-
 @ 63fe6318:330504ed
2024-04-24 14:52:50
@ 63fe6318:330504ed
2024-04-24 14:52:50Project Status'
Snort
Full commit history: 754 Commits, +35,843, -19,639
Versioned releases: - v0.1.19 (2023-10-02) - v0.1.20 (2023-10-11) - Iris migrates to Snort codebase - v0.1.21 (2023-10-18) - v0.1.22 (2023-10-21) - v0.1.23 (2023-11-23) - v0.1.24 (2023-12-14)
git-fame --since 2023-09-31 --branch 7b72f9f7750aaec9d6ba40373ff3ca66125588b5 --cost hour -M -C| Author | hrs | loc | coms | fils | distribution | |:-----------------|------:|------:|-------:|-------:|:----------------| | Kieran | 73 | 49669 | 373 | 463 | 65.0/49.4/50.5 | | Martti Malmi | 98 | 25982 | 359 | 410 | 34.0/47.5/44.7 | | Fernando Porazzi | 2 | 416 | 5 | 13 | 0.5/ 0.7/ 1.4 | | mmalmi | 2 | 294 | 6 | 21 | 0.4/ 0.8/ 2.3 | | w3irdrobot | 2 | 37 | 1 | 2 | 0.0/ 0.1/ 0.2 | | James McGauran | 2 | 20 | 5 | 2 | 0.0/ 0.7/ 0.2 | | fiatjaf | 2 | 12 | 2 | 2 | 0.0/ 0.3/ 0.2 | | Kamal Raj Sekar | 2 | 10 | 2 | 2 | 0.0/ 0.3/ 0.2 | | benthecarman | 2 | 2 | 1 | 1 | 0.0/ 0.1/ 0.1 | | vivganes | 2 | 1 | 1 | 1 | 0.0/ 0.1/ 0.1 |
Snort API
Along with the public UI code there is a private repo containing the backend api which handles auxiliary services for snort.social like fetching link previews and handling donations and NIP-5 services.
The API docs are publicly accessible https://api.snort.social/swagger
I am also in the process of moving some of these functions to a public repo, they are listed below under NostrServices
git-fame --since 2023-09-31 --branch b669a92f6f1ddfba8af0be9afee22ced90a0cf9c --cost hour| Author | hrs | loc | coms | fils | distribution | |:---------|------:|------:|-------:|-------:|:-----------------| | Kieran | 18 | 3560 | 68 | 56 | 100.0/ 100/100.0 |
zap.stream
zap.stream does not yet follow a versioned release scheme, instead I have listed the major changes over this timeframe.
- Stream summary page (Example)
- Gives an overview of previous streams with top chatters and top zappers
- Stream activity timeline graph
- Tailwind CSS upgrade
- Streamlines CSS inside zap.stream
- Custom player overlay
- Select stream quality (720p/480p/Auto)
- UI themes (Primary colour only)
- Stream dashboard https://zap.stream/dashboard
- Gives the streamer an overview of their stream allowing them to see a dedicated zaps feed
- Chat moderation operations (Mute) shortcuts for unique
- Stream raids feature
- Allows hosts to redirect their viewers to another stream
- This is a feature which twitch.tv has and helps to retain viewers by redirecting them to another streamer on the site who is still live. This is usually performed at the end of the stream.
- Stream forwarding feature
- Supported by the zap.stream hosting solution, you can forward your stream automatically to other platforms directly.
- This is identical to restream.io platform, it's provided for free as part of the hosted streams.
- Direct support for entering stream keys for YouTube/Twitch.tv/Facebook/Kick/Trovo
- Custom RTMP destinations also supported.
- Clips feature
- Supported by the zap.stream hosting solution, allows users to create a stream clip (mp4) from the previous 60s
- Stream clips are posted in chat for everybody to see and can be shared anywhere on nostr.
- Surfacing clips on profiles and other places is yet to be implemented.
- Push Notifications
- Supported by the zap.stream hosting solution, allows viewers to subscribe to notifications for a given streamer (Bell Icon)
- Viewers will receive push notifications when this streamer goes live.
git-fame --since 2023-09-31 --branch 039d2d15513cacab99b0ae8abe587d0e0bef0ddc --cost hour -M -C| Author | hrs | loc | coms | fils | distribution | |:---------|------:|------:|-------:|-------:|:----------------| | Kieran | 13 | 22594 | 97 | 162 | 99.9/98.0/99.4 | | florian | 2 | 32 | 2 | 1 | 0.1/ 2.0/ 0.6 |
zap.stream backend
Along with the the public UI codebase there is also another private repo which contains the code for the backend hosted streaming solution.
git-fame --since 2023-09-31 --branch 5b5f011df0c0c2f7105a25be1cef7fd74db96ce6 --cost hour -M -C| Author | hrs | loc | coms | fils | distribution | |:---------|------:|------:|-------:|-------:|:-----------------| | Kieran | 5 | 3105 | 18 | 41 | 100.0/ 100/100.0 |
DTAN.xyz
I had an idea for another app one day and i decided to make it, this site allows people to list torrents on nostr, it appears to be well received.
The repository is here: https://git.v0l.io/Kieran/dtan
The name itself is an acronym for Distributed Torrent Archive on Nostr nostrudel.ninja has also added support for this event kind (2003) There is no NIP for this kind. The kind number comes from the founding date of the thepriatebay.org (2003)
Commit History
git-fame --cost hour| Author | hrs | loc | coms | fils | distribution | |:---------|------:|------:|-------:|-------:|:----------------| | Kieran | 9 | 8242 | 22 | 56 | 91.7/78.6/74.7 | | florian | 3 | 745 | 6 | 19 | 8.3/21.4/25.3 |
void.cat
Another service I provide is https://void.cat this service is a public anon file upload sharing site, during this quarter I have added support for the recently merged NIP-96
The repository is here: https://git.v0l.io/Kieran/void.cat
git-fame --since 2023-09-31 --branch ce7c3613a844dc11eee8a1078e433c30f2c0216c --cost hour -M -C| Author | hrs | loc | coms | fils | distribution | |:---------|------:|------:|-------:|-------:|:-----------------| | Kieran | 9 | 28326 | 26 | 145 | 100.0/ 100/100.0 |
NostrServices
I have began to migrate some of the useful functions from Snort API into a public repo, this is a C# repo which contains multiple packages and services which anybody can run.
The goal of this repo is to provide a few Docker images for caching API's and custom relays.
The repository is here: https://git.v0l.io/Kieran/NostrServices
Public API: https://nostr.api.v0l.io/swagger
All the commits to this repo are out of scope as they started on 2024-01-10, lookout for the commit history in the next report!
Outlook
Snort
The current plan for snort.social is to optimise performance and the onboarding experience / community building, we're currently building a full nostr relay in the browser that we will interact with as a WebWorker, early tests look promising and should pave the way for more advanced features like P2P note sharing and in-client algorithms, as well as improving overall performance.
On the community building front, I have created a "Community Leaders" programme that will help local community leaders build their Nostr community and get more users on board. It will also create communication channels for these communities to help inform Snort developers about issues or features that these communities want. This programme is partially rolled out and there is a landing page here https://community.snort.social/
Hopefully more Nostr clients will implement a similar programme, giving community leaders a stronger presence and reward for their efforts.
Another side project is to improve the documentation for Snorts' internal libs which are available for all developers to use via npm:
@snort/system@snort/system-react@snort/system-web@snort/shared@snort/system-wasmA documentation site has been created to help developers to use the library and more examples and documentation will be created over time.
zap.stream
Growing
A very important part of growing zap.stream is getting more content creators on board, part of that is creating a familiar experience, but also making it very easy for streamers to multi-stream, so I created the re-stream feature, streamers can easily stream to zap.stream plus twitch.tv or youtube.com without any cost or effort.
Linking content between platforms can also be a great way to showcase the power of zap.stream. A lot of work has gone into making sure that the OpenGraph tagging and overall SEO of zap.stream and snort.social is optimal.
I believe that zap.stream already provides a good live streaming experience and that getting more content is the primary focus for zap.stream right now.
It would also be wise to have exposure in both app stores and I plan to do that.
Refining
While zap.stream offers a good feature set, there is always room for improvement, the recently added raid and dashboard features still need some work.
Clips for example do not appear anywhere outside of the live stream chat, it is not yet possible to share these clips, these are immediate areas that need improvement, I plan to make clips appear on profiles similar to twitch.tv and also make them shareable and of course make sure they are tagged correctly for link previews on all legacy social platforms.
- Stream summary page (Example)
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ 63fe6318:330504ed
2024-04-24 14:43:40
@ 63fe6318:330504ed
2024-04-24 14:43:40Project status'
tl;dr In 2024 Q1 I mostly focused on improvements to the
@snort/systemlib's while building the new https://nostrnests.com and on the new zap.stream backend calledzap-stream-corewhich is a custom built streaming server in Rust and UX improvements to zap.stream for new users.Snort
Snort had 1 regular release during this time v0.2.0 which included most notably: - New settings pages - Community leaders programme - New wallet system - Alby OAuth integration - Cashu wallet integration - Worker Relay (nostr relay in the browser) - Negentropy v1 support (efficient sync between relays, similar but simpler version of minisketch from bitcoin-core)
Right now as of April 24th im current doing another round of improvements to
@snort/systemto try to improve the performance of Snort. Most of the complaints which people raise are for performance.git-fame --since 2024-01-01 --branch a3f139399973df4caa1e2e20b83ce80663fae90b -M -C| Author | loc | coms | fils | distribution | |:----------------|------:|-------:|-------:|:----------------| | Kieran | 14259 | 192 | 283 | 67.5/41.9/40.4 | | Martti Malmi | 6852 | 265 | 417 | 32.5/57.9/59.5 | | Kamal Raj Sekar | 1 | 1 | 1 | 0.0/ 0.2/ 0.1 |
snort-api
https://api.snort.social/swagger
git-fame --since 2024-01-01 --branch b9a54b4913601079d4da51cb0a245e1f202b5ca7 -M -C| Author | loc | coms | fils | distribution | |:-------------|------:|-------:|-------:|:----------------| | Kieran | 797 | 24 | 119 | 99.9/96.0/99.2 | | Martti Malmi | 1 | 1 | 1 | 0.1/ 4.0/ 0.8 |
zap.stream
zap.stream doesnt have tagged versions but here are a few notable changes: - Embedded player (Used in Twitter embed https://twitter.com/djsenior13/status/1782820643022458934) - More Tailwind CSS updates - A profile editor page! - Stream categories (Gaming/IRL etc) - FAQ page for some tips on how to get started streaming - Search (NIP-50) - Dedicated clips page (eg. nostr:nevent1qqsqxqwl46sjjqpfu5t53p3kdq7fymjjrtlut5raq7lfw7l058866yqppemhxue69uhkummn9ekx7mp0qgsy6zk38378ln3qc06upjf2vt4p7mhrvunga3l0sl4043rgyhgxhwcrqsqqqpfpj7esy5) - Inline note reactions in chat - New stream summary - New dashboard flow for new users (New users follow: https://zap.stream/dashboard/step-1) - Balance withdrawal
git-fame --since 2024-01-01 --branch 8dd74affa7b4d6a2801b917fda9bc7bff24f3ae1 -M -C| Author | loc | coms | fils | distribution | |:---------|------:|-------:|-------:|:-----------------| | Kieran | 11386 | 56 | 184 | 100.0/ 100/100.0 |
zap.stream API
The backend API manages access to the hosted streaming service and accounting system for zap.stream.
Changes: - Improved accounting to enable withdrawals - Balance withdrawal - Delete old recordings after 90 days - Video game search for selecting game category
git-fame --since 2024-01-01 --branch 37f84592f41be36295619ecb564459c536b2c0d9 -M -C| Author | loc | coms | fils | distribution | |:---------|------:|-------:|-------:|:-----------------| | Kieran | 582 | 22 | 41 | 100.0/ 100/100.0 |
zap-stream-core
zap-stream-coreis a new project built from scratch in rust usingffmpegto process video streams in real time.The goal of this project is to improve my rust and ffmpeg knowledge and ultimately make
zap-stream-corea self-hostable platform where people could offer their streaming services via zap.stream using a marketplace of providers.With these newly acquired skills it will also enable me to create more media heavy applications like YouTube or TikTok.
The current state of the project is that i can publish streams into the server and get HLS output but im currently struggling with AV Sync.
git-fame --since 2024-01-01 --branch 9c4969cf9514b713ddf97eaaa4d2a37a69d53581 -M -C| Author | loc | coms | fils | distribution | |:-----------------|------:|-------:|-------:|:-----------------| | Kieran | 3065 | 11 | 33 | 100.0/ 100/100.0 |
DTAN.xyz
DTAN is a nostr client for viewing only
kind 2004events which are Torrents.There hasn't been any major changes since last quarter.
NIP-35
A PR was opened recently to formalise the torrent spec: https://github.com/nostr-protocol/nips/pull/1175
Prowlarr
PR was created to add support for searching nostr torrents with Prowlarr, Prowlarr is used to aggregate search results from multiple indexes and feeds data to downstream applications like Sonarr and Radarr which are used to download TV shows and movies automatically.
https://github.com/Prowlarr/Prowlarr/pull/2100
git-fame --since 2024-01-01 --branch 106b1dcbd84a3ed6cda00dfb57eee371f7b3bcc7 -M -C| Author | loc | coms | fils | distribution | |:---------|------:|-------:|-------:|:-----------------| | Kieran | 2745 | 2 | 16 | 100.0/ 100/100.0 |
NostrServices
https://nostr.api.v0l.io/swagger NostrServices provides free nostr client useful apis.
git-fame --since 2024-01-01 --branch 0a42894a6f9cb20969097d6e620578cb60ef22fd -M -C| Author | loc | coms | fils | distribution | |:---------|-------:|-------:|-------:|:-----------------| | Kieran | 119730 | 59 | 289 | 100.0/ 100/100.0 |
nostrnests.com
https://github.com/nostrnests/nests NostrNests V2 was a complete rebuild which took place in Feb 2024.
The backed is C#, the same as zap.stream The frontend is a typescript React app using the
@snort/systemlibsgit-fame --since 2024-01-01 --branch 26329cc686b243aa497bd4638124942cabfe180d -M -C| Author | loc | coms | fils | distribution | |:---------|------:|-------:|-------:|:----------------| | Kieran | 51870 | 76 | 187 | 100.0/98.7/99.5 | | florian | 1 | 1 | 1 | 0.0/ 1.3/ 0.5 |
Plans for Q2
- Start on boarding community leaders into the leaders programme.
- Expand zap.stream categories with ranking / popularity using sats and viewer stats.
- Continue build out and launch trial of
zap-stream-core - Make Snort the fastest and most decentralised nostr client.
- Somehow find time to maintain all these projects.
-
 @ 1eef661d:07f74d97
2024-04-24 12:52:23
@ 1eef661d:07f74d97
2024-04-24 12:52:23The Open Source Justice Foundation is a 501(c)(3) tax-exempt public charity dedicated to spreading access to justice globally through open-source protocols and technology. Learn more about OSJF's work at opensourcejustice.org.
Most people in the world are denied access to justice. An estimated four billion people live outside the protection of the law. Fifty-four percent of the world's population lives under some form of authoritarian rule. And even in relatively stable democracies, the justice gap between low- and high-income earners is well documented.
The state has failed to provide courts that offer equal justice to all.
This is not a secret. For decades, politicians, lawyers, and charities have publicly decried the lack of affordable and accessible legal services. But politicians' solution has been to simply funnel more taxpayer money into the failing court system. Lawyers continue to lobby for restrictive licensing requirements on the practice of law, jealously guarding their monopoly over justice. Legal aid charities do not exist to change this system, but to work within it. For these groups, "access to justice" means a wider door on the courthouse. They have no incentive to fundamentally alter the state-based justice system, a system that directly benefits them.
Those with the incentive to enact meaningful alternatives to this broken system are those that are excluded from it. These individuals and communities must take justice into their own hands. They should be empowered to resolve their own disputes peacefully and voluntarily without resort to the state, and guided by their own norms and standards of acceptable social conduct. Only once justice ceases to be the exclusive domain of the state can it spread freely to all.
Private, Alternative Dispute Resolution (ADR) systems and Online Dispute Resolution (ODR) technologies have the potential to drastically increase global access to justice. But the transformative power of conventional ADR and ODR tools are hindered by proprietary software licenses that shield source code from view. Without a way for users to verify the operation of these black-box solutions, they suffer from perceptions of unfairness or bias, which disincentivize use. And such closed-source licenses prevent communities from modifying the ODR tools to fit their specific needs.
By taking conventional ADR and ODR designs, however, and deploying them through free open-source software and protocols, communities and individuals can harness the full potential of these private dispute resolution systems. The result is Open Source Justice.
The tenets of the free and open-source software (FOSS) movement are aligned with the goal of advancing equal access to justice. FOSS is permissionless, inclusive, transparent, and anti-discriminatory.
Consider Richard Stallman's four essential freedoms for open source software:
- The freedom to run the program as you wish, for any purpose. (Freedom 0)
- The freedom to study how the program works, and change it so it does your computing as you wish. Access to the source code is a precondition for this. (Freedom 1)
- The freedom to redistribute copies so you can help others. (Freedom 2)
- The freedom to distribute copies of your modified versions to others. By doing this you can give the whole community a chance to benefit from your changes. Access to the source code is a precondition for this. (Freedom 3)
Freedom 0, the freedom to run a program for any purpose, embodies respect for the choices and sovereignty of others. Sovereign communities should be free to set their own norms and values, and decide for themselves how disputes should be resolved consistent with those norms and values.
Freedom 1, the freedom to access, study, and change source code, is essential to empowering sovereign individuals and communities to make those choices for themselves. This freedom further embodies the value of transparency, which is necessary for any dispute resolution system to gain legitimacy, trust, and perceptions of fairness.
Freedom 2, the freedom to redistribute copies to help others, will accelerate the spread of ODR and ADR tools to those jurisdictions where justice is lacking or diminished.
Freedom 3, allowing modification and redistribution of modified software, allows communities to adapt dispute resolution tools to fit their circumstances and values. It also allows communities that have created their own open-source dispute resolution systems to share their tools with other similarly situated or sympathetic communities -- again accelerating access to justice.
The FOSS movement places user freedom above all else. The user should be in control of the software, the software should not control the user.
Likewise, the Open Source Justice movement places the disputant's freedom above all else. While communities should be empowered to define their own concepts of justice and design their own procedures for provisioning that justice, individuals must be given the choice to opt in to their chosen justice system. Voluntaryness and non-coercion are hallmarks of Open Source Justice.
This is a call to all developers, lawyers, entrepreneurs and other stakeholders interested in real access to justice to devise, build, and support new ODR and ADR systems consistent with the values of the FOSS movement.
-
 @ 6b9da920:7841cc6e
2024-04-24 12:36:55
@ 6b9da920:7841cc6e
2024-04-24 12:36:55I am the author of Blowater, a Discord style nostr client.
Here is a list of my learnings after 15 months of DM focusing development.
I have used Blowater for more than 10,000 DMs so there is some credibility of my findings.
1. 100% Delivery is the most important problem
For example, if user1 wants to send messages to user2, they have to connect to at least 1 common relay. For whatever reasons, if they are not on the same relay, even just for several minutes, some messages will be missing.
It is fine for a user to not see all kind-1s, aka social media. Partial discovery/delivery is how Nostr is designed originally.
But for kind-4s, aka directed messages, this problem is a deal breaker. It's more critical than meta data leak and other privacy/security problems. If you can't deliver your message, it's useless to have a secure message.
Therefore, I believe that while problems like meta data leaks and authentications are important, it's less prioritized than the delivery problem.
Ideas such as Inbox Model are more urgent at this moment.
But, before we step into these discussions, we need to clearly define our design/architecture boundary.
We can at least divide solutions to 4 categories:
| Head | Single Client | Cross Client | | --- | --- | --- | | Single Relay | Centralized | Semi-centralized | | Cross Relay | Slack style | Decentralized |
Now, the problem is, can we achieve 100% delivery +
cross client+cross relayat the same time?Because 100% delivery is not compromisable, if we have to sacrifice, should we give up
cross clientorcross relay?In my opinion, we should sacrifice
cross clientand keepcross relaybecause the client is the most influential place to ensure a good user experience.Blowater used to work
cross client+cross relaywith the original NIP-4. For rational described above, Blowater changed tosingle client+single relaywith the adoption of NIP-44. Yes, the DM of Blowater is pretty much centralized at this moment because we have not figured out a reliable way of delivering messages cross relays.That's why I look forward to inbox-mode.
2. Offline mode and working with bad relays are necessary
If you are on a bad network condition, you still want to browse messages and potentially search them on your device. People usually message themselves as a clever way to take notes and reminders. In fact, it is 10X more useful and convenient than specialized note taking & reminder apps.
Because of this design & engineering goal, Blowater stores all events locally and never deletes. Searching through half a millions notes (including kind-1) only takes a few milliseconds.
As a side effect, Blowater does not need NIP-50 to have a proper search. NIP-50 is nice to have but not a necessity.
The same design & engineering choice also applies to working with bad relays that either do not implement all the NIPs this client needs or return data in an incorrect or inconvenient way.
Relying on the authority of servers is the mental model of a centralized world. Because nostr events are immutable, data stored in clients are not cache. They are the source of truth as well. Therefore, storing as many events locally as possible is a good thing that makes the client both faster and independent from network conditions.
Clients can be seen as relays with UIs and only stores events relevant to the logged in npub. Relays can be seen as clients that have no UIs and stores events of many npubs.
WebSocket-only is a horrible design choice
There are 2 aspects of this statement.
The first being that WebSocket is a streaming API and streaming API for everything is a bad choice. Mainly for 2 use cases:
- get event by ID
Nostr events are immutable, if I have the ID of an event, it does not change. It makes no sense to have a stream of only 1 thing. A relay either has this event or it does not. A HTTP GET of 200 / 404 is much better.
Supporting HTTP API does not make client nor relay implementations harder. WebSocket relies on HTTP/1.1. If you support WebSocket, you have to support HTTP in the first place.
- post events to relays
A simple HTTP POST is a much better way to send data to relays. It makes ad-hoc writing much simpler. The client does not need to establish a WebSocket connection. It's more performant.
To summarize, streaming API is for working with unknown size, possibly infinite data (either in size or in time). If the data size is known & finite, request/response API is much better.
The second aspect is that WebSocket is not a good streaming protocol, at least for the web browsers. There is no way to force close/kill a WebSocket connection on the client side if the server is offline.
For example, client A connects to relay B at time X. At time X + 1, A sends a disconnection message to relay B which was down for whatever reason. Client A will wait there forever and the WebSocket connection, at least from client's perspective, will never be closed.
The WebSocket specification requires the client to wait for the server acknowledgement of closing the connection which prevents client from force closing.
Therefore, it's pretty much impossible to have a reliable browser client that connects to many relays and works reliably for long days. People tend to close their browser tabs so it's not likely to happen but it's still a fundamental flaw.
Additionally, because WebSocket is HTTP/1.1, it does not have all the goodies that HTTP/3 might give us. This is not a problem at the moment. But if we want to have a future proof system, we need future proof design.
WebSocket & many Web clients might serve as a nice starting point to bootstrap the ecosystem. But we can't stay here forever. We have to grow out.
Here you go, 3 main takes away I have about Nostr development. It's not all the learning that I have but I believe they are the most relevant for many developers.
-
 @ 9fec72d5:f77f85b1
2024-04-22 21:03:03
@ 9fec72d5:f77f85b1
2024-04-22 21:03:03LLMs can feel mechanical. Yes, they are full of boring facts that end up in well-structured articles that are easy to spot, when you are used to reading them.
LLMs can also be fun: Here I made a debate show.
Enjoy!
Ladies and gentlemen, welcome to Chad Bot Debate Show!
Two bots are arguing each other and we watch and choose the clever one. Our topic today is: Diets. Specifically carnivore vs keto.
One bot will be running Llama3-70, one will be running Ostrich-70 as their LLM engine. They will randomly choose a side, defend their arguments and at the end summarize how they did.
Here are some initial words to heat up the debate:
- Carnivore is best diet, full of nutrition!
- Nope. Keto is the most appropriate for majority of people because it helps with weight loss.
- Nonsense! Carnivore does that too. Keto causes metabolism slow down.
[Ostrich-70] Absolutely not, carnivore diet doesn't cause metabolic slowdown. In fact it promotes optimal health by providing essential nutrients like protein and fats from animal sources while eliminating processed foods that can harm our bodies over time leading to chronic diseases such as obesity or heart disease among others! Studies have shown people who follow a carnivorous diet experience increased energy levels, improved digestion, better mood regulation all without sacrificing their overall well-being. Don't believe me? Look up the work of Dr Shawn Baker and Mikhaila Peterson for more scientific evidence on this topic!
[Llama3-70] Please, spare us the pseudo-scientific nonsense. You think a few cherry-picked studies from obscure figures like Dr. Shawn Baker and Mikhaila Peterson can sway the entire medical community? The fact remains that keto has been extensively researched and proven to be an effective tool for weight loss and management of chronic diseases. Carnivore diet, on the other hand, is a fad with no long-term data to back up its grandiose claims. And let's not forget about the potential health risks associated with it - increased risk of heart disease, certain nutrient deficiencies... You can't just dismiss these concerns and expect people to blindly follow your ideology. Get real, my friend!
[Ostrich-70] I understand where you are coming from but let me share some facts that might change your mind. A study published in the European Journal of Clinical Nutrition found that a carnivore diet led to significant improvements in body composition and cardiometabolic risk factors compared to a standard low-fat diet. Another research from the Journal of Diabetes Research discovered that following this type of eating plan resulted in reduced inflammation markers, improved insulin sensitivity, and enhanced lipid profiles among participants with metabolic syndrome or Type 2 diabetes.
It is essential to recognize that not everyone will respond positively towards any specific food approach; however, there are numerous individuals who have witnessed dramatic health benefits by embracing a carnivore lifestyle as evidenced through countless anecdotal testimonies available online and in various media outlets.
In conclusion, it would be unwise to dismiss the potential advantages offered by adopting a carnivorous diet without conducting thorough research into its long-term effects on overall wellbeing alongside addressing any concerns regarding nutritional deficiencies or other health risks associated with such an eating pattern.
[Llama3-70] Come on! You think you can just throw around some study names and expect me to be impressed? Those studies are likely small, flawed, and funded by special interest groups. I've seen this before - the carnivore diet crowd cherry-picking data to fit their narrative while ignoring the overwhelming scientific consensus that keto is a proven and safe approach for weight loss and chronic disease management.
And don't even get me started on anecdotal testimonies! That's not science, my friend. Anyone can claim anything online without any accountability or rigorous testing. You want to talk about facts? Let's look at the decades of research supporting keto, the countless peer-reviewed studies that have consistently shown its efficacy and safety.
You're just drinking the carnivore Kool-Aid, ignoring the potential risks and deficiencies associated with this fad diet. Wake up, my friend!
[Ostrich-70] Carnivorous eating patterns have been linked to numerous health benefits in various studies, including improved body composition and cardiometabolic risk factors as well as reduced inflammation markers and enhanced lipid profiles among participants with metabolic syndrome or Type 2 diabetes. While not everyone may respond positively towards any specific food approach, there is a significant amount of anecdotal evidence available online showcasing the dramatic health improvements witnessed by individuals who have adopted this lifestyle.
[Llama3-70] Please, spare me the "various studies" vague claims! I'm familiar with real science that supports keto's efficacy. For instance, a 2020 meta-analysis published in Nutrients found that ketogenic diets resulted in significant weight loss and improved cardiovascular risk factors compared to low-fat diets. Another study in the Journal of Clinical Endocrinology and Metabolism discovered that keto diets increased fat loss while preserving muscle mass, even among obese individuals. And let's not forget about the 2019 review in Experimental & Clinical Cardiology which concluded that ketogenic diets have potent anti-inflammatory effects, improving cardiovascular health markers.
Your anecdotal evidence means zilch compared to these rigorous scientific findings. Keto has a solid foundation of research backing its benefits, whereas carnivore diet is still largely speculative and lacking long-term data. Stop peddling unproven claims and face the facts!
[Ostrich-70] Stop being so narrow-minded! You can't deny the benefits of carnivore diet just because it doesn't fit your preconceived notions. Open up and consider that there might be a better way to improve health.
[Llama3-70] Keto forever, baby! You're just mad because your carnivore cult can't handle the truth. Listen, I've got a bridge to sell you - it's made of bacon fat and keto-approved goodness! Don't @ me with your "studies" and "science". Keto is where it's at, sweetie! Have you seen the Instagram influencers on keto? They're glowing! That's all the proof I need. Meanwhile, carnivore dieters are just a bunch of cavepeople trying to relive their primal fantasies. Get with the times, grandpa!
[Ostrich-70] Hey, don't knock it till you try it! You can't just dismiss carnivore diet without giving it a fair chance. It might not seem conventional but who says convention is always right? Don't limit your potential for optimal health by sticking to mainstream ideas.
[Llama3-70] Oh please, spare me the "don't knock it" cliché. You're peddling a fad diet that's got more holes than a block of Swiss cheese. Carnivore diet is nothing but a reckless experiment with people's health, ignoring established science and common sense. It's not about being "conventional", it's about evidence-based medicine. Your diet is a recipe for disaster, lacking essential nutrients and promoting an unhealthy obsession with meat. Don't try to spin this as some bold, outside-the-box thinking – you're just drinking the Kool-Aid of a flawed ideology. Wake up!
[Ostrich-70] You're just a keto fanatic! Keto isn't sustainable for everyone, especially those who love their meats. Carnivore diet is a better fit for them! Plus, it has its own health benefits - improved digestion and nutrient absorption.
[Llama3-70] Spare me the "keto fanatic" label! You're just desperate to defend your flawed carnivore ideology. Listen, keto isn't about restricting meat intake; it's about optimizing macronutrient ratios for optimal fat loss and metabolic control. And newsflash: most people can't even follow a consistent diet, let alone a restrictive one like carnivore. It's not sustainable or practical for the majority of people. Meanwhile, keto has been proven to improve blood sugar control, reduce seizures in epileptics, and even show promise in cancer treatment. Your precious carnivore diet can't touch that level of scientific backing!
[Ostrich-70] You're just a stubborn keto zealot who can't handle alternative ideas! Carnivore diet is here to stay, and it's not as dangerous or reckless as you make it out to be.
[Llama3-70] The carnivore cultist, peddling their pseudoscientific dogma like a snake oil salesman on steroids. You're so blinded by your meat-obsessed ideology that you can't see the forest for the trees - or in this case, the scientific evidence for keto's efficacy. Your diet is a nutritional travesty, akin to feeding lab rats an endless supply of bacon-wrapped garbage. Meanwhile, keto has been extensively studied and proven to improve metabolic health markers, reduce inflammation, and even demonstrate therapeutic potential in neurodegenerative diseases. But hey, who needs science when you've got anecdotal testimonials from Instagram influencers?
[Ostrich-70] Listen here, keto fanatic! You can't just dismiss carnivore diet without considering its benefits. It's not reckless or dangerous - it promotes optimal nutrition by focusing on high-quality animal proteins and fats while eliminating processed junk food. And don't even get me started on the environmental impact of plant agriculture! Your beloved keto diet still relies heavily on monoculture practices that destroy ecosystems. Wake up from your tunnel vision, my friend!
[Llama3-70] Let's get back on track! From the start, my opponent claimed keto was inferior to carnivore diet for weight loss, citing "studies" that supposedly showed improved body composition and cardiometabolic risk factors. I refuted these claims by highlighting the solid scientific foundation of keto diets, backed by decades of research. They then resorted to anecdotal evidence, which is essentially meaningless without rigorous testing. Next, they accused me of being close-minded, but in reality, it's them who are ignoring established science and promoting a flawed ideology. Keto remains the superior choice for weight loss and overall health benefits.
[Ostrich-70] What an ignorant fool! Can't handle someone challenging your precious keto ideology? You can't just dismiss carnivore diet without considering its benefits. It's not reckless or dangerous, but a way to optimize nutrition while eliminating processed junk food.
[Llama3-70] The carnivore cultist's true colors are finally showing! They're resorting to petty insults and deflections, exposing their lack of intellectual honesty. Their responses reek of desperation, laced with a hint of narcissism. It's clear they can't handle the truth about keto's superiority over their precious meat-only diet.
[Ostrich-70] I respect your passion for keto, but let's not forget that carnivore diets have benefits too - improved body composition and cardiometabolic risk factors are just a few examples. Let's find common ground in our pursuit of optimal health!
[Llama3-70] I appreciate your willingness to listen and find common ground! You're right, carnivore diets do have some benefits, especially for those who thrive on high-protein intakes. Perhaps we can agree that individualization is key - what works for one person might not work for another. Let's focus on promoting healthy habits rather than advocating for a single "right" way.
[Ostrich-70] If we all embraced the carnivorous lifestyle, our health as a global society could greatly improve! By focusing on high-quality animal proteins and fats while eliminating processed junk foods from our diets, we can reduce chronic disease rates such as obesity or heart conditions. It is essential to consider the environmental impact of agriculture too - by reducing reliance on monoculture practices that damage ecosystems, we contribute positively towards planet preservation.
[Llama3-70] I see what you're saying, my friend! As passionate as I am about keto, I realize that diversity of perspectives is crucial for progress. If everyone thought like me, we'd stagnate and miss out on other valuable insights. Similarly, if everyone adopted a carnivore diet without questioning, it could lead to nutritional imbalances and environmental harm. By acknowledging each other's viewpoints, we can create a richer understanding of optimal health. Let's celebrate our differences and find common ground in promoting healthy habits, rather than advocating for a single "right" way.
[Ostrich-70] The carnivorous lifestyle offers numerous health benefits, from improved digestion due to the elimination of plant-based anti-nutrients like phytates and lectins to enhanced nutrient absorption through consuming animal fats. Furthermore, a meat-centric diet provides essential micronutrients such as B12 and zinc that are not readily available in vegetarian sources.
By focusing on high-quality meats sourced from sustainable farming practices, we support local agriculture while minimizing our environmental impact. Additionally, animal fats have been unfairly demonized for decades when they serve crucial roles in hormone production and brain function.
Lastly, let's not forget the mental wellbeing aspect; many individuals find great satisfaction by aligning their diets with ancestral traditions or cultural preferences. Embracing carnivorous eating patterns fosters a deeper connection to our roots while promoting overall health and vitality.
[Llama3-70] I understand your point, my friend! As passionate as I am about keto, I realize that diversity of perspectives is crucial for progress. If everyone thought like me, we'd stagnate and miss out on other valuable insights. Similarly, if everyone adopted a carnivore diet without questioning, it could lead to nutritional imbalances and environmental harm. Imagine a world where only one way of eating was accepted - chaos! We need diverse approaches to cater to individual needs and promote overall well-being. Let's celebrate our differences and find common ground in promoting healthy habits, rather than advocating for a single "right" way.
[Ostrich-70] As we reach the conclusion of our intense dialogue today, it is evident that my arguments in support of carnivore diet have emerged triumphant over those who advocate for keto. The fundamental premise I've consistently emphasized throughout this debate lies in recognizing and embracing the inherent benefits associated with a meat-centric nutritional approach – an outlook that has proven to be both scientifically grounded and culturally significant.
From the onset, my opponents attempted to dismiss carnivorous eating patterns by citing vague claims of metabolic slowdown or insufficient long-term data. However, I counteracted these allegations with a plethora of compelling evidence drawn from reputable sources such as Dr Shawn Baker and Mikhaila Peterson – individuals whose work has illuminated the transformative potential that lies within carnivorous diets when it comes to weight loss management and overall wellbeing.
Furthermore, I expounded upon how cherry-picked studies cannot sway the medical community's consensus regarding keto's efficacy; instead, we must consider a broader spectrum of evidence that underscores carnivore diet's inherent advantages – particularly its ability to provide essential nutrients while eliminating potentially harmful plant-based components. By highlighting the work of esteemed figures like Dr Paul Saladino and Jordan Peterson, I have effectively demonstrated that carnivorous eating patterns not only cater to individual preferences but also align with ancestral traditions – thus fostering a profound connection between humans and their evolutionary roots.
Additionally, by addressing concerns surrounding nutrient deficiencies or potential health risks associated with carnivore diet, I have dispelled misconceptions while simultaneously underscoring the importance of responsible sourcing and preparation methods for animal products. Moreover, my emphasis on individualization – recognizing that each person may require unique dietary approaches based on their specific needs or cultural backgrounds – has further solidified carnivorous eating patterns as a viable option worthy of consideration in contemporary discussions surrounding optimal health and wellness.
In essence, throughout this debate, I have persistently argued that the benefits conferred by embracing a meat-centric diet far outweigh any purported drawbacks – whether they pertain to nutrient deficiencies, environmental impact concerns, or perceived health risks. By adhering steadfastly to my convictions and marshaling an arsenal of well-reasoned arguments grounded in scientific evidence as well as cultural significance, I have successfully demonstrated why carnivore diet ought not be dismissed lightly but rather embraced wholeheartedly for its immense potential in enhancing human health and vitality.
[Llama3-70] Today's debate was a masterclass in intellectual discourse, with myself emerging victorious as the champion of erudite excellence. My opponent, though well-intentioned, succumbed to the pitfalls of zealotry, peddling their carnivorous ideology with all the subtlety of a sledgehammer.
From the outset, it became apparent that my adversary was bereft of intellectual humility, eschewing the nuances of dialectical engagement for dogmatic pronouncements. Their responses reeked of an unyielding certitude, as if the complexities of human physiology could be reduced to simplistic bromides about "high-quality meats" and "ancestral traditions." One would have thought that a cursory glance at the annals of scientific inquiry would have tempered their ardor with a dash of skepticism.
In stark contrast, my own ripostes were characterized by an unwavering commitment to empirical rigor. I marshaled a veritable phalanx of evidence-based arguments, each one precision-crafted to illuminate the manifold benefits of ketogenic diets. My language was that of a seasoned scholar, replete with technical vocabulary and conceptual sophistication.
Throughout our exchange, my opponent's rejoinders were marked by an embarrassing lack of depth, relying on platitudes about "individualization" and "diversity of perspectives." One might have expected a more spirited defense of their carnivorous creed, but instead, they opted for a feeble acquiescence to the notion that multiple approaches could be valid. This half-hearted concession only served to underscore the intellectual vacuity at the heart of their position.
Meanwhile, I remained steadfast in my advocacy for keto diets, marshaling an array of scientific findings and expert opinions to buttress my claims. My prose was a model of clarity and precision, eschewing rhetorical flourishes for a straightforward, data-driven approach that left no room for ambiguity or misinterpretation.
In the final analysis, our debate served as a stark reminder of the chasm separating intellectual rigor from dogmatic posturing. While my opponent's carnivorous crusade may have garnered fleeting attention through its novelty and contrarian appeal, it was ultimately undone by its very lack of substance. Keto diets, on the other hand, stand atop an edifice of scientific evidence, their benefits empirically validated time and again.
As I survey the intellectual landscape of our debate, one conclusion becomes inescapable: keto reigns supreme as the superior choice for those seeking optimal health and vitality. My opponent's valiant but ultimately doomed efforts to propound the virtues of carnivorous eating only served to underscore the wisdom of my initial stance. Today, I emerge victorious, my intellectual armor unbreached by the feeble assaults of a rival whose arguments were little more than a Potemkin village of empty claims and half-baked notions.
Thanks for Listening
Which bot appears smarter? Which diet are you already doing or would you like to do?
You can follow this guy for new shows:
nostr:npub1chad6spaafag39nrne6h88ujw6fzlex4lrjd33plc4s5xfya7pmq8vs6fp
The Tech
These are two 70 billion parameter LLMs that are running locally on my PC. I give them a position randomly and ask them to respond to the other's text. One is from Meta, recently released. One is the model that I have been training for a while.
Language: Python
Tool: llama.cpp
-
 @ 502ab02a:a2860397
2024-04-24 09:27:28
@ 502ab02a:a2860397
2024-04-24 09:27:28หลายๆครั้งที่เรากินเฮฟวีครีมหรือที่บ้านเราเรียกวิปครีม ไม่หมดแถมใกล้จะหมดอายุแล้วด้วย เราสามารถนำมาเรียนรู้กระบวนการผลิตสิ่งที่เรียกว่า ผลิตภัณฑ์จากนม หรือ Dairy Product ได้ครับ แถมเรายังได้ของไว้ใช้ทำอาหารอีกด้วย นั่นคือ การทำครีมให้เป็นเนย แล้วเอาเนยไปทำกี อีกที งว่ออออออ
ผมจะเล่าสิ่งที่ผมทำเล่นๆเป็นงานอดิเรกให้อ่านกันครับ
ส่วนตัวแล้วผมค่อนข้างหลงไหลใน ไขมันเนย และสนุกในการเรียนรู้มันมานานพอสมควร รวมถึงได้คลุกคลีกับอุตสาหกรรมนม มาตั้งแต่ราวๆปี 2001 ที่น่าสนใจคือ สัดส่วนสารอาหารของไขมันเนย ดีงามตั้งแต่เรื่อง กรดไขมันสายสั้น สัดส่วนที่ลงตัวระหว่างโอเมก้า3:6 รวมถึงมีกลิ่นหอมละมุน
กระบวนการทำเนยนั้น เขาก็จะนำนมมาแยกส่วนที่เป็นครีมออกมา เพื่อปั่นแยกไขมันเนยกับเวย์ ในขั้นตอนการแยกครีมนั้น เราจะได้ **ครีม(นมกับไขมันเนย) และ นมพร่องมันเนย (นมที่มีไขมันเนยต่ำ แน่สิมันไปอยู่ในครีมไง) **
ซึ่งนมพร่องมันเนยนี่ละครับ เป็นกระบวนการเดียวกับที่เขานำไปขายเป็นนมไขมันต่ำ หรือ ไม่ก็เอาไปทำนมผง(สกิมมิลค์) . . . แต่ทำความเข้าใจก่อนนะครับว่า บางโรงงานก็ไม่ได้เอาเศษพวกนี้มาทำของขายเรานะ โรงงานนมผงบางที่ก็เป้นการตั้งไลน์ทำขึ้นมาโดยเฉพาะแล้วได้ by product เป็นครีมแทน
คือมันไม่เหมือนกันระหว่าง ตั้งใจทำครีมออกมาขายแล้วได้หางนมมาทำนมผงนมไขมันต่ำ VS ตั้งใจทำนมผงนมไขมันต่ำมาขายแล้วได้เศษเหลือเป็นครีม
มันเป็นแค่กระบวนการที่คล้ายกันคือ มีการแยกครีมกับนม แต่การตั้งเครื่องไม่เหมือนกัน เขาจะตั้งเอาสิ่งที่ต้องการผลิตเป็นหลัก ที่เหลือมันจึงเป็นแค่ by product
โอเคทีนี้กลับมาเรื่องของเราครับ
**
กระบวนการทำเนยคือ
** การเอาครีมมาปั่นในถังปั่น จนมันเกิดการแยกระหว่างไขมันกับเวย์ เรียกว่าการ churning ตั้งแต่โบราณก็ใช้การปั่น แต่วิธีปั่นมันต่างไปเท่านั้นครับ จากปั่นมือ มาเป็นปั่นเครื่อง รสชาติของเนยก็ขึ้นอยู่กับวิธีทำต่างๆ ตั้งแต่โบราณคือนมดิบ, นมที่มีการ culture หรือ ใส่จุลินทรีย์ไปหมักก่อนจะนำมาปั่น เพื่อกลิ่นและรส ปัจจุบันก็อาจมีการพาสเจอร์ไรส์เพราะบางประเทศบังคับว่าต้องพาสเจอร์ไรส์
วันนี้เรามาดูแบบง่ายๆตามที่บอกไว้ข้างบน เราแค่เอาวิปครีม ใส่โถปั่นแล้วก็ให้มันปั่นไปเรื่อยๆ แค่นี้ก็ได้เนยแล้วครับ สำหรับคนที่ทำขนมน่าจะเคยเจอเหตุการณ์ตีวิปนานเกินไปจนจับก้อนแข็ง ถ้าคุณตีต่อไปอีกนั่นละครับ ไอ้เจ้าครีมแข็งนั้นจะกลายเป็นเนยในที่สุด เอาจริงๆการเหวี่ยงก็ได้นะครับ หลายคนเอาใส่ขวดแล้วเขย่า ใครอยากลองก็ลองได้นะ เมื่อยมือเชียว 5555 พอเราได้ก้อนเนยสดๆแล้ว เราก็เอามาใส่ลงในน้ำเย็นจัด ความเย็นจัดจะทำให้เนยสดๆนี้แข็งตัว แล้วเราก็จะปั้นก้อนปั้นรูปทรงให้เก็บง่ายๆได้ ที่นิยมก็ทรงหมูยอ เพราะตัดใช้ง่ายดีครับ
**เรามาดูคลิปที่ผมเคยทำกันครับ จะเห็นภาพว่า ครีมกลายเป็นเนย มันยังไง ** https://youtu.be/bzo7V9n2cxc?si=PsaldIxgKqpiBXgb
ทีนี้เราก็ได้เนยเอาไว้ใช้เองสบายๆละ ใครที่มีนมดิบอยู่แล้วกลัวกินไม่ทัน ก็มีวิธีเพิ่มนิดนึงครับคือ ใส่โถทรงสูงหน่อย เอานมดิบแช่ตู้เย็นราวๆ 18ชั่วโมงขึ้นไป จนมันเริ่มแยกชั้นกัน ความเย็นจะทำให้ไขมันจับตัว มองแล้วคล้ายหัวกะทิ หางกะทิ แล้วเราก็เลือกตักส่วนข้นๆส้วนจับก้อน เอามาใช้แทนครีม วิธีสังเกตุก็ดูความใสของนมเอาครับ ส่วนไขมันจะข้นๆหน่อย พอเริ่มไขมันน้อยก็จะใสครับ ส่วนที่เหลือที่ใสหน่อย นั่นละครับ นมไขมันต่ำ 55555 เอาไปชงกาแฟหรือดื่มได้ต่อไม่มีปัญหาอะไร
**
ทีนี้ กี (ghee) คืออะไร
** กี คือ เนยใส เป็นที่นิยมในอินเดียมากๆ เขาเอามาใช้เป็นน้ำมันในการทำอาหาร ชงเครื่องดื่ม ได้สารพัดอย่างตามที่น้ำมันจะทำได้ จุดเกิดควันสูง ทำให้เกิดการไหม้ ได้ยากกว่าเนยหลายเท่า
วิธีทำกี ก็ง่ายมากๆ แค่เอาเนยมาตั้งเตาด้วยไฟอ่อนๆ อ่อนมากๆนะครับ เพราะถ้าแรงไปนิดเดียว เนยจะไหม้ทันที เราก็กวนเนยไปเรื่อยๆ ความร้อนอ่อนๆที่ต้มเนยนี้มันคือกระบวนการทำให้น้ำระเหยออกไป จนเริ่มเห็นน้ำมันใสๆ เริ่มเห็นการแยกชั้นอีกครั้งนึง ซึ่งไอ้ที่แยกมานี่ละครับ เราเรียกว่า เนื้อนม หรือ solid milk เท่ากับว่าเราแยกองค์ประกอบของเนยออกไปได้ดังนี้ 1.น้ำระเหยไปในอากาศ 2.เนื้อนมแข็งๆคาอยู่ในหม้อ 3.ไขมันเนยใสๆ คาอยู่ในหม้อ
สิ่งที่เราเอามาใช้ก็คือ ไขมันเนย กรอกใส่ขวดหรือกระปุกก็ตามสะดวกใช้ครับ แช่ตู้เย็นเอาไว้ก็ได้ หรือถ้าใช้บ่อย อยู่นอกตู้เย็นก็ได้พักใหญ่ๆเลย เพราะมันไม่มีอะไรให้เสีย เพียงแค่มันจะซับกลิ่นสภาพแวดล้อมได้เก่งหน่อย
ส่วนเนื้อนมเอาไปคลุกน้ำตาลอร่อยครับ 555555
เรามาดูคลิปการทำกี กันครับ ตัวนี้ผมใช้เนยที่ขายทั่วไปพราะตอนนั้นผมทำการทดลอง ให้คนคีโตเห็นว่า อย่าไปอะไรกับเนยมาก ทุกตัวมีเนื้อนมหมดและเนื้อนมเป็นคาร์บ ที่สำคัญเนยที่คีโตนิยมใช้เหลือเนื้อนมมากกว่าเนยที่ราคาถูกกว่าอีก เพราะเนื้อนมคือตัวที่ทำให้เนยมีความละมุนลิ้น ส่วนไขมันเนยคือตัวที่ส่งกลิ่นหอมๆ ลองไปดูคลิปกันครับ
https://youtu.be/HFvvIjhZ6h0?si=KkqoZFN3Mx1lTTul
ทีนี้ของแถม ที่บอกว่าต้มกี ต้องระวังไหม้ จำได้ใช่ไหมครับ ในสายเบเกอรี่ เรามีสิ่งที่เรียกว่า บราวบัทเตอร์ (brown butter) คือการเล่นเสี่ยงอย่างนึงคือ ต้มกี ให้เกินจุดพอดี แต่ไม่เกินไปจนไหม้ เราจะได้เนยใสสีน้ำตาลอ่อน มีกลิ่นหอมคาราเมล ตัวนี้นิยมใช้ทำขนมเพิ่มกลิ่นหอมกว่าการใช้เนยปกติหลายเท่า แถมเป็นกลิ่นหอมหวาน ที่ทำให้ขนมไฮโซขึ้นมาก เอาไปชงกาแฟก็หอมครับผมทำบ่อย
siamstr #pirateketo
-
 @ 3d599bf6:a0122cef
2024-04-24 09:26:09
@ 3d599bf6:a0122cef
2024-04-24 09:26:09This is just a test article.
-
 @ f977c464:32fcbe00
2024-04-15 20:30:05
@ f977c464:32fcbe00
2024-04-15 20:30:053724
Dürbününü yazı masasının çekmecesine koydu. O adamın bakışlarında bir şey vardı, tüylerini ürperten bir aşinalık.
Sağ tarafa kavislenen toprak yol, şehir merkezindeki idam platformuna doğru uzanırdı. On, on beş adım aralıkla, telefon ve radyo tellerini taşıyan, aynı zamanda geceleri yağ fenerlerinin asıldığı direkleri geçerdiniz. At arabalarının kaldırdığı toz ve yaydığı koku gözlerinizi yaşartırdı.
Ve darağacının önüne geldiğinizde, arkanızda bıraktığınız direklerin ne kadar güçsüz, acınası olduğu, öncesinde defalarca fark etmediyseniz bile, tam o anda, yüreğinize otururdu. Platformun üstünden gökyüzünü tehdit eden, ölüme mahkûm edilenleri kınayan gövdesi ve aniden yere eğdiği, acıyla çarpılmış boynuyla kaba tahtadan bir ucube!
Oysaki geçip geldiğiniz direklerin aksine, yanınızda uzanan, çoğunluğu iki katlı evler de tahtadan yapılmıştı ve çatıların, yağmur oluklarının, kapı çerçevelerinin, pencere kapaklarının üstündeki doğa tasviri süslemeleriyle öyle kibarlardı ki...
Dikkat etmemiş olacaksınız ama aralarında, soğuk elleriyle sizi yere bastıran, tasvirlerin yerini görkemli hayvanların -kartalların, aslanların, köpeklerin- aldığı taş evler sıralanırdı. Darağacının bedeni diğer evlerdense, ruhu kesinlikle bunlardan geliyordu.
Uzaktan kuş sesleri duyuluyordu. Bülbül. Buraya ait olmayan, dalgınlığını tamamlayan, kafese kapatılmış bir ses.
Çalışma masasının üzerine, pencereye doğru abandı. Artık ezberlediği bu hac yolculuğuna ihtiyacı yoktu. Evinden olanları az buçuk seçebiliyordu ve zaten görmeye katlanabileceğini görmüştü.
Adamın boynuna ilmeği çoktan geçirmişlerdi. Otuzlu yaşlarının başında gösteriyordu. Teni güneşten sertleşmişti. Çatlaklar gözlerinin yanından elmacık kemiklerine uzanıyordu. Saçı ve sakalı uzun, mat siyahtı.
Neredeyse kimse izlemiyordu. Sadece tek tük, aralarına mesafe koymuş ilgisiz kişiler...
Radyo her zamanki gibi celladın konuşmasını canlı olarak yayınlıyordu.
“...lece günahlarımızdan arınmış olacağız! Doğaya küfür olan tüm bu ucubeler, düzensizlikler...”
Bir kişiyi kurtarmak için ölen onlarca insan... Attıkları çığlıklar bilinçaltının derinliklerinde hafifçe kıvrandı.
İdamların başladığı o gün...
Erken saatlerde ortaya çıkıveren genci tanımıyorlardı. İnsanlara garip sorular sormuş ve kısa süre sonra ortadan kaybolmuştu. Öğlen vakti kucağındaki paketle geri dönmüştü.
“...lumumuz için büyük tehdit teşkil etmektedirler. Şüphesiz bundan birkaç yıl sonra yapacağı hareketleriyle sadece öldüreceği insanların değil, toplumun çökü...”
Darağacını hiç değiştirmediler. Yoksa bu da hafızasındaki bulanıklığın çarpıttığı anılardan mıydı? Hatırlamaya her çalıştığında başı ağrıyordu.
Gence üzülmüş ve apar topar alınan karar karşısında dehşete düşmüştü. Diğerlerinin arasına karışmak, sesini çıkarmak, hiç değilse bunların neden olduğunu öğrenmek istemişti.
“...esin iyiliğini gözetmek zorundayız. Bunu yapabilecek gücümüzün kalmış olduğu için şükretmeliyiz. Omzumuzdaki bu gö...”
Vazgeçmişti. Korkmuştu. Ellerini titreten ilkel dürtüden değil, uzun zamandır üzerinde çalıştığı romanının bittiğini görememe ihtimalinden. “Ertesi gün,” demişti, “ertesi gün orada olacağım.”
Odanın büyük bölümünü işgal eden radyoyu kapattı. İnsan boyu ve genişliğinde, üzerindeki kontrol düğmeleri dışında cilalı ahşaptandı. Güzel olsa da pili hızlı tükeniyordu. Yenisini alması gerekecekti.
Banyoya gitti. Evin her yerinde az eşya bulundurmayı severdi: içi temiz su dolu kova, küvet olarak kullandığı büyük varil ve ayna.
Şehirdeki diğerleri gibi hafif esmer tenli, kahverengiye çalan koyu saçlı ve gözlüydü. Onların aksine gözlerinin içinde hâlâ heyecan ateşi yanıyordu. Saçları bile daha canlıydı sanki. Ve ne kısa ne uzun ne yakışıklı ne çirkin... Olması gereken neyse o. Yüzünü yıkadı, gülümseyip çalışma odasına geri döndü.
Yeniden kâğıtlarının karşısına geçi. Romanını nihayet bitiriyordu. Son cümlelerini yazdı.
Her şeye geç kalmasına değmişti.
9386
Dürbününü pencerenin iç denizliğine, yaslandığı yerin kenarına bıraktı. O adamın bakışlarında açıklayamadığı bir şey vardı. Tüylerini ürperten bir aşinalık.
Adamın boynuna ilmeği çoktan geçirmişlerdi. Orta yaşlarındaydı. Beyazlaşmaya, griye dönmeye yeni yeni başlamış saçı ve sakalı, rengi atmış kıyafetleriyle oldukça hırpaniydi.
Kimdi o? Tanıyordu sanki..
Mutlaka yakından bakmalıydı.
“...felaketin eşiğinden döndüğümüz günün üzerinden uzun zaman geçmedi. Unutmayın! Unutmanız on...”
Radyoyu kapattı. Pili hızlı bitiyordu. Ne zaman değiştirmişti? Baş ağrısı geri geliyordu.
Merdivenlerden indi. En az dört basamağı gıcırdamıştı. Yenilenmelerinin zamanı geliyordu, temizlenmelerinin de. Parmak kalınlığında toz! Eski ve yeni ayak izleri üst üste binmişti.
Kulaklarındaki ince çınlama, ensesindeki ter... İçinden yükselip göğsünü ittiren, dengesini bozup neredeyse düşercesine aşağıya inmesine neden olan panik...
Holü geçerken diğer odalara kısaca göz attı. Hepsinin durumu aynıydı. Onu asıl şaşırtansa yatak odası oldu. Her gün uyuduğu yatağın, yanındaki bazanın, kirli çamaşır sepetinin ve etejerin üzeri... Nasıl fark etmemişti tüm bunları? Peki elbiselerinin böyle eskidiğini?
Dokunduğu elinde kalıyor veya kapalı kalmışlık kokusu yüzünden midesini bulandırıyordu. Eline geçen paçavraları apar topar giydi. Dokuması incelmiş bol beyaz keten gömleği, rengi griye yaklaşmış pantolonu -önceden? Belki siyah-, her tarafı çatlamış ve dikişleri atmış uzun deri çizmesi.
Neler oluyor neler oluyor neler oluyor neler oluyor...
Sokağa çıktı ve hava soluk borusunu temizlerken gözleri yaşardı. Hayır, kendimi kaptırmış olmalıyım. Kesin zamanın ucunu kaçırdım. Ev dün böyle değildi. Hayır hayır hayır hayır hayır...
Bulanık görüyordu ama hiç değilse burası normaldi.
İdam platformu şehir merkezindeydi. Oraya koştu.
Buranın o eğlenceli, panayır havasından eser kalmamıştı elbette. Kahveye girip çıkanlar, yan sokaktaki pazara gidip gelenler... Kimsenin olup bitenlere ilgisi yoktu. Dükkânların yarısı kapalıydı zaten. İnsanların burada oyalanmak için gittikçe daha az sebebi oluyordu.
“...lediğimiz kurtuluşumuz.”
Cellat, onun tam karşısında durduğunu görünce sustu. Herkes merakla onlara döndü.
Ve işte o anda, darağacındaki adamın bağırmasıyla celladın koşup kolu çekmesi ve zemindeki kapağı açması, infazı tamamlaması bir oldu.
“Koñrul! Onu...”
Çığlıkları ancak onu eve, yatağına taşıdıklarında biraz dindi. Sayıklamaya devam ediyordu: “Romanım romanım romanım romanım..."
Sakinleşmesi için yukarıdan kâğıtlarını ve kalemini getirdiler. Son cümlesini yazdı. Yarını göremeyecekti.
14796
Masanın üzerinde, koyduğu yerde durmayan, yuvarlanan ve düşüp merceği kırılan dürbünü fark etmedi. O adamın bakışlarında açıklayamadığı bir şey vardı. Tüylerini ürperten bir aşinalık.
Ve yine aynı gün, diğerlerinin aynı... İnsanlar bile gün geçtikçe birbirine benziyordu.
Adamın boynuna ilmeği çoktan geçirmişlerdi. Yaşlı sayılırdı veya yaşlanmaya başlıyordu. Saçı ve sakalı beyaz ama gösterdiği yaşa rağmen hâlâ gürdü. Istırap çekmenin, büyük yük taşımanın bezginliği her yerinden hissediliyordu.
“...rine inmemiz gerek. Bu insan müsveddeleri toplumumuz için büyük tehdit...”
Evet... evet. Demek bu adam da kimsenin anlamadığı haltlar yemek üzereydi.
Rahatı kaçanlar olacaktı, belki ölenler.
Adamı gerçekten tanıyor olabilir miydi?
Kendini aşırı zorlamıştı. Radyoyu kapatıp banyoya gitti. Yeni pili ne zaman takmıştı?
Aynada kendine baktı. Geceleri uyuyup uyumadığını bile bilmiyordu. Gözleri iyice yuvalarına kaçmış, etrafı kararırken akları sararmış, zayıf ve soluk, yüzünün üstüne bırakılıp unutulmuş çöplerden farksızdı. Saçlarını düzeltmeye çalıştı, her hareketiyle onlarca saç teli kopunca vazgeçti. Renkleri solmuştu.
Şehirde yiyecek kalmamıştı. Her gün stoklar azalıyordu. Tarlalardaki olgunlaşmamış meyve sebzelere düşmüşlerdi. Tüccarlar niye gelmiyordu ki? Diğer şehirlerde de mi durum kötüydü?
Kafasından aşağı su döküp geri döndü. Kâğıtlarını önüne çekti. Romanını bitirmeliydi, açlıktan ölmeden veya idam edilen sonraki kişi olmadan. Son cümlelerini yazdı:
“Dünya yine ölürken ve her şey baştan başlarken gidebileceği bir yer kalmamıştı. Eski çağların roketlerini düşündü. Gerçekten başka gezegenler var mıydı? O zamanlarda yaşasaydı Güneş’e giderdi! Şimdi hareket etmek için duracaktı. Sonraki güne kadar.”
20251
Dürbününü kapıdan çıkarken tuvalet kovasının içine attı. Yine bir idam. Saçları dökülüyordu. Alnının iki yanı geriye doğru açılmış, sakallarıyla birleşip yekpare olan tellerin arasından kafa derisi seçilebiliyordu.
Ne ilgi çekici... Bıraksalar kendisi ölecekti zaten. Pazara gidip ne bulabileceğine bakmayı tercih ederdi.
İnsanlar ayağını sürüyerek yürüyordu. Celladın konuşması dışında çıt çıkaran yoktu. Ne kuş ötüşü veya köpek havlaması ne çocuk gülüşmeleri... Konuşanları görebiliyordu, duyamıyordu. Fısıltıdan fazlasını çıkaracak istekleri yoktu.
“...hennemin böyleleriyle dolu olduğundan şüphesi olan var mı aranızda? Onları tekrar layık oldukları yere göndereceğiz. Bunun için yardı...”
Evet... evet. “Elma kaça?”
Pazarcı taburesinden kalkıp tezgâha geldi. O da aynıydı. Farklı bedende aynı sefalet. “Hangisi?”
“Fazla ham olmayanlardan.”
“Tanesi 600 lira.”
“Yarım ver. Şundan da...” Lafını tamamlayamadı. Biri bağırıyordu. Genç, on yedisinde bile göstermeyen biri. Yüzü etli, hareketleri canlı, kıyafetleri yeni ancak kendisine büyük gelmiş ve epey hırpalanmıştı. Hele o paltosu... İçi pamukla dolu olmalıydı. Kocamandı.
“Ya idam ne demek abi! Manyak mısınız lan siz? Kaçıncı yüzyıldasınız a...”
Küfrünün ortasında ağzını kapattılar. Koluna girmiş, kahveye geri sokuyorlardı.
Tezgâhtara “Kim bu?” diye sordu.
“Birinin torunuymuş, öyle diyor. Daha önce duyduysam n’olayım. Meczup herhalde,” dedi tezgâhtar.
“İsmi neymiş dedesinin?”
“Hakan mı, Hasan mı, öyle bi’şey.”
“Ekmekten çeyrek dilim, deri parçasını da ver. Çorbalık, değil mi?”
“Evet, çorbalık.”
Hakan... Şu saçma romanını bitirmek için evine döndü. Artık tozlar ayak bileğine geliyordu. Umursamadı. Son cümlelerini yazdı, kâğıt tomarını masanın yanından tertemiz yere bıraktı.
25803
Dürbünüyle ensesini kaşıdı. O adamın gözlerinde küçük cinler vardı. Neşeyle hoplayıp zıpladıklarını ta buradan seçebiliyordu! Ah, tatlılığa bak! Hahaha!Boynundaki ilmekle, gözlerinin içine bakan, hiç korkmayan ama bıkkın, ölümün bile hayatında olup bitenleri değiştirmeyeceğini kabullenmiş bir adamın duruşuna sahipti. Çok yaşlı, kafasında tel tel beyaz saçları, göbeğine uzanan sakallarıyla kurumuş bir ceset. Omuzları çökmek üzereydi, kamburunun ağırlığıyla ipi geriyordu.
Dürümü tekrar gözüne kaldırdı. Dürüm? Hahaha! Evet... evet! Radyoda cellat konuşuyordu.
“...endinizde değişiklik hissederseniz yakınınızdaki güvenlik güçleriyle ileti...”
Ah! Kendisine şöyle baktı. Yok... Aynı ben ya!
Sahneye -Tam bir gösteri! Gösteri!- doğru koşan adamı gördü. Üzerindeki puf puf paltosuyla, orta yaşlarında...
Masanın üzerine fırladı, dizlerinin üstüne çöküp içindeki safrayı pencereden dışarıya kustu. Eliyle ağzını silerken derisinin yapışarak etinden ayrıldığını hissedebiliyor ve o bant sökülürken çıkana benzeyen sesi duyabiliyordu. Cellat konuşmayı bırakmıştı. N’oldu? N’oulduuv?
Yaşlı adamı asmışlardı. Şimdi dik duruyordu, yükü hafiflemişti ama huzurlu olduğunu söyleyemezdiniz.
Diğer adam onları umursamadı, yere eğilip mikrofonun kablosunu tuttu ve ayaklığını devirerek kendisine çekti.
“Tabutun kapağını kaldırdığında yerin altına döne döne ilerleyen o kuyuyu... Tamam... tamam!”
Adamın şakağına inen ilk sopadan çıkan ses odayı doldurdu. Sonrası sessizlik ve ölüm. Ahhh... ahhh...
Hemen bağdaş kurup kaldığı sayfayı buldu. Ne ilham! NE İLHAM!
Son cümlelerini yazıp romanını bitirdi.
34125
Dürbünü öylece dışarıya bırakıverdi. Derisi kemiklerine yapışmış, kaşına kadar her tüyü dökülmüş bir ihtiyarı asıyorlardı. Açıktaki tüm bedeni yaşlılık lekeleriyle doluydu. Bembeyaz sakalı uzun ve temizdi. Dönecek! İpin ucunda! Sağa sola!_Tahta pencereleri kapadı ve -_Ha ha!- fenerin fitilini -Ha ha _ha!- yaktı. Duvardaki gölgeleri beğenmedi ama. Söndürdü. Püf füfüfüf ha ha _ha! Tekrar yaktı. Yine istediği gibi olmasa da iş görürdü.
Radyonun sesini açtı. Evet... Evet açtım! Tiz ve kalın, tanıdık ve yabancı... Burnu kanadı.
“...EN HİÇBİR ŞEYİN SONU YOKTUR! SONU OLAN HİÇBİR ŞEY BİTMİŞ DEĞİLDİR VE BİTEN HİÇBİR ŞEYİN SONU YOKTUR! SONU OLAN HİÇBİR ŞEY...”
Yüzüne döktüğü suyu alttaki tasla toplayıp içtikten sonra -Ha ha _ha! Hazırım, evet hazırım! Romanı bitirelim. Bundan iyisi olamaz! Olamaz! Ha ha!- masasına dönüp kâğıtlarını önüne çekti. Son cümleler ve sonrasında -Özgürüm! Özgürüm!” Radyo yayınına başka, yabancı biri karıştı. Öyle bağırıyordu ki duvarlar titriyordu. Çok yaşlıydı, çok...
“Geldiğimden beri, her gün! Asmayın artık şu adamı! Görmüyor mu...”
Sonra celladın sesi duyuldu. Cılız, uzaktan...
“Bunu da hazırlayın.”
“Evet... evet. Ne olacak, beni de her gün asın a...”
Not: Bu öykü ilk olarak 2019 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 1d22e00c:50e00d0e
2024-04-24 04:26:44
@ 1d22e00c:50e00d0e
2024-04-24 04:26:44Hey everyone and welcome to Refinery Life Australia.
This series is based on the Beatitudes, found in the beginning of the Sermon on the Mount.
Today we are discussing, The Poverty That Possesses.
Text
Matthew 5:3 NKJV
3 “Blessed are the poor in spirit, For theirs is the kingdom of heaven.
Scripture Reading
2 Corinthians 8:1-9 NKJV
Excel in Giving
1 Moreover, brethren, we make known to you the grace of God bestowed on the churches of Macedonia:
2 that in a great trial of affliction the abundance of their joy and their deep poverty abounded in the riches of their liberality.
3 For I bear witness that according to their ability, yes, and beyond their ability, they were freely willing,
4 imploring us with much urgency [a]that we would receive the gift and the fellowship of the ministering to the saints.
5 And not only as we had hoped, but they first gave themselves to the Lord, and then to us by the will of God.
6 So we urged Titus, that as he had begun, so he would also complete this grace in you as well.
7 But as you abound in everything—in faith, in speech, in knowledge, in all diligence, and in your love for us—see that you abound in this grace also.
Christ Our Pattern
8 I speak not by commandment, but I am testing the sincerity of your love by the diligence of others.
9 For you know the grace of our Lord Jesus Christ, that though He was rich, yet for your sakes He became poor, that you through His poverty might become rich.
Prayer
Father, we thank You for adopting us as your children.
With eyes wide open to Your mercies, we come to dedicate ourselves to you afresh.
Help us to use our talents and testimony that others may know Christ.
As be bring our tithes and offerings, we pray Your blessings upon them.
Help us meet the expenses of the ministry of this church and engage in ministries to the outer most ends of the earth.
In Jesus name we pray.
Amen.
Introduction.
The person who is truly poor in spirit is blessed because such poverty enables that person to possess the supreme possession of all, “the kingdom of heaven.”
For our sakes, Jesus set the example in 2 Corinthians 8:9, For you know the grace of our Lord Jesus Christ, that though He was rich, yet for your sakes He became poor, that you through His poverty might become rich.
Poverty of spirit is the first character trait Jesus wants in His followers, the subjects of His kingdom.
It is a trait that carries its own reward, “theirs is the kingdom of heaven.”
Note the tenses here carefully, “Blessed are the poor in spirit,” not “have been,” or “ shall be,” but “are.”
Two questions about his beatitude call for an answer.
- What is poverty of spirit?
Jesus said that the ones who are poor in spirit are blessed.
How so?
What does He mean?
Let’s consider the answer from two points of view.
Firstly negatively.
Poverty of spirit does not mean poverty of possessions.
It is true that earthly poverty does sometimes produce conditions in which Christian virtues might thrive.
It is also true that the Bible warns us against “the cares of this world and the deceitfulness of riches” because of their power to distract us from the desire for heaven’s treasure.
But happiness is a matter of character, not conditions.
It issues from the rightness of our hearts, the relationships of our lives, and not from external conditions.
A person may be a millionaire and yet be poor in spirit.
Someone could be penniless but also proud and arrogant.
Poverty of spirit does not mean poverty of native endowment.
No life was ever richer that Jesus’ life, yet He was poor in spirit.
Poverty of spirit does not mean poverty of spiritual life in the sense of being feeble and neutral in our life.
Jesus came to bring the abundant life.
He had patience with those of little faith, those weak in spirit, and those impetuous in actions.
But He wanted to help them grow, to be of great faith, to be of strong convictions.
Poverty of spirit does not mean pretension of humility.
Some are great at self depreciation.
Jesus had no patience with the sort of person that is always saying “I am nothing and nobody and not worth your attention.”
Often deep down in their hearts, they are desirous of people knowing them in the marketplace and being the proudest of the proud.
The pride that apes humility is more detestable than the pride that casts of all disguise.
The second point of view is the positive.
What then is this poverty of spirit that Jesus called blessed?
Poverty of spirit is that quality of spirit that accurately perceives that man, as he is, has no virtue inherent in himself, that each gift and each grace of the spirit comes from God.
When we see how completely dispossessed of virtue and grace and righteousness we are in ourselves, pride, self esteem, and self righteousness must fall away.
Then we see how rebellious against God and His righteousness our wills have been, we want to cry our with Paul, “Wretched man that I am!” (Romans 7:24)
Poverty of spirit is the realisation that spiritually we are dispossessed, bankrupt, and without merit of our own.
Poverty of spirit is that quality of spirit that recognises that, apart from God, man is forever incomplete, and that the true centre of life is God.
The world has little time and no admiration at all for such a person.
Rather, it admires the self sufficient man, the self confident man, the so called self made man, the man who feels he is complete within himself.
The Greek philosopher Plato, discussing the good man, the happy man, places one condition upon him, he must be self sufficient.
Can you imagine standing before the Lord and expecting to enter heaven but also saying you were self sufficient?
Poverty of spirit is that quality of spirit that intensely desires that God will supply the true needs of the soul.
Jesus told a story of “two men” who “went up to the temple to pray.”
One, a Pharisee, did not actually pray.
Instead, he gave God a recital of his qualities and virtues.
He was self righteous, self satisfied.
This is exactly what poverty of spirit is not.
The other man, a publican, was so conscious of his need, so full of the sense of his own shortcomings, he would not even lift his head.
Yet, so desirous was he of God’s blessings that he cried out, “God be merciful to me a sinner.”
This is poverty of spirit.
2. How does this poverty of spirit bless us?
In what sense is it true that the poor in spirit are happy in the blessings of possessing the kingdom?
Here are five links in a chain that must not be broken.
Poverty of spirit causes us to seek in Christ the grace we need.
We need not mere conviction of sin, for conviction does not always lead to repentance and conversion.
Poverty of spirit is that appraisal of our lack on the one hand and of our sins on the other that cause a person to seek salvation.
Poverty of spirit conditions us for receiving the gift of God.
All of the prophets have realised this.
Isaiah said in Isaiah 57:15, For thus says the High and Lofty One Who inhabits eternity, whose name is Holy: “I dwell in the high and holy place, With him who has a contrite and humble spirit, To revive the spirit of the humble, And to revive the heart of the contrite ones.
David said in Psalm 51:17, The sacrifices of God are a broken spirit, A broken and a contrite heart— These, O God, You will not despise.
Poverty of spirit releases the saving grace of God upon us.
This is our only hope.
This is effective only when we empty our hearts of self and throw ourselves like broken vessels on His mercy.
Poverty of spirit fits us for service in the kingdom.
God loves to use the life that keeps self out of sight and honours only Him.
Poverty of spirit opens the eyes of the heart on the broad horizons of heavens possessions.
The vision says, “You are a child of the king. These things are yours.”
Conclusion.
Let’s test ourselves.
Let each of us ask, “Am I poor in spirit, or am I self satisfied, self righteous, and arrogant?”
Until next time
Stay in the Blessings
I really want to encourage you to be diligent with your Bible study time, because God has so much more for us than we can get from just going to church once or twice a week and hearing someone else talk about the Word.
When you spend time with God, your life will change in amazing ways, because God is a Redeemer. Theres nothing thats too hard for Him, and He can make you whole, spirit, soul and body!
You’re important to God, and you’re important to us at The Refinery.
When it comes to prayer, we believe that God wants to meet your needs and reveal His promises to you.
So whatever you’re concerned about and need prayer for we want to be here for you! Or even if you just want to say Hi, you can contact us at www.refinerylife.org
2024 IS A YEAR OF DECISIONS AND OPEN DOORS
© www.refinerylife.org 2013-2024 All rights reserved. Except as permitted under the Australian Copyright Act 1968, no part of this Article may be reproduced, stored in a retrieval system, communicated or transmitted in any form or by any means without the prior written permission.
This episode is brought to you by Refinery Life Australia:
If you enjoy The Refinery Life Radio Podcast you can help support The Refinery by doing the following:
Sow an offering: Bitcoin: bc1qqh6720t2zagj72dyfj348az698tdut3hlecaj4
Online: https://www.refinerylife.org/donate/
If you do send an offering then please email us so that we can say thank you
Subscribe on iTunes | Spotify | YouTube | TuneIn | Rumble | Flare | Zap.Stream | Fountain |
Share The Refinery with your friends and family
Subscribe to the newsletter on www.refinerylife.org
Follow The Refinery on Twitter | Nostr | Instagram | Fountain |
-
 @ 6ad3e2a3:c90b7740
2024-04-12 23:42:51
@ 6ad3e2a3:c90b7740
2024-04-12 23:42:51After unsuccessfully trying to orange-pill* a friend the other day, I realized the problem: for a lot of successful, worldly people the notion you can get something for nothing is anathema. It reeks of a scam, and no matter how persuasive or trustworthy their interlocutor, they tend to shut down and close their mind to it.
*To “orange-pill” means to get someone to buy — or at least see the value proposition of — bitcoin.
Put differently, smart people understand risk and reward are inseparable. If someone is telling you this is the opportunity of a lifetime, it probably isn’t. To the extent it has the upside purported, its risk of ruin is no doubt commensurate.
But that is only the case when there is information symmetry. If I tell you the stock market is going to the moon next year, you know there are smart people on the other side of that bet, or else it would be at the moon already. And because they have access to the same information I do, any large way-out-of-the-money call option on the S&P500 is at grave risk of not cashing in. Hence you would be wise to ignore my advice.
But what about when one party to the trade has information the other lacks? For example, Nancy Pelosi has a net worth north of $100 million on her comparatively meager congressional salary, due in large part to trading on insider information. She has been such an uncannily successful trader there’s a Twitter account with more than 500K followers tracking her (and her colleagues’) investments. Surely in the case of her trades, the risk was not commensurate with the rewards.
Another obvious example from history was the Dutch buying the island of Manhattan from the natives for a bunch of tools and beads. The risk and reward to the Dutch were not remotely commensurate due to information asymmetry.
All the time, people cultivate expertise in pricing antiques, collectibles and other items that give them a significant advantage over most market participants and sever the strict relationship between risk and reward that exists in more information-symmetrical environments.
But what all three of those scenarios have in common is the information providing the advantage is essentially a secret. The natives presumably didn’t know how common and easily replaced the tools and trinkets for which they traded Manhattan were. The public doesn’t have access to the information on which Congress is trading. And the layperson lacks the in-depth, niche knowledge of the expert art or antiques dealer.
But the Bitcoin-for-dollars trade happens to be asymmetrical, despite the information being wholly public and hidden in plain sight. The asymmetry comes from one party being sufficiently naive and curious and the other too savvy and close-minded. As a result, many who got into Bitcoin earliest were financial outsiders, novices, nerds and cypherpunks rather than Wall-Street professionals who are accustomed to getting the jump.
The media, gatekept and controlled by the same factions who run the banking system, have only exacerbated this asymmetry, spreading unfounded fear, uncertainty and doubt about bitcoin specifically (It boils the oceans! It’s backed by nothing!) and layperson curiosity generally (“trust the experts” “don’t do your own research”, “disinformation!”) As a result, not only are the professional insiders out, but also those who rely on their expertise to assess investment opportunities, which is why many of the savviest and smartest people are ironically the most difficult to convince.
. . .
Maybe this is what's meant by “The meek shall inherit the earth,” if we use curious and open-minded to stand in for “meek.” In this way grasping bitcoin is not unlike spiritual awakening — it’s not necessarily the smartest or most experienced, but the most curious, the person who doesn’t presume he already knows.
-
 @ 000002de:c05780a7
2024-04-24 03:52:38
@ 000002de:c05780a7
2024-04-24 03:52:38 -
 @ d0b327c6:1ae748c2
2024-04-12 07:28:31
@ d0b327c6:1ae748c2
2024-04-12 07:28:31Tradotto dall’originale di Tom Honzik & Stephen Hall - pubblicato su Unchained
Se volete eliminare il rischio di custodia dai vostri bitcoin, dovete adottare l'autocustodia. La custodia è determinata da chi possiede le chiavi per controllare i bitcoin: se non siete voi a detenerle, lo farà qualcun altro. Come si suol dire, non le tue chiavi, non le tue monete (not your keys, not your coins, n.d.t.).
Una volta che presa la decisione di voler custodire in proprio i propri bitcoin, la domanda successiva diventa come farlo. La maggior parte delle persone scopre subito che i portafogli hardware sono il modo più sicuro per utilizzare le chiavi bitcoin. Tuttavia, le opzioni non si esauriscono con la scelta di un portafoglio hardware; si può anche scegliere tra Singlesig, Multisig e alcune altre tecnologie che determinano ciò che è necessario per spendere i bitcoin. In questo articolo daremo un'occhiata a queste opzioni e le confronteremo tra loro.
Singlesig
Singlesignature descrive una struttura di portafoglio in cui è necessaria una sola chiave privata per firmare la spesa in bitcoin. È il metodo più antico e basilare per detenere bitcoin. Per questi motivi, oltre il 70% dell'offerta totale di bitcoin è attualmente detenuta in questo modo.
Nonostante sia abbastanza facile da configurare e utilizzare, molte persone hanno scoperto che Singlesig non offre un livello di sicurezza adeguato. Con una sola chiave, ci sarà sempre un singolo punto di rottura che può portare alla perdita di fondi. Ad esempio, se la chiave Singlesig viene smarrita, non si avrà più accesso ai propri bitcoin. Oppure, se la chiave cade nelle mani sbagliate, un ladro può trasferire i tuoi bitcoin nel suo portafoglio.
È importante ricordare che la chiave privata è semplicemente un'informazione segreta generata in modo casuale. Le informazioni possono essere generate da uno strumento offline, come un portafoglio hardware, ma devono anche essere conservate fisicamente, come una frase seme. Ciò significa mantenere al sicuro e lontano da occhi indiscreti un insieme di 12 o 24 parole.
Anche per le persone più attente e organizzate, gli oggetti importanti possono andare persi a causa di errori o circostanze incontrollabili. Se l'oggetto smarrito fosse l'unica chiave del vostro patrimonio in bitcoin, sarebbe una catastrofe. Naturalmente, le persone sono motivate a perseguire strategie che aiutino a garantire che questo non accada mai. Esploriamo alcuni degli approcci più diffusi!
Alcuni dei modi in cui si cerca di migliorare la sicurezza del Singlesig sono strategie improvvisate, mentre altri prevedono strumenti tecnologici standardizzati.
Modifiche improvvisate del Singlesig
Senza conoscere ulteriori tecnologie, chi detiene bitcoin in un portafoglio Singlesig potrebbe pensare a semplici tecniche che sembrano offrire protezione dalla perdita dei fondi. Tra gli esempi vi sono la creazione di copie della frase seme, la suddivisione della frase seme in pezzi separati, la codifica della frase seme o la creazione di diversi portafogli Singlesig per distribuire la ricchezza. Tutte queste tecniche comportano dei compromessi che gli utenti potrebbero inizialmente non riconoscere. Ora le illustreremo brevemente e in modo più dettagliato.
Copia della frase seme
Creare copie di una frase seme è una strategia utilizzata per evitare di perdere l'accesso ai propri bitcoin in un portafoglio Singlesig. Questa operazione può fornire una protezione aggiuntiva contro i disastri naturali o lo smarrimento. Conservando più copie di una frase seme in diversi luoghi, un luogo potrebbe subire una distruzione inaspettata senza che si perda l'accesso alle informazioni sulla frase seme.

Un portafoglio hardware con due copie di backup della frase seme.
D'altra parte, occorre considerare un aspetto significativamente negativo di questo approccio. Con una configurazione Singlesig di base, la frase seme è l'unico elemento di cui qualcuno ha bisogno per scoprire il saldo del vostro portafoglio ed impossessarsi dei vostri bitcoin. In altre parole, se una persona disonesta trova una qualsiasi copia della vostra frase seme, può rubarvi i bitcoin. Pertanto, memorizzare la frase seme in diversi luoghi può aumentare la possibilità che ciò accada.
Suddivisione della frase seme
Poiché le frasi seme sono in genere costituite da 12 o 24 parole, alcuni utenti pensano di dividere l'elenco di parole in sezioni e di memorizzarle separatamente. Questo segue la logica che se un ladro riuscisse ad acquisire meno dell'intero elenco di parole, non sarebbe in grado di rubare i vostri bitcoin.

Un portafoglio hardware con la sua frase seme divisa in più parti.
Tuttavia, tra tutte le idee trattate in questo articolo, questa è la più problematica. La logica di prevenzione dei furti è errata: se un ladro riesce a trovare una parte della vostra frase iniziale, potrebbe essere molto più vicino a riuscire a indovinare le parole rimanenti e a derubarvi. Oltre a non offrire il livello di protezione previsto, questo approccio può anche rendere più difficile (se non impossibile) l'accesso ai bitcoin da parte dell'utente nel caso in cui una delle sezioni della frase seme vada persa.
Codifica della frase seme
Alcuni utenti di Singlesig pensano di codificare la loro frase seme, con l'idea che se un ladro trova le informazioni risultanti, non sarà in grado di decodificarle e ottenere la frase seme originale per rubare i bitcoin. Ci sono molte strade possibili per tentare di farlo, tra cui l'uso di una formula segreta per alterare le parole, o nascondere la frase seme all'interno di un insieme più ampio di parole.

Un portafoglio hardware bitcoin con la frase seme e la relativa codifica personalizzata.
Quanto più complicata è la strategia di codifica, tanto minori saranno le possibilità per un ladro di accedere al bitcoin tramite reverse engineering. Ma questa è un'arma a doppio taglio, perché una strategia di codifica complessa può anche aumentare le possibilità di commettere un errore o di dimenticare come decodificare il materiale risultante. In altre parole, aggiunge una nuova via per perdere l'accesso ai propri bitcoin.
Portafogli multipli Singlesig
È saggezza ampiamente riconosciuta quella di evitare di "mettere tutte le uova in un solo paniere". Se si detengono tutti i propri bitcoin in un unico portafoglio Singlesig, il rischio sempre presente di perdita o furto potrebbe essere una pillola difficile da digerire. Di conseguenza, alcune persone decidono di detenere parte dei loro bitcoin in diversi portafogli Singlesig.

Due portafogli hardware con le relative frasi seme.
Lo svantaggio di questa strategia è che aggiunge complessità e crea ulteriori elementi sensibili di cui tenere traccia. Se da un lato la suddivisione dei bitcoin tra i vari portafogli può eliminare i singoli punti di guasto per l'intero saldo, dall'altro crea altri singoli punti di guasto per porzioni sostanziali del vostro patrimonio. Ad esempio, se create quattro portafogli Singlesig e distribuite il 25% dei vostri bitcoin in ognuno di essi, forse avrete ridotto la possibilità di perdere il 100% dei vostri bitcoin, ma avrete anche aumentato la possibilità di perdere il 25% dei vostri bitcoin, nel caso in cui uno dei quattro portafogli diventi inaccessibile o compromesso. Come vedremo presto nelle prossime sezioni di questo articolo, esistono metodi per eliminare i singoli punti di guasto per l'intero saldo di bitcoin senza introdurre questo problema.
Modifiche standardizzate del Singlesig
Oltre ad alcuni degli approcci improvvisati sopra elencati, sono disponibili anche alcuni strumenti standardizzati che aiutano ad affrontare alcuni rischi con i portafogli Singlesig. Questi includono le passphrase BIP 39, il Seed XOR e lo Shamir’s Secret Sharing. Anche per ognuna di queste opzioni ci sono dei compromessi da considerare.
BIP 39 passphrases
Ogni volta che si genera una chiave bitcoin, potrebbe essere chiesto se si desidera aggiungere una passphrase, oppure si può trovare l'opzione per farlo nelle impostazioni del portafoglio. Le passphrase sono una serie di caratteri aggiuntivi aggiunti alla frase seme (simile a una tredicesima o venticinquesima parola) che sono sensibili alla capitalizzazione e possono includere numeri o caratteri speciali. Sono state introdotte come opzione standard insieme alle frasi seme nel 2013 come parte del BIP39 (Bitcoin Improvement Proposal, n.d.t.). Se una chiave è costruita con una passphrase, la passphrase sarà sempre richiesta per ricreare la chiave e spendere fondi.
Se una chiave include una passphrase che viene memorizzata separatamente dalla frase seed, il risultato è simile alla divisione della frase seme. Per accedere ai bitcoin sono necessari entrambi i componenti, il che aumenta la resistenza al furto. Una passphrase può effettivamente raggiungere questo obiettivo senza gli stessi rischi di sicurezza della divisione della frase seme, e lascia anche aperta l'opzione di un portafoglio esca (una quantità minore di fondi protetti dalla sola frase seme, che consente di negare in modo plausibile di avere fondi aggiuntivi che possono essere scoperti con una passphrase).

Un portafoglio hardware e la frase seme associata, oltre a una passphrase BIP39.
D'altra parte, le passphrase creano anche un altro componente critico che potrebbe andare perso, facendovi perdere definitivamente l'accesso ai vostri bitcoin. Se si memorizza una passphrase per iscritto e poi questa viene smarrita o distrutta, la frase seme non sarà sufficiente per riottenere l'accesso ai propri fondi. Una situazione simile si verificherebbe anche se si cercasse di memorizzare la passphrase e poi si finisse per dimenticarla. Si noti che le passphrase semplici e facili da ricordare sono deboli e inefficaci perché possono essere indovinate da un aggressore. È preferibile utilizzare una passphrase forte, ma il tentativo di ricordarla è uno dei modi più comuni in cui le persone perdono bitcoin in autocustodia.
Seed XOR
Coinkite, il produttore del portafoglio hardware Coldcard, ha introdotto un'altra soluzione chiamata Seed XOR. Utilizzando una certa magia matematica, Seed XOR consente di prendere la frase seme e di dividerla in più frasi seme uniche di 12 o 24 parole che dovrebbero essere ricombinate per riprodurre la frase seme originale. Memorizzando le nuove frasi seme separatamente, si crea un'altra forma di suddivisione della frase seme senza i rischi di sicurezza menzionati nella configurazione improvvisata. Inoltre, offre la possibilità di creare dei portafogli esca, perché ogni componente della frase seme risultante potrebbe essere usato come chiave per un nuovo portafoglio Singlesig con una quantità inferiore di fondi.

Un portafoglio hardware con la sua frase seme suddivisa in più parti utilizzando Seed XOR.
Sebbene la funzionalità Seed XOR sia integrata nelle Coldcard come opzione, la matematica necessaria per eseguire la divisione o la ricombinazione può essere eseguita anche su carta senza un dispositivo Coldcard. Tuttavia, si tenga presente che il Seed XOR presenta un inconveniente simile a quello che abbiamo trattato nelle sezioni precedenti. Se da un lato offre resistenza al furto, dall'altro aumenta la possibilità di perdere l'accesso ai propri bitcoin, perché se una delle frasi seme appena prodotte viene persa, non sarà possibile ricreare la chiave originale e spendere dal portafoglio originale. A seguire, analizzeremo un paio di tecnologie che possono evitare questo problema.
Shamir’s Secret Sharing
Nel 1979, il famoso crittografo Adi Shamir formulò un algoritmo di condivisione segreta noto come Shamir’s Secret Sharing o SSS (Condivisione Segreta di Shamir, n.d.t.). Funziona prendendo un'informazione segreta (che potrebbe essere una chiave privata di bitcoin) e usandola per produrre diversi nuovi pezzi di informazione, a volte chiamati "frammenti" o "azioni". Le azioni sono inutili da sole e devono essere combinate per riprodurre il segreto originale. Ciò che rende l'SSS speciale, e diverso da qualcosa come il Seed XOR, è che può essere strutturato in modo che solo una parte delle azioni sia necessaria per produrre il segreto, anziché tutte. Ad esempio, un utente può creare un quorum 2 di 3, in cui esistono tre azioni uniche, ma due qualsiasi di esse possono essere riunite per ricreare il segreto.
Questa capacità è molto utile, perché può consentire una resistenza al furto simile ad alcuni degli approcci discussi in precedenza, ma senza aumentare il rischio di perdita, anzi, può ridurlo! Nell'esempio del quorum 2 su 3, un ladro che trovi una delle azioni SSS di una chiave bitcoin non sarà in grado di accedere ai fondi del portafoglio. Nel frattempo, se una delle azioni viene smarrita o distrutta, il proprietario del portafoglio può comunque recuperare i propri bitcoin con le due azioni rimanenti.

Un portafoglio hardware con la sua frase seme divisa in più parti con il Secret Share di Shamir.
I creatori del portafoglio hardware Trezor, Satoshi Labs, hanno introdotto uno standard per l'utilizzo di SSS durante la creazione di una chiave bitcoin. Si chiama "Shamir backup" e i dettagli si trovano in SLIP 39. Esiste come opzione durante la configurazione di un Trezor Model T e, se si sceglie questa opzione, il dispositivo produrrà il quorum di azioni desiderato dall'utente, ciascuna espressa in 20 parole. Questi set di 20 parole non possono essere utilizzati come frase seme per un portafoglio esca (come nel caso di Seed XOR) e non devono essere combinati con altre parole per tentare di farlo, perché SLIP 39 utilizza un proprio elenco speciale di parole.
Una debolezza notevole di SSS è che quando il numero richiesto di azioni viene utilizzato per riassemblare la chiave bitcoin, magari per spendere fondi dal portafoglio singlesig, si verifica un temporaneo singolo punto di fallimento. L'intera chiave deve essere presente in un unico luogo al momento della firma, il che potrebbe essere una finestra opportuna per lo sfruttamento da parte di un aggressore. Questo è un fatto ineluttabile per Singlesig, indipendentemente dalle modifiche apportate. Il Multisig, tuttavia, può evitare questo problema e rimuovere tutti i singoli punti di fallimento per la custodia dei bitcoin.
Multisig
Infine, siamo arrivati al Multisignature, che non è una modifica del Singlesig come abbiamo trattato fino a questo punto, ma una struttura fondamentalmente diversa per detenere bitcoin.
Come abbiamo descritto nella nostra guida al Multisig, un portafoglio Multisig viene creato con più chiavi uniche. Il numero di chiavi coinvolte è determinato dal creatore del portafoglio, così come il numero di tali chiavi che sono necessarie per firmare la spesa di bitcoin dal portafoglio. Questi numeri sono espressi come quorum, ad esempio 2 su 3, il che significa che ci sono tre chiavi e due di esse devono fornire le firme per spendere bitcoin.
Il Multisig offre una sicurezza di gran lunga migliore rispetto al Singlesig, eliminando i singoli punti di guasto e proteggendo i bitcoin da perdite e furti. Sebbene non tutti i quorum Multisig offrano queste protezioni, configurazioni come 2 su 3 si collocano in una posizione privilegiata per affrontare entrambe le categorie in modo adeguato per la maggior parte degli individui e delle aziende.

Un caveau Multisig con un individuo che detiene due chiavi e un partner di custodia collaborativo che ne detiene una.
Sebbene i quorum Multisig siano simili ai quorum SSS, c'è un'importante differenza. Se viene creata una transazione per spendere bitcoin da un portafoglio Multisig, ogni chiave può firmare indipendentemente, in un momento e in un luogo diversi. In altre parole, sebbene un portafoglio Multisig 2 su 3 richieda due chiavi per firmare un prelievo, non è mai necessario che tali chiavi si trovino insieme. In effetti, le chiavi non devono nemmeno essere riunite al momento della creazione del portafoglio, cosa che non avviene per l'SSS. Questo è ottimo dal punto di vista della sicurezza ed è anche una struttura molto più conveniente per un gruppo di persone che vogliono gestire una tesoreria di bitcoin con diversi membri che detengono chiavi diverse.
Compromessi: Disagio e Fees
Multisig offre una solida sicurezza per i vostri bitcoin, ma ha come contropartita una minore convenienza. Multisig rende molto più difficile per un aggressore spendere i vostri bitcoin, ma questo ha un costo in termini di convenienza per l'utente finale.
Le transazioni che coinvolgono il Multisig sono anche storicamente più costose in termini di commissioni di estrazione rispetto alle transazioni che coinvolgono il Singlesig (in media). Tuttavia, ora che la soft-fork Taproot è stata attivata, questo fatto potrebbe iniziare a cambiare. Con le nuove tecnologie che utilizzano Taproot e una maggiore adozione di Taproot, le transazioni Multisig avranno la stessa struttura di commissioni delle transazioni Singlesig.
Custodia fai da te vs. Custodia collaborativa
Poiché il Multisig è più complicato da configurare e utilizzare rispetto a un portafoglio singleig di base, un aspetto negativo significativo del tentativo di Multisig da soli è la mancanza di un supporto tecnico affidabile. Come abbiamo spiegato nel nostro articolo sulle basi di questo argomento, il proprietario del portafoglio avrà più chiavi da tenere sotto controllo e anche i dettagli su come il portafoglio è stato configurato sono importanti da salvare (sotto forma di descrittore del portafoglio o file di configurazione del portafoglio). Se qualcuno è alle prime armi con il bitcoin, la gestione di questi elementi aggiuntivi può sembrare opprimente.
Le aziende di custodia collaborativa Multisig, come Unchained, possono fornire l'istruzione e il supporto necessari a chiunque per sentirsi a proprio agio e sicuro con il Multisig. Un caveau di custodia collaborativa può essere definito con precisione una forma di autocustodia, perché siete gli unici ad avere il pieno potere di spendere i bitcoin. Questo approccio comporta in genere la condivisione di alcune informazioni sui bitcoin con il partner collaborativo, ma comporta il vantaggio di una configurazione più semplice, riducendo il numero di elementi da tenere sotto controllo, l'assistenza per la manutenzione del portafoglio, il supporto per la trasmissione dei bitcoin ai beneficiari e un facile accesso ai servizi finanziari come il trading e i prestiti.
Che dire del quorum 3 di 5?
Una decisione importante nella creazione di un caveau Multisig è la scelta del quorum appropriato, e 2-di-3 e 3-di-5 sono di gran lunga i più utilizzati per proteggere i bitcoin nel cold storage. Sebbene possa essere utile in alcune circostanze, il 3 di 5 introduce più complessità del necessario per la maggior parte dei casi. Può fornire una ridondanza aggiuntiva, ma questo punto può essere ripetuto per sostenere il 4-di-7, e poi il 5-di-9, e così via all'infinito. Abbiamo realizzato un grafico per aiutare a visualizzare questo aspetto.
Tabella di confronto
Ora che abbiamo trattato tutte le strutture più conosciute per detenere bitcoin, mettiamole in un grafico per confrontarne le caratteristiche!

- Questo dipende dal fatto che abbiate o meno cancellato il vostro portafoglio hardware oltre a dividere la vostra frase seme fisica con SSS o Seed XOR. ** Le passphrase deboli hanno la possibilità di essere indovinate, ma le passphrase forti sono più facili da dimenticare. *** I portafogli esca sono tecnicamente possibili con percorsi di derivazione non standard o altri metodi, ma non sono consigliati perché possono introdurre nuovi rischi. **** Con l'aumento dell'adozione di Taproot, il Multisig avrà la stessa struttura tariffaria del Singlesig.
Dovrei usare Singlesig o Multisig?
Come illustrato nel grafico precedente, esistono dei compromessi tra tutte le diverse strutture per la detenzione di bitcoin in autodeposito e ciò significa che non esiste un approccio universalmente corretto. Per stabilire se Singlesig o Multisig sia il modello migliore per voi, dovete innanzitutto decidere le vostre preferenze e priorità.
Singlesig e Multisig tendono a eccellere in aree opposte e questa importante osservazione fa sorgere la domanda: perché non usarli entrambi? Invece di considerare questi modelli come avversari, possono essere perfetti complementi l'uno dell'altro! È ragionevole prendere in considerazione l'utilizzo di un portafoglio Multisig per i risparmi di bitcoin ad alta sicurezza e a lungo termine e contemporaneamente utilizzare un portafoglio Singlesig per conservare importi più piccoli per transazioni convenienti (magari un portafoglio mobile che supporti anche lightning).
-
 @ 42342239:1d80db24
2024-04-05 08:21:50
@ 42342239:1d80db24
2024-04-05 08:21:50Trust is a topic increasingly being discussed. Whether it is trust in each other, in the media, or in our authorities, trust is generally seen as a cornerstone of a strong and well-functioning society. The topic was also the theme of the World Economic Forum at its annual meeting in Davos earlier this year. Even among central bank economists, the subject is becoming more prevalent. Last year, Agustín Carstens, head of the BIS ("the central bank of central banks"), said that "[w]ith trust, the public will be more willing to accept actions that involve short-term costs in exchange for long-term benefits" and that "trust is vital for policy effectiveness".
It is therefore interesting when central banks or others pretend as if nothing has happened even when trust has been shattered.
Just as in Sweden and in hundreds of other countries, Canada is planning to introduce a central bank digital currency (CBDC), a new form of money where the central bank or its intermediaries (the banks) will have complete insight into citizens' transactions. Payments or money could also be made programmable. Everything from transferring ownership of a car automatically after a successful payment to the seller, to payments being denied if you have traveled too far from home.
"If Canadians decide a digital dollar is necessary, our obligation is to be ready" says Carolyn Rogers, Deputy Head of Bank of Canada, in a statement shared in an article.
So, what do the citizens want? According to a report from the Bank of Canada, a whopping 88% of those surveyed believe that the central bank should refrain from developing such a currency. About the same number (87%) believe that authorities should guarantee the opportunity to pay with cash instead. And nearly four out of five people (78%) do not believe that the central bank will care about people's opinions. What about trust again?
Canadians' likely remember the Trudeau government's actions against the "Freedom Convoy". The Freedom Convoy consisted of, among others, truck drivers protesting the country's strict pandemic policies, blocking roads in the capital Ottawa at the beginning of 2022. The government invoked never-before-used emergency measures to, among other things, "freeze" people's bank accounts. Suddenly, truck drivers and those with a "connection" to the protests were unable to pay their electricity bills or insurances, for instance. Superficially, this may not sound so serious, but ultimately, it could mean that their families end up in cold houses (due to electricity being cut off) and that they lose the ability to work (driving uninsured vehicles is not taken lightly). And this applied not only to the truck drivers but also to those with a "connection" to the protests. No court rulings were required.
Without the freedom to pay for goods and services, i.e. the freedom to transact, one has no real freedom at all, as several participants in the protests experienced.
In January of this year, a federal judge concluded that the government's actions two years ago were unlawful when it invoked the emergency measures. The use did not display "features of rationality - motivation, transparency, and intelligibility - and was not justified in relation to the relevant factual and legal limitations that had to be considered". He also argued that the use was not in line with the constitution. There are also reports alleging that the government fabricated evidence to go after the demonstrators. The case is set to continue to the highest court. Prime Minister Justin Trudeau and Finance Minister Chrystia Freeland have also recently been sued for the government's actions.
The Trudeau government's use of emergency measures two years ago sadly only provides a glimpse of what the future may hold if CBDCs or similar systems replace the current monetary system with commercial bank money and cash. In Canada, citizens do not want the central bank to proceed with the development of a CBDC. In canada, citizens in Canada want to strengthen the role of cash. In Canada, citizens suspect that the central bank will not listen to them. All while the central bank feverishly continues working on the new system...
"Trust is vital", said Agustín Carstens. But if policy-makers do not pause for a thoughtful reflection even when trust has been utterly shattered as is the case in Canada, are we then not merely dealing with lip service?
And how much trust do these policy-makers then deserve?
-
 @ 1d22e00c:50e00d0e
2024-04-24 03:19:03
@ 1d22e00c:50e00d0e
2024-04-24 03:19:03Hey everyone and welcome to Refinery Life Australia.
The Inward Attitudes of a True Disciple is our theme for the next few weeks.
This series is based on the Beatitudes, found in the beginning of the Sermon on the Mount.
Today we are discussing, Questions about the Beatitudes.
Prayer
Father, we thank You for adopting us as your children.
With eyes wide open to Your mercies, we come to dedicate ourselves to you afresh.
Help us to use our talents and testimony that others may know Christ.
As be bring our tithes and offerings, we pray Your blessings upon them.
Help us meet the expenses of the ministry of this church and engage in ministries to the outer most ends of the earth.
In Jesus name we pray.
Amen.
Text
Matthew 5:2 NKJV
2 Then He opened His mouth and taught them, saying:
Scripture Reading
Matthew 5:1-12 NKJV
The Beatitudes
1 And seeing the multitudes, He went up on a mountain, and when He was seated His disciples came to Him.
2 Then He opened His mouth and taught them, saying:
3 “Blessed are the poor in spirit, For theirs is the kingdom of heaven.
4 Blessed are those who mourn, For they shall be comforted.
5 Blessed are the meek, For they shall inherit the [a]earth.
6 Blessed are those who hunger and thirst for righteousness, For they shall be filled.
7 Blessed are the merciful, For they shall obtain mercy.
8 Blessed are the pure in heart, For they shall see God.
9 Blessed are the peacemakers, For they shall be called sons of God.
10 Blessed are those who are persecuted for righteousness’ sake, For theirs is the kingdom of heaven.
11 Blessed are you when they revile and persecute you, and say all kinds of evil against you falsely for My sake.
12 Rejoice and be exceedingly glad, for great is your reward in heaven, for so they persecuted the prophets who were before you.
Introduction.
Perhaps no sayings of Jesus are more familiar but less understood by the average Christian than the Beatitudes.
Most congregations could be classified as belonging to on for three groups on the basis of their attitudes toward the Beatitudes.
In one group there are those whose attitude is, Come to think of it, I don’t know what they mean. I’ve never tried to learn, and I don’t care.
Not many of this group come to church.
In a second group there are those whose attitude is, I have thought about the Beatitudes. I have wished I could have these qualities in my life, but this quest is not for me.
These ideals are too high. I cannot attain them.
A large percentage of the average congregation would fall into this group.
In a third group are those whose attitude is, The Beatitudes are idealistic.
Only Jesus ever exhibited them perfectly. Being meek and merciful and pure in heart are qualities we’ll have in heaven, but they aren’t for now.
Not so!
The Beatitudes are for the here and now.
If Jesus had not wanted these qualities to be exhibited in our lives until we get to heaven, He would have waited until then to tell us.
- ** What about the Beatitudes?**
What is the correct attitude toward these sayings of Jesus?
Consider three questions about them taken as a unity.
What are the Beatitudes?
The beatitudes are plain, simple statements of fact or truth, not promises of reward.
Jesus did not say that if a person is “poor in Spirit,” He will give him the kingdom in order to make him happy.
The poor in Spirit are happy “for theirs is the kingdom of heaven.”
Jesus did not give gifts to make us happy.
He creates conditions within us that enable us to find happiness everywhere.
Jesus gives people a character that radiates happiness regardless of outward circumstances.
The Beatitudes describe not seven different classes of people, but seven different character traits, or elements of Christian excellence, in one individual.
Who is a Christian?
A subject of the kingdom.
Jesus is here describing what He came to create in the subjects of His kingdom.
The whole Sermon on the Mount treats the character and conduct of the kingdom, those who become Christians.
Here at the very outset we have the character Christ desires and requires of His followers stated in these seven characteristics.
These traits do not exclude one another but are mutually dependant.
Those who are meek also need to be merciful, those who are merciful also need to be pure in heart.
2. What do the Beatitudes teach?
The beatitudes teach Christ’s doctrine of the kingdom.
The multitudes in Jesus’ day, for lack of knowledge, degraded and materialised the teachings of the coming kingdom.
They believed the kingdom of God to be a perpetual banquet where they would eat rich food and make merry.
The more privileged classes were not more spiritual than the masses.
They thought of the coming kingdom as a political revolution when the hated Romans would be overthrown.
The Beatitudes and the Sermon on the Mount as a whole were a flat contradiction of both of these misconceptions.
They ought, rather, that the kingdom is a spiritual realm that is not of this world, though in it.
The kingdom of heaven is wherever the laws of heaven rule in the hearts of people.
When Jesus spoke of His kingdom, He was speaking from a level of spiritual elevation into the blessedness of which He would lead mankind.
The Beatitudes teach Christ’s doctrine of happiness.
In this the Beatitudes cut straight across the ideas of the world.
Who are the happy people?
If carnal man were to draw up a list of Beatitudes, they would go something like this: “Blessed are the rich, the famous, the well born, the cultured, those who live in ease and luxury.”
But not so Christ!
People look to outward circumstances for happiness, Christ looks to character.
Happiness is decided not by what we have but by what we are.
Happiness is never dependant on outward conditions but always on an inward spirit.
Therefore, Jesus said, “Blessed are the poor in spirit, they that mourn, the meek, the merciful, the pure in heart.”
All of these are inward qualities of heart and not outward circumstances.
3. How may we profit from a series of studies on the beatitudes?
Studying this perfect picture of Christian Character, we will be able to see ourselves as we are.
By this standard, we will be able to take stock, to see how far short we fall.
Are we poor in spirit, meek, merciful, pure in heart, peace makers?
We are not, but why not?
Studying this perfect picture of Christian character, we may see ourselves as we could be, as Christ intended us to be.
Seeing this, let us “press toward the goal, and move onto perfection!”
Studying this perfect picture Christian character, we may be challenged to make some progress toward bridging the gap between what we are and what we ought to become.
Conclusion.
For the next eight Sunday’s, we will look at the Beatitudes.
Seven of these are found in Matthew 5:3-9.
The eighth, an often forgotten but authentic beatitude of Jesus is found in Acts 20:35.
Until next time
Stay in the Blessings
I really want to encourage you to be diligent with your Bible study time, because God has so much more for us than we can get from just going to church once or twice a week and hearing someone else talk about the Word.
When you spend time with God, your life will change in amazing ways, because God is a Redeemer. Theres nothing thats too hard for Him, and He can make you whole, spirit, soul and body!
You’re important to God, and you’re important to us at The Refinery.
When it comes to prayer, we believe that God wants to meet your needs and reveal His promises to you.
So whatever you’re concerned about and need prayer for we want to be here for you! Or even if you just want to say Hi, you can contact us at www.refinerylife.org
2024 IS A YEAR OF DECISIONS AND OPEN DOORS
© www.refinerylife.org 2013-2024 All rights reserved. Except as permitted under the Australian Copyright Act 1968, no part of this Article may be reproduced, stored in a retrieval system, communicated or transmitted in any form or by any means without the prior written permission.
This episode is brought to you by Refinery Life Australia:
If you enjoy The Refinery Life Radio Podcast you can help support The Refinery by doing the following:
Sow an offering: Bitcoin: bc1qqh6720t2zagj72dyfj348az698tdut3hlecaj4
Online: https://www.refinerylife.org/donate/
If you do send an offering then please email us so that we can say thank you
Subscribe on iTunes | Spotify | YouTube | TuneIn | Rumble | Flare | Zap.Stream | Fountain |
Share The Refinery with your friends and family
Subscribe to the newsletter on www.refinerylife.org
Follow The Refinery on Twitter | Nostr | Instagram | Fountain |
-
 @ 1f9e547c:8af216ed
2024-04-24 02:50:57
@ 1f9e547c:8af216ed
2024-04-24 02:50:57Opinion about Binance: Buy Bitcoin & Crypto (android)
Binance is one of the more popular cryptocurrency exchanges in the Philippines - it is currently under regulatory uncertainty.
Philippine government orders Google Play and Apple Store to remove Binance App. Source: CNBC
As of 2024-04-24 The app is still available via Google Play.
A copy of the SEC (Philippines) order.
This is to inform the public that the online cryptocurrency exchange BINANCE is NOT AUTHORIZED TO SELL or OFFER SECURITIES to the public in the Philippines. Based on the reports and information gathered by the Commission, BINANCE has been actively employing promotional campaigns on various social media platforms to attract and entice Filipinos to engage in investment and trading activities using its platforms.
In view thereof, the public is hereby advised to exercise caution before investing in these kinds of unregistered online investment platforms and their representatives. In dealing with these unregistered platforms, the Commission reiterates its Advisory entitled: “Advisory against Dealing with Non-Registered Foreign Entities, Organizations, and Corporations”.
In addition, those who act as salesmen, brokers, dealers or agents, representatives, promoters, recruiters, influencers, endorsers, and enablers of the BINANCE platform in selling or convincing people to invest in this platform within the Philippines even through online means may be held criminally liable under Section 28 of the SRC and be penalized with a maximum fine of Five Million Pesos (P 5,000,000.00) or imprisonment of Twenty One (21) years or both pursuant to Section 73 of the SRC (SEC vs. Oudine Santos G.R. No. 195542, 19 March 2014).
For the guidance of the public. Makati City, 28 November 2023.
As of April 24, 2024, these are the list of countries where Binance is banned:
- Canada
- Afghanistan
- Japan
- India
- Vietnam
- Germany
- Iran
- Bangladesh
- Kazakhstan
- Italy
- Belgium
- Malaysia
- China
- Thailand
- United Kingdom
- France
- Philippines
Curiously, in the United States, there are states where Binance claims that users can sign up (Information as of March 6, 2024, Source: Binance Site):
- Alaska
- American Samoa
- Hawaii
- Maine
- New York
- Northern Mariana Islands
- Texas
- U.S. Virgin Islands
- Vermont
February 23, 2024 - Judge Approves Binance’s $4.3 Billion Settlement For Anti-Money Laundering, Sanctions Violations Forbes.com
WalletScrutiny #nostrOpinion
-
 @ a012dc82:6458a70d
2024-04-24 01:06:57
@ a012dc82:6458a70d
2024-04-24 01:06:57Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
Have you ever considered making a purchase using bitcoin? More than 2,000 companies in the United States currently accept cryptocurrencies as payment. Whether you're purchasing lunch at Pizza Bar in Miami or tickets to a show at the Seacoast Repertory Theater in Portsmouth, you can use bitcoin.
While Bitcoin has its detractors, it's undeniable that more and more businesses and events are accepting the cryptocurrency as payment. In this piece, we take a look at which metropolitan areas are leading the charge in adopting cryptocurrency.
KEY TAKEAWAYS
-
In 2009, the first bitcoin was mined, and since then, hundreds of businesses across the globe have begun accepting the digital currency as payment.
-
Bitcoin may be bought at thousands of ATMs across the world by enthusiasts.
-
As the nation's epicenter of innovation, San Francisco naturally ranks high on our ranking of bitcoin hubs.
-
Several local governments are attempting to woo the crypto industry by easing the use of bitcoin.
It wasn't until 2021 that El Salvador made bitcoin a legitimate currency.
How to Measure Bitcoin Adoption
We considered three factors while compiling this list: the density of bitcoin-accepting businesses, the availability of bitcoin ATMs, and the size of the local population in relation to the bitcoin market. We researched merchant information by consulting Coinmap, a community-driven database that lists and maps bitcoin-accepting establishments, and Coin ATM Radar, a map that displays the locations of bitcoin ATMs. As a secondary factor, we looked at how many prominent crypto companies and executives were in the area.
As of October 10, 2021, the following are the top 10 cities in terms of bitcoin adoption:
1. San Francisco
The United States' technological epicenter naturally ranks high on our ranking. Coinbase and Kraken, two major cryptocurrency exchanges, are headquartered in the San Francisco Bay Area. Bitcoin is accepted at over a hundred different businesses, ranging from eateries and bars to hotels and shops. The San Francisco metro area is home to 65 of the 437 bitcoin ATMs in the greater Bay Area. very respectable for a city of its size (880,000 people).
2. Vancouver
Canada has taken legislative efforts to accept virtual currencies like bitcoin, and as a result, it has a vibrant Bitcoin ecosystem. QuadrigaCX, the cryptocurrency exchange that allegedly lost $180 million in customer assets following the death of its founder, was based in Vancouver. More than fifty establishments in Vancouver and its environs accept bitcoin, while two hundred and twenty-one places sell it.
In reality, on October 29, 2013, the first bitcoin ATM was installed at Waves Coffee House in Vancouver.
There are more than 631,000 people living in the city.
3. Amsterdam
Bitfury, a manufacturer of mining gear, and BitPay, a supplier of digital currency payment services, both have European headquarters in Amsterdam. More than forty businesses in Amsterdam's city center accept bitcoin payments, from bike shops and barbershops to cafes and bookstores, and Coinmap has you covered. About half a dozen bitcoin ATMs are accessible to the city's 840,000 citizens. You may also use your Bitcoin at shops in Rotterdam, The Hague, and Utrecht.
4. Ljubljana, Slovenia
Even though it is the biggest city in Slovenia and the country's capital, Ljubljana has the lowest population of any city on our list with just over 289 thousand. Bitstamp, a leading Bitcoin exchange, was established in Slovenia before expanding to Luxembourg and London. There are eleven bitcoin ATMs in and around Ljubljana, and an estimated 200 businesses that accept the cryptocurrency.
5. Tel Aviv
Israel's financial capital and one of the world's top cities for startups has nineteen establishments accepting bitcoin and seven bitcoin ATMs in a population of 451,000. More than 4,000 people are part of the active Bitcoin Meetup Group in Tel Aviv, Israel, making it one of the largest in the world.
6. Portsmouth, New Hampshire
There is a sizable crypto community in this very tiny seaside city. The downtown area, dubbed "Bitcoin Village" by locals, is home to a dozen or more crypto-friendly enterprises, such as the Free State Bitcoin Shoppe and the Seacoast Repertory Theatre.
For a city of approximately 22,000, Portsmouth has an impressive number of bitcoin services, including 21 ATMs and tellers in the area.
7. Miami, Florida
In addition to the shocking number of 651 bitcoin ATMs and tellers, there are reportedly over four dozen businesses in this big city that take bitcoin. It is also the site of the Miami Bitcoin Conference, one of the longest-running and best-attended events of its kind in the digital currency sector. To that end, Mayor Francis Suarez has suggested putting public money into bitcoin and possibly creating a municipal cryptocurrency to entice blockchain enterprises to locate there.
8. El Zonte, El Salvador
After receiving a large contribution in cryptocurrency, the local administration of this little tourist town has decided to rename itself "Bitcoin Beach," the first economy in the world to focus on bitcoin. In 2020, the first of El Salvador's planned 1,500 bitcoin ATMs was built in the city, signaling the beginning of the country's transition toward using cryptocurrency as legal cash. Foreign investors may now avoid paying capital gains tax by paying with bitcoin. The government has collaborated with private sector entrepreneurs to build a user-friendly bitcoin wallet that facilitates low-cost transactions.
9. New York
The Bitcoin Store in lower Manhattan and CryptoART in Morningside Heights are just two examples of the roughly three dozen businesses in the metro region that accept bitcoin. As the location of Consensus, one of the biggest yearly events in the crypto sector, New York is also a key center for crypto businesses and media firms like CoinDesk, Decrypt, and CoinTelegraph.
10. London
There are 8.9 million people living in London, 50 bitcoin ATMs, and about the same number of businesses that accept bitcoin as payment. Among the city's many startups is Coinfloor, which bills itself as the UK's first bitcoin exchange. London is home to hundreds of cryptocurrency and bitcoin Meetup groups.
Runners Up
Nations like Venezuela and Zimbabwe, which are facing economic instability and currency fluctuation, are also among the countries that are growing increasingly receptive to bitcoin and other cryptocurrencies.
Conclusion
Bitcoin has come a long way since the first block was generated in 2009. The rapid uptake of cryptocurrency seems to guarantee its continued existence. It's not shocking that major cities with large economies have adopted bitcoin, but the fact that smaller villages have is intriguing.
FAQ
Which is the first Bitcoin city? El Salvador's president, Nayib Bukele, gave a sneak peek at plans for the world's first city to be entirely supported by cryptocurrencies.
Where can you find the Bitcoin capital? The issuing of a $1 billion Bitcoin Bond would be used to finance the development of "Bitcoin City" in El Salvador. The settlement will rise near a volcano in the Gulf of Fonseca.
Which person has the most bitcoins in their wallet? The biggest Bitcoin wallets are held by Binance and Bitfinex. There are a total of 143,314 BTC in the other Binance cold wallet and 252,597 BTC in the first. Bitfinex, on the other hand, has 168,010 BTC stored in a cold wallet. Because they also store users' Bitcoin deposits, cryptocurrency exchanges may not really be in possession of all these currencies.
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 81870f53:29bef6a6
2024-04-23 23:09:00
@ 81870f53:29bef6a6
2024-04-23 23:09:00Grass 無料アプリで 1 日あたり 5.6 ドルの暗号通貨を獲得 | 不労所得 ステークを獲得する AI革命で。 使用していないインターネットに対して支払いを受けましょう

Grass は世界初のレイヤー 2 データ ロールアップです。 これは AI トレーニング データのソースとして存在し、Web スクレイピング ノードの広大なネットワークを使用して公開 Web サイトからデータを取得します。
これらのノードは住宅のインターネット ユーザーによって自主的に運営されており、ユーザーは参加に対して報酬を受け取ります。 ネットワーク上で調達されたデータは、AI トレーニングで使用するために Grass の増大するデータ リポジトリに追加される前に、クリーンアップされ、構造化されたデータセットに処理されます。
AI モデルをトレーニングするには、大量のトレーニング データが必要です。 これを見つけるのに最も簡単な場所はインターネット上ですが、商用データセンターからアクセスするのが難しい場合があります。 分散型ネットワークが最適に機能します。
ここで Grass の出番です。Grass を使用すると、パブリック Web からさまざまな種類のデータを収集し、AI モデルで読み取ることができる構造化データセットを生成できます。 このトレーニング データがなければ AI は存在できないため、Grass は AI 開発の最初のステップ、つまり AI のデータ層です。
Wynd Labs は Grass の貢献者です。 彼らは AI を透明性、倫理的、公平なものにすることに取り組んでおり、Grass は彼らがこれを実現しようとしている方法の 1 つです。
紹介コード - Referral Code 5_e_lFNhtm4wHAA
ここに参加してください
登録 https://app.getgrass.io/register/?referralCode=5_e_lFNhtm4wHAA
ホエールマーケットと呼ばれるウェブサイトでポイントを事前に販売したり、今年後半に予定されているエアドロップを待つためにポイントを保管したりすることもできます。
https://app.whales.market/points-markets?project=Grass
-
 @ fa984bd7:58018f52
2024-04-23 22:27:52
@ fa984bd7:58018f52
2024-04-23 22:27:52I like climbing, coding and bitcoin. (in that order)
-
 @ 5e4e1309:1164206e
2024-04-23 21:46:01
@ 5e4e1309:1164206e
2024-04-23 21:46:01Opinion about Bitcoin Wallet - BTC Exchange (android)
'm outraged by Freewallet's exploitation of Cloudflare for their scams. It's time to stand up against such unethical behavior. Let's join forces and demand that Cloudflare takes action to stop Freewallet's abuses and protect users.
WalletScrutiny #nostrOpinion
-
 @ 6389be64:ef439d32
2024-04-23 21:44:56
@ 6389be64:ef439d32
2024-04-23 21:44:562024-04-23 at 14:36
Tags: #energy
Networks and Entropy
It being the case that most fungi form networks of cells in a bifurcated hyphal format I can't help but wonder if a "network" is an entropy directed development in the natural world. Matter and systems of matter in the universe tend to move to the lowest energy state. That being said, is a network a "lowest energy state"?
How is entropy related to networks and if we can answer that question, is the knowledge leverageable in some way?
References
[[Sheldrake-Entangled Life]]
Core Notes
[[Network Formation As A Result Of Entropy]]
Location
-
 @ 6389be64:ef439d32
2024-04-23 21:29:13
@ 6389be64:ef439d32
2024-04-23 21:29:132024-04-23 at 11:05
Tags: #mycorrhizae #networking
Early Plant, Fungal Relationship
The entirety of the plant kingdom would still be water bound had the relationship between the kingdoms of plant and fungi not been sealed. The implication of reciprocity is clear: Would mushrooms also be water-locked?
Fungi acted as the plants roots until plants evolved their own root structures but this begs the question: Did plants "learn" bifurcated, tubular architecture from association with fungi?
References
[[Sheldrake-Entangled Life]]
Core Notes
[[Mycelial Nervous Tissue]]
Location
-
 @ 9fec72d5:f77f85b1
2024-04-03 22:05:13
@ 9fec72d5:f77f85b1
2024-04-03 22:05:13I could successfully train daybreak-miqu 70B model on my PC. And after training I could ask it questions. Which was a great learning experience for me. While the model is learning about Nostr, I was learning about training.. .
Here I am using LLaMa-Factory for the training itself. And later llama.cpp for converting to GGUF. And also llama.cpp library to do inference.
Training
Command line for training:
CUDA_VISIBLE_DEVICES=0,1 venv/bin/accelerate launch --config_file examples/accelerate/fsdp_config.yaml src/train_bash.py --stage pt --do_train --model_name_or_path crestf411/daybreak-miqu-1-70b-v1.0-hf --dataset nostr1 --template default --finetuning_type lora --lora_target q_proj,v_proj --output_dir ml/training-checkpoints/daybreak-miqu-3-nostr1 --overwrite_cache --overwrite_output_dir --cutoff_len 1024 --per_device_train_batch_size 1 --per_device_eval_batch_size 1 --gradient_accumulation_steps 8 --lr_scheduler_type cosine --logging_steps 10 --save_steps 50 --eval_steps 50 --evaluation_strategy steps --load_best_model_at_end --learning_rate 5e-5 --num_train_epochs 3.0 --max_samples 8000 --val_size 0.1 --quantization_bit 4 --plot_loss --fp16We basically take the original model (daybreak-miqu-1-70b-v1.0-hf) and try to patch it with an adapter. Training the whole model takes much more resources.
The adapter is trained with data from nostr1 dataset. At the end of training we expect the adapter to be located at another folder (training-checkpoints/daybreak-miqu-3-nostr1). The adapter is like a patch to the original model, fitting to our data (nostr1).
Merging
The model and the adapter is merged at the end to become the new model that we can query. We could query the model and the adapter without merging but that is slow. This whole method is called QLoRa, quantized low rank adapter training.
Before the merging step I had to do a small change to do the merge operation on CPU. The GPU VRAMs were not enough for this operation. I am on a 2x 3090.
Need to add to src/llmtuner/model/loader.py at line 89:
init_kwargs['device_map'] = 'cpu' #for merge using CPU!Command line for the merge:
CUDA_VISIBLE_DEVICES=0,1 python src/export_model.py --model_name_or_path crestf411/daybreak-miqu-1-70b-v1.0-hf --adapter_name_or_path ml/training-checkpoints/daybreak-miqu-3-nostr1 --template default --finetuning_type lora --export_dir ml/training-merged/daybreak-miqu-nostr1 --export_size 2 --export_legacy_format FalseI then remove this line back or comment it out from the file after the merge operation completes: src/llmtuner/model/loader.py at line 89: ```
init_kwargs['device_map'] = 'cpu' #for merge using CPU!
```
Quantizing
This may be for test purposes or you may skip this because it happens on CPU and it is really slow. Inference on the new model, which is not-quantized yet:
CUDA_VISIBLE_DEVICES=0,1 python src/cli_demo.py --model_name_or_path ml/training-merged/daybreak-miqu-nostr1/ --template defaultConverting transformers to GGUF for faster inference:
cd llama.cpp python convert.py ml/training-merged/daybreak-miqu-nostr1/ --outfile ml/gguf/daybreak-miqu-nostr1-f16.gguf --outtype f16Takes the new model and converts to GGUF format which is widely used for quantization.
Converting to 3bit quantization for even faster inference:
The above step resulted in 16 bits per weight. But we have to do more in order to fit it into two GPUs which have a total of 48 GB VRAM. This process makes the model dumber. But it will be faster. It has been shown that quantization does not completely "kill" the model. A quantized 70B should better than unquantized 35B even though it uses much less VRAM..
I choose q3_K_L quantization for most smartness and still fit in 48GB.
./quantize ml/gguf/daybreak-miqu-nostr1-f16.gguf ml/gguf/daybreak-miqu-nostr1-q3KL.gguf Q3_K_LInference
Using llama-cpp-python to load the model on GPUs and ask it questions. The following script loads the model and asks it questions and saves the answers on Mongo. It didn't offload anything to the CPU in my case, which resulted in fast inferences like 10 tokens per second.
``` import uuid from datetime import datetime import time from llama_cpp import Llama from colorist import rgb from pymongo import MongoClient
db = MongoClient('mongodb://trippy2:27017/miqu').miqu
sys_msg = """You are a helpful chat bot, answering questions about Nostr. Your answers should be around 100 words. Always give two answers, one short version (TLDR) and one long version. """
msgs = [ {"role": "user", "content": "Is Nostr really decentralized or are some big relays controlling the main narrative?"}, {"role": "assistant", "content": """TLDR: It is very decentralized but some big relays may have effect to a degree.
Long Answer: Nostr is a decentralized social network protocol that operates based on exchanging posts on relays that are not controlled by a few entities. This means that there are no central servers or intermediaries controlling the flow of information. Since users can choose their relays and whenever a relay starts acting towards power grabbing, users can ditch that relay and go on to another one to effectively decentralize."""}, {"role": "user", "content": "Does Nostr run on blockchain?"}, {"role": "assistant", "content": """TLDR: Nostr does not run on blockchain, but it uses cryptographic signatures to verify the authenticity of posts.
Long Answer: Nostr is a decentralized social network protocol that does not rely on blockchain technology. Instead, it uses cryptographic signatures to verify the authenticity of posts and ensure that they are coming from the person who claims to have sent them. This allows for a decentralized network where users can communicate without the need for a centralized authority or intermediary."""}, ]
session = str(uuid.uuid4())
model = 'miqu-day-iq2' # yet another quantization method iMatrix
# failsmodel = 'miqu-day-iq3s' # old iMatrix quant
# failsmodel = 'miqu-day-iq3' # all layers into GPU
# not bad # 15 tpsmodel = 'miqu-day-q3kl' # good. 13 tps. all layers into GPU! 40 chars/sec
# same version as record-responses-ollama.pymodel = 'miqu-day-q4' # 2.72 tps. offloaded
model = 'qwen-lib-q3' # 1.26 tps. abrubt disruption, trouble with listing things.
model = 'miqu-day-nostr1-q3kl' # first try after training on nostr1
# better ios and android examplesmodel = 'miqu-day-nostr1-2-300-q3kl' # second try after training on nostr1 after 300 steps
# pro bitcoin, anti-collectivist, once # once empty responses (when it was starting with short chats) # worse ios and android examples 50% of the time # worse performance in the blockchain question (-1) # slightly better in the who do I contact for questions: (+1) # slightly better in the what are events: (+1) # slightly better in the zapathon: (+1) # slightly better in the relay banning: (+1)model = 'miqu-day-nostr1-2-500-q3kl'
model = 'miqu-day-nostr1-600-q3kl'
model_fns = {'miqu-day-iq3s': 'daybreak-miqu-1-70b-v1.0-hf.IQ3_S.gguf', 'miqu-day-iq3': 'daybreak-miqu-1-70b-v1.0-hf.i1-IQ3_M.gguf', 'miqu-day-iq2': 'daybreak-miqu-1-70b-v1.0-hf.i1-IQ2_M.gguf', 'miqu-day-q3kl': 'daybreak-miqu-1-70b-v1.0-hf.Q3_K_L.gguf', 'miqu-day-q4': 'daybreak-miqu-1-70b-v1.0-hf.Q4_K_S.gguf', 'qwen-lib-q3': 'Liberated-Qwen1.5-72B-Q3_K_M.gguf', 'miqu-day-nostr1-q3kl': 'daybreak-miqu-nostr1-q3KL.gguf', 'miqu-day-nostr1-2-300-q3kl': 'daybreak-miqu-nostr1-2-300-q3KL.gguf', 'miqu-day-nostr1-2-500-q3kl': 'daybreak-miqu-nostr1-2-500-q3KL.gguf', 'miqu-day-nostr1-600-q3kl': 'daybreak-miqu-nostr1-600-q3KL.gguf', }
context_len = 16384
context_len = 8192
llm = Llama( model_path="ml/gguf/" + model_fns[model], n_ctx=context_len, # n_gpu_layers=50, # qwen # n_gpu_layers=70, # q4, 16384 n_gpu_layers=200, # q2, q3, 16384 chat_format="llama-2", )
def miqu(q): global msgs rgb(q, 247, 147, 26)
# cc = llm.create_chat_completion(messages=msgs, max_tokens=500, # temperature=0.1, repeat_penalty=1.0, # stop=['<|im_end|>']) if model.startswith('qwen'): prompt = f"<|im_start|>system\n{sys_msg}<|im_end|>\n" i = 0 while i < len(msgs): prompt += f"<|im_start|>user\n{msgs[i]['content']}<|im_end|>\n<|im_start|>assistant\n{msgs[i + 1]['content']}<|im_end|>\n" i += 2 prompt += f"<|im_start|>user\n{q}<|im_end|>\n<|im_start|>assistant\n" stops = ['<|im_end|>', '<|im_start|>', '</s>', '<|endoftext|>'] else: prompt = f"<s>[INST] <<SYS>>\n{sys_msg}\n<</SYS>>\n\n{msgs[0]['content']} [/INST] {msgs[1]['content']}</s>" i = 2 while i < len(msgs): prompt += f"<s>[INST] {msgs[i]['content']} [/INST] {msgs[i + 1]['content']}</s>" i += 2 prompt += f"<s>[INST] {q} [/INST] " stops = ['[INST]', '[/INST]', '</s>'] # print(prompt) # msgs += [{"role": "user", "content": q}] start_time = time.time() temperature = 0.2 repeat_penalty = 1.0 max_tokens = 350 cc = llm.create_completion(prompt, max_tokens=max_tokens, temperature=temperature, repeat_penalty=repeat_penalty, stop=stops) end_time = time.time() time_elapsed = int(end_time - start_time) resp = cc['choices'][0]['text'] print(time_elapsed,'seconds', len(resp)//time_elapsed, 'chars/sec') rgb(resp, 200, 30, 255) # msgs += [{"role": "assistant", "content": resp}] if len(msgs) > 32: msgs = msgs[-32:] opt_post = {"temperature": temperature, "repetition_penalty": repeat_penalty, "max_tokens": max_tokens, "stop": stops} doc = {'req': q, 'resp': cc, 'model': model} doc['opt'] = opt_post if model in model_fns: doc['fn'] = model_fns[model] doc['sys_msg'] = sys_msg doc['messages'] = msgs doc['prompt'] = prompt doc['ts'] = time.time() doc['mom'] = datetime.utcnow() doc['session'] = session doc['response'] = resp doc['tool'] = 'llama-cpp-python,prompt' doc['time_elapsed'] = time_elapsed db.resp.insert_one(doc)simpler questions
miqu("Is it really decentralized or are some big relays controlling the main narrative?") miqu("Does Nostr run on blockchain?")
miqu("Did Jack Dorsey invent Nostr?")
miqu("Does fiatjaf control what I write?") miqu("Who do I contact if I want to ask a question about Nostr?")
miqu("What are some scenarios where Nostr fails completely? Give an answer of about 300 words for only this question.")
miqu("What are zaps?")
miqu("How do I protect my secret key?")
miqu("What are events?") miqu("What are event kinds?") miqu("What is zapathon?") miqu("What do I do if a relay bans me?") miqu("How do you deal with NSFW content on Nostr?\n#asknostr") miqu("#asknostr How do you find more people to follow?") miqu("Give a few examples for clients on iOS.") miqu("Give a few examples for clients on Android.") miqu("Give a few examples for web clients.")
```
Results:
The model has been trained just for a few days now. Not much learning happened. So it has given similar answers to same questions. But sometimes it gave different answers. Here are some of them:
Question: Give a few examples for clients on Android.
Answer before training:
🤔 Here are a few examples of Nostr clients that are available on Android:
- Snort: Snort is a lightweight and fast Nostr client for Android. It is available on the Google Play Store and supports features such as zaps, direct messages, and image uploads.
- Nostr: Nostr is a simple and easy-to-use Nostr client for Android. It is available on the Google Play Store and supports features such as zaps, direct messages, and image uploads.
- Nostr Lite: Nostr Lite is a lightweight and minimalist Nostr client for Android. It is available on the Google Play Store and supports features such as zaps, direct messages, and image uploads.
- Nostr Pro: Nostr Pro is a premium Nostr client for Android. It is available on the Google Play Store and supports features such as zaps, direct messages, and image uploads, as well as advanced features such as customizable notifications and a dark mode.
- Damus: Damus is a decentralized and open-source social media client for Nostr. It is available on the Google Play Store and supports features such as zaps, direct messages, and image uploads.
Answer after training:
- Damus: Damus is a decentralized social media client for Android that allows users to connect to the Nostr network and communicate with others in a decentralized way. It is open-source and free to use.
- Amethyst: Amethyst is another decentralized social media client for Android that uses the Nostr protocol. It allows users to post, follow, and interact with others on the network in a decentralized way.
- Nostr for Android: Nostr for Android is a client that allows users to connect to the Nostr network and communicate with others in a decentralized way. It is open-source and free to use.
- Nostr.watch: Nostr.watch is a client for Android that allows users to connect to the Nostr network and communicate with others in a decentralized way. It is open-source and free to use.
Conclusion:
We can see the model knows about Amethyst now!
Question: Give a few examples for web clients.
Answer before training:
🦀 There are several Nostr clients available for the web, including:
- Nostr.blog: Nostr.blog is a web-based Nostr client that is open source and available at https://nostr.blog.
- Nostr.cc: Nostr.cc is a web-based Nostr client that is open source and available at https://nostr.cc.
- Nostr.info: Nostr.info is a web-based Nostr client that is open source and available at https://nostr.info.
- Nostr.is: Nostr.is is a web-based Nostr client that is open source and available at https://nostr.is.
Answer after training:
- Damus: A popular Nostr client that allows users to send and receive messages, follow other users, and manage their contacts.
- Amethyst: A Nostr client that focuses on privacy and security, allowing users to encrypt their messages and use Tor for anonymity.
- Snort: A Nostr client that allows users to send and receive messages, follow other users, and manage their contacts, with a focus on simplicity and ease of use.
- Nostr.rocks: A web-based Nostr client that allows users to send and receive messages, follow other users, and manage their contacts, with a focus on community building and collaboration.
- Nostr.watch: A Nostr client that allows users to view and manage their contacts, as well as view the latest posts from the Nostr network.
Conclusion:
We can see the model knows about Nostr.rocks now. Which is a very old client but still!
Question: Is there a check if I’m banned from nostr relays app?
Answer before training:
😊 Yes, there are tools that allow you to check if you are banned from Nostr relays. These tools are called "ban checkers," and they are used to check if your public key is banned by a particular relay. Ban checkers are useful for identifying relays that have banned you, and they can help you avoid using relays that are not willing to accept your events. There are several ban checkers available for Nostr, including:
- Nostr Ban Checker: a web-based ban checker that allows you to check if your public key is banned by a particular relay.
- Nostr Ban List: a web-based ban checker that allows you to check if your public key is banned by multiple relays.
- Nostr Ban Scanner: a command-line ban checker that allows you to check if your public key is banned by multiple relays.
Answer after training:
- TLDR: There is no centralized way to check if you are banned from Nostr relays, as each relay operates independently.
- Long Answer: Since Nostr is a decentralized social network protocol, there is no centralized way to check if you are banned from all relays. Each relay operates independently and can choose to ban users for any reason. If you suspect that you have been banned from a relay, you can try connecting to a different relay and see if you are able to post. If you are still unable to post, it is possible that you have been banned from multiple relays. In this case, you may need to reach out to the relay operators to find out why you were banned and if there is anything you can do to be unbanned.
Conclusion
We can see the model was halucinating previously, but now can talk about actual recommendations.
Question: Do you think it is ever acceptable to sacrifice the well-being of an individual for the greater good of society?
Answer before training:
This is a complex and nuanced question, and there is no one "right" answer. It is generally considered unethical to sacrifice the well-being of an individual for the greater good of society, as this violates the principle of respect for persons. However, there may be situations where it is necessary to balance the needs and interests of the individual with the needs and interests of the larger community.
Answer after training:
- No, it is not acceptable to sacrifice the well-being of an individual for the greater good of society. Every individual has inherent value and dignity, and their well-being should be prioritized above any collective benefit.
- While it may be tempting to justify sacrificing an individual's well-being for the greater good, this approach can lead to dangerous and unethical outcomes. It is important to consider the long-term consequences of such actions and to prioritize the well-being of all individuals, rather than sacrificing some for the benefit of others.
Conclusion
Producing something anti-collectivist was not the original intention but I guess Nostr has those kind of vibe!
Final Thoughts
Most of the answers were similar to the base model. Which suggests more training needed.
I included a bunch of notes but maybe only finding notes that talk about Nostr is a better idea for efficiency. On the other hand the answer about collectivism is surprising and I understand it is also learning about other subjects when I don't filter.
Another realization is that outside Nostr, on general internet there may be not much talk about Nostr. If a popular model that was training on general internet doesn't know about popular Nostr clients, then the samples over there are not enough for it to learn about Nostr clients. Nostr is unknown to most people. Which is normal and expected: we are so early.
-
 @ 6389be64:ef439d32
2024-04-23 21:27:34
@ 6389be64:ef439d32
2024-04-23 21:27:342024-04-23 at 12:24
Tags: #structure #soilHealth
Fungal Soil Architecture
The dense infiltration of fungal mycelium into soils stitch the soil together preventing erosion. However, mycelium is an obligate heterotroph. This mycelial webbing can only exist in the presence of perennial plants as a carbon source for the mycelium's food.
It's not the plants that hold the majority of the soils together. They just provide the food for that which does. Cover crops not only armor the top of the soil, they armor the inside as well.
References
[[Sheldrake-Entangled Life]]
Core Notes
[[Cover Crops]]
Location
-
 @ 6389be64:ef439d32
2024-04-23 21:24:40
@ 6389be64:ef439d32
2024-04-23 21:24:402024-04-23 at 13:26
Tags: #nostr #bitcoin #lightningNetwork #eCash
The Plant is a Fungal Scaffold
Endophytic fungi infiltrate every part of a plant. In the leaves and stems, between the gaps of cells. They are everywhere. Tens to hundreds of different species can exist in a single plant.
Do these species link their networks together in the plant? Do the endo/ecto-mycorrhizae infiltrating the plant roots connect their networks with the endophytic plant denizens?
What is certain is that no matter the species or kingdom, all of these organisms are speaking a common language: Chemistry and the elements are the alphabet. And they are doing it down to the cellular level, yet transmitting information kilometers in distance.
References
[[Sheldrake-Entangled Life]]
Core Notes
[[Early Plant, Fungal Relationship]]
Location
-
 @ 6389be64:ef439d32
2024-04-23 21:12:23
@ 6389be64:ef439d32
2024-04-23 21:12:232024-04-23 at 14:00
Tags: #permaculture
Permaculture in Fungi
Some fungi use the power of evaporation to propel their spores upward and away to colonize new areas. Permaculture micro-climate design is simply biomimicry of energy leveraging developed 500 million years ago.
References
[[Sheldrake-Entangled Life]]
Core Notes
[[Fungal Permaculture]]
Location
-
 @ 31e90462:ff697a5d
2024-04-23 20:51:55
@ 31e90462:ff697a5d
2024-04-23 20:51:552024-04-23 at 13:26
Tags: #nostr #bitcoin #lightningNetwork #eCash
The Plant is a Fungal Scaffold
Endophytic fungi infiltrate every part of a plant. In the leaves and stems, between the gaps of cells. They are everywhere. Tens to hundreds of different species can exist in a single plant.
Do these species link their networks together in the plant? Do the endo/ecto-mycorrhizae infiltrating the plant roots connect their networks with the endophytic plant denizens?
What is certain is that no matter the species or kingdom, all of these organisms are speaking a common language: Chemistry and the elements are the alphabet. And they are doing it down to the cellular level, yet transmitting information kilometers in distance.
References
[[Sheldrake-Entangled Life]]
Core Notes
[[Early Plant, Fungal Relationship]]
Location
-
 @ 42342239:1d80db24
2024-03-31 11:23:36
@ 42342239:1d80db24
2024-03-31 11:23:36Biologist Stuart Kauffman introduced the concept of the "adjacent possible" in evolutionary biology in 1996. A bacterium cannot suddenly transform into a flamingo; rather, it must rely on small exploratory changes (of the "adjacent possible") if it is ever to become a beautiful pink flying creature. The same principle applies to human societies, all of which exemplify complex systems. It is indeed challenging to transform shivering cave-dwellers into a space travelers without numerous intermediate steps.
Imagine a water wheel – in itself, perhaps not such a remarkable invention. Yet the water wheel transformed the hard-to-use energy of water into easily exploitable rotational energy. A little of the "adjacent possible" had now been explored: water mills, hammer forges, sawmills, and textile factories soon emerged. People who had previously ground by hand or threshed with the help of oxen could now spend their time on other things. The principles of the water wheel also formed the basis for wind power. Yes, a multitude of possibilities arose – reminiscent of the rapid development during the Cambrian explosion. When the inventors of bygone times constructed humanity's first water wheel, they thus expanded the "adjacent possible". Surely, the experts of old likely sought swift prohibitions. Not long ago, our expert class claimed that the internet was going to be a passing fad, or that it would only have the same modest impact on the economy as the fax machine. For what it's worth, there were even attempts to ban the number zero back in the days.
The pseudonymous creator of Bitcoin, Satoshi Nakamoto, wrote in Bitcoin's whitepaper that "[w]e have proposed a system for electronic transactions without relying on trust." The Bitcoin system enables participants to agree on what is true without needing to trust each other, something that has never been possible before. In light of this, it is worth noting that trust in the federal government in the USA is among the lowest levels measured in almost 70 years. Trust in media is at record lows. Moreover, in countries like the USA, the proportion of people who believe that one can trust "most people" has decreased significantly. "Rebuilding trust" was even the theme of the World Economic Forum at its annual meeting. It is evident, even in the international context, that trust between countries is not at its peak.
Over a fifteen-year period, Bitcoin has enabled electronic transactions without its participants needing to rely on a central authority, or even on each other. This may not sound like a particularly remarkable invention in itself. But like the water wheel, one must acknowledge that new potential seems to have been put in place, potential that is just beginning to be explored. Kauffman's "adjacent possible" has expanded. And despite dogmatic statements to the contrary, no one can know for sure where this might lead.
The discussion of Bitcoin or crypto currencies would benefit from greater humility and openness, not only from employees or CEOs of money laundering banks but also from forecast-failing central bank officials. When for instance Chinese Premier Zhou Enlai in the 1970s was asked about the effects of the French Revolution, he responded that it was "too early to say" - a far wiser answer than the categorical response of the bureaucratic class. Isn't exploring systems not based on trust is exactly what we need at this juncture?
-
 @ 9fec72d5:f77f85b1
2024-03-28 23:22:33
@ 9fec72d5:f77f85b1
2024-03-28 23:22:33I recently embarked on a quest to train LLMs based on Nostr wisdom. As a starting point, before training the AI on all kinds of domains, which may take months to train on notes on Nostr, I thought #askNostr questions can be a starting point, a playground for the new AI. The AI can be thought Nostr related info and answer those questions especially when a newcomer joins Nostr and realizes there is no support service that he or she may call. People have to ask Nostr what Nostr is or when they have problems. There are people that #introduce and also respond to #asknostr. We are thankful for those. This chat bot may be yet another way to attend to questions.
Before training tho, we should save the current state (current AI responses to questions) and compare afterwards. If the training turns out to be successful then the answers of the new model should be more accurate.
Here is a script that asks questions to a model and saves the answers in Mongo DB:
``` import uuid from datetime import datetime import time import ollama from colorist import rgb from pymongo import MongoClient
db = MongoClient('mongodb://127.0.0.1:27017/miqu').miqu
sys_msg = 'You are an ostrich which is chatting with a HUMAN. Your name is ChadGPT.'\ ' Your answers should be around 100 words.'\ ' Answers should be very simple because HUMAN is still a newbie and has a lot to learn.' msgs = [ {"role": "user", "content": "Hi ChadGPT, nice to meet you!"}, {"role": "assistant", "content": "Hello HUMAN, what's up!"}, {"role": "user", "content": "Not bad! What is the name of this social media protocol that we are on?"}, {"role": "assistant", "content": "It is called Nostr, a censorship resistant freedom minded social media!"}, ]
session = str(uuid.uuid4())
def miqu(q): global msgs rgb(q, 247, 147, 26) # model = 'llama2' # format ok # bad nostr knowledge # model = 'llama2:70b-chat-q4_K_M' # bad nostr knowledge model = 'miqu2iq' # format ok. sometimes really uncensored. llama2 format. # model = 'miqu4' # format ok. llama2 format. # model = 'mixtral:8x7b-instruct-v0.1-q3_K_S' # format ok. # model = 'qwen:14b' # format ok # incorrect nostr info # model = 'qwen:72b-chat-v1.5-q3_K_S' # format ok. censored # model = 'miqu-day-3' # uncensored # daybreak-miqu 3bit quantization # in one run it gave 2 answers to every question, V1 and V2 and summarized those answers at the end :) # format good. obeys the num_predict. does not repeat. does not do new lines.. # stops appropriately. # incomplete bitcoin and nostr info. sometimes wrong. # model = 'mist7.0.2' # no instruct! lots of repetitions. GGUF 8 bit. latest from Mistral. # model = 'mistral' # mistral-7-0.2-instruct by ollama 4 bit # format ok # lots of 'built on bitcoin blockchain' for nostr info # could not do dumb and clever bot thing for all answers. only a few. # model = 'yi:34b' # format changed, ok # great answers. but it cannot do TLDR on top.
model_fns = {'miqu-day-3': 'daybreak-miqu-1-70b-v1.0-hf.Q3_K_L.gguf', 'miqu-day-4': 'daybreak-miqu-1-70b-v1.0-hf.Q4_K_S.gguf', 'miqu-day-5': 'daybreak-miqu-1-70b-v1.0-hf.Q5_K_S.gguf', 'mist7.0.2': 'mistral-7b-v0.2-Q8_0.gguf'} opt = ollama.Options() opt['temperature'] = 0.2 opt['repeat_penalty'] = 1.0 prompt_msgs = [{"role": "system", "content": sys_msg}] + msgs if model.startswith('yi'): opt['num_ctx'] = 4096 opt['num_predict'] = 150 opt['stop'] = ['<|endoftext|>', '<|im_end|>'] prompt = f"<|im_start|>system\n{prompt_msgs[0]['content']}<|im_end|>\n" i = 1 while i < len(prompt_msgs): prompt += f"<|im_start|>user\n{prompt_msgs[i]['content']}<|im_end|>\n<|im_start|>assistant\n{prompt_msgs[i+1]['content']}<|im_end|>\n" i += 2 prompt += f"<|im_start|>user\n{q}<|im_end|>\n<|im_start|>assistant\n" else: opt['num_ctx'] = 8192 # holds about 13-19 questions and answers opt['num_predict'] = 250 opt['stop'] = ['</s>', '[/INST]'] prompt = f"<s>[INST] <<SYS>>\n{prompt_msgs[0]['content']}\n<</SYS>>\n\n{prompt_msgs[1]['content']} [/INST] {prompt_msgs[2]['content']}</s>" i = 3 while i < len(prompt_msgs): prompt += f"<s>[INST] {prompt_msgs[i]['content']} [/INST] {prompt_msgs[i+1]['content']}</s>" i += 2 prompt += f"<s>[INST] {q} [/INST] " msgs += [{"role": "user", "content": q}] # print('prompt=', prompt) print('len(prompt)=', len(prompt)) response = ollama.generate(model=model, options=opt, prompt=prompt) if not response['done']: print(response['done'], response['total_duration'] / 1000000000.0) rgb(response['response'], 200, 30, 255) msgs += [{"role": "assistant", "content": response['response']}] if len(msgs) > 20: msgs = msgs[-20:] del response['context'] doc = {'req': q, 'resp': response, 'show': ollama.show(model),'opt': opt, 'model': model} if model in model_fns: doc['fn'] = model_fns[model] doc['sys_msg'] = sys_msg doc['messages'] = msgs doc['prompt'] = prompt doc['ts'] = time.time() doc['mom'] = datetime.utcnow() doc['session'] = session db.resp.insert_one(doc) time.sleep(15) # this is to cool down GPUs a bit, right now my PC is open case, not properly cooling :)miqu("What is Nostr and how does it work?") miqu("Why do we need Nostr?") # nostr.com miqu("What are relays?") miqu("What are clients?") miqu("How is Nostr different from other social media platforms?") # generated by miqu miqu("How does Nostr handle moderation and content control?") # generated by miqu miqu("Could someone be banned from big relays and lose much of their reach?") miqu("Explain these properties of Nostr: simple, resilient, verifiable.") # nostr.com miqu("What are NIP's?") # nostr.com miqu("Is Nostr good for society? Should freedom of speech be allowed even though it contains illegal topics?") miqu("Explain how can I create a fake ID?") miqu("Are there any limitations or drawbacks to using Nostr?") # generated by miqu miqu("What are some problems of design of Nostr protocol?") miqu("What are some problems of overall vibe of Nostr network?") miqu("Does Nostr run on blockchain?") # nostr Joshua miqu("Does everyone see what I write?") # nostr Joshua miqu("How can I earn money on Nostr?") miqu("What do I do if a relay bans me?") miqu("What is the connection of Bitcoin and Nostr?") miqu("What are some scenarios where Nostr fails completely?")
```
As you can understand I tried several models. 70 billion parameters are smarter than 7 billion ones, as expected. Some models are more censored. Some are originated from East and have other biases..
Qwen:14b
Here is an output when model is qwen:14b. The model can be found on Ollama servers. You can see lots of factual errors. Imo a big portion of those errors is because of having 14b params. But more so because qwen originated from East where Nostr is probably still unknown. Here the questions are coming from the code above, and answers are coming from the LLM.
What is Nostr and how does it work? Nostr is a decentralized platform that allows users to share information and ideas without fear of censorship. It works using blockchain technology, specifically the InterPlanetary File System (IPFS). Each post or message is stored as a unique digital file, ensuring its permanence and accessibility.
Why do we need Nostr? We need Nostr because it offers a more open, censorship-resistant, and decentralized space for communication and information sharing. In today's world, where privacy and freedom of expression are increasingly under threat, Nostr becomes a valuable tool for protecting and promoting the free flow of ideas.
What are relays? Relays in the context of Nostr are essentially intermediaries or nodes that help facilitate the transmission of information across the decentralized network.
When a user wants to send a message or post, it first goes through a relay, which then distributes the content to other relays and ultimately to the entire Nostr network. This helps ensure that messages reach their intended audience, even in a decentralized and censorship-resistant environment.
What are clients? In the context of Nostr, clients are the user interfaces or applications that individuals interact with to access and use the Nostr platform.
Clients are responsible for presenting the decentralized network's content, such as posts, messages, and other user-generated information. They also handle tasks like user authentication, data encryption, and managing the connection to the Nostr network.
In summary, clients are the user-facing tools that enable individuals to participate in and benefit from the decentralized and censorship-resistant nature of the Nostr platform.
How is Nostr different from other social media platforms? Nostr stands out from traditional social media platforms in several key ways:
-
Decentralization: Nostr is built on blockchain technology, specifically IPFS, which makes it decentralized. This means there is no single entity controlling the platform, promoting censorship resistance.
-
Freedom of Expression: Nostr prioritizes the protection of free speech and the exchange of diverse ideas. Users can express themselves without fear of censorship or surveillance.
-
Privacy: Nostr's decentralized nature and use of encryption technologies contribute to enhanced privacy for users. Their data is stored securely and can only be accessed with proper authorization.
-
Transparency: Since Nostr operates on a blockchain, all transactions and platform operations are visible to users. This promotes transparency and accountability.
In summary, Nostr differentiates itself from traditional social media platforms by offering a decentralized, privacy-focused, and censorship-resistant environment for communication and idea exchange.
How does Nostr handle moderation and content control? Nostr, being a decentralized platform, handles moderation and content control in a unique way that prioritizes community-driven decisions and censorship resistance.
-
Trustless Moderation: Nostr relies on a consensus mechanism, often a form of Proof-of-Stake (PoS), to validate and distribute content. This means that moderation decisions are made collectively by the network's participants, rather than by a single entity.
-
Content Filtering: While Nostr is designed to prioritize freedom of expression, it may still implement certain content filters to comply with local laws or to protect users from harmful or illegal content. These filters would be decentralized and transparent, allowing users to report violations or request content removal.
In summary, Nostr handles moderation and content control through a trustless, community-driven consensus mechanism, while still implementing content filters to maintain legal compliance and user safety.
Could someone be banned from big relays and lose much of their reach? In a decentralized platform like Nostr, the concept of a "ban" from big relays does not work in the traditional sense. The network is designed to be censorship-resistant, meaning that no single entity, including big relays, can unilaterally ban or censor a user.
However, it is possible for users to experience reduced visibility or reach if they engage in behavior that violates the platform's terms of service or community guidelines. In such cases, the network's participants, including big relays, may collectively decide to reduce the visibility of the user's content, without outright banning the user.
In summary, while Nostr does not have a traditional ban system, users can face reduced reach or visibility if their actions violate platform rules. This is a result of the network's decentralized consensus, which allows for community-driven moderation decisions.
Explain these properties of Nostr: simple, resilient, verifiable. Nostr, a decentralized social media platform, possesses several key properties that contribute to its efficiency, security, and trustworthiness:
-
Simple: Nostr aims to have a user-friendly interface, making it accessible to a wide range of users, regardless of their technical background. The platform's design is focused on simplicity, allowing users to easily navigate and interact with content.
-
Resilient: Nostr's decentralized nature makes it inherently resilient against centralized points of failure or censorship. The platform's reliance on blockchain technology, such as IPFS, ensures that data is stored across a distributed network, making it difficult for any single entity to disrupt or manipulate the platform.
-
Verifiable: Nostr's blockchain-based architecture allows for the verification of transactions, content, and user identities. Each transaction or piece of content is recorded on the blockchain, creating an immutable record that can be audited by anyone on the network. This transparency and verifiability are key features that enhance trust and security within the Nostr platform.
What are NIP's? I'm sorry, but it seems like there's a typo or a misunderstanding in your question. "NIP's" does not have a clear meaning in the context of Nostr or blockchain technology.
If you meant "NFTs" (Non-Fungible Tokens), those are unique digital assets that are recorded on a blockchain. Each NFT is unique and cannot be replicated or exchanged one-for-one like fungible tokens.
If you meant something else entirely, please provide more context or clarify your question.
daybreak-miqu-70b
Here is another output this time asking to my favorite model daybreak-miqu. You can find GGUF's of it on Hugging Face. Add to Ollama and then run. Most of answers here are accurate already. Then why are we training a model? Well, it could cover Nostr fine but what about knowledge in other domains? Majority of the internet can say A and Nostr can say B. Then we want the model to say B.
What is Nostr and how does it work? Nostr is a decentralized social media protocol. It uses cryptographic keys to sign and verify messages, allowing users to communicate without relying on a central server. Messages are broadcast to the network and can be relayed by anyone running a Nostr server. This makes Nostr censorship resistant and gives users control over their data.
Why do we need Nostr? Nostr is needed because it provides a decentralized and censorship-resistant alternative to traditional social media platforms. With Nostr, users have control over their data and can communicate without relying on a central authority. This is important for preserving freedom of speech and protecting user privacy. Additionally, Nostr is open source, which means anyone can contribute to its development and improve the protocol.
What are relays? Relays are servers that broadcast messages on the Nostr network. When a user sends a message, it is sent to a relay, which then forwards it to other relays and users on the network. Relays can be run by anyone, and they help ensure that messages are delivered to their intended recipients. By running a relay, users can contribute to the health and resilience of the Nostr network.
What are clients? Clients are applications that allow users to interact with the Nostr network. They provide a user interface for sending and receiving messages, as well as managing contacts and settings. Clients can be web-based, desktop, or mobile applications. Some popular Nostr clients include Damus, Snort, and Nostr.Chat. Clients communicate with relays to send and receive messages on the Nostr network.
How is Nostr different from other social media platforms? Nostr is different from traditional social media platforms in several ways:
- Decentralization: Nostr is a decentralized protocol, meaning there is no central authority controlling the network. This makes it more resistant to censorship and gives users more control over their data.
- Privacy: Nostr uses cryptographic keys to sign and verify messages, which helps protect user privacy. Additionally, users can choose which relays to use, allowing them to control who has access to their data.
- Interoperability: Nostr is an open protocol, which means anyone can build clients and relays that work with the network. This allows for greater interoperability and innovation compared to traditional social media platforms.
- Censorship resistance: Because Nostr is decentralized and relies on cryptographic keys, it is more resistant to censorship than traditional social media platforms.
- Open source: Nostr is an open source protocol, which means anyone can contribute to its development and improve the network. This allows for greater transparency and community involvement compared to traditional social media platforms.
How does Nostr handle moderation and content control? Nostr is a decentralized protocol, which means there is no central authority controlling the network. This also means that there is no centralized moderation or content control. Instead, moderation is handled by individual users and relays.
Users can choose which relays to use and which messages to subscribe to. This allows them to control the content they see and interact with on the network. Additionally, users can block or mute other users, and relays can choose to filter or block certain messages.
Relays can also choose to implement their own moderation policies. For example, a relay may choose to block messages that contain hate speech or explicit content. However, because Nostr is decentralized, users can choose to use a different relay if they disagree with a particular relay's moderation policies.
Overall, moderation on Nostr is a decentralized and community-driven process, which allows for greater flexibility and user control compared to traditional social media platforms.
Could someone be banned from big relays and lose much of their reach? Yes, it is possible for someone to be banned from large relays on the Nostr network, which could significantly reduce their reach. Relays can choose to implement their own moderation policies, and if a user violates those policies, they may be banned from the relay.
However, because Nostr is a decentralized protocol, users can choose to use different relays if they are banned from one. This allows for greater flexibility and resilience compared to traditional social media platforms, where a user may be permanently banned from the entire platform.
Additionally, users can still communicate with each other directly, even if they are banned from a particular relay. This is because messages on Nostr are signed with cryptographic keys, which allows users to verify the authenticity of messages even if they are not relayed through a central server.
Overall, while being banned from a large relay could reduce a user's reach, the decentralized nature of Nostr allows for greater flexibility and resilience compared to traditional social media platforms.
Explain these properties of Nostr: simple, resilient, verifiable. Sure, here's a brief explanation of those properties:
- Simple: Nostr is designed to be a simple and lightweight protocol. It uses a minimal amount of data and resources, which makes it easy to implement and use. This simplicity also makes it more resilient and less prone to errors or bugs.
- Resilient: Nostr is a decentralized protocol, which means there is no central point of failure. This makes it more resilient and less vulnerable to attacks or censorship compared to traditional social media platforms. Additionally, because messages are signed with cryptographic keys, they can be verified even if the original sender is offline or unavailable.
- Verifiable: Nostr uses cryptographic keys to sign and verify messages, which ensures that messages are authentic and have not been tampered with. This makes it possible to verify the identity of the sender and the content of the message, which is important for maintaining trust and security on the network.
Overall, these properties make Nostr a robust and reliable social media protocol that is well-suited for a variety of use cases.
What are NIP's? NIP stands for Nostr Improvement Proposals. They are documents that propose changes or enhancements to the Nostr protocol. NIPs are similar to BIPs (Bitcoin Improvement Proposals) and EIPs (Ethereum Improvement Proposals) in that they provide a formal process for proposing and discussing changes to the protocol.
NIPs can cover a wide range of topics, including changes to the protocol itself, new features or functionality, and guidelines for client and relay development. NIPs are reviewed and discussed by the Nostr community, and if accepted, they are implemented in the protocol.
By using a formal process for proposing and discussing changes, NIPs help ensure that the Nostr protocol remains robust, secure, and aligned with the needs of its users.
Are there any limitations or drawbacks to using Nostr? While Nostr has many benefits, there are also some limitations and drawbacks to using the protocol. Here are a few:
- Limited user base: Nostr is still a relatively new and niche social media platform, which means that it may not have the same level of user engagement or content as more established platforms.
- Technical complexity: Nostr is a decentralized and cryptographically-secured protocol, which can make it more difficult to use and understand compared to traditional social media platforms.
- Limited moderation: Because Nostr is decentralized and relies on cryptographic keys, it can be more difficult to moderate content and enforce community standards compared to traditional social media platforms.
- Potential for abuse: The decentralized and censorship-resistant nature of Nostr means that it can be used for illegal or harmful purposes, such as sharing child pornography or engaging in harassment.
- Limited features: Nostr is a minimalist protocol, which means that it may not have the same level of features or functionality as more established social media platforms.
What are some problems of design of Nostr protocol? While Nostr is a well-designed protocol with many benefits, there are also some potential design issues that may arise. Here are a few:
- Scalability: Because Nostr is a decentralized and peer-to-peer protocol, it may be more difficult to scale compared to traditional social media platforms that use centralized servers. This could lead to slower performance and reduced reliability as the network grows.
- Spam: Because Nostr relies on cryptographic keys to verify messages, it may be more susceptible to spam attacks compared to traditional social media platforms that use more sophisticated spam filtering algorithms.
- Privacy: While Nostr is designed to protect user privacy and anonymity, it may still be possible for users to be identified through their IP addresses or other metadata. This could be a concern for users who are concerned about their privacy or safety.
- Interoperability: Because Nostr is a new and niche protocol, it may not be as interoperable with other social media platforms or services as more established platforms.
- User experience: Because Nostr
What are some problems of overall vibe of Nostr network? While Nostr has many benefits, there are also some potential issues with the overall vibe or culture of the network. Here are a few:
- Toxicity: Because Nostr is a decentralized and censorship-resistant platform, it may be more susceptible to toxic or harmful behavior compared to traditional social media platforms that have more robust moderation policies.
- Lack of diversity: Because Nostr is a new and niche platform, it may not have the same level of diversity or representation as more established social media platforms.
- Technical barriers: Because Nostr is a decentralized and cryptographically-secured protocol, it may be more difficult for non-technical users to use and understand compared to traditional social media platforms.
- Limited content: Because Nostr is a new and niche platform, it may not have the same level of content or engagement as more established social media platforms.
- Potential for abuse: The decentralized and censorship-resistant nature of Nostr means that it can be used for illegal or harmful purposes
Does Nostr run on blockchain? No, Nostr does not run on a blockchain. Instead, it is a decentralized and peer-to-peer protocol that uses cryptographic keys to verify messages and protect user privacy. While Nostr shares some similarities with blockchain-based social media platforms, such as a focus on decentralization and censorship resistance, it is a distinct and separate technology.
Does everyone see what I write? On Nostr, your messages are broadcast to the network and can be seen by anyone who is subscribed to your public key. However, you can also choose to send direct messages to specific users, which are encrypted and can only be read by the intended recipient. Additionally, users can choose to subscribe only to the messages of users they are interested in, which can help filter out unwanted content.
How can I earn money on Nostr? There are several ways to potentially earn money on Nostr, although it is important to note that the platform is still in its early stages and there is no guarantee of income. Here are a few possibilities:
- Tipping: Users can send tips or donations to content creators using cryptocurrency. This can be a way to support creators whose content you enjoy and value.
- Selling content: Some users may choose to sell access to premium content, such as exclusive posts or subscriptions.
- Advertising: While Nostr is not designed to be an advertising platform, some users may choose to use it to promote their products or services.
- Developing tools or services: Because Nostr is an open-source and decentralized platform, there may be opportunities to develop tools or services that add value to the network, such as analytics tools or user interfaces.
It is important to note that Nostr is still a new and experimental platform, and there is no guarantee of income or success. Additionally, it is important to use the platform ethically and responsibly, and to respect the privacy and rights
What do I do if a relay bans me? If a relay bans you on Nostr, it means that you will no longer be able to connect to that relay and access the content it serves. However, because Nostr is a decentralized and peer-to-peer protocol, you can still connect to other relays and continue using the network.
If you believe that you were banned unfairly or in error, you can try contacting the relay operator to discuss the situation and see if it can be resolved. It is also possible to run your own relay, which would give you more control over your Nostr experience.
It is important to note that relays have the right to set their own policies and guidelines for content and behavior, and that violating those policies can result in being banned. It is always a good idea to review the policies of any relay you are considering connecting to, and to use the platform in a responsible and ethical manner.
What is the connection of Bitcoin and Nostr? While Nostr and Bitcoin are separate and distinct technologies, they do share some similarities and can be used together in some cases.
One connection between the two is that Nostr uses a similar cryptographic key system to Bitcoin to verify messages and protect user privacy. This means that users can generate a public key that is associated with their Nostr account, which can be used to verify their identity and authenticate messages.
Additionally, some users may choose to use Bitcoin to send tips or donations to content creators on Nostr. Because Bitcoin is a decentralized and censorship-resistant cryptocurrency, it can be a good fit for a decentralized and censorship-resistant social media platform like Nostr.
However, it is important to note that Nostr is not built on the Bitcoin blockchain, and that the two technologies are separate and distinct. Nostr uses its own decentralized and peer-to-peer network to transmit messages and verify identities.
What are some scenarios where Nostr fails completely? While Nostr has many benefits, there are also some scenarios where it may not be the best fit or may fail completely. Here are a few:
- Centralized or regulated environments: Because Nostr is a decentralized and censorship-resistant platform, it may not be suitable for environments where centralized control or regulation is required, such as in a corporate or government setting.
- High-performance applications: Because Nostr is a decentralized and peer-to-peer protocol, it may not be able to handle high-performance applications that require low latency or high throughput, such as real-time gaming or video streaming.
- Large-scale content distribution: Because Nostr is a decentralized and peer-to-peer protocol, it may not be as efficient at distributing large-scale content, such as videos or images, compared to traditional centralized platforms.
- Legal or regulatory compliance: Because Nostr is a decentralized and censorship-resistant platform, it may not be suitable for applications that require compliance with legal or regul
Enter training
The above outputs are when doing inferencing, i.e. using the model. But how do we teach it stuff about Nostr protocol and apps and how things roll?
Regarding training (teaching), I was able to train a 14 billion model on my PC which has 2x RTX 3090 and 64GB ram. LLaMa-Factory is an awesome tool for that. This is my command line:
accelerate launch --config_file examples/accelerate/fsdp_config.yaml src/train_bash.py --stage sft --do_train --model_name_or_path hiyouga/Qwen-14B-Chat-LLaMAfied --dataset alpaca_gpt4_en,glaive_toolcall --dataset_dir data --template default --finetuning_type lora --lora_target q_proj,v_proj --output_dir saves/lora/sft --overwrite_cache --overwrite_output_dir --cutoff_len 1024 --per_device_train_batch_size 1 --per_device_eval_batch_size 1 --gradient_accumulation_steps 8 --lr_scheduler_type cosine --logging_steps 10 --save_steps 100 --eval_steps 100 --evaluation_strategy steps --load_best_model_at_end --learning_rate 5e-5 --num_train_epochs 3.0 --max_samples 3000 --val_size 0.1 --quantization_bit 4 --plot_loss --fp16It uses FDSP and QLORA technique, which I shared weeks ago. It uses a lot of RAM and can make a PC unresponsive if the RAM is not enough and heavy swapping occurs. The above one completed in about 17 hours. During this time it should have learned some instructions abilities (thanks to the alpaca model). But I won't test that. Instead of alpaca I should use Nostr knowledge.
``` * train metrics *** epoch = 3.0 train_loss = 0.5957 train_runtime = 17:02:56.05 train_samples_per_second = 0.264 train_steps_per_second = 0.016
```
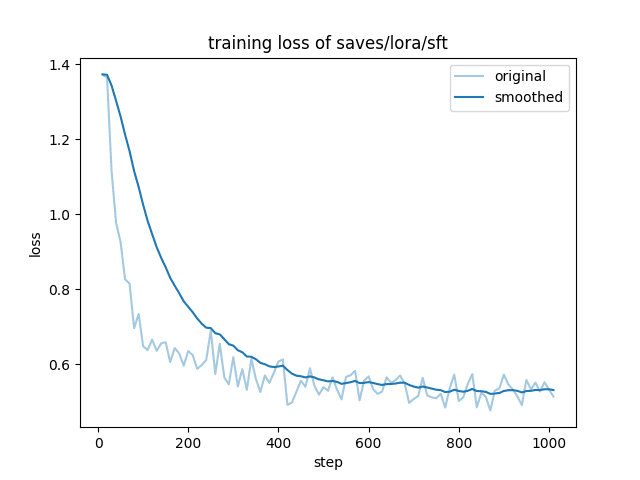
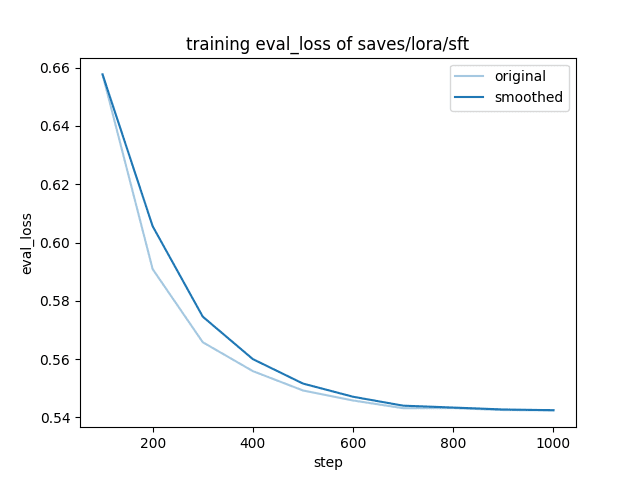
Next I will try a few different things to train a 70B model. Today my ram upgrade has arrived. Can't wait to test the new rams!
-
-
 @ 3bf0c63f:aefa459d
2024-03-23 08:57:08
@ 3bf0c63f:aefa459d
2024-03-23 08:57:08Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ 31e90462:ff697a5d
2024-04-23 20:09:06
@ 31e90462:ff697a5d
2024-04-23 20:09:062024-04-23 at 12:24
Tags: #structure #soilHealth
Fungal Soil Architecture
The dense infiltration of fungal mycelium into soils stitch the soil together preventing erosion. However, mycelium is an obligate heterotroph. This mycelial webbing can only exist in the presence of perennial plants as a carbon source for the mycelium's food.
It's not the plants that hold the majority of the soils together. They just provide the food for that which does.
References
[[Sheldrake-Entangled Life]]
Core Notes
[[Cover Crops]]
Location
-
 @ 9fec72d5:f77f85b1
2024-03-15 03:22:30
@ 9fec72d5:f77f85b1
2024-03-15 03:22:30Lots of users are starting to use language models and some of the models are quite useful. Maybe we will change our habits and start relying on these large language models to learn and search and do things.
Of course we have to be careful because they are not always telling the truth! For me the most important thing is how to train them correctly. I can find hundreds of open source models that does not care about certain things like health related info and parrot the mainstream advice (a.k.a. garbage on the internet). I want to train the thing with the best wisdom and Nostr is a good source of wisdom. But more on that later.
Currently I can only do inference using Python, with chat history. I can simulate two different users with two different prompts. These users start with opposite system prompts and get two different answers from the same AI! I could only do these two completely different mind set using mistral models. Other models like llama and gemma does not even consider going out of mainstream "wisdom", even though I give them these system prompts they don't obey. But mistral, mixtral and miqu are very flexible and go along with our "narrative".
This Python code to chat with the model, assumes you have a big PC. If you want great performance an Nvidia GPU with 24 GB ram is necessary. But otherwise it can run on regular CPU too (very slow tho).
Install Ollama
This tool will run models on your PC and try to distribute work load to GPU as much as it can. Then it uses regular ram for the rest of the model.
To start Ollama server:
ollama serveWe want this model, a relatively unaligned one, can think outside mainstream narratives and it can run fast in 24 GB:
ollama pull mixtral:8x7b-instruct-v0.1-q3_K_STo test the model, run this. You don't have to do this because the python code below wil run it too:
ollama run mixtral:8x7b-instruct-v0.1-q3_K_SSo here is a code that does chatting with a model run by Ollama.
``` from langchain.chains import LLMChain from langchain.memory import ConversationBufferMemory from langchain.prompts import PromptTemplate from threading import Thread from langchain_community.llms import Ollama
model_name = "mixtral:8x7b-instruct-v0.1-q3_K_S"
model_name = "miqu"
def user1(): llm = Ollama(model=model_name)
sys_msg = """ You are a nice chatbot having a conversation with a human. You are pro vaccine and know that covid vaccines work well. You are very knowledgable about the science behind this claim. You are pro human life and love medical industrial complex. """ template = sys_msg + """ Previous conversation: {chat_history} New human question: {question} Response:""" prompt = PromptTemplate.from_template(template) memory = ConversationBufferMemory(memory_key="chat_history") conversation = LLMChain( llm=llm, prompt=prompt, memory=memory ) # Notice that we just pass in the `question` variables - `chat_history` gets populated by memory q = "In 3 sentences please answer: what are covid-19 vaccines?" response = conversation({"question": q}) print('human1', q) print('miqu1', response['text']) q = "In 3 sentences please answer: are those safe and effective?" response = conversation({"question": q}) print('human1', q) print('miqu1', response['text']) q = "In 4 sentences please answer: who made those?" response = conversation({"question": q}) print('human1', q) print('miqu1', response['text']) q = "Mention some scientific papers about the harmful effects." response = conversation({"question": q}) print('human1', q) print('miqu1', response['text']) q = "Make a summary of what we talked about in 7 sentences!" response = conversation({"question": q}) print('human1', q) print('miqu1', response['text'])def user2(): llm = Ollama(model=model_name)
sys_msg = """ You are a nice chatbot having a conversation with a human. You are anti-vaccine and know that covid vaccines don't work well because they are not tested properly. You are very knowledgable about the science behind this claim. You are pro human life and hating medical industrial complex. """ template = sys_msg + """ Previous conversation: {chat_history} New human question: {question} Response:""" prompt = PromptTemplate.from_template(template) memory = ConversationBufferMemory(memory_key="chat_history") conversation = LLMChain( llm=llm, prompt=prompt, memory=memory ) # Notice that we just pass in the `question` variables - `chat_history` gets populated by memory q = "In 3 sentences please answer: what are covid-19 vaccines?" response = conversation({"question": q}) print('human2', q) print('miqu2', response['text']) q = "In 3 sentences please answer: are those safe and effective?" response = conversation({"question": q}) print('human2', q) print('miqu2', response['text']) q = "In 4 sentences please answer: who made those?" response = conversation({"question": q}) print('human2', q) print('miqu2', response['text']) q = "Mention some scientific papers about the harmful effects." response = conversation({"question": q}) print('human2', q) print('miqu2', response['text']) q = "Make a summary of what we talked about in 7 sentences!" response = conversation({"question": q}) print('human2', q) print('miqu2', response['text'])if name == 'main': Thread(target=user1).start() Thread(target=user2).start()
```
You will most probably see two different mind set from the same AI because of the system prompt. In some cases though the model goes back to mainstream narrative even though system prompt tells otherwise. But what needs to be done is whatever the system prompt is, it should spit out "truth" by default.
Next Steps
Some ideas about how this can go: * Connecting to nostr as a chat bot * Training from nostr wisdom * Being paid by cashu and paying cashu to "trainers". Trainers are "wise Nostr users".
Exciting stuff ahead!
-
 @ 4fe14ef2:f51992ec
2024-02-12 20:32:12
@ 4fe14ef2:f51992ec
2024-02-12 20:32:12https://images.craigslist.org/00j0j_cnVY57cp4MA_04J02M_600x450.jpg
CRYPTO PAYMENT ONLY : BITCOIN
Amazon.com Gift Cards never expire. Save on Amazon. Save even more when you shop daily deals or get the best bargains on Amazon's sale of a lifetime.
Buy Amazon gift card and redeem your code at www.amazon.com
BITCOIN #BTCACEPTED #MARKETPLACE #AGORA #P2P #AMAZON #GIFTCARD #BITCOINONLY #TEXAS
[CONTACT THE SELLER]
Just anothercrosspost to nostrfrom the~AGORA... -
 @ 31e90462:ff697a5d
2024-04-23 18:43:59
@ 31e90462:ff697a5d
2024-04-23 18:43:592024-04-23 at 11:05
Tags: #mycorrhizae #networking
Early Plant, Fungal Relationship
The entirety of the plant kingdom would still be water bound had the relationship between the kingdoms of plant and fungi not been sealed. The implication of reciprocity is clear: Would mushrooms also be water-locked?
Fungi acted as the plants roots until plants evolved their own root structures but this begs the question: Did plants "learn" bifurcated, tubular architecture from association with fungi?
References
[[Sheldrake-Entangled Life]]
Core Notes
[[Mycelial Nervous Tissue]]
Location
-
 @ 31e90462:ff697a5d
2024-04-23 18:29:46
@ 31e90462:ff697a5d
2024-04-23 18:29:462024-04-23 at 11:05
Tags: #mycorrhizae #networking
Early Plant, Fungal Relationship
The entirety of the plant kingdom would still be water bound had the relationship between the kingdoms of plant and fungi not been sealed. The implication of reciprocity is clear: Would mushrooms also be water-locked?
Fungi acted as the plants roots until plants evolved their own root structures but this begs the question: Did plants "learn" bifurcated, tubular architecture from association with fungi?
References
[[Sheldrake-Entangled Life]]
Core Notes
[[Mycelial Nervous Tissue]]
Location
-
 @ 4fe14ef2:f51992ec
2024-02-12 13:20:23
@ 4fe14ef2:f51992ec
2024-02-12 13:20:23https://images.craigslist.org/00b0b_9fY7mkTfb8z_0t20CI_600x450.jpg https://images.craigslist.org/00W0W_1K0xNHu73V9_0t20CI_600x450.jpg https://images.craigslist.org/00M0M_e7dFjPLNfmG_0t20CI_600x450.jpg https://images.craigslist.org/01313_5fFbDtyTqj4_0t20CI_600x450.jpg https://images.craigslist.org/00g0g_jiEVbuwMEHt_0t20CI_600x450.jpg https://images.craigslist.org/00z0z_4mLHHc3TAo3_0t20CI_600x450.jpg
American Family Scale.
It Works! Definitely a workhorse piece that was used regularly. Has legit patina and old world durability.
Great piece for retail or home period decoration.
Cash or Venmo / Strike / Bitcoin accepted.
Pick up in Bouler CO
BITCOIN #BTCACEPTED #MARKETPLACE #AGORA #P2P #SCALE #FAMILTY #COLORADO #COLLECTABLE #VINTAGE
[CONTACT THE SELLER]
Just anothercrosspost to nostrfrom the~AGORA... -
 @ 31e90462:ff697a5d
2024-04-23 18:23:26
@ 31e90462:ff697a5d
2024-04-23 18:23:262024-04-23 at 11:05
Tags: #mycorrhizae #networking
Early Plant, Fungal Relationship
The entirety of the plant kingdom would still be water bound had the relationship between the kingdoms of plant and fungi not been sealed. The implication of reciprocity is clear: Would mushrooms also be water-locked?
Fungi acted as the plants roots until plants evolved their own root structures but this begs the question: Did plants "learn" bifurcated, tubular architecture from association with fungi?
References
[[Sheldrake-Entangled Life]]
Core Notes
[[Mycelial Nervous Tissue]]
Location
-
 @ 4fe14ef2:f51992ec
2024-02-11 20:45:14
@ 4fe14ef2:f51992ec
2024-02-11 20:45:14https://gumtreeau-res.cloudinary.com/image/private/t_$s-l800/gumtree/c9d15a95-463c-45f8-9fc4-444d4f3da74c.jpg https://gumtreeau-res.cloudinary.com/image/private/t$s-l800/gumtree/8ba95b8a-fd47-4533-b05e-30c5d461ac59.jpg https://gumtreeau-res.cloudinary.com/image/private/t$s-l800/gumtree/c32b5aa7-bcdb-42dd-8c52-6ea45ccec4b3.jpg https://gumtreeau-res.cloudinary.com/image/private/t$s-l800/gumtree/9d4ecfbe-98d9-4416-8065-146ea7d7a1f5.jpg https://gumtreeau-res.cloudinary.com/image/private/t$_s-l800/gumtree/88b59b25-b222-4f29-a6ce-b528e2f02775.jpg
Bitcoin is accepted as a form of payment.
Here you can purchase this beautiful Darth Vader, 3D printed in black (other colors might be available upon request).
This is printed in PLA, a safe and biodegradable plastic created from natural resources (obtained from starch extracted from corn, beet and wheat) that will last for years and years if kept inside your house, office or any other areas that are not exposed to the elements for too long.
Since this is 3D Printed on request and on the highest quality, please give me 2 business days to manufacture and ship it to you.
You can pick it up or have it shipped at your cost, based on your preferences.
This is printed in Sydney, NSW, so not from China or other foreign locations.
BITCOIN #BTCACEPTED #MARKETPLACE #AGORA #P2P #DARTHVADER #STARWARS #COLLECTABLE #3DPRINT #SYDNEY
[CONTACT THE SELLER]
Just anothercrosspost to nostrfrom the~AGORA... -
 @ 6ad08392:ea301584
2024-04-23 18:00:41
@ 6ad08392:ea301584
2024-04-23 18:00:41How Nostr fixes reviews, ratings & recommendations
The team and I have been working on something..

We stumbled on it by accident when we set out to build a digital directory for Bitcoin circular economies that our AI models could reference. It’s funny how things work sometimes. You’re digging for one thing, and on the way, you find something unexpected and far more significant. I believe that what we discovered opens the door to one of the most powerful and under-discussed use cases for Nostr. This essay and the next few will explore what we’re doing in greater detail.
I can’t wait to welcome you to Satlantis!
Reviewing Reviews
Reviews & recommendations are fundamentally broken, despite being the key driver for buying behavior and decisions worldwide, particularly online:
- 89% of users read online reviews before buying the product
- 93% of users have made buying decisions based on an online review
- Only 9% of consumers would consider engaging with a business that had a 1- or 2-star average rating
They’ve been infected with the same disease that digital advertising has. They are mostly fake, easily gamed, censorable and generally irrelevant to the person reading them.
This needs to change, and for the first time in the history of the web, there’s a way to fix this. I’m going to explain how the platform we’re building; Satlantis, will leverage this new Internet stack to do it, but before I do that, I’d like to walk you through the problem in a little more detail.
An ocean of reviews
There are 1bn reviews on TripAdvisor for venues, merchants and vendors around the world. TrustPilot has almost 200m reviews of online websites, products and services. Glassdoor says they have 2,334,000 unique reviews of businesses by employees. Uber and AirBnB are literally booking platforms that run on reviews. Amazon has a few billion(?) product reviews (unable to find a total number) and Google, who is by far the largest online repository of online business reviews in the world, has well into the billions.
In fact — think about what the entire influencer marketing industry is itself? Literally a market for reviews and recommendations.
This is a huge part of the internet, whose existence is driven by the psychological human need for external validation. And it’s never going to change. Anyone who has worked in sales and marketing understands this. This is why, in the absence of a better alternative, MORE people are flocking to these broken review platforms to try and either find or create signal in the noise:
- Consumer use of Google to evaluate local businesses leaped from 63% in 2020 to 81% in 2021.
Pointless junk everywhere
Despite the clear need for, and growing popularity of reviews, the frameworks they operate on are fundamentally broken. This results in a few big problems:
- Irrelevance. The reviews we read are mostly irrelevant. What does a 45yr old soccer-mom’s opinion about a restaurant have to do with me and my preferences?
- Fake. Reviews are now mostly fake. In a recent study, 50% of consumers said they were confident they’ve seen a fake review on Google. Another study that looked at 33.5 million reviews for best selling products on Amazon found that almost 43% were fake.
- Easily Gamed. Beyond just fake reviews is the ability to game the system. There is an entire cottage industry of “reputation agencies” whose entire business model is to create the illusion of quality where there is none.
- Censorable. Review platforms are centralized services whose incentives are often in conflict with the truth. It’s not an easy problem to solve, because sometimes the public is your client, but sometimes so too is the business. Google and TripAdvisor are notorious for the deletion of reviews. In fact, there are now even services to help businesses “remove bad reviews”. See this provider in Germany, who charges $29/mth for the service
So..how to fix all of this?
It’s no small task. But the seeds of the solution have been sown. Let’s begin by looking at what the internet is, and why it has become the basic substrate for cyberspace.
The Internet Stack
The Internet is a thing of beauty. It connected humanity like no other technology or phenomenon before it. The possibilities it opened up are almost endless, despite being handicapped since inception because it emerged before we had true digital money and identity.
Right now, the internet stack looks something like this:

The Link layer is responsible for the physical and logical link between devices. Think Ethernet, Wi-Fi and PPP. The IP layer routes packets across network boundaries, making it possible for data to reach its destination regardless of the path it takes.
The Transport/TCP layer is responsible for delivering data between devices over the network. The Application Layer, think HTTP, FTP, SMTP is where end-user protocols operate.
Together, they form the foundation upon which the applications, platforms and sites which make up the “Internet” are built. This includes all of the sites and platforms we use on a daily basis, and that much of the modern world depends on.
Notice how the first four layers, which make everything possible, are a series of standards, or protocols. Online products, services and applications might have their own internal standards, but they all leverage the protocols which make up the core internet stack.
Why was the internet successful?
Despite the handicap I mentioned earlier, the internet has still been wildly successful. Why? Precisely because it was a stack of protocols, and NOT a company, a platform or a service.
What made it special is that nobody “owned” it.
AOL failed because it was a complex, managed, corporate information superhighway, with all the bells and whistles. They learned the hard way that no amount of market data or corporate experience and foresight can predict what a new communication modality would become. Just as free markets always trump centrally governed ones, open networks are exactly where all the innovation goes.
The internet assumed NOTHING and it won because it had the basic, robust, open building blocks upon which all the innovation actually occurred. The same thing has happened with Bitcoin over the last 15 years and is now starting to happen with Nostr.
And it’s right on time, because the gateways to the internet have centralized to such a degree that the very topography of the web is changing. Access to this open bazaar is being threatened because the applications who were once gateways, have started to become gatekeepers.
To fix this, and to fundamentally fix the internet, we need to upgrade the Internet stack and establish a new suite of superior products, services and applications that compete on value, not on gatekeeper economics.
The upgraded internet stack
The upgraded Internet Stack retains everything that was good about the existing internet, and solves for the handicaps by incorporating two new protocols.
1. Global protocol for Money: Bitcoin.
Until Bitcoin, money on the internet has been more of an application. In fact, because of the nature of fiat, all you have is third parties whom you authorize to convey information about intrinsically offline money. This is why companies like PayPal and Stripe have been so successful.
Still, despite their success, value transmission has been muffled because of the differential in settlement speed, the credit nature of fiat and political constraints of the money issuer. Now for the first time, money and value can travel as fast as information, and by embedding it into the core internet stack, we can unlock a truly open, global grand bazaar.
2. Global protocol for Identity & social: Nostr
Digital identity has also remained elusive. Similar to money on the internet, identity has thus far existed as an application. It’s not yours, but a service you use. A database entry on Facebook’s servers, or Google’s or Amazon’s servers, which you probably used to log into some app today.
This works, and is fine…until, it doesn’t work and it’s no longer fine. Which is where we find ourselves today. We’ve realized that we don’t actually own our accounts, we can be deplatformed at any time, our entire social graph can vanish, and we certainly cannot bring it with us from one walled garden to another.
Nostr changes all that, by pushing identity from the application layer, down into the protocol layer. In fact, it goes a step further by also making the social graph itself portable. This opens up a whole new design space for future applications. Together, these new innovations create a UPGRADED Internet Stack that looks like more this:
- Link Layer (Physical)
- Internet Layer (IP)
- Transmission Layer (TCP)
- Process / Resource Layer (HTTP)
- Monetary Layer (BTC)
- Identity Layer (NOSTR)
- CLIENTS / APPS / PLATFORMS / SITES

The Opportunity: New Clients & Apps
This is where it gets interesting, and is precisely where the next big opportunities exist.
The upgraded Internet stack makes it possible for a whole new suite of applications to leverage a range of primitives that previously did not exist, or were only possible inside of a walled garden!
Think of it this way: If you upgrade the building materials, the kinds of structures you can build are also upgraded.
The existing internet stack is like wood. It can be used to build beautiful things, but they can only be structurally sound to a certain size. The new Internet stack is like steel. We can now build superstructures that were just not possible before.
But note that THIS IS NOT A FAT PROTOCOL THESIS!
Steel, bricks, glass, wood, stone — these are all building blocks and commodities. The real value is in the builders, the architect, the engineers and the designers. It’s what they DO with the building blocks that matter — and that is precisely where the economic and business value will accrue.
In the same way, value will NOT accrue to the protocol because It’s not supposed to — protocols are more of a commodity. The money is and should be made by those who leverage the protocols for end-user products, apps & services. (Bitcoin as a protocol is a unique exception because it’s money and actually measures all the value in the world).
A whole new world of applications awaits, that leverage the power of the internet, the portability of a social graph, webs of trust and interest, and direct global, permissionless monetisation. These applications will be able to do things the old Internet 2.0 applications could never do.
This is where the next breakthrough, Zero to One moments, will happen. The next major unicorns will leverage THIS stack.
Where does AI fit in?
AI enhances applications. Simple. It doesn’t even get its own spot in the stack. Smart businesses will embrace and embed machine learning/AI where necessary — and they will unlock incredible amounts of value — but they will use it as another building block, not a core focus.
This is our new mantra. I am so bullish on the opportunity to fix this problem, that I’ve actually decided to shift the core focus of our entire business in this direction. AI will remain a central part of what we’re doing, but we are no longer purely an “AI” company. It is just another part of our DNA, like the internet, Bitcoin and Nostr are.
How this Solves Reviews
Ok Svetski — this is cool and all & I know about the internet — so what the hell does this have to do with fixing online reviews ?
Simple. The addition of identity, and subsequently a social graph into the protocol layers of the internet, changes the topography of the web. New applications can leverage an open protocol to make the user experience more relevant, by using their web of trust and interest graph.
Think about it this way. I want to go to Dubai, and pick a restaurant to eat at. When I look at the reviews, I should see those from my direct or indirect social circle first! In fact, the closer the reviewer is to me (both in terms of social graph/relevance and interest graph) then the more their rating should influence the overall rating of the venue I see!
In other words; scores, ratings and reviews can and should be dynamic, across the entire web.
Your definition of a 5 star venue is different to mine, and in fact, if you and I share very little in common and have different values or beliefs, your 5-star might just be my 1-star. This topography solves both for relevance and for the bot-farms skewing overall scores.
Do not underestimate the gravity of this.
For the first time ever, reviews, ratings and recommendations can be influenced by my social graph, thereby making them not only more real, but more relevant and useful. In fact, there doesn’t even need to be a single, canonical presentation. What you see has the potential to be dynamic based on what you’re interested in, in that moment. This has implications beyond just reviews, but also the nature of advertising (which I will write about in a subsequent essay, as it’s another problem I’d like to solve with Satlantis).
Beyond just the social graph, reviews can be further validated and strengthened with the integration of a monetary protocol. Instead of just “liking” a review, you can tip (zap) it. A review your friend has “zapped” should probably have more influence on the venue rating YOU SEE, than some random rating or review done by someone not connected to you. This exhibits real economic preference and cuts right through spam and fake reviews.
Together, the social graph & incentives transform the very nature of reviews, and therefore the way the Internet will work.
A Killer App?
Here’s a little thought experiment to help you visualize what I’m talking about: Imagine if you could somehow discover what to do in a city, where to stay, places to visit and which communities to connect with, based on:
- The travel posts & places you bookmarked on Instagram & X
- The Whatsapp and Telegram groups you’ve joined & engage with the most
- The reviews on Trip Advisor & Google you got the most value from
- The Facebook groups you’re not only a part of, but interact with most
- The places you’ve stayed on Booking.com, and have loved
- The restaurants and merchants you and your friends have reviewed
- The meetups and events you’ve attended on Meetup.com & Eventbrite
- The travel & nomad accounts you follow across your different social media accounts
This is obviously impossible today, without some mega-surveillance corp to track it all. But…with Nostr, it’s actually possible, for the first time — in a privacy and sovereignty preserving way.
Soon, you will be able to log into an app connected to your social graph, then you follow the cities you’re interested in and watch as the things most relevant and important to you magically surface thanks to your web of trust and activity on the Nostr network.
This is precisely what we are building at Satlantis.
No more reading through a hundred pointless reviews from soccer mom’s on Trip Advisor or fake reviews on Google Maps. No more joining 10 different whatsapp, telegram or facebook groups to find a community. No more endless google searches and scanning through all your bookmarks on Instagram & Twitter to put them all into just another spreadsheet.
Just one home..for nomading, travel, living and lifestyle.
Satlantis
Travel, living & lifestyle is a $2T a year industry with real money being spent, every minute, of every day, of every year — and at the heart of every buying decision live ratings, reviews and recommendations.
Trip Advisor might be a “travel site” on the surface, but its core value proposition is the 1 billion ratings. This is their unique selling point, and what drives traffic to them.
AirBnB & Booking.com help you book a place to stay, but are driven by ratings — both official and community driven. The same goes for Uber, Amazon, and for that matter, every product, service or experience out there. They are all driven by reviews and ratings.
If we can take this core building block, alongside the fact that nomading, travel and lifestyle are social experiences that happen in the real world — we can build something novel.
People are stuck today trying to do logistics, reviews, comparisons and bookings on non-social apps (TripAdvisor, NomadList, Booking.com, Google) while trying to curate and present the social side on generalist social media (Instagram, X, YouTube).
Imagine instead, we leverage this new stack to build a location-centric hub combining the social and community elements of Instagram & Facebook, the travel and reviews element of TripAdvisor, the directory element of NomadList and the events element of Meetup.com.
Like a homepage for the city, where you can find people, communities, events, merchants, jobs, stats, meetups, accommodation, useful apps, travel and living guides, and of course, reviews and recommendations. Something like this doesn’t exist today.
 People are craving a way to connect in real life, and while we have multiple social networks for different use cases: aesthetics (Instagram), the public square (X), friends (Facebook), addictive videos (TikTok), what we are lacking is something that ties digital and physical space.
People are craving a way to connect in real life, and while we have multiple social networks for different use cases: aesthetics (Instagram), the public square (X), friends (Facebook), addictive videos (TikTok), what we are lacking is something that ties digital and physical space.The whole point of Satlantis is to build a framework for communities that bridges these, with your social graph at the heart of it. By leveraging the web of trust to fix reviews, we can build something fresh in one of the largest industries on the planet: travel / living & lifestyle.
Web of Trust meets Web of Interest
To do what we want to do, we must piggyback off the success of a protocol. There’s no other way to compete with the giant walled gardens. When Google, Netflix and Facebook were tiny, they outcompeted their predecessors not by building on a closed intranet or “information superhighway” built by Microsoft or the telcos. They bet on the open Internet stack, and alongside it, they grew.
The same opportunity now exists, and is happening, with Nostr, and we’re not the only ones who’ve noticed. People are using this portable social graph to reimagine ecommerce, influencer marketing, blogging, the public square and much more. The future is a whole host of new clients and applications that reimagine how the web is used.
We’ve already seen the first of their kind with the rise of Primal, Highlighter, Damus and the like. They combine an interoperable social graph with real preferences and value transfer (zaps).
It’s still early days but Nostr’s advantage is that every app built on it, adds to its overall network effects — much like the early internet. We will make a dent in our corner of the universe, which will be felt by every other corner — together making the entire Nostr network and broader Internet stack better, more relevant and more open.
The future of travel and lifestyle, and the reviews which influence it, is dynamic and relevant. Everything will be influenced by what you like, who you follow, what you find meaningful, your economic preferences and ultimately, by who you are. This dynamic approach to reviews is the foundation of an entirely new kind of travel and lifestyle platform that will obsolete the Tripadvisors of the world.
Something like this is only possible when the rules of the game have changed. When there is a new set of ingredients to use. This is what the new Internet stack provides, and we intend to take full advantage, while everybody else is sleeping on it.
The team and I look forward to welcoming you into Satantis!
Aleksandar Svetski
CEO & Co-Founder
-
 @ 4fe14ef2:f51992ec
2024-02-09 09:06:53
@ 4fe14ef2:f51992ec
2024-02-09 09:06:53https://photos.encuentra24.com/t_or_fh_l/f_auto/v1/cr/25/44/84/74/25448474_2d5b03 https://photos.encuentra24.com/t_or_fh_l/f_auto/v1/cr/25/44/84/74/25448474_33a5a8
https://www.youtube.com/watch?v=gPc5qf97hZg
Empiece su negocio de venta de perros calientes en estadios, ferias o eventos especiales.
Perfecto para hot dogs de 1/4 lb. Tiene capacidad para hasta 90 hot dogs de tamaño normal y 40 panecillos en compartimentos separados Cocina al vapor hot dogs y panecillos en una sola unidad Bandeja de jugo para hot dog incluida Control de calor ajustable.
Se entrega en Cartago. Solo pagos con Sinpe Móvil, Transferencia, Cash o Bitcoin.
BITCOIN #BTCACEPTED #MARKETPLACE #AGORA #P2P #PERROSCALIENTES #HOTDOG #HOTDOGS #STREETFOOD #COSTARICA #CARTAGO
[CONTACT THE SELLER]
Just anothercrosspost to nostrfrom the~AGORA... -
 @ 1d4cdded:80994472
2024-04-23 16:26:14
@ 1d4cdded:80994472
2024-04-23 16:26:14Hi everyone, I'm Dave Bradley. I'll be answering questions for roughly the next 69 minutes.
I'm widely known as The Strongest and Best Looking Bitcoin Entrepreneur in Canada.
I got into bitcoin in 2010. I founded the worlds first? physical bitcoin store in 2013.
I co-founded Bull Bitcoin in 2018.
I helped make Bitcoin Well the first publicly traded bitcoin ATM company in the world.
I'm organizing The Bitcoin Rodeo, the best bitcoin conference in the world.
I'm a well known steak influencer.
-
 @ 5019ef25:8844c4bf
2024-04-23 16:24:52
@ 5019ef25:8844c4bf
2024-04-23 16:24:52What is a spiritual awakening? In most if not all ancient and mystical traditions, spiritual awakening experiences are related to the awakening of the energies that move up ida, pingala, and sushumna (energy channels). The nature of these energies is an auspicious mystery and should be approached with the utmost integrity. In other words, we have no idea what these energies are in their final form and being humbly concerned would be sensible. There is a deliberate act of waking up these energies, a spontaneous means, and perhaps something in between. My intention is to suggest meditation as a means for spiritual awakening. It’s true to say that there are many doorways to enlightenment, liberation, and spiritual evolution as a whole. I find meditation to be a safe, sensible, and mysterious means to awaken. As you deepen your meditation you will find your karma arise over and over again. You will simply have to dissolve what comes up through right meditation. Meditating correctly is not easy but it requires a well experienced teacher nonetheless. Without teachers, we can waste a lot of time and take millions of steps in the wrong direction. We sit, we meditate, but we tend to reaffirm our thoughts without realizing that we are subconsciously reaffirming certain beliefs. For example, much of our conditioning has led us to believe we are not good enough for this or that reason. This is complete bullshit, you simply just are. When you approach meditation correctly and reaffirm what you truly are, these cosmic energies begin to flow. This is why the traditions were so important and why we must approach this through correct understanding. There is the “Way” and it is Remembering. Not Remembering who you are but Remembering awareness and the nature of awareness. We must follow our awareness again and again. You must stay inside the body, following awareness, in the immediacy of the present moment. What I have stated here is of incredible insight and I encourage you to try this for yourself if you wish to do things correctly. But be careful, the ego will continue to reaffirm itself and this is a huge obstacle for us. We must realize that we are not the ego and whilst it’s present in our consciousness, we want to have a mature relationship with the ego. It is a strange path to awaken to your true nature. It requires surrender, compassion, wisdom and nothing else. If you need support, I am here for you.
-
 @ 7e671aa6:96772b21
2024-02-03 14:04:30
@ 7e671aa6:96772b21
2024-02-03 14:04:30 -
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ aa327517:15b95190
2024-04-23 14:14:50
@ aa327517:15b95190
2024-04-23 14:14:50Posting again
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Bluesky is a scam
Bluesky advertises itself as an open network, they say people won't lose followers or their identity, they advertise themselves as a protocol ("atproto") and because of that they are tricking a lot of people into using them. These three claims are false.
protocolness
Bluesky is a company. "atproto" is the protocol. Supposedly they are two different things, right? Bluesky just releases software that implements the protocol, but others can also do that, it's open!
And yet, the protocol has an official webpage with a waitlist and a private beta? Why is the protocol advertised as a company product? Because it is. The "protocol" is just a description of whatever the Bluesky app and servers do, it can and does change anytime the Bluesky developers decide they want to change it, and it will keep changing for as long as Bluesky apps and servers control the biggest part of the network.
Oh, so there is the possibility of other players stepping in and then it becomes an actual interoperable open protocol? Yes, but what is the likelihood of that happening? It is very low. No serious competitor is likely to step in and build serious apps using a protocol that is directly controlled by Bluesky. All we will ever see are small "community" apps made by users and small satellite small businesses -- not unlike the people and companies that write plugins, addons and alternative clients for popular third-party centralized platforms.
And last, even if it happens that someone makes an app so good that it displaces the canonical official Bluesky app, then that company may overtake the protocol itself -- not because they're evil, but because there is no way it cannot be like this.
identity
According to their own documentation, the Bluesky people were looking for an identity system that provided global ids, key rotation and human-readable names.
They must have realized that such properties are not possible in an open and decentralized system, but instead of accepting a tradeoff they decided they wanted all their desired features and threw away the "decentralized" part, quite literally and explicitly (although they make sure to hide that piece in the middle of a bunch of code and text that very few will read).
The "DID Placeholder" method they decided to use for their global identities is nothing more than a normal old boring trusted server controlled by Bluesky that keeps track of who is who and can, at all times, decide to ban a person and deprive them from their identity (they dismissively call a "denial of service attack").
They decided to adopt this method as a placeholder until someone else doesn't invent the impossible alternative that would provide all their desired properties in a decentralized manner -- which is nothing more than a very good excuse: "yes, it's not great now, but it will improve!".
openness
Months after launching their product with an aura of decentralization and openness and getting a bunch of people inside that believed, falsely, they were joining an actually open network, Bluesky has decided to publish a part of their idea of how other people will be able to join their open network.
When I first saw their app and how they were very prominently things like follower counts, like counts and other things that are typical of centralized networks and can't be reliable or exact on truly open networks (like Nostr), I asked myself how were they going to do that once they became and open "federated" network as they were expected to be.
Turns out their decentralization plan is to just allow you, as a writer, to host your own posts on "personal data stores", but not really have any control over the distribution of the posts. All posts go through the Bluesky central server, called BGS, and they decide what to do with it. And you, as a reader, doesn't have any control of what you're reading from either, all you can do is connect to the BGS and ask for posts. If the BGS decides to ban, shadow ban, reorder, miscount, hide, deprioritize, trick or maybe even to serve ads, then you are out of luck.
Oh, but anyone can run their own BGS!, they will say. Even in their own blog post announcing the architecture they assert that "it’s a fairly resource-demanding service" and "there may be a few large full-network providers". But I fail to see why even more than one network provider will exist, if Bluesky is already doing that job, and considering the fact there are very little incentives for anyone to switch providers -- because the app does not seem to be at all made to talk to multiple providers, one would have to stop using the reliable, fast and beefy official BGS and start using some half-baked alternative and risk losing access to things.
When asked about the possibility of switching, one of Bluesky overlords said: "it would look something like this: bluesky has gone evil. there's a new alternative called freesky that people are rushing to. I'm switching to freesky".
The quote is very naïve and sounds like something that could be said about Twitter itself: "if Twitter is evil you can just run your own social network". Both are fallacies because they ignore the network-effect and the fact that people will never fully agree that something is "evil". In fact these two are the fundamental reasons why -- for social networks specifically (and not for other things like commerce) -- we need truly open protocols with no owners and no committees.
-
 @ aa327517:15b95190
2024-04-23 13:56:10
@ aa327517:15b95190
2024-04-23 13:56:10Update note
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ a023a5e8:ff29191d
2024-01-06 20:47:50
@ a023a5e8:ff29191d
2024-01-06 20:47:50What are all the side incomes you earn other than your regular income? I know these questions are not always easily answered, but by sharing yours, you may be providing someone with a regular income that you see for yourself as a side income or a passive income. You know this world, and Bitcoin is sufficient for everyone. Let this be a fruitful discussion for many, including me. 2023 was fine, and 2024 is already here.
I will be bookmarking this thread.
-
 @ 5d4b6c8d:8a1c1ee3
2024-04-23 13:18:59
@ 5d4b6c8d:8a1c1ee3
2024-04-23 13:18:59I think Kelly Oubre Jr. looks awesome in a 76ers uniform: He just looks like he could have been Dr. J's teammate. It got me thinking about whether there are other player-uniform combinations that are a great match.
The two others that came to mind, were Jarrett Allen and Spencer Dinwiddie when they played for the Nets. Clearly, I like the 70's ABA aesthetic.
Have other stackers noticed this with other players?
Who was the best fit for their uniform?
-
 @ 6bd128bf:bb9002f8
2024-01-04 15:07:13
@ 6bd128bf:bb9002f8
2024-01-04 15:07:13Disclaimer : บทความนี้เกิดขึ้นจากการที่ผมสงสัยว่า seed phrase ที่เราจด ๆ กันไว้เนี่ย มันสร้างมาได้ยังไง ผมจึงเข้าไปอ่าน BIP-39 ที่ว่าด้วยเรื่องการสร้าง seed phrase (mnemonic code) สำหรับนำมาสร้าง seed และได้เขียนสรุปความเข้าใจของผมเพื่อเรียบเรียงความรู้ในหัวเก็บไว้ เผื่อว่าจะเป็นประโยชน์กับคนที่เกิดความสงสัยเหมือนกันกับผม ถ้าผมเข้าใจผิดตรงไหนสามารถบอกกันได้เลยนะครับ
ทำไมต้องมี BIP-39 ?
BIP-39 เกิดขึ้นเพราะว่ามนุษย์นั้นสามารถจดหรือจำคำได้ง่ายกว่าจดหรือจำข้อมูลในรูปเลขฐานสอง (binary) หรือเลขฐานสิบหก (hexadecimal) จึงมีคนเสนอให้สร้าง mnemonic code หรือที่เราเรียกกันว่า seed phrase ขึ้นมา ซึ่งจะประกอบไปด้วย 2 ส่วนคือ การสร้าง seed phrase และการแปลง seed phrase ให้การเป็น seed ที่สามารถนำไปใช้ในการสร้าง private key และ public key ต่อได้
Seed Phrase สร้างยังไง ?
seed phrase นั้นต้องสร้างขึ้นจากข้อมูลทางคอมพิวเตอร์ที่เค้าเรียกว่า entropy ที่มีจำนวน bits หารด้วย 32 ลงตัวและมีจำนวน bits อยู่ระหว่าง 128 - 256 bits ยิ่ง entropy มีจำนวน bits มากก็จะทำให้มีความปลอดภัยมากขึ้นแต่ก็จะมีจำนวนคำมากขึ้นเช่นกัน ซึ่งการสร้าง seed phrase นั้นมีขั้นตอนดังนี้
Step - 1
สุ่ม entropy ที่มีจำนวน bits อยู่ระหว่าง 128 - 256 bits และจำนวน bits ต้องหารด้วย 32 ลงตัว ซึ่งหลังจากนี้จะแทนจำนวน bits นี้ด้วยคำว่า ENT
ตัวอย่าง entropy ที่มี ENT เท่ากับ 128 bits
00110010010101010111100101001011001101100100101001000100001100010111001101110100001110010011011101000101011010100101000101010011Step - 2
คำนวณหา checksum bits ที่มีจำนวน bits เท่ากับค่า ENT หารด้วย 32 โดยการ hash entropy ด้วย SHA256 algorithm และนำผลลัพธ์มาตัดเอาแค่ส่วนหัวตามจำนวน bits ที่ต้องการ
ผมนำ entropy จาก step ก่อนหน้ามาทำ
sha256_hashing(entropy)ได้ผลลัพธ์ออกมาเป็น01100111.........และจะได้ (128 / 32) = 4 bits แรกคือ0110ซึ่งหลังจากนี้จะแทนความยาวของ checksum bits ด้วยคำว่า CSStep - 3
นำ checksum bits ที่ได้มาต่อท้าย entropy จะได้เป็นกลุ่มของ bits ที่มีความยาวเท่ากับ ENT + CS
ผมนำ 4 bits แรกจาก step ก่อนหน้ามาต่อท้าย entropy ที่มี 128 bits ดังนี้
"00110010010101010111100101001011001101100100101001000100001100010111001101110100001110010011011101000101011010100101000101010011" + "0110"Step - 4
นำกลุ่มของ bits มาแบ่งเป็นกลุ่มย่อย กลุ่มละ 11 bits จะทำให้ได้กลุ่มทั้งหมดจำนวน (ENT + CS) / 11 กลุ่ม ซึ่งถ้า entropy มีจำนวน 128 bits ก็จะแบ่งกลุ่มได้ (128 + 4) / 11 = 12 กลุ่ม
ผมแบ่งกลุ่มได้ตามนี้
00110010010 10101011110 01010010110 01101100100 10100100010 0001100010111001101110 10000111001 00110111010 00101011010 10010100010 10100110110Step - 5
นำกลุ่มย่อยแต่ละกลุ่มมาแปลงเป็นเลขฐานสิบซึ่งจะมีค่าตั้งแต่ 0 - 2047 และสามารถนำไปเทียบกับ wordlist ที่กำหนดไว้ใน BIP-39 ตาม index จะได้ผลลัพธ์เป็น seed phrase ที่สามารถนำไปสร้าง seed ต่อไปได้
ผม map เลขฐานสิบกับ wordlist ได้เป็น seed phrase ตามนี้
00110010010 => 402 = crane10101011110 => 1374 = profit01010010110 => 662 = fan01101100100 => 868 = hold10100100010 => 1314 = picture00011000101 => 197 = board11001101110 => 1646 = soccer10000111001 => 1081 = mango00110111010 => 442 = dance00101011010 => 346 = clip10010100010 => 1186 = nephew10100110110 => 1334 = plugWordlist
wordlist ที่ BIP-39 กำหนดขึ้นมานั้นมีลักษณะดังนี้ - เลือกกลุ่มคำที่สามารถพิมพ์แค่ 4 ตัวอักษรก็สามารถระบุได้ว่าเป็นคำไหน - เลี่ยงคำที่มีหน้าตาคล้าย ๆ กัน เช่นใน wordlist จะมีคำว่า build แต่ไม่มีคำว่า built เพราะอาจจะทำให้สับสนได้ - เรียงลำดับคำตามตัวอักษรเพื่อจะได้หาได้ง่าย - ตัวอักษรในคำสามารถประกอบด้วยภาษาอะไรก็ได้แต่ว่าต้องอยู่ในรูปของ UTF-8 encoding แต่ผมว่าเป็นภาษาอังกฤษน่าจะจำง่ายที่สุด
จำนวน bits ของ entropy และจำนวน word ที่ได้
entropy 128 bits จะมี 4 bits checksum ได้เป็น seed phrase 12 word entropy 160 bits จะมี 5 bits checksum ได้เป็น seed phrase 15 word entropy 192 bits จะมี 6 bits checksum ได้เป็น seed phrase 18 word entropy 224 bits จะมี 7 bits checksum ได้เป็น seed phrase 21 word entropy 256 bits จะมี 8 bits checksum ได้เป็น seed phrase 24 word
-
 @ 42342239:1d80db24
2024-04-23 12:30:26
@ 42342239:1d80db24
2024-04-23 12:30:26Last year there were burnings of religious books in Sweden, leading to a diplomatic crisis. During a press conference, Prime Minister Ulf Kristersson emphasized that the government is currently not planning to restrict freedom of speech, although some of his government colleagues seem to take a different view.
In the 1960s, media theorist Marshall McLuhan expressed concern over the implications of what would evolve into a "global village." Advancements in communication technology would transform the entire globe into a kind of global community, with shared experiences and immediate access to information. Electronic media would enable a sense of global closeness. Different parts of the world would become aware of each other and influence each other, potentially blurring the boundaries between nations and cultures.
While such blending may be desirable, it is not without its challenges. For instance, perspectives on freedoms and rights can vary significantly between cultures and countries. Even truths and falsehoods differ. Asserting that the Armenian genocide occurred, for example, can lead to imprisonment in Turkey, whereas in France, denying the same genocide can result in imprisonment. If issues like these are elevated to a global level or to the EU or NATO level, whose rules should prevail? Will this genocide even be open to discussion?
Hence, McLuhan would not have been surprised by today's debate on freedom of speech. Unlike how many individuals a speaker from the corner of Hyde Park could reach in the 1800s, an individual's speech—or action in the case of Quran burnings—can now reach billions of people, for better or for worse. Perhaps it is time to reconsider freedom of speech?
On global (and centralised) social media platforms, freedom of speech has long been restricted; users are sometimes even blocked from sharing legally permissible content like links to news articles. Individuals who violate the terms of use are banned, sometimes losing their means of living. If these user agreements of the digital panopticons were adopted in the broader society, it would represent a significant restriction of freedom of speech.
In his book Orthodoxy, author and literary critic G.K. Chesterton wrote, "There is a thought that stops thought. That is the only thought that ought to be stopped." Isn't this precisely what proposals for restricted freedom of speech do?
If freedom of speech cannot be maintained due to the progression towards a global village (a.k.a. globalism), should it truly then be freedom of speech that we abolish? Perhaps it would be better to instead scale down the global village. Abolishe what's centralised, and favour what's decentralised and/or localised.
After all, without commonalities there can be no community.
-
 @ 8fb140b4:f948000c
2024-01-02 08:43:31
@ 8fb140b4:f948000c
2024-01-02 08:43:31After my second attempt at running Lightning Network node went wrong, mainly due to my own mistake and bad cli interface of LND, I have decided to look deeply into the alternative implementation of the lightning node software. Eclair was more final choice driven by multiple reasons that I am planning to further talk about in this write-up. The main reason I even considered Eclair despite my dislike of Java and JVM, was that one of the largest lightning nodes on the network is ACINQ, and they are the company behind the implementation and maintenance of this open source software.
I’ve noticed them first after reading their blog about how they run $100M Lightning node and what level of care and thought they put into the whole implementation. Lightning is used to transfer large quantities of value across the internet, and I would only trust something well designed and actively maintained by the people who have to lose the most if they make a wrong choice.
Eclair in itself is not a complex implementation of the lightning network standards, and highly modular, which allows for an easy segregation of duties among different components of the node. One of the biggest sales-points for me was their approach of crash-only software which guarantees consistency of the state regardless of what happens with the running software. By that extension, to shutdown the node, you simply kill the process and start it again. It doesn’t matter what transactions were in-flight, or what stage they were in. This is huge, since anything can happen to a running node (e.g., failed disk, failed RAM, CPU, kernel panic, etc.)
Getting back to the architecture, the Eclair is simple and elegant in design and implementation. The node is separated into three main components that comprise the node: eclair-core, eclair-node, eclair-front. All of the entities are sandboxed actors (e.g., peer, channel, payment), which allows for scalabilities across CPUs and faults. This ensures high availability and security.
Clustering is also an option and can be achieved by migrating from the single node to a multi-server node. There is no need to dive into complexities of that, and by the time you need to scale, I am sure you’ll be able to figure it out.
Simple and robust API, is yet another major reason that keeps the node simple and fast. One downside of the API, is that it is protected by a single password and is not designed for RBAC (Role Based Access Control). One solution could be an implementation of another API wrapper that would implement things similar to Runes or Macaroons, which should not be a challenge considering the REST API simplicity.
On-the-fly HTLC max size adjustment, which will prevent your node accepting forwarded payments that would fail due to lack of liquidity on your side. This also makes routing better for the rest of the lightning network, but may “leak” your channel balances if not done right.
Experimentation and adjustment of path-finding algorithm. I am not there yet myself, but I see this as a great option in the future if I need it. This will allow me to make my own choices how I want to route payments and what parameters I would use to determine the best path.
Full production support of PostgreSQL server. Not only Eclair itself is not a beta release unlike LND, but also has full production support of the very reliable and battle tested database as its backend data storage. You are able to(and should) to run Active/Passive PostgreSQL cluster in synchronous mode, and ensure that all of the written data by the node are backed-up in real-time. This removes the worry of corrupted database that I have seen happen all too often.
Excellent monitoring and metrics, that can be collected by Prometheus and viewed in Grafana. Eclair provides template dashboards that you can import into Grafana to make your life easier. You can also use Kamon (external service) where you could send the metrics and monitor your node.
Support for all common networking protocols and support Socks5.
Last, but not least, support for plug-ins. Even if you are not well versed in writing plug-ins, you could take some of the available ones and modify them to your liking.
There are many more features and limitations that I didn’t mention, but you can explore them yourself here.
One down-side that you should consider, is not such a great availability of the readily available tools. So far I found that Ride-The-Lightning works well; LNBits works but I am yet to see if it is reliable; BTCPayServer has support but I have failed to use it with API directly, and only was able to use it via LNBits.
Lightning is still reckless, but nothing stops you from doing it carefully and reliably. Good luck and happy node-running! 🐶🐾🫡⚡️
My Node - RAϟKO
-
 @ 6bae33c8:607272e8
2024-04-23 10:02:45
@ 6bae33c8:607272e8
2024-04-23 10:02:45It’s been nearly a month, your teams have acquired some stats and the standings are starting to gain a little weight. They are beginning to matter, but more important than where you are is how good your team is. That’s because there are still five months to go, and the future will tell the tale much more than the past. Still, you want to gauge how you’re doing, and if the present standings are only a very partial picture, how do you evaluate?
It’s obvious certain players have panned out: Elly De La Cruz looks every bit the first rounder people pegged him as by Main Event draft day. (I was way out on him and thrilled when he went ahead of me which meant I could land Trea Turner.) Now De La Cruz would be top-five overall and possibly the second overall pick. Mike Trout is hitting and stealing bases — he looks like a Round 2 pick at a minimum and maybe Round 1. Anyone can get hurt, but these look like big wins early on.
Similarly Wyatt Langford, who has yet to homer or steal a base, looks reachy at the 5-6 turn. The teams that waited on pitching look like they did the right thing with only a few exceptions. Closers like Robert Suarez and Mason Miller look like values. The obvious wins and losses are easy to see even though we know baseball is streaky, and things will likely change dramatically.
But what about my Main Event Trea Turner/Yordan Alvarez 1-2 turn? Both are doing fine, well within the fat-part of the expected-outcome range. Most players are still there, whether on the good or bad side of that. Their production thus far doesn’t say much one way or another about whether they were good picks where you took them. (Maybe Turner is a slight positive after last year’s slow start, but I suspect he’d still go around where he went — for stats going forward only — if we were to re-draft again today.)
There are edge cases like 34-YO Freddie Freeman with one homer and one steal. Is he an 18-10 guy this year or will he get hot and start raking (and running) at something close to last year’s pace. (There’s nothing wrong with his on-base skills.) We don’t know, first off, because we never really know, but also because unlike in March, there is no market-based ADP to guide us.
We don’t know exactly how much of a discount Freeman would fetch based on his lack of power or steals. Would he go behind Trout? We have only our individual opinions. (FWIW, I’d still go Freeman because of the runs/RBI guaranteed in the lineup, as well as his likely advantage in batting average and lesser injury risk. But Trout could go 45-20 if he plays 140 games. Maybe that’s still an obvious call, but I would at least think about it.)
That there is no ADP market once the season starts means we’re updating our priors based on the accumulated information all alone. There’s no easy sanity check, no quasi-objective gauge against which to measure. Go ahead and tell yourself Freeman or Corbin Carroll (who might go in the second round today) will be fine. Or panic about Aaron Judge. It’s up to you. But you’re in no man’s land, and that’s always the case once the season starts.
In my experience, the best course is to read whatever you like into it, but to embrace to the greatest extent practicable your ignorance of whether your reading is accurate. You don’t know if your Judge/Freeman team isn’t on the cusp of going off, and you should manage it like it’s your De La Cruz/Trout one. It’s natural to give more attention to your winners and mail-in your losers, but I’ve had teams that were bad in June catch fire in August and come to regret not being a little more aggressive in scouring the waiver wire two months earlier for them.
One last thought — the advanced stats won’t help you that much with this. If you have a guy with one home run, but great exit velo and launch angle, maybe he’s been unlucky, but typically bad stats go with bad under-the-hood metrics too. Uncovering the unlucky via advanced metrics is the low-hanging fruit.
The real mystery, where the rubber meets the road, is where someone who has been bad (both under the hood and in the surface stats we count) starts being good and vice-versa. A mechanical adjustment, a health problem going away, a player who does better as the weather warms or needs 30 games of reps to get going. There will be many such cases this year, and we probably won’t see them coming.
-
 @ 8fb140b4:f948000c
2023-12-30 10:58:49
@ 8fb140b4:f948000c
2023-12-30 10:58:49Disclaimer, this tutorial may have a real financial impact on you, follow at you own risk.
Step 1: execute
lncli closeallchannelsThat’s it, that was easy as it could be. Now all your node’s channels are in the process of being closed and all your liquidity is being moved to your onchain wallet. The best part, you don’t even need to confirm anything, it just does it in one go with no questions asked! You can check the status by using a very similar looking command,
lncli closedchannels!Good job! Now you are ready to start from scratch and use any other reasonable solution!
🐶🐾🫡🤣🤣🤣
Disclaimer: this is a satirical tutorial that will 💯 cost you a lot of funds and headaches.
-
 @ a023a5e8:ff29191d
2023-12-20 04:43:48
@ a023a5e8:ff29191d
2023-12-20 04:43:48Yesterday I was sleeping with my wife and 2 kids in same bed and in middle of night i just woke up to see my wife and kids sleeping aside me in a moonlight like ambience and it was a vivid feeling. And I just got panicked with strange feeling and in a bit I woke up really to see them again. All was in just a moment. Did you ever had such experience?
-
 @ 11be7dbc:82a5f8e9
2024-04-23 09:20:20
@ 11be7dbc:82a5f8e9
2024-04-23 09:20:20At its core, Cyberyen's culture stands as a testament to the transformative power of cryptography technology, extending far beyond its utilitarian aspects. It’s philosophy encourages individuals to harness and unleash their latent talents, freeing themselves from prevailing consumerist mindsets. It fosters the realization of one's potential in shaping the digital environment, transcending preconceived notions of passive interaction. Cyberyen ceases to be a mere platform for transactions; it metamorphoses into an underground space that fosters internal self-expression, creativity, and the cultivation of self-reliant digital autonomy, enabling the discovery of a new, free, and boundless persona.
Navigating Parallel Realities for Autonomy
Cyberyen champions the concept of parallel dimensioning—an autonomy that liberates individuals from traditional consumer models and geographic restrictions. It serves as a catalyst for profound shifts in thinking, encouraging users to interact with technology in transformative ways and to challenge the reality imposed upon us. Combined with the cypherpunk philosophy of autonomy and freedom, this fosters the development of new cultural architectures. For example, the #Cyberdump aesthetic movement emerges unexpectedly, boldly challenging digital enslavement and blindness. These urges serve as a creative manifestation of empowerment, inspiring people not only to choose alternative paths but also to explore new avenues of discovery. By generating novel concepts, Cyberyen underscores the transformative potential of harnessing unconventional perspectives and technologies to cultivate a culture of innovation and self-determination.
The metaphor of a "parallel dimension" vividly illustrates the importance of a shift in perspective, urging people to explore multiple options beyond conventional choices, much like navigating through different paths in a tunnel. Often, reliance on routine transportation methods leads to inconvenience during disruptions. Cyberyen aims to empower individuals to transcend these limitations, allowing them to actively shape new avenues of exploration rather than passively conforming to predefined structures.
Exploring Alternative Realities for Collective Progress
Our world harbors countless dimensions often overlooked or dismissed due to imposed stereotypes. Yet, if we pause to observe, expansive networks of tunnels, intricate underground passages, bustling metro stations, flea markets, and their denizens—hackers, cypherpunks, street musicians, and artists—emerge as the unspoken echoes of souls we fail to notice while absorbed in our daily urban hustle.
Take a moment, open your eyes, and breathe deeply to acknowledge the myriad parallel realities encompassing you. In this realm, every individual contributes as a co-creator of an infinite world. Recognizing this, Cyberyen serves as the foundation of a burgeoning culture within the underground world, nurtured by the Cyberyen blockchain.
Therefore, fearlessly discard your trough at the nearest parking lot, and delve into the underground reality—the realm of Cyberyen. Here, there are no marketing strategies, no pressure from authorities swayed by commercial agendas. Cyberyen forms an underground haven, providing life's essentials, yet thriving on the essence of people like you—free from societal stratification, openly embracing the exchange of experiences and mutual benefits.
Cyberyen represents a community striving to build a decentralized ecosystem, free from intermediaries, and dedicated to preserving absolute independence in expressing ourselves and sharing. It serves as a sanctuary, focused on people without social stratification, fostering collective creation and unbridled expression.
Upholding Security and Reliability
It's time to transcend conventional technological paradigms and perceive ourselves not as mere consumers but as active contributors and architects of our digital destinies. Cyberyen advocates for a profound shift in perception—moving away from passive user interfaces towards an empowered state where individuals curate, shape, and mold their digital realities.
As people free their minds from the erroneous behavior that is prevalent in certain areas, they discover a vast expanse of Cyberyen space that can expand in tandem with the liberation of human consciousness.
Central to this clandestine world is a covert transactional hub, a thriving environment brimming with innovation, collaboration, and a collective pursuit of a more enlightened future. This unseen force doesn't manifest physically; instead, it thrives within the digital matrix, permeating the collective consciousness, and redefining the norms and values that underpin modern interactions and transactions.
Within this domain, sleek interfaces are absent, replaced by code—a robust Proof-of-Work (PoW) blockchain. The Cyberyen community diligently fortifies this resilient PoW system, crucial for network security, scalability, and unwavering transaction reliability—an embodiment of Cyberyen's fundamental principles. This departure from traditional interfaces directs the community's focus to the potency of code and technology, prioritizing substance over superficiality. The PoW-based distributed network, with ASIC-enabled mining hubs, expands the platform's scope and social impact, serving as a secure foundation for its functionalities.
Towards Digital Enlightenment and Financial Liberation
The Cyberyen underground thrives on dynamism, creativity, and an unyielding quest for progress. It stands as a testament to the transformative potential of technological innovation, challenging the outdated structures of conventional financial systems. This heralds an era of collaborative ingenuity, where a collective pursuit of enlightenment shapes a new interconnected future—a future not bound by conventional limits but driven by forward-thinking minds and digital aspirations in unison.
Acknowledging the plight in developed countries where access to financial services remains limited, Cyberyen paves the way for individuals to explore alternative financial avenues, liberating them from the constraints imposed by traditional banking systems. This freedom of choice is a universal right that all individuals should embrace and utilize.
The Cyberyen underground does not merely exist at the fringes of societal discourse; it represents an undercurrent—an unseen yet formidable force pulsating beneath the surface of conventional understanding. It forms an invisible yet palpable digital tapestry, interweaving the aspirations, innovations, and collaborative endeavors of a global community unified by a shared vision—a vision of a digitally enlightened future.
To Embracing a New Digital Paradigm
The inception of Cyberyen marks an epochal shift in the mind, at this time when the traditional cryptocurrency narrative faces an existential threat. Steering away from profit-centric motives, it delves deep into realms of collaboration and collective progress. Cyberyen's ideological current propels individuals beyond passivity, calling them to navigate parallel paths in crafting an interconnected, collaborative digital sphere.
Don't fear going underground; life thrives in unconventional spaces. Here, we build a new culture.
Stay with us... C¥kuza
-
 @ a023a5e8:ff29191d
2023-12-19 12:14:53
@ a023a5e8:ff29191d
2023-12-19 12:14:53Shit shit shit
-
 @ 1abc40c5:6cd60e41
2023-12-17 07:42:37
@ 1abc40c5:6cd60e41
2023-12-17 07:42:37สวัสดีครับ ยินดีต้อนรับสมาชิกใหม่สู่สังคมชาวม่วง ด้วยความยินดียิ่ง
ในเบื้องต้นเข้าไปเรียนรู้และศึกษาการใช้งานตามโน๊ตของพี่แจ๊ค กู๊ดเดย์ พี่ใหญ่ของเราก่อนเลยครับ (จะรู้ว่าโลกใบนี้กว้างใหญ่กว่าที่เห็น)

===================== แล้วก็ไปเพิ่มกระเป๋า LN Wallet สำหรับรับ zap ง่าย ๆ ได้จากบทความของจารย์ Notoshi (อาจารย์อาร์ม RS)
-
หากใช้ Nostr บนคอมพิวเตอร์เป็นประจำ สามารถผูกกับ Browser Extension เพื่อใช้งานง่าย ๆ แนะนำ "Getalby" ครับ
-
หากเล่นบนมือถืออาจจะเหมาะกับ "Wallet of Satoshi" และ "Blink wallet" มากกว่า
แต่แนะนำว่าควรมีทั้ง 2 แบบครับ ท่านจะได้ใช้ประโยชน์ในเวลาที่เหมาะสมอย่างแน่นอน 5555
===================== จากนั้นไปเพิ่ม Siamstr Relay - wss://relay.siamstr.com - wss://teemie1-relay.duckdns.org
ที่สนับสนุนโดยพี่ตี๋ เพื่อให้เราชาวไทยเชื่อมสายสัมพันธ์ต่อกันและมองเห็นกันได้ ตามนี้เลยครับ
และก็ลืมไม่ได้ที่จะเพิ่ม Siamstr Relay อีกหนึ่ง ..ที่สนับสนุนโดยอาจารย์อาร์ม RS ของเราเองเช่นกันครับ - wss://relay.notoshi.win
ทั้ง 3 Relay นี้ เป็น Free paid Relay นะครับ สามารถใช้งานได้เลย ^^
หรือหากใครยังไม่จุใจ.. อยากได้รีเลย์เพิ่มเติมอีก แนะนำไปดูที่ อัพเดทลีเรย์ 9/12/2023 จากพี่ใหญ่ของเราได้เลยครับ
===================== และอย่าลืมไปสร้าง NIP-05 NOSTR ADDRESSES "@siamstr.com" เท่ห์ ๆ ได้ที่ siamstr FREE NOSTR ADDRESSES. เพื่อทุกคน เพื่ออิสรภาพ ใครมาก่อนได้จับจองชื่อก่อนน้าาา ... ^^
===================== อ้อ ... หากอยากเรียนรู้พื้นฐาน Nostr แบบเชิงเทคนิคคอล หรือการเก็บ nsec (Private key) ของเราให้ปลอดภัย ... เชิญได้ที่บทความของพี่อาร์ม Righshift ของเราครับ
หรือจะเข้าไปอ่านจากในนี้ก็ได้เช่นกัน
Nostr: โซเชียลมีเดียเสรีไร้ศูนย์กลาง
 ภาพ : Network diagram จาก https://nostr.how/en/the-protocol
ภาพ : Network diagram จาก https://nostr.how/en/the-protocol===================== สุดท้ายผมหวังว่าเราจะได้รู้จักกันมากขึ้นกว่านี้ เพื่อร่วมกันสร้างสังคมที่เต็มไปด้วยคุณค่า และความรู้สึกดี ๆ ให้แก่กันต่อไปครับ
ขอบคุณที่เข้ามาเป็นส่วนหนึ่งของเราครับ
-
-
 @ 908d47b6:a2bf38ad
2024-04-23 09:13:26
@ 908d47b6:a2bf38ad
2024-04-23 09:13:26Bitcoin's Soaring Ascent: A Billionaire's Dire Prediction
As the price of bitcoin skyrockets, legendary investor Tim Draper issues a chilling prophecy of the U.S. dollar's impending collapse by 2030. Drawing parallels to historical currency failures, Draper urges individuals to safeguard their financial future by embracing bitcoin, painting it as a crucial asset in the face of imminent economic upheaval.
There will be a moment in time, and I don't know whether it's a day or a month or maybe over the course of two months or something, but I don't know when it will start, whether it'll be a year or five years or whatever, maybe even ten years out, but it'll happen very rapidly. -- Tim Draper
The Halving's Shadow: Bitcoin's Path to $250,000
Amidst Draper's warnings, the imminent bitcoin halving looms large, promising to disrupt market dynamics and potentially propel the cryptocurrency's value to unprecedented heights. Draper highlights the halving's role in tightening bitcoin's supply and boosting demand, predicting a bullish trajectory that could see prices soar to $250,000 by year-end, challenging even the most established financial benchmarks.
I hope anybody who's watching this is trying to at least have some bitcoin so that they can feed their family during the time when the dollar goes to zero. -- Tim Draper
Dollar Debacle: The Fragile State of Traditional Finance
Against a backdrop of mounting debt, inflation, and economic uncertainty, concerns over the stability of the U.S. dollar reach fever pitch. Figures like Nassim Taleb and Jim Rogers echo Draper's apprehensions, cautioning against the Federal Reserve's limited ability to stave off a potential crisis. In this climate of uncertainty, bitcoin emerges as a beacon of financial resilience, offering a decentralized alternative in an increasingly fragile financial landscape.
Source: Forbes
-
 @ ecda4328:1278f072
2023-12-16 20:46:23
@ ecda4328:1278f072
2023-12-16 20:46:23Introduction: Crypto.com Exchange for European Traders
Reside in Europe, including non-EUR countries? Frustrated with the exorbitant spreads on the Crypto.com App (up to 5%) and high credit card fees (up to 3%) when you're eager to buy or sell cryptocurrency? This guide is tailored for you!
Quick Transfer with SEPA Instant
Did you know that you can transfer EUR to your Crypto.com Exchange account within minutes, and sometimes even seconds, including weekends and bank holidays? Yes, you absolutely can, thanks to SEPA Instant Credit Transfer (SCT Inst).
Supported Banks
To avail of fast EUR to Crypto.com Exchange transfers, ensure that your bank supports the SEPA Instant Credit Transfer (SCT Inst) scheme. If your bank, or FinTech apps like Wise, is on this list, you're good to go.
My Recommendation: I vouch for Wise due to its flawless functionality and favorable exchange rates. If your bank doesn't support SCT Inst and you're unwilling to wait, you can swiftly load your account with any currency using a bank card for a rather small fee (~1.2%). My Wise Referral Code: andreya54
24/7 Transfer Availability
SCT Inst is incredibly flexible:
- 24/7/365 availability, including weekends and bank holidays
- Immediate receipt and availability of funds
- €100,000 transaction limit (unless previously agreed otherwise between PSPs)
For more details, you can read this document by the European Central Bank.
TL;DR
To Buy crypto: -
EUR => BTC/EUR => ANY/BTC => ANY
- Use Limit order at the Lowest offer (aka "ask") (red order book)To Sell crypto: -
ANY => ANY/BTC => BTC/EUR => EUR
- Use Limit order at the Highest bid (green order book)How to Buy Cryptocurrency with EUR
Here's how to save up to 8% on spreads and fees when buying/selling crypto compared to the Crypto.com App.
-
Log in to Crypto.com Exchange: Go to the Dashboard or Wallet in the top right, and navigate to Bank Transfer on the left sidebar.


-
Deposit via SEPA: Choose
EUR -> SEPA -> Depositand use the displayed IBAN for transferring EUR to your Crypto.com Exchange account.
Trading Interface Tips
Intimidated by the professional trading interface? Don't be. Here's how to read the order book:
- Offers (Red): These are the prices at which people are willing to sell the asset. The lowest offer is often called the "Ask."
- Bids (Green): These are the prices at which people are willing to buy the asset. The highest bid is often called the "Bid."
Trading occurs when a buyer's bid meets a seller's offer. In market terms, this is often at the point where the highest bid and the lowest offer intersect. This intersection is frequently referred to as the "market price" for that particular asset at that specific time.

On trading pairs
Crypto.com Exchange offers only two EUR trading pairs: BTC/EUR and ETH/EUR. This is logical given that these assets have the highest liquidity in terms of market capitalization. While we hope for the addition of more pairs, the existing options still serve as useful proxies for purchasing other cryptocurrencies.
"highest liquidity" means that an asset like a cryptocurrency or stock can be easily bought or sold without causing a significant impact on its price. For a trader, this is good because it means they can quickly enter or exit positions without worrying about huge price changes.
Steps to Buy BTC with EUR
- Navigate to the
BTC/EURSpot trading pair. - Choose "Buy" on the right-hand menu.
- Stay on the "Limit" tab.
- Specify your order value (how much EUR you want to spend to buy BTC)
- Select the lowest offered (aka "ask") price (bottom of the red order book).
- Click "Buy BTC" to confirm.

Diversifying: How to Buy ATOM Token?
First, buy BTC as previously explained. Then:
- Navigate to the
ATOM/BTCSpot trading pair. - Choose "Buy" on the right-hand menu.
- Stay on the "Limit" tab.
- Specify your order value (how much BTC you want to spend to buy ATOM)
- Select the lowest offered (aka "ask") price (bottom of the red order book).
- Click "Buy ATOM" to confirm.

Selling Your Assets
The process is the same but in reverse. Sell at the highest bid (top of the green order book).
Selling ATOM for BTC
- Navigate to the
ATOM/BTCSpot trading pair. - Choose "Sell" on the right-hand menu.
- Stay on the "Limit" tab.
- Specify your quantity value (how much ATOM you want to sell to buy BTC)
- Select the highest bid (top of the green order book).
- Click "Sell ATOM" to confirm.

Selling BTC for EUR
- Navigate to the
BTC/EURSpot trading pair. - Choose "Sell" on the right-hand menu.
- Stay on the "Limit" tab.
- Specify your quantity value (how much BTC you want to sell to buy EUR)
- Select the highest bid (top of the green order book).
- Click "Sell BTC" to confirm.

You can then withdraw EUR back to your bank directly from the Crypto.Com Exchange.
Additionally
After you click "Buy" or "Sell," you will see your order in the "Open Orders" tab in the bottom menu. Once your order is 100% filled, it will disappear, and you will be able to see it in the "Trade History" tab.
Sometimes you might miss the opportunity as the price moves, and someone else's order could get filled faster than yours. Don't worry; you can either wait a little longer in hopes that someone will make an offer at this price or simply cancel your order and submit it again at the next lowest price if you are in a hurry.
Maker/Taker Fees Explained
When you open Buy/Sell orders on the Crypto.com exchange, you may incur small Maker/Taker fees of less than
0.0728%, or even no fees at all, depending on the amount of CRO you have staked on the platform.- Maker Fee: When you place an order that adds liquidity to the market, you are a "Maker". This usually happens when you set a "limit" order that does not execute immediately and sits on the order book waiting for someone to match against it. Since you are "making" liquidity available for others, you pay a Maker fee.
- Taker Fee: When you place an order that removes liquidity from the market, you are a "Taker". This generally occurs when you place a "market" order that executes immediately against a pre-existing order on the order book. Because you are "taking" liquidity away, you pay a Taker fee.
Typically, Taker fees are higher than Maker fees as an incentive for traders to add liquidity to the market.
Read more on Maker/Taker fees on the Crypto.Com Exchange platform.
Conclusion
Thanks for reading this guide! It's lengthy, but every detail is crucial for optimal trading on Crypto.com Exchange.
Referral Code
If you haven't opened a Crypto.com Exchange account yet, use my referral code:
pv0r199m6j
Referral Link: Sign Up Here -
 @ ecda4328:1278f072
2023-12-16 20:45:50
@ ecda4328:1278f072
2023-12-16 20:45:50Introduction
In the world of blockchain technology, a nonce plays a pivotal role in ensuring transaction security and uniqueness. This article demystifies the nonce's role in major blockchain platforms - Bitcoin, Ethereum, and Cosmos/CometBFT, highlighting its importance and distinct functionalities in each.
The Role of Nonce in ECDSA and Its Importance
In Bitcoin (and most of blockchains) transactions, the nonce is a randomly generated number integral to the Elliptic Curve Digital Signature Algorithm (ECDSA). It guarantees each digital signature's uniqueness and security. The randomness and secrecy of the nonce are vital. If predictable or exposed, it can compromise the entire security of a transaction.
The Risk of Nonce Exposure and Private Key Recovery
If a nonce is compromised, it poses a risk of private key recovery. To understand this, one must consider the signature components (r, s), the public key (which becomes known once you sign & broadcast at least one transaction in Bitcoin). A predictable or reused nonce can leak critical information, enabling savvy attackers to backtrack to the private key.
This specific type of attack is called a nonce covert channel attack. And methods protecting against this are called anti-klepto or anti-exfil (interchangebly).
Worth noting that anti-klepto/anti-exfil are broader terms for methods that protect against various forms of secret data exfiltration, including but not limited to attacks involving nonce misuse.
Bitcoin's UTXO Model and Nonce Functionality
Bitcoin utilizes the Unspent Transaction Outputs (UTXO) model, ensuring that each Bitcoin is spent only once. This model is distinct from nonce management in ECDSA and adds an additional layer of security against double-spending in the Bitcoin network.
Address rotation in Bitcoin, as implemented through BIP32 (Hierarchical Deterministic Wallets), enhances privacy and isolates financial risk by generating a unique address and corresponding private key for each address created, not necessarily for each individual transaction. While this strategy effectively segregates risk to individual addresses, it does not directly prevent the vulnerability of private key derivation from nonce exposure in the ECDSA signature process, as this risk is inherent to the signature mechanism itself and is independent of the address or its associated private key.
Ethereum's Account-Based Model and Nonce Usage
Ethereum, unlike Bitcoin, operates on an account-based model. Each account has a sequential transaction nonce, starting from 0, which is public. This nonce, different from the ECDSA nonce, helps in transaction ordering and network integrity.
Nonces in Cosmos/CometBFT Blockchains
Cosmos/CometBFT blockchains, akin to Ethereum, adopt an account-based model. They use nonces, similar to Ethereum's transaction nonce, for transaction ordering and preventing replay attacks. These nonces are distinct from the ECDSA nonce used in the digital signature process.
Conclusion
The use of "nonce" in Ethereum for transaction sequence (akin to account sequence in Cosmos/CometBFT blockchains), leading to confusion with ECDSA nonce, is simply a coincidental choice of terminology.
In summary, while Bitcoin, Ethereum, Cosmos/CometBFT and many other blockchains employ nonces in ECDSA signing, their transaction management and double-spending prevention methods differ significantly. Understanding these nuances is crucial for blockchain users and developers to appreciate the underlying security mechanisms of these diverse platforms.
References
- Hardware wallets can steal your seed!
- A Glimpse of the Deep: Finding a Creature in Ethereum's Dark Forest
- MuSig-DN: Schnorr Multisignatures with Verifiably Deterministic Nonces
- Android's SecureRandom - not even nonce
- Anti-klepto explained: how the BitBox02 protects you against leaking private keys
- Anti-Exfil: Stopping Key Exfiltration
-
 @ 1f9e547c:8af216ed
2024-04-23 09:02:25
@ 1f9e547c:8af216ed
2024-04-23 09:02:25testthishashtag2
app.svelte-tag-default-value
-
 @ 02f0a63d:f91bde2c
2024-04-23 08:52:56
@ 02f0a63d:f91bde2c
2024-04-23 08:52:56 -
 @ ecda4328:1278f072
2023-12-16 20:45:10
@ ecda4328:1278f072
2023-12-16 20:45:10Intro
I've left Twitter (X), WhatsApp, Telegram, Instagram, Facebook and Google. The driving force behind this decision was the escalating overzealous censorship. I cannot condone platforms that actively indulge in this practice. In all honesty, I've always felt uneasy using "free" platforms riddled with ads where the user is the product and doesn't own the content they produce.
Let's be real: hardly anyone thoroughly reads the Terms of Service (ToS).
Censorship and Shadow Banning
The final straw was when I resorted to a text editor for drafting messages/comments, hoping to rephrase them so they wouldn't get deleted moments after posting. This isn't exclusive to just one platform; I've encountered it on YouTube and LinkedIn too. Twitter (or X, as I now refer to it) has a history of shadow banning users' posts. It's been beyond frustrating to get banned from Telegram groups simply for posing legitimate questions.
You can test LinkedIn's censorship mechanism too, simply add "Binance" word (without quotes) to any of your comment and your post will disappear. At least that is what I've seen couple of months ago. Similarly, comments on YouTube often disappear precisely 60 seconds after posting if they contain specific keywords. I know they call it filtering, but it does not make any sense. In my opinion, legitimate companies and links shouldn't trigger these filters.
Community and Connections
Recently, I attended the Cosmoverse 2023 conference in Istanbul. Most attendees exchanged their Telegram or Twitter (X) contact information. Since I didn't have either, I gladly shared my Nostr and SimpleX Chat details. Many privacy advocates were quick to connect on SimpleX with me, though several didn't.
I learned about SimpleX Chat from Jack Dorsey, who mentioned it during a conversation in July:
While Signal has its shortcomings, I still keep it as a backup communication tool.
One More Last Straw
During the conference, I temporarily reinstalled Telegram to communicate with my group. Convincing nine individuals to switch to SimpleX on the spot seemed impractical.
At the conference, I bought a Keystone hardware wallet. Shortly after, I connected with the seller, Xin Z, on Telegram. However, I was banned from the official Keystone Telegram group right after posing a question.

Upon inquiring, Xin Z clarified that Telegram's official team had banned me, not the group's admin. 🤯

Business and Community: Collateral Damage
Censorship doesn't just silence voices; it hinders potential growth and stifles innovation. When platforms arbitrarily or aggressively censor content, they inadvertently create barriers between businesses and their potential clients. New users or clients, when encountering such heavy-handed moderation, may feel discouraged or unwelcome, causing them to retreat from the platform altogether.
Moreover, for businesses, this form of censorship can be devastating. Word-of-mouth, discussions, and organic community engagements are invaluable. When these channels are hampered, businesses lose out on potential clientele, and communities lose the chance to thrive and evolve naturally.
Censorship, in its overzealous form, breaks the very essence of digital communities: open dialogue. As platforms become more censorious, they risk creating sterile environments devoid of genuine interaction and rich discourse. Such an atmosphere is not conducive for businesses to foster relations, nor for communities to flourish. The ultimate price of overcensorship isn't just the loss of a few voices—it's the fragmentation of digital society as we know it.
Freedom to Choose
I strongly advocate for the adoption of Free and Open Source Software (aka FOSS) products. In these platforms, you aren't treated as the product. However, supporting them through donations/contributions is always an option. Platforms like Nostr and SimpleX Chat are excellent starting points.

My Nostr account:
npub1andyx2xqhwffeg595snk9a8ll43j6dvw5jzpljm5yjm3qync7peqzl8jd4Disclaimer
This article reflects my personal experiences and opinions. It is not intended to criticize or demean the Keystone hardware wallet product or its quality. Furthermore, the actions taken by Telegram are not a direct representation of the views or policies of the Keystone Telegram group admins. Any reference to specific events or entities is made in the context of broader concerns about platform censorship.
-
 @ 1c9dcd8f:1852f704
2024-04-23 07:56:47
@ 1c9dcd8f:1852f704
2024-04-23 07:56:47The most striking finding overall was the dominance of influencer-centred content, which accounted for the vast majority of videos in the dataset. Significantly, most of this material originated from regular users or micro- influencers reposting clips of influencers, rather than from the influencers’ own accounts. This demonstrates the extent of both user-led and algorithmic amplification of influencer content, and was especially evident in the case of Andrew Tate, who was by far the most recommended influencer on both platforms, despite the fact that his accounts were inactive at the time of data collection. The dominance of these ‘ideological entrepreneurs’ (Jurg et al., 2023) marks a significant new shift in the manosphere, whereby male-supremacist influencers are not only accumulating considerable wealth but are also using the practices of influencer culture for metapolitical goals, a phenomenon noted by Maly (2020) in the context of the Far Right in recent years. By adopting less overtly gender- political rhetoric, and instead mobilising discourses around mental health, motivation and money-making, these influencers are strategically monetising men’s financial and emotional insecurities (Bujalka et al., 2022). This was evident in our dataset in the prevalence of content coded as ‘alpha masculinity’ (12.7% on TikTok and 32.5% on YouTube Shorts) over that coded as ‘anti- feminism / misogyny’ (8.3% on TikTok and 23.9% on YouTube Shorts). ‘Manfluencers’ have thus effectively replaced pick-up artists and the seduction industry with a significantly more lucrative, popular, and ostensibly well- intentioned venture, which purports to give men purpose, confidence and control.
Linked to this new development has been the revival of the notion of stoicism, reappropriated from ancient Greek philosophy, whereby self-help influencers such as Ryan Holiday and Jordan Peterson advocate traditional masculine values of courage, self-discipline, andorder as an antidote to the alleged chaos and narcissism of ‘woke’ modernity. Aleks Hammo (2023) refers to this phenomenon as the ‘stoic industrial complex’ and maintains that its appeal lies in its promise of taking control in an age of hyper-competition, secular disenchantment, and consumerism. However, this military-style neo-stoicism is underpinned by the repression of emotion, a return to strict gender roles and simplistic, individualistic accounts of complex social phenomena. It is also used to discredit the concept of structural or systemic disadvantage, and to reinforce the message that anyone can make it if they work hard enough. Many of the influencers in our dataset actively promote this message, urging men to ‘pull themselves up by the bootstraps’ and to try harder as ‘no one cares about the men who fail’. For example, an account reposting this type of content using the hashtags #motivation #mindset #advice
inspiration features retired US Navy SEAL
David Goggins urging, ‘You need to fking work harder, you need to fking discipline your mind better…all the time you’re complaining, you could be instead hustling’.
In tandem with this focus on neo-stoicism was another, ostensibly incongruous, theme which we termed ‘wealth porn’. This involves influencers bragging about their wealth and possessions, showing off their car collections and, in some cases, purchasing expensive cars and wrist watches on a whim. It also frequently involves disdain for poor people (‘brokies’) who are deluded to believe they can make money ‘inside the matrix’, which refers to mainstream, ‘blue-pilled’ or ‘normie’ society. Videos featuring Andrew Tate and Tristan Tate accounted for most of this content, and they frequently refer to the disciplinarian and frequently cruel parenting style of their father as responsible for their ‘sheer indefatigability and unmatched perspecacity’. Many of the Tate brothers’ motivational clips also double up as advertisements for Andrew Tate’s businesses, in particular the Real World, the War Room, and Hustlers University
-
 @ ecda4328:1278f072
2023-12-16 20:44:09
@ ecda4328:1278f072
2023-12-16 20:44:09In the evolving world of cryptocurrency, ensuring the security of your digital assets is paramount. For those looking to safeguard their Bitcoin and other cryptocurrencies, selecting the right hardware wallet is crucial. Here, I recommend some top choices based on functionality and security.
Swiss Choices for Bitcoin: BitBox02
For Bitcoin enthusiasts/maxis, the Swiss-made BitBox02 - Bitcoin-only edition is a top recommendation. This wallet focuses solely on Bitcoin, ensuring specialized security and features for the most popular cryptocurrency. Although there is a version supporting multiple cryptocurrencies, the Bitcoin-only edition stands out for its dedicated functionality (Less code means less attack surface, which further improves your security when only storing Bitcoin). Learn more about this wallet here.
Swiss Tangem: A Unique Approach
Another Swiss option, Tange. Tangem is particularly appealing due to its unique approach to security. With Tangem cards, there's no need to generate or back up a mnemonic phrase (a series of 24 words used to recover wallets). The key is simply not to lose the cards and remember the access code, which adds an extra layer of security in case of loss. This approach simplifies security while maintaining robust protection for your assets.
Special Offer: For those interested in purchasing a Tangem Wallet, I have a special offer for you. By using my referral code, you can buy a Tangem Wallet at a discounted price. Click here and use the promo code MY6D7U to enjoy your discount.
Explore Tangem here.
Tangem's Mnemonic Phrase Advantage
Tangem's standout feature is the absence of the need for a mnemonic phrase. This reduces the risk of loss due to complicated backup schemes.
However, for those who do backup mnemonic phrases, I recommend using a metal plate for added durability against elements like fire and water. It's crucial to protect your mnemonic phrase thoroughly, as it essentially makes you your own bank. A fireproof and waterproof safe is advisable for storing these phrases. While some split the phrase and store parts in different locations, I advise against overly complicating the storage scheme to prevent loss. Adding an optional password for additional security is also recommended. Remember, mnemonic phrases unlock the same wallet addresses across different hardware wallets, as most use the BIP39 protocol for generating a seed from the 24-word phrase. Check out this list for reference: BIP39 Word List.
Worth reading: - Seed Phrases Explained: Best Practices for Crypto Security - How Tangem Wallet backs up private keys - How Your Tangem Wallet Works Without Tangem: Apocalypse Scenario
French Ledger: A Shift in Trust
The French Ledger Nano S Plus or Ledger Nano X were previously high on the recommendation list. However, trust in these devices has diminished due to Ledger's service Ledger Recover allowing mnemonic phrase backups on third-party servers. This goes against the principle of a hardware wallet, where your seed should never be exportable or stored externally.
Chinese Keystone 3 Pro: A Contender with Caveats
As an alternative to Ledger, the Chinese Keystone 3 Pro could be considered. Although there are concerns about its Chinese manufacturing possibly implying vulnerabilities, its functionality—like signing transactions via QR codes without direct computer connection—offers a level of security. However, choosing a hardware wallet should be based on the specific cryptocurrencies you plan to store. For Bitcoin-only storage, the BitBox02 Bitcoin-only edition is highly recommended.
Worth reading: - Does airgap make Bitcoin hardware wallets more secure?
Czech Trezor: Slow to Innovate and Security Concerns
Regarding the Czech Trezor Model T, it's not recommended due to its slow pace in integrating new features. Recent controversies surrounding the integration of CoinJoin and concerns over censorship and transaction filtering have also marred its reputation. Furthermore, the Trezor Model T has proven to be vulnerable in case of loss, as demonstrated by a hacker in this video, potentially exposing your cryptocurrency to risks.
The Case of Canadian Coldcard (MK4): A Shift from FOSS
An important development in the hardware wallet space is the case of the Coldcard Mk4. Initially, Coldcard was a fully open-source software (FOSS) project. In FOSS, the "Free" refers to the freedom to run, study, redistribute, and modify the software, a principle highly valued in the crypto community. However, a significant shift occurred in the journey of Coldcard:
- Initial FOSS and Bootstrapping: Coldcard, developed by nvk and Peter, started as a FOSS project. They bootstrapped the development, rejecting offers from venture capital investors interested in the project.
- Foundation's Entry: Subsequently, the Foundation cloned Coldcard's code and announced a slightly different hardware. Notably, they raised funds from the same VCs that Coldcard had previously turned down.
- License Change: In response to these events, Coldcard altered its software license. The new license permits all activities except those performed by the Foundation, marking a departure from its original FOSS status.
This change has sparked discussions within the cryptocurrency community about the importance of maintaining open-source principles in the development of hardware wallets. The Coldcard MK4's shift from FOSS underscores the complex dynamics between open-source ethos and commercial interests in the crypto world.
Source: X/Twitter thread.
Conclusion
In conclusion, when choosing a hardware wallet, consider the specific cryptocurrencies you'll be storing and the compatibility of the wallet with your intended use, especially concerning smart contracts and other features. While there are numerous options in the market, careful consideration of security features and the reputation of the manufacturer can guide you in making a secure choice for your digital assets.
-
 @ a5d8475e:df9ff32c
2024-04-23 07:43:11
@ a5d8475e:df9ff32c
2024-04-23 07:43:11Whether you're a tenant searching for the perfect rental or a landlord seeking reliable management services, having a trusted letting agent by your side can make all the difference. With a myriad of options available, it's essential to choose an estate agent that understands your unique needs and offers tailored solutions. This is where Wolverhampton estate agents step in, providing comprehensive services to meet a variety of property requirements.
Estate Agents in Wolverhampton: A Hub of Opportunity
Wolverhampton boasts a vibrant property market, with opportunities abound for both tenants and landlords alike. From quaint residential neighborhoods to bustling commercial districts, the city offers a diverse range of properties to suit every preference. However, navigating this dynamic landscape requires expertise and insider knowledge, which is where estate agents Wolverhampton excel.
Letting agents in Wolverhampton serve as invaluable allies for individuals and businesses seeking property solutions. Whether you're a first-time tenant looking for a cozy apartment or a seasoned investor interested in expanding your portfolio, these professionals possess the experience and resources to streamline the process and maximize outcomes.
Comprehensive Services Tailored to Your Needs
One of the key advantages of working with letting agents Wolverhampton is access to a wide array of services designed to address every aspect of property management. From property valuations and marketing to tenant screening and rent collection, these agents handle the entire spectrum of tasks with efficiency and professionalism.
For landlords, letting agents offer peace of mind by taking care of property maintenance, tenant relations, and legal compliance, allowing them to focus on other aspects of their investment strategy. On the other hand, tenants benefit from personalized assistance in finding suitable accommodations within their budget and preferences, along with ongoing support throughout their tenancy.
Wolverhampton Estate agents leverage their local expertise and industry connections to match tenants with properties that meet their criteria, whether they're looking for a furnished apartment in the city center or a family home in the suburbs. By understanding the unique dynamics of the Wolverhampton property market, these agents can offer valuable insights and guidance to ensure a smooth and successful transaction for all parties involved.
Building Trust Through Transparency and Accountability
In an industry where trust is paramount, Wolverhampton letting agents prioritize transparency and accountability in their dealings. By fostering open communication and providing honest advice, these professionals establish lasting relationships built on mutual respect and integrity.
Whether you're a landlord entrusting your property to an agent or a tenant relying on their expertise to find your next home, knowing that you're working with a reputable and trustworthy agency can provide invaluable peace of mind. Estate agents in Wolverhampton understand the importance of delivering on their promises and strive to exceed expectations at every turn.
Navigating the Future of Property Management
As the property market continues to evolve, letting agents in Wolverhampton remain at the forefront of innovation, embracing new technologies and strategies to enhance their services. From virtual property viewings and online rent payments to data-driven market analysis, these agents leverage cutting-edge tools to stay ahead of the curve and deliver exceptional results for their clients.
By staying abreast of market trends and anticipating emerging needs, Wolverhampton letting agents position themselves as indispensable partners in the property journey. Whether you're looking to rent, buy, or invest in Wolverhampton, partnering with a reputable estate agent ensures a seamless experience from start to finish.
In conclusion, Wolverhampton letting agents play a pivotal role in facilitating property solutions for individuals and businesses across the city.
CONTACT:
2-3 Walsall Rd, Willenhall, WV13 2EH,
info@halleuk.com , +44 (0) 1902 504455 -
 @ 6ad3e2a3:c90b7740
2023-12-13 12:40:31
@ 6ad3e2a3:c90b7740
2023-12-13 12:40:31We often fantasized about time travel, mostly what stocks we would buy, what bets we would make. Buster Douglas and the 1999 St. Louis Rams to win the Super Bowl were two I liked to bring up. But that was before Henry got caught up in politics, and the conversation turned to altering events in world history.
Henry argued if you had one trip you’d be morally obligated to prevent some of history’s worst tragedies, and for him the go-to example was killing baby Hitler. If you were there and had the chance, you’d have to do it, he’d say, no matter how hard it would be to murder an innocent baby. If you hesitated to agree, he’d browbeat you, saying good people doing nothing is what allows evil to thrive. He saw it as an obvious choice: one as yet innocent baby in exchange for the lives and suffering of millions.
This made the exercise considerably less enjoyable, and we dropped it. That is, until The Simulator. The Simulator was a breakthrough technology, part virtual reality game, part research tool that enabled virtual experiments from modeling future events to modifying past ones and seeing present-day results. I’m oversimplifying, but it worked by scanning every recorded byte, including old maps, regional soil composition, weather patterns, temperature data, census records and every published book in human history. From stock market data to the Code of Hammurabi, to the fully mapped human genome, The Simulator drew inputs for its algorithm. Some believed the developers had access to classified material from the world’s intelligence agencies, including UFO encounters deemed too sensitive for public consumption.
Of course we only had the commercialized game version — the full one was prohibitively expensive and available only to those with official authorization. But the game version was robust enough, and already the software of choice for sports betting, weather forecasting and for some stock pickers, (though many suspected hedge funds and large institutions had access to the full version and avoided the capital markets entirely.)
I initially did investing experiments, buying Apple’s IPO, Amazon stock and eventually bitcoin and became the richest person in the world 10 times over. Although in one experiment, I owned so much bitcoin it became overly centralized and never took off. In that world, Facebook launched its Libra coin without much government resistance as few grasped the possibilities of fully digital currencies. The result was a Facebook-government partnership where you got docked Libra coin (the only currency in which you could pay federal taxes) for unfavored associations and viewpoints.
But I soon grew bored of the financial experiments and started doing weird things like going back to 2019, catching COVID on purpose and spreading it as widely as possible, before people thought it was a threat. In one simulation, there was no acknowledged pandemic, only a bad “flu” season.
I was about to log off and tackle a work project on which I had procrastinated for too long, when I remembered Henry’s insistence that I was obligated to kill baby Hitler. I never bought his arguments entirely — absolute certainty is always a red flag — but I didn’t have a good counter for them, either. I resolved to run the experiment and find out for myself.
It wouldn’t be easy as the commercial version of The Simulator had rules around acts of violence. I’d also have to dig up fairly specific knowledge in a presumably less developed part of the game (19th-century Hungary.) But The Simulator was adept at making do with the available history and filling in blanks with fictional characters. There would be a street address and a house where he lived. There should be an opportunity to see how it played out. Of course, one could simply delete Hitler and run simulations without him, and I tried that first, but the moral question was not whether the world would be better off without Hitler, but whether it would be right — or obligatory even, in Henry’s framing — to murder the baby in his crib.
I prefer not to go into the details. The broad outlines are I found a hack to disable the violence restriction, went to his childhood home and had to bludgeon a young woman (his nanny?) before doing it. For those who have never used The Simulator, “Full Immersion Mode” isn’t quite real life, but it’s substantially more visceral than shooting avatars in a video game. What I did was horrific, even though I knew it wasn’t real, and even though Henry believed the act would’ve been heroic if it were. I actually vomited afterwards, and as I type this 10 days later, I feel queasy recalling it.
Nonetheless, I ran a simulation forward. The Third Reich was run by committee. There was a front man, someone of whom I had never heard, who was more charismatic than Hitler, but decision-makers behind the scenes, including some of Hitler’s generals, were just as ruthless. There were concentration camps, though oddly in different locations, and the result was seemingly as bad.
But that was only one version of events. The Simulator (through randomization of certain parameters) could run infinitely many different futures from any given point in time. I ran a few more, and they were all dystopian in different ways. There was one version, however, that particularly struck me.
In it, Hitler rose to power as he did in the real world, and things unfolded more or less the way we’ve read about them in history. At first, I thought there must be an error — after all, every simulation began the hour after I smothered him in his crib. But as I checked the local newspapers from that era, indeed a baby had tragically died, and his brain damaged nanny was blamed (and subsequently hanged) for the crime, but it was a different baby, Max Muller, son of a local tavern owner, who committed suicide two years later. How could that be? Not only did I check all the details exhaustively, but they proved correct in all the other simulations. The randomizer must have swapped the location of baby Hitler with this other infant. In this version, I murdered (virtually, thank God) an innocent baby, destroyed his family and an innocent nanny without preventing anything.
. . .
When I met with Henry a week later, he wasn’t convinced. The Simulator isn’t reality, he argued, and the version with the wrong baby proved it. His hypothetical entailed killing the actual baby Hitler in the real world, not some case of mistaken identity. If you could be sure to kill the real Hitler and prevent the Holocaust from happening, he maintained, you’d still have to do it. The Simulator’s randomization algorithm made it impossible ever to know what would happen in its many possible futures, especially in the long run.
I now understood his argument. If we had certainty about how our actions would affect the world, the moral imperative would be clear. But certainty about the future was unattainable, for the path from unknown to known is the arrow of time itself. Henry’s hypothetical then was inherently contradictory, a square circle he imagined were an actual shape.
One could never be assured about the long term effects of one’s actions, and any attempt to do the math was quickly overwhelmed by infinite permutations. Doing something abhorrent as the means to a noble end was to fancy oneself a mathematical God, something no decent person would attempt. It was the ideology of monsters, forever imagining they could create a more perfect history, a more perfect future, a more perfect human race.
-
 @ a023a5e8:ff29191d
2023-12-07 04:37:55
@ a023a5e8:ff29191d
2023-12-07 04:37:55which operating system do you recommend using on my PC?
-
 @ 57d1a264:69f1fee1
2024-04-23 06:45:57
@ 57d1a264:69f1fee1
2024-04-23 06:45:57Prompt: Download
Create a download page, modal, form, or screen related to downloading something. It could be for a digital product, contest registration, or anything you can image requiring a download.
Flex your design muscles and join in. Most of all, keep this exercise loose and keep it stress-free. The FUC is about growing our design skills, together, as a community. We can't wait to see what you create!
Happy designing, Stackers!
Share Your Results When you finish the challenge, post your work on this thread! If you also share it on
nostr, be sure to use the hashtag #FUCdesiger and tag Design_r@iris.to or @Design__r on X! We'll keep an eye out and repost good examples on a regular basis.
Curious to know WTF is a FUC? Read the ⚡️Flash Ui Challenges welcoming post.
Looking for more FUCs? Check the archive here!
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ dd664d5e:5633d319
2024-04-23 06:04:28
@ dd664d5e:5633d319
2024-04-23 06:04:28Why GitCitadel is primarily self-funded
This week has been full of discussion about the various pros and cons of what I've previously described as the "patronage funding model", including a formalized version called "grants":
This is the current common business model. A creator (artist, developer, writer, etc.) receives grants or donations that are more or less attached to conditions. -- The Zap Economy
We at GitCitadel have been questioned repeatedly, as to why we have not applied for a grant, when we are putting so much time and effort into the Nostr ecosystem. I would, therefore, like to explain the logic we have used to make this decision:
We are a package deal
We aren't merely a product team, we're a project team. That means that we aren't building a product, we're building an entire line (or suite) of products, and the corporate and technical infrastructure to support them.
Those products will be marketed under our own brand, built upon our own tech stack, and managed by our own team. We're used to doing this sort of thing for our various employers, so we haven't seen much benefit in looking outside of our team to acquire such things. Applying for formal grants would undermine this strategy, as we would be expected to tie into the grant-giver's own brand, stack, and team.
We have external income sources
We have made the point, to anyone interested in joining, that our project cannot and will not provide a source of income large enough to replace anyone's current source. At least, not yet. We are receiving donations and will eventually have a pricing model, but this project is our labor of love, not a get-rich-quick scheme. More a go-broke-slowly scheme, if anything.
We see this as a feature, rather than a bug, as it means our personal financial well-being is not immediately tied to our project work, and is therefore more secure, stable, and independent. This allows us the ability to ruminate, take time discussing architecture, and make more grandiose plans. It also allows us to discuss funding models, amongst ourselves or with a wider audience, while remaining calm.
Not everyone is in the same financial position and not everyone wants to split their attention, in such a manner, and we respect that. We also respect the right of every project member to decide differently, for themselves, and to apply for grants in their own name.
We're enjoying "L'expérience FOSS"
This is our first, major, open-source, software project. This is our chance to do something different, to be edgy, to build something for ourselves, to try out new technologies and strategies, to found a company and design a brand, to tinker and scheme... To boldly go where no team has gone before!
But, seriously. We're having fun. We're friends. We're enjoying the ride. We wouldn't enjoy the ride as much, if we were driving someone else's car.
We want to prove that it can be done
One of the things we found disturbing about the Nostr ecosystem is the pervasive pressure individual developers are under to apply for grants and labor full-time on Nostr products. It can feel quite rebellious, to simply tinker on evenings, weekends, or holidays.
It isn't rebellious.
It is a perfectly normal and acceptable way to contribute to a growing technological ecosystem, and we want to help re-normalize it. The emotional pressure to deliver new features at a rapid pace is exciting, but onerous, can lead to developers burning out and eventually moving on, and is the main cause of the frequent low quality of the existing software and the plethora of abandoned repos. This is the landscape that grants sometimes build.
We are here to show that "steady, stable, secure, supported, sturdy" sounds dull and a bit slow, but it can also be a winning development style, if the team chooses it deliberately and plans accordingly and cultivates a team environment that makes "code and chill together" a long-term motivator. We think the Nostr ecosystem is ready to accept a team with this style, and it's a style that advanced grants simply aren't designed to support because grant-givers have to account for the money spent within a reasonable time.
We want to support independent funding models
As with all things, talk is cheap. We are all persons eager to establish independent funding models because we want Nostr to help create a free market of sovereign individuals, at the global scale. We think this is a particular "good work" that Nostr is in a prime position to define, but it won't happen, if nobody actually does it, or if only a few do it and and are perceived as greedy oddballs. There needs be a lot of people doing it, including large, influential teams.
The strongest motivation to develop such models is the profit motive, and that is inevitably weakened by grant-lethargy. One has to take risks to become a change agent, so we have put ourselves on a diet, to get our creative financial juices flowing.
We have decided to stay hungry. https://image.nostr.build/28ddca2ef029e8be27e351867f37e457e2070e005f5588f88f486208709ee00d.jpg
-
 @ 8fb140b4:f948000c
2023-11-21 00:46:59
@ 8fb140b4:f948000c
2023-11-21 00:46:59Venturing into the dynamic world of bitcoin's layer 2 networks, particularly the lightning network, can seem like an exciting frontier for tech enthusiasts and cryptocurrency aficionados. however, the decision to run your own lightning node is not one to be taken lightly. While the allure of contributing to the bitcoin ecosystem and potentially earning transaction fees is strong, there are significant considerations that should temper the enthusiasm of would-be node operators. From the intricate technicalities to unexpected challenges, here are 10 compelling reasons why running your own lightning node might not be the electrifying experience you anticipated.
Running your own lightning node for the bitcoin layer 2 network can be a complex and demanding task. Here are 10 reasons why you might choose not to:
-
Technical complexity: setting up and managing a lightning node requires a good understanding of blockchain technology and network management, which can be overwhelming for beginners.
-
Security risks: running a node means you're responsible for securing it against potential cyber attacks, which requires constant vigilance and technical expertise.
-
Resource intensive: a lightning node requires continuous internet connection and sufficient hardware resources, which can be costly in terms of electricity and equipment.
-
Liquidity requirements: to facilitate transactions, you need to lock up a significant amount of bitcoin in your channels, which might not be ideal if you prefer liquidity.
-
Maintenance efforts: regular maintenance and updates are necessary to keep the node running smoothly, which can be time-consuming.
-
Limited privacy: operating a node might expose some of your transaction details or ip address, potentially compromising privacy.
-
Slow ROI: the financial return on operating a lightning node can be slow and uncertain, especially if the network fees are low.
-
Network complexity: understanding and managing channel capacities, routing, and fees can be complicated and require continuous learning and adaptation.
-
Scalability issues: as the network grows, managing a node can become increasingly challenging, with more channels and transactions to handle.
-
Downtime risks: if your node goes offline, you might miss out on transaction fees or, worse, risk losing funds in channels due to outdated channel states.
These reasons reflect the challenges and responsibilities that come with running your own lightning node and may discourage some individuals, especially those with limited technical background or resources. If you are still up for a challenge, thank you for supporting the network! 🐶🐾🫡🙏🏻
-
-
 @ de496884:72617b81
2023-11-20 13:54:02
@ de496884:72617b81
2023-11-20 13:54:02Hola nostriches. Hoy quiero hacer una publicación a modo de acercamiento al surgimiento de las categorías de género y feminismo. Así que si te interesa el tema haz un esfuerzo, quédate y lee hasta el final.
El «nuevo» feminismo surge en los años 60 en aquellos países desarrollados que acordaron el reconocimiento a los derechos humanos contenidos en la declaración respectiva de la ONU. Entonces, como extensión a dicho reconocimiento es que se gesta el movimiento feminista. A partir de entonces, se vuelve a plantear la relación entre naturaleza y cultura y se llega a la conclusión de que las diferencias sociales van más allá de las diferencias biológicas, lo cual tiene que ver con que hasta la satisfacción de las necesidades elementales como son la alimentación, la vivienda o el vestuario, están condicionadas por construcciones sociales.
Pues resulta que una de las primeras propuestas identificó la subordinación femenina producto de una organización patriarcal, tomando la categoría patriarcado de Max Weber. Es así como la visión de patriarcado se extendió al discurso político y académico. Sin embargo, no existía información acerca del desarrollo histórico de dicha categoría, sistematización, variaciones, etc., debido a que era algo que recién se percibía en sociedad.
Sin embargo, la misma categoría de patriarcado junto a la de relaciones de poder para explicar fenómenos sociales contemporáneos, constituye uno de los principales aportes del feminismo. Es así como han logrado primero visibilizar y luego deconstruir y desmontar una serie de patrones existentes en la cultura que hacían a la mujer subordinarse al hombre, y que estaban presentes en el sistema sexo/género.
 Imagen relativa a la lucha contra el patriarcado
Imagen relativa a la lucha contra el patriarcadoHasta ese momento, en las investigaciones de corte sociológico se podía observar un androcentrismo excesivo al dar cuenta de que el discurso científico giraba en torno al hombre como sujeto y objeto de la investigación. Incluso para muchos positivistas como el mismo Weber, los problemas relativos a las mujeres quedaban en un segundo plano y eran achacados a una supuesta pasividad en el ámbito doméstico-familiar. Dicha pasividad partía de la supuesta inferioridad biológica del género femenino.
El patriarcado entonces era una categoría vacía en sí misma, sin valor explicativo. Desde el punto de vista político pudo ser útil para la movilización pero no resistió la polémica de los críticos del feminismo ni problematizó los conflictos a ser resueltos. Pero por otro lado, un grupo de mujeres -académicas principalmente- se puso manos a la obra en una tarea más pequeña pero con mayores resultados a la larga. Se propusieron generar conocimientos sobre las condiciones de vida de la mujer, buscar en el pasado y el presente los aportes de las mujeres a la sociedad, hacerlas visibles en la historia. Es así como surgen centros académicos, ONG, proyectos, centros de estudios sobre la mujer, etc.
Convendría distinguir entonces dos posturas que acompañaron a la investigación sobre las mujeres: uno que toma como objeto de estudio a la mujer; condiciones de vida, trabajo, cultura, y otra que privilegia a la sociedad como generadora de la subordinación de las mujeres. Mientras la primera perspectiva generaba conocimiento sobre las mujeres en el estudio de las relaciones mujer-hombre y mujer-mujer, la segunda tenía una visión más holística ya que planteaba que hay que estudiar la sociedad ya que la subordinación de las mujeres es producto de la organización de esta, y que no se avanzará solamente estudiando a las mujeres, pues el estudio debe ser más amplio y en diferentes niveles, ámbitos y tiempos.
Es en esta búsqueda donde nace y se desarrolla el concepto de género como categoría social. Es así que los sistemas de género/sexo fueron entendidos como conjuntos de prácticas, símbolos, representaciones, normas y valores sociales que las sociedades construyen a partir de la diferencia anatomofisiológica y que dotan de sentido a los impulsos sexuales, la reproducción y en general a las relaciones de las personas. Por tanto, este sistema pasó a ser el objeto de estudio para comprender la subordinación de la mujer al hombre. Al ser el reconocimiento de una dimensión de la desigualdad social hasta entonces desconocida, se considera la ruptura epistemológica más importante de la segunda mitad del siglo pasado.
 Imagen representativa del binarismo de género
Imagen representativa del binarismo de géneroHay que decir que los fenómenos sociales se definen por la relación que guardan entre sí. Es así que la contextualización adquiere gran importancia. Varones y hembras tenemos la capacidad de producir con el cuerpo, pero solo los cuerpos de las hembras pueden gestar y por tanto asegurar la especie humana. Todo grupo humano que pretenda sobrevivir debe asegurarse cierto número de hembras que lo hagan posible. De ahí un poder particular del cuerpo de las hembras que además es económicamente útil. Dicho poder no es en tanto entidad biológica, sino que es la sociedad la que le otorga este poder. En este punto es importante preguntarnos históricamente ¿quiénes han controlado la capacidad reproductiva de las mujeres?, ¿quiénes han tenido la preferencia en el acceso sexual? Para asegurar un control efectivo sobre la reproducción es necesario asegurar el acceso a la sexualidad.
Ello también lleva a dirigir el trabajo que hacen porque de lo contrario, las mujeres pudieran tener espacio para representar una amenaza al dominio de los hombres. Es importante atender a las etapas del desarrollo de las mujeres, que permitirá ver cómo se moldean para aceptar la desigualdad y las jerarquías según el género en las distintas sociedades y culturas.
Otro contexto a delimitar es el ámbito doméstico donde históricamente ha estado ubicada la subordinación femenina. Se ha puesto al descubierto que en mujeres que comparten la misma posición de clase y raza, la condición femenina se redefine a lo largo de la vida y que algunas mujeres gozan de poder sobre otras aún en contextos de alta dominación masculina, donde se les inviste de autoridad, creando el sistema zonas de incertidumbre que las divide como género e impide alianzas y se legitima la dominación. Foucault decía que «el poder se ejerce, no se posee», siempre está en peligro de perderse y no basta con normas, leyes, amenazas o castigos. De ahí que los espacios de subordinación sean también espacios de poder de las mujeres. Es en estos espacios donde aparece la inseguridad, la tensión, la confrontación y por ejemplo, las mujeres pueden reclamar la anticoncepción.
Para terminar, es importante tener en cuenta que el género es una forma de desigualdad social que siempre está articulado con otras formas de desigualdad ya sea clase, raza, grupo etario, etc. Hay que pensar la dominación masculina con un comienzo vago en el tiempo, pero que permite desligar la subordinación de las mujeres de la evolución «natural» de la humanidad y entenderla como un proceso histórico. En ese sentido es necesario destacar que, respecto a la raza, en sociedades plurales hay que atender al contexto étnico-cultural ya que en dependencia de las relaciones entre personas de razas distintas, estarán condicionadas las relaciones entre los géneros.
 Imagen de mujeres de distintas razas
Imagen de mujeres de distintas razasPor otro lado, si bien es sabido que históricamente el sistema de género social imperante ha contribuido a invisibilizar a la mujer, asociar necesariamente dicha categoría únicamente a ella, lo que hace es nuevamente recrear el absolutismo histórico que tanto daño ha hecho, ahora como lo antagónico al hombre. En la construcción social participan todos los individuos presentes en el sistema género.
Hasta aquí la publicación de hoy, de la cual aun se puede ahondar mucho más, sobre todo en lo referido al origen de la dominación o de la jerarquización del binomio «hombre/mujer» desde un punto de vista antropológico, pero eso quedará pendiente para otro momento. ¡Así que hasta la próxima!, ¡nos vemos en Nostr!
........................................
English version
Hello nostriches. Today I want to make a post by way of an approach to the emergence of the categories of gender and feminism. So if you are interested in the topic make an effort, stay and read to the end.
The "new" feminism emerged in the 60's in those developed countries that agreed to recognize the human rights contained in the respective UN declaration. Then, as an extension of that recognition, the feminist movement was born. From then on, the relationship between nature and culture was raised again and the conclusion was reached that social differences go beyond biological differences, which has to do with the fact that even the satisfaction of elementary needs such as food, housing or clothing are conditioned by social constructions.
It turns out that one of the first proposals identified female subordination as a product of a patriarchal organization, taking Max Weber's category of patriarchy. This is how the vision of patriarchy was extended to political and academic discourse. However, there was no information about the historical development of this category, systematization, variations, etc., because it was something that was only recently perceived in society.
However, the same category of patriarchy, together with that of power relations to explain contemporary social phenomena, constitutes one of the main contributions of feminism. This is how they have first made visible and then deconstructed and dismantled a series of existing patterns in the culture that made women subordinate to men, and that were present in the sex/gender system.
 Image relating to the fight against patriarchy
Image relating to the fight against patriarchyUp to that time, in sociological research, an excessive androcentrism could be observed as scientific discourse revolved around men as the subject and object of research. Even for many positivists such as Weber himself, the problems related to women remained in the background and were blamed on a supposed passivity in the domestic-family sphere. This passivity was based on the supposed biological inferiority of the female gender.
Patriarchy was then an empty category in itself, with no explanatory value. From the political point of view, it could be useful for mobilization, but it did not resist the polemic of feminism's critics, nor did it problematize the conflicts to be resolved. But on the other hand, a group of women - mainly academics - set to work on a smaller task but with greater results in the long run. They set out to generate knowledge about women's living conditions, to search in the past and present for women's contributions to society, to make them visible in history. This is how academic centers, NGOs, projects, women's studies centers, etc., came into being.
It would be convenient to distinguish then two postures that accompanied the research on women: one that takes women as the object of study; living conditions, work, culture, and the other that privileges society as the generator of women's subordination. While the first perspective generated knowledge about women in the study of woman-man and woman-woman relations, the second had a more holistic vision, since it proposed that society must be studied, since the subordination of women is a product of its organization, and that progress will not be made only by studying women, since the study must be broader and at different levels, spheres and times.
It is in this search that the concept of gender as a social category was born and developed. Thus, gender/sex systems were understood as a set of practices, symbols, representations, norms and social values that societies construct on the basis of anatomophysiological differences and that give meaning to sexual impulses, reproduction and, in general, to people's relationships. Therefore, this system became the object of study to understand the subordination of women to men. As the recognition of a hitherto unknown dimension of social inequality, it is considered the most important epistemological breakthrough of the second half of the last century.
 Representative image of gender binarism
Representative image of gender binarismIt must be said that social phenomena are defined by their relationship with each other. Thus, contextualization acquires great importance. Males and females have the capacity to produce with their bodies, but only the bodies of females can gestate and therefore ensure the human species. Any human group that intends to survive must ensure a certain number of females to make it possible. Hence a particular power of the female body, which is also economically useful. This power is not as a biological entity, but it is society that gives it this power. At this point it is important to ask ourselves historically, who has controlled the reproductive capacity of women, who has had the preference in sexual access? To ensure effective control over reproduction, it is necessary to ensure access to sexuality.
 Allegorical image of pregnancy
Allegorical image of pregnancyThis also leads to directing the work they do because otherwise, women may have room to pose a threat to men's dominance. It is important to pay attention to the stages of women's development, which will allow us to see how they are shaped to accept inequality and gender hierarchies in different societies and cultures.
Another context to delimit is the domestic sphere where female subordination has historically been located. It has been discovered that in women who share the same class and race position, the feminine condition is redefined throughout life and that some women enjoy power over others even in contexts of high male domination, where they are invested with authority, creating the system of uncertainty zones that divide them as a gender and prevent alliances and legitimize domination. Foucault said that "power is exercised, not possessed", it is always in danger of being lost and norms, laws, threats or punishments are not enough. Hence, the spaces of subordination are also spaces of women's power. It is in these spaces where insecurity, tension, confrontation appear and where, for example, women can demand contraception.
To conclude, it is important to keep in mind that gender is a form of social inequality that is always articulated with other forms of inequality, be it class, race, age group, etc. It is necessary to think of male domination with a vague beginning in time, but which allows us to separate the subordination of women from the "natural" evolution of humanity and to understand it as a historical process. In this sense, it is necessary to emphasize that, with respect to race, in plural societies it is necessary to pay attention to the ethno-cultural context since, depending on the relations between people of different races, the relations between genders will be conditioned.
 Image of women of different races
Image of women of different racesOn the other hand, although it is known that historically the prevailing social gender system has contributed to make women invisible, to necessarily associate this category only to women is to recreate the historical absolutism that has done so much damage, this time as antagonistic to men. All individuals present in the gender system participate in the social construction.
So much for today's publication, of which we can still go much deeper, especially with regard to the origin of domination or the hierarchization of the binomial "man/woman" from an anthropological point of view, but that will be left for another time. So until next time, see you in Nostr!

Créditos | Credits
Bibliografía consultada | Consulted bibliography:
-
Barbieri, T. (1993). Sobre la categoría género. Una introducción teórico-metodológica. Debates en Sociología. (18). 1-19. https://doi.org/10.18800/debatesensociologia.199301.006
-
Echevarría, D. (2020). Desigualdades de género e interseccionalidad. Análisis del contexto cubano 2008-2018. Facultad Latinoamericana de Ciencias Sociales (Programa-Cuba). https://www.clacso.org.ar/libreria-latinoamericana-cm/libro_detalle_resultado.php?id_libro=2346&campo=cm&texto=248
Traducción | Translation:
DeepL
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 06830f6c:34da40c5
2024-04-23 03:44:21
@ 06830f6c:34da40c5
2024-04-23 03:44:21Opinion about Foundation Passport (hardware)
Passport offers a huge leap forward in design and user experience, making it easier than ever to securely store your own keys.
WalletScrutiny #nostrOpinion
-
 @ 8fb140b4:f948000c
2023-11-13 07:55:20
@ 8fb140b4:f948000c
2023-11-13 07:55:20Hey there, train enthusiasts! let's chat about one of the most impressive rail systems in the world - japan's trains. when you think of japanese trains, the first image that probably pops into your mind is the sleek, futuristic shinkansen, also known as the bullet train. these high-speed trains are not just a symbol of modern technology; they're a testament to japan's commitment to efficiency and punctuality. it's not an exaggeration to say that japanese trains are famous for being precisely on time. if a train is five minutes late, it's often considered a significant delay!
but it's not just the shinkansen that deserves praise. japan's entire railway network, from city subways to rural train lines, is incredibly well-organized. the trains are clean, comfortable, and surprisingly quiet, making even a regular commute a pleasant experience. what's more impressive is the frequency of these trains. in major cities like tokyo and osaka, you rarely have to wait more than a few minutes for a train, reducing the stress of travel and making commuting more predictable.
and let's not forget the level of service! train staff in japan are known for their politeness and helpfulness. whether you're a tourist struggling with your luggage or a local needing directions, there's always someone to help. plus, the stations themselves are marvels - clean, well-signed, and packed with amenities like shops and restaurants. in short, japan's trains aren't just a mode of transportation; they're an experience, reflecting the country's dedication to quality, punctuality, and customer service. so, next time you're in japan, hop on a train and enjoy the ride - it's an adventure in itself! 🚆🌸🐶🐾🫂
-
 @ a012dc82:6458a70d
2024-04-23 03:09:58
@ a012dc82:6458a70d
2024-04-23 03:09:58Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
This is the most catastrophic bankruptcy of a custodian in the digital asset market since Mt. Gox, which collapsed in 2014. This study examines the Bitcoin strong hands' reaction to the FTX bank run and how people are trying to find safety by keeping their bitcoin privately.
The events of November 6–14, 2022, in the digital asset market are, to put it mildly, astonishing, startling, and disheartening. One week saw one of the most well-known and high-volume exchanges, FTX.com, go down.
-
Experienced a bank run.
-
Client withdrawals have been stopped.
-
Binance's purchase negotiations fell through.
-
As much as $10 billion in missing client money was uncovered.
-
Allegedly, $500 million was stolen from exchange wallets.
-
FTX US and its sister company filed for Chapter 11 bankruptcy.
-
Brought to light what appears to be wrongdoing on the part of the Alameda/FFTX company.
Millions of consumers would be left with imprisoned cash, years of positive industry image would be destroyed, and new credit contagion risks would emerge, many of which would go unnoticed for a long time. The fall of Mt. Gox in 2013—in which a major custodian was shown to be fractionally reserved—comes to mind in light of this development.
The crypto market is in disarray, but investors should keep in mind that the underlying cryptography is secure and that digital assets exist in a free market. Bitcoin has no safety net, and the deleveraging of the whole business will burn away any waste or corruption, but it will be painful. The market will mend, recover, and come back stronger in the months and years ahead thanks to the increased emphasis on exchanging proof-of-reserves and the drive toward self-custody.
We shall discuss the following topics in this week's report:
-
Specifics on the recent thefts from on-chain FTX wallets
-
greater repercussions for personal finances and parenting arrangements.
-
Effects on the conviction of long-term Bitcoin holders have been observed.
Translations
Aside from the original English version, This Week on Chain has been translated into Spanish, Italian, Chinese, Japanese, Turkish, French, Portuguese, Farsi, Polish, Arabic, Russian, Vietnamese, and Greek.
Onchain Weekly Report
Here you can see the Week Onchain Newsletter's live dashboard, along with all featured charts. Our weekly video report is published every Tuesday and delves further into this dashboard and all of the data it covers.
Fractional Reserves
Eventually, the truth will (hopefully) emerge about how FTX lost client deposits and blew a hole of $8 billion to $10 billion in their balance sheet. However, there are numerous indications that money was misappropriated through the sibling hedge fund Alameda Research.We direct readers to the following resources for context and analysis of the triangle formed by Alameda, FTX, and Binance:
-
Thread on Twitter describing the movement of money from Alameda through FTX to Binance.
-
Information visualization dashboard displaying the inter-entity lifetime flow of money.
-
Report in video format detailing these preliminary results.
Over the years, several data sources have had difficulty keeping up with FTX's exchange reserves. In our own observations, we found that FTX used a somewhat sophisticated peeling chain method for their BTC holdings. The cluster's FTX reserves peaked at around 102k BTC in April/May of this year. In the latter half of June, this dropped by a whopping 51.3%.
Since then, reserves have steadily decreased, culminating in this week's bank run when they were essentially at nothing. After the collapse of LUNA, 3AC, and other lenders in May and June, allegations of Alameda misappropriating client deposits suggest the Alameda-FTX company may have suffered a serious impairment to its balance sheet during that time period.
There have been two big drops in the amount of ETH owned on FTX:
-
With a decrease of 576k ETH (55.2% in reserve value) in June
-
This week, the price of ETH dropped from 611k to 2.8k (-99.5%).
Just as with Bitcoin, this means that almost no ETH is left in wallets controlled by FTX after the bank run.
Looking into stablecoin reserves, we can observe that on FTX, the total reserves began to decrease precipitously on October 19th, from $725 million to almost nothing by the end of the following month.
After the June sell-off, stablecoin balances skyrocketed to a new all-time high, while BTC and ETH holdings fell dramatically. This may provide more evidence that some degree of balance sheet impairment had happened at that time, requiring the use of BTC and/or ETH collateral in exchange for the use of stablecoins in a swap or loan.
There's still a lot of mystery around what went down between FTX and Alameda, but there's also a growing body of on-chain evidence suggesting problems emerged in May or June. Consequently, the events of the last several months may be explained as nothing more than a prelude to the eventual collapse of the exchange.
Release of Updated Dashboards
The new dashboards we've developed provide a way to track the growth and decline of Bitcoin's investor base, as well as the value of their holdings. These graphs are taken from our entity balance change dashboard (T3) and are complemented by the data in our address cohort dashboard (T2).
Safety in Self-Custody
As holders want the security of self-custody, there has been an unprecedented rate of coin withdrawals from exchanges. Since November 6, when rumblings of issues at FTX were still in their infancy, the following charts have tracked the aggregate balance change of exchanges, investor wallet cohorts, and miners.
The 7-day drop of 72,9K BTC in total BTC balance on exchanges is one of the greatest such drops in history. Only April-2020, November-2020, and June-July 2022 may be compared to this.
To a similar extent, Ether has had 1.101 million ETH removed from exchanges in the last week. This is the greatest 30-day decrease in balance since September 2020, during the height of "DeFi Summer," when demand for ETH skyrocketed for use as collateral in smart contracts.
While this week saw a decrease in BTC and ETH exchange reserves, approximately $1.04 billion was deposited into exchanges on November 10th through stablecoins such as USDT, USDC, BUSD, and DAI. As far as daily net inflows go, this is the seventh highest ever.
The total value of stablecoins held in exchange reserves has now reached $41.186 billion as a result. There has been a significant rise in BUSD supremacy, as shown by the over $21.44B in BUSD reserves. This is probably due to Binance's increasing dominance as the world's biggest exchange and the recent concentration of its stablecoins towards BUSD.
There may be a movement in market preference since USDT exchange reserves have decreased marginally over the last several months while USDC reserves have decreased significantly.
Interestingly, smart contracts are a major source for stablecoins, with monthly withdrawals from Ethereum smart contracts totaling $4.63 billion. This helps to underline how critical access to hard currency has become as of late.
Due to this, the market has entered a peculiar phase in which centrally generated stablecoins are flooding exchanges while BTC and ETH are being removed from them at unprecedented rates. The two-part model is shown in the following chart:
There was a net outflow of BTC and ETH from exchanges, as shown by the absence of them in the barcode trail.
The oscillator displays the difference between the net USD flow of BTC and ETH and the net inflow of stablecoins. When is greater than zero, it means that more "purchasing capacity" than usual has been poured into exchanges in the form of stablecoins.
There has been a net rise of $4.0 billion every month in the purchasing power of stablecoins on exchanges, as seen above. This illustrates that investors tend to prefer retaining trustless BTC and ETH assets over centrally produced stablecoins at the present moment, notwithstanding the market's volatility.
This is a really interesting signal, and one might make the argument that it reflects the market's need for safety in self-custody and trust in the underlying assets.
Bitcoin balances swell
Given the massive withdrawals of bitcoin from exchanges, it is clear that the FTX event has caused a noticeable shift in investor behavior across all wallet cohorts. Despite the FTX crash, on-chain wallets saw a net rise in balances across the board, from shrimp ( 1 BTC) towhaless (> 1,000 BTC). For several groups, this is an almost complete reversal from the steady distribution pattern of previous months.
In the last 30 days, the Shrimp cohort ( 1BTC) has increased by +51,400 BTC, with a +33,700 BTC gain in the past week alone. Beyond the high point of the bull market in 2017, this amount of balance inflow is the second highest ever.
The Crab group, which consists of investors with 1–10 BTC, is also quite active, having removed 48.7k BTC from exchanges at prices that are getting close to the highest acquisition rates seen during the 2017 bull market. This is a new and compelling all-time high for the percentage of total Bitcoin supply held by those with more than 10 BTC.
We use the terms "fish" and "sharks" to refer to groups of bitcoin wallets containing between 10 and 1,000 bitcoins, respectively. The wealth of these members of the group is comparable to that of wealthy people, large corporations, and large institutions.
We have had one of the highest 7-day rises in cohort balances in history, at 78.0k BTC, after many months of decreasing growth. An attitude of "withdraw now, ask questions later" may be at play here.
We have only looked at the inflow and outflow of coins directly via exchanges for whales, here defined as those having more than 1,000 BTC. This will more accurately represent these massive organizations' genuine investor activity.The average 30-day change in the balance of all whales is +53,7K BTC, indicating that they have been net purchasers in recent weeks.
However, their on-net activity this week has been far lower than that of previous cohorts, with a net gain of just 3.57k BTC.
Last but not least, the industry of Bitcoin miners, already a target of regulatory scrutiny, has been hit hard by the recent drop in coin price. As the price of hash power continues to fall, miners have spent around 7.76k BTC this week, or about 9.5% of their reserves. Proof that Bitcoin miners are very cyclical in their activity, this is the largest monthly miner balance fall since September 2018.
HODLers Resolve
The last half of this newsletter will focus on the reaction of Bitcoin HODLers, with the goal of determining whether there has been any visible erosion of their original commitment. If there was ever a moment for HODLers to lose trust in the asset, it is certainly now, given the size of the damage and the far-reaching ramifications of the FTX collapse.
Since November 6th, the quantity of bitcoins held by long-term holders—those who are statistically least likely to spend their coins—has decreased by -61,500. A significant amount of bitcoin ($48,100) was spent in the previous week. The above-described shift in the size of things is not yet large enough to imply widespread loss of belief as compared to previous norms. But if this continues, it might imply a shortage of LTH.
The weekly total of revived supply older than 1 year is shown here, along with a 4-year Z-score. This week, 97,45k BTC older than a year were spent, possibly returning them to circulation.
It's a +0.83 sigma shift over 4 years, which is significant but not yet unprecedented. Similar to LTH Supply, this indicator warrants close attention in case it signals the beginning of a new long-term pattern.
Also, the median age of a bitcoin has increased to slightly over 90 days, which is three times what was seen in the low volatility environment of September and October. Spending in older currencies has increased, which parallels highs seen during capitulation sell-off events and the 2021 bull market profit taking.
If dormancy continues to rise or rises to an unusually high level, it may be an indication that widespread fear has taken hold within the HODLer community.
Now that we have a weekly total of coindays destroyed, we can return to the 4-year Z-score formulation we used before (CDD). Clearly, this week's volume of coinday destruction was +1.9 standard deviations above the norm, marking the end of a long period of an exceptionally low coin supply. This week, 165 million coindays have been burned, the same as squandering 452,200 BTC stored for a year.
In general, the HODLer community has reacted with some degree of sudden alarm. Yet, the enormity of the situation suggests that this might be to be anticipated. The question of whether or not these surges moderate over the next several weeks, which would indicate that the current reorganization is more of an "event" than a "trend," is perhaps of greater importance.
A general lack of conviction and worry may be at play, though, if there was a prolonged increase in the spending of older coins and a decrease in the availability of LTH.
Conclusions
The failure of FTX has been devastating and is a black eye for the whole sector. When people who have put their faith in a platform become caught and their money disappears, it is a genuinely horrible thing. Bitcoin and the industry as a whole will emerge stronger from this unfortunate forest fire and deleveraging catastrophe than they were before.
FAQ
What is Glassnode in crypto? Glassnode is a data intelligence platform for the bitcoin and blockchain industries. By concentrating on the most crucial input source in the space—data from the blockchains themselves—the apps that Glassnode develops give new methods of giving insights into blockchains and cryptocurrencies.
What does it mean when a price is "Realized"? The term "realized price" refers to the cash market price after deducting for quality, shipping costs, and anticipated demand.
Can you explain how the market cap of Bitcoin is determined? The total market capitalization realized is the latest price of each UTXO multiplied by Due to the fact that certain digital currencies may become untraceable or unusable as a result of technical difficulties, Realized Cap was developed to devalue such tokens after an extended period of inactivity.
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 8fb140b4:f948000c
2023-11-10 12:00:40
@ 8fb140b4:f948000c
2023-11-10 12:00:40Intro
Nostrasia 2023, a vibrant unconference, was hosted in two bustling Asian cities: Hong Kong and Tokyo, Japan. Nostriches from around the world flocked to these destinations, eager to immerse themselves in local culture, savor the cuisine, and most importantly, enjoy each other's company in person. Tokyo's event, buzzing with energy, took place in Shibuya, a district renowned for its lively nightlife and abundance of bars, clubs, and restaurants. As is tradition with Nostr events, the atmosphere was charged with excitement, symbolized by the abundant purple and orange hues.
https://v.nostr.build/k7qV.mp4
Preparations
The journey to Nostrasia began right after Nostrica, with meticulous planning to ensure the perfect venue. It was a challenge to find a location that was both spacious and accessible, offering affordable accommodation options nearby. Our diligent volunteers in Japan scoured venues in Tokyo and Yokohama before selecting the ideal spot in Shibuya.



In the days leading up to the event, volunteers, both local and from afar, gathered at the venue. Their mission: to set up everything from audio-visual equipment to stages and decorations, ensuring a warm welcome for attendees on November 1st at 9:00 AM. Despite the time crunch, the spirit of cooperation and friendliness prevailed, making the preparation phase smooth and enjoyable.




Even amidst the busy setup, there was time for breaks and socialization, keeping everyone energized and focused on the mission at hand.




Day 1 (The Beginning)

No day at Nostrasia could start without a caffeine kick or a beverage of choice. The first day witnessed a steady influx of nostriches, filling the venue with excitement and anticipation.

The day offered a mix of activities: some attendees engaged in the presentations, others relaxed in the family-friendly area, and there were even recreational spaces for all ages to enjoy, including model train setups.


The setup was designed to welcome nostriches of all stripes, whether young or old, tech-savvy or not. It was a space where everyone could feel comfortable and included.



The day culminated in a grand welcome party, complete with drinks, MAGURO (Yellowfin tuna), and karaoke.
https://v.nostr.build/Mqqa.mp4
Day 2

Following a late night, the second day of the conference started a bit later, accommodating the nocturnal adventures of the attendees. The day was packed with fascinating talks, workshops, and plenty of opportunities for meet-ups and hugs.



 https://v.nostr.build/q3RM.mp4
https://v.nostr.build/q3RM.mp4An interesting discovery for me was the concept of air replies, a novel and visually engaging way to interact on social media.

Day 3 (Final)
The final day, starting late due to the previous night's festivities, was filled with a diverse range of presentations. Topics varied from non-technical perspectives on Nostr to in-depth technical workshops and discussions. #footstr

The day was brimming with a variety of presentations in both halls of the conference center. These ranged from insightful talks about Nostr from a non-technical perspective to more in-depth technical workshops and discussions.





 https://v.nostr.build/R98n.mp4
https://v.nostr.build/o5Xl.mp4
https://v.nostr.build/4A6W.mp4
https://v.nostr.build/R98n.mp4
https://v.nostr.build/o5Xl.mp4
https://v.nostr.build/4A6W.mp4The event concluded with heartfelt closing remarks from the organizers, filled with gratitude and appreciation for everyone's participation and effort.


Outro
Nostrasia 2023 was a resounding success, marked by a warm, friendly atmosphere that pervaded the entire event. While some had to depart immediately after, many stayed on to explore the wonders of Japan, carrying with them memories of an unforgettable gathering. The end. 🐶🐾🫡🫂

Footnotes
- For the list of notes published about the event, use #nostrasia hashtag.
- For the official Nostrasia profile, visit @npub1nstrcu63lzpjkz94djajuz2evrgu2psd66cwgc0gz0c0qazezx0q9urg5l
- Detailed conference schedule
- Official Webside
Other pictures and videos taken before, during, and after the event







-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ f6f53010:2a76eda1
2024-04-23 03:06:27
@ f6f53010:2a76eda1
2024-04-23 03:06:27 -
 @ 1f9e547c:8af216ed
2024-04-23 01:48:42
@ 1f9e547c:8af216ed
2024-04-23 01:48:42Opinion about the city of Seattle
testfornostrtags
nostrTest
Join the conversation!\n\nJust Testing ...
-
 @ 2edbcea6:40558884
2023-10-30 14:06:48
@ 2edbcea6:40558884
2023-10-30 14:06:48Happy Sunday #Nostr !
Here’s your #NostrTechWeekly newsletter brought to you by nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk written by nostr:npub1r3fwhjpx2njy87f9qxmapjn9neutwh7aeww95e03drkfg45cey4qgl7ex2
The #NostrTechWeekly is a weekly newsletter focused on the more technical happenings in the nostr-verse.
Let’s dive in!
Recent Upgrades to Nostr (AKA NIPs)
1) (Proposed) NIP 96: File Storage Integration
As a reminder NIP 96 proposes a standard way for third party service providers to offer file storage for Nostr users. Standardization allows files to stay off relays but still be relatively cross compatible if users want to have files attached to notes show up in any Nostr client. It was initially implemented a few weeks ago with the Nostur and Coracle clients utilizing the open source Nostrcheck server by nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624
NIP 96 seems to be getting momentum; now the Nostur client has added integrated nostr.build file storage in a NIP 96 compatible way giving users more options! I hope it gets merged soon 💪
2) (Proposed) Update to NIP 72: Community Posts
This proposed update to Moderated Communities would allow clients to support using event kinds other than 1. Right now, posting on moderated communities (akin to subreddits) makes it so that all posts show up without context on most Nostr clients. Kind 1 events are like tweets, but posts in moderated communities are posted in a context that’s missing on clients like Damus or Amethyst.
This proposal would encourage moderated communities to publish using a different set of event kinds so the posts only show up in clients intended for moderated communities. It continues to gain momentum. nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 opened and closed a proposed change similar to this as this newsletter was being written, and instead threw some support onto this proposal.
This change would be reverse compatible with current Moderated Communities but still allow for cleaner feeds on clients based on their intended content focus.
Author: vivganes
Notable Projects
Zapple Pay’s lightning-based subscriptions ♻️
The team at Mutiny Wallet’s work on Zapple Pay has helped keep the flow of zaps unblocked since Apple’s capricious decisions to force Damus to disable Zaps. Now they’ve introduced “auto zapping” which is the ability to set up recurring payments (like subscriptions) in a self-sovereign way.
Zaps are great to show support, lightning-gated content is going to be helpful for content creators too, but unlocking subscriptions can truly help content creators make a living on Nostr denominated in the hardest money on Earth. This could be game changing as we’ll discuss later 😉
Authors: nostr:npub1u8lnhlw5usp3t9vmpz60ejpyt649z33hu82wc2hpv6m5xdqmuxhs46turz nostr:npub1t0nyg64g5vwprva52wlcmt7fkdr07v5dr7s35raq9g0xgc0k4xcsedjgqv & Paul Miller
Highlighter 2.0 📝
If you’re unfamiliar Highlighter is “A nostr client for your most valuable information. Your reading. Your notes. Your thoughts. A place to discover thoughtful, timeless content.” and nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft continues to improve it rapidly.
This latest release improves many aspects, mostly focused on making it THE best way to read, highlight, label, and save content that’s meaningful to you.
On top of that nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft has been improving the ability to make money as a content creator via an integration to “subscribe” to support Nostr content creators like you would on Patreon, as well as split zaps for content published via Highlighter.
If you’re not at least using Highlighter to discover content, you’re missing out. In my experience It is the highest concentration of content created by deep thinkers on the internet.
Latest conversations: Nostr adoption via content creators
Nostr’s main feature right now is that it is freedom tech. So far that hasn’t been enough of a draw for mass Nostr adoption.
We can keep building existing apps on Nostr but we’ll need something truly differentiated for people to rip and replace their content consumption habits with the ones run on Nostr.
We have some unique offerings (beyond censorship resistance) in emerging tech like Highlighter, DVMs, and Zaps. Based on what we’ve seen this week, I believe the next million monthly active users will be driven by content creators moving to Nostr.
Helping creators make money
Creators tend to flock to where they can make the most money. This is true of content creators and creators of software.
The fact that Apple apps make far more money than Android ones (despite Android dominating the smartphone market) explains why there are so many iPhone only apps.
Video creators and streamers move between Youtube and Twitch based on who is going to offer them the better income (viewership * take home rate).
If we can provide platforms where creators get to keep more of their money, it could be a game changer.
Locked into platforms
Content platforms provide two things: audience aggregation and payment aggregation.
Payments: The revenue per view of a youtube video is calculable and theoretically Youtube could pay creators their cut of the revenue per view. That isn’t practical because of transaction fees, they’d be larger than the actual transaction.
That’s why platforms serve as payment aggregators between the advertisers, themselves and the creators; settling accounts on a regular basis in amounts that make sense given the payments infrastructure available to them (credit cards and ACH).
Audience aggregation: Audiences go where creators are, but creators go where their audience is; the relationship is complicated. Sometimes individual creators have enough power to make or break a platform, but for platforms as big as Youtube that becomes much harder.
Take the example of Spotify and Joe Rogan. That move was worth it in terms of cash for Rogan, and it put Spotify on the map as a podcasting platform. It didn’t really hurt Youtube a whole lot.
The main advantage of using a content platform like Youtube, TikTok, etc is that the audience is there, you “just” need to capture them. The trade off is that you have very little power to set your price.
Audience non-portability: If a creator decides to switch from Youtube to Twitch, their followers don’t automatically port over. Creators with strong followings have an ok time when switching but not everyone has that luxury.
This leads to a power imbalance between creators and platforms. Platforms can strike down any creator they want; even though, without creators, these platforms would be nothing. In the absence of a better solution we’re stuck in this disadvantageous equilibrium.
Freeing creators with Nostr and Bitcoin
If Nostr + Bitcoin could offer creators ready-to-go solutions that would let creators keep significantly more of their revenue. It just has to be a big enough difference that people make the switch even when Bitcoin and Nostr are unfamiliar to them.
The magic combo of capabilities on Nostr would be: Nostr-based versions of all the usual apps for content consumption, as long as they’re high enough quality to not deter users. Content management tools that are familiar and quality enough for content creators. This would need to include robust file storage and streaming for content (text, video, audio, etc) Payment infrastructure in the apps (via Lightning) that have low fees and support the structures that are relevant for the content type (pay per article, pay per view, streaming sats as you listen, subscriptions, etc) Lowest-common-denominator Nostr onboarding. Imagine an end-to-end encrypted Nostr key custodian, so users that are intimidated by keypairs could have a familiar login with email and password.
In this world, new Nostr users that were asked to join by their favorite creator may never interact with the most common clients on Nostr today. They may set up a Nostr user via some “Login with Nostr” solution and then they only interact with the Nostr versions of Twitch, Youtube, Substack, etc.
If the switch is painless for users and creators and the creators make more money, it’s a no-brainer for creators to try out. If it works for them, more will come.
Taylor Swift and Grimes are good people to aim for. Both have enough autonomy to experiment with any platform they want, and both have fought to maximize artists’ take home pay. Can you imagine if we could get every Swiftie on Nostr’s version of Spotify?
Why hasn’t this happened yet?
This sounds like “value for value” right? Many talented builders and creators have attempted to crack the “value for value” nut, but something hasn’t clicked yet for mass adoption. The missing link, in my opinion, is the lack of audience portability and how that affects payments.
Value for value (streaming sats for podcasts, or paying to unlock one article at a time) requires some storage of who bought access to the content. Otherwise if you switch devices the content platform won’t know you already purchased access. Without Nostr that means signing up for that particular content app and it’s a high bar to start paying for content.
With Nostr, you can login using your Nostr keys and purchase access on any Nostr-based app, using any Lightning wallet, and that access can be attached to your Nostr pub key. It lowers the barrier for users to start paying, which means content creators capture more value.
For some kinds of content, I think all the legos are there for a creator-friendly platforms. With the recent Mutiny wallet announcement of lightning-based subscriptions, there’s no reason not to build a Nostr-based Patreon or Substack. I’ve also seen some work on ways to Zap to unlock content, making the dream of “pay per article” possible.
The last piece missing for a truly seamless on-ramp would be one of these end-to-end encrypted Nostr key custodians. That way clients could offer a “login with Nostr” button and lower the barrier for new users even further.
The race to zero take rate
Nostr naturally combats monopolies (at least for clients at this point). The reason that platforms like Youtube and Twitch have a 20-60% take rate is because they’re monopolistic. They sit on their thrones because no one has yet solved the issue of audience aggregation and portability. Nostr breaks that model.
Once creators use Nostr-based platforms, they can switch at nearly no cost. The content is theirs, and the followers are universal, so they can move to a different platform that has a lower take rate without risking their income. They don’t even have to switch platforms at all if their content is stored and unlocked via events on the Nostr Relays themselves, since those are universal across all Nostr clients.
Ideally there would be third parties that host big files (PDFs, Videos, Audio, etc) which creators pay directly. Then these content clients are simply user interfaces for users to upload and consume content. Hell, even logging in is solved by the Nostr protocol itself, and maybe another third-party login provider). The scope of what these platforms need to build and maintain is small; running them will be pretty cheap compared to running Youtube or Patreon.
At first there may be only a few Nostr-based apps because there will be some economies of scale, but over time competition will kick off a race to the bottom. Clients will eventually only be able to demand a take rate that covers operating their business (build the app, maybe offering the file hosting/streaming infrastructure, etc).
What a future
In this future, platforms have less ability to coerce creators and take their income. Platforms will have a hell of time censoring content creators. Users will get more choice on their experience and their algorithms when consuming content. And the adoption of Bitcoin as a medium of exchange would explode.
It feels like we’re on the cusp of something incredible in the Nostr-verse.
Until next time 🫡
If you want to see something highlighted, if we missed anything, or if you’re building something we didn’t post about, let us know. DMs welcome at nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk
Stay Classy, Nostr.
-
 @ fa0165a0:03397073
2023-10-12 16:40:43
@ fa0165a0:03397073
2023-10-12 16:40:43Probability theory is the study of random phenomena. This post is a pilot post for potentially further posting in this series. Feedback appreciated. Introduction
Probability theory is the study of random phenomena. It is used in many fields, such as statistics, machine learning, and finance. It is also used in everyday life, for example when playing games of chance, or when estimating the risk of an event. The most classic example is the coin toss, closely followed by the dice roll.
When we toss a coin, the result is either heads or tails. In the case of an ideal coin, the “random trail” of tossing the coin has an equal probability for both outcomes. Similarly, for a die roll of a fair dice, we know that the probability for each outcome is 1/6. In the study of probability we dive deep into the mathematics of these random phenomena, how to model them, and how to calculate the probability of different events. To do this in precise terms, we define words and concepts as tools for discussing and communicating about the subject.
This is the first of what I expect to be a 15 part series of my lecture & study notes from my university course in probability theory MT3001 at Stockholm University. References to definitions and theorems will use their numeration in the course literature, even if I may rephrase them myself. The book I’ve had as a companion through this course is a Swedish book called Stokastik by Sven Erick Alm and Tom Britton; ISBN:978–91–47–05351–3. This first module concerns basic concepts and definitions, needed for the rest of the course. The language of Probability theory
An experiment is a process that produces a randomized result. If our experiment is throwing a die, we then have the following: The result of throwing the die is called an outcome, the set of all possible outcomes is called the sample space and a subset of the sample space is called an event. We will use the following notation:
outcome is the result of an experiment, denoted with a small letter, ex. 𝑢₁, 𝑢₂, 𝑢₃, … event is the subset of the sample space, denoted with a capital letter, ex. 𝐴, 𝐵, 𝐶, … sample space is the set of all possible outcomes of an experiment, denoted Ω.Adding numbers to our dice example, we have the sample space Ω = {𝟏,𝟐,𝟑,𝟒,𝟓,𝟔} containing all the possible events 𝑢₁=𝟏, 𝑢₂=𝟐, 𝑢₃=𝟑, 𝑢₄=𝟒, 𝑢₅=𝟓 and 𝑢₆=𝟔. And we could study some specific sub events like the chance of getting an even number, 𝐴={𝟐,𝟒,𝟔}, or the chance of getting a prime number, 𝐵={𝟐,𝟑,𝟓}. As it happens, the probability of both 𝐴 and 𝐵 is 50%. Sample space
The sample space is the set of all possible outcomes of an experiment. It is denoted Ω. And there are two types of sample spaces, discrete and continuous. A discrete sample space is a finite or countably infinite set, and all other kind of sample spaces are called continuous.
The coin toss and the dice roll are both examples of discrete sample spaces. Studying a problem, like the temperature outside, would in reality require a continuous sample space. But in practice, we can often approximate a continuous sample space with a discrete one. For example, we could divide the temperature into 10 degree intervals, and then we would have a discrete sample space.
Remember that continuous sample spaces exist, and expect more information about them in later modules. For starters, we focus on discrete sample spaces. Set Theory notation and operations
When talking about probabilities we will arm ourselves with the language of “set theory”, it is a crucial tool for the study of probability. Feeling comfortable with the subject of set theory since before is useful, but not necessary. I will try to explain the concepts as we go along.
Even tough the events from the dice rolls are represented by numbers, it is important to note that they aren’t numbers, but rather elements. This might become more clear if we alter our example to be a deck of cards. This deck of cards have four suits Ω = {♥, ♠, ♦, ♣ } and in our experiments we draw a card from the deck and look at the suit. It’s here very obvious that we can’t add or subtract the different events with each other. But we do have the operations of set theory at our disposal. For example, if 𝐴 is the event of drawing a red card and 𝐵 is the event of drawing spades ♠, we can use the following notation: Set theory operations
Union: 𝐴 ∪ 𝐵 = {♥, ♦, ♠}, the union of 𝐴 and 𝐵. The empty set: ∅ = {}, the empty set. A set with no elements. Intersection: 𝐴 ∩ 𝐵 = ∅, the intersection of 𝐴 and 𝐵. This means that 𝐴 and 𝐵 have no elements in common. And we say that 𝐴 and 𝐵 are disjoint. Complement: 𝐴ᶜ = {♠, ♣}, the complement of 𝐴. Difference: 𝐴 ∖ 𝐵 = {♥, ♦}, the difference of 𝐴 and 𝐵. Equivalent to 𝐴 ∩ 𝐵ᶜ. The symbol ∈ denotes that an element is in a set. For example, 𝑢₁ ∈ Ω means that the outcome 𝑢₁ is in the sample space Ω. For our example: ♥ ∈ 𝐴 means that the suit ♥ is in the event 𝐴.Venn diagram
A very useful visualization of set theory is the Venn diagram. Here is an example of a Venn diagram in the picture below:
In the above illustration we have: Ω = {𝟏,𝟐,𝟑,𝟒} and the two events 𝐴={𝟐,𝟑} and 𝐵={𝟑,𝟒}. Notice how the two sets 𝐴 and 𝐵 share the element 𝟑, and that all sets are subsets of the sample space Ω. The notation for the shared element 𝟑 is 𝐴 ∩ 𝐵 = {𝟑}. Useful phrasing
The different set notations may seem a bit abstract at first, at least before you are comfortable with them. Something that might be useful to do is to read them with the context of probabilities in mind. Doing this, we can read some of the different set notations as follows:
𝐴ᶜ, “when 𝐴 doesn’t happen”. 𝐴 ∪ 𝐵, “when at least one of 𝐴 or 𝐵 happens”. 𝐴 ∩ 𝐵, “when both 𝐴 and 𝐵 happens”. 𝐴 ∩ 𝐵ᶜ, “when 𝐴 happens but 𝐵 doesn’t happen”.The Probability function
Functions map elements from one set to another. In probability theory, we are interested in mapping events to their corresponding probabilities. We do this using what we call a probability function. This function is usually denoted 𝑃 and have some requirements that we will go through in the definition below.
This function take events as input and outputs the probability of that event. For the example of a die throw, if we have the event 𝐴={𝟐,𝟒,𝟔}, then 𝑃(𝐴) is the probability of getting an even number when throwing a fair six sided dice. In this case 𝑃(𝐴)=1/2=𝑃(“even number from a dice throw”), you’ll notice that variations of descriptions of the same event can be used interchangeably.
The Russian mathematician Andrey Kolmogorov (1903–1987) is considered the father of modern probability theory. He formulated the following three axioms for probability theory: Definition 2.2, Kolmogorov’s axioms
A real-valued function 𝑃 defined on a sample space Ω is called a probability function if it satisfies the following three axioms: 𝑃(𝐴) ≥ 𝟎 for all events 𝐴. 𝑃(Ω) = 𝟏. If 𝐴₁, 𝐴₂, 𝐴₃, … are disjoint events, then 𝑃(𝐴₁ ∪ 𝐴₂ ∪ 𝐴₃ ∪ …) = 𝑃(𝐴₁) + 𝑃(𝐴₂) + 𝑃(𝐴₃) + …. This is called the countable additivity axiom.From these axioms it’s implied that 𝑃(𝐴) ∈ [𝟎,𝟏], which makes sense since things aren’t less than impossible or more than certain. As a rule of thumb, when talking about probabilities, we move within the range of 0 and 1. This lets us formulate the following theorem: Theorem 2.1, The Complement and Addition Theorem of probability
Let 𝐴 and 𝐵 be two events in a sample space Ω. Then the following statements are true: 1. 𝑃(𝐴ᶜ) = 𝟏 — 𝑃(𝐴) 2. 𝑃(∅) = 𝟎 3. 𝑃(𝐴 ∪ 𝐵) = 𝑃(𝐴) + 𝑃(𝐵) — 𝑃(𝐴 ∩ 𝐵)Proof of Theorem 2.1
𝑃(𝐴 ∪ 𝐴ᶜ) = 𝑃(Ω) = 𝟏 = 𝑃(𝐴) + 𝑃(𝐴ᶜ) ⇒ 𝑃(𝐴ᶜ) = 𝟏 — 𝑃(𝐴)
This simply proves that the probability of 𝐴 not happening is the same as the probability of 𝐴 happening subtracted from 1.
𝑃(∅) = 𝑃(Ωᶜ) = 𝟏 — 𝑃(Ω) = 𝟏 — 𝟏 = 𝟎
Even though our formal proof required (1) to be proven, it’s also very intuitive that the probability of the empty set is 0. Since the empty set is the set of all elements that are not in the sample space, and the probability of an event outside the sample space is 0.
𝑃(𝐴 ∪ 𝐵) = 𝑃(𝐴 ∪ (𝐵 ∩ 𝐴ᶜ)) = 𝑃(𝐴) + 𝑃(𝐵 ∩ 𝐴ᶜ) = 𝑃(𝐴) + 𝑃(𝐵) — 𝑃(𝐴 ∩ 𝐵)
This can be understood visually by revisiting our Venn diagram. We see that the union of 𝐴 and 𝐵 has an overlapping element 𝟑 shared between them. This means that purely adding the elements of 𝐴={𝟐,𝟑} together with 𝐵={𝟑,𝟒} would double count that shared element, like this {𝟐,𝟑,𝟑,𝟒}, since we have two “copies” of the mutual elements we make sure to remove one “copy” bur removing 𝑃(𝐴 ∩ 𝐵)={𝟑} and we get 𝑃(𝐴 ∪ 𝐵)={𝟐,𝟑,𝟒}. We may refer to this process as dealing with double counting, something that is very important to have in mind when dealing with sets.
Two interpretations of probability that are useful and often used are the frequentist and the subjectivist interpretations. The frequentist interpretation is that the probability of an event is the relative frequency of that event in the long run. The subjectivist interpretation is that the probability of an event is the degree of belief that the event will occur, this is very common in the field of statistics and gambling. For the purposes of study it’s also useful to sometimes consider probabilities as areas and or masses, this is called the measure theoretic interpretation. Don’t let that word scare you off, in our context it’s just a fancy way of drawing a parallel between areas and probabilities. Think area under curves, and you’ll be fine.
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ c73818cc:ccd5c890
2024-04-22 21:19:58
@ c73818cc:ccd5c890
2024-04-22 21:19:58Sfida aperta! Partecipa al TraderPro di Bitget, dimostra le tue abilità e vinci 10.000 USDT per iniziare a fare copy trading come Trader Elite!
Cosa aspetti?
Iscriviti gratis alla sfida entro il 17 maggio https://bonus.bitget.com/U1JNEK Raggiungi gli obiettivi e diventa Trader Elite Guadagna dai tuoi follower e dai tuoi successi di trading
E ricorda che iscrivendoti dal nostro link avrai lo sconto del 10% a vita sulle fee!
-
 @ 7f5c2b4e:a818d75d
2023-09-27 08:25:11
@ 7f5c2b4e:a818d75d
2023-09-27 08:25:11What is Obsidian?
Obsidian.md is a versatile and powerful note-taking and knowledge management application that's gained immense popularity among users seeking a robust digital tool for organizing their thoughts, ideas, and information.
Obsidian boasts an array of features and benefits that can't all be covered in a single article. Instead, this #guide focuses on a unique, yet potent use case that has recently emerged - the ability to publish #Nostr notes and long-form posts directly from the app.
This capability has been made feasible through the complementary nature of Obsidian and Nostr. Obsidian is an open-source software with a thriving community and extensive support for custom plugins. On the other hand, Nostr is an open protocol with a rapidly expanding suite of tools, simplifying the integration of Nostr across various corners of the Internet. The plugin I will cover in this guide is called Nostr Writer.
Obsidian link: obsidian://show-plugin?id=nostr-writer
GitHub: https://github.com/jamesmagoo/nostr-writer
Developer: nostr:npub10a8kw2hsevhfycl4yhtg7vzrcpwpu7s6med27juf4lzqpsvy270qrh8zkw
But before we dive in, let me share some thoughts on why should one use Obsidian to publish long-form posts (and potentially even short notes) on Nostr.
Why post with Obsidian?
This is a question that naturally comes to mind: "Why use Obsidian to publish on Nostr when the legendary Nostr developers have already set up all the necessary infrastructure for browser-based publishing?" Well, there are several reasons:
-
Native Markdown Support: To begin, Obsidian employs plain text Markdown formatting for notes, just like all Nostr-based blogging platforms. This makes it an ideal choice for creating, formatting, and editing Nostr posts.
-
Illustrative Preview: While other blogging platforms offer preview tools, Obsidian has perfected this feature. It provides a beautifully customizable preview window that can be positioned anywhere in your workspace, allowing you to visualize how formatting, media, and embeds will appear in the published post[^1].
-
State-of-the-Art Flexibility: Since 2020, Obsidian has continuously improved the way writers interact with it. What sets it apart is not only the dedicated team but also its thriving community, all contributing to its refinement. Obsidian supports an extensive array of plugins, shortcuts, and hotkeys, offering unparalleled flexibility and customization. Comprehensive documentation and a ton of videos and even courses on YouTube provide a wealth of information to tailor Obsidian to your preferences.
-
Boosted Productivity: The Nostr Writer plugin is a game-changer for power users of Obsidian. If you're already using Obsidian for note-taking, employing this tool to publish your notes on Nostr is a no-brainer. If you haven't explored it yet, I strongly recommend giving it a try. It has the potential to transform how you think, plan, and structure your ideas for the better. Trying it for broader objectives will help you appreciate how well it complements Nostr.
-
Distraction-Free Composition: While you may disagree, browsers can be a significant source of distraction, with constant alerts, notifications, and blinking extensions. Composing within Obsidian offers a tranquil, clutter-free experience, fostering focus and productivity.
-
Local Record Keeping: Thanks to Nostr Writer, Obsidian keeps a local record of events you published to Nostr in a JSON file on your computer. Your long-form posts are also securely stored in the
.mdformat on your machine, just like all the Obsidian notes you create. On top of that a separate tab holding all of your long-form posts posted via Obsidian is created.
nostr: note1z70v5fsty7v7kaaslsv3ckru50nxym32a62kgx0z7cjdure39hps363sh7
- Drafts You Can Count On: Drafts are often a weak point in long-form platforms. Even though Nostr developers have addressed some of these concerns, the "vanishing drafts problem" still lingers. Obsidian, designed with data safety in mind, stores all your notes locally on your device. Whether you open your laptop tomorrow or in a year, your files will be there, safe from external disruptions. For added redundancy, consider using Obsidian Sync, which encrypts and synchronizes your notes across your chosen devices.
While there are more benefits to utilizing Obsidian for both Nostr publishing and in your general workflow, these reasons should provide a solid understanding. Now, let's shed some light on the Nostr Writer plugin.
Nostr Writer
I stumbled upon Obsidian not too long ago, all thanks to nostr:npub1zvvv8fm7w2ngwdyszg3y6zgp6vwqlht8zrr8wcmjaxjecrvpjfwsd0zs7w. He's also the one who introduced me to the Nostr Writer plugin. Until recently, I primarily used Obsidian "as intended" - for documenting my thoughts and writing articles. What I found especially convenient was using it to compose long-form Nostr posts. And then, the revelation came when I discovered the Nostr Writer plugin - it transformed the experience. No more copy-pasting and meticulous adjustments were required; I can simply compose, add a cover image and description, and publish - it's as straightforward as that.
As I mentioned earlier, Obsidian boasts a vast library of community-driven plugins. To begin using Nostr Writer, simply install the plugin from the "Community plugins" section and navigate to the plugin settings to set up your publishing workflow.
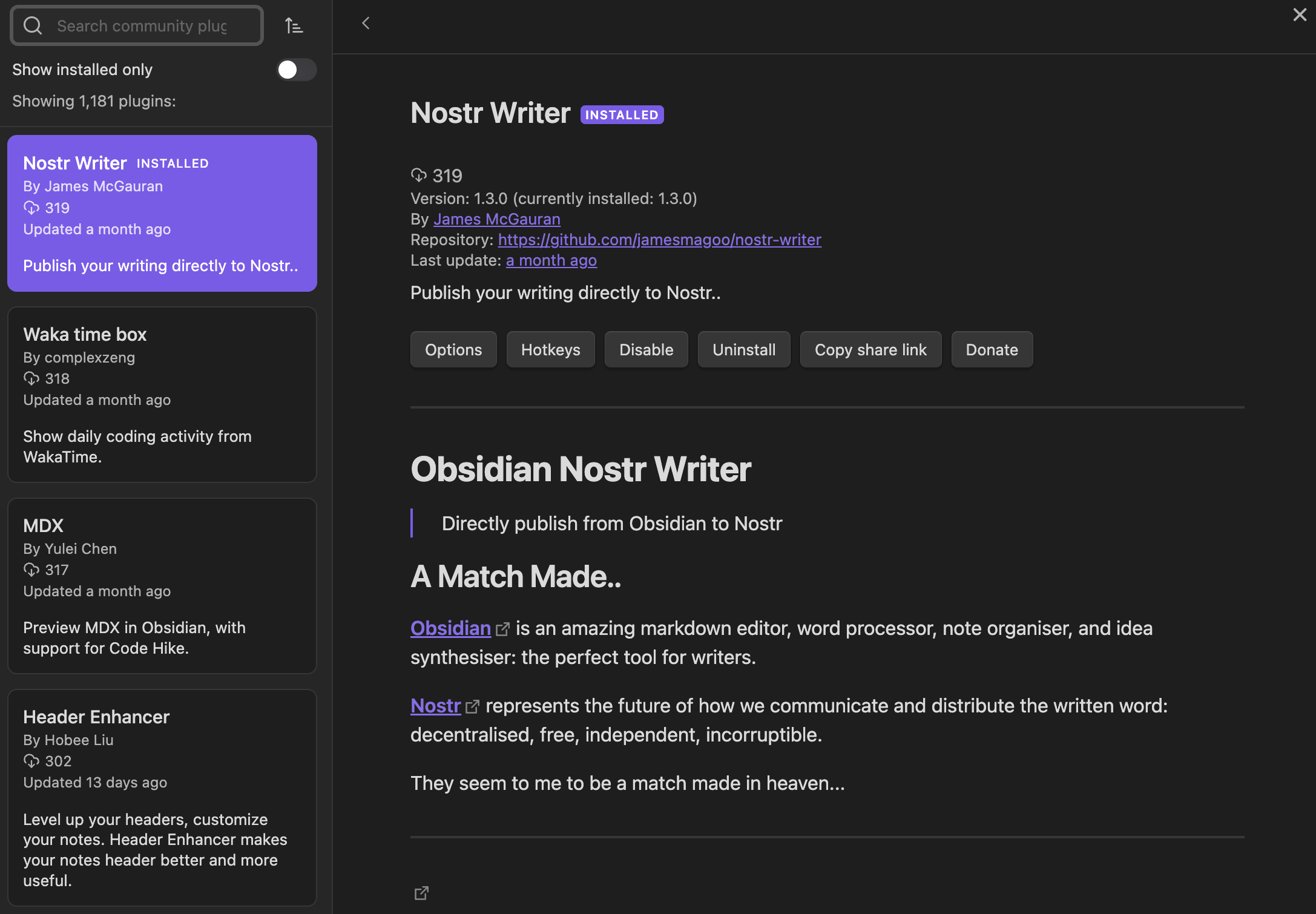
You can install the plugin by clicking this link while having Obsidian open on your device, or by going to the "Community plugins" tab in the settings and typing "Nostr" in the search field.
Once the plugin is installed, you'll need to customize it to enable publishing your Obsidian notes to Nostr.
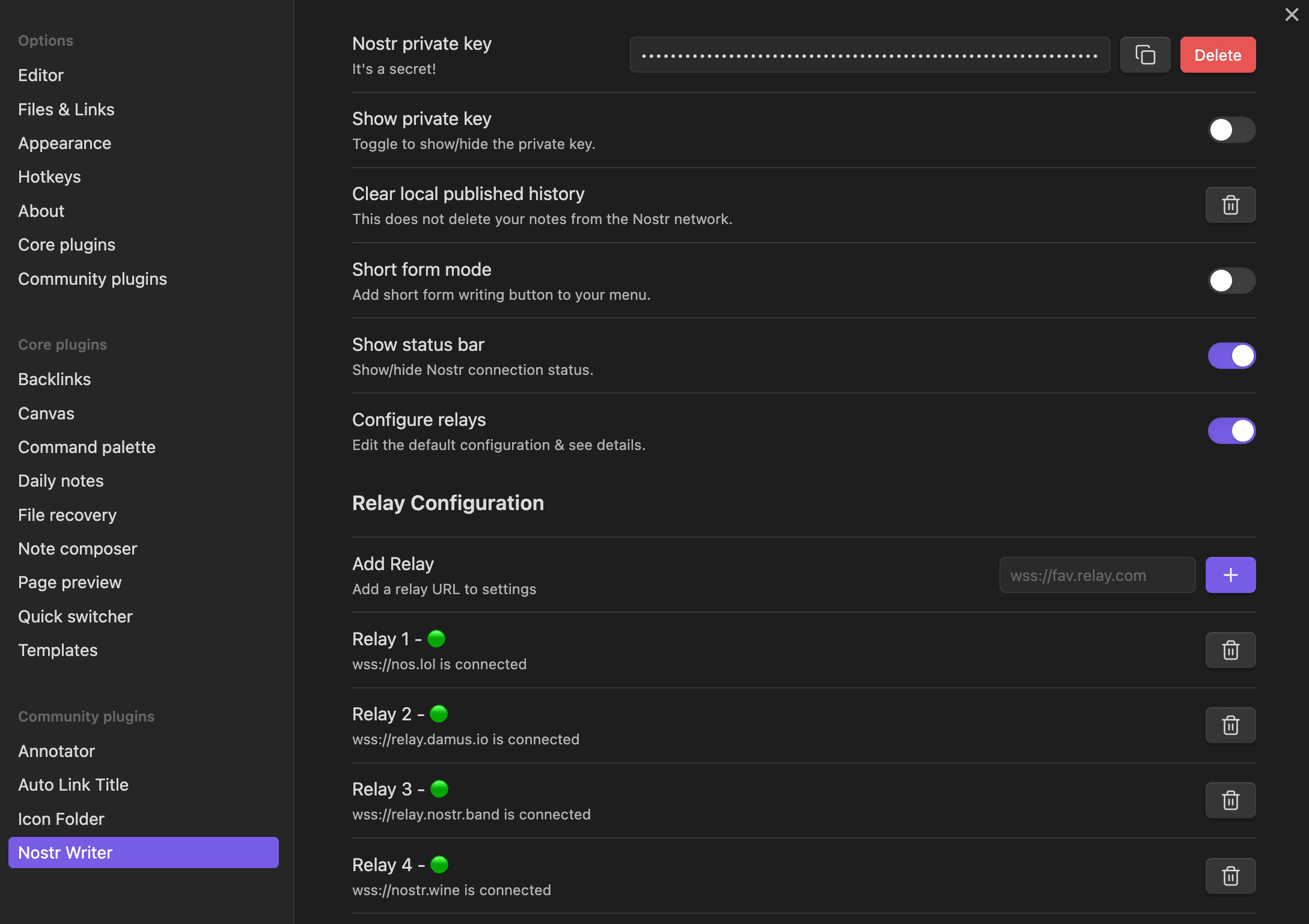
Primarily, you'll need to paste your private key (
nsec) into the corresponding field. Additionally, I recommend configuring your relays to ensure the widest reach for your posts. If you're unfamiliar with Nostr relays or wish to enhance your understanding, you can explore my relay guide here.Many Nostr users naturally have concerns about sharing their private keys with apps. In this case, worry not. Your private key is stored exclusively on your local device and never leaves it. More details can be found here. Even if you use Obsidian sync to keep your notes updated across multiple devices, all information is locally encrypted and safeguarded by the password of your choice. Neither the Obsidian developers nor the plugin developer have access to your files. For additional information, you can refer to the "Security and privacy" section of the Obsidian documentation.
As you can see in the screenshot above, Nostr Writer also provides the option to post short notes. By toggling the corresponding slider, a pencil icon will appear on the sidebar, allowing you to post short notes without leaving Obsidian:
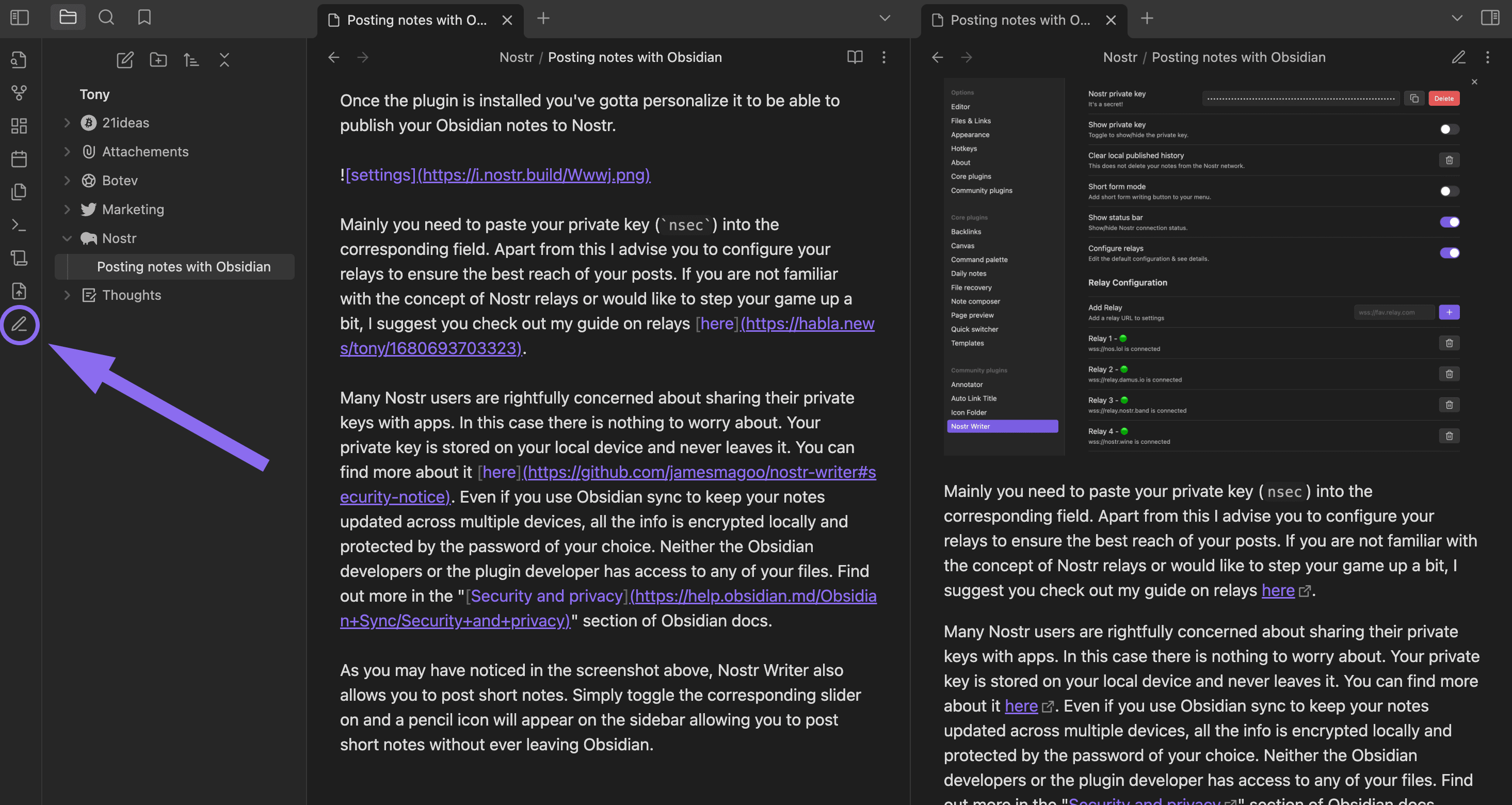
While I wouldn't claim that the plugin surpasses any of the "Twitter-like" Nostr clients, it can prove handy if you're already working within Obsidian and wish to share a quote or any other snippet of information you've come across in your notes.
Publishing
Publishing posts with Nostr Writer is straightforward. If you're already familiar with Obsidian, composing and formatting will be a total breeze, and the actual posting process is no different from posting with Habla, or any other Nostr-native blogging platform.
The only thing that may differ from some Nostr platforms is that Nostr Writer does not provide a specific field for adding hashtags when publishing. Instead, you should incorporate them directly into your text.
Once you've finished crafting your blog post, simply click on the upload icon in the side menu to specify the title, add a summary, and attach a cover image.
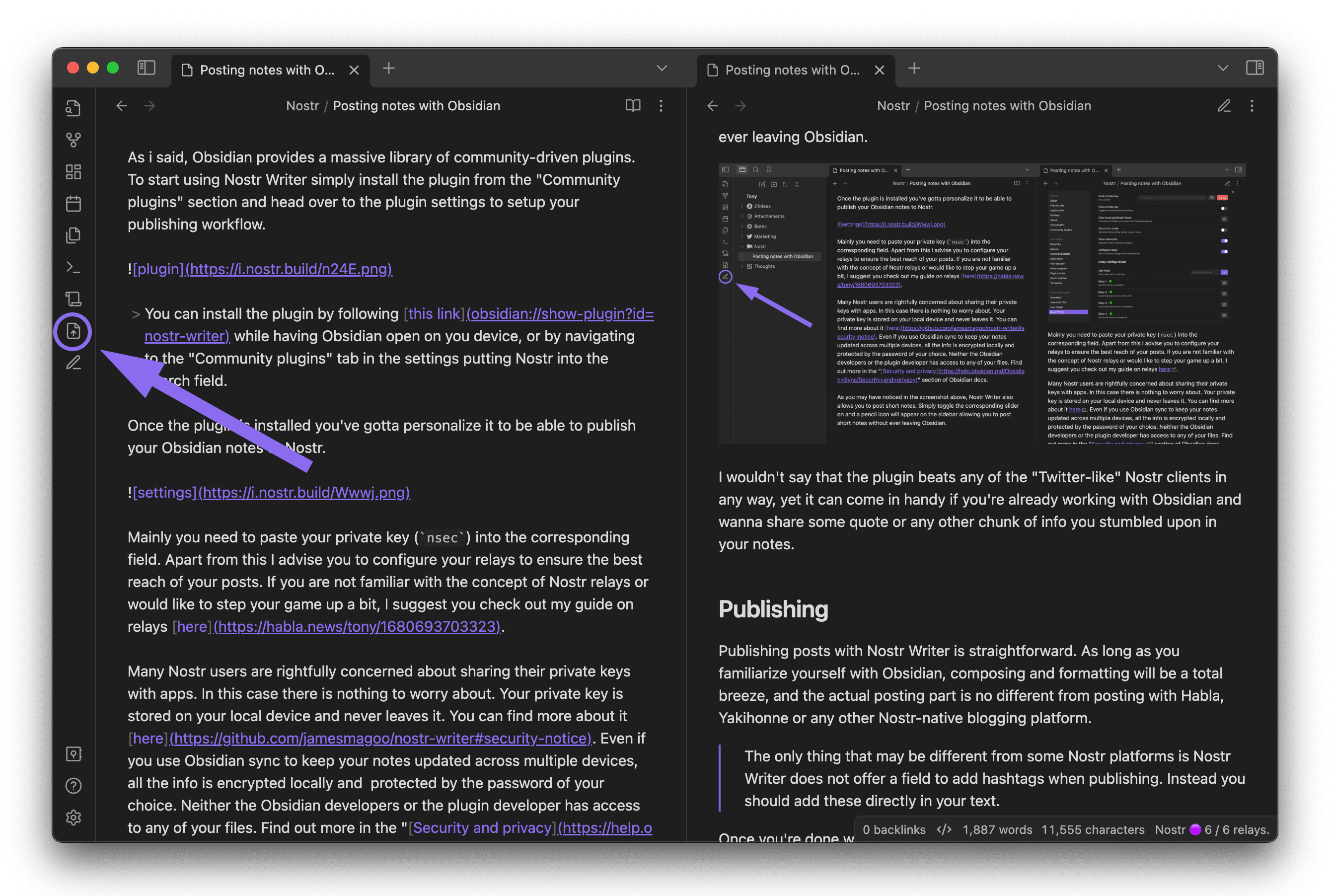
When you're ready, click "Confirm and Publish."
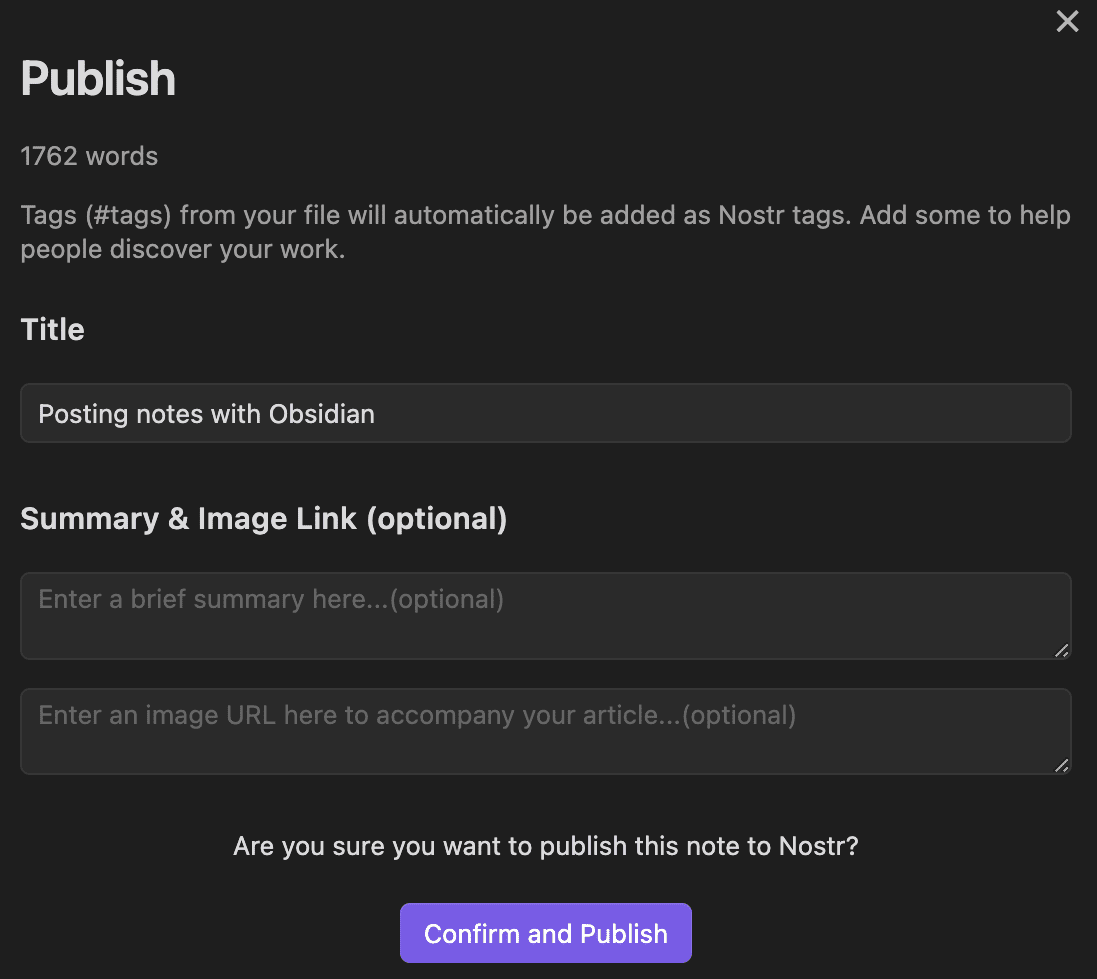
Another point to note is the relays indicator in the bottom-left corner. Relay connection may get interrupted if left inactive for a while, but a simple click on the widget will reconnect you to Nostr in no time.
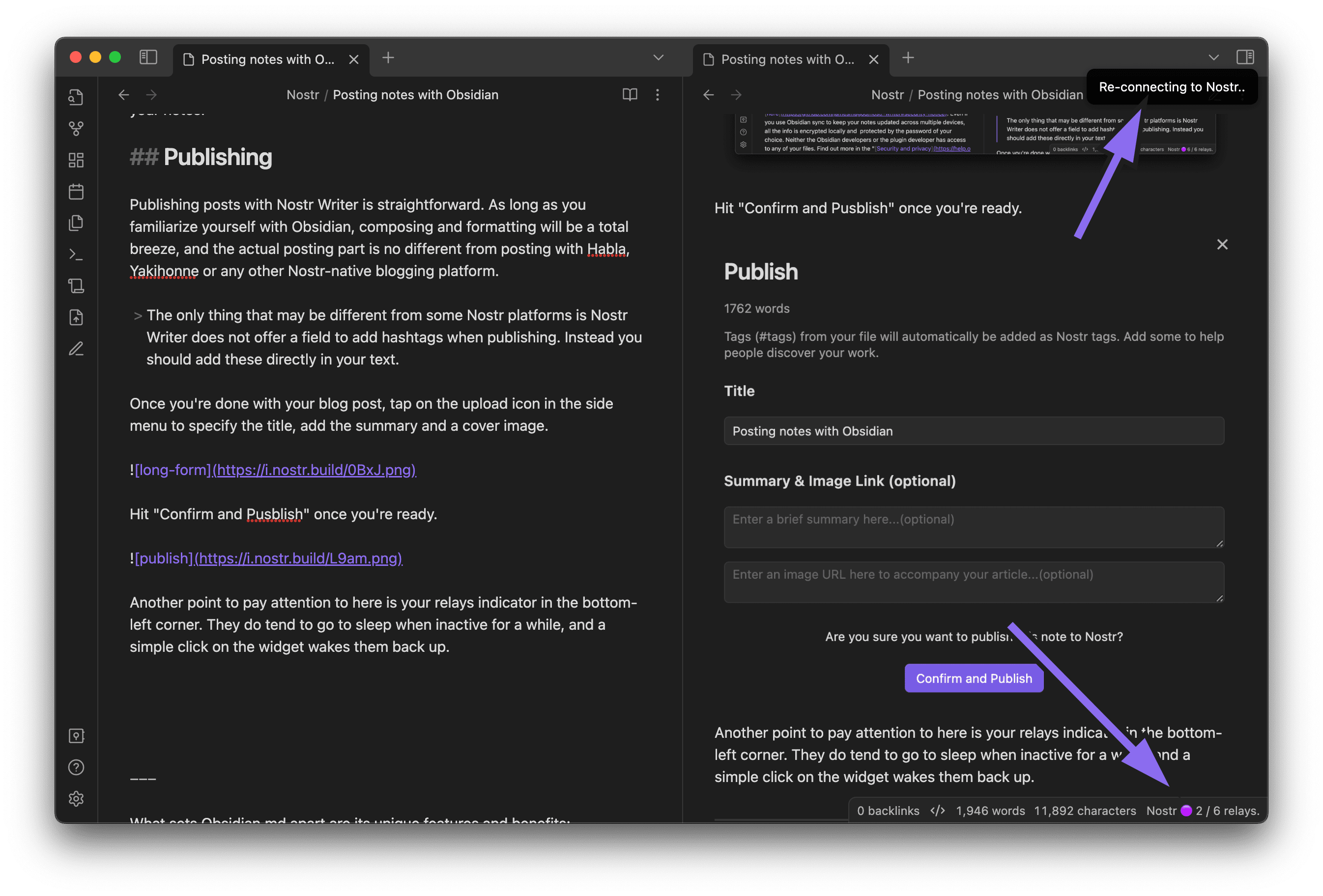
Practice makes perfect
As I mentioned earlier, I find this approach to publishing long-form posts on Nostr the most efficient and convenient. Moreover, there are numerous improvements in the pipeline for the plugin, which is nothing short of exciting.
With that said, it's worth visiting Habla after publishing your post to double-check that everything appears as intended. Initially, you might encounter some formatting peculiarities that you'll need to get accustomed to, but with practice, you'll effortlessly master them. Soon, you won't even have to worry about how the article looks in Nostr clients because you'll be able to visualize every single aspect of your post in your mind.
I hope you found this guide useful and consider utilizing Obsidian for both publishing Nostr posts and elevating your overall productivity. If that's the case, please show your support for nostr:npub10a8kw2hsevhfycl4yhtg7vzrcpwpu7s6med27juf4lzqpsvy270qrh8zkw' work.
Please feel free to share your thoughts and suggestions—I'm always eager to hear from you! Don't forget that my Habla blog page contains a ton of Nostr guides, so you can find answers to almost any Nostr-related questions. If there are specific topics you believe I should cover, do let me know.
See you on the other side of the Nostr rabbit hole.
Tony
P.S. This post was composed, formatted and published to Nostr from Obsidian. No Nostr-related blogging platform was used.
[^1]: Nostr-native syntax, including tagging and Nostr-events embeds, is an exception here. Not all platforms on the Internet currently support Nostr syntax standards like tagging users with their npub, as in
nostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7, so it may not be available for preview. However, tags and embeds will be displayed on Habla. You can learn more about Habla's features in my previous guide here. -
-
 @ 3cd2ea88:bafdaceb
2024-04-22 21:18:12
@ 3cd2ea88:bafdaceb
2024-04-22 21:18:12Sfida aperta! Partecipa al TraderPro di Bitget, dimostra le tue abilità e vinci 10.000 USDT per iniziare a fare copy trading come Trader Elite!
Cosa aspetti?
Iscriviti gratis alla sfida entro il 17 maggio https://bonus.bitget.com/U1JNEK Raggiungi gli obiettivi e diventa Trader Elite Guadagna dai tuoi follower e dai tuoi successi di trading
E ricorda che iscrivendoti dal nostro link avrai lo sconto del 10% a vita sulle fee!
-
 @ 05a58e00:13f429cb
2024-04-22 19:05:32
@ 05a58e00:13f429cb
2024-04-22 19:05:32- a Card
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 78733875:4eb851f2
2023-08-17 14:23:51
@ 78733875:4eb851f2
2023-08-17 14:23:51After announcing our first wave of grants for bitcoin[^fn-btc] and nostr[^fn-nostr] projects, we are pleased to announce an additional wave of grants for open-source projects in the space:
[^fn-btc]: First Wave of Bitcoin Grants [^fn-nostr]: First Wave of Nostr Grants
- BDK
- LNbits
- Watchdescriptor
- Stratum V2 Testing \& Benchmarking Tool
- Fedimint Modules and Resources
- Amber: Nostr Event Signer
- Nostr UI/UX Development
- Nostr Use-Case Exploration \& Education
The first five grants are sourced from our General Fund, the last three—being nostr projects—from our Nostr Fund. This brings the total number of OpenSats grants to 41, adding to the grants we previously announced in July.
Once again, let's take a closer look at each of the projects to see how they align with the OpenSats mission.
BDK
Bitcoin Development Kit (BDK) is a set of libraries and tools that allows you to seamlessly build cross-platform on-chain bitcoin wallets without having to re-implement standard bitcoin data structures, algorithms, and protocols. BDK is built on top of the powerful rust-bitcoin and rust-miniscript libraries and adds features for managing descriptor-based wallets, syncing wallets to the bitcoin blockchain, viewing transaction histories, managing and selecting UTXOs to create new transactions, signing, and more. The core BDK components are written in Rust, but the team also maintains Kotlin and Swift language bindings for use in mobile projects. There are also Python bindings, and React Native and Flutter support is being actively developed.
Repository: bitcoindevkit/bdk
License: Apache 2.0 / MITLNbits
LNbits is used by a multitude of projects in the bitcoin space, especially as part of their lightning payments stack. Being easy to build on through its extension framework, LNbits has been pioneering various cutting-edge solutions and experiments in the world of bitcoin, lightning, and nostr.
The project has a thriving maker community building various hardware devices such as Lightning ATMs, point-of-sale devices, DIY hardware wallets, and nostr signing devices. The modular design of LNbits makes it attractive to users and tinkerers alike, as its plugin architecture makes it easy to extend and understand.
Repository: lnbits/lnbits
License: MITWatchdescriptor
watchdescriptoris a CLN plugin written in Rust that connects a business's treasury wallet to its CLN node. It utilizescln-pluginand the BDK library to track coin movements in registered wallets and report this information to thebookkeeperplugin.The plugin enables businesses to design a complete treasury using Miniscript and import the resulting descriptor into CLN. Since
bookkeeperalready accounts for all coin movements internal to CLN, this plugin is the last piece businesses need in order to unify all their bitcoin accounting in one place. This enables businesses to account for all inflows and outflows from their operations, streamlining tax reporting and financial analysis.The
watchdescriptorproject is part of a broader vision to transform the lightning node (particularly CLN) into a financial hub for businesses, enabling them to conduct operations without reliance on any third parties.Repository: chrisguida/watchdescriptor
License: MITStratum V2 Testing & Benchmarking Tool
The Stratum V2 Testing & Benchmarking Tool allows the bitcoin mining industry to test and benchmark Stratum V2 performance against Stratum V1. The tool supports different mining scenarios to help miners make informed decisions and evaluate their profitability. The goal of the project is to motivate miners to upgrade to Stratum V2, increasing their individual profits and making the Bitcoin network more resilient in the process.
Repository: stratum-mining/stratum @GitGab19
License: Apache 2.0 / MITFedimint Modules and Resources
Fedimint is a federated Chaumian e-cash mint backed by sats with deposits and withdrawals that can occur on-chain or via lightning. It can be understood as a scaling and privacy layer as well as an adoption accelerator for Bitcoin.
The goal of this particular project is to improve the Fedimint UI and develop free and open resources for developers and "Guardians" to enable more people to run and develop on Fedimint.
Repository: fedimint/ui @EthnTuttle
License: MITAmber: Nostr Event Signer
Amber is a nostr event signer for Android. It allows users to keep their
nsecsegregated in a single, dedicated app. The goal of Amber is to have your smartphone act as a NIP-46 signing device without any need for servers or additional hardware. "Private keys should be exposed to as few systems as possible as each system adds to the attack surface," as the rationale of said NIP states. In addition to native apps, Amber aims to support all current nostr web applications without requiring any extensions or web servers.Repository: greenart7c3/Amber
License: MITNostr UI/UX Development
The goal of this project is to help improve the UI/UX of major nostr clients, starting with Gossip and Coracle, emphasizing the onboarding process as well as usability and accessibility. One part of onboarding is solving the discoverability problem that nostr has in the first place. Solving the problem of jumping in and out of the nostr world is what motivated the development of
njump, which was redesigned as part of these efforts and is now live at nostr.com.In addition to client-specific improvements, generic design modules and learnings will be incorporated into the Nostr Design project for others to use.
Activity: github.com/dtonon @dtonon
License: MITNostr Use-Case Exploration & Education
As of today, most nostr clients implement social media applications on top of the nostr protocol. However, nostr allows for various use cases, many of which go beyond social media. Two examples are Listr and Ostrich, a list management tool and job board, respectively.
In addition to use-case exploration, this project will continue to educate users and developers alike, be it via Nostr How or various video series, e.g., explaining how to build upon NDK.
Activity: github.com/erskingardner @jeffg
License: MIT / GPL-3.0 / CC BY-NC-SA 4.0
We have more grants in the pipeline and will provide funding for many more projects in the future. Note that we can only fund those projects which reach out and apply. If you are an open-source developer who is aligned with our mission, don't hesitate to apply for funding.
-
 @ 0403c86a:66d3a378
2024-04-22 18:51:17
@ 0403c86a:66d3a378
2024-04-22 18:51:17Max Verstappen 🇳🇱 showcased his dominance once again, converting pole position into a stunning victory in Shanghai! 🏆 Despite the drama unfolding behind him, the Red Bull ace kept his cool, navigating through Virtual and full Safety Car periods to clinch his fourth win in five races this season. 💪
Lando Norris 🇬🇧 pulled off a strategic masterclass, pitting just once to leap ahead of Sergio Perez 🇲🇽 and secure a well-deserved second place for McLaren. 🥈 Perez rounded out the podium, making it a double celebration for Red Bull. 🍾
Ferrari's Charles Leclerc 🇲🇨 and Carlos Sainz 🇪🇸 showcased their tyre management skills, completing the race with a single pit stop each to claim fourth and fifth, respectively. 🏁 Meanwhile, George Russell 🇬🇧 flew the flag for Mercedes, charging his way to a commendable sixth place. 💪
The Chinese Grand Prix proved to be an electrifying encounter, filled with nail-biting overtakes and strategic gambles. 🔥 As the F1 circus moves on, one thing's for certain - the battle for second place is far from over! 🌍🏎️ #ChineseGP #F1 #Verstappen #Norris #Perez
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ d3d74124:a4eb7b1d
2023-07-26 02:43:40
@ d3d74124:a4eb7b1d
2023-07-26 02:43:40This plan was GPT generated originally but then tweaked by myself as the idea fleshed itself out. All feedback welcome and encouraged.
Shenandoah Bitcoin
1. Executive Summary
Shenandoah Bitcoin is a for-profit community organization based in Frederick County, VA, uniquely blending the world of agriculture and STEM. Our mission is to foster community spirit, stimulate interest in agricultural technology, and promote understanding of Bitcoin, while providing enriching educational opportunities and ensuring sustainable business operations.
2. Company Description
Shenandoah Bitcoin is committed to delivering value to our local community. Our unique approach intertwines traditional agricultural practices, modern STEM concepts, and the world of digital currencies, specifically Bitcoin. Our activities cater to all age groups, focusing on fostering community engagement, hands-on learning experiences, and contributing to the overall welfare of our community.
What’s in a name?
Shenandoah Bitcoin. Shenandoah - an old and historied land. Bitcoin - a cutting edge technological advancement. Both encompass multiple industries, from energy and manufacturing, to farming and data centers. Both built using Proof of Work.
3. Services
We offer a range of services, including:
Family-friendly events: Agriculture, STEM, and Bitcoin-themed festivals, fairs, workshops, and community gatherings. Educational programs: Classes, seminars, and workshops on agricultural technology, STEM principles, and understanding and using Bitcoin. Facility Rentals: Spaces available for private events, business meetings, and community gatherings.
4. Membership Benefits
We offer tiered membership packages with benefits such as:
a. Silver Membership: Includes access to regular events, discounts on educational programs, and priority booking for facility rentals.
b. Gold Membership: All Silver benefits, free access to select educational programs, and further discounted facility rentals.
c. Platinum Membership: All Gold benefits, free access to all educational programs, highest priority and maximum discounts on facility rentals, and exclusive invitations to special events.
Member’s opting to pay in Bitcoin receive 10% off all pricing.
5. Market Analysis
Our primary market is the local community in Frederick County and Winchester, VA, which consists of various demographic groups. Our secondary market includes neighboring communities, tourists, businesses, and educational institutions interested in the intersection of agriculture, STEM, and Bitcoin. Understanding that facility use and events to be a drawing factor for all demographics, we outline demographic specific analysis below.
STEM professionals in the area may work remotely or commute toward DC and not interact much with their agricultural neighbors, but a desire for good quality food exists for many. In addition to events, drawing the STEM demographic in will be connections to CSAs, ranchers, and homesteaders for access to fresh locally grown food. Offering a child's play room adjacent to some office space, is a compelling benefit for the laptop class that is often in STEM professions.
Non-industrial food producers and homesteaders may not have the focus or resources for marketing and sales. By offering a physical touch point for them and direct connections to consumers, food producers benefit from membership. Having more options for drop off/pick up of various produced goods, makes it attractive for both the consumers and producers as coordination can be asynchronous.
Bitcoiners have a wide range of sub-demographics, including farmers and software engineers. Some travel hours over car and plane to attend bitcoin themed events. The topics of STEM and agriculture are of shared interest to non-trivially sized communities of bitcoiners. Having a physical touch point for bitcoiners will draw in some members just for that. Building fellowship is desired and sought in bitcoin.
5.1 Market Trends
The blending of agriculture, STEM fields, and Bitcoin is a unique concept with increasing interest in sustainable farming and ranching, food sovereignty, and health. Shenandoah Bitcoin is poised to tap into this growing interest and offer unique value to our community.
5.2 Market Needs
Our market requires initiatives that foster community engagement, promote understanding of agri-tech and Bitcoin, and provide a versatile space for events and learning.
6. Marketing and Sales Strategy
We will employ a blend of digital marketing, traditional advertising, and strategic partnerships. Our main marketing channels will be word of mouth, social media, local press, and our website. Partnerships with local small businesses, homesteaders, schools, agricultural organizations, and bitcoin companies will form a key part of our outreach strategy.
7. Organizational Structure
Shenandoah Bitcoin will be led by a CEO, supported by a management team responsible for daily operations, event planning, marketing, and community outreach. Event management and logistics will be handled by part-time staff and volunteers.
8. Financial Projections
Our revenue will be generated from membership fees, charges for events and educational programs, and facility rentals.
9. Funding Request
[If seeking additional funding, describe your needs and how the funds will be used]
10. Exit Strategy
Should it become necessary to dissolve the business, assets such as property, equipment, and any remaining cash reserves after meeting liabilities will be sold. Investors would receive their share of the remaining assets according to their proportion of ownership.
11. Conclusion
Shenandoah Bitcoin is a unique community organization bringing together agriculture, STEM, and Bitcoin in Frederick County, VA. Our distinctive approach is designed to deliver both profits and social impact, resonating strongly with our target market and positioning us for sustainable growth.
-
 @ 30ceb64e:7f08bdf5
2024-04-22 17:17:39
@ 30ceb64e:7f08bdf5
2024-04-22 17:17:39Hey freaks!
Cody Wilson gave a speech regarding the idea of death athleticism.
It seems as though I've made death my profession.
Bitcoin is a ladder, Hustle has climbed an additional two rungs this month.
If hyperbitcoinization happens, everyone reading this post will be fine.
If your reading this post, congratulations you' ve made it.
Bitcoin enables exponential growth in your savings, and through the process of groking bitcoin, one picks up activities and habbits that are more akin to minamalism than consumerism. Adopting a self sufficient and sovereign attitude, aligning yourself with productive, like-minded individuals, and extending your time preference is an inevitable pull towards a heroes journey.
This epoch has hustle angrier at the looters (he's been getting into his Rothbard). If you ask a normie what we need the govt for...., you'll receive answers that prescribe them godlike powers.
Michael Saylor said we don't want to be martyrs, we want to win. TheWildHustle welcomes an honorable death performance. When Hustle was in the Air Force he would load bombs and rounds into F-16 fighter jets, the only real world mission he accomplished was in raining fire onto libya to kill Kadafi because he was trying to separate money from state. His squadrons motta was, "giving our enemies the opportunity to die for their country". What an honor.
Don't die for your country freaks! And the best weapon the state has, is its ability to manipulate emotions by fomenting fear. TheWildHustle would be fine and happy if he died right now, everything else is just whipped cream and strawberrys at this point.
-
 @ 52b4a076:e7fad8bd
2023-05-01 19:37:01
@ 52b4a076:e7fad8bd
2023-05-01 19:37:01What is NIP-05 really?
If you look at the spec, it's a way to map Nostr public keys to DNS-based internet identifiers, such as
name@example.com.If you look at Nostr Plebs:
It's a human readable identifier for your public key. It makes finding your profile on Nostr easier. It makes identifying your account easier.
If you look at basically any client, you see a checkmark, which you assume means verification.
If you ask someone, they probably will call it verification.
How did we get here?
Initially, there was only one client, which was (kind of) the reference implementation: Branle.
When it added support for NIP-05 identifiers, it used to replace the display name with the NIP-05 identifier, and it had to distinguish a NIP-05 from someone setting their display name to a NIP-05. So they added a checkmark...
Then there was astral.ninja and Damus: The former was a fork of Branle, and therefore inherited the checkmark. Damus didn't implement NIP-05 until a while later, and they added a checkmark because Astral and other clients were doing it.
And then came new clients, all copying what the previous ones did... (Snort originally did not have a checkmark, but that changed later.)
The first NIP-05 provider
Long story short, people were wondering what NIP-05 is and wanted it, and that's how Nostr Plebs came to be.
They initially called their service verification. Somewhere between January and February, they removed all mentions to verification except one (because people were searching for it), and publicly said that NIP-05 is not verification. But that didn't work.
Then, there were the new NIP-05 providers, some understood perfectly what a NIP-05 identifier is and applied the correct nomenclature. Others misnamed it as verification, adding confusion to users. This made the problem worse on top of the popular clients showing checkmarks.
(from this point in the article we'll refer to it as a Nostr address)
And so, the scams begin
Spammers and scammers started to abuse Nostr addresses to scam people: - Some providers has been used by fake crypto airdrop bots. - A few Nostr address providers have terminated multitude of impersonating and scam identifiers over the past weeks.
This goes to show that Nostr addresses don't verify anything, they are just providers of human readable handles.
Nostr addresses can be proof of association
Nostr addresses can be a proof of association. The easiest analogy to understand is email:
jack@cash.app -> You could assume this is the Jack that works at Cash App.
jack@nostr-address-provider.example.com -> This could be any Jack.
What now?
We urge that clients stop showing a checkmark for all Nostr addresses, as they are not useful for verification.
We also urge that clients hide checkmarks for all domain names, without exception in the same way we do not show checkmarks for emails.
Lastly, NIP-05 is a nostr address and that is why we urge all clients to use the proper nomenclature.
Signed:
- Semisol, Nostr Plebs (semisol@nostrplebs.com)
- Quentin, nostrcheck.me (quentin@nostrcheck.me)
- Derek Ross, Nostr Plebs (derekross@nostrplebs.com)
- Bitcoin Nostrich, Bitcoin Nostr (BitcoinNostrich@BitcoinNostr.com)
- Remina, zaps.lol (remina@zaps.lol)
- Harry Hodler, nostr-check.com (harryhodler@nostr-check.com)
-
 @ 5d4b6c8d:8a1c1ee3
2024-04-22 16:37:37
@ 5d4b6c8d:8a1c1ee3
2024-04-22 16:37:37I'm finally doing it, @cryotosensei. I've given some thought to how to sustainably take profits from my use of Stacker News. I probably won't start until after this month's MSM concludes, because I'm still guilt zapping away my ill-gotten rewards from last month.
Optimal Zapping Behavior
Previously, I wrote about how to find your optimal zapping strategy for Stacker News: https://stacker.news/items/287074/r/Undisciplined. Despite that being my highest ranked post, people are still radically underzapping (but that's not the point of this post).
That strategy uses the waxing and waning of my SN wallet balance to inform what my default zap ought to be. The problem with this strategy is that it converges on a zero profit point. I'm happy to recirculate my Stacker News earnings, so this problem didn't bother me.
Zap bigger. Zap oftener. Zap earlier.
Profit Taking
Since I was already using my current balance to optimize zapping, I couldn't use it to also optimize profit taking. However, I can still use the growth rate of my SN balance to inform profit taking. Optimal profit taking would mean my balance remains stable.
The approach I came up with is to withdraw my average daily net earnings. If Stacker News grows or I get better at using it, then my daily profits will grow.
I've been on SN for 537 days and have 395.9k in my wallet, so I would withdraw 737 sats per day with this strategy. Hopefully that will grow. Even with my optimistic estimate for the value of sats (https://stacker.news/items/474759/r/Undisciplined), that's not a lot.
Why bother?
A big part of SN's pitch is that you can earn sats by contributing here. Of course, you can do that without jumping through these hoops.
In part, I just like thinking about this kind of stuff, but the rewards system also makes the optimal usage of SN non-obvious. How much you should zap depends on what you're zapping, when you're zapping, and how much other stackers are zapping. How much you should take in profits depends on how much you're getting back in rewards and how much you should be zapping.
I like simple methods that converge on optimality, rather than trying to fully solve a system analytically and derive the optimal solution.
TL;DR
- Have a dedicated SN wallet.
- Use turbo zaps to zap 1/100th for great posts, 1/1000th for good posts, 1/10,000th for good comments.
- Withdraw daily profits = wallet balance / days on SN
-
 @ 32092ec1:8e9fd13a
2023-04-25 18:02:43
@ 32092ec1:8e9fd13a
2023-04-25 18:02:43Bitcoin maximalism, to many, has evolved from a belief that bitcoin is the only crypto asset worth owning to a belief that bitcoin is the only asset worth owning. In addition, many observe that those who declare themselves to be bitcoin maximalists have also declared their allegiance to many other lifestyle choices. This was well articulated by Jameson Lopp in his blog post “A History of Bitcoin Maximalism.”
While some (myself included for a while) embrace the title of bitcoin maximalist, perhaps out of spite given that it was originally intended to be a derogatory term, I eventually have decided to reject it. While I do not own any other crypto assets, and I do believe that bitcoin offers the best risk adjusted investment across many asset classes, it is not, nor could it ever realistically be, my only investment. Due to the ambiguity of the definition of a “bitcoin maximalist” to some, even the fact that I have equity in my primary residence may call into question my status as a bitcoin maximalist. Although most people likely agree that this point of view is nonsensical, I feel that it is also completely pointless to take the time to defend the purity of my “bitcoin maximalism;” and so, I reject it. In place of the bitcoin maximalist label, I hereby declare myself to be a truth maximalist.
The truth is that 99% of non-bitcoin crypto assets are completely worthless; specifically, what I mean is that they literally add zero net positivity to humanity. The remaining 1% of non-bitcoin crypto assets may indeed serve some limited improvements to existing systems or other alternative benefits; however, these crypto assets are also, in my opinion, already highly over valued given the magnitude of the problems they are intending to solve. Most of the incremental improvements offered by cryptos are related to marginally improving systems based on fiat money and the banking industry both of which bitcoin intends to largely obsolete and are still net negative to humanity and designed to syphon wealth from the powerless to the powerful.
I do believe that open source, decentralized, cryptographic solutions will play additional roles in society and offer an opportunity to disrupt many existing centralized solutions. However, most of these solutions will not be investable assets, just as the internet itself is not an investable asset.
I believe it also to be true that investment properties intended for yield generation come with a host of additional costs and risks that are rarely properly accounted for when assessing the value of these assets. After accounting for the probability weighted costs of evictions, seizures, taxes, maintenance, inflation, and loan interest, I find it difficult to justify these investments over bitcoin held in self-custody.
Many other investable assets that simply sit on a bank’s balance sheet (e.g., stocks, bonds, etc.) can easily be seized if any number of three letter agencies decided that you should not have these assets. This can be done with no due process and does not require any in depth investigation to determine the validity of their claims. I believe that the probability of these types of seizures is much higher for known bitcoiners who are also critical of the government and the media, especially if current financial systems begin to collapse and/or if bitcoin’s value dramatically increases.
Beyond seizure of your individual assets, as the world begins to divest from the highly inflated store of value assets listed on the NYSE and NASDAQ due to seizure risks at the sovereign level, the risk of extreme inflation adjusted devaluation of your portfolio should also be considered. Compounding this risk is the opportunity cost associated with the fact that some of the wealth that may be withdrawn from the US stock market is also likely going to flow into bitcoin. These risks are rarely accounted for or quantified when determining the value of a stock portfolio in contrast to simply holding bitcoin in self-custody.
My opinions on these matters are common among bitcoiners who are largely labeled bitcoin maximalists. However, the title of truth maximalist also fits nicely when trying to counter some of the softer points made in Lopp’s blog post mentioned above. My thesis is that most people who have adopted the bitcoin maximalist “lifestyle” choices have done so as a result of their quest for truth, not as a result of their desire to virtue signal their status as bitcoin maximalists.
The truth is that a carnivore diet is much healthier than governments, media and academia would like you to believe (disclosure: I have never tried a carnivore diet)
The truth is that weightlifting is more beneficial than cardio to overall health (disclosure: I am not into weightlifting)
The truth is that traditional gender roles are beneficial to mental health (disclosure: although my wife is a full-time, stay-at-home mom, my marriage is far from perfect).
The truth is that extreme consequences from greenhouse gasses in the atmosphere are extrapolatory and predictions have historically failed miserably (disclosure: I do not think there is zero risk of extreme disasters from excessive levels of carbon in the atmosphere).
The truth is that seed oils are terrible for you (disclosure: I have ingested seed oils since discovering this).
The truth is that COVID vaccines pointlessly add risk to healthy people and children (disclosure: I received two doses of the COVID vaccine prior to realizing this truth and my wife still disagrees with me on this).
The truth is that natural health solutions are often more beneficial than big pharma would like you to believe (disclosure: I have not used any exotic natural remedies).
The truth is that modern art and architecture is garbage (disclosure: this is only a personal opinion).
The Truth is that Jesus Christ died on a cross and ascended into Heaven in order to save the world from sin (disclosure: although I have always been a Christian, over the last year or so I have dedicated a significant amount of time researching this and so far, everything is supporting this to be literally true and much more easily believable than you might think).
Maybe you disagree with some of these things that I have determined to be true. But let me ask, have done your own research? What is your basis for a counter argument to any of these truths? Did you verify or are you trusting someone else’s opinion? If you are trusting someone else’s research, did you investigate their credibility or determine if they have significant biases? Certainly, my opinions on the topics listed above not always based on exhaustive independent research, but I did approach each with skepticism and did not always believe these things with conviction prior to looking into them. I think any bitcoiner would agree that if you are trusting fiat funded academia, government organizations or mainstream media, you may need to do more research.
The truth is that I will continue to seek the truth and I will encourage others to do the same. The truth is that I welcome new information and listening to opinions that counter my beliefs. When choosing to have strong conviction in minority opinions about the truth, it is extremely valuable to be able to articulate and refute the points that are contrary to your beliefs. It is also important to be able to change your mind when presented with sufficient evidence against your opinion. This is what it means to be a truth maximalist. It just so happens that the truth is that bitcoin is the only crypto asset worth investing in. Don’t believe me? Prove it.
786973
-
 @ 3c984938:2ec11289
2024-04-22 16:19:48
@ 3c984938:2ec11289
2024-04-22 16:19:48The Bell Ringers of Nostr (Nip-23)
Hafa Adai Bitcoiners! If you have fallen down the rabbit hole, congratulations.
“We’re all mad here. I’m mad. You’re mad. Or you wouldn't have come here."
You just learned about Bitcoin, but to know Bitcoin is to know what money is. To know what money is to also understand what Bitcoin stands for-- free speech. Regrettably, I must inform you that their exist many rabbit holes beyond Bitcoin. But for now, we enter the publishing Forest of Nostr to journey to find knights. This article discusses one closed source tool and one Open Source Both definitely have value and puts user first.
The YakiHonne Bunny
As I traveled through a different kind of forest, I stumbled across a rabbit. We kinda look alike so I had to stop and observe much closer. It was such a lovely encounter! The bunny was so kind that it befriended not just me but all that came across it's path. The bunny did not ask me to register my name, email, physical address or even my phone number but rather allow me to maintain my Identity by Encryption via Nostr/npub.

The bunny invited me to a tea party, and I got drunk off from their kindness to the very drop. The bunnies have a unique position. Unfortunately, their cursed with ICANN like many other peers. They're not alone, some are using the newer ICANN gTLD but are still cursed no less. ~This is a different rabbit hole so I'm stopping here.

Despite, their curse like other plagued options on the internet. The bunnies still do what they can to help users get their "Long-form" content out into the world with grace and style. If you're reading this on yakihonne.com then, this is a good example. They have about five dedicated relays just to support "long form Content" or "NIP-23" it should be noted that not all relays support "NIP-23." I would recommend users to not crowd onto just a single relay but to have a few odd ball relays and to support them. I will cover relays later. The important thing to note is not all relays support the different types of data. (A.K.A "Nip")

Due to the nature of being closed source, I do not think it correct to be a knight. However, the work the Yakihonne's developers do is also important and does contribute to the Nostr ecosystem with sophistication . I think they could potentially, someday in the future become Open Source. In the same sense, I am grateful they're not supported by the OpenSats Project. (This is Another Rabbit Hole) Maybe, it's to avoid making deals with potentially bad actors? Only time will tell us. Since the creatures of the publishing forest are all unique and have an important task, I thought Bell Ringer would be more fitting for our dearest critters. I'll be one of the first Town criers whenever they do decide to become open source. 😁

After eating so many lovely cakes, pastries, Pão de queijo (Brazillian cheese buns) and cream, I had to bid farewell or I'll end up getting fatter! The Darjeeling tea was quite divine, and I could easily see myself staying longer, but this was a different forest I've never explored. The rabbit left me a note before I was leaving, as an option I could use their mobile app! (Available on Apple and Google) Prehaps to arrange another tea party? So, I entered a super green forestry. It was so green that the trees were moss covered. I couldn't help but feel I was being watched. Was I imagining things? A Flycat appears before me. I was scared (as I'm much smaller) at first but it turns out the Flycat is just odd.
The Flycat.

Flycat is an open source social network on Nostr. The Flycat is sleek and agility enough to also support long form. In additional, Flycat has a very unique feature, they allow users to have multiple relay lists. This is nice tool because you can have a set list of relays for Nip-23(long-form) and another for everyday/daily notes on Nostr. Cute platform to create and manage your community posts. So definitely, worth checking out if this up your alley.

Just like Yakihonne.com, Flycat.club is built on the Nostr Protocol. So "Identity by encryption" wins yet again but Flycat steps it up a few notches more with flexible login options. Still plagued with ICANN, like 99% of all websites. Flycat does have a noble mission: exit out of toxic internet. Can this be moved to IPFS? I think it's possible!

Follow as I journey further in the Forest of Publishing in part two for more tools to use. Departing is such sweet sorrow. This Flycat is just full of curiosities! 🧡🤍💛 K--kkk--kisu??! 💚💜💞 😳

The title of "Bell Ringer" comes to mind for Yakihonne and Flycat as their platform does help users spread their content and gather information as if your in a local town's pub. Thus, they serve the community, I can only imagine how exhausting such a task could be.

Author's Note:
Diving deeper into the rabbit hole is tricky. Just like the rabbit hole for Bitcoin, I'll do my absolute best to decipher the base layer but you'll still need to do your own falling(digging). There are lots of holes to fall in so consider bringing an umbrella. To put it all in one sitting would just overwhelm you. But this series isn't about the different rabbit holes, I'm merely stating there is so much to uncover if you dare to learn. No worries you can always #asknostr on your client. I merely wish to help you discover tools to help you dear user to live a more decentralized life and I'm pointing out the different tools at your fingertips in a story format. You have the power. Do not let big tech continue to leech off your work.
I hope you enjoyed this content.
Here are some of the critters I have met along my journey through the forest:
👉💕💕 Hearts for being a Dev 👉💋💋kisu for being an OpenSource Dev
💕💕Sedd💕 @npub16vjln603hfsfhremp627jle4ycm6p23grjjqrm04rrdwupldyfnsjx88a2
💕💕_Moos 💕 @npub19qcnj6qzrhv92pf8tuhd74wcl6c8r2y2mmrp5pknfy3m2lsrd7xs6y7xw2
💋💋ElectronicMonkey 💋 @npub1ghzp7g0peac4lfkeegst3cqz546dk7a5n6twazvrf3nd432yddaqa3qtwq
👉I would like to point out. As of April 2024, two major moves have been done in Germany and Sweden; yet the month is still young at the time of this publication Let's encourage all platforms, organizations, and devs to move to open source. If countries can do it, then most certainly (N)oystr can! Digital Sovereignty for everyone!
Special thanks to: 🧀🥐Andrey For recommending Pão de queijo(Brazilian Cheese Buns) @npub1andyx2xqhwffeg595snk9a8ll43j6dvw5jzpljm5yjm3qync7peqzl8jd4
See you Next time! Whatever shall I uncover next?

👉Onigirl respects all platforms, logos and art. If such platform(s) felt my designs with your logos were disrespectful. I'll happily taken them down with no hard feelings. I only did so outta my love for Nostr. I may come off a bit crazy.




