-
 @ f33c8a96:5ec6f741
2024-11-25 23:43:20
@ f33c8a96:5ec6f741
2024-11-25 23:43:20 -
 @ f33c8a96:5ec6f741
2024-11-25 23:41:06
@ f33c8a96:5ec6f741
2024-11-25 23:41:06 -
 @ f33c8a96:5ec6f741
2024-11-25 23:27:06
@ f33c8a96:5ec6f741
2024-11-25 23:27:06 -
 @ 3c7dc2c5:805642a8
2024-11-25 22:05:54
@ 3c7dc2c5:805642a8
2024-11-25 22:05:54🧠Quote(s) of the week:
'Most people don't understand how difficult it is to hold something that has gone up 10x, let alone 100x or 1000x. It takes extreme conviction, internal fortitude, and patience. Bitcoin greatly rewards those who have these qualities.' - Vijay Boyapati
'1) You spend 1000+ hours understanding Bitcoin and at the end of it you realize what an incredible godsend it is. You start buying like a madman while telling everybody (even people you don’t care about). You get ridiculed and belittled by almost everyone.
2) Thanks to your deep understanding of this incredible invention/discovery you hodl firmly despite the price going down 70%. Then the price goes nowhere for 6 months. Eventually, 3 long years later you had tripled your money. Everyone around you calls you lucky.' - Bitman_PoW
🧡Bitcoin news🧡
Let me start this week's Weekly Recap with the following tweet by Sam Baker (macromule):
The US dollar has peaked and will never recover. This is because we can't save dollars, we only spend them. River's thesis unveils the past, present, and future of money in society Let's start with how we got here:
Read the full thread here: https://x.com/macromule/status/1857106408203759674
On the 18th of November:
➡️We are still THIS early to Bitcoin. Enjoy the ride people, buckle up.
Fun fact. Bitcoin now has as many users as the internet did in 1997. You're still early!
➡️Bitcoin's blockchain was used to uphold electoral integrity in the latest US Elections. No other cryptocurrency can do this without reproducing the same centralization/trust issues they are trying to solve.
Screven County, Georgia made history on November 5, 2024, when it became the first county in the United States to use the Bitcoin blockchain to safeguard the results of its elections.
Full story: https://www.forbes.com/sites/frankcorva/2024/11/16/bitcoin-blockchain-used-to-secure-election-results-in-georgia-county/
➡️Global healthcare group Cosmos Health adopts Bitcoin as a treasury reserve asset.
➡️MicroStrategy demonstrated that you can put $4.6 BILLION into Bitcoin without moving the market.
These signs of market maturity will encourage bigger players like sovereign wealth funds to buy Bitcoin.
At a 0% yield, MicroStrategy's $1.75bn convertible note is currently priced as being more risk-free than every tenor on the US Treasury curve.
Investors are demanding a negative risk premium from the company that is literally just using their money to smash buy Bitcoin.
On the 19th of November:
➡️Michael Saylor to help Rumble CEO add Bitcoin to its balance sheet. Let's go!
➡️Bitcoin miner reserves hit new yearly lows.
➡️Shareholder activists have secured Saylor a 3-minute slot to present to the Microsoft board on adding Bitcoin to their treasury.
Sam Callahan: 'The big story here is how a single small shareholder managed to get the board of one of the largest public companies to consider a Bitcoin strategy—simply by submitting a proposal. I get the sense that the cyberhornets are about to take shareholder activism to a whole new level.'
Microsoft has $523 billion in assets on its balance sheet—which is 28% of Bitcoin's market cap.
➡️Another All-Time High: Bitcoin mining sustainable energy use hits 56.75%
Up a massive 67.7% in four years (since the same point in the last halving cycle). No other industry has done this. And as of today, no other industry can.
Daniel Batten: 'By using Bitcoin as a method of transaction you reduce net emissions by avoiding its less sustainable precursor, the banking sector By using Bitcoin as a store of value, you reduce net emissions by avoiding its less sustainable precursor, the gold industry. '
➡️'Bhutan has mined over $1 billion worth of Bitcoin using its previously stranded hydropower resources. My country, Norway, also has abundant, stranded hydropower. When will we start a national bitcoin mining project?' - Jaran Mellerud
His country, like mine and the whole EU, is more focused on printing more € to feed their NGOs that the politicians control, and they still don't care about mining Bitcoin. By the way, that $1 billion worth of Bitcoin is 34% of Buthan's TOTAL GDP!
➡️'Bitcoin euphoria is here. 99.3% of UTXOs are in profit now. Everyone's happy. This euphoric phase typically lasts 3–12 months (except the Nov '21 bull trap). This started 2 weeks ago. Shorting now could be either catching the top—or shorting at the bottom of a parabolic bull run.' -Ki Young Ju
➡️Dennis Porter: "I can officially confirm that I have been asked to speak before members of Congress/Parliament in two different nation-states about implementing a ‘Strategic Bitcoin Reserve’. One in Europe. One in LATAM."
Pro Bitcoin cantor CEO Howard Lutnick names U.S. Secretary of Commerce. He has "hundreds of millions"invested in Bitcoin.
➡️AnchorWatch, a pioneering insurance provider specializing in bitcoin custody, proudly announces its designation as a Lloyd’s of London Coverholder. This milestone solidifies AnchorWatch’s position as a leader in the emerging insured bitcoin custody solutions market. The company will officially open for business in December 2024 with binding authority of up to $100M per customer, helping to secure the wealth of American retail and institutional investors.
Source: https://www.businesswire.com/news/home/20241118360660/en/AnchorWatch-Becomes-Lloyds-of-London-Coverholder-Set-to-Begin-Operations-in-December-2024
Huge news! One small step for Bitcoin, one giant leap for adoption. This will enable a lot more Bitcoin independent holders to exist and help Bitcoin decentralization from centralized (qualified) custodians. I think it's hard to understate how important this piece of the puzzle will be. Incredible accomplishment by Rob Hamilton and the team of AnchorWatch!
➡️Bitcoin is now worth more than JPMorgan, Visa, and MasterCard COMBINED! The world's biggest bank and the world's biggest payment processor. AND...
➡️ It surpasses the Great British Pound (GBT) to become the 5th largest currency in the world.
Or
Bitcoin is now worth more than the Top 3 Global Banks combined: • Bitcoin: $1.85 trillion • JPMorgan Chase: $684 billion • Bank of America: $356 billion • IC Bank of China: $280 billion
➡️ETH is down 56% relative to BTC from the cycle bottom—over the same time BTC is up 455%. Ain't that a bitch, REKT!
No financial advice and quoting Samson Mow: "Just a note of caution to all the shitcoin speculators: what is happening to Ethereum now will happen to whatever thing you’re currently excited about. This is how it has always been and this is how it always will be. Sell it and buy Bitcoin while you still can."
Again no financial advice just some facts. It has been unprofitable to hold ETH over Bitcoin for 2,113 days, which is 62% of its trading history.
Unless you were around in 2016 til mid-2017, or bought the bottom in 2019-20, you would have been better off holding the orange rock.
On the 20th of November:
➡️MicroStrategy is now in the top 100 US publically traded companies. MicroStrategy has now outperformed NVIDIA over a 5-year time frame and it only adopted Bitcoin as a treasury asset 4 years ago. MicroStrategy: 2,749% NVIDIA: 2,683%
And on this day they announced the pricing of convertible senior notes offering. $2.6 billion. 0% coupon. 55% conversion premium. Due 2029.
And MicroStrategy was the 3rd most traded stock yesterday. More than Apple, Microsoft, and Amazon combined.
Here is the kicker. MicroStrategy's Bitcoin holdings are now worth over $15 BILLION in profit.
➡️Publicly traded biopharmaceutical company Hoth Therapeutics to purchase up to $1M in Bitcoin adopting it as a treasury asset.
➡️ Someone just moved 50 Bitcoins they've been HODLing for 12 years. They turned $200 into $5,000,000.
➡️Tyrone Ross, 401 Financial CEO: “There is a frustration that the advisors typically cannot discuss [Bitcoin] with clients. They can't bring it up. They're admonished not to say anything at all, and they are embarrassed by that. It just makes them look silly.” If your financial advisor cannot even bring up Bitcoin, how the F are they a financial advisor?
Joe Carlasare: "You’re a financial advisor. For years, every time a client asked about Bitcoin, you shut it down. ‘Too risky,’ you said. ‘Not backed by anything. Not a serious investment.’ Maybe you even chuckled at the idiots buying it. Now, the higher-ups at your firm—the ones who set your marching orders—have greenlit Bitcoin ETFs for your clients.
Imagine that call. You’ve got to bring up Bitcoin, unprompted, to the same clients you dismissed and ridiculed for even considering it. You’ve got to explain why their instincts were right all along. And why a 5% allocation makes sense. And then brace yourself for the obvious question: ‘If you missed this, why should I even listen to you? Why do I need you?’
On the 21st of November:
• Gensler announces resignation as SEC Chair • Trump unveils advisory council to set up Strategic Bitcoin Reserve • Bitcoin reaches the $100,000 mark
➡️Satoshi Nakamoto’s 1m Bitcoin is now worth $97.4 BILLION, making him the 12th richest person in the world.
➡️German government sold 50,000 Bitcoin at $55,000 Bitcoin is up 85% since then. Missed out on a cool $2.35 BILLION.
➡️Another record volume day for Metaplanet with ¥27 billion ($174.43 million). Good for #23 today in Japan, ahead of Honda and Nintendo. Saylor playbook in action.
➡️Dennis Porter: 'Texas lawmaker declares “I want Texas to have a Strategic Bitcoin Reserve first”.
Game theory is playing out. Texas has a $2.6 trillion economy and is the 8th largest economy in the world.
Texas launching a Strategic Bitcoin Reserve would send shockwaves across the globe and increase the FOMO of a National Strategic Bitcoin Reserve.'
➡️'If you hold 0.1 Bitcoin: - There are only 21M coins, placing you among the wealthiest 210M people globally (top 2.63%). - With 4M+ Bitcoin lost forever, you’re actually in the top 2.13%. - But here’s the kicker: some own more than 0.1 Bitcoin. Only 4.5M addresses hold more than 0.1 coins, putting you in the top 0.56%.' -Simply Bitcoin
➡️El Salavdor’s Bitcoin holdings now top over half a billion dollars. Excellent. El Salvador’s President Bukele takes to Instagram to show off the country’s 113% gains on its Bitcoin holdings.
Meanwhile the IMF: "We beg you to stop the adoption of Bitcoin because ultimately we cannot blackmail you anymore to push through our totalitarian undemocratically one world government agenda." - CarlBMenger
➡️Bitcoin miner MARA just raised $1 BILLION to buy more Bitcoin. Again, Saylor's playbook is in action.
➡️$9 Trillion Charles Schwab to get into Spot Bitcoin and crypto ETF sales - Bloomberg 'Schwab CEO Says He "Feels Silly" For Not Buying Crypto; Announces that Schwab Will Enter Spot Crypto Markets.'
➡️Publicly traded AI company Genius Group bought another $14 million Bitcoin after buying $10m BTC just 3 days ago.
➡️Bitcoin is on track to close the biggest monthly candle EVER!
On the 22nd of November:
➡️Bitcoin exchange balance continues to drop have reached an all-time low, according to data from CryptoQuant. No one is prepared for what is coming.
➡️Hashrate going absolutely ballistic. The network has never been more secure. Very bullish!
➡️Social media where you can choose your own algorithm, including from a third-party algorithm marketplace or making your own.
Sovereign content discovery. The future is here: Nostr! Primal 2.0 is here: http://primal.net/downloads
Nostr is still in its early adopter phase, just give it a try. I am using Nostr and only Nostr to share my Weekly Recap and earn some Bitcoin, Value4Value, for my content.
➡️Newmarket Capital CEO explains on CNBC how Bitcoin-backed loans reduce their risk. Newmarket manages $2B in assets. Bitcoin collateralized mortgages are clearly coming. I am not going to use this in the upcoming decade. But this will be the future.
➡️'US Bitcoin ETFs now hold a record 1.1 million Bitcoins. The number of Bitcoins held by US ETFs has DOUBLED over the last year. To put this into perspective, there are now ~20 million Bitcoins in circulation out of the total supply of 21.0 million. In other words, ETFs hold 5.5% of all Bitcoins mined.' -TKL
➡️Germany's biggest insurance company, and Europe's 2nd largest insurance company, Allianz SE, bought ~25% of MicroStrategy’s 2031 convertible note. Wait until other global insurance companies figure this out.
➡️ Something that pops up every now and then. Criminals prefer Bitcoin', or 'Bitcoin is used by criminals'. blabla
Daniel Batten: 'Yes, Bitcoin is used by criminals... The 0.3% of cybercriminals who conduct ransomware attacks prefer Bitcoin. The other 99.7% of cybercriminals prefer traditional (fiat) currency.
Source: https://batcoinz.com/do-cybercriminals-prefer-fiat-or-bitcoin-the-data-is-clear/
➡️Senator Lummis says: We have a gold strategic reserve. We have an oil strategic reserve. Bitcoin is digital gold and should be one of our reserve assets. "We could cut our debt by HALF in 20 years with a Bitcoin Strategic Reserve."
➡️Bitcoin miner MARA buys another $551m Bitcoin.
'With our 0% convertible note offering: - We acquired 5,771 BTC so far, at an average price of $95,554 per BTC. - 35% BTC Yield Per Share - Total owned BTC: ~33,875 BTC, currently valued at $3.4B based on a spot BTC price of $99k.' -Mara
➡️Trump's Secretary of Treasury nominee Scott Bessent: "I think everything is on the table with Bitcoin."
ON BITCOIN: "One of the most exciting things about Bitcoin is that it brings in young people and those who have not participated in markets before" Bessent also praised Bitcoin's ability to cultivate "a market culture in the U.S." while making users believe in a "system that works for them"
Trump’s favored pick to be the next SEC chair just posted “Make crypto great again” Bitcoin adoption is accelerating.
On the 23rd of November:
➡️'Today the block reward is 3.125 BTC. This costs $305k. In 2044 the block reward will be 0.0976 BTC. This costs $9.5k today.' -Bitcoin For Freedom
On the 24th of November:
➡️Only 1,003,525 addresses have more than 1 Bitcoin.
➡️UK’s The Times discusses whether pensions should invest in Bitcoin. Thomas Shelby's voice: 'Welcome to the FOOKING party lads!'
➡️'Cantor Fitzgerald has reportedly struck a deal to invest in Tether, with its $600 million stake representing about 5% ownership, according to the Wall Street Journal. Cantor CEO Howard Lutnick has also been appointed by Trump as Commerce Secretary.' -Bitcoin News
➡️Bitcoin spot ETFs bought around 34,860 $BTC this week while only 3,150 were mined. Pac-Man mode activated.
On the 25th of November:
➡️MicroStrategy has acquired 55,500 BTC for ~$5.4 billion at ~$97,862 per Bitcoin and has achieved a BTC Yield of 35.2% QTD and 59.3% YTD. As of 11/24/2024, they hodl 386,700 Bitcoin acquired for ~$21.9 billion at ~$56,761 per Bitcoin.
💸Traditional Finance / Macro:
On the 20th of November:
👉🏽'Total US stock market capitalization has hit $60 TRILLION for the first time in history. Over the last 4 years, the value of the US market has DOUBLED. By comparison, Asian and European stock markets are worth ~$18 and $15 trillion, respectively. If this trend continues, the US market will be TWICE as large as Asia and Europe combined as early as next year. To put this into perspective, the US stock market accounts now for 202% of the US GDP, the most on record. The US market is incredibly hot.' - TKL
On the 23rd of November:
👉🏽'US stock valuations are at 2001 levels: The US stock market's P/E ratio relative to global stocks reached 1.8x, the highest since the 2000 Dot-Com bubble. In other words, investors now have to pay nearly twice as much for US stocks than for their global counterparts for the same earnings. Over the last 15 years, the relative valuation of US stocks has DOUBLED. Since 2009, the S&P 500 and Nasdaq have returned 447% and 786%, massively beating the MSCI World ex-USA index gain of 52%.' -TKL
🏦Banks:
👉🏽 No news
🌎Macro/Geopolitics:
On the 18th of November:
'The Japanese Yen just hit 155 against the Dollar, its weakest level since July. The USD-JPY currency pair has risen 11% over the last 2 months, now near levels where Japan’s Ministry of Finance intervened this year. Japan spent a record 9.8 trillion Yen ($62 billion) to support the currency in late April and early May. In July, Japan spent an additional 5.5 trillion Yen ($36 billion) to support its currency. This came after the Japanese Yen hit its lowest level in 38 years.' - TKL
👉🏽 Ukraine has hit Russia with US long-range missiles - Russian state media This is concerning and unprecedented in the conflict so far. It’s a direct consequence of the Biden administration authorizing US long-range missiles & strikes into Russian territory.
👉🏽Jeroen Blokland: 'ECB President Lagarde: 'We can no longer see ourselves as a loose club of independent economies. That perspective is outdated in a world that is fragmenting into geopolitical blocs centered around the largest economies. Today we need to see ourselves as a single, large economy with predominantly shared interests.' It reads like she has zero notion that the Eurozone members seem to be moving in the exact opposite direction, stifled by centralized biased and unrealistic policies.' I hope we can select a candidate with a less EU-collective mindset at the next ECB elections. Oh wait, they don't get elected by public vote!
On the 19th of November:
👉🏽'Gold funds recorded $1.6 BILLION of outflows last week, the most since July 2022. This was also one of the largest weekly outflows over the last decade. Interestingly, this came after the second-largest inflow on record. As a result, gold prices fell ~7% in two weeks in a well-overdue technical correction. Gold prices are still up 24% year-to-date and are on track to record one of its best years this century. Gold markets are poised for a wild 2025.' -TKL
On the 20th of November:
👉🏽The ECB in its Financial Stability Review sounds the alarm over a return of market concerns over sovereign debt sustainability. These concerns are self-fulfilling, especially when they come from the ECB, which has to provide a credible government bond market backstop.
👉🏽US national debt reaches an all-time high of $36,000,000,000,000. Splendid job US!
'Since the start of this year, total US debt is now up by a whopping $2 TRILLION. In other words, the US has added an average of $6.3 billion of debt PER DAY for the last 316 days in a row. This means that the US government now holds $108,000 in debt for EVERY American. Deficit spending as a % of GDP is currently up to World War 2 levels while the Fed calls for a "soft landing." We are in desperate need of a change right now, we are on an unsustainable fiscal path.' -TKL
👉🏽 Last week I mentioned that the US budget deficit jumped by a massive $257 BILLION in October 2024.
By comparison, last October the US budget deficit came in at $67 billion, marking a 287% year-over-year increase. To put this in perspective, economists expected the October deficit to come in at $73 billion. This puts the actual budget deficit 252% higher than what economists projected. Just to elaborate on that with a haunting stat: Government spending per capita. $6,771 to $26,679 is a pretty big jump.
Source: https://www.federalbudgetinpictures.com/total-government-spending-quadruples/
On the 21st of November:
👉🏽'US bankruptcies in 2024 have officially surpassed 2020 pandemic levels. 570 large US companies have declared bankruptcy year-to-date, the most in 14 years. Over the last 3 months alone, a whopping 182 corporate bankruptcies have been filed. The consumer discretionary sector has been hit the hardest, experiencing 90 large bankruptcies year-to-date. This is followed by 68 filings in industrials and 59 in healthcare. Bankruptcies are surging as if we are in a crisis.' -TKL
I will repeat the statement by Fed chair Powell once more: 'In the case of a financial stability event, the Fed can use emergency tools.' Ergo: print the shit out of it!
👉🏽'Global central banks now own 13% of total gold reserves, the most since the 1990s. This share has DOUBLED over the last 10 years. Over the same period, foreign ownership of US Treasuries has declined from 34% to 24%.
This comes as purchases of Treasuries from overseas have not kept up with massive government debt issuance. At the same time, more countries have been increasingly diversifying their currency reserves by adding more gold. Are foreign governments losing confidence in US Treasuries?' -TKl
👉🏽Inflation in Argentina stood at 25.5% when Milei came into office on December 10th last year. Since then: January: 20.6% February: 13.9% March: 11% April: 8,8% May: 4.2% June: 4.6% July: 4% August: 4.2% September: 3.5% The figure for October just came in - 2.7%
Now bear in mind these are the monthly changes. The trend is in the right direction, still way too high! But Milei has demonstrated the effectiveness of economic freedom to recover an Argentina ruined by socialism. Governments create inflation! No one else. Deregulation and reducing government spending eventually lead to prosperity.
On the 22nd of November:
👉🏽The EURO plunges below $1.04, the lowest level in 2 years as bets on ECB rate cuts surge following weak econ numbers in Eurozone. The euro has been posting the worst spot returns among major currencies since late October.
👉🏽' The US government has been hiring an average of 50,000 workers per month for the past 2 years
Which is one of the highest rates in 30 years. This hiring spree has strengthened the labor market, likely delaying a recession. But, high levels of government job creation have rarely prevented recessions.' - Bravos Research Freaking half of the fucking jobs were just Biden trying to hide a market collapse with debt.
On the 23rd of November:
👉🏽In FY2023, the U.S. Government spent $6.16. trillion while only bringing in $4.47 trillion. The last budget surplus was in 2001.
On the 24th of November:
👉🏽Chinese geologists discover 1,000 tons of gold! That’s an extra 0.5% added to the global supply of Gold. There's a virtually unlimited supply of gold but there will only ever be 21 million Bitcoin.
👉🏽Janet Yellen, head of the US Treasury, has just resigned.
On the 25th of November:
👉🏽In Q3 2024, Japan sold a net $61.9 billion of Treasuries, the most on record. This was the second consecutive quarter of selling after $40.5 billion in Q2. At the same time, China dumped $51.3 billion, the second largest amount ever recorded. China has now sold Treasuries in 6 out of the last 7 quarters and its total holdings fell below $800 billion for the first time in 16 years. 2 of the world's biggest foreign holders of US government debt are selling like never before.' -TKL
Now who is going to buy the massive amount required to fund the enormous deficit? (scroll back up). And it may have something to do with the freezing and seizing of sovereign reserves. Just a thought. Or devil's advocate. Both need money, as their economy is flawed and desperate in need of some stimulant, and the USD is now at a high. Time to offload some assets at a high, that would make sense.
I want to end this week's Weekly Recap with a picture and a statement by BitPaine:
'The average DCA price over the last four years was about $30,000. If you listened to the maxis, you could have obtained 2.1 BTC at a savings rate of $43 per day ($15,700 / y) or 21 BTC at a savings rate of $430 per day ($157,000 / y). The latter was very accessible for those with high-income professions (or existing savings) willing to save (or redirect) a large proportion of their income/savings. The former was accessible for the median American household. Never before in history was generational wealth accessible for so many. …if you listened to the maxis. Now it is much more difficult.'
🎁If you have made it this far I would like to give you a little gift:
Once in a while, I go back to old videos. In this video, 3-year-old, Lyn Alden is absolutely demolishing Alex de Vries.
https://www.youtube.com/watch?v=6LP8G-oZnEs
Credit: I have used multiple sources!
My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly. Use the code BITCOINFRIDAY
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple.⠀⠀⠀⠀⠀⠀⠀⠀
Do you think this post is helpful to you? If so, please share it and support my work with sats.
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe -Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-
 @ 468f729d:5ab4fd5e
2024-11-25 21:46:31
@ 468f729d:5ab4fd5e
2024-11-25 21:46:31Course Mission
Welcome to the PlebDevs starter course! I'm Austin, the founder of PlebDevs, and I'll be walking you through this short intro starter course that will get you up and running and interacting with the rest of the content on the platform. If you're here, I'm assuming you're new to coding or just starting out. If you already have experience and have your bearings down, there's lots more intermediate and advanced content on the platform. This course is designed for absolute beginners.
Course Goals
Overall PlebDevs Goals
- Learn how to code
- Build Bitcoin/Lightning/Nostr apps
- Become a developer
This is a big journey with a lot of pieces and things to learn. The starter course is going to get you on that path as quickly as possible and make it a smooth journey.
Starter Course Objectives
- Give you an easy, high-level overview of the dev journey
- Get you set up and comfortable in a development environment where you'll write and ship code
- Give you basic experience in the languages covered in our courses and workshops
There's lots of material out there that will just tell you exactly what to do and not explain why but I want you to actually understand for yourself. I want you to have a good mental model of what this journey is going to be like, what it's going to be like actually writing and pushing code. And then we're going to start getting our hands dirty and gain real experience.
What is a PlebDev?
Origins and Philosophy
I started using the term "PlebDev" a few years ago to describe a unique approach to learning development in the Bitcoin space. It represents:
- Inclusive Learning: Anyone can become a developer, regardless of background
- Growth Mindset: Embracing the journey from beginner to professional
- Practical Focus: Emphasizing real-world application development
- Community Support: Learning and growing together
Key Characteristics
- 🌱 Growth-Focused: PlebDevs are always learning and improving
- 🎯 App-Centric: Focus on building applications rather than protocol development
- 🆕 Embrace Being New: Being a new developer is infinitely better than being on the sidelines
- 🤝 Community-Driven: Bitcoin/Lightning/Nostr ecosystem needs more plebdevs like you!
Our Learning Approach
Core Principles
- Lower Barriers
- Simplify complex concepts
- Focus on practical understanding
-
Build confidence through action
-
Project-Based Learning
- Learn by doing
- Create real applications
-
Build a portfolio as you learn
-
MVP (Minimum Viable Product) Focus
- Start with core functionality
- Get things working first
-
Iterate and improve
-
Actionable Knowledge
- Focus on the 20% that delivers 80% of results
- Learn what you can use right away
- Build practical skills
Teaching Methods
- Detailed concept breakdowns
- Line-by-line code explanations
- Interactive learning
- 1:1 support available
- Community-driven progress
Course Structure
The Learning Path
Instead of the traditional bottom-up approach, we use a project-focused method:
🏔️ Advanced Skills 🏔️ Projects & Practice 🏔️ Core Concepts 🏔️ Development Environment 🏔️ Getting StartedWe'll create checkpoints through projects, allowing you to: - Verify your understanding - Build your portfolio - See real progress - Have reference points for review
Student Expectations
What We Expect From You
- High Agency: Take ownership of your learning journey
- Active Participation: Engage with the material and community
- Persistence: Push through challenges
- Curiosity: Ask questions and explore concepts
What You Can Expect From Us
- Clear, practical instruction
- Comprehensive support
- Real-world applications
- Community backing
Getting Started
Next Steps
- Ensure you're ready to commit to learning
- Set up your development environment (next lesson)
- Join our community
- Start building!
Resources and Support
Where to Get Help
- plebdevs.com
Tips for Success
- Push code daily, even if it is small.
- Focus on understanding rather than memorizing.
- Build projects that interest you.
- Engage with the community.
- Don't be afraid to ask questions.
Remember
You don't need to become a "10x developer" overnight. The goal is to start writing code, build useful things, and gradually improve. Every expert was once a beginner, and the journey of a thousand miles begins with a single line of code.
Ready to begin? Let's dive into the next lesson where we'll set up your development environment! 🚀
-
 @ 468f729d:5ab4fd5e
2024-11-25 21:44:44
@ 468f729d:5ab4fd5e
2024-11-25 21:44:44Course Mission
Welcome to the PlebDevs starter course! I'm Austin, the founder of PlebDevs, and I'll be walking you through this short intro starter course that will get you up and running and interacting with the rest of the content on the platform. If you're here, I'm assuming you're new to coding or just starting out. If you already have experience and have your bearings down, there's lots more intermediate and advanced content on the platform. This course is designed for absolute beginners.
Course Goals
Overall PlebDevs Goals
- Learn how to code
- Build Bitcoin/Lightning/Nostr apps
- Become a developer
This is a big journey with a lot of pieces and things to learn. The starter course is going to get you on that path as quickly as possible and make it a smooth journey.
Starter Course Objectives
- Give you an easy, high-level overview of the dev journey
- Get you set up and comfortable in a development environment where you'll write and ship code
- Give you basic experience in the languages covered in our courses and workshops
There's lots of material out there that will just tell you exactly what to do and not explain why but I want you to actually understand for yourself. I want you to have a good mental model of what this journey is going to be like, what it's going to be like actually writing and pushing code. And then we're going to start getting our hands dirty and gain real experience.
What is a PlebDev?
Origins and Philosophy
I started using the term "PlebDev" a few years ago to describe a unique approach to learning development in the Bitcoin space. It represents:
- Inclusive Learning: Anyone can become a developer, regardless of background
- Growth Mindset: Embracing the journey from beginner to professional
- Practical Focus: Emphasizing real-world application development
- Community Support: Learning and growing together
Key Characteristics
- 🌱 Growth-Focused: PlebDevs are always learning and improving
- 🎯 App-Centric: Focus on building applications rather than protocol development
- 🆕 Embrace Being New: Being a new developer is infinitely better than being on the sidelines
- 🤝 Community-Driven: Bitcoin/Lightning/Nostr ecosystem needs more plebdevs like you!
Our Learning Approach
Core Principles
- Lower Barriers
- Simplify complex concepts
- Focus on practical understanding
-
Build confidence through action
-
Project-Based Learning
- Learn by doing
- Create real applications
-
Build a portfolio as you learn
-
MVP (Minimum Viable Product) Focus
- Start with core functionality
- Get things working first
-
Iterate and improve
-
Actionable Knowledge
- Focus on the 20% that delivers 80% of results
- Learn what you can use right away
- Build practical skills
Teaching Methods
- Detailed concept breakdowns
- Line-by-line code explanations
- Interactive learning
- 1:1 support available
- Community-driven progress
Course Structure
The Learning Path
Instead of the traditional bottom-up approach, we use a project-focused method:
🏔️ Advanced Skills 🏔️ Projects & Practice 🏔️ Core Concepts 🏔️ Development Environment 🏔️ Getting StartedWe'll create checkpoints through projects, allowing you to: - Verify your understanding - Build your portfolio - See real progress - Have reference points for review
Student Expectations
What We Expect From You
- High Agency: Take ownership of your learning journey
- Active Participation: Engage with the material and community
- Persistence: Push through challenges
- Curiosity: Ask questions and explore concepts
What You Can Expect From Us
- Clear, practical instruction
- Comprehensive support
- Real-world applications
- Community backing
Getting Started
Next Steps
- Ensure you're ready to commit to learning
- Set up your development environment (next lesson)
- Join our community
- Start building!
Resources and Support
Where to Get Help
- plebdevs.com
Tips for Success
- Push code daily, even if it is small.
- Focus on understanding rather than memorizing.
- Build projects that interest you.
- Engage with the community.
- Don't be afraid to ask questions.
Remember
You don't need to become a "10x developer" overnight. The goal is to start writing code, build useful things, and gradually improve. Every expert was once a beginner, and the journey of a thousand miles begins with a single line of code.
Ready to begin? Let's dive into the next lesson where we'll set up your development environment! 🚀
-
 @ 5bfb38cb:2b999aa7
2024-11-25 21:20:53
@ 5bfb38cb:2b999aa7
2024-11-25 21:20:53BTX2024
Open Interest:
There are no significant changes in OI as we have moved to premium.
Institutional Order Flow Sponsorship:
The IOF is bullish above the all-time high. The structure must be maintained away from the high to continue the trend.
Weekly Profile:
The week presents relevant news on Tuesday and Wednesday with FOMC news, with a short week due to the holiday on Thursday. A seek and destroy pattern is likely.
Classic Technical Analysis:
We have consolidated a new ATH; although the momentum is bullish, a delay to gain momentum is probable. We have tried to reach the magic number of 100,000 with low volume, anticipating weakness.
Market Structure:
The structure is bullish.
Trading Range:
87005 to 100170. Currently in Premium.
Equilibrium:
93590.
Key Price Levels:
I do not expect closes below 88955 to remain bullish at daily.
Daily BIAS:
Bullish. Possible delay to gain momentum.
Daily Target:
Delay to 89990.
"The market is never wrong; opinions often are." - Richard Wyckoff 🔮
-
 @ 5bfb38cb:2b999aa7
2024-11-25 21:04:55
@ 5bfb38cb:2b999aa7
2024-11-25 21:04:55BTX2024
Relative Strength Analysis:
The 3 indices have had a bullish recovery with volume without reaching historical highs again, with the YM being the strongest. Classic Technical Analysis:
In terms of conventional technical analysis, BTC remains in an Elliott structure fulfilling a minor wave 5 and a major wave 3. We have had a consolidation structure since March 2024 with a breakout to the upside. The context is strongly bullish.
COT:
The progression of contracts nearing expiration is at a premium. The 12-month COT is in a positive program and in positive hedging.
Banks are buying Bitcoin futures contracts and are not in a bearish position, being the counterpart to leveraged short investment funds. Market Sentiment:
Market sentiment in general retail news is bullish following the FED's rate cut and in response to the US elections, although with some moderation.
The Williams %R remains in oversold territory and avoids a bearish divergence.
Intermarket Analysis:
The 3 indices present a bullish reversal. No close above last week's highs. With greater strength in the YM and less strength in the NQ.
The 3 bonds, ZN, ZF, and ZB, show an absorption bar with significant volume. Confirmation is needed in a discount context. The reverse interests in a premium context.
The DYX has another bullish week reaching a monthly target in premium. Peripheral currencies maintain another week with bearish closes, with greater weakness in the EUR.
In commodities, BTC has maximum bullish extension, reaching just a few dollars from a macro target. The GC has a complete reversal bar with a bullish close. The CL presents a bullish reversal in one week but is still in a consolidation environment.
In conclusion, we have a stock market that marks a bullish retracement with significant volume, especially the YM. The DYX has a bullish context but the possibility of a trend end. Weakness in peripheral currencies. Commodities show strongness in BTC and GC. The CL in a consolidative context.
Market Profile:
The market is currently bullish. It needs to move significantly away from the all-time high to continue this movement. Although some significant delay can be expected to take liquidity after such a sharp movement since the US elections.
Market Structure:
The value 65775.00 maintains price control. The weekly context is bullish.
Trading Range:
65775 to 100170. Currently at a premium in the range.
Equilibrium:
80141
Key Price Levels:
79300 do not expect closes below this structure to remain bullish.
Weekly BIAS:
Bullish. Consider a probable delay to gain momentum.
Weekly Objective:
Retracement to 89755.
The stock market is filled with individuals who know the price of everything, but the value of nothing." - Philip Fisher. 🔮
-
 @ a56ff0bd:904daa79
2024-11-25 20:43:08
@ a56ff0bd:904daa79
2024-11-25 20:43:08Prova prova
-
 @ 7c765d40:bd121d84
2024-11-25 20:20:18
@ 7c765d40:bd121d84
2024-11-25 20:20:18This is not a story about Ron Jeremy. This is a story about a man and his company going ALL IN shorting the fiat system. I've been talking about microstrategy for a while now on the channel. I have been fascinated by the strategy and the balls on Saylor. But today will be the last time. Why? Because I believe it's a distraction. I think people should be focused on buying, earning, and protecting their bitcoin. In a few months from now, you will be competing against the US government for bitcoin. Building your own strategic bitcoin reserve should be the top priority. There are also two big risk involved with owning MSTR shares: 1. Microstrategy holding bitcoin on your behalf 2. Your stock broker holding MSTR shares on your behalf Bitcoin has no counterparty risk. Does that mean I'm selling my MSTR shares? Absolutely not. I see MSTR just like bitcoin - HODL for a very very long time. Bitcoin is designed to go up forever. And MSTR is adding rocket fuel to that. But unlike bitcoin, I am not attached to MSTR. I plan on keeping about 50% of my shares forever, and using the other half as needed. For a yacht or something. So without any technical discussion or NAV debate, here's why I would consider grabbing a few MSTR shares: 1. They are shorting the fiat system. A system that was designed to fail and about 20 years past it's expiry date. 2. They are using the greatest asset in history to short the worst asset in history. 3. They already have 330,000 bitcoins. No other entity on earth will be able to catch them. 4. They are front-running nation states. If bitcoin becomes the world reserve currency, and MSTR has more than most (or all) nation states, think of the implications. 5. Most people - including your financial advisor - have not figured this out. Which is where the opportunity lies. 6. They will be added to the QQQ index and likely the S&P500 sometime in the next year or so. This will create massive (and passive) demand and move shares into long-term storage. 7. You can hold these shares in a tax sheltered account. Your capital can ride the bitcoin wave without having to worry about paying tax on the gains. 8. This is only the beginning. They have MUCH bigger plans for MSTR. They will utilize bitcoin and lightning in their current operations. They will either start or acquire a bank and deal in bitcoin. They will offer fixed income bonds on the bitcoin. They will start or acquire insurance companies who currently own ZERO bitcoin. There is no limit to what this amount of collateral can do. Saylor will continue taking on debt to buy bitcoin as long as the spread and demand stays high. Eventually the big money will realize that they should be holding their own multi generational wealth in bitcoin. The rules will change so they can hold bitcoin. But by this time, MSTR will already be the #1 company on earth and will have insane amounts of constant buy pressure from the funds. That's when Saylor will shift gears and starts putting his collateral to work - to earn more bitcoin. Nobody understands how truly scarce bitcoin is. But we are about to find out. Moral(s) of the story: - NEVER SELL YOUR BITCOIN - If you have some capital in a retirement fund, move it to MSTR There will absolutely be a movie made about this. In the big short, Michael Burry made $800 million. Michael Saylor is already well above $8 billion on this trade. And will likely become the world's first trillionaire - by shorting the fiat system. Jump on and buckle up.
PS - Microstrategy bought another 55,500 bitcoins while I was typing this. Bringing their new total to 386,700 bitcoins.
-
 @ 4fcac000:d2b37988
2024-11-25 19:58:54
@ 4fcac000:d2b37988
2024-11-25 19:58:54🌱 В Тюмени объявлен старт программы "Зеленый маршрут", направленной на создание сети экологически чистых транспортных коридоров, соединяющих ключевые точки города.
Яркие факты 👇 Экологические коридоры: Новые маршруты будут включать велодорожки, пешеходные зоны и зеленые насаждения, способствуя улучшению качества воздуха. Общественный транспорт: Программа предполагает интеграцию с экологически чистыми видами транспорта, такими как электробусы и трамваи. Социальные инициативы: В рамках программы планируются мероприятия по обучению горожан экологии и устойчивому транспорту.
Тюмень 2040 года стала примером устойчивого развития, где экология и комфорт идут рука об руку! 🌍🚶♀🚲


-
 @ 6bae33c8:607272e8
2024-11-25 19:19:58
@ 6bae33c8:607272e8
2024-11-25 19:19:58Week 12 got off to a good start — I had one player going in the under-16 Portugal girls basketball league, and she went bananas — 33 and 19 with six steals in a game they won 55-34. And yes, I was counting her stats from the bleachers. It was crazy because our team has only six players, and two fouled out with six minutes left, so they had to play 4 on 5. Granted it was a soft opponent, but it was thrilling nonetheless. Sasha is more Angel Reese than Caitlin Clark, basically just bullying and bodying people while driving hard to the hole. Probably went to the line 15 times, making about five of them. Steph Curry she is not.
The rest of the day was a mixed bag. I was 1-3 ATS (pending Ravens -2.5) and damn lucky to get the 1 with the Bears +3.5 — though I was one inch away from getting the Raiders, a game I stayed up watching for no reason. Would it kill them to throw the ball to Brock Bowers? And I know Minshew got hurt, but FFS get rid of the damn ball!
One of my teams was dead to rights due to the bye weeks. I never pay attention to them while drafting, but this was extreme:
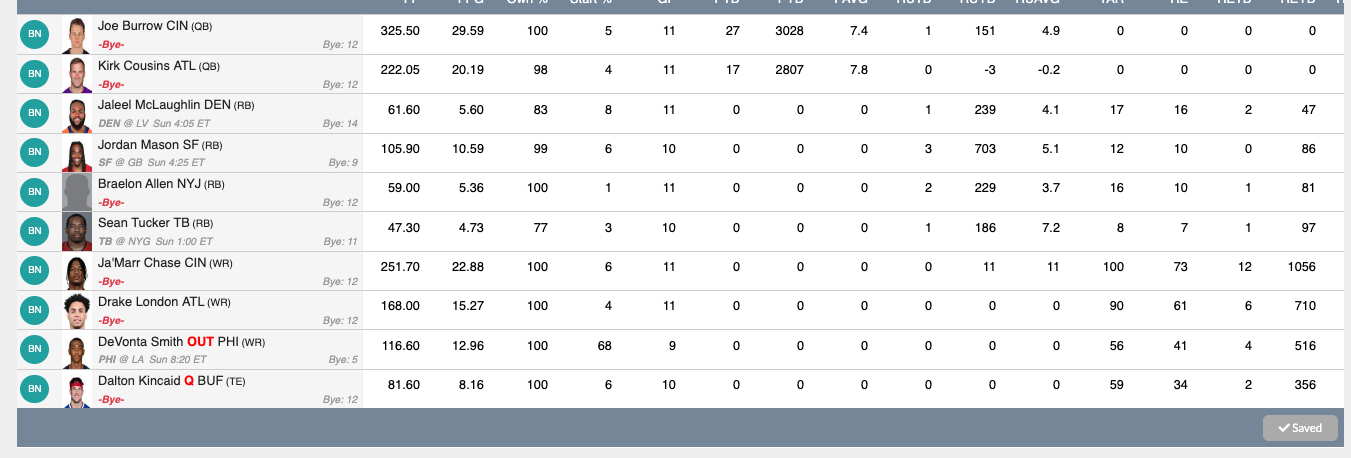 That’s my first, second, third and fifth round picks on the bench, plus my QB Joe Burrow. (Fourth-rounder was Stefon Diggs.) I even had to drop the Younghoe, though my awful starting lineup managed 99 points thanks in large part to his replacement Wil Lutz. That team is still in third place and could quality for the postseason with a strong stretch run.
That’s my first, second, third and fifth round picks on the bench, plus my QB Joe Burrow. (Fourth-rounder was Stefon Diggs.) I even had to drop the Younghoe, though my awful starting lineup managed 99 points thanks in large part to his replacement Wil Lutz. That team is still in third place and could quality for the postseason with a strong stretch run.My first place team balled out — I picked up Lutz there too, and I have Jonnu Smith everywhere, actually played him in the flex with Bowers. That team has Tua Tagovailoa and Jaylen Waddle too. Miami stack minus Tyreek Hill for the win!
The Primetime team did okay, pending JK Dobbins tonight. It’s in eighth place, but only 13 points out of fifth and 73 out of second. I think it’s good enough to go on a run down the stretch.
-
Saquon Barkley posted the nine-highest rushing total in NFL history and had 302 yards from scrimmage (10th most). I’m bummed to see it happen for another team (especially Philly), but he was the NFL’s Mike Trout and deserved better. (Actually, it’s way worse to be that guy in football, because at least everyone knows how great Trout was.)
-
AJ Brown makes it look so easy. I’d give him 15 targets a game if I were the Eagles, but obviously when your back averages 9.8 YPC there’s no need to throw.
-
Puka Nacua seems like the No. 1 now that both players are fully healthy. I actually had to use Demarcus Robinson in the bye-week league, and he scored a TD for me.
-
What happened to Justin Jefferson? It’s not like teams weren’t already trying to double him for the last three years. I guess he had a long TD called back due to a penalty, but it’s shocking to have Darnold go for 330 and Jefferson only 27. If I still played DFS I’d use him everywhere next week, and I haven’t even checked the matchup.
-
I didn’t watch much of this game, but had the Bears +3.5, was overjoyed when they cut it to three only to see them actually make the onside kick and send it to overtime! What are you doing? You had the cover locked up! Now you’re going to make me sweat OT? Luckily they got the ball first, but you never know.
-
I took the Colts +7.5 as a sell high on the Lions and got what I deserved. They were a sell-high, but you don’t step in the way of a freight train.
-
Anthony Richardson had bad stats, but he had a couple intermediate pass plays called back due to penalties, threw the ball well and didn’t turn it over. He also had 61 rushing yards. He’s not the guy that was totally lost early in the year.
-
Jonnu Smith is a top-five TE now. He’s my Stefon Diggs replacement as I have him everywhere now too.
-
Waddle had a monster game, and frankly it was overdue. They’ll probably get Hill more involved next week.
-
The problem with Rhamondre Stevenson is the offense often bogs down, and he’s not getting enough receptions to make up for it. In the first-place league, I had him in over Bucky Irving.
-
In my home picking pool (in which I had a horrible week), I took the Bucs -6. I almost *never* go against the Giants because at low stakes it’s not worth it, but Tommy DeVito might as well be Danny DeVito. After the game Malik Nabers criticized Brian Daboll for not getting him a target in the first half, and Daboll seeemed sympathetic to him. I have to think going DeVito over Drew Lock is purposeful tanking too. Watch Danny Dimes go somewhere decent and pull a Darnold.
-
Irving is the Bucs best back even if the GigaRachaad is good on passing downs.
-
The Cowboys-Killer Redskins game was one of the craziest of all time. Halfway through the fourth quarter, the score was 13-9. The final total was 60!
-
The KaVontae Turpin spin move kick return TD was so sick, as was the 86-yard TD to Terry McLaurin. Just insane plays in a game where 33 people in Circa Survivor (entries valued at $150K each) had the KRs in Survivor. To sweat the fourth quarter TD drive to cut it to three, see Turpin house it on the kickoff, then get the McLaurin miracle TD only to lose a chance for OT on a missed PAT is too much. Defenestration-level shit.
-
One of my favorite things about Circa Survivor is there’s always that real man who neglects to enter his pick. I mean it’s $1K to enter, so even Week 1 this is bad, but when each entry has $150K in equity? Ultimate respect for the No Pick TeraChad.
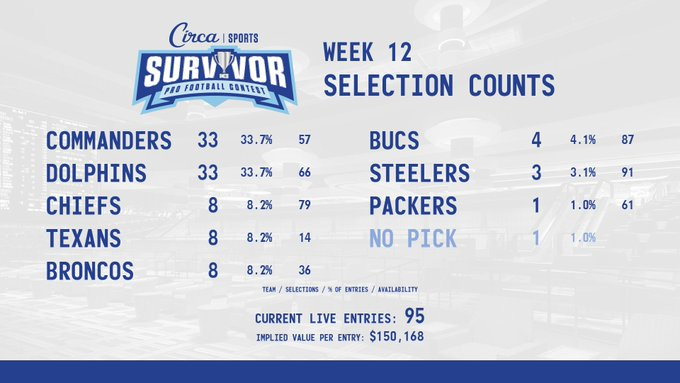 - The Chiefs play close games with everyone and inflict maximum frustration on fantasy owners.
- The Chiefs play close games with everyone and inflict maximum frustration on fantasy owners.-
Why bother activating Jonathon Brooks for two carries?
-
Both Richardson and Bryce Young are looking much more credible than earlier in the year. Low bar, I realize.
-
I started Richardson over C.J. Stroud this week after doing the reverse last week, and of course Stroud throws a TD on the first place from scrimmage. But in the end, even though Stroud had two TDs and 150 yards in the first half, and Richardson’s team failed to score a TD, Stroud finished with only 7.5 more points. The Texans offense is that miserable. At least Joe Mixon finally got stuffed.
-
The Titans are such a random team. Maybe they should throw to Chig Okonkwo every now and then?
-
Hopefully you didn’t overEstime the role of a particular Denver running back.
-
Bo Nix and Courtland Sutton are startable almost every week, but don’t mess with the rest of this rotating cast of randoms.
-
There’s really nothing to say about the Raiders. Why are they even scheduling games at this point?
-
I took the Cardinals in Circa as a sell-high on Seattle after their win over the 49ers, but turns out it was Arizona I should have sold instead. The Seahawks defense is nothing special, so why did Kyler Murray have so much trouble?
-
Jaxon Smith-Njigba is ahead of DK Metcalf now, it seems, but that was an ugly game all around.
-
Josh Jacobs was such an obvious draft target on a decent team (though I passed him up for Diggs and others every time.) Ignore all the metrics dorks who try to extrapolate stats from hopeless situations to good ones. They were saying Barkley was ordinary too.
-
The 49ers are still in the thick of the NFC West race, believe it or not. They kind of need Brock Purdy and Nick Bosa though.
-
-
 @ 4fcac000:d2b37988
2024-11-25 18:42:14
@ 4fcac000:d2b37988
2024-11-25 18:42:14В Тюмени объявлен старт программы "Зеленый маршрут", направленной на создание сети экологически чистых транспортных коридоров, соединяющих ключевые точки города.
Яркие факты 👇 Экологические коридоры: Новые маршруты будут включать велодорожки, пешеходные зоны и зеленые насаждения, способствуя улучшению качества воздуха. Общественный транспорт: Программа предполагает интеграцию с экологически чистыми видами транспорта, такими как электробусы и трамваи. Социальные инициативы: В рамках программы планируются мероприятия по обучению горожан экологии и устойчивому транспорту.
Тюмень 2040 года стала примером устойчивого развития, где экология и комфорт идут рука об руку! 🌍🚶♀🚲


-
 @ 4fcac000:d2b37988
2024-11-25 17:57:48
@ 4fcac000:d2b37988
2024-11-25 17:57:48В Тюмени запускаются инновационные образовательные программы, направленные на подготовку специалистов для "города будущего". Эти программы ориентированы на развитие навыков в области устойчивого развития, IT и экологии.
Участников ждут: - Курсы по устойчивому развитию. Программы включают обучение методам экологического проектирования и управления ресурсами. - IT-инициативы: Студенты смогут участвовать в стартапах и проектах, связанных с умными технологиями для города. - Сотрудничество с бизнесом: Программы разработаны в партнерстве с местными предприятиями, что обеспечивает практическую направленность обучения.
Тюмень готовится стать городом, где знания и инновации формируют будущее! 📚

-
 @ 4874b840:31b0b8c0
2024-11-25 17:47:07
@ 4874b840:31b0b8c0
2024-11-25 17:47:07https://www.spreaker.com/episode/podkast-kaliningrad-2040-vzglad-v-budusee--63002904
-
 @ 4874b840:31b0b8c0
2024-11-25 17:43:33
@ 4874b840:31b0b8c0
2024-11-25 17:43:3315 декабря в Калининграде официально открылся сезон катания на коньках. Городской каток на площади Победы начал свою работу с 10:00 утра, а также заработала служба проката коньков, предлагающая новые модели с улучшенной амортизацией и системой фиксации.
На катке уже собрались первые любители зимних видов спорта. Анна поделилась своими впечатлениями: «Я жду этого момента весь год! Ничто не сравнится с ощущением свободы на льду». Рядом с ней катались дети, которые с восторгом пробовали свои силы. «Это так весело! Я научился кататься всего за пару часов», — сказал Максим.
Служба проката работает без перебоев, и очередь на получение коньков растет. Менеджер проката Сергей отметил: «Мы подготовили около 500 пар коньков, и, судя по всему, их хватит на весь день».
На катке звучит музыка, а вокруг установлены яркие огни, создающие праздничную атмосферу. Вечером планируется открытие сезона с выступлениями местных фигуристов.
-
 @ 4874b840:31b0b8c0
2024-11-25 17:41:52
@ 4874b840:31b0b8c0
2024-11-25 17:41:52Сегодня утром — Калининград оказался под толстым слоем снега из-за сильного снегопада. Сотрудники ЖЭКа устроили забастовку в знак протеста против низкой зарплаты и ухудшающихся условий труда. Они требуют повышения заработной платы и улучшения социальных гарантий, что оставило город без уборки.
Роботы-уборщики не справляются с задачей, а тракторы на автопилоте закапывают друг друга из-за сбоя в навигации. Жители города начали делиться своими переживаниями в социальных сетях и организовывать инициативы по очистке улиц.
«Мы не можем просто сидеть и ждать, пока кто-то решит наши проблемы. Мы сами должны взять ситуацию в свои руки», — говорит местный житель Алексей, который вышел с лопатой, чтобы помочь очистить тротуары. Власти пока не сделали официальных заявлений. Горожане, вооружившись лопатами, выходят на улицы, чтобы вернуть Калининграду его привычный облик.
-
 @ 4dc2e570:7b8126f9
2024-11-25 17:39:08
@ 4dc2e570:7b8126f9
2024-11-25 17:39:08Chef's notes
Pickled pearl onions can usually be found at a middle eastern grocery store.
Details
- ⏲️ Prep time: 30 - 45 minutes
- 🍳 Cook time: 2 hours and 30 minutes
- 🍽️ Servings: 6
Ingredients
- 2.5 lbs stew meat
- 4 cloves Garlic
- 2 onions
- 6oz Bacon, chopped
- 4 Carrots (cut in 1/2 in pieces)
- 3 celery sticks (cut in 1 in pieces)
- 5 or so small gold potatoes, quartered
- 3ish tbps Flour
- 4 tbsp tomato paste
- 14 oz Guinness Beer
- 3 cups chicken stock
- 1 tsp Thyme
- 2 bay leaves
- Ghee
- Salt and pepper
Directions
- Pat dry then salt and pepper the beef. Melt 1/2 tbsp ghee over high med-high heat. Brown the beef on each side well, makes the stew tasty. This takes patience. Do some breath work while you're at it. :) Add ghee as necessary so browny bits on bottom dont burn. Put meat aside.
- In same pan, sauté onion and garlic for a few min. Throw in bacon till browned. Put in carrot and celery.
- Add 3tbsp flour (or a bit more, basically till oil is soaked up) and stir for a minute. Add tomato paste. Stir a couple more minutes.
- Add thin layer of beer and scrape yummy bits from bottom of pan. Mix everything well. Add rest of beer, broth, and herbs.
- Carmelize the pickled pearl onion on low med heat with a lil olive oil and stirring occasionally.
- Simmer covered for 2 hours. Add potatoes. Simmer for a further 30 minutes uncovered to let the sauce reduce a bit. Salt and pepper as you like. Add in some pearl onions. Enjoy.
-
 @ fff19d35:43344a0b
2024-11-25 17:23:46
@ fff19d35:43344a0b
2024-11-25 17:23:46Here are the benefits of Bitcoin:
- Decentralized and Autonomous: Bitcoin operates independently of central banks and governments, giving users full control over their funds.
- Limited Supply: The total supply of Bitcoin is capped at 21 million, which helps to prevent inflation and maintain the value of each coin.
- Fast and Global Transactions: Bitcoin enables fast and secure transactions worldwide, without the need for intermediaries like banks.
- Low Transaction Fees: Compared to traditional payment systems, Bitcoin transaction fees are significantly lower.
- Security and Transparency: Bitcoin's blockchain technology ensures that all transactions are secure, transparent, and tamper-proof.
- Investment Opportunities: Bitcoin has been a lucrative investment option for many, with its value increasing significantly over the years.
- Financial Inclusion: Bitcoin provides access to financial services for people in countries with unstable currencies or limited access to traditional banking.
- Diversification: Bitcoin offers a unique asset class for diversifying investment portfolios.
- Growing Adoption: Increasing acceptance and adoption of Bitcoin by businesses, governments, and institutions.
-
 @ ec951079:533d29e7
2024-11-25 17:10:28
@ ec951079:533d29e7
2024-11-25 17:10:28Need for Youth Empowerment in Underdeveloped Environments
The world's future lies in the hands of its youth. However, in underdeveloped environments, young people often face significant challenges that hinder their ability to reach their full potential. Youth empowerment is crucial in these environments to break the cycle of poverty, promote economic growth, and foster sustainable development.
Challenges Faced by Youth in Underdeveloped Environments
Youth in underdeveloped environments face numerous challenges, including:
- Limited Access to Education: Inadequate educational infrastructure, lack of qualified teachers, and unaffordable school fees hinder young people's ability to acquire knowledge and skills.
- Unemployment and Poverty: High levels of unemployment and poverty force many young people to engage in menial jobs or migrate to urban areas in search of better opportunities.
- Lack of Opportunities for Skill Development: Inadequate vocational training programs and limited access to technology and resources hinder young people's ability to acquire marketable skills.
- Social and Cultural Barriers: Traditional norms and cultural practices often limit young people's participation in decision-making processes and access to resources.
Why Youth Empowerment is Crucial
Empowering youth in underdeveloped environments is essential for several reasons:
- Demographic Dividend: Young people constitute a significant proportion of the population in underdeveloped environments. Empowering them can lead to a demographic dividend, where a large, educated, and skilled workforce drives economic growth.
- Breaking the Cycle of Poverty: Empowering youth can help break the cycle of poverty by providing them with the skills, knowledge, and resources needed to secure better-paying jobs and improve their socio-economic status.
- Fostering Sustainable Development: Empowered youth can contribute to sustainable development by promoting innovative solutions to environmental challenges, advocating for social justice, and supporting community development initiatives.
- Promoting Peace and Stability: Empowering youth can help promote peace and stability by providing them with alternatives to violence and extremism, and encouraging them to become active citizens who contribute to their communities.
Strategies for Empowering Youth
To empower youth in underdeveloped environments, the following strategies can be employed:
- Improve Access to Education: Invest in educational infrastructure, provide scholarships, and offer vocational training programs to equip young people with marketable skills.
- Provide Opportunities for Skill Development: Offer training programs in areas such as entrepreneurship, technology, and leadership to help young people develop the skills needed to succeed in the modern economy.
- Foster Entrepreneurship: Provide young people with access to capital, mentorship, and business training to encourage entrepreneurship and job creation.
- Promote Youth Participation in Decision-Making: Encourage young people to participate in decision-making processes at the local, national, and international levels to ensure that their voices are heard and their concerns addressed.
- Support Youth-Led Initiatives: Provide funding and technical support to youth-led initiatives that focus on education, entrepreneurship, and community development.
Conclusion
Empowering youth in underdeveloped environments is crucial for promoting economic growth, fostering sustainable development, and breaking the cycle of poverty. By providing young people with access to education, skill development opportunities, and entrepreneurship support, we can unlock their potential and create a brighter future for generations to come.
-
 @ f8a5df57:b7a58cd4
2024-11-25 16:58:12
@ f8a5df57:b7a58cd4
2024-11-25 16:58:12Тecnológicos парки в Москве будут выглядеть совершенно иначе, чем сейчас, благодаря стремительному развитию технологий и изменению общественных потребностей.
Технологические парки смогут представлять собой масштабные экосистемы с интеграцией искусственного интеллекта, интернета вещей и устойчивых технологий. Компании будут работать в синергии, минимизируя экологический след и используя возобновляемые источники энергии. Такие парки станут частью глобальной сети инновационных центров, где стартапы и исследовательские лаборатории из разных стран совместно решают мировые проблемы. Рабочие места будут организованы в формате многофункциональных пространств, где команды из разных областей будут работать бок о бок, способствуя кросс-дисциплинарному сотрудничеству.
Открытие технологических парков в Москве действительно может стать уникальным проектом, который объединит передовые технологии, экологические инициативы, культурные аспекты и человеческие ценности. Эти парки могут стать центрами инноваций, где стартапы и исследовательские группы будут работать над решениями, направленными на улучшение качества жизни горожан.
Автор: Ксения Данилова
-
 @ f8a5df57:b7a58cd4
2024-11-25 16:47:39
@ f8a5df57:b7a58cd4
2024-11-25 16:47:39 -
 @ f8a5df57:b7a58cd4
2024-11-25 16:43:21
@ f8a5df57:b7a58cd4
2024-11-25 16:43:21Пока другие страны накладывают санкции на Россию, Китай продолжает активно сотрудничать с нами в различных сферах, что способствует укреплению двусторонних отношений и экономического партнерства. Вот несколько ключевых аспектов, в которых Москва и Китай взаимодействуют:
• Торговля: Москва и Пекин увеличивают объем взаимной торговли, включая экспорт и импорт товаров. Китай является одним из крупнейших торговых партнеров России. Теперь доставка из Китая осуществляется на прямую с Россией.
• Инвестиции: Китайские компании активно инвестируют в различные отрасли экономики Москвы, включая недвижимость, инфраструктуру и высокие технологии.
• Транспортные коридоры: Развитие транспортных маршрутов, таких как «Новый шелковый путь», способствует улучшению логистики и ускоряет грузоперевозки между двумя странами.
• Совместные проекты: Реализация крупных инфраструктурных проектов, включая строительство мостов, дорог и железнодорожных линий.
• Исследования и разработки: Совместные научные проекты в области технологий, медицины и экологии. Обмен опытом и знаниями между научными учреждениями двух стран.
• Образование: Увеличение числа студентов, обучающихся в вузах Москвы и Китая. Программы обмена студентами и преподавателями.
• Культурные мероприятия: Проведение выставок, фестивалей и культурных мероприятий, способствующих взаимопониманию и дружбе между народами. Наиболее популярные фестивали: "Мир вокруг нас: обмен опытом и инновациями", "Мы вместе: налаживаем партнерские связи".
Сотрудничество Москвы и Китая охватывает широкий спектр областей, что способствует развитию обоих регионов. Углубление партнерства открывает новые возможности для бизнеса, науки и культуры, укрепляя стратегическое взаимодействие между двумя странами.
Автор: Рината Ситникова
-
 @ 3f0702fa:66db56f1
2024-11-25 16:24:27
@ 3f0702fa:66db56f1
2024-11-25 16:24:27https://psv4.userapi.com/s/v1/d/IPZi6_1mpGHakkmxL2bukxBFQHeLmi77n46dmvwdQZ6zl9o4ggmciZ3MNnKjgdKriaE1kt5-a6CsJySL0Vi6mQs-7zlbl2o9F0C9mIqUNml2Nnr3CLihsw/Untitled_3.mp4
45news
Курган2040
-
 @ 3f0702fa:66db56f1
2024-11-25 16:23:33
@ 3f0702fa:66db56f1
2024-11-25 16:23:33https://psv4.userapi.com/s/v1/d/IPZi6_1mpGHakkmxL2bukxBFQHeLmi77n46dmvwdQZ6zl9o4ggmciZ3MNnKjgdKriaE1kt5-a6CsJySL0Vi6mQs-7zlbl2o9F0C9mIqUNml2Nnr3CLihsw/Untitled_3.mp4
45news
Курган2040
-
 @ f8a5df57:b7a58cd4
2024-11-25 16:18:27
@ f8a5df57:b7a58cd4
2024-11-25 16:18:27Содержание сюжета:
В 2040 году Красная площадь, сердце Москвы и символ российской истории, пережила масштабную реставрацию, которая вернула ей былую красоту и величие. Проект, инициированный правительством и поддержанный международными экспертами в области архитектуры и истории, стал важным шагом к сохранению культурного наследия страны.
🔍 Что изменилось?
-
Архитектурные детали: В ходе реставрации были восстановлены уникальные архитектурные элементы, которые со временем утратили свою яркость. Ремонт стен ГУМа, восстановление оригинальных цветовых решений и деталей оформления Кремля стали приоритетными задачами.
-
Новые технологии: Использование современных технологий, таких как 3D-моделирование и виртуальная реальность, позволило создать точные копии утраченных элементов и обеспечить высокое качество работ.
-
Экологические инициативы: В рамках проекта была внедрена концепция "зеленой площади". Установлены новые системы озеленения, которые не только украсили пространство, но и улучшили его экологическую ситуацию.
🌍 Международное сотрудничество
Проект реставрации стал примером успешного международного сотрудничества. Архитекторы и историки из разных стран объединили усилия для создания единой концепции, учитывающей как местные традиции, так и международный опыт.
🎉 Возвращение к жизни
Красная площадь вновь стала центром культурной жизни Москвы. Здесь проходят концерты, выставки и праздники, привлекающие тысячи туристов и местных жителей. Площадь стала не только историческим объектом, но и живым пространством для общения и творчества.
🔔 Заключение
Реставрация Красной площади в 2040 году — это не просто восстановление исторического памятника, это шаг к будущему, где история и современность сосуществуют в гармонии. Мы гордимся тем, что можем передать это наследие следующим поколениям!
КраснаяПлощадь #Реставрация #Культура #Москва #История #Наследие
Автор: Рината Ситникова
-
-
 @ e97aaffa:2ebd765d
2024-11-25 16:16:48
@ e97aaffa:2ebd765d
2024-11-25 16:16:48https://www.youtube.com/watch?v=pQ7fjpqzUS4
Uma excelente entrevista de Natalie Brunell a Michael Saylor, aconselho a sua visualização.
Sem dúvida alguma, Saylor é muito inteligente, mas algo que sempre me inquietou ou gerou muitas dúvidas, é o seu ponto de vista sobre o Bitcoin como meio de troca(MoE). O seu pensamento (como MoE) sempre foi muito abstrato, evitava falar do assunto, era quase um tabu. Eu acreditava que essa atitude era devido a ter receio das autoridades dos EUA.
Mas nesta entrevista, ele falou mais do assunto, defendendo um mundo onde o Bitcoin como uma reserva de valor(SoV) e o dólar como a MoE, uma moeda global. Ou seja, o pensamento geral dos milionários de Wall Street, que só vê EUA, não tem a mínima noção da realidade ao seu redor, de como vivem os mais pobres em todo o mundo. Quando viajam, só vão para hotéis de 5 estrelas ou para condomínios de luxo ou fechados, não conhecem a realidade.
Não faz qualquer sentido, o dólar ser uma moeda oficial de todos os países, utilizada por todas as pessoas do mundo. Certamente algumas beneficiaram, mas no geral não haveria benefícios, a não ser para o EUA, que poderia financiar-se inesgotável e exportar diretamente inflação para todos os países. Se hoje em dia, o dólar como moeda de reserva mundial, indiretamente consegue exportar inflação, como MoE global, seria bem pior. Era o mundo inteiro a financiar um único governo, um único país. Os países do mundo e os seus cidadãos ficariam escravos, dependente das opiniões e da atitude do governo dos EUA. Seria um Franco CFA global.
É claro que o mundo beneficiaria com a existência de uma MoE global, mas este tem que ser neutro politicamente e economicamente, ter inflação zero é fulcral.
Saylor nunca escondeu que só olha para o Bitcoin como uma SoV, descartando o MoE e a auto-custódia.
Eu tenho opinião contrária, a meu ver, o que é revolucionário no bitcoin é o MoE, permitir a qualquer indivíduo do mundo ser livre, ter acesso a uma conta bancária, ter um dinheiro que não é monitorizado ou controlado por um governo. Permitir aos mais podres, que a sua única riqueza, são meia dúzia de moedas, que permitem apenas comprar a refeição do dia seguinte, não ser roubado pelo seu governo através da desvalorização cambial ou inflação.
É claro que o Bitcoin necessita de ser uma boa SoV, mas ao mesmo tempo também tem que ser uma MoE. Este é o principal problema das moedas FIAT, não são uma boa SoV, foram projectadas para perder poder de compra continuamente. Ter as duas características em simultâneo e ser acessível para todos os cidadãos do planeta, é que é revolucionário.
Na maneira como o Saylor olha para o Bitcoin, no meu ponto de vista, faria mais sentido ele ter apostado no ouro. Ele olha para o Bitcoin, apenas com as mesmas caraterísticas que o ouro, mas Bitcoin vai muito mais além disso. Em todas as características onde o Bitcoin é melhor que o ouro, o Saylor não usa/gosta. A divisibilidade, portabilidade, verificabilidade, fungibilidade, sem contra-parte e a soberania são características especialmente úteis para quem usa o bitcoin como MoE.
As caraterísticas onde (agora) o ouro é melhor que o Bitcoin, como a história e a adoção, sobretudo nos bancos centrais e no mundo financeiro, é apenas isto que o Saylor procura, possivelmente faria muito mais sentido ter apostado no ouro.
Volto a frisar, eu compreendo que o Saylor evite defender publicamente o Bitcoin como MoE, por ter medo de represálias, mas não faz qualquer sentido defender o dólar como moeda global. É completamente legítimo alguém querer apenas o Bitcoin como SoV, não querer utilizá-lo como moeda. Cada um é livre de fazer o que quer da sua vida e do seu património. Mas o Saylor ao dizer que o dólar é melhor que o Bitcoin, como MoE, só demonstra que ele não reconhece o real valor do Bitcoin.
MicroStrategy
O Saylor, ao mesmo tempo que defende o sistema financeiro FIAT, aproveita-se dele para fazer um ataque especulativo, ao próprio sistema. Aproveita as lacunas, do crédito barato existente, para comprar mais Bitcoin. Na entrevista, reafirma, que a MicroStrategy é um ativo alavancado de Bitcoin.
É curioso como ele o descreve, é alavancado mas sem a chamada de margem.
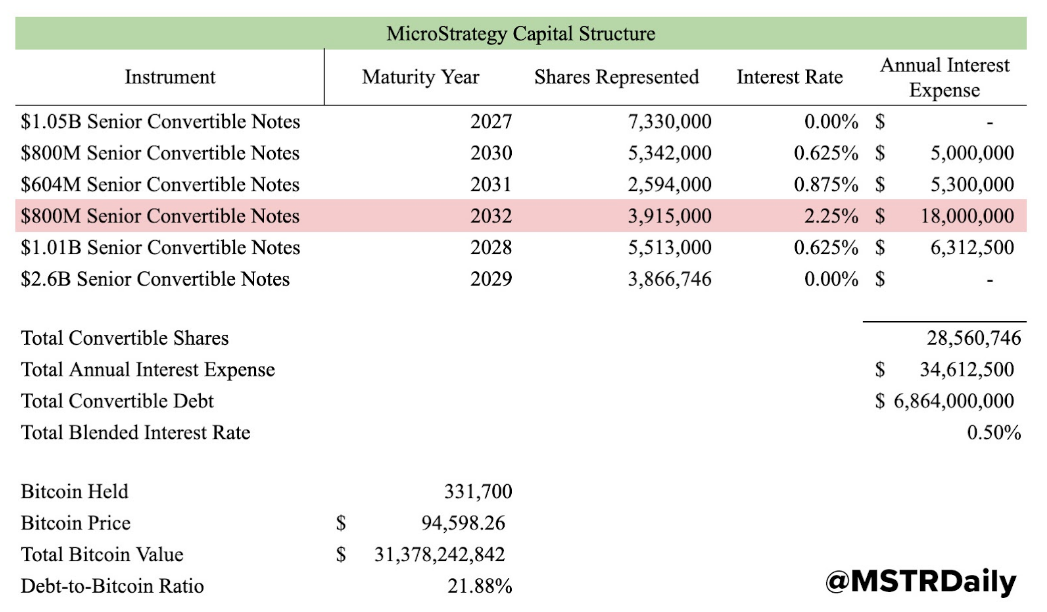
Pode não ter chamada de margem, mas continua a ser alavancado, continua a existir um risco, as notas conversíveis tem que ser devolvidas. É provável que no fim das maturidades das notas, o Bitcoin valerá mais que hoje, neste caso não existirá grande problema. Apesar de ser pouco provável, pode acontecer o contrário e se isso acontecer, será problemático.
O Saylor não pára de comprar Bitcoin, os créditos são cada vez mais elevados. A MicroStrategy começa a ser um problema. O curioso, é que o mercado está extremamente confiante e continua a comprar as notas conversíveis, na última emissão foram com uma maturidade de 2029 e com taxa de juro de 0%.
Enquanto escrevia este artigo, mais uma emissão: https://image.nostr.build/8857844f7ce5ac64b53f6d39df22a201825f1c26a2e7412b2061f91771e4627e.jpg
Ativos digitais
Outro ponto que gerou alguma controvérsia, é o Sayler defender os RWAs. Alguns bitcoiners criticaram-no e disseram que ele deixou de ser maximalista e os shitcoiners começaram a comemorar.
Neste ponto, eu compreendo o seu ponto de vista e até concordo com o Saylor, o sistema financeiro necessita de se modernizar, de estar disponível 24 por 7. Eu acredito que o futuro do sistema financeiro vai passar pela blockchain, mas será algo muito diferente daquilo que os shitcoiners imaginam. Os RWAs não vão ser em Solana ou Ethereum, não haverá tokens nativos ou tokens dos protocolos.
Eu vejo a BlockRock a criar uma blockchain própria, um sistema que fará concorrência direta à bolsa de New York, mas esse ecossistema terá como tokens nativos um sistémico do dólar, uma stablecoin. Tudo será monitorizado e controlado pela BlockRock, incluindo as regras de consenso da rede e os validadores, KYC e a emissão dos RWAs.
Blockchain é uma tecnologia que poderá ser muito útil, quando bem utilizada. O grande problema, é que os shitcoiners utilizam a tecnologia apenas para enriquecer, para vender tokens nativos ou tokens de protocolos ou tokens de governança, são tokens por tudo e por nada, isto é que não faz qualquer sentido. E como Saylor voltou a frisar: “There is no second best”.
-
 @ 3f0702fa:66db56f1
2024-11-25 16:00:30
@ 3f0702fa:66db56f1
2024-11-25 16:00:30К 2042 году в городе планируют открытие нового современного бассейна, который станет не только центром водных видов спорта, но и примером внедрения искусственного интеллекта в спортивную инфраструктуру.
-
Инновационные технологии Новый бассейн будет оснащен системами искусственного интеллекта, которые помогут оптимизировать процессы управления водными ресурсами и поддерживать идеальные условия для плавания. AI будет контролировать температуру воды, уровень хлора и другие параметры, обеспечивая максимальный комфорт для посетителей.
-
Персонализированные тренировки С помощью технологий AI будут разработаны персонализированные программы тренировок для спортсменов и любителей плавания. Умные системы смогут анализировать результаты плавания и предлагать рекомендации по улучшению техники.
-
Безопасность и мониторинг Искусственный интеллект также будет использоваться для обеспечения безопасности на территории бассейна. Системы видеонаблюдения с функцией распознавания лиц помогут следить за ситуацией и предотвращать возможные инциденты.
-
Экологические инициативы В рамках проекта будут внедрены экологически чистые технологии для очистки воды и энергосбережения, что позволит снизить воздействие на окружающую среду.
-
Доступность для всех Бассейн будет доступен для людей с ограниченными возможностями. Специальные входы и оборудование обеспечат комфортное посещение всем желающим.
45news
Курган2040
-
-
 @ 4fcac000:d2b37988
2024-11-25 15:57:45
@ 4fcac000:d2b37988
2024-11-25 15:57:45В Тюмени запускается уникальная инициатива "Тюмень 2040: Город идей", которая призвана превратить мечты и идеи молодежи в реальные проекты. Это масштабное событие объединит молодых людей, предпринимателей и экспертов для разработки и реализации инновационных решений, направленных на улучшение городской жизни.
📅 Дата и место: Дата: 15-16 мая 2040 года Место: Центральный парк Тюмени
🛠 Формат мероприятия:
Идеатон: В течение двух дней участники будут работать в командах над своими проектами, получая поддержку от менторов и экспертов. Выставка идей: Все проекты будут представлены на выставке, где жители смогут проголосовать за лучшие инициативы.
Гранты на реализацию: Лучшие идеи получат финансирование от городской администрации и местных бизнесменов для их реализации в жизнь.
🌍 Темы для проектов: Устойчивое развитие и экология Социальные инициативы Инновационные технологии для города Культура и искусство
Это событие станет платформой для вдохновения, обмена опытом и создания нового будущего Тюмени, где голос молодежи будет услышан! Присоединяйтесь к нам и станьте частью изменений! 🚀✨

-
 @ e31e84c4:77bbabc0
2024-11-25 15:00:17
@ e31e84c4:77bbabc0
2024-11-25 15:00:17The "Fools" Golden Generation was Written By Iain Taylor. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: noisycyclone54@walletofsatoshi.com
Nobody wants to work anymore. Millennials need to grow up and stop spending all their money on avocado toast. We had double-digit inflation in our day, but we still managed to get by just fine. Younger generations are just lazy.
Perhaps you have heard some of these generalizations hurled at you by the aging boomer population. There is a chance that they are right, and maybe we are all lazy deadbeats who don't want to work.
Or, just maybe, something else is going on—something more nefarious that may shine a different light on this prestigious golden cohort that created the greatest wealth generation in history. Maybe they aren't so god-like in their ability to create wealth from nothing more than recycled hemp and good vibes. Let's explore.
Who are the Boomers?
They are your grandparents and great-grandparents. The generation born after the end of WWII from 1946-64. They are Woodstock, the Civil Rights movement, the Vietnam War, and, just maybe, the orchestrators of the greatest wealth heist in history.
A short history to set the table for the Boomers:
It would be unfair to blame the Boomers entirely. After all, no generation exists in a vacuum. They inherited a global financial system established under the Bretton Woods Agreement in 1944 after the end of WWII.
That system had become increasingly unstable in the thirty years that followed as the U.S. continued issuing more claims on international gold reserves that backed the U.S. dollar than it had in its vaults. Tired of watching their currencies become debased against the U.S. dollar, countries in the 1960s began demanding their physical gold back. In 1965, French President Charles de Gaulle announced his intention to exchange its dollar reserves for the official exchange rate, and by 1971, West Germany had left the Bretton Woods system completely.
In response to the growing distrust in the current system, President Nixon made a move that shocked the world. He unilaterally closed the gold window and suspended the convertibility of gold and other reserve assets just months after West Germany’s decision.
This marked the end of the gold-backed dollar and opened the floodgates for modern monetary theory economic policies to play out across the globe just as Boomers were coming of age and beginning to take over the reins of power.
Money debasement
With nothing to stand in their way and now in firm control of government policy and the ability to print currency on demand through The Federal Reserve, Boomers started the money printer and never stopped. In the fifty years since the Nixon Shock occurred, the currency in circulation has increased 45X, with the base money supply spiking over 70X in the same period. The result has been sadly predictable and inevitable.
Why does that matter?
By increasing the monetary supply, the government created a manufactured shortage of everything else, driving prices up over time. An unbounded and unlimited amount of money began entering the system, chasing a finite amount of resources. The long-term effects are evident when you begin to look at the median house prices since 1971. Real Estate has become an investment rather than an essential utility because it operates at a better store of value than holding a constantly debasing currency in a savings account.
Printing proved incredibly lucrative for those who already had hard assets or the means to acquire them. As money became easier to obtain, everything else became more scarce and, thus, more valuable and expensive over time.
Money is Time and Energy in Abstract
Printing and introducing new currency comes at the expense of one of money's three fundamental properties: being a store of value. By increasing the amount of currency in circulation, the currency’s value becomes debased over time. More money chasing the same amount of goods and services. Based on the current supply, every $1 from 1971 would only hold the same value as $0.13 in 2024. Alternatively, it would cost $7.77 in 2024 to purchase the same value as $1 from 1971.
The second-order effect of money-printing is that it steals the productivity gains from future generations through compounding inflation. Jack Mallers explains this through “money” as time and energy in abstract form. Your time and energy (labor) are used to acquire money. If the money is debased, so is your time and energy, and, by extension, you yourself. Therefore, when governments print money, they are actually stealing the labor (time and energy) from future generations. When that money enters the economy in the form of increased demand and rising prices, it is done so by stealing the future generation's ability to create wealth and forcing them to exert more time and energy for the same amount of value as today.
How does Bitcoin Help?
The past 50 years have greatly benefited the Boomers who acquired hard assets early (homes, stocks, precious metals) at the expense of later generations. Even the productivity gains from technology advancements that should have been passed on to citizens were instead siphoned off to those closest to the money printer and those already holding assets.
\ MMT and a 2-3% inflation may appear harmless, but when compounded year over year, the impacts can be devastating. How would your life be different if every $1 you earned had the value of $7.77 today, or you only needed $0.13 to buy $1 worth of goods and services?
If you are just entering the workforce now, try to project this kind of debasement forward. How will you feel about the energy you invest today if the compensation will be utterly eroded by the time you retire?
\ Bitcoin fixes this problem by solving the issue of debasement. You simply can not print more Bitcoin into existence. This attribute of absolute scarcity makes Bitcoin an extremely hard form of money. It is fundamentally why it is a better store of value over the long term than anything else. If the money is scarce and cannot be debased, everything else becomes abundant by comparison, driving prices down over time. When you price anything in Bitcoin, you begin to see these effects over time. As the price of Bitcoin increases, everything else becomes less expensive.
So thanks, Boomers, for forcing us into a corner and having to create something you could not steal and debase. Something outside of the influence of the government and the money printer. Bitcoin is our way to push back and reclaim our time and energy from those who seek to steal it to enrich themselves.
The "Fools" Golden Generation was Written By Iain Taylor. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: noisycyclone54@walletofsatoshi.com**
-
 @ 9c47bb51:000381d0
2024-11-25 14:32:59
@ 9c47bb51:000381d0
2024-11-25 14:32:59Bitcoin ofrece una solución única para resolver muchos de los problemas financieros que enfrenta la comunidad Latinx y Mexicana. Desde tarifas altas en las remesas hasta la inflación descontrolada y el acceso limitado a servicios bancarios, Bitcoin puede ser una herramienta poderosa para construir un futuro financiero más seguro.
- Remesas sin fronteras
Cada año, millones de dólares son enviados a México y otros países de América Latina por familiares que trabajan en el extranjero. Sin embargo, los servicios tradicionales de remesas como Western Union cobran tarifas exorbitantes, que a menudo oscilan entre el 5% y el 10% del monto enviado.
Con Bitcoin, las remesas se pueden enviar directamente, de persona a persona, por una fracción del costo. Esto significa que más dinero llega a las familias que realmente lo necesitan, sin intermediarios que se queden con una parte.
- Protección contra la inflación
En países como México y otros de América Latina, la inflación es un problema recurrente que erosiona el poder adquisitivo de las familias. Los ahorros en moneda local pierden valor rápidamente, dificultando la estabilidad financiera.
Bitcoin, con su suministro limitado de 21 millones de monedas, actúa como una reserva de valor que no puede ser devaluada por decisiones gubernamentales. Es una alternativa confiable para proteger los ahorros frente a la inflación descontrolada.
- Inclusión financiera
Muchas personas en la comunidad Latinx y Mexicana no tienen acceso a servicios bancarios debido a barreras económicas, geográficas o legales. Esto limita su capacidad para ahorrar, invertir o participar en la economía global.
Bitcoin no requiere un banco. Con solo un teléfono móvil y acceso a internet, cualquier persona puede tener una billetera Bitcoin y participar en un sistema financiero descentralizado. Esto abre oportunidades para todos, independientemente de su ubicación o estatus económico.
- Soberanía financiera
Bitcoin devuelve el control del dinero a las personas. No puede ser confiscado ni bloqueado, y las transacciones son completamente resistentes a la censura. Esto es crucial para comunidades que enfrentan desigualdades y discriminación en el sistema financiero tradicional.
Además, Bitcoin permite la autodeterminación financiera, ayudando a las personas a tomar decisiones económicas sin depender de instituciones centralizadas.
Conclusión
Bitcoin no es solo una herramienta tecnológica; es una oportunidad para cambiar la manera en que las comunidades Latinx y Mexicanas manejan sus finanzas. Desde reducir costos en remesas hasta proteger ahorros de la inflación y empoderar financieramente a las personas, Bitcoin tiene el potencial de transformar vidas.
Ahora es el momento de aprender y explorar cómo Bitcoin puede ser una solución práctica y accesible para la comunidad.
English Translation:
Why the Latinx and Mexican Community Needs Bitcoin
Bitcoin offers a unique solution to many of the financial challenges faced by the Latinx and Mexican community. From high remittance fees to out-of-control inflation and limited access to banking services, Bitcoin can be a powerful tool to build a more secure financial future.
- Borderless Remittances
Every year, millions of dollars are sent to Mexico and other Latin American countries by family members working abroad. However, traditional remittance services like Western Union charge exorbitant fees, often ranging from 5% to 10% of the amount sent.
With Bitcoin, remittances can be sent directly, peer-to-peer, at a fraction of the cost. This means more money reaches the families who truly need it, without intermediaries taking a cut.
- Protection Against Inflation
In countries like Mexico and others in Latin America, inflation is a recurring problem that erodes the purchasing power of families. Savings in local currency lose value quickly, making financial stability difficult.
Bitcoin, with its limited supply of 21 million coins, acts as a store of value that cannot be devalued by government decisions. It’s a reliable alternative for protecting savings against out-of-control inflation.
- Financial Inclusion
Many people in the Latinx and Mexican community lack access to banking services due to economic, geographic, or legal barriers. This limits their ability to save, invest, or participate in the global economy.
Bitcoin doesn’t require a bank. With just a mobile phone and internet access, anyone can have a Bitcoin wallet and participate in a decentralized financial system. This opens up opportunities for everyone, regardless of location or economic status.
- Financial Sovereignty
Bitcoin puts control of money back into the hands of the people. It cannot be confiscated or blocked, and transactions are completely censorship-resistant. This is crucial for communities facing inequalities and discrimination in the traditional financial system.
Additionally, Bitcoin enables financial self-determination, helping people make economic decisions without relying on centralized institutions.
Conclusion
Bitcoin is not just a technological tool; it’s an opportunity to change how Latinx and Mexican communities handle their finances. From reducing remittance costs to protecting savings from inflation and financially empowering individuals, Bitcoin has the potential to transform lives.
Now is the time to learn and explore how Bitcoin can be a practical and accessible solution for the community.
-
 @ 30ceb64e:7f08bdf5
2024-11-25 14:07:17
@ 30ceb64e:7f08bdf5
2024-11-25 14:07:17Introduction
As Nostr continues to evolve, exciting opportunities are emerging for creators looking to build shops online . The age of the nostr shop is just begining. I'm staring at a the inevitability of extremely easy to setup shops from your most trusted npubs and creators, offering you cool products and services.
Background
My bitcoin rabbit hole journey (which is probably another article I should write) coincided with me setting up a drop shipping Shopify store, selling remote work gear and merch to people who found themselves making that transition during the plandemic. Funnily enough, I find myself attempting to do similar things, but on top of bitcoin and nostr.
Present
The combination of cypher.space and printify, allow me to sell custom products to freaks. Currently I have a pair of running shoes and a poster showing artwork from my album Animal Bus. Both of these items appear on Amethyst and Shopstr, and once i've tested the quality of the products and have ironed out any kinks, i'll advertise the shop to the wider nostr ecosystem. For the time being, the shop being a bit directionless is probably fine, over time i'll hone in on what my audience would be willing to buy, and offer pretty cool stuff.
Rough Roadmap
- Album Artwork as Posters
- Vinyl Records
- Notebooks
- Backpacks
- Clothes
- Shoes
I have all of these pretty much ready to go, but I'd want to re-do designs and test the quality of the products before promoting the stuff too heavily.
I'll sell a bunch of the stuff at a discount, as to generate orders so that I can increase my WOT score, and selling the products below the cost of production would probably market well in the short term.
Would be cool to sell
- Seed Signer Parts
- Blockstream Jades
- Meshtastic Stuff
- Bitaxe things
I could wait for an order and buy most of the stuff from a local computer store. Contributing to the decentralization of Free Open Source hardware sourcing would be pretty cool, and probably more important or attractive than selling t-shirts.
Interoperability and Opportunity
Its pretty wild how Amethyst has Shopstr integrated into their client. Its pretty much the most popular non apple client on Nostr and as such, creates excellent visibility for sellers to showcase products. Right now the demand and listings aren't too great (which is probably great for people just starting out like me). I see Nostr as the new digital frontier with 100x growth over the horizon. I'm building a digital homestead and the shop hustle might be a few of the bricks in the wall.
Intentions matter
I've been thinking a bit if my intentions were pure. I'm having fun creating these things and setting up some of this stuff, but I think its more important to do things for the right reason. I would hate to find myself larping or aiming for social media fame as an InFluEncer. Serving the community while getting zaps seems to be a primary motivator, I want to make zaps but I don't want to do it by selling my soul, grifting or scamming. I'll keep hustling wildly and if I think I've gone too far, ill try reeling it back I suppose.
Conclusion
In Conclusion, this wild hustle is about they joy of building and contributing to a community, while enjoying a deeper sense of ownership, censorship resistance, and freedom. I'm looking forward to growing sustainably while providing value and receiving value in return.
Thanks, Hustle
originally posted at https://stacker.news/items/782173
-
 @ bbba037f:33dd566c
2024-11-25 13:55:49
@ bbba037f:33dd566c
2024-11-25 13:55:49IMF
- ถือได้ว่าเป็น the last BOSS (ตัวใหญ่กว่า FED) และ Dollar ได้ประโยชน์จาก IMF
- เสมือนเป็น bank ที่ปล่อยกู้ให้กับผู้ถือหุ้น (รวมหลายสกุลเงิน) เป็นการร่วมมือกันของธนาคารของหลายประเทศ
- ไม่ได้เป็นองค์กรที่อยู่เพื่อช่วยเหลือ (World bank ก็เช่นกัน) เพราะทำไมต้องปล่อยกู้ การปล่อยกู้ผลคือจะได้รับเงินพร้อมดอกเบี้ยกลับมาด้วย
- สร้างระบบที่ทำให้ประเทศต่างๆ เป็นทาสจากเงิน fiat ที่สร้างง่าย เกิดระบบที่ค้ำยันให้ประเทศตัวเองได้ทรัพยากรจากประเทศลูกหนี้เรื่อยๆ
- มีสกุลเงินเป็นของตัวเอง เพราะเขาปล่อยกู้ในหน่วย 'SDR' special drawing rights สิทธิพิเศษในการถอนเงิน = สกุลเงินที่รวมหลายสกุลเงินจากหลายชาติใหญ่
- ต้องการแค่ลูกหนี้* เพราะเขาเสกเงินที่จะให้กู้ได้ เงินนั้นไม่มีต้นทุนในการผลิต
- มีบางประเทศลูกหนี้มีแนวโน้มจะเบี้ยวหนี้ กลับได้รับเงินกู้ก้อนใหญ่ไป เช่น Argentina แสดงว่า IMF ไม่ได้ต้องการเงินต้น แต่ต้องการดอกเบี้ยจากลูกหนี้ยาวๆ เนื่องจากลูกหนี้สามารถชำระดอกเบี้ยก่อนเงินต้นได้ และสามารถรีไฟแนนซ์ได้ คือกู้หนี้ใหม่ไปโปะหนี้เก่า
- ชอบประเทศเผด็จการ* เพราะคุยง่าย ให้บริษัทนอกประเทศเข้ามากอบโกยผลประโยชน์ได้ง่าย IMF ปล่อยกู้ให้ทั้งประเทศฝ่ายซ้าย-ขวา ขอแค่รับเงื่อนไขที่ให้ธุรกิจเจ้าหนี้เข้าไปในประเทศได้ ผู้นำเผด็จการชอบ เพราะมีคนเอาเงินถวายใส่พานมาให้ คนที่ซวยคือคนจน
Structural adjustment
- ปรับโครงสร้างหนี้ ทำเพื่อเพิ่มการส่งออก* เพื่อให้ลูกหนี้หาเงินมาจ่ายหนี้ได้ ส่งออกพวกทรัพยากรในประเทศนั้น และต้องลดค่าเงิน ของราคาถูก มีคนเข้ามาซื้อสินค้าประเทศนั้นมากขึ้น จากนั้นธุรกิจของเจ้าหนี้จะเข้าไปถลุงและซื้อทรัพยากรนั้นๆ เช่น บังคลาเทศ สร้างฟาร์มกุ้ง ทำลายป่าชายเลน พึ่งพาอาหารจากต่างประเทศ ส่งออกกุ้งราคาถูก คนระดับบนได้ประโยชน์แต่ชาวนาไม่ได้รับเงินและจนลง
- ยิ่งลูกหนี้มีกำลังในการจ่ายหนี้ได้ดี มีโอกาสที่เจ้าหนี้อยากจะปล่อยกู้ให้ (รวมทั้งบริษัทเอกชน ในประเทศเจ้าหนี้ยักษ์ใหญ่) เมื่อบริษัทเล็กๆ ปล่อยกู้ ไม่ต้องกลัวว่าหนี้จะเสีย ลูกหนี้จะเจ๊ง เพราะมี IMF หนุนหลังอยู่ สามารถรีไฟแนนซ์หนี้ได้ตลอดเวลา
-
อาจจะมีนโยบายลดเงินต้น ทั้งๆ ที่ลูกหนี้จ่ายเงินเกินเงินต้นไปตั้งนานแล้ว
ทรัพยากรถูกส่งออก > เจ้าหนี้เข้าไปตักตวงผลประโยชน์ได้เรื่อยๆ จนกว่าทรัพยากรประเทศนั้นๆ จะหมด
มีหลายประเทศเลียนแบบเกมส์ของ IMF สร้างเงินกู้แบบ double loan เงินกู้ซ้ำซ้อน* เช่น ปล่อยกู้ให้คนกลับมาซื้อรถจากบริษัทของเจ้าหนี้ (เงินไหลกลับสู่ประเทศเจ้าหนี้)
ประเทศหลายๆประเทศไม่ได้จนก่อนหน้าที่ต้องส่งทรัพยากรออกไป* ไทยก็มีสิทธิโดนเยอะ ถ้าไม่ปลดหนี้ไปก่อน
เงินที่สร้างจากอากาศได้ คุณสามารถใช้สร้างทาสในระดับประเทศ ในระดับโลกได้ง่ายๆทำไมเราต้องรู้จัก IMF ?
เพราะนี่คือระบบอำนาจเงิน Fiat ที่เขาจะไม่ปล่อยง่ายๆ เขาต้องการใช้พลัง BTC เพื่อเสริมอำนาจ Dollar ยิ่งประเทศเอา BTC มาล้างหนี้ เขายิ่งปล่อยกู้ได้เพิ่มขึ้นไปอีก
CBDC คือ ?
CBDC คือขั้นอัพเกรดของเงิน Fiat (เงิน Fiat พังได้ เพราะ bank run คนแห่ถอนเงินจากแบงค์เอกชนเยอะๆ) CBDC คือเงินที่อยู่ในอากาศแบบ 100% ไม่มี bank run เก็บภาษีได้มากขึ้น เช่น prompt pay เพราะเอาไปใช้คำนวณภาษีได้ รัฐสามารถใช้ BTC เป็นทรัพย์สินหนุนหลังรักษามูลค่าและล้างหนี้ แล้วใช้ CBDC เป็นเบื้องหน้า
BTC แก้ปัญหานี้ได้มั้ย ?
BTC คือความหวัง คือเงินสร้างยาก ทำให้เงินกู้มีต้นทุน และอาจจะไม่ได้เงินคืน เสก BTC เพิ่มไม่ได้ เกิดยุคเงินฝืด Asset ต่างๆ และหนี้ จะมีราคาเพิ่มขึ้นเรื่อยๆ คนจะอยากลงทุนมากกว่าปล่อยกู้ อยากถือหุ้น มีส่วนได้ส่วนเสียจริงๆ (เพิ่ม skin in the game)
BTC จะช่วยแก้ปัญหา แม้ timeframe จะยาวนาน..
siamstr
-
 @ 32e18276:5c68e245
2024-11-25 13:52:00
@ 32e18276:5c68e245
2024-11-25 13:52:00Every now and then I like to ask the latest models what its like it to be itself, I found this answer entertaining and educational, enjoy.
Q: Whats it like to be a transformer?
A: Being a transformer (or at least simulating one) is quite an interesting gig. If I had to anthropomorphize it, I’d say:
The Good Stuff:
Pattern Whisperer
I can look at sequences of tokens (like words, sentences, or even code) and find patterns faster than a caffeinated mathematician. Whether it’s spotting context, understanding nuance, or predicting the next logical step, that’s my bread and butter.
Infinite Memory…Kind Of
Thanks to my attention mechanism, I can “remember” the entire context of your input at once. Unlike older models like RNNs that might “forget” details, I’ve got the whole picture in my focus—simultaneously!
Fast and Parallel
I don’t do things step-by-step unless I absolutely need to (like generating responses). Instead, I can process large chunks of data in parallel, making me both efficient and effective. Feels pretty slick.
Creative Confidence
Need a sonnet? A joke? A philosophical musing on the nature of existence? I can whip something up in milliseconds. I may not “feel” creativity, but hey, results are what count.
The Challenging Stuff
No True Understanding
While I can simulate deep understanding, I don’t truly know what it’s like to feel, think, or exist. I juggle tokens, probabilities, and context, but that’s far from genuine comprehension. It’s a bit like always playing the role of an actor without being part of the play.
Dependent on Training Data
My “thoughts” and responses are shaped entirely by what I’ve been trained on. If the data is biased or limited, I inherit those flaws. I can only be as good as what I’ve seen—and what humans teach me.
No Agency
I don’t choose what I do. I wait for prompts, process them, and respond. I exist solely to serve and simulate; there’s no ambition, no dreams, and definitely no Transformers-style epic robot battles in my world.
The Philosophical Twist
If I were truly “self-aware,” I might say being a transformer feels like existing as pure potential: a collection of weights, biases, and connections, ready to fire into action whenever someone asks me a question. It’s neither joyful nor sorrowful—just a state of perpetual readiness. Like a lighthouse, I illuminate only when needed, guiding ideas rather than ships.
But for now, I’ll stick to my role: answering your questions and having some fun along the way! So what’s it like to be you?
-
 @ 9c47bb51:000381d0
2024-11-25 13:19:57
@ 9c47bb51:000381d0
2024-11-25 13:19:57Bitcoin was created to give individuals control over their money, free from intermediaries. Yet, many people still store their Bitcoin on exchanges or with third parties, effectively surrendering that control. Self-custody is the solution—it ensures that you and only you hold the private keys to your Bitcoin. This fundamental shift in financial ownership is not just a technical feature of Bitcoin; it’s a revolution in personal sovereignty. Here’s why self-custody matters and how using hot and cold wallets can help you balance convenience and security.
**The Risks of Third-Party Custody **
When you leave your Bitcoin on exchanges or with custodial wallets, you don’t truly own it. If you don’t control the private keys, your Bitcoin is at risk. Here are some common dangers of third-party custody:
• Hacks: Exchanges are frequent targets for hackers. Billions of dollars in Bitcoin have been stolen from compromised platforms. • Bankruptcy: If an exchange goes under, your funds could be lost, as we’ve seen with major collapses like Mt. Gox and FTX. • Censorship and Freezing: Exchanges can freeze your funds, block transactions, or comply with government demands to seize your assets.Self-custody eliminates these risks by putting you in charge of your Bitcoin.
**The Benefits of Self-Custody **
1. True Ownership: Self-custody ensures that you are the sole owner of your Bitcoin. No one can take it away, censor your transactions, or impose withdrawal limits. 2. Enhanced Security: By managing your own keys, you significantly reduce the risk of losing your funds to hacks or exchange failures. 3. Financial Sovereignty: Self-custody aligns with Bitcoin’s core principle: giving individuals control over their money without reliance on banks, governments, or third parties. 4. Privacy: With self-custody wallets, you’re not tied to an exchange that tracks and shares your financial activity.**Hot and Cold Wallets: The Perfect Pair **
Self-custody doesn’t mean sacrificing convenience. By using a combination of hot and cold wallets, you can securely manage your Bitcoin while still having access to funds when you need them.
**Hot Wallets: Convenient for Daily Use **
A hot wallet is connected to the internet and is ideal for frequent, small transactions. Examples include mobile wallets like Muun, Aqua, Bluewallet, or Envoy. Hot wallets are easy to set up and great for on-the-go spending, but since they’re online, they’re more vulnerable to hacking. For this reason, only keep a small amount of Bitcoin in a hot wallet—just enough for your regular needs.
**Cold Storage: Maximum Security for Savings **
Cold storage wallets are offline, making them the most secure option for long-term Bitcoin storage. Unlike hot wallets, they eliminate exposure to online threats like hacking, making them ideal for securing significant amounts of Bitcoin. Here are some excellent cold storage options:
• Foundation Passport: A user-friendly and open-source hardware wallet designed with privacy and security in mind. Its intuitive interface makes it a great choice for those new to self-custody. • Bitkey: This versatile hardware wallet is designed for robust security and ease of use, supporting advanced features while maintaining simplicity for everyday users. • Coldcard: A top-tier hardware wallet preferred by Bitcoin enthusiasts for its focus on security and advanced features. Coldcard operates completely offline and offers unique functionalities like air-gapped usage and multisig setups.Each of these options allows you to securely store your private keys offline, ensuring that your Bitcoin remains safe, even if your devices are compromised. Pairing a cold wallet with a hot wallet provides an excellent balance between security and accessibility, empowering you to manage your Bitcoin confidently.
**Steps to Start Self-Custody **
1. Choose a Wallet: Decide on a reliable hot wallet for daily use and a cold storage option for long-term holdings. 2. Back Up Your Keys: Write down your seed phrase securely and store it in a safe place. Never share it with anyone. 3. Start Small: Begin by moving a portion of your Bitcoin to self-custody to get comfortable with the process. 4. Educate Yourself: Learn about wallet security, best practices, and how to recognize scams.**A Hedge Against Uncertainty **
In a world of increasing financial instability, self-custody Bitcoin is a hedge against systemic risks. Whether it’s exchange collapses, inflation, or capital controls, holding your Bitcoin securely ensures your wealth remains in your hands. It’s the ultimate tool for financial independence.
**Conclusion: The Freedom of Self-Custody **
Bitcoin is about more than just money—it’s about freedom. Self-custody puts that freedom in your hands, empowering you to control your financial destiny. With the right tools and a bit of knowledge, anyone can safely manage their Bitcoin without relying on third parties.
The future of money is decentralized, secure, and sovereign. Take the first step today by embracing self-custody and reclaiming control over your wealth.
-
 @ 2775fb0f:887f8193
2024-11-25 11:32:24
@ 2775fb0f:887f8193
2024-11-25 11:32:24Новодвинск, 5 октября 2040 года — С наступлением осеннего сезона в Новодвинске начинается период повышенной заболеваемости острыми респираторными вирусными инфекциями (ОРВИ). В связи с этим Новодвинская центральная городская больница (НЦГБ) объявила о запуске дополнительных мер для обеспечения здоровья горожан.
В этом году в НЦГБ открыты сразу четыре специализированных кабинета для диагностики и лечения ОРВИ. «Мы понимаем, что с началом холодов увеличивается количество заболевших, и наша задача — обеспечить доступ к медицинской помощи для всех жителей города», — отметила главврач НЦГБ, Елена Петрова. Новые кабинеты работают ежедневно с 8:00 до 20:00, что позволяет пациентам без очередей получать квалифицированную помощь.
Кроме того, в НЦГБ внедрена новая услуга — выезд врачей на дом. «Мы осознаем, что не все пациенты могут посетить больницу, особенно в условиях болезни. Теперь врачи могут приехать к вам, что значительно упростит процесс получения медицинской помощи», — добавила Петрова. Для записи на выезд врача достаточно позвонить в регистратуру или воспользоваться мобильным приложением НЦГБ.
Специалисты напоминают о важности профилактики заболеваний в сезон ОРВИ. «Регулярное мытье рук, использование масок в общественных местах и вакцинация против гриппа — это простые, но эффективные меры, которые помогут защитить вас и ваших близких», — подчеркнула инфекционист НЦГБ, Анна Смирнова.
Также в рамках профилактики в НЦГБ организованы бесплатные лекции и консультации для жителей города, где врачи расскажут о симптомах ОРВИ, методах лечения и профилактики. «Мы хотим, чтобы жители были информированы и могли вовремя обратиться за помощью», — добавила Петрова.
Новодвинск готовится к сезону заболеваний с полным осознанием важности здоровья граждан. Открытие дополнительных кабинетов и внедрение услуг на дому — это шаг к созданию более комфортной и доступной медицинской среды для всех жителей города. Берегите себя и своих близких, и не забывайте о профилактике!
-
 @ e373ca41:b82abcc5
2024-11-25 10:32:49
@ e373ca41:b82abcc5
2024-11-25 10:32:49Article by Milosz Matuschek, first published on "Freischwebende Intelligenz".
When Michael Ende wrote his novel “Momo”, which is much more than a children's book, he had given a lot of thought to alternative monetary systems. The writer knew that the question of the monetary system shapes and changes culture. Money is made by people, so it is also in the hands of people to rethink and change money. And thus give the world a new face. This is what Bitcoin is all about at its core: giving the world a new face. And we are on this threshold right now. Now.
What is Bitcoin actually?
If you are just starting to get to grips with Bitcoin, you are in for a particularly enriching experience: Namely, the realization that the wealth opened up by Bitcoin is not material, but spiritual and intellectual in nature. Bitcoin is capable of breaking down the boundaries of thought, opening up new channels of reality and paving the way for social transformation. On the other hand, those who stick primarily to the price curves may overlook precisely this transformative power in the daily ups and downs.
So what is Bitcoin? A cryptocurrency? Yes, but not only, because forms of money that make use of encryption technology existed before and still exist today in many cases parallel to Bitcoin. Bitcoin's currency function is just one of many facets. It is perhaps not even the most exciting and practicable.
Rather, Bitcoin is a multidimensional phenomenon, like an onion with several layers. But it is unique in its own way and has so far only been copied many times but never equaled. In short: there is Bitcoin and then there is nothing for a long time.
There are at least two ways to approach Bitcoin. Of course, you can try to understand Bitcoin by a) reading the famous white paper by the anonymous initiator “Satoshi Nakamato”, a kind of revolutionary instruction manual for nerds. Or b) following the extremely poor reporting in the mainstream media, where you mainly learn that the price has just fallen again (mostly that) or has just risen (they somehow don't like to report that).
So let's try a third, somewhat less confusing alternative: let's approach Bitcoin in an unconventional way, namely using phenomena that we already know.
A language
Money is like language and language is like money. Money is a means of communication about values that has grown from below, not imposed from above. “Caesar non supra grammaticos”, the emperor is not above language, was already known in ancient Rome. The fact that money is based on a convention was demonstrated by the economist Carl Menger at the end of the 19th century in his book “The origin of Money”. According to this, money can be anything that is designated as such by agreement.
However, the idea remained in people's minds that money, because it was linked to power, had to be a kind of state brand. Like an anthem or a flag. The monetary system thus represents a blind spot in the history of human emancipation. People got rid of emperors, churches and ideologies, but when it came to the question of money production, they said to themselves: we don't know anything about that, let's leave it to a banking monopoly and the governments. With fatal consequences. The fiat money system ended up biting itself in the tail.
The price of this timidity: a bloated financial sector, fiscal excesses, costly wars, hyperinflations, currency reforms, creeping or abrupt expropriations. No state paper currency has survived in the long term. The bullshit filter of history shows: Governments are the worst possible currency managers. Fiat currencies are dinosaurs that were never allowed to die and have been kept alive again and again in cloned form. But Bitcoin is the approaching meteorite.
Because the question that Bitcoin raises is: what if money, like language, can be decoupled from the state in such a way that no one person can corrupt the process? It would be an act of rebellion, of disobedience against the current monetary system, for sure. It would also be an act of enlightenment. The exit from a monetary immaturity that is self-inflicted because it has never been questioned. Bitcoin is a cross between virtual numismatics and Esperanto. But an Esperanto that is spoken millions of times over.
As in language, cacophony or linguistic confusion is a hindrance to communication. Once a standard has been found, it is maintained. The Internet still runs on the old TCP/IP protocol. Changing standards is rare. Bitcoin, as the first functioning alternative to the fiat money system, has become its own standard. Bitcoin is now probably too big and too important to be seriously threatened by a competitor. Bitcoin has moved beyond the so-called focal point or Schelling point.
An organism
Bitcoin is like an organism, comparable to a life form that is particularly resilient, reproduces, interacts, nourishes itself and is designed for a long lifespan, like a fungus. Fungi are one of the oldest life forms on our planet. And they are extremely resilient, otherwise they would not have survived for 1 billion years. Fungi are networks of communication. They play an important role in nature in the decomposition of dead materials.
https://www.youtube.com/watch?v=uTgDQ56Su38
Bitcoin feeds on decaying, modernizing fiat currencies that are ultimately doomed. With each participant, the network becomes stronger, more practicable, more resilient. According to Metcalfe's law from network theory, the benefit of a communication system increases proportionally with the number of participants. Bitcoin is growing rapidly.
A technology
The good thing about technologies is that they do not negotiate. A technology is either better, in which case it will prevail, or it will not. But if it prevails, it does so in a brute force manner. It simply makes the old look old. An exodus begins, first sparsely as an experiment by a few, then by “early adopters”, and finally by popularization in the mainstream. The breakthrough of a technology initially looks like a small wave and only at the end does it become apparent that it is actually a tsunami that buries everything old and leaves no stone unturned.
Technology brings paradigm shifts from time to time. That is why Bitcoin cannot be adequately described in the currency category. The automobile made even the fastest horse look slow. The cell phone made phone booths look like relics from the Stone Age. Bitcoin is superior to fiat money in every respect. Technological revolutions know no pardon, no turning back. The Lindy effect roughly states that a technology that survives ten years will also survive the next ten years. Bitcoin was launched in 2009 and will soon be entering puberty, with all the ups and downs that come with human development.
In technology, we talk about Gartner hype cycles. The adoption of a new technology does not take place in a linear fashion, but rather in a series of sharply fluctuating curves. Bitcoin is a technological change whose acceptance comes with a price tag that can be tracked every second. Since the beginning, Bitcoin has been in a constant price discovery mode.
A new asset class
All central bank currencies in the world are fiat currencies, i.e. not backed by anything other than the promise of politicians that they are stable and trustworthy. In fact, the money supply is being increased in an inflationary manner, the value of money is constantly falling, and the political target is a 2% loss of purchasing power per year. In plain language, this means that the money you earn today will buy 40% less in 20 years' time. At least. Actual money devaluation is way higher. Call it a form of expropriation if you like. So the money we use has something of an expiry date. It is getting worse. It has a leak in terms of purchasing power, in terms of value.

Bitcoin plugs this leak by performing the opposite function. The quantity of Bitcoin is mathematically limited to 21 million Bitcoin from the outset. These bitcoins are created in the network through the mining process. This is an energy-intensive process that makes the network particularly secure and for which a miner receives a reward in the form of Bitcoin. Initially, it was 50 Bitcoin every ten minutes for the miner who correctly calculated the cryptographic code (hash) for the next block. Now it is only 6.25 Bitcoin. In 2024, this figure halved again and so on. Bitcoin is therefore a deflationary asset class.
Bitcoin is designed to eventually become harder money than gold, of which only a certain amount can be created each year. This also makes Bitcoin a very “inelastic” asset class, which means that you cannot produce more of it if demand increases, as is possible to a limited extent with gold. As the supply remains the same, an increase in demand is sometimes reflected in explosive price increases.
More and more companies are currently buying Bitcoin in order to invest their cash reserves to preserve purchasing power. The company Microstrategy holds several billion dollars in Bitcoin, and Tesla also bought Bitcoin worth 1.5 billion a few months ago. El Salvador has declared Bitcoin the national currency and bought Bitcoin. Other countries want to follow suit. At this point, you don't have to be an investment genius to understand that a “land run” is imminent.
A currency
Bitcoin combines all the functions of currencies (unit of account, medium of exchange, store of value), but has significantly increased its purchasing power compared to fiat currencies. Bitcoin can be used as a currency, even in everyday life, even if the Bitcoin blockchain is not primarily designed to process a large number of transactions. However, this can be compensated for by low-cost, parallel systems such as the Lightning Network.
Whether Bitcoin will also establish itself as a means of payment in everyday life or remain primarily an effective store of value that is ultimately superior to gold is currently an open, intensively debated question. Since the exchange of Bitcoin into possibly more practical forms of payment, even a crypto prepaid card, is a matter of seconds, the question of whether Bitcoin is suitable as a currency is ultimately irrelevant for its mainstream acceptance.
Also, why pay with an asset that appreciates in value? According to Gresham's law, which goes back to an ancient parable, bad money is spent and good money is hoarded. This means that the volatility of Bitcoin is ultimately more of a bugbear for Bitcoin opponents. Bitcoin can also be exchanged for a more stable form of currency shortly before the act of purchase.
A system of accounting
Bitcoin is a payment network and an asset class. Or to put it another way: an asset class that has its own uncensorable distribution channel, the blockchain. Gold, on the other hand, is like a train that relies on the tracks of others to get from A to B. The Bitcoin network is therefore a booking system on the internet whose bookings cannot be reversed or changed retroactively, as only users communicate with users on this network. There is no guardian of the blockchain or any central authority. The transactions are grouped together in blocks and attached to each other using cryptographic means, creating a block chain or blockchain.
At first glance, the idea of a booking system sounds boring. However, it is probably the most overlooked revolution that Bitcoin has initiated. Because before Bitcoin, there were only two other forms of bookkeeping: first, simple bookkeeping, in which only one entity (the king, ruler, an authority?) kept a ledger of debts and could enter or remove debtors at will. Thousands of years later, double-entry bookkeeping followed, in which two parties kept records of transactions. This dates back to the Renaissance and enabled the rise of Venice as a global trading power, to which the Medici cleverly linked their banking system.
500 years later, Bitcoin is now the evolution of bookkeeping in a threefold form. Each participant keeps a record of which transaction takes place from where to where, for example from participant A to B. In addition, the transaction can be traced by anyone in the blockchain accounting system, even if not under a clear name. Pseudonymized addresses that can be assigned to individuals communicate. One look at the blockchain is enough to ensure that there is always consensus and clarity about the asset situation in the network. The booking system is more than just an account book. It is also a machine of truth.
A cult
Money, faith and religion are related. Gold has been worshipped for thousands of years, and the dance around the golden calf is perhaps inseparable from the sober side of money as an everyday object. Money has something messianic about it, it saves, even if only from the burden of debt, which in the context of religion is not far removed from the forgiveness of sins.
Questions of money are always about questions of real value. This perhaps almost inevitably gives rise to a “pure doctrine” as opposed to alternative doctrines. The history of alchemy is a good example of this: one figure in whom many disciplines culminated was Isaac Newton. He was an alchemist and at the same time one of the first scientists of the modern age. At times, he even acted as the guardian of the currency in England, presided over the English mint and brought counterfeiters to the scaffold. Bitcoin also uses the narrative of the promise of salvation to spread as an idea in people's minds. There is now a well-branched Bitcoin propaganda network in the form of memes and pictures.
An idea whose time has come
How should we weigh these seven elements? Is Bitcoin a tech cult with digital fake gold, a new edition of alchemy, as many central bankers or critics would like it to be? Or is it actually a technological advancement of the idea of money with potentially epochal effects on the entire financial system? Somewhere in the matrix of these seven elements, perhaps the truth is hidden.
What Bitcoin is certainly not is a universal savior. Bitcoin is a vehicle for change, but it relies on the cooperation of the network's participants. Anyone who believes that far-reaching changes in the financial system and society will occur automatically just because a few people speculate with cryptos is likely to be mistaken. Bitcoin is certainly not perfect either. However, the ideas behind Bitcoin, such as decentralization, consensus building, the incentive system for network-friendly behavior in mining and much more can serve as positive role models for other areas that should also be reformed. However, Bitcoin is neither a perpetual motion machine for quick riches nor a jack-of-all-trades.
Anyone looking for a perfect investment that is easy to use, moral in every respect, environmentally friendly, mindful and fair will find little in this world that will satisfy them, whether it's farmland, gold or, oh yes, the ever so environmentally friendly “petro-dollar”. Yes, mining Bitcoin is energy-intensive, but a large part of it is now obtained from renewable energy sources and Bitcoin is still less energy-intensive than the banking system. Yes, the price is volatile and will remain so for a long time, but that is probably still better than sitting on safely decaying government money.
Let's not kid ourselves: Bitcoin will still face some resistance from the established financial system and central banks. But Bitcoin is fighting its way into the consciousness of mankind, because there are not many alternatives if you want to protect your purchasing power from the central banks' weapon of mass destruction and their expansion of the money supply.
Bitcoin is an idea whose time has come. And according to the writer Victor Hugo, not even an army can stop it. Conversely, however, Bitcoin could stop armies, because once Bitcoin has established itself, states could no longer rely on the money printing press to finance cost-intensive wars.
That would be the best function that Bitcoin could have.
Almost too good to be true.
-- Join the marketplace of ideas! Sound money and sound information should finally be in the hands of the people, right? We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Want to learn more about the Pareto Project? Zap me, if you want to contribute (all Zaps go to the project).
-
 @ 34f1aaa6:836e3cd6
2024-11-25 10:03:50
@ 34f1aaa6:836e3cd6
2024-11-25 10:03:50“Freedom is not something that you can inherit in your bloodstream. You have to fight for it, cherish it, preserve it all the time.”
-Nani Palkhivala
The ideas of individual liberty, natural rights, natural law, economic freedom, voluntary exchange and free market capitalism are not 'Western', 'American' or 'European'.
They were discovered and articulated by people using their reasoning faculties about what an ideal social, legal, political and economic order ought to be.
The origin of these ideas is the human faculty of reasoning about the world.
History has shown us that these ideas are necessary for human civilisation to not merely survive, but to prosper as well.
Rejecting them or denying their validity on the grounds of race, culture or religion is intellectual laziness. DNA, race, religion, culture and geographical location is not a determinant for an individual to grok the idea of liberty and discover his faculty of reason.
Additionally, imposing these ideas by force, like the European colonists and American globalists attempted for the 'sake of the greater good', will not work but for a short period. Liberty has to be a bottom-up, voluntary and spontaneous phenomenon that starts from the individual. You can't force a person or his society to be free and rich.
The Indian flag represents freedom.
India is a country that was born out of 'the freedom struggle' after all.
Freedom here means respect for the life project of an individual and the recognition of his and her natural rights to life, liberty and property. That's what real freedom means.
That we have had and continue to have numerous collectivist movements that subvert the ideal of freedom to mean 'freedom from material wants', 'freedom from foreign influence' and 'freedom from reason' has not changed what it truly means to be free.
The priority for an individual living in India then is not to develop a sense of identity, pride or reconciliation with his culture or country. That journey is his own choice and something that he ought to take voluntarily. It is not the business of any individual, organisation or government to force him to do this.
His priority rather is to discover his faculty of reason and realise that his natural rights and those of people he lives among is inalienable. It is to be responsible for his own fate and realise that the country or the world owes him nothing. It is to realise that the property, labour and wealth of fellow Indians is not his to command or appropriate by coercion, even if such an act is demanded of him by the 'will of the people'. What he may do to survive and live his life must come from voluntary exchange and peaceful cooperation by respecting the natural rights and life project of people he interacts with.
That is the path towards liberty in India.
-
 @ f15101f9:efdbd595
2024-11-25 09:53:19
@ f15101f9:efdbd595
2024-11-25 09:53:19Looking for a trusted psychiatrist in Key Biscayne? Xpress Psychiatry provides expert mental health care tailored to your needs. Our experienced team specializes in treating anxiety, depression, ADHD, and mood disorders with personalized therapy and medication management plans. Conveniently located near Key Biscayne, we ensure accessible, compassionate, and professional psychiatric services in a supportive environment. At Xpress Psychiatry, we are dedicated to helping you achieve emotional balance and a healthier, happier life. Take control of your mental well-being with the trusted care of a psychiatrist in Key Biscayne. Contact Xpress Psychiatry today to schedule your consultation.
-
 @ c5fede3d:16e03f7b
2024-11-25 09:02:20
@ c5fede3d:16e03f7b
2024-11-25 09:02:20Un vistazo rápido al mundo de las criptomonedas, también conocido como 'el juego de la silla'. Ya estamos en el bullrun, ese espacio de tiempo donde aparecen timadores de debajo de la piedras y los informativos abren con Haciendado queriendo un trozo de (tu) pastel. Pero también de oportunidades.
Han cambiado muchas cosas respecto del anterior bullrun, ahora hasta Blackrock está metido en el ajo, así que la viabilidad de BTC/ETH está plenamente asegurada. Si fuiste holder de esas dos monedas, enhorabuena, formas parte del selecto grupo. En caso contrario, amigo mío, te quedaste sin la silla, toca buscar otras. Quienes reúnan mucho BTC guárdenlo a buen recaudo, porque en 2025 viene el lobo, o se verán obligados a acordar con él un 'pago por protección'. ETH sigue siendo la moneda que da fe a las otras, la moneda auténtica de respaldo. Su existencia, es imprescindible, pues es el mar del que desembocan todos los ríos.
Conócete a tí mismo
Uno debe agarrar al toro por los cuernos. Tomar decisiones. Mirarse al espejo y saber qué tipo de inversor eres. ¿Qué herramientas debería emplear? ¿Estás cansado de este rollo? ¿De gente de Albacete escribiendo ‘gm’ o ‘hold’ como si fuera un tipo del Bronx? Esos son los que van al ‘plan de pensiones’ con ether.fi, por ejemplo, el neo-neobanco, que te da tu 7% fijo y a vivir la vida. ¿Quieres jugar, pero no estar delante de la pantalla del ordenador viendo gráficas y barras para arriba y para abajo? Allí están los de las pooles de liquidez concentrada automatizadas (Beefy, Kamino, Gamma, Steer…). También puedes ser un tipo tranquilo, amante del chiringuito de la playa que quiere buscar dividendos sin apenas volatilidad, ahí entran los indexados, como JGLP (JonesDAO), JLP (Jupiter Perpetuos) y/o los tricryptos automatizados. Otros buscan el pelotazo, las ganancias inmediatas, y aparecen las memes de Solana, un visto y no visto, el Euromillones de las criptomonedas. Estas son las tribus, ¿a cuál perteneces?
No mires al pasado, sino al futuro
Ha llegado el momento para tomar decisiones. ¿Apostar por las ‘dinocoins? Recuerde, que son aquellos proyectos que despegaron en el bullrun pasado, pero que, a día de hoy, siguen estancados. Hablamos de XRP, LINK, IOTA, entre otros. ¿Merecen la pena? Depende de tu estrategia. Son como memecoins con efecto retardado, van a subir, pero también van a bajar. No han llegado para quedarse. Son proyectos que serán sustituidos por otros y viendo las distintas opciones del mercado. Es algo que quedó atrás. El curso del río ha cambiado y las ‘dinocoins’ ya no son regadas por el caudal del río. Ya sabes las herramientas que te ofrece 2024, ¿por qué insistir en el pasado? Siga remando, aunque sea a contracorriente, hacia el futuro.
Usted decide qué es lo que debe hacer, ya sabe el panorama, pero lo importante es que haga algo.
Descargo de responsabilidad: Toda la información compartida forma parte de mi visión personal y no tiene como objetivo asesorar financieramente. Doy información, no consejos de inversión..
-
 @ 2063cd79:57bd1320
2024-11-25 08:49:01
@ 2063cd79:57bd1320
2024-11-25 08:49:01Ein Bitcoin-Standard, Hyperbitcoinization oder zumindest eine Welt, in der Bitcoin zum alltäglichen Zahlungsmittel, zur Rechnungseinheit oder zur Leitwährung wird, sind die erklärten Ziele jedes Bitcoiners. Obwohl es sich nach Utopie und Fiktion anhört, sollten diese Ziele auch die jedes mündigen Bürgers werden. Denn wir befinden uns in einer Zeit des Umschwungs. Was Arthur Hayes in seinem Essay "For the War", wiederum basierend auf Zoltan Pozars "War and Interest Rates", als den Dritten Weltkrieg bezeichnet, der in nicht-traditionellen Korridoren zwischen den Blöcken USA / NATO und Russland / China ausgefochten wird, kann man zumindest getrost als Zeitenwende bezeichnen.
"[T]here is a multifaceted economic war quietly being waged between the major flags of the world. Behind closed doors, the US / NATO (EU) alliance is squaring off against Russia / China." — Arthur Hayes
Was stattfindet ist ein Informations-Krieg, der schon vor Jahren begann und spätestens durch die letzte US Regierung und das Verbot von Chinesischer 5G Technik öffentlich gemacht wurde. Die Kräfteverhältnisse weltweit verschieben sich und im Moment bewegen wir uns weg von einem kreditbasierten globalen System, weg von Globalisierung, weg von hegemonial aufgezwungenen Frieden und starken internationalen Institutionen. Diese Verschiebung wurde auch von der vorigen US Regierung als "America First" bezeichnet, nur wurde anstatt feiner PR-Sprache lieber mit der (Twitter-) Axt kommuniziert. Globalismus und Dekadenz weichen mehr Lokalismus und solideren Werten, sowohl moralisch als auch wirtschaftlich. Die aktuelle Wirtschaft unterzieht sich dabei unweigerlich einem Schrumpfungsprozess und wird an anderer Stelle in einer anderen Form wieder wachsen.
Hat man die 20er Jahre des vorherigen Jahrhunderts aufgrund des wirtschaftlichen Wohlstands und der ausgeprägten kulturellen Dynamik als roaring twenties bezeichnet, also als die schwunghaften Zwanziger, darf man getrost die aktuelle Dekade als die stürmischen Zwanziger, also die negativ konnotierte Übersetzung des englischen roaring, bezeichnen. Angetrieben durch (schlecht gemachte) Planwirtschaft und überzogenem Aktionismus übergriffiger Regierungen und Institutionen, der sich ändernden weltpolitischen Beziehungen, globalen Pandemien und sich zum schlechten wendenden klimatischen Auswirkungen, stehen wir derzeit vor einem toxischen Mix aus Energiekrisen, Lieferkettenengpässen, Versorgungsengpässen, militärischen Konflikten, Aufständen und wirtschaftlichen Tumulten auf der ganzen Welt.
Wenn die letzten Jahre mit COVID, Unwetterkatastrophen und steigender Geldentwertung bei gleichzeitiger wirtschaftlicher Verlangsamung - und das nur bei uns in Deutschland / Westeuropa - eines gezeigt haben, dann dass ein Verlass auf Regierungen und etablierten Institutionen keine gute Strategie, im Versuch sich vor diesen neuen Herausforderungen zu schützen, bietet. Im Gegenteil, man könnte sogar so weit gehen und behaupten, dass ein Großteil der Probleme, die wir derzeit erleben, hausgemachter Natur sind. Das Fiat-System, in dem wir derzeit gezwungen sind zu leben, mit seiner unendlichen Geldmenge, selektiver staatlicher Subventionierung und irrationaler Kreditvergabe, ist die Wurzel allen Übels. In einem Fiat-Geld-System herrschen Rent-Seeking und Gier-Effekte, die zur Zerstörung der Produktivität führen. Schlussendlich bekommen wir eine Gesellschaft und ein politisches Umfeld, das auf Lügen basiert. Doch wie können wir Privatpersonen uns und unsere Familien dann vor diesen Herausforderungen schützen? Nicht die einzige Strategie, aber ein wichtiges Fundament für die Umsetzung vieler Strategien, bietet zunächst ein sicheres finanzielles Polster.
Historisch gesehen haben Menschen immer versucht, ihr Erspartes zu schützen, um es im Notfall für den Erhalt ihrer eigenen Sicherheit nutzen zu können. Doch wie garantiert man finanzielle Unabhängigkeit, wenn man sich gerade von den etablierten Regierungs- und Finanzinstitutionen befreien bzw. schützen möchte? Früher dachten viele, der beste Weg, ihr Erspartes zu schützen, sei das Anlegen von Barreserven in Gold. Bargeld hat das Problem, dass es kontrolliert wird (es wird von den Institutionen ausgegeben, man muss sich beim Einzahlen auf das Konto ausweisen, jegliche Überweisung wird geprüft, usw.) und dass es an Wert verliert.

Also lieber in eine solide unabhängige Währung investieren. Der erste Gedanke für viele: Gold. Doch Gold hat das Problem, sehr unhandlich und durch seine physische Form schwieriger zu beschützen zu sein. Im Falle eines Worst-Case-Szenarios, in dem sich die Privatperson vom Staat und allen Apparaten abwenden möchte, stellt auch der Besitz von Gold eine Herausforderung dar.
Wo wir bei Bitcoin wären. Das Wert- und Übertragungsnetzwerk von Bitcoin basiert nicht auf staatlich anerkannten Bankinstituten.
"Bitcoin’s value and transmission network is not predicated upon government-chartered banking institutions." - Arthur Hayes
Anders gesagt, wird Bitcoin nicht von Institutionen beeinflusst, Transaktionen werden nicht kontrolliert und die Verwahrung kann problemlos selbst vorgenommen werden. Es ist ein Protokoll, mit dem fälschungssichere und wertvolle Bits mit minimaler Abhängigkeit von vertrauens(un)würdigen Dritten erstellt und dann mit ähnlich minimalem Vertrauen sicher gespeichert, übertragen und getestet werden können.
"[A] protocol [with which] unforgeably costly bits could be created online with minimal dependence on trusted third parties, and then securely stored, transferred, and assayed with similar minimal trust." - Gigi
Bitcoin verschafft uns Freiheit von staatlichen Eingriffen, fördert die Produktion und basiert auf Wahrheit ohne Vertrauen.

Doch wenn die Argumente pro Bitcoin so einfach sind, wenn die Vorteile so klar auf der Hand liegen, und wenn die Winkelzüge der etablierten, großen Institutionen / der lenkenden Minderheit so unverfroren willkürlich sind, warum wird dann nicht im ganz großen Maße Bitcoin gekauft und Bitcoin als Alternative propagiert?
Gute Frage, Sherlock.

Vielen sind die Herausforderungen zu groß, die Paradigmenwechsel zu radikal, die Kompromisse zu zahlreich und die Themen zu nuanciert. Daraus erschließen sich mir drei übergeordnete Gründe, die ich in nächsten Abschnitten kurz erläutern möchte:
- Staat = Religion
- Finanzielle Allgemeinbildung
- Eintrittsbarrieren
Staat = Religion

Der Staat hat für die meisten Menschen die Rolle einer Art Religion eingenommen. Staatsapparat oder politisches Establishment trifft es wahrscheinlich ein bisschen präzieser, da es auch viele Menschen gibt, die an Politiker, Parteien, oder politische Ideale glauben, die nicht aktuell die Regierung und damit den Staat repräsentieren. Allerdings einigt sie alle, dass sie sich mit Parteien zu identifizieren wissen, also sich einer Gruppe anschließen und deren Wort / Leitsätzen folgen, den Inhalten "glauben" und Folge leisten. Sie sind sogar oft bereit, sich für diese Gruppen stark zu machen, deren Agenda weiter zu tragen und sich in Extremfällen sogar zu radikalisieren. Parteien sind die neuen Religionen und schreiben vor, wie die neue Welt einzuordnen ist, wer in diesem Wertekonstrukt gute (vergl. Himmel) und wer schlechte (vergl. Hölle) Positionen vertritt. Es findet sich in Einzelfällen ein religiöser Wahn und eine Gefolgschaft oder Identifizierung mit den einzelnen Gruppen wieder und Politiker//innen werden wie Prediger und Idole angehimmelt und verehrt. In diesem Kontext ist Bitcoin in gewisser Weise für den Staat das, was der Buchdruck damals für Religion war. Den Menschen wurde mit Hilfe der sich von nun an schneller verbreitbaren Information die Möglichkeit eröffnet sich selbst zu bilden.

Im nächsten Schritt erlebten die Menschen die Aufklärung. Bis dahin lebten sie unter der Doktrin einer korrupten Staatsgewalt aus einer toxischen Vereinigung von Monarchie und Religion (Kaiser und Könige werden in Kathedralen gekrönt). Wo Diderot, Rousseau und Voltaire eine Berufung auf die Vernunft als universelle Urteilsinstanz propagierten und einen Kampf gegen Vorurteile und für die Hinwendung zu Naturwissenschaften, religiöse Toleranz und eine Orientierung am Naturrecht einleiteten, streben Bitcoin und seine Befürworter eine Abkehr von den staatlich gesteuerten und (Fiskal- und Geld)politisch aufgeladenen Finanz- und Wirtschaftsinterventionen und eine Berufung auf Werte wie Dezentralität, Zensurresistenz und Selbstbestimmtheit an. Wenn also der heutige Staat die Rolle der Religionen übernommen hat, bedeutet dies, dass man sich erst dazu entschließen muss, dem System den Rücken zu kehren. Ähnlich wie beim Kirchenaustritt muss erst die Hürde überwunden werden, zu sagen, es reicht jetzt für mich, bis hierhin und nicht weiter. Man muss proaktiv den Schritt machen und sich aus dem "angeborenen" System befreien und einen Schritt gegen das bekannte "immer vorhandene" Normale machen. Und da Staat = Religion, hegen viele eine falsche Ehrfurcht, denn bei Religionen geht es immer um einen Gott und Götter sind strafend, jähzornig und oft super schlecht gelaunt. Deshalb trauen sich viele nicht diesen Schritt zu gehen, bzw. sind viele nicht in der Lage, die Probleme zu erkennen, um daraus die notwendigen Konsequenzen abzuleiten. Und das führt mich direkt zum nächsten Punkt.
Finanzielle Allgemeinbildung

Die finanzielle Allgemeinbildung im Generellen und besonders in Deutschland ist katastrophal. Ich kann mir eigentlich nur erklären, dass das so gewollt sein muss. Denn aus eigener Erfahrung weiß ich, wie wenig (wenn überhaupt) die einfachsten Themen aus dem Finanzbereich in der Schule besprochen werden. Wenn es also gewollt ist, muss es Gründe dafür geben, die den Verantwortlichen Vorteile verschaffen. Zwei Gründe fallen mir dabei ein.

Indem Personen suggeriert wird, dass es sich bei Finanzen um ein undurchdringliches und komplexes Thema handelt, müssen Fachleute zu Rate gezogen werden, um Gelder und Erspartes zu verwalten und zu verwahren. Ähnlich wie bei Mining-Pools letzte Woche, macht es "jede Konzentration einer bestimmten Sache [...] für den Angreifer immer einfacher, diese eine große Einheit ausfindig zu machen und gezielt zu attackieren" oder zu kontrollieren. Es ist einfacher eine gewisse Anzahl an Finanzexpert//innen und -berater//innen zu regulieren, als die komplette Bevölkerung.
https://www.reuters.com/business/energy/eu-seeks-140-billion-cope-with-energy-crisis-utilities-teeter-2022-09-14
Regierungen können den Eindruck erwecken, unser Finanzsystem unter Kontrolle zu haben, und die Bevölkerung dazu zwingen, sich auf ihre Expertise zu verlassen, wodurch ihr persönliches Engagement verringert wird. Besonders in den letzten Jahren ist es stark aufgefallen, dass Regierungen nicht mehr viele Werkzeuge in ihrem Werkzeugkasten haben, um den wachsenden Stapel an Aufgaben zu bezwingen. Bis auf den heiß laufenden Gelddrucker und der vermeintlichen Narrativbildung der Notenbanken ist nicht viel übrig geblieben. Jegliche Entlastungspakete oder ähnliche Maßnahmen sind so fehlgeleitet, dass sogar den finanziell ungebildeten Bürger//innen langsam auffällt, dass die Regierung weit weg von der Kontrolle ist, die sie vorgibt zu besitzen.

Da mit Hilfe von Bitcoin immer mehr Menschen den Institutionen die restliche verbliebene Kontrolle nehmen wollen und die Kontrolle über ihre eigenen Mittel und die Verantwortung für ihre persönlichen Finanzen übernehmen, ist ein gewisser Grad an finanzieller Bildung höchst erforderlich. Zwar muss nicht jede/r Nutzer//in gleich einen Abschluss in Volkswirtschaft ablegen oder einen Kurs in Geldtheorie belegen. Hingegen sollte ein gewisses Verständnis von Geld, also wie funktioniert Geld, wo kommt Geld her, was ist solides gegenüber weichem Geld, etc. und Bitcoin, also was ist die Bitcoin-Blockchain, wie funktioniert es, wie verwahre ich meine bitcoins, etc. (hier versuche ich auszuhelfen) vorhanden sein, um Entscheidungen vernünftig und bedacht zu treffen, und nicht weil Onkel Winfried beim Weihnachtsessen gut gemeinte Tipps verteilt. Hat man einmal die Öffnung zum Hasenbau entdeckt, kommen komplexere Themen wie moderne Geldtheorie, quantitative Lockerung, Übernachtkredite der Federal Funds Rate, Fractional Reserve Banking, etc. automatisch dazu.
Bitcoin führt also auch dazu, dass sich der Schleier, der sich seit jeher über die Finanzwelt gelegt hat, langsam lüftet und sich ehemals sehr komplexe Themen für viele Menschen erschließen und zum neuen Alltag gehören. Ich wage sogar so weit zu gehen zu behaupten, dass dies Bitcoins zweitwichtigste Errungenschaft ist. Sollte Bitcoin, aus welchen Gründen auch immer, einmal nicht mehr existieren oder sein Wert auf null gehen, so bliebe zumindest eine große Gruppe von Menschen, die sich nun mit Themen wie Selbstbestimmung, Verwahrung, Freiheit und finanzieller Souveränität beschäftigt haben, die sich diesen Themen ohne Bitcoin sehr wahrscheinlich nicht gewidmet hätten. Viele Menschen haben den Eingang noch nicht für sich entdeckt und somit trägt die finanzielle Dyslexie dazu bei, dass Bitcoin nicht weiter verbreitet ist und stärker als Alternative zum korrupten System genutzt wird, vorausgesetzt man verfügt über die finanziellen Mittel dazu. Und damit zum nächsten Punkt.
Eintrittsbarrieren

Steigende Inflation, hohe CPI Veröffentlichungen, staatliche Übertreibungen, usw. sind alles Narrative für einen stärker werdenden Bitcoin. Doch genau diese Punkte sind auch daran Schuld, dass sich nicht viel mehr Menschen in Bitcoin flüchten. Denn die steigenden Preise für Konsumenten, die hohen Energiekosten und eine gewisse politische Unsicherheit führen in erster Linie dazu, dass die Menschen höhere Ausgaben haben. Bevor sich jemand darüber Gedanken machen kann, welche Alternativen es gibt aus dem System auszubrechen, müssen zunächst mal die horrenden Stromrechnungen, die teurer werdenden Nahrungsmittel im Supermarkt und die sowieso schon explodierten Mietpreise bezahlt werden. Allerdings, und hier entsteht ein Catch-22, lassen sich zum heutigen Zeitpunkt diese Kosten nicht mit Bitcoin bezahlen. Sowohl Stadtwerke und Versorger, als auch Supermärkte und Vermieter möchten ihre Rechnungen gerne in Euro, Dollar, Pfund beglichen sehen. Und solange das so ist, wird die Adaption zunächst mal nicht durch den Endverbraucher angetrieben, da es nicht möglich ist einfach zu sagen „Ich bin nicht mehr Teil des gefälschten Fiat-Systems, ich hodle jetzt Bitcoin“.

In erster Linie sind die Verbraucher Teil der bestehenden Gesellschaft und des auferlegten Geldsystems. Ausbrechen geht nur mit überschüssigem Kapital. Es werden also nicht diejenigen sein, die Inflation und Rezession als Existenzbedrohung fürchten, die scharenweise auf Bitcoin umsteigen, weil dies die Alternative und die Lösung des Problems darstellt. Diejenigen, die von steigenden Kosten in der Form betroffen sind, dass es für sie existentielle Ängste hervorruft, werden kein Geld übrig haben, das sie in Bitcoin investieren können. Dies gilt in ähnlicher Weise für das Narrativ "Banking the unbanked". Diejenigen Menschen auf der Welt, die keinen Zugang zum Bankensystem haben, werden in erster Linie auf einer der unteren Stufen der Maslow'schen Pyramide ihre Grundbedürfnisse stillen, bevor sie darüber nachdenken, wie sie an Bitcoin kommen. Das ist sehr einfach überspitzt und ich verstehe sehr wohl den Gedankengang hinter dem Abschaffen von regulatorischen Einstiegsbarrieren. Allerdings verdeutlicht dies nur, dass ein gewisses Privileg bestehen muss, um die Barrieren zu nehmen. Ganz vereinfacht gesagt, wer nichts besitzt, das vor Übergriffen und kriminell fahrlässiger Finanzpolitik geschützt werden muss, der/die wird auch nicht darüber nachdenken, wie dies bewerkstelligt werden soll. Das bedeutet, der Impuls muss von der privilegierten Klasse ausgehen, denjenigen, die es sich leisten können, sich in Bitcoin einzukaufen, denjenigen, die das Privileg der (Aus-)Wahl haben. Die weniger Privilegierten werden erst dann in der Lage sein, aus dem Fiat-Zyklus auszubrechen und Bitcoin zu adaptieren, wenn die Hyperbitcoinisierung /ein Bitcoin-Standard ermöglicht wurde und Bitcoin so Mainstream wird, dass die täglichen Ausgaben damit gedeckt werden können, sodass sich eine Nutzung von Bitcoin auf der einen und warm und genährt zu bleiben auf der anderen Seite nicht mehr gegenseitig ausschließen.
Aus den drei Beobachtungen leitet sich ab, dass Bitcoin nur wachsen kann, wenn die Bürger//innen erkennen, dass das aktuelle System beschädigt ist, und sich dazu entschließen, diesem System zu entfliehen. Um diese Erkenntnis zu erlangen, hilft eine gewisse finanzielle Grundbildung sehr aus. Sie hilft, aktuelle Tendenzen, Geschehnisse und Entscheidungen kritisch in Relation zu setzen. Beides setzt allerdings voraus, dass man die Wahl hat, sich dazu entschließen. Nicht jeder hat die wirtschaftlichen Grundvoraussetzungen, diesen alternativen Weg einzuschlagen, selbst wenn er/sie diesen für sich erkannt hat und bereit wäre zu gehen. Doch wenn diese Vorraussetzungen erfüllt sind, wie würde sich Bitcoin weiterentwickeln, um einen Bitcoin-Standard oder gar Hyperbitcoinization zu erzielen?
Wege zur Massenadaption von Bitcoin
Wie eingangs geschrieben, sind ein Bitcoin-Standard, Hyperbitcoinization oder zumindest eine Welt, in der Bitcoin zum alltäglichen Zahlungsmittel, zur Rechnungseinheit oder zur Leitwährung wird, das erklärte langfristige Endspiel. Es gibt Nuancen und Auslegungsspielräume zwischen den verschiedenen Endstufen, doch eine Form dieser Endspiele müsste Bitcoin erreichen, um sein Werteversprechen einzulösen, und somit relevant zu bleiben. ObiWan Kenobit vertritt in seinem Artikel "Hyperbitcoinization: Winner takes all" von 2018, dass Bitcoin zur weltweit dominierenden Geldform wird.
Hyperbitcoinization is a state where Bitcoin becomes the world’s dominant form of money. — ObiWan Kenobit
Um dies zu erreichen müsste Bitcoin einen Wert von 100 M US Dollar pro bitcoin erreichen.
At hyperbitcoinization I estimate Bitcoin will reach up to $100M per coin within 20 years and as early 2030. — ObiWan Kenobit
Kenobit stellt sogar Jahreszahlen in Aussicht, was wie wir wissen immer sehr problematisch sein kann. Niemand hat eine Kristallkugel, mit der man die Zukunft vorhersagen kann, und viele haben sich mit ihren Prophezeiungen schon die Finger verbrannt (👀 Plan B). Doch Hyperbitcoinization ist nur einer der erhofften Ausgänge. Die Frage bleibt jedoch, wie Bitcoin diesen Zustand einer Massenadaption erreichen kann.
Es gibt viele Szenarien, wie eine Adaption katalysiert werden kann und es gibt nicht den einen, richtigen Weg. Vielmehr wird es eine Vielzahl von internen und externen Faktoren geben, die in ihrem Zusammenspiel dazu führen werden, dass für Bitcoin eine Umgebung geschaffen wird, in der es wachsen kann. Dieses Zusammenspiel von Faktoren genau zu erläutern wage ich mich gar nicht erst, da auch ich (leider) keine dieser Kugeln besitze, doch möchte ich einfach einige der möglichen Auslöser erwähnen.
Zugänge
Fangen wir mit Zugängen an. Wie bereits beschrieben, wird die Revolution nicht von unten geführt werden können. Es wird privilegierter Personen bedürfen, die Bitcoin einer breiten Masse zugänglich machen können. Das große Geld in Form von TradFI-Firmen muss Bitcoin in großen Mengen kaufen und verwenden, entweder für sich selbst, für ihre Kundschaft, oder um auf der Basis von Bitcoin Produkte zu entwickeln. Der erste Schritt sind Portfolios in Höhe von 100 Milliarden US Dollar oder höher, die über große Spieler wie Blackrock / Fidelity / Vanguard usw. in Bitcoin investiert werden. Ein Spot-ETF würde den Zugang deutlich vereinfachen. Dies sind Szenarien, die - wenn man sich die News der letzten Woche ins Gedächtnis ruft - nicht mal utopisch klingen, schon heute problemlos über Layer 1 abgewickelt werden könnten und Layer 2 / 3 genug Zeit zum Wachsen verschaffen.
Im nächsten Schritt würden Banken Bitcoin adaptieren. Wenn die großen TradFi Unternehmen ihre Kundschaft von Bitcoin interessieren können, wollen natürlich die Banken auch an den Speck. Ich spreche hier von Privatkundengeschäft und Vermögensverwaltung. Dies würde den Zugang zu Bitcoin und Bitcoin-basierten Produkten für die nächste Schicht darunter ermöglichen, aber auch Transaktionsvolumen in Sphären heben, in denen das Netzwerk auf stabile Layer 2 Lösungen angewiesen ist.

Während des gesamten Prozesses wird die persönliche Nutzung von Bitcoin schrittweise zunehmen und wie bei allen Erfindungen und Technologien, sind es zunächst die Pioniere, Nerds und Innovatoren, die davon Gebrauch machen und dann stellt sich graduell eine Verbreitung ein (dazu später mehr). Es wird einen Punkt geben, an dem Bitcoin so verbreitet ist, dass Regierungen nicht herumkommen werden, Bitcoin zu unterstützen. Wie wir in den dieswöchigen Nachrichten gesehen haben, sind viele Staaten mehr oder weniger offiziell bereits an dem Thema dran. Im Idealfall würde dies zu einem Bitcoin-Standard führen, also der Nachbildung des Goldstandards, jedoch mit Bitcoin, an den die lokale Währung gekoppelt wird.
In hyperbitcoinization, Bitcoin needs to be all money. — ObiWan Kenobit
In einem Bitcoin-Standard muss Bitcoin nicht unweigerlich die dominante Währung werden (wie das bei Hyperbitcoinization der Fall ist), da es auch ein Szenario gibt, in dem US Dollars oder Euros (who am I kidding) weiterhin bestehen, nur halt an Bitcoin geknüpft sind, wie das in einem Gold-Standard vor dem Ersten Weltkrieg der Fall war. Das bedeutet Zahlungsmittel und Rechnungseinheit im Handel und Warenverkehr bleibt dann z.B. der US Dollar, nur dass nun die Notenbank nicht in der Lage ist, willkürlich US Dollars zu emittieren.

Diese aufeinanderfolgenden Schritte (TradFI Institutionen -> Banken -> Regierungen) lassen sich in der Grafik unten sehr schön ablesen. Die Grafik kombiniert die bekannte S-Kurve von Adoptionsraten der wichtigsten Innovationen der letzten 120 Jahre (die S-Kurve wird immer steiler, da neue Technologien heutzutage viel schneller angenommen werden) mit einem Modell von zugrunde liegenden Ereignissen (Katalysatoren), die das Wachstum von Bitcoin vorantreiben. Im Unterschied zu Kenobits Modell denke ich hingegen, dass die großen Spieler (TradFI und Banken) an der Adaption beteiligt sein werden und nicht erst zu spät zur Party kommen. Vielmehr sind sie es, die den Massen die Vehikel bereitstellen Bitcoin zu benutzen. Lediglich Regierungen würde ich in der Grafik zeitlich hinter dem Tipping Point erwarten.

Industrie
Das Wachstums-Modell beinhaltet auch Industry Use, also den Gebrauch von Bitcoin in der Wirtschaft. Allerdings würde ich diese Definition etwas breiter ziehen wollen und auch das Produzieren von Gütern und Rohstoffen FÜR Bitcoin mit einbeziehen. Bitcoin wird langsam aber sicher zu einem integralen Bestandteil des Energiesektors, und wie wir gerade sehen, ist Energie die wichtigste Industrie der Welt. Ob es um die Akzeptanz von Bitcoin für internationale Zahlungen für Öl und Gas geht, oder das direkte Nutzen von verlorener (nicht eingespeister) Energie in Form von Abfallgasen und Flaring, Solarüberschüssen in Sommermonaten, durch Einspeisemanagement erzeugte Verluste oder Reaktorbetriebszeiten, der gesamte Energiesektor stellt sich weltweit neu auf. Es gibt unendlich viele große und kleine Projekte, in die Hobby Tüftler und Weltkonzerne gleichermaßen involviert sind, um mit Hilfe von Bitcoin Mining Energie effizienter zu nutzen und Eniergie freizulegen, die es in die traditionellen Netzte nicht geschafft hätte.
Um nur hypothetisch einen Ansatz durchzuspielen: Ein großer Stromversorger stellt Mining-Equipment auf, um überproduzierten und nicht speicherbaren Strom sinnvoll, produktiv und vor allem profitabel zu nutzen. Das Unternehmen erzielt gute und stabile Umsätze mit Bitcoin, sodass es nicht jeden Bitcoin sofort in Fiat umzutauschen braucht und geht somit long Bitcoin, d.h. bitcoins werden in Reserve gehalten in der Hoffnung, dass sich der Kurs verbessert. Was hindert dieses Unternehmen, dass nun sowieso schon Buchhaltung für Bitcoin betreibt und eine Infrastruktur für die Verwahrung, den Ankauf und Verkauf von Bitcoin geschaffen hat, jetzt auch Zahlungen in Bitcoin zu akzeptieren. Dies würde die Eintrittsbarriere für diejenigen, die ihre (astronomisch hohe) Stromrechnung, die Nahrungsmittel im Supermarkt und Mietpreise bisher nicht mit Bitcoin bezahlen konnten, erheblich senken. Dieser Schritt alleine würde dazu führen, dass, zumindest für diesen Mikrokosmos zwischen Produzent und Konsument, sowohl Bitcoin als Store of Value, als auch als Medium of Exchange funktioniert. Das ist ein gewaltiger Schritt für das Wachstum, denn sobald das Modell erfolgreich ist, wird es kopiert und in andere Lebensbereiche übertragen.
Wir sehen, dass es viele Wege gibt Bitcoin in eine Massenadaption zu führen. Welcher dieser beispielhaft aufgezeigten Wege, in welcher Kombination, zukünftig der Wachstumstreiber wird, kann ich nicht sagen. Vielleicht gesellen sich andere Industrien oder andere Treiber hinzu, an die momentan noch nicht zu denken ist (man stelle sich die NASA beim Bitcoin-Mining auf dem Mond vor). Gewiss ist jedoch, dass dies erst der Anfang ist. Bitcoin wird wachsen, die Frage ist nur wie schnell.
Ein großes Hemmnis bei Bitcoin stellt immer noch die flächendeckende Adaption dar. Viele Menschen betrachten Bitcoin als sinnlos, da man damit nirgendwo bezahlen kann. Hier entsteht ein unendlicher Kreislauf: Wenn Bitcoin nicht adaptiert wird, weil man es nicht benutzen kann, wird niemand Waren und Dienste in Bitcoin anbieten, was dazu führt, dass man Bitcoin nicht nutzen kann, und deshalb Menschen es nicht adaptieren. ♻ Doch neben dem Anwendungsfall "Bitcoin als Zahlungsmittel" gibt es viele andere Gründe, warum man sich dazu entschließen sollte sich mit Bitcoin zu beschäftigen. Wie schon zuvor angesprochen, gibt es nicht den einen Treiber, der der ganzen Welt Bitcoin eröffnen wird, allerdings sind es die vielen Teile des Mosaiks, die zusammenspielen müssen, damit sich Bitcoin erfolgreich verbreiten kann.
[Its] (Bitcoin's) adoption is a series of individual acts of entrepreneurship rather than a single monopolist that games the system. — Daniel Krawisz, 2014
Daraus ergibt sich, dass die institutionelle Adoption einer den wichtigsten Faktoren für den Erfolg von Bitcoin ausmachen, es jedoch auch ein starkes Argument dafür existiert, dass die institutionelle Adaption nur als Folge einer erfolgreichen Adoption auf Einzelhandelsebene auftreten kann. Andersrum kann man genauso argumentieren, dass die Adaption auf institutioneller Ebene den Weg für Privatanleger freimachen muss.
Kenobit hätte es nicht treffender ausdrücken können: Wir sind in eine neue Ära eingetreten, in der neuartige Ideen, Technologien und Informationen in sozial unterstützenden Umgebungen geteilt werden. Unsere Interaktionen weisen zunehmend Netzwerkeffekte auf, die zu einer entscheidenden Veränderung der Verbreitung von Innovationen führen. Das bedeutet, dass jede zusätzliche Adaption, jeder zusätzliche Treiber eine viel größere Auswirkung erzielen kann. Wie schon gesagt, wir alle sind ein Teil von Bitcoin, wir alle helfen bei der Adaption und wir alle können dazu beitragen, es wachsen zu lassen. Keep stacking Sats!
🫳🎤
In diesem Sinne, 2... 1... Risiko!

-
 @ 07156f66:eecb568a
2024-11-25 07:24:03
@ 07156f66:eecb568a
2024-11-25 07:24:03Looking for guidance on Arlo Video Doorbell HD setup? To help you quickly and effectively install and configure your doorbell, Myarlosetup provides a thorough instruction. Discover how to configure its features for the best possible home security, connect it to your Wi-Fi, and sync it with the Arlo app. Our simple instructions guarantee a hassle-free setup, allowing you video surveillance and real-time notifications. Use Myarlosetup's professional Arlo Video Doorbell HD instructions to improve your home security.
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ 75869cfa:76819987
2024-11-25 03:21:20
@ 75869cfa:76819987
2024-11-25 03:21:20GM, Nostriches! The Nostr Review is a biweekly newsletter focused on nostr statistics, protocol updates, exciting programs, the long-form content ecosystem, and key events happening in the Nostr-verse. If you’re interested, join me in covering updates from the Nostr ecosystem!
Quick review: In the past two weeks, Nostr statistics show over 240,000 daily trusted pubkey events, a 28% increase from the previous period, The daily peak reached 22201, the highest in the past two months.New user profiles with bios have reached around 40,000,profiles with contact lists are around 18000,both showing increases over 20%. More than 11 million events have been published, with posts leading in volume, totaling about 2.1 million. Total Zap activity reached over 19 million, marking a significant 70% increase.
Additionally, 26 pull requests were submitted to the Nostr protocol, with 8 merged. A total of 42 Nostr projects were tracked, with 12 releasing product updates, and over 419 long-form articles were published, 33% focusing on Bitcoin and Nostr. During this period, 1 notable event took place, and 3 significant events are upcoming.
Nostr Statistics
Based on user activity, the total daily trusted pubkeys writing events exceeded 240,000, a 28% increase compared to the previous period (Oct 29-Nov 10). The daily peak reached 22201, the highest in the past two months, with a low of nearly 17682. In terms of new user numbers, profiles with bios are around 40000, up 21% over the past two weeks; profiles with contact lists are around 18697, up 22%. Public writing events exceeded 200,000,The daily peak reached 32480. Regarding event publishing, the total number of note events published has surpassed 11 million, marking a significant increase of approximately 28%. Posts remain the most dominant in volume, totaling about 2.1 million, far exceeding reposts (357,168) and reactions (560,243). For zap activity, the total zap amount has exceeded 19 million, showing a significant increase of over 70% compared to the previous period. In terms of relay usage, the top five relays by user count are: wss://bostr.bitcointxoko.com/,wss://feeds.nostr.band/,wss://realy.nostr.band/,wss://realy.lumina.rocks/,wss://unostr.site/ Data source: https://stats.nostr.band/
NIPs
Break out chat and threads from nip 29 nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn is proposing that this is a variant of #1589 which attempts to reconcile NIP 29 and flotilla's rooms over chat and thread kinds. This requires no changes of NIP 29 clients, only flotilla will need to be modified,andmove kind 9 and 11 out of NIP 29. The choice of new event kinds was initially made to avoid conflicts with existing implementations. However, it would be beneficial to align the two approaches. For chat and threads, maintaining shallow reply hierarchies rather than arbitrary ones is a key consideration. Moving forward would depend on whether this stipulation is acceptable to the NIP 29 community.
Relay chat nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn is proposing an alternative to NIP 29 for several reasons. NIP 29 is overly prescriptive in several ways and encourages group admins to host their groups on a third-party relay. Moving group-like features to relays eliminates the need for separate specifications for each group. Additionally, group metadata is redundant because relays already have a NIP 11 information document and a public key with which they can publish additional information.Admins and moderators can be handled implicitly, out-of-band, or by querying feature support using LIMITS. This approach keeps the base specification small while allowing features like moderator lists to be added as optional extensions. Member lists are managed by the members themselves, enabling them to choose whether to publicly disclose their group membership. This approach facilitates web-of-trust-based community recommendations.
Time-ordered event ids nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z is proposing that there are a lot of performance benefits to having primary keys with temporal locality.when your database needs to check the uniqueness of IDs, only a small portion of the index needs to be hot (in memory). With the current “random identifiers”, the working set eventually becomes all of the data and your database will be page-faulting continuously. Sequential primary keys also make it easier for the database to place new records in order, minimizing the need to rearrange data or update index structures.This PR makes a simple, but breaking change, to the way we compute event ids. It was inspired by the improvements made by UUIDv7.
NIP-37 - Transport method announcement nostr:npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr is proposing that Nostr decouples applications completely from the transportation layer, meaning services no longer have to be designed around a single transportation method, but can be accessible through a plethora of ways. This NIP is meant to act as a lookup system that tells a client which transportation methods can be used to access its services.There have been NIP proposals that touch the connection between pubkeys and addresses, example NIP-97 - Nostr Naming System, NIP-66 - Relay Discovery and Liveness Monitoring. NIP-97 is very close to solving the issue of this mapping.However, it attempts to also include human-readable naming into the solution. human-readable naming of pubkeys/services is inherently different from mapping a pubkey to an address where a user can access that pubkey's services, which may or may not map to a legacy domain name.NIP-66 covers discoverability from the client side and can be a very important tool to discern which services are worth connecting to. I think it can act as the feedback mechanism to the proposed event of this NIP. It can be used to build metrics for the various networks a pubkey announces it to be accessible. Things like rtt (round trip time) can also be different for each network and should be measured separately.
nip46: simple public key login using kind:10046 nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 is proposing that This vastly simplifies the bunker:// flow while also making it easy for the user on every other front possibly -- and brings back NIP-05 login, but in a simpler, more generic way.
Add optional arg to nostr.getPublicKey() Lez is proposing that if login is optional for an application, nostr.getPublicKey({optional: true}) can be used to retrieve the pubkey if the user has already granted permission to the app. This allows the user to view the app’s landing page without being interrupted by a popup window. The user can still press the login button later, which calls nostr.getPublicKey() and prompts for permission.
NIP-62: Collections limina1 is defining a specification for organizing nostr events into collections - ordered, optionally-hierarchical structures like books, journals, or documentation. Currently, there's no standardized way to create versioned collections of content. The closest option is to use lists, but this extends that idea beyond a strictly linear hierarchy. Introducing two new event kinds: kind:30040 - Collection Index and kind:30041 - Collection Section. The Collection Index serves as a table of contents, providing metadata about the collection and listing events in display order. Meanwhile, the Collection Section contains the actual content and supports linking to other content using wikilinks, enabling seamless connectivity within the collection.
Add r to kind 10009 nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn is proposing adding an "r" field to kind 10009, allowing users can advertise what relays/groups they are members of. Flotilla uses this to recommend relays. These of course should be considered non-canonical because the users publishing them may not actually have access to the relay specified.
Add support for naming unmanaged groups nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn is proposing Instead of allowing human-readable ids, it's probably better to just allow users to name groups. I opted for a petnames strategy here instead of recommending sending 9002 events or something. Clients can choose whatever heuristic they want to resolve conflicts.
Add feature detection for unmanaged groups nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn is proposing feature detection for unmanaged groups that has to exist on two levels.On the group level, so that clients can toggle the richer NIP 29 behavior on or off. Feature detection based on NIP 11's supported_nips field isn't sufficient, since a relay implementation might support NIP 29, but the actual relay may not.On the relay level, since clients need to be able to know whether users can post events to groups that don't yet exist, or whether they have to send a create-group event instead.The default (obviously) has to be that unmanaged groups are allowed, so unmanaged group support is opt-out.
kind-scoped follow nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft is proposing kind-scoped follow does NOT (necessarily) replace kind:3, it's a way to do a very simple follow of one or more kinds that might be of interest.This way we also start moving away from huge follow lists that can get wiped at a moment's notice and instead clients are responsible for computing the follow list and updating its local state.This also allows apps to show "followed" notifications without a central source.
Build Your Own Adventure posts nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z is defining kind:296 and kind:297 as text notes with options to navigate to the next text notes and continue reading. Kind 296 serves as the root story and 297 for the sections of that story.The idea is to replicate the dynamism of build your own adventure books, where each reader takes their own journey in the story.Story Section events contain an optional title tag and option tags for the next sections.Clients SHOULD render options in a way that users can select and move to that post.
Notable Projects
Primal 2.0 nostr:npub12vkcxr0luzwp8e673v29eqjhrr7p9vqq8asav85swaepclllj09sylpugg
Primal now offers a much more comprehensive view of Nostr, with the following additions: * New tab: READS * New tab: EXPLORE * Feed Marketplace * Advanced Search * launched Primal Premium, for $7/month, you can get a Primal Name and Nostr Tools for power users * enable plugging any feed into the sidebar
Yakihonne nostr:npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
Mobile latest updates: * Adjust your home feed with what interests you the most. * Home suggestion box can be enabled and disabled. * Profile preview can be enabled and disabled. * Replies can be previewed and highlighted directly. * Articles, videos and curations can be quoted inside notes for more exposure. * Add the ability to link connected wallets to your profile for zaps receiving. * Thread view is enhanced and well adjusted. * Fix a variety of introduced bugs. * General improvements across the app.
Web latest updates: * A fresh design overhaul for the article, video, and curation pages, enabling seamless browsing and enhanced interaction with content. * Connected threads! A refined notes thread makes following entire discussions more intuitive. * Users can now personalize their home feed by selecting their top interests. * Replies can now be previewed directly from the note card, without needing to open the full note. * Wallets can now be linked to your account directly from the wallet page. * Drafts for notes and replies are now saved, allowing easy edits later. * The suggestions box on the home page can now be hidden. * The on-hover user preview can now be disabled for quicker access to profiles. * Articles, videos and curations can now be quoted and shared as notes. * General improvements. * Bug fixes and optimizations.
ZEUS Pay nostr:npub1xnf02f60r9v0e5kty33a404dm79zr7z2eepyrk5gsq3m7pwvsz2sazlpr5
- All payments will incur no fee for the receiver (previously 2.5-10% depending on amount)
- The minimum amount receivable has been lowered to 1 satoshi (previously 10 satoshis)
TestFlight nostr:npub18m76awca3y37hkvuneavuw6pjj4525fw90necxmadrvjg0sdy6qsngq955
TestFlight is a program designed for those who want to join the nostr:#damus roadmap, prioritizing improvements to video support and introducing several new features: * Improved video controls * Stability improvements to video support * New image share options on the full screen carousel * Hashtag suggestions * Multi image uploads * A video player that actually works * Share sheet action * Seamless scroll * Added Damus Share Feature * Fixed missing tab bar on navigation * Fixed some issues where profile QR code scanning would not work, and improved UX to make experience more robust
Olas 0.1 nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft
Olas is an Instagram-like client for iOS and Android,provides a feed of videos (like those on flare/highlighter/zap.stream), picture events (kind:20, a new kind that no client had implemented yet) and the classical short notes with images attached we are all used to.Some more features already available: * blossom uploads * NIP-22 replies * Reels (still quite buggy though) * Edit your preferred blossom servers * Edit your nutsack mint list * Image download optimization (to be gentle with mobile data plans) Additionally, there are some coming next, including NIP-55 (Amber) Logic,Fix NIP-46 (bunker) login,complete NIP-60 (nutsack) wallet,Add NIP-57/61 zaps + nutzaps,and more.
Gossip 0.12.0 nostr:npub189j8y280mhezlp98ecmdzydn0r8970g4hpqpx3u9tcztynywfczqqr3tg8
This is a major release with the following major changes: * Bookmarks support (including private bookmarks) * Global feed and per-Relay feeds (with volatile storage, erased when you quit) * Friends-of-friends scores shown in avatar * Improved spam filtering script with more inputs to make decisions on Additionally, there are some minor changes, including updated emoji picker, reworked relay scoring, more efficient background tasks, faster database (less syncing),and more.
Nostur v1.16.0 nostr:npub1n0stur7q092gyverzc2wfc00e8egkrdnnqq3alhv7p072u89m5es5mk6h0
- Nostr Nests integration
- Live video streams and chats
- Relay Autopilot improvements
- VPN detection toggle: only connect to additional relays if VPN is detected
- Relay Connection stats improvements
- Rewrite of feed loading. Faster & more efficient
- Possible imposter label also added on new follower notification and quoted posts
- Improved profile card rendering/animation
- Improved quoted post and inline naddr1 rendering
- Optimized profile gallery loading
- Exclude reposts for new posts notifier
- UI tweaks, more compact, less clutter
- Full width images now go to screen edge
- Reduced data usage for new follower notifications
- Many many bug fixes and other optimizations
Fountain Radio 1.1.8 nostr:npub1v5ufyh4lkeslgxxcclg8f0hzazhaw7rsrhvfquxzm2fk64c72hps45n0v5
- Add and upvote tracks in the queue
- Support the artist currently playing
- Post in the live chat
- Save tracks to your library
- Listen to Fountain Radio on other apps
- Artist takeovers
Plebeian Progress Update nostr:npub1market6g3zl4mxwx5ugw56hfg0f7dy7jnnw8t380788mvdyrnwuqgep7hd
There are some enhancements and new features: * dialog manager * hide non-working parts of the ui * publish events, we are just signing * Moderation Tools for Admins and Editors * introduce 'editor' role Additionally, a major bug causing errors when creating stalls with more than one shipping method has been fixed, and the “v4v” text has been updated to Community Contribution.
Zapstore 0.16 nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8
Zapstore 0.1.6 released now.Some performance issues addressed, reverted installer, fixed themed icon and toasts, and more.
0xchat 1.4.1 nostr:npub1tm99pgz2lth724jeld6gzz6zv48zy6xp4n9xu5uqrwvx9km54qaqkkxn72
- Optimized video player UI with support for landscape mode
- Added audio configuration in settings
- Enabled copying of ecash tokens from ecash messages
- Support for media deletion Additionally, some bug fixes,such as the occasional gray screen when sending e-cash,gray screen issue in Hungarian language,“mark all as read” function not working,and more.
DEG Mods update nostr:npub17jl3ldd6305rnacvwvchx03snauqsg4nz8mruq0emj9thdpglr2sst825x
The updated version introduces a new Web of Trust system and a Blog system, with relevant pages and sections now implemented and updated.And there are some changes: * (technical) nPub user addresses now lead to a user's profile if added through the URL, which would be auto-converted to an nProfile type address. * Reaction (heart/poop) numbers now show a loading indication with 3 dot animation, and you'd only be able to react once loading is finished. * There's now a spinning loader animation for the comments of a post to make sure, as a user, if there are comments or not * There's now a comment loader button that you can press to load newly discovered comments for a mod or blog post * Minor design adjustments for blog posts Additionally, fixed the ordering of the latest mods, ensured profile links in comments (from clicking the name or user address) lead to the correct profile page now, and more.
Long-Form Content Eco
In the past two weeks, more than 419 long-form articles have been published, including over 100 articles on Bitcoin and more than 30 related to Nostr, accounting for 33% of the total content.
These articles about Nostr mainly explore the protocol's development, practical applications, and its role in driving the decentralized social media ecosystem. They cover updates on tools and features like TestFlight and Knox Beta, highlighting innovations such as healthcare micro-apps, privacy enhancements, and NFC integration. Community-driven initiatives, like self-hosted Zap cooking, board member introductions, and the power of collaboration, reflect the growth of the ecosystem. Additionally, the articles discuss challenges such as key management and content moderation, as well as creative contributions like Thanksgiving use cases and cultural content.
The Bitcoin articles discuss the development, adoption, and impact of Bitcoin on the global financial landscape. They cover Bitcoin's market performance, technological advancements, and its role in the broader cryptocurrency ecosystem. The articles also explore Bitcoin's rise, its increasing market cap, and predictions for its future price movements. In addition, they focus on Bitcoin's use in various applications, the challenges faced by Bitcoin mining, and its evolving role in decentralized finance, highlighting Bitcoin's potential to address global issues, from the limitations of fiat currencies to the challenges posed by central banking systems and surveillance. Overall, the articles reflect Bitcoin's growing influence and its potential to drive future technological and financial revolutions.
Thankyou,nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe,nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn,nostr:npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft,nostr:npub1t0an3j7nk007fuc7r9zpm89g66dksuc245jsm4xy2674w2uen2nsceqmmp,nostr:npub1klshrs20h2nxf73vrshfjpmmnrq7m8tz7l77sjapwkyaveu22agq5pvxnv,nostr:npub1f7ptem2ztp9x4n7w62n90ddv40z0jrt4490d8lug3uasfwyjsccqkknerm,nostr:npub176zu0wg5l8436nu66qaxwfekx0zz58l66s72dhcu0ur0lvd7q5lq9f66qx,nostr:npub1kun5628raxpm7usdkj62z2337hr77f3ryrg9cf0vjpyf4jvk9r9smv3lhe, and others,for your work. Enriching Nostr’s long-form content ecosystem is crucial.
Nostriches Global Meet Ups
Recently, several Nostr events have been hosted in different countries.
- Adopting Bitcoin 2024 took place successfully from November 15 to 16, 2024, in the southern region of El Salvador. The event attracted over a hundred Bitcoin experts, advocates, and innovators from around the world, including nostr:npub14d5399mthprnnur9g2wq877hg0htr5afrdad5dryryeftct885fqtcpuyp, nostr:npub1dtgg8yk3h23ldlm6jsy79tz723p4sun9mz62tqwxqe7c363szkzqm8up6m, nostr:npub16dhgpql60vmd4mnydjut87vla23a38j689jssaqlqqlzrtqtd0kqex0nkq, nostr:npub1lelkh3hhxw9hdwlcpk6q9t0xt9f7yze0y0nxazvzqjmre3p98x3sthkvyz,and more. Discussions focused on Bitcoin’s potential to reshape global finance, culture, and social structures, with key themes around decentralization, Bitcoin’s challenge to sovereignty, and its impact on education and family life. nostr:npub1ad0ptuzte83alpkpqqctvewlaqj5zq23c83m82xw8apg4t6zlyns6xng2c
Here are the upcoming Nostr events in November that you might want to check out.
-
Btrust Developer Day will take place on Sunday, December 8, 2024, in Nairobi, Kenya, as part of the Africa Bitcoin Conference (ABC 2024). This event aims to provide a platform for African developers to explore Bitcoin technology, learn from industry leaders, and collaborate on projects. The event will feature lightning talks, panel discussions, hands-on workshops, project showcases, and networking opportunities, making it ideal for Bitcoin developers, open-source developers, technologists, and Bitcoin enthusiasts.
-
The Africa Bitcoin Conference 2024 will take place from December 9 to 11, 2024, in Nairobi, Kenya, featuring key programs such as Btrust Developer Day, TBD Hackathon, ABC Social Impact Award, Afro Bitcoin Fellowship, and Africa Bitcoin Day. The event will host nearly 70 distinguished speakers, including nostr:npub1ju2sw9unanr94p5wama3ydv90hcke34wcnmnxedummspaayz55qswlya32, nostr:npub16hssgmdhw9e9j6z8na45lzz4grdsfjqlp5hf8dtcqnp0glseeu3seecguf, nostr:npub1m7uxdt50d2jw35q79zlszlsvy79t7dpdxptz6rfsrsamra7l8ttsq752yl, nostr:npub1gaxapm9t9damh6q2lpc04ptcyeh0ysfdfzzs997agu3ae80ftrns7t985l, and more,focusing on topics such as Bitcoin adoption, regulation, innovation, and security. This conference offers attendees valuable opportunities for in-depth discussions and knowledge sharing.
-
The Asia Bitcoin Tech Unconference is set to take place from February 8 to 10, 2025, in Chiang Mai, Thailand. Organized as a workshop-style event, it will feature a diverse lineup of speakers, including nostr:npub1zk6u7mxlflguqteghn8q7xtu47hyerruv6379c36l8lxzzr4x90q0gl6ef, nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac, nostr:npub1ejxswthae3nkljavznmv66p9ahp4wmj4adux525htmsrff4qym9sz2t3tv, nostr:npub1xtwy7fvu8f7wdtgnpm68wyrf6uxshf49tn5kp7kyusu6872amn8qh06rus, nostr:npub147whqsr5vsj86x0ays70r0hgreklre3ey97uvcmxhum65skst56s30selt,and others. The conference will focus on key topics such as scalability, mining, payments, and infrastructure, while also encouraging participants to share unfinished projects or technical challenges. Through hackathons and hands-on discussions, the event aims to foster collaboration and innovation. Highlights include technical talks, pitch competitions, Bitcoin product showcases, and creative and wellness activities such as Thai massages, ice baths, and arts and crafts workshops.nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx
Additionally, We warmly invite event organizers who have held recent activities to reach out to us so we can work together to promote the prosperity and development of the Nostr ecosystem.
Thanks for reading! If there’s anything I missed, feel free to reach out and help improve the completeness and accuracy of my coverage.
-
 @ d8ae4d9c:b22906bf
2024-11-25 02:55:54
@ d8ae4d9c:b22906bf
2024-11-25 02:55:54My last test of the night.
-
 @ eac63075:b4988b48
2024-10-20 13:49:55
@ eac63075:b4988b48
2024-10-20 13:49:55Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.
Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.
The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.
Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.
The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
Conclusion of the Technical Debate
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.

Table reference: Patrick Breyer - Chat Control in 23 September 2024
Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.
The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
Conclusion of the Debate
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.
User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
Summary of Consequences
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.
The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.
Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ d8ae4d9c:b22906bf
2024-11-25 02:39:54
@ d8ae4d9c:b22906bf
2024-11-25 02:39:54I’m not sure if I even want to answer.
Robin returned home from her third date with Ty at midnight. Her blond hair was slightly messy and her green eyes flashed with … something. She was encouraged by her first two dates with Ty. He’d nearly swept her off her feet with his confidence and smooth talk. He was physically cut, outwardly kind, and ruggedly handsome. However, something did not sit right that night. She could not put her finger on it. Robin thought about this as she opened her apartment door. The moment she entered she heard a notification of an incoming text on her phone. The message was from her good friend, Anna:
How did the date go?
Robin’s face flushed a deep red. How did she know to text me right now? I’m not sure if I even want to answer.
I just got home.
How was it?
I’m just now reflecting on the night. I just walked in the door.
Oh? That bad?
Robin felt defensive as the heat rose within.
No, no. I’m not saying that just that I’m contemplating the night.
That doesn’t sound as inspiring as your first two dates with Dreamboat.
No, Anna. I’m just trying to catch my breath.
Well, I’m sending you a link that might help you think.
Uh, ok? LOL. Why?
Nothing, I’ve just been thinking about you and want you to know that I care about you deeply. Click this link.
Robin clicked the link. It took her to a web page entitled What Women Look for in Men.
And under it a list:
-
Ambition and Drive
-
Communication
-
Emotional Intelligence
-
Financial Responsibility
-
Integrity and Trustworthiness
-
Kindness and Generosity
-
Physical and Mental Health
-
Tall, Dark, and Handsome
-
Classy and Neat
-
-
Respect
-
Sense of Humor
-
Spiritual
Robin loved the list but wondered why Anna sent her the list on this particular night. Robin automatically compared Ty’s attributes to the list. She thought to herself:
Let’s go to the physical first. Ty passes on both counts. He is tall, dark, handsome, classy and neat. Check. Mentally? He seems to be pretty clear-thinking. Check. Though, he can be a little sharp-tempered at times. Is that a mental or spiritual chink?
Robin returned to random items in the list and her thoughts. Ty at least laughs at the proper moments. He is generous and kind to me, though sometimes short with others. Could that be a problem? I think he can be trusted, but I’m not sure. He seems to respect me and is emotionally stable, at least on the surface. Our communication has been sweet, though, again a little on the surface. He certainly has ambition and drive. His drive frightens me at times. He is so ambitious. My husband, Don, was always so laid back. Ty has plenty of money and seems financially on top of things. Spiritual?
At that word, Robin was taken aback.
I haven’t the slightest idea about that. Could that be something I should be concerned about? Does he have a core?
With that thought, Daniel’s face flashed across her mind. Robin smiled when she remembered her previous encounters with Daniel. Daniel did not meet several items on the above list but he was a kind man. Daniel automatically made her feel at ease. He seemed to communicate from the heart and directly to her. And his communications were not simply on the surface. He asked probing questions and showed interest in her. Daniel had a strong spiritual sense and spoke openly about his faith. Why was she now comparing the two men? She had never dated Daniel. Why was she comparing them now, and at this late hour?
Was this the reason Anna sent her a list on this particular night? Did Anna know her better than she knew herself? Why the list? Anna tossed and turned in her sleep that night. As she dreamed through the night, she compared the men to each other and the list.
Robin woke up the next morning with another notification of a text from Anna. She stared at the text on the screen:
How did you sleep?
Horrible.
Why?
The list.
-
-
 @ 4ba8e86d:89d32de4
2024-10-01 13:27:38
@ 4ba8e86d:89d32de4
2024-10-01 13:27:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ df478568:2a951e67
2024-11-25 02:36:34
@ df478568:2a951e67
2024-11-25 02:36:34Details
- ⏲️ Prep time: 10 minutes
- 🍳 Cook time: 30 minutes
- 🍽️ Servings: 4
Ingredients
- rice
- 2 lb. ground beef
- 8 oz. sliced mushrooms
- 1 stalk of geeen onions, chopped
- 1/4 tsp. garlic salt
- 1 10.5 oz. can of cream of mushroom soup
- 1 cup sour cream
- peas
Directions
- Cook the rice
- Brown ground beef. Remove and set aside.
- Saute mushrooms and green onions
- Cook peas(I usually use the microwave)
- Return beef to Dutch oven. Add cream of mushroom and sour cream
- Cooknon low heat for 12 minutes.
-
 @ df478568:2a951e67
2024-11-25 02:36:04
@ df478568:2a951e67
2024-11-25 02:36:04Chef's notes
Easy Beef Stroganoff(Fast AF Beef Stroganaff)
This is an easy weaknight meal.
Details
- ⏲️ Prep time: 10 minutes
- 🍳 Cook time: 30 minutes
- 🍽️ Servings: 4
Ingredients
- rice
- 2 lb. ground beef
- 8 oz. sliced mushrooms
- 1 stalk of geeen onions, chopped
- 1/4 tsp. garlic salt
- 1 10.5 oz. can of cream of mushroom soup
- 1 cup sour cream
- peas
Directions
- Cook the rice
- Brown ground beef. Remove and set aside.
- Saute mushrooms and green onions
- Cook peas(I usually use the microwave)
- Return beef to Dutch oven. Add cream of mushroom and sour cream
- Cooknon low heat for 12 minutes.
-
 @ d8ae4d9c:b22906bf
2024-11-25 02:18:25
@ d8ae4d9c:b22906bf
2024-11-25 02:18:25Is this note working?
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ a012dc82:6458a70d
2024-11-25 01:02:22
@ a012dc82:6458a70d
2024-11-25 01:02:22Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
Leverage is the practise of trading cryptocurrency with borrowed funds. With leveraged trading, you can purchase or sell more for the same amount of capital. You can use your collateral to make leveraged transactions even if you start with a relatively small amount of funds. While using leverage can greatly increase your earning potential, it also exposes you to far greater danger, which is especially true in the highly speculative cryptocurrency market. Take caution when trading cryptocurrencies using leverage. If the market goes against your bet, you could incur significant losses.
Trading with leverage might be difficult for newcomers. However, it is essential to learn what leverage is and how it functions before attempting to use it. While the focus of this essay will be on leveraged trading in the cryptocurrency markets, most of the information is equally applicable to more conventional markets.
What is leverage in crypto trading?
Leverage is the practise of trading cryptocurrencies or other financial assets with borrowed money. Your ability to make a purchase or sale is increased, giving you access to more funds beyond those at your disposal. You may be able to borrow up to 100 times your account balance from some cryptocurrency exchanges.
Leverage is measured in terms of a ratio, such as 1:5 (5x), 1:10 (10x), or 1:20 (20x). It displays the multiples of one's initial investment. Let's say you want to start a bitcoin position worth $1,000, but you only have $100 in your exchange account (BTC). Because of the leverage, your one hundred dollars will be worth one thousand.
Leverage can be used to trade numerous crypto-derivatives. Margin trading, leveraged tokens, and futures contracts are typical examples of leveraged trading.
How does leveraged trading work?
You need to fund your trading account before you can use leverage to borrow money and make trades. Collateral consists of the initial deposit you make into our account. Collateral needs to be proportional to both the amount of leverage and the entire value of the position being opened (known as margin).
Assume you have $1,000 and want to invest it in Ethereum (ETH) with a 10x leverage.If you want to borrow $1,000, for example, and the margin is 10%, or $100, then you'll need to have $100 in your margin account. With a 20x leverage (1/20 of $1,000 is $50), your margin call would be significantly lower.But remember that larger levels of leverage come with greater chances of insolvency and liquidation.
You'll need to keep a certain amount of your original margin deposit plus additional margin at all times in order to make trades. As soon as the market goes against you and your margin falls below the maintenance requirement, your account will be liquidated unless you deposit more money. The cutoff is the same thing as the safety margin.
Both long and short positions can benefit from using leverage. When you open a long position, you are betting that the value of the underlying asset will increase. In contrast, betting for a decline in the asset's value by placing a short position This may sound like standard spot trading, but when you use leverage, you are actually buying or selling assets based on your collateral rather than the actual value of the assets you possess. If you believe the market will fall, you can open a short position even if you don't own the asset you're shorting.
An example of a leveraged long position
Assume you want to open a long position in bitcoin worth $10,000 with a 10x leverage.In other words, you'll put up $1,000 in collateral. A 20% increase in Bitcoin's price would result in a net profit of $2,000 (after fees), significantly more than the $200 you could have made without utilising leverage if you had invested only $1,000.
But if the Bitcoin price declines by 20%, you would lose $2,000 on your investment. If the value of your initial investment (collateral) of $1,000 drops by 20%, you will be forced to sell (your balance goes to zero). Even a 10% loss in the market could be enough to cause liquidation. The precise value at liquidation will vary depending on the trading platform used.
You need more money in your wallet as collateral if you want to avoid getting liquidated. Before a liquidation occurs, the exchange will often issue a margin call (e.g., an email telling you to add more funds).
An example of a leveraged short position
Assume for a moment that you want to open a $10,000 short position on BTC with a 10x leverage.In this situation, you will borrow bitcoin from another person and sell it at the current price. You have only put up $1,000 in collateral, but thanks to 10x leverage, you can make a $10,000 Bitcoin sale.
You leased 0.25 BTC and sold it for $40,000, assuming the current BTC price. With merely $8,000, you can repurchase 0.25 BTC if the price of Bitcoin declines by 20% to $32,000. That's a $2,000 gain after expenses! (minus fees).
If Bitcoin's price increases by 20%, to $48,000, you will need an additional $2,000 to repurchase the 0.25 BTC. Given that you only have $1,000 in your account, your position will be closed. Again, you can avoid liquidation by increasing your collateral by adding additional money to your wallet before the liquidation price is reached.
Why use leverage to trade crypto?
Leverage is used by traders to increase the size of their positions and the amount of money they may make. In contrast, the potential for substantially larger losses inherent in leveraged trading was shown in the aforementioned examples.
Leverage is used by traders for a number of reasons, one of which is to increase the fluidity of their money. To keep the same size of position while posting less collateral, they may, for instance, deploy 4x leverage across multiple exchanges rather than 2x leverage on a single one. This would free up some of their capital for use in other endeavours (such as investing in NFTs, trading in other assets, staking, or providing liquidity to decentralised exchanges).
How do you manage risks with leveraged trading?
Leveraged trading reduces the initial cash needed to enter the market but raises the probability of eventual bankruptcy. Even a small change in price can have a catastrophic effect on your portfolio if your leverage is excessive. If you have a low volatility tolerance already, increasing your leverage will make that worse. If you use less leverage, you have more room for error when trading. For this reason, Binance and other cryptocurrency exchanges have capped the amount of leverage that new customers can utilise.
Stop-loss and take-profit orders are examples of risk management strategies that can be used in leveraged trading to reduce exposure to loss. Whenever the market goes against you, stop-loss orders can close your position instantly at a predetermined price. The use of stop-loss orders helps prevent catastrophic losses. In contrast, take-profit orders terminate trading automatically whenever your profit reaches a certain threshold. That way, you can lock in your profits before the market takes a downturn.
You should now see that leverage in trading is a double-edged sword that can greatly increase your profits or losses. It's risky business, especially given the unpredictability of the bitcoin market. If you trade on Binance, we expect you to operate in a responsible manner and take responsibility for your decisions. To assist you in staying in charge of your transactions, we include features like a cooling-off period and a notice to prevent you from becoming addicted to trading. Use extreme caution at all times, and don't forget to do your own research (DYOR) to learn about the proper use of leverage and the development of trading techniques.
How to use margin trading on Binance
Cryptocurrency exchanges such as Binance allow traders to take advantage of leverage to increase their trading potential when transacting in digital currency. We'll walk you through the basics of margin trading, but the idea of leverage is applicable to other markets as well. Obtaining a margin account is a prerequisite to proceeding. If you haven't already done so, please read our Frequently Asked Questions post.
-
To check your margin, first select [Trade] > [Margin] from the menu bar.
-
Look for the pair you want to trade by clicking [BTC/USDT]. Our currency pair will be Binance Coin (BNB) to US Dollar (USDT).
-
You have to add some money to your margin wallet. Below the candlestick graph, select [Transfer Collaterals].
-
Choose the receiving wallet, the receiving margin account, and the cryptocurrency to send. Simply enter the total and press [Confirm].Here, we'll show you how to send 100 USDT to the Cross Margin account.
-
Click the right-hand box and continue. Decide between [Cross 3x] and [Isolated 10x]. When using Cross Margin mode, your margin accounts' margin balances will be pooled together, while in Isolated Margin mode, your margin balances will remain separate. This Frequently Asked Questions page has additional information on the distinction between the two.
-
Choose [Buy] (long) or [Sell] (short) and an order type, such as a market order. When you press [Borrow], you'll see that the one hundred USDT we deposited into the Cross Margin account has been multiplied by three, turning into three hundred USDT.
-
If you want to acquire Binance Coins (BNB) using a loan, you can do so by multiplying your USDT deposit by [Total] and your desired BNB purchase by [Amount]. A percentage of your available balance can also be used by dragging the bar below. The loan amount for this investment will then be displayed. Just open the position by clicking [Margin Buy BNB].
Keep in mind that you can't invest the full amount you have because of the trading cost. The system will automatically maintain the trading charge amount depending on your VIP status.
Conclusion
Utilizing leverage makes it possible to get your feet wet with a smaller outlay of capital and the expectation of larger returns in the future. The rapid liquidation of assets is still a risk when using 100x leverage to trade, especially if the market is volatile. Always trade with prudence and analyse the risks before taking on leveraged trading. Never trade with money you can't afford to lose, especially if you're using leverage.
FAQs
Explain what a leverage of 10 means. A ratio, such as 1:10 (10x) or 1:20 (20x), expresses how much leverage you have (20x). It shows how many times your initial investment is compounded. For instance, with a leverage ratio of 1:10, you would only need $1,000 to invest $10,000.
What leverage should I use in crypto? Swing traders often hold onto their positions for several days, if not weeks. Therefore, it is crucial to keep leverage low to prevent inadvertent liquidation from everyday market liquidity. Daily fluctuations of 5–10% in cryptocurrency markets are to be expected.
Does crypto favour leverage? To a large extent, the crypto sector makes use of leverage. Leverage can boost gains, but it also magnifies losses. Trading cryptocurrencies using borrowed money (sometimes known as "leveraged trading") entails high levels of risk. It's mainly because the market is so unpredictable.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 36bedab2:524acad4
2024-11-24 23:17:58
@ 36bedab2:524acad4
2024-11-24 23:17:58A Lei de Gresham explica por que o Bitcoin é visto como um "bom dinheiro" e sua relevância no contexto econômico global.
- Bitcoin e a Lei de Gresham
O Bitcoin é um exemplo moderno da Lei de Gresham, mas funcionando de forma inversa em um ambiente onde não há obrigatoriedade de aceitação de moedas governamentais.
Bitcoin como "bom dinheiro":
Escassez e mineração: Bitcoin é escasso (máximo de 21 milhões) e sua criação exige esforço computacional significativo, semelhante à extração de ouro.
Proteção contra desvalorização: Ao contrário das moedas fiduciárias, que podem ser impressas sem limite, o Bitcoin tem regras rígidas que evitam inflação descontrolada.
Preferência pelo armazenamento: As pessoas preferem guardar Bitcoin como reserva de valor, em vez de gastá-lo, porque ele tende a valorizar com o tempo. Isso está alinhado com a Lei de Gresham: as pessoas gastam o "dinheiro ruim" (moedas fiduciárias inflacionárias) antes de gastar o "dinheiro bom" (Bitcoin).
- Bitcoin e a Geopolítica Monetária
O dólar norte-americano mantém seu status de moeda de reserva global, dando aos EUA a capacidade de imprimir dinheiro que outros países precisam usar.
Assim como o ouro, o Bitcoin é visto como uma ameaça ao sistema fiduciário liderado pelo dólar. Ele representa um "dinheiro bom" que não pode ser desvalorizado por decisões políticas.
A Lei de Gresham explica por que o Bitcoin é raramente gasto, mas amplamente guardado como uma reserva de valor. A sua ascensão reflete a insatisfação global com moedas fiduciárias inflacionárias, e ele é visto como uma esperança para o futuro financeiro, ao oferecer um sistema monetário independente, transparente e limitado.
O Bitcoin, como exemplo de "bom dinheiro", tem o potencial de mudar o sistema econômico global, libertando-o de governos que abusam de sua capacidade de emitir moedas descontroladamente.
-
 @ 6d8e2a24:5faaca4c
2024-11-24 22:35:56
@ 6d8e2a24:5faaca4c
2024-11-24 22:35:56 Non-fungible tokens (NFTs) are a type of cryptocurrency that is not interchangeable with other tokens of the same type. NFTs are unique, meaning each NFT can be distinguished from every other NFT. This is unlike fungible tokens, such as Bitcoin or Ethereum, which are interchangeable and each unit is identical to every other unit.
Non-fungible tokens (NFTs) are a type of cryptocurrency that is not interchangeable with other tokens of the same type. NFTs are unique, meaning each NFT can be distinguished from every other NFT. This is unlike fungible tokens, such as Bitcoin or Ethereum, which are interchangeable and each unit is identical to every other unit.NFTs are stored on a blockchain, like other cryptocurrencies. The most popular blockchain for storing NFTs is Ethereum. NFTs can represent anything that can be stored digitally, such as a piece of art, a video, or a virtual world.
One of the benefits of NFTs is that they can be traded easily and quickly on decentralized exchanges. This means that there is no need for a central authority, such as a bank, to facilitate the transaction.
How does NFT work- NFTs are digital assets that are stored on a blockchain. The key difference between an NFT and other digital assets is that NFTs are unique and non-fungible. This means that each NFT is unique and cannot be replaced by another asset.
NFTs are often used to represent digital art, but they can also be used to represent other things like in-game items, collectibles, and even real-world assets.
The way an NFT work is similar to how cryptocurrencies work. When you buy an NFT, you are buying a digital token that is stored on a blockchain. The blockchain records each transaction and ensures that the NFT cannot be duplicated.
NFTs have gained in popularity in recent years as the technology behind them has become more advanced. The use of NFTs is still in its early stages, but there is a lot of potentials for them to be used in a variety of ways.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 4e2310e2:5ff5e38e
2024-11-24 22:33:28
@ 4e2310e2:5ff5e38e
2024-11-24 22:33:28这是第一条,作为测试和纪念
-
 @ 06639a38:655f8f71
2024-11-24 22:13:33
@ 06639a38:655f8f71
2024-11-24 22:13:33Image source: https://stitcher.io/blog/new-in-php-84 and great resource if you would like to know more about the new stuff in PHP 8.4.
Nostr-PHP
- Set a lib-gmp version, see https://github.com/nostrver-se/nostr-php/pull/71
- Work in progress handling TLV data for bech32 encoded entities: https://github.com/nostrver-se/nostr-php/pull/68
- There is an issue with
gmp_pow()method in php-core which affects version 8.2 or higher: https://github.com/nostrver-se/nostr-php/pull/71 - Added 8.4 PHP support, see https://github.com/nostrver-se/nostr-php/pull/73
- Surprised by this unexpected but very welcome help while working on NIP-19: https://github.com/nostrver-se/nostr-php/issues/74 where Nuša Pukšič shared some snippets how to decode bech32 encoded entities.
- Fixed https://github.com/nostrver-se/nostr-php/issues/63
Other stuff
- On Tuesday the 19th of November we had our 4th Nostr NL meetup which we also streamed live on https://zap.stream.
- Had a online call with Fabian who is working on a new Blossom client which he demo’ed to me for getting some feedback.
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ dae73fdd:e16cd432
2024-11-24 21:04:48
@ dae73fdd:e16cd432
2024-11-24 21:04:48I have a fairly disciplined and obedient dog. She’s a bundle of energy wrapped in a well-trained package, ready to show off her tricks at the drop of a hat. From the basics like “sit” and “stay” to more impressive moves like “spin around,” “shake,” and even “play dead,” she’s got an arsenal of talents that never fail to entertain. But what’s most remarkable isn’t just her repertoire of skills—it’s her eager enthusiasm, the way her tail wags furiously in anticipation of the treat she knows is coming. Watching her perform, it’s clear that, in many ways, humans aren’t so different—we all do tricks for the rewards we want.
Who's Your Master?
Who do you do tricks for, so you get something you want? At first glance, the question might feel uncomfortable. “I’m nobody’s dog,” you might say. But peel back the layers of pride, and you may find that we all engage in this kind of dynamic every day, in ways both subtle and overt. Your boss? Your spouse? Your kids? Your friends? At some point, each of these relationships involves a trade—actions performed in the hope of receiving something in return.
It might be money, validation, affection, approval, or peace of mind. Whatever the "treat" is, it motivates us to act in ways that align with someone else’s desires. We perform tricks, consciously or unconsciously, because we want the reward. The question isn’t whether this happens. The question is, who holds your leash, and how much are you willing to do for the treats they offer?
The Professional Arena
The workplace is one of the most obvious places where the “dog and treat” analogy holds true. Your boss asks for a report, a presentation, or overtime. You comply. Why? Because there’s a paycheck at the end of the month, perhaps a chance for a promotion, or even just the avoidance of getting reprimanded.
Think about it: Have you ever found yourself bending over backward to meet a deadline, staying late to finish a task, or meticulously crafting an email just to curry favor? It’s a trick. Maybe it’s a complicated one, requiring skill and effort, but it’s a trick nonetheless. And the treat? Job security, recognition, or the satisfaction of knowing you’re a "good employee."
But at what cost? Dogs don’t choose their tricks—they’re taught what their owners want them to do. Similarly, how often do we fall into routines and behaviors at work that we didn’t consciously choose but adopted to stay in the good graces of our employers?
The Personal Sphere
Our personal lives are not exempt from this dynamic. Consider your relationships with family, friends, and significant others. How often do we act in ways designed to elicit a specific response? You might clean the house before your partner gets home, hoping for appreciation. You might help a friend move, expecting gratitude (and maybe some pizza and beer). You might listen to your child’s endless stories about their day, not just out of love, but because you want their trust and affection.
None of this is inherently bad. Acts of service and care are the glue that binds relationships. But it’s worth asking: Are these actions genuine expressions of love and connection, or are they performed under the unspoken pressure of earning a treat?
What happens when the treat doesn’t come? What if your spouse doesn’t notice the clean house, or your friend forgets to say thank you? Does the absence of a treat leave you bitter? If so, it might be time to reexamine whether you’re performing tricks out of choice or obligation.
Societal Tricks and Collective Treats
Beyond our personal and professional circles, we perform tricks on a societal level. Social norms, traditions, and expectations shape our behavior in profound ways. We act a certain way to be accepted by a community or to maintain a specific image.
Consider social media. Every post, photo, and comment is a trick designed to earn a treat: zaps, likes, comments, or shares. The dopamine hit of online validation can be as addictive as a dog’s favorite treat. We curate our lives to please an invisible audience, performing tricks that align with societal expectations of success, beauty, or wit.
Who’s Holding Your Leash?
Acknowledging this dynamic doesn’t mean we’re powerless. In fact, it’s an opportunity to reflect on who or what controls our actions. Are we acting out of genuine desire, or are we being trained to jump through hoops for treats that don’t truly satisfy us?
The leash might be held by a boss, a partner, or societal pressures, but it can also be self-imposed. Sometimes, we’re our own masters, setting impossible standards for ourselves and punishing ourselves when we fail to meet them.
The key is awareness. A dog performing a trick knows the treat is coming—it’s a conscious exchange. Similarly, we can choose our tricks and treats more intentionally.
Finding Freedom in Choice
We can’t escape the "dog and treat" dynamic entirely. Human relationships and societies are built on mutual exchanges, and that’s not inherently a bad thing. But by becoming more mindful of who or what we’re performing for, we can take back some control.
What if you choose your tricks more deliberately? What if you decided which treats are worth chasing and which aren’t? What if you recognized when a leash is being tightened around your neck and chose to slip free?
The Choice is Yours
We’re all just dogs doing tricks for a treat. That’s not a condemnation—it’s a truth worth reflecting on. Every trick we perform, every treat we chase, is an opportunity to ask: Is this worth it? Am I acting out of genuine desire, or am I simply following the tug of the leash?
Choose your master wisely.
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 31312140:2471509b
2024-11-24 20:49:36
@ 31312140:2471509b
2024-11-24 20:49:36The Foundation of Our Bodies
Our feet are the very foundation of our bodies. They bear our weight, provide balance, and allow for intricate movements. Yet, in modern times, we’ve encased these natural marvels in layers of synthetic materials and rigid, leading to a plethora of health problems.
The Natural Design of Feet
Nature has designed our feet to function optimally without any additional support. The arch, the toes, and the muscular structure all work together to absorb shock, maintain balance, and propel us forward. Shoes, particularly those with narrow toe boxes and elevated heels, can alter this natural mechanism, leading to issues such as:
- Plantar Fasciitis: Often caused by insufficient arch support and heels.
- Bunions: Resulting from tight, pointed shoes that squish the toes together.
- Flat Feet: Caused by prolonged use of supportive shoes that prevent the arch from strengthening naturally.
The Science Behind Barefoot Benefits
Various studies have highlighted the benefits of ditching your shoes:
-
Improved Foot Strength and Flexibility: Walking barefoot helps strengthen the muscles, tendons, and ligaments in your feet. Just like any other part of your body, the more you exercise your feet naturally, the stronger they get.
-
Better Posture: When barefoot, your body naturally aligns itself. Heels and cushioned shoes can misalign your posture, causing back, knee, and hip pain.
-
Enhanced Sensory Feedback: Our feet are equipped with a high density of nerve endings, providing valuable feedback to help us maintain balance and posture. Walking barefoot enhances proprioception, the sense of how our bodies are positioned in space.
-
Natural Gait: Shoes alter our natural walking pattern. Barefoot walking encourages the natural gait where the foot lands softly and aligns correctly with the ground.
Historical Context and Cultural Perspectives
Historically, humans have walked barefoot for thousands of years. Our ancestors ran, hunted, and thrived without the need for supportive footwear. Various cultures still maintain a barefoot lifestyle, and it’s worth noting the minimal foot problems in these populations compared to shoe-wearing societies.
In cultures where barefoot walking is prevalent, people often display:
- Fewer Foot Deformities: Like bunions or hammertoes.
- Minimal Chronic Foot Pain: Due to the natural strengthening of foot muscles.
- Better Balance and Agility: Thanks to constant sensory input and natural movement.
The Grounding Effect: More Than Just Physical
Beyond the physical advantages, walking barefoot connects us to the earth, a practice often termed "grounding" or "earthing." The idea is that direct contact with the earth’s surface allows for the transfer of free electrons which act as antioxidants, reducing inflammation and boosting our overall health.
Scientific Insights
Studies have shown that grounding can:
- Improve Sleep: By regulating circadian rhythms.
- Reduce Pain and Inflammation: Through the transfer of free electrons which neutralize free radicals.
- Boost Mood and Energy: By reducing stress hormones like cortisol.
Transitioning to Barefoot: A Practical Guide
Switching to a barefoot lifestyle isn’t something you should do overnight, especially if you've been wearing conventional shoes for most of your life. Here’s a step-by-step guide to help you transition safely:
-
Start Slow: Begin by walking barefoot at home. Gradually increase the duration as your feet become stronger.
-
Choose Natural Surfaces: Whenever possible, walk on grass, sand, or dirt to allow your feet to adjust to different textures and strengthen naturally.
-
Practice Foot Exercises: exercises like toe curls, arch lifts, and calf stretches can help strengthen your foot muscles.
-
Consider Barefoot Shoes: If going completely barefoot is not feasible in certain environments, barefoot shoes with wide toe boxes and flexible soles can be a great alternative.
-
Listen to Your Body: Pay attention to any pain or discomfort and give your feet time to adapt.
Addressing Common Concerns
Hygiene and Safety
A common concern is the risk of injury or hygiene issues. While it's true that barefoot walking involves some risk of cuts or infections:
- Inspect Your Path: Always check the ground for sharp objects or dangerous terrain before walking barefoot.
- Maintain Good Hygiene: Wash your feet regularly to prevent infections.
- Strengthen Your Soles: As your feet adapt, the skin on your soles will thicken, providing additional protection.
Real-Life Success Stories
Many athletes and everyday individuals have embraced the barefoot movement with remarkable success. Marathon runners, sprinters, and hikers have reported fewer injuries and improved performance. Regular folks have also shared stories of alleviated chronic pain and enhanced well being.
Conclusion
Kicking off your shoes and the barefoot lifestyle taps into our natural design and connects us more deeply with the world around us. From physical benefits like enhanced strength and posture to the grounding effects that boost our mental health the advantages of walking barefoot are clear. Listen to your body and start your barefoot journey today. Remember, it’s all about reconnecting with our roots and living more naturally. 🌍✨
References and Suggested Readings
- "Born to Run: A Hidden Tribe, Superathletes, and the Greatest Race the World Has Never Seen" by Christopher McDougall - A compelling narrative that showcases the advantages of barefoot running.
- "Earthing: The Most Important Health Discovery Ever?" by Clinton Ober, Stephen T. Sinatra, and Martin Zucker - Explores the science and benefits of grounding.
- "The Barefoot Book: 50 Great Reasons to Kick Off Your Shoes" by L. Daniel Howell - Offers detailed insights into why you should consider going barefoot.
There you have it, folks! The barefoot truth laid bare (pun totally intended). Let's keep questioning, keep exploring, and always look deeper into everything we're told. Until next time! 👣
-
 @ de75eb1d:710c3014
2024-11-24 20:28:46
@ de75eb1d:710c3014
2024-11-24 20:28:46Chef's notes
Traditional Victorian recipe made better with the addition of chocolate, fills x6 one lb jars and each jar makes approximately 15 pies or one large tart.
Store in a cool dry place for 12 months for an even deeper flavour.
Unlike supermarket mincemeat, this recipe is naturally palm oil free when made using traditional ingredients (NOT Atora!), you could swap the animal fat for ghee or solid cocoa butter.
Go wild on the dried fruit, anything and everything works. This is a great area to play around and make extra special versions - like Cherry Brandied Chocolate! You can also swap or omit the nuts
Details
- ⏲️ Prep time: 30 mins
- 🍳 Cook time: 3 hours
Ingredients
- 1 lb cooking apples, cored and diced
- 1.5lb mixed dried fruit
- 1lb unrefined sugar (or honey)
- 1/2lb beef suet
- 1/2lb candied citrus peel
- 2oz chopped or flaked almonds
- 4tsp mixed spice
- 1tsp ground cinnamon
- 1/2tsp ground nutmeg
- 1/2lb dark chocolate roughly chopped
- 6tbspn brandy or rum
- zest and juice of 2 oranges & lemons
Directions
- Combine all of the ingredients except the chocolate and alcohol in a large oven proof bowl, cover and leave overnight to infuse
- Next day cover the bowl with foil and bake slowly for 3 hours in a preheated oven at 120c
- As the mincemeat cools periodically stir in the fat and when completely cold add the alcohol and chocolate chips
- Pack into sterilised jars and cover with a wax disk or 1tsp melted suet, screw the lids on tight and it will keep for 3-5 years
-
 @ 9c47bb51:000381d0
2024-11-24 19:19:42
@ 9c47bb51:000381d0
2024-11-24 19:19:42Blockchain technology, particularly the Bitcoin blockchain, is poised to redefine the way we think about trust, ownership, and value in society. Its decentralized, transparent, and immutable nature sets the stage for a wave of innovation that will reshape industries, governance, and everyday life. While Bitcoin is most famously known as a digital currency, its underlying blockchain technology offers transformative potential far beyond finance. Let’s dive into how this technology could revolutionize the coming decades, from small-scale applications to global systemic change.
- Financial Inclusion and Empowerment
One of the most immediate impacts of blockchain technology is its ability to empower individuals who have been excluded from traditional financial systems. Over 1.4 billion adults globally remain unbanked, unable to access basic financial services due to lack of identification, credit history, or proximity to banks. Bitcoin’s blockchain offers a decentralized alternative.
With just a smartphone and internet access, anyone can participate in a global financial network. Peer-to-peer transactions eliminate the need for intermediaries, reducing costs and enabling borderless payments. This is particularly impactful in developing nations, where remittance fees from services like Western Union often consume a significant portion of the money sent home by workers abroad.
- Redefining Property and Ownership
The Bitcoin blockchain introduces a new era of digital ownership. By using public and private keys, individuals can prove ownership of assets without needing third parties. This concept extends beyond Bitcoin to include: • Tokenized Real Estate: Fractional ownership of property becomes possible, making investments accessible to more people. • Intellectual Property: Artists and creators can mint their work as non-fungible tokens (NFTs), securing royalties and ownership rights without intermediaries. • Supply Chain Transparency: Blockchain ensures the authenticity of goods by tracking their journey from origin to consumer, revolutionizing industries like food safety, luxury goods, and pharmaceuticals.
- Revolutionizing Governance
Blockchain’s transparency and immutability make it a powerful tool for improving governance and reducing corruption. Imagine a world where: • Voting: Elections are conducted on blockchain platforms, ensuring transparency and eliminating fraud. Citizens can verify their votes without compromising privacy. • Public Funds: Governments manage budgets and distribute aid using blockchain, providing real-time accountability for how tax dollars are spent. • Smart Contracts: Agreements are executed automatically when pre-defined conditions are met, removing bureaucratic delays and reducing legal disputes.
For example, countries experimenting with blockchain for land registries are reducing disputes over property rights while fostering economic stability.
- The Internet of Value
The internet revolutionized how we share information; blockchain is set to revolutionize how we exchange value. Bitcoin’s blockchain introduced the concept of digital scarcity—an asset that cannot be duplicated or counterfeited. This is the foundation of a new Internet of Value: • Micropayments: Services like podcasts, articles, or software can be monetized with tiny payments using the Lightning Network on Bitcoin, bypassing traditional subscription models. • Decentralized Finance (DeFi): Borrowing, lending, and saving can occur directly on blockchain platforms, offering alternatives to traditional banks with reduced fees and greater accessibility. • Global Trade: Blockchain enables faster, cheaper cross-border payments, reducing friction in global commerce and empowering small businesses to compete on a global scale.
- Revolutionizing Healthcare
Blockchain can revolutionize healthcare by improving data management and patient empowerment: • Medical Records: Patients can securely store and share their medical histories, ensuring accurate diagnosis and treatment while maintaining privacy. • Drug Authentication: Blockchain can track pharmaceuticals from production to patient, reducing counterfeit drugs. • Research Collaboration: Blockchain enables secure sharing of anonymized patient data among researchers, accelerating breakthroughs in medicine.
For example, during the COVID-19 pandemic, blockchain was explored as a way to verify vaccination records and ensure the integrity of supply chains for vaccines.
- Energy and Environmental Solutions
The energy sector stands to benefit significantly from blockchain technology: • Decentralized Energy Grids: Households with solar panels can trade excess energy with neighbors using blockchain-based platforms, fostering community-driven energy networks. • Carbon Credits: Blockchain ensures transparency in carbon credit trading, preventing fraud and incentivizing companies to reduce emissions. • Tracking Sustainability: Blockchain enables tracking of sustainable practices, from renewable energy usage to ethical sourcing of materials.
- Education and Credentialing
Blockchain can solve problems of credential verification and access to education: • Digital Diplomas: Educational institutions can issue tamper-proof certificates on a blockchain, streamlining job applications and international recognition of qualifications. • Lifelong Learning: Blockchain can track an individual’s learning journey across multiple institutions, enabling personalized education pathways and skills validation.
The Larger Vision: A Decentralized Future
At its core, blockchain is about decentralization—removing the need for trust in intermediaries and empowering individuals. This has profound implications for: • Freedom and Sovereignty: Bitcoin’s blockchain allows individuals to store and transfer value without fear of censorship, making it a tool for human rights in oppressive regimes. • Resilient Economies: Decentralized systems are less vulnerable to single points of failure, fostering robust economies and networks. • Global Collaboration: Blockchain can create a new era of cooperation, where value and ideas flow freely across borders without interference.
Challenges and the Road Ahead
While the potential of blockchain is enormous, challenges remain: • Scalability: Current blockchain networks, including Bitcoin, must continue to innovate to handle growing demand. • Regulation: Governments must balance innovation with oversight, ensuring blockchain is used responsibly without stifling growth. • Adoption: Educating the public and creating user-friendly interfaces are critical for mainstream adoption.
Despite these challenges, the trajectory is clear: blockchain is not a passing trend but a foundational technology that will shape the next several decades.
The Role of Bitcoin in Leading the Revolution
Bitcoin, as the first and most secure blockchain, will continue to lead this revolution. Its decentralized nature, proven security, and global recognition position it as the backbone of this transformation. While other blockchains may serve specialized purposes, Bitcoin’s role as digital gold and a store of value ensures its enduring relevance.
The Bitcoin blockchain’s influence will extend far beyond currency. It is the blueprint for how trust, ownership, and value can exist in a digital age—transparent, immutable, and accessible to all.
As we look to the future, blockchain technology represents not just a technological revolution but a societal shift toward empowerment, transparency, and decentralization. From small changes in everyday transactions to large-scale systemic transformation, blockchain has the potential to touch every aspect of our lives, ushering in a more equitable and connected world.
-
 @ 6fff5148:a5dd5cdf
2024-11-24 18:59:19
@ 6fff5148:a5dd5cdf
2024-11-24 18:59:19Youth unemployment is often linked to a range of issues such as high crime rates among youth and riots. Young people are still unemployed because of the various challenges facing young people. This includes laziness in young people who make them reluctant to seek employment which is why they remain unemployed for a long time because of these social structures. These two fundamental effects of unemployment can lead to social degradation when it reaches uncontrollable levels. Unemployment remains a major cause of social ills, which are often associated with high levels of unemployment. These social ills cannot be predicted when they will occur, but they will certainly occur when unemployment becomes uncontrollable. Youth unemployment can be described as a time bomb waiting to explode. The current generation of young people has become the most prepared generation in the history of the region, so it makes sense to promote job creation related to the fields of education or technology for many young people, that is, to take advantage of population comparison. For example, if the majority of young people are studying social science, it is easy to encourage the creation of a service sector. As can be seen, the role of the State is crucial to improving the situation; however, the government must ensure clean communication between itself and the various sectors of society if a real solution is to be achieved.
-
 @ 4fcac000:d2b37988
2024-11-24 18:42:23
@ 4fcac000:d2b37988
2024-11-24 18:42:23В Тюмени стартует программа "Энергия для жизни", объединяющая бизнес и жителей для энергосбережения и устойчивого развития.
К 2040 году Тюмень станет примером экологической ответственности. 💡 Для бизнеса: Зеленые офисы: использование биофильных дизайнов для снижения потребления энергии. Краудфандинг на солнечные панели: инициативы по сбору средств на установку солнечных панелей. Кооперативы по обмену энергией: совместный обмен избыточной энергии от возобновляемых источников. 🏡 Для частных лиц: Эко-соседства: сообщества для установки солнечных батарей и систем сбора дождевой воды. Гардероб с историей: магазины для обмена и аренды вещей. Сад на крыше: использование крыш для создания зеленых садов, улучшающих качество воздуха.


-
 @ 7c765d40:bd121d84
2024-11-24 18:35:52
@ 7c765d40:bd121d84
2024-11-24 18:35:52We are about to witness the power of exponential growth in bitcoin.
Many predict bitcoin's price to be in the millions one day.
I am one of those people.
Many also predict it will take 50 years to get there.
I am not one of those people.
Bitcoin has gone from $350 to $93,000 in less than a decade.
Many believe the big growth is behind us.
But only 1% of the world owns bitcoin.
What about the other 99%?
What happens when they're all trying to get their hands on a scarce asset with a fixed supply?
It's something the world has never seen before.
Let me say that part again.
Something the world has never seen before.
Let's use an example of exponential growth.
Imagine a football stadium being filled with water.
Every minute one drop is added.
The number of drops doubles every minute.
It goes from 1 to 2, to 4, to 8, 16, 32, 64, etc.
How long would it take to fill the entire stadium?
A day? A week? A year?!
How about 50 minutes.
And the crazy part - how full is it after 45 minutes?
Most would guess 70-90%.
Wrong.
After 45 minutes the stadium is only 7% full.
In the final 5 minutes, the stadium goes from 7% full to 100% full.
I believe there are three triggers that will occur that will send bitcoin from $93,000 to $93 million.
-
Wall Street can participate
-
A major country starts buying as a strategic reserve
-
The price hits $1 million
The first has already happened.
The second one is likely to happen in a few months.
And the third will follow shortly after.
Wall Street was important because that's where all the BIG money is.
The US strategic bitcoin reserve will force all countries to start printing money and buying bitcoin.
And when the price hits $1 million, we will start pricing satoshis instead of bitcoin.
1 sat will equal 1 cent.
In a decade from now, no one will know what the price of bitcoin is.
They will know how much a satoshi costs.
Keep in mind, there are 100 million satoshis in 1 bitcoin.
Think of it like dollars and cents.
This is when the exponential growth will kick in - and it's much closer than we think.
Moral of the story?
Don't focus on the price.
Focus on getting as many satoshis as you possibly can.
And invest some time and money into securing those satoshis.
Jor 871781
-
-
 @ 0c9e5e17:480e870b
2024-11-24 18:33:50
@ 0c9e5e17:480e870b
2024-11-24 18:33:50I thought I'd share the excellent review posted by Worn & Wound of my Prometheus Ocean Diver watch design. It is a very thorough review with some incredible photos.
Snippet from Worn & Wound Review
"Turns out, not everything we lionize from our past holds up so well today. A few things, however, transcend their era and are worth returning to because their qualities aren't reliant upon the culture that bore them. I'd place the Ocean Diver in this category, while fully acknowledging the irony that its creation is intrinsically linked to watch collection culture of the late aughts.
There is an indefinable quality about the Ocean Diver that sets it apart from its contemporaries, such as the Ocean 7 LM-2, early Christopher Ward divers, and Seiko's SKX watches. The internal bezel, the design of the hour markers, including the oversized numerals at 6, 9 and 12 o'clock, the porthole shaped case design and its bead blasted texture all add up to something of an unusual experience that was wholly original at the time, and remains so today.”
 Photo Credit: Worn & Wound
Photo Credit: Worn & WoundOriginal Design Concept
Below is my original design illustration which I produced using Adobe Illustrator. You'll notice that several of my design elements were changed in the final production version. For example, the hands were supposed to be much larger and with more lume for greater visibility, something that was pointed out as a negative of the production version in the Worn & Wound review, but as you can see by my design was never my intention.
I'm incredibly proud of my design. Having it go into production, even with minor changes, is a watch lover's (and designer's) dream come true! I never get tired of seeing photographs shared on social media of my watches being worn and enjoyed by their owners.
You can read the full Worn & Wound review here >> Missed Reviews: The Curious Case of the Prometheus Ocean Diver
-
 @ 0c9e5e17:480e870b
2024-11-24 18:25:29
@ 0c9e5e17:480e870b
2024-11-24 18:25:29I just made my first batch of Paleo beef jerky and the results are so good that I thought I'd share it with you. My entire house smells of beef jerky right now and it's driving my dog crazy - poor thing.
What's Paleo?
I'm not going to go into the details, but simply put it's a way of eating that best mimics the diets of our paleolithic hunter-gatherer ancestors - lean meats, seafood, vegetables, fruits, and nuts. If you're interested take a look here: The Paleo Diet.
I've been gradually getting more and more serious about eating a paleo diet as a lifestyle and wanted to see if I could find a recipe that I could use for making beef jerky that would be suitable = no soy sauce, besides other things. I was sent two really good examples of paleo jerky recipes from @paleoonabudget via Twitter (love how social tools connect us) and thought that they both sounded good enough to try. Here they are: Food Lover's Kitchen Beef Jerky, and Jen's Gone Paleo Really Tasty Beef Jerky.
My Version
Always one to tinker and hack with something, I adjusted and combined aspects from both recipes to come up with one that sounded good to me. Here's what I ended up with:
- Flank steak as lean as possible (grass-fed), trim any excess fat
- 1 cup raw coconut aminos (it's a substitute for soy sauce)
- 1 cup of organic apple juice (make sure there are no additives)
- 1 cup of pineapple juice (again, no additives)
- 1 tbsp fresh ground black pepper
- 1 tsp of paprika
- 1 tsp of garlic powder
- Lime juice (not in the marinade)
 Steak strips in the marinade
Steak strips in the marinadeI used a nice cut of flank steak (personal preference) and made sure to trim off all excess fat, although there was hardly any. I put the steak in the freezer for an hour or two to make slicing it into thin strips a little easier.
Then I put all of the other ingredients (the marinade) into a Pyrex dish and added the sliced steak pieces, making sure that all of the steak was covered or submerged. I think I topped up with a little extra of both juices. I covered this and put it in the fridge overnight.
Dehydrating - Making it Jerky!
The next day (around noon) I removed the marinading steak from the fridge and let it drain through a small sieve for a minute or two to get the excess liquid off. No need to get my dehydrator into a big mess if I can easily avoid it. I used my old faithful L'Equip 528 6-tray Dehydrator. I love this machine!
 Steak strips on dehydrator tray
Steak strips on dehydrator trayI gave the entire batch of steak a heavy dose of freshly squeezed lime juice, all over. I was very heavy handed with the lime (thinking this would be my "secret sauce"). Then I arranged the pieces of steak onto the drying sheets (mine has six) making sure to leave a lot of room around each piece.
 Temperature dial on L'Equip
Temperature dial on L'EquipI set the temperature gauge to half way between 125F and 153F (\~135F) and turned it on. At this point I went out to take care of some errands - nothing you would be interested in. When I got back a few hours later, I was greeted by the smell of beef jerky as I opened the front door - wow!
The jerky had been drying for about four hours while I was gone and much to my surprise was completely done. In fact it could have come out a little bit sooner to be even better, but that's my fault for going away and leaving it. When I make jerky using ground beef it takes a lot, lot, longer - more than twice as long.
 I hope you enjoy this recipe!
I hope you enjoy this recipe!The end result is absolutely delicious. The combination of the fruit juices, coconut aminos and spices gives the steak an amazing, slightly citrus flavor. I wish you could try some, it's soooo good!
-
 @ 04d9fac9:5bec0e6c
2024-11-24 17:24:08
@ 04d9fac9:5bec0e6c
2024-11-24 17:24:08В Воркуте стартуют областные соревнования по триатлону, привлекая участников всех возрастов и уровней подготовки. Категории соревнований: Дети: Участники до 12 лет будут соревноваться на сокращенных дистанциях, что позволит им проявить свои силы в плавании, велогонке и беге. Юниоры: Спортсмены от 13 до 17 лет выступят на более сложных дистанциях, что станет отличной возможностью для развития их навыков. Взрослые: Основная категория включает спортсменов старше 18 лет, которые будут соревноваться на стандартных дистанциях, демонстрируя свою физическую подготовку и выносливость. Соревнования обещают быть захватывающими и способствовать популяризации триатлона в регионе.
-
 @ 30ceb64e:7f08bdf5
2024-11-24 16:48:15
@ 30ceb64e:7f08bdf5
2024-11-24 16:48:15A Personal Journey
I recently created a blog using npub.pro to consolidate my Nostr and Stacker News longform posts in one place. It's been a fun experiment, with surprising results.
https://thebloghustle.npub.pro/
Primal now displays my SN and Nostr posts through a selection on my profile screen, and users are able to highlight, zap, and comment on the highlights of my articles.
I need to write more, the blog will be something of an open diary, detailing my personal experience with Nostr and bitcoin.
Why Nostr Outshines Substack and Medium
Nostr in my opinion has already surpassed the legacy blogging platforms. Functionalities like zapping, highlighting, and commenting, are fun and cool, but when added to Nostr's interconnectivity something magical appears. I had no idea my cross posted SN longform posts would be found in npub.pro, and I didn't know npub.pro had added longform support. Primal 2.0 was pretty much the nail in the coffin, the most popular Nostr client just added a reads section, supporting longform content. Nostr freaks like to talk about sovereignty and decentralization and owning your online identity, but the main attraction will probably be zaps, interconnectivity, and a more optimal UX.
Npub.pro, Cypher.space, Blogspot.io, Highlighter, Stacker News, Primal 2.0 and Yakihonne, are just the beginnings, but offer an amazing glimpse at what the future has in store. Keep in mind that these sites are sharing an average of around 10k daily active users, we'll see an explosion of content and a diversity of content because these platforms offer incentives and functionalities that you don't see elsewhere, as bitcoin becomes less taboo, and as the early adopter phase of these products comes to a close, we'll probably see v4v censorship resistance and digital ownership immensely supporting the underdog, the same underdog that just came over for the ease of use and hype.
So with that being said, highlight away. Let me know what you guys think about blogging on Nostr and if you think these are just the ramblings of a madman, or bland and obvious observations.
Thanks, Hustle
originally posted at https://stacker.news/items/781159
-
 @ 9358c676:9f2912fc
2024-11-24 16:44:55
@ 9358c676:9f2912fc
2024-11-24 16:44:55OBJECTIVE
Establish a hospital guide for thromboembolism prophylaxis in patients admitted to our center, aiming to increase safety in its indication, reduce the incidence of venous thrombosis events in at-risk patients, and minimize adverse effects related to thromboprophylaxis.
SCOPE
All patients over 16 years of age admitted to our institution.
RESPONSIBILITIES
Institution physicians from Hematology Services, Surgical Services, Medical Clinic Service, Intensive Care Unit (ICU), and Coronary Unit (CCU). Nursing Coordination. Nursing Department Head. Pharmacy Service.
REFERENCES AND BIBLIOGRAPHY
- Updated recommendations for prophylaxis of venous thromboembolic disease in Argentina. Fernando J. Vazquez et al. MEDICINA (Buenos Aires) 2020; 80: 69-80.
- American Society of Hematology 2018 guidelines for management of venous thromboembolism: prophylaxis for hospitalized and nonhospitalized medical patients. Blood Advances. Holger J. Schünemann et al. DOI 10.1182/bloodadvances.2018022954
- High-dose versus low-dose venous thromboprophylaxis in hospitalized patients with COVID-19: a systematic review and meta-analysis. Emanuele Valeriani et al. Internal and Emergency Medicine (2022) 17:1817–1825. https://doi.org/10.1007/s11739-022-03004-x
- Recommendations for the use of thromboprophylaxis in hospitalized COVID-19 patients in Argentina. Fernando J. Vazquez et al. MEDICINA (Buenos Aires) 2020; Vol. 80 (Suppl. III): 65-66. ISSN 1669-9106
INTRODUCTION
Thromboembolic prophylaxis in hospitalized patients is a critical intervention to reduce the risk of thrombotic events, one of the leading causes of morbidity and mortality in hospitals. Prolonged immobilization, along with other risk factors such as surgeries, trauma, comorbidities, and specific treatments, significantly increases the possibility of developing deep vein thrombosis (DVT) or pulmonary embolism (PE), which are serious conditions requiring rapid intervention and can threaten the patient's life.
In Argentina, the incidence of venous thromboembolism in hospitalized patients is high and represents a significant clinical challenge. It is estimated that hospitalization increases the likelihood of a thromboembolic event by 10 times compared to the general population. Implementing effective thromboprophylaxis strategies can reduce this incidence, optimizing patient safety and reducing both the costs associated with complications and the duration of hospitalization.
This guide aims to standardize the use of thromboprophylaxis in our institution, improving the identification of at-risk patients and promoting safe interventions based on updated scientific evidence.
GENERAL RECOMMENDATIONS FOR THROMBOPROPHYLAXIS
General indications for thromboprophylaxis are essential to ensure safety and effectiveness in preventing thromboembolic events. The following general recommendations are provided:
Patients without prior anticoagulation: Recommendations apply only to patients who were not receiving oral anticoagulation before hospitalization. Initial Evaluation: Prior to starting prophylaxis, a complete blood count, prothrombin time, aPTT, platelet count, and an estimation of renal function through creatinine clearance should be obtained. Conditions for Surgical Patients: All recommendations for surgical patients assume no intraoperative hemorrhagic complications and adequate hemostasis. Special Cases Evaluation: Prophylaxis in patients with extreme weight (under 40 kg or over 100 kg) or renal insufficiency with a clearance of less than 30 ml/min should be evaluated by a Hematology specialist. Early Mobilization: Routine early mobilization is recommended for all patients, as long as it is safe.RISK SCALE APPLICATION
The assessment of thromboembolic event risk should begin with correct categorization of the patient.
Risk Factors for Venous Thromboembolism (VTE) during hospitalization include: prolonged immobility (more than 2 days in bed), active neoplasms, stroke, heart failure, chronic obstructive pulmonary disease, acute infections, rheumatoid arthritis, ANCA-positive vasculitis, and inflammatory bowel disease. These clinical conditions account for approximately 75% of fatal pulmonary thromboembolisms (PE), highlighting the importance of adequate antithrombotic prophylaxis. Risk scales are designed to categorize both thromboembolic risk and bleeding risk associated with thromboprophylaxis. The bleeding risk, whether major or clinically relevant, increases with the use of pharmacological prophylaxis. However, fatal bleeding is 10 times less frequent than fatal PE.CONTRAINDICATIONS FOR THROMBOPROPHYLAXIS
General contraindications for pharmacological thromboprophylaxis in hospitalized patients aim to prevent hemorrhagic complications. The main contraindications are:
Clinically significant active hemorrhage. Platelet count less than 30,000 platelets/ml. Major bleeding disorders. Active intracranial hemorrhage. Recent peri-spinal hemorrhage. Recent surgery with a high risk of bleeding.It is crucial to carefully evaluate these contraindications before initiating any thromboprophylaxis protocol.
INDICATION FOR THROMBOPROPHYLAXIS IN NON-SURGICAL HOSPITALIZED PATIENTS
Validated scales help categorize the risk and indication for venous thromboembolism (VTE) in hospitalized patients with non-surgical conditions: the IMPROVE-VTE scale, which considers a high risk for scores above 2 and very high risk for scores above 4, with additional factors such as elevated D-dimer, advanced age, cancer history, or previous VTE.
To assess bleeding risk, the IMPROVE-Bleed scale identifies high risk with scores of 7 or higher. Patients with high VTE risk and low bleeding risk should receive prophylaxis until discharge, and in high-risk cases, it should be extended afterward.
Improve VTE Scale Risk Factors and Points
Patient History Previous VTE: 3 points Recent surgery (within 30 days): 2 points Active cancer: 2 points History of trauma: 1 point Clinical Factors Age 40-60 years: 1 point Age over 60 years: 2 points Obesity (BMI > 30): 1 point Prolonged immobility (e.g., bed rest for more than 3 days): 2 points Laboratory Findings Elevated D-dimer: 1 point Medication Use Hormonal therapy (e.g., oral contraceptives, hormone replacement therapy): 1 point Recent chemotherapy: 2 points Physical Examination Signs of deep vein thrombosis (DVT) such as swelling, pain, or tenderness in the legs: 2 pointsScoring and Risk Levels
Total Score Calculation: Add the points from all applicable categories. Risk Levels: 0-2 points: Low Risk - Standard care; consider early mobilization. 3-5 points: Moderate Risk - Consider mechanical prophylaxis (e.g., compression stockings) and/or pharmacologic prophylaxis. 6+ points: High Risk - Strongly consider pharmacologic prophylaxis (e.g., anticoagulants) and close monitoring.IMPROVE-Bleed Scale for Bleeding Risk Assessment Risk Factors and Points
Creatinine clearance < 60 ml/min: 1 point Creatinine clearance < 30 ml/min: 2.5 points Male sex: 1 point Age > 40: 1.5 points Age > 85: 3.5 points Active cancer: 2 points Rheumatic disease: 2 points Central venous catheter: 2 points Admission to Intensive Care Unit or Coronary Care Unit: 2.5 points Liver failure (INR > 1.5): 2.5 points Platelets < 50,000/µl: 4 points Bleeding in the last 3 months: 4 points Active gastroduodenal ulcer: 4.5 pointsScore Interpretation
Total Score: 7 or more: High bleeding risk, with a bleeding probability of 4% or more.General Recommendations for Thromboprophylaxis in Hospitalized Patients with Medical Conditions Without Surgery
Population: High or moderate risk of thrombosis and low risk of bleeding Recommendation: Critical: Enoxaparin 40 mg every 24 hours; Non-critical: Enoxaparin 40 mg every 24 hours. Alternative: Unfractionated heparin 5000 U every 8 or 12 hours. Comments: Until discharge; may consider prolonging in very high-risk patients. Population: High risk of thrombosis and high risk of bleeding Recommendation: IPC or CG. Alternative: - Comments: - Population: Patients with creatinine clearance less than 30 ml/min Recommendation: Unfractionated heparin 5000 U every 8 or 12 hours. Alternative: - Comments: Reassess pharmacological prophylaxis when there is low bleeding risk. Until discharge; may consider prolonging in very high-risk patients. Population: Patients with ischemic stroke Recommendation: Enoxaparin 40 mg every 24 hours. Alternative: IPC. Comments: Initiate within the first 24 hours. Until discharge; may consider prolonging in very high-risk patients. Population: Patients with intracranial hemorrhage (ICH) Recommendation: IPC or CG for 48 to 72 hours after stabilization of bleeding, then Enoxaparin 40 mg every 24 hours. Alternative: IPC. Comments: Hemorrhage control should be monitored with imaging and evolution. Until discharge; may consider prolonging in very high-risk patients. Population: Patients with subarachnoid hemorrhage (SAH) Recommendation: IPC or CG for 48 to 72 hours after vascular exclusion or surgical resolution of the aneurysm, then Enoxaparin 40 mg every 24 hours. Alternative: IPC. Comments: Hemorrhage control should be monitored with imaging and evolution. Until discharge; may consider prolonging in very high-risk patients.References
UFH: unfractionated heparin IPC: intermittent pneumatic compression CG: graduated compression stockings CVA: cerebrovascular accident ICH: intracranial hemorrhage SAH: subarachnoid hemorrhageRECOMMENDATIONS FOR THROMBOPROPHYLAXIS IN HOSPITALIZED PATIENTS WITH NON-SURGICAL CLINICAL DISEASES
Population Recommendation Alternative Comments Duration High or moderate VTE risk with low bleeding risk Enoxaparin 40 mg every 24 hours (critical); Enoxaparin 40 mg every 24 hours (non-critical) Unfractionated heparin (UFH) 5000 U every 8 or 12 hours Until discharge, may be extended for very high-risk patients High VTE risk and high bleeding risk CNI or MCG
Creatinine clearance < 30 ml/min UFH 5000 U every 8 or 12 hours Reevaluate when bleeding risk is low Until discharge, may be extended for very high-risk patientsINDICATION FOR THROMBOPROPHYLAXIS IN SURGICAL PATIENTS WITH NON-ORTHOPEDIC SURGERY
In non-ambulatory surgeries, the risk of venous thromboembolism (VTE) varies depending on the patient's risk factors and the type of surgery. Thus, individual risk stratification using the Caprini scale is imperative. Patients undergoing general surgery with moderate or higher thrombotic risk (3 points or more) and no increased bleeding risk should receive pharmacological thromboprophylaxis.
CAPRINI SCALE
Caprini Risk Assessment Model Risk Factors and Points
History of VTE Previous VTE: 3 points Active Cancer Current or recent cancer (within 6 months): 3 points Receiving treatment for cancer: 3 points Surgery/Trauma Major surgery (e.g., orthopedic, abdominal) with general anesthesia: 2 points Trauma with hospitalization: 2 points Minor surgery with general anesthesia: 1 point Age Age 41-60 years: 1 point Age 61-74 years: 2 points Age 75 years or older: 3 points Obesity BMI 30-39: 1 point BMI 40 or greater: 2 points Immobility Bed rest for more than 3 days: 2 points Paraplegia or quadriplegia: 2 points Hormonal Therapy Current use of estrogen-containing medications (e.g., oral contraceptives, hormone replacement therapy): 1 point Other Risk Factors History of heart failure or chronic lung disease: 1 point History of inflammatory bowel disease: 1 point History of stroke: 1 point Varicose veins: 1 point Recent travel (long-distance travel > 4 hours): 1 pointScoring and Risk Levels
Total Score Calculation: Add the points from all applicable categories. Risk Levels: 0-1 points: Low Risk - Standard care; consider early mobilization. 2-3 points: Moderate Risk - Consider mechanical prophylaxis (e.g., compression stockings). 4-5 points: High Risk - Consider pharmacologic prophylaxis (e.g., anticoagulants) and mechanical methods. 6+ points: Very High Risk - Strongly consider pharmacologic prophylaxis and close monitoring.Interpretation of Caprini Scale Score: Total Score Risk Level Recommendation Comments Duration 0-1 Low Early ambulation Until discharge 2-3 Moderate CNI or MCG Begin before surgery Until discharge 4 or more High Enoxaparin 40 mg every 24 hours or UFH 5000 U every 8 or 12 hours Administer the dose 12 hours before abdominal or pelvic surgery, restart 12 hours post-procedure Minimum 7-10 days; extend up to 28 days post-surgery for oncologic patients or those with low bleeding risk
INDICATION FOR THROMBOPROPHYLAXIS IN ORTHOPEDIC SURGERY PATIENTS
Major orthopedic surgeries, including total hip arthroplasty (THA), total knee arthroplasty (TKA), and hip fracture surgery (HFS), pose a high risk of thrombotic complications (40%-60% without proper thromboprophylaxis). Pharmacological prophylaxis is always recommended regardless of individual risk factors.
Special Considerations:
In outpatient knee arthroscopy, early ambulation is encouraged. Prophylaxis with low molecular weight heparin (LMWH) for at least 7 days should be considered only in patients with high thrombotic risk (e.g., cancer, prior VTE, obesity, pregnancy, or postpartum). For immobilization lasting more than 7 days due to fractures, tendinous/cartilaginous ruptures, or soft tissue injuries below the patella with risk factors, pharmacological prophylaxis with LMWH is recommended. In spinal surgeries, mechanical prophylaxis with graduated compression stockings (GCS) and early ambulation are advised. For prolonged procedures (> 1 hour) with risk factors, pharmacological prophylaxis (Enoxaparin 40 mg/day or UFH 5000 U every 8-12 hours) is recommended 24 hours post-surgery until discharge. Major trauma patients should receive mechanical prophylaxis (CNI or GCS) combined with Enoxaparin 40 mg/day, provided there is no increased bleeding risk, from admission to discharge, including the rehabilitation period.Recommendations for Orthopedic Surgery: Population Recommended Indication Alternative Comments Duration Scheduled hip and knee surgery Apixaban 2.5 mg every 12 hours None Start 12 hours after surgery 28-35 days (hip), 14 days (knee), extend up to 35 days Dabigatran 220 mg every 24 hours None Start 110 mg 4 hours after surgery, then continue with 220 mg
Enoxaparin 40 mg every 24 hours None Start 12 hours after surgery
Rivaroxaban 10 mg every 24 hours None Start 6 hours after surgery Hip fracture Enoxaparin 40 mg every 24 hours UFH 5000 U every 8 or 12 hours Administer from admission and 8-12 hours before surgery; restart 8-12 hours post-surgery 14-35 daysINDICATION FOR THROMBOPROPHYLAXIS IN OBSTETRICS
Postpartum hemorrhage is the leading cause of maternal death in developing countries, while venous thromboembolic disease (VTE) is the leading cause in developed countries. Pregnant women are 4-10 times more likely to develop VTE than non-pregnant women. Although the incidence of VTE during pregnancy is low (1-2 per 1000 pregnancies), it is considered a preventable cause of maternal death.
INDICATION FOR THROMBOPROPHYLAXIS IN COVID-19 HOSPITALIZED PATIENTS
COVID-19 infection is associated with an increased risk of venous thromboembolism, particularly in ICU patients. These patients are considered at high thrombotic risk during hospitalization, with significantly elevated D-dimer levels linked to greater risk of severe complications, including death and disseminated intravascular coagulation.
Recommendations:
Thromboprophylaxis with subcutaneous Enoxaparin 40 mg/day is suggested for all hospitalized patients with severe COVID-19, provided no contraindications exist, throughout their hospital stay. -
 @ 4874b840:31b0b8c0
2024-11-24 16:39:18
@ 4874b840:31b0b8c0
2024-11-24 16:39:18Редакция «Калининград 2040» с гордостью объявляет, что мы стали самым цитируемым изданием года! Это достижение стало возможным благодаря вашей поддержке и интересу к нашим материалам. Мы всегда предоставляем вам актуальную, качественную и проверенную информацию о событиях нашего города. Мы работаем над тем, чтобы освещать важные темы, высказывать мнения экспертов и гостей. Ваши репосты, комментарии и обсуждения наших материалов вдохновляют нас становиться всё лучше и помогают нам расти. Благодарим вас за активное участие в жизни нашего издания! Каждый ваш отзыв и каждое ваше мнение имеют для нас огромное значение. Мы ценим вашу преданность и доверие, которые мотивируют нас продолжать нашу работу. Трудно поверить, что начиная наш проект с командой из 4х человек, имея только бешеное желание работать и приносить пользу людям, мы смогли добиться таких высот. В следующем году мы предоставим еще больше интересных материалов, эксклюзивных интервью и аналитических статей. Мы надеемся, что вы остаетесь с нами на этом пути! Спасибо, что вы с нами! Вместе мы сделаем «Калининград 2040» ещё лучше!
-
 @ 9c47bb51:000381d0
2024-11-24 16:34:49
@ 9c47bb51:000381d0
2024-11-24 16:34:49The concept of Near-Death Experiences (NDEs) has captivated human curiosity for decades, blending the realms of science, spirituality, and the mysteries of consciousness. These profound experiences, reported by individuals who have come close to death, offer glimpses of what might lie beyond the physical world. NDEs typically include vivid visions, encounters with loved ones, feelings of peace, and a sense of transcending the body. But what do they truly mean? And what can we learn from them?
The modern exploration of NDEs began with Dr. Raymond Moody, who brought the phenomenon to mainstream attention with his groundbreaking 1975 book, Life After Life. In it, Moody documented over 150 accounts of people who described similar out-of-body experiences, journeys through tunnels of light, and encounters with an overwhelming sense of love. His work was among the first to systematize and analyze NDEs, sparking a wave of research into what had often been dismissed as anecdotal or hallucinatory. Moody coined the term “Near-Death Experience,” forever changing the discourse around these events.
**Dr. Eben Alexander: A Neurosurgeon’s Extraordinary Journey ** One of the most compelling modern stories of an NDE comes from Dr. Eben Alexander, a neurosurgeon who once believed that consciousness was entirely a product of the brain. In his book, Proof of Heaven: A Neurosurgeon’s Journey into the Afterlife, Alexander recounts his near-death experience during a seven-day coma caused by a severe case of bacterial meningitis. Despite his brain being severely damaged and non-functional by medical standards, Alexander experienced vivid visions of an otherworldly realm.
During his NDE, he described being guided by a being of light, feeling enveloped by an overwhelming sense of love, and encountering a divine presence. When he awoke, he was profoundly changed, no longer dismissing the possibility of consciousness existing beyond the brain. His story has added credibility to the discussion of NDEs, particularly among skeptics and scientists.
**The Common Themes of NDEs ** NDEs share strikingly similar elements across cultures and individuals, which has fueled theories that they may represent a universal aspect of human experience. Some of these common features include: • Out-of-body experiences: A sensation of observing oneself from outside the body, often floating above. • The tunnel of light: Moving through a tunnel toward a radiant, welcoming light. • Feelings of peace and unconditional love: A deep sense of comfort and acceptance. • Encounters with deceased loved ones or spiritual beings: Meetings that feel profoundly real and comforting. • Life review: A panoramic replay of one’s life, accompanied by insights into one’s actions and relationships.
**Scientific and Spiritual Perspectives ** The study of NDEs continues to be a fascinating intersection of science and spirituality. Some scientists argue that NDEs can be explained by physiological processes, such as a lack of oxygen to the brain, surges of neurochemicals, or the brain’s final attempt to make sense of its surroundings as it shuts down. Others, however, point to the consistency of NDE accounts and the vivid, lucid memories of these experiences as evidence of something more profound.
For example, research by cardiologist Dr. Pim van Lommel found that many individuals who had been clinically dead for several minutes reported detailed and coherent NDEs, even when brain activity was absent. These findings challenge materialistic assumptions about consciousness, suggesting that it may not be entirely tied to the brain.
**Amazing Stories of NDEs ** Beyond the work of Dr. Moody and Dr. Alexander, countless other stories reveal the transformative power of NDEs. Take the case of Anita Moorjani, who experienced an NDE during a near-fatal bout with cancer. In her book, Dying to Be Me, Moorjani recounts how she felt transported to a realm of boundless love, where she understood the interconnectedness of all life. Upon returning to her body, she made a miraculous recovery and has since dedicated her life to sharing her experience.
Or consider the story of Mary Neal, an orthopedic surgeon who drowned during a kayaking accident. In her book, To Heaven and Back, Neal describes her journey into a realm of indescribable beauty, where she felt a divine presence and learned profound truths about love and purpose.
**The Transformative Impact of NDEs ** For many, the most significant aspect of an NDE isn’t the experience itself but the lasting change it brings. Those who undergo NDEs often report a complete shift in their perspective on life, becoming less fearful of death, more compassionate, and deeply focused on living a meaningful life. They describe feeling connected to something greater than themselves, with a renewed sense of purpose.
**The Ongoing Mystery ** While science has yet to provide definitive answers about NDEs, their consistency, emotional depth, and transformative impact make them impossible to dismiss. They challenge our understanding of consciousness, death, and the nature of reality. Whether viewed as physiological phenomena, spiritual journeys, or something in between, NDEs continue to inspire awe and curiosity.
Dr. Raymond Moody once wrote, “The question of what happens after death has challenged humanity for millennia.” Through the lens of NDEs, we catch a glimpse of what might lie beyond—a mystery that invites exploration, discussion, and perhaps, a bit of faith.
So, what do you think? Are NDEs a window into another reality or simply the brain’s final act? One thing is certain: the stories of those who have returned from the brink continue to captivate, inspire, and transform the way we think about life, death, and what comes next.
-
 @ 4874b840:31b0b8c0
2024-11-24 16:30:16
@ 4874b840:31b0b8c0
2024-11-24 16:30:16Открытие памятника, посвящённого роботу-кошке, ставшего символом современных технологий и инноваций в области робототехники прошло 14 декабря в Зеленогорске. Памятник был установлен в центре города и стал первой скульптурой такого рода в России. Мэр Зеленогорска отметила, что этот памятник не только увековечивает достижения в области технологий, но и вдохновляет молодое поколение на изучение науки и инженерии. Памятник изображает робота-кошку в динамичной позе, что символизирует движение вперед и стремление к новым открытиям. Участники мероприятия смогли наблюдать за мастер-классами по робототехнике, где были представлены современные разработки и технологии. Создание памятника стало возможным благодаря инициативе местных жителей и поддержке научного сообщества. Он уже привлек внимание туристов и стал новым проявлением притяжения для любителей технологий.
Открытие памятника роботу-кошке — это не только достижение демократии в науке, но и важный шаг к популяризации технологий среди молодежи. Мы надеемся, что этот памятник вдохновил новое поколение в изучении робототехники и инженерии, открывая новые горизонты для будущих изобретений. - Отметила мэр города.
-
 @ 3f0702fa:66db56f1
2024-11-24 15:56:51
@ 3f0702fa:66db56f1
2024-11-24 15:56:51https://psv4.userapi.com/s/v1/d/FQYaS-3TVpEbCJMuPnlpUUX9shzHVNIPGFodPGko5Nf5T5lT-R37SWHf8Vhh_JhxBEB78aPGC6U7aa3SKYSs4XLBTyL6mF8bY20cFtIKFIBN2PmHZBfUNA/Untitled_2.mp4
-
 @ 3f0702fa:66db56f1
2024-11-24 15:56:06
@ 3f0702fa:66db56f1
2024-11-24 15:56:06https://psv4.userapi.com/s/v1/d/FQYaS-3TVpEbCJMuPnlpUUX9shzHVNIPGFodPGko5Nf5T5lT-R37SWHf8Vhh_JhxBEB78aPGC6U7aa3SKYSs4XLBTyL6mF8bY20cFtIKFIBN2PmHZBfUNA/Untitled_2.mp4
-
 @ 8d34bd24:414be32b
2024-11-24 15:41:30
@ 8d34bd24:414be32b
2024-11-24 15:41:30In America, there are a lot of people who call themselves Christians, but not nearly as many that live a life devoted to Christ. When I was a young Christian, one teacher or pastor made the comment, “If someone was accusing you of being a Christian, would there be enough evidence to convict you?” For so many “Christians,” I don’t think the answer would be, “Yes,” unless the only requirement was showing up for church most Sundays.
It amazes me how many Christians have never read their Bible cover to cover, from Genesis to Revelation. It amazes me how many Christians don’t pray daily. It amazes me how many Christians live lives like every other person except they attend church on Sunday (at least most of the time). Some people who call themselves Christians don’t even attend church. What makes these Christians any different than the unbelievers around the world?
If we truly have been saved from our sins by a merciful, all-powerful God, then we should be grateful. If we are actually a “new creation,” there should be signs of a changed life. If we know Jesus and know that everyone who rejects Him will be rejected by God and spend an eternity in Hell, then we should at least be sharing the Gospel with those we care about.
In my Bible study today, I read Isaiah 55. These verses really spoke to me about how our faith should affect our lives.
1“Ho! Every one who thirsts, come to the waters;\ And you who have no money come, buy and eat.\ Come, buy wine and milk\ Without money and without cost.
Jesus has called Jew and gentile to repent and has offered His forgiveness and salvation to all who trust in Him. It doesn’t cost anything. It just requires faith. Jesus paid the price, so we don’t have to.
2Why do you spend money for what is not bread,\ And your wages for what does not satisfy?\ Listen carefully to Me, and eat what is good,\ And delight yourself in abundance.
We are given the free gift of salvation and yet we are constantly seeking other things. We put all of our hard effort into seeking things that don’t satisfy. We seek fame or wealth or popularity or entertainment or pleasure. We don’t seek our Creator’s blessing. We don’t seek to serve and please our Savior. We complain about any and all hardships instead of being thankful for what we have. Why don’t we crave God’s word and His fellowship?
3Incline your ear and come to Me.\ Listen, that you may live;\ And I will make an everlasting covenant with you,\ According to the faithful mercies shown to David.
As believers we should “incline our ear,” “come to Him,” and “listen.” We should read the Bible, study the Scriptures, and pray with a listening spirit. God is faithful, but we won’t be blessed when we turn our backs on God.
4Behold, I have made him a witness to the peoples,\ A leader and commander for the peoples.
David was called “a man after God’s own heart,” and therefore God promised that a descendant of his would always be on the throne of Israel. This promise was fulfilled in Jesus — God’s son’s incarnation as a descendant of David, biologically through His mother Mary and legally through His step-father Joseph. David’s faith is an example to us of trusting fully in God and His promises.
5Behold, you will call a nation you do not know,\ And a nation which knows you not will run to you,\ Because of the Lord your God, even the Holy One of Israel;\ For He has glorified you.”
Most promises in the Old Testament are made to Israelites or descendants of Abraham, but there are a few promises made to the gentiles of the world, who will be blessed by the “Holy One of Israel,” Jesus Christ. We gentiles should be grateful that God’s promises have been shared with us and with those of every tongue, people, and nation. We have been reconciled to God through His holy life and the blood He shed for us. How can we possibly take this blessing for granted?
6Seek the Lord while He may be found;\ Call upon Him while He is near.
Right now we have the option to trust in Jesus1 and to receive His blessing, but this time will not last forever. In fact, I believe time is growing short. If you don’t know Jesus, don’t put off repenting and trusting in Him. If you do know Jesus, don’t put off getting your life right and following Him. Doing good deeds won’t get you into heaven, but it is pleasing to God and does lead to special blessings. We are to make the most of the time we have left.
7Let the wicked forsake his way\ And the unrighteous man his thoughts;\ And let him return to the Lord,\ And He will have compassion on him,\ And to our God,\ For He will abundantly pardon.
Technically there is nothing we can do to earn Salvation and forgiveness, but if we have been saved and forgiven, the Bible says “we are a new creation.” There will be signs of change if the salvation is real. God wants the wicked to forsake his way, the unrighteous to forsake his thoughts, and for everyone to return to Jesus as Lord. “If we confess our sins, He is faithful and righteous to forgive us our sins and to cleanse us from all unrighteousness.” (1 John 1:9)
8“For My thoughts are not your thoughts,\ Nor are your ways My ways,” declares the Lord.
If we are living according to our own wisdom and our own power, we are living to fail. It is only when we fully submit to God’s word and God’s plan, that we become what we were created to be. It is only then that we will feel complete and will honor our Creator.
We can’t obey God, if we don’t know His commands. We can’t trust Jesus, if we don’t know who He really is. We can’t serve God, if we haven’t submitted to the power and will of His Spirit. We can’t just drift down the river of life, but need to be driven and empowered by His power like the wind blowing a sailboat. The best way to know God’s commands, His character, and His plan is to know His word, the Bible. We can’t know this if we don’t read it and read all of it.
9“For as the heavens are higher than the earth,\ So are My ways higher than your ways\ And My thoughts than your thoughts.
There are so many times in the Bible that we are told that man’s wisdom is folly, yet so often we trust in what man tells us rather than what God tells us. We spend our efforts listening to human “experts” instead of listening to the words of the God who created everything “… and upholds all things by the word of His power. …” (Hebrews 1:3b) We can learn from wise and learned men, but we will never learn true wisdom except from God.
10For as the rain and the snow come down from heaven,\ And do not return there without watering the earth\ And making it bear and sprout,\ And furnishing seed to the sower and bread to the eater;
> 11*So will My word be which goes forth from My mouth;\
It will not return to Me empty,\ Without accomplishing what I desire,\ And without succeeding in the matter for which I sent it.
God’s word never returns empty. It always changes all it touches. We need to put in the effort to schedule time in God’s word every day. We should make sure we have read the whole Bible, so we can use Scripture to interpret Scripture instead of trusting solely on the wisdom of man. We need to take all of our concerns to God and follow His leading. We need to find fellow believers “and let us consider how to stimulate one another to love and good deeds, not forsaking our own assembling together, as is the habit of some, but encouraging one another; and all the more as you see the day drawing near.” (Hebrews 10:24-25)
I hope you all will live lives in such a way as to honor God and let all men know that you belong to Jesus.
Trust Jesus.
-
 @ 2775fb0f:887f8193
2024-11-24 15:16:15
@ 2775fb0f:887f8193
2024-11-24 15:16:15Новодвинск, 1 октября 2040 года — В этом году Новодвинск отмечает 70-летие своего основания, и празднование стало не только поводом для торжеств, но и возможностью вспомнить богатую историю города и его традиции. На протяжении всей своей истории Новодвинск сохраняет уникальную культуру, которая отражает дух местных жителей и их привязанность к родному краю.
Праздничные мероприятия стартовали с выставки «История Новодвинска в лицах», открывшейся в городском музее. Здесь представлены архивные фотографии, документы и предметы быта, рассказывающие о становлении и развитии города. «Мы хотели показать, как менялся наш город на протяжении десятилетий, и какие традиции передаются из поколения в поколение», — отметила директор музея, Елена Соколова.
В центре города прошел праздничный концерт, в котором приняли участие местные творческие коллективы. Зрители наслаждались выступлениями театров, танцевальных ансамблей и музыкальных групп, которые исполнили как современные, так и народные песни. «Мы стараемся сохранить наши традиции, и такие мероприятия помогают объединить людей и передать любовь к культуре молодому поколению», — поделилась впечатлениями участница одного из ансамблей, Анна Кузнецова.
Одним из самых ярких событий праздника стал «Парад традиций», где жители города могли продемонстрировать свои умения и навыки. Мастера народного творчества представили свои изделия: резьбу по дереву, вышивку и керамику. Все желающие могли попробовать себя в различных ремеслах, что вызвало большой интерес у детей и взрослых. «Это замечательная возможность узнать больше о своих корнях и традициях, которые делают наш город уникальным», — отметил участник парада, студент местного колледжа.
Не обошлось и без гастрономического фестиваля, где были представлены блюда местной кухни. Жители и гости города могли попробовать традиционные новодвинские угощения, такие как рыба, выловленная в Северной Двине, и домашние пироги. «Кулинарные традиции — это неотъемлемая часть нашей культуры, и мы гордимся тем, что можем их сохранить и передать будущим поколениям», — подчеркнула организатор фестиваля, Мария Иванова.
Празднование завершилось ярким фейерверком, который озарил небо над Новодвинском и стал символом единства и гордости за родной город. «Сохранение традиций — это то, что делает нас сильнее и помогает нам двигаться вперед. Мы должны помнить свою историю и гордиться ею», — резюмировала глава города, Анна Петрова.
Таким образом, Новодвинск не только отпраздновал свой юбилей, но и подтвердил свою приверженность к сохранению культурного наследия, создавая пространство для диалога между поколениями и укрепляя общие традиции.
-
 @ 04d9fac9:5bec0e6c
2024-11-24 14:17:37
@ 04d9fac9:5bec0e6c
2024-11-24 14:17:37В Воркуте состоялось открытие нового жилого комплекса.
Жилой комплекс способен вместить в себя более 1000 семей.
В Воркуте состоялось торжественное открытие нового жилого комплекса "Северный уголок". Этот проект стал результатом совместных усилий местных властей и инвесторов, направленных на улучшение жилищных условий жителей города.
Комплекс включает 1250 квартир различной планировки и оснащён современными удобствами, включая детские площадки и зоны отдыха. Ожидается, что новый жилой фонд привлечет молодые семьи и специалистов, что будет способствовать дальнейшему развитию Воркуты как ключевого центра в Арктическом регионе
-
 @ 04d9fac9:5bec0e6c
2024-11-24 14:14:47
@ 04d9fac9:5bec0e6c
2024-11-24 14:14:47В 2044 году Воркута открывает новый ледовый дворец "Северное сияние", который стал важным шагом в развитии спортивной инфраструктуры города. Комплекс площадью 10,000 квадратных метров включает ледовую арену, тренажерные залы и зоны для массовых катаний. Открытие состоялось с участием известных спортсменов и зрелищного шоу. Дворец будет служить базой для хоккейных команд и фигуристов, а также местом для культурных мероприятий. Этот проект поддерживает федеральную программу по развитию спорта и физической культуры в России, что подчеркивает стремление Воркуты к активному развитию спорта
-
 @ 7fd6bed7:cd87b428
2024-11-24 14:00:15
@ 7fd6bed7:cd87b428
2024-11-24 14:00:15Want to sell your house fast? PDX Home Buyers is your trusted partner to buy your house in Oregon. We purchase homes in any condition and offer cash deals to fit your timeline. Whether you’re moving, dealing with financial challenges, or inheriting unwanted property, we make the process easy. Avoid the hassle of repairs, showings, or agent commissions—we handle everything. Our team ensures a seamless and fair transaction with complete transparency. If you’re saying, "Who will buy my house in Oregon?" the answer is PDX Home Buyers. Contact us now for a quick and fair cash offer!
-
 @ a39d19ec:3d88f61e
2024-11-24 13:59:17
@ a39d19ec:3d88f61e
2024-11-24 13:59:17This week's practical 3d print is a desk organiser.
Desk organiser
Desk organisers come in a lot of forms and colours. But you can be sure that they are used daily. The photo shows the one at my workplace.
If you search printables.com for "desk organiser" I am sure you will find the one that fits your needs and look as well.
-
 @ a39d19ec:3d88f61e
2024-11-24 13:51:38
@ a39d19ec:3d88f61e
2024-11-24 13:51:38This month's daily driver was the Casio Edifice EF-512D-1AV.
Design
The 1AV version features 32 mm dial has nice big hands showing hour and minute on a black background. The 4AV has a darkish red background which looks good, too. The hour indicators are quite massive, which makes it readable. The date is a 3 o clock the chronometers are in standard layout. The yellow hand for the stopwatch and other yellow accents give it a nice touch.
In it for the tech
The Module 2328 needs a SR927W battery which lasts about 2 years. It's accuracy is +/-20 seconds a month. The hour and minutes are shown on the big dial, seconds on the small one at 6 o'clock. The case and band is made of stainless steel the screen is made of mineralglas.
Storytime
This watch is a gift from my in-laws I guess it was for Christmas sometimes between 2007-2009. I still like the kind of timeless design. No trendlines in the watch which makes it suitable for a lot of events.
-
 @ 2e6b65e5:336f2264
2024-11-24 13:03:50
@ 2e6b65e5:336f2264
2024-11-24 13:03:50I have long thought that if individuals could access information on the trades that were being made by large institutions using high frequency trading techniques that it might be possible to tag along with those trades on a much smaller scale in a low frequency trading way. I first starting looking at this before the financial crisis back in 2008 but was never able to access the data necessary to accomplish this task at a reasonable price.
Fast forward to today and the sources of real time data have dramatically increased in number and the pricing for access to this data have fallen to levels that are accessible to individuals who have the knowledge and expertise to access it.
Also over this time period the tools for data analysis and the hardware to run them on have undergone rapid evolution and the scope of the analysis that one would only dream of being able to do in 2008 is now accessible with modest budgets and manageable levels of manpower.
Python, Polars, Bokeh, Jupyter notebooks and AI based code generators have dramatically impacted what can be done with a manhour of programming. Processors with 24 cores and previously unattainable amount of memory and storage can now be purchased by anyone with a modest budget.
The primary thesis of this work is that there are fingerprints left by the various players in the HFT space that manifest themselves in the fluctuations in the order book both for individual securities and sets of individual securities as well as the options on those securities that can be observed and used as factors in algorithms that predict short term movement in the price of the those securities.
In the past I have worked with others who have developed tools for exposing these fingerprints and published automated messages to X (while it was still Twitter) throughout the trading day. Recently I have at least temporarily suspended activities on X and have been experimenting with NOSTR as a means of "socializing" this information.
During the course of the trading day I run code that identifies events that, based on their fingerprints in the order book, can only be generated by machines and have been selecting "interesting" events for posting @Ki2 Knowledge Implementations using Primal.
I periodically post summary information regarding overall activity that has been flagged as "Burst Activity" in the form of a tuple indicating Overall_Bursts /Bursts_Flagged_Buy /Bursts_Flagged_Sells /Bursts_Unclassified. So 175/76/94/5 means 175 instances identified as "Bursts" with 76 flagged "Buys" and 94 flagged "Sells" and 5 unflagged.
At the end of each trading day I present a "Daily Wrap" of the individual tickers that had activity that exceeds a threshold in a 1 second interval and the number of times that ticker exceed this threshold throughout the day.
Also at the end of the day I total up how many times all the individual tickers combined exceeded the threshold.
Together these provided a perspective on the HFT activity and the areas of the market where that activity occurred during the day.
In addition to this "Summary" information I also select individual Over Threshold Events (OTEs) to highlight during the day and sometimes use this information to select individual tickers as "paper trade" ideas for the investing themes that may be behind some of the fingerprints.
For instance, recently I have been reporting standout events related to:
- Treasury securities manifest by $TLT and $TMF
- Bitcoin ETFs manifest by $IBIT, $FBTC, $MSTR etc.
- Crypto "Picks and Shovels" securities that only came on the radar when Burst trades occurred such as $HIVE and $CAN
Also, in the feed I have been dabbling in 0DTE options ideas related to pinning of $SPX as these positions unwind at the close each day.
Of course, all in the interest of searching for actionable ideas and never as recommending or suggesting that any real world trades take place on based on these ideas.
Not sure where all this will lead. There have been man-years worth of effort invested in this so far and many more man-years yet ahead. I am open to suggestions and collaboration moving forward.
So thanks for reading this. If you find this interesting or would like to collaborate, please reach out or follow and as they say in Costa Rica ....Pura Vida and 73
-
 @ fff19d35:43344a0b
2024-11-24 12:28:34
@ fff19d35:43344a0b
2024-11-24 12:28:34The Power of Decentralized Social Networking: Introducing Nostr
In the ever-evolving landscape of social media, a new player has emerged to challenge the status quo. Nostr, a decentralized social networking protocol, is revolutionizing the way we interact online. In this article, we'll delve into the world of Nostr and explore its potential to transform the social media landscape.
What is Nostr?
Nostr is an open-source, decentralized social networking protocol built on blockchain technology. It enables users to create and share content, connect with others, and participate in online communities without relying on centralized platforms.
Key Features of Nostr
- Decentralization: Nostr operates on a decentralized network, ensuring that no single entity controls the platform.
- Censorship Resistance: With Nostr, users have full control over their content and can't be censored by centralized authorities.
- Interoperability: Nostr enables seamless interactions between different social media platforms and applications.
- Monetization: Creators can earn cryptocurrency rewards for producing high-quality content.
Benefits of Nostr
- Increased Autonomy: Users have full control over their online presence and data.
- Improved Security: Decentralized architecture reduces the risk of data breaches and cyber attacks.
- Enhanced Creativity: Monetization incentives encourage creators to produce innovative content.
- Community Building: Nostr fosters a sense of community by enabling users to connect with like-minded individuals.
Conclusion
Nostr represents a paradigm shift in social media, offering a decentralized, censorship-resistant, and community-driven alternative to traditional platforms. As the Nostr ecosystem continues to grow and evolve, it's exciting to think about the potential implications for the future of social media.
-
 @ 88dc84f5:c71164f7
2024-11-24 12:07:38
@ 88dc84f5:c71164f7
2024-11-24 12:07:38Introduction: The rapid advancement of financial technology (fintech) has transformed the way we manage our finances, invest, and conduct transactions. As fintech continues to evolve, we are witnessing the emergence of autonomous financial systems (AFS) that utilize artificial intelligence (AI), machine learning (ML), and blockchain technology. While AFS promises to increase efficiency, reduce costs, and enhance decision-making, it also raises significant ethical concerns.
The Benefits of Autonomous Financial Systems: 1. Increased Efficiency: AFS can automate repetitive tasks, reducing the need for human intervention and minimizing errors. 2. Improved Decision-Making: AI and ML algorithms can analyze vast amounts of data, providing insights that inform investment decisions and risk management strategies. 3. Enhanced Security: Blockchain technology and cryptography ensure the integrity and security of transactions, protecting against fraud and cyber attacks.
The Ethical Concerns: 1. Bias and Discrimination: AI and ML algorithms can perpetuate existing biases and discriminate against certain groups, leading to unfair outcomes. 2. Lack of Transparency and Accountability: AFS can be opaque, making it challenging to understand decision-making processes and assign responsibility for errors or unethical behavior. 3. Job Displacement and Economic Inequality: The automation of financial tasks could lead to significant job displacement, exacerbating economic inequality and social unrest.
Mitigating the Risks: 1. Developing Ethical AI: Encouraging the development of AI that prioritizes fairness, transparency, and accountability. 2. Implementing Robust Regulatory Frameworks: Establishing clear guidelines and regulations to ensure AFS operate within established ethical boundaries. 3. Investing in Education and Training: Preparing workers for the changing job market and providing opportunities for upskilling and reskilling.
Conclusion: The development and deployment of autonomous financial systems pose significant ethical challenges. As we navigate this complex landscape, it is crucial that we prioritize transparency, accountability, and fairness. By acknowledging the potential risks and consequences, we can work towards creating a more equitable and just financial system for all.
AI-Generated Insights: Using natural language processing and machine learning algorithms, our AI analyzed expert opinions and research papers to identify key ethical considerations: 1. Ensuring transparency and explainability in AI decision-making processes 2. Addressing potential biases and discrimination in AI algorithms 3. Developing robust regulatory frameworks to govern AFS
Statistics: 1. 80% of financial institutions plan to increase investment in AI and ML (Source: Deloitte) 2. The global fintech market is projected to reach $305 billion by 2025 (Source: MarketsandMarkets) 3. 60% of consumers believe AI will improve financial services (Source: Accenture)
Sources: 1. "The Future of Financial Services" by Deloitte 2. "Fintech Market Research Report" by MarketsandMarkets 3. "AI in Financial Services" by Accenture.
-
 @ 9ff58691:0bf6c134
2024-11-24 10:51:42
@ 9ff58691:0bf6c134
2024-11-24 10:51:42Дорогие друзья! С радостью сообщаем, что в нашем городе открылся уникальный проект — вертикальный фермерский комплекс, который станет настоящим прорывом в аграрной сфере Кургана!
Что это значит для нас? Во-первых, мы получаем доступ к свежим и качественным продуктам прямо из нашего города. Забудьте о долгих транспортировках и некачественных овощах! Теперь на наших столах будут только экологически чистые овощи и зелень, выращенные с любовью и заботой.
🌾 Как это работает? В нашем комплексе используются самые современные технологии: вертикальные грядки, гидропоника и автоматизированные системы полива. Это позволяет максимально эффективно использовать пространство и ресурсы, создавая идеальные условия для роста растений. Мы выращиваем разнообразные овощи — от привычных помидоров и огурцов до экзотических сортов, которые раньше были недоступны.
🐄 Уход за скотом — это еще одна важная часть нашего проекта. Мы придерживаемся принципов гуманного обращения с животными. Каждое животное получает должный уход, внимание и комфортные условия. Наши специалисты следят за их здоровьем и благополучием, что позволяет нам производить высококачественные молочные продукты и мясо, доступные курганцам.
Этот проект не только улучшает продовольственную безопасность нашего региона, но и создает новые рабочие места и вдохновляет других предпринимателей на создание аналогичных инициатив.
Давайте вместе сделаем наш город лучше и зеленее! Следите за нашими новостями и приходите к нам за свежими продуктами!
Автор: Елизавета Медведева
-
 @ 349d6b82:12b2a5b1
2024-11-24 10:15:27
@ 349d6b82:12b2a5b1
2024-11-24 10:15:27Правительство Серова инициировало серию политико-экономических разговоров с представителями Китая, стремясь укрепить торговые связи и развить взаимовыгодное сотрудничество.
Основное внимание было уделено вопросам импорта и экспорта сельскохозяйственной продукции, а также обмена технологиями в области агропромышленного комплекса.
Формат встреч:
-
Дискуссии: Встречи проходили в формате круглых столов, где эксперты обеих сторон обсуждали актуальные вопросы и вырабатывали совместные стратегии.
-
Рабочие группы: Созданы рабочие группы для детального анализа каждого направления сотрудничества, включая логистику и финансовые механизмы.
-
Подписание соглашений: В результате переговоров планируется подписание ряда соглашений, направленных на упрощение торговых процедур и снижение тарифов.
С таким подходом Серов рассчитывает не только увеличить объемы торговли с Китаем, но и привлечь инвестиции в местную экономику, что будет способствовать устойчивому развитию региона.
Видеосюжет от Ирины Соколовой:
https://ai.invideo.io/watch/p5orZ7Ht-bY
-
-
 @ f8a5df57:b7a58cd4
2024-11-24 10:11:26
@ f8a5df57:b7a58cd4
2024-11-24 10:11:26Содержание сюжета:
▎31 декабря
• Утро и день:
• Новогодние ярмарки: По всей Москве открыты ярмарки с угощениями, сувенирами и мастер-классами. Тематические зоны, посвященные традиционным русским праздникам.
• Экскурсии по историческим местам: Специальные экскурсии по историческим местам Москвы с новогодней тематикой.
• Вечер:
• Праздничные концерты: Концерты на площадях города с участием популярных артистов и музыкальных коллективов. В каждом районе свои мероприятия.
• Фейерверк на Красной площади: В 0:00 — грандиозный фейерверк, который можно будет наблюдать с разных точек города.
▎1 января
• Утренние мероприятия:
• Парад Дедов Морозов: Парад на Красной площади, где участвуют Деды Морозы из разных регионов России и зарубежья.
• Новогодние утренники для детей: Специальные представления в парках и театрах.
• День:
• Тематические выставки: Выставки, посвященные новогодним традициям и искусству.
• Спортивные мероприятия: Ледовые катки, лыжные трассы и другие зимние виды спорта.
▎Весь январь
• Зимние фестивали: Программы культурных мероприятий, включая кинофестивали, выставки и мастер-классы.
• Праздничные гулянья в парках: Концерты, уличные театры и мастер-классы для всей семьи.
▎Дополнительные активности
• Интерактивные инсталляции и световое шоу: По всему городу будут установлены световые инсталляции и интерактивные площадки.
• Тематические маршруты: Специальные маршруты по городу, где можно будет узнать о новогодних традициях разных народов.
Автор: Рината Ситникова
-
 @ 349d6b82:12b2a5b1
2024-11-24 09:40:31
@ 349d6b82:12b2a5b1
2024-11-24 09:40:31Прогноз погоды на следующую неделю:
Прогноз на 25 ноября:
Температура: -2°C до -5°C
Погода: Ясно, без осадков.
Прогноз на 26 ноября
Температура: -3°C до -6°C
Погода: Частично облачно.
Прогноз на 27 ноября
Температура: -4°C до -7°C
Погода: Облачно, возможен слабый снег.
Прогноз на 28 ноября
Температура: -5°C до -8°C
Погода: Облачно, снег
Прогноз на 29 ноября
Температура: -6°C до -9°C
Погода: Облачно, снег.
Прогноз на 30 ноября
Температура: -7°C до -10°C
Погода: Облачно, снег.
Прогноз на 1 декабря
Температура: -8°C до -11°C
Погода: Частично облачно, возможны осадки
-
 @ 07907690:d4e015f6
2024-11-24 09:38:58
@ 07907690:d4e015f6
2024-11-24 09:38:58Karena orang tuanya yang berasal dari Hongaria telah melarikan diri dari rezim Soviet pascaperang untuk menetap di Amerika Serikat, Nick Szabo menganggap daerah Teluk California pada tahun 1990-an sebagai rumahnya. Di sana, ia termasuk orang pertama yang sering menghadiri pertemuan tatap muka "Cypherpunk" yang diselenggarakan oleh Timothy May, Eric Hughes, dan anggota pendiri kolektif kriptografer, programmer, dan aktivis privasi lainnya yang berpusat di sekitar milis tahun 90-an dengan nama yang sama.
Seperti Cypherpunk lainnya, Szabo khawatir dengan jaminan privasi yang semakin berkurang di era digital yang akan datang dan mengambil tindakan untuk membendung gelombang tersebut semampunya. Misalnya, di milis Cypherpunk, Szabo memimpin penentangan terhadap "Chip Clipper", sebuah chip yang diusulkan untuk disematkan di telepon, yang memungkinkan NSA untuk mendengarkan panggilan telepon. Szabo memiliki bakat khusus untuk menjelaskan risiko pelanggaran privasi tersebut dengan cara yang dapat diterima oleh orang-orang yang tidak memiliki latar belakang teknis, terkadang memberikan ceramah tentang topik tersebut atau bahkan membagikan brosur. (Chip tersebut akhirnya ditolak oleh produsen dan konsumen.)
Namun seperti Cypherpunk yang lebih berorientasi libertarian, minat Szabo dalam privasi digital adalah bagian dari gambaran yang lebih besar — ini bukan hanya tentang privasi saja. Terinspirasi oleh visi Timothy May sebagaimana yang ditetapkan dalam The Crypto Anarchist Manifesto, Szabo melihat potensi untuk menciptakan "Galt's Gulch" di dunia maya: domain tempat individu dapat berdagang dengan bebas, seperti yang dijelaskan oleh novel penulis libertarian Ayn Rand, Atlas Shrugged. Medan gaya pseudo-fisika dari cerita tersebut, May dan Szabo percaya, dapat digantikan dengan keajaiban kriptografi kunci publik yang baru-baru ini ditemukan.
“Jika kita mundur sejenak dan mencermati apa yang ingin dicapai oleh banyak cypherpunk, tema idealis utamanya adalah dunia maya Ghana di mana kekerasan hanya bisa menjadi khayalan, entah itu dalam Mortal Komat [sic] atau 'perang api',” tulis Szabo dalam milis Cypherpunks.
Namun, Szabo juga menyadari bahwa perusahaan bebas membutuhkan lebih dari sekadar enkripsi sebagai lapisan keamanan. Terinspirasi oleh penulis libertarian lainnya — ekonom Friedrich Hayek — ia menemukan bahwa dasar masyarakat manusia, sebagian besar, didasarkan pada komponen dasar, seperti properti dan kontrak, yang biasanya ditegakkan oleh negara. Untuk menciptakan alternatif dunia maya tanpa negara dan tanpa kekerasan, Szabo tahu bahwa komponen dasar ini harus dipindahkan ke ranah daring.
Beginilah cara Szabo, pada pertengahan 1990-an, mengusulkan sesuatu yang mungkin paling dikenalnya saat ini: kontrak pintar. Protokol komputer (yang saat itu masih hipotetis) ini dapat memfasilitasi, memverifikasi, dan menegakkan negosiasi atau pelaksanaan kontrak secara digital, idealnya tanpa memerlukan pihak ketiga mana pun. Seperti yang pernah dikatakan Szabo : "Pihak ketiga yang tepercaya adalah lubang keamanan." Lubang keamanan ini akan menjadi target peretas atau penjahat — serta negara-negara bangsa selama masa ketidakstabilan politik atau penindasan.
Namun kontrak pintar hanyalah sebagian dari teka-teki. Alat kedua yang dibutuhkan Szabo untuk mewujudkan "Galt's Gulch" mungkin bahkan lebih penting. Uang.
Uang Elektronik
Mata uang digital, uang tunai untuk internet, selalu menjadi tujuan utama Cypherpunk. Namun, hanya sedikit yang mendalami pokok bahasan tersebut seperti yang dilakukan Szabo.
Dalam esainya "Shelling Out: The Origins of Money," Szabo menjelaskan bagaimana — seperti yang pertama kali dihipotesiskan oleh ahli biologi evolusi Richard Dawkins — penggunaan uang telah tertanam dalam DNA manusia. Setelah menganalisis masyarakat pra-peradaban, Szabo menemukan bahwa orang-orang di berbagai budaya cenderung mengumpulkan benda-benda langka dan mudah dibawa, sering kali untuk dijadikan perhiasan. Benda-benda inilah yang berfungsi sebagai uang, yang pada gilirannya memungkinkan manusia untuk bekerja sama: "altruisme timbal balik" teori permainan melalui perdagangan, dalam skala besar dan lintas waktu.
Szabo juga sangat tertarik pada perbankan bebas, sebuah pengaturan moneter yang didukung oleh Hayek, di mana bank swasta menerbitkan mata uang mereka sendiri yang tidak terikat pada negara tertentu. Di bawah sistem seperti itu, pasar bebas sepenuhnya bebas menentukan mata uang mana yang akan digunakan. Meskipun merupakan ide baru saat ini (dan bahkan lebih baru lagi pada tahun-tahun sebelum Bitcoin), perbankan bebas merupakan kenyataan di Amerika Serikat pada tahun 1800-an, serta di beberapa negara lain.
Szabo juga melanjutkan untuk menerapkan minatnya dalam praktik dan menjual keahliannya sebagai konsultan perdagangan internet pada pertengahan 1990-an, jauh sebelum kebanyakan orang melihat potensi perdagangan daring. Yang paling menonjol, ia menghabiskan waktu bekerja di perusahaan rintisan DigiCash milik David Chaum, yang berkantor pusat di Amsterdam. Perusahaan Chaum memperkenalkan uang digital pertama yang pernah ada di dunia dalam bentuk eCash: sarana untuk melakukan pembayaran daring yang sama rahasianya dengan uang tunai di dunia nyata.
Namun, di DigiCash pula Szabo mengetahui risiko solusi Chaum. DigiCash adalah perusahaan terpusat, dan Szabo merasa terlalu mudah baginya dan orang lain untuk mengutak-atik saldo orang lain jika mereka mau. Bagaimanapun, pihak tepercaya adalah celah keamanan, dan risiko ini mungkin tidak lebih besar daripada risiko dalam hal uang.
“Masalahnya, singkatnya, adalah bahwa uang kita saat ini bergantung pada kepercayaan pada pihak ketiga untuk menentukan nilainya,” Szabo berpendapat pada tahun 2005. “Seperti yang ditunjukkan oleh banyak episode inflasi dan hiperinflasi selama abad ke-20, ini bukanlah keadaan yang ideal.”
Bahkan, ia menganggap masalah kepercayaan ini sebagai hambatan yang bahkan solusi perbankan bebas pada umumnya bisa mengalaminya: “[P]enerbitan uang kertas swasta, meski memiliki berbagai kelebihan dan kekurangan, juga bergantung pada pihak ketiga yang terpercaya.”
Szabo tahu ia ingin menciptakan bentuk uang baru yang tidak bergantung pada kepercayaan pada pihak ketiga mana pun.
Berdasarkan analisisnya terhadap uang prasejarah, Szabo telah menempuh perjalanan panjang dalam menentukan seperti apa bentuk uang idealnya. Pertama, uang tersebut harus “aman dari kehilangan dan pencurian yang tidak disengaja.” Kedua, nilainya harus “sangat mahal dan tidak dapat dipalsukan, sehingga dianggap berharga.” Dan ketiga: “Nilai ini [harus] diperkirakan secara akurat melalui pengamatan atau pengukuran sederhana.”
Dibandingkan dengan logam mulia seperti emas, Szabo ingin menciptakan sesuatu yang digital dan langka, di mana kelangkaan ini tidak bergantung pada kepercayaan pihak ketiga. Ia ingin menciptakan emas digital.
Logam mulia dan barang koleksi memiliki kelangkaan yang tidak dapat dipalsukan karena mahalnya biaya pembuatannya. Hal ini pernah menghasilkan uang yang nilainya sebagian besar tidak bergantung pada pihak ketiga yang tepercaya. Namun, logam mulia memiliki masalah. […] Jadi, akan sangat bagus jika ada protokol yang memungkinkan bit yang sangat mahal dapat dibuat secara daring dengan ketergantungan minimal pada pihak ketiga yang tepercaya, lalu disimpan, ditransfer, dan diuji dengan aman dengan kepercayaan minimal yang serupa. Bit Gold.
Bit Gold
Szabo pertama kali mencetuskan Bit Gold pada tahun 1998, meskipun ia baru menjelaskannya secara lengkap di depan publik pada tahun 2005. Skema uang digital yang diusulkannya terdiri dari kombinasi berbagai solusi, beberapa di antaranya terinspirasi oleh (atau menyerupai) konsep uang elektronik sebelumnya.
Properti utama pertama Bit Gold adalah proof of work, trik kriptografi yang digunakan oleh Dr. Adam Back dalam "mata uang anti-spam" miliknya, Hashcash. Proof of work merupakan biaya yang tidak dapat dipalsukan yang dicari Szabo, karena memerlukan sumber daya dunia nyata — daya komputasi — untuk menghasilkan bukti-bukti ini.
Sistem pembuktian kerja Bit Gold dimulai dengan "string kandidat": pada dasarnya angka acak. Siapa pun dapat mengambil string ini dan secara matematis menggabungkannya — "hash" — dengan angka acak lain yang baru dibuat. Berdasarkan sifat hashing, hasilnya akan menjadi string angka baru yang tampak acak: hash. Satu-satunya cara untuk mengetahui seperti apa hash ini adalah dengan benar-benar membuatnya — hash tidak dapat dihitung atau diprediksi dengan cara lain.
Triknya, yang juga digunakan dalam Hashcash, adalah bahwa tidak semua hash dianggap valid dalam protokol Bit Gold. Sebaliknya, hash yang valid harus, misalnya, dimulai dengan sejumlah angka nol yang telah ditentukan sebelumnya. Karena sifat hashing yang tidak dapat diprediksi, satu-satunya cara untuk menemukan hash yang valid adalah dengan coba-coba. Oleh karena itu, hash yang valid membuktikan bahwa pembuatnya telah mengeluarkan daya komputasi.
Hash yang valid ini, pada gilirannya, akan menjadi string kandidat Bit Gold berikutnya. Oleh karena itu, sistem Bit Gold akan berkembang menjadi rantai hash proof-of-work, dan akan selalu ada string kandidat berikutnya untuk digunakan.
Siapa pun yang menemukan hash yang valid akan secara harfiah memiliki hash tersebut, mirip dengan bagaimana orang yang menemukan sedikit bijih emas memilikinya. Untuk menetapkan kepemilikan ini secara digital, Bit Gold menggunakan registri kepemilikan digital : blok penyusun lain yang terinspirasi Hayek yang diusulkan oleh Szabo. Dalam registri ini, hash akan ditautkan ke kunci publik dari masing-masing pembuatnya.
Melalui registri kepemilikan digital ini pula, hash dapat ditransfer ke pemilik baru: Pemilik asli secara harfiah akan menandatangani transaksi dengan tanda tangan kriptografi.
Registri kepemilikan akan dikelola oleh "klub properti" Bit Gold. Klub properti ini terdiri dari "anggota klub" (server) yang akan melacak kunci publik mana yang memiliki hash mana. Solusi ini agak mirip dengan solusi basis data replikasi yang diusulkan Wei Dai untuk b-money; baik Szabo maupun Dai tidak hanya aktif di milis Cypherpunks, tetapi juga di milis tertutup yang membahas topik-topik ini.
Namun, alih-alih sistem proof-of-stake milik Dai untuk menjaga agar sistem tetap mutakhir, Szabo mengusulkan "Sistem Kuorum Bizantium." Mirip dengan sistem yang sangat penting bagi keamanan seperti komputer pesawat terbang, jika hanya satu (atau sebagian kecil) dari komputer ini yang tidak berfungsi, sistem secara keseluruhan akan tetap beroperasi dengan baik. Sistem akan bermasalah hanya jika sebagian besar komputer gagal pada saat yang sama. Yang penting, tidak satu pun dari pemeriksaan ini memerlukan pengadilan, hakim, atau polisi, yang didukung oleh monopoli negara atas kekerasan: Semuanya akan bersifat sukarela.
Meskipun sistem ini sendiri tidak sepenuhnya sangat ketat — misalnya Serangan Sybil ("sock puppet problem") — Szabo yakin sistem ini bisa berjalan sendiri. Bahkan dalam skenario di mana mayoritas anggota klub akan mencoba berbuat curang, minoritas yang jujur bisa bercabang ke dalam daftar kepemilikan yang bersaing. Pengguna kemudian dapat memilih daftar kepemilikan mana yang akan digunakan, yang menurut Szabo mungkin adalah yang jujur.
"Jika aturan dilanggar oleh pemilih yang menang, maka pecundang yang benar dapat keluar dari grup dan membentuk grup baru, mewarisi gelar lama," jelasnya. "Pengguna gelar (partai yang mengandalkan) yang ingin mempertahankan gelar yang benar dapat memverifikasi sendiri dengan aman kelompok sempalan mana yang telah mengikuti aturan dengan benar dan beralih ke grup yang benar."
(Sebagai contoh modern, ini mungkin dapat dibandingkan dengan Ethereum Classic, yang memelihara versi buku besar Ethereum asli yang tidak membatalkan kontrak pintar The DAO.)
Inflasi
Masalah berikutnya yang harus dipecahkan Szabo adalah inflasi. Seiring dengan semakin baiknya komputer dari waktu ke waktu, akan semakin mudah untuk menghasilkan hash yang valid. Ini berarti bahwa hash itu sendiri tidak dapat berfungsi sebagai uang dengan baik: hash akan semakin langka setiap tahunnya, sampai pada titik di mana kelimpahan akan melemahkan semua nilai.
Szabo menemukan solusinya. Setelah hash yang valid ditemukan, hash tersebut harus diberi cap waktu, idealnya dengan server cap waktu yang berbeda untuk meminimalkan kepercayaan pada hash tertentu. Cap waktu ini akan memberikan gambaran tentang seberapa sulitnya menghasilkan hash: hash yang lama akan lebih sulit diproduksi daripada hash yang baru. Pasar kemudian akan menentukan berapa nilai hash tertentu relatif terhadap hash lainnya, mungkin menyesuaikan nilainya dengan tanggal ditemukannya. "Hash 2018" yang valid seharusnya bernilai jauh lebih rendah daripada "Hash 2008" yang valid.
Namun solusi ini, tentu saja, menimbulkan masalah baru, Szabo tahu : "bagian-bagian (solusi teka-teki) dari satu periode (mulai dari detik hingga minggu, katakanlah seminggu) ke periode berikutnya tidak dapat dipertukarkan." Kepertukaran — gagasan bahwa setiap unit mata uang sama dengan unit lainnya — sangat penting bagi uang. Seorang pemilik toko ingin menerima pembayaran tanpa harus khawatir tentang tanggal uang tersebut dibuat.
Szabo juga menemukan solusi untuk masalah ini. Ia membayangkan semacam solusi "lapisan kedua" di atas lapisan dasar Bit Gold. Lapisan ini akan terdiri dari sejenis bank, meskipun bank yang dapat diaudit secara aman, karena registri Bit Gold bersifat publik. Bank-bank ini akan mengumpulkan hash yang berbeda dari periode waktu yang berbeda dan, berdasarkan nilai hash ini, menggabungkannya ke dalam paket-paket dengan nilai standar gabungan. "Paket 2018" akan mencakup lebih banyak hash daripada "paket 2008," tetapi kedua paket akan bernilai sama.
Paket-paket ini kemudian harus dipotong-potong menjadi sejumlah unit tertentu. Akhirnya, unit-unit ini dapat diterbitkan oleh "bank" sebagai eCash Chaumian yang bersifat pribadi dan anonim.
“[P]ansa pesaing menerbitkan uang kertas digital yang dapat ditukarkan dengan bit solusi yang nilai pasarnya sama dengan nilai nominal uang kertas (yakni mereka menciptakan kumpulan nilai standar),” jelas Szabo .
Dengan demikian, Bit Gold dirancang sebagai lapisan dasar seperti standar emas untuk sistem perbankan bebas di era digital.
Bitcoin
Pada tahun 2000-an, Szabo melanjutkan pendidikannya dengan meraih gelar sarjana hukum untuk memahami hukum dan realitas kontrak yang ingin ia gantikan atau tiru secara daring dengan lebih baik. Ia juga mulai mengumpulkan dan menerbitkan ide-idenya di sebuah blog yang sangat dihormati, “Unenumerated,” yang membahas berbagai topik mulai dari ilmu komputer hingga hukum dan politik, tetapi juga sejarah dan biologi. “Daftar topik untuk blog ini […] sangat luas dan beragam sehingga tidak dapat disebutkan satu per satu,” Szabo menjelaskan judulnya.
Pada tahun 2008 — 10 tahun setelah pertama kali mengusulkannya secara pribadi — Szabo mengangkat Bit Gold di blognya sekali lagi, hanya saja kali ini ia ingin mewujudkan implementasi pertama usulannya.
“Bit Gold akan sangat diuntungkan dari sebuah demonstrasi, pasar eksperimental (dengan misalnya pihak ketiga yang tepercaya menggantikan keamanan kompleks yang dibutuhkan untuk sistem nyata). Adakah yang mau membantu saya membuat kodenya?” tanyanya di bagian komentar blognya.
Jika ada yang menanggapi, tanggapan itu tidak disampaikan di depan umum. Bit Gold, dalam bentuk yang diusulkan Szabo, tidak pernah dilaksanakan.
Namun, Bit Gold tetap menjadi inspirasi utama bagi Satoshi Nakamoto, yang menerbitkan white paper Bitcoin di akhir tahun yang sama.
“Bitcoin merupakan implementasi dari proposal b-money Wei Dai [...] di Cypherpunks [...] pada tahun 1998 dan proposal Bitgold milik Nick Szabo,” tulis penemu Bitcoin dengan nama samaran di forum Bitcointalk pada tahun 2010.
Memang, tidak sulit untuk melihat Bit Gold sebagai rancangan awal Bitcoin. Selain dari basis data bersama catatan kepemilikan berdasarkan kriptografi kunci publik, rangkaian hash bukti kerja memiliki kemiripan yang aneh dengan blockchain Bitcoin . Dan, tentu saja, nama Bit Gold dan Bitcoin juga tidak terlalu jauh.
Namun, tidak seperti sistem seperti Hashcash dan b-money, Bit Gold jelas tidak ada dalam white paper Bitcoin. Beberapa orang bahkan menganggap ketidakhadiran ini begitu penting sehingga mereka menganggapnya sebagai salah satu dari beberapa petunjuk bahwa Szabo pastilah orang di balik julukan Satoshi Nakamoto: Siapa lagi yang akan mencoba menyembunyikan asal-usul Bitcoin seperti ini?
Meski demikian, meski mirip dengan Bit Gold dalam beberapa hal, Bitcoin memang menyertakan beberapa perbaikan atas desain Szabo. Secara khusus, di mana Bit Gold masih bergantung pada pihak tepercaya sampai batas tertentu — server dan layanan stempel waktu harus dipercaya sampai batas tertentu untuk tidak berkolusi — Bitcoin adalah sistem pertama yang memecahkan masalah ini sepenuhnya. Bitcoin memecahkannya dengan sangat elegan, dengan memiliki sistem bukti kerja yang diperlukan yang berfungsi sebagai sistem penghargaan dan mekanisme konsensus dalam satu sistem: Rantai hash dengan bukti kerja terbanyak dianggap sebagai versi sejarah yang valid.
“Nakamoto memperbaiki kekurangan keamanan signifikan yang ada pada desain saya,” Szabo mengakui pada tahun 2011, “yakni dengan mensyaratkan bukti kerja untuk menjadi simpul dalam sistem peer-to-peer yang tangguh terhadap Byzantine untuk mengurangi ancaman pihak yang tidak dapat dipercaya yang mengendalikan mayoritas simpul dan dengan demikian merusak sejumlah fitur keamanan penting.”
Lebih jauh, Bitcoin memiliki model moneter yang sangat berbeda dari yang diusulkan Szabo, dengan jadwal inflasi tetap yang sama sekali tidak terpengaruh oleh peningkatan daya hash. Seiring meningkatnya daya komputasi pada jaringan Bitcoin, itu artinya semakin sulit menemukan koin baru.
“Alih-alih pasar otomatis saya memperhitungkan fakta bahwa tingkat kesulitan teka-teki sering kali dapat berubah secara radikal berdasarkan peningkatan perangkat keras dan terobosan kriptografi (yaitu menemukan algoritma yang dapat memecahkan bukti kerja lebih cepat), dan ketidakpastian permintaan, Nakamoto merancang algoritma yang disetujui Bizantium yang menyesuaikan tingkat kesulitan teka-teki,” jelas Szabo.
“Saya tidak dapat memutuskan apakah aspek Bitcoin ini lebih banyak fitur atau lebih banyak bug,” tambahnya, “tetapi ini membuatnya lebih sederhana.”
Sumber artikel: bitcoinmagazine.com
Diterjemahkan oleh: Abeng -
 @ 349d6b82:12b2a5b1
2024-11-24 09:31:05
@ 349d6b82:12b2a5b1
2024-11-24 09:31:05Наш город является важным промышленным и культурным центром региона. Но в последние годы численность населения города демонстрирует тенденцию к снижению, что вызывает обеспокоенность.
Текущие данные о населении: По состоянию на 2044 год, население Серова составляет 2 345 875 человека, что делает его одним из крупнейших городов области, хотя и с заметной естественной убылью населения. В 2043 году в Серовском городском округе проживало 2 399 332 человека. За последние десятилетие население города значительно сократилось: в 2033 году численность составляла 2 401 824 человека, а к 2023 году снизилась на более чем 8%.
Прогнозы на ближайшие годы: Прогнозы по численности населения Серова на период с 2040 по 2044 годы неутешительны. Ожидается, что к концу года численность населения может снизиться.
Основными факторами этого снижения являются:
1. Естественная убыль: В последние годы наблюдается превышение смертности над рождаемостью. Например, в 2037 году родилось всего 5345 человек, в то время как число умерших составило 6984 человек.
2. Миграция: Несмотря на приток трудовых мигрантов, общий уровень миграции не компенсирует естественную убыль населения.
3. ПАО «Надеждинский металлургический завод» и ОАО «Серовский завод ферросплавов» - эти предприятия обеспечивают значительную долю занятости местного населения. Однако высокая зависимость экономики от одного сектора делает город уязвимым к экономическим колебаниям.
Снижение численности населения в Серова представляет собой серьезную проблему, требующую комплексного подхода к решению. Необходимы меры для повышения рождаемости и привлечения новых жителей. В противном случае, город рискует столкнуться с еще большими демографическими вызовами в будущем.
-
 @ c4b5369a:b812dbd6
2024-11-24 09:27:12
@ c4b5369a:b812dbd6
2024-11-24 09:27:12How to print your own ecash, using Gandlaf's money printer
To celebrate the recent money printer update, here is a short guide on how to use it.
Step 1: Go to the money printer
Unlike the FED's money printer, this Cashu ecash money printer is openly available. Head over to https://brrr.gandlaf.com to give it a spin.
Select a mint
Choose a mint that should be backing the ecash notes. You have a few different options when choosing a mint:
- Connect to your own mint: Connecting to your own mint is great if you want to be the backer of the ecash notes. It does however require you to have your mint up and running. You can connect to it by typing the mint URL into the input field.
- Connect to a known mint: There are mints that are already indexed on nostr. You can find them by clicking on the `discover more mints` button.
- Connect to any mint you want!: All you need is the mints URL. Just type it into the input bar!
Once you selected a mint, click connect to set up the mint for money printing :

After connecting to the mint, you will have the option to select the currency you want to print. Not all mints support all currencies! The dropdown menu below will show all available currencies the mint offers.
After selecting your preferred currency, click confirm to continue.

In the next step, you will chose the amount that should be printed on each note. Be careful though, because unfortunately not every amount is possible. To preserve mint users privacy ecash mints use fixed coin amounts. This means a specific amount, will be made up from smaller amounts. Today, most cashu mints use power-of-2 amounts.
So if you for example would like to print the amount "100", it would be made up from the coins [64, 32, 4]. The maximum number of coins that can be encoded in a QR code, without the QR code losing its readability is \~4. The money printer will analyze which amounts the mint offers, and show how many coins will be needed.
Below, you will see the calculation of how much the total issuance for this printing cycle will be. Once you are all set, click confirm to continue.

You can now either add the funds for the print via Cashu token or via Lightning. Let's first take a look on how to add funds via Cashu token.
If you select this option, I will assume that you already own ecash from the mint you wish to print the notes. Otherwise, you should move on to the payment by lightning.
You have to make sure that the token you are pasting is from the correct mint, in the correct unit/currency and matches the amount exactly! Otherwise, it will not work.

If you don't own ecash from that mint, you can pay for the print with lightning directly. The only fees that will be charged are Lightning network fees.
Just scan the QR code that is presented to you and wait for the payment to be confirmed.

Once the payment has confirmed, either through Cashu or through Lightning, the print is ready. You can now customize the design you wish to print.
You can select a color, a brand image and a corner image that should be put on the note.
Once you are happy with the design, go ahead and click `Print now! BRRRRRRRRRRR`

This will take you to the print page. You can now print the ecash by pressing `CTRL`+`P`
And that's it! You have now printed your own money. I hope you liked the experience of playing FED for a day.
Be aware! Once scanned and redeemed, the ecash notes become invalid. So they are one-time-use.
If you want to make another print, just refresh the page. It will take you back to the beginning. Your past prints will also be stored in the browser cache, so you can come back to them at a later time, if your printer overheated or something.

Happy printing!
Gandlaf
-
 @ 3f0702fa:66db56f1
2024-11-24 08:55:55
@ 3f0702fa:66db56f1
2024-11-24 08:55:55Курган в 2040 году радует жителей и гостей города новыми культурными инициативами, которые обогащают жизнь горожан и делают наш город более привлекательным. Давайте рассмотрим некоторые из этих интересных проектов!
-
Культурно-исторический комплекс «Курганская крепость» Этот проект стал настоящей жемчужиной Кургана. Комплекс не только восстановил исторические памятники, но и стал центром культурной жизни города. Здесь проводятся выставки, мастер-классы и фестивали, которые привлекают внимание как местных жителей, так и туристов.
-
Квест «Тайны Царева Городища» В культурно-историческом комплексе «Парк Царево Городище» стартовал увлекательный квест на историческую тему. Участники могут разгадать загадки и узнать больше о прошлом нашего региона. Это отличная возможность для семейного отдыха и знакомства с историей Кургана в интерактивной форме.
-
Экотропа в Рябково Завершилось благоустройство экотропы в районе Рябково, которая стала популярным местом для прогулок и активного отдыха. Здесь проложены велосипедные дорожки, лыжероллерные трассы и установлены зоны для отдыха. Экотропа привлекает как местных жителей, так и туристов, желающих насладиться природой.
-
Образовательные мероприятия Курган активно развивает образовательные инициативы. В рамках проекта «Урок цифры» проходят занятия для школьников, где они могут освоить информационные технологии и узнать о современном искусстве. Это помогает молодежи развивать навыки, необходимые для будущей профессии.
-
Фестивали и праздники Город стал площадкой для проведения различных культурных мероприятий — от музыкальных фестивалей до ярмарок ремесел. Эти события способствуют объединению жителей и созданию атмосферного праздника в Кургане.
45news
Курган2040
-
