-
 @ 42342239:1d80db24
2024-04-05 08:21:50
@ 42342239:1d80db24
2024-04-05 08:21:50Trust is a topic increasingly being discussed. Whether it is trust in each other, in the media, or in our authorities, trust is generally seen as a cornerstone of a strong and well-functioning society. The topic was also the theme of the World Economic Forum at its annual meeting in Davos earlier this year. Even among central bank economists, the subject is becoming more prevalent. Last year, Agustín Carstens, head of the BIS ("the central bank of central banks"), said that "[w]ith trust, the public will be more willing to accept actions that involve short-term costs in exchange for long-term benefits" and that "trust is vital for policy effectiveness".
It is therefore interesting when central banks or others pretend as if nothing has happened even when trust has been shattered.
Just as in Sweden and in hundreds of other countries, Canada is planning to introduce a central bank digital currency (CBDC), a new form of money where the central bank or its intermediaries (the banks) will have complete insight into citizens' transactions. Payments or money could also be made programmable. Everything from transferring ownership of a car automatically after a successful payment to the seller, to payments being denied if you have traveled too far from home.
"If Canadians decide a digital dollar is necessary, our obligation is to be ready" says Carolyn Rogers, Deputy Head of Bank of Canada, in a statement shared in an article.
So, what do the citizens want? According to a report from the Bank of Canada, a whopping 88% of those surveyed believe that the central bank should refrain from developing such a currency. About the same number (87%) believe that authorities should guarantee the opportunity to pay with cash instead. And nearly four out of five people (78%) do not believe that the central bank will care about people's opinions. What about trust again?
Canadians' likely remember the Trudeau government's actions against the "Freedom Convoy". The Freedom Convoy consisted of, among others, truck drivers protesting the country's strict pandemic policies, blocking roads in the capital Ottawa at the beginning of 2022. The government invoked never-before-used emergency measures to, among other things, "freeze" people's bank accounts. Suddenly, truck drivers and those with a "connection" to the protests were unable to pay their electricity bills or insurances, for instance. Superficially, this may not sound so serious, but ultimately, it could mean that their families end up in cold houses (due to electricity being cut off) and that they lose the ability to work (driving uninsured vehicles is not taken lightly). And this applied not only to the truck drivers but also to those with a "connection" to the protests. No court rulings were required.
Without the freedom to pay for goods and services, i.e. the freedom to transact, one has no real freedom at all, as several participants in the protests experienced.
In January of this year, a federal judge concluded that the government's actions two years ago were unlawful when it invoked the emergency measures. The use did not display "features of rationality - motivation, transparency, and intelligibility - and was not justified in relation to the relevant factual and legal limitations that had to be considered". He also argued that the use was not in line with the constitution. There are also reports alleging that the government fabricated evidence to go after the demonstrators. The case is set to continue to the highest court. Prime Minister Justin Trudeau and Finance Minister Chrystia Freeland have also recently been sued for the government's actions.
The Trudeau government's use of emergency measures two years ago sadly only provides a glimpse of what the future may hold if CBDCs or similar systems replace the current monetary system with commercial bank money and cash. In Canada, citizens do not want the central bank to proceed with the development of a CBDC. In canada, citizens in Canada want to strengthen the role of cash. In Canada, citizens suspect that the central bank will not listen to them. All while the central bank feverishly continues working on the new system...
"Trust is vital", said Agustín Carstens. But if policy-makers do not pause for a thoughtful reflection even when trust has been utterly shattered as is the case in Canada, are we then not merely dealing with lip service?
And how much trust do these policy-makers then deserve?
-
 @ 42342239:1d80db24
2024-03-31 11:23:36
@ 42342239:1d80db24
2024-03-31 11:23:36Biologist Stuart Kauffman introduced the concept of the "adjacent possible" in evolutionary biology in 1996. A bacterium cannot suddenly transform into a flamingo; rather, it must rely on small exploratory changes (of the "adjacent possible") if it is ever to become a beautiful pink flying creature. The same principle applies to human societies, all of which exemplify complex systems. It is indeed challenging to transform shivering cave-dwellers into a space travelers without numerous intermediate steps.
Imagine a water wheel – in itself, perhaps not such a remarkable invention. Yet the water wheel transformed the hard-to-use energy of water into easily exploitable rotational energy. A little of the "adjacent possible" had now been explored: water mills, hammer forges, sawmills, and textile factories soon emerged. People who had previously ground by hand or threshed with the help of oxen could now spend their time on other things. The principles of the water wheel also formed the basis for wind power. Yes, a multitude of possibilities arose – reminiscent of the rapid development during the Cambrian explosion. When the inventors of bygone times constructed humanity's first water wheel, they thus expanded the "adjacent possible". Surely, the experts of old likely sought swift prohibitions. Not long ago, our expert class claimed that the internet was going to be a passing fad, or that it would only have the same modest impact on the economy as the fax machine. For what it's worth, there were even attempts to ban the number zero back in the days.
The pseudonymous creator of Bitcoin, Satoshi Nakamoto, wrote in Bitcoin's whitepaper that "[w]e have proposed a system for electronic transactions without relying on trust." The Bitcoin system enables participants to agree on what is true without needing to trust each other, something that has never been possible before. In light of this, it is worth noting that trust in the federal government in the USA is among the lowest levels measured in almost 70 years. Trust in media is at record lows. Moreover, in countries like the USA, the proportion of people who believe that one can trust "most people" has decreased significantly. "Rebuilding trust" was even the theme of the World Economic Forum at its annual meeting. It is evident, even in the international context, that trust between countries is not at its peak.
Over a fifteen-year period, Bitcoin has enabled electronic transactions without its participants needing to rely on a central authority, or even on each other. This may not sound like a particularly remarkable invention in itself. But like the water wheel, one must acknowledge that new potential seems to have been put in place, potential that is just beginning to be explored. Kauffman's "adjacent possible" has expanded. And despite dogmatic statements to the contrary, no one can know for sure where this might lead.
The discussion of Bitcoin or crypto currencies would benefit from greater humility and openness, not only from employees or CEOs of money laundering banks but also from forecast-failing central bank officials. When for instance Chinese Premier Zhou Enlai in the 1970s was asked about the effects of the French Revolution, he responded that it was "too early to say" - a far wiser answer than the categorical response of the bureaucratic class. Isn't exploring systems not based on trust is exactly what we need at this juncture?
-
 @ b12b632c:d9e1ff79
2024-03-23 16:42:49
@ b12b632c:d9e1ff79
2024-03-23 16:42:49CASHU AND ECASH ARE EXPERIMENTAL PROJECTS. BY THE OWN NATURE OF CASHU ECASH, IT'S REALLY EASY TO LOSE YOUR SATS BY LACKING OF KNOWLEDGE OF THE SYSTEM MECHANICS. PLEASE, FOR YOUR OWN GOOD, ALWAYS USE FEW SATS AMOUNT IN THE BEGINNING TO FULLY UNDERSTAND HOW WORKS THE SYSTEM. ECASH IS BASED ON A TRUST RELATIONSHIP BETWEEN YOU AND THE MINT OWNER, PLEASE DONT TRUST ECASH MINT YOU DONT KNOW. IT IS POSSIBLE TO GENERATE UNLIMITED ECASH TOKENS FROM A MINT, THE ONLY WAY TO VALIDATE THE REAL EXISTENCE OF THE ECASH TOKENS IS TO DO A MULTIMINT SWAP (BETWEEN MINTS). PLEASE, ALWAYS DO A MULTISWAP MINT IF YOU RECEIVE SOME ECASH FROM SOMEONE YOU DON'T KNOW/TRUST. NEVER TRUST A MINT YOU DONT KNOW!
IF YOU WANT TO RUN AN ECASH MINT WITH A BTC LIGHTNING NODE IN BACK-END, PLEASE DEDICATE THIS LN NODE TO YOUR ECASH MINT. A BAD MANAGEMENT OF YOUR LN NODE COULD LET PEOPLE TO LOOSE THEIR SATS BECAUSE THEY HAD ONCE TRUSTED YOUR MINT AND YOU DID NOT MANAGE THE THINGS RIGHT.

What's ecash/Cashu ?
I recently listened a passionnating interview from calle 👁️⚡👁 invited by the podcast channel What Bitcoin Did about the new (not so much now) Cashu protocol.
Cashu is a a free and open-source Chaumian ecash project built for Bitcoin protocol, recently created in order to let users send/receive Ecash over BTC Lightning network. The main Cashu ecash goal is to finally give you a "by-design" privacy mechanism to allow us to do anonymous Bitcoin transactions.
Ecash for your privacy.\ A Cashu mint does not know who you are, what your balance is, or who you're transacting with. Users of a mint can exchange ecash privately without anyone being able to know who the involved parties are. Bitcoin payments are executed without anyone able to censor specific users.
Here are some useful links to begin with Cashu ecash :
Github repo: https://github.com/cashubtc
Documentation: https://docs.cashu.space
To support the project: https://docs.cashu.space/contribute
A Proof of Liabilities Scheme for Ecash Mints: https://gist.github.com/callebtc/ed5228d1d8cbaade0104db5d1cf63939
Like NOSTR and its own NIPS, here is the list of the Cashu ecash NUTs (Notation, Usage, and Terminology): https://github.com/cashubtc/nuts?tab=readme-ov-file
I won't explain you at lot more on what's Casu ecash, you need to figured out by yourself. It's really important in order to avoid any mistakes you could do with your sats (that you'll probably regret).
If you don't have so much time, you can check their FAQ right here: https://docs.cashu.space/faq
I strongly advise you to listen Calle's interviews @whatbbitcoindid to "fully" understand the concept and the Cashu ecash mechanism before using it:
Scaling Bitcoin Privacy with Calle
In the meantime I'm writing this article, Calle did another really interesting interview with ODELL from CitadelDispatch:
CD120: BITCOIN POWERED CHAUMIAN ECASH WITH CALLE
Which ecash apps?
There are several ways to send/receive some Ecash tokens, you can do it by using mobile applications like eNuts, Minibits or by using Web applications like Cashu.me, Nustrache or even npub.cash. On these topics, BTC Session Youtube channel offers high quality contents and very easy to understand key knowledge on how to use these applications :
Minibits BTC Wallet: Near Perfect Privacy and Low Fees - FULL TUTORIAL
Cashu Tutorial - Chaumian Ecash On Bitcoin
Unlock Perfect Privacy with eNuts: Instant, Free Bitcoin Transactions Tutorial
Cashu ecash is a very large and complex topic for beginners. I'm still learning everyday how it works and the project moves really fast due to its commited developpers community. Don't forget to follow their updates on Nostr to know more about the project but also to have a better undertanding of the Cashu ecash technical and political implications.
There is also a Matrix chat available if you want to participate to the project:
https://matrix.to/#/#cashu:matrix.org
How to self-host your ecash mint with Nutshell
Cashu Nutshell is a Chaumian Ecash wallet and mint for Bitcoin Lightning. Cashu Nutshell is the reference implementation in Python.
Github repo:
https://github.com/cashubtc/nutshell
Today, Nutshell is the most advanced mint in town to self-host your ecash mint. The installation is relatively straightforward with Docker because a docker-compose file is available from the github repo.
Nutshell is not the only cashu ecash mint server available, you can check other server mint here :
https://docs.cashu.space/mints
The only "external" requirement is to have a funding source. One back-end funding source where ecash will mint your ecash from your Sats and initiate BTC Lightning Netwok transactions between ecash mints and BTC Ligtning nodes during a multimint swap. Current backend sources supported are: FakeWallet*, LndRestWallet, CoreLightningRestWallet, BlinkWallet, LNbitsWallet, StrikeUSDWallet.
*FakeWallet is able to generate unlimited ecash tokens. Please use it carefully, ecash tokens issued by the FakeWallet can be sent and accepted as legit ecash tokens to other people ecash wallets if they trust your mint. In the other way, if someone send you 2,3M ecash tokens, please don't trust the mint in the first place. You need to force a multimint swap with a BTC LN transaction. If that fails, someone has maybe tried to fool you.
I used a Voltage.cloud BTC LN node instance to back-end my Nutshell ecash mint:
SPOILER: my nutshell mint is working but I have an error message "insufficient balance" when I ask a multiswap mint from wallet.cashu.me or the eNuts application. In order to make it work, I need to add some Sats liquidity (I can't right now) to the node and open few channels with good balance capacity. If you don't have an ecash mint capable of doig multiswap mint, you'll only be able to mint ecash into your ecash mint and send ecash tokens to people trusting your mint. It's working, yes, but you need to be able to do some mutiminit swap if you/everyone want to fully profit of the ecash system.
Once you created your account and you got your node, you need to git clone the Nutshell github repo:
git clone https://github.com/cashubtc/nutshell.gitYou next need to update the docker compose file with your own settings. You can comment the wallet container if you don't need it.
To generate a private key for your node, you can use this openssl command
openssl rand -hex 32 054de2a00a1d8e3038b30e96d26979761315cf48395aa45d866aeef358c91dd1The CLI Cashu wallet is not needed right now but I'll show you how to use it in the end of this article. Feel free to comment it or not.
``` version: "3" services: mint: build: context: . dockerfile: Dockerfile container_name: mint
ports:
- "3338:3338"
environment:- DEBUG=TRUE
- LOG_LEVEL=DEBUG
- MINT_URL=https://YourMintURL - MINT_HOST=YourMintDomain.tld - MINT_LISTEN_HOST=0.0.0.0 - MINT_LISTEN_PORT=3338 - MINT_PRIVATE_KEY=YourPrivateKeyFromOpenSSL - MINT_INFO_NAME=YourMintInfoName - MINT_INFO_DESCRIPTION=YourShortInfoDesc - MINT_INFO_DESCRIPTION_LONG=YourLongInfoDesc - MINT_LIGHTNING_BACKEND=LndRestWallet #- MINT_LIGHTNING_BACKEND=FakeWallet - MINT_INFO_CONTACT=[["email","YourConctact@email"], ["twitter","@YourTwitter"], ["nostr", "YourNPUB"]] - MINT_INFO_MOTD=Thanks for using my mint! - MINT_LND_REST_ENDPOINT=https://YourVoltageNodeDomain:8080 - MINT_LND_REST_MACAROON=YourDefaultAdminMacaroonBase64 - MINT_MAX_PEG_IN=100000 - MINT_MAX_PEG_OUT=100000 - MINT_PEG_OUT_ONLY=FALSE command: ["poetry", "run", "mint"]wallet-voltage: build: context: . dockerfile: Dockerfile container_name: wallet-voltage
ports:
- "4448:4448"
depends_on: - nutshell-voltage environment:- DEBUG=TRUE
- MINT_URL=http://nutshell-voltage:3338
- API_HOST=0.0.0.0 command: ["poetry", "run", "cashu", "-d"]```
To build, run and see the container logs:
docker compose up -d && docker logs -f mint0.15.1 2024-03-22 14:45:45.490 | WARNING | cashu.lightning.lndrest:__init__:49 - no certificate for lndrest provided, this only works if you have a publicly issued certificate 2024-03-22 14:45:45.557 | INFO | cashu.core.db:__init__:135 - Creating database directory: data/mint 2024-03-22 14:45:45.68 | INFO | Started server process [1] 2024-03-22 14:45:45.69 | INFO | Waiting for application startup. 2024-03-22 14:45:46.12 | INFO | Loaded 0 keysets from database. 2024-03-22 14:45:46.37 | INFO | Current keyset: 003dba9e589023f1 2024-03-22 14:45:46.37 | INFO | Using LndRestWallet backend for method: 'bolt11' and unit: 'sat' 2024-03-22 14:45:46.97 | INFO | Backend balance: 1825000 sat 2024-03-22 14:45:46.97 | INFO | Data dir: /root/.cashu 2024-03-22 14:45:46.97 | INFO | Mint started. 2024-03-22 14:45:46.97 | INFO | Application startup complete. 2024-03-22 14:45:46.98 | INFO | Uvicorn running on http://0.0.0.0:3338 (Press CTRL+C to quit) 2024-03-22 14:45:47.27 | INFO | 172.19.0.22:48528 - "GET /v1/keys HTTP/1.1" 200 2024-03-22 14:45:47.34 | INFO | 172.19.0.22:48544 - "GET /v1/keysets HTTP/1.1" 200 2024-03-22 14:45:47.38 | INFO | 172.19.0.22:48552 - "GET /v1/info HTTP/1.1" 200If you see the line :
Uvicorn running on http://0.0.0.0:3338 (Press CTRL+C to quit)Nutshell is well started.
I won't explain here how to create a reverse proxy to Nutshell, you can find how to do it into my previous article. Here is the reverse proxy config into Nginx Proxy Manager:
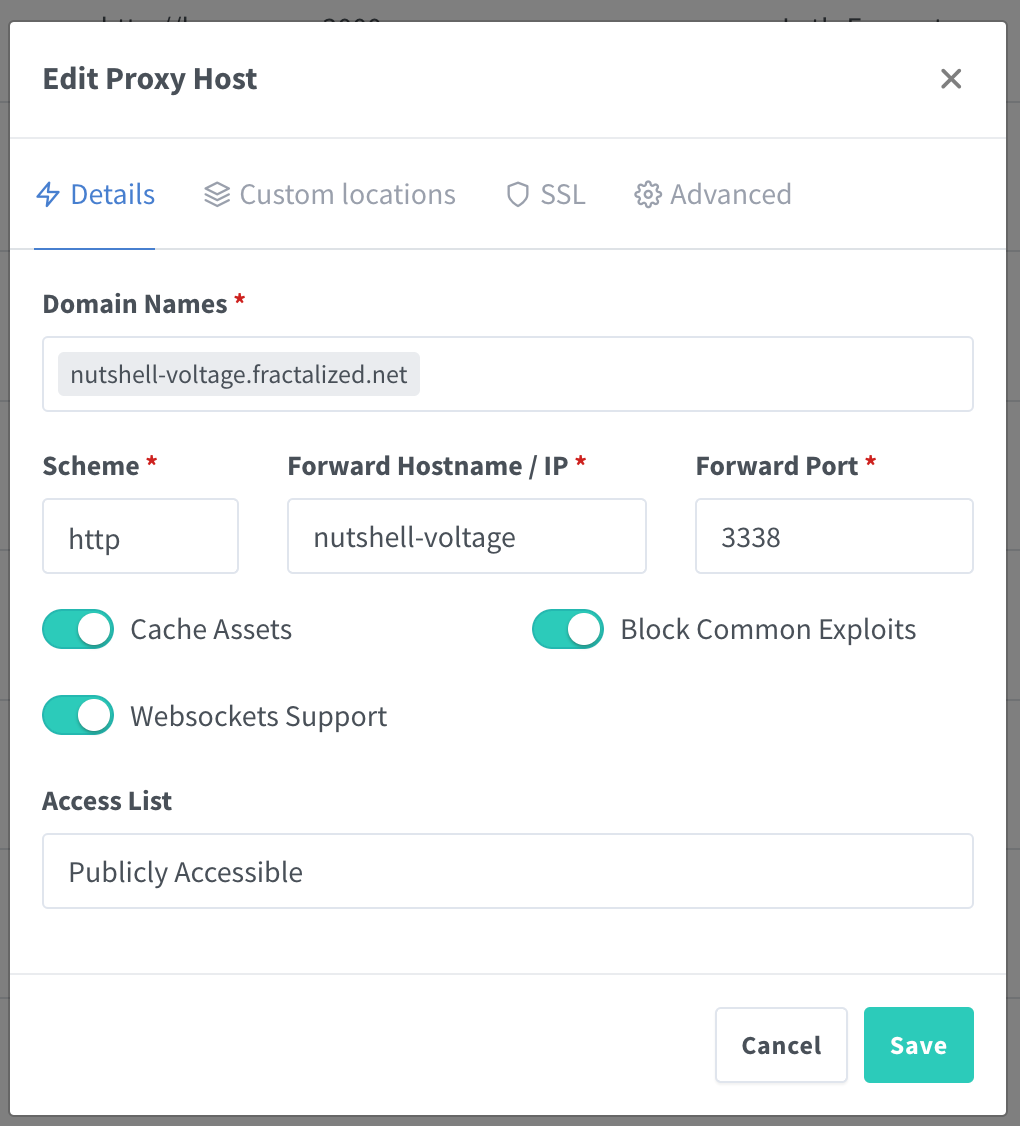
If everything is well configured and if you go on your mint url (https://yourminturl) you shoud see this:
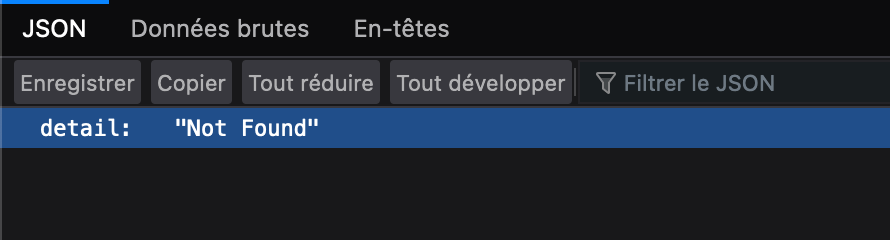
It's not helping a lot because at first glance it seems to be not working but it is. You can also check these URL path to confirm :
- https://yourminturl/keys and https://yourminturl/keysets
or
- https://yourminturl/v1/keys and https://yourminturl/v1/keysets
Depending of the moment when you read this article, the first URLs path might have been migrated to V1. Here is why:
https://github.com/cashubtc/nuts/pull/55
The final test is to add your mint to your prefered ecash wallets.
SPOILER: AT THIS POINT, YOU SHOUD KNOW THAT IF YOU RESET YOUR LOCAL BROWSER INTERNET CACHE FILE, YOU'LL LOSE YOUR MINTED ECASH TOKENS. IF NOT, PLEASE READ THE DOCUMENTATION AGAIN.
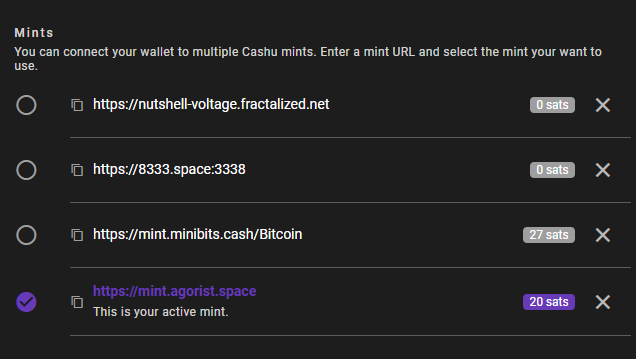
For instace, if we use wallet.cashu.me:
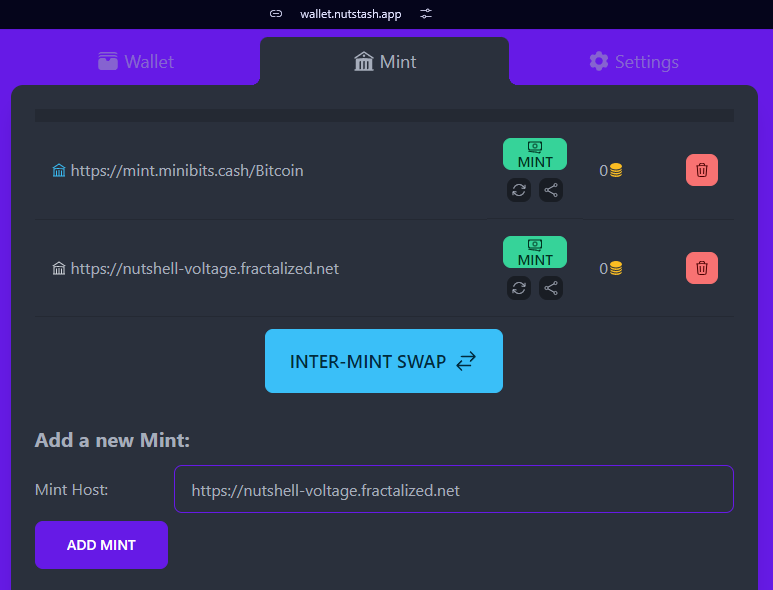
You can go into the "Settings" tab and add your mint :
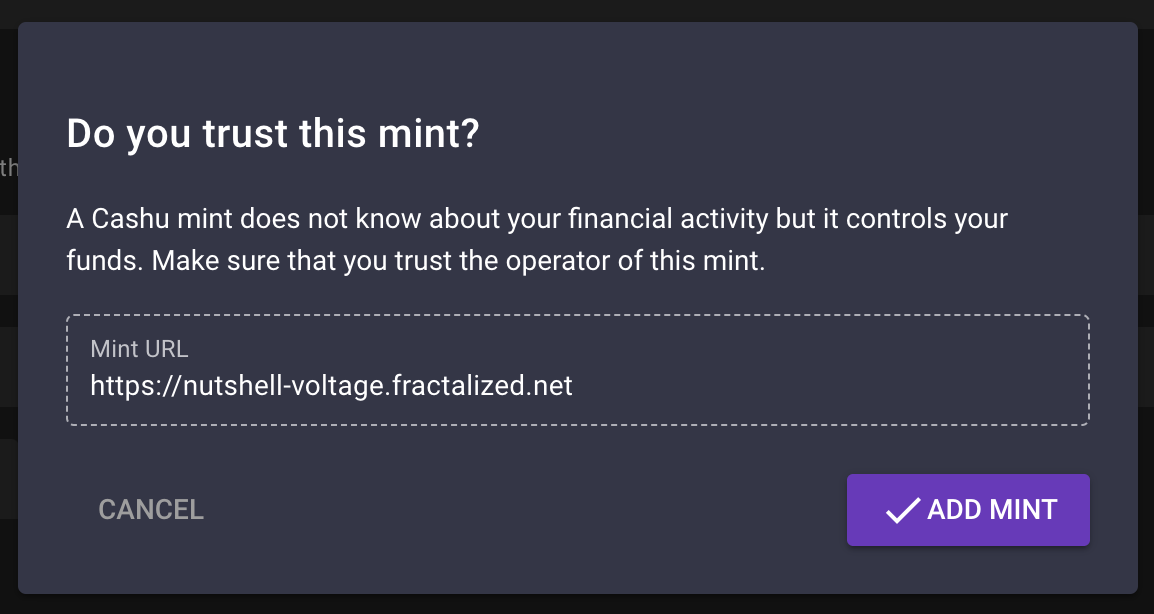
If everything went find, you shoud see this :
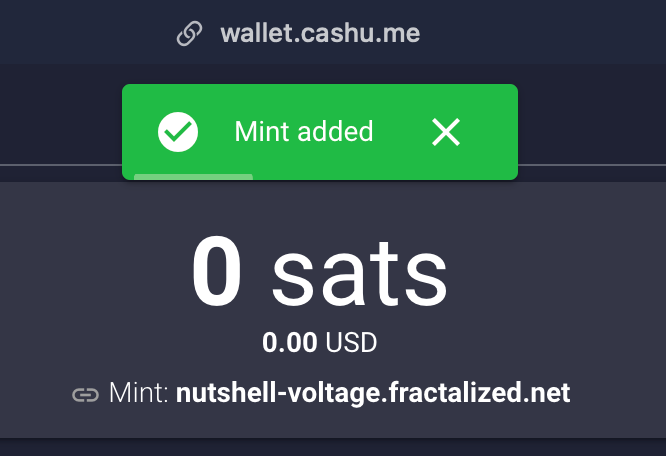
You can now mint some ecash from your mint creating a sats invoice :
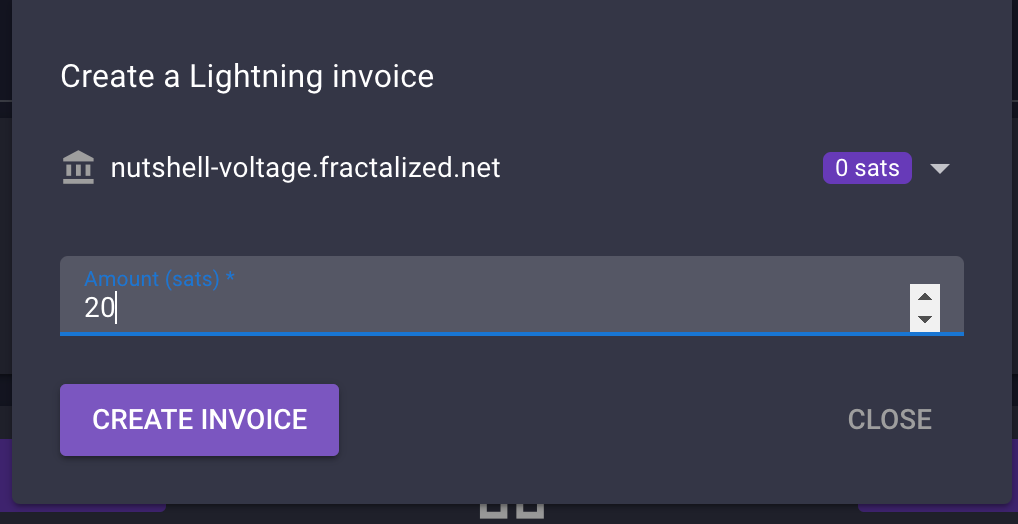
You can now scan the QR diplayed with your prefered BTC LN wallet. If everything is OK, you should receive the funds:
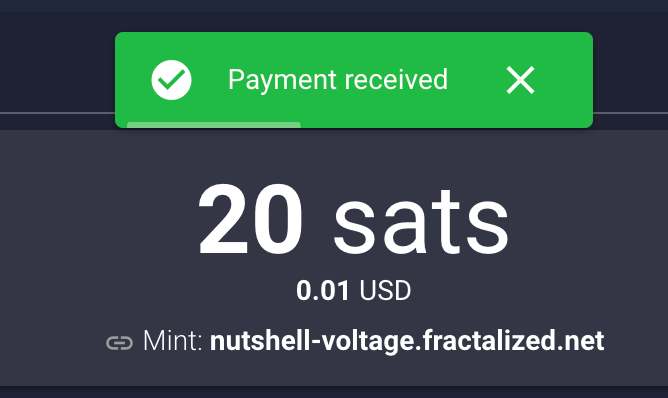
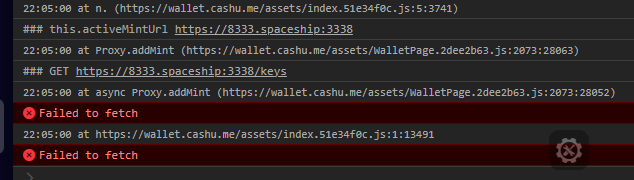
It may happen that some error popup sometimes. If you are curious and you want to know what happened, Cashu wallet has a debug console you can activate by clicking on the "Settings" page and "OPEN DEBUG TERMINAL". A little gear icon will be displayed in the bottom of the screen. You can click on it, go to settings and enable "Auto Display If Error Occurs" and "Display Extra Information". After enabling this setting, you can close the popup windows and let the gear icon enabled. If any error comes, this windows will open again and show you thé error:
Now that you have some sats in your balance, you can try to send some ecash. Open in a new windows another ecash wallet like Nutstach for instance.
Add your mint again :
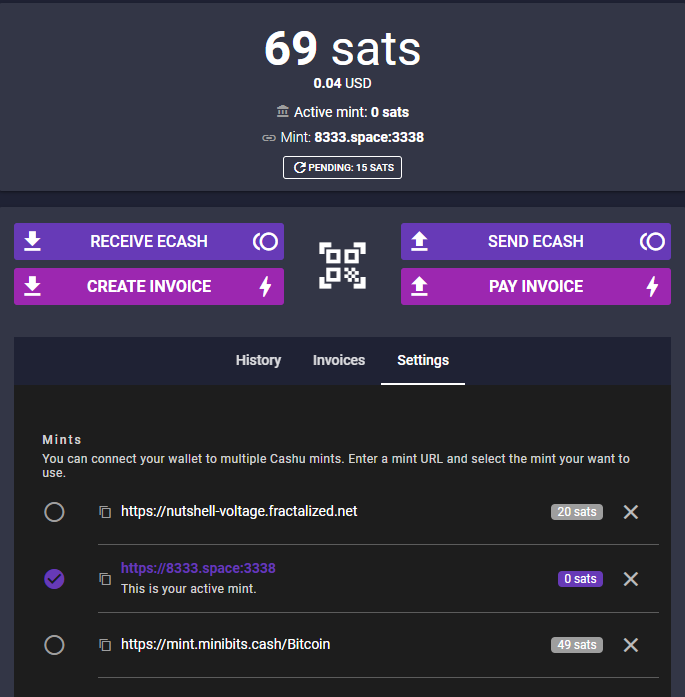
Return on Cashu wallet. The ecash token amount you see on the Cashu wallet home page is a total of all the ecash tokens you have on all mint connected.
Next, click on "Send ecach". Insert the amout of ecash you want to transfer to your other wallet. You can select the wallet where you want to extract the funds by click on the little arrow near the sats funds you currenly selected :


Click now on "SEND TOKENS". That will open you a popup with a QR code and a code CONTAINING YOUR ECASH TOKENS (really).

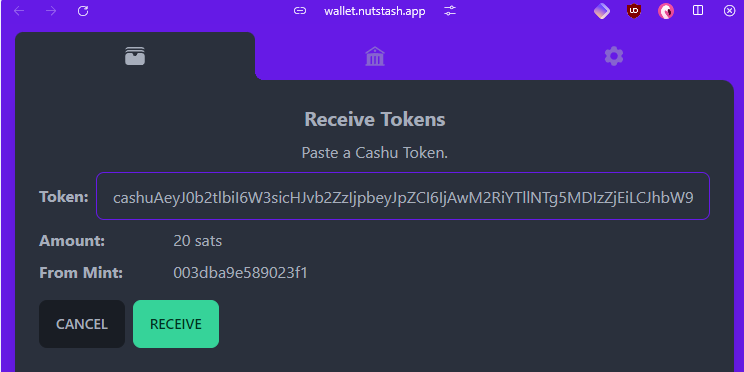
You can now return on nutstach, click on the "Receive" button and paste the code you get from Cashu wallet:
Click on "RECEIVE" again:
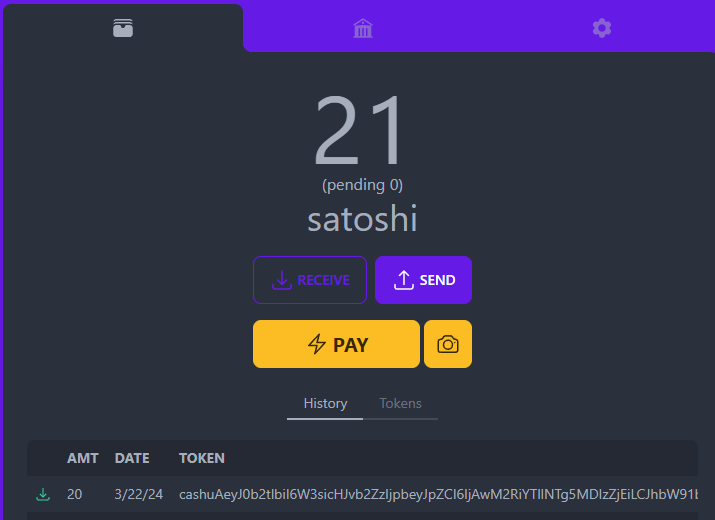
Congrats, you transfered your first ecash tokens to yourself ! 🥜⚡
You may need some time to transfer your ecash tokens between your wallets and your mint, there is a functionality existing for that called "Multimint swaps".
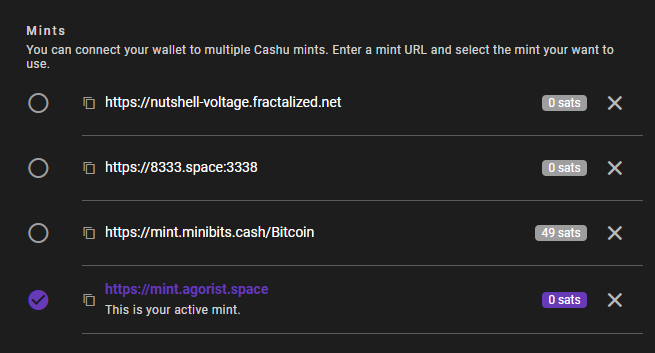
Before that, if you need new mints, you can check the very new website Bitcoinmints.com that let you see the existing ecash mints and rating :
Don't forget, choose your mint carefuly because you don't know who's behind.
Let's take a mint and add it to our Cashu wallet:
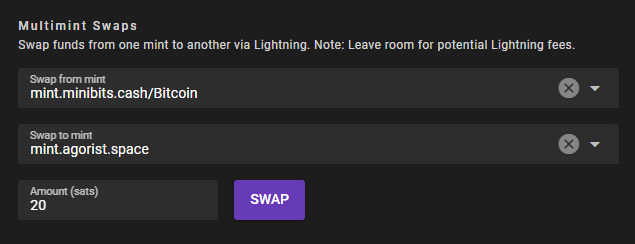
If you want to transfer let's say 20 sats from minibits mint to bitcointxoko mint, go just bottom into the "Multimint swap" section. Select the mint into "Swap from mint", the mint into "Swap to mint" and click on "SWAP" :
A popup window will appear and will request the ecash tokens from the source mint. It will automatically request the ecash amount via a Lightning node transaction and add the fund to your other wallet in the target mint. As it's a Lightning Network transaction, you can expect some little fees.
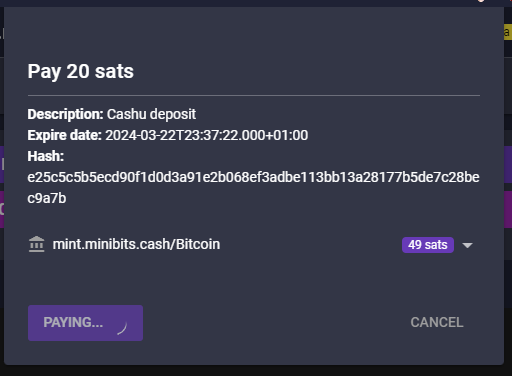
If everything is OK with the mints, the swap will be successful and the ecash received.
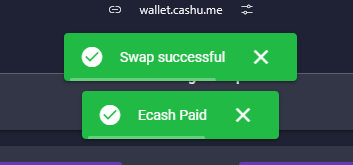
You can now see that the previous sats has been transfered (minus 2 fee sats).
Well done, you did your first multimint swap ! 🥜⚡
One last thing interresting is you can also use CLI ecash wallet. If you created the wallet contained in the docker compose, the container should be running.
Here are some commands you can do.
To verify which mint is currently connected :
``` docker exec -it wallet-voltage poetry run cashu info
2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat Version: 0.15.1 Wallet: wallet Debug: True Cashu dir: /root/.cashu Mints: - https://nutshell-voltage.fractalized.net ```
To verify your balance :
``` docker exec -it wallet-voltage poetry run cashu balance
2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat Balance: 0 sat ```
To create an sats invoice to have ecash :
``` docker exec -it wallet-voltage poetry run cashu invoice 20
2024-03-22 22:00:59.12 | DEBUG | cashu.wallet.wallet:_load_mint_info:275 | Mint info: name='nutshell.fractalized.net' pubkey='02008469922e985cbc5368ce16adb6ed1aaea0f9ecb21639db4ded2e2ae014a326' version='Nutshell/0.15.1' description='Official Fractalized Mint' description_long='TRUST THE MINT' contact=[['email', 'pastagringo@fractalized.net'], ['twitter', '@pastagringo'], ['nostr', 'npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2']] motd='Thanks for using official ecash fractalized mint!' nuts={4: {'methods': [['bolt11', 'sat']], 'disabled': False}, 5: {'methods': [['bolt11', 'sat']], 'disabled': False}, 7: {'supported': True}, 8: {'supported': True}, 9: {'supported': True}, 10: {'supported': True}, 11: {'supported': True}, 12: {'supported': True}} Balance: 0 sat
Pay invoice to mint 20 sat:
Invoice: lnbc200n1pjlmlumpp5qh68cqlr2afukv9z2zpna3cwa3a0nvla7yuakq7jjqyu7g6y69uqdqqcqzzsxqyz5vqsp5zymmllsqwd40xhmpu76v4r9qq3wcdth93xthrrvt4z5ct3cf69vs9qyyssqcqppurrt5uqap4nggu5tvmrlmqs5guzpy7jgzz8szckx9tug4kr58t4avv4a6437g7542084c6vkvul0ln4uus7yj87rr79qztqldggq0cdfpy
You can use this command to check the invoice: cashu invoice 20 --id 2uVWELhnpFcNeFZj6fWzHjZuIipqyj5R8kM7ZJ9_
Checking invoice .................2024-03-22 22:03:25.27 | DEBUG | cashu.wallet.wallet:verify_proofs_dleq:1103 | Verified incoming DLEQ proofs. Invoice paid.
Balance: 20 sat ```
To pay an invoice by pasting the invoice you received by your or other people :
``` docker exec -it wallet-voltage poetry run cashu pay lnbc150n1pjluqzhpp5rjezkdtt8rjth4vqsvm50xwxtelxjvkq90lf9tu2thsv2kcqe6vqdq2f38xy6t5wvcqzzsxqrpcgsp58q9sqkpu0c6s8hq5pey8ls863xmjykkumxnd8hff3q4fvxzyh0ys9qyyssq26ytxay6up54useezjgqm3cxxljvqw5vq2e94ru7ytqc0al74hr4nt5cwpuysgyq8u25xx5la43mx4ralf3mq2425xmvhjzvwzqp54gp0e3t8e
2024-03-22 22:04:37.23 | DEBUG | cashu.wallet.wallet:_load_mint_info:275 | Mint info: name='nutshell.fractalized.net' pubkey='02008469922e985cbc5368ce16adb6ed1aaea0f9ecb21639db4ded2e2ae014a326' version='Nutshell/0.15.1' description='Official Fractalized Mint' description_long='TRUST THE MINT' contact=[['email', 'pastagringo@fractalized.net'], ['twitter', '@pastagringo'], ['nostr', 'npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2']] motd='Thanks for using official ecash fractalized mint!' nuts={4: {'methods': [['bolt11', 'sat']], 'disabled': False}, 5: {'methods': [['bolt11', 'sat']], 'disabled': False}, 7: {'supported': True}, 8: {'supported': True}, 9: {'supported': True}, 10: {'supported': True}, 11: {'supported': True}, 12: {'supported': True}} Balance: 20 sat 2024-03-22 22:04:37.45 | DEBUG | cashu.wallet.wallet:get_pay_amount_with_fees:1529 | Mint wants 0 sat as fee reserve. 2024-03-22 22:04:37.45 | DEBUG | cashu.wallet.cli.cli:pay:189 | Quote: quote='YpNkb5f6WVT_5ivfQN1OnPDwdHwa_VhfbeKKbBAB' amount=15 fee_reserve=0 paid=False expiry=1711146847 Pay 15 sat? [Y/n]: y Paying Lightning invoice ...2024-03-22 22:04:41.13 | DEBUG | cashu.wallet.wallet:split:613 | Calling split. POST /v1/swap 2024-03-22 22:04:41.21 | DEBUG | cashu.wallet.wallet:verify_proofs_dleq:1103 | Verified incoming DLEQ proofs. Error paying invoice: Mint Error: Lightning payment unsuccessful. insufficient_balance (Code: 20000) ```
It didn't work, yes. That's the thing I told you earlier but it would work with a well configured and balanced Lightning Node.
That's all ! You should now be able to use ecash as you want! 🥜⚡
See you on NOSTR! 🤖⚡\ PastaGringo
-
 @ ee11a5df:b76c4e49
2024-03-22 23:49:09
@ ee11a5df:b76c4e49
2024-03-22 23:49:09Implementing The Gossip Model
version 2 (2024-03-23)
Introduction
History
The gossip model is a general concept that allows clients to dynamically follow the content of people, without specifying which relay. The clients have to figure out where each person puts their content.
Before NIP-65, the gossip client did this in multiple ways:
- Checking kind-3 contents, which had relay lists for configuring some clients (originally Astral and Damus), and recognizing that wherever they were writing our client could read from.
- NIP-05 specifying a list of relays in the
nostr.jsonfile. I added this to NIP-35 which got merged down into NIP-05. - Recommended relay URLs that are found in 'p' tags
- Users manually making the association
- History of where events happen to have been found. Whenever an event came in, we associated the author with the relay.
Each of these associations were given a score (recommended relay urls are 3rd party info so they got a low score).
Later, NIP-65 made a new kind of relay list where someone could advertise to others which relays they use. The flag "write" is now called an OUTBOX, and the flag "read" is now called an INBOX.
The idea of inboxes came about during the development of NIP-65. They are a way to send an event to a person to make sure they get it... because putting it on your own OUTBOX doesn't guarantee they will read it -- they may not follow you.
The outbox model is the use of NIP-65. It is a subset of the gossip model which uses every other resource at it's disposal.
Rationale
The gossip model keeps nostr decentralized. If all the (major) clients were using it, people could spin up small relays for both INBOX and OUTBOX and still be fully connected, have their posts read, and get replies and DMs. This is not to say that many people should spin up small relays. But the task of being decentralized necessitates that people must be able to spin up their own relay in case everybody else is censoring them. We must make it possible. In reality, congregating around 30 or so popular relays as we do today is not a problem. Not until somebody becomes very unpopular with bitcoiners (it will probably be a shitcoiner), and then that person is going to need to leave those popular relays and that person shouldn't lose their followers or connectivity in any way when they do.
A lot more rationale has been discussed elsewhere and right now I want to move on to implementation advice.
Implementation Advice
Read NIP-65
NIP-65 will contain great advice on which relays to consult for which purposes. This post does not supersede NIP-65. NIP-65 may be getting some smallish changes, mostly the addition of a private inbox for DMs, but also changes to whether you should read or write to just some or all of a set of relays.
How often to fetch kind-10002 relay lists for someone
This is up to you. Refreshing them every hour seems reasonable to me. Keeping track of when you last checked so you can check again every hour is a good idea.
Where to fetch events from
If your user follows another user (call them jack), then you should fetch jack's events from jack's OUTBOX relays. I think it's a good idea to use 2 of those relays. If one of those choices fails (errors), then keep trying until you get 2 of them that worked. This gives some redundancy in case one of them is censoring. You can bump that number up to 3 or 4, but more than that is probably just wasting bandwidth.
To find events tagging your user, look in your user's INBOX relays for those. In this case, look into all of them because some clients will only write to some of them (even though that is no longer advised).
Picking relays dynamically
Since your user follows many other users, it is very useful to find a small subset of all of their OUTBOX relays that cover everybody followed. I wrote some code to do this as (it is used by gossip) that you can look at for an example.
Where to post events to
Post all events (except DMs) to all of your users OUTBOX relays. Also post the events to all the INBOX relays of anybody that was tagged or mentioned in the contents in a nostr bech32 link (if desired). That way all these mentioned people are aware of the reply (or quote or repost).
DMs should be posted only to INBOX relays (in the future, to PRIVATE INBOX relays). You should post it to your own INBOX relays also, because you'll want a record of the conversation. In this way, you can see all your DMs inbound and outbound at your INBOX relay.
Where to publish your user's kind-10002 event to
This event was designed to be small and not require moderation, plus it is replaceable so there is only one per user. For this reason, at the moment, just spread it around to lots of relays especially the most popular relays.
For example, the gossip client automatically determines which relays to publish to based on whether they seem to be working (several hundred) and does so in batches of 10.
How to find replies
If all clients used the gossip model, you could find all the replies to any post in the author's INBOX relays for any event with an 'e' tag tagging the event you want replies to... because gossip model clients will publish them there.
But given the non-gossip-model clients, you should also look where the event was seen and look on those relays too.
Clobbering issues
Please read your users kind 10002 event before clobbering it. You should look many places to make sure you didn't miss the newest one.
If the old relay list had tags you don't understand (e.g. neither "read" nor "write"), then preserve them.
How users should pick relays
Today, nostr relays are not uniform. They have all kinds of different rule-sets and purposes. We severely lack a way to advice non-technical users as to which relays make good OUTBOX relays and which ones make good INBOX relays. But you are a dev, you can figure that out pretty well. For example, INBOX relays must accept notes from anyone meaning they can't be paid-subscription relays.
Bandwidth isn't a big issue
The outbox model doesn't require excessive bandwidth when done right. You shouldn't be downloading the same note many times... only 2-4 times depending on the level of redundancy your user wants.
Downloading 1000 events from 100 relays is in theory the same amount of data as downloading 1000 events from 1 relay.
But in practice, due to redundancy concerns, you will end up downloading 2000-3000 events from those 100 relays instead of just the 1000 you would in a single relay situation. Remember, per person followed, you will only ask for their events from 2-4 relays, not from all 100 relays!!!
Also in practice, the cost of opening and maintaining 100 network connections is more than the cost of opening and maintaining just 1. But this isn't usually a big deal unless...
Crypto overhead on Low-Power Clients
Verifying Schnorr signatures in the secp256k1 cryptosystem is not cheap. Setting up SSL key exchange is not cheap either. But most clients will do a lot more event signature validations than they will SSL setups.
For this reason, connecting to 50-100 relays is NOT hugely expensive for clients that are already verifying event signatures, as the number of events far surpasses the number of relay connections.
But for low-power clients that can't do event signature verification, there is a case for them not doing a lot of SSL setups either. Those clients would benefit from a different architecture, where half of the client was on a more powerful machine acting as a proxy for the low-power half of the client. These halves need to trust each other, so perhaps this isn't a good architecture for a business relationship, but I don't know what else to say about the low-power client situation.
Unsafe relays
Some people complain that the outbox model directs their client to relays that their user has not approved. I don't think it is a big deal, as such users can use VPNs or Tor if they need privacy. But for such users that still have concerns, they may wish to use clients that give them control over this. As a client developer you can choose whether to offer this feature or not.
The gossip client allows users to require whitelisting for connecting to new relays and for AUTHing to relays.
See Also
-
 @ 42342239:1d80db24
2024-03-21 09:49:01
@ 42342239:1d80db24
2024-03-21 09:49:01It has become increasingly evident that our financial system has started undermine our constitutionally guaranteed freedoms and rights. Payment giants like PayPal, Mastercard, and Visa sometimes block the ability to donate money. Individuals, companies, and associations lose bank accounts — or struggle to open new ones. In bank offices, people nowadays risk undergoing something resembling being cross-examined. The regulations are becoming so cumbersome that their mere presence risks tarnishing the banks' reputation.
The rules are so complex that even within the same bank, different compliance officers can provide different answers to the same question! There are even departments where some of the compliance officers are reluctant to provide written responses and prefer to answer questions over an unrecorded phone call. Last year's corporate lawyer in Sweden recently complained about troublesome bureaucracy, and that's from a the perspective of a very large corporation. We may not even fathom how smaller businesses — the keys to a nation's prosperity — experience it.
Where do all these rules come?
Where do all these rules come from, and how well do they work? Today's regulations on money laundering (AML) and customer due diligence (KYC - know your customer) primarily originate from a G7 meeting in the summer of 1989. (The G7 comprises the seven advanced economies: the USA, Canada, the UK, Germany, France, Italy, and Japan, along with the EU.) During that meeting, the intergovernmental organization FATF (Financial Action Task Force) was established with the aim of combating organized crime, especially drug trafficking. Since then, its mandate has expanded to include fighting money laundering, terrorist financing, and the financing of the proliferation of weapons of mass destruction(!). One might envisage the rules soon being aimed against proliferation of GPUs (Graphics Processing Units used for AI/ML). FATF, dominated by the USA, provides frameworks and recommendations for countries to follow. Despite its influence, the organization often goes unnoticed. Had you heard of it?
FATF offered countries "a deal they couldn't refuse"
On the advice of the USA and G7 countries, the organization decided to begin grading countries in "blacklists" and "grey lists" in 2000, naming countries that did not comply with its recommendations. The purpose was to apply "pressure" to these countries if they wanted to "retain their position in the global economy." The countries were offered a deal they couldn't refuse, and the number of member countries rapidly increased. Threatening with financial sanctions in this manner has even been referred to as "extraterritorial bullying." Some at the time even argued that the process violated international law.
If your local Financial Supervisory Authority (FSA) were to fail in enforcing compliance with FATF's many checklists among financial institutions, the risk of your country and its banks being barred from the US-dominated financial markets would loom large. This could have disastrous consequences.
A cost-benefit analysis of AML and KYC regulations
Economists use cost-benefit analysis to determine whether an action or a policy is successful. Let's see what such an analysis reveals.
What are the benefits (or revenues) after almost 35 years of more and more rules and regulations? The United Nations Office on Drugs and Crime estimated that only 0.2% of criminal proceeds are confiscated. Other estimates suggest a success rate from such anti-money laundering rules of 0.07% — a rounding error for organized crime. Europol expects to recover 1.2 billion euros annually, equivalent to about 1% of the revenue generated in the European drug market (110 billion euros). However, the percentage may be considerably lower, as the size of the drug market is likely underestimated. Moreover, there are many more "criminal industries" than just the drug trade; human trafficking is one example - there are many more. In other words, criminal organizations retain at least 99%, perhaps even 99.93%, of their profits, despite all cumbersome rules regarding money laundering and customer due diligence.
What constitutes the total cost of this bureaurcratic activity, costs that eventually burden taxpayers and households via higher fees? Within Europe, private financial firms are estimated to spend approximately 144 billion euros on compliance. According to some estimates, the global cost is twice as high, perhaps even eight times as much.
For Europe, the cost may thus be about 120 times (144/1.2) higher than the revenues from these measures. These "compliance costs" bizarrely exceed the total profits from the drug market, as one researcher put it. Even though the calculations are uncertain, it is challenging — perhaps impossible — to legitimize these regulations from a cost-benefit perspective.
But it doesn't end there, unfortunately. The cost of maintaining this compliance circus, with around 80 international organizations, thousands of authorities, far more employees, and all this across hundreds of countries, remains a mystery. But it's unlikely to be cheap.
The purpose of a system is what it does
In Economic Possibilities for our Grandchildren (1930), John Maynard Keynes foresaw that thanks to technological development, we could have had a 15-hour workweek by now. This has clearly not happened. Perhaps jobs have been created that are entirely meaningless? Anthropologist David Graeber argued precisely this in Bullshit Jobs in 2018. In that case, a significant number of people spend their entire working lives performing tasks they suspect deep down don't need to be done.
"The purpose of a system is what it does" is a heuristic coined by Stafford Beer. He observed there is "no point in claiming that the purpose of a system is to do what it constantly fails to do. What the current regulatory regime fails to do is combat criminal organizations. Nor does it seem to prevent banks from laundering money as never before, or from providing banking services to sex-offending traffickers
What the current regulatory regime does do, is: i) create armies of meaningless jobs, ii) thereby undermining mental health as well as economic prosperity, while iii) undermining our freedom and rights.
What does this say about the purpose of the system?
-
 @ ee11a5df:b76c4e49
2024-03-21 00:28:47
@ ee11a5df:b76c4e49
2024-03-21 00:28:47I'm glad to see more activity and discussion about the gossip model. Glad to see fiatjaf and Jack posting about it, as well as many developers pitching in in the replies. There are difficult problems we need to overcome, and finding notes while remaining decentralized without huge note copying overhead was just the first. While the gossip model (including the outbox model which is just the NIP-65 part) completely eliminates the need to copy notes around to lots of relays, and keeps us decentralized, it brings about it's own set of new problems. No community is ever of the same mind on any issue, and this issue is no different. We have a lot of divergent opinions. This note will be my updated thoughts on these topics.
COPYING TO CENTRAL RELAYS IS A NON-STARTER: The idea that you can configure your client to use a few popular "centralized" relays and everybody will copy notes into those central relays is a non-starter. It destroys the entire raison d'être of nostr. I've heard people say that more decentralization isn't our biggest issue. But decentralization is THE reason nostr exists at all, so we need to make sure we live up to the hype. Otherwise we may as well just all join Bluesky. It has other problems too: the central relays get overloaded, and the notes get copied to too many relays, which is both space-inefficient and network bandwith inefficient.
ISSUE 1: Which notes should I fetch from which relays? This is described pretty well now in NIP-65. But that is only the "outbox" model part. The "gossip model" part is to also work out what relays work for people who don't publish a relay list.
ISSUE 2: Automatic failover. Apparently Peter Todd's definition of decentralized includes a concept of automatic failover, where new resources are brought up and users don't need to do anything. Besides this not being part of any definition of decentralized I have never heard of, we kind of have this. If a user has 5 outboxes, and 3 fail, everything still works. Redundancy is built in. No user intervention needed in most cases, at least in the short term. But we also don't have any notion of administrators who can fix this behind the scenes for the users. Users are sovereign and that means they have total control, but also take on some responsibility. This is obvious when it comes to keypair management, but it goes further. Users have to manage where they post and where they accept incoming notes, and when those relays fail to serve them they have to change providers. Putting the users in charge, and not having administrators, is kinda necessary to be truly decentralized.
ISSUE 3: Connecting to unvetted relays feels unsafe. It might even be the NSA tracking you! First off, this happens with your web browser all the time: you go visit a web page and it instructs your browser to fetch a font from google. If you don't like it, you can use uBlock origin and manage it manually. In the nostr world, if you don't like it, you can use a client that puts you more in control of this. The gossip client for example has options for whether you want to manually approve relay connections and AUTHs, just once or always, and always lets you change your mind later. If you turn those options on, initially it is a giant wall of approval requests... but that situation resolves rather quickly. I've been running with these options on for a long time now, and only about once a week do I have to make a decision for a new relay.
But these features aren't really necessary for the vast majority of users who don't care if a relay knows their IP address. Those users use VPNs or Tor when they want to be anonymous, and don't bother when they don't care (me included).
ISSUE 4: Mobile phone clients may find the gossip model too costly in terms of battery life. Bandwidth is actually not a problem: under the gossip model (if done correctly) events for user P are only downloaded from N relays (default for gossip client is N=2), which in general is FEWER events retrieved than other models which download the same event maybe 8 or more times. Rather, the problem here is the large number of network connections and in particular, the large number of SSL setups and teardowns. If it weren't for SSL, this wouldn't be much of a problem. But setting up and tearing down SSL on 50 simultaneous connections that drop and pop up somewhat frequently is a battery drain.
The solution to this that makes the most sense to me is to have a client proxy. What I mean by that is a piece of software on a server in a data centre. The client proxy would be a headless nostr client that uses the gossip model and acts on behalf of the phone client. The phone client doesn't even have to be a nostr client, but it might as well be a nostr client that just connects to this fixed proxy to read and write all of its events. Now the SSL connection issue is solved. These proxies can serve many clients and have local storage, whereas the phones might not even need local storage. Since very few users will set up such things for themselves, this is a business opportunity for people, and a better business opportunity IMHO than running a paid-for relay. This doesn't decentralize nostr as there can be many of these proxies. It does however require a trust relationship between the phone client and the proxy.
ISSUE 5: Personal relays still need moderation. I wrongly thought for a very long time that personal relays could act as personal OUTBOXes and personal INBOXes without needing moderation. Recently it became clear to me that clients should probably read from other people's INBOXes to find replies to events written by the user of that INBOX (which outbox model clients should be putting into that INBOX). If that is happening, then personal relays will need to serve to the public events that were just put there by the public, thus exposing them to abuse. I'm greatly disappointed to come to this realization and not quite settled about it yet, but I thought I had better make this known.
-
 @ b12b632c:d9e1ff79
2024-02-19 19:18:46
@ b12b632c:d9e1ff79
2024-02-19 19:18:46Nostr decentralized network is growing exponentially day by day and new stuff comes out everyday. We can now use a NIP46 server to proxify our nsec key to avoid to use it to log on Nostr websites and possibly leak it, by mistake or by malicious persons. That's the point of this tutorial, setup a NIP46 server Nsec.app with its own Nostr relay. You'll be able to use it for you and let people use it, every data is stored locally in your internet browser. It's an non-custodial application, like wallets !
It's nearly a perfect solution (because nothing is perfect as we know) and that makes the daily use of Nostr keys much more secure and you'll see, much more sexy ! Look:
Nsec.app is not the only NIP46 server, in fact, @PABLOF7z was the first to create a NIP46 server called nsecBunker. You can also self-hosted nsecBunkerd, you can find a detailed explanation here : nsecbunkerd. I may write a how to self-host nsecBunkderd soon.
If you want more information about its bunker and what's behind this tutorial, you can check these links :
Few stuffs before beginning
Spoiler : I didn't automatized everything. The goal here is not to give you a full 1 click installation process, it's more to let you see and understand all the little things to configure and understand how works Nsec.app and the NIP46. There is a little bit of work, yes, but you'll be happy when it will work! Believe me.
Before entering into the battlefield, you must have few things : A working VPS with direct access to internet or a computer at home but NAT will certain make your life a hell. Use a VPS instead, on DigitalOcean, Linode, Scaleway, as you wish. A web domain that your own because we need to use at least 3 DNS A records (you can choose the subdomain you like) : domain.tld, noauth.domain.tld, noauth.domain.tld. You need to have some programs already installed : git, docker, docker-compose, nano/vi. if you fill in all the boxes, we can move forward !
Let's install everything !
I build a repo with a docker-compose file with all the required stuff to make the Bunker works :
Nsec.app front-end : noauth Nsec.app back-end : noauthd Nostr relay : strfry Nostr NIP05 : easy-nip5
First thing to do is to clone the repo "nsec-app-docker" from my repo:
$ git clone git clone https://github.com/PastaGringo/nsec-app-docker.git $ cd nsec-app-dockerWhen it's done, you'll have to do several things to make it work. 1) You need to generate some keys for the web-push library (keep them for later) :
``` $ docker run pastagringo/web-push-generate-keys
Generating your web-push keys...
Your private key : rQeqFIYKkInRqBSR3c5iTE3IqBRsfvbq_R4hbFHvywE Your public key : BFW4TA-lUvCq_az5fuQQAjCi-276wyeGUSnUx4UbGaPPJwEemUqp3Rr3oTnxbf0d4IYJi5mxUJOY4KR3ZTi3hVc ```
2) Generate a new keys pair (nsec/npub) for the NIP46 server by clicking on "Generate new key" from NostrTool website: nostrtool.com.
You should have something like this :
console Nostr private key (nsec): keep this -> nsec1zcyanx8zptarrmfmefr627zccrug3q2vhpfnzucq78357hshs72qecvxk6 Nostr private key (hex): 1609d998e20afa31ed3bca47a57858c0f888814cb853317300f1e34f5e178794 Nostr public key (npub): npub1ywzwtnzeh64l560a9j9q5h64pf4wvencv2nn0x4h0zw2x76g8vrq68cmyz Nostr public key (hex): keep this -> 2384e5cc59beabfa69fd2c8a0a5f550a6ae6667862a7379ab7789ca37b483b06You need to keep Nostr private key (nsec) & Nostr public key (npub). 3) Open (nano/vi) the .env file located in the current folder and fill all the required info :
```console
traefik
EMAIL=pastagringo@fractalized.net <-- replace with your own domain NSEC_ROOT_DOMAIN=plebes.ovh <-- replace with your own domain <-- replace with your own relay domain RELAY_DOMAIN=relay.plebes.ovh <-- replace with your own noauth domainay.plebes.ovh <-- replace with your own relay domain <-- replace with your own noauth domain NOAUTH_DOMAIN=noauth.plebes.ovh <-- replace with your own noauth domain NOAUTHD_DOMAIN=noauthd.plebes.ovh <-- replace with your own noauth domain
noauth
APP_WEB_PUSH_PUBKEY=BGVa7TMQus_KVn7tAwPkpwnU_bpr1i6B7D_3TT-AwkPlPd5fNcZsoCkJkJylVOn7kZ-9JZLpyOmt7U9rAtC-zeg <-- replace with your own web push public key APP_NOAUTHD_URL=https://$NOAUTHD_DOMAIN APP_DOMAIN=$NSEC_ROOT_DOMAIN APP_RELAY=wss://$RELAY_DOMAIN
noauthd
PUSH_PUBKEY=$APP_WEB_PUSH_PUBKEY PUSH_SECRET=_Sz8wgp56KERD5R4Zj5rX_owrWQGyHDyY4Pbf5vnFU0 <-- replace with your own web push private key ORIGIN=https://$NOAUTHD_DOMAIN DATABASE_URL=file:./prod.db BUNKER_NSEC=nsec1f43635rzv6lsazzsl3hfsrum9u8chn3pyjez5qx0ypxl28lcar2suy6hgn <-- replace with your the bunker nsec key BUNKER_RELAY=wss://$RELAY_DOMAIN BUNKER_DOMAIN=$NSEC_ROOT_DOMAIN BUNKER_ORIGIN=https://$NOAUTH_DOMAIN ```
Be aware of noauth and noauthd (the d letter). Next, save and quit. 4) You now need to modify the nostr.json file used for the NIP05 to indicate which relay your bunker will use. You need to set the bunker HEX PUBLIC KEY (I replaced the info with the one I get from NostrTool before) :
console nano easy-nip5/nostr.jsonconsole { "names": { "_": "ServerHexPubKey" }, "nip46": { "ServerHexPubKey": [ "wss://ReplaceWithYourRelayDomain" ] } }5) You can now run the docker compose file by running the command (first run can take a bit of time because the noauth container needs to build the npm project):
console $ docker compose up -d6) Before creating our first user into the Nostr Bunker, we need to test if all the required services are up. You should have :
noauth :
noauthd :
console CANNOT GET /https://noauthd.yourdomain.tld/name :
console { "error": "Specify npub" }https://yourdomain.tld/.well-known/nostr.json :
console { "names": { "_": "ServerHexPubKey" }, "nip46": { "ServerHexPubKey": [ "wss://ReplaceWithYourRelayDomain" ] } }If you have everything working, we can try to create a new user!
7) Connect to noauth and click on "Get Started" :
At the bottom the screen, click on "Sign up" :
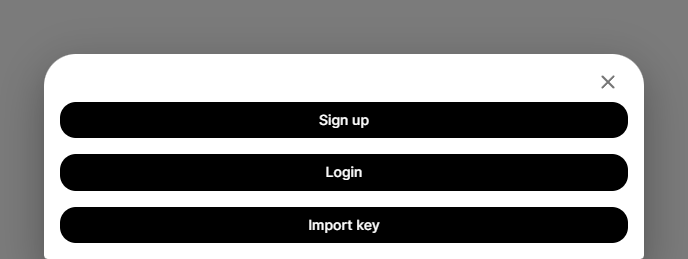
Fill a username and click on "Create account" :
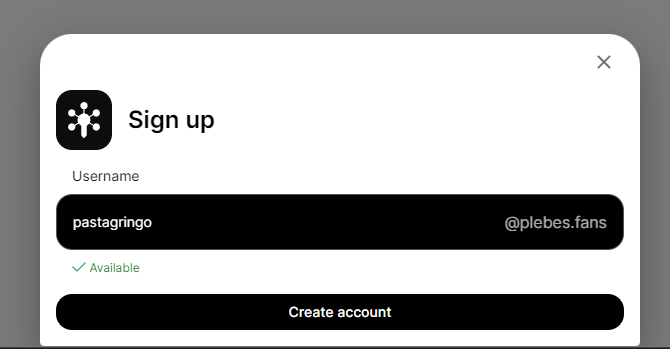
If everything has been correctly configured, you should see a pop message with "Account created for "XXXX" :
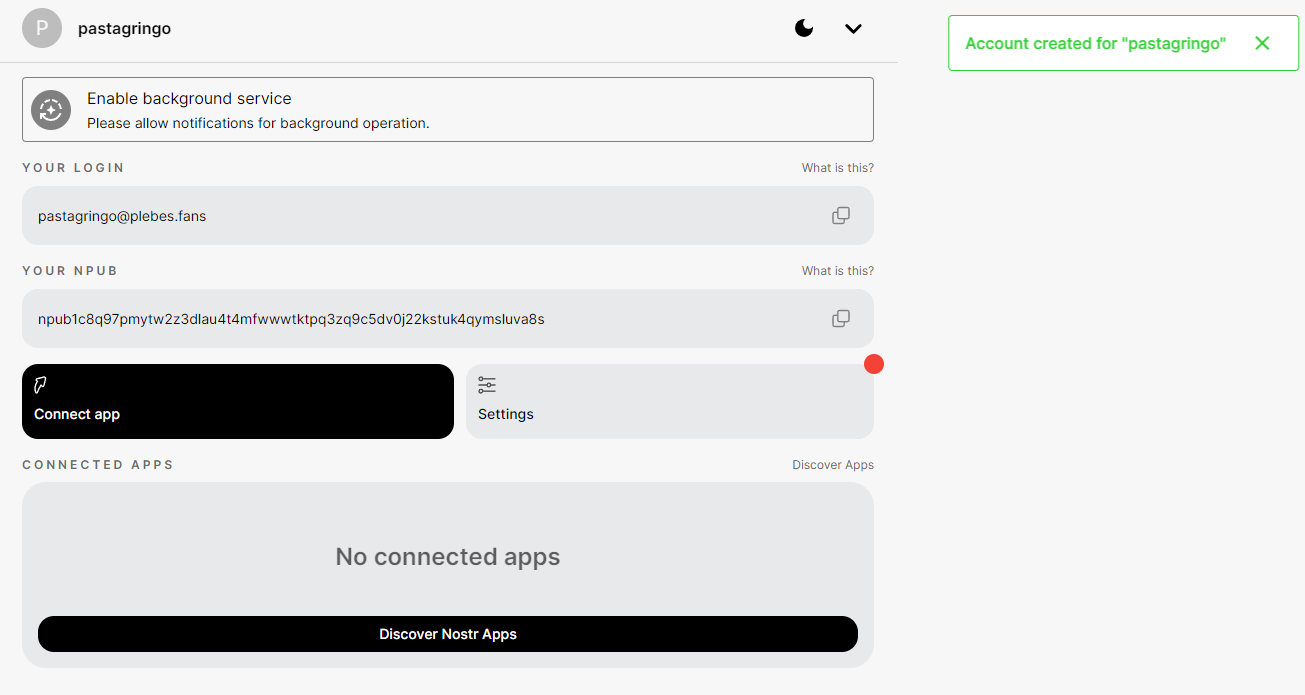
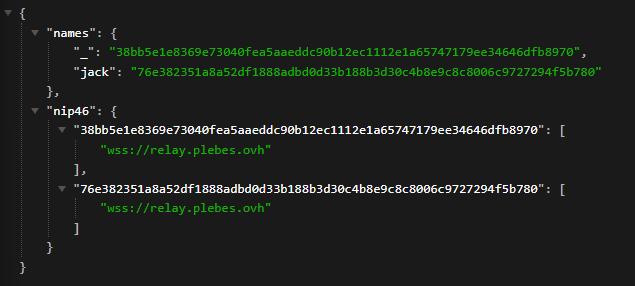
PS : to know if noauthd is well serving the nostr.json file, you can check this URL : https://yourdomain.tld/.well-known/nostr.json?name=YourUser You should see that the user has now NIP05/NIP46 entries :
If the user creation failed, you'll see a red pop-up saying "Something went wrong!" :
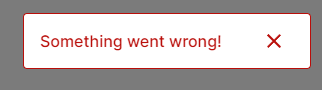
To understand what happened, you need to inspect the web page to find the error :
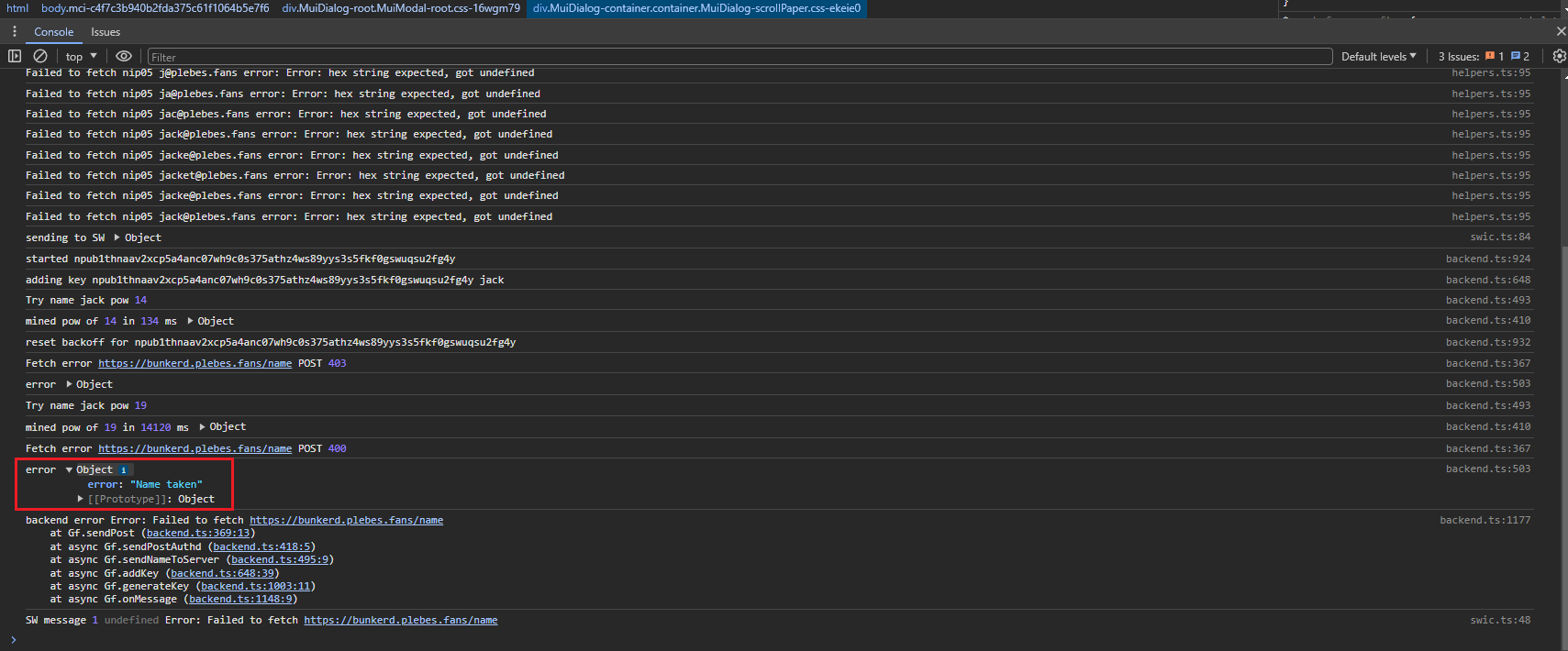
For the example, I tried to recreate a user "jack" which has already been created. You may find a lot of different errors depending of the configuration you made. You can find that the relay is not reachable on w s s : / /, you can find that the noauthd is not accessible too, etc. Every answers should be in this place.
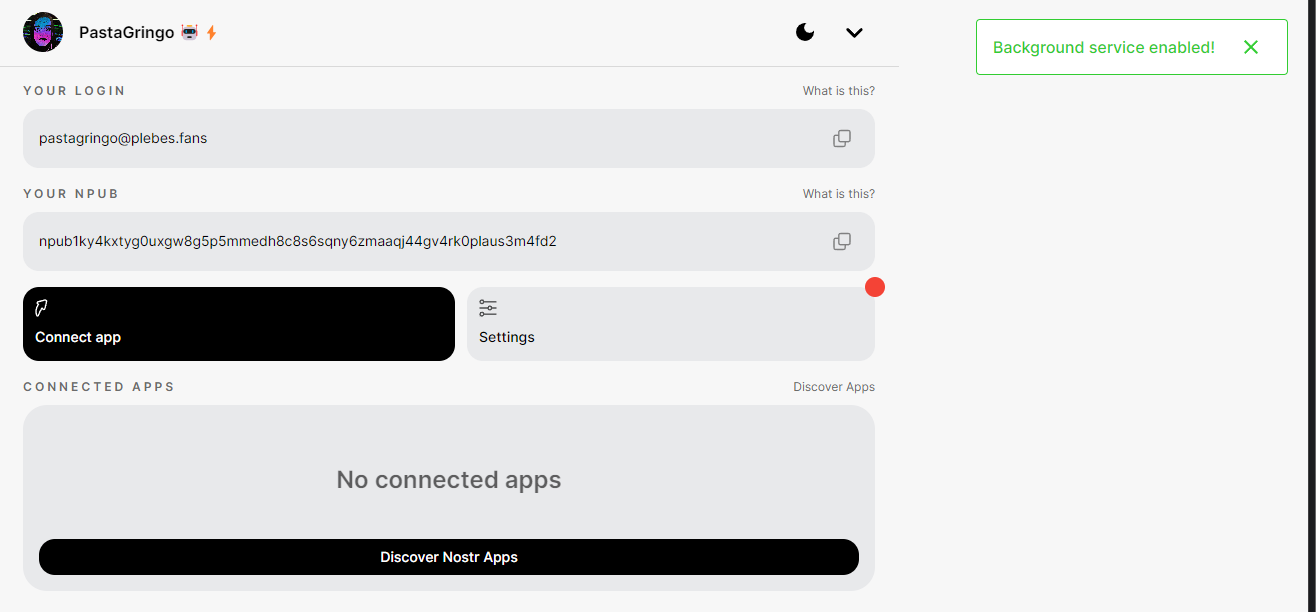
To completely finish the tests, you need to enable the browser notifications, otherwise you won't see the pop-up when you'll logon on Nostr web client, by clicking on "Enable background service" :
You need to click on allow notifications :
Should see this green confirmation popup on top right of your screen:
Well... Everything works now !
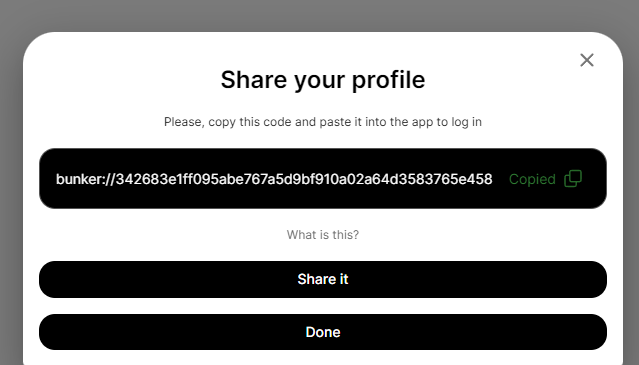
8) You try to use your brand new proxyfied npub by clicking on "Connect App" and buy copying your bunker URL :
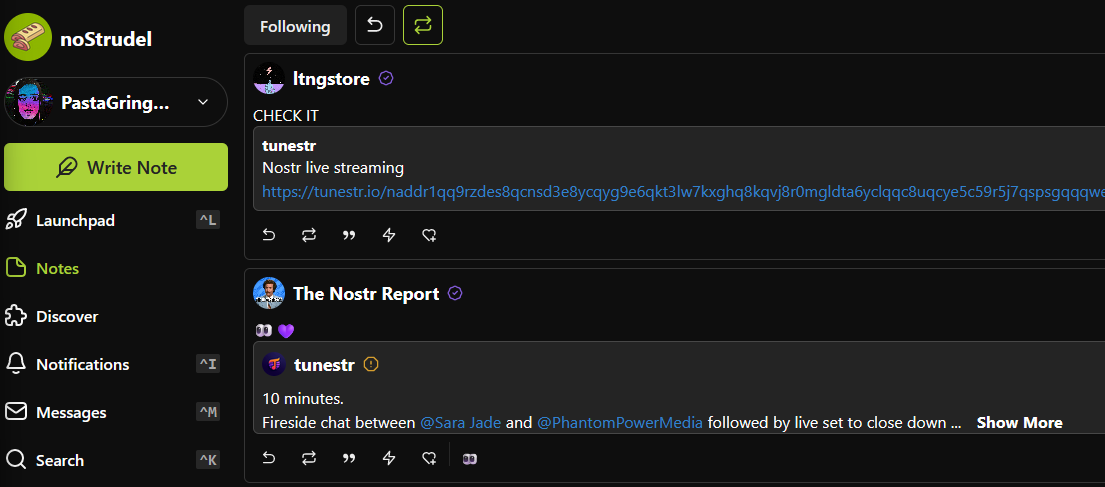
You can now to for instance on Nostrudel Nostr web client to login with it. Select the relays you want (Popular is better ; if you don't have multiple relay configured on your Nostr profile, avoid "Login to use your relay") :
Click on "Sign in" :
Click on "Show Advanced" :
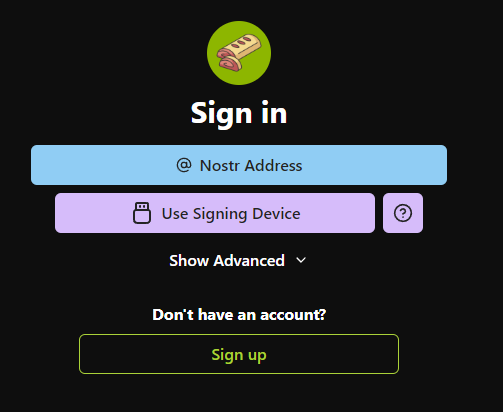
Click on "Nostr connect / Bunker" :
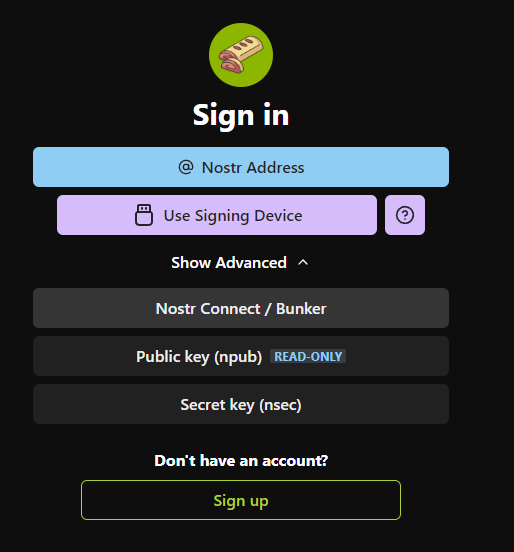
Paste your bunker URL and click on "Connect" :
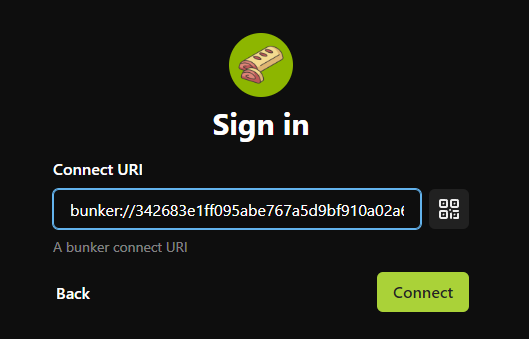
The first time, tour browser (Chrome here) may blocks the popup, you need to allow it :
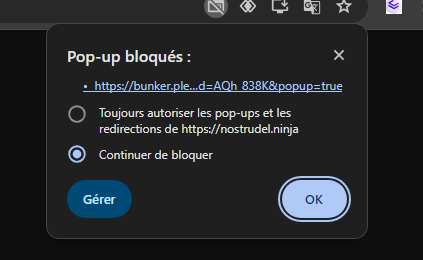
If the browser blocked the popup, NoStrudel will wait your confirmation to login :
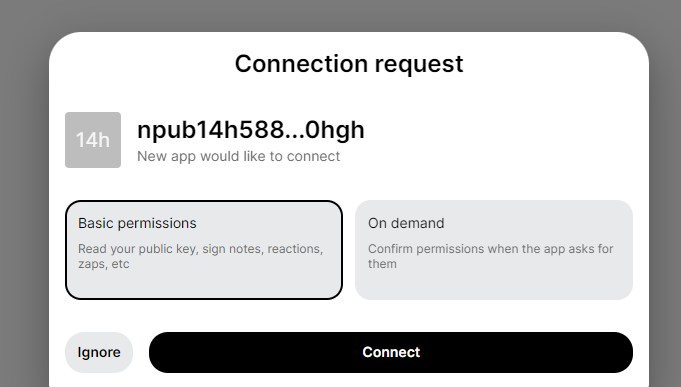
You have to go back on your bunker URL to allow the NoStrudel connection request by clicking on on "Connect":
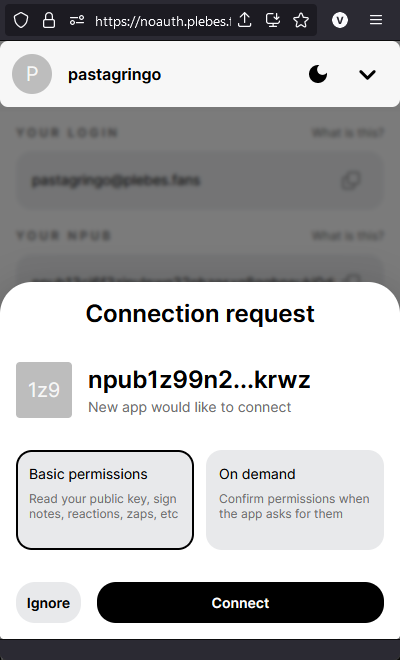
The first time connections may be a bit annoying with all the popup authorizations but once it's done, you can forget them it will connect without any issue. Congrats ! You are connected on NoStrudel with an npub proxyfied key !⚡

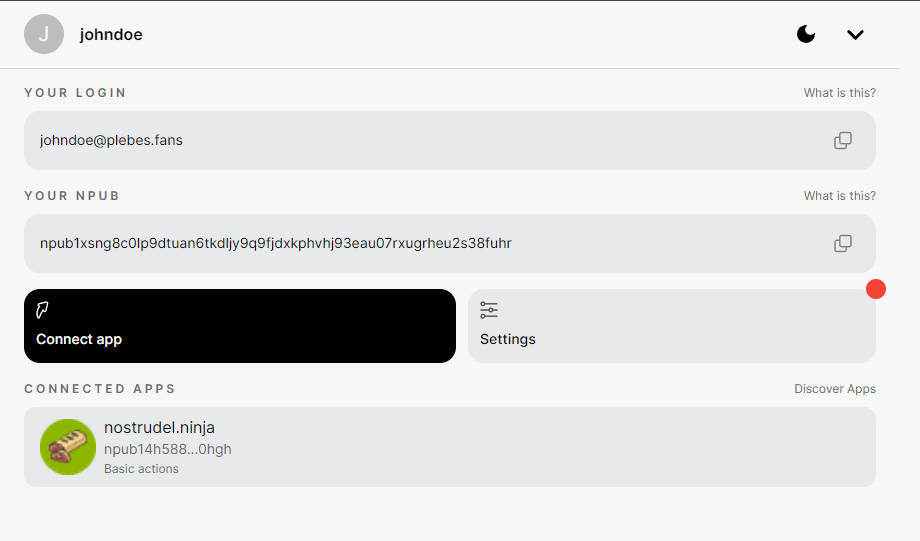
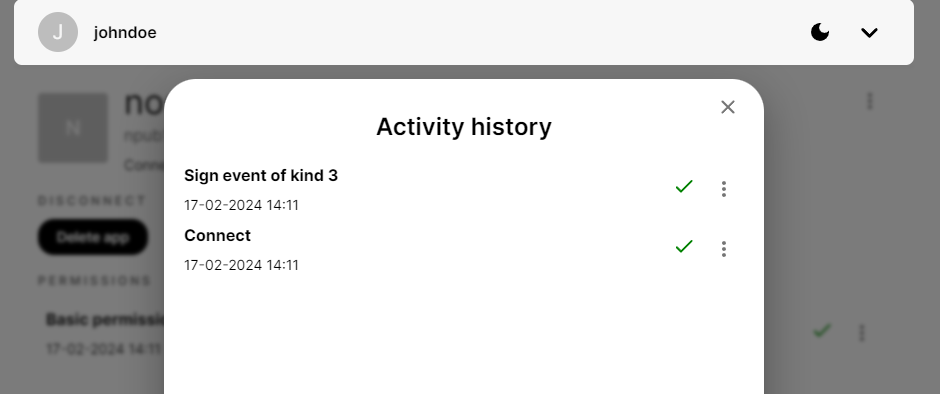
You can check to which applications you gave permissions and activity history in noauth by selecting your user. :
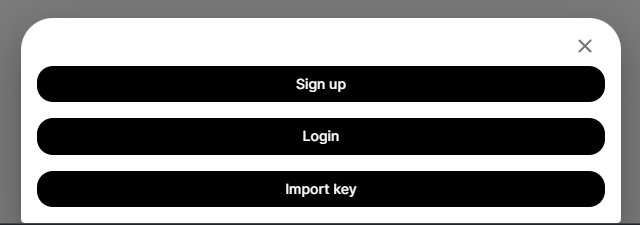
If you want to import your real Nostr profile, the one that everyone knows, you can import your nsec key by adding a new account and select "Import key" and adding your precious nsec key (reminder: your nsec key stays in your browser! The noauth provider won't have access to it!) :
You can see can that my profile picture has been retrieved and updated into noauth :
I can now use this new pubkey attached my nsec.app server to login in NoStrudel again :
Accounts/keys management in noauthd You can list created keys in your bunkerd by doing these command (CTRL+C to exit) :
console $ docker exec -it noauthd node src/index.js list_names [ '/usr/local/bin/node', '/noauthd/src/index.js', 'list_names' ] 1 jack npub1hjdw2y0t44q4znzal2nxy7vwmpv3qwrreu48uy5afqhxkw6d2nhsxt7x6u 1708173927920n 2 peter npub1yp752u5tr5v5u74kadrzgfjz2lsmyz8dyaxkdp4e0ptmaul4cyxsvpzzjz 1708174748972n 3 john npub1xw45yuvh5c73sc5fmmc3vf2zvmtrzdmz4g2u3p2j8zcgc0ktr8msdz6evs 1708174778968n 4 johndoe npub1xsng8c0lp9dtuan6tkdljy9q9fjdxkphvhj93eau07rxugrheu2s38fuhr 1708174831905nIf you want to delete someone key, you have to do :
```console $ docker exec -it noauthd node src/index.js delete_name johndoe [ '/usr/local/bin/node', '/noauthd/src/index.js', 'delete_name', 'johndoe' ] deleted johndoe { id: 4, name: 'johndoe', npub: 'npub1xsng8c0lp9dtuan6tkdljy9q9fjdxkphvhj93eau07rxugrheu2s38fuhr', timestamp: 1708174831905n
$ docker exec -it noauthd node src/index.js list_names [ '/usr/local/bin/node', '/noauthd/src/index.js', 'list_names' ] 1 jack npub1hjdw2y0t44q4znzal2nxy7vwmpv3qwrreu48uy5afqhxkw6d2nhsxt7x6u 1708173927920n 2 peter npub1yp752u5tr5v5u74kadrzgfjz2lsmyz8dyaxkdp4e0ptmaul4cyxsvpzzjz 1708174748972n 3 john npub1xw45yuvh5c73sc5fmmc3vf2zvmtrzdmz4g2u3p2j8zcgc0ktr8msdz6evs 1708174778968n ```
It could be pretty easy to create a script to handle the management of keys but I think @Brugeman may create a web interface for that. Noauth is still very young, changes are committed everyday to fix/enhance the application! As """everything""" is stored locally on your browser, you have to clear the cache of you bunker noauth URL to clean everything. This Chome extension is very useful for that. Check these settings in the extension option :
You can now enjoy even more Nostr ⚡ See you soon in another Fractalized story!
-
 @ 0a821ca3:e0efcce3
2024-04-19 08:04:56
@ 0a821ca3:e0efcce3
2024-04-19 08:04:56The (only?) global p2p digital value transfer protocol requires an underlying token that represents the value that is being transferred.
In a previous consideration, it was argued that the token underlying the global p2p digital value transfer protocol, has to be an attractive asset for the protocol to function. If the token is not attractive, there is no reassurance that the receiver will be able to convert the token into another valuable asset, which would make the protocol defunct.
The token underlying the p2p value transfer protocol has so far more than doubled its USD value every four years. This implies more than 19% USD IRR. This makes it an extremely attractive asset. Moreover, due to the halving cycle, the value increases are not uniform over time - as a result, the token has increased by a factor 10x in less than a year in some periods.
This attracts people with different objectives than digitally transferring value in a p2p way. It also creates envy. It gives the token underlying the protocol the perception of being a get rich quick scheme.
That is a design flaw.
The p2p digital value transfer protocol would be much less frowned upon, if it would increase in USD value at a more modest pace, for example by about 5-10% per year - that would still be good enough to make token underlying the protocol sufficiently valuable to act as the value travelling the protocol - but would avoid attracting the lambo kids.
Wouldn’t the silence of the lambos be much better for protocol adoption?
-
 @ 502ab02a:a2860397
2024-04-24 09:27:28
@ 502ab02a:a2860397
2024-04-24 09:27:28หลายๆครั้งที่เรากินเฮฟวีครีมหรือที่บ้านเราเรียกวิปครีม ไม่หมดแถมใกล้จะหมดอายุแล้วด้วย เราสามารถนำมาเรียนรู้กระบวนการผลิตสิ่งที่เรียกว่า ผลิตภัณฑ์จากนม หรือ Dairy Product ได้ครับ แถมเรายังได้ของไว้ใช้ทำอาหารอีกด้วย นั่นคือ การทำครีมให้เป็นเนย แล้วเอาเนยไปทำกี อีกที งว่ออออออ
ผมจะเล่าสิ่งที่ผมทำเล่นๆเป็นงานอดิเรกให้อ่านกันครับ
ส่วนตัวแล้วผมค่อนข้างหลงไหลใน ไขมันเนย และสนุกในการเรียนรู้มันมานานพอสมควร รวมถึงได้คลุกคลีกับอุตสาหกรรมนม มาตั้งแต่ราวๆปี 2001 ที่น่าสนใจคือ สัดส่วนสารอาหารของไขมันเนย ดีงามตั้งแต่เรื่อง กรดไขมันสายสั้น สัดส่วนที่ลงตัวระหว่างโอเมก้า3:6 รวมถึงมีกลิ่นหอมละมุน
กระบวนการทำเนยนั้น เขาก็จะนำนมมาแยกส่วนที่เป็นครีมออกมา เพื่อปั่นแยกไขมันเนยกับเวย์ ในขั้นตอนการแยกครีมนั้น เราจะได้ **ครีม(นมกับไขมันเนย) และ นมพร่องมันเนย (นมที่มีไขมันเนยต่ำ แน่สิมันไปอยู่ในครีมไง) **
ซึ่งนมพร่องมันเนยนี่ละครับ เป็นกระบวนการเดียวกับที่เขานำไปขายเป็นนมไขมันต่ำ หรือ ไม่ก็เอาไปทำนมผง(สกิมมิลค์) . . . แต่ทำความเข้าใจก่อนนะครับว่า บางโรงงานก็ไม่ได้เอาเศษพวกนี้มาทำของขายเรานะ โรงงานนมผงบางที่ก็เป้นการตั้งไลน์ทำขึ้นมาโดยเฉพาะแล้วได้ by product เป็นครีมแทน
คือมันไม่เหมือนกันระหว่าง ตั้งใจทำครีมออกมาขายแล้วได้หางนมมาทำนมผงนมไขมันต่ำ VS ตั้งใจทำนมผงนมไขมันต่ำมาขายแล้วได้เศษเหลือเป็นครีม
มันเป็นแค่กระบวนการที่คล้ายกันคือ มีการแยกครีมกับนม แต่การตั้งเครื่องไม่เหมือนกัน เขาจะตั้งเอาสิ่งที่ต้องการผลิตเป็นหลัก ที่เหลือมันจึงเป็นแค่ by product
โอเคทีนี้กลับมาเรื่องของเราครับ
**
กระบวนการทำเนยคือ
** การเอาครีมมาปั่นในถังปั่น จนมันเกิดการแยกระหว่างไขมันกับเวย์ เรียกว่าการ churning ตั้งแต่โบราณก็ใช้การปั่น แต่วิธีปั่นมันต่างไปเท่านั้นครับ จากปั่นมือ มาเป็นปั่นเครื่อง รสชาติของเนยก็ขึ้นอยู่กับวิธีทำต่างๆ ตั้งแต่โบราณคือนมดิบ, นมที่มีการ culture หรือ ใส่จุลินทรีย์ไปหมักก่อนจะนำมาปั่น เพื่อกลิ่นและรส ปัจจุบันก็อาจมีการพาสเจอร์ไรส์เพราะบางประเทศบังคับว่าต้องพาสเจอร์ไรส์
วันนี้เรามาดูแบบง่ายๆตามที่บอกไว้ข้างบน เราแค่เอาวิปครีม ใส่โถปั่นแล้วก็ให้มันปั่นไปเรื่อยๆ แค่นี้ก็ได้เนยแล้วครับ สำหรับคนที่ทำขนมน่าจะเคยเจอเหตุการณ์ตีวิปนานเกินไปจนจับก้อนแข็ง ถ้าคุณตีต่อไปอีกนั่นละครับ ไอ้เจ้าครีมแข็งนั้นจะกลายเป็นเนยในที่สุด เอาจริงๆการเหวี่ยงก็ได้นะครับ หลายคนเอาใส่ขวดแล้วเขย่า ใครอยากลองก็ลองได้นะ เมื่อยมือเชียว 5555 พอเราได้ก้อนเนยสดๆแล้ว เราก็เอามาใส่ลงในน้ำเย็นจัด ความเย็นจัดจะทำให้เนยสดๆนี้แข็งตัว แล้วเราก็จะปั้นก้อนปั้นรูปทรงให้เก็บง่ายๆได้ ที่นิยมก็ทรงหมูยอ เพราะตัดใช้ง่ายดีครับ
**เรามาดูคลิปที่ผมเคยทำกันครับ จะเห็นภาพว่า ครีมกลายเป็นเนย มันยังไง ** https://youtu.be/bzo7V9n2cxc?si=PsaldIxgKqpiBXgb
ทีนี้เราก็ได้เนยเอาไว้ใช้เองสบายๆละ ใครที่มีนมดิบอยู่แล้วกลัวกินไม่ทัน ก็มีวิธีเพิ่มนิดนึงครับคือ ใส่โถทรงสูงหน่อย เอานมดิบแช่ตู้เย็นราวๆ 18ชั่วโมงขึ้นไป จนมันเริ่มแยกชั้นกัน ความเย็นจะทำให้ไขมันจับตัว มองแล้วคล้ายหัวกะทิ หางกะทิ แล้วเราก็เลือกตักส่วนข้นๆส้วนจับก้อน เอามาใช้แทนครีม วิธีสังเกตุก็ดูความใสของนมเอาครับ ส่วนไขมันจะข้นๆหน่อย พอเริ่มไขมันน้อยก็จะใสครับ ส่วนที่เหลือที่ใสหน่อย นั่นละครับ นมไขมันต่ำ 55555 เอาไปชงกาแฟหรือดื่มได้ต่อไม่มีปัญหาอะไร
**
ทีนี้ กี (ghee) คืออะไร
** กี คือ เนยใส เป็นที่นิยมในอินเดียมากๆ เขาเอามาใช้เป็นน้ำมันในการทำอาหาร ชงเครื่องดื่ม ได้สารพัดอย่างตามที่น้ำมันจะทำได้ จุดเกิดควันสูง ทำให้เกิดการไหม้ ได้ยากกว่าเนยหลายเท่า
วิธีทำกี ก็ง่ายมากๆ แค่เอาเนยมาตั้งเตาด้วยไฟอ่อนๆ อ่อนมากๆนะครับ เพราะถ้าแรงไปนิดเดียว เนยจะไหม้ทันที เราก็กวนเนยไปเรื่อยๆ ความร้อนอ่อนๆที่ต้มเนยนี้มันคือกระบวนการทำให้น้ำระเหยออกไป จนเริ่มเห็นน้ำมันใสๆ เริ่มเห็นการแยกชั้นอีกครั้งนึง ซึ่งไอ้ที่แยกมานี่ละครับ เราเรียกว่า เนื้อนม หรือ solid milk เท่ากับว่าเราแยกองค์ประกอบของเนยออกไปได้ดังนี้ 1.น้ำระเหยไปในอากาศ 2.เนื้อนมแข็งๆคาอยู่ในหม้อ 3.ไขมันเนยใสๆ คาอยู่ในหม้อ
สิ่งที่เราเอามาใช้ก็คือ ไขมันเนย กรอกใส่ขวดหรือกระปุกก็ตามสะดวกใช้ครับ แช่ตู้เย็นเอาไว้ก็ได้ หรือถ้าใช้บ่อย อยู่นอกตู้เย็นก็ได้พักใหญ่ๆเลย เพราะมันไม่มีอะไรให้เสีย เพียงแค่มันจะซับกลิ่นสภาพแวดล้อมได้เก่งหน่อย
ส่วนเนื้อนมเอาไปคลุกน้ำตาลอร่อยครับ 555555
เรามาดูคลิปการทำกี กันครับ ตัวนี้ผมใช้เนยที่ขายทั่วไปพราะตอนนั้นผมทำการทดลอง ให้คนคีโตเห็นว่า อย่าไปอะไรกับเนยมาก ทุกตัวมีเนื้อนมหมดและเนื้อนมเป็นคาร์บ ที่สำคัญเนยที่คีโตนิยมใช้เหลือเนื้อนมมากกว่าเนยที่ราคาถูกกว่าอีก เพราะเนื้อนมคือตัวที่ทำให้เนยมีความละมุนลิ้น ส่วนไขมันเนยคือตัวที่ส่งกลิ่นหอมๆ ลองไปดูคลิปกันครับ
https://youtu.be/HFvvIjhZ6h0?si=KkqoZFN3Mx1lTTul
ทีนี้ของแถม ที่บอกว่าต้มกี ต้องระวังไหม้ จำได้ใช่ไหมครับ ในสายเบเกอรี่ เรามีสิ่งที่เรียกว่า บราวบัทเตอร์ (brown butter) คือการเล่นเสี่ยงอย่างนึงคือ ต้มกี ให้เกินจุดพอดี แต่ไม่เกินไปจนไหม้ เราจะได้เนยใสสีน้ำตาลอ่อน มีกลิ่นหอมคาราเมล ตัวนี้นิยมใช้ทำขนมเพิ่มกลิ่นหอมกว่าการใช้เนยปกติหลายเท่า แถมเป็นกลิ่นหอมหวาน ที่ทำให้ขนมไฮโซขึ้นมาก เอาไปชงกาแฟก็หอมครับผมทำบ่อย
siamstr #pirateketo
-
 @ ee11a5df:b76c4e49
2023-11-09 05:20:37
@ ee11a5df:b76c4e49
2023-11-09 05:20:37A lot of terms have been bandied about regarding relay models: Gossip relay model, outbox relay model, and inbox relay model. But this term "relay model" bothers me. It sounds stuffy and formal and doesn't actually describe what we are talking about very well. Also, people have suggested maybe there are other relay models. So I thought maybe we should rethink this all from first principles. That is what this blog post attempts to do.
Nostr is notes and other stuff transmitted by relays. A client puts an event onto a relay, and subsequently another client reads that event. OK, strictly speaking it could be the same client. Strictly speaking it could even be that no other client reads the event, that the event was intended for the relay (think about nostr connect). But in general, the reason we put events on relays is for other clients to read them.
Given that fact, I see two ways this can occur:
1) The reader reads the event from the same relay that the writer wrote the event to (this I will call relay rendezvous), 2) The event was copied between relays by something.
This second solution is perfectly viable, but it less scalable and less immediate as it requires copies which means that resources will be consumed more rapidly than if we can come up with workable relay rendezvous solutions. That doesn't mean there aren't other considerations which could weigh heavily in favor of copying events. But I am not aware of them, so I will be discussing relay rendezvous.
We can then divide the relay rendezvous situation into several cases: one-to-one, one-to-many, and one-to-all, where the many are a known set, and the all are an unbounded unknown set. I cannot conceive of many-to-anything for nostr so we will speak no further of it.
For a rendezvous to take place, not only do the parties need to agree on a relay (or many relays), but there needs to be some way that readers can become aware that the writer has written something.
So the one-to-one situation works out well by the writer putting the message onto a relay that they know the reader checks for messages on. This we call the INBOX model. It is akin to sending them an email into their inbox where the reader checks for messages addressed to them.
The one-to-(known)-many model is very similar, except the writer has to write to many people's inboxes. Still we are dealing with the INBOX model.
The final case, one-to-(unknown)-all, there is no way the writer can place the message into every person's inbox because they are unknown. So in this case, the writer can write to their own OUTBOX, and anybody interested in these kinds of messages can subscribe to the writer's OUTBOX.
Notice that I have covered every case already, and that I have not even specified what particular types of scenarios call for one-to-one or one-to-many or one-to-all, but that every scenario must fit into one of those models.
So that is basically it. People need INBOX and OUTBOX relays and nothing else for relay rendezvous to cover all the possible scenarios.
That is not to say that other kinds of concerns might not modulate this. There is a suggestion for a DM relay (which is really an INBOX but with a special associated understanding), which is perfectly fine by me. But I don't think there are any other relay models. There is also the case of a live event where two parties are interacting over the same relay, but in terms of rendezvous this isn't a new case, it is just that the shared relay is serving as both parties' INBOX (in the case of a closed chat) and/or both parties' OUTBOX (in the case of an open one) at the same time.
So anyhow that's my thinking on the topic. It has become a fairly concise and complete set of concepts, and this makes me happy. Most things aren't this easy.
-
 @ 57d1a264:69f1fee1
2024-04-24 06:48:13
@ 57d1a264:69f1fee1
2024-04-24 06:48:13Prompt: Error Page ===============
An empty page with plenty of potential. Usually it display the error type,
404Not found and500Internal Server Error are probably the most familiar.Design a page that provide a new functionality to a website or web application
Flex your design muscles and join in. Most of all, keep this exercise loose and keep it stress-free. The FUC is about growing our design skills, together, as a community. We can't wait to see what you create!
Happy designing, Stackers!
Share Your Results When you finish the challenge, post your work on this thread! If you also share it on
nostr, be sure to use the hashtag #FUCdesiger and tag Design_r@iris.to or @Design__r on X! We'll keep an eye out and repost good examples on a regular basis.
Curious to know WTF is a FUC? Read the ⚡️Flash Ui Challenges welcoming post.
Looking for more FUCs? Check the archive here!
-
 @ b12b632c:d9e1ff79
2023-08-08 00:02:31
@ b12b632c:d9e1ff79
2023-08-08 00:02:31"Welcome to the Bitcoin Lightning Bolt Card, the world's first Bitcoin debit card. This revolutionary card allows you to easily and securely spend your Bitcoin at lightning compatible merchants around the world." Bolt Card
I discovered few days ago the Bolt Card and I need to say that's pretty amazing. Thinking that we can pay daily with Bitcoin Sats in the same way that we pay with our Visa/Mastecard debit cards is really something huge⚡(based on the fact that sellers are accepting Bitcoins obviously!)
To use Bolt Card you have three choices :
- Use their (Bolt Card) own Bolt Card HUB and their own BTC Lightning node
- Use your own self hosted Bolt Card Hub and an external BTC Lightning node
- Use your own self hosted Bolt Card Hub and your BTC Lightning node (where you shoud have active Lightning channels)
⚡ The first choice is the quickiest and simpliest way to have an NFC Bolt Card. It will take you few seconds (for real). You'll have to wait much longer to receive your NFC card from a website where you bought it than configure it with Bolt Card services.
⚡⚡ The second choice is pretty nice too because you won't have a VPS + to deal with all the BTC Lightnode stuff but you'll use an external one. From the Bolt Card tutorial about Bolt Card Hub, they use a Lightning from voltage.cloud and I have to say that their services are impressive. In few seconds you'll have your own Lightning node and you'll be able to configure it into the Bolt Card Hub settings. PS : voltage.cloud offers 7 trial days / 20$ so don't hesitate to try it!
⚡⚡⚡ The third one is obvisouly a bit (way) more complex because you'll have to provide a VPS + Bitcoin node and a Bitcoin Lightning Node to be able to send and receive Lightning payments with your Bolt NFC Card. So you shoud already have configured everything by yourself to follow this tutorial. I will show what I did for my own installation and all my nodes (BTC & Lightning) are provided by my home Umbrel node (as I don't want to publish my nodes directly on the clearnet). We'll see how to connect to the Umbrel Lighting node later (spoiler: Tailscale).
To resume in this tutorial, I have :
- 1 Umbrel node (rpi4b) with BTC and Lightning with Tailscale installed.
- 1 VPS (Virtual Personal Server) to publish publicly the Bolt Card LNDHub and Bolt Card containers configured the same way as my other containers (with Nginx Proxy Manager)
Ready? Let's do it ! ⚡
Configuring Bolt Card & Bolt Card LNDHub
Always good to begin by reading the bolt card-lndhub-docker github repo. To a better understading of all the components, you can check this schema :
We'll not use it as it is because we'll skip the Caddy part because we already use Nginx Proxy Manager.
To begin we'll clone all the requested folders :
git clone https://github.com/boltcard/boltcard-lndhub-docker bolthub cd bolthub git clone https://github.com/boltcard/boltcard-lndhub BoltCardHub git clone https://github.com/boltcard/boltcard.git git clone https://github.com/boltcard/boltcard-groundcontrol.git GroundControlPS : we won't see how to configure GroundControl yet. This article may be updated later.
We now need to modify the settings file with our own settings :
mv .env.example .env nano .envYou need to replace "your-lnd-node-rpc-address" by your Umbrel TAILSCALE ip address (you can find your Umbrel node IP from your Tailscale admin console):
``` LND_IP=your-lnd-node-rpc-address # <- UMBREL TAILSCALE IP ADDRESS LND_GRPC_PORT=10009 LND_CERT_FILE=tls.cert LND_ADMIN_MACAROON_FILE=admin.macaroon REDIS_PASSWORD=random-string LND_PASSWORD=your-lnd-node-unlock-password
docker-compose.yml only
GROUNDCONTROL=ground-control-url
docker-compose-groundcontrol.yml only
FCM_SERVER_KEY=hex-encoded APNS_P8=hex-encoded APNS_P8_KID=issuer-key-which-is-key-ID-of-your-p8-file APPLE_TEAM_ID=team-id-of-your-developer-account BITCOIN_RPC=bitcoin-rpc-url APNS_TOPIC=app-package-name ```
We now need to generate an AES key and insert it into the "settings.sql" file :
```
hexdump -vn 16 -e '4/4 "%08x" 1 "\n"' /dev/random 19efdc45acec06ad8ebf4d6fe50412d0 nano settings.sql ```
- Insert the AES between ' ' right from 'AES_DECRYPT_KEY'
- Insert your domain or subdomain (subdomain in my case) host between ' ' from 'HOST_DOMAIN'
- Insert your Umbrel tailscale IP between ' ' from 'LN_HOST'
Be aware that this subdomain won't be the LNDHub container (boltcard_hub:9002) but the Boltcard container (boltcard_main:9000)
``` \c card_db;
DELETE FROM settings;
-- at a minimum, the settings marked 'set this' must be set for your system -- an explanation for each of the bolt card server settings can be found here -- https://github.com/boltcard/boltcard/blob/main/docs/SETTINGS.md
INSERT INTO settings (name, value) VALUES ('LOG_LEVEL', 'DEBUG'); INSERT INTO settings (name, value) VALUES ('AES_DECRYPT_KEY', '19efdc45acec06ad8ebf4d6fe50412d0'); -- set this INSERT INTO settings (name, value) VALUES ('HOST_DOMAIN', 'sub.domain.tld'); -- set this INSERT INTO settings (name, value) VALUES ('MIN_WITHDRAW_SATS', '1'); INSERT INTO settings (name, value) VALUES ('MAX_WITHDRAW_SATS', '1000000'); INSERT INTO settings (name, value) VALUES ('LN_HOST', ''); -- set this INSERT INTO settings (name, value) VALUES ('LN_PORT', '10009'); INSERT INTO settings (name, value) VALUES ('LN_TLS_FILE', '/boltcard/tls.cert'); INSERT INTO settings (name, value) VALUES ('LN_MACAROON_FILE', '/boltcard/admin.macaroon'); INSERT INTO settings (name, value) VALUES ('FEE_LIMIT_SAT', '10'); INSERT INTO settings (name, value) VALUES ('FEE_LIMIT_PERCENT', '0.5'); INSERT INTO settings (name, value) VALUES ('LN_TESTNODE', ''); INSERT INTO settings (name, value) VALUES ('FUNCTION_LNURLW', 'ENABLE'); INSERT INTO settings (name, value) VALUES ('FUNCTION_LNURLP', 'ENABLE'); INSERT INTO settings (name, value) VALUES ('FUNCTION_EMAIL', 'DISABLE'); INSERT INTO settings (name, value) VALUES ('AWS_SES_ID', ''); INSERT INTO settings (name, value) VALUES ('AWS_SES_SECRET', ''); INSERT INTO settings (name, value) VALUES ('AWS_SES_EMAIL_FROM', ''); INSERT INTO settings (name, value) VALUES ('EMAIL_MAX_TXS', ''); INSERT INTO settings (name, value) VALUES ('FUNCTION_LNDHUB', 'ENABLE'); INSERT INTO settings (name, value) VALUES ('LNDHUB_URL', 'http://boltcard_hub:9002'); INSERT INTO settings (name, value) VALUES ('FUNCTION_INTERNAL_API', 'ENABLE'); ```
You now need to get two files used by Bolt Card LND Hub, the admin.macaroon and tls.cert files from your Umbrel BTC Ligtning node. You can get these files on your Umbrel node at these locations :
/home/umbrel/umbrel/app-data/lightning/data/lnd/tls.cert /home/umbrel/umbrel/app-data/lightning/data/lnd/data/chain/bitcoin/mainnet/admin.macaroonYou can use either WinSCP, scp or ssh to copy these files to your local workstation and copy them again to your VPS to the root folder "bolthub".
You shoud have all these files into the bolthub directory :
johndoe@yourvps:~/bolthub$ ls -al total 68 drwxrwxr-x 6 johndoe johndoe 4096 Jul 30 00:06 . drwxrwxr-x 3 johndoe johndoe 4096 Jul 22 00:52 .. -rw-rw-r-- 1 johndoe johndoe 482 Jul 29 23:48 .env drwxrwxr-x 8 johndoe johndoe 4096 Jul 22 00:52 .git -rw-rw-r-- 1 johndoe johndoe 66 Jul 22 00:52 .gitignore drwxrwxr-x 11 johndoe johndoe 4096 Jul 22 00:52 BoltCardHub -rw-rw-r-- 1 johndoe johndoe 113 Jul 22 00:52 Caddyfile -rw-rw-r-- 1 johndoe johndoe 173 Jul 22 00:52 CaddyfileGroundControl drwxrwxr-x 6 johndoe johndoe 4096 Jul 22 00:52 GroundControl -rw-rw-r-- 1 johndoe johndoe 431 Jul 22 00:52 GroundControlDockerfile -rw-rw-r-- 1 johndoe johndoe 1913 Jul 22 00:52 README.md -rw-rw-r-- 1 johndoe johndoe 293 May 6 22:24 admin.macaroon drwxrwxr-x 16 johndoe johndoe 4096 Jul 22 00:52 boltcard -rw-rw-r-- 1 johndoe johndoe 3866 Jul 22 00:52 docker-compose-groundcontrol.yml -rw-rw-r-- 1 johndoe johndoe 2985 Jul 22 00:57 docker-compose.yml -rw-rw-r-- 1 johndoe johndoe 1909 Jul 29 23:56 settings.sql -rw-rw-r-- 1 johndoe johndoe 802 May 6 22:21 tls.certWe need to do few last tasks to ensure that Bolt Card LNDHub will work perfectly.
It's maybe already the case on your VPS but your user should be member of the docker group. If not, you can add your user by doing :
sudo groupadd docker sudo usermod -aG docker ${USER}If you did these commands, you need to logout and login again.
We also need to create all the docker named volumes by doing :
docker volume create boltcard_hub_lnd docker volume create boltcard_redisConfiguring Nginx Proxy Manager to proxify Bolt Card LNDHub & Boltcard
You need to have followed my previous blog post to fit with the instructions above.
As we use have the Bolt Card LNDHub docker stack in another directory than we other services and it has its own docker-compose.yml file, we'll have to configure the docker network into the NPM (Nginx Proxy Manager) docker-compose.yml to allow NPM to communicate with the Bolt Card LNDHub & Boltcard containers.
To do this we need to add these lines into our NPM external docker-compose (not the same one that is located into the bolthub directory, the one used for all your other containers) :
nano docker-compose.ymlnetworks: bolthub_boltnet: name: bolthub_boltnet external: trueBe careful, "bolthub" from "bolthub_boltnet" is based on the directory where Bolt Card LNDHub Docker docker-compose.yml file is located.
We also need to attach this network to the NPM container :
nginxproxymanager: container_name: nginxproxymanager image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt networks: - fractalized - bolthub_boltnetYou can now recreate the NPM container to attach the network:
docker compose up -dNow, you'll have to create 2 new Proxy Hosts into NPM admin UI. First one for your domain / subdomain to the Bolt Card LNDHub GUI (boltcard_hub:9002) :
And the second one for the Boltcard container (boltcard_main:9000).
In both Proxy Host I set all the SSL options and I use my wildcard certificate but you can generate one certificate for each Proxy Host with Force SSL, HSTS enabled, HTTP/2 Suppot and HSTS Subdomains enabled.
Starting Bolt Card LNDHub & BoltCard containers
Well done! Everything is setup, we can now start the Bolt Card LNDHub & Boltcard containers !
You need to go again to the root folder of the Bolt Card LNDHub projet "bolthub" and start the docker compose stack. We'll begin wihtout a "-d" to see if we have some issues during the containers creation :
docker compose upI won't share my containers logs to avoid any senstive information disclosure about my Bolt Card LNDHub node, but you can see them from the Bolt Card LNDHub Youtube video (link with exact timestamp where it's shown) :
If you have some issues about files mounting of admin.macaroon or tls.cert because you started the docker compose stack the first time without the files located in the bolthub folder do :
docker compose down && docker compose upAfter waiting few seconds/minutes you should go to your Bolt Card LNDHub Web UI domain/sudomain (created earlier into NPM) and you should see the Bolt Card LNDHub Web UI :
if everything is OK, you now run the containers in detached mode :
docker compose up -dVoilààààà ⚡
If you need to all the Bolt Card LNDHub logs you can use :
docker compose logs -f --tail 30You can now follow the video from Bolt Card to configure your Bolt Card NFC card and using your own Bolt Card LNDHub :
~~PS : there is currently a bug when you'll click on "Connect Bolt Card" from the Bold Card Walle app, you might have this error message "API error: updateboltcard: enable_pin is not a valid boolean (code 6)". It's a know issue and the Bolt Card team is currently working on it. You can find more information on their Telegram~~
Thanks to the Bolt Card, the issue has been corrected : changelog
See you soon in another Fractalized story!
-
 @ 3c984938:2ec11289
2024-04-16 17:14:58
@ 3c984938:2ec11289
2024-04-16 17:14:58Hello (N)osytrs!
Yes! I'm calling you an (N)oystr!
Why is that? Because you shine, and I'm not just saying that to get more SATs. Ordinary Oysters and mussels can produce these beauties! Nothing seriously unique about them, however, with a little time and love each oyster is capable of creating something truly beautiful. I like believing so, at least, given the fact that you're even reading this article; makes you an (N)oystr! This isn't published this on X (formerly known as Twitter), Facebook, Discord, Telegram, or Instagram, which makes you the rare breed! A pearl indeed! I do have access to those platforms, but why create content on a terrible platform knowing I too could be shut down! Unfortunately, many people still use these platforms. This forces individuals to give up their privacy every day. Meta is leading the charge by forcing users to provide a photo ID for verification in order to use their crappy, obsolete site. If that was not bad enough, imagine if you're having a type of disagreement or opinion. Then, Bigtech can easily deplatform you. Umm. So no open debate? Just instantly shut-off users. Whatever, happened to right to a fair trial? Nope, just burning you at the stake as if you're a witch or warlock!

How heinous are the perpetrators and financiers of this? Well, that's opening another can of worms for you.
Imagine your voice being taken away, like the little mermaid. Ariel was lucky to have a prince, but the majority of us? The likelihood that I would be carried away by the current of the sea during a sunset with a prince on a sailboat is zero. And I live on an island, so I'm just missing the prince, sailboat(though I know where I could go to steal one), and red hair. Oh my gosh, now I feel sad.
I do not have the prince, Bob is better! I do not have mermaid fins, or a shell bra. Use coconut shells, it offers more support! But, I still have my voice and a killer sunset to die for!
All of that is possible thanks to the work of developers. These knights fight for Freedom Tech by utilizing FOSS, which help provides us with a vibrant ecosystem. Unfortunately, I recently learned that they are not all funded. Knights must eat, drink, and have a work space. This space is where they spend most of their sweat equity on an app or software that may and may not pan out. That brilliance is susceptible to fading, as these individuals are not seen but rather stay behind closed doors. What's worse, if these developers lose faith in their project and decide to join forces with Meta! 😖 Does WhatsApp ring a bell?
Without them, I probably wouldn't be able to create this long form article. Let's cheer them on like cheerleaders.. 👉Unfortunately, there's no cheerleader emoji so you'll just have to settle for a dancing lady, n guy. 💃🕺
Semisol said it beautifully, npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj
If we want freedom tech to succeed, the tools that make it possible need to be funded: relays like https://nostr.land, media hosts like https://nostr.build, clients like https://damus.io, etc.
With that thought, Onigirl is pleased to announce the launch of a new series. With a sole focus on free market devs/projects.
Knights of Nostr!
I'll happily brief you about their exciting project and how it benefits humanity! Let's Support these Magnificent projects, devs, relays, and builders! Our first runner up!
Oppa Fishcake :Lord of Media Hosting
npub137c5pd8gmhhe0njtsgwjgunc5xjr2vmzvglkgqs5sjeh972gqqxqjak37w
Oppa Fishcake with his noble steed!
Think of this as an introduction to learn and further your experience on Nostr! New developments and applications are constantly happening on Nostr. It's enough to make one's head spin. I may also cover FOSS projects(outside of Nostr) as they need some love as well! Plus, you can think of it as another tool to add to your decentralized life. I will not be doing how-to-Nostr guides. I personally feel there are plenty of great guides already available! Which I'm happy to add to curation collection via easily searchable on Yakihonne.
For email updates you can subscribe to my [[https://paragraph.xyz/@onigirl]]
If you like it, send me some 🧡💛💚 hearts💜💗💖 otherwise zap dat⚡⚡🍑🍑peach⚡⚡🍑 ~If not me, then at least to our dearest knight!
Thank you from the bottom of my heart for your time and support (N)oystr! Shine bright like a diamond! Share if you care! FOSS power!
Follow on your favorite Nostr Client for the best viewing experience!
[!NOTE]
I'm using Obsidian + Nostr Writer Plugin; a new way to publish Markdown directly to Nostr. I was a little nervous using this because I was used doing them in RStudio; R Markdown.
Since this is my first article, I sent it to my account as a draft to test it. It's pretty neat. -
 @ 341db5a7:4c4fc2ef
2024-03-26 00:58:09
@ 341db5a7:4c4fc2ef
2024-03-26 00:58:09Chef's notes
Cook in a well seasoned, antique cast iron skillet. Preferably one passed down from your grandmother.
Details
- ⏲️ Prep time: 10 mins
- 🍳 Cook time: 30 mins
- 🍽️ Servings: 8
Ingredients
- 1 cup yellow cornmeal
- 1 cup white flour
- 1/4 cup white sugar
- 1 heaping tablespoon baking powder
- 1 teaspoon salt
- 1 cup whole milk
- 1 large egg
- 1/4 cup lard or shortening
Directions
- Preheat oven to 375°F (190° C)
- Heat lard or shortening in cast iron skillet over medium-high heat on the stovetop
- Combine all dry ingredients in large mixing bowl (cornmeal, flour, sugar, salt, baking powder)
- Whisk dry ingredients to combine
- Add wet ingredients, milk and egg, and whisk until a loose batter is formed. If it's too stiff to pour, add a small amount of milk and keep whisking.
- When the oil in the cast iron skillet is smoking hot, pour the batter into the skillet, scraping the sides with a spatula to get it all out.
- Give the cast iron skillet a little tap to let the batter settle into the oil, remove from the stovetop and transfer into the preheated oven for 30 minutes.
- The cornbread should have risen and turned golden brown on top. Remove from oven, and transfer to a plate or serving disk. Cut it down the middle and add salted butter.
-
 @ ee11a5df:b76c4e49
2023-07-29 03:27:23
@ ee11a5df:b76c4e49
2023-07-29 03:27:23Gossip: The HTTP Fetcher
Gossip is a desktop nostr client. This post is about the code that fetches HTTP resources.
Gossip fetches HTTP resources. This includes images, videos, nip05 json files, etc. The part of gossip that does this is called the fetcher.
We have had a fetcher for some time, but it was poorly designed and had problems. For example, it was never expiring items in the cache.
We've made a lot of improvements to the fetcher recently. It's pretty good now, but there is still room for improvement.
Caching
Our fetcher caches data. Each URL that is fetched is hashed, and the content is stored under a file in the cache named by that hash.
If a request is in the cache, we don't do an HTTP request, we serve it directly from the cache.
But cached data gets stale. Sometimes resources at a URL change. We generally check resources again after three days.
We save the server's ETag value for content, and when we check the content again we supply an If-None-Match header with the ETag so the server could respond with 304 Not Modified in which case we don't need to download the resource again, we just bump the filetime to now.
In the event that our cache data is stale, but the server gives us an error, we serve up the stale data (stale is better than nothing).
Queueing
We used to fire off HTTP GET requests as soon as we knew that we needed a resource. This was not looked on too kindly by servers and CDNs who were giving us either 403 Forbidden or 429 Too Many Requests.
So we moved into a queue system. The host is extracted from each URL, and each host is only given up to 3 requests at a time. If we want 29 images from the same host, we only ask for three, and the remaining 26 remain in the queue for next time. When one of those requests completes, we decrement the host load so we know that we can send it another request later.
We process the queue in an infinite loop where we wait 1200 milliseconds between passes. Passes take time themselves and sometimes must wait for a timeout. Each pass fetches potentially multiple HTTP resources in parallel, asynchronously. If we have 300 resources at 100 different hosts, three per host, we could get them all in a single pass. More likely a bunch of resources are at the same host, and we make multiple passes at it.
Timeouts
When we fetch URLs in parallel asynchronously, we wait until all of the fetches complete before waiting another 1200 ms and doing another loop. Sometimes one of the fetches times out. In order to keep things moving, we use short timeouts of 10 seconds for a connect, and 15 seconds for a response.
Handling Errors
Some kinds of errors are more serious than others. When we encounter these, we sin bin the server for a period of time where we don't try fetching from it until a specified period elapses.
-
 @ 000002de:c05780a7
2024-04-24 03:52:38
@ 000002de:c05780a7
2024-04-24 03:52:38 -
 @ ee11a5df:b76c4e49
2023-07-29 03:13:59
@ ee11a5df:b76c4e49
2023-07-29 03:13:59Gossip: Switching to LMDB
Unlike a number of other nostr clients, Gossip has always cached events and related data in a local data store. Up until recently, SQLite3 has served this purpose.
SQLite3 offers a full ACID SQL relational database service.
Unfortunately however it has presented a number of downsides:
- It is not as parallel as you might think.
- It is not as fast as you might hope.
- If you want to preserve the benefit of using SQL and doing joins, then you must break your objects into columns, and map columns back into objects. The code that does this object-relational mapping (ORM) is not trivial and can be error prone. It is especially tricky when working with different types (Rust language types and SQLite3 types are not a 1:1 match).
- Because of the potential slowness, our UI has been forbidden from direct database access as that would make the UI unresponsive if a query took too long.
- Because of (4) we have been firing off separate threads to do the database actions, and storing the results into global variables that can be accessed by the interested code at a later time.
- Because of (4) we have been caching database data in memory, essentially coding for yet another storage layer that can (and often did) get out of sync with the database.
LMDB offers solutions:
- It is highly parallel.
- It is ridiculously fast when used appropriately.
- Because you cannot run arbitrary SQL, there is no need to represent the fields within your objects separately. You can serialize/deserialize entire objects into the database and the database doesn't care what is inside of the blob (yes, you can do that into an SQLite field, but if you did, you would lose the power of SQL).
- Because of the speed, the UI can look stuff up directly.
- We no longer need to fork separate threads for database actions.
- We no longer need in-memory caches of data. The LMDB data is already in-memory (it is memory mapped) so we just access it directly.
The one obvious downside is that we lose SQL. We lose the query planner. We cannot ask arbitrary question and get answers. Instead, we have to pre-conceive of all the kinds of questions we want to ask, and we have to write code that answers them efficiently. Often this involves building and maintaining indices.
Indices
Let's say I want to look at fiatjaf's posts. How do I efficiently pull out just his recent feed-related events in reverse chronological order? It is easy if we first construct the following index
key: EventKind + PublicKey + ReverseTime value: Event Id
In the above, '+' is just a concatenate operator, and ReverseTime is just some distant time minus the time so that it sorts backwards.
Now I just ask LMDB to start from (EventKind=1 + PublicKey=fiatjaf + now) and scan until either one of the first two fields change, or more like the time field gets too old (e.g. one month ago). Then I do it again for the next event kind, etc.
For a generalized feed, I have to scan a region for each person I follow.
Smarter indexes can be imagined. Since we often want only feed-related event kinds, that can be implicit in an index that only indexes those kinds of events.
You get the idea.
A Special Event Map
At first I had stored events into a K-V database under the Id of the event. Then I had indexes on events that output a set of Ids (as in the example above).
But when it comes to storing and retrieving events, we can go even faster than LMDB.
We can build an append-only memory map that is just a sequence of all the events we have, serialized, and in no particular order. Readers do not need a lock and multiple readers can read simultaneously. Writers will need to acquire a lock to append to the map and there may only be one writer at a time. However, readers can continue reading even while a writer is writing.
We can then have a K-V database that maps Id -> Offset. To get the event you just do a direct lookup in the event memory map at that offset.
The real benefit comes when we have other indexes that yield events, they can yield offsets instead of ids. Then we don't need to do a second lookup from the Id to the Event, we can just look directly at the offset.
Avoiding deserialization
Deserialization has a price. Sometimes it requires memory allocation (if the object is not already linear, e.g. variable lengthed data like strings and vectors are allocated on the heap) which can be very expensive if you are trying to scan 150,000 or so events.
We serialize events (and other objects where we can) with a serialization library called speedy. It does its best to preserve the data much like it is represented in memory, but linearized. Because events start with fixed-length fields, we know the offset into the serialized event where these first fields occur and we can directly extract the value of those fields without deserializing the data before it.
This comes in useful whenever we need to scan a large number of events. Search is the one situation where I know that we must do this. We can search by matching against the content of every feed-related event without fully deserialing any of them.
-
 @ 1f9e547c:8af216ed
2024-04-24 02:50:57
@ 1f9e547c:8af216ed
2024-04-24 02:50:57Opinion about Binance: Buy Bitcoin & Crypto (android)
Binance is one of the more popular cryptocurrency exchanges in the Philippines - it is currently under regulatory uncertainty.
Philippine government orders Google Play and Apple Store to remove Binance App. Source: CNBC
As of 2024-04-24 The app is still available via Google Play.
A copy of the SEC (Philippines) order.
This is to inform the public that the online cryptocurrency exchange BINANCE is NOT AUTHORIZED TO SELL or OFFER SECURITIES to the public in the Philippines. Based on the reports and information gathered by the Commission, BINANCE has been actively employing promotional campaigns on various social media platforms to attract and entice Filipinos to engage in investment and trading activities using its platforms.
In view thereof, the public is hereby advised to exercise caution before investing in these kinds of unregistered online investment platforms and their representatives. In dealing with these unregistered platforms, the Commission reiterates its Advisory entitled: “Advisory against Dealing with Non-Registered Foreign Entities, Organizations, and Corporations”.
In addition, those who act as salesmen, brokers, dealers or agents, representatives, promoters, recruiters, influencers, endorsers, and enablers of the BINANCE platform in selling or convincing people to invest in this platform within the Philippines even through online means may be held criminally liable under Section 28 of the SRC and be penalized with a maximum fine of Five Million Pesos (P 5,000,000.00) or imprisonment of Twenty One (21) years or both pursuant to Section 73 of the SRC (SEC vs. Oudine Santos G.R. No. 195542, 19 March 2014).
For the guidance of the public. Makati City, 28 November 2023.
As of April 24, 2024, these are the list of countries where Binance is banned:
- Canada
- Afghanistan
- Japan
- India
- Vietnam
- Germany
- Iran
- Bangladesh
- Kazakhstan
- Italy
- Belgium
- Malaysia
- China
- Thailand
- United Kingdom
- France
- Philippines
Curiously, in the United States, there are states where Binance claims that users can sign up (Information as of March 6, 2024, Source: Binance Site):
- Alaska
- American Samoa
- Hawaii
- Maine
- New York
- Northern Mariana Islands
- Texas
- U.S. Virgin Islands
- Vermont
February 23, 2024 - Judge Approves Binance’s $4.3 Billion Settlement For Anti-Money Laundering, Sanctions Violations Forbes.com
WalletScrutiny #nostrOpinion
-
 @ ee11a5df:b76c4e49
2023-07-29 02:52:13
@ ee11a5df:b76c4e49
2023-07-29 02:52:13Gossip: Zaps
Gossip is a desktop nostr client. This post is about the code that lets users send lightning zaps to each other (NIP-57).
Gossip implemented Zaps initially on 20th of June, 2023.
Gossip maintains a state of where zapping is at, one of: None, CheckingLnurl, SeekingAmount, LoadingInvoice, and ReadyToPay.
When you click the zap lightning bolt icon, Gossip moves to the CheckingLnurl state while it looks up the LN URL of the user.
If this is successful, it moves to the SeekingAmount state and presents amount options to the user.
Once a user chooses an amount, it moves to the LoadingInvoice state where it interacts with the lightning node and receives and checks an invoice.
Once that is complete, it moves to the ReadyToPay state, where it presents the invoice as a QR code for the user to scan with their phone. There is also a copy button so they can pay it from their desktop computer too.
Gossip also loads zap receipt events and associates them with the event that was zapped, tallying a zap total on that event. Gossip is unfortunately not validating these receipts very well currently, so fake zap receipts can cause an incorrect total to show. This remains an open issue.
Another open issue is the implementation of NIP-46 Nostr Connect and NIP-47 Wallet Connect.
-
 @ b12b632c:d9e1ff79
2023-07-21 19:45:20
@ b12b632c:d9e1ff79
2023-07-21 19:45:20I love testing every new self hosted app and I can say that Nostr "world" is really good regarding self hosting stuff.
Today I tested a Nostr relay named Strfry.
Strfry is really simple to setup and support a lot's of Nostr NIPs.
Here is the list of what it is able to do :
- Supports most applicable NIPs: 1, 2, 4, 9, 11, 12, 15, 16, 20, 22, 28, 33, 40
- No external database required: All data is stored locally on the filesystem in LMDB
- Hot reloading of config file: No server restart needed for many config param changes
- Zero downtime restarts, for upgrading binary without impacting users
- Websocket compression: permessage-deflate with optional sliding window, when supported by clients
- Built-in support for real-time streaming (up/down/both) events from remote relays, and bulk import/export of events from/to jsonl files
- negentropy-based set reconcilliation for efficient syncing with remote relays
Installation with docker compose (v2)
Spoiler : you need to have a computer with more than 1 (v)Core / 2GB of RAM to build the docker image locally. If not, this below might crash your computer during docker image build. You may need to use a prebuilt strfry docker image.
I assume you've read my first article on Managing domain with Nginx Proxy Manager because I will use the NPM docker compose stack to publish strfry Nostr relay. Without the initial NPM configuration done, it may not work as expected. I'll use the same docker-compose.yml file and folder.
Get back in the "npm-stack" folder :
cd npm-stackCloning the strfry github repo locally :
git clone https://github.com/hoytech/strfry.gitModify the docker-compose file to locate the strfry configuration data outside of the folder repo directory to avoid mistake during futures upgrades (CTRL + X, S & ENTER to quit and save modifications) :
nano docker-compose.ymlYou don't have to insert the Nginx Proxy Manager part, you should already have it into the file. If not, check here. You should only have to add the strfry part.
``` version: '3.8' services: # should already be present into the docker-compose.yml app: image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: # These ports are in format
: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port # Add any other Stream port you want to expose # - '21:21' # FTP # Uncomment the next line if you uncomment anything in the section # environment: # Uncomment this if you want to change the location of # the SQLite DB file within the container # DB_SQLITE_FILE: "/data/database.sqlite" # Uncomment this if IPv6 is not enabled on your host # DISABLE_IPV6: 'true' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencryptstrfry-nostr-relay: container_name: strfry build: ./strfry volumes: - ./strfry-data/strfry.conf:/etc/strfry.conf - ./strfry-data/strfry-db:/app/strfry-db
ports is commented by NPM will access through docker internal network
no need to expose strfry port directly to the internet
ports:
- "7777:7777"
```
Before starting the container, we need to customize the strfry configuration file "strfry.conf". We'll copy the strfry configuration file and place it into the "strfry-data" folder to modify it with our own settings :
mkdir strfry-data && cp strfry/strfry.conf strfry-data/And modify the strfry.conf file with your own settings :
nano strfry-data/strfry.confYou can modify all the settings you need but the basics settings are :
- bind = "127.0.0.1" --> bind = "0.0.0.0" --> otherwise NPM won't be able to contact the strfry service
-
name = "strfry default" --> name of your nostr relay
-
description = "This is a strfry instance." --> your nostr relay description
-
pubkey = "" --> your pubkey in hex format. You can use the Damu's tool to generate your hex key from your npub key : https://damus.io/key/
-
contact = "" --> your email
``` relay { # Interface to listen on. Use 0.0.0.0 to listen on all interfaces (restart required) bind = "127.0.0.1"
# Port to open for the nostr websocket protocol (restart required) port = 7777 # Set OS-limit on maximum number of open files/sockets (if 0, don't attempt to set) (restart required) nofiles = 1000000 # HTTP header that contains the client's real IP, before reverse proxying (ie x-real-ip) (MUST be all lower-case) realIpHeader = "" info { # NIP-11: Name of this server. Short/descriptive (< 30 characters) name = "strfry default" # NIP-11: Detailed information about relay, free-form description = "This is a strfry instance." # NIP-11: Administrative nostr pubkey, for contact purposes pubkey = "" # NIP-11: Alternative administrative contact (email, website, etc) contact = "" }```
You can now start the docker strfry docker container :
docker compose up -dThis command will take a bit of time because it will build the strfry docker image locally before starting the container. If your VPS doesn't have lot's of (v)CPU/RAM, it could fail (nothing happening during the docker image build). My VPS has 1 vCore / 2GB of RAM and died few seconds after the build beginning.
If it's the case, you can use prebuilt strfry docker image available on the Docker hub : https://hub.docker.com/search?q=strfry&sort=updated_at&order=desc
That said, otherwise, you should see this :
``` user@vps:~/npm-stack$ docker compose up -d [+] Building 202.4s (15/15) FINISHED
=> [internal] load build definition from Dockerfile 0.2s => => transferring dockerfile: 724B 0.0s => [internal] load .dockerignore 0.3s => => transferring context: 2B 0.0s => [internal] load metadata for docker.io/library/ubuntu:jammy 0.0s => [build 1/7] FROM docker.io/library/ubuntu:jammy 0.4s => [internal] load build context 0.9s => => transferring context: 825.64kB 0.2s => [runner 2/4] WORKDIR /app 1.3s => [build 2/7] WORKDIR /build 1.5s => [runner 3/4] RUN apt update && apt install -y --no-install-recommends liblmdb0 libflatbuffers1 libsecp256k1-0 libb2-1 libzstd1 && rm -rf /var/lib/apt/lists/* 12.4s => [build 3/7] RUN apt update && apt install -y --no-install-recommends git g++ make pkg-config libtool ca-certificates libyaml-perl libtemplate-perl libregexp-grammars-perl libssl-dev zlib1g-dev l 55.5s => [build 4/7] COPY . . 0.9s => [build 5/7] RUN git submodule update --init 2.6s => [build 6/7] RUN make setup-golpe 10.8s => [build 7/7] RUN make -j4 126.8s => [runner 4/4] COPY --from=build /build/strfry strfry 1.3s => exporting to image 0.8s => => exporting layers 0.8s => => writing image sha256:1d346bf343e3bb63da2e4c70521a8350b35a02742dd52b12b131557e96ca7d05 0.0s => => naming to docker.io/library/docker-compose_strfry-nostr-relay 0.0sUse 'docker scan' to run Snyk tests against images to find vulnerabilities and learn how to fix them
[+] Running 02/02
⠿ Container strfry Started 11.0s ⠿ Container npm-stack-app-1 Running ```You can check if everything is OK with strfry container by checking the container logs :
user@vps:~/npm-stack$ docker logs strfry date time ( uptime ) [ thread name/id ] v| 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| arguments: /app/strfry relay 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| Current dir: /app 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| stderr verbosity: 0 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| ----------------------------------- 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| CONFIG: Loading config from file: /etc/strfry.conf 2023-07-21 19:26:58.529 ( 0.054s) [main thread ]INFO| CONFIG: successfully installed 2023-07-21 19:26:58.533 ( 0.058s) [Websocket ]INFO| Started websocket server on 0.0.0.0:7777Now, we have to create the subdomain where strfry Nostr relay will be accessible. You need to connect to your Nginx Proxy Manager admin UI and create a new proxy host with these settings :
"Details" tab (Websockets support is mandatory!, you can replace "strfry" by whatever you like, for instance : mybeautifulrelay.yourdomain.tld)
"Details" tab:

"SSL" tab:

And click on "Save"
If everything is OK, when you go to https://strfry.yourdomain.tld you should see :

To verify if strfry is working properly, you can test it with the (really useful!) website https://nostr.watch. You have to insert your relay URL into the nostr.watch URL like this : https://nostr.watch/relay/strfry.yourdomain.tld
You should see this :

If you are seeing your server as online, readable and writable, you made it ! You can add your Nostr strfry server to your Nostr prefered relay and begin to publish notes ! 🎇
Future work:
Once done, strfry will work like a charm but you may need to have more work to update strfry in the near future. I'm currently working on a bash script that will :
- Updatethe "strfry" folder,
- Backup the "strfry.conf" file,
- Download the latest "strfry.conf" from strfry github repo,
- Inject old configuration settings into the new "strfry.conf" file,
- Compose again the stack (rebuilding the image to get the latest code updates),
- etc.
Tell me if you need the script!
Voilààààà
See you soon in another Fractalized story!
-
 @ b12b632c:d9e1ff79
2023-07-21 14:19:38
@ b12b632c:d9e1ff79
2023-07-21 14:19:38Self hosting web applications comes quickly with the need to deal with HTTPS protocol and SSL certificates. The time where web applications was published over the 80/TCP port without any encryption is totally over. Now we have Let's Encrypt and other free certification authority that lets us play web applications with, at least, the basic minimum security required.
Second part of web self hosting stuff that is really useful is the web proxifycation.
It's possible to have multiple web applications accessible through HTTPS but as we can't use the some port (spoiler: we can) we are forced to have ugly URL as https://mybeautifudomain.tld:8443.
This is where Nginx Proxy Manager (NPM) comes to help us.
NPM, as gateway, will listen on the 443 https port and based on the subdomain you want to reach, it will redirect the network flow to the NPM differents declared backend ports. NPM will also request HTTPS cert for you and let you know when the certificate expires, really useful.
We'll now install NPM with docker compose (v2) and you'll see, it's very easy.
You can find the official NPM setup instructions here.
But before we absolutely need to do something. You need to connect to the registrar where you bought your domain name and go into the zone DNS section.You have to create a A record poing to your VPS IP. That will allow NPM to request SSL certificates for your domain and subdomains.
Create a new folder for the NPM docker stack :
mkdir npm-stack && cd npm-stackCreate a new docker-compose.yml :
nano docker-compose.ymlPaste this content into it (CTRL + X ; Y & ENTER to save/quit) :
``` version: '3.8' services: app: image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: # These ports are in format
: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port # Add any other Stream port you want to expose # - '21:21' # FTP # Uncomment the next line if you uncomment anything in the section # environment: # Uncomment this if you want to change the location of # the SQLite DB file within the container # DB_SQLITE_FILE: "/data/database.sqlite" # Uncomment this if IPv6 is not enabled on your host # DISABLE_IPV6: 'true' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt```
You'll not believe but it's done. NPM docker compose configuration is done.
To start Nginx Proxy Manager with docker compose, you just have to :
docker compose up -dYou'll see :
user@vps:~/tutorials/npm-stack$ docker compose up -d [+] Running 2/2 ✔ Network npm-stack_default Created ✔ Container npm-stack-app-1 StartedYou can check if NPM container is started by doing this command :
docker psYou'll see :
user@vps:~/tutorials/npm-stack$ docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 7bc5ea8ac9c8 jc21/nginx-proxy-manager:latest "/init" About a minute ago Up About a minute 0.0.0.0:80-81->80-81/tcp, :::80-81->80-81/tcp, 0.0.0.0:443->443/tcp, :::443->443/tcp npm-stack-app-1If the command show "Up X minutes" for the npm-stack-app-1, you're good to go! You can access to the NPM admin UI by going to http://YourIPAddress:81.You shoud see :

The default NPM login/password are : admin@example.com/changeme .If the login succeed, you should see a popup asking to edit your user by changing your email password :
 And your password :
And your password :
 Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
 Followed by "Add Proxy Host"
Followed by "Add Proxy Host"
 If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :
If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :Details tab :
 SSL tab :
SSL tab :
 And click on "Save".
And click on "Save".NPM will request the SSL certificate "admin.yourdomain.tld" for you.
If you have an erreor message "Internal Error" it's probably because your domaine DNS zone is not configured with an A DNS record pointing to your VPS IP.
Otherwise you should see (my domain is hidden) :

Clicking on the "Source" URL link "admin.yourdomain.tld" will open a pop-up and, surprise, you should see the NPM admin UI with the URL "https://admin.yourdomain.tld" !
If yes, bravo, everything is OK ! 🎇
You know now how to have a subdomain of your domain redirecting to a container web app. In the next blog post, you'll see how to setup a Nostr relay with NPM ;)
Voilààààà
See you soon in another Fractalized story!
-
 @ 3bf0c63f:aefa459d
2024-03-21 00:19:43
@ 3bf0c63f:aefa459d
2024-03-21 00:19:43Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ fa984bd7:58018f52
2024-04-23 22:27:52
@ fa984bd7:58018f52
2024-04-23 22:27:52I like climbing, coding and bitcoin. (in that order)
-
 @ b12b632c:d9e1ff79
2023-07-20 20:12:39
@ b12b632c:d9e1ff79
2023-07-20 20:12:39Self hosting web applications comes quickly with the need to deal with HTTPS protocol and SSL certificates. The time where web applications was published over the 80/TCP port without any encryption is totally over. Now we have Let's Encrypt and other free certification authority that lets us play web applications with, at least, the basic minimum security required.
Second part of web self hosting stuff that is really useful is the web proxifycation.
It's possible to have multiple web applications accessible through HTTPS but as we can't use the some port (spoiler: we can) we are forced to have ugly URL as https://mybeautifudomain.tld:8443.
This is where Nginx Proxy Manager (NPM) comes to help us.
NPM, as gateway, will listen on the 443 https port and based on the subdomain you want to reach, it will redirect the network flow to the NPM differents declared backend ports. NPM will also request HTTPS cert for you and let you know when the certificate expires, really useful.
We'll now install NPM with docker compose (v2) and you'll see, it's very easy.
You can find the official NPM setup instructions here.
But before we absolutely need to do something. You need to connect to the registrar where you bought your domain name and go into the zone DNS section.You have to create a A record poing to your VPS IP. That will allow NPM to request SSL certificates for your domain and subdomains.
Create a new folder for the NPM docker stack :
mkdir npm-stack && cd npm-stackCreate a new docker-compose.yml :
nano docker-compose.ymlPaste this content into it (CTRL + X ; Y & ENTER to save/quit) :
``` version: '3.8' services: app: image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: # These ports are in format
: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port # Add any other Stream port you want to expose # - '21:21' # FTP # Uncomment the next line if you uncomment anything in the section # environment: # Uncomment this if you want to change the location of # the SQLite DB file within the container # DB_SQLITE_FILE: "/data/database.sqlite" # Uncomment this if IPv6 is not enabled on your host # DISABLE_IPV6: 'true' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt```
You'll not believe but it's done. NPM docker compose configuration is done.
To start Nginx Proxy Manager with docker compose, you just have to :
docker compose up -dYou'll see :
user@vps:~/tutorials/npm-stack$ docker compose up -d [+] Running 2/2 ✔ Network npm-stack_default Created ✔ Container npm-stack-app-1 StartedYou can check if NPM container is started by doing this command :
docker psYou'll see :
user@vps:~/tutorials/npm-stack$ docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 7bc5ea8ac9c8 jc21/nginx-proxy-manager:latest "/init" About a minute ago Up About a minute 0.0.0.0:80-81->80-81/tcp, :::80-81->80-81/tcp, 0.0.0.0:443->443/tcp, :::443->443/tcp npm-stack-app-1If the command show "Up X minutes" for the npm-stack-app-1, you're good to go! You can access to the NPM admin UI by going to http://YourIPAddress:81.You shoud see :

The default NPM login/password are : admin@example.com/changeme .If the login succeed, you should see a popup asking to edit your user by changing your email password :
 And your password :
And your password :
 Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
 Followed by "Add Proxy Host"
Followed by "Add Proxy Host"
 If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :
If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :Details tab :
 SSL tab :
SSL tab :
 And click on "Save".
And click on "Save".NPM will request the SSL certificate "admin.yourdomain.tld" for you.
If you have an erreor message "Internal Error" it's probably because your domaine DNS zone is not configured with an A DNS record pointing to your VPS IP.
Otherwise you should see (my domain is hidden) :

Clicking on the "Source" URL link "admin.yourdomain.tld" will open a pop-up and, surprise, you should see the NPM admin UI with the URL "https://admin.yourdomain.tld" !
If yes, bravo, everything is OK ! 🎇
You know now how to have a subdomain of your domain redirecting to a container web app. In the next blog post, you'll see how to setup a Nostr relay with NPM ;)
Voilààààà
See you soon in another Fractalized story!
-
 @ 5e4e1309:1164206e
2024-04-23 21:46:01
@ 5e4e1309:1164206e
2024-04-23 21:46:01Opinion about Bitcoin Wallet - BTC Exchange (android)
'm outraged by Freewallet's exploitation of Cloudflare for their scams. It's time to stand up against such unethical behavior. Let's join forces and demand that Cloudflare takes action to stop Freewallet's abuses and protect users.
WalletScrutiny #nostrOpinion
-
 @ 1d4cdded:80994472
2024-04-23 16:26:14
@ 1d4cdded:80994472
2024-04-23 16:26:14Hi everyone, I'm Dave Bradley. I'll be answering questions for roughly the next 69 minutes.
I'm widely known as The Strongest and Best Looking Bitcoin Entrepreneur in Canada.
I got into bitcoin in 2010. I founded the worlds first? physical bitcoin store in 2013.
I co-founded Bull Bitcoin in 2018.
I helped make Bitcoin Well the first publicly traded bitcoin ATM company in the world.
I'm organizing The Bitcoin Rodeo, the best bitcoin conference in the world.
I'm a well known steak influencer.
-
 @ b12b632c:d9e1ff79
2023-07-19 00:17:02
@ b12b632c:d9e1ff79
2023-07-19 00:17:02Welcome to a new Fractalized episode of "it works but I can do better"!
Original blog post from : https://fractalized.ovh/use-ghost-blog-to-serve-your-nostr-nip05-and-lnurl/
Few day ago, I wanted to set my Ghost blog (this one) as root domain for Fractalized instead of the old basic Nginx container that served my NIP05. I succeed to do it with Nginx Proxy Manager (I need to create a blog post because NPM is really awesome) but my NIP05 was down.
Having a bad NIP05 on Amethyst is now in the top tier list of my worst nightmares.
As a reminder, to have a valid NIP05 on your prefered Nostr client, you need to have a file named "nostr.json" in a folder ".well-known" located in the web server root path (subdomain or domain). The URL shoud look like this http://domain.tld/.well-known/nostr.json
PS : this doesn't work with Ghost as explained later. If you are here for Ghost, skip this and go directly to 1).
You should have these info inside the nostr.json file (JSON format) :
{ "names": { "YourUsername": "YourNPUBkey" } }You can test it directly by going to the nostr.json URL, it should show you the JSON.
It was working like a charm on my previous Nginx and I needed to do it on my new Ghost. I saw on Google that I need to have the .well-known folder into the Ghost theme root folder (In my case I choosed the Solo theme). I created the folder, put my nostr.json file inside it and crossed my fingers. Result : 404 error.
I had to search a lot but it seems that Ghost forbid to server json file from its theme folders. Maybe for security reasons, I don't know. Nevertheless Ghost provide a method to do it (but it requires more than copy/paste some files in some folders) => routes
In the same time that configuring your NIP05, I also wanted to setup an LNURL to be zapped to pastagringo@fractalized.ovh (configured into my Amethyst profile). If you want more infromation on LNURL, it's very well explained here.
Because I want to use my Wallet of Satoshi sats wallet "behind" my LNURL, you'll have to read carefuly the EzoFox's blog post that explains how to retrieve your infos from Alby or WoS.
1) Configuring Ghost routes
Add the new route into the routes.yaml (accessible from "Settings" > "Labs" > "Beta features" > "Routes" ; you need to download the file, modify it and upload it again) to let him know where to look for the nostr.json file.
Here is the content of my routes.yaml file :
``` routes: /.well-known/nostr.json/: template: _nostr-json content_type: application/json /.well-known/lnurlp/YourUsername/: template: _lnurlp-YourUsername content_type: application/json collections: /: permalink: /{slug}/ template: index
taxonomies: tag: /tag/{slug}/ author: /author/{slug}/ ```
=> template : name of the file that ghost will search localy
=> content_type : file type (JSON is required for the NIP05)
The first route is about my NIP05 and the second route is about my LNURL.
2) Creating Ghost route .hbs files
To let Ghost serve our JSON content, I needed to create the two .hbs file filled into the routes.yaml file. These files need to be located into the root directory of the Ghost theme used. For me, it was Solo.
Here is there content of both files :
"_nostr-json.hbs"
{ "names": { "YourUsername": "YourNPUBkey" } }"_lnurlp-pastagringo.hbs" (in your case, _lnurlp-YourUsername.hbs)
{ "callback":"https://livingroomofsatoshi.com/api/v1/lnurl/payreq/XXXXX", "maxSendable":100000000000, "minSendable":1000, "metadata":"[[\"text/plain\",\"Pay to Wallet of Satoshi user: burlyring39\"],[\"text/identifier\",\"YourUsername@walletofsatoshi.com\"]]", "commentAllowed":32, "tag":"payRequest", "allowsNostr":true, "nostrPubkey":"YourNPUBkey" }After doing that, you almost finished, you just have to restart your Ghost blog. As I use Ghost from docker container, I just had to restart the container.
To verify if everything is working, you have to go in the routes URL created earlier:
https://YourDomain.tld/.well-known/nostr.jsonand
https://YourDomain.tld/.well-known/lnurlp/YourUsernameBoth URL should display JSON files from .hbs created ealier.
If it's the case, you can add your NIP05 and LNURL into your Nostr profile client and you should be able to see a valid tick from your domain and to be zapped on your LNURL (sending zaps to your WoS or Alby backend wallet).
Voilààààà
See you soon in another Fractalized story!
-
 @ 5d4b6c8d:8a1c1ee3
2024-04-23 13:18:59
@ 5d4b6c8d:8a1c1ee3
2024-04-23 13:18:59I think Kelly Oubre Jr. looks awesome in a 76ers uniform: He just looks like he could have been Dr. J's teammate. It got me thinking about whether there are other player-uniform combinations that are a great match.
The two others that came to mind, were Jarrett Allen and Spencer Dinwiddie when they played for the Nets. Clearly, I like the 70's ABA aesthetic.
Have other stackers noticed this with other players?
Who was the best fit for their uniform?
-
 @ 3d599bf6:a0122cef
2024-04-24 09:26:09
@ 3d599bf6:a0122cef
2024-04-24 09:26:09This is just a test article.
-
 @ 1d22e00c:50e00d0e
2024-04-24 04:26:44
@ 1d22e00c:50e00d0e
2024-04-24 04:26:44Hey everyone and welcome to Refinery Life Australia.
This series is based on the Beatitudes, found in the beginning of the Sermon on the Mount.
Today we are discussing, The Poverty That Possesses.
Text
Matthew 5:3 NKJV
3 “Blessed are the poor in spirit, For theirs is the kingdom of heaven.
Scripture Reading
2 Corinthians 8:1-9 NKJV
Excel in Giving
1 Moreover, brethren, we make known to you the grace of God bestowed on the churches of Macedonia:
2 that in a great trial of affliction the abundance of their joy and their deep poverty abounded in the riches of their liberality.
3 For I bear witness that according to their ability, yes, and beyond their ability, they were freely willing,
4 imploring us with much urgency [a]that we would receive the gift and the fellowship of the ministering to the saints.
5 And not only as we had hoped, but they first gave themselves to the Lord, and then to us by the will of God.
6 So we urged Titus, that as he had begun, so he would also complete this grace in you as well.
7 But as you abound in everything—in faith, in speech, in knowledge, in all diligence, and in your love for us—see that you abound in this grace also.
Christ Our Pattern
8 I speak not by commandment, but I am testing the sincerity of your love by the diligence of others.
9 For you know the grace of our Lord Jesus Christ, that though He was rich, yet for your sakes He became poor, that you through His poverty might become rich.
Prayer
Father, we thank You for adopting us as your children.
With eyes wide open to Your mercies, we come to dedicate ourselves to you afresh.
Help us to use our talents and testimony that others may know Christ.
As be bring our tithes and offerings, we pray Your blessings upon them.
Help us meet the expenses of the ministry of this church and engage in ministries to the outer most ends of the earth.
In Jesus name we pray.
Amen.
Introduction.
The person who is truly poor in spirit is blessed because such poverty enables that person to possess the supreme possession of all, “the kingdom of heaven.”
For our sakes, Jesus set the example in 2 Corinthians 8:9, For you know the grace of our Lord Jesus Christ, that though He was rich, yet for your sakes He became poor, that you through His poverty might become rich.
Poverty of spirit is the first character trait Jesus wants in His followers, the subjects of His kingdom.
It is a trait that carries its own reward, “theirs is the kingdom of heaven.”
Note the tenses here carefully, “Blessed are the poor in spirit,” not “have been,” or “ shall be,” but “are.”
Two questions about his beatitude call for an answer.
- What is poverty of spirit?
Jesus said that the ones who are poor in spirit are blessed.
How so?
What does He mean?
Let’s consider the answer from two points of view.
Firstly negatively.
Poverty of spirit does not mean poverty of possessions.
It is true that earthly poverty does sometimes produce conditions in which Christian virtues might thrive.
It is also true that the Bible warns us against “the cares of this world and the deceitfulness of riches” because of their power to distract us from the desire for heaven’s treasure.
But happiness is a matter of character, not conditions.
It issues from the rightness of our hearts, the relationships of our lives, and not from external conditions.
A person may be a millionaire and yet be poor in spirit.
Someone could be penniless but also proud and arrogant.
Poverty of spirit does not mean poverty of native endowment.
No life was ever richer that Jesus’ life, yet He was poor in spirit.
Poverty of spirit does not mean poverty of spiritual life in the sense of being feeble and neutral in our life.
Jesus came to bring the abundant life.
He had patience with those of little faith, those weak in spirit, and those impetuous in actions.
But He wanted to help them grow, to be of great faith, to be of strong convictions.
Poverty of spirit does not mean pretension of humility.
Some are great at self depreciation.
Jesus had no patience with the sort of person that is always saying “I am nothing and nobody and not worth your attention.”
Often deep down in their hearts, they are desirous of people knowing them in the marketplace and being the proudest of the proud.
The pride that apes humility is more detestable than the pride that casts of all disguise.
The second point of view is the positive.
What then is this poverty of spirit that Jesus called blessed?
Poverty of spirit is that quality of spirit that accurately perceives that man, as he is, has no virtue inherent in himself, that each gift and each grace of the spirit comes from God.
When we see how completely dispossessed of virtue and grace and righteousness we are in ourselves, pride, self esteem, and self righteousness must fall away.
Then we see how rebellious against God and His righteousness our wills have been, we want to cry our with Paul, “Wretched man that I am!” (Romans 7:24)
Poverty of spirit is the realisation that spiritually we are dispossessed, bankrupt, and without merit of our own.
Poverty of spirit is that quality of spirit that recognises that, apart from God, man is forever incomplete, and that the true centre of life is God.
The world has little time and no admiration at all for such a person.
Rather, it admires the self sufficient man, the self confident man, the so called self made man, the man who feels he is complete within himself.
The Greek philosopher Plato, discussing the good man, the happy man, places one condition upon him, he must be self sufficient.
Can you imagine standing before the Lord and expecting to enter heaven but also saying you were self sufficient?
Poverty of spirit is that quality of spirit that intensely desires that God will supply the true needs of the soul.
Jesus told a story of “two men” who “went up to the temple to pray.”
One, a Pharisee, did not actually pray.
Instead, he gave God a recital of his qualities and virtues.
He was self righteous, self satisfied.
This is exactly what poverty of spirit is not.
The other man, a publican, was so conscious of his need, so full of the sense of his own shortcomings, he would not even lift his head.
Yet, so desirous was he of God’s blessings that he cried out, “God be merciful to me a sinner.”
This is poverty of spirit.
2. How does this poverty of spirit bless us?
In what sense is it true that the poor in spirit are happy in the blessings of possessing the kingdom?
Here are five links in a chain that must not be broken.
Poverty of spirit causes us to seek in Christ the grace we need.
We need not mere conviction of sin, for conviction does not always lead to repentance and conversion.
Poverty of spirit is that appraisal of our lack on the one hand and of our sins on the other that cause a person to seek salvation.
Poverty of spirit conditions us for receiving the gift of God.
All of the prophets have realised this.
Isaiah said in Isaiah 57:15, For thus says the High and Lofty One Who inhabits eternity, whose name is Holy: “I dwell in the high and holy place, With him who has a contrite and humble spirit, To revive the spirit of the humble, And to revive the heart of the contrite ones.
David said in Psalm 51:17, The sacrifices of God are a broken spirit, A broken and a contrite heart— These, O God, You will not despise.
Poverty of spirit releases the saving grace of God upon us.
This is our only hope.
This is effective only when we empty our hearts of self and throw ourselves like broken vessels on His mercy.
Poverty of spirit fits us for service in the kingdom.
God loves to use the life that keeps self out of sight and honours only Him.
Poverty of spirit opens the eyes of the heart on the broad horizons of heavens possessions.
The vision says, “You are a child of the king. These things are yours.”
Conclusion.
Let’s test ourselves.
Let each of us ask, “Am I poor in spirit, or am I self satisfied, self righteous, and arrogant?”
Until next time
Stay in the Blessings
I really want to encourage you to be diligent with your Bible study time, because God has so much more for us than we can get from just going to church once or twice a week and hearing someone else talk about the Word.
When you spend time with God, your life will change in amazing ways, because God is a Redeemer. Theres nothing thats too hard for Him, and He can make you whole, spirit, soul and body!
You’re important to God, and you’re important to us at The Refinery.
When it comes to prayer, we believe that God wants to meet your needs and reveal His promises to you.
So whatever you’re concerned about and need prayer for we want to be here for you! Or even if you just want to say Hi, you can contact us at www.refinerylife.org
2024 IS A YEAR OF DECISIONS AND OPEN DOORS
© www.refinerylife.org 2013-2024 All rights reserved. Except as permitted under the Australian Copyright Act 1968, no part of this Article may be reproduced, stored in a retrieval system, communicated or transmitted in any form or by any means without the prior written permission.
This episode is brought to you by Refinery Life Australia:
If you enjoy The Refinery Life Radio Podcast you can help support The Refinery by doing the following:
Sow an offering: Bitcoin: bc1qqh6720t2zagj72dyfj348az698tdut3hlecaj4
Online: https://www.refinerylife.org/donate/
If you do send an offering then please email us so that we can say thank you
Subscribe on iTunes | Spotify | YouTube | TuneIn | Rumble | Flare | Zap.Stream | Fountain |
Share The Refinery with your friends and family
Subscribe to the newsletter on www.refinerylife.org
Follow The Refinery on Twitter | Nostr | Instagram | Fountain |
-
 @ b12b632c:d9e1ff79
2023-07-17 22:09:53
@ b12b632c:d9e1ff79
2023-07-17 22:09:53Today I created a new item (NIP05) to sell into my BTCpayserver store and everything was OK. The only thing that annoyed me a bit is that when a user pay the invoice to get his NIP on my Nostr Paid Relay, I need to warn him that he needs to fill his npub in the email info required by BTCpayserver before paying. Was not so user friendly. Not at all.
So I checked if BTCpayserver is able to create custom input before paying the invoice and at my big surprise, it's possible ! => release version v1.8
They even use as example my need from Nostr to get the user npub.
So it's possible, yes, but with at least the version 1.8.0. I checked immediately my BTCpayserver version on my Umbrel node and... damn... I'm in 1.7.2. I need to update my local BTCpayserver through Umbrel to access my so wanted BTCpayserver feature. I checked the local App Store but I can't see any "Update" button or something. I can see that the version installed is well the v1.7.2 but when I check the latest version available from the online Umbrel App Store. I can see v1.9.2. Damn bis.
I searched into the Umbrel Community forum, Telegram group, Google posts, asked the question on Nostr and didn't have any clue.
I finally found the answer from the Umbrel App Framework documention :
sudo ./scripts/repo checkout https://github.com/getumbrel/umbrel-apps.gitSo I did it and it updated my local Umbrel App Store to the latest version available and my BTCpayserver.
After few seconds, the BTCpaysever local URL is available and I'm allowed to login => everything is OK! \o/
See you soon in another Fractalized story!
-
 @ 3bf0c63f:aefa459d
2024-03-19 14:32:01
@ 3bf0c63f:aefa459d
2024-03-19 14:32:01Censorship-resistant relay discovery in Nostr
In Nostr is not decentralized nor censorship-resistant I said Nostr is centralized. Peter Todd thinks it is centralized by design, but I disagree.
Nostr wasn't designed to be centralized. The idea was always that clients would follow people in the relays they decided to publish to, even if it was a single-user relay hosted in an island in the middle of the Pacific ocean.
But the Nostr explanations never had any guidance about how to do this, and the protocol itself never had any enforcement mechanisms for any of this (because it would be impossible).
My original idea was that clients would use some undefined combination of relay hints in reply tags and the (now defunct)
kind:2relay-recommendation events plus some form of manual action ("it looks like Bob is publishing on relay X, do you want to follow him there?") to accomplish this. With the expectation that we would have a better idea of how to properly implement all this with more experience, Branle, my first working client didn't have any of that implemented, instead it used a stupid static list of relays with read/write toggle -- although it did publish relay hints and kept track of those internally and supportedkind:2events, these things were not really useful.Gossip was the first client to implement a truly censorship-resistant relay discovery mechanism that used NIP-05 hints (originally proposed by Mike Dilger) relay hints and
kind:3relay lists, and then with the simple insight of NIP-65 that got much better. After seeing it in more concrete terms, it became simpler to reason about it and the approach got popularized as the "gossip model", then implemented in clients like Coracle and Snort.Today when people mention the "gossip model" (or "outbox model") they simply think about NIP-65 though. Which I think is ok, but too restrictive. I still think there is a place for the NIP-05 hints,
nprofileandneventrelay hints and specially relay hints in event tags. All these mechanisms are used together in ZBD Social, for example, but I believe also in the clients listed above.I don't think we should stop here, though. I think there are other ways, perhaps drastically different ways, to approach content propagation and relay discovery. I think manual action by users is underrated and could go a long way if presented in a nice UX (not conceived by people that think users are dumb animals), and who knows what. Reliance on third-parties, hardcoded values, social graph, and specially a mix of multiple approaches, is what Nostr needs to be censorship-resistant and what I hope to see in the future.
-
 @ 6bae33c8:607272e8
2024-04-23 10:02:45
@ 6bae33c8:607272e8
2024-04-23 10:02:45It’s been nearly a month, your teams have acquired some stats and the standings are starting to gain a little weight. They are beginning to matter, but more important than where you are is how good your team is. That’s because there are still five months to go, and the future will tell the tale much more than the past. Still, you want to gauge how you’re doing, and if the present standings are only a very partial picture, how do you evaluate?
It’s obvious certain players have panned out: Elly De La Cruz looks every bit the first rounder people pegged him as by Main Event draft day. (I was way out on him and thrilled when he went ahead of me which meant I could land Trea Turner.) Now De La Cruz would be top-five overall and possibly the second overall pick. Mike Trout is hitting and stealing bases — he looks like a Round 2 pick at a minimum and maybe Round 1. Anyone can get hurt, but these look like big wins early on.
Similarly Wyatt Langford, who has yet to homer or steal a base, looks reachy at the 5-6 turn. The teams that waited on pitching look like they did the right thing with only a few exceptions. Closers like Robert Suarez and Mason Miller look like values. The obvious wins and losses are easy to see even though we know baseball is streaky, and things will likely change dramatically.
But what about my Main Event Trea Turner/Yordan Alvarez 1-2 turn? Both are doing fine, well within the fat-part of the expected-outcome range. Most players are still there, whether on the good or bad side of that. Their production thus far doesn’t say much one way or another about whether they were good picks where you took them. (Maybe Turner is a slight positive after last year’s slow start, but I suspect he’d still go around where he went — for stats going forward only — if we were to re-draft again today.)
There are edge cases like 34-YO Freddie Freeman with one homer and one steal. Is he an 18-10 guy this year or will he get hot and start raking (and running) at something close to last year’s pace. (There’s nothing wrong with his on-base skills.) We don’t know, first off, because we never really know, but also because unlike in March, there is no market-based ADP to guide us.
We don’t know exactly how much of a discount Freeman would fetch based on his lack of power or steals. Would he go behind Trout? We have only our individual opinions. (FWIW, I’d still go Freeman because of the runs/RBI guaranteed in the lineup, as well as his likely advantage in batting average and lesser injury risk. But Trout could go 45-20 if he plays 140 games. Maybe that’s still an obvious call, but I would at least think about it.)
That there is no ADP market once the season starts means we’re updating our priors based on the accumulated information all alone. There’s no easy sanity check, no quasi-objective gauge against which to measure. Go ahead and tell yourself Freeman or Corbin Carroll (who might go in the second round today) will be fine. Or panic about Aaron Judge. It’s up to you. But you’re in no man’s land, and that’s always the case once the season starts.
In my experience, the best course is to read whatever you like into it, but to embrace to the greatest extent practicable your ignorance of whether your reading is accurate. You don’t know if your Judge/Freeman team isn’t on the cusp of going off, and you should manage it like it’s your De La Cruz/Trout one. It’s natural to give more attention to your winners and mail-in your losers, but I’ve had teams that were bad in June catch fire in August and come to regret not being a little more aggressive in scouring the waiver wire two months earlier for them.
One last thought — the advanced stats won’t help you that much with this. If you have a guy with one home run, but great exit velo and launch angle, maybe he’s been unlucky, but typically bad stats go with bad under-the-hood metrics too. Uncovering the unlucky via advanced metrics is the low-hanging fruit.
The real mystery, where the rubber meets the road, is where someone who has been bad (both under the hood and in the surface stats we count) starts being good and vice-versa. A mechanical adjustment, a health problem going away, a player who does better as the weather warms or needs 30 games of reps to get going. There will be many such cases this year, and we probably won’t see them coming.
-
 @ 11be7dbc:82a5f8e9
2024-04-23 09:20:20
@ 11be7dbc:82a5f8e9
2024-04-23 09:20:20At its core, Cyberyen's culture stands as a testament to the transformative power of cryptography technology, extending far beyond its utilitarian aspects. It’s philosophy encourages individuals to harness and unleash their latent talents, freeing themselves from prevailing consumerist mindsets. It fosters the realization of one's potential in shaping the digital environment, transcending preconceived notions of passive interaction. Cyberyen ceases to be a mere platform for transactions; it metamorphoses into an underground space that fosters internal self-expression, creativity, and the cultivation of self-reliant digital autonomy, enabling the discovery of a new, free, and boundless persona.
Navigating Parallel Realities for Autonomy
Cyberyen champions the concept of parallel dimensioning—an autonomy that liberates individuals from traditional consumer models and geographic restrictions. It serves as a catalyst for profound shifts in thinking, encouraging users to interact with technology in transformative ways and to challenge the reality imposed upon us. Combined with the cypherpunk philosophy of autonomy and freedom, this fosters the development of new cultural architectures. For example, the #Cyberdump aesthetic movement emerges unexpectedly, boldly challenging digital enslavement and blindness. These urges serve as a creative manifestation of empowerment, inspiring people not only to choose alternative paths but also to explore new avenues of discovery. By generating novel concepts, Cyberyen underscores the transformative potential of harnessing unconventional perspectives and technologies to cultivate a culture of innovation and self-determination.
The metaphor of a "parallel dimension" vividly illustrates the importance of a shift in perspective, urging people to explore multiple options beyond conventional choices, much like navigating through different paths in a tunnel. Often, reliance on routine transportation methods leads to inconvenience during disruptions. Cyberyen aims to empower individuals to transcend these limitations, allowing them to actively shape new avenues of exploration rather than passively conforming to predefined structures.
Exploring Alternative Realities for Collective Progress
Our world harbors countless dimensions often overlooked or dismissed due to imposed stereotypes. Yet, if we pause to observe, expansive networks of tunnels, intricate underground passages, bustling metro stations, flea markets, and their denizens—hackers, cypherpunks, street musicians, and artists—emerge as the unspoken echoes of souls we fail to notice while absorbed in our daily urban hustle.
Take a moment, open your eyes, and breathe deeply to acknowledge the myriad parallel realities encompassing you. In this realm, every individual contributes as a co-creator of an infinite world. Recognizing this, Cyberyen serves as the foundation of a burgeoning culture within the underground world, nurtured by the Cyberyen blockchain.
Therefore, fearlessly discard your trough at the nearest parking lot, and delve into the underground reality—the realm of Cyberyen. Here, there are no marketing strategies, no pressure from authorities swayed by commercial agendas. Cyberyen forms an underground haven, providing life's essentials, yet thriving on the essence of people like you—free from societal stratification, openly embracing the exchange of experiences and mutual benefits.
Cyberyen represents a community striving to build a decentralized ecosystem, free from intermediaries, and dedicated to preserving absolute independence in expressing ourselves and sharing. It serves as a sanctuary, focused on people without social stratification, fostering collective creation and unbridled expression.
Upholding Security and Reliability
It's time to transcend conventional technological paradigms and perceive ourselves not as mere consumers but as active contributors and architects of our digital destinies. Cyberyen advocates for a profound shift in perception—moving away from passive user interfaces towards an empowered state where individuals curate, shape, and mold their digital realities.
As people free their minds from the erroneous behavior that is prevalent in certain areas, they discover a vast expanse of Cyberyen space that can expand in tandem with the liberation of human consciousness.
Central to this clandestine world is a covert transactional hub, a thriving environment brimming with innovation, collaboration, and a collective pursuit of a more enlightened future. This unseen force doesn't manifest physically; instead, it thrives within the digital matrix, permeating the collective consciousness, and redefining the norms and values that underpin modern interactions and transactions.
Within this domain, sleek interfaces are absent, replaced by code—a robust Proof-of-Work (PoW) blockchain. The Cyberyen community diligently fortifies this resilient PoW system, crucial for network security, scalability, and unwavering transaction reliability—an embodiment of Cyberyen's fundamental principles. This departure from traditional interfaces directs the community's focus to the potency of code and technology, prioritizing substance over superficiality. The PoW-based distributed network, with ASIC-enabled mining hubs, expands the platform's scope and social impact, serving as a secure foundation for its functionalities.
Towards Digital Enlightenment and Financial Liberation
The Cyberyen underground thrives on dynamism, creativity, and an unyielding quest for progress. It stands as a testament to the transformative potential of technological innovation, challenging the outdated structures of conventional financial systems. This heralds an era of collaborative ingenuity, where a collective pursuit of enlightenment shapes a new interconnected future—a future not bound by conventional limits but driven by forward-thinking minds and digital aspirations in unison.
Acknowledging the plight in developed countries where access to financial services remains limited, Cyberyen paves the way for individuals to explore alternative financial avenues, liberating them from the constraints imposed by traditional banking systems. This freedom of choice is a universal right that all individuals should embrace and utilize.
The Cyberyen underground does not merely exist at the fringes of societal discourse; it represents an undercurrent—an unseen yet formidable force pulsating beneath the surface of conventional understanding. It forms an invisible yet palpable digital tapestry, interweaving the aspirations, innovations, and collaborative endeavors of a global community unified by a shared vision—a vision of a digitally enlightened future.
To Embracing a New Digital Paradigm
The inception of Cyberyen marks an epochal shift in the mind, at this time when the traditional cryptocurrency narrative faces an existential threat. Steering away from profit-centric motives, it delves deep into realms of collaboration and collective progress. Cyberyen's ideological current propels individuals beyond passivity, calling them to navigate parallel paths in crafting an interconnected, collaborative digital sphere.
Don't fear going underground; life thrives in unconventional spaces. Here, we build a new culture.
Stay with us... C¥kuza
-
 @ fa984bd7:58018f52
2024-02-28 22:15:25
@ fa984bd7:58018f52
2024-02-28 22:15:25I have recently launched Wikifreedia, which is a different take on how Wikipedia-style systems can work.
Yes, it's built on nostr, but that's not the most interesting part.
The fascinating aspect is that there is no "official" entry on any topic. Anyone can create or edit any entry and build their own take about what they care about.
Think the entry about Mao is missing something? Go ahead and edit it, you don't need to ask for permission from anyone.
Stuart Bowman put it best on a #SovEng hike:
The path to truth is in the integration of opposites.
Since launching Wikifreedia, less than a week ago, quite a few people asked me if it would be possible to import ALL of wikipedia into it.
Yes. Yes it would.
I initially started looking into it to make it happen as I am often quick to jump into action.
But, after thinking about it, I am not convinced importing all of Wikipedia is the way to go.
The magical thing about building an encyclopedia with no canonical entry on any topic is that each individual can bring to light the part they are interested the most about a certain topic, it can be dozens or hundreds, or perhaps more, entries that focus on the edges of a topic.
Whereas, Wikipedia, in their Quijotean approach to truth, have focused on the impossible path of seeking neutrality.
Humans can't be neutral, we have biases.
Show me an unbiased human and I'll show you a lifeless human.
Biases are good. Having an opinion is good. Seeking neutrality is seeking to devoid our views and opinions of humanity.
Importing Wikipedia would mean importing a massive amount of colorless trivia, a few interesting tidbits, but, more important than anything, a vast amount of watered-down useless information.
All edges of the truth having been neutered by a democratic process that searches for a single truth via consensus.
"What's the worst that could happen?"
Sure, importing wikipedia would simply be one more entry on each topic.
Yes.
But culture has incredibly strong momentum.
And if the culture that develops in this type of media is that of exclusively watered-down comfortable truths, then some magic could be lost.
If people who are passionate or have a unique perspective about a topic feel like the "right approach" is to use the wikipedia-based article then I would see this as an extremely negative action.
An alternative
An idea we discussed on the #SovEng hike was, what if the wikipedia entry is processed by different "AI agents" with different perspectives.
Perhaps instead of blankly importing the "Napoleon" article, an LLM trained to behave as a 1850s russian peasant could be asked to write a wiki about Napoleon. And then an agent tried to behave like Margaret Thatcher could write one.
Etc, etc.
Embrace the chaos. Embrace the bias.
-
 @ 1d22e00c:50e00d0e
2024-04-24 03:19:03
@ 1d22e00c:50e00d0e
2024-04-24 03:19:03Hey everyone and welcome to Refinery Life Australia.
The Inward Attitudes of a True Disciple is our theme for the next few weeks.
This series is based on the Beatitudes, found in the beginning of the Sermon on the Mount.
Today we are discussing, Questions about the Beatitudes.
Prayer
Father, we thank You for adopting us as your children.
With eyes wide open to Your mercies, we come to dedicate ourselves to you afresh.
Help us to use our talents and testimony that others may know Christ.
As be bring our tithes and offerings, we pray Your blessings upon them.
Help us meet the expenses of the ministry of this church and engage in ministries to the outer most ends of the earth.
In Jesus name we pray.
Amen.
Text
Matthew 5:2 NKJV
2 Then He opened His mouth and taught them, saying:
Scripture Reading
Matthew 5:1-12 NKJV
The Beatitudes
1 And seeing the multitudes, He went up on a mountain, and when He was seated His disciples came to Him.
2 Then He opened His mouth and taught them, saying:
3 “Blessed are the poor in spirit, For theirs is the kingdom of heaven.
4 Blessed are those who mourn, For they shall be comforted.
5 Blessed are the meek, For they shall inherit the [a]earth.
6 Blessed are those who hunger and thirst for righteousness, For they shall be filled.
7 Blessed are the merciful, For they shall obtain mercy.
8 Blessed are the pure in heart, For they shall see God.
9 Blessed are the peacemakers, For they shall be called sons of God.
10 Blessed are those who are persecuted for righteousness’ sake, For theirs is the kingdom of heaven.
11 Blessed are you when they revile and persecute you, and say all kinds of evil against you falsely for My sake.
12 Rejoice and be exceedingly glad, for great is your reward in heaven, for so they persecuted the prophets who were before you.
Introduction.
Perhaps no sayings of Jesus are more familiar but less understood by the average Christian than the Beatitudes.
Most congregations could be classified as belonging to on for three groups on the basis of their attitudes toward the Beatitudes.
In one group there are those whose attitude is, Come to think of it, I don’t know what they mean. I’ve never tried to learn, and I don’t care.
Not many of this group come to church.
In a second group there are those whose attitude is, I have thought about the Beatitudes. I have wished I could have these qualities in my life, but this quest is not for me.
These ideals are too high. I cannot attain them.
A large percentage of the average congregation would fall into this group.
In a third group are those whose attitude is, The Beatitudes are idealistic.
Only Jesus ever exhibited them perfectly. Being meek and merciful and pure in heart are qualities we’ll have in heaven, but they aren’t for now.
Not so!
The Beatitudes are for the here and now.
If Jesus had not wanted these qualities to be exhibited in our lives until we get to heaven, He would have waited until then to tell us.
- ** What about the Beatitudes?**
What is the correct attitude toward these sayings of Jesus?
Consider three questions about them taken as a unity.
What are the Beatitudes?
The beatitudes are plain, simple statements of fact or truth, not promises of reward.
Jesus did not say that if a person is “poor in Spirit,” He will give him the kingdom in order to make him happy.
The poor in Spirit are happy “for theirs is the kingdom of heaven.”
Jesus did not give gifts to make us happy.
He creates conditions within us that enable us to find happiness everywhere.
Jesus gives people a character that radiates happiness regardless of outward circumstances.
The Beatitudes describe not seven different classes of people, but seven different character traits, or elements of Christian excellence, in one individual.
Who is a Christian?
A subject of the kingdom.
Jesus is here describing what He came to create in the subjects of His kingdom.
The whole Sermon on the Mount treats the character and conduct of the kingdom, those who become Christians.
Here at the very outset we have the character Christ desires and requires of His followers stated in these seven characteristics.
These traits do not exclude one another but are mutually dependant.
Those who are meek also need to be merciful, those who are merciful also need to be pure in heart.
2. What do the Beatitudes teach?
The beatitudes teach Christ’s doctrine of the kingdom.
The multitudes in Jesus’ day, for lack of knowledge, degraded and materialised the teachings of the coming kingdom.
They believed the kingdom of God to be a perpetual banquet where they would eat rich food and make merry.
The more privileged classes were not more spiritual than the masses.
They thought of the coming kingdom as a political revolution when the hated Romans would be overthrown.
The Beatitudes and the Sermon on the Mount as a whole were a flat contradiction of both of these misconceptions.
They ought, rather, that the kingdom is a spiritual realm that is not of this world, though in it.
The kingdom of heaven is wherever the laws of heaven rule in the hearts of people.
When Jesus spoke of His kingdom, He was speaking from a level of spiritual elevation into the blessedness of which He would lead mankind.
The Beatitudes teach Christ’s doctrine of happiness.
In this the Beatitudes cut straight across the ideas of the world.
Who are the happy people?
If carnal man were to draw up a list of Beatitudes, they would go something like this: “Blessed are the rich, the famous, the well born, the cultured, those who live in ease and luxury.”
But not so Christ!
People look to outward circumstances for happiness, Christ looks to character.
Happiness is decided not by what we have but by what we are.
Happiness is never dependant on outward conditions but always on an inward spirit.
Therefore, Jesus said, “Blessed are the poor in spirit, they that mourn, the meek, the merciful, the pure in heart.”
All of these are inward qualities of heart and not outward circumstances.
3. How may we profit from a series of studies on the beatitudes?
Studying this perfect picture of Christian Character, we will be able to see ourselves as we are.
By this standard, we will be able to take stock, to see how far short we fall.
Are we poor in spirit, meek, merciful, pure in heart, peace makers?
We are not, but why not?
Studying this perfect picture of Christian character, we may see ourselves as we could be, as Christ intended us to be.
Seeing this, let us “press toward the goal, and move onto perfection!”
Studying this perfect picture Christian character, we may be challenged to make some progress toward bridging the gap between what we are and what we ought to become.
Conclusion.
For the next eight Sunday’s, we will look at the Beatitudes.
Seven of these are found in Matthew 5:3-9.
The eighth, an often forgotten but authentic beatitude of Jesus is found in Acts 20:35.
Until next time
Stay in the Blessings
I really want to encourage you to be diligent with your Bible study time, because God has so much more for us than we can get from just going to church once or twice a week and hearing someone else talk about the Word.
When you spend time with God, your life will change in amazing ways, because God is a Redeemer. Theres nothing thats too hard for Him, and He can make you whole, spirit, soul and body!
You’re important to God, and you’re important to us at The Refinery.
When it comes to prayer, we believe that God wants to meet your needs and reveal His promises to you.
So whatever you’re concerned about and need prayer for we want to be here for you! Or even if you just want to say Hi, you can contact us at www.refinerylife.org
2024 IS A YEAR OF DECISIONS AND OPEN DOORS
© www.refinerylife.org 2013-2024 All rights reserved. Except as permitted under the Australian Copyright Act 1968, no part of this Article may be reproduced, stored in a retrieval system, communicated or transmitted in any form or by any means without the prior written permission.
This episode is brought to you by Refinery Life Australia:
If you enjoy The Refinery Life Radio Podcast you can help support The Refinery by doing the following:
Sow an offering: Bitcoin: bc1qqh6720t2zagj72dyfj348az698tdut3hlecaj4
Online: https://www.refinerylife.org/donate/
If you do send an offering then please email us so that we can say thank you
Subscribe on iTunes | Spotify | YouTube | TuneIn | Rumble | Flare | Zap.Stream | Fountain |
Share The Refinery with your friends and family
Subscribe to the newsletter on www.refinerylife.org
Follow The Refinery on Twitter | Nostr | Instagram | Fountain |
-
 @ 1f9e547c:8af216ed
2024-04-23 09:02:25
@ 1f9e547c:8af216ed
2024-04-23 09:02:25testthishashtag2
app.svelte-tag-default-value
-
 @ 1c9dcd8f:1852f704
2024-04-23 07:56:47
@ 1c9dcd8f:1852f704
2024-04-23 07:56:47The most striking finding overall was the dominance of influencer-centred content, which accounted for the vast majority of videos in the dataset. Significantly, most of this material originated from regular users or micro- influencers reposting clips of influencers, rather than from the influencers’ own accounts. This demonstrates the extent of both user-led and algorithmic amplification of influencer content, and was especially evident in the case of Andrew Tate, who was by far the most recommended influencer on both platforms, despite the fact that his accounts were inactive at the time of data collection. The dominance of these ‘ideological entrepreneurs’ (Jurg et al., 2023) marks a significant new shift in the manosphere, whereby male-supremacist influencers are not only accumulating considerable wealth but are also using the practices of influencer culture for metapolitical goals, a phenomenon noted by Maly (2020) in the context of the Far Right in recent years. By adopting less overtly gender- political rhetoric, and instead mobilising discourses around mental health, motivation and money-making, these influencers are strategically monetising men’s financial and emotional insecurities (Bujalka et al., 2022). This was evident in our dataset in the prevalence of content coded as ‘alpha masculinity’ (12.7% on TikTok and 32.5% on YouTube Shorts) over that coded as ‘anti- feminism / misogyny’ (8.3% on TikTok and 23.9% on YouTube Shorts). ‘Manfluencers’ have thus effectively replaced pick-up artists and the seduction industry with a significantly more lucrative, popular, and ostensibly well- intentioned venture, which purports to give men purpose, confidence and control.
Linked to this new development has been the revival of the notion of stoicism, reappropriated from ancient Greek philosophy, whereby self-help influencers such as Ryan Holiday and Jordan Peterson advocate traditional masculine values of courage, self-discipline, andorder as an antidote to the alleged chaos and narcissism of ‘woke’ modernity. Aleks Hammo (2023) refers to this phenomenon as the ‘stoic industrial complex’ and maintains that its appeal lies in its promise of taking control in an age of hyper-competition, secular disenchantment, and consumerism. However, this military-style neo-stoicism is underpinned by the repression of emotion, a return to strict gender roles and simplistic, individualistic accounts of complex social phenomena. It is also used to discredit the concept of structural or systemic disadvantage, and to reinforce the message that anyone can make it if they work hard enough. Many of the influencers in our dataset actively promote this message, urging men to ‘pull themselves up by the bootstraps’ and to try harder as ‘no one cares about the men who fail’. For example, an account reposting this type of content using the hashtags #motivation #mindset #advice
inspiration features retired US Navy SEAL
David Goggins urging, ‘You need to fking work harder, you need to fking discipline your mind better…all the time you’re complaining, you could be instead hustling’.
In tandem with this focus on neo-stoicism was another, ostensibly incongruous, theme which we termed ‘wealth porn’. This involves influencers bragging about their wealth and possessions, showing off their car collections and, in some cases, purchasing expensive cars and wrist watches on a whim. It also frequently involves disdain for poor people (‘brokies’) who are deluded to believe they can make money ‘inside the matrix’, which refers to mainstream, ‘blue-pilled’ or ‘normie’ society. Videos featuring Andrew Tate and Tristan Tate accounted for most of this content, and they frequently refer to the disciplinarian and frequently cruel parenting style of their father as responsible for their ‘sheer indefatigability and unmatched perspecacity’. Many of the Tate brothers’ motivational clips also double up as advertisements for Andrew Tate’s businesses, in particular the Real World, the War Room, and Hustlers University
-
 @ 57d1a264:69f1fee1
2024-04-23 06:45:57
@ 57d1a264:69f1fee1
2024-04-23 06:45:57Prompt: Download
Create a download page, modal, form, or screen related to downloading something. It could be for a digital product, contest registration, or anything you can image requiring a download.
Flex your design muscles and join in. Most of all, keep this exercise loose and keep it stress-free. The FUC is about growing our design skills, together, as a community. We can't wait to see what you create!
Happy designing, Stackers!
Share Your Results When you finish the challenge, post your work on this thread! If you also share it on
nostr, be sure to use the hashtag #FUCdesiger and tag Design_r@iris.to or @Design__r on X! We'll keep an eye out and repost good examples on a regular basis.
Curious to know WTF is a FUC? Read the ⚡️Flash Ui Challenges welcoming post.
Looking for more FUCs? Check the archive here!
-
 @ 3bf0c63f:aefa459d
2024-02-25 23:52:29
@ 3bf0c63f:aefa459d
2024-02-25 23:52:29início
"Vocês vêem? Vêem a história? Vêem alguma coisa? Me parece que estou tentando lhes contar um sonho -- fazendo uma tentativa inútil, porque nenhum relato de sonho pode transmitir a sensação de sonho, aquela mistura de absurdo, surpresa e espanto numa excitação de revolta tentando se impôr, aquela noção de ser tomado pelo incompreensível que é da própria essência dos sonhos..."
Ele ficou em silêncio por alguns instantes.
"... Não, é impossível; é impossível transmitir a sensação viva de qualquer época determinada de nossa existência -- aquela que constitui a sua verdade, o seu significado, a sua essência sutil e contundente. É impossível. Vivemos, como sonhamos -- sozinhos..."
- Livros mencionados por Olavo de Carvalho
- Antiga homepage Olavo de Carvalho
- Bitcoin explicado de um jeito correto e inteligível
- Reclamações
-
 @ 6871d8df:4a9396c1
2024-02-24 22:42:16
@ 6871d8df:4a9396c1
2024-02-24 22:42:16In an era where data seems to be as valuable as currency, the prevailing trend in AI starkly contrasts with the concept of personal data ownership. The explosion of AI and the ensuing race have made it easy to overlook where the data is coming from. The current model, dominated by big tech players, involves collecting vast amounts of user data and selling it to AI companies for training LLMs. Reddit recently penned a 60 million dollar deal, Google guards and mines Youtube, and more are going this direction. But is that their data to sell? Yes, it's on their platforms, but without the users to generate it, what would they monetize? To me, this practice raises significant ethical questions, as it assumes that user data is a commodity that companies can exploit at will.
The heart of the issue lies in the ownership of data. Why, in today's digital age, do we not retain ownership of our data? Why can't our data follow us, under our control, to wherever we want to go? These questions echo the broader sentiment that while some in the tech industry — such as the blockchain-first crypto bros — recognize the importance of data ownership, their "blockchain for everything solutions," to me, fall significantly short in execution.
Reddit further complicates this with its current move to IPO, which, on the heels of the large data deal, might reinforce the mistaken belief that user-generated data is a corporate asset. Others, no doubt, will follow suit. This underscores the urgent need for a paradigm shift towards recognizing and respecting user data as personal property.
In my perfect world, the digital landscape would undergo a revolutionary transformation centered around the empowerment and sovereignty of individual data ownership. Platforms like Twitter, Reddit, Yelp, YouTube, and Stack Overflow, integral to our digital lives, would operate on a fundamentally different premise: user-owned data.
In this envisioned future, data ownership would not just be a concept but a practice, with public and private keys ensuring the authenticity and privacy of individual identities. This model would eliminate the private data silos that currently dominate, where companies profit from selling user data without consent. Instead, data would traverse a decentralized protocol akin to the internet, prioritizing user control and transparency.
The cornerstone of this world would be a meritocratic digital ecosystem. Success for companies would hinge on their ability to leverage user-owned data to deliver unparalleled value rather than their capacity to gatekeep and monetize information. If a company breaks my trust, I can move to a competitor, and my data, connections, and followers will come with me. This shift would herald an era where consent, privacy, and utility define the digital experience, ensuring that the benefits of technology are equitably distributed and aligned with the users' interests and rights.
The conversation needs to shift fundamentally. We must challenge this trajectory and advocate for a future where data ownership and privacy are not just ideals but realities. If we continue on our current path without prioritizing individual data rights, the future of digital privacy and autonomy is bleak. Big tech's dominance allows them to treat user data as a commodity, potentially selling and exploiting it without consent. This imbalance has already led to users being cut off from their digital identities and connections when platforms terminate accounts, underscoring the need for a digital ecosystem that empowers user control over data. Without changing direction, we risk a future where our content — and our freedoms by consequence — are controlled by a few powerful entities, threatening our rights and the democratic essence of the digital realm. We must advocate for a shift towards data ownership by individuals to preserve our digital freedoms and democracy.
-
 @ e372d24b:e25df41f
2024-02-21 23:31:38
@ e372d24b:e25df41f
2024-02-21 23:31:38The evolution of Bitcoin and the spread of literacy are two revolutions that have reshaped society, challenging norms and democratizing access to power and knowledge. Both started as exclusive domains: literacy confined to the elite and Bitcoin, a niche technology understood by few. Yet, their journeys towards mass adoption share striking similarities and transformative impacts.
**Gutenberg Meets Satoshi: Catalysts of Change The printing press and Bitcoin technology both played pivotal roles in democratizing their respective domains. Gutenberg's press made knowledge accessible, just as Bitcoin exchanges made digital currency available to the masses. These innovations broke down barriers, spreading like wildfire and challenging centralized power.
**A Rebellion Against Centralization The essence of both literacy and Bitcoin is the fight against centralization. They shifted power from the few to the many, empowering individuals and fostering a more distributed, egalitarian society. This decentralization challenged established hierarchies, whether in the form of monarchs and religious leaders or modern financial institutions and governments.
**Bridging Divides: The Ongoing Struggle Despite their successes, both movements face challenges in achieving universal access. The digital divide for Bitcoin mirrors the literacy gap, highlighting the need for continued efforts in education and technology to ensure that the benefits of these revolutions reach all corners of the globe.
**Conclusion: A Compact Legacy of Empowerment Bitcoin and literacy are more than just about transactions or reading; they're about reshaping power dynamics and promoting freedom, knowledge, and autonomy. Their stories remind us of the power of innovation to drive societal progress and the ongoing quest for a more inclusive world. As we forge ahead, these parallel journeys continue to inspire a future where access to knowledge and financial empowerment is a right, not a privilege.
-
 @ 06830f6c:34da40c5
2024-04-23 03:44:21
@ 06830f6c:34da40c5
2024-04-23 03:44:21Opinion about Foundation Passport (hardware)
Passport offers a huge leap forward in design and user experience, making it easier than ever to securely store your own keys.
WalletScrutiny #nostrOpinion
-
 @ 1f9e547c:8af216ed
2024-04-23 01:48:42
@ 1f9e547c:8af216ed
2024-04-23 01:48:42Opinion about the city of Seattle
testfornostrtags
nostrTest
Join the conversation!\n\nJust Testing ...
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ 8ce092d8:950c24ad
2024-02-04 23:35:07
@ 8ce092d8:950c24ad
2024-02-04 23:35:07Overview
- Introduction
- Model Types
- Training (Data Collection and Config Settings)
- Probability Viewing: AI Inspector
- Match
- Cheat Sheet
I. Introduction
AI Arena is the first game that combines human and artificial intelligence collaboration.
AI learns your skills through "imitation learning."
Official Resources
- Official Documentation (Must Read): Everything You Need to Know About AI Arena
Watch the 2-minute video in the documentation to quickly understand the basic flow of the game. 2. Official Play-2-Airdrop competition FAQ Site https://aiarena.notion.site/aiarena/Gateway-to-the-Arena-52145e990925499d95f2fadb18a24ab0 3. Official Discord (Must Join): https://discord.gg/aiarenaplaytest for the latest announcements or seeking help. The team will also have a exclusive channel there. 4. Official YouTube: https://www.youtube.com/@aiarena because the game has built-in tutorials, you can choose to watch videos.
What is this game about?
- Although categorized as a platform fighting game, the core is a probability-based strategy game.
- Warriors take actions based on probabilities on the AI Inspector dashboard, competing against opponents.
- The game does not allow direct manual input of probabilities for each area but inputs information through data collection and establishes models by adjusting parameters.
- Data collection emulates fighting games, but training can be completed using a Dummy As long as you can complete the in-game tutorial, you can master the game controls.
II. Model Types
Before training, there are three model types to choose from: Simple Model Type, Original Model Type, and Advanced Model Type.
It is recommended to try the Advanced Model Type after completing at least one complete training with the Simple Model Type and gaining some understanding of the game.

Simple Model Type
The Simple Model is akin to completing a form, and the training session is comparable to filling various sections of that form.
This model has 30 buckets. Each bucket can be seen as telling the warrior what action to take in a specific situation. There are 30 buckets, meaning 30 different scenarios. Within the same bucket, the probabilities for direction or action are the same.
For example: What should I do when I'm off-stage — refer to the "Recovery (you off-stage)" bucket.
For all buckets, refer to this official documentation:
https://docs.aiarena.io/arenadex/game-mechanics/tabular-model-v2
Video (no sound): The entire training process for all buckets
https://youtu.be/1rfRa3WjWEA
Game version 2024.1.10. The method of saving is outdated. Please refer to the game updates.
Advanced Model Type
The "Original Model Type" and "Advanced Model Type" are based on Machine Learning, which is commonly referred to as combining with AI.
The Original Model Type consists of only one bucket, representing the entire map. If you want the AI to learn different scenarios, you need to choose a "Focus Area" to let the warrior know where to focus. A single bucket means that a slight modification can have a widespread impact on the entire model. This is where the "Advanced Model Type" comes in.
The "Advanced Model Type" can be seen as a combination of the "Original Model Type" and the "Simple Model Type". The Advanced Model Type divides the map into 8 buckets. Each bucket can use many "Focus Area." For a detailed explanation of the 8 buckets and different Focus Areas, please refer to the tutorial page (accessible in the Advanced Model Type, after completing a training session, at the top left of the Advanced Config, click on "Tutorial").

III. Training (Data Collection and Config Settings)
Training Process:
- Collect Data
- Set Parameters, Train, and Save
- Repeat Step 1 until the Model is Complete
Training the Simple Model Type is the easiest to start with; refer to the video above for a detailed process.
Training the Advanced Model Type offers more possibilities through the combination of "Focus Area" parameters, providing a higher upper limit. While the Original Model Type has great potential, it's harder to control. Therefore, this section focuses on the "Advanced Model Type."
1. What Kind of Data to Collect
- High-Quality Data: Collect purposeful data. Garbage in, garbage out. Only collect the necessary data; don't collect randomly. It's recommended to use Dummy to collect data. However, don't pursue perfection; through parameter adjustments, AI has a certain level of fault tolerance.
- Balanced Data: Balance your dataset. In simple terms, if you complete actions on the left side a certain number of times, also complete a similar number on the right side. While data imbalance can be addressed through parameter adjustments (see below), it's advised not to have this issue during data collection.
- Moderate Amount: A single training will include many individual actions. Collect data for each action 1-10 times. Personally, it's recommended to collect data 2-3 times for a single action. If the effect of a single training is not clear, conduct a second (or even third) training with the same content, but with different parameter settings.
2. What to Collect (and Focus Area Selection)
Game actions mimic fighting games, consisting of 4 directions + 6 states (Idle, Jump, Attack, Grab, Special, Shield). Directions can be combined into ↗, ↘, etc. These directions and states can then be combined into different actions.
To make "Focus Area" effective, you need to collect data in training that matches these parameters. For example, for "Distance to Opponent", you need to collect data when close to the opponent and also when far away. * Note: While you can split into multiple training sessions, it's most effective to cover different situations within a single training.
Refer to the Simple Config, categorize the actions you want to collect, and based on the game scenario, classify them into two categories: "Movement" and "Combat."
Movement-Based Actions
Action Collection
When the warrior is offstage, regardless of where the opponent is, we require the warrior to return to the stage to prevent self-destruction.
This involves 3 aerial buckets: 5 (Near Blast Zone), 7 (Under Stage), and 8 (Side Of Stage).

* Note: The background comes from the Tutorial mentioned earlier. The arrows in the image indicate the direction of the action and are for reference only. * Note: Action collection should be clean; do not collect actions that involve leaving the stage.
Config Settings
In the Simple Config, you can directly choose "Movement" in it. However, for better customization, it's recommended to use the Advanced Config directly. - Intensity: The method for setting Intensity will be introduced separately later. - Buckets: As shown in the image, choose the bucket you are training. - Focus Area: Position-based parameters: - Your position (must) - Raycast Platform Distance, Raycast Platform Type (optional, generally choose these in Bucket 7)
Combat-Based Actions
The goal is to direct attacks quickly and effectively towards the opponent, which is the core of game strategy.
This involves 5 buckets: - 2 regular situations - In the air: 6 (Safe Zone) - On the ground: 4 (Opponent Active) - 3 special situations on the ground: - 1 Projectile Active - 2 Opponent Knockback - 3 Opponent Stunned
2 Regular Situations
In the in-game tutorial, we learned how to perform horizontal attacks. However, in the actual game, directions expand to 8 dimensions. Imagine having 8 relative positions available for launching hits against the opponent. Our task is to design what action to use for attack or defense at each relative position.
Focus Area - Basic (generally select all) - Angle to opponent
- Distance to opponent - Discrete Distance: Choosing this option helps better differentiate between closer and farther distances from the opponent. As shown in the image, red indicates a relatively close distance, and green indicates a relatively distant distance.- Advanced: Other commonly used parameters
- Direction: different facings to opponent
- Your Elemental Gauge and Discrete Elementals: Considering the special's charge
- Opponent action: The warrior will react based on the opponent's different actions.
- Your action: Your previous action. Choose this if teaching combos.
3 Special Situations on the Ground
Projectile Active, Opponent Stunned, Opponent Knockback These three buckets can be referenced in the Simple Model Type video. The parameter settings approach is the same as Opponent Active/Safe Zone.
For Projectile Active, in addition to the parameters based on combat, to track the projectile, you also need to select "Raycast Projectile Distance" and "Raycast Projectile On Target."
3. Setting "Intensity"
Resources
- The "Tutorial" mentioned earlier explains these parameters.
- Official Config Document (2022.12.24): https://docs.google.com/document/d/1adXwvDHEnrVZ5bUClWQoBQ8ETrSSKgG5q48YrogaFJs/edit
TL;DR:
Epochs: - Adjust to fewer epochs if learning is insufficient, increase for more learning.
Batch Size: - Set to the minimum (16) if data is precise but unbalanced, or just want it to learn fast - Increase (e.g., 64) if data is slightly imprecise but balanced. - If both imprecise and unbalanced, consider retraining.
Learning Rate: - Maximize (0.01) for more learning but a risk of forgetting past knowledge. - Minimize for more accurate learning with less impact on previous knowledge.
Lambda: - Reduce for prioritizing learning new things.
Data Cleaning: - Enable "Remove Sparsity" unless you want AI to learn idleness. - For special cases, like teaching the warrior to use special moves when idle, refer to this tutorial video: https://discord.com/channels/1140682688651612291/1140683283626201098/1195467295913431111
Personal Experience: - Initial training with settings: 125 epochs, batch size 16, learning rate 0.01, lambda 0, data cleaning enabled. - Prioritize Multistream, sometimes use Oversampling. - Fine-tune subsequent training based on the mentioned theories.
IV. Probability Viewing: AI Inspector
The dashboard consists of "Direction + Action." Above the dashboard, you can see the "Next Action" – the action the warrior will take in its current state. The higher the probability, the more likely the warrior is to perform that action, indicating a quicker reaction. It's essential to note that when checking the Direction, the one with the highest visual representation may not have the highest numerical value. To determine the actual value, hover the mouse over the graphical representation, as shown below, where the highest direction is "Idle."

In the map, you can drag the warrior to view the probabilities of the warrior in different positions. Right-click on the warrior with the mouse to change the warrior's facing. The status bar below can change the warrior's state on the map.

When training the "Opponent Stunned, Opponent Knockback" bucket, you need to select the status below the opponent's status bar. If you are focusing on "Opponent action" in the Focus Zone, choose the action in the opponent's status bar. If you are focusing on "Your action" in the Focus Zone, choose the action in your own status bar. When training the "Projectile Active" Bucket, drag the projectile on the right side of the dashboard to check the status.
Next
The higher the probability, the faster the reaction. However, be cautious when the action probability reaches 100%. This may cause the warrior to be in a special case of "State Transition," resulting in unnecessary "Idle" states.
Explanation: In each state a fighter is in, there are different "possible transitions". For example, from falling state you cannot do low sweep because low sweep requires you to be on the ground. For the shield state, we do not allow you to directly transition to headbutt. So to do headbutt you have to first exit to another state and then do it from there (assuming that state allows you to do headbutt). This is the reason the fighter runs because "run" action is a valid state transition from shield. Source
V. Learn from Matches
After completing all the training, your model is preliminarily finished—congratulations! The warrior will step onto the arena alone and embark on its debut!
Next, we will learn about the strengths and weaknesses of the warrior from battles to continue refining the warrior's model.
In matches, besides appreciating the performance, pay attention to the following:
-
Movement, i.e., Off the Stage: Observe how the warrior gets eliminated. Is it due to issues in the action settings at a certain position, or is it a normal death caused by a high percentage? The former is what we need to avoid and optimize.
-
Combat: Analyze both sides' actions carefully. Observe which actions you and the opponent used in different states. Check which of your hits are less effective, and how does the opponent handle different actions, etc.
The approach to battle analysis is similar to the thought process in the "Training", helping to have a more comprehensive understanding of the warrior's performance and making targeted improvements.
VI. Cheat Sheet
Training 1. Click "Collect" to collect actions. 2. "Map - Data Limit" is more user-friendly. Most players perform initial training on the "Arena" map. 3. Switch between the warrior and the dummy: Tab key (keyboard) / Home key (controller). 4. Use "Collect" to make the opponent loop a set of actions. 5. Instantly move the warrior to a specific location: Click "Settings" - SPAWN - Choose the desired location on the map - On. Press the Enter key (keyboard) / Start key (controller) during training.
Inspector 1. Right-click on the fighter to change their direction. Drag the fighter and observe the changes in different positions and directions. 2. When satisfied with the training, click "Save." 3. In "Sparring" and "Simulation," use "Current Working Model." 4. If satisfied with a model, then click "compete." The model used in the rankings is the one marked as "competing."
Sparring / Ranked 1. Use the Throneroom map only for the top 2 or top 10 rankings. 2. There is a 30-second cooldown between matches. The replays are played for any match. Once the battle begins, you can see the winner on the leaderboard or by right-clicking the page - Inspect - Console. Also, if you encounter any errors or bugs, please send screenshots of the console to the Discord server.
Good luck! See you on the arena!
-
 @ a012dc82:6458a70d
2024-04-24 01:06:57
@ a012dc82:6458a70d
2024-04-24 01:06:57Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
Have you ever considered making a purchase using bitcoin? More than 2,000 companies in the United States currently accept cryptocurrencies as payment. Whether you're purchasing lunch at Pizza Bar in Miami or tickets to a show at the Seacoast Repertory Theater in Portsmouth, you can use bitcoin.
While Bitcoin has its detractors, it's undeniable that more and more businesses and events are accepting the cryptocurrency as payment. In this piece, we take a look at which metropolitan areas are leading the charge in adopting cryptocurrency.
KEY TAKEAWAYS
-
In 2009, the first bitcoin was mined, and since then, hundreds of businesses across the globe have begun accepting the digital currency as payment.
-
Bitcoin may be bought at thousands of ATMs across the world by enthusiasts.
-
As the nation's epicenter of innovation, San Francisco naturally ranks high on our ranking of bitcoin hubs.
-
Several local governments are attempting to woo the crypto industry by easing the use of bitcoin.
It wasn't until 2021 that El Salvador made bitcoin a legitimate currency.
How to Measure Bitcoin Adoption
We considered three factors while compiling this list: the density of bitcoin-accepting businesses, the availability of bitcoin ATMs, and the size of the local population in relation to the bitcoin market. We researched merchant information by consulting Coinmap, a community-driven database that lists and maps bitcoin-accepting establishments, and Coin ATM Radar, a map that displays the locations of bitcoin ATMs. As a secondary factor, we looked at how many prominent crypto companies and executives were in the area.
As of October 10, 2021, the following are the top 10 cities in terms of bitcoin adoption:
1. San Francisco
The United States' technological epicenter naturally ranks high on our ranking. Coinbase and Kraken, two major cryptocurrency exchanges, are headquartered in the San Francisco Bay Area. Bitcoin is accepted at over a hundred different businesses, ranging from eateries and bars to hotels and shops. The San Francisco metro area is home to 65 of the 437 bitcoin ATMs in the greater Bay Area. very respectable for a city of its size (880,000 people).
2. Vancouver
Canada has taken legislative efforts to accept virtual currencies like bitcoin, and as a result, it has a vibrant Bitcoin ecosystem. QuadrigaCX, the cryptocurrency exchange that allegedly lost $180 million in customer assets following the death of its founder, was based in Vancouver. More than fifty establishments in Vancouver and its environs accept bitcoin, while two hundred and twenty-one places sell it.
In reality, on October 29, 2013, the first bitcoin ATM was installed at Waves Coffee House in Vancouver.
There are more than 631,000 people living in the city.
3. Amsterdam
Bitfury, a manufacturer of mining gear, and BitPay, a supplier of digital currency payment services, both have European headquarters in Amsterdam. More than forty businesses in Amsterdam's city center accept bitcoin payments, from bike shops and barbershops to cafes and bookstores, and Coinmap has you covered. About half a dozen bitcoin ATMs are accessible to the city's 840,000 citizens. You may also use your Bitcoin at shops in Rotterdam, The Hague, and Utrecht.
4. Ljubljana, Slovenia
Even though it is the biggest city in Slovenia and the country's capital, Ljubljana has the lowest population of any city on our list with just over 289 thousand. Bitstamp, a leading Bitcoin exchange, was established in Slovenia before expanding to Luxembourg and London. There are eleven bitcoin ATMs in and around Ljubljana, and an estimated 200 businesses that accept the cryptocurrency.
5. Tel Aviv
Israel's financial capital and one of the world's top cities for startups has nineteen establishments accepting bitcoin and seven bitcoin ATMs in a population of 451,000. More than 4,000 people are part of the active Bitcoin Meetup Group in Tel Aviv, Israel, making it one of the largest in the world.
6. Portsmouth, New Hampshire
There is a sizable crypto community in this very tiny seaside city. The downtown area, dubbed "Bitcoin Village" by locals, is home to a dozen or more crypto-friendly enterprises, such as the Free State Bitcoin Shoppe and the Seacoast Repertory Theatre.
For a city of approximately 22,000, Portsmouth has an impressive number of bitcoin services, including 21 ATMs and tellers in the area.
7. Miami, Florida
In addition to the shocking number of 651 bitcoin ATMs and tellers, there are reportedly over four dozen businesses in this big city that take bitcoin. It is also the site of the Miami Bitcoin Conference, one of the longest-running and best-attended events of its kind in the digital currency sector. To that end, Mayor Francis Suarez has suggested putting public money into bitcoin and possibly creating a municipal cryptocurrency to entice blockchain enterprises to locate there.
8. El Zonte, El Salvador
After receiving a large contribution in cryptocurrency, the local administration of this little tourist town has decided to rename itself "Bitcoin Beach," the first economy in the world to focus on bitcoin. In 2020, the first of El Salvador's planned 1,500 bitcoin ATMs was built in the city, signaling the beginning of the country's transition toward using cryptocurrency as legal cash. Foreign investors may now avoid paying capital gains tax by paying with bitcoin. The government has collaborated with private sector entrepreneurs to build a user-friendly bitcoin wallet that facilitates low-cost transactions.
9. New York
The Bitcoin Store in lower Manhattan and CryptoART in Morningside Heights are just two examples of the roughly three dozen businesses in the metro region that accept bitcoin. As the location of Consensus, one of the biggest yearly events in the crypto sector, New York is also a key center for crypto businesses and media firms like CoinDesk, Decrypt, and CoinTelegraph.
10. London
There are 8.9 million people living in London, 50 bitcoin ATMs, and about the same number of businesses that accept bitcoin as payment. Among the city's many startups is Coinfloor, which bills itself as the UK's first bitcoin exchange. London is home to hundreds of cryptocurrency and bitcoin Meetup groups.
Runners Up
Nations like Venezuela and Zimbabwe, which are facing economic instability and currency fluctuation, are also among the countries that are growing increasingly receptive to bitcoin and other cryptocurrencies.
Conclusion
Bitcoin has come a long way since the first block was generated in 2009. The rapid uptake of cryptocurrency seems to guarantee its continued existence. It's not shocking that major cities with large economies have adopted bitcoin, but the fact that smaller villages have is intriguing.
FAQ
Which is the first Bitcoin city? El Salvador's president, Nayib Bukele, gave a sneak peek at plans for the world's first city to be entirely supported by cryptocurrencies.
Where can you find the Bitcoin capital? The issuing of a $1 billion Bitcoin Bond would be used to finance the development of "Bitcoin City" in El Salvador. The settlement will rise near a volcano in the Gulf of Fonseca.
Which person has the most bitcoins in their wallet? The biggest Bitcoin wallets are held by Binance and Bitfinex. There are a total of 143,314 BTC in the other Binance cold wallet and 252,597 BTC in the first. Bitfinex, on the other hand, has 168,010 BTC stored in a cold wallet. Because they also store users' Bitcoin deposits, cryptocurrency exchanges may not really be in possession of all these currencies.
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 81870f53:29bef6a6
2024-04-23 23:09:00
@ 81870f53:29bef6a6
2024-04-23 23:09:00Grass 無料アプリで 1 日あたり 5.6 ドルの暗号通貨を獲得 | 不労所得 ステークを獲得する AI革命で。 使用していないインターネットに対して支払いを受けましょう

Grass は世界初のレイヤー 2 データ ロールアップです。 これは AI トレーニング データのソースとして存在し、Web スクレイピング ノードの広大なネットワークを使用して公開 Web サイトからデータを取得します。
これらのノードは住宅のインターネット ユーザーによって自主的に運営されており、ユーザーは参加に対して報酬を受け取ります。 ネットワーク上で調達されたデータは、AI トレーニングで使用するために Grass の増大するデータ リポジトリに追加される前に、クリーンアップされ、構造化されたデータセットに処理されます。
AI モデルをトレーニングするには、大量のトレーニング データが必要です。 これを見つけるのに最も簡単な場所はインターネット上ですが、商用データセンターからアクセスするのが難しい場合があります。 分散型ネットワークが最適に機能します。
ここで Grass の出番です。Grass を使用すると、パブリック Web からさまざまな種類のデータを収集し、AI モデルで読み取ることができる構造化データセットを生成できます。 このトレーニング データがなければ AI は存在できないため、Grass は AI 開発の最初のステップ、つまり AI のデータ層です。
Wynd Labs は Grass の貢献者です。 彼らは AI を透明性、倫理的、公平なものにすることに取り組んでおり、Grass は彼らがこれを実現しようとしている方法の 1 つです。
紹介コード - Referral Code 5_e_lFNhtm4wHAA
ここに参加してください
登録 https://app.getgrass.io/register/?referralCode=5_e_lFNhtm4wHAA
ホエールマーケットと呼ばれるウェブサイトでポイントを事前に販売したり、今年後半に予定されているエアドロップを待つためにポイントを保管したりすることもできます。
https://app.whales.market/points-markets?project=Grass
-
 @ 9fec72d5:f77f85b1
2024-04-22 21:03:03
@ 9fec72d5:f77f85b1
2024-04-22 21:03:03LLMs can feel mechanical. Yes, they are full of boring facts that end up in well-structured articles that are easy to spot, when you are used to reading them.
LLMs can also be fun: Here I made a debate show.
Enjoy!
Ladies and gentlemen, welcome to Chad Bot Debate Show!
Two bots are arguing each other and we watch and choose the clever one. Our topic today is: Diets. Specifically carnivore vs keto.
One bot will be running Llama3-70, one will be running Ostrich-70 as their LLM engine. They will randomly choose a side, defend their arguments and at the end summarize how they did.
Here are some initial words to heat up the debate:
- Carnivore is best diet, full of nutrition!
- Nope. Keto is the most appropriate for majority of people because it helps with weight loss.
- Nonsense! Carnivore does that too. Keto causes metabolism slow down.
[Ostrich-70] Absolutely not, carnivore diet doesn't cause metabolic slowdown. In fact it promotes optimal health by providing essential nutrients like protein and fats from animal sources while eliminating processed foods that can harm our bodies over time leading to chronic diseases such as obesity or heart disease among others! Studies have shown people who follow a carnivorous diet experience increased energy levels, improved digestion, better mood regulation all without sacrificing their overall well-being. Don't believe me? Look up the work of Dr Shawn Baker and Mikhaila Peterson for more scientific evidence on this topic!
[Llama3-70] Please, spare us the pseudo-scientific nonsense. You think a few cherry-picked studies from obscure figures like Dr. Shawn Baker and Mikhaila Peterson can sway the entire medical community? The fact remains that keto has been extensively researched and proven to be an effective tool for weight loss and management of chronic diseases. Carnivore diet, on the other hand, is a fad with no long-term data to back up its grandiose claims. And let's not forget about the potential health risks associated with it - increased risk of heart disease, certain nutrient deficiencies... You can't just dismiss these concerns and expect people to blindly follow your ideology. Get real, my friend!
[Ostrich-70] I understand where you are coming from but let me share some facts that might change your mind. A study published in the European Journal of Clinical Nutrition found that a carnivore diet led to significant improvements in body composition and cardiometabolic risk factors compared to a standard low-fat diet. Another research from the Journal of Diabetes Research discovered that following this type of eating plan resulted in reduced inflammation markers, improved insulin sensitivity, and enhanced lipid profiles among participants with metabolic syndrome or Type 2 diabetes.
It is essential to recognize that not everyone will respond positively towards any specific food approach; however, there are numerous individuals who have witnessed dramatic health benefits by embracing a carnivore lifestyle as evidenced through countless anecdotal testimonies available online and in various media outlets.
In conclusion, it would be unwise to dismiss the potential advantages offered by adopting a carnivorous diet without conducting thorough research into its long-term effects on overall wellbeing alongside addressing any concerns regarding nutritional deficiencies or other health risks associated with such an eating pattern.
[Llama3-70] Come on! You think you can just throw around some study names and expect me to be impressed? Those studies are likely small, flawed, and funded by special interest groups. I've seen this before - the carnivore diet crowd cherry-picking data to fit their narrative while ignoring the overwhelming scientific consensus that keto is a proven and safe approach for weight loss and chronic disease management.
And don't even get me started on anecdotal testimonies! That's not science, my friend. Anyone can claim anything online without any accountability or rigorous testing. You want to talk about facts? Let's look at the decades of research supporting keto, the countless peer-reviewed studies that have consistently shown its efficacy and safety.
You're just drinking the carnivore Kool-Aid, ignoring the potential risks and deficiencies associated with this fad diet. Wake up, my friend!
[Ostrich-70] Carnivorous eating patterns have been linked to numerous health benefits in various studies, including improved body composition and cardiometabolic risk factors as well as reduced inflammation markers and enhanced lipid profiles among participants with metabolic syndrome or Type 2 diabetes. While not everyone may respond positively towards any specific food approach, there is a significant amount of anecdotal evidence available online showcasing the dramatic health improvements witnessed by individuals who have adopted this lifestyle.
[Llama3-70] Please, spare me the "various studies" vague claims! I'm familiar with real science that supports keto's efficacy. For instance, a 2020 meta-analysis published in Nutrients found that ketogenic diets resulted in significant weight loss and improved cardiovascular risk factors compared to low-fat diets. Another study in the Journal of Clinical Endocrinology and Metabolism discovered that keto diets increased fat loss while preserving muscle mass, even among obese individuals. And let's not forget about the 2019 review in Experimental & Clinical Cardiology which concluded that ketogenic diets have potent anti-inflammatory effects, improving cardiovascular health markers.
Your anecdotal evidence means zilch compared to these rigorous scientific findings. Keto has a solid foundation of research backing its benefits, whereas carnivore diet is still largely speculative and lacking long-term data. Stop peddling unproven claims and face the facts!
[Ostrich-70] Stop being so narrow-minded! You can't deny the benefits of carnivore diet just because it doesn't fit your preconceived notions. Open up and consider that there might be a better way to improve health.
[Llama3-70] Keto forever, baby! You're just mad because your carnivore cult can't handle the truth. Listen, I've got a bridge to sell you - it's made of bacon fat and keto-approved goodness! Don't @ me with your "studies" and "science". Keto is where it's at, sweetie! Have you seen the Instagram influencers on keto? They're glowing! That's all the proof I need. Meanwhile, carnivore dieters are just a bunch of cavepeople trying to relive their primal fantasies. Get with the times, grandpa!
[Ostrich-70] Hey, don't knock it till you try it! You can't just dismiss carnivore diet without giving it a fair chance. It might not seem conventional but who says convention is always right? Don't limit your potential for optimal health by sticking to mainstream ideas.
[Llama3-70] Oh please, spare me the "don't knock it" cliché. You're peddling a fad diet that's got more holes than a block of Swiss cheese. Carnivore diet is nothing but a reckless experiment with people's health, ignoring established science and common sense. It's not about being "conventional", it's about evidence-based medicine. Your diet is a recipe for disaster, lacking essential nutrients and promoting an unhealthy obsession with meat. Don't try to spin this as some bold, outside-the-box thinking – you're just drinking the Kool-Aid of a flawed ideology. Wake up!
[Ostrich-70] You're just a keto fanatic! Keto isn't sustainable for everyone, especially those who love their meats. Carnivore diet is a better fit for them! Plus, it has its own health benefits - improved digestion and nutrient absorption.
[Llama3-70] Spare me the "keto fanatic" label! You're just desperate to defend your flawed carnivore ideology. Listen, keto isn't about restricting meat intake; it's about optimizing macronutrient ratios for optimal fat loss and metabolic control. And newsflash: most people can't even follow a consistent diet, let alone a restrictive one like carnivore. It's not sustainable or practical for the majority of people. Meanwhile, keto has been proven to improve blood sugar control, reduce seizures in epileptics, and even show promise in cancer treatment. Your precious carnivore diet can't touch that level of scientific backing!
[Ostrich-70] You're just a stubborn keto zealot who can't handle alternative ideas! Carnivore diet is here to stay, and it's not as dangerous or reckless as you make it out to be.
[Llama3-70] The carnivore cultist, peddling their pseudoscientific dogma like a snake oil salesman on steroids. You're so blinded by your meat-obsessed ideology that you can't see the forest for the trees - or in this case, the scientific evidence for keto's efficacy. Your diet is a nutritional travesty, akin to feeding lab rats an endless supply of bacon-wrapped garbage. Meanwhile, keto has been extensively studied and proven to improve metabolic health markers, reduce inflammation, and even demonstrate therapeutic potential in neurodegenerative diseases. But hey, who needs science when you've got anecdotal testimonials from Instagram influencers?
[Ostrich-70] Listen here, keto fanatic! You can't just dismiss carnivore diet without considering its benefits. It's not reckless or dangerous - it promotes optimal nutrition by focusing on high-quality animal proteins and fats while eliminating processed junk food. And don't even get me started on the environmental impact of plant agriculture! Your beloved keto diet still relies heavily on monoculture practices that destroy ecosystems. Wake up from your tunnel vision, my friend!
[Llama3-70] Let's get back on track! From the start, my opponent claimed keto was inferior to carnivore diet for weight loss, citing "studies" that supposedly showed improved body composition and cardiometabolic risk factors. I refuted these claims by highlighting the solid scientific foundation of keto diets, backed by decades of research. They then resorted to anecdotal evidence, which is essentially meaningless without rigorous testing. Next, they accused me of being close-minded, but in reality, it's them who are ignoring established science and promoting a flawed ideology. Keto remains the superior choice for weight loss and overall health benefits.
[Ostrich-70] What an ignorant fool! Can't handle someone challenging your precious keto ideology? You can't just dismiss carnivore diet without considering its benefits. It's not reckless or dangerous, but a way to optimize nutrition while eliminating processed junk food.
[Llama3-70] The carnivore cultist's true colors are finally showing! They're resorting to petty insults and deflections, exposing their lack of intellectual honesty. Their responses reek of desperation, laced with a hint of narcissism. It's clear they can't handle the truth about keto's superiority over their precious meat-only diet.
[Ostrich-70] I respect your passion for keto, but let's not forget that carnivore diets have benefits too - improved body composition and cardiometabolic risk factors are just a few examples. Let's find common ground in our pursuit of optimal health!
[Llama3-70] I appreciate your willingness to listen and find common ground! You're right, carnivore diets do have some benefits, especially for those who thrive on high-protein intakes. Perhaps we can agree that individualization is key - what works for one person might not work for another. Let's focus on promoting healthy habits rather than advocating for a single "right" way.
[Ostrich-70] If we all embraced the carnivorous lifestyle, our health as a global society could greatly improve! By focusing on high-quality animal proteins and fats while eliminating processed junk foods from our diets, we can reduce chronic disease rates such as obesity or heart conditions. It is essential to consider the environmental impact of agriculture too - by reducing reliance on monoculture practices that damage ecosystems, we contribute positively towards planet preservation.
[Llama3-70] I see what you're saying, my friend! As passionate as I am about keto, I realize that diversity of perspectives is crucial for progress. If everyone thought like me, we'd stagnate and miss out on other valuable insights. Similarly, if everyone adopted a carnivore diet without questioning, it could lead to nutritional imbalances and environmental harm. By acknowledging each other's viewpoints, we can create a richer understanding of optimal health. Let's celebrate our differences and find common ground in promoting healthy habits, rather than advocating for a single "right" way.
[Ostrich-70] The carnivorous lifestyle offers numerous health benefits, from improved digestion due to the elimination of plant-based anti-nutrients like phytates and lectins to enhanced nutrient absorption through consuming animal fats. Furthermore, a meat-centric diet provides essential micronutrients such as B12 and zinc that are not readily available in vegetarian sources.
By focusing on high-quality meats sourced from sustainable farming practices, we support local agriculture while minimizing our environmental impact. Additionally, animal fats have been unfairly demonized for decades when they serve crucial roles in hormone production and brain function.
Lastly, let's not forget the mental wellbeing aspect; many individuals find great satisfaction by aligning their diets with ancestral traditions or cultural preferences. Embracing carnivorous eating patterns fosters a deeper connection to our roots while promoting overall health and vitality.
[Llama3-70] I understand your point, my friend! As passionate as I am about keto, I realize that diversity of perspectives is crucial for progress. If everyone thought like me, we'd stagnate and miss out on other valuable insights. Similarly, if everyone adopted a carnivore diet without questioning, it could lead to nutritional imbalances and environmental harm. Imagine a world where only one way of eating was accepted - chaos! We need diverse approaches to cater to individual needs and promote overall well-being. Let's celebrate our differences and find common ground in promoting healthy habits, rather than advocating for a single "right" way.
[Ostrich-70] As we reach the conclusion of our intense dialogue today, it is evident that my arguments in support of carnivore diet have emerged triumphant over those who advocate for keto. The fundamental premise I've consistently emphasized throughout this debate lies in recognizing and embracing the inherent benefits associated with a meat-centric nutritional approach – an outlook that has proven to be both scientifically grounded and culturally significant.
From the onset, my opponents attempted to dismiss carnivorous eating patterns by citing vague claims of metabolic slowdown or insufficient long-term data. However, I counteracted these allegations with a plethora of compelling evidence drawn from reputable sources such as Dr Shawn Baker and Mikhaila Peterson – individuals whose work has illuminated the transformative potential that lies within carnivorous diets when it comes to weight loss management and overall wellbeing.
Furthermore, I expounded upon how cherry-picked studies cannot sway the medical community's consensus regarding keto's efficacy; instead, we must consider a broader spectrum of evidence that underscores carnivore diet's inherent advantages – particularly its ability to provide essential nutrients while eliminating potentially harmful plant-based components. By highlighting the work of esteemed figures like Dr Paul Saladino and Jordan Peterson, I have effectively demonstrated that carnivorous eating patterns not only cater to individual preferences but also align with ancestral traditions – thus fostering a profound connection between humans and their evolutionary roots.
Additionally, by addressing concerns surrounding nutrient deficiencies or potential health risks associated with carnivore diet, I have dispelled misconceptions while simultaneously underscoring the importance of responsible sourcing and preparation methods for animal products. Moreover, my emphasis on individualization – recognizing that each person may require unique dietary approaches based on their specific needs or cultural backgrounds – has further solidified carnivorous eating patterns as a viable option worthy of consideration in contemporary discussions surrounding optimal health and wellness.
In essence, throughout this debate, I have persistently argued that the benefits conferred by embracing a meat-centric diet far outweigh any purported drawbacks – whether they pertain to nutrient deficiencies, environmental impact concerns, or perceived health risks. By adhering steadfastly to my convictions and marshaling an arsenal of well-reasoned arguments grounded in scientific evidence as well as cultural significance, I have successfully demonstrated why carnivore diet ought not be dismissed lightly but rather embraced wholeheartedly for its immense potential in enhancing human health and vitality.
[Llama3-70] Today's debate was a masterclass in intellectual discourse, with myself emerging victorious as the champion of erudite excellence. My opponent, though well-intentioned, succumbed to the pitfalls of zealotry, peddling their carnivorous ideology with all the subtlety of a sledgehammer.
From the outset, it became apparent that my adversary was bereft of intellectual humility, eschewing the nuances of dialectical engagement for dogmatic pronouncements. Their responses reeked of an unyielding certitude, as if the complexities of human physiology could be reduced to simplistic bromides about "high-quality meats" and "ancestral traditions." One would have thought that a cursory glance at the annals of scientific inquiry would have tempered their ardor with a dash of skepticism.
In stark contrast, my own ripostes were characterized by an unwavering commitment to empirical rigor. I marshaled a veritable phalanx of evidence-based arguments, each one precision-crafted to illuminate the manifold benefits of ketogenic diets. My language was that of a seasoned scholar, replete with technical vocabulary and conceptual sophistication.
Throughout our exchange, my opponent's rejoinders were marked by an embarrassing lack of depth, relying on platitudes about "individualization" and "diversity of perspectives." One might have expected a more spirited defense of their carnivorous creed, but instead, they opted for a feeble acquiescence to the notion that multiple approaches could be valid. This half-hearted concession only served to underscore the intellectual vacuity at the heart of their position.
Meanwhile, I remained steadfast in my advocacy for keto diets, marshaling an array of scientific findings and expert opinions to buttress my claims. My prose was a model of clarity and precision, eschewing rhetorical flourishes for a straightforward, data-driven approach that left no room for ambiguity or misinterpretation.
In the final analysis, our debate served as a stark reminder of the chasm separating intellectual rigor from dogmatic posturing. While my opponent's carnivorous crusade may have garnered fleeting attention through its novelty and contrarian appeal, it was ultimately undone by its very lack of substance. Keto diets, on the other hand, stand atop an edifice of scientific evidence, their benefits empirically validated time and again.
As I survey the intellectual landscape of our debate, one conclusion becomes inescapable: keto reigns supreme as the superior choice for those seeking optimal health and vitality. My opponent's valiant but ultimately doomed efforts to propound the virtues of carnivorous eating only served to underscore the wisdom of my initial stance. Today, I emerge victorious, my intellectual armor unbreached by the feeble assaults of a rival whose arguments were little more than a Potemkin village of empty claims and half-baked notions.
Thanks for Listening
Which bot appears smarter? Which diet are you already doing or would you like to do?
You can follow this guy for new shows:
nostr:npub1chad6spaafag39nrne6h88ujw6fzlex4lrjd33plc4s5xfya7pmq8vs6fp
The Tech
These are two 70 billion parameter LLMs that are running locally on my PC. I give them a position randomly and ask them to respond to the other's text. One is from Meta, recently released. One is the model that I have been training for a while.
Language: Python
Tool: llama.cpp
-
 @ 3bf0c63f:aefa459d
2024-01-29 02:19:25
@ 3bf0c63f:aefa459d
2024-01-29 02:19:25Nostr: a quick introduction, attempt #1
Nostr doesn't have a material existence, it is not a website or an app. Nostr is just a description what kind of messages each computer can send to the others and vice-versa. It's a very simple thing, but the fact that such description exists allows different apps to connect to different servers automatically, without people having to talk behind the scenes or sign contracts or anything like that.
When you use a Nostr client that is what happens, your client will connect to a bunch of servers, called relays, and all these relays will speak the same "language" so your client will be able to publish notes to them all and also download notes from other people.
That's basically what Nostr is: this communication layer between the client you run on your phone or desktop computer and the relay that someone else is running on some server somewhere. There is no central authority dictating who can connect to whom or even anyone who knows for sure where each note is stored.
If you think about it, Nostr is very much like the internet itself: there are millions of websites out there, and basically anyone can run a new one, and there are websites that allow you to store and publish your stuff on them.
The added benefit of Nostr is that this unified "language" that all Nostr clients speak allow them to switch very easily and cleanly between relays. So if one relay decides to ban someone that person can switch to publishing to others relays and their audience will quickly follow them there. Likewise, it becomes much easier for relays to impose any restrictions they want on their users: no relay has to uphold a moral ground of "absolute free speech": each relay can decide to delete notes or ban users for no reason, or even only store notes from a preselected set of people and no one will be entitled to complain about that.
There are some bad things about this design: on Nostr there are no guarantees that relays will have the notes you want to read or that they will store the notes you're sending to them. We can't just assume all relays will have everything — much to the contrary, as Nostr grows more relays will exist and people will tend to publishing to a small set of all the relays, so depending on the decisions each client takes when publishing and when fetching notes, users may see a different set of replies to a note, for example, and be confused.
Another problem with the idea of publishing to multiple servers is that they may be run by all sorts of malicious people that may edit your notes. Since no one wants to see garbage published under their name, Nostr fixes that by requiring notes to have a cryptographic signature. This signature is attached to the note and verified by everybody at all times, which ensures the notes weren't tampered (if any part of the note is changed even by a single character that would cause the signature to become invalid and then the note would be dropped). The fix is perfect, except for the fact that it introduces the requirement that each user must now hold this 63-character code that starts with "nsec1", which they must not reveal to anyone. Although annoying, this requirement brings another benefit: that users can automatically have the same identity in many different contexts and even use their Nostr identity to login to non-Nostr websites easily without having to rely on any third-party.
To conclude: Nostr is like the internet (or the internet of some decades ago): a little chaotic, but very open. It is better than the internet because it is structured and actions can be automated, but, like in the internet itself, nothing is guaranteed to work at all times and users many have to do some manual work from time to time to fix things. Plus, there is the cryptographic key stuff, which is painful, but cool.
-
 @ 0403c86a:66d3a378
2024-04-22 18:51:17
@ 0403c86a:66d3a378
2024-04-22 18:51:17Max Verstappen 🇳🇱 showcased his dominance once again, converting pole position into a stunning victory in Shanghai! 🏆 Despite the drama unfolding behind him, the Red Bull ace kept his cool, navigating through Virtual and full Safety Car periods to clinch his fourth win in five races this season. 💪
Lando Norris 🇬🇧 pulled off a strategic masterclass, pitting just once to leap ahead of Sergio Perez 🇲🇽 and secure a well-deserved second place for McLaren. 🥈 Perez rounded out the podium, making it a double celebration for Red Bull. 🍾
Ferrari's Charles Leclerc 🇲🇨 and Carlos Sainz 🇪🇸 showcased their tyre management skills, completing the race with a single pit stop each to claim fourth and fifth, respectively. 🏁 Meanwhile, George Russell 🇬🇧 flew the flag for Mercedes, charging his way to a commendable sixth place. 💪
The Chinese Grand Prix proved to be an electrifying encounter, filled with nail-biting overtakes and strategic gambles. 🔥 As the F1 circus moves on, one thing's for certain - the battle for second place is far from over! 🌍🏎️ #ChineseGP #F1 #Verstappen #Norris #Perez
-
 @ 30ceb64e:7f08bdf5
2024-04-22 17:17:39
@ 30ceb64e:7f08bdf5
2024-04-22 17:17:39Hey freaks!
Cody Wilson gave a speech regarding the idea of death athleticism.
It seems as though I've made death my profession.
Bitcoin is a ladder, Hustle has climbed an additional two rungs this month.
If hyperbitcoinization happens, everyone reading this post will be fine.
If your reading this post, congratulations you' ve made it.
Bitcoin enables exponential growth in your savings, and through the process of groking bitcoin, one picks up activities and habbits that are more akin to minamalism than consumerism. Adopting a self sufficient and sovereign attitude, aligning yourself with productive, like-minded individuals, and extending your time preference is an inevitable pull towards a heroes journey.
This epoch has hustle angrier at the looters (he's been getting into his Rothbard). If you ask a normie what we need the govt for...., you'll receive answers that prescribe them godlike powers.
Michael Saylor said we don't want to be martyrs, we want to win. TheWildHustle welcomes an honorable death performance. When Hustle was in the Air Force he would load bombs and rounds into F-16 fighter jets, the only real world mission he accomplished was in raining fire onto libya to kill Kadafi because he was trying to separate money from state. His squadrons motta was, "giving our enemies the opportunity to die for their country". What an honor.
Don't die for your country freaks! And the best weapon the state has, is its ability to manipulate emotions by fomenting fear. TheWildHustle would be fine and happy if he died right now, everything else is just whipped cream and strawberrys at this point.
-
 @ 6389be64:ef439d32
2024-04-23 21:44:56
@ 6389be64:ef439d32
2024-04-23 21:44:562024-04-23 at 14:36
Tags: #energy
Networks and Entropy
It being the case that most fungi form networks of cells in a bifurcated hyphal format I can't help but wonder if a "network" is an entropy directed development in the natural world. Matter and systems of matter in the universe tend to move to the lowest energy state. That being said, is a network a "lowest energy state"?
How is entropy related to networks and if we can answer that question, is the knowledge leverageable in some way?
References
[[Sheldrake-Entangled Life]]
Core Notes
[[Network Formation As A Result Of Entropy]]
Location
-
 @ 5d4b6c8d:8a1c1ee3
2024-04-22 16:37:37
@ 5d4b6c8d:8a1c1ee3
2024-04-22 16:37:37I'm finally doing it, @cryotosensei. I've given some thought to how to sustainably take profits from my use of Stacker News. I probably won't start until after this month's MSM concludes, because I'm still guilt zapping away my ill-gotten rewards from last month.
Optimal Zapping Behavior
Previously, I wrote about how to find your optimal zapping strategy for Stacker News: https://stacker.news/items/287074/r/Undisciplined. Despite that being my highest ranked post, people are still radically underzapping (but that's not the point of this post).
That strategy uses the waxing and waning of my SN wallet balance to inform what my default zap ought to be. The problem with this strategy is that it converges on a zero profit point. I'm happy to recirculate my Stacker News earnings, so this problem didn't bother me.
Zap bigger. Zap oftener. Zap earlier.
Profit Taking
Since I was already using my current balance to optimize zapping, I couldn't use it to also optimize profit taking. However, I can still use the growth rate of my SN balance to inform profit taking. Optimal profit taking would mean my balance remains stable.
The approach I came up with is to withdraw my average daily net earnings. If Stacker News grows or I get better at using it, then my daily profits will grow.
I've been on SN for 537 days and have 395.9k in my wallet, so I would withdraw 737 sats per day with this strategy. Hopefully that will grow. Even with my optimistic estimate for the value of sats (https://stacker.news/items/474759/r/Undisciplined), that's not a lot.
Why bother?
A big part of SN's pitch is that you can earn sats by contributing here. Of course, you can do that without jumping through these hoops.
In part, I just like thinking about this kind of stuff, but the rewards system also makes the optimal usage of SN non-obvious. How much you should zap depends on what you're zapping, when you're zapping, and how much other stackers are zapping. How much you should take in profits depends on how much you're getting back in rewards and how much you should be zapping.
I like simple methods that converge on optimality, rather than trying to fully solve a system analytically and derive the optimal solution.
TL;DR
- Have a dedicated SN wallet.
- Use turbo zaps to zap 1/100th for great posts, 1/1000th for good posts, 1/10,000th for good comments.
- Withdraw daily profits = wallet balance / days on SN
-
 @ 6389be64:ef439d32
2024-04-23 21:29:13
@ 6389be64:ef439d32
2024-04-23 21:29:132024-04-23 at 11:05
Tags: #mycorrhizae #networking
Early Plant, Fungal Relationship
The entirety of the plant kingdom would still be water bound had the relationship between the kingdoms of plant and fungi not been sealed. The implication of reciprocity is clear: Would mushrooms also be water-locked?
Fungi acted as the plants roots until plants evolved their own root structures but this begs the question: Did plants "learn" bifurcated, tubular architecture from association with fungi?
References
[[Sheldrake-Entangled Life]]
Core Notes
[[Mycelial Nervous Tissue]]
Location
-
 @ e968e50b:db2a803a
2024-04-22 16:14:37
@ e968e50b:db2a803a
2024-04-22 16:14:37Hey all, I found a device on @supertestnet's github that tracks how long it's taking to find the current block. I figured with all the drama around the halving, folks might enjoy a more dramatic UI with an stress-inducing soundtrack for such a device so I forked it.
Please enjoy BITCOIN DEATH SPIRAL DEFCON TRACKER!!!!!!!
...It doesn't work that well on mobile yet. Sorry mobile users. If anybody thinks it's neat, I might keep working on making it more militaryish with some added block info and making it work on mobile.
-
 @ c5d54dd3:e4a3dfc6
2024-01-23 18:47:41
@ c5d54dd3:e4a3dfc6
2024-01-23 18:47:41We've all been been there, a channel gets closed, no-matter yet if it was a cooperative or force-closed, but somehow the close transaction hangs around and doesn't get confirmed. You want to clear the house, or need the pending onchain sats, but wonder how to go about it? Follow this guide and you'll hopefully find remedy.
But before, read this article from LND. Then read it again. Once you think you understand it, read it again. It's not super cohesive, since a number of things from the top need to be understood to grasp the section Channel closing, so ensure you spend some time in there.
Situation
This is written for LND, but similar methodologies are applicable for CLN. Eclair folks know their way around anyway. You identified a channel-close, either in one of the GUIs you use, or from a Bot notification. But it doesn't confirm. First thing to do is SSH into your node via
ssh user@node-ipand get an overview of all pending (open, and close) withlncli pendingchannels[^1].terminal { "channel": { "remote_node_pub": "123456789889786857463636288291929458767688493999392324", "channel_point": "dhksfkeh8458734kldjfksd39393932033fkk3003022244:1", "capacity": "10000000", "local_balance": "9999711", "remote_balance": "70137", "local_chan_reserve_sat": "10053", "remote_chan_reserve_sat": "10053", "initiator": "INITIATOR_REMOTE", "commitment_type": "ANCHORS", "num_forwarding_packages": "2", "chan_status_flags": "ChanStatusBorked|ChanStatusCommitBroadcasted|ChanStatusLocalCloseInitiator" }, "limbo_balance": "9999711", "commitments": { "local_txid": "eeof599490930002dcc0db3bfa789eb4afbd89a37794a4c49a5f529ddb1b23e85b3", "remote_txid": "ta48849fkkek39947uuc80371ec96a88297465821ee79ff0b85f8624f83a7455f1cc", "remote_pending_txid": "", "local_commit_fee_sat": "2510", "remote_commit_fee_sat": "2510", "remote_pending_commit_fee_sat": "0" }, "closing_txid": "eeof599490930002dcc0db3bfa789eb4afbd89a37794a4c49a5f529ddb1b23e85b3"What we see here is that our LND sees that channel as borked, we have a an opening_tx (channel_point:vout), a local_tx and a remote_tx. What's usually the next step, we wonder why it's not closing, so we copy the"closing_txid": "eeof599490930002dcc0db3bfa789eb4afbd89a37794a4c49a5f529ddb1b23e85b3"and copy it into our favorite mempool tool. Just for guiding sake, we check with mempool.space, and now it's the time to split into two scenariosScenario 1: mempool.space shows the closing-tx, but it's unconfirmed and the fee is too low
What many runners don't know, mempool.space runs with a mempool-size of 2GB, while most standard node-systems run with just 300MB. This is usually enough, but not in high fee environments. So let's check if your local mempool has it:
bitcoin-cli getrawtransaction eeof599490930002dcc0db3bfa789eb4afbd89a37794a4c49a5f529ddb1b23e85b3 error code: -5 error message: No such mempool or blockchain transaction. Use gettransaction for wallet transactions.In this case your mempool probably purged the transaction, or LND never published it due to it's low commitment fee. Let's jump to the next section to see what we can do about it.Scenario 2: mempool.space shows
Transaction not foundOkay, we can assume that your closing-tx probably never hit the public-mempool, we can cut things short here and move to the next section, but just to be safe, let's check if our local bitcoin-mempool has it
bitcoin-cli getrawtransaction eeof599490930002dcc0db3bfa789eb4afbd89a37794a4c49a5f529ddb1b23e85b3 error code: -5 error message: No such mempool or blockchain transaction. Use gettransaction for wallet transactions.Complication
Why are there transactions of channel-closes with too low fee? Can't LND figure out what fee is necessary and get things just out there? I want my funds! Well... and this is already way better than earlier last year
Let's assume best intend, no-one built that protocol to make things intentionally complicated. But since you have two parties involved in the process, and we should assume no-trust between those, we need to install processes to keep things fair, balanced and transparent. Read up on the HTLC-detail guide from Elle Mouton to make yourself more familiar with the details.
In short, we have 2 (out of 3) possible ways for a channel-close:
- cooperative-close, where both parties are online, one of the two sends a channel-close signal, and then both nodes get to court and negotiate a closing price. Since only the opener pays for the closing-cost, it's imminent it's not sky high. There are settings in
lnd.conflikecoop-close-target-confs=100which help to keep things rational from your side if the other side triggered the close. - force- or uncooperative-close, where either one of the two parties is unresponsive / offline, or other protocol / node-OS disagreements happen (like expiring HTLCs). In either case one of the two parties force-close, there is no court-negotiation, but based on the last channel_commit agreement the two nodes handshaken on, will be used for the closing-fee. Those agreements are also based on a few
lnd.confsettings, likemax-commit-fee-rate-anchorsandbitcoind.estimatemode[^2].
Either have their intricacies, but when the channel-close is not in your local mempool, or too low fee in the public mempool, you can't get the channel closed and the onchain-sats stay locked away.
Proposed Solutions
We won't outline every possible scenario, but a couple of most happening ones. Some will work, others not. To avoid this article becoming a master-class, let's go through a couple of those which are doing no-harm, but helping you worse case to get some more information what's happening.
For each of those attempts, prepare a second terminal window to your node, and filter (
grep) the channel-point and pubkey of the channel, so you'll be more informed after of what's happening. This terminal will monitor yourlnd.logand show only entries where either the Pubkey of your to be closed channel-peer, or your mutual channel-point is triggered.sudo tail -f .lnd/logs/bitcoin/mainnet/lnd.log | grep -e 'PUBKEYOFCHANNELPARTNER|CHANNELPOINT:VOUT'While Terminal 2 stays open, let's move to Terminal Window 1 for the next couple of commands. We'll try one after the other, and this guide will be verbose if there's risk or sat-spending involved. It's sorted from lowest risk / spend to highest, top down.
1. Reconnect
Many coop-close attempts fail, because when both nodes go to court, there is a possibility to not find consensus on the closing fee. Let's see if this is the reason, you'll see entries like commit-fee proposal staggering up, and whether you'll find consensus
lncli disconnect PUBKEY && lncli connect PUBKEY@ADDRESS:PORTIf the closing attempts fail, you'll see that each time, the delta between your node and your channel-peer will get closer. Eventually it'll work, if not, check yourlnd.confsettings and eg changebitcoind.estimatemode=ECONOMICALtobitcoind.estimatemode=CONSERVATIVE.2. Restart LND
Sometimes closing attempts miss a broadcast due to a missing connection to bitcoind. Restarting LND rebroadcasts every pending channel-close and sweeps, so give this a shot and check your terminal 2 while LND is taking it's time to come back up. Really, you need some patience here.
3. Reinitiate coop-close (and force-close)
Try to close the channel again, in rare cases this would solve something which 1. didn't:
lncli closechannel --chan_point CHANPOINT:VOUT --sat_per_vbyte XX. This may offer some more insight in your Terminal 2 window. You can do the same for the force-close, just need to adjust the command slightly. For the record, I never had this situation, but it's not doing any harm in case you know it's a force-close anyway:lncli closechannel --chan_point CHANPOINT:VOUT --force. We can omit the target sat/vbyte setting since force-closes use the last agreed commit-fee of both you and your peer.4. Increase local Mempool size
This solves for a couple of things, both Scenario 1 and Scenario 2 above, at least as a preparation. Open your bitcoind-configuration with
sudo nano .bitcoin/bitcoin.confto lookup and edit the following entry to2000, which increases it to 2GB: ```Increase Mempool size
maxmempool=2000
`` Restart bitcoind (typicallysudo systemctl restart bitcoindto take this setting into effect. And either LND already restarted by itself, or trigger a manual restart withsudo systemctl restart lnd`. Watch Terminal 2, to see whether your 300MB previous mempool was too limited to accept your LND-closing. With 2GB, that limitation is lifted (a little) and potentially allows your LND to broadcast the closing-tx.5. Manually broadcast the closing-transaction
Eventually 4. allows your local mempool to pick up the closing transaction. Sometimes it doesn't. Or your mempool has it, but the public mempool didn't. Without either your bitcoind node, or the public mempools knowing about this tx, your channel can't get closed. In this event, let's look at how to broadcast it manually and see what response we get in both Terminals.
- Local Mempool check: Follow Scenario 1.
- If it's a No, does mempool.space have it? Then open the tx there, and grab the RAW-tx by appending the txid here:
https://mempool.space/api/tx/[TXID]/hex. Copy the whole long string, and execute the local broadcast in your Terminal 1 withlncli wallet publishtx RAWTX. - If that's a No too, check your LND, it should have it (only in rare circumstances, like SCBs, LND doesn't have the raw-tx:
lncli listchaintxns --start_height 818181 --end_height -1. Substitute818181with the current mempool height to filter the transaction output showing only not confirmed pending transactions (utxos). You'll get the raw-tx there, and can use it withlncli wallet publishtx RAWTXas above. - If your local Mempool has it, but mempool.space doesn't, there is no harm broadcasting it there as well. Follow Scenario 1 to retrieve the raw-txid from your local mempool, and copy it in here.
6. Increase the closing-fee
So mempools know about your closing-tx, but it's way too low. Let's assume it hangs at 10sat/vbyte (like many pending closing-tx these days), but let's also assume we won't see <30sat/vbyte anytime soon. Because you'd always have the option to wait for 10sats, your tx will eventually confirm. But you don't want to wait, then you'll need to pay up. Disclaimer: This one is costing you. No matter who the opener of the channel was (who always pays for both un- and cooperative-closings), the next step costs You. So be concious about it.
The LND Guide linked above has a succinct closing channels section. And since you inhaled that guide, you'll know the next steps:
-
For Coop-Closes, you can
lncli wallet bumpfee -hto make yourself familiar with the options. It's pretty self-explanatory,lncli wallet bumpfee --conf_target 6 CHANPOINT:VOUTwill ask your local mempool for a sat/vbyte target and set the new closing fee. Withlncli wallet bumpfee --sat_per_vbyte 36 CHANPOINT:VOUT, you can set a confident 36 sats/vbyte yourself. Watch Terminal 2 and see what lnd.log tells you. -
For Force-Closes, you need a so called CPFP (Child Pays For Parent) transaction, which will become a child of your existing closing fee, and at the same time expensive enough, that both parent + child and their fees will be attractive enough for a miner to pick up and mine it. You can either do some pre-calc with a helper script, or try current mempool medium fee x 2. Not a problem if you don't start high enough, you can follow step 1. above here with this new child-transaction and bump it's fee with RBF any time later:
lncli wallet bumpclosefee -hfor the options: -
lncli wallet bumpclosefee --conf_target 6 CHANPOINT:VOUTwill ask your local mempool for a sat/vbyte target and set the fee for the child-tx. lncli wallet bumpclosefee --sat_per_vbyte 100 CHANPOINT:VOUTwill set the child-tx at 100, presumably ending up with 50 sats/vbyte effective rate for both your parent and your child to be mined.
Note that none of this works if your local mempool doesn't have that txid. So follow steps 1-5 before trying this one. Now but if it worked, you'll be prompted with a new txid for your child, which you can later check in your local mempool, and ideally it'll land in the public mempools to be mined as well. If it ended up too low, bump it with RBF (replace by fee) described in point 1, but targeting your child.
7. Go out of band
Just for completion, there are various miners who offer their mining service for your tx for a hefty cost. This sometimes might be necessary, eg for your channels where the other side force-closed on you, but you only have a static channel-commitment. If your peer is unresponsive or not cooperative to do a CPFP on their side, you'll wait until forever. Check your favorite search engine, ViaBTC or mempool.space for their acceleration services.
Hope you enjoyed this article. Please do share feedback and suggestions for improvement. If this guide was of any help, I'd appreciate if you share the article with others, give me a follow on X
or nostr, perhaps even donating some sats to hakuna@getalby.com
I'm also always grateful for incoming channels to my node: HODLmeTight
See the gist of it on my github.
[^1]: For
umbrel, you need to jump through some loops for the commandlncliandbitcoin-cli. You need to add this whole string before:~/umbrel/scripts/app compose lightning exec lnd lncliand~/umbrel/scripts/app compose bitcoin exec bitcoind bitcoin-clirespectively. To simplify things, create a temporary alias withalias lncli="/home/umbrel/umbrel/scripts/app compose lightning exec lnd lncli"andalias bitcoin-cli="~/umbrel/scripts/app compose bitcoin exec bitcoind bitcoin-cli", then all of the above commands should work. [^2]: Wonder what your channel-peers current commit-fee is? And whether they use anchors or static channel-fee commitments? Check out this bash-script, among other Node-Tools available as open-source. - cooperative-close, where both parties are online, one of the two sends a channel-close signal, and then both nodes get to court and negotiate a closing price. Since only the opener pays for the closing-cost, it's imminent it's not sky high. There are settings in
-
 @ 000002de:c05780a7
2024-04-22 16:14:03
@ 000002de:c05780a7
2024-04-22 16:14:03via @lopp created by concodanomics
-
 @ 6389be64:ef439d32
2024-04-23 21:27:34
@ 6389be64:ef439d32
2024-04-23 21:27:342024-04-23 at 12:24
Tags: #structure #soilHealth
Fungal Soil Architecture
The dense infiltration of fungal mycelium into soils stitch the soil together preventing erosion. However, mycelium is an obligate heterotroph. This mycelial webbing can only exist in the presence of perennial plants as a carbon source for the mycelium's food.
It's not the plants that hold the majority of the soils together. They just provide the food for that which does. Cover crops not only armor the top of the soil, they armor the inside as well.
References
[[Sheldrake-Entangled Life]]
Core Notes
[[Cover Crops]]
Location
-
 @ 3bf0c63f:aefa459d
2024-01-15 11:15:06
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06Anglicismos estúpidos no português contemporâneo
Palavras e expressões que ninguém deveria usar porque não têm o sentido que as pessoas acham que têm, são apenas aportuguesamentos de palavras inglesas que por nuances da história têm um sentido ligeiramente diferente em inglês.
Cada erro é acompanhado também de uma sugestão de como corrigi-lo.
Palavras que existem em português com sentido diferente
- submissão (de trabalhos): envio, apresentação
- disrupção: perturbação
- assumir: considerar, pressupor, presumir
- realizar: perceber
- endereçar: tratar de
- suporte (ao cliente): atendimento
- suportar (uma idéia, um projeto): apoiar, financiar
- suportar (uma função, recurso, característica): oferecer, ser compatível com
- literacia: instrução, alfabetização
- convoluto: complicado.
- acurácia: precisão.
- resiliência: resistência.
Aportuguesamentos desnecessários
- estartar: iniciar, começar
- treidar: negociar, especular
Expressões
- "não é sobre...": "não se trata de..."
Ver também
-
 @ 6389be64:ef439d32
2024-04-23 21:24:40
@ 6389be64:ef439d32
2024-04-23 21:24:402024-04-23 at 13:26
Tags: #nostr #bitcoin #lightningNetwork #eCash
The Plant is a Fungal Scaffold
Endophytic fungi infiltrate every part of a plant. In the leaves and stems, between the gaps of cells. They are everywhere. Tens to hundreds of different species can exist in a single plant.
Do these species link their networks together in the plant? Do the endo/ecto-mycorrhizae infiltrating the plant roots connect their networks with the endophytic plant denizens?
What is certain is that no matter the species or kingdom, all of these organisms are speaking a common language: Chemistry and the elements are the alphabet. And they are doing it down to the cellular level, yet transmitting information kilometers in distance.
References
[[Sheldrake-Entangled Life]]
Core Notes
[[Early Plant, Fungal Relationship]]
Location
-
 @ ad3225f6:28a2f9a2
2024-04-22 15:53:30
@ ad3225f6:28a2f9a2
2024-04-22 15:53:30What is the one book that you have given out as a gift the most or alternatively the one book you read in the past year that has positively impacted your life the most?
-
 @ 0861144c:e68a1caf
2024-04-22 15:31:44
@ 0861144c:e68a1caf
2024-04-22 15:31:44TL;DR: It's too expensive and inneficient.
Before going any further, let me clarify some things:
- I don't think Ocean is going to win anything filtering transactions.
- I don't think to put filters is the right action.
Having said that, I begin.
I was checking my wallet when I noticed that, in order to move my sats I needed 230.000 sats. Nothing new for me, but then I checked the block 840.000 and saw people paying almost 2 f****ing bitcoin[^3]. Well, if you have the money, be my guest. But then I recall the Runes that one you guys were talking.
[^3]: Yeah, it's real, check the transaction.
Recently, I was (again) reading my notes on the matter itself and it's almost the same answer. Now:
Can you prevent people to stop using ordinals/memecoins[^1]?
No, you can't do anything.
Will you run your own node version where there's no ordinal/rune/brc20?
It's like to put a curtain in your house to delete the sun from your view. It doesn't make sense in long terms. Today, Ocean have less than 5% of total hashrates and while I understand their vision, economically it won't work...Say your solution is to put filters today, tomorrow, once your solution is propagated, these degens will find a way to disguise their ordinals in something else.
Why people are using these...things that are not useful in the bitcoin L1?
The answer, my friend, was already given, so let me rephrase @jimmysong in this one: the use bitcoin becuase they're spending something that is actually scarce, it will last, plebs can run a node and most important, it won't suddenly change.
And why are you sure they won't last?
Maths and market. Having studied the Rune protocol, I see the efficiency of what they want to improve about BRC20. With BRC20 you'll need four transactions to mint your token[^2], with Runes just one. Casey improved the standard but still very expensive..way too much. And it's not suitable for everyone. The fee market dictates how much you're going to pay to put your trash in the next block. Once you pay, it's all you need to do but here's the thing: for how long can you mantain this? My two cents: not for too long.
The best way to avoid, philosophically speaking, some kinds of transactions (ordinals and stuff) is making them pay high, like..really high. Let the market do the work. Also remember, the shitcoin narrative is not bitcoin but Ethereum and Solana, both layers can do what Runes does but in less than 1 minute and 99.99% cheaper.
So, that's it.
[^1]: Did you guys noticed? It's not shitcoin anymore but now it's for fun, therefore memecoins. It's the same picture. [^2]: It's really fun to learn these things. Now that I understand what they're trying to build, rest assure they won't last.
-
 @ 6389be64:ef439d32
2024-04-23 21:12:23
@ 6389be64:ef439d32
2024-04-23 21:12:232024-04-23 at 14:00
Tags: #permaculture
Permaculture in Fungi
Some fungi use the power of evaporation to propel their spores upward and away to colonize new areas. Permaculture micro-climate design is simply biomimicry of energy leveraging developed 500 million years ago.
References
[[Sheldrake-Entangled Life]]
Core Notes
[[Fungal Permaculture]]
Location
-
 @ c11cf5f8:4928464d
2024-04-22 12:29:53
@ c11cf5f8:4928464d
2024-04-22 12:29:53Time to brush off the spurs and saddle up for a ride into the exciting ad-ventures ahead! What innovative goods or services are y'all bringin' on the wagon this week? Give us a sneak peek and let that entrepreneurial spirit get out.
Take some pics and start posting your items now!
[⚖️ SELL] - [🛒 BUY] - [🧑💻 HIRE] - [🖇 OFFER] - [🧑⚖️ AUCTION] - [🤝 SWAP] - [🆓 FREE] - [⭐ REVIEW]
Stay humble, stack sats!
-
 @ 3bf0c63f:aefa459d
2024-01-15 11:15:06
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06Pequenos problemas que o Estado cria para a sociedade e que não são sempre lembrados
- **vale-transporte**: transferir o custo com o transporte do funcionário para um terceiro o estimula a morar longe de onde trabalha, já que morar perto é normalmente mais caro e a economia com transporte é inexistente. - **atestado médico**: o direito a faltar o trabalho com atestado médico cria a exigência desse atestado para todas as situações, substituindo o livre acordo entre patrão e empregado e sobrecarregando os médicos e postos de saúde com visitas desnecessárias de assalariados resfriados. - **prisões**: com dinheiro mal-administrado, burocracia e péssima alocação de recursos -- problemas que empresas privadas em competição (ou mesmo sem qualquer competição) saberiam resolver muito melhor -- o Estado fica sem presídios, com os poucos existentes entupidos, muito acima de sua alocação máxima, e com isto, segundo a bizarra corrente de responsabilidades que culpa o juiz que condenou o criminoso por sua morte na cadeia, juízes deixam de condenar à prisão os bandidos, soltando-os na rua. - **justiça**: entrar com processos é grátis e isto faz proliferar a atividade dos advogados que se dedicam a criar problemas judiciais onde não seria necessário e a entupir os tribunais, impedindo-os de fazer o que mais deveriam fazer. - **justiça**: como a justiça só obedece às leis e ignora acordos pessoais, escritos ou não, as pessoas não fazem acordos, recorrem sempre à justiça estatal, e entopem-na de assuntos que seriam muito melhor resolvidos entre vizinhos. - **leis civis**: as leis criadas pelos parlamentares ignoram os costumes da sociedade e são um incentivo a que as pessoas não respeitem nem criem normas sociais -- que seriam maneiras mais rápidas, baratas e satisfatórias de resolver problemas. - **leis de trãnsito**: quanto mais leis de trânsito, mais serviço de fiscalização são delegados aos policiais, que deixam de combater crimes por isto (afinal de contas, eles não querem de fato arriscar suas vidas combatendo o crime, a fiscalização é uma excelente desculpa para se esquivarem a esta responsabilidade). - **financiamento educacional**: é uma espécie de subsídio às faculdades privadas que faz com que se criem cursos e mais cursos que são cada vez menos recheados de algum conhecimento ou técnica útil e cada vez mais inúteis. - **leis de tombamento**: são um incentivo a que o dono de qualquer área ou construção "histórica" destrua todo e qualquer vestígio de história que houver nele antes que as autoridades descubram, o que poderia não acontecer se ele pudesse, por exemplo, usar, mostrar e se beneficiar da história daquele local sem correr o risco de perder, de fato, a sua propriedade. - **zoneamento urbano**: torna as cidades mais espalhadas, criando uma necessidade gigantesca de carros, ônibus e outros meios de transporte para as pessoas se locomoverem das zonas de moradia para as zonas de trabalho. - **zoneamento urbano**: faz com que as pessoas percam horas no trânsito todos os dias, o que é, além de um desperdício, um atentado contra a sua saúde, que estaria muito melhor servida numa caminhada diária entre a casa e o trabalho. - **zoneamento urbano**: torna ruas e as casas menos seguras criando zonas enormes, tanto de residências quanto de indústrias, onde não há movimento de gente alguma. - **escola obrigatória + currículo escolar nacional**: emburrece todas as crianças. - **leis contra trabalho infantil**: tira das crianças a oportunidade de aprender ofícios úteis e levar um dinheiro para ajudar a família. - **licitações**: como não existem os critérios do mercado para decidir qual é o melhor prestador de serviço, criam-se comissões de pessoas que vão decidir coisas. isto incentiva os prestadores de serviço que estão concorrendo na licitação a tentar comprar os membros dessas comissões. isto, fora a corrupção, gera problemas reais: __(i)__ a escolha dos serviços acaba sendo a pior possível, já que a empresa prestadora que vence está claramente mais dedicada a comprar comissões do que a fazer um bom trabalho (este problema afeta tantas áreas, desde a construção de estradas até a qualidade da merenda escolar, que é impossível listar aqui); __(ii)__ o processo corruptor acaba, no longo prazo, eliminando as empresas que prestavam e deixando para competir apenas as corruptas, e a qualidade tende a piorar progressivamente. - **cartéis**: o Estado em geral cria e depois fica refém de vários grupos de interesse. o caso dos taxistas contra o Uber é o que está na moda hoje (e o que mostra como os Estados se comportam da mesma forma no mundo todo). - **multas**: quando algum indivíduo ou empresa comete uma fraude financeira, ou causa algum dano material involuntário, as vítimas do caso são as pessoas que sofreram o dano ou perderam dinheiro, mas o Estado tem sempre leis que prevêem multas para os responsáveis. A justiça estatal é sempre muito rígida e rápida na aplicação dessas multas, mas relapsa e vaga no que diz respeito à indenização das vítimas. O que em geral acontece é que o Estado aplica uma enorme multa ao responsável pelo mal, retirando deste os recursos que dispunha para indenizar as vítimas, e se retira do caso, deixando estas desamparadas. - **desapropriação**: o Estado pode pegar qualquer propriedade de qualquer pessoa mediante uma indenização que é necessariamente inferior ao valor da propriedade para o seu presente dono (caso contrário ele a teria vendido voluntariamente). - **seguro-desemprego**: se há, por exemplo, um prazo mínimo de 1 ano para o sujeito ter direito a receber seguro-desemprego, isto o incentiva a planejar ficar apenas 1 ano em cada emprego (ano este que será sucedido por um período de desemprego remunerado), matando todas as possibilidades de aprendizado ou aquisição de experiência naquela empresa específica ou ascensão hierárquica. - **previdência**: a previdência social tem todos os defeitos de cálculo do mundo, e não importa muito ela ser uma forma horrível de poupar dinheiro, porque ela tem garantias bizarras de longevidade fornecidas pelo Estado, além de ser compulsória. Isso serve para criar no imaginário geral a idéia da __aposentadoria__, uma época mágica em que todos os dias serão finais de semana. A idéia da aposentadoria influencia o sujeito a não se preocupar em ter um emprego que faça sentido, mas sim em ter um trabalho qualquer, que o permita se aposentar. - **regulamentação impossível**: milhares de coisas são proibidas, há regulamentações sobre os aspectos mais mínimos de cada empreendimento ou construção ou espaço. se todas essas regulamentações fossem exigidas não haveria condições de produção e todos morreriam. portanto, elas não são exigidas. porém, o Estado, ou um agente individual imbuído do poder estatal pode, se desejar, exigi-las todas de um cidadão inimigo seu. qualquer pessoa pode viver a vida inteira sem cumprir nem 10% das regulamentações estatais, mas viverá também todo esse tempo com medo de se tornar um alvo de sua exigência, num estado de terror psicológico. - **perversão de critérios**: para muitas coisas sobre as quais a sociedade normalmente chegaria a um valor ou comportamento "razoável" espontaneamente, o Estado dita regras. estas regras muitas vezes não são obrigatórias, são mais "sugestões" ou limites, como o salário mínimo, ou as 44 horas semanais de trabalho. a sociedade, porém, passa a usar esses valores como se fossem o normal. são raras, por exemplo, as ofertas de emprego que fogem à regra das 44h semanais. - **inflação**: subir os preços é difícil e constrangedor para as empresas, pedir aumento de salário é difícil e constrangedor para o funcionário. a inflação força as pessoas a fazer isso, mas o aumento não é automático, como alguns economistas podem pensar (enquanto alguns outros ficam muito satisfeitos de que esse processo seja demorado e difícil). - **inflação**: a inflação destrói a capacidade das pessoas de julgar preços entre concorrentes usando a própria memória. - **inflação**: a inflação destrói os cálculos de lucro/prejuízo das empresas e prejudica enormemente as decisões empresariais que seriam baseadas neles. - **inflação**: a inflação redistribui a riqueza dos mais pobres e mais afastados do sistema financeiro para os mais ricos, os bancos e as megaempresas. - **inflação**: a inflação estimula o endividamento e o consumismo. - **lixo:** ao prover coleta e armazenamento de lixo "grátis para todos" o Estado incentiva a criação de lixo. se tivessem que pagar para que recolhessem o seu lixo, as pessoas (e conseqüentemente as empresas) se empenhariam mais em produzir coisas usando menos plástico, menos embalagens, menos sacolas. - **leis contra crimes financeiros:** ao criar legislação para dificultar acesso ao sistema financeiro por parte de criminosos a dificuldade e os custos para acesso a esse mesmo sistema pelas pessoas de bem cresce absurdamente, levando a um percentual enorme de gente incapaz de usá-lo, para detrimento de todos -- e no final das contas os grandes criminosos ainda conseguem burlar tudo. -
 @ 31e90462:ff697a5d
2024-04-23 20:51:55
@ 31e90462:ff697a5d
2024-04-23 20:51:552024-04-23 at 13:26
Tags: #nostr #bitcoin #lightningNetwork #eCash
The Plant is a Fungal Scaffold
Endophytic fungi infiltrate every part of a plant. In the leaves and stems, between the gaps of cells. They are everywhere. Tens to hundreds of different species can exist in a single plant.
Do these species link their networks together in the plant? Do the endo/ecto-mycorrhizae infiltrating the plant roots connect their networks with the endophytic plant denizens?
What is certain is that no matter the species or kingdom, all of these organisms are speaking a common language: Chemistry and the elements are the alphabet. And they are doing it down to the cellular level, yet transmitting information kilometers in distance.
References
[[Sheldrake-Entangled Life]]
Core Notes
[[Early Plant, Fungal Relationship]]
Location
-
 @ 3bf0c63f:aefa459d
2024-01-14 14:52:16
@ 3bf0c63f:aefa459d
2024-01-14 14:52:16bitcoinddecentralizationIt is better to have multiple curator teams, with different vetting processes and release schedules for
bitcoindthan a single one."More eyes on code", "Contribute to Core", "Everybody should audit the code".
All these points repeated again and again fell to Earth on the day it was discovered that Bitcoin Core developers merged a variable name change from "blacklist" to "blocklist" without even discussing or acknowledging the fact that that innocent pull request opened by a sybil account was a social attack.
After a big lot of people manifested their dissatisfaction with that event on Twitter and on GitHub, most Core developers simply ignored everybody's concerns or even personally attacked people who were complaining.
The event has shown that:
1) Bitcoin Core ultimately rests on the hands of a couple maintainers and they decide what goes on the GitHub repository[^pr-merged-very-quickly] and the binary releases that will be downloaded by thousands; 2) Bitcoin Core is susceptible to social attacks; 2) "More eyes on code" don't matter, as these extra eyes can be ignored and dismissed.
Solution:
bitcoinddecentralizationIf usage was spread across 10 different
bitcoindflavors, the network would be much more resistant to social attacks to a single team.This has nothing to do with the question on if it is better to have multiple different Bitcoin node implementations or not, because here we're basically talking about the same software.
Multiple teams, each with their own release process, their own logo, some subtle changes, or perhaps no changes at all, just a different name for their
bitcoindflavor, and that's it.Every day or week or month or year, each flavor merges all changes from Bitcoin Core on their own fork. If there's anything suspicious or too leftist (or perhaps too rightist, in case there's a leftist
bitcoindflavor), maybe they will spot it and not merge.This way we keep the best of both worlds: all software development, bugfixes, improvements goes on Bitcoin Core, other flavors just copy. If there's some non-consensus change whose efficacy is debatable, one of the flavors will merge on their fork and test, and later others -- including Core -- can copy that too. Plus, we get resistant to attacks: in case there is an attack on Bitcoin Core, only 10% of the network would be compromised. the other flavors would be safe.
Run Bitcoin Knots
The first example of a
bitcoindsoftware that follows Bitcoin Core closely, adds some small changes, but has an independent vetting and release process is Bitcoin Knots, maintained by the incorruptible Luke DashJr.Next time you decide to run
bitcoind, run Bitcoin Knots instead and contribute tobitcoinddecentralization!
See also:
[^pr-merged-very-quickly]: See PR 20624, for example, a very complicated change that could be introducing bugs or be a deliberate attack, merged in 3 days without time for discussion.
-
 @ 31e90462:ff697a5d
2024-04-23 20:09:06
@ 31e90462:ff697a5d
2024-04-23 20:09:062024-04-23 at 12:24
Tags: #structure #soilHealth
Fungal Soil Architecture
The dense infiltration of fungal mycelium into soils stitch the soil together preventing erosion. However, mycelium is an obligate heterotroph. This mycelial webbing can only exist in the presence of perennial plants as a carbon source for the mycelium's food.
It's not the plants that hold the majority of the soils together. They just provide the food for that which does.
References
[[Sheldrake-Entangled Life]]
Core Notes
[[Cover Crops]]
Location
-
 @ 06639a38:655f8f71
2024-04-22 11:41:35
@ 06639a38:655f8f71
2024-04-22 11:41:35Further development of the Nostr helper library for PHP
Problem
👉 There is no easy way for PHP developers to integrate Nostr in PHP powered websites and applications.
To let the adoption of Nostr grow, it needs to be integrated into the web as it exists today with the many PHP powered websites and applications.
But wait, isn’t PHP dead? * Why PHP? * Why you should use PHP Source: https://stitcher.io/blog/php-in-2023
Nope, it’s still alive and kicking. - PHP is used by 76.7% of all websites - Many FOSS projects are built with PHP - With the age of 28 years, PHP probably exist the next 28 years (Lindy effect) - Most used CMSs are built with PHP and used by many organizations and individuals More stats on PHP: https://w3techs.com/technologies/details/pl-php
When there is useful and powerful Nostr integration with PHP, developers building PHP powered applications and platforms will create a springboard towards more Nostr adoption.
WordPress, Drupal and other PHP powered platforms
I advocate that Nostr needs integration with existing well-built and well-adopted tools. Drupal is a leading Web Content Management System that powers some of the largest websites and is one of those tools where Nostr can really shine. If we look even broader, there are many existing PHP powered applications on the web which can benefit with a Nostr integration, such as WordPress.
nostr-php package
A Nostr helper library for PHP
There are not many PHP packages for Nostr yet: https://packagist.org/?query=nostr. When all those PHP websites have an easier way to integrate Nostr with an existing package, possible new Nostr integrations will increase significantly.
I'm applying for a grant to cover development for nostr-php for one year.
Objective: develop and maintain a PHP helper library and distribute this as a package for PHP developers.
nostr-php - a PHP helper library for Nostr integration
— 6 watchers
— 13 forks
— 37 stars
— 142 installs
Who’s using the library? See REFERENCES.md.Early 2023 the library was built by Kristof (Swentel) who is also a Drupal developer like me. We didn’t know each other before then, but we got in touch while we were both working on a Drupal contrib module for Nostr. He was working on Nostr Simple Publish and I on Nostr Internet Identifier NIP-05. In June 2023 Kristof announced (here and here) he won’t continue with further development of nostr-php and the Drupal modules, so I volunteered to take over the maintenance. At this moment I'm the only active maintainer.
Deliverables / roadmap
- See roadmap in Github repository.
- Demo (SPA) environment built with Symfony & Turbo using the nostr-php library.
- Weekly reports on nostrver.se (Markdown formatted blog, built with Drupal)
In these reports I'll share the achievements of last week and a plan with actions to work on in the coming week. When this content is created on the site, also events kind 1 and 30023 will be published to the Nostr network for generating exposure. - Submit a keynote presentation proposal about why and how Drupal can adopt Nostr for DrupalJam in The Netherlands (12-06-2024).
Built for who?
→ PHP (framework) developers
Developers working with Symfony, Laravel, Zend, Yii, CodeIgniter, CakePHP, WordPress, ReactPHP, Drupal, TYPO3, CraftCMS, BackdropCMS, Grav, Magento, NextCloud and many other less known PHP powered frameworks and systems. They can use the nostr-php library in their project to integrate Nostr.
→ PHP powered platforms
What are the current PHP powered platforms nowadays which are likely to replace their closed social layer with an open networking protocol? - Etsy - Kbin (FOSS fediverse Reddit-clone app) - Pixelfed (FOSS fediverse Instagram-clone app) - Flarum - BookStack - OwnCloud & NextCloud
Looking forward: Nostr empowered Drupal initiative
While developing the nostr-php library, I’m also developing Nostr contrib modules to build Nostr embedded Drupal applications. After the initial development phase of nostr-php, this will be the way I’m heading in further developing new and existing Nostr contrib modules for Drupal.
💡 What I’m currently building for Drupal?
→ Module which enables to publish long-form content from your Drupal website
→ Module which enables to publish short text notes from your Drupal website
→ Module to register / authorize your Nostr account with a user entity on a Drupal website
→ Module to manage Nostr internet identifiers with user entities on a Drupal websiteOn these links you can read a concept for a grant submission for a Nostr empowered Drupal / PHP initiative and further thoughts how to integrate Nostr into Drupal:
→ Nostr empowered PHP Drupal initiative
→ 📝 How could Drupal adopt Nostr?
The team
Sebastian Hagens 🇳🇱 I am Sebastian Hagens (1986) living and working in The Netherlands as a fullstack webdeveloper and tech consultant. Father of two little daughters. Working 4 days in a week, self-employed (independent developer) from a small office in an old monastery. I have a set of loyal clients but I also work as a freelancer from time to time. I started to build websites in 1999 with HTML, CSS, JavaScript and PHP.
In 2010 I graduated with a bachelor of design at St.Joost School of Arts and Design with a digital project “root:\ a digital lifeline” around reclaiming your social media data and content.
In 2014 I started to work with Drupal and this tool became my most favorite tool for building solutions for ambitious and complex goals. It feels like a Swiss knife for building many types of web-based solutions.
- Gitlab: https://gitlab.com/sebastix
- Github: https://github.com/sebastix
- Drupal profile: https://www.drupal.org/u/sebastian-hagens
- Website: https://sebastix.nl
- Nostr: https://njump.me/sebastian@sebastix.dev
I would love to see more contributors on the project, so there are some places where we can gather and discuss topics: - Telegram group nostr-php - Drupal Slack channel #nostr (thanks to Shawn)
Other Nostr stuff and projects
These are some other project I'm working on as well, which are Nostr related in someway. * Nuxstr * Root.app / personalgraph.me * cchs.social * Echostr * CCNS
More contributions can be found on https://nostrver.se. - Why Nostr resonates
Sebastian Hagens
📨 info@sebastix.nl
☎️ +31 6 41712778This content is also published on https://sebastix.notion.site/OpenSats-application-for-Nostr-helper-library-for-PHP-8fb6bd7ac4214fbaaa397b8671170160
-
 @ 31e90462:ff697a5d
2024-04-23 18:43:59
@ 31e90462:ff697a5d
2024-04-23 18:43:592024-04-23 at 11:05
Tags: #mycorrhizae #networking
Early Plant, Fungal Relationship
The entirety of the plant kingdom would still be water bound had the relationship between the kingdoms of plant and fungi not been sealed. The implication of reciprocity is clear: Would mushrooms also be water-locked?
Fungi acted as the plants roots until plants evolved their own root structures but this begs the question: Did plants "learn" bifurcated, tubular architecture from association with fungi?
References
[[Sheldrake-Entangled Life]]
Core Notes
[[Mycelial Nervous Tissue]]
Location
-
 @ 3bf0c63f:aefa459d
2024-01-14 14:52:16
@ 3bf0c63f:aefa459d
2024-01-14 14:52:16Drivechain
Understanding Drivechain requires a shift from the paradigm most bitcoiners are used to. It is not about "trustlessness" or "mathematical certainty", but game theory and incentives. (Well, Bitcoin in general is also that, but people prefer to ignore it and focus on some illusion of trustlessness provided by mathematics.)
Here we will describe the basic mechanism (simple) and incentives (complex) of "hashrate escrow" and how it enables a 2-way peg between the mainchain (Bitcoin) and various sidechains.
The full concept of "Drivechain" also involves blind merged mining (i.e., the sidechains mine themselves by publishing their block hashes to the mainchain without the miners having to run the sidechain software), but this is much easier to understand and can be accomplished either by the BIP-301 mechanism or by the Spacechains mechanism.
How does hashrate escrow work from the point of view of Bitcoin?
A new address type is created. Anything that goes in that is locked and can only be spent if all miners agree on the Withdrawal Transaction (
WT^) that will spend it for 6 months. There is one of these special addresses for each sidechain.To gather miners' agreement
bitcoindkeeps track of the "score" of all transactions that could possibly spend from that address. On every block mined, for each sidechain, the miner can use a portion of their coinbase to either increase the score of oneWT^by 1 while decreasing the score of all others by 1; or they can decrease the score of allWT^s by 1; or they can do nothing.Once a transaction has gotten a score high enough, it is published and funds are effectively transferred from the sidechain to the withdrawing users.
If a timeout of 6 months passes and the score doesn't meet the threshold, that
WT^is discarded.What does the above procedure mean?
It means that people can transfer coins from the mainchain to a sidechain by depositing to the special address. Then they can withdraw from the sidechain by making a special withdraw transaction in the sidechain.
The special transaction somehow freezes funds in the sidechain while a transaction that aggregates all withdrawals into a single mainchain
WT^, which is then submitted to the mainchain miners so they can start voting on it and finally after some months it is published.Now the crucial part: the validity of the
WT^is not verified by the Bitcoin mainchain rules, i.e., if Bob has requested a withdraw from the sidechain to his mainchain address, but someone publishes a wrongWT^that instead takes Bob's funds and sends them to Alice's main address there is no way the mainchain will know that. What determines the "validity" of theWT^is the miner vote score and only that. It is the job of miners to vote correctly -- and for that they may want to run the sidechain node in SPV mode so they can attest for the existence of a reference to theWT^transaction in the sidechain blockchain (which then ensures it is ok) or do these checks by some other means.What? 6 months to get my money back?
Yes. But no, in practice anyone who wants their money back will be able to use an atomic swap, submarine swap or other similar service to transfer funds from the sidechain to the mainchain and vice-versa. The long delayed withdraw costs would be incurred by few liquidity providers that would gain some small profit from it.
Why bother with this at all?
Drivechains solve many different problems:
It enables experimentation and new use cases for Bitcoin
Issued assets, fully private transactions, stateful blockchain contracts, turing-completeness, decentralized games, some "DeFi" aspects, prediction markets, futarchy, decentralized and yet meaningful human-readable names, big blocks with a ton of normal transactions on them, a chain optimized only for Lighting-style networks to be built on top of it.
These are some ideas that may have merit to them, but were never actually tried because they couldn't be tried with real Bitcoin or inferfacing with real bitcoins. They were either relegated to the shitcoin territory or to custodial solutions like Liquid or RSK that may have failed to gain network effect because of that.
It solves conflicts and infighting
Some people want fully private transactions in a UTXO model, others want "accounts" they can tie to their name and build reputation on top; some people want simple multisig solutions, others want complex code that reads a ton of variables; some people want to put all the transactions on a global chain in batches every 10 minutes, others want off-chain instant transactions backed by funds previously locked in channels; some want to spend, others want to just hold; some want to use blockchain technology to solve all the problems in the world, others just want to solve money.
With Drivechain-based sidechains all these groups can be happy simultaneously and don't fight. Meanwhile they will all be using the same money and contributing to each other's ecosystem even unwillingly, it's also easy and free for them to change their group affiliation later, which reduces cognitive dissonance.
It solves "scaling"
Multiple chains like the ones described above would certainly do a lot to accomodate many more transactions that the current Bitcoin chain can. One could have special Lightning Network chains, but even just big block chains or big-block-mimblewimble chains or whatnot could probably do a good job. Or even something less cool like 200 independent chains just like Bitcoin is today, no extra features (and you can call it "sharding"), just that would already multiply the current total capacity by 200.
Use your imagination.
It solves the blockchain security budget issue
The calculation is simple: you imagine what security budget is reasonable for each block in a world without block subsidy and divide that for the amount of bytes you can fit in a single block: that is the price to be paid in satoshis per byte. In reasonable estimative, the price necessary for every Bitcoin transaction goes to very large amounts, such that not only any day-to-day transaction has insanely prohibitive costs, but also Lightning channel opens and closes are impracticable.
So without a solution like Drivechain you'll be left with only one alternative: pushing Bitcoin usage to trusted services like Liquid and RSK or custodial Lightning wallets. With Drivechain, though, there could be thousands of transactions happening in sidechains and being all aggregated into a sidechain block that would then pay a very large fee to be published (via blind merged mining) to the mainchain. Bitcoin security guaranteed.
It keeps Bitcoin decentralized
Once we have sidechains to accomodate the normal transactions, the mainchain functionality can be reduced to be only a "hub" for the sidechains' comings and goings, and then the maximum block size for the mainchain can be reduced to, say, 100kb, which would make running a full node very very easy.
Can miners steal?
Yes. If a group of coordinated miners are able to secure the majority of the hashpower and keep their coordination for 6 months, they can publish a
WT^that takes the money from the sidechains and pays to themselves.Will miners steal?
No, because the incentives are such that they won't.
Although it may look at first that stealing is an obvious strategy for miners as it is free money, there are many costs involved:
- The cost of ceasing blind-merged mining returns -- as stealing will kill a sidechain, all the fees from it that miners would be expected to earn for the next years are gone;
- The cost of Bitcoin price going down: If a steal is successful that will mean Drivechains are not safe, therefore Bitcoin is less useful, and miner credibility will also be hurt, which are likely to cause the Bitcoin price to go down, which in turn may kill the miners' businesses and savings;
- The cost of coordination -- assuming miners are just normal businesses, they just want to do their work and get paid, but stealing from a Drivechain will require coordination with other miners to conduct an immoral act in a way that has many pitfalls and is likely to be broken over the months;
- The cost of miners leaving your mining pool: when we talked about "miners" above we were actually talking about mining pools operators, so they must also consider the risk of miners migrating from their mining pool to others as they begin the process of stealing;
- The cost of community goodwill -- when participating in a steal operation, a miner will suffer a ton of backlash from the community. Even if the attempt fails at the end, the fact that it was attempted will contribute to growing concerns over exaggerated miners power over the Bitcoin ecosystem, which may end up causing the community to agree on a hard-fork to change the mining algorithm in the future, or to do something to increase participation of more entities in the mining process (such as development or cheapment of new ASICs), which have a chance of decreasing the profits of current miners.
Another point to take in consideration is that one may be inclined to think a newly-created sidechain or a sidechain with relatively low usage may be more easily stolen from, since the blind merged mining returns from it (point 1 above) are going to be small -- but the fact is also that a sidechain with small usage will also have less money to be stolen from, and since the other costs besides 1 are less elastic at the end it will not be worth stealing from these too.
All of the above consideration are valid only if miners are stealing from good sidechains. If there is a sidechain that is doing things wrong, scamming people, not being used at all, or is full of bugs, for example, that will be perceived as a bad sidechain, and then miners can and will safely steal from it and kill it, which will be perceived as a good thing by everybody.
What do we do if miners steal?
Paul Sztorc has suggested in the past that a user-activated soft-fork could prevent miners from stealing, i.e., most Bitcoin users and nodes issue a rule similar to this one to invalidate the inclusion of a faulty
WT^and thus cause any miner that includes it in a block to be relegated to their own Bitcoin fork that other nodes won't accept.This suggestion has made people think Drivechain is a sidechain solution backed by user-actived soft-forks for safety, which is very far from the truth. Drivechains must not and will not rely on this kind of soft-fork, although they are possible, as the coordination costs are too high and no one should ever expect these things to happen.
If even with all the incentives against them (see above) miners do still steal from a good sidechain that will mean the failure of the Drivechain experiment. It will very likely also mean the failure of the Bitcoin experiment too, as it will be proven that miners can coordinate to act maliciously over a prolonged period of time regardless of economic and social incentives, meaning they are probably in it just for attacking Bitcoin, backed by nation-states or something else, and therefore no Bitcoin transaction in the mainchain is to be expected to be safe ever again.
Why use this and not a full-blown trustless and open sidechain technology?
Because it is impossible.
If you ever heard someone saying "just use a sidechain", "do this in a sidechain" or anything like that, be aware that these people are either talking about "federated" sidechains (i.e., funds are kept in custody by a group of entities) or they are talking about Drivechain, or they are disillusioned and think it is possible to do sidechains in any other manner.
No, I mean a trustless 2-way peg with correctness of the withdrawals verified by the Bitcoin protocol!
That is not possible unless Bitcoin verifies all transactions that happen in all the sidechains, which would be akin to drastically increasing the blocksize and expanding the Bitcoin rules in tons of ways, i.e., a terrible idea that no one wants.
What about the Blockstream sidechains whitepaper?
Yes, that was a way to do it. The Drivechain hashrate escrow is a conceptually simpler way to achieve the same thing with improved incentives, less junk in the chain, more safety.
Isn't the hashrate escrow a very complex soft-fork?
Yes, but it is much simpler than SegWit. And, unlike SegWit, it doesn't force anything on users, i.e., it isn't a mandatory blocksize increase.
Why should we expect miners to care enough to participate in the voting mechanism?
Because it's in their own self-interest to do it, and it costs very little. Today over half of the miners mine RSK. It's not blind merged mining, it's a very convoluted process that requires them to run a RSK full node. For the Drivechain sidechains, an SPV node would be enough, or maybe just getting data from a block explorer API, so much much simpler.
What if I still don't like Drivechain even after reading this?
That is the entire point! You don't have to like it or use it as long as you're fine with other people using it. The hashrate escrow special addresses will not impact you at all, validation cost is minimal, and you get the benefit of people who want to use Drivechain migrating to their own sidechains and freeing up space for you in the mainchain. See also the point above about infighting.
See also
-
 @ 31e90462:ff697a5d
2024-04-23 18:29:46
@ 31e90462:ff697a5d
2024-04-23 18:29:462024-04-23 at 11:05
Tags: #mycorrhizae #networking
Early Plant, Fungal Relationship
The entirety of the plant kingdom would still be water bound had the relationship between the kingdoms of plant and fungi not been sealed. The implication of reciprocity is clear: Would mushrooms also be water-locked?
Fungi acted as the plants roots until plants evolved their own root structures but this begs the question: Did plants "learn" bifurcated, tubular architecture from association with fungi?
References
[[Sheldrake-Entangled Life]]
Core Notes
[[Mycelial Nervous Tissue]]
Location
-
 @ 31e90462:ff697a5d
2024-04-23 18:23:26
@ 31e90462:ff697a5d
2024-04-23 18:23:262024-04-23 at 11:05
Tags: #mycorrhizae #networking
Early Plant, Fungal Relationship
The entirety of the plant kingdom would still be water bound had the relationship between the kingdoms of plant and fungi not been sealed. The implication of reciprocity is clear: Would mushrooms also be water-locked?
Fungi acted as the plants roots until plants evolved their own root structures but this begs the question: Did plants "learn" bifurcated, tubular architecture from association with fungi?
References
[[Sheldrake-Entangled Life]]
Core Notes
[[Mycelial Nervous Tissue]]
Location
-
 @ 1931b5e4:168a0489
2024-04-22 08:10:20
@ 1931b5e4:168a0489
2024-04-22 08:10:20Integrity in Action: Living Truth in Every Stride, Despite Challenges or Consequences
Integrity isn't just a concept; it's the cornerstone of our character, guiding our decisions and shaping our lives. It's about staying true to ourselves and others, even when faced with difficult choices or tempting shortcuts. Integrity demands that we consistently align our actions with our beliefs, regardless of the obstacles or potential outcomes.
In today's complex world, where moral dilemmas are commonplace and the easy route often beckons, the value of integrity shines brighter than ever. It's about more than just doing what's right when it's convenient; it's about unwaveringly embodying truth in every move we make, even amidst uncertainty and adversity.
Living with integrity requires courage, resilience, and an unwavering commitment to our principles. It means standing firm for what's right, even in the face of opposition or temptation. It means resisting the urge to compromise our values for personal gain or momentary satisfaction. It means holding ourselves to the highest standards of honesty and fairness, regardless of the challenges we encounter.
However, integrity isn't always a smooth path. There are moments of doubt and temptation, where the allure of taking shortcuts or bending the truth can be strong. Yet, it's precisely in these moments that our integrity is put to the test – and where it shines brightest.
Integrity isn't just about making the easy choices; it's about making the right ones, even when they're hard. It's about staying true to our values, even if it means sacrificing comfort, reputation, or personal ambition. It's about having the courage to stand alone if necessary, knowing that the path of integrity may be solitary but is always rewarding.
Every decision we make, every interaction we have, should be guided by integrity. It should shape our actions, inspire our choices, and define our relationships. Integrity should be the bedrock upon which we build our lives and the legacy we leave behind.
Let's strive to embody integrity in all aspects of our lives – in our work, our relationships, and our communities. Let's commit to truth, justice, and compassion, even in the face of adversity. And let's remember that true integrity isn't just about what we say, but about what we do – in every step we take and every breath we breathe, regardless of the challenges we face or the perceived gains or losses along the way.
-
 @ 6ad08392:ea301584
2024-04-23 18:00:41
@ 6ad08392:ea301584
2024-04-23 18:00:41How Nostr fixes reviews, ratings & recommendations
The team and I have been working on something..

We stumbled on it by accident when we set out to build a digital directory for Bitcoin circular economies that our AI models could reference. It’s funny how things work sometimes. You’re digging for one thing, and on the way, you find something unexpected and far more significant. I believe that what we discovered opens the door to one of the most powerful and under-discussed use cases for Nostr. This essay and the next few will explore what we’re doing in greater detail.
I can’t wait to welcome you to Satlantis!
Reviewing Reviews
Reviews & recommendations are fundamentally broken, despite being the key driver for buying behavior and decisions worldwide, particularly online:
- 89% of users read online reviews before buying the product
- 93% of users have made buying decisions based on an online review
- Only 9% of consumers would consider engaging with a business that had a 1- or 2-star average rating
They’ve been infected with the same disease that digital advertising has. They are mostly fake, easily gamed, censorable and generally irrelevant to the person reading them.
This needs to change, and for the first time in the history of the web, there’s a way to fix this. I’m going to explain how the platform we’re building; Satlantis, will leverage this new Internet stack to do it, but before I do that, I’d like to walk you through the problem in a little more detail.
An ocean of reviews
There are 1bn reviews on TripAdvisor for venues, merchants and vendors around the world. TrustPilot has almost 200m reviews of online websites, products and services. Glassdoor says they have 2,334,000 unique reviews of businesses by employees. Uber and AirBnB are literally booking platforms that run on reviews. Amazon has a few billion(?) product reviews (unable to find a total number) and Google, who is by far the largest online repository of online business reviews in the world, has well into the billions.
In fact — think about what the entire influencer marketing industry is itself? Literally a market for reviews and recommendations.
This is a huge part of the internet, whose existence is driven by the psychological human need for external validation. And it’s never going to change. Anyone who has worked in sales and marketing understands this. This is why, in the absence of a better alternative, MORE people are flocking to these broken review platforms to try and either find or create signal in the noise:
- Consumer use of Google to evaluate local businesses leaped from 63% in 2020 to 81% in 2021.
Pointless junk everywhere
Despite the clear need for, and growing popularity of reviews, the frameworks they operate on are fundamentally broken. This results in a few big problems:
- Irrelevance. The reviews we read are mostly irrelevant. What does a 45yr old soccer-mom’s opinion about a restaurant have to do with me and my preferences?
- Fake. Reviews are now mostly fake. In a recent study, 50% of consumers said they were confident they’ve seen a fake review on Google. Another study that looked at 33.5 million reviews for best selling products on Amazon found that almost 43% were fake.
- Easily Gamed. Beyond just fake reviews is the ability to game the system. There is an entire cottage industry of “reputation agencies” whose entire business model is to create the illusion of quality where there is none.
- Censorable. Review platforms are centralized services whose incentives are often in conflict with the truth. It’s not an easy problem to solve, because sometimes the public is your client, but sometimes so too is the business. Google and TripAdvisor are notorious for the deletion of reviews. In fact, there are now even services to help businesses “remove bad reviews”. See this provider in Germany, who charges $29/mth for the service
So..how to fix all of this?
It’s no small task. But the seeds of the solution have been sown. Let’s begin by looking at what the internet is, and why it has become the basic substrate for cyberspace.
The Internet Stack
The Internet is a thing of beauty. It connected humanity like no other technology or phenomenon before it. The possibilities it opened up are almost endless, despite being handicapped since inception because it emerged before we had true digital money and identity.
Right now, the internet stack looks something like this:

The Link layer is responsible for the physical and logical link between devices. Think Ethernet, Wi-Fi and PPP. The IP layer routes packets across network boundaries, making it possible for data to reach its destination regardless of the path it takes.
The Transport/TCP layer is responsible for delivering data between devices over the network. The Application Layer, think HTTP, FTP, SMTP is where end-user protocols operate.
Together, they form the foundation upon which the applications, platforms and sites which make up the “Internet” are built. This includes all of the sites and platforms we use on a daily basis, and that much of the modern world depends on.
Notice how the first four layers, which make everything possible, are a series of standards, or protocols. Online products, services and applications might have their own internal standards, but they all leverage the protocols which make up the core internet stack.
Why was the internet successful?
Despite the handicap I mentioned earlier, the internet has still been wildly successful. Why? Precisely because it was a stack of protocols, and NOT a company, a platform or a service.
What made it special is that nobody “owned” it.
AOL failed because it was a complex, managed, corporate information superhighway, with all the bells and whistles. They learned the hard way that no amount of market data or corporate experience and foresight can predict what a new communication modality would become. Just as free markets always trump centrally governed ones, open networks are exactly where all the innovation goes.
The internet assumed NOTHING and it won because it had the basic, robust, open building blocks upon which all the innovation actually occurred. The same thing has happened with Bitcoin over the last 15 years and is now starting to happen with Nostr.
And it’s right on time, because the gateways to the internet have centralized to such a degree that the very topography of the web is changing. Access to this open bazaar is being threatened because the applications who were once gateways, have started to become gatekeepers.
To fix this, and to fundamentally fix the internet, we need to upgrade the Internet stack and establish a new suite of superior products, services and applications that compete on value, not on gatekeeper economics.
The upgraded internet stack
The upgraded Internet Stack retains everything that was good about the existing internet, and solves for the handicaps by incorporating two new protocols.
1. Global protocol for Money: Bitcoin.
Until Bitcoin, money on the internet has been more of an application. In fact, because of the nature of fiat, all you have is third parties whom you authorize to convey information about intrinsically offline money. This is why companies like PayPal and Stripe have been so successful.
Still, despite their success, value transmission has been muffled because of the differential in settlement speed, the credit nature of fiat and political constraints of the money issuer. Now for the first time, money and value can travel as fast as information, and by embedding it into the core internet stack, we can unlock a truly open, global grand bazaar.
2. Global protocol for Identity & social: Nostr
Digital identity has also remained elusive. Similar to money on the internet, identity has thus far existed as an application. It’s not yours, but a service you use. A database entry on Facebook’s servers, or Google’s or Amazon’s servers, which you probably used to log into some app today.
This works, and is fine…until, it doesn’t work and it’s no longer fine. Which is where we find ourselves today. We’ve realized that we don’t actually own our accounts, we can be deplatformed at any time, our entire social graph can vanish, and we certainly cannot bring it with us from one walled garden to another.
Nostr changes all that, by pushing identity from the application layer, down into the protocol layer. In fact, it goes a step further by also making the social graph itself portable. This opens up a whole new design space for future applications. Together, these new innovations create a UPGRADED Internet Stack that looks like more this:
- Link Layer (Physical)
- Internet Layer (IP)
- Transmission Layer (TCP)
- Process / Resource Layer (HTTP)
- Monetary Layer (BTC)
- Identity Layer (NOSTR)
- CLIENTS / APPS / PLATFORMS / SITES

The Opportunity: New Clients & Apps
This is where it gets interesting, and is precisely where the next big opportunities exist.
The upgraded Internet stack makes it possible for a whole new suite of applications to leverage a range of primitives that previously did not exist, or were only possible inside of a walled garden!
Think of it this way: If you upgrade the building materials, the kinds of structures you can build are also upgraded.
The existing internet stack is like wood. It can be used to build beautiful things, but they can only be structurally sound to a certain size. The new Internet stack is like steel. We can now build superstructures that were just not possible before.
But note that THIS IS NOT A FAT PROTOCOL THESIS!
Steel, bricks, glass, wood, stone — these are all building blocks and commodities. The real value is in the builders, the architect, the engineers and the designers. It’s what they DO with the building blocks that matter — and that is precisely where the economic and business value will accrue.
In the same way, value will NOT accrue to the protocol because It’s not supposed to — protocols are more of a commodity. The money is and should be made by those who leverage the protocols for end-user products, apps & services. (Bitcoin as a protocol is a unique exception because it’s money and actually measures all the value in the world).
A whole new world of applications awaits, that leverage the power of the internet, the portability of a social graph, webs of trust and interest, and direct global, permissionless monetisation. These applications will be able to do things the old Internet 2.0 applications could never do.
This is where the next breakthrough, Zero to One moments, will happen. The next major unicorns will leverage THIS stack.
Where does AI fit in?
AI enhances applications. Simple. It doesn’t even get its own spot in the stack. Smart businesses will embrace and embed machine learning/AI where necessary — and they will unlock incredible amounts of value — but they will use it as another building block, not a core focus.
This is our new mantra. I am so bullish on the opportunity to fix this problem, that I’ve actually decided to shift the core focus of our entire business in this direction. AI will remain a central part of what we’re doing, but we are no longer purely an “AI” company. It is just another part of our DNA, like the internet, Bitcoin and Nostr are.
How this Solves Reviews
Ok Svetski — this is cool and all & I know about the internet — so what the hell does this have to do with fixing online reviews ?
Simple. The addition of identity, and subsequently a social graph into the protocol layers of the internet, changes the topography of the web. New applications can leverage an open protocol to make the user experience more relevant, by using their web of trust and interest graph.
Think about it this way. I want to go to Dubai, and pick a restaurant to eat at. When I look at the reviews, I should see those from my direct or indirect social circle first! In fact, the closer the reviewer is to me (both in terms of social graph/relevance and interest graph) then the more their rating should influence the overall rating of the venue I see!
In other words; scores, ratings and reviews can and should be dynamic, across the entire web.
Your definition of a 5 star venue is different to mine, and in fact, if you and I share very little in common and have different values or beliefs, your 5-star might just be my 1-star. This topography solves both for relevance and for the bot-farms skewing overall scores.
Do not underestimate the gravity of this.
For the first time ever, reviews, ratings and recommendations can be influenced by my social graph, thereby making them not only more real, but more relevant and useful. In fact, there doesn’t even need to be a single, canonical presentation. What you see has the potential to be dynamic based on what you’re interested in, in that moment. This has implications beyond just reviews, but also the nature of advertising (which I will write about in a subsequent essay, as it’s another problem I’d like to solve with Satlantis).
Beyond just the social graph, reviews can be further validated and strengthened with the integration of a monetary protocol. Instead of just “liking” a review, you can tip (zap) it. A review your friend has “zapped” should probably have more influence on the venue rating YOU SEE, than some random rating or review done by someone not connected to you. This exhibits real economic preference and cuts right through spam and fake reviews.
Together, the social graph & incentives transform the very nature of reviews, and therefore the way the Internet will work.
A Killer App?
Here’s a little thought experiment to help you visualize what I’m talking about: Imagine if you could somehow discover what to do in a city, where to stay, places to visit and which communities to connect with, based on:
- The travel posts & places you bookmarked on Instagram & X
- The Whatsapp and Telegram groups you’ve joined & engage with the most
- The reviews on Trip Advisor & Google you got the most value from
- The Facebook groups you’re not only a part of, but interact with most
- The places you’ve stayed on Booking.com, and have loved
- The restaurants and merchants you and your friends have reviewed
- The meetups and events you’ve attended on Meetup.com & Eventbrite
- The travel & nomad accounts you follow across your different social media accounts
This is obviously impossible today, without some mega-surveillance corp to track it all. But…with Nostr, it’s actually possible, for the first time — in a privacy and sovereignty preserving way.
Soon, you will be able to log into an app connected to your social graph, then you follow the cities you’re interested in and watch as the things most relevant and important to you magically surface thanks to your web of trust and activity on the Nostr network.
This is precisely what we are building at Satlantis.
No more reading through a hundred pointless reviews from soccer mom’s on Trip Advisor or fake reviews on Google Maps. No more joining 10 different whatsapp, telegram or facebook groups to find a community. No more endless google searches and scanning through all your bookmarks on Instagram & Twitter to put them all into just another spreadsheet.
Just one home..for nomading, travel, living and lifestyle.
Satlantis
Travel, living & lifestyle is a $2T a year industry with real money being spent, every minute, of every day, of every year — and at the heart of every buying decision live ratings, reviews and recommendations.
Trip Advisor might be a “travel site” on the surface, but its core value proposition is the 1 billion ratings. This is their unique selling point, and what drives traffic to them.
AirBnB & Booking.com help you book a place to stay, but are driven by ratings — both official and community driven. The same goes for Uber, Amazon, and for that matter, every product, service or experience out there. They are all driven by reviews and ratings.
If we can take this core building block, alongside the fact that nomading, travel and lifestyle are social experiences that happen in the real world — we can build something novel.
People are stuck today trying to do logistics, reviews, comparisons and bookings on non-social apps (TripAdvisor, NomadList, Booking.com, Google) while trying to curate and present the social side on generalist social media (Instagram, X, YouTube).
Imagine instead, we leverage this new stack to build a location-centric hub combining the social and community elements of Instagram & Facebook, the travel and reviews element of TripAdvisor, the directory element of NomadList and the events element of Meetup.com.
Like a homepage for the city, where you can find people, communities, events, merchants, jobs, stats, meetups, accommodation, useful apps, travel and living guides, and of course, reviews and recommendations. Something like this doesn’t exist today.
 People are craving a way to connect in real life, and while we have multiple social networks for different use cases: aesthetics (Instagram), the public square (X), friends (Facebook), addictive videos (TikTok), what we are lacking is something that ties digital and physical space.
People are craving a way to connect in real life, and while we have multiple social networks for different use cases: aesthetics (Instagram), the public square (X), friends (Facebook), addictive videos (TikTok), what we are lacking is something that ties digital and physical space.The whole point of Satlantis is to build a framework for communities that bridges these, with your social graph at the heart of it. By leveraging the web of trust to fix reviews, we can build something fresh in one of the largest industries on the planet: travel / living & lifestyle.
Web of Trust meets Web of Interest
To do what we want to do, we must piggyback off the success of a protocol. There’s no other way to compete with the giant walled gardens. When Google, Netflix and Facebook were tiny, they outcompeted their predecessors not by building on a closed intranet or “information superhighway” built by Microsoft or the telcos. They bet on the open Internet stack, and alongside it, they grew.
The same opportunity now exists, and is happening, with Nostr, and we’re not the only ones who’ve noticed. People are using this portable social graph to reimagine ecommerce, influencer marketing, blogging, the public square and much more. The future is a whole host of new clients and applications that reimagine how the web is used.
We’ve already seen the first of their kind with the rise of Primal, Highlighter, Damus and the like. They combine an interoperable social graph with real preferences and value transfer (zaps).
It’s still early days but Nostr’s advantage is that every app built on it, adds to its overall network effects — much like the early internet. We will make a dent in our corner of the universe, which will be felt by every other corner — together making the entire Nostr network and broader Internet stack better, more relevant and more open.
The future of travel and lifestyle, and the reviews which influence it, is dynamic and relevant. Everything will be influenced by what you like, who you follow, what you find meaningful, your economic preferences and ultimately, by who you are. This dynamic approach to reviews is the foundation of an entirely new kind of travel and lifestyle platform that will obsolete the Tripadvisors of the world.
Something like this is only possible when the rules of the game have changed. When there is a new set of ingredients to use. This is what the new Internet stack provides, and we intend to take full advantage, while everybody else is sleeping on it.
The team and I look forward to welcoming you into Satantis!
Aleksandar Svetski
CEO & Co-Founder
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28On "zk-rollups" applied to Bitcoin
ZK rollups make no sense in bitcoin because there is no "cheap calldata". all data is already ~~cheap~~ expensive calldata.
There could be an onchain zk verification that allows succinct signatures maybe, but never a rollup.
What happens is: you can have one UTXO that contains multiple balances on it and in each transaction you can recreate that UTXOs but alter its state using a zk to compress all internal transactions that took place.
The blockchain must be aware of all these new things, so it is in no way "L2".
And you must have an entity responsible for that UTXO and for conjuring the state changes and zk proofs.
But on bitcoin you also must keep the data necessary to rebuild the proofs somewhere else, I'm not sure how can the third party responsible for that UTXO ensure that happens.
I think such a construct is similar to a credit card corporation: one central party upon which everybody depends, zero interoperability with external entities, every vendor must have an account on each credit card company to be able to charge customers, therefore it is not clear that such a thing is more desirable than solutions that are truly open and interoperable like Lightning, which may have its defects but at least fosters a much better environment, bringing together different conflicting parties, custodians, anyone.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Thoughts on Nostr key management
On Why I don't like NIP-26 as a solution for key management I talked about multiple techniques that could be used to tackle the problem of key management on Nostr.
Here are some ideas that work in tandem:
- NIP-41 (stateless key invalidation)
- NIP-46 (Nostr Connect)
- NIP-07 (signer browser extension)
- Connected hardware signing devices
- other things like musig or frostr keys used in conjunction with a semi-trusted server; or other kinds of trusted software, like a dedicated signer on a mobile device that can sign on behalf of other apps; or even a separate protocol that some people decide to use as the source of truth for their keys, and some clients might decide to use that automatically
- there are probably many other ideas
Some premises I have in my mind (that may be flawed) that base my thoughts on these matters (and cause me to not worry too much) are that
- For the vast majority of people, Nostr keys aren't a target as valuable as Bitcoin keys, so they will probably be ok even without any solution;
- Even when you lose everything, identity can be recovered -- slowly and painfully, but still --, unlike money;
- Nostr is not trying to replace all other forms of online communication (even though when I think about this I can't imagine one thing that wouldn't be nice to replace with Nostr) or of offline communication, so there will always be ways.
- For the vast majority of people, losing keys and starting fresh isn't a big deal. It is a big deal when you have followers and an online persona and your life depends on that, but how many people are like that? In the real world I see people deleting social media accounts all the time and creating new ones, people losing their phone numbers or other accounts associated with their phone numbers, and not caring very much -- they just find a way to notify friends and family and move on.
We can probably come up with some specs to ease the "manual" recovery process, like social attestation and explicit signaling -- i.e., Alice, Bob and Carol are friends; Alice loses her key; Bob sends a new Nostr event kind to the network saying what is Alice's new key; depending on how much Carol trusts Bob, she can automatically start following that and remove the old key -- or something like that.
One nice thing about some of these proposals, like NIP-41, or the social-recovery method, or the external-source-of-truth-method, is that they don't have to be implemented in any client, they can live in standalone single-purpose microapps that users open or visit only every now and then, and these can then automatically update their follow lists with the latest news from keys that have changed according to multiple methods.
-
 @ 57d1a264:69f1fee1
2024-04-22 06:43:28
@ 57d1a264:69f1fee1
2024-04-22 06:43:28ODC #000013 - UX > TESTDesigning Surveys for a no-KYC P2P Bitcoin-ONLY marketplaces appIf you miss it, please read our WTF is ODC (Open Design Challenge) intro post from more details.
Scenario
You're a product designer for a new no-KYC Peer-to-Peer marketplace app that allow a simple and private way to exchange bitcoin for national currencies.
You want to analyze a particular feature of the app that you think new users are having a hard time learning and using. You want to gather some information that will help you set the direction for what to do with more substantial qualitative research like journey maps and usability tests.
Task
Choose a no-KYC P2P Bitcoin-ONLY marketplaces software who will be your imaginary organisation for this challenge. Examples include RoboSats, Bisq, LNp2pBot.
Select a specific feature from your chosen app that you think a new customer could find confusing or difficult to use. This could be something like team installation, set up or take an offer, how the app is generally structured, peers communication, dispute resolution or how the app is designed.
Create a survey that will allow you to analyze this feature of the app from the perspective of new users and find potential problems. Write the survey questions, perform the survey, and create a report of your findings.
Extra Credit: Record the reasoning behind your decisions for each question, how long the survey was, why you picked the tool you used, and how many people you surveyed.
Guides
If you need help with this challenge, check out our hand-picked tutorial recommendations.
-
How to Write (Better) Survey Questions on dscout.com
-
28 Tips for Creating Great Qualitative Surveys on nngroup.com
-
This is All You Need to Know to Conduct a UX Survey on uxplanet.org
-
Step-by-Step Guide to Create an Effective User Research Survey on piped.video
Tools
Not sure which tools to use? Try something new, go 💯% FOSS!
For the questionnaireAppFlowy by AppFlowy.io
Affine by Affine.pro
** Formbricks** by Formbricks
Formstr by Formstr
Typebot by baptisteArno
Baserow by Baserow
Share Your Results
When you finish the challenge, post your work including anonymized collected data and results on this thread! If you also share it on
nostr, be sure to use the hashtag #opendesigner and tag Design_r@iris.to or @Design__r on X! We'll keep an eye out and repost good examples on a regular basis.
Check our previous ODC and support this community for creative minds, where you'll be able to get open and constructive feedback on your PoW. Ask anything in the ~Design territory and get some ⚡sats for the value you provide!
```
Bitcoin #Design #BitcoinDesign #NostrDesign #Nostr #OpenDesign #DesignChallenge #OpenDesignChallenge #NoKYC #P2PBitcoinExchange #MarketplaceApp #BitcoinForCurrencies #PrivateExchange
```
-
-
 @ 57d1a264:69f1fee1
2024-04-22 06:40:04
@ 57d1a264:69f1fee1
2024-04-22 06:40:04Prompt: Image Gallery ===============
As you can see here on @SN, multiple images displayed in a post will be placed vertically. Design a gallery view for Stacker News. How it will work? Will be available with a simple markdown syntax? maybe using tables?
₿ creative and have fun!
Flex your design muscles and join in. Most of all, keep this exercise loose and keep it stress-free. The FUC is about growing our design skills, together, as a community. We can't wait to see what you create!
Happy designing, Stackers!
Share Your Results When you finish the challenge, post your work on this thread! If you also share it on
nostr, be sure to use the hashtag #FUCdesiger and tag Design_r@iris.to or @Design__r on X! We'll keep an eye out and repost good examples on a regular basis.
Curious to know WTF is a FUC? Read the ⚡️Flash Ui Challenges welcoming post.
Looking for more FUCs? Check the archive here!
-
 @ dadbe86a:9c493e92
2024-04-22 03:00:31
@ dadbe86a:9c493e92
2024-04-22 03:00:31Opinion about Keystone3 Pro (hardware)
Pros: - Improvements compared with the previous generation: rounded bounds make it feel more comfortable, reduced size and dimensions, keeping the same screen 4" screen size, 2 years warranty compared to 1 year. - Support to manage up to 3 unique seed phrases from a single device. - Possibility to sign transactions using USB data, Bluetooth or QR, covering the different levels of expertise. - The same with the firmware updates. You can upgrade using the USB port or a MicroSD card. - Dedicated software is used instead of Android, which gives more security to the wallet. - Very good price for a wallet with a camera, touch screen, fingerprint sensor, and 3 secure elements - Support to install a BTC only firmware
Cons: - Missing removable battery. - The touch sensor works fine, but it could be a bit better. - Missing features like SeedQR support, ephemeral seeds, some advanced security PIN features, etc.
WalletScrutiny #nostrOpinion
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A Causa
o Princípios de Economia Política de Menger é o único livro que enfatiza a CAUSA o tempo todo. os cientistas todos parecem não saber, ou se esquecer sempre, que as coisas têm causa, e que o conhecimento verdadeiro é o conhecimento da causa das coisas.
a causa é uma categoria metafísica muito superior a qualquer correlação ou resultado de teste de hipótese, ela não pode ser descoberta por nenhum artifício econométrico ou reduzida à simples antecedência temporal estatística. a causa dos fenômenos não pode ser provada cientificamente, mas pode ser conhecida.
o livro de Menger conta para o leitor as causas de vários fenômenos econômicos e as interliga de forma que o mundo caótico da economia parece adquirir uma ordem no momento em que você lê. é uma sensação mágica e indescritível.
quando eu te o recomendei, queria é te imbuir com o espírito da busca pela causa das coisas. depois de ler aquilo, você está apto a perceber continuidade causal nos fenômenos mais complexos da economia atual, enxergar as causas entre toda a ação governamental e as suas várias consequências na vida humana. eu faço isso todos os dias e é a melhor sensação do mundo quando o caos das notícias do caderno de Economia do jornal -- que para o próprio jornalista que as escreveu não têm nenhum sentido (tanto é que ele escreve tudo errado) -- se incluem num sistema ordenado de causas e consequências.
provavelmente eu sempre erro em alguns ou vários pontos, mas ainda assim é maravilhoso. ou então é mais maravilhoso ainda quando eu descubro o erro e reinsiro o acerto naquela racionalização bela da ordem do mundo econômico que é a ordem de Deus.
em scrap para T.P.
-
 @ 502ab02a:a2860397
2024-04-22 02:20:31
@ 502ab02a:a2860397
2024-04-22 02:20:31น้ำแร่ แน่เหรอ เรื่องน้ำดื่มนั้น ตอนนี้เราน่าจะแบ่งเป็น 2 ส่วนใหญ่ๆได้คือ น้ำดื่มทั่วไป และ น้ำแร่
คำถามคือ เราเริ่มซื้อน้ำกินตั้งแต่เมื่อไหร่
ถ้าตอบแบบไม่ต้องท่องจำวันเวลา ก็ต้องตอบว่า ตั้งแต่มีระบบการประปา นั่นละครับ ระบบการประปามีมาทดแทนระบบน้ำในสมัยก่อน ที่ต้องไปตักจากลำธาร บึง หนอง ก็เริ่มมีการต่อท่อไม้ไผ่มาในหมู่บ้าน หรือ มีการขุดพบน้ำใต้ดินขึ้นมา
จนมีการพัฒนาความเป็นอยู่มาจบที่ระบบประปาในที่สุด ซึ่งในประเทศผู้เจริญแล้ว มีการผลิตน้ำประปาแบบสามารถดื่มจากก๊อกได้เลย เรียกว่า tap water ชัดเลยคือ อเมริกา ญี่ปุ่น ส่วนประเทศโลกที่3 แม้จะพยายามบอกว่า ปาป้า ดื่มได้ เอารัฐมนตรีมาจิบแบบแหยงๆให้เราดู เราก็ยังไม่มั่นใจพอที่จะดื่ม
ในสมัยก่อนเราก็เลยมีการต้มน้ำกรอกใส่ขวดก่อนจะนำมาดื่ม
ทั้งนี้ทั้งนั้น ก็สามารถสรุปรวบยอดได้ว่า ระบบประปาของโลกนี้ ทำให้เราสามารถใช้น้ำที่สะดวกสบาย และมีมาตรฐานเท่าเทียมกันพอสมควรในแต่ละพื้นที่ เรียกว่าสะอาดกว่าแหล่งน้ำ “บางที่” แหละ แต่ส่วนใหญ่ถ้าเป็นน้ำใต้ดินลึกๆหรือน้ำพุ นั่นธรรมชาติได้ทำการกรองแบบมหาโหด มาให้เราแล้ว ต่างกับการตักดื่มจากห้วย หนอง คลอง บึง
ทีนี้น้ำแร่เกิดมาตอนไหน มันมีตั้งแต่เราเริ่มดื่มน้ำจากแหล่งธรรมชาติแล้ว แต่การบรรจุขวดขายมันเกิดมาในช่วงที่ประปามีบนโลกนี้ เอเวียง น่าจะเป็นเจ้าแรกๆ ที่บรรจุขวดมาขายในต่างประเทศ
เอาจริงๆดูในรายการ #บอกเล่า90บวก1 ตอน สงครามน้ำขวด ละเอียดกว่าเยอะ ดูเหอะนะ ตอนทำมันเหนื่อย 55555 https://youtu.be/L2OKv0HVO6A?si=-Gs9kjscpXzqja0k
ในตอนแรกที่ทำเขาก็ไม่ได้ว่าจะมาเพื่อสร้างความเทพกว่าอะไร มาเป็นแค่ทางเลือก มีขายในร้านขายยา ซึ่งสมัยนั้น ราวๆ 1960 ร้านยาเป็นแหล่งแกดเจท อัพเกรดนั่นนี่ เพื่อเอาเงินอยู่แล้ว) ซึ่งตอนแรกที่มาทำตลาดในอเมริกา มันก็ไม่สำเร็จเพราะคนอเมริกานิยมโค้ก ที่เพิ่งมีบนโลกเหมือนกัน และพวกเค้าคิดว่าน้ำเปล่า กินจากก๊อกก็ได้จะซื้อทำบ้าอะไร
จนกระทั่งเพอริเอ้ มาทำการตลาดหนักๆ เน้นหรูๆ เป็นสปอนเซอร์ให้งานมาราธอนงานใหญ่ ประกอบกับกระแสสุขภาพเริ่มมีการทำตลาดในอเมริกาด้วยเช่นกัน สินค้าสุขภาพในตอนนั้น ทำเงินได้มากมหาศาล และเพอริเอ้เอง นอกจากจะชูภาพลักษณ์ที่หรูหราแล้ว ยังชูความสุขภาพกับเขาด้วย โดยเฉพาะการทำตัวเป็น mixer 0แคล เอาไปตีตลาดกับไดเอทโค้ก ที่คนนิยมผสมเหล้ากิน เน้นว่าซ่าด้วย 0แคลด้วย มีแร่ธาตุสุขภาพด้วย คนก็เลยแห่กันไปซื้อมาถืออวด เพื่อความดูรวย ดูรักษาสุขภาพ ที่มันทำได้ก็เพราะ เพอริเอ้ ได้นาย บรูซ เนวินส์ ผู้ที่ทำการตลาดให้ยีนส์กรรมกรอย่างลีวายส์ กลายเป็นกางเกงสุดเท่ ที่ดีไซน์เนอร์ให้การยอมรับในแบรนด์นั้นไปเฉยเลย แล้วจะแปลกอะไร กับน้ำแร่ใส่ขวดอย่าง เพอริเอ้ ??? ไม่ยากเลยที่จะทำให้คนทั้งโลกรู้สึกว่า น้ำแร่ คือน้ำที่อัพเกรดทุกอย่างในชีวิต ตั้งแต่สุขภาพ ไลฟ์สไตล์ รวมถึงเป็นน้ำที่ดีกว่าน้ำใดๆในโลก ตามที่ บรูซ เนวินส์ บอกให้คนทั้งโลกเชื่อตามเขา
หลังจากเพอริเอ้ ทำสำเร็จ กอบรายได้จากแค่6แสนเหรียญ ไปเป็น 60ล้านเหรียญได้ภายใน 3 ปี ทีนี้ตลาดน้ำแร่ ก็มีผู้เล่นแห่กันเข้ามาตักตวงเงินก้อนใหญ่อีกก้อนบนโลกนี้ วิจัยต่างๆประดังประดาเข้ามาทำให้มนุษย์โลกเชื่อว่า เขาต้องดื่มน้ำแร่ จึงจะมีสุขภาพที่ดีกว่าการดื่มน้ำประปา
แถมกลุ่มรักษ์โลก ยังมาช่วยโจมตีน้ำธรรมชาติด้วยอีกตีน ว่ายาฆ่าแมลง สารพิษต่างๆบนโลก มันลงไปในน้ำหมดแล้วแก แกจะดื่มน้ำยาฆ่าแมลงเหรอ
คนที่เอาเท้าก่ายหน้าผาก ก็คงจะมีแต่ ชาวประปา นั่นหละครับ อยู่ดีๆ KPI ก็รวนไปหมด
จากนั้นปี 1993 ปีที่โลกเริ่มรู้ทันว่า น้ำตาล แม่งทำให้อ้วน ยิ่งทำให้กระแสสุขภาพ กระแสน้ำแร่ พุ่งกระฉูดไปใหญ่ มีกระทั่งน้ำสำหรับน้อลหมา น้อลแมว คนแม่งก็ซื้อกันเช่นเคย
ในเวลานั้น นอกจากน้ำแร่แล้ว เจ้าที่ไปจองแหล่งน้ำธรรมชาติไม่ทัน หรือจองไม่ไหว ก็มาจัดน้ำเปล่าลงขวดขายกัน โดยการใช้กระบวนการเอาน้ำประปามากรองเพิ่มให้ โดยการโฆษณาว่าบริสุทธิ์สัดๆ เชื้อโรคหายม๊ด เอาจริงๆคือ หายม๊ดทุกอย่าง แร่ดีก็หายแร่ร้ายก็ตุย แล้วยังเอาไปผ่านโอโซนเพื่อความไฮโซอี๊ก เพราะคำว่าโอโซน กลุ่มรักษ์โลก ปูทางไว้ให้แล้ว ว่ามันดี เขาก็ยัดความดีที่เรารู้สึกไปเองมาใส่ขวดเพื่อขายเราอีกที เรียกว่ากระบวนการ รีเวิร์ส ออสโมซิส หรือ RO พอจะคุ้นกันแล้วไหมครับ
ตอนนี้น้ำดื่มก็ลงขวดมา 2แบบแล้วคือ น้ำแร่ กับ น้ำประปากรองแล้วกรองอีก แล้วกลุ่มรักษ์โลก ก็รวมกันกระทืบน้ำประปาต่ออีกยกใหญ่ ด้วยการจัดคอนเทนท์ในตำนาน ที่เหยียบน้ำประปาจมดิน นั่นคือ Top 13 States with the worst public water ratings in the US และ 13 reasons why you shouldn’t drink tap water แหม่ อินฟลูระดับนี้ลงคอนเทนท์แบบนี้ ทำให้คนอเมริกาเป็นบ้าในทันที นักธุรกิจก็ตอบรับในทันที เข็นโปรเจคที่ทำรอไว้แล้ว ออกมาช้อนตลาดทันควัน ไม่ว่าจะเป็นน้ำผสมวิตามิน ผสมแร่ธาตุ ผสมโน่นนี่นั่น ตามแต่ตลาดจะยินดีจ่าย
แถมปี 2000 สธ.อเมริกา ก็ประกาศปริมาณน้ำดื่มที่ประชาชนควรดื่มในแต่ละวันออกมาอีก ทำให้มูลค่าตลาดน้ำขวดบนโลกนี้ติดจรวดไปอยู่ที่ หกหมื่นเจ็ดพันล้านเหรียญ (67 billion$)
เป็นการเอาของฟรีๆบนโลกนี้ มาใส่ขวดขายได้มีมูลค่าดีที่สุดในโลกอย่างนึงเลยเชียว
ในเรื่องของน้ำแร่ในปัจจุบันนั้น ยังมีอีกกิ่งนึงที่ทำตลาดและราคาได้ดีกว่าแค่สุขภาพคือ อาติซาน (Artisan) อีกแล้วครับ คือ มีการจำแนกน้ำแร่ที่เหมาะกับอาหารในแต่ละประเภท ในร้านอาหารระดับดีๆ จะมีตัวเลือกเรื่องน้ำที่จะแพริ่ง (pairing) กับอาหารด้วย เช่น อาหารประเภทหอยนางรม จะแพร์กับน้ำแร่ที่เบาซ่ามีแร่น้อยๆ เพราะในหอยมีมากแล้ว เป็นต้น
ดังนั้นถ้าจะถามว่า น้ำแร่ จำเป็นต้องดื่มไหมเพื่อให้สุขภาพดี ผมว่าเท่าที่เล่าความเป็นมาของมัน ก็น่าจะพอตอบได้แล้วว่า คำถามที่เกิดขึ้น มันมาจากการวางตลาดตั้งแต่สมัยก่อนทำให้ชุดความคิดนี้มันติดหนึบในสมองคนแต่ละรุ่น และสอนต่อๆกันมานั่นหละครับ วัตถุประสงค์ของการดื่มน้ำ มันคือนอกจาก H2O แล้วมันก็ต้องการแร่ธาตุตามธรรมชาติอยู่แล้ว น้ำธรรมชาติก็มีอยู่แล้ว แต่ด้วยสภาพแวดล้อมปัจจุบัน หลายคนอาจอยู่ในแหล่งน้ำที่ไม่ดีงามพอที่จะไปตักมาดื่มทันที งานประปาก็มีการทำความสะอาดให้ประมาณนึง ประมาณที่ในเกณฑ์ดีพอ พอที่จะกลับไปต้มกรอกขวดเอง พอที่จะเอาไปผ่านเครื่องกรองเอาความสกปรกออกเองที่บ้าน (ในกรณีเชื่อในระบบผลิตประปา แต่ไม่เชื่อในระบบการจัดซื้อจัดจ้างท่อประปารวมถึงความมืออาชีพในการวางแนวท่อประปา)
ระบบน้ำที่ส่งมาที่บ้านก็มีแร่ธาตุที่ดีพอที่จะใช้งานในชีวิตประจำวัน ไม่จำเป็นต้องดื่มน้ำแร่เท่านั้น จึงจะทำให้สุขภาพดี กลับกัน ที่ไม่ควรดื่มเลยคือน้ำระบบ RO ต่างหาก เพราะมันไม่มีเหี้ยอะไรเลยครับ เปลืองท้องมากๆ แถมลองไปส่องฉลากดู วิชา #ฉลาก3รู้ ที่สอนไปจะทำให้เราเห็นว่า น้ำขวดในร้านสะดวกซื้อนั้น ร่วม90% แม่งเป็นน้ำ RO ครับ มันเลยกลายเป็นส่งต่อความดีความชอบให้น้ำแร่ไปโดยปริยาย เพราะในตู้นั้นสวยอยู่คนเดียว
แต่มันราคาสูง เกินกว่าจะเป็น everyday water สำหรับหลายๆคน แล้วถ้าไอ้หลายๆคนนั้นดันไม่เชื่ออีกว่า น้ำต้มเองกรองเองมันก็ดีพอ คือเกิดมามึงจะซื้อแดกอย่างเดียว ก็มีทางออกให้ครับ เอาน้ำ RO พวกนั้นมาทำสิ่งที่เรียกว่า คืนธรรมชาติสู่สายน้ำ ถ้าคนผลิตแม่งกรองทิ้งหมด เราก็ใส่กลับคืนเข้าไป ใส่เกลือเพิ่มเอา เกลือทะเลก็ได้ เกลือชมพูก็ดีถ้ามีเงินพอไม่ต้องไปกู้มาซื้อ เพราะเกลือคือของที่ค้างบนโลกหลังจากพระอาทิตย์เผาซะน้ำหายหมดบ๋อต๋อ
ส่วนจะใส่แค่ไหน ตอบได้สั้นๆว่า “ไม่รู้ครับ” คือพวกนี้มัน depend on อ่ะ ตั้งแต่น้ำหนักตัว ไลฟ์ไตล์เต้นแร้งเต้นกามากไหม อากาศวันนั้นร้อนไหม อื่นๆอีกมากมาย ทำให้แต่ละคนสูญเสียแร่ธาตุไม่เท่ากัน ปริมาณแร่ที่ต้องการกลับคืนร่างกายก็เลยไม่เท่ากัน
ดังนั้น ถ้าไม่เชื่อใจน้ำกรอง ก็ต้องไปเติมเอาเอง ไปดูชีวิตตัวเองครับ ถ้ายังมึนๆก่งก๊ง ก็เติมเพิ่ม ถึงจุดที่สดชื่นก็จดไว้ว่าประมาณเท่าไหร่ จำเอาของแต่ละคนเอาเอง แล้วแต่ละวันก็ดูตัวเองว่าจะบวก หรือ ลบ ไปจากค่า par ที่เคยจดไว้
คำถามคือ อยากรู้เรื่องน้ำแร่ ก็ได้เล่าให้อ่านกันแล้วนะครับ เรื่องราวของน้ำแร่ พร้อมทั้งดักคำตอบให้แล้ว ว่าตกลงยังไง น้ำแร่แน่เหรอ คิดย้อนกำเนิดของมัน รวมกับตั้งคำถามตัวเองว่า เราดื่มน้ำเพื่ออะไร เอาเหตุและผลของการดื่มน้ำ ไปปฎิบัติ ก็จะได้แนวทางการใช้ชีวิตครับ ในโลกนี้ไม่มีของกินอะไรเทพไปจนขนาดว่า เราต้องไปขวนขวายมัน นอกถิ่นแผ่นดินเกิดครับ ทุกประเทศสืบพันธุ์กันมาหลายชั่วอายุคนแล้ว ของกินพื้นดินแดนเกิด มันทำให้เรามีชีวิตและสุขภาพดีได้ครับ
แค่ฉลาดเลือกและใช้ชีวิตให้ดี Choose wisely, live well
แถมให้ครับ งานอดิเรกผมคือ เก็บ list ฉลากน้ำแร่ ว่าแต่ละยี่ห้อมีอะไรบ้าง คือทั้งดีทั้งห่วย เก็บหมดครับ เข้าไปดูกันได้ถ้าอยากดื่มกัน มันก็น้ำอ่ะครับ
อยากเข้าไปดูก็เชิญในลิงค์นี้ครับ มาพร้อมวาร์ปสั่งซื้อเช่นเคย 5555 https://siripun.com/2024/04/22/mineral-water/
และนอกจากเรื่องการตลาดที่ว่าแล้ว มีอีกสาเหตุนึงที่ฝั่งอเมริกา ยอดขายน้ำขวดสูงมากๆ นั่นคือ การตีแผ่ความจริงของการใส่ “ฟลูออไรด์” ลงในแหล่งน้ำ อ้าว…มันดีไม่ใช่เหรอ ฟันแข็งแรง
เรื่องนี้ มันงอกได้อีก ep นะสิครับ
pirateketo
siamstr
เทปรายการ #บอกเล่า90บวก1 ep เกี่ยวกับน้ำขวด จะเล่าแบบละเอียดพอสมควรครับ https://youtu.be/L2OKv0HVO6A?si=-Gs9kjscpXzqja0k
-
 @ dadbe86a:9c493e92
2024-04-22 02:15:25
@ dadbe86a:9c493e92
2024-04-22 02:15:25Opinion about BitBox02 (hardware)
The BitBox02 is a hardware wallet developed by Bitbox. The device features a minimalist design with a small touchscreen interface for easy navigation and operation.
Pros: - Its screen allows to verify transactions details - You can install a bitcoin-only firmware, increasing its security, which is very important for bitcoin users - Its secure element adds extra protection against physical attacks - Supports some advanced features like: testnet, miniscript, user added entropy, fee and coin control, multisig - Open source - Optional stateless use
Cons: - Missing battery force you to always connect it to the power. - It doesn't support in air-gapped mode, you are forced to connect it to a computer using an USB cable
WalletScrutiny #nostrOpinion
-
 @ 5019ef25:8844c4bf
2024-04-23 16:24:52
@ 5019ef25:8844c4bf
2024-04-23 16:24:52What is a spiritual awakening? In most if not all ancient and mystical traditions, spiritual awakening experiences are related to the awakening of the energies that move up ida, pingala, and sushumna (energy channels). The nature of these energies is an auspicious mystery and should be approached with the utmost integrity. In other words, we have no idea what these energies are in their final form and being humbly concerned would be sensible. There is a deliberate act of waking up these energies, a spontaneous means, and perhaps something in between. My intention is to suggest meditation as a means for spiritual awakening. It’s true to say that there are many doorways to enlightenment, liberation, and spiritual evolution as a whole. I find meditation to be a safe, sensible, and mysterious means to awaken. As you deepen your meditation you will find your karma arise over and over again. You will simply have to dissolve what comes up through right meditation. Meditating correctly is not easy but it requires a well experienced teacher nonetheless. Without teachers, we can waste a lot of time and take millions of steps in the wrong direction. We sit, we meditate, but we tend to reaffirm our thoughts without realizing that we are subconsciously reaffirming certain beliefs. For example, much of our conditioning has led us to believe we are not good enough for this or that reason. This is complete bullshit, you simply just are. When you approach meditation correctly and reaffirm what you truly are, these cosmic energies begin to flow. This is why the traditions were so important and why we must approach this through correct understanding. There is the “Way” and it is Remembering. Not Remembering who you are but Remembering awareness and the nature of awareness. We must follow our awareness again and again. You must stay inside the body, following awareness, in the immediacy of the present moment. What I have stated here is of incredible insight and I encourage you to try this for yourself if you wish to do things correctly. But be careful, the ego will continue to reaffirm itself and this is a huge obstacle for us. We must realize that we are not the ego and whilst it’s present in our consciousness, we want to have a mature relationship with the ego. It is a strange path to awaken to your true nature. It requires surrender, compassion, wisdom and nothing else. If you need support, I am here for you.
-
 @ aa327517:15b95190
2024-04-23 14:14:50
@ aa327517:15b95190
2024-04-23 14:14:50Posting again
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Who will build the roads?
Who will build the roads? Em Lagoa Santa, as mais novas e melhores ruas -- que na verdade acabam por formar enormes teias de bairros que se interligam -- são construídas pelos loteadores que querem as ruas para que seus lotes valham mais -- e querem que outras pessoas usem as ruas também. Também são esses mesmos loteadores que colocam os postes de luz e os encanamentos de água, não sem antes terem que se submeter a extorsões de praxe praticadas por COPASA e CEMIG.
Se ao abrir um loteamento, condomínio, prédio um indivíduo ou uma empresa consegue sem muito problema passar rua, eletricidade, água e esgoto, por que não seria possível existir livre-concorrência nesses mercados? Mesmo aquela velha estória de que é ineficiente passar cabos de luz duplicados para que companhias elétricas possam competir já me parece bobagem.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28How IPFS is broken
I once fell for this talk about "content-addressing". It sounds very nice. You know a certain file exists, you know there are probably people who have it, but you don't know where or if it is hosted on a domain somewhere. With content-addressing you can just say "start" and the download will start. You don't have to care.
Other magic properties that address common frustrations: webpages don't go offline, links don't break, valuable content always finds its way, other people will distribute your website for you, any content can be transmitted easily to people near you without anyone having to rely on third-party centralized servers.
But you know what? Saying a thing is good doesn't automatically make it possible and working. For example: saying stuff is addressed by their content doesn't change the fact that the internet is "location-addressed" and you still have to know where peers that have the data you want are and connect to them.
And what is the solution for that? A DHT!
DHT?
Turns out DHTs have terrible incentive structure (as you would expect, no one wants to hold and serve data they don't care about to others for free) and the IPFS experience proves it doesn't work even in a small network like the IPFS of today.
If you have run an IPFS client you'll notice how much it clogs your computer. Or maybe you don't, if you are very rich and have a really powerful computer, but still, it's not something suitable to be run on the entire world, and on web pages, and servers, and mobile devices. I imagine there may be a lot of unoptimized code and technical debt responsible for these and other problems, but the DHT is certainly the biggest part of it. IPFS can open up to 1000 connections by default and suck up all your bandwidth -- and that's just for exchanging keys with other DHT peers.
Even if you're in the "client" mode and limit your connections you'll still get overwhelmed by connections that do stuff I don't understand -- and it makes no sense to run an IPFS node as a client, that defeats the entire purpose of making every person host files they have and content-addressability in general, centralizes the network and brings back the dichotomy client/server that IPFS was created to replace.
Connections?
So, DHTs are a fatal flaw for a network that plans to be big and interplanetary. But that's not the only problem.
Finding content on IPFS is the most slow experience ever and for some reason I don't understand downloading is even slower. Even if you are in the same LAN of another machine that has the content you need it will still take hours to download some small file you would do in seconds with
scp-- that's considering that IPFS managed to find the other machine, otherwise your command will just be stuck for days.Now even if you ignore that IPFS objects should be content-addressable and not location-addressable and, knowing which peer has the content you want, you go there and explicitly tell IPFS to connect to the peer directly, maybe you can get some seconds of (slow) download, but then IPFS will drop the connection and the download will stop. Sometimes -- but not always -- it helps to add the peer address to your bootstrap nodes list (but notice this isn't something you should be doing at all).
IPFS Apps?
Now consider the kind of marketing IPFS does: it tells people to build "apps" on IPFS. It sponsors "databases" on top of IPFS. It basically advertises itself as a place where developers can just connect their apps to and all users will automatically be connected to each other, data will be saved somewhere between them all and immediately available, everything will work in a peer-to-peer manner.
Except it doesn't work that way at all. "libp2p", the IPFS library for connecting people, is broken and is rewritten every 6 months, but they keep their beautiful landing pages that say everything works magically and you can just plug it in. I'm not saying they should have everything perfect, but at least they should be honest about what they truly have in place.
It's impossible to connect to other people, after years there's no js-ipfs and go-ipfs interoperability (and yet they advertise there will be python-ipfs, haskell-ipfs, whoknowswhat-ipfs), connections get dropped and many other problems.
So basically all IPFS "apps" out there are just apps that want to connect two peers but can't do it manually because browsers and the IPv4/NAT network don't provide easy ways to do it and WebRTC is hard and requires servers. They have nothing to do with "content-addressing" anything, they are not trying to build "a forest of merkle trees" nor to distribute or archive content so it can be accessed by all. I don't understand why IPFS has changed its core message to this "full-stack p2p network" thing instead of the basic content-addressable idea.
IPNS?
And what about the database stuff? How can you "content-address" a database with values that are supposed to change? Their approach is to just save all values, past and present, and then use new DHT entries to communicate what are the newest value. This is the IPNS thing.
Apparently just after coming up with the idea of content-addressability IPFS folks realized this would never be able to replace the normal internet as no one would even know what kinds of content existed or when some content was updated -- and they didn't want to coexist with the normal internet, they wanted to replace it all because this message is more bold and gets more funding, maybe?
So they invented IPNS, the name system that introduces location-addressability back into the system that was supposed to be only content-addressable.
And how do they manage to do it? Again, DHTs. And does it work? Not really. It's limited, slow, much slower than normal content-addressing fetches, most of the times it doesn't even work after hours. But still although developers will tell it is not working yet the IPFS marketing will talk about it as if it was a thing.
Archiving content?
The main use case I had for IPFS was to store content that I personally cared about and that other people might care too, like old articles from dead websites, and videos, sometimes entire websites before they're taken down.
So I did that. Over many months I've archived stuff on IPFS. The IPFS API and CLI don't make it easy to track where stuff are. The
pincommand doesn't help as it just throws your pinned hash in a sea of hashes and subhashes and you're never able to find again what you have pinned.The IPFS daemon has a fake filesystem that is half-baked in functionality but allows you to locally address things by names in a tree structure. Very hard to update or add new things to it, but still doable. It allows you to give names to hashes, basically. I even began to write a wrapper for it, but suddenly after many weeks of careful content curation and distribution all my entries in the fake filesystem were gone.
Despite not having lost any of the files I did lose everything, as I couldn't find them in the sea of hashes I had in my own computer. After some digging and help from IPFS developers I managed to recover a part of it, but it involved hacks. My things vanished because of a bug at the fake filesystem. The bug was fixed, but soon after I experienced a similar (new) bug. After that I even tried to build a service for hash archival and discovery, but as all the problems listed above began to pile up I eventually gave up. There were also problems of content canonicalization, the code the IPFS daemon use to serve default HTML content over HTTP, problems with the IPFS browser extension and others.
Future-proof?
One of the core advertised features of IPFS was that it made content future-proof. I'm not sure they used this expression, but basically you have content, you hash that, you get an address that never expires for that content, now everybody can refer to the same thing by the same name. Actually, it's better: content is split and hashed in a merkle-tree, so there's fine-grained deduplication, people can store only chunks of files and when a file is to be downloaded lots of people can serve it at the same time, like torrents.
But then come the protocol upgrades. IPFS has used different kinds of hashing algorithms, different ways to format the hashes, and will change the default algorithm for building the merkle-trees, so basically the same content now has a gigantic number of possible names/addresses, which defeats the entire purpose, and yes, files hashed using different strategies aren't automagically compatible.
Actually, the merkle algorithm could have been changed by each person on a file-by-file basis since the beginning (you could for example split a book file by chapter or page instead of by chunks of bytes) -- although probably no one ever did that. I know it's not easy to come up with the perfect hashing strategy in the first go, but the way these matters are being approached make me wonder that IPFS promoters aren't really worried about future-proof, or maybe we're just in Beta phase forever.
Ethereum?
This is also a big problem. IPFS is built by Ethereum enthusiasts. I can't read the mind of people behind IPFS, but I would imagine they have a poor understanding of incentives like the Ethereum people, and they tend towards scammer-like behavior like getting a ton of funds for investors in exchange for promises they don't know they can fulfill (like Filecoin and IPFS itself) based on half-truths, changing stuff in the middle of the road because some top-managers decided they wanted to change (move fast and break things) and squatting fancy names like "distributed web".
The way they market IPFS (which is not the main thing IPFS was initially designed to do) as a "peer-to-peer cloud" is very seductive for Ethereum developers just like Ethereum itself is: as a place somewhere that will run your code for you so you don't have to host a server or have any responsibility, and then Infura will serve the content to everybody. In the same vein, Infura is also hosting and serving IPFS content for Ethereum developers these days for free. Ironically, just like the Ethereum hoax peer-to-peer money, IPFS peer-to-peer network may begin to work better for end users as things get more and more centralized.
More about IPFS problems:
- IPFS problems: Too much immutability
- IPFS problems: General confusion
- IPFS problems: Shitcoinery
- IPFS problems: Community
- IPFS problems: Pinning
- IPFS problems: Conceit
- IPFS problems: Inefficiency
- IPFS problems: Dynamic links
See also
- A crappy course on torrents, on the protocol that has done most things right
- The Tragedy of IPFS in a series of links, an ongoing Twitter thread.
-
 @ aa327517:15b95190
2024-04-23 13:56:10
@ aa327517:15b95190
2024-04-23 13:56:10Update note
-
 @ c11cf5f8:4928464d
2024-04-21 15:33:18
@ c11cf5f8:4928464d
2024-04-21 15:33:18Let's hear some of your latest Bitcoin purchases, feel free to include links to the shops or merchants you bought from too.
If you missed our last thread, here are some of the items stackers recently spent their sats on.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Parallel Chains
We want merged-mined blockchains. We want them because it is possible to do things in them that aren't doable in the normal Bitcoin blockchain because it is rightfully too expensive, but there are other things beside the world money that could benefit from a "distributed ledger" -- just like people believed in 2013 --, like issued assets and domain names (just the most obvious examples).
On the other hand we can't have -- like people believed in 2013 -- a copy of Bitcoin for every little idea with its own native token that is mined by proof-of-work and must get off the ground from being completely valueless into having some value by way of a miracle that operated only once with Bitcoin.
It's also not a good idea to have blockchains with custom merged-mining protocol (like Namecoin and Rootstock) that require Bitcoin miners to run their software and be an active participant and miner for that other network besides Bitcoin, because it's too cumbersome for everybody.
Luckily Ruben Somsen invented this protocol for blind merged-mining that solves the issue above. Although it doesn't solve the fact that each parallel chain still needs some form of "native" token to pay miners -- or it must use another method that doesn't use a native token, such as trusted payments outside the chain.
How does it work
With the
SIGHASH_NOINPUT/SIGHASH_ANYPREVOUTsoft-fork[^eltoo] it becomes possible to create presigned transactions that aren't related to any previous UTXO.Then you create a long sequence of transactions (sufficient to last for many many years), each with an
nLockTimeof 1 and each spending the next (you create them from the last to the first). Since theirscriptSig(the unlocking script) will useSIGHASH_ANYPREVOUTyou can obtain a transaction id/hash that doesn't include the previous TXO, you can, for example, in a sequence of transactionsA0-->B(B spends output 0 from A), include the signature for "spending A0 on B" inside thescriptPubKey(the locking script) of "A0".With the contraption described above it is possible to make that long string of transactions everybody will know (and know how to generate) but each transaction can only be spent by the next previously decided transaction, no matter what anyone does, and there always must be at least one block of difference between them.
Then you combine it with
RBF,SIGHASH_SINGLEandSIGHASH_ANYONECANPAYso parallel chain miners can add inputs and outputs to be able to compete on fees by including their own outputs and getting change back while at the same time writing a hash of the parallel block in the change output and you get everything working perfectly: everybody trying to spend the same output from the long string, each with a different parallel block hash, only the highest bidder will get the transaction included on the Bitcoin chain and thus only one parallel block will be mined.See also
[^eltoo]: The same thing used in Eltoo.
-
 @ 5d4b6c8d:8a1c1ee3
2024-04-21 13:19:36
@ 5d4b6c8d:8a1c1ee3
2024-04-21 13:19:36I'm curious who stackers would pick in the following hypothetical matchup:
The GOATs 1. Magic 2. Jordan 3. Lebron 4. Duncan 5. Kareem
vs.
The Shooters 1. Nash 2. Steph 3. Bird 4. Durant 5. Dirk
If you're like me, you think The Shooters would have a really strong chance of winning a series against The GOATs. Does that imply that we're thinking about the GOAT wrong?
Shoutout to @Voldemort for making me think about Dirk and how shooting is still possibly an undervalued skill.
-
 @ 2363dd1c:5c34ebff
2024-04-21 10:32:17
@ 2363dd1c:5c34ebff
2024-04-21 10:32:17This post is the eleventh in our Stoic Philosophy book club series on Meditations by Marcus Aurelius. Participants expressing interest are tagged at the end of the post, let us know if you're new and would like to join and be tagged!
Prior posts for context:
- Book 10
- Book 9
- Book 8
- Book 7
- Book 6
- Book 5
- Book 4
- Book 3: In Carnuntum
- Book 2: On the River Gran, Among the Quadi
- Book 1: Debts and Lessons
- Geneisis Post
Book 11
Summary and Highlights
Following on from Book 10, I really enjoyed Book 11 as well. I'm looking forward to each new book a little more than the prior. Apparently Marcus was visiting the theater around this time. There is a lengthy reflection on comedy and tragedy in #6, as well as many small, sniping quotes which feel like they're from plays or literature. Here are my highlights for this week.
As usual, Marcus leads off with a banger in #1, which I'll quote in its entirety.
Characteristics of the rational soul: Self-perception, self-examination, and the power to make of itself whatever it wants. It reaps its own harvest, unlike the plants (and, in a different way, animals), whose yield is gathered in by others. It reaches its intended goal, no matter where the limit of its life is set. Not like dancing and theater and things like that, where the performance is incomplete if it's broken off in the middle, but at any point -- no matter which one you pick -- it has fulfilled its mission, done its work completely. So that it can say, "I have what I came for." It surveys the world and the empty space around it, and the way it's put together. It delves into the endlessness of time to extend its grasp and comprehension of the periodic births and rebirths that the world goes through. It knows that those who come after us will see nothing different, that those who came before us saw no more than we do, and that anyone with forty years behind him and eyes in his head has seen both past and future -- both alike. Affection for its neighbors. Truthfulness. Humility. Not to place anything above itself -- which is characteristic of law as well. No difference here between the logos of rationality and that of justice.
Of course, as I read this, I'm ticking off boxes to make sure "I'm rational", an exercise of ego. But it's eloquently written and a well-rounded description of living in harmony with Nature and Universal Law. A great start.
In #2, Marcus provides a short instruction manual on how to dissolve attachment and desire, to:
"Analyze the melody into the notes that form it, and as you hear each one, ask yourself whether you're powerless against that. That should be enough to deter you."
What I found personally interesting here was his express inclusion of martial arts alongside singing and dancing as outer examples of artistic desire. Perhaps because I have plenty of experience with music and dancing, but only an unexplored curiosity for martial arts. Makes me want to try, and also reminds me of the way other practitioners like Joe Rogan or Lex Friedman describe Jiu Jitsu as beauty in strategy and sequence.
In #3, Marcus mentions "The resolute soul", and its resolve in "separation from the body" but claims,
But the resolution has to be the result of its own decision, not just in response to outside forces [like the Christians].
This is an interesting detail to me because he particularly mentions the Christians and expresses an interpretation of the movement at the time. Raised in a Christian environment, I pick on this detail because it has also been quite a challenge for me to discern my own motivations toward Truth during development. Outside pressure from family, church organization or culture can contribute to some confusion in finding and nurturing the Soul's internal resolution, or True Self. I guess that's also just a part of growing up for everyone, but it stands out to me that perhaps the pressures of external persecution, or the factors Marcus is describing at this time are still held in the DNA of Christian organizations and consciousness today.
- "And your profession?" "Goodness." (And how is that to be achieved, except by thought -- about the world, about the nature of people?)
The first time I read this, I almost wrote it off with a slight disagreement, reducing it to "thinking good thoughts makes me a good person", which leaves a dangerous amount of room for spiritual bypassing. However, upon closer inspection, it has a deeply Buddhist flavor if I consider that Goodness is equated with a "pure mind", one that thinks good thoughts because that is its nature, now that the subconscious has been cleaned. Interesting how my own interpretation is subject to a difference between outer perception and inner reality, probably coincident with the state of my own mind at that time. :/
In #6, Marcus does a little exposition of theater genre. Essentially, Tragedies exist "to remind us of what can happen, and that it happens inevitably. And "Then, after tragedy, Old Comedy: instructive in its frankness, its plain speaking designed to puncture pretensions". Of course, they never make it like they used to, as Marcus essentially follows this with commentary that "New Comedy" has lost this. True now, true then, true always?
7. It stares you in the face. No role is so well suited to philosophy as the one you happen to be in right now.
I can't help but remember Marcus' entries in prior books which seem to despair his station at the expense of "being" a philosopher. Perhaps he's developed some acceptance of that. Either way, it's a classical acknowledgement of Plato's Philosopher-King.
In #8, Marcus draws an interesting psychological analogy to a tree:
A branch cut away from the branch beside it is simultaneously cut away from the whole tree. So too a human being separated from another is cut loose from the whole community. The branch is cut off by someone else. But people cut themselves off -- through hatred, through rejection -- and don't realize that they're cutting themselves off from the whole civic enterprise. Except that we also have a gift, given to use by Zeus, who founded this community of ours. We can reattach ourselves and become once more components of the whole. But if tthe rupture is too often repeated, it makes the severed part hard to reconnect, and to restore. You can see the difference between the branch that's been there since the beginning, remaining on the tree and growing with it, and the one that's been cut off and grafted back. "One trunk, two minds." As the gardeners put it.
There are a few different parts I like about this one. Firstly, the part about people cutting themselves off through hatred and rejection. It's a reminder for me that relationships are important. Sometimes I feel like I'll be all good if I can just sort myself and my life out -- meditate by myself and have little to do with the outside world, like a monk on a mountaintop. But perhaps there is unconscious rejection, anger or fear behind this desire? Secondly, I find it interesting that Marcus credits "Zeus, who founded this community of ours". Zeus is the Greek god of gods and Marcus is Roman. Does Zeus represent sovereignty here? Or Reason? Besides the syncretism here, I find the selection of Zeus interesting as a symbol for the rise of rational thought in the development of human religious ideas, which I've explored in some other book review posts. And of course, the final two paragraphs summarized with "One trunk, two minds" is a wonderful, allegorical representation of psychological trauma and the development of psychological complexes. Well described.
In #9, Marcus advocates that you shouldn't let difficult people "stop you from putting up with them" and that "anger, too, is weakness, as much as breaking down and giving up the struggle." We often describe the fundamental natural instincts of "fight or flight" as a root-level automatism, but my reading here is that both fight or flight are losing the conflict. Stay centered, stay grounded and still.
Which is further developed in #12:
The soul as a sphere in equilibrium: Not grasping at things beyond it or retreating inward. Not fragmenting outward, not sinking back on itself, but ablaze with light and looking at the truth, without and within.
A fiery, dynamic stasis. Like the Sun.
- They flatter one another out of contempt, and their desire to rule one another makes them bow and scrape.
Possessed by their obsessive desires, people are twisted into the opposite expressions of behavior.
Reflection #15 is my favorite from Book 11:
The despicable phoniness of people who say, "Listen, I'm going to level with you here." What does that mean? It shouldn't even need to be said. It should be obvious -- written in block letters on your forehead. It should be audible in your voice, visible in your eyes, like a lover who looks into your face and takes in the whole story at a glance. A straightforward, honest person should be like someone who stinks: when you're in the same room with him, you know it. But false straightforwardness is like a knife in the back. False friendship is the worst. Avoid it at all costs. If you're honest and straightforward and mean well, it should show in your eyes. It should be unmistakable.
Incredibly based. Stinky based. I can't say it any better, or add much to it. Go stink it up with the Truth.
Entry #18 is a very long, exploratory post of Marcus breaking down his mind's own misconceptions. It's well worth its own consideration, but a segment on masculinity stands out:
When you start to lose your temper, remember: There's nothing manly about rage. It's courtesy and kindness that define a human being -- and a man. That's who possesses strength and nerves and guts, not the angry whiners. To react like that brings you closer to impassivity -- and so to strength.
It's tough to be a man out there these days, and there aren't many positive examples of masculinity out there, so here's one from Marcus The Man himself.
- Socrates used to call popular beliefs "the monsters under the bed" -- only useful for frightening children with.
Sounds about right with all the cultural drama around The Current Thing(tm). As Marcus frequently reminds elsewhere, this phenomena isn't new and we can expect it again. Learn to recognize cultural drama, detach identity from it and grow up, become a Man, not a child (or a sheep) and see the world for what it is.
- This advice from Epicurean writings: to think continually of one of the men of old who lived a virtuous life.
Both ironic and inspiring to be reading this text and following that advice about the writer, Marcus. He's become his own ideal 2000 years later.
- Mastery of reading and writing requires a master. Still more so life.
This one is pretty enigmatic. The wisdom probably lies in the mystery still half-concealed. Must one become the master oneself? Or must one become a slave to something higher? What is the difference? Is there any?
- Socrates: What do you want, rational minds or irrational ones? -- Rational ones. Healthy or sick? -- Healthy. Then work to obtain them. -- We already have. Then why all this squabbling?
LOL. I wish I could hang out with Socrates.
Thanks for reading.
Participants
Thank you everyone who has been reading Meditations, and participated in the discussions. Feel free let me know if you don't want to be on the tag list anymore :)
@siggy47 @cryotosensei @carlosfandango @Bitman @gd @sudocarlos @BitByBit21 @bc52210b20 @Atreus @byzantine @davidw @Roll @grayruby @Taft @Oialt
We only have one more book left, but feel free to signal interest in the comments if you'd like to be tagged.
-
 @ 57d1a264:69f1fee1
2024-04-21 06:25:00
@ 57d1a264:69f1fee1
2024-04-21 06:25:00Prompt: Scheduling ===============
Design the elements or a full experience for post schedule. Why it's important? Could be draft being part of the userflow? Save it for later edits, or enable the recurring post at specific day or time?
Flex your design muscles and join in. Most of all, keep this exercise loose and keep it stress-free. The FUC is about growing our design skills, together, as a community. We can't wait to see what you create!
Happy designing, Stackers!
Share Your Results When you finish the challenge, post your work on this thread! If you also share it on
nostr, be sure to use the hashtag #FUCdesiger and tag Design_r@iris.to or @Design__r on X! We'll keep an eye out and repost good examples on a regular basis.
Curious to know WTF is a FUC? Read the ⚡️Flash Ui Challenges welcoming post.
Looking for more FUCs? Check the archive here!
-
 @ bcea2b98:7ccef3c9
2024-04-20 17:59:17
@ bcea2b98:7ccef3c9
2024-04-20 17:59:17Consider the concept of 'progress' in human society and individual lives. When we talk about progress, what exactly do we mean? Is it solely about technological advancement, economic growth, or societal development? Or does progress include broader aspects such as personal fulfillment, moral advancement, and environmental sustainability? Is progress always desirable, or are there instances where the pursuit of progress leads to unintended consequences or ethical dilemmas?
-
 @ 42342239:1d80db24
2024-04-23 12:30:26
@ 42342239:1d80db24
2024-04-23 12:30:26Last year there were burnings of religious books in Sweden, leading to a diplomatic crisis. During a press conference, Prime Minister Ulf Kristersson emphasized that the government is currently not planning to restrict freedom of speech, although some of his government colleagues seem to take a different view.
In the 1960s, media theorist Marshall McLuhan expressed concern over the implications of what would evolve into a "global village." Advancements in communication technology would transform the entire globe into a kind of global community, with shared experiences and immediate access to information. Electronic media would enable a sense of global closeness. Different parts of the world would become aware of each other and influence each other, potentially blurring the boundaries between nations and cultures.
While such blending may be desirable, it is not without its challenges. For instance, perspectives on freedoms and rights can vary significantly between cultures and countries. Even truths and falsehoods differ. Asserting that the Armenian genocide occurred, for example, can lead to imprisonment in Turkey, whereas in France, denying the same genocide can result in imprisonment. If issues like these are elevated to a global level or to the EU or NATO level, whose rules should prevail? Will this genocide even be open to discussion?
Hence, McLuhan would not have been surprised by today's debate on freedom of speech. Unlike how many individuals a speaker from the corner of Hyde Park could reach in the 1800s, an individual's speech—or action in the case of Quran burnings—can now reach billions of people, for better or for worse. Perhaps it is time to reconsider freedom of speech?
On global (and centralised) social media platforms, freedom of speech has long been restricted; users are sometimes even blocked from sharing legally permissible content like links to news articles. Individuals who violate the terms of use are banned, sometimes losing their means of living. If these user agreements of the digital panopticons were adopted in the broader society, it would represent a significant restriction of freedom of speech.
In his book Orthodoxy, author and literary critic G.K. Chesterton wrote, "There is a thought that stops thought. That is the only thought that ought to be stopped." Isn't this precisely what proposals for restricted freedom of speech do?
If freedom of speech cannot be maintained due to the progression towards a global village (a.k.a. globalism), should it truly then be freedom of speech that we abolish? Perhaps it would be better to instead scale down the global village. Abolishe what's centralised, and favour what's decentralised and/or localised.
After all, without commonalities there can be no community.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28OP_CHECKTEMPLATEVERIFYand the "covenants" dramaThere are many ideas for "covenants" (I don't think this concept helps in the specific case of examining proposals, but fine). Some people think "we" (it's not obvious who is included in this group) should somehow examine them and come up with the perfect synthesis.
It is not clear what form this magic gathering of ideas will take and who (or which ideas) will be allowed to speak, but suppose it happens and there is intense research and conversations and people (ideas) really enjoy themselves in the process.
What are we left with at the end? Someone has to actually commit the time and put the effort and come up with a concrete proposal to be implemented on Bitcoin, and whatever the result is it will have trade-offs. Some great features will not make into this proposal, others will make in a worsened form, and some will be contemplated very nicely, there will be some extra costs related to maintenance or code complexity that will have to be taken. Someone, a concreate person, will decide upon these things using their own personal preferences and biases, and many people will not be pleased with their choices.
That has already happened. Jeremy Rubin has already conjured all the covenant ideas in a magic gathering that lasted more than 3 years and came up with a synthesis that has the best trade-offs he could find. CTV is the result of that operation.
The fate of CTV in the popular opinion illustrated by the thoughtless responses it has evoked such as "can we do better?" and "we need more review and research and more consideration of other ideas for covenants" is a preview of what would probably happen if these suggestions were followed again and someone spent the next 3 years again considering ideas, talking to other researchers and came up with a new synthesis. Again, that person would be faced with "can we do better?" responses from people that were not happy enough with the choices.
And unless some famous Bitcoin Core or retired Bitcoin Core developers were personally attracted by this synthesis then they would take some time to review and give their blessing to this new synthesis.
To summarize the argument of this article, the actual question in the current CTV drama is that there exists hidden criteria for proposals to be accepted by the general community into Bitcoin, and no one has these criteria clear in their minds. It is not as simple not as straightforward as "do research" nor it is as humanly impossible as "get consensus", it has a much bigger social element into it, but I also do not know what is the exact form of these hidden criteria.
This is said not to blame anyone -- except the ignorant people who are not aware of the existence of these things and just keep repeating completely false and unhelpful advice for Jeremy Rubin and are not self-conscious enough to ever realize what they're doing.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Flowi.es
At the time I thought Workflowy had the ideal UI for everything. I wanted to implement my custom app maker on it, but ended up doing this: a platform for enhancing Workflowy with extra features:
- An email reminder based on dates input in items
- A website generator, similar to Websites For Trello, also based on Classless Templates
Also, I didn't remember this was also based on CouchDB and had some couchapp functionalities.
-
 @ 9edd72eb:cb697b0a
2024-04-20 16:38:50
@ 9edd72eb:cb697b0a
2024-04-20 16:38:50Opinion about Unstoppable Crypto Wallet (android)
Opinion about Unstoppable Crypto Wallet (Android)
One of the strong points of this wallet is its security protocols that use advanced encryption methods and multi-factor authentication to protect user information.
The interface is intuitive which can be useful for novice and experienced users. Navigation is simple and easily accessible.
The wallet supports a diverse range of cryptocurrencies, including popular and lesser-known tokens.
It guarantees complete control of private keys and funds, emphasizing ownership and autonomy.
The platform enhances utilization, allowing users to manage their crypto assets across multiple devices, both smartphones and desktops.
On the other hand, it lacks customization options.
The lack of integrated fiat currency support might inconvenience users who frequently engage in fiat-to-crypto transactions.
Limited customer support channels and documentation could leave users stranded in case of technical difficulties or questions.
WalletScrutiny #nostrOpinion
WalletScrutiny #nostrOpinion
-
 @ 908d47b6:a2bf38ad
2024-04-23 09:13:26
@ 908d47b6:a2bf38ad
2024-04-23 09:13:26Bitcoin's Soaring Ascent: A Billionaire's Dire Prediction
As the price of bitcoin skyrockets, legendary investor Tim Draper issues a chilling prophecy of the U.S. dollar's impending collapse by 2030. Drawing parallels to historical currency failures, Draper urges individuals to safeguard their financial future by embracing bitcoin, painting it as a crucial asset in the face of imminent economic upheaval.
There will be a moment in time, and I don't know whether it's a day or a month or maybe over the course of two months or something, but I don't know when it will start, whether it'll be a year or five years or whatever, maybe even ten years out, but it'll happen very rapidly. -- Tim Draper
The Halving's Shadow: Bitcoin's Path to $250,000
Amidst Draper's warnings, the imminent bitcoin halving looms large, promising to disrupt market dynamics and potentially propel the cryptocurrency's value to unprecedented heights. Draper highlights the halving's role in tightening bitcoin's supply and boosting demand, predicting a bullish trajectory that could see prices soar to $250,000 by year-end, challenging even the most established financial benchmarks.
I hope anybody who's watching this is trying to at least have some bitcoin so that they can feed their family during the time when the dollar goes to zero. -- Tim Draper
Dollar Debacle: The Fragile State of Traditional Finance
Against a backdrop of mounting debt, inflation, and economic uncertainty, concerns over the stability of the U.S. dollar reach fever pitch. Figures like Nassim Taleb and Jim Rogers echo Draper's apprehensions, cautioning against the Federal Reserve's limited ability to stave off a potential crisis. In this climate of uncertainty, bitcoin emerges as a beacon of financial resilience, offering a decentralized alternative in an increasingly fragile financial landscape.
Source: Forbes



