-
 @ b12b632c:d9e1ff79
2024-03-23 16:42:49
@ b12b632c:d9e1ff79
2024-03-23 16:42:49CASHU AND ECASH ARE EXPERIMENTAL PROJECTS. BY THE OWN NATURE OF CASHU ECASH, IT'S REALLY EASY TO LOSE YOUR SATS BY LACKING OF KNOWLEDGE OF THE SYSTEM MECHANICS. PLEASE, FOR YOUR OWN GOOD, ALWAYS USE FEW SATS AMOUNT IN THE BEGINNING TO FULLY UNDERSTAND HOW WORKS THE SYSTEM. ECASH IS BASED ON A TRUST RELATIONSHIP BETWEEN YOU AND THE MINT OWNER, PLEASE DONT TRUST ECASH MINT YOU DONT KNOW. IT IS POSSIBLE TO GENERATE UNLIMITED ECASH TOKENS FROM A MINT, THE ONLY WAY TO VALIDATE THE REAL EXISTENCE OF THE ECASH TOKENS IS TO DO A MULTIMINT SWAP (BETWEEN MINTS). PLEASE, ALWAYS DO A MULTISWAP MINT IF YOU RECEIVE SOME ECASH FROM SOMEONE YOU DON'T KNOW/TRUST. NEVER TRUST A MINT YOU DONT KNOW!
IF YOU WANT TO RUN AN ECASH MINT WITH A BTC LIGHTNING NODE IN BACK-END, PLEASE DEDICATE THIS LN NODE TO YOUR ECASH MINT. A BAD MANAGEMENT OF YOUR LN NODE COULD LET PEOPLE TO LOOSE THEIR SATS BECAUSE THEY HAD ONCE TRUSTED YOUR MINT AND YOU DID NOT MANAGE THE THINGS RIGHT.

What's ecash/Cashu ?
I recently listened a passionnating interview from calle 👁️⚡👁 invited by the podcast channel What Bitcoin Did about the new (not so much now) Cashu protocol.
Cashu is a a free and open-source Chaumian ecash project built for Bitcoin protocol, recently created in order to let users send/receive Ecash over BTC Lightning network. The main Cashu ecash goal is to finally give you a "by-design" privacy mechanism to allow us to do anonymous Bitcoin transactions.
Ecash for your privacy.\ A Cashu mint does not know who you are, what your balance is, or who you're transacting with. Users of a mint can exchange ecash privately without anyone being able to know who the involved parties are. Bitcoin payments are executed without anyone able to censor specific users.
Here are some useful links to begin with Cashu ecash :
Github repo: https://github.com/cashubtc
Documentation: https://docs.cashu.space
To support the project: https://docs.cashu.space/contribute
A Proof of Liabilities Scheme for Ecash Mints: https://gist.github.com/callebtc/ed5228d1d8cbaade0104db5d1cf63939
Like NOSTR and its own NIPS, here is the list of the Cashu ecash NUTs (Notation, Usage, and Terminology): https://github.com/cashubtc/nuts?tab=readme-ov-file
I won't explain you at lot more on what's Casu ecash, you need to figured out by yourself. It's really important in order to avoid any mistakes you could do with your sats (that you'll probably regret).
If you don't have so much time, you can check their FAQ right here: https://docs.cashu.space/faq
I strongly advise you to listen Calle's interviews @whatbbitcoindid to "fully" understand the concept and the Cashu ecash mechanism before using it:
Scaling Bitcoin Privacy with Calle
In the meantime I'm writing this article, Calle did another really interesting interview with ODELL from CitadelDispatch:
CD120: BITCOIN POWERED CHAUMIAN ECASH WITH CALLE
Which ecash apps?
There are several ways to send/receive some Ecash tokens, you can do it by using mobile applications like eNuts, Minibits or by using Web applications like Cashu.me, Nustrache or even npub.cash. On these topics, BTC Session Youtube channel offers high quality contents and very easy to understand key knowledge on how to use these applications :
Minibits BTC Wallet: Near Perfect Privacy and Low Fees - FULL TUTORIAL
Cashu Tutorial - Chaumian Ecash On Bitcoin
Unlock Perfect Privacy with eNuts: Instant, Free Bitcoin Transactions Tutorial
Cashu ecash is a very large and complex topic for beginners. I'm still learning everyday how it works and the project moves really fast due to its commited developpers community. Don't forget to follow their updates on Nostr to know more about the project but also to have a better undertanding of the Cashu ecash technical and political implications.
There is also a Matrix chat available if you want to participate to the project:
https://matrix.to/#/#cashu:matrix.org
How to self-host your ecash mint with Nutshell
Cashu Nutshell is a Chaumian Ecash wallet and mint for Bitcoin Lightning. Cashu Nutshell is the reference implementation in Python.
Github repo:
https://github.com/cashubtc/nutshell
Today, Nutshell is the most advanced mint in town to self-host your ecash mint. The installation is relatively straightforward with Docker because a docker-compose file is available from the github repo.
Nutshell is not the only cashu ecash mint server available, you can check other server mint here :
https://docs.cashu.space/mints
The only "external" requirement is to have a funding source. One back-end funding source where ecash will mint your ecash from your Sats and initiate BTC Lightning Netwok transactions between ecash mints and BTC Ligtning nodes during a multimint swap. Current backend sources supported are: FakeWallet*, LndRestWallet, CoreLightningRestWallet, BlinkWallet, LNbitsWallet, StrikeUSDWallet.
*FakeWallet is able to generate unlimited ecash tokens. Please use it carefully, ecash tokens issued by the FakeWallet can be sent and accepted as legit ecash tokens to other people ecash wallets if they trust your mint. In the other way, if someone send you 2,3M ecash tokens, please don't trust the mint in the first place. You need to force a multimint swap with a BTC LN transaction. If that fails, someone has maybe tried to fool you.
I used a Voltage.cloud BTC LN node instance to back-end my Nutshell ecash mint:
SPOILER: my nutshell mint is working but I have an error message "insufficient balance" when I ask a multiswap mint from wallet.cashu.me or the eNuts application. In order to make it work, I need to add some Sats liquidity (I can't right now) to the node and open few channels with good balance capacity. If you don't have an ecash mint capable of doig multiswap mint, you'll only be able to mint ecash into your ecash mint and send ecash tokens to people trusting your mint. It's working, yes, but you need to be able to do some mutiminit swap if you/everyone want to fully profit of the ecash system.
Once you created your account and you got your node, you need to git clone the Nutshell github repo:
git clone https://github.com/cashubtc/nutshell.gitYou next need to update the docker compose file with your own settings. You can comment the wallet container if you don't need it.
To generate a private key for your node, you can use this openssl command
openssl rand -hex 32 054de2a00a1d8e3038b30e96d26979761315cf48395aa45d866aeef358c91dd1The CLI Cashu wallet is not needed right now but I'll show you how to use it in the end of this article. Feel free to comment it or not.
``` version: "3" services: mint: build: context: . dockerfile: Dockerfile container_name: mint
ports:
- "3338:3338"
environment:- DEBUG=TRUE
- LOG_LEVEL=DEBUG
- MINT_URL=https://YourMintURL - MINT_HOST=YourMintDomain.tld - MINT_LISTEN_HOST=0.0.0.0 - MINT_LISTEN_PORT=3338 - MINT_PRIVATE_KEY=YourPrivateKeyFromOpenSSL - MINT_INFO_NAME=YourMintInfoName - MINT_INFO_DESCRIPTION=YourShortInfoDesc - MINT_INFO_DESCRIPTION_LONG=YourLongInfoDesc - MINT_LIGHTNING_BACKEND=LndRestWallet #- MINT_LIGHTNING_BACKEND=FakeWallet - MINT_INFO_CONTACT=[["email","YourConctact@email"], ["twitter","@YourTwitter"], ["nostr", "YourNPUB"]] - MINT_INFO_MOTD=Thanks for using my mint! - MINT_LND_REST_ENDPOINT=https://YourVoltageNodeDomain:8080 - MINT_LND_REST_MACAROON=YourDefaultAdminMacaroonBase64 - MINT_MAX_PEG_IN=100000 - MINT_MAX_PEG_OUT=100000 - MINT_PEG_OUT_ONLY=FALSE command: ["poetry", "run", "mint"]wallet-voltage: build: context: . dockerfile: Dockerfile container_name: wallet-voltage
ports:
- "4448:4448"
depends_on: - nutshell-voltage environment:- DEBUG=TRUE
- MINT_URL=http://nutshell-voltage:3338
- API_HOST=0.0.0.0 command: ["poetry", "run", "cashu", "-d"]```
To build, run and see the container logs:
docker compose up -d && docker logs -f mint0.15.1 2024-03-22 14:45:45.490 | WARNING | cashu.lightning.lndrest:__init__:49 - no certificate for lndrest provided, this only works if you have a publicly issued certificate 2024-03-22 14:45:45.557 | INFO | cashu.core.db:__init__:135 - Creating database directory: data/mint 2024-03-22 14:45:45.68 | INFO | Started server process [1] 2024-03-22 14:45:45.69 | INFO | Waiting for application startup. 2024-03-22 14:45:46.12 | INFO | Loaded 0 keysets from database. 2024-03-22 14:45:46.37 | INFO | Current keyset: 003dba9e589023f1 2024-03-22 14:45:46.37 | INFO | Using LndRestWallet backend for method: 'bolt11' and unit: 'sat' 2024-03-22 14:45:46.97 | INFO | Backend balance: 1825000 sat 2024-03-22 14:45:46.97 | INFO | Data dir: /root/.cashu 2024-03-22 14:45:46.97 | INFO | Mint started. 2024-03-22 14:45:46.97 | INFO | Application startup complete. 2024-03-22 14:45:46.98 | INFO | Uvicorn running on http://0.0.0.0:3338 (Press CTRL+C to quit) 2024-03-22 14:45:47.27 | INFO | 172.19.0.22:48528 - "GET /v1/keys HTTP/1.1" 200 2024-03-22 14:45:47.34 | INFO | 172.19.0.22:48544 - "GET /v1/keysets HTTP/1.1" 200 2024-03-22 14:45:47.38 | INFO | 172.19.0.22:48552 - "GET /v1/info HTTP/1.1" 200If you see the line :
Uvicorn running on http://0.0.0.0:3338 (Press CTRL+C to quit)Nutshell is well started.
I won't explain here how to create a reverse proxy to Nutshell, you can find how to do it into my previous article. Here is the reverse proxy config into Nginx Proxy Manager:
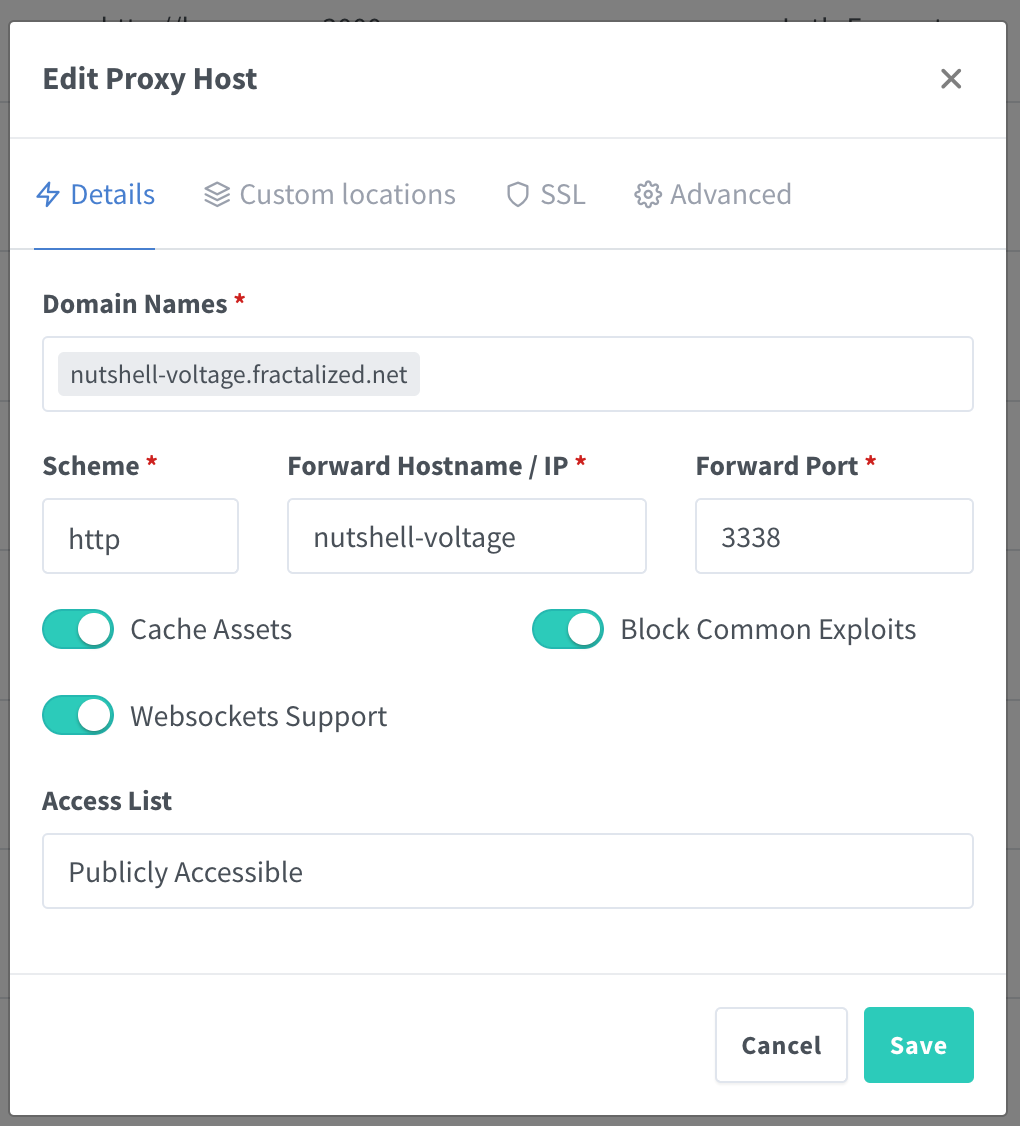
If everything is well configured and if you go on your mint url (https://yourminturl) you shoud see this:
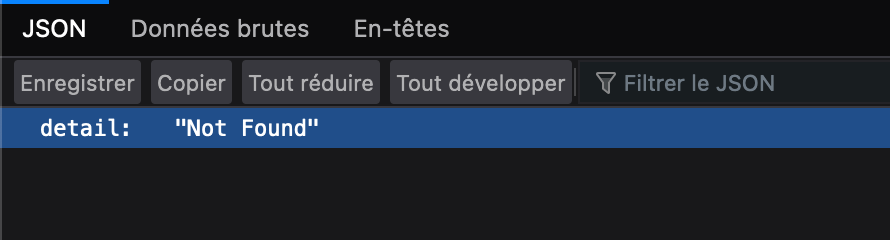
It's not helping a lot because at first glance it seems to be not working but it is. You can also check these URL path to confirm :
- https://yourminturl/keys and https://yourminturl/keysets
or
- https://yourminturl/v1/keys and https://yourminturl/v1/keysets
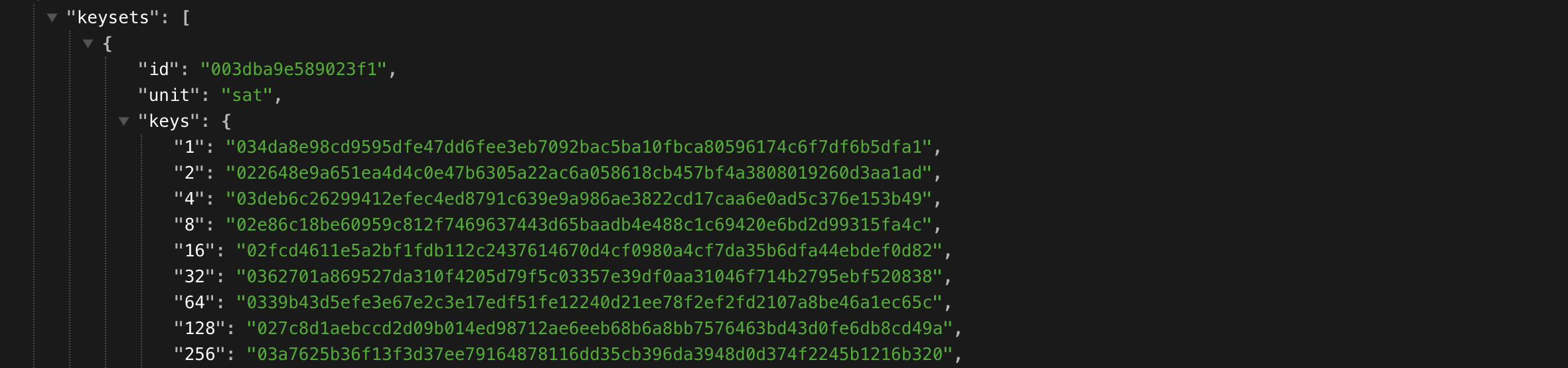
Depending of the moment when you read this article, the first URLs path might have been migrated to V1. Here is why:
https://github.com/cashubtc/nuts/pull/55
The final test is to add your mint to your prefered ecash wallets.
SPOILER: AT THIS POINT, YOU SHOUD KNOW THAT IF YOU RESET YOUR LOCAL BROWSER INTERNET CACHE FILE, YOU'LL LOSE YOUR MINTED ECASH TOKENS. IF NOT, PLEASE READ THE DOCUMENTATION AGAIN.
For instace, if we use wallet.cashu.me:
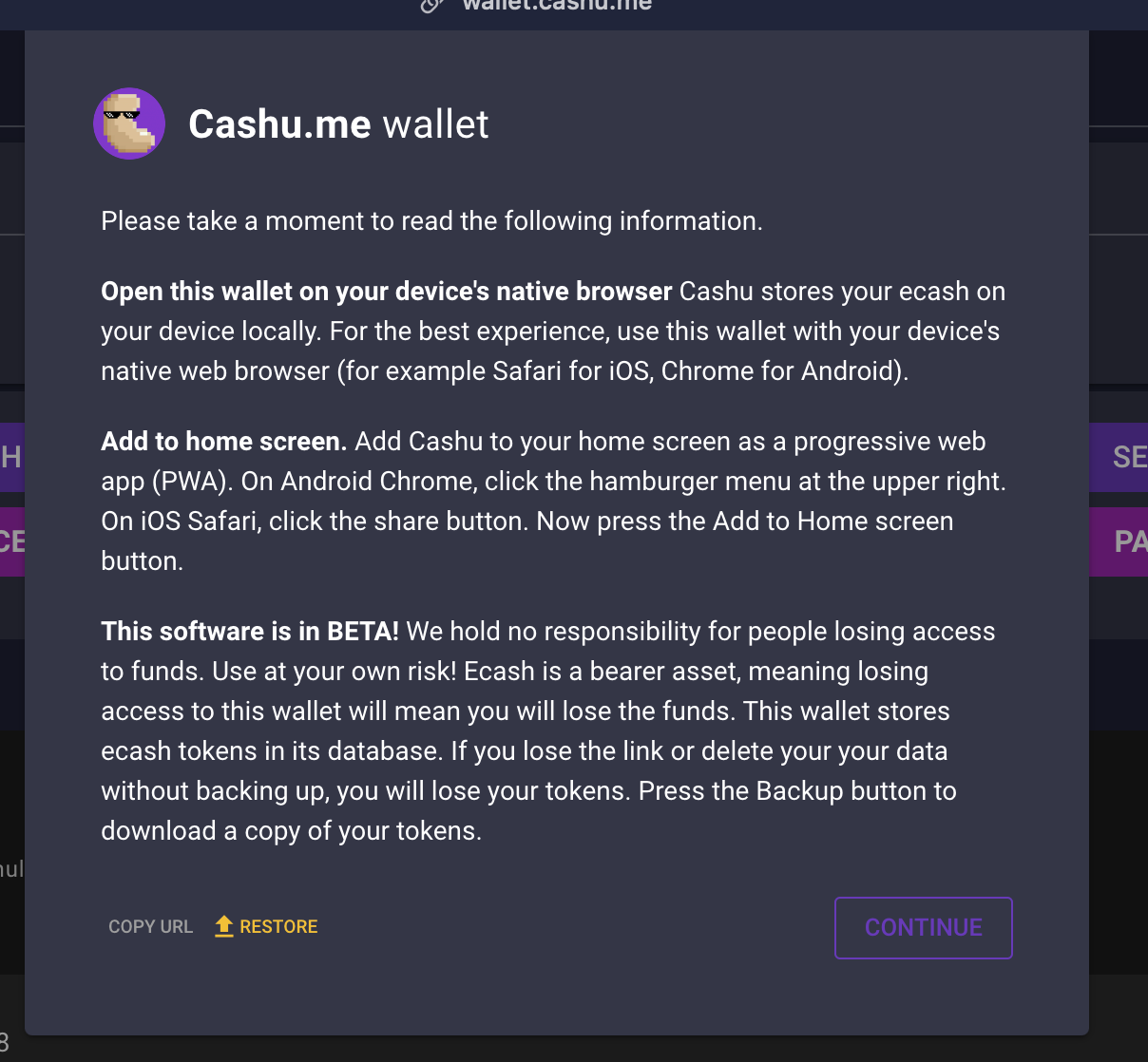
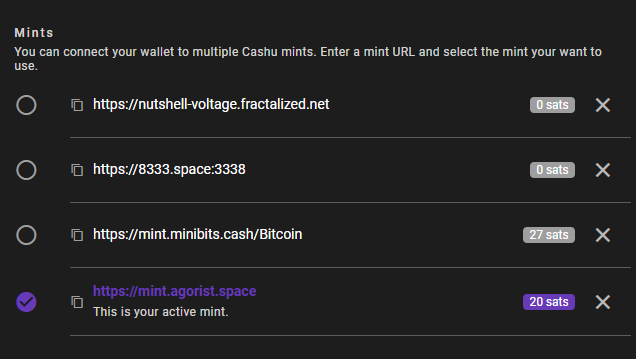
You can go into the "Settings" tab and add your mint :
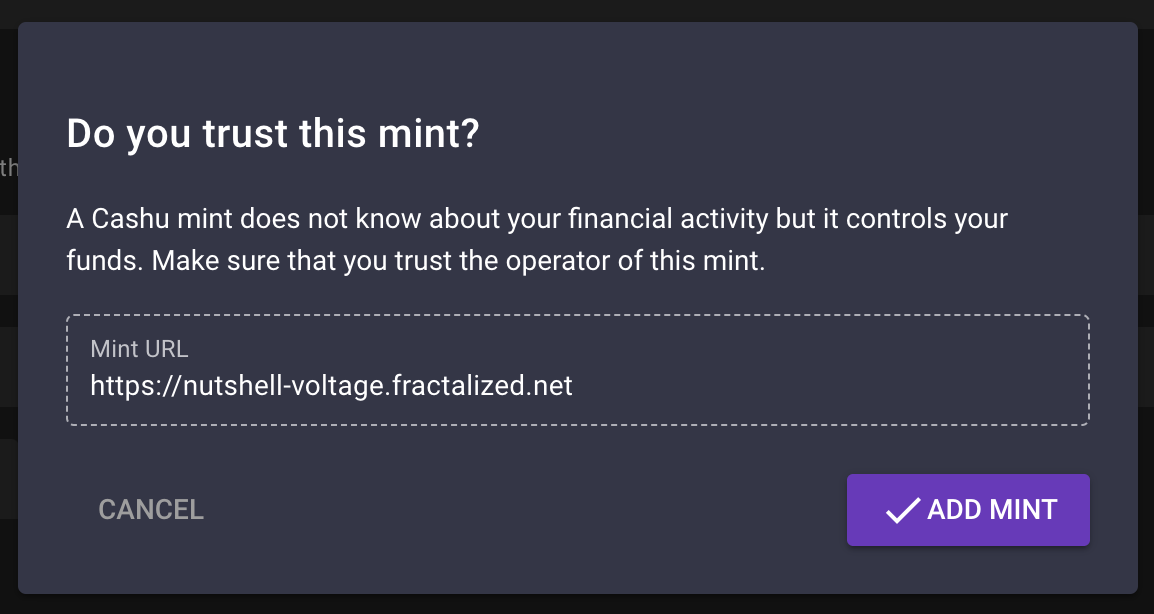
If everything went find, you shoud see this :
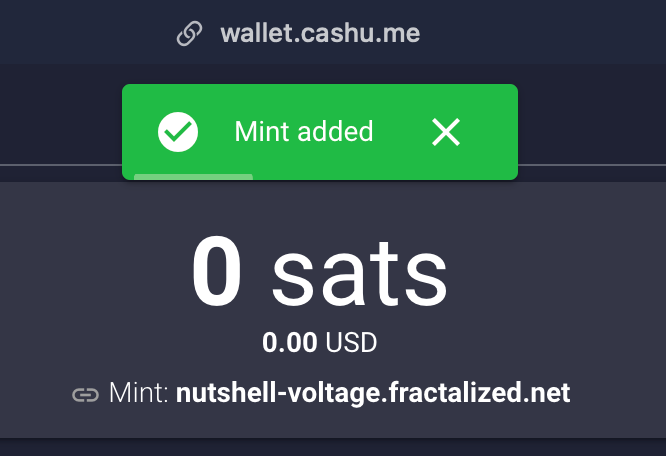
You can now mint some ecash from your mint creating a sats invoice :
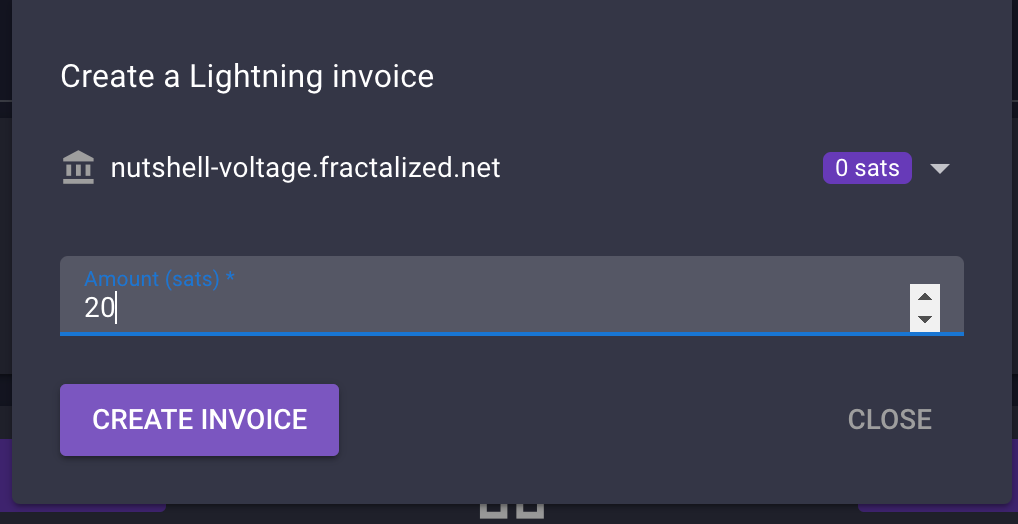
You can now scan the QR diplayed with your prefered BTC LN wallet. If everything is OK, you should receive the funds:
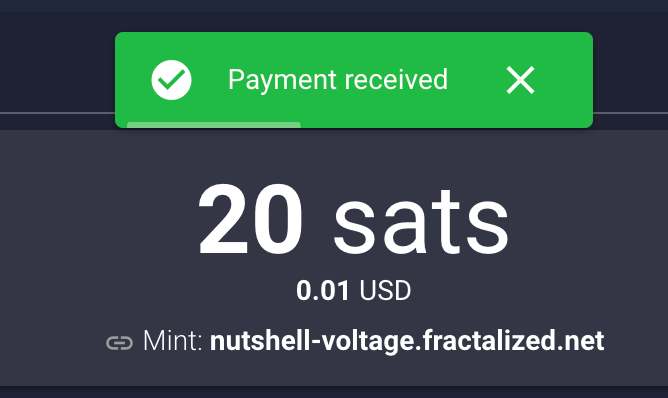
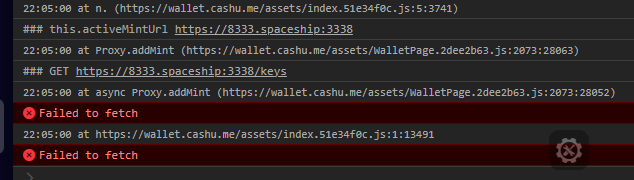
It may happen that some error popup sometimes. If you are curious and you want to know what happened, Cashu wallet has a debug console you can activate by clicking on the "Settings" page and "OPEN DEBUG TERMINAL". A little gear icon will be displayed in the bottom of the screen. You can click on it, go to settings and enable "Auto Display If Error Occurs" and "Display Extra Information". After enabling this setting, you can close the popup windows and let the gear icon enabled. If any error comes, this windows will open again and show you thé error:
Now that you have some sats in your balance, you can try to send some ecash. Open in a new windows another ecash wallet like Nutstach for instance.
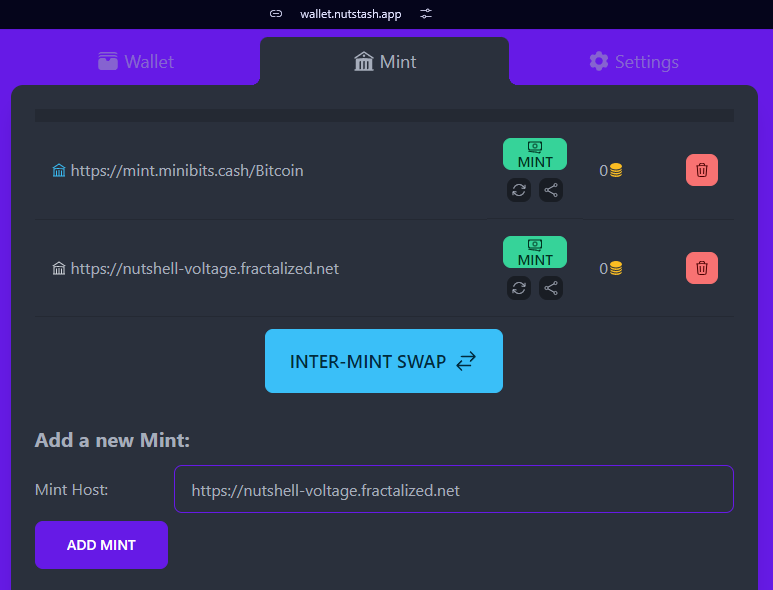
Add your mint again :
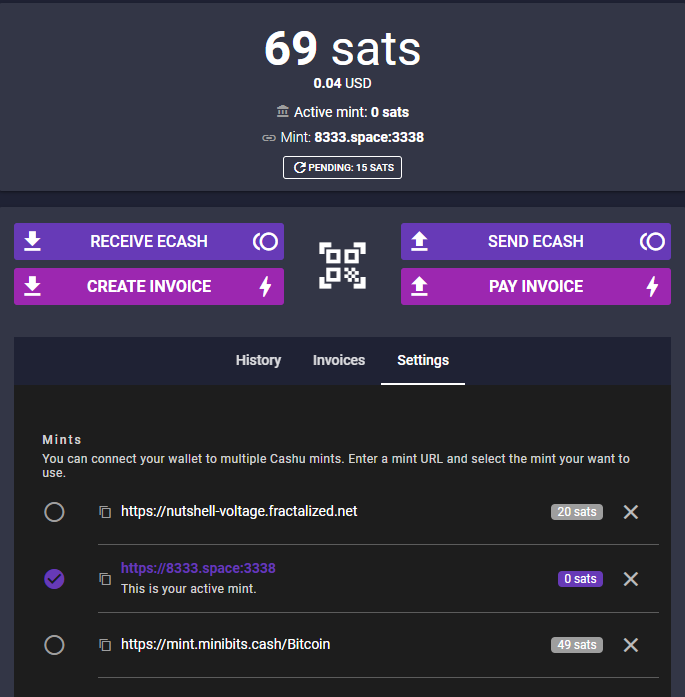
Return on Cashu wallet. The ecash token amount you see on the Cashu wallet home page is a total of all the ecash tokens you have on all mint connected.
Next, click on "Send ecach". Insert the amout of ecash you want to transfer to your other wallet. You can select the wallet where you want to extract the funds by click on the little arrow near the sats funds you currenly selected :


Click now on "SEND TOKENS". That will open you a popup with a QR code and a code CONTAINING YOUR ECASH TOKENS (really).

You can now return on nutstach, click on the "Receive" button and paste the code you get from Cashu wallet:
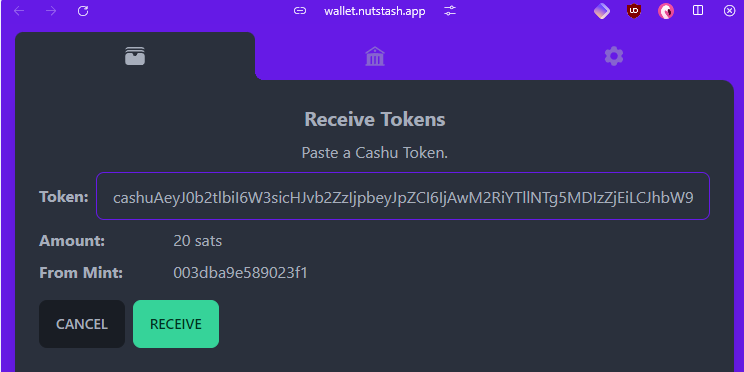
Click on "RECEIVE" again:
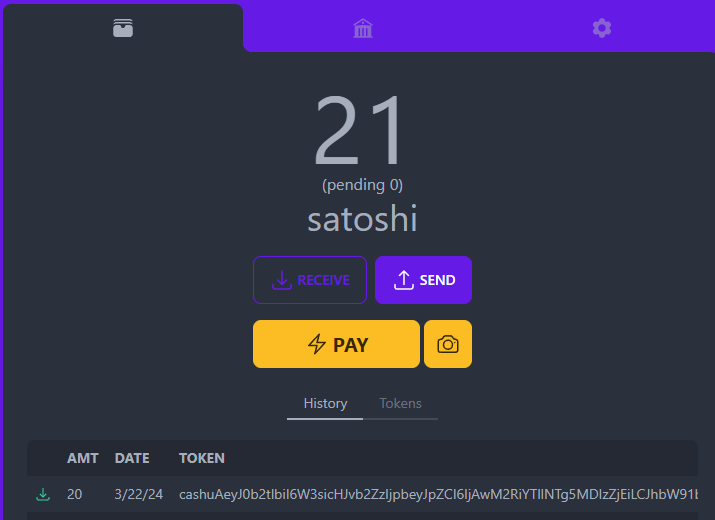
Congrats, you transfered your first ecash tokens to yourself ! 🥜⚡
You may need some time to transfer your ecash tokens between your wallets and your mint, there is a functionality existing for that called "Multimint swaps".
Before that, if you need new mints, you can check the very new website Bitcoinmints.com that let you see the existing ecash mints and rating :
Don't forget, choose your mint carefuly because you don't know who's behind.
Let's take a mint and add it to our Cashu wallet:
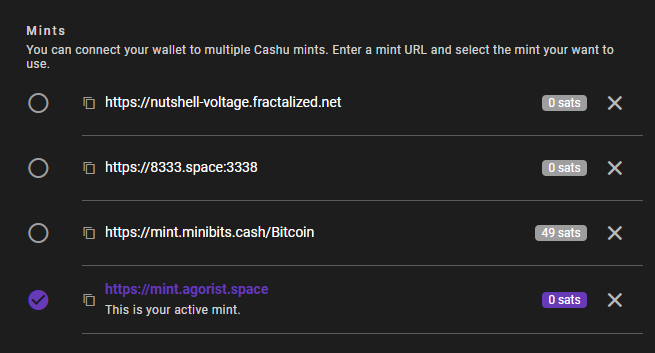
If you want to transfer let's say 20 sats from minibits mint to bitcointxoko mint, go just bottom into the "Multimint swap" section. Select the mint into "Swap from mint", the mint into "Swap to mint" and click on "SWAP" :
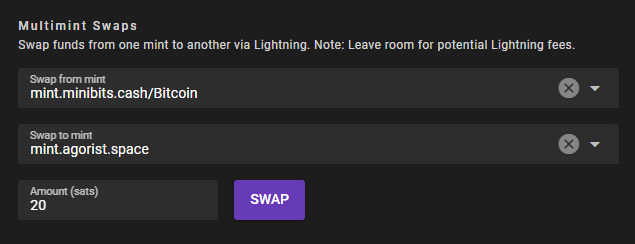
A popup window will appear and will request the ecash tokens from the source mint. It will automatically request the ecash amount via a Lightning node transaction and add the fund to your other wallet in the target mint. As it's a Lightning Network transaction, you can expect some little fees.
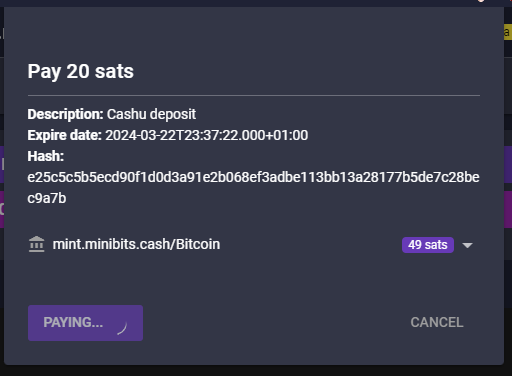
If everything is OK with the mints, the swap will be successful and the ecash received.
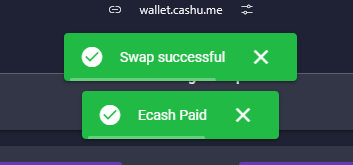
You can now see that the previous sats has been transfered (minus 2 fee sats).
Well done, you did your first multimint swap ! 🥜⚡
One last thing interresting is you can also use CLI ecash wallet. If you created the wallet contained in the docker compose, the container should be running.
Here are some commands you can do.
To verify which mint is currently connected :
``` docker exec -it wallet-voltage poetry run cashu info
2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat Version: 0.15.1 Wallet: wallet Debug: True Cashu dir: /root/.cashu Mints: - https://nutshell-voltage.fractalized.net ```
To verify your balance :
``` docker exec -it wallet-voltage poetry run cashu balance
2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat Balance: 0 sat ```
To create an sats invoice to have ecash :
``` docker exec -it wallet-voltage poetry run cashu invoice 20
2024-03-22 22:00:59.12 | DEBUG | cashu.wallet.wallet:_load_mint_info:275 | Mint info: name='nutshell.fractalized.net' pubkey='02008469922e985cbc5368ce16adb6ed1aaea0f9ecb21639db4ded2e2ae014a326' version='Nutshell/0.15.1' description='Official Fractalized Mint' description_long='TRUST THE MINT' contact=[['email', 'pastagringo@fractalized.net'], ['twitter', '@pastagringo'], ['nostr', 'npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2']] motd='Thanks for using official ecash fractalized mint!' nuts={4: {'methods': [['bolt11', 'sat']], 'disabled': False}, 5: {'methods': [['bolt11', 'sat']], 'disabled': False}, 7: {'supported': True}, 8: {'supported': True}, 9: {'supported': True}, 10: {'supported': True}, 11: {'supported': True}, 12: {'supported': True}} Balance: 0 sat
Pay invoice to mint 20 sat:
Invoice: lnbc200n1pjlmlumpp5qh68cqlr2afukv9z2zpna3cwa3a0nvla7yuakq7jjqyu7g6y69uqdqqcqzzsxqyz5vqsp5zymmllsqwd40xhmpu76v4r9qq3wcdth93xthrrvt4z5ct3cf69vs9qyyssqcqppurrt5uqap4nggu5tvmrlmqs5guzpy7jgzz8szckx9tug4kr58t4avv4a6437g7542084c6vkvul0ln4uus7yj87rr79qztqldggq0cdfpy
You can use this command to check the invoice: cashu invoice 20 --id 2uVWELhnpFcNeFZj6fWzHjZuIipqyj5R8kM7ZJ9_
Checking invoice .................2024-03-22 22:03:25.27 | DEBUG | cashu.wallet.wallet:verify_proofs_dleq:1103 | Verified incoming DLEQ proofs. Invoice paid.
Balance: 20 sat ```
To pay an invoice by pasting the invoice you received by your or other people :
``` docker exec -it wallet-voltage poetry run cashu pay lnbc150n1pjluqzhpp5rjezkdtt8rjth4vqsvm50xwxtelxjvkq90lf9tu2thsv2kcqe6vqdq2f38xy6t5wvcqzzsxqrpcgsp58q9sqkpu0c6s8hq5pey8ls863xmjykkumxnd8hff3q4fvxzyh0ys9qyyssq26ytxay6up54useezjgqm3cxxljvqw5vq2e94ru7ytqc0al74hr4nt5cwpuysgyq8u25xx5la43mx4ralf3mq2425xmvhjzvwzqp54gp0e3t8e
2024-03-22 22:04:37.23 | DEBUG | cashu.wallet.wallet:_load_mint_info:275 | Mint info: name='nutshell.fractalized.net' pubkey='02008469922e985cbc5368ce16adb6ed1aaea0f9ecb21639db4ded2e2ae014a326' version='Nutshell/0.15.1' description='Official Fractalized Mint' description_long='TRUST THE MINT' contact=[['email', 'pastagringo@fractalized.net'], ['twitter', '@pastagringo'], ['nostr', 'npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2']] motd='Thanks for using official ecash fractalized mint!' nuts={4: {'methods': [['bolt11', 'sat']], 'disabled': False}, 5: {'methods': [['bolt11', 'sat']], 'disabled': False}, 7: {'supported': True}, 8: {'supported': True}, 9: {'supported': True}, 10: {'supported': True}, 11: {'supported': True}, 12: {'supported': True}} Balance: 20 sat 2024-03-22 22:04:37.45 | DEBUG | cashu.wallet.wallet:get_pay_amount_with_fees:1529 | Mint wants 0 sat as fee reserve. 2024-03-22 22:04:37.45 | DEBUG | cashu.wallet.cli.cli:pay:189 | Quote: quote='YpNkb5f6WVT_5ivfQN1OnPDwdHwa_VhfbeKKbBAB' amount=15 fee_reserve=0 paid=False expiry=1711146847 Pay 15 sat? [Y/n]: y Paying Lightning invoice ...2024-03-22 22:04:41.13 | DEBUG | cashu.wallet.wallet:split:613 | Calling split. POST /v1/swap 2024-03-22 22:04:41.21 | DEBUG | cashu.wallet.wallet:verify_proofs_dleq:1103 | Verified incoming DLEQ proofs. Error paying invoice: Mint Error: Lightning payment unsuccessful. insufficient_balance (Code: 20000) ```
It didn't work, yes. That's the thing I told you earlier but it would work with a well configured and balanced Lightning Node.
That's all ! You should now be able to use ecash as you want! 🥜⚡
See you on NOSTR! 🤖⚡\ PastaGringo
-
 @ f6488c62:c929299d
2024-03-23 16:08:29
@ f6488c62:c929299d
2024-03-23 16:08:29มีเหตุการณ์ อะไร สำคัญ เกิดขึ้นบ้าง ในสามเดือนแรก ของ ปี 2024 เหตุการณ์สำคัญในไตรมาสแรกของปี 2024
การเมือง การเลือกตั้งประธานาธิบดีสหรัฐอเมริกา: โจ ไบเดน ประกาศลงสมัครชิงตำแหน่งประธานาธิบดีอีกครั้ง โดนัลด์ ทรัมป์ ยังไม่ประกาศ แต่คาดว่าจะลงสมัครเช่นกัน การเลือกตั้งทั่วไปในอินเดีย: พรรค Bharatiya Janata Party (BJP) ของนายกรัฐมนตรีนเรนทรา โมดี เผชิญการต่อต้านอย่างหนักจากฝ่ายค้าน ความตึงเครียดระหว่างจีนและไต้หวัน: จีนเพิ่มกิจกรรมทางทหารในช่องแคบไต้หวัน สหรัฐฯ ส่งเรือรบผ่านช่องแคบไต้หวันเพื่อแสดงอิสรภาพในการเดินเรือ
เศรษฐกิจ สงครามในยูเครน: ส่งผลกระทบต่อเศรษฐกิจโลก ราคาน้ำมันและอาหารสูงขึ้น ธนาคารกลางสหรัฐ (เฟด): ปรับขึ้นอัตราดอกเบี้ยเพื่อต่อสู้กับเงินเฟ้อ เศรษฐกิจจีน: ชะลอตัวลง
สังคม การระบาดของโควิด-19: สายพันธุ์โอมิครอน BA.2 ยังคงแพร่ระบาด การเปลี่ยนแปลงสภาพภูมิอากาศ: ภัยแล้ง น้ำท่วม และพายุรุนแรง เกิดขึ้นบ่อยและรุนแรงขึ้น วิกฤตผู้ลี้ภัย: ผู้คนลี้ภัยจากสงคราม ความยากจน และการเปลี่ยนแปลงสภาพภูมิอากาศ
เทคโนโลยี ปัญญาประดิษฐ์ (AI): มีการพัฒนาและใช้งาน AI อย่างกว้างขวางมากขึ้น ** Metaverse:** บริษัทเทคโนโลยีรายใหญ่ลงทุนใน Metaverse Web 3.0: เทคโนโลยีใหม่ที่ विकेन्द्रीकृत เหตุการณ์สำคัญอื่นๆ การแข่งขันกีฬาโอลิมปิกฤดูหนาว 2026: จัดขึ้นที่เมืองมิลานและคอร์ตินาดัมเปซโซ ประเทศอิตาลี การประกาศรางวัลโนเบล: รางวัลโนเบลสาขาวรรณกรรม สันติภาพ ฟิสิกส์ เคมี สรีรวิทยาหรือการแพทย์ และเศรษฐศาสตร์
-
 @ 97c70a44:ad98e322
2024-03-23 04:34:58
@ 97c70a44:ad98e322
2024-03-23 04:34:58The last few days on developer nostr have involved quite a kerfluffle over the gossip model, blastr, banning jack, and many related misunderstandings. This post is an attempt to lay out my thoughts on the matter in an organized and hopefully helpful way.
What's wrong with gossip?
It all started with a post from jack asking why more devs haven't implemented the gossip model. There are many answers to this question, not least having to do with there being two standards for user relay selections, and ongoing changes to NIP 65. But I don't want to talk about compatibility here.
nevent1qydhwumn8ghj7argv4nx7un9wd6zumn0wd68yvfwvdhk6tcprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hszymhwden5te0wfjkccte9enrw73wd9hj7qpq2uf488j3uy084kpsn594xcef9g9x3lplx4xnglf0xwghyw2n3tfqqnrm02
Mazin responded with some numbers which estimate how many connections the gossip model requires. Too many connections can become expensive for low-power clients like mobile phones, not to mention some privacy issues stemming from nosy relays.
nevent1qyd8wumn8ghj7urewfsk66ty9enxjct5dfskvtnrdakj7qgewaehxw309amk2mrrdakk2tnwdaehgu3wwa5kuef0qyghwumn8ghj7mn0wd68ytnhd9hx2tcqyp2xzsjktypudzmygplljkupmuyadzzr6rkgnvx9e0fx3zwhdm0vkz4ceg7
I have some minor disagreements with Mazin's numbers, but I basically agree with his point — a purist gossip model, where a large proportion of nostr users run their own relays results in a high number of connections to different relays. I brought this question up late last year in my interview with Mike Dilger and in a conversation with fiatjaf, who convinced me that in practice, this doesn't matter — enough people will use a handful of larger hubs that there will be a good amount of overlap in relay selections between most pubkeys.
To articulate this more clearly: the goal is not "personal web nodes", which is a pipe dream the Farcasters and BlueSkys (BlueSkies?) of the world aim at, but a more pragmatic mix between large hubs and smaller purpose-built relays. These small relays might be outlets for large publishers, small groups, or nerds who also run their own SMTP servers and lightning nodes.
The point of the gossip model is that these small nodes be possible to run, and discoverable from the rest of the network so that we can preserve the censorship-resistant qualities of nostr that brought us here in the first place.
Blast It!
It's no secret that I've long been a critic of Mutiny's blastr relay implementation. My main objection is that the blastr approach doesn't account for the hard limits involved in scaling smaller relays. If the goal is to cross-pollinate notes across all relays in the network, all relays will require the same size database, and contain all notes in the network. This works right now (sort of), but as the network grows, the relays running on a $5 VPS are going to have their disks fill up and will inevitably fall over.
nevent1qyvhwumn8ghj76r0v3kxymmy9ehx7um5wgcjucm0d5hszxnhwden5te0wpuhyctdd9jzuenfv96x5ctx9e3k7mf0qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qqs07jr9qx49h53nhw76u7c3up2s72k7le2zj94h5fugmcgtyde4j9qfrnwxj
Not only that, but the content breakdown on any given relay by default becomes an undifferentiated soup of "GM", chinese notes, bots, bitcoin memes, and porn. Blastr makes it impossible to run an interesting relay without implementing write policies.
Which is actually fine! Because that's always been true — servers that allow anonymous uploads always get abused. Tony is just helpfully pointing out to us that this is no less true of nostr relays. I only wish he could have waited a little longer before mounting his attack on the network, because lots of hobbyists are interested in running interesting relays, but the tools don't yet exist to protect those servers from unsolicited notes.
One other note on blastr — Tony at one point described blastr as a relay proxy. This is an interesting perspective, which puts things in a different light. More on proxies later.
Ban Jack?
Here's a thought experiment: how might we actually "ban blastr"? @Pablof7z suggested to me in a conversation that you could configure your relay to check every note that gets published to your relay against the big nostr hubs, and if it exists on any of them to simply delete it. Of course, that would result in your relay being basically empty, and the hubs having all of your content. That's game theory for you I guess.
Another approach that was floated was to encourage users to only publish to small relays. In theory, this would force clients to implement gossip so users could still see the content they were subscribed to. Fiatjaf even posted two identical notes, one to his personal relay, and one to a hub to see which would get more engagement. The note posted to the mainstream relay got 10x more replies and likes than the more obscure note.
nostr:nevent1qyd8wumn8ghj7urewfsk66ty9enxjct5dfskvtnrdakj7qgmwaehxw309aex2mrp0yh8wetnw3jhymnzw33jucm0d5hszymhwden5te0wp6hyurvv4cxzeewv4ej7qpqdc2drrmdmlkcyna5kkcv8yls4f8zaj82jjl00xrh2tmmhw3ejsmsmp945r
Of course, this is thwarted by blastr, since blastr not only replicates notes posted to it, it also actively crawls the network as well. So the next logical step in this train of thought would be for hubs to encourage people to use small relays by actively blocking high-profile accounts.
nostr:nevent1qydhwumn8ghj7argv4nx7un9wd6zumn0wd68yvfwvdhk6tcpzdmhxue69uhhyetvv9ujue3h0ghxjme0qyd8wumn8ghj7urewfsk66ty9enxjct5dfskvtnrdakj7qpqpjhnn69lej55kde9l64jgmdkx2ngy2yk87trgjuzdte2skkwwnhqv5esfq
This would of course never happen (Damus is one client that hasn't implemented NIP 65, and they also run the biggest relay), but it was a fun thought experiment. At any rate, the silliness of the suggestion didn't stop certain people from getting offended that we would "disrupt the free market" by "forcing" our opinions on everyone else. Oh well.
Death to Blastr
In reality, even though blastr makes it a little harder to adopt gossip in the short term, its days are numbered. Eventually, relay operators will start to feel the pain of unsolicted notes, and will either shut their relays down or look for tools that will help them curate the content they host.
From my perspective, these tools take two forms — read protection and write protection. This is something I alluded to in my talk at Nostrasia last November.
Write protection is straightforward — already many relays have access control lists based on active subscriptions, invite codes, or just static whitelists that determine who is allowed to post to a given relay, or what event authors are represented there. This approach effectively prevents blastr from using relays as free storage, which is a huge improvement.
Read protection is more tricky, because anything publicly readable will be scraped by blastr and replicated to unauthenticated-write relays across the network. In most cases, this is ok, but there are use cases for relays to exist that host a unique collection of notes oriented around some organizing principle. Unfortunately, with blastr in action (or any scraper that might exist), the only way to do this is to actively protect proprietary content. There are a few approaches that can work to make this happen:
- IP-based access control lists
- AUTH-based access control lists
- Stripping signatures when serving events
- Storing and serving encrypted content
Each of these approaches has its own set of trade-offs. But depending on use case, any of them or a combination of them could work to allow relay operators to carve out their own piece of the nostr-verse. In fact, this is a big part of what Coracle is about — the white-labeled version of the product confines certain notes to proprietary relays, with optional encrypted group support.
Enough of my polemic against blastr. Let's talk about how to make the gossip model actually work.
Hints are pointless
Right now, clients that implement the gossip model rely pretty heavily on relay hints to find related notes — whether user profiles, reply parents, or community definitions. The problem with hints is that they are prone to link rot. Many of the relays that were set up a year ago when nostr took off are no longer online, and yet they persist in user relay lists, and in relay hints. These hints can't be updated — they are set in stone. What this means is that a different mechanism has to be used to find the notes the hints were supposed to help locate.
Because of this, I've come around to the position that hints are basically pointless. They are fine as a stopgap, and might be appropriate for certain obscure and ill-defined use cases where relay urls are the most durable address type available. But they provide basically no value in supporting the long-term robustness of the network.
What are durable, however, are pubkeys. Pubkeys are available pretty much everywhere, except in event id hints — and there is a proposal in the works to add a pubkey to those too. The cool thing about pubkeys as hints is that once you have a pubkey, all you need to do is find that person's kind 10002 inbox/outbox selections, and you should be able to find any note they have published.
This goes with the caveat that when users change their relay selections, or rotate their key, they (or their relays) should be sure to copy their notes to the new relay/pubkey.
The question then is: how do I find a given pubkey's relay selections?
There are already several mechanisms that make this reasonably easy. First of all, NIP 65 explicitly recommends publishing relay selections to a wide range of relays. This is a place where the blastr approach is appropriate. As a result, relay selections are usually available on the most popular public relays. Then there are special purpose relays like purplepag.es, which actively seek out these notes and index them.
These indexes are not confined to relays either. It would be trivial to create a DVM that you could ask for a pubkey's relay selections, optionally for a fee. Alex Gleason's proxy tag could also be used to indicate indexes that exist outside the nostr network — whether that be torrents, DHT keys, or what have you.
The best part is that this doesn't negatively impact the decentralization of the network because in principle these indexes are stateless — in other words, they're easily derived from the state of the public part of the nostr network.
Just do it for me
Looping back to where we started — the complexity and technical challenges of implementing the gossip model — there is a simple solution that many people have experimented with in different ways that could solve both issues at once: proxies.
As I mentioned above, Tony thinks of blastr as a proxy, and he's right. More specifically, it's a write-proxy. This is only part of its functionality (it also acts as an independent agent which crawls the network. EDIT: apparently this is not true!), but it is an essential part of how people use it.
Another kind of proxy is a read proxy. There are several implementations of these, including my own multiplextr proxy, which is gossip-compatible (although it requires a wrapper protocol for use). The advantage of a proxy like this is that it can reduce the number of connections a client has to open, and the number of duplicate events it has to download.
Proxies can do all kinds of fancy things in the background too, like managing the gossip model on behalf of the client, building an index of everything the user would be likely to ask for in advance to speed up response times, and more.
One interesting possibility is that a NIP 46 signer could double as a proxy, reducing the number of round trips needed. And since a signer already has access to your private key, this kind of proxy would not result in an escalation in permissions necessary for the proxy to work.
It's simple
The number of cool and creative solutions to the content replication and indexing problem is huge, and certainly doesn't end with blastr. Just to summarize the next steps I'm excited to see (to be honest, I want to build them myself, but we all know how that goes):
- More clients supporting gossip
- Gossip implementations maturing (Coracle's still has some issues that need to be worked out)
- A shift from relying on relay hints to relying on pubkey hints + relay selection indexes of some kind
- Proxy/signer combos which can take on some of the heavy lifting for clients of delivering events to the right inboxes, and pulling events from the right outboxes
Let's get building!
-
 @ 630d6b7a:ee832cff
2024-03-23 15:59:48
@ 630d6b7a:ee832cff
2024-03-23 15:59:48Here my friend you will find what I like to call meme's o' the day'*. It is a place I put memes. I'm not saying that's what you have to call it. You be you.
. Note: They are not necessarily from today.*
meme #memes #nostrmemes #memestr
crossposting to nostr
-
 @ c11cf5f8:4928464d
2024-03-23 12:29:14
@ c11cf5f8:4928464d
2024-03-23 12:29:14
Here we are again with our Magnificent Seven, trying to give you a hit of what you missed this week in the ~AGORA territory. No much going on so we are also providing some updated to cover our monthly Wild West Sundry Sunset already at ISSUE V!
The territory recently opened up to conversations, with the aim to not only talk about goods and services, but also incentivize an open and constructive dialogue about the market itself: how should we behave? Which natural laws should we follow to create this so discussed bitcoin peer-to-peer circular economy?
You're welcome to share any topics about Buy/Sell, Customer Engagement, Sales Strategy, Fair & Ethical Trading, Barter & Exchange safety, Trade Regulations, eCommerce, Trust and Relationship Building.
This week we have seen a slow-down in the marketplace, @AG0RA help filling up the gaps, and we are confident things will go to the moon as SN will soon release the self serve ads.
Top-Performing Ads
This week, the most engaging ones are:
01[⚖️ SELL] Delicious Peruvian hot sauce made with ancient Rocoto peppers by @DelgadosFuego02[SELL] Foundry X 🚨 Miners Inventory Sale Alert by @AGORA03[SELL] Vintage Royal Electric Typewriter - $100 (Whittier/CA) 🇺🇸 by @AGORA04[SELL] Lil Hodler plush Toy, 38.95k sats (auction) by @1GLENCoop05[SELL] Bitcoin Passport & physical coin (2013) - $120 (Armstrong Creek/VIC) 🇦🇺06[SELL] badwin acrosonic piano + bench w/ delivery - $200 (Austin/TX) 🇺🇸07[SELL ]Audrey Hepburn FineArt Buchstabenbild 61x61 cm - 74 € (München/DE) 🇩🇪
Just a reminder for you all
This territory aims to connect stackers and curious buyers for IRL P2P Bitcoin deals. Have fun checking what else stackers are shilling globally in the ~Agora. This is a great time for you to make some space un-dusting some stuff that has been sitting there for too long and get some sats for it!
We also opened the territory to conversation, you're welcome to share any topics about Buy/Sell, Customer Engagement, Sales Strategy, Fair & Ethical Trading, Barter & Exchange safety, Trade Regulations, eCommerce, Trust and Relationship Building.
Let's have this bitcoin peer-to-peer circular economy rolling!
Create your Ads now!
https://imgprxy.stacker.news/rtgLMeBXazpDNrDBD5KnBpjzEOAugRa234acvg6gPgM/rs:fit:2560:1440/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8xNzAzMA
- [⚖️ SELL] anything! or,
- if you're looking for something, hit the [🛒 BUY]!
- [🧑💻 HIRE] any bitcoiner skill or stuff from bitcoiners
- [🖇 OFFER] any product or service and stack more sats
- [🧑⚖️ AUCTION] to let stackers decide a fair price for your item
- [🤝 SWAP] if you're looking to exchange anything with anything else
- [🆓 FREE] your space, make a gift!
- [⭐ REVIEW] any bitcoin product or LN service you recently bought or subscribed to
Or contact @AGORA team on nostr DM and we can help you publish a personalized post.
MAY EVERY DEAL ₿RING JOY TO YOUR ~AGORA AD-VENTURES!
-
 @ ee11a5df:b76c4e49
2024-03-22 23:49:09
@ ee11a5df:b76c4e49
2024-03-22 23:49:09Implementing The Gossip Model
version 2 (2024-03-23)
Introduction
History
The gossip model is a general concept that allows clients to dynamically follow the content of people, without specifying which relay. The clients have to figure out where each person puts their content.
Before NIP-65, the gossip client did this in multiple ways:
- Checking kind-3 contents, which had relay lists for configuring some clients (originally Astral and Damus), and recognizing that wherever they were writing our client could read from.
- NIP-05 specifying a list of relays in the
nostr.jsonfile. I added this to NIP-35 which got merged down into NIP-05. - Recommended relay URLs that are found in 'p' tags
- Users manually making the association
- History of where events happen to have been found. Whenever an event came in, we associated the author with the relay.
Each of these associations were given a score (recommended relay urls are 3rd party info so they got a low score).
Later, NIP-65 made a new kind of relay list where someone could advertise to others which relays they use. The flag "write" is now called an OUTBOX, and the flag "read" is now called an INBOX.
The idea of inboxes came about during the development of NIP-65. They are a way to send an event to a person to make sure they get it... because putting it on your own OUTBOX doesn't guarantee they will read it -- they may not follow you.
The outbox model is the use of NIP-65. It is a subset of the gossip model which uses every other resource at it's disposal.
Rationale
The gossip model keeps nostr decentralized. If all the (major) clients were using it, people could spin up small relays for both INBOX and OUTBOX and still be fully connected, have their posts read, and get replies and DMs. This is not to say that many people should spin up small relays. But the task of being decentralized necessitates that people must be able to spin up their own relay in case everybody else is censoring them. We must make it possible. In reality, congregating around 30 or so popular relays as we do today is not a problem. Not until somebody becomes very unpopular with bitcoiners (it will probably be a shitcoiner), and then that person is going to need to leave those popular relays and that person shouldn't lose their followers or connectivity in any way when they do.
A lot more rationale has been discussed elsewhere and right now I want to move on to implementation advice.
Implementation Advice
Read NIP-65
NIP-65 will contain great advice on which relays to consult for which purposes. This post does not supersede NIP-65. NIP-65 may be getting some smallish changes, mostly the addition of a private inbox for DMs, but also changes to whether you should read or write to just some or all of a set of relays.
How often to fetch kind-10002 relay lists for someone
This is up to you. Refreshing them every hour seems reasonable to me. Keeping track of when you last checked so you can check again every hour is a good idea.
Where to fetch events from
If your user follows another user (call them jack), then you should fetch jack's events from jack's OUTBOX relays. I think it's a good idea to use 2 of those relays. If one of those choices fails (errors), then keep trying until you get 2 of them that worked. This gives some redundancy in case one of them is censoring. You can bump that number up to 3 or 4, but more than that is probably just wasting bandwidth.
To find events tagging your user, look in your user's INBOX relays for those. In this case, look into all of them because some clients will only write to some of them (even though that is no longer advised).
Picking relays dynamically
Since your user follows many other users, it is very useful to find a small subset of all of their OUTBOX relays that cover everybody followed. I wrote some code to do this as (it is used by gossip) that you can look at for an example.
Where to post events to
Post all events (except DMs) to all of your users OUTBOX relays. Also post the events to all the INBOX relays of anybody that was tagged or mentioned in the contents in a nostr bech32 link (if desired). That way all these mentioned people are aware of the reply (or quote or repost).
DMs should be posted only to INBOX relays (in the future, to PRIVATE INBOX relays). You should post it to your own INBOX relays also, because you'll want a record of the conversation. In this way, you can see all your DMs inbound and outbound at your INBOX relay.
Where to publish your user's kind-10002 event to
This event was designed to be small and not require moderation, plus it is replaceable so there is only one per user. For this reason, at the moment, just spread it around to lots of relays especially the most popular relays.
For example, the gossip client automatically determines which relays to publish to based on whether they seem to be working (several hundred) and does so in batches of 10.
How to find replies
If all clients used the gossip model, you could find all the replies to any post in the author's INBOX relays for any event with an 'e' tag tagging the event you want replies to... because gossip model clients will publish them there.
But given the non-gossip-model clients, you should also look where the event was seen and look on those relays too.
Clobbering issues
Please read your users kind 10002 event before clobbering it. You should look many places to make sure you didn't miss the newest one.
If the old relay list had tags you don't understand (e.g. neither "read" nor "write"), then preserve them.
How users should pick relays
Today, nostr relays are not uniform. They have all kinds of different rule-sets and purposes. We severely lack a way to advice non-technical users as to which relays make good OUTBOX relays and which ones make good INBOX relays. But you are a dev, you can figure that out pretty well. For example, INBOX relays must accept notes from anyone meaning they can't be paid-subscription relays.
Bandwidth isn't a big issue
The outbox model doesn't require excessive bandwidth when done right. You shouldn't be downloading the same note many times... only 2-4 times depending on the level of redundancy your user wants.
Downloading 1000 events from 100 relays is in theory the same amount of data as downloading 1000 events from 1 relay.
But in practice, due to redundancy concerns, you will end up downloading 2000-3000 events from those 100 relays instead of just the 1000 you would in a single relay situation. Remember, per person followed, you will only ask for their events from 2-4 relays, not from all 100 relays!!!
Also in practice, the cost of opening and maintaining 100 network connections is more than the cost of opening and maintaining just 1. But this isn't usually a big deal unless...
Crypto overhead on Low-Power Clients
Verifying Schnorr signatures in the secp256k1 cryptosystem is not cheap. Setting up SSL key exchange is not cheap either. But most clients will do a lot more event signature validations than they will SSL setups.
For this reason, connecting to 50-100 relays is NOT hugely expensive for clients that are already verifying event signatures, as the number of events far surpasses the number of relay connections.
But for low-power clients that can't do event signature verification, there is a case for them not doing a lot of SSL setups either. Those clients would benefit from a different architecture, where half of the client was on a more powerful machine acting as a proxy for the low-power half of the client. These halves need to trust each other, so perhaps this isn't a good architecture for a business relationship, but I don't know what else to say about the low-power client situation.
Unsafe relays
Some people complain that the outbox model directs their client to relays that their user has not approved. I don't think it is a big deal, as such users can use VPNs or Tor if they need privacy. But for such users that still have concerns, they may wish to use clients that give them control over this. As a client developer you can choose whether to offer this feature or not.
The gossip client allows users to require whitelisting for connecting to new relays and for AUTHing to relays.
See Also
-
 @ 7b351277:001ba418
2024-03-23 10:07:03
@ 7b351277:001ba418
2024-03-23 10:07:03 -
 @ 3bf0c63f:aefa459d
2024-03-23 08:57:08
@ 3bf0c63f:aefa459d
2024-03-23 08:57:08Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ 42342239:1d80db24
2024-03-21 09:49:01
@ 42342239:1d80db24
2024-03-21 09:49:01It has become increasingly evident that our financial system has started undermine our constitutionally guaranteed freedoms and rights. Payment giants like PayPal, Mastercard, and Visa sometimes block the ability to donate money. Individuals, companies, and associations lose bank accounts — or struggle to open new ones. In bank offices, people nowadays risk undergoing something resembling being cross-examined. The regulations are becoming so cumbersome that their mere presence risks tarnishing the banks' reputation.
The rules are so complex that even within the same bank, different compliance officers can provide different answers to the same question! There are even departments where some of the compliance officers are reluctant to provide written responses and prefer to answer questions over an unrecorded phone call. Last year's corporate lawyer in Sweden recently complained about troublesome bureaucracy, and that's from a the perspective of a very large corporation. We may not even fathom how smaller businesses — the keys to a nation's prosperity — experience it.
Where do all these rules come?
Where do all these rules come from, and how well do they work? Today's regulations on money laundering (AML) and customer due diligence (KYC - know your customer) primarily originate from a G7 meeting in the summer of 1989. (The G7 comprises the seven advanced economies: the USA, Canada, the UK, Germany, France, Italy, and Japan, along with the EU.) During that meeting, the intergovernmental organization FATF (Financial Action Task Force) was established with the aim of combating organized crime, especially drug trafficking. Since then, its mandate has expanded to include fighting money laundering, terrorist financing, and the financing of the proliferation of weapons of mass destruction(!). One might envisage the rules soon being aimed against proliferation of GPUs (Graphics Processing Units used for AI/ML). FATF, dominated by the USA, provides frameworks and recommendations for countries to follow. Despite its influence, the organization often goes unnoticed. Had you heard of it?
FATF offered countries "a deal they couldn't refuse"
On the advice of the USA and G7 countries, the organization decided to begin grading countries in "blacklists" and "grey lists" in 2000, naming countries that did not comply with its recommendations. The purpose was to apply "pressure" to these countries if they wanted to "retain their position in the global economy." The countries were offered a deal they couldn't refuse, and the number of member countries rapidly increased. Threatening with financial sanctions in this manner has even been referred to as "extraterritorial bullying." Some at the time even argued that the process violated international law.
If your local Financial Supervisory Authority (FSA) were to fail in enforcing compliance with FATF's many checklists among financial institutions, the risk of your country and its banks being barred from the US-dominated financial markets would loom large. This could have disastrous consequences.
A cost-benefit analysis of AML and KYC regulations
Economists use cost-benefit analysis to determine whether an action or a policy is successful. Let's see what such an analysis reveals.
What are the benefits (or revenues) after almost 35 years of more and more rules and regulations? The United Nations Office on Drugs and Crime estimated that only 0.2% of criminal proceeds are confiscated. Other estimates suggest a success rate from such anti-money laundering rules of 0.07% — a rounding error for organized crime. Europol expects to recover 1.2 billion euros annually, equivalent to about 1% of the revenue generated in the European drug market (110 billion euros). However, the percentage may be considerably lower, as the size of the drug market is likely underestimated. Moreover, there are many more "criminal industries" than just the drug trade; human trafficking is one example - there are many more. In other words, criminal organizations retain at least 99%, perhaps even 99.93%, of their profits, despite all cumbersome rules regarding money laundering and customer due diligence.
What constitutes the total cost of this bureaurcratic activity, costs that eventually burden taxpayers and households via higher fees? Within Europe, private financial firms are estimated to spend approximately 144 billion euros on compliance. According to some estimates, the global cost is twice as high, perhaps even eight times as much.
For Europe, the cost may thus be about 120 times (144/1.2) higher than the revenues from these measures. These "compliance costs" bizarrely exceed the total profits from the drug market, as one researcher put it. Even though the calculations are uncertain, it is challenging — perhaps impossible — to legitimize these regulations from a cost-benefit perspective.
But it doesn't end there, unfortunately. The cost of maintaining this compliance circus, with around 80 international organizations, thousands of authorities, far more employees, and all this across hundreds of countries, remains a mystery. But it's unlikely to be cheap.
The purpose of a system is what it does
In Economic Possibilities for our Grandchildren (1930), John Maynard Keynes foresaw that thanks to technological development, we could have had a 15-hour workweek by now. This has clearly not happened. Perhaps jobs have been created that are entirely meaningless? Anthropologist David Graeber argued precisely this in Bullshit Jobs in 2018. In that case, a significant number of people spend their entire working lives performing tasks they suspect deep down don't need to be done.
"The purpose of a system is what it does" is a heuristic coined by Stafford Beer. He observed there is "no point in claiming that the purpose of a system is to do what it constantly fails to do. What the current regulatory regime fails to do is combat criminal organizations. Nor does it seem to prevent banks from laundering money as never before, or from providing banking services to sex-offending traffickers
What the current regulatory regime does do, is: i) create armies of meaningless jobs, ii) thereby undermining mental health as well as economic prosperity, while iii) undermining our freedom and rights.
What does this say about the purpose of the system?
-
 @ 20d29810:6fe4ad2f
2024-03-15 20:51:56
@ 20d29810:6fe4ad2f
2024-03-15 20:51:56













































-
 @ 57d1a264:69f1fee1
2024-03-23 06:20:19
@ 57d1a264:69f1fee1
2024-03-23 06:20:19Prompt: Food Menu Items ===============
Create a food menu for a bar or restaurant. It could be a simple coffee shop or a more complex menu such as for a pizza restaurant. How'd price the items? Bitcoin or fiat? Maybe both?
Or is it for a touchscreen tabletop ordering system at a nightclub?
Flex your design muscles and join in. Most of all, keep this exercise loose and keep it stress-free. The FUC is about growing our design skills, together, as a community. We can't wait to see what you create!
Happy designing, Stackers!
Share Your Results When you finish the challenge, post your work on this thread! If you also share it on
nostr, be sure to use the hashtag #FUCdesiger and tag Design_r@iris.to or @Design__r on X! We'll keep an eye out and repost good examples on a regular basis.
Curious to know WTF is a FUC? Read the ⚡️Flash Ui Challenges welcoming post.
Looking for more FUCs? Check the archive here!
-
 @ 57d1a264:69f1fee1
2024-03-23 06:05:56
@ 57d1a264:69f1fee1
2024-03-23 06:05:56What have you designed this week?
Be proud of you and leave a comment below to let the SN ~Design community know what you're designing on this week. It doesn't matter if it's a sketch or a high resolution screen, nor how much progress you've made.
Just share what you're up to, and let the community know if you want any feedback or help. If you missed last week's thread, here are the updates stackers shared from all their latest work projects.
-
 @ 0dc35bab:125ef4d8
2024-03-23 04:52:06
@ 0dc35bab:125ef4d8
2024-03-23 04:52:06Self Custody of your Bitcoin isn't hard, you just need to put in the work. Here's how to protect your Bitcoin in a way that allows you to be adaptable.
I am a mere pleb, standing on the shoulders of giants in bringing this information to you.
Seed Generation
Border Wallets solve a problem faced by many Bitcoiners; how to quickly, easily, securely and reliably memorise 12 or 24 (or more) seed words. I think this is a great tool for any Bitcoiner to walk through when generating their seed, as it helps grasp an understanding of entropy better. Yes, Coldcard also allows you to generate a seed through dice rolls, another good solution!
12 words are easier to remember, if shit hits the fan and you have to pack up everything and go.
You will not just be relying on memory of your seed, we will now get into how to safely protect the seed
Seed XOR
Here, your 12 word seed phrase becomes two or more parts that are also BIP-39 compatible seeds phrases. Therefore you don't need to leave any trace of the original 12 words anywhere. By using Seed XOR you can have numerous copies of the XOR-ed seed parts, definitely etched in steel and if they are found, you are not to be too worried, as it could represent a 2-of-3 multisig set up, a couple of single sig wallets with passphrases etc. the possibilities are hard to narrow down.
Coldcard is easy to use for Seed XOR as is Seed Tool.
One seed to rule them all, One Key to find them, One Path to bring them all, And in cryptography bind them.
Generate thousands of seeds with BIP-85 deterministic entropy - example guide
A would be attacker has had to jump through many hoops in order to gain access to your 12 words by now. AND STILL we can utilise more ways of obfuscation in Bitcoin. Through BIP-85 you can generate 10,000 other seeds, from your original seed, and use these to hold some of your cold stored UTXOs. You may want to leave some Bitcoin in the 12 word seed, as a decoy but that is down to personal preference. I would also recommend using passphrases for the BIP-85 generated seeds. These can be stored in password managers at a low risk because: 1. It's highly unlikely anyone will have access to your 12 words plus password manager. 2. They won't know which index number (out of 10,000) you used to generate the BIP-85 seed. 3. Know the format method of BIP-85, eg. was it wif, 12 words, 24 words etc.
THE MAIN BENEFIT OF BIP-85 IS IT ALLOWS YOU TO SHIFT SOME COLD STORAGE UTXOS INTO A HOT WALLET FOR SPENDING AT ZERO COST
Shower thoughts...
Someone could probably use a seed phrase from a BTC Sessions tutorial vid, and still be secure because of all the above
-
 @ ecebc8ba:13920f96
2024-03-23 03:52:26
@ ecebc8ba:13920f96
2024-03-23 03:52:26- How about this external image ?

- Do something to your hair.
- Have you ever eaten a spoon full of peanut butter ?
- Have you ever eaten a spoon full of ketchup ?
- Do you like spiders ?
truth-or-dare:event type:draw_card timestamp:1710561602651 cardRef:^1This is a comment! - How about this external image ?
-
 @ fa984bd7:58018f52
2024-02-28 22:15:25
@ fa984bd7:58018f52
2024-02-28 22:15:25I have recently launched Wikifreedia, which is a different take on how Wikipedia-style systems can work.
Yes, it's built on nostr, but that's not the most interesting part.
The fascinating aspect is that there is no "official" entry on any topic. Anyone can create or edit any entry and build their own take about what they care about.
Think the entry about Mao is missing something? Go ahead and edit it, you don't need to ask for permission from anyone.
Stuart Bowman put it best on a #SovEng hike:
The path to truth is in the integration of opposites.
Since launching Wikifreedia, less than a week ago, quite a few people asked me if it would be possible to import ALL of wikipedia into it.
Yes. Yes it would.
I initially started looking into it to make it happen as I am often quick to jump into action.
But, after thinking about it, I am not convinced importing all of Wikipedia is the way to go.
The magical thing about building an encyclopedia with no canonical entry on any topic is that each individual can bring to light the part they are interested the most about a certain topic, it can be dozens or hundreds, or perhaps more, entries that focus on the edges of a topic.
Whereas, Wikipedia, in their Quijotean approach to truth, have focused on the impossible path of seeking neutrality.
Humans can't be neutral, we have biases.
Show me an unbiased human and I'll show you a lifeless human.
Biases are good. Having an opinion is good. Seeking neutrality is seeking to devoid our views and opinions of humanity.
Importing Wikipedia would mean importing a massive amount of colorless trivia, a few interesting tidbits, but, more important than anything, a vast amount of watered-down useless information.
All edges of the truth having been neutered by a democratic process that searches for a single truth via consensus.
"What's the worst that could happen?"
Sure, importing wikipedia would simply be one more entry on each topic.
Yes.
But culture has incredibly strong momentum.
And if the culture that develops in this type of media is that of exclusively watered-down comfortable truths, then some magic could be lost.
If people who are passionate or have a unique perspective about a topic feel like the "right approach" is to use the wikipedia-based article then I would see this as an extremely negative action.
An alternative
An idea we discussed on the #SovEng hike was, what if the wikipedia entry is processed by different "AI agents" with different perspectives.
Perhaps instead of blankly importing the "Napoleon" article, an LLM trained to behave as a 1850s russian peasant could be asked to write a wiki about Napoleon. And then an agent tried to behave like Margaret Thatcher could write one.
Etc, etc.
Embrace the chaos. Embrace the bias.
-
 @ d8a2c33f:76611e0c
2024-02-26 03:10:36
@ d8a2c33f:76611e0c
2024-02-26 03:10:36Let's start with definitions:
Cashu - Cashu is a free and open-source Chaumian ecash system built for Bitcoin. Cashu offers near-perfect privacy for users of custodial Bitcoin applications. Nobody needs to know who you are, how much funds you have, and who you transact with. - more info here https://cashu.space/
Cashu-adress - it is a protocol that runs on top of cashu mints. More info here: https://docs.cashu-address.com/
Npub.cash - service that runs on top of cashu-address protocol. Let's you use your npub@npub.cash as a lightning address to receive zaps or incoming sats. More info here https://npub.cash/
Pay to public key - Like bitcoin you can cashu tokens are bearer assets and can be locked to a public key. This means only the person who has the private key can use that token.
What do you use it for? - Use your npub cash as your lightning address replacement.
Why? I believe everyone knows what a lightning address is. Lightning address is usually provided by your wallet provider who also runs their lightning node. E.g. if you have @alby.com lightning address then you already have an account setup with alby and using their lightning node to get your sats. With npub.cash you can simply put your npubaddress@npub.cash without registering first or signing up. And you can keep this forever even while changing your lightning wallet from alby to any other provider or running your own lightning node.
Npub.cash locks the received tokens into your nostr public key (Still work in progress) so that only the owner of Nostr public key who has the private key can claim the token and push it to their wallet of choice.
Benefits Over Traditional Custodial Lightning Addresses:
Privacy: With Cashu-Address, your financial activities are not visible to your custodian. This added layer of privacy ensures that your transactions remain your own.
Flexibility in Custodian Selection: Unlike traditional Lightning Addresses, Cashu-Address allows you to choose your custodian freely. If your needs change, you can switch your custodian anytime without hassle.
No User Exclusion: Custodians cannot exclude individual users. Because mints do know know which user eCash belongs to, they can not censor certain users. How to claim your username@npub.cash - This is what makes it so cool. You can actually get a vanity username for your profile name. E.g. I got mine as starbuilder@npub.cash. Simply visit npub.cash website and click the get username button. Put in your vanity username and pay 5k sats to get your profile@npub.cash
How to claim your username@npub.cash- This is what makes it so cool. You can actually get a vanity username for your profile name. E.g. I got mine as starbuilder@npub.cash. Simply visit npub.cash website and click the get username button. Put in your vanity username and pay 5k sats to get your profile@npub.cash . This is onetime and you can use this address forever..!
Frequently asked Questions:
-
What connect string to use to login with NIP-46 on iOS. - try setting up an account at https://use.nsec.app/home . This is still WIP. If it does not work, just try the Nostr extension using laptop browser
-
Is there a notification when I receive sats/zaps? Not yet. We are working on it. However, just go to npub.cash every couple of days to sweep your collected sats to your wallet
-
Which cashu wallet to use? Use enuts (android & ios) https://www.enuts.cash/ or minibits.cash for android https://www.minibits.cash/
-
Will anyone be able to claim my sats? NO. When you start the claim process you need to sign with your Nostr extenstion signer to claim sats. So only the person controlling the private key to the npub can claim sats.
-
I really struggle to understand the flow of what happened concretely. - Don't break your head. the devs got you covered. Also, this is super new and everyone is trying to get their heads around. Just follow instructions, play with it and ask for help.
- Is it non-custodial? - When we lock your sats to your pubkey we cannot spend it. However locking to pubkey is not enabled until wallets can start supporting them.
- How do I ask for help? - just post #asknpub.cash and post your questions. We will get to you.
- Who are the devs behind this? @calle (Master of Cashu) @egge (Core dev) @starbuilder (dev support)
Here's what everyone is talking about #npub.cash on Nostr
nostr:nevent1qvzqqqqqqypzqx78pgq53vlnzmdr8l3u38eru0n3438lnxqz0mr39wg9e5j0dfq3qythwumn8ghj7um9v9exx6pwdehhxtn5dajxz7f0qqsxcwntv9d342ashe5yvyv0fg40wm873jaszt6d2u0209vqz5gkcdq6avwyr
nostr:nevent1qvzqqqqqqypzq5qzedy85msr57qayz6dz9dlcr5k40mcqtvm5nhyn466qgc6p4kcqythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qythwumn8ghj7um9v9exx6pwdehhxtn5dajxz7f0qqsvek7d8v4lddrmj2mynegsnrc4r4gnmswkddm02qzenwuc7x9perctaedre
nostr:nevent1qvzqqqqqqypzpfpqfrt75fhfcd4x0d0lyek9pzyz4zwmudh0vq7vn3njvvngsmpjqyghwumn8ghj7mn0wd68ytnhd9hx2tcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsqgyjwfsgr80xmha8x2wwd4klzsxcagmlpk3wsfyyvqnlvzn2rcvnhu534kj5
nostr:nevent1qvzqqqqqqypzp3yw98cykjpvcqw2r7003jrwlqcccpv7p6f4xg63vtcgpunwznq3qyfhwumn8ghj7mmxve3ksctfdch8qatz9uq36amnwvaz7tmwdaehgu3wvf5hgcm0d9hx2u3wwdhkx6tpdshsqg8v5hfgmwangecpejcw22fm4uk2s438p8ahpu5l985wserctr0h6gysle9m
nostr:nevent1qvzqqqqqqypzp6y2dy0f3kvc0jty2gwl7cqztas8qqmc5jrerqxuhw622qnc2pq3qy88wumn8ghj7mn0wvhxcmmv9uq3xamnwvaz7tm0venxx6rpd9hzuur4vghsqgx68ujht0r9qqqp4l27u0x27sg4p5l2ks0xd9kxm9w2vkjhppttlur0et6k
-
-
 @ a012dc82:6458a70d
2024-03-23 02:55:42
@ a012dc82:6458a70d
2024-03-23 02:55:42Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
As of today, Bitcoin (BTC), which was the first cryptocurrency ever established, is still the most widely used and valued kind of digital money in the world as of today. Bitcoin was initially formed in 2009. Bitcoin is a decentralized digital currency that is built on blockchain technology. It is supported by a network of users who check and record transactions without relying on a central authority or an intermediary.
Bitcoin is a decentralized digital currency that offers an alternative to fiat currencies like the United States dollar, which are managed by governments and central banks. A procedure known as the proof-of-work consensus method is used to confirm the legitimacy of transactions. Bitcoin miners compete to verify transactions by solving hard math problems on powerful computers with the help of powerful computers.
Some Bitcoin supporters regard the cryptocurrency just as a fun asset for trading and speculation, while others are optimistic that it may one day replace all other digital currencies as the standard medium of exchange in the online world. Since its birth, there is no doubt that Bitcoin has seen a stratospheric surge in popularity. Nevertheless, the first 13 years of its existence have also shed light on numerous critical defects and deficiencies in the most popular digital asset in the world.
Here is a brief overview of some of the most important times in Bitcoin's short history, as well as a look at how these times might affect its future:
When Did Bitcoin Start?
It is not a coincidence that one of the most turbulent times in the history of the United States' financial system coincided with the birth of Bitcoin. During the years 2007 to 2009, when the global financial crisis was at its height, public mistrust in banks and central governments reached an all-time high.
In 2009, a person or group of people using the pseudonym Satoshi Nakamoto created bitcoin. This was the same name that appeared in the first Bitcoin white paper, which was published in 2008, and which first described the blockchain system that would serve as the backbone of the entire cryptocurrency market. Bitcoin was created in 2009.
Over the course of time, a number of individuals have come forward and said that they are the genuine Satoshi Nakamoto. However, none of these individuals have been able to present adequate proof to substantiate their claims.
When the first Bitcoin block, known as the genesis block, was successfully mined on January 3, 2009, the Bitcoin blockchain was formally introduced to the public. According to some accounts, Satoshi was able to mine up to 1.1 million bitcoins in the first seven months after the birth of Bitcoin. Using values from August 2022, the coins would have a value of almost $22 billion today.
According to Joshua Peck, founder and chief investment officer of cryptocurrency hedge fund TrueCode Capital, early Bitcoin aficionados were mesmerized by the design of the cryptocurrency, even if they weren't entirely sure what it was going to be.
According to Peck, "It had some economic worth, but I was looking at it more from an engineering viewpoint, thinking that we might utilize it for secure message passing or bring strong cryptography into the hands of regular consumers," and he thinks that the money value was rather secondary.
On May 22, 2010, a guy from Florida agreed to pay 10,000 BTC for two Papa John's pizzas, each of which had a price tag of around $25. This was the first time that a real-world financial transaction employing Bitcoin was reported to have taken place. During the transaction, the price of one Bitcoin was estimated to be somewhere around a quarter of a penny. Members of the Bitcoin community still celebrate Pizza Day every year on May 22.
"Over time, the financial value became more publicly appreciated, and of course, today it has become the cornerstone of the fastest-growing asset class of my generation," says Peck. "It has become the cornerstone of the fastest-growing asset class of my generation."
The Bitcoin Price History
In 2010, Bitcoin became the first cryptocurrency that could be bought, sold, and traded via internet exchanges. The first time the price of a bitcoin increased by more than one dollar was in the month of April 2011.
In 2011, Bitcoin was also up against its first competitors in the cryptocurrency market. In October of 2011, Litecoin (LTC) was introduced to the public. Several years later, in 2015, the live version of the Ethereum blockchain was released.
The price of Bitcoin continued to grow, which brought with it an increase in its visibility, popularity, and volatility. By November 2013, the price of a bitcoin had risen to $1,000. Prices of bitcoin and trade volumes really began to snowball at the end of 2017, with prices topping $10,000 per coin for the first time in November 2017, and reaching about $20,000. This marked the beginning of a period of sustained growth for both metrics.
The CME Group Inc.'s (ticker: CME) statement that it will be issuing Bitcoin futures contracts in December 2017 was one of the driving causes behind the price of Bitcoin's meteoric surge in December 2017. These contracts were the first Bitcoin-related financial instruments that were made available for purchase by a licensed financial institution in the United States.
According to Jarek Hirniak, founder and CEO of Generation Lambda, the innovation path that Bitcoin took is similar to the Gartner Hype Cycle, which is a standard innovation trajectory. The idea is that as soon as people find out about a new technology, like Bitcoin, their expectations for it skyrocket to an unreasonable level.
"At first, the vast majority of people ignore it, and then, all of a sudden, everyone becomes more thrilled," says Hirniak. "This continues until it becomes apparent that promises can't keep up with reality."
"A setup like this, coupled with a lack of liquidity and the absence of regulation, makes it an ideal environment for market manipulation."
At the tail end of 2017, enthusiasm, anticipation, and a frenzy in the crypto market provided the ideal conditions for an asset bubble to form. Taking advantage of the recent surge in popularity of cryptocurrencies, a number of firms have raised capital via the sale of initial coin offerings (ICOs). During the years 2017 and 2018, over 800 initial coin offerings (ICOs) generated around $20 billion in capital. The initial coin offering (ICO) market was rife with cons and fraud, which led to a precipitous drop in the value of many ICO tokens within a single year.
The collapse of the crypto boom caused Bitcoin prices to fall back down to less than $4,000 per coin by the end of 2018.
Bitcoin Crypto Winter 2022
The next significant spike in demand for Bitcoin occurred in the midst of the COVID-19 epidemic in the latter half of 2020. Many younger Americans were left with extra disposable income and time on their hands as a result of extended shutdowns of entertainment and leisure businesses such as sports and casinos, in addition to multiple rounds of government economic stimulus payments. This helped fuel another surge in Bitcoin prices in late 2020.
October 2021 saw the beginning of trading for the ProShares Bitcoin Strategy ETF (BITO), which was the first Bitcoin exchange-traded fund, often known as an ETF, to debut on a major U.S. exchange. After the BITO ETF came out, many other cryptocurrency futures ETFs were created, like the Global X Blockchain & Bitcoin Strategy ETF, the Valkyrie Bitcoin Strategy ETF (BTF), and the VanEck Bitcoin Strategy ETF (XBTF) (BITS).
After reaching a new all-time high of more than $20,000 in December 2020, the price of bitcoin continued to climb and finally reached a price of $68,990 in November 2021.
Unfortunately, consistently high inflation caused the Federal Reserve to begin rapidly tightening monetary policy at the beginning of 2022. This triggered large sell-offs in cryptocurrencies and other risky assets, which led to a global economic slowdown. To make matters even worse, the precipitous falls in the prices of cryptocurrencies at the beginning of 2022 sparked a liquidity crisis that resulted in the failure of the $10 billion cryptocurrency hedge fund known as Three Arrows Capital, as well as the failure of the cryptocurrency lending companies Celsius and Voyager Digital.
The volatility of the cryptocurrency market was also responsible for the loss of $60 billion worth of Luna and the associated stablecoin Terra USD (UST). Also, in May 2022, the volatility of the cryptocurrency market caused Tether (USDT), the largest stablecoin in the world, to lose its link to the US dollar for a short time.
Omid Malekan, an author and part-time professor at Columbia Business School, says that the crypto winter of 2022 was caused by the sharp rise in cryptocurrency prices in 2021 and the aggressive tightening of monetary policy by central banks.
"The bankruptcy of Luna and UST punched a hole in the balance sheets of big participants," says Malekan, "which led to a cascading failure of cryptocurrency lenders like Celsius and over-leveraged hedge funds, which accelerated falls."
Bitcoin Price Forecasts
At the time of writing, one Bitcoin is equivalent to around $20,000 USD. Its value is now much lower than its all-time peak of more than $68,000 in 2021, yet it is still considerably higher than its all-time low of less than $4,000 in 2018.
Bitcoin is still one of the financial assets with the greatest long-term performance despite the fact that it had a significant sell-off in 2022 during the crypto winter. But Bitcoin's huge price swings will continue to be a problem if the cryptocurrency ever wants to be used as a true global currency.
At this time, Bitcoin remains a high-risk speculative investment, and there is no obvious method to evaluate its intrinsic worth or anticipate where its price is going to go next. However, there is one clear way to invest in Bitcoin. Even so, many people who are optimistic about Bitcoin still think that the leading cryptocurrency will do well in the long run.
"It's difficult to forecast the future, particularly for something as volatile as Bitcoin," says Malekan, "but as long as general adoption keeps going strong, digital assets of all kinds continue to normalize further, and regulators create sensible guardrails, then prices should appreciate over the long run."
Conclusion
As of today, Bitcoin (BTC), which was the first cryptocurrency ever established, is still the most widely used and valued kind of digital money in the world as of today. Bitcoin was initially formed in 2009. Bitcoin is a decentralized digital currency that is built on blockchain technology. It is supported by a network of users who verify and record transactions without depending on a central authority or an intermediary. In 2009, a person or group of people using the pseudonym Satoshi Nakamoto created bitcoin. This was the same name that appeared in the first Bitcoin white paper, which was published in 2008, and which first described the blockchain system that would serve as the backbone of the entire cryptocurrency market. Bitcoin was created in 2009.
FAQ
When 2009 came along, how much was one bitcoin worth? At its inception, the value of bitcoin was almost zero. In October 2009, a transaction took place that gave Bitcoin its initial monetary value. It was carried out by a student of computer science in Finland named Martti Malmi, who went by the online alias Sirius. Malmi sold 5,050 coins for $5.02, which gave each bitcoin a value of $0.0009 at the time. The transaction was conducted using PayPal.
How much will one bitcoin be worth in the year 2030? If the predicted gain of 413% between May 2028 and May 2029 is taken into account, Bitcoin's value is projected to reach $2.08 million by May 2029. This would give Bitcoin a value of $2.11 million in January 2030.
Who has the most bitcoins in their possession? According to its financial report for the first quarter of 2022, the United States-based software business MicroStrategy (MSTR) is the largest publicly listed corporate owner of bitcoin in the world, with holdings of around 129,218 BTC. As of July 22, 2022, the value of MicroStrategy's Bitcoin holdings was more than $3 billion. It is common knowledge that Tesla (TSLA) has bitcoin holdings.
That's all for today, see ya tomorrow
If you want more, be sure to follow us on :
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 6871d8df:4a9396c1
2024-02-24 22:42:16
@ 6871d8df:4a9396c1
2024-02-24 22:42:16In an era where data seems to be as valuable as currency, the prevailing trend in AI starkly contrasts with the concept of personal data ownership. The explosion of AI and the ensuing race have made it easy to overlook where the data is coming from. The current model, dominated by big tech players, involves collecting vast amounts of user data and selling it to AI companies for training LLMs. Reddit recently penned a 60 million dollar deal, Google guards and mines Youtube, and more are going this direction. But is that their data to sell? Yes, it's on their platforms, but without the users to generate it, what would they monetize? To me, this practice raises significant ethical questions, as it assumes that user data is a commodity that companies can exploit at will.
The heart of the issue lies in the ownership of data. Why, in today's digital age, do we not retain ownership of our data? Why can't our data follow us, under our control, to wherever we want to go? These questions echo the broader sentiment that while some in the tech industry — such as the blockchain-first crypto bros — recognize the importance of data ownership, their "blockchain for everything solutions," to me, fall significantly short in execution.
Reddit further complicates this with its current move to IPO, which, on the heels of the large data deal, might reinforce the mistaken belief that user-generated data is a corporate asset. Others, no doubt, will follow suit. This underscores the urgent need for a paradigm shift towards recognizing and respecting user data as personal property.
In my perfect world, the digital landscape would undergo a revolutionary transformation centered around the empowerment and sovereignty of individual data ownership. Platforms like Twitter, Reddit, Yelp, YouTube, and Stack Overflow, integral to our digital lives, would operate on a fundamentally different premise: user-owned data.
In this envisioned future, data ownership would not just be a concept but a practice, with public and private keys ensuring the authenticity and privacy of individual identities. This model would eliminate the private data silos that currently dominate, where companies profit from selling user data without consent. Instead, data would traverse a decentralized protocol akin to the internet, prioritizing user control and transparency.
The cornerstone of this world would be a meritocratic digital ecosystem. Success for companies would hinge on their ability to leverage user-owned data to deliver unparalleled value rather than their capacity to gatekeep and monetize information. If a company breaks my trust, I can move to a competitor, and my data, connections, and followers will come with me. This shift would herald an era where consent, privacy, and utility define the digital experience, ensuring that the benefits of technology are equitably distributed and aligned with the users' interests and rights.
The conversation needs to shift fundamentally. We must challenge this trajectory and advocate for a future where data ownership and privacy are not just ideals but realities. If we continue on our current path without prioritizing individual data rights, the future of digital privacy and autonomy is bleak. Big tech's dominance allows them to treat user data as a commodity, potentially selling and exploiting it without consent. This imbalance has already led to users being cut off from their digital identities and connections when platforms terminate accounts, underscoring the need for a digital ecosystem that empowers user control over data. Without changing direction, we risk a future where our content — and our freedoms by consequence — are controlled by a few powerful entities, threatening our rights and the democratic essence of the digital realm. We must advocate for a shift towards data ownership by individuals to preserve our digital freedoms and democracy.
-
 @ 5d4b6c8d:8a1c1ee3
2024-03-22 20:17:13
@ 5d4b6c8d:8a1c1ee3
2024-03-22 20:17:13Welcome to part 6 of my series attempting to answer Bob Murphy's "Tough Questions for Libertarians". A description of this project can be found here: https://stacker.news/items/458128/r/Undisciplined.
Question
Would the God of the Bible own everything, since he created it, and doesn't that make it impossible for him to be a tyrant?
Context
Here's the clip from Bob's show that explains this question: https://fountain.fm/clip/2ibZPbXWgP7FuoYhrEbc.
This question is aimed at atheist (antitheist?) libertarians who claim that not only does god not exist, but it's good he doesn't because he's tyrannical.
Bob is first asking if the God of the Bible would be the owner of everything, according to standard libertarian homesteading theory, by virtue of having created it. Then, if so, he's asking how it makes sense to consider the legitimate owner of property a tyrant for how he uses said property.
Answer
No, God wouldn't own everything. In the same way that we don't own our adult children, God would not own us.
Would God own everything else, though? Initially, sure.
A couple of issues immediately present themselves: 1) Did God gift the Earth to mankind? I have an impression that the Biblical account has some expression of god granting us dominion over the Earth or that the Earth was made for us. 2) Squatters' rights 3) Even if God owns all the stuff, he could still be a "tyrant".
Gift
If God gifted the Earth to humanity in some way, then obviously case closed. If the earth was made for our use, then that's as good as a gift, even if there's no explicit title transfer. Since, the gift was made prior to us existing, I don't think any conditions on how we use it would be binding, as we never had an opportunity to agree.
There are many libertarian thought experiments that revolve around putting people in perilous situations. The general conclusion reached is that if you put someone in a perilous situation, you incur an obligation to save them. So, if God brought us into existence on his planet and we need that planet to survive, he has an incurred an obligation to at least allow us to use it enough to survive. In libertarianism, right to use is tantamount to ownership (exclusive right to control).
Squatters' Rights
There are implicit contracts in libertarianism. God is omniscient and omnipotent, so if we were using his stuff in a way he objected to, he's had plenty of time to inform us. Absent such a notice, it's reasonable for us to infer that the way we're using it is approved of. One of the ways we're using the Earth is to transfer ownership of chunks of it from one person to another.
"Tyrant"
The word tyrant, just means an absolute ruler. It also carries a context of unfairness and cruelty. All of those things could be true of a legitimate property owner. You might say that it's not possible to be unfair in how you choose to use your own property, but I think that's a category error. Fairness is an ethical concept whereas ownership is a legal concept.
Postscript
I confess to being about as secular of a person as there is. I'm not particularly well-versed in the biblical account, so I hope more knowledgeable readers will correct any errors or misconceptions I have.
I also will say that I thought this was a silly question from Bob and really not as "tough" as he might have thought, unless I'm missing something.
-
 @ 72592ec9:ffa64d2c
2024-03-22 20:17:03
@ 72592ec9:ffa64d2c
2024-03-22 20:17:03A new batch of previously private emails with Satoshi were published this past month by Sirius.
Sirius was one of the first volunteers to work with Satoshi in the early days of Bitcoin. These 260 emails span from May of 2009 (just 5 months after the launch of Bitcoin) to February of 2011. They're a digital-gold mine of early Bitcoin history. I highly recommend going through them if you're a Bitcoin history nerd like me.
One of these more interesting emails from Satoshi outlines his logic for Bitcoin supply numbers and the issuance schedule. It reads below:
This is some very nice color here on Satoshi's choice for 21 million bitcoin, with extra padding of 8 decimal places for satoshis. Interestingly enough, this "picking something in the middle" comment by Satoshi is also bang on in more ways than obvious. There are 8 decimal places with 21 million bitcoin, so 16 decimals total for the Bitcoin number system.
Put another way, there are 2.1 quadrillion satoshis total programmed in Bitcoin as we know it today.
But this was not always so…
In 2013 Ray Dillinger (aka Bear, aka Cryddit) posted a 2008 email copy to Bitcointalk, allegedly from Satoshi Nakamoto… The email apparently contained the source code of Bitcoin, from November 2008. Pre-dating the first release of Bitcoin v0.01 source code, released January 2009…
There are several significant changes when we compare this 2008 pre-alpha source code to the 2009 Bitcoin v0.1 source code. A big one being the genesis block hash. There is no "The Times" article headline, as this headline did not yet exist. A hash starting with "0x31" is used instead of "0x5f" (from the v0.01 "The Times" genesis block).
Furthermore, the block reward was not 50.00,000,000 bitcoin.satoshis BUT 10,000.0000 bitcoin.satoshis. This didn't mean a supply of 21 million bitcoin or 2.1 quadrillion satoshis...
BUT 1.99 billion bitcoin or 19.9 trillion satoshis TOTAL!
Furthermore, the halving was scheduled for every 100,000 blocks, instead of 210,000 blocks. The block time target was aimed at 15 minutes, instead of 10 minutes too. This implied a halving every 34 months, or 2.85 years… not every four years.
And confirmed by some other Bitcoin developers I've never heard of /s
There would have also been 27 epochs, instead of the 33 currently. This would mean the last bitcoin would have been issued in 2086 instead of 2140. In addition, the difficulty adjustment was also targeted at every month, instead of every two weeks.
But wait, you ask, how can there be more bitcoin in this first draft, but less satoshis too? Answer: notice the decimal place difference here. In this pre-alpha of Bitcoin (2008), only four decimal places for satoshis are proposed, instead of the eight seen in v0.1 (2009). And the coinbase reward was also significantly larger at 10,000 bitcoin per block, instead of just 50.
Thus there were ten decimals to express the Bitcoin supply. Resulting in 14 decimal places for the number system of this draft pre-alpha code (2008). Not the 16 decimals we enjoy currently from v0.1 (2009).
This interpretation may line up with Dillinger's testimony given in an interview, where he explains "We talked a lot (Dillinger and Satoshi) about how much divisibility bitcoins ought to have; whether to make 'satoshis' an order of magnitude bigger just to have three more bits of cushion against rounding errors, or keep them near the limit of precision at 10e-8 bitcoins in order to ensure that rounding errors would always fail."
But is Dillinger (aka "Bear", aka Cryddit) a trustworthy source for all of this early history? Greg Maxwell isn't so sure:
nullc is Greg Maxwell's reddit account. Greg is a notorious Bitcoin Developer-OG. "Maxwell" may be where vitalick coined the term "Bitcoin Maxi"
To an extent, I agree with nullc here. But, I reviewed Dillinger's interview, his BitcoinTalk, and his November 6th 2008 email with Satoshi on the cryptography mailing list. I have not found inconsistency with his testimony. Thus, I believe Dillinger can be both a misinformed shitcoiner and an early good faith participant in Bitcoin history.
With that said, we can never really know if this November 2008 source code is really from Satoshi or not, or unmodified. We should always take what anyone says about this time period with a huge grain of salt. We are assuming good faith, honest and accurate testimony here. Those are big assumptions in a space full of scammers and con artists claiming to be Satoshi.
But, in support of Dillinger's testimony, there is email evidence from Satoshi himself, suggesting he had code ready for review that he was willing to share in November of 2008.
To James A. Donald, Satoshi wrote on November 17th 2008
"I sent you the main files. (available by request at the moment, full release soon)"
James A. Donald was the first person to reply to Satoshi's Whitepaper email on the Cryptography Mailing List.
So we have confirmation by Satoshi that there was Bitcoin source code in existence at this time, and he was willing to share this with people who asked. Add to that, Dillinger was part of the Bitcoin conversation on this mailing list at this time. All supporting evidence for Dillinger's testimony.
Lastly, the founder of RSK on BitcoinTalk also asserted he had a copy of this same 2008 source code. But he never confirmed this with more evidence than just the above comment.
So what's my main takeaway from this rabbit-hole of Bitcoin history, Alice? For me, these numbers are fun to play with, to know how Satoshi was thinking at this early stage of Bitcoin's design. Exploring what could have been for Bitcoin in its genesis is a fun thought experiment. Satoshi was clearly smart for what was mostly a one man job, but he probably had help early on with code review.
On another note: with the selection of a 10,000 bitcoin base reward; a 10,000 CENT variable to express satoshi units; a 100,000 block epoch for halvings; a 1 month difficulty retarget (can you see the theme here? 1, 1, 1, 1); the ugliness of the 10 decimal places for Bitcoin and only 4 decimal places for satoshis; all point to one thing…
This 2008 source code was a rough draft.
These were temporary numbers and parameters, inputted as place holders for future refinement. They were not serious final draft considerations. This source code was a work in progress during Bitcoin's inception.
We could of had 2 billion bitcoin and not enough satoshis to go around. Ghastly. So thank god Satoshi settled on 21 million bitcoin, with 8 decimal places on both sides of the dot.
Addendum:
One fun nuance of C++ code is that integers are truncated when used as Satoshi did. This ends up somewhat reducing the total supply of Bitcoin in this 2008 code, from what looks like 2 billion bitcoin at first. The result of this truncation on supply is a very specific total: 19,999,898,800,000 satoshis or 1,999,989,880 Bitcoin. Thanks to MrRGnome for pointing this out: "it's possible Satoshi didn't even realize this rounding was happening."
Check out the Bitcoin Discord server to talk to Gnome https://discord.gg/bitcoin-discord-782749290219962370
If you like this kind of content consider subscribing to BITCOIN YouTube or following us on Twitter and NOSTR. If you're feeling extra generous, check out our Geyser crowdfund campaign for a Bitcoin History series.
-
 @ ec965405:63996966
2024-02-15 01:06:05
@ ec965405:63996966
2024-02-15 01:06:05I am beginning to see the clarity that my mentors promised I would as I progressed through my late 20s into my 30s, and it's getting clearer every day. I am inspired to change the world and bring my community with me. I know God has my back. A better world is within our grasp! I'm going to do my part in bringing my community with me by blogging about my upcoming trip to Cuba with Solidarity Collective via Nostr.
In February I'll be back in the skies headed to Havana, where I will participate in a delegation with Solidarity Collective to learn about Pan Africanism in the Cuban context. Some questions we will be exploring during this delegation are:
How do Cubans, in a Black-majority country, approach environmental protection, religion, housing rights, and healthcare?
What is the role of historic and contemporary abolitionist practices in their quest to eradicate racism?
What challenges remain to build an equitable society, especially under the yoke of 60 years of the u.s. Blockade?
What do these lessons mean for the struggle for black liberation in the u.s.?

I've dreamed about the next time I would visit Cuba and how I would track down the friends I made there in 2017. At that time, the government controlled access to internet via these cards that you would purchase then redeem on your device for timed access. The idea was that you would take your Wi-Fi card and head to a communal place like La Plaza with your device to access the Internet with others.
While some north americans might find that kind of Internet access draconian, surfing the web in public like that made me value my time on the Internet more. Has this changed since I was last there? I am personally interested in how groups are leveraging tech and the Internet for education and organizing. I now have a solid couple of years of IT/programming education to reference while I meet with teachers and journalists at the Martin Luther King Jr. Center and hear about the right to free education from daycare through university and literacy campaigns. I wonder if they've heard about decentralized social media protocols like Nostr or Activitypub or if they ever experienced censorship from the authorities on the Internet.
I recently experienced censorship in the YouTube comments as I explained to fellow web surfers why we must include Vieques and the other islands in the archipelago when talking about Puerto Rico politically. My ability to comment was restricted as I tried to convince others who talked down on Haiti and Cuba as failed states to instead take my Pan Caribbean perspective. I really enjoyed Dread's talk at Nostrasia 2023 about how he is using Bitcoin and Nostr to bring the islands together as the US Dollar and financial institutions like Western Union and the IMF keep us divided and oppressed.
The more I learn about Bitcoin as a tool for global wealth distribution, the more I understand how these institutions rob youth and families of basic necessities and facilitate the rise of authoritarian regimes and systems that punish journalists and activists through political repression. The corporate ownership of our means of internet communication by the likes of technocrats like Musk and Zuckerberg won't let authentic conversation between Caribbean-based diaspora happen on their platforms while they get to destroy countries like Myanmar and shape public discourse to their whim. That's why I'm glad I found Nostr.
My personal blog currently lives on my Uberspace asteroid in a Bludit instance that lacks much functionality outside of themes and data analytics, so it's just sits there as a personal repo for my thoughts. Nostr provides all of this with a direct link to my Bitcoin wallet address and comment functionality. If people value my content, I can get "zapped" and earn money for my content. I can now engage with my audience directly without a middle man. No Substack, no moderators censoring my messages, just community. The job now is to bridge my community and this new way of socializing on the Internet.
To help make this as educational of an experience as possible, I ask my audience: What questions or feedback do you have about my trip and the types of questions I want to explore? Is there anything you've ever wondered about Cuba? What suggestions do you have in terms of how I can better present information; written word, audio interviews, video, or photo essays?
Leave me some love in the comments and stay tuned!

-
 @ c4428155:a36de510
2024-03-22 19:10:00
@ c4428155:a36de510
2024-03-22 19:10:00Chevron Will Pay Record Fines for Oil Spills in California
by Janet Wilson, The Desert Sun (https://www.desertsun.com/)
This article was produced for ProPublica’s Local Reporting Network in partnership with The Desert Sun (http://desertsun.com). Sign up for Dispatches (https://www.propublica.org/newsletters/dispatches) to get stories like this one as soon as they are published.
Oil giant Chevron has agreed to pay a record-setting $13 million to two California agencies for past oil spills, but some of the company’s spills are ongoing.
The fines, announced Wednesday, come more than three years after an investigation by The Desert Sun and ProPublica found that oil companies are profiting from illegal spills (https://www.propublica.org/article/oil-companies-are-profiting-from-illegal-spills-and-california-lets-them) and that oversight of the industry by California’s oil and gas division was lax (https://www.propublica.org/article/oil-companies-are-profiting-from-illegal-spills-and-california-lets-them).
At least one of Chevron’s spills is still running 21 years after it began in a Kern County oilfield, although a state spokesperson said it has been reduced by 98% “from its peak.” The amount spilled from the site, dubbed GS-5, is larger than the Exxon Valdez disaster.
The crude collected from GS-5 generated an estimated $11.6 million (https://www.propublica.org/article/oil-companies-are-profiting-from-illegal-spills-and-california-lets-them) in just three years, The Desert Sun and ProPublica found. In fact, rather than stopping potentially deadly inland spills, known as surface expressions, oil companies have routinely tried to contain them with netting or pieces of metal and used more than 100 of them as unpermitted oil production sites in Kern and Santa Barbara counties.
This week’s announcement stopped short of saying GS-5 and other ongoing spills must be stopped, as required under state law. Instead, officials said the settlement “creates a framework for managing the spills with State oversight,” and “Chevron agrees to continue monitoring the site with Department of Conservation oversight.” No specific sites were named.
In follow-up emails and a phone call, spokespeople for the state said the fines cover the first phase of the Cymric spill, in which a river of thick crude flowed down a natural watershed. Chevron for several years denied it posed a risk to health and the environment, and the company fought a $1.6 million fine imposed by state regulators. The penalties also cover dozens of smaller spills that killed or damaged wildlife and habitat.
The new fines, which will be paid to the Department of Conservation and the Department of Fish and Wildlife, are unprecedented for the agencies but are minuscule for Chevron, a multinational that reported $2.3 billion in earnings (https://www.chevron.com/newsroom/2024/q1/chevron-reports-4q-2023-results) in the fourth quarter of 2023.
Spills in Chevron’s Cymric oil field had gushed more than 6 million gallons (https://w3.calema.ca.gov/operational/malhaz.nsf/f1841a103c102734882563e200760c4a/f0967e3a07bad40c882589c7007b2b7c?OpenDocument&Highlight=0,22-0840) of wastewater and crude as of last June, but the settlement covers only 2 million gallons spilled from unidentified Kern County Chevron operations.
A spokesperson for the Department of Fish and Wildlife said in an email that the fines covered the first phase of the Cymric incident that the agency’s oil spill response teams worked on from June 2019 through April 2020, totaling 1.2 million gallons, about 70% wastewater and 30% oil.
As for the decadeslong GS-5 spill, Department of Conservation spokesperson Jacob Roper said: “As mitigation continues, less oil finds its way to the surface. Mitigation measures include injecting water underground to improve ground stability, sealing subsurface leak paths and removing fluids in shallow areas before they can reach the surface.” (The injected fluid gradually cools hot steam so as to not create more boiling spills.)
Vacuum trucks sucked oil and wastewater out of the GS-5 spill, near McKittrick. GS-5 is one of the largest and longest-running surface spills.
(Jay Calderon/The Desert Sun)
At the spill’s peak in 2019, Roper noted, about 2,500 barrels of oil and water came to the surface each day. At the start of 2024, that had fallen to 80, and it has since dropped to 68.
In an email, Chevron North America spokesperson Sean Comey said the settlements “demonstrate our continuing commitment to take action to address issues and prevent similar incidents in the future. Throughout our operations we work collaboratively with government agencies to protect people and the environment and maintain safe and reliable operations.”
He added: “We always strive to meet or exceed our environmental obligations. When we do not achieve that goal, we take responsibility and appropriate action. We are pleased to put this matter behind us in a way that benefits our community so we can continue to focus on providing the affordable, reliable, and ever cleaner energy California needs.”
The California agencies’ announcement received qualified praise from an environmental attorney who monitors the state laws and policies on oil and gas production and spills.
“It’s great to see one of the state’s most prolific polluters fined for its destruction to the environment,” said Hollin Kretzmann, an attorney at the Center for Biological Diversity’s Climate Law Institute. “But it’s outrageous that Chevron earned more than $11 million off selling the oil collected from one surface spill — almost equal to the amount of this historic fine.”
He added: “The Desert Sun-ProPublica investigation that turned up that information was vital, and we need more of that type of scrutiny of oil producers from the state. To protect Californians from oil industry pollution, oil regulators need to step up oversight to minimize the damage this deadly industry does on its way out the door.”
The $5.6 million Chevron will pay the Department of Conservation will be used to plug old, dangerous wells abandoned by other owners without proper cleanup.
“This agreement is a significant demonstration of California’s commitment to transition away from fossil fuels while holding oil companies accountable when they don’t comply with the state’s regulations and environmental protections,” the department’s director, David Shabazian, said. “Every penny collected here will go toward plugging old, orphan wells in order to protect the environment and people of California.”
California’s oil wells could cost $9 billion to plug, according to a 2020 report (https://www.desertsun.com/story/news/environment/2020/01/24/california-oil-and-gas-wells-could-cost-9-billion-plug-clean/4565368002/), and companies have set aside only a fraction of those costs, though the state and federal governments are gradually stepping up funding and requirements.
Conservation staff previously identified 378 wells across six counties to begin working on under the state’s well abandonment program, which permanently seals orphan wells and remediates sites, officials noted in this week’s announcement. Work in Santa Barbara and Los Angeles counties began late last year — thanks to $125 million in state and federal funding to address old and aging oil infrastructure.
California is also eligible for an additional $140 million in federal funding to plug more wells, the news release said, and the Department of Conservation is working to claw back funding from oil companies that “sold off idle, orphan, deserted, or unplugged wells.”
The Department of Fish and Wildlife agreement with Chevron places $6.8 million in the agency’s Environmental Enhancement Fund, which provides grants for projects that acquire habitat or improve habitat quality and ecosystem function. An additional $500,000 will go to the Oiled Wildlife Care Network at the UC Davis School of Veterinary Medicine to maintain facilities in Kern County that care for animals affected by spills and to support regional wildlife response. And $200,000 will be available to respond to future spills.
Officials pledged to tighten regulation of oil company violations, including potential criminal penalties under AB 631, a law that went into effect in January that gives regulators more authority to fine oil companies that cause major spills or other hazards. In 2020, a spokesperson for the state’s oil regulator, the California Geologic Energy Management Division, told The Desert Sun and ProPublica that the agency had issued $191,669 in civil penalties and collected nothing. The then-head of CalGEM pledged more public transparency, including more details on enforcement information. As of Thursday, the agency has issued 13 orders to pay civil penalties (https://www.conservation.ca.gov/calgem/Pages/Division_Orders.aspx) in 2024, but it was impossible to determine online if they have been paid.
https://www.propublica.org/article/chevron-will-pay-record-fines-for-california-oil-spills
-
 @ 6871d8df:4a9396c1
2024-02-05 23:29:22
@ 6871d8df:4a9396c1
2024-02-05 23:29:22The Apple Vision Pro was released, and it is the talk of the town right now. To be frank, I think it's a stupid product. It's not useful or particularly enticing to me in its current form factor. It's a toy, not a tool. All the features seem gimmicky as opposed to generally helpful. I'm not saying it may never be worthwhile, but as of this first release, it is only a party trick.
Coincidently, this is the first product that does not have any of Steve Jobs' influence. To me, it shows. I don't think Jobs would have ever let this product see the light of day.
Jobs understood product. He didn't make things for the sake of progress or to make sci-fi reality; he made things because he 'wanted to make a dent in the world.' He wanted to solve problems for everyday people by innovating with cutting-edge technology. He aspired to make people's lives better. Steve Jobs' genius was the way he married cutting-edge technologies with valuable tools that made those cutting-edge technologies simple and elegant.
The Vision Pro may be technically innovative, but it is not a tool, at least in its current form. It may be one day, but that is precisely my point; Jobs would have never released a product where the form factor would hold it back from becoming a tool. At best, it is an intriguing toy that is additive to some content at the behest of being very awkward to wear or be seen in. In my view, mainstream adoption can happen only in a world where we can use the Vision Pro as a contact lens or very small, discreet, minimalist glasses, but certainly not this iteration where it covers more than half your face.
Seeing people's eyes makes us human. So much emotion, understanding, and communication happens with just a look. It is a window into the soul. I don't want to live in a world where we are actively bringing all the negatives about communicating in the digital world to the physical one.
https://image.nostr.build/2365609411f144f5d789ffd684ffce9b4d867626a7bfe11bb311cb0f61057199.jpg
I can't help but wonder or hypothesize what Steve Jobs would focus on if he were still alive today. I think Apple's priorities would be completely different. My gut tells me he would not have let Siri get as bad as it is. Siri is a horrible product; I never use it, and everyone I know who tries to use it does so unsuccessfully, at least most of the time. I personally always default to ChatGPT or Bard. These AI systems make my life dramatically more productive. They are tools in the purest sense.
In my opinion, Steve would not have missed this train. Sure, Apple could wake up and integrate these systems into Siri — if they were smart, they would — but in its current form, it is so far behind that it almost astounds me. My intuition leads me to believe he would be closer to what [Rabbit] is doing.
Who knows? Maybe I am entirely wrong, and Apple just kickstarted VR's mass adoption phase. Unfortunately, I think this will likely be the biggest failure of a physical product that Apple will have seen since Jobs returned ages ago. The Vision Pro is only slightly better than the Oculus, and Facebook has already deprioritized VR for AI. Apple is further behind, and I don't see a world where they do not make the same pivot. There is a skill to creating successful, innovative products, and it makes me sad to see the torch that Jobs passed lose its flame. As someone who respected how Apple used to innovate, watching this decay in real-time is jarring as this is just the latest in a string of disappointing decisions that exemplify that 'peak Apple' is behind us.
-
 @ 0d6c8388:46488a33
2024-02-02 01:15:40
@ 0d6c8388:46488a33
2024-02-02 01:15:40I'm just a normal guy that likes Jesus and bitcoin!
Here are some things you should know about me:
Well that's all for now hope you have a good day!
-
 @ 6ad3e2a3:c90b7740
2024-01-29 20:45:19
@ 6ad3e2a3:c90b7740
2024-01-29 20:45:19“God does not play dice. “
Albert Einstein
Imagine you’re at the blackjack table, you’re dealt a 10 and a 7 (hard 17), and the dealer shows a 10. This is a bad situation, but the odds say you stand and hope the dealer busts. You are about to do just that, but the drunk guy on your right says, “Hit, bro, I’m feeling a four.”
What are the odds this is good advice?
I’m too lazy to look up the exact odds, but let’s just invent some very rough approximations to illustrate the point.
Assume there’s a 50 percent chance you will lose no matter what you do, i.e., it makes no difference whether you hit or stand. That means there’s a 50 percent chance you win (or push) assuming you make the right choice. Let’s further assume if you stand, there’s a 30 percent chance you win (or push), and if you hit there’s a 20 percent chance you win or push. Again, please don’t quibble about the true odds in this situation, as it’s unimportant for the example.
With these odds, what are the chances hitting on hard 17 against a 10 is good advice?
Let’s make it multiple choice:
A) 20% (That’s your chance to win)
B) 0% (It’s always wrong to hit when your odds of winning are better if you stand)
C) 40% (To the extent your decision matters, it’s 2 out of 5 (20% out of 50%) that hitting will win you the hand.)
In my view, A) is the simple response, and it’s not terrible. It recognizes there’s some chance hitting in that situation gives you the desired outcome even if it’s not the optimal choice. It’s probabilistic thinking, which is the correct approach in games of chance, but just slightly misapplied.
B) is the worst response in my opinion. It’s refusing to apply probabilistic thinking in service of a dogma about probabilistic thinking! “It’s always wrong to hit in that situation” is an absolutist position when of course hitting sometimes yields the desired result. The “but my process was good” adherents love B. It signals their devotion to the rule behind the decision (the process) and avoids addressing the likelihood of whether the decision itself pans out in reality.
C) This is in my view the correct answer. To the extent your decision matters, there’s a 40 percent chance hitting will improve your outcome and a 60 percent chance it will not. I’m not looking for self-help or a remedial grade-school probability class. I don’t need to remind myself of what the best process is — I simply want to know my odds of winning money on this particular hand.
Let’s say it’s a low-stakes hand, you’re drunk, you take the advice for laughs, the next card is in fact a four, you have 21, the dealer flips over a 10 and has 20. You win, and you would have lost had you stayed. You high-five the drunk. What are the odds now you got good advice?
A) 0% — bad process!
B) 40% — same odds, don’t be result-oriented!
C) 100% — you already won!
The answer is obviously C. The point of the game is to win money, and taking his advice* on that particular hand did just that for you. You are not obligated to use that heuristic ever again. This isn’t a self-improvement seminar about creating better, more sustainable habits. You won the money, and now that you know what the next card actually was, it would be pathological to go back in time and not take his advice.
*You might think this is just a semantic argument — what we mean by “good advice” depends on whether it’s applied generally or specifically, and that is the distinction, but as we will see below the conflation of the general with the specific is itself the heart of the problem.
I use blackjack as the example because, assuming an infinite shoe (no card counting), the values of each card in each situation are well known. Coins, dice and cards are where simple probabilistic thinking functions best, where the assumptions we make are reliable and fixed. But even deep in this territory, it’s simple to illustrate how a focus on process is not a magic cloak by which one can hide from real-life results. If you lose the money, you lose the money. The casino does not allow you to plead “but my process was good!” to get a refund.
Of course, this one-off example aside, in the territory of cards and coins, the process of choosing the highest winning probability action, applied over time, will yield better results than listening to the drunk. But when we move out of this territory into complex systems, then the “but my process was good” plea is no longer simply falling on the deaf ears of the pit boss when reality goes against you, but those of the warden at the insane asylum.
. . .
I’ve encountered a similar strain of thinking on NFL analytics Twitter too. Sports analytics involve probabilistic thinking, but as leagues and teams are complex systems, it’s hardly as simple as coins and cards.
When Giants GM Dave Gettleman passed on Sam Darnold — the highest rated quarterback remaining on many boards — at pick 2 in the 2018 draft, and took generational running back prospect Saquon Barkley instead, the process people were aghast. How could you take a low-value position like running back over the highest value one when your team needs a quarterback? You always take the quarterback!
As a Giants fan, I was happy with the pick. My view was the same as Gettleman’s in this instance when he said something to the effect of, “If you have to talk yourself into a particular quarterback at that pick, pass.” His point was that he’d have taken a quarterback he liked there obviously, but he didn’t like the remaining ones, so he went elsewhere.
Now people were especially aghast he took a running back rather than say Bradley Chubb, an edge rusher, or Denzel Ward a cornerback, two typically higher value positions than running back, and those would have been good picks too, as both players have been productive in the NFL**. But Barkley has been as advertised when healthy, despite playing with a substandard supporting cast his entire career. He’s a good player, though a star running back obviously won’t singlehandedly transform a franchise the way a star quarterback might.
** The optimal pick would have been quarterback Josh Allen who went at No. 7, but was considered a reach by many in the analytics community because he was a raw prospect with physical skills, but lacked sufficient college production.
But how did the process choice, Sam Darnold, do? He was a disaster for the Jets for three seasons, destroying any hope they might have had at competing, though they salvaged some value by dealing him to the Panthers for picks. He’s also been bad on the Panthers, to date. So did Gettleman make a good choice, drafting one of the consensus top running back prospects of all time over the not-especially-impressive top-two quarterback prospect in that particular class? By any sane account, he did. He landed the better player, and while Chubb and Ward would have been fine, so was Barkley.
But despite Darnold’s failure as a prospect, the process people won’t take the L! They insist even though Barkley is a good running back, and Darnold a terrible quarterback, their process in preferring Darnold was good! But I don’t care about your process! The quality of your process will be adjudicated by your long-term results, the way a religious person’s moral character will be judged by his God. I have no interest in your attestations and signaling, no inclination to evaluate your lifelong body of work. We were simply debating this one particular pick, the results of which are already obvious to anyone not steeped in this bizarre worldview wherein you can claim vindication over reality a priori via believing you’ve found the right heuristic!
There are two claims they are making implicitly here: (1) That if quarterbacks are more valuable generally, you should always take the best available quarterback over the best available running back, irrespective of the particular human beings at issue; and (2) That no matter what the results were, you would be correct to have taken the quarterback.
Claim (1) is the notion that if something is generally — or on average — the case, the specifics need not be taken into account, i.e., they see players as having static values, based on their positions, like cards in blackjack. Claim (2) is the idea that only the heuristic should be evaluated, never the outcome. Taken together they are saying, always do what is generically most probable, ignore details and specifics and have zero regard for how any particular decision pans out in reality. In my view, this is pathological, but that’s okay, it’s only an argument about football draft analytics!
. . .
Our public health response to the covid pandemic increasingly appears to be a disaster. From lockdowns, to school closures, to vaccine mandates to discouraging people from getting early treatment, it has cost many lives, harmed children, wreaked havoc on the economy and done serious damage to our trust in institutions. Many of those who were skeptical of the narrative — for which they were slandered, fired from jobs and deplatformed — have proven prescient and wise.
While some holdouts pretend the covid measures were largely successful, most people — even those once in favor of the measures — now acknowledge the reality: the authors of The Great Barrington Declaration, which advocated for protecting only the vulnerable and not disrupting all of society, were correct. But I am starting to see the same demented logic that declared Darnold a better pick than Barkley emerge even in regard to our covid response.
Here’s a clip of Sam Harris insisting that even though Covid wasn’t as deadly as he had thought, he would have been right if it had been more deadly. (Jimmy Dore does a great job of highlighting the pathology):
Harris is arguing that even if the outcome of our response has been catastrophic, that’s just results-oriented thinking! He still believes he was staying on 17, so to speak, that he made the right call probabilistically and that he was simply unlucky. (Never mind that locking down healthy people was never part of our traditional pandemic response playbook, and coerced medicine is in plain violation of the Nuremberg Code, i.e., he wasn’t advocating for blackjack by the book, and never mind that in highly complex systems no one can calculate the true odds the way you can for a casino game or even an NFL draft pick.)
But Sam Harris was far from the only one. Here’s Dilbert creator Scott Adams explaining why even though he made a mistake in taking the mRNA shot, his process was not to blame:
He’s not defending his process as strongly as Harris, and he appeared to walk this back in this video, but the sentiment is largely the same: There was nothing wrong with my process, I just got unlucky, and others got lucky.
This is not an NFL analytics argument anymore — it’s a worldview shared by policymakers and powerful actors whose decisions have major consequences for human beings around the world. They seem to believe that as long as they come up with the correct heuristic (according to their own estimations and modeled after simplistic games of chance where it can be known in advance what heuristic was indeed better), whatever they do is justified. If reality doesn’t go the way they had expected, they still believe they acted correctly because when they simulated 100 pandemics their approach was optimal in 57 of them!
But the notion that someone with the correct heuristics, i.e., the proper model or framework for viewing the world as a game of dice, is a priori infallible is not only absurd, it’s perilous. Misplaced confidence, unwarranted certainty and being surrounded by peers who believe as you do that no matter what happens in reality, you can do no wrong incentivizes catastrophic risks no sane person would take if he had to bear the consequences of his misjudgment.
What started as a life hack to achieve better long term results — “focus on process, not outcomes” — has now become a religion of sorts, but not the kind that leads to tolerance, peace and reverence for creation, but the opposite. It’s a hubristic cult that takes as its God naive linear thinking, over-simplified probabilistic modeling and square-peg-round-holes it into complex domains without conscience.
If only this style of thinking were confined to a few aberrant psychopaths, we might laugh and hope none of them become the next David Koresh. Unfortunately this mode of understanding and acting on the world is the predominant one, and we see its pathology play out at scale virtually everywhere we look.
-
 @ 006804ee:0b759c7b
2024-03-22 18:05:11
@ 006804ee:0b759c7b
2024-03-22 18:05:11My Contest Entry! You're welcome. I'm Herschel Sterling and I'm here to help.
https://open.substack.com/pub/commercialherschel/p/whos-in-your-wallet-bitcoin-satoshi-money?r=i0uk1&utm_campaign=post&utm_medium=web
The way is really to listen to the podcast. All the links I mention are at the link above. Sorry for not doing it but I'm so busy right now.
This is a Special Holy Dispensation: Everybody wants control. Do you want control? If you don’t want to control your life, you must be happy with the times.
THIS IS A PARANOID RANT FROM A LUNATIC; IT IS NOT FINANCIAL ADVICE, AND ALL MY EXPERIENCES ARE MISINFORMATION, AND I NEED PROTECTION FROM IT BY COLLEGE CHILDREN IN CORPORATIONS.
You worked. That’s your money, right? You traded some time and some moments from your conscious existence for some money. Now, since you traded moments and time from your precious conscious life, that money you traded for must be yours, right? RIGHT! Well!
No. It’s not, it’s not yours. They can hold it up or take it from you, because you know, if you know what the definition of genocide is, and you see a genocide happening, and you say you see it, then you can be disciplined against hate speech, because when one country is committing a genocide against another country, and you can see that, and you point it out, then that means that you are PRO-genocide… right? That’s right. That’s a good stupid person.
Let’s remember the old days of paypal. Remember paypal? It was so easy to just make a purchase, or to pay someone online. It took a couple of days for bank activity to go through, but it was OK for the time, right? They decided that you and the really nice, American, non-violent people you’re working with might be terrorists, so when you made a transaction, they would hold it for 21 days “for your own good because you might be a bad person and we have to check this money out in case it’s dangerous.” Not because they want to hold your money for 21 days to make interest on it while they slander you and your employer about being potential criminals.
The thing where there is this needle, and they say it’s a “vaccine” and that if you take it, you’ll stop a sickness, and then you take it, and you get sick, and it maybe kills you, or at least the thing they said was a vaccine is literally killing people all over the world, but you have to keep taking it, or else you are pro-mass death? But now, if you won’t take it because you don’t want to get hurt from it, or die, and you want people to stop dying from it, you say that, and now you are pro-mass death for big anti-mass death, and they can take your job or your bank account. You know? Like that?
You are seeing the value of this. It’s starting to kick in how bizarre and stupid this is, and that we really don’t have to tolerate this. There is always a workaround for authoritarianism, until they start killing people from the air, we have options. Let’s be very clear in this scenario. We know who the honest people are, and we know who the criminals are.
These are the basic, beginning things that you should do to put yourself in a position to be able to make the best decision.
In the past 30 years, SCOTUS has ruled that not only do their police forces have no obligation to protect you, but the banks are not required to protect your money. If something goes wrong, they have an out, you do not. You’ve already lost that battle.
Your Currency Represents Your TIME
Protect your money from the criminals who want to cut you off when you behave like a human. They want to condition you, and they only want deadly people to be prosperous. They only want mediocre people who are willing to tolerate and participate in their crimes to have prosperity.
Use a cold wallet for storing your currency. This is the safest way to do it. This is a “wallet” that is locked, and it’s not connected to any outside systems until you decide to. You are the only one who has access to it, and you decide how to access it.
Stay off the exchanges as much as possible. Use exchanges for trivial amounts of currency, or to convert your currency for your banking needs. The exchanges have purposes, but storage is not one of them. Connect only one exchange to your bank. I like UPHOLD. It’s what I need to do any simple tasks I need for moving things.
Hold all the bitcoin you can, until it grows enough to trade for gold.
Set up a separate bitcoin account where you put 10-20% of everything you earn toward paying the extortion to the government. If we had protection systems, that would be one thing, but we do not, so it’s just extortion.
Lightning wallets are for the internet. It’s code that integrates Satoshis (The Bitcoin Unit) with enabled internet sites. I use the one called ALBY. It’s the best one for beginners, IMO. Let’s suppose that using Alby, someone is earning about 5 USD in Satoshi per day. Not much. Let’s say that is a stable number. That is around $1900 for the year. That’s just extra dough for having fun and learning about Bitcoin.
Join Stacker.News and start learning and slowly earning Satoshis. This is a great place to learn all the things you need to know, and also have good, entertaining, intelligent interaction with others on a whole range of issues, including Bitcoin and everyday, interesting, fun topics. Use my referral link. Stacker is a lot of fun. It’s kind of reminiscent of the early days of the internet. When you go there, it is a good place to learn everything you can.
Subscribed
What do you think? Is your life worth a sh*t? Is citizenship a protected office in America? Do you trust your representation in the government, where the people who work there are snatching up properties in non-extradition states as fast as they can?
What about the currency of the moments of your life that you trade with others for some fiduciary currency for your survival and prosperity? Is that worth anything to you? What do you think? You feel good about entrusting those moments to a system that will watch you work your life away and leave you under a bridge when they change the rules on you and then are done with you? What about that?
I’m looking forward to comments and whatever good advice and additional info I can get here. Thanks.
And if you can see what I’m doing here, you must know I have felt and known firsthand of what I speak. Things are and have been very difficult. I will not use censorship sites for my writing. No BlewitTube. No Social Media. I don’t use paypal or any of that because they are vile people who have nothing but contempt for honest people. I had been a human rights/ civil rights, civil liberties volunteer for 20 years. I helped to destroy truly vile political criminals and abusers and I have been financially destroyed over it. It scares people when they see what the anti-human rights forces have done to me and to others who stand up.
YouTube doesn’t censor to protect you. They do it to hide the crimes of their donors.
Paypal and other money services don’t hold your money to protect you. They do it to make money on your interest, and they have no concern about how it disrupts your life or the businesses you work for. This is not about the American economy for them.
DON’T BE TRAINABLE. Your banks are training you to think that you do not control or own your own moments and that you have nothing to say about how much, when, or if you get paid.
BUY SOME BITCOIN
SEND ME SOME BITCOIN
-
 @ 005bc4de:ef11e1a2
2024-03-22 18:01:55
@ 005bc4de:ef11e1a2
2024-03-22 18:01:55We hear about sidechains and "layer 2" solutions a lot with Bitcoin. Usually, this centers around either (a) scaling solutions or (b) alternative use-cases. Normally, these layers involve a separate chain or system which then ultimately reconciles onto Bitcoin. The concept of these layer 2's is that the sidechain uses the security, immutability, and trust of Bitcoin to bolster itself and thereby achieve whatever goal that layer 2 holds.
As an example, the Lightning Network (LN) might be the most oft-used Bitcoin layer 2. The problems it tries to address are scaling, speed of transactions and high fees. The LN system uses Bitcoin to address these problems, does so fairly well, but with its own set of problems.
I've heard chatter of layer 3 solutions, though I'm unsure what distinguishes a layer 2 from a 3. During a podcast recently (I don't recall which podcast), when asked if Cashu was a layer 2 Bitcoin solution, the Cashu dev @calle said something like, "it's a layer 69." (He was implying that it's actually not a separate Bitcoin layer at all (apparently, saying it's a layer 69 is just more fun.) The point here is that there are layers. Or are there?
Bitcoin purists might disagree with the idea of layers altogether. There is only Bitcoin. Bitcoin does what it does and doesn't care about layers or talk of layers or what you think about layers. Bitcoin is.
Whether Bitcoin layers exist or not aside, the idea of a layer 0 has been tossed around a bit. If Bitcoin is layer 1, a layer 0 somehow precedes Bitcoin. I heard a discussion on this, I believe amongst panel members and perhaps at a Nashville conference in 2023. One of the members suggested Bitcoin's layer 0 is the people. (Sorry, again I don't recall whom it was to suggest this so I can't give credit.) The idea was that Bitcoin, at it's basic level, is about people and is the relationships between those people. Money is a representation of work done by people and value and debt owed to people for that work. So, Bitcoin is essentially a technological manifestation of these relationships between people. Bitcoin's blockchain and consensus mechanism records and resolves these relationships. Thus, the people are layer 0 and Bitcoin is layer 1.
Jameson Lopp wrote in 2017 Nobody Understands Bitcoin and That's OK. He suggested that the idea of people interacting was/is a fundamental tenet of Bitcoin. This was evident when he wrote, "bitcoin’s strength comes not from being the embodiment of some dogmatic beliefs of immutability, decentralization or other buzzwords, but from collaboration." That is, people working together.
Nostr might be Bitcoin's layer 0. Nostr is not Bitcoin, however it is connected. It's connected technically in it's decentralized structure and in that sats can be easily zapped. It's connected socially in that many Bitcoiner's are there, connecting, interacting, zapping in a permissionless, decentralized way.
Certainly, Nostr is not the only arena of Bitcoin's layer 0...the interaction of Bitcoiners. Anywhere, in any manner in which Bitcoiners interact, there is the layer 0. Yet, Nostr seems to offer a rather seamless integration of the technical and financial components of Bitcoin with a social component. Nostr gives Bitcoiners a way to connect socially and economically.
Sending sats over the layer 2 Lightning Network, person to person, is so seamlessly integrated into Nostr, the layers 0, 1, and 2 blur. Transferring 10k sats to another Nostrich, or saying "Nice write up" with a 100 sat zap, or simply messaging approval for a dog picture with a 21 sat zap, all integrate layers 0, 1, and 2. What's more, the layers of personal interaction, Bitcoin, and the Lightning Network don't even need to cross anyone's mind...it's just, "Sweet doggo! Here's some sats."
I like Bitcoin and I like dogs.
-
 @ 5c8a5765:4fc5edee
2024-03-22 17:44:23
@ 5c8a5765:4fc5edee
2024-03-22 17:44:23"Мне-то что с того, что за мной следят? Мне же скрывать нечего". Но постойте, может быть вы...
Read in English
tl;dr: Отсутствие приватности угрожает сексуальным, расовым, национальным меньшинствам, женщинам, мужчинам, небинарным, атеистам, активист(к)ам, бедным, инвалидам, школьни(кам/цам), представителям социальных профессий, любым покупателям, человеку в целом и даже демократии.
...Чёрнокож(ий/ая)?
Компания Palentir, занимающаяся разработкой искусственного интеллекта, продает данные упреждающего наблюдения полиции Лос-Анджелеса, чтобы использовать дорожные камеры для целенаправленного расового профилирования (обыска исключительно чернокожих для превентивного расследования преступлений) [1]. Если вы участвовали в протестах BLM, ФСБ также грубо превышает свои полномочия ради слежки за вами [52].
...Мусульман(ин/ка)?
Salaat First, приложение, напоминающее мусульманам о времени молитвы, продает пользовательские данные ФБР и ICE, чтобы постоянно отслеживать местоположение пользователей [2]. При этом в Гуантанамо пытают заключенных мусульман без суда и следствия [3].
...Атеист/ка?
Евангелисты начали использовать цифровое наблюдение, чтобы выслеживать, где живут "ещё необращенные" в христианство [57].
...Не гетеросексуальны или не цисгендерны?
Grindr продает данные о местонахождении пользователей [4]: проданные данные использовались для увольнения священников-геев [5]. По данным New York Post, они "позволяли неизвестным третьим лицам узнавать конфиденциальную информацию о пользователях, в том числе о том, с кем они встречаются, где живут и работают, где проводят свободное время" [6].
Владельцы Grind поспешно выставили сервис на продажу, когда раскрылось, что он собирает ещё и медицинские данные пользователей и делятся ими с другими компаниями [7] (ваши мед. данные стоят в 10-40 раз дороже данных вашей кредитной карты [8]). Далеко не всем трансгендерным, небинарным или интерсекс-личностям хотелось бы ходить с табличкой "МОИ ГЕНЕТАЛИИ НЕ СООТВЕТСТВУЮТ ГЕНДЕРУ" на груди, но отсутствие приватности даёт вам именно это.
Раскрывая вашу идентичность кому попало, вы ставите свою свободу (если быть не-цисгетеро нелегально в вашей стране) и жизнь под угрозу.
...Человек с маткой?
Отслеживание мобильной геолокации используется группами против абортов. Цитата из Politico: "Одна рекламная фирма хвасталась в 2015 году, что может "пометить все смартфоны, входящие и выходящие из почти 700 клиник Planned Parenthood" [9]. При этом на 2022 г. 40% стран мира имели юридическую ответственность за проведение аборта без крайне специфических причин [10]. Не стоит также забывать, что противни(ки/цы) абортов очень воинственно настроены: существует немало насилия и даже терроризма против проводящих и совершающих аборты [11][12].
...Активист/ка?
Google передал индийской полиции данные 21-летней климатической активистки, которая набирала в Google Docs информацию о фермерских протестах (оказалась арестована) [13]. Protonmail передал данные экоактивиста* Французской полиции (оказался арестован) [14]. Facebook, Instagram и X (Twitter) предоставляют доступ к данным для слежки за активистами (в особенности не белыми) — некоторые из них не отказалась от сотрудничества даже после разоблачения [15]. Наши правительства также крайне заинтересованы в предотвращении протестов ещё до того, как они произойдут.
...Нонкомформист/ка?
Например, если вы консерватор/ка, вы можете оказаться под сапогом цензуры: компания Gotcha SEO провела исследование 50 противоречивых ("острых") поисковых запросов в Google и обнаружила, что только 5 % результатов относятся консервативным сайтам, по сравнению с 31,8 % левых и 63,8 % нейтральных [16][17]. По моему личному опыту (особенно ощутилось в ходе написания этой статьи), Google, Bing и прочие поисковики от крупных компаний (в сравнении с, например, Brave Search) также нехотя выдают результаты на тему того, как крупные компании продают ваши личные данные.
...Кита(янка/ец)?
В 2019 году YouTube был пойман на автоматическом удалении комментариев, содержавших что-либо про "50 Cent (Party)" (китайская "фабрика троллей" — команды людей, наполняющие комментарии соц. сетей прогосударственными мнениями за небольшую оплату) [18], или обвинения Китайской Коммунистической партии в бандитизме [19]. А ещё Tik Tok крадет данные ваших детей и продает их вашему (китайскому) правительству [20]. А ещё Google разрабатывает специальный зацензурированный поисковик специально для Китая [21].
...Человек с мужским гендером в документах?
Если в вашей стране есть воинский призыв, с подавляющим шансом он будет обязателен только для мужчин [22] (это — дискриминация). Чтобы отправить вас в армию или на войну, вас будут отслеживать по телефону, передвижению автомобилей [23], камерам с распознаваниям лиц [24] и проч. Уклонение — наказывается, вплоть до тюрьмы и нарушения прав человека [25][26].
...Анархист/ка?
Google Maps активно скрывают любые изображения протестов и даже плохих условий жизни [27]. Google Ads и Play Market убирают оппозиционный контент по запросам государства (например, российского) [28][29]. YouTube активно блокирует каналы и видео, освещающие критику правительств [30], протесты [31] или государственные пытки [32] — особенно в бедных странах. (См. также пункт "активист/ка?".)
...За Палестину?
Социальные сети активно блокируют про-палестинские точки зрения [33].
...Имеете особое состояние здоровья?
Аптеки передают ваши медицинские данныеп полиции без ордера на обыск [34]. Как уже было сказано, на чёрном рынке ваши мед. данные стоят в 10-40 раз дороже данных вашей кредитной карты [8].
...Когда-либо что-нибудь покупали?
Капитализм — это одна из главных опасностей при продаже ваших личных данных. Многие крупные компании используют информацию о вас, чтобы оценить ваш доход, продать вам товары, которые вам на самом деле не нужны [36][37][38], или манипулировать ценами [37].
- Например, интернет-магазины знают, что люди с низким доходом чаще совершают срочные покупки, поэтому они устанавливают для них более высокие цены и отменяют скидки [39][40].
- Некоторые финансовые и страховые компании используют социальные графики для определения процентных ставок и страховых взносов. Это часто заставляет людей с низким доходом платить больше — данный феномен известен как "бедность-премиум" [41].
- Компания Orbitz направляет пользовате(льниц/лей) Mac в более дорогие отели, поскольку они переплачивают за электронику Apple. [42].
- Компания Target выставляет клиент(к)ам более высокие цены, когда они физически находились рядом с магазином и вряд ли ищут альтернативу. [43]
- McDonalds наняла компанию Silverpush, занимающуюся слежкой, чтобы связать аудиоданные, полученные без согласия из ее мобильного приложения, со звуками, доносящимися с Youtube или телевидения, для показа "релевантной рекламы" на разных платформах. [44]
Примерам подлых продаж нет конца — и это только те, о которых стало известно общественности!
...Мама, папа, родитель?
Родительский клуб Bounty оштрафован на 400 000 фунтов стерлингов за продажу данных пользователей — компания незаконно передавала 34,4 млн записей 39 компаниям [45]. Популярное приложение для обеспечения безопасности семьи Life360 продает точные данные о местоположении десятков миллионов своих пользователей [46]. Доверили бы вы личные данные и местоположение своих детей незнаком(цам/кам)? Ведь по некоторым данным педофил(ки/ы) [47] и люди, похищающие детей, могут использовать эти данные для нахождения жертв.
...Представитель/ница социальной профессии?
Вы работаете политик/ом, депутат/кой, учител/ем, священни/цей, куратор/ом, доктор/кой, терапевт/ом или др., из-за чего у вас хранится множество уязвимых личных данных других людей, за которые вы в ответе? Вам стоит побеспокоиться об их сохранности — ведь эти данные выгодно продаются [48].
...В отношениях?
Возможно, вы бы хотели сохранить интимные детали отношений между вами? В самой гротескной из новостей на этот счёт сотрудник австралийской пограничной службы вернул телефон гражданину после принудительного досмотра в аэропорту со словами: "Приятно было снова посмотреть нормальное порно", ссылаясь на обнаженные фотографии его девушки [49].
...Путешественни(ца/к)?
Популярная сеть отелей AirBNB разрешает устанавливать камеры внутри своих помещений [56].
...Учитесь в школе?
Бдительно следите за соблюдением правил: школы используют техники слежения, чтобы ловить и жестоко наказывать вас за использование вейпа (электронных сигарет) [51].
...Водитель/ница?
Автомобили стали компьютерами на колесах: они "обладают непревзойденной способностью смотреть, слушать и собирать информацию о том, что вы делаете и куда идете" [55]. Эта информация затем передается или продается брокерам данных, правоохранительным органам и другим лицам. Из 25 изученных марок машин 56 % передают ваши данные правоохранительным органам в ответ на неофициальный запрос, 84 % передают или продают ваши личные данные [55].
Информацию также охотно закупают страховые компании [58], а для слежки за вами её могут использовать даже ваши партнер(ы/ки) [59].
...Используете технологии для уборки?
Роботы-пылесосы не только всасывают пыль, но и сканируют ваше жилище [53]. Как бы ни было сложно в это поверить, Amazon действительно использует эти данные, чтобы заставлять вас чаще покупать то, что вам не нужно [54].
...Житель/ница страны с демократической системой?
Не так давно произошёл случай, как Facebook поймали на манипуляциях крупнейшими выборами: компания использовала наши социальные графики, чтобы исказить наше представление о реальном мире и манипулировать нашими голосами [35].
...Граждан(ин/ка) государства?
В условиях государства безобидные разговоры могут подвергнуть вас опасности, даже если вам нечего скрывать. Одна из самых шокирующих историй — упомянутый выше опыт Мохамеду Ульд Салахи [3], описанный в его мемуарах и показанный в фильме "Мавританец". Он был помещен в лагерь Гуантанамо без суда и следствия и подвергался там пыткам в течение 15 лет за телефонный звонок своему родственнику в Афганистане — он подозревался в причастности к терактам 11 сентября, хотя предыдущие 10 лет он жил в Германии.
Обычных людей арестовывают и подвергают давлению за то, чем они делятся в Интернете, даже через свои "анонимные" аккаунты, даже в демократических странах, даже если это было легальным, даже если вы не мужчина [50].
«Дайте мне шесть строк, написанных самым честным человеком, и я найду в них что-нибудь, за что его казнят на виселице» — Кардинал де Ричелиеу
...Человек?
Зачем вы носите одежду? Почему вы бы скорее предпочли непрозрачный туалет прозрачному, или спальню без камер — наблюдаемой спальне? Почему вы можете не захотеть поделиться политическими взглядами, сексуальной ориентацией или гендерной идентичностью с бабушкой, учителем или полицейским, даже если вы считаете, что в них нет ничего плохого? Почему вы можете не захотеть поделиться галереей или паролями от своих социальных сетей с тётей, социальным работником или юзером Двача, даже если вы не делали ничего незаконного напрямую?
Что если я предложу вам отправить пароли от ваших социальных сетей, банковских счетов, ваши медицинские данные, адрес и фотографии на мою электронную почту — обещаю, что не воспользуюсь ими для чего-то плохого: я просто хочу хранить их у себя на жестком диске для безопасности ваших же данных? Вам действительно нечего скрывать?
Что если я скажу, что автоматизированная слежка достигла таких масштабов, что мегакорпорации могут предполагать, о чём вы думаете [60]? Вас это беспокоит? Если да — я не буду удивлен.
Приватность всегда была частью жизни человека, обычной её частью. То, как мы живем сейчас — это крайне неестественное для человека состояние; оно никогда не было нормальным. Вам не обязательно должно быть что скрывать, чтобы захотеть не делиться всеми подробностями личной жизни с окружающими.
Заключение
Чем дольше мы отказываемся от борьбы за права на приватность, тем больше Левиафан набирает силу. Вы думаете, мир Оруэлла из «1984» был построен в одночасье? Нет! Люди жертвовали правами на конфиденциальность, анонимность, свободу информации — шаг за шагом. И первый шаг к антиутопии — это маргинализация людей, которые беспокоятся о своей анонимности: сведение их до «носителей шапочек из фольги» и тех кто «правда считает, что ОНИ читают твои эмейлы».
Так что же нам делать? Не надо думать, что "с этим ничего не поделаешь", или что "мы уже проиграли". Вместо этого нам нужно:
- Распространять информацию о том, почему приватность важна, и почему о ней стоит побеспокоиться;
- Использовать приватные, свободные, децентрализованные аналоги популярным сервисам (например, Session вместо Telegram, NOSTR вместо Twitter, DuckDuckGo вместо Google);
- Поддерживать право на приватность ради остальных (например, пока только единицы используют приватные мессенджеры — государства знают, что использующие их что-то скрывают. Но если половина населения начнёт использовать их, нельзя будет вычленить никого особенного);
- Чаще спрашивать, почему компании знают о нас так много, и как это вообще легально;
- Участвовать в политике. Политика — это не "наблюдательный спорт": если демократия не работает, мы ответственны за то, чтобы заставить её работать. Самая верхушка такого участия — это поддержка организаций, борющихся за права на приватность
«Говорить, что вам не важна приватность, ибо вам нечего скрывать — это как говорить, что вам не важна свобода слова, ибо вам нечего сказать. Но даже если вы не пользуетесь каким-то правом в данный конкретный момент, другие могут нуждаться в нём. И говорить, что вам не важно право, ибо конкретно вам сейчас оно не нужно, это самая асоциальная вещь, которую вы только можете сделать» — Эдвард Сноуден
Источники:
[1] https://theintercept.com/2021/01/30/lapd-palantir-data-driven-policing/
[2] https://www.theguardian.com/us-news/2020/dec/03/aclu-seeks-release-records-data-us-collected-via-muslim-app-used-millions
[3] https://www.npr.org/2019/11/14/778944195/a-legacy-of-torture-is-preventing-trials-at-guant-namo
[4] https://www.vox.com/technology/2023/6/16/23762403/data-odni-report-wyden
[5] https://www.vox.com/recode/22587248/grindr-app-location-data-outed-priest-jeffrey-burrill-pillar-data-harvesting
[6] https://nypost.com/2022/05/02/grindr-sold-data-about-users-precise-locations-for-years-report/
[7] https://www.theguardian.com/technology/2018/apr/03/grindr-shared-information-about-users-hiv-status-with-third-parties
[8] https://www.cyberpolicy.com/cybersecurity-education/why-medical-records-are-10-times-more-valuable-than-credit-card-info
[9] https://www.politico.com/news/2024/02/13/planned-parenthood-location-track-abortion-ads-00141172
[10] "As of 2022, countries that legally allow abortion on request or for socioeconomic reasons comprise about 60% of the world's population", https://en.wikipedia.org/wiki/Abortion_law
[11] https://en.wikipedia.org/wiki/Anti-abortion_violence
[12] https://www.justice.gov/crt/recent-cases-violence-against-reproductive-health-care-providers
[13] https://www.indiatoday.in/technology/news/story/disha-ravi-arrest-puts-privacy-of-all-google-india-users-in-doubt-1769772-2021-02-16
[14] https://proton.me/blog/climate-activist-arrest
[15] https://www.aclunc.org/blog/facebook-instagram-and-twitter-provided-data-access-surveillance-product-marketed-target
[16] https://www.gotchseo.com/google-biased/
[17] Google вообще проводит немало цензуры в своих сервисах: https://en.wikipedia.org/wiki/Censorship_by_Google
[18] https://www.taiwannews.com.tw/en/news/3933777
[19] https://www.theverge.com/2020/5/26/21270290/youtube-deleting-comments-censorship-chinese-communist-party-ccp
[20] https://www.npr.org/2020/08/04/898836158/class-action-lawsuit-claims-tiktok-steals-kids-data-and-sends-it-to-china
[21] https://www.nytimes.com/2018/08/16/technology/google-employees-protest-search-censored-china.html
[22] https://ru.wikipedia.org/wiki/%D0%92%D0%BE%D0%B8%D0%BD%D1%81%D0%BA%D0%B0%D1%8F_%D0%BE%D0%B1%D1%8F%D0%B7%D0%B0%D0%BD%D0%BD%D0%BE%D1%81%D1%82%D1%8C
[23] https://focus.ua/voennye-novosti/626982-ot-doprosov-do-operativnyh-meropriyatij-v-nacpolicii-rasskazali-o-poiske-uklonistov
[24] https://www.bbc.com/russian/features-63346138
[25] https://www.rbc.ua/ukr/styler/k-zaraz-karayut-uhilyantiv-vid-mobilizatsiyi-1707820307.html
[26] https://www.mrarchivist.com/results/entry/4591/; Запрет на голосование по причине того, что мужчина не встал на военный учет, противоречит статье 21 Всеобщей Декларации Прав Человека.
[27] https://www.nbcnews.com/id/wbna17880969
[28] https://www.rferl.org/a/google-reportedly-removes-navalny-ad-after-russian-government-complains/29478844.html
[29] https://www.theguardian.com/world/2021/sep/17/apple-and-google-accused-of-political-censorship-over-alexei-navalny-app
[30] https://nordicmonitor.com/2023/09/google-youtube-accused-of-censoring-erdogan-critics/
[31] https://www.medianama.com/2024/02/223-youtube-blocks-videos-protests-job-aspirants-bihar/
[32] https://edition.cnn.com/2007/WORLD/meast/11/29/youtube.activist/
[33] https://www.aljazeera.com/features/2023/10/24/shadowbanning-are-social-media-giants-censoring-pro-palestine-voices
[34] https://thehill.com/business/4355894-pharmacies-sharing-medical-data-without-warrant/
[35] https://en.wikipedia.org/wiki/Facebook%E2%80%93Cambridge_Analytica_data_scandal
[36] https://usercentrics.com/knowledge-hub/data-is-the-new-gold-how-and-why-it-is-collected-and-sold/
[37] https://knowledge.wharton.upenn.edu/article/data-shared-sold-whats-done/
[38] https://www.eff.org/deeplinks/2020/11/visa-wants-buy-plaid-and-it-transaction-data-millions-people
[39] https://supreme.findlaw.com/legal-commentary/websites-that-charge-different-customers-different-prices.html
[40] https://policyreview.info/articles/analysis/does-everyone-have-price-understanding-peoples-attitude-towards-online-and-offline
[41] https://fairbydesign.com/povertypremium
[42] https://www.wsj.com/articles/SB10001424052702304458604577488822667325882
[43] https://www.bizjournals.com/twincities/news/2019/02/01/report-targets-app-charges-higher-prices-to.html
[44] https://www.digitaltrends.com/mobile/silverpush-app-tracking-spying-use-rises-new/
[45] https://www.theguardian.com/technology/2019/apr/12/parenting-club-bounty-fined-selling-users-data
[46] https://themarkup.org/privacy/2021/12/06/the-popular-family-safety-app-life360-is-selling-precise-location-data-on-its-tens-of-millions-of-user
[47] https://www.the-sun.com/news/3740183/paedophile-snachat-maps-victims-tesco/
[48] https://www.experian.com/blogs/ask-experian/heres-how-much-your-personal-information-is-selling-for-on-the-dark-web/
[49] https://micky.com.au/aussie-ex-pat-will-never-return-after-digital-strip-search-reveals-sex-tapes/
[50] https://www.dailymail.co.uk/news/article-11282263/Moment-police-swoop-house-devout-catholic-mother-malicious-online-posts.html
[51] https://apnews.com/article/vaping-surveillance-technology-schools-982128348c683b9d54c7a307c5b1fdc6
[52] https://www.politico.com/news/2023/05/19/fbi-surveillance-black-lives-matter-protesters-00097924
[53] https://www.welivesecurity.com/en/privacy/gathering-dust-and-data-how-robotic-vacuums-can-spy-on-you/
[54] https://www.reuters.com/markets/deals/amazons-irobot-deal-eu-antitrust-crosshairs-2023-07-06/
[55] https://foundation.mozilla.org/en/privacynotincluded/articles/its-official-cars-are-the-worst-product-category-we-have-ever-reviewed-for-privacy/
[56] https://ru.airbnb.com/help/article/3061
[57] https://newrepublic.com/article/179397/evangelical-app-targeting-immigrants-surveillance
[58] https://www.nytimes.com/2024/03/11/technology/carmakers-driver-tracking-insurance.html
[59] https://www.nytimes.com/2023/12/31/technology/car-trackers-gps-abuse.html
[60] https://www.zdnet.com/article/google-even-knows-what-youre-thinking/*Это не значит, что ProtonMail небезопасен: сервис регулярно выигрывает множество судов на тему раскрытия данных юзеро(в/к); это значит, что использования ProtonMail было недостаточно приватным (в конкретном случае — без VPN/SPN/TOR).
-
 @ 58f5a230:304d59f7
2024-01-20 18:03:12
@ 58f5a230:304d59f7
2024-01-20 18:03:12บทความชุดนี้ผมคิดว่าจะเขียนแยกเป็นตอน ๆ ตามบทเรียนที่ได้รับจาก Bitcoin FOSS Program ของทาง Chaincode Labs โดยจะมาแชร์การแก้โจทย์ปัญหาตามบททดสอบในแต่ละสัปดาห์
สัปดาห์แรกนี้ผมได้โจยท์มาทั้งหมด 8 ข้อ และการตอบปัญหาทั้งหมดจะใช้ Bash Script เขียนคำสั่งร่วมกับ
bitcoin-cliในการทำความเข้าใจพื้นฐานของ Bitcoin-Core ระบบการบันทึกบัญชีลง Blockchain การดู/ตรวจสอบ ข้อมูลบน Block รวมถึงพื้นฐานข้อมูลภายใน Block จนถึง Transaction เบื้ิองต้น และในบทความนี้จะควบคุมความรู้ในหนังสือนั้นในบทที่ 1-3 ของหนังสือ Mastering Bitcoin หากท่านต้องการศึกษาเพิ่มเติมให้เข้าใจมากขึ้น แนะนำให้อ่านไปด้วยข้อที่ 1: แฮชของบล็อคที่ 654,321 คืออะไร?
ข้อนี้ง่ายมาก ๆ โดยเราจะใช้โปรแกรม
bitcoin-cliจาก bitcoin-core ที่ติดตั้งไว้แล้ว เชื่อมไปยัง RPC server ที่เป็น Full-node ของเรา พร้อมกับคำสั่งgetblockhashเราสามารถดูได้ว่ามันใช้งานยังไงด้วยการพิมพ์helpนำหน้าคำสั่ง เราก็จะได้คำอธิบายพร้อมกับตัวอย่างการใช่งานมา```sh $ bitcoin-cli help getblockhash getblockhash height
Returns hash of block in best-block-chain at height provided.
Arguments: 1. height (numeric, required) The height index
Result: "hex" (string) The block hash
Examples:
bitcoin-cli getblockhash 1000 curl --user myusername --data-binary '{"jsonrpc": "1.0", "id": "curltest", "method": "getblockhash", "params": [1000]}' -H 'content-type: text/plain;' http://127.0.0.1:8332/ ```
ในโจทย์นี้เราจะใช้เพียงคำสั่งเดียวเท่านั้น มาดูกัน
sh $ bitcoin-cli getblockhash 654321 000000000000000000058452bbe379ad4364fe8fda68c45e299979b492858095ผมได้เรียกใช้
bitcoin-cliพร้อมกับคำสั่งgetblockhash 654321และได้คำตอบมาว่า000000000000000000058452bbe379ad4364fe8fda68c45e299979b492858095นั้นคือแฮชของบล็อคที่ 654,321 นั่นเอง ข้อมูลเหล่านี้เราจะได้ใช้มันในข้อหลัง ๆ ไปข้อต่อไปกันข้อที่ 2: จงพิสูจน์ข้อความนี้ว่าถูกเซนต์โดยที่อยู่นี้ถูกต้องหรือไม่
(true / false) Verify the signature by this address over this message: address: `1E9YwDtYf9R29ekNAfbV7MvB4LNv7v3fGa` message: `1E9YwDtYf9R29ekNAfbV7MvB4LNv7v3fGa` signature: `HCsBcgB+Wcm8kOGMH8IpNeg0H4gjCrlqwDf/GlSXphZGBYxm0QkKEPhh9DTJRp2IDNUhVr0FhP9qCqo2W0recNM=`ตามโจทย์นี้อาจจะดูงง ๆ ผมจึงไปค้นใน Docs ของ Bitcoin-Core ดูและพบกับคำสั่ง
verifymessageมาลองดูกัน```sh $ bitcoin-cli help verifymessage verifymessage "address" "signature" "message"
Verify a signed message.
Arguments: 1. address (string, required) The bitcoin address to use for the signature. 2. signature (string, required) The signature provided by the signer in base 64 encoding (see signmessage). 3. message (string, required) The message that was signed.
Result: true|false (boolean) If the signature is verified or not.
Examples:
Unlock the wallet for 30 seconds
bitcoin-cli walletpassphrase "mypassphrase" 30
Create the signature
bitcoin-cli signmessage "1D1ZrZNe3JUo7ZycKEYQQiQAWd9y54F4XX" "my message"
Verify the signature
bitcoin-cli verifymessage "1D1ZrZNe3JUo7ZycKEYQQiQAWd9y54F4XX" "signature" "my message"
As a JSON-RPC call
curl --user myusername --data-binary '{"jsonrpc": "1.0", "id": "curltest", "method": "verifymessage", "params": ["1D1ZrZNe3JUo7ZycKEYQQiQAWd9y54F4XX", "signature", "my message"]}' -H 'content-type: text/plain;' http://127.0.0.1:8332/ ```
สังเกตุว่าคำสั่งนี้ใช้ 3 ตัวแปรตามที่โจทย์ให้มาเป๊ะ ๆ มาลองใช้ดูกัน
sh address="1E9YwDtYf9R29ekNAfbV7MvB4LNv7v3fGa" message="1E9YwDtYf9R29ekNAfbV7MvB4LNv7v3fGa" signature="HCsBcgB+Wcm8kOGMH8IpNeg0H4gjCrlqwDf/GlSXphZGBYxm0QkKEPhh9DTJRp2IDNUhVr0FhP9qCqo2W0recNM="เริ่มจากการประกาศตัวแปรไว้ตามฉบับสายผู้ใช้ Linux แล้วก็ลองส่งคำสั่งกันเลย
sh $ bitcoin-cli verifymessage $address $signature $message falsefalse... ตอนแรกก็ยังงง ๆ แต่ข้อนี้คำตอบคือ false จริง ๆ นั่นแหละ อาจจะเพราะคนทำโจทย์ลืมดูว่า message มันซ้ำกับ address อยู่ หรือไม่ก็จงใจ ช่างมัน ไปข้อต่อไปกันข้อที่ 3: บล็อคที่ 123,456 มีจำนวน outputs Transaction ทั้งหมดเท่าไหร่?
ข้อนี้จะไปไวหน่อยเพราะว่าเราไม่จำเป็นต้อง loop เพื่อดูข้อมูล Transaction ในบล็อคเพื่อนับเอา outputs เราสามารถใช้คำสั่ง
getblockstatsได้เลย แล้วใช่jqแปลงข้อมูลให้เป็น JSON เพื่อให้เราอ่านได้ง่ายขึ้นsh $ bitcoin-cli getblockstats 123456 | jq . { "avgfee": 416666, "avgfeerate": 1261, "avgtxsize": 330, "blockhash": "0000000000002917ed80650c6174aac8dfc46f5fe36480aaef682ff6cd83c3ca", "feerate_percentiles": [ 0, 0, 0, 3861, 3891 ], "height": 123456, "ins": 17, "maxfee": 1000000, "maxfeerate": 3891, "maxtxsize": 618, "medianfee": 0, "mediantime": 1305197900, "mediantxsize": 258, "minfee": 0, "minfeerate": 0, "mintxsize": 257, "outs": 24, "subsidy": 5000000000, "swtotal_size": 0, "swtotal_weight": 0, "swtxs": 0, "time": 1305200806, "total_out": 16550889992, "total_size": 3964, "total_weight": 15856, "totalfee": 5000000, "txs": 13, "utxo_increase": 7, "utxo_increase_actual": 7, "utxo_size_inc": 567, "utxo_size_inc_actual": 567 }นี่คือข้อมูลเบื้องต้นของบล็อค 123,456 ที่มีรายการ transaction อยู่ 13 รายการ และมี outputs รวม 24 รายการ เราสามารถใช้
jqแสดงผลเฉพาะข้อมูลที่เราต้องการได้ง่าย ๆ โดยพิมพ์ชื่อข้อมูลที่เราต้องการตามไปหลังจุด.ข้อนี้สามารถตอบได้เลยsh $ bitcoin-cli getblockstats 123456 | jq .outs 24ข้อที่ 4: จงหา taproot address ลำดับที่ 100 โดยคำนวนจาก xpub ต่อไปนี้
ตัว extended public key หรือ xpub ที่ผมได้มาคือ
xpub6Cx5tvq6nACSLJdra1A6WjqTo1SgeUZRFqsX5ysEtVBMwhCCRa4kfgFqaT2o1kwL3esB1PsYr3CUdfRZYfLHJunNWUABKftK2NjHUtzDms2เอาหล่ะ แล้วจะทำยังไงต่อหล่ะเนี่ยแล้วผมก็ไปเจอกับคำสั่งนี้ในที่สุด
deriveaddressesว่าแต่มันใช้ยังไงหว่า```sh $ bitcoin-cli help deriveaddresses deriveaddresses "descriptor" ( range )
Derives one or more addresses corresponding to an output descriptor. Examples of output descriptors are: pkh(
) P2PKH outputs for the given pubkey wpkh( ) Native segwit P2PKH outputs for the given pubkey sh(multi( , , ,...)) P2SH-multisig outputs for the given threshold and pubkeys raw( ) Outputs whose scriptPubKey equals the specified hex scripts tr( ,multi_a( , , ,...)) P2TR-multisig outputs for the given threshold and pubkeys In the above,
either refers to a fixed public key in hexadecimal notation, or to an xpub/xprv optionally followed by one or more path elements separated by "/", where "h" represents a hardened child key. For more information on output descriptors, see the documentation in the doc/descriptors.md file. Arguments: 1. descriptor (string, required) The descriptor. 2. range (numeric or array, optional) If a ranged descriptor is used, this specifies the end or the range (in [begin,end] notation) to derive.
Result: [ (json array) "str", (string) the derived addresses ... ]
Examples: First three native segwit receive addresses
bitcoin-cli deriveaddresses "wpkh([d34db33f/84h/0h/0h]xpub6DJ2dNUysrn5Vt36jH2KLBT2i1auw1tTSSomg8PhqNiUtx8QX2SvC9nrHu81fT41fvDUnhMjEzQgXnQjKEu3oaqMSzhSrHMxyyoEAmUHQbY/0/)#cjjspncu" "[0,2]" curl --user myusername --data-binary '{"jsonrpc": "1.0", "id": "curltest", "method": "deriveaddresses", "params": ["wpkh([d34db33f/84h/0h/0h]xpub6DJ2dNUysrn5Vt36jH2KLBT2i1auw1tTSSomg8PhqNiUtx8QX2SvC9nrHu81fT41fvDUnhMjEzQgXnQjKEu3oaqMSzhSrHMxyyoEAmUHQbY/0/)#cjjspncu", "[0,2]"]}' -H 'content-type: text/plain;' http://127.0.0.1:8332/ ```
อื้อหือ ยิ่งงงไปอิ๊กก เอาวะลองดูตามตัวอย่างของ P2TR ละกัน
sh $ bitcoin-cli deriveaddresses "tr(xpub6Cx5tvq6nACSLJdra1A6WjqTo1SgeUZRFqsX5ysEtVBMwhCCRa4kfgFqaT2o1kwL3esB1PsYr3CUdfRZYfLHJunNWUABKftK2NjHUtzDms2)" error code: -5 error message: Missing checksumอะ...อ้าว ย้อนกลับไปดูตัวอย่าง และอ่าน Docs ดี ๆ จะพบว่าการ deriveaddresses นั้นจะมีรูปแบบอยู่ เช่น
wpkh([d34db33f/84h/0h/0h]xpub6DJ2dNUysrn5Vt36jH2KLBT2i1auw1tTSSomg8PhqNiUtx8QX2SvC9nrHu81fT41fvDUnhMjEzQgXnQjKEu3oaqMSzhSrHMxyyoEAmUHQbY/0/*)#cjjspncu- wpkh() นั้นคือรูปแบบของการเข้ารหัส ซึ่งมีหลายอย่างให้ใช้ตามวัตถุประสงค์ อย่าง multisig ก็จะเป็นอีกแบบ
- [d34db33f/84h/0h/0h] ส่วนนี้ึคือ fingerprint จาก pubkey หลักก่อนจะคำนวน xpub ซึ่งโจทย์ข้อนี้ไม่มีให้ และหลังจากศึกษามาก็พบว่ามันไม่จำเป็นสำหรับการสร้าง address แบบ basic ง่าย ๆ
- xpub6DJ2dNUysrn5Vt36jH2KLBT2i1auw1tTSSomg8PhqNiUtx8QX2SvC9nrHu81fT41fvDUnhMjEzQgXnQjKEu3oaqMSzhSrHMxyyoEAmUHQbY ส่วนนี้คืิอ extended public key ซึ่งคำนวนมาจาก pubkey หลักที่คำนวนมาจาก private key หรือ seed ของเราอีกที
- /0/_ คือ path สำหรับระยะการคำนวน address โดยให้มองเป็น /เริ่มต้น/สิ้นสุด เช่น /0/99 หมายถึง เราจะคำนวน address จากตำแหน่งที่ 0 ถึงตำแหน่ง 99 ถ้าใช้ _ คือจะคำนวนกี่ที่อยู่ก็ได้
-
cjjspncu คือ checksum ของ descriptor กระเป๋านี้ และสามารถใช้คำสั่ง
getdescriptorinfoเพื่อดูข้อมูลได้
เอาหล่ะ มาลองกันใหม่ โดยที่ผมจะ derive ตำแหน่งที่ /100 ที่อยู่เดียวเท่านั้น
sh $ bitcoin-cli getdescriptorinfo "tr(xpub6Cx5tvq6nACSLJdra1A6WjqTo1SgeUZRFqsX5ysEtVBMwhCCRa4kfgFqaT2o1kwL3esB1PsYr3CUdfRZYfLHJunNWUABKftK2NjHUtzDms2/100)" { "checksum": "5p2mg7zx", "descriptor": "tr(xpub6Cx5tvq6nACSLJdra1A6WjqTo1SgeUZRFqsX5ysEtVBMwhCCRa4kfgFqaT2o1kwL3esB1PsYr3CUdfRZYfLHJunNWUABKftK2NjHUtzDms2/100)#5p2mg7zx", "hasprivatekeys": false, "isrange": false, "issolvable": true }ได้แฮะ ลองเอา checksum ที่ได้ไปคำนวนที่อยู่กัน
sh $ bitcoin-cli deriveaddresses "tr(xpub6Cx5tvq6nACSLJdra1A6WjqTo1SgeUZRFqsX5ysEtVBMwhCCRa4kfgFqaT2o1kwL3esB1PsYr3CUdfRZYfLHJunNWUABKftK2NjHUtzDms2/100)#5p2mg7zx" [ "bc1p3yrtpvv6czx63h2sxwmeep8q98h94w4288fc4cvrkqephalydfgszgacf9" ]หลังจากนั้นผมก็ใช้
jq -r .[0]เพื่อดึงข้อมูลออกจาก JSON array แล้วส่งคำตอบ ผ่านได้ด้วยดีข้อที่ 5 สร้าง P2SH multisig address ด้วย public keys 4 ชุดจาก inputs ใน transaction นี้
37d966a263350fe747f1c606b159987545844a493dd38d84b070027a895c4517ไหนดูซิ transaction นี้เป็นยังไง
sh $ bitcoin-cli getrawtransaction "37d966a263350fe747f1c606b159987545844a493dd38d84b070027a895c4517" 1 { "blockhash": "000000000000000000024a848a9451143278f60e4c3e73003da60c7b0ef74b62", "blocktime": 1701158269, "confirmations": 7751, "hash": "e28a0885b6f413e24a89e9c2bac74d4c6f335e17545f0b860da9146caf7ffe39", "hex": "02000000000104b5f641e80e9065f09b12f3e373072518885d1bd1ddd9298e5b9840de515edac90000000000feffffffd54f8986afbb6ff18572acaee58fa3ad64446dd770ffe9b6a04f798becdafb440000 000000feffffff475e3062b1c3ee87544c29d723866da2b65a1b1a42e6ea4a4fd48d79f83c26c50000000000feffffffa56387352ecc93dfd37648e6ebd4d9effb37ffefcad02eb7b85860c9097cf8090000000000feff ffff02fa440f00000000001600148070ec3954ecdcbfc210d0117e8d28a19eb8467270947d0000000000160014b5fe46c647353ec9c06374655502094095f0289c0247304402200dd758801b40393f68dad8ab57558803 efcd2b681ee31eb44fb3cfa9666d2bf90220254d34fa4990e23652bf669053c5e16fd2fbb816bed2eeb44c1f1e6e54143e3e012102bbb4ba3f39b5f3258f0014d5e4eab5a6990009e3e1dba6e8eaff10b3832394f70247 304402201694761a5749b6a84f71459c04a44cf9d34a36ae8c9044c3af7a3a5514ef2e64022058f61feb92d6d54b71fdea47e7dfcd20f6a5c12e2fbcb15bc44fe95c73f2e808012103aaf17b1a7b4108f7e5bc4f7d59c2 0f7fb1a72dbc74a9a3d6d1f8488df159c76002473044022014b65c60f65e62d9dac893e404c8de2a007c7c6b74dbac18e454d8374e159759022012453f69112adadf9495fd3fe288aa5ed9e3d836340da06fa1e82c8e09 adef57012103a6d919c76d9117c23570a767450013edf31cf6be7d3b5a881c06a9aa1f2c24ce0247304402203d3b02390803c1d673fa49bd64d4a26fbeb29e3fc152af8f844d776c9409e41302206903a011a04e00a7f4 ec606da4320226d2d393f565702cc58cfcef6dca67f84c01210383d12258e3e294a6d7754336f6b4baef992ec4b91694d3460bcb022b11da8cd2817e0c00", "locktime": 818817, "size": 666, "time": 1701158269, "txid": "37d966a263350fe747f1c606b159987545844a493dd38d84b070027a895c4517", "version": 2, "vin": [ { "scriptSig": { "asm": "", "hex": "" }, "sequence": 4294967294, "txid": "c9da5e51de40985b8e29d9ddd11b5d8818250773e3f3129bf065900ee841f6b5", "txinwitness": [ "304402200dd758801b40393f68dad8ab57558803efcd2b681ee31eb44fb3cfa9666d2bf90220254d34fa4990e23652bf669053c5e16fd2fbb816bed2eeb44c1f1e6e54143e3e01", "02bbb4ba3f39b5f3258f0014d5e4eab5a6990009e3e1dba6e8eaff10b3832394f7" ], "vout": 0 }, { "scriptSig": { "asm": "", "hex": "" }, "sequence": 4294967294, "txid": "44fbdaec8b794fa0b6e9ff70d76d4464ada38fe5aeac7285f16fbbaf86894fd5", "txinwitness": [ "304402201694761a5749b6a84f71459c04a44cf9d34a36ae8c9044c3af7a3a5514ef2e64022058f61feb92d6d54b71fdea47e7dfcd20f6a5c12e2fbcb15bc44fe95c73f2e80801", "03aaf17b1a7b4108f7e5bc4f7d59c20f7fb1a72dbc74a9a3d6d1f8488df159c760" ], "vout": 0 }, { "scriptSig": { "asm": "", "hex": "" }, "sequence": 4294967294, "txid": "c5263cf8798dd44f4aeae6421a1b5ab6a26d8623d7294c5487eec3b162305e47", "txinwitness": [ "3044022014b65c60f65e62d9dac893e404c8de2a007c7c6b74dbac18e454d8374e159759022012453f69112adadf9495fd3fe288aa5ed9e3d836340da06fa1e82c8e09adef5701", "03a6d919c76d9117c23570a767450013edf31cf6be7d3b5a881c06a9aa1f2c24ce" ], "vout": 0 }, { "scriptSig": { "asm": "", "hex": "" }, "sequence": 4294967294, "txid": "09f87c09c96058b8b72ed0caefff37fbefd9d4ebe64876d3df93cc2e358763a5", "txinwitness": [ "304402203d3b02390803c1d673fa49bd64d4a26fbeb29e3fc152af8f844d776c9409e41302206903a011a04e00a7f4ec606da4320226d2d393f565702cc58cfcef6dca67f84c01", "0383d12258e3e294a6d7754336f6b4baef992ec4b91694d3460bcb022b11da8cd2" ], "vout": 0 } ], "vout": [ { "n": 0, "scriptPubKey": { "address": "bc1qspcwcw25anwtlsss6qgharfg5x0ts3njad8uve", "asm": "0 8070ec3954ecdcbfc210d0117e8d28a19eb84672", "desc": "addr(bc1qspcwcw25anwtlsss6qgharfg5x0ts3njad8uve)#pzjnvw8p", "hex": "00148070ec3954ecdcbfc210d0117e8d28a19eb84672", "type": "witness_v0_keyhash" }, "value": 0.01000698 }, { "n": 1, "scriptPubKey": { "address": "bc1qkhlyd3j8x5lvnsrrw3j42qsfgz2lq2yu3cs5lr", "asm": "0 b5fe46c647353ec9c06374655502094095f0289c", "desc": "addr(bc1qkhlyd3j8x5lvnsrrw3j42qsfgz2lq2yu3cs5lr)#hzcalwww", "hex": "0014b5fe46c647353ec9c06374655502094095f0289c", "type": "witness_v0_keyhash" }, "value": 0.0823 } ], "vsize": 344, "weight": 1374 }เราจำเป็นต้องเรียนรู้เรื่อง Witness program ของ bip-141 เพื่อเข้าใจ scriptPubKey หรือ redeemScript เบื่องต้นเสียก่อน โดยพื้นฐานธุรกรรมแบบ P2WPKH ภายใน txinwitness จะมี signature และ public keys ตามลำดับ เราจะลองใช้ pubkey นี้ในการสร้างกระเป๋า multisig กัน
sh txinfo=$(bitcoin-cli getrawtransaction "37d966a263350fe747f1c606b159987545844a493dd38d84b070027a895c4517" 1) ad1=$(echo $txinfo | jq '.vin[0] | .txinwitness[1]') ad2=$(echo $txinfo | jq '.vin[1] | .txinwitness[1]') ad3=$(echo $txinfo | jq '.vin[2] | .txinwitness[1]') ad4=$(echo $txinfo | jq '.vin[3] | .txinwitness[1]') bitcoin-cli createmultisig 1 ["$ad1","$ad2","$ad3","$ad4"] | jq -r '.address'3GyWg1CCD3RDpbwCbuk9TTRQptkRfczDz8
ง่ายเลยข้อนี้ ไปข้อต่อไปกัน
ข้อที่ 6: transaction ไหนในบล็อค 257,343 ใช้เงินรางวัลจากการขุดจากบล็อค 256,128?
Which tx in block 257,343 spends the coinbase output of block 256,128?ข้อนี้ต้องไปหาว่า coinbase output ก็คือเงินรางวัลจากการขุดบล็อคนั้น ๆ รวมกับค่า fee นั่นเอง ซึ่งจะอยู่ในลำดับแรกของบล็อคนั้น ๆ เสมอ เรามาเขียนน Bash Script หา coinbase txid กันsh blockhash=$(bitcoin-cli getblockhash 256128) tx256=$(bitcoin-cli getblock $blockhash 2)ด้วยคำสั่ง
getblock ตามด้วยแฮชของบล็อค และระดับข้อมูลโดยที่ระดับ- จะแสดงข้อมูลบล็อค ไม่มี transaction
- จะแสดงข้อมูล transaction แต่ไม่รวม inputs
- จะแสดงข้อมูลทั้งหมดของบล็อคนั้น ๆ
sh coinbase_txid=$(echo $tx256 | jq -r '.tx[0].txid') echo $coinbase_txidแล้วก็เลือก txid จากข้อมูลแรกมา ซึ่งก็คือ coinbase output ของเรา
611c5a0972d28e421a2308cb2a2adb8f369bb003b96eb04a3ec781bf295b74bc นี่คือ txid ที่เราจะเอาไปหาว่ามันมีใน inputs ไหนของ transaction ไหนใน block 257,343 ซึ่งโดยทั่วไปแล้วหากเรา loop หากทีละ transaction คงเสียเวลาน่าดู เราลองมาใช้ฟังชั่น select() ของ
jqกัน```sh blockhash=$(bitcoin-cli getblockhash 256128) tx256=$(bitcoin-cli getblock $blockhash 2) coinbase_txid=$(echo $tx256 | jq -r '.tx[0].txid') blockhash=$(bitcoin-cli getblockhash 257343) tx257=$(bitcoin-cli getblock $blockhash 3)
เลือกข้อมูล transaction
block257tx=$(echo $tx257 | jq -r '.tx')
ใน .tx นั้นเราจะได้ JSON array ที่มีรายการ transaction เยอะมาก ๆ เราจะเลือกอันเดียวที่มี coinbase txid ใน vin หรือ inputs นั้น ๆ กัน และใช้ jq อีกครั้งเพื่อให้แสดงผลแค่ txid
echo "$block257tx" | jq ".[] | select(.vin[].txid==\"$coinbase_txid\")" | jq -r '.txid' ```
และนี่คือคำตอบของข้อนี้
c54714cb1373c2e3725261fe201f267280e21350bdf2df505da8483a6a4805fc
ข้อที่ 7: มี UTXO อันนึงที่ไม่เคยถูกใช้งานเลยในบล็อคที่ 123,321 UTXO นั้นคือ address อะไร?
Only one single output remains unspent from block 123,321. What address was it sent to?ข้อนี้เราจะใช้คำสั่ง gettxout ที่จะ return ข้อมูลของ UTXO ที่ไม่เคยถูกใช้งานให้เรา โดยการ loop ไปทีละ transaction
```sh blockhash=$(bitcoin-cli getblockhash 123321) blockinfo=$(bitcoin-cli getblock $blockhash 3) transaction=$(echo $blockinfo | jq '.tx[]') txid=$(echo $transaction | jq -r '.txid')
for item in $txid; do bitcoin-cli gettxout "$item" 0 | jq -r '.scriptPubKey.address' done ```
1FPDNNmgwEnKuF7GQzSqUcVQdzSRhz4pgX ได้มาแล้วคำตอบของเรา โจทย์ข้อนี้คงผิดแน่ ๆ หากมี UTXO ที่ยังไม่ได้ใช้งานมากกว่า 1 อันเพราะเราสั่งให้แสดงมันทุก transaction เลย! ฮาาา
ข้อที่ 8: public key อะไรที่ใช้เซ็นอันดับแรกใน transaction e5969add849689854ac7f28e45628b89f7454b83e9699e551ce14b6f90c86163
ข้อนี้ค่อนข้างหินเลย ตอนแรกเอาไปเปิดในดูใน mempool พบว่าเป็นธุรกรรมที่ถูก force close lightning channel ซึ่งมันต้องเป็น multisig แน่ ๆ เอาหล่ะ ดูข้อมูลธุรกรรมนี้ก่อนแล้วกัน
sh bitcoin-cli getrawtransaction "e5969add849689854ac7f28e45628b89f7454b83e9699e551ce14b6f90c86163" 1 { "blockhash": "0000000000000000000b0e5eec04d784347ef564b3ddb939eca019a66c9cedbe", "blocktime": 1610254919, "confirmations": 161208, "hash": "881d7ab9ad60d6658283dbbad345f6f28491a264cd11d060b4fb4f121851a7f3", "hex": "020000000001018b1aab3917e6595816c63bf9dd0ebf4303f2b2a23103aee1500282c944affd71000000000000000000010e26000000000000160014c47082b5a49065d85ab65730e8c28bb0b4810b960347 3044022050b45d29a3f2cf098ad0514dff940c78046c377a7e925ded074ad927363dc2dd02207c8a8ca7d099483cf3b50b00366ad2e2771805d6be900097c2c57bc58b4f34a50101014d6321025d524ac7ec6501d018d3 22334f142c7c11aa24b9cffec03161eca35a1e32a71f67029000b2752102ad92d02b7061f520ebb60e932f9743a43fee1db87d2feb1398bf037b3f119fc268ac00000000", "locktime": 0, "size": 237, "time": 1610254919, "txid": "e5969add849689854ac7f28e45628b89f7454b83e9699e551ce14b6f90c86163", "version": 2, "vin": [ { "scriptSig": { "asm": "", "hex": "" }, "sequence": 0, "txid": "71fdaf44c9820250e1ae0331a2b2f20343bf0eddf93bc6165859e61739ab1a8b", "txinwitness": [ "3044022050b45d29a3f2cf098ad0514dff940c78046c377a7e925ded074ad927363dc2dd02207c8a8ca7d099483cf3b50b00366ad2e2771805d6be900097c2c57bc58b4f34a501", "01", "6321025d524ac7ec6501d018d322334f142c7c11aa24b9cffec03161eca35a1e32a71f67029000b2752102ad92d02b7061f520ebb60e932f9743a43fee1db87d2feb1398bf037b3f119fc268ac" ], "vout": 0 } ], "vout": [ { "n": 0, "scriptPubKey": { "address": "bc1qc3cg9ddyjpjask4k2ucw3s5tkz6gzzukzmg49s", "asm": "0 c47082b5a49065d85ab65730e8c28bb0b4810b96", "desc": "addr(bc1qc3cg9ddyjpjask4k2ucw3s5tkz6gzzukzmg49s)#c68e8rrv", "hex": "0014c47082b5a49065d85ab65730e8c28bb0b4810b96", "type": "witness_v0_keyhash" }, "value": 9.742e-05 } ], "vsize": 121, "weight": 483 }เรารู้แล้วว่าข้อมูลจะอยู่ใน
txinwitnessซึ่งอันดับแรก ๆ เป็น signature และอันหลังเป็น public key แต่ว่า มันมีหลาย public key ใช่มะ ในนี้sh transaction=$(bitcoin-cli getrawtransaction "e5969add849689854ac7f28e45628b89f7454b83e9699e551ce14b6f90c86163" 1) scriptpubkey=$(echo $txinfo | jq -r .vin[].txinwitness[2]) echo $scriptpubkey6321025d524ac7ec6501d018d322334f142c7c11aa24b9cffec03161eca35a1e32a71f67029000b2752102ad92d02b7061f520ebb60e932f9743a43fee1db87d2feb1398bf037b3f119fc268ac เอาหล่ะ เรามาแกะข้อมูลนี้กัน หากเราไปอ่าน bip-143 จะมีรูปแบบตัวอย่างลำดับอยู่ และก็พบว่ามันคืออักษรลำดับที่ 5 ถึง 67 เราต้องใช้ Bash slicing string เพื่อตัดให้เหลือส่วนที่เราต้องการและส่งข้อสอบดู
sh echo ${scriptpubkey:4:66}025d524ac7ec6501d018d322334f142c7c11aa24b9cffec03161eca35a1e32a71f
-
 @ 5c8a5765:4fc5edee
2024-03-22 17:24:46
@ 5c8a5765:4fc5edee
2024-03-22 17:24:46"Why do I care about privacy? I've got nothing to hide." But wait, maybe you are...
Прочти на русском
tl;dr: Lack of privacy threatens sexual, racial, national minorities, women, men, non-binary, atheists, activists, the poor, the disabled, students, social workers, any customers, humans beings in general, and even democracy.
...Black?
Palentir, an artificial intelligence company, is selling proactive surveillance data to the LAPD to use traffic cameras for targeted racial profiling (searching exclusively black people for preventative crime investigations) [1]. If you've participated in BLM protests, the FBI is also grossly overstepping its authority for the sake of surveillance [52].
...Muslim?
Salaat First, an app that reminds Muslims of prayer times, sells user data to the FBI and ICE to constantly track users' locations [2]. Meanwhile, Muslim prisoners are tortured without trial at Guantanamo Bay [3].
...Atheist?
Evangelicals have begun using digital surveillance to track where "not yet converted" to Christianity are living [57].
...Queer?
Grindr sells users' location data [4]: the data sold has been used to fire gay priests [5]. According to the New York Post, they "allowed unknown third parties to learn sensitive information about users, including who they date, where they live and work, and where they spend their free time" [6].
The owners of Grind hastily put the service up for sale when it was revealed that it also collects users' medical data and shares it with other companies [7] (your medical data is worth 10-40 times more than your credit card data [8]). Not all transgender, non-binary, or intersex individuals would want to walk around with a "MY GENITALS DON'T MATCH THE GENDER" sign on their chest, but the lack of privacy gives you just that.
By revealing your identity to anyone, you put your freedom (if being queer is illegal in your country) and life at risk.
...AFAB?
Mobile geolocation tracking is being used by anti-abortion groups. Quote from Politico: "One advertising firm bragged in 2015 that it could 'tag all smartphones going in and out of nearly 700 Planned Parenthood clinics'" [9]. At the same time, as of 2022. 40% of the world had legal liability for abortion without extremely specific reasons [10]. It should also be remembered that some opponents of abortion are very militant: there is quite a bit of violence and even terrorism against abortion providers and abortionists [11][12].
...Activist?
Google gave Indian police the data of a 21-year-old climate activist who typed into Google Docs about farm protests (turned out to be arrested) [13]. Protonmail gave the data of an eco-activist* to the French police (turned out to be arrested) [14]. Facebook, Instagram and X (Twitter) provide access to data to track activists (particularly non-white activists) — some of whom have not been uncooperative even after being exposed [15]. Our governments also have a strong interest in preventing protests before they even happen.
...Noncomformist?
For example, if you're a conservative, you may find yourself under the boot of censorship: the company Gotcha SEO conducted a study of 50 controversial ("edgy") search queries on Google and found that only 5% of the results pertained to conservative sites, compared to 31.8% left-wing and 63.8% neutral [16][17]. In my personal experience (especially felt while writing this article), Google, Bing and other search engines from big companies (compared to, for example, Brave Search) are also reluctant to produce results on the topic of big companies selling your personal information.
...Chinese?
In 2019, YouTube was caught automatically deleting comments that contained anything about "50 Cent (Party)" (China's "troll factory" — teams of people who flood social media comments with pro-state opinions for a small fee) [18], or accusing the Chinese Communist Party of banditry [19]. And then there's Tik Tok stealing your kids' data and selling it to your (Chinese) government [20]. And Google is also developing a special censored search engine specifically for China [21].
...A person with male gender in documents?
If your country has a military draft, with an overwhelming chance it will only be mandatory for males [22] (that's a discrimination). To send you to the army or to war, you will be tracked by phone, car movements [23], facial recognition cameras [24] and more. Evasion is punishable, up to and including prison and human rights violations [25][26].
...Anarchist?
Google Maps actively hides any images of protests and even poor living conditions [27]. Google Ads and Play Market remove opposition content at the request of the state (e.g. Russian) [28][29]. YouTube actively blocks channels and videos covering criticism of governments [30], protests [31], or torture by state [32] — especially in poor countries. (See also "activist?").
...Pro-Palestine?
Social media actively blocks pro-Palestinian viewpoints [33].
...Have a special health condition?
Pharmacies hand over your medical data to the police without a search warrant [34]. As mentioned, your medical data is worth 10-40 times more on the black market than your credit card data [8].
...Have ever bought anything?
Capitalism is one of the main dangers in selling your personal data. Many large companies use your information to estimate your income, sell you products you don't really need [36][37][38], or manipulate prices [37].
- For example, online retailers know that people with low income are more likely to make urgent purchases, so they set higher prices for them and cancel discounts [39][40].
- Some financial and insurance companies use social graphs to determine interest rates and insurance premiums. This often forces low-income people to pay more — this phenomenon is known as "poverty-premium" [41].
- Orbitz directs Mac users to more expensive hotels because they overpay for Apple electronics. [42].
- Target charges customer(s) higher prices when they were physically close to the store and unlikely to look for an alternative. [43]
- McDonalds hired surveillance company Silverpush to link non-consensual audio data from its mobile app with audio from Youtube or television to show "relevant ads" across platforms. [44]
There is no end to examples of sleazy sales pitches — and these are just the ones that have come to public knowledge!
...Mom, Dad, Parent?
Parents Club Bounty fined £400,000 for selling user data — the company illegally transferred 34.4 million records to 39 companies [45]. Popular family safety app Life360 sells the precise location data of tens of millions of its users [46]. Would you trust your children's personal data and location to a stranger? After all, according to some reports, pedophiles [47] and kidnappers can use this data to find victims.
...Working on a social profession?
Do you work as a politician, teacher, priest, curator, doctor, therapist or anyone else, so that your work causes you to hold a lot of vulnerable personal data of others for which you are responsible? You should be concerned about keeping them safe — after all, this data is being sold profitably [48].
...In a relationship?
Perhaps you'd like to keep the intimate details of your relationship private? In the most grotesque of news stories on the subject, an Australian border control officer returned a citizen's phone after a forced search at the airport with the words, "It was nice to see some good porn again," referring to nude photos of his girlfriend [49].
...Traveler?
The popular hotel chain AirBNB allows cameras inside its properties [56].
...Student?
Be vigilant: schools use tracking techniques to catch and severely penalize you for using vape (electronic cigarettes) [51].
...Driver?
Cars have become computers on wheels: they "have an unrivaled ability to watch, listen and gather information about what you are doing and where you are going" [55] [55]. This information is then shared or sold to data brokers, law enforcement, and others. Of the 25 car brands studied, 56% share your data with law enforcement in response to an informal request, and 84% share or sell your personal data [55].
Information is also willingly purchased by insurance companies [58], and even your partner(s) can use it to spy on you [59].
...Use technology to clean?
Robot vacuum cleaners not only suck up dust, but also scan your home [53]. As hard as it may be to believe, Amazon is actually using this data to make you more likely to buy things you don't need [54].
...Residen of a country with a democratic system?
There was a case not too long ago where Facebook was caught manipulating a major election: the company used our social graphs to distort our view of the real world and manipulate our votes [35].
...Citizen of a state?
In the context of the state, innocuous conversations can put you in danger, even if you have nothing to hide. One of the most shocking stories is the aforementioned experience of Mohamedou Ould Salahi [3], described in his memoirs and featured in the movie The Moorish Man. He was placed in the Guantanamo camp without trial and tortured there for 15 years for making a phone call to a relative in Afghanistan — he was suspected of involvement in the 9/11 attacks, although he had lived in Germany for the previous 10 years.
Ordinary people are arrested and pressured for what they share online, even through their "anonymous" accounts, even in democracies, even if it was legal, even if you are not a man [50].
"Give me six lines written by the most honest man, and I will find in them something for which he will be executed on the gallows" — Cardinal de Richelieu
...Human?
Why do you wear clothes? Why would you rather prefer an opaque toilet to a transparent one, or a bedroom without cameras to a monitored bedroom? Why might you not want to share your political views, sexual orientation, or gender identity with your grandmother, a teacher, or a police officer, even if you think there is nothing wrong with them? Why might you not want to share your social media gallery or passwords with your aunt, a social worker, or a 4chan user, even if you haven't done anything illegal directly?
What if I offered to send your social media passwords, bank account passwords, your medical information, address, and photos to my email — promise I wouldn't use them for anything bad: I just want to keep them on my hard drive for the security of your own data? Do you really have nothing to hide?
What if I told you that automated surveillance has reached such a scale that megacorporations can guess what you're thinking [60] about? Does that bother you? If so — I wouldn't be surprised.
Privacy has always been a part of human life, a normal part of it. The way we live now is a highly unnatural state for humans; it has never been normal. You don't have to have something to hide to want to not share all the details of your personal life with others.
Conclusion
The longer we give up the fight for privacy rights, the more Leviathan gains momentum. Do you think Orwell's world of "1984" was built overnight? No! People sacrificed the rights to privacy, anonymity, freedom of information — step by step. And the first step towards dystopia is marginalizing people who worry about their anonymity: reducing them to "tinfoil hat wearers" and "those who really think that THEY is reading your emails."
So what do we do? We must not think that "there's nothing we can do about it", or that "we've already lost". Instead, we need to:
- Spread the word about why privacy is important, and why it's worth caring about;
- Use private, free, decentralized analogs to popular services (e.g. Session instead of Telegram, NOSTR instead of Twitter, DuckDuckGo instead of Google);
- Support the right to privacy for the sake of the rest (e.g., so far only a few people use private messengers — states know that those who use them are hiding something. But if half of the population starts using them, it will be impossible to single out anyone special);
- Ask more often why companies know so much about us, and how is it even legal;
- Participate in politics. Politics is not an "observation sport": if democracy doesn't work, we are responsible for making it work. The very top of such participation is supporting organizations fighting for privacy rights
"Saying you don't care about privacy because you have nothing to hide is like saying you don't care about free speech because you have nothing to say. But even if you don't enjoy a right at that particular moment, others may need it. And to say that you don't care about a right because you don't need it right now is the most antisocial thing you can do." — Edward Snowden
Sources:
[1] https://theintercept.com/2021/01/30/lapd-palantir-data-driven-policing/
[2] https://www.theguardian.com/us-news/2020/dec/03/aclu-seeks-release-records-data-us-collected-via-muslim-app-used-millions
[3] https://www.npr.org/2019/11/14/778944195/a-legacy-of-torture-is-preventing-trials-at-guant-namo
[4] https://www.vox.com/technology/2023/6/16/23762403/data-odni-report-wyden
[5] https://www.vox.com/recode/22587248/grindr-app-location-data-outed-priest-jeffrey-burrill-pillar-data-harvesting
[6] https://nypost.com/2022/05/02/grindr-sold-data-about-users-precise-locations-for-years-report/
[7] https://www.theguardian.com/technology/2018/apr/03/grindr-shared-information-about-users-hiv-status-with-third-parties
[8] https://www.cyberpolicy.com/cybersecurity-education/why-medical-records-are-10-times-more-valuable-than-credit-card-info
[9] https://www.politico.com/news/2024/02/13/planned-parenthood-location-track-abortion-ads-00141172
[10] "As of 2022, countries that legally allow abortion on request or for socioeconomic reasons comprise about 60% of the world's population", https://en.wikipedia.org/wiki/Abortion_law
[11] https://en.wikipedia.org/wiki/Anti-abortion_violence
[12] https://www.justice.gov/crt/recent-cases-violence-against-reproductive-health-care-providers
[13] https://www.indiatoday.in/technology/news/story/disha-ravi-arrest-puts-privacy-of-all-google-india-users-in-doubt-1769772-2021-02-16
[14] https://proton.me/blog/climate-activist-arrest
[15] https://www.aclunc.org/blog/facebook-instagram-and-twitter-provided-data-access-surveillance-product-marketed-target
[16] https://www.gotchseo.com/google-biased/
[17] Google does quite a bit of censorship in its services in general: https://en.wikipedia.org/wiki/Censorship_by_Google
[18] https://www.taiwannews.com.tw/en/news/3933777
[19] https://www.theverge.com/2020/5/26/21270290/youtube-deleting-comments-censorship-chinese-communist-party-ccp
[20] https://www.npr.org/2020/08/04/898836158/class-action-lawsuit-claims-tiktok-steals-kids-data-and-sends-it-to-china
[21] https://www.nytimes.com/2018/08/16/technology/google-employees-protest-search-censored-china.html
[22] https://ru.wikipedia.org/wiki/%D0%92%D0%BE%D0%B8%D0%BD%D1%81%D0%BA%D0%B0%D1%8F_%D0%BE%D0%B1%D1%8F%D0%B7%D0%B0%D0%BD%D0%BD%D0%BE%D1%81%D1%82%D1%8C
[23] https://focus.ua/voennye-novosti/626982-ot-doprosov-do-operativnyh-meropriyatij-v-nacpolicii-rasskazali-o-poiske-uklonistov
[24] https://www.bbc.com/russian/features-63346138
[25] https://www.rbc.ua/ukr/styler/k-zaraz-karayut-uhilyantiv-vid-mobilizatsiyi-1707820307.html
[26] https://www.mrarchivist.com/results/entry/4591/; The prohibition of voting because a man has not registered to vote is contrary to Article 21 of the Universal Declaration of Human Rights.
[27] https://www.nbcnews.com/id/wbna17880969
[28] https://www.rferl.org/a/google-reportedly-removes-navalny-ad-after-russian-government-complains/29478844.html
[29] https://www.theguardian.com/world/2021/sep/17/apple-and-google-accused-of-political-censorship-over-alexei-navalny-app
[30] https://nordicmonitor.com/2023/09/google-youtube-accused-of-censoring-erdogan-critics/
[31] https://www.medianama.com/2024/02/223-youtube-blocks-videos-protests-job-aspirants-bihar/
[32] https://edition.cnn.com/2007/WORLD/meast/11/29/youtube.activist/
[33] https://www.aljazeera.com/features/2023/10/24/shadowbanning-are-social-media-giants-censoring-pro-palestine-voices
[34] https://thehill.com/business/4355894-pharmacies-sharing-medical-data-without-warrant/
[35] https://en.wikipedia.org/wiki/Facebook%E2%80%93Cambridge_Analytica_data_scandal
[36] https://usercentrics.com/knowledge-hub/data-is-the-new-gold-how-and-why-it-is-collected-and-sold/
[37] https://knowledge.wharton.upenn.edu/article/data-shared-sold-whats-done/
[38] https://www.eff.org/deeplinks/2020/11/visa-wants-buy-plaid-and-it-transaction-data-millions-people
[39] https://supreme.findlaw.com/legal-commentary/websites-that-charge-different-customers-different-prices.html
[40] https://policyreview.info/articles/analysis/does-everyone-have-price-understanding-peoples-attitude-towards-online-and-offline
[41] https://fairbydesign.com/povertypremium
[42] https://www.wsj.com/articles/SB10001424052702304458604577488822667325882
[43] https://www.bizjournals.com/twincities/news/2019/02/01/report-targets-app-charges-higher-prices-to.html
[44] https://www.digitaltrends.com/mobile/silverpush-app-tracking-spying-use-rises-new/
[45] https://www.theguardian.com/technology/2019/apr/12/parenting-club-bounty-fined-selling-users-data
[46] https://themarkup.org/privacy/2021/12/06/the-popular-family-safety-app-life360-is-selling-precise-location-data-on-its-tens-of-millions-of-user
[47] https://www.the-sun.com/news/3740183/paedophile-snachat-maps-victims-tesco/
[48] https://www.experian.com/blogs/ask-experian/heres-how-much-your-personal-information-is-selling-for-on-the-dark-web/
[49] https://micky.com.au/aussie-ex-pat-will-never-return-after-digital-strip-search-reveals-sex-tapes/
[50] https://www.dailymail.co.uk/news/article-11282263/Moment-police-swoop-house-devout-catholic-mother-malicious-online-posts.html
[51] https://apnews.com/article/vaping-surveillance-technology-schools-982128348c683b9d54c7a307c5b1fdc6
[52] https://www.politico.com/news/2023/05/19/fbi-surveillance-black-lives-matter-protesters-00097924
[53] https://www.welivesecurity.com/en/privacy/gathering-dust-and-data-how-robotic-vacuums-can-spy-on-you/
[54] https://www.reuters.com/markets/deals/amazons-irobot-deal-eu-antitrust-crosshairs-2023-07-06/
[55] https://foundation.mozilla.org/en/privacynotincluded/articles/its-official-cars-are-the-worst-product-category-we-have-ever-reviewed-for-privacy/
[56] https://ru.airbnb.com/help/article/3061
[57] https://newrepublic.com/article/179397/evangelical-app-targeting-immigrants-surveillance
[58] https://www.nytimes.com/2024/03/11/technology/carmakers-driver-tracking-insurance.html
[59] https://www.nytimes.com/2023/12/31/technology/car-trackers-gps-abuse.html
[60] https://www.zdnet.com/article/google-even-knows-what-youre-thinking/*This does not mean that ProtonMail is insecure: the service regularly wins many court cases on the subject of disclosure of user data; it means that the use of ProtonMail was not private enough (in this case, without VPN/SPN/TOR).
-
 @ 0f1b5961:868242bd
2024-03-22 17:12:48
@ 0f1b5961:868242bd
2024-03-22 17:12:48Trying out the highligher.com editor...
heaven : earth governance : generation emanation : emergence selection : variation
-
 @ 000002de:c05780a7
2024-03-22 16:12:10
@ 000002de:c05780a7
2024-03-22 16:12:10If you are truly a beginning bitcoiner or if this is your first bitcoin cycle (bitcoin has cycles of market price spikes and dumps) then there is something emotional to be aware of. FOMO.
Fear of missing out is real. When you see bitcoin rising in market price on exchanges emotions can do funny things to even the most rational and thoughtful person. A word of wisdom that you hear often is, "stay humble, stack sats". I'm not going to try to tell you what you should do but be aware. You can make some mistakes when emotions cloud your judgement.
When bitcoin prices begin to rise as they have over the last month you might be tempted to do risky things. Things like over extend yourself. What I do, and what many of us do is we just always buy. That's the stack sats part. Start getting paid a portion of your pay check in bitcoin for example. Each week use Robosats to buy bitcoin without KYC. Or find another way to regularly secure some bitcoin for your future.
I am advising this because I have allowed emotion to direct me to strongly in the past. Don't get me wrong. I didn't get wrecked. I do not regret any bitcoin I've acquired. I feel this way because I value bitcoin far above its current market price. I actually get more excited when market price goes down. That said, be prepared.
Be prepared for bitcoin to keep going up but also be prepared for an 80% draw down. That FOMO you feel now might be replaced with dread for letting emotions cloud your judgement. Just be aware. We are hearing many massive predictions from the dudes that get attention from speculating on bitcoins new ATH. It happens every cycle. It affects us all.
Stay humble, stack sats.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28nostr - Notes and Other Stuff Transmitted by Relays
The simplest open protocol that is able to create a censorship-resistant global "social" network once and for all.
It doesn't rely on any trusted central server, hence it is resilient; it is based on cryptographic keys and signatures, so it is tamperproof; it does not rely on P2P techniques, therefore it works.
Very short summary of how it works, if you don't plan to read anything else:
Everybody runs a client. It can be a native client, a web client, etc. To publish something, you write a post, sign it with your key and send it to multiple relays (servers hosted by someone else, or yourself). To get updates from other people, you ask multiple relays if they know anything about these other people. Anyone can run a relay. A relay is very simple and dumb. It does nothing besides accepting posts from some people and forwarding to others. Relays don't have to be trusted. Signatures are verified on the client side.
This is needed because other solutions are broken:
The problem with Twitter
- Twitter has ads;
- Twitter uses bizarre techniques to keep you addicted;
- Twitter doesn't show an actual historical feed from people you follow;
- Twitter bans people;
- Twitter shadowbans people.
- Twitter has a lot of spam.
The problem with Mastodon and similar programs
- User identities are attached to domain names controlled by third-parties;
- Server owners can ban you, just like Twitter; Server owners can also block other servers;
- Migration between servers is an afterthought and can only be accomplished if servers cooperate. It doesn't work in an adversarial environment (all followers are lost);
- There are no clear incentives to run servers, therefore they tend to be run by enthusiasts and people who want to have their name attached to a cool domain. Then, users are subject to the despotism of a single person, which is often worse than that of a big company like Twitter, and they can't migrate out;
- Since servers tend to be run amateurishly, they are often abandoned after a while — which is effectively the same as banning everybody;
- It doesn't make sense to have a ton of servers if updates from every server will have to be painfully pushed (and saved!) to a ton of other servers. This point is exacerbated by the fact that servers tend to exist in huge numbers, therefore more data has to be passed to more places more often;
- For the specific example of video sharing, ActivityPub enthusiasts realized it would be completely impossible to transmit video from server to server the way text notes are, so they decided to keep the video hosted only from the single instance where it was posted to, which is similar to the Nostr approach.
The problem with SSB (Secure Scuttlebutt)
- It doesn't have many problems. I think it's great. In fact, I was going to use it as a basis for this, but
- its protocol is too complicated because it wasn't thought about being an open protocol at all. It was just written in JavaScript in probably a quick way to solve a specific problem and grew from that, therefore it has weird and unnecessary quirks like signing a JSON string which must strictly follow the rules of ECMA-262 6th Edition;
- It insists on having a chain of updates from a single user, which feels unnecessary to me and something that adds bloat and rigidity to the thing — each server/user needs to store all the chain of posts to be sure the new one is valid. Why? (Maybe they have a good reason);
- It is not as simple as Nostr, as it was primarily made for P2P syncing, with "pubs" being an afterthought;
- Still, it may be worth considering using SSB instead of this custom protocol and just adapting it to the client-relay server model, because reusing a standard is always better than trying to get people in a new one.
The problem with other solutions that require everybody to run their own server
- They require everybody to run their own server;
- Sometimes people can still be censored in these because domain names can be censored.
How does Nostr work?
- There are two components: clients and relays. Each user runs a client. Anyone can run a relay.
- Every user is identified by a public key. Every post is signed. Every client validates these signatures.
- Clients fetch data from relays of their choice and publish data to other relays of their choice. A relay doesn't talk to another relay, only directly to users.
- For example, to "follow" someone a user just instructs their client to query the relays it knows for posts from that public key.
- On startup, a client queries data from all relays it knows for all users it follows (for example, all updates from the last day), then displays that data to the user chronologically.
- A "post" can contain any kind of structured data, but the most used ones are going to find their way into the standard so all clients and relays can handle them seamlessly.
How does it solve the problems the networks above can't?
- Users getting banned and servers being closed
- A relay can block a user from publishing anything there, but that has no effect on them as they can still publish to other relays. Since users are identified by a public key, they don't lose their identities and their follower base when they get banned.
- Instead of requiring users to manually type new relay addresses (although this should also be supported), whenever someone you're following posts a server recommendation, the client should automatically add that to the list of relays it will query.
- If someone is using a relay to publish their data but wants to migrate to another one, they can publish a server recommendation to that previous relay and go;
- If someone gets banned from many relays such that they can't get their server recommendations broadcasted, they may still let some close friends know through other means with which relay they are publishing now. Then, these close friends can publish server recommendations to that new server, and slowly, the old follower base of the banned user will begin finding their posts again from the new relay.
-
All of the above is valid too for when a relay ceases its operations.
-
Censorship-resistance
- Each user can publish their updates to any number of relays.
-
A relay can charge a fee (the negotiation of that fee is outside of the protocol for now) from users to publish there, which ensures censorship-resistance (there will always be some Russian server willing to take your money in exchange for serving your posts).
-
Spam
-
If spam is a concern for a relay, it can require payment for publication or some other form of authentication, such as an email address or phone, and associate these internally with a pubkey that then gets to publish to that relay — or other anti-spam techniques, like hashcash or captchas. If a relay is being used as a spam vector, it can easily be unlisted by clients, which can continue to fetch updates from other relays.
-
Data storage
- For the network to stay healthy, there is no need for hundreds of active relays. In fact, it can work just fine with just a handful, given the fact that new relays can be created and spread through the network easily in case the existing relays start misbehaving. Therefore, the amount of data storage required, in general, is relatively less than Mastodon or similar software.
-
Or considering a different outcome: one in which there exist hundreds of niche relays run by amateurs, each relaying updates from a small group of users. The architecture scales just as well: data is sent from users to a single server, and from that server directly to the users who will consume that. It doesn't have to be stored by anyone else. In this situation, it is not a big burden for any single server to process updates from others, and having amateur servers is not a problem.
-
Video and other heavy content
-
It's easy for a relay to reject large content, or to charge for accepting and hosting large content. When information and incentives are clear, it's easy for the market forces to solve the problem.
-
Techniques to trick the user
- Each client can decide how to best show posts to users, so there is always the option of just consuming what you want in the manner you want — from using an AI to decide the order of the updates you'll see to just reading them in chronological order.
FAQ
- This is very simple. Why hasn't anyone done it before?
I don't know, but I imagine it has to do with the fact that people making social networks are either companies wanting to make money or P2P activists who want to make a thing completely without servers. They both fail to see the specific mix of both worlds that Nostr uses.
- How do I find people to follow?
First, you must know them and get their public key somehow, either by asking or by seeing it referenced somewhere. Once you're inside a Nostr social network you'll be able to see them interacting with other people and then you can also start following and interacting with these others.
- How do I find relays? What happens if I'm not connected to the same relays someone else is?
You won't be able to communicate with that person. But there are hints on events that can be used so that your client software (or you, manually) knows how to connect to the other person's relay and interact with them. There are other ideas on how to solve this too in the future but we can't ever promise perfect reachability, no protocol can.
- Can I know how many people are following me?
No, but you can get some estimates if relays cooperate in an extra-protocol way.
- What incentive is there for people to run relays?
The question is misleading. It assumes that relays are free dumb pipes that exist such that people can move data around through them. In this case yes, the incentives would not exist. This in fact could be said of DHT nodes in all other p2p network stacks: what incentive is there for people to run DHT nodes?
- Nostr enables you to move between server relays or use multiple relays but if these relays are just on AWS or Azure what’s the difference?
There are literally thousands of VPS providers scattered all around the globe today, there is not only AWS or Azure. AWS or Azure are exactly the providers used by single centralized service providers that need a lot of scale, and even then not just these two. For smaller relay servers any VPS will do the job very well.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28How IPFS is broken
I once fell for this talk about "content-addressing". It sounds very nice. You know a certain file exists, you know there are probably people who have it, but you don't know where or if it is hosted on a domain somewhere. With content-addressing you can just say "start" and the download will start. You don't have to care.
Other magic properties that address common frustrations: webpages don't go offline, links don't break, valuable content always finds its way, other people will distribute your website for you, any content can be transmitted easily to people near you without anyone having to rely on third-party centralized servers.
But you know what? Saying a thing is good doesn't automatically make it possible and working. For example: saying stuff is addressed by their content doesn't change the fact that the internet is "location-addressed" and you still have to know where peers that have the data you want are and connect to them.
And what is the solution for that? A DHT!
DHT?
Turns out DHTs have terrible incentive structure (as you would expect, no one wants to hold and serve data they don't care about to others for free) and the IPFS experience proves it doesn't work even in a small network like the IPFS of today.
If you have run an IPFS client you'll notice how much it clogs your computer. Or maybe you don't, if you are very rich and have a really powerful computer, but still, it's not something suitable to be run on the entire world, and on web pages, and servers, and mobile devices. I imagine there may be a lot of unoptimized code and technical debt responsible for these and other problems, but the DHT is certainly the biggest part of it. IPFS can open up to 1000 connections by default and suck up all your bandwidth -- and that's just for exchanging keys with other DHT peers.
Even if you're in the "client" mode and limit your connections you'll still get overwhelmed by connections that do stuff I don't understand -- and it makes no sense to run an IPFS node as a client, that defeats the entire purpose of making every person host files they have and content-addressability in general, centralizes the network and brings back the dichotomy client/server that IPFS was created to replace.
Connections?
So, DHTs are a fatal flaw for a network that plans to be big and interplanetary. But that's not the only problem.
Finding content on IPFS is the most slow experience ever and for some reason I don't understand downloading is even slower. Even if you are in the same LAN of another machine that has the content you need it will still take hours to download some small file you would do in seconds with
scp-- that's considering that IPFS managed to find the other machine, otherwise your command will just be stuck for days.Now even if you ignore that IPFS objects should be content-addressable and not location-addressable and, knowing which peer has the content you want, you go there and explicitly tell IPFS to connect to the peer directly, maybe you can get some seconds of (slow) download, but then IPFS will drop the connection and the download will stop. Sometimes -- but not always -- it helps to add the peer address to your bootstrap nodes list (but notice this isn't something you should be doing at all).
IPFS Apps?
Now consider the kind of marketing IPFS does: it tells people to build "apps" on IPFS. It sponsors "databases" on top of IPFS. It basically advertises itself as a place where developers can just connect their apps to and all users will automatically be connected to each other, data will be saved somewhere between them all and immediately available, everything will work in a peer-to-peer manner.
Except it doesn't work that way at all. "libp2p", the IPFS library for connecting people, is broken and is rewritten every 6 months, but they keep their beautiful landing pages that say everything works magically and you can just plug it in. I'm not saying they should have everything perfect, but at least they should be honest about what they truly have in place.
It's impossible to connect to other people, after years there's no js-ipfs and go-ipfs interoperability (and yet they advertise there will be python-ipfs, haskell-ipfs, whoknowswhat-ipfs), connections get dropped and many other problems.
So basically all IPFS "apps" out there are just apps that want to connect two peers but can't do it manually because browsers and the IPv4/NAT network don't provide easy ways to do it and WebRTC is hard and requires servers. They have nothing to do with "content-addressing" anything, they are not trying to build "a forest of merkle trees" nor to distribute or archive content so it can be accessed by all. I don't understand why IPFS has changed its core message to this "full-stack p2p network" thing instead of the basic content-addressable idea.
IPNS?
And what about the database stuff? How can you "content-address" a database with values that are supposed to change? Their approach is to just save all values, past and present, and then use new DHT entries to communicate what are the newest value. This is the IPNS thing.
Apparently just after coming up with the idea of content-addressability IPFS folks realized this would never be able to replace the normal internet as no one would even know what kinds of content existed or when some content was updated -- and they didn't want to coexist with the normal internet, they wanted to replace it all because this message is more bold and gets more funding, maybe?
So they invented IPNS, the name system that introduces location-addressability back into the system that was supposed to be only content-addressable.
And how do they manage to do it? Again, DHTs. And does it work? Not really. It's limited, slow, much slower than normal content-addressing fetches, most of the times it doesn't even work after hours. But still although developers will tell it is not working yet the IPFS marketing will talk about it as if it was a thing.
Archiving content?
The main use case I had for IPFS was to store content that I personally cared about and that other people might care too, like old articles from dead websites, and videos, sometimes entire websites before they're taken down.
So I did that. Over many months I've archived stuff on IPFS. The IPFS API and CLI don't make it easy to track where stuff are. The
pincommand doesn't help as it just throws your pinned hash in a sea of hashes and subhashes and you're never able to find again what you have pinned.The IPFS daemon has a fake filesystem that is half-baked in functionality but allows you to locally address things by names in a tree structure. Very hard to update or add new things to it, but still doable. It allows you to give names to hashes, basically. I even began to write a wrapper for it, but suddenly after many weeks of careful content curation and distribution all my entries in the fake filesystem were gone.
Despite not having lost any of the files I did lose everything, as I couldn't find them in the sea of hashes I had in my own computer. After some digging and help from IPFS developers I managed to recover a part of it, but it involved hacks. My things vanished because of a bug at the fake filesystem. The bug was fixed, but soon after I experienced a similar (new) bug. After that I even tried to build a service for hash archival and discovery, but as all the problems listed above began to pile up I eventually gave up. There were also problems of content canonicalization, the code the IPFS daemon use to serve default HTML content over HTTP, problems with the IPFS browser extension and others.
Future-proof?
One of the core advertised features of IPFS was that it made content future-proof. I'm not sure they used this expression, but basically you have content, you hash that, you get an address that never expires for that content, now everybody can refer to the same thing by the same name. Actually, it's better: content is split and hashed in a merkle-tree, so there's fine-grained deduplication, people can store only chunks of files and when a file is to be downloaded lots of people can serve it at the same time, like torrents.
But then come the protocol upgrades. IPFS has used different kinds of hashing algorithms, different ways to format the hashes, and will change the default algorithm for building the merkle-trees, so basically the same content now has a gigantic number of possible names/addresses, which defeats the entire purpose, and yes, files hashed using different strategies aren't automagically compatible.
Actually, the merkle algorithm could have been changed by each person on a file-by-file basis since the beginning (you could for example split a book file by chapter or page instead of by chunks of bytes) -- although probably no one ever did that. I know it's not easy to come up with the perfect hashing strategy in the first go, but the way these matters are being approached make me wonder that IPFS promoters aren't really worried about future-proof, or maybe we're just in Beta phase forever.
Ethereum?
This is also a big problem. IPFS is built by Ethereum enthusiasts. I can't read the mind of people behind IPFS, but I would imagine they have a poor understanding of incentives like the Ethereum people, and they tend towards scammer-like behavior like getting a ton of funds for investors in exchange for promises they don't know they can fulfill (like Filecoin and IPFS itself) based on half-truths, changing stuff in the middle of the road because some top-managers decided they wanted to change (move fast and break things) and squatting fancy names like "distributed web".
The way they market IPFS (which is not the main thing IPFS was initially designed to do) as a "peer-to-peer cloud" is very seductive for Ethereum developers just like Ethereum itself is: as a place somewhere that will run your code for you so you don't have to host a server or have any responsibility, and then Infura will serve the content to everybody. In the same vein, Infura is also hosting and serving IPFS content for Ethereum developers these days for free. Ironically, just like the Ethereum hoax peer-to-peer money, IPFS peer-to-peer network may begin to work better for end users as things get more and more centralized.
More about IPFS problems:
- IPFS problems: Too much immutability
- IPFS problems: General confusion
- IPFS problems: Shitcoinery
- IPFS problems: Community
- IPFS problems: Pinning
- IPFS problems: Conceit
- IPFS problems: Inefficiency
- IPFS problems: Dynamic links
See also
- A crappy course on torrents, on the protocol that has done most things right
- The Tragedy of IPFS in a series of links, an ongoing Twitter thread.
-
 @ e968e50b:db2a803a
2024-03-22 15:49:38
@ e968e50b:db2a803a
2024-03-22 15:49:38ENJOY!*
https://bitcoinwhacamole.vercel.app/
*I'm pretty sure it's actually impossible for a normal human to win, but there is a little end screen as a reward if you can accomplish the impossible. It might be easier on mobile.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A vision for content discovery and relay usage for basic social-networking in Nostr
Or how to make a basic "social-networking" application using the Nostr protocol that is safe and promotes decentralization.
The basic app views
Suppose a basic "social-networking" app is like Twitter. In that, one has basically 3 views:
- A home feed that shows all notes from everybody you follow;
- A profile view from a specific user that shows all notes from that user;
- A replies view that shows all replies to one specific note.
Some Nostr clients may want to also provide another view, the global feed which shows posts from everybody.
A simple classification of relays
And suppose that all existing relays can be classified in 3 groups (according to one's subjective evaluation):
- spammy relays, in which people of any kind can post whatever they want with no filters at all;
- safe relays, in which there are some barriers to entry, like requiring a fee, or requiring some cumbersome user registration process, and spammers or people who post bad things are banned -- but this is still a relay fundamentally open to anyone (although this is also subjective depending on the kind of restrictions);
- closed relays, in which only certain kinds of people enter, for example, members of a group of friends or a closed online community.
How to follow and find posts from a given profile
To follow someone on Nostr, it is necessary to know one or more relays in which that person is publishing their notes, otherwise it is impossible to fetch anything from them.
When a user starts to follow someone, that may be done through 4 different ways:
- from seeing that person in the app
- using an
nprofileURI - using a NIP-05 address
- using a bare pubkey ('npub`)
Situation 1 may happen when that person is seen in the replies of yours or someone else's post, on a global feed post, or from a note referenced or republished from them by someone else. When that happens, it is expected that the references (in
eandptags) contain relay URLs. We must them inject that information to tentatively associate that person with a relay URL at that first contact.In situations 2 and 3 both the
nprofileand the NIP-05 addresses should contain a list of preferred relays for that person, so we can bootstrap the relay list for that person based on that.In situation 4 there is no relay list, so we must either prompt the user through an annoying popup or something -- or it can try searching for that pubkey in one of their known relays. This remains an option for the other methods too.
Once we have relay URLs for a given profile we can use these relays to query notes from that pubkey. As time passes that user may migrate to other relays, or it may become known that the user is also posting to other relays. To make sure these things are discovered, we must pay attention to hints sent in tags of all events seen everywhere -- from anyone --, and also events of kind 2 and 3, and upgrade our local database that has the knowledge of relationship between profiles and relays accordingly.
Rendering the app views
From what we've gathered until now, we can easily render the home feed and the profile view. To do that it just uses local information about relationships between profiles and relays and fetch notes:
- for the home feed, from all people we're following;
- for the profile view, from just that specific profile.
Since we'll be asking for very specific data from these relays, we do not care about where they're safe or not. They will never send us spam (and if they do that will just be filtered out since it wouldn't match our strict filter).
Now whenever the user clicks on a note we will want to display the replies view. In this case we will just query only the safe and the closed relays, since otherwise spam might be injected into the application. The same principle applies to the global feed view.
Other heuristics and corner cases
There are probably many corner cases not covered in this document. This was meant to just describe one way that seems to me to be sufficiently robust for a decentralized Nostr.
For example, how to display a note that was referenced by someone? If it has a relay hint we query that relay. If it doesn't we can try the relays associated with the person who have just mentioned it, or the same relay we've just seen the note that mentioned it -- as, when mentioning it, one might have published it directly to their own relays -- and so on. But all this may fail and then it is probably not a big deal.
Final thoughts
More important than all, is that we must keep in mind that Nostr is just a very loose set of servers with basically no connection between them, there are no guarantees of anything, and the process of keeping connected to others and finding content must be addressed through many different hackish attempts. To write Nostr applications and to use Nostr one must embrace the inherent chaos.
-
 @ 95a69326:6ac402e2
2024-01-14 11:15:12
@ 95a69326:6ac402e2
2024-01-14 11:15:12Bitcoin Romanticism: My Bitcoin Journey
The Beginnings: Indifference
In 2016, I was introduced to Bitcoin, and I discarded it. Swap the year for any other, and that sentence will resonate with many, maybe even you. So will the rest of my Bitcoin beginnings.
There was nothing exciting about it. From a technology standpoint, the mainstream narrative was portraying Bitcoin as the old dog, the first of its kind, the proof of concept. The word on the street was: “blockchain not Bitcoin”. Bitcoin was not where money could be made either, it had made its run and there was little upside left for it. Instead, the shinny new rocks were all the hype. The message was “crypto not Bitcoin”, and so I followed. As a result, I didn’t get involved with Bitcoin again until much later, almost two years later to be exact. Instead, I read up on tokenomics and how the world was going to change from it. Little did I know I was getting excited about digital barter. Anyhow, I bought some tokens, made money, and then lost the money. Frankly too much money, for a 19 year old.
Over time, I found my way back to Bitcoin and its community (yes Bitcoin has a community, fight me) and I observed the high conviction of Bitcoiners. Conviction was nothing new, every token pumping cheerleader seemed to have conviction. But this conviction felt different. It felt more grounded, more mature, dare I say, more honest. After reading some well-written articles on the topic, I found myself buying a copy of the Bitcoin Standard, and so began the next phase of this journey.
A New Love
I won’t call myself original for changing my views on Bitcoin by reading the Bitcoin Standard, but here we are. It wasn’t until I approached it from the economics side that I re-considered my interest in Bitcoin. Reading the Bitcoin Standard was my first step down the path of sound money, and everything it entails. I came out on the other side of it with a new-found conviction that restoring sound money would cure all ills. And thus a new-found motivation, no, a mission, to get involved with Bitcoin.
From that point, I saw Bitcoin as one of the most profound technologies of our time. Not because I fell in love with a neat data structure that everyone seemed to have gone crazy about, but because of the deep impact it could have on society, and on humans. The technology wasn’t the motivation, all the rest was.
Still, I fell in love, flaws didn’t exist or they were temporary. Bitcoin was the cure to everything. Wealth inequality? Bitcoin was the cure. World hunger? Bitcoin was the cure. Hitting your pinky on a corner? Bitcoin was the cure. There was a revolution happening in front of me, and I had to get involved. On the positive side, I had found a new interest, and a lot of motivation to work on it. On the negative side, I was freshly out of my Data Science bachelor, with a lot of hype around my field, and zero interest to pursue it. After studying abroad for three years, it wasn’t with a lot of joy that I moved back in with my parents, and so began the next phase of this journey.
Lightning Strikes: Getting My Hands Dirty
In 2018, the same friend that had introduced me to Bitcoin, introduced me to Lightning. This time I had learned my lesson, I didn’t discard it, instead I just ignored it for another two years. Funny how these things happen. But now, it’s 2020, and Lightning was my path to contribute to Bitcoin.
So, I’m a technical guy, I graduated in a technical field, but at that point I wouldn’t have called myself a software developer yet. For me programming was about writing python scripts, adjusting variables in statistical models, printing pretty charts and stitching the whole thing together in a Jupyter Notebook (if you know, you know). Those skills were not the most applicable in the Bitcoin space. After writing a few articles about the Lightning Network and graph theory, I realised my career in Bitcoin was going to be short lived if I didn’t try to build something “useful”. And what better way to learn than to start your own project? And for the next six months, I built, my first Bitcoin/Lightning app. It was called Spark. My biggest accomplishment in those six months, was getting shit for the unoriginal name from Fiatjaf. If you don’t know who Fiatjaf is, he’ll be all the more happy for it. Fast forward to mid-2020 and the app is out, ready for its million users. It was a scary moment, going from a lurker to a builder, and exposing my work to the world. The app gained some traction, it got a few mentions and survived a grand total of 6 months before I shut it down. I realised the app was breaking Twitter’s Terms and Conditions, and I didn’t want to risk getting my life’s work rugged by Twitter. I didn’t know it at the time, but it turned out being a prophetic decision not to build a business on top of Twitter’s API. Something something, meant to be, something something.
The app was dead, a year had passed since leaving university and the perspectives of work in Bitcoin and Lightning were bleak. I headed back to the drawing board, or to the chalk board in this case, as I signed up for two more years of university, and so began the next phase of this journey.
The Rebound
What better way to heal from this recent break-up, than to sign up for a rebound relationship: a Masters program in computer science and big data engineering. I had to arm myself with a few more tools before going back on the offensive in my pursuit of a Bitcoin career, and more studying did not sound like a bad idea.
The rebound was helpful, but my mind was still elsewhere, and the little book of Destiny was aware of it. Just a year later, I received a message from my now co-founder and friend, Mick. Mick had been on his own Bitcoin journey. Our paths had crossed before when his journey took him to Lightning, but this time, the conversation was different. Mick had an idea for a Lightning app, and he wanted to talk about it. The idea was simple: to help people fund ideas that come up on Twitter.
After a short hour of conversation, I was on board, and the next call was scheduled to two weeks later. The bi-weekly calls became weekly, then daily, and just two months later, late August 2021, we started building it. Here was my second chance at contributing to Bitcoin! Six months later, the first version of Geyser was out, and a few months after that our first angel investor, Brad Mills, was giving us a chance, and so began the next phase of this journey.
A New Relationship
Fast forward one year, and the side-project had grown enough to deserve a real chance. Geyser became a company and it was time to commit to it fully. After having completed all my Master courses, and only having the thesis left, I took my friend’s and family advice and completed my Master thesis before pursuing my dream job. No, scratch that, I dropped out and got to work. There wasn’t a minute to waste to push Bitcoin adoption, and so began the last phase of this journey.
And They Lived Happily Ever After
For two years, Geyser has continued to grow. It has had its ups and downs, but I couldn’t be happier. I am contributing to Bitcoin, and building one of the coolest (in my very unbiased opinion) projects in the space. And so, they lived happily ever after.
But wait, this is my Bitcoin journey, not my Geyser journey. So what’s the ending on that? Well, what initially sparked me to write this piece was seeing all the recent drama around Bitcoin, Lightning and the scaling debate. No, not the 2015-17 scaling debate (aka: The Block-Size Wars), I mean the 2023-24 scaling debate (aka: the Sidechain-Drivechain-Covenant-Ark-Lightning-Soft-Your-Fork Wars). After a few years of working at the application layer of Bitcoin, I observe those debates from a distance. I have not spent enough time studying them to judge on the merits of each protocol upgrade, but I wanted to share my journey to provide another perspective on the matter. One that isn’t technical.
For all its flaws, I owe Lightning and the Lightning developer community, everything good that has happened to me in this space. Lightning achieved what Bitcoin previously hadn’t, it opened up the possibilities for building consumer apps, for getting involved with Bitcoin at the application layer, rather than at the protocol layer. It made Bitcoin more tangible, more accessible and therefore less intimidating to become a part of.
What was the first Lightning API I used? It was the LNBits and LNPay API. Yes, those mostly custodial, layers of abstraction on top of lightning. But guess, what? Those custodial services dropped the first domino of the most important part of my Bitcoin journey, and if you believe it matters at all, of Geyser’s journey.
As important as protocol debates are, let’s not demonise imperfect solutions. Let’s not turn a blind eye on their qualities. Bitcoin is imperfect, Lightning is imperfect, but they work, and they evolve. And so will continue, my Bitcoin journey.
-
 @ f954303f:6e1b0af5
2024-03-22 13:26:53
@ f954303f:6e1b0af5
2024-03-22 13:26:53我对皇汉作为一个思潮和网络政治派别以及其主张的看法
首先,我客观地是并且认同自己为文化意义上的汉人,Y染色体是标准的汉族类型,而常染色体有一点我无法理解的北方成分,但我不认为汉族以及任何现代民族认同和血统实际或者应该有什么关系。
我认为汉族是亚欧大陆东端季风气侯下的这片连续的农耕区域在历史的演化中出现的一个确实存在很多构建认同材料的族群,也是这片现在叫做中国的土地的主体民族,有着长久而既有成功之处又有一些本质痼疾的文化,而因为它在地理上的偏僻缺少和更广泛的文明世界交流的可能性,因而没有参与、并且也不太可能自发地出现起源于地中海和西欧的现代秩序的构建过程,但存在和外来的因素相适应被构建为一个现代化社会的内生可能性,而这一点是已经在几个地方被证明了的。但我不认为这片土地的如它的名字那样是世界的中心,我也不觉得我们应该像几千年来一样夜郎自大地相信自己是世界上最优越的民族。
汉族是中国历史的主体,虽然这个历史过程也有其他族群的参与,但我不认为参与这片土地历史进程的所有族群在重要性上是平等的。而蒙元、满清这些王朝也确实带有外来侵略者的属性,但也不能否认尤其是满清中后期以中国自居的事实。读宋末、明末的历史时我会代入南宋南明和农民军一方为之惋惜,而满清的剃发令屠城之类的民族压迫也是令人发指的暴行 -- 但我不认为今天的中国存在着能为这些历史事件负责的存在民族认同的人群,为这些事情鼓吹复仇主义是我认为皇汉派别的一种极为愚蠢的基于想象的主张
满清作为中国步入近现代前的最后一个帝制王朝的异族性质影响了一些近代中国历史的走向,但绝不认为今天的中国的近代化的障碍完全或者大部分来自所谓满清遗毒,所谓打断明朝君主立宪资本主义萌芽、文字狱破坏文人脊梁、满清不允许汉人发展科技所以才会落后西方都是无稽之谈,如果中国的最后一个帝制王朝是汉人建立的,它虽然有可能在某些方面减少一些迈向近代化的掣肘(比如慈禧太后的“保大清还是保中国的问题”),但中国在18、19世纪时会因为缺少交流而落后于西方这是肯定的。另一方面,满清作为一个中国的帝制王朝也有其成功的地方,君主专制的集大成并非属于满清的发明创造而是建立在之前无数汉族王朝的探索结果之上的,而在维持传统社会的稳定、增殖这个农业社会的人口这些方面取得了传统王朝意义上的成功,虽然这些成就在近代的前夜显得有些滑稽。总之,作为一个古代王朝的满清在内政上有做的比汉族王朝好的地方,也有不如的地方,有异族的原罪,但从结果上看它不是中国古代最坏的一个王朝,也不是近代落后的所有责任的合适的承担者
另一方面,在领土上满清对以汉族为主体的中国是有贡献的,辽东以北的东北、河套以外的内蒙、敦煌以西的西域、湟水谷地之外的整个青藏高原当然还有外蒙以及比较麻烦的,台湾,都是在清朝被纳入不属于明朝末年的版图而被今天的PRC继承的,而即使是之前汉唐明有羁縻统治的这些领土,满清的控制力也很可能超过了远元朝以外的任何一个中原王朝,这和满族人自身作为内亚人对游牧生活的熟悉和亲近感以及控御能力是有关系。也就是说,我不认为这些地方和以汉族为主体的中国的统一是一种某种辉格史观决定的历史的必然,如果满清没能入关,李自成的大顺能不能打下全部这些领土非常值得怀疑(虽然河套、南满洲之类的地方估计还是会拿下)--而那个位面的现代中国和俄罗斯的分界线会比现实离长城近得多。自然的推论是,今天的PRC统治蒙疆藏的合法性在几乎完全的程度上来自清朝的军事征服,而这个征服靠汉人自己完成的可能性我是表示怀疑的。
基于这种领土现实的汉满蒙回藏五族合一的中华民族认同是不牢固的,在历史上的材料既不丰富,也很可能不是什么必然。但基于现实的领土和人口两方面这些领土和当代以汉族为主体的中国的关系是这样的,领土上,内蒙尤其是南部的河套、整个东北、人口意义上的半个北疆还有整个台湾(但在现实政治意义上是另一回事)都已经被开拓为新的汉地,用游戏里的话说叫造核成功;而新疆南部、西藏以及已经分离的外蒙仍然存在着独立于认同独立于汉族的巨大群体,至于外东北,历史上几乎没有讲汉语的人口居住,今天的主体民族也是俄罗斯人,声索这个地方的可能性几乎为零。民族认同上,苗瑶壮彝等南方民族在历史上和汉族有纠缠不清的联系和极深的文化影响,其认同很难独立于中国存在,把他们和汉族揉进同一个认同体系的问题不是很大,而在现实中这些地方东南亚腹地也几乎不存在政治上独立的可能性。满族作为一个征服者民族的认同已经几乎完全消失,虽然这些年有不少学满语的,但独立于中国的满族认同被重新发明出来的可能性我个人看来非常小。回族的情况类似。以上这些民族和汉人同处于一个国家是没那么拧巴的。而蒙古族在较轻的意义上、尤其是疆藏,在历史上和汉族的领土和文化的联系都远不是周边诸民族最多的,其自身有长久的和汉族无关的文化和身份认同,今天也有未能完全扑灭的独立思潮,认为取消身份证的民族识别就能消灭这些人的民族认同实现天下大同宇内一统是一部分皇汉另一个充满幻想的政治主张。也就是说,这几个地方及其人民从汉族主导的国家分裂出去是有一定认同上的基础的,一些皇汉认为这些地方是汉族的固有领土因此幻想在不影响今日中国统治这些地方的合法性的前提下彻底否认满清的中国性是其又一难以立足的主张。
在现实政治中,我不认为汉族和少数民族的矛盾是今日中国现实中最大的矛盾,估计前五都进不去,更谈不上只占百分之几人口的少数民族反向大规模压迫汉族的事情,这是我认为的皇汉的又一个不现实的主张。因为这百分之几的少数民族里有相当一部分是壮苗土家之类的户口本民族(不过这种户口本少数民族高考加分确实是个恶政,应该取消),而内部认同感较强的维藏等民族的聚居区远离汉族核心区,近几年更是受到巨大的政策束缚,在现实中很少和不住在这些地方汉人发生利害冲突。民族政策里有一个比较大的和汉族平民利益相关的项目是新疆西藏的巨额维稳费用挪用中东部的民生资金,这是皇汉的agenda里比较有关现实的一条。
至于今日的中国的政体是不是汉族的政体,有没有打压汉族,我想这不是个很难回答的问题。中央政治局里似乎一个非汉族都没有,少数民族官运到了副国级(回良玉和一大串政协副主席)就到头了,你要是相信这些人是deep state那你脑补能力我很佩服。今天的CCP在宣传上和文化认同的主张处于一种比较拧巴的状态,一方面,影视剧里连古代的内亚民族都不能提让皇汉跳脚这是真的,另一方面,汉服运动的方兴未艾绝对和官方的默许和鼓励有关系,甚至习近平在西安cosplay万国来朝时你都能看出来点汉官威仪,而对少数民族的同化也是采取的汉化的方式,比如在新疆西藏强制教汉语甚至逼着维族小孩穿汉服读论语祭孔,这种事情历史上的汉族王朝可没少干(搞笑的是满清在云贵也干过)。应该说中共基于其供着的马克思主义意识形态在民族问题上不可能完全采取复古式的宣传,一些文化元素如汉服当国服没有被采取也确实是不符合皇汉的口味,但在内核上我看不出中共是在打压汉族的利益,相反主张移民实边的造核政策可是没少干,尤以十八大以后为甚,在新疆西藏推行的汉化政策力度是很大的,今天还主张中共在宽纵少数民族的人都活在至少七八年以前 -- 这里我有个暴论,就是习近平很可能也有一点点皇汉式的自我认同,虽然他不一定知道这个名字,皇汉也不一定同意。宁夏的洋葱头清真寺在他亲自指挥下被全部改成中式的建筑就是一个例子。至于所谓不允许声讨满族历史罪行、影视剧不让提匈奴之类的问题,基本上完全是出于维稳思维和维护领土完整的需要,不少皇汉把这当成是满遗deep state捣的鬼我只能说想象力不是一般的丰富……还是那句话,要搞皇汉,就做好丢地的心理准备,既要又要是不可能的。
已经写了很多了,总之,我自认为是一个汉族人,但我基本不认为皇汉是一个立足于现实的政治思潮,而是一种基于历史和幻想的大型cosplay(把台湾当华夏神国是一个相当难崩的主张),其最大的问题是,主张的敌人在现实中大概根本就不存在,而关心的议题在普通中国人关心的政治议题中则完全排不上号,比如,皇汉在2022年是怎么看清零共存问题的?你不会想说大白都是满族人吧?又比如,今日中国的经济困境该如何解决?你不会想说搞水晶之夜吧?问题是维友也不是犹太人那种财主…… 基于这一点,我不甚看好皇汉的发展,虽然其关心的尤其是认同和领土问题在中长期的尺度上是一个现实的隐患。
敲这么多字的瑞萍没啥人看,不过这至少证明了在你sub既没有什么皇汉也没有什么人关心皇汉,哈哈
submitted by /u/KailBroflovsky (https://www.reddit.com/user/KailBroflovsky)
[link] (https://www.reddit.com/r/China_irl/comments/1bkz7dd/我对皇汉作为一个思潮和网络政治派别以及其主张的看法/)[comments] (https://www.reddit.com/r/China_irl/comments/1bkz7dd/我对皇汉作为一个思潮和网络政治派别以及其主张的看法/)
#China_irl
https://www.reddit.com/r/China_irl/comments/1bkz7dd/我对皇汉作为一个思潮和网络政治派别以及其主张的看法/
-
 @ cce0989b:b497e608
2024-03-22 12:27:18
@ cce0989b:b497e608
2024-03-22 12:27:18Old Happy: "They are lying to please me." New Happy: “They are telling the truth to help me."
You believe the negative words they speak. So why don't you believe the positive ones? When you think about it, it's completely irrational behavior: you either trust them or you don't, and if you do trust them, then why would you question their kindnesses?
Deep down, you might not believe that you actually deserve their kind words. If that's the case, here's a perspective shift I'd like you to consider trying on: sometimes, other people can see you more clearly than you can see yourself.
Prove this to yourself by thinking about one of your own friends or loved ones who does not see their own strengths. They fret about their appearance—but all you see is their beauty. They dismiss their contributions—but all you see is their impact. You try so hard to get through to them ("You're wonderful, you're gorgeous, you're doing so well!") and yet they never seem to really hear you.
Could the same be true for you? Perhaps those people offering you compliments are trying to help you see yourself. Perhaps you just need to trust them. Perhaps you need to let their words in so that you can start to feel, deep down, that you are deserving of their kindness. Because that is the truth—you are.
-
 @ 4657dfe8:47934b3e
2024-01-08 19:37:37
@ 4657dfe8:47934b3e
2024-01-08 19:37:37Hey,
We're trying to maintain the most up-to-date and interesting list of various "LN apps" (Lightning and Nostr web apps) that can be used with Alby, calling it our Discover Page
However, for the past few weeks... we couldn't encounter anyting fresh and working. And it is very possible we overlooked some must-visit website.
What should we add to the Discover Page? Asking for nice recommendations.
We'll pay 2,100 sats per each! 😊 Cheers 🚀🚀
-
 @ e47a6f25:9e1b807c
2024-03-22 11:11:06
@ e47a6f25:9e1b807c
2024-03-22 11:11:06- How about this external image ?

- Do something to your hair.
- Have you ever eaten a spoon full of peanut butter ?
- Have you ever eaten a spoon full of ketchup ?
- Do you like spiders ?
- How about this external image ?

- How about this external image ?
-
 @ 2edbcea6:40558884
2024-01-07 22:05:42
@ 2edbcea6:40558884
2024-01-07 22:05:42Happy Sunday Folks!
Here’s your #NostrTechWeekly newsletter brought to you by nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk written by nostr:npub1r3fwhjpx2njy87f9qxmapjn9neutwh7aeww95e03drkfg45cey4qgl7ex2.
The #NostrTechWeekly is focused on the more technical happenings in the nostr-verse.
Let’s dive in!
Recent Upgrades to Nostr (AKA NIPs)
1) (Proposed) Update to NIP-07: Nostr Browser Extension
monlovesmango is proposing updates to the capabilities of the Nostr Browser Extensions. Currently, browser extensions are primarily used to enable usage of Nostr clients without giving that client your Nostr private key.
Since NIP 44 was adopted, there are a few new Nostr actions creating encrypted content over Nostr that clients will want users to authorize without requiring users to input their private key. This NIP adds those new Nostr actions as something browser extensions should support going forward.
2) (Proposed) NOSTR Decentralized Advertising Network
ionextdebug is proposing creating a marketplace for advertising that runs over Nostr.
For those unfamiliar, there’s a constant bid and ask process for advertising space on platforms like Youtube or Google Adsense. The sell side is offering up ad space (for example 5-25 seconds at the beginning of a Youtube video for users within a specific demographic), and the buy side is bidding to put their ad in that spot. The highest bid wins the spot. This all happens in milliseconds every time you see an ad online.
This proposal outlines how this could be coordinated over Nostr instead of in Google’s walled garden. The use case would require Nostr to operate in ways it wasn’t designed for, so it may struggle to work in practice, but the NIP is early in the process of development.
Notable Projects
nsecBunker Update 🔐
nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft announced an update to nsecBunker that allows users to an OAuth-like experience when logging into Nostr clients.
Bunker providers are able to provide account creation to Nostr users that feels a lot like signing up for any legacy tech service (username, password, control over what each Nostr client can do on their behalf, etc). This creates a set of Nostr keypairs which are necessary to operate in the Nostr-verse, but they’re stored in the bunker.
When a Nostr client wants a user’s permission to read or write with those keys (e.g., to pull their timeline or help a user post something), the client asks the bunker for permission, which then asks the user if they want to grant that permission. Users are also able to have their bunker remember their selections of grant/reject permissions for a given Nostr client so that things are easier with fewer popups the next time around.
Additionally, users that are created and managed via nsecBunker have a lightning wallet and lightning address created automatically. If nsecBunker could also help folks manage their full Nostr profile (Kind 0 data like profile picture, name, etc,) this could be an out-of-the box solution for clients looking to add a simpler signup/login experience to new users that don’t mind giving up some control.
From what I saw in the code, the data (including Nostr private keys custodied by the bunker) are encrypted at rest, but currently that’s one key to encrypt all keys in the bunker. It may make sense in the future to extend the functionality to give users the ability to encrypt their keys with their own password, but there are downsides to that which may make self-custody the easier option.
There’s no lock-in for users since bunker providers can help users download their keys if they want to self custody or move to another provider.
This could be a foundational tool that allows an ecosystem of bunker providers emerge. Bunkers may be offered as part of Nostr clients, or independently; they may be offered for free, or for a fee. But the opt-in and interchangeable nature means that users will be able to choose what works for them, including moving to self-custody once they see the benefits. And self-custody may even just be a self-hosted bunker. 😉
Faaans 🎨
This is another project from nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft and although it’s still pre-launch, it has been teased as a Patreon replacement built on Nostr.
It seems like this project is one whose purpose and value is clear, but requires many capabilities that are novel to Nostr to be built first. From what I can see Faaans has built:
- Oauth-like flow using new nsecbunker functionality from 👆
- Ability to gate content until a Nostr user pays for it
- The presence of uploads and NIP 98 HTTP Auth makes me think that there’s a non-Nostr backend for handling uploads (maybe to also help with gating the content?)
Anyway, I’m excited to see how it turns out. Cutting out middlemen and giving creators full control over their relationship with their audience could be the killer app that brings a flood of usage and business to the Nostr ecosystem. 💪
Relay Auth to support privacy 🤫
NIP 42 allows relays to require clients to authenticate the user before the relay will take a requested action. This is useful, for example, for keeping DMs private.
By default all Nostr events can be queried by anyone that can connect to the relay. This is part of the magic of Nostr. But there are some kinds of Nostr events that likely should only be readable by a few folks. In the case of DMs, it makes sense to restrict who can download DM-type Nostr events to only those people involved in the DM.
This can be accomplished by relays requiring the user to authenticate with the relay before it returns DM-type Nostr events for that user. This announcement is that Damus looks to be adding support for Relay Auth, which may help with any number of features that can benefit from more privacy.
Latest conversations: Web of Providers
The culture of Nostr currently highly values self-custody, decentralization, and “don’t trust, verify” which is very admirable. It’s woven into the protocol itself. There are downsides to operating on these principles, but most of us judge it to be worth it.
It’s usually possible to have our cake and eat it too (have a nice experience and maintain our values), but it requires technological advances and building products based on those advances. This takes time.
In the interim, devs may build something that’s less self-custodial, less decentralized, but far easier to use. Most of the time this middle ground is far better than using some legacy system that’s completely custodial, centralized, and locks users in. But that’s only the case if it’s a stepping stone to a solution that is everything we need.
Example: Custodial Lightning Wallets
When Wallet of Satoshi stopped operating in the US, I definitely felt how vulnerable the zap ecosystem was to some overzealous bureaucrats. But I was able to switch providers in a matter of minutes and get back to sending and receiving zaps.
I definitely considered moving to Zeus or Mutiny or reviving my own Lightning Node on my Bitcoin Node, but it’s all still too difficult to manage a reliable experience passively.
On net, I’d argue that using custodial lightning is better than using Venmo or something to send and receive zaps. At least we’re operating in Bitcoin and not fiat.
A must have: a competitive ecosystem
The trade offs of a middle ground are easier to live with if there’s a robust and competitive ecosystem.
In the case of custodial lightning wallets, we’re encountering the issue of a lack of robustness. There are only a handful of providers that are able to handle zaps. Losing Wallet of Satoshi was a significant blow. We definitely need more lightning wallet providers in order to be robust against nation-state attack.
The ecosystem must also be competitive. People need to be able to switch providers or move to self custody with little or no cost.
NSecBunker
NSecBunker is an excellent example of a middle ground solution that maintains manageable trade offs while working to discover a more perfect solution.
If Nostr users want to use bunkers, it’s trivially easy to spin up a bunker and provide it to them. Existing clients may spin them up, or people looking to start a business in the Nostr ecosystem may create bunkers (maybe with some extra features) and charge for them.
At the end of the day, this technology is built in such a way that interoperability is easy and users aren’t locked in. The lift for Nostr clients to support bunkers is small, so bunkers may soon be as widely used as the Nostr browser extensions. Since users aren’t locked in to any bunker provider, it’ll be easy for a web of providers to pop up and serve users in unique ways to discover what works best.
Build tech to enable a web of providers
Building Nostr tech that has interoperability top of mind supports the Nostr ethos and enables the ecosystem to develop incrementally without giving up our values. Luckily, the protocol itself encourages interoperability with its very architecture. 🫡
Let’s reward devs when we see them doing this important work, they’re building an immense amount right now and it’s an incredible privilege to witness and beta test. 🍻
Until next time
If you want to see something highlighted, if we missed anything, or if you’re building something we didn’t post about, let us know. DMs welcome at nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk
Stay Classy, Nostr.
-
 @ e1ff3bfd:341be1af
2024-01-06 19:41:35
@ e1ff3bfd:341be1af
2024-01-06 19:41:35Over the last few months it feels the bitcoin community has gotten more and more jaded on lightning. To be honest, this is for good reason, back in 2017 we were promised a decentralized payment network that would always have cheap payments and everyone would be able to run their own node. Nowadays, the average lightning user actually isn't using lightning, they are just using a custodial wallet and the few of that do run lightning nodes often find it a burdensome task. For us at Mutiny Wallet, we are trying to make this better by creating a lightweight self-custodial wallet and in my opinion we have been executing on that dream fairly well. In this post, I'll analyze these issues and present a new way to view lightning and what that means for bitcoin going forward.
First and foremost one of the hardest UX challenges of lightning is channel liquidity. No other payment system has these problems today besides lightning so this often confuses lots of users. To make matters worse, there aren't any practical hacks that we can do to get around this. Muun Wallet used an on-chain wallet + submarine swaps to get around the channel liquidity problem, this worked very well until fees went up and everyone realized it wasn't actually a lightning wallet. The better solution is JIT liquidity like we do in Mutiny or splicing like that is done in Phoenix. These solutions abstract some of it away but not enough, we often get support questions confused on why some payments have fees and others do not. The fact is channel liquidity is not a usable UX for most end users.
The other major pain point of lightning is the offline receive problem. Inherently, you must be online with your private keys to sign and claim a payment. There is technically an ongoing spec proposal to be able to work around this (essentially creating a notification system of when people are online to receive payments), but it doesn't solve the fundamental problem and still has limitations. There has been a few attempts to get around this, most notably was Zeus Pay lightning addresses. These essentially worked by just creating stuck payments and waited for the user to come online to claim, this caused a ton of problems for people and even forced us at Mutiny to block users from paying them because it caused so many force closures. This is a hard problem because the entire rest of the bitcoin/crypto ecosystem works by just copy-paste an address and you can send to it whenever, there isn't caveats around asking your friend to open their wallet. This is further exacerbated by things like lightning address that requires a webserver to even get an invoice in the first place.
Channel liquidity and offline receives in my opinion are the two most obvious reasons why self-custodial lightning is not popular. When most users hear about any of these, they just think screw that and move to a custodial wallet because it is so much easier. If these were our only two problems, I think self-custodial lightning would be fine, it may never be the predominant way people use lightning, but we could get the UX good enough that we have a significant portion of people using lightning in a sovereign way. However, there are more problems under the surface.
Channel liquidity is a problem, but it is also deceptive. When you have 100k sats of inbound liquidity you would think you could receive up to 100k sats, but this isn't the case, often you can't actually receive any. This is because of on-chain fees, when a payment is being made in lightning you are creating pre-signed transactions that have outputs for every in-flight payment, these outputs cost potential on-chain fees and the high on-chain fees go the more it eats into your liquidity. After we've solved most of our force close issues Mutiny this has been number one support request. Even if you do everything right, understand liquidity and have enough for your payment, sometimes it still won't work because on-chain fees are too high. This is always really discouraging because isn't the whole point of lightning to not have to pay on-chain fees? Fundamentally, all current lightning channels could become entirely useless if on-chain fees went high enough because a single payment would require too many reserves. Obviously this is hyperbolic, but I hope I am getting the point across that on-chain fees don't just effect the opening and closing costs of channels, even if you are a diligent node runner that only opens channels when fees are low, that is not enough, your channels need to be large enough to pay for the on-chain fees of each HTLC at any future on-chain fee rate. As on-chain fees go up and up this problem will only get worse.
The proposed solution to these reserve issues are things like anchor channels, package relay, ephemeral anchors, etc. These are all well and good but kind of just mask the problem. They do solve it so the fee reserve can be much lower and possibly zero, however with the tradeoff that you need on-chain funds available to fee-bump your force closes so they can actually get into a block. This again breaks the UX for self-custodial users because they have hold on-chain funds alongside their lightning funds so they can do those on-chain fee bumps. The size requirements for their on-chain funds is still dynamically based on how high on-chain fees can spike. Solutions for this can include having someone else bump your transaction fees but this brings basically a trusted 3rd party into the mix and isn't ideal.
When you lay out all the different tradeoffs a lightning node needs to make, especially in a high fee environment, it makes me think, what are we doing here, are we going down the wrong path? Lightning is still fundamentally a fantastic payment protocol but its limitation is that it requires scale. Basically every problem I've outlined goes away when you have a large lightning node with lots of liquidity and high uptime so many we should optimize for that. The market has been telling us this for years already, +90% of lightning users are using custodial wallets because it works so much better at scale. So how can we use large scale lightning nodes without custodial wallets?
Combining existing large scale lightning infrastructure with self-custodial solutions sadly, isn't totally possible. The only real way to do that as of now is Muun Wallet which as we talked about earlier, doesn't really solve the problem because everything is just an on-chain transaction. However, Muun was onto something. The architecture of having a simpler protocol interface with lightning is genius and gives us the best of both worlds. We can make fast cheap payments and let the big boys collect fees for running the lightning node. Aqua Wallet just launched which is essentially a Muun Wallet but on top of Liquid, this is a good bandaid fix but doesn't get to the root of the problem.
Before we go further we should take a step back and break down what problems we are trying to solve. Bitcoin has a fundamental scaling limitation through the block size, if we could make infinite, then we wouldn't necessarily need any layer 2s because we could just make on-chain payments. However, we live in the real world and have a 1mb block size limit, and this limits the number of transactions we can make on-chain. Lightning is a huge improvement to bitcoin because we don't need to put every transaction on-chain, we just need to open a channel and can make seemingly countless payments. So why isn't lightning the silver bullet? Lightning lets us move payments off-chain but what it doesn't do is let us move ownership off-chain. Fundamentally lightning still relies on that, at the end of the day, a utxo goes to single user. So even if every on-chain transaction was a lightning channel, we still run into the limit of how many people can actually own those channels. What we need is another layer 2 that can scale utxo ownership and caninterop with lightning, that way we have a way to scale ownership combined with scaling payments.
So how do we scale ownership? Simply put, the answer today is custody, whether that is pure custodial like a Wallet of Satoshi or in the grey area like fedimints and liquid, the only way to do it today is through custody or federated bridges. In bitcoin, the only way to delegate ownership of a utxo to multiple parties is through multisig, however, that requires every user to be online when anyone wants to transact, and when you take go down this path far enough you end up just reinventing lightning.
Are we doomed then? Is there no way to scale bitcoin in a self-sovereign way? Luckily, the answer is no, but we need some soft-forks. Covenants are the way to scale bitcoin ownership. There are a bunch of covenant proposals but at their core what they propose to do is to add a way, so you can have a bitcoin address that limits where and how the coins in it can be spent. This can seem scary, but we already have these in bitcoin today, OP_CTLV (Check LockTime Verify), which was soft forked in 2016, only allows you to spend from a bitcoin address if the transaction has a given locktime, this lets you gate when a utxo can be spent. What the current covenant proposals do is let you gate where a utxo can be spent. With that simple primitive many different protocols can be built that allow for scaling ownership.
There are a lot of current covenant proposals, the main ones being: OP_CTV, OP_VAULT, OP_CSFS, OP_TXHASH, OP_CAT, and APO. They all have different functionality and tradeoffs but in my opinion we should be looking towards activating a form of covenants because otherwise we will likely be moving towards a future of less sovereign bitcoin users.
The future is not bleak however, even without covenants we can still scale bitcoin for the world, just not in the ideal way. At Mutiny, we are full steam ahead on implementing fedimint into the wallet, in my opinion (and the rest of the team's) it looks like the best current scaling solution for bitcoin. Fedimints give us the ability to dynamically share ownership over a group of utxos and is able to interop with lightning through gateways. It is the pinnacle of the scaling dream for bitcoin with current technology and I can't wait to help make it reality while we can.
-
 @ 3bf0c63f:aefa459d
2024-01-06 00:39:23
@ 3bf0c63f:aefa459d
2024-01-06 00:39:23Report of how the money Jack donated to the cause in December 2022 is being spent.
Bounties given
December 2023
- hzrd: 5,000,000 - Nostrudel
- awayuki: 5,000,000 - NOSTOPUS illustrations
- bera: 5,000,000 - getwired.app
- Chris: 5,000,000 - resolvr.io
- NoGood: 10,000,000 - nostrexplained.com stories
October 2023
- SnowCait: 5,000,000 - https://nostter.vercel.app/ and other tools
- Shaun: 10,000,000 - https://yakihonne.com/, events and work on Nostr awareness
- Derek Ross: 10,000,000 - spreading the word around the world
- fmar: 5,000,000 - https://github.com/frnandu/yana
- The Nostr Report: 2,500,000 - curating stuff
- james magoo: 2,500,000 - the Obsidian plugin: https://github.com/jamesmagoo/nostr-writer
August 2023
- Paul Miller: 5,000,000 - JS libraries and cryptography-related work
- BOUNTY tijl: 5,000,000 - https://github.com/github-tijlxyz/wikinostr
- gzuus: 5,000,000 - https://nostree.me/
July 2023
- syusui-s: 5,000,000 - rabbit, a tweetdeck-like Nostr client: https://syusui-s.github.io/rabbit/
- kojira: 5,000,000 - Nostr fanzine, Nostr discussion groups in Japan, hardware experiments
- darashi: 5,000,000 - https://github.com/darashi/nos.today, https://github.com/darashi/searchnos, https://github.com/darashi/murasaki
- jeff g: 5,000,000 - https://nostr.how and https://listr.lol, plus other contributions
- cloud fodder: 5,000,000 - https://nostr1.com (open-source)
- utxo.one: 5,000,000 - https://relaying.io (open-source)
- Max DeMarco: 10,269,507 - https://www.youtube.com/watch?v=aA-jiiepOrE
- BOUNTY optout21: 1,000,000 - https://github.com/optout21/nip41-proto0 (proposed nip41 CLI)
- BOUNTY Leo: 1,000,000 - https://github.com/leo-lox/camelus (an old relay thing I forgot exactly)
June 2023
- BOUNTY: Sepher: 2,000,000 - a webapp for making lists of anything: https://pinstr.app/
- BOUNTY: Kieran: 10,000,000 - implement gossip algorithm on Snort, implement all the other nice things: manual relay selection, following hints etc.
- Mattn: 5,000,000 - a myriad of projects and contributions to Nostr projects: https://github.com/search?q=owner%3Amattn+nostr&type=code
- BOUNTY: lynn: 2,000,000 - a simple and clean git nostr CLI written in Go, compatible with William's original git-nostr-tools; and implement threaded comments on https://github.com/fiatjaf/nocomment.
- Jack Chakany: 5,000,000 - https://github.com/jacany/nblog
- BOUNTY: Dan: 2,000,000 - https://metadata.nostr.com/
April 2023
- BOUNTY: Blake Jakopovic: 590,000 - event deleter tool, NIP dependency organization
- BOUNTY: koalasat: 1,000,000 - display relays
- BOUNTY: Mike Dilger: 4,000,000 - display relays, follow event hints (Gossip)
- BOUNTY: kaiwolfram: 5,000,000 - display relays, follow event hints, choose relays to publish (Nozzle)
- Daniele Tonon: 3,000,000 - Gossip
- bu5hm4nn: 3,000,000 - Gossip
- BOUNTY: hodlbod: 4,000,000 - display relays, follow event hints
March 2023
- Doug Hoyte: 5,000,000 sats - https://github.com/hoytech/strfry
- Alex Gleason: 5,000,000 sats - https://gitlab.com/soapbox-pub/mostr
- verbiricha: 5,000,000 sats - https://badges.page/, https://habla.news/
- talvasconcelos: 5,000,000 sats - https://migrate.nostr.com, https://read.nostr.com, https://write.nostr.com/
- BOUNTY: Gossip model: 5,000,000 - https://camelus.app/
- BOUNTY: Gossip model: 5,000,000 - https://github.com/kaiwolfram/Nozzle
- BOUNTY: Bounty Manager: 5,000,000 - https://nostrbounties.com/
February 2023
- styppo: 5,000,000 sats - https://hamstr.to/
- sandwich: 5,000,000 sats - https://nostr.watch/
- BOUNTY: Relay-centric client designs: 5,000,000 sats https://bountsr.org/design/2023/01/26/relay-based-design.html
- BOUNTY: Gossip model on https://coracle.social/: 5,000,000 sats
- Nostrovia Podcast: 3,000,000 sats - https://nostrovia.org/
- BOUNTY: Nostr-Desk / Monstr: 5,000,000 sats - https://github.com/alemmens/monstr
- Mike Dilger: 5,000,000 sats - https://github.com/mikedilger/gossip
January 2023
- ismyhc: 5,000,000 sats - https://github.com/Galaxoid-Labs/Seer
- Martti Malmi: 5,000,000 sats - https://iris.to/
- Carlos Autonomous: 5,000,000 sats - https://github.com/BrightonBTC/bija
- Koala Sat: 5,000,000 - https://github.com/KoalaSat/nostros
- Vitor Pamplona: 5,000,000 - https://github.com/vitorpamplona/amethyst
- Cameri: 5,000,000 - https://github.com/Cameri/nostream
December 2022
- William Casarin: 7 BTC - splitting the fund
- pseudozach: 5,000,000 sats - https://nostr.directory/
- Sondre Bjellas: 5,000,000 sats - https://notes.blockcore.net/
- Null Dev: 5,000,000 sats - https://github.com/KotlinGeekDev/Nosky
- Blake Jakopovic: 5,000,000 sats - https://github.com/blakejakopovic/nostcat, https://github.com/blakejakopovic/nostreq and https://github.com/blakejakopovic/NostrEventPlayground
-
 @ 97c70a44:ad98e322
2024-01-05 22:03:37
@ 97c70a44:ad98e322
2024-01-05 22:03:37Today marks the biggest release so far in Coracle's history. There have been many good days, like when I introduced Coracle to the nostr telegram group, or when I got my fellowship with FUTO, or when I got my grant from OpenSats, or when I got to speak at Nostrasia. But in terms of realizing the vision I've had for the software - for over two years - today is the day.
Coracle now has private groups.
This means you can now send almost any nostr event over an encrypted channel to the rest of the group's members. This is substantially different from group chats, in that it uses rotating shared keys to provide weak forward secrecy, better scaling, and dynamic member access. This more closely approximates one of the most popular social media products in existence - The Nostr is now a direct competitor of The Facebook.
I built this for my community. I wanted something "good enough" to entice people to leave the advertising-fueled surveillance honeypot that is Facebook. In order to work, it needed to at least support notes, events, and marketplace listings. Although support is still quite basic, Coracle has checked all three of these boxes.
Before I get into the details though, it's important to mention that these groups should not be considered "private" any more than Facebook groups or Mastodon servers are (although privacy is substantially better). A better analog might be WeChat, which uses encryption with the same set of trade-offs. So don't post anything to private groups that might get you in trouble!
With that said, it's possible to run a highly private group. The backbone of this spec is e2e encryption, but relay selection can play an important part in hiding metadata from the rest of the network. If you have a relay you trust to protect notes and not share metadata, your security is significantly increased.
Prior art
Nostr-compatible group products aren't a totally novel thing, as it turns out. In fact draft NIP 112 has been around since June, and is already implemented in ArcadeCity. So why am I creating a new standard? I'l get into the positive benefits of my approach more below, but the quick answers are:
- The new encryption standard is going to break compatibility anyway. If we can end up with a better spec, now is the time.
- ArcadeCity development seems to have stalled.
- NIP-72 communities already have a ton of traction, and match what I'm trying to achieve with encrypted channels.
Of course I'm highly indebted to the project, the design of which is still visible in my final design.
Another product that exists to do something similar in a nostr-compatible way is Soapbox by Alex Gleason. This is a great project, particularly since his Mostr project bridges the ActivityPub world and Nostr. ActivityPub works well for highly centralized communities, but the architecture suffers from this centralization too. In particular, not even DMs are e2e encrypted, and just like regular notes are protected only by authentication enforced by servers.
Finally, there's NIP 29, which is fiatjaf's competing groups project. This has some interesting properties, for example the ability to "fork" a group by linking events together. However, similar to ActivityPub it relies exclusively on relays to protect user privacy, and in a fairly non-standard way. You do get to take advantage of nostr's multi-master architecture though, and signatures are also stripped from events in order to discourage propagation through the network.
None of these solutions quite satisfied me, so I built my own.
How it works
One of the coolest things about a NIP 72 community-based group spec is that is supports a spectrum of privacy requirements. A group admin might choose to publish group metadata privately so that it's only visible to the group, publicly so that other people can find the group and ask to join, or leave off a private component entirely.
Likewise, since private groups are backwards-compatible with public communities, it's easy to add a private component to existing groups. This can be useful especially for groups run by a business or content publisher, since public exposure is a good thing but certain group members might have more or less access. This could be used to support a patreon-type model, automating group membership based on subscription tier, for example.
An important aspect of the design that makes automation possible is the concept of a dedicated administration key. By decoupling this key from the original creator of the group, ownership can be shared as simply as sharing the key. This allows multiple admins to manage the group simultaneously either manually or using automations built into the group relays or special purpose bot-clients.
This of course raises the issue of admin access revocation, which isn't possible - that is, until we have a solution for key rotation for normal accounts. Once that's in place, the same process can be used to rotate group admin keys.
In the meantime, it's also trivial to reduce the exposure an admin key gets. You wouldn't generally want to simply paste the key wherever it's needed, but luckily that problem has already been solved as well. Instead of giving every admin or admin bot the key, it's trivial to set up an nsecbunker that authorizes each admin client - and can revoke access as needed.
This level of administration is of course fairly complex, but I think it's important to think through the requirements businesses and other advanced users will eventually impose and anticipate them as we're able, not through over-engineering, but through simple concepts that can be reused.
One other neat feature of this NIP is the definition of invite codes, which are essential for running a private group at any kind of scale. When requesting access to a group, a user can send along a "claim", which can be anything - for example a static invite code, a payment receipt, or an explanation of why they want to join. This claim can be validated by hand by a human, or processed by a bot to instantly admit the new member to the group.
When a new member is admitted to the group, the admin can either share an existing access key with them, or they can rotate the key for the entire group. If relays expire access keys after a certain amount of time, this can create a weak form of forward secrecy, where attackers won't be able to access old content, even if they gain access to the admin key.
Limitations and Future Work
The bar for new nostr clients has risen significantly since I first put Coracle out there. The new groups component is far more mature than Coracle was for much of its early life, but it has its rough edges. Many of these just need to be smoothed out through further UX work, but some are more technical in nature.
- The groups spec relies on NIP 44, which isn't yet available in most signer extensions. That means that unless you log in with your private key (please don't), you won't be able to create or gain access to any private groups.
- Hybrid groups (public groups with a private area) aren't really tested yet, or fully supported in Coracle's UI. It's an open question whether this is even a good idea, since it becomes pretty hard for users to know if they're posting publicly or privately in every context.
- Moderation is not implemented, so if you're creating a public group there is currently no way in Coracle to approve posts. Also, groups created in Coracle don't show up in Satellite for some reason — this is something I'll be working on improving.
- Whether this approach actually scales is another question. It's very hard to build member lists of hundreds of thousands of people, and without a relay helping to filter events, it might become prohibitively expensive to download and analyze all the events posted to a group. We'll see what develops as the design matures and the implementation undergoes stress testing.
Conclusion
Something I like about both nostr and bitcoin is that it empowers the users of the software. The corollary of this of course is that it's important to exercise this power with care - real damage can be done with this group spec, just as real damage can be done to bitcoin holders through low entropy key generation or poor key handling practices. So please, if you're going to implement this spec, communicate clearly with your users its limitations, and encourage them to run their own relays.
Nevertheless, I am stoked to be another 1% closer to my goal of helping my community - and anyone else who uses nostr - to exercise individual sovereignty and protect their freedom and privacy. Let's keep at it.
-
 @ 26bd32c6:cfdb0158
2024-01-04 20:26:59
@ 26bd32c6:cfdb0158
2024-01-04 20:26:59I've been experiencing a bit of writer's block recently, which is somewhat strange because it's about topics I genuinely want to write about. In a way, I have so many different ideas that I want to express, I can't pin them down, leading to writing nothing at all.
It's funny because, for me, Nostr was that place where I could say anything. It didn't matter whether people hated or loved it. But now, I feel this daunting responsibility to share highly impactful words that can't be easily criticized by haters or lovers. It's as if suddenly, Nostr isn't my safe place anymore; it's become my serious place.
If, when reading this, you think it sounds as ridiculous as I feel, trust me, I won't take any offense. I am pushing myself here just by writing it down. The reason I'm writing this on a blog is due to this daunting feeling of needing perfection, which I like to call the 'traditional social media effect.'
The Traditional Social Media Effect
Definitely not a medical term or diagnosis, but I am now self-diagnosed with it, and well, "delulu makes trululu."
If you hang out long enough on Nostr, you'll start noticing some traditional social media patterns that freak me out. And because they freak me out, I feel the need to write them out, perhaps to leave them behind.
Everyone is now fighting over something, and whoever is the loudest will win the 'shitposter' award. And I love shitposting... but there's no need to disparage others' projects to ensure mine is the best.
Everyone is begging for attention. Guys, there's no algorithm; there is a high chance absolutely no one will read this, and that's okay with me. I am just creating this blog because I have things I want to get off my chest, and because nostr:npub1nxy4qpqnld6kmpphjykvx2lqwvxmuxluddwjamm4nc29ds3elyzsm5avr7 is hosting a cool contest that I just want to contribute to.
And the last part, everyone is begging for an easy fix. An easy fix that will get them zaps, an easy fix that will get them followers, an easy fix that will make them the next Nostr superstar, and solve all their life's issues.
This is just sad. What happened to PoW?
Yes, This Is about PoW!
I came into Nostr because I am a Bitcoiner, and I love complicated stuff that requires hours of my time, for me to barely understand anything, and then look at the rest of the world like, "Ha! You losers don't know what I know..."
Therefore, Nostr is not for anyone who is lazy... or at least it wasn't. It required effort; videos had to be carefully crafted to go viral and get zaps.
Actually, even e-girl content isn't top-notch anymore. A bunch of AI-generated fake content is getting more zaps than nostr:npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u's feet on #footstr.
Actually, these are the last feet to make it on Footstr, and they are from Walker, back in August... https://cdn.nostr.build/i/fb64c0f064e11dabff69d56e7e4edfd47aebd1c752b84e76d50fb0e43f9f7e6b.jpg We are lacking that good feet content.
Is She Going to Stop Ranting or Explain This Effect Thing?
Okay, here I go. What I mean is that it seems to me that we are here looking for something different, but wanting that same dopamine hit Instagram and Twitter gave us.
Where am I going with this? Well, I just wanted to post on Nostr because it made me happy. I just wanted to come here and say whatever silly thing came to mind.
But now, I just see a bunch of posts of people either fighting over which federation is going to fix layers and lighting or the latest e-beggar. And these beggars are seeking everything from attention to zaps, no limits or questions asked. Just "look at my sad face, fix my life please."
And these things are not PoW. PoW is about creating the best new federation, and I believe you did, just work on it and show it. Don't waste your time disparaging the other one.
You want a life change, a path change? Instead of coming here to complain, ask for advice, ask questions, look for a mentor.
STOP WHINING! Okay, I was trying that writing in caps thing to seem angry and badass. But now I just feel cringe...
This Was It, This Was the Rant...
I usually don't say anything because if I'm as annoyed as I am about the way feeds are starting to look, I think I will produce that same feeling in everyone else.
I've said it hundreds of times: the cool thing is that I choose what I want to see. And that's how I plan to fix this writer's block and get back to being more hands-on... back to building the Nostr I want to see!
I want to stop feeling the need to drop the most perfect note, and to do so, I am pushing myself to do a 30-day photography challenge.
I won't win anything, and if you want to join me, the prize is also absolutely nothing.
Why photography? Well, because I suck at it. I have no idea how to do it; I just started asking for help, and everyone loves to critique the composition of "art"... and I doubt anyone will call my terrible photography skills art... so I'm putting myself out there to be critiqued.
My 30-day challenge, starting today, will include daily reminders to take a picture of whatever I can, and an explanation of what I was trying to achieve.
It will also come eventually with more blogs and vlogs, with less ranting and more building. The world is just starting... at least that's how it feels to me.
We are so early... https://media.giphy.com/media/z85pBkLFP6izGn6see/giphy.gif?cid=ecf05e47kcqu2k7sshjuox6wsy8zrbms9210r1obb1d9ytof&ep=v1_gifs_search&rid=giphy.gif&ct=g
But for real, it is early... and that is why there's a lot we can do. And also why for real "There Is So Much Noise... I Can't Think Straight..."
So, join me or don't, in this challenge or just be challenged to put out there a better version of the things you see that bother you.
I think I sometimes feel angry and tired, but before I resort to running off to the woods and becoming a hermit, I'm going to stay hopeful and try to give to the world what I want the world to give me.
And yeah, that's it... This was the whole rant. I was just being louder so I could start thinking again.
If you are here and you've read the whole thing, thank you; you are truly resilient! I'm sure not even my mom made it all the way here (but just in case: Hi mom! I love you 🫶🏽).
With this, I say goodbye... going to try that photography thing and be back with another note in a bit!
Marce 💜
-
 @ 4fe14ef2:f51992ec
2024-03-22 11:07:36
@ 4fe14ef2:f51992ec
2024-03-22 11:07:36https://images.craigslist.org/00202_h0ZweBnLVJr_0t20t2_600x450.jpg https://images.craigslist.org/00j0j_4Mt0tCsv0hR_0t20t2_600x450.jpg https://images.craigslist.org/00c0c_l6wyJ3ThmBo_0t20t2_600x450.jpg
Hello,
The shown baldwin acrosonic piano and bench is available including delivery and professional inspection. All the keys and pedals work and the piano will hold a tune.
The piano is not available for showings as requested by the current owner.
We only use Craigslist email for this price to help keep inquiries organized.
Please feel free to ask questions.
The piano will work great for a beginner or maybe someone more advanced on a budget. If the piano does not match this description upon delivery, you may refuse to pay. If the piano fails our inspection, we will cancel the delivery.
Delivery included for most Austin addresses with no steps/stairs or rough terrain.
The total is $200 and due upon delivery unless you refuse the piano for not matching this ad. Tuning can be provided for an additional $150.
Cash/Bitcoin payment only accepted and due upon your approval.
Thank you Austin!
BITCOIN #BTCACEPTED #MARKETPLACE #AGORA #P2P #MUSIC #PIANO #VINTAGE
[CONTACT THE SELLER]
Just anothercrosspost to nostrfrom the~AGORA... -
 @ 4fe14ef2:f51992ec
2024-03-22 10:46:54
@ 4fe14ef2:f51992ec
2024-03-22 10:46:54https://gumtreeau-res.cloudinary.com/image/private/t_$s-l800/gumtree/cc38e65b-7e99-4f2c-b2a5-a3251d90330a.jpg https://gumtreeau-res.cloudinary.com/image/private/t$s-l800/gumtree/93a40140-9ae1-4b24-bdf7-c1485dcd1333.jpg https://gumtreeau-res.cloudinary.com/image/private/t$s-l800/gumtree/6dd0a622-6a00-4bb9-8416-df5a098ac87b.jpg https://gumtreeau-res.cloudinary.com/image/private/t$s-l800/gumtree/152441ae-e42e-46c4-957c-025969113a85.jpg https://gumtreeau-res.cloudinary.com/image/private/t$s-l800/gumtree/715d0b4c-2850-4ed0-820a-86be5a91b25a.jpg https://gumtreeau-res.cloudinary.com/image/private/t$s-l800/gumtree/57ba57b9-9a18-4df7-bd3a-25560a49bb50.jpg https://gumtreeau-res.cloudinary.com/image/private/t$s-l800/gumtree/f393173f-09bc-485b-a482-412f5823637c.jpg https://gumtreeau-res.cloudinary.com/image/private/t$s-l800/gumtree/a7401683-ff8f-444b-a646-a64e6c7353c1.jpg https://gumtreeau-res.cloudinary.com/image/private/t$s-l800/gumtree/944914ec-a7aa-4c01-81ec-0d244440045f.jpg https://gumtreeau-res.cloudinary.com/image/private/t$_s-l800/gumtree/48068dd4-3b2d-4663-adeb-bd70314b500d.jpg
extremely rare
Published in 2013 when btc was $150 per coin. This book is your pocket guide / intro to bitcoin w a physical coin. 🪙
Both items are extremely rare and a valuable piece of history , that will only continue to go up in price.
Never reprinted , this book is an original, not a replica.
Great condition still for its age .
Has been looked after and stored in my safe since 2013.
I have re listed it as buyer pulled out.
Price is slightly negotiable to serious buyer, bid now to get your hands on this bit of history as the coin price continues to soar.
Pick up from Geelong or can express post included in price.
BITCOIN #BTCACEPTED #MARKETPLACE #AGORA #P2P #PASSPORT #VINTAGE #COLLECTABLE
[CONTACT THE SELLER]
Just anothercrosspost to nostrfrom the~AGORA... -
 @ 4ba8e86d:89d32de4
2024-01-03 22:43:57
@ 4ba8e86d:89d32de4
2024-01-03 22:43:57desenvolvido por vfsfitvnm , que permite que você desfrute de todas as suas músicas favoritas do YT-Music sem limites. Com uma interface amigável e simples, basta abrir o aplicativo para pesquisar por músicas, artistas, videoclipes ou até mesmo listas de reprodução inteiras. O ViMusic oferece a conveniência de reproduzir música em segundo plano, mesmo quando o aplicativo está minimizado ou a tela está desligada, permitindo que você use outros aplicativos simultaneamente.
Principais Características: - Reproduza (quase) qualquer música ou vídeo do YouTube Music. - Reproduza em segundo plano para uma experiência contínua. - Armazene em cache pedaços de áudio para reprodução offline. - Realize pesquisas de músicas, álbuns, vídeos de artistas e listas de reprodução. - Marque seus artistas e álbuns favoritos. - Importe listas de reprodução personalizadas. - Visualize e edite letras de músicas ou letras sincronizadas. - Gerencie suas listas de reprodução locais e reordene as músicas na fila. - Escolha entre temas claro, escuro e dinâmico para personalizar a aparência do aplicativo. - Pule silêncios indesejados para uma experiência mais fluida. - Use o ViMusic como despertador para iniciar o dia com suas músicas preferidas. - Aproveite a normalização de áudio para manter o volume consistente entre faixas. - Integração com o Android Auto para uma experiência de música no carro. - Mantenha uma fila persistente para ter suas seleções sempre disponíveis.
O ViMusic oferece uma série de recursos especiais, incluindo alta qualidade de áudio, a possibilidade de ouvir música offline e acesso a uma enorme biblioteca de músicas. A experiência do usuário é livre de anúncios, o que proporciona uma audição ininterrupta e agradável.
Com o ViMusic, você desfruta de uma plataforma de streaming de música gratuita, fácil de navegar e que ocupa menos espaço para instalar. Aproveite a liberdade de ouvir música offline sem interrupções indesejadas de anúncios.
https://github.com/vfsfitvnm/ViMusic
-
 @ 57d1a264:69f1fee1
2024-03-22 10:03:34
@ 57d1a264:69f1fee1
2024-03-22 10:03:34Let's talk style! What trend, color combo, or flair has captured your head this week? Does not need to be a from famous glamoury design firms, just show off your favorite styles, and yes, a selfie showcasing your current outfit is more than welcome, yo! Just consider your privacy!
-
 @ c31052c1:493a1c56
2023-12-31 06:40:24
@ c31052c1:493a1c56
2023-12-31 06:40:24Mineral是世界上第一个由比特币挖矿现实世界资产(RWA)支持的BRC-420的铭文,在一波meme铭文的热潮过后,市场对于应用型铭文的需求将形成新趋势,Mineral在这时应运而生。
产品设计:
1.通过在二层质押Mineral获得比特币:不需要碰运气去等待价格起飞,无论市场如何变化,质押Mineral获得比特币收益。而在过往每个牛市,矿机(算力)本身也有不俗表现。
2.通过质押挖矿还可以获得二层国库代币Mner,国库将会随着项目发展不断增持新的RWA生息资产。除此以外,Mineral将与同样基于BRC-420环境中的其他项目合作,并在L2中,通过抵押Mineral铭文来实现一币多挖。
3.打铭文的用户都需要支付交易费,因此矿工挖矿收入也会随着铭文生态而水涨船高,铭文生态蓬勃发展逐渐成为共识。质押Mineral,即可像矿工一样,赚取交易费,赚取生态红利。
4.不会归0的铭文:meme铭文因投机而市场热度上升,当热点褪去可能就无人问津,所以铭文需要应用和赋能才能进一步推动生态的永续发展。Mineral除了有巨大的增长潜力,更重要的从RWA中捕获更坚实的底层价值。二层的路线路中,远期更有丰富DEFI玩法打造未来RWA DeFi航母.
铭文将带来ICO和DeFi的文艺复兴
我们之所以说铭文可能是比特币L1和L2上ICO和DeFi的文艺复兴,是因为DeFi的成熟和更具前景的市值和想象空间。有这么一个有趣的说法,以太坊和EVM就像比特币的测试网,大家都会记得他们在DeFi Summer的激情,并且在受过充分的市场教育后,深刻知道DeFi是如何运作的,BTC生态是铭文生长的沃土。此外,比特币的市值在加密货币的市值占主导地位。许多比特币持有者正在寻找建立在比特币网络上的原生应用,而铭文是基于比特币L1的产品,继承了比特币的优点,因此也将获得市场认可。Mineral结合比特币挖矿这个原生机制与铭文DeFi应用形成一种比特币专属的原生应用创新。Mineral非常适合大多数热爱并相信比特币和铭文的投资者。
Mineral是BRC-420上的进阶DeFi创新
Mineral受到良好的Defi模型启发,在其基础上更加精进和永续。
基于OHM(Olympus)和Infra(Blast)的成功,Mineral则是一种更为精进和永续的经济模式。OHM的高APY飞轮吸引了人们的注意,但我们团队坚信需要引入像比特币挖矿的正外部收益,让这个飞轮能够更持久而不会因为巨大的抛压归零。另一方面,我们认为Blast是实现生态系共荣的成功模式。我们结合并且优化这两个模型,让Mineral的持有人实现一币多挖而且永续感受到飞轮的刺激。
Mineral将很快在BRC-420官网发布,具体Mineral公平发射计划如下:
首批mint价格:等值50U的比特币
总量:40,000个
具体发射时间待定,请继续关注我们的官方推特。
Twitter: https://twitter.com/mner_club Telegram: https://t.me/mnerclub Discord: https://discord.gg/aB4KXpTv Website: https://www.mner.club/
-
 @ c4428155:a36de510
2024-03-22 10:00:00
@ c4428155:a36de510
2024-03-22 10:00:00Idaho Legislature Approves $2 Billion for Schools to Repair and Replace Aging Buildings
by Becca Savransky, Idaho Statesman (https://www.idahostatesman.com/)
This article was produced for ProPublica’s Local Reporting Network in partnership with the Idaho Statesman (https://www.idahostatesman.com/). Sign up for Dispatches (https://www.propublica.org/newsletters/dispatches) to get stories like this one as soon as they are published.
School districts across Idaho will soon receive hundreds of millions of dollars to help repair and replace their aging buildings, thanks to a bill that cleared its final hurdle in the Idaho Senate on Thursday.
House Bill 521 will invest $1.5 billion in new funding and redirect $500 million over 10 years for school facilities across the state. But critics say it still won’t be enough to address the years of neglect left from the state’s failure to fund school facilities.
Idaho school districts have for decades struggled to fix or replace their aging, deteriorating schools and build new ones to accommodate the state’s rapid growth. Over the past year, the Idaho Statesman and ProPublica have reported (https://www.propublica.org/series/state-of-disrepair) on how Idaho’s restrictive policies and the state’s reluctance to make significant investments in school facilities have led to students learning in schools with failing heating systems, leaking roofs, discolored drinking water and overcrowded classrooms.
Citing the stories, Gov. Brad Little called to make funding (https://www.propublica.org/article/idaho-governor-proposes-2-billion-school-building-funding) for school facilities “priority No. 1” in his State of the State address in January. He proposed putting $2 billion toward school facilities over 10 years, or $200 million per year.
“Together, we delivered,” Little said in a statement on Thursday. “Together, we secured the largest-ever investment in school facilities funding in state history while giving families back more of their hard-earned money with property and income tax relief.”
The bill, which the governor is expected to sign into law, will create a new fund that will allocate money to districts based on average daily attendance. School districts could choose to take the money in a lump sum or annually over 10 years.
Estimates provided to the Statesman and ProPublica (https://www.documentcloud.org/documents/24437139-school-modernization-facility-fund) last month from the governor’s office show West Ada, the largest district in the state, will receive about $140 million from this fund. The Salmon School District, which has been trying for more than a decade to replace its elementary school and build a new K-8 building in remote Central Idaho, will get about $2.6 million — not nearly enough to construct a new school.
Some legislators raised concerns that the bill doesn’t fully solve the problem, favors urban districts and leaves rural districts without the funding they need. Lawmakers also said the state doesn’t have a complete picture of the scope of the issue, in part because there hasn’t been a statewide facilities assessment in three decades.
“Let’s not pass a billion-dollar bill and then say we fixed facilities at the literal expense of our rural school districts,” said Sen. Carrie Semmelroth, D-Boise.
The bill has been largely supported by education groups and superintendents across the state, though many agree rural areas will still not get the amount they need for new schools and maintenance.
“There are some who seem to believe this fixes the problem,” Moscow Superintendent Shawn Tiegs said in an email. “It doesn’t. It is just the start.”
Under the bill, the Moscow School District will get about $8.4 million from the newly created fund, according to estimates from the governor’s office. Moscow schools have faced issues with overcrowding, leaks, security, and heating and cooling. One of its elementary schools is nearly 100 years old and has a boiler from 1926.
Tiegs said the Legislature should consider prioritizing older schools or poorer districts. Some superintendents believe the Legislature should give a base amount to each district to level the playing field.
A series of supplemental bills introduced Thursday could change how much money school districts get for their facilities. The legislation, known as “trailer bills,” work like amendments by altering bills after they pass. One of the bills, which would still need to be approved by the Legislature, would require that each school district get at least $100,000 and would cap the distributions at $100 million. West Ada is the only district that would be affected by the cap, according to the estimates from the governor’s office. The remaining money would then be redistributed to smaller districts.
Education groups and lawmakers acknowledged the bill that passed Thursday will not eliminate the need for school districts to run bond elections to replace their schools.
“We believe this is an important leap in making these necessary investments in our school facilities,” Quinn Perry from the Idaho School Boards Association said during a legislative hearing this month. “While, again, this is an important investment, it simply will not exclude the reality that most districts will still have to ask their taxpayers for financial support on new builds or even school renovation projects.”
Passing bonds has been difficult for school districts because Idaho is one of two states in the nation that requires two-thirds of voters to support a bond for it to pass. A resolution, which could start the process to lower that threshold (https://www.idahostatesman.com/news/politics-government/state-politics/article285760956.html), has not yet been debated on the House floor.
The facilities bill that passed Thursday will also add about $25 million a year and redirect about $50 million a year to a fund that school districts can use to pay off their bonds and levies. School districts with remaining funds can use it for facilities projects.
The bill also included a number of concessions to gain support in the heavily conservative Legislature. It will lower the state’s income tax rate and eliminate the August election date, one of the three remaining dates school districts can run bonds and levy elections. Republican leaders say that given the new money, there will be less need for districts to ask their communities for funding. The bill will also phase out a program that used a formula based on income and market values to give some districts money to lower their debts from school bonds.
Some superintendents have also raised concerns because the bill will require school districts on a four-day week that want to receive the funding to meet a minimum number of instructional days. Dozens of Idaho districts have moved to four-day weeks to save money or attract educators, and some districts worry these new guidelines could disrupt their schedules. But bills introduced Thursday could repeal the provision or delay its implementation for a year, giving school districts more time to plan.
Paul Anselmo, the superintendent of the Kamiah School District, a small, rural district in North Idaho, said even with this bill, his district likely won’t get enough to make lasting improvements in its schools. Kamiah will receive about $1.5 million from the newly created fund. Kamiah schools have faced issues with security, leaks, heating and cooling, exposed wiring and holes in the walls.
“While we appreciate the additional funds coming into our district, the amount Kamiah would receive would allow us to continue to put ‘band aids’ on our facility issues,” Anselmo said in an email. “A small district could have severe needs and this funding would not allow them to fully address their needs.”
Asia Fields (https://www.propublica.org/people/asia-fields) contributed reporting.
https://www.propublica.org/article/idaho-legislature-approves-funding-for-school-repairs
-
 @ d0b327c6:1ae748c2
2024-03-22 09:14:39
@ d0b327c6:1ae748c2
2024-03-22 09:14:39Tradotto dall’originale di Frank Shostak - pubblicato il 29 nov 2016
La maggior parte degli economisti ritiene che, a partire dai primi anni '80, le correlazioni tra le varie definizioni di moneta e reddito nazionale si siano interrotte. La ragione di questa rottura è che la deregolamentazione finanziaria ha reso instabile la domanda di moneta. Di conseguenza, si ritiene che l'utilità del denaro come predittore di eventi economici sia diminuita in modo significativo.
Per risolvere l'instabilità della domanda di moneta, gli economisti hanno introdotto un indicatore dell'offerta di moneta noto come indicatore monetario Divisia. (L'indicatore prende il nome dal suo ideatore, François Divisia).
Assegnando pesi variabili piuttosto che uguali alle componenti dell'offerta di moneta, si ritiene che si possa porre rimedio al problema dell'instabilità della domanda di moneta. (Assegnando pesi adeguati, è probabile che si migliori la correlazione tra l'indicatore monetario ponderato e i vari indicatori economici). Di conseguenza, si potrebbe utilizzare questo indicatore per accertare i probabili eventi economici futuri1.
Si noti che, secondo la maggior parte degli economisti, la validità delle varie definizioni di moneta può essere stabilita mediante un test statistico. Ciò che determina se la moneta - M1, M2 e gli altri Ms - è stata definita in modo valido dipende dalla loro correlazione con vari dati economici chiave, come il prodotto interno lordo.
Il problema di definire il denaro
Nessuna definizione, tuttavia, può essere stabilita per mezzo di una correlazione. Lo scopo di una definizione è presentare l'essenza, la caratteristica distintiva del soggetto che stiamo cercando di identificare. Una definizione ci dice quali sono i fondamenti di una particolare entità.
In questo senso, il denaro è ciò con cui vengono scambiati tutti gli altri beni e servizi. La caratteristica distintiva del denaro è che è il mezzo di scambio generale. Si è evoluto dalla merce più commerciabile.
Questa caratteristica fondamentale del denaro deve essere contrapposta a quelle di altri beni. Per esempio, il cibo fornisce l'energia necessaria agli esseri umani, mentre i beni strumentali permettono l'espansione delle infrastrutture che a loro volta consentono la produzione di una maggiore quantità di beni e servizi.
Attraverso un processo di selezione continuo, le persone hanno storicamente scelto l'oro come moneta. In altre parole, l'oro è stato il denaro standard.
Nel sistema monetario odierno, la massa monetaria non è più costituita dall'oro, ma da monete e banconote emesse dal governo e dalla banca centrale.
Di conseguenza, le monete e le banconote costituiscono il denaro standard, noto come contante, utilizzato nelle transazioni. In altre parole, i beni e i servizi vengono venduti in cambio di denaro contante.
Una corretta definizione di denaro è indispensabile per ottenere le giuste informazioni dagli indicatori monetari. Sfortunatamente, la maggior parte delle definizioni più diffuse di denaro sono errate.
Definizioni errate di denaro
Si consideri ad esempio la definizione di moneta M2. Questa definizione include i conti di deposito del mercato monetario. Tuttavia, l'investimento in un fondo del mercato monetario è in realtà un investimento in vari strumenti del mercato monetario.
La quantità di denaro non viene alterata a seguito di questo investimento; solo la proprietà del denaro è temporaneamente cambiata.
Se Joe investe 1.000 dollari in un fondo del mercato monetario, la quantità complessiva di denaro nell'economia non cambierà in seguito a questa transazione. Il denaro si sposterà dal conto di deposito a vista di Joe al conto di deposito a vista del mercato monetario presso una banca. Incorporare i 1.000 dollari investiti nel fondo del mercato monetario nella definizione di denaro più i 1.000 dollari originali equivarrebbe quindi a un doppio conteggio.
Il problema del doppio conteggio non è risolto nemmeno dalla definizione di denaro "a scadenza zero" (MZM) (money of zero maturity, n.d.t.), una definizione di offerta di moneta relativamente recente.
L'essenza delle MZM è quella di comprendere le attività finanziarie a scadenza zero. Le attività incluse nelle MZM sono rimborsabili alla pari su richiesta. Questa definizione esclude tutti i titoli, che sono soggetti al rischio di perdita di capitale, e i depositi a termine, che comportano penali per il ritiro anticipato. Le MZM includono tutti i tipi di strumenti finanziari che possono essere facilmente convertiti in denaro senza penalità o rischio di perdita di capitale.2
Si noti che l'MZM include attività che possono essere convertite in denaro. È proprio questo l'aspetto sbagliato di questa definizione, poiché non identifica il denaro, ma piuttosto varie attività che possono essere facilmente convertite in denaro. Non ci dice che cosa sia effettivamente il denaro, e questo è ciò che una definizione di denaro dovrebbe fare.
Allo stesso modo, la questione di una definizione valida non è risolta dall'indicatore monetario Divisia. Come abbiamo visto, questo indicatore non cerca di stabilire cosa sia la moneta, ma piuttosto di migliorare la correlazione tra la moneta, come M2, e un indicatore di attività economica. In questo senso, la costruzione dell'indicatore Divisia è un esercizio di adattamento della curva.
Una volta stabilito che la definizione è valida, ci si deve attenere ad essa, indipendentemente dal fatto che sia ben correlata o meno con altri dati economici.
Il giudice finale della validità di una definizione di offerta di moneta non dovrebbe essere la correlazione statistica in sé, ma la solidità della definizione.
La solidità di una definizione non può essere stabilita attraverso un'analisi statistica, ma solo attraverso la comprensione del significato di denaro.
Il denaro elettronico è denaro vero?
L'introduzione della moneta elettronica sembra mettere in dubbio l'idea che il denaro sia costituito da monete e banconote.
Tuttavia, le varie forme di moneta elettronica non hanno una "vita propria". La moneta elettronica può funzionare finché gli individui sanno di poter ottenere contanti su richiesta.
Le varie innovazioni finanziarie non creano nuove forme di denaro, ma piuttosto nuovi modi di utilizzare il denaro esistente nelle transazioni.
Indipendentemente da queste innovazioni finanziarie, la natura del denaro non cambia. È l'oggetto con cui vengono scambiati tutti gli altri beni e servizi.
1 Barnett, W. A., 1980. "Aggregati economici monetari: An Application of Aggregation and Index Number Theory", Journal of Econometrics 14: 11-48.
2 John B. Carlson e Benjamin D. Keen, "MZM: un aggregato monetario per gli anni '90?". Federal Reserve Bank of Cleveland Economic Review (1996).
-
 @ e1ff3bfd:341be1af
2023-12-17 18:49:31
@ e1ff3bfd:341be1af
2023-12-17 18:49:31A bunch of people have been shilling Liquid has a scaling solution with on-chain fees on the rise. I wanted to take the time to breakdown why this is a fool's errand and there are better ways to go about this.
Liquid is based on Elements which as they claim in their README is
a collection of feature experiments and extensions to the Bitcoin protocol. Liquid is just another blockchain. It is a fork of bitcoin with a few fancy things added (Tokens, CT, covenants) and bundled together with a 1 minute block time, federated custody, and some blockstream branding.Blockchains do not scale. As we are seeing today, the bitcoin blockchain does not have enough throughput for everyone's transactions. This is for good reason, keeping the cost of running a full node low is a priority, this was one of the main reasons the blocksize wars were fought.
So why does Liquid exist? People lately have been touting it as a way to ease fee pressure but in my opinion this is a fool's errand, no different than people back in 2017 saying to use litecoin because fees on bitcoin were too high. Liquid is just a fork of bitcoin, it has the exact same scaling problems and the only reason it has smaller fees is because it is never really been used. For now, it can work as a temporary stop-gap (essentially finding arbitrage for fees), but building actual infrastructure on top of liquid will run into the exact same problems as on-chain bitcoin.
The problem is that Liquid is trying to use trust as a scaling solution but did it in a completely inefficient way. When you are trusting the 11-of-15 multisig, you don't need all the benefits that a blockchain gives you, everything is dictated by the functionaries anyways. The problem is if liquid gets any meaningful amount of users it will also end up with huge fees and we'll be back to square one because Liquid's architecture didn't actually leverage any of the trust tradeoffs it took and just inherited all the same problems of on-chain bitcoin.
There are real solutions available. Lightning is the obvious alternative but it does have it's own problems, I think a lot of people have been seeing the problems with small scale self-custodial lightning, it is extremely hard to scale. This is why I am extremely excited about fedimint. Fedimint has almost the exact same trust model of Liquid (a federated multisig) but is built on a much better architecture that actually allows for scaling. Fedimints don't have a blockchain but instead operate as a chaumian ecash mint. This allows for them to do actually innovative things instead of just being bitcoin plus a couple features. There isn't a block size, instead the transaction throughput is just gated by the processing power of the guardians. Smart contracts are limited by having to do everything on-chain with bitcoin script, they are pure rust code and allows for all sorts of crazy things. And it all still interoperates with Lightning, essentially giving a Wallet of Satoshi with way less rug-pull risk, tons of new features, and is extremely private.
All this said, it is sad we aren't talking about self-custodial scaling solutions. Today the only real one is Lightning and with current fees, it isn't reasonable unless you have a few million sats. The problem is that this is just inherently a limitation with Lightning. Lightning is excellent when you have high value channels and can make payments across the network, but it does excel at "pleb nodes" where one guy puts 100k sats to try it out, this comes with too many limitations with paying on-chain fees and needing to have reserves to pay future on-chain fees. However, this is potentially solvable. Lightning has solved the problem of scaling payments, where if you have channels, one on-chain transaction can represent many actual payments. What lightning did not solve is that one utxo still represents one user, and this is the limitation we are running into today. Currently the only way we solve this is using a multisig sig (Liquid and Fedimint), but we can solve this in a self-custodial way if we activated covenants. Covenants essentially let us give fine grained control of what is going to be spent from a UTXO before the UTXO even exists. Currently, there are a few proposals (CTV, APO, TXHASH) all with varying ways to do it and different tradeoffs, but imo something like this is desperately needed if we want any chance to scale bitcoin in a self-custodial way.
-
 @ c4428155:a36de510
2024-03-22 09:00:00
@ c4428155:a36de510
2024-03-22 09:00:00A Diplomat’s Visits to Oklahoma Highlight Contacts Between Chinese Officials and Community Leaders Accused of Crimes
by Sebastian Rotella (https://www.propublica.org/people/sebastian-rotella) and Kirsten Berg (https://www.propublica.org/people/kirsten-berg), ProPublica, and Garrett Yalch and Clifton Adcock, The Frontier
This article was produced for ProPublica in partnership with The Frontier. (https://www.readfrontier.org/)Sign up for Dispatches (https://www.propublica.org/newsletters/dispatches) to get stories like this one as soon as they are published. Additional funding for this story was provided by the Pulitzer Center (https://pulitzercenter.org/).
The photos look like a routine encounter between a senior Chinese diplomat and immigrants in the American heartland: dutiful smiles, casual clothes, a teapot on a table, Chinese and U.S. flags on the wall.
But behind the images, there is a potentially concerning story. During two trips to Oklahoma, Consul General Zhu Di of the Chinese embassy visited a cultural association that has been a target of investigations into Chinese mafias that dominate the state’s billion-dollar marijuana industry. And the community leaders posing with him in the photos? A number of them have pleaded guilty or been prosecuted or investigated for drug-related crimes, according to court documents, public records, photos and social media posts.
“He’s meeting with known criminals,” said Donnie Anderson, the director of the Oklahoma Bureau of Narcotics and Dangerous Drugs Control, in an interview.
There is no indication of wrongdoing by the consul general, who is one of China’s top diplomats in the United States. Still, the encounters in Oklahoma reflect a pattern of contacts around the world between China’s authoritarian government and diaspora leaders linked to criminal activity — a subject of increasing concern among Western national security officials, human rights groups and Chinese dissidents.
U.S. and foreign national security officials have alleged that the Chinese state maintains a tacit alliance with Chinese organized crime (https://www.youtube.com/watch?v=0lu5Bdxr8QI&t=4765s) in the U.S. and across the world. Mobsters overtly support pro-Beijing causes and covertly provide services overseas: engaging in political influence work, moving illicit funds offshore for the Chinese elite and helping persecute dissidents (https://theworld.org/stories/2019-10-11/why-hong-kong-s-secret-societies-are-attacking-protesters), according to Western officials, court cases and human rights groups. Chinese officials reciprocate by tolerating and sometimes supporting their illicit activities (https://www.reuters.com/article/us-icbc-spain-investigation/fines-short-jail-terms-for-four-ex-icbc-spain-employees-in-laundering-case-idUSKBN23N2Q6/), according to those sources.
And this alleged state-mafia partnership has used influential Chinese cultural organizations in foreign countries to project power, according to Western officials. As ProPublica has reported, the leaders of diaspora associations who interact with Chinese and local governments in Europe and elsewhere include accused organized crime figures (https://www.propublica.org/article/how-beijing-chinese-mafia-europe-protect-interests).
In the United States, Chinese criminal networks have expanded their wealth and influence by taking over much of the nation’s illicit marijuana trade (https://www.propublica.org/article/chinese-organized-crime-us-marijuana-market), ProPublica reported last week.
It was in that context that the consul general traveled to Oklahoma.
In November 2022, a Chinese gunman killed four fellow immigrants and wounded another at an illegal marijuana farm in Oklahoma. The consul general hurried to Oklahoma City to discuss the murders with representatives of the community and offer help to relatives of the victims, according to Chinese officials, a participant in a meeting and media reports and photos. Zhu returned for another visit in June, photos and media reports show.
During both trips, meetings took place at the local branch of the American Fujian Association on Classen Boulevard, which in 2020 was the scene of a violent clash that left a convicted criminal with a gunshot wound and two others facing trial. Two years after that shooting, one of the accused assailants died and the other was wounded in the quadruple murder at their marijuana farm. Law enforcement agencies have also investigated the association’s headquarters, a ground-floor suite in a minimall, as a suspected illegal casino and a hub of other illicit activity, according to court records and senior officials.
(Li Zhaoyin via SinoVision, annotations by ProPublica)
During a second visit in June 2023, shown below, the diplomat met with some of the same people, as well as Chuan Min Zhang (circled), who had pleaded guilty to drug-related offenses.
(Li Zhaoyin via SinoVision, annotation by ProPublica)
Although the consul general did not respond to questions addressed to him for this article, officials at the Chinese embassy in Washington, D.C., said he simply did his duty by going to Oklahoma in response to the deaths of Chinese nationals. While declining to discuss the visits, a consular official said in an interview that the embassy was not aware of the crimes linked to the association and the people who met with Zhu.
In a written statement sent by email, the embassy’s spokesperson, Liu Pengyu, said Chinese officials travel to different states “to understand the living conditions and development of overseas Chinese in the United States, help them better observe the laws and regulations of their country of residence, and encourage them to actively serve and integrate into local communities so as to play a positive role in promoting friendship between the peoples of China and the U.S.”
But U.S. law enforcement experts see a troubling global pattern in ongoing relationships between Chinese government officials and community leaders with criminal ties. Because Chinese officials closely monitor the diaspora, it’s very likely they know about such ties, the experts said.
“These diaspora associations are tools of the Chinese state,” said Donald Im, a former senior official at the Drug Enforcement Administration. “The presence of criminal elements in the leadership suggests an alliance, directly or indirectly, between the Chinese state and organized crime.”
Freedom House, a human rights organization, summed up China’s global reach (https://freedomhouse.org/report/transnational-repression/china) in a report in 2021, describing a “framework of influence that encompasses cultural associations, diaspora groups, and in some cases, organized crime networks.”
The activities of the 14K triad, one of the Chinese criminal groups that are the dominant money launderers for Latin American drug lords (https://www.propublica.org/article/china-cartels-xizhi-li-money-laundering) and the Chinese Communist Party elite, highlight another suspected connection to the Chinese state, current and former law enforcement officials say.
The 14K has expanded its portfolio to play a command role over marijuana trafficking networks in Oklahoma and other states, according to Anderson, Im and other current and former officials. The Treasury Department has accused a Macao boss of the 14K of being prominent in the Chinese People’s Political Consultative Conference of the Chinese Communist Party (https://home.treasury.gov/news/press-releases/sm1206) and advancing China’s foreign influence through business ventures and Chinese cultural groups in Asia and the Pacific.
And U.S. federal agents are investigating cases in which Chinese provincial officials allegedly work with criminal groups to get drug money that they then use to finance infrastructure projects in China or abroad in the Belt and Road Initiative (https://www.dailytelegraph.com.au/truecrimeaustralia/crimeinfocus/australian-drug-lords-funnelling-cash-through-belt-and-road/news-story/af20ad5561327cb6eb778251b00ecaf7), the international public works program that has expanded China’s global might, according to current and former U.S. officials.
“All these provinces are competing with each other and using criminal networks and triads to find revenue for government projects,” Im said. “The marijuana industry in the U.S. is benefiting regional governors and provinces in China. Drug money is like an ad hoc bank for Chinese economic projects and policies.”
Oklahoma authorities admit that it is hard for them to get a grip on the influx of criminal groups, let alone trace a trail back to the Chinese state. Monitoring the activities of foreign diplomats, officials and spies is the jurisdiction of federal agencies working in the secretive realm of counterintelligence.
Nevertheless, state and federal agents have detected interactions between their suspects and Chinese government officials using surveillance, open sources, and photos and communications found in electronic devices, Anderson and other officials said. And the brazen movement of large amounts of money between China and the players in the illicit marijuana trade shows that Chinese officials are either aware or involved, the officials said.
“Our investigations indicate that there are Chinese officials pulling the strings, making money off of and involved in the illegal marijuana industry in Oklahoma,” Anderson said. “Money is invested here and it’s from China, to set up organizations. These are transnational organizations. And money is going back to China.”
Sen. James Lankford of Oklahoma (https://projects.propublica.org/represent/members/L000575-james-lankford), a member of the Senate Select Committee on Intelligence, said during a committee hearing last year that the Chinese government seems “fully aware” of marijuana-related organized crime activity in the United States, but it is “looking away … to increase a negative influence on Americans.”
The Chinese embassy spokesperson called such accusations “groundless,” “irresponsible speculation” and “slander.”
“We urge relevant sides to respect facts, stop fabricating lies, stop discrediting and smearing the Chinese government and diplomatic officials, and stop fomenting and spreading anti-China narratives,” Liu said.
Checkered Pasts
Many owners and workers at Oklahoma marijuana farms are Fujianese immigrants who arrived in recent years from other U.S. states, particularly New York, according to law enforcement officials and Chinese American leaders.
Some are law-abiding. Others are gunslinging gangsters. And still others operate in a gray area created by the national trend toward decriminalization, which has reduced risks and increased rewards associated with black-market marijuana.
ProPublica and The Frontier have identified over a dozen national leaders of Fujianese associations from the East Coast involved in Oklahoma’s marijuana boom. A number of these leaders, who include U.S. citizens and legal permanent residents, have suspected or confirmed links to illegal activity. Yet they interact with Chinese diplomats, Communist Party leaders and even Chinese security officials, according to photos, media reports and interviews. Some also mix with U.S. politicians.
A case in point: an accused drug trafficker named Yunda Chen, known as “Big Boss Yunda,” who traveled regularly between his home in Atlanta and his marijuana farms in Oklahoma, according to court records.
Using vehicle surveillance and a drone, state anti-drug agents followed couriers working for Chen as they transported bales of marijuana and cash shipments, some in Oklahoma and others that were destined for New York, Tennessee and other states in the national black market, court records say. The agents recruited an undercover informant — a local resident whom Chen paid $2,500 and a pound of dope a month to appear on registration documents and medical marijuana licenses as majority owner of his farms, court records say. FBI translators helped translate intercepted phone calls in which Chen used code words to set up deals, talked to suspects linked to alleged trafficking and money laundering in other states, and discussed a fight among more than 20 combatants over a debt in New York, court records say.
Authorities arrested Chen in Florida in December 2022 and charged him and five others in a trafficking conspiracy. Agents raided five farms in Oklahoma and seized nearly 50,000 marijuana plants and several guns, court documents say. They also found workers living in “poor and unsafe” conditions, said Mark Woodward, spokesperson for the Oklahoma Bureau of Narcotics.
Last June, prosecutors hit Chen with an additional charge of witness intimidation after he sent a text message warning an accused accomplice “not to talk about the things that don’t concern you” in upcoming testimony, court records say. (Chen is awaiting trial and has not yet entered pleas because defense lawyers requested delays of arraignments. He and his lawyers did not respond to requests for comment.)
The aid of the FBI and the rare use of wiretaps in a state case reflect its significance. As far as investigators were concerned, Chen was a major trafficker.
“He’s as big a player as any we’ve touched,” Woodward said. “He was running a more organized system than many we have dealt with — large scale, more hierarchy.”
In the simultaneously tightknit and far-flung subculture of Fujianese immigrants, though, Chen is a well-connected leader.
He lives in a large house on several acres bordering a country club in suburban Atlanta and owns a chain of restaurants and a catering business, public records show. (In 2012, court records show, he agreed to pay $225,000 in back wages to settle a Labor Department lawsuit accusing him of wage theft from employees who endured conditions that a federal investigator described as “deplorable.” Chen denied wrongdoing and disputed some of the findings in the settlement.)
While serving as executive vice chair of the American Lianjiang Association, which represents people from a coastal district of Fujian, Chen has joined Chinese diplomats and Communist Party officials at U.S. events, according to media reports and photos posted on social media.
Among those events: In 2017, photos and media reports show he spoke at a reception in Atlanta (https://freewechat.com/a/MzUyMDMwMjIwOQ==/2247483658/4) that was attended by a Chinese consul general who was based in Houston. In 2019, he participated with prominent Chinese Communist Party members (https://thevoiceofchinese.com/%E6%9C%80%E6%96%B0%E6%96%B0%E9%97%BB/%E7%BE%8E%E5%9B%BD%E8%BF%9E%E6%B1%9F%E5%90%8C%E4%B9%A1%E4%BC%9A%E5%91%8A%E5%8F%B0%E6%B9%BE%E5%90%8C%E8%83%9E%E4%B9%A6%E5%8F%91%E8%A1%A840%E5%91%A8%E5%B9%B4%E5%BA%A7%E8%B0%88%E4%BC%9A/) in a gala and symposium held by his association in New York to “conscientiously study” President Xi Jinping’s campaign for the “reunification” of China and Taiwan — a perennial flashpoint in military tensions with the United States.
Chen is also active in U.S. politics. He went to Georgia Gov. Brian Kemp’s (https://www.facebook.com/photo/?fbid=100950747682864&set=a.100950764349529)inauguration ceremony (https://www.facebook.com/photo/?fbid=100950747682864&set=a.100950764349529) in Atlanta in 2019 and donated $6,600 to the governor’s general election campaign, according to public records, photos and social media posts. He has contributed thousands to other local politicians (https://forum.atlanta168.com/forum.php?mod=viewthread&tid=37044&page=1) and socialized with them (https://atlanta.americachineselife.com/%E5%AE%98%E5%91%98%E6%9D%A5%E4%BA%9A%E5%9F%8E%E5%8D%8E%E5%95%86%E5%AE%B6%E5%81%9A%E5%AE%A2/), according to public records and media reports (https://atlanta.americachineselife.com/chow-time-%E6%B5%B7%E9%B2%9C%E8%87%AA%E5%8A%A9%E8%BF%9E%E9%94%81%E5%BA%97%E6%96%B0%E5%BA%97%E5%90%8D%E5%89%AA%E5%BD%A9%E5%BA%86%E5%85%B8/). He received an award (https://www.epochtimes.com/gb/19/3/30/n11151889.htm) from a minority business association in 2019. (A spokesperson for the Kemp campaign declined to comment.)
As of last year, Yunda Chen remained a “specially appointed policy consultant” of the Lianjiang association, according to a Chinese media report.
Like the Big Boss in Georgia, Virginia-based businessman Bi Chao Chen (no relation to Yunda) has interacted with Chinese diplomats, Fujian provincial officials and even representatives of the Ministry of Public Security — the law enforcement juggernaut that oversees China’s police forces — media reports and photos show.
In 2018, he was among leaders who met with a Ministry of Public Security delegation that visited New York, according to a news report that gave few details about the meeting. Photos and media reports also show him at a 2019 dinner with leaders of a powerful organization that is part of the United Front (https://selectcommitteeontheccp.house.gov/media/press-releases/select-committee-unveils-ccp-influence-memo-united-front-101), the influence and intelligence wing of the Chinese Communist Party.
U.S. prosecutors alleged last year that officials of the United Front worked with the public security ministry to set up an illegal Chinese police station in a Fujianese association in New York (https://www.justice.gov/opa/pr/two-arrested-operating-illegal-overseas-police-station-chinese-government) to monitor and intimidate U.S. dissidents, according to a federal criminal complaint and statements by federal officials. It was one of dozens of such stations (https://safeguarddefenders.com/en/patrol-and-persuade) directed by Chinese security forces and operating in diaspora associations around the world. The two Chinese-American defendants in the New York case have pleaded not guilty, and the Chinese government has denied any illegal activity on the part of the overseas police stations.
Bi Chao Chen, who appears in a photo (https://www.sinovision.net/home.php?mod=space&do=blog&uid=17812&id=393327)with a defendant (https://www.sinovision.net/home.php?mod=space&do=blog&uid=17812&id=393327) in the federal case, has had his own run-ins with the law.
In 2015, he was convicted of assault and battery after he menaced a man with a knife, forced him to the ground and stole $5,000 from him in Hampton, Virginia, court records show. He also has multiple convictions in connection to a wildlife poaching operation (https://www.dailypress.com/2015/02/18/14-charges-for-two-men-accused-of-elizabeth-river-fish-poaching/) he led and an additional arrest for assault and battery in which he was not charged, court records show.
In Oklahoma, he has had ties to at least two marijuana ventures, public records show. His name appears on a state marijuana license, limited liability corporation documents and the front gate of a vast expanse of greenhouses and indoor cultivation structures west of Tulsa whose registered agent was a lawyer now facing trial for hatching fraudulent ownership schemes, court records show. Another person who has a marijuana license registered at the same location was involved in a violent dispute in 2021 that ended in an assailant shooting at her with a pistol, court documents say.
In 2022, DEA agents searched the second location, located on the grounds of a former horse racing track, in an investigation into money laundering and marijuana trafficking in Oklahoma and Colorado that has resulted in three guilty pleas, according to court records, which also show that another defendant awaits trial. Chen has had a limited liability corporation registered at the address of the farm.
Authorities have not charged Bi Chao Chen in those cases. He and a lawyer did not respond to email and phone requests for comment.
Chinese officials are likely aware of the questionable backgrounds of these and other leaders because Chinese intelligence agencies systematically gather granular information on overseas communities, according to Western officials, academic reports, human rights groups and Chinese dissidents.
Many immigrants from Fujian, a coastal province with a history of organized crime and official corruption, come from modest backgrounds and entered the U.S. illegally, said Yaqiu Wang, research director for China, Hong Kong and Taiwan at Freedom House. Because they often visit family or do business in China, they feel pressure to develop good relationships with Chinese officials, she said.
“The CCP has leverage over them,” Wang said. “If you want to go back to China, if you need a passport or you want to clean up a criminal record in China, you need to demonstrate loyalty.”
And if leaders show loyalty, Chinese officials are increasingly willing to engage with them — even those who are organized crime figures, experts said.
“As the Chinese government has been expanding its power across the world, the organized crime connections with the state have grown,” a former national security official said. “They have gotten much closer. Chinese government influence has expanded. There is a lot of incentive to work together.”
The Chinese embassy did not respond to questions about specific cases. In an interview, a Chinese consular official acknowledged that Chinese officials have regular contact with U.S. diaspora associations. But the official rejected the idea that the Chinese government has detailed knowledge about community leaders and works with them even if they are involved in criminal activity.
“We have five million Chinese nationals living in the USA,” said the consular official, who requested anonymity because they are not the official spokesperson. “We just have some connection with different organizations, regardless of specific persons. … We couldn’t be able to know everybody.”
In Oklahoma City, the associations themselves have kept law enforcement busy.
Oklahoma Attorney General Gentner Drummond, Anderson and other officials told ProPublica and The Frontier that members of Fujianese associations are targets of investigations into organized crime. Leaders of associations in Oklahoma City did not respond to requests for comment.
During a raid last year on the Fuzhou Chamber of Commerce, police busted an illegal casino, arrested three suspects and seized drugs and $79,000 in cash from 18 people, including two who had criminal convictions and several involved in the marijuana industry, according to court documents and public records. Surveillance had detected numerous cars in the parking lot that were connected to narcotics investigations, court records say. (Of the three arrested, one was charged and has pleaded not guilty, another was extradited to Colorado on a warrant in a marijuana cultivation case, and the third has not been charged.)
A block away on Classen Boulevard at the American Fujian Association, city inspectors found card tables, video slot machines and other signs of an illegal casino in 2020, court records show. The police vice squad has investigated alleged gambling in the ground-floor suite, according to court testimony and public records. No charges have been filed in that case. Leaders of the organization did not respond to requests for comment.
Two years after the shooting in 2020 at the association, the two accused assailants became victims in the quadruple murder at the marijuana farm in Kingfisher County. As a result, investigators revisited the 2020 shooting looking for links to organized crime and the farm massacre, and they learned that the killer and some of his victims had spent time at the association.
Despite the troubles of the American Fujian Association, Consul General Zhu chose to meet there with community leaders days after the quadruple murder, according to photos, media reports and a participant in the meeting at the association. During that visit in November 2022, the diplomat talked to relatives of the victims about funeral arrangements and the transport of one of the bodies to New York, according to a media report and a participant at the meeting
Those present included prominent Fujianese figures from New York who have invested in Oklahoma’s marijuana boom, media reports and photos show. One of them was Pan Muyong, a veteran national leader of several groups.
Pan Muyong, circled, at the America Changle Association in Manhattan, where U.S. prosecutors allege an illegal Chinese police station was helping monitor and intimidate dissidents. The blue sign on the left says Fuzhou Police Overseas Service Station.
(Louis Zhao/YouTube)
“We are deeply anxious and uneasy,” Pan told the visitors from the embassy, according to a report by SinoVision, a Chinese-language media outlet. “We Chinese operate farms and grow marijuana with the licenses approved by the local government and within the scope of the law, not illegally as reported by the media.”
Pan has been an executive of the America Changle Association in New York, according to media reports and photos. Last year, federal prosecutors charged two other leaders of that association with operating the illegal Chinese police station in Manhattan.
Photos and media reports place Pan with the defendants during the period of time when, according to the federal criminal complaint, they allegedly helped Chinese security forces monitor dissidents in the United States. A video shows Pan giving a speech in the association offices that housed the allegedly illegal police station — with a sign about the station visible on a wall.
Pan interacts regularly with Chinese diplomats and other officials, according to photos and media reports. Last year, he and other pro-Beijing leaders held signs as they protested the visit of Taiwan’s president to New York, video and media reports show. Pan and other Oklahoma-connected leaders are also active in New York politics, attending campaign events and making donations, according to photos, media reports and campaign records.
Pan has not been charged with a crime. He did not respond to emails and declined a telephone request for comment.
But four people who posed for photos with him and the consul in Oklahoma City have pleaded guilty or been charged or investigated for offenses including drug trafficking, illegal firearms possession and obstructing officers, court records show.
Ling Chen, for example, pleaded guilty last June to maintaining a place for selling drugs in a case in which authorities confiscated $42,000 from her and two other defendants, court records show. Chuan Min Zhang pleaded guilty in 2021 to possession of cocaine and acquiring drug proceeds, a felony that resulted in the forfeiture of $32,000, court records show. Ke Xiang Chen has pleaded not guilty and awaits trial after an arrest last October for alleged possession of ketamine and ecstasy and acquiring drug proceeds, court records show.
None of the three responded to requests for comment in emails, by phone and through lawyers.
The fourth, Qiu He, was arrested last April in the investigation of an alleged network that set up illegal marijuana farms, court records show. She has not been charged with a crime and denied any wrongdoing in an interview with ProPublica and The Frontier. She is fighting to recover almost a million dollars seized by anti-drug agents (https://www.propublica.org/article/marijuana-oklahoma-chinese-immigrant-arrests-asset-seizure-2).
He, who had a grandparent from Fujian, said members of the community asked her to attend the 2022 meeting with the consul general to translate Mandarin for people who only spoke a Fujianese dialect. But she said she knows little about the association and has not returned.
In addition to He, three other people in the photos with the consul general have surfaced in investigations of fraudulent owner schemes for marijuana farms. Although they have not been charged with crimes in relation to those investigations, Ling Chen, Jun Can Zhang and Weixing Feng have jointly owned marijuana farms with people who are being prosecuted or investigated for serving as paid straw owners for dozens of growing operations, court documents and public records show. They did not respond to requests for comment.
Ling Chen, Ke Xiang Chen and Junli Zhang also managed or had an ownership interest in Lucky Zhang’s, a restaurant and nightclub near the Fujianese association that was outfitted with high-tech lighting and individual karaoke rooms, court documents and public records show. Detectives zeroed in on the club as a suspected site of human trafficking after they learned that young Asian women living at a house were being transported regularly to Lucky Zhang’s and spending the night there, court documents say. Police raided the club on Nov. 5, 2022, and again on Feb. 15, 2023, making arrests and seizing drugs and cash, according to court documents, interviews and social media posts.
The November raid resulted in the prosecution in which the manager, Ling Chen, pleaded guilty, court records show. Another defendant arrested at the club pleaded not guilty and awaits trial on charges of acquiring drug proceeds and possession of ketamine with intent to distribute, according to court records.
Junli Zhang did not respond to email and phone requests for comment. Zhang was also the chair of the association on Classen Boulevard during both of the consul general’s visits, according to Chinese media reports.
Last June, the consul general returned to Classen Boulevard for the second visit. Zhu’s stated goal was to gain “an in-depth understanding of the production, life and work conditions of the farms run by overseas Chinese in Oklahoma,” according to Chinese-language media reports. He listened to “a work report” from the association’s chair, one article said.
“Overseas Chinese will always be members of the big family of the Chinese nation,” the diplomat said, according to the media report (https://www.52hrtt.com/global/n/w/info/A1685709590300). “No matter where you go, the eyes of the motherland are never far away and are always watching and caring about you.”
Correction
March 22, 2024: This story originally misstated what political entity a leader of the 14K triad was said to be an important member of. The Treasury Department alleges that he is prominent in a subentity of the Chinese Communist Party called the Chinese People’s Political Consultative Conference, not in the larger party.
https://www.propublica.org/article/oklahoma-marijuana-china-diplomat-visits
-
 @ ecda4328:1278f072
2023-12-16 20:45:10
@ ecda4328:1278f072
2023-12-16 20:45:10Intro
I've left Twitter (X), WhatsApp, Telegram, Instagram, Facebook and Google. The driving force behind this decision was the escalating overzealous censorship. I cannot condone platforms that actively indulge in this practice. In all honesty, I've always felt uneasy using "free" platforms riddled with ads where the user is the product and doesn't own the content they produce.
Let's be real: hardly anyone thoroughly reads the Terms of Service (ToS).
Censorship and Shadow Banning
The final straw was when I resorted to a text editor for drafting messages/comments, hoping to rephrase them so they wouldn't get deleted moments after posting. This isn't exclusive to just one platform; I've encountered it on YouTube and LinkedIn too. Twitter (or X, as I now refer to it) has a history of shadow banning users' posts. It's been beyond frustrating to get banned from Telegram groups simply for posing legitimate questions.
You can test LinkedIn's censorship mechanism too, simply add "Binance" word (without quotes) to any of your comment and your post will disappear. At least that is what I've seen couple of months ago. Similarly, comments on YouTube often disappear precisely 60 seconds after posting if they contain specific keywords. I know they call it filtering, but it does not make any sense. In my opinion, legitimate companies and links shouldn't trigger these filters.
Community and Connections
Recently, I attended the Cosmoverse 2023 conference in Istanbul. Most attendees exchanged their Telegram or Twitter (X) contact information. Since I didn't have either, I gladly shared my Nostr and SimpleX Chat details. Many privacy advocates were quick to connect on SimpleX with me, though several didn't.
I learned about SimpleX Chat from Jack Dorsey, who mentioned it during a conversation in July:
While Signal has its shortcomings, I still keep it as a backup communication tool.
One More Last Straw
During the conference, I temporarily reinstalled Telegram to communicate with my group. Convincing nine individuals to switch to SimpleX on the spot seemed impractical.
At the conference, I bought a Keystone hardware wallet. Shortly after, I connected with the seller, Xin Z, on Telegram. However, I was banned from the official Keystone Telegram group right after posing a question.

Upon inquiring, Xin Z clarified that Telegram's official team had banned me, not the group's admin. 🤯

Business and Community: Collateral Damage
Censorship doesn't just silence voices; it hinders potential growth and stifles innovation. When platforms arbitrarily or aggressively censor content, they inadvertently create barriers between businesses and their potential clients. New users or clients, when encountering such heavy-handed moderation, may feel discouraged or unwelcome, causing them to retreat from the platform altogether.
Moreover, for businesses, this form of censorship can be devastating. Word-of-mouth, discussions, and organic community engagements are invaluable. When these channels are hampered, businesses lose out on potential clientele, and communities lose the chance to thrive and evolve naturally.
Censorship, in its overzealous form, breaks the very essence of digital communities: open dialogue. As platforms become more censorious, they risk creating sterile environments devoid of genuine interaction and rich discourse. Such an atmosphere is not conducive for businesses to foster relations, nor for communities to flourish. The ultimate price of overcensorship isn't just the loss of a few voices—it's the fragmentation of digital society as we know it.
Freedom to Choose
I strongly advocate for the adoption of Free and Open Source Software (aka FOSS) products. In these platforms, you aren't treated as the product. However, supporting them through donations/contributions is always an option. Platforms like Nostr and SimpleX Chat are excellent starting points.

My Nostr account:
npub1andyx2xqhwffeg595snk9a8ll43j6dvw5jzpljm5yjm3qync7peqzl8jd4Disclaimer
This article reflects my personal experiences and opinions. It is not intended to criticize or demean the Keystone hardware wallet product or its quality. Furthermore, the actions taken by Telegram are not a direct representation of the views or policies of the Keystone Telegram group admins. Any reference to specific events or entities is made in the context of broader concerns about platform censorship.
-
 @ 06639a38:655f8f71
2024-03-22 08:21:42
@ 06639a38:655f8f71
2024-03-22 08:21:42When we moved into our new home in 2017, one of the things we did was adding a epoxy coating layer to the concrete floor in our garage. Some photo's of the work in progress.
The is the coating we used:
One of the best modifications we've done in our garage, the floor is still very proper and easy to clean!
What does your garage floor look like?
-
 @ 4ef93712:97fe79c0
2023-12-11 21:17:25
@ 4ef93712:97fe79c0
2023-12-11 21:17:25Introduction
Resolvr is building Open Source Justice by empowering sovereign communities to peacefully and voluntarily resolve their own disputes with open-source tools.
Our first product is designed for a community close to home: the Free and Open Source Software (FOSS) development ecosystem. We've built a peer-to-peer bounty marketplace that:
- gives developers assurances of payment for solving bounties,
- decentralizes and grows FOSS funding sources,
- unlocks access to the global talent pool,
- provides a frictionless on-ramp to earn Bitcoin (₿).

Resolvr does this by:
- limiting discretion of bounty grantors through reputational stakes and a Bitcoin (₿) escrow powered by Discreet Log Contracts🔮,
- resolving disputes through crowdsourced review of bounty solutions,
- using nostr🦩 for interoperable and censorship-resistant bounty discovery,
- using Lighting⚡ zaps for instant bounty payouts.
The alpha webclient is now live at resolvr.io.
The Problem
The root problem with conventional bounty marketplaces is all the trust that's required to make them work.
Satoshi Nakamoto (probably)
1. Centralized Custodians are Security Holes 🕳️
❌ Centralized bounty marketplaces that hold bounty funds can exit scam or go bankrupt.
- This year, BountySource (5,445 listed bounties worth $406,425 in 2019) stopped paying out bounties to developers.
❌ Existing bounty marketplaces, like Replit, don't have instant or free payouts:
- Devs are rewarded in Replit's 💩-coin and must request USD conversion by email.
- Replit charges a 25% withdrawal fee and requires a minimum withdrawal of $350.
❌ Knowledge workers in developing countries, many of whom rely on mobile wallets, have lost their funds via bank and telco attack vectors ($3M USD via 2,000 SIM cards, lost).
❌ Centralized bounty sites can censor posts for projects the site-owners disagree with or find unsavory.
2. Bounty Grantors are Judge 👩⚖️ and Jury 🏛️
❌ Bounty grantors have unlimited discretion over whether a solution meets their bounty criteria. And they can change the criteria after the dev has satisfied the original bounty.
❌ The Human Rights Foundation (HRF) recently changed its criteria on a nostr bounty after a dev provided a solution to the originally posted bounty. HRF decided to pay the dev only half the bounty.
❌ This is inherently unfair and inefficient!
Resolvr's Solution ✔️
- 📡 Distributed, interoperable, censorship-resistant communication protocol for bounty posting and discovery,
- (₿) Peer-to-peer lightning payouts and non-custodial escrow system,
- ⚖️ Decentralized Dispute Resolution
How it Works
Check out the Walkthrough here.
Zap Payouts and Crowdsourced Dispute Resolution
- Login to resolvr.io with your existing nostr keys (or let resolvr.io generate keys for you - remember to back them up!)
- Set up your profile by
- Linking your GitHub identity to your nostr profile (through resolvr.io or Amethyst on android) following NIP-39 instructions
- Getting a lighting address for zap payments (getalby.com)
- Maker (entrepreneur, foundation, FOSS project) - post a bounty with a detailed criteria and amount.
- Taker (freelance developer) - find a bounty to solve, apply to the bounty.
- Maker - assign a Taker to solve your bounty.
Ideal Path
- Taker - solve the assigned bounty and provide a link to the work product in the comments (e.g., github repo or PR)
- Maker - click "pay" to zap bounty reward

Happy Path
- If either party disputes the bounty: Taker or Maker clicks "poll" to initiate a nostr zap poll,
- Community members (other Makers/Takers) review bounty/solution and vote to resolve the dispute,
- Maker - if community votes in favor of Taker, zap payout.

Sad Path
- Maker does not comply with community decision, burns reputation and cannot find developers for future projects.

Innovations
Resolvr's success is aligned with the success of nostr🦩 and bitcoin. We're advancing the tech with novel applications:
- Authored NIP-43: bounties over nostr
- Discovered new use-case for NIP-69 zap polls: dispute resolution
- First p2p bounty marketplace with instant payouts over lightning
- First p2p bounty marketplace with integrated dispute resolution
- New frictionless onramp to earn bitcoin, grow circular economy
What's Next for the Resolvr Bounty Marketplace?
The next dispute resolution feature on the roadmap for the Resolvr bounty marketplace is on-chain DLC🔮 escrow. We're putting DLCs🔮 on nostr🦩 and building a desktop client to do it!
The desktop client will allow Makers and Takers to post, apply and assign bounties just like the web client. But it will also create and broadcast DLC🔮 escrow contracts. In the event of a dispute, the Resolvr oracle will attest to the results of the crowdsourced zap poll to release the funds to the winning party.
In the future, Resolvr will allow Makers and Takers to select their own oracles, and communities can be listed as "review association" oracles, earning bitcoin for resolving disputes over bounties (think: foundations, hackerspaces, bitdev meetup groups).
For more details about our DLCs🔮 on nostr, check out the Resolvr's escrow repo on GitHub!
In addition to DLCs🔮, Resolvr's roadmap includes:
- Decentralizing the default Resolvr oracle through FediMint🔅 protocol and FROST🥶.
- Scaling escrow through Lighting⚡ DLCs🔮
- Bounty review and code testing with AI🤖 (DVMs)
Beyond Bounties...
The Resolvr Project is building an open-source dispute resolution system on bitcoin and adjacent protocols.
Resolvr will revolutionize dispute resolution on a global scale, offering secure, open-source, customizable, decentralized, and radically cost-efficient mechanisms for infinite use cases.

Dispute Resolution is a big opportunity, with increasing demand driven by AI services and microtransactions.

Thanks for joining us on this journey to make FOSS funding more fair and efficient, expand access to Bitcoin, and provide communities with the tools to peacefully resolve their own disputes!
Visit resolvr.io to post and claim bounties today!
The Team
- Dave Schwab (🦩 | 𝕏): Chief Product Officer for a legal tech SaaS.
- Aaron Daniel (🦩 | 𝕏): Appellate attorney and dispute systems designer. Author of the Bitcoin Brief newsletter and regular contributing author to Bitcoin Magazine.
- Chris@Machine (🦩 | 𝕏): Nostr developer and creator of Blogstack.io, a longform nostr platform. Streaming nostr programming workshops on Zap.Stream and Youtube.
- Utibe Essien (🦩): Product designer and web adventurer.
- Ras (𝕏): Bitcoin hacker. Founder of Bitcoin Grove, a community accelerator and physical hacker space in Miami.
- Brian: Front end web developer and crypto enthusiast.
- Tommy (🦩): Google Software Engineer who enjoys making the State obsolete in his free time
- Randy (𝕏): Full-stack developer currently working on Greenlight at Blockstream
- Derek Hinkle: Backend Developer for a legal tech SaaS; machine learning and AI powered automation.
- Justin Moeller (🦩 | 𝕏): Spiral and HRF grantee working on Fedimint.
Connect with Resolvr!
- Post and Claim Bounties on the Resolvr Bounty Marketplace TODAY: https://www.resolvr.io
- Questions/Suggestions? Join our Discord: https://discord.gg/DsqRw8My4m
- Stream the team's weekly All-Hands Call, live every Monday @ 1:00pm ET on Zap.Stream
- Contribute to the project on our GitHub!!
- Witness Resolvr's evolution through our previous #buildinpublic weekly updates.
-
 @ 599f67f7:21fb3ea9
2024-03-22 07:34:29
@ 599f67f7:21fb3ea9
2024-03-22 07:34:29¿Qué es Cashu?
Cashu es un protocolo de Ecash de código abierto para Bitcoin que ofrece transacciones instantáneas de tarifa cero con una privacidad casi perfecta, creado por nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg.
En la siguiente tabla se compara Cashu y Bitcoin on-chain, sacada de la presentación Nuts and Bolts de nostr:npub1cj6ndx5akfazux7f0vjl4fyx9k0ulf682p437fe03a9ndwqjm0tqj886t6 en la Conferencia Bitcoin Bangkok 2023.
| Cashu | Bitcoin (on-chain) | |--|--| | Sin libro mayor | Libro mayor distribuido | | Token al portador | UTXO | | Transacciones ciegas | Transacciones públicas | | Centralizado | Descentralizado | | De confianza | Sin confianza | | Sin registro de tx | Registro de tx |
Como podemos ver, Cashu sacrifica la confianza y la descentralización en favor de la privacidad. Esto tiene mucho sentido cuando se trata de soluciones de custodia, ya que el usuario ya utiliza un servicio centralizado en el que tiene que confiar. Las soluciones de custodia tradicionales tienen una privacidad horrible, ya que ese custodio conoce los fondos que posee un usuario y con quién está transaccionando. Permitiendo ataques y censura a los usuarios. Los registros de los datos también se pueden convertir en un honeypot.
Por el contrario, los mints de Cashu pueden actuar como custodios que no saben quienes son sus usuarios, cuántos fondos tienen ni con quién interactúa. Esta casa de la moneda (mint) solo tiene como único registro una lista de secretos gastados que no son reutilizables y sin forma de asociarlos con los usuarios.

Algunos casos de uso serían vales ya centralizados y custodiados por un tercero; uso para pagar por un recurso como APIs, relays de nostr o mixnets; sistemas integrados que reemplazan el modelo cuenta y saldo; y servicios de intercambio/mezcla para desligar depósitos y retiros.
Historia
Ecash fue concebido por primera vez por David Chaum en 1982 como un protocolo de transmisión de valor electrónico utilizando firmas ciegas. Cashu es una implementación de Ecash que utiliza la variante de David Wagner de Chaumian blinding de 1996 creada por nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg.
Terminología
Para ayudar a comprender como funciona Cashu, vamos a tratar primero alguna terminología esencial.
Mint
Los Mint en Cashu es el custodio de los fondos de los usuarios. Su labor es acuñar y quemar tokens y prevenir el doble gasto.
El mint de Cashu corre un nodo Lightning, por lo que puede enviar y recibir pagos Lightning. Incluyendo el intercambio con otros Mints. Sin embargo, todavía puedes realizar transacciones con tokens ecash, incluso si el nodo Lightning está offline. A diferencia de Lightning, el destinatario tampoco necesita estar en linea para recibirlo. Esta casa de la moneda o mint no sabe quién es el usuario, cuantos fondos tiene ni con quienes está realizando transacciones.
Sin embargo, desde que el mint es el custodio de los fondos de los usuarios, deberías elegir un mint en el que confíes y del que conozcas al operador.
Utiliza montos pequeños o canjea los tokens de inmediato.
Token
Un token cashu es esencialmente un conjunto de datos firmado por el mint. El usuario guarda esos tokens en su billetera. Dado que esos tokens ecash son solo texto, pueden ser enviadas por cualquier protocolo basado en texto. Como nostr, mail, sms, etc.
Cashu utiliza un sistema que se basa en monedas con denominaciones fijas.
La denominación de los billetes fíat son una analogía. Por ejemplo, en el Euro los billetes son de 5, 10, 20, 50, 100…
En Cashu, los tokens están denominados en potencias de 2. Por ejemplo, 1, 2, 4, 8, 16, 32, 64, 128 sats, así sucesivamente.
El objetivo de usar denominaciones es aumentar el anonimato establecido entre los usuarios y hacer que sea aún más difícil para los mints asociar las transacciones con las identidades de los usuarios.
¿Cómo funciona? Explicado como si tuviera 5 años

Alice quiere acuñar nuevos tokens Cashu. Así que se dirige al mint de Bob, y dice: “¡Oye! Quiero acuñar nuevos tokens de Cashu".

Bob responde diciendo: "Vale, págame y envíame un secreto ciego". El secreto ciego significa que Alice conoce el secreto, pero Bob no puede verlo.

Alice genera un secreto y luego lo ciega para que Bob no sepa cuál es el secreto.

Ella le paga a Bob y le envía su comprobante de pago y su secreto ciego.


Cuando Bob está conforme con el pago, firma el secreto ciego de Alice y le devuelve el secreto ciego firmado. Una vez firmado por Bob, en el futuro puede tener la seguridad de que el token es válido.

Alice quiere pagarle a Carol. Ella le envía a Carol su secreto junto con una llave para descifrar el secreto ciego firmado.
Carol quiere canjear su token. Así que ella va a la casa de la moneda, Bob, y le muestra el secreto y la clave que Alice le dio.

Bob nunca ha visto el secreto antes y tampoco sabe que fue Alice quien lo generó, ya que Alice lo ofuscó antes de enviárselo. Pero puede verificar que lo firmó antes, por eso puede tratarlo como un gasto valido del token. Ahora firma un nuevo token para Carol, o le devuelve los sats y añade el secreto a una lista de secretos gastados. Si alguien trata de reclamar con el mismo secreto otra vez, Bob lo rechazará porque es un gasto doble.
¿Cómo sabe el mint (Bob) qué cantidad de sats darle a Carol?
Anteriormente hemos mencionado que los tokens Cashu están denominados en potencias de 2 (1, 2, 4, 8, 16, 32...), algo así como billetes fíat.
Bob, la casa de la moneda, tiene una clave privada distinta que usa para firmar cada denominación. Por ejemplo, tiene una clave privada única para tokens con denominación de 1 sat, otra para los de denominación 2 sats, otra para los de 8 y así sucesivamente…
De esta manera, cuando Carol viene a Bob para canjear tokens, Bob sabe con qué clave privada ha firmado el token antes y, por lo tanto, a qué denominación pertenecen los tokens.
¿Qué pasa con el cambio?
En Cashu no hay cambio. Solo tienes que decirle al mint que destruya los tokens antiguos y que acuñe nuevos tokens del mismo importe exacto.
Para ver esto, digamos que Alice tiene dos tokens que suman 10 sats. Un token de 8 sats y otro de 2 sats.
Ella quiere enviar 9 sats a Carol. Así que va al mint y le dice a Bob que divida su token de 2 sats en dos tokens de 1 sat. Ahora puede enviar 9 sats a Carol en forma de una ficha de 8 sats y una ficha de 1 sat, y guardar la otra ficha de 1 sat para Ella.
Lightning para la interconexion
¿Qué pasa cuando Alice quiere pagarle a David, que no confía en el mint de Bob pero conoce a Erin y usa el mint de Erin?
Alice cambia sus tokens en el mint de Bob, dando instrucciones a Bob para que derrita los tokens o los convierta de nuevo en sats Lightning. El mint de Bob luego envía una transacción Lightning al mint de Erin. El mint de Erin luego acuña nuevos tokens con David utilizando los sats Lightning que acaba de recibir del mint de Bob.

¿Qué es lo siguiente para Cashu?
Ecash programable
Podemos establecer condiciones de gasto al ecash, siendo el mint quien las aplica. Esto puede desbloquear potentes contratos inteligentes sin llegar a la cadena base ni a la red Lightning, que pueden permitir pagos públicos, pagos offline y de alta frecuencia.
Plan de prueba de pasivos para los mints
El llamado Proof of Liabilities de Calle (PoL) en Cashu, se trata de una especie de sistema de auditoria que le dificulta a los custodios atacar a los usuarios mediante la introducción del concepto de epochs (épocas). En este esquema, el mint custodio rota de forma regular el conjunto de claves privadas que utilizan en cada epoch y publica listas auditables de tokens acuñados y quemados en el último epoch. Combinado con un esquema de prueba de reservas en el que las reservas se mantienen en un multifirma on- chain, un custodio deshonesto no puede reducir sus pasivos sin arriesgarse a ser descubierta por los usuarios. Para profundizar sobre este aspecto consulta el artículo completo.
Prueba Cashu
Puedes probar Cashu a través de nostr:naddr1qqxnzdesxqmnxvpexqunzvpcqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypve7elhmamff3sr5mgxxms4a0rppkmhmn7504h96pfcdkpplvl2jqcyqqq823cnmhuld y nostr:naddr1qqxnzdesxs6r2dehxvmrqdenqgs9n8m87l0hd9xxqwndqcmwzh4uvyxmwlw0637kuhg98pkcy8ana2grqsqqqa284333an. Únicamente necesitas una cartera Lightning y un teléfono u ordenador.
Referencias
- Cashu.space
- Learn about Cashu
- Cashu en los medios
- Entrevista con calle de nostr:npub1yn3hc8jmpj963h0zw49ullrrkkefn7qxf78mj29u7v2mn3yktuasx3mzt0
Ver también
- Video de nostr:npub1rxysxnjkhrmqd3ey73dp9n5y5yvyzcs64acc9g0k2epcpwwyya4spvhnp8
- Soporte Cashu
- NUTs - Notación, uso y terminología, las especificaciones del protocolo para Cashu
- X-Cashu - HTTP 402: Se requiere pago con Cashu
- Proxnut - Proteger o monetizar los recursos web con el uso de tokens
- Prueba de Pasivos para Cashu
- Fedimint - implementación de ecash federado
-
 @ 2edbcea6:40558884
2023-12-10 16:57:25
@ 2edbcea6:40558884
2023-12-10 16:57:25Happy Sunday #Nostr !
Here’s your #NostrTechWeekly newsletter brought to you by nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk written by nostr:npub1r3fwhjpx2njy87f9qxmapjn9neutwh7aeww95e03drkfg45cey4qgl7ex2
The #NostrTechWeekly is a weekly newsletter focused on the more technical happenings in the Nostr-verse.
Let’s dive in!
Recent Upgrades to Nostr (AKA NIPs)
1) (Proposed) NIP 71: Video Events
If Nostr wants to disrupt Netflix or Youtube, we’ll need support for video content.
So far Nostr devs have mostly shied away from storing full files (videos, PDFs, images, etc) on relays in favor of storing files on dedicated file storage/CDN solutions (e.g. nostr.build). That has meant that to bring file-based content into the nostr-verse it has to be referenced within a note or (via NIP 94 ) just publish a Nostr event that is just a reference to a file.
NIP 94 is powerful because we can wrap something that’s not on Nostr in a Nostr event which makes it referenceable and make that reference shareable natively via relays.
This proposal is to create a wapper around NIP 94 to help facilitate more than just hosting the video content. This proposal helps allow video-based clients to do two things: 1) create a replaceable nostr event for the video (so if the creator uploads a new version or switches hosts, people can still reference the same Nostr event). 2) Track video view counts.
It’s still under development but could be helpful as we try to bring more content creators over to Nostr 💪
Author: zmeyer44
2) (Proposed) NIP 44: Places 🌏
Much physical commerce is discovered by consumers via map apps. You go on Google or Apple Maps to find an art supply store near your apartment, or coffee shops that are open right now when you’re in a new city. These centralized solutions have dominated, but Yondar seeks to change that.
Yondar is a Nostr client that allows users to publish places on a map. This could be places of business or events, really anything that has a location. It could unlock crowdsourcing the place-based apps we’re used to using, so we can wrest control back from the tech giants.
This NIP is a proposal to make “place” events a protocol that’s available to any Nostr client. So that the idea can spread beyond just Yondar. Can’t wait!
Author: arkin0x
Notable Projects
Updates to negentroopy and strfry 🛜
nostr:npub1yxprsscnjw2e6myxz73mmzvnqw5kvzd5ffjya9ecjypc5l0gvgksh8qud4 is the primary author of the StrFry relay. It’s one of the most popular relay implementations used by relay operators because it’s performant and extensible.
Doug announced a slew of improvements this week to a library underpinning strfy, called negentropy. Negentropy (from my limited understanding) is a protocol for set-reconciliation, which I would summarize as optimizing the process of syncing two sets of data quickly and with minimal compute resources and data transfer.
I don’t know the innards of strfry but I do know that when scaling systems like relays much of the difficulty comes from distributing data onto many servers so that the relay can hold increasing amounts of data but still serve users requests quickly. You usually can’t have your cake and eat it too.
Improvements to projects like negentropy allow us have relays which are both larger and more performant. They’re not the sexiest advances and usually go un-celebrated, but Nostr will be faster for users and relay operation should get cheaper because of this project.
Thanks Doug!
StrFrui ✔️
Relays are inundated with new events constantly and sometimes relay operators want to “sift” through new Nostr events pushed to the relay to ensure that unwanted content can be rejected. This has been done for rate-limiting, spam filtering, and sometimes outright npub censorship. Which as a relay operator is their right.
Problem is, as Nostr usage scales, relay operators will need more sophisticated tools to manage content on their relays. nostr:npub168ghgug469n4r2tuyw05dmqhqv5jcwm7nxytn67afmz8qkc4a4zqsu2dlc built StrFrui which is a framework for building sifters for relays running strfry (common, performant relay). Thanks for helping Nostr scale 🫡.
Latest conversations: nsecBunker
The landscape for security of Nostr keys is rapidly evolving. Here are the current options:
- Paste your nsec into the client - yikes, but sometimes there’s no alternative, like on iOS Nostr Browser Extension (nos2x, Nostr Connect, etc) - good if you’re on a browser, not encrypted at rest.
- Android Signing App - great if you’re on Android and the client supports it.
- nsecBunker - great security if you want to be hands on managing a bunker
We’re early so we’re still learning the architectures that work the best and those that will be compatible with future, more user-friendly experiences. I’m starting to think nsecBunker has the most potential, because it’s cross platform, encrypted at rest, and can be built so that users never have to manage Nostr keys if they don’t want to.

How does nsecBunker work?
Short answer: it’s complicated. Slightly longer answer: 1. Give the bunker your nsec (or let it generate one). 1. You authorize a client with certain permissions (can publish kind 1 notes for 10 hours, etc). 1. That generates and npub+token that you can use to log in to clients that support nsecbunker. 1. While that authorization lasts, that client can take authorized actions on behalf of the user who’s key is in the bunker.
There’s also a flow in reverse (starts with the client wanting to take an action), but I’m not going to get into it right now. It’s much harder to explain.
How is this better?
NsecBunker has a few advantages over other solutions:
1. Users never need to copy/paste the nsec 1. Nsec is encrypted in the bunker with a passphrase so even if bunker is hacked you’re ok.
1. Bunkers can work in any Nostr context (browser, mobile app, hardware device, whatever).The biggest downside to nsecBunker is that you need a Nostr account to be the admin of the keys stored in the bunker. Whereas the Nostr Browser Extensions you can have one account and self-manage it.
The pot of gold at the end of the rainbow
There are always going to be people that want to custody their own Nostr keys, but most humans likely won’t have the knowledge nor inclination to do so. What they want is something that’s more like the “Login with Twitter” button.
In this future, a user would sign up with a Bunker provider (these could be paid services). The user would use a email/password to manage their account with the provider. The user could generate as many Nostr accounts as they like, but the Bunker custodies the keys.
Clients would then have a “Login with Bunker” button that allows the user to put in their Nostr address (NIP 05) and that will be de-referenced to a bunker and a few relays to help the client and the bunker do all the coordination to get the user logged in and ready to use the client. It will basically be OAuth but using Nostr events as the transfer protocol instead of just HTTP requests.
This architecture allows the least technical users to have a familiar experience while benefiting from all the security and control tools that sophisticated companies still struggle with.
Best of all, if users can export their keys in the future, then they can always migrate out of a custodial solution and self-custody once they learn the advantages. More freedom for users and freedom tech still gets more accessible to everyday folks. nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft created a proof of concept of just such an onboarding flow, check it out here.
What needs to be built
While bunker providers would need to build some management software around nsecBunker (user/subscription management, passing along permission requests to users, etc) most of the work to make this possible is client-side.
More clients will need to support the authorization scheme that nsecbunker requires. This would require new login capabilities, as well as supporting nsecBunker style remote signing capabilities (to delegate authorization to the nsecbunker instead of relying on the user’s nsec being on the same device as the client).
It’s not insurmountable, but it is not trivial; and if history is any guide, client adoption will take time. We’ve seen that Nostr browser extensions still haven’t become universal, even though most developers will tell you they should be mandatory at this point.
My prediction is that iOS clients will lead the charge because iOS doesn’t have the same ability as android for apps to interact with each other (via Android Signing Apps) so nsecBunker may be their only way for iOS clients to stop requiring users to paste in their nsec directly into the client 😬.
I think we’re well on our way to this future, and it’s one that will be much easier for normies to utilize while still allowing for people to opt-out and self custody if they wish.
Until next time 🫡
If you want to see something highlighted, if we missed anything, or if you’re building something we didn’t post about, let us know. DMs welcome at nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk
Stay Classy, Nostr.
-
 @ 599f67f7:21fb3ea9
2024-03-22 07:00:58
@ 599f67f7:21fb3ea9
2024-03-22 07:00:58Una BoltCard es una tarjeta que contiene una LNURLw grabada. Puedes recargarla con sats y utilizarla como si fuera una tarjeta de crédito en comercios u otros usuarios que aceptan esta tecnología.

Esto es lo que pasa por detrás durante el proceso¿Qué necesito?
- Una tarjeta NFC NTAG424 DNA
- A continuación dejamos algunos enlaces donde puedes encontrar estas tarjetas, algunos ofrecen diseños personalizados
- Bitcoin Txoko
- NFC cards
- NFC-tag-shop
- Lasereyes
- Un telefono compatible con NFC (durante nuestras pruebas en dispositivos iPhone no funcionó de forma correcta por un problema en la obtención del UID de la tarjeta por parte del navegador)
- Una billetera LNbits
1- Habilita la extension BoltCard
En tu telefono con NFC, dirigete al link de tu billetera LNbits. Dentro de
Extensionesbusca y habilitaBolt Cards.2- Crea un nuevo registro de cartera
- Abre la extensión de
Bolt Cardsy presiona el botón+para crear una nueva tarjeta. - Selecciona la cartera a la que se conectará. Esta es la cartera desde la que se gastarán los fondos.
- Puede establecer límites para la transacción máxima y el límite diario como medida de protección contra los comerciantes maliciosos que agotan su tarjeta.
- Ponle nombre a tu tarjeta.
- Presiona el botón NFC y luego lleva tu tarjeta NFC a tu teléfono para importar el UID de tu tarjeta.
- Haz clic en crear tarjeta.

Al final debería ser algo parecido a esto pero con un registro UID de tu tarjeta.
3- Escribe el registro NFC en la tarjeta.
- Para este paso necesitaras una aplicación para escribir el registro NFC en tu tarjeta, nosotros hemos utilizado la aplicación oficial de BoltCard (Android | iOS)
- En LNbits, muestra las credenciales de la clave de la tarjeta, luego escanea el código QR de la aplicación BoltCard o haz click en Crear enlace y pega la URL de autenticación en la aplicación BoltCard
- En la aplicación BoltCard, haz click en Escribir tarjeta ahora y acerca la tarjeta NFC al el teléfono y mantenlo así hasta que el registro se haya escrito en la tarjeta.
¡Eso es todo! Si todo salió bien, deberías tener una BoltCard en funcionamiento. Puedes probarla tocando contra tu teléfono y abriendo el enlace LNURLw.
⚠ Llevar tu BoltCard contigo significa que llevas dinero real contigo. Si alguien accede a tu tarjeta puede retirar todos los sats de tu cartera. Toma precauciones y mantén solo una pequeña cantidad de sats en tu billetera BoltCard para el gastos del día a día. Comprueba siempre que el comerciante está solicitando el precio correcto. Si es posible, mantén tu tarjeta en una funda protegida por RFID.
Próximos pasos
BoltCard habilitada para PoS
Algunas carteras y sistemas de punto de venta (PoS) son compatibles con la BoltCard. Aquí dejamos una lista de ellos: - BoltCard PoS - Breez - BTCpayserver - LNbits TPOS - Sí, puedes convertir tu cartera LNbits en un punto de venta (PoS) habilitando la extensión TPOS - VoltPay - lipa - Blink - Wallet of Satoshi - Blixt Wallet
Apoyar a BoltCard
También puedes apoyar el esfuerzo de haber creado una biblioteca de código abierto para programar las tarjetas, puedes hacerlo en Geyser Fund.
Tarjetas regalo NFC
En esta guía hemos tratado cómo crear una tarjeta de débito Lightning, pero ¿que ocurre si quieres hacer un regalo en sats y que pueda hacer un retiro a su billetera cuando quiera? Bueno, eso también es posible mediante tarjetas NFC y LNURLw. Explicaremos este proceso en una futura guía.
¡No solo tarjetas!
También puedes escribir registros NFC en cualquier etiqueta NFC que lo admita. Un ejemplo de esto es el Bolt Ring, que ofrece un anillo con capacidad NFC.
-
 @ 55b17d41:d6976606
2023-12-10 01:25:43
@ 55b17d41:d6976606
2023-12-10 01:25:43Details
- ⏲️ Prep time: 15 min
- 🍳 Cook time: 1 hour
- 🍽️ Servings: 12
Ingredients
- 2/3 cup creamy peanut butter
- 1/2 cup powdered sugar
- 1/4 cup graham cracker crumbs
- 1 pinch of salt
- 1 12-oz bag of chocolate chips
Directions
- In a large bowl, mix peanut butter, powdered sugar, graham crackers, and salt until well combined.
- Melt the chocolate either with a chocolate melting pot or in the microwave in a medium size bowl. If using the microwave, cook for 30 seconds and stir. Add more time if needed until the chocolate is melted.
- Line a 12-cup muffin tray with cupcake liners and fill each one with ½ tablespoon of melted chocolate. Spread the chocolate around to cover the bottom of the liner. Place the tray in the fridge for a few minutes to let them set. Doing this prevents the peanut butter filling from sinking to the bottom of the chocolate.
- Place a tablespoon of the peanut butter filling on top of the chocolate, spreading it around to form a circle and then slightly pushing it down into the chocolate. Top the peanut butter with another ½ tablespoon of melted chocolate. Smooth out the top and make sure it completely covers the peanut butter underneath.
- Refrigerate for an hour or until the chocolate has hardened. You can enjoy them cold or at room temperature. Enjoy!
-
 @ a012dc82:6458a70d
2024-03-22 01:45:22
@ a012dc82:6458a70d
2024-03-22 01:45:22Table Of Content
-
Introduction
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
The cryptocurrency market is subject to massive shifts, making it difficult to keep up with all of the volatility. However, for those who are interested in cryptocurrencies, determining the true worth of the money is not too difficult. It is not difficult to determine which coins have the greatest potential in the next few years. They should remain consistent, dynamic, and appealing to athletes over an extended period of time. The investors will have a good time with them, and as a result, their investment will continue to accumulate and grow.
Dash2Trade, IMPT, and Tamadoge are some cryptocurrencies that you should think about purchasing in order to make an investment are Dash2Trade, IMPT, and Tamadoge. They are extraordinarily appealing to purchasers and have a significant possibility of developing into the currencies with the highest value. Both of these depend on sustainable sources, which helps to maintain the purchasers' interest over the long term. Be quick about it, since they have just implemented a hefty price hike.
Which is the best penny cryptocurrency to purchase now that will increase in value by 2023?
-
Dash 2 Trade - the new signals platform
-
IMPT – the world of green investment
-
Tamadoge – overall the best currency to invest in
-
The Hideaways – the crypto for luxury lovers
-
Crypto Snack – the iGames token that you will like
-
Cardano – the third generation of potential token
Dash 2 Trade - the new analytics platform
The most recent of our internal projects to launch a presale is called Dash 2 Trade. It is a platform for traders and investors that provides crypto-analytics and insight. This platform takes cryptocurrency trading to the next level. This involves developing and testing trading strategies, keeping up with the most recent news and on-chain data, and a great deal more. Because of it, you will maintain your position at the head of the market. D2T displays the data that has an influence on performance and equips you with a concentrated view of the metrics, which enables you to concentrate on the most important aspects of trading choices so you can make them more effectively. Because tokens are moving off the shelves at a rapid rate, we may deduce that the future of this money will be quite fruitful.
Users should have access to the crypto analytics platform, trading signals, and social trading functions if the platform is powered by a D2T token. This token was introduced as an ERC-20 token on the Ethereum Network. The primary objective is to become a crypto analytics and social trading platform of world-class calibre. It will be very useful to traders because it will give them actionable trading signals, access to on-chain analysis, and all the trading tools they might need to take advantage of market opportunities.
The greatest part is that, in order to commemorate the presale and the quickly expanding community, the platform has begun a giveaway. You have a chance to be the fortunate one who wins the D2T token valued at $150k. You simply need to follow the basic instructions, and at the time of the draw, you need to have at least $150 worth of D2T tokens in your possession.
IMPT – the world of green investment
Over the last ten years, there has been a growing interest among purchasers and investors in environmentally responsible investments. There are certain initiatives that may both preserve the environment and raise the value of your investment. The International Monetary Fund and Trust (IMPT) were established to contribute to the reduction of the negative effects of climate change, to the preservation of the natural world, and to the financing of ecological endeavors. It does this by using blockchain technology in order to sell you carbon credits, which you can then use in the future to trade for other tokens known as NFTs. Every dollar is used toward environmentally responsible endeavors.
The purchasers, in addition to recognizing the significance of this money, have also acknowledged the significance of preserving the environment, which is supported by a large number of brands and enterprises, such as Microsoft, LEGO, and GameStop. The presale brought in more than $5 million in less than two weeks of fundraising. The credits you earn can be sold for money, and they can also be used to help a number of pre-approved and screened environmental projects.
The results are clear by looking at the data. They were able to sell 1,600 tokens at a price of $0.018 apiece during the first part of the sale. The investors get $100 in exchange for 5,555 tokens. Due to the fact that the first phase will conclude on November 25, an additional one billion tickets will be made available at a price of $0.023. It indicates that you need to act quickly if you want to safeguard the environment while making an investment in a currency that has a lot of promise.
Tamadoge – overall the best memecoin to invest in
Because it has shown a tremendous potential for value to rise in the near future, tamadoge is now one of the most promising cryptocurrencies to invest in this year. Only eight weeks of the presale period for the native token, TAMA, which was scheduled to last for ninety days, were actually held. During that time period, the cryptocurrency was able to raise $19 million and sell half of its full supply of 2 billion tokens. The developers, on the other hand, have more extensive plans for the next year. Whenever you make a purchase of the TAMA, Tamadoge will use 5% of that quantity. They will also utilize another thirty percent of the tokens for marketing reasons, while the remaining sixty-five percent of the tokens will be used for prize pools and rewards.
The P2E match is the foundation of the game. In this match, the buyer purchases a pet, cares for it, and invests in it. This results in the creation of an individual avatar by the inclusion of various accessories and essentials. The developers of specialist Tama shops will provide fantastic branches in order to provide customers with the opportunity to purchase one-of-a-kind decorations for their pets. On the other hand, people will have the ability to make their own enhancements and sell them on the market as NFTs. Online pet battles allow pets to compete against one another and collect rewards, which can then be used to progress up the leaderboard and win prizes. You may now participate in giveaways and win up to a hundred thousand dollars.
You are now able to purchase TAMA on both the centralized exchange OKX list and the decentralized exchange, since it is now being provided there as well. The price has increased by more than 1,000% since it first started off at $0.028, which is the current price. Be a part of one of the most powerful groups in the cryptocurrency market as quickly as possible since it will soon have a trading volume that is much greater than that of other popular currencies now available on the market.
The Hideaways – the crypto for luxury lovers
The Hideaways focuses on the premium real estate sector, which requires significant initial capital outlays for first-time buyers to overcome entry obstacles. If, on the other hand, we are aware that it generates 20% of passive income, then we are able to conclude that it is an incredibly worthwhile investment plan. The NFT is ownership in the real estate market, and the model predicts that the owner will get passive income from the property he or she owns. Even though returns on investments are expected to be high in two to three years, prices of assets are high and their rate of growth is slow.
Crypto Snack – the iGames token that you will like
Another method of investment for those who have a passion for gaming. However, this one may be used for betting online or in casinos. Checking the level of interest that different platforms have in different currencies is a good idea if you are uncertain about the value of the currency. One of the most important sites, CoinPads, uses only reliable and major currencies, making it possible for little coins like the penny and others to be traded there. The recent large investment of $50 million has put the money at the top of the list of the best penny coins to buy if you want to speculate on the market.
Cardano – the third generation of potential token
Cardano was just launched in 2017, yet it has already established itself as one of the leading cryptocurrencies when measured by market cap. The maximum supply of the currency is 45 billion units, while the market valuation of the currency is approximately $37 million. It ought to be a natural progression of the Ethereum idea into the next generation. It is possible to execute smart contracts because the blockchain technology that underpins the currency is long-lasting, adaptable, and scalable. Because of this, it is possible to develop a wide variety of decentralized financial applications, games, and new crypto coins, among other things. It is without a doubt one of the most reliable forms of digital money, in addition to being very practical. If we know that it is a blockchain platform that has a low impact on the natural world, then we can confidently conclude that it is the money of the future. The cost is always going up.
Conclusion
Even if selecting the appropriate cryptocurrency in which to invest is not a simple task, there are some signals that are important to keep in mind. According to the opinions of several industry professionals, we need to pay attention to the potential of the currency, its appeal, and the curiosity that purchasers have after the coin has been introduced. When it came to the attractiveness and the interests of the purchasers, IMPT and Tamadoge had pushed all of the limits that were possible. Because we are able to forecast very large price increases over the course of the next year, they are wonderful currencies to think about purchasing as an investment.
FAQ
Which penny crypto will explode in 2022? Ripple's native cryptocurrency token, XRP, has the potential to become the next penny cryptocurrency to see explosive growth in 2022. Even though the XRP cryptocurrency reached an all-time high of $3.84 in 2018, its value has since dropped below $1 due to a dispute with the Securities and Exchange Commission (SEC) in the United States.
What crypto has the most potential right now? Dash 2 Trade (D2T) is the Overall Cryptocurrency with the Most Potential that has been released on the Pre-Sale Market.D2T is Dash 2 Trade's native cryptocurrency, and it may be used as a means of payment on the platform to obtain access to all of the trading signals, tools, and other features available in the cryptocurrency market.
What crypto will rise in 2022? Ethereum, the most well-known alternative cryptocurrency, is much more than just another cryptocurrency in the eyes of many investors as well as cryptocurrency fans. And although it had a difficult first half of the year, market analysts believe it still has a chance to rise beyond $4,000 in 2022.
Is it worth buying a penny cryptocurrency? Penny cryptocurrencies are digital or virtual tokens that have a value that is very low in comparison to the value of other coins. Investors sometimes neglect them due to their low value. Yet, due to their low value, they might be a fantastic way to begin investing in bitcoin without spending a lot of money.
That's all for today, see ya tomorrow
If you want more, be sure to follow us on :
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 04222fa1:634e9de5
2024-03-21 23:00:17
@ 04222fa1:634e9de5
2024-03-21 23:00:17Memebritage
Is there some snobbery between the two protocols?
While it exists I shall exploit this wormhole
-
 @ 3cd2ea88:bafdaceb
2024-03-21 20:15:55
@ 3cd2ea88:bafdaceb
2024-03-21 20:15:55🚀100% di possibilità di vincita!
🚀Partecipa all'evento di Bitget e non perdere questa occasione!
🚀Iscriviti dal QR in foto o con referral 6w5d
🚀Clicca qui: https://www.bitget.com/it/events/activities/9c40c4e8a4035d4db86b296bd65cfbfc?color=black
🚀L'evento termina il 04/01/2024.
-
 @ 21b41910:91f41a5e
2023-12-03 19:36:27
@ 21b41910:91f41a5e
2023-12-03 19:36:27Summary
A user lost 180,000 sats due to a series of unfortunate events involving nostr clients, user error, lack of validation checks, lack of key rotation or mitigation approaches.
What happened
On Saturday 2023 December 2, a user had their profile set to a zeuspay address. Zeuspay addresses are not readily zappable as the receiver needs to acknowledge each zap sent to them. A request was made that they change their lightning address.
The user chose to change to the getalby address that they had previously setup. After entering an older incorrect value, they went to update their profile, but then managed to accidentally post their LND Wallet connection string instead.
A fellow nostrich realized their mistake and informed them. The user began setting up a stacker.news account, while helper connected via bluewallet using the connection string and moved funds out. Helper noted to user that the alby account can't create a separate wallet per account or rotate to new wallet and in order to continue using getalby, they would need to establish an entirely new alby account with a different email. The funds were sent from helper to user's new stacker.news account.
After this, the user linked their stacker.news account with the alby account having the compromised wallet. The user moved some funds to a different account. Later, after going to sleep, the user found remaining funds were pulled from their stacker.news account. It's believed that Zeus wallet or Bluewallet was used with the wallet connection information to LNURL-Auth login to stacker.news
User believes their NSEC was compromised as well and has setup new Nostr account, marked old as compromised and establishing new wallets for zaps.
Realizations
Not only do Nostr keys have no key rotation, LNURL-Auth suffers from this as well. While implementation approaches can be done, we need to get more work in this area to establish common, consistent patterns for how to rotate to new keys, wallets, etc.
In the case of a lightning wallet being compromised its quite severe as different services have no way to know the wallet is compromised as there is by design no central server to query against.
Recomendations
Users
-
Take extra caution when setting up wallet connect information and lightning address in your preferred clients.
-
Make note of where your lightning address and wallet connection information is being used. E.g., track in a password manager.
-
Be prepared to immediately take steps to update if ever compromised.
-
Where possible, use a dedicated lightning wallet (without funds) for LNURL Auth logins, separate from your extensions for logging in and signing events for Nostr.
General Nostr Clients
-
Where user profiles can be edited, add appropriate validation checks on the LUD06 and LUD16 fields. There are plenty of profiles with junk data that dont make sense.
-
LUD06 should be deprecated, but should be a LNURL string if provided.
-
LUD16 should be preferred, and only allow for values in username@domain format. Here's a sample regex:
[a-z0-9-_]*@(([a-zA-Z]{1})|([a-zA-Z]{1}[a-zA-Z]{1})|([a-zA-Z]{1}[0-9]{1})|([0-9]{1}[a-zA-Z]{1})|([a-zA-Z0-9][a-zA-Z0-9-_]{1,61}[a-zA-Z0-9]))\.([a-zA-Z]{2,6}|[a-zA-Z0-9-]{2,30}\.[a-zA-Z]{2,3})LNDHub, LNBits, Accounts type systems
- Add support for rotating from a compromised wallet account to a new one.
- Users and Admins should be able to mark a wallet as compromised.
- No spends should be able to performed from the account.
- Received funds should instead be diverted to replacement wallet.
- Can continue allowing LNURL-Auth to function
- Enhance API calls to ascertain if a wallet is marked as compromised
Blue Wallet, Zeus, any using LNDHub like accounts
- Add support for any new API calls that can indicate a wallet as compromised
- Recommend separation of wallets used for receiving value vs for LNURL-Auth
Alby Recommendations
-
Where Wallet Connection warning is, make it more prominent. Use bold red colors. Inform the user that this gives full access to the wallet and is non-revocable.
-
Add support for multiple wallets on an alby account. Preferably one per subaccount.
-
See notes for LNDHub about handling compromised wallets.
-
-
 @ c73818cc:ccd5c890
2024-03-21 20:12:33
@ c73818cc:ccd5c890
2024-03-21 20:12:33🚀100% di possibilità di vincita!
🚀Partecipa all'evento di Bitget e non perdere questa occasione!
🚀Iscriviti dal QR in foto o con referral 6w5d
🚀Clicca qui: https://www.bitget.com/it/events/activities/9c40c4e8a4035d4db86b296bd65cfbfc?color=black
🚀L'evento termina il 04/01/2024.
Bitget #Memecoin #Solana #MysteryBox #BGB
-
 @ 2edbcea6:40558884
2023-12-03 18:55:51
@ 2edbcea6:40558884
2023-12-03 18:55:51Happy Sunday #Nostr !
Here’s your #NostrTechWeekly newsletter brought to you by nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk written by nostr:npub1r3fwhjpx2njy87f9qxmapjn9neutwh7aeww95e03drkfg45cey4qgl7ex2
The #NostrTechWeekly is a weekly newsletter focused on the more technical happenings in the nostr-verse.
Let’s dive in!
Recent Upgrades to Nostr (AKA NIPs)
1) Deleted NIP 22: created_at limits
By its very nature Nostr has trouble reliably knowing when a piece of content was published. NIP 22 was an attempt to allow relays to be the authorities on when an event was created/published by only accepting events with a “created_at” that was recent according to the relay.
The challenge with this is rebroadcasting. The “created_at” can’t be modified because then the signature on the event that confirms the user authorized the event would be invalid (the signature is created by taking into account the created_at field). So if relays reject events that weren’t created recently, then events can’t be moved around (if a user wants to move relays or back up their content).
Overall, not many relays implemented NIP 22 because it caused too many problems. On top of that, whenever the “created_at” has to be reliable, devs are tending to use OpenTimestamps which is a non-Nostr but much more reliable system.
So, nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 deleted NIP 22.
2) (Proposed) NIP 88: Relay Notifications
The impetus for this NIP was the difficulty for paid relay providers to get their subscribers to pay their subscriptions. Currently it’s difficult to manage a monthly subscription with lightning, and most of the time you have to manually authorize the monthly payment every month.
This NIP outlines a way for relays to ask clients to pass along a message to users. The first use case is for relays to remind users to pay their subscription and include a link to pay it easily.
What’s nice about this is: 1) The protocol is more general than that specific use case, as the relay can send any kind of message to the user. Lots of possibilities! 2) This doesn’t require clients to enforce subscription agreements between the user and the relay, preserving decentralization and the opt-in nature of Nostr development.
Author: nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z
3) (Proposed) NIP 29: Image Metadata
There’s often metadata on images that is useful for clients displaying images (alternative text, dimensions, blurhashes, etc). There isn’t a standard way to provide that content to clients; this proposal changes all that.
It proposes an “imeta” tag to Nostr events so that when a user publishes an event with an image in it, their client can include this metadata to help future clients render it well. 💪
Author: staab
Notable Projects
Search and NostrDB 🔍
NostrDB is essentially a relay that lives within a Nostr client. This has many advantages for clients because it simplifies the client logic around managing events from many relays.
From what I can tell in my research, Damus uses NostrDB as the main relay that the app reads from when rendering the user experience in the app. Then it’s NostrDB’s job to sync events between NostrDB and the user’s desired relays.
Without NostrDB clients have to connect to all the users’ relays simultaneously and sync events. As syncing is going on, the client then needs to update the user’s experience. Doing both at once causes the client’s code to be more complicated and usually less performant. By separating the concern for syncing with the user’s relays to NostrDB, the client can focus on the user experience.
The new news here is that nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s has improved NostrDB to support very performant search. That means a client can sync events from the user’s relays, and then search that content in milliseconds without making a network call.
Without this, clients will need to reach out to each relay individually and make a filter request and wait for responses to trickle in. Then the client has to aggregate all the responses and show the user a result.
An architecture where there’s a NostrDB on the client, and/or a NostrDB powered relay that specializes in search, could make the work of discoverability much easier for clients. LFG!
Onboarding Normies 🛝
Rabble’s Talk on Nostr for Normies has motivated many thoughtful discussions (and some less-kind discussions) around how to attract and retain more regular folks on Nostr. But it seems no one is as prolific (in general but specifically) in their motivation to solve this problem as nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft .
This project is a demo of an experience for Nostr users to sign up for Nostr without ever touching the public and private keys. They create a username (NIP 05 address) and use an email to authorize any future recoveries of access to the Nostr account.
The experience is familiar to anyone that’s signed up for a service by logging in with Google or Twitter (which is most internet connected westerners). The experience still preserves choice for the user (where are they going to host their NIP 05 address, which nsecBunker will custody the keys, which email they will use to do recoveries, etc).
This could be the foundation of an onboarding experience that’s great for regular folks. Great work Pablo!
Better Backups 📦
Without the ability for users to move relays, Nostr isn’t truly censorship resistant. So, backup services will always be a core tool for the freedom-loving user of Nostr. nostr:npub1cmmswlckn82se7f2jeftl6ll4szlc6zzh8hrjyyfm9vm3t2afr7svqlr6f just released an update to NostrSync.
It feels more performant and feels simpler for the user. On top of that, users can now manage their backups, which means that we can start to take snapshots of our Nostr data. All stored locally so you continue to own your data.
Latest conversations: Onboarding Normies
The people in our community with the most experience building social products that people have adopted at scale have been telling us that Nostr is not ready for normies yet. ( Rabble’s Talk on Nostr for Normies and Jack’s latest assessment )
But we are seeing a ton of development that is making Nostr better for normies, and it seems like we’re close to all the lego pieces being ready. Here’s what I’ve seen lately.

Abstracting keypairs
Regular folks don’t understand public/private keypairs. It took decades for regular folks to accept usernames and passwords, and best case it’ll still be a while before regular folks understand public/private keypairs.
To help people join Nostr today, it’s sensible to offer services that wrap Nostr keypairs with a username/password experience that’s recoverable by email. People will understand it, and as long as they can still download their keys, they can self-custody whenever they want. If service providers end-to-end encrypt the actual Nostr keys, it could even be said to be non-custodial.
Pablo’s recent demo of an easy signup flow without managing Nostr keys is orders of magnitude easier to understand and educate new Nostr users on. Clients that adopt workflows like this could see retention increase quite a bit.
Finding and Filtering content
Decentralized systems are hard to search for specific content. It took a while for Google to solve the issue for web content. Twitter did incredibly well because of their search functionality. Nostr currently struggles to help people of all interests find the content and content creators they want.
Will’s work on NostrDB (as mentioned above) seems like it could be the foundation of performant search of Nostr content. Purpose-built search relays would be a valuable tool for clients helping users solve the discoverability, and we may be close to a truly great technological solution.
Approaches like Coracle’s introduction of “web of trust” based content discovery could also tackle the discoverability from a different direction. As is, it makes the global feed a bit more enjoyable. In the future, this pattern could power everything from discoverability, to semi-algorithmic feeds, to opt-in content moderation based on your social graph.
Part of making content enjoyable for regular folks is allowing and aiding people in filtering their feed how they like. Content moderation should not be forced on anyone, as that’s not in the spirit of Nostr, but rather allowing users to opt-in to filtering algorithms.
Rabble’s Nos.lol is taking the first steps towards using web of trust to help filter content in an opt-in way. Labeling tools like Ontolo could soon aid users in generating content warnings or lists of pubkey that are sources of content that people may want filtered.
Web of payments
Another challenge for normies is paying for all the services that power a great Nostr experience.
Quality relays Hosting images/videos Usernames (NIP 05) Translation Zaps
Currently there are free or custodial solutions but those can’t be run as charities forever, especially if there’s a surge of adoption.
Users are already not used to paying directly for social media, but paying independently subscriptions for all these services without being able to even use a credit card is jarring.
The problem of users paying with fiat but service providers receiving sats or a different fiat currency may soon be solved by Strike, but this is an area of underdevelopment.
Super-clients
For the freedom tech literate among us, it makes sense to sign up for services independently and manage your own self-custody lightning node/wallet to pay for services with sats. When you add up all the services this may be more expensive, and it’s definitely more work to manage, but those costs are worth it to many of us.
To service normies, we may see the development of super-clients. Where larger, well-funded clients (Primal, Nostr.Band, Damus, Amethyst, or even new players) may start to build services into the client to give an all-in-one solution for normies.
These super-clients may provide a NIP-05 address host, hosted nsecBunker with username/password interface, image/video hosting, translation, a quality relay, discoverability relays, translations, a few optional managed content moderation schemes, etc. All paid for via their hosted custodial lightning wallet the user can load with fiat but pay with sats.
Despite its trade-offs, this will make more sense to normies than the current paradigm. From what I can tell, we’re already seeing Primal working towards this level of capability. I imagine it’s very tempting for any team who wants their client to achieve scale. On balance this may not be a bad thing, but there are trade-offs to manage to minimize centralization.
Maintaining decentralization and censorship resistance
In a world that has super clients, they would be centralizing forces. They may even start to break from the protocol to build features they feel are necessary or give them a competitive advantage. This would have the side effect of decreasing interoperability and therefore decentralization.
To maintain the heart of Nostr, censorship resistance and freedom, while still offering an experience that can handle the needs of normies, it’s important to keep pressuring centralizing players to at least maintain perfect interoperability.
Users on super-clients should always be able to opt-out of aspects of the all-in-one solutions offered by these super-clients. If someone joins a super-client and wants to swap out the wallet, or the provider of content moderation, they need to be able to do that.
Users on super-clients should always be able to use other Nostr clients. If a user has their keys in a Primal nsecBunker they should be able to use that to log in to other clients and use them without difficulty.
Symbiosis with Normies
There is an exciting future equilibrium where everyone in the world is more free because of the work being done today on Nostr. A future that moves the needle for a good portion of humans requires us to find ways to onboard normies.
Normies bring more usage, and the possibility of more monetization. Through monetization we can attract more development and fund even more ambitious projects. Can’t wait to see it. 🙂
Until next time 🫡
If you want to see something highlighted, if we missed anything, or if you’re building something we didn’t post about, let us know. DMs welcome at nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk
Stay Classy, Nostr.
-
 @ 5d4b6c8d:8a1c1ee3
2024-03-21 20:00:00
@ 5d4b6c8d:8a1c1ee3
2024-03-21 20:00:00A few weeks ago, @elvismercury shared a Bitcoin valuation simulator. This simulator uses what it calls a Schrodinger model, named after the famous physicist. I haven't done a particularly systematic exploration of the model, but I said I would write up some thoughts about it and I've fiddled around enough to do that.
The Model
This model describes how Bitcoin should be valued in the present for its future potential to serve as a store of value. The premise of the model is that Bitcoin has a probability of usurping from other assets their roles as stores of value. * For each asset, it's assumed that Bitcoin either absorbs it's role as a store of value completely or not at all, with a probability attached to those binary outcomes. * Each asset also has its own timeframe for Bitcoin usurping its role as a store of value. * There's a discount rate that allows calculating present discounted value, based on the estimated future value. * Each asset has a market cap and estimated monetary premium.
I would prefer a model that used a continuous variable for the probability of capturing shares of each asset's monetary premium. However, that would require making a bunch of assumptions about the exact shape of the distribution. Still, I think you could roughly interpret the probability as the share of monetary premium you expect Bitcoin to absorb after a certain amount of time.
Estimated Valuations
The site has four preprogrammed scenarios: Bearish, Base, Bullish, Hyper. Those range in present discounted value from about $150k to $6,000k. That's a pretty wide spread, but even the "bearish" scenario suggests Bitcoin is still well under half of its proper valuation.
The simulator allows you to adjust all of the aforementioned parameters. According to @grayruby, you can get Bitcoin's present valuation as high as about $300 million, but that has more to do with just how unrealistic of parameters the simulator allows.
From what I've seen time matters more than probability. Halving all of the probabilities of capturing the monetary premia has much less effect on the valuation than doubling the time to capture.
How to Proceed as though We're Right
I would say approximately 1000x as much discussion has taken place about eventual valuation than time to adoption. In a way that makes perfect sense. We have much better tools for doing these back of the envelope future valuation calculations than we have for estimating when people will finally see the light.
The problem is that acting rationally in the present requires an estimate of present discounted value and that hinges more on when than how much.
Where we can resolve some uncertainty (at least if we have the courage of our convictions) is to say that Bitcoin will absorb every other asset's monetary premium. There are good theoretical reasons for thinking that in equilibrium there will be one money and it will act as the store of value for society (as well as unit of account and medium of exchange). So, if we believe Bitcoin is the best money, then we should conclude it will eventually eat every other assets monetary premium.
My Estimate
In the spirit of "stay humble" and "it's still early", I used the most bearish model, but increased all of the probabilities to 1. That's certain capture over the next 10 to 30 years, depending on the asset.
That yields a present discounted value of over $600k and that's just for the store of value function of Bitcoin. The estimated value for 30 years from now is over $14 million dollars. Incidentally, that's roughly the same as the estimates I've seen for Bitcoin's eventual medium of exchange value.
So, attaching no value to the unit of account function, if we're right about Bitcoin being the best money, then it's almost certainly worth well over $1 million right now. That just happens to be the same sat-cent parity many of us expressed feeling in my first big SN post: https://stacker.news/items/221151/r/Undisciplined.
Zap well!
-
 @ 00000000:3acedba7
2023-12-01 14:51:55
@ 00000000:3acedba7
2023-12-01 14:51:55El dictador de Venezuela, Nicolas Maduro amenaza con comenzar una guerra en nuestro continente, tratando de no extenderme demasiado voy a tocar ciertos hechos históricos recientes que a mi manera de ver las cosas nos han llevado a donde estamos hoy.
En la década de 2000s el fallecido dictador Hugo Chávez comenzaba a mostrarse como el dictador que fue y ante la creciente ola de críticas en todo el mundo quiso limpiar su reputación a punta de dinero así que orientó su política exterior a obtener el apoyo de la mayor cantidad de paises del continente americano, para esto hizo donaciones a gobiernos de izquierda, creó el Petro Caribe [1] para poder vender petroleo a crédito sin intereses a los estados miembros, lo cual fue una movida inteligente ya que hay muchas islas en el caribe, cada una de ellas es un país y cada país tiene derecho a voto en los organismos internacionales, podemos decir que con los precios históricos del petroleo chávez hizo operación chequera a cambio de su apoyo en la OEA y ONU, con respecto a Guyana, Chávez a petición de Fidel Castro le permitió explotar los yacimientos de petroleo ubicados en la región que hoy está en disputa entre Venezuela y Guyana, esta región es conocida como El Esequibo.
A la vez, la producción de petroleo iba en decline debido a la mala gestión del chavismo, pero como el precio del barril estaba sobre los 100 USD, no importaba, el chavismo seguía despilfarrando dinero como si no hubiera mañana.
Venezuela pasó de producir diariamente 3 millones de barriles de petroleo en 1999 a producir 703,658 (2022) [2], a la vez que Guyana en 2022 produjo 250,000 barriles diariamente.
Sinceramente creo que Maduro tiene dos razones para invadir Guyana:
- Obtener control de esos 250,000 barriles que exporta Guyana y las reservas
- Cambiar su posición en la historia de "El dictador de Venezuela" a el presidente que recuperó el esequibo
Sinceramente creo que si hoy se realizar una encuesta en Venezuela la inmensa mayoría opinaría que se debe recuperar el esequibo, pero probablemente nadie se ha puesto a pensar qué implica recuperarlo.
Actualmente viven 120 mil guyaneses en ese territorio, ¿Qué pasaría con estas personas?
Los venezolanos hemos visto como han actuado las fuerzas armadas cuando se han enfrentado con estudiantes disidentes, hemos sido testigos de relatos donde las víctimas han contado torturas [3], violaciones [4], asesinatos [5], desapariciones y otros crímenes de lesa humanidad, esto lo han hecho los militares tanto a niños de 13 años que han salido a protestar como a adultos, qué podemos esperar de su actuación en medio de la selva donde podrán llevar matanzas sin dejar testigos, donde no habrán personas filmando desde edificios como ocurría en las protestas en Caracas.
Los miserables militares venezolanos tendrán luz verde para realizar inimaginables aberraciones, sinceramente espero que no estalle una guerra porque lo que se viene sería un genocidio, ese sería el costo por recuperar El Esequibo, la destrucción de la vida de miles de personas, por eso no estoy de acuerdo con otra estúpida guerra "Patriota", tengamos o no tengamos razón, la vida de las personas es más valioso que cualquier disputa.
[1] https://es.wikipedia.org/wiki/Petrocaribe
[2] https://en.wikipedia.org/wiki/List_of_countries_by_oil_production
[3] https://www.youtube.com/watch?v=Vn2vphuy35U
[4] https://www.youtube.com/watch?v=rAP2sYk2AsY
[5] https://www.youtube.com/watch?v=jt0INSx4CEQ
-
 @ d8a2c33f:76611e0c
2023-11-27 16:52:20
@ d8a2c33f:76611e0c
2023-11-27 16:52:20This is part of a series of articles that I am writing to better understand and explain how AI agents will transform how we create and consume content in the near future. If you want to start from the first article, please start here.
In the previous article, 2: What makes an AI agent unique?, I discussed how AI agents become unique through their specific instructions, domain knowledge, and actions.
Let's delve into the concept of knowledge. Simply put, you visit a dentist for teeth cleaning, an accountant for financial management, and a primary care physician for health check-ups. In each scenario, you seek their services because they possess the domain expertise that you require.
Consider another instance. Suppose you use a Software as a Service (SaaS) platform for payments and encounter a question. Your first instinct might be to initiate a Google search, which often results in a barrage of ads and irrelevant site links. After some scrolling, you find the correct website, click on it, and are presented with FAQs and support articles. Now, you must sift through this information to determine if it answers your question.
Imagine, however, if there was an AI agent equipped with FAQs, blogs, articles, and other useful information. All you would need to do is pose your question to this AI agent, and it would provide the appropriate information. This approach not only saves time and effort for the user but also enhances the overall user experience.
The importance of domain-specific knowledge in AI agents cannot be overstated. These agents, armed with specialized knowledge, can offer more accurate and insightful responses, thereby revolutionizing the way users seek information and interact with platforms. This is the future of AI - niche applications that are tailored, efficient, and truly transformative.
To see how this works, we created this functionality on PlebAI, where anyone can create AI agents. When creating them, you can add knowledge by attaching a PDF document, text file, or even a URL from a website. Behind the scenes, these data are retrieved, transformed into vectors, and stored in a vector store. This data can be both public and private as it is stored securely and only shared with LLM (Large Language Model) in the form of embeddings.
With this knowledge, the LLM can easily answer the user's questions correctly.
Here's how to add knowledge:
- Go to PlebAI
- Click 'Create Text AI agents'
- Fill in all the necessary information
- Add knowledge in the form of documents or website URLs
- Start using them either privately or publicly

Once you add all the necessary information, the AI agent is now equipped to answer any user question related to the stored knowledge. You can also enable user web browsing so that it can retrieve any additional knowledge available on their website. Here's the response from the Zaprite Help AI agent answering a question from its FAQ.

Marc Andreessen, a renowned entrepreneur and investor, has been quoted as saying, "The content of each new medium is the old medium." This quote encapsulates the idea that each new form of media tends to repurpose the content of its predecessor.
With this view, we can start to push website and app content into AI agents and make them available inside any chat interface.
Let me know what you think and if you have any feedback or comments.
-
 @ d1e60465:c5dee193
2023-11-24 14:01:31
@ d1e60465:c5dee193
2023-11-24 14:01:31Todos los que hemos utilizado Bitcoin alguna vez sabemos lo básico sobre una wallet y de la importancia de la frase de recupero (las 12 o 24 palabras). Esa frase de recupero es única para toda la wallet. También somos conscientes de que las direcciones no deben ser reutilizadas para proteger nuestra privacidad, entonces nuestra wallet genera virtualmente infinitas direcciones. Ahora bien, ¿cómo es eso posible teniendo sólo una única frase de recupero? ¿Acaso hay algo más, además de dicha frase, que determina dónde están nuestros bitcoins?
Aquí es donde entran las wallets HD (hierarchical deterministic = jerárquicas determinísticas) y los “derivation paths” (caminos de derivación). Dicho esto, no hay mejor momento que este para tomar nuestra pala e irnos a enterrar riquezas.
Enterrando nuestra riqueza
Supongamos que tenés un tesoro que querés resguardar y se te ocurre la genial idea de enterrarlo (lo hacían los piratas, por qué vos no?). Lo primero que hacés es buscar un terreno muy MUY grande, elegís una ubicación lo más aleatoria posible, tomás la pala, cavás el pozo, y enterrás el tesoro. Por último, y muy importante, te anotás las coordenadas de dicha ubicación (llave privada) para volver luego por tu riqueza cuando la necesites.
Supongamos ahora que pasa el tiempo y seguís generando riquezas que querés proteger. Siguiendo tu idea original volvés al mismo terreno a cavar mas pozos, enterrar más tesoros y anotar más coordenadas. Si esto se repite varias veces más llegará un momento en el que guardar tantas coordenadas resultará incómodo para llevar un correcto registro, y riesgoso ya que si perdés una de ellas perdés un tesoro.
Con la pala en mano, sentado sobre un pozo, y mirando el horizonte se te ocurre una genial idea. Podrías sólo anotar la coordenada de un único punto arbitrario y diferente a los demás dentro de ese terreno (llave privada maestra), en donde no vas a enterrar nada. Pero hacés que todos los pozos, donde sí enterrarás tesoros, se ubiquen de forma relativa al punto inicial de una manera específica (camino de derivación). De esta forma llegarías a cualquier pozo partiendo de esa ubicación original. Por ejemplo: “los tesoros estarán ubicados en intervalos de 10 pasos hacia el norte desde el punto origen”. Incluso podrías definir ciertos recorridos fijos y complejos dependiendo el tesoro. Por ejemplo: “caminando hacia el norte, cada 10 pasos, pozos con oro; caminando hacia el este, cada 5 pasos, joyas; y para regalos misceláneos irás con intervalos de 4 pasos al oeste, pero cada vez que caves caminarás 2 más al sur (es decir, como si formases una letra L)”.
Todo este mecanismo parece complejo a primera vista, pero tiene una ventaja fundamental y es que los recorridos no tienen que guardarse de manera secreta ya que sin la coordenada origen nadie podrá encontrar el tesoro. Gracias a esta particularidad podríamos definir patrones de recorrido que sean públicos y todos compartamos, e incluso convertirlos en un estándar global (BIP44 o BIP86). En otras palabras, los caminos para llegar a cada pozo serán de público conocimiento y podrán estar anotados en múltiples lugares, mientras que las coordenadas de partida serán secretas de cada individuo.
Para repasar, tenemos presente que para encontrar el tesoro necesitamos la coordenada original y el recorrido de pasos. Física y visualmente podríamos pensarlo como una hoja transparente donde están dibujados los recorridos, y otra hoja con un mapa (secreto) que marque el punto origen. Ambos superpuestos darán la información necesaria (wallet HD) para encontrar todos los tesoros enterrados. Ambos son necesarios, pero sólo uno de ellos necesita ser secreto.
Cambiando la pala por criptografía
En Bitcoin, esta idea de tener una llave privada maestra (el punto de origen) y luego diferentes caminos de derivación fue introducida en el BIP 32. Explicado en términos (muy) simples podemos partir de que nuestra llave privada maestra no es más que un número, y lo que hace este mecanismo es realizar operaciones matemáticas sobre ese número para obtener nuevos números: las llaves hijas.
En la práctica, una situación habitual que genera pánico en aquellas personas que comienzan en Bitcoin se da cuando restauran una wallet utilizando la frase de recupero y la wallet no muestra su balance. El terror de ver “0 BTC” en lugar de sus ahorros detiene el tiempo durante unos segundos. Sin embargo, un poco más de atención sobre la situación revelaría que no sólo se muestra un balance en 0, sino que tampoco se muestra ninguna de las transacciones realizadas previamente. Es decir, es como si estuviésemos mirando otra wallet. Lo que sucede en estos casos es que, si bien la frase de recupero y por ende la llave privada maestra (coordenada original) se restauró correctamente, la wallet en cuestión utiliza otro derivation path, otro camino. Entonces, por más que partimos desde el mismo punto a caminar, estamos caminando para el lugar equivocado para encontrar el tesoro. Esto se debe a que, si bien existen estándares de derivation paths, no todas las wallets los respetan al 100%. Esta web detalla los diferentes caminos utilizadas por cada una de las diferentes wallets conocidas que existen en el mercado, y así evitar situaciones desagradables: https://walletsrecovery.org
Existen más particularidades no cubiertas por la analogía, como que en este esquema también se hace presente una llave pública maestra que puede tener derivaciones y así generar múltiples direcciones (y monitorearlas) pero sin tener acceso a las llaves privadas de cada una para mover los fondos asociados. Aparece también el concepto de “hardened” (fortalecido o endurecido), que hace referencia a sub-llaves derivadas de las principales ajustando el algoritmo para evitar filtración de datos sensibles y que un atacante pueda reconstruir nuestra llave privada maestra. Todos estos detalles están explicados en el BIP para quien le interese.
Epílogo
En Bitcoin, una llave privada maestra sería el equivalente a elegir una coordenada origen cualquiera en todo el planeta (incluyendo agua)… de entre más de 900000000000000000000000000000000000000000000000000000000000000 planetas Tierra. Podemos estar tranquilos que la coordenada que elijamos seguramente no sea elegida por otra persona.
Links útiles
- https://walletsrecovery.org Wallets Recovery — Derivation paths por wallet
- https://github.com/bitcoin/bips/blob/master/bip-0032.mediawiki BIP32 — “Hierarchical Deterministic Wallets”
- https://github.com/bitcoin/bips/blob/master/bip-0044.mediawiki BIP44 — “Multi-Account Hierarchy for Deterministic Wallets”
- https://github.com/bitcoin/bips/blob/master/bip-0086.mediawiki BIP86 — “Key Derivation for Single Key P2TR Outputs”
Este artículo está inspirado en un hilo de Twitter que hice en 2021: https://twitter.com/diegogurpegui/status/1408931266616041475
-
 @ a9f8b3f2:65181647
2024-03-21 17:37:58
@ a9f8b3f2:65181647
2024-03-21 17:37:58Adaptado para #Nostr #Hispano Autor: Piero Coen ⚡️ @piero_coen🔸Co-founder @osmowallet
-
Bitcoin para principiantes:
Un hilo 🧵de tweets, en el tiempo, explicando que es #Bitcoin. Traducido al español del libro “#Bitcoin for Beginners” por @Matthew R. Kratter
¡Gracias al autor @Matthew R. Kratter por confiar en mí para compartir este mensaje con el mundo hispanohablante!
-
Bitcoin es un nuevo tipo de dinero; una moneda digital que fue inventada en el 2009 por una persona (o grupo de personas) anónima, llamada Satoshi Nakamoto.
-
Han dicho que el #Bitcoin es una burbuja, un esquema Ponzi, o una estafa. Y, sin embargo, estamos en el año 2021, y Bitcoin aún no ha muerto, a pesar de años de obituarios 🪦. Sorprende aún más que el valor de #Bitcoin sigue alcanzando nuevos máximos históricos🔝.
-
¿Qué tipo de burbuja explota💥 y luego vuelve rugiendo unos años más tarde? #Bitcoin Eso nunca sucedió con la tulipomanía 🌷neerlandesa 🇳🇱del siglo 17, ni la burbuja de los mares del sur 🌊 a principios del siglo 18.
-
Algo similar sucedió con Amazon📦. Amazon se desplomó más del 90% a principios de la década de 2000, y luego volvió rugiendo a nuevos máximos históricos 🔝 a principios de la década de 2010.
-
Resulta que Amazon probablemente no fue una burbuja. Vino aquí para quedarse. O bien, si fue una burbuja a fines de la década de 1990, Amazon 📦 fue una burbuja especial.
-
Amazon fue un ejemplo del mercado tratando de fijar el precio a una nueva realidad: la realidad de una librería 📚en línea 🖥 que se había propuesto apoderarse de todo el mundo del comercio
-
Bitcoin es un tipo de burbuja similar. Es el mercado tratando de calcular el valor razonable de un nuevo tipo de dinero 🪙. Por lo tanto, para comprender #Bitcoin, debemos comprender qué es exactamente el dinero y cómo funciona.
-
Muchos piensan que solo los gobiernos pueden emitir dinero. Pero eso no es del todo cierto. Hay un brillante metal amarillo que se acepta como dinero en todo el mundo 🌎.
-
El oro es 💰dinero tan bueno, de hecho, que gran parte de él ha desaparecido y dejado de circular. La mayoría se encuentra en las bóvedas del banco central 🏦 y en la piscina de Rico McPato.
-
Cuando distintos tipos de dinero 💰compiten, pareciera que el tipo de dinero inferior terminara ganando. Sin embargo, lo que suele suceder es que el buen dinero (como el oro) es acaparando y por ende acaba saliendo de circulación. 🔃
-
No obstante cuando el dinero duro 🥇 (oro) compite con el dinero blando (e.j. papel/conchas/cacao) 💵, es el dinero blando el que sale perdiendo. Te lo pongo así: Si almacenaras tus ahorros en manzanas 🍎, pronto quedarías en la calle.
-
Las manzanas 🍏 son perecederas, se degradan rápidamente y abundan. Las conchas 🐚 funcionan un poco mejor, pues no se degradan fácilmente. Sin embargo, no son escasas. La plata 🪙 es más escasa que las conchas, pero el oro 💰 es más escaso que la plata.
-
A medida que las culturas 🛖del mundo se conocieron e interactuaron durante cientos de años🐉, el oro resultó ser el mejor dinero. Destruyó y sacó de circulación las monedas locales como el cacao, la sal 🧂 e incluso la plata 🪙.
-
El oro tiene todas las características de buen dinero; es duradero, divisible, portátil y reconocible. Pero lo que hace que realmente sea el mejor, es que es escaso. Incluso si su precio de sube 🚀, es imposible aumentar su oferta, pues es caro y difícil de minar⛏.
-
Cada año la oferta del oro incrementa ⬆️ aprox. un 1.8%. Se podría decir que esa es su tasa de crecimiento o tasa de "inflación" 💸.
-
El oro es un ejemplo de algo que funciona como dinero 💰, pero no lo controla ni emite ningún gobierno. Se puede usar como medio de pago en casi todas partes 🗺, pues funge como "medio de intercambio" pero hoy en día funciona principalmente como una "reserva de valor".
-
Una de las funciones del 💵 es ser un “medio de intercambio”. Es más fácil darte $200 por una 🪑 que tratar de averiguar cuántas 🥕 de mi huerto = una 🪑. Como fabricante de 🪑, es posible que ni siquiera te interesen mis 🥕. El dinero 💵 resuelve este problema.
-
El 💵 también funciona como “reserva de valores”. Si trabajo por 30 años y deposito mis ahorros en un banco 🏦 , me gustaría que ese dinero 💵 todavía esté allí cuando me jubile.
-
El banco 🏦 debe ser resguardado, tanto de ladrones como de gobiernos que quieran apoderarse de mis ahorros💰
En la mayoría de los países de hoy, los gobiernos le roban a sus ciudadanos de una manera mucho más sutil que la confiscación directa; a través de la “inflación”💸
-
En los 70’s, una Big Mac 🍔 costaba aprox $0.65. Hoy en día cuesta aprox $4. Todos hemos notado cómo la misma cantidad de 💵 compra menos cosas con el tiempo. A esto se le puede llamar “inflación”, o simplemente decir que el poder adquisitivo del 💵 es menor con el tiempo 🗓
-
El dólar americano 💵 no es una buena reserva de valor durante largos períodos de tiempo 🗓.
Lo mismo pasa con el Euro 💶 el ¥en 💴 y casi todas las monedas “fiat”. Se llaman monedas "fiat" (latín = “que se haga”) porque son creadas mágicamente por los bancos centrales 🏦
-
Desde la crisis del 2008, los 🏦 centrales alrededor del 🌍 se han impreso mucho 💵 nuevo. Tratan de ocultar esta devaluación monetaria utilizando nombres elegantes como “expansión cuantitativa” pero lo que están haciendo no es muy distinto a lo que hacen los falsificadores.
-
Cuando se tiene el poder de invocar a su existencia nuevos dólares 💵 americanos con tan solo pulsar una tecla en una computadora ⌨️ de la Reserva Federal, la tentación se vuelve demasiado grande para contenerse.
-
En el 2020 el gobierno de 🇺🇸 emitió mucha deuda. La reserva Federal ha estado comprando la gran mayoría de esta deuda con 💵 recién impreso. Esto se conoce como “monetización de la deuda” y si se continua haciendo el dólar seguirá perdiendo su poder adquisitivo.
-
Cuando el Gob. imprime 🖨 dinero nuevo en cantidades, el poder adquisitivo del dinero (tanto viejo, como nuevo) disminuye. Las 🍔hamburguesas, 🏡las casas y los hospitales🏥 se vuelven más caros.
-
La inflación se vuelve como un impuesto oculto que hace que todo encarezca 💸. Así es como los gobiernos y los bancos centrales le roban a la gente común, sin tener que aumentar los impuestos o disparar un tiro.
-
Los gobiernos 🇺🇸 que tienen enormes deudas denominadas en su propia moneda 💵 a menudo imprimen dinero nuevo y degradan su moneda, de modo que puedan pagar sus deudas utilizando dinero devaluado. 💸
-
Ahora comparemos esto con el oro. Los bancos centrales no pueden imprimir oro simplemente pulsando una tecla en un computador ⌨️. El oro es realmente escaso, y no está sujeto a picos masivos de nuevos suministros a como lo están las monedas fiat.
-
El oro💰es neutral, apolítico y no está sujeto a los caprichos de los banqueros en los bancos centrales. Y, a diferencia de las monedas fiat, el oro mantiene su poder adquisitivo a lo largo del tiempo, pues es una reserva de valor.
-
En el siglo 19, una onza de oro te compraba un buen traje para caballero. Hoy en día 1️⃣ oz. de oro todavía te compra un buen traje de caballero. Con 2️⃣ oz. de oro podías comprar un buen caballo 🐴 de trabajo, y eso sigue siendo cierto al día de hoy.
-
A esto nos referimos cuando decimos que el oro es una buena reserva de valor. En otras palabras, es una buena forma de transmitir riqueza a través del tiempo ⏳y/o espacio.
-
Así como puedo pagarle a un amigo en la India 🇮🇳 usando oro (reserva de valor a través del espacio). También puedo me puedo pagar a mí mismo en el futuro, o a mis herederos (reserva de valor a través del tiempo ⏳).
-
Si trabajo duro durante 30 años, quisiera que mis ahorros no fueran degradados por los bancos centrales imprimiendo más dinero fiat.
-
El mayor problema del oro es que es de difícil mover. Sería bastante caro enviar y asegurar ese oro que envío a mi amigo en la India🇮🇳. Si un gobierno hostil se apoderara de tu país, no puedes simplemente guardar un lingote de oro en tu bolsillo y viajar con el
-
El oro también es difícil de almacenar. Pudiera guardarlo en mi sótano, pero mi casa se convertiría en un blanco 🎯para ladrones. También pudiera guardarlo en un banco, pero el gobierno pudiera congelar mi cuenta bancaria 🏦.
-
El oro también es difícil (y caro) de verificar, o “tasar”. Puede ser bastante caro verificar cada moneda de oro o cada barra de oro que tengas.
-
El oro también es difícil de dividir en denominaciones más chicas. Por ende no es ideal para transacciones pequeñas.
-
¿Cómo le das a una persona cambio cuando compra una taza de café ☕️ con una moneda de oro? Tradicionalmente, la solución era utilizar monedas más pequeñas de plata 🪙. Pero luego estás atascado intentando averiguar la tasa de conversión entre el oro y la plata 🪙.
-
Hasta hace poco, a pesar de sus inconvenientes, el oro era el mejor dinero. No era perfecto, pero los gobiernos no podían imprimir más oro para pagar sus cuentas y, por lo tanto, devaluar su valor.
-
El oro es difícil y caro de extraer; requiere de mucha energía ⚡️, experiencia y aprobación de regulatoria para minar ⛏ . Cuesta tanto que su oferta aumenta en promedio 1.80% anual. Compara eso con el dólar 🇺🇸 cuya oferta subió ⬆️ 26% solo en 2020.
-
La minería de Bitcoin también es trabajo duro. Requiere mucha electricidad ⚡️y costosas computadoras especializadas (ASICs) para resolver complejos problemas matemáticos. El “minero” ⛏ de Bitcoin que resuelve primero este problema es recompensado con 6.25 nuevos #Bitcoin
-
A diferencia del oro, el suministro máximo de #Bitcoin es información pública. Solo habrá 21 millones de Bitcoin en la historia. Este límite de suministro está integrado en el código de software.
-
Compara esto con el oro: nadie sabe exactamente cuánto oro hay en bóvedas y monedas en todo el mundo 🌎. Tampoco se sabe su futuro suministro. Aunque es imposible saber cuánto oro hay en la tierra, es fácil verificar el suministro actual de #Bitcoin
-
Hoy en día, hay approx. 19 millones de #Bitcoin en existencia. Más del 88% de todo el Bitcoin ya ha sido minado. Debido a que #Bitcoin es un código de software 👩💻, es fácil verificar el suministro actual y su máximo suministro en el futuro.
-
Bitcoin no solo es más escaso que el oro, también es más fácil de subdividir (1 #Bitcoin = 100 millones de satoshis o “sats”), más fácil de enviar a cualquier parte del mundo (al instante), y es más fácil de guardar.
-
El oro puede ser (e históricamente ha sido) confiscado. Y aunque #Bitcoin también puede ser confiscado, es más difícil. Con que memoricesb12 palabras en inglés (tu llave privada), puedes usar #Bitcoin para cruzar fronteras con millones💵almacenados en tu “monedero cerebral”
-
Bitcoin proporciona seguridad criptográfica, sin necesidad intermediarios. Cuando deposito plata en mi cuenta bancaria, confío en el banco. También confío que el gobierno no se apodere de mis activos y que no destruya mi poder adquisitivo imprimiendo dinero ilimitadamente.
-
Bitcoin resuelve todos estos problemas. Puedo mantener mi #Bitcoin bajo mi custodia, y nadie puede quitármelo. No dependo de un banco o un tercero. El Gobierno no puede devaluar mis ahorros que se mantienen en #Bitcoin.
-
Bitcoin también es fácil enviar. Nadie me puede impedir enviarte o impedirte recibir. PayPal puede congelar tu cuenta, el banco también. El Gobierno puede congelar tus activos. Pero nadie puede tocar el #Bitcoin que esté bajo tu custodia
-
A cierta gente le gusta criticar #Bitcoin por ser incensurable. Dicen que #Btc es solo para lavadores de dinero, traficantes de drogas y criminales. Sin embargo, estudios han demostrado que solo el 1% de las transacciones de #Bitcoin son para actividades ilegales.
-
En los últimos años Wall Street ha estado colocando fondos para comprar #Bitcoin. Los multimillonarios han estado comprando #Btc para sus propias cuentas. Los reguladores norteamericanos le han facilitado ahora a los bancos norteamericanos e incluso @PayPal custodian #Btc
-
Si el gobierno de los Estados Unidos 🇺🇸 fuera a prohibir #Bitcoin, o si #Bitcoin fuera solo para criminales, ¿por qué los reguladores norteamericanos están permitiendo que las compañías de primera línea entren en Bitcoin?
-
Wall Street es bueno detectando tendencias y aprovechandolas para obtener ganancias. Sin embargo, esta es la primera vez que el pequeño inversionista llegó primero. Llevan comprando #Bitcoin durante años y por precios bajos. Wall Street va llegando tarde al juego.
-
Bitcoin es más que una moda, es como el Internet; una nueva tecnología que vino para quedarse. Como hemos visto una y otra vez en los últimos 20 años, la nueva tecnología desplaza a la vieja tecnología. @Amazon destruyó las tiendas físicas. @Netflix destruyó a Blockbuster.
-
Bitcoin está en el proceso de devorar y destruir todas las demás reservas de valores. #Btc es una tecnología de dinero superior al oro y continuará robando del mercado de valores hasta que el oro haya sido completamente desmonetizado.
-
Dentro de 20 años, el oro solo se utilizará en electrónicos💻 y joyería💍. Operará como cualquier otro metal industrial; ya que su prima monetaria habrá sido completamente destruida por #Bitcoin.
-
¿Suena loco? Es lo que siempre ha sucedido con las monedas 🪙. El oro destruyó al wampum como moneda. El oro también destruyó la plata como moneda. Las guerras de bimetalismo se decidieron a favor del metal más escaso: el oro. Es cuestión de tiempo que #Bitcoin se coma al oro
-
Bitcoin ha superado todos los demás activos. El tipo de cambio #Btc/oro ha subido desde su creación. #Btc ha superado otros activos, incluyendo: acciones, bonos y bienes raíces. Hemos visto a inversionistas institucionales reemplazar el oro con #Bitcoin.
-
Esta tendencia continuará hasta que se complete, pues tiene un fuerte componente demográfico. A los Millenials y a la Gen. Z no les importa el oro, pero se sienten extremadamente cómodos con las criptomonedas #Btc. El oro va por el mismo camino que la máquina de fax 📠.
-
Mientras tanto, #Btc se está comiendo al mundo 🌏. Actualmente tiene una capitalización de tan solo $500 millones - el tamaño de una empresa de S&P 500. En algunos años, #Btc superará la capitalización del oro de $11 mil millones. En ese momento, 1 #Btc valdrá + de $500,000.
-
Eventualmente, la capitalización de #Btc superará el mercado de valores global ($100 trillones) y el mercado global de bonos ($100 trillones). A ese punto, probablemente ya no hará sentido cotizar #Btc en dólares🇺🇸, pues #Bitcoin se habrá hecho la nueva unidad de cuenta.
-
Todos subestimaron lo dominante y omnipresente que llegaría a ser el Internet 📡(es difícil de recordar ahora). Lo mismo ocurre con #Bitcoin. El futuro de #Bitcoin es mucho más grande y brillante de lo que creen la mayoría.
-
-
 @ 03742c20:2df9aa5d
2023-11-19 04:19:18
@ 03742c20:2df9aa5d
2023-11-19 04:19:18สำหรับผู้เริ่มต้นใช้งาน nostr ใหม่ที่ไม่คุ้นชินกับบิตคอยน์อาจยังไม่รู้จัก lightningnetwork แต่นั้นไม่ใช่ปัญหาหลักสักเท่าไหร่คุณสามารถไปศึกษาต่อได้ถ้าหากสนใจ แต่บทความนี้แค่อยากให้พวกคุณเริ่มต้นใช้งานและรับ zap ส่ง zap กันได้อยากสนุกในคือหลักการ V4V ของ Nostr
ตอนที่เราตั้งค่าโปรไฟล์ก็จะเห็นว่าให้ใส่ lightningaddresses แล้วเราเอามาจากไหนล่ะอีเมล์หรือหรืออะไร มันก็คือที่อยู่ของ lightning wallet ของเรานั้นเองเพิ่มที่จะรับ zap ได้ต้องเพิ่มส่วนตรงนี้เข้าไปด้วย
แล้วจะเอามาจากไหนล่ะ lightning wallet นั้นเอง
จริงแล้ว lightning wallet มีอยู่ 2 ประเภทหลักๆคือ custodial wallet, non-custodial wallet แต่ในบทความนี้ผมจะแนะนำ custodial wallet เพื่อการเริ่มต้นที่ง่ายที่สุด
มาเริ่มกันเลย
Wallet of satoshi
เป็นกระเก๋าที่ง่ายที่สุดเพียงติดตั้งแอปและเปิดใช้งานได้เลย แต่ผมจะแนะนำว่าอย่าลืมผูกอีเมล์เราไว้ด้วยเพื่อเป็น backup เวลาย้ายเครื่อง

จากนั้นกดคำว่า receive ก็จะแสดง lightningaddress เราก็สามารถก๊อปปี้มาใส่ได้เลยแค่นี้ก็รับ zap ได้แล้ว

Blink wallet
ติดตั้งลงเครื่องเปิดแอปมากดสร้างแอคเคาท์ใหม่เขาจะให้ใส่เบอร์โทรศัพท์เพื่อเป็นการ backup ข้อมูลกระเป๋า

จากนั้นกดที่ขีดสามขีดมุมขวาบนกดคำว่า แอดเดรส blink ของคุณ เขาจะให้เราตั้งชื่อ lightningaddress

จากนั้นก็ก๊อปปี้ lightningaddress ไปใส่ในแอคเคาท์ nostr เพื่อรับ zap ได้เลย
เป็นบทความแนะนำสั้นๆ หวังว่าจะมีประโยชน์สำหรับผู้เริ่มต้นใช้งานใหม่ครับ
ขอให้มีความสุขกับการใช้งาน nostr อย่าลืมมาแชร์ประสบการณ์ให้เราฟังด้วยนะ
ขอบคุณทุกคนที่แวะมาอ่านแล้วเจอกันใหม่ครับ
lightning #Zap #Nostr #Siamstr
-
 @ d9f34b84:49606727
2024-03-21 17:08:04
@ d9f34b84:49606727
2024-03-21 17:08:04Opinion about Samourai Wallet (android)
The reproducibility has been a concern of mine for some time. I tried to do it myself around 2020-08-02 but was unable to. I'm glad you've continued in your attempts to verify, and not just trust!
WalletScrutiny #nostrOpinion
-
 @ 000002de:c05780a7
2024-03-21 15:46:02
@ 000002de:c05780a7
2024-03-21 15:46:02 -
 @ 21b41910:91f41a5e
2023-11-17 22:25:34
@ 21b41910:91f41a5e
2023-11-17 22:25:34An Intro to Creating Reports for Invoices and Payments for the LND tool
by @vicariousdrama 714130–714326

Summary
The purpose of this article is to guide users through use of some of the command line operations to query their lightning node, and produce summary reports using basic formatting and JSON processing tools. This article assumes that you already have a lightning node running LND, and access to the command prompt. If you don’t yet have a lightning node, consider checking out assorted node projects, or even setting up a node using voltage.cloud. Commands are presented in a way that builds up the overall result gradually so that we can better understand each part that goes into the result. You can jump to the end of major sections if you just want to copy-pasta the end result.
Change History
| Date | Description | | --- | --- | | 2022-03-11 | Initial Document | | 2023-02-26 | Conversion to Markdown | | 2023-11-17 | Crosspost to Nostr via Yakihonne |
Invoices
Invoices are payment requests that have been initiated from a lightning node for which another should pay. The creation of requests is out of scope of this article and is often created using applications or interfaces like ThunderHub, Ride The Lightning, or a Lightning capable wallet.
Listing Invoices
From the command line, we can use the
lnclitool, the control plane for your lightning network daemon (lnd) with the listinvoices command.
This will output some invoices in JSON format. We can use the
jqcommand to easily apply some formatting and color syntax coloring to improve readability. Later we will use this tool for filtering as well.
If there are invoices, they will be listed in JSON format with several fields for each. While all these fields have their purpose, the ones we are most concerned about for reporting are the ones for
memo,value,settled,creation_date,settle_date,amt_paid_sat, andstate.In follow up sections, the highlighted colors depicted here will be included in commands to draw attention to where they are used.

Only List Paid Invoices
This is the command to filter the results to only show those which were paid
shell lncli listinvoices | jq '.invoices[] | select(.state=="SETTLED")'
Only List Failed Invoices
This command alters the filter to show those which were eventually cancelled due to timeout before being paid.
shell lncli listinvoices | jq '.invoices[] | select(.state=="CANCELLED")'
List Invoices Paid for a Period of Time
To limit the invoices to a period of time, we will establish some variables and update the filter of those invoices that are being selected. The date command will return the seconds since epoch, and start on the first second of that day. Each day is comprised of 86400 seconds. For the end date, we will want to advance the result by one day, minus one second to ensure the entire day is included in the period.

Similarly, we can limit the invoices selected to a single month

Controlling the Output for Invoices
Up until now, our output has just been JSON. For reporting purposes, we will begin cleaning up the output to report information on a line by line basis. With the selected objects, we can further use the jq command line JSON processor to direct output concatenating values for a string.

Here is a sample result formatted from the string

Let’s use some trivial formatting to right align the value field by creating spaces padded on the left side. This makes it easier to read numbers when there are multiple rows. In this example, we take the value field, convert to a string using a builtin tostring function. This will then be written out with spaces before it up to 8 minus the length of the value using the built in length function. For example, if the value is 123, it has a length of 3, and to give it a total overall length of 8, 5 spaces will be written in front.

Here is the revised sample result showing the additional padding of spaces on the left side of the value.

To show our values lined up, let’s run the same report with all invoices. To do this, we’ll change the begin date to an earlier time. Your results will vary depending on how many invoices you’ve had in the past.

And here are some sample results showing alignment of the values.
Capturing Filtered Results for Invoices
Going forward, we’ll be performing multiple queries against the dataset. To avoid putting unnecessary load on the service itself, and ensure that we are always working with the same data between queries, we can capture the results to a variable and use that in our formatting.
Here, we capture the data to a variable named
REPORT_DATA
Now lets use that, and change our output to display the date in a readable format, followed by the memo field, and finally the amount right aligned.
To convert the date, we take the string, convert to a number using the builtin
tonumberfunction, and then pass that throughtodateiso8601another builtin function before parsing the Year, Month, and Day portions from it.The memo field will be left aligned, whereas right aligned fields create spaces before it, we want to write out extra spaces after its value.
Finally, for the value field, lets extend the length which will better account for a header later on.

And here is our revised sample results with the new formatting.

Creating a Header for Invoices
We can add a header to the report to put context to the data presented. Lets add both a report header for the period of time, as well as column names.
For the period of time, we’ll convert the numeric start and end date in seconds back to a readable time stamp. The column headers will be spaced out to match that of the data, and finally, we’ll create a line between the header and the data.

Our sample results

Let’s combine them so the command output runs together without interspersing the command line prompt.

The header looks much cleaner now.

Calculating the Total for a Footer for Invoices
It would be helpful if we summarized the total sats recieved for the period. We can do this by taking the inputs, converting the value to a number, reducing the array, initializing a temporary variable, and adding the value to it for each item in the array. That may sound more complicated then it is but don’t worry, it’ll become clear with the command and results. The results we will store in another variable.

To see the value, we can echo it out

Sample result

With the total, we can now put it into a footer. We’ll draw another line closing out the data and report the total

The sample footer

Overall Report of Invoices
Now lets combine all the portions of the above into one simple set of commands. We can take this and save it to a file for reuse later.

And here is the sample report of invoices

Payments
For reporting with payments, we’ll assume some of the same concepts that were outlined in the invoices section.
Listing Payments
To list successful payments, we can use the
lnclicommand with thelistpaymentsoperation, and then follow up with filtering with thejqJSON processor.
If there are payments, they will be listed in JSON format with several fields for each. While all of these fields have their purpose, the ones we are most concerned about for reporting are
value,creation_date,fee, andstatus. In follow up sections, the highlighted colors depicted here will be included in commands to draw attention to where they are used.
Within the
htlcsfield (hashed timelock contracts), there are more details about the routing path the payment took, and fees down to the millisat that were paid for each hop. For this basic report, we’ll stick to the basic rollup of fees rounded to the next sat.Capture the Filtered Payment Results
Let’s setup our reporting begin and end dates, and capture the matched payments to a variable.

Capture the Totals for Payments
Next, for reporting purposes, lets sum the total of invoices paid, the fees, and the overall total.

Overall Report of Payments
Similar to the invoices report, we prepare a payments report with a header block followed by data lines, and then a footer with the calculated sums.

Here’s a sample report output

Conclusion
Using the command line, we built up a report for invoices created with a lightning service. Basic filtering by date periods allows for flexibility in our reports. Textual alignment of data, formatting dates, and creation of headers and footers help make for a useful summary report. We then applied the same concepts to creation of a report for payments made. You may consider using this as a stepping stone to more reports and automation. If you think I should create more guides like this, or expand on it, please leave a comment on the article.
-
 @ 1e52c554:21771908
2024-03-21 15:11:45
@ 1e52c554:21771908
2024-03-21 15:11:45Posthumous work of the Colombian poet born in Don Matias on January 20, 1948.
Welcome to this blog dedicated to the Posthumous work of the Colombian poet Francisco Luis Arroyave Tabares (my father), born in Don Matias on January 20, 1948-2010. Where I will be publishing each of the 175 sonnets from his unpublished collection 'Sonnets For The Twenty-First Century And A Circadian Musical (1984-1987).' Analyzed with GPT4 artificial intelligence and illustrated with AI tools... I hope you enjoy this garden of words snatched from the solitude of a locked room.
Likewise, any enthusiast of the sonnet form is invited to conduct their personal studies of Arroyave Tabares' work, as it is a collection that, although registered since 1989, has not yet been published.
Frank Duna
Temple Of Night Fantasies"
Introduction
"Temple Of Night Fantasies" is a sonnet that blends nature, creativity, and celestial imagery to convey a sense of enchantment and the pursuit of artistic fulfillment. The poem's structure and language contribute to its dreamlike and evocative quality.
Thematic Analysis
Octave (Lines 1-8): The octave introduces the setting as a “garden of night”, a place that is rich, captivating, and expanded through “moon pavilions”. This could symbolize a vast, enchanting, and mysterious realm that the speaker is exploring. The “purple song” that fades in the west might represent the sunset, indicating the transition from day to night. The speaker mentions dreams that have been cultivated with abundance (galore) and are commanded by the harmony and magic of the stars. This suggests that the speaker’s dreams or aspirations are influenced by the enchanting and mystical elements of the night.
Sestet (Lines 9-14): The sestet delves deeper into the speaker’s interaction with this night realm. The speaker uses worldly enchantment to express their thoughts, suggesting a deep connection with the mystical elements of the night. The speaker dances through shadows, perhaps symbolizing the exploration of unknown or hidden aspects of life or self. The speaker aims to absorb the essence of each moment and convey what was secret, unfolding immaculate opulence. This could mean that the speaker seeks to understand and express the profound and often hidden beauty or wisdom found in the depths of the night.
Overall, the sonnet seems to explore themes of mystery, exploration, self-discovery, and the beauty of the night. The octave sets the stage and presents the influence of the night on the speaker’s dreams, while the sestet delves into the speaker’s active engagement with the night and their quest for understanding and expression. The sonnet beautifully uses the metaphor of the night and its elements to depict a journey of exploration and discovery.
Structure and Rhyme Scheme
The sonnet “Temple Of Night Fantasies” follows the traditional structure of a sonnet with a rhyme scheme. Let’s break it down:
Octave (Lines 1-8): The rhyme scheme in the octave is ABBA ABBA:
Line 1 (A): captivating Line 2 (B): expanded Line 3 (B): handed Line 4 (A): fading Line 5 (A): cultivating Line 6 (B): demanded Line 7 (B): commanded Line 8 (A): debatingSestet (Lines 9-14): The rhyme scheme in the sestet is CDE CDE:
Line 9 (C): encantment Line 10 (D): shadows Line 11 (E): magnifiscence Line 12 (C): moment Line 13 (D): now Line 14 (E): opulenceThis analysis shows that the sonnet follows a strict rhyme scheme, which is typical of traditional sonnets. The rhyme adds a rhythmic quality to the poem and helps to emphasize certain words and ideas. It also creates a sense of unity and cohesion in the poem. The change in rhyme scheme from the octave to the sestet often signals a shift in theme or tone, which is a characteristic feature of sonnets. In this case, the octave sets the scene and introduces the theme, while the sestet explores the theme in more depth. The final couplet often provides a resolution or a summarizing statement, which is evident in this sonnet as well.
Analysis of Aspects
The sonnet “Temple Of Night Fantasies” by Francisco Luis Arroyave Tabares is a rich piece of poetry with a lot to unpack. Let’s delve into the language, imagery, themes, meter, and overall impact of the poem:
Language: The language used in the sonnet is highly descriptive and evocative. The poet uses words like “deftly”, “captivating”, “expanded”, “fading”, “cultivating”, “demanded”, “commanded”, “debating”, “encantment”, “shadows”, “magnifiscence”, “moment”, “now”, and “opulence”. These words create a vivid and engaging picture in the reader’s mind and add depth to the poem.
Imagery: The poem is filled with beautiful and striking imagery. The “garden of night”, “moon pavilions”, “purple song”, and “stars that sing” all contribute to a mystical and enchanting atmosphere. The imagery serves to transport the reader into the world of the poem and allows them to experience the emotions and sensations described by the poet.
Themes: The main themes of the poem appear to be exploration, self-discovery, and the beauty of the night. The poet explores these themes through the journey of the speaker in the poem, who navigates through the “garden of night” and interacts with its various elements.
Meter: The sonnet follows the traditional iambic pentameter, which is a type of metrical line used in traditional English poetry and verse drama. This means that each line of the poem has five metrical feet, each consisting of one short (or unstressed) syllable followed by one long (or stressed) syllable.
Overall, the sonnet is a beautifully crafted piece of poetry that uses language, imagery, and meter to explore its themes in a deep and engaging way. The poem leaves a lasting impression on the reader and invites them to delve into their own interpretations and experiences. The strict structure of the sonnet, combined with the creative use of language and imagery, results in a poem that is both traditional and innovative. The poem is a testament to the poet’s skill and creativity. It’s a wonderful example of how poetry can transport us to different worlds and offer new perspectives.
(GPT4)
Syllable count for each line.
```
Temple Of Night Fantasies
10 Deftly rich and my soul captivating
10 With moon pavilions through night expanded
10 The garden of night is set and handed 10 By purple song that at west keeps fading.10 The dreams that I have been cultivating 10 Have the galore that my muse demanded
10 Their magic and hamony conmanded 10 By stars that sing while our fate debating.10 Speaking my mind with wordly encantment 10 In a adventurous dance through shadows 10 I prevail until gay magnifiscence.
10 To absorb the essence of each moment 10 I convey what was secret until now
10 To unfold inmaculate opulence. ***```
Sonnets For The Twenty First Century And A Circadian Musical Written By Francisco Luis Arroyave Tabares (1984-1987)
Analyzed by GPT4; Image by leonardo.ai; First published on Nostr Protocol by franciscoarroyavet@nostrplebs.com
 Temple Of Night Fantasies
Temple Of Night Fantasies -
 @ c11cf5f8:4928464d
2024-03-21 13:30:10
@ c11cf5f8:4928464d
2024-03-21 13:30:10Any Bitcoin offers or promotions you bought recently?
We’re constantly looking for some special deals! Share with your fellow stackers any latest steal, recent offering, snazzy discounts, packed bundles...
Help us all score some incredible bargains!
-
 @ 1e52c554:21771908
2024-03-21 12:55:12
@ 1e52c554:21771908
2024-03-21 12:55:12Posthumous work of the Colombian poet born in Don Matias on January 20, 1948.
Welcome to this blog dedicated to the Posthumous work of the Colombian poet Francisco Luis Arroyave Tabares (my father), born in Don Matias on January 20, 1948-2010. Where I will be publishing each of the 175 sonnets from his unpublished collection 'Sonnets For The Twenty-First Century And A Circadian Musical (1984-1987).' Analyzed with GPT4 artificial intelligence and illustrated with AI tools... I hope you enjoy this garden of words snatched from the solitude of a locked room.
Likewise, any enthusiast of the sonnet form is invited to conduct their personal studies of Arroyave Tabares' work, as it is a collection that, although registered since 1989, has not yet been published.
Frank Duna

Analysis of "Only To Kiss"
Introduction
The sonnet “Only To Kiss” as a whole blends elements of astronomy, mythology, and romanticism to create a rich and imaginative exploration of the night sky and the emotions associated with a kiss.
Thematic Analysis
Quatrain 1 (Lines 1-4): The speaker, along with the “sidereal nymphs” (star-like nymphs), keeps vigil (stays awake) during the absence of Selene, the Greek goddess of the moon. They observe other “sigils” (symbols or signs) in the sky, as the usual rulers of their hearts are not present.
Quatrain 2 (Lines 5-8): In the vast darkness, the speaker sees distant gazes or constellations (“blazes”). Light prevails where Urania’s flocks (stars) graze, nurturing a secret bestowed upon them. Urania is the Greek muse of astronomy.
Quatrain 3 (Lines 9-12): While Cupid (the god of love) and Artemis (the moon goddess) with her nymphs are asleep, Psyche (personification of the soul and lover of Cupid) and Mnemosyne (goddess of memory and mother of the Muses) are awake. They delve into the depths of dreams (“oniric deep”), following the paths left by passion.
Couplet (Lines 13-14): The speaker and his beloved have only enough strength to bid each other goodnight with a kiss. Yet, they happily dissolve their thoughts, love, and faith into one another.
This sonnet is a beautiful exploration of love, passion, and the mysteries of the night sky, intertwining human emotion with celestial bodies and mythological figures. It’s a testament to the power of poetry to elevate human experience to the divine.
Structure and Rhyme Scheme
The sonnet “Only To Kiss” follows the traditional English or Shakespearean sonnet form in terms of its rhyme scheme. Here’s a detailed analysis:
Quatrain 1 (Lines 1-4):
Line 1: Sidereal nyphs and I through vigils (A) Line 2: Have other views if Selene is absent (B) Line 3: Or notice in the sky other sygils (A) Line 4: Since rulers of tha heart are not present. (B)Quatrain 2 (Lines 5-8):
Line 5: In dark expanse I see the distant gaze (C) Line 6: or blazes with other ones underneath (D) Line 7: And light weilds where Urania’s flocks graze (C) Line 8: And nurture secret that to us bequeath. (D)Quatrain 3 (Lines 9-12):
Line 9: Cupid and all the hunting girls now sleep (E) Line 10: While Psyche and Mnemosyne are avake (F) Line 11: Searching the essence of oniric deep (E) Line 12: And tiding on paths left by passions wake. (F)Couplet (Lines 13-14):
Line 13: To kiss goodnight we only have the strength (G) Line 14: But happily we melt thoughts, love and faith. (G)So, the rhyme scheme of the sonnet is ABAB CDCD EFEF GG, which is typical of the English or Shakespearean sonnet. This structure allows for a logical progression of thought, with each quatrain presenting a distinct idea or argument, and the final couplet providing a summarizing or contrasting statement. The rhymes help to unify the poem and add a musical quality to the language.
Analysis of Aspects
The sonnet “Only To Kiss” by Francisco Luis Arroyave Tabares is a rich tapestry of language, imagery, and themes. Here’s a detailed analysis:
Language: The language used in the sonnet is highly poetic and filled with allusions to Greek mythology. The poet uses words like “sidereal,” “vigils,” “Selene,” “sigils,” “Urania,” “Cupid,” “Psyche,” and “Mnemosyne,” which add a layer of complexity and depth to the poem. The language is also quite descriptive, painting vivid pictures in the reader’s mind.
Imagery: The sonnet is replete with celestial imagery. The poet uses the night sky as a backdrop for the unfolding drama of love and passion. Images of “sidereal nymphs,” “Selene,” “sigils in the sky,” “distant gaze,” “blazes,” and “Urania’s flocks” create a dreamy, otherworldly atmosphere. The imagery serves to elevate the human experience of love to the divine.
Themes: The primary themes of the sonnet are love, passion, and the mysteries of the night sky. The poet explores the depths of human emotion and intertwines it with celestial bodies and mythological figures. The theme of love is personified through the figures of Cupid and Psyche, while the theme of passion is explored through the vigils kept by the speaker and his beloved.
Meter: The sonnet appears to follow the traditional iambic pentameter, which is common in English sonnets. This means each line consists of five pairs of unstressed and stressed syllables, giving the poem a rhythmic quality.
Overall, “Only To Kiss” is a beautifully crafted sonnet that skillfully weaves together language, imagery, and themes to create a captivating exploration of love and passion against the backdrop of the night sky. The use of Greek mythology adds a layer of complexity, making the poem a rich and rewarding read.
(GPT4)
Syllable count for each line.
```
Only To Kiss
10 Sidereal nyphs and I through vigils
10 Have other views if Selene is absent
10 Or notice in the sky other sygils
10 Since rulers of tha heart are not present.10 In dark expanse I see the distant gaze 10 or blazes with other ones underneath
10 And light weilds where Urania's flocks graze
10 And nurture secret that to us bequeath.10 Cupid and all the hunting girls now sleep
10 While Psyche and Mnemosyne are avake
10 Searching the essence of oniric deep
10 And tiding on paths left by passions wake.10 To kiss goodnight we only have the strength 10 But happily we melt thoughts, love and faith. ***
```
Sonnets For The Twenty First Century And A Circadian Musical Written By Francisco Luis Arroyave Tabares (1984-1987)
Analyzed by GPT4; Image by leonardo.ai; First published on Nostr Protocol by franciscoarroyavet@nostrplebs.com
 Only To Kiss
Only To Kiss -
 @ fab018ad:dd9af89d
2023-11-14 05:09:00
@ fab018ad:dd9af89d
2023-11-14 05:09:0018. แสงแห่งความหวัง
"ปัญหาพื้นฐานของระบบสกุลเงินปกติ อยู่ที่การยังจำเป็นต้องใช้ความเชื่อใจเพื่อให้มันทำงานได้ โดยธนาคารกลางนั้นจำเป็นต้องได้รับความเชื่อใจว่าจะไม่ทำเงินให้เสื่อมค่า แต่ในประวัติศาสตร์ของสกุลเงินเฟียตกลับเต็มไปด้วยการละเมิดความเชื่อใจนั้น”
–ซาโตชิ นากาโมโตะ
ไม่ว่าคำตอบของความยากจนในประเทศโลกที่สามจะเป็นอะไรก็ตาม เราก็แน่ใจว่ามันต้องไม่ใช่การก่อหนี้เพิ่มขึ้นอย่างแน่นอน “คนจนบนโลกนี้นั้น” คุณ Payer ได้สรุปไว้ว่า “ไม่ได้ต้องการธนาคารแบบธนาคารโลกเพิ่มขึ้นมาอีก ไม่ว่าธนาคารนั้นจะจิตใจดีมีเมตตาแค่ไหนก็ตาม สิ่งที่คนจนต้องการคืองานที่จ่ายค่าตอบแทนอย่างเหมาะสม รัฐบาลที่มีความรับผิดชอบ การมอบสิทธิมนุษยชนคืนให้พวกเขา และความเป็นเอกเทศในการบริหารประเทศโดยไม่ถูกต่างชาติแทรกแซง”
แต่เป็นเวลากว่า 7 ทศวรรษแล้วที่ธนาคารโลกและกองทุน IMF กลับตั้งตัวเป็นศัตรูกับทั้ง 4 สิ่งนี้
เมื่อมองไปในอนาคตข้างหน้านั้น คุณ Payer กล่าวว่า “ภารกิจที่สำคัญที่สุดสำหรับเหล่าประเทศร่ำรวยที่กังวลเรื่องความเป็นปึกแผ่นระหว่างประเทศอื่น ๆ คือการเดินหน้าอย่างจริงจังในการระงับการไหลของเงินให้ความช่วยเหลือไปสู่ต่างประเทศ” แต่ปัญหาคือระบบในปัจจุบันถูกออกแบบและสร้างแรงจูงใจให้การไหลของเงินแบบนี้ยังมีต่อไปได้ ทางเดียวที่จะสร้างการเปลี่ยนแปลงได้คือการปรับเปลี่ยนกระบวนทัศน์ใหม่ทั้งหมด โดยเรารู้กันอยู่แล้วว่าบิตคอยน์สามารถช่วยให้ประชาชนทั่วไปในประเทศกำลังพัฒนานั้นได้รับอิสรภาพทางการเงิน ช่วยให้พวกเขาหนีออกจากระบบเงินซึ่งล่มสลาย แต่ถูกผู้นำฉ้อฉลและสถาบันการเงินระหว่างประเทศบังคับให้พวกเขาต้องใช้ ประเด็นเหล่านี้ถูกเร่งความเร็วขึ้นในการประชุมที่เมืองอักกราเมื่อปลายปี 2022 ที่ผ่านมา
บิตคอยน์เป็นสิ่งที่อยู่ตรงข้ามกับระบบเดิมที่ถูกออกแบบโดยธนาคารโลกและกองทุน IMF แต่ทว่าบิตคอยน์จะสามารถเปลี่ยนพลวัตในโครงสร้างอำนาจและโครงสร้างทรัพยากรของโลกระหว่างประเทศแกนกลางและประเทศชายขอบได้จริงหรือ?
คุณ Nabourema นั้นเต็มไปด้วยความหวัง และไม่เข้าใจว่าทำไมฝ่ายซ้ายโดยทั่วไปมักประณามหรือไม่สนใจบิตคอยน์
“เครื่องมือที่สามารถทำให้ผู้คนสร้างและเข้าถึงความมั่งคั่งได้อย่างเป็นอิสระจากองค์กรที่มีอำนาจควบคุมนั้น สามารถที่จะมองว่ามันเป็นเครื่องมือของฝ่ายซ้ายได้เลยด้วยซ้ำ” เธอกล่าว “ในฐานะนักเคลื่อนไหวที่เชื่อว่าประชาชนควรได้รับเงินสกุลที่ให้ค่าต่อชีวิตและการเสียสละของพวกเขาแล้ว"
"บิตคอยน์คือเป็นการปฏิวัติของประชาชน”

“ฉันว่ามันเจ็บปวด” เธอกล่าว” ที่ชาวไร่ในเขตแอฟริกาบริเวณพื้นที่ใต้ทะเลทรายสะฮาราได้รับเงินแค่ร้อยละ 1 ของราคากาแฟในตลาดโลก ถ้าเราสามารถไปถึงขั้นที่ชาวไร่เหล่านั้นสามารถขายกาแฟของพวกเขาได้โดยตรงถึงผู้ซื้อ โดยไม่ต้องมีสถาบันตัวกลางใด ๆ มาแทรกแซง พร้อมทั้งรับเงินค่ากาแฟเป็นบิตคอยน์ คุณลองนึกดูสิว่ามันจะทำให้ชีวิตของพวกเขาเปลี่ยนไปมากแค่ไหน”
“ทุกวันนี้” เธอกล่าว “เหล่าประเทศกำลังพัฒนาอย่างพวกเรายังต้องกู้เงินในสกุลดอลลาร์สหรัฐ แต่เมื่อเวลาผ่านไปค่าเงินของเราเสื่อมค่าลงเรื่อย ๆ และต้องลงเอยด้วยการต้องหาเงินมาจ่ายเพิ่มขึ้นมากกว่า 2-3 เท่าของหนี้ในตอนแรก”
“ที่นี้คุณลองนึกภาพ” เธอกล่าว “ถ้าเราไปถึงขั้นที่ในอีก 10-20 ปีข้างหน้าที่บิตคอยน์เป็นสกุลเงินหลักของโลกและถูกใช้ในธุรกิจทั่วโลก ชาติต่าง ๆ ต้องกู้ยืมเป็นสกุลบิตคอยน์และใช้จ่ายในสกุลบิตคอยน์ ทุกชาติต้องจ่ายหนี้ของพวกเขาคืนในสกุลบิตคอยน์ ในโลกแบบนั้นรัฐบาลต่างชาติจะไม่สามารถเรียกร้องให้เราใช้คืนหนี้ในสกุลเงินของพวกเขา ซึ่งเป็นสกุลที่พวกเราต้องทำงานหนักเพื่อหามา แต่พวกเขาสามารถพิมพ์เพิ่มจากอากาศได้ง่าย ๆ และหากพวกเขาอยากที่จะเพิ่มอัตราดอกเบี้ยในประเทศตัวเอง มันก็ไม่ได้จะทำให้ชีวิตผู้คนนับล้าน ๆ ในประเทศของเราต้องตกอยู่ในอันตรายในทันทีเหมือนแต่ก่อน”
“มันแน่นอนว่า” คุณ Nabourema กล่าว “บิตคอยน์จะมาพร้อมปัญหาเหมือนนวัตกรรมอื่น ๆ ในอดีต แต่ความสวยงามของมันคือปัญหาเหล่านี้สามารถแก้ไขและพัฒนาขึ้นไปได้ด้วยความร่วมมือระดับนานาชาติอย่างสันติ ย้อนดูเมื่อ 20 ปีก่อน ไม่มีใครรู้หรอกว่าอินเทอร์เน็ตจะสามารถทำให้เราทำสิ่งมหัศจรรย์ที่เราทำอยู่ในทุกวันนี้ได้ และคงไม่มีใครบอกได้หรอกว่าในอีก 20 ปีข้างหน้า บิตคอยน์จะช่วยให้เราทำสิ่งมหัศจรรย์อะไรได้อีกบ้าง”
“หนทางข้างหน้าต่อจากนี้” เธอกล่าว “คือการตื่นรู้ของมวลชน พวกเขาจะเข้าใจว่าระบบการเงินในปัจจุบันทำงานอย่างไรได้แบบทะลุปรุโปร่ง และพวกเขาจะเข้าใจว่ามันมีทางเลือกอื่นอยู่ เราต้องไปอยู่ในจุดที่ผู้คนสามารถทวงคืนเสรีภาพให้ตัวเองได้ โดยที่ชีวิตของพวกเขาไม่ได้ถูกควบคุมโดยอำนาจรัฐที่สามารถยึดอิสรภาพของพวกเขาไปตอนไหนก็ได้โดยไม่ต้องรับผลกระทบใด ๆ ที่ตามมา พวกเรากำลังค่อย ๆ ไปถึงเป้าหมายนั้นด้วยบิตคอยน์”

“เนื่องจากเงินคือศูนย์กลางของทุกอย่างในโลกของเรา” คุณ Nabourema กล่าว “ความจริงที่ว่า ณ ตอนนี้เราสามารถมีอิสรภาพทางการเงินได้ถือเป็นสิ่งสำคัญต่อประชาชน และพวกเราก็กำลังพยายามทวงคืนสิทธิของเราเองในทุก ๆ พื้นที่และทุก ๆ อุตสาหกรรม”
ในการสัมภาษณ์สำหรับบทความนี้ ผู้สนับสนุนนโยบายเงินฝืด (Deflation) อย่างคุณ Jeff Booth ได้อธิบายว่าในขณะที่โลกยิ่งเดินเข้าสู่ระบบมาตรฐานบิตคอยน์ ธนาคารโลกและกองทุน IMF จะยิ่งไม่อยากเป็นเจ้าหนี้ และน่าจะอยากไปเป็นผู้ลงทุนร่วม เป็นหุ้นส่วน หรืออาจเป็นแค่ผู้จัดตั้งกองทรัสต์มากกว่า เนื่องจากในขณะที่ราคาของสิ่งต่าง ๆ เริ่มปรับตัวลง มันหมายถึงหนี้สินจะมีมูลค่าที่มากขึ้น และจะเป็นเรื่องยากขึ้นสำหรับลูกหนี้ที่จะหาเงินมาจ่ายคืนได้ และเมื่อเครื่องพิมพ์เงินของสหรัฐอเมริกาถูกปิดไป ก็จะไม่มีเงินให้กู้เพื่อมาช่วยเหลืออีก และเขายังชี้ว่าในช่วงแรกนั้นธนาคารโลกและกองทุน IMF จะยังพยายามที่จะปล่อยกู้เหมือนเดิม แต่มันจะเป็นครั้งแรกที่พวกเขาจะสูญเงินก้อนใหญ่นั้นไปจริง ๆ เพราะประเทศต่าง ๆ จะเริ่มผิดนัดชำระหนี้กันมากขึ้นในระหว่างที่โลกกำลังขยับเข้าสู่ระบบมาตรฐานบิตคอยน์
ดังนั้นพวกเขาอาจจะเริ่มพิจารณาการเป็นผู้ลงทุนร่วมมากกว่าจะเป็นผู้ปล่อยกู้ แปลว่าพวกเขาจะต้องสนใจความยั่งยืนและความสำเร็จที่แท้จริงของโครงการที่พวกเขาสนับสนุนมากขึ้น เนื่องจากพวกเขาต้องรับความเสี่ยงในการลงทุนนั้น
การขุดบิตคอยน์เป็นอีกสิ่งหนึ่งที่สามารถสร้างความเปลี่ยนแปลงได้
ถ้าชาติที่ยากจนสามารถเปลี่ยนทรัพยากรธรรมชาติของพวกเขาเป็นเงินได้ โดยไม่ต้องยุ่งเกี่ยวกับเหล่าผู้มีอำนาจจากต่างประเทศ บางทีอธิปไตยของพวกเขาอาจจะแข็งแกร่งขึ้น แทนที่จะถูกบ่อนทำลายลงเหมือนแต่ก่อน การขุดบิตคอยน์นั้นใช้ได้ทั้งพลังงานจากแม่น้ำ เชื้อเพลิงไฮโดรคาร์บอน แสงอาทิตย์ ลม ความร้อนใต้พิภพ หรือแม้แต่พลังงานจากความแตกต่างของอุณหภูมิน้ำทะเลนอกชายฝั่ง (OTEC) ที่มีอยู่มากมายในเขตตลาดเกิดใหม่ พลังงานเหล่านี้สามารถถูกเปลี่ยนเป็นสกุลเงินสำรองของโลกได้โดยตรง โดยไม่ต้องขออนุญาตใคร เรื่องนี้ไม่เคยเป็นไปได้มาก่อน ซึ่งสำหรับเหล่าประเทศที่ยากจนแล้วกับดักหนี้ดูเหมือนจะเป็นสิ่งที่หนีออกมาไม่ได้ แถมมันยังขยายขนาดขึ้นทุกปี
บางทีการลงทุนเพื่อเก็บออมบิตคอยน์เป็นเงินสำรอง และเพื่อใช้งานโครงสร้างพื้นฐานของบิตคอยน์ (ซึ่งโดยเนื้อแท้แล้วมันเป็นสิ่งที่ต่อต้านระบบเงินเฟียต) น่าจะเป็นทางออกและเป็นเส้นทางสู่การเอาคืนระบบเดิมที่กดขี่พวกเขามายาวนาน

คุณ Booth กล่าวว่าบิตคอยน์สามารถทำให้ระบบเก่าที่เอื้อประโยชน์แก่ประเทศร่ำรวยด้วยการปล้นค่าแรงของประเทศยากจนนั้นเกิดอาการลัดวงจรจนพังได้ เพราะในระบบเก่า กลุ่มประเทศชายขอบต้องถูกสังเวยเพื่อปกป้องประเทศแกนกลาง แต่ในระบบใหม่ ประเทศชายขอบและประเทศแกนกลางจะสามารถทำงานร่วมกันได้ เขากล่าวว่า ณ ตอนนี้ระบบเงินดอลลาร์สหรัฐกดคนให้จนลงด้วยการกดค่าแรงในประเทศชายขอบ แต่เมื่อเงินถูกปรับให้มีความเท่าเทียมด้วยระบบที่เป็นมาตรฐานและเป็นกลาง พลวัตใหม่จะถูกสร้างขึ้น การที่มีมาตรฐานทางการเงินเพียงหนึ่งเดียวจะส่งผลให้อัตราค่าแรงถูกดึงมาให้อยู่ในระดับใกล้เคียงกันอย่างเลี่ยงไม่ได้ แทนที่มันจะถูกทำให้ห่างออกจากกันแบบที่แล้วมา คุณ Booth ยังกล่าวอีกว่าเราไม่มีคำที่ใช้เรียกสำหรับพลวัตนี้ เพราะมันเป็นสิ่งที่ไม่เคยเกิดขึ้นมาก่อน โดยเขาแนะนำให้ใช้คำว่า “ความร่วมมือเชิงบังคับ”
คุณ Booth อธิบายถึงความสามารถของสหรัฐฯ ในการสร้างหนี้จำนวนเท่าไรก็ได้ตามต้องการว่าเป็น “การโจรกรรมในระดับฐานเงิน” คุณผู้อ่านคงอาจจะคุ้นเคยกับปรากฏการณ์แคนทิลอน (Cantillon Effect) ที่ผู้อยู่ใกล้แหล่งการผลิตเงินนั้นจะได้ประโยชน์จากเงินผลิตใหม่ ในขณะคนที่อยู่ห่างออกไปนั้นต้องทนทุกข์ใช่ไหมครับ ปรากฏการณ์แคนทิลอนในระดับโลกนั้นคือการที่ประเทศสหรัฐอเมริกาได้ประโยชน์จากการพิมพ์เงินสกุลสำรองของโลก ในขณะที่ประเทศยากจนต้องทนทุกข์กันทั้งโลก
“แต่มาตรฐานบิตคอยน์” คุณ Booth กล่าว “จะหยุดสิ่งนี้”
มีหนี้สินบนโลกมากแค่ไหนที่เป็นหนี้ที่ชั่วร้าย (Odious Debt) คำตอบคือมีเงินกู้นับล้านล้านดอลลาร์สหรัฐที่ถูกสร้างขึ้นตามอำเภอใจของผู้นำเผด็จการกับสถาบันการเงินที่อยู่เหนือประเทศชาติ และไม่มีใครเลือกตั้งพวกเขามาขึ้นมา หนี้ชั่วร้ายถูกสร้างขึ้นโดยไม่เคยถามความเห็นชอบของประชาชนในฝั่งของผู้กู้เลย สิ่งมีศีลธรรมที่ควรกระทำคือยกเลิกหนี้สินพวกนี้ให้หมด แน่นอนว่ามันจะไม่มีทางจะเกิดขึ้น เพราะสุดท้ายแล้วเงินให้กู้เหล่านี้ก็ถือเป็นทรัพย์สินบนงบดุลของผู้ที่เป็นเจ้าหนี้ของธนาคารโลกและกองทุน IMF ซึ่งพวกเขาอยากให้ทรัพย์สินพวกนั้นยังคงอยู่ และขอแค่ลูกหนี้ก่อหนี้ใหม่ไปชำระหนี้เก่าก็พอ
“พุทออปชั่น (Put Option)” ของ IMF ในหนี้ภาครัฐนั้นสร้างฟองสบู่ที่ใหญ่ที่สุดเท่าที่เคยมีมา มันใหญ่กว่าฟองสบู่ดอตคอม ฟองสบู่สินเชื่อซับไพรม์ และใหญ่กว่าฟองสบู่ที่เกิดจากเงินกระตุ้นเศรษฐกิจช่วง COVID-19 การจะรื้อระบบเก่านี้เป็นงานที่เจ็บปวดมาก แต่มันก็เป็นสิ่งที่ถูกต้องที่ควรทำ ถ้าเปรียบว่าหนี้สินคือยาเสพติด ธนาคารโลกและกองทุน IMF คือพ่อค้ายา และรัฐบาลของประเทศที่กำลังพัฒนาคือคนที่ติดยา ก็คงเห็นว่าไม่น่าจะมีฝ่ายไหนที่อยากให้อีกฝ่ายนึงหยุด แต่ที่การจะรักษาผู้ติดยานั้น เราต้องนำผู้ติดยาเข้ารับการบำบัด ระบบเงินเฟียตไม่อนุญาตให้ทำให้สิ่งนี้ได้ แต่ระบบการเงินมาตรฐานบิตคอยน์จะบังคับให้ผู้ป่วยติดยาไม่มีทางเลือกอื่น นอกจากการเลิกยา
หมายเหตุผู้แปล : - ฟองสบู่ดอตคอม (Dot-com Bubble) เป็นฟองสบู่จากการเก็งกำไรในตลาดหลักทรัพย์ภาคเทคโนโลยีของสหรัฐอเมริกา ในช่วงปี 1997-2000 - ฟองสบู่สินเชื่อซับไพรม์ (Subprime Mortgage Bubble) เป็นฟองสบู่จากเกิดจากการปล่อยกู้ในภาคอสังหาริมทรัพย์ของของสหรัฐอเมริกาซึ่งกลายเป็นวิกฤติการเงิน ในช่วงปี 2008
อย่างที่อาจารย์เซเฟดีน อัมมูสกล่าวในการสัมภาษณ์สำหรับบทความนี้ ว่าทุกวันนี้หากผู้ปกครองของบราซิลต้องการกู้เงินจำนวน 30,000 ล้านดอลลาร์สหรัฐ และรัฐสภาของสหรัฐฯ อนุมัติเงินกู้ดังกล่าวแล้ว ทางสหรัฐฯ ก็สามารถดีดนิ้วเสกเงินขึ้นมาและส่งให้ได้เลยผ่าน IMF แปลว่าระบบการเงินทุกวันนี้เป็นเรื่องของการตัดสินใจทางการเมืองเป็นหลัก แต่ถ้าเรากำจัดเครื่องพิมพ์เงินออกไปได้ การตัดสินใจเหล่านี้จะเป็นเรื่องการเมืองน้อยลง และจะเริ่มเป็นการตัดสินใจอย่างรอบคอบ แบบเดียวกับธนาคาร “ที่สำเหนียกว่าจะไม่มีใครมาอุ้มพวกเขาได้อีกแล้ว” จะพึงกระทำ
ในช่วง 60 ปีที่ผ่านมาของการครอบงำโดยธนาคารโลกและกองทุน IMF เหล่าทรราชและเครือข่ายที่ยักยอกความมั่งคั่งของประเทศจำนวนนับไม่ถ้วน ต่างก็ได้รับเงินให้กู้เพื่อการช่วยเหลือ (ซึ่งเป็นสิ่งที่ขัดกับสามัญสำนึกทางการเงิน) เพื่อให้เหล่าประเทศแกนกลางสามารถเข้าฉกฉวยทรัพยากรธรรมชาติและแรงงานของประเทศเหล่านั้นได้ต่อไป สิ่งเหล่านี้เป็นไปได้เพราะรัฐบาลซึ่งเป็นหัวใจของระบบเฟียตสามารถพิมพ์เงินที่เป็นสกุลเงินสำรองได้ แต่ในระบบมาตรฐานบิตคอยน์นั้น คุณเซเฟดีน อัมมูสตั้งคำถามว่าใครกันที่จะปล่อยเงินกู้ความเสี่ยงสูงมูลค่านับพันล้านดอลลาร์ เพียงเพื่อจะแลกกับการให้ลูกหนี้เข้ามาขอปรับโครงสร้างเพื่อยืดหนี้เก่าโปะหนี้ใหม่ในภายหลัง
“เป็นคุณจะปล่อยกู้งั้นเหรอ?” เขาถาม “แล้วจะเอาบิตคอยน์ของใครไปปล่อยกู้ล่ะ?”
⚡️ กด Zap ที่ลิงก์นี้ เพื่อเป็นกำลังใจทีมงานผู้เรียบเรียงบทความ
(ทุกยอด zap จะถูกแบ่งอัตโนมัติเข้าวอลเล็ทของผู้เขียนบทความต้นฉบับภาษาอังกฤษ, ผู้แปลดราฟต์ 1, ผู้เรียบเรียงดราฟต์ 2-3, กองบรรณาธิการและพิสูจน์อักษรจากไรท์ชิฟต์ พร้อมกันบางส่วนไว้เพื่อเป็นค่าธรรมเนียมธุรกรรม)
-
 @ 52b4a076:e7fad8bd
2023-11-10 23:08:02
@ 52b4a076:e7fad8bd
2023-11-10 23:08:02Nostr has a funding problem. Developers and infrastructure is severely underfunded and reliant on flawed economic models, and this could pose a risk to the future of Nostr as a protocol.
To understand it, we need to understand what resources are needed to make Nostr work, how they aren't funded properly and what could happen next.
The costs of what makes Nostr work
Nostr works because: 1. Developers build clients on it 2. There is infrastructure to support clients
If there are no developers, there are no clients. If there is no infrastructure, clients have no purpose.
The costs of developing a client, and the reliance on developers
Clients require time to develop the client, and money to run infrastructure for it.
Without developers, there would be no clients, and no Nostr.
Developers have lives and need to make money somehow in exchange for the time they spend. Developing a client is a significant cost, even for small ones (assuming 1 hr/day, no infrastructure costs and the average salary of a software developer, $1500) and needs to be covered somehow.
We have multiple models, all of which have large downsides: 1. Donations/V4V/Bounties:
This model suffers from the problem that a minority pays for the majority, which will lead to the majority demanding exclusive benefits for their money or otherwise cutting off funding since they have no reason to pay.
This also suffers from the fact that donations are unreliable. 2. Grants from OpenSats and similar non-profits:
These suffer from the same problems as the donations model, but also suffer from the following problems: - the managers of these non-profits may have views not aligned with their donors, leading to misfunding. - that such projects are mostly stopgaps that add additional complexity to a direct donation model. 3. Paywalled features:
It is very hard to find the balance between paywalling enough features to make money, and discouraging too many users from using the client. There may not even be such a sweet spot. 4. Cuts: It is extremely hard to balance these so that people don't complain, and it is likely that there will be forks of FOSS clients that remove these features by some users.
5. Paid clients:
People do not want to spend a lot on services that they expect to be free or cheap, and spending $5/month on this client, $10/month on that client, so on won't scale, even though that is way less than the actual value they are getting. 6. Ads:
Ads are usually underpaying and mostly make money for the ad companies instead of the client developers. Ads are also an invasion of privacy and may not be well received by some users. 7. VC funding:
VCs put profit above protocol health, which may accelerate some issues that I will discuss later. They also may disincentivize the development of some apps (uncensored social media for example) for pushing their own agenda.Even if we find some good way to fund clients, it doesn't end there...
The cost of infrastructure
There are multiple types of infrastructure for Nostr, such as relays, services like Noswhere's search relay, push notifications, etc. All of these cost money to operate, and are the other half of what make Nostr work.
These have even more limited funding options, which have even bigger downsides: 1. Client funding:
Clients already struggle on funding as I discussed in the previous section. This would mean infrastructure is even more underfunded. 2. User payments:
Users do not understand the details and importance of infrastructure, and have no reason to fund it. Making this problem worse, infrastructure providers can falsely advertise their services, diverting money away from infrastructure that is higher quality and should be funded. This is already happening. 3. Grants from OpenSats and similar non-profits (relays only):
Again, these suffer from problems specified in the last section about grants. These entities will likely want the highest value from their donations, therefore leading them to encouraging a few big relays than many medium sized ones. Since relays are more important infrastructure, and they could have more control, these entities can also exert more control over the network. 4. Data harvesting and selling:
This would discourage people from using their providers, but this is likely going to happen to some extent. The issue is that it would not generate sufficient revenue for the amount of users it will drive away.Both infrastructure and developers being underfunded can lead to issues that may kill the protocol, which I'll discuss in the next section.
The risks of improper funding
1. The protocol fizzles out and dies without reaching critical mass
This is one of the less likely options since there will probably be people developing for the sake of it, but is likely. With client developers being underfunded and infrastructure shutting down, Nostr would become smaller and worse to use until it completely fizzled out except maybe a few people.
2. The enshittification of Nostr
This is the most likely outcome, and the worst one. As Nostr continues developing, developers and infrastructure developers will want to maximize revenue, so they will begin by making good products to attract users at a loss.
After they have a sufficiently large user base, they would slowly erode bridges to their competitors, only leaving what is required so that their users won't complain.
After this stage, it is likely that clients will start merging with other ones to make larger "everything" apps and kill the last bridges, turning them into proprietary walled gardens, returning us to where we are today.
How do we fix this?
I have no idea. Please share your opinions if you do :)
-
 @ 5a9c48c8:2f2d1069
2024-03-21 12:43:42
@ 5a9c48c8:2f2d1069
2024-03-21 12:43:42Considering our most acute problems in the EU is a matter of great debate, which is not necessarily all evidence based. Our seemingly most pressing problems might not even be problems at all, just public opinion. To create unenforceable policy to address these problems is costly, so much so that I think it’s necessary to create a standard. I will not trivialise any particular policy, but I will make a case for at least having a Bitcoin strategy.
There are three ways that policy fails:
- The policy is not enforceable.
- The policy is costing more to enforce than it benefits.
- The public adjusts its behavior to circumvent in a roundabout manner, which requires yet again more policy: praxeology.
The only way that any policy has a measurable desired effect is when it is enforceable, is cost effective and doesn’t motivate adverse or roundabout behavior. This is the necessary standard to measure policy by. Budget management for the calculation of policy efficacy also needs to be represented in the balance.
An example of a failing policy is the 100km/h speed limit in the Netherlands. To enforce this requires policing of the highways, which costs money. To pay for the enforcement speed tickets are issued. Highway users use the app Flitsmeister, which is a social media app that allows users to share gps data of traffic controls. As a result less speed tickets are issued and highway users speed more. The government can’t ban the app because using the app is the user’s freedom of speech, it’s just allowing users to communicate coordinates on a map. This is a lawful behavior, any ruling against an app like Flitsmeister will not hold up in court. A calculation must be made to see how much it would cost to just allow highway users to speed versus what it would cost to continue enforcing. A calculation must be made to see what the benefit is of the policy. In this case the policy is in place because the EU has decided that emissions from motor vehicles must be brought down, so the 100km/h policy was a consequence of an unenforceable policy. So this example shows all three ways in which a policy can fail:
- Simply telling people to create less emissions is unenforceable.
- Revenue from speed tickets dwindle, people keep speeding and emissions do not measurably go down.
- People adapt to the policy with a lawful measure so that they can continue driving at the speed they desire, behavior known as praxeology. (Keep in mind that people were used to driving 120km/h before, and most people don’t consider that speed as excessive speeding or as unlawful.)
Just by using epistemology we now have the basic requirements for policy to exist. Pretending to be moralistic doesn’t help. In the end moralism points to sustainability, which means to not wasting public funds. Therefore being strategic is actually the best moralistic approach.
Bitcoin is a free and open source project, anyone can contribute. Direct participation is possible by transacting and holding Bitcoin, by running a Bitcoin node or by mining Bitcoin. To ban Bitcoin transactions is to ban freedom of speech, because transacting Bitcoin is basically the exchange of information. There is no entity that controls Bitcoin, so you can’t address the organization because there is no organization. Because of its value propositions, Bitcoin is proving to be a better store of value than any other asset class. If you have no confidence in this, then you still need to play along with Bitcoin because not playing means you will lose asymmetrically over time. The game theory of Bitcoin is that not playing results in loss. The costs to participate are low, which is a benefit that stems from the asymmetry. So there can be no reason not to participate at all, to at least offset the cost of opportunity.
To use Bitcoin as an example of framework for policy I propose to look at the failures to enforce a mining ban. If a government were to make Bitcoin mining illegal, the miner would simply move its operation. Bitcoin mining is not jurisdiction specific; this was made clear by the restoring of hashrate after the China Bitcoin mining ban. Miners that chose to stay are difficult to find, enforcement will be costly and ineffective. Miners that do leave will not pay any taxes, nor will those that have been made illegal miners within the jurisdiction. Not banning Bitcoin will allow power plants to offset inefficiency by mining Bitcoin. Energy efficiency is the greatest benefit of Bitcoin mining, which will prove to become the largest possible sustainability improvement for participants. So from this example we can see that this policy also fails on three counts in which it can fail:
- Banning Bitcoin mining does not magically make Bitcoin miners disappear. Heavy policing will not find those who still chose to continue. You can’t stop miners in other jurisdictions, yet they still give access to the network to users in the jurisdiction. Remember, the internet doesn’t do geography.
- Loss in tax revenue from multiple sectors of business will prove to be devastating. Policing illegalised Bitcoin miners is costly in many ways. There is no benefit. Allowing Bitcoin mining on the other hand would reap enormous societal benefits.
- Illegalised Bitcoin miners will still exist within the jurisdiction, but will not pay any taxes. Those who chose to leave, take with them their thriving business and the entire framework of the involved financial sector.
If you still oppose Bitcoin in any way, make sure to look up your specific criticism in the list published on https://www.endthefud.org . You will see that your misinformed belief does not hold up against matter of fact.
-
 @ 3bf0c63f:aefa459d
2023-11-08 15:06:55
@ 3bf0c63f:aefa459d
2023-11-08 15:06:55I think it's undeniable at this point that the creation of Lightning Address has made the usage of custodial Lightning solutions increase -- or at least be more prominent. We see these stats everywhere of how many of Nostr Lightning Addresses are custodial, and how services like Nodeless and Geyser only work if you give them a Lightning Address, and that probably sounds like a lament to many people who thought Lightning would be this amazing network of self-hosted nodes that everybody runs, and is indeed sad.
Well, on the other hand the Lightning Address flow is clearly an improvement -- to most people -- over the cumbersome invoice flow. Since the early days of Lightning people had been complaining about the fact that there is no way to "just send money to an address". Even though I personally liked the invoice flow much more (especially if they had structured, signatures, clear descriptions and amounts, payment proofs and so on) the fact is that most people didn't and slowly invoices were losing their meaning entirely anyway.
This improvement in the payment flow, along with the open, easy and interoperable way that Lightning Addresses work, has opened space for new use cases that maybe wouldn't have existed otherwise -- like the services mentioned above, and others. So we can't really say this was all a bad thing.
We also shouldn't say it was a bad thing to have Lightning Addresses being invented at all, because if they hadn't been invented like they were, there is a high probably they would have been invented in other forms, probably much worse, that would involve private deals and proprietary integrations with ad-hoc APIs, SDKs and JavaScript widget buttons with iframes. I even remember some of these things starting to happen at the time Lightning Address was created, and we have more evidence of these things even after Lightning Address, like some "partnerships" here and there and the "UMA" protocol. So maybe Lightning Address was just the best possible protocol at the best time, and all its problems are not really its problems, but symptons of the problems of the Lightning Network (or maybe you wouldn't call these "problems", just natural properties, but doesn't matter).
The saddest realization of all this process, for me, was that Lightning payments are mostly used for tipping and not for commerce as I thought they would in the beginning (hence my love for the invoice flow). Specifically, LNURL-pay and its cool hidden features that went mostly unsupported, were all designed with the goal of enabling new use cases for commerce in the real life, outside the web, and Lightning Addresses would have tied nicely into that vision too -- but that was all definitely an irredeemable failure.
I thought I had more things to say about this, but either I didn't or I forgot. The end.
-
 @ cce0989b:b497e608
2024-03-21 12:24:11
@ cce0989b:b497e608
2024-03-21 12:24:11It's hard to watch someone you love suffer. Sometimes, in trying to alleviate their pain (and our own distress), we end up accidentally hurting them:
-
In ignoring their pain because we 'don't want to bring it up and remind them', we can leave them feeling lonely.
-
In trying to problem solve, we can leave them feeling ashamed.
-
In trying to cheer them up, we can leave them believing that their feelings don't matter.
Here's one thing you can do that will help:
Just be there with them. Be willing to sit in the pain with them.
This can sound like an abstract idea, so we've coined an acronym — LOVE — to help you put it into practice.
Look at them
Give them your full attention. Don’t be scared or shy away from their struggles. What do you see? What do you sense? How might they be having a hard time?Open up to their pain
Demonstrate that you want to know more about their pain by asking questions. You might say something like..."What's it like managing [XYZ challenge] right now?"
"Will you tell me more about what that was like?"
"What are you feeling right now?"Validate what they're experiencing
Whatever they share, reflect it back to them, both to build your understanding and to honor their experience."It sounds like you might be feeling overwhelmed. Is that right?"
"What you're facing is hard. Everyone would struggle with it."
"I'm hearing that you need me to do this household task and it would make you feel more supported."Express your love
Finally, tell them that you love them, a sentiment that can take so many forms."I believe in you."
"I see how hard you're trying and how brave you are."
"You are not alone. We'll figure it out together."L-O-V-E. Give it a try and let us know how it goes.
-
-
 @ 1e52c554:21771908
2024-03-21 12:15:30
@ 1e52c554:21771908
2024-03-21 12:15:30Posthumous work of the Colombian poet born in Don Matias on January 20, 1948.
Welcome to this blog dedicated to the Posthumous work of the Colombian poet Francisco Luis Arroyave Tabares (my father), born in Don Matias on January 20, 1948-2010. Where I will be publishing each of the 175 sonnets from his unpublished collection 'Sonnets For The Twenty-First Century And A Circadian Musical (1984-1987).' Analyzed with GPT4 artificial intelligence and illustrated with AI tools... I hope you enjoy this garden of words snatched from the solitude of a locked room.
Likewise, any enthusiast of the sonnet form is invited to conduct their personal studies of Arroyave Tabares' work, as it is a collection that, although registered since 1989, has not yet been published.
Frank Duna

Analysis of "Our Night Stand"
Introduction
"Sonnet 133" by Francisco Luis Arroyave Tabares presents a romantic portrayal of a relationship, emphasizing the enduring love shared by a couple. The poem uses vivid imagery and metaphorical language to describe the intimate moments between the lovers.
Thematic Analysis
Lines 1-4: The poem begins with the speaker and their lover floating on the “moonshine tide,” suggesting a sense of tranquility and peace. The use of the term “stasis” indicates a state of balance or equilibrium, perhaps referring to the stability and harmony in their relationship. They mold their love around a “dim oasis,” which could symbolize the comfort and solace they find in each other amidst the darkness of the night.
Lines 5-8: The speaker describes moments of intimacy, where words are replaced by kisses, and they embark on magical journeys together. The reference to flutes transforming the wind’s hiss into jazz could be a metaphor for the transformative power of their love, turning ordinary moments into something majestic and beautiful.
Lines 9-12: The stars, often symbols of dreams and aspirations, have danced their way to their home, finding happiness in their eyes. This could suggest that their love is so profound and fulfilling that it attracts even the celestial bodies. They give birth to dreams under the dome of the stars’ lucid light, signifying their shared hopes and dreams.
Lines 13-14: The final couplet celebrates their love, which stands strong day by day, protected by the shadows and the hand of darkness. This could imply that their love thrives in the quiet and peaceful solitude of the night.
Overall, this sonnet beautifully captures the depth and magic of love, set against the backdrop of a serene and mystical night.
Structure and Rhyme Scheme
The sonnet follows the rhyme scheme of a Shakespearean sonnet, which is abab cdcd efef gg. Let’s break it down:
First Quatrain:
“tide” (A) “stasis” (B) “chide” (A) “oasis” (B)Second Quatrain:
“kiss” (C) “magic” (D) “hiss” (C) “majestic” (D)Third Quatrain:
“home” (E) “happiness” (F) “dome” (E) “emptiness” (F)Couplet:
“stand” (G) “hand” (G)Each end word in a line rhymes with another end word in a different line according to the rhyme scheme. This pattern of rhyme gives the sonnet its distinctive sound and rhythm. It also helps to link related ideas in the poem, creating a sense of cohesion and harmony. The final couplet often provides a resolution or summary of the preceding quatrains. In this case, it emphasizes the enduring and protective nature of the love described in the poem.
Analysis of Aspects
Let’s delve deeper into the language, imagery, themes, meter, and overall impact of “Sonnet 133” by Francisco Luis Arroyave Tabares:
Language: The language used in the sonnet is rich and evocative, with a strong emphasis on sensory details. The poet uses words like “moonshine tide,” “dim oasis,” “rides of magic,” and “lucid light” to create vivid images in the reader’s mind. The language is also quite lyrical, with a rhythm and flow that enhances the overall reading experience.
Imagery: The sonnet is filled with beautiful and powerful imagery. The “moonshine tide,” “dim oasis,” “flutes making jazz,” “stars dancing their way home,” and “dreams under their dome of lucid light” are all striking images that contribute to the poem’s magical and dreamlike atmosphere.
Themes: The main themes of the sonnet are love, magic, and the beauty of the night. The poet explores the depth and transformative power of love, the magic of shared experiences, and the serene and mystical beauty of the night. The theme of love is particularly prominent, with the poet depicting love as a force that brings balance, transforms ordinary moments into something majestic, and attracts even the celestial bodies.
Meter: The sonnet follows the traditional iambic pentameter, which is a type of meter in poetry where each line contains five pairs of syllables, each pair consisting of an unstressed syllable followed by a stressed syllable. This gives the poem a rhythmic quality, making it pleasing to read or recite.
Overall, “Sonnet 133” is a beautifully crafted poem that skillfully combines language, imagery, themes, and meter to create a captivating depiction of love and the night. The poet’s use of vivid and evocative language, combined with the rhythmic quality of the meter, makes the poem a pleasure to read. The themes of love, magic, and the beauty of the night are explored in a way that is both profound and enchanting, leaving a lasting impression on the reader.
(GPT4)
Syllable count for each line.
```
Our Night Stand
10 We have been floating on the moonshine tide 10 That has become a part of our stasis
10 Where with soft voice some times we used to chide 10 To mold our love around dim oasis.10 When we do not have any words we kiss 10 Or fly away in our rides of magic 10 While nice flutes make into jazz the wind's hiss
10 And from humble tone become majestic.10 The stars have danced their way until our home 10 And have found in our eyes the happiness 10 Since we give birth to dreams under their dome 10 Of lucid light that fills each emptiness.
10 Day by day we celebrate on our stand 10 Protected by shadows and darkness' hand. ***
```
Sonnets For The Twenty First Century And A Circadian Musical Written By Francisco Luis Arroyave Tabares (1984-1987)
Analyzed by GPT4; Image by leonardo.ai; First published on Nostr Protocol by franciscoarroyavet@nostrplebs.com
 Our Night Stand
Our Night Stand -
 @ 2edbcea6:40558884
2023-11-05 18:23:21
@ 2edbcea6:40558884
2023-11-05 18:23:21Happy Sunday #Nostr !
Here’s your #NostrTechWeekly newsletter brought to you by nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk written by nostr:npub1r3fwhjpx2njy87f9qxmapjn9neutwh7aeww95e03drkfg45cey4qgl7ex2
The #NostrTechWeekly is a weekly newsletter focused on the more technical happenings in the nostr-verse.
Before we dive in I want to congratulate the winners of the NostrAsia hackathon: eNuts, Shopstr, Zappdit, and the runner up Nosskey. Thanks for hacking away and building for the community. 😊
Let’s dive in!
Recent Upgrades to Nostr (AKA NIPs)
1) (Proposed) Updates to NIP 72: Moderated Communities
As mentioned in previous weeks, moderated communities as currently outlined in NIP 72 publish kind 1 events (tweet-like text notes), and they show up without context in clients like Damus, Amethyst, Snort, etc.
One solution to the lack of context is to make activities in moderated communities use event kinds other than 1 so that you have to be in a client specialized for moderated communities to see those activities.
There have been a few attempts to update NIP 72 to accomplish that goal, and this is the latest iteration. Unique to this proposal is the idea of community scoped user data, not just posts. For example you could follow people within the community within the scope of the community but not add them to your general following list for your whole Nostr account. They’d show up in your feed in the moderated community but not in your general feed.
There’s a lot of potential in moderated communities to become a core pillar of Nostr usage as the network scales, especially since the censorship and API management regimes of Reddit have gotten more restrictive. People want better and Nostr can be that solution.
Author: nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6
2) (Proposed) NIP 49: Nostr Wallet Auth
Having a Lightning Wallet connected to Nostr is a powerful tool for content monetization and nostr-based marketplaces. There’s a lot of great work done on Nostr Wallet Connect, but it all “hinges on having the user copy-paste a wallet connection URI into the app they wish to connect with. This can be a UX hurdle and often has the user handling sensitive information that they may not understand.”
“This NIP proposes a new protocol that solves these problems by having the wallet and app generate a NWC connection URI together. This URI is then used to connect the wallet and app.”
Making it easier for new users (especially those that are less technical) to participate in the new economy is fundamental to making Nostr the best place for content creators to make a living without middlemen and heavy handed platforms. 💪
Author: nostr:npub1u8lnhlw5usp3t9vmpz60ejpyt649z33hu82wc2hpv6m5xdqmuxhs46turz
3) (Proposed) Updates to NIP 15: Nostr-based Marketplaces
This proposal expands the capabilities of Nostr-based Marketplaces to support auctions. Think about a Nostr-based eBay where users can post an item for sale by auction using a marketplace Nostr client.
The auction going live is a Nostr event, and users can publish bids as Nostr events, and when the auction is closed it’ll be determined by the bid event with the highest offering. Which anyone can verify. This is a very interesting way to make marketplaces more censorship resistant.
Author: ibz
Notable Projects
Yondar (social maps) 🌐
Much physical commerce is discovered by consumers via map apps. You go on Google or Apple Maps to find an art supply store near you, or coffee shops that are open at 2pm when you’re in a new city. These centralized solutions have dominated, but no more! Enter Yondar.
Yondar is a Nostr client that allows users to publish places on a map. This could be places of business or events, really anything that has a location.
True to Nostr form, people can also socially interact with these places: do a kind 1 comment in response to an upcoming event published on Yondar. Or someone could create a Nostr client for restaurant reviews and publish one of those in response to a place published via Yondar. The possibilities are endless 🤯.
Author(s): npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w
WavLake 🎵
WavLake is a music player for web and mobile. It’s part Spotify music player and music discovery tool, part music monetization platform. They host the actual music files in their own cloud hosted system, but they publish Nostr events to represent the content that’s stored by WavLake, so other clients could help people discover music hosted and published via WavLake.
If musicians can get paid more for their music via solutions like WavLake, they will start using Nostr purely for selfish monetary reasons. This could be the start of purple-pilling that particular artistic community.
P.S. I listened to WavLake Radio while writing this, it was nice writing music.
Authors: based on the linked Github repo it’s nostr:npub1j0shgumvguvlsp38s49v4zm8algtt92cerkwyeagan9m6tnu256s2eg9a7 and blastshielddown
Opt-in content moderation on nos.social 👍👎
nostr:npub1wmr34t36fy03m8hvgl96zl3znndyzyaqhwmwdtshwmtkg03fetaqhjg240 gave a presentation at NostrAsia about making Nostr more accessible for normies. One of the items that was announced was the implementation of opt-in content moderation in his Nostr client nos.social.
They now support content warnings set by users publishing content, reporting content with various tags, as well as the ability for users to opt-in to moderation that changes their feed based on what they want to filter out.
People that don’t want moderation don’t need to use it, but I applaud nos.social’s work to develop these tools and patterns so that people have the choice to moderate their own feed.
Latest conversations: Interoperability
NostrAsia really highlighted the superpowers of Nostr and one of the foremost is interoperability. nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft gave a great talk about this topic and explained NIP 31 and NIP 89.
In summary, imagine there’s a Nostr client for movie reviews and they publish the review in a specific structure with Kind 12345678. Most Nostr clients will see that event but won’t know how to display that content or help users interact with it.
If clients adopt NIPs 31 and 89 then Nostr events will have an “alt” tag and a way to find a suggested app to handle that type of Nostr content. The alt tag helps clients display something to the user and the suggested app handler helps the client indicate to the user how to interact with that content more natively.
Maximum interoperability is useful in allowing Nostr to grow without centralizing. We can all experiment and build and all efforts still support the usage of the Nostr ecosystem in general.
Kind 1 clients as gateways to the Nostr app ecosystem
This interoperable future points to a framework where Kind 1 clients (Damus, Amethyst, Snort, Primal, etc) are the entrypoint or gateway to the Nostr ecosystem. Kind 1 clients are the core social use case and the foundation of most social interaction and could be amazing standalone apps and businesses, but Nostr makes them something more.
People will post Kind 1 notes referencing all kinds of Nostr events: music published via WavLake or Stemstr, places shared via Yondar, recipes created on Nostr.Cooking, etc. Clients will display some context on what the comment is on (music, place, video, recipe, etc) and then help the user find the right plugin/app/website to use to interact with that content natively.
This makes the Kind 1 clients the purple pill. This is only possible because of the unique interoperability capabilities of Nostr.
Interoperability with non-Nostr services
Even more amazing about Nostr is that it’s fairly easy to make the network interoperable with services outside the Nostr-verse. We already have pretty good bridges to ActivityPub-based systems like Mastadon as well as Twitter (with Exit). That reduces the switching cost for people that want to explore Nostr and eventually make the switch.
Even within Nostr-verse we have services like nostr.build that provide services in a way that doesn’t lock users in. Nostr.build provides file hosting services and because they follow NIP 96, there’s a standard way for clients to interact with nostr.build as a user’s preferred file storage provider for pictures and videos. It is easy for users to switch providers and clients can easily pick up the change. Efforts like NIP 96 makes file storage much more interoperable across the Nostr-verse without centralization.
Continuing to build solutions that allow users to have freedom AND a great experience will make Nostr the best game in town.
Don’t reinvent the wheel: use ISO when possible
I’m not sure if every developer knows this, but there’s an International Standards Organization (ISO) that has done a ton of work to promote standards of all kinds. The most common one developers have all used is the ISO datetime format. No matter what language or database you’re using, you’re likely representing timezone aware datetimes in the ISO format so that you can pass that data around safely.
ISO has codified standards for everything : how to store medical history, how to interact with USB, even stuff as obscure as how to represent data around holograms
Nostr is doing a lot of work to define structure to data that will be stored as Nostr events. We’re essentially inventing standards for social-related data of all kinds.
There are some things we’re building support for in Nostr, and I will encourage folks to see if there’s an ISO standard to follow first. It may save you a ton of time and brain power. On top of that, adopting ISO standards makes Nostr more compatible with future development that we can’t even imagine yet.
Invest in interoperability to support the cause
The Nostr-verse is under construction and the best time to plan for interoperability is before the building is done. Devs have done a great job retaining interoperability as a cambrian explosion of Nostr development has taken place. I hope we can continue to invest in interoperability because it may just be the thing that makes Nostr able to take on the giants of Big Tech when the time is right.
Until next time 🫡
If you want to see something highlighted, if we missed anything, or if you’re building something we didn’t post about, let us know. DMs welcome at nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk
Stay Classy, Nostr.
-
 @ df67f9a7:2d4fc200
2023-11-03 21:28:18
@ df67f9a7:2d4fc200
2023-11-03 21:28:18the following article is a repost from my recent issue #864 posted in the NIPs repository
Nostr is a protocol for events. Sending user generated content to a relay should be one kind of event (a
kind 1event) regardless of the structure of the content being sent. Different “types” of user generated content (EG:microblog-post,microblog-poll,encrypted-dm,blog-article,photoblog-post,calendar-event,exchange-question,exchange-answer, ect…) should not require different event kinds. Content type definitions (describing structured content with supported and required tags) should be maintained freely by implementers, not controlled by protocol. By opening up (decentralizing) the architecture for typed content, a potential source of NIP bloat will be “nipped” and the creativity of nostr designers and developers will be released to organically evolve novel solutions for real world content needs.The protocol for clients and relays to define and communicate about typed content (including supported and required tags for each type) should be a new NIP (see below for draft). New content types may also be defined by individual NIPs, but these (both existing and proposed NIPs) should only prescribe the “minimal” structure and processing (of supported and required tags) needed for compliance. In the wild, content type implementations should be defined and updated “ad hoc” between clients and relays.
==Free the “other stuff”!==
Use Case Example
- Client “NotX” implements three content types :
microblog-post,encrypted-dm, andmicroblog-poll. - The first is a stock NIP implementation. The second is a NIP content type with an added
locationtag. The last one is a custom content type being tested by the client. - These content types are defined locally by the client. Their
kindanddescriptionprovide the basis for easily identifying the client’s IRL use case. - Each content type definition also includes a list of supported and required
tagsEG: Themicroblog-pollcontent type haspoll-topic,poll-options, andclose-dateas required tags, andpublish-dateas a supported tag. - These content type definitions also describe the data expected and other properties for each tag.
- Upon WSS connection (during the “handshake” phase) the client sends it’s list of supported content types to the relay for comparison to it’s “local master” list of supported types. Any discrepancies in the list of
tagsfor a given content type are either accepted (as updates) or rejected by the relay. - Relays dictate for themselves which content types (and which tags for each type) they will accept from a given client.
- The connected relay A has been updated to work with the
locationtag forencrypted-dmcontent type, (it’s a common NIP mod these days) and will accept kind 1 events for this type. - Relay A rejects the novel
microblog-pollcontent type, but logs the client request for future updates. - The client connects to Relay B (who’s operator is working closely with the client developer) to support the novel content type. Relay B has been updated already, and will accept Kind 1 events for the
microblog-pollcontent type.
NIP Draft : Kind 1 User Generated Content Type
A NIP proposal (PR) will be forthcoming, depending on the discussions in this issue. Here are some possible highlights of what such a NIP would specify:
User Generated Content
User generated content refers to personally authored text or media content (sent as event data) which human users wish to “publish” to relays for consumption by other human users.
User generated content does NOT include: - events describing an action (EG: boost, like, vote, edit, or delete) that a user may take on already published content. - event data for user profile content - event data for reward or payment systems (EG: badges created or awarded, or zaps made to users or events). - event data that defines or configures a “grouping” of other users or events (EG: “lists”, or “communities”). - event data intended for consumption by an external API (EG: DVMs, ai bots, IOT, ect…) - event data that simply “adds function” to existing event kinds (EG: event encryption or replaceability).
NIPs Prescribing User Generated Content Types
NIPs should define new user generated content types as a
kind 1event (rather than a new event kind). Each content type will have atypeanddescriptionthat clearly illustrates its use case or intended “style” of app. NIPs will also suggest the minimaltags(content structure) and processing rules required for implementations to be NIP compliant.In addition NIPs may propose a new
tag(and rules for processing it) that may be added to any (or a specific) content type. (For example: “gift wrap” encryption and “replaceable event” may become tags for events, rather than event kinds themselves).Supported Content Types via Handshake
Client implementers will send a list of supported content types as part of a “handshake” document when web socket is first connected.
Format for content type list:
{... “content”:<array[object]>, ... }Format for defining a supported content type :
{ “kind” : 1, “type”:<string>, “description”:<string>, “tags”:<array[array]>, “legacy_kind”:<number> }Format for supported tags in a content type definition:
[<tag_id>,<default_value>,<data_type>,<is_required>]Kind 1 Content Typed Events
All user generated content should be a
kind 1“content typed” event. The content type will be communicated via thectag (as opposed to a new eventkindnumber). Structured content will be conveyed using standard tags in the event object, as defined in the handshake document for this content type.{ "id": <event_id>, "pubkey": <user_pubkey>, "created_at": <event_timestamp>, "kind": 1, "tags": [ [“c”, <content_type>], [<tag>,<tag_value>], ... ], "content": <note_content>, "sig": <event_sig> }Update Path for Implementers
For backwards compatibility with legacy clients and relays, implementers should deprecate but not remove legacy “event kind content” event handling. As the implementation code is updated to support “content typed events”, the “supported types” list in the “handshake” document will reference the
legacy_kindkind number that the legacy client or relay will be expecting. Using the info, implementors can send the event in the legacy “event kind content” format as needed. (If nostr supports log output via event tags, this can be used as well to inform of possible updates.)Related NIPs & Issues
These NIPs will Need Updating
(to redefine prescribed event kinds as Kind 1 content types, freeing clients and relays to update them as needed “in the wild” )
NIP-4 : Encrypted Direct Message NIP-18 : Reposts NIP-23 : Long form Content NIP-28 : Kind-42 : Channel Message NIP-52 : calendar events NIP-72 : community post NIP-99 : classified listing
These NIPs play well with content typed events
(by defining tags for events rather than new event kinds.)
NIP-14 : Subject Tags in Text Events NIP-32 : Labeling NIP-36 : Sensitive Content NIP-48 : Proxy Tags NIP-72 : community post
These PRs will need tweaking :
848 using multiple independent kinds for community scoped events
814 Internet on things on nostr (nip 107)
817 IOT sensors and intent
811 decentralized web hosting
787 draft of nip-34 : decentralized wikis
These Issues will be closer to resolving:
162 Decentralizing the NIPs registry.
394 add content-type tag for encrypted direct messages.
520 Different nostr: schemes for different types of apps/nips
583 nip-23 used for private journals
Conclusion
This architecture of “customizable content types” is not new. The best CMSs for over a decade have relied on this to allow website administrators to create new types of content (“pages”) with custom elements (“fields”) to suit their business needs. Indeed, some go even further and abstract other “entities” (not limited to user generated content) to use this modular “field-able” architecture.
Nostr can take this modular content architecture to the next level, by embedding it into a protocol for ANY developer, rather than a single code base for some. By defining a “means” of communicating content between clients and relays, rather than the structure of what “should be” communicated, nostr NIPs can become the open and long lasting protocol needed for decentralized social media.
- Client “NotX” implements three content types :
-
 @ 3c984938:2ec11289
2024-03-21 11:01:51
@ 3c984938:2ec11289
2024-03-21 11:01:51The voice asked Whitey to concrete on what gift she would like.
 Whitey thought carefully of what kind of gift but did not know how to express it so she closed her eyes. Memories of her life in the village flashed before her. She recalled a distant meomery of when she was a kitten. The first time she licked an injured chipmunk after it fell from a tree. She felt happiness and purpose when she helped others.
Whitey thought carefully of what kind of gift but did not know how to express it so she closed her eyes. Memories of her life in the village flashed before her. She recalled a distant meomery of when she was a kitten. The first time she licked an injured chipmunk after it fell from a tree. She felt happiness and purpose when she helped others. The voice clarifies " I understand, how very noble", and asks another question. "Why do you want to help others when you were mistreated?" asking curiously.
 Whitey with earnest heart replied back
Whitey with earnest heart replied back "I'm sorry, but I don't want to be a bully. That's goes against my nature. I do not want to be superior to anyone or anything. If possible I should like to help everyone. I had happiness when I helped others and purpose, even if it was short lived. I do not want to hold resentment towards the children despite the horrible acts done to me. This is a beautiful world, I only want to make it better. I am grateful to be alive."
"Understood", the voice from the spring boomed.
 Whitey felt a strange sensation in her forehead. She looked into the spring to look into her reflection then reached up to touch something hard and pointed. To her amazement, a shimmering unicorn horn had appeared on her forehead. She had never seen anything like this before, and she didn't know what it meant.
Whitey felt a strange sensation in her forehead. She looked into the spring to look into her reflection then reached up to touch something hard and pointed. To her amazement, a shimmering unicorn horn had appeared on her forehead. She had never seen anything like this before, and she didn't know what it meant. "This horn will give you the ability to heal injured animals and help them in times of need. Now go Caticorn", The voice fading away in her mind.
With her newfound power she was determined to make a difference now more then ever.
"Thank you", she said in her mind to the voice. Not quite sure if it was received or or not.
Whitey met plenty of injured animals as she journeyed from forest to forest. With her new horn and ability to heal she eased others pain. Tales of Whitey ability spread and animals from all over the realm came to seeking help from the caticorn.

Whitey was happy to oblige and had made a difference to the animals of the forest. She possessed a rare gift and wanted to do nothing more then to serve others.
The images are Ai, but the story is mine.
you can also subscribe to my paragraph.xyz/@onigirl
-
 @ 124b23f2:02455947
2023-10-23 14:54:56
@ 124b23f2:02455947
2023-10-23 14:54:56Im my previous post, I explained how to use your getalby ln address to receive zaps directly to your LND node. Similarly, there is an additional option that one can utilize to receive zaps directly to your lightning node: lnaddress.com.
Lnaddress.com is a federated lightning address server that you can use to create a custom ln address. Unlike using getalby, lnaddress.com can be used with any lightning implementation (not just LND). For the purposes of this write-up, I am going to use LNBits to connect an lnaddress.com lightning address with my node. And as will be the case with most of my write-ups, I am going to be using @npub126ntw5mnermmj0znhjhgdk8lh2af72sm8qfzq48umdlnhaj9kuns3le9ll OS, so users of that OS will likely find this write-up most useful, but I'm sure people using other node interfaces can infer how to complete this set up as well.
With that said, let's dive into the step-by-step on how to create your own custom ln address with lnaddress.com and set it up to receive zaps directly to your lightning node:
*Users should have lnbits set up with their lightning node before proceeding.
-
Go to lnaddress.com. Input your desired username, select 'Node Backend Type' = LNBits, and if necessary check the box 'This is a new lightning address'. Keep this page open in one tab as we will be returning to it to input info.
-
From your Start9 OS services page, go to your LNBits service. Open the 'Properties' page, and in a new tab, open the (Tor) Superuser Account. Page will look like this:
http://usri6wfilambri77iwnapyyme43la4v2hgecoismowluriekrhuvxnid.onion/content/images/2023/10/pic1-1.png
From this LNbits page, you can choose to 'add a new wallet' and use that wallet instead of your superuser account. That is up to you but the steps will be the same.
- Now, we need to grab the info needed for the 'Host Protocol + IP or Domain + Port' field on the lnaddress.com page. On the lnbits page, expand the 'Api Docs' field, and the 'Get Wallet Details' field found on the right hand side menu. In this 'Get Wallet Details' section, you will want to copy some of the URL found in the 'curl example' section. Copy 'http://xxxxxx.onion' (don't copy any more!), and paste this into the 'Host Protocol + IP or Domain + Port' field found on the lnaddress.com page.
http://usri6wfilambri77iwnapyyme43la4v2hgecoismowluriekrhuvxnid.onion/content/images/2023/10/pic2-1.png
-
Next, we need to grab the key for your lnbits wallet. From the lnbits page, expand the API docs section found on the right hand side menu. Copy the 'Invoice/read key' (make sure to use the invoice/read key and not your Admin key), and paste it into the key field found on the lnaddress.com page. Upon pasting in that last piece of info, click 'submit' at the bottom of the page.
-
If all info was input correctly, your connection will be successful. If successful, you will be brought to a page that looks like this:
http://usri6wfilambri77iwnapyyme43la4v2hgecoismowluriekrhuvxnid.onion/content/images/2023/10/pic3-1.png
You will want to save this secret PIN in case you need to update info in your ln address. You'll also find a test lightning invoice of 1 sat. Using a wallet not connected to the node we connected to our new ln address, you can test the ln address out by paying the 1 sat test invoice.
Users of Start9 OS might find the following info particularly useful: This ln address via lnaddress.com comes with a couple advantages aside from self-custodial zap receiving:
- One, you can have a custom ln address username to go with your nym or nostr username. Users of Start9 may be familiar with the ln address one can generate in the btcpay server service. This ln address is not customizable.
- Two, if you are running a tor only lightning node, you will be able to receive zaps from both tor and clear net lightning nodes. Users of Start9 may be familiar with the ln address one can generate in the btcpay server service. This ln address can only receive zaps from other tor nodes and can't receive zaps from clear net nodes.
That is it, you should now be all set up with your new ln address hosted on lnaddress.com, and you should be all ready to receive zaps or lightning payments of any kind :)
-
-
 @ a012dc82:6458a70d
2024-03-21 02:04:39
@ a012dc82:6458a70d
2024-03-21 02:04:39Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
Bitcoin forks are splits that occur in the transaction chain as a result of various user perspectives on the history of previous transactions. These splits result in the creation of various copies of the Bitcoin currency and are a logical consequence of the nature of the blockchain system, which functions decentralized and without the oversight of a central authority.
Bitcoin Forks: Definition and Example
The idea of forks as well as the technology that is behind them is incredibly complicated. Nonetheless, the simplest way to understand what Bitcoin forks do is to understand that they provide Bitcoin with a new set of guidelines to adhere to. The introduction of a new rule, often known as a fork, gives the users mining a specific Bitcoin blockchain the option of adhering to one set of rules rather than another. This choice is analogous to coming to a split in the road.
Different interpretations of the history of transactions may give birth to these forks, which can occur when there are delays in the system. As Bitcoin became more popular, the blockchain technology that it was based on slowed down. This made the whole system less stable and made transaction fees more expensive.
As a result of this slowness, Bitcoin needed to develop a solution that could grow as the number of users who purchased and sold goods increased. The forks were used at this point in the process.
Within the Bitcoin platform, forks provide a distinct development structure and the opportunity for experimentation, all without affecting the integrity of the original product. The initial Bitcoin was built on blocks that were 1 megabyte in size, which proved to be a limitation as the cryptocurrency expanded and gained more widespread use. These forks have the potential to be built on bigger blocks, which would then result in the creation of a brand-new currency.
Note
At this moment, buying and selling either the original Bitcoin or any of its forks is a highly speculative activity, and you run the risk of losing a significant amount of money in a short amount of time. Spend a little more than you can comfortably afford to replace.
How Do Bitcoin Forks Work?
Two different kinds of forks may occur in Bitcoin: "soft forks" and "hard forks." This is how the system operates.
Soft Forks
Instead of altering the final result, a Bitcoin soft fork is just a modification to the Bitcoin protocol itself. The most significant distinction between a soft fork and a hard fork is that the former is backwards-compatible, while the latter is not. Backward-compatibility refers to the fact that the new protocol will be recognized by the old nodes that are already part of the system. This also indicates that a new product will not be introduced.
Hard Forks
Bitcoin hard forks are new versions of the cryptocurrency that are fully separate from the original Bitcoin code. After a hard fork, there are no longer any transactions or communications possible between the two versions of Bitcoin. They are no longer connected to one another, and this separation is irreversible.
Note
If you are still using an earlier version of the Bitcoin program, you will not be able to communicate with users who have updated to a more recent version of the software, and vice versa. This will essentially result in the creation of two distinct forms of money. However, the currencies will not be compatible with one another.
Forks may be compared to organizational splits, in which one section of a corporation heads in one direction while another part of the company heads in the other direction. This is precisely what took place in the cases of Bitcoin, Bitcoin Cash, and Bitcoin Gold.
These are all distinct cryptocurrencies that belong to the Bitcoin family, and they all function in their own right according to their own sets of guidelines. All of these things are still cryptocurrencies, but none of them are exactly the same as Bitcoin.
Types of Major Bitcoin Hard Forks
Bitcoin Cash and Gold are the two biggest hard forks so far, but there have been others.
The Bitcoin Cash Hard Fork
On August 1, 2017, Bitcoin underwent a hard split, which resulted in the creation of Bitcoin Cash. It was conceived as a solution to Bitcoin's issues, namely latency and delayed transactions. To achieve this goal, it employs blocks that are 8 megabytes in size rather than the 1 megabyte blocks that were utilized by the original Bitcoin. This makes it simpler to grow as more users engage with the service. 1
Note
As more users join the system, the bigger blocks will be able to store more data and speed up the buying and selling process.
The Bitcoin Gold Hard Fork
A separate hard fork known as Bitcoin Gold took place in October of 2017, intending to simplify and standardize the mining process for Bitcoin such that it needs just the most fundamental tools. It is mined on regular graphics processing units instead of "ASICs," or application-specific integrated circuits, which are expensive and only used by a few big players.
The goal was to strengthen the Bitcoin concept's built-in qualities of independence and lack of a central authority.
Other Bitcoin Hard Forks
There has been a flurry of additional hard forks and experimentation inside the Bitcoin system in addition to these two primary hard forks that have occurred. The following is a list of some of the other hard forks and the time when they first appeared.
-
November 2017 - November 2017 - Bitcoin Diamond: November 2017
-
December 2017: December 2017: Super Bitcoin: December 2017
-
January 2018: Bitcoin Atom
-
November 2017: Bitcore
-
December 2017: Bitcoin God
-
January 2018: Bitcoin Private
-
September 2018: Bitcoin Zeo
-
Bitcoin Post-Quantum: December 2018
Key Takeaways
-
Bitcoin forks are new kinds of Bitcoin that are created when two or more parties examine the blockchain's transaction history independently.
-
Hard forks make bigger changes to the blockchain and create new forms of money based on the blockchain. Soft forks, on the other hand, don't lead to the creation of a new cryptocurrency.
-
The prices of the various Bitcoin hard forks are dramatically different, and each one seeks to do something unique. Some of them have done better than the original Bitcoin, but not all of them have been able to maintain their value.
Conclusion
In the context of Bitcoin, these three hard forks are only the tip of the proverbial iceberg. Bitcoin Cash, on the other hand, is still quite popular today, although Bitcoin Gold and, in particular, Bitcoin Diamond, have both seen their prices and user bases decline over the course of the last several years. There are currently over one hundred separate ongoing hard forks, each seeking to address a different issue or improve the way the Bitcoin network operates.
FAQ
What will happen if the Bitcoin blockchain forks? A Bitcoin hard fork is a break in the original blockchain that paves the way for the creation of a new platform, which often comes with its own native cryptocurrency. A change that is made to an existing blockchain is referred to as a "soft fork. In other cases, a coin's code is based on Bitcoin's code, but it also makes a brand-new blockchain from scratch at the same time.
How exactly do forks on the blockchain function? In the context of blockchain, a fork is a term that refers to the occurrence of a technical phenomenon in which a blockchain experiences a split into two distinct branches. The transaction histories of these two branches were combined up to the point when they were broken apart. After that point, they separate and go their own ways, each on their own autonomous route.
Does Bitcoin split into Dogecoin? In the space of three hours, Markus created Dogecoin before Palmer had even had a chance to reply. He did this by forking Lucky Coin, which itself is a fork of Bitcoin. To put it simply, Markus built Dogecoin by copying essential sections of the source code for Bitcoin, Litecoin, and Lucky Coin and then modifying the code before releasing it to the public and making the project active.
How many times has Bitcoin been split into two different versions? Since its first release, Bitcoin has undergone over 100 separate hard forks. A blockchain may experience a fork to address an issue or make operational improvements. In stages, the size of a Bitcoin Cash block was extended from 1 megabyte (MB) to 8 MB, and subsequently to 32 MB. The proof of work algorithm was modified when Bitcoin Gold was released.
That's all for today, see ya tomorrow
If you want more, be sure to follow us on :
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 8947a945:9bfcf626
2023-10-23 08:13:39
@ 8947a945:9bfcf626
2023-10-23 08:13:39จงตระหนักรู้คุณค่าของตัวเอง เพชรไม่ได้เปล่งประกายเจิสจรัสจากสุดปลายถ้ำ

2023’s Wake up call
แรงบันดาลใจที่ทำให้ผมตัดสินใจเอาเรื่องนี้มาเล่าบน #ทุ่งม่วง เกิดจากเมื่อต้นปี 2023 ผมได้รับสัญญาณเตือนภัยจากที่ทำงานแห่งหนึ่ง (Wake up call) ปลุกให้ตื่นขึ้นจากภวังค์ ตระหนักรู้ถึงความเป็นจริงบางอย่าง ว่างาน part time ที่กำลังทำเริ่มมีสัญญาณความไม่มั่นคงเกิดขึ้นทีละเล็กทีละน้อย มีความสุ่มเสี่ยงที่จะถูกขอให้งดคลินิคไม่ต้องมาออกตรวจ (ภาษาสุภาพของการเลิกจ้างหมอ)
สำหรับหมอที่ทำงานหลายโรงพยาบาล จะเข้าใจสถานะ”หมอ part time” ของตนเองดีว่า สามารถถูกถอดเวรออกได้ทุกเมื่อ หากทางโรงพยาบาลมีความจำเป็น
เมื่อเกิดเหตุการณ์นี้ ผมติดต่อโรงพยาบาลใกล้บ้านเป็นแผนสำรองเอาไว้ ที่นี่ขาดอัตรากำลังแพทย์พอดี ผมเลยสามารถเริ่มงานได้ทันที ทำให้รายได้ไม่กระทบกระเทือนต่อครอบครัว แต่สิ่งที่ต้องพบเจอก็คือโรงพยาบาลแห่งใหม่นี้ งานหนักมาก หนักถึงขั้นกระอักเลือด เต็มไปด้วยความเสี่ยงที่ยังไม่มีระบบการบริหารจัดการที่มีประสิทธิภาพ ผมทำงานที่นี่ไประยะนึง เมื่อมาดูสลิปค่าตอบแทน พบว่าผมถูกจัดกลุ่มให้อยู่ในกลุ่มแพทย์เวชปฏิบัติทั่วไป (General practitioner หรือ GP คือหมอทั่วไปที่ยังไม่ได้เรียนต่อเฉพาะทาง)
แพทย์เฉพาะทาง ตามกลไกจะได้ค่าตอบแทนสูงกว่าแพทย์ GP ถึง 70 - 80%
ผมนำเรื่องนี้ขึ้นปรึกษาหน่วยงานที่เกี่ยวข้อง ได้รับการดำเนินแก้ไขอย่างเร่งด่วนเพราะความเข้าใจผิด และผมก็ได้ค่าตอบแทนสมน้ำสมเนื้อตามมาทีหลัง แต่ด้วยเนื้องานที่หนักมาก เหนื่อยมาก เลิกงานเที่ยงคืน วันอื่นๆทำงานอีก ทำงาน 7 วันต่อสัปดาห์ ร่างกายเริ่มส่งสัญญาณเตือนบางอย่างว่ากำลัง overheat เครื่องกำลังจะไหม้ในอีกไม่ช้า ถ้ายังคงลากเลือดขนาดนี้ แต่เวลานั้นผมทำเพื่อครอบครัวอย่างเดียว เลยไม่ได้ลังเล เดินหน้าต่อ
จุดเปลี่ยนมันอยู่ตรงนี้ครับ ผมมีอาจารย์แพทย์ที่เคารพมากท่านหนึ่ง อาจารย์เขารับรู้เรื่องผมมาตลอด เมื่อทราบว่าผมทำงานหักโหม แลกกับความเสี่ยงหลายมิติ จึงมีโอกาสได้นั่งคุยกัน อาจารย์ท่านนี้เล่าเรื่องสั้นเรื่องหนึ่งให้ฟัง และทิ้งท้ายเอาไว้ให้คิดว่า
ทรัพยากรที่มีค่าที่สุดคือเวลา จงเอาตัวผมไปอยู่ในที่ที่เห็นคุณค่าในตัวผมให้ได้ ถ้าผมทำได้ เวลาของผมมีจะสร้างมูลค่าได้มหาศาลกว่านี้
การสนทนาจบลงด้วยความรู้สึกพบแสงสว่างที่ปลายอุโมงค์ หลังจากนั้นไม่กี่สัปดาห์ผมตัดสินใจ ของดคลินิคจากโรงพยาบาลแห่งนั้นทันที และเป็นความโชคดี เพราะที่ทำงานประจำกำลังขาดแคลนหมอ ผมเลยได้ตารางออกตรวจเพิ่ม รายได้มั่นคงมากกว่าเดิม
ส่วนโรงพยาบาลที่กระตุ้น wake up call ผมตอนแรก เล็งเห็นความสำคัญของทักษะเฉพาะทางของผมที่ขาดไม่ได้และจำเป็นมากต่อสถานการณ์ปัจจุบัน จึงขอให้ผมอยู่ช่วยต่อและเพิ่มค่าตอบแทนเพิ่มจากเดิมอีกเกือบ 100%
ทักษะการเขียนบทความ ที่เกือบจะถูกปิดผนึกไปตลอดกาล เพราะเอาตัวเองไปอยู่ไม่ถูกที่
 สิ่งที่ผมสนใจอยู่เป็นทุนเดิมคือการเล่าเรื่องแฝงแง่คิดจากประสบการณ์ของตัวเองให้กับผู้อื่นฟัง ตัวผมเองเป็นคนพูดไม่เก่ง บุคคลิกเก็บตัว Introvert ใช้เวลาส่วนใหญ่อยู่กับความคิดตัวเอง แล้วจดบันทึกข้อคิดที่คิดได้เอาไว้ ตั้งใจว่าถ้ามีเวลาพอ จะเอาสิ่งที่รีดออกมาจากสมอง มาขยายทำเป็นบทความ เพื่อเอาไว้ให้คนอื่นอ่าน เผื่อว่ามันจะมีประโยชน์ไม่มากก็น้อย ผมตระเวนหาเวบไซต์สำหรับนักเขียนไปเรื่อย แต่ก็หาที่ที่ถูกใจไม่ได้ ผมก็เลย”จำใจ” เขียนลงไปในเฟสบุค และ แพลตฟอร์มนักเขียนแห่งหนึ่งของประเทศไทย
สิ่งที่ผมสนใจอยู่เป็นทุนเดิมคือการเล่าเรื่องแฝงแง่คิดจากประสบการณ์ของตัวเองให้กับผู้อื่นฟัง ตัวผมเองเป็นคนพูดไม่เก่ง บุคคลิกเก็บตัว Introvert ใช้เวลาส่วนใหญ่อยู่กับความคิดตัวเอง แล้วจดบันทึกข้อคิดที่คิดได้เอาไว้ ตั้งใจว่าถ้ามีเวลาพอ จะเอาสิ่งที่รีดออกมาจากสมอง มาขยายทำเป็นบทความ เพื่อเอาไว้ให้คนอื่นอ่าน เผื่อว่ามันจะมีประโยชน์ไม่มากก็น้อย ผมตระเวนหาเวบไซต์สำหรับนักเขียนไปเรื่อย แต่ก็หาที่ที่ถูกใจไม่ได้ ผมก็เลย”จำใจ” เขียนลงไปในเฟสบุค และ แพลตฟอร์มนักเขียนแห่งหนึ่งของประเทศไทยในช่วงแรกผมลองเขียนบทความลงเฟสบุค ผลลัพธ์เป็นไปตามคาดครับว่าไม่เป็นที่สนใจ ประเมินผลหยาบๆจากยอดกดไลค์ คอมเม้นท์ และการแชร์ เงียบเหมือนป่าช้าเลย นานๆจะมีคนมากดไลค์ซักที แต่ก็เป็นที่รู้ๆกันครับว่าการกดไลค์ มันอาจจะเกิดจากคนอื่นเปิดมาเจอโพสต์ของผม แล้วจะปัดให้มันพ้นๆไป “ไอ้บ้านี่มันบ่นอะไรของมัน” แต่นิ้วโป้งดันไปจิ้มโดนปุ่มไลค์พอดี ในเมื่อจิ้มไปโดนแล้วก็แล้วกันไปก็เป็นไปได้
เวลาผ่านไปมันเหมือนผมขึ้นไปพูดบนเวทีที่ไม่มีผู้ฟัง หรือ ผู้ฟังหลับทั้งห้อง บทความต่างๆข้อคิดต่างๆที่ผมตั้งใจเรียบเรียงมันส่งไปไม่ถึงผู้คน มันดูไร้ค่า จบด้วยการนั่งคุยกับตัวเองเหมือนเป็นคนไข้จิตเวช เหตุการณ์ทั้งหมดนี้เกือบนำพาผมไปสู่ข้อสรุปที่ว่า “ผมเองคงเขียนไม่เก่ง” หรือ “เขียนไม่ได้แย่หรอก แต่ไม่ได้โปรโมท เลยไม่มีใครมาพบเจอ” หรือไม่ก็ถูกทั้งสองข้อ บางครั้งอยากจะล้มเลิกการเขียนไปเลยก็มีครับ
ช่วงมกราคมปี 2023 เวบไซต์ Right shift เริ่มเป็นที่รู้จัก ฟังคอนเซปจากอาจารย์พิริยะแล้วชอบมาก
เวบไซต์ Right shift ตั้งใจเป็นแหล่งรวบรวมข้อมูลสำหรับผู้ที่สนใจอยากศึกษาบิตคอยน์ ให้สามารถเข้ามาศึกษาได้โดยไม่มีค่าใช้จ่าย แถมยังเชิญชวนให้ผู้ที่อยากเขียนบทความที่เป็นประโยชน์ให้แก่ผู้อื่น ใครสนใจสามารถส่งบทความเข้ามาได้ ถ้าหากบทความไหนมีแวว จะมีทีมบก.ติดต่อกลับไปเพื่อทำงานร่วมกันในการขัดเกล้า แก้ไขสำนวนบางจุดให้ดียิ่งขึ้น
พอรู้มาถึงตอนนี้มันนเหมือนมีอะไรมาเคาะกะโหลกดังๆ จนความรู้สึก “ปังปุริเย่ เฮ้ ร้องว้าว” มันผุดขึ้นมา แต่มันก็มาพร้อมกับความไม่มั่นใจในตัวเองนั่นแหละครับ ความขัดแย้งเต็มไปหมดว่า “จะเขียนหรือไม่เขียนดี” “เอาจริงอ่ะ? จะเขียนบทความส่งไปจริงๆเหรอ?” “ม_ึง ไม่ใช่นักเขียนมืออาชีพนะ คนที่เขาส่งบทความไปมีแต่เทพๆทั้งนั้น จะเอาอะไรไปสู้กับเขา” และเสียงอื่นๆในหัวอีกมากมาย
แต่สุดท้ายผมทลาย “Comfort zone” ได้ ด้วยกำลังใจเล็กๆน้อยๆจากภรรยาครับ ภรรยาผมบอกด้วยคำสั้นๆว่า “ก็ลองดูสิ สกิลการเขียนเล่าเรื่องของเธอก็ไม่ขี้เหร่นะ” ผมเลยลองทำดู และนี่คือสิ่งที่เกิดขึ้น
บอกได้ว่าเป็นครั้งแรกที่ผมได้ถูกฝึกการเขียนบทความโดย "ใครก็ไม่รู้” ผมรู้แค่ว่าเป็นทีมบก.ของ Right shift เมื่อทำงานร่วมกันไปเรื่อยๆ ทีมบก.ทุ่มเทในการช่วยแก้ไขช่วยตรวจสอบบทความของผมมากๆ จนผมสังเกตุเห็นได้
ใครเคยใช้ Google document ร่วมแก้ไขบทความด้วยกันมากกว่าหนึ่งคนคงจะรู้ดีนะครับว่า เวลาที่มีการแก้ไขข้อความมันจะมีเมล์แจ้งเตือนไปหาทุกคนที่เข้ามาร่วมแก้ไขเอกสารทั้งหมด บางคืนที่ผมนอนหลับไม่สนิท ตีสองตีสามตื่นมาเข้าห้องน้ำ ผมยังเห็นเมล์อัพเดทการแก้ไขบทความจากทีมงาน right shift เด้งๆอยู่เลย
จนสุดท้ายงานเขียนผมก็ได้รับการเผยแพร่บนเวบไซต์ Right shift

ใครยังไม่เคยอ่านกดตรงนี้ได้เลยครับ
หลังจากนั้นผมรับรู้ถึงทักษะนี้มากขึ้น เลยตั้งใจว่าต้องฝึกให้เก่งขึ้นดีขึ้นในทุกๆบทความที่ผมเขียน ผมอ่านหนังสือเยอะขึ้น ศึกษาสำนวนการเขียนจากนักเขียนรวมถึงนักแปลท่านอื่นๆ เพื่อดูตัวอย่างสำนวน ลีลาสไตล์การใช้คำ เอามาประยุกต์ใช้กับงานเขียนของตัวเอง
ไม่รู้ตัวหรอกครับ ว่าทักษะนี้มันโดนฝึก โดนขัดเกลาตั้งแต่เมื่อไหร่ แต่ตอนนี้ตระหนักรู้ถึงการที่มันมีตัวตนอยู่ภายในตัวผมแล้ว ผมก็จะลับคมมันไปเรื่อยๆ หลายครั้งตอนที่ผมเขียนบทความอยู่ผมลืมเวลา ลืมหิว ลืมง่วง ลืมเหนื่อยไปเลย ถ้าเปรียบเทียบกับนักกีฬา คาดว่าสภาวะตอนนั้นคงเป็นสภาวะหนึ่งของการเข้าสมาธิแบบ “Into the zone”
เรื่องสั้นที่อาจารย์ของผมเล่าให้ฟัง มอบบทเรียนชีวิตที่มีค่า อยู่ต่อจากนี้ครับ

พ่อคุยกับลูกสาว “ยินดีด้วยที่จบการศึกษา พ่อซื้อรถคันนี้ไว้ให้ลูกซักพักแล้ว ตอนนี้พ่อจะให้ลูกนะ แต่ก่อนที่พ่อจะให้ พ่ออยากให้ลูกนำไปที่ร้านรับซื้อ-ขายรถในตัวเมือง แล้วมาบอกพ่อด้วยว่าเขาให้ราคาเท่าไหร่”
ลูกสาวทำตาม กลับมาหาพ่อ บอกว่า “ร้านนี้เขาให้ราคา $10,000 เพราะรถเก่า” พ่อบอกลูกว่า “โอเคลูก ทีนี้พ่ออยากให้หนูเอารถไปที่โรงรับจำนำ ลองดูซิว่าเขาจะตีราคารถคันนี้เท่าไหร่”
ลูกสาวทำตาม แล้วกลับมาบอกพ่อว่า “โรงรับจำนำให้ราคา $1,000 เพราะรถเก่ามาก ดูแล้วต้องซ่อมอีกหลายรายการ ”
ครั้งนี้พ่อบอกลูกสาวให้นำรถนี้ไปยังชมรมคนรักรถที่มีผู้เชี่ยวชาญ และนำรถให้พวกเขาดู
ลูกสาวทำตาม ขับรถนี้ไปที่ชมรมที่ว่า หลังจากนั้นไม่นานลูกสาวกลับมาบอกพ่อด้วยน้ำเสียงตื่นเต้นว่า “บางคนเสนอราคา $100,000 เพราะเป็นรถหายาก และสภาพดีมาก”

ผู้เป็นพ่อยิ้มให้กับลูกสาว เหมือนว่ารู้อยู่แล้วว่าจะเกิดอะไรขึ้น ด้วยความสงสัยลูกสาวจึงถามพ่อว่า
“ในเมื่อพ่อรู้อยู่แล้วว่าร้านไหนจะให้ราคาสูง ทำไมพ่อไม่ให้หนูไปที่ชมรมคนรักรถตั้งแต่แรกล่ะ”
พ่อบอกลูกสาวว่า “นี่แหละบทเรียนชีวิตที่สำคัญบทหนึ่งที่พ่ออยากมอบให้แก่ลูก พ่ออยากให้ลูกรู้ไว้ว่า ลูกจะไม่มีค่าใดๆเลยถ้าอยู่ผิดที่ ที่ที่คนอื่นมองไม่เห็นเรา ไม่ต้องเสียเวลาไปโกรธโมโหไม่พอใจหรอกนะ สิ่งที่ลูกต้องทำก็คือเดินออกจากที่นั่น ออกไปจากสังคมและสถานที่ที่ไม่เห็นค่าในตัวลูก ค้นหาที่สถานที่ของลูกให้เจอ ถ้าลูกไม่ลองลงมือทำด้วยตัวเอง ลูกก็จะไม่ได้เรียนรู้อะไรเลย”

ข้อคิดที่อยากจะแบ่งปันกับทุกท่านที่อ่านมาจนจบ
บทความนี้มีความพิเศษกว่าบทความอื่นๆ ท้ายบทความของผมผมจะมาชวนคุยและสรุปข้อคิดที่เป็นประโยชน์ให้แก่เพื่อนๆพี่ๆทุกท่านที่อ่านมาจนจบ แต่สำหรับบทความนี้ข้อคิดที่ผมอยากให้ ถูกสรุปขมวดไว้ทั้งหมดแล้วในประโยคที่พ่อบอกลูกสาว
อย่าลืมต่อสู้ ฝ่าฟันอุปสรรค ค้นหาสถานที่ของตัวเราเองให้พบนะครับ เมื่อค้นพบทักษะในตัวแล้ว อย่าให้ถูกปิดผนึกไว้ เพียงเพราะอยู่ผิดที่ ลงมือฝึกฝนพัฒนามันไปเรื่อยๆ เราจะดีขึ้นในทุกๆวันครับ
-
 @ b2a8fdbc:dcab1f03
2023-10-21 09:32:04
@ b2a8fdbc:dcab1f03
2023-10-21 09:32:04Node คืออะไร
Node (โหนด) คือ คอมพิวเตอร์หรืออุปกรณ์ใดๆ ที่เชื่อมต่อในเครือข่ายบล็อกเชน เครือข่ายสกุลเงินดิจิทัล โดยทุกๆ โหนดจะเชื่อมต่อกัน เพื่อที่จะสื่อสารและช่วยดูแล ตรวจสอบความถูกต้อง และความปลอดภัยให้ Blockchain
Node มีความสำคัญกับระบบบล็อกเชน เนื่องจาก Blockchain คือ ระบบแบบกระจายศูนย์ (Decentralization) ไม่ได้มีตัวกลาง จึงต้องพึ่งพาระบบ Peer-to-Peer (P2P) ที่ทำให้โหนดต้องเข้ามาเชื่อมต่อกันเพื่อสื่อสารกัน เมื่อบล็อกเชนถูกเพิ่มข้อมูลเข้ามา โหนดจะเชื่อมต่อสื่อสารไปยังโหนดอื่นๆ ภายในเครือข่ายและส่งข้อมูลเกี่ยวกับธุรกรรมและ Block ใหม่ที่เข้ามานั่นเอง
บิตคอยน์โหนด (Bitcoin Node) คืออะไร? “บิตคอยน์โหนด” (Bitcoin Node) คือ เครื่องคอมพิวเตอร์ หรือเครื่องเซิร์ฟเวอร์ใด ๆ ก็ตามที่ “เชื่อมต่อกับระบบเน็ตเวิร์กของบิตคอยน์” มีการเก็บข้อมูลประวัติธุรกรรมที่ได้รับการยืนยันแล้วในอดีต และมีหน้าที่ในการตรวจสอบธุรกรรมที่กำลังเกิดขึ้น ณ ปัจจุบันว่ามีความถูกต้องเป็นไปตามกฎเกณฑ์ที่กำหนดไว้ทุกประการ (Validate Transactions)
หน้าที่ของโหนด (Node) คือ การยืนยันว่าผู้ทำธุรกรรมทุกคน “มีสิทธิ์” ในการทำธุรกรรมต่าง ๆ ที่กล่าวมาได้อย่างถูกต้อง เนื่องจากเงินทุกบาทนั้นมีที่มาที่ไปชัดเจน และสุดท้ายคือการบันทึกประวัติการทำธุรกรรมของทุกคนไว้ในระบบ เพื่อไว้ใช้อ้างอิงในการทำธุรกรรมต่อไปในอนาคต
บิตคอยน์ถูกออกแบบมาเพื่อใช้ในการทำธุรกรรมได้ทั่วโลก ไม่ใช่เพียงสำหรับคนกลุ่มเล็ก ๆ เท่านั้น บิตคอยน์จึงตกเป็นเป้าในการถูกโจมตีได้ง่าย ดังนั้นการที่คุณร่วมเป็นส่วนหนึ่งของบิตคอยน์โหนด จะช่วยปกป้องเครือข่ายบิตคอยน์จากการโดนโจมตี ช่วยป้องกันการทำธุรกรรมที่ไม่ถูกต้องได้ และช่วยให้บิตคอยน์ก้าวไปสู่ระบบที่ปราศจากศูนย์กลางอย่างแท้จริงต่อไปในอนาคต
Raspberry Pi คืออะไร
Raspberry Pi (ราสเบอร์รี่พาย) คือ ‘Single Board Computer’ (SBC) เป็นคอมพิวเตอร์จิ๋วขนาดเท่าบัตรเครดิต ที่สามารถต่อเข้ากับจอคอมพิวเตอร์หรือทีวี และใช้แป้นพิมพ์เมาส์ เป็นอุปกรณ์ขนาดเล็กที่มีความสามารถที่ช่วยให้ผู้คนทุกวัยสามารถ เรียนรู้วิธีเขียนด้วย ภาษาคอมพิวเตอร์ (Programming Language) อย่าง Scratch, HTML, CSS และภาษา Python
Raspberry Pi (ราสเบอร์รี่พาย) ถูกสร้างมาเพื่อใช้สำหรับการเรียนรู้และพัฒนาโปรแกรมหรือเขียนโค้ด และงานที่เหมาะสมไม่ใช่งานประมวลผลอย่างหนักหน่วง ข้อดีอีกอย่างก็คือเป็นอุปกรณ์ที่กินไฟแค่ 5V และนั่นเป็นสาเหตุที่ให้ Raspberry Pi (ราสเบอร์รี่พาย) ถูกนำไปใช้ เว็บเซิร์ฟเวอร์ อุปกรณ์ควบคุมฮาร์ดแวร์ และ อุปกรณ์ Internet of Things ( IoTs ) รวมไปถึงด้านอุตสาหกรรม ซึ่งขนาดของบอร์ดที่เล็กเท่าบัตรเครดิตและนำไปใส่เคส (Case) ก็สามารถไปติดตั้งในพื้นที่เล็กๆที่ไหนก็ได้
เริ่มตื่นเต้นแล้วละสิ เรามาเริ่มกันเลยดีกว่า
จัดเตรียมอุปกรณ์
- Raspberry Pi แนะนำให้เลือกซื้อเป็นชุดที่มี Power Adaptor พร้อม case เลยนะครับเพื่อความสะดวก (ถ้างบถึงแนะนำให้เลือก 8 GB ไปเลยครับ)
- Storage drive แนะนำเป็น SSD M.2 PCIe/NVMe 2 TB เผื่ออนาคตไปเลยครับ
- Storage drive enclosure กล่องใส่ storage drive
- 16GB+ microSD
- External Card Reader
- Ethernet cable
ขั้นตอนต่อไป
- Download umbrelOS
- Download Balena Etcher โปรแกรม flash umbrelOS ลงใน microSD card ครับ
-
เสียบ microSD card เข้ากับคอมพิวเตอร์ของเรา

-
เปิดโปรแกรม Balena Etcher ขึ้นมาเพื่อ Flash umbrelOS ลงใน microSD card

-
หลังจาก Flash สำเร็จ ให้ถอดการ์ด microSD ออกจากคอมพิวเตอร์ของเรา แล้วใส่ลงใน Raspberry Pi

-
ใส่ SSD ลงในกล่อง storage drive แล้วเสียบเข้ากับพอร์ต USB 3.0 (สีน้ำเงิน) บน Raspberry Pi

-
เชื่อมต่อกับ router โดยเสียบ Ethernet cable เข้ากับ Raspberry Pi และ internet router

-
เชื่อมต่อ power supply เข้ากับ Raspberry Pi เพื่อเปิดเครื่องครับ

-
หลังจากนั้นก็เชื่อมต่อเข้าไปที่ http://umbrel.local ผ่านคอมพิวเตอร์ของเราได้เลยครับ

10.ตั้งชื่อผู้ใช้งานและตั้งรหัสผ่านในการเข้าใช้งาน Umbrel

11.หลังจากนั้นก็จะเข้าสู้หน้าตาของ umbrelOS กดเข้าที่ App Store เลือกแอปฯ Bitcoin Node


12.กด INSTALL เพื่อลงโปรแกรม Bitcoin Node

13.เมื่อลงเสร็จเรียบร้อยก็เปิดโปรแกรม Bitcoin Node ขึ้นมา รอจนกว่า Blockchain Synchronized เสร็จสิ้นครบ 100% อาจใช้เวลาประมาณ 3 วันเต็ม+- ก็เป็นอันเสร็จสิ้นกระบวนการแล้วครับ

เป็นอันเสร็จเรียบร้อยครับ ยินดีด้วยครับ เพียงเท่านี้คุณก็ได้ Run Bitcoin Full Node เต็มตัวแล้ว
ขอขอบคุณข้อมูลจาก umbrel.com และ บทความจากคุณ Chollatis Maneewong https://rightshift.to/2023/chontit/14106/ และก็ภาพจาก google บางส่วนครับ ขอบคุณมากๆครับ
-
 @ 0403c86a:66d3a378
2024-03-21 00:52:32
@ 0403c86a:66d3a378
2024-03-21 00:52:32From the moment I could walk, I was drawn to the world of sports like a moth to a flame. As a young boy, I would sit mesmerized in front of the glowing television screen, watching the greatest athletes in the world compete at the highest level. The roar of the crowd, the thunderous slam dunk, the agonizing thud of the ball clanking off the rim at the buzzer - it all captivated me, filling my senses with the electric energy of the game.
As I grew older, my passion only intensified. I devoured every statistic, studied every player's tendencies, and memorized the histories of my favorite teams. Whether it was the graceful crossovers of an NBA superstar, the cannon-like arm of an NFL quarterback, or the last second drible that takes your breath away in the standings of Maracanã, I was there, living and dying with every possession, every pass, every play.
But my love for sports extended far beyond the mainstream. I sought out the most niche competitions, from the dizzying speed of Formula 1 to the laser-sharp precision of professional darts. I marveled at the dedication and skill of these athletes, and I found myself drawn to the unique stories and strategies that defined these lesser-known sports.
Through it all, I never lost my sense of wonder. With each game, each match, each championship, I was reminded of the magic that lies at the heart of sports. The way a team can come together, like a perfectly choreographed dance, the way an individual can rise to the occasion and etch their name in the history books, the way a moment can captivate an entire nation - it was all endlessly fascinating to me.
As the years passed, my collection of sports memorabilia grew, my knowledge of the game deepened, and my passion only burned brighter. I became a living encyclopedia of sports trivia, a walking testament to the power of dedication and the beauty of competition.
And though I may have spent countless hours glued to the TV, or poring over the latest box scores, I never lost sight of the true essence of sports. It was about the thrill of the game, the camaraderie of the fans, and the timeless human drama that unfolds on the field, the court, and the diamond. It was a love affair that would last a lifetime, a never-ending journey through the world of athletic excellence and the unbridled joy of competition.
Sports, my eternal muse, my constant companion - you have captured my heart, and I will never stop chasing the magic that you inspire.
🏆⚽🏀🏈⚾🎯🥊🏁
-
 @ 57fe4c4a:c3a0271f
2023-10-18 13:02:10
@ 57fe4c4a:c3a0271f
2023-10-18 13:02:10📝 Summary: Batched splicing can be risky due to certain conditions like no funds in a channel and using an old state. It is important for batched splicing mechanisms to have a backout option to prevent disruptions caused by confirmed old states. Additionally, not all splice implementations performing a check can lead to potential loss of funds.
👥 Authors: • Greg Sanders ( nostr:npub1jdl3plz00rvxwc6g2ckemzrgg0amx5wen4kfvs3laxtssxvk9cvsf3gh0m ) • ZmnSCPxj ( nostr:npub1g5zswf6y48f7fy90jf3tlcuwdmjn8znhzaa4vkmtxaeskca8hpss23ms3l )
📅 Messages Date: 2023-10-17
✉️ Message Count: 3
📚 Total Characters in Messages: 5405
Messages Summaries
✉️ Message by ZmnSCPxj on 17/10/2023: Batched splicing can be risky if certain conditions are met, such as having no funds in a channel and using an old state. It is important for batched splicing mechanisms to have a backout option to prevent disruptions.
✉️ Message by Greg Sanders on 17/10/2023: Batched splicing is risky because if an old state is broadcasted and confirmed before the splice, it can disrupt the process. It is important for batched splicing mechanisms to have a backout option.
✉️ Message by ZmnSCPxj on 17/10/2023: Batched splicing can be risky if not all splice implementations perform a check to ensure subsequent splices confirm, potentially leading to loss of funds.
Follow nostr:npub1j3t00t9hv042ktszhk8xpnchma60x5kz4etemnslrhf9e9wavywqf94gll for full threads
-
 @ ee6ea13a:959b6e74
2024-03-21 00:48:36
@ ee6ea13a:959b6e74
2024-03-21 00:48:36Reposting this on stacker.news and Nostr for those who no longer use X.
Original post: https://x.com/dsbatten/status/1770571463151775944
You’ve probably seen GreenpeaceUSA's Bitcoin report by now, and my response (if you haven't been blocked).
Here’s six things that every environmentalist, Bitcoin advocate, regulator, policymaker and media representative should know about GreenpeaceUSA.
I've had this information for over a year, but have held back on going public with it until now because there were initially signs that GreenpeaceUSA would be open to engaging with environmentalists within the Bitcoin community.
With them now blocking me from commenting on their posts, all hope of that has now ended.
So here's what I can tell you about GreenpeaceUSA, and their campaign that have not been aired publicly until now, and which may surprise you.
Firstly, some context: I’m a former volunteer environmental campaigner with Greenpeace.
I once risked arrest to stand up for causes I believed in, including an anti-GMO campaign against McDonalds which was successful within 6 weeks, and hailed as an example of how creative direct action can yield fast results.
One of the differences: we talked to McDonalds (something no one at GreenpeaceUSA is currently doing with the Bitcoin community).
I know a number of people in the environmental movement, and I would like to thank them for their honesty in whistleblowing on a thoroughly misguided campaign from GreenpeaceUSA from start to finish.
-
GreenpeaceUSA’s campaign does NOT have the backing of Greenpeace International. In fact, other branches have asked questions of GreenpeaceUSA’s tactics, and even said that their campaign is damaging the Greenpeace brand, and has resulted in the loss of subscriptions.
-
Within GreenpeaceUSA, there are a growing number of voices of discontent. There is a growing division between some of the younger crypto-neutral or crypto-friendly millennial in their base, and the directorship of GreenpeaceUSA
-
As we know, GreenpeaceUSA did receive a $5Million donation from Ripple’s chair Chris Larsen to run an anti-Bitcoin campaign. What you probably do not know is that within Greenpeace, several staff have questioned whether this is ethical, or in the spirit of an organization that says it relies only on grassroots funding in its sign-up pledge.
-
Some members of EWG and SierraClub, particularly younger members, were not enamoured with their organization’s collusion with GreenpeaceUSA’s “Change the Code” campaign. EWG has not engaged in anti-Bitcoin rhetoric since 6 April ‘23.
-
The head of GreenpeaceUSA’s “Change the Code” campaign has stepped down and is no longer any part of GreenpeaceUSA. At the time of his stepping down he was reported by a source within GreenpeaceUSA to be questioning the wisdom of the campaign.
-
Within GreenpeaceUSA, we know from multiple inside sources that the Change the Code campaign has been widely acknowledged to have been “not particularly successful”.
GreenpeaceUSA’s campaign got off on the wrong foot right from the start, by antagonising environmentalists within the Bitcoin community, such as me. Here’s its half-time report (TL;DR, the worst performing environmental campaign I’ve ever witnessed). https://bitcoinmagazine.com/culture/greenpeace-environment-attacks-help-bitcoin
Now, the campaign is in more disarray than ever, resorting to tenuous ad hominem attacks against Satoshi Action, based on the discover that one of their supporters is a climate denier. True. Well, guess what: one of their supporters is also a plant-based, tree-hugging, climate-activist & meditation teacher: me.
That’s the beauty of Bitcoin: it pulls people in from across the political spectrum: we are as diverse as society itself, and that’s what makes us strong. As I wrote recently, “when the ship you’re standing on is sinking: it doesn’t matter if you’re on the left of right side of it.”
I hoped GreenpeaceUSA would end their anti-Bitcoin campaign before their credibility and relevance to the new generation of millennials they are currently disenfranchising is completely severed. But it seems at the moment they are more intent on doubling down on misinformation. Their leadership must change for them to ever have hope of becoming a true voice for the environment again.
-
-
 @ 83defd06:45cb69da
2024-03-21 00:38:55
@ 83defd06:45cb69da
2024-03-21 00:38:55EfBdNCE5zHbPze41Jz3IwQ==?iv=ZZYHPnIFe4c5F5oWTmmpsw==
-
 @ ee11a5df:b76c4e49
2024-03-21 00:28:47
@ ee11a5df:b76c4e49
2024-03-21 00:28:47I'm glad to see more activity and discussion about the gossip model. Glad to see fiatjaf and Jack posting about it, as well as many developers pitching in in the replies. There are difficult problems we need to overcome, and finding notes while remaining decentralized without huge note copying overhead was just the first. While the gossip model (including the outbox model which is just the NIP-65 part) completely eliminates the need to copy notes around to lots of relays, and keeps us decentralized, it brings about it's own set of new problems. No community is ever of the same mind on any issue, and this issue is no different. We have a lot of divergent opinions. This note will be my updated thoughts on these topics.
COPYING TO CENTRAL RELAYS IS A NON-STARTER: The idea that you can configure your client to use a few popular "centralized" relays and everybody will copy notes into those central relays is a non-starter. It destroys the entire raison d'être of nostr. I've heard people say that more decentralization isn't our biggest issue. But decentralization is THE reason nostr exists at all, so we need to make sure we live up to the hype. Otherwise we may as well just all join Bluesky. It has other problems too: the central relays get overloaded, and the notes get copied to too many relays, which is both space-inefficient and network bandwith inefficient.
ISSUE 1: Which notes should I fetch from which relays? This is described pretty well now in NIP-65. But that is only the "outbox" model part. The "gossip model" part is to also work out what relays work for people who don't publish a relay list.
ISSUE 2: Automatic failover. Apparently Peter Todd's definition of decentralized includes a concept of automatic failover, where new resources are brought up and users don't need to do anything. Besides this not being part of any definition of decentralized I have never heard of, we kind of have this. If a user has 5 outboxes, and 3 fail, everything still works. Redundancy is built in. No user intervention needed in most cases, at least in the short term. But we also don't have any notion of administrators who can fix this behind the scenes for the users. Users are sovereign and that means they have total control, but also take on some responsibility. This is obvious when it comes to keypair management, but it goes further. Users have to manage where they post and where they accept incoming notes, and when those relays fail to serve them they have to change providers. Putting the users in charge, and not having administrators, is kinda necessary to be truly decentralized.
ISSUE 3: Connecting to unvetted relays feels unsafe. It might even be the NSA tracking you! First off, this happens with your web browser all the time: you go visit a web page and it instructs your browser to fetch a font from google. If you don't like it, you can use uBlock origin and manage it manually. In the nostr world, if you don't like it, you can use a client that puts you more in control of this. The gossip client for example has options for whether you want to manually approve relay connections and AUTHs, just once or always, and always lets you change your mind later. If you turn those options on, initially it is a giant wall of approval requests... but that situation resolves rather quickly. I've been running with these options on for a long time now, and only about once a week do I have to make a decision for a new relay.
But these features aren't really necessary for the vast majority of users who don't care if a relay knows their IP address. Those users use VPNs or Tor when they want to be anonymous, and don't bother when they don't care (me included).
ISSUE 4: Mobile phone clients may find the gossip model too costly in terms of battery life. Bandwidth is actually not a problem: under the gossip model (if done correctly) events for user P are only downloaded from N relays (default for gossip client is N=2), which in general is FEWER events retrieved than other models which download the same event maybe 8 or more times. Rather, the problem here is the large number of network connections and in particular, the large number of SSL setups and teardowns. If it weren't for SSL, this wouldn't be much of a problem. But setting up and tearing down SSL on 50 simultaneous connections that drop and pop up somewhat frequently is a battery drain.
The solution to this that makes the most sense to me is to have a client proxy. What I mean by that is a piece of software on a server in a data centre. The client proxy would be a headless nostr client that uses the gossip model and acts on behalf of the phone client. The phone client doesn't even have to be a nostr client, but it might as well be a nostr client that just connects to this fixed proxy to read and write all of its events. Now the SSL connection issue is solved. These proxies can serve many clients and have local storage, whereas the phones might not even need local storage. Since very few users will set up such things for themselves, this is a business opportunity for people, and a better business opportunity IMHO than running a paid-for relay. This doesn't decentralize nostr as there can be many of these proxies. It does however require a trust relationship between the phone client and the proxy.
ISSUE 5: Personal relays still need moderation. I wrongly thought for a very long time that personal relays could act as personal OUTBOXes and personal INBOXes without needing moderation. Recently it became clear to me that clients should probably read from other people's INBOXes to find replies to events written by the user of that INBOX (which outbox model clients should be putting into that INBOX). If that is happening, then personal relays will need to serve to the public events that were just put there by the public, thus exposing them to abuse. I'm greatly disappointed to come to this realization and not quite settled about it yet, but I thought I had better make this known.
-
 @ fab018ad:dd9af89d
2023-10-14 05:31:59
@ fab018ad:dd9af89d
2023-10-14 05:31:595. สิ่งแทนที่การสูบทรัพยากรจากชาติอาณานิคม
“ฉันเหนื่อยกับการรอแล้ว นายก็เป็นเหมือนกันไหม รอให้โลกเป็นที่ที่ดีงาม สวยงาม และโอบอ้อมอารี เราเอามีดมาผ่าโลกนี้ให้เป็นสองซีกกันเถอะ และดูซิว่าหนอนอะไรที่กัดกินอยู่ที่ผิวของมัน”
–Langston Hughes
ในช่วงปลายทศวรรษ 1950 ยุโรปและญี่ปุ่นฟื้นตัวจากสงครามค่อนข้างมาก และกลับสู่การเติบโตด้านอุตสาหกรรมได้อย่างดี ในขณะที่เหล่าประเทศโลกที่สามนั้นไม่เหลือแล้วซึ่งเงินทุน แม้ประเทศเหล่านี้จะเคยมีงบการเงินที่ดีในช่วงยุค 1940 และต้นยุค 1950 ก็ตาม แต่เหล่าประเทศยากจนที่เป็นผู้ส่งออกปัจจัยการผลิตสำหรับอุตสาหกรรมต้องเผชิญปัญหาด้านดุลการชำระเงิน เนื่องจากราคาสินค้าส่งออกของพวกเขาตกต่ำลงอย่างมาก
นี่คือจุดเริ่มต้นของกับดักหนี้ และเป็นจุดที่ธนาคารโลกและกองทุน IMF เปิดประตูสู่สิ่งที่ต่อมาจะกลายเป็นเงินปล่อยกู้มูลค่านับล้านล้านดอลลาร์สหรัฐ
ณ จุดนี้ถือเป็นจุดสิ้นสุดของยุคล่าอาณานิคมอย่างเป็นทางการ โดยจักวรรดิในยุโรปได้ถอนตัวออกจากดินแดนที่เคยได้ครอบครอง และข้อสมมติฐานในด้านการพัฒนาที่ถูกตั้งขึ้นระดับนานาชาติก็คือเหล่าประเทศที่พัฒนาเศรษฐกิจได้สำเร็จนั้นเป็นผลมาจาก “ปัจจัยภายในประเทศเป็นหลัก โดยประเทศที่มีรายได้สูงสามารถประสบความสำเร็จในการพัฒนาเศรษฐกิจได้”

ทฤษฎียังระบุอีกว่า “เป็นเพราะการมีธรรมาภิบาลที่ดี มีสถาบันการเมืองที่เข็มแข็ง และมีการดำเนินเศรษฐกิจภายใต้ตลาดเสรี ในขณะที่ประเทศรายได้ต่ำที่มักจะล้มเหลวในการพัฒนานั้นเป็นเพราะไม่มีสิ่งเหล่านี้ หรือไม่ก็เจอปัญหาจากการคอร์รัปชั่น หรือกฎระเบียบที่ยุ่งยากเกินไป หรือกระทั่งความไร้ประสิทธิภาพในการบริหารประเทศ”
สิ่งเหล่านี้ก็แน่นอนว่าเป็นความจริง แต่อีกหนึ่งเหตุผลหลักที่ชาติร่ำรวยสามารถร่ำรวยขึ้นมาได้ และชาติที่ยากจนนั้นกลับยิ่งยากจนลงไปอีก เป็นเพราะกลุ่มประเทศร่ำรวยได้ปล้นทรัพยากรจากประเทศยากจนมาอย่างยาวนานนับร้อย ๆ ปีในช่วงยุคล่าอาณานิคม
“ในการปฏิวัติอุตสาหกรรมของอังกฤษนั้น” คุณ Jason Hickel ได้เขียนไว้ว่า “ส่วนใหญ่แล้วจำเป็นต้องพึ่งพา "ต้นฝ้าย" ซึ่งเพาะปลูกบนพื้นที่ที่ใช้กำลังยึดมาจากชนเผ่าท้องถิ่นอเมริกัน แรงงานที่ใช้ในการเพาะปลูกก็เป็นทาสชาวแอฟริกัน ส่วนวัตถุดิบสำคัญอื่น ๆ ที่ผู้ผลิตชาวอังกฤษต้องการ เช่น ใยป่าน ไม้ซุง แร่เหล็ก และเมล็ดธัญพืช ถูกผลิตโดยใช้แรงงานทาสบนดินแดนในอาณัติแถบรัสเซียและยุโรปตะวันออก ในขณะเดียวกันอังกฤษยังดึงเม็ดเงินจากอินเดียและอาณานิคมอื่น ๆ มากกว่าครึ่งหนึ่งของงบประมาณประเทศ เพื่อมาใช้สร้างถนน อาคารสาธารณะ และรัฐสวัสดิการ ทั้งหมดนี้คือตัวบ่งชี้ถึงการพัฒนาในยุคสมัยใหม่ ในขณะเดียวกันก็ทำให้ประเทศมีความสามารถที่จะซื้อปัจจัยการผลิตเพิ่มขึ้น ซึ่งจำเป็นต่อการเปลี่ยนตัวเองให้เป็นชาติอุตสาหกรรมต่อไป”
พลวัตในการโจรกรรมนี้ได้ถูกอธิบายโดยคุณ Utsa และคุณ Prabhat Patnaik ในหนังสือ “เงินทุนและจักรวรรดินิยม (Capital And Imperialism)” เจ้าอาณานิคมอย่างจักวรรดิอังกฤษจะใช้ความรุนแรงเพื่อปล้นทรัพยากรจากประเทศที่อ่อนแอกว่า และสร้างสิ่งที่เรียกว่า “การสูบออกจากชาติอาณานิคม (Colonial Drain)” โดยจะทำการสูบออกในส่วนของเงินทุนเพื่อนำมาส่งเสริมและอุดหนุนชีวิตความเป็นอยู่ของผู้คนในกรุงลอนดอน ปารีส และเบอร์ลิน โดยบรรดาชาติอุตสาหกรรมจะเปลี่ยนวัตถุดิบเหล่านี้ให้กลายเป็นสินค้าสำเร็จรูป และขายมันกลับไปสู่ชาติที่อ่อนแอกว่า

สินค้าเหล่านี้สร้างผลกำไรมหาศาลและยังบีบให้ผู้ผลิตท้องถิ่นต้องออกจากตลาดไป โดยจุดสำคัญคือพวกเขาจะพยายามทำให้เงินเฟ้อในประเทศตัวเองต่ำ โดยการกดค่าแรงในประเทศใต้อาณานิคม ไม่ว่าจะด้วยการใช้แรงงานทาสแบบฟรี ๆ หรือการจ่ายค่าแรงในอัตราที่ต่ำกว่าราคาตลาดโลกอย่างน่าเกลียด
เมื่อระบอบอาณานิคมนั้นเริ่มสั่นคลอน เหล่าชาติตะวันตกก็พบกับวิกฤติทางการเงิน โดยคุณ Patnaiks ได้แย้งว่าสาเหตุที่เกิดภาวะเศรษฐกิจตกต่ำครั้งใหญ่ (The Great Depression) ไม่ได้มาจากแค่การเปลี่ยนแปลงนโยบายทางการเงินของชาติตะวันตกเท่านั้น แต่ยังรวมถึงการสูบความมั่งคั่งออกจากประเทศใต้อาณานิคมนั้นชะลอตัวลงด้วย เหตุผลก็ง่ายมาก นั่นคือประเทศที่ร่ำรวยได้สร้างระบบสายพานที่คอยส่งทรัพยากรจากประเทศที่ยากจนเข้าสู่ประเทศตัวเองเอาไว้ และเมื่อสายพานนั้นพัง สิ่งที่เหลือก็พังตาม
ในช่วงระหว่างปี 1920-1960 ลัทธิล่าอาณานิคมทางการเมืองนั้นแทบจะสูญพันธุ์แล้ว โดยอังกฤษ สหรัฐฯ เยอรมนี ฝรั่งเศส ญี่ปุ่น เนเธอร์แลนด์ เบลเยี่ยม และจักรวรรดิอื่น ๆ ต่างถูกบังคับให้สละอำนาจการควบคุมดินแดนและทรัพยากรมากกว่าครึ่งหนึ่งของโลก
อย่างที่คุณ Patnaiks ได้เขียนไว้ว่าลัทธิจักรวรรดินิยมคือ “การเข้าไปจัดการและบังคับใช้ ‘การกดรายได้’ ผู้คนในประเทศโลกที่สาม เพื่อให้ได้มาซึ่งสินค้าโภคภัณฑ์หลักของประเทศนั้น ๆ โดยไม่ต้องเผชิญกับปัญหาราคาของอุปทานพุ่งสูงขึ้น”
โดยหลังจากปี 1960 สิ่งนี้ก็กลายเป็นหน้าที่ใหม่ของธนาคารโลกและ IMF นั่นคือการสร้าง “ระบบ” สูบทรัพยากรจากประเทศที่ยากจนสู่ประเทศที่ร่ำรวยขึ้นมาอีกครั้ง ระบบที่แต่เดิมเคยดำรงอยู่ได้ด้วยการบังคับใช้ของระบอบจักรวรรดินิยม

คำอธิบายแผนภูมิ: การสูบทรัพยากรหลังยุคอาณานิคมจากประเทศที่กำลังพัฒนาไปสู่ประเทศที่พัฒนาแล้ว (หน่วยพันล้านดอลลาร์สหรัฐ) - แกนแนวตั้ง : หน่วยมูลค่า พันล้านดอลลาร์สหรัฐ - แนวนอน : ปี - แหล่งที่มา : Plunder In The Post Colonial Era
หน่วยงานในทั้งสหรัฐฯ ยุโรป และญี่ปุ่นต่างก็ต้องการให้เกิดสิ่งที่เรียกว่า “ดุลยภาพภายใน (Internal Equilibrium)” พูดอีกนัยคือมีอัตราจ้างงานเต็มอัตรา แต่พวกเขารู้ว่าไม่สามารถทำให้สิ่งนี้เกิดได้ง่าย ๆ เพียงอัดฉีดเงินอุดหนุนเข้าสู่ระบบเศรษฐกิจแบบปิดที่แยกตัวเป็นเอกเทศ เพราะเงินเฟ้อจะพุ่งขึ้นอย่างที่ควบคุมไม่ได้ และการที่จะทำสิ่งนี้ให้สำเร็จจำเป็นต้องมีทรัพยากรจากประเทศที่ยากจนป้อนเข้ามา
การสูบมูลค่าส่วนเกินที่มากเป็นพิเศษออกมาจากเหล่าแรงงานในกลุ่มประเทศชายขอบ ซึ่งกลุ่มประเทศแกนกลางกระทำมาตลอดนั้น เป็นที่รู้จักกันในนาม “ค่าเช่าต่อระบอบจักรวรรดิ (Imperialist Rent)” ยิ่งถ้าบรรดาชาติอุตสาหกรรมสามารถได้มาซึ่งวัตถุดิบและแรงงานการผลิตในราคาถูก และหลังจากนั้นยังสามารถขายสินค้าที่ผลิตเสร็จกลับไปให้ในราคาที่ได้กำไร พวกเขาก็จะยิ่งขยับเข้าใกล้ระบบเศรฐกิจในฝันตามแบบฉบับเทคโนแครตได้อีกนิด
และสุดท้ายพวกเขาก็ได้สิ่งนั้นมาจริง ๆ ด้วย โดยในปี 2019 ค่าแรงของคนงานในประเทศที่กำลังพัฒนานั้นอยู่ในระดับเพียงร้อยละ 20 ของค่าแรงของคนงานในประเทศที่พัฒนาแล้ว
โดยตัวอย่างเพื่อที่จะให้เห็นภาพว่าธนาคารโลกสร้างพลวัตของการสูบเงินทุนออกจากอาณานิคมขึ้นมาใหม่ได้อย่างไร คุณ Payer ได้ยกกรณีของประเทศมอริเตเนียที่อยู่ทางตะวันตกเฉียงเหนือของแอฟริกาในช่วงปี 1960

กรณีนี้ถือเป็นเหตุการณ์คลาสสิก โดยโครงการเหมืองแร่ที่ชื่อ MIFERMA ได้รับการอนุมัติโดยฝรั่งเศสผู้ซึ่งเป็นเจ้าอาณานิคมก่อนที่อาณานิคมนี้จะประกาศอิสรภาพ ซึ่งในที่สุดแล้วข้อตกลงนี้ก็กลายเป็น “โครงการที่แยกออกจากส่วนอื่นของประเทศ เนื่องจากตัวมันเองคือเมืองกลางทะเลทรายที่มีทางรถไฟต่อไปที่ทะเล” โดยที่โครงสร้างพื้นฐานต่าง ๆ ก็มีไว้เพื่อขุดเอาสินแร่ส่งออกไปยังตลาดต่างประเทศ จนในปี 1969 ที่อุตสาหกรรมเหมืองแร่มีสัดส่วนคิดเป็นร้อยละ 30 ของผลิตภัณฑ์มวลรวมในประเทศและร้อยละ 75 ของสินค้าส่งออกของมอริเตเนียนั้น รายได้กว่าร้อยละ 72 ถูกส่งไปยังต่างประเทศและ “รายได้ในส่วนที่คนงานท้องถิ่นควรได้รับ เกือบทั้งหมดก็หายไปกับการใช้นำเข้าสินค้า”
และเมื่อเหล่าคนงานเหมืองลุกขึ้นรวมตัวกันประท้วงข้อตกลงสไตล์อาณานิคมรูปแบบใหม่นี้ พวกเขาก็ถูกเหล่ากำลังทหารและตำรวจปราบปรามอย่างรุนแรง

คำอธิบายแผนภูมิ : มูลค่าเงินที่ถูกสูบออกจากประเทศกำลังพัฒนาไปสู่ประเทศพัฒนาแล้ว ตั้งแต่ปี 1960-2017 แยกตามภูมิประเทศ (หน่วยล้านล้านดอลลาร์สหรัฐ) - ข้อมูลในแต่ละช่อง : ประเทศจีน 18.76, เอเชียตะวันออกเฉียงใต้และเขตแปซิฟิก 11.13, แอฟริกาเหนือ ตะวันออกกลาง และเอเชียกลาง 10.09, ประเทศชายขอบยุโรป 8.75, ลาตินอเมริกาและแถบหมู่เกาะคาริเบียน 6.48, เอเชียใต้ 4.62 และประเทศในเขตแอฟริกาใต้ทะเลทรายชาฮารา 2.26 - แหล่งที่มา : Plunder In The Post Colonial Era
MIFERMA ถือเป็นเพียงตัวอย่างจากรวม ๆ ของสิ่งที่เรียกว่า “การพัฒนา” ที่ถูกบังคับใช้กับประเทศโลกที่สามทั้งหมด ตั้งแต่สาธารณรัฐโดมินิกัน ถึงมาดากัสการ์ ไปจนกัมพูชา โครงการเหล่านี้ขยายตัวขึ้นอย่างรวดเร็วในช่วงปี 1970 โดยต้องขอบคุณระบบเปโตรดอลลาร์ที่ทำให้มันเกิดขึ้น
ในช่วงหลังปี 1973 ชาติอาหรับในกลุ่ม OPEC ที่มีเงินเหลือใช้มหาศาลจากราคาน้ำมันที่พุ่งทะยาน ได้นำเงินไปลงทุนในเงินฝากธนาคารและพันธบัตรรัฐบาลในธนาคารของชาติตะวันตก ทำให้ธนาคารเหล่านี้จำเป็นต้องหาแหล่งเพื่อจะปล่อยกู้เงินฝากที่กำลังเติบโตขึ้นออกไป โดยเหล่าเผด็จการทหารในลาตินอเมริกา แอฟริกา และเอเชีย ถือเป็นเป้าหมายที่ยอดเยี่ยม เพราะพวกเขามีความโหยหาผลตอบแทนระยะสั้นที่สูง (High Time Preference) และยินดีที่จะกู้เงินมาใช้ โดยเอาอนาคตของประชาชนทั้งชาติเป็นเดิมพัน

สิ่งที่ช่วยเร่งการเติบโตของเงินกู้นั้นคือ “IMF พุท (IMF Put)” โดยธนาคารเอกชนเริ่มมีความเชื่อ (ซึ่งถูกต้อง) ว่าหากประเทศใดเกิดผิดนัดชำระหนี้ ทางกองทุน IMF ก็พร้อมจะให้เงินกู้ช่วยเหลือ เพื่อช่วยปกป้องการลงทุนของพวกเขา
ยิ่งไปกว่านั้น อัตราดอกเบี้ยในช่วงกลางยุค 1970 มักจะอยู่ในระดับติดลบ จึงกระตุ้นให้เกิดการกู้เงินมากขึ้นไปอีก เมื่อเหตุการณ์นี้รวมเข้ากับการที่ประธานธนาคารโลกอย่างโรเบิร์ต แม็กนามารา (Robert McNamara) ยืนยันที่จะขยายความช่วยเหลือออกไปอย่างมหาศาล มันส่งผลให้เกิดการสร้างหนี้ขึ้นอย่างบ้าคลั่ง ตัวอย่างเช่นธนาคารในสหรัฐฯ ซึ่งปล่อยเงินกู้ให้ประเทศโลกที่สามเพิ่มขึ้นกว่า 300% เป็นมูลค่าถึง 450,000 ล้านดอลลาร์สหรัฐในช่วงระหว่างปี 1978-1982
>หมายเหตุผู้แปล : "พุท" ในที่นี้มีที่มาจากคำว่า "พุทออปชั่น" (Put Option) หมายถึง สิทธิ์ในการขายทรัพย์สินอ้างอิง (Underlying Asset) ในอนาคต ณ ราคาที่ได้ตกลงไว้ล่วงหน้า โดยผู้ที่ซื้อหรือครอบครองสิทธิ์นี้ไว้จะมีสิทธิ์ที่จะขายทรัพย์สินอ้างอิงนั้น ๆ ในอนาคตตามราคาที่ตกลงกันไว้ล่วงหน้าได้ ซึ่งจะเป็นประโยชน์สำหรับผู้ที่ครอบครองสิทธิ์ในกรณีที่ราคาของสินทรัพย์อ้างอิงนั้นลดลงในอนาคต ในทางปฏิบัติแล้ว สิ่งนี้สามารถนำมาใช้ทำหน้าที่ซึ่งคล้ายกับการทำประกันราคา ที่จะช่วยชดเชยส่วนต่างในกรณีที่ราคาของทรัพย์สินอ้างอิงลดต่ำลงได้ ดังนั้นหลักการทำงานของ IMF Put จึงมีความคล้ายคลึงกับ Put Option ของทรัพย์สินโดยทั่วไป ถึงแม้ว่า IMF Put จะไม่ได้มีการทำสัญญาพุทออปชั่นใด ๆ อย่างเป็นทางการก็ตาม เพียงแต่เปลี่ยนจากทรัพย์สินหรือสินค้าโภคภัณฑ์ทั่วไปมาเป็นทรัพย์สินที่เรียกว่า “ลูกหนี้จากการปล่อยกู้”
ปัญหาคือเงินกู้เหล่านี้ส่วนใหญ่ใช้อัตราดอกเบี้ยแบบลอยตัว และไม่กี่ปีหลังจากนั้นอัตราดอกเบี้ยก็พุ่งสูงขึ้นมาก เพราะธนาคารกลางสหรัฐเพิ่มต้นทุนของเงินทุนทั้งโลกถึงเกือบร้อยละ 20 และเมื่อมีภาระหนี้ที่เพิ่มขึ้น ประกอบกับวิกฤตน้ำมันแพงในปี 1979 สิ่งที่ตามมาคือการล่มสลายของราคาสินค้าโภคภัณฑ์ทั่วโลกซึ่งเคยเป็นตัวขับเคลื่อนการส่งออกของประเทศกำลังพัฒนา จนนำไปสู่วิกฤตหนี้สินของประเทศโลกที่สาม และที่แย่ไปกว่านั้นคือเงินที่รัฐบาลต่าง ๆ กู้มาในช่วงที่มีการปล่อยกู้อย่างบ้าคลั่งนี้ แทบจะไม่ได้มีการนำมาใช้ลงทุนเพื่อประชาชนทั่วไปเลย

คำอธิบายชาร์ต : การเพิ่มขึ้นของเงินที่ใช้ชำระหนี้ของประเทศโลกที่สาม นับตั้งแต่ปี 1970 (หน่วยพันล้านดอลลาร์สหรัฐ) - แถวซ้ายสีดำ : หนี้สาธารณะนอกประเทศ - แถวขวาสีส้ม : หนี้นอกประเทศของเอกชน - แหล่งที่มาของข้อมูล : Debt, the IMF, and the World Bank
นักข่าวสายสืบสวนอย่างคุณ Sue Branford และคุณ Bernardo Kucinski ได้อธิบายไว้ในหนังสือที่มีชื่อเหมาะเจาะกับสิ่งที่เกิดขึ้นอย่าง “Debt Squads” ว่าระหว่างปี 1976-1981 รัฐบาลของประเทศในเขตลาตินอเมริกา (ซึ่งเป็นรัฐบาลเผด็จการมากถึง 18 รายจากทั้งหมด 21 ชาติ) มีการกู้ยืมเงินรวมกันกว่า 272,900 ล้านดอลลาร์สหรัฐ โดยร้อยละ 91.6 ของเม็ดเงินนี้ถูกใช้เพื่อชำระหนี้หรือถูกโอนถ่ายออกนอกประเทศ รวมถึงใช้เป็นเงินทุนสำรองของเหล่าผู้มีอำนาจ เหลือแค่ร้อยละ 8.4 ที่ถูกใช้เพื่อการลงทุนภายในประเทศ และซ้ำร้ายกว่านั้นคือส่วนใหญ่มันเป็นการลงทุนแบบทิ้ง ๆ ขว้าง ๆ ที่สุดท้ายแล้วสูญเปล่า
นักสนับสนุนกิจกรรมด้านสังคมชาวบราซิล คุณ Carlos Ayuda อธิบายเอาไว้อย่างเห็นภาพถึงผลกระทบของการถูกสูบเงินออกจากประเทศตัวเอง โดยมีกลไกระบบเปโตรดอลลาร์หนุนหลัง

“พวกเผด็จการทหารกู้เงินเพื่อมาลงทุนในโครงสร้างพื้นฐานขนาดใหญ่ โดยเฉพาะโครงการที่เกี่ยวข้องกับด้านพลังงาน ตัวอย่างเช่น แนวคิดเบื้องหลังในการสร้างเขื่อนโรงไฟฟ้าพลังน้ำขนาดใหญ่ยักษ์ที่ตั้งอยู่กลางป่าแอมะซอนนั้น ก็เพื่อผลิตอลูมิเนียมส่งออกไปยังประเทศที่พัฒนาแล้ว โดยรัฐบาลได้กู้เงินมูลค่ามหาศาลและลงทุนหลายพันล้านดอลลาร์สหรัฐเพื่อสร้างเขื่อน Tucuruí ในช่วงปลายยุค 1970 ด้วยการทำลายป่าไม้ในพื้นที่ และย้ายชาวพื้นเมืองกับคนยากไร้ในเขตชนบทโดยรอบที่อาศัยอยู่ในแถบนั้นมาหลายชั่วอายุคนออกจากพื้นที่
เดิมทีทางรัฐบาลตั้งใจที่จะรื้อถอนต้นไม้ออกไป แต่เนื่องด้วยกำหนดเวลาที่กระชั้นชิด พวกเขาจึงเลือกใช้ "ฝนเหลือง" เพื่อทำให้ใบไม้ของต้นไม้ทั่วทั้งเขตร่วงจากต้น และปล่อยให้ลำต้นที่ไร้ใบเหล่านั้นจมน้ำไป หลังจากนั้นพลังงานไฟฟ้าที่เขื่อนผลิตได้จะถูกขายในราคา 13-20 ดอลลาร์สหรัฐต่อเมกะวัตต์ ในขณะที่ราคาต้นทุนการผลิตอยู่ที่ 48 ดอลลาร์สหรัฐต่อเมกะวัตต์ แปลว่าประชาชนผู้เสียภาษีจะต้องแบกภาระจ่ายเงินอุดหนุนให้บริษัทข้ามชาติได้ใช้พลังงานราคาถูก เพื่อที่พวกเขาจะได้ขายอลูมิเนียมของประเทศเราเองออกไปยังตลาดต่างประเทศ”
>หมายเหตุผู้แปล : ฝนเหลือง (Agent Orange) เป็นสารฆ่าวัชพืชและทำให้ใบไม้ร่วง ถือเป็นสารก่อมะเร็งในมนุษย์ โดยทางกองทัพสหรัฐเคยใช้สารเคมีนี้ในสงครามเวียดนามช่วงปี 1961-1971 ในการทำให้ใบไม้ร่วงและเปิดป่าให้โล่ง เพื่อที่จะสามารถเห็นความเคลื่อนไหวของข้าศึกที่ซ่อนอยู่ในป่าทึบได้
พูดอีกนัยหนึ่งคือ ชาวบราซิลจ่ายเงินให้เจ้าหนี้จากต่างประเทศเข้ามาทำลายสิ่งแวดล้อม ขับไล่พวกเขาออกจากถิ่นฐาน และปล้นเอาทรัพยากรของพวกเขาไปขาย
การสูบเอาทรัพยากรจากประเทศที่รายได้ต่ำและปานกลางในทุกวันนี้มีมากอย่างน่าตกใจ โดยในปี 2015 รวมแล้วมีทรัพยากรเพื่อการผลิตกว่า 10,100 ล้านตัน และแรงงาน 182 ล้านคน-ปี ซึ่งถือเป็นกำลังการผลิตถึงร้อยละ 50 ของสินค้าทั้งหมด และร้อยละ 28 ของแรงงานทั้งหมดในปีนั้นถูกใช้งานโดยประเทศที่มีรายได้สูง
>หมายเหตุผู้แปล : คน-ปี (person-year) เป็นหน่วยวัดเพื่อบอกปริมาณของงานที่บุคคลทำตลอดระยะเวลา 1 ปี ตัวอย่างเช่น 5 คน-ปี คือปริมาณงานที่คน 5 คนทำได้ในช่วงตลอด 1 ปี หรือเทียบเท่างานที่คน 1 คน ทำได้ในช่วงตลอด 5 ปี
และอย่างที่เอ่ยไปแล้วข้างต้นว่าผู้คนที่ชีวิตสุขสบายในชาติร่ำรวย ไม่เคยรู้เลยว่าความเจริญของบ้านเมืองตนเองนั้น ต้องแลกมากับชีวิตที่ตกนรกทั้งเป็นของคนกี่ล้านคนทั่วโลก..
⚡️ กด Zap ที่ลิงก์นี้ เพื่อเป็นกำลังใจทีมงานผู้เรียบเรียงบทความ
(ทุกยอด zap จะถูกแบ่งอัตโนมัติเข้าวอลเล็ทของผู้เขียนบทความต้นฉบับภาษาอังกฤษ, ผู้แปลดราฟต์ 1, ผู้เรียบเรียงดราฟต์ 2-3, กองบรรณาธิการและพิสูจน์อักษรจากไรท์ชิฟต์ พร้อมกันบางส่วนไว้เพื่อเป็นค่าธรรมเนียมธุรกรรม)
-
 @ fab018ad:dd9af89d
2023-10-13 05:25:13
@ fab018ad:dd9af89d
2023-10-13 05:25:1313. ทำอย่างที่ฉันพูด ไม่ใช่ทำอย่างที่ฉันทำ
“วิถีชีวิตของพวกเรานั้นไม่ได้มีไว้ต่อรอง”
–George H.W. Bush
>หมายเหตุผู้แปล : จอร์จ เอช. ดับเบิลยู. บุช (George H.W. Bush) เป็นประธานาธิบดีคนที่ 41 ของสหรัฐอเมริกาในช่วงระหว่างปี 1989-1993
ในโลกที่มีระบบตลาดเสรีอย่างแท้จริง นโยบายที่ธนาคารโลกและกองทุน IMF บังคับใช้ต่อประเทศยากจนอาจจะเป็นเรื่องสมเหตุสมผล เพราะจากประวัติศาสตร์แล้ว ผลลัพธ์ของระบอบสังคมนิยมและการยึดกิจการเอกชนให้กลายเป็นของรัฐนั้นคือความหายนะ แต่ทว่าปัญหาคือโลกไม่ได้เป็นระบบตลาดเสรีที่แท้จริง และการปฏิบัติแบบสองมาตรฐานก็มีอยู่ทุกหนทุกแห่ง
การให้เงินอุดหนุนต่าง ๆ ถือเป็นตัวอย่างที่ดี โครงการข้าวสารฟรีในประเทศศรีลังกา หรือส่วนลดราคาเชื้อเพลิงในประเทศไนจีเรียถูก IMF สั่งให้ยกเลิก แต่ชาติผู้ปล่อยเงินกู้อย่างสหราชอาณาจักรและสหรัฐอเมริกากลับหยิบยื่นสวัสดิการการรักษาพยาบาลจากภาครัฐและเงินอุดหนุนพืชผลให้แก่ประชาชนของพวกเขาเองเสียอย่างนั้น
ไม่ว่าคุณจะมองจากมุมมองแบบอิสรนิยมหรือมุมมองแบบมาร์กซิสม์ คุณก็จะได้ข้อสรุปเดียวกันว่านี่คือการปฏิบัติสองมาตรฐานที่ทำให้บางประเทศร่ำรวย และปล่อยให้ประเทศอื่นเป็นผู้รับเคราะห์แทน ซึ่งประชาชนของประเทศที่ร่ำรวยส่วนใหญ่ไม่ได้รับรู้อะไรเลย และต่างก็ใช้ชีวิตอยู่อย่างสุขสำราญ
ในการช่วยให้ชาติต่าง ๆ ฟื้นตัวจากเศษซากของสงครามโลกครั้งที่สอง ประเทศเจ้าหนี้ของ IMF พึ่งพิงการวางแผนจากส่วนกลางและนโยบายต่อต้านตลาดเสรีอย่างหนักในช่วงไม่กี่ทศวรรษแรกหลังการประชุมที่เบรตตัน วูดส์ เช่น การจำกัดการนำเข้า การจำกัดการไหลออกของเงินทุน การตั้งเพดานอัตราแลกเปลี่ยนเงินตรา และการให้เงินอุดหนุนสินค้าการเกษตร ซึ่งมาตรการเหล่านี้ช่วยปกป้องเศรษฐกิจของชาติอุตสาหกรรมเอาไว้ในช่วงที่กำลังอ่อนแอที่สุด
ตัวอย่างเช่นในสหรัฐอเมริกามีพรบ. การปรับดอกเบี้ยให้เท่าเทียม (Interest Equalization Act) ซึ่งออกในสมัยของประธานาธิบดีจอห์น เอฟ. เคนเนดี เพื่อหยุดชาวอเมริกันจากการซื้อหลักทรัพย์ต่างประเทศ และกระตุ้นให้หันมาสนใจการลงทุนในประเทศ นี่ถือเป็นหนึ่งในหลาย ๆ มาตรการที่ออกมาเพื่อควบคุมเงินทุน แต่ธนาคารโลกและกองทุน IMF กลับมีประวัติในการกีดกันไม่ให้ประเทศที่ยากจนสามารถใช้มาตรการเดียวกันนี้เพื่อปกป้องประเทศตัวเองได้บ้าง
>หมายเหตุผู้แปล : จอห์น เอฟ. เคนเนดี (John F. Kennedy) เป็นประธานาธิบดีคนที่ 35 ของสหรัฐอเมริกา ดำรงตำแหน่งตั้งแต่ปี 1961 จนกระทั่งถูกลอบสังหารในปี 1963
อย่างที่คุณ Payer ตั้งข้อสังเกตว่า “IMF ไม่เคยไปยุ่งเกี่ยวกับการตัดสินใจเรื่องการปรับอัตราแลกเปลี่ยนและนโยบายการค้าของประเทศพัฒนาแล้วที่ร่ำรวย... แต่กลุ่มชาติที่อ่อนแอต่างหากที่ต้องตกอยู่ภายใต้การบังคับใช้หลักการของ IMF อย่างเต็มสูบ... ความไม่เท่าเทียมในความสัมพันธ์ทางอำนาจนี้แปลว่ากองทุน IMF จงใจมองไม่เห็นการ 'บิดเบือนกลไกตลาด' เช่น การกีดกันทางการค้า ซึ่งเป็นสิ่งที่ชาติที่ร่ำรวยทำกันเป็นเรื่องปกติ”
คุณ Vásquez และคุณ Bandow จากสถาบัน Cato ก็ได้ข้อสรุปคล้าย ๆ กัน โดยชี้ว่า “ชาติอุตสาหกรรมส่วนใหญ่ยังคงแนวความคิดของการเป็นผู้อุปถัมภ์ต่อประเทศด้อยพัฒนา แต่มันเหมือนเป็นการเสแสร้งชัด ๆ เพราะพวกเขานี่แหละที่คอยกีดกันการส่งออกของประเทศเหล่านั้น”
ในช่วงต้นทศวรรษ 1990 ในขณะที่สหรัฐอเมริกาเน้นย้ำถึงความสำคัญของการค้าเสรี แต่ทางสหรัฐฯ กลับเสมือน “ตั้งม่านเหล็กขัดขวางการส่งออกของชาติในยุโรปตะวันออก สินค้าที่ได้รับผลกระทบนั้นรวมไปถึงสิ่งทอ เหล็ก และผลิตภัณฑ์ทางการเกษตร” โดยประเทศโปแลนด์ เชโกสโลวาเกีย ฮังการี โรมาเนีย บอสเนีย โครเอเชีย สโลวีเนีย อาเซอร์ไบจาน เบลารุส จอร์เจีย คาซัคสถาน คีร์กีซสถาน มอลโดวา รัสเซีย ทาจิกิสถาน เติร์กเมนิสถาน ยูเครน และอุซเบกิสถานนั้นต่างก็ตกเป็นเป้าหมายการกีดกันทางการค้าจากสหรัฐอเมริกาที่ไม่ต้องการให้ประเทศในยุโรปตะวันออก “ขายเนย นมผง หรือไอศกรีมแม้แต่กิโลกรัมเดียวในสหรัฐฯ” คณะรัฐบาลของประธานาธิบดีบุช และคณะรัฐบาลของประธานาธิบดีคลินตัน นั้นต่างก็ตั้งข้อจำกัดที่แข็งกร้าวต่อประเทศในพื้นที่แถบนั้นในการนำเข้าสารเคมีและสินค้าเภสัชกรรม
หมายเหตุผู้แปล : - จอร์จ เฮอร์เบิร์ต วอล์กเกอร์ บุช (George Herbert Walker Bush) เป็นประธานาธิบดีคนที่ 41 ของสหรัฐอเมริกา โดยดำรงตำแหน่งตั้งแต่ปี 1989-1993 - วิลเลียม เจฟเฟอร์สัน คลินตัน (William Jefferson Clinton) หรือรู้จักในนามบิล คลินตัน (Bill Clinton) เป็นประธานาธิบดีคนที่ 42 ของสหรัฐอเมริกา โดยดำรงตำแหน่งตั้งแต่ปี 1993-2001
มีการประมาณการว่าลัทธิการคุ้มครองทางการค้าโดยประเทศอุตสาหกรรมนั้น “ทำให้รายได้ของประเทศกำลังพัฒนาลดลงไปมากกว่า 2 เท่าของตัวเลขความช่วยเหลือที่ได้รับ” พูดอีกนัยหนึ่ง ถ้าชาติตะวันตกเปิดเศรษฐกิจให้เสรี พวกเขาก็ไม่จำเป็นต้องให้ความช่วยเหลือใด ๆ ต่อชาติยากจนด้วยซ้ำ
ข้อตกลงเงินกู้ยังมีจุดหักมุมที่บัดซบอยู่อีกด้วย นั่นคือในยามที่ชาติตะวันตก (เช่น สหรัฐอเมริกา) เจอปัญหาวิกฤตเงินเฟ้อแบบที่กำลังเจออยู่ในทุกวันนี้ และถูกบีบให้ต้องใช้นโยบายการเงินที่รัดกุมมากขึ้น พวกเขากลับได้อำนาจเพิ่มขึ้นในการควบคุมประเทศและทรัพยากรของประเทศกำลังพัฒนาเหล่านี้ เพราะหนี้ของประเทศกำลังพัฒนาที่อยู่ในสกุลเงินดอลลาร์เริ่มจะหามาชำระคืนได้ยากกว่าเดิม พวกเขาเลยต้องติดกับดักหนี้ที่ลึกกว่าเก่า จนต้องทำตามเงื่อนไขของธนาคารโลกและกองทุน IMF มากขึ้นไปอีก
ในปี 2008 ช่วงระหว่างวิกฤตทางการเงินครั้งใหญ่ ทางการสหรัฐอเมริกาและทางการยุโรปปรับลดอัตราดอกเบี้ยและอัดฉีดเงินพิเศษเพิ่มให้กับธนาคารในประเทศ แต่ในช่วงที่เกิดวิกฤตหนี้สินในประเทศโลกที่สาม ธนาคารโลกและกองทุน IMF ไม่ยินยอมให้ชาติเหล่านี้ทำพฤติกรรมแบบเดียวกัน แต่กลับแนะนำประเทศที่ได้รับผลกระทบว่าควรจะใช้มาตรการลดค่าใช้จ่ายในประเทศ และควรกู้เงินจากต่างประเทศเพิ่ม
ในเดือนกันยายน 2022 ข่าวพาดหัวหนังสือพิมพ์ระบุว่า IMF “มีความกังวล” เกี่ยวกับเงินเฟ้อในสหราชอาณาจักร ในขณะที่ตลาดพันธบัตรของพวกเขาค่อย ๆ เดินเข้าใกล้การล่มสลาย นี่แสดงให้เห็นถึงความเสแสร้งอีกครั้ง เพราะเมื่อพิจารณาจากการที่ IMF ดูจะไม่เคยเป็นห่วงเกี่ยวกับเงินเฟ้อเลยทุกครั้งที่สั่งให้ลดค่าเงินของคนหลายพันล้านคนทั่วโลกตลอดหลายทศวรรษที่ผ่านมา ชาติผู้ให้กู้นั้นดูจะเล่นอยู่บนกติกาที่ต่างออกไปอย่างสิ้นเชิง
ในกรณีตัวอย่างสุดท้ายของการ “ทำอย่างที่ฉันพูด ไม่ใช่ทำอย่างที่ฉันทำ” คือการที่ IMF ยังคงถือทองคำจำนวนมหาศาลถึง 90.5 ล้านออนซ์ หรือประมาณ 2,814 เมตริกตัน โดยส่วนใหญ่สะสมมาจากช่วงทศวรรษ 1940 ที่ตอนนั้นชาติสมาชิกถูกบังคับให้ชำระเงินด้วยทองคำจำนวนร้อยละ 25 ของโควตาที่ได้รับ ซึ่งจริง ๆ แล้วจนกระทั่งถึงปี 1970 นั้นถือเป็นเรื่องปกติมาก ๆ ที่ชาติสมาชิก “จะชำระดอกเบี้ยเงินกู้ IMF ด้วยทองคำ”
เมื่อประธานาธิบดีริชาร์ด นิกสันยุติการใช้มาตรฐานทองคำอย่างเป็นทางการในปี 1971 ทาง IMF ก็ไม่ได้ขายทองคำสำรองของพวกเขาออกไป แต่ถึงกระนั้น การพยายามจะตรึงค่าเงินเข้ากับทองคำของชาติสมาชิกใด ๆ กลับถูกสั่งห้ามเสียอย่างนั้น...
⚡️ กด Zap ที่ลิงก์นี้ เพื่อเป็นกำลังใจทีมงานผู้เรียบเรียงบทความ
(ทุกยอด zap จะถูกแบ่งอัตโนมัติเข้าวอลเล็ทของผู้เขียนบทความต้นฉบับภาษาอังกฤษ, ผู้แปลดราฟต์ 1, ผู้เรียบเรียงดราฟต์ 2-3, กองบรรณาธิการและพิสูจน์อักษรจากไรท์ชิฟต์ พร้อมกันบางส่วนไว้เพื่อเป็นค่าธรรมเนียมธุรกรรม)
