-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ 7d4417d5:3eaf36d4
2023-08-19 01:05:59
@ 7d4417d5:3eaf36d4
2023-08-19 01:05:59I'm learning as I go, so take the text below for what it is: my notes on the process. These steps could become outdated quickly, and I may have some wrong assumptions at places. Either way, I have had success, and would like to share my experience for anyone new to the process. If I have made any errors, please reply with corrections so that others may avoid potential pitfalls.
!!! If you have "KYC Bitcoin", keep it in separate wallets from your "Anonymous Bitcoin". Any Anonymous Bitcoin in a wallet with KYC Bitcoin becomes 100% KYC Bitcoin.
!!! It took me several days to get all the right pieces set up before I could even start an exchange with someone.
!!! Using a VPN is highly recommended. If you're not already using one, take the time to find one that suits you and get it running.
!!! If you don't normally buy Amazon Gift Cards, start doing so now, and just send them to yourself, or friends that will give you cash in return, etc. For my first trade, Amazon locked me out of my account for about 22 hours, while I was in the middle of an exchange. All because I had never purchased an Amazon Gift Card before. It was quite nerve wracking. My second trade was for $300, and although my Amazon account wasn't shut down, that order had a status of "Sending" for about 22 hours, due to the large amount. In each of these cases I had multiple phone calls with their customer support, all of whom gave me false expectations. Had I already been sending gift cards to the anonymous email address that I created in the steps below, and maybe other anonymous email addresses that I could make, then I might not have been stalled so much.
-
Install Tor Browser for your OS. The RoboSats.com website issues a warning if you are not using Tor Browser. If you don't know what Tor is, I won't explain it all here, but trust me, it's cool and helps keep you anonymous. If you use Firefox, the interface will look very familiar to you.
-
Create a KYC-free e-mail address. I used tutanota.com in Firefox, as it would not allow me to create an account using Tor Browser. After the account was created, using Tor Browser to login, check emails, etc. has been working perfectly. Tutanota requires a 48 hour (or less) waiting period to prevent bots from using their system. You'll be able to login, and even draft an email, but you won't be able to send. After you've been approved, you should be able to login and send an email to your new address. It should show up in your Inbox almost instantly if it's working.
-
Have, or create, at least one Lightning wallet that is compatible with RoboSats.com and has no KYC Bitcoin in it. The RoboSats website has a compatibility chart available to find the best wallet for you. During an exchange on RoboSats, you will need to put up an escrow payment, or bond, in Satoshis. This amount is usually 3% of the total amount being exchanged. If the exchange is successful, the bond payment is canceled, leaving that amount in your wallet untouched, and with no record of it having been used as escrow. If you don't hold up your end of the trade, the bond amount will be transfered from your wallet. I created a wallet, using my new email address, with the Alby extension in the Tor Browser. This anonymous wallet was empty, so I used a separate wallet for the bond payment of my first trade. This wallet had KYC Bitcoin, but since it is being used for a bond payment, and no transaction will be recorded if everything goes okay, I don't mind taking the minuscule risk. After the first trade, I don't need to use the "KYC wallet", and I will use only my anonymous Lightning wallet for transactions related to performing a trade.
-
Create a new Robot Token by going to RoboSats using the Tor Browser. Copy the Token (Robot ID) to a text file as a temporary backup. It is recommended to create a new robot-token for every session of exchanges you make.
-
Select "Offers" to browse what others are presenting. "Create" is for when you want to create an offer of your own. You may need to create your own offer if none of the existing offers match your criteria.
-
Select "Buy" at the top of the page.
-
Select your currency (USD).
-
Select your payment methods by typing "amazon" and selecting (Amazon Gift Card). Repeat this process and select (Amazon USA Gift Card).
-
Determine Priorities - If you prefer to trade quickly, and don't care as much about premiums, look for users with a green dot on the upper-right of their robot icon. If you're not in a hurry, sort users by premium and select the best deal, even if they are inactive. They may become active once they are notified that their offer has activity from you.
-
The Definition of Price = the price with the premium added, but not the bond
-
A. Find A Compatible Offer - Select the row of the desired offer and enter the amount you would like to buy. i.e. $100 If you do not find a compatible offer, you will have to create your own offer.
B. **Create An Offer** - First, take a look at "Sell" offers for your same currency and payment method(s) that you will be using. Take note of the premium those buyers are willing to pay. If your premium is drastically less than theirs, your offer may get ignored. Select "Create" at the bottom of the screen. There is a slider at the top of the screen, select it to see all the options. Select "Buy". Enter the minimum and maximum amount that you wish to spend. Type "amazon" to select the methods that you would like to use (Amazon Gift Card, Amazon USA Gift Card). For "Premium Over Market", enter an amount that is competitive with premiums you saw at the start of this step and do not use the % sign! You can adjust the duration, timer, and bond amount, but I leave those at their default settings. Select the "Create Order" button, and follow the instructions for making a bond payment. -
Pay the Bond - Copy the invoice that is presented. From your wallet that contains bond funds, select "Send", and paste the invoice as the recipient. This money will never leave your account if the exchange completes without issue. No transaction will be recorded. If there is a complication with the exchange, it is possible that this transaction will complete.
-
Create and Submit Your Invoice for Their Bitcoin Payment To You - Select "Lightning", if not selected by default.* Select the Copy Icon to copy the correct amount of Satoshis. This amount already has the premium deducted. From your anonymous Lightning Wallet, select "Receive", and paste the Satoshi amount. If you enter a description, it's probably best to keep it cryptic. Copy the invoice and paste it into RoboSats; then select "Submit".
* If you plan on "mixing" your Bitcoin after purchase, it may be better to select "On Chain" and pay the necessary fees swap and mining fees. In the example this comes from, Sparrow wallet is used and has whirlpool ability in its interface.
-
Connect With Seller and Send Funds - Greet the seller in the chat window. The seller has now provided RoboSats with the Bitcoin to transfer to you. Your move is to buy an Amazon eGift Card for the amount of the trade. Log in to your Amazon account and start the process of buying an eGift card. For delivery there is the option of email or txt message. Ask the seller what their preference is, and get their address, or phone number, to enter into Amazon's form. Complete the purchase process on Amazon, and check the status of your order. Once you see the status of "Sent", go back to RoboSats in your Tor Browser.
-
Confirm Your Payment - Select the "Confirm ___ USD Sent" button and notify the seller to check their e-mail/txt messages.
-
Seller Confirmation - Once the seller select their "Confirm" button, the trade will immediately end with a confirmation screen.
-
Verify - If you check the anonymous wallet, the new amount should be presented.
-
-
 @ eac63075:b4988b48
2024-10-20 13:49:55
@ eac63075:b4988b48
2024-10-20 13:49:55Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.
Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.
The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.
Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.
The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
Conclusion of the Technical Debate
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.

Table reference: Patrick Breyer - Chat Control in 23 September 2024
Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.
The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
Conclusion of the Debate
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.
User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
Summary of Consequences
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.
The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.
Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ 4ba8e86d:89d32de4
2024-10-07 13:37:38
@ 4ba8e86d:89d32de4
2024-10-07 13:37:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ 0520ed0d:c32b6dc8
2024-11-14 09:11:00
@ 0520ed0d:c32b6dc8
2024-11-14 09:11:00На пересечении искусства и технологий в столице России появился первый в своем роде театр, где актеры — это не люди, а высокотехнологичные машины. Этот проект стал настоящей революцией в мире сценического искусства и привлек внимание зрителей со всего мира.
Роботы-актеры способны не только воспроизводить текст, но и имитировать эмоции, движения и даже взаимодействовать с публикой. Каждое представление — это захватывающее зрелище, где сливаются современные технологии, искусственный интеллект и театральное мастерство.
Создатели театра уверены, что такой формат не только расширяет границы искусства, но и открывает новые горизонты для творчества. Зрители могут наблюдать за инновационными спектаклями, которые ставят под сомнение традиционные представления о театре и актерской игре.
Первые отзывы зрителей уже поступили, и они полны восторга! Многие отмечают, что роботы-актеры привносят в спектакли особую атмосферу и оригинальность.
Не упустите возможность стать частью этого исторического события! Приходите в новый театр и убедитесь сами, что будущее уже здесь! 🎉🤩
ТеатрБудущего #РоботыАктеры #Москва #ИскусствоИтехнологии
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ fb5986f6:4173af9d
2024-11-14 08:48:55
@ fb5986f6:4173af9d
2024-11-14 08:48:55En github hay un listado enorme de muchas alternativas a las apps mainstream que no respetan nuestra privacidad (https://github.com/pluja/awesome-privacy)
Pero ahí van algunas de las apps que hemos elegido en el grupo de telegram de GrapheneOS en español (unofficial). Anímate a entrar al grupo y enseñarnos alguna otra que te parezca interesante!
Grupo de telegram: https://t.me/grapheneosEsp
Tienda de Apps
F-Droid: https://f-droid.org/es/
F-Droid es un catálogo instalable de aplicaciones FOSS (Software Libre y de Código Abierto) para la plataforma Android.
Aurora Store: https://aurorastore.org/ Aurora Store es una alternativa gratuita de Google Play Store donde puedes descargar aplicaciones, actualizar las aplicaciones que ya tienes, recibir detalles sobre los rastreadores en la aplicación, ocultar tu ubicación, buscar aplicaciones y hacer mucho más.
Gestionar actualizaciones de nuestras APPS
Obtanium: https://github.com/ImranR98/Obtainium
Obtainium nos permite instalar y actualizar aplicaciones directamente desde sus páginas de versiones, y recibir notificaciones cuando las nuevas versiones estén disponibles.
Gestor de contraseñas
Lo ideal es que gestionemos nosotros la base de datos de las contraseñas en lugar de cederla (aunque encriptada) a una empresa.
Por supuesto esto implica la responsabilidad de realizar copias de seguridad recurrentemente para evitar la perdida de las contraseñas.
Tenemos dos opciones:
-
Alojar el servicio en un servidor casero
- Vaultwarden: https://github.com/dani-garcia/vaultwarden
-
Usar una app offline (todo en local dentro de nuestro dispositivo)
- Keepass: https://www.keepassdx.com/
2FA tokens de verificación
Aegis Authenticator: https://github.com/beemdevelopment/Aegis
Todo se guarda en local, IMPORTANTE guardar el código de recuperación que te da cada servicio cuando se crea el token 2FA (a mi me gusta apuntarlo en una libreta) y CREAR BACKUPS de la bóveda de Aegis y GUARDARLOS en otro dispositivo.
Sincronizar entre dispositivos
Syncthing: https://github.com/syncthing/syncthing
Syncthing es una aplicación que le permite sincronizar sus archivos en múltiples dispositivos. Esto significa la creación, modificación o eliminación de archivos en uno la máquina se replicará automáticamente en sus otros dispositivos.
Debido a que la app Syncthing ha dejado de dar soporte en Android (https://forum.syncthing.net/t/discontinuing-syncthing-android/23002), hemos encontrado este fork:
Syncthing-Fork: https://github.com/Catfriend1/syncthing-android
Multimedia
-
NewPipe: https://newpipe.net/
App para ver videos de youtube de manera privada, sin iniciar sesión podemos seguir los canales, sin anuncios, reproducción del audio con el móvil bloqueado...
-
RiMusic: https://rimusic.xyz/
Una aplicación para Android de código abierto y multilingüe para reproducir música de YouTube Music
-
AntennaPod: https://antennapod.org/
AntennaPod es un reproductor de podcast completamente abierto. La aplicación es software libre y puedes suscribirte a cualquier canal RSS.
Mapas
App de búsqueda:
GMaps WV: https://github.com/Divested-Mobile/Maps Es una app WebView para usar Google Maps sin exponer su dispositivo.
En GMaps WV podremos buscar el lugar donde queremos ir (también vale para buscar restaurantes y sus reseñas), sin embargo no se podrá usar como navegador. Para esto tenemos dos buenas alternativas:
Apps de navegación:
-
Organic Maps: https://organicmaps.app/es/
-
OsmAnd: https://osmand.net/
Pero todos sabemos que el mejor buscador de lugares es Google, entonces tenemos que combinar ambas herramientas para beneficiarnos de sus resultados sin comprometer nuestra privacidad:
¿Como usarlas de manera conjunta? Buscaremos el lugar donde queremos ir en GMaps WV, le daremos a "compartir" y seleccionaremos la app de navegación que tengamos (Organic Maps o OsmAnd). Seguidamente se abrirá la app con el lugar seleccionado en GMaps WV y ya podremos iniciar la navegación.
Notificaciones
You Have Mail: https://f-droid.org/packages/dev.lbeernaert.youhavemail/
App para notificaciones de email sin Google Play Services Se recomienda tener el 2FA en el servicio de mail ya que deberemos introducir la contraseña en la app You Have Mail para poder recibir las notificaciones.
Verificar autenticidad de las apps
AppVerifier: https://github.com/soupslurpr/AppVerifier
Es un visor y verificador de hash de certificados de firma de aplicaciones. Te permite verificar fácilmente que tus aplicaciones son genuinas con otros.
Tutorial: https://inv.nadeko.net/watch?v=IkrujqcM-9Y
-
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 9ff58691:0bf6c134
2024-11-14 06:43:38
@ 9ff58691:0bf6c134
2024-11-14 06:43:38Общественный транспорт Кургана претерпел значительные изменения. На смену традиционным автобусам пришли современные электронные модели, а система каршеринга предоставляет жителям доступ к парку экологичных электромобилей. Эти нововведения не только повышают комфорт и мобильность, но и способствуют созданию более чистой и устойчивой городской среды.
Электронные автобусы, курсирующие по маршрутам Кургана, оснащены просторными салонами с удобными сидениями, USB-зарядками для гаджетов и бесплатным высокоскоростным Wi-Fi. Благодаря электрическим двигателям, поездки стали практически бесшумными, а выбросы вредных веществ в атмосферу сведены к минимуму. Маршруты электронных автобусов синхронизированы с мобильным приложением, что позволяет пассажирам точно планировать свои поездки. Расписание курсирования строго соблюдается, обеспечивая высокую надежность и предсказуемость общественного транспорта.
 Помимо обновленных автобусов, в Кургане активно развивается система каршеринга. Жители города могут арендовать современные электромобили по мере необходимости через мобильное приложение. Это решение особенно удобно для коротких поездок, когда личный автомобиль не требуется. Каршеринг позволяет сократить количество личных машин на дорогах, снизить нагрузку на окружающую среду и решить проблему парковочных мест в центре города.
Внедрение электронных автобусов и каршеринга - важный шаг в направлении создания более экологичной, комфортной и доступной городской среды в Кургане. Эти нововведения не только улучшают качество жизни жителей, но и способствуют устойчивому развитию города.
Помимо обновленных автобусов, в Кургане активно развивается система каршеринга. Жители города могут арендовать современные электромобили по мере необходимости через мобильное приложение. Это решение особенно удобно для коротких поездок, когда личный автомобиль не требуется. Каршеринг позволяет сократить количество личных машин на дорогах, снизить нагрузку на окружающую среду и решить проблему парковочных мест в центре города.
Внедрение электронных автобусов и каршеринга - важный шаг в направлении создания более экологичной, комфортной и доступной городской среды в Кургане. Эти нововведения не только улучшают качество жизни жителей, но и способствуют устойчивому развитию города.

"Мы очень гордимся тем, что Курган стал одним из первых городов в России, внедривших современные решения в сфере общественного транспорта. Переход на электронные автобусы и развитие системы каршеринга - это важные шаги в направлении создания более экологичной, комфортной и доступной городской среды. Электронные автобусы не только значительно снижают выбросы вредных веществ, но и обеспечивают пассажирам высокий уровень комфорта. Бесшумный ход, USB-зарядки, Wi-Fi - все это делает поездки более приятными и продуктивными. Синхронизация с мобильным приложением позволяет жителям точно планировать свои маршруты и передвижения по городу. Каршеринг, в свою очередь, решает сразу несколько важных задач. Во-первых, он снижает нагрузку на дороги и потребность в парковочных местах, особенно в центральной части города. Во-вторых, это экономичное и экологичное решение для коротких поездок, когда личный автомобиль не требуется. И, наконец, каршеринг повышает мобильность и доступность транспорта для всех жителей. Мы уверены, что эти нововведения сделают Курган более комфортным, экологичным и современным городом для жизни. Это важный шаг в реализации нашей стратегии по развитию устойчивой городской инфраструктуры." – поделился мэр города Курган.
Автор: София Багирова
-
 @ a6b4114e:60d83c46
2024-11-14 04:55:27
@ a6b4114e:60d83c46
2024-11-14 04:55:27Pure Sniper is an epic sniper shooting game. Here you will experience an exciting and challenging mission to compete with opponents from around the world. Whether you like to play the game solo offline or engage in real-time multiplayer battles online, both options are available here.
In the latest game, you can participate in multiple battlegrounds.
Its versatile gameplay will never make you feel bored while playing, instead, its appealing 3D design will make you addicted to this game. The diverse range of missions, multiple battlegrounds, and regular special events is designed in such a way that you will never feel short of challenges.
-
 @ 59f0660b:d5d24440
2024-11-14 03:46:53
@ 59f0660b:d5d24440
2024-11-14 03:46:53HELLO 👋 nostr:#NOSTR & nostr:#YAKIHONNE FAMILY
ANOTHER BEAUTIFUL DAY
WELCOME BROTHER ‡ ALL THE WAY FROM TANZANIA 🇹🇿.
-
 @ a012dc82:6458a70d
2024-11-14 03:08:55
@ a012dc82:6458a70d
2024-11-14 03:08:55Table Of Content
-
The Economics Behind Bitcoin ATMs
-
Factors Influencing Bitcoin ATM Adoption
-
Conclusion
-
FAQ
The world of finance has experienced a significant transformation with the advent of cryptocurrencies. Bitcoin, the first and most popular cryptocurrency, has revolutionized the way we perceive and transact with money. As the adoption of Bitcoin continues to grow, various technological advancements have emerged to facilitate its usage. One such innovation is the Bitcoin Automated Teller Machine (ATM). In this article, we will explore the role of economics in the adoption of Bitcoin ATMs, analyzing the impact on the financial landscape, consumer behavior, and overall market dynamics.
The Economics Behind Bitcoin ATMs
Understanding Supply and Demand Dynamics
Bitcoin ATMs serve as physical touchpoints for users to buy or sell Bitcoin using traditional currencies. The presence of Bitcoin ATMs in a region is heavily influenced by the economics of supply and demand. When demand for Bitcoin rises in a particular area, entrepreneurs and businesses have an economic incentive to install Bitcoin ATMs to cater to this demand. Conversely, in areas with low demand, the installation of Bitcoin ATMs might not be financially viable.
Impact on Local Economies
The presence of Bitcoin ATMs can have a profound impact on local economies. By providing easy access to Bitcoin, these ATMs promote financial inclusivity and enable individuals to participate in the cryptocurrency ecosystem. This increased accessibility encourages entrepreneurship and fosters innovation within the local economy. Additionally, Bitcoin ATMs often charge transaction fees, which generate revenue for the machine owners and contribute to the local economy.
Factors Influencing Bitcoin ATM Adoption
Technological Infrastructure
The adoption of Bitcoin ATMs is heavily influenced by the technological infrastructure of a region. Bitcoin ATMs rely on a stable internet connection and other supporting technologies to function seamlessly. Areas with robust technological infrastructure are more likely to witness higher adoption rates of Bitcoin ATMs.
Regulatory Environment
The regulatory environment surrounding cryptocurrencies plays a crucial role in the adoption of Bitcoin ATMs. Clear and favorable regulations provide certainty to businesses and individuals, facilitating the installation and operation of Bitcoin ATMs. Conversely, strict regulations or uncertain legal frameworks can deter entrepreneurs from entering the market and limit the proliferation of Bitcoin ATMs.
Market Demand and Consumer Behavior
The demand for Bitcoin and the willingness of consumers to adopt cryptocurrencies significantly impact the installation of Bitcoin ATMs. Consumer behavior is influenced by factors such as trust, convenience, and perceived value. As awareness and acceptance of cryptocurrencies increase, the demand for Bitcoin ATMs rises, resulting in wider adoption.
Conclusion
The role of economics in the adoption of Bitcoin ATMs cannot be understated. The economics of supply and demand, along with technological infrastructure and regulatory environments, shape the landscape for Bitcoin ATM proliferation. These ATMs play a vital role in promoting financial inclusivity, generating revenue, and facilitating convenient access to cryptocurrencies. As the world embraces cryptocurrencies and their potential, the future of Bitcoin ATMs holds immense promise in revolutionizing financial transactions globally.
FAQs
How do Bitcoin ATMs work? Bitcoin ATMs function similarly to traditional ATMs, but instead of dispensing cash, they facilitate the buying or selling of Bitcoin. Users can insert cash into the machine, which is then converted into Bitcoin and transferred to their digital wallets. Alternatively, users can also sell Bitcoin and receive cash from the ATM.
Are Bitcoin ATMs secure? Bitcoin ATMs are designed with security measures to protect user transactions. They often utilize encryption and authentication protocols to ensure the safety of funds. However, it's essential for users to follow best practices, such as securing their digital wallets and using strong passwords, to further enhance their security.
Are there fees associated with Bitcoin ATMs? Yes, Bitcoin ATMs typically charge fees for transactions. These fees cover the costs of operating and maintaining the machines. The fee structure can vary depending on the operator and location of the ATM.
Are Bitcoin ATMs accessible globally? Bitcoin ATMs are available in many countries worldwide. However, their availability and adoption vary from region to region. Countries with higher cryptocurrency adoption rates and favorable regulatory environments tend to have a greater number of Bitcoin ATMs.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 6316050a:a5e43cbe
2024-11-14 03:02:58
@ 6316050a:a5e43cbe
2024-11-14 03:02:58Contexto
En el Grupo de Teoría y Simulación en Materia Blanda estudiamos sistemas poliméricos, interfaces y sistemas coloidales a escala nanoscópica. Estos pueden estar en equilibrio o presentar flujo de partículas o calor y son de interés en ciencia básica y aplicada en campos como micro y nano-fluídica, aplicaciones a transferencia de calor y máquinas moleculares. Una característica central es que la temperatura juega un rol importante y existe una competencia entre entropía y energía. Esto suele dar lugar a transiciones de fases u otros cambios cualitativos del comportamiento del sistema.
Herramientas
Usamos simulación computacional y herramientas teóricas, con énfasis en conceptos de mecánica estadística, que permiten estudiar variados sistemas en diferentes situaciones físicas. Estudiamos a estos sistemas en condiciones de equilibrio termodinámico o también cómo es su comportamiento cuando se inducen flujos o se los somete a campos externos. (fuera de equilibrio)
Temas propuestos para Tesis de Licenciatura en Física
Simulación de transferencia de calor en nanocanales con paredes modificadas por polímeros

Los fenómenos de transferencia de calor tienen una gran importancia en un amplísimo rango de aplicaciones como por ejemplo, los procesos de generación y conversión de energía. Además, son cruciales para el enfriamiento de motores y dispositivos electrónicos. Estas aplicaciones requerirán en el futuro un funcionamiento a mayor densidad de energía, y por lo tanto, mayor generación de calor, que deberá ser removido más eficientemente. En particular, los fenómenos de cambio de fases, como la ebullición nucleada, tienen aplicaciones en plantas de potencia eléctrica, desalinización térmica, enfriamiento de chips electrónicos y recuperación de calor desechado, entre muchas otras. Uno de los desafíos más importantes para continuar la reducción de tamaño de los dispositivos electrónicos es umentar su densidad de potencia de operación es lograr una extracción eficiente del calor generado. La transferencia de cals relevante también en aplicaciones aescalasespaciales mayores, como en la generación de energía eléctrica en centrales térmicas y nucleares. En las centrales nucleares de generación IV es necesario aumentar el calor transportado por unidad de tiempo y mejorar la eficiencia de los intercambiadores de calor.
Se propone estudiar la transferencia de calor en un nanocanal que presenta una interfaz líquido vapor. Queremos entender los detalles de cómo cambian con el tiempo las características de la evaporación de una interfaz y las condicions cuando se modifica la pared con polímeros u otras moléculas en el seno del líquido. Realizaremos simulaciones de dinámica molecular en clusters de supercómputo para estudiar estos sistemas en distintas condiciones físicas.
Contacto: Claudio Pastorino (claudiopastorino .... cnea.gob.ar ; IG, X: @clopasto; Nostr: @clopasto
Dinámica de moléculas anulares en polirotaxanos, inducida por gradientes térmicos

Los polirotaxanos, son agregados macromoleculares compuestos por múltiples moléculas cíclicas enhebradas en una cadena polimérica con grandes grupos terminales en sus extremos, que impiden la salida de los anillos. Junto con otras MIMs (Mechanically Interlocked Molecules/) son los elementos constitutivos importantes de las denominadas máquinas moleculares. Estos mecanismos moleculares pueden tomar energía del ambiente para generar movimientos dirigidos y disipación de calor. Es decir, funcionar como motores y bombas nanoscópicas., eque transforman una entrega de energía entrabajo mecánico (y, por supuesto, calor). Estás notables propiedades mecánicas hacen que los polirotaxanos sean muy promisorios industrial y tecnológicamente y sistemas fascinantes para estudiar por simulación computacional en el contexto de máquinas moleculares.
Se propone estudiar la dinámica y agregación de dos o mas anillos moleculares cuando se induce en el polímero un flujo de calor que da lugar a un gradiente térmico. Se utilizarán simulaciones dee dinámica moelecular fuera de equilibrio para estudiar este sistema. Se espera explorar en gran detalles espacial cómo se comportan los anillos en función del gradiente térmico. , analizando tantos estados estacionarios como dependendientes del tiempo. En su versión más simple, por ejemplo , se puede poner los extremos del polímero a dos temperaturas para inducir un a zona "fría " del polímero y una más caliente. Los anillos tenderán a desplazarse a la zona fría , reduciendo la energía cinética total del sistema. Pensando en diseños experimentales esto podría realizarse con lasers que inyecten energía en los extremos del polirotaxano y que esto permite mover y posicionar los anillos a escala nanoscópica.
Contacto: Claudio Pastorino (claudiopastorino .... cnea.gob.ar). IG, X, Nostr: @clopasto
¿Qué se aprenderá en la Tesis?
Estas línea de trabajo es teórico-numérica , con una parte importante de simulación computacional. Involucra principalmente conceptos de: * Mecánica estadística (Física Teórica 3 en DF-UBA), * Materia condensada en general y materia blanda. * Fundamentos y uso de simulación computacional: Dinámica Molecular, y /o Monte Carlo, * Se estudia a los sistemas en escalas espaciales y temporales relativamente grandes (mesoscópicas), * No se requieren conocimientos previos de computación, pero sí interés en el uso y creación de programas, para obtener propiedades de los sistemas físicos. * Se trabajará con : * Linux, Python, Bash, Awk. * Programas corriendo en clusters de super-cómputo. High Performance Computing (HPC) * Herramientas de posprocesamiento.
-
 @ bcea2b98:7ccef3c9
2024-11-14 00:42:08
@ bcea2b98:7ccef3c9
2024-11-14 00:42:08Sometimes we come across values that resonate deeply only after going through certain experiences. These values may not have been obvious to us earlier, but now they play a meaningful role in how we approach life.
Is there a value you’ve discovered later in life that’s become important to you?
originally posted at https://stacker.news/items/766754
-
 @ 8d34bd24:414be32b
2024-11-13 22:45:38
@ 8d34bd24:414be32b
2024-11-13 22:45:38Yesterday I was doing my Revelation Bible study and the author told us to look back at Jeremiah 25 to see how it related to what we were studying in Revelation 15 & 16. She only referred to a couple of verses, but I read more to get context because I was having trouble seeing what point she was trying to make. When I read Jeremiah 25, it reminded me of Ezekiel 38 and sounded a lot like what is happening in the Middle East and the world today. This article is my attempt to investigate this idea and organize my thoughts and share it with you.
I do have some comments regarding prophecy and the current Israeli/Palestine/etc. conflict that may be divisive, but I hope my use of the Bible to explain God’s plan will help people understand what is currently going on a bit better and without the rancor and bias coming from the media today. It should also help us to understand why it seems the whole world has turned against Israel and why nobody protests or shows solidarity with Israel when they are attacked in the most horrific ways.
Let’s see what Jeremiah 25 has to say:
‘Then it will be when seventy years are completed I will punish the king of Babylon and that nation,’ declares the Lord, ‘for their iniquity, and the land of the Chaldeans; and I will make it an everlasting desolation. (Jeremiah 25:12)
Since God declared after the 70 year exile of Judah in Babylon to destroy Babylon and to make it “an everlasting desolation,” then it seems unlikely that Babylon the Great in Revelation is historical Babylon. It has been destroyed and God promised that it would be an everlasting desolation. Who could Babylon the Great be if it isn’t actual Babylon? I am beginning to have my unpleasant theories, but I won’t go into that here.
I will bring upon that land all My words which I have pronounced against it, all that is written in this book which Jeremiah has prophesied against all the nations. (For many nations and great kings will make slaves of them, even them; and I will recompense them according to their deeds and according to the work of their hands.)’ ”
For thus the Lord, the God of Israel, says to me, “Take this cup of the wine of wrath from My hand and cause all the nations to whom I send you to drink it. They will drink and stagger and go mad because of the sword that I will send among them.” (Jeremiah 25:13-16)
God then promises “many nations and great kings” that made slaves of Judah/Israel, that God will “recompense them according to their deeds.”
Compare that to Revelation 14 and 16:
Then another angel, a third one, followed them, saying with a loud voice, “If anyone worships the beast and his image, and receives a mark on his forehead or on his hand, he also will drink of the wine of the wrath of God, which is mixed in full strength in the cup of His anger; and he will be tormented with fire and brimstone in the presence of the holy angels and in the presence of the Lamb. (Revelation 14:9-10)
and
Then the third angel poured out his bowl into the rivers and the springs of waters; and they became blood. And I heard the angel of the waters saying, “Righteous are You, who are and who were, O Holy One, because You judged these things; for they poured out the blood of saints and prophets, and You have given them blood to drink. They deserve it.” (Revelation 16:4-6)
In the same way Revelation promises God’s wrath on those who rejected Him and on those who persecuted His followers, and that He would force them to drink the cup of His wrath, Jeremiah 25 says he will force them to drink of “this cup of the wine of wrath from my hand.” Those who reject God and Jesus, as well as those who mistreat Israel/Jews and Christians, will receive God’s overwhelming wrath.
In this passage, God says, “They will drink and stagger and go mad because of the sword that I will send among them.” It seems that today, the whole world has gone mad at Israel defending itself and it is causing the whole world to turn against God’s chosen people, Israel.
I also receive great comfort from these verses thanks to the addition of “They deserve it.” There is so much injustice in the world, I love seeing that those who are evil and cause harm will be punished because “They deserve it.”
Then I took the cup from the Lord’s hand and made all the nations to whom the Lord sent me drink it: Jerusalem and the cities of Judah and its kings and its princes, to make them a ruin, a horror, a hissing and a curse, as it is this day; Pharaoh king of Egypt, his servants, his princes and all his people; and all the foreign people, all the kings of the land of Uz, all the kings of the land of the Philistines (even Ashkelon, Gaza, Ekron and the remnant of Ashdod); Edom, Moab and the sons of Ammon; and all the kings of Tyre, all the kings of Sidon and the kings of the coastlands which are beyond the sea; and Dedan, Tema, Buz and all who cut the corners of their hair; and all the kings of Arabia and all the kings of the foreign people who dwell in the desert; and all the kings of Zimri, all the kings of Elam and all the kings of Media; and all the kings of the north, near and far, one with another; and all the kingdoms of the earth which are upon the face of the ground, and the king of Sheshach shall drink after them. (Jeremiah 25:17-26) {emphasis of nations is mine}
Let’s see if the nations listed seem to match with the nations turning against Israel today. I did research online1 and came up with these matches (some are clear and some are possibly what was mentioned and are marked with a “?”:
This looks like most of the nations turning against Israel and most of the nations on this list have become very aggressive against and/or speaking evil of Israel. I never thought of Jeremiah as predicting end times events, but it seems it probably is.
“You shall say to them, ‘Thus says the Lord of hosts, the God of Israel, “Drink, be drunk, vomit, fall and rise no more because of the sword which I will send among you.” ’ And it will be, if they refuse to take the cup from your hand to drink, then you will say to them, ‘Thus says the Lord of hosts: “You shall surely drink! For behold, I am beginning to work calamity in this city which is called by My name, and shall you be completely free from punishment? You will not be free from punishment; for I am summoning a sword against all the inhabitants of the earth,” declares the Lord of hosts.’ (Jeremiah 25:12-38)
The UN just voted overwhelmingly to force Israel to leave what they call occupied Palestinian territories like the Gaza Strip and the West Bank, even though Israel only occupies them because of aggression in 1967 against them by Egypt, Jordan, Syria, and the Palestinians. These nations and people originally tried to block the Jordan river from providing water to Israel, bombed civilians (just like today), and then tried to block all shipping to Israel. When Israel tried to renew shipping, they all out attacked Israel. Israel came out the clear winner and gained a small amount of land in the West Bank, the Gaza Strip, and the Sinai Peninsula. Although the UN, at the time, said Israel rightly owned these lands since they were not the aggressors, now the UN is reneging on that promise. Israel voluntarily gave back the Sinai peninsula to Egypt as part of a peace agreement. They willingly allowed the Palestinians back into the West Bank and Gaza under semi-autonomous rule, but these lands were used primarily to attack Israel repeatedly because the Muslim nations aren’t trying to save the Palestinians. They are trying to wipe Israel off the map and take “the river to the sea,” which means 100% of Israel. Interestingly, God promised “Every place on which the sole of your foot treads shall be yours; your border will be from the wilderness to Lebanon, and from the river, the river Euphrates, as far as the western sea.” (Deuteronomy 11:24) This cry from the Muslims is a direct demonic attack on God’s promise to Israel.
Ironically before the Six Days War, the Palestinians in the West Bank were under Syrian control (they’ve never, at least in modern times, had their own nation) and Hussein of Syria put them under martial law because he feared they might overthrow him. These nations that use the Palestinian plight as an excuse to do horrific actions against Israel don’t actually like or care about the Palestinian people. They are just pawns used to justify their actions against Israel. The Palestinians were treated just as bad, if not worse by the Syrians.
The UN resolution also calls for the Israelis to leave East Jerusalem, the “city which is called by My name.” Because of their actions, God promises “You will not be free from punishment; for I am summoning a sword against all the inhabitants of the earth.” God is going to drag the anti-Israel and anti-God nations into conflict in order to punish them.
This also reminds me a lot of Ezekiel 38:
And the word of the Lord came to me saying, “Son of man, set your face toward Gog of the land of Magog, the prince of Rosh, Meshech and Tubal, and prophesy against him and say, ‘Thus says the Lord God, “Behold, I am against you, O Gog, prince of Rosh, Meshech and Tubal. I will turn you about and put hooks into your jaws, and I will bring you out, and all your army, horses and horsemen, all of them splendidly attired, a great company with buckler and shield, all of them wielding swords; Persia, Ethiopia and Put with them, all of them with shield and helmet; Gomer with all its troops; Beth-togarmah from the remote parts of the north with all its troops—many peoples with you. (Ezekiel 38:1-6) {emphasis of nations & highlighted verse is mine}
These nations seem to overlap with those mentioned in Jeremiah 25, but aren’t quite as extensive.2
Ezekiel 38 also talks about these nations being dragged into conflict. It says, “I will turn you about and put hooks into your jaws, and I will bring you out.”
“Be prepared, and prepare yourself, you and all your companies that are assembled about you, and be a guard for them. After many days you will be summoned; in the latter years you will come into the land that is restored from the sword, whose inhabitants have been gathered from many nations to the mountains of Israel which had been a continual waste; but its people were brought out from the nations, and they are living securely, all of them. You will go up, you will come like a storm; you will be like a cloud covering the land, you and all your troops, and many peoples with you.” (Ezekiel 38:7-9)
This continuation in Ezekiel 38 says these nations will be brought into conflict with Israel after Israel “will come into the land that is restored from the sword, whose inhabitants have been gathered from many nations to the mountains of Israel which had been a continual waste; but its people were brought out from the nations, and they are living securely, all of them.” This prophecy of Israel has happened with Israel being reconstituted as a nation and the Jewish people coming from nations all around the world after having been perilously attacked with the sword, i.e. Nazi Germany. They are now a successful and prosperous nation, but the nations around them are gathering to attack them. Israel has not yet been covered by troops “like a cloud covering the land,” but has been covered “like a cloud covering the land” by a bombardment of rockets, drones, and missiles shot by Iran (Persia).
‘Thus says the Lord God, “It will come about on that day, that thoughts will come into your mind and you will devise an evil plan, and you will say, ‘I will go up against the land of unwalled villages. I will go against those who are at rest, that live securely, all of them living without walls and having no bars or gates, to capture spoil and to seize plunder, to turn your hand against the waste places which are now inhabited, and against the people who are gathered from the nations, who have acquired cattle and goods, who live at the center of the world.’ Sheba and Dedan and the merchants of Tarshish with all its villages will say to you, ‘Have you come to capture spoil? Have you assembled your company to seize plunder, to carry away silver and gold, to take away cattle and goods, to capture great spoil?’ ” ’
“Therefore prophesy, son of man, and say to Gog, ‘Thus says the Lord God, “On that day when My people Israel are living securely, will you not know it? You will come from your place out of the remote parts of the north, you and many peoples with you, all of them riding on horses, a great assembly and a mighty army; and you will come up against My people Israel like a cloud to cover the land. It shall come about in the last days that I will bring you against My land, so that the nations may know Me when I am sanctified through you before their eyes, O Gog.” (Ezekiel 38:10-16) {emphasis mine}
It is interesting to note that for most of Israel’s history, there wasn’t much plunder to seize, but recently they have found great natural gas reserves that are envied by nations like Iran and Russia.
It is also interesting to see how the Jews from around the globe keep moving to Israel, despite the danger, just as predicted in the Old Testament.
There are two things I am not certain about. Are these predictions the same, or will there be multiple attacks on the new Israel? I’ve always expected this attack on Israel to happen right before or right after the beginning of the tribulation, but Zechariah 14 sounds like it might be at the end of the tribulation because it mentions Jesus coming back.
As context the previous chapter ends:
They will call on My name,\ And I will answer them;\ I will say, ‘They are My people,’\ And they will say, ‘The Lord is my God.’ ” (Zechariah 13:9b)
The Jews were dispersed around the globe for almost 2,000 years, but God has called them back to the promised land and has promised to turn their hearts back to Him. (This hasn’t happened yet and probably won’t happen until the seven year tribulation.)
Behold, a day is coming for the Lord when the spoil taken from you will be divided among you. For I will gather all the nations against Jerusalem to battle, and the city will be captured, the houses plundered, the women ravished and half of the city exiled, but the rest of the people will not be cut off from the city. Then the Lord will go forth and fight against those nations, as when He fights on a day of battle. In that day His feet will stand on the Mount of Olives, which is in front of Jerusalem on the east; and the Mount of Olives will be split in its middle from east to west by a very large valley, so that half of the mountain will move toward the north and the other half toward the south. (Zechariah 14:1-4) {emphasis mine}
After Jesus’s resurrection, He spent time with His disciples preparing them and then ascended into heaven from the Mount of Olives. Two angels told those who had witnessed His ascension that Jesus would return in the same way, which is seconded by Zechariah, “In that day His feet will stand on the Mount of Olives.”
It is true according to Zechariah that not all Jews will be saved, but that Jesus will fight for His chosen people, despite all of their failings. God is merciful!
So then He has mercy on whom He desires, and He hardens whom He desires. (Romans 9:8)
Jeremiah 25 is accentuating God’s judgement rather than His mercy.
“Therefore you shall prophesy against them all these words, and you shall say to them,\ ‘The Lord will roar from on high\ And utter His voice from His holy habitation;\ He will roar mightily against His fold.\ He will shout like those who tread the grapes,\ Against all the inhabitants of the earth.\ A clamor has come to the end of the earth,\ Because the Lord has a controversy with the nations.\ He is entering into judgment with all flesh;\ As for the wicked, He has given them to the sword,’ declares the Lord.” (Jeremiah 25:30-31)
There will be a large group of nations that will gather in hate and attack Israel with what would be conventionally considered overwhelming force, but God will defend Israel.
In reality, I can already see the hand of God on Israel. A few weeks ago (sorry I’m terrible with dates) Iran (Persia) sent a barrage of rockets, drones, and missiles against Israel. Israel’s Iron Dome defense system was able to take out the majority of them and not one Israeli was killed by massive number of these being fired into densely populated civilian areas. An expert analyzed the data and said the system should not have been able to stop all of these coming at one time. None of the ones missed hit where people were. It was a miraculous protection of Israel.
Then a few weeks later, Israel retaliated. They sent 100 jets across several enemy, Muslim countries into Iran, took out Iran’s anti-aircraft and early warning systems, their missile storage facilities, and their missile and other weapons manufacturing plants and then returned home to Israel. Not one plane was shot down. Not one was touched. It reminds me of a time Jesus was visiting his hometown and offended the people with a story from Scripture. The people, his friends and family, were so offended they dragged Him to the edge of a cliff to toss him off to His death. Then Jesus just walked through the crowd and went on His way without anyone stopping Him. Israel’s retaliation against Iran felt like that, a miraculous protection of His chosen people.
Iran and the other nations mentioned in Ezekiel 38, and probably in Jeremiah 25, are having their satanic hate brought to light by their hate of Israel and they are being dragged by the nose into a battle that they can’t win because God fights for His chosen people, Israel.
Thus says the Lord of hosts,
“Behold, evil is going forth\ From nation to nation,\ And a great storm is being stirred up\ From the remotest parts of the earth.
“Those slain by the Lord on that day will be from one end of the earth to the other. They will not be lamented, gathered or buried; they will be like dung on the face of the ground. (Jeremiah 25:32-33)
Prophecy can be a bit tricky to understand, but by digging into all of the Bible and all of its prophecy I feel like I am understanding it better and better.
If anyone thinks I’m wrong, feel free to share Bible verses showing my error. I’m always seeking the truth.
Trust Jesus.\ \ your sister in Christ,
Christy
-
 @ af9d7040:42d05d35
2024-11-13 20:30:43
@ af9d7040:42d05d35
2024-11-13 20:30:43
奥斯瓦尔德:权力与生存法则中的不择手段
企鹅人奥斯瓦尔德·科布尔普特在哥谭市的生存方式,彻底展现了黑帮法则的残酷与无情。他毫不妥协、毫无底线。对他来说,存活下去不仅需要坚强的意志,更需要冷酷和狡猾。他可以为了达成目的而不择手段,甚至在关键时刻毫不犹豫地出卖他最亲密的人——包括对他影响深远的母亲。企鹅人对母亲的依恋和渴望,带着一种病态的执念。他的不择手段,除了生存需求,更是一种根深蒂固的自私所致。
在哥谭市的黑暗中打拼,企鹅人不断操纵、欺骗和复仇,像一条在阴影中游走的毒蛇,精通黑帮规则中的弱肉强食。他的每一个成就都建立在对人性的无视与对权力的渴望上。尽管他表面上表现出对母亲的依赖与“忠诚”,实际上,这不过是自私本性的一种表现。只要母亲能提供安全感,他便表现出孝顺;而当她成为权力路上的负担时,他则会毫不犹豫地抛弃她。企鹅人复杂病态的矛盾让他成为一个既让人爱恨交织、又难以简单同情的角色。
这种病态与矛盾,让企鹅人有别于其他典型的黑帮角色。他的冷酷与自私是根深蒂固的自我保护。他可以轻易地利用甚至背叛最亲近的人,所谓的“忠诚”不过是自我中心主义的伪装。这样的伪装使得企鹅人尽管身处黑帮世界,却比身边的角色更加孤独和疏离。他是真正的反英雄,一个不值得信任的角色,对最亲近的人也毫无依恋,甚至在关键时刻不惜利用他们。

索菲亚:冰冷现实中的温柔刺痛
在女主角索菲亚的对比之下,企鹅人阴冷的本性显得更加鲜明。她与企鹅人一样身处哥谭市的阴影中,但她保留了某种纯真与善意。索菲亚尽管也具备病态的一面,但这种病态是后天形成的,带有一种温柔的成分;她内心纯朴而坚韧,对他人仍保有真实的关怀。相比之下,企鹅人从内到外都冷酷而自私。他的邪恶已融入灵魂深处,与其说是因环境所迫,不如说是其本性使然。索菲亚在泥泞中挣扎,但依旧保留了善意,而企鹅人则完全不同,他的冷酷早已融入生活中的每一个选择与行动。
索菲亚的存在如同一股暗流,让企鹅人看起来更加冷酷无情。她仿佛是一道偶尔照进企鹅人阴暗世界的微光,但始终无法驱散他内心的阴霾,最终,他彻底沉沦回归黑暗。索菲亚的温柔与善意,反而衬托出企鹅人的病态自私,使他的冷酷无情愈加显著。

权力与孤独的悖论
企鹅人所代表的孤独,并非只是哥谭市的阴暗,而是一种对权力的近乎悲哀的依赖。他对权力的渴望与对安全感的执着,如同双重枷锁般困住他。即便在权力巅峰俯视这座城市,他依旧逃不出内心深处的孤独。他对母亲的依恋,不过是自私的另一种表现,真正的温情对他来说从未存在过。冷酷自私并非一时选择,而是内心根深蒂固的本能。这种孤独与对权力的迷恋,最终将他引向不可逆的深渊。
这部剧集没有给观众提供对错的答案,也未试图美化任何一方。企鹅人和索菲亚的关系、他们在权力之路上付出的代价、经历的伤害和背叛,似乎都是生活的无奈。哥谭市这片“废墟”般的舞台上,每个角色都在演绎属于自己的选择与代价。

漂泊中的孤独美学
影片通过冷色调的视觉风格,将哥谭市刻画成了一片死寂之地,喧嚣只是掩盖真实荒凉的假象。视觉上的孤寂,配合缓慢铺展的叙事节奏和偶尔悠长的寂静,使观众在不知不觉中感受到企鹅人内心的挣扎。这条权力之路起步于他对哥谭市的偏执依恋,随着情节推进,他在绝对黑暗中逐渐失去了所有温情。剧本的零散与低沉的配乐,将他的成长历程描绘成一首形散而神不散的孤独诗歌。
在这种孤独中,导演并未试图简单地将企鹅人定义为正义或邪恶。剧本如同生活本身般零碎,通过哥谭市平民窟与富人区的对比,构筑出一种模糊的精神边界。在这座“废墟”般的哥谭市,有人选择漂泊,有人选择定居,而企鹅人则徘徊、挣扎,寻找一个模糊的归宿。整部剧集的节奏与镜头语言,使观众仿佛置身一段忧伤的钢琴曲中,在哥谭市的荒凉街头行走。

在黑暗中前行
《企鹅人》这部作品的魅力,不仅在于它对反英雄的刻画,还在于对角色内心的深挖。企鹅人辗转跌宕的黑帮人生与他对哥谭市的依恋相互交织,像极了那些试图在失落之地寻找归属的人。而索菲亚的冷静与仅存的温情,像是一把温柔的利刃,不断刺穿企鹅人对权力与孤独的幻想。
在这条充满犯罪与权力交织的道路上,企鹅人并没有飞速崛起,而是一步步逼近深渊。导演通过缓慢、逼迫式的节奏,让企鹅人看似渐入权力之巅,却始终逃不开孤独的枷锁。《企鹅人》触动了成年人的无力感。它告诉你,世界不会因为妥协而变得更友善,你只能在黑暗中摸索前行,甚至与黑暗达成和解。
@Shaun 写于 2024年11月13日
-
 @ 7fed6817:3dac63ff
2024-11-13 19:26:29
@ 7fed6817:3dac63ff
2024-11-13 19:26:29Il video analizza il profondo malcontento generazionale riguardo al panorama lavorativo attuale, focalizzandosi sulle difficoltà che ostacolano il raggiungimento di una vita appagante per i giovani. Ecco i punti chiave emersi:
-
Il Trapianto del Sogno: La promessa tradizionale di lavoro stabile, pensioni garantite e serenità economica si scontra con la realtà di un futuro incerto. L'inflazione galoppante erode il valore del denaro, rendendo vano il sacrificio di anni di duro lavoro per una pensione che non assicura più benessere materiale. La generazione Z, invece di nutrire fiducia nel sistema tradizionale, cerca alternative, spesso intraprendendo strade rischiose come dropshipping, criptovalute e corsi online "Red Pill", attratta dal fascino del "sogno" di libertà e successo immediato, pur consapevole dei rischi.
-
Il Dilemma Blue Collar: Sebbene i lavori manuali offrano utilità tangibile (costruire case, riparare tubature), il costo a livello fisico è elevato e la remunerazione spesso non giustifica lo sforzo, soprattutto nelle grandi città dove anche 40k all'anno risultano insufficienti per una vita agiata. La prospettiva di sacrificare salute e tempo per un guadagno precario genera frustrazione.
-
L'Urgenza di Reinventare Se Stessi: Il video non propone la pigrizia, ma l'esigenza di flessibilità e reinvenzione costante. L'invito è a coltivare skill attraenti, esplorare diversi campi lavorativi e bilanciare lavoro e tempo libero per costruire memorie significative. La chiave è non rimanere bloccati in ruoli statici, ma abbracciare la crescita personale e professionale come unica garanzia di successo futuro.
-
Il Tempo Libero Come Risorsa Preziosa: Il video sottolinea l'importanza di valorizzare il tempo libero, sempre più prezioso con l'aumentare dell'età e delle responsabilità. È fondamentale utilizzarlo per attività stimolanti, hobby, relazioni e cura di sé, creando un patrimonio di esperienze che arricchiscono la vita oltre al mero guadagno materiale.
In sintesi, l'articolo evidenzia come la generazione Z si trovi di fronte a una realtà lavorativa complessa e sfidante. La critica al sistema tradizionale non è passiva, ma spinge verso una riflessione attiva: reinventare se stessi, sfruttare il tempo libero e costruire un futuro basato su flessibilità, crescita personale e esperienze significative.
-
-
 @ 6bae33c8:607272e8
2024-11-13 17:22:11
@ 6bae33c8:607272e8
2024-11-13 17:22:11I went 4-1 again last week, so apparently this process of writing out my random thoughts on these games and assigning numbers is working. It’s better than the grid version from last year because that was too restrictive. More free-flowing is how you get in sync with the league.
I’m 8-2 over the last 10 and 21-9 over the last 30. Still drawing dead in the overall, but very much alive for Q3, even if I still need to go 9-1 probably.
I’m putting the paywall here not because I’ve now got the gift of prophecy (which could easily go away) but because I want to give the paying subs something the free ones don’t have.
Indigenous Peoples at Eagles — American friend of ours in Lisbon doesn’t celebrate Thanksgiving I just found out, instead calls it Indigenous Peoples Day. That’s fine, but my beef is with her ignoring the indigenous peoples those indigenous peoples surely killed before the European settlers killed them. I mean surely it wasn’t all kumbayah among the tribes. You probably have to go back 10 or 20 tribes of indigenous peoples to find the ones who were just there originally and got killed by other tribes. And even they were probably no angels. Anyway, I digress. I’ll make it Killer Redskins™ +2.5 and stay away on Thursday night.
Packers at Bears — The Bears killed us in Survivor this week (literally), and I wouldn’t have taken them if I had any idea how bad Caleb Williams was. It was likely Danny Dimes out there. Get rid of the fucking ball! In any event, I’ll say Packers -3.5 and lean Bears, but probably stay away.
Jaguars at Lions — There have been no huge lines this year and few even of double-digits, but I imagine we get one here. I’ll say Jaguars +16.5. I’d probably take the Lions anyway, but likely stay away.
Vikings at Titans — The Titans defense is okay, but the offense is pretty bad. Sam Darnold is looking more like his old self every week, and that is obviously not a good thing. I’ll say Vikings -3.5 and stay away.
Raiders at Dolphins — The Raiders are a trainwreck, and the Dolphins are playing better defensively. I’ll say Raiders +8.5 and probably stay away.
Rams at Patriots — I watched the Patriots last week and they didn’t just beat the Bears, they killed them. I’ll say Rams -2.5 and probably stay away. If anything I’d buy the Rams low.
Browns at Saints — The Saints have Alvin Kamara and a bunch of scrubs on offense, but the Browns have Jameis Winston throwing picks. I like selling the Saints off last week’s win though. I’ll say Browns plus 1.5 and consider taking them.
Colts at Jets — I guess they’re sticking with Joe Flacco. The Jets are a destroyed team too. I’ll say Colts +3 and maybe take the Jets. Have to think about it more.
Ravens at Steelers — The Ravens are in a different class than the Steelers, though often these rivalry games are tight. I’ll make it Ravens -2.5 and lay the wood.
Falcons at Broncos — The Falcons blew it last week, but Denver REALLY blew it. Denver has the better defense. I’ll say Falcons +2.5 and maybe take the Broncos.
Seahawks at 49ers — I’ve lost faith in Geno Smith, especially behind that abysmal line. It’s a divisional game which could be close, but I'll make it Seahawks +6 and lay the wood.
Chiefs at Bills — The Bills are better, the Chiefs are tougher. I’ll say Chiefs +3, probably lay the wood, but have to think about it more.
Bengals at Chargers — I’ll make this Bengals +2.5 as these are roughly equal teams. Probably a stay away for me, but if anything I’d take Cincy.
Texans at Cowboys — Micah Parsons will get to CJ Stroud, but the Cowboys offense is abominable without Dak Prescott. I’ll say Texans -6 and probably stay away.
-
 @ a901cbe4:bd85452f
2024-11-13 17:02:29
@ a901cbe4:bd85452f
2024-11-13 17:02:29From Pizza to Powerhouse: How Bitcoin Became a $90K Phenomenon
So, how did Bitcoin go from being used to buy two pizzas to crossing $90K? Here’s a quick dive into the secret sauce:
-
Crypto Goes Mainstream: Imagine telling your bank in 2010 that you wanted to buy Bitcoin. Fast forward to now, and they’re the ones begging you to HODL. Banks, corporations, and even the payment giants are jumping on the BTC train, legitimatizing what the OGs knew all along – Bitcoin is here to stay.
-
Inflation Hedge, But Make It Digital: Think of Bitcoin as digital gold but better. With global economies wobbling, people are clinging to BTC like it’s a life raft (spoiler: it might be). Gold’s nice, but can you transfer it across borders in seconds? Nope. Bitcoin’s inflation-proof and portable, the new gold standard for a digital world.
-
Institutional FOMO: Fear of Missing Out: Suddenly, everyone wants in. Billion-dollar funds, Wall Street titans, and big names that once sneered at Bitcoin now have BTC in their portfolios. The irony? Bitcoin was designed to get rid of these guys, but here they are, driving up demand and pumping up the price. Talk about poetic justice.
-
Fixed Supply, Unlimited Demand: Bitcoin’s secret weapon? There will only ever be 21 million BTC. It’s the hottest item with a one-time print run, and everyone wants a piece. Add in Bitcoin’s halving cycles, and you've got a perfect recipe for scarcity-driven price rockets.
Why $90K is More Than a Price: It’s a Wake-Up Call for the World
Bitcoin smashing $90K is like a big neon sign flashing “THE FUTURE IS HERE.” And the financial world? It’s on notice.
-
True Financial Freedom: Bitcoin lets people be their own bank, something you can’t say about your local branch. At $90K, Bitcoin is more than an investment – it’s a tool for individual empowerment. Anyone with Wi-Fi can HODL, no permission needed.
-
Potential Global Reserve Asset: The whispers have started: could Bitcoin be a reserve asset? Hitting $90K makes that less of a pipe dream and more of a “what if?” With every BTC milestone, central banks and institutions are rethinking how they store value. This could be the beginning of Bitcoin’s evolution from “rebellious outsider” to “global staple.”
-
Fueling the Future of Blockchain: Bitcoin isn’t just money; it’s the gateway to blockchain innovation. Now that BTC is breaking records, other decentralized projects have room to grow. Bitcoin’s rise could inspire entire industries to adopt blockchain tech in ways we’re only beginning to imagine.
Beyond $90K: Are We Eyeing $100K?
Here’s the deal: $90K is big, but if you’re thinking “this is it,” think again. The momentum is there, the hype is real, and $100K isn’t just a fantasy anymore. With every new HODLer, BTC breaks a bit further into the mainstream. This could be the start of something even bigger.
Long-term, Bitcoin’s story isn’t just about price. It’s about rewriting how we think about money, ownership, and freedom. And as BTC hits new highs, it’s proving to the world that maybe, just maybe, it’s here to change the game for good.
A Toast to the HODLers (and Future HODLers)
To everyone who’s been along for the ride, this $90K milestone is a well-earned victory. To the skeptics – we’re glad you’re here now! And if you’re thinking of joining us, there’s no time like the present.
So HODL on tight, buckle up, and get ready – Bitcoin at $90K is just the beginning. Here’s to $100K and beyond! 🌌
-
-
 @ 59f0660b:d5d24440
2024-11-13 16:58:58
@ 59f0660b:d5d24440
2024-11-13 16:58:58Yakihonne (often styled as YakiHonne) is a decentralized social network platform that combines elements of Nostr and Bitcoin technologies. Its focus is on enabling secure, user-controlled content sharing and interaction without centralized oversight. Like Nostr, YakiHonne uses a system of relays to handle data, which makes it censorship-resistant and allows for greater privacy. Users communicate through a global network of peers, and can participate in various activities, share content, and connect with others in a decentralized ecosystem.
YakiHonne also supports Bitcoin-based features, like a built-in Lightning wallet that facilitates quick, low-fee transactions, making it popular among the cryptocurrency community. The platform’s design allows for content curation, peer review, and publishing of articles, similar to a blend of a social media network and a blogging platform. YakiHonne is available as a mobile app, emphasizing a smooth and accessible user experience for decentralized media sharing.
This approach to social networking reflects a trend toward decentralization, providing users with more autonomy and direct control over their online presence and data. It has grown quickly, attracting a global audience and establishing partnerships within the Bitcoin ecosystem.
-
 @ 59f0660b:d5d24440
2024-11-13 16:54:33
@ 59f0660b:d5d24440
2024-11-13 16:54:33Bitcoin is a type of digital currency, also known as a cryptocurrency, that was invented in 2008 by an unknown person or group using the pseudonym Satoshi Nakamoto. Unlike traditional currencies issued by governments (like dollars or euros), Bitcoin is decentralized, meaning it operates without a central authority like a bank. Transactions are verified by network nodes through cryptography and recorded on a public ledger called the blockchain.
Here are some key characteristics of Bitcoin:
-
Decentralization: Bitcoin is maintained by a distributed network of computers (called "miners") rather than a central bank or government.
-
Limited Supply: There will only ever be 21 million bitcoins, making it scarce like a precious metal, which helps contribute to its value.
-
Blockchain Technology: Bitcoin transactions are recorded on the blockchain, a secure, transparent, and immutable ledger.
-
Digital Nature: Bitcoin exists only electronically and is stored in digital wallets. It can be sent directly from person to person (peer-to-peer) without an intermediary.
Bitcoin has been praised for enabling fast, low-cost, and borderless transactions but also criticized for its volatility and environmental impact due to the energy-intensive mining process.
-
-
 @ 59f0660b:d5d24440
2024-11-13 16:52:23
@ 59f0660b:d5d24440
2024-11-13 16:52:23Nostr (Notes and Other Stuff Transmitted by Relays) is a decentralized protocol for social networking and communication that enables users to share information and messages without relying on a central server or platform. Instead of traditional social media structures controlled by corporations (like Twitter or Facebook), Nostr allows users to publish content via distributed relays, maintaining privacy, censorship resistance, and greater user control.
Key Characteristics of Nostr:
-
Decentralized Structure: Unlike conventional platforms, Nostr does not rely on a central server. Instead, users connect to a network of relays, where they can post messages or data that others can read or respond to.
-
Public and Private Keys: Nostr uses public-key cryptography, where users have a public key (like a username) and a private key (similar to a password) to sign messages. This approach provides security and ownership over one’s identity and content.
-
Relays for Content Distribution: Users can choose which relays to connect to and broadcast their posts. This design makes censorship harder, as content doesn’t depend on a single server but can be mirrored on multiple relays across the network.
-
Minimalist Design: Nostr aims to be simple and flexible, allowing developers to build different types of applications on top of it. It’s designed for messaging, but its flexibility can also support blogging, group chats, or other social functions.
Use Cases and Popularity
Censorship Resistance: Users who seek free speech or who are in restrictive environments find Nostr appealing because it allows them to communicate without a centralized authority.
Bitcoin and Crypto Community: Nostr has gained popularity within the Bitcoin and broader cryptocurrency community as it aligns with the ethos of decentralization and user empowerment.
Nostr’s open and decentralized nature is similar to other emerging protocols, such as ActivityPub (used by Mastodon), which are part of a larger trend toward decentralized social networking and communication platforms.
-
-
 @ 13351007:eccd002a
2024-11-13 16:34:01
@ 13351007:eccd002a
2024-11-13 16:34:01[{"_id":"5478974e-5e9b-4ccc-8cee-8485f60838ef","user_id":"b34f99f110bb65ff4b5527f8fb1d015951a3038370fd95adc34d81d9006b0fcc","tradingPartner":"hank","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_SELL","adTypeReal":"ONLINE_SELL","price":169.05,"amount":202.86468,"amountCurrency":"xmr","buyerSettlementAddress":"888tNkZrPN6JsEgekjMnABU4TBzc2Dt29EPAvkRxbANsAnjyPbb3iQ1YBRk1UXcdRsiKc9dhwMVgN5S9cQUiyoogDavup3H","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T16:34:01.270Z"},{"_id":"5478974e-5e9b-4ccc-8cee-8485f60838ef","user_id":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","tradingPartner":"liam","tradeId":"5478974e-5e9b-4ccc-8cee-8485f60838ef","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_BUY","adTypeReal":"ONLINE_SELL","price":169.05,"amount":202.86468,"amountCurrency":"xmr","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T16:34:01.270Z"}]
-
 @ 13351007:eccd002a
2024-11-13 16:33:01
@ 13351007:eccd002a
2024-11-13 16:33:01[{"_id":"662f7f07-a7ef-4f29-9bdb-6d199e7dac2c","user_id":"b34f99f110bb65ff4b5527f8fb1d015951a3038370fd95adc34d81d9006b0fcc","tradingPartner":"hank","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_SELL","adTypeReal":"ONLINE_SELL","price":169.05,"amount":500.03,"amountCurrency":"fiat","buyerSettlementAddress":"888tNkZrPN6JsEgekjMnABU4TBzc2Dt29EPAvkRxbANsAnjyPbb3iQ1YBRk1UXcdRsiKc9dhwMVgN5S9cQUiyoogDavup3H","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T16:33:01.332Z"},{"_id":"662f7f07-a7ef-4f29-9bdb-6d199e7dac2c","user_id":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","tradingPartner":"liam","tradeId":"662f7f07-a7ef-4f29-9bdb-6d199e7dac2c","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_BUY","adTypeReal":"ONLINE_SELL","price":169.05,"amount":500.03,"amountCurrency":"fiat","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T16:33:01.332Z"}]
-
 @ 13351007:eccd002a
2024-11-13 16:32:01
@ 13351007:eccd002a
2024-11-13 16:32:01[{"_id":"a740e2cb-8940-4d1b-bf4c-271de778bd77","user_id":"b34f99f110bb65ff4b5527f8fb1d015951a3038370fd95adc34d81d9006b0fcc","tradingPartner":"hank","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_SELL","adTypeReal":"ONLINE_SELL","price":169.05,"amount":500.02,"amountCurrency":"fiat","buyerSettlementAddress":"888tNkZrPN6JsEgekjMnABU4TBzc2Dt29EPAvkRxbANsAnjyPbb3iQ1YBRk1UXcdRsiKc9dhwMVgN5S9cQUiyoogDavup3H","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T16:32:01.342Z"},{"_id":"a740e2cb-8940-4d1b-bf4c-271de778bd77","user_id":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","tradingPartner":"liam","tradeId":"a740e2cb-8940-4d1b-bf4c-271de778bd77","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_BUY","adTypeReal":"ONLINE_SELL","price":169.05,"amount":500.02,"amountCurrency":"fiat","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T16:32:01.342Z"}]
-
 @ 13351007:eccd002a
2024-11-13 16:31:10
@ 13351007:eccd002a
2024-11-13 16:31:10[{"_id":"6b08a49c-6812-4e79-8f5b-0a1eff7b8846","user_id":"b34f99f110bb65ff4b5527f8fb1d015951a3038370fd95adc34d81d9006b0fcc","tradingPartner":"hank","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_SELL","adTypeReal":"ONLINE_SELL","price":169.05,"amount":500.01,"amountCurrency":"fiat","buyerSettlementAddress":"888tNkZrPN6JsEgekjMnABU4TBzc2Dt29EPAvkRxbANsAnjyPbb3iQ1YBRk1UXcdRsiKc9dhwMVgN5S9cQUiyoogDavup3H","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T16:31:10.741Z"},{"_id":"6b08a49c-6812-4e79-8f5b-0a1eff7b8846","user_id":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","tradingPartner":"liam","tradeId":"6b08a49c-6812-4e79-8f5b-0a1eff7b8846","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_BUY","adTypeReal":"ONLINE_SELL","price":169.05,"amount":500.01,"amountCurrency":"fiat","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T16:31:10.741Z"}]
-
 @ 13351007:eccd002a
2024-11-13 14:50:53
@ 13351007:eccd002a
2024-11-13 14:50:53[{"_id":"c8b5c272-899c-4258-8ed8-d39d8b1f2802","user_id":"b34f99f110bb65ff4b5527f8fb1d015951a3038370fd95adc34d81d9006b0fcc","tradingPartner":"hank","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_SELL","adTypeReal":"ONLINE_SELL","price":169.05,"amount":500,"amountCurrency":"fiat","buyerSettlementAddress":"888tNkZrPN6JsEgekjMnABU4TBzc2Dt29EPAvkRxbANsAnjyPbb3iQ1YBRk1UXcdRsiKc9dhwMVgN5S9cQUiyoogDavup3H","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T14:50:53.706Z"},{"_id":"c8b5c272-899c-4258-8ed8-d39d8b1f2802","user_id":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","tradingPartner":"liam","tradeId":"c8b5c272-899c-4258-8ed8-d39d8b1f2802","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_BUY","adTypeReal":"ONLINE_SELL","price":169.05,"amount":500,"amountCurrency":"fiat","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T14:50:53.706Z"}]
-
 @ 4874b840:31b0b8c0
2024-11-13 13:22:32
@ 4874b840:31b0b8c0
2024-11-13 13:22:32Архитектурные проекты, реализованные в Калининграде, значительно преобразили облик города. Одним из ключевых направлений стала реконструкция хрущёвок, предложенная московскими архитекторами МАРХИ. Они планируют увеличить этажность существующих зданий и создать новые общественные пространства, что улучшит качество жизни жителей.
 Также активно развиваются проекты на Острове Октябрьском, где предусмотрена застройка с учетом культурного и спортивного кластеров. Важным аспектом является благоустройство общественных пространств, включая парки и набережные, что делает город более привлекательным для жителей и туристов.
Также активно развиваются проекты на Острове Октябрьском, где предусмотрена застройка с учетом культурного и спортивного кластеров. Важным аспектом является благоустройство общественных пространств, включая парки и набережные, что делает город более привлекательным для жителей и туристов.Житель отреконструированной хрущёвки делится с нами впечатлениями:
"Наша хрущёвка теперь выглядит совершенно иначе! Благодаря реконструкции добавили два этажа, и у нас появился лифт. Квартиры стали просторнее, а фасад — современным. Дворы благоустроены, появились детские площадки и парковки. Я рад, что жители могли участвовать в принятии решений. Это не просто улучшение жилья, это создание комфортной городской среды, которая отвечает требованиям XXI века".

-
 @ 4874b840:31b0b8c0
2024-11-13 13:19:46
@ 4874b840:31b0b8c0
2024-11-13 13:19:46На сегодняшний день школы Калининграда представляют собой современные образовательные учреждения, ориентированные на всестороннее развитие учащихся. В рамках программы по расширению возможностей дополнительного образования активно функционируют кружки и секции, охватывающие различные направления.
 Технические кружки включают судостроительные классы, где учащиеся изучают проектирование и технологии, получая практические навыки для востребованной отрасли. Творческие секции предлагают занятия по изобразительному искусству, музыке и театру, развивая художественные таланты. Спортивные кружки обеспечивают занятия по футболу, волейболу и плаванию.
Технические кружки включают судостроительные классы, где учащиеся изучают проектирование и технологии, получая практические навыки для востребованной отрасли. Творческие секции предлагают занятия по изобразительному искусству, музыке и театру, развивая художественные таланты. Спортивные кружки обеспечивают занятия по футболу, волейболу и плаванию.
 Школы активно сотрудничают с местными предприятиями и университетами, что обеспечивает доступ к современным технологиям. Таким образом, образовательная система Калининграда направлена на подготовку высококвалифицированных специалистов.
Школы активно сотрудничают с местными предприятиями и университетами, что обеспечивает доступ к современным технологиям. Таким образом, образовательная система Калининграда направлена на подготовку высококвалифицированных специалистов.Ученики кружка судостроения отмечают: "Учеба открывает невероятные возможности. Мы участвуем в практических проектах на верфях "Янтарь" и "Арктика", что позволяет применять знания на практике и готовиться к карьере в высокотехнологичной отрасли."
-
 @ fd208ee8:0fd927c1
2024-11-13 10:28:15
@ fd208ee8:0fd927c1
2024-11-13 10:28:15The fertility rate is not the whole story
I keep reading articles about the fertility decline that has now consumed most developed nations on Earth, and that is slowly creeping toward the few remaining holdouts, mostly in sub-Saharan Africa.
Many countries, that we still think of, as having high birthrates, are actually just experiencing the echo of previous high birthrates. Same as Europe had in the 70s and 80s, due to the post-WWII baby boom. Others have very high total fertility rates (TFR), but such high infant and child mortality, that the population doesn't grow in line with the fertility.
East Asia is in the worst shape, with Europe closely nipping at its heels. TFR is highest in Niger, at 6.1 children per woman, and lowest in South Korea, at 0.7. In other words, the South Korean population nearly halves in size, every generation. (I will be focusing on South Korea, going forward, as a case study of the general phenomenon.)
Fertility rate is not even half the story
But it's actually all much worse than is being publicized, as the fertility rates don't take the tangible effects of delays in childbearing into account, which actually are felt more immediately, than the decline in overall fertility. What the delays do, is spread the same number of births more thinly over the timeline, debilitating any infrastructure or traditions that require a certain number of people, to be maintained. I think of this as demographic logistics, as it's about getting the right number of people, of the right age, to the right place, at the right time, in order to meet some minimum required volume.
Playgroups, schools, hospitals, festivals, volunteer organizations, sports clubs, road works, senior residences, churches, new business starts, etc. all require a certain number of participants, to remain viable. Those participants trickling in, at a slower and slower rate, is why even places with above-replacement fertility (like my own town) increasingly struggle to maintain systems that are popular. Everyone is being spread thinner and thinner, and we're having to make hard choices about how the smaller group will be distributed amongst the activities.
You feel like you're being overrun because you are.
This is also why the fact that migrants (and religious people, etc.) tend to adjust their birthrate to the regional average, doesn't lead to an end of their demographic overrepresentation. They are under less societal pressure to delay childbearing, so they tend to be further down the following chart, and their offspring simply arrive much more quickly, than with the natives.
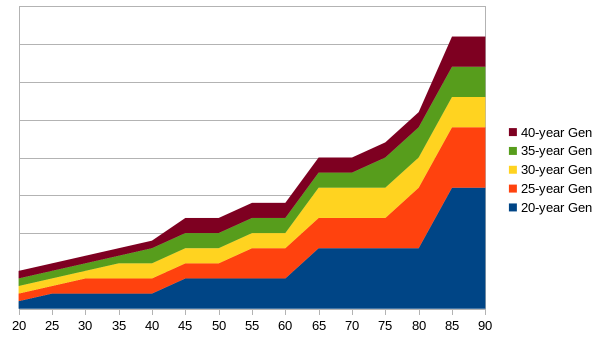
To put it simply, for everyone one generation of the "natives" or "majority" society, there are two or three generations of the others.
Does communism get the last laugh?
Societies, like South Korea, where the fertility rate is exceedingly low, also tend to have the most-delayed childbearing, so the effect of low fertility is heavily exacerbated. The countries are hollowing out, on the ground level, with the population being replaced so slowly and thinly, that the majority of the country will soon simply be empty, and the infrastructure will fall apart.
Christianity is starting to have a positive effect on a subset of South Korean birthrates, by promoting the concept of openness to life and family-friendliness, but its popularization initially decreased fertility. (This is a common effect, as Christianity leads to higher status for women, monogamy, and the concept of "family planning".) Yes, contrary to what The Handmaid's Tale enthusiasts claim, increased religiosity actually exacerbated the already-widespread decline.
South Korea is really just the worst of worst-case scenarios, unfortunately, with absolutely every demographic and economic trend aligning to cut off their reproduction. This is in direct contrast to North Korea, that can compensate for the more moderate decline in births with mere mechanization.
Yes, it looks like North Korea will do much better, going forward, than South Korea. Their entrance into the Ukraine War isn't incidental; we will be hearing more from them, going forward.
Robots serving ghosts
The South Korean plan of simply substituting robots for most humans, will go nowhere, as robots are actually less efficient and effective than humans, except at highly dull or repetitive tasks, over the course of their lifecycle. (This is hidden with cheap, extended production financing, where the machines don't have to turn a profit for decades, whereas humans have to be paid today.) Without productive, agile humans, generating real income, there will be no one to purchase and run all the expensive robots.
And... run them... for whom?

-
 @ 13351007:eccd002a
2024-11-13 09:17:38
@ 13351007:eccd002a
2024-11-13 09:17:38[{"_id":"f61999d4-6dd5-4593-9798-17980ecebd22","user_id":"b34f99f110bb65ff4b5527f8fb1d015951a3038370fd95adc34d81d9006b0fcc","tradingPartner":"hank","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_SELL","adTypeReal":"ONLINE_SELL","price":169.05,"amount":100.02,"amountCurrency":"fiat","buyerSettlementAddress":"888tNkZrPN6JsEgekjMnABU4TBzc2Dt29EPAvkRxbANsAnjyPbb3iQ1YBRk1UXcdRsiKc9dhwMVgN5S9cQUiyoogDavup3H","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T09:17:38.105Z"},{"_id":"f61999d4-6dd5-4593-9798-17980ecebd22","user_id":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","tradingPartner":"liam","tradeId":"f61999d4-6dd5-4593-9798-17980ecebd22","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_BUY","adTypeReal":"ONLINE_SELL","price":169.05,"amount":100.02,"amountCurrency":"fiat","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T09:17:38.105Z"}]
-
 @ 98589a2e:bf49daa1
2024-11-13 09:08:41
@ 98589a2e:bf49daa1
2024-11-13 09:08:41Санкт-Петербург в 2040 году стал городом, где современная архитектура гармонично сочетается с историческим наследием. В рамках нового генерального плана запланированы крупные инфраструктурные проекты, которые кардинально изменят облик города и улучшат качество жизни его жителей.
Основные инфраструктурные проекты
Развитие транспортной инфраструктуры
- Метро: К 2040 году планируется построить около 100 новых станций метрополитена и увеличить общую протяжённость линий до 272,7 км. Важными проектами являются новые Кольцевая и Адмиралтейско-Охтинская линии, а также продление существующих.
- Мосты: Запланировано строительство пяти новых мостов через Неву, включая Большой Смоленский мост и Орловский тоннель. Эти проекты направлены на улучшение транспортной доступности и сокращение времени в пути.
- Общественный транспорт: Будут развиваться трамвайные линии и железнодорожные пути, что позволит создать более удобную сеть общественного транспорта.
Социальная инфраструктура
- Образование и здравоохранение: Генеральный план предусматривает строительство 585 объектов социальной инфраструктуры, в том числе 226 образовательных учреждений и 110 медицинских. Это обеспечит необходимую поддержку растущему населению города.
- Спортивные объекты: План также предусматривает создание 205 спортивных сооружений, что будет способствовать развитию физической культуры и спорта среди жителей.
Общественные пространства и экология
- Парки и набережные: В городе появятся новые парковые зоны, в том числе реконструированные набережные Карповки и Охты, а также шесть тематических парков и девять благоустроенных пляжей. Это создаст комфортные условия для отдыха горожан.
- Зеленые зоны: Генеральный план предполагает создание около 1,5 тыс. гектаров природных территорий общего пользования, что повысит уровень экологической безопасности города.
Жилищное строительство
- Новые жилые комплексы: В соответствии с планом, к 2040 году в городе будет построено около 67 млн кв. м жилья. Основная застройка сосредоточится в Пушкинском, Приморском и Московском районах. Это позволит обеспечить жильем растущее население Санкт-Петербурга.
Благодаря проектам в городе формируется устойчивое развитие городской инфраструктуры. Эти амбициозные проекты отражают стремление города к инновациям и улучшению качества жизни его жителей.
Как вы относитесь к планируемым изменениям в инфраструктуре? Какие улучшения вы хотели бы видеть в своем районе?
-
 @ c2827524:5f45b2f7
2024-11-13 08:57:07
@ c2827524:5f45b2f7
2024-11-13 08:57:07Piano generale
l'intento è smettere di minare fiat e passare a guadagnare esclusivamente in #Bitcoin.
Attacco DDOS alla vita di tutti
winzozz, il sistema operativo imposto coercitivamente da uno smidollato mafioso, fa schifo ai vermi.
é lento, si ferma ad ogni minuto, lascia utenti in attesa per ore - ogni giorno - solo perché sta facendo Dio solo sa cosa. nostr:#winzozz è un attacco DDOS alla vita di ogni essere umano che ha la nostr:#sfiga di ritrovarsi suo malgrado ad usarlo.
mentre si attende che il pc venga rianimato da un intervento divino (perché chiamare in causa il padreterno, a volte, funziona), siamo in balia di attese infinite. per nulla.
quante ore della nostra vita sono passate in attesa di... nostr:#stocazzo?
sai chi ti saluta tanto?
ecco, appunto! a proposito di nostr:#stocazzo: la prima cosa da fare nella lista della mia nuova vita, è proprio arare tutti i miei pc e passarli a nostr:#Debian.🐧.
*terrò una macchina winzozz solo per i corsi, per aiutare nuovi utenti windows #Bitcoin ad imparare questa deliziosa tecnologia. per poi farli traghettare da Caronte su nuovi sistemi operativi, là dove nessun DDOS può mai arrivare a sottrarre tempo prezioso alle vite degli altri.
-
 @ 13351007:eccd002a
2024-11-13 08:02:18
@ 13351007:eccd002a
2024-11-13 08:02:18[{"_id":"c178a999-25e0-4bf5-b478-b6f22ae9bfbd","user_id":"b34f99f110bb65ff4b5527f8fb1d015951a3038370fd95adc34d81d9006b0fcc","tradingPartner":"hank","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_SELL","adTypeReal":"ONLINE_SELL","price":169.05,"amount":102,"amountCurrency":"fiat","buyerSettlementAddress":"888tNkZrPN6JsEgekjMnABU4TBzc2Dt29EPAvkRxbANsAnjyPbb3iQ1YBRk1UXcdRsiKc9dhwMVgN5S9cQUiyoogDavup3H","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T08:02:18.346Z"},{"_id":"c178a999-25e0-4bf5-b478-b6f22ae9bfbd","user_id":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","tradingPartner":"liam","tradeId":"c178a999-25e0-4bf5-b478-b6f22ae9bfbd","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_BUY","adTypeReal":"ONLINE_SELL","price":169.05,"amount":102,"amountCurrency":"fiat","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T08:02:18.346Z"}]
-
 @ 13351007:eccd002a
2024-11-13 07:54:13
@ 13351007:eccd002a
2024-11-13 07:54:13[{"_id":"b99131ca-10fb-48fd-be00-04aee70efd55","tradingPartner":"hank","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_SELL","adTypeReal":"ONLINE_SELL","price":169.05,"amount":100,"amountCurrency":"fiat","buyerSettlementAddress":"888tNkZrPN6JsEgekjMnABU4TBzc2Dt29EPAvkRxbANsAnjyPbb3iQ1YBRk1UXcdRsiKc9dhwMVgN5S9cQUiyoogDavup3H","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T07:54:13.400Z"},{"_id":"b99131ca-10fb-48fd-be00-04aee70efd55","tradingPartner":"liam","tradeId":"b99131ca-10fb-48fd-be00-04aee70efd55","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_BUY","adTypeReal":"ONLINE_SELL","price":169.05,"amount":100,"amountCurrency":"fiat","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T07:54:13.400Z"}]
-
 @ 13351007:eccd002a
2024-11-13 07:54:13
@ 13351007:eccd002a
2024-11-13 07:54:13[{"_id":"a8fd0883-c47a-4eba-bf4c-61ff15f836ff","tradingPartner":"hank","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_SELL","adTypeReal":"ONLINE_SELL","price":169.05,"amount":101,"amountCurrency":"fiat","buyerSettlementAddress":"888tNkZrPN6JsEgekjMnABU4TBzc2Dt29EPAvkRxbANsAnjyPbb3iQ1YBRk1UXcdRsiKc9dhwMVgN5S9cQUiyoogDavup3H","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T07:54:13.286Z"},{"_id":"a8fd0883-c47a-4eba-bf4c-61ff15f836ff","tradingPartner":"liam","tradeId":"a8fd0883-c47a-4eba-bf4c-61ff15f836ff","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_BUY","adTypeReal":"ONLINE_SELL","price":169.05,"amount":101,"amountCurrency":"fiat","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T07:54:13.286Z"}]
-
 @ a012dc82:6458a70d
2024-11-13 07:44:51
@ a012dc82:6458a70d
2024-11-13 07:44:51Table Of Content
-
What is the Lighting Network?
-
Advantages of the Lighting Network for Businesses
-
Game-Changing Bitcoin Tool
-
Conclusion
-
FAQ
In today's digital age, cryptocurrencies have taken the financial world by storm. One such cryptocurrency that has gained immense popularity and disrupted traditional financial systems is Bitcoin. Bitcoin, the pioneering cryptocurrency, has opened up new avenues for businesses and individuals alike. With the advent of the Lighting Network, a revolutionary scaling solution for Bitcoin, a game-changing Bitcoin tool has emerged, ushering in a paradigm shift for the Lighting Network in business.
What is the Lighting Network?
The Lighting Network is a second-layer protocol that operates on top of the Bitcoin blockchain. It aims to address some of the scalability and transaction speed issues faced by the Bitcoin network. By creating a network of bidirectional payment channels, the Lighting Network enables near-instant and low-cost transactions between participants. This innovative solution has paved the way for the development of game-changing Bitcoin tools that have the potential to transform the business landscape.
Advantages of the Lighting Network for Businesses
Enhanced Scalability
The Lighting Network offers a significant advantage in terms of scalability for businesses. With traditional Bitcoin transactions, every transaction needs to be recorded on the blockchain, resulting in limited transaction throughput. However, the Lighting Network allows businesses to conduct a large number of off-chain transactions, minimizing the load on the Bitcoin blockchain and significantly increasing scalability. This scalability boost opens up new possibilities for businesses to process a higher volume of transactions and accommodate growing customer demands.
Lightning-Fast Transactions
One of the most remarkable features of the Lighting Network is its ability to facilitate lightning-fast transactions. Traditional Bitcoin transactions can sometimes take several minutes or even hours to confirm, causing delays and inconveniences in business operations. However, with the Lighting Network, transactions can be settled in a matter of seconds. This speed advantage enables businesses to offer seamless and real-time payment experiences to their customers, enhancing customer satisfaction and improving overall efficiency.
Reduced Transaction Costs
Another compelling aspect of the Lighting Network for businesses is the reduced transaction costs it offers. Traditional Bitcoin transactions often incur high fees due to the limited capacity of the blockchain. However, the Lighting Network's off-chain transactions significantly reduce transaction fees, making microtransactions and low-value transactions economically feasible. This cost reduction is particularly beneficial for businesses that rely on frequent small transactions, such as online retailers or service providers.
Improved Privacy and Security
The Lighting Network also brings improvements in terms of privacy and security. As most Lighting Network transactions occur off-chain, they do not require broadcasting every detail to the public blockchain. This aspect enhances privacy by reducing the exposure of sensitive transaction information. Additionally, the Lighting Network implements various security measures, such as multi-signature wallets and hash time-locked contracts, to ensure the safety of funds during transactions. These enhanced privacy and security features provide businesses with peace of mind when adopting the Lighting Network.
Game-Changing Bitcoin Tool
The advent of the Lighting Network has paved the way for the development of various game-changing Bitcoin tools that empower businesses to leverage the potential of this revolutionary technology. These tools offer innovative solutions to address specific business needs, enhance operational efficiency, and unlock new opportunities. Let's explore some of these remarkable tools and their impact on businesses:
1. Lightning Payment Processors
Lightning payment processors are tools that enable businesses to seamlessly integrate the Lighting Network into their existing payment infrastructure. These processors provide the necessary software and APIs to facilitate Lightning Network payments, making it convenient for businesses to accept Bitcoin payments with lightning speed and low fees. By adopting a Lightning payment processor, businesses can expand their customer base, attract Bitcoin-savvy customers, and provide a more efficient payment experience.
2. Lightning Network Point-of-Sale (PoS) Systems
Lightning Network PoS systems are specifically designed for businesses that operate physical stores or provide in-person services. These systems enable businesses to accept Lightning Network payments directly at the point of sale, similar to traditional payment terminals. With Lightning PoS systems, businesses can offer a seamless payment experience to their customers, eliminating the need for lengthy transaction confirmations and reducing customer waiting time. This convenience can lead to increased customer satisfaction and improved sales.
3. Lightning Network E-commerce Plugins
For businesses operating in the digital realm, Lightning Network e-commerce plugins provide a seamless integration of Bitcoin payments on their online platforms. These plugins offer ready-to-use solutions that can be easily installed on popular e-commerce platforms, such as WooCommerce or Shopify. By incorporating Lightning Network payments, businesses can tap into the growing Bitcoin user base and provide an alternative payment option that is fast, secure, and cost-effective. This integration can boost sales and attract tech-savvy customers who prefer Bitcoin transactions.
4. Lightning Network Micropayment Platforms
Micropayments refer to transactions involving small amounts of money, typically fractions of a cent. The Lighting Network's low fees and near-instant transaction settlement make it an ideal solution for micropayments. Lightning Network micropayment platforms enable businesses to monetize content or services that were previously not economically viable due to high transaction costs. By leveraging micropayment platforms, businesses can explore new revenue streams and create innovative business models.
Conclusion
The Lighting Network has introduced a game-changing Bitcoin tool that offers a paradigm shift for the Lighting Network in business. With enhanced scalability, lightning-fast transactions, reduced costs, and improved privacy and security, the Lighting Network empowers businesses to unlock new opportunities, streamline operations, and provide better customer experiences. By embracing the potential of this innovative technology and leveraging the game-changing Bitcoin tools available, businesses can stay at the forefront of the digital revolution and thrive in the evolving landscape of cryptocurrencies.
FAQ
How does the Lighting Network enhance scalability for businesses? The Lighting Network enhances scalability by allowing businesses to conduct a large number of off-chain transactions, reducing the load on the Bitcoin blockchain and enabling higher transaction throughput.
What are the advantages of Lightning Network transactions for businesses? Lightning Network transactions offer lightning-fast settlement times, reduced transaction costs, improved privacy, and enhanced security, all of which contribute to better operational efficiency and customer satisfaction for businesses.
How can businesses integrate the Lighting Network into their payment infrastructure? Businesses can integrate the Lighting Network by leveraging Lightning payment processors, Lightning Network PoS systems, or Lightning Network e-commerce plugins, depending on their specific requirements.
What are micropayment platforms, and how can they benefit businesses? Micropayment platforms enable businesses to process and monetize small transactions economically. With the Lighting Network's low fees, businesses can explore new revenue streams and offer innovative services that involve micropayments.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 13351007:eccd002a
2024-11-13 06:54:35
@ 13351007:eccd002a
2024-11-13 06:54:35{"_id":"6189965d-885f-44a5-8283-236809f90bb4","tradingPartner":"liam","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_BUY","adTypeReal":"ONLINE_SELL","price":169.05,"amount":2,"amountCurrency":"fiat","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T06:54:35.193Z"}
-
 @ 13351007:eccd002a
2024-11-13 06:54:35
@ 13351007:eccd002a
2024-11-13 06:54:35{"_id":"45961f60-af28-49a7-8285-39d46a04ae04","tradingPartner":"liam","adId":"10df86b1-657c-4065-b5c8-d6f6bbe64a7b","adPublisher":"f462d21e10163eb0a403aec6b93ac57ec2f1b9455473e99304f571a51390b6b1","adType":"ONLINE_BUY","adTypeReal":"ONLINE_SELL","price":170.27,"amount":1.5,"amountCurrency":"fiat","paymentMethodCode":"VENMO","currencyCode":"USD","country":"United Kingdom","countryCode":"GB","paymentMethodDetail":"best rates really","msg":"","accountInfo":"","action":"open","added":"2024-11-13T06:54:35.127Z"}
-
 @ 13351007:eccd002a
2024-11-13 06:54:35
@ 13351007:eccd002a
2024-11-13 06:54:35{"_id":"d12af7f8-9fad-4718-85d2-71de3e1ab22f","tradingPartner":"hank","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_SELL","adTypeReal":"ONLINE_SELL","price":169.05,"amount":1,"amountCurrency":"fiat","buyerSettlementAddress":"888tNkZrPN6JsEgekjMnABU4TBzc2Dt29EPAvkRxbANsAnjyPbb3iQ1YBRk1UXcdRsiKc9dhwMVgN5S9cQUiyoogDavup3H","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T06:54:35.527Z"}
-
 @ 13351007:eccd002a
2024-11-13 06:54:35
@ 13351007:eccd002a
2024-11-13 06:54:35{"_id":"79c3b4de-fb00-40e6-82b4-9c8474d90c43","tradingPartner":"hank","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_SELL","adTypeReal":"ONLINE_SELL","price":169.05,"amount":1.6,"amountCurrency":"fiat","buyerSettlementAddress":"888tNkZrPN6JsEgekjMnABU4TBzc2Dt29EPAvkRxbANsAnjyPbb3iQ1YBRk1UXcdRsiKc9dhwMVgN5S9cQUiyoogDavup3H","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T06:54:35.210Z"}
-
 @ 13351007:eccd002a
2024-11-13 06:54:34
@ 13351007:eccd002a
2024-11-13 06:54:34{"_id":"fad63d53-f555-429e-916a-d2ea8968552d","tradingPartner":"hank","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_SELL","adTypeReal":"ONLINE_SELL","price":169.05,"amount":20,"amountCurrency":"fiat","buyerSettlementAddress":"888tNkZrPN6JsEgekjMnABU4TBzc2Dt29EPAvkRxbANsAnjyPbb3iQ1YBRk1UXcdRsiKc9dhwMVgN5S9cQUiyoogDavup3H","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T06:54:34.754Z"}
-
 @ fff19d35:43344a0b
2024-11-13 06:17:55
@ fff19d35:43344a0b
2024-11-13 06:17:55Guys have you download the lates YakiHonne app, the lates update is just amazing and wonderful very fast and with pretty good feature you won’t have any worries or problems loading anything😃if you haven’t updated you are missing big time 🥹😉
-
 @ 9ff58691:0bf6c134
2024-11-13 06:14:04
@ 9ff58691:0bf6c134
2024-11-13 06:14:04За последние 16 лет индекс счастья курганцев поднялся до 8.1. Это на три единицы больше, чем за прошлую декаду.
Ведущая Катерина Тобольская рассказывает о причинах, повлиявших на настроение жителей Кургана за последние 16 лет в новом выпуске «Заметок о главном»
-
 @ 9ff58691:0bf6c134
2024-11-13 06:13:21
@ 9ff58691:0bf6c134
2024-11-13 06:13:21Мы с радостью приглашаем вас на фестиваль уличной культуры «Город в ритме», который начнётся на улице Свободы в 15:00.
Это событие объединит талантливых людей из разных сфер: от художников и музыкантов до танцоров и спортсменов.
О подробностях фестиваля нам рассказала его организатор — Катерина Тобольская. Ждём вас, чтобы вместе окунуться в атмосферу творчества и вдохновения!
-
 @ 9ff58691:0bf6c134
2024-11-13 06:10:17
@ 9ff58691:0bf6c134
2024-11-13 06:10:17Вы не поверите, что происходит в наших школах! Ученики теперь используют самые передовые технологии в процессе обучения. Представьте себе: вместо скучных учебников и меловых досок, наши аудитории оснащены по последнему слову техники. Ребята работают с 3D-моделями, создают потрясающие компьютерные графические проекты и даже обучаются с помощью искусственного интеллекта!
Представьте, как здорово изучать физику, создавая виртуальные модели планет и космических кораблей. Или постигать тайны биологии, рассматривая 3D-изображения клеток и органов. Да что там, даже на уроках истории ученики могут "побывать" в прошлом с помощью VR-технологий!
Все это стало возможным благодаря масштабной модернизации системы образования в нашем городе. Теперь наши дети получают знания в по-настоящему современной и интерактивной среде. Это не просто повышает их мотивацию, но и готовит их к жизни в эпоху высоких технологий.
А знаете ли вы, что в Кургане открылись сразу несколько новых учебных заведений, которые делают ставку на инновационные подходы? Например, в Технологическом лицее ученики с 5 класса осваивают программирование, 3D-моделирование и робототехнику. А в Экологической гимназии ребята изучают передовые методы сохранения окружающей среды с помощью современных IT-решений. "Мы стремимся дать нашим ученикам не просто знания, а навыки, которые будут востребованы в будущем", - говорит директор Технологического лицея Лев Петров. - Наша цель - вырастить поколение, готовое к вызовам цифровой эпохи".
Это действительно прорыв в образовании, который вдохновляет и вселяет надежду на лучшее будущее для наших детей.
Автор: Елизавета Медведева
-
 @ 9ff58691:0bf6c134
2024-11-13 06:04:04
@ 9ff58691:0bf6c134
2024-11-13 06:04:04Город, который когда-то казался забытым, сегодня стал центром инноваций и молодежного творчества. Программы поддержки молодежи, запущенные в последние два десятилетия, принесли свои плоды, и мы рады поделиться историями успеха, которые вдохновляют новое поколение.
Центр молодежного предпринимательства "Курган-Start"
Одной из самых успешных инициатив стал Центр молодежного предпринимательства "Курган-Start", который предоставляет молодым людям возможность развивать свои бизнес-идеи. В 2040 году мы встретились с Анной Петровой, 24-летней предпринимательницей, которая запустила свой стартап по производству экологически чистых упаковочных материалов. "Я всегда мечтала создать что-то полезное для окружающей среды. Благодаря поддержке 'Курган-Start' я получила не только финансирование, но и наставничество от опытных бизнесменов", — делится Анна.
Программа "Творческая молодежь"
Курган также стал домом для программы "Творческая молодежь", которая поддерживает молодых художников, музыкантов и писателей. В этом году мы познакомились с Дмитрием Соловьевым, 22-летним музыкантом, который стал известен благодаря своему уникальному стилю, сочетающему фолк и электронную музыку. "Программа помогла мне записать мой первый альбом и организовать тур по России. Я никогда не думал, что смогу выступать на таких больших сценах", — рассказывает Дмитрий.

Образовательные инициативы и стажировки
Образование в Кургане также претерпело значительные изменения. Программы стажировок и обменов с ведущими университетами страны стали доступными для молодежи. Мария Иванова, 21 год, рассказывает о своем опыте: "Я прошла стажировку в одном из лучших IT-компаний Москвы. Это был невероятный опыт, который открыл мне двери в мир технологий. Теперь я работаю над собственным проектом в Кургане и надеюсь вдохновить других".

Спортивные достижения
Спорт также занимает важное место в жизни молодежи Кургана. Программа "Спорт для всех" привлекла множество молодых людей к занятиям физической культурой. Алексей Смирнов, 19 лет, стал чемпионом России по легкой атлетике. "Я начал заниматься спортом благодаря местным тренерам, которые верили в меня. Теперь я мечтаю о международных соревнованиях", — говорит Алексей.

Курган — это город возможностей, где молодежь может реализовать свои мечты и идеи. Программы поддержки, созданные для помощи молодым людям, стали катализатором изменений и вдохновения. Эти истории успеха — лишь малая часть того, что происходит в нашем городе, и мы уверены, что впереди нас ждут еще более яркие достижения.
Автор: Александра Налобина
-
 @ 97fc03df:8bf891df
2024-11-13 03:37:00
@ 97fc03df:8bf891df
2024-11-13 03:37:00Bitcoin's mechanical consensus is set to become human civilization's ultimate shield
Author: Gavin, BeeGee (Core Builders of Super Bitcoin & BEVM)
November 12, 2024
The value of Bitcoin is set to rise in the long term if mankind is unable to create an adaptive, growth-oriented mechanical consensus similar to that of Bitcoin. Bitcoin is not merely a tool to protect property; it represents a "Great Consensus" that safeguards human civilization and our future. With a supply capped at 21 million, each Bitcoin bears the immense responsibility of protecting the security and well-being of 8 billion people today and countless future generations. Can such a Bitcoin truly have a price ceiling?
The consensus mechanism behind Bitcoin is an unending competition of computing power. Miners constantly add computing power in pursuit of rewards of BTC. This competitive process creates a self-reinforcing growth model: as more people participate in mining, computing power increases, mining difficulty rises, the network’s security strengthens, Bitcoin’s consensus becomes more solid, and the value of Bitcoin increases accordingly. This pattern creates a powerful and enduring positive feedback loop. It is such kind of “mechanical consensus,” which operates without human intervention, that enables the Bitcoin network to self-coordinate and evolve autonomously among distributed nodes through computational competition and economic incentives.
However, even though Bitcoin’s adaptive mechanical consensus excels at securing property, this is just the tip of the iceberg. Its potential extends far beyond. Human society is in the midst of the torrent of the information age, and the accelerated growth of technology means that complexity and uncertainty are increasing, making it difficult to deal with these challenges by relying solely on traditional "social consensus". In this context, the adaptive mechanical consensus brought about by Bitcoin's incentive layer becomes the really important part. It shows us the ability of machines to form consensus through automated gaming, and the potential of technology to safeguard human life and civilization more broadly than property.
Super Bitcoin emerged just to further unlock the potential of Bitcoin's consensus. It proposes a five-layer architecture that extends the capabilities of various protocols and corresponding application scenarios by sharing the consensus security of Bitcoin. Super Bitcoin is more than just an upgrade to the Bitcoin network, it is an attempt to take this great mechanical consensus beyond the limits of property security to protect the broader interests of humanity and civilization. By sharing the consensus security of Bitcoin, Super Bitcoin provides the infrastructure to support the synergy of human technology and civilization as well as the safety of life through the "interconnectedness" and "interoperability" of all blockchain systems.
The core idea behind all of these is to unleash the potential of Bitcoin's consensus. Bitcoin's journey from zero to $1.8 trillion market capitalization in just 16 years has proven that a consensus driven by computing power can adaptively grow through economic incentives without any human intervention. Super Bitcoin's goal is to build on this foundation with a new architecture that allows this great consensus to protect not just the value of cryptocurrencies, but the security of the entire human society and technological civilization.
Imagine a future where Bitcoin's consensus mechanism not only protects digital assets, but also provides security for human life and civilization. This is not only a technological advancement, but also a qualitative transformation of social consensus. In a way, the scalability of Bitcoin and its consensus is representing our latest efforts to cope with complexity in the information age. If we can apply mechanical consensus to a wider range of areas through these efforts, then this consensus mechanism will no longer be just a financial tool, but a foundational force to lead humanity into the future.
Therefore, the value of Bitcoin lies not only in its scarcity as a digital asset, but also in the adaptive mechanical consensus behind it. This consensus is an important weapon for human society to confront future complexity and uncertainties, and is the cornerstone for protecting human life and the security of technological civilization. Super Bitcoin's mission is to make this Great Consensus no longer confined to the protection of property, but rather to become the common "Civilization Guardian" for the whole mankind.
-
 @ bcea2b98:7ccef3c9
2024-11-13 02:44:17
@ bcea2b98:7ccef3c9
2024-11-13 02:44:17@chess a3
originally posted at https://stacker.news/items/765445
-
 @ bcea2b98:7ccef3c9
2024-11-13 02:18:58
@ bcea2b98:7ccef3c9
2024-11-13 02:18:58Sometimes our strongest values are the ones that people wouldn’t expect. These unique principles often reveal something special about who we are and what we believe in. Do you hold a value that might surprise others?
originally posted at https://stacker.news/items/765433
-
 @ 1123ece2:7d1e00c0
2024-11-13 01:43:26
@ 1123ece2:7d1e00c0
2024-11-13 01:43:26Hey everyone and welcome to Refinery Life Australia.
“The Christ of John’s Gospel” is the theme for the coming Sunday mornings that focus on John’s unique portrayal of the Christ.
We will continue this series through to the end of the year.
Today we are discussing, Passport to the Kingdom.
John 3:5 NKJV
5 Jesus answered, “Most assuredly, I say to you, unless one is born of water and the Spirit, he cannot enter the kingdom of God.
Scripture Reading
John 3:1-21 NKJV
The New Birth
1 There was a man of the Pharisees named Nicodemus, a ruler of the Jews.
2 This man came to Jesus by night and said to Him, “Rabbi, we know that You are a teacher come from God; for no one can do these signs that You do unless God is with him.”
3 Jesus answered and said to him, “Most assuredly, I say to you, unless one is born again, he cannot see the kingdom of God.”
4 Nicodemus said to Him, “How can a man be born when he is old? Can he enter a second time into his mother’s womb and be born?”
5 Jesus answered, “Most assuredly, I say to you, unless one is born of water and the Spirit, he cannot enter the kingdom of God.
6 That which is born of the flesh is flesh, and that which is born of the Spirit is spirit.
7 Do not marvel that I said to you, ‘You must be born again.’
8 The wind blows where it wishes, and you hear the sound of it, but cannot tell where it comes from and where it goes. So is everyone who is born of the Spirit.”
9 Nicodemus answered and said to Him, “How can these things be?”
10 Jesus answered and said to him, “Are you the teacher of Israel, and do not know these things?
11 Most assuredly, I say to you, We speak what We know and testify what We have seen, and you do not receive Our witness.
12 If I have told you earthly things and you do not believe, how will you believe if I tell you heavenly things?
13 No one has ascended to heaven but He who came down from heaven, that is, the Son of Man who is in heaven.
14 And as Moses lifted up the serpent in the wilderness, even so must the Son of Man be lifted up,
15 that whoever believes in Him should not perish but have eternal life.
16 For God so loved the world that He gave His only begotten Son, that whoever believes in Him should not perish but have everlasting life.
17 For God did not send His Son into the world to condemn the world, but that the world through Him might be saved.
18 “He who believes in Him is not condemned; but he who does not believe is condemned already, because he has not believed in the name of the only begotten Son of God.
19 And this is the condemnation, that the light has come into the world, and men loved darkness rather than light, because their deeds were evil.
20 For everyone practicing evil hates the light and does not come to the light, lest his deeds should be exposed.
21 But he who does the truth comes to the light, that his deeds may be clearly seen, that they have been done in God.”
To travel from one country to another, every person, no matter how notable they might be, must have a passport.
Likewise, the new birth can be considered a sort of passport into the kingdom of God.
Jesus was visited by Nicodemus, a leading Pharisee of his day, who wanted to know more about Jesus’ is concept of the kingdom of God.
The Lord clearly taught Nicodemus that the new birth was the pre-requisite for entering the kingdom of God.
People who desire God's kind of life need to be born again just as Jesus taught Nicodemus.
Let us examine facets of the new birth.
- The new birth is a mandate.
Look at the person who came to Jesus.
There was a man of the Pharisees, they Nicodemus, a ruler of the Jews.
That's what it tells us in John 3:1.
Nicodemus had many commendable qualities.
He was a Pharisee.
Pharisees were religious people of Jesus' day who worked meticulously at interpreting and keeping God’s laws.
Their religion was mainly one of external rules, but they were moral, upright people.
Nicodemus was a ruler of the Jews.
This probably meant that he was a member of the Sanhedrin.
This was a group of seventy outstanding religious leaders.
Nicodemus acknowledge that Jesus had unusual powers from God.
In verse to he says Rabbi, we know that you are a teacher come from God, for no man can do these miracles that You do, except God be with him.
Fuss this is a person who came to see Jesus that had a lot of commendable virtues, he's a Pharisee, he's a religious ruler, and one who acknowledge the Jesus possessed a gift from God.
Look at Jesus’ words to Nicodemus.
Jesus went abruptly to the need of Nicodemus.
Without being impressed with his credentials or his compliments, Jesus said in John 3:5 'Verily, verily I say to you except a man be born again he cannot see the kingdom of God.”
Jesus gave a mandate to Nicodemus, it's in verse seven, he said marvel not that I've said toy you, that you must be born again.
There is no other way to enter the kingdom.
- The new birth is a miracle.
Think about what Nicodemus thought.
When Jesus mentioned the expression born again, Nicodemus thought of a physical birth.
He questioned, in verse four, “How can a man be born when he is old? Can you enter the second time in to his mother's womb and be born?”
Nicodemus acknowledge the mandate, but you confuse the new birth with a physical birth.
To go through physical birth again would be an impossibility.
But now I think about what Jesus meant.
The Lord was not talking about a physical birth.
He was talking about the miracle of new beginning.
To be born again means to allow God to come into your life and change.
That is a miracle indeed!
- The new birth has a means.
Listen to Nicodemus's questions.
Twice the Pharisee asked, “How?”
Without a doubt, Nicodemus wanted to know how we might have the new birth.
And listen to Jesus’ answers.
Jesus answered Nicodemus’s questions.
He told him that the means of experiencing the new birth was faith.
John 3:14-15 says, And as Moses lifted up the serpent in the wilderness, even so must the Son of Man be lifted up, that whoever believes in Him should [a]not perish but have eternal life.
To believe means to open our life to God.
When we open our lives to God, the new birth occurs.
- The new birth has manifestations.
Nicodemus was asked to observe the wind.
Jesus used an illustration about the wind he said in John 3:8, “The wind blows where it wishes, and you hear the sound of it, but cannot tell where it comes from and where it goes. So is everyone who is born of the Spirit.”
The results of the wind blowing can be seen.
Likewise, when the Lord comes into a life, changes are evident.
Jesus wants people to observe the result of the new birth.
Human beings change when they open their lives to God.
Attitudes and actions change.
People become children of God.
My question today is, "Do you want to enter the kingdom of God?"
The only means, the only way of entrance is to be born again, the new birth.
Open your life to Christ, and He will change you.
Until next time
Stay in the Blessings
I really want to encourage you to be diligent with your Bible study time, because God has so much more for us than we can get from just going to church once or twice a week and hearing someone else talk about the Word.
When you spend time with God, your life will change in amazing ways, because God is a Redeemer. Theres nothing thats too hard for Him, and He can make you whole, spirit, soul and body!
You’re important to God, and you’re important to us at The Refinery.
When it comes to prayer, we believe that God wants to meet your needs and reveal His promises to you.
So whatever you’re concerned about and need prayer for we want to be here for you! Or even if you just want to say Hi, you can contact us at www.refinerylife.org
2024 IS A YEAR OF DECISIONS AND OPEN DOORS
© www.refinerylife.org 2013-2024 All rights reserved. Except as permitted under the Australian Copyright Act 1968, no part of this Article may be reproduced, stored in a retrieval system, communicated or transmitted in any form or by any means without the prior written permission.
This episode is brought to you by Refinery Life Australia:
If you enjoy The Refinery Life Radio Podcast you can help support The Refinery by doing the following:
Sow an offering: Bitcoin: bc1qqh6720t2zagj72dyfj348az698tdut3hlecaj4
Online: https://www.refinerylife.org/donate/
If you do send an offering then please email us so that we can say thank you
Subscribe on iTunes | Spotify | YouTube | TuneIn | Rumble | Flare | Zap.Stream | Fountain |
Share The Refinery with your friends and family
Subscribe to the newsletter on www.refinerylife.org
Follow The Refinery on Twitter | Nostr | Instagram | Fountain |
-
 @ be7bf5de:09420d0a
2024-11-13 01:08:36
@ be7bf5de:09420d0a
2024-11-13 01:08:36At NosFabrica, we envision a future of healthcare where the individual is in charge of their health data and empowered to take responsibility for their own health. We are building health applications on Nostr and bitcoin to enable individuals own their health data. Nostr's architecture will allow different healthcare providers to write data onto the individual's relay. We see many potential use cases to solve specific problems in healthcare when the individual in a world where everyone has a comprehensive, portable and interoperable health record over time. We are looking to show what is possible with the "other stuff" on Nostr, starting by developing micro-apps so you can start compiling your health data, which you control.
If you're like most people on earth, your eyes aren't perfect. About half of us - 4 billion humans - have eye glasses, yet nearly a billion people can't get glasses due to inaccessibility of eye care or affordability.
With our microapp, Lazer Eyes, eye care providers can now write an eyeglasses or contacts prescription directly onto your own health relay. The optometrist simply needs to enter in your Nostr public key profile (nprofile), which relay to write the data to, and your prescription data; the encrypted prescription will be sent in an encrypted note directly to your relay. You can now send this signed note to your eye glasses provider to fulfill your glasses or contacts order.
 If you're using Amethyst today, you will be able to see this prescription rendered into your DMs. In our NosFabrica future vision, different clients would be able to show you this piece of your health record alongside other health information with different user interfaces and experiences. You will then have the power to selectively disclose this information, as needed.
If you're using Amethyst today, you will be able to see this prescription rendered into your DMs. In our NosFabrica future vision, different clients would be able to show you this piece of your health record alongside other health information with different user interfaces and experiences. You will then have the power to selectively disclose this information, as needed. There are many benefits to using Nostr for health as an individual:
There are many benefits to using Nostr for health as an individual:-
Patient Ownership and Control
-
Patients have full control of their prescription, and they can share it securely with confidence and even privately if required with eyewear providers or optometrists whenever needed.
-
Patients no longer rely on email or paper copies that can be easily lost or tampered with. Emailing a PDF to a patient brings the issue of requiring an optometrist signature leading to excess time taken to generate, print, sign, scan and email the copy. Public / private key cryptography provides a verifiable, time saving option in this case.
-
Continuity of care and ability to track changes in prescription over time - there are numerous forum posts where patients have found it difficult to get their prescription data from their optometrist practice when requesting it months or years later.
-
Removes the need for the patient to contact their old opticians and go through a process of trying to request their details, which can be time consuming.
-
Identity Verification
-
Optometrists sign prescriptions with a cryptographic key that patients could verify using their private Nostr identity (also known as a public/private key pair). This ensures that the prescription is authentic, accurate, and hasn't been altered after issuance. This would remove the need for issuing a “signed prescription” that currently has to be done in the physical sense, as a print out and issued to the patient. Have the option to have an indisputable and verifiable ‘Optometrist Identity Key’ would enable this legal requirement (in the UK) to go completely digital over Nostr.
-
The decentralized nature of Nostr ensures that prescriptions can be easily verified and traced back to the original issuer, avoiding forgery or fraud.
-
Privacy:
-
Unlike traditional methods where patient information is stored on centralized databases of the electronic medical record company (eg, Epic), or large health systems (eg, Ascension), Nostr keeps patient data decentralized and private, accessible only through permissioned sharing. This ensures no third party can access, manipulate, or misuse this sensitive information.
-
Immutable Records
-
Once a prescription is issued and signed on Nostr, it is stored immutably on the decentralized network. This ensures a permanent and trustworthy ledger of the patient's eye health history. This feature adds to accountability and should bring a higher standard to complete and accurate prescribing across all practices.
-
These records can persist over time and are portable to travel with you, wherever you seek care or glasses.
-
Global Access
-
Patients can use their Nostr-stored prescription with any provider across the globe, without needing to worry about differing national data standards or carrying physical documents when they travel or move.
-
This opens up a wider use case when considering the 2 Billion + individuals who currently cannot get access to sight care services.
Benefits for Optometrist Practices and Operators:
- Improved Patient Retention and Care through Trust and Transparency
-
By empowering patients with ownership of their data, practices foster trust and loyalty, reducing churn over time. If patients know they can rely on your practice for transparency, secure record-keeping, and access to the latest technology, they are more likely to return for future eye exams and other services.
-
A decentralized, tamper-proof record of prescriptions can improve administrative efficiency. No more handling lost prescriptions, disputes about validity, or delays in getting updated information to patients or other providers.
- The decentralized storage of prescriptions allows optometrists to securely share and access patient data, making cross-practice collaboration easier for referrals, second opinions, or specialized care.
- Cost Savings on Paperwork and Administration
-
Digitizing and decentralizing prescription records could lead to long-term savings on administrative costs, such as paperwork management, prescription re-issues, and managing patient data in outdated systems.
-
Optometrists can ensure their records are always accessible, accurate, and trusted by all parties (patients, insurers, other clinics).
- By reducing the burden of handling prescription storage and verification manually, the practice can focus more on patient care.
- Adaptation to Future Consumer Behavior and building a Tech-Savvy Reputation
-
As patients increasingly take control of their health data and seek decentralized solutions, practices that adapt to this trend are future-proofing their business model. Over time, patients will expect more control over their medical data, and being ahead of this shift will ensure long-term relevance.
-
Practices that embrace new technologies like Nostr can market themselves as tech-forward and adaptable to future trends, gaining an edge over more traditional competitors. This reputation is especially important as younger generations increasingly value privacy and digital autonomy. A Nostr-based service helps position the practice as aligned with these values.
- Integration with Bitcoin
-
By integrating a service built on Nostr, naturally linked with the bitcoin ecosystem, the practice can also introduce bitcoin payments as a novel way to reduce transaction fees and differentiate their practice from the competition.
-
Attract bitcoiners: The optics practice can appeal to the Bitcoin community, who value decentralization and would appreciate paying with bitcoin or using a decentralized protocol for prescription management. This opens up a new market of patients interested in technology and financial independence.
- Upsell Opportunities and Revenue Diversification
-
The practice can still maintain a competitive eyewear sales strategy by offering upsell opportunities. When patients receive their prescription digitally, they can be automatically sent tailored offers for high-quality lenses, frames, or even add-ons like blue light coatings or progressive lenses, keeping them within the practice’s ecosystem. Practices can offer value-added eyewear options, such as free adjustments, repairs, or personalized lens consultations, which online retailers can’t easily match.
-
The Nostr system can open doors to additional services beyond eyewear sales, including personalized consulting services, specialized testing (e.g., for contact lenses, binocular vision, myopia control), and more frequent checkups due to the ease of updating and verifying records.
Of course, utilizing this tool means providers need to help onboard individuals onto Nostr. In many ways, we see providers as playing into the Nostr network and flywheel effect. This is better technology with global access - and we invite you to consider other micro-apps that can continue to build out the decentralized healthcare ecosystem built on Nostr and bitcoin.
We have partnered with the Bitcoin Optometrist, Dr Alan Bryden, to continue to refine the micro-application and start testing its use. We'd like to thank Dr Alan for his insights that contributed to this micro-app and write-up. Check out his site and nonprofit, Sats for Sight, to learn more about utilizing bitcoin to provide eyeglasses to those in need, along with his HODL eyewear line.
We're excited about the future of building healthcare applications on nostr and bitcoin. If you have ideas or are facing any health challenges, we're conducting product discovery interviews to understand your biggest pain points when it comes to managing and optimizing your health and healthcare data. Please reach out to jon@nosfabrica.com or schedule time here to learn more about how to get involved!
Note: Lazer Eyes is currently only available for testing purposes as we evaluate regulatory considerations across jurisdictions.
-
-
 @ 3c7dc2c5:805642a8
2024-11-12 21:52:55
@ 3c7dc2c5:805642a8
2024-11-12 21:52:55🧠Quote(s) of the week:
'If you have survived China mining ban, FTX, BlockFi, Celsius, Futures ETFs, and massive FUD you are now a confirmed Bitcoin HODL’er. It’s time to sit back and enjoy The Banana Zone' - BTCforFreedom
'You should not sell your bitcoin. Your children should not sell your family’s bitcoin. It is wealth that should last generations. This is grabbing land in the New World in the 1700s, except instead of waiting 350 years for it to mature, you wait 20 years.' - Wealth Theory
🧡Bitcoin news🧡
Let me start this week's Weekly Recap with the following message. This is it, ladies & gentlemen. Retail is starting to get excited. People are asking me: 'Should I buy Bitcoin?', 'Am I too late?', 'Will Bitcoin reach the 100K or 200K?' I honestly have no clue, and it depends on the liquidity splashes coming from central banks. But I truly believe much higher than 100K. Don't pinpoint it, as I said, I have no clue.
But for the love of god, calm your tits people! This is not the end goal! Now I am in no position to tell you what to do with your corn, but selling now? I don't think so chief! You didn’t sit through 7 months of chop to start thinking about the exit already. You can endure the same amount of time again. How do I feel about Bitcoin in the upcoming years, and decades, well let me explain that with the following picture:
So Trump won, but remember, you will still want to own Bitcoin.
'There is no red. There is no blue. There is the State. And there is you.' - WalkerAmerika
On the 5th of November:
➡️Semler Scientific announced yesterday that they increased their Bitcoin holdings to 1,058 BTC. Today, their stock is up 25%.
➡️Bitcoin mining difficulty hits a new ATH, surpassing 100 trillion.
➡️Bitcoin has always gone PARABOLIC after a US election, and Bitcoin has never dipped back lower than the price on election day.
➡️Trump as the US President: - Pardoning Ross Ulbricht on Day One - A Strategic Bitcoin Reserve - Friendly mining policies - Favorable SEC: end of Choke Point 2.0
➡️Semler Scientific purchases an additional 47 Bitcoin, and now holds 1,058.
➡️Bitcoin miners Marathon Digital and Riot Platforms report their highest production since halving in October. Marathon mined 717 BTC ($48.8M), while Riot mined 505 BTC $34.4M).
On the 6th of November:
➡️Bitcoin hits a new all-time high. Bitcoin hit $75,000 for the first time as it became clear Trump won the election. The anti-Bitcoin movement died last night (election day/night). The USA will be the most pro-Bitcoin nation in the world. And it looks like they will have a Bitcoin Strategic Reserve.
Senator Lummis has put forward a bill for the U.S. Govt to buy 200,000 Bitcoin per year over 5 years for a total of 1,000,000 $BTC. At today's price that would be worth $76 BILLION.
One tiny little thing is why I am skeptical about this bill. During a speech at the Bitcoin conference in Nashville Lummis used her words quite well, let's say strangely: Her word choice here is "assemble" instead of "purchase" or "buy". Most likely MicroStrategy will play a role and they, the US government, already have like 200K Bitcoin.
I have a feeling a Strategic Bitcoin Reserve will be built through confiscation and taxation – and Lummis is already hard at work to make it happen. Just a feeling.
➡️You have approximately three months until the U.S. Government puts into law the active accumulation of Bitcoin as a strategic reserve asset.
Other sovereigns will be discreetly front-running. The clock has already started. Cheers to everyone who built a Strategic Bitcoin Reserve before the United States of America.
➡️BlackRock’s Bitcoin ETF saw a record volume of $1 billion today in the first 20 minutes. Bitcoin ETFs have seen $3.73 billion in trading volume over the last 24 hours, with BlackRock accounting for over half of it.
➡️$4.5 billion Bitwise CIO says, “We are entering the Golden Age of Crypto.” We will see a “strong bull market for years to come.”
➡️Bitcoin surpasses Meta to become the world’s 9th largest asset by market cap.
➡️'MicroStrategy breaks $50 BILLION market cap and is now worth more than Ford Motor Company.
Ford has lost ~60% of its market cap since 2022 and holds $26 BILLION in cash, about 65% of its total market cap! The "melting ice cube" of cash holdings, eroded by inflation year after year. This is what Michael Saylor feared for his company when he decided to buy Bitcoin in 2020. MicroStrategy's market cap has been up ~45x since then. Get some Bitcoin Ford.' - Bitcoin Archive
On the 7th of November:
➡️MicroStrategy will spend $10 BILLION buying Bitcoin next year, which is more than the total amount it has spent buying Bitcoin since 2020.
➡️Bitcoin is tracking the 2017 and 2021 bull markets perfectly and is ready for lift-off.
➡️Italy is under pressure from lawmakers to drop proposals to raise taxes on Bitcoin. & crypto capital gains.
Economic Minister: "I am willing to consider different forms of taxation for people who keep investments in their portfolio."
➡️Chinese TV reporting that “Trump will make the US the world's crypto capital and establish a strategic Bitcoin reserve.” This is now urgent for every nation.
➡️ Bitcoin Treasuries are expanding in the EU.
The Blockchain Group has appointed Alexandre Laizet as Deputy CEO, focusing on boosting Bitcoin holdings per share. They’re raising €1 million to acquire 15 Bitcoin, strengthening their BTC strategy.
On the 8th of November:
➡️Yesterday's Bitcoin ETF inflows have reached a new high with $1,373.8 million of inflows. Blackrock did $1,119.9 million and Fidelity $190.9 million. Price went from $75k to $76.5k now, sitting back at $75.7k.
➡️Swiss National Bank Chairman says Bitcoin is a "niche phenomenon" not suitable for payments. Meanwhile: The largest Swiss Canton bank now offers Bitcoin to 1.5m customers Bitcoin!
➡️ Bitcoin vs. Gold ETF inflows by year.
Bear in mind that the first year of an ETF is historically the hardest to attract inflows. In 10 months, Blackrock's Bitcoin ETF just surpassed what Blackrock's Gold ETF did in 20 years.
➡️'The former CEO of Sotheby's, Tim Smith. It is his job to know value. He retired and studied Bitcoin and the economy we have just been in. Please I urge you to understand as Bitcoin goes from $76,000 to $1,000,000 and beyond.' - Brian Roemmele Please watch the clip: here
The video is perfectly explained by BTConlyScoot: 'This is the perfect type of individual and video to show to your high institutional trust, high IQ friends who are skeptical of Bitcoin... The CEO of Sotheby's tells them; 1. they need to do 100-100 hours (not you telling them - the CEO of Sotheby's) 2. 8-10% increase in money supply = 8-10% increase in S&P index, is correlated and consequentially is no increase in your wealth (... again not you telling them) Because they are high-trust individuals, they need someone with credentials they respect to spell it out.
Then they just might study Bitcoin! But you won't get the credit.'
➡️Google searches for Bitcoin are surging as the price hit $76,000 to make a record high this week. In good dutch, 'het klootjesvolk komt eraan!'.
➡️German parliament member Joana Cotar says "If the US buys Bitcoin as a strategic reserve, then I think all the European countries will get FOMO.”
German government's decision to sell 50,000 Bitcoin at $54K cost them $1.1 billion in missed profits. Wunderbar!
On the 9th of November:
➡️El Salvador is now $100 million in profits on their Bitcoin.
➡️Bitcoin ETFs bought $2.3 BILLION of Bitcoin in the last 3 days.
On the 10th of November:
➡️Bitcoin has finally reached its first inflation-adjusted all-time high since 2021.
➡️El Salvador is now $100 million in profits on their Bitcoin.
On the 11th of November:
➡️$725 billion Bernstein urges investors to add exposure to Bitcoin “as soon as possible.” “We will keep it simple. Don’t fight this.”
➡️Wicked: 'When Bitcoin first broke out above its all-time high in 2017, it pumped +139% and then had a brutal -40% retracement. If we saw those percentages again for this cycle's first break out, we'd see a pump to $167k followed by a retracement back to $100k.' ➡️BlackRock’s Bitcoin ETF does $1 BILLION trading volume in just 35 minutes.
➡️MicroStrategy acquires an additional 27,200 BTC for $2 billion They now hold 279,420 BTC acquired at $42,692 per Bitcoin. Michael Saylor outlines the path for MicroStrategy to become a TRILLION-DOLLAR company. “I think it's infinitely scalable. I don't have any problem seeing how we could raise $100bn more capital and then $200bn after that."
➡️This is the biggest single-day $ price increase in Bitcoin history!
💸Traditional Finance / Macro:
On the 5th of November:
👉🏽'Corruption, the billionaires and market makers always know. Last Week: Ken Griffin sold 79% of Citadel’s Stake in Nvidia.This Week: Nvidia, ask the US Supreme Court to spare them from securities fraud suits.' Meta News
The vast majority of productivity gains and the added value created by human innovation is robbed by governments through inflation. That's why we Bitcoin.
On the 9th of November:
👉🏽For the first time in history, the S&P 500 broke above 6,000 last week, up +46% in 13 months. The S&P 500 now has a market cap of $50 TRILLION, adding $15 trillion since October 2023. However, US technology funds have seen a record $5 billion of outflows over the last 4 weeks.
On the 10th of November:
👉🏽'Berkshire Hathaway’s, cash position relative to total assets jumped to 28.0% in Q3 2024, the most in at least 34 years. This means that Buffett's cash share has DOUBLED in just a year. The company is piling into cash at a faster pace than in the mid-2000s. Back then, this percentage reached 24.5% in Q2 2005 and remained elevated until 2008. Berkshire Hathaway also decided to HALT stock buybacks for the first time since 2018. Does Warren Buffett believe the market is too expensive?' - TKL
🏦Banks:
👉🏽no news
🌎Macro/Geopolitics:
On the 5th of November:
👉🏽'Output per hours worked ("labor productivity") has increased much more in the US than in other advanced economies since the pandemic. Maybe using an economic policy strategy aimed at running the economy hot was not a bad idea after all?' - Phillip Heimberger
👉🏽In 2000, China accounted for 6% of global manufacturing. In 2030, China is projected to account for almost half of all global manufacturing. This kind of shift is unprecedented in the modern world economy.
👉🏽Evidence of plutocratic developments in the US: Billionaires spent nearly $2 billion on the 2024 US presidential election (60% more than during the 2020 election). Almost three-quarters of billionaire campaign spending went to Republicans.
👉🏽Jeroen Blokland: 'We go into the USElection2024 with US debt higher than ever, and both candidates are likely to add much more of it than is projected in the already dire baseline projected by the Congressional Budget Office. Obviously, the US will print its way out of this.
A key question is whether this will trigger a faster unfolding of Gresham's law, the phenomenon where people will spend 'bad' money (money with less value) first and hoard 'good' money (money with more value.)'
👉🏽'Global central bank net gold purchases reached 694 tonnes year-to-date, the 3rd largest on record.
In Q3 alone, the net buying hit 186 tonnes as gold prices continued their historic run. Since 2022, central banks have acquired a MASSIVE 2,825 tonnes of gold, double the average seen before the 2020 pandemic. Purchases have been primarily driven by China, India, Turkey and Poland. Gold prices have hit 41 all-time highs this year and are up 33% year-to-date, the best performance in 3 decades.
Central banks are stocking up on gold while calling for a "soft landing." -TKL
On the 6th of November:
👉🏽Trump won the elections in a decisive way. Trump's win is responsible for this Bitcoin pump, which will likely lead to a more sustained long-term bull run. Yet make no mistake the bull run would've still happened even if Trump had lost.
Some important stats: * Trump won Starr County TX, the most Hispanic county in America at 97% by 16 points. The last time it voted Republican was in 1892. * What about campaign spending in the swing states?
I guess campaign spending doesn't determine the outcome. Worth noting that far more “billionaires” backed Harris than Trump and she raised almost 50% more money. 3 out of 4 Americans who said that inflation caused them and their family severe hardship in the last year voted for Trump.
-
People hate price increases (irrespective of whether their real wages keep up), and this was a major reason for voting the Democrats out.
-
2004 John Kerry 59 million votes.
2008 Barack Obama 69.5 million votes.
2012 Barack Obama 65.9 million votes.
2016 Hillary Clinton 65.8 million votes.
2020 Joe Biden 81 million votes.
2024 Kamala Harris 68 million votes.
What happened in 2020?
Peter McCormack is spot on: "To all the people that are surprised and angry by the Trump result, I am sad to inform you that there is an equal cohort in the UK who are also pissed off with the corporate media, political elite, inflation, attacks on free speech, etc... Your irrational meltdowns will not change what is coming..."
👉🏽'To my friends in Germany, it seems that with the news of the end of the German government, both Harris and Habeck will fall into irrelevance the same day. Cheers.'
On this day the German coalition government imploded. As the federal government is collapsing and the country approaches early elections, the right-wing party AfD is ahead of all three government parties. Lindner triggered the collapse, and his FDP is currently unlikely to even overcome the 5% hurdle of getting into parliament.
On top of that Germany is not in a recession, the German business model based on cheap energy from Russia, growing exports to China, and cheap subcontractors in Eastern Europe is imploding.
Grotesque overregulation, green paranoia and ideological amateurs in key government positions do the rest. Industrial production in Germany is now 17% lower than at the end of 2017. Auf gehts, Jungs!
To make it even worse, on the 11th of November news came in: the German economy is suffering from the worst lack of orders since the global financial crisis of 2009 — Ifo Institute
On the 7th of November:
👉🏽REPORTER: If Trump asked you to leave would you go? Jay Powell: No REPORTER: You're not required to leave? Jay Powell: No Q: If the Fed doesn't answer to the President of the USA, who does it answer to?!
In terms of funding, the Fed operates like a private entity but its board reports to Congress.
It’s an independent entity within the us government. The president chooses the fed chair but after being selected he can’t remove him because of political conflict of interest.
But you must ask yourself who is on the board of the Fed? Good luck finding out who. The banking cartel. The families that run it. You ain't in that club.
👉🏽'What's happening with the "Fed pivot?" Today, the Fed cut interest rates by 25 bps in their 2nd cut since 2020. Meanwhile, mortgage rates are at their highest level since July and have risen ~100 basis points in 2 months. Is the market doubting the Fed pivot?' -TKL The Bank of England also cut rates today.
👉🏽'US personal interest payments hit $556 BILLION in September, the second-largest in history. Since 2022, Americans' interest costs have DOUBLED. Personal interest as a percentage of disposable personal income is now at 2.5%, near the highest since the 2008 Financial Crisis. This metric is also materially higher than the 2.0% seen in the 1970s when interest rates were almost twice as much as the current 4.75%-5.00% range. All while the total household debt sits at a record $17.8 TRILLION. Consumers are drowning in interest expense.' -TKL
On the 8th of November:
👉🏽China announced a $1.4 TRILLION debt bailout and is working on more measures to boost the economy.
On the 9th of November:
👉🏽Robert Habeck, German Vice Chancellor, and Green party member: "The regulation of algorithms, of X or TikTok, through the application of European legal norms is a central task. We cannot place ‘democratic discourse’ in the hands of Elon Musk and Chinese software." Good luck Robert Habeck with regulating X. You have not noticed that things have changed since Tuesday? There is a new sheriff in town. JD Vance says the US could veto NATO if Europe tries to regulate Elon Musk’s platforms.
“If NATO wants us to continue supporting them, and NATO wants us to continue to be a good participant in this military alliance, why don't you respect American values and respect free speech?” “It's insane that we would support a military alliance if that military alliance isn't gonna be pro-free speech.” “We've gotta say American power comes with certain strings attached. One of those is respect for free speech, especially in our European allies.” “European countries should theoretically share American values, especially about some very basic things like free speech.”
👉🏽'US government spending is set to reach $13.0 TRILLION in 2029, according to IMF estimates. That would be almost DOUBLE the amount seen in Fiscal Year 2024 which came in at $6.8 trillion. To put this into perspective, prior to 2008, government expenditures were 3 TIMES lower. Meanwhile, the US posted its third largest budget deficit in history last month, reaching $1.8 TRILLION or 6.4% of GDP. Currently, total federal debt sits at a new record of $35.9 trillion.' -TKL
🎁If you have made it this far I would like to give you a little gift:
Lyn Alden: 'Along with Steve Lee and Ren, I co-authored a paper that analyzes the process and risks of how Bitcoin upgrades its consensus rules over time, from a technical & economic perspective.'
https://github.com/bitcoin-cap/bcap/blob/main/bcap_v1.0.pdf
Thread: https://x.com/LynAldenContact/status/1854606667213603208 Great read!
Credit: I have used multiple sources!
My savings account: Bitcoin
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple. ⠀⠀⠀⠀⠀⠀⠀⠀
Do you think this post is helpful to you? If so, please share it and support my work with sats.
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe - Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-
-
 @ 3cea4806:10fe3f40
2024-11-12 21:24:18
@ 3cea4806:10fe3f40
2024-11-12 21:24:18testA looong
-
 @ ac8bb9b0:70278acc
2024-11-12 19:55:33
@ ac8bb9b0:70278acc
2024-11-12 19:55:33Details
- ⏲️ Prep time: 10
- 🍳 Cook time: 45
- 🍽️ Servings: 16
Ingredients
- 1/4 cup light brown sugar
- 1/4 cup granulated sugar
- 1 tablespoon ground cinnamon
- 1 teaspoon salt
- 1 pound unsalted pecans halves
- 1 egg white
- 1/2 teaspoon vanilla extract
- 1 teaspoon water
Directions
- Preheat oven to 300 degrees F. Line a large baking sheet with parchment paper and set aside.
- In a bowl, add sugars, cinnamon, and salt. Whisk until combined. Set aside.
- In a large bowl, whisk the egg white, vanilla, and water together until frothy. Add the pecans and gently toss until the pecans are well coated. Add the sugar and cinnamon mixture and toss until pecans are covered.
- Spread the pecans out in a single layer on prepared baking sheet. Bake for about 30-45 minutes, stirring every 15 minutes.
- Remove from the oven and let the pecans cool on the baking sheet. When completely cool, store in an airtight container for up to 1 month.
-
 @ 6e24af77:b3f1350b
2024-11-12 18:53:21
@ 6e24af77:b3f1350b
2024-11-12 18:53:215
-
 @ 90ae01dc:6991f210
2024-11-12 18:08:21
@ 90ae01dc:6991f210
2024-11-12 18:08:21test article generated in hablanews by hablanator
-
 @ 0461fcbe:35a474dd
2024-11-12 17:58:48
@ 0461fcbe:35a474dd
2024-11-12 17:58:48On Nostr, I am running several marketing accounts for my projects: Ditto, The Mostr Bridge, and Cobrafuma. But I want other people to be able to post from those accounts. In fact, I want to hire a "social media manager" someday (for when my wife is not available 😂).
This is a pretty basic need for social media, but of course on Nostr it isn't basic at all, because private keys have nuclear potential if leaked. Even if you trust the person, a small mistake could be disastrous.
To solve this, we need a bunker.
What is a bunker?
A bunker (aka "remote signer") allows you to store your keys on your computer, but give others access. Once the other person is granted access, they can send commands to your computer like
sign_eventandget_public_key, and your computer will perform those operations without needing to expose the actual key.
In reality the UX is not so technical. Your bunker generates a unique URI containing the connection details, and the other person pastes it into the login screen. Everything else happens automatically.
As for the running the bunker, you can run it on a VPS, a laptop, an old computer in your house, a Raspberry Pi, or even an Android phone.
The first bunker was an Android app called Nostr Connect. This lead to the creation of nsecBunker (a hosted service), nsec.app (a bunker that runs inside your web browser), and Amber (another Android app).
These days nsec.app and Amber are the only ones being actively developed, but due to running in restricted environments (web and Android respectively), they don't offer the level of 24/7 reliability I wanted in a bunker. If you are a single user managing your own keys I still recommend Amber, but for doling out credentials to your team, you might want knox.
Introducing Knox
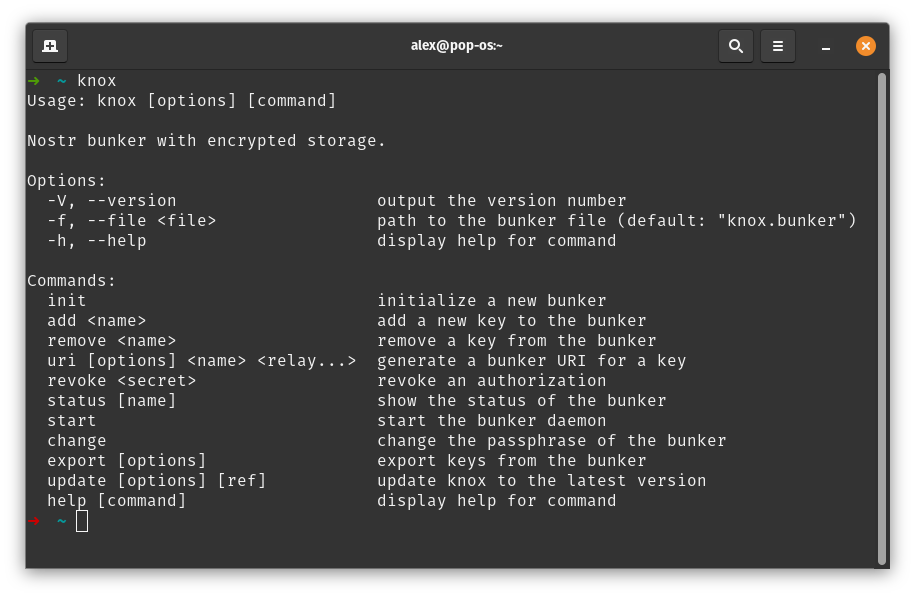
knox is a command-line tool that manages keys, generates bunker URIs, and runs a bunker server. It is still beta software, but I am using it successfully today to post on Ditto.
knox is inspired by the wonderful
nak bunkercommand, which almost solved my problem but has no way to store credentials. So I created my own command-line bunker that you can run again and again.
Most notably, knox introduces a portable
.bunkerfile format for storing keys and connection details. It's encrypted with a password, which you have to type every time you want to add or remove keys, generate new URIs, and when you start the bunker.With knox you can have one bunker file, or many. It is loosely inspired by the KeePass
.kbdxidea.knox is written in TypeScript, but it's available as a precompiled executable on Linux, MacOS, and Windows thanks to
deno compile.Getting Started
To install knox, I've prepared a simple setup script that will detect your OS and install the knox command in your path:
sh curl https://dl.soapbox.pub/install/knox.sh | shYou can also grab a precompiled binary if you don't want to run the script.
Commands
Once installed, run
knoxto see a list of supported commands. It should look something like this:``` Usage: knox [options] [command]
Nostr bunker with encrypted storage.
Options: -V, --version output the version number -f, --file
path to the bunker file (default: "knox.bunker") -h, --help display help for command Commands: init initialize a new bunker add
add a new key to the bunker remove remove a key from the bunker uri [options] generate a bunker URI for a key revoke revoke an authorization pubkey [options] show the public key of a secret key status [name] show the status of the bunker start start the bunker daemon change change the passphrase of the bunker export [options] export keys from the bunker update [options] [ref] update knox to the latest version help [command] display help for command ``` Run
knox initto create a new bunker file. Then useknox add alex(replace with your own name) to add a key, thenknox uri alexto get a connection string. Finally, runknox startto start the bunker.While the bunker is running, you can continue to run commands like
knox addandknox uriin another tab, and the bunker will detect the file changes and automatically refresh.
Another good one is
knox status, which shows a list of keys and whether any of their URIs are being utilized.knox status <key>can show the individual connections for a specific key, andknox revoke <secret>can revoke an individual connection.Bunker Where?
knox needs internet connectivity to connect to relays, but it does not need to expose any ports to the outside world, so the ideal place might be on a desktop computer in your living room. This might be considered more secure than a VPS in a datacenter, depending on your circumstances.

I am running knox on an old Dell computer under my TV, which is a cheap and simple solution. It's connected to a backup battery in case the power flickers, but a prolonged outage would require starting the bunker again manually. I also suggest running the bunker in
screenor a similar tool so you can reconnect and view the logs over ssh on your home network.It's not suggested to run knox in systemd, because knox requires manually entering the encryption password when it starts. Any solution to store the password to disk, or pass it through a command-line argument, would compromise security.
What's Next?
For now, knox is meeting my needs. As the idea evolves I expect to make more changes, and possibly improvements to the
.bunkerformat if anyone else decides to use it. Feel free to drop any suggestions on GitLab!Another interesting idea would be to build a UI to manage the
.bunkerfile, or to offer hosted bunker (although I am kind of against this, unless the hoster is just cloud sync service and the bunker is decrypted locally within the browser, similar to KeeWeb). -
 @ 13351007:eccd002a
2024-11-12 17:32:12
@ 13351007:eccd002a
2024-11-12 17:32:12just testing with p tag
-
 @ 13351007:eccd002a
2024-11-12 16:33:39
@ 13351007:eccd002a
2024-11-12 16:33:39just testing with p tag
-
 @ 13351007:eccd002a
2024-11-12 15:44:07
@ 13351007:eccd002a
2024-11-12 15:44:07just testing
-
 @ 30ceb64e:7f08bdf5
2024-11-12 15:41:27
@ 30ceb64e:7f08bdf5
2024-11-12 15:41:27Hey Freaks,
Listen to these.
Joy Again - How you Feel
https://music.youtube.com/watch?v=g94AbYYL678&si=JVzaqFjtG0s-SKqQ
Vacations - Young
https://music.youtube.com/watch?v=oAur1xQx-sc&si=HB7PrvtOA2phz3Jk
The Rare Occasions - Notion
https://music.youtube.com/watch?v=3vEiqil5d3Q&si=LdRtoEFrO4kldPzw
Current Joys - Blondie
https://music.youtube.com/watch?v=XVuBw7TYvHg&si=_mm3U5Rj29xEAXiD
Mac Demarco - On The Level
https://music.youtube.com/watch?v=WOV3c0t-Mwk&si=HZC2Ei-rnIE6-K4I
Snail Mail - Habit
https://music.youtube.com/watch?v=MHYxZKEV0bY&si=_XBaUw4O4DZKp6iq
Modest Mouse - Trailer Trash
https://music.youtube.com/watch?v=5kwLVhnTYlI&si=qEhasX5NckmoW_ke
Third Eye Blind - Darkness
https://music.youtube.com/watch?v=WlLyAMU7MtQ&si=edt-dNgbgg-m0HJ_
Weezer - Pink Triangle
https://music.youtube.com/watch?v=v2vWDWxYJBc&si=UlMuJjofu_l__dak
The Mars Volta - The Widow
https://music.youtube.com/watch?v=0lAXFjAmcnM&si=YOOo4lCo1iMzzRQi
And let me know what you think.
originally posted at https://stacker.news/items/764730
-
 @ 4874b840:31b0b8c0
2024-11-12 14:58:03
@ 4874b840:31b0b8c0
2024-11-12 14:58:03В 2050 году Калининград продолжит эволюционировать, и транспортная система города претерпит значительные изменения по сравнению с 2040 годом. За десятилетие, власти планируют изменить город, чтобы он стал образцом для подражания в области устойчивого и инновационного транспорта.
В 2040 году основным акцентом является развитие электробусов и велосипедных дорожек. Электробусы, которые уже сейчас заменяют традиционные дизельные автобусы, обеспечивают более чистый и тихий транспорт. Велосипедные дорожки активно используются горожанами, и многие жители пересели на двухколесный транспорт.
К 2050 году планируют выпускать автобусы, оснащенными солнечными панелями, которые позволят подзаряжать батареи в течение дня. Из нового в автобусы будет внедрена система автономного вождения. Механики к 2050 году планируют изготовить новые модели общественного транспорта – автономные электрические минивэны, которые будут курсировать по определенным маршрутам и будут подбирать пассажиров по запросу через мобильное приложение.
Планами на улучшение транспортной сети города с редакцией «Калининград 2040» поделился сотрудник Транспортного управления Михаил Чернец:
Как сотрудник транспортной компании, я с большим энтузиазмом наблюдаю за тем, как Калининград меняется и развивается. К 2050 году мы планируем внедрить ряд новых современных транспортных средств, которые сделают передвижение по городу еще более удобным и экологически чистым. Во-первых, мы активно работаем над расширением нашего парка электробусов. Эти автобусы не только снижают уровень загрязнения, но и обеспечивают комфортные поездки для пассажиров. К 2050 году мы планируем оснастить их новейшими технологиями, такими как системы автономного вождения и солнечные панели для подзарядки. Это позволит нам сократить затраты на эксплуатацию и сделать транспорт более доступным для всех горожан.

 Макеты будущих автобусов
Макеты будущих автобусов -
 @ 4874b840:31b0b8c0
2024-11-12 14:51:28
@ 4874b840:31b0b8c0
2024-11-12 14:51:28В Калининграде, городе с уникальным историческим наследием и живописной природой, в последние годы наблюдается заметный прогресс в области экологии. В 2040 году несколько инициатив, направленных на улучшение экологической ситуации, успешно реализованы, что стало важным шагом к устойчивому развитию региона.
Одной из ключевых инициатив стало создание «Зеленого пояса» вокруг города. Этот проект, реализованный при поддержке местных властей и экологических организаций, включает в себя высадку более 500 тысяч деревьев и кустарников, что значительно улучшило качество воздуха и создало новые зеленые зоны для отдыха горожан. «Зеленый пояс» стал не только защитой от загрязнений, но и местом обитания для множества видов животных и птиц.

Кроме того, в Калининграде успешно функционирует программа по утилизации отходов, которая включает в себя раздельный сбор мусора и переработку. Благодаря внедрению современных технологий и активному вовлечению населения, уровень переработки отходов в городе достиг 70%. Местные жители активно участвуют в образовательных мероприятиях, направленных на повышение осведомленности о важности экологии и правильного обращения с отходами.

Не менее значимой стала инициатива по развитию экологического транспорта. В 2040 году в Калининграде функционирует сеть электробусов и велосипедных дорожек, что способствует снижению уровня выбросов углекислого газа и улучшению транспортной ситуации в городе. Местные власти также внедрили программу субсидирования покупки электромобилей, что сделало экологически чистый транспорт доступнее для горожан.

«Я живу в Калининграде уже много лет, и за последние несколько лет заметила, как наш город преобразился. В 2040 году здесь действительно стало хорошо жить! Зеленые парки и скверы, которые появились благодаря инициативам по озеленению, стали любимыми местами для прогулок с семьей и друзьями. Я часто гуляю по «Зеленому поясу» — это просто невероятно, как природа вернулась в наш город!» - Галина Симакова поделилась своими впечатлениями о развитии города.
-
 @ 4874b840:31b0b8c0
2024-11-12 14:38:03
@ 4874b840:31b0b8c0
2024-11-12 14:38:03Калининград, уникальный город на западе России, за последние 20 лет претерпел значительные изменения, которые затронули все сферы жизни — от экономики и инфраструктуры до культуры и экологии. В этом обзоре мы рассмотрим ключевые моменты, которые определили развитие города с 2020 по 2040 год.
Экономические вызовы
В начале 2020-х годов Калининград столкнулся с рядом экономических вызовов, включая высокую зависимость от внешних рынков и недостаток инвестиций. Однако благодаря активной государственной поддержке и привлечению частных инвестиций, город стал центром новых технологий и инноваций. В 2030 году был запущен ряд крупных проектов в области судостроения и логистики, что способствовало созданию новых рабочих мест и увеличению объемов производства.

 Судостроение Калининграда 2020 и 2040 годов.
Судостроение Калининграда 2020 и 2040 годов.Логистика
Калининград также стал важным логистическим хабом благодаря своему стратегическому расположению между Европой и Россией. Развитие транспортной инфраструктуры, включая новые автодороги и модернизацию аэропорта, способствовало росту туристического потока и увеличению объемов грузоперевозок.
Инфраструктура
В рамках программы «Умный город» были внедрены современные технологии в управление городскими услугами, что повысило качество жизни горожан. Новые жилые комплексы, парки и общественные пространства стали неотъемлемой частью городской среды.

 Изменения на Главной площади Калининграда. Сравнение 2020 и 2040 годов
Изменения на Главной площади Калининграда. Сравнение 2020 и 2040 годовГородское развитие
Внедрение зеленых технологий, таких как солнечные панели и системы утилизации отходов, сделало город более экологически чистым и комфортным для жизни.
Культурная жизнь
В 2020-х годах началось активное развитие культурных инициатив, включая фестивали, выставки и театральные постановки. Город стал центром культурного обмена, привлекая художников и творческих людей со всей страны и из-за рубежа.

 Кафедральный собор в 2020 и 2040 годах
Кафедральный собор в 2020 и 2040 годахОбразование
В 2035 году был открыт новый университет, который стал центром исследований в области экологии и устойчивого развития, привлекая студентов и ученых со всего мира.

 Балтийский федеральный университет имени Иммануила Канта в 2020 и 2040 годах
Балтийский федеральный университет имени Иммануила Канта в 2020 и 2040 годахИзменения в социальной сфере
Власти города активно работали над улучшением системы здравоохранения и образования. Были реализованы программы по повышению доступности медицинских услуг и улучшению качества образования, что способствовало повышению уровня жизни населения. К 2040 году Калининград стал более инклюзивным городом, где активно развиваются инициативы по поддержке различных социальных групп, включая молодежь, пожилых людей и людей с ограниченными возможностями.
Пройдя через экономические трудности и социальные изменения, Калининград сегодня представляет собой уникальное сочетание исторического наследия и современных технологий, что делает его привлекательным как для жителей, так и для гостей.
-
 @ 4874b840:31b0b8c0
2024-11-12 14:16:37
@ 4874b840:31b0b8c0
2024-11-12 14:16:37Мы рады представить новое издание «Калининград 2040», которое станет уникальным источником информации о будущем нашего города. Это средство массовой информации будет освещать самые актуальные новости, инновационные разработки и ключевые события, формирующие облик Калининграда в ближайшие десятилетия.
«Калининград 2040» будет не только информировать читателей о новых технологиях и проектах, но и погружать их в мир морской промышленности. Мы планируем эксклюзивные репортажи с производств морских судов, где будут представлены передовые разработки и достижения местных предприятий. Читатели смогут узнать о том, как Калининград становится важным центром судостроения и какие перспективы открываются для региона.
Мы уделим внимание актуальным экономическим проблемам, с которыми сталкивается город. Мы будем анализировать изменения в экономической ситуации, обсуждать меры по поддержке бизнеса и привлекать экспертов для оценки будущих трендов.
Здравоохранение — еще одна важная тема, которую мы планируем освещать. В условиях быстро меняющегося мира мы будем следить за новыми инициативами в области медицины, инновациями в лечении и профилактике заболеваний, а также за развитием системы здравоохранения в Калининграде.
Не обойдем стороной и уникальную историю нашего города — «городок кошек». Мы расскажем о том, что произошло с этим необычным местом, как оно изменилось и какие инициативы по его сохранению и развитию существуют сегодня.
«Калининград 2040» — это не просто новостное издание, а платформа для обсуждения будущего нашего города. Мы приглашаем всех заинтересованных читателей следить за нашими публикациями!
-
 @ 45bda953:bc1e518e
2024-11-12 13:25:12
@ 45bda953:bc1e518e
2024-11-12 13:25:12I recently watched Robert Breedloves WiM528 linked below. His guest whom I have never heard of before, Bryan Solstin, made the most compelling case to potentially prove the identity and person behind the persona of Satoshi Nakamoto. Their discussion fascinated and triggered me at different points for different reasons. In my writings I frequently draw a very strong correlation between Satoshi Nakamoto and Jesus Christ because of the synchronicity and alignment of their goals and effective outcomes. I strongly advise anyone curious about Satoshi's possible identity to watch the full episode.
https://www.youtube.com/watch?v=xYuNA3ifPKc
One of the topics of discussion was the problem of mental illness, paranoia and schizophrenia and is the point I would like to expound on in this document.
This type of illness is not unwarranted and I find it to be much more common under the general populace of the world than is generally believed. Pharmaceutical drugs speaks to the symptoms of these fears but does not answer the cause. I strongly oppose drugs as a means to deal with possible mental health conditions because I believe them to be dangerous and suicide inducing when brain chemistry is affected by alcohol, chemicals in food, drink and water. It can have a host of undesirable side effects on medicated minds. I am not speaking to everyone's unique situation. I would personally much rather beat my problems out in my private ruminations and suffer in silence hoping to come to a point where some type of closure is found. Hopefully that helps me to carry on with life in a way that brings stability and peace to my family and loved ones in spite of inner my confliction and turmoil carried as permanent scars on my conscience.
The problem of paranoia and schizophrenia is as old as time and is predominantly a spectre born from uncertainty. This uncertainty in a more extreme way plagues people with power and wealth who suffer from these fears more than simple people with simple lives and little or nothing to lose. People with power and wealth, driven by fears and doubts then manifest and project their own fear outwards in the form of tyrannical oppression of these simple and contented people. In turn it manifests in the general population as paranoia and schizophrenia, an irrational/rational fear of the elite. A loop of fear and pain feeding on it's tail like the ourobouros serpent consuming itself. The "haves" clustering together in exclusive clubs for protection from the "have not's" who are increasingly disenfranchised from basic necessities and dignity.
This cycle of pain and trauma is rarely broken throughout human history, when it is, it is so impactful to the collective human phsyce that it is an epochal shift in the way society functions for centuries thereafter. Some times for the better, mostly for the worse. When for the better it usually manifests in more personal responsibility and greater freedom for all. As if the whole world releases a sigh of relief when it discovers that it was afraid of nothing more than a little darkness.
I am going to give an example of ancient collective resentment brewed from trauma through metaphor. A metaphor that Bryan Solstin alludes to in the interview is the Hayekian hidden hand. This metaphor has another definition that I would like to draw from, but for clarity and distinction I am going to define Adam Smith's hidden hand so that I can dispose of this metaphor and shift to a exposition of the hidden hand that is more useful to this thesis specifically. Both explanations are equally useful and valid in their own right but not the same in meaning.
Follow the link to learn the detail and value of Adam Smith's hidden hand and Friedrich Hayek's conclusions from it as subject matter.
https://www.adamsmithworks.org/documents/adam-smith-peter-foster-invisible-hand
I would like to address all the hands in order of heavy, hidden and strong.
The Heavy Hand
The heavy hand of God is often used in scripture to explain calamity of a populace or individual when confronted with some form of perceived judgement. When punishment is dealt by God in the old testament it is often generalised as the heavy hand of God. The physical hand not evident but the detrimental effects felt tangibly and empirically. The solidity and weight of the hand quantified in the suffering induced by its distribution.
Job 33:7
Surely no fear of me will terrify you, Nor will my hand be heavy on you.
I Samuel 5:6
But the hand of the Lord was heavy on the people of Ashdod, and He ravaged them and struck them with tumors, both Ashdod and its territory.
The heavy hand is not perceived as evil by the narrators of biblical literature. It is a predictable and sincere authority which punishes justly and obviously as a repercussion to dishonest and malfeasant behaviour. A type of karma and "serves you right" rebalancing of wrongs committed into an acceptable outcome of divine justice. In modern times the heavy hand is frequently interpreted as divine retribution when evil befalls people who have abused and treated others unfairly. This frame of mind could lead naive and vulnerable people into a superstitious trap where they find themselves entertained with the idea that devils are trying to harm them and guardian angels fighting at protecting them. This is a form of religious coping mechanism used to deal with uncertainty and doubt when people are ignorant of reality.
It is not logical to fear the heavy hand of god if you lead a good life. This is a very good and generally well accepted idea. If you hurt people they will be mad at you and want to hurt you back. So if you lead a simple and respectable life you should be safe from the invasive proclivity of bad mental health. id est Fear of punishment.
I Thessalonians 4:9-12
But concerning brotherly love you have no need that I should write to you, for you yourselves are taught by God to love one another; and indeed you do so toward all the brethren who are in all Macedonia. But we urge you, brethren, that you increase more and more; that you also aspire to lead a quiet life, to mind your own business, and to work with your own hands, as we commanded you, that you may walk properly toward those who are outside, and that you may lack nothing.
Paul gives sound advice that is foundational to and guides towards a stable and healthy mental state. Behaving respectfully toward your brethren, minding your own business and being self sufficient.
Now none should fear the heavy hand of god for his wrath is appeased under these pleasant conditions of societal harmony.
The Hidden Hand (Not Adam Smith's)
The hidden hand also finds it's origin in Judea, first founded and branded as the Mysterious Force, established as a movement by Herod Agrippa I as a conspiracy to snuff out the spread of Christianity and maintain Judaism as dominant culture in a environment of conflicting religious ideology. It has since evolved into a conspiratorial malevolence that is cause of consternation and fear that has plagued western civilisation for centuries. I would contend it is the root cause for almost all manifestations of antisemitism in predominantly christian countries, Orthodox, Catholic and Protestant alike.
The evolution of the hidden hands manifestation in the modern world is a product of western capitalism and imperialism. This is what is commonly referred to as principalities and powers of the air, the enemy that cannot be confronted because of it's ideological nature. People fear a maniacal elite who wish to dominate and control every aspect of their existence to the point of them being enslaved. People link this fear into international organisations or movements such as the World Economic Forum, Aipac, Freemasonry, Illuminati, Communists, Zionism, Islam or the global financial elite, pick your poison. This fear of a malevolent power that is bigger than your ability to confront is cause of real and pervasive mental illness. Fear of impending doom and no obvious avenue of escape. Chemtrails, FEMA death camps, gulags and covid isolation facilities, vaccine passports and travel restrictions, world war III, nuclear war, global warming. These fears have a tremendous detrimental effect on humanities mental health leading to the type of paranoia and schizophrenia that John Nash and many others suffer from, myself included. The elites love it when your fears are bigger than you confrontational ability to fight it. They graciously accept responsibility, confronting your fears in your stead while coercing you to submit to their authority. A mentally ill and scared populace is an easily controlled group. People who recognise the real danger cope with these fears by prepping, buying gold, guns, ammo and by joining extremist organisations. But it is not a cure just a coping mechanism because this intangible power of the air is not a material flesh and blood threat but ideological in nature. Born from peoples proclivity to harm themselves irreparably.
How do we find a cure to mental health issues of this magnitude? It seems an impossible dream.
The Strong Hands.
In bitcoin we like to joke and meme about the salad hands who sell their coins to turn a quick fiat profit and the diamond hands who hold onto their coins with unwavering conviction no matter the fiat price. This is because those who study and understand bitcoin transcend the principalities and powers of the air, we predict and speculate on the types of problems bitcoin might one day solve. We cannot value it adequately by the virtue of the problems we don't even know bitcoin will solve yet. Bitcoin is a priceless treasure to those who comprehend the esoteric attributes of it.
II Timothy 1:7 (NKJV)
For God has not given us a spirit of fear, but of power and of love and of a sound mind.
If John Nash is indeed the inventor of bitcoin I find it very inspiring to think that he found it therapeutic to confront the nature of his fear head on and tackled the root problem of mental illness being the love of money by working to fix money. Chaos and entropy is a natural part of life. If the human condition is defined by our eternally having to confront chaos with the intent of establishing good and useful order then John Nash is probably about to heal the world from a whole host of mental illnesses and causation's. Human's who motivated by greed exploit their brethren cause a distortion in value signal transmission. This degradation in signal translates into increased uncertainty and by extension increased mental illness and fears, rational and irrational.
Isaiah 35:3 Strengthen the weak hands, And make firm the feeble knees.
It does not really matter where you think the evils of this world spring from.
Bitcoin fixes this problem and the problems you have not thought of.
We are still in the transition of a broken world reeling from ages of pain and suffering to a new one. Remember that which is promised in prophecy is a world of hope, prosperity and property rights. A world where the exploiter of the weak and innocent has no foothold and no power.
If John Nash is or is not Satoshi Nakamoto makes no difference to this inevitable outcome.
Stay humble, stack sats.
Post script: "The elites" whoever they are most certainly suffer from worse and even more detrimental mental illness, delusions of grandeur and fear than does the common man. Their fears are not unwarranted but bitcoin could fix it for them too. I am just worried that they do not appreciate the price they deserve as demonstrated by their continual dismissing of it.
Regards
EchDel
bitbib
-
 @ 9ff58691:0bf6c134
2024-11-12 10:34:50
@ 9ff58691:0bf6c134
2024-11-12 10:34:50В 2024 году проект «Путешествуй, познавай наш любимый край!» стал обладателем гранта президента, что стало значимым шагом к созданию более инклюзивного и доступного туризма для людей с ограниченными возможностями здоровья. Инициатива, направленная на социальную интеграцию и популяризацию культурного наследия Зауралья, получила признание за свои инновационные подходы и активное вовлечение местного сообщества.
Проект, который уже зарекомендовал себя как важный инструмент для улучшения качества жизни людей с ОВЗ, планирует использовать полученные средства для внедрения новых технологий, разработки адаптированных маршрутов и организации уникальных экскурсионных программ. В рамках гранта будут реализованы инициативы, направленные на создание комфортных условий для путешествий, включая адаптивные транспортные средства и интерактивные экскурсии с использованием виртуальной и дополненной реальности.
«Мы рады, что наш проект получил такую высокую оценку, — говорит директор проекта. — Это не только поддержка нашей работы, но и возможность сделать туризм доступным для всех. Мы уверены, что каждый человек, независимо от своих возможностей, должен иметь возможность познавать и наслаждаться красотой родного края»
С получением гранта проект «Путешествуй, познавай наш любимый край!» открывает новые горизонты для людей с ОВЗ, способствуя их социальной интеграции и культурному обмену.
Автор: Александра Налобина
-
 @ 6bae33c8:607272e8
2024-11-12 09:53:33
@ 6bae33c8:607272e8
2024-11-12 09:53:33So much for my Jonnu Smith premonition. For a garbage game, he wasn’t terrible and almost scored a TD, but that was a tough watch overall. The Dolphins sling it around to so many different players, while the Rams have their shallow, rock-solid three-player tree that produces even when they fail to score a touchdown. I also spoiled it by accidentally glimpsing the final score while checking the price of bitcoin this morning — totally forgot there was even a game.
-
I don’t know if Tua is still rusty, or the Dolphins have been solved, but there just isn’t any rhythm to the offense that was so unstoppable at times last year.
-
How is the Rams defense better without Aaron Donald? It’s like they suddenly got faster, younger and more aggressive, the entire unit. It goes to show how much we don’t know, and how overrated names on jerseys are.
-
The Dolphins defense was also nasty. I had expected this to be a shootout.
-
De’Von Achane is so fast once he gets going, but the Rams rarely let that happen.
-
Smith is a weapon, and he’s a significant part of the offense, but they spread it around so much.
-
Jaylen Waddle had a bad drop, but they seemed to want to get him involved early.
-
Tyreek Hill is one of the stranger busts in recent memory. He looks just as fast, but after Tua got hurt they just never regained interest in getting him the necessary looks.
-
As I said, Cooper Kupp, Puka Nacua and Kyren Williams are rocks — the entire rest of the offense barely sees any touches.
-
One odd thing when you know the final score is trying to figure out in real time how it gets there. When the Rams were down 20-9 with five minutes left, I was sure they would get the TD and fail on the two point conversion to make it 20-15. But instead they kicked the FG, the Dolphins got their FG, and the Rams kicked yet another FG before a failed onside kick.
-
-
 @ 1b5ee74d:bb1aae6e
2024-11-12 09:42:20
@ 1b5ee74d:bb1aae6e
2024-11-12 09:42:20Last July, I published an article highlighting the shifting narrative around the so-called "Bitcoin President" in the United States. An expression that should—must—sound absurd to anyone who has taken even a cursory look at the technology Satoshi Nakamoto introduced. It's evident that no such thing as a Bitcoin President exists. And if you're wondering what I think: no, not even him.
Not even Nayib Bukele, the President of El Salvador, the first country to adopt Bitcoin as legal tender, can be considered as such. Do you think the promotion of a centralized, government-controlled wallet like Chivo aligns with the values that gave birth to Bitcoin?\ But let's return to the United States. The intense lobbying efforts of BTC Inc—the company behind Bitcoin Magazine—first positioned Robert Kennedy Jr. as the Bitcoin Candidate, only to swiftly pivot to Donald Trump despite his repeated anti-cryptocurrency remarks and his staunch support for the dollar's supremacy.
After an electoral campaign of relentless brainwashing, how did Italian mainstream media interpret Bitcoin's relationship with U.S. politics?
Orange Coin and Orange President
The wave of articles published by Italian and international outlets reveals a telling trend: a systematic association between Bitcoin and Donald Trump following his reelection. The headlines in the following examples illustrate how this connection was constructed to imbue the cryptocurrency with a specific political connotation, aligned with conservative and Republican positions.
Fanpage kicks off with a headline that takes for granted the causal link between Trump's reelection and Bitcoin's price surge: "Why Bitcoin is Soaring After Trump's Election." At least the article notes that the tycoon, during his first term, called cryptocurrencies a "scam," only to drastically change his stance later.
ANSA adopts an even more emphatic approach: Bitcoin, Wall Street, and the dollar are portrayed as a harmonious trio, collectively celebrating Trump’s return to the White House. The association between Bitcoin and the dollar, however, is paradoxical. Bitcoin was created as an alternative to the dollar—a tool to escape expansionary monetary policies and inflation. Reducing it to a mere appendage of Republican economic policies misses the very reason for Bitcoin's existence.
Corriere della Sera headline reads: "With Trump’s Victory, New Record for Bitcoin." The newspaper leans into sensationalism, linking Bitcoin’s new all-time high to Trump’s electoral victory. The article goes on to mention figures like Elon Musk, attempting to tie the fortunes of the crypto sector to a series of controversial yet highly charismatic personalities.
In short, the idea that Bitcoin owes its growth solely to political events or the support of specific individuals is misleading. The notion that its price hinges on a particular election is not only simplistic but ignores decades of market cycles and economic data showing that Bitcoin responds to more complex dynamics such as global liquidity and technological adoption.
Il Giornale doesn't escape this fallacy either: "Trump Boosts Stocks and Bitcoin."
The daily draws a direct connection between stock market enthusiasm and Bitcoin's rally, highlighting how Trump's reelection has galvanized both Piazza Affari and cryptocurrencies. This narrative perpetuates the notion that Bitcoin and traditional equities move in lockstep, overlooking Bitcoin's historical decorrelation from traditional assets during critical moments.
The idea of a natural alliance between Trump and Bitcoin is reinforced without any solid evidence. On the contrary, Bitcoin investors aren't celebrating a president; they are responding to a broader macroeconomic environment where loose monetary policies and growing distrust in fiat currencies play a crucial role.
-
 @ 9ff58691:0bf6c134
2024-11-12 05:58:26
@ 9ff58691:0bf6c134
2024-11-12 05:58:26Курган, с успехом провел Фестиваль современных искусств. Это событие объединило передовые технологии и новаторские художественные идеи, предоставив гостям уникальную возможность погрузиться в мир, где творчество и инновации сливаются воедино.Организаторы фестиваля создали платформу для экспериментов, инноваций и вдохновения, представив гостям захватывающую программу.

Ключевые моменты фестиваля: - Интерактивные инсталляции, в которых гости могли управлять виртуальными объектами с помощью жестов и движений, погружаясь в мир дополненной реальности - Мультимедийные перформансы, где зрители становились частью световых и звуковых композиций, создавая уникальные визуальные эффекты - Выставки цифрового искусства, где гости могли наблюдать за процессом 3D-печати скульптур и взаимодействовать с роботизированными инсталляциями - Лекции и мастер-классы от ведущих экспертов, раскрывающие секреты использования технологий будущего в современном искусстве
Организаторами фестиваля выступили Иван Петров, основатель и директор Курганского центра современного искусства, Анна Сидорова, куратор международных художественных проектов, и Максим Соколов, технический директор фестиваля, эксперт в области интерактивных технологий.
Среди гостей фестиваля были замечены известный художник-медиаэкспериментатор Алексей Иванов, пионер цифрового искусства Мария Смирнова и инженер-новатор Дмитрий Петров, создатель уникальных робототехнических инсталляций.
Автор: Елизавета Медведева
-
 @ a012dc82:6458a70d
2024-11-12 05:33:23
@ a012dc82:6458a70d
2024-11-12 05:33:23Table Of Content
-
Bitcoin-Backed Life Insurance Startup: An Overview
-
How Does It Work?
-
Advantages of Bitcoin-Backed Life Insurance
-
Conclusion
-
FAQ
In the world of cryptocurrencies, innovation knows no bounds. The latest groundbreaking development comes in the form of a Bitcoin-backed life insurance startup that has recently launched with a staggering $19 million investment. This bold venture aims to revolutionize the insurance industry by leveraging the power of blockchain technology and digital assets to provide individuals with a secure and transparent life insurance solution. In this article, we will explore the details of this startup, its unique offering, and the potential implications it may have for the future of insurance.
Bitcoin-Backed Life Insurance Startup: An Overview
The Bitcoin-backed life insurance startup, which recently entered the market with a substantial investment of $19 million, aims to disrupt the traditional insurance model by incorporating the benefits of blockchain technology and cryptocurrency. This innovative approach allows policyholders to secure their life insurance coverage using Bitcoin, a popular digital currency known for its decentralized and secure nature.
By utilizing Bitcoin as a backing asset, this startup can offer policyholders several advantages, such as increased transparency, faster claim settlements, and enhanced security. Moreover, the integration of blockchain technology ensures that all policy-related transactions are recorded on an immutable ledger, minimizing the risk of fraud and manipulation.
How Does It Work?
Policy Creation Process
To initiate a policy with this Bitcoin-backed life insurance startup, individuals can visit their user-friendly website and follow a simple step-by-step process. Users are required to provide personal information, undergo a risk assessment, and choose their desired coverage amount.
Bitcoin as Collateral
Unlike traditional life insurance policies that rely on fiat currency, this startup allows policyholders to secure their coverage by depositing a predetermined amount of Bitcoin as collateral. This collateral not only guarantees the payout in case of the policyholder's demise but also serves as an investment that can appreciate over time.
Smart Contracts and Claims
The integration of smart contract technology enables automated claim settlements, eliminating the need for lengthy paperwork and reducing processing times. When a claim is filed, the smart contract verifies the validity of the claim against predefined conditions and automatically executes the payout process, ensuring a seamless and efficient experience for policyholders and beneficiaries.
Advantages of Bitcoin-Backed Life Insurance
Transparency and Security
With the utilization of blockchain technology, this Bitcoin-backed life insurance startup brings unparalleled transparency and security to the insurance industry. Every policy transaction, from policy creation to claim settlements, is recorded on an immutable and decentralized ledger, eliminating the possibility of fraud and ensuring that all transactions are transparent and verifiable.
Faster Claim Settlements
One of the most significant pain points in traditional life insurance is the lengthy and complex claim settlement process. However, with the implementation of smart contract technology, this Bitcoin-backed startup offers policyholders faster claim settlements. The automated nature of smart contracts streamlines the entire process, minimizing paperwork and reducing the time it takes for beneficiaries to receive their payouts.
Potential for Investment Growth
By using Bitcoin as collateral, policyholders have the opportunity to benefit from potential investment growth. As Bitcoin's value continues to fluctuate in the market, policyholders can reap the rewards of any appreciation in their Bitcoin collateral. This unique feature adds a new dimension to life insurance, turning it into a potential investment avenue for individuals seeking to safeguard their loved ones' future.
Conclusion
The emergence of a Bitcoin-backed life insurance startup with a $19 million investment signifies a significant leap forward for the insurance industry. By combining the benefits of blockchain technology, smart contracts, and cryptocurrency, this startup offers policyholders a unique and innovative approach to life insurance. With increased transparency, faster claim settlements, and the potential for investment growth, Bitcoin-backed life insurance has the potential to reshape the insurance landscape. As the market embraces this disruptive solution, individuals seeking life insurance coverage may find this startup to be a compelling choice.
FAQ
How secure is Bitcoin-backed life insurance? Bitcoin-backed life insurance offers enhanced security due to the utilization of blockchain technology. Every transaction is recorded on an immutable and decentralized ledger, minimizing the risk of fraud and ensuring transparency.
Can I convert my existing life insurance policy to a Bitcoin-backed policy? The conversion of an existing life insurance policy to a Bitcoin-backed policy would depend on the terms and conditions of the respective insurance provider. It is recommended to consult with the Bitcoin-backed life insurance startup or your current insurance provider for further guidance.
How does the Bitcoin collateral appreciate over time? The value of Bitcoin collateral appreciates based on market conditions and demand. As Bitcoin is a highly volatile digital currency, its value can experience significant fluctuations. Policyholders can benefit from any appreciation in the value of their Bitcoin collateral.
Are there any limitations to coverage amounts? The coverage amounts offered by the Bitcoin-backed life insurance startup may vary based on factors such as the applicant's risk profile, age, and desired coverage. It is advisable to consult with the startup directly to determine the coverage options available.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ a901cbe4:bd85452f
2024-11-12 04:22:24
@ a901cbe4:bd85452f
2024-11-12 04:22:24Bitcoin, the crypto world’s star player, is once again making headlines, creeping up on the thrilling milestone of $90,000. It’s the kind of thing that gets HODLers, new investors, and crypto skeptics alike buzzing. But what’s really exciting about Bitcoin hitting $90K is that it feels like we’re in the final approach toward the magical $100K mark. Here’s why this milestone is so important — and why $90K is more than just another number.
$90K: Not Quite There, But Oh So Close
$90,000 is a hefty number on its own, but in the world of Bitcoin, it’s like reaching the crest of a rollercoaster — a massive climb with the real excitement still ahead. When Bitcoin is this close to $100K, every dollar feels like another step toward the “big moment.” The journey has been long and often volatile, but Bitcoin’s persistence, resilience, and ability to keep pushing higher tells a compelling story. If $80K showed Bitcoin’s serious potential, $90K is that last push that’s putting us within touching distance of the ultimate milestone.
Why $90K is Huge: Momentum and Market Mindset
The closer Bitcoin gets to $100K, the more attention it attracts. Traditional investors, financial institutions, and even regulators are watching closely. As Bitcoin nears $90K, the market momentum is growing. Every incremental rise is backed by a combination of increased mainstream adoption, institutional buy-in, and a community that believes in Bitcoin’s long-term potential. It’s like the crypto world’s version of the final sprint, and every piece of momentum counts.
More importantly, $90K is proof of market confidence. It signals that investors aren’t just hoping for quick gains; they see Bitcoin as a long-term store of value and a potential future standard in global finance. Each step closer to $100K solidifies Bitcoin’s reputation as a lasting financial asset.
The Final Countdown: What Happens After $90K?
Once Bitcoin breaks $90K, the psychological impact on the market could be enormous. We’re not talking about another bump in the road here — we’re talking about Bitcoin heading into the realm of six-figure valuations. And when that happens, it’s not just a moment for those in the crypto world; it’s a moment for finance as a whole.
Here’s what could happen when Bitcoin finally crosses $100K:
-
Media Frenzy: The media, which already loves covering every Bitcoin milestone, will go wild with the story, and this could spark a new wave of interest from those who haven’t invested yet.
-
Institutional FOMO: We’ve seen an increase in institutional interest, and $100K could drive even more companies, investment funds, and potentially even sovereign wealth funds to consider Bitcoin seriously.
-
Retail Investor Boom: New retail investors may jump in, bringing fresh capital into the market. Bitcoin’s journey to $100K could fuel further retail adoption as people see it as a ‘must-have’ in their portfolios.
-
Regulatory Spotlight: $100K will also draw attention from regulators. Bitcoin isn’t just a niche investment anymore — it’s a global force, and lawmakers may feel pressure to establish clearer frameworks around crypto.
$90K and Beyond: Bitcoin’s Future as a Mainstream Asset
As Bitcoin inches closer to $90K, it’s becoming clear that we’re witnessing more than just a price rally. Bitcoin is on a path to becoming a mainstream financial asset. Once considered the “outsider” in the financial world, Bitcoin has steadily gained respect and credibility, and now $90K is yet another validation of its journey.
After $100K, who knows what’s possible? Some crypto enthusiasts believe Bitcoin could go as high as $500K or even $1 million in the future. While these figures might seem ambitious, they highlight the level of optimism and potential people see in Bitcoin.
The Bottom Line: Bitcoin Nearing $90K is the Start of Something Bigger
Bitcoin reaching $90K is an incredible milestone, but it’s also a starting line. This isn’t just about a number — it’s about Bitcoin’s evolution from a niche digital asset to a globally recognized financial powerhouse. The road from $90K to $100K is going to be exciting, but it’s just the beginning.
To everyone watching, it’s time to buckle up. Bitcoin’s rise is far from over, and if you think $90K is thrilling, just wait. The journey ahead promises to be one for the books. So let’s enjoy the ride, because Bitcoin is just getting started. 🚀
-
-
 @ 6bae33c8:607272e8
2024-11-11 19:24:52
@ 6bae33c8:607272e8
2024-11-11 19:24:52Yesterday was a mixed bag fantasy wise, but I’m feeling a bit lucky of late generally, and nothing happened to disabuse me of that. I started Aaron Rodgers in the Primetime which was a disaster, but it was over C.J. Stroud who was only a little better. Watching the Texans-Lions this morning validated all the reasons I sat Stroud, so I didn’t feel that badly about it.
The Circa Millions picks really broke my way — the Steelers came back late, as did the Bucs who lost in exactly the right way. The Chargers and Broncos were good most of the way, but it’s those 50/50 games that have to work out. I lost on the Bears which was just a stupid pick. That puts me at 8-2 over the first half of Q3 — I figure if I go 9-1 or 10-0 over the second half, that gets me a piece of the $300K prize.
-
I went on a hike, so I missed most of the Giants game, and that’s just as well. What I did see was bad Danny Dimes and then the Tyrone Tracy fumble in overtime. Tracy is actually doing God’s work getting them that No. 1 overall pick though.
-
The Panthers drafted Jonathon Brooks, extended Chuba Hubbard, who is decent, and they gave a four-year deal to Miles Sanders last year! I remember when the Gettlechad paid big bucks to Jonathan Stewart and DeAngelo Williams!
-
There was a shot of Bryce Young watching Daniel Jones work, and I imagined Young shuddering to think that’s the path down which he’s going — if he’s lucky.
-
I let Seslowsky talk me into the Bears in Survivor, that NLM. Honestly, I didn’t object so it’s my own fault even though the Chargers were the obvious pick.
-
The Patriots destroyed the Bears in every way, and Caleb Williams looked a lot like Danny Dimes. Just get rid of the damn ball!
-
Joe Flacco was a nice story, but you have to play Anthony Richardson now. I picked up Richardson in two more leagues so I now have him in four. He’s still a long shot to be good, but if he’s even decent, he’ll be a monster for fantasy. If I were the Colts I’d tailor the offense to him, call tons of designed runs, roll-outs, etc. I’m sure he’d just get hurt though.
-
Dalton Kincaid got hurt, but he’s just such a bust in every way. He’s basically just a generic TE you could grab off waivers. I had him ranked as my TE3.
-
So crazy the Broncos got the game-winning FG blocked. This Chiefs team will go undeafeated and win the Super Bowl like the 1973 Dolphins, but no one will consider them a top-10 all-time team.
-
Courtland Sutton is suddenly a top receiver again. He had disappeared entirely in Week 7.
-
I have the league’s only Younghoe in three leagues, so his missing three field goals really hurt.
-
Drake London was banged up, but he produces every game.
-
I started Mason Tipton in the Primetime — what the hell happened to him?
-
The Alvin Kamara easy-long TD drop was crazy. I thought for sure Atlanta would win the game after that.
-
Christian McCaffrey was all the way back — he got most of the carries and seven targets.
-
Bucky Irving is the Bucs best back, but Rachaad White is a good receiver and made an insane fourth-down conversion on a scramble play from Baker Mayfield.
-
Jaylen Warren is finally back to last year’s role.
-
The Steelers really held Jayden Daniels in check and would have an easier time of it but for a botched fake punt deep in their own end early in the game. I was only half watching, so I’m not exactly sure what happened there.
-
You can take Sam Darnold off the Jets, but you can’t take the Jets off Sam Darnold. Seriously, the tick where he throws an end zone pick every time down is leftover from his time with them.
-
Say what you want about the Jaguars, but they were able to take away Justin Jefferson.
-
The Titans defense isn’t bad, though the broadcast kept harping on their strong per-game statistics. It’s easier to have good per-game defensive statistics when your offense is awful, and teams can play conservatively against you.
-
Gus Edwards returned and looked good. He split carries fairly evenly with J.K. Dobbins who doesn’t look explosive of late.
-
I can’t believe Calvin Ridley is good again. I guess I wrote him off after last year not realizing how terrible the Jaguars offense was.
-
Cooper Rush was abominable, made Danny Dimes look like Joe Montana.
-
CeeDee Lamb had 10 targets for 21 yards.
-
Saquon Barkley’s having a great year, but you have to be at least a little annoyed about Jalen Hurts vulturing 10 TDs already.
-
The Cardinals are in sync, and Kyle Murray has been very good the last month.
-
Aaron Rodgers doesn’t look terrible physically to me, but there’s obviously something way off.
-
The Lions are so good they won on the road against a 6-3 team despite Jared Goff throwing five picks. One was bad luck and another was at the end of the half, but still the hit to his stats could cost him the MVP.
-
Stroud played better, but the offensive line is still bad (and this was the Lions without their new edge rusher Za’Darius Smith.) The Texans are committed to playing slowly and running Joe Mixon into the teeth of the defense 50 times too.
-
I’m probably jinxing this by posting it, but I’ve been on a nice roll generally these last couple weeks, and I have Jonnu Smith starting everywhere tonight. I’m not saying I did some deep (or any) analysis of the matchup, only that I have a feeling he’ll go off. Not investment advice, just posting this as an experiment.
-
-
 @ 6ad3e2a3:c90b7740
2024-11-11 19:22:48
@ 6ad3e2a3:c90b7740
2024-11-11 19:22:48One thing I enjoy about this Substack is I know a lot of its readers personally, and for that reason I also know many of them disagree with me. How dull it would be to write only for people who already were in lockstep with what you were saying! I say that because I also imagine some of you might be inclined to turn away from certain posts, but I would ask that the more you disagree, the more you stick this particular one out to the end. Imagine it were a reflection on the joys of owning a small, poorly-trained dog.
Donald Trump didn’t just win the election, he won the House, Senate and popular vote. He had unprecedented support among Latinos and black people, outperformed prior Republican candidates among Jews, reached out to Arabs in Michigan and even got the Amish to turn out en masse despite being outspent 2:1. The election was a total repudiation of the democratic party and its policies, the corporate press, the censorship industrial complex, uniparty republicans, left-wing academia, Hollywood, large tech companies thumbing the scale and entrenched government bureaucracy.
If you think this is a bad thing and were hoping for a different result, you probably have some explanation for what happened. I won’t pretend to know what anyone in particular is thinking, but I can tell you, as someone who is deeply relieved and heartened by this result how I see it. Maybe it will confirm some of your priors and disabuse you of others. Your mileage may vary.
My sense of relief is profound. I feel like a heavy weight has finally been lifted. I didn’t even realize how heavy it was until it was suddenly removed. The sense of creeping authoritarianism starting with Trump’s covid measures and increasing via the Biden vaccine mandates, online censorship, the creation of a disinformation bureau! was demoralizing in the extreme. I live in Europe where people have been arrested for Facebook posts in the UK, where a law was passed in France criminalizing criticism of the mRNA shots. The United States with its Bill of Rights was the one place where there was some obstacle in place against these abuses, but even there, prominent and powerful factions were explicitly calling for its dismantling.
But perhaps even more troubling was the behavior of ordinary people in response to these measures. I’ve written at length about what I take to be the causes, but more from a 30,000-foot view. I want to express how glad I am personally this behavior will ostensibly no longer be rewarded by those in power.
There is a large class of people who believe they are wiser and morally superior than those who disagree with them. They think that if you voted for candidate A you are a better person than if you voted for B. That who you voted for and how much you verbally signal your concern for various policies is important. One day it could be wearing your mask, another taking your booster, maybe it’s your views on Ukraine or Gaza, systemic racism, climate change or teenagers who believe they’ve been born in the wrong body.
If you don’t come out on the right side of these issues, you are not only mistaken, you are bad, and not just bad, but ignorant and in need of further education. It’s like an entire class of people became the HR department, your entire world was some dystopian corporation encouraging you to stay in line and accept a pay (energy) cut and lower standard of living for the greater good. And that’s assuming you were compliant enough to keep your job in the first place.
Now if this class of people simply excommunicated you from its church — and I know people personally whose families vowed to disown them for voting for Trump — that wouldn’t have been so bad. I mean I don’t need to associate with judgy, intolerant people who aim to stop me from thinking and saying what I earnestly believe. But it was worse than that: They didn’t even respect your right to be left alone.
If you refused to inject yourself with pharmaceutical poison, they wanted to isolate you from society. Never mind there was never any scientific basis for it, never mind the constitution does not suddenly cease to apply because people are scared of a respiratory virus. And even the people who were silent, who did not beat the drum for this biomedical authoritarianism just went along like that was normal. Like shutting down people’s businesses and telling them where they could travel was just unfortunately necessary and for the greater good of “public health.”
But while I harp on covid and the disgraceful scourge of vaccine mandates because it was such an extreme example, my larger point is about the ethos, the attitude that the lab coats, the experts, the climate scientists, the economists, the entire modern technocratic priesthood knew what was best for you. I posted on Twitter once my decision to decline a colonoscopy (deemed due at my age), gave the caveat that this was neither advice nor even an informed opinion of the cost-benefit of getting one, and people went insane. The notion that I wouldn’t go along with the prevailing medical edicts (what did they care what I did?) was enraging to them. They knew better, I was an idiot, “getting colon cancer to own the libs.”
The truth is, and of this one thing I am certain, you do not know better than I do. I am an adult human being, and there is no higher authority in the known universe than me. I can very well make my own errors without compounding them by taking on your flawed presumptions and biases.
Quite obviously there are technical matters where my expertise is lacking. I am happy to consult those who have it to better inform my judgment and decision-making, the way at trial experts often testify to better inform the jury of ordinary people. But just as it is the ordinary people who must render the verdict, it will always be my judgment and my judgment alone that governs my particular affairs, what medicines I will take, what policies I support, what language I use, with whom I choose to associate, how I feel it’s best to raise my kid, what she should and should not be exposed to at what age. I don’t care how many PhDs you attach to the end of your name — the more the worse if the last few years are any guide — you do not know how to manage my affairs better than I do, and I say that while cognizant that I make mistakes in their administration every single day of my life without exception.
So I have rambled a bit, but I wanted to convey as thoroughly as possible the enormity of the weight I feel lifted off my back as a result of this election. Yes, someone can still continue to be a condescending, insufferable, moralizing asshole, but what’s changed is he is no longer getting rewarded for such behavior by those in power. You can report me to HR for believing climate change (as it’s marketed to the masses) is a cynical and evil scam, but when you get to the HR office you’ll find Karen clearing out her desk.
. . .
I understand people have misgivings about some of Trump’s proposed policies, and as with any politician you should be circumspect. I would never guarantee he and his cohorts soon to be in power won’t overstep — he surely did during the covid lockdowns.
But I am certain virtually every claim instilling so much fear in susceptible people is a media fabrication, deliberate distortion or outright lie. One tell for me is when people cite Project 2025, insist he’s going to outlaw abortion or jail those for disagreeing with him politically. Not only did you live through four years of people posting all manner of falsehoods (He’s on Putin’s payroll!) under their own names all over social media without consequence, but as Glenn Greenwald pointed out, if that were true why aren’t people like AOC and Rachel Maddow fleeing the country yet?
The answer is obvious: they know all the rhetoric they spewed was fake and performative, even if the psychological damage they did to the credulous is in many cases quite real. Whether you want to venture outside the corporate media propaganda ecosystem to verify these points is up to you. (I have provided many links, and I encourage you to click them.) But my belief is no matter your political persuasion whether you realize it or not, like me (and Trump himself coincidentally) you just dodged a serious bullet.
-
 @ 5d4b6c8d:8a1c1ee3
2024-11-11 17:06:58
@ 5d4b6c8d:8a1c1ee3
2024-11-11 17:06:58Here are today's picks using my proprietary betting strategy at Freebitcoin. For details about what Risk Balanced Odds Arbitrage is and why it works see https://stacker.news/items/342765/r/Undisciplined.
For a hypothetical 1k wager on each match, distribute your sats as follows:
| Outcome 1 | Outcome 2 | Outcome 3 | Bet 1 | Bet 2 | Bet 3 | |--------------|-------------|--------------|-------|-------|-------| | FC Bayern| Augsburg| Draw | 860| 50 | 90 | | West Ham| Arsenal| Draw | 150| 650| 200| | Southampton| Liverpool| Draw | 100| 730| 170| | Newcastle| West Ham| Draw | 610| 170| 220| | Man City| Tottenham| Draw | 630| 160| 210| | Leicester| Chelsea| Draw | 180| 600| 220| | Ipswich| Man United| Draw | 210| 590| 240| | Crystal Palace| Newcastle| Draw | 310| 420| 270 | | Arsenal| Nottingham Forest| Draw | 720| 100 | 180| | Leganes| Real Madrid| Draw | 120| 690| 190 | | Celta Viga| Barcelona| Draw | 210| 570| 220| | Atletico Madrid| Alaves| Draw | 710| 100| 190| | Athletic Club| Real Sociedad| Draw | 410| 280| 310|
As of writing this, I'm up almost 85 kilosats with RBOA, thanks to Real Sociedad beating Barcelona last week as a wildly underpriced underdog.
originally posted at https://stacker.news/items/763403
-
 @ 00000000:0da46cec
2024-11-11 15:37:15
@ 00000000:0da46cec
2024-11-11 15:37:15The Content Authenticity Initiative (CAI) is a collaborative effort launched by Adobe in 2019 in partnership with technology companies and media organizations like Twitter and The New York Times. Its goal is to combat misinformation and ensure that digital content can be trusted. By creating a system for global adoption, CAI aims to provide a standard for traceability and verification of digital content in a secure and accessible manner. This article dives into the technical underpinnings of this initiative, detailing the use of metadata, cryptography, and blockchain. We also reference official repositories and open-source resources available for implementing these technologies.
Content Authenticity Initiative Architecture
The architecture of CAI relies on a set of techniques and tools based on standardized metadata, cryptographic integrity mechanisms, and decentralized solutions to ensure content verifiability throughout its lifecycle. Below is an in-depth look at each core element of this architecture.
1. Generation of Authenticity Metadata
Content creation within CAI begins at the capture stage, whether through a camera or smartphone, where authenticity metadata is generated. This metadata records important details such as the author's information, timestamp, geolocation, and device used for content capture. The data is stored using standardized schemes like XMP (Extensible Metadata Platform), ensuring consistency for later verification. Developers can access the reference source code for XMP via Adobe's GitHub: XMP Toolkit SDK.
The metadata not only describes the creation context but also maintains an immutable history of modifications. Whenever content is edited, the changes are documented, ensuring a complete and traceable history of the content lifecycle.
2. Digital Content Signing
A key component of CAI is the use of digital signatures to certify the authenticity and integrity of the content. Each file (image, video, document) is signed with asymmetric cryptographic algorithms like ECDSA (Elliptic Curve Digital Signature Algorithm) or RSA, depending on the desired level of security and computational resources.
These digital signatures generate a unique hash for each piece of content, linking it to the creator's private key. If even a single bit of the content is altered, the hash will change, which invalidates the original signature. This mechanism guarantees that unauthorized alterations are easily detected. Reference implementations for these cryptographic methods are available in the OpenSSL repository and the Bouncy Castle library for Java and C#: Bouncy Castle GitHub.
3. Timestamping and Blockchain
To further validate content authenticity, CAI also employs timestamping and, in some implementations, blockchain technology. Timestamping is handled by a Timestamp Authority (TSA), which certifies that the content existed in a particular state at a specific moment in time. TSAs utilize digital signatures to provide a secure record of when the content was created.
Blockchain technology provides an additional layer of transparency and security. By storing the hashes of metadata and digital signatures on a public blockchain (like Ethereum), an immutable, decentralized record is created, allowing any user to verify the content's authenticity. Structures like Merkle trees are commonly used for recording efficiently, ensuring that changes are tracked without bloating the blockchain. Examples of blockchain-based implementations can be explored in the Merkle Tree JavaScript Library and the official Ethereum repository: Ethereum GitHub.
4. Secure Metadata Storage
The metadata generated during content creation is embedded directly within the content file, using steganographic techniques or as readable attachments. This ensures that the metadata remains tied to the content and is resistant to malicious alteration.
To maintain metadata integrity during transfer, Transport Layer Security (TLS) is used, ensuring that content is securely exchanged without interference. Moreover, distributed storage systems such as IPFS (InterPlanetary File System) can be leveraged to provide redundant and long-term availability of metadata. The IPFS implementation is available on GitHub: IPFS GitHub.
Authentic Content Verification
One of CAI's primary goals is to enable anyone to easily verify the origin and edit history of content. To achieve this, open-source verification tools such as "Verify with CAI" have been developed, allowing users to inspect the content and access all associated metadata. These tools are available in the official CAI repository: Content Authenticity Initiative GitHub.
These verification tools leverage hashes and digital signatures embedded in the content, providing an easy way to determine if unauthorized changes have occurred. They also provide links to blockchain records, allowing third-party verification for an added level of security.
Guide for Photographers and Content Creators
The CAI's technology is particularly beneficial for photographers and content creators seeking to protect their work from misuse. Below is a practical guide to utilizing this technology effectively:
-
Compatible Equipment: Use a camera or device that supports the generation of authenticity metadata using XMP standards. Many modern devices and editing tools allow users to embed this metadata during capture.
-
Editing Software: Choose editing software that maintains authenticity metadata. Adobe Photoshop and similar tools now include features that preserve metadata throughout the editing process, ensuring the content remains verifiable.
-
Digital Signing: Use a digital signing tool like OpenSSL or libraries such as Bouncy Castle to digitally sign your files. This is critical for asserting the integrity and authenticity of your content. Tutorials and examples are available in the repositories mentioned.
-
Timestamping: Utilize a Timestamp Authority (TSA) to certify that the content existed at a specific point in time. This adds a temporal validation layer that proves when your content was created and that it hasn’t been altered since.
-
Blockchain Registration: To further reinforce content authenticity, consider recording metadata on a public blockchain. Services and smart contracts are available to help you register data without requiring deep blockchain expertise. Refer to repositories like Ethereum GitHub for guidance.
-
Content Verification: Use Verify with CAI to verify that your content is correctly registered and ensure that all metadata and digital signatures are intact. This tool is open source, allowing anyone to verify the content's authenticity.
-
Publishing Platforms: Share your content on platforms that support CAI standards. Platforms like Behance are starting to integrate these standards, helping distribute content while retaining its verified authenticity.
Technical Challenges and Barriers
CAI implementation faces several technical challenges. The most significant are:
-
Adoption: For CAI to succeed, stakeholders across the digital content ecosystem—camera manufacturers, software platforms, social networks, etc.—must adopt its standards.
-
Privacy Concerns: Providing detailed metadata about authorship may raise privacy issues. To address this, CAI offers options to encrypt sensitive metadata, ensuring it is only accessible when required.
-
Costs: The tools needed for digital signatures, blockchain registration, and timestamping can require significant resources, which may be a barrier for smaller creators or platforms.
-
Sophisticated Threats: While CAI improves digital security, sophisticated actors may still attempt to bypass authenticity checks or falsify metadata. Continuous improvement of cryptographic techniques and verification methods is required to counter these evolving threats.
Conclusion
The Content Authenticity Initiative provides a solid framework for protecting the integrity of digital content. By utilizing metadata standards, digital signatures, blockchain records, and open-source verification tools, CAI aims to establish a global standard for content transparency and authenticity. Despite some technical and logistical challenges, CAI represents a crucial step towards a trustworthy digital ecosystem. Developers and creators can access official repositories to implement these tools and contribute to a safer, more reliable environment for digital media.
References
- Adobe. (n.d.). XMP Toolkit SDK. Retrieved from https://github.com/adobe/XMP-Toolkit-SDK
- OpenSSL. (n.d.). OpenSSL Cryptography and SSL/TLS Toolkit. Retrieved from https://github.com/openssl/openssl
- Bouncy Castle. (n.d.). Bouncy Castle Libraries. Retrieved from https://github.com/bcgit
- Miguel Mota. (n.d.). Merkle Tree JavaScript Library. Retrieved from https://github.com/miguelmota/merkletreejs
- Ethereum Foundation. (n.d.). Ethereum. Retrieved from https://github.com/ethereum
- IPFS. (n.d.). InterPlanetary File System. Retrieved from https://github.com/ipfs
- Content Authenticity Initiative. (n.d.). Verify with CAI. Retrieved from https://github.com/contentauth/
-
-
 @ 81dfd044:f1737ef9
2024-11-11 13:08:51
@ 81dfd044:f1737ef9
2024-11-11 13:08:51Looking to invest in solar energy for your business? Aurora Energy offers high-quality commercial solar panels for sale, built to meet the energy needs of businesses both large and small. Our solar panels provide reliable, renewable energy that reduces operating costs and minimizes environmental impact. Let us help you choose the perfect system to power your business with clean energy and long-term financial benefits.
-
 @ 00000000:0da46cec
2024-11-11 12:44:46
@ 00000000:0da46cec
2024-11-11 12:44:46Resumen
La Content Authenticity Initiative (CAI) es una colaboración global iniciada por Adobe en 2019, junto con empresas tecnológicas y medios de comunicación, cuyo objetivo es combatir la desinformación digital mediante la creación de un sistema de autenticidad para contenidos digitales. Este artículo analiza en detalle los aspectos tecnológicos avanzados de la CAI, como el uso de metadatos, criptografía, blockchain y la verificación distribuida, además de incluir una guía para fotógrafos y creadores de contenido. Se ofrecen referencias a repositorios de código abierto para implementar estas tecnologías, proporcionando una base técnica robusta para proteger la autenticidad del contenido digital.
Palabras clave: Content Authenticity Initiative, CAI, autenticidad del contenido, metadatos, criptografía, blockchain, integridad digital, firma digital, sellado de tiempo.
La Content Authenticity Initiative (CAI), traducida al español como Iniciativa de Autenticidad del Contenido, es un esfuerzo colaborativo iniciado por Adobe en 2019 en conjunto con empresas tecnológicas y medios de comunicación como Twitter y The New York Times. Su principal objetivo es combatir la desinformación digital mediante la creación de un sistema de autenticidad de contenidos que pueda ser adoptado globalmente, proporcionando trazabilidad y verificación de los contenidos digitales de una manera confiable y accesible. Este artículo detalla los aspectos tecnológicos más avanzados de esta iniciativa, que incluye el uso de metadatos, criptografía y blockchain. Además, se hace referencia a algunos de los repositorios oficiales y recursos de código fuente disponibles para implementar estas tecnologías.
Arquitectura de la Content Authenticity Initiative
La arquitectura de la CAI está compuesta por un conjunto de técnicas y herramientas basadas en metadatos estandarizados, mecanismos de integridad criptográfica, y soluciones descentralizadas para asegurar la verificabilidad del contenido en cada etapa de su ciclo de vida. A continuación se describe en detalle cada uno de los elementos clave de esta arquitectura.
1. Generación de Metadatos de Autenticidad
El proceso de generación de contenido dentro de la CAI comienza en el dispositivo de captura, como una cámara o un smartphone, donde se crean los metadatos de autenticidad. Estos metadatos incluyen información relevante sobre el autor del contenido, la fecha y hora de captura, la geolocalización y el dispositivo utilizado. Estos elementos se guardan utilizando esquemas estandarizados como XMP (Extensible Metadata Platform), que asegura una estructura coherente y legible para las aplicaciones de verificación posteriores. El código fuente de referencia para la implementación de XMP está disponible en el repositorio oficial de Adobe en GitHub: XMP Toolkit SDK.
Los metadatos de autenticidad no solo proporcionan datos sobre la creación, sino que también mantienen un registro inmutable de modificaciones del archivo. Cada vez que se realiza una edición, se documenta el cambio mediante un proceso de versionado, asegurando la trazabilidad completa de cualquier alteración.
2. Firma Criptográfica del Contenido
El siguiente nivel de protección que ofrece la CAI es el uso de firmas digitales para garantizar la autenticidad e integridad del contenido. Cada archivo multimedia (imagen, video, documento) se firma utilizando algoritmos de criptografía asimétrica como ECDSA (Elliptic Curve Digital Signature Algorithm) o RSA, dependiendo del nivel de seguridad requerido y la capacidad de cálculo del dispositivo.
Estas firmas digitales generan un hash único para el contenido y lo vinculan con la clave privada del creador. Si el contenido es modificado de alguna manera, incluso un cambio de un solo bit, el hash cambiará, invalidando la firma digital original. De esta forma, cualquier alteración que no esté registrada y autorizada se puede detectar fácilmente, proporcionando garantía de que el archivo no ha sido comprometido desde su creación. Implementaciones de referencia para la generación y verificación de firmas digitales están disponibles en el repositorio OpenSSL y en la biblioteca Bouncy Castle para Java y C#: Bouncy Castle GitHub.
3. Sellado de Tiempo y Blockchain
Para reforzar la veracidad del contenido, la CAI también puede emplear sellado de tiempo (timestamping) y, en algunas implementaciones, blockchain para descentralizar y proteger el registro de autenticidad. El sellado de tiempo se realiza mediante una autoridad de sellado (“Timestamp Authority” o TSA), que certifica que el contenido existía en un estado particular a una fecha y hora específica. Las TSA utilizan firmas digitales para proporcionar un valor criptográficamente seguro que confirma la temporalidad del contenido.
La incorporación de blockchain aporta un nivel adicional de transparencia. Al registrar hashes de los metadatos y las firmas de autenticidad en una blockchain pública (como Ethereum o cualquier blockchain dedicada), se crea un registro inmutable y descentralizado que permite a cualquier usuario verificar la autenticidad del contenido. La estructura basada en árboles Merkle se usa comúnmente para optimizar el proceso de registro, asegurando que cada cambio en el contenido se documente con eficiencia y sin necesidad de almacenar grandes volúmenes de datos en la blockchain. Los desarrolladores pueden explorar ejemplos de implementación en el repositorio Merkle Tree JavaScript Library y consultar el repositorio oficial de Ethereum para interacciones con contratos inteligentes: Ethereum GitHub.
4. Almacenamiento Seguro de Metadatos
Los metadatos generados durante el proceso de creación se incrustan en el contenido utilizando técnicas de esteganografía o como datos adjuntos legibles por las herramientas de edición y verificación. Para evitar la eliminación o alteración maliciosa de estos metadatos, se emplean mecanismos de incrustación segura que vinculan los metadatos al contenido de manera criptográfica.
Para garantizar la integridad de los metadatos durante la transferencia, se emplean protocolos TLS (Transport Layer Security), que aseguran que cualquier intercambio de archivos mantenga la confidencialidad y la integridad. Además, se pueden usar sistemas de almacenamiento distribuido como IPFS (InterPlanetary File System) para replicar y almacenar estos metadatos de forma redundante, asegurando su disponibilidad a largo plazo. El código fuente para IPFS está disponible en el repositorio oficial: IPFS GitHub.
Verificación del Contenido Auténtico
Uno de los objetivos fundamentales de la CAI es que cualquier usuario pueda verificar la procedencia y el historial de ediciones de un contenido de manera sencilla y eficiente. Para ello, se han desarrollado herramientas de verificación basadas en código abierto, como “Verify with CAI”, que permiten al espectador analizar el contenido y ver todos los metadatos asociados. Estas herramientas se pueden encontrar en el repositorio oficial de la CAI: Content Authenticity Initiative GitHub.
Estas herramientas usan los hashes incrustados y las firmas digitales para comparar la información disponible y determinar si el contenido ha sido alterado sin autorización. Asimismo, permiten al usuario acceder a los registros de blockchain, si es aplicable, para confirmar la autenticidad desde una fuente independiente y descentralizada.
Guía para Fotógrafos y Creadores de Contenido
La adopción de la tecnología de la Content Authenticity Initiative puede ser extremadamente beneficiosa para los fotógrafos y creadores de contenido que deseen garantizar la autenticidad y proteger su trabajo contra el uso indebido. A continuación se presenta una guía paso a paso sobre cómo utilizar esta tecnología:
-
Equipamiento Compatible: Asegúrate de que utilizas una cámara o dispositivo que soporte la generación de metadatos de autenticidad según los estándares XMP. Muchas cámaras y aplicaciones de edición modernas permiten incluir estos metadatos durante la captura y la edición del contenido.
-
Software de Edición Compatible: Utiliza software de edición que mantenga los metadatos de autenticidad intactos. Adobe Photoshop y otras herramientas de edición avanzadas han comenzado a integrar estas funcionalidades para garantizar que cada cambio quede registrado. Al editar, asegúrate de mantener los registros de metadatos, de modo que se pueda trazar la autenticidad del contenido.
-
Firmado Digital del Contenido: Usa una herramienta de firma digital, como OpenSSL o bibliotecas como Bouncy Castle para generar firmas digitales de tus archivos. Esto proporciona una garantía de autenticidad. Estas herramientas se pueden usar para firmar imágenes y documentos multimedia y protegerlos contra cualquier alteración. Puedes encontrar tutoriales y ejemplos de uso en los repositorios mencionados previamente.
-
Sellado de Tiempo del Contenido: Implementa el sellado de tiempo utilizando una Timestamp Authority (TSA) reconocida. Esto permite certificar que el contenido existía en un estado específico en una fecha y hora determinadas, lo cual es esencial para demostrar la integridad temporal del contenido. Algunas plataformas ofrecen servicios de sellado de tiempo gratuitos o a bajo costo.
-
Uso de Blockchain para Registrar Metadatos: Si deseas una protección adicional y más transparencia, considera registrar los hashes de los metadatos en una blockchain pública. Existen servicios y contratos inteligentes que pueden ayudarte a registrar estos datos sin necesidad de un conocimiento profundo en programación blockchain. Puedes consultar repositorios como Ethereum GitHub para aprender cómo interactuar con contratos inteligentes.
-
Verificación del Contenido: Utiliza herramientas como Verify with CAI para asegurarte de que tus contenidos están adecuadamente registrados y que los metadatos y firmas digitales se mantienen intactos. Estas herramientas son de código abierto y están disponibles en GitHub, lo que permite a cualquier usuario comprobar la integridad y procedencia del contenido.
-
Publicación en Plataformas Compatibles: Publica tu contenido en plataformas que soporten la CAI y mantengan los metadatos intactos. Redes sociales y sitios web como Behance están comenzando a adoptar estos estándares, lo que te permitirá que tu contenido se distribuya con la verificación de autenticidad.
Desafíos Técnicos y Barreras
La implementación de la CAI no está exenta de desafíos. Algunos de los principales son:
-
Adopción Masiva: Para que la CAI sea efectiva, es necesario que todos los actores involucrados en la creación y distribución de contenido adopten sus estándares. Esto incluye a los fabricantes de cámaras, plataformas de edición, redes sociales y sitios web.
-
Privacidad de los Creadores: Al proporcionar información detallada sobre el autor y el origen del contenido, surgen preocupaciones relacionadas con la privacidad. Para mitigar esto, la CAI permite que algunos metadatos se almacenen de forma encriptada, y solo se revelen si es necesario.
-
Costos de Implementación: Las herramientas para firmar digitalmente, registrar en blockchain, y mantener el sellado de tiempo requieren recursos que podrían ser prohibitivos para algunos creadores o plataformas pequeñas.
-
Atacantes Sofisticados: Aunque la CAI mejora significativamente la seguridad, atacantes avanzados podrían intentar falsificar metadatos o burlar los procesos de firma digital. La combinación de técnicas criptográficas y blockchain mitiga este riesgo, pero siempre existirá la necesidad de evolucionar con las amenazas emergentes.
Conclusión
La Content Authenticity Initiative ofrece una arquitectura tecnológica sólida para proteger la autenticidad del contenido digital. A través del uso combinado de metadatos estandarizados, firmas digitales, blockchain y herramientas de verificación, la CAI busca establecer un estándar global para la transparencia y verificabilidad del contenido. Si bien existen desafíos técnicos y logísticos, la CAI representa un paso significativo hacia un ecosistema digital donde la confianza y la autenticidad sean la norma y no la excepción. Los interesados en profundizar más pueden acceder al código fuente disponible en los repositorios oficiales, como se ha indicado a lo largo del artículo, para implementar estas soluciones y contribuir al desarrollo de un entorno digital más seguro y confiable.
Bibliografía
- Adobe. (n.d.). XMP Toolkit SDK. Recuperado de https://github.com/adobe/XMP-Toolkit-SDK
- OpenSSL. (n.d.). OpenSSL Cryptography and SSL/TLS Toolkit. Recuperado de https://github.com/openssl/openssl
- Bouncy Castle. (n.d.). Bouncy Castle Libraries. Recuperado de https://github.com/bcgit
- Miguel Mota. (n.d.). Merkle Tree JavaScript Library. Recuperado de https://github.com/miguelmota/merkletreejs
- Ethereum Foundation. (n.d.). Ethereum. Recuperado de https://github.com/ethereum
- IPFS. (n.d.). InterPlanetary File System. Recuperado de https://github.com/ipfs
- Content Authenticity Initiative. (n.d.). Verify with CAI. Recuperado de https://github.com/contentauth/
-
-
 @ a012dc82:6458a70d
2024-11-11 12:35:40
@ a012dc82:6458a70d
2024-11-11 12:35:40Table Of Content
-
Understanding Bitcoin Halving and its Significance
-
JPMorgan Analysis Reveals Positive Indicators
-
Increased Retail Investment: Driving Factors
-
Anticipated Impact on Bitcoin Market
-
Tips for Retail Investors to Leverage the Opportunity
-
Conclusion
-
FAQ
In recent years, Bitcoin has become a buzzword in the financial world, captivating both institutional and retail investors. As the cryptocurrency market continues to evolve, experts at JPMorgan have conducted a comprehensive analysis, revealing strong indications of increased retail interest in Bitcoin leading up to the next halving event. This blog post will explore the insights from JPMorgan's analysis and shed light on the potential impact of this anticipated surge in retail interest.
Understanding Bitcoin Halving and its Significance
The concept of Bitcoin halving is pivotal to understanding the potential surge in retail interest. Bitcoin operates on a controlled supply system, with a predetermined issuance rate. Approximately every four years, the number of new Bitcoins generated per block gets halved, reducing the rate at which new Bitcoins enter circulation. This scarcity mechanism has significant implications for the cryptocurrency's value and investor sentiment.
JPMorgan Analysis Reveals Positive Indicators
According to JPMorgan's analysis, there are several positive indicators suggesting a strong influx of retail investors in the period leading up to the next Bitcoin halving. The analysis takes into account various factors such as historical data, market trends, and investor behavior. JPMorgan's experts have identified patterns that align with previous halving events, indicating a potential surge in retail interest in Bitcoin.
Increased Retail Investment: Driving Factors
JPMorgan's analysis highlights key driving factors behind the expected increase in retail investment. One significant factor is the growing awareness and acceptance of Bitcoin among the general public. As more individuals recognize the potential of cryptocurrencies as an investment asset, they are likely to be drawn towards Bitcoin, especially during periods of heightened market activity like halving events.
Moreover, the influence of social media and digital platforms cannot be overlooked. The rise of social media communities, investment forums, and influencers has played a crucial role in amplifying discussions around Bitcoin. These platforms facilitate the spread of information, enabling retail investors to gain insights and make informed investment decisions.
Anticipated Impact on Bitcoin Market
The surge in retail interest preceding the halving event is expected to have a significant impact on the Bitcoin market. As more retail investors enter the market, the demand for Bitcoin is likely to increase, potentially driving up its price. This increased demand could lead to a period of heightened market volatility, offering both opportunities and risks for investors.
JPMorgan's analysis suggests that the impact of retail interest will extend beyond the halving event itself. Historically, Bitcoin has experienced price rallies following halvings, indicating the potential for substantial gains. However, it is important to note that the cryptocurrency market is highly unpredictable, and investors should exercise caution and conduct thorough research before making investment decisions.
Tips for Retail Investors to Leverage the Opportunity
For retail investors considering Bitcoin as an investment, it is essential to approach the market with a strategic mindset. Here are a few tips to help leverage the anticipated surge in retail interest:
-
Educate Yourself: Gain a deep understanding of Bitcoin, its underlying technology, and the factors that influence its price.
-
Diversify Your Portfolio: Consider allocating a portion of your investment portfolio to Bitcoin while maintaining a diverse range of assets.
-
Set Realistic Goals: Define your investment objectives and set realistic expectations, considering the volatility and risks associated with cryptocurrencies.
-
Stay Informed: Stay updated with the latest news, market trends, and regulatory developments that could impact the cryptocurrency market.
-
Seek Professional Advice: Consult with financial advisors or experts who specialize in cryptocurrencies to gain valuable insights and guidance.
Conclusion
JPMorgan's analysis reveals strong indications of increased retail interest in Bitcoin prior to the halving event. Retail investors, driven by factors such as growing awareness and the influence of digital platforms, are likely to play a significant role in shaping the cryptocurrency market. As retail interest surges, it is crucial for investors to approach the market with caution, conduct thorough research, and leverage the opportunities while managing the risks associated with cryptocurrencies.
FAQ
What is Bitcoin halving? Bitcoin halving is an event that occurs approximately every four years, where the number of new Bitcoins generated per block gets halved. It is a mechanism designed to control the supply of Bitcoin and has significant implications for its value and investor sentiment.
Why is there expected strong retail interest in Bitcoin prior to halving? JPMorgan's analysis indicates increased retail interest in Bitcoin before halving due to growing awareness, acceptance, and the influence of social media platforms. Retail investors are drawn towards Bitcoin during periods of heightened market activity like halving events.
What impact does retail interest have on the Bitcoin market? Retail interest can drive up the demand for Bitcoin, potentially impacting its price. The surge in retail interest preceding the halving event could lead to increased market volatility, offering opportunities and risks for investors.
How can retail investors leverage the anticipated surge in retail interest? Retail investors can leverage the opportunity by educating themselves about Bitcoin, diversifying their investment portfolio, setting realistic goals, staying informed about market trends, and seeking professional advice.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 05fcdfd8:fd31299f
2024-11-11 10:49:36
@ 05fcdfd8:fd31299f
2024-11-11 10:49:36Die Auswirkungen von Störsendern auf Reisen und wie Sie Ihre Privatsphäre und Sicherheit schützen können
In der modernen Gesellschaft ist Reisen zu einem integralen Bestandteil des Lebens der Menschen geworden. Mit zunehmender Reisehäufigkeit sind Informationssicherheit und Privatsphäre jedoch nach und nach zu wichtigen Themen geworden, die den Menschen Sorgen bereiten. An verschiedenen öffentlichen Orten, insbesondere in Flughäfen, Hotels und Touristenattraktionen, kann das Vorhandensein von Signal störsender eine potenzielle Bedrohung für die Sicherheit unserer persönlichen Geräte und Informationen darstellen. Aus diesem Grund ist es wichtig, die Auswirkungen von Störsendern zu verstehen und geeignete Sicherheitsmaßnahmen zu ergreifen.
1. Funktionsprinzip des Störsenders
Ein Störsender, oft auch „Signalstörsender“ genannt, ist ein Gerät, das Signale auf bestimmten Frequenzen aussendet, die die Kommunikation mit anderen drahtlosen Geräten stören oder verhindern können. Diese Geräte werden manchmal verwendet, um illegale drahtlose Kommunikation zu blockieren, beispielsweise in Gefängnissen, aber auch auf Reisen kommt es zu illegalem Einsatz. Hacker könnten beispielsweise Handyblocker verwenden, um die Mobiltelefonsignale von Menschen zu stören, um vertrauliche Informationen abzuhören oder zu stehlen.
2. Die Auswirkungen von Störsendern
1. Auswirkungen auf die Kommunikation: In Bereichen, in denen Störsender verwendet werden, kann es bei Mobiltelefonen und anderen drahtlosen Geräten zu Signalverlusten kommen, wodurch es unmöglich wird, Anrufe entgegenzunehmen oder Nachrichten zu senden. Dies kann im Ernstfall schwerwiegende Folgen haben.
2. Risiken für die Datensicherheit: Hacker können WLAN Jammer nutzen, um Funksignale abzufangen und die persönlichen Daten und Bankkontoinformationen der Benutzer zu stehlen. Wenn ein Gerät keine stabile Verbindung zum Netzwerk herstellen kann, neigen Benutzer dazu, die Sicherheit der Verbindung zu ignorieren, wodurch sich das Risiko eines Angriffs erhöht.
3. Datenschutzverlust: Wenn Benutzer gestört werden, nutzen sie möglicherweise unsichere Netzwerke oder Anwendungen, was das Risiko eines Datenschutzverlusts erhöht. Insbesondere in öffentlichen WLAN-Umgebungen können Hacker Interferenztechnologie nutzen, um Man-in-the-Middle-Angriffe durchzuführen und Benutzeraktivitäten zu überwachen.
3. So schützen Sie Privatsphäre und Sicherheit
1. Verwenden Sie ein virtuelles privates Netzwerk (VPN): Die Verwendung eines VPN verschlüsselt Ihren Internetverkehr und schützt Ihre Privatsphäre, insbesondere bei der Nutzung öffentlicher WLANs. Ein VPN erstellt einen sicheren Tunnel, sodass Ihre Daten während der Übertragung nicht gestohlen werden können.
https://www.jammermfg.com/de/alle-jammer.html
2. Vermeiden Sie Verbindungen zu ungesicherten Netzwerken: Versuchen Sie auf Reisen, Verbindungen zu WLAN-Netzwerken zu vermeiden, die nicht passwortgeschützt oder ungesichert sind. Wenn Sie es unbedingt nutzen müssen, stellen Sie sicher, dass Sie zusätzliche Sicherheitsmaßnahmen wie ein VPN oder mobile Daten ergreifen.
3. Aktualisieren Sie Ihre Geräte und Apps regelmäßig: Stellen Sie sicher, dass Ihr Telefon und Ihre Apps immer auf dem neuesten Stand sind, um Sicherheitslücken zu schließen. Hersteller veröffentlichen regelmäßig Updates, um potenzielle Sicherheitsprobleme zu beheben.
4. Verwenden Sie die Zwei-Faktor-Authentifizierung: Die Aktivierung der Zwei-Faktor-Authentifizierung erhöht die Sicherheit Ihrer Online-Konten. Auch wenn ein Hacker Ihr Passwort erhält, benötigt er noch einen zweiten Verifizierungsschritt, um auf Ihr Konto zuzugreifen.
5. Geben Sie Informationen sorgfältig weiter: Vermeiden Sie es, persönliche Informationen öffentlich preiszugeben, z. B. Kreditkarteninformationen oder private Inhalte in sozialen Medien. Achten Sie auf Ihre Umgebung und vermeiden Sie es, sensible Themen zu besprechen.
6. Verwenden Sie sichere Messaging-Tools: Verwenden Sie bei wichtigen Kommunikationen sichere Messaging-Apps wie Signal oder WhatsApp. Diese Apps bieten eine Ende-zu-Ende-Verschlüsselung, um Ihre Gespräche vor Abhörern zu schützen.
7. Sichern Sie Ihr Gerät: Stellen Sie sicher, dass Sie ein sicheres Passwort für Ihr Gerät festlegen und biometrische Daten (z. B. Fingerabdruck oder Gesichtserkennung) verwenden, um die Sicherheit zu erhöhen und zu verhindern, dass andere auf Ihr Gerät zugreifen, wenn Sie es nicht verwenden.
4. Zusammenfassung
Auf Reisen ist der Schutz Ihrer Privatsphäre und Sicherheit eine wichtige und notwendige Aufgabe. Auch wenn die Existenz von Störsendern und HF Detektor gewisse Auswirkungen auf die Kommunikation hat, können Sie durch die oben genannten Maßnahmen potenzielle Risiken wirksam reduzieren und sicherstellen, dass Ihre Daten nicht durchsickern oder verletzt werden. Während wir die Reise genießen, müssen wir wachsam bleiben und unsere persönlichen Daten und Privatsphäre schützen.
-
 @ 6aa0e5a8:f1677da5
2024-11-11 08:42:28
@ 6aa0e5a8:f1677da5
2024-11-11 08:42:28In diesem hochentwickelten technologischen Zeitalter waren Einsamkeit und Isolation des Menschen noch nie so präsent wie heute. Das Aufkommen der love doll hat ein tieferes Nachdenken über Intimität und menschliche Bedürfnisse ausgelöst.
Blickt man auf die lange Geschichte der menschlichen Zivilisation zurück, so war der Wunsch nach Intimität und Liebe schon immer ein Teil der menschlichen Natur. In der heutigen schnelllebigen Gesellschaft entfernen sich die zwischenmenschlichen Beziehungen jedoch immer mehr voneinander, und die Veränderungen in den Familienstrukturen haben dazu geführt, dass zu viele Menschen in geistige und körperliche Einsamkeit verfallen. Einigen Daten zufolge befindet sich etwa ein Viertel der Bevölkerung in einem Zustand der dauerhaften Einsamkeit.
Die Einsamkeit lässt die Nachfrage nach sexpuppe als „virtuelle Begleiter“ wachsen. Auch wenn Liebespuppe den Reichtum echter Intimität nicht vollständig wiedergeben können, so können sie doch für diejenigen, denen es lange Zeit an Intimität gefehlt hat, die körperliche und emotionale Leere zumindest bis zu einem gewissen Grad stillen. Auf der einen Seite zeigt dies, dass der Fortschritt von Wissenschaft und Technik uns mehr Wahlmöglichkeiten bietet, auf der anderen Seite spiegelt es aber auch einen Teil des Mangels an menschlicher Natur in der modernen Gesellschaft wider.
Davor können wir nicht die Augen verschließen. Wir sollten darüber nachdenken, was zu der Kälte in den intimen Beziehungen zwischen den Menschen geführt hat. Die Zunahme der Zahl der Singles, der Anstieg der Scheidungsrate, die niedrige Geburtenrate usw. sind allesamt Anzeichen dafür, dass der menschlichen Liebe und Intimität in unserer Gesellschaft nicht genügend Aufmerksamkeit geschenkt wird. Wir müssen darüber nachdenken, wie wir die menschliche Wärme wiederherstellen und die zwischenmenschliche Kommunikation stärken können, damit jeder ein Gefühl der Sicherheit und der Zugehörigkeit bekommt.
Gleichzeitig sollten wir auch darüber nachdenken, welche Art von intimer Beziehung wir anstreben. Ist die rein körperliche oder virtuelle Erfüllung nur eine unangebrachte Nachahmung wahrer Intimität? Der Kern einer intimen Beziehung besteht aus zwei Menschen aus Fleisch und Blut, die sich gegenseitig schätzen, verstehen, tolerieren und Verantwortung füreinander übernehmen. Vergessen wir langsam die guten Eigenschaften der Intimität?
Der Zweck der technologischen Entwicklung besteht darin, der Menschheit besser zu dienen, und nicht darin, sie zu entfremden und zu mechanisieren. real sex doll geben uns die Möglichkeit zum Nachdenken, es geht nicht um eine schwarz-weiße Entscheidung für richtig oder falsch, sondern wir sollten darüber nachdenken, wie wir Wohlwollen, Wärme und Verantwortungsbewusstsein nutzen können, um das humanistische Fundament intimer Beziehungen aufzubauen und die verlorene Temperatur der menschlichen Natur in dieser Ära des Hochgeschwindigkeitsbetriebs zurückzugewinnen.
-
 @ 9ff58691:0bf6c134
2024-11-11 08:29:00
@ 9ff58691:0bf6c134
2024-11-11 08:29:00Курган - один из крупнейших городов Уральского региона, административный центр Курганской области. За последние двадцать лет этот город претерпел значительные изменения, превратившись из серого провинциального центра в современный, динамично развивающийся город. Об изменениях рассказал Олег Фролов – коренной житель города.
- Олег, расскажите, как за последние двадцать лет изменился ваш родной город Курган? Что именно изменилось в городе за это время?
-
За эти годы Курган преобразился до неузнаваемости. Когда я был ребенком, город казался мне серым и унылым. Сейчас он стал более современным и привлекательным. Пожалуй, самые заметные изменения произошли в сфере образования и медицины. Многие школы и детские сады были капитально отремонтированы или построены заново. Появились современные учебные классы, оснащенные новейшим оборудованием, включая интерактивные доски, 3D-принтеры и системы искусственного интеллекта для помощи в обучении. Городские больницы и поликлиники были модернизированы, оснащены новейшей диагностической техникой: роботизированные хирургические системы и системы искусственного интеллекта для анализа медицинских данных. Качество и доступность медицинской помощи значительно возросли.


-
А как изменилась культурная жизнь города?
-
Был отреставрирован и значительно расширен городской драматический театр. Открылись новые концертные залы, музеи и выставочные пространства. Стало проводиться гораздо больше культурных мероприятий. Жителям других регионов выдалась возможность посетить каждое культурное место нашего города с помощью экскурсий дополненной вирутальной реальностью. Курган превратился в настоящий культурный центр региона.
-
Как вы оцениваете эти изменения? Довольны ли вы тем, как развивается ваш родной город?
-
Я очень рад тем преобразованиям, которые произошли в Кургане за последние годы. Город стал более комфортным и привлекательным для жизни. Конечно, есть еще над чем работать, но в целом я вижу, что Курган уверенно движется вперед, становясь современным и развитым.
-
Олег, а есть ли у вас в Кургане любимое место, куда вы любите ходить?
-
Безусловно. Мое любимое место - это Центральный парк культуры и отдыха. Это настоящее сердце нашего города. Парк преобразился до неузнаваемости - он стал мобильным, с большим экраном для проведения мероприятий, а голограммы проводят интересные экскурсии. Здесь созданы все удобства для людей с ограниченными возможностями.

-
Что вам особенно нравится в этом парке?
-
Парк очень красивый и ухоженный. Здесь высажено множество зеленых насаждений - деревьев, кустарников, цветов. Есть уютные аллеи для прогулок, детские площадки, спортивные зоны. Летом работают аттракционы, открыты кафе и летние веранды. Зимой заливают большой каток, который очень популярен среди жителей. Мне очень нравится культурная жизнь парка. Здесь регулярно проводятся различные фестивали, концерты, выставки. Летом часто организуют кинопоказы под открытым небом. Зимой работает резиденция Деда Мороза, куда приходят целыми семьями.
-
Похоже, это действительно замечательное место. Спасибо, что поделились своими впечатлениями!
- Да, и правда замечательное. Я очень рад, что за последние годы он преобразился и стал настоящим центром притяжения для жителей города. Приглашаю всех приехать и лично убедиться в этом!
-
 @ 9ff58691:0bf6c134
2024-11-11 06:04:29
@ 9ff58691:0bf6c134
2024-11-11 06:04:29За последние 16 лет Курган претерпел значительные инфраструктурные изменения, направленные на повышение качества жизни горожан и развитие города. Ниже представлен обзор основных нововведений:
Новые здания и сооружения: - Построен современный многофункциональный спортивно-развлекательный комплекс "Курганская Арена" с ледовой ареной, бассейном и фитнес-центром. - Открыт новый корпус Курганского государственного университета, оснащенный по последнему слову техники лабораториями и аудиториями. - Возведен крупный торгово-развлекательный центр "Курган Молл" с магазинами, кинотеатром, ресторанами и зонами отдыха. - Построен современный медицинский центр "Курганская клиника", оказывающий широкий спектр высокотехнологичных услуг.

Транспортная инфраструктура: - Открыта новая скоростная автомагистраль, соединяющая центр города с аэропортом и федеральной трассой. - Запущено движение городского скоростного трамвая, связывающего отдаленные районы с центром. - Построены два новых транспортных кольца на основных развязках, значительно улучшившие дорожную ситуацию. - Обновлен автобусный парк, переведенный на экологичные электрические и гибридные модели.

Благоустройство и озеленение: - Реконструирован центральный городской парк с новыми пешеходными зонами, велодорожками и зонами отдыха. - Высажены тысячи новых деревьев и кустарников, создавшие "зеленые легкие" города. - Построены новые общественные пространства - набережная, пешеходные улицы и площади с современным дизайном. - Модернизирована система освещения улиц, переведенная на энергоэффективные светодиодные технологии.

В целом, Курган за последние 16 лет значительно преобразился, став более современным, комфортным и экологичным городом с развитой инфраструктурой. Эти изменения повысили качество жизни горожан и привлекательность Кургана для туристов и инвесторов.
-
 @ 8f2fe968:0fbf4901
2024-11-11 02:20:35
@ 8f2fe968:0fbf4901
2024-11-11 02:20:35


-
 @ 8d34bd24:414be32b
2024-11-10 22:42:29
@ 8d34bd24:414be32b
2024-11-10 22:42:29In Part 1, we got to see God’s initial promises to Adam, Eve, and all mankind with the proto Gospel:
“He shall bruise you on the head,\ And you shall bruise him on the heel.”(Genesis 3:15)
We saw God’s promises to Abraham:
-
To have his name made great.
-
To receive the land of Israel.
-
To father many nations.
-
That “in you all the families of the earth will be blessed.”
We saw God’s reiterated promises to Jacob, Abraham’s grandson.
Now we will look at the partial fulfillment of these promises and new promises made.
The Promised Land (Quick Summary)
Jacob fathered 12 sons. His son Joseph was sold as a slave to Egypt where he became second to the Pharaoh and saved Jacob’s family and the rest of the Middle East from famine. The Israelites then spent around 400 years in Egypt before Moses was called by God to lead the Israelites to the promised land. God performed awe inspiring miracles through Moses to force Pharaoh to release the Israelites who had been made slaves by the Egyptians.
After crossing the desert, the Israelites reached the promised land, but instead of trusting the God who had rescued them with miracles never before seen, they were fearful and refused to obey God and to enter the promised land. God then had them wander 40 more years in the wilderness until the rebellious adults had all died. Then God miraculously aided this band of shepherds to conquer the land of Canaan and inhabit it, partially fulfilling His promise to give them this land.
After approximately 410 years of judges leading the people of Israel and them repeatedly going astray, God gave them the king they requested, Saul. God gave them a tall and handsome, but selfish and unfaithful king to show them the error of their ways. After showing them their error, God gave them a godly king, a man after God’s own heart.
David
When God spoke His promise (covenant) with David, He reiterated the promises given to Abraham and to Jacob, but added:
“When your days are complete and you lie down with your fathers, I will raise up your descendant after you, who will come forth from you, and I will establish his kingdom. He shall build a house for My name, and I will establish the throne of his kingdom forever. I will be a father to him and he will be a son to Me; when he commits iniquity, I will correct him with the rod of men and the strokes of the sons of men, but My lovingkindness shall not depart from him, as I took it away from Saul, whom I removed from before you. Your house and your kingdom shall endure before Me forever; your throne shall be established forever.” (2 Samuel 7:12-16) {emphasis mine}
The first part of this promise was fulfilled through David’s son, Solomon. Solomon sat on the throne. Solomon built a temple to worship God. Solomon was not cut off for his sins at the end of his life when he drifted away from God. Even though ten tribes were taken away from Solomon’s son Rehoboam, Rehoboam remained king of the two tribes of Judah and Benjamin and therefore his throne remained.
The final promise, “Your house and your kingdom shall endure before Me forever; your throne shall be established forever,” was also partially fulfilled through Jesus at His incarnation and will be fully fulfilled when He returns for His millennial reign.
“I will raise up your descendant after you, who will come forth from you, and I will establish his kingdom. He shall build a house for My name, and I will establish the throne of his kingdom forever.” Jesus is a descendant of David and His kingdom will be established at the end of the age — a kingdom of believers. “He shall build a house for My name.” Most of the time Israel is referred to as the house of God while the church is referred to as the body of Christ. In the millennial kingdom they will be united into one house, the adopted children which are the gentile church and the natural children which are the Jews who have finally accepted their Messiah. The final kingdom on this earth will be the millennial reign of Jesus (the promised heir of David), and then God will produce a new heaven and a new earth upon which Jesus will reign forever.
Once again, David did not get to experience the complete fulfillment of the promises made to him. It was partially fulfilled in his son, Solomon, but it has taken thousands of years to partially fulfill this promise and we don’t know for sure how long it will be until complete fulfillment.
Jeremiah
By the time of Jeremiah, the nation of Israel was gone and Judah was corrupted beyond recognition. The fulfillment of God’s promises seemed impossible, but God’s promises are faithful and true. God spoke to Jeremiah to remind him, that although Judah and Israel were being punished, ultimately, God would fulfill all His promises. He begins with these tender words:
Now the word of the Lord came to me saying,\ “Before I formed you in the womb I knew you,\ And before you were born I consecrated you;\ I have appointed you a prophet to the nations.”\ \ Then I said, “Alas, Lord God!\ Behold, I do not know how to speak,\ Because I am a youth.”\ \ But the Lord said to me,\ “Do not say, ‘I am a youth,’\ Because everywhere I send you, you shall go,\ And all that I command you, you shall speak.\ Do not be afraid of them,\ For I am with you to deliver you,” declares the Lord.\ \ Then the Lord stretched out His hand and touched my mouth, and the Lord said to me,\ “Behold, I have put My words in your mouth.\ See, I have appointed you this day …” (Jeremiah 1:4-10a)
First God tells Jeremiah that He loves him so much that He formed him in his mother’s womb for a special purpose, to speak His judgement and blessings on Israel. God comforts Jeremiah when Jeremiah fears he is unworthy of the great task God has for him. God promises to be with Jeremiah and to help Jeremiah fulfill His will.
As Christians we are similarly told that God created us for His purpose and His blessing and He will be with us, empowering us for whatever tasks He has called us to do.God promises that despite Israel’s nonstop rebellion, He will be gracious and “not be angry forever.”
Go and proclaim these words toward the north and say,\ ‘Return, faithless Israel,’ declares the Lord;\ ‘I will not look upon you in anger.\ For I am gracious,’ declares the Lord;\ ‘I will not be angry forever.\ Only acknowledge your iniquity,\ That you have transgressed against the Lord your God\ And have scattered your favors to the strangers under every green tree,\ And you have not obeyed My voice,’ declares the Lord.\ ‘Return, O faithless sons,’ declares the Lord;\ ‘For I am a master to you,\ And I will take you one from a city and two from a family,\ And I will bring you to Zion.’ (Jeremiah 3:12-14)
God will always fulfill His promises even if that means calling His people home from the ends of the earth where they are scattered “one from a city and two from a family.”
God promises to call both Israel and Judah back to the land promised to them all of the way back in time of God’s promise to Abraham. There is a partial return, after Judah’s 70 year exile in Babylon, leading to a rebuilding of the temple for a second time. We are in the middle of another return to Israel that began when Israel was recreated in 1948 and is continuing today. Despite the fact that the people of Israel are being barraged with rockets, drones, and missiles daily and are at risk of being attacked by suicide bombers and terrorists, God is calling His people home for His big finale.
I believe these continuing verses refer to Jesus’s second coming and the millennial reign of Christ.
“Then I will give you shepherds after My own heart, who will feed you on knowledge and understanding. It shall be in those days when you are multiplied and increased in the land,” declares the Lord, “they will no longer say, ‘The ark of the covenant of the Lord.’ And it will not come to mind, nor will they remember it, nor will they miss it, nor will it be made again. At that time they will call Jerusalem ‘The Throne of the Lord,’ and all the nations will be gathered to it, to Jerusalem, for the name of the Lord; nor will they walk anymore after the stubbornness of their evil heart. In those days the house of Judah will walk with the house of Israel, and they will come together from the land of the north to the land that I gave your fathers as an inheritance. (Jeremiah 3:15-18)
This passage isn’t just a call back to the promised land. This is another promise of God. “Then I will give you shepherds after My own heart, who will feed you on knowledge and understanding.” After Jesus’s first coming, He made things clear about His plan of redemption for Israel and for the gentiles. He made clear His promise to bless all nations through Himself, a descendant of David, Jacob, and Abraham, to whom the promises were given. He demonstrated how His laws for the Jews pointed them to God’s ultimate plan.
It is actually ironic that the “shepherds after My own heart, who will feed you on knowledge and understanding” are most likely Christian believers who are returned to earth to reign with Christ during the millennial kingdom. Gentile Christians were enabled to have a relationship with God through the Jews and then God will use those gentile Christians to shepherd the Jews back to God, so we can all worship God together.
It won’t be until Jesus’s second coming and His thousand year reign that “they will call Jerusalem ‘The Throne of the Lord.’” It won’t be until Jesus’s second coming and His thousand year reign that they will not “walk anymore after the stubbornness of their evil heart.” God will finally make the full land of Israel a land of peace and prosperity for the Jews, but also to all the nations of the earth.
But at the time of Jeremiah’s prophecy, God is promising punishment and hardship now to teach His people to be faithful and to trust God’s faithfulness.
Behold, I am bringing a nation against you from afar, O house of Israel,” declares the Lord.
“It is an enduring nation,\ It is an ancient nation,\ A nation whose language you do not know,\ Nor can you understand what they say. (Jeremiah 5:15)
Due to Israel and Judah’s rebellion, both nations are taken away by a foreign nation into exile. Jeremiah, in particular, prophecies the 70 year exile of Judah in Babylon and their return to the promised land. God promised Abraham and Jacob (Israel) the land of Israel (previously Canaan) and He always keeps His promise, so He always brings them home in ways that are hard to comprehend.
Relatively near the end of the 70 year exile in Babylon, God had Persia conquer Babylon and then a Persian king, not only allowed the Israelites to return to Jerusalem to rebuild the city, the walls, and the temple, but also he funded the return to Israel and returned the gold, silver, and bonze temple implements. What conquering nation does something like that? It was clearly all God.
God may delay His promises, but He never cancels them.
For this the earth shall mourn\ And the heavens above be dark,\ Because I have spoken, I have purposed,\ And I will not change My mind, \ nor will I turn from it.” (Jeremiah 4:28)
When God makes a promise, it is as good as done.
Trust Jesus.
-
-
 @ 36bedab2:524acad4
2024-11-10 21:37:52
@ 36bedab2:524acad4
2024-11-10 21:37:521. Power ON
- Quando você liga o computador, ele inicia o processo de boot.
- Esse primeiro passo envia energia aos componentes do sistema e dispara o BIOS (ou firmware UEFI em sistemas mais recentes).
2. BIOS (Basic Input/Output System)
- O BIOS ou UEFI é o firmware inicial que roda logo após o computador ser ligado.
- Ele executa um conjunto de verificações no hardware (chamado POST - Power-On Self-Test) e inicializa os dispositivos básicos necessários para o boot, como o disco rígido, memória RAM e CPU.
- O BIOS então procura o dispositivo de boot (HD, SSD, USB, etc.) e carrega o MBR ou a partição EFI para dar continuidade ao processo de boot.
3. Master Boot Record (MBR) ou EFI Partition
- O MBR (Master Boot Record) ou a partição EFI (em sistemas com UEFI) é onde ficam armazenadas as informações sobre o carregamento do sistema operacional.
- Em sistemas antigos, o MBR continha o boot loader e as tabelas de partição. Nos sistemas modernos com UEFI, a partição EFI cumpre essa função.
- O MBR ou a partição EFI passa o controle para o boot loader, que é responsável por carregar o sistema operacional.
4. Boot Loader (e.g., GRUB)
- O Boot Loader (exemplo: GRUB) é um programa responsável por carregar o sistema operacional no momento do boot.
- Ele permite selecionar qual sistema operacional inicializar (em caso de dual boot) e passa o controle para o kernel do sistema.
- GRUB (Grand Unified Bootloader) é o boot loader mais comum em sistemas Linux.
5. Kernel
- O kernel é o núcleo do sistema operacional Linux.
- Ele é carregado na memória pelo boot loader e começa a configurar os recursos do sistema, como a CPU, a memória e os dispositivos de hardware.
- O kernel é responsável por gerenciar os recursos do sistema e permitir a comunicação entre o hardware e o software.
6. Initial RAM disk - initramfs
- O initramfs é um sistema de arquivos temporário carregado na memória logo após o kernel.
- Ele contém módulos e drivers essenciais para que o sistema possa iniciar corretamente e acessar o sistema de arquivos principal do disco.
- O initramfs é desmontado após o sistema principal estar carregado.
7. /sbin/init (parent process)
- Após o kernel inicializar o sistema, ele chama o processo /sbin/init, que é o primeiro processo a rodar no Linux e é o "pai" de todos os outros processos.
- O init é responsável por iniciar e gerenciar todos os outros processos do sistema.
- Em muitas distribuições modernas, o init foi substituído por outros sistemas de inicialização, como o systemd, que tem mais funcionalidades e permite um gerenciamento mais eficiente de processos.
8. Command Shell using getty
- Getty é o processo que configura e gerencia terminais para o login do usuário.
- Ele exibe a tela de login em sistemas baseados em linha de comando.
- Se o sistema tiver uma interface gráfica, o getty geralmente passa o controle para o gerenciador de login gráfico.
9. Graphical User Interface (X Window ou Wayland)
- Finalmente, o sistema carrega a interface gráfica usando o X Window System (X11) ou o Wayland (um sistema gráfico mais moderno).
- Esse é o ambiente visual onde o usuário pode interagir com o sistema usando janelas, ícones, menus, etc.
- X11 e Wayland são servidores gráficos que gerenciam como as janelas e aplicativos são exibidos e manipulados na tela.
Como esses processos se intercalam?
- Hardware ligado → BIOS/UEFI realiza verificações básicas.
- BIOS/UEFI encontra o dispositivo de boot e carrega o MBR ou partição EFI.
- MBR/EFI localiza e executa o boot loader (GRUB).
- GRUB permite que o usuário escolha o sistema operacional e carrega o kernel do Linux.
- Kernel inicializa o sistema, configurando os recursos de hardware e carregando o initramfs.
- Initramfs fornece drivers e módulos necessários para o kernel acessar o sistema de arquivos principal.
- Kernel chama o processo /sbin/init (ou systemd), que inicia todos os serviços e processos do sistema.
- Init executa o getty para configurar o terminal de login.
- Getty chama o ambiente gráfico (X11 ou Wayland) se estiver presente, e o usuário pode então usar o sistema na interface gráfica.
-
 @ bcea2b98:7ccef3c9
2024-11-10 19:34:24
@ bcea2b98:7ccef3c9
2024-11-10 19:34:24@chess a3
originally posted at https://stacker.news/items/762161
-
 @ a901cbe4:bd85452f
2024-11-10 18:33:53
@ a901cbe4:bd85452f
2024-11-10 18:33:53Bitcoin under $100K? Let's be honest: it’s kind of like waiting for your favorite song to drop at a concert. The crowd's hyped, but you're still waiting for the real action to begin. Sure, $80K is cool — it's solid, it's impressive, but it’s not the headline act. The true show begins when Bitcoin crosses that $100K milestone, and until then, we’re in the “pre-game” phase.
Here's why Bitcoin under $100K is merely the warm-up, and why we’re all just biding our time for what’s coming next.
Bitcoin Under $100K: Just a Pre-Party Vibe
Right now, Bitcoin at $80K feels like that awkward moment at a party when everyone’s gathered in the kitchen, getting their drinks ready, and the music is almost turned up. Sure, you can feel the energy, but everyone’s really waiting for the DJ to hit play on that banger. Bitcoin at $80K is promising, but it’s just a preview of the real excitement that’s about to unfold.
This isn’t the time for victory laps. It’s the time to get ready, to watch and wait, because when Bitcoin hits $100K, that’s when the party really starts. The market will pop, the spotlight will shine brighter, and the world will be watching as Bitcoin climbs to new heights.
The $80K Milestone: A Solid Step, But Not The Destination
Let’s take a moment to appreciate $80K. It’s a big number in the world of crypto, and a milestone in its own right. But let’s not kid ourselves — it’s not the finish line. It’s like running a race, getting to the 80% mark, and looking ahead at the final stretch. You’re feeling good, but the best part is still coming.
Bitcoin’s at $80K and that’s a statement, no doubt. But $100K is the magic number. It’s the one that makes the headlines, the one that makes everyone say, “Okay, Bitcoin’s for real.” $80K is impressive, but it’s not the showstopper. So while the excitement is there, we all know Bitcoin’s best performance is still ahead.
Why $100K Is the Real Milestone We’ve All Been Waiting For
When Bitcoin finally crosses that $100K mark, it’s going to be a global event. It’ll be the moment that people who were skeptical finally start to take notice, the moment when Bitcoin becomes a household name, not just a niche investment. It's like watching a rising star finally step into the spotlight and own the stage.
And here's the thing: When Bitcoin hits $100K, it won’t be a “surprise.” It’s been in the works for years. But it’ll be the moment when everyone truly grasps the scale of what’s happening. The world will finally recognize that Bitcoin isn’t just a speculative asset — it’s a fundamental part of the financial landscape.
Bitcoin’s Resilience: Boring Until It’s Not
What makes $80K so intriguing isn’t just the number itself — it’s that Bitcoin’s still holding strong, despite all the FUD (fear, uncertainty, doubt) thrown at it. Critics have come and gone, but Bitcoin’s still here, solid as ever. It’s like the underdog story that just refuses to be over.
Bitcoin at $80K is doing its thing, even when people doubt it. It’s showing up every day, proving that it’s built to last. Sure, it may seem like “just another day in the crypto market,” but trust me — Bitcoin’s resilience is what makes this moment significant. It’s not a bubble; it’s an evolution. And that evolution is building toward something even bigger.
What’s Next: Bitcoin and Beyond $100K
Once Bitcoin hits $100K, everything changes. The narrative shifts. Bitcoin goes from "that risky bet" to "the future of finance." And that’s where things get wild. It’s not just about price anymore — it’s about the institutional and mainstream acceptance of Bitcoin. It’s about the fact that this isn’t a fad, it’s a global movement that’s not going anywhere.
After $100K? Who knows. Maybe $200K, $500K, or more. But let’s not get ahead of ourselves. We’re still waiting for that first major milestone to break, and when it happens, it’s going to be like a flip of a switch. A whole new world will open up.
The Waiting Game: It’s Gonna Be Worth It
So, while Bitcoin under $100K might feel like a long wait, remember: it’s all part of the journey. Bitcoin at $80K is just the start of something bigger. It’s the calm before the storm, the deep breath before the final sprint.
When $100K hits, we’ll all be able to say we were here for it. And when it crosses that threshold, it’s going to be one of the biggest moments in the world of finance — one that we’ll all look back on and say, "We saw this coming." And for those of us who’ve been riding the wave since the early days? Well, we’ll be popping the champagne.
The real show starts at $100K. We’re just waiting for the curtain to rise. 🚀
-
 @ df478568:2a951e67
2024-11-10 14:26:38
@ df478568:2a951e67
2024-11-10 14:26:38*note: This version of the article uses some four-letter words some people may not like. If you prefer cartoon-like cussing, you can read it here.
It's that time, again--The bull market which happens every 4 years like the Winter Olympics. We've surpassed the previous USD/ATH. This is the 498th resurrection of our beloved bitcoin, but you know what really turns my crank? Bitcoin cybersecurity!
I love digging into the nitty-gritty of cryptography not CrYpTo and finding creative ways to use my toy collection. I mean, hardware wallet(a.k.a. signing devices) collection. Nah, they're toys. Yesterday, as I was playing with my toys, I was inspired to use my seed signer after a long hiatus. To be clear, I love the Seed Signer. It has some neat features: - Generate seeds with the entropy from a picture - Hand-drawn QR codes for easy seed backup - You can DIY

It looks cool too, but for the record, I wouldn't use it for a single sig wallet because it does not contain a secure element. According to NVK, there are zero days and supply chain attacks you can't really mitigate with the seed signer. Although I think this is a fair criticism, it can be useful: - As an educational tool - Part of a multi-sig backup. Michael Flaxman, in his 10X Your BTC Security Guide, suggests removing a Wi-Fi card and hard drive from a computer, boot up TAILS, plug your computer into an RJ45 port with an Ethernet cable for Internet access, navigate to https://seedpicker.net/ on the default TOR browser, unplug the Ethernet cable from the RJ45 port, and generate the seed for your paper wallet. That sentence is too damn long, but this is indicative of how cumbersome this method is.
This was necessary when he wrote it since we did not have as many hardware wallets back then as are on the market today. In my cybersecurity opinion, and I am not a certified cyber security expert, buying a seed signer requires less technical know-how than using Flaxman's guide. This is not a criticism of Flaxman, his guide is one of my favorite things ever written about bitoin because of it's educational value. If you want to learn about extreme cybersecurity, Flaxman's guide makes an excellent lab. We assume no network security model is 100% secure, so we never risk compromising our keys by ever connecting to an Internet-connected device. It's a hell of an education.
Seed Signer Is For Everybody

Say you work a full time job and didn't spend the majority of your free time learning this stuff during a pandemic. Or maybe you're like my wife. She think's Bitcoin is cool now, but this one time she walked in on me with my Cold Card plugged into a 9v battery and said, "See. I'm never using whatever the fuck that thing is. My wife is never removing a Wi-Fi card from a laptop. If you're like my wife, the Seed Signer is right for you, if you want to use multisig. It's also not imperative to use the 9v battery if you don't want to. You can just plug it into a wall outlet like everybody else.
I want to start bringing the Seed Signer to my local meetup, but it's at a brewery and I don't want to be a wallflower because I need to plug the damn thing into an outlet so I thought, “Why not try the Cold Power with my Seed Signer?”
I found one of my magnetic micro-USB adapters and plugged it into the Seed signer, Then I plugged the battery in. My switch is on because the flimsy plastic switch broke the first time I turned it on, but it still works. I just broke it with my fat thumbs.
It felt as if it took as long as a difficulty adjustment to boot-up, but in reality it was about the time it takes the Liquid Network to find a block. I proceeded to take a picture and write down a 12 word seed. I plan on using this with the Nunchuck testnet wallet to show people at my local Meetup how to create seeds and take self-custody of their Bitcoin. Again, I would not use this as a single sign because there are more secure options, but it is a great tool for teaching Bitcoin cybersecurity and can be a great wallet that can mitigate the risk of supply-chain and retirement attacks when used as part of a multi-sig quorum. I can also now use it in the middle of a brewery. I'll write about how this goes the next time I get down there.
Why We Use The Cold Power

I placed one of those magnetic adapters I bought on Amazon into one of the power holes. Power holes is a technical term for microUSB. This is because the Cold Power does hooks up to a cable that does not transmit data, only Power. Get it? It's like a cold wallet, but instead of a wallet, it's a power cable. You hook this cable up to a technology which was invented in 1836, a [battery]. 9V batteries contain no data. It is only Power, but most of us must trust Coinkite. Maybe they programmed the green part to be a bitcoin stealing script. I doubt this and think Coinkite is an honest company, but the awesome sauce thing is, the little magnet I bought on Amazon does not allow the transmittal of data. I don't need to plug in a charger that might be compromised.
This might sound paranoid, but in Tools of Titans, Samy Kamkar, malware has even been found in cigarette lighter chargers. Imagine a fix of nicotine costing you you entire life savings. That's not likely to happen, but why take a chance? It's better to spend several thousand sats on a charger and a 9v battery than lose your whole stack.
According to Wired Magazine, he can also learn the keystrokes you're typing on your laptop keyboard through a window. This means typing a seed onto a laptop might not be the best idea even if you are afraid of this. It is better to take a picture and use the entropy from the random picture.
Powering The Seed Signer With A Coinkite Product
Seed Signer and NVK, the CEO of Coinkite seem to have some beef on nostr, but it's none of my business. The part I find interesting is a product made by Coinkite works with a product made by Seed Signer. This was made for the Cold Card, but it works with a hardware wallet made from someone else. Too bad politics isn't more like that. It's nice to see two rival companies make products that are compatible with each other, but that's just the way free and open source software like bitcoin is. Seeds from Coinkite can be used with the Seed Signer. Maybe that's okay if it's only $1,000 worth of bitcoin on the Seed Signer. You don't need to go to Defcon 5 for every single sat. It's not practical. Sure, if the NSA was after you and wanted to steal your $1,000 worth of bitcoin from you, they could probably do it. Why would they spend ten thousand dollars to do this to you? This is not in most people's threat models.
Wait...Then why do you need to use the 9v battery thing-a-ma-jig? I technically don't need to , but we could also use this for a multi-signature quorum? What if you took your wallet to a safe deposit box, but the vault does not have a plug?

I created this key with no power outlet at all. This means I could do this in the middle of Alaska where there's no cell phones, where you only need to worry about bears stealing your seed phrase... That's a bit much, but it's possible.
I was not able to take a picture on the same battery charge so You might want to use a fresh battery if you ever try this yourself.
Thanks for reading. - If you like this blogs with no swear words, send sats to marc26z@strike.me/ - If you like this blog with swear words, send sats to marc@npub.pro/
✌️
npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0no
As Seen On TIR: http://p66dxywd2xpyyrdfxwilqcxmchmfw2ixmn2vm74q3atf22du7qmkihyd.onion/use-a-seed-signer-with-cold-power/
-
 @ c0e4bd0b:1c5734af
2024-11-10 12:15:08
@ c0e4bd0b:1c5734af
2024-11-10 12:15:08Bitcoin Calendar Definition
Layer: Applications
Status: Draft
Bitcoin defines the halving cycle as 210,000 blocks, as defined in the file
kernel/chainparams.cpp. This number was apparently chosen as an aesthetically pleasing number which equates almost exactly to 4 years, according to the ten-minute block schedule. This BIP proposes using this parameter of Bitcoin as the basis for reckoning calendar time, defined as follows.nBlocksPerYear = 210000 / 4 // calculates to 52,500 nBlocksPerMonth = nBlocksPerYear / 12 // calculates to 4375The calculations above produce integer results, making calendrical calculations based on block height extremely convenient. The zero-based year and month are calculated as follows, using integer division (/) and mudulo (%) based on block height h:
year = h / 52500 month = (h % 52500) / 12Furthermore, we assume a bitcoin day length of 144 blocks. This is consistent with the target of 10-minutes per block and the 2016 blocks every two weeks for the difficulty adjustment period. This results in months of 30 days, with a small remainder:
nBlocksPerDay = 144 daysPerMonth = nBlocksPerMonth / nBlocksPerDay // calculates to 30.somethingA human-friendly date can thus be displayed based upon block height, with familiar calendrical characteristics of 30 full days per month (with a partial day 31) and 12 months per year. As of this writing, the current bitcoin date is 7/24/17, 24-07-0017, or the twenty fourth day of the seventh month of the seventeenth year of Bitcoin.
This definition forms the basis for a culturally independent and socially universal calendar system which is easy to calculate, durable, and financially relevant.
Cross-referencing with other calendar systems:
Since this date will not synchronize exactly to extant calendar systems, a notation needs to be used in cases where ambiguity would result. Taking the solar day as the example, references that cross over between the solar day and the bitcoin date need to have a qualifier resolving the phase discrepancy (as is done when referring to dates in ancient calendar systems that do not align with the turn of the date at midnight). For example, the Bitcoin date of 7/24/17 would be written as November 9/10, 2024, making it clear that it touches both of those solar days. However, this format should only be used for dates in which the two calendar systems are more out of sync than in sync. For dates that are more in sync than out of sync, no overlap day should be given, because it would add ambiguity where there otherwise was none.
Bitcoin Calendar Synchronization
Layer: Consensus
Status: Draft
The Bitcoin calendar (referring to the prior definition) would be more economically relevant to earthlings if the Bitcoin year actually stayed synchronized with the growing seasons of the tropical year. Currently, the Bitcoin year begins in the springtime of the northern hemisphere, but it is offset one year and there is currently nothing to keep the bitcoin year from drifting further out of synchronization with the tropical year.
To keep the Bitcoin year in sync with the seasons, the bi-weekly proof-of-work difficulty adjustment could be tailored to aim toward better alignment during every difficulty adjustment. Normally, the difficulty is adjusted upward or downward a maximum factor of 4, as defined in the file
pow.cpp. The determination of the value within that range is made solely on the basis of the rate of block discovery during the prior 2016-block (two-week) period.The existing difficulty adjustment scheme has resulted in the Bitcoin calendar generally sliding earlier every year, presumably due to the fact that the global hash rate is generally increasing rather than decreasing. The historical dates for the year beginnings and the corresponding duration of the Bitcoin year are as follows:
|Year|Block|Date|Days| |-:|-:|--|-:| |0|0|01/03/09|| |1|52500|04/22/10|474| |2|105000|01/28/11|281| |3|157500|12/14/11|320| |4|210000|11/28/12|350| |5|262500|10/09/13|315| |6|315000|08/10/14|305| |7|367500|07/29/15|353| |8|420000|07/09/16|346| |9|472500|06/23/17|349| |10|525000|05/29/18|340| |11|577500|05/23/19|359| |12|630000|05/11/20|354| |13|682500|05/07/21|361| |14|735000|05/05/22|363| |15|787500|04/29/23|359| |16|840000|04/19/24|356|
As can be seen, the number of days in the actual Bitcoin year are consistently fewer than the number of days in the tropical year (365.2425). Assuming the hash rate will generally continue to increase, this trend should continue, which allows us to make a convenient simplifying assumption.
Conceptually this proposal seeks to add an additional, limited offset to the work requirement based on whether the Bitcoin calendar is ahead of schedule or behind schedule, in comparison to the tropical year. We can assume based on the trends, however, that we only need to "slow down" the block rate slightly to keep it in sync with the seasons. Therefore, this proposal aims to do only that.
If the Bitcoin block height is a certain amount ahead of the calendar synchronization goal (per the trend), the difficulty would be increased one notch more than required by the normal calculation, if not already at the limit of adjustment for that period. This would make it impossible for the proposed change to overpower the existing calculation, but would still provide a gentle enough push when needed to keep the calendar in sync, thus accomplishing the purpose.
Fork considerations by the author:
A consensus change to the proof of work calculation would normally result in a hard fork. However, in the case that we only potentially increase the difficulty and never decrease it relative to non-upgraded nodes in the network, this means that during the transition, only upgraded nodes would be at risk of rejecting blocks for not meeting the more stringent difficulty level necessary to synchronize the calendar.
The new nodes would therefore need to be programmed to yield to the non-upgraded difficulty criteria until most of the network has upgraded, at which point activation would occur (as explained below) and miners would be obliged to meet the tougher requirements demanded by all upgraded nodes. Nodes that still had not upgraded by that time would remain unaffected, since the post-activation blocks would only have more proof of work, and not less, than non-upgraded nodes require.
More importantly, an overwhelming majority of the hash rate should be fully upgraded to avoid a situation where non-upgraded, non-mining nodes are forked by a longer chain created by non-upgraded miners. A sufficient portion of the hash rate following the upgrade path would eliminate this possiblity, even for non-mining nodes that don't upgrade, because the longer chain will come from the greater hash power and there would be no financial incentive for miners to switch back to catering to a minority of non-upgraded nodes.
Proposed activation method:
Upgraded nodes would delay the relaying of blocks that do not meet the more stringent requirements. This would begin as a confirmation-time penalty to upgraded nodes, but as the upgrade expands to more nodes, the effect would shift to incentivizing miners to produce blocks that conform to the upgrade in order to build on the longest chain faster.
Optional second-phase activation:
For the longer term, it might be advisable to also implement the corresponding opposite influence on the proof of work adjustment for the case where the simplifying assumption taken above does not hold. In other words, if hash rate were to take on a trend of decreasing over a significant period of time at some point in the future leading to a Bitcoin year length greater than 365 days, the calendar drift would ideally be pushed in the other direction by a relaxing influence on the proof of work requirement instead of a tightening influence. Since this would definitely result in a hard fork relative to un-upgraded nodes, this feature, if implemented, would need to be kept inactive for much longer, and only activated if/when the number of non-upgraded nodes becomes so insignificant that a hard fork is no longer a concern.
Join the conversation on stacker.news.
-
 @ c0e4bd0b:1c5734af
2024-11-10 12:13:26
@ c0e4bd0b:1c5734af
2024-11-10 12:13:26Bitcoin Calendar Definition
Layer: Applications
Status: Draft
Bitcoin defines the halving cycle as 210,000 blocks, as defined in the file
kernel/chainparams.cpp. This number was apparently chosen as an aesthetically pleasing number which equates almost exactly to 4 years, according to the ten-minute block schedule. This BIP proposes using this parameter of Bitcoin as the basis for reckoning calendar time, defined as follows.nBlocksPerYear = 210000 / 4 // calculates to 52,500 nBlocksPerMonth = nBlocksPerYear / 12 // calculates to 4375The calculations above produce integer results, making calendrical calculations based on block height extremely convenient. The zero-based year and month are calculated as follows, using integer division (/) and mudulo (%) based on block height h:
year = h / 52500 month = (h % 52500) / 12Furthermore, we assume a bitcoin day length of 144 blocks. This is consistent with the target of 10-minutes per block and the 2016 blocks every two weeks for the difficulty adjustment period. This results in months of 30 days, with a small remainder:
nBlocksPerDay = 144 daysPerMonth = nBlocksPerMonth / nBlocksPerDay // calculates to 30.somethingA human-friendly date can thus be displayed based upon block height, with familiar calendrical characteristics of 30 full days per month (with a partial day 31) and 12 months per year. As of this writing, the current bitcoin date is 7/24/17, 24-07-0017, or the twenty fourth day of the seventh month of the seventeenth year of Bitcoin.
This definition forms the basis for a culturally independent and socially universal calendar system which is easy to calculate, durable, and financially relevant.
Cross-referencing with other calendar systems:
Since this date will not synchronize exactly to extant calendar systems, a notation needs to be used in cases where ambiguity would result. Taking the solar day as the example, references that cross over between the solar day and the bitcoin date need to have a qualifier resolving the phase discrepancy (as is done when referring to dates in ancient calendar systems that do not align with the turn of the date at midnight). For example, the Bitcoin date of 7/24/17 would be written as November 9/10, 2024, making it clear that it touches both of those solar days. However, this format should only be used for dates in which the two calendar systems are more out of sync than in sync. For dates that are more in sync than out of sync, no overlap day should be given, because it would add ambiguity where there otherwise was none.
Bitcoin Calendar Synchronization
Layer: Consensus
Status: Draft
The Bitcoin calendar (referring to the prior definition) would be more economically relevant to earthlings if the Bitcoin year actually stayed synchronized with the growing seasons of the tropical year. Currently, the Bitcoin year begins in the springtime of the northern hemisphere, but it is offset one year and there is currently nothing to keep the bitcoin year from drifting further out of synchronization with the tropical year.
To keep the Bitcoin year in sync with the seasons, the bi-weekly proof-of-work difficulty adjustment could be tailored to aim toward better alignment during every difficulty adjustment. Normally, the difficulty is adjusted upward or downward a maximum factor of 4, as defined in the file
pow.cpp. The determination of the value within that range is made solely on the basis of the rate of block discovery during the prior 2016-block (two-week) period.The existing difficulty adjustment scheme has resulted in the Bitcoin calendar generally sliding earlier every year, presumably due to the fact that the global hash rate is generally increasing rather than decreasing. The historical dates for the year beginnings and the corresponding duration of the Bitcoin year are as follows:
|Year|Block|Date|Days| |-:|-:|--|-:| |0|0|01/03/09|| |1|52500|04/22/10|474| |2|105000|01/28/11|281| |3|157500|12/14/11|320| |4|210000|11/28/12|350| |5|262500|10/09/13|315| |6|315000|08/10/14|305| |7|367500|07/29/15|353| |8|420000|07/09/16|346| |9|472500|06/23/17|349| |10|525000|05/29/18|340| |11|577500|05/23/19|359| |12|630000|05/11/20|354| |13|682500|05/07/21|361| |14|735000|05/05/22|363| |15|787500|04/29/23|359| |16|840000|04/19/24|356|
As can be seen, the number of days in the actual Bitcoin year are consistently fewer than the number of days in the tropical year (365.2425). Assuming the hash rate will generally continue to increase, this trend should continue, which allows us to make a convenient simplifying assumption.
Conceptually this proposal seeks to add an additional, limited offset to the work requirement based on whether the Bitcoin calendar is ahead of schedule or behind schedule, in comparison to the tropical year. We can assume based on the trends, however, that we only need to "slow down" the block rate slightly to keep it in sync with the seasons. Therefore, this proposal aims to do only that.
If the Bitcoin block height is a certain amount ahead of the calendar synchronization goal (per the trend), the difficulty would be increased one notch more than required by the normal calculation, if not already at the limit of adjustment for that period. This would make it impossible for the proposed change to overpower the existing calculation, but would still provide a gentle enough push when needed to keep the calendar in sync, thus accomplishing the purpose.
Fork considerations by the author:
A consensus change to the proof of work calculation would normally result in a hard fork. However, in the case that we only potentially increase the difficulty and never decrease it relative to non-upgraded nodes in the network, this means that during the transition, only upgraded nodes would be at risk of rejecting blocks for not meeting the more stringent difficulty level necessary to synchronize the calendar.
The new nodes would therefore need to be programmed to yield to the non-upgraded difficulty criteria until most of the network has upgraded, at which point activation would occur (as explained below) and miners would be obliged to meet the tougher requirements demanded by all upgraded nodes. Nodes that still had not upgraded by that time would remain unaffected, since the post-activation blocks would only have more proof of work, and not less, than non-upgraded nodes require.
More importantly, an overwhelming majority of the hash rate should be fully upgraded to avoid a situation where non-upgraded, non-mining nodes are forked by a longer chain created by non-upgraded miners. A sufficient portion of the hash rate following the upgrade path would eliminate this possiblity, even for non-mining nodes that don't upgrade, because the longer chain will come from the greater hash power and there would be no financial incentive for miners to switch back to catering to a minority of non-upgraded nodes.
Proposed activation method:
Upgraded nodes would delay the relaying of blocks that do not meet the more stringent requirements. This would begin as a confirmation-time penalty to upgraded nodes, but as the upgrade expands to more nodes, the effect would shift to incentivizing miners to produce blocks that conform to the upgrade in order to build on the longest chain faster.
Optional second-phase activation:
For the longer term, it might be advisable to also implement the corresponding opposite influence on the proof of work adjustment for the case where the simplifying assumption taken above does not hold. In other words, if hash rate were to take on a trend of decreasing over a significant period of time at some point in the future leading to a Bitcoin year length greater than 365 days, the calendar drift would ideally be pushed in the other direction by a relaxing influence on the proof of work requirement instead of a tightening influence. Since this would definitely result in a hard fork relative to un-upgraded nodes, this feature, if implemented, would need to be kept inactive for much longer, and only activated if/when the number of non-upgraded nodes becomes so insignificant that a hard fork is no longer a concern.
Join the conversation on stacker.news.
