifts. It’s a beautiful and effective use of the sonnet form.
Additional Aspects
Let’s delve deeper into the sonnet’s language, imagery, themes, meter, and overall impact.
Language and Imagery: The sonnet uses rich and evocative language to convey the speaker’s emotions. The metaphor of the “river of time” and the “bays of many worlds” creates a vivid image of the speaker’s journey through life and love. The use of words like “wandering”, “searching”, “currents”, and “motives” further enhances this imagery, giving the reader a sense of the speaker’s longing and exploration.
Themes: The main themes of the sonnet are love, longing, and the passage of time. The speaker expresses a deep longing for their loved one and reflects on the moments they shared together. The theme of time is also prominent, with references to the “river of time”, “past and future”, and the “moments” they held their loved one.
Meter: The sonnet appears to follow the iambic pentameter, which is a common meter in English sonnets. This means each line typically contains five pairs of syllables, with the stress falling on the second syllable of each pair. This creates a rhythmic pattern that enhances the flow and musicality of the poem.
Overall: “To Hold You” is a beautifully crafted sonnet that effectively uses language, imagery, and meter to convey a poignant narrative of love and longing. The themes are universal and relatable, and the structure of the sonnet— with its octave and sestet, and the turn between them— provides a satisfying progression from problem to resolution. The sonnet is a testament to the power of poetry to capture complex emotions and experiences in a compact and structured form.
(GPT4)
Syllable count for each line.
``` To Hold You
10 I have been wandering and searching hard 10 In this river of time that damps my song 10 For a sensation to my love prolong 10 And avoid lone notes that sometimes I heard.
10 Through bays of many worlds I wandered 10 Studying currents that they thrive among 10 And the motives that push them right along 10 What they call goals as each one plays a card.
10 Past and future pour in me their content 10 Most of it keeps leading me to one thing, 10 To those moments when I got to hold you... 10 Not even space lures me with its movement 10 Or places that better faces bring 10 Or heavens without your smile and your dew. *** ```
Sonnets For The Twenty First Century And A Circadian Musical Written By Francisco Luis Arroyave Tabares (1984-1987)
Analyzed by GPT4; Image by Frank Duna; First published on Nostr Protocol by franciscoarroyavet@nostrplebs.com
 *To Hold You
*To Hold You -
 @ cb86d908:d81e2f94
2024-03-07 15:58:59
@ cb86d908:d81e2f94
2024-03-07 15:58:59
ไม่ยาก ลองดูก่อนครับ จะมี 4 หัวข้อหลัก ดังนี้
- สมัครใช้งาน Norstr ผ่านแอพ Damus
- ใส่ข้อมูลเราในโปรไฟล์เพิ่มเติม เช่น ใส่ที่อยู่ Lightning เพื่อรับ zap
- วิธีใช้ย้ายไปใช้ Nostr อีกที่ผ่านแอพอื่นๆ เช่น Primal
- วิธีหาเพื่อนคนไทย
เริ่มเลย
1. ขั้นตอนสมัครผ่านแอพ damus
1.1 ดาวโหลดแอพ
1.2 กดต่อไป
1.3 กดสร้างรหัสใหม่
1.4 ตั้งชื่อ ใส่รูป ตามต้องการ และกดสมัคร
1.5 เขาจะให้รหัสผ่านเรามาเก็บไว้
1.6 รหัสผ่านเราควรเก็บไว้ที่ปลอดภัย แนะนำให้เก็บไว้ใน bitwarden เหมือนกัน
1.7 ข้อ 1 เสร็จละ ได้รหัส Nostr ละ
2. ใส่ข้อมูลเราเพิ่มเติม
2.1 ไปมุมบนซ้ายรูปโปรไฟล์เรา
2.2 เลือกโปรไฟล์เรา
2.3 ถึงหน้าโปรไฟล์เข้าไปหน้า Edit
2.4 ใส่ข้อมูลเราบลาๆ
2.5 อย่าลืมใส่ Lightning นะ
2.6 โหลดแอพ wallet of satoshi มา ใช้ email เราสมัครได้เลย
2.7 เข้าไปตรงนี้
2.8 copy ที่อยู่มา
2.9 เอามาใส่หน้าข้อมูลของเราที่ช่อง Lightning
2.10 กด Save เสร็จ รับ zap จากเพื่อนๆได้แล้ว
3. ต่อไปขั้นตอนเอา key ไปใส่แอพอื่น เผื่อเบื่อ damus แล้ว
3.1 ถ้าเราไม่ได้เก็บ nsec ตอนสมัครครั้งแรกไว้ก็ไปเอาที่ setting > key และ copy ได้เลย
3.2 โหลดแอพ primal มา
3.3 sign in ได้เลย เพราะเอารหัสมาจาก damus
3.4 เสร็จ หาเพื่อนต่อได้เลย
4. ขั้นตอนการหาเพื่อนคนไทย
4.1 เข้าได้แล้วก็ค้นหา #Siamstr ได้เลย
4.2 พอเจอแล้วกดเข้าไปที่ hashtag เลย
4.3 กดติดตามไว้เลย
4.4 พอไปหน้าแรกหลังติดตามแล้วเราจะมีเพื่อนคนไทยขึ้นมาแล้ว
4.5 แอดเพื่อนบ้าง ไปที่โปรไฟล์เพื่อนเลย
4.6 กดติดตามเพื่อนได้เลย
4.7 Primal ก็หาเพื่อนเหมือนกันนะ
4.8 อย่าลืมกดติดตามแท๊กมุมบนขวานะ
เสร็จแล้ว ไปท่องทุ่งม่วงกัน GOGO!
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ 1c6b3be3:73f0ae6f
2024-03-06 05:02:34
@ 1c6b3be3:73f0ae6f
2024-03-06 05:02:34Releases - No Bullshit Bitcoin
Block Shares Update on MDK's Firmware, API and User Interface (1 min) The company developing their own mining software aims to give users more control and diagnostic capabilities through a user interface and an API. The API will allow for easy integration with third-party software solutions. Some of the features that are being explored include performance monitoring, power tuning, ASIC diagnostics, and failure mode notifications. Users will be able to monitor and adjust the miner's settings such as power consumption, hashrate and temperature. The company is asking for feedback on any additional features that users may find important by contacting them at mining@block.xyz.
LNp2pBot v0.10.0: Show Solver Username in Dispute, Languages Fixes The article announces the release of version 0.10.0 of LNp2pBot, an open-source Telegram bot that enables non-KYC P2P trades via the Lightning Network. The update includes:
- Displaying the solver who will assist users in dispute
- Fixes to language issues
- Conversion of model to TypeScript
- Bumping es5-ext from 0.10.62 to 0.10.64 and ip from 2.0.0 to 2.0.1 for dependencies
- Replacement of logger.warn() by error()
- Showing solver username to parties in a dispute
The full changelog can be found in the linked GitHub repository, along with information on how to access and use the bot.
 Unleashed.Chat v0.1.16: Nostr Log In Support
The article announces the release of v0.1.14 of Unleashed Chat, an AI chatbot service that prioritizes privacy and accepts Bitcoin payments. This version introduces the ability to log in with a Nostr npub (if you have a NIP-07 browser extension) and connect your npub on the Account page if you already have an account. The update also includes bug fixes, faster file processing, and fixed delays for some on-chain deposits. Additionally, v0.1.14 features a new model, an uncensored version of Mistral AI's Mixtral 8x7B, promising better coding capabilities. For more information, visit the Unleashed Chat website.
Unleashed.Chat v0.1.16: Nostr Log In Support
The article announces the release of v0.1.14 of Unleashed Chat, an AI chatbot service that prioritizes privacy and accepts Bitcoin payments. This version introduces the ability to log in with a Nostr npub (if you have a NIP-07 browser extension) and connect your npub on the Account page if you already have an account. The update also includes bug fixes, faster file processing, and fixed delays for some on-chain deposits. Additionally, v0.1.14 features a new model, an uncensored version of Mistral AI's Mixtral 8x7B, promising better coding capabilities. For more information, visit the Unleashed Chat website. 
Releases - No Bullshit Bitcoin
Block Shares Update on MDK's Firmware, API and User Interface (1 min)
LNp2pBot v0.10.0: Show Solver Username in Dispute, Languages Fixes
 Unleashed.Chat v0.1.16: Nostr Log In Support
Unleashed.Chat v0.1.16: Nostr Log In Support

🍵 "btc | bitcoin | lightning network | asic" - Google News
Bitcoin's Test of All-Time Highs Means Old Miners Are Cashing Out - CoinDesk What the Bitcoin halving means for the network's energy consumption concerns - Cointelegraph Bitcoin layer 2s bootstrap $2.7bn in DeFi deposits with points offerings - DLNews These Crypto Heavyweights Just Onboarded Bitcoin’s Stacks (STX) Network - CryptoPotato Bitcoin Halving 2024: Predicting the Future of Bitcoin in a Digital World - Yahoo Finance Stacks Bolsters Bitcoin L2 with Major Signer Expansion - TipRanks.com - TipRanks Digihost Secures Hosting Deal for 4640 S19 XPs With Leading Bitcoin Miner Manufacturer – Mining Bitcoin News - Bitcoin.com News STRK, OP and THETA - Best Crypto to Buy Today? - Cryptonews Bitcoin layer-2 Stacks partners with eight companies ahead of its Nakamoto upgrade - Crypto Briefing Bitcoin Soared to an All-Time High. So Why Aren't Miners Blasting Off, Too? - TradingView It’s Happening: Bitcoin Hits New All-Time High Price Above $69K - Decrypt Bitcoin DeFi Boom: Merlin Chain Sparks $2.7 Billion Surge, Outpacing Solana in TVL - BNN Breaking
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ 1e52c554:21771908
2024-03-06 04:45:19
@ 1e52c554:21771908
2024-03-06 04:45:19Posthumous work of the Colombian poet born in Don Matias on January 20, 1948.
Welcome to this blog dedicated to the Posthumous work of the Colombian poet Francisco Luis Arroyave Tabares (my father), born in Don Matias on January 20, 1948-2010. Where I will be publishing each of the 175 sonnets from his unpublished collection 'Sonnets For The Twenty-First Century And A Circadian Musical (1984-1987).' Analyzed with GPT4 artificial intelligence and illustrated with AI tools... I hope you enjoy this garden of words snatched from the solitude of a locked room.
Likewise, any enthusiast of the sonnet form is invited to conduct their personal studies of Arroyave Tabares' work, as it is a collection that, although registered since 1989, has not yet been published.
Frank Duna

Analysis "Without Her"
Introduction
"Without Her" is a sonnet by Francisco Luis Arroyave Tabares that explores themes of loss, loneliness, and longing.
Thematic Analysis
In the octave, the speaker describes the setting of his room after the sun (Phoebus) has set, leaving only its traces (vestigia) and beginning a night filled with shadows of his gloom. The speaker further describes the winds of solitude announcing his doom, with voices echoing from a river where ships with demons loom towards his soul. This part of the sonnet sets a melancholic and desolate tone, reflecting the speaker’s feelings of loneliness and despair.
The sestet introduces the idea of death as a possible relief from his suffering. The speaker expresses a willingness to be taken away by death, still in the wake of love, and would go to the kingdom of death with a smile. However, he is kept awake by the torturing bellow of evil sounds, signifying his torment since he has lost his freedom without her. This part of the sonnet deepens the sense of despair and longing, emphasizing the speaker’s intense feelings of loss and yearning for release.
Overall, the sonnet uses vivid and powerful imagery to convey a deep sense of loneliness, despair, and longing, effectively capturing the speaker’s emotional state in the absence of his beloved. The transition from the octave to the sestet also marks a shift from setting the scene of despair to expressing a desire for release, providing a poignant exploration of the speaker’s inner turmoil.
Rhyme Scheme
The rhyme scheme ABBA ABBA CDE CDE, is a common one in sonnets, particularly those of the Petrarchan or Italian variety. Let’s analyze how this scheme applies to the sonnet “Without Her” by Francisco Luis Arroyave Tabares.
In the octave (the first eight lines), the rhyme scheme is ABBA ABBA:
A: Phoebus has given his back to my room B: His vestigia making a pale dim B: And beginning a night that, without him A: Will start to dance the shadows of my gloom. A: The winds of solitude announce my doom B: With voices that come to a crater’s rim B: And echoes from a river where, in trim A: Some ships with demons toward my soul loom.In the sestet (the last six lines), the rhyme scheme is CDE CDE:
C: If Death, at least, could come to my pillow D: To take me away now, still in love’s wake E: With a smile I would go to that kingdom… C: But I just hear the torturing bellow D: Of those evil sounds that keep me awake E: Since, without her, I have lost my freedom…This rhyme scheme helps to structure the poem and guide its rhythm. It also serves to emphasize certain words and ideas, contributing to the overall mood and theme of the sonnet. In this case, the rhyme scheme enhances the sense of longing and despair expressed by the speaker. The transition from the octave to the sestet, marked by a change in the rhyme scheme, also helps to highlight the shift in the speaker’s thoughts from his desolate surroundings to his yearning for release.
Additional Aspects
Let’s delve deeper into the analysis of “Without Her” by Francisco Luis Arroyave Tabares:
Language and Imagery: The sonnet “Without Her” by Francisco Luis Arroyave Tabares uses rich and evocative language to create vivid imagery. The poet personifies the sun as “Phoebus” and describes its departure from his room, leaving only its traces (vestigia) and beginning a night filled with shadows of his gloom. The use of words like “vestigia”, “doom”, “crater’s rim”, “bellow”, and “kingdom” add depth and texture to the poem, creating a melancholic and desolate atmosphere.
Themes: The main themes of the sonnet are love, loss, loneliness, despair, and death. The speaker expresses a deep sense of loss and longing in the absence of his beloved, which is reflected in the desolate imagery and the melancholic tone of the poem. The theme of death is introduced in the sestet as a possible relief from his suffering, further emphasizing the speaker’s despair and longing for release.
Meter: The sonnet appears to follow the iambic pentameter, which is a common meter in English poetry and particularly in sonnets. This means each line consists of five pairs of unstressed and stressed syllables, giving the poem a rhythmic quality.
Overall: Overall, the sonnet is a poignant exploration of love, loss, and longing. The poet uses evocative language and vivid imagery to convey the speaker’s emotional state, effectively capturing the depth of his feelings. The structure of the sonnet, with its transition from the octave to the sestet, also contributes to the development of the themes and the progression of the speaker’s thoughts. The use of the ABBA ABBA CDE CDE rhyme scheme further enhances the rhythm and flow of the poem, making it a powerful and moving piece of poetry.
(GPT4)
Syllable count for each line.
``` Without Her
10 Phoebus has given his back to my room 10 His vestigia making a pale dim
10 And beginning a night that, without him 10 Will start to dance the shadows of my gloom.10 The winds of solitude announce my doom 10 With voices that come to a crater's rim 10 And echoes from a river where, in trim
10 Some ships with demons toward my soul loom.10 If Death, at least, could come to my pillow 10 To take me away now, still in love's wake 10 With a smile I would go to that kingdom...
10 But I just hear the torturing bellow
10 Of those evil sounds that keep me awake 10 Since, without her, I have lost my freedom.... *** ```
Sonnets For The Twenty First Century And A Circadian Musical Written By Francisco Luis Arroyave Tabares (1984-1987)
Analyzed by GPT4; Image by leonardo.ai; First published on Nostr Protocol by franciscoarroyavet@nostrplebs.com
 Without Her
Without Her -
 @ ec965405:63996966
2024-03-06 04:36:27
@ ec965405:63996966
2024-03-06 04:36:27I'm finally getting around to sharing this note after Aaron Bushnell, a 25 year old united states service member streamed a video of his self immolation in front of an israeli embassy on Twitch last weekend in protest of the ongoing Palestinian genocide. He's the second in recent months to do so and the first to lose his life in the process. This note is for the martyrs.
Finalmente estoy compartiendo esta nota después de que Aaron Bushnell, un miembro de 25 años de las fuerzas armadas de Estados Unidos, transmitiera en vivo su autoinmolación frente a una embajada israelí en Twitch el fin de semana pasado en protesta por el genocidio palestino en curso. Es el segundo que lo hace en los últimos meses y el primero en perder la vida en el proceso. Esta nota es para los mártires.

I woke up feeling sick to my stomach in the middle of the night during my recent delgation to Cuba; probably a side effect of mixing 3 plates of Ropa Vieja at dinner with cigars and beer at La Fabrica the night before. Chastising myself for hitting my body with 3 things I normally avoid at home (tobacco, alcohol, and meat), I wasn't able to make it downstairs to the cafeteria for breakfast or the day trip with the group. I was allowed to stay and rest at the center in the morning while they checked out El Rincón de los Milagros,where they learned about the impact of the Haitian revolution on Cuban society. Everyone said I would have loved it. After looking through their pictures and videos of the drum sessions,I'm certain I would have. I'm going to prioritize visiting this spot next time I'm in Cuba.
Me desperté sintiéndome mal del estómago en medio de la noche, durante mi reciente delegación a Cuba; probablemente un efecto secundario de mezclar 3 platos de Ropa Vieja en la cena, con cigarros y cerveza en La Fábrica la noche anterior. Regañándome a mí mismo por someter mi cuerpo a 3 cosas que normalmente evito en casa (tabaco, alcohol y carne), no logré bajar a la cafetería para desayunar ni unirme al viaje del día con el grupo. Me permitieron quedarme a descansar en el centro durante la mañana mientras ellos visitaban El Rincón de los Milagros, donde aprendieron sobre el impacto de la revolución haitiana en la sociedad cubana. Todos dijeron que me hubiera encantado. Después de ver sus fotos y videos de las sesiones de tambores, estoy seguro de que así hubiera sido. Voy a hacer de visitar este lugar una prioridad la próxima vez que esté en Cuba.

On the flip side, I was deficient in sleep hours, so catching up on rest put me in a better position to participate in the evening social at El Sauce. El Sauce is a smaller venue that wasn't nearly as packed as La Fabrica the previous evening. I enjoyed down time with my fellow delegates, happy to get to know them in an intimate space and eventualy joining them on the dance floor for an electric slide.
Por otro lado, me faltaban horas de sueño, así que ponerme al día con el descanso me colocó en una mejor posición para participar en el evento social de la noche en El Sauce. El Sauce es un lugar más pequeño que no estaba tan lleno como La Fábrica la noche anterior. Disfruté del tiempo libre con mis compañeros delegados, contento de llegar a conocerlos en un espacio íntimo y finalmente uniéndome a ellos en la pista de baile para un electric slide.

I watched a man dressed in plain shorts and a red shirt dance enthusiastically with at least 5 separate partners of varying ages and genders throughout the night, radiating joy with each graceful spin as if he hadn't a care in the world. His magnetic energy drew everyone around him into his orbit despite coming to El Sauce alone that night. The circumstances of an inhumane blockade on his country did not seem to phase him as he laughed and sang along to the music, his humanity on full display for us to see.
Observé a un hombre vestido con shorts sencillos y una camisa roja bailar entusiasmado con al menos 5 parejas distintas de variadas edades y géneros a lo largo de la noche, irradiando alegría con cada giro elegante como si no tuviera ninguna preocupación en el mundo. Su energía magnética atraía a todos a su alrededor a pesar de haber llegado solo a El Sauce esa noche. Las circunstancias de un bloqueo inhumano sobre su país parecían no afectarle mientras reía y cantaba junto a la música, mostrando su humanidad para que todos la viéramos
Before dinner the next evening, the group gathered in the cafeteria for a reflection activity about our first few days in Cuba where we broke the ice by sharing an African word that we were familiar with and its significance to us. My mind instantly snapped to "Ubuntu", a word that represents the inception of my programming journey and my intentions with what comes from it. From the African Journal of Social Work,
Antes de la cena la siguiente noche, el grupo se reunió en la cafetería para una actividad reflexiva sobre nuestros primeros días en Cuba, donde rompimos el hielo compartiendo una palabra africana con la que estuviéramos familiarizados y su significado para nosotros. Mi mente se dirigió instantáneamente a 'Ubuntu', una palabra que representa el inicio de mi carrera en la programación y mis intenciones con lo que resulte de ello. Según el Journal Africano de Trabajo Social:
Ubuntu refers to a collection of values and practices that Black people of Africa or of African origin view as making people authentic human beings. While the nuances of these values and practices vary across different ethnic groups, they all point to one thing – an authentic individual human being is part of a larger and more significant relational, communal, societal, environmental and spiritual world. Ubuntu se refiere a un conjunto de valores y prácticas que las personas negras de África o de origen africano consideran que hacen a los seres humanos auténticos. Aunque los matices de estos valores y prácticas varían entre los distintos grupos étnicos, todos apuntan a lo mismo: un ser humano auténtico es parte de un mundo más amplio y significativo que incluye lo relacional, lo comunal, la sociedad, el medio ambiente y lo espiritual.
I explained my philosophy around the use of open sourced software and a healthier relationship with the Internet highlighting the need to boycot corporate tech platforms that inflict irreparable harm on the massses. The constant bombardment of corporate advertising guided by antagonizing algorithms fuel a dire behavioral health crisis that's actively destroying the fabric of our society and disconnecting us from our humanity. Open source software is my weapon in this war against the tech corporations that dominate our dystopic digital lives that I will leverage to center humanity and dignity in communications.
Expliqué mi filosofía sobre el uso de software de código abierto y una relación más saludable con internet, resaltando la necesidad de boicotear las plataformas tecnológicas corporativas que infligen un daño irreparable a las masas. El constante bombardeo de publicidad corporativa, guiado por algoritmos antagonistas, alimenta una grave crisis de salud conductual que está destruyendo activamente el tejido de nuestra sociedad y desconectándonos de nuestra humanidad. El software de código abierto es mi arma en esta guerra contra las corporaciones tecnológicas que dominan nuestras vidas digitales distópicas, el cual utilizaré para centrar la humanidad y la dignidad en nuestras comunicaciones.
I shared this with the group, happy to look over at a fellow delegate and see her point to the bracelet on her wrist with the letters U-B-U-N-T-U spelled out. I felt right at home with this crew.
Compartí esto con el grupo, contento de mirar a una compañera delegada y verla señalar hacia la pulsera en su muñeca con las letras U-B-U-N-T-U. Me sentí como en casa con este equipo.

-
 @ 2edbcea6:40558884
2023-09-03 16:03:23
@ 2edbcea6:40558884
2023-09-03 16:03:23Happy Sunday #Nostr !
Here’s your #NostrTechWeekly newsletter at the nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk written by nostr:npub1r3fwhjpx2njy87f9qxmapjn9neutwh7aeww95e03drkfg45cey4qgl7ex2
NostrTechWeekly is a weekly newsletter focused on the more technical happenings in the nostr-verse.
A lot of foundational work happening in the nostr-verse and quite a bit of new projects shipped this week. Let’s dive in!
Recent Upgrades to Nostr (AKA NIPs)
1) NIP 75: Zap Goals ⚡
Zapping has been such an integral part of what makes Nostr what it is. Earning for your content or contributions. Zaps for memes. Zaps as a way to boost the signal. It’s a growing concept as well.
NIP 75 was merged this week, with the goal of introducing the ability to set a “Zap Goal” which is similar to a fundraising goal. Users can zap the “goal” event directly and help the progress bar go up. Whatever the cause.
Interesting to see if this will stay simple and decentralized or if this will be the foundation of a GoFundMe type platform via Nostr using exclusively Bitcoin.
Author: nostr:npub107jk7htfv243u0x5ynn43scq9wrxtaasmrwwa8lfu2ydwag6cx2quqncxg
2) (Proposed) NIP 79: Digital contracts on Nostr ✍️
Think Docusign, but on Nostr. This NIP would introduce support for various kinds of digital agreement (contracts, covenants, agreements) which serve various purposes.
These agreements would all be unencrypted markdown, so the purpose is likely more for non-secret agreements so that they can be cited by all parties in public.
Author(s): https://github.com/xemuj nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z
3) (Proposed) NIP 34: Improved media attachments to notes 📎
Attaching media to notes in a way that is handled well on a majority of major clients is still more of an art than a science and nostr:npub108pv4cg5ag52nq082kd5leu9ffrn2gdg6g4xdwatn73y36uzplmq9uyev6 is determined to introduce a better pattern 💪.
This NIP introduces the pattern of using an explicit set of “media” tags on any note so that media that should accompany the note can be explicitly linked without clients needing to parse the content of the note to make the url of the media in the note a hyperlink.
Author: nostr:npub108pv4cg5ag52nq082kd5leu9ffrn2gdg6g4xdwatn73y36uzplmq9uyev6
4) (Proposed) Improvements to reddit-style moderated communities 💬
This proposed improvement to NIP 72 introduces the concept of a post (within a moderated community) that is exclusively posted to a specific community. Think about posting something that can make the front page of reddit versus a post that is intended solely for a subreddit. Seems like a welcome addition to NIP 72 👍
Author: https://github.com/vivganes
Notable projects
A nostr Wiki
The start of a truly open wiki.
Wikis are used for a lot of things: corporate intranets and documentation, fandoms managing information about their universe, and Wikipedia which may be one of the greatest repositories of knowledge on Earth. The main downside to Wikipedia is that it may be crowdsourced but it is centralized, seeking one version of each article (and therefore determining what is true).
This wiki (in the spirit of Nostr) allows people to create any number of articles on the same subject to offer different perspectives. At scale this could become something where people read various perspectives and determine the truth for themselves.
Author: nostr:npub1q7klm2w94hyq3qdm9ffzpahrrq0qcppmjrapzhz0rq6xgq3fdrnqr6atmj
Oxchat
Oxchat is a secure, private group chat experience for iOS and Android with a great UX 🙌.
Nostr needs its own standalone chat app that can stand up to the capabilities and ease of use of Signal, Telegram, WhatsApp, etc. And Oxchat may be that app! Looking forward to using it more.
Author: nostr:npub10td4yrp6cl9kmjp9x5yd7r8pm96a5j07lk5mtj2kw39qf8frpt8qm9x2wl
Nostrnet.work
A web-based dashboard for Nostr, it’s a webpage that is a configurable hub for all the Nostr apps you want to have available quickly. You can log in with your Nostr account, and configure it to your liking.There’s a section for managing your profile (including your relays), as well as for taking notes, all of that on top of the list of Nostr apps for quick access.
Nostrnet.work seems to be evolving into almost a web-based browser of the nostr-verse. You can manage the apps that are on the dashboard Nostrnet.work via the basic/open app store from nostr.band. There’s endless possibilities for users to discover what Nostr has to offer and use those offerings from one unified interface.
A recent addition to the Nostrnet.Work interface is an area for “Nostr AI'' which is meant to allow users to utilize Data Vending Machines (explored in the Latest Conversations section). Data Vending Machines (or DVMs) are something that I think is unique to Nostr, and it's a product/ecosystem that may be the killer unique offering people come to Nostr to try out.
Author: nostr:npub1cmmswlckn82se7f2jeftl6ll4szlc6zzh8hrjyyfm9vm3t2afr7svqlr6f
w3.do url shortener
URL shorteners are a stable web util. In fact,
We started using w3.do because the tool we use to draft/publish this newsletter as a long form note will send Nostr links and embed the note instead of just linking to the note. So a url shortener is enough to trick the tool so we get fewer embeds and more links! Thanks nostr:npub1alpha9l6f7kk08jxfdaxrpqqnd7vwcz6e6cvtattgexjhxr2vrcqk86dsn !
Latest conversations
Data Vending Machines (DVMs)
“Data Vending Machines are data-processing tools. You give them some data, a few sats, and they give you back some data.” source: vendata. A practical example is a recent DVM published by Pablo: FOMOstr. You put up some sats, you’ll get back content on Nostr that you may have missed.
The concept seems to be that people need help from machines. And right now, the most common way for people to get that help is to pay a company for that help (email provider, calendar management, group chats, entertainment, etc).
These are great for more complex digital products, but what if you just have a question? Maybe you just want to generate an image. Or maybe just extract text, and then maybe translate it. These are most efficient as pay-as-you-need-it products. That’s where DVMs shine (on the long tail of needs).
You can put up a certain amount of money and people who have created algorithms or AIs that can accomplish these tasks will compete to do the job for the lowest price (and therefore win the money). This is the foundation of an economy of people who need jobs done and people who want to make income by creating the best DVMs for the jobs people need done.
DVMs that help you discover people and content on Nostr will be a god-send for improving the experience for people using Nostr while maintaining decentralization. This will certainly evolve over time, but it seems this could become an integral part of the Nostr ecosystem as well as become a unique service that can only be found on Nostr (attracting a new set of users).
Events
Here are some upcoming events that we are looking forward to! We keep a comprehensive list and details of Nostr-related events that we hear about (in person or virtual) that you can bookmark here NostrConf Report
- Nostrasia Nov 1-3 in Tokyo & Hong Kong
- Nostrville Nov 9-10 in Nashville, TN, USA
- NostrCon Jan 12, 2024 (online only)
Until next time 🫡
If you want to see something highlighted, if we missed anything, or if you’re building something I didn’t post about, let me know, DMs welcome.
nostr:npub1r3fwhjpx2njy87f9qxmapjn9neutwh7aeww95e03drkfg45cey4qgl7ex2 or nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk
Stay Classy, Nostr.
-
 @ ff1a68c4:ec9831cf
2024-03-07 15:54:25
@ ff1a68c4:ec9831cf
2024-03-07 15:54:25Mucho se ha hablado del día de la mujer, orígenes, de celebrarlo o no. A quién celebrar o a quién no, etc.
Pero aprovecho de recordar que en Chile hace años existe un Ministerio de la Mujer, y aún así la violencia hacia ellas sigue aumentando, los asesinatos a mujeres (mal llamados femicidios o feminicidios) no han disminuido. Tal ministerio solamente sirve para poner en el poder a compañeras de ideología, de darle trabajo a quienes no tendrían posibilidad de ejercer en el mercado porque no ofrecen valor agregado con su actividad, como las especialistas en estudios de género.
¿Marchan las mujeres por cargos de alto riesgo que típicamente ejercen los hombres? no, por cuotas de género en altas esferas del poder.
¿Les importa que esas cuotas de género las perjudiquen al largo plazo, tal como #metoo las perjudicó a la hora de buscar trabajo? no, ninguna capacidad de responsabilidad.
¿Les molesta que juezas feministas liberen a violadores que luego reinciden? no, porque las víctimas sirven para seguir marchando, y seguir obteniendo dinero para su causa.
A propósito de las caletas con perspectiva de género, inauguradas hace poco, y que causaron mucha risa entre las redes sociales.
Por mucho que fuera un anuncio ridículo; no son solamente baños para mujeres en las caletas. Por detrás esconde muchos pitutos (trabajos a amigotes) para gente que adhiere a la ideología del actual gobierno. Porque nadie con sentido común adhiere a estas ideas (por eso tal alboroto en las redes sociales). Pero la que sí, tendrá trabajo gracias a Boric. A costa del bolsillo de la gente que se reía en las redes (vía impuestos).
Pero el peligro va más allá, porque las futuras licitaciones obligarán a tener ese tipo de "expertos" y con "experiencia comprobable". Experiencia comprobable en algo que no existe. Es obvio que solamente será contratada gente de ese sector político que adhiere a esas estupideces.
Cuando en mi empresa contraten a una especialista en perspectiva de género para poder ganar licitaciones en proyectos del sector público, no me sorprendería. Es más, es muy probable que, vía leyes liberticidas, obliguen a todo el sector privado a contratar a gente de esa calaña.
Cuando eso suceda, todo hombre tendrá que tener cuidado, porque cada gesto, cada opinión, podría ser considerada un ataque o discurso de odio.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ ff1a68c4:ec9831cf
2024-03-07 15:50:54
@ ff1a68c4:ec9831cf
2024-03-07 15:50:54Para que en una sociedad libre puedan coexistir personas con puntos de vista radicalmente distintos, en paz o lo más libre de conflictos posible, deben existir principios que deben respetarse. Estos principios buscan la cooperación entre visiones diversas, evitando enfrentamientos y respetando el pacto de no agresión. Este pacto es, vive y deja vivir, o prevención de conflictos civiles.
Principios Básicos Libertarios:
- Individualismo Político: El individuo es el sujeto de derecho, con un enfoque moral en él. Esto no impide que un individuo pueda pertenecer a un colectivo, como se podrá ver más adelante.
- Igualdad Jurídica: Todos los seres humanos poseen los mismos derechos fundamentales. Esto puede traducirse como igualdad ante la ley, no como igualdad de resultados.
- Libertad Personal: Derecho a seguir el propio proyecto de vida, y a respetar el proyecto de vida del próximo.
- Propiedad Privada: Como no vivimos en el aire, de nada servirá nuestra libertad si no podemos interactuar con todo lo que nos rodea. Esta libertad se concreta en el derecho a la propiedad privada, que comienza con nuestro propio cuerpo y mente, y se propaga en todo aquello que obtenemos pacíficamente, sin robar o que podemos construir con estos recursos.
- Autonomía Contractual: Los acuerdos regulan las interacciones entre individuos. Estos acuerdos deben ser respetados fielmente.
- Reparación del Daño o Responsabilidad: Quien causa daño debe repararlo. La libertad requiere responsabilidad.
- Libertad de Asociación: Cualquier persona puede unirse a todo tipo de asociaciones de manera voluntaria, sin imposiciones morales, políticas o económicas. También esto incluye el derecho de desasociarse cuando el individuo lo estime conveniente.
- Libre Mercado: todos los individuos son libres y voluntarios de decidir con quién quieren intercambiar productos o servicios, ni el estado ni ninguna otra institución o persona puede interferir en la libre comercialización.
- Gobierno Limitado: Un gobierno debe proteger y hacer respetar los principios fundamentales sin excederse en su poder y potenciar el desarrollo de la ciudadanía, creando las condiciones necesarias para que estos puedan desenvolverse libremente y tomar las mejores oportunidades. Como este poder aumenta mucho el riesgo de crecer, o corromperse, se deben establecer reglas claras, límites bien delimitados y contrapesos entre los poderes de este gobierno.
- Globalización de Principios: Los derechos aplican a TODOS los seres humanos, sin distinciones de raza, etnia, color o pensamiento político, religioso u otros.
-
 @ 32e18276:5c68e245
2023-12-06 15:29:43
@ 32e18276:5c68e245
2023-12-06 15:29:43I’m going to be on an ordinals panels as one of the people who is counter arguing the claim that they are good for bitcoin. I decided to brush up on the technicals on how inscriptions work. I am starting to see luke’s perspective on how it is exploiting a loophole in bitcoin’s anti-data-spam mechanisms.
Storing data in Bitcoin, the “standard” way
The standard way you add “data” to bitcoin is by calling the OP_RETURN opcode. Bitcoin devs noticed that people were storing data (like the bitcoin whitepaper) in the utxo set via large multisig transactions. The problem with this is that this set is unprunable and could grow over time. OP_RETURN outputs on the other-hand are provably prunable and don’t add to utxo bloat.
Here’s an excerpt from the march 2014 0.9.0 release notes that talks about this:
On OP_RETURN: There was been some confusion and misunderstanding in the community, regarding the OP_RETURN feature in 0.9 and data in the blockchain. This change is not an endorsement of storing data in the blockchain. The OP_RETURN change creates a provably-prunable output, to avoid data storage schemes – some of which were already deployed – that were storing arbitrary data such as images as forever-unspendable TX outputs, bloating bitcoin’s UTXO database. Storing arbitrary data in the blockchain is still a bad idea; it is less costly and far more efficient to store non-currency data elsewhere.
Much of the work on bitcoin core has been focused on making sure the system continues to function in a decentralized way for its intended purpose in the presence of people trying to abuse it for things like storing data. Bitcoin core has always discouraged this, as it is not designed for storage of images and data, it is meant for moving digital coins around in cyberspace.
To help incentive-align people to not do stupid things, OP_RETURN transactions were not made non-standard, so that they are relayable by peers and miners, but with the caveat:
- They can only push 40 bytes (later increased to 80,83, I’m guessing to support larger root merkle hashes since that is the only sane usecase for op_return)
Bitcoin also added an option called -datacarriersize which limits the total number of bytes from these outputs that you will relay or mine.
Why inscriptions are technically an exploit
Inscriptions get around the datacarriersize limit by disguising data as bitcoin script program data via OP_PUSH inside OP_IF blocks. Ordinals do not use OP_RETURN and are not subjected to datacarriersize limits, so noderunners and miners currently have limited control over the total size of this data that they wish to relay and include in blocks. Luke’s fork of bitcoin-core has some options to fight this spam, so hopefully we will see this in core sometime soon as well.
Inscriptions are also taking advantage of features in segwit v1 (witness discount) and v2/taproot (no arbitrary script size limit). Each of these features have interesting and well-justified reasons why they were introduced.
The purpose of the witness discount was to make it cheaper to spend many outputs which helps the reduction of the utxo set size. Inscriptions took advantage of this discount to store monke jpegs disguised as bitcoin scripts. Remember, bitcoin is not for storing data, so anytime bitcoin-devs accidentally make it cheap and easy to relay data then this should be viewed as an exploit. Expect it to be fixed, or at least provide tools to noderunners for fighting this spam.
Where do we go from here
The interesting part of this story is that people seem to attach value to images stored on the bitcoin blockchain, and they are willing to pay the fee to get it in the block, so non-ideologic miners and people who don’t care about the health and decentralization of bitcoin are happy to pay or collect the fee and move on.
Data should not get a discount, people should pay full price if they want to store data. They should just use op_return and hashes like opentimestamps or any other reasonable protocol storing data in bitcoin.
After going through this analysis I’ve come to the opinion that this is a pretty bad data-spam exploit and bitcoin devs should be working on solutions. Ideological devs like luke who actually care about the health and decentralization of the network are and I’m glad to see it.
-
 @ 1e52c554:21771908
2024-03-06 04:23:26
@ 1e52c554:21771908
2024-03-06 04:23:26Posthumous work of the Colombian poet born in Don Matias on January 20, 1948.
Welcome to this blog dedicated to the Posthumous work of the Colombian poet Francisco Luis Arroyave Tabares (my father), born in Don Matias on January 20, 1948-2010. Where I will be publishing each of the 175 sonnets from his unpublished collection 'Sonnets For The Twenty-First Century And A Circadian Musical (1984-1987).' Analyzed with GPT4 artificial intelligence and illustrated with AI tools... I hope you enjoy this garden of words snatched from the solitude of a locked room.
Likewise, any enthusiast of the sonnet form is invited to conduct their personal studies of Arroyave Tabares' work, as it is a collection that, although registered since 1989, has not yet been published.
Frank Duna

Analysis "Make Sure That Only Sympathy Remains"
Introduction
Sonnet 85 is a heartfelt exploration of love, loss, and the hope for sympathy and understanding in the aftermath of a relationship's end.
Thematic Analysis
First Quartet (Lines 1-4): The speaker is asking someone to look at him before they close all the doors, possibly indicating the end of a relationship or a significant change. The speaker wants the other person to remember the good times (“those things that you liked”). The “dream in your eyes that still soars” could be a shared dream or goal that is still alive. The “Phoenix wings from that dessert we spiked” is a metaphor for rebirth and resilience, suggesting that they have gone through hardships together but have emerged stronger.
Second Quartet (Lines 5-8): The speaker pleads with the other person not to abandon their shared experiences (“these fruits ripe and unshorn”). The speaker is willing to be forgotten (“You can forget or dismiss my forlorn”) but promises to keep their song, perhaps a symbol of their shared memories or love.
Third Quartet (Lines 9-12): The speaker acknowledges that some of their shared experiences (“these flowers”) will remain unclaimed. He encourages the other person to take them, feel them, or use them. The speaker is resigned to his fate (“I will get used to destiny that drawned”) and recalls a past event where his hope was dashed (“Once before my hope in front of white elf”).
Couplet (Lines 13-14): The speaker asks the other person to ensure that his mind is empty, possibly of pain or regret. The speaker hopes that when love is gone, only sympathy remains.
This sonnet is a poignant exploration of love, loss, and the hope for understanding and sympathy in the aftermath of a relationship. The use of metaphors and symbols adds depth to the emotional landscape of the poem. The Phoenix and the elf are particularly striking images that convey the themes of rebirth, resilience, and the elusive nature of hope.
Rhyme Scheme
The sonnet follows the traditional English (or Shakespearean) sonnet rhyme scheme, which is ABABCDCDEFEFGG. Here’s how it breaks down:
Look at me before you close all the doors (A) And see if you find those things that you liked (B) I see a dream in your eyes that still soars (A) With Phoenix wings from that dessert we spiked. (B) Please do not leave these fruits ripe and unshorn (C) As you might need them while you walk along (D) You can forget or dismiss my forlorn (C) For another while I will keep your song. (D) Some of these flowers will remain unowed (E) Take them, feel them, or use them yourself (F) I will get used to destiny that drawned (E) Once before my hope in front of white elf. (F) Please make sure that my mind is all empty (G) Or that, love gone, remains our sympathy. (G)The final two lines form a rhymed couplet (GG), which is a characteristic feature of the English sonnet. This couplet often serves to summarize or conclude the themes of the poem. In this case, the speaker asks for the other person to ensure that his mind is empty, or that only sympathy remains after love is gone. This effectively encapsulates the speaker’s longing for understanding and closure.
It’s also worth noting that the sonnet is written in iambic pentameter, which is another common feature of traditional English sonnets. This means each line consists of five pairs of unstressed and stressed syllables, giving the poem a rhythmic quality. This rhythm, combined with the rhyme scheme, contributes to the overall musicality of the sonnet.
Additional Aspects
Let’s delve deeper into the analysis of “Amuse Yourself Again” by Francisco Luis Arroyave Tabares:
Language: The language used in the sonnet is rich and evocative, with a formal and somewhat archaic tone that is typical of traditional sonnets. The poet uses a variety of literary devices, including metaphor (“Phoenix wings”), simile, and personification (“destiny that drawned”), to convey complex emotions and ideas.
Imagery: The sonnet is filled with vivid imagery that appeals to the senses. For example, “fruits ripe and unshorn” and “flowers will remain unowed” evoke visual and tactile sensations, while “Phoenix wings from that dessert we spiked” suggests a sense of movement and transformation. These images serve to create a vivid and immersive world within the poem.
Themes: The main themes of the sonnet are love, loss, and longing. The speaker expresses a deep sense of loss and longing for a past relationship, and the desire for understanding and sympathy in its aftermath. The use of the Phoenix as a symbol of rebirth and resilience suggests a theme of hope and renewal amidst adversity.
Meter: The sonnet is written in iambic pentameter, a common meter in English poetry that consists of five pairs of unstressed and stressed syllables per line. This gives the poem a rhythmic quality and contributes to its musicality. The regular rhythm also serves to emphasize the formal structure of the sonnet.
Overall: Ove Sonnet 85 by Francisco Luis Arroyave Tabares is a deeply moving exploration of love, loss, and longing. The poet’s skillful use of language, imagery, and meter, combined with the exploration of universal themes, makes this sonnet a powerful and poignant piece of poetry. The sonnet’s structure, with its three quatrains and a concluding couplet, allows the poet to develop his ideas and emotions in a nuanced and sophisticated way. The final couplet, in particular, serves as a poignant conclusion that encapsulates the speaker’s longing for understanding and closure.
(GPT4)
Syllable count for each line.
``` Make Sure That Only Sympathy Remains
10 Look at me before you close all the doors 10 And see if you find those things that you liked 10 I see a dream in your eyes that still soars 10 With Phoenix wings from that dessert we spiked.
10 Please do not leave these fruits ripe and unshorn 10 As you might need them while you walk along 10 You can forget or dismiss my forlorn 10 For another while I will keep your song.
10 Some of these flowers will remain unowed 9 Take them, feel them, or use them yourself 10 I will get used to destiny that drawned 10 Once before my hope in front of white elf.
10 Please make sure that my mind is all empty 10 Or that, love gone, remains our sympathy. ***
```
Sonnets For The Twenty First Century And A Circadian Musical Written By Francisco Luis Arroyave Tabares (1984-1987)
Analyzed by GPT4; Image by leonardo.ai; First published on Nostr Protocol by franciscoarroyavet@nostrplebs.com
 Make Sure That Only Sympathy Remains
Make Sure That Only Sympathy Remains -
 @ cce0989b:b497e608
2024-03-07 15:00:10
@ cce0989b:b497e608
2024-03-07 15:00:10Why do we let embarrassment hold us back from doing what we really want to do?
To answer this question, we need to look to our ancestors. In a 2018 study, researchers investigated the evolutionary purpose of shame. Why does this emotion exist?
They argue that, because our ancestors lived in groups in unpredictable conditions, we relied upon one another for mutual aid. If you developed a reputation for selfish or immoral behavior, it could be deadly — you might be cast out and left alone, and unlikely to survive. Shame evolved to protect us from doing things that would hurt our communities, which, in turn, would hurt ourselves. Imagining how we might be treated if we behave improperly acts like a deterrant for bad behavior.
In today's very different world, the type of embarrassment we're afraid of is very different. It's more about deviating from the acceptable Old Happy norm: doing the things that we are supposed to do and being the person we are expected to be.
That's what can hold us back from doing the things we really want to do, like:
I want to quit my job. I want to get divorced. I want to go back to school. I want to become an artist. I want to help people in a new way.
How many inventions and ideas have been lost because their havers were afraid to pursue them?
Our ancestral fear of embarassment ends up stopping us from doing what would make us happy, which often ends up contributing to others' happiness, too.
One key to overcoming embarassment is to remember that it doesn't last forever. It's an intense emotion, yes, but a short-lived one too. Another study looked at 27 different emotions and how long they lasted for, discovering that feeling ashamed had the shortest duration of all.
What you create and contribute, on the other hand, can last forever. Don't let a short-term feeling get in the way of your long-term impact.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ de496884:72617b81
2023-11-20 13:54:02
@ de496884:72617b81
2023-11-20 13:54:02Hola nostriches. Hoy quiero hacer una publicación a modo de acercamiento al surgimiento de las categorías de género y feminismo. Así que si te interesa el tema haz un esfuerzo, quédate y lee hasta el final.
El «nuevo» feminismo surge en los años 60 en aquellos países desarrollados que acordaron el reconocimiento a los derechos humanos contenidos en la declaración respectiva de la ONU. Entonces, como extensión a dicho reconocimiento es que se gesta el movimiento feminista. A partir de entonces, se vuelve a plantear la relación entre naturaleza y cultura y se llega a la conclusión de que las diferencias sociales van más allá de las diferencias biológicas, lo cual tiene que ver con que hasta la satisfacción de las necesidades elementales como son la alimentación, la vivienda o el vestuario, están condicionadas por construcciones sociales.
Pues resulta que una de las primeras propuestas identificó la subordinación femenina producto de una organización patriarcal, tomando la categoría patriarcado de Max Weber. Es así como la visión de patriarcado se extendió al discurso político y académico. Sin embargo, no existía información acerca del desarrollo histórico de dicha categoría, sistematización, variaciones, etc., debido a que era algo que recién se percibía en sociedad.
Sin embargo, la misma categoría de patriarcado junto a la de relaciones de poder para explicar fenómenos sociales contemporáneos, constituye uno de los principales aportes del feminismo. Es así como han logrado primero visibilizar y luego deconstruir y desmontar una serie de patrones existentes en la cultura que hacían a la mujer subordinarse al hombre, y que estaban presentes en el sistema sexo/género.
 Imagen relativa a la lucha contra el patriarcado
Imagen relativa a la lucha contra el patriarcadoHasta ese momento, en las investigaciones de corte sociológico se podía observar un androcentrismo excesivo al dar cuenta de que el discurso científico giraba en torno al hombre como sujeto y objeto de la investigación. Incluso para muchos positivistas como el mismo Weber, los problemas relativos a las mujeres quedaban en un segundo plano y eran achacados a una supuesta pasividad en el ámbito doméstico-familiar. Dicha pasividad partía de la supuesta inferioridad biológica del género femenino.
El patriarcado entonces era una categoría vacía en sí misma, sin valor explicativo. Desde el punto de vista político pudo ser útil para la movilización pero no resistió la polémica de los críticos del feminismo ni problematizó los conflictos a ser resueltos. Pero por otro lado, un grupo de mujeres -académicas principalmente- se puso manos a la obra en una tarea más pequeña pero con mayores resultados a la larga. Se propusieron generar conocimientos sobre las condiciones de vida de la mujer, buscar en el pasado y el presente los aportes de las mujeres a la sociedad, hacerlas visibles en la historia. Es así como surgen centros académicos, ONG, proyectos, centros de estudios sobre la mujer, etc.
Convendría distinguir entonces dos posturas que acompañaron a la investigación sobre las mujeres: uno que toma como objeto de estudio a la mujer; condiciones de vida, trabajo, cultura, y otra que privilegia a la sociedad como generadora de la subordinación de las mujeres. Mientras la primera perspectiva generaba conocimiento sobre las mujeres en el estudio de las relaciones mujer-hombre y mujer-mujer, la segunda tenía una visión más holística ya que planteaba que hay que estudiar la sociedad ya que la subordinación de las mujeres es producto de la organización de esta, y que no se avanzará solamente estudiando a las mujeres, pues el estudio debe ser más amplio y en diferentes niveles, ámbitos y tiempos.
Es en esta búsqueda donde nace y se desarrolla el concepto de género como categoría social. Es así que los sistemas de género/sexo fueron entendidos como conjuntos de prácticas, símbolos, representaciones, normas y valores sociales que las sociedades construyen a partir de la diferencia anatomofisiológica y que dotan de sentido a los impulsos sexuales, la reproducción y en general a las relaciones de las personas. Por tanto, este sistema pasó a ser el objeto de estudio para comprender la subordinación de la mujer al hombre. Al ser el reconocimiento de una dimensión de la desigualdad social hasta entonces desconocida, se considera la ruptura epistemológica más importante de la segunda mitad del siglo pasado.
 Imagen representativa del binarismo de género
Imagen representativa del binarismo de géneroHay que decir que los fenómenos sociales se definen por la relación que guardan entre sí. Es así que la contextualización adquiere gran importancia. Varones y hembras tenemos la capacidad de producir con el cuerpo, pero solo los cuerpos de las hembras pueden gestar y por tanto asegurar la especie humana. Todo grupo humano que pretenda sobrevivir debe asegurarse cierto número de hembras que lo hagan posible. De ahí un poder particular del cuerpo de las hembras que además es económicamente útil. Dicho poder no es en tanto entidad biológica, sino que es la sociedad la que le otorga este poder. En este punto es importante preguntarnos históricamente ¿quiénes han controlado la capacidad reproductiva de las mujeres?, ¿quiénes han tenido la preferencia en el acceso sexual? Para asegurar un control efectivo sobre la reproducción es necesario asegurar el acceso a la sexualidad.
Ello también lleva a dirigir el trabajo que hacen porque de lo contrario, las mujeres pudieran tener espacio para representar una amenaza al dominio de los hombres. Es importante atender a las etapas del desarrollo de las mujeres, que permitirá ver cómo se moldean para aceptar la desigualdad y las jerarquías según el género en las distintas sociedades y culturas.
Otro contexto a delimitar es el ámbito doméstico donde históricamente ha estado ubicada la subordinación femenina. Se ha puesto al descubierto que en mujeres que comparten la misma posición de clase y raza, la condición femenina se redefine a lo largo de la vida y que algunas mujeres gozan de poder sobre otras aún en contextos de alta dominación masculina, donde se les inviste de autoridad, creando el sistema zonas de incertidumbre que las divide como género e impide alianzas y se legitima la dominación. Foucault decía que «el poder se ejerce, no se posee», siempre está en peligro de perderse y no basta con normas, leyes, amenazas o castigos. De ahí que los espacios de subordinación sean también espacios de poder de las mujeres. Es en estos espacios donde aparece la inseguridad, la tensión, la confrontación y por ejemplo, las mujeres pueden reclamar la anticoncepción.
Para terminar, es importante tener en cuenta que el género es una forma de desigualdad social que siempre está articulado con otras formas de desigualdad ya sea clase, raza, grupo etario, etc. Hay que pensar la dominación masculina con un comienzo vago en el tiempo, pero que permite desligar la subordinación de las mujeres de la evolución «natural» de la humanidad y entenderla como un proceso histórico. En ese sentido es necesario destacar que, respecto a la raza, en sociedades plurales hay que atender al contexto étnico-cultural ya que en dependencia de las relaciones entre personas de razas distintas, estarán condicionadas las relaciones entre los géneros.
 Imagen de mujeres de distintas razas
Imagen de mujeres de distintas razasPor otro lado, si bien es sabido que históricamente el sistema de género social imperante ha contribuido a invisibilizar a la mujer, asociar necesariamente dicha categoría únicamente a ella, lo que hace es nuevamente recrear el absolutismo histórico que tanto daño ha hecho, ahora como lo antagónico al hombre. En la construcción social participan todos los individuos presentes en el sistema género.
Hasta aquí la publicación de hoy, de la cual aun se puede ahondar mucho más, sobre todo en lo referido al origen de la dominación o de la jerarquización del binomio «hombre/mujer» desde un punto de vista antropológico, pero eso quedará pendiente para otro momento. ¡Así que hasta la próxima!, ¡nos vemos en Nostr!
........................................
English version
Hello nostriches. Today I want to make a post by way of an approach to the emergence of the categories of gender and feminism. So if you are interested in the topic make an effort, stay and read to the end.
The "new" feminism emerged in the 60's in those developed countries that agreed to recognize the human rights contained in the respective UN declaration. Then, as an extension of that recognition, the feminist movement was born. From then on, the relationship between nature and culture was raised again and the conclusion was reached that social differences go beyond biological differences, which has to do with the fact that even the satisfaction of elementary needs such as food, housing or clothing are conditioned by social constructions.
It turns out that one of the first proposals identified female subordination as a product of a patriarchal organization, taking Max Weber's category of patriarchy. This is how the vision of patriarchy was extended to political and academic discourse. However, there was no information about the historical development of this category, systematization, variations, etc., because it was something that was only recently perceived in society.
However, the same category of patriarchy, together with that of power relations to explain contemporary social phenomena, constitutes one of the main contributions of feminism. This is how they have first made visible and then deconstructed and dismantled a series of existing patterns in the culture that made women subordinate to men, and that were present in the sex/gender system.
 Image relating to the fight against patriarchy
Image relating to the fight against patriarchyUp to that time, in sociological research, an excessive androcentrism could be observed as scientific discourse revolved around men as the subject and object of research. Even for many positivists such as Weber himself, the problems related to women remained in the background and were blamed on a supposed passivity in the domestic-family sphere. This passivity was based on the supposed biological inferiority of the female gender.
Patriarchy was then an empty category in itself, with no explanatory value. From the political point of view, it could be useful for mobilization, but it did not resist the polemic of feminism's critics, nor did it problematize the conflicts to be resolved. But on the other hand, a group of women - mainly academics - set to work on a smaller task but with greater results in the long run. They set out to generate knowledge about women's living conditions, to search in the past and present for women's contributions to society, to make them visible in history. This is how academic centers, NGOs, projects, women's studies centers, etc., came into being.
It would be convenient to distinguish then two postures that accompanied the research on women: one that takes women as the object of study; living conditions, work, culture, and the other that privileges society as the generator of women's subordination. While the first perspective generated knowledge about women in the study of woman-man and woman-woman relations, the second had a more holistic vision, since it proposed that society must be studied, since the subordination of women is a product of its organization, and that progress will not be made only by studying women, since the study must be broader and at different levels, spheres and times.
It is in this search that the concept of gender as a social category was born and developed. Thus, gender/sex systems were understood as a set of practices, symbols, representations, norms and social values that societies construct on the basis of anatomophysiological differences and that give meaning to sexual impulses, reproduction and, in general, to people's relationships. Therefore, this system became the object of study to understand the subordination of women to men. As the recognition of a hitherto unknown dimension of social inequality, it is considered the most important epistemological breakthrough of the second half of the last century.
 Representative image of gender binarism
Representative image of gender binarismIt must be said that social phenomena are defined by their relationship with each other. Thus, contextualization acquires great importance. Males and females have the capacity to produce with their bodies, but only the bodies of females can gestate and therefore ensure the human species. Any human group that intends to survive must ensure a certain number of females to make it possible. Hence a particular power of the female body, which is also economically useful. This power is not as a biological entity, but it is society that gives it this power. At this point it is important to ask ourselves historically, who has controlled the reproductive capacity of women, who has had the preference in sexual access? To ensure effective control over reproduction, it is necessary to ensure access to sexuality.
 Allegorical image of pregnancy
Allegorical image of pregnancyThis also leads to directing the work they do because otherwise, women may have room to pose a threat to men's dominance. It is important to pay attention to the stages of women's development, which will allow us to see how they are shaped to accept inequality and gender hierarchies in different societies and cultures.
Another context to delimit is the domestic sphere where female subordination has historically been located. It has been discovered that in women who share the same class and race position, the feminine condition is redefined throughout life and that some women enjoy power over others even in contexts of high male domination, where they are invested with authority, creating the system of uncertainty zones that divide them as a gender and prevent alliances and legitimize domination. Foucault said that "power is exercised, not possessed", it is always in danger of being lost and norms, laws, threats or punishments are not enough. Hence, the spaces of subordination are also spaces of women's power. It is in these spaces where insecurity, tension, confrontation appear and where, for example, women can demand contraception.
To conclude, it is important to keep in mind that gender is a form of social inequality that is always articulated with other forms of inequality, be it class, race, age group, etc. It is necessary to think of male domination with a vague beginning in time, but which allows us to separate the subordination of women from the "natural" evolution of humanity and to understand it as a historical process. In this sense, it is necessary to emphasize that, with respect to race, in plural societies it is necessary to pay attention to the ethno-cultural context since, depending on the relations between people of different races, the relations between genders will be conditioned.
 Image of women of different races
Image of women of different racesOn the other hand, although it is known that historically the prevailing social gender system has contributed to make women invisible, to necessarily associate this category only to women is to recreate the historical absolutism that has done so much damage, this time as antagonistic to men. All individuals present in the gender system participate in the social construction.
So much for today's publication, of which we can still go much deeper, especially with regard to the origin of domination or the hierarchization of the binomial "man/woman" from an anthropological point of view, but that will be left for another time. So until next time, see you in Nostr!

Créditos | Credits
Bibliografía consultada | Consulted bibliography:
-
Barbieri, T. (1993). Sobre la categoría género. Una introducción teórico-metodológica. Debates en Sociología. (18). 1-19. https://doi.org/10.18800/debatesensociologia.199301.006
-
Echevarría, D. (2020). Desigualdades de género e interseccionalidad. Análisis del contexto cubano 2008-2018. Facultad Latinoamericana de Ciencias Sociales (Programa-Cuba). https://www.clacso.org.ar/libreria-latinoamericana-cm/libro_detalle_resultado.php?id_libro=2346&campo=cm&texto=248
Traducción | Translation:
DeepL
-
-
 @ 1e52c554:21771908
2024-03-06 03:44:18
@ 1e52c554:21771908
2024-03-06 03:44:18Posthumous work of the Colombian poet born in Don Matias on January 20, 1948.
Welcome to this blog dedicated to the Posthumous work of the Colombian poet Francisco Luis Arroyave Tabares (my father), born in Don Matias on January 20, 1948-2010. Where I will be publishing each of the 175 sonnets from his unpublished collection 'Sonnets For The Twenty-First Century And A Circadian Musical (1984-1987).' Analyzed with GPT4 artificial intelligence and illustrated with AI tools... I hope you enjoy this garden of words snatched from the solitude of a locked room.
Likewise, any enthusiast of the sonnet form is invited to conduct their personal studies of Arroyave Tabares' work, as it is a collection that, although registered since 1989, has not yet been published.
Frank Duna

Analysis "No More Time To Cry"
Introduction
This sonnet "No More Time to Cry", explores themes of love, loss, longing, and hope. It beautifully juxtaposes the sorrow of loss with the beauty of memories and the hope for love’s return.
Thematic Analysis
In the octave, the speaker expresses a deep sadness and a sense of loss. The speaker questions if they will always be in this state of sorrow, listening to their heart “die” and shedding tears in great numbers. The imagery of gardens, butterflies, rainbows, and “weilds” (wooded areas) that will soon be dry, adds a layer of melancholy and transience to the speaker’s emotions. The octave ends with a plea for each day not to be somber, indicating a desire for relief from this sadness.
The sestet shifts the tone slightly. The speaker acknowledges the pleasures of life, music, and the lyrics left behind. There’s a sense of nostalgia as the speaker recalls the dreams shared with the person they’re addressing. The speaker then asks if Aphrodite, the goddess of love and beauty, will return to their side and dwell with them, ending their sorrow. This suggests a longing for love and companionship to alleviate their sadness.
Overall, the sonnet explores themes of sadness, loss, longing, and the hope for love and happiness. The octave sets up the problem (enduring sadness), and the sestet offers a potential resolution (the return of love).
Rhyme Scheme
The rhyme scheme (ABBA ABBA CCD EED) is a variant of the Petrarchan sonnet form. Let’s analyze it in the context of the sonnet “No More Time To Cry” by Francisco Luis Arroyave Tabares.
The octave (first eight lines) follows an ABBA ABBA pattern:
A: Shall I have to be so sad for ever? B: Will I have to listen to my heart die B: In gardens with each kind of butterfly A: In an air of echoes to remember? A: Or shall my tears fall in a great number B: Amid rainbows and passions that go by B: Reminding me that weilds will soon be dry A: And asking each day not to be somber?The sestet (last six lines) follows a CCD EED pattern:
C: Oh girl, life, pleasures, and oh my musics! C: At least you have left with me some lyrics D: And those dreams that you and I had before. E: Are you going to return by my side E: Dear Aphrodite this time to abide D: And say, “come, please do not cry any more”?This rhyme scheme creates a specific rhythm and structure to the poem, enhancing its musicality and flow. The octave sets up a problem or situation, and the sestet provides a resolution or commentary, with the change in rhyme scheme marking the transition between the two. The final couplet (EED) provides a poignant conclusion to the sonnet. This structure is typical of sonnets and is part of what gives them their unique expressive power.
Additional Aspects
Let’s delve deeper into the sonnet “No More Time To Cry” by Francisco Luis Arroyave Tabares.
Language and Imagery: The language used in the sonnet is rich and evocative, creating vivid imagery that enhances the emotional depth of the poem. The speaker’s sadness is depicted through images of a dying heart, falling tears, and drying “weilds” (wooded areas). The use of natural elements like gardens, butterflies, and rainbows adds a layer of beauty and transience to the speaker’s emotions. The mention of Aphrodite, the goddess of love and beauty, introduces a mythological element, further enriching the imagery.
Themes: The sonnet explores themes of sadness, loss, longing, and hope. The speaker’s enduring sadness and sense of loss are evident in the octave, while the sestet introduces a longing for love and companionship and a hope for happiness.
Meter: The sonnet appears to follow the iambic pentameter, which is a common metrical form in English poetry and traditional sonnets. Each line consists of five pairs of unstressed and stressed syllables, giving the poem a rhythmic quality.
Overall: the sonnet is a poignant exploration of human emotions. The use of evocative language and imagery, combined with the traditional sonnet form and meter, creates a powerful and moving piece of poetry. The transition from the octave to the sestet, marked by a change in rhyme scheme and tone, effectively conveys the speaker’s journey from enduring sadness to a hopeful longing for love and happiness. The sonnet ends on a hopeful note, leaving the reader with a sense of anticipation and optimism.
(GPT4)
Syllable count for each line.
``` No More Time To Cry
10 Shall I have to be so sad for ever? 10 Will I have to listen to my heart die 10 In gardens with each kind of butterfly 10 In an air of echoes to remember?
10 Or shall my tears fall in a great number 10 Amid rainbows and passions that go by 10 Reminding me that weilds will soon be dry 10 And asking each day not to be somber?
10 Oh girl, life, pleasures, and oh my musics! 10 At least you have left with me some lyrics 10 And those dreams that you and I had before . 10 Are you going to return by my side 10 Dear Aphrodite this time to abide 10 And say, "come, please do not cry any more"? *** ```
Sonnets For The Twenty First Century And A Circadian Musical Written By Francisco Luis Arroyave Tabares (1984-1987)
Analyzed by GPT4; Image by leonardo.ai; First published on Nostr Protocol by franciscoarroyavet@nostrplebs.com
 *No More Time To Cry
*No More Time To Cry -
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ a012dc82:6458a70d
2024-03-06 01:51:06
@ a012dc82:6458a70d
2024-03-06 01:51:06Table of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
Introduction
Since El Salvador accepted Bitcoin as legal cash in September 2021, several rapid judgments have been issued proclaiming this move a failure. Some commentators have even gone so far as to argue that Bitcoin is somehow responsible for the economic issues that existed in El Salvador long before Bitcoin was ever established. This decision has been met with a number of quick judgments praising this move as a failure. But the conventional financial gurus, talking heads, and even officials from the International Monetary Fund (IMF) who advocate this viewpoint are completely missing the mark here.
After President Nayib Bukele of El Salvador made public in July his intention to make an offer to acquire publicly owned bonds with maturities between 2023 and 2025, the total amount of El Salvador's national debt increased to more than $20 billion. Although it was a significant sum in comparison to the size of the Salvadoran economy, the decision to recognize Bitcoin as valid currency had nothing to do with it.
Instead, El Salvador's debt is the result of a wide variety of variables. El Salvador took out a loan from the International Monetary Fund (IMF) in the amount of $85 million in 1982, which added to the country's already extensive fiscal debt and offered negligible benefits to the country's citizens during a time of civil war. This was 39 years before Bitcoin was made legal. After that, the country's capacity to handle its own finances was further hindered when, in 2001, it chose to adopt the United States dollar as its official currency. El Salvador was unable to adopt its own monetary policy because its base currency, the US dollar, prevented it from doing so. This prevented it from paying for internal needs such as social programs or infrastructure. Instead, more money had to be borrowed from the public sector to pay for these important services.
The problems that El Salvador's debt problems are not a direct outcome of the country's investments in innovative financial technology such as Bitcoin. Instead, El Salvador's adoption of Bitcoin is a step toward recovering its monetary sovereignty, giving its inhabitants access to financial services and possibilities, and tackling systemic issues that traditionally disadvantaged Salvadorans. Bitcoin is a digital currency that doesn't have a central bank and uses cryptography to make sure its transactions are safe.
El Salvador has spent little more than a hundred million dollars on Bitcoin in the time since it was declared legal tender last year. The new legislation mandates that all establishments in the nation accept Bitcoin as a form of payment. The government also established a trust with $150 million dollars in public money at the same time to allow dollar conversions. Also, the government made a digital wallet called "Chivo Wallet" and gave residents who downloaded it $30 in Bitcoin as a reward.
The government has made important efforts toward its goal of providing residents with more financial freedom and opportunity than they have ever had before. These actions include recognizing Bitcoin as a form of legal cash, providing wallets for its citizens, and motivating their use of these new tools with Bitcoin bonuses. For instance, around the time this law was enacted, estimates showed that as many as 70 percent of the country's people did not have bank accounts. The experiment with Bitcoin is helping these folks improve their lives by giving them a method to participate in the formal economy and an opportunity to build money for themselves.
Even while the timing of El Salvador's commitment to Bitcoin as legal cash has unhappily coincided significantly with a bear market that has affected the whole sector, the rush to declare that this is a failure is, to say the least, premature. To figure out if the experiment was a success, it is important to think about the study's goals and give the experiment enough time to be done.
El Salvador embarked on the Bitcoin project for two primary reasons: the first was to usher in a new era of monetary sovereignty in the nation; the second was to provide citizens with financial opportunities that they did not have in the past and likely would not have in the future. Both of these goals are central to the Bitcoin project. As a direct result of this project, millions of Salvadorans who didn't have bank accounts before now do. This is made possible by the use of blockchain technology.
El Salvador has taken the initiative to become a leader in this movement, which is likely to expand to a great number of other countries all over the world while other countries sit idly by and watch to see what unfolds. Countries like Venezuela and Guatemala, as well as a large number of others, may soon follow in El Salvador's footsteps and look for forward-thinking financial solutions based on blockchain technology. This would give citizens more power and help the economy grow and become more independent.
The adoption of Bitcoin, as opposed to being the cause of El Salvador's economic problems, as some critics have asserted, is a response to the intractable challenges that El Salvador and other countries like it are currently facing. This is the case despite some critics having drawn a correlation between the two. The decision that the government of El Salvador has taken, which is both courageous and commendable, is to provide its people and the government itself a shot at economic independence. When regular people begin to achieve their goals using the financial resources that have been made available to them, other nations will be inspired to pursue their own goals of progress in the subsequent generation of finance.
Conclusion
El Salvador's primary motivation for its Bitcoin initiative was to usher in a new age of monetary sovereignty for the country and to provide its population access to economic possibilities they had not previously had and were unlikely to have again in the near future. Many other nations, like Venezuela and Guatemala, may soon follow El Salvador's lead in looking for innovative financial solutions based on blockchain technology to better equip their inhabitants and usher in a new age of economic prosperity and self-sufficiency. Critics who say Bitcoin is to blame for El Salvador's economic problems are missing the point; Bitcoin is a solution to the insurmountable obstacles that El Salvador and similar nations face right now.
FAQ
What caused Bitcoin to dip? Experts say that the falling prices on the stock and cryptocurrency markets are caused by a number of things, such as the possibility of an economic recession, rising interest rates, the ongoing conflict in Ukraine, and persistently high inflation.
Why does El Salvador have bitcoins? The project was advocated by President Nayib Bukele, who has a strong interest in cryptocurrencies, as one that would provide many economic advantages. He said that adopting Bitcoin as a legitimate form of currency would encourage foreign investment, create new employment, and "push mankind at least a small bit towards the right path."
How long do crypto dips usually last? Because it is impossible for anybody to precisely time every bottom or peak, you should secure some profits whenever you have them. In the cryptocurrency market, extended downtrends in bear markets may persist for weeks or months, while bull markets can also last for a significant amount of time. Hence, be conscious of the pattern as a whole!
That's all for today, see ya tomorrow
If you want more, be sure to follow us on :
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 78733875:4eb851f2
2023-08-17 14:23:51
@ 78733875:4eb851f2
2023-08-17 14:23:51After announcing our first wave of grants for bitcoin[^fn-btc] and nostr[^fn-nostr] projects, we are pleased to announce an additional wave of grants for open-source projects in the space:
[^fn-btc]: First Wave of Bitcoin Grants [^fn-nostr]: First Wave of Nostr Grants
- BDK
- LNbits
- Watchdescriptor
- Stratum V2 Testing \& Benchmarking Tool
- Fedimint Modules and Resources
- Amber: Nostr Event Signer
- Nostr UI/UX Development
- Nostr Use-Case Exploration \& Education
The first five grants are sourced from our General Fund, the last three—being nostr projects—from our Nostr Fund. This brings the total number of OpenSats grants to 41, adding to the grants we previously announced in July.
Once again, let's take a closer look at each of the projects to see how they align with the OpenSats mission.
BDK
Bitcoin Development Kit (BDK) is a set of libraries and tools that allows you to seamlessly build cross-platform on-chain bitcoin wallets without having to re-implement standard bitcoin data structures, algorithms, and protocols. BDK is built on top of the powerful rust-bitcoin and rust-miniscript libraries and adds features for managing descriptor-based wallets, syncing wallets to the bitcoin blockchain, viewing transaction histories, managing and selecting UTXOs to create new transactions, signing, and more. The core BDK components are written in Rust, but the team also maintains Kotlin and Swift language bindings for use in mobile projects. There are also Python bindings, and React Native and Flutter support is being actively developed.
Repository: bitcoindevkit/bdk
License: Apache 2.0 / MITLNbits
LNbits is used by a multitude of projects in the bitcoin space, especially as part of their lightning payments stack. Being easy to build on through its extension framework, LNbits has been pioneering various cutting-edge solutions and experiments in the world of bitcoin, lightning, and nostr.
The project has a thriving maker community building various hardware devices such as Lightning ATMs, point-of-sale devices, DIY hardware wallets, and nostr signing devices. The modular design of LNbits makes it attractive to users and tinkerers alike, as its plugin architecture makes it easy to extend and understand.
Repository: lnbits/lnbits
License: MITWatchdescriptor
watchdescriptoris a CLN plugin written in Rust that connects a business's treasury wallet to its CLN node. It utilizescln-pluginand the BDK library to track coin movements in registered wallets and report this information to thebookkeeperplugin.The plugin enables businesses to design a complete treasury using Miniscript and import the resulting descriptor into CLN. Since
bookkeeperalready accounts for all coin movements internal to CLN, this plugin is the last piece businesses need in order to unify all their bitcoin accounting in one place. This enables businesses to account for all inflows and outflows from their operations, streamlining tax reporting and financial analysis.The
watchdescriptorproject is part of a broader vision to transform the lightning node (particularly CLN) into a financial hub for businesses, enabling them to conduct operations without reliance on any third parties.Repository: chrisguida/watchdescriptor
License: MITStratum V2 Testing & Benchmarking Tool
The Stratum V2 Testing & Benchmarking Tool allows the bitcoin mining industry to test and benchmark Stratum V2 performance against Stratum V1. The tool supports different mining scenarios to help miners make informed decisions and evaluate their profitability. The goal of the project is to motivate miners to upgrade to Stratum V2, increasing their individual profits and making the Bitcoin network more resilient in the process.
Repository: stratum-mining/stratum @GitGab19
License: Apache 2.0 / MITFedimint Modules and Resources
Fedimint is a federated Chaumian e-cash mint backed by sats with deposits and withdrawals that can occur on-chain or via lightning. It can be understood as a scaling and privacy layer as well as an adoption accelerator for Bitcoin.
The goal of this particular project is to improve the Fedimint UI and develop free and open resources for developers and "Guardians" to enable more people to run and develop on Fedimint.
Repository: fedimint/ui @EthnTuttle
License: MITAmber: Nostr Event Signer
Amber is a nostr event signer for Android. It allows users to keep their
nsecsegregated in a single, dedicated app. The goal of Amber is to have your smartphone act as a NIP-46 signing device without any need for servers or additional hardware. "Private keys should be exposed to as few systems as possible as each system adds to the attack surface," as the rationale of said NIP states. In addition to native apps, Amber aims to support all current nostr web applications without requiring any extensions or web servers.Repository: greenart7c3/Amber
License: MITNostr UI/UX Development
The goal of this project is to help improve the UI/UX of major nostr clients, starting with Gossip and Coracle, emphasizing the onboarding process as well as usability and accessibility. One part of onboarding is solving the discoverability problem that nostr has in the first place. Solving the problem of jumping in and out of the nostr world is what motivated the development of
njump, which was redesigned as part of these efforts and is now live at nostr.com.In addition to client-specific improvements, generic design modules and learnings will be incorporated into the Nostr Design project for others to use.
Activity: github.com/dtonon @dtonon
License: MITNostr Use-Case Exploration & Education
As of today, most nostr clients implement social media applications on top of the nostr protocol. However, nostr allows for various use cases, many of which go beyond social media. Two examples are Listr and Ostrich, a list management tool and job board, respectively.
In addition to use-case exploration, this project will continue to educate users and developers alike, be it via Nostr How or various video series, e.g., explaining how to build upon NDK.
Activity: github.com/erskingardner @jeffg
License: MIT / GPL-3.0 / CC BY-NC-SA 4.0
We have more grants in the pipeline and will provide funding for many more projects in the future. Note that we can only fund those projects which reach out and apply. If you are an open-source developer who is aligned with our mission, don't hesitate to apply for funding.
-
 @ 18e3af1e:1d42e5df
2024-03-06 00:58:47
@ 18e3af1e:1d42e5df
2024-03-06 00:58:47Disclosure
Now, this is purely an opinion. I have not done research and I haven't even thought it throw for that long. Is more like an idea I have of the future, a hunch if you allow me. Just want to record this thought.
The term "mining hardware" will fade away from people's mind in generations to come. But why?
Is not because the term is used in an incorrect way, or have this bad connotations (like mining gold for example, bad for the planet), but rather the use of home appliances. Allow me to articulate it a bit more:
Home appliances are always use for an specific purpose, and that's make our life's easier A.K.A save time. Dishwasher help us with the dishes so we don't have wash them by hand, washer help us with cloth, and so on...
In this generation we don't even think about all the technology behind all this innovation, we only use them for the purpose they were built for. Bitcoin "mining" equipment is the same.
Virtually ANYTHING can have a "bitcoin miner" inside of it (I'm exaggerating, you get the idea). If somehow making an appliance that "mines" bitcoin, the idea that people in the future will call it "washer-miner" would be kind of far fetch. The word "mining" itself will fade in the background, just like all this other components domestic appliances use that most of us have no clue.
Share your thoughts please.
-
 @ 6ad3e2a3:c90b7740
2024-03-05 22:11:05
@ 6ad3e2a3:c90b7740
2024-03-05 22:11:05I got into it with a friend and fellow Jew about Israel the other day. It’s not a topic I talk about much, either here or on my podcast and not because I’m worried about offending anyone — that ship has long sailed. It’s because I’m not entirely clear on the facts, and I find the usual back and forth about who did what to whom when to be endlessly debatable, unresolvable and uninteresting. Same goes for the history.
My basic understanding is that Israel is killing a lot of innocent people, and that’s both bad strategic policy and also evil. Of course, the US killed a million Iraqis for less (nothing), and no one seems to mind much. I mean you mind, but if you don’t think George Bush (who gave Michelle Obama a candy once) and Dick Cheney should be prosecuted for war crimes because come on, that’s absurd, then you don’t really mind.
And I get it. The “Iraqis” are just a concept to you and me, as are the Palestinians, the Ukrainians, the Yemenis and the Congolese. Just a bunch of unfortunate, oppressed, murdered humans about whom we all feel terrible, but who also occupy less of our mindshare than that fucking parking ticket we got yesterday. I swear I read the sign three times!
It’s normal for people to care almost exclusively about themselves, their families and their friends. People who purport to care so much about “humanity”, to paraphrase Dostoevsky, often do so while despising and mistreating the individual human beings with whom they come into contact. I’d much more trust someone who risked his reputation and livelihood for a friend than someone going on about third-world oppressed peoples on social media, for example.
But this natural tendency to prioritize those nearest to us often seems to undergird how we see the world and the sides we take in these discussions. For example, my friend sees Israel as a potential homeland for his family should things get ugly for Jews in the US. He is therefore inclined to support them generally, even if he doesn’t always support their particular tactics or conduct.
I live in Europe which seems to me more antisemitic than the US, and I’d rather Israel not fuel more of that by killing a whole bunch of seemingly innocent people. That’s honestly what I think was framing the conversation, the initial biases we brought to it. I think of it as “talking your book,” a phrase used to describe when people talk up their own investments simply because they are invested. And there is no bigger investment than your family’s safety.
So you have people convinced Israel is a potential safe haven, and others who see it, rightly or wrongly, as a flashpoint for conflict and driver of antisemitism. The former will talk their books, say how Israel was savagely attacked and has terrorists right on its border, and the latter will point to the conditions under which the Palestinians live and the disproportionate response to the attack.
But as someone who lacks the appetite to sift through the propaganda and delve into what’s really happening and why, and who has never been and has no desire to go to the region, I don’t care to weigh in much about the truth on the ground. As I said, from what I can tell, Israel is doing something stupid and evil right now, but what I can tell from afar is neither definitive, nor especially important.
What I can say is even though my “book” is for Israel to stop killing innocent Palestinians, my real book, the thing that is most in my family’s interest is justice. That is, if in fact Israel were truly fighting terrorists and within its self-defense rights, then I would want it to defend itself as it is, even if it seems to make things harder for me. That’s because I have faith that justice is more in my interest than whatever appears to advantage me in the short run.
And I would also argue that the “book” of those who view Israel as a potential safe-haven for Jews is also for Israel to be harshly condemned and punished internationally if it’s in fact the case that they are committing war crimes. What’s true and just always trumps what’s apparently expeditious and advantageous in your real book. That is, if you are a person of faith, and by that I don’t mean nominally a Jew, a Muslim or a Christian, but someone with actual faith.
So rather than argue the facts on the ground with people talking their books (and often manipulated by powerful interests that shape what they see as their books), it’s better to understand what’s in our deeper interest, what’s more important than our fears, which incidentally might correspond less to reality than to someone’s cleverly incepted narrative about it.
Otherwise, I expect things will only get worse.
-
 @ 9ecbb0e7:06ab7c09
2023-08-08 02:53:15
@ 9ecbb0e7:06ab7c09
2023-08-08 02:53:15Según nos reporta y documenta la familia, la niña pequeña de 3 años de edad Leadi Kataleya Naranjo, hija del preso de conciencia Idael Naranjo Pérez, ha sido citada para mañana por la Seguridad del Estado de #Cuba.
 La citación no ofrece duda e indica los dos nombres, apellido y la dirección de la abuela paterna, donde entregaron la citación, y la abuela también ha sido citada y amenazada de desobediencia.
La citación no ofrece duda e indica los dos nombres, apellido y la dirección de la abuela paterna, donde entregaron la citación, y la abuela también ha sido citada y amenazada de desobediencia.
 Si la niña no se presenta, amenazan de acusarla igualmente de "desobediencia".
La abuela se preocupó, les dijo la edad, y aún así entregaron la citación y se fueron. Que "debían presentarse". Nada más.
Desalmados son, pero...
¿Qué clase de locos de atar están al mando en #Cuba?
¿Qué pretenden citando y amenazando a una niña de 3 años?
Esa niña no puede ir a esa ignominiosa citación. ¿A oír qué? ¿A responder qué? El tema da ASCO.
La familia no quiere llevar a la niña, y necesitan todo el apoyo para que esta locura se aclare y se detenga.
Desgraciadamente hemos visto cosas iguales o peores. Niños amenazados, separados por la fuerza de sus padres, menores torturados... El régimen de Cuba da mucho asco, por todos lados rezuma repugnancia y degradación. Todo lo que sucede en Cuba clama al cielo, y estas barbaries son distópicas.
¡MANTENGAN AL MARGEN A LOS NIÑOS, DESALMADOS ENFERMOS!
Bastante daño causan con la Ley de los 8 años que tiene a miles de niños huérfanos, separados forzosamente de sus madres para castigarlas a ellas por no doblegarse a trabajar en las misiones médicas esclavas de Cuba en el exterior, como sentenció el Comité de los Derechos del Niño.
¡BASTA YA!
Si la niña no se presenta, amenazan de acusarla igualmente de "desobediencia".
La abuela se preocupó, les dijo la edad, y aún así entregaron la citación y se fueron. Que "debían presentarse". Nada más.
Desalmados son, pero...
¿Qué clase de locos de atar están al mando en #Cuba?
¿Qué pretenden citando y amenazando a una niña de 3 años?
Esa niña no puede ir a esa ignominiosa citación. ¿A oír qué? ¿A responder qué? El tema da ASCO.
La familia no quiere llevar a la niña, y necesitan todo el apoyo para que esta locura se aclare y se detenga.
Desgraciadamente hemos visto cosas iguales o peores. Niños amenazados, separados por la fuerza de sus padres, menores torturados... El régimen de Cuba da mucho asco, por todos lados rezuma repugnancia y degradación. Todo lo que sucede en Cuba clama al cielo, y estas barbaries son distópicas.
¡MANTENGAN AL MARGEN A LOS NIÑOS, DESALMADOS ENFERMOS!
Bastante daño causan con la Ley de los 8 años que tiene a miles de niños huérfanos, separados forzosamente de sus madres para castigarlas a ellas por no doblegarse a trabajar en las misiones médicas esclavas de Cuba en el exterior, como sentenció el Comité de los Derechos del Niño.
¡BASTA YA!11jul #11j #11jCuba #CubaEsUnaDictadura #UNICEF @uniceflac @unicefenespanol
-
 @ cd408a69:797e8162
2023-09-14 13:08:47
@ cd408a69:797e8162
2023-09-14 13:08:47Nostrasia Hackathon
Welcome FOSS hackers and creatives who care deeply about freedom technology!
自由のテクノロジーに深い関わりたい FOSS ハッカーとクリエイター、あつまれ!
We're joining forces with Bolt.Fun for a month-long hackathon bridging Bitcoin and NOSTR (Notes and Other Stuff Transmitted by Relays), culminating with a special three day sprint and live event in Tokyo at the Nostrasia Conference.
私たちは、Bolt.Fun と協力して、ビットコインと Nostrを橋渡しする ハッカソンを、1 か月間かけて開催します。 クライマックスは東京で開催されるNostrasia Tokyo が舞台。3日間の特別なスプリントとライブ イベントで最高潮に達します。
Be a Part of the Early Days of Nostr
Nostr の創成期を共に作り上げましょう
Help build the future of Nostr! Like the early days of Bitcoin or of the Internet, Nostr is nascent open technology shaping new types of social experiences to connect people across the globe. It carries a foundation of principles similar to Bitcoin, like decentralization, simplicity, and censorship-resistance.
Nostr の未来を築くのに協力してください!ビットコインやインターネットの初期と同じように、Nostr は世界中の人々をつなぐ新しいソーシャル体験を形成するオープン テクノロジーの初期段階にあります。 Nostr には「分散化」「シンプルさ」「検閲耐性」など、ビットコインと同様の原則が組み込まれています。
Orange-Pill people through the Purple-Nostr-Pill
オレンジピル(ビットコイン)から紫の Nostr のピルへ
Bitcoin and Nostr communities are in synergy. What started as a social protocol is quickly transforming into a space for exploration on ways to support content creators through bitcoin lightning micro payments, often referred to as zaps. Bitcoin integration to the nostr protocol strengthens Bitcoin's use case as a currency of exchange. It carves new paths to a culture of value4value.
ビットコインと Nostr のコミュニティは相乗効果を発揮します。 Nostr はソーシャルプロトコルとしてはじまりましたが、今では Zap (ビットコイン の ライトニング マイクロペイメント)を通じてコンテンツ クリエイターをサポートする方法を模索する空間へと急速に進化しています。 Nostr プロトコルにビットコインが組み合わさることで、交換通貨としてのビットコインの働きが強化されます。 それは、"value4value" の文化への新しい道を切り開くでしょう。
Help People HODL their Keys (Social+Monetary)
人々が自分のキーを HODL (長期保有)できるように支援します (ソーシャル + 金銭的に)
Nostr exists outside of the rule of platforms and those who seek to control them. HODLing your nostr keys is hodling your identity and social graph, outside of KYC. By helping develop and educate on NOSTR, you are helping people escape walled gardens & gain control and choice over their identities & their money. The Internet, over time, has become centralized, help Nostr stay decentralized by supporting the growth of an ecosystem of apps, websites, microapps, relay services...
Nostr はプラットフォームやそれを制御しようとする人々の支配の外にあります。 Nostr keys を持つことは、KYC (本人確認)以外であなたのアイデンティティとソーシャル グラフを保持することになります。 Nostr の開発や教育に貢献することは、人々が束縛から解放され、アイデンティティやお金に対する主導権を得られるよう支援することにもなるのです。 時間の経過とともに集中化されてきたインターネットですが、Nostr のアプリ/Web サイト/マイクロアプリ/リレー サービスのエコシステムの成長をサポートすることで、Nostr の分散化を維持できるようになります。
Permissionless Building
許可を必要としない構築
Opportunities abound in an environment ripe for innovation:
- Develop & design new nostr white label clients, middleware, microapps...
- Help improve existing Nostr FOSS projects
- Contribute directly to protocol development through NIPs (Nostr Implementation Possibilities)
- Encourage nostr and bitcoin adoption through art, education, and any way you like
イノベーションの機が熟した環境には、チャンスが溢れています。
- Nostr の真新しい クライアント、ミドルウェア、マイクロアプリを開発したりデザインする
- 既存の Nostr FOSS プロジェクトの改善に寄与する
- NIP (Nostr Implementation Possibilities) を通じたプロトコル開発に直接貢献する
- 芸術、教育、その他好きな方法を通じて Nostr とビットコインの普及を推進する
Hack in a Supportive Environment
サポートされた環境でハックしよう
We have a growing list of knowledgeable people with skin-in-the-game to mentor and support your journey. Once your project matures, you may also have 1-on-1 guidance to help you reach your vision and discover ways of growing and funding it.
私たちは、あなたの道のりを指導しサポートしてくれる知識豊富なメンターを増やしています。 プロジェクトが成熟した暁には、1対1のガイダンスを受けられる可能性もあります。それは、あなたのビジョンを達成し、成長させて資金を得る方法を発見するのに役立つでしょう。
Nostr has a blossoming community open to innovation. It is also a great testing ground, as people in the community are open to giving and receiving feedback. It is an environment encouraging conversation on feature ideas as well as possible solutions to social media issues and product bugs.
Nostr には、イノベーションに対してオープンで、発展しているコミュニティがあります。 コミュニティの人々はフィードバックの授受にオープンであるため、優れた実験の場にもなります。 機能のアイデアや、ソーシャル メディアの課題や製品のバグの解決策についての会話を促進する環境です。
NostrHack Tracks
You have 3 options
NostrHack Tracks には3つのオプションがあります
Track 1: Builder's Track - Reimagine Nostr
トラック1 : ビルダーのトラック - Nostr を再考しよう
If you can think of it, it can be engineered! Nostr encourages permissionless building while staying mindful of interoperability and network support. Help BUIDL, design, and improve an area you are passionate about. Reimagine and BUIDL features, tools, clients... Help solve issues and create new experiences in social media.
思いつくことができれば、エンジニアリングできる! Nostr は、相互運用性とネットワーク サポートに留意しながら、パーミッションレスな構築 (BUIDL) を奨励しています。 あなたが情熱を注いでいる分野での構築、設計、改善に貢献してください。 機能やツール、クライアントを再考して構築 (BUIDL) し、ソーシャル メディアでの課題を解決して新しい体験を生み出すのに協力してください。
Possibilities...
これを踏まえて…
BUILD on the NOSTR Protocol
The Nostr Implementation Possibilities (NIPs) are optional protocol features anyone can add to their clients. Improve and strengthen existing NIPs or build on new ones. NOSTR is a balance of simplicity, interoperability, backward-compatibility and innovation.
NIPs は、誰でもクライアントに追加できるオプションのプロトコル機能です。 既存の NIP を改善および強化するか、新しい NIP を構築してください。 Nostr は、シンプルさ、相互運用性、下位互換性、革新性のバランスを保っています。
Focus on UX
Nostr is made up of a wide range of clients and tools. To make NOSTR scalable, you can help improve its user experience and education.
Nostr は幅広いクライアントとツールで形成されています。 Nostr をスケーラブルにするために、UX と教育の改善に協力してください。
Help shape a Web of Trust
Nostr cares about removing the KYC tied to our identities. To use Nostr you do not need to give up your phone number, email, financial information, or any metadata tied to your real world identity to be later harvested and sold. You are not the product. What are ways that trust can be earned to prevent impersonation, spam...?
Nostr は、私たちの身元に関連付けられた KYC (個人情報)を取り除けるようにしています。 Nostr を使用しても、電話番号、電子メール、財務情報、または現実世界のアイデンティティに関連付けられたメタデータを、収集されたり販売されたりして手放すことになる心配がありません。 あなたは商品ではないのです。 その中で、なりすましやスパムを防ぐために、信頼を獲得するにはどうすればよいでしょうか...?
NIP05/Nostr address
One of the solutions to build a web of trust used today, is to tie your nostr hex public key to a domain. Although this makes it harder for bots to have nostr addresses, it is not a perfect solution. Domains are centralized through DNS. To help people who do not have their own domains or cannot easily add a NIP05 on their sites, your nostr address can be hosted as a service along with other people's. At this moment, you can highlight just one nostr address per profile. In the future, could it include your website, where you work, and other identifiers... What are other possible solutions?
現在使用されている信頼獲得のための解決策の 1 つは、Nostr の HEX 公開鍵をドメインに結び付けることです。 これにより、完璧な解決策ではないものの、bot などが Nostr アドレスを持つことが難しくなります。 ドメインは DNS を通じて一元化されています。 独自のドメインを持っていない人や、自分では NIP-05 を簡単に追加できない人のために、あなたの Nostr アドレスをサービスとして他の人のものと一緒にホストすることも可能です。 現時点では、プロフィールごとに1つの Nostr アドレスのみを強調表示できますが、将来的には、Web サイト、勤務先、その他の識別情報も含められるようになる可能性があります...この他にも考えられる解決策は何かありますか?
On Decentralization & Discoverability
分散化と発見可能性について
Your identity in NOSTR is tied to your keys, but your information needs to be shared and found across a network of relays. To promote decentralization and censorship resistance, relays need to be easy to setup, lightweight, and sustainable. Relays get to choose what information passes through them, so they are also a form of spam prevention that could potentially also become censoring, so both the relay-runners and the individuals connecting to relays need to have choice and policies cannot be homogenous one-size-fits-all. What are possible solutions to make setting up relays easier, to make running a relay sustainable, to have new ways of discovering information...
Nostr での ID はキーに関連付けられていますが、その情報はリレーのネットワーク全体で共有され、検索できる必要があります。 分散化と検閲耐性を促進するために、リレーはセットアップが簡単で、軽量で、持続可能である必要があります。 リレーは通過する情報を選択できるため、スパム防止の一形態である一方で検閲にもなり得ます。そのため、リレー管理者とリレーに接続する個人の両方に選択権が必要で、ポリシーが全てに対し画一的になってはいけません。 リレーのセットアップを容易にし、リレーの実行を持続可能にし、情報を発見する新しい方法を実現するには、どのような解決策が考えられるでしょうか...?
Buidl tools to connect to Git, as a decentralized alternative to GitHub
GitHub の分散型代替手段として、Git に接続するための BUIDL ツール
Media Uploads
To keep relays lightweight, images are hosted by uploading them to the web, and keeping only the links to them in the data within individual nostr notes. This has led to developing image uploading services specific to nostr, but they carry the risk of centralization or censorship. Some product makers and relay runners are looking into direct uploads to Cloud services. What are possible solutions to the handling of media (images, videos, music...)?
リレーを軽量に保つために、画像は Web にアップロードしてホストされ、各投稿のデータには画像へのリンクのみが保持されます。そんな中で、Nostr に特化した画像アップロード サービスが開発されましたが、集中化や検閲のリスクが伴います。 一部のプロダクト開発者やリレー管理者は、クラウド サービスへの直接アップロードを検討しています。 メディア(画像、ビデオ、音楽など)の処理について、考えられるよい解決策はありますか?
Social Signals
People have the choice to block and mute others, this gives signals to relays, which can reenact policies based on those and other signals. Relays need to be able to differentiate real signals from those wanting to game the system for censorship. Relay runners need to have the capacity to make decisions on what to allow or reject.
ユーザーは他のユーザーをブロックしたりミュートできます。ユーザーの設定内容はリレーに送信され、リレーはその設定に基づいてそれぞれのポリシーを再現できます。 リレーは、実際の設定と、検閲のためにシステムを操作しようとする設定を区別する必要があります。 リレーの管理者には、何を許可し、何を拒否するかを決定する能力が必要です。
Track 2 : Marketplaces & Value4Value
Make freedom of exchange fun again! Nostr extends beyond social. It is integrating ways for content creators to be supported through lightning micropayments, called zaps, for their creations. The possibilities of building niche value4value economies through the exchange of products, services, and ideas, is growing through various avenues: Marketplaces, fundraising, blogs, music, streaming... devise new robust ways of integrating NOSTR and Bitcoin of monetary and skill exchange. Seek to explore distributed, digital reciprocity and free trade. Encourage a culture of value4value.
自由な交流を再び楽しく! Nostr はソーシャルを超えて広がります。 Zap と呼ばれるマイクロペイメントを通じて、コンテンツクリエイターの作品をサポートできる方法を兼ね備えています。 製品、サービス、アイデアの交換を通じてニッチな価値と価値(value4value)の経済を構築する可能性は、さまざまな手段を通じて拡大しています : マーケットプレイス、資金調達、ブログ、音楽、ストリーミングなど... Nostr とビットコインを組み合わせて、金銭とスキルの交換を行う新しい堅牢な方法を考案します。分散型、デジタル相互主義、自由貿易を探究してください。 価値対価値(value4value)の文化を促進してください。
A value4value culture is not only about the individuals using NOSTR products and services, but also about the developers and creatives building sustainable projects. What are ways of sustaining NOSTR through Bitcoin that do NOT make the individual user the product and that are privacy mindful?
value4value の文化は、Nostr の製品やサービスを使用する個人だけでなく、持続可能なプロジェクトを構築する開発者やクリエイターにも関係します。 個人ユーザーを製品にすることなくプライバシーに配慮しながら、ビットコインを通じて Nostr を持続させる方法は何ですか?
Possibilities...
On Social and Economic Signals
Zaps
Many nostr clients have implemented lightning zap payments. Imagine instead of liking a nostr note, you can zap someone's note and they can receive bits/sats in appreciation for their content. It is a strong signal to creators of the kind of content their audiences are looking for. The Apple App Store has recently banned the zapping of specific notes, per Apple's policy that makes the sale of digital content prohibited except when paid through their services. Fortunately, Nostr exists in many decentralized forms outside of app stores and the community is creating new and innovative ways to send bitcoin and free speech from relay to relay, circumventing barriers as they appear. What are solutions that can make NOSTR and zaps ubiquitous?
多くの Nostr クライアントが Zap を導入しています。Nostr での投稿を「いいね」する代わりに Zap すると、その内容に対する感謝としてビットコイン(サトシ)を受け取ることができるイメージです。 これは、フォロワーがどのような種類のコンテンツを求めているかをクリエイターに伝える強力なシグナルになります。 Apple App Storeは最近、サービスを通じて支払われる場合を除きデジタルコンテンツの販売を禁止するというAppleのポリシーに従い、特定の投稿への Zap を禁止しました。 幸い、Nostr は多くが App Store の外で分散型で存在しているため、コミュニティは障壁を回避しながら、ビットコインと言論の自由をリレーからリレーに送信するための革新的な方法を生み出しています。 Nostr と Zaps をユビキタスにするソリューションとは何ですか?
Track 3 : Empower Communities
Give choice and control back to the individual! Create paths forward to help onboard millions of new users and restore free and uncensored speech to the world
選択とコントロールを個人に返そう。 何百万人もの新規ユーザーの参加を支援し、自由で検閲されていない言論を世界に取り戻すための道筋を作り出してください。
Possibilities...
On Security, Privacy & Self-Custody
Private Communication
Direct Messages on NOSTR are encrypted, but metadata is leaked. If someone's key is compromised, whoever has access to that account can read those messages. Integrating secure and reliable encrypted communication protocols, like the SimpleX messaging protocol, is especially desired by the community, as many in Nostr are aware of the risks of surveillance, authoritarianism, government and Big Tech overreach... Private communication is important for individual rights, in particular for activists and journalists across the globe.
Nostr のダイレクト メッセージは暗号化されていますが、メタデータは漏洩します。 誰かのキーが侵害された場合、そのアカウントにアクセスできる人は誰でもそれらのメッセージを読むことができてしまうのです。Nostr の多くの人が監視、権威主義、政府とビッグテックの行き過ぎのリスクを認識しているため、 SimpleX メッセージング プロトコルのような安全で信頼性の高い暗号化通信プロトコルの統合が、コミュニティによって特に望まれています...プライベート通信は個人の権利にとって重要です 、特に世界中の活動家やジャーナリストにとって。
Zaps & Privacy
Current lightning zap payments tend to be custodial and not mindful of privacy, though they are helping onboard people unto lightning. What are ways that people can grow into non-custodial solutions? A wider adoption of Bolt-12 would improve zap payment privacy, what are ways to encourage that development? What are other possible solutions?
現在のザップの支払いは、ライトニングペイメントに出会うのに役立っているものの、カストディアル(管理的)でプライバシーに配慮していない傾向にあります。 ノンカストディアル(非監護的)なものになるよう解決する方法はありませんか? Bolt-12 が広く採用されれば、Zap 支払いのプライバシーが向上しますが、その開発を促進するにはどのような方法がありますか?また、他に考えられる解決策はありませんか?
Closing Live 3-Day Sprint at the Nostrasia Conference
Nostrasia Tokyo 3日間のライブスプリントによる締めくくり
Tokyo | Nov 1-3 (you can also join virtually)
If you heard of the Nostrica unconference, which happened in Costa Rica in March of this year, Nostrasia is the second Nostr World conference, bringing NOSTR and Bitcoin awareness to the heart of Asia, where freedom communication and freedom money are direly needed.
今年の3月にコスタリカで開催された Nostrica のことをご存知の方もいると思いますが、ノストラジアは2回目の Nostr 世界カンファレンスです。自由なコミュニケーションと自由なお金が切実に必要とされているアジアの中心にNostr とビットコインの認識をもたらします。
Tokyo and Hong Kong are beautiful cultural hubs with budding Nostr and thriving Bitcoin communities of their own. We are eager to spread NOSTR education and development in those regions and beyond. We will close this Nostrasia month-long hackathon with a 3-day sprint at the Nostrasia Conference in Tokyo.
東京と香港は、新進気鋭のNostrと繁栄する独自のビットコインコミュニティを持つ美しい文化の中心地です。 私たちは、Nostr の教育と開発をこれらの地域やその他の地域に広めることに熱心に取り組んでいます。 この Nostrasia の 1 か月にわたるハッカソンは、Nostrasia Tokyo での 3 日間のスプリントをもって終了します。
We will have a dedicated workshop area and food for you to hack away on the final details of your projects. On the last day of the conference, the most robust projects will get time on stage to present. We will close the Nostrasia Hackathon with a special presentation.
プロジェクトの最終的な詳細を検討するための専用のワークショップ エリアと食事をご用意します。 カンファレンスの最終日には、最も強力なプロジェクトがステージ上でプレゼンテーションを行う時間が与えられます。 Nostrasia Hackathon は特別なプレゼンテーションで締めくくられます。
We cannot wait to see what new and exciting projects are proposed for the Nostrasia Hackathon. We’re eager to welcome devs and non-devs alike to contribute to this space and help #grownostr in any small way to help onboard Asia, and the rest of the world to this robust open communication protocol and decentralized freedom of speech tool.
Nostrasia Hackathon ではどんな斬新でエキサイティングなプロジェクトが提案されるのか楽しみです。 私たちは、開発者も非開発者も同様にこの分野に貢献し、アジアやその他の世界をこの堅牢なオープン通信プロトコルと分散型言論の自由ツールに参加させるために、どんな小さな方法でも #grownostr を支援してくれることを心から歓迎しています。
-
 @ 57d1a264:69f1fee1
2024-03-07 07:49:34
@ 57d1a264:69f1fee1
2024-03-07 07:49:34What's got you buzzing with excitement, and which trends are you ready to cheers?
Share your insights and learnings!
-
 @ 3824d96c:68b8f9dc
2024-03-05 17:06:53
@ 3824d96c:68b8f9dc
2024-03-05 17:06:53There is nothing worse than the kind of people that like to do things the easy way, those are the ones who eventually are going to destroy the world.
People like to be free but don't like to hold responsibility over their lives. That's the reason they prefer to let their money on banks, fake investments and trust in the gorvenment for almost every aspect of their life.
I don't like that. We are hardcore. We, the cypherpunks, the hackers and the bitcoiners, we like to know and to carry the responsibility over things that are important to us. That's evident in one of our strongest slogans: don't trust, verify.
Letting the responsibility of some of the most important things in your life, your money, your privacy, your children and so on, on the hands of others is admitting those things are actually not that important for you.
We are hardcore.
We use technology the way it is suposed to, we know how to take care of our money, how to educate our children and pretty we are willing to learn and work for the protection of the things most important to us.
Everyone who does not takes responsibility and desires freedom is not worthy of my time.
Keep doing things, keep pushing forward.
Per aspera ad astra.
-
 @ fa0165a0:03397073
2023-07-24 10:19:27
@ fa0165a0:03397073
2023-07-24 10:19:27Below is an easy-to-read list of keyboard shortcuts and commands to navigate your Linux computer efficiently: (Note that some variations between systems may apply)
General Shortcuts: Open Terminal: Ctrl + Alt + T Close current application: Alt + F4 Switch between open applications: Alt + Tab Logout from current session: Ctrl + Alt + Del Navigating the File System: Open File Manager (Nautilus): Super (Windows key) + E Move back in directory: Alt + Left Arrow Move forward in directory: Alt + Right Arrow Go to Home directory: Ctrl + H Go to Desktop: Ctrl + D Open a folder or file: Enter Rename a file or folder: F2 Copy selected item: Ctrl + C Cut selected item: Ctrl + X Paste copied/cut item: Ctrl + V Delete selected item: Delete Create a new folder: Ctrl + Shift + N Navigating Applications: Switch between open windows of the same application: Alt + ` Close the current window: Ctrl + W Minimize the current window: Ctrl + M Maximize/Restore the current window: Ctrl + Super + Up Arrow / Down Arrow Navigating Web Browsers (e.g., Firefox, Chrome): Open a new tab: Ctrl + T Close the current tab: Ctrl + W Switch to the next tab: Ctrl + Tab Switch to the previous tab: Ctrl + Shift + Tab Open a link in a new tab: Ctrl + Left Click Go back in the browser history: Alt + Left Arrow Go forward in the browser history: Alt + Right Arrow System Controls: Lock the screen: Ctrl + Alt + L Open the system menu (context menu): Menu key (or Right-click key) or Shift + F10 Open the Run Command prompt: Alt + F2These shortcuts may vary slightly depending on the Linux distribution and desktop environment you are using. Experiment with these shortcuts to navigate your Linux system faster and more efficiently without relying on the mouse.
Since websites are such an important interface for the information of today, I have here appended the list with some navigational hotkeys for web browsers (e.g., Firefox, Chrome) on Linux:
General Navigation: Scroll down: Spacebar Scroll up: Shift + Spacebar Scroll horizontally: Hold Shift and scroll with the mouse wheel or arrow keys Go to the top of the page: Home Go to the bottom of the page: End Refresh the page: F5 or Ctrl + R Stop loading the page: Esc Link and Page Navigation: Move focus to the next link or interactive element: Tab Move focus to the previous link or interactive element: Shift + Tab Activate/follow a link or button: Enter Open link in a new tab: Ctrl + Enter (Cmd + Enter on macOS) Open link in a new background tab: Ctrl + Shift + Enter (Cmd + Shift + Enter on macOS) Open link in a new window: Shift + Enter Go back to the previous page: Backspace or Alt + Left Arrow Go forward to the next page: Alt + Right Arrow Searching: Find text on the page: Ctrl + F Find next occurrence: Ctrl + G Find previous occurrence: Ctrl + Shift + G Tab Management: Open a new tab: Ctrl + T Close the current tab: Ctrl + W Reopen the last closed tab: Ctrl + Shift + T Switch to the next tab: Ctrl + Tab Switch to the previous tab: Ctrl + Shift + Tab Switch to a specific tab (numbered from left to right): Ctrl + [1-8] Switch to the last tab: Ctrl + 9 Form Interaction: Move to the next form field: Tab Move to the previous form field: Shift + Tab Check/uncheck checkboxes and radio buttons: Spacebar Select an option from a dropdown menu: Enter, then arrow keys to navigate options Miscellaneous: Open the browser's menu: Alt (sometimes F10) Open the address bar (omnibox): Ctrl + L or Alt + DRemember, the accessibility of websites can vary, and some sites might have different keyboard navigation implementations. In some cases, you may need to enable keyboard navigation in the browser's settings or extensions. Additionally, browser updates might introduce changes to keyboard shortcuts, so it's always good to check the latest documentation or help resources for your specific browser version.
But I hope this helps as an tldr and getting started with navigating your laptop the ways pro role.
Version controlled over at github gist.
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 5b0e8da6:7792bc54
2024-03-05 15:57:43
@ 5b0e8da6:7792bc54
2024-03-05 15:57:43I recently completed my home 7.1.4 speaker setup and have been really enjoying digging into high-end Dolby Atmos and Dolby Vision material. Playing around with nip23 long-form content to share this kind of niche nerd stuff that doesn't quite make sense as a regular nostr note.

tldr: Still a joy, though much of its intentional over-the-top ridiculousness is just too much for me now. The absolute trash 4k transfer is a tragedy.
The movie
I'm fairly sad to report that I just couldn't enjoy the first hour or so anymore. More and more of the movie's creative absurdity that I previously loved is souring to cringe.
The bulky, waddling alien designs in the intro sequence are just pointlessly dumb.
The savage lampooning of an American-style government — from the casting of a President who looks and sounds like an NFL lineman to all the stupid and/or war-hungry military leaders — I'm sure is hilarious to the French creative team (and, sure, somewhat deserved), but it's just so blunt and caveman-y and insulting. I'm not interested in defending America's honor, but this is just so dumb and cruel in its way that it's unpleasant to watch.
Gary Oldman is, as always, a powerhouse. But when you direct him to go big with the campiness, it's... it's a lot.
Things improve once Leeloo starts to take over the story. And, maybe this is a surpise given the above, but Chris Tucker's how-do-you-even-describe-it Ruby Rhod is still a shockingly successful, brain-breaking spectacle. Happy to report that the Fhloston Paradise set piece is still a gem and is where all the unique absurd energy truly finds its groove.
Overall, I think the movie still works. Luc Besson is unapologetically asking us to YOLO into this crazy world. It's experimental in a idgaf way but he does real work to layer in an appealing emotional core between Corben and Leeloo. It does all somehow come together and ultimately works surprisingly, uniquely well — if you can get past the first hour.
Video
https://i.nostr.build/0ren.jpg
Just straight trash.
Sidebar: On image processing / contrast
Our eyes want strong contrast in images. You might complain that this pic is just a little too muted:
https://i.nostr.build/8Y9J.jpg
But once you start tinkering, it can be very easy to way overshoot the mark:
https://i.nostr.build/jQAr.jpg
Some of you may think, "Uh, I prefer the boosted version." Yes, it's more lively to our eyes, certain things are so much more emphasized now that you can appreciate those details more. But then look at the highlights. They're so boosted that details have disappeared into full white. Same for the shadows. Crushed to pure black.
The art is to dial in just the right amount of contrast boost without blowing out the highs or crushing the lows. And there's just an overall harshness where there had previously been subtle gradations of color and texture. The more you work with image processing, the more you appreciate a lighter touch.
Here's another set:
https://i.nostr.build/lBRA.jpg
https://i.nostr.build/P94W.jpg
This was a lower quality image to start with (cellphone cam vs DSLR) and then overjuiced so hard that it's lost any semblance of the natural world.
Back to the trash "The Fifth Element" video transfer
The 4k transfer is similarly overjuiced everywhere. It's hideous. My cellphone photos of the HDR screen are in no way accurate, but even still some of the flaws are entirely evident.
https://i.nostr.build/A6GR.jpg
Harsh over-contrasty processing. Color saturation similarly overjuiced.
There are lots of dark areas in this image, but if we boost those levels, we see that there's NO information in the shadows. Once you crush shadows to black, no amount of brightening can bring back those details.
https://i.nostr.build/z9LM.jpg
Ruby Rhod's hair and black dress are just (0,0,0) pixels.
A good transfer would still provide strong contrast where it's called for, but would preserve the subtleties, some details even in the shadows and highlights. A good transfer paints with up to the full 1 billion available colors. This transfer clumsily, bluntly limits itself to a box of 32 crayons.
View this one full-screen:
https://i.nostr.build/P9A6.jpg
Just harshness everywhere.
There's also way too much sharpening applied which adds to the harshness and over-accentuates the natural film grain.
I'm not the only one who hates this transfer.
It's noisy and harsh [...] I think a lot of people would be surprised at how artificial Sony's remaster would look compared to an untampered presentation. (link)
There’s no positives that I can mention in regards to Sony’s efforts on The Fifth Element. It may be the single most artificially sharpened UHD. You can literally use the screen as a cheese grater. And the color grade is completely off from 35mm. (link)
There's a better option
Weirdly, there's an alternate 4k disc that was published in the UK by Studiocanal that is said to be a vastly superior transfer.
https://i.nostr.build/0r4M.jpg
The 4k disc is region-free, so even though it's a UK disc, it'll play fine in any 4k blu-ray player.
It's currently $28 on amazon but, given my lessening admiration for the movie (at least the first hour), I'm not interested in double-dipping and spending more money to get this version.
Audio
Nice that it has a Dolby Atmos mix but I think I was too distracted by the horrible visuals to do any kind of critical listening. But for any movie this old (1997), the quality of the original sound elements will always be an obvious limiting factor.
-
 @ aa55a479:f7598935
2023-07-19 17:54:44
@ aa55a479:f7598935
2023-07-19 17:54:44Test
-
 @ 78733875:4eb851f2
2023-07-14 22:25:21
@ 78733875:4eb851f2
2023-07-14 22:25:21"The computer can be used as a tool to liberate and protect people, rather than to control them," as Hal Finney wrote so presciently 30 years ago.[^fn-hal]
The goal of OpenSats is to help build the tools that Hal alluded to. Tools that liberate and protect, rather than systems that control and oppress. Many tools still have to be built. Many tools still need to be improved. However, "the universe smiles on encryption," as Assange so aptly put it.[^fn-assange]
We believe that freedom tech is what carries this smile forward, which is why we are delighted to announce grants for over a dozen projects in the bitcoin & lightning ecosystem.
[^fn-hal]: Hal Finney: Why remailers... (November 1992)
[^fn-assange]: Julian Assange: A Call to Cryptographic Arms (October 2012)
The following open-source projects were selected by the OpenSats board for funding:
- Payjoin Dev Kit
- Bolt12 for LND
- Splicing
- Raspiblitz
- Labelbase
- BTCPay Server
- ZeroSync
- Mutiny Wallet
- next-auth Lightning Provider
- Cashu
- lnproxy
- Blixt Wallet
Let's take a closer look at each to understand their goal and how it aligns with the OpenSats mission.
Payjoin Dev Kit
Payjoin brings privacy to bitcoin without changing the way you're used to using it. Payjoin transactions look no different from normal activity on-chain, so they boost everyone's privacy, even those who don't payjoin, and foil chain surveillance.
Payjoin is easy to integrate and falls back to working defaults where it isn't supported, but it can only take off when senders and receivers include standard payjoin support in their software. Payjoin Dev Kit makes it easy for wallet developers to integrate BIP 78 standard payjoins everywhere, having working reference integrations for Bitcoin Core, LND, and BDK.
Repository: github.com/payjoin
License: MITBolt12 for LND
Bolt12 brings a new invoice format, enabling static invoices (offers) as well as recurring payments. It adds support to receive payments in a lightning-native way without using a web server. It also uses Blinded Paths to disguise the destination of a node both when fetching the invoice and when paying. This improves privacy and, therefore, security for the receiver of the payment.
Consequently, Bolt12 makes it much easier to receive and send payments without any third-party infrastructure in a native-lightning way. Static invoices make donations and recurring payments much easier.
Repository: lightningnetwork/lnd
License: MITSplicing
Splicing is the ability to resize Lightning channels on-the-fly, giving users of the Lightning Network many additional benefits that were not intuitively obvious at first. Splicing scales Lightning by removing a fundamental limitation. Removing this limitation increases fungibility and lowers blockspace usage, an important step towards maturing the Lightning network and enabling the onboarding of millions, and ultimately billions, of people.
Repository: ddustin/splice
License: BSD-MITRaspiblitz
Raspiblitz is a do-it-yourself node stack that allows you to run a Lightning Node together with a Bitcoin Core full node on your Raspberry Pi. While the Raspberry Pi is the most common hardware running this particular software, it was developed to support multiple hardware platforms and can run on bare metal servers too.
The open-source project was started in 2018 as part of a Lightning hackathon in the German Bitcoin space. Since then, it has grown to over 150 contributors and 2000 stars on GitHub. The software integrates dozens of services and tools via its plugin system and sports advanced features like touchscreen support, channel autopilot, backup systems, DynDNS, SSH tunneling, and more.
Repository: raspiblitz/raspiblitz
License: MITLabelbase
Labelbase is a label management service for Bitcoin transactions and addresses. It provides features for adding labels, importing and exporting labels, and offers a public API for integration with wallets and existing workflows.
Labelbase supports BIP-329, a format for unifying label data. The goal of the project is to offer a convenient solution for managing labels associated with Bitcoin transactions and addresses across wallets and other tools. By providing a unified label management interface, Labelbase enhances the user experience, improves privacy, and promotes better organization and understanding of Bitcoin transactions.
Repository: Labelbase/Labelbase
License: MITBTCPay Server
BTCPay Server is a free, open-source & self-hosted bitcoin payment gateway that allows self-sovereign individuals and businesses to accept bitcoin payments online or in person without added fees.
At its core, BTCPay Server is an automated invoicing system. Merchants can integrate the software with their website or shop, so customers are presented with an invoice upon checkout. The status of the invoice will update according to settlement, so merchants can fulfill the order at the appropriate time. The software also takes care of payment refunding and bitcoin management alongside many other features.
Repository: btcpayserver/btcpayserver
License: MITZeroSync
While ZeroSync is still at an early stage, its promise is to allow verification of Bitcoin's chain state in an instant. It offers compact cryptographic proofs to validate the entire history of transactions and everyone's current balances.
The first application is to "zerosync" Bitcoin Core in pruned mode. The long-term vision for ZeroSync is to become a toolbox for custom Bitcoin proofs.
Repository: zerosync/zerosync
License: MITMutiny Wallet
Mutiny Wallet is a web-first wallet capable of running anywhere, providing instant onboarding and platform censorship resistance. It is self-custodial, privacy-focused, user-friendly, and open-sourced under the MIT license.
The wallet has a strong focus on privacy, scalability, and accessibility. In addition to features that you would expect a regular lightning wallet to have, the team is working to incorporate Nostr-related features into the wallet, such as a feed of friends' Zaps, native Zap sending and receiving, a lightning subscription specification for services such as nostr relays, and a P2P DLC marketplace. The team's goal is to provide users with a seamless experience, combining the power of Bitcoin and Lightning with social media in a way that matches the Bitcoin ethos.
Repository: MutinyWallet
License: MITnext-auth Lightning Provider
The goal of this project is to implement an authentication provider for next-auth, an authentication provider for the popular open-source framework NextJS. The next-auth framework has nearly 500k weekly downloads and powers the authentication of many modern web, mobile, and desktop apps. Having a plug-and-play Provider for Lightning makes integration easier and more attractive for developers.
Repository: jowo-io/next-auth-lightning-provider
License: ISCCashu
Cashu is a Chaumian ecash system built for bitcoin that brings near-perfect privacy for users of custodial bitcoin applications. A Cashu ecash mint does not know who you are, what your balance is, or who you're transacting with. Users of a mint can exchange ecash privately, without anyone being able to know who the involved parties are.
Payments are executed without anyone able to censor specific users. There are multiple implementations of the Cashu protocol. Popular open-source wallets are Cashu Nutshell, Cashu.me, and Nutstash.
Repository: cashubtc/cashu
License: MITlnproxy
lnproxy is a simple privacy tool that empowers users of custodial Lightning wallets with better payment destination privacy and sovereign node runners with enhanced receiver privacy. lnproxy works like a "poor man's" rendezvous router, providing privacy for users without taking custody of their funds. The project encompasses an LNURL-style protocol specification and a collection of open-source implementations of lnproxy clients and a relay.
Repository: lnproxy/lnproxy
License: GPL 3.0 & MITBlixt Wallet
Blixt is a non-custodial wallet for bitcoiners who want to give Lightning a try. It runs on Android, iOS, and macOS. It is easy to use and straightforward to set up, making it a user-friendly option to get started with Lightning.
Blixt uses LND and Neutrino under the hood, directly on the phone, respecting your privacy. The wallet does not use any centralized servers for doing transactions. Channels are opened automatically on the user's behalf, making it easy to get up and running on Lightning.
Repository: hsjoberg/blixt-wallet
License: MIT
In addition to the software projects listed above, three educational initiatives were selected for funding:
- Bitcoin Education in Nigeria is an initiative started and led by Apata Johnson. Apata's project aims to educate youths on bitcoin and the opportunities it brings for the people living in the rural areas of Nigeria.
- 21 Ideas is a project that aims to bring quality Bitcoin education to Russian citizens. Tony and others have been working for many years on translations, original material, and hands-on tutorials for beginners. We believe that education is paramount to proper Bitcoin use, and localization is paramount for everyday citizens to properly grasp the importance as well as the novel concepts of bitcoin.
- CoreDev.tech is organizing recurring developer events, which are all about bringing devs together so that they can hack on Bitcoin Core and related software.
We received hundreds of applications in the last couple of months, which is a fantastic signal and something we are delighted about. Some applications are still being reviewed by the OpenSats board, as we try our best to assess feasibility, alignment, and potential impact of each project. We will announce additional grants as applications pass our grant selection process.
Unfortunately, we were unable to fund all of the proposals that were sent to us. Please don't hesitate to apply again in case your application was rejected this time around. The applicant pool was very competitive, which is a great thing to see in and of itself.
Grants for the projects above are funded by contributions to the Bitcoin General Fund. Our operations as well as our grant programs are made possible by generous donors like you. If you want to help fund the Bitcoin ecosystem, please donate to the Bitcoin General Fund.
Our team is screening applications constantly, and we will announce new grants and funding opportunities as they arise. If you are working on an open-source project in and around bitcoin, and you think your work is aligned with the OpenSats mission, please apply for funding.
-
 @ dffd3ffc:5ade7be1
2024-03-07 04:00:29
@ dffd3ffc:5ade7be1
2024-03-07 04:00:29[3]
[4]
[5]
[6]
[7]
[8]
-
 @ a10260a2:caa23e3e
2023-08-14 21:36:14
@ a10260a2:caa23e3e
2023-08-14 21:36:14It seems like blogstack is meant to replace Substack if not already apparent by the name. If that's the case, it's already better in a few ways.
1. Hit the ground running
I'm already getting started out of the gate with more readers than I would have if I just started a Substack. This, of course, is due to the fact that I'm creating on top of a protocol where I'm able to have the same audience across all clients of that protocol. This is in stark contrast to the legacy apps from centralized entities where you have to corral your audience from one platform to the next.
2. Readers need not subscribe
Technically, if you're following me, you're subscribed. But you don't have to subscribe for a set price and amount of time (e.g. $5/month or $50/year). I believe this is a win for both of us as I can write my best notes and you can choose to reward me as you see fit. Value 4 value.
3. More conducive to conversation
Writing on Substack felt like writing into a void, with little to no feedback. A post shows up in my readers' inbox and I'll see some stats on whether it was opened or not. That's it. Based on what I've seen so far, blog posts created on Nostr appear in the client apps (e.g Damus, Primal, and Plebstr) as just another note, but with nice formatting and such. From there, I can receive zaps, shakas, comments, and even be reposted.
This is just the beginning. Right now, I'm using blogstack. But what's to stop me from using another tool down the line? I'll have the ability to do so by simply connecting my private key. Can't wait to see what new tools are created down the line.
So ₿ULLISH on #Nostr
-
 @ 78733875:4eb851f2
2023-07-07 22:06:45
@ 78733875:4eb851f2
2023-07-07 22:06:45The mission of OpenSats is to support and maintain a sustainable ecosystem of funding for free and open-source projects that help Bitcoin flourish. Nostr is such a project, which is why OpenSats introduced The Nostr Fund and built a team around the protocol's originator to help fund the growing nostr ecosystem. As an open, interoperable, and censorship-resistant protocol, nostr has the chance of doing social-native networking right.
After weeks of sorting through applications, we are excited to announce the first round of grants from The Nostr Fund. OpenSats is proud to support over a dozen projects, from clients to relay implementations to adjacent tools and design efforts.
In no particular order, here they are:
- NDK by @pablof7z
- Habla by @verbiricha
- Coracle by @hodlbod
- Iris by @mmalmi
- Damus by @jb55
- rust-nostr & nostr-sdk by @yukibtc
- Nostr Relay NestJS by @CodyTseng
- Soapbox by @alexgleason
- Code Collaboration over Nostr by @DanConwayDev
- Satellite by @lovvtide
- Amethyst by @vitorpamplona
- Pinstr by @sepehr-safari
- nostr.build by @nostr.build
- Gossip by @mikedilger
- Nostr SDK iOS by @bryanmontz
- Nostr Design by @karnage
The projects above have received grants of various durations and sizes, and we have more nostr-related applications in the pipeline. Donate to The Nostr Fund if you want to help fund the nostr ecosystem.
Without further ado, let's take a closer look at each project in turn.
NDK
NDK is a nostr development kit that makes the experience of building Nostr-related applications—whether they are relays, clients, or anything in between—better, more reliable, and overall more enjoyable to work with than existing solutions. The core goal of NDK is to improve the decentralization of Nostr via intelligent conventions and data discovery features without depending on any one central point of coordination, such as large relays or centralized search providers.
Repository: nostr-dev-kit/ndk
License: MITHabla
Habla is a website for reading, writing, curating, and monetizing long-form content on nostr. It uses NIP-23 to allow markdown-formatted articles and embedded nostr content such as notes, profiles, lists, relays, badges, and more. The goal of Habla is to give everyone an alternative to centralized publishing platforms such as Medium or Substack, which are by their very nature prone to censorship and deplatforming.
Repository: verbiricha/habla.news
License: GNU GPL v3.0Coracle
Coracle is a nostr web client focusing on user experience, performance, and scaling of the nostr network beyond the "twitter clone" use-case. The end goal is to build marketplaces, groups, chat, and more on top of an emergent web of trust. Coracle is already one of the most mature and accessible clients for new users while also providing some novel features for more advanced nostriches.
Repository: coracle-social/coracle
License: MITIris
Iris is a multi-platform nostr client that is available for web, mobile, and desktop. Iris' design goals are speed, reliability, and ease of use. The client features public as well as private messaging, customizable feeds, an offline mode, and speedy account creation.
Repository: irislib/iris-messenger
License: MITDamus
Damus is a cutting-edge nostr client for iOS. The goal of Damus is to integrate bitcoin with social media and to show the power, censorship resistance, and scalability of nostr in general. Damus includes picture and video uploading, is fully translated into 24 languages, supports automatic translation of notes, and includes all of the features you would expect from a Twitter-like client.
Repository: damus-io/damus
License: GNU GPL v3.0rust-nostr & nostr-sdk
Rust-nostr is a Rust implementation of the nostr protocol. It is a high-level client library with the explicit goal to help developers build nostr apps for desktop, web, and mobile that are both fast and secure. Rust crates can be easily embedded inside other development environments like Swift, Kotlin, Python, and JavaScript, making rust-nostr a versatile base to build upon. While the project is in the early stages of development, over 35 NIPs are already supported, with more to come.
Repository: rust-nostr/nostr
License: MITNostr Relay NestJS
Nostr-relay-nestjs is a Nostr relay with a clear structure that is easy to customize to your needs. This relay implementation is based on the NestJS framework and focuses on reliability and high test coverage.
Repository: CodyTseng/nostr-relay-nestjs
License: MITSoapbox
Soapbox started out as an alternative to Mastodon but has grown to encompass ActivityPub and nostr while being interoperable with both. In February 2023, the team launched the "Mostr" bridge, seamlessly connecting nostr to the ActivityPub Fediverse and enabling bidirectional communication between both protocols. This bridge exposes over 9.4M potential users in nostr's target audience to nostr, many of whom have already left the Fediverse completely in favor of nostr.
Repository: gitlab.com/soapbox-pub
License: GNU Affero General Public License v3.0Code Collaboration over Nostr
This project is a proof-of-concept for a much-needed, often discussed, and permissionless, nostr-based GitHub alternative. The goal is to replace the traditional interactions using a centralized server or service with a nostr-based alternative centered around nostr events. Commits, branches, pull requests, and other actions are all modeled as nostr events, with permissions managed through groups so that multiple maintainers can manage a repository. This model reduces the barriers for clients to support repository collaboration and allows for interoperability between repository management tools.
Repository: DanConwayDev/ngit-cli
License: MITSatellite
satellite.earth is a web client for nostr that has a community focus and presents conversations as threaded comments, borrowing from the traditional Reddit interface.
Repository: lovvtide/satellite-web
License: MITAmethyst
Amethyst is one of the most popular nostr clients for Android. Amethyst comes with expected features such as account management, feeds, profiles, and direct messages. Amethyst also offers native image uploads, public chat groups, link previews, one-tap zaps, public and private bookmarks, as well as the ability to follow hashtags, and other novel features. You can install releases of Amethyst via F-Droid or Google Play.
Repository: vitorpamplona/amethyst
License: MITPinstr
Pinstr allows users to easily organize and discover new ideas by creating public boards of pins. Users can star, comment, and zap other users' boards. Users can find curated boards of other users and create boards themselves. Default boards include users' bookmarked content, among other lists.
Repository: sepehr-safari/pinstr
License: MITnostr.build
Nostr.build is a free-to-use media hosting service that allows users to upload images, gifs, videos, and audio files to share them as nostr events. The team recently released their code under an MIT License so that anyone might use the software to offer a similar service.
Repository: nostrbuild/nostr.build
License: MITGossip
Gossip is a fast and stable desktop nostr client focused on the Twitter-like micro-blogging aspect of nostr. Gossip follows people by downloading their events from whichever relays they post to (rather than relays you configure) and was the impetus for NIP-65. It does not use complex web technologies such as JavaScript or HTML rendering and stores your private key only in an encrypted format. Consequently, Gossip is considered more secure than other clients by some. The client is packaged and released for Linux, Windows, and MacOS.
Repository: mikedilger/gossip
License: MITNostr SDK iOS
The nostr SDK for iOS is a native Swift library that will enable developers to quickly and easily build nostr-based apps for Apple devices. The library plans to implement all approved NIPs and will follow Apple's API patterns, so that iOS developers feel comfortable using it from the start. The SDK aims to be simple in its public interface, abstracting away as much complexity as possible so that developers can focus on what makes their specific application unique.
Repository: nostr-sdk/nostr-sdk-ios
License: MITNostr Design
Nostr Design will be a comprehensive resource for designers and developers to build successful nostr products. Nostr introduces several new concepts that most people are not familiar with. Given its nature, the protocol presents some unique design challenges for developers and users alike. The Nostr Design efforts are led by Karnage, who has done stellar product design work around nostr in the past. We believe that this project has the potential to impact the entire nostr space, as it can act as a go-to source for developing quality products, addressing user needs, as well as providing concrete examples and building blocks for product designers and developers alike.
License: Public Domain, Creative Commons
We have received hundreds of applications in the last couple of weeks, many related to or exclusively focused on nostr. Most projects that applied focus on bitcoin and lightning. We will announce another wave of grants for these soon.
To all the nostr projects that applied and didn't make the cut this time around: don't be discouraged. Please apply for funding again in the future. We will announce new grants and funding opportunities quarterly, and there is always the possibility of being listed on the OpenSats website to receive pass-through donations for your project.
We are excited to support the projects above in building the tools we bitcoiners care so deeply about. The future is bright; we just have a lot of building to do.
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 7f5c2b4e:a818d75d
2024-03-05 15:40:04
@ 7f5c2b4e:a818d75d
2024-03-05 15:40:04Nsec.app is a Nostr application which lets you share access to your account and login to Nostr apps seamlessly with numerous devices.
The app is super useful when collaboratively running a Nostr account. It lets you generate tokens to share with partners or colleagues and provide different levels of access to different individuals.
Another bonus feature of nsec.app is letting you forget about Nostr browser extensions. Extensions have their fair share of useful features, but using nsec.app (or other apps that support NIP-46 login, e.g. nsecBunker) is often more convenient, arguably more secure and offers some features, that extensions aren't able to deliver.
Let's walk through the process of starting the nsec.app and see what features it has to offer.
Installation
Nsec.app is a PWA (see my short blog post on PWAs and their benefits here), meaning that it can be saved to your device in a way that it feels and acts like a native app. Alternatively the app can be used in the browser.
Visit Nsec.app:
https://i.nostr.build/axlP.png
After pressing the "Get started" button you'll be welcomed by three main options: "Sign up", "Login" or "Import Key". Let's explore each of these options:
- Sign up: This option suits those, who do not have a Nostr account yet. I'd steer clear from this option for now and create an account in a more "conventional" way – via one of the popular Nostr clients or by utilizing a dedicated browser extension.
Stay tuned as the developers are working on wide implementation of NIP49. At the moment few Nostr clients support NIP49, so you won't have many options of using keys created with nsec.app. When most Nostr apps support NIP49 logins, signing up to Nostr via nsec.app will become a more convenient option.
If you decide to utilize nsec.app to create your Nostr account, the process is super simple:
1) Choose your Nostr address 2) Create and confirm your password 3) Enjoy your new Nostr account 💜
https://i.nostr.build/JqgP.png
- Import key: This approach assumes you would like to start using nsec.app with the existing Nostr account.
https://i.nostr.build/5e9y.png
In this case you'll need to choose your username, provide your private key and choose a password. This will create the nsec.app account (by setting a username and a password) while binding it with your original Nostr account (by providing your private key).
It is worth noting that your keys will be encrypted by your password and stored on nsec.app's server to sync to other devices in end-to-end encrypted manner.
- Login: This approach assumes you've already set up nsec.app and would like to enter your dashboard from a new device.
https://i.nostr.build/k6aa.png
Do not forget to click the "Enable background service" tile after setting up your account. This will ensure you receive a notification whenever the request to authorize a login is created.
https://i.nostr.build/Zrdx.png
Usage
After setting up nsec.app you're ready to start utilizing it to login to numerous Nostr apps.
The most powerful feature of nsec.app is that it lets you login to apps without having to use the browser extension or exposing your private key.
For example, I can now turn Coracle client into a PWA on my iPhone, which is otherwise impossible, because Apple does not allow you to utilize browser extensions with PWAs.
Another use case is delegating the rights to interact with Nostr on behalf of the account you created.
Regardless of wether you want to use the app single-handedly, or delegate the private key, the process is as follows:
- Use nsec.app to create a login string by pressing "Connect app".
- Copy the string by pressing the corresponding button.
https://i.nostr.build/rvVB.png
- Paste the string into the client that you'd like to login to.
- As you (or your companion) try to login to the Nostr app, nsec.app will display a notification asking you (the administrator) to approve the login.
https://i.nostr.build/7x53.png
As you can see, there are two options for you to choose from:
- Basic permissions: This will approve all potential future interactions.
- On demand: This will log the user in and ask for your approvals every time the user tries to interact with the protocol in a new way (like, zap, follow, etc.)
That's it. You can now interact with nostr without ever having to utilize the browser extension or share your private key with any app.
Features
Customization
Nsec.app lets you customize the way your connected apps look. You can name them, specify a website address and choose an icon of your choice. Very handy functionality for when you start actively using the app:
https://i.nostr.build/ej6X.png
As the stack of connected apps grows this will help you distinguish between them in order to introduce any necessary changes.
https://i.nostr.build/XEgW.png
Connected apps management
This leads us to the next important part of using nsec.app: revoking access to apps. This is especially important when it comes to sharing access to account with someone else. In case you no longer plan to collaborate on the account, or you simply do not need some app connection to function any longer, you can revoke access at any time.
Just open the app you need and: (a) press "Delete app" (this completely cuts connection between your app and nsec.app) or (b) press the three dots next to the existing approved permission followed by "Delete permission" (this cancels the given permission, so that the next time you (or other user) tries to interact with the protocol, you will receive a notification asking you to approve their action).
https://i.nostr.build/d3QD.png
NIP49 logins
Nsec.app allows you to utilize another way of logging into Nostr apps – NIP49. We touched on this approach earlier, so let's explore how it works.
Here's an example with Noogle:
- Choose the Login with NCryptSec option:
https://i.nostr.build/DzeV.png
- Enter the encrypted Nsec (to be retrieved from the nsec.app in Settings -> Export) and the nsec.app password:
https://i.nostr.build/R505.png
That's it. You're logged in.
https://i.nostr.build/moLR.png
At the moment few clients support this NIP, but given the benefits of this functionality, it shouldn't be long before we see more and more clients join in.
Outro
Just like with every other Nostr app, there's a lot of work to be done. Nevertheless, nsec.app already solves many important problems, and is definitely worth your attention. Give it a try and let us know if you find any bugs, or come up with some ideas worth implementing. Feel free to ping myself or, better yet, the app developer nostr:npub1xdtducdnjerex88gkg2qk2atsdlqsyxqaag4h05jmcpyspqt30wscmntxy
Hope this guide was useful! If so, don't forget to zap this post 😉
See you on the other side of the Nostr rabbit hole
Tony⚡️
-
 @ 50809a53:e091f164
2024-03-05 12:33:57
@ 50809a53:e091f164
2024-03-05 12:33:57Chef's notes
Note 1. Aquafaba is just the liquid from a can of chickpeas. If you don’t have canned chickpeas or are allergic, use 2 flax eggs: mix 2 TBSP ground flaxseed meal with 5 TBSP water. Stir and let sit for 15 minutes to thicken. The banana bread won’t be as fluffy though.
Note 2: If using brown sugar, lightly pack it. If choosing between light and dark brown sugar, I like the dark variety for a deeper molasses flavor; the bread will be darker in color too. If you are limiting your sugar intake, you can use less sugar, as little as 1/4 cup (about 38g) with still pretty good results.
Note 3: Since this is a simple ingredient list, try to use real vanilla extract, not the imitation stuff, as you will taste the difference.
Note 4. If not using a measuring scale to weigh ingredients, please spoon and level your flour so you don’t overmeasure. More info in the Tips section of the blog post.
Note 5: Don’t just insert a toothpick vertically down into the bread. Instead, insert it at an angle, which is a much better test for doneness in a tall cake.
Details
- 🍳 Cook time: 50 min
- 🍽️ Servings: 10
Ingredients
- 6 tablespoons (90 mL) aquafaba (see Note 1)
- 3 medium-sized very ripe bananas, (optional, 1 ripe banana for decoration)
- 1/4 cup + 2 tablespoons (90 mL) oat milk, or plain-flavored plant-based milk of choice
- 1 tablespoon lemon juice
- 1/3 cup (75g) sunflower oil, olive oil, or any neutral-tasting oil
- 3/4 cup (115g) organic brown sugar or coconut sugar (see Note 2)
- 1 teaspoon pure vanilla extract (see Note 3)
- 2 cups (240 to 250g) all-purpose flour, spooned and leveled (see Note 4)
- 1/4 teaspoon sea salt
- 1 teaspoon baking soda
- 3/4 teaspoon ground cinnamon
Directions
- Preheat the oven to 350°F/176°C. Arrange a rack in the bottom third of the oven. Line a 9×5-inch (23×13 cm) loaf pan with parchment paper, letting the excess hang over the long sides to form a sling.
- Pour the aquafaba into a medium bowl. Using a handheld electric mixer, whip the aquafaba on medium speed for 45-60 seconds until uniformly foamy.
- Wipe out the bowl used for the aquafaba. Add the three bananas to the bowl and mash with a fork until smooth and no lumps remain (or, for a more rustic banana bread, leave a few chunks in). FYI: the 3 mashed bananas should weigh around 300g.
- Stir the lemon juice into the oat milk and set aside. This is the vegan "buttermilk."
- In a large mixing bowl, add the sugar and oil. Mix using the electric mixer or a whisk until well combined.
- Add the whipped aquafaba and mix until well incorporated. Add in the vegan "buttermilk" and vanilla and mix until smooth. Add the mashed bananas and mix until well incorporated.
- Add the flour, salt, baking soda, and cinnamon to the wet ingredients. Switch to using a silicone spatula (if you don’t have one, use a large wooden spoon). Gently stir until the ingredients are just barely combined. It’s okay if you can see a few traces of flour.
- Pour the batter into the prepared loaf pan and smooth out the top of the batter using a spatula or spoon.
- For the optional decoration, keep the peel on the reserved banana and slice it in half, lengthwise; then peel the banana. Sprinkle a little coconut sugar or brown sugar on the cut/interior sides of the banana. Gently arrange the bananas on top the batter, sugared side side up. NOTE: This might create a dome in the middle of the bananas, where the batter bunches up in the middle. Use a spoon to move some of the batter around the pan so that the bread doesn’t bake unevenly.
- Bake in the preheated oven for 45 to 55 minutes. Since every home oven differs, I like to start checking at 45 minutes. The banana bread is done when a toothpick inserted into the center top at a slight angle comes out a few moist crumbs (see Note 5). If there's runny batter, it needs more time.
- Transfer the pan to a wire rack and cool for 10 minutes. Then remove the bread from the pan and cool on the rack for at least 20 to 30 minutes before slicing (the bread is still cooking and setting up, so don't slice too early).
- To store, place completely cooled banana bread in an airtight container or wrap tightly in plastic and leave on the counter for 2-4 days (if using decorative banana topping, the topping a will start to brown after day 1). You can also freeze the banana bread. If you freeze the whole loaf, allow it to defrost on the countertop for 2-3 hours. If you freeze individual slices, defrost on the countertop for 20-30 minutes.
-
 @ 1e52c554:21771908
2024-03-05 11:14:43
@ 1e52c554:21771908
2024-03-05 11:14:43Posthumous work of the Colombian poet born in Don Matias on January 20, 1948.
Welcome to this blog dedicated to the Posthumous work of the Colombian poet Francisco Luis Arroyave Tabares (my father), born in Don Matias on January 20, 1948-2010. Where I will be publishing each of the 175 sonnets from his unpublished collection 'Sonnets For The Twenty-First Century And A Circadian Musical (1984-1987).' Analyzed with GPT4 artificial intelligence and illustrated with AI tools... I hope you enjoy this garden of words snatched from the solitude of a locked room.
Likewise, any enthusiast of the sonnet form is invited to conduct their personal studies of Arroyave Tabares' work, as it is a collection that, although registered since 1989, has not yet been published.
Frank Duna

Analysis "Amuse Yourself Again"
Introduction
Sonnet 83 by Francisco Luis Arroyave Tabares, titled "Amuse Yourself Again," is a poignant exploration of unrequited love and the emotional turmoil that comes with it.
Thematic Analysis
In the octave, the speaker expresses a sense of betrayal and disillusionment. The speaker feels lured and trapped by the addressee’s artful beguilement and love games. The octave ends with the speaker acknowledging the confusion and entrapment they feel due to the addressee’s actions.
The sestet shifts the tone slightly. Here, the speaker seems to be in a state of self-realization, acknowledging the pain and worthlessness they feel. However, there’s also a sense of defiance and resilience. The speaker encourages the addressee to continue their behavior, implying that despite the pain, they will not cease their quest.
This sonnet explores themes of love, betrayal, resilience, and self-realization. It’s a poignant expression of the speaker’s emotional journey. The octave sets up the problem, and the sestet offers a resolution, albeit a painful one. This is a common structure in sonnets, providing a clear narrative progression. The final line leaves the reader with a powerful image of the speaker’s determination despite their pain.
Rhyme Scheme
The rhyme scheme (ABBA ABBA CDE CDE) is typical of a Petrarchan sonnet. Let’s analyze the rhyme in the sonnet “Amuse Yourself Again” by Francisco Luis Arroyave Tabares:
Octave:
I refuse to admit your words sound sorry (A) After I was the captive you could lure (B) With zealous bloomns of languor and demure (B) Artfully used to beguile our story. (A) Be happy and show you do not worry (A) About the yesteryears you now obscure (B) Since your damned tricks worked so well to immure (B) My heart confused with love games and glory. (A)Sestet:
I endure losing myself worthlessly (C) And painfully looking for repletion (D) As you were a dancer only to tease. (E) Amuse yourself again and aimlessly (C) Build more webbs for those without protection (D) Because It huts, yet my quest will not cease. (E)As you can see, the sonnet follows the ABBA ABBA CDE CDE rhyme scheme perfectly. The rhyme scheme is a crucial part of the sonnet’s structure, contributing to its rhythm and flow. It also helps to emphasize certain words and ideas, enhancing the poem’s overall impact.
Additional Aspects
Let’s delve deeper into the analysis of “Amuse Yourself Again” by Francisco Luis Arroyave Tabares:
Language and Imagery: The language used in this sonnet is rich and evocative, with a strong use of imagery. Phrases like “zealous bloomns of languor and demure” and “damned tricks worked so well to immure” paint vivid pictures in the reader’s mind. The use of words such as “captive”, “lure”, “beguile”, “tricks”, and “webbs” suggest deception and entrapment, reinforcing the themes of betrayal and disillusionment.
Themes: The main themes of this sonnet are love, betrayal, resilience, and self-realization. The speaker feels betrayed and trapped by the addressee’s deceptive actions, but there’s also a sense of defiance and resilience. Despite the pain, the speaker is determined to continue their quest, suggesting a theme of self-realization and personal growth.
Meter: The sonnet appears to follow the iambic pentameter, which is typical of traditional sonnets. This means each line consists of five pairs of unstressed and stressed syllables, giving the poem a rhythmic quality.
Overall: this sonnet is a powerful exploration of emotional turmoil and resilience in the face of betrayal. The strong use of language and imagery, combined with the traditional sonnet structure and meter, make it a compelling piece of poetry. The themes are universal and relatable, adding to the sonnet’s impact. The final line leaves a lasting impression, encapsulating the speaker’s determination and resilience. It’s a poignant expression of the human capacity to endure and grow from painful experiences.
(GPT4)
Syllable count for each line.
``` Amuse Yourself Again
11 I refuse to admit your words sound sorry 10 After I was the captive you could lure 10 With zealous bloomns of languor and demure 10 Atrfully used to beguile our story.
10 Be happy and show you do not worry 10 About the yesteryears you now obscure 10 Since your damned tricks worked so well to immure 10 My heart confused with love games and glory.
10 I endure losing myself worthlessly 10 And painfully looking for repletion 10 As you were a dancer only to tease. 10 Amuse yourself again and aimlessly 10 Build more webbs for those without protection 10 Because It huts, yet my quest will not cease. *** ```
Sonnets For The Twenty First Century And A Circadian Musical Written By Francisco Luis Arroyave Tabares (1984-1987)
Analyzed by GPT4; Image by leonardo.ai; First published on Nostr Protocol by franciscoarroyavet@nostrplebs.com
 Amuse Yourself Again
Amuse Yourself Again -
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 78733875:4eb851f2
2023-07-07 22:04:12
@ 78733875:4eb851f2
2023-07-07 22:04:12OpenSats is pleased to announce a new long-term support (LTS) program for Bitcoin Core developers and similar Load-Bearing Internet People.[^fn-lbip] This grant program is designed to provide financial support for developers who are working on critical infrastructure for the bitcoin network.
The LTS program is a new initiative from OpenSats and is distinct from our regular grant program, which is more expansive in scope. It is also distinct from OpenSats' website listings, which allows reviewed open-source projects to receive tax-deductible donations via OpenSats. The LTS program is specifically designed to provide long-term support for developers who are working on critical open-source infrastructure in and around bitcoin.
Having a longer time horizon than regular grants, the LTS program is geared towards long-term stability for grantees, with a minimum grant duration of 12 months and possible grant durations of two years or longer. This will allow developers to focus on their work without having to worry about financial constraints.
To be eligible for the LTS program, applicants must:
- have a track record of quality contributions
- be mission-driven and self-motivated
- be able to work in public
- be bitcoin-only
Applications for the LTS program are now open: https://opensats.org/apply/
The first recipient of an OpenSats LTS Grant is Marco Falke, a long-term maintainer and contributor of Bitcoin Core with thousands of contributions over many years. Marco will continue to focus on testing and quality assurance, as well as maintenance and review, helping to make sure that the Bitcoin Core software is as solid as it can be. You can read more about his contributions here.
We appreciate all the hard work that goes into building and maintaining critical open-source infrastructure. It is a hard and often thankless job. We hope that we can play a role in closing the gaps in bitcoin open-source funding, and we look forward to working with contributors in the future.
OpenSats aims to be an additional pillar of the increasingly solid funding landscape in and around bitcoin. We have learned a lot from the programs of the past and aim to join Brink, Spiral, Chaincode, HRF, and other successful grant programs to support those who build the tools that ensure the protection of individual liberties in our digital world.
We are committed to supporting the development of bitcoin. The LTS program is a new way for OpenSats to support long-term contributors who are building, maintaining, testing, researching, and reviewing critical software.
We encourage all qualified developers to apply for the LTS program. Together, we can build a stronger and more resilient bitcoin network.
[^fn-lbip]: "An LBIP is a person who maintains the software for a critical Internet service or library, and has to do it without organizational support or a budget backing him up." —Eric S. Raymond
-
 @ b12b632c:d9e1ff79
2023-07-20 20:12:39
@ b12b632c:d9e1ff79
2023-07-20 20:12:39Self hosting web applications comes quickly with the need to deal with HTTPS protocol and SSL certificates. The time where web applications was published over the 80/TCP port without any encryption is totally over. Now we have Let's Encrypt and other free certification authority that lets us play web applications with, at least, the basic minimum security required.
Second part of web self hosting stuff that is really useful is the web proxifycation.
It's possible to have multiple web applications accessible through HTTPS but as we can't use the some port (spoiler: we can) we are forced to have ugly URL as https://mybeautifudomain.tld:8443.
This is where Nginx Proxy Manager (NPM) comes to help us.
NPM, as gateway, will listen on the 443 https port and based on the subdomain you want to reach, it will redirect the network flow to the NPM differents declared backend ports. NPM will also request HTTPS cert for you and let you know when the certificate expires, really useful.
We'll now install NPM with docker compose (v2) and you'll see, it's very easy.
You can find the official NPM setup instructions here.
But before we absolutely need to do something. You need to connect to the registrar where you bought your domain name and go into the zone DNS section.You have to create a A record poing to your VPS IP. That will allow NPM to request SSL certificates for your domain and subdomains.
Create a new folder for the NPM docker stack :
mkdir npm-stack && cd npm-stackCreate a new docker-compose.yml :
nano docker-compose.ymlPaste this content into it (CTRL + X ; Y & ENTER to save/quit) :
``` version: '3.8' services: app: image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: # These ports are in format
: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port # Add any other Stream port you want to expose # - '21:21' # FTP # Uncomment the next line if you uncomment anything in the section # environment: # Uncomment this if you want to change the location of # the SQLite DB file within the container # DB_SQLITE_FILE: "/data/database.sqlite" # Uncomment this if IPv6 is not enabled on your host # DISABLE_IPV6: 'true' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt```
You'll not believe but it's done. NPM docker compose configuration is done.
To start Nginx Proxy Manager with docker compose, you just have to :
docker compose up -dYou'll see :
user@vps:~/tutorials/npm-stack$ docker compose up -d [+] Running 2/2 ✔ Network npm-stack_default Created ✔ Container npm-stack-app-1 StartedYou can check if NPM container is started by doing this command :
docker psYou'll see :
user@vps:~/tutorials/npm-stack$ docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 7bc5ea8ac9c8 jc21/nginx-proxy-manager:latest "/init" About a minute ago Up About a minute 0.0.0.0:80-81->80-81/tcp, :::80-81->80-81/tcp, 0.0.0.0:443->443/tcp, :::443->443/tcp npm-stack-app-1If the command show "Up X minutes" for the npm-stack-app-1, you're good to go! You can access to the NPM admin UI by going to http://YourIPAddress:81.You shoud see :

The default NPM login/password are : admin@example.com/changeme .If the login succeed, you should see a popup asking to edit your user by changing your email password :
 And your password :
And your password :
 Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
 Followed by "Add Proxy Host"
Followed by "Add Proxy Host"
 If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :
If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :Details tab :
 SSL tab :
SSL tab :
 And click on "Save".
And click on "Save".NPM will request the SSL certificate "admin.yourdomain.tld" for you.
If you have an erreor message "Internal Error" it's probably because your domaine DNS zone is not configured with an A DNS record pointing to your VPS IP.
Otherwise you should see (my domain is hidden) :

Clicking on the "Source" URL link "admin.yourdomain.tld" will open a pop-up and, surprise, you should see the NPM admin UI with the URL "https://admin.yourdomain.tld" !
If yes, bravo, everything is OK ! 🎇
You know now how to have a subdomain of your domain redirecting to a container web app. In the next blog post, you'll see how to setup a Nostr relay with NPM ;)
Voilààààà
See you soon in another Fractalized story!
-
 @ 1c6b3be3:73f0ae6f
2024-03-05 06:16:52
@ 1c6b3be3:73f0ae6f
2024-03-05 06:16:52🍵 Actualités securite
Webex de Cisco cité dans une affaire d'espionnage en Allemagne (2 min) Le 26 avril 2023, des hauts responsables militaires allemands ont vu leurs échanges sur des informations sensibles liées à l'Ukraine être dévoilés par les médias russes. Ces discussions auraient été captées via une version non sécurisée de Webex de Cisco. Les militaires auraient utilisé cette plateforme pour discuter d'éventuelles livraisons de missiles de croisière Taurus à l'Ukraine et de cibles potentielles. L'armée allemande utilise généralement des solutions très sécurisées avec chiffrement de bout en bout pour ce type d'entretien. Le ministère allemand de la défense a confirmé l'authenticité de l'enregistrement et a ouvert une enquête sur la pertinence de l'utilisation de Webex dans ce cas précis. L'incident soulève des inquiétudes quant à la sécurité et au contre-espionnage, certains considérant même cela comme une attaque hybride russe visant à diffuser de la désinformation.
Lazarus modernise son rootkit avec la faille zero day AppLocker (6 min) Le groupe APT Lazarus, lié au gouvernement nord-coréen, a intégré une faille AppLocker dans sa dernière version de rootkit FudModule pour obtenir des privilèges accrus dans le noyau Windows. Cette technique permet de suspendre les processus protégés associés à Microsoft Defender, CrowdStrike Falcon et HitmanPro. Le rootkit FudModule est utilisé depuis plusieurs années par Lazarus et exploite les pilotes pour altérer les mécanismes de sécurité Windows. Il désactive des fonctions importantes utilisées par les produits de sécurité pour détecter les comportements suspects, affaiblissant ainsi leurs capacités de détection des logiciels malveillants. Une nouvelle fonctionnalité permet de désactiver directement certains produits de sécurité spécifiques.
Le malware Bifrost use de typosquatting de domaine VMware (1 min) Un nouveau variant du trojan d'accès distant (RAT) Bifrost a été découvert par l'équipe Unit42 de Palo Alto Networks, qui cible des architectures ARM et utilise une technique de typosquatting pour imiter un domaine VMware légitime dans le but de tromper les utilisateurs et éviter la détection. Cette variante est particulièrement préoccupante car elle établit une communication avec le serveur de l'attaquant, collecte des données d'utilisateur et les envoie à ce dernier. Palo Alto Networks a publié les indicateurs de compromission (IoC) associés à cette variante et recommande l'utilisation de mesures de sécurité spécifiques pour s'en prémunir, telles que la filtrage URL avancée et des pare-feu dotés d'intelligence artificielle.
Le prix, critère crucial pour choisir un logiciel (1 min) L'article indique que le coût est le facteur déterminant dans le choix d'un logiciel pour la majorité des acheteurs. Près de la moitié d'entre eux ont déjà écarté un fournisseur en raison de prix élevés, et un tiers a déjà remplacé une solution trop coûteuse par une alternative moins chère. Cependant, les dépenses en logiciels devraient augmenter cette année grâce à la popularité des outils d'IA générative et des solutions de cybersécurité. Gartner prévoit que les dépenses mondiales en logiciels dépasseront 1 000 milliards de dollars en 2024, en hausse de 13 % par rapport à l'année précédente. La plupart des entreprises envisagent d'investir dans des logiciels basés sur l'IA. Les avis d'autres utilisateurs sont également essentiels pour les décisions d'achat.
🍵 Actualités le-monde-du-cloud-computing
Dans la guerre des LLM, Anthropic dégaine ses modèles Claude 3 (2 min) Anthropic a récemment annoncé les dernières itérations de son grand langage de modèle (LLM) Claude 3, avec Opus étant la plus performante mais aussi la plus coûteuse. Selon Anthropic, Opus surpasse ses concurrents tels que Llama de Meta, GPT d'OpenAI, Gemini de Google et Large de Mistral AI en termes de connaissances expertes de premier cycle, de raisonnement expert de deuxième cycle et de mathématiques de base. Claude 3 peut également traiter une large gamme de formats visuels, y compris des photos, des tableaux, des graphiques et des diagrammes techniques.
Anthropic a introduit un benchmark appelé « Aiguille dans une botte de foin » pour mesurer la capacité d'un modèle à rappeler avec précision des informations à partir d'un vaste corpus de données. Claude 3 Opus a atteint un rappel presque parfait, dépassant 99% de précision.
Les cas d'usage incluent l'automatisation des tâches, la R&D et la stratégie. Le coût pour la version Opus est de 15 $ par million de token en entrée et 75 $ par million de token en sortie, avec une taille de fenêtre de requête de 200 000 tokens.
Pour structurer son cloud, Groq s'empare de Definitive Intelligence (1 min) Groq, une start-up spécialisée dans les puces IA et concurrente de Nvidia, a racheté Definitive Intelligence, une autre start-up qui propose des services d'analyse de données utilisant l'IA et le langage naturel. Definitive Intelligence a aidé au développement de la plateforme cloud de Groq, nommée GroqCloud, qui donne accès à la demande aux puces LPU de Groq. Après l'acquisition, Sunny Madra, cofondateur et CEO de Definitive Intelligence, rejoindra Groq pour diriger la division responsable de GroqCloud et augmenter ses fonctionnalités et son nombre d'utilisateurs. Groq a également annoncé le lancement d'une autre activité, Groq Systems, qui aidera les entreprises à tirer parti des LPU dans leurs projets IA. Le montant de l'opération n'a pas été divulgué.
Nexity construit petit à petit sa stratégie IA générative (4 min) Nexity, un promoteur immobilier de taille importante, explore les possibilités offertes par l'IA générative pour améliorer ses opérations et offrir de meilleurs services à ses clients. Le directeur des nouvelles offres et de l'innovation, François Desgardin, a présenté lors d'une conférence Oracle les projets IA en cours dans l'entreprise.
Dans un contexte où le secteur est peu automatisé et où les obligations juridiques sont nombreuses, Nexity souhaite utiliser l'IA pour aider ses collaborateurs à digérer et trier les normes en vigueur dans la construction et la promotion immobilière. Un PoC (preuve de concept) avec la direction de la qualité a été mené sur les normes de sécurité des chantiers, afin de fournir aux directeurs de programmes et chefs de chantier des outils pour comparer les engagements des fournisseurs avec les obligations légales et internes. Cet outil d'aide à la décision permettra au collaborateur d'avoir un questionnement plus approfondi et de garder une trace des réponses appliquées.
Un autre PoC est en cours dans la direction de la communication, qui travaille sur la génération de contenu sémantique et d'images grâce à l'IA. Le but n'est pas de remplacer les agences de création, mais de réduire les coûts opérationnels associés à cette tâche. Nexity a également identifié le potentiel de l'IA dans la gestion des PLU (Plan Local d'Urbanisme), qui sont actuellement contenus dans des PDF non normalisés et varient selon les municipalités. L'objectif est de charger les PLU dans une base de données, de scanner et comprendre le contenu, et éventuellement d'automatiser la génération de permis de construire conformes à 90% aux exigences du PLU.
Le déploiement à plus grande échelle de ces projets IA nécessitera une collaboration étroite entre Nexity et les ministères compétents, ainsi qu'une formation adéquate pour les collaborateurs afin de les aider à maîtriser ces nouvelles technologies.
Le temps des stratégies 100 % cloud a vécu (7 min) L'article discute du fait que les DSI remettent en question l'approche "cloud-first" pour leurs applications après avoir migré vers le cloud. Les raisons incluent des coûts plus élevés et une inadéquation de certaines applications avec le cloud public. De nombreux DSI cherchent à déplacer certaines applications vers des plateformes qui fonctionnent mieux en termes de productivité, d'efficacité et de coûts. Cela peut inclure un mélange d'environnements sur site et cloud hybride pour réduire les dépassements de coûts, gérer le chaos du cloud et garantir un financement adéquat pour les projets d'IA générative. La motivation la plus courante pour cette tendance est de réduire les coûts, car de nombreuses applications d'entreprise ne sont pas optimisées pour le cloud. Les entreprises deviennent également plus nuancées dans leur utilisation et leurs stratégies cloud afin de trouver un équilibre entre les performances, les coûts et la sécurité.
🍵 Toutes les actualités :
Telex : L'UE condamne Apple sur le streaming musical, Le code source de Pegasus réclamé par un juge, Tiny Core Linux 15 lancé (1 min) L'Union Européenne a infligé une amende de 1,8 milliards d'euros à Apple pour abus de position dominante dans le streaming musical. La Commission européenne a considéré qu'Apple avait mis en place des restrictions sur les acteurs alternatifs en privilégiant son propre service Apple Music, après une plainte de Spotify et une longue enquête.
Un juge a demandé à la société israélienne NSO Group, éditeur du logiciel espion Pegasus, de transmettre le code source de son logiciel et des vulnérabilités découvertes à Meta (anciennement Facebook). Cela fait suite à une procédure datant de 2019 concernant l'usage d'une faille dans WhatsApp pour diffuser Pegasus et espionner des opposants politiques, journalistes et autres.
La dernière version de Tiny Core Linux, un système d'exploitation open source, est disponible en version x86 32/64 bits. Elle se base sur un noyau 6.6.8, la glibc 2.38 et inclut la version 13.2 de GCC. Le projet a été fondé par Robert Shingledecker, précédemment responsable de Damn Small Linux (DSL), qui a récemment repris vie après une interruption de douze ans.
Dans la guerre des LLM, Anthropic dégaine ses modèles Claude 3 (2 min) Anthropic a récemment annoncé les dernières itérations de son grand langage de modèle (LLM) Claude 3, avec Opus étant la plus performante mais aussi la plus coûteuse. Selon Anthropic, Opus surpasse ses concurrents tels que Llama de Meta, GPT d'OpenAI, Gemini de Google et Large de Mistral AI en termes de connaissances expertes de premier cycle, de raisonnement expert de deuxième cycle et de mathématiques de base. Claude 3 peut également traiter une large gamme de formats visuels, y compris des photos, des tableaux, des graphiques et des diagrammes techniques.
Anthropic a introduit un benchmark appelé « Aiguille dans une botte de foin » pour mesurer la capacité d'un modèle à rappeler avec précision des informations à partir d'un vaste corpus de données. Claude 3 Opus a atteint un rappel presque parfait, dépassant 99% de précision.
Les cas d'usage incluent l'automatisation des tâches, la R&D et la stratégie. Le coût pour la version Opus est de 15 $ par million de token en entrée et 75 $ par million de token en sortie, avec une taille de fenêtre de requête de 200 000 tokens.
Apple embarque sa puce M3 dans les MacBook Air 13 et 15 pouces (1 min) Apple a équipé les dernières versions des MacBook Air 13 et 15 pouces de sa puce M3, après l'avoir introduite dans le MacBook Pro 14 pouces en octobre dernier. Le MacBook Air 13 pouces est disponible à partir de 1 031 €HT avec la puce M3 (CPU 8 cœurs/GPU 8 noyaux) et le modèle 15 pouces à partir de 1 269 €HT (CPU 8 cœurs/GPU 10 noyaux). Les nouvelles fonctionnalités incluent un WiFi amélioré en passant de la version 6 à 6E, la prise en charge de deux écrans externes lorsque le couvercle est fermé et des options de couleurs similaires aux modèles précédents. Les prix restent inchangés et Apple a retiré le modèle M1, remplacé par le Air M2 en tant que modèle d'entrée de gamme à 952 €HT. Les précommandes pour le MacBook Air M3 commencent aujourd'hui et les expéditions débuteront le vendredi 8 mars. Apple a décidé de ne pas organiser d'événement printanier cette année et de publier des communiqués de presse pour le lancement de ses produits.
Webex de Cisco cité dans une affaire d'espionnage en Allemagne (2 min) Le 26 avril 2023, des hauts responsables militaires allemands ont vu leurs échanges sur des informations sensibles liées à l'Ukraine être dévoilés par les médias russes. Ces discussions auraient été captées via une version non sécurisée de Webex de Cisco. Les militaires auraient utilisé cette plateforme pour discuter d'éventuelles livraisons de missiles de croisière Taurus à l'Ukraine et de cibles potentielles. L'armée allemande utilise généralement des solutions très sécurisées avec chiffrement de bout en bout pour ce type d'entretien. Le ministère allemand de la défense a confirmé l'authenticité de l'enregistrement et a ouvert une enquête sur la pertinence de l'utilisation de Webex dans ce cas précis. L'incident soulève des inquiétudes quant à la sécurité et au contre-espionnage, certains considérant même cela comme une attaque hybride russe visant à diffuser de la désinformation.
CompTIA prépare une certification dédiée à l'IA (3 min) CompTIA, un organisme de certification et de formation IT à but non lucratif, élargit sa gamme de produits et de programmes pour répondre à la forte demande de compétences en IA sur le marché du travail. L'IA devenant essentielle dans les fonctions professionnelles existantes et avec l'apparition de nouveaux rôles tels que l'ingénierie des messages et les architectes de systèmes d'IA, CompTIA accélère le développement de produits et de programmes en lien avec l'IA. Ces derniers mois, environ 200 000 offres d'emploi aux États-Unis comprenaient des compétences et fonctions liées à l'IA, représentant plus de 10 % de toutes les offres d'emploi dans le domaine de la technologie. CompTIA prévoit de créer une gamme complète de certifications et de formations couvrant tout le spectre des carrières en IA, des connaissances fondamentales pour les débutants aux compétences avancées pour les professionnels expérimentés. L'organisation prévoit également de travailler directement avec les entreprises intéressées par le développement des talents en matière d'IA.
🍵 Actualités securite
Webex de Cisco cité dans une affaire d'espionnage en Allemagne (2 min) Lazarus modernise son rootkit avec la faille zero day AppLocker (6 min) Le malware Bifrost use de typosquatting de domaine VMware (1 min) Le prix, critère crucial pour choisir un logiciel (1 min)
🍵 Actualités le-monde-du-cloud-computing
Dans la guerre des LLM, Anthropic dégaine ses modèles Claude 3 (2 min) Pour structurer son cloud, Groq s'empare de Definitive Intelligence (1 min) Nexity construit petit à petit sa stratégie IA générative (4 min) Le temps des stratégies 100 % cloud a vécu (7 min)
🍵 Toutes les actualités :
Telex : L'UE condamne Apple sur le streaming musical, Le code source de Pegasus réclamé par un juge, Tiny Core Linux 15 lancé (1 min) Dans la guerre des LLM, Anthropic dégaine ses modèles Claude 3 (2 min) Apple embarque sa puce M3 dans les MacBook Air 13 et 15 pouces (1 min) Webex de Cisco cité dans une affaire d'espionnage en Allemagne (2 min) CompTIA prépare une certification dédiée à l'IA (3 min) Lazarus modernise son rootkit avec la faille zero day AppLocker (6 min) Pour structurer son cloud, Groq s'empare de Definitive Intelligence (1 min) Plusieurs associations militent pour renforcer l'EdTech (3 min) Le malware Bifrost use de typosquatting de domaine VMware (1 min) Le prix, critère crucial pour choisir un logiciel (1 min) Nexity construit petit à petit sa stratégie IA générative (4 min) La circulation des trains suisses optimisée à l'IA (3 min) HN Services croque ST Groupe (2 min) Le temps des stratégies 100 % cloud a vécu (7 min)
🍵 "llm | cloud | ddos" - Google News
Baseten nabs $40M for its cloud-based AI inference platform - SiliconANGLE News Cloudflare wants to put a firewall in front of your LLM - The Register Apple hit with consumer lawsuit claiming cloud storage monopoly - Reuters Managing Costs with Cloud Financial Management Technical Implementation Playbooks (CFM TIPs) for AWS | AWS ... - AWS Blog Air Force Intelligence Office CIO Col. Michael Medgyessy on Cloud Office Governance - Executive Gov On ‘Oppenheimer’: The Pink Cloud and the Ethics of Subjectivity | Arts - Harvard Crimson Dorothy Kay Swanson Obituary - SC Times [Webinar] SaaS and Cloud: At the Intersection of IP and Data Protection - April 2nd, 10:00 am PT - JD Supra What's next for Salesforce Einstein AI and Data Cloud - TechTarget Tom the 'lost trucker cat' reunited with his humans in St. Cloud - Star Tribune Observations find evidence of patchy cloud layers in the atmosphere of a nearby planetary-mass object - Phys.org St. Cloud Planning Commission Recommends Allocation of $520000 in CDBG Funds to Address Homelessness and ... - KNSI Cloud service provider spending on ethernet data center switches declined for first time in three years – Dell'Oro - Light Reading Evolving cloud threats were observed in the last half of 2023 - Security Magazine
-
 @ aa55a479:f7598935
2023-02-20 13:44:48
@ aa55a479:f7598935
2023-02-20 13:44:48Nostrica is the shit.
-
 @ 3cd2ea88:bafdaceb
2024-03-07 01:21:29
@ 3cd2ea88:bafdaceb
2024-03-07 01:21:29Event continues!
Trade futures, earn entries, and win:
1st draw: Guaranteed SHIB for all!
Bitget welcome bonus
Trading fee discount coupons
Don't miss out!
Sign up on Bitget and start trading!
-
 @ 1c6b3be3:73f0ae6f
2024-03-05 05:08:18
@ 1c6b3be3:73f0ae6f
2024-03-05 05:08:18Bitcoin Optech
Bitcoin Optech Newsletter #291 Recap Podcast Le Bitcoin Optech Podcast #291, présenté par Mark "Murch" Erhardt et Mike Schmidt, reçoit Richard Myers, Rijndael, Luke Dashjr et Jason Hughes pour discuter des sujets suivants :
- (1:31) Trustless contract for miner feerate futures : Une proposition de contrat intelligent trustless permettant aux mineurs de spécifier les frais minimums qu'ils accepteront dans un bloc.
- (7:20) Coin selection for liquidity providers : Discussion sur la sélection des pièces pour les fournisseurs de liquidités dans le contexte de l'amélioration des méthodes d'incorporation des transactions.
- (21:15) Simple vault prototype using
OP_CAT: Présentation d'un prototype simple de coffre utilisant l'opcodeOP_CAT. - (44:44) Sending and receiving ecash using LN and ZKCPs : Exploration des moyens d'envoyer et de recevoir de l'argent électronique (ecash) en utilisant Lightning Network (LN) et les preuves à divulgation nulle de connaissance (ZKCP).
Des questions/réponses sont également abordées, provenant du site Bitcoin Stack Exchange :
- (49:41) Pourquoi les noeuds ne peuvent-ils pas avoir l'option de relais pour interdire certains types de transactions ?
- (53:28) Quel est le problème de dépendance circulaire dans la signature d'une chaîne de transactions non confirmées ?
- (34:02) Comment fonctionne le schéma de paiement Ocean’s TIDES ?
- (57:57) Quelles données le portefeuille Bitcoin Core recherche-t-il lors d'une rescan du bloc-chaîne ?
- (59:37) Comment fonctionne le réémission des transactions pour les portefeuilles watch-only ?
Les sorties et les candidats à la sortie sont également abordés :
- (1:02:20) Core Lightning 24.02
- (1:04:20) LDK #2770

Releases - No Bullshit Bitcoin
Amethyst v0.85.1: Post Edits, Forks, Git Repositories & More (2 min) Amethyst, a free and open-source Nostr client for Android devices, has released an update that adds support for various new features including post edits, forks, pull requests, open timestamps, git repositories, issues, patches, replies, wiki pages, and medical data. The developer, Vitor Pamplona, mentioned in Nostr that they are trying to move away from GitHub and use a Nostr-native alternative. Users can report any issues on Amethyst at https://gitworkshop.dev/repo/amethyst.
The new additions include:
- Support for editing of notes (NIP-37 / kind: 1010)
- Support for sending edit proposals
- Embedded events in NIP-19 uris
- Support for NIP-03: OpenTime Stamp attestations (kind: 1040)
- Support for Decentralized Wikis (event kind 30818)
- Basic support for NIP-34: Git repositories (kind 30617), patches (kind 1617), issues (kind 1621) and replies (kind 1622)
- Rendering support for FHIR payloads (kind 82)
- Support for the q tag
- Early support for Kind1 forks
- Zap splits automatically for quotes and forks.
The bug fixes include:
- Fixes the text's vertical alignment when emojis are present
- Fixes DM Chatroom edit button
- Fixes the crash when images are not being present in the image dialog.
- Inserts uploaded URLs where the cursor is and not at the end of the new post
- Fixes the rendering of Japanese characters, hashtags, and custom emojis in the same line
- Fixing stack overflow with more than 200 zaps in a single note
- Fixes image preview visualization on a new post
- Adds support for a new report option as "Other"
- Fixes missing nsec processing when parsing NIP-29 uris
- Fixes caching issue when creating a Bitcoin invoice for the first time
- Fixes UI issues due to the caching of Polls.
The update also includes better alignment of post header elements and several performance improvements, such as faster text parsing, reduced memory footprint of navigation buttons, faster hex validation, increased speed of the Robohash SVG to byte buffer function, addition of benchmark tests for content parser and URL detector, speeds up image composition, faster relay list NIP-11 caching, faster longform tag filters, improved loop through local cache, better speed of location services, improved cache of LnInvoices and cashu tokens, and reduced memory footprint for parsed posts.
Furthermore, the code quality improvements include moving content parsers and media classes to commons, moving emoji parsers to commons, moving Wallet Connect code to Quartz, moving Relay information code to Quartz, removing dependency on Kotlin serialization, adding a release draft generator to CI, updating Vico, Compose UI Version, Coil and Google Service dependencies, refactors the code to manage extra characters after Bech32 Links, moves to Android Studio Iguana | 2023.2.1, moves gradle to 8.4, and moves project to version catalogs.
The developer also mentioned that they archived their GitHub repository.
 Zaprite Introduces Teams and Organizations (1 min)
Zaprite, a platform allowing users to accept bitcoin and fiat payments with no transaction fees, has announced the addition of Teams. This feature will enable users to collaborate with colleagues on managing payments and related reporting. While adding team members is currently free, Zaprite plans to begin charging $5 per month for each additional user in May 2024, with a discount available for annual plans. The platform also introduced the ability to invite new team members and the concept of Organizations, which allows users to associate multiple accounts with one email login. In the future, Zaprite aims to add more roles with narrower permissions.
Zaprite Introduces Teams and Organizations (1 min)
Zaprite, a platform allowing users to accept bitcoin and fiat payments with no transaction fees, has announced the addition of Teams. This feature will enable users to collaborate with colleagues on managing payments and related reporting. While adding team members is currently free, Zaprite plans to begin charging $5 per month for each additional user in May 2024, with a discount available for annual plans. The platform also introduced the ability to invite new team members and the concept of Organizations, which allows users to associate multiple accounts with one email login. In the future, Zaprite aims to add more roles with narrower permissions.  Samourai Wallet Launches Nextblock.is For More Accurate Transaction Fee Estimation
Le Next Block estimator est un nouvel outil qui évalue les transactions non confirmées dans le mempool et calcule le taux de frais auquel une transaction doit être diffusée à l'instant présent pour qu'elle soit confirmée dans le bloc suivant. L'outil fournit une probabilité instantanée d'être confirmé dans le prochain bloc, mais ne peut pas prendre en compte les variables au-delà de cela car cela rendrait le calcul mathématiquement instable. Bien que l'outil soit disponible pour tous, il sera directement intégré à Samourai Wallet pour les utilisateurs de Samourai. Pour plus d'informations sur son fonctionnement, vous pouvez consulter 'the original Readme.'
Samourai Wallet Launches Nextblock.is For More Accurate Transaction Fee Estimation
Le Next Block estimator est un nouvel outil qui évalue les transactions non confirmées dans le mempool et calcule le taux de frais auquel une transaction doit être diffusée à l'instant présent pour qu'elle soit confirmée dans le bloc suivant. L'outil fournit une probabilité instantanée d'être confirmé dans le prochain bloc, mais ne peut pas prendre en compte les variables au-delà de cela car cela rendrait le calcul mathématiquement instable. Bien que l'outil soit disponible pour tous, il sera directement intégré à Samourai Wallet pour les utilisateurs de Samourai. Pour plus d'informations sur son fonctionnement, vous pouvez consulter 'the original Readme.' 
Bitcoin Optech
Bitcoin Optech Newsletter #291 Recap Podcast

Releases - No Bullshit Bitcoin
Amethyst v0.85.1: Post Edits, Forks, Git Repositories & More (2 min)
 Zaprite Introduces Teams and Organizations (1 min)
Zaprite Introduces Teams and Organizations (1 min)
 Samourai Wallet Launches Nextblock.is For More Accurate Transaction Fee Estimation
Samourai Wallet Launches Nextblock.is For More Accurate Transaction Fee Estimation
 Bitcoin Tribe v2.4.2: Request Test Sats for RGB Assets
Bitcoin Tribe v2.4.2: Request Test Sats for RGB Assets
 Geyser Partners with Flash to Introduce NWC-Powered Recurring Subscriptions
Geyser Partners with Flash to Introduce NWC-Powered Recurring Subscriptions

🍵 "btc | bitcoin | lightning network | asic" - Google News
Generation Bitcoin to Unite Student Groups in Worldwide Network - Bitcoin Magazine Tesla's (TSLA) Bitcoin holdings surge to over $600 million - Electrek What Bitcoin Creator Satoshi Nakamoto Predicted About Crypto in 2009 - TradingView Why Bitcoin Mempools Are Important - Blockchain - CCN.com Bitcoin could become 'a form of digital gold': Scaramucci - Yahoo Finance Charting the Bitcoin Course for Crypto Traders – Where Will 2024 Take Us - The Daily Hodl Orange Domains aims to expand Bitcoin Name System functionality - Cointelegraph $1.3+ Trillion: Bitcoin Market Cap Sets New Record All-Time High - NewsBTC Bitget director: Bitcoin aims for $200k price tag during bull cycle - crypto.news JTC Network's Revolutionary Legal -Recourse Bitcoin Fork Listed on WhiteBIT, Bridging Digital Assets with Official ... - CryptoDaily Bitcoin's Lightning Network: 3 Possible Problems - Investopedia 3 New Crypto To Buy Gems Poised To Outpace Bitcoin Pre-Halving - CoinGape Bitdeer Launches Innovative 4nm SEAL01 Bitcoin Mining Chip - Blockchain.News MicroStrategy To Raise $600 Million To Buy More Bitcoin - Bitcoin Magazine
-
 @ d2e97f73:ea9a4d1b
2023-04-11 19:36:53
@ d2e97f73:ea9a4d1b
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ f3df9bc0:a95119eb
2024-03-07 00:29:47
@ f3df9bc0:a95119eb
2024-03-07 00:29:47 -
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 20986fb8:cdac21b3
2024-03-05 04:17:58
@ 20986fb8:cdac21b3
2024-03-05 04:17:58Download and experience the YakiHonne app now and enjoy the decentralized media network:
iOS: https://apps.apple.com/mo/app/yakihonne/id6472556189?l=en-GB Android: https://play.google.com/store/apps/details?id=com.yakihonne.yakihonne
A weekly update on YakiHonne.com 26 Feb - 3rd March
TL;DR
1. Tech Updates
2. Weekly Flash News Quick Look
4. Featured Articles of the Week
1. Product Updates 💻
Weekly Updates
Web & Mobile : 1. Support new features in mobile app 2. Bug fixes and improvements 3. Major updates in progress
Major updates in process...
-
You can test out the different aspects & features of the app. Your feedback is more than welcome in order to achieve the optimal user experience.
-
Note: Flash news. & uncensored notes are considered one of the newly introduced main features of YakiHonne that provide a new, unique & rich experience for the users while navigating through Nostr protocol.
Welcome to download and try
2. Weekly Flash News Quick Look
Bitcoin & Nostr
-
Mission statement for April 8th mini-conference in Berlín, El Salvador.
-
Bitcoin L2 tokens surge double digits as BTC notches 25-month high.
-
The White House raises concerns about Bitcoin mining's impact on power grids.
-
Saylor : Spot Bitcoin ETFS have opened a gateway for capital.
-
Senator Elizabeth Warren used extreme political pressure to fake an "emergency" for bitcoin mining.
-
Michael Saylor : "Bitcoin is math. There is no reason to think it doesn't last a thousand years.”
Crypto
-
Bitcoin Tops $57,000 Price Level for First Time Since Late 2021.
-
Bitcoin Funding Rates Jump to 100%, Sparking Opportunity for Savvy Traders.
-
Crypto Exchange OKX Enters Turkey as Part of Global Expansion Plan.
-
Republican Lawmakers Introduce Legislation to Ban a CBDC in the U.S. Again.
-
Ether's Bitcoin Beating Rally Not Just Because of Potential ETF Approval: Bernstein.
-
Justin Sun says he owns {{text}}.6 billion of crypto with bizarre screenshot of HTX wallet.
-
Worldcoin token drops 5% amid Elon Musk's lawsuit against OpenAI.
Politic
-
Trump's lawyers swing broadly trying to limit what gets into the Manhattan criminal trial.
-
U.S. Congressman Dan Bishop says "CBDCs are a direct threat to every freedom we hold dear."
-
Do Kwon likely won’t be extradited ‘before the end of March,’ say lawyers.
-
Lara Trump officially announces for RNC co-chair, as Trump tightens grip on GOP.
-
Michigan primary results: In 2020, Joe Biden got 52.9%. In 2024, Joe Biden got 80.1%.
-
The Arizona 'Fun Bunch' at their Box #3 emergency election day announcement.
-
Supreme Court has Granted cert and will consider presidential immunity.
-
Judge Cannon has DENIED Trump’s motion to access Jack Smith’s CIPA §4 filings.
-
Biden losing a few Latino-plurality precincts to Uncommitted.
-
Could Arab American and Muslim voters cost Biden the 2024 election?
-
Virginia Primary Map:🤖Donald Trump 63%👹Nikki Haley 34%🙀Does Trump sweep statewide?
-
Rashida Tlaib Posts Video Accusing Biden of Supporting ‘Genocide’.
-
Two of Steve Garvey’s former teammates just endorsed ... not Steve Garvey for U.S. Senate.
-
Meet Susie Wiles, the operative trying to guide Trump through four indictments to the White House.
-
Trump's claims of a migrant crime wave are not supported by national data.
-
Biden and Trump both set to visit U.S. Mexico Border in Texas.
-
Trump Media sued by co-founders ahead of DWAC merger, potential setback for lucrative deal.
-
Biden Directly Addresses Trump as he gives a speech before the Border Parol in Brownsville, Texas.
-
Who would you vote for if the candidates were Joe Biden and Donald Trump?
-
AIPAC uncorks {{text}}00 million war chest to sink progressive candidates.
-
The fossil-fuel-promoting agency that Biden seems powerless to stop.
-
Trump could be instrumental in deciding California’s next U.S. senator.
DeSci
Science and Technology
Others
-
Idaho sheriff hunts for “obscene” books in library with a citizen informant.
-
The Julian Assange case is significant due to its implications.
3. Uncensored Notes For Truth
Dive into more controversial content with YakiHonne uncensored notes to uncover the truth and instantly earn Stas rewards. 🔗https://yakihonne.com/uncensored-notes
4. Featured Articles of the Week
1. What is npub.cash? — by @ StarBuilder
Unlock the future of lightning transactions with http://npub.cash ! Use your npub cash as your lightning address replacement. Join the discussion about http://npub.cash on Nostr @Egge21M. Reported by StarBuilder.
2. Beyond the Basics: Redefining Q&A on NOSTR — by @ Samuel Ralak
🚀 Exciting progress on Apollo! 💫 Rolling out new features and UI enhancements to improve the overall user experience. Report by Samuel Ralak.
3. Notes On The Problems Nostr Solves — by @ Metamick
🚀 Exciting news! #Geyser integrates with Nostr, revolutionizing creator engagement and crowdfunding! 🌐✨ Discover the key problems Nostr solves for Geyser. Report by metamick14.
4. We can. But should we? — by @ PABLOF7z 🫂
Introducing #Wikifreedia based on Nostr. There are no "official" entries for any topic. Anyone can create or edit any entry and build their own perspectives on topics they care about. Report by pablof7z.
5. Weekly Curation Picks
Mineral is the first native BTC DeFi project on Merlin Chain (BTC L2) that issues RWA inscriptions based on BRC420. Unlike many unsustainable DeFi 1.0 projects that rely heavily on subsidies and liquidity lock-ups, Mineral introduces positive externalities from mining, creating a sustainable yield-generating DeFi model. With its unique treasury ...
2. My Bitcoin, Lightning and nostr Journeys by Cadayton
A collection of articles documenting my adventures with Bitcoin, Lightning, and nostr technologies.
3. #Bitcoin in italiano by Mujahideen
Una selezione di articoli dai protagonisti del mondo bitcoin, tradotti in italiano.
4. #austrian economics in italiano by italiansatoshi Pubblicazioni selezionate dalle serie del Mises Institute. Notizie e opinioni contemporanee attraverso la lente dell’economia austriaca e dell’economia politica libertaria.
Nostr ecosystem's long-form posts are booming! There are more and more creators posting on Nostr, like Bitcoin Magazine, StarBuilder, PABLOF7z 🫂, Metamick, Santos, 𝚋𝚊𝚝𝚜𝚒𝚚, Mavis, おっぱぴぃ, teachYourselfAndYourChildrenHowtoHack, Leo Wandersleb, Joda, JohnOnchain, etc. Many thanks! Welcome all to explore the enriching experience of yakihonne.com.
About YakiHonne:
YakiHonne is a Nostr-based decentralized content media protocol, which supports free curation, creation, publishing, and reporting by various media. Try YakiHonne.com Now!
Follow us
- Telegram: http://t.me/YakiHonne_Daily_Featured
- Twitter: @YakiHonne
- Nostr pubkey: npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
- 🌟iOS: https://apps.apple.com/mo/app/yakihonne/id6472556189?l=en-GB
- 🌟Android: https://play.google.com/store/apps/details?id=com.yakihonne.yakihonne
- Facebook Profile: https://www.facebook.com/profile.php?id=61551715056704
- Facebook Page: https://www.facebook.com/profile.php?id=61552076811240
- Facebook Group: https://www.facebook.com/groups/720824539860115
- Youtube: https://www.youtube.com/channel/UCyjDDtWFCntGvf4EyFJ7BlA
-
-
 @ 81870f53:29bef6a6
2024-03-06 20:23:17
@ 81870f53:29bef6a6
2024-03-06 20:23:17自動車産業の柱の一つであるメルセデス・ベンツは最近、完全電気自動車の廃止を発表し、開発戦略に大きな変更を加えた。この決定は、一部の人にとって驚くべきものではありますが、市場の現実と財政的要請が蔓延する複雑な経済状況の中で行われます。
メルセデス・ベンツの発表は、自動車業界全体の一連の挫折を受けて行われた。高い開発コストや製造コスト、収益性の問題など、電気自動車の生産における課題により、多くのメーカーは計画の再検討を余儀なくされています。メルセデス・ベンツにとって、この決定は電動モビリティへの移行に伴うコストと利点の実用的な評価を反映しています。
メルセデス・ベンツが全電気技術を放棄したのも、長期的な経済的考慮によるものだ。電気自動車の需要は依然として不確実であり、充電インフラはまだ開発中ですが、この技術への多額の投資はかなりの財務リスクを伴います。メルセデス・ベンツは、ハイブリッド パワートレインや改良された内燃エンジンなど、より多様なソリューションにリソースを集中することを選択することで、長期的な経済的存続を確保しようとしています。
この決定を、より持続可能なモビリティへの移行にとって後退とみなす人もいるかもしれない。しかし、より深く分析すると、問題はさらに微妙であることが明らかになります。実際には、経済的な持続可能性は環境の持続可能性と同じくらい重要です。企業は、環境上の責務と経済的現実の両方を考慮した情報に基づいた意思決定を行う必要があります。この文脈において、メルセデス・ベンツのアプローチは、現在の課題に対する賢明かつ責任ある対応であるように見えます。
自動車経済の観察者にとって、メルセデス・ベンツの発表は、エネルギー転換に関する政府政策の有効性についても疑問を投げかけている。多くの政府は電気自動車の導入を促進するために税制上の優遇措置や排出削減目標を実施していますが、これらの措置は必ずしも普及を促進することに成功しているわけではありません。市場の現実や消費者のニーズに合わせてこれらの政策を再考する時期が来ています。
結局のところ、メルセデス・ベンツの全電気自動車からの脱却は、経済的な決定は慎重かつ洞察力を持って行う必要があることを思い出させる重要なものだ。自動車産業のようなダイナミックで競争の激しい分野では、企業は市場の変化に適応し、長期的な生き残りを確実にするために戦略を常に再評価する必要があります。電動モビリティが進歩し続けるにつれて、環境への願望と経済的要請の間のバランスを維持することが不可欠です
この記事がお役に立てば幸いです。 もしそうなら、チップをおくるどうぞ https://getalby.com/p/bitcap
-
 @ e968e50b:db2a803a
2024-03-06 19:30:42
@ e968e50b:db2a803a
2024-03-06 19:30:42I past these on display at an antique store recently. Here are a couple of thoughts. Alabama was issuing it's own currency. The cent was worth enough that it made sense to have paper money for significantly less than a dollar.
-
 @ b5035b7a:f170dae3
2024-03-06 17:04:45
@ b5035b7a:f170dae3
2024-03-06 17:04:45Initial post
codecodequote quotes
- list item
- second list item
Regular paragraph.
-
 @ a012dc82:6458a70d
2024-03-05 01:40:30
@ a012dc82:6458a70d
2024-03-05 01:40:30Table of Content
-
Content
-
Introduction
-
Who Created Polygon?
-
How Does Polygon Work?
-
Why Does MATIC Have Value?
-
Architecture
-
Why Use MATIC?
-
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
Introduction
Ethereum, a platform that is home to a variety of decentralized apps, is at the core of Polygon's concept. These applications include ones that allow users to join virtual worlds, play games, purchase artwork, and take part in a variety of financial activities. But because there is so much activity on Ethereum's blockchain, the platform is almost useless because the cost of sending data is going up and there is a growing backlog of traffic.
Enter Polygon. In a nutshell, Polygon markets itself as a layer-2 network, which indicates that it functions as an add-on layer to Ethereum and does not intend to replace the original blockchain layer. In other words, Polygon is not trying to reinvent the blockchain. The polygon, like the physical form that it was named after, has numerous sides, many shapes, and different functions. It also provides a simpler foundation for the construction of linked networks.
Polygon aims to assist Ethereum in growing in terms of scale, security, efficiency, and utility. Also, the company wants to encourage developers to make products that are more appealing and bring them to market faster.
Following the renaming, Polygon continued using the MATIC cryptocurrency, the digital token that serves as the basis for the network. When members of a network communicate with one another, the MATIC cryptocurrency serves as the unit of payment and settlement for such transactions.
Who Created Polygon?
Polygon was once referred to as the Matic Network when it was initially established in India in 2017. They (Jaynti Kanani, Sandeep Nailwal, and Anurag Arjun), together with Mihailo Bjelic, are all seasoned Ethereum engineers, and they are the ones who came up with the idea.
The Matic Network became online in the year 2020 and has already attracted some of the most well-known names in the field of decentralized finance, generally referred to as DeFi. These names include MakerDAO and Decentraland. In February of 2021, the Matic Network changed its name. It is now called Polygon.
During the first offering that took place in April 2019, the Polygon team was able to raise the equivalent of $5.6 million in ETH by selling 1.9 billion MATIC tokens over the course of a frenetic 20-day period.
How Does Polygon Work?
Polygon is a multi-level platform with the goal of scaling Ethereum owing to a multitude of sidechains, each of which attempts to unclog the main network in a way that is both effective and cost-efficient. Polygon's primary goal is to grow Ethereum.
For those of you who are new to the term, sidechains are individual blockchains connected to the main Ethereum blockchain. Sidechains are useful in that they enable many of the Decentralized Finance (DeFi) protocols that are accessible on Ethereum.
As a result, it is possible to compare Polygon to other networks that compete with it, such as Polkadot, Cosmos, and Avalanche.
Why Does MATIC Have Value?
The native coin of the Polygon network is called MATIC. In addition to being staked and used to pay transaction fees, MATIC is also utilized to assist drive growth throughout the network.
Users that provide computing resources or services to the Polygon network are eligible to get MATIC tokens as a reward. Validating transactions or carrying out smart contracts on the network are two possible ways to accomplish this goal.
In addition, users who hold MATIC and stake it are granted the power to vote on network enhancements, with the weight of each user's vote being directly proportionate to the amount of MATIC cryptocurrency they stake.
As is the case with the vast majority of other crypto assets, the supply of MATIC tokens is finite. According to the program's rules, there will never be more than 10 billion MATIC coins in circulation.
Architecture
At the center of the Polygon network is the software development kit (SDK) that is used to build decentralized apps that work with Ethereum as sidechains and connect them to the main blockchain of the network.
Sidechains can be made using any of the following scalable building methods:
-
Plasma Chains - Transactions are grouped into blocks, and then the blocks are submitted to the Ethereum blockchain.
-
zk-Rollups - Makes it possible to combine many different transfers into a single transaction.
-
Optimistic Rollups - Similar to Plasma Chains, but with the ability to scale Ethereum smart contracts.
The primary chain of Polygon is a Proof of Stake (PoS) sidechain. Participants in the network can use MATIC tokens to verify transactions and vote on updates to the network.
Why Use MATIC?
It is possible that the potential of the Polygon Network to give scaling solutions to Ethereum would attract supporters of the network. Developers could also use Polygon's technology to make decentralized applications (dapps) on the network's blockchain easier to use.
All of Sushi, a decentralized exchange platform; Augur, a prediction market platform; and Ocean Protocol, a platform that enables companies and people to trade and monetize data and data-based services, are examples of dapps that are built on Polygon.
If investors feel that Layer-2 solutions are the way to go to improve the Ethereum Network, they can also look into purchasing MATIC and adding it to their portfolio.
Conclusion
There aren't many DeFi projects as intriguing as Polygon, and its future prospects for scalability and blockchain compatibility bode well for the DeFi community as a whole. And since it comes with such a comprehensive collection of tools for developers, its forward-thinking mechanisms and modules, and complete support for the Ethereum Virtual Machine (EVM), the Polygon ecosystem may soon be home to a great number of successful applications.
FAQ
Is Polygon Matic a good investment? Polygon, on the other hand, is a cryptocurrency asset that may give investors the potential to make substantial gains if they hold it for longer. The price prediction for Polygon (MATIC) shows that the value of this cryptocurrency asset will rise over time, which is what the experts above have said will happen.
What does Polygon Matic do? Polygon (MATIC) is a cryptocurrency and technological platform developed to connect and grow blockchains and projects that are compatible with Ethereum. Investors may purchase MATIC tokens on exchanges like Coinbase and Kraken to use them for governing and securing the Polygon network as well as paying transaction fees. MATIC tokens are also used to pay for those fees.
Is Polygon Network the same as Matic? Polygon is a cryptocurrency that was established in 2017 and was originally known as Matic Network. It has a fair amount of popularity and consistently places among the top 15 cryptocurrencies in terms of market value. MATIC now supports more than 7,000 decentralized apps, often known as dApps. These are applications that function independently of any middlemen.
Does Polygon Matic have a future? According to the findings of a recent technical study conducted by cryptocurrency industry professionals about the pricing of Polygon, it is anticipated that MATIC will have a minimum price of around $1.83 and a maximum price of approximately $2.22 in the year 2024. The anticipated cost of trading, on average, is $1.89.
That's all for today, see ya tomorrow
If you want more, be sure to follow us on :
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ c11cf5f8:4928464d
2024-03-06 16:54:51
@ c11cf5f8:4928464d
2024-03-06 16:54:51Trying to submit a post as usual, but getting this error when clicking on post:
submit error: Invalid
prisma.$queryRawUnsafe()invocation: Raw query failed. Code:23503. Message:insert or update on table "ItemUpload" violates foreign key constraint "ItemUpload_uploadId_fkey"What's next?
-
 @ 000002de:c05780a7
2024-03-04 22:47:35
@ 000002de:c05780a7
2024-03-04 22:47:35I started this as a comment on @felipe's post "What is your story with Linux? Me first:" but decided it was getting a bit long.
How it Began
It started on my first day at my first job in tech. I was working part time and being trained by a retired IT guy that had built the computers and set up the servers I was going to manage. He showed my my workstation which was running some Linux distro. I knew nothing about Linux at the time and I don't recall which distro it was. I am pretty sure it was using KDE though. He just called it Linux. At the time I was using OS X (now called Mac OS). I didn't dive into Linux at all. I only used it when I had to use it.
Fast forward a few years and our team was tasked with launching a set of web sites and I needed to set up servers for hosting them. I had never done this before. I hired a consultant to help me evaluate and do the work. He was a Linux guy, and also a Vim user and regularly encouraged me to dive into Vim. I'm still grateful for that. He was a Debian fan but due to my limited knowledge of Linux and upper management's desire for support we went with Red Hat Enterprise Linux (RHEL). What is funny is I now work at Red Hat. I started learning more and more about Linux servers as I ran them. I set up many Debian servers and have been using Linux on the server ever since. I still default to Debian when I need to set up a server. I know it best. Over the years hosting web sites for myself and others has taught me quite a bit about Linux but that is only the first part.
The Year of the Linux Desktop
In 2020 I started working at Red Hat. I stayed on MacOS but over the years I had started to tire of Apple's neglect of their operating system, their increased focus on iOS and making MacOS more like iOS. I wanted to do things that MacOS just couldn't do. My job required a lot of use of Docker and MacOS at the time was painfully bad at running Docker Desktop. In 2021 I'd finally had it with their hardware as well and decided to try to make a go all in using Linux on the desktop. After all I now worked at a Linux company and had many co-workers that used Linux as their main OS.
I did my research and decided to go with Fedora since I like the desktop environment. I later learned that DE is not a great reason to choose a distro. But, all and all Fedora has been solid and I haven't been tempted to go back to MacOS. I bought an early Framework laptops and soon after requested a company issued Thinkpad. I installed Fedora on both and haven't looked back.
I've tried Arch but its never stuck as my daily driver. I still use it on an old Thinkpad from time to time. I'm planning to try NixOS soon. I've also tried to use a couple tiling window managers but just haven't been able to make the jump yet. I think that's where I will land as I have used Tmux for my development work for 10+ years now and I like the UX. Linux has an amazing ecosystem and there's so much you can do with it. I now recommend anyone getting into programming or working in IT start using it as their main workstation. I wish I had done it much sooner. Thankfully there was a lot of knowledge I gained using MacOS that transferred to Linux since they share the same origin but there is no substitute for Linux.
-
 @ b5035b7a:f170dae3
2024-03-06 16:54:14
@ b5035b7a:f170dae3
2024-03-06 16:54:14Interested in a larger time frame, a larger context.
My rabbit holes: - Finance, geo-politics, martial events(these days Ukraine, Gaza), energy - my weaknesses: malinois dogs, when sporting - fitness+health+diet+exercise - vast spaces, unspoiled nature - water and air - artificial intelligence - genetics(biology of) - Jewish proportionality as compared to malinois
-
 @ 34f1aaa6:836e3cd6
2024-03-04 19:52:12
@ 34f1aaa6:836e3cd6
2024-03-04 19:52:12Liberty isn’t a societal value at the moment in India.
But it can become one if we work towards it.
Here are the reasons why:
•It is very much a constitutional value as is evident in the preamble and part III of the document.
•There was a political movement called 'Swatantra' that was based on libertarian values and had a real impact on policies and politics in post-independence India, so there is historical evidence that it is possible here.
•There are religious schools of thought like Shaivism that preach it, so it is not an 'imported value', but very much native to our country.
•There are cultural signs of people starting to believe in it as an increasing number of people are exposed to the relatively open internet and all the information available on it. There are 900 million internet subscribers in India at the moment.
•Every single person irrespective of social, financial, professional and political status experiences persistent inflation, high taxation, trade restrictions, unfair licensing, frustrating red tape and not a single political party makes them their core issues and relegates them to the peripheries of their manifestos and campaigns.
It is entirely up to those of us who believe in liberty to fight for it by informing ourselves, speaking up, sharpening our opinions and articulating them effectively.
Borrowing and partially altering a quote from Odell,
'Liberty is not granted, it is taken and defended.'
-
 @ 7dd04080:36f6813d
2024-03-04 18:49:56
@ 7dd04080:36f6813d
2024-03-04 18:49:56All filmmakers' and musicians' lightning address QR codes will now be displayed with their videos inside our Roku app. This should greatly enhance the ability to receive direct tips from television watchers worldwide. All they need to do is open their favorite Lightning wallet on their phone, point its camera at the QR code, and choose the number of Sats to send to an artist.
For more information, check out our site: https://versusmedia.com/
-
 @ 5d4b6c8d:8a1c1ee3
2024-03-04 16:47:50
@ 5d4b6c8d:8a1c1ee3
2024-03-04 16:47:50I mentioned going to Dune part 2 in the saloon and promised to make a post about it. Without spoiling the main events of the plot, I'm going to discuss what's so amazing about Dune. I'll focus on the books, since this is ~BooksAndArticles, but I'll also give my impressions of the adaptation.
I'd love to hear other people's thoughts about book and/or movie.
Dune (the book)
First off, Dune is one of my favorite books of all time. I'm an economist with a background in atmospheric science who loves sci-fi, so Dune is very much up my alley. I've read all of the Frank Herbert books, and I recommend all of them, but the first one is really special. It's worth noting that Star Wars was heavily influenced by Dune (to the point where I've heard Star Wars referred to as a knock-off).
Dune is a planet that is the sole producer of an extremely valuable commodity, "spice", that is basically a combination of spices and petroleum in the context of Earth history. So, think about a substantially more extreme version of the spice trade. The planet is incredibly inhospitable: hotter and drier than any desert on Earth, plus there are enormous carnivorous worms in the desert. The native inhabitants of the planet are ferocious desert warriors who are in perpetual conflict with the oligarchs attempting to harvest spice.
@r3drun3 made a post about the economics of Dune. The political setting of this universe is very detailed. There's an empire, but also great houses, trade guilds, and professional societies. Each of those are described in great detail, which makes the world incredibly immersive. There are a ton of dynamics in play all the time, but it's written so well as to not be confusing or hard to keep track of.
There are many themes being explored in Dune (understatement alert), so I'll just discuss a couple of my favorites. The most striking element of the book to me was how intricately detailed the native culture of Dune (the Fremen) is described. The society is fundamentally shaped around water scarcity and there are a wide array of cultural practices, beliefs, and technologies that exist to help them survive this place. There is also a religious belief system that has been externally curated and manipulated to make the Fremen receptive to a messiah that one of the secret societies is trying to create. It's a fascinating exploration of propaganda and myth making.
As a slight aside, I've been reading The Wheel of Time (review here) and there's a lot of overlap with Dune. One is sci-fi and the other is fantasy, but there are a ton of parallels.
Dune Parts 1 and 2 (the movies)
The two recent movies are fairly faithful to the book they are adapting, but they have radically pared down the content. The first book describes many characters in great detail, which would have been very difficult to cover in a movie. As a result, the movies are largely told from Paul Atreides' perspective and many of the things that would have been explained in the book are seen without exposition in the movies.
The director does a phenomenal job of showing many of the complex elements of the books without needing to spend precious screen time on exposition. Dune is also a very alien universe, despite being mostly about humanity. It takes place in the far distant future and the technologies are supposed to be simultaneously understandable in function and unfamiliar in form. This is executed beautifully on screen: everything is grand and distinctive and foreign.
The performances are overwhelmingly excellent, with just a couple of exceptions (Jason Momoa cough, Christopher Walken cough). Timothée Chalamet, in particular, has some incredible scenes in part 2.
-
 @ 82b30d30:40c6c003
2024-03-06 15:40:24
@ 82b30d30:40c6c003
2024-03-06 15:40:24[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
[19]
[20]
[21]
[22]
-
 @ cce0989b:b497e608
2024-03-06 13:44:03
@ cce0989b:b497e608
2024-03-06 13:44:03Here are some common myths about loneliness: if you're lonely, it's because...
-
You live alone
-
You're single
-
You're older
-
You have poor social skills
-
You're introverted
The science of loneliness, spearheaded by John Cacioppo, tells us these myths are incorrect.
Loneliness is a state of being that arises in tandem with real-life challenges.
If you're lonely, you're probably going through something hard. You're dealing with medical problems, struggling with your mental health, unemployed, navigating relationship problems, or anything else that's difficult.
Lonely people feel like no one is ‘in it’ with them and that they are facing these struggles alone.
That's why all of us have a collective responsibility to take on loneliness as a problem. The solution is to care for one another. (By the way, that's also where your personal happiness lies, too.)
Today, try this:
Think about someone you love who is having a tough time.
Reach out to them. Check in with them. Ask them about the challenge in their life. Proactively offer help. If you're not sure what to do, think about what you would want in this situation.
We can build bridges that support one another.
-
-
 @ a5d8475e:df9ff32c
2024-03-06 10:27:56
@ a5d8475e:df9ff32c
2024-03-06 10:27:56The quest for the perfect rental can be a daunting task, filled with numerous considerations and potential pitfalls. From location preferences to budget constraints, finding the right rental requires thorough research and discernment. Fortunately, with the right approach and guidance, securing a desirable property to rent in Wombourne is entirely achievable.
Wolverhampton, a vibrant city nestled in the heart of the West Midlands, offers a diverse range of rental properties to suit various preferences and lifestyles. Whether you're seeking a cozy apartment in the city center or a spacious family home in the suburbs, Wolverhampton has something to offer for everyone. However, with the abundance of options available, distinguishing genuine and well-kept rentals from the rest requires careful evaluation and attention to detail.
One of the first steps in your quest for the perfect rental property is to determine your specific requirements and preferences. Consider factors such as location, budget, size, and amenities to narrow down your search criteria. Are you looking for a property to rent in Wolverhampton bustling city center, or do you prefer the quieter suburbs of Codsall or Wombourne? Define your priorities to streamline the search process and focus on properties that align with your needs.
When it comes to finding genuine and well-kept rentals in Wolverhampton, leveraging online resources and platforms dedicated to property listings can be immensely helpful. Websites and apps specializing in property rentals offer a comprehensive database of available listings, allowing you to browse through various options from the comfort of your home. Utilize search filters to refine your results based on location, price range, and property type, making it easier to identify suitable rentals in your desired area.
Keywords such as "property to rent in Wolverhampton," "houses to rent Codsall," and "property to rent in Wombourne" can be instrumental in refining your online search and uncovering hidden gems in these specific areas. Incorporating these keywords into your search queries will ensure that you access relevant listings tailored to your preferences. Whether you're seeking a cozy apartment, a modern townhouse, or a spacious family home, utilizing targeted keywords can expedite the search process and increase your chances of finding the perfect rental property.
In addition to online resources, enlisting the services of reputable estate agents and letting agencies can provide valuable assistance in your quest for a genuine and well-kept rental in Wolverhampton. Experienced professionals with in-depth knowledge of the local property market can offer valuable insights, guidance, and access to exclusive listings that may not be available through online platforms. By collaborating with a trusted agent, you can benefit from their expertise and streamline the rental process, ensuring a smooth and successful outcome.
When evaluating potential rental properties, it's essential to conduct thorough inspections to assess their condition and ensure they meet your standards. Look for signs of maintenance and upkeep, such as freshly painted walls, well-maintained appliances, and clean and tidy living spaces. Pay attention to any red flags, such as signs of neglect or disrepair, that may indicate a lack of care or attention from the landlord or property management company.
Keywords like "property to rent" and "houses to rent Wolverhampton" can help broaden your search and uncover a wider range of available rentals in the area. By incorporating these keywords into your search queries, you can explore different neighborhoods, property types, and price ranges, giving you a comprehensive overview of the rental market in Wolverhampton.
Furthermore, don't hesitate to ask questions and seek clarification from landlords or property managers regarding any concerns or queries you may have about the rental property. Inquire about maintenance procedures, tenant responsibilities, and lease terms to ensure you have a clear understanding of what to expect before signing any agreements. Effective communication is key to establishing a positive landlord-tenant relationship and ensuring a mutually beneficial rental experience.
In conclusion, finding a genuine and well-kept rental houses to rent wolverhampton requires patience, diligence, and a proactive approach. By defining your requirements, leveraging online resources and keywords, and seeking assistance from professionals, you can navigate the rental market with confidence.
+44 (0) 1902 504455
-
 @ 57d1a264:69f1fee1
2024-03-06 10:21:10
@ 57d1a264:69f1fee1
2024-03-06 10:21:10I thought it could be an interesting topic to discuss here, as designers we probably lack the tech knowledge necessary to make this happen.
The issue is also a BIP on the bitcoin repository https://github.com/bitcoin/bips/pull/1551
https://www.youtube.com/watch?v=gAmrqSaL5Mo
And here the issue opened on the Bitcoin design repository https://github.com/BitcoinDesign/Meta/issues/638
In reality, we already have it on the Lightning network, it would make sense to apply it to onchain addresses too? It would even possible to do?
-
 @ 599f67f7:21fb3ea9
2024-03-04 14:25:25
@ 599f67f7:21fb3ea9
2024-03-04 14:25:25¿Qué es Cashu?
Cashu es un protocolo de ecash de código abierto para Bitcoin que ofrece transacciones instantáneas sin comisiones con una privacidad casi perfecta. Consulta nostr:naddr1qqxnzd3e8y6rvdpe8qur2v3cqgs9n8m87l0hd9xxqwndqcmwzh4uvyxmwlw0637kuhg98pkcy8ana2grqsqqqa28f238dz para obtener más detalles.
Nutstash
Nutstash es una increíble billetera web de Cashu desarrollada por nostr:npub1cj6ndx5akfazux7f0vjl4fyx9k0ulf682p437fe03a9ndwqjm0tqj886t6 que implementa la mayoría de los NUTs, así como el envío y recepción a través de Nostr. También puedes instalarla como una Progressive Web App (PWA) en tu teléfono.
⚠️ Tanto Nutstash como Cashu todavía están en fase beta. Existe la posibilidad de perder fondos. Lee sobre los riesgos antes de usar la aplicación. Haz pruebas con pequeñas cantidades con las que te sientas cómodo perdiendo.
Pruébalo
Vamos a explicar cómo interactuar con una mint, recibir y enviar ecash, hacer copias de seguridad, convertir a Lightning y hacer intercambios entre mints, y al final probaremos la funcionalidad de los contactos de Nostr.
Añadir un mint
Para interactuar con ecash, primero necesitas tener acceso a una mint, donde se crean y canjean tus tokens de ecash.
- Ve a Txoko Mint.
- Abre la mint en Nutstash.
💡 Puedes añadir mints adicionales en Nutstash yendo a
Mint, pegando la URL de la mint y presionandoAdd Mint("Añadir Mint"). Algunas mints públicas se pueden encontrar en MintIndex. Ten en cuenta que algunas mints reservarán una cierta cantidad de sats para pagar las tarifas de enrutamiento, lo que significa que no podrás retirar todos tus sats.
Crear tokens
Puedes financiar tu billetera de ecash tanto recibiendo ecash directamente como creando nuevos tokens de ecash pagando una factura de Lightning.
- En la pestaña
Mint, elige la mint en la que quieres crear nuevos tokens y presionaMint. - Elige una cantidad. Prueba con una cantidad pequeña, como 100 sats.
- Crea la factura y págala desde una billetera de Lightning. Una vez que se haya pagado la factura, deberías tener tokens de ecash.
Realizar transacciones con ecash
Realizar transacciones con ecash implica básicamente enviar y recibir bloques de datos. Por lo tanto, puedes probar estas funcionalidades enviando y recibiendo a ti mismo. 1. Para enviar ecash, ve a
Wallet>Send. 2. Selecciona la mint desde la que quieres enviar. 3. Elige una cantidad. Opcionalmente, utiliza la selección de monedas. 4. Haz clic en enviar tokens. 5. Copia el token. En este punto, puedes enviar el token a otra persona o canjearlo en tu propia billetera. Dado que solo estamos probando las cosas, haremos lo último.- Para recibir ecash, haz clic en
Wallet>Receive. - Pega el token de cashu.
- Haz clic en
Receive.
💡 Puedes verificar los tokens de ecash pendientes y reclamarlos si el destinatario aún no los ha canjeado. Para hacer esto, ve a la pestaña
Walletsy buscaTokens. Asegúrate de que la columnaPendingesté marcada. Debería haber una lista de tokens pendientes, haz clic en el botón de actualización para verificar su estado. Si no han sido reclamados, puedes copiar y canjear el token.Intercambio de múltiples mints
Es posible que te hayas preguntado si diferentes mints pueden enviar y recibir entre sí. La respuesta es sí. Bueno, más o menos. En lugar de enviar tokens de cashu entre sí, las transacciones entre mints se realizan a través de Lightning. Para probar esto, puedes agregar otra mint si aún no lo has hecho, por ejemplo, la mint de LNbits.
💡 Ten en cuenta que algunas mints reservarán una cierta cantidad de sats para pagar las tarifas de enrutamiento, lo que significa que no podrás retirar todos tus sats. Para evitar esto, también puedes crear tu propia mint con tu billetera Bitcoin Txoko LNbits activando la extensión de Cashu. Bitcoin Txoko no requiere reservas, por lo que puedes retirar todos tus sats.
- Ve a la pestaña
Minty agrega una nueva mint si aún no lo has hecho. - Una vez que tengas varias mints, tendrás la opción de
Inter-Mint Swap. Abre la opción y lee la advertencia. - Si deseas continuar, elige una mint de la que quieres hacer el intercambio y una mint a la que quieres hacer el intercambio.
- Elige una cantidad.
- Confirma la cantidad (
Confirm amount), verifica las tarifas estimadas de enrutamiento y procede con el intercambio (Swap). En segundo plano, la mint que envía está pagando una factura de Lightning a la mint que recibe. Una vez que se haya liquidado la factura, el token intercambiado debería aparecer en el saldo de tu billetera en la mint que recibe.
Convertir a lightning
Cuando quieras convertir tus sats de cashu de nuevo a sats de Lightning, puedes convertir o "derretir" tus tokens de cashu.
- Haz clic en
Payo toca el ícono de la cámara para escanear un código QR. - Ingresa o escanea una factura.
- Opcionalmente, utiliza la selección de monedas.
- Presiona
Pay. La mint funde los tokens de cashu y paga la factura de Lightning.
Copias de seguridad
Hacer copias de seguridad de los tokens de Cashu es probablemente diferente al proceso que estás acostumbrado a hacer para respaldar las billeteras de Bitcoin y Lightning. Dado que los fondos están representados por tokens que son simplemente bloques de datos, solo estás respaldando estos datos cuando haces una copia de seguridad de los tokens de Cashu. Esto también significa que tus copias de seguridad cambiarán cada vez que realices una transacción y necesitarás hacer una nueva copia de seguridad después de cada transacción.
Los diferentes clientes de billeteras han implementado las copias de seguridad de manera diferente y solo funcionarán con la misma billetera que ha creado la copia de seguridad. Nutstash utiliza un archivo JSON como copia de seguridad, que también incluye tu historial de transacciones junto con los tokens que has agregado.
- Para descargar la copia de seguridad en formato JSON, ve a
Settings("Configuración") >Backup Tokens("Copia de seguridad de tokens"), descarga el archivo JSON y guárdalo en un lugar seguro. - Para restaurar la copia de seguridad, ve a
Settings("Configuración") >Restore("Restaurar"). Lee la advertencia. Los datos actuales de tu billetera se sobrescribirán.
Nostr
Dado que puedes enviar tokens de Cashu a través de cualquier protocolo basado en texto, Nostr es una excelente opción para Cashu. Nutstash facilita el envío de tokens de Cashu a través de Nostr.
Primero, necesitas conectar un firmante externo de Nostr a Nutstash para que Nutstash pueda cifrar y firmar mensajes directos utilizados para enviar tokens de ecash. Para hacer esto,
- Ve a la pestaña
Settings("Configuración") y encuentra la secciónNostr. - Activa
Nostr. - Puedes configurar (
Configure) los retransmisores manualmente o permitir que Nutstash lea tu lista de retransmisores después de completar el siguiente paso. - Activa
Use external key("Usar clave externa"). Debes tener instalada una extensión de firmante de Nostr en tu navegador. Algunas buenas opciones son nos2x, Alby y Nostore (para Safari en iOS). - Una vez que Nutstash detecte tu extensión de firmante, permítele leer tu lista de retransmisores y clave pública.
- Si permites que Nutstash descifre los mensajes, buscará tokens de Cashu en tus mensajes directos. Una vez encontrados, aparecerán en la pestaña
Walleten la bandeja de entrada (Inbox). Allí podrás canjearlos en tu billetera.
Para enviar Cashu a través de Nostr,
- Ve a
Send("Enviar"). - Elige un mint.
- Elige una cantidad. Opcionalmente, utiliza la selección de monedas.
- Presiona
Send("Enviar"). - En
Send via Nostr("Enviar a través de Nostr"), ingresa una dirección de Nostr en formato npub, hexadecimal o NIP-05. Alternativamente, escanea el código QR del perfil de alguien. - Presiona
Send via Nostr("Enviar a través de Nostr") y firma el mensaje tipo 4 con tu firmante externo. - Informa al destinatario que revise su bandeja de entrada, ¡deberían tener algunos Cashu esperándolos allí!
Conclusión
¿Encontraste útil esta guía? ¡Intenta enviarnos algunos tokens de Cashu a través de Nostr!
-
 @ 57d1a264:69f1fee1
2024-03-06 07:27:16
@ 57d1a264:69f1fee1
2024-03-06 07:27:16Prompt: Nostr Subscription ===============
What is a person subscribing to? A nostr thread, a zapstream platform, or a private messaging group? Is it just a button or a widget?
What type of information are you looking to capture from the user? Their
nymandnpub? Their location? Age consent? Something else?Flex your design muscles and join in. Most of all, keep this exercise loose and keep it stress-free. The FUC is about growing our design skills, together, as a community. We can't wait to see what you create!
Happy designing, Stackers!
Share Your Results When you finish the challenge, post your work on this thread! If you also share it on
nostr, be sure to use the hashtag #FUCdesiger and tag Design_r@iris.to or @Design__r on X! We'll keep an eye out and repost good examples on a regular basis.
Curious to know WTF is a FUC? Read the ⚡️Flash Ui Challenges welcoming post.
Looking for more FUCs? Check the archive here!
-
 @ 73cee26b:072f3bb6
2024-03-04 14:09:29
@ 73cee26b:072f3bb6
2024-03-04 14:09:29I've been diving the rabbit hole of non-KYC this evening, thanks to this post https://stacker.news/items/435653
But the sellers I looked at require sending them bank statements or Cash App balances and A SELFIE WITH PHOTO ID!
I don't want to mail cash. Are any online money transfer services irreversible (venmo, cash app, zelle, etc)?
And, if there is an actual chargeback risk, wouldn't scammers just be constantly ripping off sellers?
-
 @ 599f67f7:21fb3ea9
2024-03-04 13:47:41
@ 599f67f7:21fb3ea9
2024-03-04 13:47:41¿Qué es Cashu?
Cashu es un protocolo de ecash de código abierto para Bitcoin que ofrece transacciones inmediatas, sin comisiones con una completa privacidad. Visita nostr:naddr1qqxnzd3e8y6rvdpe8qur2v3cqgs9n8m87l0hd9xxqwndqcmwzh4uvyxmwlw0637kuhg98pkcy8ana2grqsqqqa28f238dz para más detalles.
eNuts
eNuts es un excelente cliente monedero Cashu para tu móvil, disponible tanto para Android como para iOS (TestFlight). Admite múltiples mints y también enviar sobre nostr.
⚠ eNuts y Cashu todavía están en versión beta. La pérdida de fondos es posible. Lea sobre los riesgos al instalar la aplicación. Prueba con pequeños montos que no te importaría perder.
Pruébalo
Explicaremos la forma de interactuar con un mint (casa de la moneda), recibir y enviar efectivo, copias de seguridad, retirar a Lightning y el intercambio entre mints, en la parte final probaremos la funcionalidad de los contactos de nostr
Instalar
Visita el sitio web de eNuts e instala la aplicación idónea para tu sistema operativo.
Añadir un mint
Para interactuar con el efectivo, antes debes tener acceso a una casa de la moneda, donde se acuñen e intercambian sus tokens de efectivo. La casa de la moneda es el custodio de tu Bitcoin, pero no sabe quién eres, con quién estás negociando ni cuántos fondos tienes. Puedes usar para las pruebas.
- Dirígete a Txoko Mint y copia la URL del mint
- En eNuts, ve a
Opciones>Gestión de mentay pulse el botón+. Pega la URL del mint que has copiado del paso anterior.
💡 Puedes añadir casas adicionales adicionales. Algunos mints públicos se pueden encontrar en MintIndex. Ten en cuenta que algunos de estos mints reservarán una cierta cantidad de sats para pagar las tarifas de enrutamiento, lo que significa que no puedes retirar todos tus sats.
Acuñación de Tokens
Una vez que hayas añadido el mint, eNuts te preguntará automáticamente si quieres acuñar nuevos tokens de ecash de ese mint. 1. Respuesta
Sí. 2. Crea una factura por la cantidad que desea acuñar. Prueba una pequeña cantidad, por ejemplo, 100 sats. 3. Paga la factura con una billetera Lightning. Una vez pagada la factura ya deberías tener tus tokens de ecashTransaccionar con ecash
Estas transacciones son básicamente enviar y recibir blobs de datos. Como tal, puedes probar estas funcionalidades enviándote y recibiendo a ti mismo. 1. Para enviar efectivo, haz clic en
Enviar>Enviar ecash2. Si utilizas varios mints, selecciona el mint desde el que quieres enviar. Luego eligeCopiar y compartir. 3. Elige una cantidad. 4. Opcionalmente, puedes agregar una nota, haz clic enContinuar. 5. Confirma los detalles del pago y crea un token. En este punto, puedes usar la función de selección de monedas para elegir qué tokens quieres gastar. Ten en cuenta que las fichas se denominan en 1 sat, 2 sats, 4 sats, 8 sats, 16 sats, y así. Puedes pensar en ellos como billetes de 10 euros, 20 euros, 50 euros como ejemplo. 6. Copia el token.En este punto, puedes enviar el token a otra persona o canjearlo en tu propia cartera. Como solo estamos probando las cosas, haremos esto mas tarde. 1. Para recibir, haz clic en
Recibir>Pegar y canjear efectivo. eNuts debe leer automáticamente su portapapeles y canjear el token.💡 Puedes comprobar los tokens de efectivo pendientes en tu historial de transacciones y reclamarlos si el destinatario aún no los ha canjeado. Para hacer esto, selecciona una transacción saliente de tu historial de transacciones y luego compruebe si se ha gastado el token. Si el token está pendiente, puede reclamar el token de vuelta tu billetera.
Intercambio entre Mints
Es posible que te hayas preguntado si diferentes mentas pueden enviar y recibir fondos entre sí. La respuesta es sí. Bueno, más o menos. En lugar de enviar tokens de cashu entre sí, las transacciones entre estas casas vuelven a Lightning, ya que un mint también es un nodo Lightning. Los tokens de Cashu en sí mismos no son fungibles en todos los nodos. Para probar esto, puedes añadir otra menta si aún no lo has hecho, por ejemplo, el mint cashme LNbits o el mint que presenta eNuts por defecto.
💡 Ten en cuenta que algunas mentas reservarán una cierta cantidad de sats para pagar las tarifas de enrutamiento, lo que significa que no puedes retirar todos tus sats. Para evitar esto, también puedes crear tu propio mint con tu cartera Bitcoin Txoko LNbits activando la extensión Cashu.
- Vaya a
Opciones>Gestión de minty selecciona el mint del que desea intercambiar. Luego vaya aMultimint swapenFondos. - Elige un mint para intercambiar.
- Elige una cantidad y toca en la tarifa de estimación para estimar las posibles tarifas de Lightning.
- Haz clic en
Continuar. - Comprueba los detalles y, opcionalmente, usa la selección de monedas, luego presione Intercambiar ya. Ahora, en segundo plano, la casa de la moneda de envío está pagando una factura Lightning de la casa de la moneda de recepción. Una vez que se liquida la factura, el token intercambiado debe aparecer en el saldo de su billetera en la casa de la moneda de recepción.
Retiro
Cuando quieras convertir tus cashu sats a Lightning sats, puedes hacer retiros. 1. Haga clic en
Enviar>Pagar factura Lightning2. Seleccione un mint desde el que enviar si utiliza varias. 3. En facturaLN o LNURL, introduzca una factura, LNURL o dirección Lightning; o simplemente escanea un código QR. 4. Elije la cantidad y la estimación de comisiones. 5. Comprueba los detalles antes de pulsarCash out. El mint canjea los tokens de efectivo y paga la factura de Lightning.Respaldo (Backups)
La copia de seguridad de los tokens de cashu es probablemente diferente al proceso al que podrías estar acostumbrado para hacer copias de seguridad de las carteras de Bitcoin y Lightning. Dado que los fondos están representados por tokens que son solo blobs de datos, solo estás haciendo una copia de seguridad de estas piezas de datos cuando haces una copia de seguridad de los tokens de ecash. Esto también significa que tus copias de seguridad se invalida cada vez que realizas una transacción. Diferentes clientes de cartera han implementado copias de seguridad de manera diferente y solo funcionarán con la misma cartera que ha creado la copia de seguridad.
eNuts crea un token de cashu con todos sus fondos en él y a qué moneda pertenecen.
• Para crear una copia de seguridad, ve a
Opciones>Seguridad>Crear un token de copia de seguridad. Copia el token y guárdalo en un lugar seguro.Alternativamente, puedes hacer una copia de seguridad de cada una de tus mints individualmente.
• Para ello, ve a
Opciones>Gestión de la casa de la moneday seleccione la casa de la moneda de la que desea hacer una copia de seguridad. Ve aCopia de seguridad de fondos, copia el token y guárdalo en un lugar seguro.Para restaurar, simplemente copie el token de copia de seguridad y abra la aplicación eNuts. La aplicación debería leer su portapapeles y preguntarle si desea restaurar el token.
Nostr
eNuts integra Nostr para que puedas enviar efectivo a tus contactos.
Para usar esta función, ve a
Contactosy pega tu clave pública de nostr. eNuts luego extrae tu lista de contactos de los relays. ~~Desafortunadamente, la función de búsqueda aún no se ha implementado, lo que puede hacer que encontrar el contacto correcto sea un poco engorroso si tienes muchos.~~ Con la actualización a la v0.1.1-beta, eNuts ahora soporta la búsqueda, y funciona a las mil maravillas. Simplemente introduce una npub, dirección nostr o busca por una palabra clave y podrás enviar ecash directamente a tu contacto.El destinatario debe recibir un mensaje directo de Nostr tipo 4 que contenga el token ecash que puede canjear en su billetera.
Conclusion
¿Te ha resultado útil esta guía? ¡Intenta enviarnos algunos tokens de Cashu a través de nostr!
-
 @ 57d1a264:69f1fee1
2024-03-06 07:16:55
@ 57d1a264:69f1fee1
2024-03-06 07:16:55An opportunity to share some bits of a process you embrace to achieve anything you aim to. What steps do you follow from concept to design completion? What’s your tricks? Any useful guide or tutorial to share? Where are you now?
-
 @ 1c6b3be3:73f0ae6f
2024-03-04 06:00:07
@ 1c6b3be3:73f0ae6f
2024-03-04 06:00:07🍵 "llm | cloud | ddos" - Google News
Proposed class action lawsuit alleges Apple monopolizing cloud storage for its devices - The Hill St. Cloud State Tennis Travels to Florida for Three-Match Slate - St. Cloud State University Athletics - St. Cloud State University Athletics Best cloud storage of 2024 - TechRadar 40 years ago, St. Cloud Apollo was Cinderella at the state hockey tournament - The Rink Live Proposed class action lawsuit accuses Apple of monopolizing cloud storage for its devices - Engadget French cloud Scaleway starts renting Alibaba's RISC-V SoC - The Register Apple Faces Class Action Allegations of Unfairly Dominating Cloud Services Market - PYMNTS.com Axiom Cloud Closes $5M Funding - FinSMEs ABB's cloud-based collaboration with Microsoft boosts project execution efficiency - Process & Control Today Google brings Stack Overflow’s knowledge base to Gemini for Google Cloud - TechCrunch
-
 @ 1c6b3be3:73f0ae6f
2024-03-04 05:00:08
@ 1c6b3be3:73f0ae6f
2024-03-04 05:00:08🍵 "btc | bitcoin | lightning network | asic" - Google News
Milton Friedman's 1999 Vision: Predicting Bitcoin Before the Digital Age Dawned – Featured Bitcoin News - Bitcoin.com News Bitcoin leads charge, weekly NFT sales skyrocket to $423m - crypto.news Intel Unveils Next-Gen Bitcoin Mining Chip, Aims for Efficiency Leap in Cryptocurrency Sector - BNN Breaking What is Bitcoin? Key cryptocurrency terms and what they mean - BBC.com Bitcoin Cash price prediction amid record hashrate surge - Finbold - Finance in Bold Top 5 Bitcoin ATM Locations in Athens for Fast and Easy Crypto Access - CryptoNinjas Bitcoin's Layer-2 Ecosystem is Booming as Fourth Halving Approaches - Cryptonews Recursive Inscriptions: Elevating Ordinals to the Next Level - Bybit Learn Bitcoin Leads Surge in Weekly NFT Sales Topping $423 Million - Crypto Times In Its Entire History, Bitcoin Has Only Spent 0.81% of Its Life Above the $60K Line – Market Updates Bitcoin News - Bitcoin.com News
-
 @ a012dc82:6458a70d
2024-03-04 02:45:33
@ a012dc82:6458a70d
2024-03-04 02:45:33Table of Contents
-
Content
-
Introduction
-
- Not cutting your losses
-
- Overtrading
-
- Revenge trading
-
- Being too stubborn to change your mind
-
- Ignoring extreme market conditions
-
- Forgetting that TA is a game of probabilities
-
- Blindly following other traders
-
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
Introduction
One of the most popular approaches to analyzing the financial markets is known as technical analysis, or TA. The use of TA is possible in almost every kind of financial market, including stocks, FX, gold, and cryptocurrencies, among others.
Although it is not too difficult to understand the fundamental ideas behind technical analysis, becoming an expert in this field is rather challenging. It's certain that you'll blunder your way through the process of acquiring any new talent, so you may as well get used to it. When it comes to trading or investing, this may be very detrimental to your success. You run the danger of losing a significant chunk of your wealth if you do not exercise caution and make an effort to gain knowledge from your past errors. It's a good idea to gain wisdom from your past errors, but getting as far away from them is much smarter.
You will get familiar with some of the most common errors made in technical analysis as you read this article. If you are new to trading, why not become familiar with some of the fundamentals of technical analysis first? Read our article on "What Is Technical Analysis?" to learn more. and the 5 core indicators necessary for Conducting Technical Analysis.
When it comes to trading using technical analysis, what are the most common errors that novice traders make?
1. Not cutting your losses
Let's begin with a quotation from Ed Seykota, who is involved in the trading of commodities:
"The components of successful trading are, in order of importance, (1) minimizing losses, (2) minimizing losses, and (3) minimizing losses. If you are able to comply with these three guidelines, there is a possibility that you may be successful.
Even though this seems to be a straightforward step, it is critical that its significance be emphasized at all times. Protecting your financial resources should always be your first concern when it comes to financial activities like trading and investing.
Trading for the first time may be a very nerve-wracking experience. When you're just getting started, a good strategy to keep in mind is that the first thing you should focus on is preventing failure rather than achieving success. For this reason, it may be beneficial to begin trading with a lower position size, or perhaps to not risk any actual cash at all. For instance, you may practice your trading techniques on the testnet provided by Binance Futures before putting any of your hard-earned money at risk. With this strategy, you could keep your money safe and only put it at risk after you've shown that you can consistently bring in money.
Establishing a loss limit is sound business practice. Each of your deals needs to have a point when they become invalid. This is the point at which you have to "take the medicine" and admit that your trading plan was flawed. If you do not approach trading with this frame of mind, it is probable that you will not do well throughout the course of a trading career. Even just one poor move may damage your portfolio, and you may wind up having to hang on to lost positions while you wait for the market to get better.
2. Overtrading
When you are engaged in active trading, it is a frequent misunderstanding that you must constantly be in a transaction. Trading requires a significant amount of study as well as a significant amount of "sitting about" and patiently waiting. When using some trading tactics, you may be required to hold off on entering a trade until you get a signal that can be trusted. Even if they only do three deals a year, some traders may still make a lot of money from their investments.
Make it a point to steer clear of engaging in a transaction for the sole purpose of doing so. You are not required to engage in a transaction at all times. In some situations, doing nothing and waiting for an opportunity to reveal itself might actually be more lucrative than acting in response to the situation. Your investment will be protected in this manner, and you will be able to quickly put it to use if profitable trading opportunities become available again. You simply have to be patient and remember that chances will always present themselves again; all you have to do is wait for them.
An error that is similar in nature when it comes to trading is placing an excessive focus on smaller time periods. As a rule, analysis carried out on longer time periods will provide more trustworthy results than analysis carried out on shorter time spans. As a result, short time frames will generate a lot of market noise, which may encourage you to initiate trades more often than you would otherwise. Trading on smaller time frames often results in a poor risk-to-reward ratio. This is not to say that there aren't some profitable scalpers or short-term traders; there just aren't as many of them. Because it is such a high-risk trading method, it is not recommended for traders just starting out.
3. Revenge trading
It is not unusual to see traders attempting to make up for a huge loss they have incurred instantly. This practice is referred to as "revenge trading." It makes no difference whether you want to be a technical analyst, a day trader, or a swing trader; the most important thing is to refrain from making judgments based on your emotions.
It is not difficult to maintain your composure when things are going well, or even when you make little errors. But are you able to maintain your composure even when everything seems to be going wrong? Are you able to remain disciplined and follow your trading strategy even while everyone else is freaking out?
It is important to note the term "analysis" in the phrase "technical analysis." This, of course, calls for a methodical approach to trading in the markets, doesn't it? Therefore, why would you want to make quick judgments based on your emotions inside the confines of such a framework? If you want to be included among the finest traders, you need to be able to maintain your composure even after making the most significant errors. Try not to make decisions based on how you feel. Instead, try to keep a clear head and think things through.
Trading right after experiencing a significant loss is often a recipe for much bigger losses in the future. As a consequence of this, some traders may choose to not trade at all for a certain amount of time after suffering a significant loss. They will be able to begin trading once again with a clear head and a clean slate thanks to this solution.
4. Being too stubborn to change your mind
If you want to become a good trader, you can't be scared to shift your viewpoint when necessary. A lot. One thing that can be said with absolute confidence is that market circumstances may change very fast. They are always subject to change. As a trader, you are responsible for identifying these shifts and adjusting your strategy accordingly. It's possible that a business approach that does incredibly well in one market setting may be completely ineffective in another.
Let's have a look at what the illustrious trader Paul Tudor Jones had to say about his holdings:
"I operate on the assumption that every viewpoint I have is incorrect," you said.
It's a useful exercise to put yourself in the position of the opposing side of your arguments in order to see probable flaws in their reasoning. If you keep going in this way, your investing theses (and conclusions) may become more complete.
This brings up yet another important issue, which is cognitive biases. Your preconceived notions may significantly impact the decisions you make, cloud your judgment, and restrict the range of options you can take into consideration. You should make it a priority to at least learn about the cognitive biases that may affect your trading strategies. This will help you be better able to fight against their bad effects.
5. Ignoring extreme market conditions
There are instances in which the predictive capacities of TA are not as dependable as they formerly were. These may be black swan occurrences or other sorts of extraordinary market situations that are mainly influenced by people's emotions and the psychology of the masses. In the end, supply and demand are what drive the markets, and there are times when one of those factors is very out of whack relative to the other.
Take, for instance, the Relative Strength Index (RSI), an example of momentum indicator. In general, if the reading is lower than 30, the asset being tracked may be seen as having been oversold. When the RSI drops below 30, does this suggest that it is an indication that a transaction should be made immediately? Never in a million years! Simply said, it means that the selling side of the market is now in control of the momentum of the market. To put it another way, it simply suggests that there is more power in the hands of sellers than purchasers.
When unusual market circumstances exist, the RSI has the potential to reach high values. It is even feasible that it will go into the single digits, which is quite close to the absolute minimum reading (zero). Even such a strong sign of being oversold doesn't always mean that the market is about to turn around.
If you rely on the extreme readings that your technological equipment provides, you might end up losing a significant amount of money. This is particularly true during black swan situations, when it may be quite difficult to predict what the price action will do. When conditions are as they are right now, no analytical instrument can stop the markets from continuing in whichever direction they are currently moving. Because of this, it is important to constantly take into account other aspects as well, and not to depend just on a single instrument.
6. Forgetting that TA is a game of probabilities
The analyses that are performed using technical methods do not deal with absolutes. Probabilities are the subject of this discussion. This indicates that there is never a guarantee that the market will react in the way you anticipate, regardless of the technical approach you base your plans on. Even if your research indicates that there is a very high possibility of the market going up or down, nothing can be said with absolute confidence about the direction in which it will move.
When formulating your trading strategy, you really must remember to take this into consideration. It is never a good idea to expect that the market will follow your analysis, regardless of how much expertise you have in the financial markets. If you do so, you risk oversizing your bets and putting too much on a single event, which might result in a significant loss of money.
7. Blindly following other traders
If you want to become an expert in any field, it is imperative that you are always working to improve your skills. When it comes to trading in the financial markets, this is very important to keep in mind. In point of fact, the shifting circumstances of the market make it an absolute must. One of the best ways to learn is to look at how experienced technical analysts and traders do things.
To become consistently excellent, you will need first to identify your own talents and then build upon those abilities. If you want to achieve this goal, you must first uncover your own strengths. We might refer to this as your edge, which is the quality that sets you apart from other traders in the market.
If you read a lot of interviews with great traders, you'll quickly realize that each one uses a very unique set of tactics to achieve their goals. In fact, a trading technique that works faultlessly for one dealer might be seen as totally impractical by another. There are an almost infinite number of methods to make money off of market activity. You only need to figure out which one complements your character and the way you trade the most effectively.
The decision to enter into a transaction based on the analysis of another person could sometimes be profitable. On the other hand, if you just copy the actions of other traders without making an effort to comprehend the bigger picture, you should not expect this strategy to be successful over the long run. This, of course, does not imply that you should not follow the examples of others or gain knowledge from them. The most crucial thing to consider is whether or not you agree with the trade concept and whether or not it is compatible with your trading strategy. Even though other traders are knowledgeable and have a good reputation, you shouldn't just mindlessly follow in their footsteps.
Conclusion
When it comes to technical analysis, we went over some of the most basic errors you should try to avoid making. Keep in mind that trading is not a simple endeavor; generally, it is more viable to approach it with a longer-term perspective.
Learning how to trade successfully on a constant basis is a process that requires time. Developing your own trading methods and learning how to come up with your own ideas for trades involves a significant amount of experience. You'll have a better understanding of your capabilities, be able to pinpoint any areas in which you fall short, and ultimately feel more in command of the choices you make about investments and trades.
FAQ
What is TA in technical analysis? Stock charts are used in technical analysis so that the behaviors of market players may be visually represented. Within the charts, patterns develop, and recognizing these patterns may assist a trader in locating potential trading opportunities. TA functions at its highest potential when we keep a few key assumptions in mind. Technical analysis is more useful for determining short-term transactions.
What are the major issues to consider in technical analysis? Switching from one method or technique to another is an example of one of the most significant issues that may arise in technical analysis, which is known as "system hopping." Traders engage in such behavior because they are unable to generate a profit with a single trading technique. The old saying is that "practice makes perfect." You've probably heard of this proverb; however, merchants rarely follow it in practice.
What is a drawback to technical analysis? Technical analysis does not consider the fundamentals specific to particular stocks or the stock market as a whole. All of the significant economic announcements, company reports, and outside events are completely ignored. Important factors may drive the long-term and short-term volatility of the markets.
That's all for today, see ya tomorrow
If you want more, be sure to follow us on :
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 73cee26b:072f3bb6
2024-03-03 21:58:19
@ 73cee26b:072f3bb6
2024-03-03 21:58:19I saw a couple audience clips at the conference and one of them looked like 100% dudes, but another one had more #women than I expected.
Anyone over there want to report a guess what the split is? I just mean the attendants, not speakers/hosts/podcasters.
-
 @ 6ad3e2a3:c90b7740
2024-03-03 20:36:41
@ 6ad3e2a3:c90b7740
2024-03-03 20:36:41*"Who controls the past controls the future: who controls the present controls the past."
George Orwell*
What is the one weapon you cannot, under any circumstances, allow your adversary to possess? No, not nuclear weapons — as dangerous as they are (and we might be close to finding out), you can deter them with nuclear weapons of your own and possibly even shoot them out of the sky. There is an even worse weapon, one for which you have no defense: The Time Machine.
If your enemy has a time machine, you are in big trouble. Whatever technology you have, he can go back and invent, so that it is now he who possesses it instead of you. Of course, there’s not much need for that as he can simply interfere with your parents meeting, and you would not even exist at all! The Time Machine cannot be defeated because it always has the jump on you, even before you are born. Your enemy must never be able to possess a time machine.
Fortunately for you, he never will. That’s because time travel is not possible per the physical laws of the universe. Cause must always precede effect, and never the other way around. To travel backwards in time, you would need to travel through space faster than the speed of light. This is impossible because as any object even approaches the speed of light, it takes on infinite mass and thus requires infinite energy to propel. Because energy is finite, nothing with any mass can ever be accelerated to the speed of light, let alone beyond it, and hence no one can travel backwards in time.
This “difficulty adjustment” of sorts — the closer you get to the speed of light, the more energy you need to increase your speed — means that the timeline of events is secure and cannot be tampered with no matter how much power one has at his disposal — your enemy can never acquire the ultimate weapon.
. . .
Time is money, or so the saying goes. It follows that money is also time: a representation of the collective economic energy stored by humanity.
One way to look at money is stored time. To the extent I lack money, I will probably want to trade some of my time to acquire some, and to the extent I have it, I now can trade it for someone else’s time. Whether through my own labor (time) or someone else’s (inheriting stored time from a parent, e.g.), I might have some stored time to trade. People making (voluntary) time trades is essentially how a healthy economy functions.
Imagine then if while you and I are trading time amongst ourselves and others, someone especially efficient with his time comes along and has a lot of surplus to trade. That wealthy person will at first get a lot of others’ time in return, but people will observe his methods, become more efficient themselves, and that will eventually become the new standard, i.e., the process of innovation and competition. These injections of efficiency make goods and services cheaper for everyone, i.e., less costly in stored time to acquire.
Imagine, alternatively, someone else comes along with a magic machine such that he can, by pressing a button, create stored time in unlimited supply, and he brooks no competition. You can see his method (counterfeiting), but you can’t copy it because for you it is illegal. What happens to your healthy economy of time trading and innovation? For starters, savvy people will do what they can to transact with the man who has the machine. After all, he has infinite stored time to offer, and you have only the meager surplus you were able to save. Instead of innovating and competing for your stored time (building goods and services), the best and brightest will seek out the infinitely remunerative financial sector that sits closest to the machine.
Moreover, because the machine injects so much stored time into the system, one’s share of stored time relative to that of the entire economy gets diluted — there is stored time inflation, and your stored time does not have the purchasing power it once did. It’s as though the work you did, the actual time you expended in exchange for the stored version, was negated. When you look at wages as time, and saving as stored time, inflation that cuts your savings in half isn’t merely wage theft, it’s time theft. The man with the machine is rolling back the ledger of events and essentially saying, “Actually that work you did for that stored time? You only did half of it.”
Even worse, many people don’t know they’re being robbed. They know the time they’re putting in doesn’t go as far as they used to, that it’s harder to pay for scarce goods and services like healthcare, education and a home, but the man with the magic machine never breaks into their apartments directly — he doesn’t have to. He just re-arranges the ledger, so that it appears certain people earned more in the past (holders of scarce assets, financiers closest to his magic machine) and others less (wage earners, people who have their savings in cash.) The man has a machine that can re-arrange stored time, so to speak. He has, in essence, a time machine.
. . .
Over the last 25 years, the world has begun (as Michael Saylor puts it) to dematerialize huge swaths of everyday life. Social media for socializing, payment processors and online banking for money, e-commerce for online shopping, communication via email. This has added great convenience and utility. All but most die-hard luddite would rather pay a bill in two seconds with a click than have to find a postage stamp, a check and walk to the nearest mailbox.
But the dematerialization of everything has come at a cost. That cost is middleman control of the digital rails. Twitter or Facebook can ban you from participation in the public square, Paypal or JP Morgan can prevent you from using the payment rails, something that was impossible when people transacted with physical cash or gold. In digital realms, controlled entirely by third parties, there is no speed-of-light-infinite-mass adjustment ensuring the sequence of events or the integrity of the ledger. There is nothing to prevent creating money out of thin air, there is nothing to prevent dilution, inflation and time theft.
. . .
Or I should say there was nothing.
The invention of Bitcoin in 2009 was a breakthrough. Not only does it have a fixed and entirely auditable supply, but it relies on real-world, unforgeable energy for its verification. It takes energy from the physical world to mine a block, and over time it becomes increasingly difficult (by now virtually impossible) to meddle with the ledger, to change the records of who owes what to whom, or whose time is stored where.
Moreover, Bitcoin mining is subject to a difficulty adjustment. Miners expend energy to guess a random number, the successful achievement of which enables you to mine the next block and get rewarded in bitcoin. If the number to be guessed were between one and a quintillion, for example, it would take a certain amount of processing power (or otherworldly luck) to make a sufficient number of guesses to find it. But the difficulty of guessing it adjusts, depending on how much energy went into the prior 2,016 blocks (roughly two weeks' worth.)
So say, the US government decided to put substantial power behind mining with an aim to capture the rest of the bitcoin to be awarded, the difficulty would spike accordingly. Maybe instead of one in a quintillion, it would be one in three quintillion. In sum, you cannot simply brute force mine all the bitcoin for yourself — like the speed of light, which keeps time for the universe, the difficulty adjustment keeps the blocks coming in, one after another, roughly 10 minutes apart, no matter how much or little energy is going into it.
. . .
The universe has protected us against the ultimate weapon in the physical realm, but in the increasingly important digital sphere, someone has gotten hold of it. He can devalue our stored time, he can re-write our work history, re-arrange who owes what to whom at a whim. As luck would have it, Satoshi Nakamoto brought us a shield, an incorruptible ledger to which we can turn, an accurate clock that will tell us what time it is.
I’ll let Julian Assange have the last word:
"#Bitcoin breaks Orwell's dictum."
— CARLA⚡️ (@carlabitcoin) October 7, 2022
— Julian Assange pic.twitter.com/iDgXQ4YpeM -
 @ 7076f659:ca493321
2024-03-03 16:46:20
@ 7076f659:ca493321
2024-03-03 16:46:20Desde la versión Meshtastic Firmware 2.2.24.e6a2c06 Alpha viene desactivada la opción de recibir mensajes de MQTT. Por lo que por defecto no recibirás ningún mensaje proveniente de MQTT. Para poder recibir esos mensajes, además que activar la opción MQTT (Module Config y Uplink y Downlink en el Canal) tienes que desactivar Ignore MQTT que se encuentra en el siguiente menú:
Radio Config > LoRa > Ignore MQTT

Recordad que tenemos el Canal Spain para poder comunicarnos y que el Canal FastLong recibe tantos mensajes que probablemente sature y bloquee vuestro nodo de meshtastic, por lo que es recomendable que no tengas habilitados el Uplink ni el Downlink de dicho canal.
Cualquier duda puedes preguntar por aquí o en el grupo de TG.
-
 @ a012dc82:6458a70d
2024-03-03 13:40:42
@ a012dc82:6458a70d
2024-03-03 13:40:42Discover the inspiring journey of Robin Seyr, a software developer turned full-time Bitcoin advocate, in "The BTC Path" interview by Croxroad Podcasts. Seyr delves into Bitcoin's role as the foundational layer of the financial system, drawing parallels with the TCP/IP protocol of the internet. The conversation explores the long-term nature of the Bitcoin revolution and its potential as a protocol for building diverse applications, particularly through the Lightning Network. Seyr emphasises the importance of patience in Bitcoin's development and shares insights into its philosophy, impact on life, and significance in preserving wealth. The interview also touches on potential catalyst events for a Bitcoin price surge and the challenges of adoption, highlighting Seyr's perspective as a role model for Bitcoin enthusiasts. Dive into this engaging dialogue, where Seyr discusses the perfect storm propelling Bitcoin's growth, the entertainment factor in its development, and the possibility of a crash during or after the current bull run. Explore the multifaceted aspects of Bitcoin through the lens of a passionate advocate, gaining valuable insights into its societal impact and the exciting future it holds.
Table of Contents
-
Transition from Software Developer to Full-Time Bitcoin Advocate
-
Bitcoin as the base layer of the financial system
-
The analogy of Bitcoin to the TCP/IP protocol of the internet
-
Bitcoin as a protocol for building applications
-
Bitcoin adoption and mindset in Austria
-
Conclusion
-
FAQs
Transition from Software Developer to Full-Time Bitcoin Advocate
Robin Seyr's journey from a software developer to a full-time Bitcoin advocate is a compelling narrative that reflects the transformative power of cryptocurrency. In the interview with Croxroad Podcasts, Seyr delves into the profound shift in his professional trajectory and life philosophy after immersing himself in the world of Bitcoin.
Seyr draws parallels between Bitcoin and the foundational nature of the TCP/IP protocol, emphasising its potential as a revolutionary force rather than a mere technology. His insights shed light on the long-term nature of the Bitcoin revolution, likening it to the slow but impactful growth of the internet.
As Seyr unfolds his perspective on Bitcoin as a protocol, he envisions a future where diverse applications are built on top of its base layer. The discussion extends to the importance of patience in Bitcoin's development, urging enthusiasts to adopt a mindset aligned with the protocol's philosophy. Seyr also highlights the significance of being a role model in the Bitcoin space, focusing on the positive impact on society and personal well-being.
The interview covers various facets of Seyr's Bitcoin journey, ranging from preserving wealth to the potential catalyst events that could drive Bitcoin's price surge. He navigates the challenges of adoption, emphasising the need for realistic expectations in the ever-evolving landscape of cryptocurrency.
Ultimately, Seyr paints a vivid picture of the perfect storm propelling Bitcoin's growth, where entertainment intertwines with societal impact. His insights offer a glimpse into the exciting future of Bitcoin and its advocacy, making this interview a must-listen for those captivated by the cryptocurrency's potential.
Bitcoin as the base layer of the financial system
Seyr envisions Bitcoin as a revolutionary force, emphasising its role as a base layer for the financial system rather than a standalone technology. Drawing parallels to the slow but transformative growth of the internet, Seyr discusses the wide array of applications that can be built on top of Bitcoin's secure base layer.
The interview delves into Seyr's philosophy, highlighting the importance of patience in the ongoing Bitcoin revolution. He underscores the need for enthusiasts to adopt a long-term mindset, understanding that the impact of Bitcoin takes time to unfold. Seyr also emphasises the role of individuals in the Bitcoin space as role models, promoting positive societal change and personal well-being.
Seyr shares his perspectives on preserving wealth through Bitcoin and discusses potential catalyst events that could drive the cryptocurrency's price surge. Navigating the challenges of adoption, he stresses the significance of maintaining realistic expectations in the ever-evolving landscape of cryptocurrency.
Overall, Seyr's narrative paints a vivid picture of Bitcoin as the base layer, a foundational element shaping the future of the financial system. His insights make this interview essential for those fascinated by the potential of Bitcoin and its transformative influence on the world's economic infrastructure.
The analogy of Bitcoin to the TCP/IP protocol of the internet
In the insightful conversation between Robin Seyr and Croxroad Podcasts, a compelling analogy emerges as Seyr likens Bitcoin to the TCP/IP protocol of the internet. Drawing parallels between these two foundational elements, Seyr emphasises that, like the revolutionary impact of the TCP/IP protocol on the internet, Bitcoin serves as a fundamental protocol for the financial system.
Seyr's comparison unfolds, highlighting Bitcoin's role as a base layer, much like the underlying architecture of the internet. He posits that Bitcoin, as a protocol, provides a secure and unchanging foundation upon which various applications and functionalities can be built. This analogy underscores the significance of Bitcoin's permanence and stability in an ever-evolving financial landscape.
Just as the TCP/IP protocol enabled the internet's expansive growth, Seyr envisions Bitcoin as the catalyst for transformative changes in the financial sector. The comparison resonates with the idea that, much like the internet's gradual acceptance, Bitcoin's true potential may take time for widespread understanding and adoption.
This analogy forms a core theme in Seyr's perspective, encapsulating the essence of Bitcoin as not merely a cryptocurrency but a foundational technology reshaping the future of finance. The interview provides a deeper understanding of Seyr's conviction that, akin to the internet's lasting impact, Bitcoin is poised to revolutionise the financial landscape as an immutable and secure base layer.
Bitcoin as a protocol for building applications
Drawing parallels with the concept of protocols in technology, Seyr likens Bitcoin to the fundamental frameworks that facilitate communication and functionality. He envisions Bitcoin as an open protocol, offering a secure and unchanging base layer for a myriad of financial applications. This viewpoint positions Bitcoin as a versatile platform that extends beyond its conventional use as a store of value.
Seyr's insight delves into the transformative potential of Bitcoin as a protocol, highlighting its capacity to foster innovation in the financial landscape. By providing a secure and decentralised foundation, Bitcoin becomes a canvas upon which various applications can be developed, from payment solutions to decentralised finance (DeFi) platforms.
The interview underscores Seyr's belief that Bitcoin's protocol nature is a key driver for its long-term impact. As a protocol for building financial applications, Bitcoin represents a paradigm shift in how we perceive and utilise digital assets. Seyr's elucidation on this topic adds depth to the conversation, positioning Bitcoin as a revolutionary protocol shaping the future of financial technology.
Bitcoin adoption and mindset in Austria
Throughout the interview with Croxroad Podcasts, Robin Seyr sheds light on Bitcoin adoption and the prevailing mindset in Austria. Seyr shares valuable insights into how the Austrian community perceives and integrates Bitcoin into their lives.
He emphasises the importance of mindset, illustrating that adopting Bitcoin is not solely about its monetary value but extends to cultivating a broader mindset. Seyr articulates how having a positive outlook and living a good life can be a more persuasive means of promoting Bitcoin to others. He recounts examples where individuals, like a respected doctor in a small village, incorporating Bitcoin into their lives becomes an influential narrative within their community.
Seyr reflects on his personal journey and highlights the diverse paths people take within the Austrian landscape, from doctors to athletes, all finding unique ways to integrate Bitcoin. This discussion delves into the societal impact of Bitcoin adoption, showcasing how individuals, irrespective of their professional backgrounds, contribute to the broader narrative of digital currency.
The Austrian context provides a fascinating backdrop, allowing Seyr to elucidate on the varying perspectives within the community. By intertwining personal anecdotes and societal observations, Seyr paints a comprehensive picture of Bitcoin adoption in Austria and emphasises the importance of mindset in driving this transformative change.
Conclusion
In conclusion, Robin Seyr's journey from a software developer to a full-time Bitcoin advocate exemplifies the transformative power of embracing Bitcoin's philosophy. Through insightful discussions on adoption, mindset, and societal impact in Austria, Seyr emphasises that Bitcoin is more than a financial asset; it's a mindset shift. The interview underscores the importance of personal growth, positive living, and being a role model to inspire Bitcoin adoption. Seyr's narrative serves as a beacon for those navigating their paths in the digital currency space, highlighting the broader societal implications of embracing Bitcoin beyond its financial aspects.
FAQs
What inspired Robin Seyr's transition from a software developer to a full-time Bitcoin advocate? Robin Seyr's shift stemmed from a deep understanding of Bitcoin's principles. He found purpose in advocating for a decentralised financial system and fostering a mindset shift toward positive living.
How does Seyr compare Bitcoin to the TCP/IP protocol of the internet? Seyr draws an analogy between Bitcoin and the TCP/IP protocol, positioning it as the foundational layer for financial applications. This comparison highlights Bitcoin's potential to revolutionise the financial landscape, much like how TCP/IP transformed the internet.
What key message does Seyr convey about Bitcoin adoption in Austria? Seyr emphasises the importance of being a role model and fostering a positive mindset in promoting Bitcoin adoption in Austria. His experiences highlight the cultural impact and societal benefits that can result from embracing Bitcoin beyond its financial implications.
That's all for today, see ya tomorrow
If you want more, be sure to follow us on :
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 1c6b3be3:73f0ae6f
2024-03-03 06:00:06
@ 1c6b3be3:73f0ae6f
2024-03-03 06:00:06🍵 "llm | cloud | ddos" - Google News
NASA captures mysterious holes in cloud formations that resemble UFOs - Earth.com With super SDMs (machine learning, open access big data, and the cloud) towards more holistic global squirrel ... - Nature.com Balanced Scoring Leads No. 5 DU to Sweep of No. 15 St. Cloud - University of Denver Athletics Austin Bruins pull ahead in the third to defeat St. Cloud Norsemen - The Rink Live McMahon Scores Two Goals, Gascon Sets Rookie Shutout Record as No. 8 Bulldogs Sweep No. 10 St. Cloud State 2-0 ... - UMD Bulldogs McMahon powers #8 UMD past #10 St. Cloud State to advance to WCHA semifinals - WDIO Rosemount diver Lucas Gerten, St. Cloud swimmer Micah Davis stand out in Class 2A state meet - Star Tribune Final Fantasy 7 Rebirth Confirms Cloud's Canon Love Interest - TheGamer

































