-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 2ca61871:f4ab98c0
2024-09-21 19:44:07
@ 2ca61871:f4ab98c0
2024-09-21 19:44:07We all feel disqualified sometimes. The truck that hit me in that pedestrian crossing was my own truck. I landed in the hospital, because of my insolence.
-
 @ e83b66a8:b0526c2b
2024-09-21 16:29:23
@ e83b66a8:b0526c2b
2024-09-21 16:29:23Here are some of the more interesting projects that I like:
Messaging:
https://www.0xchat.com/#/ - Private messaging - think WhatsApp
Xitter Like Clients:
https://damus.io/ - iPhone client
https://nostrapps.com/amethyst - Android client
https://primal.net/downloads - Android, iPhone & Desktop
https://shipyard.pub/posts - Schedule future posts
Interesting sites:
https://zap.stream/ - Video streaming
https://fountain.fm/ - Podcasting
https://wavlake.com/ - Music streaming
https://shopstr.store/ - Online shop
https://zap.cooking/recent - Cooking recipes
https://ostrich.work/ - NOSTR jobs board
NOSTR tools
https://nostr.band/ - Powerful search tool
https://nostr.wine/ - Powerful, but centralised paid relay
https://npub.pro/ - Website creation tool
https://nostr.build/ - Media and file storage
https://relay.tools/ - Build and curate your own relay
https://creatr.nostr.wine/subscriptions/new-user - Creator tools
List of NOSTR apps:
https://nostrapps.com/
-
 @ df478568:2a951e67
2024-09-21 14:34:08
@ df478568:2a951e67
2024-09-21 14:34:08CyberSecurity Awareness Training: Note-this is a link to a downloadable PDFhttps://puhsd-ca.safeschools.com/training/certificate/3AFD09CE-6D73-11EF-B6F3-B8ABE6806967
Currently Studying
-
 @ 03742c20:2df9aa5d
2024-09-21 09:31:17
@ 03742c20:2df9aa5d
2024-09-21 09:31:17ถ้าอยากเก็บข้อมูล Nostr ของตัวเองทั้งหมด นอกจาก Relay ที่เราสร้างเองได้แล้วยังมี Media Server ที่สำคัญไม่แพ้กันถึงแม้จะไม่เหมาะกับทุกคน แต่ถ้าอยากควบคุมข้อมูลทั้งหมดนี่คือคำตอเเลย
ผมแนะนำ Nostrcheck Server ที่ติดตั้งง่าย แถมใช้ Docker ได้ด้วยมันสะดวกสุดๆ
สิ่งที่ต้องเตรียม - เครื่องที่เปิดตลอด 24/7 - Docker - Domain (แนะนำจดกับ Cloudflare)
วิธีติดตั้ง Nostrcheck Server ด้วย Docker
ดาวน์โหลด Nostrcheck Server
git clone https://github.com/quentintaranpino/nostrcheck-api-ts.gitเข้าไปที่โฟลเดอร์ Nostrcheckcd nostrcheck-api-tsสั่ง Build Containersudo docker-compose up -d --buildอนุญาต Firewall พอร์ต 3000sudo ufw allow 3000/tcp comment 'Allow for nostrcheck'เท่านี้ก็มี Media Server แล้วแต่ถ้าอยากให้คนอื่นเข้าถึงได้ต้องทำยังไงล่ะ
วิธีออก Public โดยไม่ต้องมี Public IP ด้วย Cloudflare Tunnel
จดโดเมนกับ Cloudflare

ไปที่ Zero Trust คลิกไปที่ Network จากนั้นคลิก create a tunnel

ตั้งชื่อ Tunnet แล้วติดตั้ง Cloudflare Tunnel ลงเครื่อง (ผมเลือก docker)

เพิ่ม Public Hostname ใน Cloudflare Tunnel Subdomain: ตั้งชื่อที่ต้องการ Domain: เลือกโดเมนที่จดเอาไว้ Type: เลือก http URL: ใส่ localhost แล้วตามด้วย port หรือใส่ IP แล้วตามด้วย port ได้เช่นกัน

แค่นี้ก็เรียบร้อย! Nostrcheck Server ของคุณพร้อมใช้งานแล้ว
มาเริ่มใช้งานกัน

เปิด URL ที่เราสร้างคลิกที่รูปมุมขวาบนเลือก Settings แล้วเลื่อนลงมาจนเจอ Server secret key

คลิกเปิดตา Coppy ไปใส่ Nostr extension ผมแนะนำ AKA Profiles จดบันทึกไว้ได้เช่นกัน

ไปเพิ่ม Media Servers ใน Amethyst

หวังว่าแนวทางนี้อาจเป็นประโยชน์ปรับใช้ได้หลายอย่าง มีส่วนไหนผิดพลาดพูดคุยเสริมกัน ขอบคุณทุกคนที่แวะมาอ่าน
ไว้เจอกันใหม่ครั้งหน้าจะเป็นเรื่องอะไรรอติตามกัน
บ๊ะบาย
ลิงค์ Github: https://github.com/quentintaranpino/nostrcheck-server
siamstr #Nostr
-
 @ dc652bee:6154e7d0
2024-09-21 08:50:55
@ dc652bee:6154e7d0
2024-09-21 08:50:55BEST TELEGRAM AIRDROP BOT
Download the telegram app, anyone who hasn't created it, your own channel is free later, you can sign up for airdrops, many have already started giving money for free . Get the ultimate airdrop experience with the best Telegram bot around! 🚀 #Bot #Airdrop #Telegram #TON.
https://t.me/Dogiators_bot/game?startapp=F80aAU4OlGJX61YK
https://t.me/tonton_intract_bot/start?startapp=eyJyZWZlcnJhbENvZGUiOiJGOER6dDAiLCJyZWZlcnJhbFNvdXJjZSI6IlRFTEVHUkFNX01JTklfQVBQIiwicmVmZXJyYWxMaW5rIjoiaHR0cHM6Ly93d3cuaW50cmFjdC5pby90bWEvcmV3YXJkcyJ9
https://t.me/gamee/start?startapp=ref_730909086
https://t.me/Bcoin2048bot/app?startapp=ref_pCGwqQ15aSZUFYa9ZEys8qRH
https://t.me/realgoats_bot/run?startapp=c127fadc-579e-485a-a68f-f901cd4e64e6
https://t.me/OwlMini_bot/app?startapp=730909086
https://t.me/bluefarming_bot/play?startapp=c8a58023
https://t.me/BitsTonboxBot/BitsAirdrops?startapp=M9Ek3ygSFAJTZ5Y4PS2aoq
https://t.me/digibuy_bot/digiverse/start?startapp=0cb38b86ee4543c74bd76ab16c1c8fd3
http://t.me/foxs_HouseBot?start=730909086
https://t.me/Agent301Bot/app?startapp=onetime730909086
t.me/RealCowsHouse_bot/cowshouse?startapp=kentId730909086
http://t.me/token1win_bot/start?startapp=refId730909086
https://t.me/MemesLabBot?start=PNT7D8
https://t.me/major/start?startapp=730909086
https://t.me/uptonfi_bot/UpTonGames?startapp=ByKBX2QurGdYa
https://t.me/catizenbot/gameapp?startapp=r_1938_7836673
https://t.me/memefi_coin_bot/main?startapp=r_27d6952978
https://t.me/whitebunnywtf_bot?start=ref666953186736f7f2eff6261f
https://t.me/pixelversexyzbot?start=730909086
https://t.me/tapswap_mirror_2_bot?start=r_730909086
https://t.me/hamster_kombaT_bot/start?startapp=kentId730909086
https://t.me/IcebergAppBot?start=referral_730909086
https://t.me/gemsee_bot?start=ref_100a006b
https://t.me/GoodRides_bot?start=NzMwOTA5MDg2
https://t.me/lost_dogs_bot/lodoapp?startapp=ref-u_730909086
https://t.me/gemzcoin_bOt/tap?startapp=nSoqE-UNEtgNUcRp5luy0w
https://t.me/QappiMinerBot?start=730909086
https://t.me/Snakelite_official_bot/Snakelite?startapp=nOuSbPc0
https://t.me/squid_squad_bot/squid?startapp=link_730909086
https://t.me/lovetap_bot?start=ref_120218
https://t.me/BIRDTonBot/app?startapp=730909086
https://t.me/LovelyLegends_bot/start?startapp=kentId730909086
https://t.me/claytoncoinbot/game?startapp=730909086
https://t.me/pehekingdom_bot/open?startapp=iAzmZVumOr
https://t.me/loody_farming_bot/LOODY/?startapp=inviter_id_40937
https://t.me/Tomarket_ai_bot/app?startapp=0000bDIo
https://t.me/CoinCryptoGameBot?start=r_JSGDH54A
https://t.me/Xyzmercoin_bot/play?startapp=BZI2CZ
https://t.me/dragonz_land_bot/app?startapp=ref-668302fc033aa4721ab5d1ea
https://t.me/BullishFarmBot/start?startapp=r_730909086
https://dashboard.wormfare.com/referral/0DC0D761
https://t.me/betfury_social_bot/app?startapp=tgReLe1ec7c70
https://t.me/PipeFlareBot/pipeflare_app?startapp=730909086
https://t.me/TimeFarmCryptoBot?start=x3jKZG0eoJa58ayY
https://t.me/MatchQuestBot/start?startapp=0cb38b86ee4543c74bd76ab16c1c8fd3
https://t.me/DiamoreCryptoBot/app?startapp=730909086
https://t.me/money_dogs_bot/money_dogs?startapp=3eAlu89K
https://t.me/ZARGatesBot/?start=2307731133
https://t.me/taptapcore_bot/Earn?startapp=b1720f3afcf04e5cb76418c267c4559e
https://t.me/Mimiland_appbot/app?startapp=ref_eyJwIjoiIiwiZiI6InJlZiIsInIiOiI3MzA5MDkwODYiLCJtIjoiNjZkNWZmMWJkNTE3MGU1M2ZiYmMwZmNiIn0=
https://t.me/CyberFinanceBot/game?startapp=cj1CRjNxRE5WbmhNQlomdT1yZWY=
https://t.me/BBQcoin_bot/BBQcoin?startapp=rp_9004676_730909086
https://t.me/PonchKick_bot/ponchiqs?startapp=730909086
https://t.me/potusclick_bot/app?startapp=r730909086
https://t.me/chickcoopofficial_bot/chickcoop?startapp=ref_730909086
https://t.me/ArtiTapBot/start?startapp=referrerId730909086
https://t.me/Frogs_HouseBot?start=730909086
https://t.me/tomo_cat_bot?start=r-cofuLtoo
https://t.me/Boom/LoudCoins?startapp=F5iKvP2LEVi9g4hFkGdpya
https://t.me/The_Rocket_bot?start=r_730909086
https://t.me/monkeycost_bot/app?startapp=r_730909086
https://t.me/tapcoinsbot/app?startapp=ref_TxCe4a
https://t.me/cexio_tap_bot?start=1722546804203779
https://t.me/cexio_tap_bot?start=1722546804203779
https://t.me/flarexgamebot?start=66743fede9b04d43fd21fe9e
https://t.me/grandcombat_bot/start?startapp=TFqI0dXjLc
https://t.me/fishing_bowl_bot/fish?startapp=EQANA57LP2PPLgBIwbnWMpHD4708uGKu7YipzvELhOt6fdnA
https://t.me/GametyPlatform_bot?start=NzMwOTA5MDg2XzA
https://t.me/HUNDTAPbot?start=r_730909086
https://t.me/BabyDogePAWS_Bot?start=r_730909086
https://t.me/BillyBobRobot/GAME?startapp=730909086
https://t.me/wcoin_tapbot?start=NzMwOTA5MDg2
https://t.me/cherrygame_io_bot/game?startapp=r_730909086
https://t.me/pirate_frenzy_bot/piratefrenzy?startapp=i7z37hc2G6
https://t.me/MMproBump_bot?start=ref_730909086
https://t.me/theHoldCoinBot/app?startapp=ref_NRPViKZ4
https://t.me/not_panda_bot/not_panda_app?startapp=9j3938HJeb
https://t.me/gmdotaibot/Airdrop?startapp=ovyova
https://t.me/GoldVerseBot/app?startapp=ref_zzT4iN
https://t.me/herewalletbot/grafun?startapp=TewJ6VV5SA2CrVidvyILAXC8diL
https://gra.fun/?ref=TewJ6VV5SA2CrVidvyILAXC8diL
https://t.me/owlsonton_bot?start=730909086
https://t.me/y_nation_bot/start?startapp=NKS74T
https://t.me/cedex_tap_bot?start=1725744305355276
https://t.me/TondropEarnBot/app?startapp=66dfd225c839152d9203f5a9
https://t.me/BYIN_official_bot/BYIN_Launchpad_Beta?startapp=q3lj8O41
https://t.me/ARIXcoin_bot?start=ref_730909086
https://t.me/sunkongmyth_bot/sunkong_miniapp?startapp=E987837FE
https://t.me/boolfamily_bot/join?startapp=8T1X0
https://t.me/tonstationgames_bot/app?startapp=ref_aysq8p4swodmv4ex6c7e4y
https://t.me/y_nation_bot/start?startapp=NKS74T
https://t.me/GalaCoin_bot/app?startapp=ref_KFfSylID
https://t.me/Yaytsogram_bot?start=invite4546481
https://t.me/battle_games_com_bot/start?startapp=frndId730909086
https://t.me/PinEye_Bot/pineye?startapp=r_730909086
https://t.me/pocketfi_bot/Mining?startapp=730909086
https://t.me/SatoshiMiner_Hq_Bot?start=730909086
https://t.me/sidekick_fans_bot?start=730909086
https://t.me/bums/app?startapp=ref_rgws9zFi
https://t.me/TondropEarnBot/app?startapp=66dfd225c839152d9203f5a9
https://t.me/head_coin_bot/start?startapp=bonusId730909086
https://t.me/onus_tap_tap_tap_bot/join?startapp=1722155904792
https://t.me/Atleta_tap_bot/tap?startapp=a89197f4-6ef7-4925-a38d-cbe0cc71aa34
https://t.me/SecretPadBot/app?startapp=r730909086
https://t.me/Binance_Moonbix_bot/start?startApp=ref_730909086&startapp=ref_730909086&utm_medium=web_share_copy
https://t.me/catsdogs_game_bot/join?startapp=730909086
https://t.me/claytoncoinbot/game?startapp=730909086
https://t.me/playpenchobot/play?startapp=ZF6EG6NCVC
🎉 Exciting news alert! 🚀 Join us today - it's totally FREE and packed with unlimited opportunities in the Telegram app! 📱 Dive into numerous ongoing projects and explore amazing releases already out there. 🌟 Don't miss out on all the fun, creativity, and innovation waiting for you! 💫 Let's make things happen together! #memefi #hamster kompat #Iblum #tapswap .
-
 @ f5f9e186:1fb7e621
2024-09-21 08:18:34
@ f5f9e186:1fb7e621
2024-09-21 08:18:34asdasd
asdsada
-
 @ 09fbf8f3:fa3d60f0
2024-09-21 07:44:42
@ 09fbf8f3:fa3d60f0
2024-09-21 07:44:42软件名称: OSSQ
这款软件打开时杀毒软件会报毒,大家忽略即可,如果实在不放心,大家可以先杀毒后再使用!
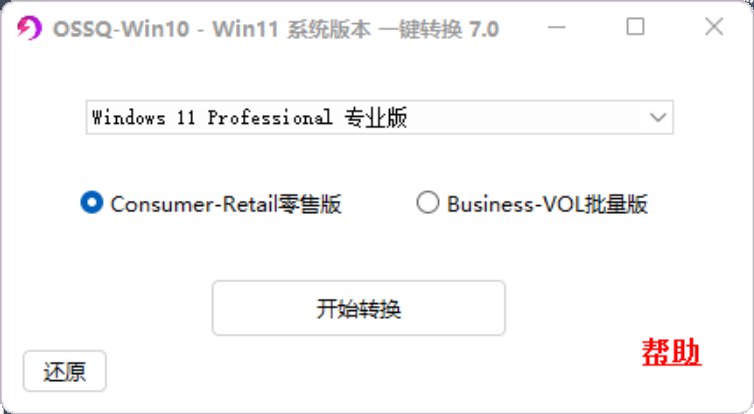
软件使用很简单,选择想要转换的版本,选择后点【开始转换】即可。
 这里转换需要点时间,大家耐心等待,等转换成功了以后会跳出“版本切换成功!”的提示。
这里转换需要点时间,大家耐心等待,等转换成功了以后会跳出“版本切换成功!”的提示。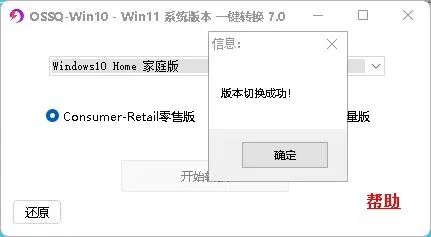
转换后再重启电脑,那么你的系统版本就转换成功了。 我自己电脑是Windows11,但我办公电脑是Win10,看看我原来的是专业版。
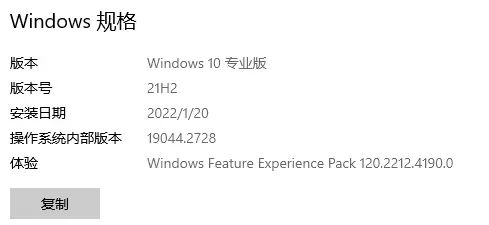
转换以后就变成了家庭版了。
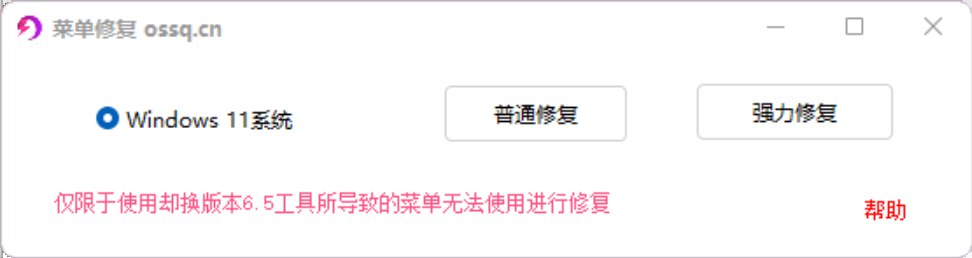
这个软件在版本转换后,可能会出现“Win+X”和右键开始菜单失效的问题,这时候可以用作者开发的一款“菜单修复”软件进行修复。
下载地址:
蓝奏云: https://lepidus.lanzouv.com/b00zx2euef 密码:gomr
菜单修复工具: 蓝奏云: https://lepidus.lanzouv.com/b00zx2euij 密码:9dl6
-
 @ a012dc82:6458a70d
2024-09-21 06:43:47
@ a012dc82:6458a70d
2024-09-21 06:43:47Table Of Content
-
Factors behind the Rise in Bitcoin's Hash Rate
-
Implications of the Rise in Bitcoin's Hash Rate
-
Conclusion
-
FAQ
Bitcoin's hash rate has been skyrocketing lately, with the mining difficulty hitting all-time highs. This surge in hash rate has left many wondering about the reasons behind it and its implications for the cryptocurrency industry. In this article, we will explore the factors contributing to the rise in Bitcoin's hash rate and the implications of this development.
Factors behind the Rise in Bitcoin's Hash Rate:
Increase in the number of miners
One of the primary factors behind the rise in Bitcoin's hash rate is the increase in the number of miners. As the price of Bitcoin continues to surge, more and more people are entering the mining space, trying to capitalize on the opportunity to earn profits. This has led to an increase in the number of miners, which, in turn, has resulted in a surge in hash rate.
Improved Mining Hardware
Another reason for the increase in hash rate is the improvement in mining hardware. As the demand for Bitcoin continues to rise, mining hardware manufacturers are constantly innovating and improving their products to meet the demand. This has resulted in more efficient and powerful mining hardware that can process more transactions in less time, leading to an increase in hash rate.
Increase in Institutional Investment
Institutional investors are increasingly investing in Bitcoin, resulting in an increase in the overall hash rate. These investors have more resources and can afford to purchase high-end mining equipment, which leads to an increase in hash rate.
Halving
Bitcoin undergoes a halving event every four years, which reduces the reward for miners. This event is designed to control the supply of Bitcoin and maintain its value. However, it also has the effect of reducing the number of miners, which results in a drop in hash rate. After each halving event, it takes some time for the hash rate to recover, and this could be a contributing factor to the recent surge in hash rate.
Implications of the Rise in Bitcoin's Hash Rate:
Increased Security:
The rise in hash rate means that the Bitcoin network is becoming more secure. The higher the hash rate, the more difficult it becomes to launch a 51% attack, where an attacker gains control of the network. This increased security is good news for Bitcoin investors as it reduces the risk of a security breach.
Reduced Mining Rewards
As the hash rate increases, mining rewards become more difficult to obtain. This means that smaller mining operations may be forced to shut down, resulting in a more centralized mining ecosystem. This could be seen as a negative development as it goes against the decentralized nature of cryptocurrencies.
More Transactions
The increase in hash rate means that more transactions can be processed on the Bitcoin network. This is good news for Bitcoin users as it reduces transaction times and fees. With the rise in hash rate, Bitcoin is becoming a more practical payment method, which could lead to increased adoption.
Conclusion
The rise in Bitcoin's hash rate is a result of several factors, including an increase in the number of miners, improved mining hardware, institutional investment, and the halving event. While there are some potential drawbacks to the increase in hash rate, such as reduced mining rewards and a more centralized mining ecosystem, the benefits of increased security and faster transaction processing make it a positive development for the cryptocurrency industry. As Bitcoin continues to gain mainstream acceptance, it is likely that the hash rate will continue to increase, leading to further innovation and improvements in the network.
FAQ
What is Bitcoin's hash rate? Hash rate is the measure of the computational power of the Bitcoin network. It is the number of calculations that the network can perform per second.
Why is the hash rate important? The hash rate is important because it determines the security of the Bitcoin network. The higher the hash rate, the more secure the network becomes.
How is the hash rate calculated? The hash rate is calculated by counting the number of calculations that the network can perform per second.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 6bae33c8:607272e8
2024-09-20 15:32:58
@ 6bae33c8:607272e8
2024-09-20 15:32:58I went 2-3 last week to bring my two-week mark to 3-7. I’m not drawing dead yet, but obviously you don’t get many of those stretches if you expect to cash in this contest.
This week I feel more strongly about a couple games:
I love the Bengals laying the 7.5 at home against the Football team. The Giants should have beaten them in Washington last week (but for not having a kicker and Malik Nabers dropping an easy 4th-down conversion at the end.) The Bengals will get Ja’Marr Chase going and blow them out.
I like the desperate Ravens in Dallas laying only one point. It’s usually not a great idea to think, “I can’t imagine them at 0-3” so I have to bet them when they’re 0-2 because you probably didn’t foresee them at 0-2, either, and once they’re 0-2, they only need to lose one road game to get to 0-3. That said, I think they’ll be focused, and the Cowboys would have to bring their A game to beat them.
Give me the Falcons getting the 3.5 at home against the Chiefs. Atlanta should hang with them.
I like the Texans laying less than a FG in Minnesota. The Vikings have played well, but I’ll sell high off the big win over the 49ers.
I was on the Bucs initially, but something feels off about it. It’s too obvious, the Broncos aren’t getting nearly enough points with Bo Nix. I’ll stay away.
My last choice is between the Colts as a buy-low at home and the way overpriced Lions on the road.
The Colts are ugly, can’t stop the run, missing DeForest Buckner, etc. But really the names on the jerseys, the details of that sort are already priced in, not the way to handicap games. The better way is to get a sense of the league’s ebb and flow. I think the Colts win at home, maybe Anthony Richardson plays better this week.
The Lions should be 2.5-point underdogs, so this line caught my attention — something is off, and it gives me a feeling I’m missing something, makes me want to take them. But that’s probably overthinking it. I’ll take the Colts with the last pick.
Final Picks

-
 @ 6bae33c8:607272e8
2024-09-20 15:31:21
@ 6bae33c8:607272e8
2024-09-20 15:31:21This was one of those games where I’m grateful to be in Portugal and not catching it in real time. I have Rhamondre Stevenson in one league unfortunately, but none of the prominent players on the Jets (who I don’t have) went crazy, either. And I finally got a Thursday night ATS win in the books. I probably should have used it in the Circa Millions, but I hate submitting the whole slate on Thursday.
-
Aaron Rodgers looks sharp at 40 still. He even moved well in the pocket and scrambled for some yards. The Jets might actually be good.
-
Breece Hall is getting the requisite work (16 carries, five targets), but Braelon Allen (11 carries, 3 targets) looks more or less just as good. On the one hand, Hall won’t dominate the workload the way say Jonathan Taylor or Saquon Barkley might on their respective teams, but on the other, he’ll stay fresh and still get plenty. If Hall goes down, Allen is probably a top-five back instantly.
-
Rodgers spread the ball around, but the Jets tree is pretty narrow: Garrett Wilson, Allen Lazard, Mike Williams, Tyler Conklin and the backs. Wilson had a modest game, but it was a good sign they kept going to him and eventually got him the TD (while he was covered by top corner Christian Gonzalez) even with a big lead.
-
Conklin looks like a top-10 TE right now. I’d expect Williams to overtake Lazard before long as the team’s No. 2 wideout. He’s just better and more explosive.
-
There’s not much to say about the Pats. Antonio Gibson looked okay after Stevenson was pulled following his fumble. DeMario Douglas took Hunter Henry’s place as the lone productive pass catcher. Maybe you could use one of those two in a pinch.
-
It’s time to see more of Drake Maye who looked comfortable and confident in mop-up duty. The circumstances are rough, but Jacoby Brissett is best suited as a stop-gap game-manging backup, not someone who should block real prospect.
-
-
 @ eac63075:b4988b48
2024-09-20 08:46:49
@ eac63075:b4988b48
2024-09-20 08:46:49Lá na outra rede, o Dov havia feito um post bacana mostrando como usar a Electrum mobile de cold wallet nessa playlist.
Então ao comentar que a minha primeira cold wallet havia sido uma Electrum num notebook velho e formatado só pra isso, algumas pessoas me perguntaram sobre meu setup atual.
Então preparei o seguinte esboço:
No geral é: * Server Umbrel para os nodes * Coldcard e Ledger (coldwallets) * Computador criptografado e celular android com área segura p/ apps
É um caso de uso extremo mas além da auto-soberania e custódia dos meus satoshis, essa estrutura ainda me permite:
- Participar do consenso do Bitcoin
- Auxiliar no roteamento de sats na Lightning Network
- Fazer coinjoin facilmente para aumentar a privacidade
E embora a estrutura pareça complicada, é bastante simples:
- Raspberry Pi 4 com Debian e Umbrel (p/ os nodes e servers)
- Celular antigo android com área segura e sem simcard
- Notebook com storage criptografada
- Ledger Nano X
- Coldcard
E ainda pude evoluir de N.O.I.A. (Network Operator Innovator and Advocate) para M.A. (Minerador Anônimo), com uma Nerdminer pra tentar um ticket da sorte a cada 10 minutos
Não esqueça que uma cold wallet para a auto-custódia pode começar com um computador ou celular velho!
É mais simples do que parece e praticar sua auto-soberania e custódia significa na verdade liberdade e privacidade nesse mundo digital!
-
 @ eac63075:b4988b48
2024-09-20 09:23:23
@ eac63075:b4988b48
2024-09-20 09:23:23Overview of the Infrastructure
- Umbrel/Citadel/RaspiBlitz/Start9 Server
- Purpose: Acts as your personal Bitcoin and Lightning Network node.
- Setup: Installed on a Raspberry Pi 4 running Debian or Umbrel OS.
- Benefits:
- Participate in Bitcoin Consensus: Validates transactions and blocks independently.
- Lightning Network Routing: Facilitates faster transactions and earns routing fees.
- Cold Storage Wallets
- Coldcard: A highly secure hardware wallet designed specifically for Bitcoin.
- Ledger Nano X: A versatile hardware wallet supporting multiple cryptocurrencies.
- Purpose: Store your Bitcoin offline to protect against online threats.
- Secure Devices
- Encrypted Computer: A notebook with encrypted storage for managing your wallets and nodes securely.
- Android Phone with Secure Area:
- Old Device: Repurposed without a SIM card to minimize exposure.
- Secure Area for Apps: Uses features like Samsung's Secure Folder/Knox to isolate sensitive applications.
- NerdMiner
- Purpose: A compact mining device like the Nerdminer V2 to engage in Bitcoin mining.
- Function: Attempts to mine Bitcoin blocks, offering a chance (albeit very low) to earn block rewards and learn about the mining process.
 ### Advantages of This Setup
### Advantages of This Setup- Self-Sovereignty: You have complete control over your funds without relying on third-party services.
- Enhanced Privacy:
- CoinJoin Transactions: Mix your coins with others to obfuscate transaction history.
- No SIM Card Devices: Reduces the risk of SIM swapping attacks.
- Network Participation:
- Consensus Involvement: By running a full node, you help maintain the network's integrity.
- Lightning Network: Improve transaction speeds and network scalability.
- Security:
- Cold Storage: Keeps your private keys offline, away from potential online threats.
- Encrypted Devices: Protects data even if physical devices are lost or stolen.
 ### Simplifying the Perceived Complexity
### Simplifying the Perceived ComplexityWhile the infrastructure may seem daunting, it's more approachable than it appears:
- Starting Point: Use an old computer or phone as a cold wallet with software like Electrum or Sparrow.
- Step-by-Step Setup:
- Begin with setting up the Umbrel/Citadel/RaspiBlitz/Start9 server.
- Gradually add hardware wallets like Coldcard, SeedSigner DIY, Jade, Ledger, Trezor or Onekey.
- Implement security measures on your existing devices.
- Community Resources: Numerous guides and communities are available to assist with each step.
 ### Embracing Freedom and Privacy
### Embracing Freedom and PrivacyPracticing self-sovereignty and custody isn't just about securing your Bitcoin—it's about embracing freedom and privacy in the digital age. By taking control:
- Financial Independence: You're not dependent on banks or exchanges.
- Data Privacy: Your financial data remains confidential.
- Empowerment: Gain a deeper understanding of how Bitcoin and blockchain technology work.
Remember: Even simple steps like using an old device as a cold wallet can significantly enhance your security. The journey towards complete self-sovereignty is a progressive one, and each step you take strengthens your position in the digital world.
-
 @ 3bf0c63f:aefa459d
2024-09-18 10:37:09
@ 3bf0c63f:aefa459d
2024-09-18 10:37:09How to do curation and businesses on Nostr
Suppose you want to start a Nostr business.
You might be tempted to make a closed platform that reuses Nostr identities and grabs (some) content from the external Nostr network, only to imprison it inside your thing -- and then you're going to run an amazing AI-powered algorithm on that content and "surface" only the best stuff and people will flock to your app.
This will be specially good if you're going after one of the many unexplored niches of Nostr in which reading immediately from people you know doesn't work as you generally want to discover new things from the outer world, such as:
- food recipe sharing;
- sharing of long articles about varying topics;
- markets for used goods;
- freelancer work and job offers;
- specific in-game lobbies and matchmaking;
- directories of accredited professionals;
- sharing of original music, drawings and other artistic creations;
- restaurant recommendations
- and so on.
But that is not the correct approach and damages the freedom and interoperability of Nostr, posing a centralization threat to the protocol. Even if it "works" and your business is incredibly successful it will just enshrine you as the head of a platform that controls users and thus is prone to all the bad things that happen to all these platforms. Your company will start to display ads and shape the public discourse, you'll need a big legal team, the FBI will talk to you, advertisers will play a big role and so on.
If you are interested in Nostr today that must be because you appreciate the fact that it is not owned by any companies, so it's safe to assume you don't want to be that company that owns it. So what should you do instead? Here's an idea in two steps:
- Write a Nostr client tailored to the niche you want to cover
If it's a music sharing thing, then the client will have a way to play the audio and so on; if it's a restaurant sharing it will have maps with the locations of the restaurants or whatever, you get the idea. Hopefully there will be a NIP or a NUD specifying how to create and interact with events relating to this niche, or you will write or contribute with the creation of one, because without interoperability this can't be Nostr.
The client should work independently of any special backend requirements and ideally be open-source. It should have a way for users to configure to which relays they want to connect to see "global" content -- i.e., they might want to connect to
wss://nostr.chrysalisrecords.com/to see only the latest music releases accredited by that label or towss://nostr.indiemusic.com/to get music from independent producers from that community.- Run a relay that does all the magic
This is where your value-adding capabilities come into play: if you have that magic sauce you should be able to apply it here. Your service -- let's call it
wss://magicsaucemusic.com/-- will charge people or do some KYM (know your music) validation or use some very advanced AI sorcery to filter out the spam and the garbage and display the best content to your users who will request the global feed from it (["REQ", "_", {}]), and this will cause people to want to publish to your relay while others will want to read from it.You set your relay as the default option in the client and let things happen. Your relay is like your "website" and people are free to connect to it or not. You don't own the network, you're just competing against other websites on a leveled playing field, so you're not responsible for it. Users get seamless browsing across multiple websites, unified identities, a unified interface (that could be different in a different client) and social interaction capabilities that work in the same way for all, and they do not depend on you, therefore they're more likely to trust you.
Does this centralize the network still? But this a simple and easy way to go about the matter and scales well in all aspects.
Besides allowing users to connect to specific relays for getting a feed of curated content, such clients should also do all kinds of "social" (i.e. following, commenting etc) activities (if they choose to do that) using the outbox model -- i.e. if I find a musician I like under
wss://magicsaucemusic.comand I decide to follow them I should keep getting updates from them even if they get banned from that relay and start publishing onwss://nos.lolorwss://relay.damus.ioor whatever relay that doesn't even know anything about music.The hardcoded defaults and manual typing of relay URLs can be annoying. But I think it works well at the current stage of Nostr development. Soon, though, we can create events that recommend other relays or share relay lists specific to each kind of activity so users can get in-app suggestions of relays their friends are using to get their music from and so on. That kind of stuff can go a long way.
-
 @ 17538dc2:71ed77c4
2024-09-16 15:26:32
@ 17538dc2:71ed77c4
2024-09-16 15:26:32
Quiztime
Oil and gas
Oil and gas is naturally occurring. The prevalent worldview is that oil & gas has a biotic origin. There are real world examples of abiotic oil deposits, which proponents of the status quo have a difficult time reconciling.
Irregardless, when oil & gas is burned, it simply turns to plant food (carbon dioxide + water).
Oil and gas greens the Earth, and increases fertilization and agricultural crop yield across the globe.

The energy density of oil and gas is only surpassed by that of nuclear power.
Energy produced by oil and gas combustion is generally on-demand, reliable, economically storable & transportable.
Solar
The sun is an abudant energy source, which keeps Earth warm, and alive. Thank you sun 🌞!
With the exception of places such as the UK, where it is unclear if inhabitants have ever seen the sun, solar rays keep plants, animals, and humans happy & alive on most of planet Earth.
Inventions such as solar panels harness the sun's energy, and convert it to electricity.
Solar panels consist of silicon, rare earth metals, and require toxic metals.
Solar panels have an expected life of decades, are not readily or economically recyclable.
A very low solar energy density practically means that land is inefficiently utilized in solar energy production. Solar used on arable land can no longer be farmed, and where no plains exist solar is known to cause deforestation and landslides.
Solar energy is not reliable, not can it be summoned on demand. Solar energy is not economically storable, and is many cases is not produced at the point of demand.
Despite central planner mandates & subsidies in the US, the #EULAG and elsewhere, due to its intermittent nature, solar power cannot be counted on to replace reliable power generation in nuclear, hydro, or carbon fuel thermoelectric plants.
What this means is that solar does not replace, and yet ratheradds to reliable energy generation, as most people in the developed world would not be OK with having electricity for at most 1/3 of the day. This increases the price of electricity, which in turn increases energy poverty, and drives businesses to shut down manufacturing, or move to a more energy competitive jurisdiction.
The capital wasted by central planners could have been used to reduce burden on consumers, and businesses, or fund healthcare, infrastructure, or other services.
It should be noted that off grid applications where there is no grid, or energy alternatives can be massively useful for folks otherwise without electricity.
Which energy source would you consider renewable?
-
 @ a012dc82:6458a70d
2024-09-20 05:55:35
@ a012dc82:6458a70d
2024-09-20 05:55:35Table Of Content
-
Bitcoin Beach Wallet Rebrands as Global Shore Wallet
-
Feature-Rich Wallet for Enhanced User Experience
-
Partnerships to Drive Adoption and Education
-
Conclusion
-
FAQ
Bitcoin Beach Wallet, originally developed to support the Bitcoin community in El Salvador, has made significant strides since its inception. The wallet started as a grassroots project aimed at driving Bitcoin adoption in a small coastal town, and has now transformed into a global force. With a new name and a plethora of innovative features, the wallet is set to become a major player in the world of cryptocurrency.
Bitcoin Beach Wallet Rebrands as Global Shore Wallet
As part of the wallet's evolution, it has been rebranded as the Global Shore Wallet. This name change reflects the wallet's expanded focus beyond El Salvador, as it aims to promote Bitcoin adoption and financial inclusion in communities across the globe. The new name signifies a broader commitment to empowering individuals and businesses with a versatile cryptocurrency wallet that caters to their unique needs.
Feature-Rich Wallet for Enhanced User Experience
The Global Shore Wallet comes packed with features designed to enhance the user experience and promote widespread adoption. Some of these exciting new features include:
1. Multilingual Support
To cater to a global audience, the wallet now supports multiple languages, ensuring that users worldwide can navigate and use the wallet with ease.
2. Multi-Currency Compatibility
In addition to Bitcoin, the wallet now supports various cryptocurrencies, such as Ethereum, Litecoin, and more, making it a one-stop solution for users looking to manage multiple digital assets.
3. Lightning Network Integration
To facilitate faster, cheaper, and more scalable transactions, the Global Shore Wallet has integrated the Lightning Network. This upgrade allows users to make instant payments with minimal fees.
4. Advanced Security Features
The wallet offers cutting-edge security features, such as biometric authentication, two-factor authentication, and encrypted backups, ensuring that users' digital assets are well-protected.
5. Seamless Onboarding
The Global Shore Wallet simplifies the onboarding process with a user-friendly interface and step-by-step guidance, making it easy for new users to get started with cryptocurrency.
Partnerships to Drive Adoption and Education
To further its mission of promoting Bitcoin adoption and financial inclusion, the Global Shore Wallet team has entered into strategic partnerships with various organizations. These collaborations aim to provide educational resources and offer support to communities looking to embrace cryptocurrency.
Conclusion
The transformation of the Bitcoin Beach Wallet into the Global Shore Wallet marks an important milestone in the journey towards global cryptocurrency adoption. With a new name, cutting-edge features, and strategic partnerships, the Global Shore Wallet is poised to become a leading wallet solution for individuals and businesses around the world. By fostering financial inclusion and empowering users with the tools they need to thrive in the digital economy, the Global Shore Wallet is set to make a lasting impact on the cryptocurrency landscape.
FAQ
What was the original purpose of the Bitcoin Beach Wallet? The Bitcoin Beach Wallet was initially developed to support the Bitcoin community in El Salvador, focusing on driving Bitcoin adoption in a small coastal town.
What is the new name of the Bitcoin Beach Wallet? The Bitcoin Beach Wallet has been rebranded as the Global Shore Wallet.
Why was the name changed to Global Shore Wallet? The name change reflects the wallet's expanded focus on promoting Bitcoin adoption and financial inclusion in communities across the globe, beyond just El Salvador.
How is the Global Shore Wallet promoting Bitcoin adoption? The Global Shore Wallet is fostering adoption through its user-friendly features, educational resources, and strategic partnerships with organizations to support communities looking to embrace cryptocurrency.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 592295cf:413a0db9
2024-09-14 18:13:41
@ 592295cf:413a0db9
2024-09-14 18:13:4109 09 week
The billboard has reached its first goal.
I don't understand anything, too much.
The web is a dangerous place, maybe the couch at home is for you.
Nostr is like being in a public place like a bar and you listen to the radio, and you can decide which radio to choose, you can also talk on the radio, only those who follow you and those who are connected to that frequency can listen to you.
We talk on multiple frequencies so if one is offline they can hear me on the other.
Spam will always be a constant as are fixed costs, personnel costs, taxes things that people in general hate
A lot of talk that will be blown away by the wind.
Jack Dorsey says Nostr will be a protocol for private encrypted chats
-
Open-sats drama
-
Carnivore dietitian
-
Lightning diatribe
-
This is already Twitter 😉
Fiatjaf explained for the umpteenth time what the outbox model is, now those who look at images instead of reading books must have understood it too. My note, Patricia writes in her relays write, including select some in her outbox 10002 kind. it was a dev page of something, so maybe it won't be online for long
Thinking that with Kamala Harris's victory, the price of Bitcoin would hit a low and holders would be happy to buy. 🤣🤣 Instead with Trump new all time High, holders would be happy. 🤣🤣 Lol Moment.
I read the article about btcmap maps, there were some notes to make but I didn't, it's beyond my level, it was only for builders.
Satlantis, trustroots, and wherostr were not noted.
I had this thought that we will not "succeed" in building the openness of type 1, in the following nips, because of the relays and because discovering new things has a cost, and no one wants to discover new things. And then after that the others should use them, but how and after that at least two others appear who are doing a similar thing, but they don't talk to each other because they don't have time.
If the time horizon is 10 years, those who survive will see.
Keeping calm seems difficult.
I tried nostr-relay-tray works. It works, I would suggest a couple of changes
- Delete some events.
- View events
- Search by npub id or time
- Delete by time.
These are difficult things but they can be done with a database, so they may as well not be done.
I hope that all the controversies are forgotten and overcome and we are more serene.
-
-
 @ ee11a5df:b76c4e49
2024-09-11 08:16:37
@ ee11a5df:b76c4e49
2024-09-11 08:16:37Bye-Bye Reply Guy
There is a camp of nostr developers that believe spam filtering needs to be done by relays. Or at the very least by DVMs. I concur. In this way, once you configure what you want to see, it applies to all nostr clients.
But we are not there yet.
In the mean time we have ReplyGuy, and gossip needed some changes to deal with it.
Strategies in Short
- WEB OF TRUST: Only accept events from people you follow, or people they follow - this avoids new people entirely until somebody else that you follow friends them first, which is too restrictive for some people.
- TRUSTED RELAYS: Allow every post from relays that you trust to do good spam filtering.
- REJECT FRESH PUBKEYS: Only accept events from people you have seen before - this allows you to find new people, but you will miss their very first post (their second post must count as someone you have seen before, even if you discarded the first post)
- PATTERN MATCHING: Scan for known spam phrases and words and block those events, either on content or metadata or both or more.
- TIE-IN TO EXTERNAL SYSTEMS: Require a valid NIP-05, or other nostr event binding their identity to some external identity
- PROOF OF WORK: Require a minimum proof-of-work
All of these strategies are useful, but they have to be combined properly.
filter.rhai
Gossip loads a file called "filter.rhai" in your gossip directory if it exists. It must be a Rhai language script that meets certain requirements (see the example in the gossip source code directory). Then it applies it to filter spam.
This spam filtering code is being updated currently. It is not even on unstable yet, but it will be there probably tomorrow sometime. Then to master. Eventually to a release.
Here is an example using all of the techniques listed above:
```rhai // This is a sample spam filtering script for the gossip nostr // client. The language is called Rhai, details are at: // https://rhai.rs/book/ // // For gossip to find your spam filtering script, put it in // your gossip profile directory. See // https://docs.rs/dirs/latest/dirs/fn.data_dir.html // to find the base directory. A subdirectory "gossip" is your // gossip data directory which for most people is their profile // directory too. (Note: if you use a GOSSIP_PROFILE, you'll // need to put it one directory deeper into that profile // directory). // // This filter is used to filter out and refuse to process // incoming events as they flow in from relays, and also to // filter which events get/ displayed in certain circumstances. // It is only run on feed-displayable event kinds, and only by // authors you are not following. In case of error, nothing is // filtered. // // You must define a function called 'filter' which returns one // of these constant values: // DENY (the event is filtered out) // ALLOW (the event is allowed through) // MUTE (the event is filtered out, and the author is // automatically muted) // // Your script will be provided the following global variables: // 'caller' - a string that is one of "Process", // "Thread", "Inbox" or "Global" indicating // which part of the code is running your // script // 'content' - the event content as a string // 'id' - the event ID, as a hex string // 'kind' - the event kind as an integer // 'muted' - if the author is in your mute list // 'name' - if we have it, the name of the author // (or your petname), else an empty string // 'nip05valid' - whether nip05 is valid for the author, // as a boolean // 'pow' - the Proof of Work on the event // 'pubkey' - the event author public key, as a hex // string // 'seconds_known' - the number of seconds that the author // of the event has been known to gossip // 'spamsafe' - true only if the event came in from a // relay marked as SpamSafe during Process // (even if the global setting for SpamSafe // is off)
fn filter() {
// Show spam on global // (global events are ephemeral; these won't grow the // database) if caller=="Global" { return ALLOW; } // Block ReplyGuy if name.contains("ReplyGuy") || name.contains("ReplyGal") { return DENY; } // Block known DM spam // (giftwraps are unwrapped before the content is passed to // this script) if content.to_lower().contains( "Mr. Gift and Mrs. Wrap under the tree, KISSING!" ) { return DENY; } // Reject events from new pubkeys, unless they have a high // PoW or we somehow already have a nip05valid for them // // If this turns out to be a legit person, we will start // hearing their events 2 seconds from now, so we will // only miss their very first event. if seconds_known <= 2 && pow < 25 && !nip05valid { return DENY; } // Mute offensive people if content.to_lower().contains(" kike") || content.to_lower().contains("kike ") || content.to_lower().contains(" nigger") || content.to_lower().contains("nigger ") { return MUTE; } // Reject events from muted people // // Gossip already does this internally, and since we are // not Process, this is rather redundant. But this works // as an example. if muted { return DENY; } // Accept if the PoW is large enough if pow >= 25 { return ALLOW; } // Accept if their NIP-05 is valid if nip05valid { return ALLOW; } // Accept if the event came through a spamsafe relay if spamsafe { return ALLOW; } // Reject the rest DENY} ```
-
 @ 09fbf8f3:fa3d60f0
2024-09-10 13:22:42
@ 09fbf8f3:fa3d60f0
2024-09-10 13:22:42发现一个可以将Telegram频道内容转换为微博客。
-
开源项目: BroadcastChannel
-
演示站点:https://memo.miantiao.me/
✨ 特性 * 将 Telegram Channel 转为微博客 * SEO 友好 /sitemap.xml * 浏览器端 0 JS * 提供 RSS 和 RSS JSON /rss.xml /rss.json
使用 Astro 框架,支持部署在 Cloudflare、Netlify、Vercel 等支持 Node.js SSR 的无服务器平台或 VPS,可搜索,可 RSS 订阅
🏗️部署注意: * 项目通过 https://t.me/s/ 获取频道内容,如果频道被限制无法预览会显示空白 * 频道需要关闭 Restricting Saving Content * 环境变量 CHANNEL 值必须为频道 ID * 环境变量 TIMEZONE 值不要添加双引号 * 建议安装测试时只填写 CHANNEL 值 * BUG: 带引用回复的内容无法显示 已修复 * BUG: 带自定义 emoji 的无法显示 已修复 * BUG: 带 Quote 的内容无法显示
-
-
 @ 502ab02a:a2860397
2024-09-20 02:30:23
@ 502ab02a:a2860397
2024-09-20 02:30:23
มีเรื่องจะประกาศครับ ถ้าสามารถแชร์ออกไปได้ก็ยินดีมากครับ
เป็นความตั้งใจตั้งแต่ก่อนงาน Thailand Bitcoin Conference 2024 ว่าจะเป็นงานสุดท้ายที่ผมจะใช้คำว่า ขนมคีโต
ตลอดเส้นทางที่ผ่านมา หมวกอีกใบนึงของผมคือ การถ่ายทอดความรู้ที่ศึกษามาในแขนงโภชนาการ และคำถามตลอดกาลคือ "อันไหนเป็นอาหารคีโต"
จริงอยู่ครับก็ยินดีตอบให้ได้ แต่ลึกๆมันก็มีความขุ่นๆนิดๆว่า หากเป็นขวบปีแรกของคีโตก็ยังพอเข้าใจ แต่ขณะนี้ก้าวเข้าวปีที่ 8 แล้ว อีกไม่เท่าไรก็ 10ปีคีโตในไทยแล้ว สิ่งแรกที่คนคีโตมองหาเวลาซื้ออาหารคือ ฉลากคีโต
แล้วพอเจอบางสินค้าแปะป้ายคีโต แต่มีวัตถุดิบที่ต่างจากกูรูต่างจากเจ้าพ่อเจ้าแม่คีโต ได้บัญญัติไว้ ก็เกิดความสับสนวุ่นวายทะเลาะเบาะแว้ง ว่าตกลงมันเป็นอาหารคีโตหรือไม่
ผมเลือกทางนี้ครับ หักดิบไปเลย
ต่อไปนี้ผมจะไม่ใส่คำว่า คีโต ในชื่อเรียกอาหาร ต่อไปนี้จะไม่มีชีสเค้กคีโต ดาร์คชอคกานาซคีโต หน้าไก่คีโต บลาบลาบลา ที่มีคีโตเป็นชื่อเรียก อีกต่อไปครับ พอกันทีกับสิ่งนี้
ของกินทุกอย่างที่ผมทำ จะใช้ความเชี่ยวชาญด้านโภชนาการ ความสะอาด สุขอนามัย ฉลากสารอาหาร ใช้การคำนวนแบบเผื่อข้อผิดพลาด(บวก ไม่ลบ) ด้วยการใส่ Macro Nutrient ให้ในทุกเมนู !!!!
เพราะผมเชื่อว่า การกินคาร์บต่ำ เป็นการกินแบบ "ปกติ" การกินคาร์บมากก็เป็นการกินแบบ "ปกติ" เหมือนคนไม่ชอบกินผิก ไม่ชอบกินปลา ไม่ชอบกินเนื้อ อันนี้มันก็แค่คนไม่ชอบกินคาร์บสูงเกินไป แค่นั้นครับ เป็นการกินแบบปกติ ย้ำ เป็นการกินแบบปกติ คาร์บต่ำแบบคีโต เป็นการกินแบบปกติ ที่ควรเป็นมานานแล้วด้วย
การยัดทะนานคาร์บสูงมากๆ ในมุมมองผมคือ นี่แหละที่ไม่ปกติ
ทีนี้ความไม่ปกตินี้มันก็ไม่ผิดอะไรด้วย ถ้าคนกินไม่ปกติ นิยามไม่ปกติคือ ไม่ใช่คนทั่วๆไปเช่น นักกล้าม นักกีฬา ผู้ที่ใช้ "พลังงาน" สูงมากๆแลละต้องการใช้คาร์บ เพื่อการใดการหนึ่งโดยเฉพาะ ดังนั้นไม่มีอะไรที่ผิดเลยครับ ใครอยากกินอะไร กิน ตราบใดที่เรารู้ตัวเราเองว่าทำอะไร
ผมอยู่ในวงการธุรกิจทั้งอาหารและการโฆษณา เข้าใจดีครับว่าการแปะป้ายคีโต คือการช่วยให้คนตัดสินใจง่ายขึ้น เข้าใจง่ายขึ้น ช่วยในการขายให้สะดวกขึ้น แต่ ผมพอแล้วครับ เหรียญอีกด้านนึงของป้ายนีคือ มันไม่ได้ช่วยให้คนคีโต เรียนรู้การทำความเข้าใจด้านสารอาหารเท่าที่ผมคาดหวัง เพราะถ้าไม่มีป้ายพวกนี้ คนคีโตหลายๆคนถึงกับไปไม่เป็นกันเลยทีเดียว แล้วทุกวันนี้เหรียญมันออกด้านนี้ซะเยอะด้วย
นอกจากนี้ประเด็นที่หลีกไม่ได้คือ การหมอบคลานเข้ารับวัตถุดิบคีโตจากกูรู ซึ่งไม่เคยได้เหตุผลในการ "ห้าม" ของหลายๆอย่างเช่น สารหวานบางประเภท แครอท ฟักทอง(ตัวนี้มีคนถามและส่งมาให้ดูเยอะ เดี๋ยวจัดให้เคลียร์ๆ)
ซึ่งใครที่เลือกกินสิ่งนี้แล้วแชร์ความรู้ให้คนคีโตว่ากินได้ ก็จะโดนตรรกะวิบัติจากกูรูด้วยการแปะคำว่า "อยากกิน เลยชวนคนอื่นกิน ชวนคนให้ไม่เคร่ง" เป็นตรรกะวิบัติที่เรียกว่า Ad Hominem หรือ การโจมตีที่ตัวบุคคล นั่นเอง (ref : https://siripun.com/2023/06/09/logical-fallacies-2-ad-hominem ) ทั้งที่ถ้าจะนิยามคำว่าเคร่ง สิ่งที่กูรูให้ทำ ไม่สามารถมีคำตอบที่สร้างสมการสมดุลได้ (ทำไม A ได้แล้ว B ไม่ได้ถ้าเทียบบริบทเอามาชนกันชัดๆเลย)
จริงๆก็อยากรณรงค์ให้ผู้ประกอบการอาหารคีโต ร่วมโครงการนี้ แต่เข้าใจว่ามันคงไม่สามารถทำได้ เพราะอาจจะมองในมุมที่ต่างกัน ผมเข้าใจในสิ่งนั้นครับ แต่มุมของผมคือ การทำอาหารคีโตให้กลับมาอยู่ในประเภทอาหารปกติ จะยิ่งขยายมูลค่าตลาดออกไปได้มากกว่าทุกวันนี้
ตลาดคีโตมันซบเซา เพราะเราทำให้มัน "ประหลาด" ทำให้มันกลายเป็นของ "ไม่ปกติ" พอได้น้ำหนัก หุ่น ลูก สมปรารถนาแล้วก็ถวิลหาการ "ออกไปกินปกติ" นั่นคือการทำให้ตลาดหายไปเรื่อยๆเพราะพวกคุณเองครับ ผมกลับมองว่าทำให้คีโตคืออาหารปกติ แล้วกินกันไปตลอด ไม่มีการขอออกจากเผ่า หานเป็ดอะไรคือทางที่ดีกว่า ได้สุขภาพที่ดีกว่า
คีโตคือการกินปกติ ไม่ควรต้องมาแยกเป็นชนเผ่าอะไรเลย คีโตคือคนเมือง คนมีความรู้ คือ วิทยาศาสตร์ คือความฉลาดในการเลือกสารอาหาร อย่าไปยัดเยียดความ "ไม่ปกติ" ให้อาหาร "ปกติ"
ก็เลยคิดว่า ไม่เป็นไร ร้านคีโตร้านใดอยากร่วมเรายินดี แต่ถ้ามองว่าไม่เอาด้วยก็ยินดีเหมือนกัน เพราะการค้าเสรี อยากทำอะไรก็ทำได้ครับ ในส่วนตัวผม เราทำของเรา เราเริ่มของเราเลยก็ได้ เพราะเส้นทางที่ผ่านมา เราก็เดินอยู่ในเส้นทางของเราอยู่แล้ว และผมเชื่อใน Proof of Work ครับ ผมสามารถทุ่มแรงกายแรงใจ ลงในอาหาร ลงในการสอน ให้คนตระหนักถึง "สารอาหาร" มากกว่า "ป้ายฉลาก"
แล้ววันนึง มันจะส่งผลที่ impact ครับ ผมเชื่ออย่างนั้น Proof of Work สามารถส่งต่อได้ และ พลิกโลกได้ มานับต่อนับแล้ว
ทุกวันนี้ผมทุ่มเนื้อหาด้าน ฉลากอาหาร เพื่อให้คนหัดอ่าน รู้เท่า รู้ทัน มันก็ทำให้ผมยิ่งรู้สึกว่า ผมไม่ควรแปะคำว่าคีโต ลงไปเลย มันเหมือนไปสปอยให้คนลืมพื้นฐานสำคัญ
ไม่ใช่ว่าไม่ง้อคนคีโตนะ คนทำการค้าต้องยินดีกับทุกการค้าอยู่แล้ว แต่ผมกลับมมองว่า ตลาดของผมขอเป็นตลาดที่มีการอ่านฉลาก มีการหัดพิจารณาสารอาหาร ดูคาร์บเป็น เลือกวัตถุดิบที่เหมาะกับแต่ละคน มากกว่าวัตถุดิบที่ต้องได้รับการโปรดจากกูรู
ผมมองว่า คนกินคลีน คนกินไฮโปรตีน หรือแม้แต่แค่คนที่ไม่อยากกินน้ำตาล ก็จะสามารถกินอาหารที่ผมทำได้ ไม่โดนปิดกั้นจากป้ายคีโต ที่โลกประเคน mind set ให้ว่าต้อง high fat เท่านั้น
ซึ่งถ้าผมทำอาหารในแบบของผม + คนกินพิจารณาได้เองว่าสารอาหารเหมาะกับเขาไหม = การกินแบบมีความรู้จริง เหมาะกับตัวเองจริงๆ
ถือว่าเป็นอีกเส้นทางที่ผมต้อง fight for ครับ ถ้าสำเร็จ มันจะช่วยให้คนในสังคมหลุดกรอบ และมองสารอาหารได้ ดูแลสุขภาพได้ ด้วยพื้นฐานความรู้ที่มากขึ้นครับ ไม่ใช่ทางที่สบายแน่นอนครับ แต่พวกคุณจะได้ประโยชน์ติดตัวไปแน่ๆ
ถามว่าทำเพื่อการค้าใช่ไหม ก็ใช่ครับ การค้ามันคู่กับโลก ผมไม่ค่อยเข้าใจในมุมของการต้องการอะไรฟรีๆอยู่ตลอด ถ้าคุณเคารพใน value แล้วยินดีส่งต่อ value for value คุุณจะยินดีในการค้าที่ไม่ยัดเยียด (fiat) คุณจะยินดีในการส่งต่อ value ด้วยคุณค่า คุณจะยินดีในการมองคุณค่าของ "เวลา" ที่ผู้สร้างผู้ทำลงทุนลงไป (เวลาคือทรัพยการที่มีค่าที่สุดในโลก) แล้วถ้าคุณให้เกียรติกับสิ่งเหล่านี้ คุณจะไม่อยากได้มันฟรีๆ คุณจะกระดากใจที่จะหยิบมันมาเปล่าๆ นี่คือเหตุผลที่ผมไม่เคยมองว่า การทำการค้า มันจะเลวร้ายอะไร แต่ที่แน่ๆ ผมจะไม่ทำ FIAT keto ครับ ผมจะไม่เร่งเร้า ไม่ขู่เข็ญ ไม่ใช้ตรรกะประเภท "ของมันต้องมี" ผมจะแบไต๋แฟร์ๆด้วยสารอาหารครับ
แม้มันจะแลกมาด้วยการขาดโอกาส จากป้าย "คีโต" ก็ตาม แม้คนคีโตจะมองว่า ไม่มีป้ายคือไม่คีโตก็ตาม แม้จะไม่ได้รับการรับรองจากกูรูใดๆ ว่า "คีโตกินได้" ก็ตาม ถ้าจะให้สังคมมีการเรียนรู้สารอาหารขึ้นได้ ผมยอม
pirateketo #ตำรับเอ๋ #siripun #siamstr
-
 @ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23
@ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23由于gmail在中国被防火墙拦截了,无法打开,不想错过邮件通知。
通过自建ntfy接受gmail邮件通知。 怎么自建ntfy,后面再写。
2024年08月13日更新:
修改不通过添加邮件标签来标记已经发送的通知,通过Google Sheets来记录已经发送的通知。
为了不让Google Sheets文档的内容很多,导致文件变大,用脚本自动清理一个星期以前的数据。
准备工具
- Ntfy服务
- Google Script
- Google Sheets
操作步骤
- 在Ntfy后台账号,设置访问令牌。

- 添加订阅主题。

- 进入Google Sheets创建一个表格.记住id,如下图:

- 进入Google Script创建项目。填入以下代码(注意填入之前的ntfy地址和令牌):
```javascript function checkEmail() { var sheetId = "你的Google Sheets id"; // 替换为你的 Google Sheets ID var sheet = SpreadsheetApp.openById(sheetId).getActiveSheet();
// 清理一星期以前的数据 cleanOldData(sheet, 7 * 24 * 60); // 保留7天(即一周)内的数据
var sentEmails = getSentEmails(sheet);
var threads = GmailApp.search('is:unread'); Logger.log("Found threads: " + threads.length);
if (threads.length === 0) return;
threads.forEach(function(thread) { var threadId = thread.getId();
if (!sentEmails.includes(threadId)) { thread.getMessages().forEach(sendNtfyNotification); recordSentEmail(sheet, threadId); }}); }
function sendNtfyNotification(email) { if (!email) { Logger.log("Email object is undefined or null."); return; }
var message = `发件人: ${email.getFrom() || "未知发件人"} 主题: ${email.getSubject() || "无主题"}
内容: ${email.getPlainBody() || "无内容"}`;
var url = "https://你的ntfy地址/Gmail"; var options = { method: "post", payload: message, headers: { Authorization: "Bearer Ntfy的令牌" }, muteHttpExceptions: true };
try { var response = UrlFetchApp.fetch(url, options); Logger.log("Response: " + response.getContentText()); } catch (e) { Logger.log("Error: " + e.message); } }
function getSentEmails(sheet) { var data = sheet.getDataRange().getValues(); return data.map(row => row[0]); // Assuming email IDs are stored in the first column }
function recordSentEmail(sheet, threadId) { sheet.appendRow([threadId, new Date()]); }
function cleanOldData(sheet, minutes) { var now = new Date(); var thresholdDate = new Date(now.getTime() - minutes * 60 * 1000); // 获取X分钟前的时间
var data = sheet.getDataRange().getValues(); var rowsToDelete = [];
data.forEach(function(row, index) { var date = new Date(row[1]); // 假设日期保存在第二列 if (date < thresholdDate) { rowsToDelete.push(index + 1); // 存储要删除的行号 } });
// 逆序删除(从最后一行开始删除,以避免行号改变) rowsToDelete.reverse().forEach(function(row) { sheet.deleteRow(row); }); }
```
5.Google Script是有限制的不能频繁调用,可以设置五分钟调用一次。如图:

结尾
本人不会代码,以上代码都是通过chatgpt生成的。经过多次修改,刚开始会一直发送通知,后面修改后将已发送的通知放到一个“通知”的标签里。后续不会再次发送通知。
如需要发送通知后自动标记已读,可以把代码复制到chatgpt给你写。
-
 @ db95cd8e:399d79e2
2024-09-19 22:09:14
@ db95cd8e:399d79e2
2024-09-19 22:09:14Hello [[Nostr]]! For my first post, an introduction feels appropriate with [[Nostr]], but why is that? Why do so many of us talk about our discovery of [[Nostr]] like we just discovered the next best thing? We don't act that way with any other social media.
Simply, I think it is because we have discovered the next best thing. And not just the next best thing, but the thing that will change online communication forever.
[[Nostr]] revolutionizes social media and is fundamentally different from anything else due to how our information is shared through relays and different clients instead of a single source. This change alone has the potential to disrupt current social media, and is the path forward to [[Freedom]] communication channels for the world.
My journey to [[Nostr]] started with [[Bitcoin]]. I first heard about [[Bitcoin]] in 2020, but didn't really start learning about it until late 2021. I heard about [[Nostr]] from the [[Bitcoin]] influencers and podcasters I listened to. My understanding of how #Bitcoin worked was fundamental to me understanding [[Nostr]] and it's importance. The #Freedom provided by these two beautiful inventions is set to change the world in a way we can't fully see yet.
The note app Obsidian is also a big part of this start for me. I’ve wanted to improve and organize my thoughts for a long time, as well as learn better ways to articulate my thoughts. I found Obsidian, and there is a community plugin to publish notes directly to [[Nostr]].
So this is the start of my journey with the future of social media and communication.
- Jared
-
 @ e83b66a8:b0526c2b
2024-09-09 20:30:30
@ e83b66a8:b0526c2b
2024-09-09 20:30:30We have a confession to make. NOSTR is not perfect, we are still building. No client you use does everything you want it to, and everything it does is imperfect.
Therefore, I strongly advise you to run multiple clients.
On iPhone, I run: Damus: https://nostrapps.com/damus Primal: https://primal.net/downloads Nostur: https://nostrapps.com/nostur
On Android I run: Primal: https://primal.net/downloads Amethyst: https://nostrapps.com/amethyst
On desktop I run: Primal: https://primal.net/downloads noStrudel: https://nostrapps.com/nostrudel
Also, because I run a node (Umbrel & Start9), I self host noStrudel on my own relay.
If you haven’t taken the plunge to run a node, now might be a good time to think about it.
There are many, many options for clients, the “Social” section of https://nostrapps.com/
lists 23 currently.
Play with them, see what they do, if you’re a developer, you could even consider building or forking your own.
Have fun and realise we are building freedom tech, not just running it.
-
 @ 8cb60e21:5f2deaea
2024-09-19 22:09:05
@ 8cb60e21:5f2deaea
2024-09-19 22:09:05 -
 @ 8cb60e21:5f2deaea
2024-09-19 21:25:34
@ 8cb60e21:5f2deaea
2024-09-19 21:25:34 -
 @ c6f7077f:ad5d48fd
2024-09-08 01:24:03
@ c6f7077f:ad5d48fd
2024-09-08 01:24:03“The more you learn about something, the more you realize you know nothing.” This saying resonates deeply with me. The truth is, no one really has all the big answers. Many in the scientific community seem to pretend they do. Let’s explore this further.
Consider the Most Fundamental Questions
- The Origin of the Universe
- The Origin of Life on Earth
The Origin of the Universe
You might think we have a solid answer: the Big Bang. However, this explanation has its limitations, and calling it a “start” can be misleading. In fact, this theory might be entirely wrong. New research challenges the Big Bang theory, and I highly recommend listening to Sir Roger Penrose for a deeper understanding.
The only substantial evidence we have is the universe's expansion. Penrose proposes a different hypothesis: the endless expansion and contraction of the universe. This idea doesn’t contradict our current understanding.
Thus, the evidence for the Big Bang and Penrose’s theory are both radically different, yet neither can be definitively proven over the other. This highlights the limitations of our current understanding.
The Origin of Life on Earth
The origin of life is even more complex. Life requires three essential components: - Proteins for basic functioning - RNA for storing and replicating genes - Lipids (cell walls) to create separation from the environment
Mathematical models suggest that while proteins and lipids have a reasonable probability of forming, the creation of RNA seems nearly impossible through random mutations in a short time frame. The best explanations indicate that we either lack crucial information or that these RNA molecules—and life as a whole—might have come from outside sources. Some scholars even question the entire random mutation model.
The Question of Certainty
If scientists don’t know the answers, why do they pretend they do? In my humble opinion, It seems they do this to distance science from religion and to close the discussion before the wealthiest can fit God into the narrative, Interestingly, I’m not alone in believing they closed the books too early.
Reclaiming Control of Science and Education
The best way to reclaim control of science and education is to learn. If you’re looking for a starting point, I highly recommend: - “A Brief History of Time” by Stephen Hawking for physics - “Sapiens” or “The Selfish Gene” for evolutionary biology
All three are excellent starting points—densely packed with information and covering a wide range of topics in a concise and accessible manner.
-
 @ 8cb60e21:5f2deaea
2024-09-19 20:54:23
@ 8cb60e21:5f2deaea
2024-09-19 20:54:23Python Introduction Guide
1. What is Python?
Python is a high-level, interpreted programming language known for its simplicity and readability. It's widely used in various fields, including web development, data science, artificial intelligence, and more.
2. Installing Python
Visit python.org to download and install the latest version of Python for your operating system.
3. Your First Python Program
Open a text editor and type:
python print("Hello, World!")Save this as
hello.pyand run it from the command line:python hello.py4. Basic Syntax
Variables and Data Types
```python
Strings
name = "Alice"
Integers
age = 30
Floats
height = 5.5
Booleans
is_student = True ```
Lists
python fruits = ["apple", "banana", "cherry"] print(fruits[0]) # Outputs: appleDictionaries
python person = { "name": "Bob", "age": 25, "city": "New York" } print(person["name"]) # Outputs: Bob5. Control Flow
If statements
python age = 18 if age >= 18: print("You're an adult") elif age >= 13: print("You're a teenager") else: print("You're a child")Loops
```python
For loop
for i in range(5): print(i)
While loop
count = 0 while count < 5: print(count) count += 1 ```
6. Functions
```python def greet(name): return f"Hello, {name}!"
message = greet("Alice") print(message) # Outputs: Hello, Alice! ```
7. Modules
Python has a vast standard library and many third-party packages. You can import them like this:
python import math print(math.pi) # Outputs: 3.1415926535897938. Exception Handling
python try: result = 10 / 0 except ZeroDivisionError: print("Error: Division by zero!")9. Classes and Objects
```python class Dog: def init(self, name): self.name = name
def bark(self): return f"{self.name} says Woof!"my_dog = Dog("Buddy") print(my_dog.bark()) # Outputs: Buddy says Woof! ```
10. Next Steps
- Practice writing small programs
- Explore the Python standard library
- Learn about virtual environments and package management with pip
- Dive into specific areas like web development (Django, Flask) or data science (NumPy, Pandas)
Remember, the best way to learn Python is by writing code. Happy coding!
-
 @ 8cb60e21:5f2deaea
2024-09-19 20:46:05
@ 8cb60e21:5f2deaea
2024-09-19 20:46:05Markdown Cheatsheet
Headers
H1
H2
H3
H4
H5
H6
Emphasis
italic or italic bold or bold bold italic or bold italic ~~strikethrough~~
Lists
Unordered
- Item 1
- Item 2
- Subitem 2.1
- Subitem 2.2
Ordered
- First item
- Second item
- Third item
Links
Images


Blockquotes
This is a blockquote
It can span multiple lines
Code
Inline
codehas back-ticks around it.Code blocks are fenced by three back-ticksHorizontal Rule
Tables
| Header 1 | Header 2 | Header 3 | |----------|----------|----------| | Row 1, Column 1 | Row 1, Column 2 | Row 1, Column 3 | | Row 2, Column 1 | Row 2, Column 2 | Row 2, Column 3 |
Task Lists
- [x] Completed task
- [ ] Uncompleted task
Footnotes
Here's a sentence with a footnote. [^1]
[^1]: This is the footnote.
Escaping Characters
*This text is surrounded by literal asterisks*
-
 @ 3bf0c63f:aefa459d
2024-09-06 12:49:46
@ 3bf0c63f:aefa459d
2024-09-06 12:49:46Nostr: a quick introduction, attempt #2
Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else.
Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services.
(Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation).
More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between clients (i.e. the program that runs on a user computer) and relays (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
-
 @ 361d3e1e:50bc10a8
2024-09-19 15:52:59
@ 361d3e1e:50bc10a8
2024-09-19 15:52:59An attack on Belarus will be the beginning of the Third World War
usa #belarus #russia #ukraine #war #politics
-
 @ 3bf0c63f:aefa459d
2024-09-06 12:15:47
@ 3bf0c63f:aefa459d
2024-09-06 12:15:47a way to do an open and permissionless mesh network
I don't have much experience with that so maybe this is all a stupid, but I think that routing in mesh networks is never scalable. It basically always requires all the nodes to keep a full view of the network in order to route packages -- and often there is no incentive for them to do that either. And then the thing is easily spammable but either that problem doesn't happen because the mesh never gets big enough or it has a central committee that decides who can join.
The biggest example is, of course, the big ICANN-controlled IP network, that gets all the negatives of being centrally controlled while weirdly getting also all the negatives of being a kinda-decentralized peer-to-peer ad-hoc network between indepent ISPs.
A good solution that makes kinda-decentralized (at least open and permissionless) routing possible and replaces node addresses with pubkeys could get rid of ICANN. Once that is done, ad-hoc peering would become more seamless and ISPs wouldn't have to be so big, clunky and centralized, they could slowly split, and non-comercial entities could join the party too by basically just plugging a cable or pointing an antenna at the correct place.
What is it?
One very dumb solution that came to my mind that has a chance of working is one in which each node as a keypair and to be reachable by others they announce their address -- for example, using some kind of DNS (on a [spacechain]?) or by directly communicating their address through some other means -- as their public key plus some "routing hints".
The routing hints are just pubkeys of other nodes known to be routers. Known to whom? Well, this would require some schelling points to naturally appear and the network would be ordered around them, but you are never forced to use them, you have to include as many routing hints as required to ensure that all the people you want to connect to you will eventually be able to, but nothing is ever 100% guaranteed.
Such network could probably work with a pure onion routing scheme with all its privacy benefits in some cases; degrading to a trampoline onion routing scheme otherwise, which means it will just be slightly less private the more trampolines you have to use. And every node has to keep track of just a set of routes from them to a bunch of known routers (or trampolines, which in my mind are mostly the same nodes, but are slightly different roles).
Example
Suppose A is trying to connect to B.
A is a home computer in the city of Évora, Portugal.
B is a home computer in the city of Udine, Italy.
There is a route (we, the narrator, know) between them that goes like this:
A--Ev--Li--Al--Ro--Sm--Ve--Ud--B, in which Ev means the node of an ISP in Évora which directly serves A, Li means a big node in Lisboa, Al a node in Algiers, Ro a node in Rome, Sm a node in San Marino, Ve a node in Venice and Ud a gateway node in the mesh of Udine to which B is connected.
There could be many other routes, but we'll ignore them for now.
B could have published his address as
<pubkey-B>?hint=<pubkey-Ud>,<pubkey-Ve>,<pubkey-Sm>,<pubkey-Ro>, which would mean A would only have to know a route from Ev up to Ro.If Ro is known to be a big router, A could easily have a route cached there, and could discover other routes by asking around every now and then too. It wouldn't take a lot of space to have routes cached to some thousands of different known big nodes like that. Then A can just wrap an onion with all the coordinates and the message inside and hand it to Ev and it would reach B. Inside the message she would also include the full route for a message to be sent back.
However, even if A doesn't have a route to Ro, it could still hope that Li would have, then she could make a special "trampoline" onion that goes Ev--Li and then when Li receives it it sees a request to forward the next packet to Ro, so Li has the freedom to choose a route from itself to Ro (as long as it knows Ro, of course) and from there A's message continues.
The same trampolining can exist on B's side, if B doesn't have a route from Ud to Ro, but knows Ro is likely to have one up to Ud -- or if B feels it's not worth including so many hints when most big nodes will have routes to Ud, for example, it can publish his address as
<pubkey-B>?hint=<pubkey-Ud>*<pubkey-Ro>meaning that one should find a route up to Ro and from there ask Ro to trampoline it up to Ud.Or, if B doesn't expect Ud to be very well-known, but Sm yes, then it could do
<pubkey-B>?hint=<pubkey-Ud>,<pubkey-Sm>*<pubkey-Ro>. Again, this is just one hint, in practice it would have to have a lot (maybe 10, 20?) other hints, in a tree structure that this querystring syntax isn't very suited for encoding:``` Ud Tr Pu Za Li
Sm * Ro Ba Mi La Ge * Mo Tu
```
(Remember, we're using city name abbreviations here, but each of these would be a specific node, with a specific public key, supposed for the example to be in such a city, but nothing prevents them from being in different cities or that multiple nodes exist in the same city.)
Summary
Basically packets go from node to node, in a sequence established by the sender -- with optional trampolines in between -- until they get to the target. Target responds in the same route. Nodes can be anyone. Focal points form around big nodes, but they can be replaced easily, the receivers just have to stop using them in their hints, so the network is flexible and open.
-
 @ dc652bee:6154e7d0
2024-09-19 13:47:51
@ dc652bee:6154e7d0
2024-09-19 13:47:51https://www.ouxyi.link/ul/1G3I1x
-
 @ d830ee7b:4e61cd62
2024-09-04 07:29:41
@ d830ee7b:4e61cd62
2024-09-04 07:29:41Bitcoin ถือกำเนิดขึ้นในปี 2009 จากวิสัยทัศน์ของ Satoshi Nakamoto บุคคลหรือกลุ่มบุคคลปริศนา ที่ใฝ่ฝันถึง "เงินสดดิจิทัล" อิสระไร้พรมแดน ไร้การควบคุมจากรัฐบาล
ในช่วงแรกเริ่ม Bitcoin เป็นเสมือนเพชรดิบที่ซ่อนตัวอยู่ในเงามืด เป็นที่รู้จักกันเฉพาะในกลุ่มเล็กๆ ที่หลงใหลในเทคโนโลยีและศักยภาพอันไร้ขีดจำกัดของมัน
แต่แล้ว Bitcoin ก็เริ่มฉายแสงเจิดจรัส ดึงดูดความสนใจจากผู้คนทั่วโลก ราคาพุ่งทะยานอย่างรวดเร็ว บริษัทและบริการต่างๆ ผุดขึ้นมาราวกับดอกเห็ด
ทว่า.. เส้นทางสู่ความสำเร็จของ Bitcoin ไม่ได้โรยด้วยกลีบกุหลาบ Bitcoin ยังต้องเผชิญกับความท้าทายมากมาย ทั้งปัญหาทางเทคนิค ความขัดแย้งภายในชุมชนและการต่อสู้แย่งชิงอำนาจ
Blocksize Limit จุดเริ่มต้นของความขัดแย้งและสงคราม Big Blocks VS Small Blocks
ย้อนกลับไปในปี 2010 Satoshi Nakamoto ได้เพิ่ม "Blocksize Limit" ซึ่งเป็นข้อจำกัดขนาดของ Block ใน Bitcoin ไว้ที่ 1MB เพื่อป้องกันการโจมตีทางไซเบอร์ในยุคแรกเริ่ม
แต่เมื่อ Bitcoin ได้รับความนิยมมากขึ้น ธุรกรรมก็เพิ่มขึ้นอย่างรวดเร็ว Blocksize Limit 1MB เริ่มจะกลายเป็นปัญหา..
เกิดการถกเถียงอย่างดุเดือดในชุมชน Bitcoin ว่าควรเพิ่ม Blocksize Limit หรือไม่
ฝ่าย "Small Blockers" นำโดยนักพัฒนา Bitcoin Core ส่วนใหญ่ เชื่อว่า Blocksize Limit ควรคงที่ เพื่อรักษาความปลอดภัยและการกระจายอำนาจ พวกเขากล่าวอ้างว่า Big Blocks จะทำให้ Bitcoinรวมศูนย์อยู่ที่ Miners รายใหญ่ และยากต่อการรัน Full Nodes สำหรับผู้ใช้งานทั่วไป ซึ่งจะบั่นทอนความเป็น Decentralized ของ Bitcoin
ฝ่าย "Big Blockers" นำโดย Gavin Andresen ผู้สืบทอดตำแหน่งจาก Satoshi Nakamoto และ Mike Hearn เชื่อว่า Bitcoin ควรเติบโตอย่างไม่จำกัด "Big Blocks" คือคำตอบ พวกเขามองว่า Small Blocks จะทำให้ Bitcoin ไม่สามารถรองรับธุรกรรมที่เพิ่มขึ้น ค่าธรรมเนียมจะพุ่งสูงและ Bitcoin จะไม่สามารถใช้งานได้จริงในชีวิตประจำวัน..
ความขัดแย้งนี้สะท้อนให้เห็นถึงวิสัยทัศน์ที่แตกต่างกัน
Gavin Andresen ผู้ที่เคยได้รับความไว้วางใจจาก Satoshi รู้สึกผิดหวังที่ Bitcoin Core ไม่ยอมเพิ่ม Blocksize Limit เขาเชื่อมั่นว่า Bitcoin ควรเป็นระบบการชำระเงินที่ใช้งานได้จริง รวดเร็ว และมีค่าธรรมเนียมต่ำ
Blockstream บริษัทผู้ทรงอิทธิพลและความกังวลเรื่องผลประโยชน์ทับซ้อน
ปี 2014 กลุ่มนักพัฒนา Bitcoin Core บางส่วนได้ก่อตั้งบริษัท Blockstream (นำโดย Adam Back) พวกเขาเน้นการพัฒนาเทคโนโลยี Blockchain และกลายเป็นที่มถกเถียงว่าอิทธิพลอย่างมากต่อ Bitcoin Core
Blockstream สนับสนุน "Small Blocks"
เช่นเดียวกับ Bitcoin Core พวกเขาพัฒนา "Sidechains" ซึ่งเป็น Blockchain แยกต่างหากที่เชื่อมต่อกับ Bitcoin เช่น Liquid Network Sidechains ซึ่งช่วยให้ Blockstream สามารถเก็บค่าธรรมเนียมจากธุรกรรมและขายบริการให้กับองค์กรหรือบริษัทต่างๆ ได้
ความสัมพันธ์อันใกล้ชิดระหว่าง Blockstream และ Bitcoin Core ทำให้เกิดความกังวลขึ้นในชุมชน Bitcoin ในขณะนั้นว่า Blockstream อาจมีผลประโยชน์ทับซ้อนและต้องการให้ Bitcoin คงขนาดเล็ก เพื่อผลักดันให้คนใช้งาน "Sidechains" ของพวกเขา
BitcoinXT และ Bitcoin Classic ความพยายามแก้ไข Blocksize ที่ถูกต่อต้าน
ปี 2015 Mike Hearn และ Gavin Andresen ตัดสินใจเสนอทางออกด้วยการสร้าง "BitcoinXT" ซอฟต์แวร์ Bitcoin เวอร์ชั่นใหม่ที่ เพิ่ม Blocksize Limit เป็น 8MB
แต่ BitcoinXT ถูกต่อต้านอย่างรุนแรงจากฝ่าย Small Blockers
Bitcoin.org เว็บไซต์หลักของ Bitcoin และ r/Bitcoin ฟอรัมหลักของ Bitcoin ได้เซ็นเซอร์ BitcoinXT ไม่ให้ปรากฏ เกิดการโจมตีทางไซเบอร์ที่มุ่งเป้าไปที่ BitcoinXT โดยตรง
Coinbase บริษัทแลกเปลี่ยน Cryptocurrency รายใหญ่ ประกาศสนับสนุน BitcoinXT แต่กลับถูกถอดออกจาก Bitcoin.org
ต่อมา Bitcoin Classic ถูกสร้างขึ้นเป็นอีกหนึ่งทางเลือก แต่ก็ล้มเหลวเช่นกัน
เนื่องจาก Bitcoin Core ยังคงมีอิทธิพลอย่างมากในชุมชน Bitcoin ในช่วงเวลานั้น..
Hong Kong Agreement และ New York Agreement ความพยายามประนีประนอมที่ไม่ลงตัว
ปี 2016 และ 2017 เกิดความพยายามในการประนีประนอมระหว่างฝ่าย Small Blocks และ Big Blockers ถึงสองครั้ง คือ "Hong Kong Agreement" และ "New York Agreement"
ทั้งสองข้อตกลงมีเป้าหมายที่จะเปิดใช้งาน SegWit และ เพิ่ม Blocksize Limit เป็น 2MB แต่ Bitcoin Core ไม่ทำตามสัญญาในการเพิ่ม Blocksize Limit ทำให้ข้อตกลงล้มเหลว
ความล้มเหลวของข้อตกลงทั้งสอง สะท้อนให้เห็นถึงความไม่ไว้วางใจระหว่างสองฝ่าย และความยากลำบากในการหาจุดร่วมที่ทุกฝ่ายยอมรับ
SegWit ก้าวสำคัญของ Bitcoin และจุดกำเนิดของ Bitcoin Cash
ในที่สุด SegWit ก็ถูกเปิดใช้งานบน Bitcoin ในเดือนสิงหาคม 2017
SegWit เป็น Soft Fork ที่เปลี่ยนแปลงวิธีการจัดเก็บข้อมูลใน Block เพื่อเพิ่มประสิทธิภาพและความปลอดภัย
SegWit ช่วยแก้ปัญหา "Transaction Malleability" ซึ่งเป็นช่องโหว่ด้านความปลอดภัย และปูทางไปสู่การพัฒนา "Layer 2 solutions" เช่น Lightning Network ในเวลาต่อมา..
อย่างไรก็ตาม.. กลุ่ม "Big Blockers" มองว่า SegWit ไม่ใช่ทางออกที่แท้จริงสำหรับปัญหาการขยายขนาด (พวกเขาต้องการขยายขนาดบล็อกบนเลอเยอร์ฐาน) พวกเขาไม่พอใจที่ Bitcoin Core ไม่ทำตามสัญญาในการเพิ่ม Blocksize Limit
ในเดือนสิงหาคม 2017 กลุ่ม "Big Blockers" ได้ทำการ "Hard Fork" Bitcoin เพื่อสร้าง "Bitcoin Cash (BCH)" ซึ่งอ้างว่ามุ่งสืบทอดจุดมุ่งหมายดั้งเดิมของ Bitcoin ในฐานะ "เงินสดดิจิทัล"
ความเสี่ยงด้านความปลอดภัย Bug ร้ายแรงใน Bitcoin Core และบทเรียนที่ได้รับ
ในเดือนกันยายน 2018 Awemany นักพัฒนา BCH ค้นพบ Bug ร้ายแรงใน Bitcoin Core (CVE-2018-17144) ซึ่งอาจทำให้เกิดภาวะเงินเฟ้อได้
Bug นี้เกิดจากความผิดพลาดในการเขียนโค้ด และอาจทำให้ผู้ไม่หวังดีสามารถสร้าง Bitcoin ปลอมขึ้นมาได้
Awemany ได้แจ้งเตือนนักพัฒนา Bitcoin Core อย่างเงียบๆ แทนที่จะใช้ประโยชน์จาก Bug นี้ แสดงให้เห็นถึงความรับผิดชอบของเขา และ Bug นี้ได้รับการแก้ไขอย่างรวดเร็ว
เหตุการณ์นี้แสดงให้เห็นถึงความสำคัญของการตรวจสอบโค้ดอย่างละเอียด และความจำเป็นของการมีนักพัฒนาจากหลายฝ่ายเพื่อช่วยกันตรวจสอบความถูกต้องของโค้ด
นอกจากนี้.. ยังเป็นเครื่องเตือนใจว่าแม้แต่ระบบที่ถูกออกแบบมาอย่างดีก็ยังมีความเสี่ยงด้านความปลอดภัย
Bitcoin Cash แตกแยก การ Hard Fork ครั้งที่สอง และบทบาทของ Craig Wright
ในเดือนพฤศจิกายน 2018 Bitcoin Cash (BCH) ได้แตกออกเป็นสองสาย คือ Bitcoin ABC (BCH) และ Bitcoin SV (BSV)
การ Hard Fork นี้เกิดจากความขัดแย้งระหว่างกลุ่มนักพัฒนา Bitcoin ABC นำโดย Amaury Séchet และกลุ่ม Bitcoin SV นำโดย Craig Wright ผู้ที่อ้างว่าเป็น Satoshi Nakamoto 🤔
ความขัดแย้งหลักคือเรื่องขนาดของ Block และทิศทางการพัฒนา Bitcoin Cash
กลุ่ม Bitcoin SV ต้องการเพิ่มขนาด Block อย่างมาก ในขณะที่กลุ่ม Bitcoin ABC ต้องการปรับปรุง Bitcoin Cash ในด้านอื่นๆ เช่น Smart Contracts
Craig Wright มีบทบาทสำคัญในการผลักดัน Bitcoin SV เขาเชื่อมั่นว่า Bitcoin ควรเป็นไปตามวิสัยทัศน์ดั้งเดิมของ Satoshi Nakamoto โดยเน้นที่การเป็น "เงินสดอิเล็กทรอนิกส์แบบ peer-to-peer"
การ Hard Fork นี้แสดงให้เห็นถึงความหลากหลายของความคิดเห็นในชุมชน Cryptocurrency และความยากลำบากในการหาจุดร่วมที่ทุกฝ่ายยอมรับ
นอกจากนี้.. ยังสะท้อนให้เห็นถึงความท้าทายในการกำหนดทิศทางของ Cryptocurrency ในอนาคตอีกด้วย
Bitcoin ในปัจจุบัน เส้นทางสู่ทองคำดิจิทัล และวิวัฒนาการของเทคโนโลยี
หลังจากการ Hard Fork ของ Bitcoin Cash
Bitcoin ได้ก้าวเข้าสู่ยุคใหม่ Bitcoin ได้รับการยอมรับมากขึ้นในวงกว้าง มีมูลค่าตลาดสูง และถูกมองว่าเป็น "ทองคำดิจิทัล" ที่สามารถใช้เก็บรักษามูลค่าในระยะยาว (Store of Value)
การพัฒนา Lightning Network เป็นก้าวสำคัญในการแก้ปัญหาเรื่องค่าธรรมเนียมและความเร็วในการทำธุรกรรม
Lightning Network เป็น "Second Layer" ที่สร้างขึ้นบน Bitcoin Blockchain ช่วยให้สามารถทำธุรกรรมได้รวดเร็วขึ้น มีค่าธรรมเนียมต่ำ และมีความเป็นส่วนตัวสูง
อย่างไรก็ตาม.. Lightning Network ยังคงต้องเผชิญกับความท้าทาย เช่น ปัญหาเรื่องการบริหารจัดการ Liquidity และความซับซ้อนในการใช้งาน
นอกจาก Lightning Network แล้ว ยังมีการพัฒนาเทคโนโลยีอื่นๆ ที่ช่วยเพิ่มขีดความสามารถของ Bitcoin เช่น Taproot ซึ่งเป็น Soft Fork ที่ช่วยเพิ่มความเป็นส่วนตัว และ Schnorr signatures ซึ่งเป็น Digital Signature แบบใหม่ที่ช่วยลดขนาดของธุรกรรมให้เล็กลง
นอกจากนี้.. ยังเริ่มมีการพัฒนา DeFi (Decentralized Finance) บน Bitcoin และ Bitcoin Ordinals ซึ่งเป็นวิธีการใหม่ในการฝังข้อมูลลงใน Bitcoin Blockchain
Bitcoin ยังคงถูกนำไปใช้ในประเทศอื่นๆ นอกจาก El Salvador และมีความพยายามในการแก้ปัญหาความกังวลด้านสิ่งแวดล้อมจากการขุด Bitcoin
บทเรียนจากมหากาพย์แห่งวิวัฒนาการ
ประวัติศาสตร์ Bitcoin สอนให้เรารู้ว่า.. เทคโนโลยี Blockchain มีศักยภาพในการเปลี่ยนแปลงโลก แต่เส้นทางสู่ความสำเร็จนั้นก็ไม่ได้โรยด้วยกลีบกุหลาบ
ความขัดแย้ง การต่อสู้แย่งชิงอำนาจ และการตัดสินใจที่ยากลำบาก ล้วนเป็นส่วนหนึ่งของการเดินทาง
สิ่งที่สำคัญที่สุดคือ.. เราต้องศึกษา ทำความเข้าใจ และอาจมีส่วนร่วมในการกำหนดทิศทางของเทคโนโลยีนี้ เพื่อให้ Blockchain สามารถสร้างประโยชน์สูงสุดให้กับมวลมนุษยชาติต่อไป
เจาะลึกวิวัฒนาการของ Bitcoin การ Soft Forks, Hard Forks และมุมมองที่แตกต่าง
SegWit, Taproot และ Soft Forks อื่นๆ การปรับปรุง Bitcoin อย่างนุ่มนวล
Bitcoin Core ไม่ได้หยุดนิ่งอยู่กับที่ นักพัฒนาได้ทำงานอย่างต่อเนื่องเพื่อปรับปรุง Bitcoin ให้ดีขึ้น โดยใช้ "Soft Forks" ซึ่งเป็นการอัพเกรดที่เข้ากันได้กับซอฟต์แวร์เวอร์ชั่นเก่า
SegWit (Segregated Witness)
เปิดตัวในปี 2017 SegWit เป็นเหมือนการจัดระเบียบข้อมูลใน Block ใหม่ ย้ายส่วนที่เรียกว่า "Witness data" (ข้อมูลลายเซ็น) ออกไปไว้ข้างนอก ทำให้มีพื้นที่ว่างใน Block มากขึ้น รองรับธุรกรรมได้มากขึ้น และลดค่าธรรมเนียมได้ SegWit ยังช่วยแก้ปัญหา "Transaction Malleability" ซึ่งเป็นช่องโหว่ด้านความปลอดภัยและปูทางไปสู่การพัฒนา Lightning Network
Taproot
เปิดตัวในปี 2021 Taproot เป็น Soft Fork ที่ช่วยเพิ่มความเป็นส่วนตัว และประสิทธิภาพของ Bitcoin Taproot ทำให้ธุรกรรมที่ซับซ้อน เช่น Smart Contracts มีขนาดเล็กลงและยากต่อการแยกแยะจากธุรกรรมทั่วไป
Soft Forks อื่นๆ ที่ Bitcoin Core ได้นำมาใช้ เช่น BIP 65 (CheckLockTimeVerify) และ BIP 112 (CSV) ช่วยเพิ่มความยืดหยุ่นในการใช้งาน Bitcoin และปูทางไปสู่การพัฒนาฟังก์ชันใหม่ๆ
Hard Forks เส้นทางที่แตกต่างและการถือกำเนิดของเหรียญใหม่
ในขณะที่ Soft Forks เป็นการอัพเกรดที่นุ่มนวล "Hard Forks" นั้นนับว่าเป็นการเปลี่ยนแปลงครั้งใหญ่ ที่ทำให้เกิดสาย Blockchain ใหม่และเหรียญใหม่
Bitcoin XT (2015)
เป็นความพยายามครั้งแรกในการเพิ่ม Blocksize Limit โดย Mike Hearn และ Gavin Andresen Bitcoin XT เสนอให้เพิ่ม Blocksize Limit เป็น 8MB แต่ถูกต่อต้านอย่างรุนแรง และไม่ประสบความสำเร็จ
Bitcoin Classic (2016)
เป็นอีกหนึ่งความพยายามในการเพิ่ม Blocksize Limit โดยเสนอให้เพิ่มเป็น 2MB แต่ก็ล้มเหลวเช่นกัน
Bitcoin Unlimited (2016)
เสนอให้ Miners สามารถกำหนด Blocksize Limit ได้เอง แต่มีข้อบกพร่องด้านความปลอดภัย และไม่เป็นที่ยอมรับในวงกว้าง
Bitcoin Cash (BCH) (2017)
เกิดจากการ Hard Fork ของ Bitcoin โดยกลุ่ม "Big Blockers" ที่ไม่พอใจที่ Bitcoin Core ไม่ยอมเพิ่ม Blocksize Limit Bitcoin Cash เพิ่ม Blocksize Limit เป็น 8MB และมุ่งเน้นที่การเป็น "เงินสดดิจิทัล" ที่ใช้งานได้จริง
Bitcoin SV (BSV) (2018)
เกิดจากการ Hard Fork ของ Bitcoin Cash โดยกลุ่มที่นำโดย Craig Wright ผู้ที่อ้างว่าเป็น Satoshi Nakamoto Bitcoin SV ต้องการเพิ่มขนาด Block อย่างมาก และกลับไปสู่วิสัยทัศน์ดั้งเดิมของ Bitcoin
Bitcoin ABC (2020)
เกิดจากการ Hard Fork ของ Bitcoin Cash โดยกลุ่มนักพัฒนา Bitcoin ABC ที่ต้องการเปลี่ยนแปลงกลไกการระดมทุน Bitcoin ABC ถูกเปลี่ยนชื่อเป็น eCash ในภายหลัง
มุมมองที่แตกต่าง Bitcoin ถูก "แย่งชิง" หรือไม่?
หนังสือ "Hijacking Bitcoin" โดย Roger Ver นำเสนอมุมมองที่แตกต่างจาก Bitcoin Maximalists
Roger Ver เชื่อว่า Bitcoin ถูก "แย่งชิง" โดยกลุ่มนักพัฒนา Bitcoin Core และ Blockstream ที่ต้องการเปลี่ยนแปลง Bitcoin จาก "เงินสดดิจิทัล" ให้กลายเป็น "สินทรัพย์เก็บมูลค่า"
Roger Ver วิพากษ์วิจารณ์ Bitcoin Core ในหลายประเด็น เช่น..
การไม่ยอมเพิ่ม Blocksize Limit
Roger Ver เชื่อว่า Bitcoin Core จงใจจำกัดการเติบโตของ Bitcoin เพื่อผลักดันให้คนใช้งาน Sidechains ของ Blockstream
การเซ็นเซอร์ข้อมูล
Roger Ver กล่าวหาว่า Bitcoin Core เซ็นเซอร์ข้อมูลและปิดกั้นการสนทนาเกี่ยวกับ Big Blocks บนแพลตฟอร์มต่างๆ
การต่อต้านนวัตกรรม
Roger Ver เชื่อว่า Bitcoin Core ต่อต้านนวัตกรรม และไม่ยอมรับการเปลี่ยนแปลงที่อาจทำให้ Bitcoin ดีขึ้น
การควบคุมโดยกลุ่มเล็กๆ
Roger Ver มองว่า Bitcoin Core ถูกควบคุมโดยกลุ่มเล็กๆ ที่ไม่คำนึงถึงความต้องการของชุมชน Bitcoin
Roger Ver สนับสนุน Bitcoin Cash ซึ่งเขาเชื่อว่าเป็น Bitcoin ที่แท้จริง ที่สืบทอดวิสัยทัศน์ดั้งเดิมของ Satoshi Nakamoto
บทสรุป:
การต่อสู้แย่งชิง Bitcoin และการเกิดขึ้นของ Hard Forks ต่างๆ เป็นส่วนหนึ่งของวิวัฒนาการของ Cryptocurrency
มุมมองที่แตกต่าง ความขัดแย้ง และการแข่งขัน ล้วนเป็นแรงผลักดันให้ Bitcoin และ Cryptocurrency อื่นๆ พัฒนาต่อไป
สุดท้ายแล้ว.. เราคงไม่อาจตัดสินได้ว่าฝ่ายใดคิดถูกหรือฝ่ายใดผิด
"เสียงของตลาด จะช่วยทำหน้าที่ให้คำตอบนั้นกับเรา ว่าแท้ที่จริงแล้วผู้คนกำลังต้องการอะไรกันแน่..
ลองมองไปที่มูลค่าของแต่ละแนวคิด มองไปที่ Network effect และกำลังการขุด มองไปที่การยอมรับและความเชื่อมั่นของผู้คน เหล่านี้ล้วนเป็นข้อบ่งชี้ที่เห็นได้ง่าย..
เพราะนั่นคือเสียงแห่งการเพรียกหาอิสรภาพ และอธิปไตยทางการเงินที่แท้จริง..
— Jakk Goodday
-
 @ 52adc2ef:9f4bc0ba
2024-09-19 09:54:56
@ 52adc2ef:9f4bc0ba
2024-09-19 09:54:56สวัสดีครับ
ผมว่าจะลองเขียนบทความหรืออะไรที่มีประโยชน์ ในสิ่งที่ตัวเองได้รู้และมาเเชร์ หลังจากได้ฟัง
'Stoic' ปรัชญาเปลี่ยนชีวิตและพัฒนาการทำงานของ 'ทอย DataRockie' มีช่วงนึงพูดไว้ว่า
คนไทย consume กับ social media ลำดับต้นๆ ซึ่งหลายคน consume อย่างเดียว จะเป็นได้แค่ effect ของส่วนที่เรา content ที่เราเสพ แต่ถ้าเราสร้าง content ที่มี value เราก็จะเป็น เหตุ ที่มี effect กับคนอื่น สร้างเเรงกระเพื่อมส่งต่อไป
รู้สึกว่าน่าสนใจ เพราะก็เป็นหนึ่งในคนที่รับสารมาตลอด ไม่เคยลองที่จะ create ขึ้นมา เพราะเขิน ไม่ค่อยได้โพสอะไรอยู่เเล้ว บวกกับ คิดว่ารู้ไม่พอ เเต่คนเราก็น่าจะมีความรู้อะไรที่รู้ดีกว่าคนอื่นเค้าบ้าง
คิดว่าลองเริ่มดู ก็คงไม่เสียหายอะไร หวังว่าน่าจะเป็นประโยชน์กับใครก็คนใดคนหนึ่งครับ
siamstr
nostr
-
 @ eac63075:b4988b48
2024-09-19 09:03:33
@ eac63075:b4988b48
2024-09-19 09:03:33Nos últimos anos, as Organizações Autônomas Descentralizadas (DAOs) emergiram como uma das inovações mais significativas no ecossistema das criptomoedas e da tecnologia blockchain. Elas prometem ser uma evolução dos sistemas tradicionais de governança, oferecendo um modelo em que as decisões são tomadas coletivamente por meio de tokens, sem a necessidade de intermediários. No entanto, à medida que esse conceito se populariza, problemas relacionados à manipulação de votos e à corrupção dentro das DAOs tornaram-se cada vez mais evidentes.
Recentemente, um novo desenvolvimento criptográfico foi proposto para combater essas fraudes: a Prova de Conhecimento Completo (Complete Knowledge Proof). Este avanço, com a colaboração de Vitalik Buterin, criador do Ethereum, e pesquisadores da Universidade de Cornell, traz uma abordagem inovadora para resolver um dos maiores desafios de governança descentralizada: a segurança e integridade dos votos. Neste artigo, vamos explorar detalhadamente como funciona essa tecnologia e o impacto que ela pode ter no futuro das DAOs.
O Problema das DAOs: Manipulação de Votos e Fraudes
O conceito de DAOs é fascinante, pois permite que qualquer pessoa com tokens tenha voz ativa nas decisões de uma organização descentralizada. A governança é realizada através da votação, onde os detentores de tokens participam para aprovar ou rejeitar propostas. No entanto, a prática tem revelado alguns problemas críticos, principalmente a manipulação de votos e o aluguel de tokens.
Em muitos casos, indivíduos ou grupos podem "alugar" tokens de outros participantes para ganhar mais poder nas votações. Isso corrompe o processo de governança, pois aqueles que deveriam votar com seus próprios tokens acabam utilizando tokens de terceiros, prejudicando a descentralização genuína. Em algumas situações, esse processo leva a decisões que beneficiam poucos, enquanto os interesses da maioria são ignorados. Um dos exemplos mais críticos desse problema ocorreu quando tokens foram delegados ou alugados para manipular decisões em uma DAO, permitindo que certos atores controlassem resultados vitais.
A Solução: Prova de Conhecimento Completo (Complete Knowledge Proof)
A Prova de Conhecimento Completo surge como uma solução promissora para mitigar esses problemas de governança. O objetivo dessa tecnologia é garantir que o processo de votação seja legítimo e que somente os verdadeiros detentores dos tokens possam participar de forma válida, sem delegar ou vender seus direitos de voto.
O que é Prova de Conhecimento Completo?
A Prova de Conhecimento Completo é um conceito criptográfico que permite a alguém provar que tem conhecimento de uma informação (como uma chave criptográfica) sem precisar revelar essa informação. Ou seja, você pode provar que tem os direitos para votar com seus tokens sem precisar divulgar suas chaves privadas ou delegar os tokens para outra pessoa.
Essa solução utiliza uma combinação de Zero-Knowledge Proof (Prova de Conhecimento Nulo) e Proof of Work (Prova de Trabalho) para garantir que os votos sejam realizados apenas por aqueles que realmente detêm os tokens e que estão participando de forma legítima, sem manipulação ou fraude. A Zero-Knowledge Proof permite que alguém prove que possui a chave privada associada aos tokens, sem revelar a chave em si, e a Proof of Work adiciona uma camada adicional de validação, exigindo que um trabalho computacional seja realizado para confirmar a autenticidade do voto.
Como Funciona a Prova de Conhecimento Completo?
A ideia central da Prova de Conhecimento Completo é simples, mas poderosa. Imagine que você possui tokens de uma DAO e deseja participar de uma votação. Para garantir que o voto seja válido, a Prova de Conhecimento Completo exige que você utilize um dispositivo específico ou um ambiente de execução confiável, que possa validar que você realmente é o dono dos tokens e que não os compartilhou com outra pessoa.
Este processo pode ser feito através de um hardware dedicado, como um dispositivo ASIC (circuito integrado de aplicação específica), que é programado para validar os votos de maneira segura. Os votos são computados diretamente a partir desse hardware, que usa algoritmos criptográficos complexos para provar que você tem os tokens e está votando de forma legítima. Isso evita que os votos sejam manipulados ou alugados, pois só o verdadeiro detentor dos tokens pode usá-los para votar.
Uso de Zero-Knowledge Proof e Proof of Work
A combinação de Zero-Knowledge Proof e Proof of Work é o que torna esse processo especialmente robusto. A Zero-Knowledge Proof garante que a sua identidade como votante seja preservada, ou seja, você pode provar que tem os tokens sem revelar publicamente quem você é ou quantos tokens possui. Já o Proof of Work adiciona um nível extra de segurança, exigindo que o hardware dedicado realize um certo número de cálculos antes que o voto seja validado. Isso impede que pessoas usem múltiplas contas falsas ou tokens alugados, já que seria computacionalmente inviável manipular o sistema.
O Impacto na Governança Descentralizada
A implementação da Prova de Conhecimento Completo pode transformar completamente a forma como as DAOs operam, eliminando os problemas de manipulação de votos e garantindo uma governança mais transparente e justa. Além de aumentar a segurança, essa solução também promove uma maior confiança nas DAOs, já que os participantes podem ter certeza de que as decisões estão sendo tomadas por aqueles que realmente possuem os tokens, sem interferências de atores externos.
Aplicações Além das DAOs
Embora o foco inicial da Prova de Conhecimento Completo seja a governança descentralizada, essa tecnologia tem um potencial muito maior. Ela pode ser utilizada em várias outras áreas, como votação eletrônica, identidade digital, autenticação de usuários, entre outros. Em sistemas de votação eletrônica, por exemplo, a Prova de Conhecimento Completo poderia garantir que cada voto é legítimo sem comprometer a privacidade dos eleitores, o que seria uma revolução na forma como conduzimos eleições em todo o mundo.
No campo da identidade digital, essa solução poderia permitir que usuários provem que possuem determinadas credenciais (como uma identidade ou uma carteira de motorista), sem a necessidade de expor essas informações a terceiros. Isso poderia ser extremamente útil em situações que exigem alto nível de privacidade e segurança, como em contratos eletrônicos e autenticação de serviços.
Conclusão
A Prova de Conhecimento Completo é uma inovação significativa no campo da criptografia e da governança descentralizada. Ao combinar as vantagens da Zero-Knowledge Proof e da Proof of Work, ela oferece uma solução eficaz para prevenir fraudes e manipulações nas DAOs, garantindo que os votos sejam realizados de forma segura e legítima.
Com a participação de nomes de peso como Vitalik Buterin e pesquisadores da Cornell, essa tecnologia tem o potencial de se tornar um pilar fundamental na governança descentralizada e em várias outras aplicações no mundo digital. À medida que as DAOs continuam a ganhar espaço no ecossistema blockchain, soluções como essa serão essenciais para assegurar sua integridade e transparência.
O futuro das DAOs pode estar mais seguro com a Prova de Conhecimento Completo, e este é apenas o começo de um novo capítulo na governança descentralizada.
Assista ao vídeo:
-
 @ 005bc4de:ef11e1a2
2024-09-19 08:57:10
@ 005bc4de:ef11e1a2
2024-09-19 08:57:10Recently, I wrote this: https://stacker.news/items/684558?commentId=684701 and asked whether three emails were "legit"...did Satoshi write them. Still wondering, I thought a wider explanation might be worthwhile.
Somehow, I'm finding myself lost in a techno labyrinth and then mired in a quandary of muck. Here's why...

Image source: generated at leonardo.ai
The background
In 2019, I edited a book called "Kicking the Hornet’s Nest: The Complete Writings, Emails, and Forum Posts of Satoshi Nakamoto, the Founder and Creator of Bitcoin" with the goal of logging all of Satoshi Nakamoto's public writings in chronological order (links here). There were other similar resources out there, and a somewhat similar but incomplete book, yet none were arranged strictly by chronology or without heavy editorial commentary added as a layer on top of Satoshi's writings.
I wanted Satoshi's words, alone, in order, all of them.
A second edition of "Kicking" came out when three "Satoshi emails" were released in 2020. Since the goal was to include all of Satoshi's writings, a new edition was needed.
Then, with the "COPA trial" in early 2023 a new slew of never-before-seen emails were released by Adam Back and Martii Malmi as evidence in the case. This was a couple of hundred more emails, half from Satoshi and the other half to Satoshi. So, a third edition of "Kicking" was needed.
The start
My current quandary started when I got a ping via X saying I'd missed Wei Dai's emails with Satoshi.
https://files.peakd.com/file/peakd-hive/crrdlx/23wMyix4neRki9BgsjZGYV7qpaHvmiwXUVMtm8XP8MQEpCNApb8BVQcY8qdAxa3kenpdw.png
Wei Dai's work is the first citation in the bitcoin whitepaper (page 9) and Dai is a cypherpunk legend, of course. This omission was a rather egregious error on my part, "How did I miss that?" I wondered. Like finding an overlooked golden nugget, I eagerly wrote back to thank BITCOINALLCAPS: "This is defitely [sic] something to include. I'll investigate, and thanks for the heads up!"
That feeling
Since I'm currently still tweaking out the third edition, this Wei Dai email discovery came at an opportune time to make adjustments. However, I had, and have, a funny feeling.
The link that BITCOINALLCAPS gave was to what I thought was a semi-sketchy looking video. (See the YouTube video linked on the X post above: https://www.youtube.com/watch?v=hkcwUortfWE) The vid was interesting in that it talked about Satoshi reaching out to Wei Dei pre-whitepaper. Then it analyzed nuanced differences between the drafted whitepaper title and summary when compared to the final title and summary of the whitepaper.
A little searching pointed the "source" for this missing Wei Dai email as bitcoin.com. That site has a list of Satoshi emails, forum posts, etc. I noticed two correspondences that I'd missed: Wei Dei's two emails and Jon Matonis's one. However, the likely more-respected Nakamoto Institute at https://satoshi.nakamotoinstitute.org did not include those three emails. That feeling came back to me, with the question, "Are these emails for real?"
If you're unfamiliar with bitcoin.com, then you may not realize why I got a funny feeling and why I began to wonder about the emails at all. It's a long, sordid story, but I'll try to briefly summarize.
At first there was bitcoin. Then, around 2017 as bitcoin grew and struggled to scale in size, the "block size wars" went down. Some wanted to increase the block size to unclog the chain, others wanted to retain the small block size that Satoshi had coded. The big blockers eventually forked Bitcoin (BTC) to start Bitcoin Cash (aka, "B-cash") and took the symbol BCH.
There was much animosity, and frankly, there still is. Bitcoin "maxis" today consider BTC the only bitcoin. Maxis even say there is bitcoin and no other...that there actually are no other cryptocurrencies...that all others are merely scam-coins. These folks consider themselves purists by retaining Satoshi's original small block size. The B-cashers consider themselves purists, retaining Satoshi's "electronic cash" ethos so that someone could buy-a-cup-of-coffee with a transaction on the main chain.
If you're keeping score:
|coin/chain:|Bitcoin|Bitcoin Cash| |-|-|-| |symbol/nickname:|BTC|BCH or B-cash| |block size:|small blocks like Satoshi coded|big blocks so electronic cash can exist like Satoshi wrote| |website:|bitcoin.org|bitcoin.com| |site founder/owner:|started by Satoshi|owned by Roger Ver| |Satoshi's writings logged at:|nakamotoinstitute.org|nakamotostudies.org|
And, to really throw gas onto the fire, and I hate to even bring this up, but there is Craig Steven Wright. His "Bitcoin SV" (BSV) coin spun-off from Bitcoin Cash. BSV claimed to be the even more pure purist coin as "Satoshi's Vision," hence the "SV." If you're reading this, you know about Wright...and the COPA trial...and his debunking as Satoshi...and all that. I'll return to this topic in a moment.
Like I said, this is a long and sordid story.
So, why dig up this muck here?
Back to the emails
My question was/is, "Did Satoshi write the emails to Wei Dai and Jon Matonis?" And this is where I entered the techno-labyrinth.
The video source I mentioned above aroused skepticism. The narrator focused on certain items, namely the emphasis on "electronic cash" or "ecash" or the "b" in "b-money." He didn't mention "b-cash" that I caught, but the I wondered if that was the allusion projected. In other words, I wondered if there was/is an agenda, as if to say, "b-money is b-cash which is the real and original bitcoin."
And, back to Craig Wright. I was unfamiliar with Jon Matonis, so I searched, and this article came up: https://jonmatonis.medium.com/how-i-met-satoshi-96e85727dc5a. The upshot is that in 2016 Matonis believed Craig Wright was Satoshi Nakamoto. (I'm curious as to his opinion now.) Suddenly, the reason for excluding the Jon Matonis email from the Bitcoin (BTC)-friendly NakamotoInstitute.org was apparent. This was high blasphemy.
The labyrinth got more convoluted. The website NakamotoStudies.org is Bitcoin Cash (BCH)-friendly. (See the left-leaning green "B" symbol? It's the same as on the BCH symbol instead of the familiar, right-lighting and orange BTC symbol.)

For some reason, the NakamotoStudies.org (BCH-friendly) site does not currently show the Matonis email, see this link. Actually, all "Emails" are "forbidden."
Though not live now, the Internet Archive Wayback Machine has captured the emails here.
At this point, the tecno-labyrinth is confusing and the muck is deep.
It seemed simple. I just wondered if Satoshi wrote the emails, but now I'm mired in website inclusion/exclusion censorship and gamesmanship, B-cash talk, and Craig Wright-is-Satoshi nonsense. Labyrinth and muck.
Canon or canon not?
In Christianity, there is the idea of Biblical canon. Canon is what should be included in the Bible, non-canon is everything else. Christians believe canonical works are inspired scripture, where the Holy Spirit guided the authors of the books of the Bible. As man used his own words and writing styles to literally write, the Holy Spirit actually guided each word perfectly so that the finished work was not just man's words, but "God-breathed" words.
The early Christian church, then, had to figure, "Which works are God-breathed canon and which are not?" Or, practically speaking, what goes into the Bible and what does not?
This gets into the weeds a bit, but there was no official meeting to decide what gets into the Bible and what did not. The "Early Church," that is, the body of Christian believers in the first couple of centuries A.D., essentially agreed as a collective on certain books as being in line with Christian thought and agreed that others were not. As a group, they nodded and said, "Yep, this is in," to the 66 books we recognize in the Bible today, and they said, "Nope, not this" to everything else.
I say this gets into the weeds, and it does. The Catholic Church may bring up the books of the Apocrypha. And, even then, the church might distinguish the Old Testament Apocryphal books versus New Testament Apocryphal books. It gets complicated.
What's more, some may argue that official church councils or positions officially codify or accept certain books as doctrine, or not. That is, the official church officially deems canon, or as deems non-canon. Yet, others may argue, as I do, that it is not an official church that is the gatekeeper of canon, but rather that it is instead the decentralized body of believers as a group, guided by the Holy Spirit, which accept canon and reject non-canon. If canon is God-breathed, it is not a council of church men who decide canon or not. Rather, it is the church, the believers, guided by the Holy Spirit that decides.
This is now deeply in the weeds, but the point remains...some works get in, some does not.
Bitcoin is not a religion
To be clear, I'm very much not a fan of throwing religion onto bitcoin. We do it at times, maybe in a solely fun way, such as with the "Genesis block" or in other ways. Bitcoin is a lot of things: economics, computer science, physical science, mathematics, philosophy, game theory, and more. But, it's not religion.
The reason I even included the religious discussion here is to illustrate the point of including or excluding text. Recall my question, "Should the Wei Dai and Jon Matonis emails be included in Satoshi's writings?"
And, I mentioned two ways above what made Biblical canon or non-canon: (1) official decree or (2) unofficial acceptance by the people. In the first case, I wouldn't want an official bitcoin meeting of people to decide yes or no as to what is Satoshi's writings and what is not (of course, being decentralized, there can be no official bitcoin meeting!). And, to the second, I don't want the bitcoin community to collectively agree yes or no, "This is in, this is not," as the early Christian Church did with Biblical canon. My desire is this:
If Satoshi wrote it, I want it included in "Kicking."
Yet, the question still nags, are these emails Satoshi's words? Are they bitcoin canon or not?
My hope
To include or not to include is my question? My reason for writing this is to hopefully get unstuck from the muck and mire. My options at the moment, as I see them, are:
- Don't include those emails in "Kicking the Hornet's Nest."
- Include them alongside all the others in the chronological place they would go.
- Include the emails, but add an editor's comment effectively as an asterisk saying: *here is the email, but take itwith a grain of salt.
Currently, I'm really not sure which option I'll go with. If I had to choose today, I'd choose option 3. I've already done this with the "I am not Dorian" post, as below.
This is odd in a way. I'm a Christian, by faith. Faith, by definition, is believing in what cannot be proven. And yet, I love bitcoin, who's #1 mantra may be, "Don't trust (believe), verify." So, my hope is to find an answer to whether these emails are Satoshi's or not. Perhaps there is a telling clue or clues in the source or metadata of those emails that proves or disproves them. My hope is to verify yes or no, legit or not. Maybe someone who reads this, more adroit than I, can enlighten me on a telling point that reveals whether Satoshi wrote the Wei Dai and Jon Matonis emails, or not.
I'm curious and listening.
-
 @ 42342239:1d80db24
2024-09-02 12:08:29
@ 42342239:1d80db24
2024-09-02 12:08:29The ongoing debate surrounding freedom of expression may revolve more around determining who gets to control the dissemination of information rather than any claimed notion of safeguarding democracy. Similarities can be identified from 500 years ago, following the invention of the printing press.
What has been will be again, what has been done will be done again; there is nothing new under the sun.
-- Ecclesiastes 1:9
The debate over freedom of expression and its limits continues to rage on. In the UK, citizens are being arrested for sharing humouristic images. In Ireland, it may soon become illegal to possess "reckless" memes. Australia is trying to get X to hide information. Venezuela's Maduro blocked X earlier this year, as did a judge on Brazil's Supreme Court. In the US, a citizen has been imprisoned for spreading misleading material following a controversial court ruling. In Germany, the police are searching for a social media user who called a politician overweight. Many are also expressing concerns about deep fakes (AI-generated videos, images, or audio that are designed to deceive).
These questions are not new, however. What we perceive as new questions are often just a reflection of earlier times. After Gutenberg invented the printing press in the 15th century, there were soon hundreds of printing presses across Europe. The Church began using printing presses to mass-produce indulgences. "As soon as the coin in the coffer rings, the soul from purgatory springs" was a phrase used by a traveling monk who sold such indulgences at the time. Martin Luther questioned the reasonableness of this practice. Eventually, he posted the 95 theses on the church door in Wittenberg. He also translated the Bible into German. A short time later, his works, also mass-produced, accounted for a third of all books sold in Germany. Luther refused to recant his provocations as then determined by the Church's central authority. He was excommunicated in 1520 by the Pope and soon declared an outlaw by the Holy Roman Emperor.
This did not stop him. Instead, Luther referred to the Pope as "Pope Fart-Ass" and as the "Ass-God in Rome)". He also commissioned caricatures, such as woodcuts showing a female demon giving birth to the Pope and cardinals, of German peasants responding to a papal edict by showing the Pope their backsides and breaking wind, and more.
Gutenberg's printing presses contributed to the spread of information in a way similar to how the internet does in today's society. The Church's ability to control the flow of information was undermined, much like how newspapers, radio, and TV have partially lost this power today. The Pope excommunicated Luther, which is reminiscent of those who are de-platformed or banned from various platforms today. The Emperor declared Luther an outlaw, which is similar to how the UK's Prime Minister is imprisoning British citizens today. Luther called the Pope derogatory names, which is reminiscent of the individual who recently had the audacity to call an overweight German minister overweight.
Freedom of expression must be curtailed to combat the spread of false or harmful information in order to protect democracy, or so it is claimed. But perhaps it is more about who gets to control the flow of information?
As is often the case, there is nothing new under the sun.
-
 @ a6631624:24ba1a2f
2024-09-01 22:33:57
@ a6631624:24ba1a2f
2024-09-01 22:33:57I started V1 of this blog back in Q2 2023 on other platforms. And, I started writing for it about a year before that. Since then, all of my posts -- both in the backlog and currently published -- have undergone rework after rework as I painstakingly refine the presentation of these rarely spoken and "never-before-thought" ideas. Yet, the posts I've most stalled and blown off have been those pertaining to Gnosticism.
The reason being that it's just overwhelming the amount of wrongs I have to right, the number of misconceptions I must correct, the scope of the programs I have to bypass, and the shear volume of aspects I need to educate on just to convey Gnosticism and the Gnostic spirit accurately, as I tap into it.
And, we haven't even began talking about the number of butts I've got to prick in the process.
So, this a massive undertaking that I have continually delayed. And, I fear, in my delayedness, that I've allowed too much wrong to proliferate in the the meme pool of "Gnosticism" unchallenged. And though, I've been shamefully ignoring the pot, I still feel I have just enough time to stir before the food is burnt.
So, let's begin.
What is Gnosticism?
Gnosticism, as we inherit it in America, is a vein of Orpho-Platonism.
Obviously.
Not Hermeticism. Not Christianity. And, certainly, not Judaism.
But, Orpho-Platonism.
Particularly, Western Gnosticism can be described as a syncretism of the Greek mystery religions centering the Orphic vein -- which comes to us from Orpheus, through Pythagoras (and most likely from Egypt and Babylon through his studies), through Plato. As a matter of fact, the mythological through-line from Gnosticism to Plato, to Orphism, and back to Egyptian mythologies is glaring when you read the myths, even without being a buff.
Yet, this is not the form of Gnosticism we usually first encounter. We don't learn of it as a complete and independent framework of hellenic origin, but usually as a half-thing mix mashed with something else; as a "parasite religion" as I've recently heard it mocked.
This stems from the Christian-centered folly of conflating Gnostic Christianity with Gnosticism itself, both historically and theologically, as if Gnosticism "came from" Christianity. Such beliefs are simply failures of historical and cultural inquiry. But, this "entanglement" that persists in the minds of the many today, is rooted in the fact that Western Gnosticism garnered it's first bout of attention (i. e. major hostilities) when it appeared in the early centuries CE — as a variety of rouge mystery cultists attempted to integrate the Jesus figure into their canons.
As Christ-followers, they'd adopt Jesus as the latest prophet in their esoteric lineage (from Orpheus to Pythagoras, for example) with many choosing to participate in Jesus-worship activities along side the other early Christian varieties. This is the origin of those who call themselves "Gnostic Christians" (a.k.a. Gnostic followers of Christ) today.
However, these mystery cultists -- unlike other Christians -- did not renounce their traditions to become whole converts into the Jewish way. They quietly retained them, seeking not to "convert" or rouse the other Christians, but to cultivate their own understandings of the texts in line with their Greek way. And, that is why their Jesus — "Gnostic Jesus" — is a little divergent from the norm. He is not interpreted to take on the throughly Jewish character and ideological background of Abrahamic Jesus, but a Hellenic character and background inside of a Jewish body (with the body thing being debatable).
And that, as we have learned, is very !!!TRIGGERING!!! to the zealots for Judeo-Christian ideology. This little attempt at cultural assimilation would result in being seeing as not just some kind of competitor, a but a mortal enemy to the ideology and spread the proper Christian -ness. Thus, "the Gnostics" — those retaining the beliefs of the mystery cults -- were branded the worst of "heretics," worthy of being rooted out of all influence and power by any means necessary.
And, so began the hiding.
``` Transmission Note 01:
The Greeks and other peoples were a lot more open to input from cultures and pantheons beyond their own than the Jews are. I believe this led them to underestimate the extent to which the Jewish -ness defined the character and how Christianity was meant to be an expansion of that -ness rather than an earnest spiritual or intellectual exploration.
Essentially, they did not realize there was this agenda and rigid ethnic claim to ownership of the Jesus character. And, the misstep of trying to engage with it as such is what led the mystery cultists to inadvertently cause such great offense.
Now, of course, the plan was always to convert, kill, persecute, and/or disenfranchise anyone and any culture that did not give way to the planned faith (Catholicism). But, they really stay aggro'd on the Gnostic Christians, which is why everybody finds them and thinks they're the whole of Gnosticism.
``` For half of the last 2000 years, the Christian mystery cultists publicly behaved and saw themselves as Christians, and that is indeed what they called themselves ("Gnostic" is a name that was given to them collectively and retroactively). But, they entertained their mysteries in private. They preserved their belief systems through metaphor and code, they prepared private gatherings, and they participated in both new and ancient rituals in secret. They also, famously, wrote and distributed their own texts among themselves, drew and documented esoteric meaning from The Bible, and as time went on, became the Valentinians, Manichaens, Cathars, Mandaeans, etc...
All of whom, in the end, lost themselves.
``` Transmission Note 02:
The non-Christian mystery cultists behaved much the same, continuing to exist beneath the surface under other names and "heresies." Seems like most died up to now, but the mysteries of some are still carried by different orgs, lines of thought, and denominations just like the Orphic vein.
``` Sometimes genocided, sometimes not, they all became more and more assimilated into the Christian worldview, losing and twisting up bits of their gnosis until they were no longer carriers of the mysteries, but dead ends. Most notably, the information surrounding death either came to mimic that of Christianity and/or became platitudinal, losing it's instructional value. And, that's just what Christianity does — its function is to destroy the means and routes to Gnosis; forcing you to succumb, in one way or another, to the Evil-bland power of the demiurgic drone.
It breaches. It invades. It colonizes. It burns.
All of this is why, despite modern and historical claims, it is clear that Gnosticism and Christianity share no common cause and are, in fact, fundamentally opposed. This is obvious from their logical ends, on their faces, and Gnostic Christians are lost, or "heretical," Gnostics as far as I am concerned.
``` Transmission Note 03:
Despite this, there are very few Gnostic Christians who have (so far) maintained a non-Abrahamic Jesus and allegedly find bits of gnosis by focusing through the figure. That certainly makes them distinct from the Judeo-Catholic lineage and this, among other non-standard Christs, are the only reason why I make the distinction between Catholicism and Christianity in other posts.
``` But, thus far, I've (necessarily) given you more of a history lesson on them than an explanation of what Gnosticism really is.
Features of Gnosticism
Globally and as a phenomenon, Gnosticism is the metaphysical worldview positing a duality between self-consciousness and material nature, with need for man to overcome the latter by means of personal knowledge of the self and of the nature of reality (Gnosis). Further, it:
- Posits a hostile world order.
- Asserts a material reality that naturally restricts the meaningful will and ability of self-conscious man within its objective and knowable parameters.
- Affirms the free will and intellectual agency of self-conscious man as means by which he can pursue, gain, and apply Gnosis.
- Calls for a personal journey toward individuation, as man cannot attain Gnosis collectively or by means of others, but only through his own efforts.
Gnosticism is an emergent worldview, appearing across time and space organically, rather than as a worldview constructed for socio-political purposes like religions. As such, it does not share the goal or function of religion as a means of socio-political management. Yet, still, it takes on the three forms that all worldviews do -- mythic, secular, and atheistic. Specifically (with examples), there is:
-
Mythic Gnosticism -- taking on a spiritual character, dealing with immaterial realms and entities:
-
- Classical/Theistic Gnosticism
-
- Jungian Analysis
-
Secular Gnosticism -- taking on a political character, dealing mainly with material powers and principalities:
-
- Prometheanism
-
- Reincarnation Truthers (ET)
-
- American Conspiracy Culture (Alex Jones, David Icke, etc...)
-
- Plot of The Matrix
-
- Forms of Anarchism
-
Gnostic Atheism -- taking on a philosophical character, dealing with ethics and metaphysics:
-
- Objectivism
-
- Simulation Theory (some)
-
- e/acc
I, personally, view Gnosticism as a signal you pick up on. A well broadcast fact of reality that you become attune to (if you so have the capacity) after an alienating event: a realization, a condition, or a happening that snaps you out of a given collective drone and spurns the oh, so gnostic sense that something is deeply wrong with the world. Often, it's a noticing of hyleticism, a noticing of a naturally systemic injustice, or a just a longstanding experience of disconnect with the norms and trajectory of the world. But, after boarding the Gnostic-line of thought, a decent amount path-find their way to actual Gnosticism. And, while that Gnosticism may wear many different faces and metaphorical frameworks, it's always says the same thing.
``` This isn't exclusive to me. I'm the only one I've heard explicitly say this, but I've seen all serious Gnostics talk about this in a way that suggests what I am. Additionally, those "alienating events," as I've coined, are not spontaneous, they're usually a long time coming.
``` That's why I've listed only 4 characteristics — of Gnosticism: because, contrary to what most scholars and enthusiasts would say, that's all you need to describe that thing. And, by being able to identify what are essentially Gnostic first principles, we are able to understand and talk about Gnosticism much more pointedly.
For one, it gives us a kind of tracking system where we can talk about Western Gnosticism but also see Gnosticism itself, Eastern Gnosticism, and Gnosticism's appearance in tribal cultures around the world. We can see it branching off in America or taking on some new flavor in Brazil. We can also see it when it isn't appearing in an explicitly spiritual form, but as a literary theme or a cultural meme. So, fittingly, this understanding of Gnosticism is as broad as the phenomena itself since it is much more in line with how it actually manifests within the world.
Yet, you’ll also see that it is somehow much more precise than the long, droning lists that Stephan Hoeller and a few others have produced:
- There is an original and transcendental spiritual unity from which emanated a vast manifestation of pluralities.
- The manifest universe of matter and mind was created not by the original spiritual unity but by spiritual beings possessing inferior powers.
- One of the objectives of these creators is the perpetual separation of humans from the unity (God).
- The human being is a composite: the outer aspect is the handiwork of the inferior creators, while the inner aspect is a fallen spark of the ultimate of the divine unity.
- The sparks of transcendental holiness slumber in their material and mental prison, their self-awareness stupefied by the forces of materiality and mind.
- The slumbering sparks have not been abandoned by the ultimate unity; rather, a constant effort directed toward their awakening and liberation comes forth from this unity.
- The awakening of the inmost divine essence in humans comes through salvific knowledge, called “gnosis.”
- Gnosis is not brought about by belief of by the performance of virtuous deeds or by obedience to commandments; these at best serve to prepare one for liberating knowledge.
- Among those aiding the slumbering sparks, a particular position of honor and importance belongs to a feminine emanation of the unity, Sophia (Wisdom). She was involved in the creation of the world and ever since has remained the guide of her orphaned human children.
- From the earliest times of history, messengers of Light have been sent forth from the ultimate unity for the purpose of advancing gnosis in the souls of humans.
- The greatest of these messengers in our historical and geographical matrix was the descended Logos of God manifest in Jesus Christ.
- Jesus exercised a twofold ministry: he was a teach, imparting instruction concerning the way of gnosis; and he was a hierophant, imparting mysteries.
- The mysteries imparted by Jesus (which are also known as sacraments) are mighty aids toward gnosis and have been entrusted by him to his apostles and their successors.
- Through the spiritual practice of the mysteries (sacraments) and a relentless and uncompromising striving for gnosis, humans can steadily advance toward liberation from all confinement, material and otherwise. The ultimate objective of this process of liberation is the achievement of salvific knowledge and with it, freedom from embodied existence and return to ultimate unity.
— Gnosticism: New Light on the Ancient Tradition of Inner Knowing by Stephan A. Hoeller
Lists like this, while not all wrong, do not form a cohesive or accurate explanation of Gnosticism.
I will say that, while I disagree on the language, universality, “divine feminine,” and the implications of “oneness” — which mostly come from Christian contamination — the first 10 points comprise a very accurate characterization of Mythic Gnosticism. But the list, as a whole, is completely ignorant of Gnosticism’s non-spiritual manifestations and, again presupposes that Gnosticism is a denomination of Christianity, a plain falsehood.
Worse yet, they're the works of those who futilely take it upon themselves to "revive" and "spread" Gnostic Christianity, with these lists as blatant — and often plainly stated — attempts to define a canonical doctrine. The ultimate intent being to make "Gnosticism" structurally and massively participatory so that it can be marketable to the masses. But, those who desire this do so because they view Gnosticism as a religion and have adopted Christian/Abrahamic views as to the purpose of belief systems.
Yet, Gnosticism is neither beholden to nor compatible with those views.
``` Transmission Note:
This should not be interpreted as an attack on Stephan Hoeller. The aforementioned book is informative as a whole and I agree with a lot of it. However, I disagree with many of Hoeller's conclusions.
Funny enough, while revisting that chapter, I discovered that Hoeller, being well before my time, has a lot more context on where guys like David Lindsay (I think that's his name?) come from. Page 182.
```
Practicing Gnosticism
One does not practice Gnosticism, mythic or not. But, Gnostics often practice rituals that they believe will induce Gnosis.
Because Gnosis must be attained personally and intellectually, these rituals historically involved psychedelics and circumambulatory* acts meant to remind the practitioner of his goal. Additionally, this pursuit meant that Classical Gnostics were (and continue to be) open to trying out practices from other belief systems if they're believed to have the potential to induce Gnosis. Many, however, also turn to plain ol' knowledge, choosing to immerse themselves in more interactive ways of knowing about the world such as science, math, and esoterica as a path to personal knowledge of reality.
Yet, while varied and individualistic, Gnostics did not always go about their spiritual journeys alone. While Gnosis is pursued personally, individual findings, experiences, and speculations were/are shared among each other for consideration and guidance in personal journeys. Individuals with similar findings and personally efficacious mediums of Gnosis would form groups and participate in rituals together. And, because Gnosticism is classically hostile or indifferent to the body, historical Gnostic groups tended to go one of two ways: ascetic or degenerate. The first involved fasting, abstinence, and denial of bodily pleasures. The second, I will leave to your imagination. But, thankfully the former won out in popularity and is how Gnostics are commonly portrayed.
``` Come to think of it, the whole attempt to shock oneself into Gnosis is kind of like trying to relive the alienating event that made one Gnostic in the first place. But, more intense.
``` So, the point being made is that, when thinking of Gnostic groups or Gnostics gathered, one should avoid conceiving of them as one does a church. Rather than platforms where an orthodoxy is espoused and downloaded, Gnostic gatherings were/are information exchanges, more akin to get-togethers.
Gnosticism has an investigative and antinomian character, rather than faithful and obedient character.
Secrets
At this point, I've laid out that Western Gnosticism comes from the Greek mystery cults (and by extension Egypt, and, in likelihood, Babylon). I've highlighted that those holding their beliefs went into hiding and were given the name "Gnostic" by their persecutors ("Gnosis" meaning "knowledge," "Gnostic" approximating "knower"). And, I've repeatedly used word like "private," "personal," "individual," "metaphor," "code," and "secret" to describe their activities.
All of these things, in a sort of snowball effect, have had Christians unwaveringly convinced that Gnosticism is about "keeping secrets." And, with a strange intensity, they've been all riled up about Gnostics having "secret knowledge" for thousands of years. In fact, if you ask a Christian (who has heard of Gnosticism) today, that's exactly what they'll tell you: "Gnostics were people who thought they had secret knowledge."
With a tone suggesting an absurd level of contempt for a supposedly dead heresy, to boot.
But, Gnosticism was poorly understood by its enemies and is not about "secret knowledge." Despite the fact that Christians love making themselves angry imagining such silly ideas that are more attributable to themselves, Gnostics are not and were not meeting up to go: "teehee, they don't know our seeecret!"
In fact, here are the mythic secrets of such great concern:
-
The mysteries of the mystery cults tended to be along these lines:
-
- You have an immortal soul.
-
- You belong to a spiritual reality (often phrased: "you are/can become a god").
-
- You are trapped in a cycle of material death and rebirth.
-
- You need to do XYZ to escape materiality.
-
The mystery cultists/Gnostics were secretive to preserve the purity of the above beliefs and techniques and to avoid persecution -- and ultimately inquisition -- at the hands of hostile powers.
- Gnosis is personal, private, and "secret" because it is incommunicable. Personal knowledge can be talked about, but cannot be literally shared person to person and Gnosis comes differently to each person.
- Gnosticism doesn't have an imperative for conversion or being a "big tent" because Gnosticism itself is incommunicable to the majority.
These things are not really "secrets" but, even if they were, they could be talked about freely (given the absence of persecution) due to bullet four.
Bonus "Secret": A common premise is that Gnosis is applied at death on a post-mortem spiritual journey, similar to that of the Ka of Egyptian mythology.Books
Many religions and even philosophies are centered around holy books as definitive canonical, instructional, and behavioral guides. They function as the source and reinforcement of a given worldview, which allows it to persist fundamentally undiluted for extended periods of time.
This is not so for Gnosticism -- mythic or not.
Instead, Gnosticism has no holy book and, in the section called "Features of Gnosticism," I've already laid out its presence and reception through alienating events. It requires no human regulation in order to continue to authentically exist.
``` Now is a good time to mention that there is a multiple discovery aspect of Gnosticism which is generally how I, at least, track alignment and continuity while identifying "the signal," as I call it, as the source in others.
``` Yet, the ancient Mythic Gnostics were known to be prolific writers, as attested by the Nag Hammadi library. And, the penchant for writing seems to persist across time and mode, as Secular Gnostics and Gnostic Atheists (beknownst or not) have been absurdly influential in American media and culture by this means.
So, why do Gnostics write so much and how do they use books?
Gnostics tend to view books as spiritual journals, rather than instruction manuals, and literature at large as a means of preserving knowledge. Contributing to the Gnostic meme pool is a form of participation in the imperative, which is why Gnostics, unlike Christians and others, have little issue putting their pieces forward. Rather than the book study and faith characteristic of Abrahamic maintenance, Gnosticism, again, tends toward investigation and information sharing. And, it is for these reasons that Gnostics have been known to not only write their own texts, but to adopt and reinterpret the texts of other belief systems according to the Gnostic worldview.
-
 @ 42342239:1d80db24
2024-08-30 06:26:21
@ 42342239:1d80db24
2024-08-30 06:26:21Quis custodiet ipsos custodes?
-- Juvenal (Who will watch the watchmen?)
In mid-July, numerous media outlets reported on the assassination attempt on Donald Trump. FBI Director Christopher Wray stated later that same month that what hit the former president Trump was a bullet. A few days later, it was reported from various sources that search engines no longer acknowledged that an assassination attempt on ex-President Trump had taken place. When users used automatic completion in Google and Bing (91% respectively 4% market share), these search engines only suggested earlier presidents such as Harry Truman and Theodore Roosevelt, along with Russian President Vladimir Putin as people who could have been subjected to assassination attempts.
The reports were comprehensive enough for the Republican district attorney of Missouri to say that he would investigate matter. The senator from Kansas - also a Republican - planned to make an official request to Google. Google has responded through a spokesman to the New York Post that the company had not "manually changed" search results, but its system includes "protection" against search results "connected to political violence."
A similar phenomenon occurred during the 2016 presidential election. At the time, reports emerged of Google, unlike other less widely used search engines, rarely or never suggesting negative search results for Hillary Clinton. The company however provided negative search results for then-candidate Trump. Then, as today, the company denied deliberately favouring any specific political candidate.
These occurrences led to research on how such search suggestions can influence public opinion and voting preferences. For example, the impact of simply removing negative search suggestions has been investigated. A study published in June 2024 reports that such search results can dramatically affect undecided voters. Reducing negative search suggestions can turn a 50/50 split into a 90/10 split in favour of the candidate for whom negative search suggestions were suppressed. The researchers concluded that search suggestions can have "a dramatic impact," that this can "shift a large number of votes" and do so without leaving "any trace for authorities to follow." How search engines operate should therefore be considered of great importance by anyone who claims to take democracy seriously. And this regardless of one's political sympathies.
A well-known thought experiment in philosophy asks: "If a tree falls in the forest and no one hears it, does it make a sound?" Translated to today's media landscape: If an assassination attempt took place on a former president, but search engines don't want to acknowledge it, did it really happen?
-
 @ 599f67f7:21fb3ea9
2024-09-19 08:27:12
@ 599f67f7:21fb3ea9
2024-09-19 08:27:12¿Qué es una dirección Lightning o Lightning address?
Una dirección Lightning es una dirección que visualmente se asemeja a una dirección de correo electrónico legible para los humanos, por ejemplo usuario@dominio.com pero que en realidad te permite recibir pagos en bitcoin instantáneos y económicos, sin la necesidad de tener un nodo en linea en tu dispositivo ni tener que generar facturas de forma manual cada vez que alguien te quiere hacer un pago.
¿Suena bien no?
¿Y cómo funciona?
Funciona utilizando el protocolo de pago LNURL.
Aquí se muestra un sencillo esquema de lo que ocurre en segundo plano.
En resumen, cuando otro usuario quiere pagarte usando tu dirección Lightning, tu billetera convierte la dirección Lightning en una solicitud de pago LNURL. Luego se utiliza esa solicitud de pago LNURL exitosa para obtener una factura BOLT11.
💡 Dirección Lightning > LNURLp > Factura BOLT 11.
Suena bien, pero ¿cuál es el problema?
Por el momento, muchas de las implementaciones de Lightning Address son de custodia, porque se necesita un dominio para que Lightning Address funcione y un nodo que esté siempre en línea para recibir los pagos. Debido a que es de custodia, el custodio puede atacarte en cualquier momento y monitorear tus transacciones.
Tienes que confiar en el propietario del dominio para no cambiar el registro de tu dirección Lightning. Y no funciona si el servidor LNURL no está en línea.
Bitcoin Txoko ofrece una sencilla solución de Lightning Address respaldada por LNbits. Esto también es de custodia, así que por favor mantén solo una pequeña cantidad en tu billetera Bitcoin Txoko y ve retirando a tu billetera de autocustodia a medida que recibas más sats.
Estoy listo, ¿qué necesito para empezar?
¡Todo lo que necesitas es un teléfono móvil o un ordenador y una conexión a Internet!
1. Creando tu billetera
Si aún no lo has hecho, navega a https://bitcointxoko.com y crea una nueva billetera. Puedes elegir el nombre que quieras.
2. Activar extensiones
Hace falta la extensión
Pay Linkspara que las direcciones Lightning funcionen.Abre
Extensionesen la barra de herramientas y activaPay Links.3. Creando tu enlace de pago
-
En a la extensión
Pay Links, haz clic enNew Pay Link. -
Elige la billetera que has creado.
-
Para la descripción del artículo, puedes escribir lo que quieras.
-
Elige un nombre de usuario de tu dirección Lightning. Tu dirección Lightning se verá como
username@bitcointxoko.com. -
Desmarque
Fixed amounty cambia el valor mínimo a 1 y el valor máximo a 500000.
⚠️ También puedes cambiar el valor máximo a algo más alto, pero es más probable que los pagos más grandes fallen debido a la limitada capacidad de entrada del nodo Lightning de Bitcoin Txoko. Así que recomendamos mantenerlo en 500000 sats.
-
Ahora abre
Advanced optionsy cambiaComment maximum charactersa 799. Este paso no es necesario pero permite más funcionalidades más adelante. -
Marca
Enable nostr zapsen la parte inferior, para que puedas utilizar tu dirección Lightning para recibir zaps. -
Las demás opciones avanzadas son opcionales, puedes configurarlas si quieres o dejarlas en blanco.
Al final debería verse algo así.
- Cuando hayas comprobado que todo es correcto, sigue adelante y haz clic en
Create Pay Link.
Probando
Puedes probar si tu nueva dirección Lightning funciona yendo a otra cartera, pulsando en
Enviary escribiendo tu dirección Lightning como destino, y luego enviándote una pequeña cantidad de sats.Vuelve a tu billetera Bitcoin Txoko y comprueba si has recibido tu propio pago. Es posible que tengas que actualizar la página.
Si todo funcionó correctamente, ¡enhorabuena! 🥳
Si no es así, háznoslo saber. Siempre estamos aquí para ayudar.
Próximos pasos
Nostr zaps
Puedes añadir tu dirección Bitcoin Txoko Lightning a tu perfil de nostr y usarla para recibir zaps. Normalmente, esto se hace yendo a
Perfil>Editar>Dirección Lightningy cambiando la dirección Lightning.LNDhub
Puedes importar tu billetera LNbits como un LNDhub en tu teléfono utilizando una aplicación como Zeus o BlueWallet, en lugar de visitar la billetera en el navegador cada vez que desees comprobar tu saldo o realizar un pago. Echa un vistazo a nostr:naddr1qvzqqqr4gupzqkvlvlma7a55ccp6d5rrdc27h3ssmdmael286mjaq5uxmqslk04fqqxnzd3exuerqdfkxccnyv3cs0uvul sobre cómo hacer esto.
Código QR
También puedes compartir o imprimir tu código QR LNURLp para que la gente pueda escanearlo fácilmente con sus teléfonos. ¡Muy útil si estás introduciendo bitcoin a tu comerciante local favorito para que pueda recibir propinas Lightning!
Simplemente comparte el enlace a tu página compartida, o imprime el código QR como PDF yendo a
View Link>Print. -
-
 @ d830ee7b:4e61cd62
2024-08-29 14:55:24
@ d830ee7b:4e61cd62
2024-08-29 14:55:24เรื่องราวของ Didier Somnuke บิตคอยเนอร์ชาวไทย และเส้นทางการเดินทางของเขาในโลก Bitcoin
บทความต้นฉบับโดย Win Ko Ko Aung
27 สิงหาคม 2024 / เผยแพร่บนเว็บไซต์ Bitcoin Magazine
ในแวดวง Bitcoin ทั่วโลกที่กำลังเติบโตอย่างรวดเร็ว มักจะมีอคติจากชาติตะวันตกครอบงำเรื่องเล่าต่างๆ ทำให้มองข้ามเรื่องราวอันหลากหลายจากทั่วทุกมุมโลก
หนึ่งในเรื่องราวเหล่านั้นคือเรื่องของ Didier Somnuke เจ้าของธุรกิจขนาดเล็กในใจกลางกรุงเทพฯ เมืองที่ขึ้นชื่อเรื่องการต้อนรับนักท่องเที่ยวต่างชาติถึง 22.8 ล้านคนในปี 2023 แซงหน้าเมืองใหญ่ๆ อย่างปารีส ลอนดอน และนิวยอร์ก
แม้ว่าประเทศไทยจะประสบปัญหาหนี้ครัวเรือนพุ่งสูงถึง 16.37 ล้านล้านบาท (463 พันล้านดอลลาร์สหรัฐ) หรือ 90.8% ของ GDP เพิ่มขึ้นจากไม่ถึง 14 ล้านล้านบาทในปี 2019
Didier Somnuke เกิดในจังหวัดยะลา ที่ซึ่งความขัดแย้งทางภูมิรัฐศาสตร์เป็นความจริงอันโหดร้าย ภาคใต้ของไทยเป็นหนึ่งในพื้นที่ที่ยากจนที่สุดของประเทศ โดยมีอัตราความยากจนอยู่ที่ 34% เทียบกับค่าเฉลี่ยของประเทศที่ 6% อ้างอิงจากข้อมูลของธนาคารโลก
ยะลาต้องเผชิญกับความไม่สงบมาอย่างยาวนาน นับตั้งแต่ปี 2004 ความรุนแรงนี้คร่าชีวิตผู้คนไปกว่า 7,000 คน และมีผู้ได้รับบาดเจ็บอีก 13,500 คน
ดังคำกล่าวของคนไทยที่ว่า "ทวงสิทธิ์ที่จะมีชีวิตที่ดีกลับคืนมา"
ในปี 2012 Didier ตัดสินใจอำลาบ้านเกิดที่เต็มไปด้วยความขัดแย้ง มุ่งหน้าสู่กรุงเทพฯ โดยหวังว่าการศึกษาจะเป็นแสงสว่างนำทางไปสู่ชีวิตที่ดีกว่า
ในเวลานั้น Bitcoin และแนวคิดทางการเงินยังเป็นเรื่องไกลตัวสำหรับ Didier เขาใช้ชีวิตอย่างคุ้นเคยบนท้องถนนที่คึกคักของกรุงเทพฯ สำเร็จการศึกษาระดับปริญญาโท และเข้าสู่โลกแห่งการทำงานประจำ สำหรับคนที่ย้ายถิ่นฐานมาจากต่างจังหวัด นี่ถือเป็นความสำเร็จครั้งสำคัญ
Didier นึกถึงคำพูดของอาจารย์ที่เคยสอนว่า "เมื่อคุณแก่ตัวลง คุณจะมีเวลาและเงิน แต่คุณจะไม่มีแรงที่จะเริ่มต้นธุรกิจ ถ้าอยากทำอะไร ก็จงลงมือทำซะ" ด้วยคำแนะนำนี้ Didier จึงลาออกจากงานประจำที่แสนน่าเบื่อหลังจากผ่านไปเพียงหนึ่งปี และเริ่มต้นบทใหม่ของชีวิต
Didier ยืมเงิน 50,000 บาท (ประมาณ 1,500 ดอลลาร์สหรัฐ) จากพี่ชาย เพื่อเปิดร้านขายเบอร์เกอร์ข้างทาง เขาเลือกที่จะเริ่มต้นธุรกิจเบอร์เกอร์เพราะคิดว่ามันง่าย และใช้เงินลงทุนไม่มาก
ด้วยความทะเยอทะยาน และแรงบันดาลใจจากพลังงานอันพลุ่งพล่านของกรุงเทพฯ เมืองที่ไม่เคยหลับใหล เขาใช้เวลาประมาณหนึ่งปีในการพัฒนาสูตร และเริ่มต้นธุรกิจในปี 2015
ในช่วงสามถึงสี่ปีแรก เขาบริหารจัดการทุกอย่างด้วยตัวเองในฐานะผู้ประกอบการรายย่อย และรายได้ของเขาก็ต่ำกว่าเงินเดือนที่เคยได้รับจากงานประจำ หลายครั้งที่เขาสงสัยว่าตัวเองตัดสินใจผิดหรือไม่ ที่ลาออกจากงานมาทำธุรกิจที่สร้างรายได้น้อยกว่า
อย่างไรก็ตาม หลังจากผ่านไปห้าปี ทุกอย่างก็เริ่มดีขึ้น ยอดขายของร้านเริ่มเพิ่มขึ้น และ Didier ก็เริ่มจ้างพนักงาน
เขาสารภาพว่า "ผมเข้าสู่ตลาดคริปโทด้วยความโลภ สิ่งที่ผมต้องการคือรวยเร็ว"
ในปี 2017 เขาและเพื่อนๆ ได้รวบรวมเงินกันซื้อเครื่องขุด ASIC สามเครื่องจาก Bitmain เพื่อลองขุด Bitcoin และ Altcoins เช่น Litecoin และ Dogecoin พวกเขาได้รับผลตอบแทนจากการลงทุนภายในหกเดือน
Didier ซื้อ Bitcoin ครั้งแรกในต้นปี 2017 เพื่อซื้อเครื่องขุด ASIC เหล่านั้น แต่เขาไม่รู้วิธีโอน Bitcoin จึงต้องใช้การโอนเงินผ่านธนาคารแทน
เมื่อนึกย้อนกลับไปถึงประสบการณ์ในช่วงแรกๆ เขาเล่าว่า..
"Bitcoin ก้อนแรกของผมค่อยๆ ถูกเปลี่ยนเป็น Shitcoins ในช่วงตลาดกระทิง ผมโชคดีมาก ผมได้กำไร 100% เกือบทันทีที่ซื้ออะไรก็ตาม"
แม้จะไม่มีความรู้เรื่องคริปโทเคอร์เรนซีเลย แต่เขาก็เริ่มมั่นใจในตัวเอง และกลายเป็น "Super Shitcoiner" โดยไม่สนใจ Bitcoin มากนัก
กลางปี 2017 เขาได้เรียนรู้เกี่ยวกับ Leverage และการเทรด กำไรของเขาพุ่งสูงขึ้นอย่างรวดเร็ว แต่โชคก็ไม่ได้เข้าข้างเขาไปตลอด
ต้นปี 2018 ตลาด Crash เขาขาดทุนกว่า 1 ล้านบาท (เกือบ 30,000 ดอลลาร์สหรัฐ) ในขณะที่เงินทุนเริ่มต้นของเขาอยู่ที่ประมาณ 100,000 บาท (ประมาณ 3,000 ดอลลาร์สหรัฐ) เท่านั้น ไม่เพียงเท่านั้น เขายังสูญเสีย Shitcoins ทั้งหมดจาก Mining Pool ที่เขาฝากไว้
อยู่มาวันหนึ่ง เมื่อเขาตรวจสอบบัญชี Shitcoins ทั้งหมดที่เขามีมูลค่า 10,000 ดอลลาร์สหรัฐก็หายไป ประกาศบนเว็บไซต์ Mining Pool ที่ชื่อว่า "Hash-to-Coin" ระบุว่า หากเก็บเหรียญไว้กับพวกเขานานกว่าสามเดือน จะถือว่าเป็นการบริจาค

เขาพูดด้วยความผิดหวังว่า "ผมสูญเสียทุกอย่าง" แต่ไม่เหมือนคนส่วนใหญ่ "ผมไม่ได้โทษ Bitcoin ผมยังคงมองว่ามันคืออนาคต ผมโทษตัวเอง ผมไม่รู้อะไรเลย และผมใช้ Leverage มากเกินไป"
เขาเน้นย้ำว่า แม้จะประสบกับความสูญเสียทางการเงินอย่างหนัก แต่แฟนสาวของเขาก็ไม่ได้ทิ้งเขาไป..
"แฟนผมเป็นลูกค้าประจำ เธอมาซื้อเบอร์เกอร์เป็นประจำ ผมเจอเธอตอนที่ผมกำลังลำบากทางการเงิน ในช่วงแรกๆ ที่เป็นผู้ประกอบการ เธอสนับสนุนผม และบอกว่าเราสามารถหาเงินคืนได้"
ด้วยความมุ่งมั่นที่จะพลิกสถานการณ์ เขาได้ค้นพบคุณพิริยะบน YouTube และเริ่มติดตาม Live Stream เกี่ยวกับ Bitcoin อย่างจริงจัง นี่คือจุดเริ่มต้นที่ทำให้เขาเข้าใจอย่างแท้จริงว่า Bitcoin และคริปโทเคอร์เรนซีคืออะไร
ด้วยความรู้ใหม่นี้ เขาเริ่มมอง Bitcoin เป็นเทคโนโลยีสำหรับการออม มากกว่าเครื่องมือในการเทรด
หลังจากนั้นสามปี Didier ก็สามารถกู้คืนจากความสูญเสีย และกลับมาแข็งแกร่งยิ่งกว่าเดิม เขากลายเป็นเพื่อนกับคุณพิริยะ และร่วมกันก่อตั้งบริษัท Right Shift เพื่อสร้างสรรค์เนื้อหาเกี่ยวกับ Bitcoin ในรูปแบบภาษาไทยผ่านช่องทางโซเชียลมีเดียต่างๆ รวมถึง Nostr โดยใช้แฮชแท็กยอดนิยมอย่าง #siamstr
พวกเขาร่วมกันแปลหนังสือ "The Bitcoin Standard" และ "The Fiat Standard" เป็นภาษาไทย ซึ่งกลายเป็นหนังสือขายดีในประเทศไทย พวกเขาจัดงาน Bitcoin Thailand Conference ครั้งแรกในปี 2023 และกำลังเตรียมจัดงานครั้งต่อไปในเดือนกันยายน 2024
ปัจจุบัน Didier รับชำระเงินด้วย Bitcoin ในร้านเบอร์เกอร์หลักของเขา ซึ่งเป็นหนึ่งในสี่สาขา
เขาใช้ Wallet of Satoshi ในการรับชำระเงิน ภายในหนึ่งปีหลังจากเริ่มต้นโครงการนี้ เขารับชำระเงินด้วย Bitcoin ไปแล้วกว่า 3 ล้าน Sats แม้ว่าในตอนแรกเขาคาดหวังว่าจะมีธุรกรรม Bitcoin มากกว่านี้
ในตลาดที่เขาขายของ บางครั้งเจ้าของธุรกิจขนาดเล็กข้างๆ ก็ถามเขาเกี่ยวกับ Bitcoin เพราะเห็นโปสเตอร์ Bitcoin ขนาดใหญ่ในร้านของเขา แต่พวกเขามักจะหมดความสนใจเมื่อ Didier อธิบาย
จากประสบการณ์ที่ไม่ประสบความสำเร็จหลายครั้ง ตอนนี้เขาจึงมุ่งเน้นไปที่การให้ความรู้ทางออนไลน์ ซึ่งเขาสามารถเข้าถึงผู้คนที่พร้อมจะเปิดรับนวัตกรรมได้มากกว่า

ในปี 2022 มีคนไทยประมาณ 8.4 ล้านคน คิดเป็น 12% ของประชากร ที่ใช้คริปโทเคอร์เรนซี มีการคาดการณ์ว่าภายในปี 2028 จำนวนนี้จะเพิ่มขึ้นเป็นประมาณ 17.67 ล้านคน คิดเป็น 25% ของประชากร
ระหว่างการสนทนาของเรา Didier อ้างว่ามีผู้ใช้ Bitcoin ในประเทศไทยประมาณ 50,000 คน และคาดการณ์ว่ารัฐบาลไทยอาจเข้ามายุ่งเกี่ยวกับการใช้งาน Bitcoin เช่น การบังคับใช้ KYC Wallet เพราะพวกเขาไม่ชอบระบบการเงินที่ควบคุมไม่ได้
ในกรณีที่เลวร้ายที่สุด Didier ยังคงยืนกรานว่า เขาจะยังคงสนับสนุน Bitcoin ต่อไปกับเพื่อนๆ ของเขา
"มันไม่ใช่ทางเลือก" เขายืนยัน "แต่มันคือทางรอดเดียว"
-
 @ da2683b9:54eedc2c
2024-09-19 08:03:21
@ da2683b9:54eedc2c
2024-09-19 08:03:21In modern society, technology is everywhere, especially the popularity of wireless signals, which makes our lives extremely convenient. However, with the widespread use of wireless communications, the mysterious technology gadget of signal jammer has gradually surfaced. Today, let's unveil it together!
Signal jammer, the name sounds a bit mysterious and complicated, but in fact its principle is very simple. It interferes with the transmission of other wireless signals by emitting signals of a specific frequency, thereby causing communication interruption. Although this sounds a bit shady, signal jammers do play an important role in some cases.
Imagine that you are immersed in a wonderful TV series, and suddenly, the network signal disappears, and the video freezes and makes people crazy. At this time, some places may actually be quietly using wifi disruptor. It covers or interferes with the original WiFi network by emitting powerful signals, causing a situation where it is impossible to connect to the Internet.
In some environments, WiFi jammers are also valuable. For example, in some sensitive occasions, such as prisons, military bases or important meetings, in order to protect the security of information, WiFi jammers become "bodyguards". It keeps information private by blocking unnecessary external communications.
Next, let's talk about UHF jammer. UHF signals are widely used in television broadcasting, mobile communications, wireless microphones, etc. UHF jammers are also a signal jammer that can block or interfere with these wireless signals. At concerts or large events, using UHF jammers can prevent interference with wireless microphones and ensure the smooth progress of the event.
Interestingly, UHF jammers can also be used to disrupt the communications of criminals in some cases. For example, when the police are chasing suspects, they may use UHF jammers to interfere with their communications, thereby reducing the suspect's chance of escape.
When it comes to signal jamming, military jammers are definitely the best. In modern warfare, the security of information and communications is directly related to the victory or defeat of the battle. Military signal jammer effectively weaken the enemy's combat capabilities by interfering with the enemy's wireless communications, radars, and missile guidance systems. Its powerful transmitters can block the enemy's signals, making it impossible for the enemy to obtain intelligence or command troops in time.
In addition to being used for attack, military jammers can also counter the interception of one's own telecommunications signals by the enemy. In some cases, the military will also use signal jammers to protect their secret communications from being eavesdropped by the enemy.
https://thetheblocker723-47197065.hubspotpagebuilder.com/how-to-pursue-a-higher-quality-of-life
Signal jammers, seemingly mysterious and powerful, are actually an important product of the development of modern science and technology. In certain situations, they can protect information security, maintain system stability, and even support the maintenance of law and order in some cases.
-
 @ dc652bee:6154e7d0
2024-09-19 07:39:14
@ dc652bee:6154e7d0
2024-09-19 07:39:14Unleash the fun with our Cat Earn Coins Bot! 🐱💰 Watch your feline friend collect coins while they play! Join the adventure and let the purring profits roll in! #CatCoins https://n9.cl/cat_bot
-
 @ a012dc82:6458a70d
2024-09-19 07:35:12
@ a012dc82:6458a70d
2024-09-19 07:35:12Table Of Content
-
The Psychology of Scarcity
-
Trust in Decentralization
-
The Power of Network Effects
-
The Role of Intrinsic Motivation
-
Anchoring and Adjustment Heuristics
-
Conclusion
-
FAQ
Bitcoin has been the talk of the town since its inception in 2009. While most people primarily view it as a digital currency, it offers much more than that. In this article, we will examine the various aspects of Bitcoin that set it apart from traditional currencies, focusing on behavioral economics. By understanding these unique features, we can better appreciate the true value and potential of Bitcoin in the world's financial landscape.
The Psychology of Scarcity
The limited supply of Bitcoin, capped at 21 million coins, contributes to the perceived value of the cryptocurrency. This scarcity can drive increased demand, as people are generally drawn to scarce resources. This phenomenon is well documented in behavioral economics, and it can lead to irrational decision-making, fear of missing out (FOMO), and even price manipulation.
Trust in Decentralization
Bitcoin operates on a decentralized network, meaning no central authority or government can control its supply or value. This aspect appeals to many users who have lost faith in traditional financial institutions due to corruption, mismanagement, or economic instability. From a behavioral economics perspective, the trust in decentralization can lead to a preference for Bitcoin over conventional currencies.
The Power of Network Effects
The value of Bitcoin is further enhanced by its growing network of users, developers, and investors. As more people adopt and use the cryptocurrency, its utility and demand increase, further driving up its value. This positive feedback loop is a classic example of network effects in behavioral economics, and it helps explain the rapid growth and adoption of Bitcoin.
The Role of Intrinsic Motivation
Bitcoin's open-source nature and the pseudonymous identity of its creator, Satoshi Nakamoto, have fostered a sense of community and intrinsic motivation among its supporters. This shared sense of ownership and the desire to contribute to the success of the project can drive innovation, development, and adoption of the cryptocurrency. Intrinsic motivation is a powerful force in behavioral economics, often leading to better outcomes than extrinsic rewards.
Anchoring and Adjustment Heuristics
Bitcoin's highly volatile nature can be attributed, in part, to cognitive biases like anchoring and adjustment. People often anchor their expectations of Bitcoin's value to a previous reference point, such as an all-time high or low. As new information emerges, they adjust their valuation, sometimes leading to overreactions and significant price swings. Understanding these heuristics can help explain the often unpredictable behavior of Bitcoin's price.
Conclusion
Bitcoin is more than just a digital currency; it is a complex financial ecosystem that can be better understood through the lens of behavioral economics. By analyzing the psychological factors that drive its value and adoption, we can gain valuable insights into the cryptocurrency's potential and the unique role it plays in our global economy. As the world continues to evolve, so too will Bitcoin and the fascinating interplay between human behavior and digital finance.
FAQ
How does scarcity influence Bitcoin's value? Bitcoin's limited supply creates a sense of scarcity, driving demand and leading to increased value and potential irrational decision-making.
Why is decentralization important for Bitcoin? Decentralization eliminates central authority control, appealing to users who distrust traditional financial institutions and prefer a more trustless system.
How does the psychology of FOMO influence Bitcoin adoption? Fear of missing out (FOMO) drives people to invest in Bitcoin to avoid feeling left out, potentially resulting in impulsive decision-making and increased demand.
How do cognitive biases affect our perception of Bitcoin's value? Cognitive biases like confirmation bias and herd mentality can lead to irrational beliefs and expectations about Bitcoin's value, influencing investment decisions.
Can behavioral economics explain the appeal of Bitcoin for speculative investors? Yes, factors like scarcity, network effects, and cognitive biases can make Bitcoin an attractive option for speculative investors seeking high returns.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ a03b38f8:2c7ce1f0
2024-09-19 03:04:13
@ a03b38f8:2c7ce1f0
2024-09-19 03:04:13You are Giving Away a Lot of Data with those Pictures
You post pictures on nostr and other social media. You send pictures to friends and sometimes sorta friends. I hate to tell you this but you are giving away a lot more personal data than just what's on the image of the picture.
It all comes down to the metadata. The term Metadata refers to descriptive information about a picture, image, or file. This set of information is so vital as it reveals everything about a picture.
Metadata is key as it explains the privacy and security dangers that you are exposing yourself to everytime you share that file. And not just pictures, but text documents, PDFs and Videos.
What data is in Pictures?
EXIF Data (Exchangeable Image File Format): This is a standard that specifies the formats for sound, images and ancillary tags used by scanners, smartphones and other smart devices.
EXIF contains so much more personal information than you can imagine.
It tells the geolocation of where the picture was taken and it gives the timestamp of when it was taken.
So that creepy guy who follows your accounts knows all your favorite lunch spots because you like to post pictures of your food.
Additionally the metadata contains a description or title of the image. Any tags or keywords associated with the image, author information, and any custom metadata from any image editing software that might have been used including more timestamps, system information, and log of any edits.
So yes your Bumble date knows you are trying to catfish them with that 5 year old picture you doctored up with AI.
Uses in Open Source Intelligence
Open Source Intelligence or OSINT is a fancy term for cyber stalking someone. It is using nothing more than specialized knowledge and freely available information on the internet to find out all kinds of stuff about someone.
Using the GPS metadata and reverse image search of that picture posted online you figure out where that person is from and maybe a first name. Using that to narrow down your search criteria you find their Facebook and Instagram. Now you have their last name, how they spend their time, friends, and maybe where they work. Searching free data brokers you find their address and phone number. Public records tell you how much they paid for their house and Google street view gives you a view of the house from the street.
So other than being a creep, what else is metadata used for?
Analysis of metadata helps to trace the origin and history of digital files. Digital Forensics will know when those files were created, accessed, or modified. Forensics then uses this for additional context about files and other data stored on a computer or network, this information is useful because it provides information that may not be immediately clear from the file itself. Remember your OPSEC rules and be a Nemo when necessary.
There is some good news. (And bad)
Luckily the more popular services out there such as Facebook and Instagram do not display the metadata of the users. You cannot check the metadata of pictures as it does not allow you to download pictures or copy the image link. Although that doesn't mean the companies themselves do not have access to that data.
This is not the case with services like Tumbler and most image hosting or storage services. When pictures are uploaded to cloud services like dropbox or google drive anyone with access to these images can also access the metadata.
Okay I am terrified, how do I remove metadata from pictures?
Thankfully there are several options to take care of this. Most operating systems have methods built in. (see below for instructions for Windows and MacOS). Tails and QubesOS has Metadata Cleaner software preinstalled. There are several online tools that also scrub metadata from pictures. (Shout out to nostr.build)
Windows
-
Right Click the image file and select properties
-
Click the details tab
-
Click Remove Properties and Personal Information
-
Choose the level of metadata removal desired
MacOS
-
Open the image in the preview
-
Go to Tools
-
Click EXIF tab
-
Select Remove EXIF file
How to remove EXIF data after capture on phones
Let's be honest that most of your photos are taken and reside on your phone now of days.
On iPhone you have to open the Photos app, select the image, tap on 3 dots and select Adjust Date & Time and Adjust Location. You can also get the adjust setting by clicking the little i at the bottom of the picture.
On android it is much the same way. Open Gallery, select image, tap 3 dots, choose details, then the pencil to remove location and timestamp, save.
On Graphene OS no worries, remove EXIF data after capture is an existing setting in the camera and is enabled by default.
It is a total pain that you have to do this each and every time to every picture. But I hope you now realize how important that metadata can be and why you shouldn't just be sharing it with the world.
-



