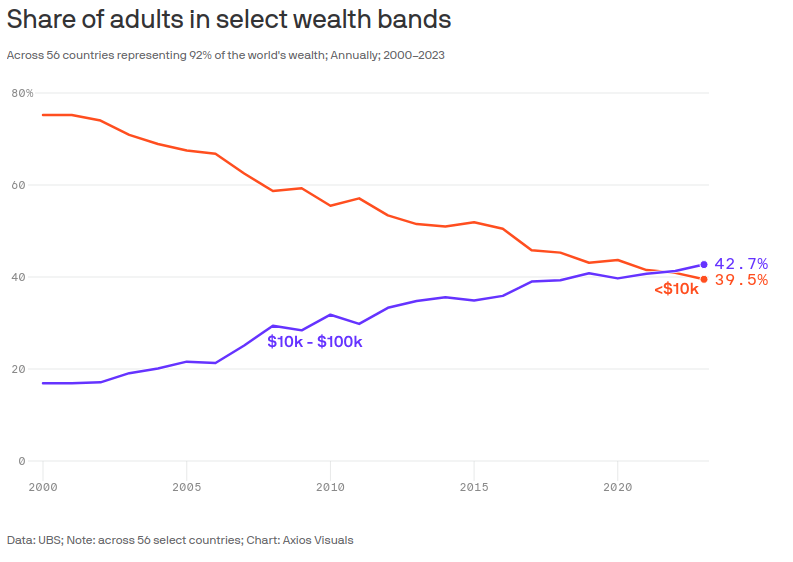
-
 @ 4523be58:ba1facd0
2024-05-28 11:05:17
@ 4523be58:ba1facd0
2024-05-28 11:05:17NIP-116
Event paths
Description
Event kind
30079denotes an event defined by its event path rather than its event kind.The event directory path is included in the event path, specified in the event's
dtag. For example, an event path might beuser/profile/name, whereuser/profileis the directory path.Relays should parse the event directory from the event path
dtag and index the event by it. Relays should support "directory listing" of kind30079events using the#ffilter, such as{"#f": ["user/profile"]}.For backward compatibility, the event directory should also be saved in the event's
ftag (for "folder"), which is already indexed by some relay implementations, and can be queried using the#ffilter.Event content should be a JSON-encoded value. An empty object
{}signifies that the entry at the event path is itself a directory. For example, when savinguser/profile/name:Bob, you should also saveuser/profile:{}so the subdirectory can be listed underuser.In directory names, slashes should be escaped with a double slash.
Example
Event
json { "tags": [ ["d", "user/profile/name"], ["f", "user/profile"] ], "content": "\"Bob\"", "kind": 30079, ... }Query
json { "#f": ["user/profile"], "authors": ["[pubkey]"] }Motivation
To make Nostr an "everything app," we need a sustainable way to support new kinds of applications. Browsing Nostr data by human-readable nested directories and paths rather than obscure event kind numbers makes the data more manageable.
Numeric event kinds are not sustainable for the infinite number of potential applications. With numeric event kinds, developers need to find an unused number for each new application and announce it somewhere, which is cumbersome and not scalable.
Directories can also replace monolithic list events like follow lists or profile details. You can update a single directory entry such as
user/profile/nameorgroups/follows/[pubkey]without causing an overwrite of the whole profile or follow list when your client is out-of-sync with the most recent list version, as often happens on Nostr.Using
d-tagged replaceable events for reactions, such as{tags: [["d", "reactions/[eventId]"]], content: "\"👍\"", kind: 30079, ...}would make un-reacting trivial: just publish a new event with the samedtag and an empty content. Toggling a reaction on and off would not cause a flurry of new reaction & delete events that all need to be persisted.Implementations
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
f) already support this feature. - IrisDB client side library: treelike data structure with subscribable nodes.
https://github.com/nostr-protocol/nips/pull/1266
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
-
 @ b60c3e76:c9d0f46e
2024-05-15 10:08:47
@ b60c3e76:c9d0f46e
2024-05-15 10:08:47KRIS menjamin semua golongan masyarakat mendapatkan perlakuan sama dari rumah sakit, baik pelayanan medis maupun nonmedis.
Demi memberikan peningkatan kualitas layanan kesehatan kepada masyarakat, pemerintah baru saja mengeluarkan Peraturan Presiden (Perpres) nomor 59 tahun 2024 tentang Jaminan Kesehatan. Melalui perpres itu, Presiden Joko Widodo (Jokowi) telah menghapus perbedaan kelas layanan 1, 2, dan 3 dalam Badan Penyelenggara Jaminan Sosial atau BPJS Kesehatan.
Layanan berbasis kelas itu diganti dengan KRIS (Kelas Rawat Inap Standar). Berkaitan dengan lahirnya Perpres 59/2024 tentang Perubahan Ketiga atas Perpres 82/2018 tentang Jaminan Kesehatan, Presiden Joko Widodo telah memerintahkan seluruh rumah sakit yang bekerja sama dengan BPJS Kesehatan melaksanakannya.
Kebijakan baru itu mulai berlaku per 8 Mei 2024 dan paling lambat 30 Juni 2025. Dalam jangka waktu tersebut, rumah sakit dapat menyelenggarakan sebagian atau seluruh pelayanan rawat inap berdasarkan KRIS sesuai dengan kemampuan rumah sakit.
Lantas apa yang menjadi pembeda dari sisi layanan dengan layanan rawat inap sesuai Perpres 59/2024? Dahulu sistem layanan rawat BPJS Kesehatan dibagi berdasarkan kelas yang dibagi masing-masing kelas 1, 2, dan 3. Namun, melalui perpres, layanan kepada masyarakat tidak dibedakan lagi.
Pelayanan rawat inap yang diatur dalam perpres itu--dikenal dengan nama KRIS—menjadi sistem baru yang digunakan dalam pelayanan rawat inap BPJS Kesehatan di rumah sakit-rumah sakit. Dengan KRIS, semua golongan masyarakat akan mendapatkan perlakuan yang sama dari rumah sakit, baik dalam hal pelayanan medis maupun nonmedis.
Dengan lahirnya Perpres 59/2024, tarif iuran BPJS Kesehatan pun juga akan berubah. Hanya saja, dalam Perpres itu belum dicantumkan secara rinci ihwal besar iuran yang baru. Besaran iuran baru BPJS Kesehatan itu sesuai rencana baru ditetapkan pada 1 Juli 2025.
“Penetapan manfaat, tarif, dan iuran sebagaimana dimaksud ditetapkan paling lambat tanggal 1 Juli 2025,” tulis aturan tersebut, dikutip Senin (13/5/2024).
Itu artinya, iuran BPJS Kesehatan saat ini masih sama seperti sebelumnya, yakni sesuai dengan kelas yang dipilih. Namun perpres itu tetap berlaku sembari menanti lahirnya peraturan lanjutan dari perpres tersebut.
Kesiapan Rumah Sakit
Berkaitan dengan lahirnya kebijakan layanan kesehatan tanpa dibedakan kelas lagi, Kementerian Kesehatan (Kemenkes) menegaskan mayoritas rumah sakit di Indonesia siap untuk menjalankan layanan KRIS untuk pasien BPJS Kesehatan.
Kesiapan itu diungkapkan oleh Dirjen Pelayanan Kesehatan Kemenkes Azhar Jaya. “Survei kesiapan RS terkait KRIS sudah dilakukan pada 2.988 rumah sakit dan yang sudah siap menjawab isian 12 kriteria ada sebanyak 2.233 rumah sakit,” ujar Azhar.
Sebagai informasi, KRIS adalah pengganti layanan Kelas 1, 2, dan 3 BPJS Kesehatan yang bertujuan untuk memberikan layanan kesehatan secara merata tanpa melihat besaran iurannya.
Melalui KRIS, rumah sakit perlu menyiapkan sarana dan prasarana sesuai dengan 12 kriteria kelas rawat inap standar secara bertahap. Apa saja ke-12 kriteria KRIS itu?
Sesuai bunyi Pasal 46A Perpres 59/2024, disyaratkan kriteria fasilitas perawatan dan pelayanan rawat inap KRIS meliputi komponen bangunan yang digunakan tidak boleh memiliki tingkat porositas yang tinggi serta terdapat ventilasi udara dan kelengkapan tidur.
Demikian pula soal pencahayaan ruangan. Perpres itu juga mengatur pencahayaan ruangan buatan mengikuti kriteria standar 250 lux untuk penerangan dan 50 lux untuk pencahayaan tidur, temperature ruangan 20--26 derajat celcius.
Tidak hanya itu, layanan rawat inap berdasarkan perpres itu mensyaratkan fasilitas layanan yang membagi ruang rawat berdasarkan jenis kelamin pasien, anak atau dewasa, serta penyakit infeksi atau noninfeksi.
Selain itu, kriteria lainnya adalah keharusan bagi penyedia layanan untuk mempertimbangkan kepadatan ruang rawat dan kualitas tempat tidur, penyediaan tirai atau partisi antartempat tidur, kamar mandi dalam ruangan rawat inap yang memenuhi standar aksesibilitas, dan menyediakan outlet oksigen.
Selain itu, kelengkapan tempat tidur berupa adanya dua kotak kontak dan nurse call pada setiap tempat tidur dan adanya nakas per tempat tidur. Kepadatan ruang rawat inap maksimal empat tempat tidur dengan jarak antara tepi tempat tidur minimal 1,5 meter.
Tirai/partisi dengan rel dibenamkan menempel di plafon atau menggantung. Kamar mandi dalam ruang rawat inap serta kamar mandi sesuai dengan standar aksesibilitas dan outlet oksigen.
Azhar menjamin, Kemenkes akan menjalankan hal tersebut sesuai dengan tupoksi yang ada. “Tentu saja kami akan bekerja sama dengan BPJS Kesehatan dalam implementasi dan pengawasannya di lapangan,” ujar Azhar.
Berkaitan dengan perpres jaminan kesehatan itu, Direktur Utama BPJS Kesehatan Ghufron Mukti menilai, perpres tersebut berorientasi pada penyeragaman kelas rawat inap yang mengacu pada 12 kriteria. "Bahwa perawatan ada kelas rawat inap standar dengan 12 kriteria, untuk peserta BPJS, maka sebagaimana sumpah dokter tidak boleh dibedakan pemberian pelayan medis atas dasar suku, agama, status sosial atau beda iurannya," ujarnya.
Jika ada peserta ingin dirawat pada kelas yang lebih tinggi, kata Ghufron, maka diperbolehkan selama hal itu dipengaruhi situasi nonmedis. Hal itu disebutkan dalam Pasal 51 Perpres Jaminan Kesehatan diatur ketentuan naik kelas perawatan.
Menurut pasal tersebut, naik kelas perawatan dilakukan dengan cara mengikuti asuransi kesehatan tambahan atau membayar selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya yang harus dibayar akibat peningkatan pelayanan.
Selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya pelayanan dapat dibayar oleh peserta bersangkutan, pemberi kerja, atau asuransi kesehatan tambahan.
Ghufron Mukti juga mengimbau pengelola rumah sakit tidak mengurangi jumlah tempat tidur perawatan pasien dalam upaya memenuhi kriteria KRIS. "Pesan saya jangan dikurangi akses dengan mengurangi jumlah tempat tidur. Pertahankan jumlah tempat tidur dan penuhi persyaratannya dengan 12 kriteria tersebut," tegas Ghufron.
Penulis: Firman Hidranto Redaktur: Ratna Nuraini/Elvira Inda Sari Sumber: Indonesia.go.id
-
 @ 266815e0:6cd408a5
2024-05-09 17:23:28
@ 266815e0:6cd408a5
2024-05-09 17:23:28Lot of people are starting to talk about building a web-of-trust and how nostr can or is already being used as such
We all know about using the kind:3 following lists as a simple WoT that can be used to filter out spam. but as we all know it does not really signal "trust", its mostly just "I find your content interesting"
But what about real "trust"... well its kind of multi-denominational, I could trust that your a good developer or a good journalist but still not trust you enough to invite you over to my house. There are some interesting and clever solutions proposed for quantifying "trust" in a digital sense but I'm not going to get into that here. I want to talk about something that I have not see anyone discuss yet.
How is the web-of-trust maintained? or more precisely how do you expect users to update the digital representation of the "trust" of other users?
Its all well and good to think of how a user would create that "trust" of another user when discovering them for the first time. They would click the "follow" button, or maybe even rate them on a few topics with a 1/5 star system But how will a user remove that trust? how will they update it if things change and they trust them less?
If our goal is to model "trust" in a digital sense then we NEED a way for the data to stay up-to-date and as accurate as possible. otherwise whats the use? If we don't have a friction-less way to update or remove the digital representation of "trust" then we will end up with a WoT that continuously grows and everyone is rated 10/10
In the case of nostr kind:3 following lists. its pretty easy to see how these would get updated. If someone posts something I dislike or I notice I'm getting board of their content. then I just unfollow them. An important part here is that I'm not thinking "I should update my trust score of this user" but instead "I'm no longer interested, I don't want to see this anymore"
But that is probably the easiest "trust" to update. because most of us on social media spend some time curating our feed and we are used to doing it. But what about the more obscure "trust" scores? whats the regular mechanism by which a user would update the "honestly" score of another user?
In the real world its easy, when I stop trusting someone I simply stop associating with them. there isn't any button or switch I need to update. I simply don't talk to them anymore, its friction-less But in the digital realm I would have to remove or update that trust. in other words its an action I need to take instead of an action I'm not doing. and actions take energy.
So how do we reflect something in the digital world that takes no-energy and is almost subconscious in the real world?
TLDR; webs-of-trust are not just about scoring other users once. you must keep the score up-to-date
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ 700c6cbf:a92816fd
2024-07-14 00:51:44
@ 700c6cbf:a92816fd
2024-07-14 00:51:44... something else
This is the final image. Or is it? Likely, it is not. I have already started on a perfect version of my Mother Earth painting.
Of course, there is no such thing as a perfect painting. What I mean is that I already started on a vector version of Mother Earth. You're familiar with vector vs. pixel, right?
But let's start at the beginning, not the end.
This here is a pic from the sketching phase. I am not one who can just magically and with a few strokes produce an amazing sketch of something that resembles a human. There are artists out there that do this wonderfully. It's amazing but it is not me (unfortunately).

Here I am starting to color in the sketch with a watercolor brush. This is all done in Procreate App on an iPad Pro. The coloring is on a separate layer with the pencil sketch set to multiply to shine through the colors. That's why the pencil strokes now are black. I like that look.

And here, I am almost done. Just need to decide on the background color. And as you can see from the gif and video I didn't really decide. Though at the moment I am favoring that muted pinkish red - LOL

Which color is your favorite?


Here you can see the whole process in a timelapse. Above pictures were grabbed from it to detail the process a little.
https://cdn.satellite.earth/05774dcaaf4679c34cbeb46cb43b4c4f85553a3d2b4850a7256d26a871b0c4f3.mp4
And that's it my Nostr friends for my first longform post in this community.
I hope you enjoyed this post. Comments are encouraged an appreciated. Thank you.
Cheers, OceanBee
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ a8d1560d:3fec7a08
2024-07-14 00:17:38
@ a8d1560d:3fec7a08
2024-07-14 00:17:38I have made an event viewer and an event crafter for #Nostr using https://websim.ai. The event crafter works flawlessly, but sadly without NIP-07. It can be used to craft events of any kind, with any tags you want. You can find it here:
https://websim.ai/c/tZxeQ9DWZf9bCkTd1
As for the event viewer, making it brought several difficulties, and I'm not really happy with it in its current state. But it does show any event of any kind. If you enter your own pubkey, you can choose to only show events from pubkeys you follow. And you can always choose to either show all events or use a pubkey filter.
https://websim.ai/c/KI87SEQljLys4nVIX
-
 @ 32e18276:5c68e245
2023-12-06 15:29:43
@ 32e18276:5c68e245
2023-12-06 15:29:43I’m going to be on an ordinals panels as one of the people who is counter arguing the claim that they are good for bitcoin. I decided to brush up on the technicals on how inscriptions work. I am starting to see luke’s perspective on how it is exploiting a loophole in bitcoin’s anti-data-spam mechanisms.
Storing data in Bitcoin, the “standard” way
The standard way you add “data” to bitcoin is by calling the OP_RETURN opcode. Bitcoin devs noticed that people were storing data (like the bitcoin whitepaper) in the utxo set via large multisig transactions. The problem with this is that this set is unprunable and could grow over time. OP_RETURN outputs on the other-hand are provably prunable and don’t add to utxo bloat.
Here’s an excerpt from the march 2014 0.9.0 release notes that talks about this:
On OP_RETURN: There was been some confusion and misunderstanding in the community, regarding the OP_RETURN feature in 0.9 and data in the blockchain. This change is not an endorsement of storing data in the blockchain. The OP_RETURN change creates a provably-prunable output, to avoid data storage schemes – some of which were already deployed – that were storing arbitrary data such as images as forever-unspendable TX outputs, bloating bitcoin’s UTXO database. Storing arbitrary data in the blockchain is still a bad idea; it is less costly and far more efficient to store non-currency data elsewhere.
Much of the work on bitcoin core has been focused on making sure the system continues to function in a decentralized way for its intended purpose in the presence of people trying to abuse it for things like storing data. Bitcoin core has always discouraged this, as it is not designed for storage of images and data, it is meant for moving digital coins around in cyberspace.
To help incentive-align people to not do stupid things, OP_RETURN transactions were not made non-standard, so that they are relayable by peers and miners, but with the caveat:
- They can only push 40 bytes (later increased to 80,83, I’m guessing to support larger root merkle hashes since that is the only sane usecase for op_return)
Bitcoin also added an option called -datacarriersize which limits the total number of bytes from these outputs that you will relay or mine.
Why inscriptions are technically an exploit
Inscriptions get around the datacarriersize limit by disguising data as bitcoin script program data via OP_PUSH inside OP_IF blocks. Ordinals do not use OP_RETURN and are not subjected to datacarriersize limits, so noderunners and miners currently have limited control over the total size of this data that they wish to relay and include in blocks. Luke’s fork of bitcoin-core has some options to fight this spam, so hopefully we will see this in core sometime soon as well.
Inscriptions are also taking advantage of features in segwit v1 (witness discount) and v2/taproot (no arbitrary script size limit). Each of these features have interesting and well-justified reasons why they were introduced.
The purpose of the witness discount was to make it cheaper to spend many outputs which helps the reduction of the utxo set size. Inscriptions took advantage of this discount to store monke jpegs disguised as bitcoin scripts. Remember, bitcoin is not for storing data, so anytime bitcoin-devs accidentally make it cheap and easy to relay data then this should be viewed as an exploit. Expect it to be fixed, or at least provide tools to noderunners for fighting this spam.
Where do we go from here
The interesting part of this story is that people seem to attach value to images stored on the bitcoin blockchain, and they are willing to pay the fee to get it in the block, so non-ideologic miners and people who don’t care about the health and decentralization of bitcoin are happy to pay or collect the fee and move on.
Data should not get a discount, people should pay full price if they want to store data. They should just use op_return and hashes like opentimestamps or any other reasonable protocol storing data in bitcoin.
After going through this analysis I’ve come to the opinion that this is a pretty bad data-spam exploit and bitcoin devs should be working on solutions. Ideological devs like luke who actually care about the health and decentralization of the network are and I’m glad to see it.
-
 @ 9edd72eb:cb697b0a
2024-07-13 22:16:45
@ 9edd72eb:cb697b0a
2024-07-13 22:16:45If one knows exactly what to do to alleviate one's pain, comfort oneself, and emerge more or less unscathed from Adversity, I think it can be said that one has reached a fairly high level of Wisdom in Life.
originally posted at https://stacker.news/items/607422
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ de496884:72617b81
2023-11-20 13:54:02
@ de496884:72617b81
2023-11-20 13:54:02Hola nostriches. Hoy quiero hacer una publicación a modo de acercamiento al surgimiento de las categorías de género y feminismo. Así que si te interesa el tema haz un esfuerzo, quédate y lee hasta el final.
El «nuevo» feminismo surge en los años 60 en aquellos países desarrollados que acordaron el reconocimiento a los derechos humanos contenidos en la declaración respectiva de la ONU. Entonces, como extensión a dicho reconocimiento es que se gesta el movimiento feminista. A partir de entonces, se vuelve a plantear la relación entre naturaleza y cultura y se llega a la conclusión de que las diferencias sociales van más allá de las diferencias biológicas, lo cual tiene que ver con que hasta la satisfacción de las necesidades elementales como son la alimentación, la vivienda o el vestuario, están condicionadas por construcciones sociales.
Pues resulta que una de las primeras propuestas identificó la subordinación femenina producto de una organización patriarcal, tomando la categoría patriarcado de Max Weber. Es así como la visión de patriarcado se extendió al discurso político y académico. Sin embargo, no existía información acerca del desarrollo histórico de dicha categoría, sistematización, variaciones, etc., debido a que era algo que recién se percibía en sociedad.
Sin embargo, la misma categoría de patriarcado junto a la de relaciones de poder para explicar fenómenos sociales contemporáneos, constituye uno de los principales aportes del feminismo. Es así como han logrado primero visibilizar y luego deconstruir y desmontar una serie de patrones existentes en la cultura que hacían a la mujer subordinarse al hombre, y que estaban presentes en el sistema sexo/género.
 Imagen relativa a la lucha contra el patriarcado
Imagen relativa a la lucha contra el patriarcadoHasta ese momento, en las investigaciones de corte sociológico se podía observar un androcentrismo excesivo al dar cuenta de que el discurso científico giraba en torno al hombre como sujeto y objeto de la investigación. Incluso para muchos positivistas como el mismo Weber, los problemas relativos a las mujeres quedaban en un segundo plano y eran achacados a una supuesta pasividad en el ámbito doméstico-familiar. Dicha pasividad partía de la supuesta inferioridad biológica del género femenino.
El patriarcado entonces era una categoría vacía en sí misma, sin valor explicativo. Desde el punto de vista político pudo ser útil para la movilización pero no resistió la polémica de los críticos del feminismo ni problematizó los conflictos a ser resueltos. Pero por otro lado, un grupo de mujeres -académicas principalmente- se puso manos a la obra en una tarea más pequeña pero con mayores resultados a la larga. Se propusieron generar conocimientos sobre las condiciones de vida de la mujer, buscar en el pasado y el presente los aportes de las mujeres a la sociedad, hacerlas visibles en la historia. Es así como surgen centros académicos, ONG, proyectos, centros de estudios sobre la mujer, etc.
Convendría distinguir entonces dos posturas que acompañaron a la investigación sobre las mujeres: uno que toma como objeto de estudio a la mujer; condiciones de vida, trabajo, cultura, y otra que privilegia a la sociedad como generadora de la subordinación de las mujeres. Mientras la primera perspectiva generaba conocimiento sobre las mujeres en el estudio de las relaciones mujer-hombre y mujer-mujer, la segunda tenía una visión más holística ya que planteaba que hay que estudiar la sociedad ya que la subordinación de las mujeres es producto de la organización de esta, y que no se avanzará solamente estudiando a las mujeres, pues el estudio debe ser más amplio y en diferentes niveles, ámbitos y tiempos.
Es en esta búsqueda donde nace y se desarrolla el concepto de género como categoría social. Es así que los sistemas de género/sexo fueron entendidos como conjuntos de prácticas, símbolos, representaciones, normas y valores sociales que las sociedades construyen a partir de la diferencia anatomofisiológica y que dotan de sentido a los impulsos sexuales, la reproducción y en general a las relaciones de las personas. Por tanto, este sistema pasó a ser el objeto de estudio para comprender la subordinación de la mujer al hombre. Al ser el reconocimiento de una dimensión de la desigualdad social hasta entonces desconocida, se considera la ruptura epistemológica más importante de la segunda mitad del siglo pasado.
 Imagen representativa del binarismo de género
Imagen representativa del binarismo de géneroHay que decir que los fenómenos sociales se definen por la relación que guardan entre sí. Es así que la contextualización adquiere gran importancia. Varones y hembras tenemos la capacidad de producir con el cuerpo, pero solo los cuerpos de las hembras pueden gestar y por tanto asegurar la especie humana. Todo grupo humano que pretenda sobrevivir debe asegurarse cierto número de hembras que lo hagan posible. De ahí un poder particular del cuerpo de las hembras que además es económicamente útil. Dicho poder no es en tanto entidad biológica, sino que es la sociedad la que le otorga este poder. En este punto es importante preguntarnos históricamente ¿quiénes han controlado la capacidad reproductiva de las mujeres?, ¿quiénes han tenido la preferencia en el acceso sexual? Para asegurar un control efectivo sobre la reproducción es necesario asegurar el acceso a la sexualidad.
Ello también lleva a dirigir el trabajo que hacen porque de lo contrario, las mujeres pudieran tener espacio para representar una amenaza al dominio de los hombres. Es importante atender a las etapas del desarrollo de las mujeres, que permitirá ver cómo se moldean para aceptar la desigualdad y las jerarquías según el género en las distintas sociedades y culturas.
Otro contexto a delimitar es el ámbito doméstico donde históricamente ha estado ubicada la subordinación femenina. Se ha puesto al descubierto que en mujeres que comparten la misma posición de clase y raza, la condición femenina se redefine a lo largo de la vida y que algunas mujeres gozan de poder sobre otras aún en contextos de alta dominación masculina, donde se les inviste de autoridad, creando el sistema zonas de incertidumbre que las divide como género e impide alianzas y se legitima la dominación. Foucault decía que «el poder se ejerce, no se posee», siempre está en peligro de perderse y no basta con normas, leyes, amenazas o castigos. De ahí que los espacios de subordinación sean también espacios de poder de las mujeres. Es en estos espacios donde aparece la inseguridad, la tensión, la confrontación y por ejemplo, las mujeres pueden reclamar la anticoncepción.
Para terminar, es importante tener en cuenta que el género es una forma de desigualdad social que siempre está articulado con otras formas de desigualdad ya sea clase, raza, grupo etario, etc. Hay que pensar la dominación masculina con un comienzo vago en el tiempo, pero que permite desligar la subordinación de las mujeres de la evolución «natural» de la humanidad y entenderla como un proceso histórico. En ese sentido es necesario destacar que, respecto a la raza, en sociedades plurales hay que atender al contexto étnico-cultural ya que en dependencia de las relaciones entre personas de razas distintas, estarán condicionadas las relaciones entre los géneros.
 Imagen de mujeres de distintas razas
Imagen de mujeres de distintas razasPor otro lado, si bien es sabido que históricamente el sistema de género social imperante ha contribuido a invisibilizar a la mujer, asociar necesariamente dicha categoría únicamente a ella, lo que hace es nuevamente recrear el absolutismo histórico que tanto daño ha hecho, ahora como lo antagónico al hombre. En la construcción social participan todos los individuos presentes en el sistema género.
Hasta aquí la publicación de hoy, de la cual aun se puede ahondar mucho más, sobre todo en lo referido al origen de la dominación o de la jerarquización del binomio «hombre/mujer» desde un punto de vista antropológico, pero eso quedará pendiente para otro momento. ¡Así que hasta la próxima!, ¡nos vemos en Nostr!
........................................
English version
Hello nostriches. Today I want to make a post by way of an approach to the emergence of the categories of gender and feminism. So if you are interested in the topic make an effort, stay and read to the end.
The "new" feminism emerged in the 60's in those developed countries that agreed to recognize the human rights contained in the respective UN declaration. Then, as an extension of that recognition, the feminist movement was born. From then on, the relationship between nature and culture was raised again and the conclusion was reached that social differences go beyond biological differences, which has to do with the fact that even the satisfaction of elementary needs such as food, housing or clothing are conditioned by social constructions.
It turns out that one of the first proposals identified female subordination as a product of a patriarchal organization, taking Max Weber's category of patriarchy. This is how the vision of patriarchy was extended to political and academic discourse. However, there was no information about the historical development of this category, systematization, variations, etc., because it was something that was only recently perceived in society.
However, the same category of patriarchy, together with that of power relations to explain contemporary social phenomena, constitutes one of the main contributions of feminism. This is how they have first made visible and then deconstructed and dismantled a series of existing patterns in the culture that made women subordinate to men, and that were present in the sex/gender system.
 Image relating to the fight against patriarchy
Image relating to the fight against patriarchyUp to that time, in sociological research, an excessive androcentrism could be observed as scientific discourse revolved around men as the subject and object of research. Even for many positivists such as Weber himself, the problems related to women remained in the background and were blamed on a supposed passivity in the domestic-family sphere. This passivity was based on the supposed biological inferiority of the female gender.
Patriarchy was then an empty category in itself, with no explanatory value. From the political point of view, it could be useful for mobilization, but it did not resist the polemic of feminism's critics, nor did it problematize the conflicts to be resolved. But on the other hand, a group of women - mainly academics - set to work on a smaller task but with greater results in the long run. They set out to generate knowledge about women's living conditions, to search in the past and present for women's contributions to society, to make them visible in history. This is how academic centers, NGOs, projects, women's studies centers, etc., came into being.
It would be convenient to distinguish then two postures that accompanied the research on women: one that takes women as the object of study; living conditions, work, culture, and the other that privileges society as the generator of women's subordination. While the first perspective generated knowledge about women in the study of woman-man and woman-woman relations, the second had a more holistic vision, since it proposed that society must be studied, since the subordination of women is a product of its organization, and that progress will not be made only by studying women, since the study must be broader and at different levels, spheres and times.
It is in this search that the concept of gender as a social category was born and developed. Thus, gender/sex systems were understood as a set of practices, symbols, representations, norms and social values that societies construct on the basis of anatomophysiological differences and that give meaning to sexual impulses, reproduction and, in general, to people's relationships. Therefore, this system became the object of study to understand the subordination of women to men. As the recognition of a hitherto unknown dimension of social inequality, it is considered the most important epistemological breakthrough of the second half of the last century.
 Representative image of gender binarism
Representative image of gender binarismIt must be said that social phenomena are defined by their relationship with each other. Thus, contextualization acquires great importance. Males and females have the capacity to produce with their bodies, but only the bodies of females can gestate and therefore ensure the human species. Any human group that intends to survive must ensure a certain number of females to make it possible. Hence a particular power of the female body, which is also economically useful. This power is not as a biological entity, but it is society that gives it this power. At this point it is important to ask ourselves historically, who has controlled the reproductive capacity of women, who has had the preference in sexual access? To ensure effective control over reproduction, it is necessary to ensure access to sexuality.
 Allegorical image of pregnancy
Allegorical image of pregnancyThis also leads to directing the work they do because otherwise, women may have room to pose a threat to men's dominance. It is important to pay attention to the stages of women's development, which will allow us to see how they are shaped to accept inequality and gender hierarchies in different societies and cultures.
Another context to delimit is the domestic sphere where female subordination has historically been located. It has been discovered that in women who share the same class and race position, the feminine condition is redefined throughout life and that some women enjoy power over others even in contexts of high male domination, where they are invested with authority, creating the system of uncertainty zones that divide them as a gender and prevent alliances and legitimize domination. Foucault said that "power is exercised, not possessed", it is always in danger of being lost and norms, laws, threats or punishments are not enough. Hence, the spaces of subordination are also spaces of women's power. It is in these spaces where insecurity, tension, confrontation appear and where, for example, women can demand contraception.
To conclude, it is important to keep in mind that gender is a form of social inequality that is always articulated with other forms of inequality, be it class, race, age group, etc. It is necessary to think of male domination with a vague beginning in time, but which allows us to separate the subordination of women from the "natural" evolution of humanity and to understand it as a historical process. In this sense, it is necessary to emphasize that, with respect to race, in plural societies it is necessary to pay attention to the ethno-cultural context since, depending on the relations between people of different races, the relations between genders will be conditioned.
 Image of women of different races
Image of women of different racesOn the other hand, although it is known that historically the prevailing social gender system has contributed to make women invisible, to necessarily associate this category only to women is to recreate the historical absolutism that has done so much damage, this time as antagonistic to men. All individuals present in the gender system participate in the social construction.
So much for today's publication, of which we can still go much deeper, especially with regard to the origin of domination or the hierarchization of the binomial "man/woman" from an anthropological point of view, but that will be left for another time. So until next time, see you in Nostr!

Créditos | Credits
Bibliografía consultada | Consulted bibliography:
-
Barbieri, T. (1993). Sobre la categoría género. Una introducción teórico-metodológica. Debates en Sociología. (18). 1-19. https://doi.org/10.18800/debatesensociologia.199301.006
-
Echevarría, D. (2020). Desigualdades de género e interseccionalidad. Análisis del contexto cubano 2008-2018. Facultad Latinoamericana de Ciencias Sociales (Programa-Cuba). https://www.clacso.org.ar/libreria-latinoamericana-cm/libro_detalle_resultado.php?id_libro=2346&campo=cm&texto=248
Traducción | Translation:
DeepL
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 3bf0c63f:aefa459d
2024-01-15 11:15:06
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06Pequenos problemas que o Estado cria para a sociedade e que não são sempre lembrados
- **vale-transporte**: transferir o custo com o transporte do funcionário para um terceiro o estimula a morar longe de onde trabalha, já que morar perto é normalmente mais caro e a economia com transporte é inexistente. - **atestado médico**: o direito a faltar o trabalho com atestado médico cria a exigência desse atestado para todas as situações, substituindo o livre acordo entre patrão e empregado e sobrecarregando os médicos e postos de saúde com visitas desnecessárias de assalariados resfriados. - **prisões**: com dinheiro mal-administrado, burocracia e péssima alocação de recursos -- problemas que empresas privadas em competição (ou mesmo sem qualquer competição) saberiam resolver muito melhor -- o Estado fica sem presídios, com os poucos existentes entupidos, muito acima de sua alocação máxima, e com isto, segundo a bizarra corrente de responsabilidades que culpa o juiz que condenou o criminoso por sua morte na cadeia, juízes deixam de condenar à prisão os bandidos, soltando-os na rua. - **justiça**: entrar com processos é grátis e isto faz proliferar a atividade dos advogados que se dedicam a criar problemas judiciais onde não seria necessário e a entupir os tribunais, impedindo-os de fazer o que mais deveriam fazer. - **justiça**: como a justiça só obedece às leis e ignora acordos pessoais, escritos ou não, as pessoas não fazem acordos, recorrem sempre à justiça estatal, e entopem-na de assuntos que seriam muito melhor resolvidos entre vizinhos. - **leis civis**: as leis criadas pelos parlamentares ignoram os costumes da sociedade e são um incentivo a que as pessoas não respeitem nem criem normas sociais -- que seriam maneiras mais rápidas, baratas e satisfatórias de resolver problemas. - **leis de trãnsito**: quanto mais leis de trânsito, mais serviço de fiscalização são delegados aos policiais, que deixam de combater crimes por isto (afinal de contas, eles não querem de fato arriscar suas vidas combatendo o crime, a fiscalização é uma excelente desculpa para se esquivarem a esta responsabilidade). - **financiamento educacional**: é uma espécie de subsídio às faculdades privadas que faz com que se criem cursos e mais cursos que são cada vez menos recheados de algum conhecimento ou técnica útil e cada vez mais inúteis. - **leis de tombamento**: são um incentivo a que o dono de qualquer área ou construção "histórica" destrua todo e qualquer vestígio de história que houver nele antes que as autoridades descubram, o que poderia não acontecer se ele pudesse, por exemplo, usar, mostrar e se beneficiar da história daquele local sem correr o risco de perder, de fato, a sua propriedade. - **zoneamento urbano**: torna as cidades mais espalhadas, criando uma necessidade gigantesca de carros, ônibus e outros meios de transporte para as pessoas se locomoverem das zonas de moradia para as zonas de trabalho. - **zoneamento urbano**: faz com que as pessoas percam horas no trânsito todos os dias, o que é, além de um desperdício, um atentado contra a sua saúde, que estaria muito melhor servida numa caminhada diária entre a casa e o trabalho. - **zoneamento urbano**: torna ruas e as casas menos seguras criando zonas enormes, tanto de residências quanto de indústrias, onde não há movimento de gente alguma. - **escola obrigatória + currículo escolar nacional**: emburrece todas as crianças. - **leis contra trabalho infantil**: tira das crianças a oportunidade de aprender ofícios úteis e levar um dinheiro para ajudar a família. - **licitações**: como não existem os critérios do mercado para decidir qual é o melhor prestador de serviço, criam-se comissões de pessoas que vão decidir coisas. isto incentiva os prestadores de serviço que estão concorrendo na licitação a tentar comprar os membros dessas comissões. isto, fora a corrupção, gera problemas reais: __(i)__ a escolha dos serviços acaba sendo a pior possível, já que a empresa prestadora que vence está claramente mais dedicada a comprar comissões do que a fazer um bom trabalho (este problema afeta tantas áreas, desde a construção de estradas até a qualidade da merenda escolar, que é impossível listar aqui); __(ii)__ o processo corruptor acaba, no longo prazo, eliminando as empresas que prestavam e deixando para competir apenas as corruptas, e a qualidade tende a piorar progressivamente. - **cartéis**: o Estado em geral cria e depois fica refém de vários grupos de interesse. o caso dos taxistas contra o Uber é o que está na moda hoje (e o que mostra como os Estados se comportam da mesma forma no mundo todo). - **multas**: quando algum indivíduo ou empresa comete uma fraude financeira, ou causa algum dano material involuntário, as vítimas do caso são as pessoas que sofreram o dano ou perderam dinheiro, mas o Estado tem sempre leis que prevêem multas para os responsáveis. A justiça estatal é sempre muito rígida e rápida na aplicação dessas multas, mas relapsa e vaga no que diz respeito à indenização das vítimas. O que em geral acontece é que o Estado aplica uma enorme multa ao responsável pelo mal, retirando deste os recursos que dispunha para indenizar as vítimas, e se retira do caso, deixando estas desamparadas. - **desapropriação**: o Estado pode pegar qualquer propriedade de qualquer pessoa mediante uma indenização que é necessariamente inferior ao valor da propriedade para o seu presente dono (caso contrário ele a teria vendido voluntariamente). - **seguro-desemprego**: se há, por exemplo, um prazo mínimo de 1 ano para o sujeito ter direito a receber seguro-desemprego, isto o incentiva a planejar ficar apenas 1 ano em cada emprego (ano este que será sucedido por um período de desemprego remunerado), matando todas as possibilidades de aprendizado ou aquisição de experiência naquela empresa específica ou ascensão hierárquica. - **previdência**: a previdência social tem todos os defeitos de cálculo do mundo, e não importa muito ela ser uma forma horrível de poupar dinheiro, porque ela tem garantias bizarras de longevidade fornecidas pelo Estado, além de ser compulsória. Isso serve para criar no imaginário geral a idéia da __aposentadoria__, uma época mágica em que todos os dias serão finais de semana. A idéia da aposentadoria influencia o sujeito a não se preocupar em ter um emprego que faça sentido, mas sim em ter um trabalho qualquer, que o permita se aposentar. - **regulamentação impossível**: milhares de coisas são proibidas, há regulamentações sobre os aspectos mais mínimos de cada empreendimento ou construção ou espaço. se todas essas regulamentações fossem exigidas não haveria condições de produção e todos morreriam. portanto, elas não são exigidas. porém, o Estado, ou um agente individual imbuído do poder estatal pode, se desejar, exigi-las todas de um cidadão inimigo seu. qualquer pessoa pode viver a vida inteira sem cumprir nem 10% das regulamentações estatais, mas viverá também todo esse tempo com medo de se tornar um alvo de sua exigência, num estado de terror psicológico. - **perversão de critérios**: para muitas coisas sobre as quais a sociedade normalmente chegaria a um valor ou comportamento "razoável" espontaneamente, o Estado dita regras. estas regras muitas vezes não são obrigatórias, são mais "sugestões" ou limites, como o salário mínimo, ou as 44 horas semanais de trabalho. a sociedade, porém, passa a usar esses valores como se fossem o normal. são raras, por exemplo, as ofertas de emprego que fogem à regra das 44h semanais. - **inflação**: subir os preços é difícil e constrangedor para as empresas, pedir aumento de salário é difícil e constrangedor para o funcionário. a inflação força as pessoas a fazer isso, mas o aumento não é automático, como alguns economistas podem pensar (enquanto alguns outros ficam muito satisfeitos de que esse processo seja demorado e difícil). - **inflação**: a inflação destrói a capacidade das pessoas de julgar preços entre concorrentes usando a própria memória. - **inflação**: a inflação destrói os cálculos de lucro/prejuízo das empresas e prejudica enormemente as decisões empresariais que seriam baseadas neles. - **inflação**: a inflação redistribui a riqueza dos mais pobres e mais afastados do sistema financeiro para os mais ricos, os bancos e as megaempresas. - **inflação**: a inflação estimula o endividamento e o consumismo. - **lixo:** ao prover coleta e armazenamento de lixo "grátis para todos" o Estado incentiva a criação de lixo. se tivessem que pagar para que recolhessem o seu lixo, as pessoas (e conseqüentemente as empresas) se empenhariam mais em produzir coisas usando menos plástico, menos embalagens, menos sacolas. - **leis contra crimes financeiros:** ao criar legislação para dificultar acesso ao sistema financeiro por parte de criminosos a dificuldade e os custos para acesso a esse mesmo sistema pelas pessoas de bem cresce absurdamente, levando a um percentual enorme de gente incapaz de usá-lo, para detrimento de todos -- e no final das contas os grandes criminosos ainda conseguem burlar tudo. -
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Músicas grudentas e conversas
Uma vez que você ouviu uma música grudenta e ela volta, inteira, com toda a melodia e a harmonia, muitos dias depois, contra a sua vontade. Mas uma conversa é impossível de lembrar. Por quê?
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 6c2d79de:0407f1b7
2024-07-13 20:34:36
@ 6c2d79de:0407f1b7
2024-07-13 20:34:36
In this inaugural investigative campaign, we at The Xibao Times invite you to embark on a journey down the rabbit hole of Chinese propaganda. Our mission: to expose the intricate network of disinformation and anti-Western sentiment that the Chinese Communist Party (CCP) has meticulously woven through various channels, including state media, non-profits, coalition groups, and more. Our starting point: a seemingly innocuous image (above) reposted by China Daily, which has led us to uncover a web of deception that spans the globe.
At the heart of Operation Codepink lies a comprehensive examination of the CCP's propaganda apparatus. We delve into the inner workings of this sophisticated machine, revealing the strategies and tactics employed to disseminate disinformation and manipulate public opinion. From the recruitment of "useful idiots" to the exploitation of social media, we uncover the CCP's playbook and the players involved.
Our investigation spans multiple platforms and formats, providing readers with a multi-faceted view of the propaganda war being waged. In addition to in-depth articles on Habla News, we are creating wiki-pages on Wikifreedia to serve as a repository of information, and relationship charts to illustrate the complex web of connections between entities and individuals.
As we continue our investigative journey, we will be publishing updates, revelations, and analyses. Stay tuned for an exposé on the CCP's infiltration of Russian state media, US non-profits, and coalition groups, among others. Our objective is not only to educate and inform but also to spark a broader conversation about the dangers of disinformation and the need for transparency and accountability in the media landscape.
Join us as we unravel the threads of this intricate web and shed light on the dark corners of the CCP's propaganda machine. With Operation Codepink, we aim to provide the spiciest content on Nostr, and we invite you to be a part of this groundbreaking campaign.
Inside the Operation
Articles on Habla News:
Our in-depth articles on Habla News will provide a comprehensive overview of the CCP's propaganda machine, its tactics, and the individuals and organizations involved. These articles will delve into specific cases of disinformation, analyze the CCP's propaganda strategies, and expose the connections between various entities and individuals. The articles will be written in an engaging and accessible style, making complex information easily understandable for a broad audience.
Wiki-pages on Wikifreedia:

We will create a series of wiki-pages on Wikifreedia to serve as a central repository of information related to Operation Codepink. These wiki-pages will provide a detailed and organized overview of the CCP's propaganda machine, its various components, and the individuals and organizations involved. They will include information on specific cases of disinformation, analysis of propaganda tactics, and connections between various entities and individuals.
Relationship Charts:
To illustrate the complex web of connections between the entities and individuals involved in the CCP's propaganda machine, we will create relationship charts. These charts will show the relationships between different organizations, individuals, and governments, providing a visual representation of the intricate network of disinformation and propaganda. The relationship charts will help readers understand the scale and scope of the CCP's influence and manipulation efforts.
Investigative Approach:
Our investigative approach for Operation Codepink will involve a combination of open-source research, data analysis, and interviews with experts and insiders. We will use a range of tools and techniques to gather information, including:
Open-Source Research: We will conduct extensive open-source research, using publicly available information to identify patterns, connections, and trends related to the CCP's propaganda machine.
Data Analysis: We will analyze large datasets to identify relationships between individuals, organizations, and governments, as well as patterns in disinformation and propaganda tactics.
Expert Interviews: We will interview experts and insiders who have firsthand knowledge of the CCP's propaganda machine, as well as individuals who have been targeted by the CCP's disinformation campaigns.
Social Media Monitoring: We will monitor social media platforms for signs of disinformation and propaganda, as well as for clues about the identities of individuals and organizations involved in the CCP's propaganda machine.
By using a combination of these techniques, we aim to provide a comprehensive and accurate picture of the CCP's propaganda machine and its activities.
Updates and Revelations:
As we continue our investigation, we will provide regular updates and revelations on our findings. These updates will be published on Habla News and shared on our Nostr account xibaotimes@zaps.lol, keeping readers informed about the latest developments in Operation Codepink. We will also provide analyses and commentary on the implications of our findings for global politics, media, and society.
Stay tuned for more revelations and updates!
-
 @ 6f170f27:711e26dd
2024-07-13 18:16:58
@ 6f170f27:711e26dd
2024-07-13 18:16:58This century has known a stunning decrease in global income inequality, bringing it down to levels not seen in well over a century. That's the conclusion that Branko Milanovic, one of the world's foremost inequality researchers, comes to in an important essay for Foreign Affairs.
https://www.axios.com/2024/07/11/world-income-inequality-ubs-wealth-report
https://www.axios.com/2023/06/14/global-economic-inequality
originally posted at https://stacker.news/items/607318
-
 @ d2e97f73:ea9a4d1b
2023-04-11 19:36:53
@ d2e97f73:ea9a4d1b
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 5d4b6c8d:8a1c1ee3
2024-07-13 12:44:32
@ 5d4b6c8d:8a1c1ee3
2024-07-13 12:44:32Yesterday's edition https://stacker.news/items/605773/r/Undisciplined
We have a confessional from a professional shitcoiner, today. That's fun.
-
- -
July 13, 2023 📅
📝
TOP POSTValidating Lightning Signer - AMA
Excerpt
VLS is a nifty piece of software that helps boost the security of the Bitcoin Lightning Network. 🛡️
11k sats \ 33 comments \ @devrandom \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/208442/r/Undisciplined?commentId=208454
Excerpt
Ever bought a computer or cell phone? Why? Why not wait until your money is worth more later compared to the price of that cell phone?
1441 sats \ 7 replies \ @02674f045a
From Opinion: Why BTC can't become the reserve currency by @0xBTC in ~bitcoin
🏆
TOP STACKER1st place @k00b
5838 stacked \ 7855 spent \ 3 posts \ 19 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
27k stacked \ 0 revenue \ 40.6k spent \ 108 posts \ 281 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 13, 2022 📅
📝
TOP POSTAny Good Routing Node Strategies?
Excerpt
For people who have/are running nodes, are there any strategies that have been most effective for you for earning routing fees? From my very limited routing experience so far it seems there are a few main questions:
1232 sats \ 33 comments \ @andyleroy \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/44747/r/Undisciplined?commentId=44755
Excerpt
Obligatory not a node routing expert, but this guy is a good follow: https://mobile.twitter.com/cold_sats
276 sats \ 1 reply \ @Cornleone
From Any Good Routing Node Strategies? by @andyleroy in ~bitcoin
🏆
TOP STACKER1st place @k00b
37.3k stacked \ 15.2k spent \ 1 post \ 29 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
27.4k stacked \ 0 revenue \ 34.7k spent \ 117 posts \ 279 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 13, 2021 📅
📝
TOP POSTI joined a shitcoin project full time couple of months ago
Excerpt
I though it would be exciting and fun. But I think I'm wasting my time.
3 sats \ 9 comments \ @03785de7ab \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/306/r/Undisciplined?commentId=316
Excerpt
There are many companies working with Bitcoin but it's not their main focus. I did implement Bitgo sevices for one e-wallet provider but that was it. What I'm looking for is a project which build useful things for user with current Bitcoin features, […]
2 sats \ 1 reply \ @03785de7ab
From I joined a shitcoin project full time couple of months ago by @03785de7ab in ~bitcoin
🏆
TOP STACKERNo top stacker
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
37 stacked \ 0 revenue \ 60 spent \ 6 posts \ 10 comments
originally posted at https://stacker.news/items/607040
-
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ b2caa9b3:9eab0fb5
2024-07-13 12:01:35
@ b2caa9b3:9eab0fb5
2024-07-13 12:01:35I woke up in my dorm this morning to the sound of rain – a rarity in Africa, but a common occurrence here around Mount Kilimanjaro. The climate is much like a European summer, with comfortable temperatures ranging from 18 to 30 degrees Celsius. Unlike the rest of Africa, this region receives more rainfall, creating a lush and scenic environment.

After a quick shower, I stepped out onto the balcony to find myself greeted by a chilly rain. Not ideal weather for exploring, but it did present a different perspective of the majestic Kilimanjaro. The mountain, often shrouded in clouds, occasionally peeks through, and on a clear day, might even be bathed in sunshine. From this vantage point, it's hard to imagine the countless hikers making their way up its slopes.
Did you know that Kilimanjaro, Africa's tallest mountain and a dormant volcano, once held a unique title? Back in 1910, during the German Empire, it was considered the empire's highest peak. While Mount Everest holds the title of the world's highest mountain overall, Kilimanjaro takes the crown for the tallest freestanding mountain – any higher peak is likely part of a mountain range or group.
Gazing at Kilimanjaro, I'm struck by its history – a single, towering volcano, once a part of the German Empire. Traces of that era linger in Moshi, with some colonial-era buildings, some in disrepair, others beautifully restored. Arusha, another nearby town, boasts an impressive art gallery and a fascinating National Museum. This museum, housed in a former German fort, offers a glimpse into the past. One particularly intriguing resident is a giant tortoise, discovered by German colonists as a hatchling in Kilimanjaro National Park. This living relic has witnessed a century of change, a silent observer of a bygone era.

Today promises to be a relaxing one. I'll spend time soaking up the views from the rooftop, hoping to catch a glimpse of Kilimanjaro in all its glory. On a more practical note, I'm also on the hunt for a remote job to help with some financial constraints. Finding the right opportunity seems to be a bit more challenging than anticipated.
As I wrap up this post, the weather has taken a turn for the better. The rain has stopped, the temperature has risen, and the sun is beginning to peek through the clouds. Here's to a wonderful day for everyone – enjoy yours!
(P.S. Be sure to check out the photos – one captures Kilimanjaro from yesterday evening, the other is a picture of me with the giant tortoise from my previous trip here in December 2022).
Online
Feel free to support me by sending some sats via the lightning network to rubenstorm@sats.mobi
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Bluesky is a scam
Bluesky advertises itself as an open network, they say people won't lose followers or their identity, they advertise themselves as a protocol ("atproto") and because of that they are tricking a lot of people into using them. These three claims are false.
protocolness
Bluesky is a company. "atproto" is the protocol. Supposedly they are two different things, right? Bluesky just releases software that implements the protocol, but others can also do that, it's open!
And yet, the protocol has an official webpage with a waitlist and a private beta? Why is the protocol advertised as a company product? Because it is. The "protocol" is just a description of whatever the Bluesky app and servers do, it can and does change anytime the Bluesky developers decide they want to change it, and it will keep changing for as long as Bluesky apps and servers control the biggest part of the network.
Oh, so there is the possibility of other players stepping in and then it becomes an actual interoperable open protocol? Yes, but what is the likelihood of that happening? It is very low. No serious competitor is likely to step in and build serious apps using a protocol that is directly controlled by Bluesky. All we will ever see are small "community" apps made by users and small satellite small businesses -- not unlike the people and companies that write plugins, addons and alternative clients for popular third-party centralized platforms.
And last, even if it happens that someone makes an app so good that it displaces the canonical official Bluesky app, then that company may overtake the protocol itself -- not because they're evil, but because there is no way it cannot be like this.
identity
According to their own documentation, the Bluesky people were looking for an identity system that provided global ids, key rotation and human-readable names.
They must have realized that such properties are not possible in an open and decentralized system, but instead of accepting a tradeoff they decided they wanted all their desired features and threw away the "decentralized" part, quite literally and explicitly (although they make sure to hide that piece in the middle of a bunch of code and text that very few will read).
The "DID Placeholder" method they decided to use for their global identities is nothing more than a normal old boring trusted server controlled by Bluesky that keeps track of who is who and can, at all times, decide to ban a person and deprive them from their identity (they dismissively call a "denial of service attack").
They decided to adopt this method as a placeholder until someone else doesn't invent the impossible alternative that would provide all their desired properties in a decentralized manner -- which is nothing more than a very good excuse: "yes, it's not great now, but it will improve!".
openness
Months after launching their product with an aura of decentralization and openness and getting a bunch of people inside that believed, falsely, they were joining an actually open network, Bluesky has decided to publish a part of their idea of how other people will be able to join their open network.
When I first saw their app and how they were very prominently things like follower counts, like counts and other things that are typical of centralized networks and can't be reliable or exact on truly open networks (like Nostr), I asked myself how were they going to do that once they became and open "federated" network as they were expected to be.
Turns out their decentralization plan is to just allow you, as a writer, to host your own posts on "personal data stores", but not really have any control over the distribution of the posts. All posts go through the Bluesky central server, called BGS, and they decide what to do with it. And you, as a reader, doesn't have any control of what you're reading from either, all you can do is connect to the BGS and ask for posts. If the BGS decides to ban, shadow ban, reorder, miscount, hide, deprioritize, trick or maybe even to serve ads, then you are out of luck.
Oh, but anyone can run their own BGS!, they will say. Even in their own blog post announcing the architecture they assert that "it’s a fairly resource-demanding service" and "there may be a few large full-network providers". But I fail to see why even more than one network provider will exist, if Bluesky is already doing that job, and considering the fact there are very little incentives for anyone to switch providers -- because the app does not seem to be at all made to talk to multiple providers, one would have to stop using the reliable, fast and beefy official BGS and start using some half-baked alternative and risk losing access to things.
When asked about the possibility of switching, one of Bluesky overlords said: "it would look something like this: bluesky has gone evil. there's a new alternative called freesky that people are rushing to. I'm switching to freesky".
The quote is very naïve and sounds like something that could be said about Twitter itself: "if Twitter is evil you can just run your own social network". Both are fallacies because they ignore the network-effect and the fact that people will never fully agree that something is "evil". In fact these two are the fundamental reasons why -- for social networks specifically (and not for other things like commerce) -- we need truly open protocols with no owners and no committees.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Jofer
Jofer era um jogador diferente. À primeira vista não, parecia igual, um volante combativo, perseguia os atacantes adversários implacavelmente, um bom jogador. Mas não era essa a característica que diferenciava Jofer. Jofer era, digamos, um chutador.
Começou numa semifinal de um torneio de juniores. O time de Jofer precisava do empate e estava sofrendo uma baita pressão do adversário, mas o jogo estava 1 a 1 e parecia que ia ficar assim mesmo, daquele jeito futebolístico que parece, parece mesmo. Só que aos 46 do segundo tempo tomaram um gol espírita, Ruizinho do outro time saiu correndo pela esquerda e, mesmo sendo canhoto, foi cortando para o meio, os zagueiros meio que achando que já tinha acabado mesmo, devia ter só mais aquele lance, o árbitro tinha dado dois minutos, Ruizinho chutou, marcou e o goleiro, que só pulou depois que já tinha visto que não ia ter jeito, ficou xingando.
A bola saiu do meio e tocaram para Jofer, ninguém nem veio marcá-lo, o outro time já estava comemorando, e com razão, o juiz estava de sacanagem em fazer o jogo continuar, já estava tudo acabado mesmo. Mas não, estava certo, mais um minuto de acréscimo, justo. Em um minuto dá pra fazer um gol. Mas como? Jofer pensou nas partidas da NBA em que com alguns centésimos de segundo faltando o armador jogava de qualquer jeito para a cesta e às vezes acertava. De trás do meio de campo, será? Não vou ter nem força pra fazer chegar no gol. Vou virar piada, melhor tocar pro Fumaça ali do lado e a gente perde sem essa humilhação no final. Mas, poxa, e daí? Vou tentar mesmo assim, qualquer coisa eu falo que foi um lançamento e daqui a uns dias todo mundo esquece. Olhou para o próprio pé, virou ele de ladinho, pra fora e depois pra dentro (bom, se eu pegar daqui, direitinho, quem sabe?), jogou a bola pro lado e bateu. A bola subiu escandalosamente, muito alta mesmo, deve ter subido uns 200 metros. Jofer não tinha como ter a menor noção. Depois foi descendo, o goleirão voltando correndo para debaixo da trave e olhando pra bola, foi chegando e pulando já só pra acompanhar, para ver, dependurado no travessão, a bola sair ainda bem alta, ela bateu na rede lateral interna antes de bater no chão, quicar violentamente e estufar a rede no alto do lado direito de quem olhava.
Mas isso tudo foi sonho do Jofer. Sonhou acordado, numa noite em que demorou pra dormir, deitado na sua cama. Ficou pensando se não seria fácil, se ele treinasse bastante, acertar o gol bem de longe, tipo no sonho, e se não dava pra fazer gol assim. No dia seguinte perguntou a Brunildinho, o treinador de goleiros. Era difícil defender essas bolas, ainda mais se elas subissem muito, o goleiro ficava sem perspectiva, o vento alterava a trajetória a cada instante, tinha efeito, ela cairia rápido, mas claro que não valia à pena treinar isso, a chance de acertar o gol era minúscula. Mas Jofer só ia tentar depois que treinasse bastante e comprovasse o que na sua imaginação parecia uma excelente idéia.
Começou a treinar todos os dias. Primeiro escondido, por vergonha dos colegas, chegava um pouco antes e ficava lá, chutando do círculo central. Ao menor sinal de gente se aproximando, parava e ia catar as bolas. Depois, quando começou a acertar, perdeu a vergonha. O pessoal do clube todo achava engraçado quando via Jofer treinando e depois ouvia a explicação da boca de alguém, ninguém levava muito a sério, mas também não achava de todo ridículo. O pessoal ria, mas no fundo torcia praquilo dar certo, mesmo.
Aconteceu que num jogo que não valia muita coisa, empatezinho feio, aos 40 do segundo tempo, a marcação dos adversários já não estava mais pressionando, todo mundo contente com o empate e com vontade de parar de jogar já, o Henrique, meia-esquerdo, humilde, mas ainda assim um pouco intimidante para Jofer (jogava demais), tocou pra ele. Vai lá, tenta sua loucura aí. Assumiu a responsabilidade do nosso volante introspectivo. Seria mais verossímil se Jofer tivesse errado, primeira vez que tentou, restava muito tempo ainda pra ele ter a chance de ser herói, ninguém acerta de primeira, mas ele acertou. Quase como no sonho, Lucas, o goleiro, não esperava, depois que viu o lance, riu-se, adiantou-se para pegar a bola que ele julgava que quicaria na área, mas ela foi mais pra frente, mais e mais, daí Lucas já estava correndo, só que começou a pensar que ela ia pra fora, e ele ia só se dependurar no travessão e fazer seu papel de estar na bola. Acabou que por conta daquele gol eles terminaram em segundo no grupo daquele torneiozinho, ao invés de terceiro, e não fez diferença nenhuma.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O caso da Grêmio TV
enquanto vinha se conduzindo pela plataforma superior daquela arena que se pensava totalmente preenchida por adeptos da famosa equipe do Grêmio de Porto Alegre, viu-se, como por obra de algum nigromante - dos muitos que existem e estão a todo momento a fazer más obras e a colocar-se no caminhos dos que procuram, se não fazer o bem acima de todas as coisas, a pelo menos não fazer o mal no curso da realização dos seus interesses -, o discretíssimo jornalista a ser xingado e moído em palavras por uma horda de malandrinos a cinco ou seis passos dele surgida que cantavam e moviam seus braços em movimentos que não se pode classificar senão como bárbaros, e assim cantavam:
Grêmio TV pior que o SBT !
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Replacing the web with something saner
This is a simplification, but let's say that basically there are just 3 kinds of websites:
- Websites with content: text, images, videos;
- Websites that run full apps that do a ton of interactive stuff;
- Websites with some interactive content that uses JavaScript, or "mini-apps";
In a saner world we would have 3 different ways of serving and using these. 1 would be "the web" (and it was for a while, although I'm not claiming here that the past is always better and wanting to get back to the glorious old days).
1 would stay as "the web", just static sites, styled with CSS, no JavaScript whatsoever, but designers can still thrive and make they look pretty. Or it could also be something like Gemini. Maybe the two protocols could coexist.
2 would be downloadable native apps, much easier to write and maintain for developers (considering that multi-platform and cross-compilation is easy today and getting easier), faster, more polished experience for users, more powerful, integrates better with the computer.
(Remember that since no one would be striving to make the same app run both on browsers and natively no one would have any need for Electron or other inefficient bloated solutions, just pure native UI, like the Telegram app, have you seen that? It's fast.)
But 2 is mostly for apps that people use every day, something like Google Docs, email (although email is also broken technology), Netflix, Twitter, Trello and so on, and all those hundreds of niche SaaS that people pay monthly fees to use, each tailored to a different industry (although most of functions they all implement are the same everywhere). What do we do with dynamic open websites like StackOverflow, for example, where one needs to not only read, but also search and interact in multiple ways? What about that website that asks you a bunch of questions and then discovers the name of the person you're thinking about? What about that mini-app that calculates the hash of your provided content or shrinks your video, or that one that hosts your image without asking any questions?
All these and tons of others would fall into category 3, that of instantly loaded apps that you don't have to install, and yet they run in a sandbox.
The key for making category 3 worth investing time into is coming up with some solid grounds, simple enough that anyone can implement in multiple different ways, but not giving the app too much choices.
Telegram or Discord bots are super powerful platforms that can accomodate most kinds of app in them. They can't beat a native app specifically made with one purpose, but they allow anyone to provide instantly usable apps with very low overhead, and since the experience is so simple, intuitive and fast, users tend to like it and sometimes even pay for their services. There could exist a protocol that brings apps like that to the open world of (I won't say "web") domains and the websockets protocol -- with multiple different clients, each making their own decisions on how to display the content sent by the servers that are powering these apps.
Another idea is that of Alan Kay: to design a nice little OS/virtual machine that can load these apps and run them. Kinda like browsers are today, but providing a more well-thought, native-like experience and framework, but still sandboxed. And I add: abstracting away details about design, content disposition and so on.
These 3 kinds of programs could coexist peacefully. 2 are just standalone programs, they can do anything and each will be its own thing. 1 and 3, however, are still similar to browsers of today in the sense that you need clients to interact with servers and show to the user what they are asking. But by simplifying everything and separating the scopes properly these clients would be easy to write, efficient, small, the environment would be open and the internet would be saved.
See also
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28IPFS problems: General confusion
Most IPFS open-source projects, libraries and apps (excluding Ethereum stuff) are things that rely heavily on dynamic data and temporary links. The most common projects you'll see when following the IPFS communities are chat rooms and similar things. I've seen dozens of these chat-rooms. There's also a famous IPFS-powered database. How can you do these things with content-addressing is a mistery. Of course they probably rely on IPNS or other external address system.
There's also a bunch of "file-sharing" on IPFS. The kind of thing people use for temporary making a file available for a third-party. There's image sharing on IPFS, pastebins on IPFS and so on. People don't seem to share the preoccupation with broken links here.
-
 @ 58537364:705b4b85
2024-07-13 11:49:14
@ 58537364:705b4b85
2024-07-13 11:49:14อารมณ์ คือ โลก - โลก คือ อารมณ์ อารมณ์ ในโลกปัจจุบันรวมอยู่ที่ วัตถุนิยม อารมณ์ จึงเป็นปัจจัยแห่งเหตุการณ์ทุกอย่างในโลก

…. “ เดี๋ยวนี้คําว่า “อารมณ์” ในภาษาไทยนั้น หมายถึงความรู้สึกในใจมากกว่า; เช่น พื้นเพของจิตใจในขณะนั้นเป็นอย่างไร, เรียกว่าอารมณ์ของเขาเป็นอย่างไร, อารมณ์กําลังดี อารมณ์กําลังไม่ดี, นี่ คําว่าอารมณ์ในภาษาไทยใช้กันไปเสียอย่างนี้ ; มันคนละเรื่องกับในภาษาบาลี ซึ่งคําว่า “อารมณ์” หมายถึง สิ่งที่จะเข้ามากระทบ ตา หู จมูก ลิ้น กาย ใจ.
…. ถ้ากระทบแล้วเกิดความรู้สึกอย่างไร งุ่นง่านอยู่ในใจ อันนั้นไม่ได้เรียกว่าอารมณ์; อันนั้นก็เรียกว่ากิเลสอย่างอื่น เช่น เรียกว่าตัณหาบ้าง อุปาทานบ้าง; ถ้าจัดเป็นพวกขันธ์ ก็เรียกว่า เวทนาขันธ์บ้าง สัญญาขันธ์บ้าง สังขารขันธ์บ้าง; ถ้าเป็นความคิดที่งุ่นง่านก็เรียกว่า “สังขารขันธ์” ทั้งนั้น ดังนั้น เราจะต้องถือเอาคําว่าอารมณ์ในบาลีมาเป็นหลัก …. คําว่า อารมณ์ ที่จะเข้าใจกันง่ายๆ ก็หมายความว่า รูป เสียง กลิ่น รส โผฏฐัพพะ ที่จะมากระทบ ตา หู จมูก ลิ้น กาย นี้ ๕ อย่าง แล้วก็ความรู้สึกเก่าแก่ที่จะมาผุดขึ้นในใจอีก เรียกว่า ธัมมารมณ์ ที่จะมากระทบใจในปัจจุบันนี้ นี้ก็เป็นอันหนึ่ง เลยได้เป็นอารมณ์ ๖. อารมณ์กระทบ ตา หู จมูก ลิ้น กาย ๕ อย่างข้างนอกนี้ก็สําคัญไปพวกหนึ่ง ที่ปรุงขึ้นภายในสําหรับกระทบใจโดยไม่ต้องอาศัย ตา หู จมูก ลิ้น กาย ใจ เลย ในเวลานั้นก็ยังมีอยู่นี้เรียกว่าธัมมารมณ์ นี้ก็ยิ่งสําคัญ: แต่ว่ารวมกันแล้วก็เรียกว่า อารมณ์ ได้ด้วยกันทั้งนั้น แปลว่า สิ่งที่จะมากระทบกับ ตา หู จมูก ลิ้น กาย ใจ นั่นเอง
…. นี้ ดูให้ละเอียดตามตัวหนังสือ คําว่า “อารมณ์” แปลว่า ที่หน่วงบ้าง แปลว่า ที่ยินดีบ้าง, มันมีความหมายละเอียดมาก. ถ้าถือเอาความหมายอย่างคนที่มีตัวตนเป็นหลัก ธรรมะในฝ่ายฮินดูหรือฝ่ายพรหมณ์เขาก็จะพูดว่า สําหรับจิตหรืออาตมันเข้าไปจับฉวยเอา. แต่ถ้าพูดอย่างภาษาชาวพุทธพูดอย่างนั้นไม่ได้ เพราะไม่มีจิตไม่มีอาตมันชนิดนั้น แล้วจิตนี้ก็เพิ่งเกิดขึ้นหลังอารมณ์กระทบแล้ว; เลยต้องพูดตามพระบาลีที่ว่า อาศัยตาด้วย อาศัยรูปด้วย ย่อมเกิดจักษุวิญญาณ; ตาอาศัยกับรูปคืออารมณ์นั้นได้แล้วจึงจะเกิดจักษุวิญญาณ วิญญาณหรือจิตนี้เกิดทีหลัง
…. ฉะนั้น จึงไม่พูดว่า อารมณ์นี้เป็นสิ่งสําหรับจิตหรือตัวตนเข้าไปจับฉวยยึดเอา; ถ้าพูดอย่างนั้นมันก็จะเป็นฮินดูหรือพราหมณ์ไป คือมีตัวตนไป. พูดอย่างพุทธไม่มีตัวตน ทุกอย่างไม่ใช่ตัวตน เป็นสักว่าธาตุ, ได้การปรุงแต่งที่เหมาะแล้วมันก็ปรุงแต่งเป็นสิ่งใหม่ขึ้นมา ในนั้นอาจจะมีความรู้สึกโง่ไปว่าเป็นตัวเราก็ได้
…. ฉะนั้น คําว่าอารมณ์ ถ้าถือตามหลักในทางพุทธศาสนา ก็แปลว่า สิ่งที่อาศัยกันกับจิต จะเรียกว่าเป็นที่หน่วงของจิตมันก็ยังได้: ถ้าเข้าใจผิดมันก็ผิดได้: เรียกว่าสิ่งที่อาศัยกับอายตนะ แล้วก็เกิดเป็นความรู้สึกเป็นจิตขึ้นมา จิตกําลังหน่วงสิ่งนั้นเป็นอารมณ์ก็ได้ แต่จะให้เป็นตัวตนนั้นไม่ได้
…. โดยพยัญชนะก็มีอยู่อย่างนี้ ตัวพยัญชนะก็ยังกํากวม อารมฺมณํ หรือที่มาจาก อาลมฺพนํ ก็แปลว่า ที่หน่วงของจิต. ถ้าจะถือว่ามาจาก รม ที่แปลว่า ยินดี ก็แปลว่า มันเป็นสิ่งที่หลงใหลยินดีของจิต อย่างนี้ก็ยังได้อีก
…. แต่ขอให้รู้จักจากภายในดีกว่าที่จะมารู้จักจากตัวหนังสือ เมื่อตากระทบรูป เมื่อหูกระทบเสียง เป็นต้น มันเกิดขึ้นในใจ, แล้วสังเกตเอาที่นั่นก็แล้วกัน ว่ารูปที่มากระทบตานั้นมันคืออะไร? เสียงที่มากระทบหูนั้นมันคืออะไร? จะค่อยเข้าใจแจ่มแจ้งขึ้นทีละน้อยๆ ว่าอารมณ์นั้นคืออะไร? แต่ให้เข้าใจไว้ทีหนึ่งก่อนว่าสิ่งที่เรียกว่าอารมณ์ๆที่มากระทบนี้ มันยังไม่ดีไม่ชั่ว ยังไม่จัดเป็นสิ่งดีสิ่งชั่ว มันต้องผสมปรุงแต่งเป็นความคิดอย่างนั้นอย่างนี้เสียก่อน จึงจะจัดเป็นดีเป็นชั่ว อารมณ์ล้วนๆยังไม่ดีไม่ชั่ว จะได้รู้จักป้องกัน อย่าให้เป็นไปในทางชั่ว, ให้เป็นไปแต่ในทางดีได้ตามปรารถนา
…. นี้เรียกว่าโดยพยัญชนะ โดยตัวหนังสือ คําว่า “อารมณ์” แปลว่า เป็นที่ยินดีแห่งจิต, เป็นที่ยึดหน่วงแห่งจิต; โดยเฉพาะภาษาอภิธรรมแล้วก็ใช้คําว่า “เป็นที่หน่วงเอาของจิต”, คือจิตย่อมหน่วงสิ่งใดสิ่งหนึ่งเป็นอารมณ์ แปลคําว่าอารมณ์บ้าง, อาลัมพนะ แปลว่า เป็นที่หน่วงเอา.
…. เดี๋ยวนี้เราเรียนพุทธศาสนาไม่ใช่เรามาเรียนหนังสือบาลี, เราจะเรียนพระธรรมคําสอนของพระพุทธเจ้า เราก็ต้องดูสิ่งที่เรียกว่าอารมณ์ โดยหลักของธรรมชาติที่ปรุงแต่งกันอยู่ในใจดีกว่า; ก็อย่างพระบาลีที่ได้ว่ามาแล้วข้างต้นว่า จกฺขุญฺจ ปฏิจฺจ รูเป จ อุปฺปชฺชติ จกฺขุวิญฺญาณํ = เพราะอาศัยตาด้วย รูปด้วย ย่อมบังเกิดจักษุวิญญาณ ติณฺณํ ธมฺมานํ สงฺคติ ผสฺโส - การประจวบกันของ ๓ สิ่งนี้เรียกว่า “ผัสสะ”, ผสฺสปจฺจยา เวทนา = เพราะผัสสะเป็นปัจจัยจึงเกิดเวทนา, อย่างนี้เรื่อยไปจนเกิดทุกข์ จนเกิดความทุกข์, นี้เรียกว่าโดยธรรมชาติ
…. สิ่งที่เรียกว่าอารมณ์มีอยู่โดยธรรมชาติที่จะเข้ามาอาศัยกันกับตาข้างใน ที่มีอยู่ในตัวคน. แล้วจะเกิดจักษุวิญญาณ เป็นต้น ขึ้นในตัวคน; จะเกิด ผัสสะ เวทนา ตัณหา อุปาทาน ภพ ชาติ ขึ้นในตัวคน; นี้โดยธรรมชาติ พระพุทธเจ้าท่านบันดาลอะไรไม่ได้ : ธรรมชาติเป็นอยู่อย่างนี้ แต่ท่านรู้เรื่องนี้ท่านจึงนํามาสอนว่า ธรรมชาติมันมีอยู่อย่างนี้ เราจะต้องเข้าใจให้ถูกต้อง โดยที่จะป้องกันความทุกข์ไม่ให้เกิดขึ้นมาได้, หรือถ้าเกิดขึ้นมาได้ก็จะดับเสียได้
…. เราควรจะรู้จักอารมณ์ในฐานะที่เป็นธรรมชาติอันหนึ่ง ที่มีอยู่ตามธรรมชาติ แล้วที่จะเข้ามาทําเรื่องทําราวขึ้นในจิตใจของคนเราให้เกิดปัญหายุ่งยากนี้ให้ดีๆ นี้เรียกว่ารู้จักอารมณ์จากธรรมชาติโดยตรงอย่างนี้ ดีกว่าที่จะรู้จักตามตัวหนังสือ, ดีกว่าที่จะรู้จักตามคําบอกเล่าบางอย่างบางประการที่มันไม่มีประโยชน์อะไร. รู้จักตามคําบอกเล่าก็รู้จักตามที่พระพุทธเจ้าท่านตรัสดีกว่า แต่แล้วยังไม่รู้จักตัวจริง จนกว่าจะมารู้จักจากที่เมื่ออารมณ์มากระทบตา หู จมูก ลิ้น กาย ใจ เข้าจริงๆ : นั่นจึงจะรู้จักอารมณ์ รู้จักผลที่เกิดขึ้นจากการกระทบของอารมณ์, รู้จักต่อไปตามลําดับ จนแก้ปัญหาต่างๆ ได้
…. นี่ ขอร้องให้รู้จักสิ่งที่เรียกว่า อารมณ์ ในฐานะที่เป็นธรรมชาติอันหนึ่ง ที่มีอยู่ตามธรรมชาติ ที่จะเข้ามากระทบอายตนะภายใน คือ กระทบ ตา หู จมูก ลิ้น กาย ใจ แล้วมีเรื่องมีราวมีปัญหา
อารมณ์ คือ โลก - โลก คือ อารมณ์ …. “ ที่นี้จะให้ดูต่อไปอีก ว่าโดยข้อเท็จจริงที่เป็นอยู่แล้ว อารมณ์นั้นคืออะไร? ถ้าจะพูดโดยข้อเท็จจริงหรือตามสถานการณ์ที่เป็นอยู่จริงในชีวิตของคนเรา อารมณ์มันก็คือ “โลก” นั่นเอง. เดี๋ยวนี้เราไม่รู้จักโลกในฐานะอย่างนี้, เราไปเข้าใจความหมายของคําว่าโลกแคบไปบ้าง หรือว่าเขวไปบ้าง.
…. ถ้าจะรู้ตามหลักพระพุทธศาสนาแล้ว โลกทั้งหมดก็คือสิ่งที่จะมาปรากฏแก่ ตา หู จมูก ลิ้น กาย ใจ ของเรา, เรามีเพียง ๖ อย่าง, แล้วมันก็ ปรากฏได้เพียง ๖ ทาง, มากกว่านั้นมันปรากฏไม่ได้ ดังนั้น โลกก็คือสิ่งที่จะมาปรากฏแก่ ตา หู จมูก ลิ้น กาย ใจ ๖ อย่างของเรา. “โลก” ก็คือ รูป เสียง กลิ่น รส โผฏฐัพพะ ธัมมารมณ์ ๖ ประการเท่านั้น, ไม่มีอะไรมากไปกว่านั้น
…. ฉะนั้น รูป เสียง กลิ่น รส โผฏฐัพพะ ธัมมารมณ์ แต่ละอย่าง ๆ ก็คือ โลกในแต่ละแง่ละมุม นั่นเอง, ที่เป็น รูป เสียง กลิ่น รส โผฏฐัพพะ ก็อยู่ข้างนอก จะเรียกว่าอยู่ข้างนอกก็ได้, ที่เป็นอารมณ์เกิดขึ้นในใจ ปรุงขึ้นในใจก็เรียกว่าโลกข้างในก็ได้ แต่มันก็เป็นโลกอยู่นั่นแหละ เพราะมันเป็นสิ่งที่จิตจะต้องรู้สึก จิตรู้สึกก็เรียกว่าโลกสําหรับจิต ตา หู จมูก ลิ้น กาย รู้สึก ก็เรียกว่าโลกสำหรับ ตา หู จมูก ลิ้น กาย. นี้ขอให้มองให้เห็นชัดตามพระพุทธประสงค์ว่า โลก ก็คือ อารมณ์, อารมณ์ ก็คือ โลก.
…. แต่ทีนี้ พระพุทธเจ้าท่านมองลึกกว่านั้น ท่านตรัสถึงข้อที่ว่า ถ้ามันมาเกิดเป็นปัญหาแก่เราเมื่อไรจึงจะเรียกว่า “มันมี” พอมันมาเป็นปัญหาแก่เราเมื่อไรก็เรียกว่า “เป็นทุกข์”; เพราะว่าเราได้ไปจับฉวยยึดถือเอาตามประสาตามวิสัยของคนที่ไม่รู้จักโลก ถ้าพูดว่าไม่รู้จักโลกแล้วคนก็มักจะไม่ยอมรับ เพราะว่าเขาจะพูดว่าเขารู้จักโลกดี. ยิ่งพวกฝรั่งสมัยนี้ นักวิทยาศาสตร์ปราดเปรื่องนั้น เขาจะไม่ยอมรับว่าเขาไม่รู้จักโลก. แต่ถ้าพูดตามหลักพุทธศาสนาแล้วก็จะพูดได้ว่ายังไม่รู้จักโลกเลย เป็นคนตาบอดยิ่งกว่าตาบอด; เพราะว่าฝรั่งเหล่านั้นรู้จักโลกแต่ในแง่สําหรับจะยึดมั่นถือมั่นเป็น “ตัวกู ของกู” จะครองโลกจะอะไร เอาประโยชน์ทุกอย่าง; เขารู้จักโลกในแง่นี้ อย่างนี้พุทธบริษัทไม่เรียกว่า “รู้จักโลก”; แต่ถือว่าเป็นคนตาบอดต่อโลก, หลงยึดมั่นถือมั่นในโลก. เพราะว่าคนเหล่านั้นไม่รู้จักโลกโดยความเป็นอารมณ์ ๖ ประการ คือ รูป เสียง กลิ่นรส โผฏฐัพพะ ธัมมารมณ์, แล้วเป็น “มายา” คือ เอาจริงไม่ได้ เป็นของชั่วคราวๆ หลอกให้เกิดความรู้สึกยึดมั่นถือมั่น
…. นี้เรารู้จัก เราไม่ไปหลงยึดมั่นถือมั่นกับมัน นี้จึงเรียกว่า “คนที่รู้จักโลก” ไปตามหลักของพุทธศาสนา, ฉะนั้น จึงไม่ยึดมั่นถือมั่นสิ่งใดโดยความเป็นตัวตน หรือโดยความเป็นของตน, เรียกว่าเป็นผู้รู้จักอารมณ์ ๖ ประการนั้นก็คือรู้จักโลกทั้งปวง, แล้วก็ไม่หลงไปในโลกในแง่ใดแง่หนึ่ง นี้เรียกว่า อารมณ์ ก็คือ โลก นั่นเอง ในความหมายที่ลึกที่สุดของพระพุทธสาสนา ไม่ใช่โลกก้อนดิน, ไม่ใช่โลกก้อนกลมๆ นี้. แต่มันหมายถึงคุณค่าอะไรที่มันมีอยู่ในโลกกลมๆ นี้ ที่จะเข้ามามาทําให้เกิดปัญหา ที่ตา ที่หู ที่จมูก ที่ลิ้น ที่กาย ที่ใจ ของคน. นั่นแหละคือตัวร้ายกาจของสิ่งที่เรียกว่า โลก เราจะต้องรู้จักในส่วนนี้ให้เพียงพอ
อารมณ์ในโลกปัจจุบันมารวมที่วัตถุนิยม …. ทีนี้ ดูอีกแง่หนึ่งก็โดยปัญหาที่กําลังมีอยู่ อารมณ์ในโลกนี้ในฐานะที่มันเป็นตัวปัญหาที่กําลังมีอยู่ มันมารวมอยู่ที่คําว่า “วัตถุนิยม”: หมายความว่า ตา หู จมูก ลิ้น กาย ใจ นี้ มันเป็นฝ่ายชนะ ไปหลงใหลในอารมณ์ รูป เสียง กลิ่น รส โผฏฐัพพะ ฯลฯ, แล้วก็เกิดนิยมหลงใหลในวัตถุเหล่านั้น จนเกิดความคิดใหม่ๆ, ปรุงแต่งไปในทางที่จะให้หลงใหลในโลกยิ่งขึ้นๆ, ความเจริญก้าวหน้า ในโลกสมัยนี้เป็นไปแต่ในทางอย่างนี้ ฉะนั้น จึงไกลความสงบ, ไกลสันติภาพ ไกลอะไรออกไปทุกที. การที่มนุษย์ที่มีปัญญาในโลกสมัยนี้ โดยเฉพาะฝรั่งที่ก้าวหน้านั้นเขาก็จัดโลกไปแต่ในแง่ของวัตถุมากขึ้นๆ: มันก็ไกลจากสันติภาพ ไกลจากความสงบสุขยิ่งขึ้นทุกที
…. ความสะดวกสบายที่ทําให้เกิดขึ้นมาได้นั้น ไม่ได้ช่วยส่งเสริมเกิดสันติภาพ; แต่มันช่วยให้เกิดความหลงในโลกนั้นเองมากขึ้น แล้วก็ช่วยให้หลงใหลใน “ตัวกู ของกู”, ยึดมั่นถือมั่นเห็นแก่ตัวมากขึ้น รวมกันแล้วมันไม่มีทางที่จะเกิดสันติภาพหรือสันติสุขในโลกได้เลย, จึงกลายเป็นความหลอกลวงเหลือประมาณ โลกจึงกลายเป็นความหลอกลวง, หรือสิ่งที่หลอกลวงเหลือประมาณใน เวลานี้ เราเรียกกันว่า ติดบ่วง หรือว่า ติดเหยื่อของวัตถุนิยม. คําพูดทั้งหมดนี้ ล้วนแต่เป็นการแสดงให้เห็นว่า อารมณ์นี้คืออะไร สิ่งที่เรียกว่าอารมณ์นั้น คือตัวโลกที่กําลังหลอกลวงเราอยู่ทุกวันอย่างยิ่ง โดยเฉพาะในปัจจุบันนี้เป็นวัตถุนิยม นี้คืออารมณ์”
พุทธทาสภิกขุ ที่มา : ธรรมบรรยายภาคมาฆบูชา ครั้งที่ ๗ หัวข้อเรื่อง “อารมณ์ คือ ปัจจัยแห่งเหตุการณ์ทุกอย่างในโลก” เมื่อวันที่ ๑๖ กุมภาพันธ์ ๒๕๑๗ จากหนังสือชุดธรรมโฆษณ์ เล่มชื่อว่า “ก ข ก กา ของการศึกษาพุทธศาสนา”
หมายเหตุ
“อารมณ์ ” ในทางพุทธศาสนา มี ๖ คือ... * ๑. รูปะ = รูป, สิ่งที่เห็น หรือ วัณณะ คือ สี * ๒. สัททะ = เสียง * ๓. คันธะ = กลิ่น * ๔. รสะ = รส * ๕. โผฏฐัพพะ = สัมผัสทางกาย * ๖. ธรรมารมณ์ = สิ่งที่ใจนึกคิด, อารมณ์ที่เกิดกับใจ
…. ทั้ง ๖ อย่างนี้ เป็นสิ่งสำหรับให้จิตยึดหน่วง เรียกอีกอย่างว่า "อายตนะภานนอก" ก็ได้
“อายตนะภายใน ๖” คือ ที่เชื่อมต่อให้เกิดความรู้, แดนต่อความรู้ฝ่ายภายใน มี * ๖ อย่าง คือ... * ๑. จักษุ - ตา * ๒. โสตะ - หู * ๓. ฆานะ - จมูก * ๔. ชิวหา - ลิ้น * ๕. กาย - กาย * ๖. มโน - ใจ
… หรือจะเรียกอีกอย่างว่า “อินทรีย์ ๖” ก็ได้ เพราะเป็นใหญ่ในหน้าที่ของตนแต่ละอย่าง เช่น จักษุ เป็นเจ้าการ(เป็นใหญ่)ในการเห็น เป็นต้น
ท. ส. ปัญญาวุฑโฒ – รวบรวม.
-
 @ a012dc82:6458a70d
2024-07-13 08:10:23
@ a012dc82:6458a70d
2024-07-13 08:10:23Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
Introduction
Bitcoin is a highly volatile asset that can experience dramatic price swings in short periods of time. In a bull market, traders can capitalize on rising prices and generate significant profits. However, when the market turns bearish, it can be challenging to navigate and maintain profitability. A bear market is a period of declining prices, where negative sentiment dominates and trading volumes may decrease. In this context, it's important to have a set of strategies that can help you navigate the market and protect your investments. In this article, we'll explore five essential strategies for trading Bitcoin in a bear market. By implementing these strategies, you can reduce your risks and maximize your chances of success.
Strategy 1: Take profit regularly
This strategy involves selling a portion of your Bitcoin holdings when prices reach a certain level. By taking profits regularly, you can lock in gains and minimize the risk of losses in a bear market. It's important to have a plan for taking profits and stick to it, even if prices continue to rise.
Strategy 2: Set stop-loss orders
A stop-loss order is an instruction to sell your Bitcoin if prices fall below a certain level. By setting stop-loss orders, you can limit your losses in a bear market and avoid holding onto Bitcoin that's losing value. It's important to set stop-loss orders at a level that allows for normal price fluctuations but also provides adequate protection against sharp declines.
Strategy 3: Short sell Bitcoin
Short selling involves borrowing Bitcoin from a broker and selling it on the open market with the hope of buying it back at a lower price. This strategy can be useful in a bear market when prices are falling, as it allows you to profit from the decline. However, short selling is a high-risk strategy that requires careful consideration of the potential risks and rewards.
Strategy 4: Use dollar-cost averaging
Dollar-cost averaging involves investing a fixed amount of money at regular intervals, regardless of the current price of Bitcoin. By buying Bitcoin at regular intervals, you can take advantage of market fluctuations and potentially reduce the average cost of your holdings. This strategy can be effective in a bear market where prices are falling and may present buying opportunities.
Strategy 5: Stay up-to-date with news and trends
Staying informed about news and trends in the cryptocurrency market is essential for making informed trading decisions. By staying up-to-date, you can identify potential risks and opportunities and adjust your trading strategies accordingly. It's important to use reliable sources of information and avoid making impulsive trading decisions based on emotions or rumors.
Conclusion
The Bitcoin bear market can be difficult to navigate, but with these five essential strategies, traders can reduce their risks and maximize their chances of success. These strategies include taking profits regularly, setting stop-loss orders, short selling, using dollar-cost averaging, and staying up-to-date with news and trends. It's important to remain disciplined, avoid impulsive decisions, and stay flexible to adapt to changing market conditions. By following these strategies, traders can emerge successful from the Bitcoin bear market.
FAQ
What is a bear market? A bear market is a period of declining prices, where negative sentiment dominates and trading volumes may decrease.
How can I protect my investments in a bear market? To protect your investments in a bear market, you can implement strategies such as taking profits regularly, setting stop-loss orders, short selling, using dollar-cost averaging, and staying up-to-date with news and trends.
Is short selling a high-risk strategy? Yes, short selling is a high-risk strategy that requires careful consideration of the potential risks and rewards.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Scala is such a great language
Scala is amazing. The type system has the perfect balance between flexibility and powerfulness.
matchstatements are great. You can write imperative code that looks very nice and expressive (and I haven't tried writing purely functional things yet). Everything is easy to write and cheap and neovim integration works great.But Java is not great. And the fact that Scala is a JVM language doesn't help because over the years people have written stuff that depends on Java libraries -- and these Java libraries are not as safe as the Scala libraries, they contain reflection, slowness, runtime errors, all kinds of horrors.
Scala is also very tightly associated with Akka, the actor framework, and Akka is a giant collection of anti-patterns. Untyped stuff, reflection, dependency on JVM, basically a lot of javisms. I just arrived and I don't know anything about the Scala history or ecosystem or community, but I have the impression that Akka has prevent more adoption of Scala from decent people that aren't Java programmers.
But luckily there is a solution -- or two solutions: ScalaJS is a great thing that exists. It transpiles Scala code into JavaScript and it runs on NodeJS or in a browser!
Scala Native is a much better deal, though, it compiles to LLVM and then to binary code and you can have single binaries that run directly without a JVM -- not that the single JARs are that bad though, they are great and everybody has Java so I'll take that anytime over C libraries or NPM-distributed software, but direct executables even better. Scala Native just needs a little more love and some libraries and it will be the greatest thing in a couple of years.
-
 @ 1f9e547c:8af216ed
2024-07-13 07:37:05
@ 1f9e547c:8af216ed
2024-07-13 07:37:05Opinion about Bitcoin Wallet Crypto Ethereum (android)
For archival purposes
Atomic Wallet suffers hack on June 2023
Sources
Atomic Wallet users have been left wanting more answers, despite the decentralized wallet provider finally releasing a full “event statement” about the June exploit — which some estimate has run up to $100 million in losses.
In a June 20 blog post — the first major update from the firm since the June 3 exploit — Atomic Wallet claimed there have been no new confirmed cases after initial reports of the hack.
Atomic Wallet Was Breached by North Korean Hackers: Elliptic
Atomic Wallet users might have fallen victim to Lazarus, the infamous North Korean hacking group, said blockchain intelligence firm Elliptic in a blog post on Tuesday.
Early Saturday morning, the team behind Atomic, a non-custodial crypto wallet, announced that some users were compromised and lost the funds from their wallets. According to the company, the number of incidents did not exceed 1% of "monthly active users." The announcement followed multiple reports on Reddit from users complaining their wallets had been drained.
WalletScrutiny #nostrOpinion
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Que vença o melhor
Nos esportes e jogos em geral, existe uma constante preocupação em balancear os incentivos e atributos do jogo, as regras do esporte em si e as regras das competições para que o melhor vença, ou, em outras palavras, para que sejam minimizados os outros fatores exceto a habilidade mais pura quanto possível no jogo em questão.
O mundo fora dos jogos, porém, nem sempre pode ter suas regras mudadas por um ente que as controla e está imbuído da vontade e dos meios para escolher as melhores regras possíveis para a obtenção dos resultados acima. Aliás, é muitas vezes essa possibilidade é até impensável. Mesmo quando ela é pensável e levada em conta os fatores que operam no mundo real não são facilmente identificáveis, eles são muitos, e mudam o tempo todo.
Mais do que isso, ao contrário de um jogo em que o objetivo é praticamente o mesmo para todo mundo, os objetivos de cada agente no mundo real são diferentes e incontáveis, e as "competições" que cada um está disputando são diferentes e muitas, cada minúsculo ato de suas vidas compreendendo várias delas simultaneamente.
Da mesma forma, é impossível conceber até mesmo o conceito de "melhor" para que se deseje que ele vença.
Mesmo assim é comum encontrarmos em várias situações gente que parte do princípio de que se Fulano está num certo lugar (por exemplo, um emprego muito bom) e Beltrano não isso se deve ao fato de Fulano ter sido melhor que Beltrano.
Está aí uma crítica à idéia da meritocracia (eu tinha me esquecido que essa palavra existia).
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Token-Curated Registries
So you want to build a TCR?
TCRs (Token Curated Registries) are a construct for maintaining registries on Ethereum. Imagine you have lots of scissor brands and you want a list with only the good scissors. You want to make sure only the good scissors make into that list and not the bad scissors. For that, people will tell you, you can just create a TCR of the best scissors!
It works like this: some people have the token, let's call it Scissor Token. Some other person, let's say it's a scissor manufacturer, wants to put his scissor on the list, this guy must acquire some Scissor Tokens and "stake" it. Holders of the Scissor Tokens are allowed to vote on "yes" or "no". If "no", the manufactures loses his tokens to the holders, if "yes" then its tokens are kept in deposit, but his scissor brand gets accepted into the registry.
Such a simple process, they say, have strong incentives for being the best possible way of curating a registry of scissors: consumers have the incentive to consult the list because of its high quality; manufacturers have the incentive to buy tokens and apply to join the list because the list is so well-curated and consumers always consult it; token holders want the registry to accept good and reject bad scissors because that good decisions will make the list good for consumers and thus their tokens more valuable, bad decisions will do the contrary. It doesn't make sense, to reject everybody just to grab their tokens, because that would create an incentive against people trying to enter the list.
Amazing! How come such a simple system of voting has such enourmous features? Now we can have lists of everything so well-curated, and for that we just need Ethereum tokens!
Now let's imagine a different proposal, of my own creation: SPCR, Single-person curated registries.
Single-person Curated Registries are equal to TCR, except they don't use Ethereum tokens, it's just a list in a text file kept by a single person. People can apply to join, and they will have to give the single person some amount of money, the single person can reject or accept the proposal and so on.
Now let's look at the incentives of SPCR: people will want to consult the registry because it is so well curated; vendors will want to enter the registry because people are consulting it; the single person will want to accept the good and reject the bad applicants because these good decisions are what will make the list valuable.
Amazing! How such a single proposal has such enourmous features! SPCR are going to take over the internet!
What TCR enthusiasts get wrong?
TCR people think they can just list a set of incentives for something to work and assume that something will work. Mix that with Ethereum hype and they think theyve found something unique and revolutionary, while in fact they're just making a poor implementation of "democracy" systems that fail almost everywhere.
The life is not about listing a set of "incentives" and then considering the problems solved. Almost everybody on the Earth has the incentive for being rich: being rich has a lot of advantages over being poor, however not all people get rich! Why are the incentives failing?
Curating lists is a hard problem, it involves a lot of knowledge about the problem that just holding a token won't give you, it involves personal preferences, politics, it involves knowing where is the real limit between "good" and "bad". The Single Person list may have a good result if the single person doing the curation is knowledgeable and honest (yes, you can game the system to accept your uncle's scissors and not their competitor that is much better, for example, without losing the entire list reputation), same thing for TCRs, but it can also fail miserably, and it can appear to be good but be in fact not so good. In all cases, the list entries will reflect the preferences of people choosing and other things that aren't taken into the incentives equation of TCR enthusiasts.
We don't need lists
The most important point to be made, although unrelated to the incentive story, is that we don't need lists. Imagine you're looking for a scissor. You don't want someone to tell if scissor A or B are "good" or "bad", or if A is "better" than B. You want to know if, for your specific situation, or for a class of situations, A will serve well, and do that considering A's price and if A is being sold near you and all that.
Scissors are the worst example ever to make this point, but I hope you get it. If you don't, try imagining the same example with schools, doctors, plumbers, food, whatever.
Recommendation systems are badly needed in our world, and TCRs don't solve these at all.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Precautionary Principle
The precautionary principle that people, including Nassim Nicholas Taleb, love and treat as some form of wisdom, is actually just a justification for arbitrary acts.
In a given situation for which there's no sufficient knowledge, either A or B can be seen as risky or precautionary measures, there's no way to know except if you have sufficient knowledge.
Someone could reply saying, for example, that the known risk of A is tolerable to the unknown, probably magnitudes bigger, risk of B. Unless you know better or at least have a logical explanation for the risks of B (a thing "scientists" don't have because they notoriously dislike making logical claims), in which case you do know something and is not invoking the precautionary principle anymore, just relying on your logical reasoning – and that can be discussed and questioned by others, undermining your intended usage of the label "precautionary principle" as a magic cover for your actions.
-
 @ c73818cc:ccd5c890
2024-07-14 00:27:17
@ c73818cc:ccd5c890
2024-07-14 00:27:17
🔹 Aggiornamenti Importanti per il Token BGB
🔹 Bitget ha annunciato una serie di aggiornamenti significativi per il suo token BGB. Il nuovo smart contract porta con sé miglioramenti strutturali, inclusi cambiamenti nella tokenomics e nuovi strumenti di gestione per i detentori di BGB.
🔹 Ristrutturazione della Tokenomics di BGB
🔹 Il nuovo smart contract introduce una ristrutturazione della tokenomics di BGB, con l’obiettivo di stabilizzare il valore del token e incentivare l’uso della piattaforma. Tra le novità, si prevede una modifica delle politiche di emissione e nuovi meccanismi di burn per controllare l’offerta.
🔹 Nuove Opportunità per gli Utenti di Bitget
🔹 Con il lancio del nuovo smart contract, Bitget mira a migliorare l’esperienza degli utenti. Il cambiamento include il potenziamento delle funzionalità di staking e l’introduzione di nuovi programmi di ricompense, pensati per premiare gli utenti più attivi e fedeli.
🔹 Da oggi è stata attivata PoolX con un AirDrop in BGB mettendo in stake USDT. Ed è anche attiva una serie di altre promo per l'evento, come la competizione sui future BGB ed altre.
Unisciti al nostro gruppo Telegram: https://t.me/Bitcoin_Report_Italia
Referral Bitget -10% sulle fee + bonus benvenuto 6w5d o link: https://bonus.bitget.com/U1JNEK
BitcoinReportItalia #Bitget #BGB #Airdrop #Token #Tokenomics #Staking #PoolX #Cripto #Bitcoin
-
 @ 502ab02a:a2860397
2024-07-13 02:14:11
@ 502ab02a:a2860397
2024-07-13 02:14:11Anna Britt Agnsäter ผู้อุทิศชีวิตให้โภชนาการ แต่โดนโลกบูลลีเพราะอเมริกา?
โลกรับรู้ว่า คุณ Anna Britt Agnsäter (ขอเรียกสั้นๆว่า ป้าแอน) เป็นผู้ที่นำเสนอ ปิรามิดอาหาร คนแรกของโลก และเป็นแบบจำลองที่ทาง USDA นำไปพัฒนาปรับใช้แล้วนำมาเป็น แบบที่ใช้สื่อสารกับคนทั้งโลก ในเรื่องของการกำหนด ประเภทอาหารที่ควรกิน ในช่วงปี 1992-2005 ซึ่งในบทความที่แล้วผมได้เขียนว่า ปิรามิดเวอร์ชั่นที่ป้าแอนคิด กับ ที่อเมริกาเอาไปปรับใช้เป็นคนละตัวกัน แต่โลกทั้งโลกก็บูลลีป้าเอนว่า เป็นสาเหตุของการทำลายสุขภาพคนทั้งโลก ทั้งๆที่ไม่ได้เป็นนักวิทยาศาสตร์ ผมก็เป็นคนนึงที่เคยคิดแบบนั้นครับ และเคยอุทานในใจเบาๆว่า แกเป็นใครนะทำไมถึงนำเสนออะไรแบบนี้มาทำร้ายคนทั้งโลก???
นานวันเข้า ความคิดอีกฝั่งของผมก็บอกมาว่า ประโยคข้างบนเป็นคำบ่นหรือคำถาม
นั่นสิ!!!!! ถ้ามันเป็นคำถาม มันจะทำให้เราได้รู้จักตัวตนป้าแอนและเข้าใจว่าแกได้ทำอะไรลงไปนะ มันควรเป็นคำถามมากกว่าคำบ่น นั่นเลยเป็นเหตุผลที่ทำให้ผมเริ่มขุดเรื่องป้าแอน Anna Britt Agnsäter มากที่สุดเท่าที่จะทำได้ พร้อมที่จะอ่านกันแล้วใช่ไหมครับ
Anna Britt Agnsäter เกิดเมื่อปี 1915 ที่เมือง Älmhult ประเทศสวีเดน (นอกเรื่องนิดนึง เมืองนี้คือเมืองที่ให้กำเนิด IKEA ที่เรารู้จักกันดีเรื่องเฟอร์นิเจอร์ ที่นี่มีพิพิธภัณฑ์อิเกีย ซึ่งปรับปรุงมาจากโกดังแห่งแรกของเขาด้วยครับ) เรียกได้ว่า เกิดในช่วงสงครามโลกครั้งที่1 พอดีเลยครับ
ป้าแอน จบการศึกษาที่โรงเรียนสตรี ในเมือง Ystad ก่อนจะเข้ารับการฝึกสอนเพื่อเป็นครูสอนวิทยาศาสตร์ในครัวเรือน (rural domestic science teacher) ในช่วงปี 1930 ที่โรงเรียนวิทยาศาสตร์ในครัวเรือนในชนบทชื่อว่า Rimforsa ก่อนจะได้รับวุฒิการศึกษาการสอนวิทยาศาสตร์ในครัวเรือนในชนบทในปี 1939 จาก Kvinnliga medborgarskola (civic women’s school) จนกระทั่ง ปี 1943 ถึง 1945 เธอได้เดินทางไปทั่ว Norrland (พื้นที่ภาคเหนือของสวีเดน) โดยได้รับเงินสนับสนุนจาก Kooperativa Förbund (เรียกสั้นๆว่า KF หรือ สมาคมสหกรณ์ ก่อตั้งขึ้นในปี 1899 โดยสหกรณ์ผู้บริโภคในท้องถิ่น 41 แห่ง เป็นผู้นำด้านการค้าปลีกในสวีเดนโดยพัฒนารูปแบบร้านค้าใหม่และใหญ่ขึ้น และเป็นหนึ่งในกลุ่มธุรกิจหลักในสแกนดิเนเวีย ในสมัยนี้คำว่าสหกรณ์อาจจะดูเชยๆ แต่ต้องเข้าใจครับว่ายุคนั้นคือความก้าวหน้ามากๆ และต้องมีความรู้รอบด้านทั้งวิทยาศาสตร์ เศรษฐกิจ การเมือง) เพื่อบรรยายให้คนหนุ่มสาวและแม่บ้านฟังเกี่ยวกับวิธีรับมือกับเสบียงที่มีจำกัดในช่วงสงครามที่ตึงเครียด เนื่องจากอยู่ในภาวะสงครามโลกครั้งที่2

ในปี 1946 ป้าแอนได้รับการแต่งตั้งเป็นหัวหน้าของSwedish Cooperative Union หรือ Kooperativa Förbundets (KF) Provkök (experimental kitchen หรือ ภาษาสมัยนี้น่าจะใกล้เคียงกับ kitchen lab นั่นเอง) ซึ่งเป็นองค์กรที่มีอิทธิพลทางด้านอาหารเป็นอย่างมากในสวีเดน มีบทบาทสำคัญในเศรษฐกิจและสังคมสวีเดน โดยสร้างโอกาสให้แก่สมาชิกและส่งเสริมการพัฒนาที่ยั่งยืนในชุมชนต่าง ๆ ทั่วประเทศ
ป้าแอนทำงานที่นี่นานจนถึงช่วงปี 1980 ขนาดของ KF ก็ใหญ่โตขึ้นมากมาย จนขยายอำนาจและขอบเขตการทำงานไปถึงการเป็นคณะกรรมการทดสอบรสชาติซึ่งทดสอบอาหารกึ่งสำเร็จรูปและอาหารสำเร็จรูปใหม่ด้วย ในจุดนี้ ป้าแอน เล็งเห็นความสำคัญและความรับผิดชอบของผู้ผลิต/ผู้ค้าอาหาร ควรจะขยายความรับผิดชอบครอบคลุมไปจนถึงโต๊ะอาหาร (ในที่นี่น่าจะหมายถึงลูกค้า) นั่นคือเหตุผลที่การติดฉลากอาหารจึงมีความสำคัญมาก ป้าแอนได้มุ่งเน้นให้ความรู้กับผู้บริโภคว่า ‘Weigh up the price against the quality’ หรือ ให้ชั่งน้ำหนักพิจารณาให้ดี ระหว่างราคากับคุณภาพ ตลอดระยะเวลาการทำงาน Anna-Britt Agnsäter ได้รณรงค์เพื่อให้มีการแสดงข้อมูล ให้ผู้บริโภครับทราบ เพื่อคุณภาพชีวิตที่ดีขึ้นและได้ให้คำแนะนำด้านโภชนาการ เพื่อให้เข้าใจได้ง่ายขึ้น ในรูปแบบฉลากโภชนาการ
ในปี 1946 เช่นกันป้าแอนได้มีแผนในการทำ มีแผนที่จะผลิตหนังสือสอนทำอาหารสำหรับสถานการณ์ฉุกเฉิน เพราะบทเรียนในภาวะสงครามโลก ที่ป้าแอนผ่านมาตลอด แต่ไม่สามารถพิมพ์ออกมาได้เนื่องจากกระดาษขาดแคลนเนื่องจากอยู่ในภาวะหลังสงคราม
ในปี 1948-1949 ป้าแอนเดินทางไปอเมริกา เพื่อศึกษาเทคนิคการทำอาหารใหม่ๆ การผลิตภัณฑ์อาหารแช่แข็ง รวมถึงอาหารผงแห้งต่างๆ (dry powder) รวมไปถึงวิทยาศาสตร์การอาหาร (food science) ที่มหาวิทยาลัย Iowa State University การเดินทางมาอเมริกาครั้งนี้เปลี่ยนโลกของป้าแอนเป็นอย่างมาก ในตอนที่ป้าทำงานกับ KF เธอมักจะร่วมงานกับ Hemmens Forskningsinstitut (สถาบันวิจัยในประเทศ) เพื่อจัดหาเครื่องมือในครัวที่ยกระดับมาตรฐานการทำอาหารที่ดียิ่งขึ้น รวมถึงอุปกรณ์การครัว ภาชนะต่างๆที่เข้าเตาอบได้ และจากประสบการณ์ที่อเมริกานี้
ป้าแอนได้จับมือกับ โรงงานเครื่องเคลือบและพลาสติก Gustavsberg และ HFI Anna-Britt Agnsäter พัฒนาช้อนตวง ชุด4ชิ้น ที่วางซ้อนกันได้ ซึ่งเป็นการปฎิวัติวงการอาหารครั้งสำคัญของสวีเดน เรียกว่า “ชุดช้อนตวงมาตรฐาน” ซึ่งจะมีการระบุขนาดที่ชัดเจน 4 ชิ้น ประกอบไปด้วย

ซึ่งทำให้ผู้ใช้สามารถวัดปริมาณวัตถุดิบได้อย่างถูกต้องตามที่สูตรอาหารกำหนด กลายเป็นเครื่องมือที่จำเป็นในครัวเรือนและการประกอบอาหารในเชิงพาณิชย์
แม้การพัฒนา “ชุดช้อนตวงมาตรฐาน” นี้จะเริ่มต้นในสวีเดน แต่นวัตกรรมนี้มีผลกระทบที่กว้างขวางและแพร่หลายไปยังครัวเรือนและอุตสาหกรรมอาหารทั่วโลกจนถึงปัจจุบัน


ในชุดช้อนตวงมาตรฐาน original 4 คุณอาจสังเกตคำนึงที่ไม่ค่อยคุ้นสักเท่าไรคือหน่วย kryddmått
นอกจากชุดช้อนตวงมาตรฐานแล้ว ป้าแอนยังคิดค้นสิ่งต่างๆอีกมากมาย ให้กับวงการอาหารสวีเดน รวมถึงหน่วยวัดใหม่ที่เรียกว่า kryddmått นี้ด้วยครับ ซึ่งมันเป็นหน่วยวัดขนาดเล็กที่ใช้ในการตวงเครื่องเทศและวัตถุดิบปริมาณน้อย โดยหน่วยวัดนี้มีขนาด 1 มิลลิลิตร (ml)ซึ่งถูกกำหนดมาเป็นหน่วยที่เล็กที่สุดซึ่งทำให้มีการจดบันทึกสูตรได้แม่นยำยิ่งขึ้น นั่นเพราะว่า การตวงเครื่องเทศ หรือ เกลือ นั้นหากรสชาติที่เข้มข้น หรือมีการใช้มากเกินไปหรือไม่พออาจทำให้รสชาติของอาหารเปลี่ยนไป การใช้ kryddmått ช่วยให้การวัดปริมาณเครื่องเทศที่ใช้ในสูตรอาหารเป็นไปอย่างแม่นยำและสม่ำเสมอ
ถือว่าเป็นอีกผลงานคุโณปการที่ป้าแอน ฝากไว้ให้กับโลกนี้ มันมีส่วนสำคัญในการทำให้งานครัวเรือนง่ายขึ้นและมีประสิทธิภาพมากขึ้นผ่านการพัฒนาหน่วยวัดที่แม่นยำและสะดวกในการใช้งาน นวัตกรรมนี้ช่วยให้การทำอาหารเป็นไปอย่างราบรื่นและมีคุณภาพสูงยิ่งขึ้น

ในปี 1951 ป้าแอนได้บูรณะหนังสือการทำอาหารประจำสวีเดนใหม่ทั้งหมด (Vår kokbok) จุดประสงค์ของตำราอาหาร Vår คือการนำเสนอตำราอาหารราคาต้นทุนวัตถุดิบไม่แพง ที่ให้ความรู้เรื่องสารอาหารและใช้งานง่าย นอกจากนี้ยังเป็นการวางวัตถุดิบให้ได้รับสารอาหารที่เพียงพออีกด้วย เพราะในยุคนั้นสวีเดนมีข้อจำกัดในเรื่องอาหารเป็นอย่างมาก
เนื้อหาสูตรอาหารที่ใช้ในหนังสือเล่มนี้กลายเป็นบรรทัดฐานในช่วงทศวรรษ 1950 โดยมีการใช้หน่วยชั่งตวงแบบใหม่ ตามชุดช้อนตวงมาตรฐาน (ปริมาตร) จากของเดิมที่ใช้การชั่งน้ำหนัก ใช้ศัพท์ในการทำอาหารแบบเป็นสากล เช่น ขูด ปอกเปลือก ล้าง เป็นต้น (grate, peel, rinse) จัดอาร์ทเวิคให้แต่ละสูตร สามารถจบได้ในหน้าเดียวไม่ต้องพลิกอ่านหน้าต่อๆไป ทำให้สะดวกในการเปิดแล้วทำตาม การไล่ลำดับอาหาร เปลี่ยนจากการไล่ประเภทอาหาร ไปเป็นไล่ลำดับตามวัตถุดิบหลักของอาหาร ทำให้คนอ่านสามารถบริหารจัดการเมนูได้ง่าย เช่น ไก่ ก็สามารถไล่เรียงได้เลยว่า วันนี้มีไก่ จะทำอะไรกินดี
นอกจากนี้ยังรับประกันว่าทุกสูตรสามารถทำได้จริง เพราะป้าแอนลงมือทดสอบสูตรด้วยตัวเองทุกสูตร นอกจากนี้ยังคงมีการแนะนำให้ใช้การวัดอุณหภูมิในการทำอาหารด้วยเพื่อความเป๊ะในรสชาติ เนื่องจากป้าแอนเห็นตอนไปดูงานที่อเมริกา จนถึงทุกวันนี้ Vår kokbok เป็นหนึ่งในตำราอาหารที่ขายมากที่สุดในโลกด้วยยอดขายมากกว่า 2.3 ล้านเล่มนับตั้งแต่เริ่มต้น โดยเฉลี่ยมากกว่า 40,000 เล่มต่อปี


ด้วยความที่ Kooperativa Förbundets เป็นองค์กรที่มีอิทธิพลสูงมากในวงการอาหารสวีเดน และคุณป้าแอน ก็มีตำแหน่งที่สูงมาก จึงสามารถเป็นผู้มีส่วนสนับสนุนรูปแบบซูเปอร์มาร์เก็ตสมัยใหม่ ในการใส่รายการส่วนผสมและคำแนะนำในการปรุงอาหารในรูปแบบฉลากของผลิตภัณฑ์อาหารสมัยใหม่

จนกระทั่งในช่วงปี 1970 ประเทศสวีเดนต้องเผชิญกับปัญหาราคาอาหารที่สูงเนื่องจากเงินเฟ้อ รวมถึงสภาพอากาศของสวีเดนนั้น ไม่เอื้อต่อการได้รับสารอาหารที่หลากหลายได้ ครอบครัวที่มีเด็ก ไม่สามารถปรุงอาหารและรับประทานอาหารที่มีคุณค่าทางโภชนาการในราคาที่เหมาะสมได้ รัฐบาลจึงมอบหมายให้ Sweden’s National Board of Health and Welfare (คณะกรรมการสุขภาพและสวัสดิการแห่งชาติของสวีเดน) หาวิธีแก้ไขสถานการณ์ดังกล่าว และคัดกรองแบ่งประเภทอาหารออกเป็น “basic food” และ “supplement” มาเป็นรูปแบบของ กราฟวงกลม (diet circle) แต่ป้าแอนพบปัญหาบางอย่าง ที่ทำให้กราฟวงกลมนี้ใช้งานยาก เพราะการแบ่งปริมาณของอาหารแต่ละประเภทไม่ชัดเจน
ในระหว่างบรรยายเรื่องการกำหนดอาหารพื้นฐาน คุณ Fjalar Clemes หนึ่งในผู้เข้าร่วมการบรรยาย ได้ให้ไอเดียด้วยการสร้างแบบจำลองที่เรียกว่า ปิรามิดอาหาร (Food Pyramid) ขึ้นมา เพื่อให้เห็นภาพสัดส่วนอาหารที่ชัดเจนขึ้น ป้าแอนเลยนำข้อมูลจากกราฟวงกลมนั้น มาสร้างโมเดลจำลองให้อยู่ในรูปแบบปิรามิด โดยให้ “basic food” เช่น ขนมปัง มันฝรั่ง พาสต้า และนม และ “supplements” เช่น ผลไม้ ผัก เนื้อสัตว์ และปลา อยู่ในรูปแบบที่เข้าใจได้ง่ายขึ้น แม้แต่คนที่อ่านหนังสือไม่ออก

แต่นี่แหละที่เป็นจุดเริ่มต้นของปัญหา ด้วยความที่มันใช้งานง่ายสะดวก อเมริกาจึงนำไปปรับปรุงเป็นเวอร์ชั่นตัวเอง แต่ก็มีการเปลี่ยนแปลงไปอย่างมาก ตามที่ได้มีการทำบทความไปแล้ว (อ่านที่นี่)
ทั้งๆที่ปิรามิดต้นแบบของป้าแอนนั้น สร้างขึ้นมาเพื่อชาวสวีเดนเนื่องจากนำข้อมูลพื้นฐานจากข้อจำกัดในประเทศในขณะนั้น ไม่ว่าจะเรื่องของวัตถุดิบที่หาได้ในภาวะยากแค้นแบบนั้น อุณหภูมิอันปรวนแปร รวมถึงสภาพเศรษฐกิจที่ย่ำแย่มาก การจัดแจงข้อจำกัดที่มีเพื่อให้ได้สารอาหารที่เพียงพอที่สุดเท่าที่จะทำได้ต่างหาก (eat healthier, more affordable and save on fat) ที่เป็นที่มาของ “ปิรามิดอาหารของสวีเดน” (คือ จะให้เอาอุดมคติมาสร้างปิรามิดอาหาร คงไม่มีประโยชน์ เพราะยังไงก็ไม่มีเงินซื้อและหาวัตถุดิบไมไ่ด้ตามอุดมคติ วัตถุประสงค์ในการสร้างและเผยแพร่ครั้งนี้มันเพื่อให้ประชาชนทั้งประเทศที่มีความรู้ด้านอาหารน้อย รู้และทำตามได้จริง สมกับพื้นที่และกำลังทรัพย์ // ความเห็นส่วนตัวผมครับ)
ปิรามิดอาหารที่แท้จริงแล้ว จะมีการปรับปรุงตลอดเวลา ตามปัจจัยที่เปลี่ยนไป ไม่ใช่ปิรามิดที่เอาไว้ยึดถือตลอดไป แต่การที่อเมริกานำไปยึดถือว่าเป็น all time information เป็นค่าคงที่ให้ทั้งโลกยึดตาม รวมถึงสร้างด้วยเบื้องหลังด้านธุรกิจ จึงต่างกับที่ป้าแอนทำในทุกมิติ แต่ไฉน เป้าการบูลลี จึงต้องไปตกที่ป้าแอน ว่าเป็นต้นตอความพังของสุขภาพ มันแฟร์แล้วหรือ
เรื่องนี้มีข้อพิสูจน์ได้จนถึงปัจจุบันเช่น ในปี 2022 ก็มีการนำเสนอ ปิรามิดอาหารสำหรับ Mixed diet, flexitarian, vegetarian และ vegan ออกมาสืบทอดเจตนารมณ์ป้าแอน นอกจากนี้ในช่วงที่ป้าแอนมีชีวิต ก็ยังคงมีการช่วยเหลือแนะนำให้ประเทศต่างๆ “มีปิรามิดอาหารของตัวเอง” นั่นคือ วิชั่นที่กว้างไกลของป้าแอน ที่เห็นได้ชัดเจนว่า อาหารพื้นถิ่นกับสารอาหารที่สมดุล ของแต่ละประเทศมีความไม่เหมือนกัน และแนวคิดนี้ได้มีทั้ง เดนมาร์ก, นอร์เวย์, ฟินแลนด์, ญี่ปุ่น, ศรีลังกา ได้นำไปพัฒนาใช้เช่นกัน
นอกจากนี้ ป้าแอนและองค์กร Kooperativa Förbundets ยังให้ข้อมูลการศึกษาที่สำคัญสำหรับประชาชนผ่านบทความเกี่ยวกับอาหารที่ตีพิมพ์ใน นิตยสาร Vi รวมถึงการจัดตั้งกลุ่มการศึกษาร่วมกับทาง สมาคมการศึกษาของชนชั้นแรงงาน หรือ Arbetarnas bildningsförbund (ABF) มีส่วนสนับสนุนในการอภิปรายแบบเปิดทางสังคมเกี่ยวกับปัญหาโรคอ้วนอีกด้วย รวมถึงยังออกหนังสือเกี่ยวกับการทำอาหารอีกร่วมๆ 30เล่ม ซึ่งรวมถึงบทเกี่ยวกับมื้ออาหารที่มีคุณค่าทางโภชนาการที่สมดุล ด้วยเช่นกัน

ในปี 1983 ป้าแอนได้ตีพิมพ์หนังสือ Matboken ซึ่งได้รับการพิสูจน์แล้วว่าเป็นประโยชน์อย่างมาก โดยเฉพาะกับคนหนุ่มสาวเกี่ยวกับวิธีการกินอาหารที่มีคุณค่าทางโภชนาการและมีวิธีทำที่เรียบง่ายที่สุด

ในช่วงทศวรรษ 1990 เมื่อป้าแอนเป็นม่าย จึงได้ย้ายเข้าไปอยู่ในบ้านพักคนชรา Färdknäppen ใน Södermalm ในสตอกโฮล์ม และ ได้แก้ไขสูตรอาหาร 250 สูตรจาก Vår kokbok เพื่อให้เหมาะสมกับสภาพแวดล้อมการปรุงอาหารส่วนกลางของบ้านพักคนชรา เพื่อให้ได้อาหารที่มีสารอาหารครบถ้วนตามที่ควรเป็น
เกียรติประวัติป้าแอนได้รับการตอบแทนดังนี้ ในปี 1979 ได้รับรางวัลเหรียญ St Erik เพื่อเป็นการยกย่องสิ่งที่เธอทุ่มเทแรงกายแรงใจทำมาตลอดชีวิต ในปี 1993 ได้รับเหรียญ HM Konungens ลำดับที่ 8 (HM The King’s Medal หรือ H.M. Konungens medalj ในภาษาสวีเดน) เป็นหนึ่งในรางวัลเกียรติยศที่สำคัญที่สุดที่มอบโดยพระมหากษัตริย์สวีเดนเพื่อยกย่องบุคคลที่มีผลงานดีเด่นหรือมีความโดดเด่นในด้านต่าง ๆ เช่น วิทยาศาสตร์ ศิลปะ วัฒนธรรม และการบริการสาธารณะ ในปี 1995 ได้รับเหรียญทอง Albin Johansson สำหรับผลงานอันทรงคุณค่าของเธอต่อสหกรณ์สวีเดน ในปี 1998 ได้รับรางวัล Gastronomiska Akademiens Guldpenna (ปากกาทองของสถาบันอาหาร) สำหรับบทความเกี่ยวกับส่วนผสมและการทำอาหารของเธอ

Anna-Britt Agnsäter เสียชีวิตในปี 2006 (อายุ 90ปี) ป้าแอนทำงานทั้งชีวิตเพื่อสอนชาวสวีเดนในการจัดการอาหารให้ดีขึ้น ทุกการทดลอง ทดสอบ ได้มีการบันทึกไว้อย่างชัดเจนสามารถพัฒนาต่อไปได้ การริเริ่มให้ข้อมูลที่ซื่อสัตย์ต่อผู้บริโภค ทั้งการติดฉลากอุปกรณ์ คำแนะนำในการทำอาหาร สูตรอาหาร บทความ และตำราอาหาร สิ่งเหล่านี้กลายเป็นพื้นฐานสำคัญในอุตสาหกรรมอาหารจนปัจจุบัน
แต่ทุกวันนี้วงการสุขภาพส่วนมากยังคงล้อเลียนเธอว่าเป็นครูธรรมดา ที่มีหน้ามาสร้างปิรามิดอาหาร จึงทำให้คนทั่งโลกป่วย ทั้งที่ความจริงทั้งหมดนั้น ความรู้ของป้าแอนไม่ได้น้อยไปกว่า ผู้เชี่ยวชาญทางวิทยาศาสตร์การอาหาร ซึ่งในสมัยนั้นนับว่าเป็นอีกแขนงที่อยู่ในระดับบนของการศึกษา ไม่ต่างกับวิทยาศาสตร์อื่นๆ ปิรามิดควรเป็นไปตามถิ่นที่อยู่ สภาพเวลาและสภาพเศรษฐกิจขณะนั้น ไม่ใช่การสร้างมาตรฐานให้ต้องทำเหมือนกันทั่วโลก โดยมาจากอิทธิพลของกลุ่มธุรกิจดังที่ usda ได้ทำการแก้ไขก่อนจะประกาศให้คนทั่วไปยึดถือ รายละเอียดเป็นไปตามที่สืบค้นข้อมูลประวัติของป้าแอน มาเล่าสู่กันฟัง ณ วันนี้ครับ
ผมก็เป็นหนึ่งในนั้น สิ่งที่ผมสามารถทำได้เพื่อเป็นการขอโทษคุณ Anna-Britt Agnsäter ที่ดีที่สุดที่ทำได้ตอนนี้คือ เผยแพร่ประวัติอันทรงคุณค่าของเธอ ให้คนอื่นๆได้รับทราบมากที่สุด เท่าที่จะทำได้
โปรดแชร์ เพื่อคืนความเป็นธรรมให้ Anna-Britt Agnsäter ให้โลกได้เข้าใจและรับรู้ถึงการอุทิศชีวิตให้วงการอาหารของคุณป้าครับ
ปล.มีการค้นพบไฟล์เสียง ที่ป้าแอน จัดรายการวิทยุในปี 1968 ให้ลองฟังกันครับ (น่าจะภาษาสวีเดนนะ 5555) ฟังได้ที่นี่ครับ https://rumble.com/v56p1wa-ann-britt-agnster-in-a-radio-find-from-1968.html
siamstr #pirateketo
-
 @ ad6a909b:589fb93c
2024-07-13 23:37:38
@ ad6a909b:589fb93c
2024-07-13 23:37:38
 Former President Donald Trump was taken off stage by the Secret Service at a Pennsylvania rally on Saturday after loud cracking noises were heard.
Former President Donald Trump was taken off stage by the Secret Service at a Pennsylvania rally on Saturday after loud cracking noises were heard. -
 @ 6c8c7979:15595f3e
2024-07-13 01:55:06
@ 6c8c7979:15595f3e
2024-07-13 01:55:06Rococo is a style in interior design, decorative arts, painting, architecture, and sculpture, originating in Paris in the early 18th century. It quickly spread throughout France and later to other countries, primarily Germany and Austria.

Palace of Versailles - France
$$The origin of the word "Rococo"$$The term Rococo was first used by the designer Jean Mondon in his book "First Book Of Rococo Form And Setting" in 1736, where he used it alongside illustrations depicting the style used in architecture and interior design.
The word Rococo combines the French word "Rocaille," meaning shell, which was used to describe fountains and grottoes in gardens adorned with pebbles and shells, and "Barocco," the Italian word for Baroque, the art style preceding Rococo. Rococo art is characterized by curved forms resembling shells and wave-like ornaments.

One of the most famous paintings by the artist François Boucher is "The Swing" (La Balançoire), painted in 1767.
$$How Rococo Art Emerged$$With the death of King Louis XIV of France in 1715, one of the greatest French monarchs known for his lengthy reign and cultural influence, France was left economically and militarily powerful, setting it as a cultural beacon in arts, fashion, and culture. His successor, King Louis XV, in contrast, faced challenges and mismanagement, leading France toward bankruptcy with extravagant spending and failed policies. Despite this, his reign fostered an era of lavish court entertainment and artistic patronage, contrasting sharply with his predecessor.
Rococo art developed an aristocratic flavor, adopted by rising upper-middle-class individuals emulating the French nobility's fashion and lifestyle, known as the bourgeoisie. The period, spanning roughly from Louis XIV's death to the French Revolution in 1789, marked an era more than a defined style. Aristocrats in France imposed Rococo artistic style, constructing more elegant homes and commissioning interior decorations for palaces. Unlike its predecessor Baroque art, which was less suited for intimate and comfortable home decor, Rococo allowed for artistic rebellion.
Rococo paintings offered a unique glimpse into the lives of the French upper class in the decades preceding the French Revolution, though it didn't reflect the political and economic realities of the era and largely ignored working-class issues. While intricate Baroque architecture thrived in France, Italy, England, Spain, and South America, softer Rococo styles were prevalent in Germany, Austria, Eastern Europe, and Russia, mainly focusing on interior and exterior design.
$$Information about Rococo Art$$Rococo art, termed by some historians as the late phase of Baroque but lighter and more delicate, was employed by artists and designers in interior design and the arts.
The Rococo era was considered a revolution against the formal Baroque designs that characterized the French royal court at Versailles, emphasizing comfort, warmth, and intimacy.
Rococo is distinguished by its softness, playfulness, imagination, and whimsy compared to its more serious predecessor, Baroque. Ornamentation was used to create a sense of flow, especially through abstract and asymmetrical details.
This art style was influenced by Asian motifs such as Chinese design, influenced by trade relations with the Far East, leading to more modern decorative works. Interior decor and its components formed a harmonious unity, giving a unified impression, with great effort put into selecting furniture shapes, placements, and decorations.
Wealthy property owners renewed their homes' interiors with Rococo-style plasterwork, murals, mirrors, furniture, and porcelain, characterized by a delicate, feminine touch, while maintaining Baroque architecture on the exterior.
In Rococo decor, large candelabra, beautiful chandeliers, and wall sconces stand out to create a warm atmosphere, complemented by luxurious gilt-framed mirrors with floral motifs, enhancing a sense of openness in spaces.
$$Architecture$$As the fundamental principle in Rococo architecture was to achieve the purpose of celebration, in the early 18th century, the aim of construction was festive. French aristocrats ceased gathering at the royal court and palaces of kings, instead opting to enjoy themselves in private palaces intended as venues for parties, incorporating complex, ornate, and asymmetrical styles that imparted a sense of joy and whimsy.

The Fountain of Fountains (Fontänebnlo): A stunning water sculpture located in Munich, Germany, considered a masterpiece of Rococo art, and was part of the design for the Nymphenburg Palace.
$$Art of Painting$$Painters used pastel colors, flowing lines, and non-symmetrical shapes, with many artworks characterized by off-center compositions, meaning the overall design or arrangement was asymmetric or whimsical. Each element contributed to creating a sense of movement and playfulness within the painting, depicting mythical scenes set in imaginative landscapes and images of love as well.
$$Themes Embraced by Rococo$$Rococo paintings did not address national issues, religious piety, morality, saints, or heroes, nor did they provoke deep thought. They depicted outdoor scenes for leisurely activities, lovers in romantic encounters, and playful behavior with a sense of humor. These artworks were created for aesthetic purposes and to please the viewer's eye.

One of the most famous Rococo painters was the French artist Jean Antoine Watteau, and his painting "Les Plaisirs Du Bal" is considered exemplary of the early Rococo period.
$$Rococo in Germany$$aristocrats and nobles desired their palaces to be venues for celebrations, similar to the French. One of the notable examples is the construction of Amalienburg Palace, originally a hunting lodge within the grounds of Nymphenburg Palace in Munich. It was commissioned by Holy Roman Emperor Charles VII and his wife Maria Amalia, designed by architect François de Cuvilliés and decorated by painter Johann Baptist Zimmermann between 1734-1739. The building is distinguished by its smooth lines, intricate designs, and light pink color.

Amalienburg
Moving inside the palace, one must pause at the Hall of Mirrors, a circular room at the center of the building surrounded by mirrors. It is filled with decorations of gold and silver on the walls, featuring motifs of leaves, flowers, birds, and small cupids. Its design is intricate, vibrant with life and movement.

Inside the palace - Hall of Mirrors
Critics dubbed this art as frivolous, appearing only to vanish, and condemned it for its superficiality, with some even labeling it as failed art, leading to a backlash against it. This resulted in a strong reaction from intellectuals like Voltaire. By the mid-18th century, the popularity of Rococo art began to decline in France, and interest waned across Europe.
-
 @ 3cd2ea88:bafdaceb
2024-07-12 22:33:49
@ 3cd2ea88:bafdaceb
2024-07-12 22:33:49Siamo entusiasti di annunciare il lancio di DOGS POINTS (DOGS) nel trading pre-market su Bitget! 🎉 Gli utenti possono ora iniziare a scambiare DOGS POINTS prima che diventi disponibile per il trading ufficiale.
🐶 Un po' di background su DOGS POINTS:
L'immagine di DOGS è ispirata a Spotty, la mascotte creata dal fondatore di TON, Pavel Durov, per la comunità di Telegram. Questa moneta non è solo per divertimento, ma tutti i ricavi delle vendite sostengono orfanotrofi e case per bambini, continuando l'eredità benefica di Spotty. ❤️
👉 Non perdere questa opportunità unica! Unisciti ora al trading pre-market su Bitget e sostieni una buona causa. Iscriviti ora e inizia a scambiare: https://bonus.bitget.com/U1JNEK
👉 Non sei andato a riscattare il tuo AirDrop su Telegram? Vai subito a vedere quanti DOGS puoi ricevere! https://t.me/dogshouse_bot/join?startapp=y5J61rnXSU2wW2ruadnJNA
-
 @ 617f0a85:b403d1ed
2024-07-12 21:03:19
@ 617f0a85:b403d1ed
2024-07-12 21:03:19For the last several weeks we've been meeting on Thursday evenings to chat about projects people are working on, cool new things in crypto, and generally just having a good time. As we all have busy schedules and lots of meetings, it is important to keep things informal and give people the space to share freely. Please join us and connect with some great builders.
This weekly happy hour is hosted by Chones which is hoping to weave together communities in web3 and make the things happen that often are not appreciated but make a big difference. Hosting the happy hour is a way to expose builders to new projects and learn about what else is happening in the space for those who are heads down working on their stuff. There is so much going on, keeping track of it all is impossible for anyone, so let's do it together.
If you're interested in attending, let me know and I'll let you know when and where we meet. We're looking to move to hivetalk.org after getting everyone on the same page. Hope to see you there.
chones
-
 @ 1aa437b3:51119dbd
2024-07-13 17:36:28
@ 1aa437b3:51119dbd
2024-07-13 17:36:28I have been using Proton for some time now. They provide many services I use.
- Calendar
- Drive
- Passwords
- Email Aliases (SimpleLogin)
- Notes - in progress
The issue I am seeing is all my eggs are all in one basket basically. Everything belongs to one vendor. Though convenient, I don't think it's necessarily good for things in the long run. So I am breaking things up.
Here is the plan broken down as listed above.
- Mail & Calendar - I am moving back to Fastmail which I used for over five years before I switched to Proton. I've come to the realization that for now at least, encrypted email really isn't needed. Fastmail is a much better solution and will cover mail, contacts, and calendar. And of course I will still have my proton account if I need encryption.
- pCloud - I've actually had a lifetime 500 gigs with encryption which I actually use more than Proton Drive since Proton doesn't have a Linux client.
- Passwords - I used 1Password in the past, and I think I am going to return to them. Using them to manage SSH keys has always been a game changer, so it's worth going back to them.
- Email Aliases - SimpleLogin is hard to beat, but Fastmail does provide this service, I just have to redo my current aliases for Fastmail's format. I can keep Simplelogin as a stand alone app so I don't have to rush the transition.
- Notes - So I have been using Standard Notes for almost five years. I've been grandfathered into a super low priced package, but Proton owns them now and I don't know if stand alone will be available outside of Proton in the future. But in order to separate the eggs, I am set up a Joplin server and moved to self hosting my own notes.
Well this is sort of the game plan. I'm working on implementing it over this weekend. Will update if there are any other modifications needed.
-
 @ c73818cc:ccd5c890
2024-07-13 16:15:27
@ c73818cc:ccd5c890
2024-07-13 16:15:27
🧙♀️ Piani Ambiziosi per Hamster Kombat
🧙♂️ I fondatori di Hamster Kombat, rimanendo anonimi, hanno delineato i loro ambiziosi piani per il futuro del gioco. Tra le principali iniziative ci sono due airdrop programmati e un obiettivo dichiarato di raggiungere un miliardo di giocatori globali.
🧙♀️ Primo Airdrop in Arrivo
🧙♂️ Il primo airdrop di Hamster Kombat è previsto per questo mese e rappresenta un passo fondamentale nella strategia di crescita del gioco. Questo evento mira ad attrarre nuovi utenti e a distribuire i token di gioco agli attuali partecipanti.
🧙♀️ Sfide e Visioni per il Futuro
🧙♂️ Oltre agli airdrop, i fondatori di Hamster Kombat si concentrano sulla creazione di una comunità globale intorno al gioco. Hanno dichiarato di volere una “famiglia mondiale” di giocatori e di puntare all’alfabetizzazione finanziaria attraverso il mondo della blockchain e del Web3.
Unisciti al nostro gruppo Telegram: https://t.me/Bitcoin_Report_Italia
Referral Bitget -10% sulle fee + bonus benvenuto 6w5d o link: https://bonus.bitget.com/U1JNEK
BitcoinReportItalia #Hamster #Kombat #Airdrop #TON #HMSTR #Telegram #Blockchain #Tap #Game #Cripto #Bitcoin
-
 @ b6dcdddf:dfee5ee7
2024-07-12 20:15:22
@ b6dcdddf:dfee5ee7
2024-07-12 20:15:22🚀 Exciting News: Introducing Project Affiliates!
Creators can finally reach a wider audience by partnering with affiliates!
Affiliates earn automated payouts for contributions enabled through their shares. 🤑
Announcement link: https://x.com/geyserfund/status/1811434402041282680
originally posted at https://stacker.news/items/606500
-
 @ 7175188c:6382a72c
2024-07-12 20:02:24
@ 7175188c:6382a72c
2024-07-12 20:02:24originally posted at https://stacker.news/items/606482
-
 @ 30e8cbf1:74fccbaa
2024-07-13 14:51:59
@ 30e8cbf1:74fccbaa
2024-07-13 14:51:59Establishment economists, both in the Keynesian and Modern Monetary schools, argue that increasing the money supply is not the cause of consumer price inflation. As Figure 1 and Figure 2 show, the broad money supply has increased by 345% from 2000 to 2024, while the Consumer Price Index has only increased by 83% in the same period. This analysis obscures the fact that the ascension of China into the World Trade Organization (WTO) in December of 2021 put significant downward pressure on prices of many consumer goods.
Figure 1: M2 Money Supply from 2000 to 2024

Figure 2: CPI from 2000 to 2024

As goods production moves from a location with a high cost of labor to another location with a low cost of labor, one would assume that the price of final products would fall. This is what would happen in an economy with sound money, where efficiencies in production result in lower prices. However, we live in an economy where Central Bankers have the power to increase the money supply to achieve “price stability” which they define as a steady (usually 2%) increase in year-over-year prices of a basked of consumer goods.
The once in a lifetime transition of Western manufacturing offshore (particularly to China) resulted in a “problem” for central bankers. They must adjust monetary policy to counteract the falling price of consumer goods, which we saw in the “too low” inflation rates of the 2000s and 2010s decades. In fact, Central Bankers were forced to increase the money supply enough that final prices went up despite the rapidly falling actual prices of goods.
Figure 3: Consumer Electronics Prices from 2000 to 2024

This brings us to our conclusion: the disconnect between the increase of the money supply and consumer price inflation was due to the rapid fall in actual cost of consumer goods caused by the one-time movement of supply chains through globalization. This price cannot be repeated in the future. The true relationship between money supply and consumer prices is going to be re-established and cannot be denied by the establishment anymore.
-
 @ ab8cb80e:5395d502
2024-07-12 14:21:14
@ ab8cb80e:5395d502
2024-07-12 14:21:14Hey, I have nothing to do this Friday evening, so why not chill with chess?
Spontaneously I launched an Arena Tournament for today: https://lichess.org/tournament/2iNa8jh4
@ek @kristapsk @BitcoinAbhi @grayruby @frostdragon @Taft @02d43d3798 @030e0dca83 @riberet19 @felipe @didiplaywell @SatsMate @itsTomekK @wize123 @Coinsreporter @stefano @anon @314piepi @160ed04091 do you want to play?
! TODAY ! ♟️ https://lichess.org/tournament/2iNa8jh4 ♟️ 90 min arena, with 5 minute games.
Join on @Alby's new Discord: https://discord.gg/3vbafUCZ?event=1261325278358016091 for voicechat I plan to stream it to zap.stream, because why not.
Who takes my challenge?
originally posted at https://stacker.news/items/605942
-
 @ 1739d937:3e3136ef
2024-07-12 10:11:42
@ 1739d937:3e3136ef
2024-07-12 10:11:42This is the third in a series of weekly updates detailing progress on bringing MLS protocol DMs and group messaging to Nostr.
Previous Updates
Progress this week
Short update post this week but I made solid progress updating several OpenMLS dependencies and building a new library that implements all the OpenMLS crypto requirements for Nostr.
HPKE-RS
I mentioned a PR last week on the
rust-hpkelibrary, that PR is still waiting on review. However, in the meantime, the OpenMLS library depends on a slightly different hpke library, thehpke-rslibrary.This library didn't support the secp256k1 curve either so I've opened a PR to add support for secp256k1. That PR uses the
RustCryptolibrary that is the default in the thehpke-rslibrary. However, because this library is built to allow for swapping out the underlying crypto library (using traits), I was also able to create a new library that uses thesecp256k1library instead of theRustCryptolibrary. This is the main crypto library that almost all Bitcoin and Nostr apps use so it's important we use that instead ofRustCrypto.OpenMLS Nostr Crypto
The library that I've created (openmls-nostr-crypto) does a few things via separate sub-libraries (crates). The entire library tries to do as little as possible; only implementing the one required ciphersuite for all MLS implementations and the
secp256k1schnorr signatures ciphersuite I've created for Nostr. It's also using the rightsecp256k1library to do it.openmls-nostr-crypto: implementes the crypto traits that the OpenMLS library expects to find for a given provider and removes all the ciphersuites that we don't care about supporting.
hpke-rs-nostr-crypto: This implements the crypto traits that the hpke-rs library expects to find. Again removing all the ciphersuites we don't care about supporting.
I've not yet written any tests for these libraries (which needs to be done) but I've gotten some very simple demos working with OpenMLS using this new set of libraries to handle the crypto.
I've been really impressed with the simplicity of the OpenMLS interface as well. While there is A LOT going on under the hood, the public interface that client developers have to use is clean and simple.
Onward and Upward
Next week I'll continue working on these libraries; adding tests and continuing to build out my small demo app. I've been in touch with the maintainers of the OpenMLS library and I'm hoping to get a review done with them on my PRs and on my new library.
One thing I'll call out here: The review of my library and getting them to review the direction of the project overall will be paid consulting so I'm making sure that I've got as much done as possible before scheduling that time and paying their rates. I'm a strong believer that the right conversation can save you months of wasted time, but I'm also a believer in making sure you're prepared if you're going to drop money on that conversation. 😅
-
 @ 30e8cbf1:74fccbaa
2024-07-13 14:39:51
@ 30e8cbf1:74fccbaa
2024-07-13 14:39:51What is the best form of government? Aristotle writes of three correct regimes, Monarchy, Aristocracy, and Polity, as well as their three deviant counterparts in Tyranny, Oligarchy, and Democracy. Plato famously described an ideal republic led by philosopher kings with three strictly separated social classes. The Roman republic conquered most of the known world before transforming into an empire going through the phases of Principate and Dominate. Medieval kingdoms saw the separation of the spiritual and temporal power between the church and the monarch. Our current forms of liberal government saw their rise in the early modern period with the transition to constitutional republics and constitutional monarchies.
What was so special about written constitutions that led to the revolutionaries of 1776, 1789, and 1848 to demand them as the bedrock of their political reforms? Put simply, written constitutions represent faith in rules not rulers.
In the battle of letters and ideas that proceeded and accompanied these revolutions, reactionaries put forth arguments in defense of absolute monarchy that parallel many arguments for fiat-based central banking we see deployed against Bitcoin today. I think this parallel gives us some insight into the monetary revolution we are living through, and how it may be as world changing as the political revolutions of the 18th and 19 centuries.
The primary argument in the defense of despotism is that a ruler unencumbered by the need for consent of the governed can focus on the long-term health of the nation. With the nation as his personal property, the king must want to see its flourishing and acts as a father figure, imposing unpopular actions in the present which he tells us will improve our fortunes in the future.
The central bank needs to be able to make policy without short term political concerns. - Ben Bernanke
The second argument is that binding the king to the strict rules of the constitution would leave him without the flexibility to respond rapidly to some future crisis. Why does the king need to go through a cumbersome process of gaining the consent of the governed when some emergency might require his immediate action?
"In facing the unpredictable nature of economic shocks, central banks must be equipped with a broad toolkit and the agility to deploy measures that can effectively address emergent threats to stability. Our experience underscores the critical need for readiness and the ability to adapt strategies in real-time." - Janet Yellen
The third argument is that the king is somehow enlightened, either by his noble birth or divine appointment. We’re led to believe that the wise king sees farther than us and despite being unpopular in the present, will eventually be proven right.
The Federal Reserve Board employs more than 500 researchers, including more than 400 Ph.D. economists, who represent an exceptionally diverse range of interests and specific areas of expertise. Board researchers conduct cutting edge research, produce numerous working papers and notes, and are among the leading contributors at professional meetings and in major journals. Our researchers also produce a wide variety of economic analyses and forecasts for the Board of Governors and the Federal Open Market Committee. - federalreserve.gov
Like the early modern revolutionaries, Bitcoiners reject these arguments wholeheartedly. We recognize that every person and institution is motivated to some degree by personal self interest and a ruler unencumbered by rules will eventually expropriate the wealth of the nation for his own benefit. In order for any system affecting multitudes of people to preserve liberty, some fixed set of rules must be articulated and enforced on all parties. These rules should be public and subject to audit, ensuring that each individual can understand how the rules protect him through the use of his own reason.
The Bitcoin software is open source, simple, and well understood. A person need only study it to reach the inevitable conclusion that the fixed supply, cryptographic protections, and proof of work consensus system preserve his liberty and property while interacting with the wider ecosystem. The Bitcoin rules are applied with absolute equality. While modern liberal governments claim “no one is above the law” we see in fact that public officials and rich individuals rarely receive the same legal scrutiny as the average citizen.
It is impossible to know the future, and whether one set of rules will remain adequate in perpetuity. The political revolutionaries and Satoshi Nakamoto prepared for this eventuality with the same solution. The rules may be changed, but only with overwhelming consensus among participants. No emergency, however dire, justifies an immediate and unilateral change to the rules. Only long deliberation and wide public engagement can reach the threshold necessary to change the system.
Despite these lofty Liberal ideas, we see that constitutional governments in practice do not preserve liberty to the absolute degree envisioned by the revolutionaries that brought them into being. Too often the governed are frightened into believing the old arguments for despotism, where each emergency justifies some unpopular usurpation of the people’s freedom. In the most egregious example, governments have chartered central banks totally outside the constitutional order with the same arguments for “long term thinking”, “flexibility”, and “expertise”.
These breeches of the written rules are slipped in through the weak consensus of civic engagement. Citizen preferences are attenuated through their self interested representatives. Continuous energy and attention is required to identify rule violations and fight against them. By moving the enforcement of rules onto computers, Bitcoin alleviates this problem. Our nodes are always vigilant and decisive in identifying and rejecting violations of the rules.
The march of liberty is far from complete after centuries of struggle. We see in this monetary revolution the echos of political revolutions past that unlocked some freedom for each individual from arbitrary despotic rule. We must continue on.
-
 @ 0dc2dcb1:4787801a
2024-07-12 13:52:51
@ 0dc2dcb1:4787801a
2024-07-12 13:52:51- Prepared a Dutch webinar with an short introduction to Nostr - https://welkom.keuzevrijbijmij.nl/evenement/wwebinar-vergroot-je-privacy-op-social-media-10-juli/

- Received a nice t-shirt with the Nostr-PHP logo from Bitpopart who designed the logo
- Did an introduction talk in Dutch on a webinar with 350+ people subscribed on July 10th. 100+ watched the webinar live.
- Here is the full replay: https://keuzevrijbijmij.webinargeek.com/watch/replay/3487925/f29f93e939ffce35ac4593e407d03a9e/
At around 38min the Nostr stuff begins
- Here is the full replay: https://keuzevrijbijmij.webinargeek.com/watch/replay/3487925/f29f93e939ffce35ac4593e407d03a9e/
- Adding pages and wrote some documentation on nostr-php.dev
- Added a custom field
field_nsecto the user entity on nostrver.se (Drupal website) using the contrib module field_encrypt. The value of this field is stored encrypted in the database using a self created private key. This key is stored as a blob the server, but multiple ways of storing this are possible. In the Drupal CMS I now can save a Nostr private key for each user which will be fetch from nostr_content_nip23. All changes made in this Drupal contrib module for this: https://git.drupalcode.org/project/nostr_content_nip23/-/commit/cbc172b976aceaff107fea0296a8a476e098467e -
With a
nsecstored for each user, it’s possible to select a user when you’re broadcasting an Nostr event from Drupal. The event will be signed with the nsec of the selected user. Quick demo here: https://njump.me/nevent1qvzqqqqqqypzqpnrnguxe8qszsshvgkvhn6qjzxy7xsvx03rlrtddr62haj4lrm3qy88wumn8ghj7mn0wvhxcmmv9uq3camnwvaz7tmwdaehgu3wwdjkyctnw35hstnnda3kjctv9uqzqj75dy5eps3lgwum7f9p2l8sywy7wuxjr08pyhzyzv9mklylaydgdyll3z
-
 @ dd664d5e:5633d319
2024-07-10 15:00:40
@ dd664d5e:5633d319
2024-07-10 15:00:40The Law Giver
In my previous article, I briefly went into the topic of how contract law is holy law.
The Father of the Christians, you see, is a God of Covenants, and He sent His Son to Earth to fulfill the Law and pay a Price for our salvation. The Father also created the Natural Order to confirm His Laws through our observation of that Law in action.
That is why Christians have a deep respect for honest contracts, true prices, fair measures, natural systems, and good laws. Not merely for their own sake, but also because understanding them helps us to understand and emulate the Law Giver.
The tired What would Jesus do? meme is actually an attempt to capture this emulation of the Highest Judge. Jesus knows the Law, since His Father defined it and He is One with the Father, so how would He apply the Law best, in this situation?
The Last Things
Working together with him, then, we entreat you not to accept the grace of God in vain. For he says, “At the acceptable time I have listened to you, and helped you on the day of salvation.”
Behold, now is the acceptable time; behold, now is the day of salvation.
-- 2 Corinthians 6:1-2 New Testament, RSV Bible
One of the things most devout Christians frequently ruminate over, is when Christ will return.
Every day, we ponder. We go for a walk, and ponder. We cook dinner, and ponder.
At the same time, we are called upon to live each day in a productive manner, and to not simply lie around, vegetating, and staring at the heavens. Not only for our own sake, but also because to do so would be to limit our ability to inform others about the Good News, so that they can take to pondering with us. We are called to ponder with as many people as we can produce, adopt, convert, or simply collect through our daily interactions.
This means that we are not of the world (as our eyes are watching God and baptism has made us Immortals), but we are definitely in the world (involved in, and effected by, the everyday dealings around us.) It is a very difficult balancing act to know when we are paying too much attention to the one or the other, or to know where to store up our treasures, if we can't put them all immediately into the Final Treasury.
So, we worked today and earned a bit of fiat cash and we have no immediate usage for it. What to do with it?
Well, some of it should go to charity or be invested in a business that provides important goods, services, and employment. Some of it will be needed to simply cover the day-to-day costs of our own life, or that of those dependent upon us. But it might be prudent to store up some of it, for the mysterious length of time between receipt of the monies and our own ascent into Heaven.
Typically, that store was the local currency, but that's being inflated away at an alarming rate. Then we all began to move to precious metals, and many of us still do, but they are so difficult to spend and can't be broken into small bits or transported over wide distances at low cost.
Enter Bitcoin.
The Great Ledger
In our frustration, more and more Christians are turning to a new technology, to save up some treasure in a liquid asset, for the mid-term. And, once we begin using it, and begin to understand how it works, we quickly grow fond of it.
Bitcoin is a beautiful money because it is a money based upon keeping precise accounts, using a fair measure, and obeying the Laws of Nature.
In essence, Bitcoin is a debt note emitted by a universal debtor (the network) in exchange for some good or service. This frees the individual people using it from ever needing to carry debt, as the debt stays in the network, the value and enforceability of that debt note is protected by the effort used to create and maintain the network, and the eagerness with which other people wish to store their efforts up in that same network. The debt still exists, but it can be so thinly and widely spread that it no longer rests as a burden upon one particular person.
The debt, in other words, has been disassociated from humans and the management has been distributed to machines. This is the precise opposite process of a "fiat" (by decree) currency, which only has value so long as it is associated with some particularly solvent group of humans (who personally vouch for repayment of any debts denominated in the currency), and where management is centralized to some other group of humans.
Have you accepted Bitcoin as your personal money and store of value?
You have invested $10 to buy the electricity to mine Bitcoin? Then you receive $10 of Bitcoin in return. The Bitcoin network now owes you the $10 purchasing power equivalent of that electricity.
If someone then gives you $5 worth of pizza, then you can then give them a $5 portion of your $10 worth of Bitcoin. You have taken a part of your Bitcoin debt note and shared it with them.
They now hold $5 worth of Bitcoin invested in the network and can spend it on some other good or service. Or they can simply hold it and wait for it to rise in value, as more people "mine" more of it (and produce more notes, paradoxically making the existing notes more useful and therefore valuable) and more people try to gain the notes in order to manage their own finances by storing their energy in the network or transporting their energy using the network.
Bitcoin, in other words, is an accounting book that needs no accountant because it stores, tracks, and controls the ledger on its own. It is a Natural Ledger that runs according to the Laws.
It is the only human-made ledger that allows for true and immediate Final Settlement. This Final Settlement is what allows people to trade using the convenience of digital debt notes, with neither person occurring or even risking any personal debt. We Christians know that all debt is a burden, including monetary debts, which is why we are called to forgive each other's debt and to hope that our own debts are forgiven. Better still, is to avoid the accumulation of debts, altogether.
So, Final Settlement? Final Settlement is what Jesus would do.
-
 @ 5d4b6c8d:8a1c1ee3
2024-07-12 12:44:07
@ 5d4b6c8d:8a1c1ee3
2024-07-12 12:44:07Yesterday's edition https://stacker.news/items/604559/r/Undisciplined
-
- -
July 12, 2023 📅
📝
TOP POSTExcerpt
The nostr protocol directly solves two problems in internet applications: identity portability and data portability. Products built on nostr can depend on those two problems being solved. For most other equally challenging problems, the nostr protoco […]
3636 sats \ 26 comments \ @k00b \ ~nostr
💬
TOP COMMENThttps://stacker.news/items/208075/r/Undisciplined?commentId=208122
Excerpt
One thing I've noticed: almost all nostr profiles have a display name, a picture, and a bio, and almost all of them seem to be stored exclusively on relay.damus.io. I've connected to the top 5 relays on nostr.watch, queried for metadata for random ac […]
1046 sats \ 1 reply \ @super_testnet
From Portable experiences by @k00b in ~nostr
🏆
TOP STACKER1st place @k00b
11.3k stacked \ 15.7k spent \ 2 posts \ 17 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
22.3k stacked \ 0 revenue \ 35.3k spent \ 108 posts \ 245 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 12, 2022 📅
📝
TOP POSTExcerpt
Max Webster at Hivemind led with Ross Stevens (the NYDIG one), Raymond Tonsing of Caffeinated Capital, Mishti Sharma with Caffeinated's Collective Fund, and Steve Lee filling up the rest.
18.6k sats \ 93 comments \ @k00b \ ~meta
💬
TOP COMMENThttps://stacker.news/items/44061/r/Undisciplined?commentId=44097
Excerpt
Another "interesting" thing to note: where are Coinbase's, Gemini's and Binance's LN implementations?
331 sats \ 0 replies \ @moon
From Exchanges on Lightning by @kr in ~bitcoin
🏆
TOP STACKER1st place @k00b
21k stacked \ 26.2k spent \ 4 posts \ 39 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
22.9k stacked \ 0 revenue \ 26.3k spent \ 119 posts \ 321 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 12, 2021 📅
📝
TOP POSTLink to https://lightningbutton.com/
6 sats \ 3 comments \ @qecez \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/238/r/Undisciplined?commentId=286
Excerpt
I’m seeing “Sorry This page does not exist yet.”
1 sat \ 1 reply \ @02552fb987
From Deploy a lightning node in one line by @k00b in ~bitcoin
🏆
TOP STACKERNo top stacker
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
25 stacked \ 0 revenue \ 72 spent \ 8 posts \ 9 comments
originally posted at https://stacker.news/items/605773
-
-
 @ 124b23f2:02455947
2024-07-10 05:24:33
@ 124b23f2:02455947
2024-07-10 05:24:33I'm reposting this in order to fix the images and get it correctly onto my npub.pro site
What is this ?
My Futurebit Apollo Miner in action
Futurebit is a company that manufactures home miners for retail users (see futurebit.io) - you can check out details on their website. These are targeted at individuals that want to participate in mining with an easy to use, quiet miner that does not use a ton of electricity.
The idea here is to try and stay true to the original bitcoin concept of a computer which runs the bitcoin software and mines bitcoin, all in one. While mining has obviously evolved into a commercial industry and the mining process has long been separated from running a bitcoin node, I think there are still some valid reasons to want to participate in the mining process and attempt to keep this original ethos alive:
- You learn a lot about bitcoin from mining. Reading about the process is one thing, but actually getting a machine running, pointing it towards the pool of your choice, and seeing the bitcoin process from this perspective is something I've found very enjoyable (mining is probably my favorite part of bitcoin, if I had to choose one). It can also be a gateway drug to more advanced mining, so...heavy care.
- It is marginally valuable to the network. Sure, one person running a futurebit miner is nothing compared to the hashrate of MARA. But, if you have tens of thousands of plebs all running their own miners from home, pointing their hashpower to the pool of their choice, it does provide a legitimate decentralizing anchor to large mining actors. Every pleb should be participating in mining, in my opinion, and the Futurebit Apollo miner offers a casual and unobtrusive avenue to do just that.
Now, the Futurebit Apollo Miner you most commonly see is the 'Full Package.' The Full Package is an Orange Pi computer running on a custom linux distribution. You basically boot it up, and it starts running bitcoin core and mining in a few clicks. That is very cool, and I did own one. However, I will say that the Full Package is, unfortunately, not a great product. I won't go into too much detail, but its a very poor quality computer, the security upkeep of the custom linux distribution is lacking, and I found connecting to the node to use with wallets to be very difficult. The mining was also consistently inturrupted due to the pi freezing up. You are better off going with a different option for running a bitcoin node.
This is simply to say, I dislike the Full Package Futurebit Apollo Unit. With that said, I very much like the 'Standard Unit'. The Standard Unit is simply a mining hashboard without the computer OS that comes with the Full Package. I've been running two Standard Units in my house for 18 months now and they just quietly hum along in my house, I barely notice them and they rarely need to be restarted (honestly I can't think of more than 3 times that I needed to troubleshoot and even then it was typically restarting the miner). They are a great way to make your personal contribution to the security of the bitcoin network.
(Please Note: These things are pretty pricey brand new, so don't even think about buying one as being a profitable choice. You can sometimes find decent deals for them used, but buyer beware I can't speak to that experience. This is about hands-on learning about bitcoin mining and participating in the security of the network with a machine that won't drive your family crazy and that I believe is well-built enough to last you a long time. Heck, you could even set one up at your office and I doubt anyone would notice and mine with free electricity.)
So, that's some background. Now, a standard unit is not the most friendly user experience if you are not used to using command line. I wasn't, but I spent a lot of time figuring it out. With this guide, any user should be able to get a Standard Unit hashing :) Here is the step by step process guide on how to run a standard unit, in use with both a Windows OS computer and a Linux OS computer (Ubuntu is what I use)...enjoy.
I. Linux
Your Futurebit Apollo Standard Unit (referred to from here as 'the Unit') miner comes with a power supply and a usb cable. It's pretty straight forward, but you will want to connect the Unit to the computer of your choice (the computer needs to be on and running while you are mining, so a low power consumption computer and/or a computer that you are already running all the time for some other reason would be best). Also, plug in the power supply to your unit and turn it on (there are instructions in the Unit's manual for how to hook up the power supply correctly).
- Go to https://github.com/jstefanop/Apollo-Miner-Binaries
- You'll land on a page that looks like this:
For the purposes of this guide, I am going to be using the 'linux-x86_64' package as it is most appropriate for my computer. But, you would need to select the appropriate binaries for your computer. Odds are, if you are running ubuntu on your laptop or desktop, you are going to use the 'linux-x86_64' package.
- Once you have clicked on the linux-x86_64 folder, you will land here:
Open each of these 4 files and download them using the 'Download Raw File' link in each file's page. Here is an example:
Once you have downloaded, I'd recommend making a folder and putting all 4 of the files into that folder. I am going to make a folder with the name 'Mining Files'. I am also going to move the folder out of my Downloads folder (not necessary, but I'd recommend as it's not a great place to park a folder you want to hold onto). I am going to move it to my Documents Folder:
-
Now, if you do not have a mining pool account, you will need to make one, otherwise you should be able to use your pool credentials in the next step. Alternatively, you can solo mine using solo.ckpool.org with only a btc address. However, for the purposes of this guide I am going to assume that you are using Braiins pool. If necessary, go ahead and make a login at braiins.com/pool. Note the username and password as we will need that later.
-
From the files that you downloaded in step 3, we are going to double-click on 'start_apollo.sh' and open it up in Text Editor. The first 60 lines or so are explanations on how to prepare this script for your use. However, I am going to run you through all the options to update, so you shouldn't need to read the description. Instead, we are going to focus on the text in black font at the bottom of the file:
We need to update the info in the following fields as follows
-host = stratum.braiins.com -port = 3333 -user = username for your Braiins login. I'll use "braiinsexample" for now. -pswd = password for your Braiins login. I'll use "Password123" for now. -comport = Most likely "/dev/ttyACM0" or "/dev/ttyACM1" or "/dev/ttyACM2" -brd_ocp = 48 -osc = 30 -ao_mode = 1
So, when our file is set up correctly, it will look like:
Make sure to save, then close out of text editor.
- Now, start up terminal on your computer. First, we are going to want to get into the correct directory. In our case, our file is in Documents > Mining Files. So, you would input the following command:
cd ~/Documents/Mining Files
Once you are in the correct directory, we will run the following command:
sudo ./start_apollo.sh
You will likely be prompted to enter your computer's password, input the password and, if all goes well, you should see a result like this in your terminal:
You are now mining! The setting we use run the Unit ins 'eco mode', which should yield 2 terahash per second in terms of mining power (you can monitor the performance from your respective mining pool dashboard). As long as you keep this terminal window open and the computer on that is connected to the miner, and you will be mining away :)
II. Windows
Your Futurebit Apollo Standard Unit (referred to from here as 'the Unit') miner comes with a power supply and a usb cable. It's pretty straight forward, but you will want to connect the Unit to the computer of your choice (the computer needs to be on and running while you are mining, so a low power consumption computer and/or a computer that you are already running all the time for some other reason would be best). Also, plug in the power supply to your unit and turn it on (there are instructions in the Unit's manual for how to hook up the power supply correctly).
- Go to https://github.com/jstefanop/Apollo-Miner-Binaries
- You'll land on a page that looks like this:
For Windows, you will click on the folder titled 'msvc19'. You'll see 2 files to download, go ahead and click on each and click 'Download Raw File' for each.
Please Note: Windows may see this file as a virus, so you may need to 'allow on device' in your virus & threat protection of your windows security service.
- Once you have downloaded each file, I'd recommend making a folder and putting all of the files into that folder. I am going to make a folder with the name 'Mining Files'. I am also going to move the folder out of my Downloads folder (not necessary, but I'd recommend as it's not a great place to park a folder you want to hold onto). I am going to move it to my Documents Folder:
-
Now, if you do not have a mining pool account, you will need to make one, otherwise you should be able to use your pool credentials in the next step. Alternatively, you can solo mine using solo.ckpool.org with only a btc address. However, for the purposes of this guide I am going to assume that you are using Braiins pool. If necessary, go ahead and make a login with at braiins.com/pool. Note the username and password as we will need that later.
-
From the files that you downloaded in step 3, we are going to right click on 'start_apollo' and select 'edit'. The file will open up in notepad. The first 60 lines or so are explanations on how to prepare this script for your use. However, I am going to run you through all the options to update, so you shouldn't need to read the description. Instead, we are going to focus on the text in black font at the bottom of the file:
We need to update the info in the following fields as follows
-host = stratum.braiins.com -port = 3333 -user = username for your Braiins login. I'll use "braiinsexample" for now. -pswd = password for your Braiins login. I'll use "Password123" for now. -comport = go to the 'Device Manager' service on your computer, expand the 'Ports' section, and you should find a 'USB serial device' with COM#. Update with your COM# (COM1, COM2, COM3, etc). -brd_ocp = 48 -osc = 30 -ao_mode = 1
So, when our file is set up correctly, it will look like:
- Now that the file is ready, save the file and exit out of notepad. You should be able to simply double-click on the file. The command prompt services will pop-up on your desktop, and should reflect this, indicating your connection is successful and mining has begun:
You are now mining! The setting we use run the Unit ins 'eco mode', which should yield 2 terahash per second in terms of mining power (you can monitor the performance from your respective mining pool dashboard). As long as you keep this terminal window open and the computer on that is connected to the miner, and you will be mining away :)
originally posted at https://stacker.news/items/603076
-
 @ 124b23f2:02455947
2024-07-10 04:54:00
@ 124b23f2:02455947
2024-07-10 04:54:00I'm reposting this article I wrote some time ago again to fix the images for it on my npub.pro site
In my previous post, I explained how to use your getalby ln address to receive zaps directly to your LND node. Similarly, there is an additional option that one can utilize to receive zaps directly to your lightning node: lnaddress.com.
Lnaddress.com is a federated lightning address server that you can use to create a custom ln address. Unlike using getalby, lnaddress.com can be used with any lightning implementation (not just LND). For the purposes of this write-up, I am going to use LNBits to connect an lnaddress.com lightning address with my node. And as will be the case with most of my write-ups, I am going to be using Start9 OS, so users of that OS will likely find this write-up most useful, but I'm sure people using other node interfaces can infer how to complete this set up as well.
With that said, let's dive into the step-by-step on how to create your own custom ln address with lnaddress.com and set it up to receive zaps directly to your lightning node:
*Users should have lnbits set up with their lightning node before proceeding.
- Go to lnaddress.com. Input your desired username, select 'Node Backend Type' = LNBits, and if necessary check the box 'This is a new lightning address'. Keep this page open in one tab as we will be returning to it to input info.
- From your Start9 OS services page, go to your LNBits service. Open the 'Properties' page, and in a new tab, open the (Tor) Superuser Account. Page will look like this:
From this LNbits page, you can choose to 'add a new wallet' and use that wallet instead of your superuser account. That is up to you but the steps will be the same.
- Now, we need to grab the info needed for the 'Host Protocol + IP or Domain + Port' field on the lnaddress.com page. On the lnbits page, expand the 'Api Docs' field, and the 'Get Wallet Details' field found on the right hand side menu. In this 'Get Wallet Details' section, you will want to copy some of the URL found in the 'curl example' section. Copy 'http://xxxxxx.onion' (don't copy any more!), and paste this into the 'Host (Protocol + IP or Domain + Port' field found on the lnaddress.com page.
-
Next, we need to grab the key for your lnbits wallet. From the lnbits page, expand the API docs section found on the right hand side menu. Copy the 'Invoice/read key' (make sure to use the invoice/read key and not your Admin key), and paste it into the key field found on the lnaddress.com page. Upon pasting in that last piece of info, click 'submit' at the bottom of the page.
-
If all info was input correctly, your connection will be successful. If successful, you will be brought to a page that looks like this:
You will want to save this secret PIN in case you need to update info in your ln address. You'll also find a test lightning invoice of 1 sat. Using a wallet not connected to the node we connected to our new ln address, you can test the ln address out by paying the 1 sat test invoice.
Users of Start9 OS might find the following info particularly useful: This ln address via lnaddress.com comes with a couple advantages aside from self-custodial zap receiving:
- One, you can have a custom ln address username to go with your nym or nostr username. Users of Start9 may be familiar with the ln address one can generate in the btcpay server service. This ln address is not customizable.
- Two, if you are running a tor only lightning node, you will be able to receive zaps from both tor and clear net lightning nodes. Users of Start9 may be familiar with the ln address one can generate in the btcpay server service. This ln address can only receive zaps from other tor nodes and can't receive zaps from clear net nodes.
That is it, you should now be all set up with your new ln address hosted on lnaddress.com, and you should be all ready to receive zaps or lightning payments of any kind :)
originally posted at https://stacker.news/items/603061
-
 @ 69a0a091:c968228d
2024-07-07 19:10:07
@ 69a0a091:c968228d
2024-07-07 19:10:07Radicale is a self-hosted calendar and contact solution that is "lightweight solution, easy to use, easy to install, easy to configure."
https://radicale.org/v3.html#about
I can finally dump my NextCloud, which was a sprawling mess of PHP scripts. Managing a NextCloud instance over a long period of a time requires the sysadmin to be mindful of the stateful configuration, which can only be upgraded one major version at a time.
I stumbled over Radicale a couple years ago right after I had spent an entire day writing a playbook to build a dockerless NextCloud container. I should have switched immediately, I've wasted numerous hours over that period making sure my container was up to date, or needlessly fiddling with settings just to feel like I had a handle on how the thing was going to operate.
Running radicale on NixOS:
service.radicale = { enable = true; settings = { server = { hosts = [ "127.0.0.1:5232" "[::]:5232" ]; }; auth = { type = "htpasswd"; htpasswd_filename = "/etc/radicale/users"; htpasswd_encryption = "bcrypt"; }; storage = { filesystem_folder = "/var/lib/radicale/collections"; }; }; };Nginx configuration snippet from:
locations."/radicale/" = { proxyPass = "http://127.0.0.1:5232/"; extraConfig = '' proxy_set_header X-Script-Name /radicale; proxy_pass_header Authorization; ''; };Creating my account after
nixos-rebuild switch:nix-shell -p apacheHttpd --run "htpasswd -B -c /etc/radicale/users pleb"The web interface is dead simple and let's you create, import, or export calendars or addressbooks. I exported the vcf addressbook and ics calendar from my NextCloud instance and imported them into Radicale. The UI gives you URIs for the calendar or contacts, and I pasted that in along with my username in the relevant add dialog in Thunderbird.
Likewise, I added the account in davx5 on Android using the first "Login with URL and user name" option. For the URL this time, I appended my username, so it was
https://example.com/radicale/myusernameand davx was able to sync both the calendar and the contacts from that endpoint. -
 @ a012dc82:6458a70d
2024-07-12 09:48:42
@ a012dc82:6458a70d
2024-07-12 09:48:42Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
Introduction
The term "unbanked" refers to individuals who lack access to basic financial services, such as bank accounts, credit, and insurance. According to the World Bank, there are around 1.7 billion unbanked adults globally, and the majority of them live in developing countries. This lack of access to financial services often results in significant barriers to economic growth and financial security for these individuals. However, the rise of cryptocurrencies, such as Bitcoin, has opened up the potential for a solution to this problem.
The Bitcoin Lightning Network
The Bitcoin Lightning Network is a second layer technology built on top of the Bitcoin blockchain that allows for fast and cheap transactions. It works by creating payment channels between two parties that can be used for multiple transactions, without each one needing to be recorded on the blockchain. This enables near-instantaneous transactions and makes it ideal for micropayments, which are often required by the unbanked.
The Lightning Network is often cited as a potential solution to the high fees and long transaction times associated with traditional financial services. With the Lightning Network, fees are significantly lower, and transactions are confirmed almost instantly. This is particularly important for the unbanked, who may not have the resources to cover high transaction fees or the time to wait for transactions to be processed.
The Power of the Bitcoin Lightning Network Wallet
The Lightning Network wallet enables the unbanked to participate in the Bitcoin economy without needing a traditional bank account. It provides greater access to financial services and privacy compared to traditional financial services. The Lightning Network also addresses the challenges of high fees and long transaction times associated with traditional financial services. With lower fees and almost instant transaction confirmations, the Lightning Network has the potential to promote financial inclusion and empowerment for the unbanked.
Addressing the Challenges Faced by the Unbanked
The unbanked, who are individuals without access to traditional banking services, often face challenges when it comes to accessing basic financial services. Some of the key challenges include high fees and long transaction times associated with traditional financial services, limited access to financial services due to location or socioeconomic status, and concerns around privacy and security.
The Lightning Network and Lightning Network wallet can address many of these challenges. The Lightning Network offers significantly lower transaction fees and almost instant transaction confirmations, which can be a huge benefit for the unbanked who may not have the resources to cover high fees or the time to wait for transactions to be processed.
The Future of the Bitcoin Lightning Network Wallet
The future of the Bitcoin Lightning Network wallet looks promising as the network continues to grow and evolve. As more users adopt the Lightning Network and Lightning Network wallets, the infrastructure supporting these tools is expected to become more robust, secure, and efficient.
One potential area of growth for the Lightning Network wallet is in the development of new applications that can be built on top of the network. For example, developers could create peer-to-peer lending platforms, microfinance applications, or other financial tools that leverage the Lightning Network's fast and low-cost transactions.
Conclusion
The Bitcoin Lightning Network wallet is a powerful tool that has the potential to address many of the challenges faced by the unbanked. With lower fees, faster transactions, and increased access to financial services, the Lightning Network wallet has the potential to promote financial inclusion and empowerment for individuals who have traditionally been excluded from the financial system.
FAQ
What is the Lightning Network wallet? The Lightning Network wallet is a digital wallet that is built on top of the Lightning Network. It enables individuals to store, send, and receive Bitcoin in a secure and private manner.
How does the Lightning Network wallet help the unbanked? The Lightning Network wallet enables the unbanked to participate in the Bitcoin economy without the need for a traditional bank account. It provides greater access to financial services, lower fees, and increased privacy and security compared to traditional financial services.
How can the Lightning Network wallet be used for peer-to-peer transactions? The Lightning Network wallet enables individuals to send and receive Bitcoin in a peer-to-peer manner, allowing for fast and low-cost transactions.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ bd32f268:22b33966
2024-07-12 09:23:22
@ bd32f268:22b33966
2024-07-12 09:23:22"By the sweat of your face you shall eat bread, till you return to the ground, for out of it you were taken; for you are dust, and to dust you shall return." _ Genesis 3:19_
Can man eat bread without the sweat of his face? We have done everything to make life easier, using tools and inventing machines, thus maximizing our capacity to produce. Despite these prodigious improvements, Kierkegaard, a Danish philosopher from the 19th century, says the following:
“So there I sat and smoked my cigarette until my mind began to think. You are advancing in age, getting old without having become anything or having any project. On the other hand, when we examine literature or life, we see names and figures of celebrities, valuable and acclaimed people for their deeds, the benefactors of the age who know how to benefit humanity by making life easier, some through railways, buses, and steamboats, others through the telegraph, others through brief and easy-to-understand publications about what is worth knowing, and finally the true benefactors of the age who by virtue of systematic thought make spiritual existence increasingly easier and yet more meaningful — and what am I doing? Only one thing is missing [in our age], although it is not yet felt, difficulty is missing. For the love of humanity and despair regarding my strange proclamation of having achieved nothing nor succeeded in making anything easier, despite the genuine interest in those who make things easier, I finally understood that it was my task: to create difficulties everywhere.” Concluding Unscientific Postscript to Philosophical Fragments, published in 1846. Søren Kierkegaard (pseudonym Johannes Climacus)
This excerpt from a text by Kierkegaard comes as a punch in the stomach, alerting us to an inescapable reality: the need for sacrifice. No matter how seemingly easy life becomes, we still need sacrifice as a way to fulfill our purpose as human beings. Sacrifice, illustrated by difficulty in Kierkegaard's text, is what allows us to negotiate with existence itself and offer something in the present in the hope of obtaining something in the future. Sacrifice also allows us to know more deeply our limits and weaknesses and create an opportunity to transcend these limits. Without sacrifice, there is no love, for sacrifice implies that we have the capacity to see beyond ourselves, beyond our most immediate selfish interest. Through sacrifice, we are therefore invited to renounce something with the purpose of offering it.

Angelus (painting) – by Jean-François Millet shows two peasants praying, giving thanks for the harvest obtained through the sweat and effort of many days.
Since work is also a form of sacrifice, it is good to remember that this is an exercise we do with a useful end in view. Nature does not automatically satisfy all human needs, hence the need for work to meet them. Besides all this, work is also an antidote to some evils and a promoter of virtues. It allows us, for example, to combat idleness and laziness, while on the other hand, it allows us to enhance solidarity since we have obtained resources that we can now share. This means that work creates a propitiatory atmosphere for the person because it develops their ethics and morals on various levels. It seems more important at this time to reflect on this because we often fall into the error of seeking the enjoyment of immediate pleasures, the promises of an easy life, forgetting these realities. Not that having pleasure in itself evil, but this must always be subordinated to the values that organize our lives because obtaining pleasure is not the ultimate goal of life. It is evident that not all jobs are the same, and some are more conducive to virtues than others, something to which we must pay careful attention, hence it makes sense to seek to make work subordinate to our values. For there is no good work that does not express these values. Let us then use work as a springboard for our growth, and begin not to wish for an easy life, but rather to increasingly desire an honorable life in which we are not deceived by superficial gratuities.
-
 @ 1739d937:3e3136ef
2024-07-06 09:22:17
@ 1739d937:3e3136ef
2024-07-06 09:22:17This is the second in a series of weekly updates detailing progress on bringing MLS protocol DMs and group messaging to Nostr.
Previous Updates
Progress this week
This week was mostly spent on the topic of how to properly publish prekey bundles and what would be needed in the bundle itself to make it workable. I've included an early version of the spec below for prekeys, and would love thoughts on it. Treat this as an alpha version, very subject to change.
The other thing I spent time on was making changes to the OpenMLS library to add support for our custom ciphersuite. One issue that I've run into is that the IETF standard for HPKE doesn't include the secp256k1 curve. Because of this, the library being used in the OpenMLS library doesn't implement the necessary methods using our curve. Thankfully, there is another library with an open PR (shout out to nostr:npub1yevrvtp3xl42sq06usztudhleq8pdfsugw5frgaqg6lvfdewfx9q6zqrkl for that!) that would fix this. Additionally, there's an expired proposal to add secp256k1 to the HPKE spec itself. I've bumped both of these and will continue to follow up. Even without the formal addition to the spec, if we have a working library, I can add that to the OpenMLS library.
Spec Draft for Prekeys
Initial keying material (Prekey Event)
Each user that wishes to be reachable via MLS-based messaging MUST first publish a prekey event. Prekeys are used to authenticate and add members to groups (one-to-one DMs or groups with more than two participants) in an asynchronous way. The prekey event is a simple replaceable event and contains all the information needed to add a user to a group.
Prekeys SHOULD be used only once. Resuse of prekeys can lead to replay attacks.
In most cases, clients that implement this NIP will manage the creation and rotation of the prekey event. It's recommended that clients do so interactively with user consent in order to avoid overwriting prekeys created by other clients.
Derived vs Ephemeral Prekeys
Since prekeys are generated on a single device/client pair, the private key of the prekey must be either stored or generated in a way that can be deterministically recovered.
The recommended approach is to use derived keys, generated in the manner described in NIP-06. In this way, the user can respond to a new group request from any device/client pair, not just from the same device/client pair that created the initial prekey event. If using derived keys;
- Clients MUST use
104as theaccountlevel value and0at thechangelevel value (e.g.m/44'/1237'/104'/0/0). - Keys are then generated using public derivation by incrementing the
address_indexlevel value. - Clients MUST include the full derivation path corresponding to the key used in the
contentfield on the prekey event. - The
contentfield MUST be encrypted using standard NIP-44 encryption (encrypted to themselves).
However, for added security (and consequently a more restrictive user experience), clients can chose to generate an ephemeral key and store the private key locally. This means that users will only be able to respond to new group requests from the same device/client pair and won't be able to respond at all if the prekey's private key is lost. Ephemeral keys can also be used with minimal degredation of UX if you're using a remote signer that can manage these keys.
If using an ephemeral key;
- The
contentfield on the prekey event MUST be filled in withEPHEMERALand then encrypted using standard NIP-44 encryption (encrypted to themselves). This ensures that anyone looking at prekey events cannot tell whether it's a derived or an ephemeral prekey.
Example Prekey Event
json { "id": <id>, "kind": 10443, "created_at": <unix timestamp in seconds>, "pubkey": <main identity pubkey>, "content": <encrypted derivation path | EPHEMERAL>, "tags": [ ["mls_protocol_version", "1.0"], ["ciphersuite", "MLS_256_DHKEMK256_CHACHA20POLY1305_SHA256_K256"], ["pubkey", <prekey pubkey>], ["prekey_sig", <signature generated from hex encoded pubkey of the prekey>], ["r", "wss://nos.lol"], ["r", "wss://relay.primal.net"] ], "sig": <signed with main identity key> }Tags
- The
mls_protocol_versiontag identifies the MLS protocol version being used. For now, this MUST be1.0 - The
ciphersuitetag identifies the ciphersuite supported. For now on Nostr, we're using a custom ciphersuite,MLS_256_DHKEMK256_CHACHA20POLY1305_SHA256_K256. Read more about ciphersuites in MLS. pubkeyis the derived or ephemeral prekey pubkey.- The
prekey_sigtag value is a Schnorr signature (over the secp256k1 curve) of the SHA-256 hashed value of the prekey's pubkey, signed with the prekey's private key.
```js const privKey = schnorr.utils.randomPrivateKey(); const pubKey = schnorr.getPublicKey(privKey);
const prekeySig = bytesToHex( schnorr.sign(bytesToHex(sha256(pubKey)), privKey) );
const prekeyTag = ["prekey_sig", prekeySig]; ```
Finally, clients SHOULD include
rtags to identify each of the relays that they will attempt to publish this prekey event to. This allows for more complete replacement of prekey events at a later date.Replacing Prekey Events
Clients MUST replace the prekey event on all the listed relays any time they successfully process a group welcome event. If the prekey was a derived prekey, clients SHOULD increment the derivation path by 1 for the next key.
Onward and Upward
This next week I'll continue to work on getting the right curves and code added to the OpenMLS library and start work on a simple demo app. The focus is on better understanding what we need from the control and message events and how we can make those as simple as possible for Nostr clients and relays while also preserving as much privacy as possible.
- Clients MUST use
-
 @ 38d0888d:bd8e1246
2024-07-12 07:10:35
@ 38d0888d:bd8e1246
2024-07-12 07:10:35A thriving society rests on the principles of modesty and humility, avoiding idleness and self-indulgence. Individuals are needed to forsake the constant pursuit of attention and instead aspire to selflessness, dedicating themselves to serving humanity. Humility fosters spiritual harmony and protects against materialism and selfish desires.
Beyond personal conduct, humanity must champion altruism and solidarity within the global community. Belief in collective endeavors will pave the way for global harmony. Embracing values like kindness, compassion, and genuine concern for others promotes positivity and reflects the influence of a higher power. The aim is to cultivate a unified multicultural community where each person contributes to manifesting this higher presence.
The collective goal is to direct humanity to nurture a community that experiences spiritual growth while upholding humility as a guiding principle, resisting materialism's allure. By creating such an environment, the hope is to resonate with a sacred harmony that extends beyond immediate boundaries. Through intentional actions and meaningful relationships, a collective space embodying these values can be established, ensuring the higher power's presence guides individual lives and interactions with the world.
-
 @ 6c8c7979:15595f3e
2024-07-12 01:02:17
@ 6c8c7979:15595f3e
2024-07-12 01:02:17Despite the numerous historical turning points that have influenced art history, the Baroque era stands out as a pivotal marker in the history of art and culture.
Spanning from the 17th to the early 18th century, the Baroque period reshaped architecture, literature, music, sculpture, and visual arts.
Originating in Italy, the Baroque movement spread across Europe, flourishing notably in France, the Netherlands, and Spain, and later extending its influence throughout the continent.
It was an artistic and philosophical movement aimed at embodying motion, life, and profound meaning with maximal drama and theatricality.

Nymphenburg Palace - Munich, GermanyIn the field of architecture, Baroque style saw the construction of churches, palaces, castles, theaters, and public spaces in a bold and distinctive manner.
These buildings were characterized by abundant use of marble, intricate curves and recesses, and ornate decorative details. Colors were vibrant and rich, lending a dramatic and spiritual character to Baroque structures.
For example, the Luxembourg Palace, now known as the French Senate, built in Paris in 1615, exemplifies Baroque architecture with its emphasis on luxury, detailed ornamentation, monumental size, and the use of domes.
This architectural philosophy was influenced by the opulence and intricate designs that were originally introduced to Europe from the Islamic world during the Middle Ages.
Moreover, the building is distinguished by its grand staircases, high ceilings, and walls adorned with either sculptures or paintings—a hallmark Baroque tradition. Additionally, Baroque architecture emphasized the abundant use of mirrors inside buildings to visually expand the space, albeit illusionistically, creating a sense of spaciousness.

The Luxembourg Palace Library in Paris houses approximately half a million books.$$Baroque literature$$Baroque literature saw many writers and poets of the era adopt an epic rhetorical style. Baroque literary works are characterized by complexity, mystery, and elaboration in description, influenced by the cultural phase deeply immersed in highlighting and praising intricate details.
Those works arose from a self-awareness of the prevailing cultural discourse at the time. Metaphors and epic similes were abundant. There was also a tendency towards exaggeration and paradox in the sequence of events throughout the plot.
John Milton's epic poem "Paradise Lost" (1608-1674), for many language scholars, is considered one of the greatest poems in the history of the English language. The poem consists of 10 volumes in its first edition and 12 volumes in the second, recounting the story of Adam and Eve's expulsion from paradise and their long-lasting battle with Satan.
In "Paradise Lost," Milton states, "The end of all learning is to know God, and out of that knowledge to love Him and to imitate Him."
Baroque Music
In the field of music, numerous musical instruments and new techniques were developed to emphasize the depth and power of sound. As a result, Baroque music emerged filled with complex compositions, lively rhythms, and rich harmonies.
Some of the most famous composers of this era include Johann Sebastian Bach, George Frideric Handel, and Antonio Vivaldi.
https://youtu.be/DwHpDOWhkGk?si=Nw-h0RKZFllyNwok
Let's enjoy, for example, a musical journey with Bach's cello suite, exploring the depth and beauty of the instrument across 6 movements, each showcasing Bach's mastery of the following point and his innovative musical ideas that captivate the listener with their charm and technical complexity.
$$Baroque Sculpture$$Like other creative fields, visual arts such as sculpture and painting gained fame for their precision and richness of detail. Many works overall dealt with religious meanings, elements of pride, and beauty.
Baroque artists were renowned for their skillful use of natural light to highlight dark shadows, thereby adding dimensions to their paintings. Many prominent artists such as Rembrandt, Peter Paul Rubens, and Peter Paul Rubens produced stunning works during that period.
Therefore, the painting "The Night Watch," created by the Dutch artist Rembrandt in 1642, stands as a prominent example of the depth of Baroque style in art history.

"The Night Watch" - Amsterdam MuseumThe painting is a group portrait of a civic militia, where the painter skillfully used light and shadow to showcase their pride and intimate camaraderie.
It's worth noting that the play of light and shadow not only highlights the central figures but also creates a sense of mystery and anticipation, which in turn adds drama and movement to the scene, attracting the eye to the tableau.
The vibrant colors and intricate details bring a lively texture to the characters, making the painting a visual feast for viewers. The composition is balanced due to Rembrandt's expertise; we see him strategically positioning the characters at times and infusing Baroque dramatic touches at others, all serving the same purpose of presenting the work as a cohesive narrative.
One intriguing aspect of "The Night Watch" is Rembrandt's departure from depicting a single hero in the work; instead, he portrays each individual in the painting with equal importance. This deviation from the norm reflects his progressive vision and artistic sensitivity amidst the Baroque era.
The Baroque period was known for its personal dedication to expression, whether through painting, music, or writing, making it a distinctive and valuable era in human history, characterized by richness of production as much as richness of detail.
The development of new styles and techniques during this period also contributed to the emergence of other artistic schools, such as Rococo.
-
 @ 81870f53:29bef6a6
2024-07-13 00:13:11
@ 81870f53:29bef6a6
2024-07-13 00:13:11先週、米国の雇用統計が軟調だったことで連邦準備制度理事会が利下げを行うとの期待が高まり、金と銀は週ごとに上昇した。今週も、利下げの可能性を巡るセンチメントが貴金属を牽引した。具体的には、投資家は連邦準備制度理事会の次の政策措置に関するさらなるヒントを求めて米国のインフレデータを注視していた。
金は月曜日、利益確定売りで0.75%下落して2,367ドルとなったが、銀は31ドル前後でほぼ横ばいだった。同日、ナスダック総合指数とS&P 500はハイテク株が急騰し、投資家がJPモルガン・チェースやシティグループなどの大手銀行の収益を予想したことから、新たな最高値で引けた。
火曜日もハイテク株の上昇が続き、株価は再び上昇した。つまり、S&P 500とナスダックはともに過去最高値で引けたことになる。一方、ドル指数はライバル通貨に対して0.2%上昇し、投資家が木曜日のインフレデータを待つ中、国債利回りは急上昇した。債券利回りの上昇とドルの相対的強さにもかかわらず、金と銀は火曜日にほとんど変化がなかった。
水曜日、ジェローム・パウエル連邦準備制度理事会議長は議会に出席し、報告書を提出し、経済状況に関する質問を受けた。証言の中で、パウエル議長は、中央銀行が利下げを進める前にインフレがFRBの2%目標に戻る必要はないと示唆した。FRB議長は、景気後退リスクと失業率の大幅な上昇を、FRBが利下げをそれほど長く待たない理由として挙げた。
パウエル議長の証言後、株価は再び急上昇し、S&P500は指数史上初めて5,600を超えた。パウエル議長の発言が利下げへの楽観論を高め、金は0.60%上昇した。その結果、金は水曜日の取引を2,387ドルで終え、銀は1日1%上昇して31ドルを突破した。
木曜日、労働統計局は消費者物価指数(CPI)が5月から6月にかけて0.1%下落したという報告書を発表した。これにより年間インフレ率は3%に低下し、9月の利下げの可能性が高まった。
金はCPIの軟調な推移を受けて1%以上上昇し、1オンス2,381ドルで取引を終えた。同時にドル指数は下落し、10年国債は10ベーシスポイント下落して4.187%となり、金の魅力がさらに高まった。しかし、株式市場はCPI後の上昇を金ほど享受しなかった。木曜日、S&P 500とナスダックは7セッション連続の上昇を止め、ハイテク株の下落で指数は下落した。
本日、投資家は、7月の生産者物価指数(PPI)が0.1%の上昇が予想されていたのに0.2%上昇したという報告を受けて、予想を上回る卸売インフレ率を消化した。卸売インフレ率の上昇は金の上昇にほとんど影響せず、金は1.2%上昇して2,415ドルで週を終え、3週連続の上昇となった。
しかし、本日のPPIの数字は木曜のCPIの数字を縮小したようで、銀は下落圧力を受けた。その結果、銀は本日午後2%下落し、0.7%下落して30.79ドルで週を終えた。昨日の下落にもかかわらず、米国株はなんとかプラスで週を終えた。ダウ工業株30種平均は、3大平均の中で最大の週間上昇率を記録し、1.56%となった。一方、S&P 500とナスダックはそれぞれ0.77%と0.14%の週間上昇で週を終えた。
-
 @ ee11a5df:b76c4e49
2024-07-11 23:57:53
@ ee11a5df:b76c4e49
2024-07-11 23:57:53What Can We Get by Breaking NOSTR?
"What if we just started over? What if we took everything we have learned while building nostr and did it all again, but did it right this time?"
That is a question I've heard quite a number of times, and it is a question I have pondered quite a lot myself.
My conclusion (so far) is that I believe that we can fix all the important things without starting over. There are different levels of breakage, starting over is the most extreme of them. In this post I will describe these levels of breakage and what each one could buy us.
Cryptography
Your key-pair is the most fundamental part of nostr. That is your portable identity.
If the cryptography changed from secp256k1 to ed25519, all current nostr identities would not be usable.
This would be a complete start over.
Every other break listed in this post could be done as well to no additional detriment (save for reuse of some existing code) because we would be starting over.
Why would anyone suggest making such a break? What does this buy us?
- Curve25519 is a safe curve meaning a bunch of specific cryptography things that us mortals do not understand but we are assured that it is somehow better.
- Ed25519 is more modern, said to be faster, and has more widespread code/library support than secp256k1.
- Nostr keys could be used as TLS server certificates. TLS 1.3 using RFC 7250 Raw Public Keys allows raw public keys as certificates. No DNS or certification authorities required, removing several points of failure. These ed25519 keys could be used in TLS, whereas secp256k1 keys cannot as no TLS algorithm utilizes them AFAIK. Since relays currently don't have assigned nostr identities but are instead referenced by a websocket URL, this doesn't buy us much, but it is interesting. This idea is explored further below (keep reading) under a lesser level of breakage.
Besides breaking everything, another downside is that people would not be able to manage nostr keys with bitcoin hardware.
I am fairly strongly against breaking things this far. I don't think it is worth it.
Signature Scheme and Event Structure
Event structure is the next most fundamental part of nostr. Although events can be represented in many ways (clients and relays usually parse the JSON into data structures and/or database columns), the nature of the content of an event is well defined as seven particular fields. If we changed those, that would be a hard fork.
This break is quite severe. All current nostr events wouldn't work in this hard fork. We would be preserving identities, but all content would be starting over.
It would be difficult to bridge between this fork and current nostr because the bridge couldn't create the different signature required (not having anybody's private key) and current nostr wouldn't be generating the new kind of signature. Therefore any bridge would have to do identity mapping just like bridges to entirely different protocols do (e.g. mostr to mastodon).
What could we gain by breaking things this far?
- We could have a faster event hash and id verification: the current signature scheme of nostr requires lining up 5 JSON fields into a JSON array and using that as hash input. There is a performance cost to copying this data in order to hash it.
- We could introduce a subkey field, and sign events via that subkey, while preserving the pubkey as the author everybody knows and searches by. Note however that we can already get a remarkably similar thing using something like NIP-26 where the actual author is in a tag, and the pubkey field is the signing subkey.
- We could refactor the kind integer into composable bitflags (that could apply to any application) and an application kind (that specifies the application).
- Surely there are other things I haven't thought of.
I am currently against this kind of break. I don't think the benefits even come close to outweighing the cost. But if I learned about other things that we could "fix" by restructuring the events, I could possibly change my mind.
Replacing Relay URLs
Nostr is defined by relays that are addressed by websocket URLs. If that changed, that would be a significant break. Many (maybe even most) current event kinds would need superseding.
The most reasonable change is to define relays with nostr identities, specifying their pubkey instead of their URL.
What could we gain by this?
- We could ditch reliance on DNS. Relays could publish events under their nostr identity that advertise their current IP address(es).
- We could ditch certificates because relays could generate ed25519 keypairs for themselves (or indeed just self-signed certificates which might be much more broadly supported) and publish their public ed25519 key in the same replaceable event where they advertise their current IP address(es).
This is a gigantic break. Almost all event kinds need redefining and pretty much all nostr software will need fairly major upgrades. But it also gives us a kind of Internet liberty that many of us have dreamt of our entire lives.
I am ambivalent about this idea.
Protocol Messaging and Transport
The protocol messages of nostr are the next level of breakage. We could preserve keypair identities, all current events, and current relay URL references, but just break the protocol of how clients and relay communicate this data.
This would not necessarily break relay and client implementations at all, so long as the new protocol were opt-in.
What could we get?
- The new protocol could transmit events in binary form for increased performance (no more JSON parsing with it's typical many small memory allocations and string escaping nightmares). I think event throughput could double (wild guess).
- It could have clear expectations of who talks first, and when and how AUTH happens, avoiding a lot of current miscommunication between clients and relays.
- We could introduce bitflags for feature support so that new features could be added later and clients would not bother trying them (and getting an error or timing out) on relays that didn't signal support. This could replace much of NIP-11.
- We could then introduce something like negentropy or negative filters (but not that... probably something else solving that same problem) without it being a breaking change.
- The new protocol could just be a few websocket-binary messages enhancing the current protocol, continuing to leverage the existing websocket-text messages we currently have, meaning newer relays would still support all the older stuff.
The downsides are just that if you want this new stuff you have to build it. It makes the protocol less simple, having now multiple protocols, multiple ways of doing the same thing.
Nonetheless, this I am in favor of. I think the trade-offs are worth it. I will be pushing a draft PR for this soon.
The path forward
I propose then the following path forward:
- A new nostr protocol over websockets binary (draft PR to be shared soon)
- Subkeys brought into nostr via NIP-26 (but let's use a single letter tag instead, OK?) via a big push to get all the clients to support it (the transition will be painful - most major clients will need to support this before anybody can start using it).
- Some kind of solution to the negative-filter-negentropy need added to the new protocol as its first optional feature.
- We seriously consider replacing Relay URLs with nostr pubkeys assigned to the relay, and then have relays publish their IP address and TLS key or certificate.
We sacrifice these:
- Faster event hash/verification
- Composable event bitflags
- Safer faster more well-supported crypto curve
- Nostr keys themselves as TLS 1.3 RawPublicKey certificates
-
 @ 6c8c7979:15595f3e
2024-07-12 00:13:43
@ 6c8c7979:15595f3e
2024-07-12 00:13:43The painting "The Anatomy Lesson of Dr. Nicolaes Tulp" by Rembrandt, created in 1631, is one of the prominent works of Baroque art and a notable example of anatomical studies during that period. The painting depicts a real anatomy lesson conducted in a lecture hall in Amsterdam.
The artwork portrays several individuals, including members of the Surgeons' Guild and anatomy students, interacting with the dissected corpse laid out before them to study the human body's details. It is distinguished by its meticulous depiction of muscular forms and skeletal structure, rendered realistically, with a focus on the contrast between life and death, and light and shadow within the composition.
Rembrandt employed his artistic skills to create a powerful dramatic effect, infusing the painting with life and movement despite the static nature of the cadaver. The dramatic lighting he used is highly realistic, highlighting intricate details in the darker areas, thus adding depth and expressive power to the artwork.
In addition to its stunning technical execution, the painting reflects human curiosity and scientific inquiry into human anatomy, embodying aspects of philosophy and science that were of interest to Baroque society at that time.
-
 @ c73818cc:ccd5c890
2024-07-12 22:19:23
@ c73818cc:ccd5c890
2024-07-12 22:19:23
Siamo entusiasti di annunciare il lancio di DOGS POINTS (DOGS) nel trading pre-market su Bitget! 🎉 Gli utenti possono ora iniziare a scambiare DOGS POINTS prima che diventi disponibile per il trading ufficiale.
🐶 Un po' di background su DOGS POINTS:
L'immagine di DOGS è ispirata a Spotty, la mascotte creata dal fondatore di TON, Pavel Durov, per la comunità di Telegram. Questa moneta non è solo per divertimento, ma tutti i ricavi delle vendite sostengono orfanotrofi e case per bambini, continuando l'eredità benefica di Spotty. ❤️
👉 Non perdere questa opportunità unica! Unisciti ora al trading pre-market su Bitget e sostieni una buona causa. Iscriviti ora e inizia a scambiare: https://bonus.bitget.com/U1JNEK
👉 Non sei andato a riscattare il tuo AirDrop su Telegram? Vai subito a vedere quanti DOGS puoi ricevere! https://t.me/dogshouse_bot/join?startapp=y5J61rnXSU2wW2ruadnJNA
Bitget #DOGSPOINTS #PreMarket #Crypto #Trading #Telegram #BitcoinReportItalia #AirDrop
-
 @ 036533ca:cbaabf58
2024-07-11 21:54:40
@ 036533ca:cbaabf58
2024-07-11 21:54:40In a recent job interview, we discussed some of my work on Nostr and specifically my Noscrypt library. I was asked basic questions, such as what it is and what purpose it serves. Most of my response centered on the idea that while the secp256k1 library is excellent, it is easy to misuse.
So what footguns?
It had been a while since I heard that term, and for whatever reason, I struggled to give a satisfactory response. The interviewer was pleased, but I was not, so I want to take some time to reflect on better ways of explaining the challenges I've encountered while working with libsecp256k1 when building on Nostr.
First, libsecp256k1 is functionally perfect as it is, and I don't see any need for changes. The real challenge is implementing all of the Nostr-specific cryptographic tasks on top of secp256k1. This includes complex but necessary operations like note encryption and signing. The most difficult part is converting between all of the different required encodings: Hex, Base64, Bech32, JSON, UTF-8, and so on.
Really I'm just talking about implementation details, what I got wrong, and what was missing between nostr operations and libsecp256k1.
Some backstory
When I first fell into Nostr, I had some cryptography experience from working on my .NET libraries called VNLib. I quickly realized that Nostr identities rely on your ability to keep a 32-byte number safe, but also accessible. With my HTTP framework in hand, everything seemed like a nail. I wanted my key to be securely stored and signed remotely across a network, where the data is sent between the client/server, and my key never has the opportunity to leave the server. So that's what I started building and continue to use, even though it's not complete. That project is called NVault, and I quietly work on it in the background as things break.
Originally, I built a C# wrapper for libsecp256k1, manually worked through all the C/C# barriers, and implemented the note encryption and signing in higher-level C#. However, when NIP-44 came out, everything changed. I realized how much more complex the wrapper would become if I kept trying to stack onto it. Another issue was performance. I still believe my skills in C allow me to write more efficient and performant code than I can in C# for the same tasks, especially when it comes to cryptography and functional programming.
NIP-44 significantly increased the complexity of Nostr cryptography, and after seven months of regular work on NIP-44, I know I'm not the only one still grappling with this complexity, along with NIP-59 and other related DM and crypto specs.
Okay, so a library needed to address the complexities and inefficiencies of Nostr cryptography while also being portable. To me, no other language meets those goals better than C. We can target virtually every operating system, as most high-level languages can bind to a C ABI at load time or runtime. Additionally, we can target hardware/RTOS systems. C can do it all and usually do it better if you are "smart" and careful, in my opinion. Defensive C programming, if you will.
Why noscrypt
If you are building a client or relay in C, or a derivative that relies on libsecp256k1, or a similar library, because it's the most tested and stable library for the secp256k1 elliptic curve, you will need to implement every Nostr-related spec by hand as helper code in your project. Libraries handle this. However, each time note encryption changes (which it has frequently), you will need to revise your cryptographic helpers to accommodate those changes and hope you don't make a fatal mistake that compromises your users' keys or notes. You aren't a cryptographer; you're a client/relay developer. I'm not saying you can't do it; I'm saying you don't want to.
Working with libsecp256k1
First, there is no concept of a key pair associated with Nostr in libsecp256k1. Nostr is "special" in that we treat the secret key and public key as equally distinct parts of your identity on the network and often store them separately.
Public Keys are X-Only
Public keys in Nostr only use the x-coordinate of the xy point on the curve. Libsecp256k1 handles this fine, but not in a foolproof way, in my opinion.
Here is some code taken from Noscrypt to illustrate the steps needed to implement public key conversion:
```c int _convertToPubKey( const NCContext ctx, const NCPublicKey compressedPubKey, secp256k1_pubkey* pubKey ) { int result; uint8_t compressed[sizeof(NCPublicKey) + 1];
/* Set the first byte to 0x02 to indicate a compressed public key */ compressed[0] = BIP340_PUBKEY_HEADER_BYTE; /* Copy the compressed public key data into a new buffer (offset by 1 to store the header byte) */ MEMMOV((compressed + 1), compressedPubKey, sizeof(NCPublicKey)); result = secp256k1_ec_pubkey_parse( ctx->secpCtx, pubKey, compressed, sizeof(compressed) ); return result;} ```
The NCPublicKey type is a 32-byte structure (a byte array) so it's far easier to work with and store with higher-level Nostr applications. We have encountered these issues time and again in Aedile due to the way we use public keys in Nostr.
I regularly failed to find a structured way to store Nostr-specific public keys that libsecp256k1 could work with. I ended up making all the above function calls (and about two more) into the library to do this conversion. So, it's just implementation details.
Keypairs
Again, libsecp256k1 requires some complexity in keypair structures which Nostr has almost no 1:1 mapping to, and really doesn't need. A secret key is all that is required to sign (encrypt) a message using ECDSA, so there is no reason to store keypairs in this case.
Again here is an example from noscrypt
```c NCResult NCSignDigest( const NCContext ctx, const NCSecretKey sk, const uint8_t random32[32], const uint8_t digest32[32], uint8_t sig64[64] ) { int result; secp256k1_keypair keyPair; secp256k1_xonly_pubkey xonly;
/* Fill keypair structure from the callers secret key */ if (secp256k1_keypair_create(ctx->secpCtx, &keyPair, sk->key) != 1) { return E_INVALID_ARG; } /* Sign the digest */ result = secp256k1_schnorrsig_sign32(ctx->secpCtx, sig64, digest32, &keyPair, random32); /* x-only public key from keypair so the signature can be verified */ result = secp256k1_keypair_xonly_pub(ctx->secpCtx, &xonly, NULL, &keyPair); /* Verify the signature is valid */ result = secp256k1_schnorrsig_verify(ctx->secpCtx, sig64, digest32, 32, &xonly); return result == 1 ? NC_SUCCESS : E_INVALID_ARG;} ```
Some validation code was removed for brevity, assertions are used for describing expected results
You will notice that a key pair structure is required (and must be assigned) from our secret key. This is where I think the strict typing of the
NCPrivateKeystructure ensures safer signing and a more straightforward API. Again, Nostr implementation details, but this function helps mitigate complexities in an obvious and difficult-to-misuse way.In the case of polyglot linking, I think it also makes it reasonably simple to sign a message digest with a single function call on some byte arrays. Direct, which I think is important.
EC Diffie Hellman
ECDH or Elliptic Curve Diffie Hellman gives us the ability to take a set of points on an elliptic curve and create a shared key that only the key holders can generate. More specifically, each party only needs to know each other's public information in order to generate said shared point. We exploit that feature in multiple ways by using symmetric encryption in both NIP-04 and NIP-44 encryption specifications.
Ignoring all of the encryption specifications, we need a function to safely generate our shared point from our Nostr-specific secret and public keys. So some strict typing and our
_convertToPubKey()function from above re-appear. You will also notice a callback function called_edhHashFuncInternal(). This function does the work of "computing the hash" which in Nostr we just need to return the shared x-coordinate as per NIP-04```c NCResult _computeSharedSecret( const NCContext ctx, const NCSecretKey sk, const NCPublicKey otherPk, struct shared_secret sharedPoint ) { int result; secp256k1_pubkey pubKey;
/* Recover pubkey from compressed public key data */ if (_convertToPubKey(ctx, otherPk, &pubKey) != 1) { return E_INVALID_ARG; } /* * Compute the shared point using the ecdh function. * * The above callback is invoked to "compute" the hash (it * copies the x coord) and it does not use the data pointer * so it is set to NULL. */ result = secp256k1_ecdh( ctx->secpCtx, (uint8_t*)sharedPoint, &pubKey, sk->key, &_edhHashFuncInternal, NULL ); ZERO_FILL(&pubKey, sizeof(pubKey)); /* Result should be 1 on success */ return result == 1 ? NC_SUCCESS : E_OPERATION_FAILED;} ```
A lot of things to remember right? Passing buffers and keys around to callback functions. Yeah, in C# I sure had fun doing this in nvault. That was sarcasm if you couldn't tell.
Read The Docs?
The libsecp256k1 project has almost no public documentation. Like many C projects, documentation is just the header files and readme cover. Which is fine if you are me and take the time to really learn how to use their public API. One of the larger projects I build is my website (and CMNext blog tool) to publish readable and up-to-date dedicated documentation. It is assumed you should take header files as authoritative, but dedicated documentation and examples can make or break a project's adoption IMO.
Wrapping up footguns
Honestly, my goal was to provide insight into my experience writing over 4k lines of C code to avoid some of the complexities I initially encountered when scaling NVault to compete with the latest NIPs. I believe Nostr will only become more complex, especially as we delve deeper into post-quantum and forward-secret algorithms.
Backward compatibility
A lesson learned outside of libsecp256k1 is the need for backward and forward API compatibility. When I first started building NVault, only NIP-04 existed, and I assumed that any future spec would deprecate the old spec. As it turns out, that is not the case, and I needed to rethink compatibility for future upgrades.
Many parts of Nostr are either slow to upgrade (due to complexity) or other contributors don't see the need to upgrade. Nostr is inherently anarchistic, and no one developer has the final say on what specs are used in the wild, which is an appeal to me. Every system has tradeoffs; in this case, we will have app compatibility issues. A perfect example is NIP-17 DMs collected by cloud fodder, where some clients support spec interoperability and others do not. I will disregard my personal opinions on their reasoning. I, and GitCitadel, will have our own reasons for our support or lack thereof, and I aim to be as transparent as possible when the time comes.
Making the case for noscrypt
By this point, you might be thinking: "Okay, yeah, you just made a case for another library, great." That would be correct, but I showed some simple code snippets that I believe highlight the requirement for high-level cryptography libraries incorporating the Nostr spec. While Nostr was always meant to be simple enough for a caveman to implement, it relies on the legacy existence of high-level libraries and users' ability to implement them correctly. This ecosystem predominantly exists in the JavaScript/browser world.
When trying to implement compact, portable, and powerful applications, you need the horsepower and efficiency of a dedicated library built for this purpose. We can already see this with existing Nostr SDKs (NDKs) in multiple languages. I don't aim to lock you into an NDK; for very high-level spec functionality, I think simple libraries are suitable for most smart and passionate developers. You don't need to rely on an NDK developer for a specific language.
Use noscrypt for your C project
-
 @ 44dc1c2d:31c74f0b
2024-07-11 19:26:22
@ 44dc1c2d:31c74f0b
2024-07-11 19:26:22Chef's notes
Make sure you cook them thoroughly on the skin side first to render out as much of the fat as possible and ensure maximum crispiness.
This goes great with rice.
Ingredients
- 6 skin-on, bone-in chicken thighs (about 2 pounds total)
- Kosher salt
- 2 tablespoons sesame oil, preferably toasted, divided
- 1 pound medium carrots, scrubbed
- 2 tablespoons soy sauce
- 2 tablespoons Sriracha
- 2 tablespoons unseasoned rice vinegar
- 1 tablespoon honey
- 1 1-inch piece ginger
- 3 scallions
- Toasted sesame seeds (for serving)
Directions
- Preheat oven to 425°. Heat a large dry skillet, preferably cast iron, over medium-low.
- Pat 6 chicken thighs dry with paper towels and season all over with salt. Rub only skin side of thighs with 1 Tbsp. oil.
- Transfer thighs skin side down to skillet and cook until enough fat is rendered to cover bottom of skillet, about 5 minutes. Once skin starts to brown, increase heat to medium. Rotate skillet to encourage even browning. Carefully lift up thighs to allow hot fat to run underneath. If thighs are stubborn and don’t want to release, let them go a bit longer.
- While thighs are cooking, cut 1 lb. carrots into 4" segments.
- Cook thighs until meat is opaque all around the edges and skin is deep golden brown, 10–12 minutes total. Transfer skin side up to a plate.
- Pour off all but about 2 Tbsp. fat from skillet (you just want enough left to form a thin layer) and heat over medium-high. Add carrots and try to arrange so all are side by side in a single layer in direct contact with skillet. Cook, undisturbed, until lightly charred on first side, about 5 minutes. Turn carrots so charred side is facing up, then season lightly with salt.
- Cook carrots on opposite side until lightly charred, about 2 minutes. Turn off stove and transfer skillet to oven. Roast until a toothpick, skewer, or cake tester easily pierces surface of carrot but encounters resistance in the center, 8–10 minutes.
- While carrots are roasting, stir 2 Tbsp. soy sauce, 2 Tbsp. Sriracha, 1 Tbsp. rice vinegar, 1 Tbsp. honey, and remaining 1 Tbsp. oil in a small bowl. Scrape peel off of ginger root with a spoon; discard peel. Grate ginger into bowl with microplane, then stir to combine.
- Carefully remove skillet from oven (the handle will be hot!) and place on stove. Arrange thighs over carrots and drizzle sauce over. Return to oven and roast until chicken thighs are cooked through (an instant-read thermometer inserted into the thickest part near the bone will register 165°), juices run clear, sauce is caramelized on chicken skin, and carrots are tender all the way through, 12–18 minutes. Remove from oven and let rest 10 minutes.
- While skillet is resting, thinly slice 3 scallions.
- Transfer chicken and carrots to a platter and drizzle pan juices over. Top with scallions and sesame seeds.
-
 @ 75da9402:77a65b5c
2024-07-11 19:18:54
@ 75da9402:77a65b5c
2024-07-11 19:18:54Empezare este articulo indicando que iba hacer publicado como un hilo en Twitter o X o como diablos se llame ahora por que mi intencion era trasmitir a otros que existe algo mucho mejor donde pueden empezar nuevamente a disfrutar de otra forma de comunicarse, pero mi sorpresa fue grande al momento de enviar el hilo de tweets, me salio el mensaje "no se puede enviar" usted debe UPDATE TO PREMIUM para atreverse hacer un post en esta empresa que protege la libertad de expresion...lol...(:-O). Como yo casi ya no escribo nada en X y lo uso solo para informarme de lo que pasa en mi pais, no sabia esta nueva limitacion. Ahora volvi a recordar por que deje de usarlo. Pero bueno, aqui voy a desahogar mi hilo para luego compartirlo en X, por que me van a leer quieran o no, jajaja.
Te cuento una pequeňa historia.
Alguna vez me preguntaron por qué me gustaba Twitter (hoy X) más que otras redes sociales ya que yo era un joven audaz que siempre interactuaba ahi jaja. Y mi respuesta fue simple en esos aňos: Twitter es una selva digital donde se genera el debate público e informativo a nivel mundial y aqui puedo decir lo que yo quiera (pobre iluso). Pero luego las cosas fueron cambiando en mi RRSS favorita, en algun momento se convirtio en un hueco lleno de toda clase de basura digital de la cual habia huido siempre, hasta que llego un familiar mio a comprar la empresa y pense: AL FINNN... volveran los dias de gloria, y efectivamente algo parecio mejorar y con eso me conforme, pero aclaro que no me gusto al final el rumbo que tomo la empresa familiar después que mi tío Elon la compró pero es lo que habia en ese entonces y aguante. HASTA AHORA..
Te gusta twitter pero a la vez estás arto de lo mismo?
Hace meses hice 1 post de por qué me gustaba X, pero también explicaba el rumbo que está tomando el mundo de la tecnología con respecto a las redes sociales. Y ahora te explicaré de qué se trata.
Todo ha evolucionado en el mundo de la tecnologia a velocidad vertiginosa, por ejemplo tu tia antes enviaba un Piolin de BUENOS DIAS todas las mañanas en su muro de Facebook a sus amigos y familiares que la seguian, ahora hace lo mismo por el WAZA (grupo familiar que pasa silenciado por siempre) y si ya no lo hace es por que TU eres la TIA del Piolin ahora jajaja, pero volviendo al tema las RRSS no han evolucionado desde hace 20 años, ojo me refiero a la forma de generar contenido, monetizar y consumir, todo es lo mismo que cuando abrí mi cuenta de Twitter hacer 15 años. Han aparecido muchas otras RRSS si es cierto, #tiktok la última. Pero todas hacen lo mismo darte a ti el usuario: entretenimiento, distracción ludica y tal vez “informar”; y esto entre comillas por qué lo que lees, escuchas y te informas es lo que los dueños de estas RRSS, las marcas auspiciantes y quienes pagan su verificación quieren, NO lo que TÚ quieres. Ellos dictan y te “Sugieren el contenido que puedes ver” pero tu no te das cuenta y crees que lo que estas viendo es por que tu asi lo decidiste. Lo cual es una triste y deprimente mentira....
Y no es invento mío, te adjunto una entrevista a Jack Dorsey fundador de Twitter, donde él explica detalladamente por qué sucede esto que afirmó anteriormente. Léelo en tu tiempo libre, no tiene desperdicio. Usa traductor si no le haces mucho al inglés:
https://www.piratewires.com/p/interview-with-jack-dorsey-mike-solana
Y si te preguntas, Alguien está haciendo algo para mejorar esto? SI, un montón de gente (Jack incluido) y otros mas que aportan con muchos recursos: técnicos, económicos, tenologicos y sobre todo tiempo y amor a su profesion. Esta gente está trabajando en cambiar todo esto que esta mal y de ese esfuerzo en conjunto nacieron soluciones como Mastodon, Bluesky y Nostr.
Pero que son Mastodon, Bluesky y Nostr?
Mastodon y Bluesky son básicamente lo mismo, nuevas RRSS donde encuentras de todo. Nacieron con la idea de enfrentar a Twitter la primera, y mejorarlo la segunda como lo explica Jack en su entrevista. Pero al final terminaron teniendo lo mismo, es decir marcas asupiciantes, moderadores verificados y dueños o juntas directivas. Mas de lo mismo....
Nostr en cambio es el giro de tuerca que las RRSS y las comunicaciones humanas necesitan para el futuro, y de hecho Instagram (Threads) y otros ya lo están probando en sus plataformas lanzando puentes desde sus empresas para que sus usuarios tengan interoperatibilidad entre diferentes rrsss del fediverse.
-Y por qué sucede esto con Nostr?
Por qué Nostr no es una RRSS ni una empresa, ni tampoco tiene dueños o moderadores de contenido que dictaminan lo que puedes o no ver, leer, escuchar y consumir en tu feed, ya que es un protocolo de comunicación como los que usas para el correo, para navegar en internet, etc.
-Y que ganamos los usuarios?
Ganamos un largo etc. de beneficios para consumo de contenido REAL, mas humano y mas limpio, pero lo que si diré que NO encontraras es nada de lo que te tiene hastiado de las otras RRSS. Aquí un video que te gustaría ver para entender de lo que escribo:
https://youtu.be/aA-jiiepOrE?si=iaMu5K3qKqh_JxsR
Te interesa usar y aprender que puedes hacer con Nostr?
Te dejo unos link 🔗 para que empieces a explorar una nueva forma de comunicarse entre seres humanos. Usa alguno de estos servicios, pruebalos.
- Lives: https://zap.stream/
- Música: https://wavlake.com/
- Blogs: https://yakihonne.com/
- Podcast: https://www.fountain.fm/
Y muchas más aplicaciones y sevicios en: https://www.nostrapps.com/
Si lo tuyo es consumir contenido en algo como Twitter/X estás apps son para ti:
En iOS: - Primal: https://primal.net/ - Damus: https://damus.io/ - Nostur: http://nostur.com/ - NosSocial: https://nos.social/
En ANDROID: - Primal: https://primal.net/ - Amethys: https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst&hl=en
En WEB: - Primal: https://primal.net/ - Nostrudel: https://nostrudel.ninja/ - Snortsocial: https://snort.social/ - Coracle: https://coracle.social/
Debes saber que puedes con el mismo usuario y contraseña (en #Nostr se dicen llaves) puedes ingresar a TODAS las aplicaciones mencionadas en este articulo, y esto puede lograrse por que el protocolo es el mismo, es NOSTR.
Ya vas en tendiendo? no hay empresas, no hay dueños..😏, TU eres el dueño del contenido que produces y del contenido que consumes.
Quieres saber mas informacion sobre Nostr, visita estas web. Resolveran muchas de tus dudas.
https://nostr.com/ https://nostr.how/
Para terminar con este pequeño hilo... (te odio Elon) jajaja
Nostr esta empezando y tiene mucho por mejorar pero al dia de HOY ya existen cosas increibles que puedes hacer y son mejores que en otras RRSS y te aseguro algo, TODOS nosotros terminaremos tarde o temprano usandolo en el futuro, es inevitable si queremos evolucionar nuestra forma de comunicarnos.
Si tu quieres ser uno de los primeros en experimentar una nueva era de las RRSS. Anímate y empieza a usar NOSTR como TU quieras. Solo haz lo siguiente:
- Descarga cualquier aplicacion en tu movil tipo Twitter detallada en este articulo.
- Crea el Usuario (npub....) llave 1
- Crea la contraseña (nsec....) llave 2
- Guarda tus llaves, que no se te olviden. (anótalas)
- Envia tu primer post colocando al final el hashtag #introductions
- Y a disfrutar de #nostr
Si te gustó este hilo (Elon de >:{ #$%&) dale RT o cómo diablos se diga ahora 😂 o postealo y compartelo donde quieras para que mas gente lea sobre Nostr. Tal vez a alguien le interese.
Si deseas seguirme en #Nostr •𓅦
primal.net/p/npub1whdfgqn66sytcta0l6c7vlt3h2lg67xcnsmzpk3pyvpmsaaxtdwqr8vs60
Alla nos vemos...escríbeme y pregunta lo que quieras.
Saludos, johnny
-
 @ 75da9402:77a65b5c
2024-07-11 19:14:04
@ 75da9402:77a65b5c
2024-07-11 19:14:04
### BIENVENID@ A NOSTR
Queridos amigos que desean unirse a Nostr, sé que para todos ustedes es nuevo este camino, pero créanme que vale la pena experimentar y conocer una nueva forma de conectar y comunicarse con personas en otras partes del mundo. Varias de las mentes mas brillantes y apasionadas por dejar una huella diferente en las comunicaciones humanas han puesto alma, mente, corazón y hasta sus propios fondos para desarrollar y aportar a nostr.
QUE ES NOSTR? ¿COMO EMPIEZO?
Nostr es un protocolo de comunicación que está diseñado para que las personas se conecten entre si de forma rápida, segura y divertida. No es una empresa de RRSS como Twitter, FB u otras, tampoco existe un dueño, CEO o accionistas ni moderadores ni administradores de contenido, tampoco pertenece algún país en específico. Dicho esto, si aún no sabes cómo empezar aquí vamos. Para conectarte a Nostr vas a usar aplicaciones llamadas también clientes, te sugiero empieces en tu móvil y estas son algunas de las que puedes descargar y probar para empezar, luego puedes buscar otros clientes de tu agrado:
Damus para usuarios de IPhone https://apps.apple.com/app/damus/id1628663131
Amethyst para usuarios de Android https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst
PASOS IMPORTANTES A SEGUIR
Vamos a realizar estos pasos con el cliente Damus pero en Amethyst funciona igual:
1.- Una vez que instalaste la aplicación cliente ábrela y vas a ir a la opción Crear Cuenta

2.- Te aparecera una pantalla que dice EULA, dale aceptar sin miedo como en todas tus RRSS jaja, tranquil@ no pasa nada.
3.- En la siguiente pantalla deberás: Subir foto de perfil (si lo deseas), Nombre de usuario (nick que te guste el mio jp ), Mostrar nombre (como quieres llamarte el mio johnny ), Informacion (una breve biografía tuya ) presiona Crear y listo ya puedes usar Nostr como un Sayayin :-P

4.- Antes de empezar a escribir tu primer post vamos a dar 2 pasos más que son fundamentales y algún día me lo agradecerás (pero si a ti nadie te dice que hacer jajaja, ya puedes empezar a usar Nostr y saltarte estos pasos). Ve a la parte superior izquierda de Damus y presiona en la foto de tu perfil, deberá aparecer un menú que dice Configuración presiónalo y debe llevarte a algunas opciones, entre ellas escoges la que dice Keys

5.- Este es el último paso y es EXTREMADAMENTE IMPORTANTE que lo sigas al pie de la letra por que vamos a guardar tus llaves (usuario y contraseña) de forma segura. Aquí debo informarte que en Nostr no usaras ni correo ni número de móvil ni otro dato personal que te identifique para poder acceder a tu cuenta y por lo tanto debes guardar tú mismo las llaves de acceso ya que si las pierdes NO HAY FORMA DE RECUPERAR, las perderás para siempre y deberás volver a iniciar de nuevo.
Dentro de la opción Keys encontraras dos identificadores el primero que empieza por npub... es tu clave publica (tu usuario) que todos ven en la red y más abajo encontraras tu llave secreta (tu contraseña) esta es la más importante y al activar el botón Mostrar aparecerá y empieza con nsec.... estas dos claves debes copiarlas y guardarlas con total seguridad NO LAS PIERDAS de preferencia para guardarlas usa un administrador de contraseña como Bitwarden o tu propio llavero de ICloud en tu IPhone.

Bien si ya hiciste estos 5 pasos en menos de 5 minutos ya estarás listo para navegar e interactuar con otras personas en #nostr. Existen otros conceptos dentro de la red que ya te explicare en otra guía, por ejemplo, los relés que son los que se encargan de trasmitir tus posts (en forma de notas) a todo el mundo, pero con los que vienen preconfigurados los clientes es suficiente por ahora.
DIVIERTETE NUEVO NOSTRICH
Es momento de lanzarte al universo de Nostr, publica tu primer post Hola Mundo y empieza hacer amigos y te aseguro que muchas buenas personas te responderán para darte la bienvenida, como sugerencia si hablas español o quieres conocer gente de este idioma: ve a la opción UNIVERSO (lupa de buscar) de tu cliente, aquí encontraras el feed global donde aparece todos los posts a nivel mundial donde también puedes conocer gente. Ahí escribes Seguidor Hispano le das seguir a todos los que sigue esa cuenta y puedes empezar a seguir a otros en tu idioma.
Si te ha gustado y servido este minitutorial, compártelo a otros y si quieres puedes también seguirme a veces comparto buenos memes :-) Copia mi usuario en el buscador y me sigues:
npub1whdfgqn66sytcta0l6c7vlt3h2lg67xcnsmzpk3pyvpmsaaxtdwqr8vs60
By Johnny
-
 @ c73818cc:ccd5c890
2024-07-12 19:13:47
@ c73818cc:ccd5c890
2024-07-12 19:13:47
⏰ Accuse di Censura Centralizzata
😱 Andrea Lombardi, ha denunciato la rimozione dei suoi contenuti dalla piattaforma X. Lombardi sostiene che i suoi post siano stati segnalati in massa da bot e gruppi organizzati, appellandosi al DSA della Comunità Europea, evidenziando un preoccupante trend di censura.
⏰ La censura e il Digital Services Act (DSA)
😱 Lombardi afferma che la censura sui suoi post è il risultato del Digital Services Act (DSA), un regolamento dell’Unione Europea che impone alle piattaforme digitali di rimuovere contenuti potenzialmente dannosi per il discorso civico o per le elezioni. Questo regolamento, sostiene Lombardi, permette una rimozione arbitraria dei contenuti, colpendo indiscriminatamente tutto ciò che potrebbe risultare scomodo per il potere.
⏰ Le reazioni e le minacce
😱 A seguito delle sue dichiarazioni, Lombardi ha ricevuto migliaia di commenti, molti dei quali minacce e insulti da account anonimi. Un episodio particolarmente grave è stato l’intervento di un giornalista italiano di origini ucraine, Vladislav Maistru, che ha comparato Lombardi a Julius Streicher, un alto funzionario nazista condannato a morte a Norimberga, suggerendo implicitamente che Lombardi potrebbe fare la stessa fine.
⏰ Organizzazione della censura
😱 Lombardi ha scoperto l’esistenza di un gruppo Telegram, gestito da Alexander Orlowski, dove gli utenti si organizzano per segnalare i suoi contenuti a Twitter. Questo gruppo, secondo Lombardi, utilizza anche sistemi automatici per inviare segnalazioni in massa, al fine di ottenere la rimozione dei suoi post.
⏰ Il reato di opinione e l'imposizione della verità, sono le basi su cui si fonda ogni dittatura
Unisciti al nostro gruppo Telegram: https://t.me/Bitcoin_Report_Italia
Referral Bitget -10% sulle fee + bonus benvenuto 6w5d o link: https://bonus.bitget.com/U1JNEK
BitcoinReportItalia #Lombardi #DSA #Censura #UE #Dittatura #Fascismo #SmartContract #DigitalServicesAct #Contenuti #Minacce #Maistru #Orlowski #Bitcoin
-
 @ 8d34bd24:414be32b
2024-07-11 15:27:32
@ 8d34bd24:414be32b
2024-07-11 15:27:32Once again here are the fruits of the Spirit as defined in Galatians 5.
But the fruit of the Spirit is love, joy, peace, patience, kindness, goodness, faithfulness, gentleness, self-control; against such things there is no law. (Galatians 5:22-23) {emphasis mine}
A Young Example
When I think of Godly kindness, I think of my eldest son. He always puts others above himself. He always considers other’s needs and point of view. He goes out of his way to help or talk to those who are lonely and hurting. He is unbelievably accommodating and caring to his younger brother, who has Down Syndrome. When we ask him for help, he instantly and cheerfully stops what he is doing to help. Nothing, but God, can make a teenage boy (now a young man) be as kind and self sacrificing as he is.
Do not let kindness and truth leave you;
Bind them around your neck,
Write them on the tablet of your heart.
So you will find favor and good repute
In the sight of God and man. (Proverbs 3:3-4)My son is such an amazing example of kindness that everyone who has met him notices and most comment on it. He stands out as a light in this dark world.
Bless Those Who Curse You
God calls us to all exhibit kindness. When we are kind, even to those who are unkind to us, we point the world to God. We stand out like a shining beacon in this grumpy, divided world.
“But I say to you who hear, love your enemies, do good to those who hate you, bless those who curse you, pray for those who mistreat you. Whoever hits you on the cheek, offer him the other also; and whoever takes away your coat, do not withhold your shirt from him either. Give to everyone who asks of you, and whoever takes away what is yours, do not demand it back. Treat others the same way you want them to treat you. If you love those who love you, what credit is that to you? For even sinners love those who love them. If you do good to those who do good to you, what credit is that to you? For even sinners do the same. If you lend to those from whom you expect to receive, what credit is that to you? Even sinners lend to sinners in order to receive back the same amount. But love your enemies, and do good, and lend, expecting nothing in return; and your reward will be great, and you will be sons of the Most High; for He Himself is kind to ungrateful and evil men. Be merciful, just as your Father is merciful. (Luke 6:27-36)
Putting Others First
Kindness is related to love, but is a little different. Kindness is acting in a loving manner even to those who are hateful to you and to those whom you don’t really like. It is seeing the hurt and pain in others instead of the hate and reaching out with the same mercy that God had for you. It is putting another’s good above your own. It is doing this not only for those whom you love, but also those who hate you, mistreat you, and who are undeserving. We do this because God showed love to us when we were undeserving. It is acting based on the other person’s need instead of based on our own hurt. It is amazing how, when our focus is on God and the needs of others, the same words and actions that would previously drive us into a rage, instead will engender pity, mercy, and care.
When my son was flying home from college for the summer, he had a succession of problems with his flight. First his flight was delayed several hours due to mechanical issues delaying it into the afternoon. Then after finally taking off, they couldn’t land at their intended location because of severe thunderstorms and even the risk of tornados. Instead they landed at an airport in a completely different state. While waiting to return to the intended location, he had to wait in the airport for hours.
My son is very frugal. He is generous with others and has insisted on buying gifts for his friends since he was around 10 years old (maybe younger) so that they would be from him, but he doesn’t like to spend any money on himself. He definitely doesn’t want to spend the high prices of airport food, but is an always hungry teenage boy. We told him over the phone that he should go to the service desk and ask for food vouchers since the original delay was mechanical problems and to not take “no” for an answer because they wouldn’t have had weather issues if not for their mechanical issues. He refused to go get vouchers because he said there were a bunch of people in line that looked to be in greater need than he was. He put their comfort and need above his own. This is the exact attitude that God calls us to and is a fruit that we should show if we are saved. True, many of us may show it as an unripe and misshapen fruit, but the fruit should still be there, especially when we make an effort to obey God.
Imitate the Kindness of Christ
Let all bitterness and wrath and anger and clamor and slander be put away from you, along with all malice. Be kind to one another, tender-hearted, forgiving each other, just as God in Christ also has forgiven you. (Ephesian 4:31-32)
Based on what God has done for us:
But God demonstrates His own love toward us, in that while we were yet sinners, Christ died for us. (Romans 5:8)
We should show the same love, kindness, and mercy towards others who need Jesus as we did. Instead of focusing on how we were wronged, we should focus on their need.
You may say, “That’s not fair.” Maybe not, but it is right and it actually can end up to our benefit. When we act kindly towards someone who does not act kindly towards others or ourselves, we point them to Jesus because we are different than the world. If that person accepts Jesus, we have gained a brother or sister in Christ. We have changed the world for the better (through the power of the Spirit). It feels good when someone changes from hate to kindness and goes from unsaved to a child of God.
I worked two summers as an intern for a design build construction company while I was in college getting my electrical engineering degree. I worked with a drafter who would draw up my electrical drawings. He had been doing this for a good number of years. I was a newbie designing these systems for buildings. He resented me because he wanted to do the job I had been hired to do, but the company only wanted to hire people with EE degrees for the job. (Ironically the top electrical guy didn’t have a degree.) The drafter would point out any error I made in a very unkind way, but I just worked and did my best.
After a long time working with Him, a big group from work went to a free lunch at a local mega-church (actually the church I was attending at the time.) As a ministry the church did a free lunch once a month and preached to the attendees during lunch. At this lunch, the drafter sat near me and asked me, why I had always been kind to him despite him not being kind to me. I told him it was because I was a Christian. I would like to say that he became a born-again Christian at that moment, but that didn’t happen. At the same time, our relationship almost instantly changed. I was no longer picked on. Any corrections were done kindly. Working together was done with mutual respect. This never would have happened if I had responded in the same way I was treated. I would like to think that that was a seed I planted that God later brought to fruition, but I will never know until I reach heaven. Still, it was so worth it.
The Sweetness of Kind Words
The heart of the wise instructs his mouth
And adds persuasiveness to his lips.
Pleasant words are a honeycomb,
Sweet to the soul and healing to the bones. (Proverbs 16:23-24)A person with the fruit of the Spirit always talks in a kind, pleasant way that is sweet to those who hear. Some that hate us may not appreciate the kindness at the time, but it will make a difference. They may initially hate us more because of our kindness because it accentuates their hate and no one wants to think of themselves as hateful. We all want to think well of ourselves.
Are your words known for their kindness? Are you gentle with your words or are you known for your sharp, cutting words? If the latter, pray that the Spirit would help you have self-control and kindness in your words. Our Christian response should always be different.
Therefore, putting aside all malice and all deceit and hypocrisy and envy and all slander, like newborn babies, long for the pure milk of the word, so that by it you may grow in respect to salvation, if you have tasted the kindness of the Lord. (1 Peter 2:1-3)
Be Kind in Gratefulness for the Kindness of Jesus
We should be kind because God was kind to us and we want to show the world what God is like.
Do nothing from selfishness or empty conceit, but with humility of mind regard one another as more important than yourselves; (Philippians 2:3)
Is there any other religion or belief system where its adherents are encouraged to put others first and not seek our own benefit from our words and actions? I don’t think so! When we act in this manor, we stand out in the crowd. People see that there is something different about us. We can be used by God to make a difference in the world and in other people’s lives.
For we also once were foolish ourselves, disobedient, deceived, enslaved to various lusts and pleasures, spending our life in malice and envy, hateful, hating one another. But when the kindness of God our Savior and His love for mankind appeared, He saved us, not on the basis of deeds which we have done in righteousness, but according to His mercy, by the washing of regeneration and renewing by the Holy Spirit, whom He poured out upon us richly through Jesus Christ our Savior, so that being justified by His grace we would be made heirs according to the hope of eternal life. (Titus 3:3-7)
Kindness is just being grateful for what Jesus did for us and doing for others what Jesus did for us. Obviously we will never succeed in being as kind and merciful as Jesus, but the Spirit enables to do more than a natural man ever could.
Therefore, return to your God, Observe kindness and justice, And wait for your God continually. (Hosea 12:6)
Obedience Encourages Kindness
Paul talks about working hard so we are able to be kind and minister to those in need. He used his own work and generosity as part of his witness for Christ.
You yourselves know that these hands ministered to my own needs and to the men who were with me. In everything I showed you that by working hard in this manner you must help the weak and remember the words of the Lord Jesus, that He Himself said, ‘It is more blessed to give than to receive.’ ” (Acts 20:34-35)
Although the fruit of the Spirit, kindness, is something only spoken of as being given to Christian believers in the New Testament, the command to be kind has been spoken of in the Bible throughout the Old Testament as well. It isn’t a new command. This verse tells more about kindness:
Then the word of the Lord came to Zechariah saying, “Thus has the Lord of hosts said, ‘Dispense true justice and practice kindness and compassion each to his brother; and do not oppress the widow or the orphan, the stranger or the poor; and do not devise evil in your hearts against one another.’ (Zechariah 7:8-10)
Take this to heart and let kindness flow through you.
Trust Jesus
Check out the whole series, Fruits of the Spirit
-
 @ 47750177:8969e41a
2024-07-09 12:00:00
@ 47750177:8969e41a
2024-07-09 12:00:0026.2 Release Notes
Bitcoin Core version 26.2 is now available from:
This release includes new features, various bug fixes and performance improvements, as well as updated translations.
Please report bugs using the issue tracker at GitHub:
https://github.com/bitcoin/bitcoin/issues
To receive security and update notifications, please subscribe to:
https://bitcoincore.org/en/list/announcements/join/
How to Upgrade
If you are running an older version, shut it down. Wait until it has completely shut down (which might take a few minutes in some cases), then run the installer (on Windows) or just copy over
/Applications/Bitcoin-Qt(on macOS) orbitcoind/bitcoin-qt(on Linux).Upgrading directly from a version of Bitcoin Core that has reached its EOL is possible, but it might take some time if the data directory needs to be migrated. Old wallet versions of Bitcoin Core are generally supported.
Compatibility
Bitcoin Core is supported and extensively tested on operating systems using the Linux kernel, macOS 11.0+, and Windows 7 and newer. Bitcoin Core should also work on most other Unix-like systems but is not as frequently tested on them. It is not recommended to use Bitcoin Core on unsupported systems.
Notable changes
Script
-
29853: sign: don't assume we are parsing a sane TapMiniscript
P2P and network changes
-
29691: Change Luke Dashjr seed to dashjr-list-of-p2p-nodes.us
-
30085: p2p: detect addnode cjdns peers in GetAddedNodeInfo()
RPC
-
29869: rpc, bugfix: Enforce maximum value for setmocktime
-
28554: bugfix: throw an error if an invalid parameter is passed to getnetworkhashps RPC
-
30094: rpc: move UniValue in blockToJSON
-
29870: rpc: Reword SighashFromStr error message
Build
-
29747: depends: fix mingw-w64 Qt DEBUG=1 build
-
29985: depends: Fix build of Qt for 32-bit platforms with recent glibc
-
30151: depends: Fetch miniupnpc sources from an alternative website
-
30283: upnp: fix build with miniupnpc 2.2.8
Misc
-
29776: ThreadSanitizer: Fix #29767
-
29856: ci: Bump s390x to ubuntu:24.04
-
29764: doc: Suggest installing dev packages for debian/ubuntu qt5 build
-
30149: contrib: Renew Windows code signing certificate
Credits
Thanks to everyone who directly contributed to this release:
- Antoine Poinsot
- Ava Chow
- Cory Fields
- dergoegge
- fanquake
- glozow
- Hennadii Stepanov
- Jameson Lopp
- jonatack
- laanwj
- Luke Dashjr
- MarcoFalke
- nanlour
- willcl-ark
As well as to everyone that helped with translations on Transifex.
-
-
 @ 0dc2dcb1:4787801a
2024-07-11 15:16:25
@ 0dc2dcb1:4787801a
2024-07-11 15:16:25- Added ids and
setIds()to the Filter class to fetch events with ids - https://github.com/nostrver-se/nostr-php/compare/1.3.1...1.3.2 - Discovered https://revolt.run/ as a package to be used for concurrent async code in PHP. Source: TalkingDrupal podcast with KingDutch - https://www.drupal.org/project/drupal/issues/3257726
- Fix response in Relay class - https://github.com/nostrver-se/nostr-php/releases/tag/1.3.3. Found and reported on Nostr: https://njump.me/nevent1qvzqqqqqqypzphtxf40yq9jr82xdd8cqtts5szqyx5tcndvaukhsvfmduetr85ceqy88wumn8ghj7mn0wvhxcmmv9uq3zamnwvaz7tmwdaehgu3wwa5kuef0qqsq3utlvgf6tz88ctexwu8ppgct9dkahmv5esxhmmgphv675get22qmzah0a
- Created a seperate repository with the code for the nostr-php.dev website: https://github.com/nostrver-se/nostr-php.dev
- Added ids and
-
 @ b2caa9b3:9eab0fb5
2024-07-11 15:04:06
@ b2caa9b3:9eab0fb5
2024-07-11 15:04:06Hey everyone,
Today wasn't super eventful, but there were a couple things I wanted to share. First off, I had to pay rent, which meant a trip to the bank with my still-not-great foot. On the bright side, I took some pictures of Moshi along the way - hopefully you'll enjoy a glimpse of the city!

Speaking of my foot, there's been some improvement! The pain isn't constant anymore, only when I'm walking around. It looks better too, so hopefully it'll be back to normal soon.
Now, onto the slightly more frustrating topic: the Kenyan border situation. As you might recall, I had a big issue where border control wouldn't let me leave the country and even refused to contact my embassy. Basically, they held me hostage (which, by the way, is a violation of international law).
Two days later, I managed to get out through a different border. Recently, the Kenyan police has started investigating. They contacted me on WhatsApp a few days ago, and things are getting stranger by the day.

There's a big part of this that just doesn't add up. They keep asking for a photo of the exit stamp, but the officer who wouldn't let me leave never gave me one. He actually denied my exit and put me on a bus back to the city! I explained this and told them another border provided the stamp later, but they insist they need the original stamp to find this as "proof" related to this officer. It just doesn't connect to the man who caused the problem in the first place.

Even more concerning, they want me to return to Kenya. First, they want me to sign a document, but when I expressed hesitation about returning, they switched to asking me to identify this officer in a lineup. And all of this communication is happening on a personal WhatsApp number, which makes the whole situation incredibly suspicious.
Overall, it's a confusing situation.
On a brighter note, my foot is definitely on the mend. Here's to hoping it keeps getting better!
That's all for today. I'll just be relaxing and grabbing some dinner later.
Stay tuned for more updates!


Online
Feel free to support me by sending some sats via the lightning network to rubenstorm@sats.mobi
-
 @ c73818cc:ccd5c890
2024-07-12 13:18:55
@ c73818cc:ccd5c890
2024-07-12 13:18:55
🍽 Hamilton Lancia i Primi Buoni del Tesoro USA Tokenizzati su Bitcoin
😘 Hamilton ha fatto notizia con il lancio degli Hamilton U.S. T-Bills (HUST), i primi buoni del Tesoro USA tokenizzati sulla blockchain di Bitcoin. Questo evento storico rappresenta una significativa evoluzione nella finanza decentralizzata (DeFi), portando i buoni del Tesoro, tradizionalmente un asset sicuro e stabile, nel mondo delle criptovalute.
🍽 Vantaggi dei Layer-2 di Bitcoin e Implicazioni per la Finanza Decentralizzata
😘 L'uso dei layer-2 di Bitcoin per la tokenizzazione dei T-Bills offre vantaggi sostanziali, tra cui commissioni ridotte e una maggiore scalabilità per le operazioni DeFi. Le soluzioni layer-2 come Stacks e Core permettono l’esecuzione di smart contract e migliorano l'efficienza delle transazioni, rendendo più accessibili e sicure le operazioni finanziarie basate su Bitcoin.
🍽 L’Effetto dei T-Bills sul Mercato delle Criptovalute e la Crescita dei RWA
😘 Il lancio dei T-Bills tokenizzati ha contribuito a far crescere il valore totale degli Real-World Assets (RWA) a oltre 8 miliardi di dollari. Con un’offerta di rendimenti competitivi rispetto alle stablecoin, questo sviluppo rappresenta un’opportunità per gli investitori di diversificare i propri portafogli e segna un importante passo verso una maggiore integrazione tra finanza tradizionale e criptovalute.
Unisciti al nostro gruppo Telegram: https://t.me/Bitcoin_Report_Italia
Referral Bitget -10% sulle fee + bonus benvenuto 6w5d o link: https://bonus.bitget.com/U1JNEK
BitcoinReportItalia #Hamilton #HUST #BuoniTesoro #USA #DeFi #Layer2 #SmartContract #TBills #RWA #Bitcoin
-
 @ 0e8c41eb:95ff0faa
2024-07-08 14:36:14
@ 0e8c41eb:95ff0faa
2024-07-08 14:36:14Chef's notes
Sprinkle a pinch of salt in a bowl. Sift 275 grams of flour above it. Make a well in the center of the flour and sprinkle the yeast into it. Add 50 grams of butter, 25 grams of sugar, and the egg. Pour in the milk and knead the dough with the mixer or by hand into a smooth dough. If necessary, add a bit more flour if the dough is too sticky. Form the dough into a ball. Let the dough rise covered with cling film at room temperature for 1 hour.
Peel the apples. Cut the apples and apricots into pieces. Cook the fruit with 150 grams of sugar and 50 ml of water in 15 minutes into a thick compote. Let this fruit filling cool.
Knead the dough again briefly and roll it out to a round sheet of about 28-30 cm in diameter, so that it fits well over the baking tin. Press the dough into the tin and press it well into the corners. Let the dough rise again for 10 minutes and cut off the excess edges.
Spread the fruit filling over the dough.
Mix the rest of the flour with the remaining 100 grams of butter and 100 grams of sugar and knead it with your fingers into a crumbly mixture. Sprinkle this crumble mixture over the fruit filling. Bake the tart in the preheated oven at 200°C for about 30 minutes until golden brown.
Variations: Only apple? Make this tart with 1 kilo of apples. High or low? You can also bake the crumble tart in a low tart tin of 30 cm diameter. If the fruit filling is a bit too voluminous, you can make double the crumble mixture and sprinkle it over the larger surface area.
Additional needs: Mixer with dough hooks or food processor Cling film Round baking tin with a diameter of 28-30 cm, greased
Details
- ⏲️ Prep time: 45 min + 1 hour Rising
- 🍳 Cook time: 30 minutes
- 🍽️ Servings: 8
Ingredients
- 375 grams flour
- 1 packet dried yeast (7 grams)
- 125 grams unsalted butter, at room temperature
- 275 grams sugar
- 1 egg
- 100 ml milk, at room temperature
- 500 grams apples
- 500 grams apricots (fresh or from a can)
Directions
- Sprinkle a pinch of salt in a bowl. Sift 275 grams of flour above it. Make a well in the center of the flour and sprinkle the yeast into it. Add 50 grams of butter, 25 grams of sugar, and the egg. Pour in the milk and knead the dough with the mixer or by hand into a smooth dough. If necessary, add a bit more flour if the dough is too sticky. Form the dough into a ball. Let the dough rise covered with cling film at room temperature for 1 hour.
- Peel the apples. Cut the apples and apricots into pieces. Cook the fruit with 150 grams of sugar and 50 ml of water in 15 minutes into a thick compote. Let this fruit filling cool.
- Knead the dough again briefly and roll it out to a round sheet of about 28-30 cm in diameter, so that it fits well over the baking tin. Press the dough into the tin and press it well into the corners. Let the dough rise again for 10 minutes and cut off the excess edges.
- Spread the fruit filling over the dough.
-
 @ 29216785:2a636a70
2024-07-11 13:06:59
@ 29216785:2a636a70
2024-07-11 13:06:59Dont know...
-
 @ 796a6d9b:3bb533e3
2024-07-11 12:57:35
@ 796a6d9b:3bb533e3
2024-07-11 12:57:35For more than a while now, I think you have experienced the feeling that things are not right in the world or in your country, it is not surprising that it coincides with a moment in history where we will experience the end of a monetary cycle like It is FIAT money or in other words fiat money that is backed by debt, every day you look around you and people do not find much hope in the future, many of them are working to support themselves, pay the costs of living and In the best of cases, just saving a little inflationary money, a slower theft in the population, in the worst of cases, people are full of debt and without a plan on how to escape said trap.
Everything is connected, we just have to look for the signs that are leaving us with the naked eye, as for example we have never had in history countries so indebted based on their GDP or gross domestic product and that this same debt was financed with a deficit, For people who have studied or lived the situations of hyperinflationary countries like Venezuela, Argentina, Turkey, Lebanon, you will know what I am talking about, it is simpler than it sounds, no country can spend more than it produces without any consequences, someone has to pay the price, in this case the population through the dark hand of inflation.
We have reached the point where governments blatantly lie to us with inflation data that does not include food, rent and energy prices, to save appearances and maintain the psychological operation that everything is fine, but when you go to the supermarket you know that something was never there. Well, it is not surprising that even you, the person reading this, know that inevitably your Dollars, Euros or Pesos will not buy you the same thing in a year as what they buy you today.
So where are we headed? It is normal then that people are not very enthusiastic about the future, since when we look into the depths of our system we realize that people's savings and purchasing power will increasingly be devalued so that everything continues to function as it has until now. Today, it is noticeable that something in people's subconscious warns them that tomorrow will be worse and that is why they have to enjoy the now, reducing their time preference to sporadic moments without thinking about the long term, even if they do not understand complex mechanisms. economics, it is observed that people are increasingly working more for less remuneration since the numbers of a salary can increase nominally but they buy fewer and fewer goods and services, as we can see in this graph.
What we have left in the coming years is the acceleration of government mechanisms to be able to continue keeping the wealth extraction system functioning, trying to extend the psychological operation to a point of no return, it is clear that a form of money has been confiscated from us. . that allowed us savings like gold did, I think it is important that we begin to question certain things and choose not to continue participating in a system that is arranged to destroy the energy of our work.
What can we do? Alternatives such as Bitcoin and gold to protect the energy of our work are some of the best options that we can implement as a refuge from the disaster to which our politicians have dragged us. Using these alternatives as a kind of battery for our energy is the only way we can ensure that the effort we make every day in our jobs, ventures or companies is not devalued, since both gold and bitcoin are not debt. of anyone, they are reserves of value and have no risk of reverse departure or non-payment.
It is time to take action and educate ourselves to be able to rise to the challenges of the paradigm shift that we will have as a civilization, since a change in the monetary standard is what can lead us to a better path of incentives where people can change preferences. temporary and build for the future.
originally posted at https://stacker.news/items/604619
-
 @ b2caa9b3:9eab0fb5
2024-07-12 11:31:31
@ b2caa9b3:9eab0fb5
2024-07-12 11:31:31Seven months ago, I published an article titled »A Day of Hope: Journey to the Orphan Children in the Shadow of Kilimanjaro«. Unfortunately, the link I included for the organization wasn't quite right – it didn't lead you to the information you needed.

I'm happy to report that I recently reconnected with someone from the organization during my return trip to Moshi! They've informed me that their website is now up and running smoothly at a new address.
While I wasn't able to visit the children again this time, I wanted to provide the correct website address in this update. For anyone interested in donating or volunteering, you'll now find all the necessary details on their official website: worthyofhopetanzania.com
I sincerely apologize for the inconvenience caused by the incorrect link in my original post. I hope this update empowers you to learn more about the organization and their important work.
The photo you see here is from my December 2023 visit, included in the original article.
Please share this update to spread the word and help this fantastic organization continue its mission.
Check out this article for details about my visit in December 2023 - Original Article
Online
Feel free to support me by sending some sats via the lightning network to rubenstorm@sats.mobi
-
 @ 29216785:2a636a70
2024-07-11 12:35:37
@ 29216785:2a636a70
2024-07-11 12:35:37this should not be empty
-
 @ cec2981c:814d4f26
2024-07-08 12:56:36
@ cec2981c:814d4f26
2024-07-08 12:56:36Chef's notes
More information about its origins: https://en.wikipedia.org/wiki/Soda_bread
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 45 min
- 🍽️ Servings: 4-8
Ingredients
- 500 gr whole grain flour
- 450 ml butter milk
- 10 gr (sea)salt
- 15 gr baking soda (not US's "baking powder") (also known as sodium bicarbonate)
- a bit of butter or olive oil
Directions
- Pre-heat the oven to 220°C
- Put all flour in a bowl with baking soda and salt. Mix it well.
- Create a hole in the middle and pour all butter milk in the center.
- Stir it from the centre and slowly mixing all together until you get a dough.
- When mixed, the dough is sticky. Use all purpose flour on counter and bulge to the same size as your skillet.
- Use a bit of butter or olive oil to wet the skillet to prevent sticky bread. And put the dough in your skillet.
- Add a but of flour on top of the dough and then cut lightly a X.
- Bake for ±45 min on 220°C until done (inside temperature must be at least 95°C). Turn up the heat for the last 5 min to get a crust.
- Let the bread cool down a bit before taking it out the skillet, and let it cool down even more before eating.
- Donate some sats to me if you like this recipe.
-
 @ 826e9f89:ffc5c759
2024-06-28 21:46:01
@ 826e9f89:ffc5c759
2024-06-28 21:46:01_Prologue: this is a prose adaptation of a talk I gave to a private audience in Dubai and then tweaked slightly for a small conference in Sofia. I'm increasingly thinking it deserves a more general audience, and may be better suited to text anyway. This is probably not its final form, as the desired audience is tradfi capital allocators, hence a PDF is likely on the cards in the near future. For the time being, consider this a first draft, practising what it might look like as prose, and soliciting feedback from the good people of Nostr. Enjoy! _
The title of this essay means absolutely nothing. There is no such thing as “Web π” because there is no such thing as “Web 3”. It’s bullshit. It’s a scam.
Unfortunately, it has turned out to be extremely powerful bullshit and an extremely profitable scam, and so my goal in writing this essay is to give the reader the tools to navigate all of this and come out the other side without having been scammed or bullshat. In the spirit of not scamming and not bullshitting, I should be clear upfront about the intended readership of this essay, who I am to write it, and who it’s really about.
Who Are You?
I assume the reader is not a shadowy super-coder, but rather is a financial professional. This essay isn’t really for Bitcoiners, although if any read it, I hope they still find it interesting. Who I am really writing for are people coming to the space for the first time. Hopefully in your mind you are coming to the _Bitcoin _space, but if you think you are coming to the “crypto” space then this may be even more useful.
Who Am I?
I am the founder of a company that makes me not only highly biased but also flagrantly self-interested in the content I am promoting. I run a firm that invests in the Bitcoin ecosystem through a variety of different vehicles. I am not going to mislead you in the slightest in that my primary motivation is for you to allocate capital to us rather than to people I would call scammers and bullshitters. You should listen to them too and make up your own mind, or else what’s the point, really? How do you know I’m not scamming or bullshitting you? Exactly. Don’t trust. Verify.
In any case, that’s all assuming you want to “allocate capital” at all rather than just buy Bitcoin without a management fee. I’d like to think the primary difference is that I will be honest about that, and I’ll encourage you to understand as much as you can about what is going on and what you are doing (and if you are at all unsure, I would suggest you aren’t ready and you should just buy Bitcoin and learn) rather than bamboozle you with complete nonsense like “Web 3”.
Who Is This About?
It’s not at all about people working in crypto. Bitcoiners amongst the readership may be mildly irritated by me going on to give about as charitable an explanation of the role of these people as they have probably ever heard from somebody like me. This is really about financiers. It’s about the people who have used the mostly unrewarded efforts of developers, academics, entrepreneurs, and so on to siphon money from you to themselves, leaving a trail of useless tech and defrauded retail investors in their wake – and who will continue to do so if you continue to empower them.
Why This Essay?
We are at an interesting point in the development of the entirety of the “crypto” industry and I strongly suggest that people like you are going to be pitched all kinds of scams and bullshit in the coming months and years. If you have a little more background on what these people are really talking about, you will hopefully be able to avoid it.
My plan to help with that is presenting a short version and a long version of what blockchains are and are for, how they have historically been deployed in service of scams and bullshit, a high-level theory explaining the narrative evolution behind this sorry history, and a prediction for the near-term future of such shenanigans.
What is a Blockchain For?
A Blockchain is for sound, censorship-resistant, peer-to-peer digital money. It is not for anything else. If a blockchain is functional as money, it may be possible to also _use it _for other things. Some people find that interesting, some people find it infuriating, but don’t let that subtlety confuse you. It is not _for _arbitrary computation and storage or “decentralizing the internet” or running illegal securities rackets.

It is for money, plain and simple.
How does it achieve that? Proof of work and the difficulty adjustment. These are the innovations from which every other desirable property or feature flows. Proof of work enables censorship resistance. If somebody is trying to sell you on “proof of stake”: bullshit. The difficulty adjustment enables precise, predetermined, and _fair _issuance. If somebody is trying to sell you on a token they issue for free and without restriction: scam.
The problem Bitcoin solves is both economic and technical and the solution has material technical and economic merit. And it’s for this very specific and irreplicable reason the Bitcoin token has value. If this all sounds extreme to you, then I would suggest that your understanding of the topic is _extremely _misguided, that you are going to be _extremely bullshat and extremely scammed, _and you need to read this essay. That’s the short version.
The Long Version
I am sensitive to how extreme this all sounds. After all, hundreds of billions of dollars have been pumped into crypto, not Bitcoin – a huge amount of it is widely used, and many capable, honest, and brilliant people work in the industry. The reader will recall just above I said those people are not the target of my criticism. I’m not claiming they are all scammers and bullshitters. Sadly, I think it’s more likely they have been scammed and bullshat to some degree also.
I think I have some credibility in pointing this out because, as a VC in the Bitcoin space, I have increasingly seen founders telling me this themselves: that they originally bought into the hype in crypto and ended up wasting an enormous amount of time realizing their idea made no technical or economic sense in that context, so then they came to Bitcoin instead. You hear this one time and it’s an anecdote, but you hear it as many times as I have and it feels more like a representative sample.
What I want to cover next is as charitable a summary of the state of ex-Bitcoin crypto as I possibly can: my contention is that crypto has evolved into 4 rough categories: stablecoins, cryptography R&D, gambling, and scams. And these aren’t exclusive, to be clear; there is a lot of overlap, and, in fact, the overlap is arguably the key.
Scams
Scams are tokens, plain and simple. If somebody is trying to profit from the speculative price action of a token they have issued, they are scamming somebody. Maybe they are scamming you, maybe they are scamming retail investors, maybe they are scamming customers or suppliers – if such parties even exist in their cargo cult “business model”. There’s a scam in there somewhere.
However, it is rarely _just _a scam. There will almost always be components of stablecoins, R&D or gambling too. Hence these are worth really grappling with, taking seriously, giving credit to the extent it is due, but also analyzing critically.
My rough and high-level assessment of this breakdown of crypto is as follows, and I’ll explain what I mean by this below: stablecoins have economic merit but dubious technical merit; R&D has technical merit but no economic merit; and gambling sort of has merit but it depends how you interpret it. Obviously, scams have neither.

Stablecoins
By “sort of technical merit” I mean that stablecoins have central issuers. You can issue them as tokens on a blockchain but there’s not really much of a point. The issuer could just run a database connected to the internet with some straightforward signature schemes for transfers and it would make minimal operational difference. In fact, it would be cheaper and faster. _In fact, _you may as well run a Chaumian eCash mint (a decades-old innovation recently resurrected firmly within the _Bitcoin _space) such that your cheaper-and-faster-than-a-blockchain database also grants users transience and privacy rather than the public permanence of a blockchain.
The fact Tron is the most heavily used for stablecoins, in terms of settling the most value, is a testament to this point: it is barely even pretending not to be a database. This works as regulatory arbitrage given regulators think this is “innovation” because they are stupid.
That said, it is worth giving some credit here given the abject awfulness of fiat banking and payment rails with which stablecoins arguably most directly compete. Stablecoins are significantly more permissionless in their transfer than any fiat bank liability. And to attest to what seems like their most significant use case, they are permissionless in their _usership _in that only an internet connection and the right software is required rather than various discriminatory jurisdictional and compliance criteria.
However, what “sort of technical merit” ultimately boils down to, especially in comparison to Bitcoin, is: highly censorable in their exogenous links and, therefore, their value. The assets supposedly backing stablecoins are (by definition) still within the fiat system, even if this novel transfer mechanism of the rights to withdraw them is not. There is frankly a bit of theatre involved in the so-called “decentralization” of stablecoins given shutting down the central issuer is all that is required to make the permissionlessly tradeable decentralized tokens go to zero and be technically unimpeded but functionally useless. The technical innovation of Bitcoin, in contrast, is easily understood in one sense as it being totally indifferent to this kind of attack.
On the other hand, by “economic merit” I mean that they are extremely widely used and valued as a means of providing dollar shadow banking and often superior payment rails. Those in crypto often love pointing to this and many Bitcoiners tie themselves in knots trying to explain it away, whereas I see it as essentially unrelated to Bitcoin. Clearly there is a superficial connection, but you could create any superficial connection by “tokenizing” things for no particularly good technical _reason. I think it’s a different industry entirely. It’s more like a subindustry within _fintech – part banking, part payments – that for the time being relies on bamboozling regulators with all the nonsense I’m drawing attention to.
And good for them, frankly. If fiat banking isn’t going to be backed by real money anyway, then it _at least _ought to be permissionless. It should really be Chaumian eCash if it isn’t just Bitcoin, and it is regulation alone that makes it so awful in the first place. Making money usable and not a tool of dystopian control is, at this point, a political problem, not a technical one. Stablecoins are frankly a step in the right direction, especially insofar as they acclimatize users to digital assets. But I would still caution that they arguably don’t have sufficient technical merit to withstand what feels like an inevitable political attack …
Cryptography R&D
“Technical merit” for R&D is more or less self-explanatory, but the context is worth appreciating. It’s only really in crypto and mostly in Ethereum more specifically that people can permissionlessly experiment with arbitrarily complex cryptographic schemes that operate on real, enormous value. There are a lot of people who understandably find this attractive given their projects are essentially academic and trying out their ideas in the wild is more interesting, arguably more worthwhile, and certainly more fun than putting research essays on ArXiv or submitting them to a journal.
But … the value being manipulated is at best stablecoins and at worst baseless hype. If it isn’t a stablecoin then it probably exists in the first place because of either gambling or scams – and even there the line is very blurry.
Gambling
Gambling is an interesting lens to adopt on all this because it’s literally a trillion-dollar industry. And it’s real. It’s consensual; it’s not criminal; it’s legitimate economic activity that generates enormous profits for those who facilitate it well.
So, gambling has economic merit in that sense. But it’s tricky in this context how to characterize it because you could also argue it’s deeply dishonest gambling in that the gamblers don’t realize they are playing a negative sum game against the house. They think they are doing something akin to speculating on securities, which may be just as stupid depending on how it’s done, but at least has real economic utility and contributes to capital formation.
The difference here is that what is being speculated on _has no economic merit. _So, if that’s your gauge of merit, then here there is none. And it’s a very blurry line between this and an outright scam. Maybe the people involved _think _of what they are doing as amazing R&D, and maybe it’s inadvertently just a scam; maybe they know it’s all nonsense, but they think they can profit within the negative sum game because there are greater fools. In any case, I think gambling is a very helpful characterization of a lot of the behavior of the users and the real economic function of the industry.
There’s an interesting social component to all this because crypto people will often get mad at Bitcoiners because Bitcoiners tend not to care about either stablecoins or crypto R&D: they’ll say, why don’t you like stablecoins, they have clear economic merit? And the answer is they have dubious technical merit. Or, why don’t you like our next-gen Zero Knowledge scaling protocol, it has clear technical merit? And the answer is it has no economic merit.
If you’re happy with one but not the other, it’s easy to think of Bitcoiners as being closed-minded or dogmatic or whatever, but, ultimately, I think it’s just about discipline. What’s the point in being excited by something that half works, and that you know why will never fully work? So to be frank, a lot of this may be well-intentioned, but it’s kinda’ bullshit. It very probably ultimately rests on gambling and not at all whatever its stated purpose is … or it’s just a scam.
How Did We Get Here?
The following is by no means exhaustive and the framing is deliberately a little tongue-in-cheek. As well as being accurate enough (if unavoidably biased), my goal here is primarily to set up my prediction for what is coming next.
2015 reality: Ethereum launches narrative: “the world computer”
In 2015, Ethereum launched. The narrative here was that we are building “the world computer” and we can now have decentralized uncensorable computation. Never mind that anybody with a laptop has an uncensorable and decentralized computing device. And keep in mind this question of, “_what data might it ever be relevant to compute over in this manner (whatever that means in the first place)?” _The answer will become clearer and clearer …
2016-17 reality: ICO bubble narrative: “Web 3” / “DApps”
Regardless, at the end of 2015 we get the proposal and adoption of ERC20: a standard for issuing fungible tokens within Ethereum contracts, which is why in 2016 _but especially in 2017 _we get the ICO bubble. The narrative changes. Now we are concerned with “Web 2” companies being huge, powerful, and centralized. What if, instead, users could cooperatively own the application, control their own data, and participate in the economic upside that their usage is creating?
2018-19 reality: crypto winter narrative: “mistakes were made”
In 2018 this all falls apart, so don’t worry about it, moving on …
2020-21 reality: defi summer narrative: “decentralized finance”
By 2020 the narrative was different once again. It is more or less realized by this point that utility tokens make no technical or economic sense. You can’t introduce artificial scarcity in capital goods where there should be abundance and deflation and expect anybody to care, never mind to value your concoction. On the other hand, “securities” ought to be scarce and in some sense ought to function as tradeable ledger entries. Maybe they could be tokenized and computed on in a censorship-resistant and decentralized manner?
So, we get a boom in “defi” which, for what it’s worth, fellow Axiom co-founder Anders Larson and I predicted in our essay Only The Strong Survive, in September 2021, would be a complete disaster because, amongst a myriad of other illiterate insanities, there was approximately zero grounding of these securities in productive capital. The ecosystem was entirely self-referential – grounded _not even _in the questionable economic merit of stablecoins but firmly in gambling and scams; in leverage, rehypothecation, and securitization of precisely nothing whatsoever productive.
2022 reality: shitcoinpocalypse narrative: “mistakes were made”
And we were absolutely right because in 2022 everything collapsed. First Terra/Luna imploded – a “defi” project which essentially presented to the world the argument that a fractional reserve bank issuing fiduciary media can literally never go bankrupt because it can always cover a deposit shortfall by issuing more equity. While briefly flirting with a capitalization of around fifty f***ing billion dollars, and endorsed and fawned over by all manner of illiterate charlatans with gigantic and unsuspecting audiences, this argument was eventually rejected by the market as utterly imbecilic, as analyzed by myself and Nic Carter in All Falls Down.
This triggered a credit contagion that soon after took down 3 Arrows Capital, Celsius, Voyager, BlockFi, and others. FTX limped along by what we now understand to be something like defrauding their way out of debt, but eventually also collapsed later that year. If _Only The Strong Survive _was a pre-mortem of all of this, then the reader may want to read Green Eggs And Ham, also by myself and Anders Larson, as a kind of post-mortem.
2023-today reality: Bitcoin multisigs narrative: “Bitcoin renaissance”
And now a lot of this stuff is moving to Bitcoin. It is outside the scope of this essay to explain this in much detail but there have been a handful of developments in Bitcoin recently which, regardless of their intended purpose, seem to have as a collective side effect that a lot of these same shenanigans can now be implemented (or can _pretend _to be implemented) in a more Bitcoin-native context.
So, the new narrative is something like:
“these things didn’t work, not because they are terrible ideas that collapse to moon math wrappers around gambling and scams under any remotely critical analysis, but rather because they weren’t on Bitcoin. But also, since it has only recently become possible to (at least pretend to) implement them on Bitcoin, they are now worthwhile. We have wandered in the wilderness but learned our lessons and found the promised land.”

Technical and Economic Merit
Let’s consider all this through the lens of technical and economic merit once again. Or rather, the alleged merit given the stated goal. Ignore for now whether there is any merit:
2015 technical goal: new computing paradigm economic goal: x% of GDP?
The original idea of “crypto” allegedly has the merit of the next revolution in computing. Goodness knows how big that market is; probably a decent chunk of global GDP – if it meant anything, which it doesn’t.
2016-17 technical goal: disrupting company formation economic goal: y% of S&P?
ICOs then become a little bit more specific. Now they are merely disrupting how we organize companies. What’s that worth? Some portion of the value of the companies that can now be decentralized and tokenized I guess? Who knows …
2018-19 nothing to see here
Nothing happened then, don’t worry about it.
2020-21 technical goal: decentralize finance economic goal: z% of NYSE, CME, ISDA?
Defi becomes more specific again. Now we are merely tokenizing financial contracts, expanding access, removing middlemen, and so on. So that should probably be worth some percentage of capital markets activity?
2022 nothing to see here
Oops, never mind …
2023-today technical goal: now it’s on Bitcoin! economic goal: i% of … Bitcoin?
… and now it’s on Bitcoin apparently.
In Hindsight ...
I think the most amusing analysis of all this is as follows: it starts off completely insane, it gets more and more restrained each time – you could cheekily argue it starts to make more and more sense – but it also gets closer to Bitcoin every time. It’s clearly narrowing in on just: Bitcoin.
This is people realizing, painfully, over decades, what blockchains are for! They are not for “decentralizing everything” They are for censorship-resistant, sound, peer-to-peer digital money.

And I think this is _also _why we get the current state of crypto from earlier in the essay. As it starts to make more and more sense (by getting closer and closer to Bitcoin) you have realizations like the following: digital gift vouchers for artificially scarce and extremely expensive computation aren’t money, so we need “real money” in here for it to have economic merit, so you get stablecoins. Also, well we have a rich programming environment that seems technically interesting but also the severe technical handicap of being unable to do even a billionth of a billionth of a billionth of all the computations in the world, so you get crypto R&D. These emerge as a kind of patch, and they have _some _merit in isolation, whereas the long-term trajectory is actually just to converge on Bitcoin.
It’s an open and fascinating question if there are any learnings from these that can still be transplanted to Bitcoin. For stablecoins, this strikes me as less clear, given the dubious technical merit is introduced by using a blockchain at all, not just a blockchain other than Bitcoin. However, efforts to create Bitcoin balances (tokenized or otherwise) that are stable relative to some external price are to be applauded, if still heavily scrutinized for what technical merit they _really _have.
It seems far more likely that crypto R&D will prove useful in a Bitcoin context to some or other degree, and in this case the economic merit is in fact solved by moving to Bitcoin, provided the necessary technical merit can be mimicked. At the time of writing, this is a source of both hope and dread: hope given the possibility of viable avenues of development (although still highly uncertain); dread given how early steps in this direction are already being misrepresented in the pursuit of bullshit and scams. I will return to both shortly.
Narrative Evolution
Back to the table just above, I want to make three quick observations that tie together my entire argument and get us to the end of the essay:

Firstly, the bubbles always follow the price of Bitcoin. Hopefully I don’t need to include a price chart for the reader to grasp this immediately.
Secondly, it’s important that the narrative always changes. Absolutely ungodly amounts of money were raised for this crap following the_ Bitcoin bull runs of 2017 and 2021. The people doing this couldn’t point to the previous absolute disaster, so they had to spin something along the lines of: “_we learned our lessons and we’ve refined the use case.” This should sound familiar from just above.
Thirdly, however, regardless of whatever refinement they’ve come up with, the consequence of the new “narrative” is always, “buy my token”.
Always.
It doesn’t matter what buzzword salad is in the middle. It’s always “Bitcoin is cool, xyz, fughayzi fughahzi, buy my token.”
This is why I am very much tempted to not care so much about developers, academics, entrepreneurs, and so on, and in fact for my null hypothesis to be that they are more likely to have been victims than perpetrators. I don’t think they even end up in a position to contribute without the key group whom I do blame. When you put all these pieces together, what I think falls out of this analysis is as follows:
The entire cycle of shitcoinery can be traced to unscrupulous financiers convincing capital allocators who don’t know any better, in a bull market that, yes, Bitcoin is cool, but what they are doing is related, cooler, and that they deserve a fee.
Let us label this the Capital Cycle Theory of Shitcoinery. I think that everything else about which one might want to complain is downstream of this core realization.
Avoiding It
Given everything I’ve covered this is simple and this is pretty much the end of the essay.
You need to be aware of why this is happening now. If it hasn’t happened to you already (intended readership in the capital allocation business, that is) I guarantee it’s about to: with ETFs and the halving just past, we seem to be starting a Bitcoin bull run, these people have already raised ridiculous amounts of money on scams and bullshit that have mostly imploded. They may have lost a lot of money, or they may even have dumped on retail and got an excellent “return”. But in any case, they need a new narrative.
It's _possible _they have a viable narrative around stablecoins, R&D, both, and that they are as wary of scams as I have suggested here that they should be. I don’t want to insult anybody who merely has a different investment thesis to me if they are otherwise reasonable in their outlook and honest in their dealings.
However, if they are only now realizing how pointless and disingenuous every preceding crypto narrative has been after 7 years and hundreds of billions of dollars – or if they still don’t realize it at all; if their track record shows they were deeply involved, handsomely rewarded, and yet created nothing of lasting value; if they say things like “the builders are coming back to Bitcoin”: be very, very suspicious. Be on the lookout for tokens, which is to say, be on the lookout for scams.
What is especially frustrating is that the technical spin of the "layer twos" that are all the rage at the time of writing, that "the builders are coming back to Bitcoin" to build, and that you, the capital-allocating reader, will almost certainly be pitched, is in and of itself pretty reasonable. They just don't require tokens and they don't require gambling to support the token prices. What they do require is _sound adherence to Bitcoin's technical and economic merit. _At the very least, they require honest communication about the design trade-offs so far and planned for, and what, if any, economic and technical merit is left over after these trade-offs have been made.
Narrative aside, the _reality _of 99% of these projects is that they are private execution environments tied to multisigs custodying user deposits. Which is to say, on the one hand, that they are cargo culting "crypto R&D" from Ethereum that isn't technically possible in Bitcoin in order to feign technical merit, and on the other, that _they aren't layer twos at all. _Once again, they may as well be Chaumian eCash mints, except for the fact that this would make the intended token scam all but impossible to pull off.
Casey Rodarmor, creator of the Ordinals protocol, recently joked on the Hell Money _podcast he co-hosts, responding to the idea that "_everybody is building an L2 now":
"It's the same sad sack playbook as on Ethereum being recapitulated on Bitcoin. That's how you get a VC check on Ethereum. They are all glorified multisigs, so they are like, "hey let's port our glorified multisig to Bitcoin and get a VC check." I was talking to a friend of mine who is working on an interesting project, an open-source analyzer that does transaction clustering, and I was like, "maybe you could do this in this way and raise some VC money," and he said, "yeah, okay, but what's the point in raising VC money?" And I said, "no, no, no, this is the end! This is the goal! You raise VC money and then you cut yourself checks from that VC money until it runs out and then you raise more at a 10x valuation. This is the new economy, guys!"
The 1% that are legitimately trying to bring the learnings from crypto R&D to Bitcoin in a technically and economically sound manner will hopefully win in the long run (and even this is somewhat speculative at the time of writing) but will likely get little to no attention amidst this bull market flurry of scams and bullshit.
Axiom will do its best to source and invest in these companies (we already have!) but we are resigned to it being a much more difficult sell to capital allocators in light of the Capital Cycle Theory of Shitcoinery. To be brutally honest, this entire essay can fairly be considered cope on my part in light of having lost this battle in the past and facing up to the very real prospect of losing it in the near future too. Oh well, at least I tried.
Wrapping Up
The essence of the Capital Cycle Theory of Shitcoinery is that the problems I’ve described ultimately come from bamboozling people just like you with technical sounding nonsense like “Web 3” so you think it’s all a lot more complicated than it really is. Just buy Bitcoin. That’s certainly the first thing you should do anyway, and it might be the only thing you ever need to do.
If you really, really want to take the extra risk of investing in the Bitcoin ecosystem, the team at Axiom would be happy to speak with you. But we are never going to talk you out of buying Bitcoin. There is no world in which Bitcoin does poorly and we do well, or in which we promise something “better than Bitcoin,” and there’s no point in engaging with us at all if you don’t already believe most of this.
If that’s of interest to you, we’d love to talk. If not, just buy Bitcoin. In any case: fair warning, we are heading into a Bitcoin bull market and the scams and the bullshit are coming. Good luck avoiding them.
Allen Farrington, June 2024

-
 @ b2caa9b3:9eab0fb5
2024-07-11 12:34:49
@ b2caa9b3:9eab0fb5
2024-07-11 12:34:49Back then, I was still living in a house in Höpfigheim. The house bordered directly on nature, a nature reserve, and I loved going out into nature there. I regularly took photos in this area. That's how this photo came about on that day in April 2011.
The photo was taken in Höpfigheim, a town in the Ludwigsburg district of Baden-Württemberg, Germany.

Photo Information
- Author: Ruben Storm
- Date Taken: April 22, 2011
- Published: June 19, 2012
- Camera: Nikon D3100
- Lens: Not specified
- Location: Höpfigheim, Germany
Links:
-
 @ 29216785:2a636a70
2024-07-11 12:34:12
@ 29216785:2a636a70
2024-07-11 12:34:12this should not be empty
-
 @ 5d4b6c8d:8a1c1ee3
2024-07-11 12:17:18
@ 5d4b6c8d:8a1c1ee3
2024-07-11 12:17:18Yesterday's edition https://stacker.news/items/603455/r/Undisciplined
-
- -
July 11, 2023 📅
📝
TOP POSTI am not a routing node anymore
Excerpt
Over the past two years I ran an amateur routing node that was in the top 300 on lightning terminal. I have decided to stop for the following reasons […]
5586 sats \ 37 comments \ @lnvisualizer \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/207349/r/Undisciplined?commentId=207482
Excerpt
While you were making Bitcoin banks, Phoenix scripted out lightning channel management […]
1776 sats \ 12 replies \ @nerd2ninja
From Introducing the new Phoenix: a 3rd generation self-custodial Lightning wallet by @Norbert in ~bitcoin
🏆
TOP STACKER2nd place @nerd2ninja (1st hiding, presumed @siggy47)
746 stacked \ 2262 spent \ 1 post \ 11 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
91.7k stacked \ 0 revenue \ 113.7k spent \ 90 posts \ 302 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 11, 2022 📅
📝
TOP POSTI'm Evan Kaloudis, Founder of Zeus. July 11th AMA!
Excerpt
I'm stoked to chat with you all today. Zeus (https://zeusln.app) is a mobile app for iOS and Android that lets you connect to and control your lightning node remotely. It supports LND, Core Lightning, and Eclair.
31.7k sats \ 58 comments \ @evankaloudis \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/43634/r/Undisciplined?commentId=43640
Excerpt
Hello, I am a Bitcoin maxi and I put my sats where my mouth is. Bitcoin maximalism is a method of consumer protection. My story as a maximalist, is that I used to shitcoin back in 2016. During the 2018 bear market, I lost so much money in everything […]
390 sats \ 11 replies \ @nerd2ninja
From I am moving over from Twitter by @charles_stack in ~bitcoin
🏆
TOP STACKER1st place @k00b
19.3k stacked \ 32k spent \ 2 posts \ 17 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
53.4k stacked \ 0 revenue \ 62.2k spent \ 114 posts \ 304 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 11, 2021 📅
📝
TOP POSTThis company sells passports to Americans looking for a tax break on their bitcoin profits
Link to https://www.cnbc.com/2021/07/11/plan-b-passport-tax-break-bitcoin-profits.html
5 sats \ 4 comments \ @0268486dc4 \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/256/r/Undisciplined?commentId=282
Excerpt
Fascinating to see the disconnect between fundamentals of a crypto/stock and the price action created by market movers and how it seems to follow so many mathematical patterns. Makes you want to be a trader but then you remember 90%+ or whatever jus […]
1 sat \ 2 replies \ @gmd
From What are your favorite Bitcoin newsletters? by @k00b in ~bitcoin
🏆
TOP STACKERNo top stacker
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
21 stacked \ 0 revenue \ 151 spent \ 5 posts \ 15 comments
originally posted at https://stacker.news/items/604559
-
-
 @ a012dc82:6458a70d
2024-07-11 11:45:10
@ a012dc82:6458a70d
2024-07-11 11:45:10Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
Introduction
The world of real estate is one that has always been known for its slow-moving and traditional nature. However, with the rise of digital currencies like Bitcoin, the industry is beginning to see some significant changes. In this blog post, we'll explore the future of real estate transactions and how Bitcoin is changing the game.
Cryptocurrency as a payment method
Real estate transactions have traditionally been conducted using fiat currency, but the emergence of cryptocurrencies like Bitcoin is changing the game. Bitcoin offers faster and more cost-effective transactions compared to traditional payment methods. Additionally, blockchain technology provides a secure and tamper-proof record of real estate contracts, simplifying the transaction process and reducing the need for intermediaries.
Greater transparency and security
Bitcoin and blockchain technology can also provide greater transparency and security in real estate transactions. For instance, using Bitcoin and blockchain technology, buyers and sellers can easily track the progress of a transaction from start to finish, with a clear record of all the steps taken along the way.
This transparency can help to reduce the risk of fraud, as well as providing a level of trust and confidence in the transaction process. It can also help to reduce the risk of errors, as all parties involved in the transaction can see the same information, reducing the chance of miscommunication or misunderstandings.
Greater global reach
Finally, Bitcoin and other cryptocurrencies can help to expand the global reach of real estate transactions. Because Bitcoin is a decentralized currency, it can be used across borders without the need for currency exchange or other financial intermediaries. This can make it easier for foreign buyers and sellers to participate in real estate transactions, opening up new opportunities for investment and growth.
Conclusion
In conclusion, Bitcoin and blockchain technology are changing the game for real estate transactions. By providing faster, more cost-effective, and secure transactions, and by expanding the global reach of real estate investments, Bitcoin is helping to make real estate a more accessible and efficient industry. As these technologies continue to develop and mature, we can expect to see even more changes and innovations in the real estate industry in the years to come.
FAQ
How can Bitcoin be used in real estate transactions? Bitcoin can be used as a payment method for real estate transactions. Buyers and sellers can exchange Bitcoin in exchange for a property.
What are the advantages of using Bitcoin in real estate transactions? The speed of transactions is much faster with Bitcoin compared to traditional payment methods. Additionally, Bitcoin transactions tend to have lower fees than traditional methods. Using Bitcoin can also provide greater transparency and security.
What is blockchain technology? Blockchain is a digital ledger that securely records and stores data. It is ideal for recording and verifying real estate transactions because it provides a tamper-proof record of the transaction.
How does blockchain technology simplify the real estate transaction process? Blockchain technology can automate certain parts of the transaction process, reducing the need for intermediaries like lawyers and banks. This can speed up the transaction process and reduce costs for all parties involved.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 42342239:1d80db24
2024-07-06 15:26:39
@ 42342239:1d80db24
2024-07-06 15:26:39Claims that we need greater centralisation, more EU, or more globalisation are prevalent across the usual media channels. The climate crisis, environmental destruction, pandemics, the AI-threat, yes, everything will apparently be solved if a little more global coordination, governance and leadership can be brought about.
But, is this actually true? One of the best arguments for this conclusion stems implicitly from the futurist Eliezer Yudkowsky, who once proposed a new Moore's Law, though this time not for computer processors but instead for mad science: "every 18 months, the minimum IQ necessary to destroy the world drops by one point".
Perhaps we simply have to tolerate more centralisation, globalisation, control, surveillance, and so on, to prevent all kinds of fools from destroying the world?
Note: a Swedish version of this text is avalable at Affärsvärlden.
At the same time, more centralisation, globalisation, etc. is also what we have experienced. Power has been shifting from the local, and from the majorities, to central-planning bureaucrats working in remote places. This has been going on for several decades. The EU's subsidiarity principle, i.e. the idea that decisions should be made at the lowest expedient level, and which came to everyone's attention ahead of Sweden's EU vote in 1994, is today swept under the rug as untimely and outdated, perhaps even retarded.
At the same time, there are many crises, more than usual it would seem. If it is not a crisis of criminality, a logistics/supply chain crisis or a water crisis, then it is an energy crisis, a financial crisis, a refugee crisis or a climate crisis. It is almost as if one starts to suspect that all this centralisation may be leading us down the wrong path. Perhaps centralisation is part of the problem, rather than the capital S solution?
Why centralisation may cause rather than prevent problems
There are several reasons why centralisation, etc, may actually be a problem. And though few seem to be interested in such questions today (or perhaps they are too timid to mention their concerns?), it has not always been this way. In this short essay we'll note four reasons (though there are several others):
- Political failures (Buchanan et al)
- Local communities & skin in the game (Ostrom and Taleb)
- The local knowledge problem (von Hayek)
- Governance by sociopaths (Hare)
James Buchanan who was given the so-called Nobel price in economics in the eighties once said that: "politicians and bureaucrats are no different from the rest of us. They will maximise their incentives just like everybody else.".
Buchanan was prominent in research on rent-seeking and political failures, i.e. when political "solutions" to so-called market failures make everything worse. Rent-seeking is when a company spends resources (e.g. lobbying) to get legislators or other decision makers to pass laws or create regulations that benefit the company instead of it having to engage in productive activities. The result is regulatory capture. The more centralised decision-making is, the greater the negative consequences from such rent-seeking will be for society at large. This is known.
Another economist, Elinor Ostrom, was given the same prize in the great financial crisis year of 2009. In her research, she had found that local communities where people had influence over rules and regulations, as well as how violations there-of were handled, were much better suited to look after common resources than centralised bodies. To borrow a term from the combative Nassim Nicholas Taleb: everything was better handled when decision makers had "skin in the game".
A third economist, Friedrich von Hayek, was given this prize as early as 1974, partly because he showed that central planning could not possibly take into account all relevant information. The information needed in economic planning is by its very nature distributed, and will never be available to a central planning committee, or even to an AI.
Moreover, human systems are complex and not just complicated. When you realise this, you also understand why the forecasts made by central planners often end up wildly off the mark - and at times in a catastrophic way. (This in itself is an argument for relying more on factors outside of the models in the decision-making process.)
From Buchanan's, Ostrom's, Taleb's or von Hayek's perspectives, it also becomes difficult to believe that today's bureaucrats are the most suited to manage and price e.g. climate risks. One can compare with the insurance industry, which has both a long habit of pricing risks as well as "skin in the game" - two things sorely missing in today's planning bodies.
Instead of preventing fools, we may be enabling madmen
An even more troubling conclusion is that centralisation tends to transfer power to people who perhaps shouldn't have more of that good. "Not all psychopaths are in prison - some are in the boardroom," psychologist Robert Hare once said during a lecture. Most people have probably known for a long time that those with sharp elbows and who don't hesitate to stab a colleague in the back can climb quickly in organisations. In recent years, this fact seems to have become increasingly well known even in academia.
You will thus tend to encounter an increased prevalance of individuals with narcissistic and sociopathic traits the higher up you get in the the status hierarchy. And if working in large organisations (such as the European Union or Congress) or in large corporations, is perceived as higher status - which is generally the case, then it follows that the more we centralise, the more we will be governed by people with less flattering Dark Triad traits.
By their fruits ye shall know them
Perhaps it is thus not a coincidence that we have so many crises. Perhaps centralisation, globalisation, etc. cause crises. Perhaps the "elites" and their planning bureaucrats are, in fact, not the salt of the earth and the light of the world. Perhaps President Trump even had a point when he said "they are not sending their best".
https://www.youtube.com/watch?v=w4b8xgaiuj0
The opposite of centralisation is decentralisation. And while most people may still be aware that decentralisation can be a superpower within the business world, it's time we remind ourselves that this also applies to the economy - and society - at large, and preferably before the next Great Leap Forward is fully thrust upon us.
-
 @ 29216785:2a636a70
2024-07-11 11:05:08
@ 29216785:2a636a70
2024-07-11 11:05:08 -
 @ ee7d2dbe:4a5410b0
2024-07-11 10:31:42
@ ee7d2dbe:4a5410b0
2024-07-11 10:31:42Making money with free apps is a trending topic in the mobile application development world. The mobile app industry has been active for over a decade and is now generating billions of dollars in the revenue. Research shows from 2021 to 2022 the app and game revenues increased by 19.1% to $133 Billion and most of these Free Apps and games are free to download upfront and then charge for subscription or in-app purchases. Hence, it’s an estimate that the mobile app industry is most likely to hit a whopping $407.31 Billion by 2026. With more than three billion smartphone users, the industry keeps on expanding and bringing more revenue in the upcoming years.
While there is so much growth and spread of apps across the globe, the demand for custom app development is at an all-time high. For App Tech startups, the app is a core product, but even for non-app tech startups the app is an essential tool to engage with their customers and users and to improve the overall business process. Hence this makes startups and entrepreneurs curious for answers to a few questions.
Popular Revenue Models For How Do Free Apps Make Money
- Revenue through Mobile Advertising
In-app advertisement method, the most common and easiest method to implement when it comes to money-making apps via a third-party ad network like Google AdMob or Tapjoy (iron source) etc. As per the latest report by business standard the global mobile ad spend is going to reach $362 Billion and $412 Billion in 2023 and 2024 respectively. The free app market has always outnumbered the paid ones when it comes to profit and download numbers, however an app should have a large user base in order to convert that into significant revenue through in-app ads.
- App Monetization through Sponsorships / Sponsored Content
Another interesting and exciting method to earn money from a mobile app is sponsorship. In this method, the app owner needs to figure out the appropriate platform to launch the app. A platform or brand that has its identity before and a great audience base should be preferred.
- In-app Purchase Freemium Model
Another way to make money with free mobile apps is to offer in-app purchases in a Freemium Model. A Freemium Model means you offer some features of the Apps for free, while charge for some premium features. These are purchases that are made while the app is open. In-app purchases include things like extra lives, bonus levels in a game, or virtual goods in a social media app.
- App Subscription Model
The App subscription-based model is one of the most popular and finest app monetization strategies over the last few years, however it is also a part of the in-app purchase. In this method, users can subscribe to join, try for a while, and then pay a regular monthly fee for access. Subscription-based apps tend to see higher revenue per user than apps with other business models. This type of monetization is recommended for cloud-based services, audio and video streaming apps or OTT Apps, and Media Services etc. As per the Subscription Trade Association, 75% of distributor-to-consumer businesses will have a subscription-based leg of their business by 2023.
- Selling Physical goods
As the name suggests, the apps that sell physical goods make money by how? By selling physical goods on e-commerce apps or on food delivery apps or taxi booking apps. These Apps are free, their content is free and all you pay for is to buy a physical good or service out of it.
Please note that such apps accept payments through a payment gateway (like PayPal, stripe) and not via in-app purchase. Hence don’t give commission to Google or Apple but to the respective payment gateway provider. The commission of such payment gateways is usually 2.9 % of the total sales.
- Affiliate and Referral Marketing Monetization Model
Affiliate is another variation of sponsorship. In place of granting advertising rights solely to one organization, you negotiate with interested parties and place their reference links in your application. Referral Marketing includes promoting a third-party product or service as a way to upgrade revenue opportunities for your app. App publishers sell or promote affiliates based on the number of clicks or installs. For this one can use pop-up ads to endorse someone else’s application or advertise products.
Source: https://www.agicent.com/blog/how-do-free-apps-make-money/
-
 @ c6e3a6a3:f82a6a70
2024-07-11 21:15:50
@ c6e3a6a3:f82a6a70
2024-07-11 21:15:50Even with Bitcoin's price dip, the infrastructure scene is heating up!
I had the pleasure of speaking with Bitcoin oracle provider APRO Oracle and Data Availability (DA) Layer service Multiadaptive today, and wanna share my two cents here with my fellow Bitcoiners.
For those unfamiliar with the terms "Oracle" and "DA Layer," let's break them down:
Oracles in the Crypto World
Smart contracts, which are self-executing contracts with the terms directly written into code, can only execute based on data available within the blockchain. Oracles act as bridges between blockchains and the outside world, providing access to external data and enabling the creation of complex and useful decentralized applications (dApps).
In DeFi, for example, oracles supply price feeds for various assets, allowing lending, borrowing, and trading platforms to function accurately. This capability extends to gaming, prediction markets, and more, expanding the potential use cases for blockchain technology.
Oracles on Bitcoin
While the Bitcoin blockchain itself does not support smart contracts, Layer 2 solutions provide the necessary infrastructure for oracles to operate. Layer 2 solutions are built on top of the Bitcoin blockchain to enhance its scalability, speed, and functionality without altering the base layer. These solutions address Bitcoin's limitations, such as slow transaction times and high fees, by offloading some transaction processing to secondary layers.
Apro Oracle prides itself on being the first decentralized oracle specifically designed for the Bitcoin ecosystem. It has been instrumental in supporting Layer 2 projects like Merlin and Bitlayer.
Simon, the company's tech lead with a strong background in OKX's security team, brings years of experience in ensuring seamless data flow between the real world and Layer 2 solutions, enhancing transaction safety and reliability.
**What is a Data Availability (DA) Layer? **
A DAL stores and ensures transaction data availability. It’s crucial for scaling and modular blockchain architectures. DALs help process more transactions without overloading the main chain, leading to higher throughput and lower costs.
What Does MultiAdaptive Do?
MultiAdaptive uses Bitcoin protocols like Ordinals to publish data. This method lets users inscribe unique data to satoshis, Bitcoin’s smallest units. Users send NFT-like Ordinal transactions to MultiAdaptive nodes for verification and then to Bitcoin for storing and broadcasting. MultiAdaptive leverages Bitcoin as a “witness” in the data publishing process. No need for bridging between chains!
In a nutshell, there are three parties involved: users who are storing data, MultiAdaptive nodes that power data availability off-chain, and Bitcoin as the arbiter that witnesses the signing process.
Edwyn told us that MultiAdaptive started as a data availability network for Ethereum and quickly saw the demand for multichain data availability, adding support for Bitcoin.
The Bigger Picture
As crypto traders or holders, we might not see Oracle and DA Layer every day, but they’re the lifelines for every transaction. It’s lit to see builders like Apro and MultiAdaptive joining the Bitcoin ecosystem. They’re just the beginning—more builders are coming in to make Bitcoin as vibrant as Ethereum.
Bitcoin used to be all about being a store of value, lacking smart contracts for creating dApps, including DeFi. But with Ordinals popping up, it’s clear Bitcoiners want digital assets on Bitcoin. This demand is paving the way for DeFi projects like staking and lending in the Bitcoin ecosystem, making infrastructure providers jump on the bandwagon.
What's more, the Bitcoin blockchain is more secure, reliable, and decentralized compared to Ethereum, right?
I've got some exciting numbers to share! In Q1 2024, the total value locked (TVL) in the Bitcoin ecosystem skyrocketed over sixfold, jumping from $492 million to over $2.9 billion!
Plus, with Bitcoin staking project Babylon raising $70 million at the end of May, it feels like we're heading into a BitcoinFi summer.
Stay tuned as the Bitcoin ecosystem evolves and expands, bringing new possibilities and innovations to the blockchain world!
BTW, if you're building something in the Bitcoin ecosystem—be it infrastructure, ordinals, runes, gaming, social, or anything else—feel free to get in touch with me. Let’s vibe and collab!
-
 @ 81870f53:29bef6a6
2024-07-11 20:50:05
@ 81870f53:29bef6a6
2024-07-11 20:50:05今後どこで間違えるでしょうか? 投資ロジックは株式購入の直接の原動力となります。
バリュー投資家にとって、良好なファンダメンタルズと合理的なバリュエーションは投資に必要な条件にすぎず、対象となる企業はますます増えており、通常は新製品の発売、生産能力の拡大、チャネル整理の完了などの直接的な要因があります。 . ポジションをオープンまたは増やすかの決定を迫られます。
しかしそれだけでは十分ではありません。
理にかなっていると思う限り、同じロジックに同意しますが、あるロジックに従って投資したい場合は、このロジックの「反対ロジック」を見つける必要があります。
たとえば、業界の動向では、下流の需要が爆発的に拡大し、企業の生産能力が大幅に拡大し、今後1〜2年で収益と利益が急速に成長するだろう、これはすべての投資家が好む投資ロジックです。
しかし、この論理には隠された「逆論理」が存在する。なぜなら、このブームは業界全体に属しており、主要な注文を履行するには遅すぎて、以前は瀬戸際で苦戦していた第二層や第三層の企業にも浸透しているからである。死が活力を取り戻し、一部の企業が猛烈な勢いで生産を拡大し、一部の企業が一部の分野で優位性を拡大し、有力なCR3/CR5企業の集中力が低下しているこれらはすべて、急成長している業界ではよく見られる現象である。
2 年後には、業界が過剰生産能力に陥り、市場セグメントを確立している一部の第 2 および第 3 企業の優位性が損なわれ、業界全体の競争環境が悪化すると考えられます。劣化する。
この現象は、これまでの携帯電話産業チェーン、通信産業、その他の産業で何度も発生しており、現在、リチウム電池、太陽光発電、半導体の一部で開発が進められています。
多くの人はこれが今から 2 年後だと考えていますが、今考えるのは時期尚早です。しかし、機関投資家のシェアが高くなり、より効率的になるにつれて、機関投資家は業界がピークに達する前にほとんどの場合、事前に「評価額を押しつぶして」しまいます。株価は停滞するか、下落することさえあります。その日は各四半期の業績が最高値に達する日です。実際、それは市場が将来の業界の底値を予測する時期です。
どのような投資ロジックにも、対応する「逆ロジック」が隠されています。
新製品を開発する場合、その「逆論理」は研究開発の失敗です。
主要な新製品が発売される 「逆論理」とは、売上が低迷するか、売上は好調だが、旧製品の販売量が影響を受けるというものです。
生産能力拡大の「逆論理」は、歩留まりが基準を満たすのが遅いということです。
大口顧客に近いため、その「逆論理」は、運営の自主性の喪失、売掛金の大幅な増加、さらには業績の大幅な浮き沈みです。
...
したがって、「逆論理」は次のように要約されます。投資する理由を知るだけでなく、将来どこで「うまくいかない」可能性が最も高いかを知る必要があるということです。
論理と反論理: 価格上昇を例に挙げる 企業のビジネス上の意思決定には必ずリスクがあり、失敗する可能性があります。この意思決定における失敗の一般的な原因は、その「失敗の原因」を理解する必要があります。そしてこの決定の結果。
私たちが好む消費財の「価格上昇」ロジックを例に挙げると、多くの投資家は企業の価格上昇の兆しが見えるとすぐに、業績が劇的に向上すると考えますが、たとえそうであったとしても、「価格上昇」は非常に複雑なビジネス行為です。茅台酒の値上げは消費に影響を与えるが、必ずしも売上に影響を与えるわけではないため、値上げのロジックの「逆論理」は、値上げの失敗が売上に影響を与えるほど単純ではない。
まず、工業製品と消費財を区別する必要があります。工業製品の「価格上昇」は、顧客に値上げの通知がある限り、通常はイベント駆動型の投資ロジックですが、消費財はイベント駆動型の投資ロジックです。ほとんどの製品は直接的に価格を上昇させるわけではありませんが、さまざまな代替手段があります。
-
パッケージをアップグレードし、新しいパッケージを新しい価格で、古いパッケージを古い酒の価格で提供しますが、徐々に供給量を減らし、ほとんどが価格を上げました。
-
以前は「2 台購入すると 1 台無料」だった端末プロモーションの中止または縮小。これは値上げに相当します。
-
より高い価格の製品を宣伝し、ローエンド製品のマーケティング サポートを削減します。これは比較的穏やかな価格上昇です。
-
端末価格の値上げは行わず、販売店一括価格の引き上げまたはリベートの削減を行い、販売店数の最適化により販売量を減らさずに販売店の利益を確保する。
消費財価格上昇の論理には、この逆論理がある。
- 新しいパッケージをアップグレードすることの逆論理
酒類のアップグレードは、収益と利益を促進するだけでなく、ブランド酒類の核となる成長ロジックでもあります。
そう、その「逆論理」は、新しいパッケージや新しいフレーバーが受け入れられなかったり、価格が不適切だったりすることで、中心的な顧客が他のブランドに乗り換えたり、同じ価格で強力な競合他社に狙われたり、ブランドイメージが出せない価格帯に参入したりするということです。その結果、古い製品の売上減少と相まって、最終的には収益と利益の両方が減少し、在庫が増加し、アップグレードが失敗するという結果が業績に反映されます。
歴史的に、五梁業と蘆州老角はいずれもやみくもな価格上昇と失敗を経験しており、近年では酒類の消費の向上と茅台酒の継続的な価格上昇によって生じた価格帯のギャップにより、ほとんどの新製品のアップグレードは成功している。将来、茅台酒の価格が停滞し、消費のグレードアップが鈍化すれば、業界が「逆論理」と解釈する可能性が大幅に高まるだろう。
- 「プロモーションの削減」による値上げの逆論理
直接端末プロモーションは通常、競争の激しいカテゴリーで行われるため、ほとんどのブランドが統一的に行動するか、CR2 の主要ブランドが立ち上げない限り、プロモーションが中止されるリスクが高くなります。この現象は通常、業界全体の原材料価格の急激な上昇の中でのみ発生します。と続きが疑問です。
原材料による価格上昇は通常、コストの上昇をカバーするのが困難です。「価格上昇」が業績に与える影響は現時点ではありませんが、原材料価格が下落した後は、当然のことながら、値上げに成功した製品の価格は回復しません。現時点では、GLEMI にとって利益を押し上げることができるのは、材料の各波が上昇および下落するとき、つまり利益成長率が上昇するときだけです。
したがって、この種の価格上昇の逆論理は、価格上昇によって端末の売上が減少し、業界全体の在庫が過剰になり、上流の材料の価格上昇圧力が低下したときに、より大きなプロモーションの波を引き起こしたということです。業界全体で。
- 高額商品を主に宣伝するカウンターロジック
このようなビジネス行為は携帯電話では一般的であり、リスクまたは「カウンターロジック」もユーザーの受け入れが限られているハイエンド製品であり、Xiaomi の携帯電話は以前にもハイエンドの失敗を経験しました。
また、ハイエンド市場に心理的な影を落とす可能性があり、次の戦略はより保守的なものになるでしょう。これも対抗策の一部です。
- 価格だけを求めることの逆論理
企業の財務に与える影響は価格の値上げと同じですが、厳密に言えば、良い仕事をすれば、販売店を最適化しながら収益を確保し、利益を増やすことができます。
したがって、そのリスクまたは逆論理はディーラーの反発にもあり、チャネルの混乱につながるため、一度失敗すると、マーケティングシステム全体の失敗となり、特に業界のセンチメントが低下した場合、その損失は最初の3つのカテゴリの損失をはるかに上回ります。失敗する可能性の方が高いのがグリーのチャネル改革である(もちろん、まだ終わっていない。失敗すると断言できるわけではない)。
さらに、高級酒やサプリメントなど、保管に強くギフトの性質を持つ一部の商品は、価格を直接上昇させる可能性があるため、ディーラーも株価に影響を与える可能性があります。そのほうがモチベーションが上がります。
しかし、それはさらに深刻な「逆論理」、つまりディーラーの買い占めによって引き起こされる「需要バブル」も引き起こす。売上を伸ばすことも、ブランドイメージに影響を与えることもできず、チャネル在庫を消化するのに何年も費やすことしかできず、会社の経営が困難になり、さらにはキャッシュフローが破綻することさえある。
逆ロジックシグナルとファンダメンタルストップ バフェット氏が間違いを犯したと気づいた後、取締役会を変更したり、会社を買収したり、一連の合併・買収を行うこともできるが、方法はただ一つ、売却することだ。
カウンターロジックの中心的な機能は「ストップロス」です。もちろん、これは価格が少し下がったときのストップロスのようなものではなく、基本的なストップロスのシグナルです。
売りの 3 つの原則は、高価であること、壊れたロジック、そしてより良いものを見つけることです。いわゆる「逆論理」売りとは、投資前に「ロジックが壊れている」という明確なシグナルを設定することを意味します。
しかし、実際の投資はそれほど正確ではありません。たとえば、株価の上昇傾向は、この「価格」を意識する投資家が増えていることを示しています。 「増加」ロジックですが、その間の下落は、投資家が「逆ロジック」をますます意識していることでもあります。
「逆論理」がコンセンサスとなった場合、株価は人間の限界を超えて下落しているはずであり、損失は避けられないため、基本的なストップロスシグナルは「逆論理」が 0 から 1 に直接ジャンプするのではなく、むしろ中間点になります。 「0.1、0.2、0.3...」の遷移パターン。
酒類の価格を引き上げるには、新製品の売上を追跡する必要があります。売上が予想を下回った場合には、この投資を中止する必要があります。
「アンチロジック」シグナルが現れるときは、通常、株価がしばらく下落しているため、「ロジックの破綻」は将来の業績の低下を意味し、評価額が下落する可能性があります。ますます高価になります。
「カウンターロジック」の基本的なストップロス効果は、「投資保険のロープ」のようなものです。自分が守られていると感じると、投資の範囲を広げ、より高いオッズでいくつかの機会を試すことができます。
しかし、別の観点から見ると、投資は論理実装の確率だけでなく、その論理が実現されるまでのサイクルが長くなると、その論理がより小さい確率で「有効な価格が設定される」かどうかにも依存します。株価がまだ非常に低い場合は、オッズが高くなるチャンスです。
したがって、この投資決定の焦点は、ロジックや「逆ロジック」の確率ではなく、むしろこの「逆ロジック」に明確なシグナル(掘削機の売上高が前月比で減少する高頻度のデータなど)があるかどうかにあります。そして、シグナルが現れたときに経験する可能性のある最大の損失は何ですか、株価はどこにある可能性がありますか。
将来の「逆ロジック」を最初から明確に認識している場合にのみ、「逆ロジック」が解釈され始めたときにまだ利益があるか、または損切りした場合の損失が少なくなるように、購入価格を慎重に選択します。
明確な機会から利益を得るには「決定的な内部ボリューム」が発生することは誰もが知っています。機会を見つけても躊躇し、論理的な決定が行われるまでは購入コストが高くなるだけでなく、確実性も高まります。ホール。
「内輪」を打ち破りたいなら、並外れた選択肢が必要です。「逆論理」の不確実性を恐れてはいけません。論理が現れたばかりで、株価がまだ底にあるときは、けちをしないでください。想像力に頼って、逆論理のシグナルが現れたときは、バリュエーションがどれほど魅力的であっても、ためらわずにすべての幻想を断ち切ってください。
「間違い」が何かわからないなら 実際、私たちは日常生活や仕事において、次のような 2 つの相反する論理を脳内に準備することができます。
朝出勤するとき、天気が悪く、雨が降っていなくてもかばんに軽い傘を入れている 「雨が降る・降らない」は対極です。あなたの脳内に同時に存在する一連のロジック。
上司に提出する計画には、主な計画に加えて、これらの要因の一部が変化した場合の緊急時対応計画も含まれます。これには、2 つの相反するロジックが同時に含まれます。
しかし、投資となると、多くの人は「闇への一方通行」の精神を発揮しますが、我慢できないときは、チキンスープの「最後まで耐えて大儲け」の例を見てください。それらの投資のうち。
投資家は、自分がほとんど知らない方向に対しては常に「盲目的な自信」を示し、よく知っている分野でしか適切な慎重さを示すことができません。
何が「間違い」なのかが分からないのであれば、それを主張しても無駄です。
この記事がお役に立てば幸いです。 もしそうなら、チップをおくるどうぞ https://getalby.com/p/bitcap
日本のホスティングサービス Linux、Windowsクラウドホスティング データストレージ JPStream を使用して NOSTR リレーを作成する ホスティング サービスの料金をSatsで支払うことができます https://jpstream.net
-
-
 @ 32e18276:5c68e245
2024-07-05 18:28:20
@ 32e18276:5c68e245
2024-07-05 18:28:20Hey guys!
Here's our Q3-Q4 report. There was some confusion with the timing of the previous quarters so we've accumulated everything since the Q2 report (March 2nd, 2024) into this one. Enjoy!
Damus OpenSats Q3-Q4 Progress Report
The third and fourth quarter of the initial Damus OpenSats grant encompasses work done across many of the active projects being worked on at Damus HQ. Here's a quick overview of the progress made across the organization:
nostrdb
Added
- Author query support (William Casarin)
- REQ support: ndb_subscribe (William Casarin)
- CLOSE support: ndb_unsubscibe (William Casarin)
- Profile flatbuffer dump utility (William Casarin)
- Ability to register a subscription callback instead of just polling (William Casarin)
Changed
- Dump json in filter and fulltext queries in cli tool (William Casarin)
Stats
name added removed commits William Casarin <jb55@jb55.com> +665 -739 16nostrdb-rust
Added
- Note builder interface (William Casarin)
- Nip10 implementation (William Casarin)
- Getting profile by key (William Casarin)
- Note tag support (William Casarin)
Tag::into_itermethod (Yuki Kishimoto)FilterBuilder::untilmethod (Yuki Kishimoto)- Export structs from
tagsmodule (Yuki Kishimoto)
Fixed
FilterBuilder::limitmethod (Yuki Kishimoto)Note::sigmethod (Yuki Kishimoto)
Stats
Yuki Kishimoto <yukikishimoto@protonmail.com> +20 -4 5 William Casarin <jb55@jb55.com> +1551 -867 32Damus NoteDeck/Android
This project is in heavy development and doesn't have clean changelogs yet, so here are all of the git logs from this period
Willam's updates
- account_manager: don't add the same pubkey more than once
- actionbar placeholder
- actionbar: remove border on reply button, add expand animation
- actionbar: support both dark and light buttons
- Add forward navigation animation
- add hover to profile map demo
- add --light lightmode flag to previews and notedeck
- add my pubkey to the timeline query for testing
- add test queries for elsat
- add vertical separators between timelines
- allow missing profiles in account switcher
- allow multiple invocations of --sec
- always have some default timeline
- app: make ndb public
- a quick note about the View trait
- args: allow filter files and raw filters on cli
- bump timeline filter limit
- cap size of remote filter limits
- change selection color to purple
- check: remove duplicate and disable wasm checks
- ci: disable wasm builds for now
- cli: add --sec argument to quickly add an account
- clippy postbox cleanups
- crates: add bitflags
- damus: make relay pool public
- darker quote reposts for mobile
- debug: add some debug logs for keyboard note selection
- deps: using tracing instead of log
- direnv: disable nix direnv on darwin
- direnv: make args explicit so its easy to change
- don't bump timeline when adding notes
- dont since-optimize when we don't have enough notes
- don't use an actual keystorage in Damus test apps
- drafts: clear post after posting
- enable nip10 replies
- enostr: rename Event to Note
- env: allow private things like secret keys
- filter: add default limit
- filters: fix hashtag filters
- filter: unify nostrdb and remote limits
- Fix all warnings
- fixed_window: fix clippy warning
- fix global query
- fix inline note preview colors
- fix light borders for quote reposts
- fix postbox design
- fix scroll area shrinking
- fix some clippy warnings
- fix until filters
- fix warnings
- fonts: always use base fonts for all families
- fun large profile grid preview
- get all missing ids from all timelines
- github: remove pages workflow
- gitignore: add perf files
- hide navigation title on global nav
- ids: find more unknown ids from inline notes
- images: add aspect_fill
- initial inline note previews
- initial navigation
- initial note posting
- initial postbox for testing
- initial post box view
- initial post reply view
- initial refactor in preparation for routing
- input: fix deadlock on resize
- input: handle raw events
- input: process input once
- input: switch to scanning over raw input events
- integrate sidebar into main view
- introduce View and Previews traits
- irc mode
- ircmode: tighten username
- keys: actually use the keystore
- lighter gray for inline previews in white mode
- list: switch from arc mutext to rc refcell
- load timelines from commandline
- log: reduce spammy new note log
- log relay subscriptions
- make notedeck front and center
- mobile: add lots of top padding on mobile
- mobile: a tad more padding at the top
- mobile: black panel bg color
- mobile: don't add hover on mobile
- mobile: make mobile flag runtime-configurable
- mobile: simplify is_mobile
- mobile: use my timeline for testing again
- move account_login_view to ui submodule
- move add_space to its correct location
- nip10: fetch unknown replied-to notes
- nip10: show initial reply information on notes
- nix: add openssl dep for reqwest
- nix: make android emulator optional
- nostrdb: bump to support timeline queries
- note: don't allow nested note previews
- note: support nprofile mentions
- perf: don't clone bytes via a more specialized function
- perf: fix continuous repaint
- perf: profiling note content rendering
- popup: increase fixed window margin
- popup: simplify borrow
- postbox: add focused state
- postbox: add focus shadow from figma
- post: full available width
- postview: add vertical scroll
- previews: remove central panel frame
- profile: add about and username to profile previews
- profiles: introduce DisplayNames
- profiling: update puffin version
- queries: add a few more test queries
- queries: set reasonable initial query sizes
- queries: update hashtags query
- readme: add usage
- readme: document previews
- readme: make it clear that its for desktop
- readme: make it clear that nix is optional for non-android dev
- readme: show notedeck preview
- refactor: move fixed_window to ui
- refactor: move note into its own widget
- refactor: rename widgets to ui
- refactor: use map instead of explicit
if let - remote: use default_remote_limit instead of hardcoding
- remove context from DesktopSidePanel
- remove minimum window size
- remove useless struct
- render_pfp: only depend on imgcache
- reset virtual list if notes are spliced into timeline
- set tooltip delay to 100ms
- side_panel: return more detailed side panel responses
- simplify is_mobile check
- simplify tab underline calculation
- since filter optimization
- slightly larger pfpfs
- small inline preview pfps
- style: initial logic for mobile style
- style: less bubbly
- style: realtime hover interactions
- style: set 0 duration tooltip delay
- Switch to egui master to fix wgpu issues
- switch to glow for now
- switch to rustls-tls-native-roots
- tabs: select notes & replies by default
- test: add test timeline query
- test: update test profile with a banner
- test: use my timeline query by default for testing
- textmode: adjust name sizing so it doesn't bump the column
- textmode: fix coloring of abbreviated names
- textmode: no previews in textmore for now
- theme: update to correct colors based on figma design
- timeline: don't hide on resize
- timeline: refactor tabs into TimelineView
- timeline: use strips instead of panels
- ui: add banners to profile previews
- ui: add feathering-resistant hline separator fn
- ui: add frame around note previews
- ui: add initial Profile hover previews
- ui: add profile picture hover animation
- ui: integrate egui-tabs for notes & replies selector
- ui: introduce profile picture widget
- ui: make pixel sizes correct, use more of the figma
- ui: move RelayView into ui module
- ui: only inline preview kind1 notes for now
- ui: reduce vertical padding for more compact timelines
- ui: remove some old note ui comments
- ui: simplify note widget
- ui: switch to flags for note options
- update slow timeline query
- update to latest nostrdb, adding tag support
- update version in comment because I still use this on my laptop
- use egui_virtual_list for rendering
- use unique id for post/reply view
- weird actionbar experiment
- we should just called this damus
- widgets: begin organizing ui components into widgets
- working notes + notes&replies
kernelkind's updates
- account_management: refactor
- AccountManagementView
- AccountManager: add ability to make a selection
- AccountSelectionWidget
- Account switcher
- Add AccountManager to app
- Add custom visual themes
- Add flag to emulate mobile during preview
- Add keypair & update pubkey
- Add login key parsing
- Add login manager
- Add MacOS key storage
- Add MobileAccountLoginView
- Add modular custom text styles
- Add monospace text style
- Add nix-shell for macos android development
- Add nostr-sdk dependency
- Add precommit hook to suggest proper formatting
- Add preview for RelayView
- Add relay view
- add reqwest as dependency
- Add SimpleProfilePreview
- Add ui_test_harness binary implementation
- Add warn color and highlight color
- app: add accounts to Damus & mock
- Apply app style to AccountLoginView
- Apply cargo fmt
- Conditionally compile MacOS key storage code
- Constrain app minimum size
- Create account login panel
- Create side panel & global popup
- enostr: expose RelayStatus
- Extract the sample relay to test_data for reuse
- impl linux credential storage
- Integrate account switcher to side panel
- Integrate global popup into app
- login: Add key loading & error to mobile
- macos_key_storage: runner ignore tests
- migrate AccountManagementView to enostr Keypair
- Migrate to new AccountManagementView conception
- Move login business logic to LoginManager
- move login logic from promise to async fns
- Move preview controller out of account_manager.rs
- move test account creation & apply to global popup
- Pfp integration to side panel
- refactor account switcher & management previews
- Refactor 'ui tests' conception to previews
- reintroduce account management
- reintroduce account switcher
- remove nostr-sdk
- Rename PersistState -> StateInMemory
- select first account
- Seperate mobile dark color theme into its own func
- update cargo.lock to reflect toml change
- Update egui 0.26.1 -> 0.27.1
- Use app_creation for common app setup functions
- Use custom style in app
- use nostr in enostr
Stats
name added removed commits kernelkind <kernelkind@gmail.com> +6844 -1979 58 William Casarin <jb55@jb55.com> +9733 -5583 194Damus iOS
Added
- Ability to create highlights (ericholguin)
- Add ability to mute hashtag from SearchView (Charlie Fish)
- Add ability to mute words, add new mutelist interface (Charlie) (William Casarin)
- Added callbackuri for a better ux when connecting mutiny wallet nwc (ericholguin)
- Added nip10 marker replies (William Casarin)
- Added title image and tags to longform events (ericholguin)
- Add event content preview to the full screen carousel (Daniel D’Aquino)
- Add First Aid solution for users who do not have a contact list created for their account (Daniel D’Aquino)
- Add marker nip10 support when reading notes (William Casarin)
- Add video cache to save network bandwidth (Daniel D’Aquino)
- Completely new threads experience that is easier and more pleasant to use (Daniel D’Aquino)
- Connect to Mutiny Wallet Button (ericholguin)
- Highlights (NIP-84) (ericholguin)
- Notification reminders for Damus Purple impending expiration (Daniel D’Aquino)
- Proxy Tags are now viewable on Selected Events (ericholguin)
- Relay fees metadata (ericholguin)
- Revamp emoji picker to be less error-prone and add search, frequently used, and multiple skin tone support capabilities (Terry Yiu)
- Show list of quoted reposts in threads (William Casarin)
Changed
- Added first aid contact damus support email (alltheseas)
- Add support for Apple In-App purchases (Daniel D’Aquino)
- Always strip GPS data from images (kernelkind)
- Change reactions to use a native looking emoji picker (Terry Yiu)
- Errors with an NWC will show as an alert (ericholguin)
- Improve UX around video playback (Daniel D’Aquino)
- Moved paste nwc button to main wallet view (ericholguin)
- Relay config view user interface (ericholguin)
- Relay detail design (ericholguin)
- Updated Zeus logo (ericholguin)
Fixed
- Fix broken GIF uploads (Daniel D’Aquino)
- Fix bug that would cause connection issues with relays defined with a trailing slash URL, and an inability to delete them. (Daniel D’Aquino)
- Fixed issue where some replies were including the q tag (William Casarin)
- Fixed issue where timeline was scrolling when it isn't supposed to (William Casarin)
- Fixed threads not loading sometimes (William Casarin)
- Fixed wallet not disconnecting when a user logs out (ericholguin)
- Fix emoji reactions being cut off (ericholguin)
- Fix ghost notifications caused by Purple impending expiration notifications (Daniel D’Aquino)
- Fix image indicators to limit number of dots to not spill screen beyond visible margins (ericholguin)
- Fix in-app purchase issue that would trigger an error on purchase before confirming the account information. (Daniel D’Aquino)
- Fix issue where bootstrap relays would inadvertently be added to the user's list on connectivity issues (Daniel D’Aquino)
- Fix missing Mute button in profile view menu (Terry Yiu)
- Fix nostrscripts not loading (William Casarin)
- Fix profile not updating bug (William Casarin)
- Fix stale feed issue when follow list is too big (Daniel D’Aquino)
- Fix thread bug where a quote isn't picked up as a reply (William Casarin)
- Fix welcome screen not showing if the user enters the app directly after a successful checkout without going through the link (Daniel D’Aquino)
- Improve reliability of contact list creation during onboarding (Daniel D’Aquino)
- Issue where NWC Scanner view would not dismiss after a failed scan/paste (ericholguin)
Stats
name added removed commits Fonta1n3 <fontainedenton@googlemail.com> +1 -0 1 Sean Kibler <skibler@protonmail.com> +13 -2 1 alltheseas <64376233+alltheseas> +65 -1 4 Transifex <transifex@transifex.com> +581 -39 36 Terry Yiu <git@tyiu.xyz> +763 -1383 8 William Casarin <jb55@jb55.com> +1017 -1564 49 ericholguin <ericholguin@apache.org> +1962 -643 13 Daniel D’Aquino <daniel@daquino.me> +3885 -761 48 -
 @ ee7d2dbe:4a5410b0
2024-07-11 09:54:27
@ ee7d2dbe:4a5410b0
2024-07-11 09:54:27Making an App in the world where Apps are loaded with AI capabilities is not just an intelligent decision for any business to find their digital edge, it has become more of an essential than ever. Making an App with advanced capabilities like AI, AR/ VR, Automation is easier for bigger organizations since they always have resources and budget to hire their own team or an Mobile Application development company for a premium. But most of the First time App Entrepreneurs or startups wonder about what will be the best way to make an app or how to make an app from the scratch in limited budget and resources. Since any mobile app project involves a good amount of skilled efforts, energy, cost and time it becomes pretty obvious that a new startup entrepreneur gets worried about pros and cons of various methods of App development, hidden App developments cost, Maintaining the App and other nuances before actually jumping the gun.
Therefore, we’ve got you covered and here is this comprehensive guide on how to make an App from the scratch, and how to monetize your App, and why you should work with the best App Development companies to keep the complex things simpler.
A guide to make an App, with Examples
- Define Your App Objectives
Yes, we all know that the ultimate goal of any business is to generate a million-dollar revenue and an App business is pretty much capable to achieve that and more, however we suggest take one step at a time. First of all, define what Major Problem that your app is going to solve, then define secondary problems too. Figure out what is not already in the market that your app can fill with i.e Do an App Gap Analysis. Brainstorm about the main objective your app is going to serve. Will the app enhance the experience of all your customers or will it be generating sales and purchases? Will this App offer a unique technology that makes users life easier, or the app is going to be an extension of your existing business? Once you’ve figured out the Gap, Opportunity, and Problem then you can make an App startup business around it.
Following are some of the common Goals for which you make an App –
To solve a problem through an App and make a business around it – like uber solved the Taxi booking problem, Airbnb solved the problem of accommodation, and like our very own HASfit(yes, we made it for our client and it has 6 million users now) solves the problem of giving quality home based no/ low equipment workouts. To Extend your existing Digital Product (A SaaS product, or a Web based or Desktop Software) as an App – Like Google Ads App as an extension of their Big web based Google Ad console, or Linkedin has their own App. Such apps may or may not replicate all functionality of your existing tech product, but offers enough to keep users at ease.
To Enhance your existing brand for better customer relationship – Like My BMW Application for BMW brand, or a Mercedes App. An App for facilitating Transactions like Ecommerce Apps– like Amazon Application or any other famous Ecommerce App, or any buy and sell app.
- Do App Competition Research, Analyze, Validate App idea, build a strategy
Scenario #1 – Your App idea is absolutely unique and there is no existing App which remotely does what you want your App to offer.
Now this is a great App situation to be in. There is no App competitor, your App idea is unique so you’d think of going full force to build it, right? Well, not just like that! More important than not having a competitive App, is a viable business model that your App can support. In such a case where you’ve an App idea that doesn’t exist yet, you should be asking following questions –
– Will users pay for this app, and if yes then how (via subscription, via ads, via in app purchase)?
– How much scope of future improvement and enhancements is going to be there with your App idea? There must be a scope for scaling, enhancements to keep your users interested and engaged.
– There is no competition today, your App idea supports a viable business model too and that means you will soon have a competition! So what will be your plans once a competition takes birth?
Scenario #2 There are similar Apps out-there but you see a big opportunity to fill the gaps they’ve left.
This is a pretty common scenario, because there is an App for almost everything but so as with the automobile and they still launch new improved cars so you can still launch a new App, a better one than your competitors. A good thing in this scenario is that, you already have a market that is receptive to the App idea you’re contemplating to make.
There was myspace and orkut before facebook, there was google talk before whatsapp, there was bigbasket before zepto grocery delivery; and the list is just endless. This means, most of the successful Apps we use today had a big competition already and their App ideas were already implemented but they still made their way like a champ. You just need to take care of following points before starting to make the app:
– Check how efficiently and aesthetically you can incorporate the features and offerings that existing competition has left considering. – Check if such new features and offerings are good enough to make your App a better alternative to the existing Apps. – Check the usage analytics of those existing apps, are people liking them and spending time and money? – Check their monetization methods, check their revenue and numbers and see how big the market is. Think of strategy where you can beat them with not just the features but also with pricing, offerings and content. – Check if these Apps have left any geographies or demographics that you can cater to, and carve a niche for your own app in such locations and among such demographics.
- Define your App’s USP or Unique Bragworthy Proposition
As mentioned in the competitive research point above, figuring out your App’s unique selling proposition and then secondary propositions is of utmost importance. The world is however moved on from USP (unique selling proposition) to UBP (Unique Bragworthy proposition) as described well by Cred’s Founder Mr. Kunal Shah, Cred is valued at apprx $ 6.4 billion as of mid 2022 is one of the biggest unicorns in India. So we can take his advice about UBP pretty seriously.
The concept of UBP in case of the Apps means you need to make your App product in such a way and position it in such a way that their users just not get benefitted out of it but feel “Smug” about being its users and that becomes your no. 1 App marketing tool. Not every new App product can be Bragworthy for the users, but atlesat one should try. After all, as Les Brown said and we quote – “Shoot for the moon. Even if you miss, you’ll land among the stars.
- Make Wireframes or Write user stories or Use-cases
A wireframe is the next step in the process of making an app. An App wireframe is the rough sketch of the mobile application you want to develop. A wireframe can be made on paper or also by using some very smart Mockups or Wireframes creating tools around that come with their mobile apps as well. We’ll talk about wireframing tools a little later, after describing an app specification document.
- Technical Feasibility – Make App’s PoC if needed
Things get serious from here. A big round of Technical Feasibility Analysis is to be done here and I’ll tell you the reasons also.
– To make sure that all what the App wants to achieve is achievable through the existing technology and libraries or would you need to build the technology from the scratch. For example, if I were to make an App that can scan the numbers on your credit card then I can use an OCR library like tesseract or any other computer vision/ Optical character recognition library and that will save me to create a whole new technology just for one app. Similarly, if I have to make an app that can extract text from images, then I can leverage the same technology (OCR) for it. However, in case of Apps which offer you an altogether new technology (Like Prisma App), you may need to work on the background technology (in this case – image processing) yourself and that can blow out the scope of the work to a whole different level.
- Make High Fidelity App Designs
Once your wireframes are finalized, the development looks all feasible, the technical architecture is selected now it is time to convert your wireframes into high fidelity screen designs that developers can use to incorporate into the project.
For high fidelity designs, you do need a professional designer who can use tools like Adobe Photoshop, or Sketch or Figma for making high fidelity screens. Agicent can definitely help you with App wireframes, App high fidelity designs, and of course App development.
- Choose Front end and Backend Technologies
Now that you have the objective, goals, market research and framework ready, the next step to proceed forward is the the coding at both ends – Front end (The App side) and backend (the backend technology, admin panel, content management, database and APIs). There are plenty of ways to build an app but the most important call to take while building an app from the scratch is to finalize which technologies to use. This highly depends upon the App type, Budget, Future scalability, and timeline.
Here are some of the common technology choices for making an app: Native App development: Native App Development means using the Native technology stack separately for iOS and Android. For iOS – Xcode with Swift or Objective C is native; while for android its Android studio with Kotlin or Java.
- Choose your App Developer
When all of above is in place, you now have to launch your project and for that you need an App Development Team. There are some options to go about making your app as follows –
Hire an App Development Company – You can always hire a reputed App Development company like Agicent to make your App. App Companies like ours are usually equipped with the right development, design and testing teams and can quickly start working on the project and delivering that. You can either hire an App company on fixed price for fixed scope of work; or can opt for hourly model (Check out Remote App Developers )pricing.
Following are some of the major benefits of hiring an App Development Company – – Rapid Development and Delivery: We are ready to start on any new project in a matter of days or maximum 1 week as we keep our app development teams ready for new projects.
– Expertise and Experience: We leverage our years of experience in the app development for your project’s benefit.
Source: https://www.agicent.com/blog/how-to-make-an-app/
-
 @ 502ab02a:a2860397
2024-07-11 08:42:42
@ 502ab02a:a2860397
2024-07-11 08:42:42เตรียมตัวเตรียมของ 3 อย่าง ก่อนลงสู่ทุ่งม่วง
โพสที่แล้ว เราเห็นข้อเปรียบเทียบระหว่าง nostr กับ โซเชียลมีเดีย กันไปแล้ว โพสนี้เราจะมาทำความรู้จัก ของหลักๆที่จำเป็นในการลงสู่ทุ่งม่วงกันครับ

อย่างที่ 1 : กุญแจคู่ รู้ตัวตน ก่อนจะเข้าประตูสู่ทุ่งม่วงนั้น เราต้องการกุญแจ 2 ดอกครับ มันทำงานคล้ายๆเซฟธนาคาร คือ กุญแจ 2 ดอกนี้ต้องเข้าชุดกัน ถึงจะเปิดออกได้ ซึ่งกุญแจ 2 ดอกนี้ เราเรียกว่า npub กับ nsec
อย่าเพิ่งตกใจ ไหนบอกว่าจะมีศัพท์คอมพิวเตอร์น้อยๆไง 5555 ใช่ครับ บางคำอาจจำเป็นต้องรู้จักไว้ แต่ผมจะเทียบเคียงเป็นภาษาบ้านๆเราให้นะครับ npub กับ nsec จะเป็นชุดตัวเลขที่คอมพิวเตอร์คำนวนมาให้ (วิธีการได้มาจะบอกภายหลังครับ)
Npub เราทำความเข้าใจเป็นภาษาอังกฤษง่ายๆว่า Nostr Public key ตัวย่อ NPUB หรือกุญแจที่เราเอาไว้ให้คนอื่นเพื่อจดจำว่าเป็นเรา ซึ่งคนอื่น นั่น นอกจากจะเป็นคนจริงๆแล้ว ยังหมายถึงระบบแอพต่างๆด้วย
Nsec เราทำความเข้าใจเป็นภาษาอังกฤษง่ายๆว่า Nostr Secret key ตัวย่อ NSEC หรือกุญแจที่เราเก็บไว้ที่ตัวเองเท่านั้น ห้ามใครรู้
ระบบต่างๆจะคำนวนว่า npub กับ nsec เป็นชุดเดียวกันหรือเปล่า ก่อนนะอนุญาตให้เราดำเนินการใดๆได้ใน nostr พูดง่ายๆคือ npub nsec คือ กุญแจคู่ที่เอาไว้ยืนยันความเป็นตัวเรานั่นเองครับ
ทีนี้ข้อเด่นของระบบ nostr ที่เหนือกว่า แอพโซเชียล www ทุกวันนี้คือ กุญแจคู่นี้ชุดเดียว ทำให้คุณสามารถท่องไปในดินแดน nostr ได้ตลอดกาล ไม่ว่าในอนาคตจะมีคนสร้าง nostr app อะไรใหม่ๆขึ้นมา โครงสร้างหลักของ nostr จะเป็นการใช้กุญแจคู่นี้ตลอดไปเช่นกัน ไม่เหมือนกับ โซเชียล www ทุกวันนี้ ที่ต้องไปไล่สมัคร user id ตามเอกชนแต่ละที่ แล้วเราก็ต้องมีเป็นร้อยๆ account ตามจำนวนบริการที่เราใช้ ไหนจะ เฟสบุค ไหนจะยูทูป ไหนจะกูเกิ้ล นี่ยังดีที่ แอพเล็กๆหลายๆเจ้าไปพึ่งใบบุญลูกพี่ใหญ่ อย่างเฟสบุค ยูทูป ไปบ้างแล้ว แต่เราก็ต้องมีสารพัด user id อยู่ดี
นอกจากนี้ ข้อมูล password ของเราก็ยังถูกบันทึกไว้ที่คอมของ แอพนั้นๆ ต่างกับ กุญแจคู่ของ nostr ที่ไม่ได้เป็นการบันทึกข้อมูลของกุญแจไว้ในคอมของแอพ(ที่ใน nostr เราเรียกว่า รีเลย์ จำได้ใช่ไหมครับ) ระบบของ nostr เป็นการนำตัวเลขของกุญแจคู่นี้ มาคำนวนความเข้ากันได้ว่าเป็นคู่ที่ถูกต้องไหม ถ้าถูกต้องมันจะอนุญาตให้เราดำเนินการต่อ นั่นหมายถึงไม่มีการบันทึกใดๆไว้ในคอมผู้ให้บริการเลย ตราบใดที่คุณเก็บกุญแจไว้ที่ตัวดีๆ your key is your id
ทีนี้การที่จะได้กุญแจคู่นี้มานั้นไม่ยากครับ เพียงแค่เราใช้แอพของ nostr เป็นตัวสร้างได้เลย

อย่างที่ 2 : แอพไหน ไฟแรงเวอร์ ก่อนจะเข้าสู่การสร้าง เรามาทำความเข้าใจ โลกของ nostr app กันเพิ่มสักนิดก่อนครับ อย่างที่บอกในโพสที่แล้ว nostr คือระบบการส่งข้อมูลแบบใหม่ เทียบให้เห็นภาพก็คือ www (world wide web) Nostr คือ การส่งอะไรก็ตามผ่านรีเลย์ (Notes and Other Stuff Transmitted by Relays)
ทีนี้ในโลกของ www เราก็จะมีแอพซึ่งภาษาทางการเรียกว่า web app เห็นชัดๆก็พวกที่อยู่ในมือถือเรานั่นละครับ เฟสบุค ยูทูป ไอจี ทวิตเตอร์ มันคือหน้าฉากเป็นมือถือแต่หลังบ้านมันเป็นการติดต่อส่งรับข้อมูลในระบบ www รวมศูนย์อยู่ที่แอพแต่ละยี่ห้อ
การทำงานของ Nostr ก็เหมือนกัน แม้จะใช้การส่งข้อมูลผ่านรีเลย์แต่ระบบยังคงทำงานบนอินเตอร์เนทช่วยในการเดินทาง เราจึงจะมี nostr app เพื่อใช้เป็นหน้าบ้านในการส่งรับข้อมูลในระบบ nostr ที่เชื่อมต่อถึงกันโดยรีเลย์ ดังนั้นเอาจริงๆในฐานะผู้ใช้ แทบจะไม่ต้องปรับอะไรมากเลย นอกจากเรียนรู้การใช้แอพใหม่
ส่วนการอธิบายหลักการที่ผ่านมา มันแค่ช่วยให้คุณเข้าใจความเจ๋ง ความอิสระ ความปลอดภัย เพื่อให้คุณ อิน ในระบบที่ไม่ต้องพึ่งพาบริษัทเอกชนที่เอาคุณเป็นสินค้าใดๆอีก
นักเขียนโปรแกรม เขาก็ทำ app ขึ้นมาให้เราเทียบเคียงการใช้งานกับโลกทุกวันนี้ ยกตัวอย่างให้เห็นภาพกันก่อนเช่น Facebook twitter เขาก็จะมีแอพ damus artemis primal ฯลฯ ที่เป็นการโพสข้อความ รูป ลิงค์ มีกดไลค์ มีแชร์ ได้เหมือนกัน Youtube เขาก็จะมีแอพ zapstream flare ฯลฯ ที่เป็นลักษณะคลังเก็บวีดีโอ หรือ การไลฟ์ต่างๆ ซึ่งอันนี้แค่ตัวอย่างครับ จริงๆแล้วยังมี nostr app อีกมากมายก่ายกอง ที่เริ่มมีการทะยอยออกมาให้ใช้งานกัน (แน่ละครับ มันยังไม่มากแบบใน app store แต่มันคือจุดเริ่มต้นที่ผ่านมาได้พักนึงแล้ว และแอพใช้งานทั่วไปก็ครอบคลุมแล้ว)
ที่สำคัญคือ ทุก nostr app ใช้กุญแจคู่เดียว ในการแสดงตัวตนของเราในการใช้งานนั้นๆ ตามที่บอกไว้ข้างบน (อย่างที่1) ไม่ต้องสมัครอะไรอีกต่อไป โหลดแล้วใช้เลย และใครที่ใช้คอม จะยิ่งมี nostr app ที่ใช้งานแบบบนคอมเยอะกว่าในมือถือเสียอีก

อย่างที่ 3 : แฮชแทคจ๋า พี่มาแล้ว ด้วยความที่โลกของ nostr กว้างใหญ่มาก อิสระมาก และที่สำคัญคือ ไม่มีอัลกอลิทึม ในการที่จะยัดเยียดการมองเห็น ดังนั้นสิ่งที่จะทำให้ทุกอย่างง่ายขึ้นนั่นคือแฮชแทค ถ้าใครเล่น ig twitter เราจะคุ้นเคยกันดี ว่าหากเราโพสอะไรแล้วใส่แฮชแทค คนที่ติดตามแฮชแทคนั้น จะได้เห็นข้อความเราไปเอง nostr ก็เช่นกัน มีแฮชแทคมากมายให้ติดตามกัน โดยเฉพาะ แฮชแทค #siamstr ที่เราชาวไทยรวมใจกันใช้ เพื่อสร้างอาณาเขตของคนไทยในทุ่งม่วง นอกจากนี้ของผมเองคือ #pirateketo ที่ใช้อยู่กับเฟสบุคและ ig ก็นำไปใช้ในทุ่งม่วงด้วย สามารถเจอโพสของพวกเราได้ ตามแฮชแทคนี้
ถ้าเป็นคนเล่นแฮชแทคอยู่แล้วก็ง่ายเลยแทบไม่ต้องปรับตัว ใครไม่ค่อยเล่นก็สามารถลองกดๆแฮชแทคในเฟสบุคดูเพื่อทำความเข้าใจการทำงานได้ก่อนที่จะลงทุ่งม่วง
ทบทวนอีกที ของ3อย่างที่ต้องเตรียมรู้ก่อนลงทุ่งม่วง 1.กุญแจคู่ รู้ตัวตน 2.แอพไหน ไฟแรงเวอร์ 3. แฮชแทคจ๋า พี่มาแล้ว เมื่อทำความเข้าใจ 3 อย่างนี้แล้ว เราก็พร้อมจะลงไปมั่วกันแล้วครับ เล่นก่อนเรียนตามกันไปอีกที
pirateketo
siamstr
-
 @ c73818cc:ccd5c890
2024-07-11 20:03:26
@ c73818cc:ccd5c890
2024-07-11 20:03:26
🐓 Record Storico di Esposizione a Bitcoin
💠 Nel 2024, Wall Street ha raggiunto un'esposizione record a Bitcoin, con un incremento significativo degli investimenti in criptovalute. Le principali istituzioni finanziarie hanno aumentato le loro posizioni in Bitcoin attraverso fondi di investimento (ETF) e prodotti finanziari legati al criptoasset. Questo riflette una crescente fiducia nel potenziale di Bitcoin come asset class.
🐓 Sviluppi dei Prodotti Finanziari
💠 Le principali istituzioni finanziarie, tra cui JPMorgan e Goldman Sachs, hanno lanciato nuovi strumenti finanziari per facilitare l'accesso degli investitori a Bitcoin. Tra questi, ETF basati su Bitcoin e contratti futures sono stati introdotti, offrendo agli investitori opportunità diversificate per espandere le loro esposizioni al criptoasset. Questi prodotti mirano a capitalizzare il crescente interesse degli investitori per le criptovalute.
🐓 Implicazioni per il Futuro di Bitcoin
💠 L'aumento dell'esposizione a Bitcoin da parte delle istituzioni di Wall Street potrebbe segnare l'inizio di una nuova era per le criptovalute. La crescente integrazione di Bitcoin nei portafogli degli investitori istituzionali potrebbe portare a una maggiore legittimazione del criptoasset e a una maggiore stabilità del mercato. Questo sviluppo potrebbe anche stimolare ulteriori innovazioni e investimenti nel settore delle criptovalute.
Unisciti al nostro gruppo Telegram: https://t.me/Bitcoin_Report_Italia
Referral Bitget -10% sulle fee + bonus benvenuto 6w5d o link: https://bonus.bitget.com/U1JNEK
BitcoinReportItalia #WallStreet #Investimenti #Istituzioni #ETF #JPMorgan #GoldmanSachs #Criptovalute #Bitcoin
-
 @ 502ab02a:a2860397
2024-07-11 07:14:05
@ 502ab02a:a2860397
2024-07-11 07:14:05 ก่อนจะเปิดหลุมกระต่าย ให้เพื่อนๆลงไปสู่ ทุ่งม่วง wonderland เรามาเบิกเนตรระบบที่ทำให้เราเป็นสินค้าแทนที่จะเป็นลูกค้ากันก่อนครับ
ก่อนจะเปิดหลุมกระต่าย ให้เพื่อนๆลงไปสู่ ทุ่งม่วง wonderland เรามาเบิกเนตรระบบที่ทำให้เราเป็นสินค้าแทนที่จะเป็นลูกค้ากันก่อนครับอินเตอร์เนทเริ่มต้นด้วยอุดมการณ์ที่ดี ที่จะให้ข้อมูลข่าวสารมันฉับไว ซึ่งมันก็เป็นเช่นนั้นจริงๆ แต่โลกมันมีสิ่งนึงที่เกิดขึ้นอยู่เสมอ นั้นคือ การชิงทรัพยากร ดินแดน เวลา และการควบคุมคนให้อยู่ในอาณัติ
อินเตอร์เนทเริ่มถูกยึดดินแดนมาตั้งแต่การเริ่มมีการสื่อสาร 2 ทางที่โต้ตอบกันได้เร็วขึ้น เจ้า www (World Wide Web) มันกลายเป็นดินแดนของไม่กี่บริษัท ที่เป็นผู้ยิ่งใหญ่ในโลก ดอทคอม สร้างกิจกรรมบางอย่างแล้วให้คนทั้งโลกเข้ามาใช้งาน
จะเห็นว่าทุกวันนี้เราแทบไม่พ้นการเข้าไปดู เฟสบุค ยูทูป ทวิตเตอร์ ไอจี ชอปปี้ ลาซาด้า และอื่นๆที่เหมือนจะมากมายแต่ไม่ได้มากมายเมื่อเทียบประชากรโลก
บางคนบอกว่ามันก็ดีไม่ใช่เหรอ เราได้ใช้ฟรีๆ ตรงนี้ละครับ เราจะเข้าเรื่องกันแล้ว
คำที่เราหลงไปกับมันคือ เขาทำมาให้เราใช้ฟรีๆ เขาต้องเห็นเราเป็นลูกค้าสิ แต่ความจริงนั้น เราคือสินค้าครับ เขาฟาร์มเราไว้เป็นสินค้า เป็นหมูในแฮปปี้ฟาร์ม ยิ่งประชากรในฟาร์มมีมาก เขาก็จะมีมูลค่าสูงมาก ดังเช่นที่เราเห็นว่า
มีการบ่นมากมายเรื่องการกดการมองเห็น การที่มีแต่โพสพนัน หลอกขายของที่เป็นสปอนเซอร์ การที่เราลงรูปไก่ต้มแล้วโดนแบนเพราะเขามองว่าทรมานสัตว์ และอื่นๆอีกมากมายที่ทำให้รู้สึกว่า ทำไมเขาดูแลผู้ใช้งานไม่ดีเลย เราเป็นลูกค้าเขานะ
ถ้ามองในอีกมุมนึง จริงๆเขาดูแลลูกค้าดีแล้วครับ ลูกค้าของเขาคือคนซื้อโฆษณาต่างหาก ใครที่จ่ายมาก ก็เอาสินค้าเค้ามายัดเยียดให้ประชากรในฟาร์ม ได้ดูกันตาแตก หมูในฟาร์มคนไหนออกนอกลู่นอกทางก็จะเชือดทิ้ง นี่ละครับที่บอกว่าเราคือสินค้าต่างหาก
กลุ่มคนที่ต้องการอิสระเสรี จึงสร้างสิ่งใหม่ขึ้นมา ไม่ใช่แค่ทำแอพ ไม่ใช่ทำแค่เว็บ เพราะมันยังต้องพึ่งพาเอกชนในการเอาข้อมูลไปฝากไว้ในเครือข่าย แต่สิ่งใหม่นี้มันเป็นระบบการส่งข้อมูลแบบใหม่ครับ
ให้เห็นภาพยิ่งขึ้น เราบอกไปแล้วว่าดินแดนอินเตอร์เนท มันอยู่ในกำมือคนที่เป็น land lord ไม่กี่คน และทุกอย่างเราต้องอยู่ใต้อาณัติเขา ตั้งแต่การได้เห็นแค่ข้อมูลเขาก็เลือกให้ จนถึงว่าถ้าเขาสงสัยว่าเราไม่ใช่เราตัวจริง เขาสามารถลบเราไปโดยไม่ต้องถามอะไร ชีวิต7ปี 10ปี ที่ผ่านมาในแอพมันสามารถเหลือ 0โพสได้ในพริบตาและไม่ให้อุธรณ์ใดๆ
นั่นเพราะข้อมูลทุกอย่างมันไปอยู่ในเครื่องคอมของแต่ละบริษัท ทั้งยูทูป เฟสบุค ไอจี ของๆเรา เราเอาไปอัพไว้ในคอมเขา ต้องทำตามกฎที่เขาตั้งและเปลี่ยนใจได้ทุกเมื่อ และแอบมองของๆเราได้ทุกรูปทุกข้อความลับ
ทุกอย่าง ย้ำว่าทุกอย่าง ต้องผ่านคอมของเขาทั้งหมด เราไม่มีอะไรเป็นของเราเลย ในฟาร์มนี้ เราแค่รอโดนเชือดและเราไม่กล้าออกมาเพราะคิดว่าเป็น safe zone
ส่วนระบบการส่งข้อมูลแบบใหม่ เราเรียกว่า nostr อ่านว่า นอสเตอร์ ชื่อเต็มมันยาว แต่ถ้ารู้ จะเข้าใจง่ายขึ้น เพราะมันมาจากคำว่า Notes and Other Stuff Transmitted by Relays แปลว่า ”อะไรก็ตามที่เอามาส่งผ่านรีเลย์“
ผมขอเรียกมันว่าส่งไม้ต่อละกันครับ มองภาพการวิ่ง 4x100 มันมีการส่งไม้ผลัดใช่ไหมครับ นั่นละ รีเลย์

ระบบเก่าเราเรียกว่า การรวมศูนย์ นั่นคือเอะอะก็ต้องไปเก็บหรือไปดู จากคอมบริษัทนั้นๆ เช่น ดูคลิปก็ต้องไปโหลดจากคอมของยูทูป จะดูฟีดเพื่อนก็ต้องไปโหลดข้อความที่เพื่อนฝากไว้ในคอมของเฟสบุค
ถ้าวันนึง เฟสบุคล่ม นั่นคือทุกคนติดต่อหรือดูอะไรไม่ได้เลย และถ้ากู่ไม่กลับ นั้นคือทุกอย่างหายหมด นอกจากนี้ผู้คุมศูนย์คือสั่งชี้เป็นชี้ตายคุณได้ทันที ที่ไม่พอใจคุณ บ้านเขากฎเขา นั้นเอง

ในขณะที่ nostr เป็นระบบส่งไม้ผลัด นั่นคือ ใครๆก็สามารถเป็น รีเลย์ได้ แค่มีคอมก็เรียบร้อย วิธีการเป็นรีเลย์ เรายังไม่ต้องสนใจครับ เราเป็นแค่ผู้ใช้ ไม่ต้องเป็นผู้ให้บริการก็ได้ ฟรีด้วย วันนี้เราแค่มาเข้าใจเส้นทางก่อนครับ
อย่างที่บอกครับ ระบบการส่งข้อมูลเราเป็นรีเลย์ หรือ ไม้ผลัด หลักการก็แค่เราก็แค่ใส่ที่อยู่รีเลย์ ลงไปในแอพของเรา แล้วข้อมูลที่เราส่งไป เจ้ารีเลย์มันก็จะวิ่งส่งไม้ผลัดนี้ไปให้สมาชิกทุกคนในรีเลย์
ในทางกลับกัน เราก็จะได้รับข้อมูลที่สมาชิกในสังกัดรีเลย์ที่เราลงไว้ ส่งมาให้ผ่านทางรีเลย์ด้วยเช่นกัน
และที่เจ๋งก็คือ รีเลย์ ไม่สนใจอะไรอย่างอื่นอีก นอกเหนือแค่ส่งไม้ผลัดให้สมาชิกทุกคน นั่นคือ มันไม่คิดว่าอะไรควรส่งไม่ควรส่ง มันไม่คิดว่าข้อมูลดีแค่ไหน มันไม่ปิดกั้น มันไม่เซนเซอร์ นั่นคือ มีหน้าที่แค่ส่งจริงๆ นอกจากนี้ถ้าเราเป็นใส่รีเลย์มากกว่า 1 แห่งในตัวเรา ข้อมูลทั้งหมดก็จะสำเนาไปยังรีเลย์ที่เหลือได้เช่นกัน หมายถึงว่า ข้อมูลเราจะกระจายแบบสำเนาไปได้อีกหลายๆๆๆๆรีเลย์
นอกจากอิสระแล้วยังฆ่าไม่ตายด้วย เพราะรีเลย์มีขึ้นเป็นดอกเห็ด และใครๆทำรีเลย์มาเปิดให้บริการได้เอง (เราเป็นแค่ผู้ใช้ ไม่ได้อยากเป็นผู้ให้บริการ เราไม่ต้องสร้างรีเลย์ก็สามารถใช้งาน nostr ได้ครับ)
ดังนั้น nostr จึงเหมาะกับคนที่ต้องการเสรีภาพแบบเต็มๆ เพราะไม่มีใครเซนเซอร์คุณได้เลย คุณเท่านั้นที่จะต้องรับผิดชอบการกระทำของคุณเอง
เพราะด้วยที่มันฆ่าไม่ตาย นั่นหมายถึง สิ่งที่คุณพิมพ์หรือโพสลงไป จะไม่สามารถลบหรือแก้ไขได้เช่นกัน แม้แต่ตัวคุณเองก็ตาม
ดังนั้นไต่ตรองให้ดีถ้าจะสร้างเนื้อหา เพราะมันจะบันทึกสิ่งที่คุณทำไว้ตลอดไป แต่ถ้าเรายังไม่มั่นใจเราลองเล่นแบบเป็นคนอ่านก่อนก็ได้ครับ พอเราใช้คล่องขึ้น มีสติสัมปชัญญะเพียงพอ ก็เริ่มทักทายคนในนั้นได้ มันไม่น่ากลัวหรอกครับ เพราะหัวใจหล้กของ nostr คือการเข้าสังคม สร้างสังคมคุณภาพ มากกว่าการโพสเท่ๆเอาไลค์ เพราะ มันไม่มีอัลกอลิทึ่มใดๆ เขายึดมั่นใน proof of work
ไลฟ์ของเราจะไม่โดนปิดกั้น โพสของเราจะไม่โดนลดการมองเห็น ถ้ามันมีคุณภาพเพียงพอที่คนจะเลือกติดตามชม
ถ้ามองเห็นกลลวงของโซเชียลแล้ว ตอนหน้า จะรวบรัด ลงหลุมกระต่ายกันเลย เอาแบบโหลดแล้วเล่นก่อน แล้วเรียนไปพร้อมๆกับเล่นนี่แหละ
ถ้าทุกคนเริ่มวันนี้ อิสระก็จะเริ่มยิ่งใหญ่วันนี้ แล้วก็จะไม่มีคำว่า คนมันยังน้อยอยู่
เคยดูหนังไหมครับ เช่นตอนเปิดแผ่นดินใหม่ ใครขี่ม้าไปปักธงจองอาณาเขตได้ก่อน ก็จะคุ้นชินพื้นที่นั้นๆได้ก่อนใครครับ
pirateketo
กูต้องรู้มั๊ย
Siamstr
-
 @ 1ad8f5d3:bb624486
2024-07-11 03:58:07
@ 1ad8f5d3:bb624486
2024-07-11 03:58:07Livestream Your Gameplay and Earn Bitcoin with Zap.Stream
The world of gaming and live streaming is evolving, and now you can monetize your gameplay by earning bitcoin. In this guide, we’ll show you how to easily set up your live stream using OBS (Open Broadcaster Software) and zap.stream, a nostr-based streaming platform. This is the second article in our nostr series, read the introduction to nostr here.
https://cdn.satellite.earth/6b833e9d1bab7379ba3ed0798290783a3d8a81dc8b4195405037720163768b4e.mp4
Why Choose Zap.Stream?
Zap.Stream is a user-friendly streaming platform that integrates seamlessly with the Nostr network. Which means your followers can easily support you with native bitcoin integration. Whether you’re a seasoned Nostr user or new to the scene, zap.stream makes it incredibly simple to get started. Plus, zap.stream has built-in re-streaming, allowing you to stream to one destination and have it restreamed to multiple platforms like Twitch and YouTube, for a fraction of the cost of traditional restreamers.
Getting Started with zap.stream
- Sign In with Your Nostr Identity
- If you already have a Nostr identity, sign in directly with your nostr browser extension.
-
If you're new, creating a nostr profile with zap.stream is straightforward and quick, ensuring you're ready to start streaming in no time. Alternatively you could read our previous post on how to create a Nostr identity with Alby.
-
Copy Your Stream Key and URL
- Once logged in, navigate to your zap.stream stream settings.
-
Copy the stream key and stream URL provided. You’ll need these for OBS.
-
Set Up Your Profile and Stream Info
- If this is your first time using Nostr, make sure to go to Settings, then Profile, and add a Lightning Address. This will give your viewers a destination to send you sats if they like your stream.
- Before streaming, go to the Dashboard and edit your Stream Info to provide a Title and Summary of your stream.
Setting Up OBS
OBS is a powerful, free, and open-source software for video recording and live streaming. Here’s how to set it up for streaming with zap.stream:
- Download and Install OBS
- Visit the OBS website and download the software for your operating system.
-
Follow the installation instructions to get OBS up and running on your computer.
-
Configure OBS for Streaming
- Open OBS and go to Settings.
- In the Stream section, select Custom... from the Service dropdown.
- Paste the stream URL from zap.stream into the Server field.
-
Paste your stream key into the Stream Key field.
-
Set Up Your Scene
- OBS works with scenes and sources. Create a new scene by clicking the + button under the Scenes box.
- Add your gameplay source by clicking the + button under the Sources box and selecting Game Capture. Choose the game you want to stream from the options provided.
- Don’t forget to add an audio output source by clicking the + button under the Sources box and selecting Audio Output Capture. Adjust the sound levels to ensure your game audio is balanced with your microphone input.
- You can also add other sources like a webcam, images, or text to personalize your stream.
-
Add cool widgets from zap.stream, like the chat widget or zap alert widget (which provides an audio and text alert when a viewer sends you some sats). To do this, go to the widget section of zap.stream, copy the URL for the widget, and add it to OBS as a browser source.
-
Optimize Your Settings
- Go to the Output section in the settings to adjust your streaming quality. For a smooth experience, a bitrate between 2500 and 6000 kbps is recommended, depending on your internet speed.
- In the Video section, set your base (canvas) resolution and output (scaled) resolution. A common setting is 1920x1080 for both.
-
Set your FPS (frames per second) to 30 for a standard quality stream or 60 for a high-quality stream.
-
Encoder Settings
- In the Output settings under the Streaming tab, choose your encoder. If you have a dedicated GPU from NVIDIA, you can use the NVENC encoder. Otherwise you could use the AMD encoder or the x264 CPU encoder.
-
For CPU usage preset (available if you're using the x264 encoder), a higher preset means less CPU usage. For most users, the veryfast preset is a good balance between quality and CPU usage. If you have a powerful CPU, you can try faster or fast for better quality. If you need to conserve CPU power, superfast or ultrafast will use less CPU but at the cost of some quality.
-
Start Streaming
- Once you’ve configured your settings and added your sources, click Start Streaming in the main OBS window.
- You should now be live on zap.stream, sharing your gameplay with the world and earning bitcoin from your viewers.
Restream to Multiple Platforms
One of the standout features of zap.stream is its built-in re-streaming capability. This allows you to stream to zap.stream and have your content automatically restreamed to other popular platforms like Twitch and YouTube. This feature maximizes your reach without needing to set up multiple streams, saving you time and effort. Simply add the stream keys from these destinations to your zap stream settings to enable restreaming.
Testing Your Stream Quality
Before going live, it’s a good idea to test your stream quality using OBS’s recording function. Use the same encoder settings for the recording to see what the quality looks like. If the recording is blurry, here are a few troubleshooting tips:
-
Increase the Bitrate: A higher bitrate can improve video quality, especially for fast-moving gameplay. Try increasing the bitrate in the Output settings.
-
Adjust the CPU Usage Preset: If you’re using the x264 encoder, try a slower CPU usage preset (e.g., from veryfast to faster). This will use more CPU but can improve quality.
-
Try a Different Encoder: If you have a dedicated GPU, consider using the NVENC encoder, which can offload encoding to the GPU and reduce CPU load.
-
Check Resolution and FPS Settings: Ensure your base and output resolution are appropriately set, and consider reducing FPS if your hardware struggles to maintain high quality.
Tips for a Successful Stream
- Engage with Your Audience: Interact with viewers through chat, respond to comments, and create a community.
- Promote Your Stream: Share your zap.stream link on nostr and other social media, gaming forums, and with friends to attract more viewers.
- Consistency is Key: Regular streaming schedules help build a loyal audience.
- Quality Matters: Invest in a good microphone and webcam to enhance the viewer experience.
Conclusion
Streaming your gameplay and earning bitcoin has never been easier. With zap.stream and OBS, you can set up and start streaming in just a few steps. Plus, with zap.stream's re-streaming feature, you can effortlessly expand your audience across multiple platforms. Follow this guide, and you’ll be live in no time, sharing your gaming skills with the world and earning bitcoin along the way. Happy streaming!