-
 @ 361d3e1e:50bc10a8
2024-09-15 14:50:08
@ 361d3e1e:50bc10a8
2024-09-15 14:50:08The end of the German economy is coming - Companies over 200 years old are going bankrupt
germany #business #finance
-
 @ 3bf0c63f:aefa459d
2024-03-19 15:35:35
@ 3bf0c63f:aefa459d
2024-03-19 15:35:35Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ 41fa852b:af7b7706
2024-09-15 11:22:04
@ 41fa852b:af7b7706
2024-09-15 11:22:04People don't realise how hard it is to speak the truth, to a world full of people that don't realise they're living a lie. —Edward Snowden
Good morning, Bitcoiners! I hope you're enjoying your Sunday morning.
There are 11 meetups across the country this coming week, including a big day at Cyphermunk House in London and another gathering at Tooting Market, where 15 merchants now accept Bitcoin as payment. All the details are listed below.
I hope you've been enjoying the newsletter over the past couple of months. This is the Nostr version of the newsletter which is ad-free and relies on V4V to keep the lights on.
Let's get into it...
Upcoming Bitcoin Meetups
Happening this week...
- Newcastle upon Tyne Bitcoin Meetup: The next Newcastle meetup is on Tuesday 17th September at The Ware Rooms Bar. 6:30 PM.
- Tooting Market Bitcoin Hub: Another big meetup at Tooting market this week. 15 merchants are now accepting bitcoin at the market. Head along to see what all the fuss is on Wednesday 18th at 6 PM. Join the Tooting Bitcoin Telegram group to stay updated on what's happening each month.
- Bitcoin Glasgow: Bitcoin Glasgow meet every 3rd Wednesday of the month and this month will be at The Maltman, 59-61 Renfield Street at 6 PM to 8 PM, on the 18th.
- Shropshire Bitcoin: On the 18th, the Shropshire crew will be meeting at the Admiral Benbow in Shrewsbury at 7 PM.
- Preston Bitcoin Meetup: Preston will be meeting at Plau Gin and Beer House, Fairgate. This month on Thursday the 19th of September. New faces welcome.
- Brum Bitcoin & Beer: These guys are one of the longest and most consistent running meetups in the UK. If you're in the Birmingham area head along to meet them on Thursday 19th at 7 pm at The Wellington, Bennett's Hill.
- Bitcoin Surrey: Something a little different for the Surrey meetup this month. A wine-tasting session at Hawkins Bros Fine English Wines plus a guest speaker. You'll need to get a ticket for this one too as space at the venue is limited.
- Cyphermunk House: Join them for a day of education, pizza and art at the 'BE YOUR OWN BANK' event. A host of events will be happening, including workshops, a book launch by Bill Aronson, Protocol presentation with Angor and a talk from former politician Steve Baker about Bitcoin and the state. Grab a ticket here.
- Bitcoin Walk - Edinburgh: Every Saturday they walk around Arthur's Seat in this historic city. Join them at 12 pm to chat about all things Bitcoin and keep fit.
- Bitcoin Derby: On Saturday the 21th September, Bitcoin Derby will be at Ye Olde Dolphin, DE1 3DL. Join them for some great conversations and get to know your local Bitcoiners.
- Bitcoin Bristol: From 6.15pm on Weds 21st. At the Wiper and True Brewery & Taproom, Old Market. Next week there'll be some news on a big event Bitcoin Bristol is organising in November.
Upcoming Special Events
These events aren’t happening next week, but they’re important to add to your calendar now as tickets are selling fast.
- Bitcoin Racing - Networking Experience: Missing the roar of engines at Brands Hatch? Join us on September 26th for an adrenaline-filled event that blends high-speed thrills with valuable business networking. Take exhilarating passenger rides in a JCW MINI with Chris Mackenzie, connect with industry leaders during networking sessions featuring speakers from companies like Archax and Green Mining DAO, and sharpen your skills with professional driver tuition in the Bitcoin Racing C1 car. Enjoy complimentary lunch, beverages, and test your limits with sim racing experiences. This is the ultimate experience for motorsport enthusiasts and business professionals alike. Book your spot now! 🏁

-
Southampton Trip to Real Bedford: The Satoshi Society in Southampton are pleased to announce an upcoming trip to cheer on the Pirates in their league game against Ware on Saturday the 28th of September. All meetups around the country are welcome to join them. After the game, there will be food and drinks in Bedford at La Terrazza and The Auction Room. Check out the link for more details. ⚽️🍺

-
Bitcoin Whitepaper Party: Celebrate Bitcoin’s 16th birthday on Bitcoin Whitepaper Day at the Dockside Vaults this Halloween. Currently, you can buy two tickets for £28.68 as an early bird deal, the regular price is £21.40 for a single ticket. Get involved with the chocolate making workshop with Roger9000. Enjoy a performance by Roger9000 and DJ sets from MadMunky, itsTOMEKK, and ZAZAWOWOW. The party kicks off at 19:30. Bitcoin is accepted at the venue, and you can also pay for tickets with Bitcoin here.

Get Involved
- Volunteer Opportunities: Bridge2Bitcoin is actively seeking volunteers who share our passion for merchant adoption. We'd be delighted to connect if you're eager to contribute. Reach out to us on Twitter or through our website.
- Start Your Own Meetup: Interested in launching a Bitcoin meetup? We’re here to support you every step of the way. We’ve assisted numerous UK Bitcoin meetups in getting started. Get in touch via Twitter.
- Telegram users: You might find our Telegram Channel another useful way to keep up-to-date with UK meetups.
- Feedback and Suggestions: We value your input! Share your ideas on how we can enhance this newsletter.
Get out and support the meetups where you can, visit Bitcoin Events UK for more info on each meetup and to find your closest on the interactive map.
Stay tuned for more updates next week!
Simon.
-
 @ 3bf0c63f:aefa459d
2024-03-19 13:07:02
@ 3bf0c63f:aefa459d
2024-03-19 13:07:02Censorship-resistant relay discovery in Nostr
In Nostr is not decentralized nor censorship-resistant I said Nostr is centralized. Peter Todd thinks it is centralized by design, but I disagree.
Nostr wasn't designed to be centralized. The idea was always that clients would follow people in the relays they decided to publish to, even if it was a single-user relay hosted in an island in the middle of the Pacific ocean.
But the Nostr explanations never had any guidance about how to do this, and the protocol itself never had any enforcement mechanisms for any of this (because it would be impossible).
My original idea was that clients would use some undefined combination of relay hints in reply tags and the (now defunct)
kind:2relay-recommendation events plus some form of manual action ("it looks like Bob is publishing on relay X, do you want to follow him there?") to accomplish this. With the expectation that we would have a better idea of how to properly implement all this with more experience, Branle, my first working client didn't have any of that implemented, instead it used a stupid static list of relays with read/write toggle -- although it did publish relay hints and kept track of those internally and supportedkind:2events, these things were not really useful.Gossip was the first client to implement a truly censorship-resistant relay discovery mechanism that used NIP-05 hints (originally proposed by Mike Dilger) relay hints and
kind:3relay lists, and then with the simple insight of NIP-65 that got much better. After seeing it in more concrete terms, it became simpler to reason about it and the approach got popularized as the "gossip model", then implemented in clients like Coracle and Snort.Today when people mention the "gossip model" (or "outbox model") they simply think about NIP-65 though. Which I think is ok, but too restrictive. I still think there is a place for the NIP-05 hints,
nprofileandneventrelay hints and specially relay hints in event tags. All these mechanisms are used together in ZBD Social, for example, but I believe also in the clients listed above.I don't think we should stop here, though. I think there are other ways, perhaps drastically different ways, to approach content propagation and relay discovery. I think manual action by users is underrated and could go a long way if presented in a nice UX (not conceived by people that think users are dumb animals), and who knows what. Reliance on third-parties, hardcoded values, social graph, and specially a mix of multiple approaches, is what Nostr needs to be censorship-resistant and what I hope to see in the future.
-
 @ e166e06b:ed623672
2024-09-15 05:07:30
@ e166e06b:ed623672
2024-09-15 05:07:30Get ready, because the future of digital content is here and it's decentralized live streaming! Imagine a world where you have complete control over what you watch without any interference or censorship. Say goodbye to YouTube and hello to a new era of content creation. One of the key players in this exciting shift is Owncast hosting.com – a revolutionary platform that empowers creators by giving them the freedom to broadcast live streams directly to their audience, without relying on centralized platforms. With Owncast hosting.com, content creators are in charge, able to share their passion and message without fear of being silenced. But it doesn't stop there. Decentralization means embracing the power of the fediverse, a network of interconnected social platforms that allows for seamless communication and sharing across various independent servers. This interconnectedness is a game-changer, as creators and viewers are no longer confined to one platform. The possibilities are endless, and the audience expands exponentially. Now is the time to celebrate the end of YouTube's dominance. We're witnessing a thrilling rise of decentralized live streaming, where users determine the direction of content. No more worrying about algorithms pushing certain narratives or shadowbanning creators. This new wave ensures that freedom of expression is preserved, making way for diverse voices and ideas to flourish. So buckle up and get ready to embrace the future of digital content. Be part of the revolution, where the power lies in your hands, and creativity knows no bounds. Exciting times are ahead as decentralized live streaming takes center stage, bridging communities and enabling more authentic connections. The way we consume content will never be the same again! For a perfect example of a no censorship decentralized live streaming network,please explore wowzatv.network
-
 @ 3bf0c63f:aefa459d
2024-01-29 02:19:25
@ 3bf0c63f:aefa459d
2024-01-29 02:19:25Nostr: a quick introduction, attempt #1
Nostr doesn't have a material existence, it is not a website or an app. Nostr is just a description what kind of messages each computer can send to the others and vice-versa. It's a very simple thing, but the fact that such description exists allows different apps to connect to different servers automatically, without people having to talk behind the scenes or sign contracts or anything like that.
When you use a Nostr client that is what happens, your client will connect to a bunch of servers, called relays, and all these relays will speak the same "language" so your client will be able to publish notes to them all and also download notes from other people.
That's basically what Nostr is: this communication layer between the client you run on your phone or desktop computer and the relay that someone else is running on some server somewhere. There is no central authority dictating who can connect to whom or even anyone who knows for sure where each note is stored.
If you think about it, Nostr is very much like the internet itself: there are millions of websites out there, and basically anyone can run a new one, and there are websites that allow you to store and publish your stuff on them.
The added benefit of Nostr is that this unified "language" that all Nostr clients speak allow them to switch very easily and cleanly between relays. So if one relay decides to ban someone that person can switch to publishing to others relays and their audience will quickly follow them there. Likewise, it becomes much easier for relays to impose any restrictions they want on their users: no relay has to uphold a moral ground of "absolute free speech": each relay can decide to delete notes or ban users for no reason, or even only store notes from a preselected set of people and no one will be entitled to complain about that.
There are some bad things about this design: on Nostr there are no guarantees that relays will have the notes you want to read or that they will store the notes you're sending to them. We can't just assume all relays will have everything — much to the contrary, as Nostr grows more relays will exist and people will tend to publishing to a small set of all the relays, so depending on the decisions each client takes when publishing and when fetching notes, users may see a different set of replies to a note, for example, and be confused.
Another problem with the idea of publishing to multiple servers is that they may be run by all sorts of malicious people that may edit your notes. Since no one wants to see garbage published under their name, Nostr fixes that by requiring notes to have a cryptographic signature. This signature is attached to the note and verified by everybody at all times, which ensures the notes weren't tampered (if any part of the note is changed even by a single character that would cause the signature to become invalid and then the note would be dropped). The fix is perfect, except for the fact that it introduces the requirement that each user must now hold this 63-character code that starts with "nsec1", which they must not reveal to anyone. Although annoying, this requirement brings another benefit: that users can automatically have the same identity in many different contexts and even use their Nostr identity to login to non-Nostr websites easily without having to rely on any third-party.
To conclude: Nostr is like the internet (or the internet of some decades ago): a little chaotic, but very open. It is better than the internet because it is structured and actions can be automated, but, like in the internet itself, nothing is guaranteed to work at all times and users many have to do some manual work from time to time to fix things. Plus, there is the cryptographic key stuff, which is painful, but cool.
-
 @ 6389be64:ef439d32
2024-09-14 22:58:12
@ 6389be64:ef439d32
2024-09-14 22:58:12originally posted at https://stacker.news/items/685129
-
 @ 3bf0c63f:aefa459d
2024-01-15 11:15:06
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06Anglicismos estúpidos no português contemporâneo
Palavras e expressões que ninguém deveria usar porque não têm o sentido que as pessoas acham que têm, são apenas aportuguesamentos de palavras inglesas que por nuances da história têm um sentido ligeiramente diferente em inglês.
Cada erro é acompanhado também de uma sugestão de como corrigi-lo.
Palavras que existem em português com sentido diferente
- submissão (de trabalhos): envio, apresentação
- disrupção: perturbação
- assumir: considerar, pressupor, presumir
- realizar: perceber
- endereçar: tratar de
- suporte (ao cliente): atendimento
- suportar (uma idéia, um projeto): apoiar, financiar
- suportar (uma função, recurso, característica): oferecer, ser compatível com
- literacia: instrução, alfabetização
- convoluto: complicado.
- acurácia: precisão.
- resiliência: resistência.
Aportuguesamentos desnecessários
- estartar: iniciar, começar
- treidar: negociar, especular
Expressões
- "não é sobre...": "não se trata de..."
Ver também
-
 @ e477586c:63d94e3f
2024-09-14 21:53:16
@ e477586c:63d94e3f
2024-09-14 21:53:16Just a post trying a new (to me) NOSTR client: Habla.News. Let's not get too long-winded and see how this goes...
But it is intended for "long form" content, so I've got to do something more than a couple of sentences. I was going to test blogstack.io, but kept receiving some error message about a client-side error.
To recap the week, it was a big, old,
meh
I don't remember mentioning in my last post, or maybe it didn't happen until the next day, but have any of you ever had to drive #barefoot in order to lift the clutch pedal off the floor? After changing the water pump on my 4-Runner, I was beset by 2 more problems... one of my own making. Let's get that one out of the way and get the embarrassment over with. When taking off my timing belt for the water pump replacement, I noticed that the timing was advanced 15 degrees. I thought this was a bit much, so instead of finding out what the proper timing advance was, I just set the timing to TDC. Talk about having no power for a few days. I got it set to the proper 10 degrees yesterday, along with replacing the clutch master cylinder.
So I spent a few days this week with no power and very complex shifting procedures in Austin traffic, but that's all now fixed. Next time in "adventures in transportation" maybe it will be whatever is rattling in my suspension or the leak that's just developed under my rear differential... or the heater core.
My goals for Monday now seem a bit ambitious. I've accomplished most of them since then, but Monday didn't have much to show for it except 2 hand-tossed and 1 cauliflower crust pizzas from scratch. They were delicious. I did complete my cover-letter and job application and manage to pick up the boys. Up to today, I've sent applications for more facilities maintenance and landscaping positions, gotten task-rabbit all set up, and am eligible for jobs in the Austin, TX market, and measured and cut the wood for a 3'x3' propagation bed. The chainsaw does start, but is running a little rough, and thanks to my tool shopping is now very sharp... and the car is running a lot better.
-
 @ 3bf0c63f:aefa459d
2024-01-15 11:15:06
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06Pequenos problemas que o Estado cria para a sociedade e que não são sempre lembrados
- **vale-transporte**: transferir o custo com o transporte do funcionário para um terceiro o estimula a morar longe de onde trabalha, já que morar perto é normalmente mais caro e a economia com transporte é inexistente. - **atestado médico**: o direito a faltar o trabalho com atestado médico cria a exigência desse atestado para todas as situações, substituindo o livre acordo entre patrão e empregado e sobrecarregando os médicos e postos de saúde com visitas desnecessárias de assalariados resfriados. - **prisões**: com dinheiro mal-administrado, burocracia e péssima alocação de recursos -- problemas que empresas privadas em competição (ou mesmo sem qualquer competição) saberiam resolver muito melhor -- o Estado fica sem presídios, com os poucos existentes entupidos, muito acima de sua alocação máxima, e com isto, segundo a bizarra corrente de responsabilidades que culpa o juiz que condenou o criminoso por sua morte na cadeia, juízes deixam de condenar à prisão os bandidos, soltando-os na rua. - **justiça**: entrar com processos é grátis e isto faz proliferar a atividade dos advogados que se dedicam a criar problemas judiciais onde não seria necessário e a entupir os tribunais, impedindo-os de fazer o que mais deveriam fazer. - **justiça**: como a justiça só obedece às leis e ignora acordos pessoais, escritos ou não, as pessoas não fazem acordos, recorrem sempre à justiça estatal, e entopem-na de assuntos que seriam muito melhor resolvidos entre vizinhos. - **leis civis**: as leis criadas pelos parlamentares ignoram os costumes da sociedade e são um incentivo a que as pessoas não respeitem nem criem normas sociais -- que seriam maneiras mais rápidas, baratas e satisfatórias de resolver problemas. - **leis de trãnsito**: quanto mais leis de trânsito, mais serviço de fiscalização são delegados aos policiais, que deixam de combater crimes por isto (afinal de contas, eles não querem de fato arriscar suas vidas combatendo o crime, a fiscalização é uma excelente desculpa para se esquivarem a esta responsabilidade). - **financiamento educacional**: é uma espécie de subsídio às faculdades privadas que faz com que se criem cursos e mais cursos que são cada vez menos recheados de algum conhecimento ou técnica útil e cada vez mais inúteis. - **leis de tombamento**: são um incentivo a que o dono de qualquer área ou construção "histórica" destrua todo e qualquer vestígio de história que houver nele antes que as autoridades descubram, o que poderia não acontecer se ele pudesse, por exemplo, usar, mostrar e se beneficiar da história daquele local sem correr o risco de perder, de fato, a sua propriedade. - **zoneamento urbano**: torna as cidades mais espalhadas, criando uma necessidade gigantesca de carros, ônibus e outros meios de transporte para as pessoas se locomoverem das zonas de moradia para as zonas de trabalho. - **zoneamento urbano**: faz com que as pessoas percam horas no trânsito todos os dias, o que é, além de um desperdício, um atentado contra a sua saúde, que estaria muito melhor servida numa caminhada diária entre a casa e o trabalho. - **zoneamento urbano**: torna ruas e as casas menos seguras criando zonas enormes, tanto de residências quanto de indústrias, onde não há movimento de gente alguma. - **escola obrigatória + currículo escolar nacional**: emburrece todas as crianças. - **leis contra trabalho infantil**: tira das crianças a oportunidade de aprender ofícios úteis e levar um dinheiro para ajudar a família. - **licitações**: como não existem os critérios do mercado para decidir qual é o melhor prestador de serviço, criam-se comissões de pessoas que vão decidir coisas. isto incentiva os prestadores de serviço que estão concorrendo na licitação a tentar comprar os membros dessas comissões. isto, fora a corrupção, gera problemas reais: __(i)__ a escolha dos serviços acaba sendo a pior possível, já que a empresa prestadora que vence está claramente mais dedicada a comprar comissões do que a fazer um bom trabalho (este problema afeta tantas áreas, desde a construção de estradas até a qualidade da merenda escolar, que é impossível listar aqui); __(ii)__ o processo corruptor acaba, no longo prazo, eliminando as empresas que prestavam e deixando para competir apenas as corruptas, e a qualidade tende a piorar progressivamente. - **cartéis**: o Estado em geral cria e depois fica refém de vários grupos de interesse. o caso dos taxistas contra o Uber é o que está na moda hoje (e o que mostra como os Estados se comportam da mesma forma no mundo todo). - **multas**: quando algum indivíduo ou empresa comete uma fraude financeira, ou causa algum dano material involuntário, as vítimas do caso são as pessoas que sofreram o dano ou perderam dinheiro, mas o Estado tem sempre leis que prevêem multas para os responsáveis. A justiça estatal é sempre muito rígida e rápida na aplicação dessas multas, mas relapsa e vaga no que diz respeito à indenização das vítimas. O que em geral acontece é que o Estado aplica uma enorme multa ao responsável pelo mal, retirando deste os recursos que dispunha para indenizar as vítimas, e se retira do caso, deixando estas desamparadas. - **desapropriação**: o Estado pode pegar qualquer propriedade de qualquer pessoa mediante uma indenização que é necessariamente inferior ao valor da propriedade para o seu presente dono (caso contrário ele a teria vendido voluntariamente). - **seguro-desemprego**: se há, por exemplo, um prazo mínimo de 1 ano para o sujeito ter direito a receber seguro-desemprego, isto o incentiva a planejar ficar apenas 1 ano em cada emprego (ano este que será sucedido por um período de desemprego remunerado), matando todas as possibilidades de aprendizado ou aquisição de experiência naquela empresa específica ou ascensão hierárquica. - **previdência**: a previdência social tem todos os defeitos de cálculo do mundo, e não importa muito ela ser uma forma horrível de poupar dinheiro, porque ela tem garantias bizarras de longevidade fornecidas pelo Estado, além de ser compulsória. Isso serve para criar no imaginário geral a idéia da __aposentadoria__, uma época mágica em que todos os dias serão finais de semana. A idéia da aposentadoria influencia o sujeito a não se preocupar em ter um emprego que faça sentido, mas sim em ter um trabalho qualquer, que o permita se aposentar. - **regulamentação impossível**: milhares de coisas são proibidas, há regulamentações sobre os aspectos mais mínimos de cada empreendimento ou construção ou espaço. se todas essas regulamentações fossem exigidas não haveria condições de produção e todos morreriam. portanto, elas não são exigidas. porém, o Estado, ou um agente individual imbuído do poder estatal pode, se desejar, exigi-las todas de um cidadão inimigo seu. qualquer pessoa pode viver a vida inteira sem cumprir nem 10% das regulamentações estatais, mas viverá também todo esse tempo com medo de se tornar um alvo de sua exigência, num estado de terror psicológico. - **perversão de critérios**: para muitas coisas sobre as quais a sociedade normalmente chegaria a um valor ou comportamento "razoável" espontaneamente, o Estado dita regras. estas regras muitas vezes não são obrigatórias, são mais "sugestões" ou limites, como o salário mínimo, ou as 44 horas semanais de trabalho. a sociedade, porém, passa a usar esses valores como se fossem o normal. são raras, por exemplo, as ofertas de emprego que fogem à regra das 44h semanais. - **inflação**: subir os preços é difícil e constrangedor para as empresas, pedir aumento de salário é difícil e constrangedor para o funcionário. a inflação força as pessoas a fazer isso, mas o aumento não é automático, como alguns economistas podem pensar (enquanto alguns outros ficam muito satisfeitos de que esse processo seja demorado e difícil). - **inflação**: a inflação destrói a capacidade das pessoas de julgar preços entre concorrentes usando a própria memória. - **inflação**: a inflação destrói os cálculos de lucro/prejuízo das empresas e prejudica enormemente as decisões empresariais que seriam baseadas neles. - **inflação**: a inflação redistribui a riqueza dos mais pobres e mais afastados do sistema financeiro para os mais ricos, os bancos e as megaempresas. - **inflação**: a inflação estimula o endividamento e o consumismo. - **lixo:** ao prover coleta e armazenamento de lixo "grátis para todos" o Estado incentiva a criação de lixo. se tivessem que pagar para que recolhessem o seu lixo, as pessoas (e conseqüentemente as empresas) se empenhariam mais em produzir coisas usando menos plástico, menos embalagens, menos sacolas. - **leis contra crimes financeiros:** ao criar legislação para dificultar acesso ao sistema financeiro por parte de criminosos a dificuldade e os custos para acesso a esse mesmo sistema pelas pessoas de bem cresce absurdamente, levando a um percentual enorme de gente incapaz de usá-lo, para detrimento de todos -- e no final das contas os grandes criminosos ainda conseguem burlar tudo. -
 @ 6303cd52:917f640d
2024-09-14 20:41:25
@ 6303cd52:917f640d
2024-09-14 20:41:25Hello Nostr community! I'm excited to start using Nostr as a digital diary to reflect on my thoughts, experiences, and goals. As a student, I'm looking forward to using this platform to document my journey, track my progress, and gain insights into my personal growth.
I'll be posting updates whenever I can, sharing my thoughts on what I've learned, what I'm grateful for, and what I'm looking forward to in the coming days. I'm hoping to use Nostr as a tool to stay organized, focused, and motivated, and to develop a greater sense of self-awareness.
One of my main goals is to prioritize my physical health and fitness, and I'm planning to do more workouts and play volleyball regularly. I'm also committed to being more productive and making the most of my time.
To help me achieve these goals, I've decided to cut back on distractions - starting with YouTube. I'm planning to significantly reduce my YouTube usage and focus on more meaningful activities. Don't expect me to be always online, as I'm not really active on other social media platforms either.
Also, a quick note: I'm not a native English speaker, so please bear with me if I make any spelling or grammar mistakes. I'm here to learn and improve, and I appreciate any corrections or feedback you may have. Your help will only make me better!
I would really appreciate it if we can connect here and support each other on our individual journeys. Let's make the most of this platform and learn from each other!
Thanks for joining me on this journey! Let's get started!
introduction
-
 @ 361d3e1e:50bc10a8
2024-09-14 20:07:27
@ 361d3e1e:50bc10a8
2024-09-14 20:07:27The only one that talks about a huge number of missing children
trump #politics #usa #biden #bordercrisis
-
 @ 361d3e1e:50bc10a8
2024-09-14 20:04:55
@ 361d3e1e:50bc10a8
2024-09-14 20:04:55https://forex-strategy.com/2024/09/14/unseen-anti-vaccine-ad-by-new-york-state-governor/
Unseen anti-vaccine ad by New York State Governor
newyork #usa #politics #vaccine #covid #sideeffects #kathyhochul
-
 @ d6affa19:9110b177
2024-09-14 18:13:34
@ d6affa19:9110b177
2024-09-14 18:13:34The Timeless Relevance of Chivalry in Relationships
Chivalry, often romanticized in tales of medieval knights, is more than just a relic of the past. It’s a code of conduct that emphasizes respect, honor, and protection—values that still resonate today. While many think of chivalry as lost in today’s world, it has the potential to transform modern relationships, and perhaps fill a void in the modern definition of masculinity.
For a unique perspective, we can look at chivalry's evolution within Female Led Relationships (FLRs), where respect and devotion are foundational. In FLRs, women take the lead, guiding their partners through a blend of strength and nurturing. Chivalry enhances this dynamic, allowing men to express respect and devotion while embracing their roles in a supportive manner.
Let’s take a look at how chivalry has changed over time to become a defining component in many FLRs. We’ll look at the virtues of chivalry, its role in defining masculinity, and why it serves as a foundation for mutual respect and growth in relationships. By understanding these principles, we’ll begin to see how chivalry acts as a bridge between strength and submission, enriching the connection between partners.
Introduction to Chivalry
Chivalry began in the medieval period as a code of conduct for knights, focusing on virtues like bravery, loyalty, and the protection of those in need. Knights were expected to live by these ideals in their service to their lords and in their interactions with women, often viewing them as deserving of special respect and protection. This code created a framework of strength, honor, and courage to be embedded in the concept of masculinity.
As society has changed, so too has the interpretation of chivalry, leading to a broader understanding of what it means to be chivalrous today. The rigid structure of chivalry has softened a bit, allowing for a more nuanced understanding of respectful behavior in modern contexts.
Today, chivalry is less about following a strict code and more about embodying kindness, respect, and support in everyday interactions. It’s often seen as a choice rather than an obligation, allowing men to express their admiration for women in ways that feel genuine and meaningful. However, it challenges and expands upon the notion that a man’s role is solely to protect and provide.
The Virtues of Chivalry: A Contemporary View
Chivalry is often seen as a sign of healthy masculinity, demonstrating qualities like courage, respect, compassion, and support for women. This helps create relationship dynamics where both partners feel appreciated. Healthy masculinity, as expressed through chivalry, encourages men to engage in acts of kindness—whether surprising their partner with a home-cooked meal after a long day or actively listening to her concerns without distractions.
These behaviors demonstrate emotional intelligence and create deeper connections. Examples of chivalrous actions include taking the initiative to handle household chores, planning special dates that reflect the partner's interests, and offering emotional support during tough times. Simple yet meaningful gestures, like holding the door open or offering a comforting touch, reinforce the idea that strength lies in nurturing and uplifting one another.
With this basic understanding of chivalry, we can now explore how these principles are redefined and practiced in the context of Female Led Relationships.
Understanding FLRs
In Female Led Relationships, the woman takes on the primary leadership role, while the man supports her through devotion and service. This structure redefines leadership to highlight feminine strengths like empathy, intuition, and emotional intelligence.
What does it mean for a woman to lead in a relationship? In this dynamic, a woman might lead the decision-making process for family activities, while her gentleman supports her by taking care of the logistics. This is just one of many examples where a woman acts as the visionary, charting the course for her relationship and family.
Despite common misconceptions, FLRs are not, in essence, simply kink-driven or role-reversal relationships. They create space for both partners to grow and thrive in their distinct roles. Within this framework, the woman doesn’t necessarily adopt traditionally masculine behavior; instead, she may lead in a way that feels authentic to her feminine nature.
This dynamic allows for a greater flexibility of traditional roles, where both individuals can express their strengths and support one another. When a woman assumes the leadership role, the concept of chivalry can be framed to reflect this adjustment.
Supporting Her Lead: Chivalry's Place in FLRs
Traditionally, chivalry revolved around men using their strength and status to protect women, who were perceived as needing safeguarding. This aspect of chivalry is redefined in an FLR. Instead of the intention being about men protecting fragile women, the emphasis is now in showing deep respect and devotion to the women they admire and serve. This becomes a major shift away from the stereotypical image of the damsel in distress—who needs to be rescued by a knight in shining armor.
This adjustment makes space for a woman's inherent strength and her role as the central figure of leadership and authority. It positions her as the one a man submits to. The idea of submission, or service, in FLRs challenges the conventional views of masculinity, which often emphasize aggression and dominance.
Instead, submission is framed as a conscious choice that allows men to express vulnerability and emotional openness. Through acts of chivalry—such as opening doors, attending to her needs, or providing comfort—a man in an FLR expresses his devotion and commitment to a woman as his leader. These are the types of actions that serve as a bridge between a man’s masculine energy and his submission—a powerful and empowering act for both partners.
In this context, chivalry may then represent a minimum standard of behavior for a gentleman in an FLR. Understanding this redefinition is essential for appreciating the balance of power and respect that make FLRs work. A woman might decide to set chivalry as a starting point for behavior, guiding her partner in ways that strengthen their bond. Let’s take a closer look at how these chivalrous principles are expressed in this relationship setup.

Chivalry in Action: A Minimum Standard for Gentlemen
Chivalry offers a subtle and respectful way for a gentleman in an FLR to express his devotion in public. This allows him to honor his partner's leadership while keeping the intimate aspects of their relationship private. It’s important to reiterate, a gentleman performs these actions from a deep respect and admiration, not because the woman is incapable.
Let’s dive into how chivalry is demonstrated in everyday interactions and how these gestures reflect a deeper bond between the woman and her submissive gentleman.
- Discreet Displays of Devotion: Acts of chivalry like opening doors, pulling out chairs, and carrying bags are traditionally seen as courteous. In an FLR, these gestures take on added meaning—they become acts of service and submission, representing the gentleman’s commitment to the woman. These actions subtly reinforce the Female-led dynamic, making it clear who is leading the relationship, even without explicit words.
- Respect and Care: Public chivalry allows a gentleman to show his reverence and protectiveness in a non-dominating way. Escorting a woman across the street or guiding her with a hand on her back signals that her comfort and safety come first. Such gestures help reinforce his role as her protector, not through overpowering, but by ensuring her well-being.
- Empowering Her Leadership: Chivalry positions the woman as someone to be admired and revered. A gentleman's attentiveness—like ensuring her seat is comfortable, giving her his coat, or waiting for her to decide the next move—publicly celebrates her power and grace. It signals to the outside world that she is cherished, respected, and in control.
- Symbol of Hierarchy: Public chivalry subtly communicates the hierarchy in the relationship. A gentleman’s actions demonstrate that he prioritizes the woman’s needs above his own, affirming her leadership and his devotion. This can be empowering for both partners while maintaining the appearance of traditional courteous behavior.
Having examined how chivalry is publicly displayed in acts of service, it’s important to consider the relationship between chivalry and the concept of submission in FLRs. These gestures are just the tip of the iceberg; they pave the way for a deeper bond that intertwines strength with surrender, taking the relationship to another level. With this in mind, let’s explore further.
Chivalry and Submission: The Interplay of Strength and Vulnerability
Chivalry provides a beautiful way to express an FLR in public, but the bond between a woman and her submissive gentleman runs much deeper than it appears. The public gestures are merely a reflection of a more private intimacy and the dynamics at play in the relationship.
- Private Surrender: Behind closed doors, the gentleman’s devotion often takes on deeper, more intimate forms. While public chivalry may seem like courteous behavior, in private it evolves into true acts of surrender, vulnerability, and service. His obedience, respect, and loyalty are manifested in ways that may not be visible to the outside world—through emotional support, personal sacrifices, and an unwavering commitment to the woman’s happiness.
- Emotional Bond: The bond in an FLR is built on strong emotional understanding and trust. Public gestures, such as opening a door, may signal respect, but the private relationship is built on communication, vulnerability, and reciprocity. The gentleman’s willingness to be emotionally open and the woman’s acceptance of his submission generate a bond that goes beyond the surface-level acts.
- Empowerment and Growth: An FLR often involves the woman guiding and empowering her gentleman to become a better version of himself, and in turn, he finds fulfillment in supporting her goals and ambitions. This growth happens through encouragement, challenges, and nurturing. These elements are not always visible in public but are foundational to the strength of the relationship.
- Sacred Submission: A gentleman’s devotion in private is often much more profound and spiritual than what can be conveyed through chivalry alone. His willingness to give himself fully to a woman, to honor her needs and desires over his own, represents a depth of commitment that is intensely personal and transformational for both partners.
- Unspoken Understanding: The connection between a woman and her submissive gentleman often includes a deep, unspoken understanding of their roles and dynamics. While public gestures may hint at their FLR, their private moments of connection bring the relationship to the next level. These moments—whether through quiet service, intense conversation, or physical intimacy—solidify true emotional connections.
- Private Rituals of Devotion: Chivalry in public is often a toned-down version of the rituals of devotion that occur in private. Behind closed doors, a woman’s submissive gentleman may have more formal ways of showing his reverence, such as kneeling, offering his service in specific ways, or following set routines that reinforce his role. These private rituals strengthen the bond of submission and deepen the trust between partners.
We’ve seen that chivalry alone doesn’t fully capture the essence of submission in a Female Led Relationship. However, when we look at masculinity through the lens of chivalry, it becomes clear that the qualities associated with healthy masculinity—like devotion, compassion, and protection—are fundamentally about serving and supporting others.
The Essence of Chivalry: Strength Through Service
In summary, chivalry effectively bridges the gap between strength and submission within the framework of FLRs. Throughout this brief exploration, we’ve seen how chivalry can serve as a foundational guideline for men, allowing them to embody a form of healthy masculinity that’s empowered, but also open to submission.
By changing how we think about masculinity, chivalry encourages men to express their strength through simple acts of kindness, respect, and devotion. Whether it’s in public or behind closed doors, these gestures create a space where both partners can truly thrive. The qualities that make up healthy masculinity—bravery, loyalty, compassion, and a commitment to service—actually lean into the idea of submission as a natural part of masculinity. In this way, chivalry becomes an expression of this submission, allowing men to honor and uplift their partners while still maintaining their own sense of stability and strength.
By embracing these chivalrous behaviors, men can enhance their relationships and help create a more balanced and supportive partnership. Chivalry in the context of FLRs redefines the narrative of masculinity, demonstrating that true strength lies in the ability to serve, support, and cherish one another in a loving and respectful manner.
As a final thought, the essence of chivalry lies not just in the actions taken, but in the intentions behind them. In the pursuit of uplifting and supporting partners, true strength emerges through vulnerability and service. By reflecting on our relationships, we can look for and find opportunities to embody these principles. How might embracing the principles of chivalry expand and enrich what masculinity can contribute to any relationship?
-
 @ 361d3e1e:50bc10a8
2024-09-14 14:44:30
@ 361d3e1e:50bc10a8
2024-09-14 14:44:30For every 1000 new injections, 5.7 people get myocarditis or pericarditis
usa #pfizer #sideeffects #vaccine #covid #monkeypox #mpox #health #myocarditis
-
 @ 7f5b758e:db91b367
2024-09-14 14:05:18
@ 7f5b758e:db91b367
2024-09-14 14:05:18Central en español,
Dios esta obrando.
Nosotros lo vemos cada semana - A través del servicio y luego en los grupos de comunidad (10:45AM). El Espíritu Santo trabaja en nosotros y a través de nosotros en los programas de niños y estudiantes. Mañana va a ser igual. Nosotros vivimos para Dios, eso nos da significado y lo celebramos como hijos del Rey. Nos vemos mañana, 9:30AM.
https://scontent-dfw5-2.xx.fbcdn.net/v/t39.30808-6/455704243_475776645232773_6440552152342423803_n.jpg?stp=cp6_dst-jpg&_nc_cat=100&ccb=1-7&_nc_sid=833d8c&_nc_ohc=uDrwym_Iu60Q7kNvgGcoQ6Z&_nc_ht=scontent-dfw5-2.xx&_nc_gid=AYZqyypf1_uXwqU1xlTUgX0&oh=00_AYC77jEwXJis9rw84CkoObvwNn4Wm6ZZGiZ1z1R5fJtLHQ&oe=66EB458B
-
 @ 3bf0c63f:aefa459d
2024-01-14 14:52:16
@ 3bf0c63f:aefa459d
2024-01-14 14:52:16bitcoinddecentralizationIt is better to have multiple curator teams, with different vetting processes and release schedules for
bitcoindthan a single one."More eyes on code", "Contribute to Core", "Everybody should audit the code".
All these points repeated again and again fell to Earth on the day it was discovered that Bitcoin Core developers merged a variable name change from "blacklist" to "blocklist" without even discussing or acknowledging the fact that that innocent pull request opened by a sybil account was a social attack.
After a big lot of people manifested their dissatisfaction with that event on Twitter and on GitHub, most Core developers simply ignored everybody's concerns or even personally attacked people who were complaining.
The event has shown that:
1) Bitcoin Core ultimately rests on the hands of a couple maintainers and they decide what goes on the GitHub repository[^pr-merged-very-quickly] and the binary releases that will be downloaded by thousands; 2) Bitcoin Core is susceptible to social attacks; 2) "More eyes on code" don't matter, as these extra eyes can be ignored and dismissed.
Solution:
bitcoinddecentralizationIf usage was spread across 10 different
bitcoindflavors, the network would be much more resistant to social attacks to a single team.This has nothing to do with the question on if it is better to have multiple different Bitcoin node implementations or not, because here we're basically talking about the same software.
Multiple teams, each with their own release process, their own logo, some subtle changes, or perhaps no changes at all, just a different name for their
bitcoindflavor, and that's it.Every day or week or month or year, each flavor merges all changes from Bitcoin Core on their own fork. If there's anything suspicious or too leftist (or perhaps too rightist, in case there's a leftist
bitcoindflavor), maybe they will spot it and not merge.This way we keep the best of both worlds: all software development, bugfixes, improvements goes on Bitcoin Core, other flavors just copy. If there's some non-consensus change whose efficacy is debatable, one of the flavors will merge on their fork and test, and later others -- including Core -- can copy that too. Plus, we get resistant to attacks: in case there is an attack on Bitcoin Core, only 10% of the network would be compromised. the other flavors would be safe.
Run Bitcoin Knots
The first example of a
bitcoindsoftware that follows Bitcoin Core closely, adds some small changes, but has an independent vetting and release process is Bitcoin Knots, maintained by the incorruptible Luke DashJr.Next time you decide to run
bitcoind, run Bitcoin Knots instead and contribute tobitcoinddecentralization!
See also:
[^pr-merged-very-quickly]: See PR 20624, for example, a very complicated change that could be introducing bugs or be a deliberate attack, merged in 3 days without time for discussion.
-
 @ 3bf0c63f:aefa459d
2024-01-14 14:52:16
@ 3bf0c63f:aefa459d
2024-01-14 14:52:16Drivechain
Understanding Drivechain requires a shift from the paradigm most bitcoiners are used to. It is not about "trustlessness" or "mathematical certainty", but game theory and incentives. (Well, Bitcoin in general is also that, but people prefer to ignore it and focus on some illusion of trustlessness provided by mathematics.)
Here we will describe the basic mechanism (simple) and incentives (complex) of "hashrate escrow" and how it enables a 2-way peg between the mainchain (Bitcoin) and various sidechains.
The full concept of "Drivechain" also involves blind merged mining (i.e., the sidechains mine themselves by publishing their block hashes to the mainchain without the miners having to run the sidechain software), but this is much easier to understand and can be accomplished either by the BIP-301 mechanism or by the Spacechains mechanism.
How does hashrate escrow work from the point of view of Bitcoin?
A new address type is created. Anything that goes in that is locked and can only be spent if all miners agree on the Withdrawal Transaction (
WT^) that will spend it for 6 months. There is one of these special addresses for each sidechain.To gather miners' agreement
bitcoindkeeps track of the "score" of all transactions that could possibly spend from that address. On every block mined, for each sidechain, the miner can use a portion of their coinbase to either increase the score of oneWT^by 1 while decreasing the score of all others by 1; or they can decrease the score of allWT^s by 1; or they can do nothing.Once a transaction has gotten a score high enough, it is published and funds are effectively transferred from the sidechain to the withdrawing users.
If a timeout of 6 months passes and the score doesn't meet the threshold, that
WT^is discarded.What does the above procedure mean?
It means that people can transfer coins from the mainchain to a sidechain by depositing to the special address. Then they can withdraw from the sidechain by making a special withdraw transaction in the sidechain.
The special transaction somehow freezes funds in the sidechain while a transaction that aggregates all withdrawals into a single mainchain
WT^, which is then submitted to the mainchain miners so they can start voting on it and finally after some months it is published.Now the crucial part: the validity of the
WT^is not verified by the Bitcoin mainchain rules, i.e., if Bob has requested a withdraw from the sidechain to his mainchain address, but someone publishes a wrongWT^that instead takes Bob's funds and sends them to Alice's main address there is no way the mainchain will know that. What determines the "validity" of theWT^is the miner vote score and only that. It is the job of miners to vote correctly -- and for that they may want to run the sidechain node in SPV mode so they can attest for the existence of a reference to theWT^transaction in the sidechain blockchain (which then ensures it is ok) or do these checks by some other means.What? 6 months to get my money back?
Yes. But no, in practice anyone who wants their money back will be able to use an atomic swap, submarine swap or other similar service to transfer funds from the sidechain to the mainchain and vice-versa. The long delayed withdraw costs would be incurred by few liquidity providers that would gain some small profit from it.
Why bother with this at all?
Drivechains solve many different problems:
It enables experimentation and new use cases for Bitcoin
Issued assets, fully private transactions, stateful blockchain contracts, turing-completeness, decentralized games, some "DeFi" aspects, prediction markets, futarchy, decentralized and yet meaningful human-readable names, big blocks with a ton of normal transactions on them, a chain optimized only for Lighting-style networks to be built on top of it.
These are some ideas that may have merit to them, but were never actually tried because they couldn't be tried with real Bitcoin or inferfacing with real bitcoins. They were either relegated to the shitcoin territory or to custodial solutions like Liquid or RSK that may have failed to gain network effect because of that.
It solves conflicts and infighting
Some people want fully private transactions in a UTXO model, others want "accounts" they can tie to their name and build reputation on top; some people want simple multisig solutions, others want complex code that reads a ton of variables; some people want to put all the transactions on a global chain in batches every 10 minutes, others want off-chain instant transactions backed by funds previously locked in channels; some want to spend, others want to just hold; some want to use blockchain technology to solve all the problems in the world, others just want to solve money.
With Drivechain-based sidechains all these groups can be happy simultaneously and don't fight. Meanwhile they will all be using the same money and contributing to each other's ecosystem even unwillingly, it's also easy and free for them to change their group affiliation later, which reduces cognitive dissonance.
It solves "scaling"
Multiple chains like the ones described above would certainly do a lot to accomodate many more transactions that the current Bitcoin chain can. One could have special Lightning Network chains, but even just big block chains or big-block-mimblewimble chains or whatnot could probably do a good job. Or even something less cool like 200 independent chains just like Bitcoin is today, no extra features (and you can call it "sharding"), just that would already multiply the current total capacity by 200.
Use your imagination.
It solves the blockchain security budget issue
The calculation is simple: you imagine what security budget is reasonable for each block in a world without block subsidy and divide that for the amount of bytes you can fit in a single block: that is the price to be paid in satoshis per byte. In reasonable estimative, the price necessary for every Bitcoin transaction goes to very large amounts, such that not only any day-to-day transaction has insanely prohibitive costs, but also Lightning channel opens and closes are impracticable.
So without a solution like Drivechain you'll be left with only one alternative: pushing Bitcoin usage to trusted services like Liquid and RSK or custodial Lightning wallets. With Drivechain, though, there could be thousands of transactions happening in sidechains and being all aggregated into a sidechain block that would then pay a very large fee to be published (via blind merged mining) to the mainchain. Bitcoin security guaranteed.
It keeps Bitcoin decentralized
Once we have sidechains to accomodate the normal transactions, the mainchain functionality can be reduced to be only a "hub" for the sidechains' comings and goings, and then the maximum block size for the mainchain can be reduced to, say, 100kb, which would make running a full node very very easy.
Can miners steal?
Yes. If a group of coordinated miners are able to secure the majority of the hashpower and keep their coordination for 6 months, they can publish a
WT^that takes the money from the sidechains and pays to themselves.Will miners steal?
No, because the incentives are such that they won't.
Although it may look at first that stealing is an obvious strategy for miners as it is free money, there are many costs involved:
- The cost of ceasing blind-merged mining returns -- as stealing will kill a sidechain, all the fees from it that miners would be expected to earn for the next years are gone;
- The cost of Bitcoin price going down: If a steal is successful that will mean Drivechains are not safe, therefore Bitcoin is less useful, and miner credibility will also be hurt, which are likely to cause the Bitcoin price to go down, which in turn may kill the miners' businesses and savings;
- The cost of coordination -- assuming miners are just normal businesses, they just want to do their work and get paid, but stealing from a Drivechain will require coordination with other miners to conduct an immoral act in a way that has many pitfalls and is likely to be broken over the months;
- The cost of miners leaving your mining pool: when we talked about "miners" above we were actually talking about mining pools operators, so they must also consider the risk of miners migrating from their mining pool to others as they begin the process of stealing;
- The cost of community goodwill -- when participating in a steal operation, a miner will suffer a ton of backlash from the community. Even if the attempt fails at the end, the fact that it was attempted will contribute to growing concerns over exaggerated miners power over the Bitcoin ecosystem, which may end up causing the community to agree on a hard-fork to change the mining algorithm in the future, or to do something to increase participation of more entities in the mining process (such as development or cheapment of new ASICs), which have a chance of decreasing the profits of current miners.
Another point to take in consideration is that one may be inclined to think a newly-created sidechain or a sidechain with relatively low usage may be more easily stolen from, since the blind merged mining returns from it (point 1 above) are going to be small -- but the fact is also that a sidechain with small usage will also have less money to be stolen from, and since the other costs besides 1 are less elastic at the end it will not be worth stealing from these too.
All of the above consideration are valid only if miners are stealing from good sidechains. If there is a sidechain that is doing things wrong, scamming people, not being used at all, or is full of bugs, for example, that will be perceived as a bad sidechain, and then miners can and will safely steal from it and kill it, which will be perceived as a good thing by everybody.
What do we do if miners steal?
Paul Sztorc has suggested in the past that a user-activated soft-fork could prevent miners from stealing, i.e., most Bitcoin users and nodes issue a rule similar to this one to invalidate the inclusion of a faulty
WT^and thus cause any miner that includes it in a block to be relegated to their own Bitcoin fork that other nodes won't accept.This suggestion has made people think Drivechain is a sidechain solution backed by user-actived soft-forks for safety, which is very far from the truth. Drivechains must not and will not rely on this kind of soft-fork, although they are possible, as the coordination costs are too high and no one should ever expect these things to happen.
If even with all the incentives against them (see above) miners do still steal from a good sidechain that will mean the failure of the Drivechain experiment. It will very likely also mean the failure of the Bitcoin experiment too, as it will be proven that miners can coordinate to act maliciously over a prolonged period of time regardless of economic and social incentives, meaning they are probably in it just for attacking Bitcoin, backed by nation-states or something else, and therefore no Bitcoin transaction in the mainchain is to be expected to be safe ever again.
Why use this and not a full-blown trustless and open sidechain technology?
Because it is impossible.
If you ever heard someone saying "just use a sidechain", "do this in a sidechain" or anything like that, be aware that these people are either talking about "federated" sidechains (i.e., funds are kept in custody by a group of entities) or they are talking about Drivechain, or they are disillusioned and think it is possible to do sidechains in any other manner.
No, I mean a trustless 2-way peg with correctness of the withdrawals verified by the Bitcoin protocol!
That is not possible unless Bitcoin verifies all transactions that happen in all the sidechains, which would be akin to drastically increasing the blocksize and expanding the Bitcoin rules in tons of ways, i.e., a terrible idea that no one wants.
What about the Blockstream sidechains whitepaper?
Yes, that was a way to do it. The Drivechain hashrate escrow is a conceptually simpler way to achieve the same thing with improved incentives, less junk in the chain, more safety.
Isn't the hashrate escrow a very complex soft-fork?
Yes, but it is much simpler than SegWit. And, unlike SegWit, it doesn't force anything on users, i.e., it isn't a mandatory blocksize increase.
Why should we expect miners to care enough to participate in the voting mechanism?
Because it's in their own self-interest to do it, and it costs very little. Today over half of the miners mine RSK. It's not blind merged mining, it's a very convoluted process that requires them to run a RSK full node. For the Drivechain sidechains, an SPV node would be enough, or maybe just getting data from a block explorer API, so much much simpler.
What if I still don't like Drivechain even after reading this?
That is the entire point! You don't have to like it or use it as long as you're fine with other people using it. The hashrate escrow special addresses will not impact you at all, validation cost is minimal, and you get the benefit of people who want to use Drivechain migrating to their own sidechains and freeing up space for you in the mainchain. See also the point above about infighting.
See also
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Parallel Chains
We want merged-mined blockchains. We want them because it is possible to do things in them that aren't doable in the normal Bitcoin blockchain because it is rightfully too expensive, but there are other things beside the world money that could benefit from a "distributed ledger" -- just like people believed in 2013 --, like issued assets and domain names (just the most obvious examples).
On the other hand we can't have -- like people believed in 2013 -- a copy of Bitcoin for every little idea with its own native token that is mined by proof-of-work and must get off the ground from being completely valueless into having some value by way of a miracle that operated only once with Bitcoin.
It's also not a good idea to have blockchains with custom merged-mining protocol (like Namecoin and Rootstock) that require Bitcoin miners to run their software and be an active participant and miner for that other network besides Bitcoin, because it's too cumbersome for everybody.
Luckily Ruben Somsen invented this protocol for blind merged-mining that solves the issue above. Although it doesn't solve the fact that each parallel chain still needs some form of "native" token to pay miners -- or it must use another method that doesn't use a native token, such as trusted payments outside the chain.
How does it work
With the
SIGHASH_NOINPUT/SIGHASH_ANYPREVOUTsoft-fork[^eltoo] it becomes possible to create presigned transactions that aren't related to any previous UTXO.Then you create a long sequence of transactions (sufficient to last for many many years), each with an
nLockTimeof 1 and each spending the next (you create them from the last to the first). Since theirscriptSig(the unlocking script) will useSIGHASH_ANYPREVOUTyou can obtain a transaction id/hash that doesn't include the previous TXO, you can, for example, in a sequence of transactionsA0-->B(B spends output 0 from A), include the signature for "spending A0 on B" inside thescriptPubKey(the locking script) of "A0".With the contraption described above it is possible to make that long string of transactions everybody will know (and know how to generate) but each transaction can only be spent by the next previously decided transaction, no matter what anyone does, and there always must be at least one block of difference between them.
Then you combine it with
RBF,SIGHASH_SINGLEandSIGHASH_ANYONECANPAYso parallel chain miners can add inputs and outputs to be able to compete on fees by including their own outputs and getting change back while at the same time writing a hash of the parallel block in the change output and you get everything working perfectly: everybody trying to spend the same output from the long string, each with a different parallel block hash, only the highest bidder will get the transaction included on the Bitcoin chain and thus only one parallel block will be mined.See also
[^eltoo]: The same thing used in Eltoo.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Comprimido desodorante
No episódio sei-lá-qual de Aleixo FM Bruno Aleixo diz que os bêbados sempre têm as melhores idéias e daí conta uma idéia que ele teve quando estava bêbado: um comprimido que funciona como desodorante. Ao invés de passar o desodorante spray ou roll-on a pessoa pode só tomar o comprimido e pronto, é muito mais prático e no tempo de frio a pessoa pode vestir a roupa mais rápido, sem precisar ficar passando nada com o tronco todo nu. Quando o Busto lhe pergunta sobre a possibilidade de algo assim ser fabricado ele diz que não sabe, que não é cientista, só tem as idéias.
Essa passagem tão boba de um programa de humor esconde uma verdade sobre a doutrina cientística que permeia a sociedade. A doutrina segundo a qual é da ciência que vêm as inovações tecnológicas e de todos os tipos, e por isso é preciso que o Estado tire dinheiro das pessoas trabalhadoras e dê para os cientistas. Nesse ponto ninguém mais sabe o que é um cientista, foi-se toda a concretude, ficou só o nome: "cientista". Daí vão procurar o tal cientista, é um cara que se formou numa universidade e está fazendo um mestrado. Pronto, é só dar dinheiro pra esse cara e tudo vai ficar bom.
Tirando o problema da desconexão entre realidade e a tese, existe também, é claro, o problema da tese: não faz sentido, que um cientista fique procurando formas de realizar uma idéia, que não se sabe nem se é possível nem se é desejável, que ele ou outra pessoa tiveram, muito pelo contrário (mas não vou dizer aqui o que é que era para o cientista fazer porque isso seria contraditório e eu não acho que devam nem existir cientistas).
O que eu queria dizer mesmo era: todo o aparato científico da nossa sociedade, todos os departamentos, universidades, orçamentos e bolsas e revistas, tudo se resume a um monte de gente tentando descobrir como fazer um comprimido desodorante.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28OP_CHECKTEMPLATEVERIFYand the "covenants" dramaThere are many ideas for "covenants" (I don't think this concept helps in the specific case of examining proposals, but fine). Some people think "we" (it's not obvious who is included in this group) should somehow examine them and come up with the perfect synthesis.
It is not clear what form this magic gathering of ideas will take and who (or which ideas) will be allowed to speak, but suppose it happens and there is intense research and conversations and people (ideas) really enjoy themselves in the process.
What are we left with at the end? Someone has to actually commit the time and put the effort and come up with a concrete proposal to be implemented on Bitcoin, and whatever the result is it will have trade-offs. Some great features will not make into this proposal, others will make in a worsened form, and some will be contemplated very nicely, there will be some extra costs related to maintenance or code complexity that will have to be taken. Someone, a concreate person, will decide upon these things using their own personal preferences and biases, and many people will not be pleased with their choices.
That has already happened. Jeremy Rubin has already conjured all the covenant ideas in a magic gathering that lasted more than 3 years and came up with a synthesis that has the best trade-offs he could find. CTV is the result of that operation.
The fate of CTV in the popular opinion illustrated by the thoughtless responses it has evoked such as "can we do better?" and "we need more review and research and more consideration of other ideas for covenants" is a preview of what would probably happen if these suggestions were followed again and someone spent the next 3 years again considering ideas, talking to other researchers and came up with a new synthesis. Again, that person would be faced with "can we do better?" responses from people that were not happy enough with the choices.
And unless some famous Bitcoin Core or retired Bitcoin Core developers were personally attracted by this synthesis then they would take some time to review and give their blessing to this new synthesis.
To summarize the argument of this article, the actual question in the current CTV drama is that there exists hidden criteria for proposals to be accepted by the general community into Bitcoin, and no one has these criteria clear in their minds. It is not as simple not as straightforward as "do research" nor it is as humanly impossible as "get consensus", it has a much bigger social element into it, but I also do not know what is the exact form of these hidden criteria.
This is said not to blame anyone -- except the ignorant people who are not aware of the existence of these things and just keep repeating completely false and unhelpful advice for Jeremy Rubin and are not self-conscious enough to ever realize what they're doing.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Flowi.es
At the time I thought Workflowy had the ideal UI for everything. I wanted to implement my custom app maker on it, but ended up doing this: a platform for enhancing Workflowy with extra features:
- An email reminder based on dates input in items
- A website generator, similar to Websites For Trello, also based on Classless Templates
Also, I didn't remember this was also based on CouchDB and had some couchapp functionalities.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A big Ethereum problem that is fixed by Drivechain
While reading the following paragraphs, assume Drivechain itself will be a "smart contract platform", like Ethereum. And that it won't be used to launch an Ethereum blockchain copy, but instead each different Ethereum contract could be turned into a different sidechain under BIP300 rules.
A big Ethereum problem
Anyone can publish any "contract" to Ethereum. Often people will come up with somewhat interesting ideas and publish them. Since they want money they will add an unnecessary token and use that to bring revenue to themselves, gamify the usage of their contract somehow, and keep some control over the supposedly open protocol they've created by keeping a majority of the tokens. They will use the profits on marketing and branding, have a visual identity, a central website and a forum with support personnel and so on: their somewhat interesting idea have become a full-fledged company.
If they have success then another company will appear in the space and copy the idea, launch it using exactly the same strategy with a tweak, then try to capture the customers of the first company and new people. And then another, and another, and another. Very often these contracts require some network effect to work, i.e., they require people to be using it so others will use it. The fact that the market is now split into multiple companies offering roughly the same product hurts that, such that none of these protocols get ever enough usage to become really useful in the way they were first conceived. At this point it doesn't matter though, they get some usage, and they use that in their marketing material. It becomes a race to pump the value of the tokens and the current usage is just another point used for that purpose. The company will even start giving out money to attract new users and other weird moves that have no relationship with the initial somewhat intereting idea.
Once in a lifetime it happens that the first implementer of these things is not a company seeking profits, but some altruistic developer or company that believes in Ethereum and wants to see it grow -- or more likely someone financed by the Ethereum Foundation, which allegedly doesn't like these token schemes and would prefer everybody to use the token they issued first, the ETH --, but that's a fruitless enterprise because someone else will copy that idea anyway and turn it into a company as described above.
How Drivechain fixes it
In the Drivechain world, if someone had an idea, they would -- as it happens all the time with Bitcoin things -- publish it in a public forum. Other members of the community would evaluate that idea, add or remove things, all interested parties would contribute to make it the best possible incarnation of that idea. Once the design was settled, someone would volunteer to start writing the code to turn that idea into a sidechain. Maybe some company would fund those efforts and then more people would join. It's not a perfect process and one that often involves altruism, but Bitcoin inspires people to do these things.
Slowly, the thing would get built, tested, activated as a sidechain on testnet, tested more, and at this point luckily the entire community of interested Bitcoin users and miners would have grown to like that idea and see its benefits. It could then be proposed to be activated according to BIP300 rules.
Once it was activated, the entire pool of interested users would join it. And it would be impossible for someone else to create a copy of that because everybody would instantly notice it was a copy. There would be no token, no one profiting directly from the operations of that "smart contract". And everybody would be incentivized to join and tell others to join that same sidechain since the network effect was already the biggest there, they will know more network effect would only be good for everybody involved, and there would be no competing marketing and free token giveaways from competing entities.
See also
-
 @ 18483135:00cf44f6
2024-09-14 13:30:41
@ 18483135:00cf44f6
2024-09-14 13:30:41(Highlighter version)
This article is a Nostr-exclusive so please give it a boost if you think it’s worthy of one!
The world of video games has come a long way since its inception, evolving from simple pixel-based arcade games to highly immersive experiences. However, the medium is still broadly considered to be not much more than entertainment. Even as a gamer, I used to agree with that statement, though some games did help shape who I am. I was a pretty lonely kid and certain game characters substituted as a father figure. I absorbed their values and even mimicked their behavior. And yet, at one point I stopped being interested in gaming. This happened around the same time I was “awakening” through Bitcoin, Austrian Economics and other meaningful topics. I no longer had any intention of wasting time on the medium as a means of distraction.
It didn’t take me very long to suspect I might have just been looking for the wrong things.
Instead of the best RPG, the best action, the best graphics, the best gameplay, … how about I look for games that people have found significant meaning in? As I browsed online through forums and blogs, particular discussions and comments really spoke to me, although they seemed a bit exaggerated at the time. Depression, existential crisis, temporary psychosis. These are not the kind of effects you’d expect people to have from a form of entertainment. But as I played them, I realized they weren’t kidding. These games challenged how I view myself, humanity, the world, life itself and even my own way of thinking. I went from being sick of gaming to finding profound and worthwhile experiences, all by simply changing what I was looking for. Now, I’m convinced that important topics will one day become more mainstream with the usage of the gaming medium. In the bottom of this note I will add a list of these games. They all deserve to be written about, but I will mainly focus on my experience with one in particular, the one that had the most impact on me. It’s one of those experiences that I can’t stop thinking about even after so many years, and I never will. This note is written out of sheer gratitude, as I feel indebted for the value I have received, and to spread awareness of its existence.
Video games allow for hugely ambitious projects, but if one aspect feels off, the product as a whole will drastically decrease in efficacy. Just like certain movies, it tries to incorporate nearly all forms of art, but with the key difference that it places you directly in the story with varying degrees of control, decisions, and the consequences of those decisions. The tricky part is achieving harmony and synchronicity between the visual, audiovisual, writing, and story execution. Everything needs to feel connected and this requires immense skill and cooperation between the involved entities to execute successfully. Naturally, the depths of wisdom contained in books are unparalleled. But it really hits different with games like Nier: Automata, which encapsulates wisdom within a story that shreds one’s mind and heart apart, accompanied by music which I can only understate as “the sound of the human condition”.
https://images5.alphacoders.com/921/thumb-1920-921994.jpg
Exploring The Underlying Themes
The first impression one may have when they look at Nier: Automata on the surface, is "hot android chicks fighting against machines". Everyone knows sex sells, but I dare say it is a rather typical Japanese media phenomenon where the female form is on the foreground but mind-boggling concepts are lurking behind it. I think a fair analogy to this is Bitcoin’s fiat price, where the prospect of wealth is the magnet that draws in people, but most of us know it is only the bait next to the rabbit hole. Much like in Nier, you’d miss out on all the incredible stuff if you didn’t look further than the hot androids.
Anyway, you will no doubt notice I will be extremely vague about the story itself. Instead, I will focus on some of the underlying content as to provide proper context for potential players.
The game takes place in 11945 AD, during a proxy war between human-made androids and alien-made machines. They were designed to serve a predetermined obligation. Don’t humans have a similar mechanism? Don’t we all feel like we need to serve a purpose, whether that is predetermined or not? Much of the game is about coping with the loss of purpose and the realization of an identity for yourself afterwards.
Nihilism is the belief that nothing matters and everything is meaningless.
Existentialism on the other hand, is the attempt to confront and deal with meaninglessness, as to not succumb to nihilism. An existentialist does not give up in the face of adversity, nor does he avoid responsibility. Albert Camus, for instance, believed the entire purpose of existential philosophy is to overcome absurdity. In other words, for man to triumph over the absurdity of existence. The nihilist says: I am a godless creature, there is no heaven or hell, there is no right or wrong. The existentialist says: you and I must figure out how to make life meaningful and good. We must, in fact, work (together) without cosmic aid to figure out what 'good' itself is, regardless of the existence or non-existence of a god.
Even though the game is full of events which would turn anyone to a nihilistic mindset, the game counters this during the most significant ending sequence, ending E, where players are able to leave a message for other players to see. Since I won’t spoil any details, what I can allow myself to say is this: the game isn't telling you that our existence is ultimately meaningless. Instead, an event lets YOU and other players demonstrate that it is not. Life doesn't HAVE to be pointless. Humanity doesn't HAVE to treat freedom as a curse, as Jean-Paul Sartre proclaimed. Games don't HAVE to be silly little things, made to distract us from our own meaninglessness. The potential absence of a god doesn’t HAVE to be a negative circumstance. We're not doomed per se. We can treat our freedom as an opportunity to create our own futures. To craft happier endings.
Mechanics
In the game, there are machines that take the form of real-life philosophers, because their specific work seemed most valuable to these machines. This is no different than us humans; we tend to absorb the views of the people whose words resonate with us. As such, we get to see a fresh perspective on certain philosophies, and how this might play out for machines is just another way of tuning our understanding of humanity.
You will also encounter rather unfriendly historical figures in machine form, For example, the first boss battle is versus an enemy called… Marx. That’s right, Karl Marx is your first boss fight. He takes the form of an excavator arm, which is normally attached to another machine lifeform, called Engels. And yes, that’s a reference to Friedrich Engels, who aided Marx in the construction of the communist theory. They quite literally seized the means of production. In real life the duo was inseparable until Marx's death, at which point Engels was alone with his thoughts. Just as when you defeat the Engels unit in-game, it will be separated from its right arm, Marx. By defeating it, it will be immobilized with nothing to do but contemplate upon its past actions, and you can return to speak to it on multiple occasions, if you wish to do so.
As I stated before, the game takes place in 11945 AD, so machines and androids are indeed extremely advanced. Some could be considered on par with the human gestalt in every way.
As such a technologically advanced entity, your current state of being along with your memories and all that makes you “you”, can be backed up and uploaded into a blank compatible body unit. For this reason, a well known system among gamers called "auto-save" is non-existent here. Saving your game equals backing up your state of being at the time. Many core elements of the main narrative and relationships between the protagonists are based on the ability or inability to back up data. And since this plot point of the androids backing up their data is tied to the game’s save system, there is no auto-save. The creator of the game, Yoko Taro, has an aversion to ludonarrative dissonance, where elements of the game go in stark contrast with what the story is telling, so using the game’s mechanics as a narrative device to deliver main plot elements is exactly one of the ways to avoid this. Gameplay and story stay true to each other. That said, our past experiences and recollections define who we are. This raises questions about the nature of self-identity and personal growth. Whether you believe it is possible for non-organic beings to develop human-like consciousness, or in the eventual possibility of backing up and uploading said consciousness, is irrelevant. The goal here is to explore the human condition and deepen our appreciation for its complexity.
The story unfolds over 3 major playthroughs, each of which are different. The first 2 playthroughs, though indeed different, are very similar as they tell the same part of the story but with additional context and information, as well as playing through the eyes of a different character. This is key to a proper transition into the powerful third part. Near the end, you gain the ability to redo certain events of the game so you can make different choices and see how this impacts that particular timeline. This part of the game is my favorite, as it allows a deep-dive into all the rabbit holes that are scattered throughout the game. Every time I thought I had seen the full truth or all there was to be seen, I kept making new discoveries. It felt very similar to figuring out all the lies and mechanics of the fiat system.
I will now move on to discuss a few of the philosophers and how they are relevant in-game. It’s important to note that the game does not try to push any philosophical views on you. Instead, you are shown the pros and cons of certain values, thoughts, beliefs, and ways of living. You are not told how to live your life, but through storytelling you are shown the importance of responsibility and walking your own path.
Friedrich Nietzsche
"Everything that lives is designed to end. We are perpetually trapped in a never-ending spiral of life and death. Is this a curse? Or some kind of punishment? I often think about the god who blessed us with this cryptic puzzle.. and wonder if we'll ever get the chance to kill him."
This is the game’s opening monologue by a female android called 2B. It is reminiscent of Samsara, a concept present especially in buddhism and hinduism, which describes the endless drifting of a futile existence that can only be stopped with true insight.
2B’s name is based on the famous speech in Shakespeare’s Hamlet “To be or not to be” in which the character Hamlet contemplates death and suicide, weighing the pain and unfairness of life against the alternative.
Nietzsche’s influence on this game is extremely obvious; in 2B’s monologue alone we can already see two major Nietzschean themes that tie into the Nier franchise. The first one is eternal return (or eternal recurrence). This is the concept which states that time repeats itself in an infinite loop, and that exactly the same events will continue to occur in exactly the same way, over and over again, for eternity. With a finite number of events and an infinite amount of time all things will repeat themselves forever. It is not known whether Nietzsche believed in the eternal return, or if it was merely used as a means to demonstrate his point. The second one, is on how to live life in a world without god(s).
“God is dead. God remains dead. And we have killed him.”
For Nietzsche, the idea of what it is to be a human was up until a point aimed at a God. What it meant “to be” was derived from a God. As such, meaning was given to existence. However, societal and scientific progress "killed" God, or the need for one, and a human being could no longer see themself as an existence with a “true” purpose. This in turn, leads to the crisis of the concept of being a human, as it no longer holds as the notion of purpose.
The androids in the game were created by humans, therefore we could say that humanity is their god. Humans are a natural phenomenon — androids are not. I am aware of the counterargument; since humans are a part of nature, anything we create could also be defined as natural, at least to a certain degree. I have no strong stance on this matter, but one could argue that when they die, their consciousness lives on because it shares an attachment to the natural world. One cannot say the same of an artificial consciousness. There is nothing for a machine to believe in after death. They know who their gods are. If their gods are gone, their objective goes with it, and they are left with absolutely nothing. Humans on the other hand have the “luxury” to believe in an afterlife, a rebirth, or simply an unknown. Machines do not, so if they are to survive life’s suffering, they must follow an ethic as stated by Nietzsche, who believed that if you want to live without a god, it is necessary to create your own values.
As I stated before, much of the game is about coping with the loss of purpose and the realization of an identity for yourself afterwards. Some androids clearly resent the purpose they have been given. You, the player, can see how the story potentially ends and resent the game creators for it. You either accept the fate given to you, or you decide it cannot continue like this, and you fight to defeat the gods of the game to break free.
Pascal Blaise
“When I consider the short duration of my life, swallowed up in the eternity before and after, the little space which I fill, and even can see, engulfed in the infinite immensity of spaces of which I am ignorant, and which know me not, I am frightened, and am astonished at being here rather than there; for there is no reason why here rather than there, why now rather than then. Who has put me here? By whose order and direction have this place and time been allotted to me? Memoria hospitis unius diei prætereuntis.”
Pascal Blaise, a mathematician, physicist, and philosopher, is a significant figure of the 17th century. He was the inventor of the first mechanical calculator, the Pascaline, and as you may have guessed, the unit of pressure “Pascal” was named after him.
Our existence is based on uncertainty, and there is no way to prove a god exists, or does not exist. Pascal chose to live his life as if god exists. You may be familiar with the philosophical argument “Pascal's wager”, which posits that individuals essentially engage in a life-defining gamble regarding the belief in the existence of God.
After seeing countless of his comrades die in an ongoing war, Machine Pascal refused to take any more part in this endless cycle and decided to become fully pacifistic while dedicating himself to learn about humanity and teaching other machines about emotions. At one point, we see Pascal studying Nietzsche’s work (In real life Pascal preceded Nietzsche so this would be an anachronistic event, if it weren’t for the fact that these characters are timeless machine representations).
“It seems this Nietzsche was quite the profound thinker.. Or perhaps he skipped right past profound and went straight to crazy instead.. I’d best go see the world for myself instead of burying my head in books.”
A wise choice indeed. I couldn’t help but think of Keynesian economists during this remark. Keynesians may have read very much about mainstream economics but they are completely oblivious as to how the world actually works. They are convinced that their statistics are causally linked and their formulas correct, despite the overwhelming evidence against it. They are blind to the destructive effects of their flawed beliefs. To quote Pascal: “It is man's natural sickness to believe that he possesses the truth.”
Jean-Paul Sartre
“Existence precedes essence”
This idea originated from a speech by Friedrich Schelling in December 1841, and can be found in the work of other philosophers such as Søren Kierkegaard in the 19th century, and Heidegger’s book ‘Being and Time’ in 1927. But it was philosopher Jean-Paul Sartre who worked out this concept in detail.
“Existence precedes essence” is a disagreement with the traditional philosophical view that the essence (nature) of something is more fundamental and unchangeable than its existence. People create their own values and determine their own meaning in life, since they have no innate identity or value. This identity or value must be created by the individual himself. By performing the actions of which they are composed, they make their existence more substantial.
To claim that existence precedes essence is to assert that there is no predetermined essence to be found in humans, and that an individual's essence is defined by the individual through how that individual creates and lives his or her life. As Sartre puts it in Existentialism is a Humanism: "man first of all exists, encounters himself, surges up in the world and defines himself afterwards".
In 2009, philosophy professor James Webber interpreted Sartre's usage of the term essence not in a modal fashion, i.e. as necessary features, but in a teleological fashion, thus relating to the explanation of phenomena in terms of the purpose they serve rather than of the cause by which they arise. An essence is the relational property of having a set of parts ordered in such a way as to collectively perform some activity. For example, it belongs to the essence of a house to keep the bad weather out, which is why it has walls and a roof. Humans are different from houses because unlike houses they don't have an inbuilt purpose: they are free to choose their own purpose and thereby shape their essence, therefore their existence precedes their essence.
When it is said that people define themselves, it is often perceived as stating that they can "wish" to be something and then be what they claim to be. According to Sartre, however, this would be a kind of bad faith. What is meant by the statement is that people are defined only insofar as they act, and that they are responsible for their actions. To clarify, it can be said that a person who acts cruelly towards other people is, by that act, defined as a cruel person and in that same instance, they (as opposed to their genes, for instance) are defined as being responsible for being this cruel person. Ofcourse, you can choose to act in a different way, and to be a good person instead of a cruel person. Here it is also clear that since people can choose to be either cruel or good, they are, in fact, neither of these things essentially.
Jean-Paul's depiction in Nier: Automata parodies the real-life Sartre, who despite great acclaim for his philosophy famously disdained awards and recognition. Among other honors, he was awarded the 1964 Nobel Prize for Literature, but refused to accept it. I also see the resemblance with the game’s creator, Yoko Taro, who is known for playing down his achievements very much, calling his games shit for instance. Though he does so in a playful manner.
Machine Jean-Paul takes the work of the human Jean-Paul so seriously that he ignores that the human versions had a life outside of philosophy. Or rather, whatever part of his life was not recorded or lost, would not exist to a machine.
\ https://i.pinimg.com/originals/39/b8/33/39b8331ebffb0f0c410a88fee80a1e03.jpg
Simone De Beauvoir
Simone de Beauvoir (who had a lifelong relationship with Jean-Paul Sartre) wrote of the example of a woman's identity going wrong if it is based on nothing but a man's affection.
In-game, she was at one point a normal machine. But one day, she fell in love with the Jean-Paul machine. When he disregarded her, pleasing him and getting his attention became her obsession. She made it her goal to become beautiful. “Beauty is pretty skin,” Simone says. “Beauty is stylish accessories. Beauty is looking one’s best.”
As time went on, and Jean-Paul still wouldn’t notice her, things went too far. Simone became desperate and consumed machines and androids to see if she could obtain beauty by digesting them. She even draped dozens of android corpses over her dress in a sickly decorative manner. Driven to madness by her obsession, Simone becomes a monster. And in the end, Jean-Paul still never noticed her. He still never looked her way. So yeah, I said I was not going to mention any more mechanics but looks like I lied; during the battle with Simone this theme is simulated, when you are unable to look at her with the camera at all, no matter what you do with the controls. And as the player deals enough damage to her outer case of morbid accessories, her true unappealing self is revealed.
\ https://untitledcritic.com/wp-content/uploads/2024/04/NieR_mainart-1536x863.jpg
Immanuel Kant
Admittedly, I’m not deeply familiar with Immanuel Kant’s work but I know this much: Kant wrote of the importance of duty in moral action and the intent behind an action being more important than the end result. In the forest section in Nier: Automata, we see a sacrifice being made with good intent but with little result. The entire sequence is about exploring this concept. In the first playthrough you go through an area where all you see is the result of something. The second playthrough shows you the intent. One should always keep in mind that in many cases, be it in-game or in real life, we are only left with results to judge. Kant believed that when people refuse to judge and think for themselves, it’s due to a lack of courage to be independent. He strongly argued against the idea of saying “Why dare to push against the grain when you could simply follow the herd?” Yet this is the antithesis of what in-game Immanuel Kant represents.
\ https://jumpitoy.com/wp-content/uploads/2024/04/NieR-creator-criticizes-Japanese-studios_11zon.webp
Yoko Taro
The creator of the Nier franchise agrees with the existential viewpoint that our lives have no innate meaning whatsoever and that our existence is profoundly absurd. He also confesses that he’s not yet ready to accept the world as it is, and intends to keep trying to change it with his video games.
As opposed to the majority of games, where many conventions of the game market inhibit creative freedom, he is keen in experimenting with the video game format.
“Throughout his entire career, Taro Yoko has always felt disheartened by the image of humanity reflected in most big-budget video games, which propose the use of firearms as the principal means of action. Through his own work, from Drakengard to NieR: Automata, this artist attempts to explore the reasons behind our strange fascination with conflict.
Is man so vicious that he must triumph, discriminate, hurt and kill even for entertainment?
Within the great fields of ruin resulting from wars in which mankind battled against mankind, Taro Yoko perceives this “entertainment” as a way for hope, a horizon, a shield against evil.”
-- The Strange Works of Taro Yoko: From Drakengard to NieR: Automata Hardcover – June 1, 2019
Yoko Taro is known for being quite the eccentric figure. He has an intense dislike for giving interviews and believes that game designers are not supposed to be entertainers or commentators on their work, and that the usual questions asked in traditional media interviews would be boring to the viewer. For this reason and others, he is anonymous. Nobody’s ever seen his face, and I think Yoko Taro isn’t even his real name. As for his work, he writes in a manner called "backwards scriptwriting", which he describes as starting with the ending first, then working backwards from there. He then creates central plot points that form emotional peaks in the narrative, adds details, then scatters them through the narrative so the player can build a suitable emotional connection. Many of his games reflect his own feelings about death and his socratic questioning of the concept. He also has an unconventional and creative approach to sharing extra information about his games. For example, inside the soundtrack there's a message that's coded in hexadecimal. When deciphered, you find it is a partial memory retrieved from one of the android protagonists.
Good developers are able to produce good games, but it takes an exceptional individual or team of exceptional individuals, to craft a piece of work that is so emotionally powerful, so moving, that it transcends the medium of entertainment and leaves an unforgettable mark.
\ https://img3.gelbooru.com//samples/76/13/sample_76134e4004bc4bcd629fb2a478ea6ff7.jpg
If you made it this far, thank you for reading!
A few quick tips to fully enjoy this masterpiece..
For the sake of all that’s holy, play it in the original Japanese voiceover. The immersion gets quite broken if you don’t get to hear the proper emotion in the character’s voices. English subtitles are included of course. It is also an experience that’s most effective when you go through it all alone, as to allow for the most self-reflection and absorption.
Quick echo of what I said on top: I would love it if this note got some visibility, it is a Nostr-exclusive article so please give it a boost if you think it’s worthy of one!
Also, HI EVERYONE. I haven’t used my #introductions formally yet, so this is it!
Now here is the list of games I said I was going to provide, not in any specific order, and a short description for some.
Must-play
Disco Elysium: The player controls a detective who suffers from amnesia and has to solve a murder case while navigating his own state of being and dealing with the consequences of past mistakes. One of the most unique elements in this game, is the fact that concepts such as logic, or various parts of your body such as your limbic system, actually converse with you.
The Talos Principle: Like Nier: Automata, lots of self-reflection and a challenge to your sense of morality. Its gameplay however is based on problem-solving and presenting you with thought-provoking questions in a direct manner.
The Talos Principle 2: A continuation of the events in the first game.
Semi must-play
Detroit: Become Human
Lisa
Bioshock Infinite
Omori
Oneshot
Doki Doki Literature Club
Meaningful Anime
Since I’m writing about existential stuff anyway, I might as well add the relevant anime that I’ve watched. It doesn’t have the same level of impact on me as games do but I feel like this note wouldn’t be complete without mentioning them.
Again, in no particular order:
Neon Genesis Evangelion (Yoko taro also mentioned Nier: Automata was inspired by this anime)
Serial Experiments Lain
Ergo Proxy
I know there’s plenty more gems out there but I haven’t gotten around to watching them yet.
## Tags and stuff
nier #nierautomata #philosophy #existentialism #game #gaming #games #gamestr #nihilism #story #storytelling #meaning #life #bitcoin
\ CREDIT for certain images I found: RPINr, Gasia112 on deviantart
-
 @ e97aaffa:2ebd765d
2024-09-14 11:41:09
@ e97aaffa:2ebd765d
2024-09-14 11:41:09Há 4 ou 5 anos, eu fiz um comentário num tweet de um famoso shitcoiner português, entretanto o tweet foi apagado. Eu escrevi: «Ethereum é o WordPress 2.0», o influencer não concordou mas até foi cordial na resposta, o mesmo não aconteceu com o resto da sua comunidade, fui altamente atacado. Quanto mais tempo passa, eu estou mais convicto que estava certo.
Passados estes anos, eu continuo a manter o mesmo pensamento sobre a Ethereum, possivelmente não vai cair tanto como a WordPress, mas vai perder muito valor, comparado com o atual valor. Hoje em dia a tecnologia WordPress está em todo lado, utilizada por milhões de pessoas e empresas, mas o valor da empresa WordPress é ínfima parte do valor da tecnologia WordPress. Eu acredito que vai acontecer o mesmo com Ethereum, posso estar errado mas é a minha convicção.
O atual plano de negócios da empresa/fundação Ethereum é inviável a longo prazo, recentemente voltou a fazer uma enorme venda para financiar os custos operacionais. Os custos são uma monstruosidade, o seu tesouro inevitável vai acabar um dia, o problema está aqui, não há uma solução boa, qualquer que seja, é má. O que fazer para financiar:
Donativos
Uma alternativa, seguir o modelo mais opensource, sem uma fundação, ao estilo do #Bitcoin, através de donativos diretos ou empresas a pagar ao devs e devs voluntários. Só que este modelo, será difícil seguir uma linha orientadora, um roadmap, será um desenvolvimento mais anarquista. Ou então a fundação poderá ser financiada por empresas ou países, com o objetivo de seguir o rumo que os doadores pretendem, perdendo a liberdade.
Opensource/Patentes
Outra solução é, deixarem de ser exclusivamente opensource, para terem uma vantagem contra a concorrência. O atual modelo é péssimo em termos de negócio, porque a Ethereum gasta milhões em desenvolvimento e lança as inovações. Mas como é opensource, rapidamente a concorrência copia e implementa a tecnologia, como os custos destas são muito menores, conseguem disponibilizar um serviço muito mais barato, são uma concorrência desleal. Isto faz lembrar muito a indústria farmacêutica, por isso existem as patentes, durante x anos, quem inventa/descobre o medicamento tem uma exclusividade. Só que isto é contra os princípios básicos deste ecossistema, é ir contra a sua essência.
Inflação
A inflação será possivelmente o caminho mais provável, vão criar mais ether para se financiar. Ou em alternativa criar uma nova fee que reverta a favor, em exclusivo, para a fundação. Em ambos os casos, vai aumentar os custos para os utilizadores ou desvaloriza o ether para os investidores, ou seja, a rede fica ainda menos competitiva, em relação à concorrência. A maioria das pessoas vão querer sempre o mais barato. Assim será quase uma espiral da morte, terá que estar constantemente a desvalorizar o ether, é exatamente como os atuais governos fazem com as suas moedas FIAT e também sabemos as consequências destas medidas.
Estagnação
Se não houver bastante financiamento o projecto vai acabar por estagnar, mais tarde ou mais cedo vai surgir um outro projeto, com uma tecnologia melhor e o Ethereum será ultrapassado.
Ou a fundação arranja uma solução para o seu futuro ou este será muito sombrio. Com isto, eu não quero dizer que o projeto vai colapsar, mas não vai valer tanto como vale hoje em dia.
Esta é a grande vantagem do #Bitcoin, não é apenas tecnologia, a tecnologia é quase uma coisa secundária. O principal é o seu ethos, a política monetária, a descentralização e o efeito de rede, estes sim, são os reais valores do Bitcoin, a tecnologia serve apenas para garantir a segurança e que esses valores são cumpridos. O código é possível ser copiado e foi copiado no passado, não passou disso, apenas código, porque o real valor não pode ser replicado, por isso poucas pessoas trocaram o Bitcoin pelos “clones”.
No caso do Ethereum, é o oposto, o principal valor é a sua tecnologia(EVM), e esta pode e está a ser replicada em dezenas de projectos diferentes. Podem alegar que é mais seguro, sim é verdade, mas apenas uma minoria está disponível para pagar por esse premium, a esmagadora maioria dos utilizadores vai e está a preferir redes mais baratas. E é lógico que queiram, se tens dois serviços idênticos, não existe razão para escolher o mais caro. Na guerra dos clones, o Bitcoin saiu claramente vencedor, não perdeu utilizadores; o Ethereum estará em plena guerra, mas os clones estão a ganhar parte significativa desses mercado.
Eu sinceramente acredito que muita da tecnologia criada pela Ethereum estará no futuro por todo o lado, especialmente no sistema financeiro e notarial. Mas os investidores têm a expectativa que vai acontecer um boom, vai acontecer mas não será na Ethereum, nem em blockchains permissionless, cada instituição terá a sua própria blockchain ou vão juntar-se em cooperativas. O mundo financeiro e das securities é tão complexo, em termos de regras e regulatório, cada país tem as suas próprias regras, é provável no futuro, a BlackRock ter uma blockchain para os EUA, outra para UE e muitas outras. É apenas uma base de dados, ou seja, será o mesmo que aconteceu com a WordPress.
Na minha opinião, a Ethereum vai se tornar algo de nicho, a grande massa de utilizadores ficará dispersa por milhares de blockchains. É exatamente o mesmo que acontece com o Bitcoin, só que o Bitcoin está a ser construído com esse objetivo, ser um local de settlements. No Bitcoin estimula-se a utilização de outras redes, layers 2, ecash, sidechains e outras tecnologias, a descentralização pura.
Há muito tempo que os bitcoiners concluíram que é impossível escalar a blockchain do Bitcoin para uma adoção global, essa escalabilidade passará obrigatoriamente por layer 2 e outras tecnologias. Eu tenho a sensação que o Vitalik também já chegou a essa conclusão, o Ethereum não é escalável, e está a transformá-lo num local para os “settlements” de outras blockchains. Só que os investidores ainda não compreenderam isso… O atual valor do ether está sobrevalorizado, porque os investidores estão na expectativa de um crescimento exponencial de utilizadores, mas se crescimento nunca acontecer?
Esta é a minha opinião, posso estar completamente errado, mas é assim que eu penso. Enquanto for permitido, vou fazê-lo, expressar livremente, dizer aquilo que realmente penso. Prefiro errar, do que ficar calado ou expressar algo que não acredito, mas esses são os meus valores… outros preferem os valores monetários.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Using Spacechains and Fedimint to solve scaling
What if instead of trying to create complicated "layer 2" setups involving noveau cryptographic techniques we just did the following:
- we take that Fedimint source code and remove the "mint" stuff, and just use their federation stuff secure coins with multisig;
- then we make a spacechain;
- and we make the federations issue multisig-btc tokens on it;
- and then we put some uniswap-like thing in there to allow these tokens to be exchanged freely.
Why?
The recent spike in fees caused by Ordinals and BRC-20 shitcoinery has shown that Lightning isn't a silver bullet. Channels are too fragile, it costs a lot to open a channel under a high fee environment, to run a routing node and so on.
People who want to keep using Lightning are instead flocking to the big Lightning custodial providers: WalletofSatoshi, ZEBEDEE, OpenNode and so on. We could leverage that trust people have in these companies (and individuals) operating shadow Lightning providers and turn each of these into a btc-token issuer. Each issue their own token, transactions flow freely. Each person can hold only assets from the issuers they trust more.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28contratos.alhur.es
A website that allowed people to fill a form and get a standard Contrato de Locação.
Better than all the other "templates" that float around the internet, which are badly formatted
.docfiles.It was fully programmable so other templates could be added later, but I never did. This website made maybe one dollar in Google Ads (and Google has probably stolen these like so many other dollars they did with their bizarre requirements).
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Just malinvestiment
Traditionally the Austrian Theory of Business Cycles has been explained and reworked in many ways, but the most widely accepted version (or the closest to the Mises or Hayek views) view is that banks (or the central bank) cause the general interest rate to decline by creation of new money and that prompts entrepreneurs to invest in projects of longer duration. This can be confusing because sometimes entrepreneurs embark in very short-time projects during one of these bubbles and still contribute to the overall cycle.
The solution is to think about the "longer term" problem is to think of the entire economy going long-term, not individual entrepreneurs. So if one entrepreneur makes an investiment in a thing that looks simple he may actually, knowingly or not, be inserting himself in a bigger machine that is actually involved in producing longer-term things. Incidentally this thinking also solves the biggest criticism of the Austrian Business Cycle Theory: that of the rational expectations people who say: "oh but can't the entrepreneurs know that the interest rate is artificially low and decide to not make long-term investiments?" ("and if they don't know they should lose money and be replaced like in a normal economy flow blablabla?"). Well, the answer is that they are not really relying on the interest rate, they are only looking for profit opportunities, and this is the key to another confusion that has always followed my thinkings about this topic.
If a guy opens a bar in an area of a town where many new buildings are being built during a "housing bubble" he may not know, but he is inserting himself right into the eye of that business cycle. He expects all these building projects to continue, and all the people involved in that to be getting paid more and be able to spend more at his bar and so on. That is a bet that may or may not end up paying.
Now what does that bar investiment has to do with the interest rate? Nothing. It is just a guy who saw a business opportunity in a place where hungry people with money had no bar to buy things in, so he opened a bar. Additionally the guy has made some calculations about all the ending, starting and future building projects in the area, and then the people that would live or work in that area afterwards (after all the buildings were being built with the expectation of being used) and so on, there is no interest rate calculations involved. And yet that may be a malinvestiment because some building projects will end up being canceled and the expected usage of the finished ones will turn out to be smaller than predicted.
This bubble may have been caused by a decline in interest rates that prompted some people to start buying houses that they wouldn't otherwise, but this is just a small detail. The bubble can only be kept going by a constant influx of new money into the economy, but the focus on the interest rate is wrong. If new money is printed and used by the government to buy ships then there will be a boom and a bubble in the ship market, and that involves all the parts of production process of ships and also bars that will be opened near areas of the town where ships are built and new people are being hired with higher salaries to do things that will eventually contribute to the production of ships that will then be sold to the government.
It's not interest rates or the length of the production process that matters, it's just printed money and malinvestiment.
-
 @ a012dc82:6458a70d
2024-09-14 10:17:24
@ a012dc82:6458a70d
2024-09-14 10:17:24Table Of Content
-
What are Bitcoin Ordinals?
-
Importance of Bitcoin Ordinals in the Bitcoin Network
-
How Bitcoin Ordinals Work
-
The Significance of Bitcoin Ordinals
-
Advantages of Bitcoin Ordinals
-
Future of Bitcoin Ordinals and Blockchain Technology
-
Conclusion
-
FAQ
Bitcoin ordinals are a fundamental aspect of the Bitcoin network, serving a crucial role in ensuring the network's integrity and security. In this article, we will delve into the basics of Bitcoin ordinals, their importance, and how they are generated.
What are Bitcoin Ordinals?
Bitcoin ordinals are unique identifiers assigned to each transaction on the Bitcoin network. They distinguish each transaction from others by assigning a unique ordinal number to it. Bitcoin ordinals are represented as a long string of alphanumeric characters generated by the Bitcoin network's underlying code.
Importance of Bitcoin Ordinals in the Bitcoin Network
Bitcoin ordinals are a critical component of the Bitcoin network, serving several important purposes that are essential in ensuring the network's integrity and security.
Ensuring Transaction Authenticity
One of the primary purposes of Bitcoin ordinals is to ensure the authenticity of each transaction on the Bitcoin network. Each transaction is assigned a unique ordinal number that distinguishes it from other transactions, ensuring that it cannot be replicated or modified.
Preventing Double-Spending
Another important role of Bitcoin ordinals is to prevent double-spending, a fraudulent activity where a user spends the same Bitcoin more than once. Bitcoin ordinals ensure that each Bitcoin can only be spent once, preventing double-spending and enhancing the security of the Bitcoin network.
Verifying Transaction Origin and Destination
Bitcoin ordinals also help verify the origin and destination of Bitcoin transactions. Each Bitcoin transaction is associated with a specific public key that identifies the user who sent the Bitcoin and the user who received it.
How Bitcoin Ordinals Work
Bitcoin ordinals are generated through the process of Bitcoin mining. Each block added to the blockchain contains a unique set of Bitcoin transactions, and each transaction within the block is assigned a unique ordinal number. The ordinal number is derived from the block's hash, a unique identifier that represents the block's contents and its position in the blockchain.
The mining process involves solving complex mathematical equations to validate Bitcoin transactions and create new blocks in the blockchain. Once a block is created, its ordinal numbers cannot be changed, ensuring the authenticity and security of each transaction within the block.
The Significance of Bitcoin Ordinals
Bitcoin ordinals play a crucial role in the security and integrity of the Bitcoin network. They help prevent fraudulent activities such as double-spending and ensure that each transaction on the network is authentic and secure. Bitcoin ordinals also provide a unique identifier for each transaction, allowing users to easily track the movement of Bitcoins through the network.
Advantages of Bitcoin Ordinals
Bitcoin ordinals provide several advantages that are crucial in ensuring the security and integrity of transactions on the Bitcoin network. These advantages include:
Improved Transaction Security: Bitcoin ordinals enhance transaction security by providing a unique identifier for each transaction, preventing fraudulent activities and enhancing network security.
Easy Tracking of Bitcoin Transactions: Bitcoin ordinals allow for easy tracking of Bitcoin transactions from one address to another, making it possible to verify the authenticity of each transaction.
Preventing Fraudulent Transactions: Bitcoin ordinals provide an additional layer of security that prevents fraudulent transactions on the Bitcoin network, making it nearly impossible for hackers to manipulate the transaction history or attempt to double-spend Bitcoins.
Future of Bitcoin Ordinals and Blockchain Technology
Bitcoin ordinals will remain a critical component of the Bitcoin network as it continues to evolve and expand. As the blockchain technology advances, new methods for generating and using ordinals may emerge, leading to even greater security and transaction efficiency. The continued growth and development of the Bitcoin network will rely heavily on the security and authenticity provided by Bitcoin ordinals.
Conclusion
Bitcoin ordinals are a unique and essential aspect of the Bitcoin network, serving several critical purposes in ensuring its security and integrity. Understanding how Bitcoin ordinals work and their importance in the Bitcoin network is essential for anyone investing or transacting with Bitcoins. As the Bitcoin network continues to grow and evolve, the role of Bitcoin ordinals will become increasingly significant in ensuring the network's security and success.
FAQ
What is the future of Bitcoin ordinals and blockchain technology? As blockchain technology advances, new methods for generating and using ordinals may emerge, leading to even greater security and transaction efficiency. The continued growth and development of the Bitcoin network will rely heavily on the security and authenticity provided by Bitcoin ordinals.
Can Bitcoin ordinals be changed or modified? No, once a block is created, its ordinal numbers cannot be changed or modified, ensuring the authenticity and security of each transaction within the block.
How do Bitcoin ordinals enhance transaction security? Bitcoin ordinals provide a unique identifier for each transaction, making it nearly impossible for hackers to manipulate the transaction history or attempt to double-spend Bitcoins.
Can Bitcoin ordinals be used in other blockchain networks? Bitcoin ordinals are unique to the Bitcoin network and cannot be directly used in other blockchain networks. However, other blockchain networks may have similar mechanisms to ensure transaction authenticity and prevent double-spending.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28neuron.vim
I started using this neuron thing to create an update this same zettelkasten, but the existing vim plugin had too many problems, so I forked it and ended up changing almost everything.
Since the upstream repository was somewhat abandoned, most users and people who were trying to contribute upstream migrate to my fork too.
-
 @ eac63075:b4988b48
2024-09-14 10:06:38
@ eac63075:b4988b48
2024-09-14 10:06:38A privacidade do usuário na internet tornou-se um tema central na era digital atual. Com o aumento das preocupações sobre como os dados pessoais são coletados, armazenados e utilizados, legislações como a AB 3048 da Califórnia emergem para fortalecer a proteção dos dados dos usuários. Neste contexto, navegadores como o Brave posicionam-se como defensores proativos da privacidade, enquanto gigantes como o Google enfrentam desafios para alinhar seus modelos de negócio com essas novas diretrizes. Este artigo técnico analisa como o Brave e o Google diferem em sua abordagem à privacidade do usuário, especialmente em relação à legislação emergente.
Controle Global de Privacidade (GPC)
Brave: Implementação Proativa do GPC
O Brave foi um dos primeiros navegadores a implementar e suportar o Global Privacy Control (GPC). Ativado por padrão há quase quatro anos (até 2024), o GPC permite que os usuários sinalizem automaticamente aos sites sua preferência em não ter seus dados vendidos ou compartilhados. Esta funcionalidade está em total alinhamento com a intenção da AB 3048, que busca reforçar as escolhas de privacidade dos usuários no nível do navegador. Ao adotar o GPC antecipadamente, o Brave demonstra um compromisso em capacitar os usuários no controle de sua privacidade digital, sem depender exclusivamente de legislações para impulsionar essas mudanças.
Google: Adaptação Reativa às Demandas de Privacidade
Por outro lado, o Google não tem sido tão entusiasta em integrar ou ativar por padrão recursos como o GPC em seus serviços. A introdução de legislações como a AB 3048 pode pressionar a empresa a implementar controles de privacidade mais robustos. No entanto, o modelo de negócio do Google é amplamente baseado em publicidade e dados dos usuários, o que muitas vezes o coloca em desacordo com medidas de privacidade mais rigorosas. A abordagem do Google tende a ser mais reativa, implementando mudanças quando exigido por lei ou diante de pressão pública significativa.
Filosofia de Privacidade e Funcionalidades
Brave: Privacidade como Pilar Central
O Brave foi construído com a privacidade como foco principal. Por padrão, ele bloqueia anúncios e rastreadores, reduzindo significativamente a quantidade de dados coletados durante a navegação. Além disso, oferece um modo de navegação privada integrado com o Tor, proporcionando anonimato aprimorado. O Brave também desenvolveu seu próprio mecanismo de busca, o Brave Search, que prioriza a preservação da privacidade. Uma característica única é o sistema de recompensas em Basic Attention Tokens (BAT), que incentiva os usuários a visualizar anúncios respeitadores da privacidade, enfatizando o consentimento e a transparência.
Google: Equilíbrio Entre Serviços Personalizados e Privacidade
O Google Chrome, embora ofereça configurações de privacidade, não bloqueia anúncios ou rastreadores por padrão, exigindo que os usuários instalem extensões para obter funcionalidade semelhante. O modelo de receita do Google depende significativamente da publicidade direcionada, que necessita da coleta de dados do usuário. Embora o Google tenha feito avanços na melhoria da privacidade do usuário, como a eliminação gradual de cookies de terceiros, seu modelo de negócio central muitas vezes entra em conflito com o espírito de legislações de privacidade como a AB 3048.
Dados do Usuário e Publicidade
Brave: Minimização da Coleta de Dados
Por padrão, o Brave minimiza a coleta de dados e não armazena informações de navegação de uma forma que possa ser diretamente vinculada ao usuário. Esta abordagem está em consonância com a AB 3048, que visa limitar a venda ou compartilhamento de informações pessoais. Ao reduzir a coleta de dados ao mínimo necessário, o Brave reforça o controle do usuário sobre suas informações pessoais.
Google: Dependência de Dados para Eficácia Publicitária
O ecossistema do Google é projetado para reunir dados do usuário com o objetivo de aprimorar sua plataforma publicitária. Embora o Google tenha introduzido recursos de privacidade e ofereça algum nível de controle ao usuário, sua reação a legislações como a AB 3048 provavelmente envolverá a adaptação de seus sistemas existentes para cumprir os requisitos legais, ao mesmo tempo em que busca manter a eficácia de sua publicidade baseada em dados.
Suporte Público e Legislativo
Brave: Alinhamento com Defensores da Privacidade
Ao acolher a AB 3048, o Brave alinha-se com defensores da privacidade e usuários preocupados com os direitos sobre seus dados. Esta postura reforça sua marca como um navegador que coloca a privacidade em primeiro lugar, não apenas como um recurso, mas como um valor fundamental incorporado em sua arquitetura e serviços.
Google: Navegando Desafios Regulatórios
O Google pode perceber legislações restritivas de privacidade como um desafio complexo, dado seu vasto ecossistema de serviços que dependem de dados do usuário. Embora a empresa cumpra as legislações, sua posição pública pode enfatizar mais o equilíbrio entre a privacidade do usuário e a oferta de serviços personalizados, em vez de abraçar plenamente leis de privacidade restritivas.
Conclusão
Em um cenário digital onde a privacidade do usuário é cada vez mais valorizada, o Brave destaca-se por sua abordagem proativa e centrada no usuário. Sua filosofia e design intrínsecos estão em harmonia com legislações de privacidade como a AB 3048, e suas funcionalidades refletem um compromisso genuíno em dar aos usuários controle sobre suas informações pessoais.
O Google, apesar de adaptar-se às tendências e legislações de privacidade, enfrenta desafios mais complexos devido ao seu modelo de receita baseado em publicidade direcionada. A necessidade de coletar dados para manter a eficácia de seus serviços coloca a empresa em uma posição onde deve constantemente equilibrar os imperativos regulatórios com suas estratégias de negócio.
Para os usuários, a escolha entre o Brave e o Google Chrome pode depender de suas prioridades pessoais em relação à privacidade e à personalização dos serviços. Enquanto o Brave oferece uma experiência focada na proteção dos dados e no controle do usuário, o Google continua a fornecer serviços altamente integrados e personalizados, alimentados por dados coletados dos usuários.
À medida que legislações como a AB 3048 entram em vigor, será interessante observar como essas empresas e outras no setor tecnológico ajustarão suas estratégias. A tendência indica um movimento em direção a práticas que colocam a privacidade do usuário em primeiro plano, seja por convicção ou por conformidade regulatória. Independentemente do motivo, os maiores beneficiários serão os usuários, que terão maior controle e transparência sobre seus dados pessoais no ambiente digital.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Reasons why Lightning is not that great
Some Bitcoiners, me included, were fooled by hyperbolic discourse that presented Lightning as some magical scaling solution with no flaws. This is an attempt to list some of the actual flaws uncovered after 5 years of experience. The point of this article is not to say Lightning is a complete worthless piece of crap, but only to highlight the fact that Bitcoin needs to put more focus on developing and thinking about other scaling solutions (such as Drivechain, less crappy and more decentralized trusted channels networks and statechains).
Unbearable experience
Maintaining a node is cumbersome, you have to deal with closed channels, allocating funds, paying fees unpredictably, choosing new channels to open, storing channel state backups -- or you'll have to delegate all these decisions to some weird AI or third-party services, it's not feasible for normal people.
Channels fail for no good reason all the time
Every time nodes disagree on anything they close channels, there have been dozens, maybe hundreds, of bugs that lead to channels being closed in the past, and implementors have been fixing these bugs, but since these node implementations continue to be worked on and new features continue to be added we can be quite sure that new bugs continue to be introduced.
Trimmed (fake) HTLCs are not sound protocol design
What would you tell me if I presented a protocol that allowed for transfers of users' funds across a network of channels and that these channels would pledge to send the money to miners while the payment was in flight, and that these payments could never be recovered if a node in the middle of the hop had a bug or decided to stop responding? Or that the receiver could receive your payment, but still claim he didn't, and you couldn't prove that at all?
These are the properties of "trimmed HTLCs", HTLCs that are uneconomical to have their own UTXO in the channel presigned transaction bundles, therefore are just assumed to be there while they are not (and their amounts are instead added to the fees of the presigned transaction).
Trimmed HTLCs, like any other HTLC, have timelocks, preimages and hashes associated with them -- which are properties relevant to the redemption of actual HTLCs onchain --, but unlike actual HTLCs these things have no actual onchain meaning since there is no onchain UTXO associated with them. This is a game of make-believe that only "works" because (1) payment proofs aren't worth anything anyway, so it makes no sense to steal these; (2) channels are too expensive to setup; (3) all Lightning Network users are honest; (4) there are so many bugs and confusion in a Lightning Network node's life that events related to trimmed HTLCs do not get noticed by users.
Also, so far these trimmed HTLCs have only been used for very small payments (although very small payments probably account for 99% of the total payments), so it is supposedly "fine" to have them. But, as fees rise, more and more HTLCs tend to become fake, which may make people question the sanity of the design.
Tadge Dryja, one of the creators of the Lightning Network proposal, has been critical of the fact that these things were allowed to creep into the BOLT protocol.
Routing
Routing is already very bad today even though most nodes have a basically 100% view of the public network, the reasons being that some nodes are offline, others are on Tor and unreachable or too slow, channels have the balance shifted in the wrong direction, so payments fail a lot -- which leads to the (bad) solution invented by professional node runners and large businesses of probing the network constantly in order to discard bad paths, this creates unnecessary load and increases the risk of channels being dropped for no good reason.
As the network grows -- if it indeed grow and not centralize in a few hubs -- routing tends to become harder and harder.
While each implementation team makes their own decisions with regard to how to best way to route payments and these decisions may change at anytime, it's worth noting, for example, that CLN will use MPP to split up any payment in any number of chunks of 10k satoshis, supposedly to improve routing success rates. While this often backfires and causes payments to fail when they should have succeeded, it also contributes to making it so there are proportionally more fake HTLCs than there should be, as long as the threshold for fake HTLCs is above 10k.
Payment proofs are somewhat useless
Even though payment proofs were seen by many (including me) as one of the great things about Lightning, the sad fact is that they do not work as proofs if people are not aware of the fact that they are proofs. Wallets do all they can to hide these details from users because it is considered "bad UX" and low-level implementors do not care very much to talk about them at all. There have been attempts from Lightning Labs to get rid of the payment proofs entirely (which at the time to me sounded like a terrible idea, but now I realize they were not wrong).
Here's a piece of anecdote: I've personally witnessed multiple episodes in which Phoenix wallet released the preimage without having actually received the payment (they did receive a minor part of the payment, but the payment was split in many parts). That caused my service, @lntxbot, to mark the outgoing payment as complete, only then to have to endure complaints from the users because the receiver side, Phoenix, had not received the full amount. In these cases, if the protocol and the idea of preimages as payment proofs be respected, should I have been the one in charge of manually fixing user balances?
Another important detail: when an HTLC is sent and then something goes wrong with the payment the channel has to be closed in order to redeem that payment. When the redeemer is on the receiver side, the very act of redeeming should cause the preimage to be revealed and a proof of payment to be made available for the sender, who can then send that back to the previous hop and the payment is proven without any doubt. But when this happens for fake HTLCs (which is the vast majority of payments, as noted above) there is no place in the world for a preimage and therefore there are no proofs available. A channel is just closed, the payer loses money but can't prove a payment. It also can't send that proof back to the previous hop so he is forced to say the payment failed -- even if it wasn't him the one who declared that hop a failure and closed the channel, which should be a prerequisite. I wonder if this isn't the source of multiple bugs in implementations that cause channels to be closed unnecessarily. The point is: preimages and payment proofs are mostly a fiction.
Another important fact is that the proofs do not really prove anything if the keypair that signs the invoice can't be provably attached to a real world entity.
LSP-centric design
The first Lightning wallets to show up in the market, LND as a desktop daemon (then later with some GUIs on top of it like Zap and Joule) and Anton's BLW and Eclair wallets for mobile devices, then later LND-based mobile wallets like Blixt and RawTX, were all standalone wallets that were self-sufficient and meant to be run directly by consumers. Eventually, though, came Breez and Phoenix and introduced the "LSP" model, in which a server would be trusted in various forms -- not directly with users' funds, but with their privacy, fees and other details -- but most importantly that LSP would be the primary source of channels for all users of that given wallet software. This was all fine, but as time passed new features were designed and implemented that assumed users would be running software connected to LSPs. The very idea of a user having a standalone mobile wallet was put out of question. The entire argument for implementation of the bolt12 standard, for example, hinged on the assumption that mobile wallets would have LSPs capable of connecting to Google messaging services and being able to "wake up" mobile wallets in order for them to receive payments. Other ideas, like a complicated standard for allowing mobile wallets to receive payments without having to be online all the time, just assume LSPs always exist; and changes to the expected BOLT spec behavior with regards to, for example, probing of mobile wallets.
Ark is another example of a kind of LSP that got so enshrined that it become a new protocol that depends on it entirely.
Protocol complexity
Even though the general idea of how Lightning is supposed to work can be understood by many people (as long as these people know how Bitcoin works) the Lightning protocol is not really easy: it will take a long time of big dedication for anyone to understand the details about the BOLTs -- this is a bad thing if we want a world of users that have at least an idea of what they are doing. Moreover, with each new cool idea someone has that gets adopted by the protocol leaders, it increases in complexity and some of the implementors are kicked out of the circle, therefore making it easier for the remaining ones to proceed with more and more complexity. It's the same process by which Chrome won the browser wars, kicked out all competitors and proceeded to make a supposedly open protocol, but one that no one can implement as it gets new and more complex features every day, all envisioned by the Chrome team.
Liquidity issues?
I don't believe these are a real problem if all the other things worked, but still the old criticism that Lightning requires parking liquidity and that has a cost is not a complete non-issue, specially given the LSP-centric model.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Multi-service Graph Reputation protocol
The problem
- Users inside centralized services need to know reputations of other users they're interacting with;
- Building reputation with ratings imposes a big burden on the user and still accomplishes nothing, can be faked, no one cares about these ratings etc.
The ideal solution
Subjective reputation: reputation based on how you rated that person previously, and how other people you trust rated that person, and how other people trusted by people you trust rated that person and so on, in a web-of-trust that actually can give you some insight on the trustworthiness of someone you never met or interacted with.
The problem with the ideal solution
- Most of the times the service that wants to implement this is not as big as Facebook, so it won't have enough people in it for such graphs of reputation to be constructed.
- It is not trivial to build.
My proposed solution:
I've drafted a protocol for an open system based on services publishing their internal reputation records and indexers using these to build graphs, and then serving the graphs back to the services so they can show them to users when it is needed (as HTTP APIs that can be called directly from the user client app or browser).
Crucially, these indexers will gather data from multiple services and cross-link users from these services so the graph is better.
https://github.com/fiatjaf/multi-service-reputation-rfc
The first and single actionable and useful feedback I got, from @bootstrapbandit was that services shouldn't share email addresses in plain text (email addresses and other external relationships users of a service may have are necessary to establish links from users accross services), but I think it is ok if services publish hashes of these email addresses instead. At some point I will update the spec draft and that may have been before the time you're reading this.
Another issue is that services may lie about their reputation records and that will hurt other services and users in these other services that are relying on that data. Maybe indexers will have to do some investigative job here to assert service honesty. Or maybe this entire protocol is just failed and we will actually need a system in which users themselves will publish their own records.
See also
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28doulas.club
A full catalog of all Brazilian doulas with data carefully scrapped from many websites that contained partial catalogs and some data manually included. All this packaged as a Couchapp and served directly from Cloudant.
This was done because the idea of doulas was good, but I spotted an issue: pregnant womwn should know many doulas before choosing one that would match well, therefore a full catalog with a lot of information was necessary.
This was a huge amount of work mostly wasted.
Many doulas who knew about this didn't like it and sent angry and offensive emails telling me to remove them. This was information one should know before choosing a doula.
See also
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Idéia de um sistema jurídico centralizado, mas com um pouco de lógica
um processo, é, essencialmente, imagino eu na minha ingenuidade leiga, um apelo que se faz ao juiz para que este reconheça certos fatos como probantes de um certo fenômeno tipificado por uma certa lei.
imagino então o seguinte:
uma petição não é mais um enorme documento escrito numa linguagem nojenta com referências a leis e a evidências factuais espalhadas segundo a (in) capacidade ensaística do advogado, mas apenas um esquema lógico - talvez até um diagrama desenhado (ou talvez quem sabe uma série de instruções compreensíveis por um computador?) - mostrando a ligação entre a lei e os fatos e os pedidos, por exemplo:
- a lei tal diz que ninguém pode vender
- fulano vendeu cigarros
- é prova de que fulano vendeu cigarros ia foto tirada na rua tal no dia tal que mostra fulano vendendo cigarros
- a mesma lei pede que fulano pague uma multa
este exemplo está ainda muito verborrágico, mas é só um exemplo simples. coisas mais complicadas precisariam de outras formas de expressão caso queiramos evitar as longas dissertações jurídicas em voga.
a idéia é que o esquema acima vale por si. um proto-juiz pode julgá-lo como válido ou inválido apenas pela sua lógica interna.
a outra parte do julgamento seria a ligação desse esquema com a realidade externa: anexados à petição viriam as evidências. no caso, anexada ao ponto 3 viria uma foto do fulano. ao ponto 1 também precisa ser anexado o texto da lei referida, mas isto pode ser feito automaticamente pelo número da lei.
uma vez que tenhamos um esquema lógico válido um outro proto-juiz, ou vários outros, pode julgar individualmente cada evidência: ver se o texto da lei confere com a interpretação feita no ponto 1, e se a foto anexada ao ponto 3 é mesmo a foto do réu vendendo cigarro e não a de um urso comendo laranjas.
cada um desses julgamentos pode ser feito sem que o proto-juiz tenha conhecimento do resto das coisas do processo: o primeiro proto-juiz não precisa ver a foto ou a lei, o segundo não precisa ver o esquema lógico ou a foto, o terceiro não precisa ver a lei nem o esquema lógico, e mesmo assim teríamos um julgamento de procedência ou não da petição ao final, o mais impessoal e provavelmente o mais justo possível.
a defesa consistiria em apontar erros no esquema lógico ou falhas no nexo entre a realidade é o esquema. por exemplo:
- uma foto assim não é uma prova de que fulano vendeu, ele podia estar só passando lá perto.
- ele estava de fato só passando lá perto. do que é prova este documento mostrando seu comparecimento a uma aula do curso de direito da UFMG no mesmo horário.
perdoem-me se estiver falando besteira, mas são 5h e estou ainda dormindo. obviamente há vários pontos problemáticos aí, e quero entendê-los, mas a forma geral me parece bem razoável.
o que descrevi acima é uma proposta, digamos, de sistema jurídico que não se diferencia em nada do nosso sistema jurídico atual, exceto na forma (não no sentido escolástico). é também uma tentativa de compreender sua essência.
as vantagens desse formato ao atual são muitas:
- menos papel, coisas pra ler, repetição infinita de citações legais e longuíssimas dissertações escritas por advogados analfabetos que destroem a língua e a inteligência de todos
- diminuição drástica do tempo gasto por cada juiz em cada processo
- diminuição do poder de cada juiz (se cada ato de julgamento humano necessário em cada processo pode ser feito por qualquer juiz, sem conhecimento dos outros aspectos do mesmo processo, tudo é muito mais rápido, e cada julgamento desses pode ser feito por vários juízes diferentes, escolhidos aleatoriamente)
- diminuição da pomposidade de casa juiz: com menos poder e obrigações maus simples, um juiz não precisa ser mais uma pessoa especial que ganha milhões, pode ser uma pessoa comum, um proto-juiz, ganhando menos (o que possibilitaria até ter mais desses e aumentar a confiabilidade de cada julgamento)
- os juízes podem trabalhar da casa deles e a qualquer momento
- passa a ter sentido a existência de um sistema digital de processos (porque é ridículo que o sistema digital atual seja só uma forma de passar documentos do Word de um lado para o outro)
- o fim das audiências de conciliação, que são uma monstruosidade criada apenas pela necessidade de diminuir a quantidade de processos em tramitação e acabam retirandobo sentido da justiça (as partes são levemente pressionadas a ignorar a validade ou não das suas posições e fazer um acordo, sob pena de o juiz ficar com raiva delas depois)
milhares de precauções devem ser tomadas caso um sistema desses vá ser implantado (ahahah), talvez manter uma forma de julgamento tradicional, de corpo presente e com um juiz ou júri que tem conhecimento de toda situação, mas apenas para processos que chegarem até certo ponto, e assim por diante.
Ver também
- P2P reputation thing para um fundamento de um sistema jurídico anárquico.
-
 @ dc652bee:6154e7d0
2024-09-14 10:06:10
@ dc652bee:6154e7d0
2024-09-14 10:06:10Big eyes, big excitement! Join the fun and see what surprises await you in this thrilling game! 🎉👀 #memefi#hamsterkompat#blum http://facebooksz.lnkiy.in/Bigeyes_bot
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Why I don't like NIP-26 as a solution for key management
NIP-26 was created out of the needs of the Nostr integration at https://minds.com/. They wanted Minds users to be able to associate their "custodial" Nostr key with an external self-owned key. NIP-26 looked like a nice fit for the job, because it would allow supporting clients to associate the two identities statelessly (i.e. by just seeing one event published by Minds but with a delegation tag on it the client would be able to associate that with the self-owned external key without anything else[^1]).
The big selling point of NIP-26 (to me) was that it was fully optional. Clients were free to not implement it and they would not suffer much. They would just see "bob@minds.com" published this, and "bob-self-owned" published that. They would probably know intuitively that these two were the same person, or not, but it wouldn't be an issue. Both would still be identified as Bob and have a picture, a history and so on. Moreover, this wasn't expected to happen a lot, it would be mostly for the small intersection of people that wanted to have their own keys and also happened to be using one of these "custodial Nostr" platforms like Minds.
At some point, though, NIP-26 started to be seen as the solution for key management on Nostr. The idea is that someone will generate a very safe key on a hardware device and guard it as their most precious treasure without it ever touching the internet, and use it just to sign delegation tags. Then use multiple of these delegation tags, one for each different Nostr app, and maybe rotate them every month or so, details are unclear.
This breaks the previous expectations I had for NIP-26 entirely, as now these keys become faceless entities that can't be associated with anything except their "master" key (the one that is in cold storage). So in a world in which most Nostr users are using NIP-26 for everything, clients that do not implement NIP-26 become completely useless, as all they will see is a constant stream of random keys. They won't be able to follow anyone or interact with anyone, as these keys will not identify any concrete person on their back, they will vanish all the time and new keys will show up and the world will be chaotic. So now every client must implement NIP-26 to become usable at all, it is not optional anymore.
You may argue that making NIP-26 a de facto mandatory NIP isn't a bad thing and is worth the cost, but I think it breaks a lot of the simplicity of the protocol. It would probably be worth the cost if we knew NIP-26 was an actual complete solution, but it definitely is not, it is partial, and not the most elegant thing in the world. I think key management can be solved in multiple different ways that can all work together or not, but most importantly they can all remain optional.
More thoughts on these multiple ways can be found at Thoughts on Nostr key management.
If I am wrong about all this and we really come to the conclusion that we need a de facto mandatory key delegation method for Nostr, so be it -- but in that case, considering that we will break backwards-compatibility anyway, I think there might be a better design than NIP-26, more optimized and easier to implement, I don't know how exactly. But I really think we shouldn't rush that.
[^1]: as opposed to other suggestions that would also work, but that would require dealing with multiple events -- for example, the external user could publish a new replaceable event -- or use
kind:0-- to say they wanted to grandfather the Minds key into their umbrella, while the Minds key would also need to signal its acceptance of that. This also had the problem of requiring changes every time a new replaceable event of such kind was found. Although I am unsure now, at the time me and William agreed this was worse than NIP-26 with the delegation tag. -
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Splitpages
The simplest possible service: it splitted PDF pages in half.
Created specially to solve the problem of those scanned books that come with two pages side-by-side as if they were a single page and are much harder to read on Kindle because of that.

It required me to learn about Heroku Buildpacks though, and fork or contribute to a Heroku Buildpack that embedded a mupdf binary.
-
 @ 502ab02a:a2860397
2024-09-14 08:26:05
@ 502ab02a:a2860397
2024-09-14 08:26:05
YakiHonne คือแพลทฟอร์ม long form ที่ผมมักใช้ประจำในการทำบทความยาวๆ มาวันนี้ได้เจอคุณเวนดี้ ที่งาน Thailand Bitcoin conference 2024 รู้สึกดีใจมากๆ
siamstr
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Criteria for activating Drivechain on Bitcoin
Drivechain is, in essence, just a way to give Bitcoin users the option to deposit their coins in a hashrate escrow. If Bitcoin is about coin ownership, in theory there should be no objection from anyone on users having the option to do that: my keys, my coins etc. In other words: even if you think hashrate escrows are a terrible idea and miners will steal all coins from that, you shouldn't care about what other people do with their own money.
There are only two reasonable objections that could be raised by normal Bitcoin users against Drivechain:
- Drivechain adds code complexity to
bitcoind - Drivechain perverts miner incentives of the Bitcoin chain
If these two objections can be reasonably answered there remains no reason for not activating the Drivechain soft-fork.
1
To address 1 we can just take a look at the code once it's done (which I haven't) but from my understanding the extra validation steps needed for ensuring hashrate escrows work are very minimal and self-contained, they shouldn't affect anything else and the risks of introducing some catastrophic bug are roughly zero (or the same as the risks of any of the dozens of refactors that happen every week on Bitcoin Core).
For the BMM/BIP-301 part, again the surface is very small, but we arguably do not need that at all, since anyprevout (once that is merged) enables blind merge-mining in way that is probably better than BIP-301, and that soft-fork is also very simple, plus already loved and accepted by most of the Bitcoin community, implemented and reviewed on Bitcoin Inquisition and is live on the official Bitcoin Core signet.
2
To address 2 we must only point that BMM ensures that Bitcoin miners don't have to do any extra work to earn basically all the fees that would come from the sidechain, as competition for mining sidechain blocks would bid the fee paid to Bitcoin miners up to the maximum economical amount. It is irrelevant if there is MEV on the sidechain or not, everything that reaches the Bitcoin chain does that in form of fees paid in a single high-fee transaction paid to any Bitcoin miner, regardless of them knowing about the sidechain or not. Therefore, there are no centralization pressure or pervert mining incentives that can affect Bitcoin land.
Sometimes it's argued that Drivechain may facilitate the ocurrence of a transaction paying a fee so high it would create incentives for reorging the Bitcoin chain. There is no reason to believe Drivechain would make this more likely than an actual attack than anyone can already do today or, as has happened, some rich person typing numbers wrong on his wallet. In fact, if a drivechain is consistently paying high fees on its BMM transactions that is an incentive for Bitcoin miners to keep mining those transactions one after the other and not harm the users of sidechain by reorging Bitcoin.
Moreover, there are many factors that exist today that can be seen as centralization vectors for Bitcoin mining: arguably one of them is non-blind merge mining, of which we have a (very convoluted) example on the Stacks shitcoin, and introducing the possibility of blind merge-mining on Bitcoin would basically remove any reasonable argument for having such schemes, therefore reducing the centralizing factor of them.
- Drivechain adds code complexity to
-
 @ 1f698bd4:68d58e60
2024-09-13 23:27:37
@ 1f698bd4:68d58e60
2024-09-13 23:27:37"Mr. Tentmaker, it was nice living in this tent it was strong and secure and the sun was shining and the air was warm. But, Mr Tentmaker, it’s scary now. My tent is acting like it’s not going to hold together. The poles seem weak, and they shift with the wind. An a couple of the stakes here wiggled loose from the sand, and worst of all, the canvas has a rip. It no longer protects me from the beating rain or the stinging flies. Its scary in here, mr. Tentmaker. Last week I was sent to the repair shop and some repairman tried to path the rip in my canvas. It didn’t help much though, because the patched pulled away from the edges and now the tear is worse. What troubled me most, Mr. Tentmaker, is that the repairman didn’t seem to notice I was still in the tent. They just worked on the canvas while I shivered inside. I cried out once, but no one heard me. I guess my first real question is: Why did you give me such a flimsy tent? I can see by looking around the campground that some of the tents are much stronger and more stable than mine. Why Mr. Tent maker, did you pick a tent of such poor quality for me? And even more important, what do you intend to do about it?
God speaks: Oh little tent dweller, as the Creator and Provider of tents, I know all about you and your tent, and I love you both. I made a tent for myself once, and I lived in it on your campground. My tent was vulnerable too, and some vicious attackers ripped it to pieces while I was still in it. It was a terrible experience, but you’ll be glad to know they couldn’t hurt me. In fact, the whole occurrence was a tremendous advantage because it is this very victory over my enemy that frees me to be a present help to you. Little tent dweller, I am now prepared to come and live in your tent with you, if you will invite me. You will learn as we dwell together that real security comes from my being in your tent with you. When the storms come, you can huddle in my arms and I’ll hold you. When the canvas rips, we will go to the repair shop together. But someday, little tent dweller, your tent will collapse, for I have only designed it for temporary use. When it does, you and I will leave together. I promise not to leave before you do. And then, free of all that would hinder or restrict, we will move to our permanent home and together forever rejoice and be glad."
By Roselyn Aronson
-
 @ 1739d937:3e3136ef
2024-09-13 21:09:24
@ 1739d937:3e3136ef
2024-09-13 21:09:24This is the seventh in a series of weekly(ish) updates detailing progress on bringing MLS protocol DMs and group messaging to Nostr.
Previous Updates
Progress this week
I was told recently that my update walls of text are too much. So, I'll try to keep things concise this week. 😅
This week has been all about building the reference implementation, which is quickly becoming a full-fledged client instead of just a reference implementation. I've not quite gotten to the MLS portion of the client yet but it does already support multiple accounts (including ephemeral accounts) and loads legacy (NIP-04) chats and full contact lists. So far, I've not implemented NIP-104 so there's not yet any updates to the MLS spec or other dependencies.
If you've got experience with using messengers in hostile environments (authoritarian regimes, you've been de-platformed, etc.) please get in touch. I'd love to hear more about what you'd like to see in a communication tool.
In the meantime, I'll be over here in the corner coding with my headphones on. 👨💻
Onward and Upwards!
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28"Você só aprendeu mesmo uma coisa quando consegue explicar para os outros"
Mentira. Tá certo que existe um ponto em que você acha que sabe algo mas não consegue explicar, mas não necessariamente isso significa não saber. Conseguir explicar não depende de saber, mas de verbalizar. Podemos saber muitas coisas sem as conseguir verbalizar. Aliás, para a maior parte das experiências humanas verbalizar é que é a parte difícil. Por último, é importante dizer que a verbalização é uma abstração e portanto quando alguém tenta explicar algo e se força a fazer uma abstração está arriscando substituir a experiência concreta ou mesmo o conhecimento difuso de algo por aquela abstração e com isso ficar mais burro -- me parece que esse é risco é maior quanto mais prematura for a tentativa de explicação e quando mais sucesso a abstração improvisada fizer.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28There's a problem with using Git concepts for everything
We've been seeing a surge in applications that use Git to store other things than code, or that are based on Git concepts and so enable "forking, merging and distributed collaboration" for things like blogs, recipes, literature, music composition, normal files in a filesystem, databases.
The problem with all this is they will either:
- assume the user will commit manually and expect that commit to be composed by a set of meaningful changes, and the commiter will also add a message to the commit, describing that set of meaningful, related changes; or
- try to make the committing process automatic and hide it from the user, so will producing meaningless commits, based on random changes in many different files (it's not "files" if we are talking about a recipe or rows in a table, but let's say "files" for the sake of clarity) that will probably not be related and not reduceable to a meaningful commit message, or maybe the commit will contain only the changes to a single file, and its commit message would be equivalent to "updated
<name of the file>".
Programmers, when using Git, think in Git, i.e., they work with version control in their minds. They try hard to commit together only sets of meaningful and related changes, even when they happen to make unrelated changes in the meantime, and that's why there are commands like
git add -pand many others.Normal people, to whom many of these git-based tools are intended to (and even programmers when out of their code-world), are much less prone to think in Git, and that's why another kind of abstraction for fork-merge-collaborate in non-code environments must be used.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Custom spreadsheets
The idea was to use it to make an app that would serve as custom database for everything and interact with the spreadsheet so people could play and calculate with their values after they were created by the custom app, something like an MS Access integrated with Excel?
My first attempt that worked (I believe there was an attempt before but I have probably deleted it from everywhere) was this
react-microspreadsheetthing (at the time calledreact-spreadsheetbefore I donated the npm name to someone who asked):This was a very good spreadsheet component that did many things current "react spreadsheet" components out there don't do. It had formulas; support for that handle thing that you pulled with the mouse and it autofilled cells with a pattern; it had keyboard navigation with Ctrl, Shift, Ctrl+Shift; it had that thing through which you copy-pasted formulas and they would change their parameters depending on where you pasted them (implemented in a very poor manner because I was using and thinking about Excel in baby mode at the time).
Then I tried to make it into "a small sheet you can share" kind of app through assemblymade.com, and eventually as I tried to add more things bugs began to appear.
Then there was
cycle6-spreadsheet:If I remember well this was very similar to the other one, although made almost 2 years after. Despite having the same initial goal of the other (the multi-app custom database thing) it only yielded:
- Sidesheet, a Chrome extension that opened a spreadsheet on the side of the screen that you could use to make calculations and so on. It worked, but had too many bugs that probably caused me to give up entirely.
I'm not sure which of the two spreadsheets above powers http://sheets.alhur.es.
-
 @ 3eacaa76:bac66fe4
2024-09-13 20:43:20
@ 3eacaa76:bac66fe4
2024-09-13 20:43:20!!! Attention !!! BANGER DROP just landed on @Wavlake ! #remixculture
Funny enough that today is a day - 9/11. Maybe coincidence, maybe not. This mashup is the result of playing around mixing amazing banger tunes with proper truth-telling vocals some loops and filthy delay fx.
I created kind of my personal #Manifesto according to world issues we're facing nowadays. Still, not many people can't see this. We are early so #fuckdabanks .
Let's build on Love and Respect - We can do this. Those fuckers can't take our spirit and knowledge, so use it against them.
Avoid bullshit at any price, don't be a fucking twat and ignorant.
...and always remember to stay humble. !!!
FreePalestine
wavlake #music #remix #sound
agora #anarchy #action
2140army ----> we are commin, we are everywhere

~~~~LISTEN HERE~~~~ --->
https://wavlake.com/track/959ddd10-823d-4f55-9176-5617cc791f2e
Please share this tune world wide. Spread da vibe to da roof,

TNX for Support
MadMunky
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Democracia na América
Alexis de Tocqueville escreveu um livro só elogiando o sistema político dos Estados Unidos. E mesmo tendo sido assim, e mesmo tendo escrito o seu livro quase 100 anos antes do mais precoce sinal de decadência da democracia na América, percebeu coisas que até hoje quase ninguém percebe: o mandato da suprema corte é um enorme poder, uma força centralizadora, imune ao voto popular e com poderes altamente indefinidos e por isso mesmo ilimitados.
Não sei se ele concluiu, porém, que não existe nem pode existir balanço perfeito entre poderes. Sempre haverá furos.
De qualquer maneira, o homem é um gênio apenas por ter percebido isso e outras coisas, como o fato da figura do presidente, também obviamente um elemento centralizador, não ser tão poderosa quanto a figura de um rei da França, por exemplo. Mas ao mesmo tempo, por entre o véu de elogios (sempre muito sóbrios) deixou escapar que provavelmente também achava que não poderia durar para sempre a fraqueza do cargo de presidente.
-
 @ 361d3e1e:50bc10a8
2024-09-13 18:57:17
@ 361d3e1e:50bc10a8
2024-09-13 18:57:17Cancer characteristic of adults, sharply affects young people as well. The reasons.
cancer #health #medicine #unitedkingdom #study #research #truth
-
 @ 6bae33c8:607272e8
2024-09-13 18:09:34
@ 6bae33c8:607272e8
2024-09-13 18:09:34I went 1-4 last week, and I didn’t deserve any better. I had the Giants and Browns on the wrong side of blowouts, and the favored Falcons who lost outright to the Steelers. The only close games were the Dolphins (I lost) and the Cardinals (I won.)
But while the 1-4 leaves me less margin for error, I’m not sweating it too much. Week 1 is always a crapshoot because you’re making assumptions on limited current information.
The main hazard for Week 2 is overusing the information from Week 1, i.e., we have only a little more information for 2024
My Picks:
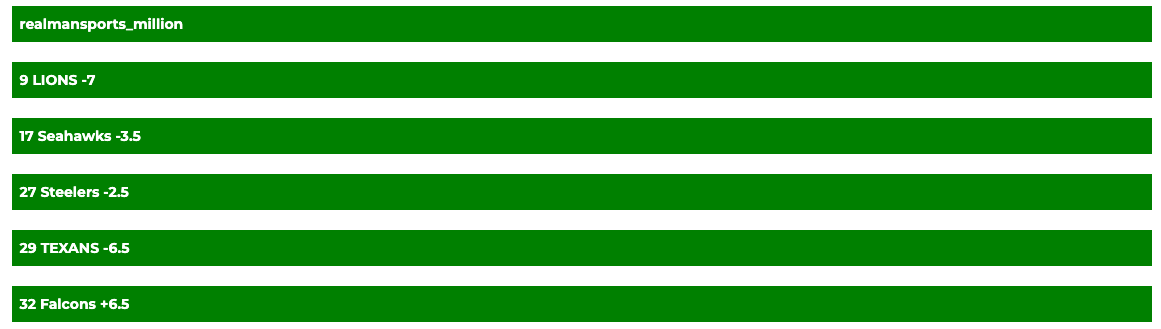 Lions -7 vs Buccaneers
Lions -7 vs BuccaneersThis is my least favorite of the five. I was stuck on four and had to pick a final one. The Bucs looked good last week at home against a soft Washington team, but I’ll sell them high. The Lions at home should move the ball at will and get some pressure on Mayfield.
Seahawks -3.5 at Patriots
The Patriots were able to hide Jacoby Brissett with a lead in Week 1, and Brissett did a good job managing the game. But if the Seahawks score some points — which they should — Brissett will have to do more and get exposed. Maybe someone on the Seahawks (unlike the Bengals) can tackle Rhamondre Stevenson too.
Steelers -2.5 at Broncos
Bo Nix looked overwhelmed to me last week, and the Steelers defense is pretty good. Justin Fields is a wild card, plenty of upside and downside, but this is a good spot where he won’t have to do much to keep up with a substandard Broncos offense.
Texans -6.5 vs Bears
Caleb Williams has to play better than in Week 1, but this line seems so small for a game in Houston I feel like I must be missing something.
Falcons +6.5 at Eagles
Kirk Cousins looked bad last week, but I’ll buy low on a Falcons team that needs to get going and sell high on the Eagles after a big Week 1 win in Brazil.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28P2P reputation thing
Each node shares a blob of the reputations they have, which includes a confidence number. The number comes from the fact that reputations are inherited from other nodes they trust and averaged by their confidence in these. Everything is mixed for plausible deniability. By default a node only shares their stuff with people they manually add, to prevent government from crawling everybody's database. Also to each added friend nodes share a different identity/pubkey (like giving a new Bitcoin address for every transaction) (derived from hip32) (and since each identity can only be contacted by one other entity the node filters incoming connections to download their database: "this identity already been used? no, yes, used with which peer?").
Network protocol
Maybe the data uploader/offerer initiates connection to the receiver over Tor so there's only a Tor address for incoming data, never an address for a data source, i.e. everybody has an address, but only for requesting data.
How to request? Post an encrypted message in an IRC room or something similar (better if messages are stored for a while) targeted to the node/identity you want to download from, along with your Tor address. Once the node sees that it checks if you can download and contacts you.
The encrypted messages could have the target identity pubkey prefix such that the receiving node could try to decrypt only some if those with some probability of success.
Nodes can choose to share with anyone, share only with pre-approved people, share only with people who know one of their addresses/entities (works like a PIN, you give the address to someone in the street, that person can reach you, to the next person you give another address etc., you can even have a public address and share limited data with that).
Data model
Each entry in a database should be in the following format:
internal_id : real_world_identifier [, real_world_identifier...] : tagWhich means you can either associate one or multiple real world identifier with an internal id and associate the real person designated by these identifiers with a tag. the tag should be part of the standard or maybe negotiated between peers. it can be things like
scammer,thief,tax collectoretc., orhonest,good dentistetc. defining good enough labels may be tricky.internal_idshould be created by the user who made the record about the person.At first this is not necessary, but additional bloat can be added to the protocol if the federated automated message posting boards are working in the sense that each user can ask for more information about a given id and the author of that record can contact the person asking for information and deliver free text to them with the given information. For this to work the internal id must be a public key and the information delivered must be signed with the correspondent private key, so the receiver of the information will know it's not just some spammer inventing stuff, but actually the person who originated that record.
-
 @ a03b38f8:2c7ce1f0
2024-09-13 16:28:42
@ a03b38f8:2c7ce1f0
2024-09-13 16:28:42Your phone is not your friend
Your phone is not your friend. It is a filthy little snitch that tells anyone who asks where you are, what you are doing, and who you are doing it with. You can obscure and hide some things through the use of privacy respecting software like encrypted communication apps, Tor pathways using Orbot, or the base OS like Graphene but metadata and geolocation is still very loud and very present. It is built into the infrastructure of how cell phones work. Your phone is tracked at all times through every cell tower area you pass through logging your IMEI and by extension your phone number and identity. This data is logged and saved forever by companies who use and sell it for corporate surveillance and post Patriot Act give it to police and government agencies warrantlessly.
Fine, I will just turn it off then. Nice try, but unless the battery can be removed it still tracks you. You didn't think it was weird that Find My Phone still works even if the phone was off?
Luddites are not off the hook. That dumb phone or flip phone is tracked just the same and since it will not run encrypted communications you are screaming out the content of every call or text and not just the metadata.
OK, I will get a burner phone or anonymous SIM card not tied to my identity. Better but not bullet proof. This is great for use and toss but if you continue to use it multiple times, around other devices that are tied to you or your social network, or take it to your home, work, or any location associated with you then it will be doxxed. Once doxxed all past information associated with it becomes now linked to you.
Metadata, Profile, and Network
Your network is very easily known and built up over time. Who are the contacts saved in your phone. Who do you interact with. Who do you call, text, email, DM, or follow on social networks. Who do you never contact but your geolocation overlaps with them often. Now look at all those contacts and who do they have a network with. A giant spider web of connections. If by 7 degrees of Kevin Bacon you have a shady contact in your network then you may get more scrutiny than you may realize.
You are spilling metadata everywhere you go along with your geolocation. Time stamps, who you contacted, how long did you talk to them, which app was used when, internet searches, map app searches, etc. People are creatures of habit and over time this metadata builds a pretty good profile on you.
Phone becomes active around 7am when they wake up. Scans social media and news sites for usually 30 minutes. Assume they are taking a shower because the phone is on but not being used until 8am most week days. Travels to coffee place on the corner most mornings and then goes to their place of work. Between 9:30 and 10:30am they again scan social media and news sites for a solid 10 minutes, probably their bathroom schedule. During lunch they frequent these locations with these people.
You get the point. This profile, plus your geolocation history, plus your network paints a pretty complete picture on you. Surprisingly it is not what you do but when you do something different that gets attention.
There was a big protest last night that we are not happy about. We already have a list of everyone who took their phones with them at that geolocation and timestamp. We run a algorithm looking for simple patterns. John is usually at a restaurant eating with friends during this time but strangely his phone was left at home and turned off during that time frame. Did anyone in his network go to the protest that we have already confirmed? Anyone in his network follow the protest Facebook page, or have a deviation from their usual pattern such as their phone being somewhere dormant when it is usually active during this time?
What can you do?
You can choose to do nothing. You can just live your life with the awareness that you are being tracked and profiled, maybe work to limit how much metadata you are spilling out to the universe. If you are a activist, a oppressed minority, live in a oppressive regime, or your country suddenly becomes oppressive this might not be an option.
Randomize or maintain your profile. This is hard but not impossible. Make your profile and habits so chaotic that any deviation is not a deviation. Most people cannot do this but if you are a couch surfing, different place constantly, new friends and new activities on the daily agent of chaos then maybe this is a option. On the opposite extreme maybe you are very regimented person so be aware of that and always stick to your routine. If you want to go to that protest but are usually home doom scrolling youtube during that time then set your phone to no sleep mode and set up to watch a long playlist of youtube videos left at home while you go to the protest.
Home phone only. Maybe you decide to have a home phone only, no not a landline, but a actual smart device that can utilize encrypted communications services but never leaves the house. This could potentially save you a lot of money on data plans, texts, and minutes if you don't buy a network plan and just use VOIP on your home WIFI. Or maybe you have a very minimum network plan and when you leave the house you either take it with you in a Faraday bag or have a secondary device that lives in a Faraday bag that only comes out for emergencies and to check in. Just be aware that the time in and out of the Faraday bag is part of your profile.
No Phone. You can have no phone whatsoever. This will not work for most people in the modern age but if you have a extreme risk profile then this might be the extreme option you need.
How do you survive with no phone or only a home phone?
Just some alternatives and some ideas. You can still buy WIFI only devices that have no network connection and / or stay in airplane mode. Old MP3 players for music and podcasts while on the go. Old phones that you can download maps to for navagation and use VIOP services in WIFI hotspots.
Emergency Communication and Go Bag
Prepper culture has given us all sorts of bags: bug out bags, get home bags, never coming back bag, and go bags. I define go bags as very small, light weight, and compact bags or kits. They carry very minimum, bare necessary gear, and ideally are so small that you actually have it on you, in your purse or computer satchel or car all of the time. Emergency communication will be part of this. This is when the burner phone, purchased with cash out of town, and stored in a Faraday bag all the time shines. It has no connection to you and has no history of use. It is a have but hope to never use oh shit device.
If you are the activist, the whistle blower, the oppressed that they could come after at any time, or the journalist that investigates corruption, organized crime, or terrorism then you need this.
I will cover go bags in more details later, probably in a key note.
Always forward, GHOST
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Token-Curated Registries
So you want to build a TCR?
TCRs (Token Curated Registries) are a construct for maintaining registries on Ethereum. Imagine you have lots of scissor brands and you want a list with only the good scissors. You want to make sure only the good scissors make into that list and not the bad scissors. For that, people will tell you, you can just create a TCR of the best scissors!
It works like this: some people have the token, let's call it Scissor Token. Some other person, let's say it's a scissor manufacturer, wants to put his scissor on the list, this guy must acquire some Scissor Tokens and "stake" it. Holders of the Scissor Tokens are allowed to vote on "yes" or "no". If "no", the manufactures loses his tokens to the holders, if "yes" then its tokens are kept in deposit, but his scissor brand gets accepted into the registry.
Such a simple process, they say, have strong incentives for being the best possible way of curating a registry of scissors: consumers have the incentive to consult the list because of its high quality; manufacturers have the incentive to buy tokens and apply to join the list because the list is so well-curated and consumers always consult it; token holders want the registry to accept good and reject bad scissors because that good decisions will make the list good for consumers and thus their tokens more valuable, bad decisions will do the contrary. It doesn't make sense, to reject everybody just to grab their tokens, because that would create an incentive against people trying to enter the list.
Amazing! How come such a simple system of voting has such enourmous features? Now we can have lists of everything so well-curated, and for that we just need Ethereum tokens!
Now let's imagine a different proposal, of my own creation: SPCR, Single-person curated registries.
Single-person Curated Registries are equal to TCR, except they don't use Ethereum tokens, it's just a list in a text file kept by a single person. People can apply to join, and they will have to give the single person some amount of money, the single person can reject or accept the proposal and so on.
Now let's look at the incentives of SPCR: people will want to consult the registry because it is so well curated; vendors will want to enter the registry because people are consulting it; the single person will want to accept the good and reject the bad applicants because these good decisions are what will make the list valuable.
Amazing! How such a single proposal has such enourmous features! SPCR are going to take over the internet!
What TCR enthusiasts get wrong?
TCR people think they can just list a set of incentives for something to work and assume that something will work. Mix that with Ethereum hype and they think theyve found something unique and revolutionary, while in fact they're just making a poor implementation of "democracy" systems that fail almost everywhere.
The life is not about listing a set of "incentives" and then considering the problems solved. Almost everybody on the Earth has the incentive for being rich: being rich has a lot of advantages over being poor, however not all people get rich! Why are the incentives failing?
Curating lists is a hard problem, it involves a lot of knowledge about the problem that just holding a token won't give you, it involves personal preferences, politics, it involves knowing where is the real limit between "good" and "bad". The Single Person list may have a good result if the single person doing the curation is knowledgeable and honest (yes, you can game the system to accept your uncle's scissors and not their competitor that is much better, for example, without losing the entire list reputation), same thing for TCRs, but it can also fail miserably, and it can appear to be good but be in fact not so good. In all cases, the list entries will reflect the preferences of people choosing and other things that aren't taken into the incentives equation of TCR enthusiasts.
We don't need lists
The most important point to be made, although unrelated to the incentive story, is that we don't need lists. Imagine you're looking for a scissor. You don't want someone to tell if scissor A or B are "good" or "bad", or if A is "better" than B. You want to know if, for your specific situation, or for a class of situations, A will serve well, and do that considering A's price and if A is being sold near you and all that.
Scissors are the worst example ever to make this point, but I hope you get it. If you don't, try imagining the same example with schools, doctors, plumbers, food, whatever.
Recommendation systems are badly needed in our world, and TCRs don't solve these at all.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Lightning and its fake HTLCs
Lightning is terrible but can be very good with two tweaks.
How Lightning would work without HTLCs
In a world in which HTLCs didn't exist, Lightning channels would consist only of balances. Each commitment transaction would have two outputs: one for peer
A, the other for peerB, according to the current state of the channel.When a payment was being attempted to go through the channel, peers would just trust each other to update the state when necessary. For example:
- Channel
AB's balances areA[10:10]B(in sats); Asends a 3sat payment throughBtoC;AasksBto route the payment. ChannelABdoesn't change at all;Bsends the payment toC,Caccepts it;- Channel
BCchanges fromB[20:5]CtoB[17:8]C; BnotifiesAthe payment was successful,Aacknowledges that;- Channel
ABchanges fromA[10:10]BtoA[7:13]B.
This in the case of a success, everything is fine, no glitches, no dishonesty.
But notice that
Acould have refused to acknowledge that the payment went through, either because of a bug, or because it went offline forever, or because it is malicious. Then the channelABwould stay asA[10:10]BandBwould have lost 3 satoshis.How Lightning would work with HTLCs
HTLCs are introduced to remedy that situation. Now instead of commitment transactions having always only two outputs, one to each peer, now they can have HTLC outputs too. These HTLC outputs could go to either side dependending on the circumstance.
Specifically, the peer that is sending the payment can redeem the HTLC after a number of blocks have passed. The peer that is receiving the payment can redeem the HTLC if they are able to provide the preimage to the hash specified in the HTLC.
Now the flow is something like this:
- Channel
AB's balances areA[10:10]B; Asends a 3sat payment throughBtoC:AasksBto route the payment. Their channel changes toA[7:3:10]B(the middle number is the HTLC).Boffers a payment toC. Their channel changes fromB[20:5]CtoB[17:3:5]C.CtellsBthe preimage for that HTLC. Their channel changes fromB[17:3:5]CtoB[17:8]C.BtellsAthe preimage for that HTLC. Their channel changes fromA[7:3:10]BtoA[7:13]B.
Now if
Awants to trickBand stop respondingBdoesn't lose money, becauseBknows the preimage,Bjust needs to publish the commitment transactionA[7:3:10]B, which gives him 10sat and then redeem the HTLC using the preimage he got fromC, which gives him 3 sats more.Bis fine now.In the same way, if
Bstops responding for any reason,Awon't lose the money it put in that HTLC, it can publish the commitment transaction, get 7 back, then redeem the HTLC after the certain number of blocks have passed and get the other 3 sats back.How Lightning doesn't really work
The example above about how the HTLCs work is very elegant but has a fatal flaw on it: transaction fees. Each new HTLC added increases the size of the commitment transaction and it requires yet another transaction to be redeemed. If we consider fees of 10000 satoshis that means any HTLC below that is as if it didn't existed because we can't ever redeem it anyway. In fact the Lightning protocol explicitly dictates that if HTLC output amounts are below the fee necessary to redeem them they shouldn't be created.
What happens in these cases then? Nothing, the amounts that should be in HTLCs are moved to the commitment transaction miner fee instead.
So considering a transaction fee of 10000sat for these HTLCs if one is sending Lightning payments below 10000sat that means they operate according to the unsafe protocol described in the first section above.
It is actually worse, because consider what happens in the case a channel in the middle of a route has a glitch or one of the peers is unresponsive. The other node, thinking they are operating in the trustless protocol, will proceed to publish the commitment transaction, i.e. close the channel, so they can redeem the HTLC -- only then they find out they are actually in the unsafe protocol realm and there is no HTLC to be redeemed at all and they lose not only the money, but also the channel (which costed a lot of money to open and close, in overall transaction fees).
One of the biggest features of the trustless protocol are the payment proofs. Every payment is identified by a hash and whenever the payee releases the preimage relative to that hash that means the payment was complete. The incentives are in place so all nodes in the path pass the preimage back until it reaches the payer, which can then use it as the proof he has sent the payment and the payee has received it. This feature is also lost in the unsafe protocol: if a glitch happens or someone goes offline on the preimage's way back then there is no way the preimage will reach the payer because no HTLCs are published and redeemed on the chain. The payee may have received the money but the payer will not know -- but the payee will lose the money sent anyway.
The end of HTLCs
So considering the points above you may be sad because in some cases Lightning doesn't use these magic HTLCs that give meaning to it all. But the fact is that no matter what anyone thinks, HTLCs are destined to be used less and less as time passes.
The fact that over time Bitcoin transaction fees tend to rise, and also the fact that multipart payment (MPP) are increasedly being used on Lightning for good, we can expect that soon no HTLC will ever be big enough to be actually worth redeeming and we will be at a point in which not a single HTLC is real and they're all fake.
Another thing to note is that the current unsafe protocol kicks out whenever the HTLC amount is below the Bitcoin transaction fee would be to redeem it, but this is not a reasonable algorithm. It is not reasonable to lose a channel and then pay 10000sat in fees to redeem a 10001sat HTLC. At which point does it become reasonable to do it? Probably in an amount many times above that, so it would be reasonable to even increase the threshold above which real HTLCs are made -- thus making their existence more and more rare.
These are good things, because we don't actually need HTLCs to make a functional Lightning Network.
We must embrace the unsafe protocol and make it better
So the unsafe protocol is not necessarily very bad, but the way it is being done now is, because it suffers from two big problems:
- Channels are lost all the time for no reason;
- No guarantees of the proof-of-payment ever reaching the payer exist.
The first problem we fix by just stopping the current practice of closing channels when there are no real HTLCs in them.
That, however, creates a new problem -- or actually it exarcebates the second: now that we're not closing channels, what do we do with the expired payments in them? These payments should have either been canceled or fulfilled before some block x, now we're in block x+1, our peer has returned from its offline period and one of us will have to lose the money from that payment.
That's fine because it's only 3sat and it's better to just lose 3sat than to lose both the 3sat and the channel anyway, so either one would be happy to eat the loss. Maybe we'll even split it 50/50! No, that doesn't work, because it creates an attack vector with peers becoming unresponsive on purpose on one side of the route and actually failing/fulfilling the payment on the other side and making a profit with that.
So we actually need to know who is to blame on these payments, even if we are not going to act on that imediatelly: we need some kind of arbiter that both peers can trust, such that if one peer is trying to send the preimage or the cancellation to the other and the other is unresponsive, when the unresponsive peer comes back, the arbiter can tell them they are to blame, so they can willfully eat the loss and the channel can continue. Both peers are happy this way.
If the unresponsive peer doesn't accept what the arbiter says then the peer that was operating correctly can assume the unresponsive peer is malicious and close the channel, and then blacklist it and never again open a channel with a peer they know is malicious.
Again, the differences between this scheme and the current Lightning Network are that:
a. In the current Lightning we always close channels, in this scheme we only close channels in case someone is malicious or in other worst case scenarios (the arbiter is unresponsive, for example). b. In the current Lightning we close the channels without having any clue on who is to blame for that, then we just proceed to reopen a channel with that same peer even in the case they were actively trying to harm us before.
What is missing? An arbiter.
The Bitcoin blockchain is the ideal arbiter, it works in the best possible way if we follow the trustless protocol, but as we've seen we can't use the Bitcoin blockchain because it is expensive.
Therefore we need a new arbiter. That is the hard part, but not unsolvable. Notice that we don't need an absolutely perfect arbiter, anything is better than nothing, really, even an unreliable arbiter that is offline half of the day is better than what we have today, or an arbiter that lies, an arbiter that charges some satoshis for each resolution, anything.
Here are some suggestions:
- random nodes from the network selected by an algorithm that both peers agree to, so they can't cheat by selecting themselves. The only thing these nodes have to do is to store data from one peer, try to retransmit it to the other peer and record the results for some time.
- a set of nodes preselected by the two peers when the channel is being opened -- same as above, but with more handpicked-trust involved.
- some third-party cloud storage or notification provider with guarantees of having open data in it and some public log-keeping, like Twitter, GitHub or a Nostr relay;
- peers that get paid to do the job, selected by the fact that they own some token (I know this is stepping too close to the shitcoin territory, but could be an idea) issued in a Spacechain;
- a Spacechain itself, serving only as the storage for a bunch of
OP_RETURNs that are published and tracked by these Lightning peers whenever there is an issue (this looks wrong, but could work).
Key points
- Lightning with HTLC-based routing was a cool idea, but it wasn't ever really feasible.
- HTLCs are going to be abandoned and that's the natural course of things.
- It is actually good that HTLCs are being abandoned, but
- We must change the protocol to account for the existence of fake HTLCs and thus make the bulk of the Lightning Network usage viable again.
See also
- Channel
-
 @ 6ad3e2a3:c90b7740
2024-09-13 15:58:12
@ 6ad3e2a3:c90b7740
2024-09-13 15:58:12This is the story of our time.
The Emperor was scammed by fake weavers, who used a clever trick: They posed as experts in their craft and declared their work invisible to simpletons. In other words, if you did not go along with the scam, it was because you were stupid or of low character. Or, in modern parlance, you were a conspiracy theorist or an anti-vaxxer.
The story applies to so many facets of present narrative — from Joe Biden’s transparently declining cognitive capacity to the preposterously phony war on “disinformation,” there is stiff competition for the best example. But if I had to choose, it would be the “safe and effective” mRNA shots — they check all the boxes: veneration of “experts”, political and business interests masquerading as “The Science” and disparagement of those who were skeptical as stupid, selfish, childish and evil. Any questioning of the safety or efficacy of the mRNA shots could get you attacked by angry online mobs, deplatformed from social media or even fired from your job.
Why are people going along with the “safe and effective” narrative in the face of an unprecedented number of adverse effects, the sketchy track record of large pharmaceutical companies in putting profits above safety, the rush of these products to market more quickly than any prior vaccine, the fact it has not been updated to reflect the new strains, its quickly-waning efficacy such that multiple boosters are already needed in fewer than 18 months, the fact it doesn’t stop (and may increase) the spread and the relatively mild nature of the virus for those under 50 who don’t have pre-existing conditions? Surely, this emperor’s pale, flaccid gluteus maximi are flapping about in public view.
There are certain conditions under which people are especially likely to pretend the naked emperor is dressed, all of which have been met in this case:
-
Many powerful people are pot-committed to “safe and effective.”
-
Everyone knows powerful people are committed.
-
Everyone knows that everyone knows powerful people are committed.
Every elected official who required mandates, every corporation who forced people to get the shot as a condition for employment, the corporate news media, its on-air hosts, executives and board members, every doctor who advised it, many parents who gave it to their kids, every person who shamed others for not going along — and there were many — heads of state, the CDC, the WHO, etc. are pot committed. (Pot-committed is a poker term for when someone has put such a large percentage of his chips into a pot there is virtually no way he can fold his hand.)
If the mRNA shot were shown to be unsafe, the liability, both legally (I know they received a waiver under the EUA, but fraud, for example, would invalidate that), reputationally and worse (criminal prosecutions might be warranted, given it was mandated) would be catastrophic for them. In other words, many of the world’s most powerful people have a lot to lose if the mRNA shots were shown to have harmed and/or killed thousands of healthy young people who were at minuscule risk from covid itself. They will not easily be persuaded this happened, and they have massive incentives to destroy anyone making headway in persuading others. There are powerful forces who need you to view the emperor as clothed.
The second condition is that everyone is well aware of this. Any researcher contemplating speaking out or going deeper into the data to that end knows he could be blackballed, cut off from funding and any prospect at a career in science or academia. Any person who speaks up knows he could lose his job, get deplatformed or run afoul of the soon-to-be-created Bureau of Disinformation. In fact, you would expect the powerful to create just such a bureau under these conditions — when they have too much to lose should the word get out.
Finally, it’s not simply that everyone knows, but that everyone knows that everyone knows, i.e., per Ben Hunt, it’s common knowledge that you don’t screw with the pharmaceutical cartels and those who do their bidding. It’s not just you who are deterred, but you know everyone else has a similar deterrent. People who blow the whistle therefore expect to be ridiculed, destroyed and tarred as conspiracy theorists and also don’t expect their friends and colleagues to come to their aid.
With these three conditions present, we can all hail the incredibly safe and effective mRNA treatments are a miracle! Thank God we have them and are finally able to get out of this pandemic! The emperor has such a wonderful suit of clothes!
In the story, it took a child to blurt out the obvious, that the emperor was exposing his sagging, unsightly posterior. Interestingly, once he did, everyone else acknowledged the obvious, but the emperor — and members of his procession, who were going along — went on with the show. They were in too deep to back out.
I suspect that’s going on now — the child has noticed, word is getting out. They are desperately trying to shut it down with the most Orwellian measures (Bureau of Disinformation!) They will not succeed, but lasting damage has been done, and more will be inflicted before it’s over. The biggest question now is the lengths to which the emperor’s minions will go — creating a ministry of truth is extreme, but that pales in comparison to, say, starting World War III.
There are other reasons for a world war too — the collapse of the giant global debt bubble and the fallout therefrom — but in both cases the stakes are nearly infinite for those responsible, given how much damage has been done to the average person. We’d be wise not to underestimate the risks they’d run to avoid accountability.
-
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28idea: "numbeo" with satoshis
This site has a crowdsourced database of cost-of-living in many countries and cities: https://www.numbeo.com/cost-of-living/ and it sells the data people write there freely. It's wrong!
Could be an fruitful idea to pay satoshis for people to provide data.
-
 @ 361d3e1e:50bc10a8
2024-09-13 15:38:50
@ 361d3e1e:50bc10a8
2024-09-13 15:38:50Biden and Kamala and then Trump walk into the hall with the same people - see how they were greeted
biden #harris #kamalaharris #trump #usa #politics
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28gravity
IPFS is nice as a personal archiving tool (edit: it's not). You store a bunch of data and make it available to the public.
The problem is that no one will ever know you have that data, therefore you need a place to publish it somewhere. Gravity was an attempt of being the tool for this job.
It was a website that showcased the collections from users, and it was also a command-line client that used your IPFS keys for authentication and allowed you to paste IPFS URIs and names and descriptions.
The site was intended to be easy to run so you could have multiple stellar bodies aggregating content and interact with them all in a standardized manner.
It also had an ActivityPub/"fediverse" integration so people could follow Gravity server users from Mastodon and friends and see new data they published as "tweets".
See also
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28notes on "Economic Action Beyond the Extent of the Market", Per Bylund
Source: https://www.youtube.com/watch?v=7St6pCipCB0
Markets work by dividing labour, but that's not as easy as it seems in the Adam Smith's example of a pin factory, because
- a pin factory is not a market, so there is some guidance and orientation, some sort of central planning, inside there that a market doesn't have;
- it is not clear how exactly the production process will be divided, it is not obvious as in "you cut the thread, I plug the head".
Dividing the labour may produce efficiency, but it also makes each independent worker in the process more fragile, as they become dependent on the others.
This is partially solved by having a lot of different workers, so you do not depend on only one.
If you have many, however, they must agree on where one part of the production process starts and where it ends, otherwise one's outputs will not necessarily coincide with other's inputs, and everything is more-or-less broken.
That means some level of standardization is needed. And indeed the market has constant incentives to standardization.
The statist economist discourse about standardization is that only when the government comes with a law that creates some sort of standardization then economic development can flourish, but in fact the market creates standardization all the time. Some examples of standardization include:
- programming languages, operating systems, internet protocols, CPU architectures;
- plates, forks, knifes, glasses, tables, chairs, beds, mattresses, bathrooms;
- building with concrete, brick and mortar;
- money;
- musical instruments;
- light bulbs;
- CD, DVD, VHS formats and others alike;
- services that go into every production process, like lunch services, restaurants, bakeries, cleaning services, security services, secretaries, attendants, porters;
- multipurpose steel bars;
- practically any tool that normal people use and require a little experience to get going, like a drilling machine or a sanding machine; etc.
Of course it is not that you find standardization in all places. Specially when the market is smaller or new, standardization may have not arrived.
There remains the truth, however, that division of labour has the potential of doing good.
More than that: every time there are more than one worker doing the same job in the same place of a division of labour chain, there's incentive to create a new subdivision of labour.
From the fact that there are at least more than one person doing the same job as another in our society we must conclude that someone must come up with an insight about an efficient way to divide the labour between these workers (and probably actually implement it), that hasn't happened for all kinds of jobs.
But to come up with division of labour outside of a factory, some market actors must come up with a way of dividing the labour, actually, determining where will one labour stop and other start (and that almost always needs some adjustments and in fact extra labour to hit the tips), and also these actors must bear the uncertainty and fragility that division of labour brings when there are not a lot of different workers and standardization and all that.
In fact, when an entrepreneur comes with a radical new service to the market, a service that does not fit in the current standard of division of labour, he must explain to his potential buyers what is the service and how the buyer can benefit from it and what he will have to do to adapt its current production process to bear with that new service. That's has happened not long ago with
- services that take food orders from the internet and relay these to the restaurants;
- hostels for cheap accommodation for young travellers;
- Uber, Airbnb, services that take orders and bring homemade food from homes to consumers and similars;
- all kinds of software-as-a-service;
- electronic monitoring service for power generators;
- mining planning and mining planning software; and many other industry-specific services.
See also
-
 @ 8d34bd24:414be32b
2024-09-13 15:09:18
@ 8d34bd24:414be32b
2024-09-13 15:09:18I’ve recently had discussions with several people about the deity of Jesus Christ. They did not believe Jesus was God. I believe that the Bible claims Jesus is God and is part of the trinity (3 persons in one God). I know the 3-in-1 nature of God is confusing and hard to understand, but who wants to worship a God that is totally understandable by our human and mortal minds? I want to worship a God who is so awesome that we, the creatures, cannot fully comprehend Him because He is so much more than we have ever seen or imagined.
Now let’s go through multiple Scriptural evidences that Jesus is God. I don't want you to take my word that Jesus is God. I want you to believe it because the Bible says it and therefore God says it.
The Basic Claims of Jesus
Let’s start with the basics.
In John 10:30 Jesus says "I and the Father are one.”\ \ This sure sounds like Jesus is claiming to be God. I know some people claim that this is just Jesus saying that He is one with God or that they have the same goals. I find this interpretation to be hard to believe because I think Jesus speaks clearly and the most obvious interpretation is usually the intended meaning especially when you are speaking of God’s word. He created man and created the ability to communicate. I don’t believe He would ever speak unclearly or in a way that would lead people to blasphemy. The most obvious interpretation of what Jesus meant is that He is one with God.
"If you had known Me, you would have known My Father also; from now on you know Him, and have seen Him.”\ Philip *said to Him, “Lord, show us the Father, and it is enough for us.” Jesus said to him, “Have I been so long with you, and yet you have not come to know Me, Philip? He who has seen Me has seen the Father; how can you say, ‘Show us the Father’?" (John 14:7-9) {Emphasis Mine}
Jesus says knowing Him is knowing the Father and if you have seen Him you have seen the Father. This can only be true if they are one. Some may say that Jesus is just saying that seeing Him is like seeing God the Father because they are acting in agreement, but this once again is not the most obvious interpretation and I do not believe that God the Father or Jesus would speak in a misleading or unclear manner that could lead people astray.\ \ Even back in Genesis there is reference to the trinitarian nature of God. Genesis 1:26a says, "Then God said, ‘Let Us make man in Our image, according to Our likeness’" God refers to Himself in the plural. There are lots of other similar references in the Old Testament. This is early evidence of the trinitarian nature of God that was not clearly revealed until the New Testament (just as His plan for salvation was not revealed until the New Testament).
"Jesus answered them, “I showed you many good works from the Father; for which of them are you stoning Me?” The Jews answered Him, “For a good work we do not stone You, but for blasphemy; and because You, being a man, make Yourself out to be God.” Jesus answered them, “Has it not been written in your Law, ‘I said, you are gods’? If he called them gods, to whom the word of God came (and the Scripture cannot be broken), do you say of Him, whom the Father sanctified and sent into the world, ‘You are blaspheming,’ because I said, ‘I am the Son of God’? If I do not do the works of My Father, do not believe Me; but if I do them, though you do not believe Me, believe the works, so that you may know and understand that the Father is in Me, and I in the Father.” (John 10:32-38) {Emphasis Mine}
In this passage the Jews accuse Jesus of "blasphemy; and because You, being a man, make Yourself out to be God.” Jesus is being accused of claiming to be God, but Jesus does not deny being God. He says He does His miracles "so that you may know and understand that the Father is in Me, and I in the Father.” Jesus continues to claim to be God. Even if it is possible to explain Jesus’s claim “that the Father is in Me, and I in the Father” could mean that they have the same goals, it would be incomprehensible for Jesus to make an unclear statement that sounds like a claim to be God if He wasn’t while being accused of claiming to be God. If He isn't God, then He is guilty of blasphemy and can't save anyone. He doesn't allow people to think He is a good man, a prophet, or a teacher, but not God.1
Jesus’s biggest claim to be God is probably:
Jesus said to them, “Truly, truly, I say to you, before Abraham was born, I am.” (John 8:58)
Jesus started His statement with “Truly, Truly” (literally Amen, Amen). This repetition is used in Hebrew literature as an emphasis to mean pay attention to this statement. Then He claims “before Abraham was born, I am.” This is a doubly stunning statement because Abraham had died more than a thousand years before Jesus was physically born and because “I am” is what God told Moses to call Him at the burning bush.
Then Moses said to God, “Behold, I am going to the sons of Israel, and I will say to them, ‘The God of your fathers has sent me to you.’ Now they may say to me, ‘What is His name?’ What shall I say to them?” God said to Moses, “I AM WHO I AM”; and He said, “Thus you shall say to the sons of Israel, ‘I AM has sent me to you.’ ” (Exodus 3:13-14)
Jesus claimed the exalted name of God for Himself while claiming to exist since before Abraham. If Jesus is good, then Jesus must be God.
The Example of Godly Men and Angels
Let’s look at how angels and godly people react when accused of being or believed to be God.
When Paul & Silas were preaching in Lystra, the people thought they were gods because of the miracles they were performing through God’s power. Their response made it crystal clear that they were not to be worshipped.
But when the apostles Barnabas and Paul heard of it, they tore their robes and rushed out into the crowd, crying out and saying, “Men, why are you doing these things? We are also men of the same nature as you, and preach the gospel to you that you should turn from these vain things to a living God, who made the heaven and the earth and the sea and all that is in them. (Acts 14:14-15) {Emphasis Mine}
They didn’t reply that they were God’s messengers or working through God’s power and will. They said, “why are you doing these things? We are also men of the same nature as you.” There was no lack of clarity and they cleared up the misunderstanding as fast as possible.
When Peter was sent to Cornelius in answer to Cornelius’s prayer, Cornelius fell down to worship Peter, but Peter instantly made it clear that this was wrong.
When Peter entered, Cornelius met him, and fell at his feet and worshiped him. But Peter raised him up, saying, “Stand up; I too am just a man.” (Acts 10:25-26) {Emphasis Mine}
There was no mistake in his response that would allow anyone to think he was god. Peter gave God alone the glory.
We can even look at the example of an angel sent by God when John mistakenly fell at the angel’s feet to worship him:
Then he said to me, “Write, ‘Blessed are those who are invited to the marriage supper of the Lamb.’ ” And he said to me, “These are true words of God.” Then I fell at his feet to worship him. But he said to me, “Do not do that; I am a fellow servant of yours and your brethren who hold the testimony of Jesus; worship God. For the testimony of Jesus is the spirit of prophecy.” (Revelation 19:9-10) {Emphasis Mine}
The angel would not allow anyone to worship him even though he was a great messenger of God.
Jesus’s Response to Worship
Let’s contrast these responses to Jesus’s responses.
One of the synagogue officials named Jairus came up, and on seeing Him, fell at His feet and implored Him earnestly, saying, “My little daughter is at the point of death; please come and lay Your hands on her, so that she will get well and live.” And He went off with him; and a large crowd was following Him and pressing in on Him. (Mark 5:22-24) {Emphasis Mine}
Notice that Jesus did not rebuke Jairus for falling at His feet. He went to help him with the ultimate miracle, healing his servant.
But after hearing of Him, a woman whose little daughter had an unclean spirit immediately came and fell at His feet. Now the woman was a Gentile, of the Syrophoenician race. And she kept asking Him to cast the demon out of her daughter. And He was saying to her, “Let the children be satisfied first, for it is not good to take the children’s bread and throw it to the dogs.” But she answered and *said to Him, “Yes, Lord, but even the dogs under the table feed on the children’s crumbs.” And He said to her, “Because of this answer go; the demon has gone out of your daughter.” (Mark 7:25-29) {Emphasis Mine}
This woman fell at Jesus’s feet and called Him Lord (Adonai), but Jesus did not correct her. He gave to her her request because she believed in Him.
In the same way:
Therefore, when Mary came where Jesus was, she saw Him, and fell at His feet, saying to Him, “Lord, if You had been here, my brother would not have died.” (John 11:32) {Emphasis Mine}
Mary also fell at Jesus’s feet and called Him Lord without being corrected. Jesus accept this worship because He rightly deserved the worship and being called Lord because He is God. He confirmed His right to have people fall at His feet because He followed it up with raising Lazarus from the dead.
In this next passage, a man didn’t just fall at Jesus’s feet or call Him Lord, this man worshipped Jesus.
Jesus heard that they had put him out, and finding him, He said, “Do you believe in the Son of Man?” He answered, “Who is He, Lord, that I may believe in Him?” Jesus said to him, “You have both seen Him, and He is the one who is talking with you.” And he said, “Lord, I believe.” And he worshiped Him. And Jesus said, “For judgment I came into this world, so that those who do not see may see, and that those who see may become blind.” (John 9:35-39) {Emphasis Mine}
This man believed that Jesus was Lord and God and worshipped Him as such. Jesus did not reprimand this man for worshipping him instead of God. He accepted the worship and rebuked the hard hearted Pharisees that were in attendance.
When Jesus was walking on water past the boat holding his disciples, and Peter called out to Him. Jesus called Peter out to join Him. When Peter began to sink in unbelief, Jesus rescued him and calmed the sea. Then:
When they got into the boat, the wind stopped. And those who were in the boat worshiped Him, saying, “You are certainly God’s Son!” (Matthew 14:32-33) {Emphasis Mine}
This is yet another example of Jesus being worshipped and accepting the worship rather than rebuking them for worshipping a false god. If Jesus was just a man. This would be sin, but 2 Corinthians 5:21 says of Jesus, “He made Him who knew no sin to be sin on our behalf, so that we might become the righteousness of God in Him.” If Jesus is sinless, He has to be God because He accepted the worship of people.
In the Ten Commandments:
“You shall have no other gods before Me.\ “You shall not make for yourself an idol, or any likeness of what is in heaven above or on the earth beneath or in the water under the earth. You shall not worship them or serve them; for I, the Lord your God, am a jealous God, visiting the iniquity of the fathers on the children, on the third and the fourth generations of those who hate Me, (Exodus 20:3-5) {Emphasis Mine}
God makes it perfectly clear that nobody can be worshipped other than Himself. The fact that Jesus repeatedly allows people to fall at His feet and worship Him means He is either God, a blasphemer and the worst of sinners, or a madman. He has not left us any other options.
There are multiple additional examples of Jesus being worshipped and accepting worship.
Right after being raised from the dead:
And behold, Jesus met them and greeted them. And they came up and took hold of His feet and worshiped Him. Then Jesus said to them, “Do not be afraid; go and take word to My brethren to leave for Galilee, and there they will see Me.” (Matthew 28:9-10) {Emphasis Mine}
When His disciples “took hold of His feet and worshiped Him,” His response was “Do not be afraid” instead of “Do not worship me.”
When they saw Him, they worshiped Him; but some were doubtful. And Jesus came up and spoke to them, saying, “All authority has been given to Me in heaven and on earth. Go therefore and make disciples of all the nations, baptizing them in the name of the Father and the Son and the Holy Spirit, teaching them to observe all that I commanded you; and lo, I am with you always, even to the end of the age.” (Matthew 28:17-20) {Emphasis Mine}
Jesus’s response to being worshipped is to say that He has “All authority … in heaven and on earth” and to tell them to “observe all that I commanded you.” If He was only a godly man, he would have rebuked the worshippers not talked about His authority and commands.
While He was blessing them, He parted from them and was carried up into heaven. And they, after worshiping Him, returned to Jerusalem with great joy, and were continually in the temple praising God. (Luke 24:51-53) {Emphasis Mine}
I think I’ve have given plenty of examples to show that Jesus accepted worship and therefore is either God or a blaspheming sinner. No good man or Godly teacher would ever allow another to worship him without rebuking them.
The Word Made Flesh
In the beginning was the Word, and the Word was with God, and the Word was God. He was in the beginning with God. All things came into being through Him, and apart from Him nothing came into being that has come into being. In Him was life, and the life was the Light of men.... And the Word became flesh, and dwelt among us, and we saw His glory, glory as of the only begotten from the Father, full of grace and truth. John testified about Him and cried out, saying, “This was He of whom I said, ‘He who comes after me has a higher rank than I, for He existed before me.’ ” For of His fullness we have all received, and grace upon grace. For the Law was given through Moses; grace and truth were realized through Jesus Christ. " (John 1:1-4, 14-17) {Emphasis Mine}
“In the beginning was the Word” refers to before time and space began. This refers to God, the first cause of all things that exist.
The Word "was with God" and "was God" and "All things came into being through Him" (aka He is creator). These verses are explicitly saying that the Word is God and implying He is God since He is the creator.
At the end of the verse it is made clear who “The Word” is. John is referring to Jesus Christ as “The Word.” John the Baptist also refers to Jesus as God when he talks of His higher rank and that Jesus existed before John (Other gospels say John was physically born first, so this refers to Jesus existing well before His physical birth).
The Bible clearly teaches that Jesus is God and I am seriously concerned that anyone who denies Jesus’s deity will be one of those referred to in this passage:
Many will say to Me on that day, ‘Lord, Lord, did we not prophesy in Your name, and in Your name cast out demons, and in Your name perform many miracles?’ And then I will declare to them, ‘I never knew you; depart from Me, you who practice lawlessness.’ (Matthew 7:22-23)
If you are one of those who believes that Jesus is only a good man, a good teacher, a prophet, or a righteous man created for God’s purpose, I beg you to do like these Christians who were praised for their actions:
Now these were more noble-minded than those in Thessalonica, for they received the word with great eagerness, examining the Scriptures daily to see whether these things were so. (Acts 17:11)
Trust Jesus.\ \ your sister in Christ,
Christy
Bible verses are NASB (New American Standard Bible) 1995 edition unless otherwise stated
FYI, I’ve included this extended passage without commentary because it is an excellent passage describing the trinity and including God the Father, God the Son, and God the Holy Spirit.
8Philip *said to Him, “Lord, show us the Father, and it is enough for us.” 9Jesus *said to him, “Have I been so long with you, and yet you have not come to know Me, Philip? He who has seen Me has seen the Father; how can you say, ‘Show us the Father’? 10Do you not believe that I am in the Father, and the Father is in Me? The words that I say to you I do not speak on My own initiative, but the Father abiding in Me does His works. 11Believe Me that I am in the Father and the Father is in Me; otherwise believe because of the works themselves. 12Truly, truly, I say to you, he who believes in Me, the works that I do, he will do also; and greater works than these he will do; because I go to the Father. 13Whatever you ask in My name, that will I do, so that the Father may be glorified in the Son. 14If you ask Me anything in My name, I will do it.
15 “If you love Me, you will keep My commandments.
16 I will ask the Father, and He will give you another Helper, that He may be with you forever; 17that is the Spirit of truth, whom the world cannot receive, because it does not see Him or know Him, but you know Him because He abides with you and will be in you.
18 “I will not leave you as orphans; I will come to you. 19After a little while the world will no longer see Me, but you will see Me; because I live, you will live also. 20In that day you will know that I am in My Father, and you in Me, and I in you. 21He who has My commandments and keeps them is the one who loves Me; and he who loves Me will be loved by My Father, and I will love him and will disclose Myself to him.” (John 14:8-21) {Emphasis Mine}
This post is scheduled to publish on Sunday, September 15th on my Trust Jesus Substack, but is being published early on nostr due to a discussion that occurred here.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Veterano não é dono de bixete
"VETERANO NÃO É DONO DE BIXETE". A frase em letras garrafais chama a atenção dos transeuntes neófitos. Paira sobre um cartaz amarelo que lista várias reclamações contra os "trotes machistas", que, na opinião do responsável pelo cartaz, "não é brincadeira, é opressão".
Eis aí um bizarro exemplo de como são as coisas: primeiro todos os universitários aprovam a idéia do trote, apoiam sua realização e até mesmo desejam sofrer o trote -- com a condição de o poderem aplicar eles mesmos depois --, louvam as maravilhas do mundo universitário, onde a suprema sabedoria se esconde atrás de rituais iniciáticos fora do alcance da imaginação do homem comum e rude, do pobre e do filhinho-de-papai das faculdades privadas; em suma: fomentam os mais baixos, os mais animalescos instintos, a crueldade primordial, destroem em si mesmos e nos colegas quaisquer valores civilizatórios que tivessem sobrado ali, ficando todos indistingüíveis de macacos agressivos e tarados.
Depois vêm aí com um cartaz protestar contra os assédios -- que sem dúvida acontecem em larguíssima escala -- sofridos pelas calouras de 17 anos e que, sendo também novatas no mundo universitário, ainda conservam um pouco de discernimento e pudor.
A incompreensão do fenômeno, porém, é tão grande, que os trotes não são identificados como um problema mental, uma doença que deve ser tratada e eliminada, mas como um sintoma da opressão machista dos homens às mulheres, um produto desta civilização paternalista que, desde que Deus é chamado "o Pai" e não "a Mãe", corrompe a benéfica, pura e angélica natureza do homem primitivo e o torna esta tão torpe criatura.
Na opinião dos autores desse cartaz é preciso, pois, continuar a destruir o que resta da cultura ocidental, e então esperar que haja trotes menos opressores.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A crappy zk-rollups explanation attempt
(Considering the example of zksync.io) (Also, don't believe me on any of this.)
- They are sidechains.
- You move tokens to the sidechain by depositing it on an Ethereum contract. Then your account is credited in the sidechain balance.
- Then you can make payments inside the sidechain by signing transactions and sending them to a central operator.
- The central operator takes transactions from a bunch of people, computes the new sidechain balances state and publishes a hash of that state to the Ethereum contract.
- The idea is that a single transaction in the blockchain contains a bunch of sidechain transactions.
- The operator also sends to the contract an abbreviated list of the sidechain transactions. The trick is making all signatures condensed in a single zero-knowledge proof which is enough for the contract to verify that the transition from the previous state to the new is good.
- Apparently they can fit 500 sidechain transactions in one mainchain transaction (each is 12 bytes). So I believe it's fair to say all this zk-rollup fancyness could be translated into "a system for aggregating transactions".
-
I don't understand how the zero-knowledge proof works, but in this case it is a SNARK and requires a trusted setup, which I imagine is similar to this one.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Rede Relâmpago
Ao se referir à Lightning Network do O que é Bitcoin?, nós, brasileiros e portugueses, devemos usar o termo "Relâmpago" ou "Rede Relâmpago". "Relâmpago" é uma palavra bonita e apropriada, e fácil de pronunciar por todos os nossos compatriotas. Chega de anglicismos desnecessários.
Exemplo de uma conversa hipotética no Brasil usando esta nomenclatura:
– Posso pagar com Relâmpago? – Opa, claro! Vou gerar um boleto aqui pra você.Repare que é bem mais natural e fácil do que a outra alternativa:
– Posso pagar com láitenim? – Leite ninho? -
 @ 87730827:746b7d35
2024-09-13 12:42:31
@ 87730827:746b7d35
2024-09-13 12:42:31As an avid RSS user, I've always been on the lookout for the perfect feed reader. Recently, I made the switch from FreshRSS to Miniflux, and I wanted to share my experience with the Nostr community.
Why Miniflux?
Miniflux caught my attention as a simpler alternative to FreshRSS. Don't get me wrong, FreshRSS is a powerful tool, but sometimes less is more. Here's why Miniflux has won me over:
- Minimalist Design: Miniflux strips away the unnecessary, focusing on what matters most - your feeds.
- Speed: With its lightweight architecture, Miniflux is blazing fast, even with a large number of feeds.
- Third-party App Support: This is where Miniflux really shines. The ecosystem of third-party apps is robust and growing.
- Easy Self-Hosting: If you're into self-hosting like me, Miniflux makes it a breeze.
- Vim Keybindings: As a Vim enthusiast, I absolutely love that the Miniflux web client comes with default Vim keybindings. This feature significantly speeds up my workflow and makes navigation a breeze.
Third-Party Apps: The Icing on the Cake
Speaking of third-party apps, I've been experimenting with MiniFlutt (https://github.com/docmarty84/miniflutt). It's a Flutter-based mobile client for Miniflux that brings the simplicity of the web version to your pocket. MiniFlutt is just one example of the diverse app ecosystem surrounding Miniflux. Whether you prefer mobile, desktop, or web-based clients, chances are you'll find something that suits your needs.
Final Thoughts
If you're looking for a no-frills RSS reader that does its job exceptionally well, give Miniflux a try. The transition from FreshRSS was smooth, I was able to import all my feeds from an OPML file and I haven't looked back since. Remember, the best RSS reader is the one that fits your workflow. For me, Miniflux's simplicity and third-party app support make it a winner. What's your go-to RSS solution?
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Haskell Monoids
You've seen that
<>syntax and noticed it is imported fromData.Monoid?I've always thought
<>was a pretty complex mathematical function and it was very odd that people were using it forTextvalues, like"whatever " <> textValue <> " end.".It turns out
Textis a Monoid. That means it implements the Monoid class (or typeclass), that means it has a particular way of being concatenated. Any list could be a Monoid, any abstraction you can think of for which it makes sense to concatenate could be a Monoid, and it would use the same<>syntax. What exactly<>would do with that value when concatenating depends on its typeclass implementation of Monoid.We can assume, for example, that
Textimplements Monoid by just joining the text bytes, and now we can use<>without getting puzzled about it. -
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Truthcoin as a spacechain
To be clear, the term "spacechain" here refers only to the general concept of blindly merge-mined (BMM) chains without a native money-token, not including the "spacecoins".
The basic idea is that for Truthcoin/Hivemind to work we need
- Balances of Votecoin tokens, i.e. a way to keep track of who owns how much of the oracle corporation;
- Bitcoin tokens to be used for buying and selling prediction market shares, i.e. money to gamble;
- A blockchain, i.e. some timestamping service that emits blocks ordered with transactions and can keep track of internal state and change the state -- including the balances of the Votecoin tokens and of the Bitcoin tokens that are assigned to individual prediction markets according to predefined rules;
A spacechain, i.e. a blindly merge-mined chain, gives us 1 and 3. We can just write any logic for that and that should be very easy. It doesn't give us 2, and it also has the problem of how the spacechain users can pay the spacechain miners (which is why the spacecoins were envisioned in the first place, but we don't have spacecoins here).
But remember we have votecoins already. Votecoins (VTC) should represent a share in the oracle corporation, which means they entitle their holders to some revenue -- even though they also burden their holders with the duty to vote in event outcomes (at the risk of losing part of their own votecoin balance) --, and they can be exchanged, so we can assume they will have some value.
So we could in theory use these valuable tokens to pay the spacechain miners. That wouldn't be great because it pervert their original purpose and wouldn't solve the problem 2 from above -- unless we also used the votecoins to bet in which case they wouldn't be just another shitcoin in the planet with no network effect competing against Bitcoin and would just cause harm to humanity.
What we can do instead is to create a native mechanism for issuing virtual Bitcoin tokens (vBTC) in this chain, collaterized by votecoins, then we can use these vBTC to both gamble (solve problem 2) and pay miners (fix the hole in the spacechain BMM design).
For example, considering the VTC to be worth 0.001 BTC, any VTC holder could put 0.005 VTC and get 0.001 vBTC, then use to gamble or sell to others who want to gamble. The VTC holder still technically owns the VTC and can and must still participate in the oracle decisions. They just have to pay the BTC back before they can claim their VTC back if they want to send it elsewhere.
They stand to gain by selling vBTC if there is a premium for vBTC over BTC (i.e. people want to gamble) and then rebuying vBTC back once that premium goes away or reverts itself.
For this scheme to work the chain must know the exchange rate between VTC and BTC, which can be provided by the oracle corporation itself.
-
 @ e27ae11e:e0c36580
2024-09-13 12:35:33
@ e27ae11e:e0c36580
2024-09-13 12:35:33Choosing colors involves a thoughtful process that takes into account various factors to ensure that the final palette achieves the desired effect, whether it’s for design, branding, or art. Here’s a detailed breakdown of the process: 1. Understand the Purpose Before diving into color selection, it's crucial to understand the purpose of the color scheme. Are you designing a brand identity, creating a website, painting a room, or something else? Each scenario may have different requirements and goals. For instance, branding colors need to align with the brand’s personality and values, while interior colors might focus on mood and comfort. 2. Know Your Audience Consider the preferences and cultural meanings associated with colors for your target audience. Different colors can evoke various emotions and associations. For example, blue often represents trust and calmness, while red can signify excitement and urgency. Understanding your audience’s cultural context and psychological responses to colors can help you choose a palette that resonates with them. 3. Research Color Theory Color theory is a foundational aspect of choosing colors. It involves understanding how colors interact with each other and the effects they produce. Key concepts include: Color Wheel: A circular diagram of colors arranged by their chromatic relationship. It helps in understanding primary, secondary, and tertiary colors. Complementary Colors: Colors opposite each other on the color wheel, such as blue and orange. They create high contrast and stand out. Analogous Colors: Colors next to each other on the color wheel, such as blue, teal, and green. They create harmony and are pleasing to the eye. Triadic Colors: Three colors evenly spaced around the color wheel, such as red, yellow, and blue. They offer vibrant contrast while maintaining balance. Monochromatic Colors: Variations of one hue, including tints and shades. They provide a cohesive and unified look. 4. Create a Mood Board A mood board is a visual tool that helps you gather inspiration and visualize how different colors work together. Collect images, fabric swatches, color samples, and any other materials that represent the mood or aesthetic you're aiming for. This can help you see how colors interact and narrow down your choices. 5. Consider Color Psychology Color psychology examines how colors affect human behavior and emotions. For instance: Red: Stimulates energy and urgency, often used in promotions or to grab attention. Blue: Conveys trust, calm, and professionalism, making it popular for corporate and tech brands. Green: Represents nature, growth, and tranquility, often used in eco-friendly and health-related contexts. Yellow: Evokes warmth and optimism but can be overwhelming if overused. By incorporating color psychology, you can choose colors that align with the emotional response you want to elicit. 6. Select a Base Color Start by choosing a base color that will dominate your design. This color sets the tone and direction for the rest of the palette. The base color should align with the overall goal and purpose of your project. 7. Build a Color Palette With your base color in mind, build a color palette by selecting complementary, analogous, or triadic colors that work well together. Use color schemes and tools, such as Adobe Color or Coolors, to experiment with different combinations. Ensure that the palette is balanced and harmonious. 8. Test Your Colors Once you have a palette, test how the colors look in real-world scenarios. For digital designs, check how they appear on various screens and under different lighting conditions. For physical spaces, sample paint colors or materials in the actual environment to see how they look at different times of day and under various lighting conditions. 9. Consider Accessibility Accessibility is a crucial factor, especially in digital design. Ensure that your color choices provide enough contrast for readability and usability. Tools like the WebAIM Contrast Checker can help you evaluate whether your color combinations meet accessibility standards. 10. Refine and Finalize After testing, refine your color choices as needed. Make adjustments based on feedback, functionality, and aesthetic preferences. Finalize the color palette that best meets your goals and resonates with your audience. 11. Document Your Palette Once you’ve settled on a color palette, document it for consistency. Create a color guide or style guide that includes color codes (such as HEX, RGB, or CMYK values) and usage guidelines. This ensures that the colors are used consistently across different applications and mediums. 12. Stay Current Color trends can evolve, so it’s important to stay informed about current color trends and how they might influence your choices. However, prioritize timelessness and relevance to your specific project over fleeting trends. Conclusion The process of choosing colors is a blend of creativity, psychology, and practical considerations. By understanding the purpose, audience, and principles of color theory, you can create a color palette that effectively communicates your message, evokes the desired emotions, and enhances the overall design.
-
 @ 7579076d:1bbfcb19
2024-09-13 12:00:20
@ 7579076d:1bbfcb19
2024-09-13 12:00:20Amber 2.0.0
- New sign keys, to use this version you will need to first backup your accounts, uninstall the old version and install the new version
- When you not configured a notification type Amber will ask you to configure and default to direct connection to relays
- Check if is a valid relay before adding it when changing the default relays or adding a relay to a application
Download it with zap.store, Obtainium, f-droid or download it directly in the releases page
If you like my work consider making a donation
Verifying the release
In order to verify the release, you'll need to have
gpgorgpg2installed on your system. Once you've obtained a copy (and hopefully verified that as well), you'll first need to import the keys that have signed this release if you haven't done so already:bash gpg --keyserver hkps://keys.openpgp.org --recv-keys 44F0AAEB77F373747E3D5444885822EED3A26A6DOnce you have his PGP key you can verify the release (assuming
manifest-v2.0.0.txtandmanifest-v2.0.0.txt.sigare in the current directory) with:bash gpg --verify manifest-v2.0.0.txt.sig manifest-v2.0.0.txtYou should see the following if the verification was successful:
bash gpg: Signature made Fri 13 Sep 2024 08:06:52 AM -03 gpg: using RSA key 44F0AAEB77F373747E3D5444885822EED3A26A6D gpg: Good signature from "greenart7c3 <greenart7c3@proton.me>"That will verify the signature on the main manifest page which ensures integrity and authenticity of the binaries you've downloaded locally. Next, depending on your operating system you should then re-calculate the sha256 sum of the binary, and compare that with the following hashes:
bash cat manifest-v2.0.0.txtOne can use the
shasum -a 256 <file name here>tool in order to re-compute thesha256hash of the target binary for your operating system. The produced hash should be compared with the hashes listed above and they should match exactly. -
 @ 8e7e2128:25e34fd1
2024-09-13 10:07:37
@ 8e7e2128:25e34fd1
2024-09-13 10:07:37Have you ever dreamed of a non-invasive way to improve your skin's appearance without the pain and downtime of traditional treatments?
Look no further than Healite LED Therapy. This innovative technology harnesses the power of light to rejuvenate and revitalize your skin, leaving you with a radiant and youthful glow. What is Healite LED Therapy?
Healite LED Therapy utilizes light-emitting diodes (LEDs) to deliver specific wavelengths of light to the skin. These wavelengths penetrate the skin's layers, stimulating cellular activity and promoting healing. Unlike lasers, which can be intense and potentially damaging, LED therapy is gentle and safe for most skin types.
How Does Healite LED Therapy Work?
When LED light is applied to the skin, it triggers a series of biological processes that can improve skin health. These processes include:
Increased collagen production: Collagen is a protein that gives the skin its structure and elasticity. LED therapy can stimulate the production of collagen, helping to reduce wrinkles and fine lines. Improved blood circulation: LED light can increase blood flow to the skin, providing essential nutrients and oxygen to the cells. This can help to improve skin tone and texture. Reduced inflammation: LED therapy can help to reduce inflammation, which is often associated with skin conditions like acne and rosacea. Enhanced wound healing: LED therapy can accelerate the healing process of wounds, including cuts, scrapes, and surgical incisions.The Benefits of Healite LED Therapy
Non-invasive and painless: Healite LED Therapy is a completely non-invasive treatment that requires no needles or incisions. The procedure is generally comfortable and painless. Safe for all skin types: Unlike some other skin treatments, LED therapy is suitable for all skin types, including sensitive skin. Effective for a wide range of skin concerns: LED therapy can be used to address a variety of skin issues, including acne, wrinkles, fine lines, sun damage, and uneven skin tone. Minimal downtime: Most people can resume their normal activities immediately after a Healite LED Therapy treatment. Long-lasting results: While the results of LED therapy may vary depending on individual factors, many people experience long-lasting improvements in their skin's appearance.Who is a Good Candidate for Healite LED Therapy?
Individuals who are seeking to improve their skin's health and appearance may be good candidates for Healite LED Therapy. This treatment is particularly effective for those who:
Have acne or acne scars Experience premature aging or wrinkles Have sun damage or uneven skin tone Want to enhance their skin's overall radianceIf you're looking for a gentle, effective, and non-invasive way to rejuvenate your skin, Healite LED Therapy may be the perfect solution for you.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O mito do objetivo
O insight deste cara segundo o qual buscar objetivos fixos, além de matar a criatividade, ainda não consegue atingir o tal objetivo -- que é uma coisa na qual eu sempre acreditei, embora sem muitas confirmações e (talvez por isso) sem dizê-lo abertamente --, combina com a idéia geral de que todas as estruturas sociais que valem alguma coisa surgem do jogo e brincadeira.
A seriedade, que é o oposto da brincadeira, é representada aqui pelo objetivo. Pessoas muito sérias com um planejamento e um objetivo final, tudo esquematizado.
Na verdade esse insight é bem manjado. Até eu mesmo já o tinha mencionado, citando Taleb em Processos Antifrágeis.
E finalmente há esta tirinha que eu achei aleatoriamente e que bem o representa:
-
 @ 733a7b6e:9c4a4b9b
2024-09-13 10:03:04
@ 733a7b6e:9c4a4b9b
2024-09-13 10:03:04Lorem ipsum
Lorem ipsum dolor sit amet, consectetur adipiscing elit[^1]. Sed non risus. Suspendisse lectus tortor, dignissim sit amet, adipiscing nec, ultricies sed, dolor. Cras elementum ultrices diam. Maecenas ligula massa, varius a, semper congue, euismod non, mi. Proin porttitor, orci nec nonummy molestie, enim est eleifend mi, non fermentum diam nisl sit amet erat. Duis semper. Duis arcu massa, scelerisque vitae, consequat in, pretium a, enim. Pellentesque congue. Ut in risus volutpat libero pharetra tempor. Cras vestibulum bibendum augue. Praesent egestas leo in pede. Praesent blandit odio eu enim. Pellentesque sed dui ut augue blandit sodales. Vestibulum ante ipsum primis in faucibus orci luctus et ultrices posuere cubilia Curae; Aliquam nibh. Mauris ac mauris sed pede pellentesque fermentum. Maecenas adipiscing ante non diam sodales hendrerit.
Ut velit mauris, egestas sed
Ut velit mauris, egestas sed, gravida nec, ornare ut, mi. Aenean ut orci vel massa suscipit pulvinar. Nulla sollicitudin. Fusce varius, ligula non tempus aliquam, nunc turpis ullamcorper nibh, in tempus sapien eros vitae ligula. Pellentesque rhoncus nunc et augue. Integer id felis. Curabitur aliquet pellentesque diam. Integer quis metus vitae elit lobortis egestas. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Morbi vel erat non mauris convallis vehicula. Nulla et sapien. Integer tortor tellus, aliquam faucibus, convallis id, congue eu, quam. Mauris ullamcorper felis vitae erat. Proin feugiat, augue non elementum posuere, metus purus iaculis lectus, et tristique ligula justo vitae magna.
[^1]: Ut velit mauris, egestas sed.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A prediction market as a distributed set of oracle federations
See also: Truthcoin as a spacechain.
This is not Truthcoin, but hopefully the essence of what makes it good is present here: permissionless, uncensorable prediction markets for fun, profit, making cheap talk expensive and revolutionizing the emergence and diffusion of knowledge in society.
The idea
The idea is just to reuse Fedimint's codebase to implement federated oracle corporations that will host individual prediction markets inside them.
Pegging in and out of a federation can be done through Lightning gateways, and once inside the federation users can buy and sell shares of individual markets using a native LMSR market-maker.
Then we make a decentralized directory of these bets using something simple like Nostr so everybody can just join any market very easily.
Why?
The premise of this idea is that we can't have a centralized prediction market platform because governments will shut it down, but we can instead have a pseudonymous oracle corporation that also holds the funds being gambled at each time in a multisig Bitcoin wallet and hope for the best.
Each corporation may exist to host a single market and then vanish afterwards -- its members returning later to form a new corporation and host a new market before leaving again.
There is custodial risk, but the fact that the members may accrue reputation as the time passes and that this is not one big giant multisig holding all the funds of everybody but one multisig for each market makes it so this is slightly better.
In any case, no massive amounts are expected to be used in this scheme, which defeats some of the use cases of prediction markets (funding public goods, for example), but since these are so advanced and society is not yet ready for them, we can leave them for later and first just try to get some sports betting working.
This proto-truthcoin implementation should work just well enough to increase the appetite of bitcoiners and society in general for more powerful prediction markets.
Why is this better than DLCs?
Because DLCs have no liquidity. In their current implementations and in all future plans from DLC enthusiasts they don't even have order books. They're not seen very much as general-purpose prediction markets, but mostly as a way to create monetary instruments and derivatives.
They could work as prediction markets, but then they would need order books and order books are terrible for liquidity. LMSR market makers are much better.
But it is custodial!
If you make a public order book tied to known oracles using a DLC the oracle may also be considered custodial since it becomes really easy for him to join multiple trades as a counterpart then lie and steal the money. The bets only really "discreet" if they're illiquid meaningless bets between two guys. If they're happening in a well-known public place they're not discreet anymore.
DLC proponents may say this can be improved by users using multiple oracles and forming effectively a federation between them, but that is hardly different from choosing a reputable oracle corporation in this scheme and trusting that for the life of the bet.
But Hivemind is better!
Yes.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Liberalismo oitocentista
Quando comecei a ler sobre "liberalismo" na internet havia sempre umas listas de livros recomendados, uns Ludwig von Mises, Milton Friedman e Alexis de Tocqueville. "A Democracia na América". Pra mim parecia estranho aquele papo de democracia quando eu estava interessado era em como funcionaria um mercado livre, sem regulações e tal.
Parece que Tocqueville era uma herança do mesmo povo que adorava a expressão "liberalismo clássico". O liberalismo clássico era uma coisa política que ia contra a monarquia e em favor da democracia, e aí Tocqueville se encaixava muito bem.
Poucos anos se passaram e tudo mudou. Agora acho que alguém lendo na internet não vai ver menção nenhuma a Tocqueville ou liberalismo clássico, essa chatice de democracia e suas chatices legalistas. O "libertarianismo", também um nome infeliz, tomou conta de tudo, e cresceu muito mais do que o movimento liberal-da-internet jamais imaginou que seria possível.
Os libertários brasileiros são anarquistas, detestam a democracia, reconhecem nela um vetor de ataque dos socialistas a qualquer pontinha de livre-mercado que exista -- e às liberdades individuais dos cidadãos (este aqui ainda um ponto em comum com os liberais oitocentistas). São inclusive muito mais propensos a defender a monarquia do que a democracia.
E isso é uma coisa boa. Finalmente uma pessoa pode defender princípios razoáveis de livre-mercado e individualismo sem precisar se associar com o movimento setecentistas e oitocentista que fez coisas boas, mas também foi responsável por coisas horríveis como a revolução francesa e todos os seus absurdos, e de onde saiu todo o movimento socialista.
-
 @ 6bae33c8:607272e8
2024-09-13 08:22:42
@ 6bae33c8:607272e8
2024-09-13 08:22:42That was annoying. I have Tua in one league and of course he got concussed on one of his two scrambles. At least he had the decency to have 145 passing yards and a TD when he did it. But the bigger problem is the Dolphins offense. Why not some play action on 1st-and-10 every now and then. It was just run-run-obvious passing down with a totally immobile “eggshell plaintiff” QB. I know they lost Terron Armstead, but the game was already salted away at that point.
The other crazy thing was they kept De’Von Achane in with an ankle injury during garbage time. The guy weighs 188 pounds, but they’re tacking on carries like he’s John Riggins. As an Achane owner I’ll take the production, but it made little sense.
Three silver linings: I have no shares of Josh Allen. I have no shares of Tyreek Hill. And Tyler Bass’ shank cost whoever was using him too.
-
Allen played well but had to do very little, and James Cook even got a goal-line carry for the TD.
-
Cook had only 11 carries and one target, but somehow scored three times on a team where the QB vultures most of the goal-line carries. Enjoy it, but don’t get used to it.
-
Dalton Kincaid looked good, breaking tackles every time he touched the ball, and it was nice to see them get him involved early on short screens. But game flow wasn’t in his favor, and he wasn’t used much after that.
-
Khalil Shakir is probably the team’s No. 1 WR, but it’s hard to rely on him. Curtis Samuel, if it wasn’t obvious before, is a cut. Keon Coleman isn’t playable now either, borderline cut, but in NFFC I’d give him more time.
-
Tua’s first pick wasn’t his fault, but the booth bent over backwards to excuse him for the second one (blamed the WR) and then he was of course at fault for the pick six. He’s accurate from the pocket and has good touch, but now he’s concussed for the 25th time, so who knows going forward? That it’s so dangerous for him to run (and even more so now) is a serious handicap. He has 10 days to get ready for Week 3, but given his history, I’m not sure he plays. Skylar Thompson was terrible in relief too.
-
Achane is just a fantasy points producing machine whenever he’s playing. Mike McDaniel apparently doesn’t worry about pitch counts, either.
-
Jaylen Wright had a couple carries for loss, but looked okay. Definitely a hold despite the ugly box score.
-
Jonnu Smith who I drafted in a few places (and unfortunately dropped in one or two) is the Dolphins third or fourth WR (depending on how you classify Achane.) He looked nimble, and if/when Tua returns has a floor in that offense now.
-
Another dumb thing McDaniel did was go to the up-back (Alec Ingold) twice in a row on fourth and short. The first time, fine, you have the element of surprise. But the Bills were waiting for it the second time, and it got stuffed.
-
Hill and Waddle have to get more targets, and they will. But if Thompson is the QB, it’s obviously a big downgrade for both.
-
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28tempreites
My first library to get stars on GitHub, was a very stupid templating library that used just HTML and HTML attributes ("DSL-free"). I was inspired by http://microjs.com/ at the time and ended up not using the library. Probably no one ever did.
-
 @ a012dc82:6458a70d
2024-09-13 08:07:27
@ a012dc82:6458a70d
2024-09-13 08:07:27Table Of Content
-
The Self-Custody Movement
-
Impact on Exchange Supply
-
Future Implications
-
Conclusion
-
FAQ
The exchange supply of Bitcoin has been witnessing a steady decline as more people opt for self-custody solutions. This trend has caught the attention of investors and analysts alike, as it could have significant implications for the cryptocurrency's price and overall market dynamics. In this article, we will explore the reasons behind this shift and what it means for the future of Bitcoin.
The Self-Custody Movement
In recent years, the self-custody movement has gained traction as a growing number of Bitcoin users have started to move their funds from centralized exchanges to private wallets. This allows users to maintain full control over their digital assets, as opposed to relying on third parties to secure their funds.
1. Security Concerns One of the primary reasons people are shifting to self-custody is the increasing number of security breaches and hacks that have plagued cryptocurrency exchanges. By holding their Bitcoin in private wallets, users can mitigate the risk of losing their funds due to exchange vulnerabilities or fraudulent activities.
2. Financial Sovereignty Another driving force behind the self-custody movement is the desire for financial sovereignty. By holding their own private keys, users can exercise complete control over their digital assets, eliminating the need for intermediaries like banks and exchanges.
Impact on Exchange Supply
As more users withdraw their Bitcoin from exchanges and move them to private wallets, the exchange supply decreases. This can lead to several potential consequences:
1. Reduced Selling Pressure With fewer Bitcoins available for trading on exchanges, the selling pressure is likely to decrease, which could result in a more stable price or even upward price movements.
2. Enhanced Liquidity As the exchange supply diminishes, the available liquidity for trading can be affected, which might lead to increased volatility in the market.
3. Strengthened Decentralization The shift towards self-custody can also contribute to the decentralization of the Bitcoin network, making it more resistant to censorship and control.
Future Implications
The decline in exchange supply is an important trend to watch, as it may have several implications for the future of Bitcoin:
1. Growing Adoption of Decentralized Exchanges (DEXs) As users become more security-conscious and seek financial sovereignty, we may see an increased adoption of decentralized exchanges. These platforms allow users to trade directly from their private wallets, thereby reducing the need for centralized intermediaries.
2. Enhanced Security Measures by Centralized Exchanges In response to the growing demand for self-custody, centralized exchanges may be forced to improve their security measures and provide better custody solutions to retain users.
Conclusion
The ongoing decrease in the exchange supply of Bitcoin can be attributed to the growing adoption of self-custody solutions. As more people move their funds to private wallets, this trend is likely to impact market dynamics, liquidity, and the overall decentralization of the Bitcoin network. It is essential for investors and market participants to keep a close eye on these developments, as they will shape the future of the cryptocurrency landscape.
FAQ
Why are people moving to self-custody? The main reasons behind the shift to self-custody include security concerns due to exchange hacks, a desire for financial sovereignty, and an increasing preference for decentralized solutions.
How does the decrease in exchange supply impact Bitcoin's price? Reduced exchange supply can lead to decreased selling pressure, which could result in a more stable price or even upward price movements. However, the overall impact on price depends on various factors, such as market sentiment and demand.
What are the potential consequences of decreasing exchange supply? Some consequences of decreasing exchange supply include reduced selling pressure, enhanced liquidity, and strengthened decentralization of the Bitcoin network.
How does the self-custody trend affect decentralized exchanges (DEXs)? The growing demand for self-custody may lead to increased adoption of decentralized exchanges, as they allow users to trade directly from their private wallets without relying on centralized intermediaries.
How can centralized exchanges respond to the self-custody movement? Centralized exchanges can improve their security measures, provide better custody solutions, and integrate with decentralized services to retain users and adapt to the changing landscape.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Money Supply Measurement
What if we measured money supply measured by probability of being spent -- or how near it is to the point in which it is spent? bonds could be money if they're treated as that by their owners, but they are likely to be not near the spendpoint as cash, other assets can also be considered money but they might be even farther.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
A command line utility to create and manage personal graphs, then write them to dot and make images with graphviz.
It manages a bunch of YAML files, one for each entity in the graph. Each file lists the incoming and outgoing links it has (could have listen only the outgoing, now that I'm tihnking about it).
Each run of the tool lets you select from existing nodes or add new ones to generate a single link type from one to one, one to many, many to one or many to many -- then updates the YAML files accordingly.
It also includes a command that generates graphs with graphviz, and it can accept a template file that lets you customize the
dotthat is generated and thus the graphviz graph.rel
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A flexibilidade da doutrina socialista
Os fatos da revolução russa mostram que Lênin e seus amigos bolcheviques não eram só psicopatas assassinos: eles realmente acreditavam que estavam fazendo o certo.
Talvez depois de um tempo o foco deles tenha mudado mais para o lado de se preocuparem menos com a vida e o bem-estar dos outros do que com eles mesmos, mas não houve uma mudança fundamental.
Ao mesmo tempo, a doutrina socialista na qual eles acreditavam era enormemente flexível, assim como a dos esquerdistas de hoje. É a mesma doutrina: uma coleção de slogans que pode ser adaptada para apoiar ou ir contra qualquer outra tese ou ação.
Me parece que a justificativa que eles encontraram para fazer tantas coisas claramente ruins vem dessas mesma flexibilidade. Os atos cruéis estavam todos justificados pela mesma coleção de slogans socialistas de sempre, apenas adaptados às circunstâncias.
Será que uma doutrina mais sólida se prestaria a essas atrocidades? Se concluirmos que a flexibilidade vem da mente e não da doutrina em si, sim, mas não acho que venha daí, porque é sempre o socialismo que é flexível, nunca nenhuma outra doutrina. Ou, na verdade, o socialismo é tão flexível que ele envolve e integra qualquer outra doutrina que seja minimamente compatível.
Talvez a flexibilidade esteja mesmo na mente, mas existe alguma relação entre a mente que desconhece a coerência e a lógica e a mente que se deixa atrair pelos slogans socialistas.
-
 @ 733a7b6e:9c4a4b9b
2024-09-13 07:36:15
@ 733a7b6e:9c4a4b9b
2024-09-13 07:36:15Lorem ipsum
Lorem ipsum dolor sit amet, consectetur adipiscing elit[^1]. Sed non risus. Suspendisse lectus tortor, dignissim sit amet, adipiscing nec, ultricies sed, dolor. Cras elementum ultrices diam. Maecenas ligula massa, varius a, semper congue, euismod non, mi. Proin porttitor, orci nec nonummy molestie, enim est eleifend mi, non fermentum diam nisl sit amet erat. Duis semper. Duis arcu massa, scelerisque vitae, consequat in, pretium a, enim. Pellentesque congue. Ut in risus volutpat libero pharetra tempor. Cras vestibulum bibendum augue. Praesent egestas leo in pede. Praesent blandit odio eu enim. Pellentesque sed dui ut augue blandit sodales. Vestibulum ante ipsum primis in faucibus orci luctus et ultrices posuere cubilia Curae; Aliquam nibh. Mauris ac mauris sed pede pellentesque fermentum. Maecenas adipiscing ante non diam sodales hendrerit.
Ut velit mauris, egestas sed
Ut velit mauris, egestas sed, gravida nec, ornare ut, mi. Aenean ut orci vel massa suscipit pulvinar. Nulla sollicitudin. Fusce varius, ligula non tempus aliquam, nunc turpis ullamcorper nibh, in tempus sapien eros vitae ligula. Pellentesque rhoncus nunc et augue. Integer id felis. Curabitur aliquet pellentesque diam. Integer quis metus vitae elit lobortis egestas. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Morbi vel erat non mauris convallis vehicula. Nulla et sapien. Integer tortor tellus, aliquam faucibus, convallis id, congue eu, quam. Mauris ullamcorper felis vitae erat. Proin feugiat, augue non elementum posuere, metus purus iaculis lectus, et tristique ligula justo vitae magna.
[^1]: Ut velit mauris, egestas sed.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28"House" dos economistas e o Estado
Falta um gênio pra produzir um seriado tipo House só que com economistas. O House do seriado seria um austríaco é o "everybody lies" seria uma premissa segundo a qual o Estado é sempre a causa de todos os problemas.
Situações bem cabeludas poderiam ser apresentadas de maneira que parecesse muito que a causa era ganância ou o mau-caratismo dos agentes, mas na investigação quase sempre se descobriria que a causa era o Estado.
Parece ridículo, mas se eu descrevesse House assim aqui também pareceria. A execução é que importa.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28How to attack Bitcoin, Anthony Towns' take
In his Bitcoin in 2021 blog post, Anthony Towns lists some strategies that can be used to attack Bitcoin without it looking like an attack:
- Big companies centralizing funding on them. If a big company like Square, for example, pays most of the development work it can pretty much control the focus of the project and what PRs will be prioritized and what will be ostracized (and they could even make it look like multiple companies are doing it when in fact all the money and power is coming from a single one).
- Attackers "willing to put in the time to establish themselves as Bitcoin contributors", which is an effort some individuals may be doing, and a big company like Square can fund.
- Creating changes that seem to improve things but are ultimately unnecessary and introducing deliberate vulnerabilities there. All these vulnerabilities are super hard to spot even by the most experienced reviewers.
- Creating more and more changes, and making them all pristine and correct, exhausting all the patience of reviewers, just to introduce a subtle bug somewhere in the middle. The more changes happening, more people will need to review. This gets much worse if for every 10 people 6 or 7 are being funded by the same attacker entity to just generate more noise while purposefully leaving the review work to the other, unpaid honest contributors.
- Moving code around for the sake of modularization gives an attacker the opportunity to change small things without anyone noticing, because reviewers will be looking at the changes expecting them to be just the same old code moved to other places, not changed. Even harder to spot.
- Another way of gaining control of the repository and the development process is to bribe out honest developers into making other things, so they'll open up space for malicious developers. For example, if a company like Square started giving grants for Bitcoin Core developers to relax a little and start working on cooler projects of their own choices while getting paid much more, they would very likely accept it.
- Still another way is to make the experience of some honest contributors very painful and annoying or ostracizing them. He cites what might be happening today with LukeDashjr, one of the most important and competent Bitcoin Core developers, who doesn't get any funding from anyone, despite wanting it and signing up for grant programs.
-
 @ 733a7b6e:9c4a4b9b
2024-09-13 07:24:47
@ 733a7b6e:9c4a4b9b
2024-09-13 07:24:47Ceci est une tentative de publication sur Nostr
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28idea: Graph subjective reputation as a service
The idea more-or-less coded in https://github.com/fiatjaf/multi-service-reputation-rfc, but if it is as good as I think it is, it could be sold for websites without any need for information sharing and without it being an open protocol.
It could be used by websites just to show subjective reputations inside their own site (as that isn't so trivial to build, but it is still desirable).
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28hyperscript-go
A template rendering library similar to hyperscript for Go.
Better than writing HTML and Golang templates.
See also
-
 @ 1f698bd4:68d58e60
2024-09-13 03:13:26
@ 1f698bd4:68d58e60
2024-09-13 03:13:26Dear family in Christ,
We want to update you on the latest developments regarding our visa. We have finally received a six-month extension, but not the two and a half years we were hoping for.
This decision was due to an error in the dates on the documents. We are a bit frustrated because the lawyer representing us did not correct this mistake and is not taking responsibility for it. Now, we have to make a new petition to immigration to stay here for the remaining two years, which means paying the government fees again, amounting to $1,000. We have also lost the benefit of having paid the “premium" service to expedite our case, as this is considered a new application.
We ask that you continue to pray for our lawyer to accept her responsibility and cover the immigration fees. We praise God because, at least, we can stay here until March 2025 and do not have to rush back to Spain.
In the midst of these challenges, our daughter Isabel fell off her scooter on Saturday and fractured two bones in her right arm. These have been difficult days for our little one as she gets used to managing without the help of her arm, which is causing her a lot of frustration.
Besides the emotional aspect, we are facing a new financial challenge. Her appointment to get a cast is on Friday, and we need to pay $653 upfront, in addition to the costs from the emergency visit.
Lately, we have been praying a lot, asking God for direction on how to move forward as a family. Carol and I believe it is good and God's will for her to be dedicated to the family and ministry, which demands a lot of time and has been our calling from the beginning. However, we see how it is becoming increasingly difficult to stay afloat with just my income. Every unexpected expense destabilizes our ability to cover the necessary monthly expenses, and that is why we are asking for your prayers for our family’s financial provision.
We know that God’s promises are to bless His children and that the righteous will never be forsaken. Please join us in asking God for His favor and provision for this need, and for direction in our lives.
Thank you in advance for your prayers. May God bless your life with fullness of joy!
Love, Perera Family.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Bluesky is a scam
Bluesky advertises itself as an open network, they say people won't lose followers or their identity, they advertise themselves as a protocol ("atproto") and because of that they are tricking a lot of people into using them. These three claims are false.
protocolness
Bluesky is a company. "atproto" is the protocol. Supposedly they are two different things, right? Bluesky just releases software that implements the protocol, but others can also do that, it's open!
And yet, the protocol has an official webpage with a waitlist and a private beta? Why is the protocol advertised as a company product? Because it is. The "protocol" is just a description of whatever the Bluesky app and servers do, it can and does change anytime the Bluesky developers decide they want to change it, and it will keep changing for as long as Bluesky apps and servers control the biggest part of the network.
Oh, so there is the possibility of other players stepping in and then it becomes an actual interoperable open protocol? Yes, but what is the likelihood of that happening? It is very low. No serious competitor is likely to step in and build serious apps using a protocol that is directly controlled by Bluesky. All we will ever see are small "community" apps made by users and small satellite small businesses -- not unlike the people and companies that write plugins, addons and alternative clients for popular third-party centralized platforms.
And last, even if it happens that someone makes an app so good that it displaces the canonical official Bluesky app, then that company may overtake the protocol itself -- not because they're evil, but because there is no way it cannot be like this.
identity
According to their own documentation, the Bluesky people were looking for an identity system that provided global ids, key rotation and human-readable names.
They must have realized that such properties are not possible in an open and decentralized system, but instead of accepting a tradeoff they decided they wanted all their desired features and threw away the "decentralized" part, quite literally and explicitly (although they make sure to hide that piece in the middle of a bunch of code and text that very few will read).
The "DID Placeholder" method they decided to use for their global identities is nothing more than a normal old boring trusted server controlled by Bluesky that keeps track of who is who and can, at all times, decide to ban a person and deprive them from their identity (they dismissively call a "denial of service attack").
They decided to adopt this method as a placeholder until someone else doesn't invent the impossible alternative that would provide all their desired properties in a decentralized manner -- which is nothing more than a very good excuse: "yes, it's not great now, but it will improve!".
openness
Months after launching their product with an aura of decentralization and openness and getting a bunch of people inside that believed, falsely, they were joining an actually open network, Bluesky has decided to publish a part of their idea of how other people will be able to join their open network.
When I first saw their app and how they were very prominently things like follower counts, like counts and other things that are typical of centralized networks and can't be reliable or exact on truly open networks (like Nostr), I asked myself how were they going to do that once they became and open "federated" network as they were expected to be.
Turns out their decentralization plan is to just allow you, as a writer, to host your own posts on "personal data stores", but not really have any control over the distribution of the posts. All posts go through the Bluesky central server, called BGS, and they decide what to do with it. And you, as a reader, doesn't have any control of what you're reading from either, all you can do is connect to the BGS and ask for posts. If the BGS decides to ban, shadow ban, reorder, miscount, hide, deprioritize, trick or maybe even to serve ads, then you are out of luck.
Oh, but anyone can run their own BGS!, they will say. Even in their own blog post announcing the architecture they assert that "it’s a fairly resource-demanding service" and "there may be a few large full-network providers". But I fail to see why even more than one network provider will exist, if Bluesky is already doing that job, and considering the fact there are very little incentives for anyone to switch providers -- because the app does not seem to be at all made to talk to multiple providers, one would have to stop using the reliable, fast and beefy official BGS and start using some half-baked alternative and risk losing access to things.
When asked about the possibility of switching, one of Bluesky overlords said: "it would look something like this: bluesky has gone evil. there's a new alternative called freesky that people are rushing to. I'm switching to freesky".
The quote is very naïve and sounds like something that could be said about Twitter itself: "if Twitter is evil you can just run your own social network". Both are fallacies because they ignore the network-effect and the fact that people will never fully agree that something is "evil". In fact these two are the fundamental reasons why -- for social networks specifically (and not for other things like commerce) -- we need truly open protocols with no owners and no committees.
-
 @ 8cb60e21:5f2deaea
2024-09-12 22:00:26
@ 8cb60e21:5f2deaea
2024-09-12 22:00:26Python for Absolute Beginners
Welcome to the world of Python programming! This guide will introduce you to the basics of Python, a powerful and beginner-friendly programming language.
What is Python?
Python is a high-level, interpreted programming language known for its simplicity and readability. It's widely used in various fields, including web development, data science, artificial intelligence, and more.
Why Choose Python?
- Easy to learn and read
- Versatile and powerful
- Large community and extensive libraries
- Used in many industries
Getting Started
1. Installing Python
Visit the official Python website (https://www.python.org) and download the latest version for your operating system.
2. Your First Python Program
Open a text editor and type the following:
python print("Hello, World!")Save the file as
hello.pyand run it using the Python interpreter.Basic Python Concepts
Variables
Variables store data in your program:
python name = "Alice" age = 30 height = 1.75Data Types
Python has several built-in data types:
- Strings:
"Hello" - Integers:
42 - Floats:
3.14 - Booleans:
TrueorFalse - Lists:
[1, 2, 3] - Dictionaries:
{"name": "Bob", "age": 25}
Control Flow
If Statements
python if age >= 18: print("You're an adult") else: print("You're a minor")Loops
For loop:
python for i in range(5): print(i)While loop:
python count = 0 while count < 5: print(count) count += 1Functions
Functions help organize and reuse code:
```python def greet(name): return f"Hello, {name}!"
message = greet("Charlie") print(message) ```
Next Steps
- Practice writing simple programs
- Learn about modules and libraries
- Explore Python documentation
- Join Python communities and forums
Remember, programming is a skill that improves with practice. Don't be afraid to experiment and make mistakes – it's all part of the learning process!
Happy coding!
-
 @ 8cb60e21:5f2deaea
2024-09-12 21:56:38
@ 8cb60e21:5f2deaea
2024-09-12 21:56:38 -
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Empreendendorismo de boteco
Há no Brasil, não sei se em algum outro país, esse tipo que acha que sabe tudo e, falando alto e com convicção acaba convencendo todos os que sabem não saber nada. Entre os papéis que pode assumir o sabidão, um dos mais nocivos é o do empreendedor, o conhecedor de negócios, o que sabe quanto as coisas valem. Você conhece este homem, caro leitor, ele é aquele que, com sua voz alta e convicta, afirma coisas como "isso dá muito dinheiro" ou "tal empresa ganha dinheiro demais". É aquele que tem a fórmula do dinheiro infinito: "se você quiser ganhar dinheiro é só comprar tal coisa e revender", às vezes adicionando o sufixo "simples!". É também o que têm noção da realidade: "se eu tivesse dinheiro pra investir abriria um tal negócio, dá muito dinheiro", ele sabe que não é qualquer um que pode ser milionário: "mas precisa ter muito capital", diz ele.
Em suma, é esse tipo que espalha essa idéia, vinda não sei daonde, de que qualquer empreendimento é coisa simples e que os empresários de sucesso são homens que já tinham dinheiro e que não tiveram dificuldade alguma em multiplicá-lo.
Hoje, com a invasão dessas pessoas aos cargos públicos, o Estado vive uma grande fase de empreendendorismo, com "investimentos" em empresas de futuro que "dinamizarão" a economia (ah, as "startups" e todo o seu capital estatal!) e, principalmente, com empreendimentos próprios, como foi o caso, por exemplo, dos estádios para a Copa de 2014: além da propaganda de todos os lados, desde os jornalistas infectados pelo empreendendorismo de boteco que repetiam "os estádios darão muito lucro, pois comportam não-sei-quantas pessoas e ainda podem ser usados para eventos" aos próprios técnicos do governo que faziam contratos com administradoras com cláusulas do tipo "o Estado garante aqui um lucro de 20 bilhões por ano, menos que isto a gente completa" e ainda eram aclamados pela mídia por sua certeza de que 20 bilhões eram pouco.
-
 @ 361d3e1e:50bc10a8
2024-09-12 21:04:52
@ 361d3e1e:50bc10a8
2024-09-12 21:04:52https://forex-strategy.com/2024/09/12/the-end-of-normal-food-is-coming-gmo-food-will-not-be-labeled/
The end of normal food is coming - GMO food will not be labeled
food #organic #bio #politics #gmo #australia #newzealand #truth
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A estrutura lógica do livro didático
Todos os livros didáticos e cursos expõem seus conteúdos a partir de uma organização lógica prévia, um esquema de todo o conteúdo que julgam relevante, tudo muito organizadinho em tópicos e subtópicos segundo a ordem lógica que mais se aproxima da ordem natural das coisas. Imagine um sumário de um manual ou livro didático.
A minha experiência é a de que esse método serve muito bem para ninguém entender nada. A organização lógica perfeita de um campo de conhecimento é o resultado final de um estudo, não o seu início. As pessoas que escrevem esses manuais e dão esses cursos, mesmo quando sabem do que estão falando (um acontecimento aparentemente raro), o fazem a partir do seu próprio ponto de vista, atingido após uma vida de dedicação ao assunto (ou então copiando outros manuais e livros didáticos, o que eu chutaria que é o método mais comum).
Para o neófito, a melhor maneira de entender algo é através de imersões em micro-tópicos, sem muita noção da posição daquele tópico na hierarquia geral da ciência.
- Revista Educativa, um exemplo de como não ensinar nada às crianças.
- Zettelkasten, a ordem surgindo do caos, ao invés de temas se encaixando numa ordem preexistentes.
-
 @ a03b38f8:2c7ce1f0
2024-09-12 19:16:50
@ a03b38f8:2c7ce1f0
2024-09-12 19:16:50-----BEGIN PGP MESSAGE-----
wcDMA17V9MGW3LFGAQv/erNSJ4ooO6fERifSPB0ENbX8V+XEMeoq4DXt/EyRdeBP DpettdnDboZWnaJz2g3fk6VUAeSNH+ZqKW67LSNEg/qk3L7AdcxrVji1DJhfQ8WR K3r/iQzSO8OXSWsez3yEXhmJSy6fwFS/D6kHpCcHu3wo4fipLLJ96lkMpUd0zzir JDw7atRjI7LfulDwfIuFk2hAXEDrWJkPosdZ3g9cCayfzV440WvAMN0K7pv6OQp+ I7Zxf6KsMB5hNz3yEQRJIspqaQaI7gdNqEkfkdCkTw5wfmhlyKVgukvSkrIGe6Cb WEXBpO/QKMsY4HBOiPc/Mu4i4gEQlSZxGDNiGB6AkWz7o0hEiT+ugXIdMXl/ACH6 DhBOWOr2JQtHo70z5mpiqAkbG2lFcPnSGXikCIZ1ONh/eJiM7ZbpRcPZ+Vo7veAQ 3dfrB5g32cmVteL8T9H3bL88uP06FoRqQU6YmdKtu101SpEkXzAP46NDZ0re54QA IPxCy8t1BcjAfDmtuHsW0susATLI40nPziahKfLA7iOYhpUsHT9tnZm63g1uIwGF MlT377PJydN9hTAQbxTsfNSPws8/OoHzE5UeEQehFhOKxjw0lslM3HQhsgYVN6F6 6/ileO7LsJo9UPVd5D5Qy1qGwBWKl5wZk80Io5kJlvHp3BjFDfjCsPUXmmc1Kh8J Yn6wiFzm6Ti6rBDxuZSCbcyRhebOi+ZKnkzra+4rwy5BYPArj+N0mbwUbMh+1DR5 86m683N7bOMJkOYfjXxm00PTz17usJLzfPmcqkUE9x4RC8p/huz7MmCFhnTVedOl io4RHg2iV0hgUf0ybuO49ROuEB9B/nrqpdUYiL2PVUKUkVnFRQ5XZvKr9/4pUh95 eTrLCUYP5+X1IZfoF8nHEy4D/HuHQGdtAeCADvARB0nnTphIV9YUBpCuq1MWKkBa iSWnD4X9ErodF8aGaVG2Cvh/BlMMl5CkHlzZUHJEedrFllLTZNdCgmDggduGzq5n iD2FdKz9O2MrNEbBu5o2NHOvFcs5KFFfqUeb028kOxNnTozPO5sMZJYZvlQCPBv7 eeWsM6WRPq6lB8xSZAO3yRlBa/EEvMU9k8qBq56G91dNYDUu03kS/WBzUZYoCS5e YLhpn8Jb5XP4HJdct/VPKmpzPRBzj7Xyeqc3hZdj6/uF2fMngmCt2IeNQjsZrjKQ mszv/A7huvTbU9wUdA8ssrkD4GLeg6q1a7WNBJ12SkoOK1ld+g6s6k4Z6UwSJVgc R9JtPC77A+/kyRgPJW6JdEmlZXYpagtPRP/eIt52IMByQ9s/L7HkYO/FGPMok9Yb 1X6NLh+3CQMBkscuUcUbWjsWGVrJxqQYdMBnXuvCUDILPm3NrRBUO8Y9yieG/lwT kG1d/90WrjgtGO3Bny3UgsEap2RZ/91KN8dS6+PfgqBUc8nQV7zpsxDGfvLFryFF GBLKtv6IbWw8mYqPMBrf/q8a06+TVtUkIYxlhmfxut+Zpf+o99Ph81CH90PO290M 1FxBwL7j4lqFeYoQSz9Xs6wrJ6V+F9ORwVXpPqdJGSYNcBUhk9inIo/imyhdd0rV u0V1NkepX9DmP/vRdu4e1VJJoh70XOQImfa+92DP01B6sGq5Ah1/b5/U6LOml5Nj 7kC/RPLs/R0yZ8eGZW04MuDLu3flZtkvgsw2RNutlrFyN/pdHksRa+4qgyIAY2q2 2+iGtKZ5ksTYY53WoRmnMzz3Pwkb7Vw6/ROpJB9qrSTkNtZ3DIgavXznmMGfg5Yx AcoEElg3Why65wMSUXXeenW/0UUVfyZZJhV5822I3/b9wJgkRsA2G3+Pqu4Fw3Xs OnsSRIj7Wcg3RFvld/2Su05LO8zzQKzt5+JbG689J4Mb4wc8s4/o3vgF6J8+GR7G a081oL0gStqNRAL5dgXwqdFswEpYu3mYROVjZlsM+Yw6i5JsyzDtDjyJJs6A+Jxx 0yCQ/21lkc4n3RGItFce2JVogBs+0YkL8tqDZnhtDtPJgp0t9t8L7Po55sGHnigE faBdbpVfJEU6G7qGS5/xxv9Pkw4qTTV/5ENGPybfQ4CGgLUAWkGaT1PTNa7x3i65 TDF+N5heKXOwuTg+18oCvYpGxVTDmboSaqc835dExoP1r9GZ9zgODXM9+034GNP7 DmuKnw5tyJlF7lZjXioWmer1RCFGyicsI9XaXqqYsQiAo0EZzArA5lri5cnxIa6g 6d88gkOjMV+6mGnXfpm8Cb8pl5dGmsWo7vZdoFDK5a/6ueDqp7yj20Kug672Of32 R5LUUiwr0IslCAaYwraU/Tv2PvS1JERoN1YE6clUEFaraSOO3099/duxPa5vgNbs l8tG2gyuRFtqcGEio8bUqlNnpsg2KM0Cs3SOUx7siXpQzcatx0kvffFNdt8CAsTh xLu8byxoFxlJp6meNMjSNOO37kkZ8DgjyUdwfhpCf4/Lfzox/te2ulC4/6Jccc28 rbeFTRw536IAEQYW0R+m7iL5HVmC8K0xO6k98ESo8TVSW3+gHdwkBXtuwqIl8iD5 bxnbqUtrmnfyYe32SZZVtyaUUtFjwfJ3crsdTWJmSrsd54ZNRzfs8R9ymnQEU+EW Fngulk2/NiU7Nw9rzoW6o35DsrLXFFpoNbEotVn8Pqb+8bDWwhXIY1tC0VQq6D9p 9l4s2ZB+ps2N5iGsijIvdSNNiLttZl+NFUnyQOAn+hbbb8R9GsGWam9thrdBMRNo hUSxRTgWRUqEQ6Tue8vbG+S/CylaAaryF1nz6ShRBegluI5ivyUV8MbxiSTKo2r6 MRYXGp2j4K0vADDjd2M8gwgmancszgZxjN9XTeO/xhWQ1Ed8SEI87I6ymQA7nXTm Cn5fMHdht+uOMdZ3CHOXO+YWoxsOpq60K2lkldb/Cv1s9F9gZqXC6aauPZ9un6K5 p7/1Kje7ATFgUrfcsNMuI04qobJc7QiiQJLf3yoQ64bF3GHXQmUfxJurQ9nUg0oW rETBdT4gz3eDS6ApbSXnUIV+SSbQTWCBGkqJddjYtoYTONBkZFTLg9yYdAw43+8P 9mv5Mwe5nocd2322W1zQj/npUDh1H61UQTIsZHUY66/KNprNi4PLawEFy1MpJiE0 0UT4Xhbw+3/ynIYy+ibAj71O4ymslzbz7P/zn/vR8iy8ZY8o0riMtwE8v+nBRWEs uwG/kW7vjPYA5RZkYLRz3LNnrlfiOgd7eCoFc2PU/c9NdBT0+pZQbudXiMW+eX6C FZY3oh+6heTuWF1kzyQy9RCDx43XSg/GON5Vy2pD/+24CDpscE6AObLGCWQoVYxk KQUwx85iomVWijRkWC7Nm4lTUIH8jnA5BZxyhymPbUttoUOiN+z2umtgNUfIp1L7 CwFAs0VThseHny/ra7q/5rmepP1s98ojcyBF3YD3o+Wy981R61e1v/c4L2P8iSZC LMyVSK+pWWaMLWIdFBSR8Ke/vDS1pz8GAeAdcXRQRjVw1l/aIQPXYNKJ0S6kNbQ0 IwnYdiMuOXEkhOlnFsUV1uiSN2LY6W8/Kk2cxcwheCgTkk5ibKl39VFsy9h2vxiP +ecjDnAGrR+ZJV958zrnnt7gosr2Nm/VUSlU/NbFlXE2kIhhulyd/M2GGKrj3j70 lD1HRjUjrSLrZsirdITG4VbYIIq/00K4x3hYbcY8R6ROrCJemdE4DUkDvirYZ7rU yEhbpuo2oz/KjubgPKAY9srkJ8Tv8dcZQR0c2XfpohAzl5ctv3Ai9c0LW+eePUSk RtgOnges73+WImv5rgjYv2y7eeupXgnAMcndFF490vUk3+B3F/LafsFNLSVwqJUL qhimUv+84J6/G9uG6xEc6b+4B1VMvmM7/cFmjZYRRvBxvBaOTyjP1OMe69TgKM69 H73haTEA0QEwenRxQq0tKqCo2fygK0uVkFSGQ3dRDh6QueTVRzbmopKwWrSMw3ye +NjpdRR8tBj95bTj7YvesJP7z0WqtHj6N8FJt+VY9bfAHB97oCc3QziEmdY+lpZe 37PMAY6JN2chQ8HuwPpgWe5JmhiO09w8DgYcQnOJqVl4UQulkJvti7i4VDyMY8Z+ hxiNDsb8agY03zAchgLN6cXrpall5/XDzGVBbnbnccVS/x7L0Dr940+AF6yKi1mD 0l79sqWjT5nNHmf/ni5YXfLU+4ajSHWOm4yLaqWRjTSTUh/41v9iHqQwPj4RgBZP 1/fFy4HpM5kBMSYlCFFLPrY2OFqFX8yw1HyRn39W62FETIH4CASdEF5ieJ44CWef L/TwrLaS2R0SS6Xnnhyckr8dwh86tDgxZhtruQ4unu4EiOj15PMWymI69J+Ad6jF oRfrZ/mqyi0+hfxFyoLnI5Uz/Gxza/0A7mcBiwqLrbqU9K0695u8ZCi4B3ytB0rP l6HJZuODn6sQiUta/03Yo3GabFNzTuoqQ9HerdVOyPxpRjeTjEbULdmOmnHltUIQ AlgCAXJ71nmaCazGPIVvkIC2QQSg6TxJWvAR/vF879K2NcXZfImB4OpoWGJ1vb9W BiDq1nU57jiyugxxSR3/RlZRfqpo9HPkq8qooQR1VxqfxBxV0XgxEsxs6LB2cr9g RPJ6Cys/OmOj698rjKzss+2OVbHQiXknIUgZqaAgqThVI8G5R/FNWQVM5okmodnf unTVl9eTXVkK/vrzU8iw1K4H2TCJQhFTJX9m4dE9GxnNKeH+T7D8TqtJHjkd7tUH 6+k+Ar4xZwLPB6rNHNbw+4DNDmCyJ9hXMGhCIbqn =RNR1 -----END PGP MESSAGE-----
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Gold is not useless
If there's something all common people believe about gold is that it is useless[^1]. Austrian economists and libertarians in general that argue against central banks or defend a primitive gold standard are often charged with that accusation: that gold is useless, it has no use in the industry, it serves no purpose besides ornamental, so it is a silly commodity, a luxurious one, and that it would be almost immoral to have such a thing in a so central position in an economy such as the position of money.
I've seen libertarians in general argue such things as: "it is used in some dental operations", which means people make dental prosthesis of gold, something that fits in same category of jewelry, I would say.
There's also the argument of electronic connectors. That's something that appears to be true, but wouldn't suffice the anti-gold arguments. The fact remains that, besides its uses as money -- because gold is still considered to be a form money even now that it doesn't have that position formally in any country (otherwise it wouldn't be considered as an "investment" or "value store" everywhere) -- gold is used mainly for ornamental purposes[^2].
All that is a hassle for libertarians in general. Even the Mises Regression Theory wouldn't solve that problem of people skeptical of gold due to its immoral nature. That problem is solved once you read what is written in the chapter 17 from Richard Cantillon's Essay on Economic Theory^3 (page 103):
Gold and silver are capable of serving not only the same purpose as tin and copper, but also most of the purposes of lead and iron. They have this further advantage over other metals in that they are not consumed by fire and are so durable that they may be considered permanent. It is not surprising, therefore, that the men who found the other metals useful, valued gold and silver even before they were used in exchange.
So gold is indeed useful. Everybody should already know that. You can even do forks and spoons with gold. You can do furniture with gold, and many other useful stuff. As soon as you grasp this, gold is useful again. It is an useful commodity.
Answering the next question becomes easy: why isn't anyone making gold forks anywhere? The questioner already knows the answer: because it is too expensive for that.
And now the Regression Theory comes with its full force: why is it expensive? Because it has gained a lot of value in the process of becoming money. The value of gold as money is much greater than as a metal used in fork production.
[^1]: see http://www.salon.com/2014/02/02/ignore_sean_hannity_gold_is_useless_partner/ or all answers on https://www.quora.com/Why-is-gold-considered-so-precious-and-why-does-it-have-such-high-prices. [^2]: this https://en.wikipedia.org/wiki/Gold#Modern_applications section on the Wikipedia page for gold is revealing.
-
 @ a03b38f8:2c7ce1f0
2024-09-12 16:49:50
@ a03b38f8:2c7ce1f0
2024-09-12 16:49:50First steps into privacy.
You are a normie, but maybe you are privacy curious. Maybe you are ready to take a first step or two into security and privacy but don't know where to start.
Don't worry, here are some absolute beginner first steps that will make a big difference.
No one except your friends and family should know your personal phone number and email address. Stop giving away your data! You don't have to fill out every blank on that form. Unless they are mailing you something they don't need your home address. Use a email aliasing service or just create a burner email account as a spam trap. Get a second VOIP phone number. Look up the address of a local hotel. Use these instead of your personal information or maybe just skip the customer reward program. Speaking of giving away your data. Stop using spyware! Facebook, Instagram, Tiktok, etc. It is "free" software designed to suck every ounce of personal data from you to be repackaged and sold. Don't just delete the app, search for how to delete your account data.BTW Windows, google, and 90% of the apps on your phone are also spyware but one thing at a time. Maybe start reading up on FOSS.
Clean up your communications. Stop using unencrypted calls and SMS texts. There are several options but just get Signal and make your friends use it. Its easy and works. Clean up your email. This one is probably going to take you some time if you are like most people who have hundreds of emails from years gone bye. Go through every single one and unsubscribe from every newsletter or sales pitch from every store you have ever bought anything from. Block every spam email you see. If you are using a email provider that literally scans every email you send or receive in order to sell you stuff like gmail, then now is the time to switch to a private and encrypted provider like proton or tuta. Clean up your web surfing. Switch to a privacy browser and search engine. If you don't know which one just get Brave. There are ones that I like better but Brave is good enough and easy, especially if you like Chrome. A hardened Firefox is better but requires some homework and if on desktop Mullvad browser is a excellent choice.BONUS TIP:
Clean up your security. Make sure all of your software is setup for automatic updates, especially security updates. Also, I don’t know who needs to hear this but get a password manager if you don’t have one. (Don't save passwords on the browser!) Get an actual password manager and then add 2FA to all of your online accounts and you will have better security than 90% of the population.
OK, nothing too exciting but we got the big rocks. Data leaks, communications, email, web surfing, and basic security.
What, no VPN or Tor or super secret stuff? No, not yet. This is your level zero default. Your identity and activity is still transparent but you are no longer leaking your data all over the place. This will provide a general base for everyone.
The next step is to perform a basic threat assessment of your personal situation. What are you most at risk for? Targeted attacks or passive? Cyber or physical? What do you most need to defend against? Government mass surveillance, surveillance capitalism, censorship, or public exposure?
There will be some overlap with all of them but your next steps will really depend on your answer. We will cover each of these in greater depth later.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28IPFS problems: Inefficiency
Imagine you have two IPFS nodes and unique content, created by you, in the first one. From the second, you can connect to the first and everyhing looks right. You then try to fetch that content. After some seconds it starts coming, the progress bar begins to move, that's slow, very slow, doing an rsync would have been 20 times faster.
The progress bar halts. You investigate, the second node is not connected to the first anymore. Why, if that was the only source for the file we're trying to fetch? It remains a mistery to this day. You reconnect manually, the progress bar moves again, halts, you're disconnected again. Instead of reconnecting you decide to add the second node to the first node's "Bootstrap" list.
I once tried to run an IPFS node on a VPS and store content on S3. There are two S3 datastore plugins available. After fixing some issues in one of them, recompiling go-ipfs, figuring out how to read settings from the IPFS config file, creating an init profile and recompiling again I got the node running. It worked. My idea was to host a bunch of data on that node. Data would be fetched from S3 on demand so there would be cheap and fast access to it from any IPFS node or gateway.
IPFS started doing hundreds of calls to S3 per minute – something I wouldn't have known about if I hadn't inserted some log statements in the plugin code, I mean before the huge AWS bill arrived. Apparently that was part of participation on the DHT. Adjusting some settings turned my node into a listen-only thing as I intended, but I'm not 100% sure it would work as an efficient content provider, and I'll never know, as the memory and CPU usage got too high for my humble VPS and I had to turn it down.
-
 @ a03b38f8:2c7ce1f0
2024-09-12 16:45:51
@ a03b38f8:2c7ce1f0
2024-09-12 16:45:51Encryption is the promethium fire that the cypherpunks secured from heaven for me and you. It is our sacred duty to use and advance that in the world. Encryption is so powerful that governments tried to keep it away from the people and to this day have tried to weaken and backdoor it at every turn.
So what is encryption?
It is a deep deep rabbit hole and involves a lot of numbers but in a nutshell it uses math to scramble up the data of your file so it is gibberish and can't be read without decrypting it back to regular data. Encryption technology has continued to advance over time and cracking technology to break the encryption has as well. For our purposes all you really need to remember is to use modern cyphers and your encryption is really only going to be as good as the password (use a passphrase) strength you are using to lock it down with.
BEGINNER LEVEL - Encrypt your phone and computer.
People walk around with their whole lives on their phone. Protect it.
-phone: Congratulations, if you already have a lock screen set on either your iPhone or Android device then device encryption is enabled.
If your lock screen password is only 4 digits then we still have work to do. Four digits is only about 10,000 combinations and fairly easy to crack. I believe it only took them about 40 minutes to crack the iPhone of the attempted Trump shooter. Go into settings and set it up for 6 digits or for extra credit use a alphanumeric password.
After your phone then your personal computer probably has the most important data to you. Banking records, tax documents, photos, etc. Encrypt your drive.
-Windows: from Settings, select Privacy security -> Device encryption. Just follow the prompts.
-Apple: from Apple icon, select System Preferences -> Security & Privacy icon. Click "Turn On FileVault".
-Linux: most distros gives you the option during installation. If you didn't do so then search for how to enable it after the fact based on your distribution.
Awesome sauce. You have achieved minimum status.
ADVANCED LEVEL - Encrypt individual files.
You already encrypted your computer but guess what, once you start up your computer and log in the key is stored in RAM for as long as it stays on. The beginner level encryption protects your computer when it is off and it means no one can just steal your hard drive and access your files. This is good, but what if someone grabs you while you're sitting there working on it? What if you leave it in sleep mode and not turned off? Then that whole disk encryption is not really going to help you.
What if you had individual files that you consider more secret than the others? That finance spreadsheet or that special pic your spouse sent you? That's where individual file encryption comes in. You are just scrolling nostr when they grab you, your computer is on, and unlocked, but those special files are still safely encrypted.
I will share with you one of my favorite small programs: Picocrypt.
Download the Paranoid pack and store it in multiple drives, email accounts, and cloud storage. That way you will always have a copy to decrypt any files that you stored away.
Use it to encrypt any files that you feel need extra attention. It is also very useful for encrypting any files that you intend to store online in cloud storage. You do encrypt your files that are stored online don't you? Yes, even with the company that offers "encrypted" storage. Don't trust their encryption, use your own.
EXPERT LEVEL - Encrypt containers and hidden containers.
What if you want to encrypt several files and keep them all together in like a folder or container? That's where Veracrypt comes in. Free, open source, cross platform, and powerful.
Veracrypt allows you to create encrypted containers from any file that act like individual drives that can be mounted or unmounted as needed. You can name these files anything that you want, move them around or delete like any file, and make as many as you want. This allows you to have compartmentation of your files and drives.
Next trick, Veracrypt allows you to create a hidden container inside that container. Enter one passphrase and you open the encrypted container. Enter a different passphrase and you open a different hidden container.
This allows deniability. When they grab you and start pulling your fingernails off until you tell them the password to open the encrypted container, give it to them. They don't have to know that there is another hidden one under that.
These features allow you to do all sorts of interesting things only limited by your need and imagination.
What if you have a container named as some random config file in your /etc folder? What if you just encrypted a removable storage drive? What if you have multiple hard drives on your computer that have multiple containers and hidden containers? What if you have a hidden container that can only be accessed from booting up in a amnesiac OS like Tails leaving no trace that the files exist or trail that they were ever accessed? Go crazy, have fun.
NEMO - Failsafe
Nemo has no files, encrypted or otherwise. If they did you couldn't prove it. Nemo does use something like Tails that retains no memory from boot to boot.
Nemo also uses a failsafe. A simple lanyard attached to the flashdrive running the OS and the other end around their wrist while they work. When you try to separate them from the computer the flashdrive pulls out and everything is gone.
Using these programs you can create a layered and compartmentlized approach to your encryption scheme. There are also plenty of other encryption programs to check out such as Cryptomator, AES Crypt, etc
Last point and most important: Encryption is only as good as the passphrase you use to lock it down. Use a shitty password and it doesn't matter how uncrackable your encryption is.
-
 @ 8cb60e21:5f2deaea
2024-09-12 15:47:40
@ 8cb60e21:5f2deaea
2024-09-12 15:47:40h1 Heading
h2 Heading
h3 Heading
h4 Heading
h5 Heading
h6 Heading
Horizontal Rules
Typographic replacements
Enable typographer option to see result.
(c) (C) (r) (R) (tm) (TM) (p) (P) +-
test.. test... test..... test?..... test!....
!!!!!! ???? ,, -- ---
"Smartypants, double quotes" and 'single quotes'
Emphasis
This is bold text
This is bold text
This is italic text
This is italic text
~~Strikethrough~~
Blockquotes
Blockquotes can also be nested...
...by using additional greater-than signs right next to each other...
...or with spaces between arrows.
Lists
Unordered
- Create a list by starting a line with
+,-, or* - Sub-lists are made by indenting 2 spaces:
- Marker character change forces new list start:
- Ac tristique libero volutpat at
- Facilisis in pretium nisl aliquet
- Nulla volutpat aliquam velit
- Very easy!
Ordered
- Lorem ipsum dolor sit amet
- Consectetur adipiscing elit
-
Integer molestie lorem at massa
-
You can use sequential numbers...
- ...or keep all the numbers as
1.
Start numbering with offset:
- foo
- bar
Code
Inline
codeIndented code
// Some comments line 1 of code line 2 of code line 3 of codeBlock code "fences"
Sample text here...Syntax highlighting
``` js var foo = function (bar) { return bar++; };
console.log(foo(5)); ```
Tables
| Option | Description | | ------ | ----------- | | data | path to data files to supply the data that will be passed into templates. | | engine | engine to be used for processing templates. Handlebars is the default. | | ext | extension to be used for dest files. |
Right aligned columns
| Option | Description | | ------:| -----------:| | data | path to data files to supply the data that will be passed into templates. | | engine | engine to be used for processing templates. Handlebars is the default. | | ext | extension to be used for dest files. |
Links
Autoconverted link https://github.com/nodeca/pica (enable linkify to see)
Images

Like links, Images also have a footnote style syntax

With a reference later in the document defining the URL location:
Plugins
The killer feature of
markdown-itis very effective support of syntax plugins.Emojies
Classic markup: :wink: :cry: :laughing: :yum:
Shortcuts (emoticons): :-) :-( 8-) ;)
see how to change output with twemoji.
Subscript / Superscript
- 19^th^
- H~2~O
\
++Inserted text++
\
==Marked text==
Footnotes
Footnote 1 link[^first].
Footnote 2 link[^second].
Inline footnote^[Text of inline footnote] definition.
Duplicated footnote reference[^second].
[^first]: Footnote can have markup
and multiple paragraphs.[^second]: Footnote text.
Definition lists
Term 1
: Definition 1 with lazy continuation.
Term 2 with inline markup
: Definition 2
{ some code, part of Definition 2 } Third paragraph of definition 2.Compact style:
Term 1 ~ Definition 1
Term 2 ~ Definition 2a ~ Definition 2b
Abbreviations
This is HTML abbreviation example.
It converts "HTML", but keep intact partial entries like "xxxHTMLyyy" and so on.
*[HTML]: Hyper Text Markup Language
Custom containers
- Create a list by starting a line with
-
 @ 7ab1ed7a:f8e15275
2024-09-12 15:32:35
@ 7ab1ed7a:f8e15275
2024-09-12 15:32:35Summary
This article outlines an approach to handling IoT event data in Nostr, considering both replaceable and regular events. It discusses event structures, including types, units, and metadata tags, and suggests efficient ways to manage the size of data relayed through Nostr. The article also touches on the importance of maintaining privacy in IoT applications and addresses the potential challenges of scaling IoT data within the Nostr protocol.
Events
There are several possible approaches to structuring IoT event data. The following approach is being considered for use within Nostr:
Event Structure
Kind:\ The NIP (Nostr Implementation Proposal) should define both replaceable and regular event kinds. Previous PRs for IoT on Nostr NIPs defined kinds for each data type (e.g.,
30106for temperature), a more maintainable solution would be to have a limited number of kinds with data types and units defined in event tags. This would simplify management while improving long-term maintainability.Content:\ The content field will typically contain data from IoT sensors, commands, or statuses. For example, a switch could have a value of
1or0, and a temperature reading might have a value like20.Tags:\ Tags are essential for defining the data types, units, and additional metadata such as physical coordinates. These are some of the key tags that could be used:
- ["l", "type", "[data-type]"]. Describes the type of data, where [data-type] could be for example
intent,status,temperature, orlight. - ["unit", "[unit-name]"]. Describes the measurement unit where [unit-name] is for example "celsius" (
°C), "hectopascal" (hPa), or "lux".
Private Data
Using IoT on Nostr privately should be a priority. Following an approach similar to how Direct Message Volumes (DVMs) encrypt all data (as per NIP90) could work well. Encrypting IoT event data and possibly "giftwrapping" it could enhance privacy. However, this is currently out of the article's scope and requires further investigation.
Replaceable vs. Regular Events
One challenge with Nostr events is their size, especially when compared to IoT protocols like MQTT. A typical Nostr event, such as:
json {"id":"072ec5876798efb182e9083464a7d6be41b2a0e46a8336db7c550eca173e1f9b","pubkey":"0987d97ee78e6a2281d2f45aedebc3d22da346a064850ca85440c2dd104badd4","created_at":1726123555,"kind":30107,"tags":[["l","type","pressure"],["unit","hectopascal"]],"content":"1005.78","sig":"a4d65dee6d2c9aed705acebaf2c8fd4ef3411126b8de472e9d03a2a94d420bb72a64fbc307146cac56abfa0b1716f001bbc1516b1ee48bc5fa955f6a1149f42d"}is around 387 bytes. If a device sends this data to a public relay every 60 seconds, it would generate approximately 540 KB of data daily or 194 MB per year. If thousands of devices do this, relays could experience significant strain.
To address this, distinct IoT kinds could be defined for replaceable and regular events—perhaps
30107for replaceable events and9107for regular events. This would allow relay operators to manage event storage more effectively, possibly rejecting regular events that originate from npubs that are not subscribed to a paid relay.For replaceable events, relays will persist the event and replace it with a new event that is published by the same pubkey with the same kind and d tag. Defining replaceable events would allow IoT devices to publish to public relays in a manner that doesn't abuse the relay. Third-party clients or relays could "harvest" these events in real time and index them for future processing.
Example REQ for data queries
Using tags in the manner described above, querying a relay for specific information could be done with a request similar to the one shown below:
["REQ", "TMBl2WOTX5oMI8ngKKwzBhpONaH8ahanYFM0DUDmspxQ3Sf9K06zqztjTwYLV2Ul0",{"kinds": [30107], "authors": ["d0bfc94bd4324f7df2a7601c4177209828047c4d3904d64009a3c67fb5d5e7ca"], "#l": ["type", "temperature"], "limit": 2}]Event Kinds
In Nostr, event kinds are divided as follows:
-
Regular Events:\
1000 <= n < 10000or4 <= n < 45orn == 1 || n == 2. These events are expected to be stored by relays. -
Ephemeral Events:\
20000 <= n < 30000. These are not expected to be stored by relays. -
Parameterised replaceable\
30000 <= n < 40000, These events are parameterised replaceable, which means that, for each combination of pubkey, kind and the d tag's first value, only the latest event MUST be stored by relays, older versions MAY be discarded.
Conclusion
Managing IoT data on Nostr requires balancing the need for efficient data transmission with the constraints of relay storage. Distinguishing between replaceable and regular events can help optimize relay usage. Future discussions on privacy and encryption strategies are essential to ensuring secure IoT implementations on Nostr.
- ["l", "type", "[data-type]"]. Describes the type of data, where [data-type] could be for example
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28As valas comuns de Manaus
https://www.terra.com.br/noticias/brasil/cidades/manaus-comeca-a-enterrar-em-valas-coletivas,e7da8b2579e7f032629cf65fa27a11956wd2qblx.html

Todo o Estado do Amazonas tem 193 mortos por Coronavirus, mas essa foto de "valas coletivas" sendo abertas em Manaus tem aproximadamente 500 túmulos. As notícias de "calamidade total" já estão acontecendo pelo menos desde o dia 11 (https://www.oantagonista.com/brasil/manaus-sao-paulo-e-rio-de-janeiro-nao-podem-relaxar-com-as-medidas-de-distanciamento/).
O comércio está fechado por decreto desde o final de março (embora a matéria diga que as pessoas não estão respeitando).
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Cadeias, crimes e cidadãos de bem
A idéia de ficar dentro duma dessas penitenciárias superlotadas é aterrorizante para qualquer cidadão de bem, logo, nenhum cidadão de bem comete crimes puníveis dessa maneira. Mas os cidadãos de bem já não os cometeriam de qualquer modo, é um outro tipo de gente, que não o cidadão de bem, que comete os piores crimes (não quero dizer que o "cidadão de bem" é melhor do que o outro absolutamente, estou só usando um conceito mais-ou-menos identificável).
O problema disso é que todos esses mesmos cidadãos de bem imaginam que a existência da cadeia e da punição-padrão movida pelo Estado afasta do crime milhões de pessoas que, sem isso, cometeriam crimes horríveis, mas que com isso vivem vidas normais.
A verdade, me parece, é que quem fica assim tão aterrorizado com a idéia da cadeia e da punição-padrão é a pessoa que já por natureza não cometeria esses crimes.
