-
 @ 3bf0c63f:aefa459d
2024-10-26 14:18:23
@ 3bf0c63f:aefa459d
2024-10-26 14:18:23kind:1maximalism and the future of other stuff and Nostr decentralizationThese two problems exist on Nostr today, and they look unrelated at first:
- People adding more stuff to
kind:1notes, such as making them editable, or adding special corky syntax thas has to be parsed and rendered in complicated UIs; - The discovery of "other stuff" content (i.e. long-form articles, podcasts, calendar events, livestreams etc) is hard due to the fact that most people only use microblogging clients and they often don't appear there for them.
Point 2 above has 3 different solutions:
- a. Just publish everything as
kind:1notes; - b. Publish different things as different kinds, but make microblogging clients fetch all the event kinds from people you follow, then render them natively or use NIP-31, or NIP-89 to point users to other clients that would render them better;
- c. Publish different things as different kinds, and reference them in
kind:1notes that would act as announcements to these other events, also relying on NIP-31 and NIP-89 for displaying references and recommending other clients.
Solution a is obviously very bad, so I won't address it.
For a while I have believed solution b was the correct one, and many others seem to tacitly agree with it, given that some clients have been fetching more and more event kinds and going out of their way to render them in the same feed where only
kind:1notes were originally expected to be.I don't think clients doing that is necessarily bad, but I do think this have some centralizing effects on the protocol, as it pushes clients to become bigger and bigger, raising the barrier to entry into the
kind:1realm. And also in the past I have talked about the fact that I disliked that some clients would display my long-form articles as if they were normalkind:1notes and just dump them into the feeds of whoever was following me: nostr:nevent1qqsdk90k9k30vtzwpj6grxys9mvsegu5kkwd4jmpyhlmtjnxet2rvggprpmhxue69uhhyetvv9ujumn0wdmksetjv5hxxmmdqy8hwumn8ghj7mn0wd68ytnddaksygpm7rrrljungc6q0tuh5hj7ue863q73qlheu4vywtzwhx42a7j9n5hae35cThese and other reasons have made me switch my preference to solution c, as it gives the most flexibility to the publisher: whoever wants to announce stuff so it can be discovered can, whoever doesn't don't have to. And it allows microblogging clients the freedom to render just render tweets and having a straightforward barrier between what they can render and what is just a link to an external app or webapp (of course they can always opt to render the referenced content in-app if they want).
It also makes the case for microapps more evident. If all microblogging clients become superapps that can render recipe events perfectly why would anyone want to use a dedicated recipes app? I guess there are still reasons, but blurring the line between content kinds in superapps would definitely remove some of the reasons and eventually kill all the microapps.
That brings us back to point 1 above (the overcomplication of
kind:1events): if solution c is what we're going to, that makeskind:1events very special in Nostr, and not just another kind among others. Microblogging clients become the central plaza of Nostr, thus protecting their neutrality and decentralization much more important. Having a lot of clients with different userbases, doing things in slightly different ways, is essential for that decentralization.It's ok if Nostr ends up having just 2 recipe-sharing clients, but it must have dozens of microblogging clients -- and maybe not even full-blown microblogging clients, but other apps that somehow deal with
kind:1events in multiple ways. It's ok if implementing a client for public audio-rooms is very hard and complicated, but at the same time it should be very simple to write a client that can render akind:1note referencing an audio-room and linking to that dedicated client.I hope you got my point and agreed because this article is ended.
- People adding more stuff to
-
 @ 592295cf:413a0db9
2024-10-26 13:39:00
@ 592295cf:413a0db9
2024-10-26 13:39:00[Week 21-10] I thinks that Saylor is on right, don't trust verify, is bullshit Bitcoin is a financial tool! I think it's good for me to get away from social media once a week. I could do things outside, like walking. Take pictures of the landscape. The weirdest thing is when the alarm calls you up in an hour.
Fiatjaf wants a cache client. I feel like I can do it, I have the set to do it, but nostrudel is no longer working, so it's a little murky. Next nostrudel does not accept changes to settings (It works now!), so maybe i can think something. I want to make a corny chat, test, read this article. Nostr doesn't work with a vpn because relays don't know who you are. jokes aside, some clients have difficulties.
I couldn't take pictures of the landscape if I didn't take the wind blades. Small local controversy.
Missing the point of content creator. Simply for final user, Simply for the creator, new feature, no missing nothing. I'm trying to limit everything to writing for a week. I almost did. Maybe another week can do well.
Meanwhile I updated apps like Amber and Voyager, coracle, nostrmo.
The experiment continues with open vibe following the trending of Nostr. I'm following almost 120 npub. He'll stop, I don't know, possible he's already reached the limit. You still can't block words on the Nostr side of Open, strange thing. The app doesn't count the follow well, still some problem cleaning the cache seems that it doesn't need. After a while open and close and seems updated. I wanted to try open librarian, but I was busy sending fake zap on Nostr. This morning i try and It keeps giving me error 500 when I try to connect to a relay.
I hate when a profile follows everyone indistinctly, why does everyone follow? and in voyage, I read with WoT setting, I probably have to do unfollow. There must be an indication in which not include the followers of this person in the web of trust, I would do it by default if you follow more than 600 people.
WoT on Nostr Visualized post on stackernews
-
 @ 4ba8e86d:89d32de4
2024-10-20 10:12:19
@ 4ba8e86d:89d32de4
2024-10-20 10:12:19M5Stick-NEMO: Firmware para Pegadinhas de Alta Tecnologia em Dispositivos M5Stack ESP32 , Este projeto oferece uma solução eficaz sem comprometer a qualidade, ideal para quem busca uma experiência educativa e divertida no universo do hacking.
https://nostrcheck.me/media/public/nostrcheck.me_2674216785970862911706546228.webp
Desenvolvido por Noah Axon-n0xa, o M5Stick-NEMO é um projeto pessoal que surgiu da vontade de aprender mais sobre o desenvolvimento do ESP32 com o Arduino IDE. Inspirado por desafios populares na comunidade de tecnologia, NEMO replica pegadinhas comuns, proporcionando uma experiência educativa e divertida.
Características Principais:
- Portal NEMO WiFi: um captive portal login que tenta criar credenciais de e-mail de engenharia social - salva nomes de usuário e senhas no cartão SD (se inserido em um leitor compatível)
- Porta TV B-Gone para desligar dispositivos controlados por infravermelho.
- Spam de emparelhamento de dispositivo AppleJuice iOS Bluetooth.
- Spam de notificação de dispositivo Bluetooth para SwiftPair (Windows) e Android.
- Spam de WiFi com SSIDs engraçados, WiFi Rickrolling e modo aleatório.
- Scanner SSID WiFi: exibe e clona SSIDs próximos.
- Relógio digital ajustável pelo usuário com suporte do M5 Stick RTC.
- Configurações apoiadas por EEPROM para rotação, brilho, escurecimento automático e SSID do Portal NEMO.
- Nível da bateria e créditos no menu de configurações.
Interface de Usuário:
- Três controles principais: Home, Próximo e Selecionar.
Portal NEMO:
No modo NEMO Portal, o NEMO ativa um Hotspot WiFi aberto chamado "Nemo Free WiFi" (configurável em portal.h) com servidores DNS, DHCP e Web ativados.
-
O Portal NEMO exibe uma página de login falsa que afirma fornecer acesso à Internet se você fizer login.
-
Este é um ataque de engenharia social e registrará o nome de usuário e as senhas inseridas na página.
-
Nos detalhes do Wifi Scan, você pode clonar um SSID existente na lista de verificação. Sair do Portal NEMO limpará o SSID Evil Twin
-
Você pode visualizar as credenciais capturadas conectando-se ao portal a partir do seu próprio dispositivo e navegando até http://172.0.0.1/creds
-
Você pode definir um SSID personalizado conectando-se ao portal a partir do seu próprio dispositivo e navegando até http://172.0.0.1/ssid
-
Se o seu dispositivo suportar EEPROM para configurações, o SSID personalizado inserido será salvo como padrão, mesmo se estiver desligado.
-
Se o seu dispositivo tiver um leitor de cartão SD com um cartão formatado em sistema de arquivos FAT inserido, os nomes de usuário e senhas serão registrados em nemo-portal-creds.txt no cartão SD para você ler mais tarde.
-
O suporte a cartão SD só está habilitado por padrão na plataforma M5Stack Cardputer. Ele pode ser habilitado em dispositivos M5Stick, mas um leitor de cartão SD deve ser construído e conectado ao pino do painel frontal.
-
O Portal NEMO deve ser usado apenas em compromissos profissionais com um escopo válido de trabalho, fins educacionais ou de demonstração.
O armazenamento, venda ou uso de informações pessoais sem consentimento é contra a lei.🤓
Instalação:
-
Visite o site oficial: M5Stack Docs https://docs.m5stack.com/en/download
-
Baixe o programa oficial M5Burner.
-
Procure pelo projeto "NEMO For M5Stick C Plus".
-
Conecte o M5 à porta USB do seu PC.
-
Abra o M5Burner, selecione o projeto e clique em "Burn".
Experimente algumas funções do FlipperZero no seu M5. Para recursos adicionais e a liberdade de personalização, compile e baixe diretamente o programa "NEMO-M5Stick C Plus" no GitHub do projeto. Isso não só permite explorar, mas também modificar e aprimorar o projeto de acordo com suas preferências.
Repositório oficial no GitHub
https://github.com/n0xa/m5stick-nemo
Assista a um tutorial sobre a implementação do M5Stick-NEMO.
https://youtu.be/uFzQTzZo-6E?si=BJJzNmiN0Jzw42Eu
https://youtu.be/uTeCbR_hWjc?si=l88w_Hl3EXuKa6gv
Além disso, você pode aprimorar seu M5 com o MURAUDER, um conjunto abrangente de ferramentas ofensivas e defensivas WiFi/Bluetooth para o ESP32.
Encontre-o no GitHub: ESP32Marauder
https://github.com/justcallmekoko/ESP32Marauder
Assista a um tutorial sobre a implementação do MURAUDER:
https://youtu.be/GQPzgYksdkg?si=dWN-GwEP5r6hk9IC
-
 @ 7ab1ed7a:f8e15275
2024-10-17 11:54:59
@ 7ab1ed7a:f8e15275
2024-10-17 11:54:59I've started building an IoT DVM simulator. It's written in TS and uses Deno for simplicity.
The project will be used to test the ideas in and support the NIP 90 PR.
https://github.com/blackcoffeexbt/nostriot-dvm-simulator
It has a basic plugin architecture so we can test a whole suite of how different IoT commands can work easily (config, intents, sensors, all the things).
This is the current, very basic roadmap for this project:
-
Add NIP 89 announcements
-
Respond to requests
- Accept payments for requests
I'll also be working on a basic - for now - IoT DVM client that can be used to interact with IoT DVMs.
-
-
 @ 4ba8e86d:89d32de4
2024-10-26 14:14:01
@ 4ba8e86d:89d32de4
2024-10-26 14:14:01I2P é uma rede anônima, oferecendo uma camada simples que aplicativos sensíveis à identidade podem usar para se comunicar com segurança. Todos os dados são agrupados com várias camadas de criptografia e a rede é distribuída e dinâmica, sem partes confiáveis.
O Invisible Internet Project começou em 2002. A visão do projeto, conforme descrito em uma entrevista com Lance James, era que a rede I2P "oferecesse total anonimato, privacidade e segurança no mais alto nível possível. Internet descentralizada e ponto a ponto significa não se preocupe mais com seu ISP controlando seu tráfego. Isso permitirá que (as pessoas) realizem atividades contínuas e mudem a maneira como vemos a segurança e até a Internet, utilizando criptografia de chave pública, esteganografia de IP e autenticação de mensagens. A Internet que deveria ter sido, será em breve." Desde então, o I2P evoluiu para especificar e implementar um conjunto completo de protocolos de rede capazes de fornecer um alto nível de privacidade, segurança e autenticação para uma variedade de aplicativos.
A rede I2P. A rede I2P é uma rede de sobreposição ponto a ponto totalmente criptografada. Um observador não pode ver o conteúdo, origem ou destino de uma mensagem. Ninguém pode ver de onde vem o tráfego, para onde está indo ou qual é o conteúdo. Além disso, os transportes I2P oferecem resistência ao reconhecimento e bloqueio por parte dos censores. Como a rede depende de pares para rotear o tráfego, o bloqueio baseado em localização é um desafio que cresce com a rede. Cada roteador na rede participa de tornar a rede anônima. Exceto nos casos em que seria inseguro, todos participam do envio e recebimento do tráfego de rede.
Como funciona o I2P?
O I2P usa criptografia para obter uma variedade de propriedades para os túneis que constrói e as comunicações que transporta. Os túneis I2P usam transportes, NTCP2 e SSU2, para ocultar o tráfego que está sendo transportado por eles. As conexões são criptografadas de roteador para roteador e de cliente para cliente (ponta a ponta). Forward-secrecy é fornecido para todas as conexões. Como o I2P é endereçado criptograficamente, os endereços de rede I2P são auto-autenticados e pertencem apenas ao usuário que os gerou.
A rede é composta por pares ("roteadores") e túneis virtuais unidirecionais de entrada e saída. Os roteadores se comunicam entre si usando protocolos construídos em mecanismos de transporte existentes (TCP, UDP), passando mensagens. As aplicações cliente possuem seu próprio identificador criptográfico ("Destino") que permite enviar e receber mensagens. Esses clientes podem se conectar a qualquer roteador e autorizar a alocação temporária ("lease") de alguns túneis que serão utilizados para envio e recebimento de mensagens pela rede. O I2P possui seu próprio banco de dados de rede interna (usando uma modificação do Kademlia DHT) para distribuir roteamento e informações de contato com segurança.
Sobre a Descentralização e a Rede I2P A rede I2P é quase totalmente descentralizada, com exceção dos chamados Reseed Servers. Isso é para lidar com o problema de bootstrap DHT (Distributed Hash Table). Basicamente, não há uma maneira boa e confiável de deixar de executar pelo menos um nó de inicialização permanente que os participantes que não são da rede possam encontrar para começar. Uma vez conectado à rede, um roteador só descobre pares construindo túneis "exploratórios", mas para fazer a conexão inicial, um host reseed é necessário para criar conexões e integrar um novo roteador à rede. Os servidores reseed podem observar quando um novo roteador baixou um reseed deles, mas nada mais sobre o tráfego na rede I2P.
Recursos do I2P
O I2P oferece uma série de recursos para proteger a privacidade do usuário. Alguns desses recursos incluem:
Ocultação do endereço IP: O I2P oculta o endereço IP do usuário, tornando impossível que alguém rastreie a atividade do usuário na rede.
Comunicação segura: Todas as comunicações dentro da rede I2P são criptografadas de ponta a ponta, garantindo a privacidade do usuário.
Anonimato: O I2P permite que os usuários se comuniquem de forma anônima, o que significa que sua identidade não é exposta durante a comunicação.
Sites ocultos: O I2P permite que os usuários criem e acessem sites ocultos, que só podem ser acessados dentro da rede I2P.
Vantagens do uso do I2P
O I2P oferece várias vantagens para os usuários que desejam proteger sua privacidade online. Algumas dessas vantagens incluem:
Proteção contra vigilância governamental: O I2P ajuda a proteger os usuários contra a vigilância governamental, tornando impossível rastrear o endereço IP do usuário.
Anonimato em redes públicas: O I2P ajuda a proteger os usuários contra ataques de hackers em redes Wi-Fi públicas.
Acesso a sites censurados: O I2P permite que os usuários acessem sites que estão bloqueados em sua região ou país.
O I2P é uma rede anônima de comunicação que oferece recursos de privacidade avançados para proteger a privacidade do usuário. Ele permite que os usuários se comuniquem de forma anônima e segura e cria uma solução eficaz para usuários que valorizam a privacidade e a segurança online. Se você está preocupado com sua privacidade online, o I2P pode ser uma ótima escolha.
https://github.com/i2p
-
 @ 592295cf:413a0db9
2024-10-13 08:29:48
@ 592295cf:413a0db9
2024-10-13 08:29:48[07/10 week]
Thinking about it, even the protocol is a cathedral, Rabble in the speech in Riga on Bluesky.
He said the protocol is a bazaar. But you have to converge on the scheme in the NIPs or between Apps.
NIPs for example are like Luther's 95 theses, but they change continuously and adapt, but they always remain those 95.
Maybe that Pr on theother curve keys could lead to saying this is "nostr" these others are similar. Creating more points, but I just think it would have led to endless diatribes.
What will be of the protocol and who knows. He can do everything or maybe nothing and from tomorrow we will see and it will be, it will be what it will be. Italian Song
Notifications with nostter are not hidden, they are in your feed and this is good, you always know if someone has searched for you. While in the others you do not know.
I saw a sliver of light pass by it was Unanimity.
It's a very stupid idea, it takes a long time. it's basically a community + channel, where you post the channel in the community and start talking about that topic in the channel. The channel is an approved message. I made musicbook channel, it's the collection of albums released on Friday. The idea of also making a blogger channel, where to put long-form articles.
Following nostr trending on Openvibe social, with a new profile, the Lost One, sad, in this One follow fiatjaf, means I won't bother him anymore . Now I follow 62 profiles, it's an account that I will use to read the notes of the top profiles. Curious if this number will grow enormously or is there a spectre.
The strength of the protocol is the developers if they collaborate together, otherwise it can still work, everyone goes their own way, but it's like saying I want to make my own fence.
One who in his long form doing an analysis of the various social networks. npub19mq9swna4dkhlm3jaux4yhgv5kjj556lkfhv3qnjtyh0kcljph6s88e295 Nostr is all based on Bitcoin. The difficult thing is Bitcoin not Nostr and he says so.
Controversies are useful, or my doubts, but maybe people who can't write code don't understand much, the so-called end users. No one is an end user at this time. The end user doesn't care about the person behind it, only having their own service, if the service is good they also do promotion, they become sponsors. We have seen in recent months sponsoring a Nostr app, result a small attack can damage that app. But the strength of having all these apps is that the other app doesn't have that problem. Spam attack example. The problem is that you can't sponsor an ecosystem, so it becomes difficult to suggest 10 apps to download. The best 10 apps of Nostr and the other 100, there is no easy way out. It's a bit like proposing a new place in NY, then everyone goes to that place and it loses a bit. What the sponsor must understand is that Nostr has only one "one shot".
I saw a video on Nostr of two people posting content on social media, making a review. Not bad, compared to the previous video, that Nostr doesn't even have a token. It doesn't give me a sign up. The main feature they say is a platform or at least they reviewed damus, damus for Bitcoin maxi. And so Nostr is populated by people who Number go up, only fiat thought they would say on Nostr. It's true in part there are those obsessed, even the non-obsessed are obsessed.
How nice it would be to call them NPs Nostr protocol specification, today supertestnet called them that. (the nice thing is that they are pronounced the same way).
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ 5e5fc143:393d5a2c
2024-10-11 22:26:08
@ 5e5fc143:393d5a2c
2024-10-11 22:26:08Just revisiting some quick tips for #newbies #pow #public #blockchain users only.
if you just getting started with bitcoin or any pow crypto coins or been using or storing them for a while, you not must forget the roots and fundamentals.
Hot Wallet — It gets connected to live internet at some point in time essentially to sign / send a tx i.e. spending transaction — exposes the private key of the address from in the process
Cold Wallet — It never ever gets connected or online and can always keep receiving inbound amounts Paper wallets are best n cheapest form of cold wallet that can used once n thrown away.
Cold wallets need to either “import”ed or “sweep”ed in order to used or spend — https://coinsutra.com/private-key-import-vs-sweep-difference/

Any thin #wallet is always dependent on connectivity to live up2date node server where-as self-sufficient qt / cli wallet takes a while to sync up to latest block height in order to be usable.
Beginners should always resist the attraction of quick and fast — thin n 3rd party wallets and always start a long learning journey of core wallets of any coin — either “qt” GUI wallet or command line “coin-cli” wallet
Almost all #proofofwork #blockchains i.e. #POW has #node #wallet - everyone who use support he #public #blockchain secures own you coin value
You can run fullnode either on clearnet or over onion 🧅 #BTC has >55% of nodes running in onion out of total 15000+ live fullnodes and 50000+ bitcoincore wallets around blockheight 777000 . Other notable pow chains are #LTC #RVN and rest are babychains for now !
Always delete hot wallet to test practice restoration before sending any large refunds to it to be safe.
Large funds are always best to keep in self custody node wallets rare n occasional use
Final word — Cannot see private key 🔑 or seed 🌱 in any wallet means not your coin. 😲
Use wallet which u learn or understand best only
That’s all for now n Thank you 🙏 ! ⚡️ https://getalby.com/p/captjack ⚡️
Some Cold wallet nostr posts nostr:note1p6ke5wqshgxtfzj5de3u04hejl2c5ygj8xk8ex6fqdsg29jmt33qnx57y2 nostr:note1rse0l220quur6vfx0htje94ezecjj03y6j7lguwl09fmvmpt6g3q0cg7yw nostr:note1q5w8dyjuqc7sz7ygl97y0ztv6sal2hm4yrf5nmur2tkz9lq2wx9qcjw90q
some nostr specific lightning ⚡️ Layer2 wallets with blockchain mainnet option nostr:naddr1qqsky6t5vdhkjm3qd35kw6r5de5kueeqf38zqampd3kx2apqdehhxarjqyv8wue69uhkummnw3e8qun00puju6t08genxven9uqkvamnwvaz7tmxd9k8getj9ehx7um5wgh8w6twv5hkuur4vgchgefsw4a8xdnkdgerjatddfshsmr3w93hgwpjdgu8zdnswpuk2enj0pcnqdnydpersepkwpm8wenpw3nkkut2d44xwams8a38ymmpv33kzum58468yat9qyt8wumn8ghj7un9d3shjtngv9kkuet59e5k7tczyqvq5m2zcltylrpetrvazrw45sgha24va288lxq8s8562vfkeatfxqcyqqq823ckqlhc8 related blog post nostr:naddr1qqxnzd3cxyenjv3c8qmr2v34qy88wumn8ghj7mn0wvhxcmmv9uq3zamnwvaz7tmwdaehgu3wwa5kuef0qydhwumn8ghj7mn0wd68ytn4wdjkcetnwdeks6t59e3k7tczyp6x5fz66g2wd9ffu4zwlzjzwek9t7mqk7w0qzksvsys2qm63k9ngqcyqqq823cpdfq87
-
 @ a95c6243:d345522c
2024-10-26 12:21:50
@ a95c6243:d345522c
2024-10-26 12:21:50Es ist besser, ein Licht zu entzünden, als auf die Dunkelheit zu schimpfen. Konfuzius
Die Bemühungen um Aufarbeitung der sogenannten Corona-Pandemie, um Aufklärung der Hintergründe, Benennung von Verantwortlichkeiten und das Ziehen von Konsequenzen sind durchaus nicht eingeschlafen. Das Interesse daran ist unter den gegebenen Umständen vielleicht nicht sonderlich groß, aber es ist vorhanden.
Der sächsische Landtag hat gestern die Einsetzung eines Untersuchungsausschusses zur Corona-Politik beschlossen. In einer Sondersitzung erhielt ein entsprechender Antrag der AfD-Fraktion die ausreichende Zustimmung, auch von einigen Abgeordneten des BSW.
In den Niederlanden wird Bill Gates vor Gericht erscheinen müssen. Sieben durch die Covid-«Impfstoffe» geschädigte Personen hatten Klage eingereicht. Sie werfen unter anderem Gates, Pfizer-Chef Bourla und dem niederländischen Staat vor, sie hätten gewusst, dass diese Präparate weder sicher noch wirksam sind.
Mit den mRNA-«Impfstoffen» von Pfizer/BioNTech befasst sich auch ein neues Buch. Darin werden die Erkenntnisse von Ärzten und Wissenschaftlern aus der Analyse interner Dokumente über die klinischen Studien der Covid-Injektion präsentiert. Es handelt sich um jene in den USA freigeklagten Papiere, die die Arzneimittelbehörde (Food and Drug Administration, FDA) 75 Jahre unter Verschluss halten wollte.
Ebenfalls Wissenschaftler und Ärzte, aber auch andere Experten organisieren als Verbundnetzwerk Corona-Solution kostenfreie Online-Konferenzen. Ihr Ziel ist es, «wissenschaftlich, demokratisch und friedlich» über Impfstoffe und Behandlungsprotokolle gegen SARS-CoV-2 aufzuklären und die Diskriminierung von Ungeimpften zu stoppen. Gestern fand eine weitere Konferenz statt. Ihr Thema: «Corona und modRNA: Von Toten, Lebenden und Physik lernen».
Aufgrund des Digital Services Acts (DSA) der Europäischen Union sei das Risiko groß, dass ihre Arbeit als «Fake-News» bezeichnet würde, so das Netzwerk. Staatlich unerwünschte wissenschaftliche Aufklärung müsse sich passende Kanäle zur Veröffentlichung suchen. Ihre Live-Streams seien deshalb zum Beispiel nicht auf YouTube zu finden.
Der vielfältige Einsatz für Aufklärung und Aufarbeitung wird sich nicht stummschalten lassen. Nicht einmal der Zensurmeister der EU, Deutschland, wird so etwas erreichen. Die frisch aktivierten «Trusted Flagger» dürften allerdings künftige Siege beim «Denunzianten-Wettbewerb» im Kontext des DSA zusätzlich absichern.
Wo sind die Grenzen der Meinungsfreiheit? Sicher gibt es sie. Aber die ideologische Gleichstellung von illegalen mit unerwünschten Äußerungen verfolgt offensichtlich eher das Ziel, ein derart elementares demokratisches Grundrecht möglichst weitgehend auszuhebeln. Vorwürfe wie «Hassrede», «Delegitimierung des Staates» oder «Volksverhetzung» werden heute inflationär verwendet, um Systemkritik zu unterbinden. Gegen solche Bestrebungen gilt es, sich zu wehren.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ b6424601:a11e4ff4
2024-10-26 12:12:56
@ b6424601:a11e4ff4
2024-10-26 12:12:56In 2007, my 10-year-old business had just signed a 5-year lease on Atlanta's Peachtree Road with enough space for my partner and our wives' separate companies to continue growing. We thought we were an overnight success 10 years in the making. 14K a month split between 3 companies, all in the housing and office design industry; what could go wrong?
As I look back on those early days, I realize that our business was fueled by the fiat jet fueled housing run-up. Two couples, three businesses, and all personally guaranteed. We thought we were an overnight success, but little did we know that the housing market was about to take a drastic turn.
In 2008, I joined a Vistage CEO group, where I was tasked with presenting to the group on my approach to designing buildings for individuals. I saw an opportunity to analyze the patterns that produced good projects for happy clients, and I teamed up with a contractor buddy to work on a joint presentation. Our efforts yielded ten principles that produced the highest ROI beyond providing a primary place to live.
These principles were the foundation of our approach to architecture, and they were based on our experiences working with individuals on their custom house projects. We focused on listening to our clients, designing buildings that stood out while fitting in, creating lifetime homes, and making projects sustainable and viable.
As I reflect on our journey, I realize that the principles we developed were an interesting reflection of what was happening to our clients in the housing market of that time and how we as architects help our clients get through the process. Over time, we had to adapt and evolve to respond to changing conditions.
In 2010, we made changes to respond to a client environment where projects happened without banks. Clients spent paper on their projects, and construction loans were not available. What the subsequent buyers wanted when the house was sold was off the table. Remember being thankful our clients had cash to spend on projects in our survival predicament.
In hindsight, our clients are probably grateful as well for being able to convert paper into a hard asset. The principles evolved slowly until the COVID came in 2020. I was ready to hunker down and go to business survival mode like back in the crash, converting staff to contractors again and only paying for billable work.
But "your" government made PPP rain from the sky on our small business with employees. In addition, clients working from home who needed change or from their vacation property added gasoline to the fire. By 2022, inflation raged, described as transitory, to change the build cost from 1.2 million to a new price of 2.2 million for the new Intown infill homes. That is 83% inflation over 2 years, no matter what the CPI said.
The principles pivoted to respond: going fast to respond to inflation, managing the stuff to deal with supply chain problems, providing a viability budget before starting work to help clients understand the cost, and guiding our clients through the choppy waters of inflation.
We added a new principle about stewardship, which has become a cornerstone of our approach. We want to become architects for life for our completed projects and owners. We want to maintain relationships, observe results, and be trusted advisors as our projects age and clients' needs evolve.
Today, we are proud to say that our principles have evolved into 10 guiding principles that organize our approach to producing architecture asset architecture for the individual. We leverage the team of clients, contractors, vendors, and our time through our principle based process to produce architecture worthy of being an asset for our clients and families.
These 10 principles are:
- Listen: Analyze and understand our client's goals, constraints, and opportunities to communicate our vision of what is possible.
- Establish Viability: Before starting our project process, we will engage our client in a pre-project viability phase to diagnose and prescribe our solutions with a timeline and budget for client approval.
- Be a Design Sherpa: Our process is the most important value we provide. Following our process milestones will lead new and experienced clients through the 1000’s of design decisions to evolve in the correct order at the proper time.
- Design in Context: We believe context is the caldron of good architecture fits into its location both from the outside and inside out. Designing in context allows a building to stand out while fitting into the adjacent network of spaces around it.
- Architecture is a team sport: We believe in custom teams for custom projects, collaborating with partners who care about our clients and believe in our process as much as we do.
- Design for the individual: We do our most fulfilling work with clients who will live in or operate architecture explicitly created for their needs.
- Investment iteration: We break down the design process into decision milestones, providing increasingly detailed pricing for initial ideas, building shell, and interior selections to empower clients to make informed decisions about the value they're willing to exchange for their desired architecture.
- Create Asset Architecture: Design and execute projects that hold long-term value and provide a return on investment beyond the currency used build the project.
- Be present: Designing and building stuff is an atypical and infrequent activity for our client. Help our clients enjoy the journey and results that could be life-changing (in a good way).
- Stewardship—We want to Become architects for life for our completed projects and owners. We want to maintain relationships, observe results, and be trusted advisors as our projects age and clients' needs evolve.
We're an architect tribe that has refined our principles to design buildings that truly matter for the people that use them. Aspire to create hard asset architecture worth exchanging for the hardest money there is.
HODL on.
-
 @ 592295cf:413a0db9
2024-10-05 09:32:22
@ 592295cf:413a0db9
2024-10-05 09:32:22Week 30th September
Wiki article on the topic. [sPhil] (https://sphil.xyz/) Religion politics philosophy history are critical. They are not objective things.
Week of updates for protocol apps, including Gossip, coracle app, nostrmo, nostur and many others.
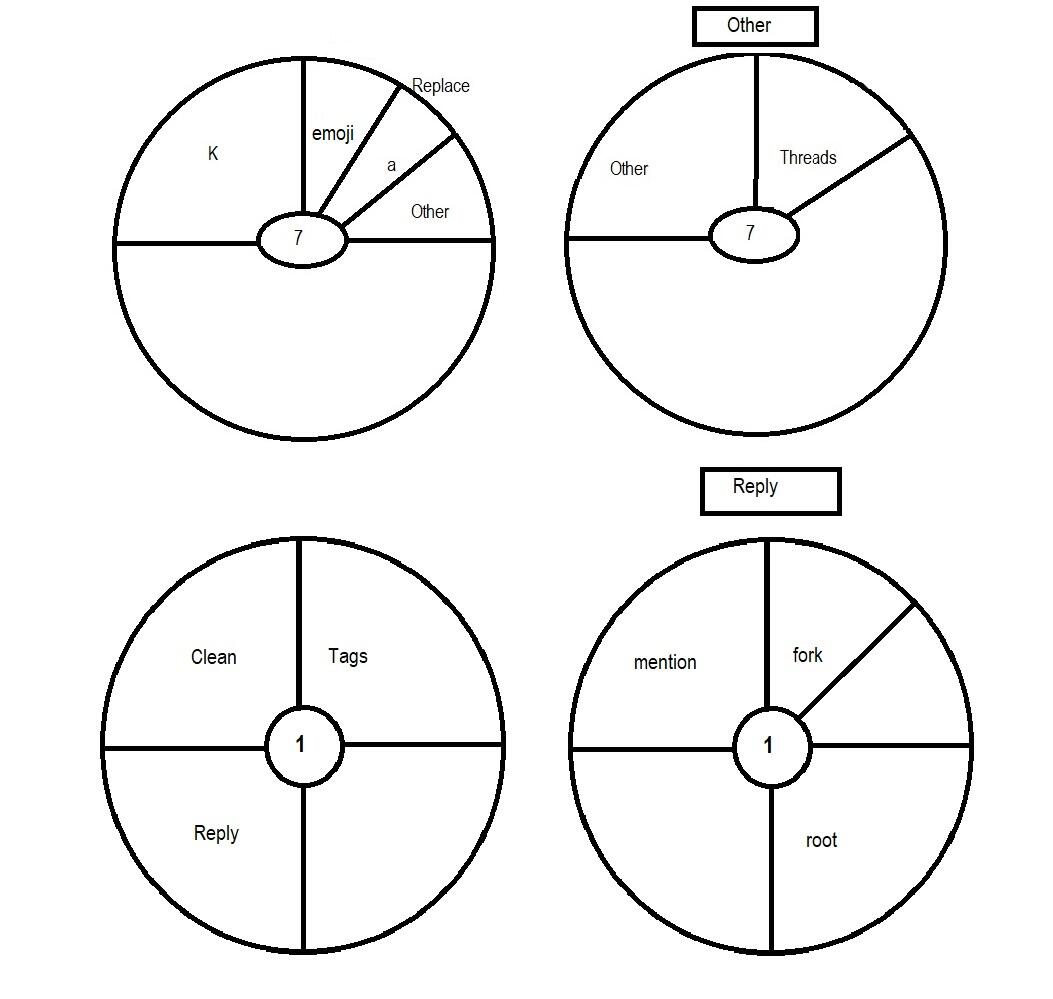
Kind7 Tags: K, emoji,a,others Others threads multi people
Show likes as kind 1 This person liked this post. Or this post has three likes in your timeline. The likes I don't know in your timeline really interest you.
The first book is the bible... Word of Alexandria.
I added cyberspace to the difficult things of the protocol ultra brain things. Low brain, middle brain, top brain, ultra.
Some alphaama codes .AA u login .AA q stuff .AA q run b .AA q run f .AA q close f
high things of alphaama nostr:nevent1qy88wumn8ghj7mn0wvhxcmmv9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcqyqlqu2vwpwax7dj420e75yws7g7vyua9e245c0x73c056gunxchluey4q99
Comment: nostr:nevent1qqs8pn0zzhgk5l2raqh736rj3ckm48pfl6r7m72rnz2r2p7lzgmx20gzyqduwzspfzelx9k6x0lrez0j8cl8rtz0lxvqylk8z2ustnfy76jpzqcyqqqqqqgpramhxue69uhkummnw3ezuetfde6kuer6wasku7nfvuh8xurpvdjsjt5rvu
You have to get to the point where you have your community relay. But you have to go down the rabbit hole of relays. General, search, local, inbox outbox, cache. Etc until you get to community relay that is being talked about these days because of NIP 29 "Relay-based Groups". In the end you have to have that table with the various types of relays clearly in your mind. If the user doesn't think about it, who should think about it, who? if I choose the relays?
NIP-100 the world to make community for me. NIP-28 + NIP-72. So you have some structure interoperability with kind1. But the Channel is another kind. You arrange the various channels in the community. No posts need to be approved.
It's useless Protocol users are becoming more reddit users or so. I don't want to deal with these people.
-
 @ 592295cf:413a0db9
2024-09-28 08:19:25
@ 592295cf:413a0db9
2024-09-28 08:19:25Week 23th September
It's not your voice anymore if it's available to everyone.
Nostr is psycho pop.
Nostrasia took place today. It all seemed beautiful. A muffled meeting, a bit in the clouds compared to the air you breathe in social media.
It seems there are two types of Nostr the one who doesn't want to grow and the one who wants to grow. 😅
-
There has always been a misconception that kind1 is the discovery layer, but in reality it is the opposite. If someone publishes a long form article there is less audience, it is true, but then it is easier to find quality content, therefore quality profiles to follow in the kind1 client aka twitter clone. And this can be true for all portable data layers, video streaming, audio, long form, ngit, wiki and whatsoever. So you have finally good follow.
-
The fact that in Nostr you don't see who follows you generally, only in a few clients, I only know one where you see who started following you. It's a strange thing, made to avoid seeing masses of bots that follow you and you can want to block, and you increase that list to the point of absurdity. It's strange because there is a lot of focus on the social graph, if you follow me it's an important aspect.
So in Nostr there are - portable data layers (Twitter style and other social) - non-portable, applications that use disposable npub, where the key is ephemeral.
- 0xchat was becoming a good client, they killed it because it has to focus on chat. I don't use chat, I don't have anyone to chat with, I follow the 0xchat channel and then I read things from Moment. I use it with my second account, because after the nos2x-amber affair with the Odell result, which I had already told you about, I no longer tried to have the first profile even on the mobile. In the end they are all keys that will be burned 😔
Maybe I won't use Nostr anymore in the future just with burn npub, pow and whatsoever. In the end you don't build anything because it's a "stateless" communication.
Lol Moment
On Nostr the poor answer guy is helping the network 🤣🤣
call the police 911: what is your emergency?
a spam bot is attacking "nostr" relays.
you want some government censorship on those relays that contain spam, yes we can do that.
-Previous week- 16 09 Machines Like Me was a good book, maybe now it will become reality.
-
The cool thing about Plebchain radio, it's not the guests, it's these two Nostr users that do a podcast. And they focused on Bitcoin and Nostr and lightning, but maybe it's just the beginning, first you have to focus on a niche and then you expand to the whole world. I think the whole world phase is starting, the podcast topics would become too repetitive. The best part is the 15 10 minute intro. Or in the live show part, there could be some interesting clips.
-
-
idea White button for activity pub user on voyage (app).
-
People hate Nostr. Don't use it
-
UnNip, now we've seen it all
-
Until the morale improves
-
-
People think Sync works like this by magic. Unfortunately it doesn't, I think, at least that's what those who are trying to do say, auto-merge, tinybase, evolu. There is an interesting local-first project. Jaguard a collaborative environment for writing empirical research papers.
-
Now I can search by id. I couldn't do it and I didn't understand the mechanism. Everything has to be instantiated. it works. Now I have to create a function maybe note_list_id and note_id. I continued to edit the NIPs page with asciidoc, categorizing this table is very fun.
New wave of Opensats grants.
- If you haven't heard about WoT this week, you probably live on Mars. There are people who didn't know you could edit on amethyst.
You need to do a podcast of NIPs, features and whatsoever, maybe doing a podcast is not the best solution because it assumes you know something more and something that could change the next day or be no longer valid. maybe you should avoid doing things you don't have full control over, or at least not spread it outside. Maybe because last year at this time I was recording audio.
-
-
 @ 599f67f7:21fb3ea9
2024-10-26 11:22:06
@ 599f67f7:21fb3ea9
2024-10-26 11:22:06Zer da Cashu?
Cashu Bitcoin-erako ecash protokolo ireki bat da, transakzio azkarrak eta komisio gabekoak eskaintzen dituena, pribatutasun ia perfektuarekin. Xehetasun gehiago nahi izanez gero, gure azalpena ikus dezakezu.
eNuts
eNuts Cashu-rako mugikorretarako zorro bikaina da, Android eta iOS (TestFlight) plataformetan eskuragarri dagoena. Mint anitzekin lan egitea ahalbidetzen du eta nostr bidez bidalketak egiteko aukera ere eskaintzen du.
⚠️ eNuts eta Cashu oraindik beta fasean daude. Funtsak galtzeko arriskua dago. Aplikazioa instalatzerakoan arriskuen inguruan irakurri. Galera ekonomikoei aurre egiteko gai zaren zenbateko txikiekin saiatu.
Probatu
Prozesu honetan zehar mint-ekin elkarreragin, ecash-a jaso eta bidali, segurtasun-kopiak egin, Lightning-era ateratzeak eta mint-en artean trukaketak egingo ditugu. Azkenik, nostr kontaktu funtzionalitatea probatuko dugu.
Instalatu
Sartu eNuts webgunera eta instalatu aplikazioa zure sistema eragilerako.
Mint bat gehitzea
Ecash-arekin elkarreragiteko, lehenik mint bat behar duzu. Mint honetan zure ecash token-ak sortzen eta itzultzen dira. Mint-a da zure Bitcoin-en zaindaria, baina ez daki nor zaren, norekin egiten duzun transakzioa, ezta zenbat diru duzun ere. Probetarako Txoko mint erabili dezakezu.
- Joan Txoko Mint-era. Kopiatu mint URL-a.
- eNuts-en, joan Aukerak > Mint kudeaketa eta sakatu + botoia. Itsatsi lehen urratsean kopiatu duzun mint URL-a.
💡 Mint gehigarriak ere gehitu ditzakezu. Mint publiko batzuk MintIndex-en aurki daitezke. Kontuan izan mint batzuek zenbateko jakin bat gordetzen dutela bideratze-gastuak ordaintzeko, eta, beraz, ezin dituzula zure sats guztiak atera.
Tokenak sortzea
Mint bat gehitu duzunean, eNuts-ek automatikoki galdetuko dizu mint horretatik Cashu token berriak sortu nahi dituzun.
- Erantzun Bai.
- Sortu faktura bat mintu nahi duzun zenbatekoarentzat. Zenbateko txiki batekin saiatu, adibidez, 100 sats.
- Ordaindu faktura Lightning zorro batetik. Faktura ordaindutakoan, ecash token-ak izango dituzu.
Prozesu honek aukera ematen dizu ecash token-ak sortzeko, eta horiek zure transakzioetarako erabiltzeko prest izango dituzu.
Ecash-ekin transakzioak egitea
Ecash-ekin transakzioak egitea, funtsean, datu multzoak bidaltzea eta jasotzea da. Funtzionalitate hauek zuk zeuk probatzeko, bidali eta jaso dezakezu zure buruari.
- Ecash bidaltzeko, sakatu Bidali > Ecash bidali.
- Mint bat baino gehiago erabiltzen baduzu, aukeratu bidali nahi duzun mint-a. Ondoren, aukeratu Kopiatu eta partekatu.
- Aukeratu zenbatekoa.
- Nahi izanez gero, gehitu ohar bat, eta sakatu Jarraitu.
- Berretsi ordainketa xehetasunak eta sortu token-a. Une honetan, coin selection funtzioa erabil dezakezu zein token erabili nahi dituzun hautatzeko.
Ohartu token-ak 1 sat, 2 sats, 4 sats, 8 sats, 16 sats eta antzeko zenbatekotan sailkatuta daudela. Horiek 10 euroko, 20 euroko edo 50 euroko billeteak bezala irudika ditzakezu. - Kopiatu token-a.
Une honetan, token-a beste norbaiti bidal diezaiokezu edo zure zorroan berreskuratu. Saiakera moduan, bigarren aukera hau egingo dugu.
- Ecash jasotzeko, sakatu Jaso > Itsatsi eta berreskuratu Ecash. eNuts-ek automatikoki irakurriko du zure arbeletik eta token-a berreskuratuko du.
💡 Zure transakzioen historian ecash token-a zain dagoen egiaztatu dezakezu, eta hartzaileak ez badu berreskuratu, itzuli dezakezu. Horretarako, sakatu zure historiako irteerako transakzioan eta aukeratu Egiaztatu token-a gastatu den. Token-a zain badago, Itzuli token-a sakatu dezakezu eta berriro zure zorroan izango duzu.
Multimint trukeak
Mint desberdinen artean bidalketak eta jasotzeak posibleak diren galdetu baduzu, erantzuna bai da, neurri batean. Hala ere, Cashu token-ak zuzenean mint batetik bestera bidaltzea ez da zuzenean egiten; horren ordez, transakzioak Lightning-era bideratzen dira, mint bat Lightning nodo bat ere badelako. Cashu token-ak ez dira bateragarriak nodo desberdinen artean.
Hau probatzeko, beste mint bat gehitu dezakezu oraindik egin ez baduzu, adibidez, cashme LNbits mint edo eNuts mint lehenetsia.
💡 Kontuan izan mint batzuek sats kopuru bat gordetzen dutela bideratze-gastuak ordaintzeko. Arazo hau konpontzeko, zure mint propioa sor dezakezu Bitcoin Txoko LNbits zorroarekin, Cashu luzapena aktibatuz.- Joan Aukerak > Mint kudeaketa atalera, eta aukeratu trukatu nahi duzun mint-a. Ondoren, joan Multimint trukeak atalean.
- Aukeratu trukatu nahi duzun mint-a.
- Aukeratu zenbatekoa eta sakatu Kuotak aurreikusi Lightning gastuen kalkulua egiteko.
- Sakatu Jarraitu.
- Egiaztatu xehetasunak, eta nahi izanez gero, coin selection funtzioa erabili. Ondoren, sakatu Orain trukatu.
Prozesu honetan, bidaltzen ari den mint-ak Lightning faktura bat ordaintzen du jasotzen ari den mint-aren bidez. Faktura osatu bezain laster, trukatuta dagoen token-a zure zorroaren saldoan agertu beharko litzateke jasotzen ari den mint-ean.
Ateratzea
Zure Cashu sats-ak berriro Lightning sats bihurtu nahi dituzunean, ateratzeko aukera duzu. Prozesua hauxe da:
- Sakatu Bidali > Lightning faktura ordaindu.
- Mint bat baino gehiago erabiltzen baduzu, aukeratu bidaliko duzun mint-a.
- LN faktura edo LNURL atalean, sartu faktura bat, LNURL edo Lightning helbide bat; edo, besterik gabe, QR kode bat eskaneatu.
- Aukeratu zenbatekoa eta sakatu Kuotak aurreikusi.
- Egiaztatu xehetasunak, eta dena zuzen dagoela ikusi ondoren, sakatu Ateratzea.
Prozesu hau amaitutakoan, mint-ak Cashu token-ak trukatzen ditu eta Lightning faktura ordaintzen du.
Segurtasun kopiak
Cashu token-ak babesteko prozesua, agian, ezberdina izango da Bitcoin eta Lightning zorroak babesteko ohiko prozesuekin alderatuta. Diru-funtsak datu blokeekin irudikatzen direnez, Cashu token-ak babesten dituzunean datu bloke horiek bakarrik babesten ari zara. Honek esan nahi du segurtasun-kopiak baliogabetzen direla transakzio berri bat egiten duzun bakoitzean.
eNuts aplikazioak Cashu token bat sortzen du zure funts guztiekin, eta token horiek zein mint-ekoak diren jasotzen du.
- Segurtasun-kopia bat sortzeko, joan Aukerak > Segurtasuna > Sortu babeskopia token. Kopiatu token-a eta gorde toki seguru batean.
Bestela, mint bakoitza banaka babestu dezakezu: - Horretarako, joan Aukerak > Mint kudeaketa atalera eta aukeratu babestu nahi duzun mint-a. Ondoren, sakatu Funtseak babestu, kopiatu token-a eta gorde toki seguru batean.
Berreskuratzea
Berreskuratzeko, kopiatu babeskopia token-a eta ireki eNuts aplikazioa. Aplikazioak automatikoki irakurriko du zure arbelean dagoena eta galdetuko dizu token-a berreskuratu nahi duzun.
Nostr
eNuts aplikazioak Nostr integrazioa eskaintzen du, horrela zure kontaktu zerrendara ecash bidali ahal izateko. Funtzio hau erabiltzeko, honako pauso hauek jarraitu behar dituzu:
- Joan Kontaktuak atalera eta itsatsi zure Nostr gako publikoa.
- eNuts-ek zure kontaktu zerrenda eskuratuko du relays-etatik. Tamalez, bilaketa funtzioa oraindik ez dago eskuragarri, eta horrek kontaktu zuzena aurkitzea zaildu dezake, kontaktu asko izanez gero.
Hartzaileak Nostr motako 4 mezu zuzena jasoko du, Cashu token-arekin. Hartzaileak mezu hau bere zorroan berreskuratu eta token-a erabili ahal izango du.
Ondorioa
Gida hau lagungarria iruditu zaizu? Saiatu Cashu token batzuk bidaltzen Nostr bidez!
-
 @ eac63075:b4988b48
2024-10-15 20:18:52
@ eac63075:b4988b48
2024-10-15 20:18:52Bitcoin emerged as a promise of financial freedom, challenging the traditional and centralized structures of governments and financial institutions. Since its inception, many enthusiasts have believed in the revolutionary potential of this cryptocurrency. However, over the years, challenges have arisen that have tested this promise, especially concerning centralization, the implementation of secondary layers like the Lightning Network, and issues of governance and privacy.
https://www.fountain.fm/episode/SDZYaFMyLEO1krL6x8RD
Centralization and the Exclusivity of Nostr
Nostr, a decentralized network aiming to be censorship resistant, emerged as an attempt to solve some inherent problems of centralization. However, it faces significant challenges. Many users point out that, despite its promise, Nostr is still not attractive to the general public, being exclusive to a specific niche.
Additionally, issues of centralization still permeate the network. Discussions on GitHub revealed that developers chose not to implement an absolute level of privacy, a decision many considered inadequate. Even with protocols developed to ensure total privacy—such as the non-identification of IPs and communicating parties—the network still lacks this robust implementation.
Individual Freedom and Data Protection
A recurring issue is the importance of demonstrating that real options exist for citizens to protect and preserve their freedom. In a world where most discussions about Bitcoin revolve around its use as an investment asset, there is an urgent need to emphasize its potential as a tool for financial freedom.
The Bitcoin community should focus on development and education, showing that the conscious use of cryptography and decentralized transactions can protect individuals against excessive government surveillance and control. Secure and private communication is fundamental, and Bitcoin, along with privacy technologies, can provide this.
Hyperbitcoinization and the Illusion of Store of Value
Hyperbitcoinization is a concept that refers to the moment when Bitcoin will replace fiat currencies worldwide. However, achieving this state is not simple, especially when Bitcoin is seen primarily as a store of value. Since 2017, this narrative has gained strength, promoting the idea that accumulating Bitcoin will lead to automatic wealth.
However, this perspective is limited. The true value of Bitcoin lies in its use as a transactional currency, not just in its scarcity. The community must work to ensure that Bitcoin is utilized in everyday transactions, strengthening its network and demonstrating its real value.
The Role of the Community in Bitcoin's Development
Bitcoin's strength comes from its community. Developers, users, and enthusiasts, through their actions and support, make Bitcoin a powerful tool. This community is responsible for ensuring that Bitcoin maintains its essence and that its functionalities are accessible to all.
It is crucial that this support network continues promoting the decentralized use of Bitcoin, without intermediaries that can censor or control transactions. Adopting Bitcoin in a centralized manner, through banks or other institutions, contradicts its original proposal and strengthens those who have historically opposed its existence.
Sidechains, Second Layers, and the Lightning Network
Sidechains and second layers, like the Lightning Network, are essential components for Bitcoin's scalability. However, they bring challenges, especially regarding the need to trust intermediaries. For these solutions to be effective, it is fundamental that they allow the unilateral withdrawal of funds, ensuring that users maintain full control over their assets.
The Lightning Network, for example, is a second layer that allows fast and cheap transactions. However, many users face difficulties when dealing with channels that do not close correctly, resulting in locked funds. These problems must be solved for the network to be truly decentralized and functional.
The Fight Against Centralization on the Internet
Centralization is not a problem exclusive to Bitcoin. The internet as a whole faces similar challenges, with data control concentrated in the hands of a few large technology companies. To ensure freedom of expression and online privacy, it is necessary to decentralize these data clusters.
Projects that seek to decentralize the internet are vital for this mission. They not only complement Bitcoin in its quest for financial freedom but also ensure that digital communication and expression are protected against censorship and corporate control.
The Future of Bitcoin and the Need for Action
The future of Bitcoin depends on the community's action. We cannot expect Bitcoin to automatically become a global medium of exchange. A conscious effort is necessary to build an ecosystem where Bitcoin can flow freely, being used in everyday transactions and valued for its utility.
Moreover, with the imminent arrival of central bank digital currencies (CBDCs), time is of the essence. CBDCs represent a significant challenge, as they can further restrict individuals' financial freedom. Therefore, accelerating Bitcoin adoption and ensuring it maintains its decentralized and uncensorable properties is a priority.
Conclusion
Bitcoin remains a powerful tool for financial freedom but faces significant challenges. Centralization, both in the context of secondary networks and the internet in general, poses a threat to its original proposal. However, with the joint action of the community and the continuous development of decentralized solutions, it is possible to maintain Bitcoin as a bastion of individual freedom.
The true revolution of Bitcoin lies in its use as a medium of exchange, not just as a store of value. To achieve hyperbitcoinization, it is necessary to build a robust ecosystem where Bitcoin can circulate freely and be accessible to all. Only then can we fulfill Bitcoin's initial promise and ensure it continues to be a tool for freedom and financial autonomy.
-
 @ 592295cf:413a0db9
2024-09-14 18:13:41
@ 592295cf:413a0db9
2024-09-14 18:13:4109 09 week
The billboard has reached its first goal.
I don't understand anything, too much.
The web is a dangerous place, maybe the couch at home is for you.
Nostr is like being in a public place like a bar and you listen to the radio, and you can decide which radio to choose, you can also talk on the radio, only those who follow you and those who are connected to that frequency can listen to you.
We talk on multiple frequencies so if one is offline they can hear me on the other.
Spam will always be a constant as are fixed costs, personnel costs, taxes things that people in general hate
A lot of talk that will be blown away by the wind.
Jack Dorsey says Nostr will be a protocol for private encrypted chats
-
Open-sats drama
-
Carnivore dietitian
-
Lightning diatribe
-
This is already Twitter 😉
Fiatjaf explained for the umpteenth time what the outbox model is, now those who look at images instead of reading books must have understood it too. My note, Patricia writes in her relays write, including select some in her outbox 10002 kind. it was a dev page of something, so maybe it won't be online for long
Thinking that with Kamala Harris's victory, the price of Bitcoin would hit a low and holders would be happy to buy. 🤣🤣 Instead with Trump new all time High, holders would be happy. 🤣🤣 Lol Moment.
I read the article about btcmap maps, there were some notes to make but I didn't, it's beyond my level, it was only for builders.
Satlantis, trustroots, and wherostr were not noted.
I had this thought that we will not "succeed" in building the openness of type 1, in the following nips, because of the relays and because discovering new things has a cost, and no one wants to discover new things. And then after that the others should use them, but how and after that at least two others appear who are doing a similar thing, but they don't talk to each other because they don't have time.
If the time horizon is 10 years, those who survive will see.
Keeping calm seems difficult.
I tried nostr-relay-tray works. It works, I would suggest a couple of changes
- Delete some events.
- View events
- Search by npub id or time
- Delete by time.
These are difficult things but they can be done with a database, so they may as well not be done.
I hope that all the controversies are forgotten and overcome and we are more serene.
-
-
 @ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23
@ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23由于gmail在中国被防火墙拦截了,无法打开,不想错过邮件通知。
通过自建ntfy接受gmail邮件通知。 怎么自建ntfy,后面再写。
2024年08月13日更新:
修改不通过添加邮件标签来标记已经发送的通知,通过Google Sheets来记录已经发送的通知。
为了不让Google Sheets文档的内容很多,导致文件变大,用脚本自动清理一个星期以前的数据。
准备工具
- Ntfy服务
- Google Script
- Google Sheets
操作步骤
- 在Ntfy后台账号,设置访问令牌。

- 添加订阅主题。

- 进入Google Sheets创建一个表格.记住id,如下图:

- 进入Google Script创建项目。填入以下代码(注意填入之前的ntfy地址和令牌):
```javascript function checkEmail() { var sheetId = "你的Google Sheets id"; // 替换为你的 Google Sheets ID var sheet = SpreadsheetApp.openById(sheetId).getActiveSheet();
// 清理一星期以前的数据 cleanOldData(sheet, 7 * 24 * 60); // 保留7天(即一周)内的数据
var sentEmails = getSentEmails(sheet);
var threads = GmailApp.search('is:unread'); Logger.log("Found threads: " + threads.length);
if (threads.length === 0) return;
threads.forEach(function(thread) { var threadId = thread.getId();
if (!sentEmails.includes(threadId)) { thread.getMessages().forEach(sendNtfyNotification); recordSentEmail(sheet, threadId); }}); }
function sendNtfyNotification(email) { if (!email) { Logger.log("Email object is undefined or null."); return; }
var message = `发件人: ${email.getFrom() || "未知发件人"} 主题: ${email.getSubject() || "无主题"}
内容: ${email.getPlainBody() || "无内容"}`;
var url = "https://你的ntfy地址/Gmail"; var options = { method: "post", payload: message, headers: { Authorization: "Bearer Ntfy的令牌" }, muteHttpExceptions: true };
try { var response = UrlFetchApp.fetch(url, options); Logger.log("Response: " + response.getContentText()); } catch (e) { Logger.log("Error: " + e.message); } }
function getSentEmails(sheet) { var data = sheet.getDataRange().getValues(); return data.map(row => row[0]); // Assuming email IDs are stored in the first column }
function recordSentEmail(sheet, threadId) { sheet.appendRow([threadId, new Date()]); }
function cleanOldData(sheet, minutes) { var now = new Date(); var thresholdDate = new Date(now.getTime() - minutes * 60 * 1000); // 获取X分钟前的时间
var data = sheet.getDataRange().getValues(); var rowsToDelete = [];
data.forEach(function(row, index) { var date = new Date(row[1]); // 假设日期保存在第二列 if (date < thresholdDate) { rowsToDelete.push(index + 1); // 存储要删除的行号 } });
// 逆序删除(从最后一行开始删除,以避免行号改变) rowsToDelete.reverse().forEach(function(row) { sheet.deleteRow(row); }); }
```
5.Google Script是有限制的不能频繁调用,可以设置五分钟调用一次。如图:

结尾
本人不会代码,以上代码都是通过chatgpt生成的。经过多次修改,刚开始会一直发送通知,后面修改后将已发送的通知放到一个“通知”的标签里。后续不会再次发送通知。
如需要发送通知后自动标记已读,可以把代码复制到chatgpt给你写。
-
 @ fa0165a0:03397073
2024-10-23 17:19:41
@ fa0165a0:03397073
2024-10-23 17:19:41Chef's notes
This recipe is for 48 buns. Total cooking time takes at least 90 minutes, but 60 minutes of that is letting the dough rest in between processing.
The baking is a simple three-step process. 1. Making the Wheat dough 2. Making and applying the filling 3. Garnishing and baking in the oven
When done: Enjoy during Fika!
PS;
-
Can be frozen and thawed in microwave for later enjoyment as well.
-
If you need unit conversion, this site may be of help: https://www.unitconverters.net/
-
Traditionally we use something we call "Pearl sugar" which is optimal, but normal sugar or sprinkles is okay too. Pearl sugar (Pärlsocker) looks like this: https://search.brave.com/images?q=p%C3%A4rlsocker
Ingredients
- 150 g butter
- 5 dl milk
- 50 g baking yeast (normal or for sweet dough)
- 1/2 teaspoon salt
- 1-1 1/2 dl sugar
- (Optional) 2 teaspoons of crushed or grounded cardamom seeds.
- 1.4 liters of wheat flour
- Filling: 50-75 g butter, room temperature
- Filling: 1/2 - 1 dl sugar
- Filling: 1 teaspoons crushed or ground cardamom and 1 teaspoons ground cinnamon (or 2 teaspoons of cinnamon)
- Garnish: 1 egg, sugar or Almond Shavings
Directions
- Melt the butter/margarine in a saucepan.
- Pour in the milk and allow the mixture to warm reach body temperature (approx. + 37 ° C).
- Dissolve the yeast in a dough bowl with the help of the salt.
- Add the 37 ° C milk/butter mixture, sugar and if you choose to the optional cardamom. (I like this option!) and just over 2/3 of the flour.
- Work the dough shiny and smooth, about 4 minutes with a machine or 8 minutes by hand.
- Add if necessary. additional flour but save at least 1 dl for baking.
- Let the dough rise covered (by a kitchen towel), about 30 minutes.
- Work the dough into the bowl and then pick it up on a floured workbench. Knead the dough smoothly. Divide the dough into 2 parts. Roll out each piece into a rectangular cake.
- Stir together the ingredients for the filling and spread it.
- Roll up and cut each roll into 24 pieces.
- Place them in paper molds or directly on baking paper with the cut surface facing up. Let them rise covered with a baking sheet, about 30 minutes.
- Brush the buns with beaten egg and sprinkle your chosen topping.
- Bake in the middle of the oven at 250 ° C, 5-8 minutes.
- Allow to cool on a wire rack under a baking sheet.
-
-
 @ 129f5189:3a441803
2024-09-09 23:28:41
@ 129f5189:3a441803
2024-09-09 23:28:41Project 2025, outlined in the Heritage Foundation's "Mandate for Leadership" document, serves as a fundamental guide for the next Republican administration. Despite Trump's extensive denial, in today's material, we will explore the deepening and continuation of many policies already employed during his first term. The idea is that this material will serve as a reference document to consult and verify what was actually implemented and/or followed. https://image.nostr.build/e3b89d71ff929258e5d9cb0b5ca8709a381598f43d8be4b17df3c69c0bc74d4a.jpg This document presents proposals for the foreign policy and the State Department of the United States of America, as well as the strategy with its political partners and adversaries. We will also address the U.S. government's communication strategy abroad. https://image.nostr.build/a4250b786f611b478aaf0be559427ad7d4296fbcacb2acc692c7f0d7eb06b0dd.jpg Reorienting U.S. Foreign Policy: Proposals for a Conservative Future In the chapter "The Department of State" from the "Mandate for Leadership," also known as "Project 2025," Kiron K. Skinner presents a comprehensive plan to reform U.S. foreign policy under a conservative administration. Skinner, a renowned foreign policy expert and former Director of Policy Planning at the U.S. State Department, outlines global threats and offers specific recommendations to strengthen the U.S. position on the international stage. Below, we present a detailed analysis of the proposals, emphasizing direct quotes and explanations of the key points discussed. https://image.nostr.build/278dcd7ef0439813ea35d0598319ee347f7a8cd7dfecac93be24ffdd0f6ecd04.jpg History and Structure of the State Department Since its founding in 1789, the State Department has been the primary diplomatic channel of the U.S. With nearly 80,000 employees and 275 posts around the world, it faces significant structural challenges. Skinner highlights that "the biggest problem of the State Department is not a lack of resources," but the belief that it is "an independent institution that knows what is best for the U.S." (Skinner). The scholar and former Director of Policy Planning at the U.S. State Department during the Trump administration emphasizes these points, considering the difficulty in accepting a conservative international approach by State Department employees (the equivalent of the Ministry of Foreign Affairs in other countries). https://image.nostr.build/049939926793e86000b300b9a962dc0ae7e271d9a607ae36d8cb08642adf4174.jpg Political Leadership and Bureaucratic Support To align the State Department with presidential priorities, Kiron suggests appointing political leaders who are committed to the president's vision. "Leadership should include political appointees in positions that do not require Senate confirmation, including senior advisors and deputy secretaries" (Skinner). Furthermore, she emphasizes the importance of training and supporting these appointees to ensure effective coordination between agencies. https://image.nostr.build/6ed704cc9612aa6489e048b143f1e489c1f8807fdf2ab011b4ba88e4a1e3619a.jpg Global Threats to the U.S. The document identifies five countries that pose significant threats to the security and prosperity of the U.S.: China, Iran, Venezuela, Russia, and North Korea. 🇨🇳 China: Skinner argues that China represents an existential threat. "The U.S. needs a strategic cost-imposing response to make Beijing's aggression economically unviable" (Skinner). Additionally, she emphasizes that the issue is not with the Chinese people, but with the communist dictatorship that oppresses them: "As with all global struggles against communist and other tyrannical regimes, the issue should never be with the Chinese people, but with the communist dictatorship that oppresses them" (Skinner). https://image.nostr.build/e707273f1d08bdc4187123a312bd116695b5f603066e11ad30fcef4466730b6b.jpg 🇮🇷 Iran: The Obama administration, through the 2015 nuclear deal, provided the Iranian regime with a "crucial cash bailout" (Skinner). Kiron criticizes this approach, asserting that the U.S. should support the Iranian people in their demands for a democratic government. "The correct policy for Iran is one that recognizes that it is in the U.S. national security interests and the human rights of Iranians that they have the democratic government they demand" (Skinner). https://image.nostr.build/cda7d29a62981f59ad8d77362b3867b552f190c8d7e0e8d9233cb7c1d1d0309e.jpg 🇻🇪 Venezuela: Under the regimes of Hugo Chávez and Nicolás Maduro, Venezuela has transitioned from a prosperous country to one of the poorest in South America. Skinner suggests that the U.S. should work to contain Venezuelan communism and support its people. "The next administration should take steps to put Venezuela's communist abusers on notice and make progress in helping the Venezuelan people" (Skinner). https://image.nostr.build/f53e12564cae74d4b50c24b0f3752dd2c53b70bd1c00a16df20736fb8588417d.jpg 🇷🇺 Russia: The war between Russia and Ukraine divides opinions among conservatives, and the document considers three lines of action. Some advocate continuing support for Ukraine, while others believe that such support does not serve U.S. security interests. "The conservative approach rejects both isolationism and interventionism, first asking: What is in the interest of the American people?" https://image.nostr.build/8fedaf77129f4801f4edb8b169b2ac93a3e518b8bf3642b3abc62575b5435fa3.jpg One conservative school of thought believes that "Moscow's illegal war of aggression against Ukraine represents major challenges to U.S. interests, as well as to peace, stability, and the post-Cold War security order in Europe" (Skinner). This view advocates for continued U.S. involvement, including military and economic aid, to defeat Russian President Vladimir Putin and return to pre-invasion border lines. Another conservative school of thought argues that U.S. support for Ukraine is not in the interest of U.S. national security. According to this view, "Ukraine is not a member of the NATO alliance and is one of the most corrupt countries in the region" (Skinner). It is argued that the European nations directly affected by the conflict should help defend Ukraine, but the U.S. should seek a swift end to the conflict through a negotiated settlement. https://image.nostr.build/22db3d0e79340c1d62344a2b8a3bfddbe4d5bd923cf77d70cfbf5ebf73e4db3e.jpg A third conservative viewpoint avoids both isolationism and interventionism, proposing that "each foreign policy decision should first ask: What is in the interest of the American people?" (Skinner). From this perspective, continued U.S. involvement should be fully funded, limited to military aid while European allies address Ukraine's economic needs, and must have a clear national security strategy that does not endanger American lives. https://image.nostr.build/939fea0bb5c69f171a3da1073e197edcff23a600430b3bc455f6d41bc8a0319f.jpg Although not stated explicitly, I believe this third viewpoint is the one Kiron Skinner desires, as she considers American intervention important but advocates for balancing the costs of the war with its partners in the European Union and NATO. https://image.nostr.build/d1d0c7fb27bfc5dd14b8dde459b98ed6b7ca2706473b2580e0fbf5383f5a9c10.jpg 🇰🇵 North Korea: North Korea must be deterred from any military conflict and cannot be allowed to remain a de facto nuclear power. "The U.S. cannot allow North Korea to remain a de facto nuclear power with the capability to threaten the U.S. or its allies" (Skinner). https://image.nostr.build/95febb04f6d2e0575974a5e645fc7b5ec3b826b8828237ccc1f49b11d11d6bce.jpg Detailed Policy Proposals Refugee Admissions: The Biden administration has caused a collapse in border security and internal immigration enforcement, according to Skinner. She argues that the U.S. Refugee Admissions Program (USRAP) should be resized. "The federal government should redirect screening and verification resources to the border crisis, indefinitely reducing the number of USRAP refugee admissions until the crisis can be contained" (Skinner). https://image.nostr.build/a5740b33842e47b9a1ab58c7b72bd6514f9b6ffbb18706deed1445c59236bc0d.jpg Corporate Collaboration with China: Skinner criticizes the collaboration of companies like BlackRock and Disney with the Chinese regime, noting that "many are invested in an unwavering faith in the international system and global norms," refusing to acknowledge Beijing's malign activities. She emphasizes that the real issue is the communist dictatorship that oppresses the Chinese people, not the Chinese citizens themselves (Skinner). https://image.nostr.build/05a3c787f144c4519c2ee8a4b22e64b8729842819ace4b439c849ef70ecd60b4.jpg Fentanyl and Mexico: The trafficking of fentanyl, facilitated by Mexican cartels in collaboration with Chinese precursor chemical manufacturers, is a critical problem. "Mexican cartels, working closely with Chinese manufacturers of fentanyl precursor chemicals, are sending this drug to the U.S., causing an unprecedented lethal impact" (Skinner). The next administration should adopt a firm stance to halt this public health crisis. https://image.nostr.build/59e32aeef5dabab3344a94a3e415d57fed91fece8bc3c5f068e9f6f7d71f99bd.jpg Re-hemispherization of Manufacturing: Kiron proposes that the U.S. promote the relocation of manufacturing to partner countries such as Mexico and Canada. "The U.S. should do everything possible to shift global manufacturing to Central and South American countries, especially to move it away from China" (Skinner). This would improve the supply chain and represent a significant economic boost for the region. https://image.nostr.build/5d5d7d792f1c94eb6e2bd7a4b86c43236765719e183be8ba8e00ed7dd07eca66.jpg Abraham Accords and a New “Quad”: Skinner suggests that the next administration should expand the Abraham Accords to include countries like Saudi Arabia and form a new security pact in the Middle East that includes Israel, Egypt, Gulf states, and possibly India. "Protecting the freedom of navigation in the Gulf and the Red Sea/Suez Canal is vital for the global economy and, therefore, for U.S. prosperity" (Skinner). https://image.nostr.build/c87cd99cb3ea2bef40e9d1f1fea48b0c9f9f031f3077fff658f15f850e7b8589.jpg Policy for Africa: The U.S. strategy for Africa should shift focus from humanitarian assistance to economic growth and countering China’s malign activities. "Development assistance should focus on fostering free market systems and involving the U.S. private sector" (Skinner). She also highlights that African nations are opposed to the imposition of policies such as abortion and LGBT lobbying. https://image.nostr.build/44df42f32e61c14786ac46c231d368b14df4dc18124a0da458e8506f917302f2.jpg Relations with Europe and Asia Europe: The U.S. should demand that NATO countries increase their contributions to defense. "The U.S. cannot be expected to provide a defense umbrella for countries that do not contribute adequately" (Skinner). Additionally, urgent trade agreements should be pursued with the post-Brexit United Kingdom. https://image.nostr.build/6c013bacfa9e6505ad717104d9a6065f27664a321dd2c3d41fd7635258042d2f.jpg Asia: The withdrawal of U.S. troops from Afghanistan was humiliating and created new challenges. Skinner emphasizes the importance of India as a critical partner to counterbalance the Chinese threat and promote a free and open Indo-Pacific. Cooperation within the Quad, which includes the U.S., India, Japan, and Australia, is essential to this strategy. "The priority is to advance U.S.-India cooperation as a pillar of the Quad" (Skinner). https://image.nostr.build/1cc988b2f70d855c9676d7e38ffdb23564d04ad6333a8d256698f416a1c6704e.jpg International Organizations Skinner criticizes the corruption and failure of the World Health Organization (WHO) during the Covid-19 pandemic. "The next administration should end blind support for international organizations and direct the Secretary of State to initiate a cost-benefit analysis of U.S. participation in all international organizations" (Skinner). She also supports the “Geneva Consensus Declaration on Women’s Health and Protection of the Family,” which is against abortion, and believes that the U.S. government should not fund international organizations that promote abortion (Skinner). https://image.nostr.build/0b583511fef16d68736804fae2f15850eb5c803af01f006a3fe10cdbc583f48c.jpg Conclusion Skinner’s document provides a detailed vision for reorienting U.S. foreign policy under a conservative administration, with an emphasis on ensuring that the State Department serves the national interests defined by the president. With these guidelines, the next administration has the opportunity to redefine the U.S. position on the global stage, promoting security, prosperity, and freedom. https://image.nostr.build/697522745c5947cd4384cdd302b531ee98ce5d59a5d72de0b4f3a52c9abd4821.jpg
-
 @ 7cc328a0:2a247c0e
2024-10-12 15:54:42
@ 7cc328a0:2a247c0e
2024-10-12 15:54:42relay.tools quarterly report
October, 2024
Project Updates
Milestone: Relay.tools is celebrating 1 year of OpenSats! Cheers to everyone that made this possible.
Relays were very popular this quarter. Scaling efforts were prioritized! This is a good indicator for relay.tools as it means that it's healthily growing. Development was executed well, completing one project at a time across the whole stack.
Relay Discovery
I've been working with @sandwich from nostr.watch on NIP66.
NIP66 will be an ABSOLUTE GAMECHANGER for clients in finding of their relays. This was always a vision for relay.tools and I am honored to be working with @sandwich on what is a pretty amazing solution. We are now in a phase of client outreach, to gather client feedback and help them implement/understand the overall goal of the NIP.
TLDR: the goal is to create a distributed version of the nostr.watch data, using nostr events.
- [x] implemented NIP66 draft7 (the 'final' design) in monitorlizard
- [x] started shipping events to the monitor relay(s) in collab with nostr.watch backends and relay.tools backends.
- [x] fixed bugs and released new binaries for monitorlizard (a NIP66 data reporting tool)
Auth Proxy Rollout
The NIP42 Auth Proxy project went really well this quarter. It's now serving tons of traffic and most bugs with clients have been squashed and the proxy hardened. This has become a very popular feature on the relays, as AUTH has many benefits beyond protecting of DMs.
- [x] testing vs. NIP17 and bugs fixed
- [x] cluster operations (multiple proxies)
UI/UX
A huge milestone this quarter was the release of the settings wizard. This is a walkthrough for new (and current) users of all the available settings for different 'relay types'. A lot of work over the last year has gone into the culmination of these settings and the wizard was a major step forward to help users understand what their options are when running a relay.
Another major UI change was the introduction of a relay feed to the landing page for a relay. This is called the relay explorer. The idea was to move to a single page app, and re-do navigation for easy relay browsing and discovery.
- [x] settings wizard released
- [x] relay explorer v2
Installer
The installer had lots of good effort put in by me and some nice contributors. We did a couple iterations on documentation and facilitated in the creation of 2-3 new relay hubs that are using this installer infrastructure.
Some additions to the installer were:
- [x] docs for building self-hosted machine images and installing on a VPS
- [x] FULLY AUTOMATIC SSL certificate handling for multiple domains with certbot
- [x] self-hosted influxDB (for relay metrics)
- [x] fix bugs with auto-deploy upgrade
Billing/Invoicing/Support
The billing system had some improvements this quarter and many invoices were sent. :) It now has better super-admin tools to notify users of past-due balances via nostr (With NDK). This took a few iterations of deciding the best way to contact users of nostr and figuring out why they don't respond to messages. It's a learning experience all the way around and the billing system will evolve over time in ways that are conducive to remaining 100% nostr for user communication and support.
The support system also showed signs of life, and people were able to use it to contact me with their questions via the various help-desk methods that I've been rolling out. (A relay, a support npub, DMs, NIP17 DMs, simplex)
Scaling!
Relay.tools successfully completed the first scale-out event. This is HUGE. Relays take more and more bandwidth and resources as they establish themselves, while at the same time needing a reasonable low-cost environment to grow in. To meet their demands the horizontal scaling is important. This will scale on commodity hardware or VPSs with ZERO vendor lock-in.
- [x] multi-server clustering with ZERO cloud vendor lock-in
- [x] deployment pipeline and capacity planning
- [x] HAproxy and additional AUTH proxies fronting all services
- [x] internal/external network support
-
 @ e97aaffa:2ebd765d
2024-10-26 10:10:21
@ e97aaffa:2ebd765d
2024-10-26 10:10:21Não é possível determinar o número exato de quantos bitcoins terá o Satoshi, já foram efectuados diversos estudos, apesar de discrepâncias nos resultados, estima-se entre os 900 mil a 1.1 milhões de moedas.
A Arkham identificou apenas 3 endereços (P2PKH) pertencentes ao Satoshi, não esquecendo que no início não existiam endereços, os bitcoins eram enviados diretamente para a pubkey (chave pública, P2PK).
Este gráfico apenas contabiliza os bitcoins em endereços. Mesmo após o desaparecimento de Satoshi, a comunidade continua a enviar moedas para os seus endereços.
O endereço principal recebe regularmente moedas, têm mais de 38 mil transações, entre elas, destaca-se as seguintes:
Este ano, um anônimo doou quase 27btc, incrível.
O problema
A muito longo prazo, com o desenvolvimento tecnológico, os computadores vão ficar cada vez mais poderosos. Conforme os computadores vão evoluindo, o desenvolvimento da computação quântica, o bitcoin vai acompanhar essa evolução tecnológica, para se manter seguro. Os utilizadores terão que migrar de endereços mais antigos para endereços mais resilientes. É uma evolução natural.
O problema está nas moedas que estão em tecnologias/endereços mais antigos, sobretudo nos que têm a pubkey exposta, estes serão os primeiros alvos. Vai demorar muitos anos, mas um dia será possível ter acesso a esses UTXOs. O pagamento para P2PK foi utilizado entre 2009 e 2010, hoje em dia é quase inexistente.
Não é necessário entrar em pânico, os endereços SegWit são muito mais seguros e resilientes, porque oculta a pubkey. A pubkey só é revelada no momento em que efetua a primeira transação(enviar), assim para garantir uma melhor segurança é essencial não reutilizar endereços.
Só que existem 45370 UTXOs que não realizaram a migração para tecnologias mais seguras, isto representa mais de 1.7 milhões de Bitcoins, ou seja, 8.73% do supply.
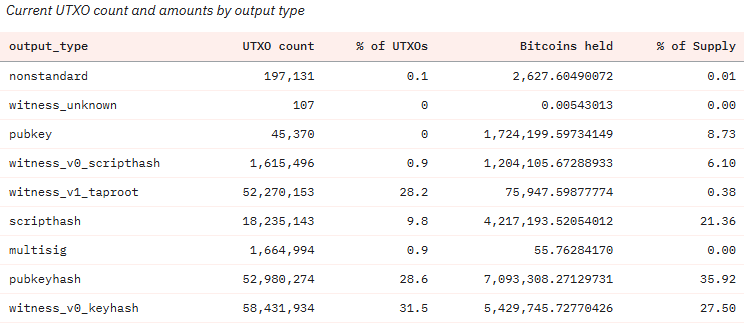
Apenas uma minoria dessas moedas pertence a bitcoiners no “ativos”, a grande maioria pertence ao Satoshi e as pessoas que perderam as chaves. Apesar de tudo, esporadicamente algumas dessas moedas são movidas, este ano já foram 172 UTXOs, equivalente a 7707 BTC.
Além dos P2PK ainda existem os endereços que foram reutilizados, que tem a chave pública exposta, assim o número aumenta para 4 milhões de moedas, apesar de ser um número elevado, não é preocupante, porque parte destas moedas ainda tem donos ativos, quando for necessário, vão se mover para endereços mais seguros.
O dilema
«Moedas perdidas apenas fazem com que as moedas de todos os outros valham um pouco mais. Pense nisso como uma doação para todos.» – Satoshi
O problema é que essas moedas não estão perdidas para sempre, talvez daqui a 5 ou 20 anos, não sei, mas uma coisa é certa, um dia vão ser recuperadas e não serão pelos legítimos donos.
Assim, nos próximos anos a comunidade de bitcoiners terá um dilema para resolver, o que fazer com os Bitcoins do Satoshi/P2PK?
Existem duas possibilidades: não fazer nada e essas moedas voltam a circular ou então, mudar o código para bloquear as moedas para sempre.
Qualquer uma das soluções será algo extremamente polémica, certamente vai dividir a comunidade, vai ser uma discussão acirrada, dificilmente haverá um consenso, por isso é mais provável ficar tudo como está.
Vendo bem, o bitcoin vai passar por uma situação similar ao ouro, periodicamente são descobertas moedas de ouro, que foram escondidas durante décadas ou séculos pelos nossos antepassados. O ouro que estava “perdido”, volta à circulação.
Será uma nova corrida ao “ouro”, o resgate das moedas do Satoshi. Se esse resgate for lento e gradual, não terá grande impacto, mas se for num curto espaço de tempo será um enorme problema, são mais de 8% de supply que entram no mercado.
O preço poderá ser um problema, mas a meu ver, o grande problema é a busca em si, porque será mais lucrativo gastar energia na procura das moedas do Satoshi do que minerar novos bitcoins.
Será que a hashrate não cairá drasticamente? Colocando em causa a segurança da rede.
Esta é a minha principal dúvida e receio.
A minha opinião
Hoje eu penso que deveríamos optar por algo intermédio, nem com a proibição total, nem sem restrições. Apenas nos blocos com o número múltiplo de 144, ou seja, um bloco por dia, seria possível incluir transações P2PK. Além disso, o número de transações por bloco seria limitado: 1 UTXO maior que 10 btc ou vários UTXOs com uma soma inferior a 10 btcs.
Este limite de “espaço” é suficiente para os legítimos donos das moedas efetuarem as transações no período pré quântica. No período pós quântica, se a quebra da criptografia for muito rápida, o limite de bloco vai criar uma gargalo, vai obrigar o aumento drástico do fee, reduzindo o lucro do “ladrão”, além de financiar os mineradores.
Conclusão
A minha ideia é muito complexa, mas o bitcoin é um protocolo simples, a comunidade é muito conservadora, dificilmente aceitaria algo assim tão complexo. Por isso eu digo, só existem dois caminhos plausíveis, ou não fazer nada ou a proibição total dos P2PK.
Mas vamos ter muitos anos para pensar sobre o assunto.
-
 @ 07e188a1:24d232f3
2024-10-26 09:16:44
@ 07e188a1:24d232f3
2024-10-26 09:16:44Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
A sub heading goes a long way
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
-
 @ 7cc328a0:2a247c0e
2024-10-12 15:33:58
@ 7cc328a0:2a247c0e
2024-10-12 15:33:58relay.tools quarterly report
January, 2024
Project updates
UI design
Relay.tools spent quite a bit of time working on UI design this quarter. Since UI is time intensive and there are many other aspects of the project that need work, I time-boxed this work to 3-4 weeks total.
I engaged with @Daniel from #nostrdesign and a freelance UI developer @freecritter. We setup a penpot instance for relay.tools and practiced using that instead of closed-source figma. We learned that penpot is not as friendly as figma from a designers point of view, but is workable. From the perspective of a frontend engineer it is no different than figma and using penpot is a big opensource win.
The following designs were implemented this quarter. There is still much to do in this area and some aspects have been brainstormed but put on hold due to other priorities.
Relay branding and directory
I wanted to give the relays personality and branding, here is a list of improvements in this area:
- [x] The home page now prominently displays the public relays that have chosen to advertise.
- [x] Relay 'Badges' were re-designed to have better contrast and fit.
- [x] Relays have a custom direct landing page at their domain. eg. frogathon.nostr1.com
### 'Paid relay' support
Relays now support lightning payments to the relay.tools operator. This helps with combating spam and allowing the relay owners to subsidize their monthly cost.
Layout / theme
The frontend code has been modified so that it is responsive on mobile/desktop using columns. The menu was re-designed to be responsive on mobile and shows user hints for login as well as additional links (explore, FAQ). Theme switcher bugs for light/dark modes have been fixed. (Nextjs bleeding edge workaround was required).
Relay Explorer Alpha
The Relay Explorer Alpha is a mini-client for interacting with a single relay. The following improvements were made:
- [x] Moderation capabilities added: Mods can delete messages, block pubkeys, and delete+block directly from the explorer.
- [x] Image and Link parsing / optional loading.
- [x] Replies implemented.
Example screenshot showing these features:
Installer
Another main focus this quarter was to implement an installer for the relay.tools software so that anyone can easily self-host this on a generic VPS.
The installer will be a simple shell script that asks the user a few questions (like their domain name) and then automatically installs the entire stack.
A new code repository was created for this called relay-tools-images
- [x] Main architecture to match production (systemd and nspawn).
- [x] Common Base OS image builds (Debian).
- [x] Haproxy, Strfry, Relaycreator and Mysql image builds.
- [x] Auto-updating of application code (including database migrations).
This is still in-progress and will be part of next quarter's priorities to finish the first stage. (described in plans for next quarter)
Lightning Node
A decent amount of time was spent managing a Bitcoin+Lightning+LnBits node and building a second node for testing and standby purposes.
I had some node issues this quarter and have been learning, re-building the node, upgrading, and aquiring more inbound liquidity to support relay operations.
Relay Management / daily operations
Relay.tools growth last quarter exceeded expectations and lots of work in the ladder part of this quarter went into daily operations.
It grew so fast that I have paused any advertising so that I have time to implement some important growth related features (as described in the plans for next quarter).
- number of relays currently running: 63
- number of unique admins/mods: 207
- events processed in last 30d: 5,091,724
- gigabytes sent/received in last 30d: 1,651GB / 175GB
Monitoring
Daily operations include checking in on the relay activity to get a feel for what's going on. I've implemented an InfluxDB integration for the strfry plugin, which helps with daily operations and in the future will provide owners, mods, and users with stats showing relay performance and event counts. This greatly improves visibility into the relays and is the backbone of data analysis for the platform.
Events by Kind (7d)
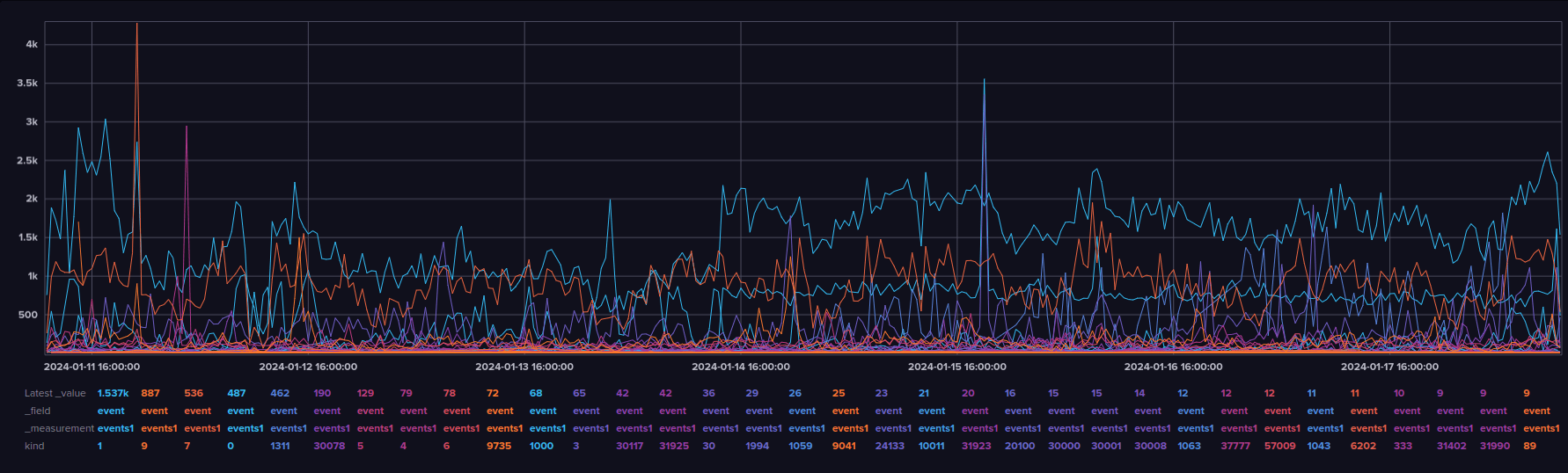
Events by Relay (7d)
Data Explorer View (single relay, kind 3)
Moderation
Daily operations time is also spent ensuring relays meet our TOS. That includes browsing the relays content for anything that does not meet the TOS and performing mitigation when necessary. This can be time consuming. I will be adding super-moderator capability so that others can assist as we grow (as described in the plans for next quarter).
Training / Feedback / Community
I promoted the use of event specific relays for nostr community events. Feedback was very positive and showed that people enjoy having event specific relays even if client support is minimal. * Nostrasia * Frogathon
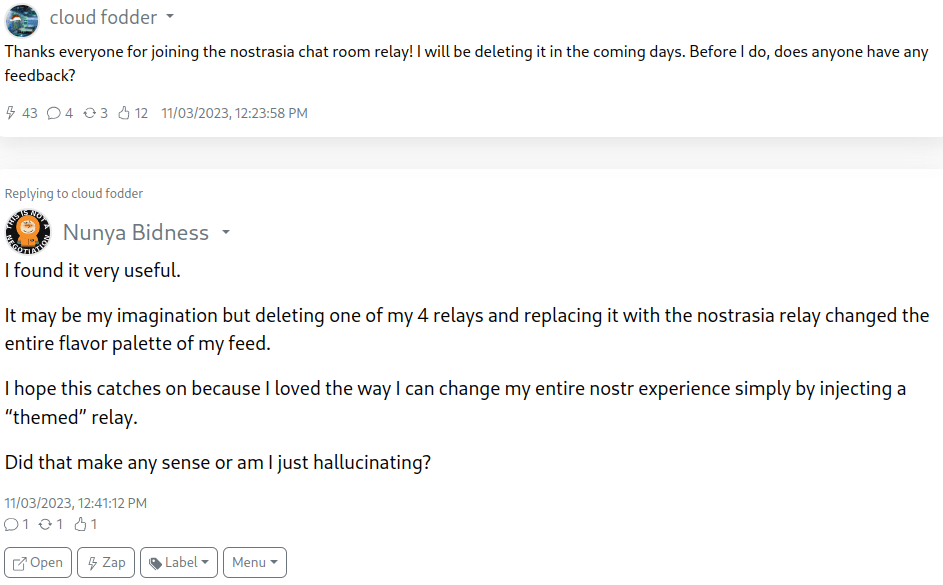
Plans for next Quarter
Finish the installer - [ ] SSL certificate management with certbot. - [ ] Nostr key generation for API credentials. - [ ] install.sh script for interactive -and- config file based one-shot installation. - [ ] Publish pre-built images and integrate their use with the installer.
Re-Occuring Billing (+ tools for interacting with community of relay runners) - [ ] Implement re-occuring billing using a credits system and lightning payments. - [ ] Implement user notification(s) for billing cycle notifications. - [ ] Implement user feedback / support channel.
Additional visibility and moderation tools - [ ] Implement super-moderator capability for TOS violations. - [ ] Engage with community to help support moderation
-
 @ eac63075:b4988b48
2024-10-10 18:12:38
@ eac63075:b4988b48
2024-10-10 18:12:38Companies like Meta (formerly Facebook) and Twitter (now X) control platforms that have become the main channels of communication for millions of people worldwide. At the center of this discussion are figures like Mark Zuckerberg and Elon Musk, whose recent actions raise serious questions about freedom of speech, censorship, and political manipulation.
https://fountain.fm/episode/VzJItfySZ8z6417prHyD
Recently, a public letter written by Mark Zuckerberg revealed how the U.S. government, under Joe Biden’s administration, pressured Facebook to censor information during the COVID-19 pandemic. The controversy involves, among other topics, the censorship of content related to Biden’s son, Hunter Biden, during the height of the laptop scandal. This revelation raises questions about the role these platforms play in spreading or withholding information, as well as the direct impact this has on democracy.
Meta and Censorship: Zuckerberg's Letter
In his letter, Zuckerberg admitted that Facebook was pressured by the Biden administration to suppress information about the pandemic and the Hunter Biden case, something he now claims to regret. This has sparked heated debate about how far social media should go in yielding to governmental pressure. Many see this as a threat to freedom of speech, while others argue that this censorship was necessary to control misinformation.
The issue here is not just about government pressure, but the fact that Facebook, as a global platform with billions of users, holds unparalleled power to shape narratives. When a platform decides what is “acceptable” or “truthful,” it directly influences public perception and opinion formation, especially during critical moments like an election.
Zuckerberg, in his letter, seems to be trying to salvage his image, but the damage has already been done. The admission that Facebook collaborated with the government to suppress certain information raises doubts about the platform’s impartiality and its commitment to free speech.
Elon Musk and Free Speech on X
Meanwhile, Elon Musk, now in control of Twitter, renamed X, has promised to transform the platform into a space for free expression. However, the reality seems more complex. Musk claims that X should be a place where all voices can be heard, regardless of political or ideological alignment. Yet, this promise has proven difficult to fulfill in practice.
X continues to ban users and censor content, especially in countries with authoritarian governments like India and Turkey. This creates a dichotomy: on the one hand, Musk advocates for unrestricted free speech, but on the other, he complies with censorship requests from these regimes. This raises questions about Musk’s true intentions and the extent to which he is willing to uphold his principles when the platform faces international pressure.
Moreover, Musk has used X as a political platform, especially in support of former President Donald Trump. The reinstatement of Trump’s account, banned during the Capitol insurrection, has raised further suspicions that Musk is turning X into a tool of political power. For many, this represents a significant risk to the neutrality of digital platforms.
The Cambridge Analytica Scandal and the Risk of Political Manipulation
The discussion of censorship and free speech on social media brings up a case that shocked the world a few years ago: the Cambridge Analytica scandal. In 2015, this British company was accused of using personal data from millions of Facebook users to manipulate elections, including the Brexit referendum and Donald Trump’s 2016 presidential election.
Although Cambridge Analytica was dissolved after the scandal, its legacy remains. Big Tech companies still have access to vast amounts of user data, and the power this grants them is alarming. Companies like Meta and X could, in theory, directly influence election outcomes by manipulating algorithms to promote certain narratives or suppress others.
This scenario raises crucial questions: to what extent can we trust these platforms to act impartially? Are they truly committed to free speech, or are they using their power to shape the political future of the world according to their own interests?
The Pablo Marçal Case and Manipulation in Brazil
In Brazil, a recent example that illustrates the complexity of the relationship between social media and political power is the case of coach Pablo Marçal. Marçal, who built a considerable following, became involved in controversies related to using his influence to manipulate public opinion. Recently, it was revealed that X hired the renowned law firm Pinheiro Neto to defend Marçal’s continued presence on the platform, even after controversies.
This move raises concerns about the selective enforcement of social media’s own rules. Why are some influencers protected while others are summarily banned? Marçal’s influence, particularly among conservative voters in Brazil, is undeniable, and the public defense of his account on X suggests that more is at stake than just free speech.
The Future of Social Media and Democracy
What we are witnessing is the rise of a new era where social media plays a central role in global politics. Control over the flow of information lies in the hands of a few giant companies, and the decisions of their leaders—whether Mark Zuckerberg, Elon Musk, or others—can have a profound impact on elections, governments, and democracies.
This raises legitimate concerns about the future of democracy in a world where private platforms have the power to control public discourse. Big Tech censorship, often disguised as “misinformation control,” can easily become a tool for manipulation.
For citizens, this means being vigilant and critical about the information they receive on social media. Freedom of expression must be defended, but we also need to question who is behind these platforms and what their true motivations are. Trust in social media is at stake, and the future of democracy may depend on how we decide to deal with this unprecedented power.
Conclusion
Recent revelations about Zuckerberg’s involvement in censorship and Musk’s use of X to promote a political agenda highlight the urgent need for transparency in social media platforms. As these companies become increasingly influential in the global political arena, the public must be aware of the risks and actively engage in the debate about the future of free speech and democracy.
-
 @ eac63075:b4988b48
2024-10-08 20:37:08
@ eac63075:b4988b48
2024-10-08 20:37:08In this botcast, we explore how technology is solving one of the biggest challenges faced by DAOs (Decentralized Autonomous Organizations): vote fraud. Learn how Vitalik Buterin and other experts from Cornell University are leading innovation using Zero-Knowledge Proofs and Proof of Work (PoW) to ensure security and privacy in blockchain voting systems.
You will discover how these technologies combat practices like token renting and lending, preventing vote manipulation in DAOs. The video also covers the importance of dedicated hardware to increase the integrity of digital elections.
Listen to the Podcast:
https://wavlake.com/episode/bdb2850b-49b4-45f6-9a00-d310e29f4528
Table of Contents:
Source: YouTube Transcript - Morning Crypto (Timestamped Excerpts)
I. Introduction and Context (0:00:00 - 0:02:37)
- This section sets the stage by briefly discussing a common problem in Decentralized Autonomous Organizations (DAOs): fraudulent voting practices.
- It highlights the issue of individuals manipulating voting systems by borrowing, renting, or delegating tokens to influence decision-making within DAOs.
II. Introducing Complete Knowledge and the Proposed Solution (0:02:37 - 0:03:39)
- Introduces a potential solution developed by Vitalik Buterin and researchers from Cornell University, utilizing Zero-Knowledge Proofs to address the challenge of fraudulent voting in DAOs.
- Explains that the proposed solution involves a dedicated hardware or wallet system that verifies voting rights without revealing the user's private key, preventing token manipulation.
III. Deep Dive into Complete Knowledge with "Ger" (0:05:54 - 0:07:57)
- This section features "Ger," a voice assistant, who explains Complete Knowledge as a cryptographic innovation.
- Ger describes how Complete Knowledge allows users to prove possession of information, like a private key, without revealing the information itself.
- The section emphasizes how Complete Knowledge enhances security and privacy in digital identity and voting systems.
IV. Proof of Work and ASICs for Enhanced Security (0:07:57 - 0:09:05)
- Examines the potential of using Proof of Work (PoW), the consensus mechanism behind Bitcoin, in conjunction with Complete Knowledge.
- Explains how PoW can act as a mechanism to further ensure that a specific secret or key is held by a user without requiring the user to reveal it.
- Discusses the use of Application-Specific Integrated Circuits (ASICs) for performing the computational tasks required for PoW and Complete Knowledge verification.
V. Practical Implementation and Conclusion (0:09:05 - 0:10:25)
- Highlights the development of a demo ASIC by the researchers, showcasing the practical application of their proposed solution.
- Emphasizes the potential of this technology to prevent fraudulent voting practices by requiring a user to generate proof of their voting rights via this specialized ASIC.
- Concludes with a message emphasizing the importance of verifiable knowledge and its implications for privacy and security in the digital age.
Reference: - https://eprint.iacr.org/2023/044 - https://medium.com/initc3org/complete-knowledge-eecdda172a81
-
 @ 09fbf8f3:fa3d60f0
2024-09-08 13:17:43
@ 09fbf8f3:fa3d60f0
2024-09-08 13:17:43由于telegram的政策调整,不允许滥用telegraph匿名上传图片了。 导致之前通过telegraph搭建的图床无法上传(已上传的能正常查看)。
有人通过原项目的基础上分支另外项目,可以通过频道上传图片。
项目是通过cloudflare pages搭建的。 - 项目地址:https://github.com/MarSeventh/CloudFlare-ImgBed
项目的教程很详细,具体去看项目教程。
telegram设置:
- 需要有telegram账号
- 通过@BotFather创建一个telegram机器人,并获取api key。
- 创建一个频道,获取频道id,通过转发一条消息到 @VersaToolsBot机器人可以查看频道id。
- 一定要添加创建的机器人到频道作为管理员才能使用。
cloudflare的设置
- 通过git项目部署,设置变量:TG_BOT_TOKEN和TG_CHAT_ID就基本可以使用了。
- 如果需要后台,需要添加kv空间,并在设置里面的函数,选择对应的kv空间,如图:
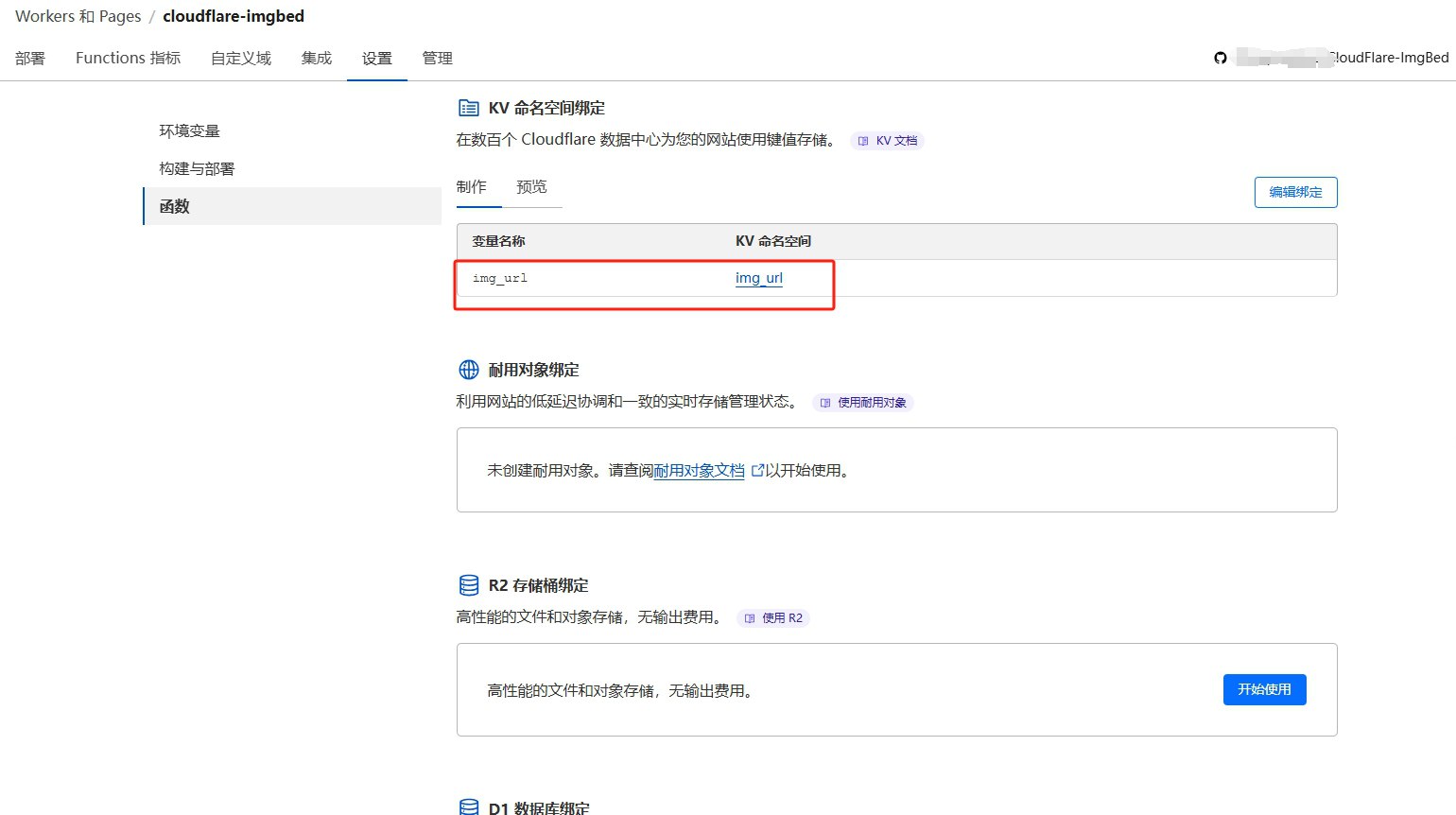
- BASIC_USER 后台登陆名
- BASIC_PASS 后台密码
- AUTH_CODE 鉴权,防止别人使用,设置后,别人使用必须输入这个。
其他
- 成人内容屏蔽
- pico 使用api接口 去项目地址看
最后
我搭建的地址: https://imgbed.lepidus.me
-
 @ d625c21c:dfa2ef0f
2024-10-26 08:26:23
@ d625c21c:dfa2ef0f
2024-10-26 08:26:23Join the best SSC coaching for top-notch faculty, comprehensive materials, and proven success. Start your journey today! Securing a position in the Staff Selection Commission (SSC) exams requires dedicated preparation, strategic guidance, and comprehensive resources. Our coaching center offers the best SSC coaching with high-quality, free study materials to streamline your journey towards success.
SSC Coaching Overview SSC exams cover multiple levels, including CGL (Combined Graduate Level), CHSL (Combined Higher Secondary Level), CPO (Central Police Organization), and JE (Junior Engineer). Each level tests different skills, but all require strong analytical abilities, time management, and a grasp of essential concepts. Scholars Academy SSC coaching program focuses on: Conceptual Clarity: Breaking down complex topics for an in-depth understanding. Practice-Centric Approach: Emphasis on solving a variety of questions to tackle different exam scenarios. Customized Plans: Adaptive study plans tailored to your strengths and weaknesses.
Why Choose SSC Coaching? Expert Guidance: Learning from experienced professionals with years of SSC coaching expertise helps streamline preparation. Time Efficiency: Structured coaching saves time, allowing candidates to cover the syllabus thoroughly and systematically. Updated Content: Our free study materials are regularly updated, following the latest SSC exam patterns and question trends. Motivational Environment: Being part of a focused, competitive setting helps maintain discipline and motivation.
The benefits of Scholars Academy SSC Coaching with free study material are as follows: Cost Efficiency: Free study material reduces the financial burden, providing students with access to top resources without additional costs. Comprehensive Coverage: From previous year question papers and e-books to mock tests, our free material includes everything essential for SSC preparation. Flexibility and Accessibility: Materials are provided in digital formats, allowing students to study anytime, anywhere. Focused Practice: Our free materials include topic-wise exercises and full-length tests to reinforce concepts and improve time management. Performance Analytics: With self-evaluation features, students can track their progress, identify areas for improvement, and receive targeted feedback.
Success Stories and Testimonials Over the years, many of our students have achieved top ranks in SSC exams, showcasing the effectiveness of our coaching methodology and materials. Here’s what some of them have to say: Anita Sharma (SSC CGL Topper): “The structured coaching, combined with regular tests and free materials, helped me focus on key areas and strengthen my weaknesses. The faculty’s insights were invaluable in my journey.” Rohit Mehta (SSC CHSL Qualifier): “The study materials were comprehensive, with questions modeled on actual exams. The coaching team’s support made a big difference in boosting my confidence.” Megha Verma (SSC JE Selection): “Getting quality materials for free and continuous guidance from experienced mentors was instrumental in my success.”
Our Coaching Methodology Personalized Learning Plans: We create individualized study schedules, focusing on each student’s specific needs and exam goals. Intensive Practice Sessions: Our program includes regular mock tests, speed drills, and concept quizzes to build both speed and accuracy. Doubt Clearing Sessions: Dedicated sessions with mentors allow students to resolve doubts, clarify complex topics, and strengthen their conceptual understanding. Real-Time Feedback: Each student receives actionable feedback on their performance, focusing on areas for improvement and boosting overall confidence. Motivational Support: We foster a positive, motivating environment to keep students engaged and confident throughout their preparation journey.
Enroll Today By joining our SSC coaching program, you’re not only investing in expert guidance but also gaining access to a wealth of resources, including free study materials, that bring you closer to your SSC aspirations. Free Study Material for SSC Exams Our SSC coaching center offers a range of free study materials designed to equip students with essential tools for effective preparation. From foundational concepts to advanced practice, we cover everything needed to excel in SSC exams.
Comprehensive Study Material for SSC Exams We provide detailed, well-organized study materials covering all SSC exam sections, including Quantitative Aptitude, Reasoning Ability, English Language, and General Awareness. Each module is crafted to ensure in-depth learning and thorough practice: Concept Notes: Detailed explanations of fundamental concepts and problem-solving techniques. Topic-Wise Exercises: Practice questions for each topic, allowing students to focus on individual sections. Revision Guides: Concise notes summarizing key concepts and formulas for quick revisions.
Free SSC Study Material Download Students can access and download our SSC study materials at no cost. These downloadable resources include: PDF Notes: Covers all topics comprehensively with examples and practice questions. Formula Sheets: Essential for quick reference, especially useful in Quantitative Aptitude. E-Books: Covering General Awareness and English, these books provide an extensive base of knowledge. How to Download: Visit our website, sign up for a free account, and access the downloadable materials instantly.
Practice Tests and Mock Exams Our practice tests and mock exams are designed to simulate real SSC exams, providing students with essential test-taking experience: Topic-Based Tests: Focus on specific areas, ideal for targeted practice. Full-Length Mock Exams: Simulate the actual SSC exam experience, helping students gauge their readiness and time management skills. Instant Feedback: After each test, students receive a detailed performance analysis with actionable insights.
Previous Year Question Papers Accessing and practicing with previous years' question papers is crucial for SSC preparation. We offer a collection of past papers, enabling students to understand the question patterns and difficulty levels: Detailed Solutions: Each question is accompanied by a step-by-step solution. Topic Distribution Analysis: Learn which topics frequently appear, allowing for focused study. Time-Based Practice: Helps students build speed and accuracy under exam conditions.
Study Material FAQs 1. What materials are included in the free downloads? We provide PDF notes, topic-specific exercises, formula sheets, mock tests, and previous year question papers. 2. Are the materials updated to match the latest SSC exam pattern? Yes, all materials are regularly updated to reflect the latest SSC exam trends and patterns. 3. Can I access the study material offline? Once downloaded, all materials can be accessed offline, allowing you to study anytime. 4. Do I need to pay for additional study resources? Our free materials cover all major topics required for SSC exams. However, for advanced guidance, premium resources are available. 5. Are there solutions provided for practice questions and mock tests? Yes, all practice questions and mock tests come with detailed solutions for effective learning. SSC Exam Preparation Guide Preparing for SSC exams demands dedication, structured study plans, and access to quality resources. Here’s a comprehensive guide to our offerings for SSC CGL, CHSL, and MTS exams, covering everything from coaching and study materials to syllabus details and preparation tips.
SSC CGL (Combined Graduate Level) Coaching Our SSC CGL coaching is designed to help students excel in one of the most competitive government exams. We offer: In-Depth Coverage of All Topics: From Quantitative Aptitude to General Awareness, every topic is thoroughly covered. Experienced Faculty: Trainers with a proven track record in SSC exams provide guidance and mentorship. Doubt Clearing Sessions: Personalized sessions to address individual queries and doubts.
SSC CGL Syllabus and Exam Pattern The SSC CGL exam consists of multiple tiers, each with a specific syllabus: Tier I: General Intelligence & Reasoning, General Awareness, Quantitative Aptitude, English Comprehension. Tier II: Quantitative Abilities, English Language & Comprehension, Statistics, and General Studies (Finance and Economics). Tier III: Descriptive Paper (Essay/Letter Writing). Tier IV: Computer Proficiency Test/Skill Test. Exam Pattern: Each section has multiple-choice questions with negative marking in Tiers I and II.
SSC CGL Free Study Material To aid students in preparation, we offer free downloadable materials: Notes and eBooks: Covers each section with explanations and examples. Formula Sheets and Tips: Key formulas and shortcuts for Quantitative Aptitude. Previous Year Papers: Solved papers for familiarity with exam patterns.
SSC CGL Preparation Tips Understand the Exam Pattern: Familiarize yourself with the tier system and focus on scoring sections. Time Management: Allocate specific hours daily for each subject to ensure balanced preparation. Daily Practice: Attempt questions regularly to build speed and accuracy. Revision: Revisit important concepts and formulas frequently.
SSC CGL Practice Tests Our mock tests include: Full-Length Mock Tests: Real exam simulation to assess your preparedness. Sectional Tests: Focus on specific sections for targeted practice. Performance Analysis: Get detailed feedback on your performance.
SSC CHSL (Combined Higher Secondary Level) Coaching Our SSC CHSL coaching program is structured to help students aiming for higher secondary level positions: Special Focus on Core Areas: Reasoning, Quantitative Aptitude, English, and General Awareness. Conceptual Learning: Breaking down complex concepts for easy understanding. Regular Mock Tests: To help students practice under timed conditions.
SSC CHSL Syllabus and Exam Pattern Tier I: General Intelligence, Quantitative Aptitude, English Language, General Awareness. Tier II: Descriptive Paper (Essay and Letter Writing). Tier III: Skill Test/Typing Test. Exam Pattern: Tier I is objective type, while Tier II is descriptive. There is negative marking in Tier I.
SSC CHSL Free Study Material We provide free resources including: PDF Study Notes: Detailed notes covering all important topics. Solved Previous Year Papers: Provides insight into commonly asked questions. Mock Papers: Realistic practice papers with varying difficulty levels.
SSC CHSL Preparation Tips Focus on Basics: Strengthen foundational knowledge in all subjects. Practice Writing: Essential for the descriptive section in Tier II. Review Past Papers: Familiarize yourself with the question types and difficulty. Stay Updated: For General Awareness, read current affairs regularly.
SSC CHSL Practice Tests Our practice tests help students gain confidence and improve time management: Sectional and Full-Length Tests: Practice in both focused and exam-like settings. Instant Feedback: Detailed analysis of each test for targeted improvement.
SSC MTS (Multi-Tasking Staff) Coaching SSC MTS coaching is designed for candidates aiming for Group C positions. Our coaching covers all essentials for this entry-level exam: Focused Coaching: Covering all required topics in Quantitative Aptitude, Reasoning, and General Awareness. Basic to Advanced Training: Sessions tailored for beginners as well as advanced learners. Mock Tests: Practice in an exam-like environment.
SSC MTS Syllabus and Exam Pattern Paper I: General Intelligence, English Language, Numerical Aptitude, General Awareness. Paper II: Descriptive Test (Essay/Letter Writing). Exam Pattern: Paper I is objective with negative marking, and Paper II is descriptive to assess writing skills.
SSC MTS Free Study Material Our free study materials include: Topic-Wise Notes: Clear explanations with practice questions. Previous Year Question Papers: Helps understand the exam pattern. Study Guides: Focus on key concepts and frequently asked questions.
SSC MTS Preparation Tips Regular Revision: Particularly for Numerical Aptitude and General Awareness. Practice Writing: Essential for the descriptive paper. Mock Tests: Practice regularly to improve speed and accuracy.
SSC MTS Practice Tests To ensure readiness, we offer: Timed Mock Tests: To simulate real exam conditions. Sectional Practice: For focused improvement in weaker areas. Performance Insights: Detailed feedback after each test. Courses Offered Our SSC coaching center provides various courses tailored to meet the unique needs of SSC aspirants. From classroom and online coaching to personalized programs, we offer a range of options with comprehensive study resources for effective SSC preparation.
-
SSC Classroom Coaching Our classroom coaching program is ideal for students who thrive in a traditional, interactive learning environment. It includes: In-Person Lectures: Delivered by expert faculty with years of experience in SSC coaching. Daily Practice and Doubt Sessions: Regular practice sessions and personalized doubt-clearing. Mock Tests and Performance Tracking: Assess your progress with regular tests and track your improvement.
-
SSC Online Coaching Our online coaching program offers flexibility for students who prefer remote learning or have time constraints: Live Online Classes: Real-time, interactive classes covering the entire syllabus. Recorded Lectures: Access recorded sessions for self-paced study and revision. 24/7 Doubt Resolution: Online discussion boards and chat support for resolving doubts.
-
Personalized Coaching Programs Our personalized coaching programs are tailored to the individual strengths and needs of each student, focusing on: Customized Study Plans: Adaptive schedules based on your strengths and areas for improvement. One-on-One Sessions: Individual mentoring sessions for focused attention. Goal Setting and Tracking: Personalized targets and regular progress reviews.
-
Study Resources Our coaching includes a variety of study resources designed for comprehensive SSC preparation, accessible across platforms.
Online Video Lectures Topic-Wise Video Lectures: Covering each subject thoroughly. Concept-Focused Videos: Explaining complex concepts in an easy-to-understand manner. Downloadable Content: Download videos for offline access and revision.
Important SSC Exam Topics and Guides Exam Guides: Complete topic breakdowns for SSC exams, focusing on high-scoring areas. Tips and Strategies: Subject-specific strategies to tackle each section efficiently. Frequently Asked Questions: Insights into commonly asked questions across all SSC exam tiers.
SSC Exam Preparation Apps and Tools We recommend and provide access to apps and tools to assist with SSC preparation: Daily Practice Apps: Mobile-friendly apps offering quizzes and daily practice questions. Performance Analytics Tools: Track your performance, identify weak areas, and customize your study plan. SSC Prep Games: Engaging apps with educational games and flashcards for easy learning.
Downloadable E-Books for SSC Exams Access a library of downloadable e-books covering key SSC topics: Quantitative Aptitude and Reasoning: Books with solved examples, formulas, and practice questions. General Awareness and English Language: Comprehensive guides with theory, practice, and revision notes. Mock Test Collections: E-books with mock tests and detailed solutions for exam practice.
Blog Our blog keeps students updated with the latest insights and tips for SSC exam preparation. SSC Exam Updates and News: Stay informed about exam dates, syllabus changes, and other key updates. SSC Exam Preparation Tips: Practical tips from experts to help students maximize their potential. Time Management for SSC Exams: Guides on managing time effectively for each section. Common Mistakes to Avoid in SSC Exams: Learn about common pitfalls and how to avoid them.
-
-
 @ eac63075:b4988b48
2024-10-03 17:17:27
@ eac63075:b4988b48
2024-10-03 17:17:27This document presents a detailed plan for best practices in Operational Security (OPSEC) and Digital Hygiene, focusing on overall online security and cryptocurrency security.
Listen on The Neural Network Botcast:
https://wavlake.com/podcast/the-neural-network
- Summary
- Introduction
- OPSEC Steps
- Privacy on Social Networks
- Password Security and Authentication
- Device Protection
- Safe Browsing
- Cryptocurrency Security
- Advanced Security Measures
- Physical Security
- Data Backup and Disaster Recovery
- Advanced Mobile Device Security
- Continuous Learning and Community Engagement
- Personalized Recommendations
- OPSEC in Cryptocurrency Events
- Conclusion
1. Introduction
This document presents a detailed plan for best practices in Operational Security (OPSEC) and Digital Hygiene, focusing on overall online security and cryptocurrency security. It is designed for users of all experience levels and includes both basic and advanced strategies.
OPSEC is a systematic process of protecting sensitive and critical information that, if disclosed, could be used by adversaries to compromise the security of an organization or individual. Originally developed for military use, the OPSEC concept has been adapted to various fields, including information security and online privacy protection.
1.1 Why is OPSEC so important for online life?
In the context of online life, OPSEC is essential to protect privacy and personal security. Here are some reasons why it is crucial:
Protection of Personal Information: Applying OPSEC practices helps protect personal data, such as addresses, phone numbers, financial information, and other sensitive information that, if leaked, could be used for identity theft, fraud, or other types of abuse. Security in Online Transactions: For cryptocurrency users and other forms of online transactions, OPSEC is vital to protect private keys, seed phrases, and other credentials that, if compromised, could result in the loss of digital assets. Prevention of Cyber Attacks: Implementing OPSEC practices helps identify and mitigate vulnerabilities that could be exploited by hackers and other cybercriminals to carry out attacks such as phishing, malware, ransomware, and others. Privacy Protection: In a world where digital surveillance is a growing concern, OPSEC helps maintain the privacy of communications and online activities, preventing personal information from being tracked and monitored by third parties in ways that could compromise personal and professional life.
2. OPSEC Steps
OPSEC is used to identify, control, and protect critical information that adversaries may exploit. Its main functions include:
Identification of Critical Information: Determine which information, if compromised, can cause significant harm. Threat Analysis: Identify potential threats and adversaries who may try to obtain this information. Vulnerability Examination: Assess weaknesses that could be exploited by these threats to access critical information. Risk Assessment: Estimate the likelihood and potential impact of a threat exploiting a vulnerability. Implementation of Countermeasures: Adopt measures to mitigate or eliminate identified risks. Continuous Effectiveness Assessment: Monitor and regularly review security practices to ensure their continued effectiveness.
3. Privacy on Social Networks
3.1 Privacy Settings
Regularly review and adjust privacy settings. Set accounts to private when possible. Restrict who can see your posts and personal information.
3.2 Friends/Followers Management
Regularly review and remove unknown or suspicious contacts. Be cautious when accepting new friend requests.
3.3 Information Sharing
Limit sharing of sensitive personal data (address, phone number, birth date, financial information). Be aware of the potential impact of shared content on your privacy and security.
3.4 Tagging Controls
Adjust settings to review tags in photos and posts before they appear on your profile. Consider disabling location tagging in posts.
3.5 Separate Accounts and Emails
Create separate accounts for different types of interactions (personal, professional, cryptocurrency). Use distinct emails for different accounts and online activities.
4. Password Security and Authentication
4.1 Password Best Practices
Use long, complex, and unique passwords for each account. Consider using a reliable password manager. Change passwords periodically and immediately after any suspicion of compromise.
4.2 Multi-Factor Authentication (MFA)
Enable MFA on all accounts that support it. Prefer authentication apps or hardware tokens over SMS-based MFA. Use biometric authentication when available and appropriate.
5. Device Protection
5.1 Software Updates
Keep operating systems, applications, and browsers updated. Enable automatic updates when possible (preferably perform manual updates).
5.2 Security Software
Use reliable antivirus and firewall software. Consider using anti-malware and anti-spyware tools.
5.3 Device Access
Use strong passwords, PINs, or biometrics to lock devices when not in use. Enable remote wipe features for mobile devices.
5.4 Secure Boot and TPM
Enable Secure Boot to prevent unauthorized operating systems from loading. Use the Trusted Platform Module (TPM) for hardware-based security functions.
5.5 Disk Encryption
Encrypt hard drives to protect data in case of theft or unauthorized access. Use integrated encryption tools such as BitLocker (Windows) or FileVault (macOS).
6. Safe Browsing
6.1 Use of VPN
Use a reliable VPN service to encrypt internet traffic. Always use VPN on public Wi-Fi networks.
6.2 Secure Browsers and Extensions
Use privacy-focused browsers like Brave or Firefox. Install extensions that enhance security, such as uBlock Origin and HTTPS Everywhere.
6.3 Phishing Prevention
Be skeptical of unsolicited emails, messages, and attachments. Verify the authenticity of URLs before clicking. Learn to identify advanced phishing techniques (e.g., spear phishing, whaling).
6.4 Privacy-Focused Browsing
Use the Tor network for greater anonymity when necessary. Manage cookies and other tracking technologies to minimize your online footprint.
7. Cryptocurrency Security
7.1 Wallet Security
7.1.1 Hardware Wallets
Use hardware wallets for long-term storage of significant amounts. Follow best practices for cold storage: Secure physical storage. Regular backups. Protection against physical attacks. Choose the right hardware wallet based on supported cryptocurrencies and security features.
7.1.2 Software Wallets
Use reliable software wallets for daily transactions. Mobile wallet security: Use official app stores. Keep the app updated. Enable additional security features (e.g., PIN, biometrics). Desktop wallet security: Use on a clean, dedicated system. Keep wallet software updated. Enable encryption and backups.
7.1.3 Cloud-Based Wallets
Understand the risks associated with cloud-based wallets. Use only when necessary and with additional security measures. Enable all available security features provided by the service.
7.2 Transaction Privacy
Use privacy-focused cryptocurrencies (e.g., Monero) for greater anonymity. Consider using mixing services to obscure transaction trails.
7.3 Key Management
Never share private keys or seed phrases. Store offline in secure and redundant locations. Consider using multi-signature configurations for large amounts.
7.4 Exchange Security
Use reliable exchanges with strong security measures. Enable all available security features (2FA, withdrawal limits, etc.). Avoid keeping large amounts on exchanges for long periods.
7.5 Social Media and Cryptocurrencies
Use separate accounts for personal and cryptocurrency-related activities. Limit disclosure of cryptocurrency involvement on public profiles. Be cautious when interacting in cryptocurrency-related groups and forums.
8. Advanced Security Measures
8.1 Network Security
Configure firewalls with custom rules for enhanced protection. Implement Intrusion Detection Systems (IDS) for early threat detection. Regularly audit the network for vulnerabilities.
8.2 Operational Security
Apply secure coding practices when developing applications or smart contracts. Develop and maintain an incident response plan. Conduct regular security audits of systems and applications.
8.3 Advanced Privacy Techniques
Responsibly and legally use cryptocurrency mixers or tumblers. Implement IP address obfuscation techniques. Consider using steganography for sensitive communications.
9. Physical Security
9.1 Device and Media Protection
Protect physical devices from theft and unauthorized access. Use cable locks, safes, or other physical security measures for valuable hardware. Implement appropriate data destruction methods for old hardware and media.
9.2 Environmental Security
Control physical access to your workspace. Be aware of onlookers in public spaces. Use privacy screens on devices when working in public.
10. Data Backup and Disaster Recovery
10.1 Backup Strategies
10.1.1 3-2-1 Rule
Keep at least 3 copies of your data. Store 2 backup copies on different storage media. Keep 1 copy off-site. 10.2 Backup Tools and Solutions
10.2.1 Local Solutions
External hard drives. Network Attached Storage (NAS).
10.2.2 Cloud Solutions
Services like Backblaze, iDrive, or Carbonite. Enterprise solutions like AWS Backup or Azure Backup.
10.2.3 Backup Software
Time Machine (for macOS). Windows Backup. Third-party solutions like Acronis True Image or Veeam.
10.3 Backup Encryption
Always encrypt backups, especially those stored off-site or in the cloud. Use AES-256 or higher encryption. Securely manage encryption keys.
10.4 Recovery Testing
Regularly perform restoration tests on backups. Simulate disaster scenarios and practice recovery. Document the recovery process.
10.5 Disaster Recovery Plan
10.5.1 Plan Elements
Asset inventory. Notification and escalation procedures. Detailed recovery steps. Emergency contact list.
10.5.2 Types of Disasters to Consider
Natural disasters (floods, fires, earthquakes). Hardware failures. Cyber attacks (ransomware, DDoS). Human error.
11. Advanced Mobile Device Security
11.1 Advanced Security Settings
11.1.1 iOS
Enable "Erase data" after 10 failed password attempts. Use Face ID or Touch ID with a complex passcode. Enable "Find My iPhone" and activation lock.
11.1.2 Android
Enable full disk encryption. Use biometric authentication with a strong password. Configure Google’s "Find My Device."
11.2 App Management
Regularly review app permissions. Uninstall unused apps. Use only official app stores (App Store, Google Play).
11.3 Mobile Network Security
Use a reliable VPN, especially on public Wi-Fi networks. Disable Wi-Fi and Bluetooth when not in use. Avoid connecting to unsecured public Wi-Fi networks.
11.4 Mobile Malware Protection
Install reliable antivirus software for mobile devices. Keep the operating system and apps updated. Be cautious when clicking links or downloading attachments.
11.5 Mobile Privacy
Review and adjust device privacy settings. Limit app access to location, camera, and microphone. Use privacy-focused browsers (e.g., Brave, Firefox Focus).
11.6 Data Security in Transit
Use 2FA for important accounts accessed via mobile. Avoid performing sensitive financial transactions on untrusted networks. Consider using encrypted messaging apps (e.g., Signal).
11.7 Secure Backup and Synchronization
Configure automatic encrypted cloud backup. Use secure synchronization for contacts and calendars. Perform local backups regularly before major updates.
11.8 Response to Loss or Theft
Configure and test remote lock and wipe features. Keep an updated list of devices and their information. Have a quick action plan to report and disable lost devices.
12. Continuous Learning and Community Engagement
12.1 Staying Informed
Follow reliable security blogs, podcasts, and news sources. Participate in cybersecurity and cryptocurrency communities. Attend workshops and conferences on digital security and cryptocurrencies.
12.2 Education and Training
Engage in continuous education on cybersecurity and cryptocurrencies. Participate in or organize security awareness training sessions. Share knowledge and best practices with colleagues and community members.
13. Recommendations
13.1 For Beginners
Focus on implementing basic security measures: Strong, unique passwords. Two-factor authentication. Regular software updates. Basic privacy settings on social networks. Start with user-friendly wallets and exchanges with strong built-in security.
13.2 For Advanced Users
Explore advanced topics such as: Setting up a secure home lab. Running a full node. Implementing multisig wallets. Contributing to open-source security projects.
14. OPSEC in Cryptocurrency Events
Participating in cryptocurrency-related events can be an excellent opportunity for networking and learning but also presents unique security and privacy risks. Follow these guidelines to stay safe:
14.1 Pre-Event Preparation
14.1.1 Identity Management
Consider using a pseudonym or alternate name for registration and networking. Create a dedicated email for cryptocurrency-related matters. Use a profile picture that is not your real image in event materials.
14.1.2 Devices and Data
Take only essential devices to the event. Backup and wipe your devices before the event. Consider using a device dedicated only for the event. Install all security updates before leaving.
14.1.3 Wallets and Funds
Create a specific wallet for the event with limited funds. Do not bring hardware wallets with significant amounts. Prepare business cards with limited information (use your pseudonym, if applicable).
14.2 During the Event
14.2.1 Physical Security
Keep your devices with you at all times or in a secure location. Use an RFID blocker to protect cards and passports. Be aware of people observing when you type passwords or show QR codes.
14.2.2 Digital Security
Use a reliable VPN on all internet connections. Avoid using public Wi-Fi; use your own mobile hotspot if possible. Disable Bluetooth and NFC when not in use. Be extremely cautious when scanning QR codes or clicking links.
14.2.3 Social Interactions
Be discreet about your cryptocurrency holdings. Avoid discussing specific details about your investment strategies. Be alert to social engineering techniques and phishing attempts.
14.2.4 Transactions
Avoid making large or important transactions during the event. If a transaction is necessary, find a private and secure location. Double-check all details before confirming any transaction.
14.3 Post-Event
14.3.1 Security Review
Conduct a full antivirus scan on all devices used during the event. Check all your accounts for suspicious activity. Change all passwords used during the event.
14.3.2 Contact Management
Carefully review new contacts before adding them to your networks. Maintain separation between your personal and cryptocurrency-related identities.
14.3.3 Reflection and Learning
Evaluate your security experience during the event. Identify areas for improvement in future events. Share (anonymously, if preferred) lessons learned with the community.
14.4 Special Considerations for Speakers and VIPs
14.4.1 Public Profile Management
Carefully manage publicly available information about you. Consider using an agent or intermediary for communications and scheduling.
14.4.2 On-Stage Security
Avoid showing wallet or transaction details in presentations. Be careful with questions that may lead you to reveal sensitive information. Prepare standard responses for questions about your holdings or personal strategies.
14.4.3 Personal Security
Consider hiring personal security for larger events. Have an emergency exit plan. Vary your routines and routes during the event.
15. Conclusion
Maintaining strong OPSEC and digital hygiene is an ongoing process that requires vigilance, education, and adaptation to new threats. By following this comprehensive plan and staying informed about the latest security developments, users can significantly enhance their online security and protect their digital assets.
Remember to regularly review and update your security practices and always err on the side of caution when dealing with sensitive information or valuable digital assets.
Watch this episode topic:
-
 @ 460c25e6:ef85065c
2024-10-10 13:22:06
@ 460c25e6:ef85065c
2024-10-10 13:22:06In the early days of Nostr, developers often competed to see who could implement the most NIPs. Although all were optional (except NIP-01), it became a point of pride and vital for the ecosystem's growth. Back then, there were only a few dozen relatively simple NIPs to implement. Fast forward to today, with nearly 100 NIPs, maintaining and implementing everything has become nearly impossible. Yet, the drive among developers to "code all things Nostr" remains as strong as ever.
nostr:nprofile1qqsrhuxx8l9ex335q7he0f09aej04zpazpl0ne2cgukyawd24mayt8gprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hszxmhwden5te0wfjkccte9emk2um5v4exucn5vvhxxmmd9uq3xamnwvaz7tmhda6zuat50phjummwv5hsx7c9z9 raised the point that everyone, even I, agrees:
nostr:nevent1qqsqqqp2zrs7836tyjlsfe7aj9c4d97zrxxqyayagkdwlcur96t4laspzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7q3q80cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsxpqqqqqqzgcrrrp
But how big is too big? How can we better understand the range of options available for devs out there?
I went out for a hunt in my own brain to figure out how to clarify the situation. I came up with the following 4 categories for Nostr Clients: - Super Clients: These apps merge vastly different domains into a single application, offering basic support for reading, writing, configuration, and data management for each use case within each domains. An example would be an app that combines a Marketplace and Live Streams under one roof.
-
Clients: These apps provide comprehensive support for a single domain, handling all its use cases in a single home. They manage the complete set of reading, writing, configuration, and long-term data management within that domain. An example is a marketplace app that helps users manage product catalogs, process orders, collect payments, and handle fulfillment and reports.
-
Mini Clients: These apps focus on read and write functionality for a single use case, including configuration management and any actions related to that specific task. For example, a fulfillment app that helps users view orders placed from another client to then pack and ship them.
-
Micro Clients: These apps have a single interface and perform one specific action. Viewing and creating a record is handled by separate micro apps. An example is an app that simply scans an order's QR code and marks it as shipped.
Based on my made-up categories described at the end, this is how I would split our most known apps.
Super Clients - amethyst - nostrudel - coracle
Clients - damus - twitter - primal - twitter - snort - twitter - gossip - twitter - lume - twitter - ditto - twitter - rabbit - twitter - freefrom - twitter - nos - twitter - flycat - twitter - straylight - twitter - nostter - twitter - iris - twitter - nostur - twitter - nostrmo - twitter - yana - twitter - openvibe - twitter - freerse - twitter - 0xchat - chats - cornychat - chats - coop - chats - nostrchat - chats - blowater - chats - habla - blogs - yakihonne - blogs - highlighter - blogs - blogstack - blogs - stemstr - music - wavlake - music - fountain - podcasts - zap.stream - live streaming - shopstr - marketplace - plebeian.market - marketplace - flotilla - communities - satellite - communities - zapddit - communities - nostr.kiwi - communities - hivetalk - video calls - flare - long-form videos - nostrnests - audio spaces - wherostr - location - yondar - location - stacker.news - news - flockstr - events - nostrocket - issue tracker - docstr - docs - satshoot - freelance - wikifreedia - wiki - formstr - forms - chesstr - chess - memestr - meme feed - npub.cash - wallet - npub.pro - websites - gitworkshop - dev tools - onosendai - metaverse - degmods - games - turdsoup - prompts
Mini Clients - amber - signer - alby - signer - nos2x - signer - nsec.app - signer - keys.band - signer - nostrame - signer - nokakoi - anon - zap.cooking - recipes - anonostr - anon - getwired - anon - lowent - anon - creatr - exclusive content - lightning.video - exclusive content - zaplinks - slides - listr - lists - zap.store - app store - badges.page - badges - oddbean - news - dtan - torrents - nosta - user pages - pinstr - pinterest - pollerama - polls - swarmstr - trending - nostrapp - apps manager - noogle - search - ostrich.work - job postings - emojito - emoji manager - nostree - links - citrine - local relay - joinstr - coinjoins - heya - crowdfunding - zapplepay - zaps - nosbin - clipboard - shipyard - scheduler - tunestr - live streams - filestr - files - nostrcheck.me - media hosting - sheetstr - spreadsheets - crafters - curriculum vitae
Micro Clients - w3 - url shortener - nosdrive - backups - zaplife - zaps dashboard - zapper.fun - payments - nostrends - trends - zephyr - trends - wavman - music player - nostrrr - relay info - nosdump - relay info - notestack - blogs - nostr.build - media hosting - nostr.watch - relay info - nostr hours - use reports - lazereyes - vision prescriptions - snakestr - games - deletestr - deletion requests - 2048str - games - nostrqr - qr generator - notanostrclient - anon
Super apps will try to do everything, but can't really do most things super well. Regular-sized Clients will try to manage most of a given domain but are likely to centralize users on themselves, an unwanted effect inside of Nostr. If we want Nostr to grow in a decentralized fashion, we have to start betting on and using more Mini and Micro clients.
-
-
 @ 592295cf:413a0db9
2024-09-07 08:32:33
@ 592295cf:413a0db9
2024-09-07 08:32:33Week 02/09
A week with a free vpn on Nostr.
I gave up using nostter by now. 😔 now it works it seems to be back From Wednesday, it should start calm on Nostr, Brazilians will not arrive, no one has more Twitter accounts where to contact them. 😅 Sorry brazilian.
I read 5 and 6 comments about Nostr, Nostr is bad I do not enroll. It's only four months to the end. Join made two zap and then we salute definitively, pura vida. I'm gonna miss Nostr.
I also thought about making a bookmark on Nostr, using the spec that already exists but using kind 1985. Convert this link to the note, but I did not find the courage. Maybe it doesn't make much sense if it only lasts four months and all the relays are turned off.
There's a bit of enthusiasm and some keep pointing the Nostr weird index by raising the stick. In practice, the new bookmark spec is used only by two clients. I think the clients who have more bookmarks in the groppone is Amethyst, if someone writes an encoding for the new bookmark, it would be nice, but I don't think it will happen, to those who care about bookmarks.
Moment aspirin, orbot, citrine, Amethyst. I don't think it's mentally sustainable, too.
Sometimes they are extremely bullish, the second after disfatist, regarding the various clients.
It would be nice to get to some foundations. That's Nostr, I don't think it'll happen so easily.
Some Events
- is Zapconf online really there?
-
1 week Bangkok, bitcoin conference Conference there will be yakihonne and wherostr.
-
24 September Nostrasia
Do not follow the bots you can make a list of bots, rankings of people You just have to follow people. Kind 982 from 892892 advertising 😅🙇♂️
{ "kind": 892, "tags": [ ["b", "91cf9..4e5ca", "wss://bot_alicerelay.com/", "bot_alice"], ["b", "14aeb..8dad4", "wss://bot_bobrelay.com/nostr", "bot_bob"], ["b", "612ae..e610f", "ws://bot_carolrelay.com/ws", "bot_carol"] ], "content": "", ...other fields }Jack Dorsey says there will be more bots than people on Nostr (useful).
The more I read about Bluesky the more I am in Fomo with Nostr, like this post post in Buesky That's why not stay in other social media 🤣
Or they all have it with Nostr, maybe Nostr is finishing, really in four months.
Nostr is over, the chain of command is now insurmountable, you have to make a scalable protocol from within, reminds me of some political party.
Internal scale 🙅
Representation of all the NIPs, neighbors
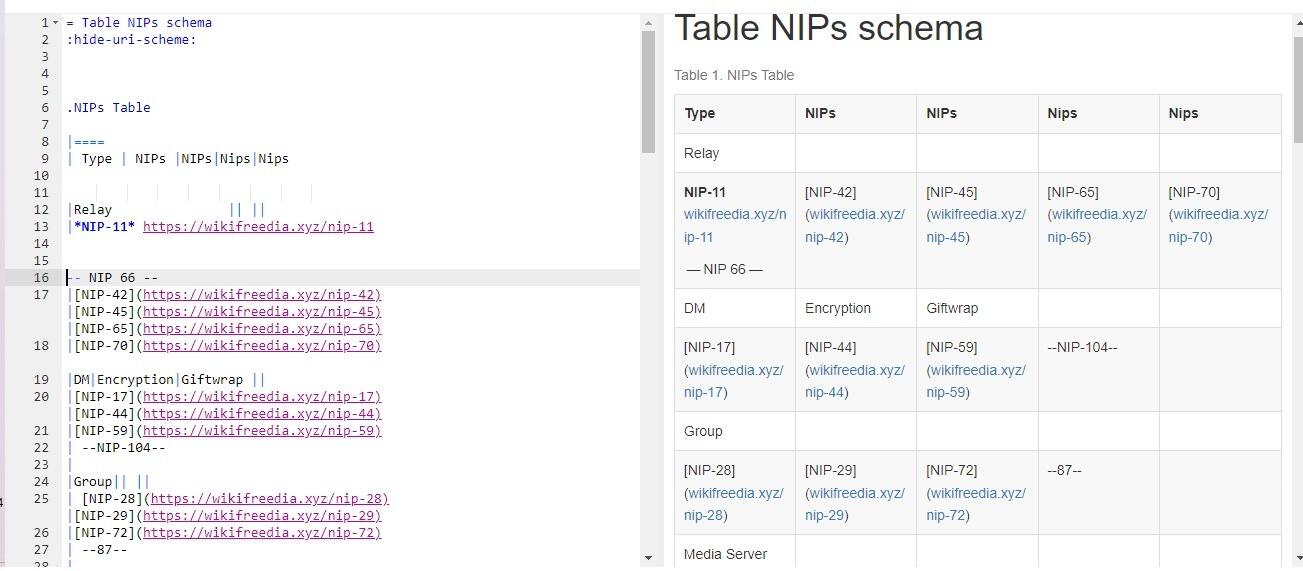
People just want proof of works, but there is so much uncompensated question, you have to create the right incentives. Your job is work only if you create a job. Nostrudel has created this tool sandbox where you can just play event consoles, event publishers, blindspots, Discovery, relays. Coracle has created custom feed, groups, supports listing events and items.
People are not important, they are important because they consent to this, but it is not quantifiable in money.
And but as I get visibility, just proof of work. Forget about the various bottle doors, think about yourself, if you want a community make yourself a community, if you don't want to do it, relax.
But only four months are missing, in fact relax, enjoy them. A world of possibilities do not waste it because everything is not perfect.
If you want to make a CMS, the road is long and uphill, but then you are using a blog, no and then.
I made an attempt with kind 1985 works, I still have to create sub category. Example live events ecash Germany Berlin.
Anyway it's a bit of a mess this "new" web. Users are angry. 😉 It's the new feature.
-
 @ 8cb60e21:5f2deaea
2024-09-06 22:23:03
@ 8cb60e21:5f2deaea
2024-09-06 22:23:03 -
 @ 2df170ea:90d2b157
2024-10-26 06:43:03
@ 2df170ea:90d2b157
2024-10-26 06:43:03If you're experiencing the issue of Orbi not connected to the internet, start by accessing the Orbi Login page through your web browser. Once logged in, check the status of your internet connection and ensure all cables are securely connected. Look for any error notices on the dashboard. If the problem persists, reset your Orbi router and modem. Additionally, check for firmware upgrades in the settings. Following these instructions will help you restore your internet connection fast and efficiently.
-
 @ eac63075:b4988b48
2024-09-28 09:13:08
@ eac63075:b4988b48
2024-09-28 09:13:08O mundo das criptomoedas sempre foi um espaço de inovação e experimentação, onde ideias revolucionárias surgem para transformar mercados. Recentemente, um conceito novo tem chamado a atenção de especuladores e investidores mais ousados: o re-staking. Ao contrário do staking tradicional, onde os tokens ficam bloqueados em uma única plataforma, o re-staking vai além e permite que os mesmos tokens sejam usados em múltiplas plataformas ao mesmo tempo, aumentando a percepção de escassez e, potencialmente, os riscos.
Mas o que isso significa para o mercado e, principalmente, para os investidores? Para entender o re-staking, precisamos primeiro compreender os princípios do staking e como ele tem sido utilizado para criar uma sensação de escassez no mercado.
A Escassez Forçada no Staking Tradicional
No staking tradicional, os investidores alocam seus tokens em um contrato inteligente, geralmente para ajudar a validar transações em uma rede blockchain, como o Ethereum. Esses tokens ficam "travados" por um período de tempo, durante o qual não podem ser negociados ou movimentados. Em troca, os investidores recebem recompensas, como juros, por ajudar a manter a segurança e a operação da rede.
O interessante é que, quando muitos tokens estão travados em staking, isso cria uma escassez artificial no mercado. Embora o número total de tokens de uma determinada criptomoeda permaneça o mesmo, os tokens em circulação — ou seja, aqueles disponíveis para compra e venda — tornam-se mais limitados. Essa "escassez forçada" pode, em teoria, aumentar o preço dos tokens circulantes, já que a demanda pode permanecer alta, mas a oferta disponível é menor.
O Problema da Ilusão de Escassez
Mas será que essa escassez é real? Em termos práticos, os tokens estão apenas temporariamente fora de circulação. Quando o período de staking termina, eles voltam ao mercado. O conceito de escassez forçada, portanto, levanta preocupações sobre a sustentabilidade desse mecanismo. Alguns críticos argumentam que isso cria uma falsa impressão de valor, já que os tokens não desapareceram — eles apenas estão "em espera".
Isso nos leva a uma das principais questões sobre o staking: ele pode realmente sustentar uma economia baseada em escassez artificial? E, mais importante, ele pode garantir a segurança e a descentralização que as blockchains precisam para funcionar de forma eficaz? Muitos acreditam que não, o que nos leva ao surgimento do re-staking como uma solução alternativa — ou seria uma armadilha?
Re-staking: A Nova Fronteira da Alavancagem em Cripto
O re-staking surge como uma tentativa de maximizar o potencial dos tokens bloqueados. Nesse modelo, os mesmos tokens que já estão alocados em uma plataforma podem ser "re-stakeados" em outras plataformas, permitindo que os investidores ganhem recompensas adicionais sem precisar comprar mais tokens. Parece uma solução perfeita, certo? Afinal, quem não gostaria de ganhar mais sem precisar gastar mais?
Porém, como muitos especialistas têm alertado, o re-staking cria uma dinâmica de alavancagem dentro do próprio mercado de staking. Ao permitir que os mesmos tokens sejam usados em múltiplas plataformas ao mesmo tempo, você cria a ilusão de que mais valor está sendo gerado, quando, na verdade, o risco subjacente está aumentando exponencialmente.
Pense nisso como um sistema de empréstimos sobre empréstimos. Se tudo correr bem, os ganhos são maiores. Mas se algo der errado, o efeito dominó pode ser catastrófico. O re-staking, de certa forma, transforma o mercado de criptomoedas em uma montanha russa de riscos, onde os investidores estão sempre um passo à frente de uma possível queda.
Os Riscos de Segurança no Re-staking
Um dos maiores riscos associados ao re-staking está relacionado à segurança. Quando você distribui seus tokens por várias plataformas, aumenta a exposição a possíveis falhas de segurança. Cada plataforma possui seus próprios contratos inteligentes, que, por mais bem auditados que sejam, estão sempre suscetíveis a falhas ou ataques.
Imagine que você está cuidando de uma planta. Se você dividir essa planta em várias partes e plantar cada uma em um solo diferente, você precisaria garantir que cada solo fosse adequado e que as condições fossem perfeitas em todos os lugares ao mesmo tempo. No mundo das criptomoedas, cada plataforma de staking é como um vaso diferente, e se um deles tiver uma rachadura — ou, no caso de uma falha em um contrato inteligente —, você pode perder parte ou até mesmo todos os seus tokens.
O risco de slashing (perda de tokens como penalidade por má conduta do validador) também é ampliado no re-staking. Se um validador com quem você está associado cometer um erro ou for desonesto em qualquer uma das plataformas onde você está re-stakeando seus tokens, você pode ser penalizado, perdendo parte do que alocou. Aumentar a quantidade de plataformas significa aumentar o risco de ser impactado por um erro de um terceiro.
Alavancagem: Uma Receita para o Colapso?
Outro fator importante a ser considerado é o impacto da alavancagem no mercado de criptomoedas. No re-staking, a alavancagem ocorre porque você está, essencialmente, duplicando o uso dos mesmos tokens, gerando mais valor do que realmente existe. Essa prática é semelhante à alavancagem no mercado financeiro tradicional, onde investidores tomam empréstimos para aumentar suas apostas.
O problema da alavancagem é que ela pode ser uma faca de dois gumes. Em um mercado em alta, ela pode amplificar os ganhos. Mas, em um mercado em queda, os prejuízos são igualmente amplificados. Se o preço das criptomoedas cair, os investidores que utilizaram re-staking podem ser forçados a liquidar suas posições para cobrir perdas, desencadeando um efeito dominó que pode colapsar todo o sistema.
Esse risco sistêmico é uma das maiores preocupações com o re-staking. Como vimos em crises financeiras anteriores, como a de 2008, o uso excessivo de alavancagem pode levar a um colapso total do mercado, e no mundo das criptomoedas, onde a volatilidade é alta e os preços podem mudar rapidamente, isso é ainda mais perigoso.
Conclusão: Re-staking — O Futuro ou uma Armadilha?
O re-staking representa um passo interessante na evolução do staking e das finanças descentralizadas. Ele oferece a promessa de maiores retornos, mas com essa promessa vêm riscos substanciais que precisam ser considerados cuidadosamente.
Para investidores que estão dispostos a assumir riscos maiores em busca de recompensas mais altas, o re-staking pode parecer uma oportunidade irresistível. No entanto, para aqueles que preferem uma abordagem mais cautelosa, o re-staking pode ser uma armadilha, criando uma falsa sensação de segurança e de crescimento, enquanto expõe o investidor a riscos potencialmente devastadores.
Assim como em qualquer investimento, a chave para o sucesso no re-staking está em compreender os riscos envolvidos e em adotar uma abordagem equilibrada. Afinal, no mundo das criptomoedas, onde o inesperado é a única certeza, um passo em falso pode ser o suficiente para transformar um grande salto em uma queda dolorosa.
Assista esse assunto no Morning Crypto
(artigo editado para ver se propaga)
-
 @ e83b66a8:b0526c2b
2024-09-06 19:16:04
@ e83b66a8:b0526c2b
2024-09-06 19:16:04The founder of Telegram has just been arrested in France. Charges include lack of cooperation with law enforcement, drug trafficking and fraud.
Aside from Telegram, social media is controlled by two billionaires who decide what you say, are themselves controlled by overbearing governments and make money through advertising and selling your personal data.
There is a different way.
NOSTR stands for Notes and Other Stuff Transmitted on Relays and it is a social media protocol in the same way http is a web protocol.
The protocol is open and anybody can build upon it. It has some fundamental concepts that are very different to existing social media platforms.
Firstly it is decentralised, it runs across relays and anybody can run a relay. They can be open or closed, public or private, free or paid.
Secondly as a user, you don’t have an account, you have a private key which is used to secure your data.
Your profile (account) is yours, you own and control it using your private keys and verified by others with your public key.
Your posts are yours and you can store them on your own relay in your own home or business or you can rely on free public relays or more feature rich paid public relays.
All your public data is signed by your private keys to verify it is you that owns it and all your private data is encrypted so nobody can read it.
Messages (i.e. think NOSTR WhatsApp) are encrypted with your private keys so NOBODY can hack it or listen in, not even the NSA through a companies backdoor. You message other users privately by encrypting messages to them using their public key, which they decrypt using their private key.
Relays store your data in a decentralised network of private and public relays and you discover relays automatically when searching for people or content.
Data is normally sent on the clearnet, but can be relayed across the darknet (Tor) in highly censored regions.
Because it is built using Bitcoin principles and technology, so it has Bitcoin money built in, meaning you actually send / receive money from / to any participant.
As money is built in, the commercial options are different to centralised corporate owned platforms. It would be technically possible to build a platform that supports advertising, however that hasn’t really happened because influencers can be paid directly from their audience in many different ways. Ad hoc tips, subscriptions, pay to view or pay per time models.
The great thing for content creators is that they control, own and keep all the money they make. There is no third party intermediary or merchant deciding whether they are allowed to be paid or not.
NOSTR is censorship resistant, as there is no way to stop anybody publishing anything they want, in the same way nobody can stop or interfere with a Bitcoin payment.
From an end users point of view, if they want to self censor, they can do this in multiple ways. You can mute users individually, or you can choose to use relays that adhere to your views or interests, so if you don’t want to see certain categories of content, you would avoid relays that carry those feeds. You can even run your own relay and curate content that you then charge other like minded users to connect to. You can of course connect to multiple relays for multiple different type of feed.
While NOSTR is a protocol, platforms have to be built to use it, so the first platforms were twitter like clients and they are still very prevalent. However, NOSTR now has clients that emulate most social media platforms, Instagram, Facebook, YouTube, Soundcloud, WhatsApp etc. They are even creating their own categories as well as emulating other functions such as Office Suite tools, collaborative calendars, contact lists or e-commerce shops.
If you want to give it a go, the easiest, but not the best, way to get started is download Primal on your phone from here:
https://primal.net/downloads
It will create a private key for you and setup a Bitcoin wallet.
Once you have done this you can visit me here:
nostr:npub1aqakd28d95muqlg6h6nwrvqq5925n354prayckr424k49vzjds4s0c237n
If you want to see a small part of the ecosystem, then visit https://www.nostrapps.com/ where volunteers are listing some of the many apps that exist already.
NOSTR is being backed by Jack Dorsey, Twitter founder, and you can see his account here:
nostr:npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m
Or you can see his account like this:
https://primal.net/jack
Edward Snowden is also on the platform and you can find him here:
https://primal.net/Snowden
NOSTR has around 2 million users or public keys, although nobody really knows how many, because it is decentralised and not controlled or run by any person or organisation.
Once you’ve setup Primal, you can use those same private keys to access any platform you wish and you can use a browser extension such as Alby to manage your keys: https://getalby.com/
Primal looks great, but there are other better functioning twitter like clients, probably the most reliable for iPhone is Damus: https://www.nostrapps.com/apps/damus
or Amethyst for Android: https://nostrapps.com/amethyst
The content and user base is very Bitcoin and freedom focused right now, but more and more people are starting to use the various platforms and some are transferring exclusively to it.
Some of the more interesting projects right now are:
https://www.0xchat.com/#/ – Private messaging – think WhatsApp
https://zap.stream/ – Video streaming
https://fountain.fm/ – Podcasting
https://wavlake.com/ – Music streaming
https://shopstr.store/ – Online shop
https://npub.pro/ – Website creation tool
https://nostr.build/ – Media and file storage
https://relay.tools/ – Build and curate your own relay
https://creatr.nostr.wine/subscriptions/new-user – Creator tools
Remember, the same keys you created for Primal can be used across the whole ecosystem.
If you want to see some of the other apps that have been built on the NOSTR protocol visit: https://nostrapps.com/
-
 @ a012dc82:6458a70d
2024-10-26 02:54:27
@ a012dc82:6458a70d
2024-10-26 02:54:27Table Of Content
-
Understanding MicroStrategy's Bitcoin Holdings
-
A Strategic Hedge Against Inflation
-
Embracing Digital Transformation
-
Maximizing Long-Term Returns
-
Enhancing Shareholder Value
-
Creating Synergies with Business Operations
-
Leveraging Bitcoin's Network Effect
-
Conclusion
-
FAQ
In the world of finance, few moves have been as bold and controversial as MicroStrategy's decision to invest heavily in Bitcoin. As uncertainty looms over traditional investment avenues, this technology-focused company has chosen to embrace the decentralized digital currency. With a commitment of billions of dollars, MicroStrategy's Bitcoin holdings have attracted attention from investors, analysts, and enthusiasts alike. This article delves into the motivations and implications of MicroStrategy's Bitcoin holdings, examining the potential risks and rewards in these uncertain times.
Bitcoin Holdings
Understanding MicroStrategy's Bitcoin Holdings To comprehend the significance of MicroStrategy's Bitcoin holdings, it is crucial to grasp their approach and strategy. Here are the key aspects to consider:
A Strategic Hedge Against Inflation
In an era of economic uncertainty, many investors seek alternative assets to protect against inflation. Bitcoin's limited supply and decentralized nature make it an appealing option for wealth preservation.
MicroStrategy recognized the potential value of Bitcoin as a hedge against inflation and made a bold move by investing a substantial portion of its treasury reserves in the cryptocurrency.
Embracing Digital Transformation
MicroStrategy, a renowned technology-focused company, believes in the power of digital transformation. By incorporating Bitcoin into its treasury strategy, the company demonstrates its confidence in the future of digital currencies and the underlying blockchain technology.
This move positions MicroStrategy as a pioneer in the corporate adoption of Bitcoin, potentially encouraging other companies to explore similar avenues.
Maximizing Long-Term Returns
MicroStrategy's CEO, Michael Saylor, has been a vocal advocate for Bitcoin, emphasizing its potential as a long-term investment. By converting a significant portion of their reserves into Bitcoin, the company aims to maximize returns over time, capitalizing on the cryptocurrency's potential growth.
Enhancing Shareholder Value
MicroStrategy's decision to invest in Bitcoin is not only driven by financial considerations but also by a commitment to enhancing shareholder value. By diversifying their assets and potentially generating substantial returns, the company aims to provide long-term benefits to its shareholders.
Creating Synergies with Business Operations
MicroStrategy's business revolves around data analytics and intelligence. By investing in Bitcoin, the company can leverage its expertise to analyze blockchain data and gain insights into market trends, potentially opening up new business opportunities and revenue streams.
Leveraging Bitcoin's Network Effect
Bitcoin's status as the largest and most recognized cryptocurrency grants it a significant network effect. MicroStrategy's investment in Bitcoin allows them to participate in this thriving ecosystem, potentially reaping benefits from increased adoption and acceptance.
Conclusion
MicroStrategy's Bitcoin holdings represent a bold move in uncertain times. By embracing Bitcoin as a strategic asset, the company positions itself at the forefront of the digital currency revolution. While risks accompany this venture, the potential rewards could reshape the corporate investment landscape. MicroStrategy's decision sets a precedent for other companies to explore the merits of Bitcoin and highlights the growing importance of cryptocurrencies in the financial world.
FAQ
Why did MicroStrategy choose Bitcoin over other cryptocurrencies? MicroStrategy's decision to focus on Bitcoin stems from its established market presence, robust infrastructure, and reputation as a store of value. Additionally, Bitcoin's limited supply and extensive adoption make it a favorable choice for long-term investment.
How does MicroStrategy's Bitcoin investment impact its financial position? MicroStrategy's investment in Bitcoin adds a new dimension to its financial position. While it introduces volatility due to Bitcoin's price fluctuations, the potential upside can significantly impact the company's overall balance sheet and shareholder value.
What are the risks associated with MicroStrategy's Bitcoin holdings? Investing in Bitcoin involves inherent risks, such as market volatility, regulatory uncertainty, and potential security breaches. MicroStrategy's substantial exposure to Bitcoin amplifies these risks, making the company vulnerable to significant losses in the event of a market downturn.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 3bf0c63f:aefa459d
2024-09-06 12:49:46
@ 3bf0c63f:aefa459d
2024-09-06 12:49:46Nostr: a quick introduction, attempt #2
Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else.
Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services.
(Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation).
More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between clients (i.e. the program that runs on a user computer) and relays (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
-
 @ eac63075:b4988b48
2024-09-25 20:28:17
@ eac63075:b4988b48
2024-09-25 20:28:17🤖 Baseado na explicação de Gerard Aithen para o Morning Crypto
Nos últimos anos, o Bitcoin se consolidou como a criptomoeda de referência, trazendo inovação e mudança para o cenário econômico global. Apesar de sua notoriedade, a tecnologia por trás do Bitcoin, especialmente em termos de escalabilidade e eficiência, ainda é um campo em constante evolução. Recentemente, um novo avanço tem gerado bastante discussão entre os entusiastas do mundo cripto: a BitVM2. Desenvolvida por Robin Linus, essa inovação promete transformar a maneira como as transações são processadas e verificadas no ecossistema do Bitcoin.
A BitVM2 está sendo apontada como uma revolução na forma como programas inteiros podem ser verificados dentro da blockchain, facilitando e tornando mais acessível a participação nas transações. Mas o que exatamente é essa nova tecnologia? Como ela funciona? E, acima de tudo, por que ela é tão importante para o futuro do Bitcoin?
Neste artigo, vamos explorar a BitVM2 em profundidade, analisando seu funcionamento, os benefícios que ela traz e suas implicações para o futuro da rede Bitcoin.
O Que é a BitVM2?
Imagine que a primeira versão da BitVM era como um quebra-cabeça gigante, onde cada peça precisava ser ajustada meticulosamente para que a transação fosse validada. Essa estrutura exigia muitas etapas e transações para garantir que tudo funcionasse corretamente, o que, claro, consumia tempo e recursos. A BitVM2 vem para mudar completamente esse cenário.
Com a BitVM2, todo esse processo se torna muito mais rápido e acessível. Agora, é como se um GPS eficiente tivesse sido instalado no lugar do velho mapa. O caminho está traçado, e tudo o que você precisa fazer é seguir as direções. A nova estrutura da BitVM2 utiliza criptografia avançada para transformar programas complexos em fragmentos menores, que podem ser verificados diretamente nas transações do Bitcoin. Em outras palavras, ela permite que contratos inteligentes e programas complexos rodem dentro da blockchain do Bitcoin, sem comprometer a segurança ou eficiência.
O principal benefício? Antes, um processo que exigia mais de 70 transações agora pode ser verificado com apenas três. Isso não apenas economiza tempo e recursos, mas também abre as portas para que mais pessoas possam participar e monitorar essas transações.
A Importância da Descentralização na BitVM2
Um dos pontos mais revolucionários da BitVM2 é que ela é completamente permissionless, ou seja, não precisa de permissão. Isso significa que qualquer pessoa pode verificar ou contestar uma transação. Antes, essa era uma tarefa restrita a operadores específicos dentro da rede. Agora, a verificação e contestação de transações suspeitas podem ser feitas por qualquer um, tornando o sistema mais democrático e transparente.
Essa descentralização aumenta a segurança da rede. Em vez de depender de um grupo centralizado de validadores, o sistema se torna autossustentável. A comunidade como um todo pode vigiar e garantir a integridade das transações, o que dificulta tentativas de fraudes ou manipulações.
Além disso, o novo design da BitVM2 foi pensado para ser compatível com a estrutura atual do Bitcoin, ou seja, não foi necessário fazer alterações no código base da criptomoeda. Isso garante que o Bitcoin continue funcionando como sempre, enquanto permite a introdução de novas funcionalidades. É como construir um novo andar em um prédio sem precisar mexer na estrutura do alicerce.
Rollups e a Eficiência das Transações no Bitcoin
Um dos temas mais discutidos na comunidade de criptomoedas nos últimos anos é a questão da escalabilidade. Conforme o Bitcoin ganha mais adoção, a rede fica mais sobrecarregada, o que pode aumentar o tempo e o custo das transações. A BitVM2 pode ajudar a resolver esse problema, especialmente quando falamos de rollups.
Rollups são soluções que permitem processar transações fora da blockchain principal, para depois consolidá-las em um único registro na blockchain do Bitcoin. Isso torna as transações mais rápidas e baratas, sem comprometer a segurança. A BitVM2 pode ser vista como uma espécie de ponte entre o Bitcoin e essa nova era de rollups, permitindo uma maior eficiência e abrindo espaço para que o Bitcoin continue evoluindo.
De forma simples, a BitVM2 garante que transações complexas possam ser processadas sem sobrecarregar a blockchain principal. Com isso, ela ajuda a diminuir as taxas e a aumentar a velocidade das transações, um avanço crucial para o futuro da criptomoeda.
O Papel dos Covenants no Bitcoin
Outro conceito-chave no desenvolvimento da BitVM2 é o uso dos Covenants. Para quem não está familiarizado, os Covenants são como pequenas promessas que os Bitcoins "fazem" durante as transações. Eles colocam condições específicas sobre como e onde os Bitcoins podem ser gastos. Isso adiciona uma camada extra de segurança e funcionalidade às transações, permitindo que os Bitcoins sejam gastos apenas sob determinadas circunstâncias.
Por exemplo, um Covenant pode especificar que os Bitcoins só podem ser transferidos para certos endereços ou que só podem ser liberados após determinado período de tempo. Esses contratos inteligentes tornam o Bitcoin ainda mais flexível e permitem a criação de soluções inovadoras dentro da rede.
Na BitVM2, os Covenants desempenham um papel importante na verificação das transações, garantindo que todas as regras sejam seguidas e que não haja brechas para fraudes ou manipulações. Isso amplia as possibilidades de uso do Bitcoin, permitindo que ele seja utilizado de formas que antes eram impensáveis.
BitVM2 e a Manipulação de Opinião Pública
Outro ponto que não podemos ignorar ao discutir as inovações tecnológicas no mundo das criptomoedas é a questão da manipulação de opinião pública. Bilionários e grandes empresas têm se posicionado como grandes influenciadores no cenário das criptomoedas. O caso de Elon Musk é um exemplo clássico, onde tweets e posicionamentos podem mudar drasticamente o valor de uma criptomoeda em questão de horas.
Com a BitVM2, no entanto, o poder de manipulação pode ser mitigado, uma vez que o sistema se torna mais descentralizado e aberto à participação de todos. A liberdade de contestar transações e a democratização do processo ajudam a garantir que o Bitcoin continue sendo uma moeda de todos, sem a influência de poucos.
Conclusão: Um Futuro Promissor para o Bitcoin
O lançamento da BitVM2 representa um salto importante para o futuro do Bitcoin. A capacidade de verificar transações complexas de forma rápida e acessível, aliada à descentralização e à possibilidade de uso dos rollups, promete tornar o Bitcoin mais eficiente e acessível para todos.
Mais do que uma simples atualização tecnológica, a BitVM2 traz à tona a discussão sobre liberdade digital, transparência e o papel das criptomoedas no futuro. É um avanço que, sem dúvida, será observado de perto pelos entusiastas e críticos da criptoeconomia.
O Bitcoin sempre foi visto como uma alternativa descentralizada ao sistema financeiro tradicional, e a BitVM2 parece reforçar essa visão. À medida que mais pessoas se envolvem e a tecnologia avança, o futuro das transações digitais parece mais promissor do que nunca. Vamos ficar de olho no que essa nova fase nos reserva e nas novas possibilidades que ela pode abrir.
***
-
 @ c6f7077f:ad5d48fd
2024-09-08 01:24:03
@ c6f7077f:ad5d48fd
2024-09-08 01:24:03“The more you learn about something, the more you realize you know nothing.” This saying resonates deeply with me. The truth is, no one really has all the big answers. Many in the scientific community seem to pretend they do. Let’s explore this further.
Consider the Most Fundamental Questions
- The Origin of the Universe
- The Origin of Life on Earth
The Origin of the Universe
You might think we have a solid answer: the Big Bang. However, this explanation has its limitations, and calling it a “start” can be misleading. In fact, this theory might be entirely wrong. New research challenges the Big Bang theory, and I highly recommend listening to Sir Roger Penrose for a deeper understanding.
The only substantial evidence we have is the universe's expansion. Penrose proposes a different hypothesis: the endless expansion and contraction of the universe. This idea doesn’t contradict our current understanding.
Thus, the evidence for the Big Bang and Penrose’s theory are both radically different, yet neither can be definitively proven over the other. This highlights the limitations of our current understanding.
The Origin of Life on Earth
The origin of life is even more complex. Life requires three essential components: - Proteins for basic functioning - RNA for storing and replicating genes - Lipids (cell walls) to create separation from the environment
Mathematical models suggest that while proteins and lipids have a reasonable probability of forming, the creation of RNA seems nearly impossible through random mutations in a short time frame. The best explanations indicate that we either lack crucial information or that these RNA molecules—and life as a whole—might have come from outside sources. Some scholars even question the entire random mutation model.
The Question of Certainty
If scientists don’t know the answers, why do they pretend they do? In my humble opinion, It seems they do this to distance science from religion and to close the discussion before the wealthiest can fit God into the narrative, Interestingly, I’m not alone in believing they closed the books too early.
Reclaiming Control of Science and Education
The best way to reclaim control of science and education is to learn. If you’re looking for a starting point, I highly recommend: - “A Brief History of Time” by Stephen Hawking for physics - “Sapiens” or “The Selfish Gene” for evolutionary biology
All three are excellent starting points—densely packed with information and covering a wide range of topics in a concise and accessible manner.
-
 @ eac63075:b4988b48
2024-09-22 11:55:42
@ eac63075:b4988b48
2024-09-22 11:55:42I've been banging this drum for almost a decade: stop using Telegram. Seriously, folks, it's high time we faced the facts about this so-called "secure" messaging app. Just the other day, someone told me my name was mentioned in the Cypherpunks Brasil Telegram group. My immediate reaction? "First of all, stop using Telegram!"
Back in December 2015—yeah, nearly ten years ago—I tweeted about the anonymity issues with Telegram. I shared an article highlighting four security flaws found by experts. The gist? Telegram's supposed privacy features were nothing more than smoke and mirrors.
Fast forward to 2021, and I was still at it. When WhatsApp updated its privacy policy, people flocked to Telegram as a safer alternative. I couldn't help but point out that Signal is infinitely superior to Telegram in terms of security. Telegram doesn't use end-to-end encryption by default, stores all your messages and files, and has possible agreements with governments to avoid legal troubles.
I even found an old post where we did a proof of concept. We proved that even if you delete a message or set it to self-destruct before it's read, it's still possible to recover the content later. Translation: everything is stored. In 2022, when Brazil temporarily banned Telegram, I noted that it aligned us with countries known for heavy censorship like China and Iran. The ban didn't last, of course. Telegram likely made some concessions to keep operating, possibly sharing data with the government.
Now, let's talk about that Wired article from earlier this year, titled "The Kremlin Has Entered the Chat". It's a must-read. It tells the story of activists in Russia who were arrested, and their private Telegram messages were already in the hands of authorities—even before their devices could be searched. One activist noted, "They already knew everything I was saying. There wasn't enough time for them to scan my phone. They had the information beforehand."
How is this possible? The article delves into the history of Telegram, including how founder Pavel Durov and his brother initially wanted to create a platform for free communication. Noble intentions, perhaps, but somewhere along the line, things went awry.
Telegram's group messages are accessible through an open API. You can retrieve information from any group, including all participants and messages, without even being a member. Yes, you read that right. You don't need to be in a group to extract all its messages. I'll even show you how.
There are scripts and tools—like Telethon and Telepathy—that allow you to automate data collection from public channels and groups. With a few lines of code, you can pull messages, media, documents—everything. There's an article on Medium that walks you through how to do this step by step. It's that easy.
But wait, there's more. You can geolocate users. There's a tool called Telepathy that lets you find Telegram users nearby. It leverages the app's "People Nearby" feature, which is enabled by default. This means anyone can find out who's using Telegram around them, down to a few meters. Think about the privacy implications of that.
Recently, Pavel Durov announced that he's disabling the personal geolocation feature on Telegram. According to a Cointelegraph article, Durov acknowledged that security researchers had found a way to use this feature to triangulate a user's exact location. So, he decided to disable it to protect user privacy.
But is that enough? Disabling one feature doesn't address the fundamental issues with Telegram's architecture. The app doesn't use end-to-end encryption by default, and group chats are not encrypted at all. Everything is stored on Telegram's servers, which could be accessed by governments or malicious actors.
Remember, the founder's reemergence has sparked debates in the crypto community. As reported by Decrypt, some see Durov as a champion of privacy, while others are skeptical of his motives and Telegram's security practices.
In the Wired article, they also discuss how Telegram was banned in Russia at one point, only to be unbanned after possible agreements were made. The speculation is that Durov may have struck a deal with the Kremlin to provide access to user data in exchange for the app's continued operation in Russia.
And let's not forget the investors behind Telegram. The article mentions that Russian entities have funneled money into Telegram. So, when Durov flies from Azerbaijan to France—where he has legal issues—you have to wonder what's really going on behind the scenes.
So, what can you do? Stop using Telegram. There are better alternatives out there. Signal is infinitely superior when it comes to security. It uses end-to-end encryption by default and doesn't store your data. There's also Session and SimpleX, which don't even require a phone number to use.
Another promising platform is Veilid, developed by the Cult of the Dead Cow—the same group that coined the term "hacktivism" and has been pioneering digital privacy since the '80s. Valet uses strong encryption and decentralization to protect your communications.
And let's not forget about Element, which operates on the Matrix protocol. It's decentralized and offers end-to-end encryption, making it another solid choice for secure messaging.
In conclusion, Telegram is not the privacy-focused app it claims to be. Its architecture and business practices raise serious concerns about user privacy and data security. With so many better alternatives available, there's no reason to keep using Telegram.
I've been saying this for years, and the evidence keeps piling up. So, please, for your own sake, stop using Telegram. Switch to a platform that genuinely respects your privacy and keeps your data secure.
Technical Considerations When Choosing a Messaging Platform
When evaluating messaging apps, it is essential to consider the following technical aspects:
- End-to-End Encryption by Default: Ensures that only the participants in the conversation can read the messages.
- Open Source: Allows the community to review the source code for vulnerabilities or backdoors.
- Metadata Collection: Minimizing or eliminating metadata collection reduces the risk of user profiling.
- Decentralization: Reduces single points of failure or control, increasing resistance to censorship and surveillance.
- Registration Requirements: Avoiding the need to provide personal information, such as phone numbers or emails, enhances anonymity.
Practical Recommendations for Users
- Disable Geolocation Features: As advised by Pavel Durov, disable "People Nearby" to prevent unwanted tracking.
- Use Secret Chats: If you continue to use Telegram, always use "secret chat" for sensitive conversations, and
- Never, ever store sensitive information like passwords or private keys in your Saved Messages.
- Keep the App Updated: Updates often contain critical security fixes.
- Explore Secure Alternatives: Consider migrating to apps like Signal, Session, or SimpleX for communications requiring a high level of privacy.
- Continuous Education: Stay informed about best practices in digital security and be aware of emerging threats.
References:
- "The Kremlin Has Entered the Chat" - Wired
- Collecting Data from Telegram Channels and Groups Using Telethon - Medium
- Durov Disabling Personal Geolocation on Telegram - Cointelegraph
- Telegram Founder’s Reemergence Sparks Split - Decrypt
Alternative Messaging Apps:
- Signal: End-to-end encryption by default, open-source, and highly respected in the security community.
- Session: No phone number required, uses blockchain technology for decentralization.
- SimpleX: Doesn't require personal identifiers, focuses on strong privacy.
- Veilid: Developed by Cult of the Dead Cow, emphasizes privacy and security.
- Element: Based on the Matrix protocol, decentralized, and offers end-to-end encryption.
Final Thoughts:
Privacy isn't just a buzzword; it's a fundamental right. Don't be lulled into a false sense of security by apps that claim to protect you but do the opposite. Do your research, choose wisely, and take control of your digital life.
-
 @ 76c71aae:3e29cafa
2024-08-13 04:30:00
@ 76c71aae:3e29cafa
2024-08-13 04:30:00On social media and in the Nostr space in particular, there’s been a lot of debate about the idea of supporting deletion and editing of notes.
Some people think they’re vital features to have, others believe that more honest and healthy social media will come from getting rid of these features. The discussion about these features quickly turns to the feasibility of completely deleting something on a decentralized protocol. We quickly get to the “We can’t really delete anything from the internet, or a decentralized network.” argument. This crowds out how Delete and Edit can mimic elements of offline interactions, how they can be used as social signals.
When it comes to issues of deletion and editing content, what matters more is if the creator can communicate their intentions around their content. Sure, on the internet, with decentralized protocols, there’s no way to be sure something’s deleted. It’s not like taking a piece of paper and burning it. Computers make copies of things all the time, computers don’t like deleting things. In particular, distributed systems tend to use a Kafka architecture with immutable logs, it’s just easier to keep everything around, as deleting and reindexing is hard. Even if the software could be made to delete something, there’s always screenshots, or even pictures of screens. We can’t provably make something disappear.
What we need to do in our software is clearly express intention. A delete is actually a kind of retraction. “I no longer want to associate myself with this content, please stop showing it to people as part of what I’ve published, stop highlighting it, stop sharing it.” Even if a relay or other server keeps a copy, and keeps sharing it, being able to clearly state “hello world, this thing I said, was a mistake, please get rid of it.” Just giving users the chance to say “I deleted this” is a way of showing intention. It’s also a way of signaling that feedback has been heard. Perhaps the post was factually incorrect or perhaps it was mean and the person wants to remove what they said. In an IRL conversation, for either of these scenarios there is some dialogue where the creator of the content is learning something and taking action based on what they’ve learned.
Without delete or edit, there is no option to signal to the rest of the community that you have learned something because of how the content is structured today. On most platforms a reply or response stating one’s learning will be lost often in a deluge of replies on the original post and subsequent posts are often not seen especially when the original goes viral. By providing tools like delete and edit we give people a chance to signal that they have heard the feedback and taken action.
The Nostr Protocol supports delete and expiring notes. It was one of the reasons we switched from secure scuttlebutt to build on Nostr. Our nos.social app offers delete and while we know that not all relays will honor this, we believe it’s important to provide social signaling tools as a means of making the internet more humane.
We believe that the power to learn from each other is more important than the need to police through moral outrage which is how the current platforms and even some Nostr clients work today.
It’s important that we don’t say Nostr doesn’t support delete. Not all apps need to support requesting a delete, some might want to call it a retraction. It is important that users know there is no way to enforce a delete and not all relays may honor their request.
Edit is similar, although not as widely supported as delete. It’s a creator making a clear statement that they’ve created a new version of their content. Maybe it’s a spelling error, or a new version of the content, or maybe they’re changing it altogether. Freedom online means freedom to retract a statement, freedom to update a statement, freedom to edit your own content. By building on these freedoms, we’ll make Nostr a space where people feel empowered and in control of their own media.
-
 @ 4ba8e86d:89d32de4
2024-10-26 02:51:21
@ 4ba8e86d:89d32de4
2024-10-26 02:51:21Inicialmente criado como uma evolução do projeto CopperheadOS, o GrapheneOS é uma versão modificada do Android que concentra seus esforços na proteção da privacidade e segurança dos usuários. Foi iniciado por Daniel Micay, também conhecido como thestinger, após um desentendimento com os cofundadores do CopperheadOS em 2018. O foco principal do GrapheneOS é fornecer um sistema operacional móvel altamente seguro e com ênfase na privacidade para dispositivos Google Pixel.
Uma das principais características do GrapheneOS é sua rápida atualização de segurança, juntamente com recursos avançados de privacidade. O sistema operacional adota tecnologias que mitigam diferentes tipos de vulnerabilidades, dificultando a exploração das principais fontes de risco. Ele também aprimora a segurança dos aplicativos em execução no sistema operacional, reforçando a sandbox do aplicativo e outros limites de segurança.
O GrapheneOS se esforça para garantir que os recursos de privacidade e segurança não afetem negativamente a experiência do usuário. Idealmente, esses recursos são projetados para estar sempre ativados, sem adicionar complexidade adicional ou opções de configuração que possam sobrecarregar o usuário. No entanto, em certos casos, são adicionados interruptores para recursos como permissões de rede, permissões de sensores e restrições quando o dispositivo está bloqueado (por exemplo, periféricos USB, câmera, ladrilhos rápidos).
O GrapheneOS tem ganhado popularidade como uma escolha confiável para usuários que valorizam a privacidade e a segurança em seus dispositivos móveis. É reconhecido como uma das opções mais seguras e privadas disponíveis para o sistema Android.
Recomenda-se a compra dos seguintes dispositivos para usar o GrapheneOS devido à sua melhor segurança e garantia mínima de 5 anos para atualizações completas de segurança:
- Pixel 7a
- Pixel 7 Pro
- Pixel 7
- Pixel 6a
- Pixel 6 Pro
- Pixel 6
Os dispositivos mais recentes possuem uma garantia mínima de 5 anos, mas o suporte real pode ser ainda maior. O Pixel 7 e o Pixel 7 Pro apresentam melhorias em relação aos modelos anteriores, como GPU e rádio celular aprimorados, além de uma atualização incremental da CPU. O Pixel 7a oferece um bom custo-benefício com recursos semelhantes ao Pixel 7, exceto pelo carregamento sem fio lento e proteção contra poeira/água mais fraca.
O Pixel 6, Pixel 6 Pro e Pixel 6a ainda podem ser uma opção válida se encontrados a um preço atrativo, pois possuem de 3,5 a 4 anos de garantia mínima de suporte restante.
Dispositivo
Google Pixel 7a , maio de 2028 , 5 anos.
Google Pixel 7 Pro , outubro de 2027 , 5 anos.
Google Pixel 7 , outubro de 2027 , 5 anos.
Google Pixel 6a, julho de 2027 ,5 anos.
Google Pixel 6 Pro , outubro de 2026 ,5 anos.
Google Pixel 6 ,outubro de 2026 ,5 anos.
Google Pixel 5a , agosto de 2024 ,3 anos.
Google Pixel 5 , outubro de 2023 , 3 anos.
Google Pixel 4a 5G , novembro de 2023 ,3 anos.
Google Pixel 4a, agosto de 2023 ,3 anos.
Google Pixel 4 , Outubro 2022 , 3 anos.
Google Pixel 4 XL ,Outubro 2022 ,3 anos.
No que diz respeito à segurança e privacidade, o GrapheneOS utiliza uma versão aprimorada da criptografia de disco baseada no sistema de arquivos do Android OpenSource Project. Os dispositivos suportados possuem suporte substancial baseado em hardware para aumentar a segurança da criptografia. A autenticidade e integridade das partições de firmware e do sistema operacional são verificadas em cada inicialização. O GrapheneOS implementa criptografia de disco completo por meio de criptografia baseada em sistema de arquivos, garantindo que todos os dados, nomes de arquivos e metadados sejam armazenados criptografados.
O sistema utiliza chaves de criptografia de disco geradas aleatoriamente e armazenadas criptografadas. Dados confidenciais são armazenados em perfis de usuário com suas próprias chaves de criptografia. O GrapheneOS permite o suporte para encerrar sessões de perfil de usuário secundário após o login, o que limpa totalmente as chaves de criptografia e coloca os perfis em repouso. Além disso, o GrapheneOS suporta o uso de armazenamento de chaves de hardware e implementações de criptografia em aplicativos para adicionar camadas adicionais de proteção. Detalhes adicionais sobre essas funcionalidades estão além do escopo desta resposta.
Um dos Recurso GrapheneOS tem é Duress PIN! Que você pode definir um PIN especial de “coação” para que, em vez de desbloquear o telefone, ele limpe imediatamente as chaves de criptografia no elemento seguro, tornando os dados de armazenamento irrecuperáveis. vídeo - Tuxsudo🐧 https://video.nostr.build/ec077345a2109811ef83afc38c33f5ee06aa687ec2bfdf8685ebc8af90293d48.mp4
Os aplicativos podem espionar a área de transferência em segundo plano ou injetar conteúdo nela? A partir do Android 10, apenas o teclado de entrada padrão configurado (o teclado de sua escolha) e o aplicativo atualmente em foco têm acesso à área de transferência. Aplicativos em segundo plano não podem acessar a área de transferência. Essa restrição é mais rigorosa do que simplesmente impedir que aplicativos em segundo plano a acessem, pois nem mesmo um aplicativo ou serviço em primeiro plano pode acessá-la, apenas o aplicativo em primeiro plano que está em foco no momento. Os gerenciadores de área de transferência precisam ser implementados pelo teclado definido como padrão pelo usuário. Anteriormente, o GrapheneOS restringia o acesso à área de transferência em segundo plano, mas essa abordagem foi substituída por uma restrição mais rigorosa implementada pelo Android 10. Assim, a funcionalidade de permitir que os gerenciadores de área de transferência estejam na lista de permissões não é mais necessária, pois os teclados devem implementar essa funcionalidade.
A partir do Android 12, o usuário recebe uma notificação quando um aplicativo lê o conteúdo da área de transferência definido por outro aplicativo. Essa notificação está ativada por padrão e pode ser alterada em Configurações -> Privacidade -> Mostrar acesso à área de transferência.
Os aplicativos podem monitorar conexões de rede ou estatísticas? Os aplicativos não podem monitorar conexões de rede, a menos que sejam realizadas por meio de um serviço de VPN ativo definido pelo usuário. Normalmente, os aplicativos não têm acesso às estatísticas de rede e não podem solicitar acesso direto a elas. No entanto, os usuários podem conceder explicitamente permissões de estatísticas de uso do aplicativo, que fornecem estatísticas específicas do aplicativo. Isso foi introduzido como parte das melhorias de privacidade do Android 10.
O GrapheneOS fornece um firewall? Sim, o GrapheneOS herda o firewall profundamente integrado do Android Open Source Project, que é usado para implementar partes do modelo de segurança e vários outros recursos. Historicamente, o projeto GrapheneOS fez várias melhorias no firewall, mas ao longo do tempo a maioria dessas mudanças foi integrada à versão principal do sistema operacional ou se tornaram irrelevantes.
O GrapheneOS adiciona uma opção de permissão de rede voltada para o usuário, oferecendo uma maneira robusta de negar o acesso direto e indireto à rede para os aplicativos. Essa opção baseia-se na permissão padrão de INTERNET, que não é voltada para o usuário, mas já é amplamente adotada pelo ecossistema de aplicativos. Ao revogar a permissão de INTERNET, o acesso indireto por meio de componentes do sistema operacional e aplicativos que exigem a permissão de INTERNET, como o DownloadManager, é negado. O acesso direto é bloqueado, impedindo o acesso a soquetes de rede de baixo nível.
O GrapheneOS incluirá suporte para serviços do Google? Assim como o Android Open Source Project, o GrapheneOS não inclui aplicativos e serviços do Google. Eles nunca serão empacotados com o sistema operacional. No entanto, o GrapheneOS possui uma camada de compatibilidade para os Serviços do Google Play, que permite que os aplicativos que dependem desses serviços sejam instalados e executados em um ambiente sandbox sem privilégios.
Essa camada de compatibilidade garante que os aplicativos do Google Play possam funcionar, mas sem comprometer a segurança e a privacidade do sistema operacional.
O GrapheneOS é um sistema operacional móvel baseado no Android Open Source Project que prioriza a segurança e a privacidade dos usuários. Ele oferece atualizações rápidas de segurança, recursos avançados de privacidade e um firewall integrado para proteger os dispositivos. O sistema operacional é projetado para garantir que recursos de segurança e privacidade não afetem negativamente a experiência do usuário. O GrapheneOS não inclui aplicativos e serviços do Google, É uma escolha confiável para aqueles que valorizam a privacidade e a segurança em seus dispositivos móveis.
Este é o instalador baseado em WebUSB para GrapheneOS e é a abordagem recomendada para a maioria dos usuários. https://grapheneos.org/install/web
O guia de instalação da linha de comando é a abordagem mais tradicional para instalar o GrapheneOS.
https://grapheneos.org/install/cli
https://grapheneos.org/
https://github.com/GrapheneOS
Pixel tem chip Titan M2 que leva o pixel outro nivel de segurança. https://www.androidauthority.com/titan-m2-google-3261547/
-
 @ 0e8c41eb:95ff0faa
2024-07-08 14:36:14
@ 0e8c41eb:95ff0faa
2024-07-08 14:36:14Chef's notes
Sprinkle a pinch of salt in a bowl. Sift 275 grams of flour above it. Make a well in the center of the flour and sprinkle the yeast into it. Add 50 grams of butter, 25 grams of sugar, and the egg. Pour in the milk and knead the dough with the mixer or by hand into a smooth dough. If necessary, add a bit more flour if the dough is too sticky. Form the dough into a ball. Let the dough rise covered with cling film at room temperature for 1 hour.
Peel the apples. Cut the apples and apricots into pieces. Cook the fruit with 150 grams of sugar and 50 ml of water in 15 minutes into a thick compote. Let this fruit filling cool.
Knead the dough again briefly and roll it out to a round sheet of about 28-30 cm in diameter, so that it fits well over the baking tin. Press the dough into the tin and press it well into the corners. Let the dough rise again for 10 minutes and cut off the excess edges.
Spread the fruit filling over the dough.
Mix the rest of the flour with the remaining 100 grams of butter and 100 grams of sugar and knead it with your fingers into a crumbly mixture. Sprinkle this crumble mixture over the fruit filling. Bake the tart in the preheated oven at 200°C for about 30 minutes until golden brown.
Variations: Only apple? Make this tart with 1 kilo of apples. High or low? You can also bake the crumble tart in a low tart tin of 30 cm diameter. If the fruit filling is a bit too voluminous, you can make double the crumble mixture and sprinkle it over the larger surface area.
Additional needs: Mixer with dough hooks or food processor Cling film Round baking tin with a diameter of 28-30 cm, greased
Details
- ⏲️ Prep time: 45 min + 1 hour Rising
- 🍳 Cook time: 30 minutes
- 🍽️ Servings: 8
Ingredients
- 375 grams flour
- 1 packet dried yeast (7 grams)
- 125 grams unsalted butter, at room temperature
- 275 grams sugar
- 1 egg
- 100 ml milk, at room temperature
- 500 grams apples
- 500 grams apricots (fresh or from a can)
Directions
- Sprinkle a pinch of salt in a bowl. Sift 275 grams of flour above it. Make a well in the center of the flour and sprinkle the yeast into it. Add 50 grams of butter, 25 grams of sugar, and the egg. Pour in the milk and knead the dough with the mixer or by hand into a smooth dough. If necessary, add a bit more flour if the dough is too sticky. Form the dough into a ball. Let the dough rise covered with cling film at room temperature for 1 hour.
- Peel the apples. Cut the apples and apricots into pieces. Cook the fruit with 150 grams of sugar and 50 ml of water in 15 minutes into a thick compote. Let this fruit filling cool.
- Knead the dough again briefly and roll it out to a round sheet of about 28-30 cm in diameter, so that it fits well over the baking tin. Press the dough into the tin and press it well into the corners. Let the dough rise again for 10 minutes and cut off the excess edges.
- Spread the fruit filling over the dough.
-
 @ dd664d5e:5633d319
2024-06-24 06:05:05
@ dd664d5e:5633d319
2024-06-24 06:05:05The new Great Library
We have all heard tales of Amazon or other booksellers banning customers from their bookstores or censoring/editing purchased books. The famous Project Gutenberg, and similar organizations, are performing a good work, to help protect many of our precious books from this fate, but it is merely a centralized website and therefore not censorship resistant. Also, it mostly posts books in English or German.
So, we at nostr:npub1s3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqd975wz have decided to move Project Gutenberg to Nostr and house it in the most distributed way possible: on relays. Specifically, our new, public Citadel relay for out-of-print books (and other documents), but also on any relay, anywhere.
And, because we are a very humble group, we're naming the effort "Alexandria". And the first book to be printed on Nostr is the Bible because obviously.
Why on relays?
Well, why not on relays? Relays are one of the few widely-distributed databases for documentation in existence. The relay database spans the entire globe and anyone can maintain their own relay on their personal computer or mobile phone.
That means that anyone can house their own books. Which books are their own? Any books they have in their own possession. Any books someone would have to physically pry out of their cold, dead, computer.
Notes are perfect for publishing
Once we begin generating eBooks from notes with an associated header (which will be quite easy to do, so long as they are written in markdown or similar), they will also be readable, downloadable, and storable in ePub format (see Pandoc). And it is, after all, only a matter of time until someone enterprising makes an ePaper Nostr client for calmer reading of notes, and then you can download and read them, without having to bother converting beforehand, which maintains their Nostr-navigation.
The new event kind 30040 allows us to take any sort of note containing any sort of characters and create a type of "note collection" or "book of notes", "journal of notes", "magazine of notes". And it can be nested or embedded in other notes, creating any sort of note-combination and note-hierarchy you can think of, only limited in size by the ability of your computer to processes the relationships.
Save the Zettels
The associated kind 30041 adds the prospect of breaking longer texts or articles up into sections or snippets (called "Zettel" in German). We can then collect or refer to particular bits of a longer text (like a chart, elegant paragraph or definition, data table), directly. Anyone can create such snippets, even of texts they didn't write, as they can add a reference to the original publication in the tags of the new event.
This means we no longer have to "copy-paste" or quote other people's works, we can simply tie them in. If we worry about them being deleted, we can fork them to create our own, digitally-linked version, and then tie that in. This means that source material can be tied to the new material, and you can trace back to the source easily (using Nostr IDs and tags, which are signed identifiers) and see who else is branching out from that source or discussing that source.
It's gonna be HUGE!
We are making a big, beautiful library... and you are going to build it for us. Anyone, anywhere can therefore publish or republish any document they wish, with Nostr, and store it wherever they have a relay, and view it on any client willing to display it.
You will own something and be happy.
-
 @ eac63075:b4988b48
2024-09-20 09:23:23
@ eac63075:b4988b48
2024-09-20 09:23:23Overview of the Infrastructure
- Umbrel/Citadel/RaspiBlitz/Start9 Server
- Purpose: Acts as your personal Bitcoin and Lightning Network node.
- Setup: Installed on a Raspberry Pi 4 running Debian or Umbrel OS.
- Benefits:
- Participate in Bitcoin Consensus: Validates transactions and blocks independently.
- Lightning Network Routing: Facilitates faster transactions and earns routing fees.
- Cold Storage Wallets
- Coldcard: A highly secure hardware wallet designed specifically for Bitcoin.
- Ledger Nano X: A versatile hardware wallet supporting multiple cryptocurrencies.
- Purpose: Store your Bitcoin offline to protect against online threats.
- Secure Devices
- Encrypted Computer: A notebook with encrypted storage for managing your wallets and nodes securely.
- Android Phone with Secure Area:
- Old Device: Repurposed without a SIM card to minimize exposure.
- Secure Area for Apps: Uses features like Samsung's Secure Folder/Knox to isolate sensitive applications.
- NerdMiner
- Purpose: A compact mining device like the Nerdminer V2 to engage in Bitcoin mining.
- Function: Attempts to mine Bitcoin blocks, offering a chance (albeit very low) to earn block rewards and learn about the mining process.
 ### Advantages of This Setup
### Advantages of This Setup- Self-Sovereignty: You have complete control over your funds without relying on third-party services.
- Enhanced Privacy:
- CoinJoin Transactions: Mix your coins with others to obfuscate transaction history.
- No SIM Card Devices: Reduces the risk of SIM swapping attacks.
- Network Participation:
- Consensus Involvement: By running a full node, you help maintain the network's integrity.
- Lightning Network: Improve transaction speeds and network scalability.
- Security:
- Cold Storage: Keeps your private keys offline, away from potential online threats.
- Encrypted Devices: Protects data even if physical devices are lost or stolen.
 ### Simplifying the Perceived Complexity
### Simplifying the Perceived ComplexityWhile the infrastructure may seem daunting, it's more approachable than it appears:
- Starting Point: Use an old computer or phone as a cold wallet with software like Electrum or Sparrow.
- Step-by-Step Setup:
- Begin with setting up the Umbrel/Citadel/RaspiBlitz/Start9 server.
- Gradually add hardware wallets like Coldcard, SeedSigner DIY, Jade, Ledger, Trezor or Onekey.
- Implement security measures on your existing devices.
- Community Resources: Numerous guides and communities are available to assist with each step.
 ### Embracing Freedom and Privacy
### Embracing Freedom and PrivacyPracticing self-sovereignty and custody isn't just about securing your Bitcoin—it's about embracing freedom and privacy in the digital age. By taking control:
- Financial Independence: You're not dependent on banks or exchanges.
- Data Privacy: Your financial data remains confidential.
- Empowerment: Gain a deeper understanding of how Bitcoin and blockchain technology work.
Remember: Even simple steps like using an old device as a cold wallet can significantly enhance your security. The journey towards complete self-sovereignty is a progressive one, and each step you take strengthens your position in the digital world.
-
 @ 472f440f:5669301e
2024-09-04 22:54:11
@ 472f440f:5669301e
2024-09-04 22:54:11For the last few months many people in bitcoin, myself included, have been focused on bitcoin's role as a macroeconomic asset. Bitcoin as a strategic reserve for the US government. Bitcoin as a strategic treasury asset for corporations. Bitcoin as a geopolitical hedge in a world that is trending toward a multi-polar power dynamic. This is where the focus has been. And for good reason. These trends will ultimately have a material effect on the price of bitcoin if they pick up steam.
However, with all of the focus on bitcoin as a strategic asset I think a couple of technical developments and trends have been overlooked. Particularly in the realm of second layer privacy. I'll touch on two of them in this letter; BOLT 12 invoices and the progression of ecash.
Yesterday afternoon the Strike (a company Ten31 is very proud to be backing) team released a blog post that detailed their journey to implementing BOLT 12 offers in their product stack. For those who are unaware of BOLT 12 and why it is important, in short, it is an upgrade to the lightning network that would make receiving bitcoin on the lightning network more private while also significantly improving the user experience. The current standard for invoicing people via the lightning network is BOLT 11, which forces users to create a unique invoice every time they want to receive bitcoin and comes with privacy tradeoffs for the party receiving bitcoin.
BOLT 12 brings with it route blinding which allows a receiver to publish a lightning offer to the network without revealing their node's public key. It also brings with it onion messaging, which allows users of the lightning network to communicate without a dependence on HTTP, which can be censored by a motivated state actor. On top of this, it enables users to create a static invoice that can be paid multiple times by multiple people. Think of a band putting their Venmo or Cash App QR code next to their tip jar on the stage. They'll be able to add a private lightning invoice their audience can pay to now.
https://strike.me/blog/bolt12-offers/
As it stands right now, Strike has only enabled BOLT 12 offers and there is work to do at the protocol layer of lightning and the different implementations of that protocol to get the full benefits of BOLT 12, but this is material progress that gets us closer to a significantly better user experience on the lightning network. If you read Strike's blog post you'll come to appreciate the collaboration between the teams working on these implementations and the companies implementing the protocol that is necessary to get these features live. Shout out to everyone who worked on this. Everyone who uses the lightning network will be better off when BOLT 12 is fully implemented.
Moving on. Earlier today the founder of the BTCPay Server open source project, Nicolas Dorier, published a blog post outlining his thoughts on how ecash has the potential to solve problems that many have tried to solve by launching their own blockchains in the past. The problem with trying to "blockchain the world" is that blockchains are very inefficient and only really work for one application; enabling a peer-to-peer digital cash system with no trusted third parties (i.e., bitcoin). However, the ultimate goals of the thousands of blockchain projects that spun up in bitcoin's wake are desirable. Cheap, private and instant transactions. The ability to trivially spin up private money tokens suited for very particular use cases. Overall great UX that makes it easy for people to realize the benefits of "blockchain technology".
The problem that has existed to date is that you don't need a blockchain for all of these things. In fact, having a blockchain for these things proves to be detrimental to their ultimate goals. Instead, what people really need is a protocol that gives you the granular control, privacy, instantaneous transactions and UX that anchors to bitcoin. This is exactly what Chaumian Mints bring to the bitcoin stack.
This is something that we've been screaming about for more than seven years in this rag. Now with ecash protocols like Cashu and Fedimint maturing, gaining traction and bringing products to market that highlight the power and flexibility of ecash systems, people are beginning to see the promise. It is only a matter of time before more and more people begin to realize this potential.
Another benefit of ecash protocols is the fact that they are siloed from each other. Ecash mints are permissionless; any one person or group of people can spin them up, offer their preferred services and maintain (or fail to maintain) their mints. The failure of one mint is not a systemic risk to other mints. This is very different from token projects that are spun up on blockchains. The last ten years have proven that individual token projects can prove to be systemic problems for individual blockchains (i.e., The DAO token on Ethereum). Being able to silo mints is the only way to ensure that the utility of ecash overall is actually scalable and robust.
Don't get so distracted by the bitcoin macro talk that you miss out on the incredible technical developments happening on top of and adjacent to bitcoin.
Final thought... Vibes are high.
-
 @ eac63075:b4988b48
2024-09-19 09:03:33
@ eac63075:b4988b48
2024-09-19 09:03:33Nos últimos anos, as Organizações Autônomas Descentralizadas (DAOs) emergiram como uma das inovações mais significativas no ecossistema das criptomoedas e da tecnologia blockchain. Elas prometem ser uma evolução dos sistemas tradicionais de governança, oferecendo um modelo em que as decisões são tomadas coletivamente por meio de tokens, sem a necessidade de intermediários. No entanto, à medida que esse conceito se populariza, problemas relacionados à manipulação de votos e à corrupção dentro das DAOs tornaram-se cada vez mais evidentes.
Recentemente, um novo desenvolvimento criptográfico foi proposto para combater essas fraudes: a Prova de Conhecimento Completo (Complete Knowledge Proof). Este avanço, com a colaboração de Vitalik Buterin, criador do Ethereum, e pesquisadores da Universidade de Cornell, traz uma abordagem inovadora para resolver um dos maiores desafios de governança descentralizada: a segurança e integridade dos votos. Neste artigo, vamos explorar detalhadamente como funciona essa tecnologia e o impacto que ela pode ter no futuro das DAOs.
O Problema das DAOs: Manipulação de Votos e Fraudes
O conceito de DAOs é fascinante, pois permite que qualquer pessoa com tokens tenha voz ativa nas decisões de uma organização descentralizada. A governança é realizada através da votação, onde os detentores de tokens participam para aprovar ou rejeitar propostas. No entanto, a prática tem revelado alguns problemas críticos, principalmente a manipulação de votos e o aluguel de tokens.
Em muitos casos, indivíduos ou grupos podem "alugar" tokens de outros participantes para ganhar mais poder nas votações. Isso corrompe o processo de governança, pois aqueles que deveriam votar com seus próprios tokens acabam utilizando tokens de terceiros, prejudicando a descentralização genuína. Em algumas situações, esse processo leva a decisões que beneficiam poucos, enquanto os interesses da maioria são ignorados. Um dos exemplos mais críticos desse problema ocorreu quando tokens foram delegados ou alugados para manipular decisões em uma DAO, permitindo que certos atores controlassem resultados vitais.
A Solução: Prova de Conhecimento Completo (Complete Knowledge Proof)
A Prova de Conhecimento Completo surge como uma solução promissora para mitigar esses problemas de governança. O objetivo dessa tecnologia é garantir que o processo de votação seja legítimo e que somente os verdadeiros detentores dos tokens possam participar de forma válida, sem delegar ou vender seus direitos de voto.
O que é Prova de Conhecimento Completo?
A Prova de Conhecimento Completo é um conceito criptográfico que permite a alguém provar que tem conhecimento de uma informação (como uma chave criptográfica) sem precisar revelar essa informação. Ou seja, você pode provar que tem os direitos para votar com seus tokens sem precisar divulgar suas chaves privadas ou delegar os tokens para outra pessoa.
Essa solução utiliza uma combinação de Zero-Knowledge Proof (Prova de Conhecimento Nulo) e Proof of Work (Prova de Trabalho) para garantir que os votos sejam realizados apenas por aqueles que realmente detêm os tokens e que estão participando de forma legítima, sem manipulação ou fraude. A Zero-Knowledge Proof permite que alguém prove que possui a chave privada associada aos tokens, sem revelar a chave em si, e a Proof of Work adiciona uma camada adicional de validação, exigindo que um trabalho computacional seja realizado para confirmar a autenticidade do voto.
Como Funciona a Prova de Conhecimento Completo?
A ideia central da Prova de Conhecimento Completo é simples, mas poderosa. Imagine que você possui tokens de uma DAO e deseja participar de uma votação. Para garantir que o voto seja válido, a Prova de Conhecimento Completo exige que você utilize um dispositivo específico ou um ambiente de execução confiável, que possa validar que você realmente é o dono dos tokens e que não os compartilhou com outra pessoa.
Este processo pode ser feito através de um hardware dedicado, como um dispositivo ASIC (circuito integrado de aplicação específica), que é programado para validar os votos de maneira segura. Os votos são computados diretamente a partir desse hardware, que usa algoritmos criptográficos complexos para provar que você tem os tokens e está votando de forma legítima. Isso evita que os votos sejam manipulados ou alugados, pois só o verdadeiro detentor dos tokens pode usá-los para votar.
Uso de Zero-Knowledge Proof e Proof of Work
A combinação de Zero-Knowledge Proof e Proof of Work é o que torna esse processo especialmente robusto. A Zero-Knowledge Proof garante que a sua identidade como votante seja preservada, ou seja, você pode provar que tem os tokens sem revelar publicamente quem você é ou quantos tokens possui. Já o Proof of Work adiciona um nível extra de segurança, exigindo que o hardware dedicado realize um certo número de cálculos antes que o voto seja validado. Isso impede que pessoas usem múltiplas contas falsas ou tokens alugados, já que seria computacionalmente inviável manipular o sistema.
O Impacto na Governança Descentralizada
A implementação da Prova de Conhecimento Completo pode transformar completamente a forma como as DAOs operam, eliminando os problemas de manipulação de votos e garantindo uma governança mais transparente e justa. Além de aumentar a segurança, essa solução também promove uma maior confiança nas DAOs, já que os participantes podem ter certeza de que as decisões estão sendo tomadas por aqueles que realmente possuem os tokens, sem interferências de atores externos.
Aplicações Além das DAOs
Embora o foco inicial da Prova de Conhecimento Completo seja a governança descentralizada, essa tecnologia tem um potencial muito maior. Ela pode ser utilizada em várias outras áreas, como votação eletrônica, identidade digital, autenticação de usuários, entre outros. Em sistemas de votação eletrônica, por exemplo, a Prova de Conhecimento Completo poderia garantir que cada voto é legítimo sem comprometer a privacidade dos eleitores, o que seria uma revolução na forma como conduzimos eleições em todo o mundo.
No campo da identidade digital, essa solução poderia permitir que usuários provem que possuem determinadas credenciais (como uma identidade ou uma carteira de motorista), sem a necessidade de expor essas informações a terceiros. Isso poderia ser extremamente útil em situações que exigem alto nível de privacidade e segurança, como em contratos eletrônicos e autenticação de serviços.
Conclusão
A Prova de Conhecimento Completo é uma inovação significativa no campo da criptografia e da governança descentralizada. Ao combinar as vantagens da Zero-Knowledge Proof e da Proof of Work, ela oferece uma solução eficaz para prevenir fraudes e manipulações nas DAOs, garantindo que os votos sejam realizados de forma segura e legítima.
Com a participação de nomes de peso como Vitalik Buterin e pesquisadores da Cornell, essa tecnologia tem o potencial de se tornar um pilar fundamental na governança descentralizada e em várias outras aplicações no mundo digital. À medida que as DAOs continuam a ganhar espaço no ecossistema blockchain, soluções como essa serão essenciais para assegurar sua integridade e transparência.
O futuro das DAOs pode estar mais seguro com a Prova de Conhecimento Completo, e este é apenas o começo de um novo capítulo na governança descentralizada.
Assista ao vídeo:
-
 @ 3bf0c63f:aefa459d
2024-05-21 12:38:08
@ 3bf0c63f:aefa459d
2024-05-21 12:38:08Bitcoin transactions explained
A transaction is a piece of data that takes inputs and produces outputs. Forget about the blockchain thing, Bitcoin is actually just a big tree of transactions. The blockchain is just a way to keep transactions ordered.
Imagine you have 10 satoshis. That means you have them in an unspent transaction output (UTXO). You want to spend them, so you create a transaction. The transaction should reference unspent outputs as its inputs. Every transaction has an immutable id, so you use that id plus the index of the output (because transactions can have multiple outputs). Then you specify a script that unlocks that transaction and related signatures, then you specify outputs along with a script that locks these outputs.

As you can see, there's this lock/unlocking thing and there are inputs and outputs. Inputs must be unlocked by fulfilling the conditions specified by the person who created the transaction they're in. And outputs must be locked so anyone wanting to spend those outputs will need to unlock them.
For most of the cases locking and unlocking means specifying a public key whose controller (the person who has the corresponding private key) will be able to spend. Other fancy things are possible too, but we can ignore them for now.
Back to the 10 satoshis you want to spend. Since you've successfully referenced 10 satoshis and unlocked them, now you can specify the outputs (this is all done in a single step). You can specify one output of 10 satoshis, two of 5, one of 3 and one of 7, three of 3 and so on. The sum of outputs can't be more than 10. And if the sum of outputs is less than 10 the difference goes to fees. In the first days of Bitcoin you didn't need any fees, but now you do, otherwise your transaction won't be included in any block.

If you're still interested in transactions maybe you could take a look at this small chapter of that Andreas Antonopoulos book.
If you hate Andreas Antonopoulos because he is a communist shitcoiner or don't want to read more than half a page, go here: https://en.bitcoin.it/wiki/Coin_analogy
-
 @ bec0c9d3:c4e9cd29
2024-10-26 01:55:04
@ bec0c9d3:c4e9cd29
2024-10-26 01:55:04The Bitcoin Culture Festival is just around the corner, and we're excited to present our artists with physical artworks at the Cyphermunk House. In addition, we will be showcasing these pieces on our 2140 Auction Portal.
The "Culture of Code" gallery will be held at:
CypherMunk House 9 John Street Bloomsbury, London, UK WC1N 2ES
Before the festival, you can read our latest article about this one-of-a-kind house here on Yakihonne.
Online auctions will be available on 2140.wtf starting from October 29th to November 2nd 2024.
During the Bitcoin Culture Festival ART Gallery, you will have the opportunity to see the works of many talented Bitcoin artists. The sale will take place through our auction.
ART Gallery opening hours:
October 29 - Private viewing: 6:30 pm - 8:30 pm October 30 - November 2 - 10:00 am - 5:00 pm November 1 and 2 - 5:00 pm - 10:00 pm during NostrLDN and ART Panels
Entry to the gallery is FREE

This event is only possible due to the passion and dedication of our crew, partners , and sponsors . All made by People for the People. Cypherpunk vibe, pure from the bottom. We look forward to seeing you there!
Follow us also on all socials NOSTREE.me - NOSTR LinkTree INSTAGRAM TWETTER - X YOUTUBE
LINKS
OUR PARNERS / SPONSORS

STAY TUNED !!
2140 Crew
Hashtags:
ArtGallery
ArtPanel
2140wtf
2140army
CyhermunkHouse
art
artstr
nostrart
craft
culture
music
bitcoin
nostr
TootingMarket
NostrLDN
NostrLondon
yakihonne
-
 @ 1e286f5c:cc2c5009
2024-10-25 21:23:22
@ 1e286f5c:cc2c5009
2024-10-25 21:23:22Running a test, publishing a note in Obsidian to Nostr with 2 photos attached to ensure all works as planned.
Photo 1: L.A.B + Spirulina

Photo 2: A peek into the scope

D.
-
 @ deab79da:88579e68
2024-05-20 20:48:09
@ deab79da:88579e68
2024-05-20 20:48:09Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 20-30 min
- 🍽️ Servings: 4
Ingredients
- 1 lb cod fillets
- 1/4 cup butter
- 1/4 cup white flour
- 1 1/4 cups milk
- 1 tsp salt
- pepper to taste
- 1 small onion
- 1 carrot
- 3 celery stalks
- 1/2 cup breadcrumbs
- 1/2 cup shredded old cheddar
Directions
- Preheat oven to 375F. Place cod in a greased baking dish.
- Make the white sauce in a heavy saucepan. Melt the butter over medium heat and stir in the flour until smooth. Remove from heat and slowly stir in half of the milk, then return to heat and beat until smooth and shiny.
- Gradually add the remaining milk, followed by salt, pepper, and your vegetables. Cook until sauce is smooth & thickened.
- Pour sauce over the fish, and sprinkle breadcrumbs and cheese over the top.
- Bake, uncovered for 20-30 minutes until sauce bubbles and the cheese begins to brown. Let rest 10 minutes after cooking completes.
-
 @ 1739d937:3e3136ef
2024-09-04 07:23:12
@ 1739d937:3e3136ef
2024-09-04 07:23:12This is the sixth in a series of weekly(ish) updates detailing progress on bringing MLS protocol DMs and group messaging to Nostr.
Previous Updates
Progress this week
Sorry about the very late update this week. Catching up on everything after a week in Riga for Nostriga and Baltic Honeybadger took a bunch of time, every other moment was spent coding. 👨💻
The response at Nostriga to NIP-104 and my two talks on the subject were overwhelmingly positive. It was very helpful to spend time with other devs going through the spec in detail. We found a few minor improvements and clarifications but no major issues surfaced. Thanks to nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49, nostr:npub1lunaq893u4hmtpvqxpk8hfmtkqmm7ggutdtnc4hyuux2skr4ttcqr827lj, and nostr:npub1ye5ptcxfyyxl5vjvdjar2ua3f0hynkjzpx552mu5snj3qmx5pzjscpknpr in particular for the lengthly interrogations and nostr:npub1wmr34t36fy03m8hvgl96zl3znndyzyaqhwmwdtshwmtkg03fetaqhjg240 for the introductions.
Last week, I started work on a reference implementation of the spec. It's still early but going quickly.
My PR adding support for secp256k1 was also merged into the hpke-rs library yesterday. That's one more step in the right direction towards having secp256k1 ciphersuite support.
The NIP
If you haven't already, check out my talk; The Past and Future of DMs and Group messaging on Nostr. This was a basic overview of the various DM and group messaging schemes and talks a little about the progress on NIP-104. I believe there is a recording of the technical talk on the spec but it hasn't yet been released. I'll link it up when it is.
At this point I've been discouraging anyone from trying to implement the NIP quite yet. As I mentioned above there are a few adjustments that need to be made and a few open questions that I'm working on answering with my implementation (which I'm very happy to have contributors on). My plan at the moment is to do this first implementation with the default ciphersuite that MLS already supports while I continue to work on the dependencies to get secp256k1 support across the board.
The Implementation
I've started on a cross-platform native client that will run on Mac, Windows, Linux, iOS, and Android. Think of it as Signal or Telegram but over Nostr. I hope that this will not only become the reference implementation for other client developers but also will be one of the most secure and privacy focused clients in the Nostr ecosystem. Building it has already been helpful in clarifying some of the more complex implementation details in the NIP. It's still early but I'll have more to share on this in the coming weeks.
HPKE-RS
My PR to add support for secp256k1 is merged!
Onward and Upward
Thanks again to everyone for the support and feedback on this stuff at Nostriga. It was hugely motivating to hear the kind words, have you introducing me to people that could help, and spending time giving me feedback! This community is the best. 🫂
-
 @ e0e92e54:d630dfaa
2024-09-04 04:13:19
@ e0e92e54:d630dfaa
2024-09-04 04:13:19This is a copy of the email received from newsletter@Rumble.com

Free Speech Under Attack -- A Note from the CEO of Rumble
Dear Rumble Users,
I don't typically send messages to our users through email, but red lines have been crossed. There have been major developments with free speech platforms, and I feel it’s important to let everyone know what is going on and how you can help Rumble.
Rumble is no longer available to the citizens of Brazil, joining the ranks of France, Russia, and China. From media reports, Brazil no longer has Elon Musk's X due to attacks on free speech by Alexandre De Moreas, a justice of Brazil's Supreme Federal Court.
World powers don’t want Rumble, they don’t want X, they don’t want Telegram, and they don't want Truth Social. They want to control information, but our companies won’t let them.
There are no other large companies fighting for freedom like we are. We put everything on the line for it, and the Telegram CEO was recently arrested for it.
Advertisers boycott our companies to try and cut our economic lifeline, but they underestimate our support among the people.
The people keep us alive and keep us going.
If you want to help us, join Rumble Premium. If Rumble Premium gets big enough, you help us change the game and fight for freedom of expression.
We are also offering a $10 dicount for any new annual subscribers when they use the promo code "brazil".
Sincerely,
Chris Pavlovski Chairman and CEO of Rumble
 444 Gulf of Mexico Dr.
Longboat Key, FL 34228, USA.
444 Gulf of Mexico Dr.
Longboat Key, FL 34228, USA. -
 @ eac63075:b4988b48
2024-09-14 10:06:38
@ eac63075:b4988b48
2024-09-14 10:06:38A privacidade do usuário na internet tornou-se um tema central na era digital atual. Com o aumento das preocupações sobre como os dados pessoais são coletados, armazenados e utilizados, legislações como a AB 3048 da Califórnia emergem para fortalecer a proteção dos dados dos usuários. Neste contexto, navegadores como o Brave posicionam-se como defensores proativos da privacidade, enquanto gigantes como o Google enfrentam desafios para alinhar seus modelos de negócio com essas novas diretrizes. Este artigo técnico analisa como o Brave e o Google diferem em sua abordagem à privacidade do usuário, especialmente em relação à legislação emergente.
Controle Global de Privacidade (GPC)
Brave: Implementação Proativa do GPC
O Brave foi um dos primeiros navegadores a implementar e suportar o Global Privacy Control (GPC). Ativado por padrão há quase quatro anos (até 2024), o GPC permite que os usuários sinalizem automaticamente aos sites sua preferência em não ter seus dados vendidos ou compartilhados. Esta funcionalidade está em total alinhamento com a intenção da AB 3048, que busca reforçar as escolhas de privacidade dos usuários no nível do navegador. Ao adotar o GPC antecipadamente, o Brave demonstra um compromisso em capacitar os usuários no controle de sua privacidade digital, sem depender exclusivamente de legislações para impulsionar essas mudanças.
Google: Adaptação Reativa às Demandas de Privacidade
Por outro lado, o Google não tem sido tão entusiasta em integrar ou ativar por padrão recursos como o GPC em seus serviços. A introdução de legislações como a AB 3048 pode pressionar a empresa a implementar controles de privacidade mais robustos. No entanto, o modelo de negócio do Google é amplamente baseado em publicidade e dados dos usuários, o que muitas vezes o coloca em desacordo com medidas de privacidade mais rigorosas. A abordagem do Google tende a ser mais reativa, implementando mudanças quando exigido por lei ou diante de pressão pública significativa.
Filosofia de Privacidade e Funcionalidades
Brave: Privacidade como Pilar Central
O Brave foi construído com a privacidade como foco principal. Por padrão, ele bloqueia anúncios e rastreadores, reduzindo significativamente a quantidade de dados coletados durante a navegação. Além disso, oferece um modo de navegação privada integrado com o Tor, proporcionando anonimato aprimorado. O Brave também desenvolveu seu próprio mecanismo de busca, o Brave Search, que prioriza a preservação da privacidade. Uma característica única é o sistema de recompensas em Basic Attention Tokens (BAT), que incentiva os usuários a visualizar anúncios respeitadores da privacidade, enfatizando o consentimento e a transparência.
Google: Equilíbrio Entre Serviços Personalizados e Privacidade
O Google Chrome, embora ofereça configurações de privacidade, não bloqueia anúncios ou rastreadores por padrão, exigindo que os usuários instalem extensões para obter funcionalidade semelhante. O modelo de receita do Google depende significativamente da publicidade direcionada, que necessita da coleta de dados do usuário. Embora o Google tenha feito avanços na melhoria da privacidade do usuário, como a eliminação gradual de cookies de terceiros, seu modelo de negócio central muitas vezes entra em conflito com o espírito de legislações de privacidade como a AB 3048.
Dados do Usuário e Publicidade
Brave: Minimização da Coleta de Dados
Por padrão, o Brave minimiza a coleta de dados e não armazena informações de navegação de uma forma que possa ser diretamente vinculada ao usuário. Esta abordagem está em consonância com a AB 3048, que visa limitar a venda ou compartilhamento de informações pessoais. Ao reduzir a coleta de dados ao mínimo necessário, o Brave reforça o controle do usuário sobre suas informações pessoais.
Google: Dependência de Dados para Eficácia Publicitária
O ecossistema do Google é projetado para reunir dados do usuário com o objetivo de aprimorar sua plataforma publicitária. Embora o Google tenha introduzido recursos de privacidade e ofereça algum nível de controle ao usuário, sua reação a legislações como a AB 3048 provavelmente envolverá a adaptação de seus sistemas existentes para cumprir os requisitos legais, ao mesmo tempo em que busca manter a eficácia de sua publicidade baseada em dados.
Suporte Público e Legislativo
Brave: Alinhamento com Defensores da Privacidade
Ao acolher a AB 3048, o Brave alinha-se com defensores da privacidade e usuários preocupados com os direitos sobre seus dados. Esta postura reforça sua marca como um navegador que coloca a privacidade em primeiro lugar, não apenas como um recurso, mas como um valor fundamental incorporado em sua arquitetura e serviços.
Google: Navegando Desafios Regulatórios
O Google pode perceber legislações restritivas de privacidade como um desafio complexo, dado seu vasto ecossistema de serviços que dependem de dados do usuário. Embora a empresa cumpra as legislações, sua posição pública pode enfatizar mais o equilíbrio entre a privacidade do usuário e a oferta de serviços personalizados, em vez de abraçar plenamente leis de privacidade restritivas.
Conclusão
Em um cenário digital onde a privacidade do usuário é cada vez mais valorizada, o Brave destaca-se por sua abordagem proativa e centrada no usuário. Sua filosofia e design intrínsecos estão em harmonia com legislações de privacidade como a AB 3048, e suas funcionalidades refletem um compromisso genuíno em dar aos usuários controle sobre suas informações pessoais.
O Google, apesar de adaptar-se às tendências e legislações de privacidade, enfrenta desafios mais complexos devido ao seu modelo de receita baseado em publicidade direcionada. A necessidade de coletar dados para manter a eficácia de seus serviços coloca a empresa em uma posição onde deve constantemente equilibrar os imperativos regulatórios com suas estratégias de negócio.
Para os usuários, a escolha entre o Brave e o Google Chrome pode depender de suas prioridades pessoais em relação à privacidade e à personalização dos serviços. Enquanto o Brave oferece uma experiência focada na proteção dos dados e no controle do usuário, o Google continua a fornecer serviços altamente integrados e personalizados, alimentados por dados coletados dos usuários.
À medida que legislações como a AB 3048 entram em vigor, será interessante observar como essas empresas e outras no setor tecnológico ajustarão suas estratégias. A tendência indica um movimento em direção a práticas que colocam a privacidade do usuário em primeiro plano, seja por convicção ou por conformidade regulatória. Independentemente do motivo, os maiores beneficiários serão os usuários, que terão maior controle e transparência sobre seus dados pessoais no ambiente digital.
-
 @ 4e4fc3e3:e935140a
2024-10-25 20:29:27
@ 4e4fc3e3:e935140a
2024-10-25 20:29:27This is a test using frost bunker from Highlighter 🤞
chances of working = \~0.1
-
 @ 3b7fc823:e194354f
2024-09-04 00:26:48
@ 3b7fc823:e194354f
2024-09-04 00:26:48Encryption is the promethium fire that the cypherpunks secured from heaven for me and you. It is our sacred duty to use and advance that in the world. Encryption is so powerful that governments tried to keep it away from the people and to this day have tried to weaken and backdoor it at every turn.
So what is encryption?
It is a deep deep rabbit hole and involves a lot of numbers but in a nutshell it uses math to scramble up the data of your file so it is gibberish and can't be read without decrypting it back to regular data. Encryption technology has continued to advance over time and cracking technology to break the encryption has as well. For our purposes all you really need to remember is to use modern cyphers and your encryption is really only going to be as good as the password (use a passphrase) strength you are using to lock it down with.
BEGINNER LEVEL - Encrypt your phone and computer.
People walk around with their whole lives on their phone. Protect it.
-phone: Congratulations, if you already have a lock screen set on either your iPhone or Android device then device encryption is enabled. If your lock screen password is only 4 digits then we still have work to do. Four digits is only about 10,000 combinations and fairly easy to crack. I believe it only took them about 40 minutes to crack the iPhone of the attempted Trump shooter. Go into settings and set it up for 6 digits or for extra credit use a alphanumeric password.
After your phone then your personal computer probably has the most important data to you. Banking records, tax documents, photos, etc. Encrypt your drive.
-Windows: from Settings, select Privacy security -> Device encryption. Just follow the prompts.
-Apple: from Apple icon, select System Preferences -> Security & Privacy icon. Click "Turn On FileVault".
-Linux: most distros gives you the option during installation. If you didn't do so then search for how to enable it after the fact based on your distribution.
Awesome sauce. You have achieved minimum status.
ADVANCED LEVEL - Encrypt individual files.
You already encrypted your computer but guess what, once you start up your computer and log in the key is stored in RAM for as long as it stays on. The beginner level encryption protects your computer when it is off and it means no one can just steal your hard drive and access your files. This is good, but what if someone grabs you while you're sitting there working on it? What if you leave it in sleep mode and not turned off? Then that whole disk encryption is not really going to help you.
What if you had individual files that you consider more secret than the others? That finance spreadsheet or that special pic your spouse sent you? That's where individual file encryption comes in. You are just scrolling nostr when they grab you, your computer is on, and unlocked, but those special files are still safely encrypted.
I will share with you one of my favorite small programs: Picocrypt.
Download the Paranoid pack and store it in multiple drives, email accounts, and cloud storage. That way you will always have a copy to decrypt any files that you stored away.
Use it to encrypt any files that you feel need extra attention. It is also very useful for encrypting any files that you intend to store online in cloud storage. You do encrypt your files that are stored online don't you? Yes, even with the company that offers "encrypted" storage. Don't trust their encryption, use your own.
EXPERT LEVEL - Encrypt containers and hidden containers.
What if you want to encrypt several files and keep them all together in like a folder or container? That's where Veracrypt comes in. Free, open source, cross platform, and powerful.
Veracrypt allows you to create encrypted containers from any file that act like individual drives that can be mounted or unmounted as needed. You can name these files anything that you want, move them around or delete like any file, and make as many as you want. This allows you to have compartmentation of your files and drives.
Next trick, Veracrypt allows you to create a hidden container inside that container. Enter one passphrase and you open the encrypted container. Enter a different passphrase and you open a different hidden container.
This allows deniability. When they grab you and start pulling your fingernails off until you tell them the password to open the encrypted container, give it to them. They don't have to know that there is another hidden one under that.
These features allow you to do all sorts of interesting things only limited by your need and imagination.
What if you have a container named as some random config file in your /etc folder? What if you just encrypted a removable storage drive? What if you have multiple hard drives on your computer that have multiple containers and hidden containers? What if you have a hidden container that can only be accessed from booting up in a amnesiac OS like Tails leaving no trace that the files exist or trail that they were ever accessed? Go crazy, have fun.
NEMO - Failsafe
Nemo has no files, encrypted or otherwise. If they did you couldn't prove it. Nemo does use something like Tails that retains no memory from boot to boot.
Nemo also uses a failsafe. A simple lanyard attached to the flashdrive running the OS and the other end around their wrist while they work. When you try to separate them from the computer the flashdrive pulls out and everything is gone.
Using these programs you can create a layered and compartmentlized approach to your encryption scheme. There are also plenty of other encryption programs to check out such as Cryptomator, AES Crypt, etc
Last point and most important: Encryption is only as good as the passphrase you use to lock it down. Use a shitty password and it doesn't matter how uncrackable your encryption is.
-
 @ 09fbf8f3:fa3d60f0
2024-10-25 18:43:59
@ 09fbf8f3:fa3d60f0
2024-10-25 18:43:59在线直播:
央视体育版CCTV5:
央视体育版CCTV16 :
翡翠台:
-
 @ 8cb60e21:5f2deaea
2024-09-03 22:26:25
@ 8cb60e21:5f2deaea
2024-09-03 22:26:25 -
 @ 8cb60e21:5f2deaea
2024-09-03 22:26:25
@ 8cb60e21:5f2deaea
2024-09-03 22:26:25 -
 @ 185e9a1b:f608e37b
2024-10-25 18:31:05
@ 185e9a1b:f608e37b
2024-10-25 18:31:05 -
 @ 266815e0:6cd408a5
2024-04-24 23:02:21
@ 266815e0:6cd408a5
2024-04-24 23:02:21NOTE: this is just a quick technical guide. sorry for the lack of details
Install NodeJS
Download it from the official website https://nodejs.org/en/download
Or use nvm https://github.com/nvm-sh/nvm?tab=readme-ov-file#install--update-script
bash wget -qO- https://raw.githubusercontent.com/nvm-sh/nvm/v0.39.7/install.sh | bash nvm install 20Clone example config.yml
bash wget https://raw.githubusercontent.com/hzrd149/blossom-server/master/config.example.yml -O config.ymlModify config.yml
```bash nano config.yml
or if your that type of person
vim config.yml ```
Run blossom-server
```bash npx blossom-server-ts
or install it locally and run using npm
npm install blossom-server-ts ./node_modules/.bin/blossom-server-ts ```
Now you can open http://localhost:3000 and see your blossom server
And if you set the
dashboard.enabledoption in theconfig.ymlyou can open http://localhost:3000/admin to see the admin dashboard -
 @ eac63075:b4988b48
2024-03-23 11:12:58
@ eac63075:b4988b48
2024-03-23 11:12:58I want to report a serious issue I had with ZBD. I was having problems with my LN node and, as a temporary alternative, I turned to ZBD as a backup, integrating their streaming service to receive donations in sats through a QR Code displayed on the screen, while my system was not working.
However, when I tried to access the ZBD app last Saturday to transfer the sats, I discovered I was blocked. I opened a support ticket and, after a long wait and opening a second ticket, the only response I got was a promise to "escalate" the problem. With no further responses, I continued opening tickets and demonstrating their lack of support live, as a real test of customer service.
Since the beginning of the Morning Crypto program in 2021, I had been recommending ZBD to our community as a good wallet option for beginners on the Lightning Network, but always warning about the risks of custodial wallets. Now, this experience reinforces the problem and serves as a great practical example: a custodial wallet can confiscate your sats without any explanation.
During the livestreams this week, I received numerous testimonies from users with similar issues on ZBD, reporting account locks without explanations and lack of support.
Therefore, I have removed ZBD from my recommendations and advise everyone: avoid using this wallet, due to the risk of losing your sats.
Spread this information among your contacts and acquaintances who may be using ZBD. The suspicious situation ZBD finds itself in is unacceptable in a market that demands reliability and transparency.
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ 8cb60e21:5f2deaea
2024-09-03 21:58:26
@ 8cb60e21:5f2deaea
2024-09-03 21:58:26Lesson 3: Arrays, Objects, and Callbacks
Arrays: Lists of Things
Arrays are ordered lists of values. They're perfect for storing multiple related items, like a list of your favorite cat toys:
javascript var catToys = ["mouse", "ball", "laser pointer"]; console.log(catToys[0]); // Prints "mouse"Objects: Grouping Related Information
Objects allow you to group related information together. They're like detailed profiles for each of your cat friends:
```javascript var myCat = { name: "Fluffy", age: 3, favoriteFood: "tuna" };
console.log(myCat.name); // Prints "Fluffy" ```
Callbacks: Doing Things Later
Callbacks are functions that are executed after another function has finished. They're useful for handling asynchronous operations, like waiting for your cat to finish eating before giving it a treat:
```javascript function feedCat(callback) { console.log("Feeding the cat..."); setTimeout(function() { console.log("Cat has finished eating!"); callback(); }, 2000); }
feedCat(function() { console.log("Time for a treat!"); }); ```
This code simulates feeding a cat, waiting 2 seconds, and then giving it a treat.
Remember, learning JavaScript is a journey. Take your time, practice regularly, and soon you'll be coding like a pro cat!
-
 @ 3cd2ea88:bafdaceb
2024-10-25 18:30:47
@ 3cd2ea88:bafdaceb
2024-10-25 18:30:47Metti in staking i tuoi SOL facilmente e approfitta di molteplici vantaggi :
1️⃣ Ricevi BGSOL : La versione tokenizzata dei tuoi SOL in staking. 2️⃣ Guadagna rendimenti sostanziali : Ottieni fino al 30.15% APR stimato e sblocca guadagni di liquidità con BGSOL. 3️⃣ Sblocca SOL con flessibilità : Nessun periodo di blocco! Puoi convertire BGSOL in SOL in qualsiasi momento.
💡Cos'è BGSOL? BGSOL è una soluzione di liquidity staking sviluppata da Bitget. Ti permette di mantenere la liquidità dei tuoi asset mentre guadagni con lo staking e partecipi ad altre attività DeFi. Approfitta ora!
🔗 Unisciti alla community BGSOL su Telegram 👉 https://t.me/BitgetBGSOL 🔗 Partecipa alla promo qui 👉 https://www.bitget.com/it/events/bitget-sol-staking?utmTerm=KOC
-
 @ eac63075:b4988b48
2024-02-16 20:34:29
@ eac63075:b4988b48
2024-02-16 20:34:29I just dropped the album Neon Revolution w/ 2 tracks part of the book Chronicles of Code Guardians: The Origin of Titan. It is an epic Bitcoin cyberpunk saga (to be released soon).
If you want to follow the song and lyrics: https://www.eddieoz.com/censorship-shadows-lyrics/ or https://soundcloud.com/eddieoz
Cyberpunk synthwave to make the Friday's mood.
-
 @ f977c464:32fcbe00
2024-04-15 20:30:05
@ f977c464:32fcbe00
2024-04-15 20:30:053724
Dürbününü yazı masasının çekmecesine koydu. O adamın bakışlarında bir şey vardı, tüylerini ürperten bir aşinalık.
Sağ tarafa kavislenen toprak yol, şehir merkezindeki idam platformuna doğru uzanırdı. On, on beş adım aralıkla, telefon ve radyo tellerini taşıyan, aynı zamanda geceleri yağ fenerlerinin asıldığı direkleri geçerdiniz. At arabalarının kaldırdığı toz ve yaydığı koku gözlerinizi yaşartırdı.
Ve darağacının önüne geldiğinizde, arkanızda bıraktığınız direklerin ne kadar güçsüz, acınası olduğu, öncesinde defalarca fark etmediyseniz bile, tam o anda, yüreğinize otururdu. Platformun üstünden gökyüzünü tehdit eden, ölüme mahkûm edilenleri kınayan gövdesi ve aniden yere eğdiği, acıyla çarpılmış boynuyla kaba tahtadan bir ucube!
Oysaki geçip geldiğiniz direklerin aksine, yanınızda uzanan, çoğunluğu iki katlı evler de tahtadan yapılmıştı ve çatıların, yağmur oluklarının, kapı çerçevelerinin, pencere kapaklarının üstündeki doğa tasviri süslemeleriyle öyle kibarlardı ki...
Dikkat etmemiş olacaksınız ama aralarında, soğuk elleriyle sizi yere bastıran, tasvirlerin yerini görkemli hayvanların -kartalların, aslanların, köpeklerin- aldığı taş evler sıralanırdı. Darağacının bedeni diğer evlerdense, ruhu kesinlikle bunlardan geliyordu.
Uzaktan kuş sesleri duyuluyordu. Bülbül. Buraya ait olmayan, dalgınlığını tamamlayan, kafese kapatılmış bir ses.
Çalışma masasının üzerine, pencereye doğru abandı. Artık ezberlediği bu hac yolculuğuna ihtiyacı yoktu. Evinden olanları az buçuk seçebiliyordu ve zaten görmeye katlanabileceğini görmüştü.
Adamın boynuna ilmeği çoktan geçirmişlerdi. Otuzlu yaşlarının başında gösteriyordu. Teni güneşten sertleşmişti. Çatlaklar gözlerinin yanından elmacık kemiklerine uzanıyordu. Saçı ve sakalı uzun, mat siyahtı.
Neredeyse kimse izlemiyordu. Sadece tek tük, aralarına mesafe koymuş ilgisiz kişiler...
Radyo her zamanki gibi celladın konuşmasını canlı olarak yayınlıyordu.
“...lece günahlarımızdan arınmış olacağız! Doğaya küfür olan tüm bu ucubeler, düzensizlikler...”
Bir kişiyi kurtarmak için ölen onlarca insan... Attıkları çığlıklar bilinçaltının derinliklerinde hafifçe kıvrandı.
İdamların başladığı o gün...
Erken saatlerde ortaya çıkıveren genci tanımıyorlardı. İnsanlara garip sorular sormuş ve kısa süre sonra ortadan kaybolmuştu. Öğlen vakti kucağındaki paketle geri dönmüştü.
“...lumumuz için büyük tehdit teşkil etmektedirler. Şüphesiz bundan birkaç yıl sonra yapacağı hareketleriyle sadece öldüreceği insanların değil, toplumun çökü...”
Darağacını hiç değiştirmediler. Yoksa bu da hafızasındaki bulanıklığın çarpıttığı anılardan mıydı? Hatırlamaya her çalıştığında başı ağrıyordu.
Gence üzülmüş ve apar topar alınan karar karşısında dehşete düşmüştü. Diğerlerinin arasına karışmak, sesini çıkarmak, hiç değilse bunların neden olduğunu öğrenmek istemişti.
“...esin iyiliğini gözetmek zorundayız. Bunu yapabilecek gücümüzün kalmış olduğu için şükretmeliyiz. Omzumuzdaki bu gö...”
Vazgeçmişti. Korkmuştu. Ellerini titreten ilkel dürtüden değil, uzun zamandır üzerinde çalıştığı romanının bittiğini görememe ihtimalinden. “Ertesi gün,” demişti, “ertesi gün orada olacağım.”
Odanın büyük bölümünü işgal eden radyoyu kapattı. İnsan boyu ve genişliğinde, üzerindeki kontrol düğmeleri dışında cilalı ahşaptandı. Güzel olsa da pili hızlı tükeniyordu. Yenisini alması gerekecekti.
Banyoya gitti. Evin her yerinde az eşya bulundurmayı severdi: içi temiz su dolu kova, küvet olarak kullandığı büyük varil ve ayna.
Şehirdeki diğerleri gibi hafif esmer tenli, kahverengiye çalan koyu saçlı ve gözlüydü. Onların aksine gözlerinin içinde hâlâ heyecan ateşi yanıyordu. Saçları bile daha canlıydı sanki. Ve ne kısa ne uzun ne yakışıklı ne çirkin... Olması gereken neyse o. Yüzünü yıkadı, gülümseyip çalışma odasına geri döndü.
Yeniden kâğıtlarının karşısına geçi. Romanını nihayet bitiriyordu. Son cümlelerini yazdı.
Her şeye geç kalmasına değmişti.
9386
Dürbününü pencerenin iç denizliğine, yaslandığı yerin kenarına bıraktı. O adamın bakışlarında açıklayamadığı bir şey vardı. Tüylerini ürperten bir aşinalık.
Adamın boynuna ilmeği çoktan geçirmişlerdi. Orta yaşlarındaydı. Beyazlaşmaya, griye dönmeye yeni yeni başlamış saçı ve sakalı, rengi atmış kıyafetleriyle oldukça hırpaniydi.
Kimdi o? Tanıyordu sanki..
Mutlaka yakından bakmalıydı.
“...felaketin eşiğinden döndüğümüz günün üzerinden uzun zaman geçmedi. Unutmayın! Unutmanız on...”
Radyoyu kapattı. Pili hızlı bitiyordu. Ne zaman değiştirmişti? Baş ağrısı geri geliyordu.
Merdivenlerden indi. En az dört basamağı gıcırdamıştı. Yenilenmelerinin zamanı geliyordu, temizlenmelerinin de. Parmak kalınlığında toz! Eski ve yeni ayak izleri üst üste binmişti.
Kulaklarındaki ince çınlama, ensesindeki ter... İçinden yükselip göğsünü ittiren, dengesini bozup neredeyse düşercesine aşağıya inmesine neden olan panik...
Holü geçerken diğer odalara kısaca göz attı. Hepsinin durumu aynıydı. Onu asıl şaşırtansa yatak odası oldu. Her gün uyuduğu yatağın, yanındaki bazanın, kirli çamaşır sepetinin ve etejerin üzeri... Nasıl fark etmemişti tüm bunları? Peki elbiselerinin böyle eskidiğini?
Dokunduğu elinde kalıyor veya kapalı kalmışlık kokusu yüzünden midesini bulandırıyordu. Eline geçen paçavraları apar topar giydi. Dokuması incelmiş bol beyaz keten gömleği, rengi griye yaklaşmış pantolonu -önceden? Belki siyah-, her tarafı çatlamış ve dikişleri atmış uzun deri çizmesi.
Neler oluyor neler oluyor neler oluyor neler oluyor...
Sokağa çıktı ve hava soluk borusunu temizlerken gözleri yaşardı. Hayır, kendimi kaptırmış olmalıyım. Kesin zamanın ucunu kaçırdım. Ev dün böyle değildi. Hayır hayır hayır hayır hayır...
Bulanık görüyordu ama hiç değilse burası normaldi.
İdam platformu şehir merkezindeydi. Oraya koştu.
Buranın o eğlenceli, panayır havasından eser kalmamıştı elbette. Kahveye girip çıkanlar, yan sokaktaki pazara gidip gelenler... Kimsenin olup bitenlere ilgisi yoktu. Dükkânların yarısı kapalıydı zaten. İnsanların burada oyalanmak için gittikçe daha az sebebi oluyordu.
“...lediğimiz kurtuluşumuz.”
Cellat, onun tam karşısında durduğunu görünce sustu. Herkes merakla onlara döndü.
Ve işte o anda, darağacındaki adamın bağırmasıyla celladın koşup kolu çekmesi ve zemindeki kapağı açması, infazı tamamlaması bir oldu.
“Koñrul! Onu...”
Çığlıkları ancak onu eve, yatağına taşıdıklarında biraz dindi. Sayıklamaya devam ediyordu: “Romanım romanım romanım romanım..."
Sakinleşmesi için yukarıdan kâğıtlarını ve kalemini getirdiler. Son cümlesini yazdı. Yarını göremeyecekti.
14796
Masanın üzerinde, koyduğu yerde durmayan, yuvarlanan ve düşüp merceği kırılan dürbünü fark etmedi. O adamın bakışlarında açıklayamadığı bir şey vardı. Tüylerini ürperten bir aşinalık.
Ve yine aynı gün, diğerlerinin aynı... İnsanlar bile gün geçtikçe birbirine benziyordu.
Adamın boynuna ilmeği çoktan geçirmişlerdi. Yaşlı sayılırdı veya yaşlanmaya başlıyordu. Saçı ve sakalı beyaz ama gösterdiği yaşa rağmen hâlâ gürdü. Istırap çekmenin, büyük yük taşımanın bezginliği her yerinden hissediliyordu.
“...rine inmemiz gerek. Bu insan müsveddeleri toplumumuz için büyük tehdit...”
Evet... evet. Demek bu adam da kimsenin anlamadığı haltlar yemek üzereydi.
Rahatı kaçanlar olacaktı, belki ölenler.
Adamı gerçekten tanıyor olabilir miydi?
Kendini aşırı zorlamıştı. Radyoyu kapatıp banyoya gitti. Yeni pili ne zaman takmıştı?
Aynada kendine baktı. Geceleri uyuyup uyumadığını bile bilmiyordu. Gözleri iyice yuvalarına kaçmış, etrafı kararırken akları sararmış, zayıf ve soluk, yüzünün üstüne bırakılıp unutulmuş çöplerden farksızdı. Saçlarını düzeltmeye çalıştı, her hareketiyle onlarca saç teli kopunca vazgeçti. Renkleri solmuştu.
Şehirde yiyecek kalmamıştı. Her gün stoklar azalıyordu. Tarlalardaki olgunlaşmamış meyve sebzelere düşmüşlerdi. Tüccarlar niye gelmiyordu ki? Diğer şehirlerde de mi durum kötüydü?
Kafasından aşağı su döküp geri döndü. Kâğıtlarını önüne çekti. Romanını bitirmeliydi, açlıktan ölmeden veya idam edilen sonraki kişi olmadan. Son cümlelerini yazdı:
“Dünya yine ölürken ve her şey baştan başlarken gidebileceği bir yer kalmamıştı. Eski çağların roketlerini düşündü. Gerçekten başka gezegenler var mıydı? O zamanlarda yaşasaydı Güneş’e giderdi! Şimdi hareket etmek için duracaktı. Sonraki güne kadar.”
20251
Dürbününü kapıdan çıkarken tuvalet kovasının içine attı. Yine bir idam. Saçları dökülüyordu. Alnının iki yanı geriye doğru açılmış, sakallarıyla birleşip yekpare olan tellerin arasından kafa derisi seçilebiliyordu.
Ne ilgi çekici... Bıraksalar kendisi ölecekti zaten. Pazara gidip ne bulabileceğine bakmayı tercih ederdi.
İnsanlar ayağını sürüyerek yürüyordu. Celladın konuşması dışında çıt çıkaran yoktu. Ne kuş ötüşü veya köpek havlaması ne çocuk gülüşmeleri... Konuşanları görebiliyordu, duyamıyordu. Fısıltıdan fazlasını çıkaracak istekleri yoktu.
“...hennemin böyleleriyle dolu olduğundan şüphesi olan var mı aranızda? Onları tekrar layık oldukları yere göndereceğiz. Bunun için yardı...”
Evet... evet. “Elma kaça?”
Pazarcı taburesinden kalkıp tezgâha geldi. O da aynıydı. Farklı bedende aynı sefalet. “Hangisi?”
“Fazla ham olmayanlardan.”
“Tanesi 600 lira.”
“Yarım ver. Şundan da...” Lafını tamamlayamadı. Biri bağırıyordu. Genç, on yedisinde bile göstermeyen biri. Yüzü etli, hareketleri canlı, kıyafetleri yeni ancak kendisine büyük gelmiş ve epey hırpalanmıştı. Hele o paltosu... İçi pamukla dolu olmalıydı. Kocamandı.
“Ya idam ne demek abi! Manyak mısınız lan siz? Kaçıncı yüzyıldasınız a...”
Küfrünün ortasında ağzını kapattılar. Koluna girmiş, kahveye geri sokuyorlardı.
Tezgâhtara “Kim bu?” diye sordu.
“Birinin torunuymuş, öyle diyor. Daha önce duyduysam n’olayım. Meczup herhalde,” dedi tezgâhtar.
“İsmi neymiş dedesinin?”
“Hakan mı, Hasan mı, öyle bi’şey.”
“Ekmekten çeyrek dilim, deri parçasını da ver. Çorbalık, değil mi?”
“Evet, çorbalık.”
Hakan... Şu saçma romanını bitirmek için evine döndü. Artık tozlar ayak bileğine geliyordu. Umursamadı. Son cümlelerini yazdı, kâğıt tomarını masanın yanından tertemiz yere bıraktı.
25803
Dürbünüyle ensesini kaşıdı. O adamın gözlerinde küçük cinler vardı. Neşeyle hoplayıp zıpladıklarını ta buradan seçebiliyordu! Ah, tatlılığa bak! Hahaha!Boynundaki ilmekle, gözlerinin içine bakan, hiç korkmayan ama bıkkın, ölümün bile hayatında olup bitenleri değiştirmeyeceğini kabullenmiş bir adamın duruşuna sahipti. Çok yaşlı, kafasında tel tel beyaz saçları, göbeğine uzanan sakallarıyla kurumuş bir ceset. Omuzları çökmek üzereydi, kamburunun ağırlığıyla ipi geriyordu.
Dürümü tekrar gözüne kaldırdı. Dürüm? Hahaha! Evet... evet! Radyoda cellat konuşuyordu.
“...endinizde değişiklik hissederseniz yakınınızdaki güvenlik güçleriyle ileti...”
Ah! Kendisine şöyle baktı. Yok... Aynı ben ya!
Sahneye -Tam bir gösteri! Gösteri!- doğru koşan adamı gördü. Üzerindeki puf puf paltosuyla, orta yaşlarında...
Masanın üzerine fırladı, dizlerinin üstüne çöküp içindeki safrayı pencereden dışarıya kustu. Eliyle ağzını silerken derisinin yapışarak etinden ayrıldığını hissedebiliyor ve o bant sökülürken çıkana benzeyen sesi duyabiliyordu. Cellat konuşmayı bırakmıştı. N’oldu? N’oulduuv?
Yaşlı adamı asmışlardı. Şimdi dik duruyordu, yükü hafiflemişti ama huzurlu olduğunu söyleyemezdiniz.
Diğer adam onları umursamadı, yere eğilip mikrofonun kablosunu tuttu ve ayaklığını devirerek kendisine çekti.
“Tabutun kapağını kaldırdığında yerin altına döne döne ilerleyen o kuyuyu... Tamam... tamam!”
Adamın şakağına inen ilk sopadan çıkan ses odayı doldurdu. Sonrası sessizlik ve ölüm. Ahhh... ahhh...
Hemen bağdaş kurup kaldığı sayfayı buldu. Ne ilham! NE İLHAM!
Son cümlelerini yazıp romanını bitirdi.
34125
Dürbünü öylece dışarıya bırakıverdi. Derisi kemiklerine yapışmış, kaşına kadar her tüyü dökülmüş bir ihtiyarı asıyorlardı. Açıktaki tüm bedeni yaşlılık lekeleriyle doluydu. Bembeyaz sakalı uzun ve temizdi. Dönecek! İpin ucunda! Sağa sola!_Tahta pencereleri kapadı ve -_Ha ha!- fenerin fitilini -Ha ha _ha!- yaktı. Duvardaki gölgeleri beğenmedi ama. Söndürdü. Püf füfüfüf ha ha _ha! Tekrar yaktı. Yine istediği gibi olmasa da iş görürdü.
Radyonun sesini açtı. Evet... Evet açtım! Tiz ve kalın, tanıdık ve yabancı... Burnu kanadı.
“...EN HİÇBİR ŞEYİN SONU YOKTUR! SONU OLAN HİÇBİR ŞEY BİTMİŞ DEĞİLDİR VE BİTEN HİÇBİR ŞEYİN SONU YOKTUR! SONU OLAN HİÇBİR ŞEY...”
Yüzüne döktüğü suyu alttaki tasla toplayıp içtikten sonra -Ha ha _ha! Hazırım, evet hazırım! Romanı bitirelim. Bundan iyisi olamaz! Olamaz! Ha ha!- masasına dönüp kâğıtlarını önüne çekti. Son cümleler ve sonrasında -Özgürüm! Özgürüm!” Radyo yayınına başka, yabancı biri karıştı. Öyle bağırıyordu ki duvarlar titriyordu. Çok yaşlıydı, çok...
“Geldiğimden beri, her gün! Asmayın artık şu adamı! Görmüyor mu...”
Sonra celladın sesi duyuldu. Cılız, uzaktan...
“Bunu da hazırlayın.”
“Evet... evet. Ne olacak, beni de her gün asın a...”
Not: Bu öykü ilk olarak 2019 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 8cb60e21:5f2deaea
2024-09-03 21:58:26
@ 8cb60e21:5f2deaea
2024-09-03 21:58:26Lesson 2: Functions and Loops
Functions: Your Own Commands
Functions are reusable blocks of code that perform specific tasks. They're like teaching your cat a new trick:
```javascript function meow(times) { for (var i = 0; i < times; i++) { console.log("Meow!"); } }
meow(3); // This will print "Meow!" three times ```
Built-in Functions
JavaScript comes with many built-in functions. For example,
console.log()is a function that prints things to the console:javascript console.log("I'm a cat!");Loops: Repeating Tasks
Loops allow you to repeat a task multiple times without writing the same code over and over. It's like telling your cat to chase its tail for a specific number of rounds:
javascript for (var i = 0; i < 5; i++) { console.log("Chasing tail, round " + (i + 1)); }This will print "Chasing tail, round X" five times, where X goes from 1 to 5.
-
 @ 8f2fe968:0fbf4901
2024-10-25 17:34:06
@ 8f2fe968:0fbf4901
2024-10-25 17:34:06 -
 @ 6bae33c8:607272e8
2024-09-03 10:47:55
@ 6bae33c8:607272e8
2024-09-03 10:47:55I do this every year, and every year I get at least one correct. Last year, I got exactly one correct and unfortunately it was the surefire prediction that not all of them would be right, i.e., I got really zero correct. But that just goes to show how bold they were. These aren’t layups, more like three pointers and half-court shots. I fared much better the previous two years, so hopefully these will get back on track.
(Actually, probably better to just link to all of them for full transparency: 2023, 2022, 2021, 2020, 2019, 2018, 2017, 2016, 2015, 2014.) I’m not going to argue it matters, or that anyone even clicks through on these, but I want to pat myself on the back for being so organized in archiving my old work.)
-
Stefon Diggs leads the Texans in targets, catches and receiving yards
Right now, he’s getting drafted more than a round behind Nico Collins and less than a round ahead of Tank Dell. Diggs is 30, but he was one of the league’s best receivers until halfway through last year when the Bills made an offensive play-calling change. Moreover, Diggs is getting paid $22.5 million, so the Texans obviously don’t think he’s washed up, and he’s also in a contract year.
-
CJ Stroud leads the NFL is passing yards
This is +600 on DraftKings, so the real odds are probably north of 8:1. Stroud adds Diggs to his receiving corps, doesn’t run much and heads into Year 2.
-
Roman Wilson (ADP 211) has more receptions than George Pickens (ADP 47)
Pickens is a boom or bust downfield playmaker, not high-target alpha, and Wilson is a good fit for the slot for the Steelers new QBs. Think Martavis Bryant not Antonio Brown. (Not that Wilson is Brown!) Van Jefferson isn’t good, and someone will need to fill the void. Moreover, because Pittsburgh has new QBs, neither has an existing rapport with the incumbent Pickens.
-
DeAndre Hopkins (ADP 82) out produces Calvin Ridley (ADP 54) in PPR
Hopkins wasn’t terrible last year, has a rapport with Will Levis and is a future Hall of Famer who can still run routes. Ridley is already 29 and is just a guy outside of his monster season in 2020.
-
The Giants will field a top-10 fantasy defense.
I’ve been crushed by my homer bold predictions in the past, but they added Brian Burns to a rush that already had Dexter Lawrence and Kayvon Thibodeaux, the offense should be on the field more and generate some leads with a real playmaking receiver in Malik Nabers.
-
One of the following Year 2 receivers will finish in the top-15 PPR: Jaxon Smith-Njigba, Jayden Reed, Jordan Addison, Dontayvion Wicks, Michael Wilson, Josh Downs, Andrei Iosivas, Quentin Johnston, Marvin Mims, Jalin Hyatt
I make this prediction every year, and it often pans out as Year 2 is when receivers typically make the leap. I left out Tank Dell because he’s now got a fifth-round ADP, as well as the obvious ones: Zay Flowers, Rashee Rice and Puka Nacua.
-
Rome Odunze (ADP 77) will outproduce Xavier Worthy (ADP 59)
Both receivers enter crowded situations, and while Worthy’s is far better, he’s also got essentially the same skill-set as teammate Marquise Brown. Moreover, Andy Reid rarely entrusts rookies with large roles, especially early on. Odunze is 6-3, 215 and has the pedigree of a true NFL alpha, while Worthy weighs only 165 pounds at 5-11. Finally, Patrick Mahomes already has an established rapport with both Travis Kelce and Rashee Rice, while Odunze gets a more open competition with the Bears veteran WRs, given all three will play with Caleb Williams for the first time.
-
Dalvin Cook will lead the Cowboys in rushing yards
Cook is 29 and looked beyond “cooked” last year on the Jets, but his 3.3 YPC was on a small sample (67 carries), and prior to that, he’d been very good for the Vikings. At the very least he should have fresh legs, and he’d only need to beat out the ancient Ezekiel Elliott and Rico Dowdle. (Of course, Cook would have to be promoted from the practice squad first, so I really should hedge and make the prediction “neither Elliott, nor Dowdle will lead the Cowboys in rushing yards,” but I’ll push it and say it’s Cook.)
-
Jonathan Taylor (ADP12 ) will lead the NFL in rushing yards.
He’s got little competition in the Indy backfield and a running QB who should open lanes for him. Draft Kings has him at +600, so his real odds are probably about 10:1, but I’d take him over the favored Christian McCaffrey (age/mileage) and all the other backs who are more hybrid types or old (Derrick Henry.)
-
Dalton Kincaid (TE4) will lead all TE in catches
I guess this is a chalky pick because he and Kelce are both favored at the position at +3000, while Evan Engram is +5000! (I’d way rather bet on Engram at those odds.) But straight up, I’m going with Kincaid who is likely Josh Allen’s de facto No. 1 target with Diggs gone. In his final 11 regular season games Kincaid had 56 catches which prorates to 87 catches over the full year. And rookie tight ends rarely do anything and often make a leap in Year 2.
-
Some of these predictions will be wrong
No one’s perfect, but you never want to get shut out.
-
-
 @ eac63075:b4988b48
2023-08-01 15:45:29
@ eac63075:b4988b48
2023-08-01 15:45:29Lá na outra rede, o Dov havia feito um post bacana mostrando como usar a Electrum mobile de cold wallet nessa playlist.
Então ao comentar que a minha primeira cold wallet havia sido uma Electrum num notebook velho e formatado só pra isso, algumas pessoas me perguntaram sobre meu setup atual.
Então preparei o seguinte esboço:
No geral é: * Server Umbrel para os nodes * Coldcard e Ledger (coldwallets) * Computador criptografado e celular android com área segura p/ apps
É um caso de uso extremo mas além da auto-soberania e custódia dos meus satoshis, essa estrutura ainda me permite:
- Participar do consenso do Bitcoin
- Auxiliar no roteamento de sats na Lightning Network
- Fazer coinjoin facilmente para aumentar a privacidade
E embora a estrutura pareça complicada, é bastante simples:
- Raspberry Pi 4 com Debian e Umbrel (p/ os nodes e servers)
- Celular antigo android com área segura e sem simcard
- Notebook com storage criptografada
- Ledger Nano X
- Coldcard
E ainda pude evoluir de N.O.I.A. (Network Operator Innovator and Advocate) para M.A. (Minerador Anônimo), com uma Nerdminer pra tentar um ticket da sorte a cada 10 minutos
Não esqueça que uma cold wallet para a auto-custódia pode começar com um computador ou celular velho!
É mais simples do que parece e praticar sua auto-soberania e custódia significa na verdade liberdade e privacidade nesse mundo digital!
-
 @ 4ba8e86d:89d32de4
2024-10-25 15:26:47
@ 4ba8e86d:89d32de4
2024-10-25 15:26:47Ele foi criado por Mark Harman e lançado sob a licença GNU General Public License (GPL), o que significa que qualquer pessoa pode acessar, modificar e distribuir o código-fonte do aplicativo.
Recursos e Funcionalidades: O Open Camera oferece uma ampla gama de recursos e funcionalidades que permitem aos usuários aproveitar ao máximo suas câmeras em dispositivos Android. Alguns dos recursos notáveis incluem:
-
Controles Manuais: O aplicativo permite ajustar manualmente as configurações da câmera, como exposição, foco, balanço de branco, ISO e muito mais. Isso oferece maior flexibilidade e controle sobre a qualidade e o estilo das fotos tiradas.
-
Suporte a Formatos de Arquivo Avançados: O Open Camera suporta uma variedade de formatos de arquivo, incluindo RAW, que é uma opção preferida por fotógrafos profissionais devido à maior quantidade de informações capturadas e à flexibilidade durante a pós-produção.
-
Modo de Gravação de Vídeo Avançado: Além da fotografia, o Open Camera também oferece recursos avançados de gravação de vídeo, como gravação em câmera lenta, gravação de lapso de tempo e suporte a taxas de quadros personalizadas.
-
Marcação de Geolocalização: O aplicativo permite que os usuários adicione informações de localização às fotos tiradas, o que pode ser útil para organizar e recordar onde cada imagem foi capturada.
-
Interface Personalizável: O Open Camera oferece opções para personalizar a interface do usuário de acordo com as preferências individuais, incluindo a escolha de cores e layouts.
O código-fonte aberto permite que os usuários examinem e verifiquem como o aplicativo funciona. Isso aumenta a transparência e a confiança na segurança e privacidade dos dados. Os desenvolvedores podem modificar o aplicativo para atender às suas necessidades específicas ou adicionar novos recursos. Isso cria um ecossistema de desenvolvimento vibrante e incentiva a inovação. O Open Camera possui uma comunidade ativa de desenvolvedores e usuários que contribuem com melhorias, correções de bugs e compartilham conhecimentos. Isso garante que o aplicativo seja continuamente atualizado e aprimorado.
O Open Camera é uma opção poderosa e personalizável para aqueles que desejam aproveitar ao máximo a câmera de seus dispositivos Android. Com recursos avançados e a flexibilidade proporcionada pelo código aberto, o aplicativo oferece uma experiência fotográfica aprimorada para entusiastas e profissionais da fotografia. Se você está procurando um aplicativo de câmera versátil e repleto de recursos, o Open Camera é definitivamente uma escolha que vale a pena considerar.
https://sourceforge.net/p/opencamera/code/ci/master/tree/
https://opencamera.org.uk/
https://f-droid.org/packages/net.sourceforge.opencamera/
-
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ eac63075:b4988b48
2023-07-22 13:28:38
@ eac63075:b4988b48
2023-07-22 13:28:38Este é um texto é baseado na transcrição do Twitter Spaces promovido pela Cointelegraph Brasil, com a participação de Edilson Osorio Jr (@eddieoz) , Pedro Magalhães e Rafaela Romano como host.
Introdução
Nos últimos anos, o mundo testemunhou um aumento significativo no uso de criptomoedas, com o Bitcoin ganhando destaque. O Brasil, como muitas outras nações, está navegando nessa nova era digital, enfrentando a introdução de sua Moeda Digital de Banco Central (CBDC), chamada Real Digital. Embora essa tecnologia ofereça um grande potencial para a inovação financeira, também traz consigo desafios, preocupações com a privacidade e ameaças potenciais às liberdades individuais. Neste artigo, vamos mergulhar nas questões que cercam a CBDC brasileira e explorar as implicações mais amplas da criptografia, Bitcoin, criptomoedas e blockchain na sociedade.

O CBDC Brasileiro - Equilibrando Vigilância e Controle
O Real Digital, distribuído pelo Banco Central do Brasil, promete trazer eficiência, transparência e inclusão de desbancarizados ao sistema financeiro. No entanto, surgem preocupações à medida que o CBDC é inicialmente lançado para corporações e instituições, com planos futuros para alcançar as carteiras dos indivíduos. Essa medida poderia resultar em vigilância em massa e questões de controle, conferindo ao governo um poder sem precedentes para monitorar as atividades financeiras dos cidadãos. Defensores da privacidade temem que tal intromissão nas finanças pessoais possa comprometer as liberdades individuais e abrir caminho para o uso autoritário dos dados financeiros.
Bitcoin como Símbolo de Liberdade
À medida que o governo brasileiro explora medidas regulatórias para a indústria de criptomoedas, o debate em torno das funções de congelamento, queima e transferência de saldos traz preocupações entre especialistas. Essas funções, se mal utilizadas, podem impactar significativamente o cidadão. Enquanto isso, amplia-se a discussão sobre a importância da inclusão financeira dos desbancarizados, e criptomoedas como o Bitcoin oferecem um caminho alternativo para que os indivíduos tenham mais controle sobre suas próprias transações financeiras. A descentralização e a capacidade de contornar intermediários financeiros tradicionais capacitam os indivíduos e promovem a liberdade financeira.
Encontrando um Equilíbrio entre Segurança e Privacidade
Governos em todo o mundo, incluindo a União Europeia, estão contemplando a criação de backdoors em sistemas criptográficos com o pretexto de combater a lavagem de dinheiro, o financiamento do terrorismo e o abuso infantil. Embora possam parecer causas justificáveis, representa sérias ameaças à privacidade e à segurança. A criptografia desempenha um papel vital na proteção das pessoas contra a vigilância e a manipulação dos governos, especialmente em uma era de crescente propaganda e manipulação nas mídias sociais. O uso de tecnologias como hardware wallets e sistemas de votação seguros destaca a importância de proteger a privacidade ao mesmo tempo em que abraçamos avanços tecnológicos.
O Futuro das Votações: Blockchain e Além
Na Estônia, a digitalização das eleições tem apresentado resultados promissores, aumentando a transparência e a eficiência, ao mesmo tempo que reduz a coerção e a compra de votos. O potencial da tecnologia blockchain para revolucionar sistemas eleitorais é significativo, oferecendo mecanismos de votação seguros e transparentes. No entanto, desafios permanecem, incluindo custos, complexidade e riscos de segurança, que requerem maior engajamento político e consenso. Sistemas financeiros acessíveis e inclusivos também desempenham um papel vital para garantir que os benefícios dos avanços tecnológicos sejam acessíveis a todos os segmentos da sociedade.
Conclusão
Conforme o Brasil embarca na jornada de seu CBDC e o mundo em geral enfrenta o impacto das criptomoedas e da tecnologia blockchain, é fundamental encontrar um delicado equilíbrio entre o progresso e a salvaguarda das liberdades individuais. Embora o potencial das criptomoedas e do blockchain seja vasto, também é crucial abordar preocupações com a privacidade, desafios regulatórios e a possibilidade de vigilância e controle governamental. A educação, o debate público e uma abordagem aberta serão fundamentais para moldar o futuro dessa tecnologia transformadora em benefício da sociedade.
Ouça/assista o spaces completo em: Twitter: https://www.youtube.com/watch?v=lxf3BdMOe50 Youtube (@eddieoz): https://www.youtube.com/watch?v=lxf3BdMOe50
-
 @ 3bf0c63f:aefa459d
2024-01-15 11:15:06
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06Pequenos problemas que o Estado cria para a sociedade e que não são sempre lembrados
- **vale-transporte**: transferir o custo com o transporte do funcionário para um terceiro o estimula a morar longe de onde trabalha, já que morar perto é normalmente mais caro e a economia com transporte é inexistente. - **atestado médico**: o direito a faltar o trabalho com atestado médico cria a exigência desse atestado para todas as situações, substituindo o livre acordo entre patrão e empregado e sobrecarregando os médicos e postos de saúde com visitas desnecessárias de assalariados resfriados. - **prisões**: com dinheiro mal-administrado, burocracia e péssima alocação de recursos -- problemas que empresas privadas em competição (ou mesmo sem qualquer competição) saberiam resolver muito melhor -- o Estado fica sem presídios, com os poucos existentes entupidos, muito acima de sua alocação máxima, e com isto, segundo a bizarra corrente de responsabilidades que culpa o juiz que condenou o criminoso por sua morte na cadeia, juízes deixam de condenar à prisão os bandidos, soltando-os na rua. - **justiça**: entrar com processos é grátis e isto faz proliferar a atividade dos advogados que se dedicam a criar problemas judiciais onde não seria necessário e a entupir os tribunais, impedindo-os de fazer o que mais deveriam fazer. - **justiça**: como a justiça só obedece às leis e ignora acordos pessoais, escritos ou não, as pessoas não fazem acordos, recorrem sempre à justiça estatal, e entopem-na de assuntos que seriam muito melhor resolvidos entre vizinhos. - **leis civis**: as leis criadas pelos parlamentares ignoram os costumes da sociedade e são um incentivo a que as pessoas não respeitem nem criem normas sociais -- que seriam maneiras mais rápidas, baratas e satisfatórias de resolver problemas. - **leis de trãnsito**: quanto mais leis de trânsito, mais serviço de fiscalização são delegados aos policiais, que deixam de combater crimes por isto (afinal de contas, eles não querem de fato arriscar suas vidas combatendo o crime, a fiscalização é uma excelente desculpa para se esquivarem a esta responsabilidade). - **financiamento educacional**: é uma espécie de subsídio às faculdades privadas que faz com que se criem cursos e mais cursos que são cada vez menos recheados de algum conhecimento ou técnica útil e cada vez mais inúteis. - **leis de tombamento**: são um incentivo a que o dono de qualquer área ou construção "histórica" destrua todo e qualquer vestígio de história que houver nele antes que as autoridades descubram, o que poderia não acontecer se ele pudesse, por exemplo, usar, mostrar e se beneficiar da história daquele local sem correr o risco de perder, de fato, a sua propriedade. - **zoneamento urbano**: torna as cidades mais espalhadas, criando uma necessidade gigantesca de carros, ônibus e outros meios de transporte para as pessoas se locomoverem das zonas de moradia para as zonas de trabalho. - **zoneamento urbano**: faz com que as pessoas percam horas no trânsito todos os dias, o que é, além de um desperdício, um atentado contra a sua saúde, que estaria muito melhor servida numa caminhada diária entre a casa e o trabalho. - **zoneamento urbano**: torna ruas e as casas menos seguras criando zonas enormes, tanto de residências quanto de indústrias, onde não há movimento de gente alguma. - **escola obrigatória + currículo escolar nacional**: emburrece todas as crianças. - **leis contra trabalho infantil**: tira das crianças a oportunidade de aprender ofícios úteis e levar um dinheiro para ajudar a família. - **licitações**: como não existem os critérios do mercado para decidir qual é o melhor prestador de serviço, criam-se comissões de pessoas que vão decidir coisas. isto incentiva os prestadores de serviço que estão concorrendo na licitação a tentar comprar os membros dessas comissões. isto, fora a corrupção, gera problemas reais: __(i)__ a escolha dos serviços acaba sendo a pior possível, já que a empresa prestadora que vence está claramente mais dedicada a comprar comissões do que a fazer um bom trabalho (este problema afeta tantas áreas, desde a construção de estradas até a qualidade da merenda escolar, que é impossível listar aqui); __(ii)__ o processo corruptor acaba, no longo prazo, eliminando as empresas que prestavam e deixando para competir apenas as corruptas, e a qualidade tende a piorar progressivamente. - **cartéis**: o Estado em geral cria e depois fica refém de vários grupos de interesse. o caso dos taxistas contra o Uber é o que está na moda hoje (e o que mostra como os Estados se comportam da mesma forma no mundo todo). - **multas**: quando algum indivíduo ou empresa comete uma fraude financeira, ou causa algum dano material involuntário, as vítimas do caso são as pessoas que sofreram o dano ou perderam dinheiro, mas o Estado tem sempre leis que prevêem multas para os responsáveis. A justiça estatal é sempre muito rígida e rápida na aplicação dessas multas, mas relapsa e vaga no que diz respeito à indenização das vítimas. O que em geral acontece é que o Estado aplica uma enorme multa ao responsável pelo mal, retirando deste os recursos que dispunha para indenizar as vítimas, e se retira do caso, deixando estas desamparadas. - **desapropriação**: o Estado pode pegar qualquer propriedade de qualquer pessoa mediante uma indenização que é necessariamente inferior ao valor da propriedade para o seu presente dono (caso contrário ele a teria vendido voluntariamente). - **seguro-desemprego**: se há, por exemplo, um prazo mínimo de 1 ano para o sujeito ter direito a receber seguro-desemprego, isto o incentiva a planejar ficar apenas 1 ano em cada emprego (ano este que será sucedido por um período de desemprego remunerado), matando todas as possibilidades de aprendizado ou aquisição de experiência naquela empresa específica ou ascensão hierárquica. - **previdência**: a previdência social tem todos os defeitos de cálculo do mundo, e não importa muito ela ser uma forma horrível de poupar dinheiro, porque ela tem garantias bizarras de longevidade fornecidas pelo Estado, além de ser compulsória. Isso serve para criar no imaginário geral a idéia da __aposentadoria__, uma época mágica em que todos os dias serão finais de semana. A idéia da aposentadoria influencia o sujeito a não se preocupar em ter um emprego que faça sentido, mas sim em ter um trabalho qualquer, que o permita se aposentar. - **regulamentação impossível**: milhares de coisas são proibidas, há regulamentações sobre os aspectos mais mínimos de cada empreendimento ou construção ou espaço. se todas essas regulamentações fossem exigidas não haveria condições de produção e todos morreriam. portanto, elas não são exigidas. porém, o Estado, ou um agente individual imbuído do poder estatal pode, se desejar, exigi-las todas de um cidadão inimigo seu. qualquer pessoa pode viver a vida inteira sem cumprir nem 10% das regulamentações estatais, mas viverá também todo esse tempo com medo de se tornar um alvo de sua exigência, num estado de terror psicológico. - **perversão de critérios**: para muitas coisas sobre as quais a sociedade normalmente chegaria a um valor ou comportamento "razoável" espontaneamente, o Estado dita regras. estas regras muitas vezes não são obrigatórias, são mais "sugestões" ou limites, como o salário mínimo, ou as 44 horas semanais de trabalho. a sociedade, porém, passa a usar esses valores como se fossem o normal. são raras, por exemplo, as ofertas de emprego que fogem à regra das 44h semanais. - **inflação**: subir os preços é difícil e constrangedor para as empresas, pedir aumento de salário é difícil e constrangedor para o funcionário. a inflação força as pessoas a fazer isso, mas o aumento não é automático, como alguns economistas podem pensar (enquanto alguns outros ficam muito satisfeitos de que esse processo seja demorado e difícil). - **inflação**: a inflação destrói a capacidade das pessoas de julgar preços entre concorrentes usando a própria memória. - **inflação**: a inflação destrói os cálculos de lucro/prejuízo das empresas e prejudica enormemente as decisões empresariais que seriam baseadas neles. - **inflação**: a inflação redistribui a riqueza dos mais pobres e mais afastados do sistema financeiro para os mais ricos, os bancos e as megaempresas. - **inflação**: a inflação estimula o endividamento e o consumismo. - **lixo:** ao prover coleta e armazenamento de lixo "grátis para todos" o Estado incentiva a criação de lixo. se tivessem que pagar para que recolhessem o seu lixo, as pessoas (e conseqüentemente as empresas) se empenhariam mais em produzir coisas usando menos plástico, menos embalagens, menos sacolas. - **leis contra crimes financeiros:** ao criar legislação para dificultar acesso ao sistema financeiro por parte de criminosos a dificuldade e os custos para acesso a esse mesmo sistema pelas pessoas de bem cresce absurdamente, levando a um percentual enorme de gente incapaz de usá-lo, para detrimento de todos -- e no final das contas os grandes criminosos ainda conseguem burlar tudo. -
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28IPFS problems: Community
I was an avid IPFS user until yesterday. Many many times I asked simple questions for which I couldn't find an answer on the internet in the #ipfs IRC channel on Freenode. Most of the times I didn't get an answer, and even when I got it was rarely by someone who knew IPFS deeply. I've had issues go unanswered on js-ipfs repositories for year – one of these was raising awareness of a problem that then got fixed some months later by a complete rewrite, I closed my own issue after realizing that by myself some couple of months later, I don't think the people responsible for the rewrite were ever acknowledge that he had fixed my issue.
Some days ago I asked some questions about how the IPFS protocol worked internally, sincerely trying to understand the inefficiencies in finding and fetching content over IPFS. I pointed it would be a good idea to have a drawing showing that so people would understand the difficulties (which I didn't) and wouldn't be pissed off by the slowness. I was told to read the whitepaper. I had already the whitepaper, but read again the relevant parts. The whitepaper doesn't explain anything about the DHT and how IPFS finds content. I said that in the room, was told to read again.
Before anyone misread this section, I want to say I understand it's a pain to keep answering people on IRC if you're busy developing stuff of interplanetary importance, and that I'm not paying anyone nor I have the right to be answered. On the other hand, if you're developing a super-important protocol, financed by many millions of dollars and a lot of people are hitting their heads against your software and there's no one to help them; you're always busy but never delivers anything that brings joy to your users, something is very wrong. I sincerely don't know what IPFS developers are working on, I wouldn't doubt they're working on important things if they said that, but what I see – and what many other users see (take a look at the IPFS Discourse forum) is bugs, bugs all over the place, confusing UX, and almost no help.
-
 @ 4ba8e86d:89d32de4
2024-10-25 15:20:13
@ 4ba8e86d:89d32de4
2024-10-25 15:20:13Imagine um mundo onde 99 pessoas estão verificando a ação de uma única pessoa para garantir a integridade das transações. Isso é exatamente o que o sidechain bitVM propõe. Aqui está uma explicação detalhada do processo:
- Prova e Verificação:
- Uma pessoa atua como uma comprovadora, enquanto 99 pessoas são verificadoras.
- Antes de depositar na sidechain, a comprovadora faz um contrato com os verificadores. Ela coloca 100 BTC como garantia.
-
Se um verificador alegar que alguém fez uma solicitação de saque válida na sidechain, a comprovadora deve provar que processou essa solicitação em X blocos. Caso contrário, qualquer verificador pode penalizá-la, resultando na perda da garantia.
-
Mecanismo de Penalidade e Rotação:
- Se a comprovadora for penalizada, o próximo verificador na fila assume como a nova comprovadora.
- Cada verificador também tem 100 BTC como garantia.
-
A nova comprovadora (ex-verificadora) deve provar que processou a solicitação de saque dentro de X blocos ou será penalizada.
-
Segurança em Camadas:
- A garantia impede comportamentos inadequados, garantindo que todos os participantes tenham algo em jogo.
-
O modelo de pegada dupla oferece camadas adicionais de segurança. Qualquer tentativa de fraude pode ser detectada e punida.
-
Contratos Laterais e Confiança Mínima:
- Um usuário pode fazer um "contrato lateral" com qualquer verificador. Se uma solicitação de saque válida for apresentada, o verificador deve provar o processamento dentro de X blocos.
-
Não é necessário confiar apenas em uma pessoa; se a comprovadora falhar, ela pode ser penalizada.
-
Prova de Ocorrência em Sidechain:
- O bitVM requer a capacidade de "provar" que algo aconteceu em uma sidechain.
-
Um cliente leve SPV no bitVM, compreendendo as regras de consenso da sidechain, é essencial.
-
Depósito e Saque:
- Para depositar, a comprovadora fornece garantia e prova que processará futuras solicitações de saque.
-
Ao sacar, o bitVM valida a solicitação. Se a comprovadora não processar, ela é penalizada, e o usuário recebe 100 BTC de um verificador.
-
Garantia como Parâmetro Variável:
- Tanto comprovadoras quanto verificadoras devem postar garantias.
- A quantidade de garantia é um parâmetro variável; mais garantia significa uma sidechain mais segura.
O sidechain bitVM propõe uma abordagem descentralizada e segura, onde a confiança é distribuída e a segurança é reforçada por penalidades significativas. Este modelo inovador tem o potencial de oferecer eficiência e confiança aprimoradas nas transações de sidechain.
Ótima explicação sobre bitVM. Supertest , Robin .
https://open.spotify.com/episode/6rcOVwcxkzcZRXnVcwKlTq?si=s5E31_HWQEqOoRbzoAzpZQ
-
 @ eac63075:b4988b48
2023-06-27 20:14:42
@ eac63075:b4988b48
2023-06-27 20:14:42Austrália
O setor financeiro australiano tem se mostrado cada vez mais interessado em criptomoedas. De acordo com os bancos australianos, 40% das transações financeiras envolvem criptomoedas. O regulador do setor bancário afirmou que o problema não é a criptomoeda, mas sim o ambiente que permite a execução de golpes. Mas lá, a Binance foi avisada com apenas 12 horas de antecedência para que se preparasse para perder a conta bancária - e a gente sempre recomenda que as criptomoedas não sejam armazenadas em exchanges, mas sim em wallets não custodiadas.
Binance
A Binance também sofreu diversas restrições e baniu várias moedas de privacidade na Europa. No entanto, ela reverteu a decisão sobre algumas moedas, como o Verge e a Secret Network. O Pornhub já usou Verge como meio de pagamento. Além disso, a Binance está considerando se mudar para os Emirados Árabes Unidos porque a região está se mostrando mais favorável a esse mercado.
Europa
Na Europa, o pessoal estava discutindo meios para tentar resolver o risco da criptomoeda. Eles queriam implementar a regra de que tem que ter a mesma quantidade em criptomoedas e em euros na conta bancária. No entanto, essa regra dificultaria a inovação. Então o Comitê de Basileia está criando regras, propondo uma regra de balanceamento de risco, com exposição em FIAT para a quantidade de cripto, com teto máximo de 1250% em EUR da quantidade de cripto.
Black Rock e amigos
Instituições financeiras que administram 27 trilhões de dólares estão adquirindo Bitcoin, incluindo Black Rock, Fidelity, JP Morgan, Morgan Stanley, Goldman Sachs, BNY Mellon, Invesco e Bank of America. Isso mostra que o Bitcoin está se tornando cada vez mais popular.
A comunidade do Bitcoin tem uma parcela que só se preocupa com o preço do Bitcoin, ignorando os motivos pelos quais foi criado. A Black Rock e outras instituições estão entrando no Bitcoin, mas apenas para especular.
Bitcoin
O Bitcoin foi criado para que as pessoas pudessem controlar suas próprias riquezas, sem intermediários. A adoção por governos e grandes instituições pode acelerar a adoção da população em geral. A disponibilidade de bitcoins pode ser impactada no futuro por uma grande concentração de bitcoins na mão de pessoas que controlam o dinheiro no mundo. O Bitcoin é mais escasso que o ouro e pode ser utilizado como reserva de valor, embora não tenha sido criado para isso. Bitcoin foi originalmente usado como meio de troca, mas em 2016-2018, a Tether pode ter manipulado o mercado comprando Bitcoin e emitindo moeda sem lastro. O preço do Bitcoin subiu e as pessoas pararam de usá-lo como meio de troca. O Bitcoin passou a ser visto como reserva de valor e a especulação em cima dele aumentou. O principal valor do Bitcoin no futuro não é o preço, mas sim a liberdade que ele proporciona.
Ordinals
Satoshi se posicionava contra o uso do Bitcoin para fins diferentes da sua criação. O protocolo do Ordinals abriu portas para novas possibilidades, mas também pode ser abusado.
Pode existir a possibilidade de governos penalizarem usuários do Bitcoin por conteúdo criminoso armazenado em seus nós. A comunidade do Bitcoin zela pelos valores pelos quais foi criado e pode filtrar ou criar incentivos para evitar o uso abusivo da rede através de consenso, caso seja considerado um ataque. Existem diversas formas diferentes de registrar coisas no Bitcoin. A disseminação de conteúdo ilícito ou criminoso, de maneira consciente, pode ser penalizada por governos no futuro. Além disso, empresas que usam o Bitcoin para fins comerciais podem ser vinculadas à distribuição de conteúdo ilícito caso rodem nós da rede. Os ordinals podem se transformar em um cavalo de tróia para governos acusarem a rede do Bitcoin de distribuir conteúdo criminoso. O limite da liberdade é onde começa a do outro, e alguns crimes extrapolam esse limite.
-
 @ 161c8564:2d633b95
2024-09-02 20:24:34
@ 161c8564:2d633b95
2024-09-02 20:24:34Opinion about Freewallet Multi Crypto Wallet (iphone)
FRWT Wallet uses deceptive marketing to lure in unsuspecting users. Once you deposit funds, they’ll block your account under the guise of KYC checks. It’s a fraudulent app—don’t download it!
WalletScrutiny #nostrOpinion
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Castas hindus em nova chave
Shudras buscam o máximo bem para os seus próprios corpos; vaishyas o máximo bem para a sua própria vida terrena e a da sua família; kshatriyas o máximo bem para a sociedade e este mundo terreno; brâmanes buscam o máximo bem.
-
 @ eed76ece:afa98124
2024-09-02 18:58:30
@ eed76ece:afa98124
2024-09-02 18:58:30As the World continues to create more and more NEW regulations. And as free speech get attacked from every angle. Bonafide business owners, especially importers will need to find ways to migrate sales offerings of goods and services. It feels like the majority of business owners have to really take this seriously.
Obviously so many different methods are used around the World already, but when the upcoming new mandatory vaccinations, vaccine passport travel restrictions really hit, businesses will have to jump to more selling online.
SN, Nostr and other unknown communication methods are Paramount. As usual it feels like no one is taking free speech attacks seriously. The amount of postings my customers around the World do daily on WhatsApp, LINE (Asia), Telegram, Twitter will move where it is allowed to move. Feels like there's an ongoing increase in the attack not just on the West, but from WITHIN the West.
Regardless if you retail, wholesale, manufacture, are an agent we try hard to be pro active on marketing on multiple methods. It seems very logical that in the future Nostr and SN will pick up International users as a way to get their goods posted somehow someway.
Examples
Customers in these regions I deal with primarily communicate with me in Japan, Thailand using LINE and Tik Tok daily. Most of the rest of the World communicate with me using WhatsApp. Certain parts of Eastern Europe and Asia Telegram.
Interestingly my resellers in the USA primarily post on WhatsApp.
Westerners especially Americans seem to have enough money, they are not hungry for making more money, or increasing their business growth, they think everything is ok. "We will always be okay, there will NEVER be a Worldwide depression, recession, deflation, increased restrictions, they will NEVER force a new vaccine on us again, they will NEVER lock business and us down again".
"So I will always have free speech, the politicians told me so".
originally posted at https://stacker.news/items/670041
-
 @ eac63075:b4988b48
2023-06-22 14:21:10
@ eac63075:b4988b48
2023-06-22 14:21:10
Introdução
O mundo das criptomoedas está em constante mudança e evolução. Com a Foxbit integrando a Lightning Network, aplicativos para converter Bitcoin em Lightning, e a SEC considerando que o Ethereum pode ser considerado um Security após a mudança para Proof-of-Stake, é importante entender o que está acontecendo no setor. Além disso, o Banco Central brasileiro vem estudando o assunto desde 2015, e a Argentina está usando criptomoedas para se resolver. Neste artigo, vamos explorar esses assuntos e muito mais.
Foxbit e Lightning Network
De acordo com membros da comunidade, a Foxbit, uma das principais exchanges brasileiras, anunciou recentemente que já integrou a Lightning Network. A Lightning Network é uma camada de pagamentos para o Bitcoin que permite que os usuários façam pagamentos instantâneos, baratos e seguros. Com a integração da Foxbit, os usuários agora podem usar a Lightning Network para converter Bitcoin na Lightning.
Além disso, existem aplicativos que permitem aos usuários converter Bitcoin em Lightning. Esses aplicativos permitem que os usuários façam pagamentos instantâneos, baratos e seguros usando a Lightning Network.
Disputa da Binance
Um juiz americano determinou recentemente que as partes envolvidas na disputa da Binance devem se sentar para conversar e chegar a um acordo. A disputa envolve a SEC, que acusa a Binance de violar as leis de segurança dos EUA ao permitir que os usuários negociem criptomoedas sem licença.
Regulação
Em 2018, o regulador americano pronunciou-se de que o Ethereum não seria considerado um Security. No entanto, a SEC está considerando que, após a mudança do Ethereum para Proof-of-Stake, o Ethereum pode ser considerado um Security. Além disso, documentos podem ajudar certos tokens ERC 20, mas não é possível implementar leis de Security.
Gary Gensler, o presidente da SEC, falou recentemente sobre Bitcoin, Ethereum, Litecoin e Bitcoin Cash. Ele disse que a regulação é difícil de ser executada, mas que a SEC já afirmou que o Bitcoin não é security.
Banco Central brasileiro
O Banco Central brasileiro vem estudando o assunto de criptomoedas desde 2015. O poder do governo é sobre a população, independente de partido político. O governo se acha dono do Estado, e isso é algo que precisa ser discutido.
Argentina
A Argentina está usando criptomoedas para se resolver. O mercado está sendo controlado desde os anos 90, e as criptomoedas podem ser usadas como forma de liberdade no futuro.
Bitcoin
O Bitcoin tem múltiplas facetas no mundo financeiro. Ele pode ser usado como forma de preservar a liberdade das pessoas para o futuro. Além disso, o Bitcoin foi criado como uma ferramenta para ser usada pelas pessoas comuns, e o acesso ao sistema bancário para os desbancarizados é complicado.
A Lightning é uma ferramenta revolucionária para pagamentos. No entanto, a bipa não lê os qr-code da LNBits, então é necessário enviar para outra plataforma e converter para Bitcoin.
Além disso, a queda da Amazon nos Estados Unidos poderia ser usada como argumento para derrubar a jurisdição do Ethereum nos Estados Unidos. É recomendado espalhar os nós por diferentes regiões para aumentar a resiliência e a descentralização. Como grande parte dos nodes do Ethereum estão nos Estados Unidos (dentro da Amazon), Gary Gensler disse que a jurisdição sobre o Ethereum é americana.
Marketing
O marketing deve ser usado de forma ética, sem usar informações falsas para enganar o público.
Mineração
A Blockstream vai lançar sua própria mineradora de Bitcoin no Q3 de 2024. A Intel suspendeu a fabricação do chip de mineração de Bitcoin.
NFTs
A Apple removeu aplicativos de NFTs por considerar que eles fazem transações financeiras. Ethereans criaram uma música para o Vitalic, que está disponível na plataforma Sound.xyz. É uma plataforma como o Spotify, mas web3. Ela permite que os criadores de música vendam suas músicas como NFTs. Os donos dos NFTs recebem uma parte das vendas. O modelo econômico do negócio é interessante, pois ao invés de pagar uma distribuidora, o criador paga as pessoas que adquiriram o NFT para distribuir.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Thoughts on Nostr key management
On Why I don't like NIP-26 as a solution for key management I talked about multiple techniques that could be used to tackle the problem of key management on Nostr.
Here are some ideas that work in tandem:
- NIP-41 (stateless key invalidation)
- NIP-46 (Nostr Connect)
- NIP-07 (signer browser extension)
- Connected hardware signing devices
- other things like musig or frostr keys used in conjunction with a semi-trusted server; or other kinds of trusted software, like a dedicated signer on a mobile device that can sign on behalf of other apps; or even a separate protocol that some people decide to use as the source of truth for their keys, and some clients might decide to use that automatically
- there are probably many other ideas
Some premises I have in my mind (that may be flawed) that base my thoughts on these matters (and cause me to not worry too much) are that
- For the vast majority of people, Nostr keys aren't a target as valuable as Bitcoin keys, so they will probably be ok even without any solution;
- Even when you lose everything, identity can be recovered -- slowly and painfully, but still --, unlike money;
- Nostr is not trying to replace all other forms of online communication (even though when I think about this I can't imagine one thing that wouldn't be nice to replace with Nostr) or of offline communication, so there will always be ways.
- For the vast majority of people, losing keys and starting fresh isn't a big deal. It is a big deal when you have followers and an online persona and your life depends on that, but how many people are like that? In the real world I see people deleting social media accounts all the time and creating new ones, people losing their phone numbers or other accounts associated with their phone numbers, and not caring very much -- they just find a way to notify friends and family and move on.
We can probably come up with some specs to ease the "manual" recovery process, like social attestation and explicit signaling -- i.e., Alice, Bob and Carol are friends; Alice loses her key; Bob sends a new Nostr event kind to the network saying what is Alice's new key; depending on how much Carol trusts Bob, she can automatically start following that and remove the old key -- or something like that.
One nice thing about some of these proposals, like NIP-41, or the social-recovery method, or the external-source-of-truth-method, is that they don't have to be implemented in any client, they can live in standalone single-purpose microapps that users open or visit only every now and then, and these can then automatically update their follow lists with the latest news from keys that have changed according to multiple methods.
-
 @ 56a6da9b:7f5a2243
2024-09-02 18:27:19
@ 56a6da9b:7f5a2243
2024-09-02 18:27:19IO used to have a lot of content and now the only thing that shows up is my fouintain stuff. when i go into other nostr things it's not there anymore and i look like an anonymous user with no profile pic, or profile and no activity.
originally posted at https://stacker.news/items/669994
-
 @ b83e6f82:73c27758
2024-10-25 14:19:14
@ b83e6f82:73c27758
2024-10-25 14:19:14Citrine 0.5.4
- Fix notification icon size
- Fix loading screen
- Update dependencies
Download it with zap.store, Obtainium, f-droid or download it directly in the releases page
If you like my work consider making a donation
Verifying the release
In order to verify the release, you'll need to have
gpgorgpg2installed on your system. Once you've obtained a copy (and hopefully verified that as well), you'll first need to import the keys that have signed this release if you haven't done so already:bash gpg --keyserver hkps://keys.openpgp.org --recv-keys 44F0AAEB77F373747E3D5444885822EED3A26A6DOnce you have his PGP key you can verify the release (assuming
manifest-v0.5.4.txtandmanifest-v0.5.4.txt.sigare in the current directory) with:bash gpg --verify manifest-v0.5.4.txt.sig manifest-v0.5.4.txtYou should see the following if the verification was successful:
bash gpg: Signature made Fri 13 Sep 2024 08:06:52 AM -03 gpg: using RSA key 44F0AAEB77F373747E3D5444885822EED3A26A6D gpg: Good signature from "greenart7c3 <greenart7c3@proton.me>"That will verify the signature on the main manifest page which ensures integrity and authenticity of the binaries you've downloaded locally. Next, depending on your operating system you should then re-calculate the sha256 sum of the binary, and compare that with the following hashes:
bash cat manifest-v0.5.4.txtOne can use the
shasum -a 256 <file name here>tool in order to re-compute thesha256hash of the target binary for your operating system. The produced hash should be compared with the hashes listed above and they should match exactly. -
 @ fd208ee8:0fd927c1
2024-10-20 18:19:48
@ fd208ee8:0fd927c1
2024-10-20 18:19:48(Please note that this is not official financial or business advice, but rather a description of something we have done, on an informal basis.)
A long, long time ago
It's been nearly a year, since nostr:nprofile1qydhwumn8ghj7argv4nx7un9wd6zumn0wd68yvfwvdhk6tcpypmhxue69uhkummnw3ezuetfde6kuer6wasku7nfvuh8xurpvdjj7qpqs3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqv5atj2 came into being, mostly as a lark, involving a couple of members of our private chat group. Our initial plan was to work toward bounties, but Nostr bounties are a bit of a biased, uncertain thing, and our enthusiasm for that quickly waned.
So, what to do? Here we are, we three (nostr:npub1ecdlntvjzexlyfale2egzvvncc8tgqsaxkl5hw7xlgjv2cxs705s9qs735, nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn, and I): IT professionals with little time, but plenty of intellectual energy, a Slack chat, a GitHub repo, and lots of frustration with the Nostr status quo.
We were, you see, Nostr end-users. We loved the idea of the protocol, but we were being regularly stymied by the poor quality of many implementations.
- Why can I not login? Oh, they fixed the login! Nope, still can't login.
- If I press this button, it says it sent, but it didn't send. Where note?
- They announced a new feature, but I tried it and it didn't work. Oh well.
- I noticed a bug in the client, reported it, and the issue is just rotting away in the project repo. Ignored.
- The website/relay/repo was here... yesterday. Today it has disappeared, and taken my zaps with it.
It was enough to make us want to tear our hair out. We decided that what Nostr needed... what it really needed... was a Nostr Stable Version. Nothing glamorous. Nothing exotic. Nothing busy or excitable. Just something that stayed where you initially found it, ran, and actually worked. Something where you could report a bug and receive a prompt response. Maybe even something, where you could pay a reasonable fee and be allowed to have expectations of some particular service being returned. And who better to build such a version, than people who want to use it, themselves?
Things working is an underrated concept
I know that the very idea of software running as expected and websites not appearing and disappearing suddenly, based upon what some particular developer had for lunch, tends to be met with little but scorn, from hardened, seasoned Nostriches (who are convinced that bugs are all features), but I think the majority of potential users would see it differently.
I'm with the majority, on this one.
I like to click "save" buttons and have them save. If I publish something, I want it to appear under my list of published somethings. I like to type in the website address I always type in, and have it magically appear on my screen, as if there were a little man sitting at controls in my laptop, just waiting for me to write H-T-T-P-S... and then jump to attention.
My unreasonable expectations have no bounds, it is true. But unreasonable people are also people, so we would also like to have our own unreasonable things to play with. Scorn away. My save button will save, and my published something will publish, and my website will load every damn time, just to spite you.
In the larger scheme of things, you see, we win even if we fail, if we at least increase the competition enough, that things working becomes the new standard. We can simply prove, definitively, that it is possible for Nostr things to work, if they are built by people who care if they work. If we also have fun together, learn something new, and come up with some cool, novel use cases, then that's pure profit.
We can only win, at this endeavor.
Where to start?
Name that brand
So, we had a team, we had a business idea, and we had a heck of a lot of motivation. What we didn't have, is a name. (Never underestimate the importance of naming things.)
We decided to name ourselves "GitCitadel" because "git" sounds techy, hints at our GitRepublic project, and is reminiscent of open-source development, and "citadel" reminds us of Bitcoin. The republic is at home in the citadel, naturally. All other products also live in the same citadel, hence the naming-convention of prefacing everything with "GC" (i.e. "GC Alexandria", "GC Sybil", "GC Aedile", etc.).
Brand yourself
The next thing we did, was rent a domain and run a webserver on it. This is an important step because it gives you an Internet presence, allows you to have company NIP-05 and email addresses (a form of promotion), and it's simply exciting to have one. Feels so much more "official" and it helps increase the name-recognition of your company.
Define yourself
We then sat down, together, over the Internet, and figured out who we are. Not who we individually are, but who we are, as a company. A company, after all, (according to the Cambridge Dictionary) is "an organization that produces or sells goods or services in order to make a profit". Now, a company's profits don't have to be monetary, but they should be something tangible. A company, in other words, is a team of people working toward some defined goal.
What is our goal? Well, we decided to think it over, sat down with the newer additions to the company (you can see who they are, on our project wiki page, and came up with a Vision and a Mission:
The vision is what the overall goals of the company are, whereas the mission describes how those goals shall be achieved. Now, this is a sort of lofty, abstract statement, so it was important that we posted it someplace publicly (to keep ourselves accountable) and look at it regularly, so that we can ponder it and realign whatever we are currently working on, with this statement. We know the statement is well-designed, if considering it helps us make decisions about what to do next.
Pay yourselves
(I'm going to switch from "we" to "you", here, as it's easier to write this part, but let's just pretend I didn't.)

The next thing on the list, is to arrange the finances, usually by setting up a Geyserfund, with an associated wallet, and then deciding how the funds from the wallet will be dispersed or stored. (I won't tell you how we are handling that, as that's internal company business, but I'm sure you'll think of something clever, yourselves. Or just google it.)
I would encourage you to arrange to pay yourselves profits. Not merely because your idea is going to make you all fabulously wealthy and internationally famous (although, that is obviously true), but because profits are the most pure form of communication that consumers in the market have with its producers, and one of the best ways to make decisions and measure increases in efficiency (increasing profits and/or output, while keeping prices steady or falling).
Cutting off this signal, in order to look pious to outsiders, is to shoot yourself in your free-market foot. Nobody says that you have to spend your profits on the proverbial lambo and a bimbo. You could donate them to charity, reinvest them, or store them for your nephews to inherit, but pay them out, you should. You don't have to love money, to value it as a tool and use it shrewdly. Money is a measure, and companies should regularly measure themselves: against their previous state, against their potential state, and against their competition.
(Also, you can use money to buy a lambo and a bimbo, but you didn't hear that from me.)
Organize yourselves
Once you've been working together, for a while, you'll find that you need to figure out how to organize yourselves. The first step is to...
Form a board of directors.
Stop laughing. I'm serious.
Any company has at least two roles (President and Secretary), ideally held by two different people, so any single-proprietor company is a man down. Find a different person, to be your Second, even if they're just your confident, who lets you cry on your shoulder on The Bad Days, when your code refuses to compile, and can tell people that you've become a Bitcoin millionaire and have gone on a sabbatical to hike the Himalayas and will be back in 3 months on The Very Good Days. Because business man was not meant to be alone.
If, like us, you're a small herd of people and have already been working together for a while, then this step is actually really, really fun. Just think about what people are already doing, and put a label on it. That role is now defined and it is clear who is in charge of what.
Scientists become "Chief Science Officer" or "Scientific Advisor". The person who always writes the okay, so this is what we've decided comment in the thread becomes the Secretary, the one managing the Lightning wallet and worrying over paying for the servers is the CFO, the person running the remote server becomes the CTO, and so on and etc.
And everyone knows who the CEO is. Everyone always knows. They do. Just write it down.
Agree how to disagree
Now, have the secretary write up a Member's Agreement. It's a contract between the members, about whatever the group thinks is important concerning the way the company will operate. According to Investopedia, common topics are:

Is this legally binding? Probably not. Maybe. I don't know and wouldn't tell you, even if I did. But it's emotionally binding, which is arguably more important.
Writing things down is an advanced form of naming things and it provides clarity, helps to manage expectations, and allows you to define a working agreement before Real Money shows up and taints your interaction. You're just accepting tips, at the moment. Everyone is calm and cheerful, so now is your best time to negotiate.
Keep it very simple and only address the most basic things. If you wish to incorporate, at a later date, then you just take this to a registered agent, or other experienced person, and have them tidy up any loose ends and add the fine print.
Go forth, together
This has probably taken you weeks, or even months, but you're now a company. Get a logo and a company npub, start dropping the company name into your notes, and get on with the business of being in business.
-
 @ 6bae33c8:607272e8
2024-09-02 18:09:19
@ 6bae33c8:607272e8
2024-09-02 18:09:19I did the third and final NFFC Beat Chris Liss league last night, and it was one of the more interesting and aggressive drafts I’ve ever done. I picked from the seven slot.
Here are the results:

1.7 Ja’Marr Chase — I made seven my first choice, but then realized I probably should have gone with four or five, or maybe nine or 10. That’s because if the first six picks went chalk (and they did), I’d be faced with Chase who is holding out for a new contract (and who I have in two other leagues already), Justin Jefferson (new, bad QB) or Garrett Wilson (new QB, never been a Round 1-level WR.) At 1.9 I’d have gotten one of those guys anyway, but earlier picks on the way back. And at 1.4, I’d have gotten a shot at Bijan Robinson for an easier hero-RB build. But I had pick seven, and I tripled-down on Chase because I think it’s very likely he’ll get his extension (or play if he doesn’t), and he’s an all-time talent with a top QB and projects for a massive target share. Plus, if he busts it’s Alan Seslowsky’s fault, and having someone to blame is paramount.
2.6 Drake London — I had it mapped out via ADP that I’d likely get De’Von Achane here, but he went at his min pick (I’m pretty sure) at the 1-2 turn, and so I was scrambling a bit. I really wanted Puka Nacua, who I missed by one pick, considered Cooper Kupp, but ended up going for the ADP-faller London who I had not remotely planned on getting. London obviously benefits from the massive QB upgrade in Atlanta, but it’s an open question whether he’s really an elite receiver or just a good one, and Kyle Pitts could easily emerge as Kurt Cousins favorite target instead.
3.6 DeVonta Smith — When Derrick Henry went one pick ahead of me, it was between Smith and Jaylen Waddle who I took in BCL2. Normally I avoid receivers this undersized but Smith has always produced at every level and is locked into his sizeable target share. Plus I read some Scott Barrett tweets about how Kellen Moore’s offense boosts the slot receiver a ton and that Smith thrives in the slot and could see more work there.
4.7 Stefon Diggs — This was ideal. I now have Diggs in all four of my leagues so far. Maybe he’s hit a cliff at age 30, but he’s getting $22.5M to play in arguably the league’s top passing game that lacks a true No. 1 alpha. I also considered Tee Higgins to pair with Chase (and serve as Chase insurance), but Diggs has more upside as a potential No. 1 target.
5.6 Dalton Kincaid — I’ve been high on him all summer, but he never quite fell to me in the right place until now. I expect him to be Josh Allen’s No. 1 receiver now that Diggs is gone.
6.7 James Conner — I needed a RB, and Conner is one. I’m a bit wary of a 29-YO guy with an extensive injury history, but he averaged 5.0 YPC last year and has never had a massive workload so he’s fresh for his age at least. Plus, the Cardinals offense should be good this year.
7.6 Anthony Richardson — I wasn’t planning on taking a QB here, or even Richardson who I have in BCL2 in Round 5!, but I couldn’t pull the trigger on Zamir White over someone with Richardson’s upside. I’m trying to win the overall contest, not simply cover the bases with starters at every position.
8.7 Jonathon Brooks — Jaylen Warren was still on the board, and he was a viable Week 1 starter for me, but Brooks who is on IR, struck me as the upside play. I heard somewhere, can’t remember where, that Brooks was an elite prospect in college before the injury, and there’s a lot of hype about Carolina’s new offensive brain trust boosting the offense generally. But it might have been a rash pick given my zero-RB build to take a rookie on IR.
9.6 Marquise Brown — I missed Warren by one pick on the way back, and instead of pivoting to Tyjae Spears I leaned into the zero-RB by taking Brown who was going in the fifth or sixth round before his injury. The beauty of this pick is I don’t need Brown right away as I wouldn’t start him anyway, so I pay no price for him missing Week 1. The ugly of this pick is I missed out on Spears, Zack Moss and Chuba Hubbard (who would have been nice to pair with Brooks.)
10.7 Joe Burrow — The obvious pick was Trey Benson to pair with Conner. In fact, I could have had Hubbard in Round 9 and Benson in 10 to lock up two backfields for my zero-RB team. But no, I had to take a second QB here because (a) Richardson has a low floor; (b) this was cheap for Burrow; and (c) I could potentially pair Burrow with Chase for the playoffs. If you’re gonna go zero RB, lean the into it. (The other problem with this pick is the weekly headache of picking my starting QB.)
11.6 Jaleel McLaughlin — The Burrow pick cost me not only Benson but JK Dobbins too, but I had my eye on McLaughlin who apparently was a god in college, and per Barrett is in an ideal spot as the RB2 in Sean Payton’s offense. Now that stat has to be tempered a bit given that peak Alvin Kamara was the source of so much of it, but how much of that was Payton’s offense? In any event, I’m seriously rolling into Week 1 with McLaughlin in my active lineup because of the Richardson, Brooks, Brown and Burrow picks.
12.7 Jordan Mason — Obviously he’s not usable unless and until Christian McCaffrey gets hurt, and the Niners badly need Trent Williams to report, but he’s a top-10 RB if McCaffrey, who played into February last year, goes down. This also furthers my extreme “what could go right” build.
13.6 Braelon Allen — Oddly I view this pick as a mistake as he was higher in ADP, so I thought I could wait another round on Giants backup Tyrone Tracy. (Tracy went three picks ahead of me in the next round.) Allen might be good, but only a Breece Hall injury could free him up whereas Tracy could just outplay Devin Singletary. Granted the Jets might be a better environment than the Giants, so Allen could have more upside if he did get a shot, but Tracy is also a converted WR and would likely catch a lot of passes if he got the job.
14.7 Khalil Herbert — Once Tracy was gone, I pivoted to Herbert. The Chicago backfield is crowded, but D’Andre Swift always gets hurt, and Roschon Johnson isn’t as good a runner as Herbert.
15.6 Jalen McMillan — I wanted to get Cam Akers because Joe Mixon is old, but I missed him by two picks and pivoted (finally) back to WR. McMillan’s created some buzz in camp, and both Mike Evans and Chris Godwin are getting old.
16.7 Will Shipley — I love Saquon Barkley, but he’s getting old and has been hurt a lot. Kenneth Gainwell is ostensibly ahead of Shipley, but is just a guy. Another top-10 upside back should the starter go down.
17.6 Dalvin Cook — He’s on the practice squad for now, and he looked beyond done last year with the Jets, but keep in mind he only got 67 carries, and the Cowboys don’t have serious obstacles ahead of him should he regain even 60 percent of his prior form. Cook was still very good in 2022, and he should have fresh legs too.
18.7 Quentin Johnston — I needed one more receiver, and Johnston is one. Seriously, though he was a first-round pick only last year, and he’s competing with only Josh Palmer and a rookie.
19.6 Younghoe Koo — All these years I was with a wonderful kicker in Justin Tucker, but I’m trading him in for a Younghoe. (That joke will get old one day, just not in any of our lifetimes.)
20.7 Giants Defense — They draw Sam Darnold and Jayden Daniels the first two weeks, and added Brian Burns to Kayvon Thibodeaux and Dexter Lawrence.
Roster By Position
QB Anthony Richardson
RB James Conner/Jaleel McLaughlin
WR Ja’Marr Chase/Drake London/DeVonta Smith
TE Dalton Kincaid
FLEX Stefon Diggs
K Younghoe Koo
D Giants
Bench Jonathan Brooks/Marquise Brown/Joe Burrow/Jordan Mason/Braelon Allen/Khalil Herbert/Jalen McMillan/Will Shipley/Dalvin Cook/Quentin Johnston
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28IPFS problems: Shitcoinery
IPFS was advertised to the Ethereum community since the beggining as a way to "store" data for their "dApps". I don't think this is harmful in any way, but for some reason it may have led IPFS developers to focus too much on Ethereum stuff. Once I watched a talk showing libp2p developers – despite being ignored by the Ethereum team (that ended up creating their own agnostic p2p library) – dedicating an enourmous amount of work on getting a libp2p app running in the browser talking to a normal Ethereum node.
The always somewhat-abandoned "Awesome IPFS" site is a big repository of "dApps", some of which don't even have their landing page up anymore, useless Ethereum smart contracts that for some reason use IPFS to store whatever the useless data their users produce.
Again, per se it isn't a problem that Ethereum people are using IPFS, but it is at least confusing, maybe misleading, that when you search for IPFS most of the use-cases are actually Ethereum useless-cases.
See also
- Bitcoin, the only non-shitcoin
-
 @ 4ba8e86d:89d32de4
2024-10-25 13:17:33
@ 4ba8e86d:89d32de4
2024-10-25 13:17:33Foi criado com o objetivo de fornecer aos usuários uma experiência de navegação mais privada e segura na internet. O LibreWolf é uma excelente alternativa ao Firefox, com algumas diferenças significativas em relação ao navegador da Mozilla.
O LibreWolf foi desenvolvido com foco na privacidade e segurança do usuário. Ele bloqueia rastreadores de terceiros, impede o envio de dados de telemetria e desabilita recursos de rastreamento de usuário que vêm ativados por padrão no Firefox. Além disso, ele vem pré-configurado com diversas extensões de privacidade, como uBlock Origin, Privacy Badger e HTTPS Everywhere, que ajudam a bloquear anúncios, scripts maliciosos e outras ameaças de segurança enquanto você navega na web.
Outra característica notável do LibreWolf é que ele usa o mecanismo de pesquisa Searx como padrão, em vez do Google. O Searx é conhecido por fornecer resultados de pesquisa mais privados e anônimos, sem rastrear as suas atividades online. O LibreWolf também possui suporte nativo ao Tor, que permite aos usuários acessar a internet anonimamente.
Além dos recursos de privacidade e segurança, o LibreWolf é muito semelhante ao Firefox em termos de usabilidade e funcionalidades. Ele é fácil de instalar e configurar, e possui um grande número de extensões disponíveis na sua loja de extensões.
O LibreWolf é uma excelente opção para usuários que buscam um navegador mais privado e seguro. Se você se preocupa com a sua privacidade online, vale a pena experimentar o LibreWolf. Ele é gratuito e de código aberto, o que significa que você pode baixá-lo e personalizá-lo de acordo com suas necessidades específicas.
https://librewolf.net/
https://github.com/librewolf-community
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Economics
Just a bunch of somewhat-related notes.
- notes on "Economic Action Beyond the Extent of the Market", Per Bylund
- Mises' interest rate theory
- Profits, not wages, as the originary factor
- Reisman on opportunity cost
- Money Supply Measurement
- Per Bylund's insight
- Maybe a new approach to the Austrian Business Cycle Theory, some disorganized thoughts
- An argument according to which fractional-reserve banking is merely theft and nothing else
- Conjecture and criticism
- Qual é o economista? (piadas)
- UBI calculations
- Donations on the internet
-
 @ 6bae33c8:607272e8
2024-10-25 12:50:49
@ 6bae33c8:607272e8
2024-10-25 12:50:49I went 4-1 last week which brings my two-week run to 8-2, though it’s not enough to salvage Q2 because I was 2-3 in Week 5. Even if I go 5-0 this week, that’s only 15-5, and that won’t cut it to get a share of the prize. But I’d like to keep it going if only to confirm that after a slow start I’m finally getting in sync.
My Picks
Lions -11.5 vs Titans — I rarely take double-digit favorites, but 11.5 seems low to me. In a normal year this would be 14 in Detroit.
Browns +8.5 vs Ravens — This is a big line on the road, and the Browns have to feel good putting the Deshaun Watson fiasco behind them. (Almost like a relaxing massage.) Might also be a look-ahead game after quality wins for the Ravens.
Jets -7 at Patriots — This line is too big, and Drake Maye might turn out to be a player. But this feels like a get-well spot for the Jets after some tough losses.
Bengals -2.5 vs Eagles — The Eagles are a good sell high off a big win against a weak Giants team. The Bengals are slow starters, but they’re starting to get going.
Raiders +8.5 vs Chiefs — This line is up to 9.5 in places, I knew that, but took the Raiders anyway. Just seems like a divisional game where the beaten-down dog shows up.
-
 @ 3b7fc823:e194354f
2024-09-02 16:26:30
@ 3b7fc823:e194354f
2024-09-02 16:26:30First steps into privacy.
You are a normie, but maybe you are privacy curious. Maybe you are ready to take a first step or two into security and privacy but don't know where to start.
Don't worry, here are some absolute beginner first steps that will make a big difference.
-
No one except your friends and family should know your personal phone number and email address. Stop giving away your data! You don't have to fill out every blank on that form. Unless they are mailing you something they don't need your home address. Use a email aliasing service or just create a burner email account as a spam trap. Get a second VOIP phone number. Look up the address of a local hotel. Use these instead of your personal information or maybe just skip the customer reward program.
-
Speaking of giving away your data. Stop using spyware! Facebook, Instagram, Tiktok, etc. It is "free" software designed to suck every ounce of personal data from you to be repackaged and sold. Don't just delete the app, search for how to delete your account data.
BTW Windows, google, and 90% of the apps on your phone are also spyware but one thing at a time. Maybe start reading up on FOSS.
-
Clean up your communications. Stop using unencrypted calls and SMS texts. There are several options but just get Signal and make your friends use it. Its easy and works.
-
Clean up your email. This one is probably going to take you some time if you are like most people who have hundreds of emails from years gone bye. Go through every single one and unsubscribe from every newsletter or sales pitch from every store you have ever bought anything from. Block every spam email you see. If you are using a email provider that literally scans every email you send or receive in order to sell you stuff like gmail, then now is the time to switch to a private and encrypted provider like proton or tuta.
-
Clean up your web surfing. Switch to a privacy browser and search engine. If you don't know which one just get Brave. There are ones that I like better but Brave is good enough and easy, especially if you like Chrome. A hardened Firefox is better but requires some homework and if on desktop Mullvad browser is a excellent choice.
BONUS TIP:
Clean up your security. Make sure all of your software is setup for automatic updates, especially security updates. Also, I don’t know who needs to hear this but get a password manager if you don’t have one. (Don't save passwords on the browser!) Get an actual password manager and then add 2FA to all of your online accounts and you will have better security than 90% of the population.
OK, nothing too exciting but we got the big rocks. Data leaks, communications, email, web surfing, and basic security.
What, no VPN or Tor or super secret stuff? No, not yet. This is your level zero default. Your identity and activity is still transparent but you are no longer leaking your data all over the place. This will provide a general base for everyone.
The next step is to perform a basic threat assessment of your personal situation. What are you most at risk for? Targeted attacks or passive? Cyber or physical? What do you most need to defend against? Government mass surveillance, surveillance capitalism, censorship, or public exposure?
There will be some overlap with all of them but your next steps will really depend on your answer. We will cover each of these in greater depth later.
-
-
 @ eac63075:b4988b48
2023-06-22 11:19:54
@ eac63075:b4988b48
2023-06-22 11:19:54Lets try this new native blog tool for Nostr!
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28tempreites
My first library to get stars on GitHub, was a very stupid templating library that used just HTML and HTML attributes ("DSL-free"). I was inspired by http://microjs.com/ at the time and ended up not using the library. Probably no one ever did.
-
 @ 599f67f7:21fb3ea9
2024-10-26 11:54:10
@ 599f67f7:21fb3ea9
2024-10-26 11:54:10Zer da Cashu?
Cashu Bitcoinentzako Ecash protokolo irekia da, transakzio azkarrak eta doakoak eskaintzen dituena. Protokolo honen ezaugarri nabarmenetako bat pribatutasun ia perfektua eskaintzea da. Nostr nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg erabiltzaileak sortu zuen.
Hona hemen Cashu eta on-chain Bitcoin alderatzen dituen taula, Bangkok 2023ko Bitcoin Konferentzian nostr:npub1cj6ndx5akfazux7f0vjl4fyx9k0ulf682p437fe03a9ndwqjm0tqj886t6-k aurkeztutako Nuts and Bolts hitzaldian oinarrituta:
| Cashu | Bitcoin (on-chain) | |-----------------------|----------------------------| | Libururik gabe | Liburu banatua | | Titulartasun tokena | UTXO (Ustiaketa Ezberdinen Irteera) | | Transakzio itsutuak | Transakzio publikoak | | Zentralizatua | Deszentralizatua | | Konfiantzazkoa | Konfiantzarik gabe | | Aldi baterako transakzioak | Betiko transakzioak |
Ikusten dugunez, Cashuk pribatutasuna hobetzeko konfiantza gabeko izaera eta deszentralizazioa sakrifikatzen ditu. Konpentsazio hauek zentzuzkoak dira zaintza-zerbitzuetan, erabiltzailea dagoeneko zerbitzu zentralizatu eta fidagarri bat erabiltzen ari baita. Zaintza tradizionaleko irtenbideek pribatutasun eskasa dute, zaintzaileak erabiltzailearen funtsak zenbat diren eta norekin ari den transakzioak egiten jakin dezakeelako. Horrek esan nahi du norbanakoak erraz helburu eta zentsura daitezkeela. Gainera, datu-erregistroek "honeypot" bihurtzeko arriskua dute, hau da, erasotzaileentzat erakargarri.
Alderantziz, Cashu-ren mint-ek zaintzaile gisa jardun dezakete, baina erabiltzaileen nortasuna, duten funtsen kopurua edo norekin ari diren transakzioak egiten ezagutzeko aukerarik gabe. Mint-ek duten datu-erregistro bakarra gastatutako sekretuen zerrenda da, berriro erabili ezin direnak, baina erabiltzaileekin lotzeko modurik gabe. Horrela, Cashu-k pribatutasuna bermatzen du, zaintzaileak ez duelako inolako informaziorik erabiltzaileen jarduerei buruz, ohiko zaintza-soluzioekin gertatzen denaren kontrara.

Cashu-ren erabilera kasu batzuk
Cashu-ren erabilera kasu batzuk honako hauek dira: bonuak, dagoeneko zentralizatuak eta zaintza-zerbitzuak dituztenak; baliabide bakoitzeko ordainketa (pay-per-resource) APIak, nostr bideratzaileak eta mixnet-ak bezalako zerbitzuetarako; sistema integratuak, kontu eta saldo eredu tradizionala ordezkatzen dutenak; eta truke/mixinge zerbitzuak, gordailuak eta ateratzeak deslotzeko, pribatutasuna hobetzeko.
Historia
Ecash David Chaum-ek 1982an asmatu zuen, sinadura itsuak erabiliz balio elektronikoaren transmisiorako protokolo gisa. Cashu Ecash-en inplementazio bat da, David Wagner-en 1996ko Chaum-en itsutze-aldaketan oinarrituta dagoena, eta nostr sortu zuen.
Terminologia
Cashu nola funtzionatzen duen ulertzen laguntzeko, lehenik eta behin funtsezko terminologia batzuk azalduko ditugu.
Mint
Cashu-ren mint-a erabiltzaileen funtsen zaintzailea da. Bere zeregina tokenak jaulkitzea eta erretzea da, baita bikoiztutako gastuak saihestea ere. Cashu-ren mint-a Lightning nodo baten gainean dago, beraz, Lightning ordainketak bidali eta jaso ditzake, beste mint batzuekin trukeak barne. Hala ere, Lightning nodoa lineaz kanpo badago ere, ecash tokenekin transakzioak egin daitezke. Lightning-ekin ez bezala, jasotzailea linean egon beharrik ez du tokenak jasotzeko.
Mint-ak ez daki nor den erabiltzailea, zenbat funts dituzten edo norekin ari diren transakzioak egiten. Hala ere, mint-a erabiltzaileen funtsen zaintzailea denez, fidagarria den mint bat aukeratu behar duzu, eta eragilea nor den jakin. Erabil ezazu funts txikiekin edo tokenak berehala trukatu.
Token
Cashu token-a mint-ak sinatutako datu-puska bat da, eta erabiltzaileak token horiek bere zorroan gordetzen ditu. Ecash tokenak testu-kate hutsak direnez, edozein testu bidezko protokoloaren bidez bidal daitezke, adibidez, nostr, posta elektronikoa, SMS, etab. Cashu-k txanpon-sistema bat erabiltzen du, zenbateko finkatuak dituena. Analogia bat eginez, hau moneta fiduziarioen billeteen zenbatekoei dagokie. Adibidez, eurotan 5, 10, 20, 50, 100 euroko billeteak daude. Cashu-n, tokenak 2ren indarren arabera sailkatzen dira. Adibidez, 1, 2, 4, 8, 16, 32, 64, 128 satoshi, eta horrela aurrera.
Zenbatekoak erabiltzea erabiltzaileen artean anonimotasuna areagotzeko egiten da, eta mint-ek transakzioak erabiltzaileen nortasunekin lotzea zailagoa bihurtzeko.
Nola funtzionatzen duen, 5 urteko bati bezala azaldua

Erabiltzaile Alice-k Cashu token berriak sortu nahi ditu. Horregatik, Bob mint-aren arduradunarengana joaten da eta esaten dio: "Kaixo! Cashu token berriak sortu nahi ditut."

Bob-ek erantzuten dio: "Ados, ordaindu iezadazu eta bidali iezadazu sekretu itsu bat." Sekretu itsua esan nahi du Alice-k sekretua ezagutzen duela, baina Bob-ek ezin duela sekretu hori ikusi.

Alice-k sekretu bat sortzen du, eta ondoren itsutzen du, horrela Bob-ek ez dezan jakin zein den sekretu hori.

Alice-k Bob-i ordainketa egiten dio eta ordainketaren egiaztagiria eta sekretu itsua bidaltzen dizkio. Bob ordainketa jaso duela ziur dagoenean, Alice-ren sekretu itsua sinatzen du eta sinatutako sekretu itsua itzultzen dio. Bob-ek sinatu duelako, etorkizunean ziur egon daiteke tokena baliozkoa dela.


Alice-k Carol-i ordaindu nahi dio. Horretarako, sekretua eta sinatutako sekretu itsua desitsutzeko gakoa bidaltzen dizkio Carol-i.


Carol-ek bere tokena trukatu nahi du. Beraz, Bob-engana (mint-aren arduradunera) joaten da eta Alice-k eman dion sekretua eta desitsututako gakoa erakusten dizkio.
Nola jakiten du mint-ak Carol-i zenbat satoshi eman behar dizkion?
Lehenago aipatu genuen bezala, Cashu tokenak 2ren indarren araberako zenbatekoetan banatuta daude (1, 2, 4, 8, 16, 32...), paperezko diru billeteen antzera. Bob mint-ak zenbateko bakoitza sinatzeko gako pribatu berezi bat du. Adibidez, 1 satoshi zenbatekoaren tokenak sinatzeko gako pribatu bat du, 2 satoshi zenbatekoaren beste bat, 8 satoshi zenbatekoaren beste bat, eta abar. Horrela, Carol tokenak trukatzera datorrenean, Bob-ek badaki zein gako pribaturekin sinatu zuen token hori, eta horren arabera, tokenak zein zenbatekotakoak diren ezagutzen du. Horrela, Bob-ek Carol-i dagokion satoshi kopurua itzuli diezaioke, sinatutako tokenaren zenbatekoa kontuan hartuta.
Zer gertatzen da itzulkinekin?
Cashu-n ez dago itzulkinik diru fisikoan bezala. Horren ordez, mint-ari (Bob-i) eskatu behar diozu token zaharrak suntsitzeko eta berriak sortzeko, zenbateko berarekin. Adibide batekin azalduz: Demagun Alice-k bi token dituela, guztira 10 satoshi balio dutenak. Bata 8 satoshi da eta bestea 2 satoshi. Alice-k 9 satoshi bidali nahi dizkio Carol-i. Horretarako, mint-ari (Bob-i) eskatzen dio bere 2 satoshi tokena bi 1 satoshi token bihurtzeko. Horrela, Alice-k 9 satoshi bidal diezazkioke Carol-i: 8 satoshi token bat eta 1 satoshi token bat erabiliz. Gainera, beste 1 satoshi tokena berarentzat gordetzen du.
Lightning sarearen papera konektatzeko elementu gisa
Zer gertatzen da Alice-k David-i ordaindu nahi dionean, baina David-ek Bob-en mint-a ez du fidatzen, eta, aldiz, Erin ezagutzen du eta bere mint-a erabiltzen du? Alice-k bere tokenak Bob-en mint-ean trukatzen ditu, eta Bob-i eskatzen dio token horiek "urtzeko" edo Lightning satoshietara bihurtzeko. Ondoren, Bob-en mint-ak Lightning transakzio bat bidaltzen dio Erin-en mint-ari. Erin-en mint-ak transakzio hori jasotzen du, eta David-entzat token berriak sortzen ditu Lightning sarearen bidez Bob-en mint-etik jasotako satoshiekin. Horrela, Lightning sareak mint ezberdinak konektatzen ditu, erabiltzaileak (Alice eta David) mint ezberdinak fidatu arren, transakzioak segurtasunez egiteko.

Zer dator hurrengoa Cashu-rentzat?
Programagarri den ecash
Cashu-ri gastatzeko baldintzak gehitu ahal izango zaizkio, mint-ak baldintza horiek betearaziko dituelarik. Horrek ahalbidetu dezake kontratu adimendun sendoak sortzea, oinarrizko katean (Bitcoin blockchain) edo Lightning sarean sartu gabe. Horrela, ordainketa publikoak, lineaz kanpokoak eta maiztasun handikoak posible izango dira.
Zorren froga eskema (Proof of Liabilities Scheme)
Zorren Froga (PoL) Eskema Cashu-rentzat zaintzailea den mint-ak erabiltzaileak iruzurrez erabiltzea zailtzen du, epoka kontzeptua aurkeztuz. Eskema honetan, zaintzaile den mint-ak epoka bakoitzean gako pribatuak aldian-aldian biratzen ditu, eta azken epokan jaulkitako eta erretako tokenen zerrenda publikoak argitaratzen ditu. Hau Erreserben Froga (Proof of Reserves) eskemarekin uztartzen da, non erreserbak katean bertan multisig batean gordetzen diren. Horrela, mint-ak ezingo du bere erantzukizunak murriztu, erabiltzaileek iruzurra detektatzeko arriskua handitu gabe. Xehetasun gehiagorako, eskema honen azalpen osoa kontsultatu dezakezu.
Saiatu Cashu
Cashu probatzeko, [Nutstash] eta [eNuts] gidak erabil ditzakezu. Horretarako Lightning zorro bat eta telefono edo ordenagailu bat besterik ez duzu behar.
-
 @ df8f0a64:057d87a5
2024-10-10 15:18:39
@ df8f0a64:057d87a5
2024-10-10 15:18:39書き散らす動機
残暑続きからの急な気温低下で鼻炎がひどくなる今日この頃、皆様お元気でしょうか
株主への抗議のために退職してから2ヶ月半、流石に暇を持て余してきました 時間がある上に能動的に働く気も起きず、ひたすらボーッとしたりうねうね考え事をする日々です 幸いにして人生も折り返しにさしかかる頃になり、時折「今、人生が終わって構わないのでは?」というようなことも考えたりします (鬱病既往歴ありますが私は元気です)
子どものお迎えを終えて、いつもどおり夕食をとり、またうねうねしているうちに ふと、6年前の年末に急死された、仕事でお世話になったTさんのことを思い出しました
子を寝かしつけてもまだ頭の中をぐるぐるしていたので、ここに吐き出してすっきりしようという魂胆です
Tさんとの出会い
私のキャリアの(ほぼ)スタートはVC(ベンチャーキャピタル)でした 誰のせいでもないとある経緯もあり、周囲からは警戒され避けられ、わずか6年ではありますが、 インナーサークルに入り込めない時期を過ごし、当時の上司と二人、とにかくやれることをやり続ける毎日でした
いつものようにピッチイベントに参加しているとき、近くの席にいたスーツ姿の3人組と目が一瞬合います
「事業会社の人だ」
協調投資やファンド出資のきっかけを掴むべく、その3人に話かけます
「よろしければ弊社投資先のご紹介や御社の...」
ひととおりの挨拶を済ませ、この人たちにも避けられるんだろうと思いながらも要件を切り出します
「是非やりましょう」
いつもとは違う嬉しい返事をくれたのがTさんでした
面倒見の良い他社の先輩
そのときの3人組であるMさん・Iさん・Tさんには、私の仕事人生の中で最もお世話になったと言っても過言ではありません
ファンドの営業を受けていただき、協調投資を行い、VCからの転職後にも協業相手として他部署のキーマンをご紹介いただき...
社会人になったばかりの私の、今思い返せば恥ずかしい(部下がこんな提案したら卒倒する)レベルの提案を、 誰もが知る一流企業の多忙な役職持ちであるにも関わらず、毎回一時間も割いて丁寧に対応してくださる心の広い方でした
当時、VCと接点をもつような事業会社の対スタートアップ部隊は、本業でご活躍されている方が兼任で取り組むパターンが多く、Mさん・Iさん・Tさんももちろんそう
その後も昇進され、最後には本社の取締役に。今年遂に退任され、所謂「あがり」でしょうか、子会社の取締役に異動 長い社会人人生をほぼ走りきり、有終の美を飾ろうとする時期にさしかかっています
でもTさんはそこにはいません
残される側
冒頭触れたとおり、Tさんは6年前のこの時期に急死されました 死因については、Tさんのご友人がFBに投稿していた文章を読んでも、Iさんに聞いてもわからない
悲しいかな、四十年近く生きていると、死因が明かされない理由がわかるようになる機会が一度や二度はあります Tさんもおそらくそうだったのでしょう
直前まで、Iさんと一緒にベイエリアに出張され、楽しそうなコメントと共に写真を投稿されていたのに 晩婚なのか再婚なのか、とにかくご結婚されて一年ちょっと。お子様も生まれたばかりだったのに Tさんは近い人間に心中を隠して、静かにこの世を去りました
あなたの快い返事に、どれほど私が救われたのか 転職後の提案のとき、受付で顔を出してすぐ「元気?」と声をかけてくださったことがどれほど私を安心させてくれたか あなたが声をかけてくれる度、私の社会人としての成果が生まれたことに、私は十分に感謝を伝えられていません
まだしばらく残る理由
振り返って、Tさんのように誰かの人生をenhanceできたのか?と自分に問うと、まだできたとは思えません。残念ですが
今ここで死んでも私は構わないけど、まだもうちょっと頑張るべきかな、老いてから誰かに感謝をしてもらうまで生きてみてもいいかな
そうふと思い直しているうちに日付が変わりました
-
 @ 4ba8e86d:89d32de4
2024-10-25 12:45:38
@ 4ba8e86d:89d32de4
2024-10-25 12:45:38A privacidade é uma preocupação crescente para muitos usuários da internet, especialmente quando se trata de pesquisar na web. É aqui que entra o Searx, um buscador de código aberto que se destaca por seu compromisso com a privacidade do usuário.
Searx é um mecanismo de metabusca descentralizado na forma de software livre, sob a licença GNU AGPLv3, desenvolvido pelo programador Húngaro, Adam Tauber, que agrega resultados por volta de 70 serviços de busca. O mecanismo não salva consultas de pesquisa e não repassa ou mesmo vende dados privados a terceiros. Os usuários não são rastreados e além disso, pode ser usado na rede Tor para o anonimato online.
O Searx foi criado em 2011 como um projeto de código aberto, o que significa que seu código-fonte está disponível para todos os usuários e desenvolvedores examinarem e contribuírem para seu desenvolvimento. Como um buscador de código aberto, o Searx não coleta ou armazena dados pessoais de seus usuários, o que o diferencia de grandes buscadores como o Google.
Uma das principais vantagens do Searx é sua capacidade de preservar a privacidade do usuário. Ele não rastreia suas pesquisas e não compartilha dados com terceiros. Ao contrário do Google e outros buscadores que exibem anúncios personalizados com base no histórico de navegação do usuário, o Searx não exibe anúncios.
O Searx é altamente personalizável, o que significa que os usuários podem escolher quais fontes de dados usar para suas pesquisas. O Searx é capaz de buscar resultados em mais de 70 fontes de dados, incluindo Google, Bing, Yahoo, Wikipedia, Reddit, entre outros. Os usuários podem personalizar suas pesquisas para excluir determinadas fontes ou incluir outras, conforme necessário.
Outra vantagem do Searx é a capacidade de utilizar motores de busca especializados. O Searx pode ser configurado para buscar em motores de busca especializados em áreas específicas, como tecnologia, ciência, artes, entre outros. Isso significa que os usuários podem encontrar resultados mais precisos e relevantes para suas pesquisas.
O Searx oferece uma experiência de busca semelhante à do Google, com uma barra de pesquisa simples e fácil de usar. No entanto, ele se destaca pela sua capacidade de preservar a privacidade do usuário e oferecer resultados personalizados e precisos. Como um projeto de código aberto, o Searx está em constante desenvolvimento e melhoria, e os usuários podem contribuir para seu desenvolvimento, sugerindo melhorias e correções.
O Searx é uma excelente opção para aqueles que se preocupam com a privacidade e segurança de seus dados pessoais na internet. Como um buscador de código aberto, ele se destaca por sua transparência e compromisso com a privacidade do usuário, além de oferecer uma experiência de busca personalizada e altamente personalizável. Se você valoriza a privacidade online, experimente o Searx.
https://searx.thegpm.org/
https://github.com/searx/searx
-
 @ 266815e0:6cd408a5
2024-09-02 15:27:16
@ 266815e0:6cd408a5
2024-09-02 15:27:16After 7 months of work and procrastination I've decided to release another version of noStrudel
There a ton of new features and a few bugs fixed. This article highlights the biggest changes but if you want to read the full changelog you can find it in the github repo
And as always if you want to check it out you can use nostrudel.ninja or run it locally using docker
sh docker run --rm -p 8080:80 ghcr.io/hzrd149/nostrudel:0.40.0New Features
Support for NIP-49 encrypted nsec
Now when logging into to the app it will prompt you to set a password to encrypt your nsec so it can be stored securely (if that's even possible for a web client...)
There is also a new "Account" settings view that lets you export you nsec as a ncryptsec so you can copy it to other apps

Blindspot feeds
There are also new "blindspot" feeds that show what others are seeing in their timeline that your missing

NIP-42 Relay authentication
The app now supports NIP-42 relay authentication. Its opt-in though, so if you want to use popular authenticated relays like nostr.wine or relay.snort.social you will have to enable it in the settings

Wasm relay and event verification
The app now supports using @snort/worker-relay as a local relay. Its at least 10x faster than the internal browser cache and can hold at least 100x more events. Its not enabled by default though so if you want to use it you have to switch to it in the "Relays" -> "Cache Relay" view

The app also supports using nostr-wasm to speed up event signature verification. This is enabled by default, but if you want to still use the JavaScript verification or no verification you can find it in the performance setting

Thread tabs
Threads now have a set of tabs that let you see the Replies, Quotes, Zaps, and other stuff related to the note


Wiki articles
Its not feature complete but you can now view and edit wiki articles in the app

Finished the launchpad
The launchpad is now usable and shows the latest notifications, messages, streams, and tools

Blossom uploads
The app now lets you upload images and video to blossom server, this isn't enabled by default though so your going to have to enable it in the settings

And then setup some blossom servers in the settings. A few good public ones are
https://cdn.satellite.earthandhttps://cdn.nostrcheck.me
Task Manager
There is also a new "Task Manager" in the side nav that lets you see whats going on under the hood in the app

You can see what relays the app is currently connected to

And which relays are requesting NIP-42 authentication

Bug fixes
- Fix null relay hints in DMs
- Fix users own events being hidden by muted words
- Fix random events showing up as DM messages
- Fix app prompting NIP-07 extension to unlock when app opens
- Remove corsproxy.io as default service for CORS proxy
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28nix
Pra instalar o neuron fui forçado a baixar e instalar o nix. Não consegui me lembrar por que não estava usando até hoje aquele maravilhoso sistema de instalar pacotes desde a primeira vez que tentei, anos atrás.
Que sofrimento pra fazer funcionar com o
fish, mas até que bem menos sofrimento que da outra vez. Tive que instalar um tal defish-foreign-environment(usando o próprio nix!, já que a outra opção era ooh-my-fishou qualquer outra porcaria dessas) e aí usá-lo para aplicar as definições de shell para bash direto nofish.E aí lembrei também que o
/nix/storefica cheio demais, o negócio instala tudo que existe neste mundo a partir do zero. É só para computadores muito ricos, mas vamos ver como vai ser. Estou gostando do neuron (veja, estou usando como diário), então vou ter que deixar o nix aí. -
 @ 38d0888d:bd8e1246
2024-09-02 11:08:05
@ 38d0888d:bd8e1246
2024-09-02 11:08:05To foster collective improvement, it is essential to implement social programs that encourage voluntary engagement and mutual support. These initiatives should serve as fertile ground, nurturing altruistic values and deepening the understanding of humanity’s true needs. By integrating spiritual connections into these efforts, a ripple effect of kindness, understanding, and enlightenment can spread throughout society. Each individual, endowed with intellectual abilities by a higher power, is invited to contribute to the creation of a harmonious and enlightened world. Sharing inspirational concepts that blend spirituality with social responsibility has the potential to profoundly influence and unite public sentiment.
A sense of community and interconnectedness must be cultivated within these programs. Creating spaces for shared experiences and collective growth extends their impact beyond individual actions, fostering a network of mutual support and understanding.
It is crucial to promote inclusive development that transcends bureaucratic constraints, aiming to dismantle inequality and confront corruption. These initiatives do more than foster a fairer world; they also reveal the latent spiritual dimensions of the human mind. To encourage spiritual growth and overcome selfishness, collaborative efforts across society, decentralized governance structures, educational institutions, and individual contributions are imperative. Moral codes must emerge from deeply rooted spiritual ethics that are interwoven into the societal fabric, surpassing the interests of a privileged few. Humanity’s ultimate goal is to transcend mere cooperation among individuals, striving for absolute transparency and openness across all spheres of existence. Achieving this vision requires unwavering dedication from every stakeholder committed to guiding society along the path of enlightenment.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Bitcoin como um sistema social humano
Afinal de contas, o que é o Bitcoin? Não vou responder a essa pergunta explicando o que é uma "blockchain" ou coisa que o valha, como todos fazem muito pessimamente. A melhor explicação em português que eu já vi está aqui, mas mesmo assim qualquer explicação jamais será definitiva.
A explicação apenas do protocolo, do que faz um programa
bitcoindsendo executado em um computador e como ele se comunica com outros em outros computadores, e os incentivos que estão em jogo para garantir com razoável probabilidade que se chegará a um consenso sobre quem é dono de qual parte de qual transação, apesar de não ser complicada demais, exigirá do iniciante que seja compreendida muitas vezes antes que ele se possa se sentir confortável para dizer que entende um pouco.E essa parte técnica, apesar de ter sido o insight fundamental que gerou o evento miraculoso chamado Bitcoin, não é a parte mais importante, hoje. Se fosse, várias dessas outras moedas seriam concorrentes do Bitcoin, mas não são, e jamais poderão ser, porque elas não estão nem próximas de ter os outros elementos que compõem o Bitcoin. São eles:
- A estrutura
O Bitcoin é um sistema composto de partes independentes.
Existem programadores que trabalham no protocolo e aplicações, e dia após dia novos programadores chegam e outros saem, e eles trabalham às vezes em conjunto, às vezes sem que um se dê conta do outro, às vezes por conta própria, às vezes pagos por empresas interessadas.
Existem os usuários que realizam validação completa, isto é, estão rodando algum programa do Bitcoin e contribuindo para a difusão dos blocos, das transações, rejeitando usuários malignos e evitando ataques de mineradores mal-intencionados.
Existem os poupadores, acumuladores ou os proprietários de bitcoins, que conhecem as possibilidades que o mundo reserva para o Bitcoin, esperam o dia em que o padrão-Bitcoin será uma realidade mundial e por isso mesmo atributem aos seus bitcoins valores muito mais altos do que os preços atuais de mercado, agarrando-se a eles.
Especuladores de "criptomoedas" não fazem parte desse sistema, nem tampouco empresas que aceitam pagamento em bitcoins para imediatamente venderem tudo em troca de dinheiro estatal, e menos ainda gente que usa bitcoins e a própria marca Bitcoin para aplicar seus golpes e coisas parecidas.
- A cultura
Mencionei que há empresas que pagam programadores para trabalharem no código aberto do BitcoinCore ou de outros programas relacionados à rede Bitcoin -- ou mesmo em aplicações não necessariamente ligadas à camada fundamental do protocolo. Nenhuma dessas empresas interessadas, porém, controla o Bitcoin, e isso é o elemento principal da cultura do Bitcoin.
O propósito do Bitcoin sempre foi ser uma rede aberta, sem chefes, sem política envolvida, sem necessidade de pedir autorização para participar. O fato do próprio Satoshi Nakamoto ter voluntariamente desaparecido das discussões foi fundamental para que o Bitcoin não fosse visto como um sistema dependente dele ou que ele fosse entendido como o chefe. Em outras "criptomoedas" nada disso aconteceu. O chefe supremo do Ethereum continua por aí mandando e desmandando e inventando novos elementos para o protocolo que são automaticamente aceitos por toda a comunidade, o mesmo vale para o Zcash, EOS, Ripple, Litecoin e até mesmo para o Bitcoin Cash. Pior ainda: Satoshi Nakamoto saiu sem nenhum dinheiro, nunca mexeu nos milhares de bitcoins que ele gerou nos primeiros blocos -- enquanto os líderes dessas porcarias supramencionadas cobraram uma fortuna pelo direito de uso dos seus primeiros usuários ou estão aí a até hoje receber dividendos.
Tudo isso e mais outras coisas -- a mentalidade anti-estatal e entusiasta de sistemas p2p abertos dos membros mais proeminentes da comunidade, por exemplo -- faz com que um ar de liberdade e suspeito de tentativas de centralização da moeda sejam percebidos e execrados.
- A história
A noção de que o Bitcoin não pode ser controlado por ninguém passou em 2017 por dois testes e saiu deles muito reforçada: o primeiro foi a divisão entre Bitcoin (BTC) e Bitcoin Cash (BCH), uma obra de engenharia social que teve um sucesso mediano em roubar parte da marca e dos usuários do verdadeiro Bitcoin e depois a tentativa de tomada por completo do Bitcoin promovida por mais ou menos as mesmas partes interessadas chamada SegWit2x, que fracassou por completo, mas não sem antes atrapalhar e difundir mentiras para todos os lados. Esses dois fracassos provaram que o Bitcoin, mesmo sendo uma comunidade desorganizada, sem líderes claros, está imune à captura por grupos interessados, o que é mais um milagre -- ou, como dizem, um ponto de Schelling.
Esse período crucial na história do Bitcoin fez com ficasse claro que hard-forks são essencialmente incompatíveis com a natureza do protocolo, de modo que no futuro não haverá a possibilidade de uma sugestão como a de imprimir mais bitcoins do que o que estava programado sejam levadas a sério (mas, claro, sempre há a possibilidade da cultura toda se perder, as pessoas esquecerem a história e o Bitcoin ser cooptado, eis a importância da auto-educação e da difusão desses princípios).
-
 @ 599f67f7:21fb3ea9
2024-10-26 11:20:48
@ 599f67f7:21fb3ea9
2024-10-26 11:20:48Zer da lightning address bat?
Lightning address bat irakurgarria den helbide elektroniko baten antza duen helbidea da, adibidez username@domein.com, baina bitcoinetan ordainketak berehala eta merke jasotzeko aukera ematen du. Ez duzu zure gailuan nodo bat linean izatea behar, eta ez duzu eskuz faktura bat sortu behar norbaitek ordainketa egin nahi dizunean.
Oso interesgarria, ezta?Nola funtzionatzen du, orduan?
Lightning Address-ek LNURL pay protokoloa erabiltzen du, Lightning Network-aren gainean dagoen geruza bat da.

Prozesua hurrengo urratsetan laburbil daiteke:
- Erabiltzaile batek zure Lightning Address erabiliz ordainketa egin nahi duenean, haien zorroak helbide hori LNURL payRequest batean bihurtzen du.
- LNURL payRequest arrakastatsu baten bidez, zorroak BOLT11 faktura bat eskuratzen du, eta faktura hori ordainketa burutzeko erabiltzen da.
Hau da, prozesuaren oinarrizko pausoak hurrengoak dira:
💡 Lightning Address > LNURLp > BOLT11 faktura.
Lightning Network-ekin integratuta dagoen sistema honi esker, ordainketak erraz, azkar eta modu automatizatuan burutu daitezke.Oso ondo dirudi, baina zein da tranpa?
Lightning Address-en inplementazio askok kustodia dute (nahiz eta ez den beti horrela), izan ere, domeinu bat eta beti linean dagoen nodo bat behar dira Lightning Address-ak funtzionatzeko. Kustodia sistema bat denez, zure fondoak kudeatzen dituenak edozein momentutan kontrolatu edo kendu ahal dizkizu eta zure transakzioak monitorizatu ditzake.
Domeinuaren jabearengan fidatu behar duzu, zure Lightning Address-aren erregistroa aldatu ez dezan. Eta, gainera, LNURL zerbitzaria linean ez badago, sistema ez da funtzionatzen.
Bitcoin Txoko-k LNbits-en oinarritutako Lightning Address irtenbide sinplea eskaintzen du. Hau ere kustodia sistemakoa da, beraz, gomendagarria da Bitcoin Txoko zorroan kopuru txiki bat bakarrik gordetzea eta gero auto-kustodia zorro batera ateratzea, satoshi gehiago jasotzen dituzun heinean.Hasteko prest bazaude, hona hemen behar duzuna:
-
Zure zorroa sortzea
Lehenik eta behin, ez baduzu oraindik egin, joan bitcointxoko.com webgunera eta zorro bat sortu. Zorroari nahi duzun izena jar diezaiokezu. -
Luzapenak aktibatzea
Lightning Address-ak funtzionatzeko Pay Links luzapena behar da. Horretarako: -
Joan tresna-barrako Extensions (Luzapenak) atalera eta Pay Links luzapena aktibatu.
-
Ordainketa esteka bat sortzea
- Ireki Pay Links luzapena eta egin klik New Pay Link (Ordainketa Esteka Berria) aukeran.
- Aukeratu sortu duzun zorroa.
- "Item Description" atalean, nahi duzun testua sar dezakezu.
- Aukeratu zure Lightning Address-erako erabiltzaile izena. Zure Lightning Address hau bezalakoa izango da: erabiltzailea@bitcointxoko.com.
-
Fixed Amount aukera desmarkatu eta jarri gutxieneko balioa 1 eta gehienekoa 500000.

⚠️ Gehienezko balioa handiagoa jar dezakezu, baina ordainketa handiek huts egiteko probabilitate handiagoa dute, Bitcoin Txoko Lightning nodoaren kanalaren sarrera-gaitasun mugatua dela eta. Gomendagarria da 500000 satoshitan mantentzea. - Orain, ireki Advanced Options (Aukera Aurreratuak) eta aldatu Comment maximum characters (Komentarioaren gehieneko karaktere kopurua) 799-ra. Ez da beharrezkoa, baina aurrerantzean funtzionalitate gehiago emango dizu. - Azkenik, markatu Enable nostr zaps aukera behealdean, Lightning Address bidez zaps jasotzeko aukera izateko.
Aukera aurreratuak beste parametro batzuk konfiguratzea ahalbidetzen dute, baina nahi baduzu hutsik utz ditzakezu.
Azkenik, dena zuzen dagoela egiaztatu ondoren, egin klik Create Pay Link (Sortu Ordainketa Esteka) botoian.Horrela, zure Lightning Address sortuta izango duzu eta ordainketak jaso ahal izango dituzu!
Proba egitea
Zure Lightning Address ondo funtzionatzen duen probatu nahi baduzu, beste zorro batera joan, Bidali (Send) aukera hautatu eta helmuga gisa zure Lightning Address idatzi. Ondoren, bidali zeure buruari satoshi batzuk.
Ondoren, itzuli Bitcoin Txoko zorrora eta egiaztatu ordainketa jaso duzun. Litekeena da orria freskatu behar izatea ordainketa agertzeko.
Dena ondo atera bada, zorionak! 🥳
Bestela, jakinarazi iezaguzu. Beti prest gaude laguntzeko.Hurrengo urratsak
Nostr zaps
Zure Bitcoin Txoko Lightning Address nostr profilean gehitu dezakezu eta horrela zaps jasotzeko erabil dezakezu. Normalean, hau hurrengo pausuekin egiten da: - Joan Profile (Profila) atalera. - Hautatu Edit (Editatu) eta Lightning Address aldatu.
LNDhub
Zure LNbits zorroa telefonoan inporta dezakezu LNDhub bezala, Zeus edo BlueWallet bezalako aplikazioak erabiliz. Horrela, ez duzu nabigatzailean zorroa ireki beharko aldian-aldian saldoa egiaztatu edo ordainketak egiteko.
Nola egin jakiteko, ikus ezazu nostr:naddr1qqxnzdej8y6ryvejxc6nvwpnqyg8wumn8ghj7mn0wd68ytnhd9hx2q3qtx0k0a7lw62vvqax6p3ku90tccgdka7ul4radews2wrdsg0m865sxpqqqp65w4hhl8s.QR kodea
Zure LNURLp QR kodea parteka edo inprima dezakezu, jendeak mugikorrarekin eskaneatu dezan. Oso erabilgarria da zure denda lokaleko jabeak Lightning ordainketak jasotzeko sistema ezartzea nahi baduzu! - Parteka ezazu Sharable Page (Parteka daitekeen Orrialdea) esteka. - Edo, QR kodea PDF formatuan inprima dezakezu: joan View Link (Esteka Ikusi) atalera eta hautatu Print (Inprimatu).
Horrela, zure Lightning Address erabilera praktikoa handitu eta errazago kudeatu dezakezu! Hasi zaitez !




