-
 @ fa0165a0:03397073
2024-10-23 17:19:41
@ fa0165a0:03397073
2024-10-23 17:19:41Chef's notes
This recipe is for 48 buns. Total cooking time takes at least 90 minutes, but 60 minutes of that is letting the dough rest in between processing.
The baking is a simple three-step process. 1. Making the Wheat dough 2. Making and applying the filling 3. Garnishing and baking in the oven
When done: Enjoy during Fika!
PS;
-
Can be frozen and thawed in microwave for later enjoyment as well.
-
If you need unit conversion, this site may be of help: https://www.unitconverters.net/
-
Traditionally we use something we call "Pearl sugar" which is optimal, but normal sugar or sprinkles is okay too. Pearl sugar (Pärlsocker) looks like this: https://search.brave.com/images?q=p%C3%A4rlsocker
Ingredients
- 150 g butter
- 5 dl milk
- 50 g baking yeast (normal or for sweet dough)
- 1/2 teaspoon salt
- 1-1 1/2 dl sugar
- (Optional) 2 teaspoons of crushed or grounded cardamom seeds.
- 1.4 liters of wheat flour
- Filling: 50-75 g butter, room temperature
- Filling: 1/2 - 1 dl sugar
- Filling: 1 teaspoons crushed or ground cardamom and 1 teaspoons ground cinnamon (or 2 teaspoons of cinnamon)
- Garnish: 1 egg, sugar or Almond Shavings
Directions
- Melt the butter/margarine in a saucepan.
- Pour in the milk and allow the mixture to warm reach body temperature (approx. + 37 ° C).
- Dissolve the yeast in a dough bowl with the help of the salt.
- Add the 37 ° C milk/butter mixture, sugar and if you choose to the optional cardamom. (I like this option!) and just over 2/3 of the flour.
- Work the dough shiny and smooth, about 4 minutes with a machine or 8 minutes by hand.
- Add if necessary. additional flour but save at least 1 dl for baking.
- Let the dough rise covered (by a kitchen towel), about 30 minutes.
- Work the dough into the bowl and then pick it up on a floured workbench. Knead the dough smoothly. Divide the dough into 2 parts. Roll out each piece into a rectangular cake.
- Stir together the ingredients for the filling and spread it.
- Roll up and cut each roll into 24 pieces.
- Place them in paper molds or directly on baking paper with the cut surface facing up. Let them rise covered with a baking sheet, about 30 minutes.
- Brush the buns with beaten egg and sprinkle your chosen topping.
- Bake in the middle of the oven at 250 ° C, 5-8 minutes.
- Allow to cool on a wire rack under a baking sheet.
-
-
 @ 5d4b6c8d:8a1c1ee3
2024-07-14 13:50:54
@ 5d4b6c8d:8a1c1ee3
2024-07-14 13:50:54Yesterday's edition https://stacker.news/items/607040/r/Undisciplined
Happy July 14th, everyone. America narrowly averted a civil war last night and I'm pretty happy about that. I was impressed by how well Stacker News covered the biggest breaking news event of the site's existence. People were pulling together lots of sources and offering generally measured thoughts.
-
- -
July 14, 2023 📅
📝
TOP POSTCommon psychological biases that bitcoiners have
Excerpt
One of the primary reasons I got involved with markets is my interest in psychology. Humans are a fickle bunch, and it's fascinating to observe the human condition in such a clear, mathematical way.
3217 sats \ 11 comments \ @birdeye21 \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/208075/r/Undisciplined?commentId=208936
Excerpt
I get your point, but this seems to me one of the (rare) differences where "technically possible but empirically infeasible" vs "technically impossible" matters a lot.
1128 sats \ 3 replies \ @elvismercury
From Portable experiences by @k00b in ~nostr
🏆
TOP STACKER2nd place @k00b (1st hiding, presumed @siggy47)
7947 stacked \ 10.5k spent \ 3 posts \ 12 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
37.3k stacked \ 0 revenue \ 51.8k spent \ 95 posts \ 214 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 14, 2022 📅
📝
TOP POSTPine – A bitcoin wallet w/ a messenger-like UI || A BTC Wallet UX for the masses
Link to https://pine.pm/
509 sats \ 15 comments \ @Spartan \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/44747/r/Undisciplined?commentId=45060
Excerpt
The user @darthcoin has way to many guides from wich you can learn a lot IMO, he is active here to most of the time, though I dont know if I've @ him correctly.
300 sats \ 4 replies \ @bangbang_u_r_done
From Any Good Routing Node Strategies? by @andyleroy in ~bitcoin
🏆
TOP STACKER1st place @nerd2ninja
544 stacked \ 1765 spent \ 3 posts \ 17 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
14.6k stacked \ 0 revenue \ 31.6k spent \ 133 posts \ 261 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 14, 2021 📅
📝
TOP POSTHow Bitcoin And Green Energy Can Save Ethiopia’s Economy
Link to https://stacker.news/items/320/r/Undisciplined
2 sats \ 1 comment \ @0268486dc4 \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/332/r/Undisciplined?commentId=333
Excerpt
From the Twitter announcement
Students will learn how to build #Bitcoin applications from the ground up using the Rust programming language. […]
18 sats \ 0 replies \ @sha256
From Fodé Diop Launches a Bitcoin Academy by @sha256 in ~bitcoin
🏆
TOP STACKER1st place @sha256
4 stacked \ 5 spent \ 2 posts \ 1 comment \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
10 stacked \ 0 revenue \ 47 spent \ 9 posts \ 8 comments
originally posted at https://stacker.news/items/608036
-
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ b2caa9b3:9eab0fb5
2024-07-14 10:52:36
@ b2caa9b3:9eab0fb5
2024-07-14 10:52:36The African sun is warming things up here at Kilimanjaro, but there's still a crispness in the morning air. My fleece jacket came in handy after a refreshing shower! I started my day with a perfect combo: coffee and breakfast on the rooftop, with a stunning view as my backdrop.

Speaking of tech, today was dedicated to getting my workspace set up. First on the agenda: Thunderbird, my trusty email client from my Linux days. It took a few hours to wrangle everything, especially the S/MIME encryption. Feeling a bit lost in the weeds, I decided to switch gears and embrace OpenPGP for end-to-end encryption – a simpler solution in my opinion.
Just as I finished conquering Thunderbird, Kilimanjaro itself decided to make an appearance! The clouds parted to reveal the majestic peak, and I couldn't resist capturing the moment with a couple of photos.
Today's another day with no set plans, just taking things minute by minute. Soaking up the beautiful scenery, the cool mornings, and the positive vibes. As soon as my foot heals, I'll be out exploring the town, snapping photos, and enjoying a delicious coffee at a local cafe.

Speaking of exploring, the world of NFTs has piqued my interest. I have a few on Opensea and WAX Blockchain, but I'm curious – where else are people showcasing their digital art? Let me know in the comments where you buy and sell your NFTs, or if they're just patiently waiting for a better future. I'd love to hear your NFT stories!

Life has a way of taking us on unexpected journeys. So, here's to embracing the unexpected, making the most of each situation, and maybe even finding a small online job to boost my budget. Wishing you all a wonderful day – and remember, don't stress yourself!

Online
Feel free to support me by sending some sats via the lightning network to rubenstorm@sats.mobi
-
 @ a10260a2:caa23e3e
2024-10-03 16:37:37
@ a10260a2:caa23e3e
2024-10-03 16:37:37Alby Hub is configurable with several different backends. Although setting up with Cashu is considered experimental, it’s a good option to have if you don’t want to run a Lightning node.
This post will give a quick overview of the steps to connect your Alby Hub with a Cashu mint.
Before you get started, you’re going to want to have Alby Hub installed already. There are many options for this as well — Linux, StartOS, and Umbrel to name a few. You can even have Alby host it for you in their cloud.
I just happen to have a Linux machine free so I went that route — the installation script made it super easy.
After the install is complete, navigating to localhost:8080 brings up this page.
- Select “Advanced Setup”
- Select “Create Wallet with Custom Node”
- Select “Cashu Mint”
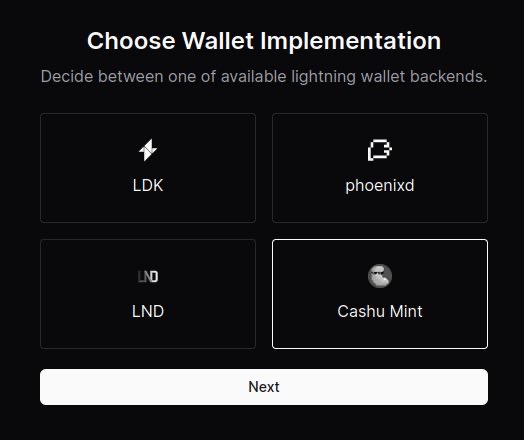
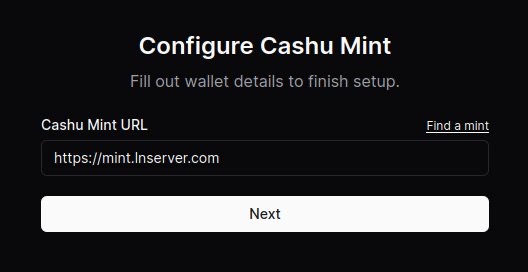
- Paste the URL of the mint you’d like to use. You can use the default one provided or click on “Find a mint” to search for others.
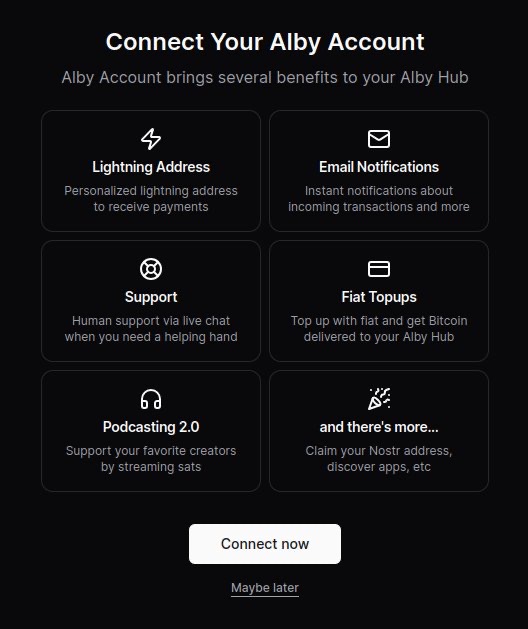
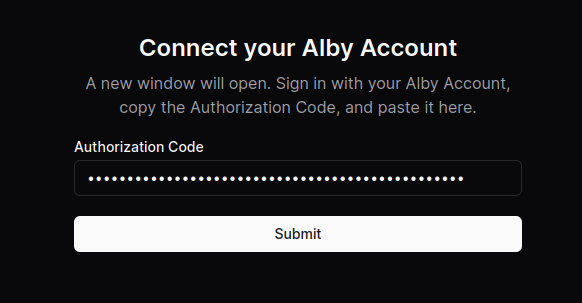
- (Optional) Connect your Alby account by requesting an authorization code. After clicking “Connect now,” a new window will open and the code displayed after signing in.
Boom. You’re all done.
Now you can use your Alby Lightning address to receive your first sats!
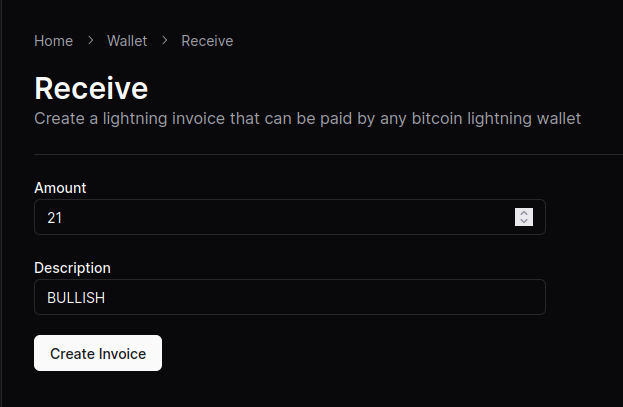
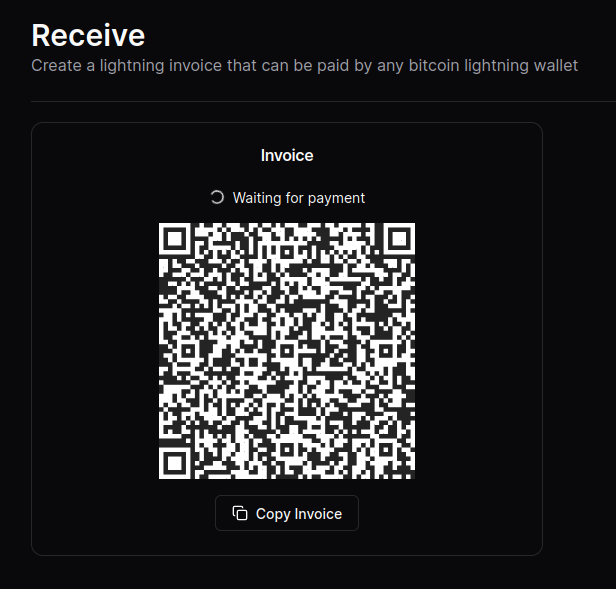
NOTE: Although the sats do make it to the wallet, the “Waiting for payment” animation seems to wait indefinitely and there’s no record in transaction history.
This seems to be a Cashu-related issue that has something to do with the preimage. An issue has been opened on GitHub if you’re curious.
Other that that, sending and receiving works like a charm.
originally posted at https://stacker.news/items/707673
-
 @ d6affa19:9110b177
2024-09-24 18:31:42
@ d6affa19:9110b177
2024-09-24 18:31:42i'm in the upstairs office. lost in some project i've been tinkering with. i feel driven with purpose.
the door is cracked open. i always leave the door open.
Her footsteps echo up the stairway. but my focus is intense; a solution just beyond my fingertips.
the door creaks open, a soft whisper of a sound.
i instantly feel Her presence. a sweet vanilla scent wraps around me, thick and intoxicating.
Her fingers brush through my hair, a gentle caress.
She grips my hair, then releases it— over and over again. it feels good.
a soothing warmth envelops me.
Her fingers glide, each stroke igniting my senses. a chill races down my spine.
the monitor becomes a bit distant.
"You're really focused, hmm?" She teases, leaning closer. "I'm just checking in on my sweet boy." Her tone alluring, already drawing me in.
"of course, my Queen." i reply, my eyes glued to the screen, struggling to concentrate. "thank You," my voice hints at annoyance. "i'm so close to finishing this up."
just when i near a breakthrough, She appears, a siren pulling me from my path. how does She know..? the quiet signals that betray my focus— that reveal my yearning.
"Hmmmm," She playfully muses.
ugh, i need to concentrate. but the way this feels...
it pulls me deeper.
Her fingers drift by my ear, lingering around my neck. nails grazing my skin, sending shivers through me.
my heart begins to race. the screen blurs, reality separates.
"Okay, sweet boy." Her voice is a soft command. Her nails dig in, a mixture of pain and pleasure. a sharp contrast to the softness of Her touch. "I'll be downstairs while you finish."
yet She remains. i close my eyes, drowning in the sensation. i should be finishing this project...
but each press feels like a silent command, an urge to abandon my thoughts, to succumb to the pull of Her presence.
the way She easily captures my attention... it makes me feel so vulnerable...
Her grip finally loosens, and slowly leaves my neck. it wants more...
i barely hear Her leave. but the air feels colder. the warmth of Her presence is fading. an aching emptiness fills the space...
the weight of Her absence settles in, another reminder of how easily She commands my thoughts...
desperately, i take in the remnants of Her scent.
i stare at my monitor. focus shattered, thoughts scattered like leaves.
i linger for a moment. fighting the urge to chase after Her.
the pull of Her absence is heavy in the air. i'm unable to resist. i rise from my seat.
the door is slightly open. She always leaves the door open.
i make my way downstairs, lost in the thoughts of serving Her. my true purpose...
-
 @ e97aaffa:2ebd765d
2024-07-14 09:57:13
@ e97aaffa:2ebd765d
2024-07-14 09:57:13Estamos numa época tão estranha da humanidade…
Onde alguns querem reescrever a história, em vez de aprender e evoluir com a mesma. São com os erros que se cresce.
Onde o termo fascista é sinónimo de alguém com uma opinião diferente da sua, sem minimamente saber o real significado dessa palavra.
Onde defendem uma liberdade, que proíba o contraditório.
Onde não se discutem ideias, mas sim combatem ideias.
Onde o ambientalmente sustentável é substituir árvores e zonas verdes por estruturas em aço e zonas negras.
Onde os políticos constroem casas ou cidades, literalmente, em cima dos rios mas depois a culpa das cheias é as alterações climáticas.
Onde os alimentos tem menos importância que um peido de uma vaca.
Onde pessoas defendem que a solução para o aquecimento, é morrer de frio.
Onde a igualdade é favorecer um grupo, em detrimento de outro.
Onde o essencial é viver para consumir, em vez de usufruir.
Onde o importante é ser rico e ostentar essa mesma riqueza, mesmo que tenha de espezinhar outros para a conquistar.
Onde o mais importante é parecer em vez de ser.
Onde políticos defendem que o conhecimento pode levar a escolhas erradas, defendem o carneirismo.
Onde um político define o que é verdade ou mentira, limitando o que as pessoas podem expressar. Mas quem controla o controlador.
Onde os revisores da verdade deixaram de estar num gabinete, passando a ser um exército de jovens atrás de um teclado.
Onde, são propostas e aprovadas limitações de liberdade, sem esclarecimento ou divulgação pública. Pior que a obscuridade, é desinteresse da comunidade por liberdade.
Onde a censura é o novo normal, defender o contrário é que é censurável.
Onde a imprensa é tão livre como uma pomba dentro de sua gaiola.
Onde, quem comete o crime é protegido, quem o denúncia é perseguido.
Onde o certo é pensar com a cabeça dos outros, sem questionar.
Onde os pais delegaram o papel de educar às escolas e aos ecrãs azuis.
Onde a escola deixou de ser um lugar de conhecimento e/ou do desenvolvimento do espírito crítico.
Onde as crianças crescem doutrinados por políticos e por AI.
Onde a sociedade é programada e com um destino predefinido, como um rato dentro da sua roda.
Onde o maior erro, é pretender construir seres que não cometem erros, que não tenham vícios. Quando isso acontecer, deixamos de ser humanos. A imperfeição é a essência dos seres humanos, é o que nos difere das máquinas.
Onde só se ensina a não cair, em vez de ajudar e incentivar a levantar.
Onde se suspende a liberdade de circulação e os direitos mais básicos, sem ninguém questionar.
Onde a privacidade é crime.
Onde Satoshi é excomungado, mas Miguel Tiago é idoleterado.
Onde a moeda é utilizado como uma arma.
Onde uma guerra é digladiada entre zeros e uns, sem o comum mortal aperceber da sua existência.
Onde crianças caem em campos de batalha, como folhas em pleno outono.
Onde o direito ao Livre-arbítrio está sob ameaça.
-
 @ d5c3d063:4d1159b3
2024-10-24 14:31:36
@ d5c3d063:4d1159b3
2024-10-24 14:31:36แว่นตา...เข็มทิศ...ชีวิต...ทางเลือก
เคยรู้สึกมั้ยครับว่า เรากำลังมองโลกต่างจากคนอื่น เหมือนใส่แว่นตาคนละแบบ เห็นภาพคนละมุม บางคนมองโลกสวยงาม บางคนมองโลกโหดร้าย บางคนมองโลกแสนสับสน...นั่นแหละครับ "ปรัชญา"
https://image.nostr.build/13ec632e4bb720d8b6729ddc07428be7f3fd89d02b117a9eff89ecb80540a1fd.jpg
หลายคนอาจมองว่า ปรัชญาเป็นเรื่องไกลตัว เป็นเรื่องของนักคิด นักปราชญ์ อยู่ในตำราเล่มหนา แต่จริงๆ แล้ว ปรัชญาอยู่รอบตัวเราและใกล้ตัวเรามากกว่าที่คิด เพราะมันคือเข็มทิศที่นำทางชีวิต มันคือระบบความคิด ชุดความเชื่อ และค่านิยมหรือคุณค่าที่เรายึดถือ ซึ่งส่งผลต่อทุกการตัดสินใจ ทุกการกระทำ และสุดท้ายก็คือชีวิตของเราเอง
นั่นหมายความว่า ทุกวันนี้ เรากำลังเลือกว่าจะเป็นมนุษย์ที่ใช้ชีวิตอย่างมีสติ มีเหตุผล และมีความรับผิดชอบต่อการกระทำของเราหรือไม่ หรือจะเป็นแค่ทาสของอารมณ์ ของความเชื่อและความงมงาย...?
ลองนึกภาพดูนะครับ ถ้าเข็มทิศของเราชี้ผิดทิศ มันจะพาเราไปถึงจุดหมายได้ยังไง การเลือกปรัชญาที่ผิดพลาด ก็เหมือนการใช้เข็มทิศที่ผุพัง และในที่สุดปลายทางนั้นก็คือความล้มเหลวหรือความทุกข์ยาก
ปรัชญาที่มีเหตุผล ใช้การคิดวิเคราะห์กับความรับผิดชอบ คือเข็มทิศที่แม่นยำที่สุดที่จะนำทางเราไปสู่ชีวิตที่ดีงาม ชีวิตที่มีอิสระมีความหมายและมีคุณค่า
เหตุผล คือแสงสว่าง นำทางเราไปสู่ความจริง ช่วยให้เรามองเห็นโลกในอย่างที่มันเป็น โดยไม่ถูกบิดเบือนด้วยอคติ อารมณ์ หรือความเชื่อแบบผิดๆ ในขณะเดียวกันความเชื่อที่ผ่านการไตร่ตรองด้วยเหตุผลบนพื้นฐานของความจริง ก็สามารถเป็นรากฐานที่มั่นคงให้กับชีวิตและเป็นแรงผลักดันให้เราก้าวไปข้างหน้าได้ การคิดวิเคราะห์คือเครื่องมือที่ทรงพลัง ช่วยให้เราเข้าใจปัญหาอย่างลึกซึ้ง มองเห็นเหตุและผลเพื่อหาทางแก้ไขได้อย่างมีประสิทธิภาพ ส่วนความรับผิดชอบคือการยืนหยัดในความเป็นมนุษย์ คือการยอมรับผลของการกระทำของเราทั้งดีและไม่ดีนั้น ที่จะส่งผลต่อตัวเราและคนรอบข้าง ซึ่งเป็นหนทางสู่ "อิสรภาพ" ที่แท้จริง
ในทางกลับกัน ปรัชญาที่ปฏิเสธเหตุผล ปล่อยให้อารมณ์ความเชื่อที่งมงายหรืออำนาจภายนอกครอบงำ ก็เหมือนเข็มทิศที่มันพัง มันก็จะพาเราไปสู่ความหายนะ ชีวิตที่ไร้สติไร้จุดหมายและการตกเป็นทาสของผู้อื่น
ชีวิตเรา เราเลือกได้ เลือกที่จะใช้ชีวิตแบบมนุษย์ที่คิดเป็น ใช้เหตุผลเป็นหลักในการตัดสินใจ หรือจะใช้ชีวิตแบบไร้สติ ปล่อยให้อารมณ์ ความเชื่อความงมงายมาควบคุม แต่อย่าลืมว่าอารมณ์เป็นส่วนหนึ่งของเรา การทำความเข้าใจและจัดการกับอารมณ์ จึงมีความสำคัญอย่างยิ่งในการนำทางชีวิตเราให้ไปในทิศทางที่ดีงาม
เลือกปรัชญาของคุณอย่างชาญฉลาด เพราะนั่นหมายถึงคุณกำลังเลือกเส้นทางชีวิตของคุณเอง
Siamstr #Philosophy #ปรัชญา
-
 @ 84b0c46a:417782f5
2024-10-22 00:04:17
@ 84b0c46a:417782f5
2024-10-22 00:04:17- 1:nan:
- 2
- 2irorio絵文字
- 1nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw
- 2
- 2
- 3
- 3
- 2
- 1
|1|2| |:--|:--| |test| :nan: |
 ---
---:nan: :nan:
- 1
- 2
- tet
- tes
- 3
- 1
-
2
t
te
test
-
19^th^
- H~2~O
本サイトはfirefoxのみサポートしています うにょ :wayo: This text will bounce wss://catstrr.swarmstr.com/
-
 @ c4f5e7a7:8856cac7
2024-09-27 08:20:16
@ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on Habla, YakiHonne or Highlighter.
TL;DR
This article explores the links between public, community-driven data sources (such as OpenStreetMap) and private, cryptographically-owned data found on networks such as Nostr.
The following concepts are explored:
- Attestations: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your web-of-trust.
- Proof of Place: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in meatspace with their digital representations in the Nostrverse.
- Check-ins: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time.
The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems.
Open Data in a public commons has a place and should not be thrown out with the Web 2.0 bathwater.
Cognitive Dissonance
Ever since discovering Nostr in August of 2022 I've been grappling with how BTC Map - a project that helps bitcoiners find places to spend sats - should most appropriately use this new protocol.
I am assuming, dear reader, that you are somewhat familiar with Nostr - a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: Nostr is Identity for the Internet and The Power of Nostr by @max and @lyn, respectively. Nostr is so much more than a short-form social media replacement.
The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting - all your silos are indeed broken - however, something fundamental has been bothering me for a while and I think it comes down to data ownership.
For those unfamiliar, BTC Map uses OpenStreetMap (OSM) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) - FOSD if you will, but more commonly referred to as Open Data.
In contrast, Notes and Other Stuff on Nostr (Places in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned.
How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data?
Self-sovereign Identity
Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something - an identity.
All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money.
Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state.
Or, as @nvk said recently: "Don't build your house on someone else's land.".
https://i.nostr.build/xpcCSkDg3uVw0yku.png
While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this.
Nostr is PGP for the masses and will take cryptographic identities mainstream.
Full NOSTARD?
Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons.
We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be.
https://i.nostr.build/s3So2JVAqoY4E1dI.png
There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a Wikifreedia variant of OpenStreetMap.
While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native - there's no need to go Full NOSTARD. H/T to @princeySOV for the original meme.
https://i.nostr.build/ot9jtM5cZtDHNKWc.png
So, how do we appropriately blend cryptographically owned data with the commons?
If a location is owned in meatspace and it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the tragedy of the commons.
The remainder of this article explores how we can:
- Verify ownership of a physical place in the real world;
- Link that ownership to the corresponding digital place in cyberspace.
As a side note, I don't see private key custodianship - or, even worse, permissioned use of Places signed by another identity's key - as any more viable than the rented identities of Web 2.0.
And as we all know, the Second Law of Infodynamics (no citation!) states that:
"The total amount of sensitive information leaked will always increase over time."
This especially holds true if that data is centralised.
Not your keys, not your notes. Not your keys, not your identity.
Places and Web-of-Trust
@Arkinox has been leading the charge on the Places NIP, introducing Nostr notes (kind 37515) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via NIP-73 - External Content IDs (championed by @oscar of @fountain).
However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world.
Ultimately, this problem can only be solved in a decentralised way by using Web-of-Trust - using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop.
This requires users to:
- Verify the owner of a Place in cyberspace is the owner of a place in meatspace.
- Signal this verification to their social graph.
Let's look at the latter idea first with the concept of Attestations ...
Attestations
A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false.
Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too.
However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc).
Here is a recent example from @lyn that would carry more signal if it were an Attestation:
https://i.nostr.build/lZAXOEwvRIghgFY4.png
Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or Data Vending Machines in accordance with:
- Your social graph;
- The type or subject of the content being attested and by whom;
- Your personal preferences.
They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places.
NIP-25 (Reactions) do allow for users to up/downvote notes with optional content (e.g., emojis) and could work for Attestations, but I think we need something less ambiguous and more definitive.
‘This is true’ resonates more strongly than ‘I like this.’.
https://i.nostr.build/s8NIG2kXzUCLcoax.jpg
There are similar concepts in the Web 3 / Web 5 world such as Verified Credentials by tdb. However, Nostr is the Web 3 now and so wen Attestation NIP?
https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg
That said, I have seen @utxo has been exploring ‘smart contracts’ on nostr and Attestations may just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust.
Proof of Place
Attestations handle the signalling of your truth, but what about the initial verification itself?
We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth.
Introducing Proof of Place, an out–of-band process where an oracle (such as BTC Map) would mail - yes physically mail- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace.
One way of doing this would be to mint a 1 sat cashu ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location.
Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places).
In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as @Gigi says in PoW is Essential:
"A failure to understand Proof of Work, is a failure to understand Bitcoin."
In the Nostrverse, Proof of Place helps bridge the digital and physical worlds.
@Gigi also observes in Memes vs The World that:
"In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone."
https://i.nostr.build/dOnpxfI4u7EL2v4e.png
This isn’t true for Nostr.
In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯
Check-ins
Although not a draft NIP yet, @Arkinox has also been exploring the familiar concept of Foursquare-style Check-ins on Nostr (with kind 13811 notes).
For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as OSM elements) if NIP-73 - External Content IDs are used.
Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices.
Bringing Check-ins to Nostr is possible (as @sebastix capably shows here), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am.
Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable.
How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene - I’m sure @blackcoffee and @Ben Arc could hack something together over a weekend!
Check-ins could also be used as a signal for bonafide Place ownership over time.
Summary: Trust Your Bros
So, to recap, we have:
Places: Digital representations of physical locations on Nostr.
Check-ins: Users signalling their presence at a location.
Attestations: Verifiable social proofs used to confirm ownership or the truth of a claim.
You can visualise how these three concepts combine in the diagram below:
https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg
And, as always, top right trumps bottom left! We have:
Level 0 - Trust Me Bro: Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all.
Level 1 - Definitely Maybe Somewhere: This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL.
Level 2 - Trust Your Bros: An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph.
https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg
Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map?
Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ - you decide.
As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities.
Thanks
With thanks to Arkinox, Avi, Ben Gunn, Kieran, Blackcoffee, Sebastix, Tomek, Calle, Short Fiat, Ben Weeks and Bitcoms for helping shape my thoughts and refine content, whether you know it or not!
-
 @ 6bcc27d2:b67d296e
2024-10-21 03:54:32
@ 6bcc27d2:b67d296e
2024-10-21 03:54:32yugoです。 この記事は「Nostrasia2024 逆アドベントカレンダー」10/19の分です。Nostrasiaの当日はリアルタイムで配信を視聴していました。Nostrを使ってアプリケーションの再発明をすべきという発表を聴き、自分だったらどんなものを作ってみたいかを考えて少し調べたり試みたりしたのでその記録を書きます。また、超簡単なものですがおそらく世界初となるvisionOS対応のNostrクライアントをつくってみたので最後の方に紹介します。
アプリケーションを再発明する話があったのは、「What is Nostr Other Stuff?」と題したkaijiさんの発表でした。
Nostrプロトコルを使って既存のアプリケーションを再発明することで、ユーザ体験を損なわずにゆるやかな分散を促すことができ、プロトコルとしてのNostrも成長していくというような内容でした。
自分はまだNostrで何かをつくった経験はなかったので、実装に必要な仕様の知識がほとんどない状態からどのようなアプリケーションをつくってみたいかを考えました。
最初に思いついたのは、Scrapboxのようなネットワーク型のナレッジベースです。自分は最近visionOS勉強会をやっており、勉強会でナレッジを共有する手段としてScrapboxの導入を検討していました。
Nostrコミュニティにも有志によるScrapboxがありますが、Nostrクライアントがあればそれを使うだろうから同じくらいの実用性を備えたクライアントはまだ存在しないのではないかという見立てでした。
長文投稿やpublic chatなどの機能を組み合わせることで実現できるだろうか。そう思っていた矢先、NIP-54のWikiという規格があることを知りました。
https://github.com/nostr-protocol/nips/blob/master/54.md
まだちゃんとは読めていないですが、Scrapboxもwikiソフトウェアだし参考になりそうと思っています。正式な仕様に組み込まれていないようで、採用しているクライアントはfiatjafによるリファレンス実装(?)のwikistrくらいしか見つかりませんでした。
Scrapboxのようなナレッジベースを志向するNostrクライアントがあれば、後述するvisionOS対応クライアントの存在もありアカウントを使いまわせて嬉しいので試してみたいです。もし他にも似たようなサービスをどなたか知っていたら教えてください。
また現在は、勉強会やワークショップ、ハッカソンなどのコラボレーションワークを支援するためのツールを自分たちでも開発しています。Apple Vision Proに搭載されているvisionOSというプラットフォームで動作します。
https://image.nostr.build/14f0c1b8fbe5ce7754825c01b09280a4c22f87bbf3c2fa6d60dd724f98919c34.png
この画面で自分が入りたいスペースを選んで共有体験を開始します。
スライドなどのコンテンツや自らのアバターを同期させることで、遠隔地にいてもまるでオフラインかのように同じ空間を共有することが可能になります。
https://image.nostr.build/cfb75d3db2a9b9cd39f502d6426d5ef4f264b3d5d693b6fc9762735d2922b85c.jpg
ということなので、急遽visionOS対応のクライアントを作ってみました。検索しても1つも事例が出てこなかったので多分まだ世界で実装しているアプリはないのではないでしょうか。
とはいえ、クライアントを名乗っているもののまだ大した機能はなく、リレーからデータを取得するだけの読み取り専用です。
https://image.nostr.build/96e088cc6a082528682989ccc12b4312f9cb6277656e491578e32a0851ce50fe.png
画像では自分のプロフィールデータをリレーから取得しています。
まだどのライブラリもvisionOSに対応していなかったりで手こずったものの仕様の勉強になりました。
ただvisionOSアプリはiOSアプリ同様NIP-7が使えないので秘密鍵を自分で保管しなくてはならず、今後どう対処すべきかわかりかねています。これから時間ある時に少しずつ調べていこうと思っていますが、ネイティブアプリの秘密鍵周りはあまりリソースが多くないようにも感じました。もしどなたかその辺の実装に詳しい方いたら教えていただけると嬉しいです。
準備ができたらそのうちコードも公開したいと思っています。
これから少しずつ色んな機能を実装しながらNostrで遊んでいきたいです!
-
 @ 700c6cbf:a92816fd
2024-07-14 00:51:44
@ 700c6cbf:a92816fd
2024-07-14 00:51:44... something else
This is the final image. Or is it? Likely, it is not. I have already started on a perfect version of my Mother Earth painting.
Of course, there is no such thing as a perfect painting. What I mean is that I already started on a vector version of Mother Earth. You're familiar with vector vs. pixel, right?
But let's start at the beginning, not the end.
This here is a pic from the sketching phase. I am not one who can just magically and with a few strokes produce an amazing sketch of something that resembles a human. There are artists out there that do this wonderfully. It's amazing but it is not me (unfortunately).

Here I am starting to color in the sketch with a watercolor brush. This is all done in Procreate App on an iPad Pro. The coloring is on a separate layer with the pencil sketch set to multiply to shine through the colors. That's why the pencil strokes now are black. I like that look.

And here, I am almost done. Just need to decide on the background color. And as you can see from the gif and video I didn't really decide. Though at the moment I am favoring that muted pinkish red - LOL

Which color is your favorite?


Here you can see the whole process in a timelapse. Above pictures were grabbed from it to detail the process a little.
https://cdn.satellite.earth/05774dcaaf4679c34cbeb46cb43b4c4f85553a3d2b4850a7256d26a871b0c4f3.mp4
And that's it my Nostr friends for my first longform post in this community.
I hope you enjoyed this post. Comments are encouraged an appreciated. Thank you.
Cheers, OceanBee
-
 @ 4ba8e86d:89d32de4
2024-10-24 14:03:14
@ 4ba8e86d:89d32de4
2024-10-24 14:03:14O Collabora Office é uma suíte de escritório baseada em código aberto que oferece uma alternativa viável e de qualidade ao popular pacote Office da Microsoft. Desenvolvido pela Collabora, uma empresa líder em serviços de consultoria e desenvolvimento de software de código aberto, o Collabora Office oferece uma gama completa de aplicativos de produtividade para a plataforma Android, incluindo processador de texto, planilha, apresentação e muito mais.
Recursos e Funcionalidades.
O Collabora Office oferece uma ampla gama de recursos e funcionalidades para dispositivos Android, comparáveis aos encontrados em outras suítes de escritório populares. Além das funcionalidades básicas, como criação e edição de documentos de texto, planilhas e apresentações, o Collabora Office suporta formatos de arquivo comuns, como o formato OpenDocument (ODF) e o formato do Microsoft Office (OOXML). Isso significa que você pode facilmente compartilhar e colaborar em documentos com usuários de outras suítes de escritório.
Uma característica notável do Collabora Office para Android é a capacidade de edição colaborativa em tempo real. Vários usuários podem trabalhar simultaneamente em um documento, visualizando as alterações em tempo real. Isso torna a colaboração em equipe mais eficiente, permitindo que os membros trabalhem juntos em projetos sem a necessidade de trocar arquivos várias vezes.
O Collabora Office para Android possui uma interface intuitiva e fácil de usar, projetada especificamente para dispositivos móveis. Isso garante uma experiência de usuário fluida e permite que os usuários aproveitem ao máximo os recursos e funcionalidades do aplicativo em seus smartphones ou tablets.
Uma das principais vantagens do Collabora Office para Android é o fato de ser baseado em código aberto. Isso significa que o software é desenvolvido de forma transparente e está disponível para qualquer pessoa utilizar, estudar, modificar e distribuir. A natureza de código aberto do Collabora Office traz vários benefícios, incluindo:
-
Custos reduzidos: O Collabora Office para Android é gratuito para download e uso, eliminando a necessidade de licenças caras. Isso é particularmente atraente para pequenas empresas e usuários domésticos que buscam uma alternativa acessível ao pacote Office tradicional.
-
Personalização e flexibilidade: Como o código-fonte está disponível, desenvolvedores e usuários avançados podem personalizar e adaptar o Collabora Office para Android às suas necessidades específicas. Isso permite criar soluções personalizadas e integrar o software a outros sistemas e fluxos de trabalho existentes.
-
Segurança: Com a comunidade de código aberto constantemente analisando e auditando o software, eventuais vulnerabilidades de segurança são identificadas e corrigidas rapidamente. Além disso, os usuários podem ter maior confiança na privacidade de seus dados, uma vez que podem verificar como o software lida com as informações.
O Collabora Office para Android é uma alternativa sólida e de código aberto ao pacote Office da Microsoft. Com recursos abrangentes, capacidade de edição colaborativa em tempo real e uma interface otimizada para dispositivos móveis, ele se tornou uma escolha popular entre empresas e usuários individuais que desejam uma solução de produtividade acessível e personalizável para seus dispositivos Android. Além disso, a natureza de código aberto do Collabora Office traz vantagens significativas, como custos reduzidos, flexibilidade e segurança aprimorada. Se você está em busca de uma alternativa confiável e gratuita ao pacote Office tradicional para Android, vale a pena considerar o Collabora Office como uma opção viável.
https://www.collaboraoffice.com/
https://github.com/CollaboraOnline/online
-
-
 @ 4f82bced:b8928630
2024-10-24 14:19:51
@ 4f82bced:b8928630
2024-10-24 14:19:51I was invited to tag along with a film crew heading to a Gridless facility in Kenya earlier this year. An exciting opportunity to see how Bitcoin mining leverages renewable energy and supports rural communities.
Two hours from Nairobi is a town with a mini-grid powered by hydroelectric energy. The river flowing downstream is captured by generators, converted into electricity, and powers the community. The community only utilizes a portion of the energy produced, resulting in a large surplus wasted. Additionally, the demand is constantly fluctuating: factories ramp up demand during the day, households require more in the evenings, and demand plummets at night.
This leaves the producer wasting energy that could be monetized otherwise. Enter Gridless! They use bitcoin miners to stabilize the mini-grid and smooth out energy demand. How? Any surplus energy at any given moment is directed to the bitcoin miners. If no surplus energy exists, the miners receive no power. The energy needs of the community come first!
If you don’t know what bitcoin miners are, a quick TLDR: they are machines that guess a combination of numbers to find a hash below a certain target value. Sound confusing? In simpler terms, the machines are rolling multiple dice, hoping for the right outcome. This results in a new block being added to the blockchain, and the miner is rewarded with bitcoin for their efforts.
Walking into the container filled with miners, you hear a loud buzzing noise similar to a large hornet’s nest. If you pay close attention, you’ll hear a symphony of miners turning on and off based on the energy available. Unlike traditional industrial systems that may require time to ramp up or down, bitcoin miners can be flipped on and off instantly. That means if only some energy is available, only some miners run. If more energy becomes available, more miners turn on.
A common misconception is that bitcoin uses too much energy. It consumes 0.21% of the world's energy production and 60% of it comes from renewable sources. This consumption increases the resilience and security of the network (an article for another day).
Gridless continues similar work around Africa to capture excess energy produced by renewable means and stabilize local grids with an extremely flexible solution. It ensures that the energy produced for local communities will never go to waste and can be monetized through bitcoin mining.
https://youtu.be/YB2q0J65VDg
-
 @ 4ba8e86d:89d32de4
2024-10-23 13:28:09
@ 4ba8e86d:89d32de4
2024-10-23 13:28:09Ele possibilita o compartilhamento seguro de arquivos e mensagens entre dispositivos próximos em uma rede Wi-Fi local, sem a necessidade de uma conexão com a Internet.
O LocalSend é um aplicativo de plataforma cruzada que utiliza uma API REST e criptografia HTTPS para garantir a segurança da comunicação. Diferentemente de outros aplicativos de mensagens que dependem de servidores externos, o LocalSend não requer acesso à Internet ou servidores de terceiros.
Para assegurar a máxima segurança, o LocalSend utiliza um protocolo de comunicação seguro em que todos os dados são enviados por HTTPS, e um certificado TLS/SSL é gerado instantaneamente em cada dispositivo durante a comunicação.
https://f-droid.org/pt_BR/packages/org.localsend.localsend_app/
https://github.com/localsend/localsend
-
 @ 9edd72eb:cb697b0a
2024-07-13 22:16:45
@ 9edd72eb:cb697b0a
2024-07-13 22:16:45If one knows exactly what to do to alleviate one's pain, comfort oneself, and emerge more or less unscathed from Adversity, I think it can be said that one has reached a fairly high level of Wisdom in Life.
originally posted at https://stacker.news/items/607422
-
 @ 3bf0c63f:aefa459d
2024-09-06 12:49:46
@ 3bf0c63f:aefa459d
2024-09-06 12:49:46Nostr: a quick introduction, attempt #2
Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else.
Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services.
(Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation).
More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between clients (i.e. the program that runs on a user computer) and relays (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
-
 @ 4ba8e86d:89d32de4
2024-10-23 00:11:19
@ 4ba8e86d:89d32de4
2024-10-23 00:11:19Ele permite que os usuários descubram, baixem e instalem aplicativos em seus dispositivos Android sem depender da Google Play Store, que é a loja de aplicativos padrão do Android.
História do F-Droid
O F-Droid foi lançado em 2010 por um grupo de desenvolvedores liderados por Ciaran Gultnieks. A ideia por trás do projeto era criar uma alternativa de código aberto para a Google Play Store, que é uma plataforma centralizada controlada por uma única empresa. O F-Droid foi desenvolvido como um catálogo de aplicativos que só inclui aplicativos de código aberto que podem ser baixados e instalados gratuitamente.
Desde o lançamento, o F-Droid cresceu significativamente e agora oferece mais de 3.500 aplicativos de código aberto para Android, com uma ampla gama de categorias, incluindo jogos, educação, produtividade, privacidade e segurança. O projeto é mantido por uma comunidade de desenvolvedores voluntários e é executado sem fins lucrativos.
Os problemas que o F-Droid resolve
O F-Droid resolve vários problemas associados à Google Play Store e outras lojas de aplicativos. O primeiro é o controle centralizado de uma única empresa. A Google Play Store pode remover aplicativos que violem suas políticas, e os desenvolvedores podem ser impedidos de distribuir aplicativos por meio da loja por motivos arbitrários. O F-Droid, por outro lado, é administrado por uma comunidade sem fins lucrativos e não há restrições sobre quais aplicativos podem ser incluídos no catálogo.
Além disso, o F-Droid oferece uma alternativa para os usuários preocupados com a privacidade que não querem depender dos serviços da Google. O F-Droid é independente do Google Play Services e não rastreia os usuários ou coleta informações pessoais, tornando-se uma escolha atraente para aqueles que buscam maior privacidade.
Por que usar o F-Droid?
Há várias razões pelas quais você pode querer usar o F-Droid em vez da Google Play Store ou outras lojas de aplicativos. Aqui estão algumas delas:
-
Privacidade: Como mencionado anteriormente, o F-Droid é independente do Google Play Services e não rastreia os usuários. Isso significa que você pode baixar e instalar aplicativos sem se preocupar com a coleta de dados pessoais.
-
Segurança: O F-Droid oferece apenas aplicativos de código aberto e de software livre, o que significa que a comunidade pode examinar o código-fonte para garantir que não haja vulnerabilidades ou backdoors mal-intencionados.
-
Controle: O F-Droid permite que os usuários controlem seus próprios dispositivos Android e decidam quais aplicativos são instalados e atualizados.
-
Escolha: O F-Droid oferece uma ampla gama de aplicativos de código aberto e de software
Também é importante observar que nem todos os aplicativos disponíveis no F-Droid são completamente livres de riscos. Portanto, é sempre recomendável ler cuidadosamente as informações sobre o aplicativo e avaliar os riscos antes de baixá-lo e instalá-lo.
Aqui está o passo a passo para instalar o F-Droid em seu dispositivo Android:
-
Acesse o site oficial do F-Droid em https://f-droid.org/ usando um navegador da web no seu dispositivo Android.
-
Verifique a assinatura PGP do arquivo APK que você irá baixar. Para isso, clique no link "PGP Signature" abaixo do botão "Download F-Droid" na página inicial do site. Na página seguinte, baixe o arquivo "F-Droid.apk.asc" clicando no botão "Download". Baixe também a chave pública do desenvolvedor do F-Droid, clicando no link "PGP key of F-Droid release signing key" na mesma página. É importante verificar a assinatura antes de prosseguir com a instalação.
-
Clique no botão "Download F-Droid" para baixar o arquivo APK.
-
Abra o arquivo APK baixado em seu dispositivo Android. Se você não sabe como abrir o arquivo, vá até o gerenciador de arquivos do seu dispositivo e encontre o arquivo APK que acabou de baixar. Toque no arquivo e siga as instruções na tela para instalar o aplicativo.
-
Se aparecer uma mensagem de alerta informando que a instalação de aplicativos de fontes desconhecidas está desativada, vá até as configurações de segurança do seu dispositivo e habilite a opção "Fontes desconhecidas". Isso permitirá que você instale aplicativos de fora da Google Play Store.
-
Clique em "Instalar" e aguarde a instalação ser concluída.
-
Após a instalação, abra o aplicativo F-Droid e aguarde a inicialização do repositório de aplicativos.
-
Pronto! Agora você pode navegar e baixar aplicativos do F-Droid em seu dispositivo Android. O F-Droid oferece uma ampla variedade de aplicativos de código aberto e de software livre, e todos são gratuitos para baixar e usar. Você pode usar o F-Droid como uma alternativa à Google Play Store se estiver preocupado com privacidade, segurança ou controle de seus próprios dispositivos Android.
https://github.com/f-droid
-
-
 @ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23
@ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23由于gmail在中国被防火墙拦截了,无法打开,不想错过邮件通知。
通过自建ntfy接受gmail邮件通知。 怎么自建ntfy,后面再写。
2024年08月13日更新:
修改不通过添加邮件标签来标记已经发送的通知,通过Google Sheets来记录已经发送的通知。
为了不让Google Sheets文档的内容很多,导致文件变大,用脚本自动清理一个星期以前的数据。
准备工具
- Ntfy服务
- Google Script
- Google Sheets
操作步骤
- 在Ntfy后台账号,设置访问令牌。

- 添加订阅主题。

- 进入Google Sheets创建一个表格.记住id,如下图:

- 进入Google Script创建项目。填入以下代码(注意填入之前的ntfy地址和令牌):
```javascript function checkEmail() { var sheetId = "你的Google Sheets id"; // 替换为你的 Google Sheets ID var sheet = SpreadsheetApp.openById(sheetId).getActiveSheet();
// 清理一星期以前的数据 cleanOldData(sheet, 7 * 24 * 60); // 保留7天(即一周)内的数据
var sentEmails = getSentEmails(sheet);
var threads = GmailApp.search('is:unread'); Logger.log("Found threads: " + threads.length);
if (threads.length === 0) return;
threads.forEach(function(thread) { var threadId = thread.getId();
if (!sentEmails.includes(threadId)) { thread.getMessages().forEach(sendNtfyNotification); recordSentEmail(sheet, threadId); }}); }
function sendNtfyNotification(email) { if (!email) { Logger.log("Email object is undefined or null."); return; }
var message = `发件人: ${email.getFrom() || "未知发件人"} 主题: ${email.getSubject() || "无主题"}
内容: ${email.getPlainBody() || "无内容"}`;
var url = "https://你的ntfy地址/Gmail"; var options = { method: "post", payload: message, headers: { Authorization: "Bearer Ntfy的令牌" }, muteHttpExceptions: true };
try { var response = UrlFetchApp.fetch(url, options); Logger.log("Response: " + response.getContentText()); } catch (e) { Logger.log("Error: " + e.message); } }
function getSentEmails(sheet) { var data = sheet.getDataRange().getValues(); return data.map(row => row[0]); // Assuming email IDs are stored in the first column }
function recordSentEmail(sheet, threadId) { sheet.appendRow([threadId, new Date()]); }
function cleanOldData(sheet, minutes) { var now = new Date(); var thresholdDate = new Date(now.getTime() - minutes * 60 * 1000); // 获取X分钟前的时间
var data = sheet.getDataRange().getValues(); var rowsToDelete = [];
data.forEach(function(row, index) { var date = new Date(row[1]); // 假设日期保存在第二列 if (date < thresholdDate) { rowsToDelete.push(index + 1); // 存储要删除的行号 } });
// 逆序删除(从最后一行开始删除,以避免行号改变) rowsToDelete.reverse().forEach(function(row) { sheet.deleteRow(row); }); }
```
5.Google Script是有限制的不能频繁调用,可以设置五分钟调用一次。如图:

结尾
本人不会代码,以上代码都是通过chatgpt生成的。经过多次修改,刚开始会一直发送通知,后面修改后将已发送的通知放到一个“通知”的标签里。后续不会再次发送通知。
如需要发送通知后自动标记已读,可以把代码复制到chatgpt给你写。
-
 @ ee11a5df:b76c4e49
2024-09-11 08:16:37
@ ee11a5df:b76c4e49
2024-09-11 08:16:37Bye-Bye Reply Guy
There is a camp of nostr developers that believe spam filtering needs to be done by relays. Or at the very least by DVMs. I concur. In this way, once you configure what you want to see, it applies to all nostr clients.
But we are not there yet.
In the mean time we have ReplyGuy, and gossip needed some changes to deal with it.
Strategies in Short
- WEB OF TRUST: Only accept events from people you follow, or people they follow - this avoids new people entirely until somebody else that you follow friends them first, which is too restrictive for some people.
- TRUSTED RELAYS: Allow every post from relays that you trust to do good spam filtering.
- REJECT FRESH PUBKEYS: Only accept events from people you have seen before - this allows you to find new people, but you will miss their very first post (their second post must count as someone you have seen before, even if you discarded the first post)
- PATTERN MATCHING: Scan for known spam phrases and words and block those events, either on content or metadata or both or more.
- TIE-IN TO EXTERNAL SYSTEMS: Require a valid NIP-05, or other nostr event binding their identity to some external identity
- PROOF OF WORK: Require a minimum proof-of-work
All of these strategies are useful, but they have to be combined properly.
filter.rhai
Gossip loads a file called "filter.rhai" in your gossip directory if it exists. It must be a Rhai language script that meets certain requirements (see the example in the gossip source code directory). Then it applies it to filter spam.
This spam filtering code is being updated currently. It is not even on unstable yet, but it will be there probably tomorrow sometime. Then to master. Eventually to a release.
Here is an example using all of the techniques listed above:
```rhai // This is a sample spam filtering script for the gossip nostr // client. The language is called Rhai, details are at: // https://rhai.rs/book/ // // For gossip to find your spam filtering script, put it in // your gossip profile directory. See // https://docs.rs/dirs/latest/dirs/fn.data_dir.html // to find the base directory. A subdirectory "gossip" is your // gossip data directory which for most people is their profile // directory too. (Note: if you use a GOSSIP_PROFILE, you'll // need to put it one directory deeper into that profile // directory). // // This filter is used to filter out and refuse to process // incoming events as they flow in from relays, and also to // filter which events get/ displayed in certain circumstances. // It is only run on feed-displayable event kinds, and only by // authors you are not following. In case of error, nothing is // filtered. // // You must define a function called 'filter' which returns one // of these constant values: // DENY (the event is filtered out) // ALLOW (the event is allowed through) // MUTE (the event is filtered out, and the author is // automatically muted) // // Your script will be provided the following global variables: // 'caller' - a string that is one of "Process", // "Thread", "Inbox" or "Global" indicating // which part of the code is running your // script // 'content' - the event content as a string // 'id' - the event ID, as a hex string // 'kind' - the event kind as an integer // 'muted' - if the author is in your mute list // 'name' - if we have it, the name of the author // (or your petname), else an empty string // 'nip05valid' - whether nip05 is valid for the author, // as a boolean // 'pow' - the Proof of Work on the event // 'pubkey' - the event author public key, as a hex // string // 'seconds_known' - the number of seconds that the author // of the event has been known to gossip // 'spamsafe' - true only if the event came in from a // relay marked as SpamSafe during Process // (even if the global setting for SpamSafe // is off)
fn filter() {
// Show spam on global // (global events are ephemeral; these won't grow the // database) if caller=="Global" { return ALLOW; } // Block ReplyGuy if name.contains("ReplyGuy") || name.contains("ReplyGal") { return DENY; } // Block known DM spam // (giftwraps are unwrapped before the content is passed to // this script) if content.to_lower().contains( "Mr. Gift and Mrs. Wrap under the tree, KISSING!" ) { return DENY; } // Reject events from new pubkeys, unless they have a high // PoW or we somehow already have a nip05valid for them // // If this turns out to be a legit person, we will start // hearing their events 2 seconds from now, so we will // only miss their very first event. if seconds_known <= 2 && pow < 25 && !nip05valid { return DENY; } // Mute offensive people if content.to_lower().contains(" kike") || content.to_lower().contains("kike ") || content.to_lower().contains(" nigger") || content.to_lower().contains("nigger ") { return MUTE; } // Reject events from muted people // // Gossip already does this internally, and since we are // not Process, this is rather redundant. But this works // as an example. if muted { return DENY; } // Accept if the PoW is large enough if pow >= 25 { return ALLOW; } // Accept if their NIP-05 is valid if nip05valid { return ALLOW; } // Accept if the event came through a spamsafe relay if spamsafe { return ALLOW; } // Reject the rest DENY} ```
-
 @ 7460b7fd:4fc4e74b
2024-09-05 08:37:48
@ 7460b7fd:4fc4e74b
2024-09-05 08:37:48请看2014年王兴的一场思维碰撞,视频27分钟开始
最后,一个当时无法解决的点:丢失
-
 @ df67f9a7:2d4fc200
2024-07-07 18:25:32
@ df67f9a7:2d4fc200
2024-07-07 18:25:32Anyone who thinks that “onboarding new users” is simply a technical challenge of educating people about “how Nostr works”, is grossly mistaken about social networks in general and blind to what makes Nostr so special.
Social Networks are for Friends
Relationship building is why people use social networks. Connecting with friends and loved ones (and colleagues and customers also) is the obvious reason to join, and should be the primary objective in any onboarding endeavor. Everything else “about the technology” only needs to be introduced “as needed” in order for each new user to achieve this goal.
The Nostr Network Requires Trusted Friendships
To thrive at scale, Nostr needs to have established and interconnected “webs of trusted friends” for “verifying” authentic profiles and quality content. This PgP strategy for decentralized trust implemented on Nostr, is the best way to keep bots and bad actors at bay while preserving freedom and sovereignty for every user. Even though Nostr still doesn’t have a standard for determining who “is trusted” for any one user across all clients, we can already build tools to onboard new friends of the highest quality trust. Leveraging existing relationships, “webs of trust” can be strengthened even at this early stage simply by advocates “inviting friends to Nostr”.
Nostr is New and Already Full of Trusted Friends
But it won’t be for long. Bots and bad actors are relatively “easy” to keep at bay today because the Nostr userbase is still small. People who come to Nostr and STAY have mostly been a self selecting group of “freedom tech fans”. We like it this way, and are generally happy to be here. The comraderie is refreshing. But the more people that come to Nostr, the more Nostr will attract different kinds of people.
This is already happening. Nostr is growing at the edges, reaching out beyond the “freedom tech fans” and attracting a number of “less committed” (and some nefarious) individuals here and there. Who sticks around? The “friends of freedom tech fans” stick around longer because they have friends here. WAY BEFORE even considering how “the network effect” will take over, Nostr needs to solve for retention by bringing more “trusted friends” into the network. Social onboarding tools will allow us to share Nostr to “friends of freedom tech fans” and beyond, establishing interconnected “webs of trust” that are increasingly impermeable to bots and bad actors.
Nostr is Freedom Tech that People Want to Share
Creators and influencers of every kind share Nostr (and Nostr content) every day. This phenomenon is a gold mine for onboarding, and can be supported with tools and incentives. Driven by the fact that Nostr is an open protocol, owned by nobody and available for anybody to build upon and profit from, the passion for sharing Nostr will never wane. But our userbase may fall off, if people become disenchanted by undesirable content or lack of good follows. This is why onboarding efforts, to attract more “friends” to the network, are so important. Leveraging the “share worthy” phenomenon of Nostr itself to grow Nostr’s networks of “trusted friends” seems like a no brainer. But for this strategy to work, it needs to be win win win for all parties.
Everybody Wins with More Trusted Users on Nostr
Even as standards for qualifying trust are still being refined, “social onboarding” increases the ratio of “more” trusted over “less” trusted users across the network.
Developers Win
With more trusted users on the network, Nostr developers win by being able to attract an increasingly diverse range of business partners to sponsor their projects.
Sponsors Win
An increase in trusted usership equates to more “real people” perusing “desired content” and more chances for brands to engage “organically” with target audiences. Marketing opportunities increase with trust.
Advocates Win
Simply by sharing Nostr with their friends, Advocates support the sustained growth of trust across the network. Valuable zap reward programs to incentivize high quality onboarding efforts are easily justified and funded by social onboarding clients and their sponsors.
Users Win
More trusted users across the network means more trustworthy content in every feed and more easily discoverable friends and new follows regardless of the client or algorithm used.
Nostr Wins
More trusted users on the network means more “high quality” trust connections between each user. Strong webs of trust is what keeps out bots and bad actors, and is essential for stability as Nostr scales.
Social Onboarding Clients Bring Trust to Nostr
Having more tools for “sharing Nostr with friends” is how Nostr wins. Any client can have capacity for “Social Onboarding”. This may be a dedicated onboarding client or a feature set within a social client. A client that offers “Social Onboarding” will support Nostr advocates and the users that they invite. These should have the following feature set :
- Nostr advocates may create and share any number of customizable “Nostr invites” for different audiences or occasions. Each may have different reccomendations, or access codes, or expiry options. (A NIP is in the works)
- Nostr invite QR codes (and shareable URLs) should resolve to a WEB based interface for prospective (and existing) users who MAY NOT have a client or browser extension already installed.
- Each invite should (within the onboarding client) provide access to low friction profile creation AND advocate reccomended lists of new friends, interest groups, preferred clients, best relays, and other stuff.
- Private key generation and management for new users should be handled entirely within the onboarding client (using NIP standards without a browser extension or external bunker app) to reduce friction at this crucial moment.
- A human readable Nostr address (NIP05 or some future NIP) should be generated automatically for all new users.
- New account creation should result immediately in a direct message or group thread of private “gift wrap” encrypted messages. This thread acts as the new user’s “first contact” with the advocate (possibly others as well) and an anchor for exploring the rest of Nostr.
- Invite “receipt” data (who invited who) should be “gift wrap” encrypted, accessible only to the advocate and new user. Clients wishing to use this data for analytics MAY request access from BOTH parties.
- Top Advocates may be calculated by the client (using data from invite receipts OR from public Nostr usage metrics), and awards may be offered.
- Advocates may also be supported by the client through access to private “advocate support” groups and communities over the Nostr network.
Support Social Onboarding for Nostr
Meet Me On Nostr is an app for sharing Nostr with friends via advocate invites. It is a reference client to demonstrate the power of Social Onboarding for Nostr. The first launch of "feature complete" client is expected in fall 2024.
This is a “bootstrap” funded project in active development. We are not grant funded or VC funded. Instead, we are looking to pay our developers by sponsorships from “Nostr adjacent” businesses who want to increase brand recognition over this new social network.
Is Your Business Nostr Adjacent?
“I’d like to advertise on Nostr but it’s “not quite ready” says our marketing team.”
“It has potential, and we have alignment, but the technology is still a bit rough.”
“Nostr is a perfect fit for our “target audience”, but there simply aren’t enough people using it.”
If your business is aligned with freedom technology, and the people who build and use Nostr, then NOW is the perfect time to sponsor Social Onboarding. Help grow Nostr’s base of trusted users and engage directly with Nostr’s most active advocates and influencers as it scales.
Release Nostr’s Superpower
When Nostr advocates are equipped and incentivized to share Nostr with their friends, nothing can stop this network from growing and growing and growing ever more secure and interconnected networks of trusted users.
Onboarding and retaining trusted users as Nostr scales will require so much more than just pointing people to “how Nostr works” content. Nostr’s true power lies dormant in the existing relationships that Nostr users already have outside of Nostr. Leveraging this power is what Social Onboarding is all about. Social Onboarding is Nostr’s superpower.
-
 @ fd208ee8:0fd927c1
2024-10-20 18:19:48
@ fd208ee8:0fd927c1
2024-10-20 18:19:48(Please note that this is not official financial or business advice, but rather a description of something we have done, on an informal basis.)
A long, long time ago
It's been nearly a year, since nostr:nprofile1qydhwumn8ghj7argv4nx7un9wd6zumn0wd68yvfwvdhk6tcpypmhxue69uhkummnw3ezuetfde6kuer6wasku7nfvuh8xurpvdjj7qpqs3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqv5atj2 came into being, mostly as a lark, involving a couple of members of our private chat group. Our initial plan was to work toward bounties, but Nostr bounties are a bit of a biased, uncertain thing, and our enthusiasm for that quickly waned.
So, what to do? Here we are, we three (nostr:npub1ecdlntvjzexlyfale2egzvvncc8tgqsaxkl5hw7xlgjv2cxs705s9qs735, nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn, and I): IT professionals with little time, but plenty of intellectual energy, a Slack chat, a GitHub repo, and lots of frustration with the Nostr status quo.
We were, you see, Nostr end-users. We loved the idea of the protocol, but we were being regularly stymied by the poor quality of many implementations.
- Why can I not login? Oh, they fixed the login! Nope, still can't login.
- If I press this button, it says it sent, but it didn't send. Where note?
- They announced a new feature, but I tried it and it didn't work. Oh well.
- I noticed a bug in the client, reported it, and the issue is just rotting away in the project repo. Ignored.
- The website/relay/repo was here... yesterday. Today it has disappeared, and taken my zaps with it.
It was enough to make us want to tear our hair out. We decided that what Nostr needed... what it really needed... was a Nostr Stable Version. Nothing glamorous. Nothing exotic. Nothing busy or excitable. Just something that stayed where you initially found it, ran, and actually worked. Something where you could report a bug and receive a prompt response. Maybe even something, where you could pay a reasonable fee and be allowed to have expectations of some particular service being returned. And who better to build such a version, than people who want to use it, themselves?
Things working is an underrated concept
I know that the very idea of software running as expected and websites not appearing and disappearing suddenly, based upon what some particular developer had for lunch, tends to be met with little but scorn, from hardened, seasoned Nostriches (who are convinced that bugs are all features), but I think the majority of potential users would see it differently.
I'm with the majority, on this one.
I like to click "save" buttons and have them save. If I publish something, I want it to appear under my list of published somethings. I like to type in the website address I always type in, and have it magically appear on my screen, as if there were a little man sitting at controls in my laptop, just waiting for me to write H-T-T-P-S... and then jump to attention.
My unreasonable expectations have no bounds, it is true. But unreasonable people are also people, so we would also like to have our own unreasonable things to play with. Scorn away. My save button will save, and my published something will publish, and my website will load every damn time, just to spite you.
In the larger scheme of things, you see, we win even if we fail, if we at least increase the competition enough, that things working becomes the new standard. We can simply prove, definitively, that it is possible for Nostr things to work, if they are built by people who care if they work. If we also have fun together, learn something new, and come up with some cool, novel use cases, then that's pure profit.
We can only win, at this endeavor.
Where to start?
Name that brand
So, we had a team, we had a business idea, and we had a heck of a lot of motivation. What we didn't have, is a name. (Never underestimate the importance of naming things.)
We decided to name ourselves "GitCitadel" because "git" sounds techy, hints at our GitRepublic project, and is reminiscent of open-source development, and "citadel" reminds us of Bitcoin. The republic is at home in the citadel, naturally. All other products also live in the same citadel, hence the naming-convention of prefacing everything with "GC" (i.e. "GC Alexandria", "GC Sybil", "GC Aedile", etc.).
Brand yourself
The next thing we did, was rent a domain and run a webserver on it. This is an important step because it gives you an Internet presence, allows you to have company NIP-05 and email addresses (a form of promotion), and it's simply exciting to have one. Feels so much more "official" and it helps increase the name-recognition of your company.
Define yourself
We then sat down, together, over the Internet, and figured out who we are. Not who we individually are, but who we are, as a company. A company, after all, (according to the Cambridge Dictionary) is "an organization that produces or sells goods or services in order to make a profit". Now, a company's profits don't have to be monetary, but they should be something tangible. A company, in other words, is a team of people working toward some defined goal.
What is our goal? Well, we decided to think it over, sat down with the newer additions to the company (you can see who they are, on our project wiki page, and came up with a Vision and a Mission:
The vision is what the overall goals of the company are, whereas the mission describes how those goals shall be achieved. Now, this is a sort of lofty, abstract statement, so it was important that we posted it someplace publicly (to keep ourselves accountable) and look at it regularly, so that we can ponder it and realign whatever we are currently working on, with this statement. We know the statement is well-designed, if considering it helps us make decisions about what to do next.
Pay yourselves
(I'm going to switch from "we" to "you", here, as it's easier to write this part, but let's just pretend I didn't.)

The next thing on the list, is to arrange the finances, usually by setting up a Geyserfund, with an associated wallet, and then deciding how the funds from the wallet will be dispersed or stored. (I won't tell you how we are handling that, as that's internal company business, but I'm sure you'll think of something clever, yourselves. Or just google it.)
I would encourage you to arrange to pay yourselves profits. Not merely because your idea is going to make you all fabulously wealthy and internationally famous (although, that is obviously true), but because profits are the most pure form of communication that consumers in the market have with its producers, and one of the best ways to make decisions and measure increases in efficiency (increasing profits and/or output, while keeping prices steady or falling).
Cutting off this signal, in order to look pious to outsiders, is to shoot yourself in your free-market foot. Nobody says that you have to spend your profits on the proverbial lambo and a bimbo. You could donate them to charity, reinvest them, or store them for your nephews to inherit, but pay them out, you should. You don't have to love money, to value it as a tool and use it shrewdly. Money is a measure, and companies should regularly measure themselves: against their previous state, against their potential state, and against their competition.
(Also, you can use money to buy a lambo and a bimbo, but you didn't hear that from me.)
Organize yourselves
Once you've been working together, for a while, you'll find that you need to figure out how to organize yourselves. The first step is to...
Form a board of directors.
Stop laughing. I'm serious.
Any company has at least two roles (President and Secretary), ideally held by two different people, so any single-proprietor company is a man down. Find a different person, to be your Second, even if they're just your confident, who lets you cry on your shoulder on The Bad Days, when your code refuses to compile, and can tell people that you've become a Bitcoin millionaire and have gone on a sabbatical to hike the Himalayas and will be back in 3 months on The Very Good Days. Because business man was not meant to be alone.
If, like us, you're a small herd of people and have already been working together for a while, then this step is actually really, really fun. Just think about what people are already doing, and put a label on it. That role is now defined and it is clear who is in charge of what.
Scientists become "Chief Science Officer" or "Scientific Advisor". The person who always writes the okay, so this is what we've decided comment in the thread becomes the Secretary, the one managing the Lightning wallet and worrying over paying for the servers is the CFO, the person running the remote server becomes the CTO, and so on and etc.
And everyone knows who the CEO is. Everyone always knows. They do. Just write it down.
Agree how to disagree
Now, have the secretary write up a Member's Agreement. It's a contract between the members, about whatever the group thinks is important concerning the way the company will operate. According to Investopedia, common topics are:

Is this legally binding? Probably not. Maybe. I don't know and wouldn't tell you, even if I did. But it's emotionally binding, which is arguably more important.
Writing things down is an advanced form of naming things and it provides clarity, helps to manage expectations, and allows you to define a working agreement before Real Money shows up and taints your interaction. You're just accepting tips, at the moment. Everyone is calm and cheerful, so now is your best time to negotiate.
Keep it very simple and only address the most basic things. If you wish to incorporate, at a later date, then you just take this to a registered agent, or other experienced person, and have them tidy up any loose ends and add the fine print.
Go forth, together
This has probably taken you weeks, or even months, but you're now a company. Get a logo and a company npub, start dropping the company name into your notes, and get on with the business of being in business.
-
 @ 76c71aae:3e29cafa
2024-08-13 04:30:00
@ 76c71aae:3e29cafa
2024-08-13 04:30:00On social media and in the Nostr space in particular, there’s been a lot of debate about the idea of supporting deletion and editing of notes.
Some people think they’re vital features to have, others believe that more honest and healthy social media will come from getting rid of these features. The discussion about these features quickly turns to the feasibility of completely deleting something on a decentralized protocol. We quickly get to the “We can’t really delete anything from the internet, or a decentralized network.” argument. This crowds out how Delete and Edit can mimic elements of offline interactions, how they can be used as social signals.
When it comes to issues of deletion and editing content, what matters more is if the creator can communicate their intentions around their content. Sure, on the internet, with decentralized protocols, there’s no way to be sure something’s deleted. It’s not like taking a piece of paper and burning it. Computers make copies of things all the time, computers don’t like deleting things. In particular, distributed systems tend to use a Kafka architecture with immutable logs, it’s just easier to keep everything around, as deleting and reindexing is hard. Even if the software could be made to delete something, there’s always screenshots, or even pictures of screens. We can’t provably make something disappear.
What we need to do in our software is clearly express intention. A delete is actually a kind of retraction. “I no longer want to associate myself with this content, please stop showing it to people as part of what I’ve published, stop highlighting it, stop sharing it.” Even if a relay or other server keeps a copy, and keeps sharing it, being able to clearly state “hello world, this thing I said, was a mistake, please get rid of it.” Just giving users the chance to say “I deleted this” is a way of showing intention. It’s also a way of signaling that feedback has been heard. Perhaps the post was factually incorrect or perhaps it was mean and the person wants to remove what they said. In an IRL conversation, for either of these scenarios there is some dialogue where the creator of the content is learning something and taking action based on what they’ve learned.
Without delete or edit, there is no option to signal to the rest of the community that you have learned something because of how the content is structured today. On most platforms a reply or response stating one’s learning will be lost often in a deluge of replies on the original post and subsequent posts are often not seen especially when the original goes viral. By providing tools like delete and edit we give people a chance to signal that they have heard the feedback and taken action.
The Nostr Protocol supports delete and expiring notes. It was one of the reasons we switched from secure scuttlebutt to build on Nostr. Our nos.social app offers delete and while we know that not all relays will honor this, we believe it’s important to provide social signaling tools as a means of making the internet more humane.
We believe that the power to learn from each other is more important than the need to police through moral outrage which is how the current platforms and even some Nostr clients work today.
It’s important that we don’t say Nostr doesn’t support delete. Not all apps need to support requesting a delete, some might want to call it a retraction. It is important that users know there is no way to enforce a delete and not all relays may honor their request.
Edit is similar, although not as widely supported as delete. It’s a creator making a clear statement that they’ve created a new version of their content. Maybe it’s a spelling error, or a new version of the content, or maybe they’re changing it altogether. Freedom online means freedom to retract a statement, freedom to update a statement, freedom to edit your own content. By building on these freedoms, we’ll make Nostr a space where people feel empowered and in control of their own media.
-
 @ 4ba8e86d:89d32de4
2024-10-22 23:04:43
@ 4ba8e86d:89d32de4
2024-10-22 23:04:43O objetivo principal do Tutanota é oferecer um serviço de e-mail protegido, onde as mensagens são criptografadas de ponta a ponta. Isso significa que as mensagens são codificadas no dispositivo do remetente e permanecem criptografadas até chegarem ao dispositivo do destinatário. Somente o remetente e o destinatário têm as chaves necessárias para descriptografar as mensagens, garantindo a confidencialidade das comunicações.
Além da criptografia de ponta a ponta, o Tutanota oferece outras medidas de segurança. Os e-mails são armazenados de forma criptografada nos servidores da empresa, o que significa que mesmo se alguém obtiver acesso aos servidores, os e-mails permanecerão ilegíveis sem a chave de descriptografia do usuário. O Tutanota também permite que os usuários protejam suas contas com senhas fortes.
O Tutanota foi fundado em 2011 na Alemanha por Arne Möhle e Matthias Pfau, com o objetivo de oferecer um serviço de e-mail seguro e privado. Eles buscavam fornecer uma alternativa aos serviços tradicionais, enfatizando a proteção da privacidade e a criptografia de ponta a ponta. Desde então, o Tutanota expandiu suas funcionalidades, adicionando recursos como armazenamento criptografado, calendário e agenda. A empresa está comprometida com a proteção dos dados dos usuários e está sediada na Alemanha, seguindo o Regulamento Geral de Proteção de Dados (GDPR). O Tutanota continua a ser reconhecido como uma referência em privacidade digital e mantém seu compromisso com a segurança e a privacidade dos usuários.
Recursos de Segurança: 1. Criptografia de ponta a ponta: Uma das principais características do Tutanota é a criptografia de ponta a ponta. Isso significa que suas mensagens são codificadas no dispositivo do remetente e permanecem criptografadas durante o trânsito até o dispositivo do destinatário. Somente o remetente e o destinatário têm as chaves para descriptografar as mensagens, tornando praticamente impossível para terceiros interceptá-las e acessar seu conteúdo.
-
Armazenamento criptografado: Além da criptografia de ponta a ponta para as mensagens em trânsito, o Tutanota também armazena seus e-mails de forma criptografada em seus servidores. Isso significa que, mesmo se alguém obtiver acesso aos servidores do Tutanota, os e-mails armazenados permanecerão ilegíveis sem a chave de descriptografia do usuário.
-
Proteção por senha: O Tutanota permite que você defina uma senha segura para proteger sua conta de e-mail. Essa senha é usada para criptografar seus dados armazenados e deve ser mantida em sigilo para garantir a segurança de sua conta.
Outros Recursos e Funcionalidades: 1. Interface amigável: O Tutanota oferece uma interface de usuário intuitiva e fácil de usar, semelhante aos serviços de e-mail convencionais. Isso torna a transição para o Tutanota suave para os usuários acostumados a outras plataformas de e-mail.
-
Aplicativos móveis: O Tutanota oferece aplicativos móveis para dispositivos iOS e Android, permitindo que você acesse sua conta de e-mail de forma segura em seu smartphone ou tablet.
-
Armazenamento e anexos: O Tutanota oferece 1 GB de armazenamento gratuito para sua conta de e-mail, permitindo que você mantenha um histórico de mensagens seguro. Além disso, você pode enviar e receber anexos com segurança, pois eles também são criptografados.
-
Proteção contra spam: O Tutanota possui um filtro de spam eficiente que verifica e filtra mensagens indesejadas, garantindo que sua caixa de entrada seja livre de spam e ameaças.
-
Calendário e Contatos: Além do serviço de e-mail, o Tutanota também oferece recursos de calendário e agenda, permitindo que você organize seus compromissos de forma segura e mantenha uma lista de contatos criptografados.
-
Personalização: O Tutanota permite que você personalize sua conta de e-mail, como escolher seu próprio domínio personalizado (para usuários pagos) e criar aliases de e-mail para maior flexibilidade na comunicação.
-
Compromisso com a privacidade: O Tutanota é conhecido por sua postura pró-privacidade e compromisso com a proteção dos dados de seus usuários. A empresa está sediada na Alemanha, onde estão sujeitos a rigorosas leis de proteção de dados, e segue o Regulamento Geral de Proteção de Dados (GDPR) da União Europeia.
O Tutanota é uma opção excelente para aqueles que valorizam a privacidade e desejam proteger suas comunicações online. Com sua criptografia de ponta a ponta, armazenamento criptografado e outros recursos de segurança, o Tutanota garante que suas mensagens e dados pessoais permaneçam privados e seguros.
https://tutanota.com/pt_br/
https://github.com/tutao/tutanota
-
-
 @ 4ba8e86d:89d32de4
2024-10-24 13:52:57
@ 4ba8e86d:89d32de4
2024-10-24 13:52:57Tecnologia de escalonamento #Bitcoin Layer-2 baseada no conceito de statechains, que permite que chaves privadas para depósitos BTC (UTXOs) sejam transferidas com segurança entre proprietários fora da cadeia.
Mercury Layer é uma implementação de um protocolo statechain de camada 2 que permite a transferência e liquidação fora da cadeia de saídas de Bitcoin que permanecem sob a custódia total do proprietário o tempo todo, enquanto se beneficia de transações instantâneas e de custo zero. A capacidade de realizar esta transferência sem exigir a confirmação (mineração) de transações em cadeia tem vantagens em uma variedade de aplicações diferentes.
um sistema de transferência e controle de propriedade do Bitcoin, especificamente focado em saídas de transações não gastas (UTXOs),
um resumo detalhado dos principais elementos e procedimentos do sistema:
-
Saída de Transação Não Gasta (UTXO): UTXO é a unidade fundamental que representa valor e propriedade no Bitcoin. Cada UTXO é identificado por um ID de transação (TxID) e um número de índice de saída (n) e possui duas propriedades essenciais: valor em BTC e condições de gasto, definidas em um Script. As condições de gasto geralmente envolvem uma chave pública que requer uma transação assinada com a chave correspondente.
-
Transferência de Propriedade sem Transação On-Chain: O sistema permite a transferência de propriedade de UTXOs controlados por uma única chave pública (P) de uma parte para outra sem a necessidade de executar transações na cadeia (on-chain) do Bitcoin ou alterar as condições de gasto. Isso é facilitado por um mecanismo chamado "Statechain Entity" (SE).
-
Compartilhamento de Chave Privada: A chave privada (s) para a chave pública P é compartilhada entre o SE e o proprietário. No entanto, nenhuma das partes conhece a chave privada completa. Isso requer cooperação entre o proprietário e o SE para gastar o UTXO.
-
Atualização/Transferência de Chave: A propriedade do UTXO pode ser transferida para um novo proprietário através de um processo de atualização de chave. Isso envolve a substituição do compartilhamento de chave privada do SE para que corresponda ao compartilhamento de chave do novo proprietário, tudo sem revelar compartilhamentos de chave ou a chave privada completa.
-
Transações de Backup: Além da transferência de propriedade, o sistema inclui transações de backup que podem ser usadas para reivindicar o valor do UTXO pelo atual proprietário, caso o SE não coopere ou desapareça. Essas transações são assinadas cooperativamente pelo proprietário atual e pelo SE e possuem um bloqueio de tempo (nLocktime) que permite a recuperação dos fundos em uma altura de bloco futura especificada.
-
Mecanismo de Redução do Backup de Timelock: Para limitar o número de transferências possíveis durante um período de tempo, o sistema utiliza um mecanismo de decremento do nLocktime. O usuário é responsável por enviar as transações de backup no momento adequado.
-
Cadeias Estaduais (Statechains): O sistema opera usando cadeias estaduais, que são uma camada adicional que permite a transferência de propriedade de UTXOs. O SE precisa seguir o protocolo, mas não armazena informações sobre compartilhamentos de chave anteriores.
-
Cegagem (Blinding): O servidor da camada Mercury (SE) é cego, o que significa que não tem conhecimento das moedas que está assinando. Isso é alcançado através do uso de criptografia de chave pública para ocultar informações de chave privada compartilhada entre as partes.
-
Protocolo de Camada Mercury: O protocolo detalha os procedimentos desde o depósito inicial até a transferência de propriedade, atualizações de chave, retiradas ordenadas e recuperação de backup.
-
Recuperação de Backup: Caso o SE não coopere ou desapareça, o proprietário atual pode recuperar os fundos, enviando a transação de backup quando o nLocktime for atingido.
-
Publicação de Compartilhamento de Chaves: O SE não tem acesso aos IDs de transação individuais das moedas, mas publica compartilhamentos de chaves públicas para cada moeda na lista de ativos. Essa lista é comprometida com a blockchain para provar a exclusividade da propriedade.
Este sistema é projetado para fornecer uma maneira segura e eficiente de transferir e controlar a propriedade do Bitcoin, permitindo a recuperação de fundos em caso de problemas com o servidor.
No sistema de controle de propriedade de saídas de transações não gastas (UTXOs), cada UTXO é uma chave compartilhada composta por duas partes: o proprietário e o servidor de compartilhamento. Juntos, eles colaboram para criar transações de backup com bloqueio de tempo, que transferem a propriedade da UTXO para o novo proprietário. Durante essa transferência, a chave pública compartilhada permanece inalterada, mas o compartilhamento da chave do servidor é atualizado por meio de um Protocolo de Computação Multifuncional (MPC) para se alinhar apenas com o novo proprietário. Essa atualização resulta na criação de uma nova transação de backup, direcionada à chave pública do novo proprietário, com um tempo de bloqueio mais curto.
A confiabilidade do servidor é essencial, pois ele é responsável por excluir o compartilhamento de chave anterior. Isso garante que não seja possível conspirar com os proprietários anteriores. O proprietário atual pode gastar a UTXO a qualquer momento, desde que o faça em cooperação com o servidor. No entanto, se o servidor for desligado ou desaparecer, o proprietário atual deve aguardar até que o tempo de bloqueio expire antes de enviar sua transação de backup.
É importante ressaltar que o remetente nunca possui a chave privada completa; ele possui apenas uma parte do compartilhamento. Assim, todas as transações requerem a assinatura conjunta do servidor. Quando a UTXO é transferida para um novo proprietário, o compartilhamento do servidor é atualizado para que ele não possa mais assinar em nome do proprietário anterior, apenas em nome do novo proprietário. Esse sistema de transações de backup com bloqueio de tempo é projetado para proteger contra cenários de não cooperação ou apreensão do servidor, garantindo a segurança das UTXOs e a integridade da rede.
https://github.com/layer2tech/mercury-wallet
https://mercurylayer.com/
https://twitter.com/TTrevethan/status/1689929527420387328?t=0f5oF6w_ZRjWRYGah3HX8Q&s=19
-
-
 @ 6f170f27:711e26dd
2024-07-13 18:16:58
@ 6f170f27:711e26dd
2024-07-13 18:16:58This century has known a stunning decrease in global income inequality, bringing it down to levels not seen in well over a century. That's the conclusion that Branko Milanovic, one of the world's foremost inequality researchers, comes to in an important essay for Foreign Affairs.
https://www.axios.com/2024/07/11/world-income-inequality-ubs-wealth-report
https://www.axios.com/2023/06/14/global-economic-inequality
originally posted at https://stacker.news/items/607318
-
 @ 0176967e:1e6f471e
2024-07-28 15:31:13
@ 0176967e:1e6f471e
2024-07-28 15:31:13Objavte, ako avatari a pseudonymné identity ovplyvňujú riadenie kryptokomunít a decentralizovaných organizácií (DAOs). V tejto prednáške sa zameriame na praktické fungovanie decentralizovaného rozhodovania, vytváranie a správu avatarových profilov, a ich rolu v online reputačných systémoch. Naučíte sa, ako si vytvoriť efektívny pseudonymný profil, zapojiť sa do rôznych krypto projektov a využiť svoje aktivity na zarábanie kryptomien. Preskúmame aj príklady úspešných projektov a stratégie, ktoré vám pomôžu zorientovať sa a uspieť v dynamickom svete decentralizovaných komunít.
-
 @ 42342239:1d80db24
2024-10-23 12:28:41
@ 42342239:1d80db24
2024-10-23 12:28:41TL;DR: The mathematics of trust says that news reporting will fall flat when the population becomes suspicious of the media. Which is now the case for growing subgroups in the U.S. as well as in Sweden.
A recent wedding celebration for Sweden Democrats leader Jimmie Åkesson resulted in controversy, as one of the guests in attendance was reportedly linked to organized crime. Following this “wedding scandal”, a columnist noted that the party’s voters had not been significantly affected. Instead of a decrease in trust - which one might have expected - 10% of them stated that their confidence in the party had actually increased. “Over the years, the Sweden Democrats have surprisingly emerged unscathed from their numerous scandals,” she wrote. But is this really so surprising?
In mathematics, a probability is expressed as the likelihood of something occurring given one or more conditions. For example, one can express a probability as “the likelihood that a certain stock will rise in price, given that the company has presented a positive quarterly report.” In this case, the company’s quarterly report is the basis for the assessment. If we add more information, such as the company’s strong market position and a large order from an important customer, the probability increases further. The more information we have to go on, the more precise we can be in our assessment.
From this perspective, the Sweden Democrats’ “numerous scandals” should lead to a more negative assessment of the party. But this perspective omits something important.
A couple of years ago, the term “gaslighting” was chosen as the word of the year in the US. The term comes from a 1944 film of the same name and refers to a type of psychological manipulation, as applied to the lovely Ingrid Bergman. Today, the term is used in politics, for example, when a large group of people is misled to achieve political goals. The techniques used can be very effective but have a limitation. When the target becomes aware of what is happening, everything changes. Then the target becomes vigilant and views all new information with great suspicion.
The Sweden Democrats’ “numerous scandals” should lead to a more negative assessment of the party. But if SD voters to a greater extent than others believe that the source of the information is unreliable, for example, by omitting information or adding unnecessary information, the conclusion is different. The Swedish SOM survey shows that these voters have lower trust in journalists and also lower confidence in the objectivity of the news. Like a victim of gaslighting, they view negative reporting with suspicion. The arguments can no longer get through. A kind of immunity has developed.
In the US, trust in the media is at an all-time low. So when American media writes that “Trump speaks like Hitler, Stalin, and Mussolini,” that his idea of deporting illegal immigrants would cost hundreds of billions of dollars, or gets worked up over his soda consumption, the consequence is likely to be similar to here at home.
The mathematics of trust says that reporting will fall flat when the population becomes suspicious of the media. Or as the Swedish columnist put it: like water off a duck’s back.
Cover image: Ingrid Bergman 1946. RKO Radio Pictures - eBay, Public Domain, Wikimedia Commons
-
 @ 0176967e:1e6f471e
2024-07-28 09:16:10
@ 0176967e:1e6f471e
2024-07-28 09:16:10Jan Kolčák pochádza zo stredného Slovenska a vystupuje pod umeleckým menom Deepologic. Hudbe sa venuje už viac než 10 rokov. Začínal ako DJ, ktorý s obľubou mixoval klubovú hudbu v štýloch deep-tech a afrohouse. Stále ho ťahalo tvoriť vlastnú hudbu, a preto sa začal vzdelávať v oblasti tvorby elektronickej hudby. Nakoniec vydal svoje prvé EP s názvom "Rezonancie". Učenie je pre neho celoživotný proces, a preto sa neustále zdokonaľuje v oblasti zvuku a kompozície, aby jeho skladby boli kvalitné na posluch aj v klube.
V roku 2023 si založil vlastnú značku EarsDeep Records, kde dáva príležitosť začínajúcim producentom. Jeho značku podporujú aj etablované mená slovenskej alternatívnej elektronickej scény. Jeho prioritou je sloboda a neškatulkovanie. Ako sa hovorí v jednej klasickej deephouseovej skladbe: "We are all equal in the house of deep." So slobodou ide ruka v ruke aj láska k novým technológiám, Bitcoinu a schopnosť udržať si v digitálnom svete prehľad, odstup a anonymitu.
V súčasnosti ďalej produkuje vlastnú hudbu, venuje sa DJingu a vedie podcast, kde zverejňuje svoje mixované sety. Na Lunarpunk festivale bude hrať DJ set tvorený vlastnou produkciou, ale aj skladby, ktoré sú blízke jeho srdcu.
Podcast Bandcamp Punk Nostr website alebo nprofile1qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qy88wumn8ghj7mn0wvhxcmmv9uq3xamnwvaz7tmsw4e8qmr9wpskwtn9wvhsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0qyg8wumn8ghj7mn0wd68ytnddakj7qghwaehxw309aex2mrp0yh8qunfd4skctnwv46z7qpqguvns4ld8k2f3sugel055w7eq8zeewq7mp6w2stpnt6j75z60z3swy7h05
-
 @ 42342239:1d80db24
2024-10-22 07:57:17
@ 42342239:1d80db24
2024-10-22 07:57:17It was recently reported that Sweden's Minister for Culture, Parisa Liljestrand, wishes to put an end to anonymous accounts on social media. The issue has been at the forefront following revelations of political parties using pseudonymous accounts on social media platforms earlier this year.
The importance of the internet is also well-known. As early as 2015, Roberta Alenius, who was then the press secretary for Fredrik Reinfeldt (Moderate Party), openly spoke about her experiences with the Social Democrats' and Moderates' internet activists: Twitter actually set the agenda for journalism at the time.
The Minister for Culture now claims, amongst other things, that anonymous accounts pose a threat to democracy, that they deceive people, and that they can be used to mislead, etc. It is indeed easy to find arguments against anonymity; perhaps the most common one is the 'nothing to hide, nothing to fear' argument.
One of the many problems with this argument is that it assumes that abuse of power never occurs. History has much to teach us here. Sometimes, authorities can act in an arbitrary, discriminatory, or even oppressive manner, at least in hindsight. Take, for instance, the struggles of the homosexual community, the courageous dissidents who defied communist regimes, or the women who fought for their right to vote in the suffragette movement.
It was difficult for homosexuals to be open about their sexuality in Sweden in the 1970s. Many risked losing their jobs, being ostracised, or harassed. Anonymity was therefore a necessity for many. Homosexuality was actually classified as a mental illness in Sweden until 1979.
A couple of decades earlier, dissidents in communist regimes in Europe used pseudonyms when publishing samizdat magazines. The Czech author and dissident Václav Havel, who later became the President of the Czech Republic, used a pseudonym when publishing his texts. The same was true for the Russian author and literary prize winner Alexander Solzhenitsyn. Indeed, in Central and Eastern Europe, anonymity was of the utmost importance.
One hundred years ago, women all over the world fought for the right to vote and to be treated as equals. Many were open in their struggle, but for others, anonymity was a necessity as they risked being socially ostracised, losing their jobs, or even being arrested.
Full transparency is not always possible or desirable. Anonymity can promote creativity and innovation as it gives people the opportunity to experiment and try out new ideas without fear of being judged or criticised. This applies not only to individuals but also to our society, in terms of ideas, laws, norms, and culture.
It is also a strange paradox that those who wish to limit freedom of speech and abolish anonymity simultaneously claim to be concerned about the possible return of fascism. The solutions they advocate are, in fact, precisely what would make it easier for a tyrannical regime to maintain its power. To advocate for the abolition of anonymity, one must also be of the (absurd) opinion that the development of history has now reached its definitive end.
-
 @ 8947a945:9bfcf626
2024-10-17 08:06:55
@ 8947a945:9bfcf626
2024-10-17 08:06:55สวัสดีทุกคนบน Nostr ครับ รวมไปถึง watchersและ ผู้ติดตามของผมจาก Deviantart และ platform งานศิลปะอื่นๆนะครับ
ตั้งแต่ต้นปี 2024 ผมใช้ AI เจนรูปงานตัวละครสาวๆจากอนิเมะ และเปิด exclusive content ให้สำหรับผู้ที่ชื่นชอบผลงานของผมเป็นพิเศษ
ผมโพสผลงานผมทั้งหมดไว้ที่เวบ Deviantart และค่อยๆสร้างฐานผู้ติดตามมาเรื่อยๆอย่างค่อยเป็นค่อยไปมาตลอดครับ ทุกอย่างเติบโตไปเรื่อยๆของมัน ส่วนตัวผมมองว่ามันเป็นพิร์ตธุรกิจออนไลน์ ของผมพอร์ตนึงได้เลย
เมื่อวันที่ 16 กย.2024 มีผู้ติดตามคนหนึ่งส่งข้อความส่วนตัวมาหาผม บอกว่าชื่นชอบผลงานของผมมาก ต้องการจะขอซื้อผลงาน แต่ขอซื้อเป็น NFT นะ เสนอราคาซื้อขายต่อชิ้นที่สูงมาก หลังจากนั้นผมกับผู้ซื้อคนนี้พูดคุยกันในเมล์ครับ
นี่คือข้อสรุปสั่นๆจากการต่อรองซื้อขายครับ
(หลังจากนี้ผมขอเรียกผู้ซื้อว่า scammer นะครับ เพราะไพ่มันหงายมาแล้ว ว่าเขาคือมิจฉาชีพ)

- Scammer รายแรก เลือกผลงานที่จะซื้อ เสนอราคาซื้อที่สูงมาก แต่ต้องเป็นเวบไซต์ NFTmarket place ที่เขากำหนดเท่านั้น มันทำงานอยู่บน ERC20 ผมเข้าไปดูเวบไซต์ที่ว่านี้แล้วรู้สึกว่ามันดูแปลกๆครับ คนที่จะลงขายผลงานจะต้องใช้ email ในการสมัครบัญชีซะก่อน ถึงจะผูก wallet อย่างเช่น metamask ได้ เมื่อผูก wallet แล้วไม่สามารถเปลี่ยนได้ด้วย ตอนนั้นผมใช้ wallet ที่ไม่ได้ link กับ HW wallet ไว้ ทดลองสลับ wallet ไปๆมาๆ มันทำไม่ได้ แถมลอง log out แล้ว เลข wallet ก็ยังคาอยู่อันเดิม อันนี้มันดูแปลกๆแล้วหนึ่งอย่าง เวบนี้ค่า ETH ในการ mint 0.15 - 0.2 ETH … ตีเป็นเงินบาทนี่แพงบรรลัยอยู่นะครับ

-
Scammer รายแรกพยายามชักจูงผม หว่านล้อมผมว่า แหม เดี๋ยวเขาก็มารับซื้องานผมน่า mint งานเสร็จ รีบบอกเขานะ เดี๋ยวเขารีบกดซื้อเลย พอขายได้กำไร ผมก็ได้ค่า gas คืนได้ แถมยังได้กำไรอีก ไม่มีอะไรต้องเสีนจริงมั้ย แต่มันเป้นความโชคดีครับ เพราะตอนนั้นผมไม่เหลือทุนสำรองที่จะมาซื้อ ETH ได้ ผมเลยต่อรองกับเขาตามนี้ครับ :
-
ผมเสนอว่า เอางี้มั้ย ผมส่งผลงานของผมแบบ low resolution ให้ก่อน แลกกับให้เขาช่วยโอน ETH ที่เป็นค่า mint งานมาให้หน่อย พอผมได้ ETH แล้ว ผมจะ upscale งานของผม แล้วเมล์ไปให้ ใจแลกใจกันไปเลย ... เขาไม่เอา
- ผมเสนอให้ไปซื้อที่ร้านค้าออนไลน์ buymeacoffee ของผมมั้ย จ่ายเป็น USD ... เขาไม่เอา
- ผมเสนอให้ซื้อขายผ่าน PPV lightning invoice ที่ผมมีสิทธิ์เข้าถึง เพราะเป็น creator ของ Creatr ... เขาไม่เอา
- ผมยอกเขาว่างั้นก็รอนะ รอเงินเดือนออก เขาบอก ok
สัปดาห์ถัดมา มี scammer คนที่สองติดต่อผมเข้ามา ใช้วิธีการใกล้เคียงกัน แต่ใช้คนละเวบ แถมเสนอราคาซื้อที่สูงกว่าคนแรกมาก เวบที่สองนี้เลวร้ายค่าเวบแรกอีกครับ คือต้องใช้เมล์สมัครบัญชี ไม่สามารถผูก metamask ได้ พอสมัครเสร็จจะได้ wallet เปล่าๆมาหนึ่งอัน ผมต้องโอน ETH เข้าไปใน wallet นั้นก่อน เพื่อเอาไปเป็นค่า mint NFT 0.2 ETH
ผมบอก scammer รายที่สองว่า ต้องรอนะ เพราะตอนนี้กำลังติดต่อซื้อขายอยู่กับผู้ซื้อรายแรกอยู่ ผมกำลังรอเงินเพื่อมาซื้อ ETH เป็นต้นทุนดำเนินงานอยู่ คนคนนี้ขอให้ผมส่งเวบแรกไปให้เขาดูหน่อย หลังจากนั้นไม่นานเขาเตือนผมมาว่าเวบแรกมันคือ scam นะ ไม่สามารถถอนเงินออกมาได้ เขายังส่งรูป cap หน้าจอที่คุยกับผู้เสียหายจากเวบแรกมาให้ดูว่าเจอปัญหาถอนเงินไม่ได้ ไม่พอ เขายังบลัฟ opensea ด้วยว่าลูกค้าขายงานได้ แต่ถอนเงินไม่ได้
Opensea ถอนเงินไม่ได้ ตรงนี้แหละครับคือตัวกระตุกต่อมเอ๊ะของผมดังมาก เพราะ opensea อ่ะ ผู้ใช้ connect wallet เข้ากับ marketplace โดยตรง ซื้อขายกันเกิดขึ้น เงินวิ่งเข้าวิ่งออก wallet ของแต่ละคนโดยตรงเลย opensea เก็บแค่ค่า fee ในการใช้ platform ไม่เก็บเงินลูกค้าไว้ แถมปีนี้ค่า gas fee ก็ถูกกว่า bull run cycle 2020 มาก ตอนนี้ค่า gas fee ประมาณ 0.0001 ETH (แต่มันก็แพงกว่า BTC อยู่ดีอ่ะครับ)
ผมเลยเอาเรื่องนี้ไปปรึกษาพี่บิท แต่แอดมินมาคุยกับผมแทน ทางแอดมินแจ้งว่ายังไม่เคยมีเพื่อนๆมาปรึกษาเรื่องนี้ กรณีที่ผมทักมาถามนี่เป็นรายแรกเลย แต่แอดมินให้ความเห็นไปในทางเดียวกับสมมุติฐานของผมว่าน่าจะ scam ในเวลาเดียวกับผมเอาเรื่องนี้ไปถามในเพจ NFT community คนไทนด้วย ได้รับการ confirm ชัดเจนว่า scam และมีคนไม่น้อยโดนหลอก หลังจากที่ผมรู้ที่มาแล้ว ผมเลยเล่นสงครามปั่นประสาท scammer ทั้งสองคนนี้ครับ เพื่อดูว่าหลอกหลวงมิจฉาชีพจริงมั้ย
โดยวันที่ 30 กย. ผมเลยปั่นประสาน scammer ทั้งสองรายนี้ โดยการ mint ผลงานที่เขาเสนอซื้อนั่นแหละ ขึ้น opensea แล้วส่งข้อความไปบอกว่า
mint ให้แล้วนะ แต่เงินไม่พอจริงๆว่ะโทษที เลย mint ขึ้น opensea แทน พอดีบ้านจน ทำได้แค่นี้ไปถึงแค่ opensea รีบไปซื้อล่ะ มีคนจ้องจะคว้างานผมเยอะอยู่ ผมไม่คิด royalty fee ด้วยนะเฮ้ย เอาไปขายต่อไม่ต้องแบ่งกำไรกับผม
เท่านั้นแหละครับ สงครามจิตวิทยาก็เริ่มขึ้น แต่เขาจนมุม กลืนน้ำลายตัวเอง ช็อตเด็ดคือ
เขา : เนี่ยอุส่ารอ บอกเพื่อนในทีมว่าวันจันทร์ที่ 30 กย. ได้ของแน่ๆ เพื่อนๆในทีมเห็นงานผมแล้วมันสวยจริง เลยใส่เงินเต็มที่ 9.3ETH (+ capture screen ส่งตัวเลขยอดเงินมาให้ดู)ไว้รอโดยเฉพาะเลยนะ ผม : เหรอ ... งั้น ขอดู wallet address ที่มี transaction มาให้ดูหน่อยสิ เขา : 2ETH นี่มัน 5000$ เลยนะ ผม : แล้วไง ขอดู wallet address ที่มีการเอายอดเงิน 9.3ETH มาให้ดูหน่อย ไหนบอกว่าเตรียมเงินไว้มากแล้วนี่ ขอดูหน่อย ว่าใส่ไว้เมื่อไหร่ ... เอามาแค่ adrress นะเว้ย ไม่ต้องทะลึ่งส่ง seed มาให้ เขา : ส่งรูปเดิม 9.3 ETH มาให้ดู ผม : รูป screenshot อ่ะ มันไม่มีความหมายหรอกเว้ย ตัดต่อเอาก็ได้ง่ายจะตาย เอา transaction hash มาดู ไหนว่าเตรียมเงินไว้รอ 9.3ETH แล้วอยากซื้องานผมจนตัวสั่นเลยไม่ใช่เหรอ ถ้าจะส่ง wallet address มาให้ดู หรือจะช่วยส่ง 0.15ETH มาให้ยืม mint งานก่อน แล้วมากดซื้อ 2ETH ไป แล้วผมใช้ 0.15ETH คืนให้ก็ได้ จะซื้อหรือไม่ซื้อเนี่ย เขา : จะเอา address เขาไปทำไม ผม : ตัดจบ รำคาญ ไม่ขายให้ละ เขา : 2ETH = 5000 USD เลยนะ ผม : แล้วไง
ผมเลยเขียนบทความนี้มาเตือนเพื่อนๆพี่ๆทุกคนครับ เผื่อใครกำลังเปิดพอร์ตทำธุรกิจขาย digital art online แล้วจะโชคดี เจอของดีแบบผม
ทำไมผมถึงมั่นใจว่ามันคือการหลอกหลวง แล้วคนโกงจะได้อะไร
อันดับแรกไปพิจารณาดู opensea ครับ เป็นเวบ NFTmarketplace ที่ volume การซื้อขายสูงที่สุด เขาไม่เก็บเงินของคนจะซื้อจะขายกันไว้กับตัวเอง เงินวิ่งเข้าวิ่งออก wallet ผู้ซื้อผู้ขายเลย ส่วนทางเวบเก็บค่าธรรมเนียมเท่านั้น แถมค่าธรรมเนียมก็ถูกกว่าเมื่อปี 2020 เยอะ ดังนั้นการที่จะไปลงขายงานบนเวบ NFT อื่นที่ค่า fee สูงกว่ากันเป็นร้อยเท่า ... จะทำไปทำไม
ผมเชื่อว่า scammer โกงเงินเจ้าของผลงานโดยการเล่นกับความโลภและความอ่อนประสบการณ์ของเจ้าของผลงานครับ เมื่อไหร่ก็ตามที่เจ้าของผลงานโอน ETH เข้าไปใน wallet เวบนั้นเมื่อไหร่ หรือเมื่อไหร่ก็ตามที่จ่ายค่า fee ในการ mint งาน เงินเหล่านั้นสิ่งเข้ากระเป๋า scammer ทันที แล้วก็จะมีการเล่นตุกติกต่อแน่นอนครับ เช่นถอนไม่ได้ หรือซื้อไม่ได้ ต้องโอนเงินมาเพิ่มเพื่อปลดล็อค smart contract อะไรก็ว่าไป แล้วคนนิสัยไม่ดีพวกเนี้ย ก็จะเล่นกับความโลภของคน เอาราคาเสนอซื้อที่สูงโคตรๆมาล่อ ... อันนี้ไม่ว่ากัน เพราะบนโลก NFT รูปภาพบางรูปที่ไม่ได้มีความเป็นศิลปะอะไรเลย มันดันขายกันได้ 100 - 150 ETH ศิลปินที่พยายามสร้างตัวก็อาจจะมองว่า ผลงานเรามีคนรับซื้อ 2 - 4 ETH ต่องานมันก็มากพอแล้ว (จริงๆมากเกินจนน่าตกใจด้วยซ้ำครับ)
บนโลกของ BTC ไม่ต้องเชื่อใจกัน โอนเงินไปหากันได้ ปิดสมุดบัญชีได้โดยไม่ต้องเชื่อใจกัน
บบโลกของ ETH "code is law" smart contract มีเขียนอยู่แล้ว ไปอ่าน มันไม่ได้ยากมากในการทำความเข้าใจ ดังนั้น การจะมาเชื่อคำสัญญาจากคนด้วยกัน เป็นอะไรที่ไม่มีเหตุผล
ผมไปเล่าเรื่องเหล่านี้ให้กับ community งานศิลปะ ก็มีทั้งเสียงตอบรับที่ดี และไม่ดีปนกันไป มีบางคนยืนยันเสียงแข็งไปในทำนองว่า ไอ้เรื่องแบบเนี้ยไม่ได้กินเขาหรอก เพราะเขาตั้งใจแน่วแน่ว่างานศิลป์ของเขา เขาไม่เอาเข้ามายุ่งในโลก digital currency เด็ดขาด ซึ่งผมก็เคารพมุมมองเขาครับ แต่มันจะดีกว่ามั้ย ถ้าเราเปิดหูเปิดตาให้ทันเทคโนโลยี โดยเฉพาะเรื่อง digital currency , blockchain โดนโกงทีนึงนี่คือหมดตัวกันง่ายกว่าเงิน fiat อีก
อยากจะมาเล่าให้ฟังครับ และอยากให้ช่วยแชร์ไปให้คนรู้จักด้วย จะได้ระวังตัวกัน
Note
- ภาพประกอบ cyber security ทั้งสองนี่ของผมเองครับ ทำเอง วางขายบน AdobeStock
- อีกบัญชีนึงของผม "HikariHarmony" npub1exdtszhpw3ep643p9z8pahkw8zw00xa9pesf0u4txyyfqvthwapqwh48sw กำลังค่อยๆเอาผลงานจากโลกข้างนอกเข้ามา nostr ครับ ตั้งใจจะมาสร้างงานศิลปะในนี้ เพื่อนๆที่ชอบงาน จะได้ไม่ต้องออกไปหาที่ไหน
ผลงานของผมครับ - Anime girl fanarts : HikariHarmony - HikariHarmony on Nostr - General art : KeshikiRakuen - KeshikiRakuen อาจจะเป็นบัญชี nostr ที่สามของผม ถ้าไหวครับ
-
 @ 0176967e:1e6f471e
2024-07-27 11:10:06
@ 0176967e:1e6f471e
2024-07-27 11:10:06Workshop je zameraný pre všetkých, ktorí sa potýkajú s vysvetľovaním Bitcoinu svojej rodine, kamarátom, partnerom alebo kolegom. Pri námietkach z druhej strany väčšinou ideme do protiútoku a snažíme sa vytiahnuť tie najlepšie argumenty. Na tomto workshope vás naučím nový prístup k zvládaniu námietok a vyskúšate si ho aj v praxi. Know-how je aplikovateľné nie len na komunikáciu Bitcoinu ale aj pre zlepšenie vzťahov, pri výchove detí a celkovo pre lepší osobný život.
-
 @ 826e9f89:ffc5c759
2024-06-28 21:46:01
@ 826e9f89:ffc5c759
2024-06-28 21:46:01_Prologue: this is a prose adaptation of a talk I gave to a private audience in Dubai and then tweaked slightly for a small conference in Sofia. I'm increasingly thinking it deserves a more general audience, and may be better suited to text anyway. This is probably not its final form, as the desired audience is tradfi capital allocators, hence a PDF is likely on the cards in the near future. For the time being, consider this a first draft, practising what it might look like as prose, and soliciting feedback from the good people of Nostr. Enjoy! _
The title of this essay means absolutely nothing. There is no such thing as “Web π” because there is no such thing as “Web 3”. It’s bullshit. It’s a scam.
Unfortunately, it has turned out to be extremely powerful bullshit and an extremely profitable scam, and so my goal in writing this essay is to give the reader the tools to navigate all of this and come out the other side without having been scammed or bullshat. In the spirit of not scamming and not bullshitting, I should be clear upfront about the intended readership of this essay, who I am to write it, and who it’s really about.
Who Are You?
I assume the reader is not a shadowy super-coder, but rather is a financial professional. This essay isn’t really for Bitcoiners, although if any read it, I hope they still find it interesting. Who I am really writing for are people coming to the space for the first time. Hopefully in your mind you are coming to the _Bitcoin _space, but if you think you are coming to the “crypto” space then this may be even more useful.
Who Am I?
I am the founder of a company that makes me not only highly biased but also flagrantly self-interested in the content I am promoting. I run a firm that invests in the Bitcoin ecosystem through a variety of different vehicles. I am not going to mislead you in the slightest in that my primary motivation is for you to allocate capital to us rather than to people I would call scammers and bullshitters. You should listen to them too and make up your own mind, or else what’s the point, really? How do you know I’m not scamming or bullshitting you? Exactly. Don’t trust. Verify.
In any case, that’s all assuming you want to “allocate capital” at all rather than just buy Bitcoin without a management fee. I’d like to think the primary difference is that I will be honest about that, and I’ll encourage you to understand as much as you can about what is going on and what you are doing (and if you are at all unsure, I would suggest you aren’t ready and you should just buy Bitcoin and learn) rather than bamboozle you with complete nonsense like “Web 3”.
Who Is This About?
It’s not at all about people working in crypto. Bitcoiners amongst the readership may be mildly irritated by me going on to give about as charitable an explanation of the role of these people as they have probably ever heard from somebody like me. This is really about financiers. It’s about the people who have used the mostly unrewarded efforts of developers, academics, entrepreneurs, and so on to siphon money from you to themselves, leaving a trail of useless tech and defrauded retail investors in their wake – and who will continue to do so if you continue to empower them.
Why This Essay?
We are at an interesting point in the development of the entirety of the “crypto” industry and I strongly suggest that people like you are going to be pitched all kinds of scams and bullshit in the coming months and years. If you have a little more background on what these people are really talking about, you will hopefully be able to avoid it.
My plan to help with that is presenting a short version and a long version of what blockchains are and are for, how they have historically been deployed in service of scams and bullshit, a high-level theory explaining the narrative evolution behind this sorry history, and a prediction for the near-term future of such shenanigans.
What is a Blockchain For?
A Blockchain is for sound, censorship-resistant, peer-to-peer digital money. It is not for anything else. If a blockchain is functional as money, it may be possible to also _use it _for other things. Some people find that interesting, some people find it infuriating, but don’t let that subtlety confuse you. It is not _for _arbitrary computation and storage or “decentralizing the internet” or running illegal securities rackets.

It is for money, plain and simple.
How does it achieve that? Proof of work and the difficulty adjustment. These are the innovations from which every other desirable property or feature flows. Proof of work enables censorship resistance. If somebody is trying to sell you on “proof of stake”: bullshit. The difficulty adjustment enables precise, predetermined, and _fair _issuance. If somebody is trying to sell you on a token they issue for free and without restriction: scam.
The problem Bitcoin solves is both economic and technical and the solution has material technical and economic merit. And it’s for this very specific and irreplicable reason the Bitcoin token has value. If this all sounds extreme to you, then I would suggest that your understanding of the topic is _extremely _misguided, that you are going to be _extremely bullshat and extremely scammed, _and you need to read this essay. That’s the short version.
The Long Version
I am sensitive to how extreme this all sounds. After all, hundreds of billions of dollars have been pumped into crypto, not Bitcoin – a huge amount of it is widely used, and many capable, honest, and brilliant people work in the industry. The reader will recall just above I said those people are not the target of my criticism. I’m not claiming they are all scammers and bullshitters. Sadly, I think it’s more likely they have been scammed and bullshat to some degree also.
I think I have some credibility in pointing this out because, as a VC in the Bitcoin space, I have increasingly seen founders telling me this themselves: that they originally bought into the hype in crypto and ended up wasting an enormous amount of time realizing their idea made no technical or economic sense in that context, so then they came to Bitcoin instead. You hear this one time and it’s an anecdote, but you hear it as many times as I have and it feels more like a representative sample.
What I want to cover next is as charitable a summary of the state of ex-Bitcoin crypto as I possibly can: my contention is that crypto has evolved into 4 rough categories: stablecoins, cryptography R&D, gambling, and scams. And these aren’t exclusive, to be clear; there is a lot of overlap, and, in fact, the overlap is arguably the key.
Scams
Scams are tokens, plain and simple. If somebody is trying to profit from the speculative price action of a token they have issued, they are scamming somebody. Maybe they are scamming you, maybe they are scamming retail investors, maybe they are scamming customers or suppliers – if such parties even exist in their cargo cult “business model”. There’s a scam in there somewhere.
However, it is rarely _just _a scam. There will almost always be components of stablecoins, R&D or gambling too. Hence these are worth really grappling with, taking seriously, giving credit to the extent it is due, but also analyzing critically.
My rough and high-level assessment of this breakdown of crypto is as follows, and I’ll explain what I mean by this below: stablecoins have economic merit but dubious technical merit; R&D has technical merit but no economic merit; and gambling sort of has merit but it depends how you interpret it. Obviously, scams have neither.

Stablecoins
By “sort of technical merit” I mean that stablecoins have central issuers. You can issue them as tokens on a blockchain but there’s not really much of a point. The issuer could just run a database connected to the internet with some straightforward signature schemes for transfers and it would make minimal operational difference. In fact, it would be cheaper and faster. _In fact, _you may as well run a Chaumian eCash mint (a decades-old innovation recently resurrected firmly within the _Bitcoin _space) such that your cheaper-and-faster-than-a-blockchain database also grants users transience and privacy rather than the public permanence of a blockchain.
The fact Tron is the most heavily used for stablecoins, in terms of settling the most value, is a testament to this point: it is barely even pretending not to be a database. This works as regulatory arbitrage given regulators think this is “innovation” because they are stupid.
That said, it is worth giving some credit here given the abject awfulness of fiat banking and payment rails with which stablecoins arguably most directly compete. Stablecoins are significantly more permissionless in their transfer than any fiat bank liability. And to attest to what seems like their most significant use case, they are permissionless in their _usership _in that only an internet connection and the right software is required rather than various discriminatory jurisdictional and compliance criteria.
However, what “sort of technical merit” ultimately boils down to, especially in comparison to Bitcoin, is: highly censorable in their exogenous links and, therefore, their value. The assets supposedly backing stablecoins are (by definition) still within the fiat system, even if this novel transfer mechanism of the rights to withdraw them is not. There is frankly a bit of theatre involved in the so-called “decentralization” of stablecoins given shutting down the central issuer is all that is required to make the permissionlessly tradeable decentralized tokens go to zero and be technically unimpeded but functionally useless. The technical innovation of Bitcoin, in contrast, is easily understood in one sense as it being totally indifferent to this kind of attack.
On the other hand, by “economic merit” I mean that they are extremely widely used and valued as a means of providing dollar shadow banking and often superior payment rails. Those in crypto often love pointing to this and many Bitcoiners tie themselves in knots trying to explain it away, whereas I see it as essentially unrelated to Bitcoin. Clearly there is a superficial connection, but you could create any superficial connection by “tokenizing” things for no particularly good technical _reason. I think it’s a different industry entirely. It’s more like a subindustry within _fintech – part banking, part payments – that for the time being relies on bamboozling regulators with all the nonsense I’m drawing attention to.
And good for them, frankly. If fiat banking isn’t going to be backed by real money anyway, then it _at least _ought to be permissionless. It should really be Chaumian eCash if it isn’t just Bitcoin, and it is regulation alone that makes it so awful in the first place. Making money usable and not a tool of dystopian control is, at this point, a political problem, not a technical one. Stablecoins are frankly a step in the right direction, especially insofar as they acclimatize users to digital assets. But I would still caution that they arguably don’t have sufficient technical merit to withstand what feels like an inevitable political attack …
Cryptography R&D
“Technical merit” for R&D is more or less self-explanatory, but the context is worth appreciating. It’s only really in crypto and mostly in Ethereum more specifically that people can permissionlessly experiment with arbitrarily complex cryptographic schemes that operate on real, enormous value. There are a lot of people who understandably find this attractive given their projects are essentially academic and trying out their ideas in the wild is more interesting, arguably more worthwhile, and certainly more fun than putting research essays on ArXiv or submitting them to a journal.
But … the value being manipulated is at best stablecoins and at worst baseless hype. If it isn’t a stablecoin then it probably exists in the first place because of either gambling or scams – and even there the line is very blurry.
Gambling
Gambling is an interesting lens to adopt on all this because it’s literally a trillion-dollar industry. And it’s real. It’s consensual; it’s not criminal; it’s legitimate economic activity that generates enormous profits for those who facilitate it well.
So, gambling has economic merit in that sense. But it’s tricky in this context how to characterize it because you could also argue it’s deeply dishonest gambling in that the gamblers don’t realize they are playing a negative sum game against the house. They think they are doing something akin to speculating on securities, which may be just as stupid depending on how it’s done, but at least has real economic utility and contributes to capital formation.
The difference here is that what is being speculated on _has no economic merit. _So, if that’s your gauge of merit, then here there is none. And it’s a very blurry line between this and an outright scam. Maybe the people involved _think _of what they are doing as amazing R&D, and maybe it’s inadvertently just a scam; maybe they know it’s all nonsense, but they think they can profit within the negative sum game because there are greater fools. In any case, I think gambling is a very helpful characterization of a lot of the behavior of the users and the real economic function of the industry.
There’s an interesting social component to all this because crypto people will often get mad at Bitcoiners because Bitcoiners tend not to care about either stablecoins or crypto R&D: they’ll say, why don’t you like stablecoins, they have clear economic merit? And the answer is they have dubious technical merit. Or, why don’t you like our next-gen Zero Knowledge scaling protocol, it has clear technical merit? And the answer is it has no economic merit.
If you’re happy with one but not the other, it’s easy to think of Bitcoiners as being closed-minded or dogmatic or whatever, but, ultimately, I think it’s just about discipline. What’s the point in being excited by something that half works, and that you know why will never fully work? So to be frank, a lot of this may be well-intentioned, but it’s kinda’ bullshit. It very probably ultimately rests on gambling and not at all whatever its stated purpose is … or it’s just a scam.
How Did We Get Here?
The following is by no means exhaustive and the framing is deliberately a little tongue-in-cheek. As well as being accurate enough (if unavoidably biased), my goal here is primarily to set up my prediction for what is coming next.
2015 reality: Ethereum launches narrative: “the world computer”
In 2015, Ethereum launched. The narrative here was that we are building “the world computer” and we can now have decentralized uncensorable computation. Never mind that anybody with a laptop has an uncensorable and decentralized computing device. And keep in mind this question of, “_what data might it ever be relevant to compute over in this manner (whatever that means in the first place)?” _The answer will become clearer and clearer …
2016-17 reality: ICO bubble narrative: “Web 3” / “DApps”
Regardless, at the end of 2015 we get the proposal and adoption of ERC20: a standard for issuing fungible tokens within Ethereum contracts, which is why in 2016 _but especially in 2017 _we get the ICO bubble. The narrative changes. Now we are concerned with “Web 2” companies being huge, powerful, and centralized. What if, instead, users could cooperatively own the application, control their own data, and participate in the economic upside that their usage is creating?
2018-19 reality: crypto winter narrative: “mistakes were made”
In 2018 this all falls apart, so don’t worry about it, moving on …
2020-21 reality: defi summer narrative: “decentralized finance”
By 2020 the narrative was different once again. It is more or less realized by this point that utility tokens make no technical or economic sense. You can’t introduce artificial scarcity in capital goods where there should be abundance and deflation and expect anybody to care, never mind to value your concoction. On the other hand, “securities” ought to be scarce and in some sense ought to function as tradeable ledger entries. Maybe they could be tokenized and computed on in a censorship-resistant and decentralized manner?
So, we get a boom in “defi” which, for what it’s worth, fellow Axiom co-founder Anders Larson and I predicted in our essay Only The Strong Survive, in September 2021, would be a complete disaster because, amongst a myriad of other illiterate insanities, there was approximately zero grounding of these securities in productive capital. The ecosystem was entirely self-referential – grounded _not even _in the questionable economic merit of stablecoins but firmly in gambling and scams; in leverage, rehypothecation, and securitization of precisely nothing whatsoever productive.
2022 reality: shitcoinpocalypse narrative: “mistakes were made”
And we were absolutely right because in 2022 everything collapsed. First Terra/Luna imploded – a “defi” project which essentially presented to the world the argument that a fractional reserve bank issuing fiduciary media can literally never go bankrupt because it can always cover a deposit shortfall by issuing more equity. While briefly flirting with a capitalization of around fifty f***ing billion dollars, and endorsed and fawned over by all manner of illiterate charlatans with gigantic and unsuspecting audiences, this argument was eventually rejected by the market as utterly imbecilic, as analyzed by myself and Nic Carter in All Falls Down.
This triggered a credit contagion that soon after took down 3 Arrows Capital, Celsius, Voyager, BlockFi, and others. FTX limped along by what we now understand to be something like defrauding their way out of debt, but eventually also collapsed later that year. If _Only The Strong Survive _was a pre-mortem of all of this, then the reader may want to read Green Eggs And Ham, also by myself and Anders Larson, as a kind of post-mortem.
2023-today reality: Bitcoin multisigs narrative: “Bitcoin renaissance”
And now a lot of this stuff is moving to Bitcoin. It is outside the scope of this essay to explain this in much detail but there have been a handful of developments in Bitcoin recently which, regardless of their intended purpose, seem to have as a collective side effect that a lot of these same shenanigans can now be implemented (or can _pretend _to be implemented) in a more Bitcoin-native context.
So, the new narrative is something like:
“these things didn’t work, not because they are terrible ideas that collapse to moon math wrappers around gambling and scams under any remotely critical analysis, but rather because they weren’t on Bitcoin. But also, since it has only recently become possible to (at least pretend to) implement them on Bitcoin, they are now worthwhile. We have wandered in the wilderness but learned our lessons and found the promised land.”

Technical and Economic Merit
Let’s consider all this through the lens of technical and economic merit once again. Or rather, the alleged merit given the stated goal. Ignore for now whether there is any merit:
2015 technical goal: new computing paradigm economic goal: x% of GDP?
The original idea of “crypto” allegedly has the merit of the next revolution in computing. Goodness knows how big that market is; probably a decent chunk of global GDP – if it meant anything, which it doesn’t.
2016-17 technical goal: disrupting company formation economic goal: y% of S&P?
ICOs then become a little bit more specific. Now they are merely disrupting how we organize companies. What’s that worth? Some portion of the value of the companies that can now be decentralized and tokenized I guess? Who knows …
2018-19 nothing to see here
Nothing happened then, don’t worry about it.
2020-21 technical goal: decentralize finance economic goal: z% of NYSE, CME, ISDA?
Defi becomes more specific again. Now we are merely tokenizing financial contracts, expanding access, removing middlemen, and so on. So that should probably be worth some percentage of capital markets activity?
2022 nothing to see here
Oops, never mind …
2023-today technical goal: now it’s on Bitcoin! economic goal: i% of … Bitcoin?
… and now it’s on Bitcoin apparently.
In Hindsight ...
I think the most amusing analysis of all this is as follows: it starts off completely insane, it gets more and more restrained each time – you could cheekily argue it starts to make more and more sense – but it also gets closer to Bitcoin every time. It’s clearly narrowing in on just: Bitcoin.
This is people realizing, painfully, over decades, what blockchains are for! They are not for “decentralizing everything” They are for censorship-resistant, sound, peer-to-peer digital money.

And I think this is _also _why we get the current state of crypto from earlier in the essay. As it starts to make more and more sense (by getting closer and closer to Bitcoin) you have realizations like the following: digital gift vouchers for artificially scarce and extremely expensive computation aren’t money, so we need “real money” in here for it to have economic merit, so you get stablecoins. Also, well we have a rich programming environment that seems technically interesting but also the severe technical handicap of being unable to do even a billionth of a billionth of a billionth of all the computations in the world, so you get crypto R&D. These emerge as a kind of patch, and they have _some _merit in isolation, whereas the long-term trajectory is actually just to converge on Bitcoin.
It’s an open and fascinating question if there are any learnings from these that can still be transplanted to Bitcoin. For stablecoins, this strikes me as less clear, given the dubious technical merit is introduced by using a blockchain at all, not just a blockchain other than Bitcoin. However, efforts to create Bitcoin balances (tokenized or otherwise) that are stable relative to some external price are to be applauded, if still heavily scrutinized for what technical merit they _really _have.
It seems far more likely that crypto R&D will prove useful in a Bitcoin context to some or other degree, and in this case the economic merit is in fact solved by moving to Bitcoin, provided the necessary technical merit can be mimicked. At the time of writing, this is a source of both hope and dread: hope given the possibility of viable avenues of development (although still highly uncertain); dread given how early steps in this direction are already being misrepresented in the pursuit of bullshit and scams. I will return to both shortly.
Narrative Evolution
Back to the table just above, I want to make three quick observations that tie together my entire argument and get us to the end of the essay:

Firstly, the bubbles always follow the price of Bitcoin. Hopefully I don’t need to include a price chart for the reader to grasp this immediately.
Secondly, it’s important that the narrative always changes. Absolutely ungodly amounts of money were raised for this crap following the_ Bitcoin bull runs of 2017 and 2021. The people doing this couldn’t point to the previous absolute disaster, so they had to spin something along the lines of: “_we learned our lessons and we’ve refined the use case.” This should sound familiar from just above.
Thirdly, however, regardless of whatever refinement they’ve come up with, the consequence of the new “narrative” is always, “buy my token”.
Always.
It doesn’t matter what buzzword salad is in the middle. It’s always “Bitcoin is cool, xyz, fughayzi fughahzi, buy my token.”
This is why I am very much tempted to not care so much about developers, academics, entrepreneurs, and so on, and in fact for my null hypothesis to be that they are more likely to have been victims than perpetrators. I don’t think they even end up in a position to contribute without the key group whom I do blame. When you put all these pieces together, what I think falls out of this analysis is as follows:
The entire cycle of shitcoinery can be traced to unscrupulous financiers convincing capital allocators who don’t know any better, in a bull market that, yes, Bitcoin is cool, but what they are doing is related, cooler, and that they deserve a fee.
Let us label this the Capital Cycle Theory of Shitcoinery. I think that everything else about which one might want to complain is downstream of this core realization.
Avoiding It
Given everything I’ve covered this is simple and this is pretty much the end of the essay.
You need to be aware of why this is happening now. If it hasn’t happened to you already (intended readership in the capital allocation business, that is) I guarantee it’s about to: with ETFs and the halving just past, we seem to be starting a Bitcoin bull run, these people have already raised ridiculous amounts of money on scams and bullshit that have mostly imploded. They may have lost a lot of money, or they may even have dumped on retail and got an excellent “return”. But in any case, they need a new narrative.
It's _possible _they have a viable narrative around stablecoins, R&D, both, and that they are as wary of scams as I have suggested here that they should be. I don’t want to insult anybody who merely has a different investment thesis to me if they are otherwise reasonable in their outlook and honest in their dealings.
However, if they are only now realizing how pointless and disingenuous every preceding crypto narrative has been after 7 years and hundreds of billions of dollars – or if they still don’t realize it at all; if their track record shows they were deeply involved, handsomely rewarded, and yet created nothing of lasting value; if they say things like “the builders are coming back to Bitcoin”: be very, very suspicious. Be on the lookout for tokens, which is to say, be on the lookout for scams.
What is especially frustrating is that the technical spin of the "layer twos" that are all the rage at the time of writing, that "the builders are coming back to Bitcoin" to build, and that you, the capital-allocating reader, will almost certainly be pitched, is in and of itself pretty reasonable. They just don't require tokens and they don't require gambling to support the token prices. What they do require is _sound adherence to Bitcoin's technical and economic merit. _At the very least, they require honest communication about the design trade-offs so far and planned for, and what, if any, economic and technical merit is left over after these trade-offs have been made.
Narrative aside, the _reality _of 99% of these projects is that they are private execution environments tied to multisigs custodying user deposits. Which is to say, on the one hand, that they are cargo culting "crypto R&D" from Ethereum that isn't technically possible in Bitcoin in order to feign technical merit, and on the other, that _they aren't layer twos at all. _Once again, they may as well be Chaumian eCash mints, except for the fact that this would make the intended token scam all but impossible to pull off.
Casey Rodarmor, creator of the Ordinals protocol, recently joked on the Hell Money _podcast he co-hosts, responding to the idea that "_everybody is building an L2 now":
"It's the same sad sack playbook as on Ethereum being recapitulated on Bitcoin. That's how you get a VC check on Ethereum. They are all glorified multisigs, so they are like, "hey let's port our glorified multisig to Bitcoin and get a VC check." I was talking to a friend of mine who is working on an interesting project, an open-source analyzer that does transaction clustering, and I was like, "maybe you could do this in this way and raise some VC money," and he said, "yeah, okay, but what's the point in raising VC money?" And I said, "no, no, no, this is the end! This is the goal! You raise VC money and then you cut yourself checks from that VC money until it runs out and then you raise more at a 10x valuation. This is the new economy, guys!"
The 1% that are legitimately trying to bring the learnings from crypto R&D to Bitcoin in a technically and economically sound manner will hopefully win in the long run (and even this is somewhat speculative at the time of writing) but will likely get little to no attention amidst this bull market flurry of scams and bullshit.
Axiom will do its best to source and invest in these companies (we already have!) but we are resigned to it being a much more difficult sell to capital allocators in light of the Capital Cycle Theory of Shitcoinery. To be brutally honest, this entire essay can fairly be considered cope on my part in light of having lost this battle in the past and facing up to the very real prospect of losing it in the near future too. Oh well, at least I tried.
Wrapping Up
The essence of the Capital Cycle Theory of Shitcoinery is that the problems I’ve described ultimately come from bamboozling people just like you with technical sounding nonsense like “Web 3” so you think it’s all a lot more complicated than it really is. Just buy Bitcoin. That’s certainly the first thing you should do anyway, and it might be the only thing you ever need to do.
If you really, really want to take the extra risk of investing in the Bitcoin ecosystem, the team at Axiom would be happy to speak with you. But we are never going to talk you out of buying Bitcoin. There is no world in which Bitcoin does poorly and we do well, or in which we promise something “better than Bitcoin,” and there’s no point in engaging with us at all if you don’t already believe most of this.
If that’s of interest to you, we’d love to talk. If not, just buy Bitcoin. In any case: fair warning, we are heading into a Bitcoin bull market and the scams and the bullshit are coming. Good luck avoiding them.
Allen Farrington, June 2024

-
 @ 4ba8e86d:89d32de4
2024-10-22 22:58:12
@ 4ba8e86d:89d32de4
2024-10-22 22:58:12Isto visa aumentar a privacidade dos utilizadores envolvidos, proteger contra a vigilância financeira e aumentar a fungibilidade da rede Bitcoin como um todo.
O coinjoin é uma técnica poderosa de privacidade para aqueles com um conhecimento intermediário do Bitcoin. Aprender o que é o coinjoin e como ele funciona pode ser uma ferramenta valiosa para sua caixa de ferramentas no mundo do Bitcoin. Antes de entrarmos em detalhes, é fundamental compreender o funcionamento dos endereços e das UTXOs (Unspent Transaction Outputs) do Bitcoin, bem como os princípios básicos da privacidade no Bitcoin.
Para começar, todas as transações padrão do Bitcoin são registradas publicamente na blockchain. Isso significa que se alguém identificar um endereço como pertencente a você, poderá rastrear o saldo desse endereço e acompanhar como seus Bitcoins são movimentados. No entanto, ao enviar Bitcoin para um coinjoin, você torna extremamente difícil para qualquer pessoa continuar associando UTXOs ou partes específicas de Bitcoin à sua identidade. Em essência, os coinjoins permitem que você recupere a privacidade perdida e, em certa medida, corrija erros de privacidade cometidos no passado.
Agora, vamos explorar como os coinjoins funcionam. O conceito é relativamente simples. Um coinjoin é uma colaboração sem confiança entre várias pessoas para criar uma transação. Na forma mais básica, cada pessoa envolvida contribui com uma quantia igual de Bitcoin como entrada para a transação e, em seguida, recebe essa mesma quantia de Bitcoin de volta como saída. Para ilustrar, considere este exemplo:
Imagine um coinjoin envolvendo você e mais quatro participantes. Cada pessoa retira 0,05 Bitcoin de um endereço vinculado à sua identidade e paga uma taxa para contribuir para a transação global. Após a transmissão e confirmação da transação, cada pessoa recebe 0,05 Bitcoin de volta como um novo UTXO em um novo endereço de carteira que controlam. As cinco novas addresses que recebem os UTXOs devem ser anônimas, o que significa que qualquer observador da blockchain não terá ideia de qual delas pertence a você. Mas Claro Você pode participar de múltiplos coinjoins com um número muito maior de participantes.
Aumento no número de maneiras pelas quais as coinjoins da Whirlpool podem ser interpretadas na cadeia
5 entradas/5 saídas = 1.496 interpretações (existentes)
6 entradas/6 saídas = 22.482 interpretações
7 entradas/7 saídas = 426.833 interpretações
8 entradas/8 saídas = 9.934.563 interpretações
Lembre-se de que, após submeter Bitcoins a um coinjoin, eles podem novamente ser associados à sua identidade por meio de ações subsequentes, como enviar Bitcoin para um serviço financeiro que conhece a sua identidade, o Bitcoin será naturalmente vinculado a você aos olhos desse provedor de serviços. #Bitcoin #privacidade
https://medium.com/oxt-research/understanding-bitcoin-privacy-with-oxt-part-1-4-8177a40a5923
https://medium.com/oxt-research/understanding-bitcoin-privacy-with-oxt-part-2-4-20010e0dab97
https://medium.com/oxt-research/understanding-bitcoin-privacy-with-oxt-part-3-4-9a1b2b572a8
https://medium.com/oxt-research/understanding-bitcoin-privacy-with-oxt-part-4-4-16cc0a8759d5
https://medium.com/samourai-wallet/introducing-whirlpool-surge-cycles-b5b484a1670f
https://medium.com/samourai-wallet/diving-head-first-into-whirlpool-anonymity-sets-4156a54b0bc7
https://blog.samourai.is/why-we-coinjoin/
https://docs.samourai.io/whirlpool
https://youtu.be/0YwiL978p1c?si=DRZNEH_aHKHjb2-m
-
 @ 4523be58:ba1facd0
2024-05-28 11:05:17
@ 4523be58:ba1facd0
2024-05-28 11:05:17NIP-116
Event paths
Description
Event kind
30079denotes an event defined by its event path rather than its event kind.The event directory path is included in the event path, specified in the event's
dtag. For example, an event path might beuser/profile/name, whereuser/profileis the directory path.Relays should parse the event directory from the event path
dtag and index the event by it. Relays should support "directory listing" of kind30079events using the#ffilter, such as{"#f": ["user/profile"]}.For backward compatibility, the event directory should also be saved in the event's
ftag (for "folder"), which is already indexed by some relay implementations, and can be queried using the#ffilter.Event content should be a JSON-encoded value. An empty object
{}signifies that the entry at the event path is itself a directory. For example, when savinguser/profile/name:Bob, you should also saveuser/profile:{}so the subdirectory can be listed underuser.In directory names, slashes should be escaped with a double slash.
Example
Event
json { "tags": [ ["d", "user/profile/name"], ["f", "user/profile"] ], "content": "\"Bob\"", "kind": 30079, ... }Query
json { "#f": ["user/profile"], "authors": ["[pubkey]"] }Motivation
To make Nostr an "everything app," we need a sustainable way to support new kinds of applications. Browsing Nostr data by human-readable nested directories and paths rather than obscure event kind numbers makes the data more manageable.
Numeric event kinds are not sustainable for the infinite number of potential applications. With numeric event kinds, developers need to find an unused number for each new application and announce it somewhere, which is cumbersome and not scalable.
Directories can also replace monolithic list events like follow lists or profile details. You can update a single directory entry such as
user/profile/nameorgroups/follows/[pubkey]without causing an overwrite of the whole profile or follow list when your client is out-of-sync with the most recent list version, as often happens on Nostr.Using
d-tagged replaceable events for reactions, such as{tags: [["d", "reactions/[eventId]"]], content: "\"👍\"", kind: 30079, ...}would make un-reacting trivial: just publish a new event with the samedtag and an empty content. Toggling a reaction on and off would not cause a flurry of new reaction & delete events that all need to be persisted.Implementations
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
f) already support this feature. - IrisDB client side library: treelike data structure with subscribable nodes.
https://github.com/nostr-protocol/nips/pull/1266
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
-
 @ 5d4b6c8d:8a1c1ee3
2024-07-13 12:44:32
@ 5d4b6c8d:8a1c1ee3
2024-07-13 12:44:32Yesterday's edition https://stacker.news/items/605773/r/Undisciplined
We have a confessional from a professional shitcoiner, today. That's fun.
-
- -
July 13, 2023 📅
📝
TOP POSTValidating Lightning Signer - AMA
Excerpt
VLS is a nifty piece of software that helps boost the security of the Bitcoin Lightning Network. 🛡️
11k sats \ 33 comments \ @devrandom \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/208442/r/Undisciplined?commentId=208454
Excerpt
Ever bought a computer or cell phone? Why? Why not wait until your money is worth more later compared to the price of that cell phone?
1441 sats \ 7 replies \ @02674f045a
From Opinion: Why BTC can't become the reserve currency by @0xBTC in ~bitcoin
🏆
TOP STACKER1st place @k00b
5838 stacked \ 7855 spent \ 3 posts \ 19 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
27k stacked \ 0 revenue \ 40.6k spent \ 108 posts \ 281 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 13, 2022 📅
📝
TOP POSTAny Good Routing Node Strategies?
Excerpt
For people who have/are running nodes, are there any strategies that have been most effective for you for earning routing fees? From my very limited routing experience so far it seems there are a few main questions:
1232 sats \ 33 comments \ @andyleroy \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/44747/r/Undisciplined?commentId=44755
Excerpt
Obligatory not a node routing expert, but this guy is a good follow: https://mobile.twitter.com/cold_sats
276 sats \ 1 reply \ @Cornleone
From Any Good Routing Node Strategies? by @andyleroy in ~bitcoin
🏆
TOP STACKER1st place @k00b
37.3k stacked \ 15.2k spent \ 1 post \ 29 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
27.4k stacked \ 0 revenue \ 34.7k spent \ 117 posts \ 279 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 13, 2021 📅
📝
TOP POSTI joined a shitcoin project full time couple of months ago
Excerpt
I though it would be exciting and fun. But I think I'm wasting my time.
3 sats \ 9 comments \ @03785de7ab \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/306/r/Undisciplined?commentId=316
Excerpt
There are many companies working with Bitcoin but it's not their main focus. I did implement Bitgo sevices for one e-wallet provider but that was it. What I'm looking for is a project which build useful things for user with current Bitcoin features, […]
2 sats \ 1 reply \ @03785de7ab
From I joined a shitcoin project full time couple of months ago by @03785de7ab in ~bitcoin
🏆
TOP STACKERNo top stacker
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
37 stacked \ 0 revenue \ 60 spent \ 6 posts \ 10 comments
originally posted at https://stacker.news/items/607040
-
-
 @ 9bc2d34d:d19d2948
2024-09-02 19:41:40
@ 9bc2d34d:d19d2948
2024-09-02 19:41:40Chef's notes
This recipe is designed for home cooks who want to recreate the delicious buttery hollandaise sauce at home without feeling overwhelmed. It focuses on teaching the basics of the sauce, allowing beginners to master the fundamentals before experimenting with seasonings, hot sauces, or herbs.
Please note the thickness of sauce in the picture. This is after ten minutes of blending.
Details
- ⏲️ Prep time: 3 minutes
- 🍳 Cook time: 10 minutes (blending)
- 🍽️ Servings: 2 - 4
Ingredients
- 4 egg yolks
- 8 tablespoons of melted butter
- 1 tablespoon of lemon juice
- Pinch of salt
- Pinch of pepper
Directions
- Melt butter in the microwave or on the stovetop.
- Separate the egg yolks from the egg whites (reserve the egg whites for another dish).
- Place the egg yolks in a blender.
- Start the blender (medium to high settings for blend mode is fine).
- Slowly pour the melted butter into the cover opening (it will splatter).
- Add the remaining ingredients.
- Blend for ten minutes (seriously, walk away and do something else).
- Taste and adjust the flavors (add extra lemon juice or salt if desired).
- Serve over your breakfast!
-
 @ d5c3d063:4d1159b3
2024-10-24 13:47:14
@ d5c3d063:4d1159b3
2024-10-24 13:47:14เราได้ยินคำว่า "สิทธิ" กันจนชินหูไปแล้ว นักการเมืองก็พูดกันจังเลยว่าให้สิทธินั่นสิทธินี่ แต่เคยสงสัยกันบ้างไหมว่าสิทธิพวกนี้มันมาจากไหนกันแน่ จริงๆ แล้วรัฐเป็นคนหยิบยื่นสิทธิให้เราเหรอ หรือจริงๆ แล้วเรามีสิทธิเหล่านี้อยู่แล้วโดยกฎธรรมชาติ
. https://image.nostr.build/d03cc1428b49045550ef7203db1de9f36c8c1f923bfdc96a4953254be5fdb6c2.png
เริ่มจากเรื่อง "กฎธรรมชาติ" (Natural Law) ย้อนเวลาหน่อยแล้วกัน ตั้งแต่สมัยกรีกโบราณโน่นเลย นักปัชญาสมัยนั้นเค้าเชื่อว่า ทั้งจักรวาลและสังคมของเรามันมีกฎเกณฑ์บางอย่างที่เป็นความจริงสากล ไม่ว่าจะอยู่ที่ไหนบนโลกก็หนีไม่พ้น เหมือนกับเวลาโยนน้ำขึ้นฟ้า ยังไงน้ำก็ต้องตกลงมาอยู่ดีถูกไหม นั่นแหละเค้าเรียกว่า "กฎธรรมชาติ" หรือยกตัวอย่างง่ายๆ เช่น "กฎอุปสงค์-อุปทาน" ที่เราเรียนกันในวิชาเศรษฐศาสตร์นั่นแหละ ลองคิดดูนะ ถ้าสินค้ามันมีน้อยแต่คนอยากได้เยอะ ราคามันก็ต้องพุ่งสูงขึ้นเป็นธรรมดา เป็นกลไกของตลาด เป็นความจริงที่เกิดขึ้นเองโดยธรรมชาติ ไม่ต้องมีใครไปบังคับเลย .
ทีนี้มาถึง Aristotle "อริสโตเติล" เขาเชื่อว่าสิ่งที่ทำให้มนุษย์เราพิเศษกว่าสัตว์อื่นๆ ก็คือ "เหตุผล" นี่แหละ เพราะเรามีเหตุผล เราถึงรู้จักผิดชอบชั่วดี รู้จักใช้ชีวิตอย่างมีคุณธรรม ต่อมานักปรัชญาสโตอิกส์ (Stoics) ก็เอาไอเดียเรื่องกฎธรรมชาติมาขยายความต่อ พวกเขาเน้นว่า เมื่อมนุษย์ทุกคนเกิดมาพร้อมกับการมี "เหตุผล" เหมือนๆ กัน เพราะฉะนั้น "กฎธรรมชาติ" จึงเปรียบเสมือน "กฎศีลธรรม" (Moral Law) ที่เป็นสากล ใช้ได้กับทุกคนบนโลกใบนี้ ไม่ว่าคุณจะเป็นใคร มาจากไหน รวยหรือจน ก็ต้องอยู่ภายใต้กฎเดียวกันหมด ไม่ใช่แค่สโตอิกส์นะ นักคิดดังๆ อีกหลายคนในโลกตะวันตก ไม่ว่าจะเป็น Cicero, Aquinas หรือ Grotius พวกเขาก็เห็นด้วยกับเรื่องกฎธรรมชาติเหมือนกัน .
ทีนี้มาถึงศตวรรษที่ 17 ก็มีนักปรัชญาคนสำคัญชื่อ John Locke (จอห์น ล็อค) เขาเอาไอเดียเรื่อง "กฎธรรมชาติ" มาเชื่อมโยงกับ "สิทธิธรรมชาติ" (Natural Rights) มาอธิบายได้อย่างเป็นระบบ โดย Locke เชื่อว่ามนุษย์ทุกคนเกิดมาพร้อมกับสิทธิพื้นฐาน 3 อย่าง นั่นก็คือ สิทธิที่จะมีชีวิต มีเสรีภาพในการเลือก และสิทธิในการเป็นเจ้าของทรัพย์สิน ซึ่งสิทธิเหล่านี้มีติดตัวเรามาตั้งแต่เกิด มีอยู่ก่อนที่จะมีรัฐชาติด้วยซ้ำ มนุษย์เราสามารถใช้ "เหตุผล" ที่เรามีอยู่ในการทำความเข้าใจสิทธิธรรมชาติเหล่านี้ได้ .
สมัยก่อนที่ยังไม่มีรัฐบาล Locke เรียกช่วงเวลานั้นว่า "สภาวะธรรมชาติ" (State of Nature) ที่จริงๆ แล้วมนุษย์เราสามารถใช้ "เหตุผล" ในการอยู่ร่วมกันได้นะ ถึงจะไม่มีรัฐบาลก็ตาม แต่! ประเด็นคือ ในสภาวะธรรมชาติ มันอาจจะไม่มีศาลหรือตำรวจแบบที่เราคุ้นเคยไง (แต่ก็อาจจะมีวิธีจัดการความยุติธรรมแบบอื่นๆ อยู่) Locke บอกว่า คนบางกลุ่มอาจจะตกลงกันว่า เรามาตั้งรัฐบาลกันดีกว่า (ซึ่งการตั้งรัฐบาลก็อาจจะไม่ได้รับความเห็นชอบจากทุกคนก็ได้นะ) เพื่อที่จะได้มีระบบยุติธรรม มีคนดูแลความสงบเรียบร้อยอย่างเป็นทางการ แต่ที่สำคัญที่สุดคือรัฐบาลต้องปกป้องสิทธิธรรมชาติที่มีก่อนที่การตั้งรัฐ
คือ Locke เขาก็รู้นะว่า "อำนาจรัฐ" มันเหมือนดาบสองคม ถ้ารัฐบาลไม่ดี เอาอำนาจไปใช้ในทางที่ผิด ก็จะกลายเป็นการละเมิดสิทธิของประชาชนซะเอง เพราะงั้น Locke ถึงเน้นย้ำมากๆ ว่า รัฐบาลต้องมี "อำนาจที่จำกัด" (Limited Government) และต้องให้ความเคารพสิทธิธรรมชาติของประชาชนเป็นอันดับแรก ซึ่งอำนาจของรัฐบาลต้องมาจากความยินยอมของประชาชน ประชาชนมีสิทธิ์ตั้งคำถาม วิพากษ์วิจารณ์ หรือแม้แต่ต่อต้านรัฐบาลที่ใช้อำนาจในทางที่ผิด .
น่าเสียดายที่ทุกวันนี้ คำว่า "สิทธิ" มันถูกนักการเมืองเอาไปใช้หาเสียงกันจัง เช่น สิทธิเรียนฟรี สิทธิรักษาฟรี สิทธิความเท่าเทียมทางเศรษฐกิจ ฟังดูดี๊ดีเนอะ แต่จริงๆ แล้วมันก็แค่นโยบายหาเสียง ไม่ใช่ "สิทธิขั้นพื้นฐาน" จริงๆ สักหน่อย
สิทธิขั้นพื้นฐานที่แท้จริงมันต้องเป็นอะไรที่ติดตัวเรามาตั้งแต่เกิด อย่างเช่น สิทธิที่จะมีชีวิตอยู่ สิทธิในการเป็นเจ้าของทรัพย์สิน สิทธิในการพูดหรือแสดงความคิดเห็น
ส่วนนโยบายเรียนฟรี รักษาฟรี แจกเงิน พวกนี้มันเป็นแค่นโยบายของรัฐ ที่รัฐจะยกเลิกเมื่อไหร่ก็ได้ ที่สำคัญคือนโยบายพวกนี้มันมักจะไปละเมิดสิทธิของคนอื่นโดยไม่รู้ตัว เช่น รัฐบาลจะเก็บภาษีเราเพิ่มขึ้น เพื่อเอาเงินไปทำโครงการต่างๆ โดยที่เราไม่เห็นด้วยหรือเต็มใจ นี่มันก็คือการละเมิดสิทธิในทรัพย์สินของเรานะ หรือบางทีรัฐบาลก็เข้าไปแทรกแซงเศรษฐกิจ เช่น บังคับให้เราต้องทำนู่นทำนี่ ซึ่งมันก็ละเมิดเสรีภาพในการเลือกของเราเหมือนกัน อีกตัวอย่างที่เห็นชัดๆ คือ รัฐบาลสร้างเงินเฟ้อ ทำให้เงินในกระเป๋าเรามันมีค่าน้อยลง นี่มันปล้นกันชัดๆ แต่เขาทำได้อย่างถูกกฎหมายนะ ซึ่งจริงๆ แล้ว รัฐบาลไม่มีสิทธิ์ทำแบบนี้ เพราะมันเป็นการละเมิดสิทธิของประชาชนอย่างชัดเจน การที่รัฐบาลก็ชอบเอา "กฎหมาย" มาอ้างก็เพื่อให้ตัวเองดูชอบธรรม .
สรุปง่ายๆ เลยนะ "สิทธิ" ที่แท้จริงมันไม่ได้เกิดจากการใช้อำนาจหรือความรุนแรง แต่มันมีรากฐานมาจาก "กฎธรรมชาติ" และสิทธิก็ต้องมาพร้อมกับ "ความรับผิดชอบ" ด้วย เราต้องไม่เอาสิทธิของเราไปละเมิดสิทธิของคนอื่น
"กฎหมาย" มีไว้เพื่อปกป้องสิทธิของทุกคนอย่างเท่าเทียม ไม่ใช่เพื่อสร้างสิทธิหรือเอาไปใช้เป็นเครื่องมือในการละเมิดสิทธิของประชาชน กฎหมายต้องเป็นเหมือนเกราะป้องกันสิทธิของเรา ไม่ใช่โซ่ตรวนที่พันธนาการเสรีภาพของเรา
เพราะฉะนั้น "สิทธิ" กับ "ความรับผิดชอบ" มันเป็นของคู่กัน เวลาเราใช้สิทธิอะไรก็ตาม ต้องคิดถึงใจเขาใจเราด้วย อย่าเผลอไปละเมิดสิทธิของคนอื่นเข้าล่ะ .
ก่อนที่จะเชื่อนักการเมืองที่ชอบโฆษณาว่าให้สิทธินั่นนี่ เราต้องตั้งคำถามกับตัวเองก่อนว่าสิทธินั้น มันมาจากการใช้อำนาจหรือการบังคับใช้โดยกฎหมายด้วยความรุนแรงหรือเปล่า และที่สำคัญคือมันไปละเมิดสิทธิของคนอื่นรึเปล่า .
การตั้งคำถามกับสิ่งเหล่านี้ มันคือจุดเริ่มต้นของการเข้าใจ "สิทธิ" ที่แท้จริง และเป็นก้าวแรกของการลุกขึ้นมาปกป้องสิทธิของเราเอง เพื่อไม่ให้กลายเป็นเหยื่อของอำนาจรัฐ เพราะท้ายที่สุดแล้ว สิ่งที่มนุษย์ต้องการก็คือการมีชีวิตที่มีอิสระ อยู่ในสังคมที่มีความยุติธรรม และมีศักดิ์ศรีของความเป็นมนุษย์
Siamstr #NaturalLaw #NaturalRights
-
 @ 9e69e420:d12360c2
2024-10-24 13:10:08
@ 9e69e420:d12360c2
2024-10-24 13:10:08Kamala Harris delivered a sharp critique of Donald Trump, comparing him to Adolf Hitler during a recent speech. She referenced comments made by former Chief of Staff John Kelly, who disclosed that Trump expressed admiration for Hitler while in office.
![Kamala Harris] (https://i.nostr.build/iyRm5cJo9YuRgh3M.png)
Harris stated, "It is deeply troubling and incredibly dangerous that Donald Trump would invoke Adolf Hitler."
She warned that if re-elected, Trump could seek unchecked power and compare him to a dictator. Harris emphasized the importance of understanding Trump's intentions and the implications for America’s future. Her remarks coincided with the fast-approaching election, intensifying her campaign's rhetoric against Trump.
-
 @ c73818cc:ccd5c890
2024-10-21 22:13:09
@ c73818cc:ccd5c890
2024-10-21 22:13:09
Siamo entusiasti di lanciare il Centro App Telegram di Bitget, una piattaforma con oltre 600 app e bot sviluppati su Telegram Open Network (TON). Ora puoi esplorare servizi blockchain, giochi innovativi e strumenti Web3 direttamente da Telegram!
✨ I primi 1.000 utenti fortunati che partecipano potranno condividere 2.000 USDT! 🎉 📅 Periodo della promozione: 14 ottobre 2024, ore 14:00 (UTC+2) – 28 ottobre 2024, ore 13:00 (UTC+1).
💡 Iscriviti con il nostro referral per:
✅ Bonus esclusivi 🔖 Sconto del 20% sulle fee a vita 📚 Accesso al gruppo privato con un corso completo su Bitcoin e trading!
🔗 Non perdere questa occasione, unisciti ora e scopri il futuro su Telegram! 💥
Unitevi da questo link! https://t.me/tg_app_center_bot/appcenter?startapp=O9oLXzD6OX
Oppure inserendo questo codice d’invito: O9oLXzD6OX
Referral Bitget: https://bonus.bitget.com/U1JNEK
BitcoinReportItalia #Bitget #Telegram #dApp #TON #Crypto #Web3 #USDT #Trading
-
 @ b2caa9b3:9eab0fb5
2024-07-13 12:01:35
@ b2caa9b3:9eab0fb5
2024-07-13 12:01:35I woke up in my dorm this morning to the sound of rain – a rarity in Africa, but a common occurrence here around Mount Kilimanjaro. The climate is much like a European summer, with comfortable temperatures ranging from 18 to 30 degrees Celsius. Unlike the rest of Africa, this region receives more rainfall, creating a lush and scenic environment.

After a quick shower, I stepped out onto the balcony to find myself greeted by a chilly rain. Not ideal weather for exploring, but it did present a different perspective of the majestic Kilimanjaro. The mountain, often shrouded in clouds, occasionally peeks through, and on a clear day, might even be bathed in sunshine. From this vantage point, it's hard to imagine the countless hikers making their way up its slopes.
Did you know that Kilimanjaro, Africa's tallest mountain and a dormant volcano, once held a unique title? Back in 1910, during the German Empire, it was considered the empire's highest peak. While Mount Everest holds the title of the world's highest mountain overall, Kilimanjaro takes the crown for the tallest freestanding mountain – any higher peak is likely part of a mountain range or group.
Gazing at Kilimanjaro, I'm struck by its history – a single, towering volcano, once a part of the German Empire. Traces of that era linger in Moshi, with some colonial-era buildings, some in disrepair, others beautifully restored. Arusha, another nearby town, boasts an impressive art gallery and a fascinating National Museum. This museum, housed in a former German fort, offers a glimpse into the past. One particularly intriguing resident is a giant tortoise, discovered by German colonists as a hatchling in Kilimanjaro National Park. This living relic has witnessed a century of change, a silent observer of a bygone era.

Today promises to be a relaxing one. I'll spend time soaking up the views from the rooftop, hoping to catch a glimpse of Kilimanjaro in all its glory. On a more practical note, I'm also on the hunt for a remote job to help with some financial constraints. Finding the right opportunity seems to be a bit more challenging than anticipated.
As I wrap up this post, the weather has taken a turn for the better. The rain has stopped, the temperature has risen, and the sun is beginning to peek through the clouds. Here's to a wonderful day for everyone – enjoy yours!
(P.S. Be sure to check out the photos – one captures Kilimanjaro from yesterday evening, the other is a picture of me with the giant tortoise from my previous trip here in December 2022).
Online
Feel free to support me by sending some sats via the lightning network to rubenstorm@sats.mobi
-
 @ c73818cc:ccd5c890
2024-10-24 13:18:26
@ c73818cc:ccd5c890
2024-10-24 13:18:26
🖕 Saylor delega la custodia dei suoi Bitcoin a istituzioni bancarie
🤮 Un cambio di rotta inaspettato
🖕 Michael Saylor, figura centrale nel panorama Bitcoin, ha sorpreso molti con la sua recente affermazione. Nonostante sia sempre stato un sostenitore della custodia personale di BTC, oggi invita i detentori a fare affidamento sulle grandi banche, considerandole più sicure. Una mossa che ha sollevato diverse critiche tra i più ferventi Bitcoiner.
🤮 Il potere delle istituzioni: pericolo o opportunità?
🖕 Secondo Saylor, la paura di un sequestro statale di Bitcoin è eccessiva. Preferisce ora affidare la custodia di BTC a banche "troppo grandi per fallire", contraddicendo la sua precedente posizione. Molti critici vedono in questo un tentativo di normalizzare Bitcoin come semplice asset speculativo, allontanandolo dal suo ruolo di strumento di libertà finanziaria.
🤮 La comunità Bitcoin è divisa
🖕 Personalità di spicco come Simon Dixon e John Carvalho hanno espresso forti perplessità. Dixon teme che MicroStrategy possa trasformarsi in una sorta di banca Bitcoin, mentre Carvalho sottolinea come questo discorso rischi di minare la visione originale di Bitcoin come "speranza per tutti", marginalizzando i veri sostenitori della decentralizzazione.
🤮 Un messaggio per le grandi aziende?
🖕 Alcuni analisti ritengono che il messaggio di Saylor sia destinato principalmente a grandi imprese e fondi di investimento. Per queste entità, la custodia personale non è praticabile, e le banche rappresentano una soluzione più adatta. Tuttavia, questo potrebbe spingere ulteriormente Bitcoin nelle mani di pochi potenti, riducendo la libertà individuale di chi lo detiene.
🤮 Un futuro incerto per Bitcoin
🖕 Mentre Saylor continua a prevedere un futuro da trilione di dollari per Bitcoin, resta da vedere se riuscirà a mantenere l'equilibrio tra le sue ambizioni finanziarie e i principi cardine delle criptovalute. Il rischio di una Bitcoin centralizzata nelle mani di istituzioni bancarie e fondi resta un'ombra incombente, soprattutto sapendo che MicroStrategy è controllata per il 30% da Vanguard.
Unisciti al nostro gruppo Telegram: https://t.me/Bitcoin_Report_Italia
Referral Bitget -20% sulle fee + bonus benvenuto 6w5d o link: https://bonus.bitget.com/U1JNEK
BitcoinReportItalia #MichaelSaylor #MicroStrategy #BlackRock #ETF #Hodl #Hold #Vanguard #Banche #Cripto #Bitcoin
-
 @ 8947a945:9bfcf626
2024-10-17 07:33:00
@ 8947a945:9bfcf626
2024-10-17 07:33:00Hello everyone on Nostr and all my watchersand followersfrom DeviantArt, as well as those from other art platforms
I have been creating and sharing AI-generated anime girl fanart since the beginning of 2024 and have been running member-exclusive content on Patreon.
I also publish showcases of my artworks to Deviantart. I organically build up my audience from time to time. I consider it as one of my online businesses of art. Everything is slowly growing
On September 16, I received a DM from someone expressing interest in purchasing my art in NFT format and offering a very high price for each piece. We later continued the conversation via email.
Here’s a brief overview of what happened

- The first scammer selected the art they wanted to buy and offered a high price for each piece. They provided a URL to an NFT marketplace site running on the Ethereum (ETH) mainnet or ERC20. The site appeared suspicious, requiring email sign-up and linking a MetaMask wallet. However, I couldn't change the wallet address later. The minting gas fees were quite expensive, ranging from 0.15 to 0.2 ETH

-
The scammers tried to convince me that the high profits would easily cover the minting gas fees, so I had nothing to lose. Luckily, I didn’t have spare funds to purchase ETH for the gas fees at the time, so I tried negotiating with them as follows:
-
I offered to send them a lower-quality version of my art via email in exchange for the minting gas fees, but they refused.
- I offered them the option to pay in USD through Buy Me a Coffee shop here, but they refused.
- I offered them the option to pay via Bitcoin using the Lightning Network invoice , but they refused.
- I asked them to wait until I could secure the funds, and they agreed to wait.
The following week, a second scammer approached me with a similar offer, this time at an even higher price and through a different NFT marketplace website.
This second site also required email registration, and after navigating to the dashboard, it asked for a minting fee of 0.2 ETH. However, the site provided a wallet address for me instead of connecting a MetaMask wallet.
I told the second scammer that I was waiting to make a profit from the first sale, and they asked me to show them the first marketplace. They then warned me that the first site was a scam and even sent screenshots of victims, including one from OpenSea saying that Opensea is not paying.
This raised a red flag, and I began suspecting I might be getting scammed. On OpenSea, funds go directly to users' wallets after transactions, and OpenSea charges a much lower platform fee compared to the previous crypto bull run in 2020. Minting fees on OpenSea are also significantly cheaper, around 0.0001 ETH per transaction.
I also consulted with Thai NFT artist communities and the ex-chairman of the Thai Digital Asset Association. According to them, no one had reported similar issues, but they agreed it seemed like a scam.
After confirming my suspicions with my own research and consulting with the Thai crypto community, I decided to test the scammers’ intentions by doing the following
I minted the artwork they were interested in, set the price they offered, and listed it for sale on OpenSea. I then messaged them, letting them know the art was available and ready to purchase, with no royalty fees if they wanted to resell it.
They became upset and angry, insisting I mint the art on their chosen platform, claiming they had already funded their wallet to support me. When I asked for proof of their wallet address and transactions, they couldn't provide any evidence that they had enough funds.
Here’s what I want to warn all artists in the DeviantArt community or other platforms If you find yourself in a similar situation, be aware that scammers may be targeting you.
My Perspective why I Believe This is a Scam and What the Scammers Gain
From my experience with BTC and crypto since 2017, here's why I believe this situation is a scam, and what the scammers aim to achieve
First, looking at OpenSea, the largest NFT marketplace on the ERC20 network, they do not hold users' funds. Instead, funds from transactions go directly to users’ wallets. OpenSea’s platform fees are also much lower now compared to the crypto bull run in 2020. This alone raises suspicion about the legitimacy of other marketplaces requiring significantly higher fees.
I believe the scammers' tactic is to lure artists into paying these exorbitant minting fees, which go directly into the scammers' wallets. They convince the artists by promising to purchase the art at a higher price, making it seem like there's no risk involved. In reality, the artist has already lost by paying the minting fee, and no purchase is ever made.
In the world of Bitcoin (BTC), the principle is "Trust no one" and “Trustless finality of transactions” In other words, transactions are secure and final without needing trust in a third party.
In the world of Ethereum (ETH), the philosophy is "Code is law" where everything is governed by smart contracts deployed on the blockchain. These contracts are transparent, and even basic code can be read and understood. Promises made by people don’t override what the code says.
I also discuss this issue with art communities. Some people have strongly expressed to me that they want nothing to do with crypto as part of their art process. I completely respect that stance.
However, I believe it's wise to keep your eyes open, have some skin in the game, and not fall into scammers’ traps. Understanding the basics of crypto and NFTs can help protect you from these kinds of schemes.
If you found this article helpful, please share it with your fellow artists.
Until next time Take care
Note
- Both cyber security images are mine , I created and approved by AdobeStock to put on sale
- I'm working very hard to bring all my digital arts into Nostr to build my Sats business here to my another npub "HikariHarmony" npub1exdtszhpw3ep643p9z8pahkw8zw00xa9pesf0u4txyyfqvthwapqwh48sw
Link to my full gallery - Anime girl fanarts : HikariHarmony - HikariHarmony on Nostr - General art : KeshikiRakuen
-
 @ 32e18276:5c68e245
2024-07-05 18:28:20
@ 32e18276:5c68e245
2024-07-05 18:28:20Hey guys!
Here's our Q3-Q4 report. There was some confusion with the timing of the previous quarters so we've accumulated everything since the Q2 report (March 2nd, 2024) into this one. Enjoy!
Damus OpenSats Q3-Q4 Progress Report
The third and fourth quarter of the initial Damus OpenSats grant encompasses work done across many of the active projects being worked on at Damus HQ. Here's a quick overview of the progress made across the organization:
nostrdb
Added
- Author query support (William Casarin)
- REQ support: ndb_subscribe (William Casarin)
- CLOSE support: ndb_unsubscibe (William Casarin)
- Profile flatbuffer dump utility (William Casarin)
- Ability to register a subscription callback instead of just polling (William Casarin)
Changed
- Dump json in filter and fulltext queries in cli tool (William Casarin)
Stats
name added removed commits William Casarin <jb55@jb55.com> +665 -739 16nostrdb-rust
Added
- Note builder interface (William Casarin)
- Nip10 implementation (William Casarin)
- Getting profile by key (William Casarin)
- Note tag support (William Casarin)
Tag::into_itermethod (Yuki Kishimoto)FilterBuilder::untilmethod (Yuki Kishimoto)- Export structs from
tagsmodule (Yuki Kishimoto)
Fixed
FilterBuilder::limitmethod (Yuki Kishimoto)Note::sigmethod (Yuki Kishimoto)
Stats
Yuki Kishimoto <yukikishimoto@protonmail.com> +20 -4 5 William Casarin <jb55@jb55.com> +1551 -867 32Damus NoteDeck/Android
This project is in heavy development and doesn't have clean changelogs yet, so here are all of the git logs from this period
Willam's updates
- account_manager: don't add the same pubkey more than once
- actionbar placeholder
- actionbar: remove border on reply button, add expand animation
- actionbar: support both dark and light buttons
- Add forward navigation animation
- add hover to profile map demo
- add --light lightmode flag to previews and notedeck
- add my pubkey to the timeline query for testing
- add test queries for elsat
- add vertical separators between timelines
- allow missing profiles in account switcher
- allow multiple invocations of --sec
- always have some default timeline
- app: make ndb public
- a quick note about the View trait
- args: allow filter files and raw filters on cli
- bump timeline filter limit
- cap size of remote filter limits
- change selection color to purple
- check: remove duplicate and disable wasm checks
- ci: disable wasm builds for now
- cli: add --sec argument to quickly add an account
- clippy postbox cleanups
- crates: add bitflags
- damus: make relay pool public
- darker quote reposts for mobile
- debug: add some debug logs for keyboard note selection
- deps: using tracing instead of log
- direnv: disable nix direnv on darwin
- direnv: make args explicit so its easy to change
- don't bump timeline when adding notes
- dont since-optimize when we don't have enough notes
- don't use an actual keystorage in Damus test apps
- drafts: clear post after posting
- enable nip10 replies
- enostr: rename Event to Note
- env: allow private things like secret keys
- filter: add default limit
- filters: fix hashtag filters
- filter: unify nostrdb and remote limits
- Fix all warnings
- fixed_window: fix clippy warning
- fix global query
- fix inline note preview colors
- fix light borders for quote reposts
- fix postbox design
- fix scroll area shrinking
- fix some clippy warnings
- fix until filters
- fix warnings
- fonts: always use base fonts for all families
- fun large profile grid preview
- get all missing ids from all timelines
- github: remove pages workflow
- gitignore: add perf files
- hide navigation title on global nav
- ids: find more unknown ids from inline notes
- images: add aspect_fill
- initial inline note previews
- initial navigation
- initial note posting
- initial postbox for testing
- initial post box view
- initial post reply view
- initial refactor in preparation for routing
- input: fix deadlock on resize
- input: handle raw events
- input: process input once
- input: switch to scanning over raw input events
- integrate sidebar into main view
- introduce View and Previews traits
- irc mode
- ircmode: tighten username
- keys: actually use the keystore
- lighter gray for inline previews in white mode
- list: switch from arc mutext to rc refcell
- load timelines from commandline
- log: reduce spammy new note log
- log relay subscriptions
- make notedeck front and center
- mobile: add lots of top padding on mobile
- mobile: a tad more padding at the top
- mobile: black panel bg color
- mobile: don't add hover on mobile
- mobile: make mobile flag runtime-configurable
- mobile: simplify is_mobile
- mobile: use my timeline for testing again
- move account_login_view to ui submodule
- move add_space to its correct location
- nip10: fetch unknown replied-to notes
- nip10: show initial reply information on notes
- nix: add openssl dep for reqwest
- nix: make android emulator optional
- nostrdb: bump to support timeline queries
- note: don't allow nested note previews
- note: support nprofile mentions
- perf: don't clone bytes via a more specialized function
- perf: fix continuous repaint
- perf: profiling note content rendering
- popup: increase fixed window margin
- popup: simplify borrow
- postbox: add focused state
- postbox: add focus shadow from figma
- post: full available width
- postview: add vertical scroll
- previews: remove central panel frame
- profile: add about and username to profile previews
- profiles: introduce DisplayNames
- profiling: update puffin version
- queries: add a few more test queries
- queries: set reasonable initial query sizes
- queries: update hashtags query
- readme: add usage
- readme: document previews
- readme: make it clear that its for desktop
- readme: make it clear that nix is optional for non-android dev
- readme: show notedeck preview
- refactor: move fixed_window to ui
- refactor: move note into its own widget
- refactor: rename widgets to ui
- refactor: use map instead of explicit
if let - remote: use default_remote_limit instead of hardcoding
- remove context from DesktopSidePanel
- remove minimum window size
- remove useless struct
- render_pfp: only depend on imgcache
- reset virtual list if notes are spliced into timeline
- set tooltip delay to 100ms
- side_panel: return more detailed side panel responses
- simplify is_mobile check
- simplify tab underline calculation
- since filter optimization
- slightly larger pfpfs
- small inline preview pfps
- style: initial logic for mobile style
- style: less bubbly
- style: realtime hover interactions
- style: set 0 duration tooltip delay
- Switch to egui master to fix wgpu issues
- switch to glow for now
- switch to rustls-tls-native-roots
- tabs: select notes & replies by default
- test: add test timeline query
- test: update test profile with a banner
- test: use my timeline query by default for testing
- textmode: adjust name sizing so it doesn't bump the column
- textmode: fix coloring of abbreviated names
- textmode: no previews in textmore for now
- theme: update to correct colors based on figma design
- timeline: don't hide on resize
- timeline: refactor tabs into TimelineView
- timeline: use strips instead of panels
- ui: add banners to profile previews
- ui: add feathering-resistant hline separator fn
- ui: add frame around note previews
- ui: add initial Profile hover previews
- ui: add profile picture hover animation
- ui: integrate egui-tabs for notes & replies selector
- ui: introduce profile picture widget
- ui: make pixel sizes correct, use more of the figma
- ui: move RelayView into ui module
- ui: only inline preview kind1 notes for now
- ui: reduce vertical padding for more compact timelines
- ui: remove some old note ui comments
- ui: simplify note widget
- ui: switch to flags for note options
- update slow timeline query
- update to latest nostrdb, adding tag support
- update version in comment because I still use this on my laptop
- use egui_virtual_list for rendering
- use unique id for post/reply view
- weird actionbar experiment
- we should just called this damus
- widgets: begin organizing ui components into widgets
- working notes + notes&replies
kernelkind's updates
- account_management: refactor
- AccountManagementView
- AccountManager: add ability to make a selection
- AccountSelectionWidget
- Account switcher
- Add AccountManager to app
- Add custom visual themes
- Add flag to emulate mobile during preview
- Add keypair & update pubkey
- Add login key parsing
- Add login manager
- Add MacOS key storage
- Add MobileAccountLoginView
- Add modular custom text styles
- Add monospace text style
- Add nix-shell for macos android development
- Add nostr-sdk dependency
- Add precommit hook to suggest proper formatting
- Add preview for RelayView
- Add relay view
- add reqwest as dependency
- Add SimpleProfilePreview
- Add ui_test_harness binary implementation
- Add warn color and highlight color
- app: add accounts to Damus & mock
- Apply app style to AccountLoginView
- Apply cargo fmt
- Conditionally compile MacOS key storage code
- Constrain app minimum size
- Create account login panel
- Create side panel & global popup
- enostr: expose RelayStatus
- Extract the sample relay to test_data for reuse
- impl linux credential storage
- Integrate account switcher to side panel
- Integrate global popup into app
- login: Add key loading & error to mobile
- macos_key_storage: runner ignore tests
- migrate AccountManagementView to enostr Keypair
- Migrate to new AccountManagementView conception
- Move login business logic to LoginManager
- move login logic from promise to async fns
- Move preview controller out of account_manager.rs
- move test account creation & apply to global popup
- Pfp integration to side panel
- refactor account switcher & management previews
- Refactor 'ui tests' conception to previews
- reintroduce account management
- reintroduce account switcher
- remove nostr-sdk
- Rename PersistState -> StateInMemory
- select first account
- Seperate mobile dark color theme into its own func
- update cargo.lock to reflect toml change
- Update egui 0.26.1 -> 0.27.1
- Use app_creation for common app setup functions
- Use custom style in app
- use nostr in enostr
Stats
name added removed commits kernelkind <kernelkind@gmail.com> +6844 -1979 58 William Casarin <jb55@jb55.com> +9733 -5583 194Damus iOS
Added
- Ability to create highlights (ericholguin)
- Add ability to mute hashtag from SearchView (Charlie Fish)
- Add ability to mute words, add new mutelist interface (Charlie) (William Casarin)
- Added callbackuri for a better ux when connecting mutiny wallet nwc (ericholguin)
- Added nip10 marker replies (William Casarin)
- Added title image and tags to longform events (ericholguin)
- Add event content preview to the full screen carousel (Daniel D’Aquino)
- Add First Aid solution for users who do not have a contact list created for their account (Daniel D’Aquino)
- Add marker nip10 support when reading notes (William Casarin)
- Add video cache to save network bandwidth (Daniel D’Aquino)
- Completely new threads experience that is easier and more pleasant to use (Daniel D’Aquino)
- Connect to Mutiny Wallet Button (ericholguin)
- Highlights (NIP-84) (ericholguin)
- Notification reminders for Damus Purple impending expiration (Daniel D’Aquino)
- Proxy Tags are now viewable on Selected Events (ericholguin)
- Relay fees metadata (ericholguin)
- Revamp emoji picker to be less error-prone and add search, frequently used, and multiple skin tone support capabilities (Terry Yiu)
- Show list of quoted reposts in threads (William Casarin)
Changed
- Added first aid contact damus support email (alltheseas)
- Add support for Apple In-App purchases (Daniel D’Aquino)
- Always strip GPS data from images (kernelkind)
- Change reactions to use a native looking emoji picker (Terry Yiu)
- Errors with an NWC will show as an alert (ericholguin)
- Improve UX around video playback (Daniel D’Aquino)
- Moved paste nwc button to main wallet view (ericholguin)
- Relay config view user interface (ericholguin)
- Relay detail design (ericholguin)
- Updated Zeus logo (ericholguin)
Fixed
- Fix broken GIF uploads (Daniel D’Aquino)
- Fix bug that would cause connection issues with relays defined with a trailing slash URL, and an inability to delete them. (Daniel D’Aquino)
- Fixed issue where some replies were including the q tag (William Casarin)
- Fixed issue where timeline was scrolling when it isn't supposed to (William Casarin)
- Fixed threads not loading sometimes (William Casarin)
- Fixed wallet not disconnecting when a user logs out (ericholguin)
- Fix emoji reactions being cut off (ericholguin)
- Fix ghost notifications caused by Purple impending expiration notifications (Daniel D’Aquino)
- Fix image indicators to limit number of dots to not spill screen beyond visible margins (ericholguin)
- Fix in-app purchase issue that would trigger an error on purchase before confirming the account information. (Daniel D’Aquino)
- Fix issue where bootstrap relays would inadvertently be added to the user's list on connectivity issues (Daniel D’Aquino)
- Fix missing Mute button in profile view menu (Terry Yiu)
- Fix nostrscripts not loading (William Casarin)
- Fix profile not updating bug (William Casarin)
- Fix stale feed issue when follow list is too big (Daniel D’Aquino)
- Fix thread bug where a quote isn't picked up as a reply (William Casarin)
- Fix welcome screen not showing if the user enters the app directly after a successful checkout without going through the link (Daniel D’Aquino)
- Improve reliability of contact list creation during onboarding (Daniel D’Aquino)
- Issue where NWC Scanner view would not dismiss after a failed scan/paste (ericholguin)
Stats
name added removed commits Fonta1n3 <fontainedenton@googlemail.com> +1 -0 1 Sean Kibler <skibler@protonmail.com> +13 -2 1 alltheseas <64376233+alltheseas> +65 -1 4 Transifex <transifex@transifex.com> +581 -39 36 Terry Yiu <git@tyiu.xyz> +763 -1383 8 William Casarin <jb55@jb55.com> +1017 -1564 49 ericholguin <ericholguin@apache.org> +1962 -643 13 Daniel D’Aquino <daniel@daquino.me> +3885 -761 48 -
 @ 8dc86882:9dc4ba5e
2024-09-02 15:50:01
@ 8dc86882:9dc4ba5e
2024-09-02 15:50:01Today I saw a YouTube video from one of the privacy related channels, Techlore maybe? I don't exactly remember. Either way this particular video was going over the pluses and minuses of Android and iOS; and it has made me reconsider some things. I have one of each type of phone and jump back and forth a bit, but always thought I would end on Android. I'm not feeling that way anymore.
After really getting to understand Apple's Advanced Data Protection I think I came to the conclusion that my iPhone more than meets my needs and does everything I like. Yeah, Android sounds like it has most of the privacy coolness as far as mods, roms, and apps, but my iPhone is easily fully encrypted along with iCloud. The few services that aren't are covered by my Proton plan. It also allows me to stop paying for services I may not really need.
- I use and pay for Ente photos, which is great, but my Apple photos are already encrypted and backed up. I don't think I need to be paying for the extra service.
- The Apple Notes app falls under the fully encrypted side, and I can use the free version of Standard Notes for other things.
- I still use Signal Messenger where the OS doesn't matter as much.
- MySudo which I use for numbers is transferable between OSs also.
That's really about it, I mainly use my phone for Email, Calendar, Messaging, Notes, some social, and photos. I don't think I need anything special beyond that. The insecure apps I use on either platform keep their risks though Apple isn't an advertising company, so I feel they are less likely to abuse anything, at least for now. I wonder what other folks thoughts are. Feel free to share.
Cheers!
plebone
-
 @ df8f0a64:057d87a5
2024-10-10 15:18:39
@ df8f0a64:057d87a5
2024-10-10 15:18:39書き散らす動機
残暑続きからの急な気温低下で鼻炎がひどくなる今日この頃、皆様お元気でしょうか
株主への抗議のために退職してから2ヶ月半、流石に暇を持て余してきました 時間がある上に能動的に働く気も起きず、ひたすらボーッとしたりうねうね考え事をする日々です 幸いにして人生も折り返しにさしかかる頃になり、時折「今、人生が終わって構わないのでは?」というようなことも考えたりします (鬱病既往歴ありますが私は元気です)
子どものお迎えを終えて、いつもどおり夕食をとり、またうねうねしているうちに ふと、6年前の年末に急死された、仕事でお世話になったTさんのことを思い出しました
子を寝かしつけてもまだ頭の中をぐるぐるしていたので、ここに吐き出してすっきりしようという魂胆です
Tさんとの出会い
私のキャリアの(ほぼ)スタートはVC(ベンチャーキャピタル)でした 誰のせいでもないとある経緯もあり、周囲からは警戒され避けられ、わずか6年ではありますが、 インナーサークルに入り込めない時期を過ごし、当時の上司と二人、とにかくやれることをやり続ける毎日でした
いつものようにピッチイベントに参加しているとき、近くの席にいたスーツ姿の3人組と目が一瞬合います
「事業会社の人だ」
協調投資やファンド出資のきっかけを掴むべく、その3人に話かけます
「よろしければ弊社投資先のご紹介や御社の...」
ひととおりの挨拶を済ませ、この人たちにも避けられるんだろうと思いながらも要件を切り出します
「是非やりましょう」
いつもとは違う嬉しい返事をくれたのがTさんでした
面倒見の良い他社の先輩
そのときの3人組であるMさん・Iさん・Tさんには、私の仕事人生の中で最もお世話になったと言っても過言ではありません
ファンドの営業を受けていただき、協調投資を行い、VCからの転職後にも協業相手として他部署のキーマンをご紹介いただき...
社会人になったばかりの私の、今思い返せば恥ずかしい(部下がこんな提案したら卒倒する)レベルの提案を、 誰もが知る一流企業の多忙な役職持ちであるにも関わらず、毎回一時間も割いて丁寧に対応してくださる心の広い方でした
当時、VCと接点をもつような事業会社の対スタートアップ部隊は、本業でご活躍されている方が兼任で取り組むパターンが多く、Mさん・Iさん・Tさんももちろんそう
その後も昇進され、最後には本社の取締役に。今年遂に退任され、所謂「あがり」でしょうか、子会社の取締役に異動 長い社会人人生をほぼ走りきり、有終の美を飾ろうとする時期にさしかかっています
でもTさんはそこにはいません
残される側
冒頭触れたとおり、Tさんは6年前のこの時期に急死されました 死因については、Tさんのご友人がFBに投稿していた文章を読んでも、Iさんに聞いてもわからない
悲しいかな、四十年近く生きていると、死因が明かされない理由がわかるようになる機会が一度や二度はあります Tさんもおそらくそうだったのでしょう
直前まで、Iさんと一緒にベイエリアに出張され、楽しそうなコメントと共に写真を投稿されていたのに 晩婚なのか再婚なのか、とにかくご結婚されて一年ちょっと。お子様も生まれたばかりだったのに Tさんは近い人間に心中を隠して、静かにこの世を去りました
あなたの快い返事に、どれほど私が救われたのか 転職後の提案のとき、受付で顔を出してすぐ「元気?」と声をかけてくださったことがどれほど私を安心させてくれたか あなたが声をかけてくれる度、私の社会人としての成果が生まれたことに、私は十分に感謝を伝えられていません
まだしばらく残る理由
振り返って、Tさんのように誰かの人生をenhanceできたのか?と自分に問うと、まだできたとは思えません。残念ですが
今ここで死んでも私は構わないけど、まだもうちょっと頑張るべきかな、老いてから誰かに感謝をしてもらうまで生きてみてもいいかな
そうふと思い直しているうちに日付が変わりました
-
 @ ff6187a2:ddbe1be7
2024-10-24 12:54:45
@ ff6187a2:ddbe1be7
2024-10-24 12:54:45Happy Halloween
-
 @ 1f9e547c:8af216ed
2024-07-13 07:37:05
@ 1f9e547c:8af216ed
2024-07-13 07:37:05Opinion about Bitcoin Wallet Crypto Ethereum (android)
For archival purposes
Atomic Wallet suffers hack on June 2023
Sources
Atomic Wallet users have been left wanting more answers, despite the decentralized wallet provider finally releasing a full “event statement” about the June exploit — which some estimate has run up to $100 million in losses.
In a June 20 blog post — the first major update from the firm since the June 3 exploit — Atomic Wallet claimed there have been no new confirmed cases after initial reports of the hack.
Atomic Wallet Was Breached by North Korean Hackers: Elliptic
Atomic Wallet users might have fallen victim to Lazarus, the infamous North Korean hacking group, said blockchain intelligence firm Elliptic in a blog post on Tuesday.
Early Saturday morning, the team behind Atomic, a non-custodial crypto wallet, announced that some users were compromised and lost the funds from their wallets. According to the company, the number of incidents did not exceed 1% of "monthly active users." The announcement followed multiple reports on Reddit from users complaining their wallets had been drained.
WalletScrutiny #nostrOpinion
-
 @ b60c3e76:c9d0f46e
2024-05-15 10:08:47
@ b60c3e76:c9d0f46e
2024-05-15 10:08:47KRIS menjamin semua golongan masyarakat mendapatkan perlakuan sama dari rumah sakit, baik pelayanan medis maupun nonmedis.
Demi memberikan peningkatan kualitas layanan kesehatan kepada masyarakat, pemerintah baru saja mengeluarkan Peraturan Presiden (Perpres) nomor 59 tahun 2024 tentang Jaminan Kesehatan. Melalui perpres itu, Presiden Joko Widodo (Jokowi) telah menghapus perbedaan kelas layanan 1, 2, dan 3 dalam Badan Penyelenggara Jaminan Sosial atau BPJS Kesehatan.
Layanan berbasis kelas itu diganti dengan KRIS (Kelas Rawat Inap Standar). Berkaitan dengan lahirnya Perpres 59/2024 tentang Perubahan Ketiga atas Perpres 82/2018 tentang Jaminan Kesehatan, Presiden Joko Widodo telah memerintahkan seluruh rumah sakit yang bekerja sama dengan BPJS Kesehatan melaksanakannya.
Kebijakan baru itu mulai berlaku per 8 Mei 2024 dan paling lambat 30 Juni 2025. Dalam jangka waktu tersebut, rumah sakit dapat menyelenggarakan sebagian atau seluruh pelayanan rawat inap berdasarkan KRIS sesuai dengan kemampuan rumah sakit.
Lantas apa yang menjadi pembeda dari sisi layanan dengan layanan rawat inap sesuai Perpres 59/2024? Dahulu sistem layanan rawat BPJS Kesehatan dibagi berdasarkan kelas yang dibagi masing-masing kelas 1, 2, dan 3. Namun, melalui perpres, layanan kepada masyarakat tidak dibedakan lagi.
Pelayanan rawat inap yang diatur dalam perpres itu--dikenal dengan nama KRIS—menjadi sistem baru yang digunakan dalam pelayanan rawat inap BPJS Kesehatan di rumah sakit-rumah sakit. Dengan KRIS, semua golongan masyarakat akan mendapatkan perlakuan yang sama dari rumah sakit, baik dalam hal pelayanan medis maupun nonmedis.
Dengan lahirnya Perpres 59/2024, tarif iuran BPJS Kesehatan pun juga akan berubah. Hanya saja, dalam Perpres itu belum dicantumkan secara rinci ihwal besar iuran yang baru. Besaran iuran baru BPJS Kesehatan itu sesuai rencana baru ditetapkan pada 1 Juli 2025.
“Penetapan manfaat, tarif, dan iuran sebagaimana dimaksud ditetapkan paling lambat tanggal 1 Juli 2025,” tulis aturan tersebut, dikutip Senin (13/5/2024).
Itu artinya, iuran BPJS Kesehatan saat ini masih sama seperti sebelumnya, yakni sesuai dengan kelas yang dipilih. Namun perpres itu tetap berlaku sembari menanti lahirnya peraturan lanjutan dari perpres tersebut.
Kesiapan Rumah Sakit
Berkaitan dengan lahirnya kebijakan layanan kesehatan tanpa dibedakan kelas lagi, Kementerian Kesehatan (Kemenkes) menegaskan mayoritas rumah sakit di Indonesia siap untuk menjalankan layanan KRIS untuk pasien BPJS Kesehatan.
Kesiapan itu diungkapkan oleh Dirjen Pelayanan Kesehatan Kemenkes Azhar Jaya. “Survei kesiapan RS terkait KRIS sudah dilakukan pada 2.988 rumah sakit dan yang sudah siap menjawab isian 12 kriteria ada sebanyak 2.233 rumah sakit,” ujar Azhar.
Sebagai informasi, KRIS adalah pengganti layanan Kelas 1, 2, dan 3 BPJS Kesehatan yang bertujuan untuk memberikan layanan kesehatan secara merata tanpa melihat besaran iurannya.
Melalui KRIS, rumah sakit perlu menyiapkan sarana dan prasarana sesuai dengan 12 kriteria kelas rawat inap standar secara bertahap. Apa saja ke-12 kriteria KRIS itu?
Sesuai bunyi Pasal 46A Perpres 59/2024, disyaratkan kriteria fasilitas perawatan dan pelayanan rawat inap KRIS meliputi komponen bangunan yang digunakan tidak boleh memiliki tingkat porositas yang tinggi serta terdapat ventilasi udara dan kelengkapan tidur.
Demikian pula soal pencahayaan ruangan. Perpres itu juga mengatur pencahayaan ruangan buatan mengikuti kriteria standar 250 lux untuk penerangan dan 50 lux untuk pencahayaan tidur, temperature ruangan 20--26 derajat celcius.
Tidak hanya itu, layanan rawat inap berdasarkan perpres itu mensyaratkan fasilitas layanan yang membagi ruang rawat berdasarkan jenis kelamin pasien, anak atau dewasa, serta penyakit infeksi atau noninfeksi.
Selain itu, kriteria lainnya adalah keharusan bagi penyedia layanan untuk mempertimbangkan kepadatan ruang rawat dan kualitas tempat tidur, penyediaan tirai atau partisi antartempat tidur, kamar mandi dalam ruangan rawat inap yang memenuhi standar aksesibilitas, dan menyediakan outlet oksigen.
Selain itu, kelengkapan tempat tidur berupa adanya dua kotak kontak dan nurse call pada setiap tempat tidur dan adanya nakas per tempat tidur. Kepadatan ruang rawat inap maksimal empat tempat tidur dengan jarak antara tepi tempat tidur minimal 1,5 meter.
Tirai/partisi dengan rel dibenamkan menempel di plafon atau menggantung. Kamar mandi dalam ruang rawat inap serta kamar mandi sesuai dengan standar aksesibilitas dan outlet oksigen.
Azhar menjamin, Kemenkes akan menjalankan hal tersebut sesuai dengan tupoksi yang ada. “Tentu saja kami akan bekerja sama dengan BPJS Kesehatan dalam implementasi dan pengawasannya di lapangan,” ujar Azhar.
Berkaitan dengan perpres jaminan kesehatan itu, Direktur Utama BPJS Kesehatan Ghufron Mukti menilai, perpres tersebut berorientasi pada penyeragaman kelas rawat inap yang mengacu pada 12 kriteria. "Bahwa perawatan ada kelas rawat inap standar dengan 12 kriteria, untuk peserta BPJS, maka sebagaimana sumpah dokter tidak boleh dibedakan pemberian pelayan medis atas dasar suku, agama, status sosial atau beda iurannya," ujarnya.
Jika ada peserta ingin dirawat pada kelas yang lebih tinggi, kata Ghufron, maka diperbolehkan selama hal itu dipengaruhi situasi nonmedis. Hal itu disebutkan dalam Pasal 51 Perpres Jaminan Kesehatan diatur ketentuan naik kelas perawatan.
Menurut pasal tersebut, naik kelas perawatan dilakukan dengan cara mengikuti asuransi kesehatan tambahan atau membayar selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya yang harus dibayar akibat peningkatan pelayanan.
Selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya pelayanan dapat dibayar oleh peserta bersangkutan, pemberi kerja, atau asuransi kesehatan tambahan.
Ghufron Mukti juga mengimbau pengelola rumah sakit tidak mengurangi jumlah tempat tidur perawatan pasien dalam upaya memenuhi kriteria KRIS. "Pesan saya jangan dikurangi akses dengan mengurangi jumlah tempat tidur. Pertahankan jumlah tempat tidur dan penuhi persyaratannya dengan 12 kriteria tersebut," tegas Ghufron.
Penulis: Firman Hidranto Redaktur: Ratna Nuraini/Elvira Inda Sari Sumber: Indonesia.go.id
-
 @ 266815e0:6cd408a5
2024-05-09 17:23:28
@ 266815e0:6cd408a5
2024-05-09 17:23:28Lot of people are starting to talk about building a web-of-trust and how nostr can or is already being used as such
We all know about using the kind:3 following lists as a simple WoT that can be used to filter out spam. but as we all know it does not really signal "trust", its mostly just "I find your content interesting"
But what about real "trust"... well its kind of multi-denominational, I could trust that your a good developer or a good journalist but still not trust you enough to invite you over to my house. There are some interesting and clever solutions proposed for quantifying "trust" in a digital sense but I'm not going to get into that here. I want to talk about something that I have not see anyone discuss yet.
How is the web-of-trust maintained? or more precisely how do you expect users to update the digital representation of the "trust" of other users?
Its all well and good to think of how a user would create that "trust" of another user when discovering them for the first time. They would click the "follow" button, or maybe even rate them on a few topics with a 1/5 star system But how will a user remove that trust? how will they update it if things change and they trust them less?
If our goal is to model "trust" in a digital sense then we NEED a way for the data to stay up-to-date and as accurate as possible. otherwise whats the use? If we don't have a friction-less way to update or remove the digital representation of "trust" then we will end up with a WoT that continuously grows and everyone is rated 10/10
In the case of nostr kind:3 following lists. its pretty easy to see how these would get updated. If someone posts something I dislike or I notice I'm getting board of their content. then I just unfollow them. An important part here is that I'm not thinking "I should update my trust score of this user" but instead "I'm no longer interested, I don't want to see this anymore"
But that is probably the easiest "trust" to update. because most of us on social media spend some time curating our feed and we are used to doing it. But what about the more obscure "trust" scores? whats the regular mechanism by which a user would update the "honestly" score of another user?
In the real world its easy, when I stop trusting someone I simply stop associating with them. there isn't any button or switch I need to update. I simply don't talk to them anymore, its friction-less But in the digital realm I would have to remove or update that trust. in other words its an action I need to take instead of an action I'm not doing. and actions take energy.
So how do we reflect something in the digital world that takes no-energy and is almost subconscious in the real world?
TLDR; webs-of-trust are not just about scoring other users once. you must keep the score up-to-date
-
 @ 4fe4a528:3ff6bf06
2024-09-01 12:45:44
@ 4fe4a528:3ff6bf06
2024-09-01 12:45:44One of the main motivational factors for people to buy bitcoin is it’s ability to store value over time. During harvest we are doing the same thing. We have now harvested our garlic and 1/2 of our onions because if we don’t use the sun’s energy to cure the plants before winter they will start to rot. Let me explain why God has made the world this way; but, first let me explain why storing things isn’t evil.
“Do not store up for yourselves treasures on earth, where moth and rust consume and where thieves break in and steal; but store up for yourselves treasures in heaven, where neither moth nor rust consumes and where thieves do not break in and steal. For where your treasure is, there your heart will be also”. Matt. 6:19-21
Is it wrong, then to have a retirement portfolio or even to care about the material things of this world for ourselves or for others? The answer is again both no and yes. The no comes from the fact that this passage is not the only one in the Bible speaking to questions of wealth and provision for those who are dependent on us. Other passages counsel prudence and forethought, such as, “Those who gather little by little will increase [wealth]” (Proverbs 13:11b), and, “The good leave an inheritance to their children’s children” (Proverbs 13:22).
God guides Joseph to store up food for seven years in advance of a famine (Genesis 41:25-36), and Jesus speaks favorably in the Parable of the Talents (Matt. 25:14-30). In light of the rest of Scripture, Matthew 6:19-21 cannot be a blanket prohibition. But the yes part of the answer is a warning, summed up beautifully in verse 21, “Where your treasure is, there will your heart be also.” In other words, the possessions you own will change you so that you care more about the possessions than about other things.” So choose carefully what you own, for you will inevitably begin to value and protect it to the potential detriment of everything else.
How are we to discern the line between appropriate and inappropriate attention to wealth? Jesus answers, “Strive first for the kingdom of God and his righteousness, and all these things will be given to you” So if you believe your heart is following God’s direction go ahead and harvest your crops and / or buy some bitcoin. If you would have bought bitcoin one year ago, you would have 127% more purchasing power now. Let’s keep on fearing God and keeping his commandments.
-
 @ af9c48b7:a3f7aaf4
2024-08-27 16:51:52
@ af9c48b7:a3f7aaf4
2024-08-27 16:51:52Chef's notes
Easy recipe with simple ingredients. This recipe uses some store bought, precooked items as way to cut down on cook time. I recommend letting the vegetables thaw if you don't like them on the firm/crunchy side.Feel free to substitute fresh ingredients if you have the time and want to make the extra effort.
Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 50 min
- 🍽️ Servings: 8-10
Ingredients
- 2 (8 oz) packages refrigerated crescent rolls (dough sheets preferred)
- 1 pound cooked rotisserie chicken (deboned and chopped)
- 2 table spoons of butter
- 2 (10 once) packages of frozen mixed vegetables
- 1 (15 once can sliced potatoes (drained)
- 1 (10.5 once) can condensed cream of chicken soup
- 1 (10.5 once) can condensed cream of mushroom soup
- 1/2 cup milk
- salt and ground pepper to taste
Directions
- Preheat oven to 350 degrees F (175 degrees C). Line the botton of 9x13-inch baking dish with one can of crescent roll dough. If you don't get the sheet dough, be sure to pinch the seams together.
- Melt the butter in a sauce pan over medium heat. Then add the chicken, mixed vegetables, and sliced potatoes (recommend cutting into smaller pieces). Cook, stirring frequently, until vegetables are thawed and mixture is heated through, 5 to 7 minutes.
- While the mixed vegetables are heating, warm both cans of condensed soup in a seperate pan over medium-low heat. Slowly add milk and cook, stirring frequently, until combined and heated through, about 3 minutes.
- Add the soup mixture to the chicken mixture, then pour into the baking dish. Top with the second can of crescent roll dough. Feel free to cut some slits in dough if you are using the dough sheets. Cover lightly with foil to prevent the crescent roll dough from browning too quickly.
- Bake in oven until heated through and dough is a golden brown. Cook time should be around 45-50 minutes I reommend removing the foil for the last 10 minutes to get a golden crust. Be sure to keep a close watch on the crust after removing the foil because it will brown quickly.
-
 @ 472f440f:5669301e
2024-10-16 01:57:41
@ 472f440f:5669301e
2024-10-16 01:57:41Over the last four years bitcoin has, among other things, established itself as an incredible corporate treasury asset that benefits those who adopt it as such. Microstrategy is the shining example of this theme going from a company that was hovering barely above a ~$1B market cap in mid-2020 to a ~$40B market cap company holding more than 1% of the 21,000,000 bitcoin that will ever exist. Microstrategy's success has emboldened a number of other publicly trader companies to follow suit. Bitcoin as a corporate treasury asset is well on its way to becoming a standard. If you run a business that doesn't hold bitcoin on its balance sheet you are doing yourself, your customers and your shareholders a disservice.
This is a trend that has its legs under it and will accelerate moving forward. A trend that I believe will emerge this cycle is incorporating bitcoin into real estate markets. Leon Wankum has been beating the drum about this for the last few years and I had the pleasure of sitting down with him this morning to record an episode of TFTC that will be published tomorrow morning. Leon is a real estate developer in Germany and he has made it his mission to educate and warn others in real estate about the demonetization of real estate that is under way due to the fact that bitcoin exists and it provides a far superior alternative.
These are pretty stark numbers. Nothing highlights the superior monetary properties of bitcoin better than looking at a chart of the average price of a home priced in USD v. bitcoin.
Since 2016: +46% in USD -99% in BTC
Since 2020: +34% in USD -70% in BTC
The funny thing is that an overwhelming majority of the individuals who make their living in real estate markets do not understand that this is happening to them. Many think they are doing exceptionally well all things considered. Sure, there may be a bit of a slow down and price retraction due to a couple of years of relatively elevated interest rates, but don't worry! The Fed is lowering rates again and the good times are about to start back up. Nothing could be further from the truth. This trend is going to continue unabated until bitcoin is fully monetized and those is the real estate industry, particularly real estate developers and those who lend capital to developers, should seriously take the time to understand what is happening to them.
Real estate is the largest store of value asset in the world at the moment. The most common number that is thrown around for the total size of the market is $300 TRILLION. $300 TRILLION of wealth being stored in an asset that is illiquid, comes with maintenance costs, taxes, insurance premiums, and susceptible to extreme weather event, among other things. Compared to bitcoin - which is extremely liquid, saleable, divisible and hard to confiscate, real estate is a far superior asset to store your wealth in. This is something that I'm sure is well understood by many of you reading this letter.
What's less understood is the dynamics of the real estate development market over the last few years, which have been severely hindered by elevated interest rates. The higher interest rate environment coupled with the inflationary pressures that forced rates higher in the first place have put developers in a predicament; they have a higher cost of capital to start new projects with raw material prices that are still much higher than they were before the economic lock downs of 2020-2022. This has led to a scenario where it isn't advantageous to start new projects and the projects that broke ground in 2021-2023 are finding that they need to incur more debt to get their developments across the finish line.
Despite the fact that interest rates are on their way back down, it doesn't seem like the economics of these projects are going to materially improve in the short to medium-term as headline inflation begins to creep back up. Couple this with the fact that the jobs market is cratering while real wages struggle to keep up with inflation and many builders are going to find themselves in a situation where they do actually complete a development problem but their cash flow suffers because their customers can't afford the inflated rents that builders will have to charge to get a return on their outlaid capital. Many will be put in a situation where they are forced to be happy with lower rents (cash flow) or sit on the sidelines making no cash flow.
The post-1971 era that brought with it a booming real estate industry is suffering the same fate as the bond market; the generation bull market is over. Real estate prices may go up, but that will be nothing more than a mirage of wealth creation. The unit of account those prices are built on is in dollars, which are being debased at an accelerating rate. Developers, banks and borrowers need to de-risk their real estate exposure and, as Leon points out, bitcoin is the only way to do this in an effective way.
Moving forward developers will have to finance by dual collateralizing their debt with the real estate and bitcoin. In the graphic below Leon illustrates what this type of financing structure will look like. Instead of taking $10m of debt to finance a project and putting it all into materials, construction and marketing, a developer will take out a $10m loan, put $1m in bitcoin and the rest toward the development project. Over the course of the construction of the real estate project, bitcoin will sit in the credit structure and, if held for 4+ years, should increase significantly in value. Saving the builder from risk of default and providing him some optionality in terms of what he can do with the project once it's finished.
In this scenario downside risk is contained - a developer isn't pouring all of the cash into bitcoin at the beginning so the worst case scenario is that bitcoin goes to zero (highly unlikely) and they can eat the small loss and hope to make up with it via cash flows once a project is finished, while upside potential is enormous. Bitcoin is still monetizing and having exposure to the hardest monetary asset the world has ever while it's monetizing has proven to be massively beneficial.
We are still in the early days of bitcoin and this idea will likely seem absolutely insane to most Tradfi investors, but I strongly believe that developers, banks and end consumers who don't leverage this type of bitcoin structured credit will be cooked in the long-run. And those that take advantage of this type of structure first will be considered geniuses in 20 years.
There are many more nuanced benefits to this strategy; holding bitcoin allows landlords and management companies to weather ongoing maintenance costs throughout the years, those who take out mortgages dual collateralized with a house and bitcoin not only protect the equity value of their property but could see their equity values increase significantly more than others using vanilla mortgages, and builders who accumulate bitcoin in their treasuries will be able to use better raw materials when building, which leads to more valuable properties that cash flow for longer.
Again, it's going to take time for these types of structures to become commonplace in the market, but I firmly believe this cycle will be the cycle that these strategies get off the ground. In four to five years they will have a track record and after that it will be considered irresponsible not to finance real estate in this way. The banks will begin to demand it.
Final thought... Sinus congestion sucks.
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ a95c6243:d345522c
2024-10-19 08:58:08
@ a95c6243:d345522c
2024-10-19 08:58:08Ein Lämmchen löschte an einem Bache seinen Durst. Fern von ihm, aber näher der Quelle, tat ein Wolf das gleiche. Kaum erblickte er das Lämmchen, so schrie er:
"Warum trübst du mir das Wasser, das ich trinken will?"
"Wie wäre das möglich", erwiderte schüchtern das Lämmchen, "ich stehe hier unten und du so weit oben; das Wasser fließt ja von dir zu mir; glaube mir, es kam mir nie in den Sinn, dir etwas Böses zu tun!"
"Ei, sieh doch! Du machst es gerade, wie dein Vater vor sechs Monaten; ich erinnere mich noch sehr wohl, daß auch du dabei warst, aber glücklich entkamst, als ich ihm für sein Schmähen das Fell abzog!"
"Ach, Herr!" flehte das zitternde Lämmchen, "ich bin ja erst vier Wochen alt und kannte meinen Vater gar nicht, so lange ist er schon tot; wie soll ich denn für ihn büßen."
"Du Unverschämter!" so endigt der Wolf mit erheuchelter Wut, indem er die Zähne fletschte. "Tot oder nicht tot, weiß ich doch, daß euer ganzes Geschlecht mich hasset, und dafür muß ich mich rächen."
Ohne weitere Umstände zu machen, zerriß er das Lämmchen und verschlang es.
Das Gewissen regt sich selbst bei dem größten Bösewichte; er sucht doch nach Vorwand, um dasselbe damit bei Begehung seiner Schlechtigkeiten zu beschwichtigen.
Quelle: https://eden.one/fabeln-aesop-das-lamm-und-der-wolf
-
 @ fd208ee8:0fd927c1
2024-10-09 12:27:53
@ fd208ee8:0fd927c1
2024-10-09 12:27:53Why waste time, looking at other people's stuff?
I get this question a lot, on Nostr, and it feeds immediately back to the next question: Why don't you just build your own client, if you're so smart?
This was a completely new question for me, as I'm used to collaborating with at least one other person, even when doing FOSS stuff. (No, this isn't my first such project; we just used to call it "volunteering" and "sharing the code", which sounds way less glamorous.) It never occurred to me, that a habit of collaboration and interaction was some sign of my ignorance and incompetence, or somehow proof that I can't vomit up "Hello World!" in 5 different programming languages.
I also made the deadly political mistake, when I entered the Nostrsphere, of refusing to call myself a "dev". For me, "dev" is a special title, given to someone doing a specific type of programming (fiddling with GUIs, mostly, which I've only done occasionally, as a sub), whereas the types I've done are "test automation", "development operations", "database management and data curation", "requirements engineering", and "application administration". Because it's so much easier to find someone interested in building a GUI, rather than building AnythingElse, I tend to slide into AnythingElse and it eventually became my professional specialty to be the Girl Friday of every project.

But, in Nostr, there is no AnythingElse category. There are only (GUI) client devs and AllOfTheIdiotsWhoMustBowDownToTheDevs. Which merely doubled my instinct to distance myself from the term. I do not want to join some cargo cult and be pedestalized and regarded as some sort of superhuman everyone owes fealty to, in return for raining GUI presents down on my loyal subjects.
Software engineers are simply people who are skilled craftsman, not gods, and it is fair to point out that some are more skilled than others. It is also completely fair to criticize their products, report bugs, and wonder aloud at endemic low-quality.
Which brings me back to the initial question:
What does the inquisitive dev know, that the others don't?
1) You learn an awful lot about an awful lot, by looking at specs, reviewing code, and trying out various implementations of concepts you are already familiar with. There are, in fact, n number of use cases for every event type, and I've seen so many of them, that I can conjure them up, or invent new ones, on the fly, rather than wasting time inventing similar events. 2) They don't have to explain their concept to you, later, when you interact. Each interaction brings you closer to parallel-levels of knowledge, which raises the signal-strength of the interaction, and widens your own knowledge base, for interacting with third parties. 3) You are increasingly-likely to contribute code or perform some other more-advanced task, for other people, as you don't face the hurdle of adjusting to a new repo or unfamiliar language, while being less-likely to merely fork-and-ignore because you have a standing business relationship with the other developer. 4) If the other dev stops maintaining the repo, you'll be inclined to continue on your own. You may even eventually receive administrative access, rather than needing to fork, as they trust you with their stuff. This means that the risk of the repo becoming abandoned falls, with each active dev snooping around it, even if that is not their primary project. 5) It helps you determine who to focus your energy on interacting with, further. Is this person new to software development, perhaps, but has some interesting transfer-knowledge from some other branch, that has resulted in a surprisingly novel concept? Is this person able to write very clean code, so that merely reading their code feels like mental training for your own craftsman's toolbox?
...and many more reasons, but this is getting too long, so, let's just cut to the chase.
What does a craftswoman want?
But, this still doesn't answer the question of my private motivation. Why do I want to gather all of this knowledge, from those further ahead, than I?
I think Nostr has long moved past the initial stage, where mere speed was of the essence, so that one npub could finally post a note and have it appear on the other npubs' client. That must have felt like a miracle, but it increasingly feels like a disaster, as the steadily-rising complexity of the Nostr ecosystem causes haphazardly-structured and largely-unexamined code bases to begin to atrophy, or result in developers running around at an exhausting speed, with their bug-extinguishers, to put out fire after fire.
I think the time has arrived, for a different kind of development. Maybe even for a different kind of developer. Not replacing the experimentalism that made Nostr fun, but adding the realm of production-quality software engineering. The sort of software development that requires relay administration, testing, support... collaboration, interaction, maybe even someone who does AnythingElse.
I want to build useful, elegant products people enjoy using and feel comfortable relying on. I want them to use them, naturally and happily, to accomplish tasks they consider worthwhile. I don't want them thinking about me, while they use it. The craftswoman should never be greater than her work.
I want them to feel free -- nay, be eager! -- to give me both positive and negative feedback. My assumption is always that our production is imperfect because we are imperfect, so you do us a favor, by pointing out where we can improve. That's why we wish to integrate a feedback form that produces ngit issue events, putting your questions and comments straight on our board.
And there will be an AnythingElse person, reading that board, and responding promptly, rest assured.
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 502ab02a:a2860397
2024-07-13 02:14:11
@ 502ab02a:a2860397
2024-07-13 02:14:11Anna Britt Agnsäter ผู้อุทิศชีวิตให้โภชนาการ แต่โดนโลกบูลลีเพราะอเมริกา?
โลกรับรู้ว่า คุณ Anna Britt Agnsäter (ขอเรียกสั้นๆว่า ป้าแอน) เป็นผู้ที่นำเสนอ ปิรามิดอาหาร คนแรกของโลก และเป็นแบบจำลองที่ทาง USDA นำไปพัฒนาปรับใช้แล้วนำมาเป็น แบบที่ใช้สื่อสารกับคนทั้งโลก ในเรื่องของการกำหนด ประเภทอาหารที่ควรกิน ในช่วงปี 1992-2005 ซึ่งในบทความที่แล้วผมได้เขียนว่า ปิรามิดเวอร์ชั่นที่ป้าแอนคิด กับ ที่อเมริกาเอาไปปรับใช้เป็นคนละตัวกัน แต่โลกทั้งโลกก็บูลลีป้าเอนว่า เป็นสาเหตุของการทำลายสุขภาพคนทั้งโลก ทั้งๆที่ไม่ได้เป็นนักวิทยาศาสตร์ ผมก็เป็นคนนึงที่เคยคิดแบบนั้นครับ และเคยอุทานในใจเบาๆว่า แกเป็นใครนะทำไมถึงนำเสนออะไรแบบนี้มาทำร้ายคนทั้งโลก???
นานวันเข้า ความคิดอีกฝั่งของผมก็บอกมาว่า ประโยคข้างบนเป็นคำบ่นหรือคำถาม
นั่นสิ!!!!! ถ้ามันเป็นคำถาม มันจะทำให้เราได้รู้จักตัวตนป้าแอนและเข้าใจว่าแกได้ทำอะไรลงไปนะ มันควรเป็นคำถามมากกว่าคำบ่น นั่นเลยเป็นเหตุผลที่ทำให้ผมเริ่มขุดเรื่องป้าแอน Anna Britt Agnsäter มากที่สุดเท่าที่จะทำได้ พร้อมที่จะอ่านกันแล้วใช่ไหมครับ
Anna Britt Agnsäter เกิดเมื่อปี 1915 ที่เมือง Älmhult ประเทศสวีเดน (นอกเรื่องนิดนึง เมืองนี้คือเมืองที่ให้กำเนิด IKEA ที่เรารู้จักกันดีเรื่องเฟอร์นิเจอร์ ที่นี่มีพิพิธภัณฑ์อิเกีย ซึ่งปรับปรุงมาจากโกดังแห่งแรกของเขาด้วยครับ) เรียกได้ว่า เกิดในช่วงสงครามโลกครั้งที่1 พอดีเลยครับ
ป้าแอน จบการศึกษาที่โรงเรียนสตรี ในเมือง Ystad ก่อนจะเข้ารับการฝึกสอนเพื่อเป็นครูสอนวิทยาศาสตร์ในครัวเรือน (rural domestic science teacher) ในช่วงปี 1930 ที่โรงเรียนวิทยาศาสตร์ในครัวเรือนในชนบทชื่อว่า Rimforsa ก่อนจะได้รับวุฒิการศึกษาการสอนวิทยาศาสตร์ในครัวเรือนในชนบทในปี 1939 จาก Kvinnliga medborgarskola (civic women’s school) จนกระทั่ง ปี 1943 ถึง 1945 เธอได้เดินทางไปทั่ว Norrland (พื้นที่ภาคเหนือของสวีเดน) โดยได้รับเงินสนับสนุนจาก Kooperativa Förbund (เรียกสั้นๆว่า KF หรือ สมาคมสหกรณ์ ก่อตั้งขึ้นในปี 1899 โดยสหกรณ์ผู้บริโภคในท้องถิ่น 41 แห่ง เป็นผู้นำด้านการค้าปลีกในสวีเดนโดยพัฒนารูปแบบร้านค้าใหม่และใหญ่ขึ้น และเป็นหนึ่งในกลุ่มธุรกิจหลักในสแกนดิเนเวีย ในสมัยนี้คำว่าสหกรณ์อาจจะดูเชยๆ แต่ต้องเข้าใจครับว่ายุคนั้นคือความก้าวหน้ามากๆ และต้องมีความรู้รอบด้านทั้งวิทยาศาสตร์ เศรษฐกิจ การเมือง) เพื่อบรรยายให้คนหนุ่มสาวและแม่บ้านฟังเกี่ยวกับวิธีรับมือกับเสบียงที่มีจำกัดในช่วงสงครามที่ตึงเครียด เนื่องจากอยู่ในภาวะสงครามโลกครั้งที่2

ในปี 1946 ป้าแอนได้รับการแต่งตั้งเป็นหัวหน้าของSwedish Cooperative Union หรือ Kooperativa Förbundets (KF) Provkök (experimental kitchen หรือ ภาษาสมัยนี้น่าจะใกล้เคียงกับ kitchen lab นั่นเอง) ซึ่งเป็นองค์กรที่มีอิทธิพลทางด้านอาหารเป็นอย่างมากในสวีเดน มีบทบาทสำคัญในเศรษฐกิจและสังคมสวีเดน โดยสร้างโอกาสให้แก่สมาชิกและส่งเสริมการพัฒนาที่ยั่งยืนในชุมชนต่าง ๆ ทั่วประเทศ
ป้าแอนทำงานที่นี่นานจนถึงช่วงปี 1980 ขนาดของ KF ก็ใหญ่โตขึ้นมากมาย จนขยายอำนาจและขอบเขตการทำงานไปถึงการเป็นคณะกรรมการทดสอบรสชาติซึ่งทดสอบอาหารกึ่งสำเร็จรูปและอาหารสำเร็จรูปใหม่ด้วย ในจุดนี้ ป้าแอน เล็งเห็นความสำคัญและความรับผิดชอบของผู้ผลิต/ผู้ค้าอาหาร ควรจะขยายความรับผิดชอบครอบคลุมไปจนถึงโต๊ะอาหาร (ในที่นี่น่าจะหมายถึงลูกค้า) นั่นคือเหตุผลที่การติดฉลากอาหารจึงมีความสำคัญมาก ป้าแอนได้มุ่งเน้นให้ความรู้กับผู้บริโภคว่า ‘Weigh up the price against the quality’ หรือ ให้ชั่งน้ำหนักพิจารณาให้ดี ระหว่างราคากับคุณภาพ ตลอดระยะเวลาการทำงาน Anna-Britt Agnsäter ได้รณรงค์เพื่อให้มีการแสดงข้อมูล ให้ผู้บริโภครับทราบ เพื่อคุณภาพชีวิตที่ดีขึ้นและได้ให้คำแนะนำด้านโภชนาการ เพื่อให้เข้าใจได้ง่ายขึ้น ในรูปแบบฉลากโภชนาการ
ในปี 1946 เช่นกันป้าแอนได้มีแผนในการทำ มีแผนที่จะผลิตหนังสือสอนทำอาหารสำหรับสถานการณ์ฉุกเฉิน เพราะบทเรียนในภาวะสงครามโลก ที่ป้าแอนผ่านมาตลอด แต่ไม่สามารถพิมพ์ออกมาได้เนื่องจากกระดาษขาดแคลนเนื่องจากอยู่ในภาวะหลังสงคราม
ในปี 1948-1949 ป้าแอนเดินทางไปอเมริกา เพื่อศึกษาเทคนิคการทำอาหารใหม่ๆ การผลิตภัณฑ์อาหารแช่แข็ง รวมถึงอาหารผงแห้งต่างๆ (dry powder) รวมไปถึงวิทยาศาสตร์การอาหาร (food science) ที่มหาวิทยาลัย Iowa State University การเดินทางมาอเมริกาครั้งนี้เปลี่ยนโลกของป้าแอนเป็นอย่างมาก ในตอนที่ป้าทำงานกับ KF เธอมักจะร่วมงานกับ Hemmens Forskningsinstitut (สถาบันวิจัยในประเทศ) เพื่อจัดหาเครื่องมือในครัวที่ยกระดับมาตรฐานการทำอาหารที่ดียิ่งขึ้น รวมถึงอุปกรณ์การครัว ภาชนะต่างๆที่เข้าเตาอบได้ และจากประสบการณ์ที่อเมริกานี้
ป้าแอนได้จับมือกับ โรงงานเครื่องเคลือบและพลาสติก Gustavsberg และ HFI Anna-Britt Agnsäter พัฒนาช้อนตวง ชุด4ชิ้น ที่วางซ้อนกันได้ ซึ่งเป็นการปฎิวัติวงการอาหารครั้งสำคัญของสวีเดน เรียกว่า “ชุดช้อนตวงมาตรฐาน” ซึ่งจะมีการระบุขนาดที่ชัดเจน 4 ชิ้น ประกอบไปด้วย

ซึ่งทำให้ผู้ใช้สามารถวัดปริมาณวัตถุดิบได้อย่างถูกต้องตามที่สูตรอาหารกำหนด กลายเป็นเครื่องมือที่จำเป็นในครัวเรือนและการประกอบอาหารในเชิงพาณิชย์
แม้การพัฒนา “ชุดช้อนตวงมาตรฐาน” นี้จะเริ่มต้นในสวีเดน แต่นวัตกรรมนี้มีผลกระทบที่กว้างขวางและแพร่หลายไปยังครัวเรือนและอุตสาหกรรมอาหารทั่วโลกจนถึงปัจจุบัน


ในชุดช้อนตวงมาตรฐาน original 4 คุณอาจสังเกตคำนึงที่ไม่ค่อยคุ้นสักเท่าไรคือหน่วย kryddmått
นอกจากชุดช้อนตวงมาตรฐานแล้ว ป้าแอนยังคิดค้นสิ่งต่างๆอีกมากมาย ให้กับวงการอาหารสวีเดน รวมถึงหน่วยวัดใหม่ที่เรียกว่า kryddmått นี้ด้วยครับ ซึ่งมันเป็นหน่วยวัดขนาดเล็กที่ใช้ในการตวงเครื่องเทศและวัตถุดิบปริมาณน้อย โดยหน่วยวัดนี้มีขนาด 1 มิลลิลิตร (ml)ซึ่งถูกกำหนดมาเป็นหน่วยที่เล็กที่สุดซึ่งทำให้มีการจดบันทึกสูตรได้แม่นยำยิ่งขึ้น นั่นเพราะว่า การตวงเครื่องเทศ หรือ เกลือ นั้นหากรสชาติที่เข้มข้น หรือมีการใช้มากเกินไปหรือไม่พออาจทำให้รสชาติของอาหารเปลี่ยนไป การใช้ kryddmått ช่วยให้การวัดปริมาณเครื่องเทศที่ใช้ในสูตรอาหารเป็นไปอย่างแม่นยำและสม่ำเสมอ
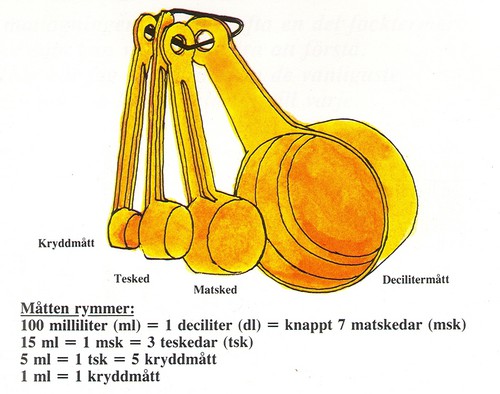
ถือว่าเป็นอีกผลงานคุโณปการที่ป้าแอน ฝากไว้ให้กับโลกนี้ มันมีส่วนสำคัญในการทำให้งานครัวเรือนง่ายขึ้นและมีประสิทธิภาพมากขึ้นผ่านการพัฒนาหน่วยวัดที่แม่นยำและสะดวกในการใช้งาน นวัตกรรมนี้ช่วยให้การทำอาหารเป็นไปอย่างราบรื่นและมีคุณภาพสูงยิ่งขึ้น

ในปี 1951 ป้าแอนได้บูรณะหนังสือการทำอาหารประจำสวีเดนใหม่ทั้งหมด (Vår kokbok) จุดประสงค์ของตำราอาหาร Vår คือการนำเสนอตำราอาหารราคาต้นทุนวัตถุดิบไม่แพง ที่ให้ความรู้เรื่องสารอาหารและใช้งานง่าย นอกจากนี้ยังเป็นการวางวัตถุดิบให้ได้รับสารอาหารที่เพียงพออีกด้วย เพราะในยุคนั้นสวีเดนมีข้อจำกัดในเรื่องอาหารเป็นอย่างมาก
เนื้อหาสูตรอาหารที่ใช้ในหนังสือเล่มนี้กลายเป็นบรรทัดฐานในช่วงทศวรรษ 1950 โดยมีการใช้หน่วยชั่งตวงแบบใหม่ ตามชุดช้อนตวงมาตรฐาน (ปริมาตร) จากของเดิมที่ใช้การชั่งน้ำหนัก ใช้ศัพท์ในการทำอาหารแบบเป็นสากล เช่น ขูด ปอกเปลือก ล้าง เป็นต้น (grate, peel, rinse) จัดอาร์ทเวิคให้แต่ละสูตร สามารถจบได้ในหน้าเดียวไม่ต้องพลิกอ่านหน้าต่อๆไป ทำให้สะดวกในการเปิดแล้วทำตาม การไล่ลำดับอาหาร เปลี่ยนจากการไล่ประเภทอาหาร ไปเป็นไล่ลำดับตามวัตถุดิบหลักของอาหาร ทำให้คนอ่านสามารถบริหารจัดการเมนูได้ง่าย เช่น ไก่ ก็สามารถไล่เรียงได้เลยว่า วันนี้มีไก่ จะทำอะไรกินดี
นอกจากนี้ยังรับประกันว่าทุกสูตรสามารถทำได้จริง เพราะป้าแอนลงมือทดสอบสูตรด้วยตัวเองทุกสูตร นอกจากนี้ยังคงมีการแนะนำให้ใช้การวัดอุณหภูมิในการทำอาหารด้วยเพื่อความเป๊ะในรสชาติ เนื่องจากป้าแอนเห็นตอนไปดูงานที่อเมริกา จนถึงทุกวันนี้ Vår kokbok เป็นหนึ่งในตำราอาหารที่ขายมากที่สุดในโลกด้วยยอดขายมากกว่า 2.3 ล้านเล่มนับตั้งแต่เริ่มต้น โดยเฉลี่ยมากกว่า 40,000 เล่มต่อปี


ด้วยความที่ Kooperativa Förbundets เป็นองค์กรที่มีอิทธิพลสูงมากในวงการอาหารสวีเดน และคุณป้าแอน ก็มีตำแหน่งที่สูงมาก จึงสามารถเป็นผู้มีส่วนสนับสนุนรูปแบบซูเปอร์มาร์เก็ตสมัยใหม่ ในการใส่รายการส่วนผสมและคำแนะนำในการปรุงอาหารในรูปแบบฉลากของผลิตภัณฑ์อาหารสมัยใหม่

จนกระทั่งในช่วงปี 1970 ประเทศสวีเดนต้องเผชิญกับปัญหาราคาอาหารที่สูงเนื่องจากเงินเฟ้อ รวมถึงสภาพอากาศของสวีเดนนั้น ไม่เอื้อต่อการได้รับสารอาหารที่หลากหลายได้ ครอบครัวที่มีเด็ก ไม่สามารถปรุงอาหารและรับประทานอาหารที่มีคุณค่าทางโภชนาการในราคาที่เหมาะสมได้ รัฐบาลจึงมอบหมายให้ Sweden’s National Board of Health and Welfare (คณะกรรมการสุขภาพและสวัสดิการแห่งชาติของสวีเดน) หาวิธีแก้ไขสถานการณ์ดังกล่าว และคัดกรองแบ่งประเภทอาหารออกเป็น “basic food” และ “supplement” มาเป็นรูปแบบของ กราฟวงกลม (diet circle) แต่ป้าแอนพบปัญหาบางอย่าง ที่ทำให้กราฟวงกลมนี้ใช้งานยาก เพราะการแบ่งปริมาณของอาหารแต่ละประเภทไม่ชัดเจน
ในระหว่างบรรยายเรื่องการกำหนดอาหารพื้นฐาน คุณ Fjalar Clemes หนึ่งในผู้เข้าร่วมการบรรยาย ได้ให้ไอเดียด้วยการสร้างแบบจำลองที่เรียกว่า ปิรามิดอาหาร (Food Pyramid) ขึ้นมา เพื่อให้เห็นภาพสัดส่วนอาหารที่ชัดเจนขึ้น ป้าแอนเลยนำข้อมูลจากกราฟวงกลมนั้น มาสร้างโมเดลจำลองให้อยู่ในรูปแบบปิรามิด โดยให้ “basic food” เช่น ขนมปัง มันฝรั่ง พาสต้า และนม และ “supplements” เช่น ผลไม้ ผัก เนื้อสัตว์ และปลา อยู่ในรูปแบบที่เข้าใจได้ง่ายขึ้น แม้แต่คนที่อ่านหนังสือไม่ออก

แต่นี่แหละที่เป็นจุดเริ่มต้นของปัญหา ด้วยความที่มันใช้งานง่ายสะดวก อเมริกาจึงนำไปปรับปรุงเป็นเวอร์ชั่นตัวเอง แต่ก็มีการเปลี่ยนแปลงไปอย่างมาก ตามที่ได้มีการทำบทความไปแล้ว (อ่านที่นี่)
ทั้งๆที่ปิรามิดต้นแบบของป้าแอนนั้น สร้างขึ้นมาเพื่อชาวสวีเดนเนื่องจากนำข้อมูลพื้นฐานจากข้อจำกัดในประเทศในขณะนั้น ไม่ว่าจะเรื่องของวัตถุดิบที่หาได้ในภาวะยากแค้นแบบนั้น อุณหภูมิอันปรวนแปร รวมถึงสภาพเศรษฐกิจที่ย่ำแย่มาก การจัดแจงข้อจำกัดที่มีเพื่อให้ได้สารอาหารที่เพียงพอที่สุดเท่าที่จะทำได้ต่างหาก (eat healthier, more affordable and save on fat) ที่เป็นที่มาของ “ปิรามิดอาหารของสวีเดน” (คือ จะให้เอาอุดมคติมาสร้างปิรามิดอาหาร คงไม่มีประโยชน์ เพราะยังไงก็ไม่มีเงินซื้อและหาวัตถุดิบไมไ่ด้ตามอุดมคติ วัตถุประสงค์ในการสร้างและเผยแพร่ครั้งนี้มันเพื่อให้ประชาชนทั้งประเทศที่มีความรู้ด้านอาหารน้อย รู้และทำตามได้จริง สมกับพื้นที่และกำลังทรัพย์ // ความเห็นส่วนตัวผมครับ)
ปิรามิดอาหารที่แท้จริงแล้ว จะมีการปรับปรุงตลอดเวลา ตามปัจจัยที่เปลี่ยนไป ไม่ใช่ปิรามิดที่เอาไว้ยึดถือตลอดไป แต่การที่อเมริกานำไปยึดถือว่าเป็น all time information เป็นค่าคงที่ให้ทั้งโลกยึดตาม รวมถึงสร้างด้วยเบื้องหลังด้านธุรกิจ จึงต่างกับที่ป้าแอนทำในทุกมิติ แต่ไฉน เป้าการบูลลี จึงต้องไปตกที่ป้าแอน ว่าเป็นต้นตอความพังของสุขภาพ มันแฟร์แล้วหรือ
เรื่องนี้มีข้อพิสูจน์ได้จนถึงปัจจุบันเช่น ในปี 2022 ก็มีการนำเสนอ ปิรามิดอาหารสำหรับ Mixed diet, flexitarian, vegetarian และ vegan ออกมาสืบทอดเจตนารมณ์ป้าแอน นอกจากนี้ในช่วงที่ป้าแอนมีชีวิต ก็ยังคงมีการช่วยเหลือแนะนำให้ประเทศต่างๆ “มีปิรามิดอาหารของตัวเอง” นั่นคือ วิชั่นที่กว้างไกลของป้าแอน ที่เห็นได้ชัดเจนว่า อาหารพื้นถิ่นกับสารอาหารที่สมดุล ของแต่ละประเทศมีความไม่เหมือนกัน และแนวคิดนี้ได้มีทั้ง เดนมาร์ก, นอร์เวย์, ฟินแลนด์, ญี่ปุ่น, ศรีลังกา ได้นำไปพัฒนาใช้เช่นกัน
นอกจากนี้ ป้าแอนและองค์กร Kooperativa Förbundets ยังให้ข้อมูลการศึกษาที่สำคัญสำหรับประชาชนผ่านบทความเกี่ยวกับอาหารที่ตีพิมพ์ใน นิตยสาร Vi รวมถึงการจัดตั้งกลุ่มการศึกษาร่วมกับทาง สมาคมการศึกษาของชนชั้นแรงงาน หรือ Arbetarnas bildningsförbund (ABF) มีส่วนสนับสนุนในการอภิปรายแบบเปิดทางสังคมเกี่ยวกับปัญหาโรคอ้วนอีกด้วย รวมถึงยังออกหนังสือเกี่ยวกับการทำอาหารอีกร่วมๆ 30เล่ม ซึ่งรวมถึงบทเกี่ยวกับมื้ออาหารที่มีคุณค่าทางโภชนาการที่สมดุล ด้วยเช่นกัน

ในปี 1983 ป้าแอนได้ตีพิมพ์หนังสือ Matboken ซึ่งได้รับการพิสูจน์แล้วว่าเป็นประโยชน์อย่างมาก โดยเฉพาะกับคนหนุ่มสาวเกี่ยวกับวิธีการกินอาหารที่มีคุณค่าทางโภชนาการและมีวิธีทำที่เรียบง่ายที่สุด

ในช่วงทศวรรษ 1990 เมื่อป้าแอนเป็นม่าย จึงได้ย้ายเข้าไปอยู่ในบ้านพักคนชรา Färdknäppen ใน Södermalm ในสตอกโฮล์ม และ ได้แก้ไขสูตรอาหาร 250 สูตรจาก Vår kokbok เพื่อให้เหมาะสมกับสภาพแวดล้อมการปรุงอาหารส่วนกลางของบ้านพักคนชรา เพื่อให้ได้อาหารที่มีสารอาหารครบถ้วนตามที่ควรเป็น
เกียรติประวัติป้าแอนได้รับการตอบแทนดังนี้ ในปี 1979 ได้รับรางวัลเหรียญ St Erik เพื่อเป็นการยกย่องสิ่งที่เธอทุ่มเทแรงกายแรงใจทำมาตลอดชีวิต ในปี 1993 ได้รับเหรียญ HM Konungens ลำดับที่ 8 (HM The King’s Medal หรือ H.M. Konungens medalj ในภาษาสวีเดน) เป็นหนึ่งในรางวัลเกียรติยศที่สำคัญที่สุดที่มอบโดยพระมหากษัตริย์สวีเดนเพื่อยกย่องบุคคลที่มีผลงานดีเด่นหรือมีความโดดเด่นในด้านต่าง ๆ เช่น วิทยาศาสตร์ ศิลปะ วัฒนธรรม และการบริการสาธารณะ ในปี 1995 ได้รับเหรียญทอง Albin Johansson สำหรับผลงานอันทรงคุณค่าของเธอต่อสหกรณ์สวีเดน ในปี 1998 ได้รับรางวัล Gastronomiska Akademiens Guldpenna (ปากกาทองของสถาบันอาหาร) สำหรับบทความเกี่ยวกับส่วนผสมและการทำอาหารของเธอ

Anna-Britt Agnsäter เสียชีวิตในปี 2006 (อายุ 90ปี) ป้าแอนทำงานทั้งชีวิตเพื่อสอนชาวสวีเดนในการจัดการอาหารให้ดีขึ้น ทุกการทดลอง ทดสอบ ได้มีการบันทึกไว้อย่างชัดเจนสามารถพัฒนาต่อไปได้ การริเริ่มให้ข้อมูลที่ซื่อสัตย์ต่อผู้บริโภค ทั้งการติดฉลากอุปกรณ์ คำแนะนำในการทำอาหาร สูตรอาหาร บทความ และตำราอาหาร สิ่งเหล่านี้กลายเป็นพื้นฐานสำคัญในอุตสาหกรรมอาหารจนปัจจุบัน
แต่ทุกวันนี้วงการสุขภาพส่วนมากยังคงล้อเลียนเธอว่าเป็นครูธรรมดา ที่มีหน้ามาสร้างปิรามิดอาหาร จึงทำให้คนทั่งโลกป่วย ทั้งที่ความจริงทั้งหมดนั้น ความรู้ของป้าแอนไม่ได้น้อยไปกว่า ผู้เชี่ยวชาญทางวิทยาศาสตร์การอาหาร ซึ่งในสมัยนั้นนับว่าเป็นอีกแขนงที่อยู่ในระดับบนของการศึกษา ไม่ต่างกับวิทยาศาสตร์อื่นๆ ปิรามิดควรเป็นไปตามถิ่นที่อยู่ สภาพเวลาและสภาพเศรษฐกิจขณะนั้น ไม่ใช่การสร้างมาตรฐานให้ต้องทำเหมือนกันทั่วโลก โดยมาจากอิทธิพลของกลุ่มธุรกิจดังที่ usda ได้ทำการแก้ไขก่อนจะประกาศให้คนทั่วไปยึดถือ รายละเอียดเป็นไปตามที่สืบค้นข้อมูลประวัติของป้าแอน มาเล่าสู่กันฟัง ณ วันนี้ครับ
ผมก็เป็นหนึ่งในนั้น สิ่งที่ผมสามารถทำได้เพื่อเป็นการขอโทษคุณ Anna-Britt Agnsäter ที่ดีที่สุดที่ทำได้ตอนนี้คือ เผยแพร่ประวัติอันทรงคุณค่าของเธอ ให้คนอื่นๆได้รับทราบมากที่สุด เท่าที่จะทำได้
โปรดแชร์ เพื่อคืนความเป็นธรรมให้ Anna-Britt Agnsäter ให้โลกได้เข้าใจและรับรู้ถึงการอุทิศชีวิตให้วงการอาหารของคุณป้าครับ
ปล.มีการค้นพบไฟล์เสียง ที่ป้าแอน จัดรายการวิทยุในปี 1968 ให้ลองฟังกันครับ (น่าจะภาษาสวีเดนนะ 5555) ฟังได้ที่นี่ครับ https://rumble.com/v56p1wa-ann-britt-agnster-in-a-radio-find-from-1968.html
siamstr #pirateketo
-
 @ 0176967e:1e6f471e
2024-07-26 17:45:08
@ 0176967e:1e6f471e
2024-07-26 17:45:08Ak ste v Bitcoine už nejaký ten rok, možno máte pocit, že už všetkému rozumiete a že vás nič neprekvapí. Viete čo je to peňaženka, čo je to seed a čo adresa, možno dokonca aj čo je to sha256. Ste si istí? Táto prednáška sa vám to pokúsi vyvrátiť. 🙂
-
 @ 0176967e:1e6f471e
2024-07-26 12:15:35
@ 0176967e:1e6f471e
2024-07-26 12:15:35Bojovať s rakovinou metabolickou metódou znamená použiť metabolizmus tela proti rakovine. Riadenie cukru a ketónov v krvi stravou a pohybom, časovanie rôznych typov cvičení, včasná kombinácia klasickej onko-liečby a hladovania. Ktoré vitamíny a suplementy prijímam a ktorým sa napríklad vyhýbam dajúc na rady mojej dietologičky z USA Miriam (ktorá sa špecializuje na rakovinu).
Hovori sa, že čo nemeriame, neriadime ... Ja som meral, veľa a dlho ... aj grafy budú ... aj sranda bude, hádam ... 😉
-
 @ 0176967e:1e6f471e
2024-07-26 09:50:53
@ 0176967e:1e6f471e
2024-07-26 09:50:53Predikčné trhy predstavujú praktický spôsob, ako môžeme nahliadnuť do budúcnosti bez nutnosti spoliehať sa na tradičné, často nepresné metódy, ako je veštenie z kávových zrniek. V prezentácii sa ponoríme do histórie a vývoja predikčných trhov, a popíšeme aký vplyv mali a majú na dostupnosť a kvalitu informácií pre širokú verejnosť, a ako menia trh s týmito informáciami. Pozrieme sa aj na to, ako tieto trhy umožňujú obyčajným ľuďom prístup k spoľahlivým predpovediam a ako môžu prispieť k lepšiemu rozhodovaniu v rôznych oblastiach života.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ 1ec45473:d38df139
2024-07-12 22:51:49
@ 1ec45473:d38df139
2024-07-12 22:51:49The probability of AGI ending us is negative.
A common tactic among doomers is to state something along the lines of the following:
"If we create AGI, there is some non-zero chance every year, that the AGI will end humanity. Whatever that chance is compounds every year, and is thus unacceptable."
The question I would ask the doomer is "How do you know that the chance of AGI ending humanity isn't negative?"
What does it mean for AGI to have a negative chance of ending humanity?
Setting aside AGI for a moment, what is the chance every year that humanity ends from other events, such as nuclear war, solar flares, super-volcanoes, asteroid hits, societal collapse, etc?
How do you even answer this question in a reasonable manner? Well lets look at past data.
Of all species that have existed 99% have gone extinct.
Of our closest 7 relatives from the genus Homo, 100% have gone extinct.
On a higher level looking at civilizational collapse. According to Wikipedia, virtually all historical societies have collapsed.
Looking out into the universe, we see no signs of life elsewhere, so if there was life in the past we can assume that they have gone extinct.
It would therefore be reasonable to say that the chance of our extinction is very high even without AGI, well above 90%. Maybe 99%.
You could argue the numbers but at least with these numbers we are using some past data to extrapolate the future, where the doomers are using no data whatsoever to support their numbers.
We can also state, that of all the species and societies that have collapsed in the past, they have done so because they did not yet have the knowledge on how to survive. They didn't know how to create antibiotics, or generate enough energy, or defend themselves from the environment.
What is AGI? AGI is a way to create knowledge. Most all societies in the past have collapsed because they didn't have the knowledge on how to survive, and the doomer argument is that we should slow down our ability to create knowledge, when we know that this has been precisely the problem in the past.
It is a certainty we will all die without more knowledge then we have now. The future death of our sun ensures that.
We have to create the knowledge on how to survive, and that is what AGI does - it creates knowledge.
AGI most certainly has a negative probability of ending humanity.
-
 @ c80b5248:6b30d720
2024-10-13 18:14:34
@ c80b5248:6b30d720
2024-10-13 18:14:34Using tools like Continue in your vault
As the capabilities of artificial intelligence continue to expand, integrating AI into our workflows has become an increasingly attractive option. One of the most exciting applications of AI is its potential to enhance the way we manage and organize information. Obsidian, a powerful knowledge management tool, provides a robust platform for building a personal knowledge base. By layering AI tools like Continue over your Obsidian vault, you can unlock new levels of efficiency, creativity, and insight. This article will start to explore how to effectively use AI tools within Obsidian to enhance your note-taking, information management, and productivity.
An Explosion of AI Tools
Over the past few years, I have tinkered with ChatGPT and other chat interfaces, but I only recently stumbled upon the rapidly growing space of AI tools for coding. In such a short time, some amazing tools have emerged, most notably:
- Aider: A command line interface tool to iteratively generate, edit, and refactor code.
- Cursor: A fork of Visual Studio Code (VS Code) with integrated AI functionality.
- Cline: A plug-in for command line and code editor built to work with Antropic's Claude 3.5.
- Continue: A customizable VS Code plug-in with chat and code editing abilities.
These tools are designed to assist developers in writing, debugging, and even generating code from natural language prompts. They are powered by large language models (LLMs) like GPT-4 and Llama 3, which are trained on vast amounts of text data and can produce human-like responses to a wide range of prompts.
In this article, I will focus on Continue, a VS Code plug-in that offers multiple ways to interact with AI. It features autocomplete powered by an LLM of your choice, as well as the ability to generate new code blocks directly in the editor. It can also incorporate context from external sources or the local codebase. Additionally, it includes a standard chat window for interacting with the LLM.
The new twist is that I won't be using Continue to write code, but rather to write notes in Obsidian. I will be using the chat window to generate notes, and the autocomplete feature to assist me in writing them. By leveraging the context feature, I can bring in information from my Obsidian vault, allowing me to create more complete, accurate, and better-organized notes. I can also use the vault as context to ask for summaries or retrieve information from my notes, even as the vault continues to grow.
It's worth mentioning that while I am focusing on Continue, there are likely other tools that can be used in a similar way or provide better features. One example is the text-generator plug-in for Obsidian. This plug-in allows you to generate text using an LLM of your choice, and it can be used to generate notes, summaries, or even entire documents. It can also generate code, but I was unable to get the plug-in working with my LLM provider. Using Continue is a bit of a hack, as it requires working through an IDE like VS Code, but it's a good way to get started with AI tools in Obsidian. I will assume that you already have an Obsidian vault set up. If you don't, you can ask your assistant to help you organize it once you have it up and running.
The system I am going to describe here relies on two primary components:
- Continue (installed in an IDE like VS Code)
- An LLM provider to power Continue
Let's start by talking about LLM Providers. If you already know how these work, feel free to skip to the next section.
LLM Providers
LLM providers are services that offer access to large language models (LLMs) like GPT-4 or Llama 3.1, typically via an API (application programming interface). These providers usually charge by the token, which is the number of words processed by the model. You can go directly to a provider like OpenAI or Anthropic, or you can use an aggregation site like OpenRouter that provides a single API to access multiple models. Each provider has its own data privacy policies, so it's important to review them carefully. For this reason, I have been using DeepInfra. They run their own models and offer a clear privacy policy - even better, they tend to have the lowest costs.
h/t nostr:npub17vhnjkt04m6thytr8dna67v2pa4tjk7uh3ut40eq9wy8d28u0kvq7qnhkq nostr:note1qfckzxm687peaddwjpmms92kj3v59wrrx0cs2fcxlkm6pm9lyu3squscxa
Another option is to use Ollama to run some of these models locally. However, the hardware requirements for achieving good results quickly are quite demanding. For example, the smaller chat model I use in my configuration, which has 72 billion parameters, requires a 48 GB GPU to run efficiently—something that is not within my budget. This is why I am using DeepInfra.
Note: If you are setting this up for the first time, consider adding a small amount (less than $5) to a provider like DeepInfra and testing it out before you invest time in setting up a local Ollama instance. I have also had some issues with shutting down Ollama on Windows, so your mileage may vary.
If you choose to use a provider like DeepInfra, you are ready to move to the next section. If you prefer to set up Ollama, you can refer to their documentation for installation instructions. I prefer to run it in Docker, which can be done in Linux by running
bash docker run -d -v ollama:/root/.ollama -p 11434:11434 --name ollama ollama/ollamaor if you want to have an interface like ChatGPT, you can even run Open WebUI in the same command with
bash docker run -d -p 3000:8080 --add-host=host.docker.internal:host-gateway -v open-webui:/app/backend/data --name open-webui --restart always ghcr.io/open-webui/open-webui:mainOnce Ollama is running in docker you can start up the models you want to use by running the following in your terminal.
docker exec ollama ollama run model_nameSee the Ollama model library to choose which models you want to run locally.
Getting Started with Continue
Continue is installed as a plug-in for VS Code or JetBrains. I personally use it with VS Code, so my instructions will be based on that. If you are using a JetBrains IDE, you should refer to the Continue documentation for installation instructions.
After installing the plug-in, continue will prompt you to set up your LLM provider. In my experience, once this initial GUI goes away, you can't get it back. Instead, you will do most of the configuration within the
config.jsonfile for Continue, which you can access by clicking in the lower right corner of the Chat box. In VS Code, if you ever can't find anything,F1is your friend and will launch a searchable menu.Continue provides recommended settings from each provider, which you can find here. For my coding and writing, I chose the very new Qwen2.5 72B Instruct due to its high benchmark scores and relatively low costs. This model costs $0.35-0.40 USD per million tokens, compared to the best available on DeepInfra, the Llama3.1 405B Instruct, which costs $1.78 per million tokens. The results may be slightly worse, but I prefer cheaper and faster for my purposes. For autocomplete, I am using a faster and code-specific model, Qwen2.5-Coder-7B. I have not yet tried changing the autocomplete model for usage with Obsidian, but that is on my to-do list. Lastly, by the time you read this article, these models may be out of date. One nice thing about having a provider API is that you can easily switch and test different models to see how they work. Aider has one of many model leaderboards that will show you some benchmarks.
After working through the configuration, your
config.jsonfile will have a list of chat models and a tab for the autocomplete model. It will look something like this:```json "models": [ { "title": "DeepInfra Qwen2.5 72B Instruct", "provider": "deepinfra", "model": "Qwen/Qwen2.5-72B-Instruct", "apiKey": "your-api-key" }, { "title": "DeepInfra Llama3.1 405B Instruct", "provider": "deepinfra", "model": "meta-llama/Meta-Llama-3.1-405B-Instruct", "apiKey": "your-api-key" }, ],
"tabAutocompleteModel": { "title": "DeepInfra Qwen/Qwen2.5-Coder-7B", "provider": "deepinfra", "model": "Qwen/Qwen2.5-Coder-7B", "apiKey": "your-api-key" } ```
Trying it Out
The Chat UI
Once you have Continue configured, you can open your Obsidian Vault in VS Code. You will want to add a
.continueignorefile in your folder that lists.obsidianand any other files or folders you want Continue to ignore for context purposes. Click the three dots in the bottom of the chat bar and check that your vault (@codebase) index is complete. You can now chat with the LLM and ask it questions using your vault as a reference.
Click the three dots in the bottom of the chat bar and check that your vault (@codebase) index is complete. You can now chat with the LLM and ask it questions using your vault as a reference.@codebase what are some common themes from this vault?Continue provides a docs page that lists some types of questions that an LLM will be able to help with. Naturally, I asked the LLM to put these in the context of an Obsidian Vault and here is what it told me:
```md
Useful Questions
- High-Level Questions About Your Notes:
- "What are the main themes in my notes on personal development?"
-
"How do I incorporate agile methodologies into my project management?"
-
Specific Information:
- "What are the key points in my notes about productivity hacks?"
-
"Can you find any references to neuropsychology in my notes on cognitive science?"
-
Generating Content:
- "Write a new note on the benefits of meditation, using the same structure as my other wellness notes."
-
"Draft a summary of my recent project retrospective, following the format of my previous summaries."
-
Contextual Questions About a Specific Folder:
- "What is the main purpose of the 'Research' folder?"
-
"How do we use the concept of 'flow' in the 'Psychology' folder?"
-
Relationships and Connections:
- "What are the connections between my notes on 'Time Management' and 'Goal Setting'?"
-
"How do my notes on 'Digital Marketing' relate to 'SEO'?"
-
Task and Project Management:
- "What are the next steps I should take based on my notes for the 'Personal Finance' project?"
-
"Can you list the tasks I need to complete for my 'Career Development' plan?"
-
Deep Dives and Analysis:
- "Can you provide a detailed explanation of the concept of 'reflective practice' found in my notes?"
-
"What insights can you derive from my notes on 'Project Management'?"
-
Insight and Reflection:
- "What have I learned from my notes on 'Mindfulness'?"
- "Can you help me reflect on my progress based on my notes for the 'Health and Wellness' topic?"
Not Useful Questions
- Literal Review of All Files:
- "Find everywhere where the term 'mindfulness' is mentioned in my entire vault."
-
"Review all my notes and find any spelling mistakes."
-
Comprehensive Tasks that Require Literal Access:
- "Add a new section to all notes that discuss 'productivity' and summarize the main points."
-
"Rewrite all my notes on 'Digital Marketing' to include the latest industry trends."
-
Refactoring and Detailed Edits:
- "Update all references to 'Scrum' to 'Kanban' in my 'Agile' folder."
- "Add a new parameter to the function
calculate_scoreand update all usages in my 'Programming' notes."
Summary
- Useful Questions: Focus on high-level insights, specific information, generating new content, contextual questions about specific folders, and reflecting on your notes.
- Not Useful Questions: Require the LLM to see and edit every file, perform comprehensive reviews, or make detailed edits across multiple notes. ```
Text Generation
Continue also offers in-editor code generation with the hotkey
Ctrl+Iand an entered prompt. I have only tried a few things with this, but it was able to successfully review a set of meeting notes I had written and summarize all of the outstanding questions. I expect you could also use this to autogenerate backlinks on a note where a follow-up note might be helpful, or quickly generate templates to be used in Obsidian. I ended up editing this entire article by selecting sections and prompting the AI with the following: "You are a proficient writer. Please edit this text for style, typos, spelling, and grammar."Autocomplete
Continue will also attempt to autocomplete unless you turn it off in the bottom right bar in VS Code. While writing this article, the autocomplete feature was somewhat helpful even though it is not code. Further configuration may optimize this even more. Keep in mind that autocomplete triggers frequently and will burn through a lot of tokens, so you will want to keep an eye on your usage. With the cheaper models I am using, I have only spent 10 cents over the past four days of moderate usage at work and at home. A bulk of that cost is due to autocomplete, and I sometimes turn it off to keep costs down. You may be able to limit these costs effectively by configuring the number of input tokens that can be sent to the API, but I am not sure how that will impact the results.
 ## Conclusion - Brought to You by Qwen 72B
## Conclusion - Brought to You by Qwen 72BIn conclusion, integrating AI tools like Continue into your Obsidian vault opens up a multitude of possibilities for enhancing your note-taking, information management, and productivity. By leveraging the chat window, text generation, and autocomplete features, you can create more comprehensive and accurate notes, generate summaries, and automate routine tasks. The integration of LLMs into your workflow not only streamlines your processes but also provides deeper insights and connections within your knowledge base. While there are initial setup steps and some considerations around cost and configuration, the benefits of AI-assisted note-taking in Obsidian are well worth the effort. As AI tools continue to evolve, the potential for further enhancements and optimizations is immense, making this an exciting and valuable addition to any knowledge management system.
-
 @ 9e69e420:d12360c2
2024-10-24 11:51:32
@ 9e69e420:d12360c2
2024-10-24 11:51:32Dr. Johanna Olson-Kennedy, a leading advocate for trans youth care, withheld a $10 million study funded by taxpayers on the effects of puberty blockers, which found no improvement in mental health among participants.
She feared the findings would be "weaponized" against transgender care. Critics argue that her decision violates research standards and denies vital information to the public. The study tracked 95 children, revealing that 25% had mental health issues prior to treatment, contradicting Olson-Kennedy's claims of good overall mental health. Experts stress the importance of publishing research regardless of outcomes.
Sauce: https://nypost.com/2024/10/23/us-news/doctor-refused-to-publish-trans-kids-study-that-showed-puberty-blockers-didnt-help-mental-health/