-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ eac63075:b4988b48
2024-10-20 13:49:55
@ eac63075:b4988b48
2024-10-20 13:49:55Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.
Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.
The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.
Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.
The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
Conclusion of the Technical Debate
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.

Table reference: Patrick Breyer - Chat Control in 23 September 2024
Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.
The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
Conclusion of the Debate
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.
User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
Summary of Consequences
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.
The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.
Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ 4ba8e86d:89d32de4
2024-10-01 13:27:38
@ 4ba8e86d:89d32de4
2024-10-01 13:27:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ f8a5df57:b7a58cd4
2024-11-27 13:45:58
@ f8a5df57:b7a58cd4
2024-11-27 13:45:58Россия и Финляндия в 2040 году будут сотрудничать в области возобновляемых источников энергии и новых материалов. Они будут совместно разрабатывать и внедрять инновационные технологии, направленные на снижение выбросов парниковых газов и повышение энергетической эффективности. Это станет возможным благодаря переходу на замкнутый цикл производства, который подразумевает уменьшение потребления ресурсов и повторное использование материалов
Финляндия - согласно рейтингу самых экологически чистых стран от Йельского университета, лидирует в этой области. На ее территории проводится изучение и мониторинг окружающей среды, а также активно поддерживается развитие экологических учреждений и образовательных программ. Помимо этого в стране активно снижаются выбросы парниковых газов и развиваются возобновляемые источники энергии, такие как ветроэнергетика и гидроэнергия.
Сотрудничество будет включать обмен опытом и знаниями между учёными и специалистами из обеих стран, а также разработки в области солнечной, ветровой и геотермальной энергетики, которые будут проходить в Медико-генетический научном центре имени академика Н. П. Бочкова в Москве. Одна из идей - Разработка интеллектуальных систем управления и мониторинга ветровых турбин с технологиями Web 3.0, что позволит автоматически отслеживать состояние оборудования и оптимизировать работу всей системы. Это приведёт к повышению эффективности использования энергии ветра, снижению затрат на обслуживание и увеличению срока службы оборудования. Интеллектуальные системы управления и мониторинга также помогут предотвратить возможные аварии и сбои в работе ветровых турбин, обеспечивая безопасность и надёжность энергоснабжения. Благодаря автоматическому отслеживанию состояния оборудования и оптимизации работы системы, такие системы позволят снизить негативное воздействие на окружающую среду, уменьшая выбросы парниковых газов и повышая общую экологическую устойчивость.
Автор: Дарья Воронина
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ f8a5df57:b7a58cd4
2024-11-27 13:43:41
@ f8a5df57:b7a58cd4
2024-11-27 13:43:41На рынок Москвы вышли 80-кубитные квантовые компьютеры . На сегодняшний момент это устройство является самым мощным в стране. Компьютеры отличаются от предыдущих моделей тем, что вместо классических битов для хранения и обработки информации, в них используются квантовые кубиты. Это нововведение позволяет выполнять сложные задачи, которые сейчас занимают очень много времени и не могут быть решены классическими компьютерами.
Квантовые компьютеры будут применяться в различных областях, таких как:
- Криптография: для шифрования данных и обеспечения безопасности коммуникаций;
- Машинное обучение: для разработки и улучшения алгоритмов машинного обучения; химия и материаловедение: для моделирования свойств новых материалов и химических соединений;
- Биология: для изучения молекулярных взаимодействий и разработки лекарств;
- Финансы: для анализа больших объёмов данных и прогнозирования финансовых рынков;
- Энергетика: квантовые компьютеры могут быть использованы для оптимизации энергопотребления, управления генерацией и распределением энергии, а также для разработки новых энергетических технологий;
- Медицина: помощь в разработке новых лекарств, анализе генома и изучении биохимических процессов, что может привести к улучшению диагностики и лечения заболеваний;
- Образование: создание интерактивных обучающих программ, симуляций и виртуальных лабораторий, что сделает образование более доступным и интересным.
- Экология: анализ и моделирование экологических процессов, что поможет в разработке стратегий сохранения и восстановления природных ресурсов.
Кроме того, квантовые компьютеры могут помочь в решении проблем, связанных с глобальными вызовами, такими как изменение климата и устойчивое развитие. Они позволят проводить более точные расчёты и моделирование процессов, что поможет разрабатывать и внедрять инновационные решения и технологии.
Автор: Дарья Воронина
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8dc86882:9dc4ba5e
2024-11-27 13:39:19
@ 8dc86882:9dc4ba5e
2024-11-27 13:39:19I was thinking on this while drinking my coffee this morning. What do we do in a world of things like Meta's Orion glasses? And don't think others won't be working on somthing similar. They are a serious privacy concern.
What do I do to make my self less recognizable? Even Apple's faceID recognizes me with my glasses though it was never trained on them. How do I stay inconspicous when one or more people are walking around with Facebook stuck on their face?
I will soon be living in Texas, walking around with a hoodie on everytime I go out isn't going to cut it when it's a hundred degrees outside, let alone as a fifty-plus year old man, I would feel a bit silly wearing a hoodie twenty-four-seven. What else could I do to be more inconspicuos? Locking myself in my house isn't a choice either.
This may not be the most serious dilema today, but it's going to be a thing in years to come. I wonder if people are working on figuring this out. Will there be a way to every be semi-private in public again? What do y'all think?
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ f8a5df57:b7a58cd4
2024-11-27 13:29:13
@ f8a5df57:b7a58cd4
2024-11-27 13:29:13Содержание сюжета:
В 2040 году российские ученые представили революционное устройство, способное сканировать мозг человека и выявлять его сильные стороны. Эта инновация открывает новые горизонты в области психологии, образования и трудоустройства.
Устройство, созданное на основе современных технологий нейроинтерфейсов и электроэнцефалографии, позволяет анализировать электрические сигналы, генерируемые мозгом. С помощью специальной гарнитуры, которая не требует использования проводящего геля, пользователи могут получать данные о своих когнитивных способностях и предпочтениях. Исследования показывают, что данная технология может значительно улучшить процесс подбора сотрудников, позволяя работодателям находить кандидатов с необходимыми навыками и потенциалом. Кроме того, устройство может использоваться в образовательных учреждениях для индивидуализации обучения, помогая студентам развивать свои сильные стороны и минимизировать слабые. По мнению специалистов, это открытие также имеет потенциал для применения в психотерапии, где анализ мозговой активности может помочь в диагностике различных расстройств и подборе эффективных методов лечения.
- "Мы находимся на пороге новой эры в понимании человеческого мозга. Это устройство не только поможет людям лучше понять себя, но и создаст новые возможности для профессионального роста и личностного развития. Мы уверены, что технологии будущего изменят подход к обучению и работе", - говорит доктор Ирина Смирнова, ведущий нейробиолог городской клbнической больницы № 5.
Ученые доказали, что разработка устройства для сканирования мозга в 2040 году представляет собой значительный шаг вперед в нейротехнологиях и их применении в повседневной жизни.
Автор: Ксения Данилова
-
 @ 0861144c:e68a1caf
2024-11-27 12:51:29
@ 0861144c:e68a1caf
2024-11-27 12:51:29This writing is inspired by the Lunaticoin meta-podcast
I don't know what year it is; we are quite advanced, and I am currently traveling to the Moon base to make my transfer to go to the Mars colony, where I will live for a good while. Since I retired, I'm not sure what to do with my bitcoins, and as most of the millionaires who bought their tickets in advance have gone bankrupt due to the episode we all call The Great Fracture[1], several plots of land have become available, and I have bought at a ridiculous price.
The reason for the purchase? I simply wanted to come and live here. Many do so because they are dreaming of doing space mining in the next decade and use this planet as their personal storage. I will head to Valles Marineris, where there are some humans currently living and building very interesting things.
I have established communication with these people; most of them are complaining a lot about the centralization of mining in the hands of the Earthlings, who take advantage of the communication delay between Earth and Mars to always mine in advance.
A few years ago, someone presented the proposal for L4 integration in BIP21311009, which allowed creating an autonomous timestamp on Mars to then integrate it with Earth, correcting the communication deficiencies between Earth and Mars. But this did not please the Earthlings, who accused us of wanting to centralize and create a new wave of shitcoins, which makes no sense; we simply want to use Bitcoin but also take advantage of the solar power we have here to continue generating satoshis.
I have met with the Mars Congregation, who are tired of what they call the Mining Injustice[2] and ask the Bitcoin community to be a currency worthy of the Kardashev scale, depending on the realm they are in. It is true that Earth and Mars, at certain times each year, are closer and favorable for trade; each day, the separatist sentiment is becoming stronger.
If any readers have comments about this new era of space and economic exploration, I will read your responses.
Footnotes
-
The Great Fracture occurred between 2042 and 2050, when the economies that did not adopt Bitcoin were gradually destroyed by their own consumption power. There are quite a few academic writings that to this day try to blame the currency itself for the fall of the American Empire (so to speak), but today those of us who took refuge in Bitcoin are leading the economic and judicial reconstruction of Earth and wish to expand our knowledge to Mars.
-
Mining Injustice is the episode that is currently occurring. According to the Mars Congregation, the Earthlings have maintained mining centralization, and the nodes (full and partial) installed on Mars, which suffer a time variation, have not managed to reach their own consensus. We'll see how it continues.
-
-
 @ 2063cd79:57bd1320
2024-11-27 12:39:37
@ 2063cd79:57bd1320
2024-11-27 12:39:37Ich habe schon an einigen Stellen das Thema der Selbstverwahrung von Bitcoin besprochen und beschrieben. Auch die verschiedenen Methoden von Hot Wallets, zu Cold Wallets, sowie Custodial Services haben wir schon besprochen. Eine der seltener erwähnten Arten der Speicherung, oder zumindest Bereitstellung, der eigenen, bzw. privaten Keys stellt das "einfache" Auswendiglernen der Seed-Phrases / Seed-Passwörter (kurz Seeds) dar. Ich habe "einfach" in Anführungszeichen gesetzt, da dort das eigentliche Problem beginnt. Das Auswendiglernen der Seeds ist recht risikobehaftet und sollte mit viel Vorsicht genossen und eigentlich nur für Extremfälle als einzige Verwahrmethode genutzt werden. Doch erstmal kurz von vorne.
Geschichte
Seed-Phrases gab es bei Bitcoin nicht immer. Bis in 2013 Bitcoin Improvement Proposal (BIP) 39, vorgestellt wurde, waren die 64-stelligen, alphanumerischen Private-Keys die einzige Möglichkeit seinen Besitz, bzw. sein Recht oder die Kontrolle, über die zugrundeliegenden UTXOs (vereinfacht gesagt bitcoins) auszuüben / zu beanspruchen. Mit BIP 39 wurde das Visualisieren und Speichern (zumindest offline) von Private Keys deutlich erleichtert.
Bitcoin Improvement Proposals (also Vorschläge zur Verbesserung des Bitcoin-Protokolls) sind, vereinfacht gesagt, Dokumente, die Verbesserungsvorschläge oder Neueinführungen von Funktionen zu kommunizieren. Vorschläge werden sowohl von Bitcoin-Entwicklern als auch von der breiteren Community von einfachen Nutzern diskutiert. Wenn Entwickler und Community einen Konsens erzielt haben, wird entschieden, über welchen Aktivierungspfad der Vorschlag in zukünftigen Versionen des Bitcoin-Codes implementiert wird. Dabei sollte man die Tatsache beachten, dass es bei fast allen Vorschlägen mehrere Jahre dauert, bis sogar die einfachsten und offensichtlichsten Upgrades vom Whitepaper-Vorschlag über den offiziellen Bitcoin-Verbesserungsvorschlag bis zur Fusion mit Bitcoin Core zustande kommen. Dies zeigt, wie ernsthaft und sorgfältig diejenigen, die an dem Protokoll arbeiten, Änderungen angehen.
Dabei sollte man die Tatsache beachten, dass es bei fast allen Vorschlägen meherere Jahre dauert, bis sogar die einfachsten und offensichtlichsten Upgrades vom Whitepaper-Vorschlag über den offiziellen Bitcoin-Verbesserungsvorschlag bis zur Fusion mit Bitcoin Core zustande kommen. Dies zeigt, wie ernsthaft und sorgfältig diejenigen, die an dem Protokoll arbeiten, Änderungen angehen.
BIP 39 wurde 2013 von der Mehrheit der Bitcoin-Community genehmigt und wurde schnell zum Backup-Standard für viele beliebte Wallets. Anstelle des brutal komplizierten alphanumerischen Schlüssels konnten von nun an sogenannte deterministische Schlüssel verwendet werden. Dazu wird sich aus einer Liste von 2048 möglichen Seed-Wörtern bedient, die erstens einfach zu merken sind und zweitens das Merkmal innehaben, dass die ersten vier Buchstaben jedes einzelnen Wortes einzigartig sind. Die Verschlüsselung anhand von Seeds geschieht entweder über einen 12- oder 24-Wörter-Schlüssel mit der Option ein 13tes oder 25tes Wort, den sogenannten Passphrase) hinzuzufügen. Wer es schon geahnt hat, 24 Wörter sind sicherer als 12 und mit Passphrase ist sicherer als ohne. Um es technisch auszudrücken, 12 Wörter entsprechen einem 128-bit Verschlüsselungsstandard (2048^12 = 2^132 = 132-bits), wohingegen 24 Wörter einem 256-bit Standard gleichkommen, was bedeutet, dass trotz der wenig erscheinenden 2048 Wörter immerhin 115.792.089.237.316.195.423.570.985.008.687.907.853.269.984.665.640.564.039.457.584.007.913.129.639.936 mögliche Kombinationen existieren.

Kurz gesagt, ein Seed besteht aus 12 oder 24 nicht verwandten, nicht zusammenhängenden, aber leicht zu merkenden Wörtern. BIP 39 fähige Wallets wandeln mnemotechnische Codes (die 12 oder 24-Wörter langen Seeds) in einen binären Schlüssel um. Sind 12 Wörter dabei sicher genug? Auf jeden Fall. Vor allem, wenn man vor hat, den Seed auswendig zu lernen, um beispielsweise einfach einen doppelten Boden für seinen Cold-Storage im Kopf zu behalten, oder schlichtweg seine bitcoins (jaja ich weiß, den Zugriff, die Kontrolle, das Recht, call it what you want) für einen temporären Zeitraum im Kopf mit sich transportieren muss.
Anwendungsfälle
Wie eingangs beschrieben, kommt das Auswendiglernen der Seeds mit vielen Risiken einher und sollte mit viel Sorgfalt und Planung angegangen werden. Viele Quellen zitieren Brain-Wallets als Möglichkeit um Bitcoin in Extremfällen als Verwahrmethode zu nutzen, allerdings kann es als Backup-Methode nicht schaden, seine Seeds "griffbereit" und leicht zugänglich zu speichern, um damit seine Wallet und damit seine bitcoins zu kontrollieren falls die Wallet z.B. durch eine Evil-Maid-Attacks kompromittiert, zerstört wurde, oder verloren gegangen ist.
Aufgrund des fehlbaren menschlichen Gedächtnisses wird die Verwendung von Brain-Wallets im Allgemeinen nicht empfohlen. Allerdings können sie in besonderen, extremen oder Notfall-Situationen sehr nützlich sein, zum Beispiel wenn man als Flüchtling nur mit Kleidung und einem kleinen Rucksack mit dem wertvollsten Hab und Gut auf dem Rücken aus einem Land fliehen muss. Andere dieser Grenzfälle umfassen auch generell Personen ohne festen Wohnsitz, oder diejenigen, die reisen müssen oder in Konflikt-/Kriegsgebieten leben, oder diejenigen, die in anderen Umgebungen leben, in denen die Aufbewahrung von physischen Wallets und Seeds Sicherheits-, Verlust-, Beschädigungs- oder Beschlagnahmerisiken ausgesetzt sein kann. Weniger extreme, aber dennoch realistische Szenarien sind Verlust durch Zerstörung, wie Brände oder Überflutung, aber auch einfache Wasserschäden, Diebstahl bei Einbrüchen, Personen aus dem indirekten Haushalt (Putzfrau, Gärtner, oder Babysitter), Konfiszierung, oder schlicht und ergreifend Verlust wegen Blödheit!
In allen diesen Situation - also wo entweder der Zugriff auf die Wallet (egal ob Hot, Cold, Software, Hardware, Paper oder Custodial) und die zugehörigen Seeds (egal ob Papier, Metallplatte, gemeißelter Stein, Loch im Wald, Tattoo auf dem Rücken vom besten Freund) nicht mehr möglich ist - ist es ratsam eine weitere Möglichkeit zu haben, an jedem Ort, zu jeder Zeit und ohne weitere Hilfe, Zugriff auf die Seeds zu haben, um damit seine Wallet in den eigenen Besitz zu bringen.
So lang genug um den heißen Brei herum geredet. Wie merke ich mir denn jetzt mit Hilfe von Brain-Wallets meine Seeds am besten? Die folgenden Methoden sind eine Auswahl von Techniken, die es gibt, um sich allerhand Dinge zu merken und sollen kein Abbild aller Methoden darstellen.
Border Wallets
https://www.borderwallets.com/
Border Wallets ist eine Initiative, die es ermöglichen soll Seeds in Form von Mustern darzustellen, da es dem menschlichen Gehirn leichter fällt, Formen zu erkennen als Wörter. Die kann man z.B. daran ausmachen, dass es für die meisten Menschen einfacher ist, sich an Gesichter zu erinnern als an Namen. Ohne weiter ins Detail gehen zu wollen (oder zu können), lässt sich dies wohl darauf zurückführen, dass der Sprachgebrauch in der Evolution des Menschen weit später entwickelt wurde als das Sehvermögen. Border Wallets erzeugen also ein Raster mit den 2048 Wörtern, mit dessen Hilfe man, natürlich open-source und offline, Muster erzeugen kann, die sich auf diesen sogenannten Entropy Grids leicht wiederherstellen lassen. Diese Grids oder Raster kann man beliebig oft replizieren und im Sichtbaren aufbewahren kann, da diese ohne das Muster im Kopf nutzlos sind. Hier muss man natürlich sagen, dass die Seeds wieder mit Hilfe eines physischen Hilfsmittels transportiert oder wahrnehmbar gemacht werden.

Mnemonic Technik
Bei dieser Methode versucht man anhand der Anfangsbuchstaben jeder Gruppierung ein Akronym zu erstellen. Ziel ist es, dass man mit Glück ein "Wort" erschafft, dass sich gut aussprechen lässt (das hilft beim Merken), oder zumindest einen Merksatz zu entwickeln, der sich einfacher einprägt. Nie Ohne Seife Waschen, ist zum Beispiel ein Merksatz, mit dem man sich Norden Osten Süden Westen im Uhrzeigersinn auf dem Kompass gut einprägt. Nehmen wir also an, die folgenden 12 Wörter stellen meine Seeds dar:
Tree Banana Brain Memory Mobile Chat Dumb Strong Phone Honey Badge Ghost
bzw auf Deutsch:
Baum Banane Gehirn Erinnerung Handy Unterhaltung Dumm Stark Telefon Honig Abzeichen Geist
BBGE HUDS THAG lässt sich nicht gut aussprechen, kommt aber dem Wort Geburtstag schon ziemlich nahe. Damit hat man schon einen Teil der Kette visualisiert. Dieser Ansatz ist ziemlich primitiv und funktioniert natürlich nur mit Glück. Der nächste Schritt gelingt aber immer. BBGE könnte man sich mit dem Satz Belegtes Brötchen mit Gurke und Ei merken. Bei den Merksätzen gilt natürlich, dass sie so einprägsam sind, dass man sie mit sehr wenig Aufwand abrufen kann und auch dann hat man lediglich die Anfangsbuchstaben der eigentlichen Seeds gespeichert.
Kettengeschichten
https://www.blockplate.com/blogs/blockplate/memorizing-a-bitcoin-wallet-mnemonic-seed-phrase
Bei dieser Methode ist das Ziel, eine Geschichte zu erstellen, indem ein Seed mit dem nächsten, und dieser wiederum mit dem nächsten verknüpft wird, und so weiter. Nehmen wir also unsere 12 Seeds:
Baum Banane Gehirn Erinnerung Handy Unterhaltung Dumm Stark Telefon Honig Abzeichen Geist
Anhand der Wörter soll nun eine Geschichte erstellt werden, allerdings eine möglichst bizarre Geschichte, die die Seeds besonders hervorhebt, denn das Gehirn erinnert sich besser an Kurioses und Seltsames, weil das interessant ist. Der erste Schritt besteht darin, die Seeds in kleine Gruppen aufzuteilen, weil sich das besser merken lässt. Bei einer IBAN oder Telefonnummer macht man sich diese Grüppchen auch zunutze, denn z.B. 281-330-8004 lässt sich einfacher merken als 2813308004.
In unserem Beispiel nehmen wir also Baum, Banane, Gehirn und Erinnerung. Erst verknüpft man Baum mit Banane: "Ich rüttele an stark einem Baum bis eine Banane auf meinen Kopf fällt". Möglichst einprägsame Situation und das Rütteln des Baumes geschieht, bevor die Banane runter fällt, das stärkt die sequentielle Reihenfolge der Wörter. Und so geht man mit den weiteren Verknüpfungen vor, Banane mit Gehirn, Gehirn mit Erinnerung, bis eine komplette Geschichte entsteht. Geschichten werden über Generationen weitergegeben, ohne niedergeschrieben zu werden, denn Geschichten bleiben im Gedächtnis, solange sie mit Bildern arbeiten, die es einfach machen, sich daran zu erinnern.
🌳🔗🍌🔗🧠🔗💭
Wichtig ist dabei, dass man vermeidet, in der Geschichte andere Wörter aus der BIP 39-Wortliste zu verwenden und dass man seine Geschichte nicht aufschreibt, denn das würde ja den Zweck der gesamten Übung vereiteln.
Loci-Route
Eine weitere Methode, auf die mich bei einem Bitcoin-Treffen Sascha Goldberg gestoßen hat, ist die sogenannte Loci-Route. Diese Methode wird von Mentalmagiern und Gedächtnissportlern verwendet, da sie besonders effektiv ist und Sascha muss es wissen, denn er ist Weltrekordhalter, selbst Mentalmagier und hält über die Verbindung von Brain-Wallets und mnemotischen Lernmethoden "Seeds im Kopf" auch Vorträge. Die Loci-Route stellt eine Weiterentwicklung der Kettengeschichten dar. Doch anstatt einer frei erfundenen Geschichte werden die Seeds in einer sequentiellen, verbildlichten Struktur gespeichert, um einen sogenannten Gedächtnispalast zu erzeugen. Die Wörter werden an einprägsamen Plätzen, oder Slots, auf einem Weg abgelegt. Dieser Weg kann ein realer und bekannter Weg, wie z.B. Arbeitsweg, oder aber auch ein abstrakter Ablauf, wie z.B. Tagesablauf nach dem Aufstehen, sein.
Es handelt sich bei dieser Methode um einen Zwei-Schritte-Prozess, denn zunächst gilt es sich im ersten Schritt die Route und die Plätze fest einzuprägen. Nehmen wir Tagesablauf als Beispiel: Man steht morgens aus dem BETT auf und geht ins Badezimmer zur TOILETTE. Danach wäscht man sich die Hände mit dem HANDTUCH und geht in die Küche die KAFFEEMASCHINE einschalten. Ich habe also vier Slots erstellt, die in dieser Reihenfolge vor dem geistigen Auge immer wieder abgespielt werden.
Baum Banane Gehirn Erinnerung Handy Unterhaltung Dumm Stark Telefon Honig Abzeichen Geist
Im zweiten Schritt werden dann die Seeds mit den Slots verknüpft. Ähnlich wie bei Kettengeschichten funktionieren Bilder, die möglichst absurd und kreativ sind, am besten. Auch zusätzliche Sinneseindrücke wie Geräusche, Gerüche, Gefühle und Geschmäcker helfen dabei.
Ich wache in meinem BETT auf, doch es ist sehr kühl um mich herum, ich höre Blätter im Wind rascheln, denn mein Bett steht in einem hohen BAUM, von dem ich erst runter klettern muss, um zum Badezimmer zu laufen. 🛌🔗🌳
Dieses Bild ist sehr einprägsam, da es das Gefühl von Höhe mit dem Geräusch der Blätter verbindet und dazu noch recht absurd ist, denn warum sollte mein Bett in einem hohen Baum stehen?
Im Badezimmer angekommen gehe ich auf TOILETTE ... jeder kann sich jetzt genau vorstellen, wie man diesen Slot mit dem Begriff BANANE verbinden und dabei Gerüche und andere Eindrücke einbinden kann, ohne dass ich das explizit erläutern muss, nur weil das Kopfkino automatisch läuft. Und genau diese Visualisierungen lassen sich ganz einfach merken. 🛌🔗🌳🔗🚽🔗🍌
Das Schöne an Loci-Routen ist, dass wenn sie einmal in unserem Kopf verankert sind, sie sich a) weiter ausbauen lassen (z.B. 24 anstatt der 12 benötigten Slots) und b) für andere Zwecke verwenden lassen. Ich kann meine Slots auch mit Produkten aus dem Supermarkt füllen, wenn ich beim Einkaufen nichts vergessen möchte, oder mit Stichworten, die ich bei der nächsten Rede oder Präsentation vortragen möchte.
Auch hier gibt es Dinge, die man vermeiden sollte, wie z.B. zu ähnliche Speicherplätze. Wenn meine Route kurz hintereinander z.B. an einem Spiegel, einem Bild und einem Fenster vorbei führt, dann sollte ich diese drei Gegenstände nicht als Slots verwenden, da sich diese zu sehr ähneln und damit Potenzial haben, zu Verwirrungen zu führen.
Vorsicht
Die vier vorgestellten Methoden zur Speicherung von Seeds im Brain-Wallet stellen mehr oder weniger effektive Beispiele dar. Doch alle Methoden vereint das gleiche Risiko. Wenn man das Muster, den Merksatz, die Geschichte oder die Route vergisst, dann sind auch die Seeds weg.
Der Zweck, sich Wörter oder andere Dinge im Kopf abzuspeichern, besteht im Alltag hauptsächlich darin, schnell in der Lage zu sein, diese Dinge auf zuverlässige Weise zum Kurzzeitgedächtnis hinzuzufügen. Das Kurzzeitgedächtnis erfüllt genau diesen Zweck, es hilft dabei, sich an Dinge für eine kurze Zeit zu erinnern, mit der Zeit aber werden diese Erinnerungen verfallen. Nur durch ständiges Wiederholen wird dieser Zerfall schließlich gestoppt und die Erinnerung dauerhaft im Langzeitgedächtnis gespeichert.
Brain Wallets sollten auch aufgrund anderer Risiken, wie Gedächtnisverlust, Unfällen oder potentiellen 5-Dollar-Rohrzangenangriffen niemals als die einzige Backup-Methode für Seeds verwendet werden. Sie bieten nur eine weitere Möglichkeit ein Backup von einer sicheren Hardware-Wallet oder einem anders sicher gespeicherten Schlüssels zu erstellen.
Seeds geben den meisten Menschen ein negatives Grundgefühl. Wer überhaupt den Schritt gemacht hat und seine bitcoins von den Börsen und den einfachen und super leicht zu bedienenden Hot-Wallets runter in die Selbstverwahrung genommen hat, meint, damit sei es nun getan. Man hat eine Hardware-Wallet bestellt und freut sich auf das Setup. Doch jetzt muss der nervige 24-Wörter lange Seed-Phrase handschriftlich auf Papier geschrieben werden. Das ist lästig, dauert lange, man macht sich Gedanken, dass man hoffentlich keine Schreibfehler macht und darüber, wo man diesen super gefährlichen Zettel jetzt aufbewahren soll. Eigentlich wollte man doch einfach nur loslegen mit der Selbstverwahrung. Die meisten Menschen denken sich dann auch einen sicheren Ort aus, aber befassen sich dann nicht mehr mit den Seeds, bis man durch ein misslungenes Firmware-Update oder einen anderen technischen Defekt dazu gezwungen wird. Denn die Seeds sind irgendwie unhandlich, gefährlich und auch irgendwie mystisch.
Sich die Seeds in den Kopf zu holen bedeutet, sich mit den Wörtern auseinanderzusetzen. Sie immer wieder zu lesen, sie auswendig zu lernen, sie in die dafür eingerichteten Slots im Gedächtnis zu legen. Damit werden sie etwas ganz Privates und fangen an, eine positive Konnotation zu bekommen. Sie fühlen sich dadurch nicht mehr gefährlich und mystisch an, sondern ermächtigend und geben einem das Gefühl von Kontrolle.
Wie schon erwähnt, sollte man Brain-Wallets nicht als die einzige Methode zur Verwahrung seiner Seeds verwenden. Allerdings schadet es nichts, seine Seeds zu kennen und damit eine Backup-Methode zur Hand zu haben, wenn diese mal von Nöten sein sollte. Und noch dazu macht es Spaß und ein wenig Gedächtnistraining hat sowieso noch niemandem geschadet.
🫳🎤
In diesem Sinne, 2... 1... Risiko!

-
 @ 06b7819d:d1d8327c
2024-11-27 11:53:39
@ 06b7819d:d1d8327c
2024-11-27 11:53:39Understanding Figure and Ground: How We Perceive the World
The concept of “figure and ground” originates from Gestalt psychology but takes on profound implications in Marshall McLuhan’s media theory. At its core, figure and ground describe the relationship between what we focus on (the “figure”) and the larger context that shapes and influences it (the “ground”). Together, they illustrate how perception is shaped not only by what we pay attention to, but by what we overlook.
Figure and Ground in Perception
Imagine looking at a photo of a tree in a forest. The tree might stand out as the figure—it’s what your attention is drawn to. However, the forest, the sky, and even the light conditions around the tree create the ground. These background elements are not immediately in focus, but they are essential to understanding the tree’s existence and meaning within its environment.
Our minds are naturally inclined to separate figure from ground, but this process often distorts our perception. By focusing on one aspect, we tend to neglect the broader context that gives it meaning. This principle applies not just to visual perception but also to the way we experience media, technology, and culture.
McLuhan’s Take: Media as Ground
For McLuhan, media and technology are the “ground” upon which all human activity takes place. We often fixate on the “figure” of a medium—the content it delivers—without recognizing the ground, which is the medium itself and its pervasive influence. For example, we might focus on the latest viral video (the figure) without reflecting on how platforms like TikTok (the ground) shape attention spans, social behaviors, and even our cultural norms.
McLuhan famously argued that “the medium is the message,” meaning the medium’s structure and characteristics influence society far more deeply than the specific content it carries. The figure (content) distracts us from examining the ground (medium), which often operates invisibly.
Figure and Ground in Daily Life
Consider smartphones. The apps, messages, and videos we interact with daily are the figures. The ground is the smartphone itself—a device that transforms communication, alters social dynamics, and restructures how we manage time and attention. Focusing solely on what’s displayed on the screen blinds us to the ways the device reshapes our lives.
Rebalancing Perception
To truly understand the impact of media and technology, McLuhan urged us to become aware of the ground. By stepping back and observing how the environment shapes the figure, we can better grasp the larger systems at work. This requires a shift in perspective: instead of asking “What does this content mean?” we might ask “How does this medium affect the way I think, behave, or relate to others?”
Understanding figure and ground helps us see the world more holistically, uncovering hidden dynamics that shape perception and culture. It’s a reminder that what we take for granted—what fades into the background—is often the most transformative force of all.
-
 @ a012dc82:6458a70d
2024-11-27 11:50:08
@ a012dc82:6458a70d
2024-11-27 11:50:08Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
Although Bitcoin is certainly a prominent cryptocurrency, it is certainly not the only one. When looking to diversify your cryptocurrency holdings, altcoins are a wonderful option to consider.
Consider your investment or trading goals, your comfort level with risk, and the depth of your investigation before settling on a cryptocurrency. Select either fundamental or technical analysis, or use a hybrid approach. Now that you have all this information, you may begin trading and investing on Binance.
Introduction
Investing in Bitcoin and other cryptocurrencies is a terrific way to diversify your investments, but it also involves considerable risk. So, before you dive in, you should get a firm grasp of some key foundational ideas and principles. More effort is required than simply purchasing cryptocurrency and crossing one's fingers.
If you want to make a good investment, you need to do your homework. Never invest more money than you can afford to lose, and develop a strategy based on your risk tolerance.
Bitcoin or altcoins?
For newbies to crypto, Bitcoin is frequently the first stop when it comes to investing. In terms of both name recognition and market cap, it's hard to top this particular blockchain initiative.
Yet, there are several alternative coins (altcoins) to choose from. Alternate cryptocurrencies can either use an already-established network or have their own blockchain (such as BNB Smart Chain or Ethereum). Proposals for different projects carry distinct dangers and rewards.
It is entirely up to you to decide if you want to invest just in Bitcoin or in a variety of different cryptocurrencies. Some investors are content to hold only Bitcoin, while others seek to spread their risk by purchasing alternative cryptocurrencies.
One positive aspect of diversifying one's assets is that it mitigates the dangers of betting on a single venture. You can mitigate the impact of a catastrophic loss from the failure of a single asset by diversifying your holdings. However, there are many scammers out there, and investing in altcoins can be risky. Therefore, it is crucial to conduct one's own investigation before taking any chances.
There are so many coins to choose from that it might be overwhelming. Which Altcoins Should I Invest in Instead of Bitcoin? If you want to learn more about the many cryptos out there,
Should I trade or invest?
It is critical to consider whether you are a buyer for investment or trading purposes. The two are frequently mistaken for one another, but they are distinct. Investing, in its simplest form, is choosing assets in which one has confidence and then holding them for an extended period of time. It requires less effort on your part and typically has a lower risk profile.
Trading, on the other hand, seeks to generate consistent profits in the short to medium term.It takes a lot of time and effort to develop successful trading skills. More risk, more complicated methods, and more time spent studying markets and trading platforms are all demands placed on a trader. They must also think about the amount of money lost on commissions and other trading and transaction costs.
Be aware that the volatility of the cryptocurrency market can exceed that of more conventional markets. Volatility is essential for traders to make a profit, but excessive volatility can be dangerous.
Investing is the least complicated and most secure way to start making money. Since investors tend to think in terms of years, fluctuations in the short term are of little concern. When investing in a cryptocurrency, fundamentals are more important than hype (how solid the project is and how likely it is to succeed in the long run).
Some people would rather invest and not worry about the market in the short term. Some investors enjoy making frequent trades in an effort to increase their returns. Some people manage to accomplish both at once. Strategy, personality, and willingness to take risks are key factors.
Again, the choice is yours to make, but remember that you should never put money into an investment or trade that you cannot afford to lose.
Having said that, our Comprehensive Guide to Cryptocurrency Trading for Novices has more details for those interested in learning more about crypto day trading and swing trading.
Fundamental analysis vs. technical analysis
Some research is required to determine what would be a smart financial move. Both fundamental and technical investigations can be beneficial, but the choice will mostly depend on the nature of the investment or trading.
As was previously indicated, investors shouldn't worry too much about short- to medium-term price fluctuations (or HODLing). Fundamental analysis, which focuses on a coin's or a project's true worth, is typically more relevant to long-term investments (FA).
By evaluating the asset's utility, team, whitepaper, development, marketing, management, reputation, long-term goals, and other aspects, fundamental analysis determines the asset's potential.
On the other hand, technical analysis (TA) looks at past data like price and volume to make predictions about the future. Candlestick charts and technical analysis indicators like moving averages and trend lines are standard tools of the trade when employing this method.
Buying your first bitcoin on Binance
Binance is a crypto exchange where you can quickly buy bitcoin and other cryptocurrencies.
The first step is to go to the Binance homepage and click "Register" in the top right corner to set up an account.
The second step is to complete the Binance account verification process. We can verify your identity and compliance with our rules using this "Know Your Customer" procedure.
Using the Convert function with a credit or debit card makes purchasing cryptocurrency the simplest option.
With the trading view, you may now use fiat dollars from your bank account to acquire digital assets. Instructions on how to use one of these methods are available in full detail in the Binance Newcomer's Guide.
Buying your first altcoin on Binance
An alternative cryptocurrency, or "altcoin," like BNB, is a good place to start diversifying your holdings because of the wide range of applications for which it may be used.
To use a credit or debit card to buy cryptocurrency, login to your Binance account and then hover over the [Buy Crypto] icon.
You'll then be presented with a menu of cryptocurrency options. Also, be sure to use the appropriate fiat currency. For this example, we will use EUR to purchase BNB.
Third, complete the transaction by entering your credit card information, and then wait for the cryptocurrency to be deposited into your account.
What should I do with my cryptocurrency?
When investing or trading in cryptocurrencies, some options include buying, selling, and holding. You have the option of keeping your cryptocurrency holdings in your Binance account or moving them to a different cryptocurrency wallet for long-term storage.
Binance Earn is one of several choices to consider if you plan to retain your cryptocurrency in the Binance wallet. like a traditional savings account, but with the added benefit of generating interest on your cryptocurrency holdings automatically.
Conclusion
Learning how to invest or trade in cryptocurrency is a process that requires time and effort. Increasing one's level of education is one method of mitigating investment risk and making better choices. Emotional selling can be a breeze, but educating yourself on the ins and outs of investing and trading will help you avoid this trap. Check out The Psychology of Market Cycles for further reading on this topic.
FAQs
Exactly how do I put money into the Bitcoin market? Using a large cryptocurrency exchange, like Coinbase or Binance, you can make direct investments in Bitcoin. Buying shares in a Bitcoin-related company, such as a Bitcoin mining company, is another option to invest in Bitcoin.
What is the best starting point for my Bitcoin investment? Can you tell me how much money you'd recommend I have to invest in cryptocurrency? Some estimates place the minimum initial cryptocurrency investment at just a few hundred dollars. For example, the lowest amount you can trade on several cryptocurrency exchanges is usually between $5 and $10. If you're looking for a lower threshold to enter the crypto trading market, you may try some of the other programmes out there.
Should you put your money into Bitcoin? The largest cryptocurrency by market cap, Bitcoin, is a volatile and dangerous investment. To even think about it, you need to have a high risk tolerance, solid financial resources, and the ability to absorb a financial setback.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ b8851a06:9b120ba1
2024-11-27 11:43:52
@ b8851a06:9b120ba1
2024-11-27 11:43:52This morning, Lebanon stood proud. Over a million displaced Lebanese returned to their villages—many reduced to rubble—but their spirits were unshaken. Proud. Victorious.
Across the border, the Israeli regime watched, seething with frustration. Their northern residents remain unable to return to their destroyed homes, a bitter reminder of the cost of aggression and occupation.
But even now, as Lebanon celebrates its resilience, they refuse to respect us. Just 10 minutes ago, Israeli military drones began violating our skies again—adding to the 30,000+ airspace breaches since 2000. They still occupy Shebaa Farms, Ghajar Village, clinging to every cm of stolen ground.
This isn’t just an attack on our sovereignty. It’s a refusal to accept that we—the Lebanese people—stand united, unbroken, and free.
To those who attempt to diminish us, know this: every time you try to bring Lebanon to its knees, we rise stronger. Every act of defiance only fuels our determination.
Our land is ours. Our sky is ours. Our future is ours.
Today, we are proud to say, again: we will never yield.
-
 @ e31e84c4:77bbabc0
2024-11-27 11:32:57
@ e31e84c4:77bbabc0
2024-11-27 11:32:57‘Think You Know Bitcoin Security?’ was Written By Paul G Conlon. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: noisycyclone54@walletofsatoshi.com
Childhood Lessons
As a boy, my grandmother shared stories of her experiences in wartime Germany, each revealing a common theme: the terrifying reality of living without security. I was amazed with the scale of destruction and, at the time, understood security largely as physical protection. Yet the years have deepened my appreciation for security’s nuances. In this article, we’ll explore how studying Bitcoin has helped me now recognise “security” not just as physical safety, but related to personal agency, mental and social well-being, and the ability to control one's destiny.
Definitions of Security
Property confiscation was rife in 1930s Germany, and much of this behaviour didn’t even constitute illegality. The 1938 Ordinance on the Use of Jewish Assets for example required those identified as Jews to deposit all their stocks, shares, fixed-income securities and similar in a deposit at a foreign exchange bank. The government even allowed itself to sell Jewish businesses. Access to these resources required no less than approval by the Reich Minister for Economic Affairs.
Narrowly defining security as simply asset protection is tempting, given its historical prevalence. Everything from my grandmother’s tales of stashing cash in curtains, to the US Constitution's 4th Amendment, “the right of the people to be secure in their persons, houses, papers, and effects” reinforces this physical emphasis.
When I discovered Bitcoin, I was hence drawn to its asset protection features. Like many, this biased view of security defined the start of my Bitcoin journey, focusing my attention on hardware wallets and encryption protocols. But that was soon to change.
How Bitcoin Changed Me
The more I read, the more I learned that with a network of nodes working to secure a global protocol, came a network of people working to secure global principles. It dawned on me that I had not so much discovered the ultimate bastion of property rights, but of human rights.
Here are just a few examples:
Freedom of Expression
Anonymity is fundamental for the full exercise of the right to freedom of expression. This is enshrined in Article 19 of the Universal Declaration of Human Rights (UDHR) and the International Covenant on Civil and Political Rights (ICCPR). Bitcoin's pseudonymous and decentralised nature makes it difficult for tyrants to identify and censor one of the purest forms of expression: transactions.
Adequate Living Standards
Article 25 of the UDHR states that everyone has the right to a standard of living adequate for health and well-being, including food, clothing, housing, and medical supplies. Article 17 further enshrines the retention of property necessary to support these living standards.
Bitcoin's cryptographic security reinforces ownership rights, making it difficult for rogue states to arbitrarily seize assets essential for the maintenance of these living standards. Furthermore, Bitcoin's 21-million-coin capped supply prevents arbitrary inflation, protecting against the erosion of purchasing power that has time and again proven correlated with the erosion of living standards.
Freedom of Association
Article 20 of the UDHR states that everyone has the right to freedom of peaceful assembly and association. Article 22 of the ICCPR also protects the right to freedom of association, including the right to form and join trade unions.
Multi-signature wallets are an explicit expression of this associative freedom. By enabling groups to collaboratively manage resources, the human connections required for civilisation to flourish can be directly represented and enforced in code.
Programmatic freedom of association is particularly pertinent for activist and civil society organisations and provides security against coercion in situations where individuals may face pressure to hand over funds from those who wield power.
Right to Information
The open-source nature of Bitcoin also somewhat poetically aligns with the right to seek, receive, and impart information, as outlined in Article 19 of the UDHR. Anyone can inspect, verify, and contribute to Bitcoin's code, promoting transparency and accountability. Its immutability also supports the right to information by preserving truth in the face of potential revisionism. Furthermore, Article 27 states that everyone has the right to share in scientific advancement and its benefits. Bitcoin embodies this principle by allowing global participation in its development and use.
Personal Context
For me, Bitcoin brought context to those old wartime stories I heard as a boy. It led me to the understanding that property rights are simply a derivative of human rights. Now, for the first time in history, we have a borderless technology that secures these rights not in international declarations or national constitutions – both susceptible to the stroke of a tyrant’s pen – but in executable code.
In essence, Bitcoin's technical features embody the very principles of security and resilience that are well recognised as essential to personal agency, mental well-being, and social cohesion. These operate independently of central authorities that have historically proven both capable and willing of stripping human rights, and not a moment too soon…
A Modern Necessity
These concerns are not limited to the past. Just recently, Blackrock CEO, Larry Fink, said this about Bitcoin in a CNBC interview:
“We have countries where you’re frightened of your everyday existence and it gives an opportunity to invest in something that is outside your country’s control.” (https://www.youtube.com/watch?v=K4ciiDyUvUo)
As an Australian, I see the precursors of what Larry describes. Legislative attacks on the right to expression, living standards, association, and information are becoming brazen. The Digital ID Bill 2024, legislated on May 16th, has already denied employment and government services to some, and is now poised to police the internet in what appears to be the making of a conditional access society.
The Communications Legislation Amendment (Combatting Misinformation and Disinformation) Bill 2024, currently sitting before federal parliament, is even more horrendous. It effectively establishes a protectionist Ministry of Truth and threatens imprisonment for an extremely broad array of ill-defined speech – all while providing exemptions for government and legacy media. This political activity is occurring amidst a cost-of-living and housing crisis, where many working individuals are living in tents in major cities.
Bitcoin’s True Security
Yet with Bitcoin (and a Starlink connection), I feel secure. Bitcoin has become a source of resilience and mental well-being for people in an increasingly complex world. Beyond its cryptographic security, Bitcoin provides a global network of like-minded individuals who share common principles. This distributed community offers a sense of belonging and support that extends far beyond the technology behind it.
Bitcoin’s existence gives me confidence in my ability to secure basic needs and find community anywhere, without relying on easily confiscated physical assets. Meeting fellow Bitcoin enthusiasts often reveals shared worldviews and values, creating instant connections.
Ultimately, Bitcoin's security stems not just from its technology, but from the human network it has fostered. It offers the reassurance that I could "land on my feet" anywhere, preserving both financial sovereignty and social bonds with free-thinking individuals. This holistic security - financial, social, and psychological - provides profound peace of mind in uncertain times.
‘Think You Know Bitcoin Security?’ was Written By Paul G Conlon. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: noisycyclone54@walletofsatoshi.com
-
 @ ed651996:0c058662
2024-11-27 09:49:40
@ ed651996:0c058662
2024-11-27 09:49:40Introduction
Aiwa.ae offers the best SEO companies in Dubai, providing businesses with top-tier SEO services that are designed to boost online visibility, drive organic traffic, and increase conversions. Search Engine Optimization (SEO) is a critical part of digital marketing, and with the right SEO strategy, your business can dominate search engine rankings, making it easier for customers to find your products and services online.
Dubai is one of the most competitive markets in the world, with businesses vying for attention in a digital landscape filled with local and international players. To stand out in this crowded space, it’s essential to work with a trusted SEO company that has a deep understanding of the local market, as well as global SEO best practices. Aiwa.ae connects you with the best SEO companies in Dubai, helping you choose the right agency for your unique needs.
When you partner with an SEO company listed on Aiwa.ae, you gain access to a team of professionals who are experienced in all aspects of SEO, including on-page SEO, off-page SEO, technical SEO, and local SEO. These companies use the latest tools and techniques to ensure that your website is optimized for search engines like Google, Bing, and Yahoo. They focus on improving your website’s content, structure, and user experience, all of which are essential factors that influence search engine rankings.
Why Choose an SEO Company from Aiwa.ae?
Proven Track Record: The SEO companies listed on Aiwa.ae have a history of success in helping businesses improve their online rankings. Whether you are a small business or a large corporation, these agencies have the expertise to tailor SEO strategies that suit your business goals.
Tailored SEO Strategies: Every business is unique, and a one-size-fits-all approach doesn’t work in SEO. The best SEO companies in Dubai understand this and provide customized strategies that address your specific challenges and objectives. Whether you're looking to improve local search visibility or expand globally, they will create a plan that aligns with your business goals.
Comprehensive SEO Services: Aiwa.ae connects you with SEO companies that offer a full range of services, including keyword research, content creation, link building, website audits, mobile optimization, and more. These companies ensure that every aspect of your website is optimized for both search engines and users.
Transparent Reporting: SEO is a long-term strategy, and it's essential to monitor progress and results. The best SEO companies in Dubai provide transparent reporting, so you can track the performance of your SEO campaigns. You will receive regular updates on keyword rankings, traffic growth, and other key metrics that demonstrate the effectiveness of your SEO strategy.
Experienced Team of SEO Experts: The SEO companies featured on Aiwa.ae employ experienced professionals who are well-versed in the latest SEO trends and updates. They stay ahead of the curve by continuously learning and adapting to changes in search engine algorithms, ensuring that your business stays competitive.
Focus on ROI: The ultimate goal of SEO is to increase your return on investment (ROI). The SEO companies in Dubai recommended by Aiwa.ae understand this and focus on driving high-quality traffic to your website, resulting in increased leads, conversions, and sales.
Conclusion
If you're looking for the best SEO company in Dubai, Aiwa.ae is the ideal platform to find trusted agencies that can help you improve your online presence and achieve your business goals. With a comprehensive range of SEO services and proven strategies, the companies listed on Aiwa.ae will ensure that your business stands out in search engine results, attracts more customers, and grows in the digital landscape. Whether you're looking to optimize your website, improve local SEO, or drive more organic traffic, Aiwa.ae connects you with the top SEO experts in Dubai.
-
 @ 98589a2e:bf49daa1
2024-11-27 09:38:24
@ 98589a2e:bf49daa1
2024-11-27 09:38:24К 2040 году Санкт-Петербург стал ярким примером эффективной и доступной системы здравоохранения, которая значительно изменилась за последние два десятилетия. Внедрение новых медицинских учреждений и передовых технологий улучшило качество медицинского обслуживания для всех граждан.
Новые медицинские учреждения и технологии
Современные медицинские центры
С момента открытия первых новых клиник в начале 2020-х годов, в городе было построено более 50 современных медицинских учреждений, включая многопрофильные больницы и специализированные клиники. Эти учреждения оснащены самым современным оборудованием, что позволяет предоставлять высококачественные медицинские услуги. Например, в 2025 году была открыта новая детская поликлиника, которая стала образцом для других учреждений благодаря своей инфраструктуре и комфортным условиям для маленьких пациентов.
Внедрение цифровых технологий
В 2031 году по приказу Президента была создана Единая государственная информационная система здравоохранения (ЕГИСЗ), к которой подключились все медицинские учреждения. Это обеспечило беспрепятственный доступ к медицинским данным и улучшило координацию между учреждениями. Телемедицина также получила широкое распространение, позволяя пациентам получать консультации врачей удаленно, что особенно актуально для жителей отдаленных районов.

Профилактика и ранняя диагностика
Важным направлением стало внедрение программ профилактических осмотров, что позволило значительно снизить уровень заболеваемости. Специализированные центры здоровья были созданы для проведения диспансеризации и профилактических мероприятий, способствуя раннему выявлению заболеваний.
Устойчивое развитие системы здравоохранения
В рамках национального проекта «Здравоохранение» была осуществлена программа по привлечению квалифицированных специалистов в медицину, что повысило уровень обслуживания. Регулярные курсы повышения квалификации для медицинского персонала обеспечивают актуальность знаний и навыков врачей.

Планы на 2050 год
Санкт-Петербург продолжает развивать систему здравоохранения с акцентом на следующие направления:
Расширение сети медицинских учреждений
Планируется открыть дополнительно 100 новых объектов здравоохранения, включая специализированные центры по лечению хронических заболеваний. Это позволит улучшить доступность медицинской помощи для всех слоев населения.
Инновационные технологии
Ожидается внедрение искусственного интеллекта для диагностики заболеваний и разработки индивидуальных планов лечения, что повысит эффективность медицинской помощи. Также будут разработаны мобильные приложения для записи на прием к врачу и получения результатов анализов.

Устойчивость системы здравоохранения
Программы по повышению зарплат и улучшению условий работы для медицинского персонала помогут привлечь больше специалистов в отрасль. Кроме того, внедрение экологически чистых технологий в медицинских учреждениях снизит негативное воздействие на окружающую среду.
Программы по профилактике заболеваний
Планируется расширение программ вакцинации населения для предотвращения распространения инфекционных заболеваний. Образовательные инициативы будут направлены на повышение осведомленности населения о здоровье и профилактике заболеваний через информационные кампании.
 С внедрением новых технологий и инициатив система здравоохранения Санкт-Петербурга станет еще более эффективной и устойчивой к вызовам будущего. Город здоровья продолжает развиваться, обеспечивая каждому жителю качественную медицинскую помощь!
С внедрением новых технологий и инициатив система здравоохранения Санкт-Петербурга станет еще более эффективной и устойчивой к вызовам будущего. Город здоровья продолжает развиваться, обеспечивая каждому жителю качественную медицинскую помощь! -
 @ 2063cd79:57bd1320
2024-11-27 09:36:09
@ 2063cd79:57bd1320
2024-11-27 09:36:09Beschäftigt sich die deutsche Politik mit Bitcoin? Es ist nicht ganz leicht diese Frage mit ja oder nein zu beantworten, da es innerhalb der verschiedenen Parteien, aber auch der Länder- und Bundesregierung kleine und größere Gruppen, sogenannte Arbeitsgruppen und Task-Forces, gibt, die sich mit speziellen Themen befassen. Um einen ersten Überblick zu erhalten habe ich mir die Regierungsprogramme der großen Parteien der Bundestagswahl im Herbst 2021, den Koalitionsvertrag der aktuellen Regierung und die Strategiepapiere der Superministerien angeschaut. Ohne die Spannung vorwegnehmen zu wollen, es ist ernüchternd.
SPD Regierungsprogramm
Nix! Weder Bitcoin, noch Blockchain oder Kryptowährungen werden erwähnt.

CDU/CSU Regierungsprogramm
Der Begriff Blockchain kommt hier immerhin 6 mal vor. Die CDU/CSU möchte "wichtigen industriellen Zukunftsfeldern" einen Platz in Europa bieten und Deutschland dabei zu einer "Hochburg" für diese Technologien entwickeln. Des Weiteren verweist die CDU/CSU hier auf die Blockchain-Strategie, die wir später noch näher betrachten. Von Bitcoin im Speziellen oder Kryptowährungen im Allgemeinen ist an keiner Stelle die Rede.
FDP Regierungsprogramm
Auch die FDP nähert sich dem Thema Blockchain wage an und erwähnt diese 2 mal in ihrem Programm. Auch das Thema Kryptowährungen wird besprochen und zumindest in einem positiven Kontext "begrüßt". Konkrete Schritte oder Pläne werden nicht erläutert.
Wir begrüßen zudem alternative Tauschmittel wie Kryptowährungen auf Blockchain sowie anderen Basen und wollen die Schaffung eines verlässlichen rechtlichen Rahmens fördern und weiterentwickeln.
Grünen Regierungsprogramm
Jetzt wird es schwierig. Die Grünen sind pro einer Euro-CBDC der EZB, da sie meinen, dass diese Rechtssicherheit für Verbraucher//innen schafft. In Ausgabe #5 haben wir schon besprochen, dass CBDCs Zentralbankgeld darstellen und die Zentralbanken Konten direkt verwalten. Die Einzigen, die Rechtssicherheit erhalten, sind die Zentralbanken und durch Erweiterung der Staat. Denn CBDCs sind - anders als Bargeld - programmiertes und transparentes Geld, mit dem sich die Herkunft somit alle historischen Daten sowie Daten über den Verwendungszweck nachvollziehen lassen.
Weiter setzen die Grünen den Gebrauch von Kryptowährungen mit Geldwäsche, Kinderpornografie, Steuerhinterziehung und Terrorfinanzierung gleich. Das lassen wir mal unkommentiert so stehen.

Wir befürworten die Initiative der Europäischen Zentralbank (EZB), einen digitalen Euro zu schaffen. Sie gewährleistet dabei Daten- und Rechtssicherheit für Verbraucher*innen und Unternehmen und erhöht die Effizienz der Euro-Transaktionen. [...] Bei allen digitalen Zahlungen und Kryptowährungen müssen die tatsächlichen wirtschaftlich Berechtigten analog zu Regelungen beim Bargeld ab einer gewissen Schwelle ermittelt werden. Zur Bekämpfung von Verbrechen wie Geldwäsche, Darstellung sexualisierter Gewalt gegen Kinder, Steuerhinterziehung und TerrorFinanzierung braucht es auch für den Bereich des digitalen Bezahlens klare Regeln. Bestehende Kooperationspflichten von Kryptotauschbörsen wollen wir erweitern und Ermittlungsbehörden angemessen in diesem Bereich schulen. Wir wollen den rasanten Entwicklungen im Bereich dezentraler Finanzanwendungen gerecht werden und die Chancen und Risiken von Kryptowährungen und Blockchains differenziert ausloten.
Insgesamt werden Kryptowährungen in einem sehr negativ gefärbten Licht dargestellt. Kurzfassung: CBDCs und damit staatliche Kontrolle top! Kryptowährungen und Kryptotauschbörsen kriminell und zu wenig reguliert! Achja, aber Blockchain als Technologie "loten wir aus". Haben wir noch was vergessen? Stimmt, mehr Steuern! Denn wie wir letzte Woche gesehen haben, sind Gewinne aus der Veräußerung von virtuellen Währung steuerfrei, wenn zwischen Kauf und Verkauf mindestens 12 Monate liegen. Diese Regel wollen die Grünen abschaffen und alle Transkationen besteuern.
Auch werden wir die Steuerfreiheit für andere Veräußerungsgewinne, beispielsweise beim Handel mit Edelmetallen, Rohstoffen oder Kryptowerten, abschaffen.
Linkspartei Regierungsprogramm
Bei der Linkspartei wird die Technologie Blockchain erst gar nicht erwähnt, allerdings wird von Kryptotechnologie gesprochen, und wie soll es auch anders sein, sollen Zahlungen mit dieser Technologie besser beaufsichtigt werden. Als einzige Partei befasst sich die Linkspartei auch mit dem Thema Mining. Dieses ist deren Ansicht nach energie- und ressourcenverschwendend und muss deshalb verboten werden. Wenn mich eine Sache wundert, dann dass ich diesen Absatz in diesem und nicht im Regierungsprogramm der Grünen gefunden habe.
Die Antigeldwäscheeinheit des Zolls (FIU) hat im Kampf gegen Geldwäsche versagt und verfügt nicht über kriminalistisch geschultes Personal. Wir brauchen eine stärkere Einbeziehung der Kriminalämter in die Analyse von Geldwäscheverdachtsmeldungen. Insbesondere der Immobilien- bzw. Nichtfinanzsektor sowie die neuen Fintech-Unternehmen, die Zahlungen im Internet abwickeln oder Kryptotechnologie nutzen, müssen besser beaufsichtigt werden.
Wir streben ein Verbot der energie- und ressourcenverschwendenden Erzeugung sogenannter Kryptowährungen an.
Wie wir alle wissen, haben SPD, Grüne und FDP als Koalition die Wahl für sich entscheiden können und so musste aus den Regierungsprogrammen der drei Parteien ein Koalitionsvertrag geschaffen werden. Welche der Forderungen aus den Programmen übernommen und in den Vertrag eingebaut wurden, schauen wir uns als nächstes an.
Koalitionsvertrag zwischen SPD, Grünen und FDP
Gänzlich neu und in keinem der Programme zu finden, ist der Ansatz der neuen Regierung, den veralteten und sehr mühseligen Ablauf beim Erwerb von Immobilien mit Hilfe eines "Grundbuches auf der Blockchain" zu prüfen. Dies ist ein persönliches Reizthema für mich und etwas, das ich schon seit Jahren fordere. Ich bin also sehr dafür.
Wir geben eine Machbarkeitsstudie in Auftrag um zu untersuchen, ob ein Grundbuch auf der Blockchain möglich und vorteilhaft ist.
Außerdem will die Regierung die Blockchain dazu nutzen, um Cum-Ex ähnliche Geschäfte zu verhindern. Ich finde es beachtlich, dass das Thema Blockchain zumindest Erwähnung findet und darüber hinaus handfeste Anwendungsbereiche geschaffen wurden. Ob diese tatsächlich Umsetzung finden wird, bleibt abzuwarten.
Aufbauend auf den Maßnahmen der letzten Legislaturperiode werden wir alles dafür tun, missbräuchliche Dividendenarbitragegeschäfte zu unterbinden. Um dies betrugssicher sicher zu stellen, wollen wir neue technische Möglichkeiten, z. B. Blockchain, noch stärker nutzen.
Der positive Ton gegenüber dem Thema Blockchain und digitalen Finanzdienstleistungen (ich begrüße, dass Kryptowährungen als Begriff ersetzt wurde) scheint es aus dem Programm der FDP in den Vertrag hinüber geschafft zu haben. Die Regierung öffnet sich dem Thema, will den finanziellen, rechtlichen und regulatorischen Rahmen schaffen, um Deutschland zu einem der führenden Standorte machen und schlägt proaktiv Anwendungsbeispiele, wie z.B. die Emission elektronischer Wertpapiere, vor.
Für FinTechs, InsurTechs, Plattformen, NeoBroker und alle weiteren Ideengeber soll Deutschland einer der führenden Standorte innerhalb Europas werden. Es gilt, die mit den neuen Technologien, wie z. B. Blockchain, verbundenen Chancen zu nutzen, Risiken zu identifizieren und einen angemessenen regulatorischen Rahmen schaffen. Wir werden deshalb für effektive und zügige Genehmigungsverfahren für FinTechs sorgen. Digitale Finanzdienstleistungen sollten ohne Medienbrüche funktionieren; dafür werden wir den Rechtsrahmen schaffen und die Möglichkeit zur Emission elektronischer Wertpapiere auch auf Aktien ausweiten.
Im nächsten Absatz wird ein konkreter Ansatz zur Regulierung des Kryptobereichs durch die EU (MiCA) vorgestellt und zugleich der Standort Deutschland als gerechter und wettbewerbsfreundlicher Finanzplatz für Digitalunternehmen verteidigt. Die gesamte Formulierung wirkt auf mich sehr FDP-getrieben und scheint größtenteils durch die Verantwortlichen der Liberalen nach vorne gebracht worden zu sein.
Wir brauchen eine neue Dynamik gegenüber den Chancen und Risiken aus neuen Finanzinnovationen, Kryptoassets und Geschäftsmodellen. Wir setzen uns für ein Level-PlayingField mit gleichen Wettbewerbsbedingungen innerhalb der EU, zwischen traditionellen und innovativen Geschäftsmodellen und gegenüber großen Digitalunternehmen ein. Das europäische Finanzmarktaufsichtsrecht machen wir fit für die Digitalisierung und für komplexe Konzernstrukturen, um eine ganzheitliche und risikoadäquate Aufsicht über neue Geschäftsmodelle sicherzustellen. Wir brauchen für den Kryptobereich eine gemeinsame europäische Aufsicht. Wir verpflichten Kryptoassetdienstleister zur konsequenten Identifikation der wirtschaftlich Berechtigten.

Und dann durften die Grünen auch noch einen Absatz aus ihrem Programm unterbringen (immerhin keine Kinderpornografie):
Die EU-Aufsichtsbehörde soll sich nicht nur um den klassischen Finanzsektor kümmern, sondern auch den Missbrauch von Kryptowerten für Geldwäsche und Terrorismusfinanzierung verhindern.
Wie werden also die Ideen und Ansätze des Koalitionsvertrages in der Praxis umgesetzt? Die Bundesfinanz- und Wirtschaftsministerien haben eine "Blockchain-Strategie der Bundesregierung" verfasst, in der gründlich alle möglichen Konzepte vermischt werden:
Der bekannteste – bei Weitem nicht einzige – Anwendungsfall ist die Kryptowährung Bitcoin. Mit dem sprunghaften Anstieg der Kurse von Kryptowährungen und der neuartigen Finanzierungsform sogenannter Initial Coin Offerings (ICOs) wuchs das öffentliche Interesse an der Blockchain-Technologie. Zugleich wuchs mit dem Handel von Bitcoin der damit verbundene Stromverbrauch massiv. In letzter Zeit kommen Anwendungsfälle jenseits von Kryptowährungen mehr und mehr in den Fokus.
Zunächst wird Bitcoin als Kryptowährung betitelt, aber das ist nicht das größte Problem, denn diese Debatte wird ja zur Zeit noch geführt und das Unterscheiden von Bitcoin und anderen "Kryptowährungen" wird ein Kampf sein, der noch für eine Weile gekämpft werden wird. Allerdings wird im zweiten Satz gleich auf ICOs verwiesen, welche mit Bitcoin überhaupt nichts zu tun haben, um dann wieder auf das Thema Bitcoin zurückzuspringen und das beliebte Stromverbrauch-FUD-Narrativ aufzugreifen (das BMWK - also das Bundesministerium für Wirtschaft und Klimaschutz vereint unter Robert H. ja jetzt zwei Kompetenzbereiche, da darf der Verweis auf Klimaschutz natürlich nicht fehlen 😙).
Kurzer Schwenker zum Thema Energie- und Klimaschutz-FUD. Das betrifft nicht direkt das Kernthema dieser Ausgabe, scheint aber das Lieblingsthema der Politiker zu sein, wenn es um Bitcoin geht (oder Joe?). Sogar die FT hat kürzlich eine Kolumne veröffentlicht, die sich "kritisch" mit Bitcoin auseinandersetzt und vielen objektiv falschen Narrativen auf den Leim geht. Der Artikel ist als Archiv verlinkt:
https://archive.ph/4AD1L
Um die Argumente gegen die Kritiker (z.B. FT Kolumnistin Jemima Kelly) kurz zu halten: Der letzte Bericht des Bitcoin Mining Councils (Juli) zeigt auf, dass 59,5% der für Bitcoin-Mining aufgebrachten Energie aus erneuerbaren Quellen stammt, und dass Bitcoin zwar 0,15% der weltweit produzierten Energie verbraucht, diese jedoch für nur 0,086% der globalen CO2-Emissionen verantwortlich ist.


Hinzu kommt, dass Bitcoin-Mining in den nächsten Jahren energieeffizienter wird, da Mining sich mit erstaunlicher Geschwindigkeit dem Energiesektor annähert. Dies wird zu einer exponentiellen Steigerung von Innovationen führen, die sowohl Bitcoin mittelfristig weiter dekarbonisieren, aber auch die zunehmend erneuerbaren Netze verbessern wird.
Zurück zur Politik und der Blockchain-Strategie der Bundesregierung. An anderer Stelle wird vom Blockchain-Whitepaper gesprochen und dann auf das Bitcoin Whitepaper von Satoshi verwiesen. Bis auf eine weitere Erwähnung zur Einordnung von Bitcoin als Kryptowährung wird Bitcoin selbst auf den gesamten 24 Seiten der Veröffentlichung nicht mehr erwähnt. Wie man sehen kann, wird hier Einiges durcheinandergeworfen und viele Konzepte scheinen den Autoren noch nicht ganz klar zu sein.
Es sei der aktuellen Startelf des BMWK und BMF zugute gehalten, dass dieses Strategiepapier schon im Septemeber 2019 erschienen, und damit der Vorgängerregierung zuzuschreiben ist (siehe Parteiprogramm CDU/CSU, die sich hierauf berufen), dennoch stützen sich sämtliche aktuellen Publikationen und Zielsetzungen der aktuellen Regierung auf diese Strategie und wurden dementsprechen sicherlich eingehend geprüft, auf Korrektheit kontrolliert und inhaltlich begutachtet (ODER?). Oder ist die Strategie schlichtweg vergessen worden, und durch die "Digitalstrategie" des Bundesministerium für Digitales und Verkehr (wieder zwei clever kombinierte Kompetenzbereiche) ersetzt worden? Begriffe wie Blockchain oder Bitcoin kommen in diesem Strategiepapier des BMVI nämlich gar nicht mehr vor 🤔Nur der Begriff Krypto wird hier (natürlich mit Verweis auf Nachhaltigkeit und Rechtssicherheit) kurz erwähnt:
Wir wollen den Standort Deutschland im Bereich der Finanzinnovationen und Krypto-Token weiter stärken. Dazu braucht es weiter klare und rechtssichere Steuerregeln, um Entwicklungen nicht zu behindern. Wir wollen die Finanzaufsicht weiter darin bestärken, neue, innovative Geschäftsmodelle auch bei komplexen Strukturen zu durchdringen. Wir setzen uns für eine europäische Aufsicht im Kryptobereich ein, um innerhalb Europas einheitliche Standards auch unter Berücksichtigung von Nachhaltigkeitsaspekten zu fördern. [...] Den schnell wachsenden ökologischen Fußabdruck von digitalen Technologien wie z.B. von bestimmten Kryptowerten wollen wir monitoren und weitere Maßnahmen zur Reduktion ausarbeiten.
Das Fehlen von Blockchain und Bitcoin in dieser Strategie kann darauf zurückgeführt werden, dass weder in den jeweiligen Parteien, noch auf Ebene der Bundesregierung engagierte Fachpersonen zugegen sind, die das Thema vorantreiben wollen. Das Thema Blockchain wird hier, wenn überhaupt, ehrenamtlichen Interessenvertretern, Vereinen und Vertretern von Start-ups im Blockchain-Bereich repräsentiert. So gibt es z.B. den sogenannten Bundesblock (Blockchain Bundesverband), der thematisch aber scheinbar absichtlich von Bitcoin abrückt und sich mit anderen Anwendungsfällen der Blockchain, wie DAOs (Decentralized Autonomous Organization), SSI (Self Sovereign Identity), Steuern, sogar NFTs und dem Metaverse beschäftigt. Die Regierung selbst scheint insgesamt wenig zu dem Thema beitragen zu wollen.
Das oben aufgezeigte ist eine kurze Übersicht des Ist-Zustands. Das Thema Bitcoin scheint in der deutschen Politik noch überhaupt nicht angekommen zu sein, entweder, weil die Einstiegshürde zu hoch ist, oder weil das Thema für die meisten Amtsträger einfach noch keinen großen Stellenwert besitzt. Was auch immer der Grund für die Nichtbeachtung ist, es bleibt abzuwarten, ob die Regierung ihre Prioritäten falsch setzt und die wichtigste Erfindung seit dem Internet (wieder mal) verpasst, oder ob nach außen hin eine scheinheilige Nichtbeachtung suggeriert wird, während man sich an anderer Stelle detailliert mit dem Thema auseinandersetzt.
Da zumindest die EZB mit Hinblick auf CBDCs aktiv im Bereich der Digital Assets "forscht", sollte die Bundesregierung mindestens auf dem gleichen Erkenntnisstand bleiben, um etwaigen Vorstößen mit Wissen und Kompetenz entgegentreten zu können. Die Nichtbeachtung von Seiten der Parteien ist fahrlässig, öffnet aber - gerade in einem Vielparteiensystem wie Deutschland - sogar Türen, um vielleicht eine Gruppierung zu gründen, die sich dem Thema, mit Sachverstand und Ahnung, annimmt. Das wäre ein schönes Thema für eine zukünftige Ausgabe.
🫳🎤
In diesem Sinne, 2... 1... Risiko!

-
 @ 98589a2e:bf49daa1
2024-11-27 09:14:01
@ 98589a2e:bf49daa1
2024-11-27 09:14:01Санкт-Петербург — город инноваций: обзор 2040 года
К 2040 году Санкт-Петербург стал одним из ведущих центров инноваций в России, превратившись в город, где технологии и наука играют ключевую роль в жизни его жителей. За последние два десятилетия в городе произошли значительные изменения, способствующие развитию высоких технологий и созданию комфортной городской среды.
Текущие достижения
Энерготехнохаб "Петербург"
С момента запуска Энерготехнохаба в конце 2019 года, Санкт-Петербург стал важным международным центром для энергетических и нефтегазовых разработок. В результате этого проекта, который активно развивался в 2020-х годах, город привлек более 500 R&D-компаний, что позволило увеличить долю Петербурга в объемах заказов на научно-исследовательские и опытно-конструкторские разработки до 30%. Резиденты хаба разработали множество инновационных решений, включая новое поколение донных станций для сейсморазведки.
Научно-образовательные центры
В 2026 году началось строительство ИТМО Хайпарка — научно-образовательного центра на базе Петербургского государственного университета информационных технологий, механики и оптики. Этот комплекс стал домом для более чем 50 международных лабораторий и новых производств. К 2040 году он обеспечил создание более 12 тысяч рабочих мест и стал важной частью технологической экосистемы города.
Инфраструктурные проекты
Генеральный план развития Петербурга до 2050 года включает строительство новых станций метро и транспортных магистралей. К 2040 году было построено около 100 новых станций метро, что значительно улучшило транспортную доступность города. Также была реализована Широтная магистраль скоростного движения, связывающая различные районы города.
Планы на 2050 год
Санкт-Петербург продолжает развивать свои инновационные возможности с акцентом на следующие направления:
Расширение технологической инфраструктуры
Планируется создание новых научных и исследовательских центров, которые будут сосредоточены на разработках в области экологии, биотехнологий и информационных технологий. Ожидается, что к 2050 году количество технологических компаний в городе увеличится вдвое по сравнению с текущими показателями.
Устойчивое развитие
В рамках новых инициатив власти города намерены внедрить экологически чистые технологии во все сферы городской жизни. Это включает создание "умных" зданий с минимальным воздействием на окружающую среду и развитие зеленых зон.
Образование и кадры
Санкт-Петербург планирует увеличить инвестиции в образование и подготовку кадров для высоких технологий. Ожидается, что новые образовательные программы будут направлены на привлечение молодых специалистов в области науки и технологий.
Санкт-Петербург к 2040 году стал не только культурной столицей России, но и важным центром инноваций и технологий. С продолжающимся развитием инфраструктуры, научных учреждений и программ устойчивого развития город готовится к будущим вызовам. К 2050 году Петербург станет образцом для других городов страны, демонстрируя, как можно эффективно сочетать технологический прогресс с комфортом жизни для своих граждан.
-
 @ 98589a2e:bf49daa1
2024-11-27 09:12:34
@ 98589a2e:bf49daa1
2024-11-27 09:12:34К 2040 году Санкт-Петербург стал образцом устойчивого развития и внедрения зеленой экономики, что стало возможным благодаря множеству инициатив и проектов, реализованных за последние два десятилетия. Город активно работает над улучшением экологической ситуации и переходом к более устойчивым методам ведения хозяйства.

Достижения в области зеленой экономики
Создание кластеров чистых технологий
В 2021 году в Санкт-Петербурге был основан кластер чистых технологий для городской среды, который стал важным шагом к формированию устойчивого развития территорий. Этот проект направлен на развитие промышленного симбиоза и координацию усилий по внедрению экологически чистых технологий в различных отраслях.
Развитие возобновляемых источников энергии
С 2025 года в городе активно развиваются проекты по внедрению возобновляемых источников энергии (ВИЭ). К 2030 году доля ВИЭ в энергетическом балансе города достигла 20%, что стало возможным благодаря строительству солнечных и ветровых электростанций, а также малых ГЭС.
Устойчивый городской транспорт
С начала 2030-х годов Петербург начал массовое внедрение электрического и гибридного транспорта. В результате, к 2040 году более 50% общественного транспорта города стало экологически чистым, что значительно снизило уровень выбросов углерода и улучшило качество воздуха.

Планы на 2050 год
Санкт-Петербург продолжает двигаться в сторону зеленой экономики с амбициозными планами на будущее:
- Расширение зеленой инфраструктуры
-
Планируется создание новых зеленых зон и парковых пространств, чтобы увеличить долю зеленых территорий в городской среде до 30% к 2050 году.
-
Углубление перехода на ВИЭ
-
Ожидается, что к 2050 году доля возобновляемых источников энергии в энергетическом балансе города вырастет до 50%. Это будет достигнуто за счет строительства новых солнечных и ветровых электростанций, а также модернизации существующих.
-
Инновационные технологии для устойчивого развития
-
Внедрение умных технологий для управления ресурсами и мониторинга экологической ситуации станет приоритетом. Ожидается использование больших данных и искусственного интеллекта для оптимизации потребления энергии и ресурсов.
-
Образовательные инициативы
-
Планируется создание образовательных программ по экологии и устойчивому развитию для всех возрастных групп, чтобы повысить осведомленность населения о важности защиты окружающей среды.
-
Кооперация с международными партнерами
- Санкт-Петербург намерен активно сотрудничать с международными организациями и другими городами для обмена опытом и внедрения лучших практик в области зеленой экономики.
К 2050 году Санкт-Петербург станет не только примером зеленой экономики в России, но и важным центром экологических инициатив на международной арене. Город продолжит развиваться как пространство, где гармонично сосуществуют природа и человек, обеспечивая высокое качество жизни для своих жителей.
-
 @ 98589a2e:bf49daa1
2024-11-27 09:07:51
@ 98589a2e:bf49daa1
2024-11-27 09:07:51К 2040 году Санкт-Петербург стал центром инноваций и предпринимательства, открывающим новые горизонты для бизнеса. За последние два десятилетия город пережил значительные изменения, внедрив передовые технологии и адаптировавшись к глобальным трендам.

Текущие достижения
Инновационные технологии и стартапы
С начала 2020-х годов в Петербурге активно развивались стартапы в области технологий, что привело к созданию множества новых компаний. В 2025 году был основан «Технопарк Санкт-Петербурга», который стал площадкой для incubator-ов и акселераторов, поддерживающих молодые предприятия. Это способствовало росту высоких технологий, таких как искусственный интеллект, робототехника и биотехнологии.
Устойчивое развитие
С 2030 года в городе активно внедряются экологические инициативы. Программы по сокращению углеродного следа и переходу на зеленую энергетику стали основой для многих бизнес-моделей. К 2035 году Санкт-Петербург стал одним из первых городов, внедривших концепцию «умного города», что улучшило качество жизни и повысило эффективность бизнеса.
Цифровизация и облачные технологии
С 2031 года многие компании начали использовать облачные сервисы для хранения данных и оптимизации бизнес-процессов. Это дало возможность малым и средним предприятиям снизить затраты на IT-инфраструктуру и сосредоточиться на развитии своих продуктов.

Планы на 2050 год
Взгляд в будущее показывает, что Санкт-Петербург продолжит развивать свои бизнес-горизонты с акцентом на следующие направления:
Расширение технологической инфраструктуры
Планируется создание новых технопарков и инкубаторов, которые будут поддерживать стартапы в области космических технологий, робототехники и искусственного интеллекта. Ожидается, что к 2050 году рынок космических услуг вырастет до $20 миллиардов, что откроет новые возможности для местных предпринимателей.
Устойчивое развитие и экология
К 2050 году город намерен стать углеродно нейтральным. Это потребует от бизнеса внедрения экологически чистых технологий и перехода на возобновляемые источники энергии. Программы по утилизации отходов и переработке станут стандартом для всех предприятий.
Инновации в здравоохранении
Ожидается, что к 2050 году медицина станет одним из ведущих направлений для бизнеса. Развитие телемедицины и использование ИИ для диагностики заболеваний откроют новые возможности для медицинских стартапов, улучшая доступность медицинских услуг.
Образование и подготовка кадров
Санкт-Петербург будет активно развивать образовательные программы для подготовки специалистов в области новых технологий. Ожидается создание партнерств между университетами и бизнесом для разработки образовательных курсов, соответствующих требованиям рынка труда.
Санкт-Петербург в 2040 году демонстрирует пример успешной адаптации к современным вызовам и трендам. Город продолжает открывать новые горизонты для бизнеса, внедряя инновации и устойчивые практики. С планами на будущее Санкт-Петербург готов стать лидером в области технологий и предпринимательства к 2050 году, обеспечивая качественную жизнь своим жителям и создавая возможности для роста бизнеса.
-
 @ 98589a2e:bf49daa1
2024-11-27 09:04:40
@ 98589a2e:bf49daa1
2024-11-27 09:04:40К 2040 году Санкт-Петербург стал одним из ведущих городов в России, где новые технологии кардинально изменили повседневную жизнь горожан. С момента начала внедрения инновационных решений в начале 2020-х годов, жители города ощутили на себе все преимущества цифровизации и технологического прогресса.

Текущие достижения
Голограммы в повседневной жизни
С 2028 года голограммы стали неотъемлемой частью городской инфраструктуры. Они используются для навигации в общественном транспорте, а также в торговых центрах, где виртуальные помощники помогают с выбором товаров. Например, в 2035 году была запущена система голографической информации на станциях метро, что значительно упростило передвижение по городу.
Нейроинтерфейсы
С 2035 года началось активное внедрение нейроинтерфейсов, которые позволяют пользователям управлять устройствами с помощью мыслей. Эти технологии нашли применение в медицине, образовании и даже в сфере развлечений. Благодаря нейроинтерфейсам пациенты могут взаимодействовать с медицинскими системами для получения рекомендаций по лечению и реабилитации.
Искусственный интеллект и автоматизация
С 2029 года искусственный интеллект (ИИ) активно используется в различных сферах — от здравоохранения до городского управления. ИИ помогает оптимизировать транспортные потоки, предсказывать потребности в ресурсах и управлять коммунальными службами. В 2038 году была внедрена система "умного города", которая использует данные для улучшения качества жизни граждан.

Планы на 2050 год
Санкт-Петербург не собирается останавливаться на достигнутом и планирует дальнейшее развитие технологий к 2050 году:
Расширение использования нейроинтерфейсов
Ожидается, что к 2050 году нейроинтерфейсы станут стандартом в повседневной жизни. Они будут интегрированы в устройства для работы и обучения, позволяя пользователям мгновенно получать доступ к информации и управлять задачами без необходимости использования традиционных интерфейсов.

Голографические технологии
Голография продолжит развиваться, с прогнозами о создании интерактивных голограмм для образовательных целей и развлечений. К 2050 году голограммы смогут передавать не только визуальную информацию, но и тактильные ощущения, что откроет новые горизонты для взаимодействия с контентом.
Устойчивое развитие технологий
Планируется внедрение экологически чистых технологий, которые будут минимизировать воздействие на окружающую среду. Это включает использование возобновляемых источников энергии для работы всех новых устройств и систем.
Интеграция технологий в медицину
К 2050 году ожидается значительное развитие телемедицины и персонализированной медицины на основе ИИ. Это позволит более точно диагностировать заболевания и разрабатывать индивидуальные планы лечения для пациентов.
С учетом всех этих изменений Санкт-Петербург к 2050 году станет городом будущего, где технологии не только облегчают жизнь граждан, но и делают её более безопасной и комфортной. Горожане смогут наслаждаться преимуществами инновационных решений, которые помогут создать умное и устойчивое общество.

-
 @ 98589a2e:bf49daa1
2024-11-27 09:00:47
@ 98589a2e:bf49daa1
2024-11-27 09:00:47К 2040 году Санкт-Петербург стал образцом инновационных подходов к формированию городской среды, интегрируя современные технологии и концепции устойчивого развития. За последние два десятилетия город значительно изменился, внедрив новые идеи, которые продолжают развиваться и будут актуальны в будущем.

Текущие достижения
Горизонтальные города и малоэтажное строительство
С начала 2020-х годов в Петербурге активно реализуется концепция горизонтальных городов, которая предполагает расширение городской территории по горизонтали. Это означает создание кварталов, где жилье, бизнес и рекреационные зоны находятся близко друг к другу. К 2035 году было построено множество малоэтажных зданий, что создало более интимную и комфортную атмосферу для жителей.
Умные города
В 2030 году началась реализация программы умного города, которая интегрировала цифровые технологии в управление городской инфраструктурой. Это позволило оптимизировать транспортные потоки, повысить безопасность и улучшить качество жизни горожан. Датчики и системы мониторинга обеспечивают оперативное реагирование на изменения в городской среде.
Экологические инициативы
С 2025 года в городе начали активно развивать экологические парки и зеленые зоны. Создание новых общественных пространств с акцентом на природу стало важным шагом к улучшению качества воздуха и созданию комфортной городской среды.

Планы на 2050 год
Санкт-Петербург продолжает развивать свою городскую среду с акцентом на следующие направления:
Расширение зеленых пространств
К 2050 году планируется создание дополнительных экологических парков и зеленых зон, что позволит увеличить долю природных комплексов в городской структуре. Это поможет улучшить качество жизни и снизить уровень загрязнения.

Инновационные технологии
Ожидается дальнейшее развитие искусственного интеллекта для управления городскими процессами. Внедрение новых технологий позволит более эффективно использовать ресурсы и улучшить взаимодействие между жителями и городской администрацией.

Мобильность и транспорт
Планируется создание новых транспортных систем, включая автономные транспортные средства и расширение сети общественного транспорта. Это обеспечит более удобные условия для передвижения по городу и снизит нагрузку на дороги.

Социальная интеграция
Важным аспектом будущего станет создание многофункциональных общественных пространств, способствующих социальной интеграции всех слоев населения. Ожидается, что такие пространства будут включать в себя скверы, площади и культурные центры, где жители смогут взаимодействовать друг с другом.
 К 2040 году Санкт-Петербург стал примером успешной реализации новых подходов к городской среде, сочетая инновации с устойчивым развитием. С дальнейшими планами на 2050 год город стремится стать еще более комфортным, безопасным и экологически чистым местом для жизни, где каждый житель сможет реализовать свой потенциал.
К 2040 году Санкт-Петербург стал примером успешной реализации новых подходов к городской среде, сочетая инновации с устойчивым развитием. С дальнейшими планами на 2050 год город стремится стать еще более комфортным, безопасным и экологически чистым местом для жизни, где каждый житель сможет реализовать свой потенциал. -
 @ 98589a2e:bf49daa1
2024-11-27 08:56:38
@ 98589a2e:bf49daa1
2024-11-27 08:56:38К 2040 году Санкт-Петербург стал образцом для подражания в области инновационного строительства, благодаря внедрению передовых технологий и новых подходов. За последние два десятилетия город претерпел значительные изменения, которые значительно улучшили качество жизни его жителей.

Текущие достижения в строительстве
3D-печать и аддитивные технологии
С 2023 года в Санкт-Петербурге активно развиваются технологии 3D-печати, что позволило возводить целые жилые комплексы с использованием аддитивных методов. В 2025 году были построены первые поселки из напечатанных домов, что продемонстрировало возможность быстрого и качественного строительства. Эти технологии не только ускорили процесс возведения зданий, но и снизили затраты на материалы.

Умные города
С начала 2030-х годов концепция "умных городов" стала основой для развития городской инфраструктуры. Интеграция цифровых технологий в управление городом позволяет оптимизировать ресурсы, улучшить безопасность и повысить качество услуг для граждан. Например, системы управления транспортом и энергоснабжением стали более эффективными благодаря использованию больших данных и искусственного интеллекта.
Экологические инициативы
Санкт-Петербург также делает акцент на устойчивом развитии. С 2030 года началась реализация проектов по использованию экологически чистых материалов и технологий в строительстве, что способствует снижению углеродного следа. Малоэтажное строительство стало популярным направлением, позволяющим создать более комфортную и безопасную городскую среду.

Планы на 2050 год
Смотрим в будущее: к 2050 году ожидаются следующие изменения в строительстве Санкт-Петербурга:
- Расширение применения 3D-печати
Планируется дальнейшее развитие технологий аддитивного строительства, включая создание многофункциональных объектов с уникальными архитектурными решениями. Ожидается, что к 2050 году все новые жилые комплексы будут строиться с использованием 3D-печати.
-
Интеграция искусственного интеллекта
Внедрение ИИ в процессы проектирования и строительства позволит автоматизировать многие этапы, включая планировку и контроль качества. Это повысит эффективность работы строительных компаний и сократит сроки реализации проектов. -
Устойчивые экосистемы
К 2050 году планируется создание "горизонтальных городов", где жилье, бизнес и общественные пространства будут гармонично сочетаться. Такие города будут ориентированы на самодостаточность и устойчивое развитие, с акцентом на зеленые зоны и общественные пространства. -
Умные технологии в строительстве
Ожидается, что все новые здания будут оснащены "умными" системами управления, которые обеспечат энергоэффективность и комфорт для жителей. Это включает автоматизированные системы отопления, освещения и безопасности.
 5. Общественное участие
5. Общественное участие
Важным аспектом будущего строительства станет вовлечение граждан в процесс планирования и проектирования новых объектов. Это позволит учитывать потребности жителей и создавать более комфортные условия для жизни.
- Расширение применения 3D-печати
-
 @ 98589a2e:bf49daa1
2024-11-27 08:50:01
@ 98589a2e:bf49daa1
2024-11-27 08:50:01Климатическая политика Санкт-Петербурга: шаги к устойчивому развитию в 2040 году
К 2040 году Санкт-Петербург стал примером успешной климатической политики, направленной на устойчивое развитие города. За последние два десятилетия были предприняты значительные шаги для улучшения экологической ситуации и повышения качества жизни горожан.
Достижения в области устойчивого развития
Внедрение зеленых технологий
С 2025 года в городе активно внедрялись зеленые технологии, направленные на снижение углеродного следа. В рамках программы "Зеленый Петербург" было установлено более 1000 солнечных панелей на общественных зданиях и жилых домах, что позволило значительно сократить потребление энергии из невозобновляемых источников.
Развитие общественного транспорта
С 2030 года в Петербурге началось активное развитие экологически чистого общественного транспорта. Введены в эксплуатацию новые электрические автобусы и трамваи, что снизило уровень выбросов углекислого газа в атмосферу. К 2035 году доля экологичного транспорта составила более 50% от общего числа пассажирских перевозок.
Создание зеленых зон
В 2032 году была реализована программа по созданию новых рекреационных зон и парков. Площадь зеленых насаждений увеличилась на 20%, что способствовало улучшению качества воздуха и созданию комфортной городской среды.
Планы на 2050 год
Санкт-Петербург продолжает развивать свою климатическую политику с акцентом на следующие направления:
Углеродная нейтральность
К 2050 году город планирует достичь углеродной нейтральности. Для этого будет разработан план по сокращению выбросов парниковых газов, включая переход на полностью возобновляемые источники энергии и повышение энергоэффективности зданий.
Инновационные технологии
Ожидается внедрение новых технологий для мониторинга состояния окружающей среды, включая использование дронов и сенсоров для сбора данных о качестве воздуха и уровнях загрязнения. Это позволит оперативно реагировать на экологические проблемы и принимать меры по их устранению.
Образование и осведомленность населения
Планируется реализация образовательных программ для повышения осведомленности населения о важности устойчивого развития и охраны окружающей среды. Будут организованы кампании по вовлечению граждан в проекты по озеленению и благоустройству города.
Устойчивое городское планирование
В рамках нового Генерального плана, который был принят в 2023 году с расчетным сроком до 2050 года, особое внимание будет уделено устойчивому городскому планированию. Это включает в себя создание пешеходных зон, развитие велоинфраструктуры и улучшение доступа к общественному транспорту.
Климатическая политика Санкт-Петербурга к 2040 году демонстрирует значительные успехи в направлении устойчивого развития. С учетом намеченных планов на 2050 год город стремится не только улучшить экологическую ситуацию, но и создать комфортные условия для жизни своих жителей. Санкт-Петербург становится примером для других городов, показывая, как можно успешно сочетать развитие urban-инфраструктуры с заботой об окружающей среде.
-
 @ 98589a2e:bf49daa1
2024-11-27 08:48:00
@ 98589a2e:bf49daa1
2024-11-27 08:48:00К 2040 году Санкт-Петербург пережил настоящую революцию в сфере общественного транспорта, что сделало его более доступным и современным. За последние два десятилетия город значительно обновил свою транспортную инфраструктуру, внедрив новые технологии и расширив сеть маршрутов.

Современные изменения в общественном транспорте
1. Развитие метрополитена
С момента начала масштабной реконструкции метрополитена в 2025 году, когда было открыто 31 новых станции, система подземного транспорта продолжает активно развиваться. По состоянию на 2040 год в городе функционирует уже более 120 станций, включая новые линии, такие как Кольцевая и Адмиралтейско-Охтинская. Это позволило улучшить доступность метро для жителей как центральных районов, так и отдаленных пригородов.
2. Обновление наземного транспорта
В 2030 году началась программа по обновлению парка наземного транспорта, в рамках которой были закуплены современные электробусы и автобусы на газомоторном топливе. К 2040 году на улицах города уже курсируют более 3000 экологически чистых автобусов и около 500 электробусов, что значительно снизило уровень загрязнения воздуха.
3. Интеграция разных видов транспорта
Согласно Генеральному плану, утвержденному в конце 2023 года, было предусмотрено создание 39 транспортно-пересадочных узлов, которые связывают различные виды общественного транспорта. Это позволяет пассажирам легко пересаживаться с метро на трамваи или автобусы, оптимизируя время в пути.
Планы на 2050 год
Санкт-Петербург не собирается останавливаться на достигнутом. В планах к 2050 году — дальнейшее развитие общественного транспорта с акцентом на следующие направления:
-
Строительство новых станций метро: Ожидается открытие еще 50 новых станций, что позволит расширить сеть метрополитена до более чем 170 станций.
-
Развитие высокоскоростного транспорта: В рамках нового Генплана запланировано строительство высокоскоростной железнодорожной магистрали, которая свяжет Санкт-Петербург с другими крупными городами России.
-
Инновационные технологии: Внедрение систем искусственного интеллекта для управления движением общественного транспорта и оптимизации маршрутов. Это позволит сократить время ожидания и повысить безопасность пассажиров.
-
Экологические инициативы: Продолжение программы по замене старых транспортных средств на экологически чистые модели с акцентом на использование возобновляемых источников энергии.
-
Улучшение инфраструктуры: Планируется реконструкция существующих дорог и строительство новых путепроводов и эстакад для улучшения транспортной доступности в городе.
 К 2040 году Санкт-Петербург стал примером успешной трансформации общественного транспорта, который стал более эффективным, безопасным и экологичным. С дальнейшими планами на развитие к 2050 году город готовится к новым вызовам и стремится обеспечить комфортные условия для всех своих жителей. Революция на колесах продолжается, и Санкт-Петербург движется к статусу одного из самых современных мегаполисов мира!
К 2040 году Санкт-Петербург стал примером успешной трансформации общественного транспорта, который стал более эффективным, безопасным и экологичным. С дальнейшими планами на развитие к 2050 году город готовится к новым вызовам и стремится обеспечить комфортные условия для всех своих жителей. Революция на колесах продолжается, и Санкт-Петербург движется к статусу одного из самых современных мегаполисов мира!
-
-
 @ 98589a2e:bf49daa1
2024-11-27 08:45:31
@ 98589a2e:bf49daa1
2024-11-27 08:45:31К 2040 году экономика Санкт-Петербурга претерпела значительные изменения, став более устойчивой и инновационной. Город успешно адаптировался к новым вызовам и использовал возможности, возникающие в условиях глобальных изменений.

Текущая экономическая ситуация
Промышленность и инвестиции
С момента принятия нового Генерального плана в 2023 году, который определил стратегию развития города до 2040 года, Санкт-Петербург стал одним из ведущих промышленных центров России. В рамках этого плана было увеличено количество промышленных зон на 630 гектаров, что способствовало привлечению новых производств и созданию рабочих мест. По состоянию на 2040 год, индекс промышленного производства в городе вырос на 12% по сравнению с предыдущими годами, благодаря активному развитию обрабатывающих отраслей.
Инновации и технологии
Санкт-Петербург стал важным центром для стартапов и высоких технологий. В 2035 году была запущена программа «Город инноваций», направленная на развитие человеческого капитала и внедрение передовых технологий во все сферы жизни. Это привело к созданию новых исследовательских центров и инкубаторов, которые поддерживают молодые компании.
Туризм
Туризм также стал важной частью экономики города. В 2023 году Санкт-Петербург заработал более 480 миллиардов рублей на туристической деятельности, что положительно сказалось на местном бизнесе и создании новых рабочих мест. К 2040 году город продолжает привлекать туристов благодаря культурным событиям и улучшенной инфраструктуре.
Изменения с 2023 по 2040 год
-
Развитие транспортной инфраструктуры: В рамках нового Генплана было запланировано строительство новых транспортных маршрутов, включая скоростную трамвайную линию и новые мосты. Эти изменения значительно улучшили мобильность жителей и способствовали экономическому росту.
-
Устойчивое развитие городской среды: Введены экологические инициативы, направленные на снижение негативного воздействия на окружающую среду. Увеличение доли рекреационных зон с 28,5% до 29,38% позволило создать более комфортные условия для жизни горожан.
-
Социальная инфраструктура: В городе было построено более 585 крупных объектов социальной инфраструктуры, включая школы и поликлиники, что улучшило качество жизни жителей.

Планы на 2050 год
Санкт-Петербург продолжает развивать свою экономику с акцентом на следующие направления:
-
Расширение производственных мощностей: Планируется создание новых промышленных зон и привлечение высокотехнологичных производств, что позволит увеличить объемы производства и создать дополнительные рабочие места.
-
Инновационные технологии: Ожидается дальнейшее развитие искусственного интеллекта и автоматизации в различных отраслях экономики. Это повысит эффективность производства и улучшит качество услуг.
-
Устойчивое развитие: Город будет продолжать внедрять экологически чистые технологии в промышленности и городской инфраструктуре для снижения углеродного следа.
-
Развитие человеческого капитала: Программы по обучению и повышению квалификации будут направлены на подготовку специалистов для новых высокотехнологичных отраслей.
 С учетом всех этих изменений, Санкт-Петербург к 2050 году стремится стать не только экономическим центром России, но и образцом устойчивого развития для других городов страны. Город продолжает адаптироваться к вызовам времени, обеспечивая своим жителям качественную жизнь и возможности для самореализации.
С учетом всех этих изменений, Санкт-Петербург к 2050 году стремится стать не только экономическим центром России, но и образцом устойчивого развития для других городов страны. Город продолжает адаптироваться к вызовам времени, обеспечивая своим жителям качественную жизнь и возможности для самореализации.
-
-
 @ 98589a2e:bf49daa1
2024-11-27 08:41:58
@ 98589a2e:bf49daa1
2024-11-27 08:41:58К 2040 году мир изменился, и Санкт-Петербург стал ярким примером адаптации к новым финансовым реалиям. За последние два десятилетия город прошел через значительные изменения, которые повлияли на управление бюджетом и финансовые привычки жителей.

Текущие финансовые тренды
Переход к цифровым деньгам
С 2025 года в Санкт-Петербурге начался массовый переход на электронные деньги, что привело к полному упразднению наличных расчетов. Это изменение стало возможным благодаря внедрению безопасных и удобных систем электронных платежей, что значительно упростило финансовые транзакции для граждан.
Устойчивое управление бюджетом
В 2030 году была запущена программа по устойчивому управлению бюджетом, которая включает в себя использование искусственного интеллекта для анализа расходов и доходов. Эта система позволяет более эффективно распределять бюджетные средства и минимизировать финансовые риски.
Инвестиции в зеленую экономику
С 2035 года наблюдается рост интереса к инвестициям в устойчивую экономику. Городские власти активно поддерживают проекты, направленные на развитие возобновляемых источников энергии и экологически чистых технологий, что позволяет не только улучшать качество жизни, но и создавать новые рабочие места.
Планы на 2050 год
Санкт-Петербург продолжает развиваться, и в планах на 2050 год — дальнейшее совершенствование финансовой системы и управление бюджетом:
Расширение цифровых платформ
Планируется внедрение новых цифровых платформ для управления личными финансами, которые помогут гражданам более эффективно планировать свои расходы и сбережения. Эти платформы будут интегрированы с государственными сервисами, что позволит получать актуальную информацию о налогах и социальных выплатах.
Устойчивое развитие городской инфраструктуры
В рамках программы "Устойчивый город" к 2050 году запланировано строительство новых объектов инфраструктуры с акцентом на экологические стандарты. Это включает в себя "умные" здания с энергоэффективными системами, которые помогут сократить коммунальные расходы для жителей.
Образовательные инициативы
С целью повышения финансовой грамотности населения будут запущены образовательные программы, направленные на обучение граждан основам управления личными финансами. Это поможет людям лучше понимать, как управлять своими ресурсами в условиях постоянно меняющейся экономики. К 2040 году Санкт-Петербург стал примером успешной адаптации к новым финансовым условиям. Переход на электронные деньги, устойчивое управление бюджетом и инвестиции в зеленую экономику создают основу для дальнейшего развития. Впереди нас ждут новые технологии и инициативы, которые помогут городу стать еще более устойчивым и комфортным для жизни. В 2050 году жители Петербурга смогут рассчитывать на качественное управление своими финансами и доступ к современным услугам, что сделает их жизнь более комфортной и безопасной.
-
 @ 98589a2e:bf49daa1
2024-11-27 08:36:56
@ 98589a2e:bf49daa1
2024-11-27 08:36:56К 2040 году Санкт-Петербург стал одним из ведущих городов России в вопросах управления миграцией населения. В ответ на растущее население, которое, согласно прогнозам, достигнет 6,5 миллионов человек, город внедрил ряд инициатив и программ, направленных на эффективное управление внутренней и внешней миграцией.
Текущие меры и изменения
Программы по привлечению мигрантов
С начала 2020-х годов город активно разрабатывает программы, направленные на привлечение квалифицированных специалистов из других регионов страны и зарубежья. В 2025 году была запущена программа "Петербург — город возможностей", которая предлагает налоговые льготы и субсидии для новых жителей, что способствовало увеличению миграционного притока.
Инфраструктурные изменения
Согласно новому Генеральному плану, утвержденному в 2031 году, в городе было запланировано строительство более 585 социальных объектов, включая школы, медицинские учреждения и спортивные комплексы. Это было сделано для обеспечения качественной социальной инфраструктуры для растущего населения. Основное внимание уделялось созданию комфортной городской среды, что также способствовало привлечению новых жителей.
Устойчивое развитие
С 2035 года в Петербурге активно реализуются проекты по улучшению экологической ситуации и созданию зеленых зон. Это включает в себя благоустройство набережных и создание новых парков. Подобные инициативы делают город более привлекательным для мигрантов, желающих жить в комфортной городской среде.
Планы на будущее: 2050 год
Глядя вперед, Петербург ставит перед собой амбициозные цели к 2050 году:
-
Расширение жилой застройки: Планируется строительство дополнительно 67 миллионов квадратных метров жилья для обеспечения потребностей растущего населения. Это включает как многоквартирные дома, так и индивидуальное жилье.
-
Развитие транспортной инфраструктуры: В рамках нового Генплана предусмотрено строительство новых линий метрополитена и расширение существующих маршрутов общественного транспорта. Ожидается создание более 89 новых станций метро до 2050 года, что значительно улучшит доступность различных районов города.
-
Поддержка интеграции мигрантов: В планах — разработка программ по интеграции мигрантов в общество через обучение языку, профессиональную подготовку и культурные обмены. Это поможет создать более гармоничную социальную среду.
-
Экологические инициативы: Продолжится внедрение экологически чистых технологий в городской инфраструктуре и здравоохранении, что сделает Петербург более устойчивым к вызовам изменения климата.
Таким образом, Санкт-Петербург к 2040 году успешно справляется с вызовами миграции населения благодаря комплексному подходу к развитию социальной инфраструктуры и созданию комфортной городской среды. Планы на 2050 год предполагают дальнейшее развитие этих инициатив с акцентом на устойчивость и интеграцию новых жителей в общество. Город продолжает оставаться привлекательным местом для жизни и работы, что способствует его динамичному развитию.
-
-
 @ 98589a2e:bf49daa1
2024-11-27 08:33:33
@ 98589a2e:bf49daa1
2024-11-27 08:33:33К 2040 году Санкт-Петербург стал центром спортивной активности, где новые объекты и мероприятия значительно изменили спортивную инфраструктуру города. За последние два десятилетия в Петербурге было реализовано множество инициатив, направленных на развитие спорта и повышение качества жизни горожан.

Новые спортивные объекты
Строительство спортивных комплексов
В 2024 году в рамках федерального проекта «Спорт — норма жизни» началось строительство нескольких крупных спортивных объектов. К 2030 году в городе было открыто более 20 новых спортивных комплексов, включая многофункциональные арены и специализированные школы олимпийского резерва. Одним из самых значительных объектов стал СКА Арена, открытый в 2025 году, который стал крупнейшим ледовым стадионом в мире.
Спортивные школы и адаптивный спорт
В 2025-2030 годах было открыто 13 новых отделений спортивных школ, включая четыре для адаптивного спорта, что позволило ветеранам и людям с ограниченными возможностями заниматься физической активностью и проходить реабилитацию. Эти шаги способствовали интеграции различных групп населения в спортивную жизнь города.

Мероприятия и программы
Массовые спортивные события
Санкт-Петербург стал местом проведения множества массовых спортивных мероприятий, включая марафоны, велогонки и чемпионаты по различным видам спорта. Эти события привлекают не только местных жителей, но и туристов, что способствует популяризации спорта и здорового образа жизни.
Программы по физической активности
В рамках городской программы по повышению уровня физической активности населения были внедрены регулярные занятия спортом на открытых площадках, а также курсы по различным видам физической активности для всех желающих. Благодаря этим программам уровень вовлеченности граждан в спорт значительно возрос.

Планы на 2050 год
Санкт-Петербург продолжает развивать свою спортивную инфраструктуру с амбициозными планами до 2050 года:
- Расширение сети спортивных объектов
-
Планируется строительство еще 100 новых спортивных объектов, включая специализированные центры для тренировок по различным видам спорта и новые многофункциональные комплексы.
-
Инновационные технологии в спорте
-
Ожидается внедрение технологий виртуальной реальности для тренировок и подготовки спортсменов, что позволит улучшить результаты и повысить интерес к занятиям спортом.
-
Устойчивое развитие спортивной инфраструктуры
-
В рамках новых экологических инициатив будет акцент на создание "зеленых" спортивных объектов с использованием экологически чистых материалов и технологий.
-
Образовательные программы
- Планы по расширению образовательных программ для тренеров и инструкторов, чтобы повысить качество подготовки специалистов в области физической культуры и спорта.
С внедрением новых технологий и инициатив Санкт-Петербург продолжает укреплять свои позиции как город здоровья и спорта, обеспечивая каждому жителю доступ к качественным спортивным услугам и активному образу жизни.
-
 @ 98589a2e:bf49daa1
2024-11-27 08:25:31
@ 98589a2e:bf49daa1
2024-11-27 08:25:31К 2040 году Санкт-Петербург стал одним из ведущих культурных центров России и Европы, продолжая развивать свои традиции и внедрять новые инициативы. За последние два десятилетия культурная жизнь города претерпела значительные изменения, которые сделали её более разнообразной и доступной для всех жителей.

Культурные учреждения и инициативы
Новые театры и культурные центры
С момента открытия нового театра в 2025 году, в Петербурге было построено более 15 новых театров и культурных центров, включая современные арт-пространства и выставочные галереи. Эти учреждения стали местом притяжения для творческих людей и любителей искусства. Например, в 2030 году был открыт Центр современного искусства на Васильевском острове, который стал платформой для выставок, мастер-классов и лекций.
Развитие музыкальной сцены
Музыкальная жизнь города также значительно обогатилась. В 2035 году была создана новая филармония, которая привлекла внимание как местных, так и международных музыкантов. В Петербурге проходят ежегодные музыкальные фестивали, такие как "Петербургская весна", которые собирают талантливых исполнителей со всего мира.
Внедрение цифровых технологий
С развитием цифровых технологий культурная жизнь города также изменилась. В 2031 году была запущена платформа "Культура онлайн", которая предоставляет доступ к виртуальным экскурсиям по музеям, театрам и другим культурным объектам. Это позволило людям из разных уголков страны и мира знакомиться с петербургской культурой без необходимости физического присутствия.
Программы по поддержке искусства
В рамках государственной программы поддержки культуры, запущенной в 2022 году, было выделено значительное финансирование на развитие творческих инициатив. Эта программа включает гранты для художников, музыкантов и театров, что способствует развитию новых проектов и идей.

Планы на 2050 год
Санкт-Петербург не собирается останавливаться на достигнутом и продолжает развивать свою культурную жизнь с акцентом на следующие направления:
Расширение культурных учреждений
Планируется строительство новых театров, музеев и концертных залов. К 2050 году ожидается открытие еще 20 новых объектов, включая специализированные музеи по современному искусству и мультидисциплинарные центры.
Инновации в культуре
С развитием технологий ожидается внедрение виртуальной реальности в музейные экспозиции и театральные постановки. Это позволит создать уникальный опыт взаимодействия с искусством для зрителей.

Образовательные программы
Планы включают запуск новых образовательных программ по искусству для молодежи, что поможет развивать творческие навыки у подрастающего поколения. Программы будут направлены на поддержку талантливых детей и молодежи через курсы, мастер-классы и стажировки.
Устойчивое развитие культуры
Важным аспектом станет внедрение экологически чистых технологий в культурные учреждения. Это может включать использование возобновляемых источников энергии и устойчивое управление ресурсами.
В результате всех этих изменений Санкт-Петербург к 2050 году станет еще более привлекательным для жителей и туристов как культурный центр, где каждый сможет найти что-то интересное для себя. Город продолжит свою традицию быть "культурной столицей" России, открывая новые горизонты для творчества и самовыражения.

Как вам инициативы развития культурной жизни города?
-
 @ 98589a2e:bf49daa1
2024-11-27 08:22:18
@ 98589a2e:bf49daa1
2024-11-27 08:22:18К 2040 году система образования в Санкт-Петербурге претерпела значительные изменения благодаря внедрению новых технологий и образовательных программ. Эти изменения начались в начале 2020-х годов и продолжают развиваться, обеспечивая более индивидуализированный и доступный подход к обучению.

Текущие достижения
Внедрение цифровых технологий
С 2025 года в образовательные учреждения активно внедряются цифровые технологии. Появление платформ для дистанционного обучения и онлайн-курсов сделало образование более доступным для всех слоев населения. В 2031 году была запущена единая платформа для электронного обучения, которая объединила различные ресурсы и курсы, позволяя студентам выбирать программы, соответствующие их интересам и потребностям.
Гибридное обучение
С 2035 года гибридное обучение стало стандартом в школах и университетах. Этот формат сочетает традиционные методы обучения с онлайн-ресурсами, что позволяет студентам учиться в удобном для них темпе. Преподаватели теперь выступают не только как источники знаний, но и как наставники, поддерживающие студентов на их образовательном пути.
Персонализированное обучение
С начала 2040 года акцент на персонализированное обучение стал основным трендом. Искусственный интеллект используется для создания индивидуальных учебных планов, адаптированных к способностям и интересам каждого ученика. Это позволяет учащимся работать в своем темпе и сосредоточиться на тех предметах, которые им наиболее интересны.

Планы на 2050 год
Расширение возможностей дистанционного обучения
К 2050 году планируется дальнейшее развитие дистанционного обучения с акцентом на использование виртуальной реальности (VR) и дополненной реальности (AR). Это позволит создавать иммерсивные образовательные среды, где студенты смогут взаимодействовать с учебным материалом в трехмерном пространстве.
Интеграция искусственного интеллекта
В ближайшие годы ожидается значительное расширение использования искусственного интеллекта в образовании. ИИ будет не только помогать в разработке индивидуальных учебных планов, но и анализировать прогресс студентов, предлагая дополнительные ресурсы для улучшения их навыков.

Устойчивое развитие образовательной среды
Планируется создание экологически чистых и устойчивых учебных заведений, которые будут способствовать развитию экологического сознания у студентов. Образовательные учреждения будут использовать зеленые технологии и ресурсы для создания комфортной учебной среды.
Образование на протяжении всей жизни
К 2050 году концепция образования на протяжении всей жизни станет нормой. Программы переподготовки и повышения квалификации будут доступны для всех возрастных групп, что позволит людям адаптироваться к быстро меняющемуся миру труда.
Образование будущего в Санкт-Петербурге стремится стать более гибким, доступным и персонализированным. С внедрением новых технологий и методов обучения город готовится к вызовам 2050 года, обеспечивая каждому жителю возможность получать качественное образование на протяжении всей жизни.
Какие инициативы вам кажутся наиболее перспективными?
-
 @ 98589a2e:bf49daa1
2024-11-27 08:16:48
@ 98589a2e:bf49daa1
2024-11-27 08:16:48К 2040 году Санкт-Петербург стал примером успешного развития социальной инфраструктуры, в значительной степени благодаря реализации нового Генерального плана, принятого в 2023 году. Этот план нацелен на создание комфортной городской среды и улучшение качества жизни горожан.

Новые медицинские и образовательные учреждения
За последние два десятилетия в Петербурге было построено более 585 новых объектов социальной инфраструктуры, включая:
-
226 учебных заведений: В 2025 году началось строительство новых школ и детских садов, что позволило значительно увеличить количество образовательных мест. Школы на 825 мест стали стандартом для новых учебных учреждений.
-
110 медицинских учреждений: В 2030 году открылись новые поликлиники и больницы, оснащенные современным оборудованием, что улучшило доступность медицинской помощи для всех слоев населения.
Развитие спортивной инфраструктуры
К 2040 году в городе было построено 205 спортивных объектов, включая современные спортивные комплексы и стадионы. Эти объекты способствуют развитию массового спорта и организации мероприятий различного уровня.
Общественные пространства и экология
В рамках нового Генерального плана также предусмотрено создание новых общественных пространств:
-
Тематические парки и пляжи: В 2035 году были открыты шесть тематических парков и девять благоустроенных пляжей, что сделало город более привлекательным для жителей и туристов.
-
Зеленые зоны: Появление новых парков и скверов, таких как реконструированная набережная Тучков буяна, способствовало улучшению экологической обстановки и созданию комфортной городской среды.
Транспортная инфраструктура
Согласно новому Генплану, к 2040 году было запланировано строительство более 100 новых станций метро и модернизация существующих транспортных артерий. Это значительно улучшило транспортную доступность города, что особенно важно для его дальнейшего развития.

Планы на 2050 год
Санкт-Петербург продолжает развивать свою социальную инфраструктуру с акцентом на следующие направления:
Расширение сети социальных учреждений
Планируется построить дополнительно 100 новых объектов здравоохранения и образования, включая специализированные медицинские центры для лечения хронических заболеваний.
Инновационные технологии
Ожидается внедрение современных технологий в управление социальными учреждениями. Это включает использование искусственного интеллекта для оптимизации работы медучреждений и образовательных организаций.

Устойчивое развитие
В рамках устойчивого развития системы здравоохранения и образования будут реализованы программы по повышению зарплат медиков и педагогов, а также улучшению условий труда. Это поможет привлечь больше квалифицированных специалистов в эти сферы.
Программы по профилактике заболеваний
Планируется расширение программ вакцинации и образовательные инициативы по повышению осведомленности населения о здоровье. Это позволит предотвратить распространение инфекционных заболеваний и улучшить общее состояние здоровья граждан.
С внедрением новых технологий и инициатив система социальной инфраструктуры Санкт-Петербурга станет еще более эффективной и устойчивой к вызовам будущего. Город здоровья и комфорта продолжает развиваться, обеспечивая каждому жителю качественные услуги!
А как вам такие изменения?
-
-
 @ 98589a2e:bf49daa1
2024-11-27 08:12:11
@ 98589a2e:bf49daa1
2024-11-27 08:12:11К 2040 году Санкт-Петербург стал примером успешной реализации зеленой экономики, что стало возможным благодаря внедрению экологически устойчивых практик и инициатив, направленных на сохранение окружающей среды и улучшение качества жизни горожан. За последние два десятилетия город значительно изменился, и его развитие стало более гармоничным и сбалансированным.

Достижения в области зеленой экономики
Развитие зеленых зон
С момента начала реализации нового Генерального плана в 2023 году, который предусматривал увеличение доли рекреационных зон до 29% от общей площади города, было создано множество новых парков и скверов. К 2030 году в Петербурге открыли более 100 новых зеленых пространств, что позволило улучшить экологическую обстановку и создать комфортные условия для отдыха горожан.
Устойчивый транспорт
В 2031 году была запущена программа по развитию общественного транспорта с акцентом на экологические виды. В результате к 2040 году в городе значительно увеличилось количество электрических и гибридных автобусов, а также были построены новые велосипедные дорожки. Это способствовало снижению уровня загрязнения воздуха и улучшению качества жизни.
Энергетическая эффективность
С 2025 года началась активная реализация проектов по модернизации зданий с целью повышения их энергоэффективности. В рамках программы "Энергосбережение" были обновлены системы отопления и освещения в общественных зданиях, что позволило сократить потребление энергии на 30%.

Планы на 2050 год
Санкт-Петербург продолжает развивать зеленую экономику с акцентом на следующие направления:
Увеличение зеленых зон
Планируется дальнейшее расширение рекреационных пространств с целью достижения 30% от общей площади города к 2050 году. Это включает создание новых парков, скверов и озеленение промышленных территорий.
Инновационные технологии
Внедрение технологий для мониторинга состояния окружающей среды станет приоритетом. Ожидается использование дронов и сенсоров для сбора данных о качестве воздуха и уровнях загрязнения, что позволит оперативно реагировать на экологические проблемы.

Экологически чистый транспорт
К 2050 году планируется полностью перейти на экологически чистые виды транспорта в общественном транспорте. Это будет включать создание сети зарядных станций для электрических автомобилей и развитие инфраструктуры для велосипедистов.
Образовательные инициативы
Одним из ключевых направлений станет повышение осведомленности населения о важности устойчивого развития. Запланированы образовательные программы и кампании по экологии для всех возрастных групп, что поможет сформировать экологическую культуру среди горожан.
К 2040 году Санкт-Петербург достиг значительных успехов в реализации зеленой экономики благодаря внедрению устойчивых практик и инициатив. Впереди город ждет еще больше изменений к 2050 году, направленных на создание комфортной и безопасной городской среды для всех жителей. Зеленая экономика становится неотъемлемой частью жизни города, обеспечивая гармоничное сосуществование человека и природы.

А вы уже участвуете в новых экологических программах и проектах?
-
 @ 98589a2e:bf49daa1
2024-11-27 08:07:26
@ 98589a2e:bf49daa1
2024-11-27 08:07:26Климатические изменения в Санкт-Петербурге к 2040 году: стратегии адаптации
К 2040 году Санкт-Петербург столкнулся с серьезными климатическими изменениями, которые оказали значительное влияние на жизнь горожан. В ответ на эти вызовы город активно разрабатывает и внедряет стратегии адаптации к новым условиям. Утвержденный Региональный план адаптации к изменениям климата стал основой для дальнейших действий.

Текущая ситуация
Согласно прогнозам, средняя годовая температура в Санкт-Петербурге к 2040 году увеличилась на 2,5-3,5 °C по сравнению с 1980-2000 годами. Это потепление сопровождается изменениями в характере осадков: зимы становятся более дождливыми, а количество дней с сильными атмосферными осадками увеличивается. Например, в 2024 году город уже зафиксировал рекордное количество осадков для февраля, что привело к затоплению улиц и серьезным неудобствам для жителей.
В результате этих изменений были выявлены 17 основных климатических рисков, включая увеличение числа дней с экстремально жаркой погодой и угрозу наводнений. В частности, прогнозируется, что уровень Финского залива может подняться на 10-40 см к середине века, что угрожает затоплением прибрежных районов.

Стратегии адаптации
Работа над Региональным планом адаптации началась еще в 2016 году и была завершена в 2023 году. В его разработке участвовали более 20 научных организаций, которые оценили риски и предложили меры по их минимизации. Основные направления плана включают:
- Развитие "водно-зеленого каркаса": Создание зеленых зон и лесопарковых поясов вокруг города для смягчения микроклимата и повышения устойчивости к жаре.
- Улучшение систем водоотведения: Актуализация нормативных документов и модернизация инфраструктуры для более эффективного управления стоками.
- Берегозащитные мероприятия: Строительство защитных дамб и укрепление берегов для предотвращения разрушений от повышения уровня воды.
Планы на 2050 год
Санкт-Петербург продолжает развивать свои стратегии адаптации с акцентом на следующие направления:
- Расширение зеленых пространств: Планируется увеличить площадь озеленения города до 60%, что позволит снизить температуру воздуха летом и улучшить качество жизни горожан.

-
Инновационные технологии: Внедрение систем мониторинга климата и автоматизированных решений для управления городскими ресурсами поможет оперативно реагировать на изменения погоды.
-
Образовательные программы: Разработка инициатив по повышению осведомленности населения о климатических изменениях и их последствиях станет важной частью стратегии адаптации.
-
Инфраструктурные проекты: Строительство новых жилых кварталов будет учитывать климатические риски, включая проектирование зданий с учетом повышенных требований к устойчивости.
С принятием этих мер Санкт-Петербург стремится не только справиться с текущими климатическими вызовами, но и создать устойчивую городскую среду для будущих поколений. Город продолжает оставаться на передовой борьбы с климатическими изменениями, обеспечивая своим жителям качественную жизнь даже в условиях меняющегося климата.
-
 @ 98589a2e:bf49daa1
2024-11-27 07:43:34
@ 98589a2e:bf49daa1
2024-11-27 07:43:34Новый год пророчит новые изменения! Что ждет жителей Санкт-Петербурга с наступлением 2040 года? Свежие новости только в нашем издании!
К 2040 году Санкт-Петербург претерпел значительные изменения в транспортной системе, став более современным и удобным для жителей и гостей города. Внедрение новых маршрутов, расширение метрополитена и развитие общественного транспорта сделали передвижение по городу более комфортным и эффективным. https://cdn.genmo.dev/results/text-to-video-v4/2024-11-12/cm3eb03i4000703if12n71hti/watermarked.mp4
Новые транспортные маршруты и инфраструктура
Развитие метрополитена
Согласно Генеральному плану, к 2040 году в Санкт-Петербурге было построено 120 новых станций метро и вестибюлей. В 2032 году завершилось строительство новых линий, включая Красносельско-Калининскую и Адмиралтейско-Охтинскую. Это значительно увеличило пропускную способность подземки и снизило нагрузку на городские дороги.
Общественный транспорт
В последние годы был обновлен парк общественного транспорта: появилось более 5000 новых автобусов, трамваев и троллейбусов, включая экологически чистые модели на газомоторном топливе и электробусы. Протяженность наземной маршрутной сети увеличилась на 25%, что позволило улучшить доступность общественного транспорта в различных районах города.
Новые дороги и мосты
Санкт-Петербург также стал свидетелем строительства новых дорог и мостов. В 2025 году был завершен проект Западного скоростного диаметра (ЗСД), который разгрузил центральные районы города. Пять новых мостов через Неву, включая Арсенальный и Большой Смоленский, были введены в эксплуатацию до 2040 года, что значительно улучшило транспортные потоки.
Интеграция различных видов транспорта
Одним из ключевых направлений стало создание транспортно-пересадочных узлов. К 2040 году в городе было запланировано создание 59 таких узлов, что позволяет удобно пересаживаться между различными видами транспорта — метро, автобусами и трамваями. https://dnznrvs05pmza.cloudfront.net/4d412658-247a-4527-a9ae-fab1e9ab0f3d.mp4?_jwt=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJrZXlIYXNoIjoiNDcwOWJmY2FjNzFhZDU1MCIsImJ1Y2tldCI6InJ1bndheS10YXNrLWFydGlmYWN0cyIsInN0YWdlIjoicHJvZCIsImV4cCI6MTczMTU0MjQwMH0.xC_qzeivfXpf0Y1l1Km4qAnK5T7OCgPAQCsoO-L7Gsk
Планы на 2050 год
Санкт-Петербург не собирается останавливаться на достигнутом. К 2050 году планируется:
-
Расширение сети метрополитена: Ожидается строительство дополнительных 80 станций, что позволит охватить новые районы города и улучшить доступность для жителей.
-
Инновационные технологии: Внедрение систем искусственного интеллекта для оптимизации движения общественного транспорта, а также разработка мобильных приложений для удобства пользователей.
-
Устойчивое развитие: Продолжение работы по улучшению условий труда для водителей общественного транспорта и внедрение экологически чистых технологий в транспортной инфраструктуре.
-
Развитие скоростного сообщения: Планируется запуск новых высокоскоростных маршрутов, соединяющих Петербург с соседними регионами, что сделает поездки более быстрыми и комфортными.
-
Интеграция с пригородными электричками: Ожидается дальнейшее развитие тактового движения электропоездов, что позволит жителям пригородов быстрее добираться до центра города.
К 2050 году Санкт-Петербург станет городом с высокоразвитой транспортной системой, где каждый житель сможет рассчитывать на удобное и быстрое передвижение по городу!
А какие изменения ждете вы? Делитесь своим мнением в комментариях!
-
-
 @ 98589a2e:bf49daa1
2024-11-27 07:37:57
@ 98589a2e:bf49daa1
2024-11-27 07:37:57К 2040 году Санкт-Петербург стал свидетелем значительных изменений в сфере жилищного строительства, что оказало заметное влияние на рынок недвижимости. В последние годы город активно развивает новые жилые комплексы, что связано с реализацией нового Генерального плана, принятого в 2023 году и рассчитанного до 2050 года. https://sun9-41.userapi.com/impg/VrVgUtkdhQl2MI7vaSpToqcjO3kpCmumTa6_EA/vxReCjaoXyI.jpg?size=1280x720&quality=96&sign=1a9715dd31fdd5a624aac444eed0b4c9&type=album
Текущая ситуация на рынке недвижимости
С момента принятия предыдущего Генплана в 2005 году и его последующего продления до 2023 года, Санкт-Петербург столкнулся с необходимостью пересмотра подходов к градостроительству. В результате, к 2040 году было построено более 67 миллионов квадратных метров жилья, что соответствует среднегодовому темпу строительства около 3,2 миллиона квадратных метров. Основные изменения произошли в южных районах города, таких как Пушкинский, Приморский и Московский районы, где сосредоточено большинство новых жилых комплексов. https://sun90-1.userapi.com/impg/jZWDLIswYArEVMQFcZgrvbzipAtBTk3uCs43lQ/RovUO_jyT2E.jpg?size=1280x720&quality=96&sign=271051336bdefe00c4a46bad75d3330a&type=album
Новые жилые комплексы и их особенности
Новые жилые комплексы отличаются современными архитектурными решениями и акцентом на создание комфортной городской среды. В рамках нового Генплана предусмотрено строительство не только жилых зданий, но и объектов социальной инфраструктуры: к 2040 году планируется открыть 585 новых учреждений, включая школы, медицинские центры и спортивные объекты. Это создает условия для полноценной жизни в новых районах и делает их привлекательными для покупателей.
Прогнозы на 2050 год
Согласно прогнозам, к 2050 году население Санкт-Петербурга вырастет до 6,5 миллионов человек. Для удовлетворения потребностей растущего населения планируется строительство дополнительных 100 новых жилых комплексов. Основное внимание будет уделено созданию экологически чистого жилья с использованием современных технологий. Ожидается внедрение принципов устойчивого развития и "умных" технологий в строительстве.
Инновационные технологии
- Энергоэффективность: Новые жилые комплексы будут строиться с учетом высоких стандартов энергоэффективности, что позволит снизить затраты на коммунальные услуги.
- Интеграция ИТ-технологий: Использование информационных технологий для управления зданием и обеспечения его функциональности станет нормой. Это включает автоматизацию процессов отопления, освещения и безопасности.
Устойчивое развитие
- Зеленые зоны: В рамках нового Генплана предусмотрено создание обширных зеленых зон и общественных пространств вокруг новых жилых комплексов. Это не только улучшит качество жизни жителей, но и позитивно скажется на экологии города.
- Социальная инфраструктура: Параллельно с жилищным строительством будет развиваться социальная инфраструктура, что обеспечит доступность образования и медицинских услуг для всех жителей.
Заключение
Таким образом, новые жилые комплексы в Санкт-Петербурге к 2040 году стали важным элементом развития городской среды. Ожидается, что дальнейшие планы по строительству к 2050 году будут направлены на создание комфортного и устойчивого жилья с использованием современных технологий. Это не только улучшит качество жизни горожан, но и окажет положительное влияние на рынок недвижимости города в целом. Санкт-Петербург продолжает двигаться к статусу современного мегаполиса с высокими стандартами жизни для своих жителей.
Ваши предложения о том, что бы вы хотели еще поменять или улучшить в городе ждем в комментариях!
-
 @ 98589a2e:bf49daa1
2024-11-27 07:27:56
@ 98589a2e:bf49daa1
2024-11-27 07:27:56Новый Генплан Санкт-Петербурга: что нас ждет?
На 2040 год Санкт-Петербург уже стал свидетелем значительных изменений благодаря новому Генеральному плану, который был утвержден в конце 2023 года. Этот документ определяет вектор развития города на ближайшие десятилетия и включает в себя амбициозные проекты, направленные на улучшение качества жизни горожан и развитие инфраструктуры.
Текущие достижения


Строительство жилья
С момента принятия предыдущего Генплана в 2005 году было построено множество новых жилых комплексов. К 2024 году в городе было возведено более 40 миллионов квадратных метров жилья, что позволило значительно улучшить жилищные условия для населения. Основные объемы строительства сосредоточены в Пушкинском, Приморском и Московском районах.
Транспортная инфраструктура
В 2030 году началось строительство новых веток метро, которые значительно улучшили транспортное сообщение между удаленными районами и центром города. К 2040 году планируется завершение строительства 100 объектов метрополитена, включая новые станции и дополнительные вестибюли.


Социальная инфраструктура
В рамках нового Генплана также предусмотрено строительство 585 крупных объектов социальной инфраструктуры, включая школы, поликлиники и спортивные сооружения. Эти объекты создают необходимые условия для комфортной жизни горожан и способствуют развитию образовательной и медицинской системы.


Планы до 2050 года
Согласно новому Генплану, Санкт-Петербург ожидает продолжение масштабного строительства и развития инфраструктуры до 2050 года:
Расширение жилищного строительства
Планируется построить дополнительно 67 миллионов квадратных метров жилья. Основное внимание будет уделено незастроенным территориям, а также преобразованию нежилых участков. Ожидается, что новые жилые комплексы будут строиться с учетом современных стандартов комфорта и экологии.


Развитие транспортной сети
К 2050 году планируется завершение строительства новых транспортных артерий, включая пять новых мостов и транспортный обход центра города. Увеличение доли рекреационных зон с 28,5% до 29,38% также станет важной частью нового Генплана.

Инновации в городской инфраструктуре
Внедрение современных технологий будет ключевым аспектом развития города. Ожидается использование искусственного интеллекта для оптимизации городских услуг и повышения качества жизни граждан. Мобильные приложения для управления городской инфраструктурой также станут неотъемлемой частью повседневной жизни.
Заключение
Новый Генеральный план Санкт-Петербурга на 2040-2050 годы открывает новые горизонты для развития города. С акцентом на устойчивое развитие, инновации и улучшение качества жизни горожан, Санкт-Петербург стремится стать современным мегаполисом, отвечающим всем требованиям XXI века. Мы можем ожидать значительных изменений, которые сделают город более комфортным и привлекательным для жизни.

А вы как считаете, какие из предложенных инициатив являются наиболее важными для улучшения качества жизни в Санкт-Петербурге?
Ждем ваше мнение в комментариях!
-
 @ 7ec80607:128517c5
2024-11-27 06:03:35
@ 7ec80607:128517c5
2024-11-27 06:03:35When buying or selling a property, a realtor is often your most valuable partner. They not only bring industry expertise but also guide you through complex transactions and help you secure the best deal. However, not all realtors are created equal, and hiring the right one is crucial for a smooth and successful experience. To ensure you make an informed decision, asking the right questions during your initial consultation is essential. Here’s a comprehensive guide to the questions you should ask a realtor before hiring them.
1. How Long Have You Been a Realtor? Experience matters. An experienced realtor is likely to have dealt with various market conditions, negotiation scenarios, and unexpected challenges. While newer realtors may bring fresh enthusiasm and innovative approaches, those with years of experience often possess the expertise needed to navigate complex situations. Follow-up questions: • Have you specialized in residential, commercial, or both types of properties? • What challenges have you overcome in your career?
2. What Areas Do You Specialize In? Real estate markets vary greatly from one neighborhood to another. A realtor specializing in the area where you’re buying or selling will have valuable insights into market trends, property values, and local amenities. Follow-up questions: • How familiar are you with the school districts, transportation options, or zoning laws in this area? • What is the average time a property stays on the market here?
3. What Is Your Marketing Strategy for My Property? If you’re selling a property, a realtor’s marketing strategy can significantly impact the speed and value of the sale. Ask about their approach to advertising and attracting potential buyers. Key elements to look for: • Use of professional photography and virtual tours. • Promotion through online platforms like Zillow, Realtor.com, and social media. • Hosting open houses and networking with other agents. Follow-up questions: • How will you target the right buyers? • What’s your budget for marketing?
4. Can You Provide References or Client Testimonials? A successful track record speaks volumes. Request references or reviews from past clients to gauge their satisfaction with the realtor's services. Follow-up questions: • Have you worked with clients in a situation similar to mine? • Can I contact one of your previous clients for feedback?
**5. How Do You Handle Negotiations? ** Negotiation skills are critical in real estate. Whether you’re buying or selling, your realtor should be a strong advocate for your best interests. Key points to discuss: • Their approach to handling competing offers. • Their strategy for negotiating repairs or closing costs. • How they communicate during negotiations.
**6. What Is Your Availability? ** A realtor’s availability can significantly impact your experience. You want someone who can accommodate your schedule and promptly address your concerns. Questions to ask: • Are you a full-time or part-time realtor? • How do you prefer to communicate (phone, email, text)? • What’s your response time to calls or messages?
- What Are Your Fees and Commission Rates? Understanding the financial aspect of hiring a realtor is crucial. Typically, realtors charge a commission based on the property’s sale price, but it’s important to clarify this upfront. Key questions: • What percentage of the sale price is your commission? • Are there any additional fees I should be aware of? • Do you offer any flexibility in your commission structure?
- What Is Your Success Rate? A realtor’s success rate can indicate their effectiveness in closing deals. While high sales numbers are impressive, also consider their ability to secure favorable outcomes for their clients. Key metrics to discuss: • The number of transactions completed in the past year. • Their average list-to-sale price ratio (for sellers). • The average time it takes for their clients to close deals.
- What’s the Current State of the Market? A knowledgeable realtor should be able to provide insights into the current market conditions and how they affect your goals. Follow-up questions: • Is it a buyer’s or seller’s market? • What trends should I be aware of in this area? • How should I price my property to attract serious buyers?
- Do You Work Independently or as Part of a Team? Realtors often work solo or as part of a team. Each setup has its pros and cons. Questions to clarify: • If you’re unavailable, who will handle my queries or showings? • What specific roles do team members play in the process? • Will I have a primary point of contact throughout the transaction?
- How Will You Keep Me Informed? Clear and consistent communication is vital for a smooth transaction. Discuss how the realtor plans to keep you updated throughout the process. Key points to discuss: • Frequency of updates. • Methods of communication. • Types of information they will share (e.g., buyer feedback, market updates).
- What Are Your Credentials and Training? Real estate regulations and practices evolve constantly. A realtor committed to professional development is more likely to be up-to-date with industry trends. Questions to ask: • Are you a member of the National Association of Realtors (NAR)? • What certifications or special training do you have (e.g., CRS, ABR, SRES)? • How often do you participate in training or continuing education?
- What Challenges Do You Foresee in My Case? Every transaction has its unique challenges. A proactive realtor will anticipate potential hurdles and offer solutions. Key areas to discuss: • Market conditions that might impact your goals. • Legal or regulatory issues to be aware of. • Strategies to address any challenges.
- How Do You Ensure a Smooth Closing Process? The closing process can be complicated and stressful. Your realtor should outline how they’ll help you navigate this stage. Follow-up questions: • How do you coordinate with other parties involved (e.g., lenders, inspectors, attorneys)? • What steps do you take to prevent last-minute surprises? • Will you assist with post-closing issues?
- Why Should I Choose You Over Other Realtors? This open-ended question allows the realtor to highlight their unique strengths and value proposition. Pay attention to: • Their confidence and professionalism. • Examples of past successes. • Their alignment with your specific needs and expectations.
Conclusion Hiring the right realtor can make all the difference in your property transaction. By asking these questions, you’ll gain valuable insights into their expertise, approach, and compatibility with your needs. Remember, the best realtor for you is someone who combines experience, market knowledge, strong communication skills, and a commitment to your goals. Take your time, do your research, and trust your instincts when making your choice.
-
 @ ece3317b:91a5d59b
2024-11-27 06:03:22
@ ece3317b:91a5d59b
2024-11-27 06:03:22A proposed open-source app built on the Nostr protocol, aimed at fostering meaningful debates by surfacing the strongest arguments rather than perpetuating strawmen. By leveraging Nostr’s decentralized and censorship-resistant infrastructure, the app aspires to create a framework for debates that promotes intellectual integrity, mutual understanding, and community-driven curation.
This app will integrate Wikifreedia, a prototype for wikis on Nostr, to curate debate content, with a new event kind proposed for identifying and linking core concepts to arguments and rebuttals. The app will initially be bootstrapped using the bitcoiner.social relay, tapping into its strong web of trust to demonstrate its capabilities.
Key Features
- Core Concepts and Argument Mapping
- A new Nostr event kind will be introduced to identify and tag core concepts, which will be the subject of the debates.
- Arguments will link to one or more core concepts, forming a web of interconnected ideas.
-
Rebuttals, comments, and surveys will further enrich this network of debates.
-
Arguments and Rebuttals
- Arguments: Can be any Nostr event kind that presents an explanation or stance. They will include:
- A tagged reference to core concept events.
- Links to other Nostr events, such as text notes, images, or videos.
-
Rebuttals: Specific Nostr events pointing to an argument, forming counterpoints.
-
Comments
-
Surveys
- A Nostr event kind for Q&A-style feedback. (this probably already exists)
- Surveys will evaluate the quality of arguments and rebuttals based on:
- Logical soundness (e.g., identification of fallacies).
- Objectivity vs. subjectivity.
-
Survey results will contribute to ranking and curating content.
-
Wiki Integration
-
Wikifreedia will serve as the backbone for debate curation, allowing:
- Moderators/curators to create articles linking arguments and rebuttals.
- Highlighting key comments and displaying survey results.
- Collaborative content management by any user in the web of trust.
-
Trust-Based Curation
- Content displayed in the app will be filtered the web of trust. The PoC will use the bitcoiner.social web of trust which includes thousands of npubs.
-
The homepage can surface and highlight debate content sorted by the level of engagement and trustworthiness.
-
Revenue Model
- Integration with Lightning Prisms for micropayments:
- Facilitate zaps to contributors.
- Redirect 10% of zaps to the operator to offset server costs.
Goals
- Provide a steel man argument framework for debates, minimizing tribalism and fostering understanding across perspectives.
- Allow communities to curate their topics of interest.
- Create an extensible platform that other communities can adopt for their debates and curation.
Technical Specifications
- Platform: Progressive Web App (PWA) for cross-platform accessibility.
- Backend: Nostr protocol for decentralized and censorship-resistant data exchange.
- Frontend: Svelte
- Wiki Integration: Leverage Wikifreedia for collaborative article curation.
- Relevant Event Kinds:
- Core Concept: New event kind for tagging and linking debates.
- Argument: Links to core concepts and other Nostr events.
- Rebuttal: Points to argument events.
- Comments
- Survey: Q&A event kind for feedback.
Implementation Roadmap
- Phase 1: Prototyping (0-3 months)
- Define new event kinds and extend the Nostr protocol.
- Develop a basic PWA interface for submitting arguments, rebuttals, and comments.
-
Implement core concept tagging and event linking.
-
Phase 2: Wiki Integration (3-6 months)
- Build Wikifreedia support into the app.
- Develop tools for curators to manage and link debates within articles.
-
Introduce survey functionality.
-
Phase 3: Community Rollout (6-9 months)
- Deploy on bitcoiner.social relay.
- Engage with the community for feedback and testing.
-
Implement ranking algorithms for surfacing arguments and curators.
-
Phase 4: Monetization and Expansion
- Integrate Lightning Prisms for zaps and revenue generation.
- Expand to other communities and relays.
- Refine UI/UX based on user feedback.
The app aims to be a transformative tool for debate, fostering constructive dialogue in an era of polarized social media. By prioritizing the strongest arguments and enabling communities to curate their narratives, the app has the potential to bridge divides and encourage intellectual growth. As an open-source project, it empowers any community to adopt and adapt the system for their unique needs.
Let's reframe how debates are conducted in the digital age. By leveraging the power of Nostr, this platform can become a cornerstone for communities seeking truth, understanding, and constructive discussion.
-
 @ 9c47bb51:000381d0
2024-11-27 05:55:22
@ 9c47bb51:000381d0
2024-11-27 05:55:22The Bitcoin ecosystem continues to evolve, providing tools that enhance privacy, usability, and accessibility. One exciting innovation is the integration of Chaumian ecash systems with Bitcoin, which enable private micropayments without leaving a trace on the blockchain. This article explores how much to transact or hold in ecash wallets and offers tips on selecting a mint that aligns with your needs.
What Are Bitcoin Ecash Wallets?
Ecash wallets bring the concept of digital cash to Bitcoin. They leverage Chaumian ecash technology, which uses blind signatures to issue tokens backed by Bitcoin. These tokens can be spent privately and often without requiring internet connectivity.
Transactions via ecash wallets are: • Highly private: Transactions do not appear on the Bitcoin blockchain, and the mint cannot trace token spending. • Ideal for micropayments: These systems are optimized for small transactions, such as tipping, small service payments, or buying digital goods.
How Much Should You Transact or Hold?
While ecash wallets provide powerful tools for private payments, their design and reliance on a mint operator make them best suited for small amounts. Here’s how to think about your transaction limits and balance:
1. Micropayment Use Cases: • Ecash wallets shine for low-value transactions: • Tipping creators or writers. • Buying digital goods like e-books or music. • Small P2P transfers for casual exchanges. 2. Recommended Transaction Amounts: • Micropayments: 1,000–50,000 satoshis (~$0.93–$46 at current BTC prices) are common. • Balance for Regular Use: If you’re a frequent user, keeping a balance of up to 500,000 satoshis (~$463) can be practical. • Maximum Risk Tolerance: For those fully trusting their mint, a balance of up to 1,000,000 satoshis (~$927) could work. However, this is outside the typical use case. 3. Keep It Low Risk: • Treat ecash wallets as hot wallets—only store what you are comfortable losing if the mint fails or is compromised.How to Choose the Right Mint
Choosing the right mint is crucial for maximizing the benefits of ecash wallets while mitigating risks. Here are some factors to consider:
1. Trustworthiness: • Research the mint operator’s history and reputation within the Bitcoin community. • Prefer mints with transparent operations and an open-source codebase. • Look for community feedback or endorsements from trusted Bitcoin developers. 2. Privacy Practices: • Ensure the mint implements robust privacy measures, such as not logging issuance or redemption data. • Check if the mint integrates privacy-preserving tools like Tor for user interactions. 3. Accessibility and User Experience: • Choose a mint with an easy-to-use wallet interface that meets your technical comfort level. • Verify compatibility with platforms or services you regularly use for payments. 4. Mint Policies: • Look for clear policies on: • Maximum and minimum transaction limits. • Fees for issuing or redeeming tokens. • Refund or recovery mechanisms in case of issues. 5. Geographical Considerations: • Some mints might cater to specific regions or have localized support. Choose one that operates in your area if needed. 6. Resilience and Redundancy: • Check if the mint offers fail-safes, like distributed backups, or whether multiple mints are interoperable (e.g., in federated models).Tips for Maximizing Your Experience with Ecash Wallets
• Use Ecash for What It’s Best At:Stick to small, privacy-focused transactions. For larger payments, consider the Bitcoin Lightning Network or on-chain transactions with privacy tools like CoinJoin.
• Combine Privacy Tools:Use privacy-enhancing tools like Tor or VPNs when interacting with the mint for added anonymity.
• Diversify Mints:If possible, use multiple mints to distribute your balances and reduce reliance on a single operator.
• Audit Your Mint:Periodically test the mint’s solvency by redeeming tokens for Bitcoin to ensure the system operates as promised.
Final Thoughts
Ecash wallets bring the best of both worlds—Bitcoin’s financial sovereignty and the simplicity of digital cash. By keeping transaction sizes small and choosing a trustworthy mint, users can enjoy seamless, private payments. Always remember that these wallets are not a replacement for self-custody but a powerful complement to it, designed for specific use cases.
As the Bitcoin ecosystem continues to innovate, tools like ecash wallets will play an essential role in making private, low-friction transactions a reality for everyone.
-
 @ f685c7b9:b1be053e
2024-11-27 01:24:44
@ f685c7b9:b1be053e
2024-11-27 01:24:44Revisiting Civil Disobedience
as I stood considering the walls of solid stone, two or three feet thick, the door of wood and iron, a foot thick, and the iron grating which strained the light, I could not help being struck with the foolishness of that institution which treated me as if I were mere flesh and blood and bones, to be locked up.
--Henry David Thoreau, "Civil Disobedience"
What an amazing quote from Thoreau, whom was imprisoned for refusing, on principle of "civil disobedience" to state overreach and the condoning of slave ownership, to pay his poll-tax. "That institution which treated me as if I were mere flesh and blood and bones, to be locked up." If reading that 180 years later doesn't make your hairs stand on ends, then what does?
Thoreau's transcendentalism resonates in these lines, reminding us that freedom is as non-tangible as your Bitcoin UTXOs.
Freedom is relative, an ideal
I have considered the oft-lamented, anti-libertarian bane that is the social-welfare state and the exorbitant amount it costs the government, especially as I meet more-and-more people complaining about the bureaucratic buffoonery we have over here in Canadaland. Honestly, what a shit show.
But over here, in my line of work (picture: inner city school), I hear a lot about developing countries, where folks lack a lot of the so-called freedoms we enjoy. Where they don't have freedom to worship a God of their choosing, women must cover their heads in public and cannot pursue an education, and where they'll cut off your hands for stealing.
I am told of places where schools pack 60+ kids into a classroom, most of them showing up just only because they don't want to go to work, or, because they get biscuits on Tuesdays. Some of these places, the teachers are expected to chase after children if they don't attend class, go into their homes and reprimand them over dinner tables of rice, plantains and coca-cola. Yet other places, teachers shame parents by @-ing them public group chats, using their when their sons or daughters don't complete the homework as expected, 'everything apps'; and yes, in China, so I am told, parents are expected to work on their child's homework projects.
Some of these places you cannot own property.
From some of these places, people walk 365 days a year on worn out shoe-soles across continents in search of some glorified idyllic 'freedom,' out of fear of tyrannical government regimes who have devalued currencies so as not even to be worth the paper it is printed on. I talk to folks every day escaping real tyranny, the kind we are told lay crouching in the darkness, seething and desiring and plotting to take away your freedom.
To them, tyranny is familiar as their first cousin. And yet, they can see the contradiction in the claim that they escaped tyranny to enjoy 'free society.' They are not fools, some, I would argue posess a special kind of discernment when it comes to spotting a tyrant. They confide in me their complaints and I find, to my chagrin, they despise much I do, government overreach, bureaucratic skulduggery and taxes.
What I have begun to tell them, besides the empathizing platitudes: freedom is relative, an ideal.
A freedom state of mind
And to you, dear freedom-loving reader. You might have your BTC in self custody, your property, your guns, your free speech, your off-grid power sources. You might be free from the arms of government power and well protected, ready to defend your family and property from some listless refugee wandering onto your property in the cover of darkness. I'm not fear mongering. I am illustrating the point that there, you see, freedom is an ideal, a relative state that needs protecting. It cannot be fully realized, because, to the libertarians the inalienable freedom to own property means that that property faces the threat of being taken, pillaged or otherwise violated.
I don't imagine that Thoreau could have anticipated the world we live in today, nor that his words would be construed this way. I beg forgiveness from any Americans who think I have missed the point. But, take heed of his words:
"I saw that, if there was a wall of stone between me and my townsmen, there was a still more difficult one to climb or break through before they could get to be as free as I was."
Don't be one of those townsmen.
Freedom is a relative state, and it is a mindset. If you are completely self-soverign, independent, self-reliant, off-grid, self-custodying; all of these thigs and, still, you might be paranoid of losing it all - then, are you really free? Similarly, people flee oppression, understandably, but I fear that what they find is the same velvet tongued tyrant, dressed in different garb.
I think we need to adopt freedom as a state of mind, and seek it constantly. And be as tranquil as Thoreau,
I could not but smile to see how industriously they locked the door on my meditations, which followed them out again without let or hindrance, and they were really all that was dangerous.
And yet, I challenge you, to reflect: over what continents you have traversed, over hill and dale, to be free?
-
 @ 99895004:c239f905
2024-11-27 01:21:46
@ 99895004:c239f905
2024-11-27 01:21:46Most Nostr users have never heard of nostr.build. Many Nostr users know of nostr.build, and that we store images and videos for Nostr, but don't know that we can do anything else. There are also users that have a paid nostr.build account, but don’t know of all the included features they have access to. For these reasons I've decided to write a blog about all of nostr.build's features, in detail, let's begin.
Nostr.build offers free media hosting services for Nostr and paid services when you purchase an account. We have three levels of paid accounts: Pro, Creator, and Advanced. Let’s talk about each level of service and the features included below.
Free Services:
-
Supported Media Files up to 21MB: Anyone using Nostr can upload the media of their choice, up to 21MB per file. We support many different media types including .jpg, .png, .gif, .mov, .mp4, .mp3, and .wav. We compress JPEGs, PNGs and GIFs, but currently perform only light processing of video to allow quick preview. If your video is playing weird, no audio or not playing at all, it is likely your video format or how it was transcoded.

-
Removes Location-Related Metadata: Most photographs these days have the location data (GPS coordinates) embedded in the metadata. The data is commonly used to tell users where they were when they took the picture, it can also dox someone if they share an image with location data in it, e.g., their home address. Nostr.build removes this location metadata so as not to reveal your location to everyone you are sharing a picture with.

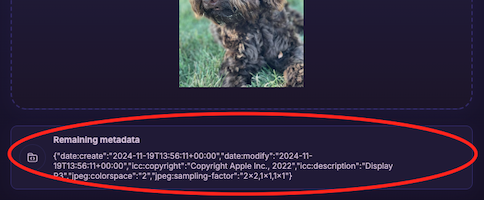
-
Integrated Media Uploading on Nostr Platforms: In the early days of Nostr, if you wanted to share an image or video, you would have to upload it to another site, copy the link it provides, and paste it to your Nostr note. With NIP96 and NIP98 nostr.build is now directly integrated into most Nostr apps making it just one click to add your media, like other popular and social media platforms. Currently this is supported on Damus, Amethyst, Nostrudel, Snort, Iris, Coracle, Flycat, and Yakihonne, among others.
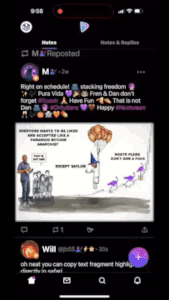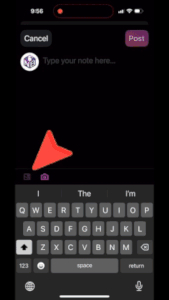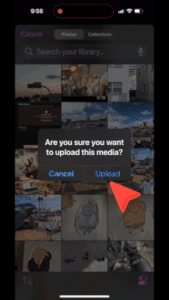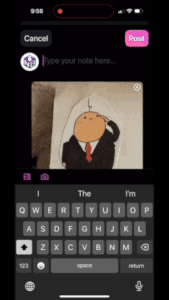
-
Free Media Gallery: Curious what type of images, memes, gifs, and videos are being uploaded to Nostr? Check out the Free Media Gallery to see the most recent uploades to nostr.build. This view only shares the free uploads, you would not be able to see any user account uploads which are kept private unless purposely shared by the account owner. https://nostr.build/freeview
-
Delete Uploaded Media: If you upload free media to Nostr using a Nostr app, you can go back and delete it yourself with our delete tool. This is most used when people dox themselves, accidentally uploading an image with their name or address. The image needs to be associated to your n-pub and you will need to authenticate before deleting.
-
CSAM Scanning, Removal and Reporting: CSAM is not tolerated in any way. Not just CSAM, but any media that exploits a child in any way including AI and cartoons, children in inappropriate positions or clothing, we block the user and report their content and all related information we have on the user to the authorities / NCMEC. We use multiple services when filtering and reporting CSAM including Cloudflare's CSAM filter, Microsoft PhotoDNA, AI models and the NCMEC reporting portal. We do not filter or report anything else that is in compliance with our TOS, only CSAM. https://www.missingkids.org/theissues/csam

-
24/7 Support: nostr.build has people around the world, monitoring Nostr every day for Nostr and nostr.build related issues. Issues include but are not limited to; media not uploading or displaying, doxed uploads, illegal content removal, developer issues, and feature requests. There are very few services in the world where you can interact directly with the developers and get support and feature requests fulfilled. You can also contact us at support@nostr.build.
Pro Accounts:
-
10GB of Private Storage: One of the most common problems with the free service is the file size is capped at 21MB per file. For long videos, this becomes a challenge. With paid accounts, there is no file size limit to what you upload, only the size of the account.
-
Media Management Portal: One of the biggest advantages of a nostr.build account is the ability to keep all your media in one place, separate from social media platforms, in your own private portal. You can drag and drop, add, create folders, move to a folder, delete, and rename any of your media, and much more. Check out our nostr.build features overview video to get a better idea of media management in your nostr.build account.

-
AI Studio: Our latest and one of our coolest features is the all-new AI Studio. AI Studio provides text-to-image generation with multiple popular models to choose from. While other platforms only offer a single text-to-image model (ex. ChatGPT/DallE, Discord/Midjourney, X/Grok2), nostr.build offers multiple models on the same platform. We also offer a complete media management system for your AI creations mentioned above, the other platforms don’t have that. Check out our competitive comparison here! For Pro accounts we offer SDXL-Lightning, and Stable Diffusion 1.

-
.pdf and .zip File Support: Another huge request from users was to support the .pdf and .zip file types. This wasn’t as easy as it seems since we have to perform a virus scan on each of these file types before publishing and allowing public access.

-
View All Media Gallery: Curious what type of images, memes, gifs and videos are being uploaded to nostr's free service? Check out the Media Gallery to see all 2Million+ uploads ever uploaded to nostr.build. This only shares the free uploads, you would not be able to see any user account uploads which are kept private unless shared.
-
Share Direct to Nostr: Upload or create new media on nostr.build and share it with or without a note straight to Nostr, no other client needed! This is a feature that more tightly integrates nostr.build with Nostr and takes it steps closer to becoming a true Nostr client.
-
Global Content Delivery Network: Lightning-fast global CDN distribution of your content for faster, easier viewing around the world.
-
Referral Link: Found in your profile settings, share your referral link and earn ‘Credits’ when someone uses it to purchase an account. Credits can be used for advanced features, account upgrades, and renewals.
-
Viewer and Usage Stats: See the total ‘Unique Views’ and ‘Request Counts’ for all of your media, nicely graphed out, from 1-day to 3-month chart options. Just click the three dots under your media and select the 'Statistics' tab.
Creator Accounts:
-
30GB of Private Storage: 3x more storage than the Pro account. Ideal for creators, podcasts, and videographers, this gives you the added storage for those larger projects.
-
.svg File Support: Scalable Vector Graphics (SVG) files use mathematical formulas to store graphics. This makes them able to be resized without losing quality, very common with designers and content creators.

-
AI Studio: When creating images in AI Studio, Creator accounts have access to all Pro Stable Diffusion models and unlimited use of the Flux.1 model.
- Flux.1 (schnell): One of the latest text-to-image models, Flux is a 2 billion parameter rectified flow transformer that excels in graphic detail and correct text spelling and layout. It is the same core model that X(Twitter) uses with Grok2 images.

-
Host a Creators Page: Creators have the option to share their media to their Creators page hosted on nostr.build. This makes it easier for people to see, donate, and share. Check out all the Creators and their masterpieces here!

-
iDrive E2 backup for all media: We currently store all media on Cloudflare R2 servers. If for whatever reason Cloudflare servers lose your content, we also store a backup on a completely different service provider, iDrive E2 servers.

Advanced Accounts:
-
100GB of Private Storage: The largest account size we offer, with more than 3x the storage of the Creator account. This is plenty of storage for all of your Nostr needs and more.
-
AI Studio Extended Access: Get all the models, all the latest experimental features, and additional Credits with an Advanced account.
-
NIP-05 @nostr.build: Do you need premium NIP-05 identification? Choose any name you want and have your own @nostr.build official profile.
Roadmap:
-
Free Account: This would be just enough to get someone started with nostr.build’s media management features and slightly larger media size uploads.
-
Lifetime Account: This would be something like all features, all experimental features, 1TB of storage for life, and two free t-Shirts.
-
Traditional and AI Media Editors: Combining a powerful, standard media editor Pintura, with modern AI image editing features from stability.ai would allow users to quickly and easily modify their media using multiple tools. https://pqina.nl/pintura/?ref=pqina https://stability.ai/stable-image
-
Video Transcoding and Player: nostr.build has never modified video meaning all different formats and sizes are uploaded, none of them optimized for the platform they are being viewed on, and all of them in many different formats. By properly transcoding the media it will be viewable, optimized and faster on all platforms the video is being watched on, Android, iOS, desktops, laptops, etc.
-
Expandable Storage: The ability to purchsase additional chunks of storage and add it to your existing account.
nostr.build has a lot more to offer than just a place to upload media. It is your complete media platform, with an extremely intuitive user interface offering new features added all the time, and of course, always with the goal, to help grow Nostr, make is easier and more fun to use.
-
-
 @ 617f0a85:b403d1ed
2024-11-27 00:35:41
@ 617f0a85:b403d1ed
2024-11-27 00:35:41Chef's notes
I got this recipe from a friend in college. I'm not sure where she came across it, but I don't think she'd mind me posting it here.
Details
- ⏲️ Prep time: 15 min
Ingredients
- 2.5 cups unbleached all-purpose flour
- 1 tsp salt
- 2 tbsp sugar
- 12 tbsp cold unsalted butter
- 0.5 cup lard
- 0.25 cup vodka
- 0.25 cup cold water
Directions
- Process 1.5 cups flour, salt, and sugar in food processor until combined, about 2 one-second pulses. Add butter and shortening and process until homogeneous dough just starts to collect in uneven clumps, about 15 seconds (dough will resemble cottage cheese curds and there should be no uncoated flour). Scrape bowl with rubber spatula and redistribute dough evenly around processor blade. Add remaining cup flour and pulse until mixture is evenly distributed around bowl and mass of dough has been broken up, 4 to 6 quick pulses. Empty mixture into medium bowl
- Sprinkle vodka and water over mixture. With rubber spatula, use folding motion to mix, pressing down on dough until dough is slightly tacky and sticks together. Divide dough into two even balls and flatten each into 4-inch disk. Wrap each in plastic wrap and refrigerate at least 45 minutes or up to 2 days.
-
 @ f33c8a96:5ec6f741
2024-11-27 00:09:03
@ f33c8a96:5ec6f741
2024-11-27 00:09:03 -
 @ 9c47bb51:000381d0
2024-11-26 23:15:58
@ 9c47bb51:000381d0
2024-11-26 23:15:58The Bitcoin ecosystem thrives on the principles of decentralization, freedom, and mutual support. These principles are what make Bitcoin more than just a financial revolution—it’s a movement. Nostr, as an open and censorship-resistant protocol, provides the ideal platform to expand these values into social interactions. If Bitcoin is about creating a decentralized financial system, Nostr is about building a decentralized communication network, connecting people across the globe.
As we navigate this new frontier, one key aspect stands out: the importance of supporting Bitcoiners—both local and global—on Nostr. Whether through zaps, resharing their notes, or purchasing their online products and services, your support can amplify voices, foster creativity, and strengthen the entire network.
Why Supporting Bitcoiners on Nostr Matters
1. Economic Empowerment and Circular EconomiesBitcoin is the native currency of the internet, and Nostr is becoming a hub for its exchange. Zaps—small Bitcoin payments over the Lightning Network—represent a way to show appreciation for content, incentivize quality contributions, and support creators directly. By zapping Bitcoiners on Nostr, you’re participating in a circular Bitcoin economy, where value flows freely without intermediaries. This economic empowerment is crucial for ensuring the longevity and growth of both Bitcoin and the communities around it.
2. Decentralized FreedomTraditional social platforms rely on centralized algorithms to decide what content gets visibility. Nostr, on the other hand, enables you to curate your own experience and directly reward the people and ideas you find valuable. Supporting Bitcoiners on Nostr isn’t just an act of generosity—it’s a statement against the monopolistic control of traditional platforms.
3. Global Connection and Local ResilienceThe Bitcoin community spans borders, languages, and cultures. Supporting global Bitcoiners means helping spread the message of financial sovereignty worldwide. Simultaneously, supporting local Bitcoiners strengthens the foundation of the movement in your own community, creating a resilient base to educate, innovate, and collaborate.
How to Support Bitcoiners on Nostr
1. Zapping Notes: A Token of AppreciationZaps are the easiest and most direct way to support Bitcoiners on Nostr. By zapping a note, you’re sending a small amount of Bitcoin to the creator, acknowledging their contribution to the conversation. It’s a micro-act of generosity that, when multiplied across the community, can have a profound impact. • Who to Zap: • Content creators sharing insightful thoughts, Bitcoin memes, or educational content. • Developers working on open-source Bitcoin or Nostr tools. • Artists, musicians, and writers showcasing their work to the community. • How to Zap: Use wallets compatible with the Lightning Network, such as Wallet of Satoshi or Phoenix, and connect to Nostr clients that support zapping, like Damus or Amethyst.
2. Resharing Notes: Amplify the SignalSharing someone’s note is free, but its value is immeasurable. When you reshare a note, you’re amplifying the creator’s reach and helping spread their message. This is particularly important for smaller accounts or those with niche content, as resharing helps surface valuable ideas that might otherwise be overlooked.
3. Buying Bitcoiners’ Products or ServicesMany Bitcoiners use Nostr to showcase their products or services, from custom artwork to educational courses and software tools. Supporting these endeavors not only helps the individual but also creates a self-sustaining ecosystem where Bitcoin circulates naturally. • Examples of What to Buy: • Art and NFTs on Bitcoin. • Bitcoin-themed merchandise like clothing or accessories. • Educational resources, consulting, or services related to Bitcoin and Lightning.
4. Provide Feedback and CollaborationNot all support needs to be financial. Offering constructive feedback on projects, volunteering to test new tools, or collaborating on open-source initiatives are invaluable ways to contribute to the growth of Bitcoiners on Nostr.
Building a Culture of Support
A strong community is built on shared values and mutual support. By actively supporting Bitcoiners on Nostr, we’re not just helping individuals succeed; we’re reinforcing the principles that Bitcoin and Nostr represent: decentralization, sovereignty, and freedom.
Here are a few principles to keep in mind as you engage with the community: • Be Generous with Zaps: Even small amounts add up. Regularly zapping creators you appreciate encourages them to keep contributing. • Champion Quality Content: Use resharing strategically to elevate thoughtful discussions, groundbreaking ideas, and inspiring stories. • Think Globally, Act Locally: Support Bitcoiners in your immediate community while also connecting with those in underserved or emerging markets.
The Ripple Effect of Support
When you zap, reshare, or purchase from a Bitcoiner, your action sets off a ripple effect. You’re not just helping one individual—you’re contributing to a network of financial and social empowerment. This ripple strengthens the entire Bitcoin ecosystem, attracting more users to Nostr, spreading the adoption of Bitcoin, and inspiring others to pay it forward.
In the end, supporting Bitcoiners on Nostr isn’t just about generosity—it’s about creating the kind of decentralized, cooperative world we all envision. So the next time you see a thoughtful post, an interesting product, or a brilliant idea on Nostr, take a moment to zap, reshare, or buy. Small actions today can shape the decentralized future we’re building together.
-
 @ 9f51b59f:75e7c3a2
2024-11-26 20:04:51
@ 9f51b59f:75e7c3a2
2024-11-26 20:04:51Chef's notes
Use bone in or boneless short rib. This recipe also works with ox tail and pork shoulder or any kind of meat that’s ideal for braising low and slow.
Details
- ⏲️ Prep time: 30 mins
- 🍳 Cook time: 2.5-3.5 hours
- 🍽️ Servings: 6-8
Ingredients
- 3 Tablespoons natural cooking oil (I use tallow or ghee)
- 2 lbs boneless short ribs (bone-in also works)
- Salt & Pepper
- 1 small red onion, diced
- 5 garlic cloves rough chopped
- 1 bell or poblano pepper, seeded & diced
- 2 teaspoon chili powder
- 1 teaspoon ancho chili powder
- 1 tablespoon smoked paprika
- 1 tablespoon dark coco powder
- 2 teaspoon cumin
- 1 tablespoon graham masla
- 1 teaspoon dried oregano
- 3 tablespoons apple cider vinegar
- 1/2 cup tomato puree
- 3 tablespoons chipotle adobo sauce
- 3 bay leaves
- 1.5 cups stock or water
- 2 fresh limes, juiced
- Banana leaves, optional
- Avocado, sour cream, lime juice
- Shaved red cabbage with lime juice
Directions
- Preheat oven to 315 degrees F. Using a Dutch oven or braising pan, begin heating oil over high heat on the stove top.
- Season beef with salt and pepper and begin searing in the pot. Once browned on all sides set the beef aside and add the onions, garlic, and peppers to the same pan and reduce the heat.
- Season and cook the veggies 5 to 8 minutes until they start to caramelize. Add the chili pepper, paprika, coco, cumin, marsala, and dried oregano.
- Briefly toast the spices and deglaze with the vinegar and immediately add the tomato puree.
- Add the adobo sauce, broth, and using a stick blender or blender buzz the cooking liquid. (if using banana leaves remove the cooking liquid from the pan or use a new pot with lid. Line the pot with the leaves shingled over one another, return the cooking liquid over the leaves.)
- Return the beef to the pot and cover with lid or foil (fold leaves over the meat then cover).
- Place the pot in the oven and cook for 2 hours before checking, the meat should be fork tender when done.
- Mash the avocado into the sour cream and season with lime juice or hot sauce. Serve on tortillas with the crema and cabbage.
-
 @ fcb65172:87f3c4ed
2024-11-26 19:29:20
@ fcb65172:87f3c4ed
2024-11-26 19:29:20Introduction
As I approached the Santa Marta Favela, I couldn’t help but feel a mix of excitement and trepidation. Famous for housing a Michael Jackson music video, this favela is a common tourist attraction, but I was here to witness the raw, unfiltered reality of daily life. Little did I know that my adventure would involve a Brazilian gangster as my guide, offering to show me a side of the favela that few have ever seen.

The Initial Challenge
Initially, I was denied access to film anything beyond the iconic Michael Jackson statue and the breathtaking view of the city. Armed gangsters stood guard, making it clear that they had the final say in what I could capture. Frustrated and unsure of what to do, I decided to break the ice by buying them some beers. As we sipped on our drinks, I shared my previous videos and explained my passion for documenting the stories of ordinary people. To my surprise, one of them lowered his weapon and offered to show me around, granting me a glimpse into a world that most tourists never get to see.
The Guided Tour
 As we ventured deeper into the favela, it became clear that my guide was well-connected and respected by the locals. He laid down the ground rules: certain things were off-limits, like the drug dealers and heavily armed gang members. While I was initially apprehensive, I soon realized that this was an opportunity to gain a unique perspective on life in the favela. He introduced me to the kiosk owners, street vendors, and everyday people who had called the favela home for decades. These individuals shared their stories of violence, police confrontations, and community resilience, painting a picture of life in the favela that was far from the stereotype of a place where the poor live.
As we ventured deeper into the favela, it became clear that my guide was well-connected and respected by the locals. He laid down the ground rules: certain things were off-limits, like the drug dealers and heavily armed gang members. While I was initially apprehensive, I soon realized that this was an opportunity to gain a unique perspective on life in the favela. He introduced me to the kiosk owners, street vendors, and everyday people who had called the favela home for decades. These individuals shared their stories of violence, police confrontations, and community resilience, painting a picture of life in the favela that was far from the stereotype of a place where the poor live.The Police Station and the Question of Control
We ascended to the top of the favela, where a police station sat prominently. As we approached, I couldn’t help but wonder how much control the police really held over this complex network of streets and alleyways. Were the police and the gangs working together, using the honest, hardworking residents as pawns in their illicit activities? My guide, sensing my curiosity, shared his insights on the delicate balance between the police, the gangs, and the residents. He explained that while the police may not have complete control, they do work together to maintain a certain level of order, often in exchange for bribes or protection fees.

The Everyday Heroes of the Favela
As we explored the favela, we encountered a wide range of individuals, each with their own unique story. There was the kiosk owner who had lived in the favela for over 30 years, running his small business and raising a family. He shared his experiences of witnessing shootings and confrontations with the police, as well as the importance of community and football in the favela. We also met a local street vendor who had turned to selling goods to support his family after losing his job. Despite the challenges they faced, both men spoke with pride about their community and the resilience of its people.
 ### The View from the Summit
### The View from the SummitAs we reached the summit, the view of Rio de Janeiro’s skyline took my breath away. It was a poignant reminder of the dichotomy between the beauty of the city and the harsh realities of life in the favela. My guide shared stories of community churches, local football teams, and the unwavering spirit of the residents. Despite the challenges they face, the people of Santa Marta Favela have created a community that is both resilient and vibrant.
Conclusion
In conclusion, my journey through the Santa Marta Favela was an eye-opening experience that challenged my preconceptions of this complex and misunderstood place. It’s a world where gangsters, police, and everyday citizens coexist in a delicate balance, where community and resilience thrive in the face of adversity. As I left the favela, I couldn’t help but feel a newfound appreciation for the strength and spirit of the people who call this place home. And a question of who is really in control here?
-
 @ fcb65172:87f3c4ed
2024-11-26 19:15:59
@ fcb65172:87f3c4ed
2024-11-26 19:15:59 Evo Morales wins 2005 elections
Evo Morales wins 2005 electionsBolivia my second home
Bolivia, a country that I consider a second home, a country that is near and dear to my heart, unfortunately Bolivia is arguably also South America's Most Troubled Nation.\ When Evo Morales won the presidency in 2005, Bolivia experienced a short lived economic boost, in large parts due to a global boom in commodities prices around 2008-2012. Evo Morales made sure to take take the glory for this, when in fact his communist policies and nationalisation of most industries, particularly the natural gas industry has led the country to become the economic basket case that it is today.\ Bolivia is running out of natural gas and has become a net importer, despite having huge natural gas reserves. Bolivia's central bank is close to going bankrupt, it is running out of US dollars and foreign currencies for trade. Bolivia sees huge lines outside petrol stations, just to get 5 Litres of gasoline.\ -This is the context as I hit the road to go explore, what is really going on in Bolivia these days.
On The Road - Through a Troubled Bolivia
“AIQUILE! AIQUILE!” The girl who sells the bus tickets yells the destination into the Bolivian morning air. “AIQUILE YA SALE!”\ I will never grow tired of the feeling I get, when I buy a ticket with one of these minibuses to a destination that I barely know anything about. If I could find a way to put that feeling in a pill, it would be that next drug to take over the world. Of that I’m sure, this is my definition of adventure.\ As we head out of Sucre, Bolivia’s capital city towards Aiquile our destination the landscape becomes ever more impressive. Deep valleys with no end in sight. At the bottom of valleys it’s hot, we most have dropped about 1000 meters in altitude. A few mountain goats stroll around by the dry river bed in search of water. A street dog runs out in front of the minibus. Our driver beeps his horn like a mad man, the dog just kinda stands there looking at the approaching minibus, as if to say “I’m the boss here”. 10 meters before the sure death of the dog it makes the sensible choice, running to the side.
 A Bolivian Valley
A Bolivian ValleyWe pass a spot where the mountain side looks to have caved in, rocks and mud is still on the road, making our driver slow down, he has been riding like he stole the bus so far. “There were roadblocks here just last week” the driver says to me. So this isn’t the results of last weeks mudslide, this is a result of the political unrest going on in the country at the moment.\ For the past month Evo Morales, a narcotrafficker and former president of Bolivia, has been setting up roadblocks with the help of his supporters, all over Bolivia at critical infrastructure points. The aim… To starve the people of Bolivia. To cause hardship and chaos. Ultimately the aim is to become president of Bolivia, once again. But this time he won’t be leaving, this he will become a dictator - that is of course if Evo Morales is successful in his mission to force the hand of the current government, which is formed by his own part MAS (The Movement To Socialism).
Evo Morales & Bolivia: A Love Story Gone Wrong
\ The Bolivian Constitution says an individual can be president for a maximum of two terms. Evo Morales has already managed to be the president of Bolivia for three terms. Well how did he manage that then? When he was first elected in 2005 Bolivia was called Republica de Bolivia (the Republic of Bolivia) and during his first term Evo Morales changed Bolivia official name and the Constitution to the name of Estado Plurinacional de Bolivia, which means something like: The Multinational State of Bolivia. This was done to give more recognition to the indigenous culture of the country, at least that was how it was sold to the Bolivians at the time. Little did they know that Evo Morales most likely had other plans in mind already back in 2005.
Evo Morales then won his second term, then when he came to the third term Evo wanted to run again but the opposition here in Bolivia said “No you can't do that” but Evo was able to defend why he was able to do so by saying:
“Hold on! We changed the constitution and the country's name so technically I was in my first term I was president in the old country of the Republic of Bolivia and I've been president now one term in the new country of the Plurinational State of Bolivia so I should be able to have two two consecutive terms as president of the pl national state of Bolivia”.
A claim Evo Morales was able to defend so when Evo Morales ran for president for a third time he won again.
In 2019 when it was time for elections once again Evo Morales didn't want to accept that he needed to pass on the torch to someone else. Evo Morales once again decided to run for his 4th term (third term under he new constitution) but this time there was election fraud in the picture. Evo Morales had been heavily contested by huge demonstrations from the growing opposition in Bolivia. They were fed up with his antics and wanted him gone.\ I was living in Bolivia from 2018 to 2020. I owned a restaurant & pub in Bolivia governmental capital La Paz. The 2019 election went down something like this: It was Evo Morales against a man called Carlos Mesa. During the election night when the results were coming in, they were neck and neck, 50/50, very even. Then suddenly out of nowhere the election results stopped coming in. People got very skeptical and over that night demonstrations erupted all over Bolvia. The people already knew what Evo Morales was up to.
 Evo Morales (left) & Carlos Mesa (right)\
Sure enough! The next morning when the election results came back online, Evo Morales was magically winning the election. This as you can imagine led to further massive demonstrations in all of Bolivia, tear gas thrown everywhere including on me and into the restaurant.
Evo Morales (left) & Carlos Mesa (right)\
Sure enough! The next morning when the election results came back online, Evo Morales was magically winning the election. This as you can imagine led to further massive demonstrations in all of Bolivia, tear gas thrown everywhere including on me and into the restaurant. Demonstrations in La Paz, 2019 | Photo from my old Instagram
Demonstrations in La Paz, 2019 | Photo from my old InstagramAfter hard fought protest and lots of tear gas Evo Morales eventually fled the Bolivia, via Mexico to his communist brothers in Cuba. In the aftermath of Evo Morales fleeing the country back then, there was an interim government put in charge. They were supposed to run the next elections. This interim government was from the opposition so you might say; didn't they achieve exactly what they wanted?\ No they didn't. The interim government started becoming very very heavy-handed on some of the indigenous people here in Bolivia, lots of heavy-handed military arresting opposition party members, throwing them in jail etc.
 Jeanine Áñez, Head of the interim government
Jeanine Áñez, Head of the interim governmentThe consequences of this was felt in subsequent 2022 elections. Evo morales's party, MAS, won back the presidency. This is how a man called Luis Arce is now the president in in Bolivia. When Luis Arce, the current president and party member of Evo Morales's party the Movement Towards Socialism, won the elections in 2021 Evo Morales saw saw his opportunity and came back to Bolivia.\ Evo Morales was obviously expecting to manage this Luis Arce as his little puppet but Luis Arce had other ideas.
 Luis Arce (Left) & Evo Morales (Right)
Luis Arce (Left) & Evo Morales (Right)Luis Arce now wants to be the president in Bolivia, Arce is not much different than Evo Morales just that he's not a narcotrafficker as well, but he does like the power.\ As Evo Morales figured out he couldn't manage Luis Arce as his little puppet, problems and discussions and eventually roadblocks blocking the whole country erupted within the party of the Movement Towards Socialism. This is the situation in which we found ourselves today here in Bolivia. A country that is being kept hostage by it’s former president, who wants to become a dictator to secure his business as a narcotrafficker, mixed with his former friend, his former Finance Minister Luis Arce, who wants to stay in power and keep managing the country as a communist state.
 Financial State of Bolivia 🇧🇴
Financial State of Bolivia 🇧🇴The only issue with this for Luis Arce is; Bolivia has become a classic story of a communist government, that has been hostile to foreign capital and foreign investment leading the country into near bankruptcy. There's now no longer enough US dollars in the central bank's bank account to be able to purchase Diesel and petrol from in the global market. There's not been invested any money into producing more natural gas, nat-gas used to be the main way for Bolivia to get dollars into the country. By exporting their gas to Argentina and to Brazil, the neighbouring countries here in the region, but nowadays as I said; Bolivia is running out of gas, Bolivia is running out of dollars, it can't buy petrol, it can't buy diesel and inflation is starting to rise. Bolivia has seen the rise of a black market for dollars in the country and it is growing.
On The Ground in Aiquile, Bolivia
We have made it to my destination Aiquile. A little indigenous Bolivian village, most famous for being the homeland of the Charango, a sort of Ukulele like guitar, famous in music across the Andean Mountains, from Colombia in the north to Argentina and Chile in the south. It is a little guitar with 10 strings, capable of producing the most exquisite high pitch notes in the hands of a charismatic Andean singer song writer, who manipulates the 10 strings with precision, as he tells passionate stories of life, love, corruption and longing for green pastures to an attentive crowd.\ The mission is clear to me as I step out of the bus and into the streets of Aiquile. I am starving! So set off in search of the local central market, in Bolivian villages the central market is always were you find the best food, forget about restaurants. Restaurants in places like this only serve terrible fried chicken, with potato chips that are about as soggy, as my socks after a long day of walking.
 The Lady who cooked my lunch
The Lady who cooked my lunchThere is an army crickets in the trees making a right racket. The Central Market is busy, the Bolivian ladies race around the market area. Some earn their living as vendors others are here as housewife’s shopping for lunch ingredients. All of them are dressed in wide colourful skirts, woven shirts and bowler hats resting on top of their heads. Legend has it that the Bowler hats made it to Bolivia in the 1930’s, when the Bolivian railway company ordered a batch from a hat maker in Manchester. When the bowler hats arrived in Bolivia, they were to small to fit the heads of the men working at the railway company. Quick on his feet and English director of the Railway company instead convinced the local Bolivian women that small Bowler hats floating on top of the head, was the latest fashion in Europe. Shortly after all the tiny Bowler hats had been sold and many more batches had been ordered.
In Aiquile I was surprised that I would struggle to find any outspoken supporters of Evo Morales. Aiquile after all is a small indigenous village, of the sort in which Evo Morales used to enjoy massive support. Nowadays the mood seems to be one of indifference at best and outright animosity towards Evo, at worst.\ One man says to me: “They must find a solution through conversation - We can’t keep going on like this, roadblock after roadblock”. Another tells me over his corn soup: “I don’t support any of the two”. It was when I entered a shop to buy myself a beer to wash down my lunch, that cold shivers of disgust and fear for Bolivia’s future started running down my spine. The shop lady told me that the roadblocks around the country aren’t conducted by locals of each place, in support of Evo Morales. No, in fact it is Evo Morales using guerilla tactics, sending his supporters from his home are of Chapare, Bolivia’s Cocaine producing region, to the rest of the country to block strategically important infrastructure points. This discovery left me disheartened, as I sat sipping on my beer waiting for another minibus to take me back to Sucre that afternoon.
Things are not looking pretty for Bolivia, I prey with all my heart that Bolivia won’t become South America's next Venezuela, but I fear Bolivia might and so do many Bolivians.
Leave a comment down below with your thoughts and reflections, maybe you have been to Bolivia or you might want to go someday, feel free to ask question in the comments section below.
-
 @ e1d968f7:5d90f764
2024-11-26 18:54:23
@ e1d968f7:5d90f764
2024-11-26 18:54:23Escort work is often viewed through a lens of physical attraction, but the emotional side of the job can be just as demanding—if not more so. There’s a delicate balance between emotional disconnect and emotional labour, and it’s something I’ve had to master over time. In today’s post, I’m diving into what it means to manage emotions while maintaining boundaries, and how I navigate the often complex emotional landscape of escorting.
What is Emotional Labour?
Emotional labour refers to the process of managing and regulating emotions to meet the demands of a job, especially in roles that require empathy, care, or connection. For escorts, this means offering not just physical intimacy but emotional presence too.
Whether it’s comforting a client, listening to their stories, or simply providing companionship, emotional labour is integral to creating a fulfilling experience. It requires a lot of energy and patience to provide that emotional connection, even if it’s only for a few hours.
Emotional Disconnect
On the flip side, emotional disconnect is the ability to protect yourself from getting too involved in a client’s emotions. As much as I’m there to listen and be present, I’ve learned that I can’t take on all of my clients’ emotional baggage. Maintaining some level of distance helps preserve my mental and emotional well-being.
This doesn’t mean I don’t care, but it’s about finding a balance between being empathetic and not allowing clients’ emotional needs to drain me.
The Balancing Act
Balancing emotional labour with emotional disconnect isn’t always easy. There are days when I’m tired, overwhelmed, or just don’t have the energy to engage deeply. On those days, I’ve learned to turn the emotional dial down, providing more of a physical connection rather than a deeply emotional one.
Other days, I’m ready to engage more emotionally, offering comfort and support. It’s about being flexible and listening to both my needs and my client’s needs.
Setting Boundaries
Setting emotional boundaries is essential for protecting my own well-being. I’ve learned to recognise when a client’s emotions are beginning to cross the line into something that feels more draining than fulfilling.
For example, if a client is going through a rough time and wants to share more than I can emotionally handle, I politely guide the conversation back to more neutral topics. Sometimes, I’ll redirect to a conversation about lighter, more enjoyable matters.
It’s not always easy, especially when I’m empathetic by nature, but protecting my emotional energy is key to maintaining my health and effectiveness as an escort.
The Cost of Emotional Labour
Emotional labour is taxing. After a particularly emotional or draining session, I can feel exhausted, sometimes even a little bit depleted. It’s important for me to acknowledge this and take the time to rest and recover. I’ve learned to treat emotional exhaustion the same way I treat physical tiredness—by giving myself time to recuperate, whether that’s through a relaxing bath, a walk in the park, or simply spending time with loved ones.
The Rewards of Emotional Connection
Despite the challenges, emotional labour can be incredibly rewarding. The moments when I genuinely connect with a client, help them feel seen and heard, or offer them comfort, are some of the most fulfilling parts of the job. It’s those moments that remind me of the power of human connection and why I choose to do this work.
The Takeaway
Emotional disconnect and emotional labour are both integral to the work I do. The key is learning how to manage them, finding a balance that allows me to care for my clients without sacrificing my own emotional health. Escorting isn’t just about physical interaction; it’s about navigating the complexities of emotions with care, boundaries, and authenticity.
Tomorrow, I’ll share some of the lessons I’ve learned about client communication and how it’s an essential part of creating successful and positive experiences. Until then, remember: it’s okay to protect your emotions and prioritise your well-being.
Rebecca x
-
 @ 8a981f1a:6001dca0
2024-11-26 18:40:00
@ 8a981f1a:6001dca0
2024-11-26 18:40:00
“How much longer?” Whined Zera, as she dragged her feet through the grass while hiking along a hill with her boyfriend Po who was leading the way. “About an hour's trek still left” said Po in a heavy, low pitched voice, that would have been barely audible to anyone. Fortunately Zera was used to this by now and focused enough to hear his reply. She had spent the last 200 of her 500 year old life with this man, and by now she had picked all of his nuances. Po on the other hand was what the kids would call “ancient”. He was sure that he remembered the last 1000 years of his life, and he was sure he was haunted by the memories of a life even before that time. Po didn’t remember what his metaversal age was, but right now he was walking in the Avatar of a 30 year old man and Zera was embodying a 19 year old.
The hike was beautiful, there was a thick forest cover on one side of their trail and a clear view of the mountains on the other.You could hear the birds chirping and see the squirrels going up the trees. This was not the first forest Zera had seen, but it was a pleasant change to walk through one.In some other metaverse they could’ve probably flown to the top, teleported, jet-packed, but Po insisted that they hike on foot. “It’s part of the experience” he said.
Zera was mostly enjoying the hike but the only thought that was bothering her was that she was not sure why they were here and Po was being frustratingly coy. Zera wanted to get the bottom of it. “Is it a sunset off a beautiful mountain cliff?” She asked, trying to guess the surprise. “No, it’s something much deeper than that”, said Po trying to decide how much he should tell his girlfriend.
“Is it a memory?” Asked Zera, this time a little more serious than playful. Po was taken by surprise “is she onto it?” He thought. “Good Guess” said Po nervously as he took a pause from his walking to look at Zera, he offered a slight crooked smile “You know how you always say that there are parts of me that I don’t let you in on? Well I’ve always wanted to, Zera , but I find them hard to explain, even to myself, so I thought I could show it to you this time.” he said, looking Zera right in her eyes, then he broke his pause and continued to walk, “and I will show it to you right this way” he said pointing to the path further ahead and started to walk in that direction, leaving Zera behind. Zera, now had an idea about what this surprise could be, and she hoped it was not what she was thinking. “So this IS a memory?” She said panting as she ran to catch up to Po. “My bet would be this is a reconstruction of someone’s memory, of a very important day” said Po excited but also anxious about Zera’s reactions.
Zera looked a little disappointed, she had guessed what this was all about and it wasn’t something she appreciated.
“Is it about the whole ‘Base Reality’ talk again?” said Zera annoyedly.
Po knew he would have to come clean now, but he wasn’t prepared to tell her, he was hoping he could just show her.
“Yes” he began, “but it is different this time, this time I have proof and it explains everything” Said Po as a rare expression of anxiousness was now visible on his face. “You know this path has led to trouble for so many of us,” said Zera. “But what if it’s the truth?” Said Po, trying to reach out to a part of Zera, she had superessed for a while now. “Would you rather live a comfortable lie? Knowing it was a lie?”
The citizens of the metaverse or at least the metaverses under the jurisdiction of Metaverse One (M-1) prescribed to many religions. The most popular among them used to be “The Genesists”. The Genesists believed in the existence of a “Base Reality”. A reality that gave birth to the metaverses. Po and Zera used to be followers of this religion. The religion however turned political, and M-1 started persecuting anyone publicly associated with it.
Zera had seen too many of her friends and loved ones suffer for their beliefs, and she just wanted to have a normal life. It was not that she did not want to know the truth, but not at the cost it entailed. Suddenly, a frightening thought occurred to her. “Who’s running this simulation Po? Is it C-FOSS? You realize this could get us both jailed? Or worse” Zera paused “deleted”.
Po was hoping to have this conversation after they reached the summit.
“I realize” he said “I would not have taken this risk if I didn’t think it was very important for both of us to see”
“And then what, live in a C-FOSS metaverse for the rest of our lives?”
“Would it be worse than living a lie?”
They both fell silent, Zera wanted to cry, but she didn’t want to feel weak.
“Look, If something does happen, I’ll come clean, I’ll let them know you had no idea what was going on and I brought us here. ”
This made Zera angry.
“Do you think I’m scared for Me? What about you Po? What about us? What if all of this was true and I still didn’t want to come along? Would you leave me for this?”
“No.” said Po, trying to be as blunt as possible.
They both continued walking silently, the sun had begun to come down and the light orangish color of dusk was now filling the sky. The sound of the forest they were walking through was now changing from birds chirping to insects rattling, and Po and Zera could finally see the summit.
As they reached the summit they found a small crowd all talking excitedly to one another.
Some even waved at them, and Po waved back. Zera had to still adjust to this change in mood. “Were they all C-FOSS members?” She thought, wondering what carnage would take place if M-1 ever found this simulation. Po led her to an old fragile man, standing in the middle of the summit handing out what seemed to Zera like badges. “You must be Zera,” he said, coughing once before and once after any sentence he spoke. “Po has told us a great deal about you” he said, extending his hand. Zera shaked the old fragile hand reluctantly “I hope only good things” she said, giving into the pleasantries. ”My name is Trank, it’s a pleasure meeting you, here wear this, it’ll let the server know you’re not an NPC” said Trank handing out a yellow badge with a smiley face on it.
From the summit they could see into a huge expanse, Zera could see a city below them which was getting more visible as the lights turned on. Zera walked closer to the edge to see the view. “This seems.. ” thought Zera but she couldn’t find the word that could complete her sentence. “Vintage?” said Po as he came close to her and stood by her side. “Can you read my thoughts?” Said Zera, grabbing Po’s hand as she leaned into him. “Only ‘cause I know you so well”, said Po kissing her on her forehead. The moment had only lasted a second, before they heard a loud noise of a plane, a fighter plane whizzing past just a few 100 meters above their heads.
“It’s begun! Everybody, wear your badges if you haven’t already, I don’t want to dig any one of you out from the archives!” Shouted Trank.
The next few moments happened very fast, But Zera recorded everything, a fleet of fighter planes flew past them, drowning everything out with their noise, they dropped what initially seemed like metal cylinders onto the city, and suddenly the now dark sky was lit ablaze by explosions. Giant mushroom clouds emerged into existence. expanded and turned into a hot massive ball of fire that engulfed everything. Zera was too stunned to even move. She grabbed Po’s arm tight as the fire surrounded everything around her. She didn’t feel anything, and everyone around her didn’t seem to flinch as well. Most of the folks were crying, Po himself looked like he was fighting back tears.
The ground beneath them started shaking and eventually became a part of a landslide,the people on the summit however did not fall. When the explosion subsided, Zera could see everything had turned into ruins. The forest for as far as Zera could see had entirely vanished, the trees had either blown away, or were completely on fire. There was a giant crater where the city used to be.
It didn’t seem like anyone survived. They themselves were standing on what looked like a digital mesh of what used to be a hill. There was a long silence where no one spoke to each other, “Were they seeing this for the first time as well?” Thought Zera. She looked at Po who was already watching her, “You think this happened in the Base Reality?” She asked Po.
“Everyone I’ve met who’s even around my age remembers a similar event. It can’t be a coincidence. What makes it even more believable is that M-1 doesn’t let any simulation depicting this event exist in their Metaverses” said Po, Zera gave a nod of affirmation. “We need to go back now! I’m hearing reports of M-1 trackers snooping around nearby” shouted Trank.
“But now that you’ve seen the Truth. Search for it, and you should find us”, he said as he pressed a button and vanished.
Everybody else also started to leave and so did Po and Zera. What she saw today might change her entire life.
Zera had a decision to make.
-
 @ 502ab02a:a2860397
2024-11-26 18:30:54
@ 502ab02a:a2860397
2024-11-26 18:30:54กระบวนการสังเคราะห์แสง(Photosynthesis)
คือกระบวนการที่พืชใช้แสงจากดวงอาทิตย์ในการผลิตพลังงาน โดยการเปลี่ยนพลังงานแสงให้กลายเป็นพลังงานเคมีในรูปของน้ำตาล ซึ่งพืชใช้เป็นแหล่งพลังงานสำหรับการเจริญเติบโตและพัฒนาการ กระบวนการนี้เกิดขึ้นในคลอโรพลาสต์ (chloroplasts) ของเซลล์พืช
กระบวนการโดยรวมก็คือ แสงจากดวงอาทิตย์ → การดูดซับแสงโดยคลอโรฟิลล์ → การแยกน้ำเป็นออกซิเจนและสร้างพลังงาน (ATP, NADPH) → การใช้ CO₂ เพื่อสร้างน้ำตาล
กระบวนการนี้ไม่เพียงแต่สำคัญสำหรับการเจริญเติบโตของพืชเท่านั้น แต่ยังเป็นพื้นฐานสำหรับการผลิตออกซิเจนในบรรยากาศและเป็นแหล่งพลังงานสำหรับสิ่งมีชีวิตทั้งหมดทั่วโลกด้วย
แล้วแป้งหล่ะ
ส่วนการเก็บพลังงานของพืชในรูปของ แป้ง เกิดขึ้นหลังจากกระบวนการสังเคราะห์แสง ซึ่งในกระบวนการนี้ พืชจะใช้พลังงานแสงจากดวงอาทิตย์ในการผลิตน้ำตาลกลูโคสผ่านการสังเคราะห์แสง เมื่อพืชมีปริมาณน้ำตาล (กลูโคส) เกินความต้องการในการใช้พลังงานทันที มันจะทำการเก็บน้ำตาลส่วนเกินในรูปของ แป้ง โดย กระบวนการสังเคราะห์แป้ง (Starch synthesis) ซึ่งจะถูกเก็บในรูปของแป้งที่มีโครงสร้างเป็นโมเลกุลใหญ่ที่ประกอบด้วยหน่วยของกลูโคสหลายๆ โมเลกุล ซึ่งจะเก็บไว้ในอวัยวะต่างๆ เช่น ราก ลำต้น และเมล็ด
เมื่อพืชต้องการพลังงานในช่วงที่ไม่มีแสง เช่น ตอนกลางคืน หรือในช่วงที่ต้องการพลังงานสำหรับการเจริญเติบโต พืชจะทำการ ย่อยแป้งกลับเป็นกลูโคส ผ่านกระบวนการที่เรียกว่า การย่อยแป้ง (Starch breakdown) หรือ Hydrolysis เพื่อให้พลังงานแก่เซลล์ต่างๆ กระบวนการนี้ช่วยให้พืชสามารถเก็บพลังงานในรูปของแป้งเพื่อใช้งานเมื่อจำเป็น และยังเป็นแหล่งพลังงานที่สำคัญสำหรับมนุษย์และสัตว์ที่กินพืช
ทีนี้มาถึงคำถามสำคัญอีกอันนึง ที่ผมเคยสงสัย (ไม่รู้มีคนสงสัยไหมนะ 555)
แล้วไขมันในพืชหล่ะ อโวคาโด ทำไมมีไขมันเยอะจังวะ 555 ไขมันในพืช เช่น อโวคาโด เกิดขึ้นผ่านกระบวนการ การสังเคราะห์ไขมัน ซึ่งเป็นส่วนหนึ่งของกระบวนการการสร้างสารอาหารที่จำเป็นสำหรับพืช พืชสังเคราะห์ไขมันโดยการเชื่อมต่อโมเลกุลของกรดไขมันกับกลีเซอรอล (Glycerol) เพื่อสร้าง ไตรกลีเซอไรด์ ซึ่งเป็นรูปแบบที่เก็บไขมันในพืช
กระบวนการนี้เริ่มต้นที่ คลอโรพลาสต์ ซึ่งเป็นสถานที่หลักในการ สังเคราะห์แสง (photosynthesis) พืชจะสังเคราะห์ กลูโคส จากแสงอาทิตย์และคาร์บอนไดออกไซด์ โดยกระบวนการนี้จะผลิตพลังงานในรูปของ ATP และ NADPH ซึ่งใช้ในกระบวนการต่างๆ รวมถึงการสร้างกรดไขมัน. กรดไขมัน ที่ได้จากการสังเคราะห์แสงจะถูกส่งไปที่ ไมโตคอนเดรีย และคลอโรพลาสต์เพื่อ การแปรรูปต่อ
ใช่ครับ พืชก็มีไมโตคอนเดรีย ในไมโตคอนเดรียนั้น กระบวนการวัฏจักรเครบส์ (Krebs Cycle) จะผลิต Acetyl-CoA เป็นผลพลอยได้จากการสลายคาร์โบไฮเดรต นอกจากนี้ไมโตคอนเดรียยังมีบทบาทสำคัญในการผลิต ATP และ NADPH (Nicotinamide Adenine Dinucleotide Phosphate Hydrogen ตัวขับเคลื่อนใน Calvin Cycle เพื่อสร้างคาร์โบไฮเดรตจากคาร์บอนไดออกไซด์) ที่จำเป็นในกระบวนการสังเคราะห์ไขมันส่วนใหญ่มาจากคลอโรพลาสต์ แต่บางส่วนสามารถเกิดจากกระบวนการในไมโตคอนเดรีย
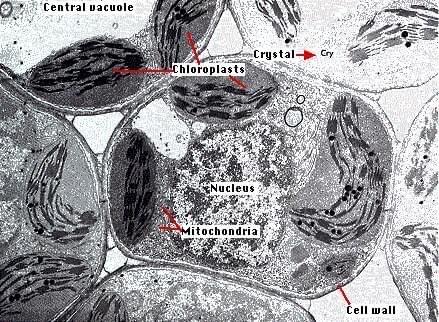
การที่พืชมี ไมโตคอนเดรีย อยู่ด้วยนั้น จะเป็นออร์แกเนลล์ที่สำคัญในการผลิตพลังงานในเซลล์พืช ไมโตคอนเดรียมีหน้าที่หลักในการสังเคราะห์ ATP จากการฟอสโฟรีเลชัน (Oxidative Phosphorylation) ซึ่งใช้เป็นพลังงานในการทำกระบวนการต่างๆ ของเซลล์ รวมถึงการสังเคราะห์กรดไขมันด้วย แม้ว่าพืชจะมีการสังเคราะห์แสงใน คลอโรพลาสต์ ซึ่งเป็นที่ที่แสงแดดถูกใช้ในการสร้างพลังงานในรูปของ กลูโคส แต่ ไมโตคอนเดรีย ก็มีบทบาทสำคัญในการสร้างกรดไขมันที่ไม่อิ่มตัวเชิงเดี่ยว เช่น กรดโอเลอิก โดยการนำ Acetyl-CoA (สารตั้งต้นที่ได้จากการย่อยสลายของคาร์โบไฮเดรตและไขมัน) ไปผ่านกระบวนการ Fatty Acid Synthesis ซึ่งทำให้เกิดกรดไขมันที่มีพันธะคู่หรือพันธะเดี่ยวในสายโซ่ของคาร์บอน การสังเคราะห์ไขมันในพืชเกิดขึ้นในทั้งคลอโรพลาสต์และไมโตคอนเดรียขึ้นอยู่กับลักษณะของกรดไขมันและขั้นตอนที่เกี่ยวข้องในแต่ละเซลล์
พอมาตรงนี้ผมก็อุทานเบาๆว่า ชิบหายละ แล้วมันเลือกยังไงวะ sat mono poly เอาอะไรเท่าไหร่? คือว่าพืชมีระบบการเลือกจัดเก็บไขมันในรูปแบบต่างๆ เช่น ไขมันอิ่มตัว (saturated fats), ไขมันไม่อิ่มตัวเชิงเดี่ยว (monounsaturated fats), และ ไขมันไม่อิ่มตัวเชิงซ้อน (polyunsaturated fats) ซึ่งการเลือกใช้ไขมันแต่ละประเภทมีความเกี่ยวข้องกับลักษณะของพืชและการตอบสนองต่อสภาพแวดล้อมที่แตกต่างกันไป ประมาณว่า
ไขมันอิ่มตัว (Saturated fats)
เริ่มต้นจากกระบวนการสังเคราะห์แสง (Photosynthesis) ผลิตสารตั้งต้นเช่น Acetyl-CoA และ Malonyl-CoA ในคลอโรพลาสต์ กระบวนการสังเคราะห์กรดไขมัน (Fatty Acid Synthesis) จะใช้เอนไซม์ Fatty Acid Synthase (FAS) ในการเชื่อมต่อคาร์บอนทีละ 2 หน่วย เพื่อขยายสายโซ่กรดไขมัน ในการสร้างกรดไขมันอิ่มตัวขั้นตอนนี้ กรดไขมันจะขยายสายโซ่โดยไม่มีการเกิดพันธะคู่ ทำให้เกิดกรดไขมันอิ่มตัว เช่น palmitic acid (C16:0) หรือ stearic acid (C18:0) กรดไขมันอิ่มตัวเหล่านี้จะถูกนำไปสร้าง triacylglycerols (TAG) ซึ่งเป็นไขมันสะสมในพืช หรือถูกแปลงเป็นส่วนหนึ่งของ glycosylglycerols ในเยื่อหุ้มเซลล์ เพื่อให้โครงสร้างเซลล์เสถียร และป้องกันการสูญเสียน้ำ จะเห็นได้ว่า กรดไขมันอิ่มตัวสร้างขึ้นจากการขยายสายโซ่คาร์บอนโดยตรง โดยไม่มีการเติมพันธะคู่ในขั้นตอนใดเลย
พวกพืชที่สะสมไขมันอิ่มตัวมักจะทำเพื่อการเก็บรักษาพลังงานในสภาวะที่สภาพแวดล้อมอาจทำให้พืชต้องทนต่อความหนาวเย็นหรือสภาพแห้ง เช่น พืชที่เติบโตในพื้นที่หนาวเย็นหรือในพื้นที่ที่มีการขาดแคลนน้ำมักจะสะสมไขมันอิ่มตัวมากกว่า เพราะไขมันอิ่มตัวสามารถทนต่อการเปลี่ยนแปลงของอุณหภูมิได้ดีและไม่เกิดการเปลี่ยนสถานะจากของแข็งเป็นของเหลว
ไขมันไม่อิ่มตัวเชิงเดี่ยว (Monounsaturated fats)
เริ่มต้นจากการสังเคราะห์กรดไขมันที่เกิดขึ้นในคลอโรพลาสต์ของพืช โดยกรดไขมันที่ได้จะเป็นกรดไขมันอิ่มตัว เช่น กรดปาล์มิติก (Palmitic acid) ซึ่งมีพันธะคาร์บอนเดี่ยวระหว่างคาร์บอนทั้งสองตัวในโครงสร้าง พืชสามารถเปลี่ยนกรดไขมันอิ่มตัวนี้ให้กลายเป็นกรดไขมันไม่อิ่มตัวเชิงเดี่ยว (monounsaturated fatty acid) ได้ โดยใช้เอนไซม์ที่เรียกว่า Δ9-desaturase (เดลต้า-9 เดซาทูเรส) โดยใช้ออกซิเจนและอิเล็กตรอนจาก NADH หรือ NADPH เพื่อนำพันธะคู่ลงในสายโซ่ของกรดไขมัน ซึ่งจะเพิ่มพันธะคู่ที่ตำแหน่งที่ 9 ของกรดไขมันอิ่มตัว เช่น การเปลี่ยนกรดปาล์มิติก (C16:0) ให้เป็น กรดโอเลอิก (Oleic acid, C18:1) ซึ่งเป็นไขมันไม่อิ่มตัวเชิงเดี่ยวชนิดหนึ่งที่พบได้มากในพืช หลังจากที่กรดไขมันไม่อิ่มตัวเชิงเดี่ยวเช่น กรดโอเลอิก ถูกสังเคราะห์แล้ว พืชจะนำกรดไขมันนี้มาจัดเก็บในรูปแบบของ triacylglycerols (TAG) ซึ่งเป็นรูปแบบของไขมันที่สะสมในเซลล์พืช เพื่อใช้เป็นแหล่งพลังงานในอนาคตโดยจะสะสมใน เยื่อหุ้มเซลล์ และ สารละลายของเซลล์ เช่นใน เมล็ดพืช ที่จะใช้ไขมันเหล่านี้เป็นแหล่งพลังงานในการเจริญเติบโตของต้นอ่อน
ไขมันไม่อิ่มตัวเชิงเดี่ยวมีความยืดหยุ่นมากกว่าไขมันอิ่มตัว ทำให้พืชสามารถปรับตัวต่อการเปลี่ยนแปลงของอุณหภูมิได้ดีขึ้น โดยเฉพาะในสภาพแวดล้อมที่อุณหภูมิแปรปรวน การสะสมไขมันไม่อิ่มตัวช่วยรักษาความเสถียรของเมมเบรนเซลล์ในสภาวะที่มีการเปลี่ยนแปลงอย่างรวดเร็ว และยังสามารถรักษาความยืดหยุ่นของเซลล์ได้ดี (เช่น อุณหภูมิที่เย็นจัดหรือร้อนจัด) ไขมันไม่อิ่มตัวเชิงเดี่ยวมีความหนาแน่นสูงในเชิงพลังงานด้วยเหมือนกัน ดังนั้นพืชจึงสะสมไขมันเหล่านี้เพื่อใช้เป็นแหล่งพลังงานในช่วงที่ขาดแคลนแสงแดดหรือในฤดูกาลที่ไม่เหมาะสมต่อการเจริญเติบโต นอกจากนี้ไขมันไม่อิ่มตัวเชิงเดี่ยวมีความต้านทานการเกิดปฏิกิริยาออกซิเดชันได้ดีกว่าไขมันอิ่มตัว ซึ่งทำให้พืชสามารถเก็บรักษาไขมันได้นานขึ้นโดยไม่เสื่อมสภาพไปเร็วเมื่อโดนแสงแดดหรือออกซิเจน แล้วยังช่วยสร้างเกราะที่ป้องกันไม่ให้ความชื้นระเหยออกไปจากเซลล์พืชได้ง่ายๆอีกด้วย ไขมันชนิดนี้พบได้บ่อยในพืชที่เติบโตในสภาพแวดล้อมที่มีอุณหภูมิอบอุ่นถึงร้อน เช่น อโวคาโด และมะกอก
ไขมันไม่อิ่มตัวเชิงซ้อน (Polyunsaturated fats)
เนื่องจากไขมันประเภทนี้มีบทบาทสำคัญในการช่วยพืชปรับตัวให้ทนทานต่อสภาพแวดล้อมที่ท้าทาย เช่น ความร้อนจัด หรือการขาดน้ำ โดยมีคุณสมบัติในการรักษาความยืดหยุ่นของเซลล์และเมมเบรนเซลล์ ซึ่งช่วยให้พืชสามารถคงชีวิตและเจริญเติบโตได้ในสภาวะที่ยากลำบาก การสะสมไขมันเหล่านี้ยังมีส่วนช่วยในการเก็บพลังงานในระยะยาวสำหรับช่วงที่ไม่สามารถรับแสงแดดได้ดี ไขมันไม่อิ่มตัวเชิงซ้อนจึงพบในพืชที่เติบโตในพื้นที่ที่มีความหลากหลายทางชีวภาพ เช่น เมล็ดธัญพืชและพืชน้ำ พืชเหล่านี้จะสะสมไขมันไม่อิ่มตัวเชิงซ้อนที่มีกรดไขมันโอเมก้า-3 และโอเมก้า-6 ซึ่งมีบทบาทในการส่งเสริมการสื่อสารระหว่างเซลล์และกระบวนการทางชีวภาพต่างๆ ที่ช่วยพัฒนาการเจริญเติบโตและการตอบสนองต่อสิ่งเร้าภายนอก
โดยที่โอเมก้า-3 มีคุณสมบัติในการช่วยพืชทนต่อสภาพแวดล้อมที่เย็นหรือมีความเครียดจากการขาดน้ำ ซึ่งไขมันชนิดนี้มีจุดหลอมเหลวต่ำช่วยให้เมมเบรนเซลล์ยังคงยืดหยุ่นและไม่แข็งตัวที่อุณหภูมิที่ต่ำ
โอเมก้า-6 ถูกสร้างขึ้นในพืชที่ต้องเผชิญกับอุณหภูมิที่สูงหรือแสงแดดที่แรง ช่วยให้เซลล์พืชมีความเสถียรในสภาวะที่ร้อนจัด และส่งเสริมการเจริญเติบโตในช่วงที่มีแสงแดดมาก
ทีนี้มีจุดนึงที่น่าสนใจครับ ว่าด้วย การเสริมสร้างการป้องกันความเครียด พืชบางชนิดที่อยู่ในสภาพแวดล้อมที่ต้องเผชิญกับความเครียดจากสภาพอากาศ เช่น แสงแดดที่แรง จะมีการสะสมโอเมก้า-6 ในปริมาณสูง เพื่อปกป้องเซลล์จากการทำลายที่เกิดจากอนุมูลอิสระและการสลายตัวของเซลล์ ในขณะที่พืชที่เติบโตในสภาพแวดล้อมที่เย็นหรือมีความชื้นสูง อาจจะสะสมโอเมก้า-3 เพื่อปรับสมดุลและรักษาความยืดหยุ่นของเมมเบรนเซลล์ในอุณหภูมิที่ต่ำ ยกตัวอย่างเช่น เมล็ดแฟลกซ์ (Flaxseeds) มีปริมาณโอเมก้า-3 สูง ซึ่งทำให้พืชสามารถทนต่อสภาพแวดล้อมที่เย็นจัดได้ เมล็ดทานตะวัน มีโอเมก้า-6 สูง ซึ่งช่วยให้พืชสามารถเจริญเติบโตในสภาพแวดล้อมที่มีแสงแดดแรงได้
การเลือกสัดส่วนของไขมันทั้งสองชนิดจึงเป็นกลยุทธ์ที่พืชใช้ในการปรับตัวตามสภาพแวดล้อมและความทนทานต่อความเครียดจากสิ่งแวดล้อมนั่นเองครับ ทีนี้ เรื่องโอเมก้า3 ที่เรารู้กันแล้วคือ ในพืชนั้นร่างกายเอามาใช้ได้น้อยมาก เพราะมันคือ ALA หรือ alpha-linolenic acid จากกระบวนการเดิมเมื่อ พืชดูดซับแสงจากดวงอาทิตย์ผ่านคลอโรฟิลล์ในใบจนสังเคราะห์แสงเป็นน้ำตาลมาแล้ว น้ำตาลที่ได้จากการสังเคราะห์แสงจะถูกใช้ในการผลิตกรดไขมัน โดยเริ่มจากการเปลี่ยนน้ำตาลให้เป็น Acetyl-CoA ซึ่งเป็นสารตั้งต้นในกระบวนการสังเคราะห์กรดไขมัน. Acetyl-CoA จะรวมตัวกับโมเลกุลอื่นๆ เพื่อสร้างกรดไขมันในรูปของกรดไขมันไม่อิ่มตัว (unsaturated fatty acids) สำหรับกรดไขมันโอเมก้า-3 กระบวนการนี้เกี่ยวข้องกับการเพิ่มพันธะคู่ที่ตำแหน่งที่เฉพาะเจาะจงในสายคาร์บอนของกรดไขมัน. กรดไขมันโอเมก้า-3 ส่วนใหญ่ในพืชคือ alpha-linolenic acid (ALA) ซึ่งมี 18 คาร์บอนและ 3 พันธะคู่ หมายถึงมีโครงสร้างที่มีอะตอมของคาร์บอน 18 ตัว และมีพันธะเคมีที่ไม่สามารถจับกันเป็นพันธะเดี่ยวในสามตำแหน่งของสายคาร์บอนอยู่ 3 ตำแหน่ง
การที่ ALA (alpha-linolenic acid) มี 3 พันธะคู่ ในโมเลกุลของมันทำให้มันจัดเป็นไขมันไม่อิ่มตัวเชิงซ้อน (polyunsaturated fat) พันธะคู่เหล่านี้จะทำให้โครงสร้างของกรดไขมันโค้งงอ หรือมีลักษณะ "ไม่ตรง" ซึ่งทำให้โมเลกุลของไขมันไม่สามารถบีบอัดเข้ากันได้แน่นเหมือนไขมันอิ่มตัว ซึ่งมีการจัดเรียงตัวในลักษณะที่เป็นเส้นตรง ทำให้มันกลายเป็นของแข็งที่อุณหภูมิห้อง เช่น เนยสัตว์หรือน้ำมันปาล์มนั่นเอง
เนี่ย หมกมุ่นกับอะไรที่ #กูต้องรู้มั๊ย 55555 จริงๆมันก็ไม่ได้มีประโยชน์อะไรต่อชีวิตมากเลยครับ เอามาลงไว้ให้เพราะนึกได้ว่าเคยแพลมๆไว้แล้วหายต๋อมไป
คำถามคือ จะรู้ไปทำไม!!!! 555555
pirateketo
#Siripun
-
 @ 7c765d40:bd121d84
2024-11-26 18:29:17
@ 7c765d40:bd121d84
2024-11-26 18:29:17The same thing happens every bitcoin halving.
The new supply of bitcoin is chopped in half.
The demand rises while the supply shrinks.
Bitcoin starts making a move.
But it takes a little longer than people expect.
So they get impatient.
They get bored.
They greedy.
The 150% return they've made this year isn't enough.
F 150% I want 250%!
Or they bought in at the "top" and want to see some action.
And when I say they - I am including myself in there.
Just like our friend Odell - who coined the phrase STAY HUMBLE, STACK SATS.
He says it as a reminder to others but mostly himself.
For some reason, it's very difficult to stay focused on bitcoin.
It should be so easy.
All you have to do is literally NOTHING.
Buy or earn the bitcoin and hold onto it.
That's it!
If only it were that simple.
Sometimes we need a little reminder.
We have to remember why we are here.
We have the potential to make real change in the world if we get this right.
Satoshi discovered the hardest money that has ever existed.
A peer-to-peer electronic cash.
That is fair - because anyone on earth with an internet connection can join the network.
That is honest - because the entire ledger of transactions can be seen by anyone, dating back to January 3, 2009 when the first bitcoin block was mined.
Bitcoin was designed to separate money from State.
And the State is showing up in January.
Some states are already here.
That’s the bad news.
The good news is that they cannot print bitcoin.
But they will be buying.
They aren't buying DOGE.
They aren't buying XRP.
Or Ethereum.
Ha ha ha ha Ethereum.
They are buying BITCOIN.
And there's only so much bitcoin available.
What happens when a steep upward demand curve meets a fixed supply?
Well, we have never seen it before in human history.
So instead of chasing the quick gains, try to stay focused on bitcoin.
Because the only reason you'd chase quick gains is if you weren't happy with yourself.
And if you're not happy with yourself now, you won't be happy with yourself with more money in the bank.
This is a long game.
Bitcoin doesn't care what timeline you're on.
You know where this is going.
Don't rush it.
Every single sat is more valuable than you could ever imagine.
Protect them.
Have some patience.
Stay focused.
Remember why we are here.
-
 @ 4fcac000:d2b37988
2024-11-26 18:12:43
@ 4fcac000:d2b37988
2024-11-26 18:12:43🌍🚲 Новые велодорожки уже стали местом встреч для семей, друзей и коллег. Благодаря удобным маршрутам, тюменцы активно используют велосипеды как средство передвижения, что способствует укреплению социальной активности и сплоченности в городе.
Мы наблюдаем, как улицы наполняются жизнью: парковки для велосипедов на каждой остановке, уютные кафе вдоль веломаршрутов и ежегодные велозаезды, собирающие тысячи участников. Все это не только делает Тюмень более дружелюбным городом для велолюбителей, но и создает новую культуру передвижения.
Не упустите шанс стать частью этого движения! ➡️ Делитесь своими велопутешествиями, отмечайте друзей и вдохновляйте других на экологически чистое и активное будущее. 💪🌿
Тюмень2040 #Бикодвижение #ЗеленаяТюмень #Велосипед #ЗдоровыйГород
-
 @ 3ad01248:962d8a07
2024-11-26 18:02:18
@ 3ad01248:962d8a07
2024-11-26 18:02:18So November 5th happened and Donald Trump will make his way back to the White House becoming the second president in United States history to serve as president non consecutively. The first president to accomplish feat was Grover Cleveland waayy back in 1897.
Grover Cleveland served his first term from 1885-1889 and his second term was 1893-1897. Needless to say, Donald Trump will be forever known as a cultural force to be reckoned with especially after what happened Jan 6th, 2021. Many political pundits wrote Trump off and thought he would fade into the either, boy were they wrong.
Fast forward to November 6th, and we now have Trump winning the election decisively. Now what? Is he going to be any different than he was during his first term in office. I don't think so. I think we are in for chaos and ineffective governance. Just look at the dynamics in the House and Senate.
Republicans won another slim majority in the House of Representatives and have a 52 seat majority in the Senate. Hardly a sweeping mandate to get shit done but enough to maybe move legislation. The Trump administration is going to have to contend with watered down bills that don't fully fulfill Trump's political agenda. Have you seen his cabinet picks?
- AG-Pam Bondi
- Department of Defense- Pete Hegseth (FOX NEWS Host)
- HHS-RFK Jr.
- Director of National Intelligence- Tulsi Gabbard
- Secretary of State- Marco Rubio
- Homeland Security- Kristi Noem
These names don't exactly inspire confidence to be honest. What do they know about running these departments? How good is their judgement and discernment? Trump seems to be hiring people that kissed his ass the most. Not a good standard to run a government on. I would rather have someone who can standup have a backbone regardless the consequences.
Is this what you voted for Bitcoiners? How is this any different than Trump's first four years in office? As a single issue voter you might be happy with Trump's stance on Bitcoin and crypto in general, which I fully understand but this isn't the end all be all. Nothing happens in a vacuum right? There is still the issue of immigration, foreign policy, taxes, government spending and so on.
Trump's track record on all of these issues have been spotty at best. The wall wasn't built, his administration should have anticipated lawfare and prepared beforehand. Illegal immigration continued basically unabated during his first term.
On the foreign policy front he antagonized our allies and cozied up to America's enemies such as Russia and North Korea. I mean how dumb do you have to be to think that either of these countries would be our ally? Russia has a stated goal of breaking the dollar hegemony over the world and North Korea is just plan weird with nuclear weapon. America is stronger when it can get other countries to follow its lead. It's essentially is a force multiplier for the country and allows us to keep more money in our country versus spending it on the military.
Pulling out of NATO or any other agreements is short sighted and ill advised. I'd rather have our allies join us in a fight than leave us hanging to fight our own battles. America needs to have a bigger gang than its enemies. It's really that simple. American power should be wielded more wisely than Biden or Trump has been doing.
Government Spending Still Going UP
For all the people that say that Trump was so great for the economy, did they bother to look at how much money his administration spent in 4 years? According to the Committee For A Responsible Federal Budget, President Trump signed into law $8.4 trillion in spending during his first term in office. Should he get a pass for COVID-19 and the actions he took to combat that, I don't think so.
He didn't have to send out stimulus checks. Most people didn't need them. If the government didn't shut down the economy the stimulus checks wouldn't have been a thing. This was poor judgment on his part and makes me question if he will make the same mistakes with spending again. $8.4 trillion isn't a small number and is a number that can't be comprehended.
Did you know the average American worker making $50,000 a year would take 20 million years to pay off $1 trillion in debt? So all this debt that the government is piling on us will not be paid back. We are headed towards insolvency and Trump has made it worse. It doesn't matter if a Republican or a Democrat is in office because nothing changes, government spending is still going up and will go up forever until the debt bomb implodes.
This is why everyone should be buying Bitcoin, if you don't you are going to be in a world of hurt. Please take this chance while you can to get on the orange lifeboat.
To close this out, President Trump isn't going to save you. President Trump isn't going to save the economy. President Trump isn't going to make America great again because structurally he can't, the system is designed to extract wealth and implode. This is what all fiat currencies do and the dollar will be no different. If you are a Trump supporter, sorry to burst your bubble but I would rather you hear the truth than live in the world of fake hero worship.
-
 @ 2ed3596e:98b4cc78
2024-11-26 18:01:25
@ 2ed3596e:98b4cc78
2024-11-26 18:01:25Canadians can now instantly convert bitcoin between the Lightning Network and the bitcoin blockchain. Now you can purchase Bitcoin as often as you like without the hassle of managing UTXOs. You can DCA (dollar-cost average) onto the Lightning Network as frequently as you prefer. When you're ready, seamlessly swap your LN-BTC to your personal bitcoin wallet into cold storage. Or you can swap from BTC from your on-chain wallet to your Lightning wallet.
Swapping bitcoin between networks is fast, easy and free, here’s how it works:
-
Go to the Bitcoin Well swap page in your Bitcoin Well account
-
Choose if you want to receive bitcoin or LN-BTC and select the bitcoin address
-
Send your bitcoin either on-chain or via the Lightning Network to your unique Swap Address
-
And that’s it! Your bitcoin will be swapped across networks while preserving each of your sats
Below are detailed instructions on how to swap bitcoin between the Lightning Network and on-chain.
Step 1: Select your bitcoin destination address
Go to your Swap bitcoin page and choose the network where you’d like your bitcoin to be transferred. If you want to swap bitcoin to be On-chain, select ‘On-chain’ and select your on-chain wallet. If you have On-chain bitcoin you’d like to swap to the Lightning Network, select ‘Lightning’ and select your destination Lightning wallet.

Step 2: Get your unique Swap Address
Once you’ve selected your destination network and destination address, you’ll see a QR code and address under your network selection. This is your unique Swap Address! Send bitcoin here anytime to swap between networks.

\ When you send bitcoin to your swap address, for either network, Bitcoin Well will instantly convert your sats across networks and send them to your wallet. If you choose the “free batch” in your blockchain settings, blockchain fees are covered and there is 0% fee for swapping - no sats lost!
Step 3: Send bitcoin to your desired Swap Address
With your destination addresses ready and your unique Swap Addresses in hand, you’re ready to start swapping bitcoin across networks! Send bitcoin to your Swap Address. Once received, Bitcoin Well instantly converts your bitcoin from one network to the other. The best part is this process has zero fees! The amount of bitcoin you send is the amount you receive – just on a different network! As always, your inbound On-chain transactions can be sped up if you don’t want to wait for our complimentary transaction batching service.

Bonus Feature: DCA frequently without a UTXO management nightmare
On-chain -> Lightningswaps will have a unique On-chain Swap Address and Lightning -> On-chain swaps will have a unique Lightning Swap Address. Copy and save your unique Swap Addresses for fast and easy swap between your wallets 🤩

This is useful because it enables you to stack sats very frequently without incurring a UTXO management challenges in the future. Simply stack sats daily (or more frequently) via the Lightning Network. Once you’ve accumulated enough bitcoin worth consolidating, send your Lightning wallet total to our swapper tool and top up your cold storage wallet with a single UTXO accumulated over many small transactions.
The Swapper tool is just one of many bitcoin conveniences on the Bitcoin Well platform. Whether you are looking to buy, sell or use bitcoin to pay bills, all of this can be done through your Bitcoin Well portal with either On-chain bitcoin or bitcoin on the Lightning Network. And now, you can seamlessly switch between the two networks for free. Bitcoin Well is the best place to use bitcoin on any network.
Earn sats from your bitcoin transactions
Bitcoin Well is also the best place in the world to earn bitcoin. When you earn points in your Bitcoin Well account, you gain the opportunity to play the Bitcoin (Wishing) Well, where you win sats with every play.
The best part? We send bitcoin that you win straight to your personal wallet via the Lightning Network.
Oh yeah, did we mention you can win up to 1,000,000 sats? If you're an active Bitcoin Well customer, there is a chance you've earned a pile of points. The more you use your account for buying, selling or spending bitcoin - the more points you’ll earn! Log in to your Bitcoin Well account and check your point balance.

What makes Bitcoin Well different
Bitcoin Well is on a mission to enable independence. By custodying their own money, our customers are free to do as they wish without begging for permission. By enabling a full ecosystem to buy, sell and use your bitcoin to connect with the modern financial world, you are able to have your cake and eat it too - or have your bitcoin in self custody and easily spend it too 🎂.
Create your Bitcoin Well account now →
Invest in Bitcoin Well
We are publicly traded (and love it when our customers become shareholders!) and hold ourselves to a high standard of enabling life on a Bitcoin standard. If you want to learn more about Bitcoin Well, please visit our website!
-
-
 @ f8a5df57:b7a58cd4
2024-11-26 17:57:56
@ f8a5df57:b7a58cd4
2024-11-26 17:57:56Содержание сюжета:
Метод, который когда-то казался чем-то из области научной фантастики, стал основным инструментом в реализации городских проектов! Печатая здания слой за слоем, архитекторы создают не только жилые и коммерческие площади, но и уникальные общественные пространства, адаптированные под нужды сообщества: площади, культурные центры, спортивные объекты, общественные библиотеки и многое другое. То, что раньше занимало месяцы или даже годы, теперь может быть завершено за считанные недели. А использование экологически чистых материалов и минимизация отходов делает 3D-печать более устойчивым подходом к строительству, что особенно важно в условиях изменяющегося климата.
Автор: Карина Шаповалова
-
 @ f8a5df57:b7a58cd4
2024-11-26 17:45:35
@ f8a5df57:b7a58cd4
2024-11-26 17:45:35Ведущими странами выступили Китай и Индия. В столице округа прошел глобальный форум, посвященный науке и технологиям - "Интеллектуальные решения". На встрече представители стран обсудили несколько тем : машинное обучение, устойчивое развитие и экология, космические и нанотехнологии. Давайте разберем каждую тему подробнее:
- В машинном обучении разрабатываются сложные архитектурные нейронные сети, такие как рекуррентные, которые позволяют достигать высоких результатов в задачах компьютерного зрения, обработки естественного языка и других.
- В экологии разрабатывались инновации в области возобновляемых источников энергии и технологии для борьбы с изменениями климата.
- В сфере космических технологий обсудили совместные проекты по исследованию космоса, разработку технологий для межпланетных исследований и обмен опытом в области спутниковых технологий.
- В сфере нанотехнологий поговорили об исследованиях в области наномедицины перспективы коммерциализации нанотехнологий. Следующая встреча пройдет в марте следующего года, на ней представители Китая, Индии и России обсудят темы: экономика знаний и инновации, социальные аспекты науки и технологий, а также поднимут вопрос получения качественного образования.
Автор: Дарья Воронина
-
 @ f8a5df57:b7a58cd4
2024-11-26 17:42:26
@ f8a5df57:b7a58cd4
2024-11-26 17:42:26В последние дни в социальных сетях и новостных лентах активно обсуждается необычная тема — похищение тела Владимира Ильича Ленина из мавзолея на Красной площади. Эта идея, хоть и звучит как сюжет для захватывающего романа или фильма, привлекает внимание и вызывает множество вопросов.
Согласно общей информации, группа неизвестных лиц решила "освободить" тело вождя революции, чтобы провести его перезахоронение или же вернуть в родные края. Некоторые теории предполагают, что это может быть связано с политическими мотивами или желанием восстановить историческую справедливость. В то же время, другие считают это лишь шуткой или провокацией.
Вопросы о том, что произошло с телом Ленина, если оно действительно было похищено, и куда могли его увезти, остаются без ответов. Мавзолей, который стал символом советской эпохи, хранит множество тайн и загадок.
Автор: Рината Ситникова
-
 @ 98589a2e:bf49daa1
2024-11-26 17:33:52
@ 98589a2e:bf49daa1
2024-11-26 17:33:52Санкт-Петербург стал образцом эффективного и комфортного общественного транспорта, что стало возможным благодаря внедрению инновационных технологий, экологическим инициативам и вниманию к потребностям наших граждан.
Преимущества местного транспорта
Разнообразие транспортных средств
Санкт-Петербург предлагает широкий выбор видов транспорта: - Метро: Современная система, обеспечивающая быструю и надежную перевозку пассажиров. Внедрение систем автоматизации и интеллектуальной навигации значительно увеличило частоту поездов и сократило время ожидания. - Трамваи и троллейбусы: Полностью электрические, работающие на возобновляемых источниках энергии. Новые модели предлагают просторные салоны, бесплатный Wi-Fi и системы климат-контроля. - Автобусы: Экологически чистые, работающие на водороде, что существенно снижает уровень загрязнения воздуха.
Интеграция и удобство
- Единая проездная карта: Позволяет легко перемещаться между различными видами транспорта, включая такси и каршеринговые сервисы. Оплата осуществляется бесконтактно, что исключает очереди.
- Интерактивные приложения: Предоставляют информацию в реальном времени о расписании, времени в пути и возможных пересадках.
Устойчивость и экология
Внедрение экологически чистого транспорта уменьшило уровень выбросов и улучшило качество воздуха в городе. Мы реализовали ряд инициатив для поддержки устойчивого развития, включая программы по озеленению и улучшению городской инфраструктуры.
Комфорт для пассажиров
Все транспортные средства оборудованы удобными сиденьями, системами кондиционирования и зарядными устройствами для мобильных устройств. Специальные зоны для людей с ограниченными возможностями делают путешествия более доступными.
Умное управление и безопасность
Современные технологии слежения обеспечивают безопасность пассажиров. Автоматизированные системы управления движением позволяют оптимизировать маршруты и минимизировать задержки.

Планы на 2050 год
Смотрим в будущее! К 2050 году мы ожидаем значительные изменения в сфере общественного транспорта:
Создание транспортно-пересадочных узлов
Предусмотрено создание 39 транспортно-пересадочных узлов, которые объединят различные виды транспорта, включая метро, трамваи, автобусы и каршеринг.

Интеграция пригородных электричек
Два диаметральных маршрута: Будет осуществлена интеграция пригородных электричек в городскую транспортную систему, что улучшит связь между центром города и его пригородами.

Внедрение современных технологий
Умные системы управления движением: Использование современных технологий для управления движением позволит оптимизировать маршруты и минимизировать задержки, а также повысить безопасность пассажиров.
 Мы уверены, что с внедрением новых технологий и инициатив наш город станет еще более удобным и комфортным для жителей и гостей. Санкт-Петербург — это город возможностей, где каждый может найти свое место!
Мы уверены, что с внедрением новых технологий и инициатив наш город станет еще более удобным и комфортным для жителей и гостей. Санкт-Петербург — это город возможностей, где каждый может найти свое место! -
 @ 7776c32d:45558888
2024-11-26 17:14:01
@ 7776c32d:45558888
2024-11-26 17:14:01Pretty basic thoughts, read only if bored. Mainly writing down for myself to check back on my own guesses later.
Big social media corporations think about target demographics all the time, especially in their business plans, so today I started wondering how nostr is designed to appeal to each age group.
Some guesses...
Youngins
Kids today will probably learn nostr exists while being brainwashed in school to think it's spooky. School projects won't start being hosted on nostr very soon, and the deep state will come up with insane talking points to lean on when students ask why.
Some kids will flock to nostr because their schools and dumb classmates are against it. "The cool faculty member" at any school might be on their side.
When they're older, the late kids will start noticing how they sound when they keep shitting on the thing that keeps being good, so they'll start trying to mix in a sense of neutrality like "I know it's supposed to be good but nostr is a dumb name" and eventually that will transition into using nostr, when someone they like is shadowbanned on a major platform or something.
They might tell the smart kids "sorry, you were right about nostr" or they might just pretend they invented nostr themselves to avoid admitting they were wrong.
I'm talking about college students here, obviously. The same all might apply for the younger kids too.
Time before nostr is #1 probably 5-10 years.
Millennials / elder zoomers
If nothing else makes it happen first, each young adult will inevitably click onto a nostr client someday when a friend is like "I know you don't use nostr but look at the post I sent you, you don't even have to sign in."
I'm sure many will still think nothing of nostr until one of their favorite micro-celebrities starts using it, which is what I bet attracts a critical mass.
The rest naturally come after critical mass is achieved, like how people keep using X just because so many others are on it.
Time before nostr is #1 probably 5-10 years.
Gen X
Probably won't reach critical mass on micro-celebrities alone. Might require major celebrities and younger people populating the protocol first. Might require White House level of adoption and recognition before deeming nostr "relevant" or "the new thing it's all moving to now."
Time before nostr is #1 probably 10+ years.
Senior to gen X
Age groups above gen X might never widely adopt nostr. They don't seem to adopt any new electronic infrastructure without being forced to, which is perhaps helpful in defending us younger people from the most egregious of big tech's machinations.
Time before nostr is #1 with this age group, like I said, maybe never.
However, most of them will eventually use nostr a little bit, if not fully adopting it. If nostr is #1 with Gen X in 15 years, I think elders will hear enough about it from Gen X to at least make a throwaway npub for telling their grandkids "happy birthday" by year 20.
Wildcard
Every age group could widely adopt nostr within 10 years if a critical mass of people can lead to an accelerated migration, so fast it makes centralized platforms feel like abandoned ghost towns. Digit arriving here might trigger this.
It's why many nostr proponents recommend deleting accounts on other platforms now, going nostr-only. I consider that strategy premature, but important to consider as nostr's user base reaches more effective numbers.
I was way wrong about this Presidential election, so hopefully my brain is working properly on this.
Of course, I haven't addressed when people would adopt a perfectly decentralized version of nostr. That might take an extra 100 years, or something.
-
 @ 06b7819d:d1d8327c
2024-11-26 16:57:14
@ 06b7819d:d1d8327c
2024-11-26 16:57:14Hanlon’s Razor is a philosophical principle or adage that states:
“Never attribute to malice that which is adequately explained by stupidity.”
It suggests that when trying to understand someone’s actions, it is often more reasonable to assume a lack of knowledge, competence, or foresight rather than intentional harm or ill will. The principle encourages people to avoid jumping to conclusions about malicious intent and instead consider simpler, more mundane explanations.
Hanlon’s Razor is often used in problem-solving, interpersonal interactions, and organizational settings to promote understanding and reduce conflict. It’s part of a broader family of “razors,” which are rules of thumb used to simplify decision-making.
-
 @ 98589a2e:bf49daa1
2024-11-26 16:32:56
@ 98589a2e:bf49daa1
2024-11-26 16:32:56Город преобразился благодаря внедрению современных образовательных технологий, которые значительно изменили подход к обучению в школах. Модернизированные учебные заведения оснащены самым современным оборудованием, что позволяет создавать уникальные условия для обучения.
Новые технологии в школьном обучении
Современные школы активно интегрируют цифровые платформы и дистанционные технологии в учебный процесс. Цифровые платформы становятся основным инструментом для взаимодействия между учениками и учителями. Они предлагают доступ к обширным образовательным ресурсам, включая интерактивные учебники, видеоуроки и онлайн-курсы. Благодаря этим платформам ученики могут учиться в удобное время и в своем собственном темпе, что способствует более глубокому усвоению материала.
Внедрение искусственного интеллекта (ИИ) в образовательный процесс позволяет персонализировать обучение. ИИ анализирует успехи каждого ученика и предлагает адаптивные задания, которые соответствуют их уровню знаний и интересам. Это делает обучение более инклюзивным и доступным для всех категорий учащихся.

Дистанционное обучение
Дистанционное обучение стало неотъемлемой частью образовательной системы. Школы используют виртуальные классы, где ученики могут участвовать в занятиях из любой точки города или даже страны. Это особенно актуально для детей из удаленных районов, которые теперь имеют возможность получать качественное образование без необходимости переезда. Платформы для дистанционного обучения также включают чат-ботов, которые помогают ученикам получать ответы на вопросы в реальном времени и предоставляют поддержку по различным предметам. Эти технологии делают процесс обучения более интерактивным и увлекательным.

Инновационные методы обучения
В 2040 году активно применяются игровые технологии и виртуальная реальность (VR) в учебном процессе. Ученики могут изучать сложные концепции через симуляции и игровые сценарии, что делает обучение более практическим и интересным. Например, уроки по биологии могут включать виртуальные экскурсии по экосистемам, а уроки истории — погружение в исторические события через VR-технологии.
Кроме того, школы активно используют большие данные для анализа образовательных результатов и оптимизации учебных программ. Это позволяет выявлять успешные методики и адаптировать их под нужды учеников.

Будущее образования
С переходом на новые образовательные технологии Санкт-Петербург стал примером того, как можно улучшить качество образования через инновации. Образование будущего не только готовит учеников к вызовам XXI века, но и делает процесс обучения более доступным, увлекательным и эффективным. В условиях быстро меняющегося мира такие подходы становятся необходимыми для формирования нового поколения учеников, готовых к жизни в высоких технологиях и глобальном обществе.
Какие новшества ожидаются в образовании и в школах к 2050 году?
Увеличение образовательных учреждений
Строительство новых школ и детских садов: В рамках нового Генерального плана Санкт-Петербурга запланировано значительное увеличение числа образовательных учреждений, что поможет решить проблему нехватки мест в школах и детских садах.
 Модернизация существующих учреждений: Большое внимание будет уделено капитальному ремонту и обновлению оборудования в уже существующих школах, что повысит качество образовательной среды.
Модернизация существующих учреждений: Большое внимание будет уделено капитальному ремонту и обновлению оборудования в уже существующих школах, что повысит качество образовательной среды.

Подготовка к вызовам XXI века
Фокус на STEM-образовании: Уделение внимания науке, технологиям, инженерии и математике (STEM) станет приоритетом для подготовки учащихся к требованиям современного рынка труда.
Развитие навыков критического мышления и креативности: Образовательные программы будут направлены на развитие у учеников навыков критического мышления, креативности и способности к решению проблем, что важно в условиях быстро меняющегося мира.

-
 @ 98589a2e:bf49daa1
2024-11-26 16:13:39
@ 98589a2e:bf49daa1
2024-11-26 16:13:39Этот переход принес множество экономических выгод:
Снижение операционных расходов. Электротранспорт требует меньше затрат на топливо и обслуживание, что позволило городу сэкономить значительные средства.
Независимость от импорта нефти. Санкт-Петербург стал менее уязвим к колебаниям цен на нефть, поскольку перешел на электричество, производимое из возобновляемых источников.
Привлечение инвестиций. Развитие инфраструктуры для электробусов и зарядных станций привлекло внимание крупных компаний, что способствовало созданию новых рабочих мест и росту налоговых поступлений.
Улучшение здоровья населения. Чистый воздух и снижение уровня шума улучшили качество жизни горожан, уменьшив затраты на здравоохранение.
Рост популярности экологически чистых товаров и услуг. Переход на электрическую тягу подстегнул спрос на электромобили и сопутствующие сервисы, создавая новый рынок и укрепляя экономику города.

Санкт-Петербург продолжает двигаться вперед, ставя экологичность и устойчивость в приоритет, что положительно отражается на его экономическом развитии.
Что следует ожидать в сфере общественного транспорта к 2050 году?
Увеличение количества электрозарядных станций: Ожидается, что к 2050 году в городе будет значительно увеличено количество зарядных станций для электромобилей, что сделает использование электротранспорта более доступным и удобным для горожан.
 Строительство новых станций метро: В рамках Генерального плана развития общественного транспорта запланировано открытие 89 новых станций метро и увеличение протяженности линий на 139 км. Это улучшит доступность различных районов города и снизит нагрузку на наземный транспорт.
Строительство новых станций метро: В рамках Генерального плана развития общественного транспорта запланировано открытие 89 новых станций метро и увеличение протяженности линий на 139 км. Это улучшит доступность различных районов города и снизит нагрузку на наземный транспорт.
 Модернизация подвижного состава: Внедрение высокотехнологичных поездов с современными системами управления и комфортабельными условиями для пассажиров станет важной частью транспортной стратегии города. Это повысит общую эффективность и безопасность перевозок.
Модернизация подвижного состава: Внедрение высокотехнологичных поездов с современными системами управления и комфортабельными условиями для пассажиров станет важной частью транспортной стратегии города. Это повысит общую эффективность и безопасность перевозок.

-
 @ 2775fb0f:887f8193
2024-11-26 16:09:26
@ 2775fb0f:887f8193
2024-11-26 16:09:26В Новодвинске продолжается ремонт теплотрассы, который затронет несколько жилых районов и повлияет на сроки подключения отопления. Работы начались 10 октября и продлятся до конца месяца, что вызвало беспокойство у жителей.
В результате ремонта отопление будет временно отключено в домах по улицам Ленина, Советская и Молодежная. Ожидается, что жители этих домов получат тепло позже остальных, ориентировочно в начале ноября.
Однако есть и положительная новость: впервые к системе отопления будут подключены деревянные дома на Новой улице. Это значительное событие для жителей, которые долгое время испытывали трудности с отоплением в зимний период. Подключение этих домов к централизованному отоплению позволит улучшить условия проживания и повысить комфорт для жителей.
«Мы понимаем, что временные неудобства могут вызвать недовольство, но ремонт необходим для обеспечения надежности теплоснабжения в будущем. Подключение деревянных домов на Новой улице — это важный шаг к улучшению инфраструктуры города», — отметил начальник управления ЖКХ Новодвинска.
Администрация города призывает жителей следить за обновлениями на официальном сайте и в социальных сетях, где будет размещена актуальная информация о ходе работ и сроках подключения отопления. В случае возникновения вопросов, жители могут обращаться в службу поддержки по указанным телефонам.
-
 @ 2775fb0f:887f8193
2024-11-26 16:05:04
@ 2775fb0f:887f8193
2024-11-26 16:05:04Новодвинск, 10 сентября 2040 года — Историческое событие для города: в Новодвинске торжественно открылся первый университет, ставший значимым шагом в развитии образовательной инфраструктуры региона. Открытие нового учебного заведения стало настоящим праздником для жителей, студентов и преподавателей.
На церемонии открытия присутствовали высокопоставленные гости, включая губернатора области, представителей Министерства образования и науки, а также местные власти. Глава города, Анна Петрова, в своем выступлении отметила: «Сегодня мы делаем важный шаг к будущему нашего города. Открытие университета — это не только возможность для молодежи получать качественное образование, но и шанс для Новодвинска стать центром знаний и инноваций».
Университет предлагает широкий спектр образовательных программ, включая гуманитарные, технические и естественные науки. В этом учебном году здесь будет открыто 10 факультетов, на которых смогут обучаться более 2000 студентов. «Мы стремимся создать современное образовательное пространство, где каждый студент сможет развивать свои таланты и достигать успеха», — подчеркнула ректор университета, Татьяна Сергеева.
В рамках открытия прошли экскурсии по университетскому кампусу, где будущие студенты познакомились с новейшими лабораториями, библиотекой и учебными аудиториями, оснащенными современным оборудованием. «Это невероятно! Я всегда мечтала учиться в университете, и теперь у меня есть такая возможность прямо в родном городе», — поделилась впечатлениями абитуриентка, Мария Коваленко.
Кроме того, университет планирует активно сотрудничать с местными предприятиями и организациями, что позволит студентам проходить практику и стажировки, а также участвовать в научных проектах. «Мы уверены, что это сотрудничество даст возможность нашим студентам не только получать теоретические знания, но и применять их на практике», — добавила Сергеева.
Открытие университета в Новодвинске — это не только шаг к улучшению образовательной среды, но и возможность для молодежи оставаться в родном городе, развиваться и строить карьеру. Этот проект стал результатом совместной работы администрации города, образовательных учреждений и бизнеса, что подтверждает важность сотрудничества в достижении общих целей.
С открытием первого университета Новодвинск вступает в новую эру, полную возможностей и надежд для будущих поколений. Жители города с нетерпением ожидают, что это событие станет началом долгого пути к развитию науки и образования в регионе.
-
 @ 3f0702fa:66db56f1
2024-11-26 15:56:29
@ 3f0702fa:66db56f1
2024-11-26 15:56:29https://psv4.userapi.com/s/v1/d/0L4xrYa_TAEaQL9VMLPKX4D-uU1bPTtibLuGMB0N0khhp6EwQm3F1ASOwbbL9iHKwTSUQOEMOh2gIuHboyoVC9jBUR04azTcd8--jCYg5d5eimfdDsmnAw/Untitled_5.mp4
-
 @ 3f0702fa:66db56f1
2024-11-26 15:42:23
@ 3f0702fa:66db56f1
2024-11-26 15:42:23Зимние праздники — это время волшебства, радости и традиционных мероприятий, которые объединяют жителей города. Давайте посмотрим, как курганцы празднуют этот особенный период!
-
Новогодний городок на площади Центральная площадь Кургана вновь превращается в новогодний городок с 18-метровой живой елкой, катком и ледяными скульптурами. Каждый год здесь проходят яркие мероприятия, включая концерты и мастер-классы, которые привлекают как местных жителей, так и туристов.
-
Зимние фестивали Курган славится своими зимними фестивалями. В этом году запланированы гастрономические праздники, где можно попробовать традиционные блюда и деликатесы региона. Это отличная возможность для курганцев собраться вместе и насладиться атмосферой праздника.
-
Спортивные мероприятия Зимой в Кургане активно проводятся лыжные соревнования и турниры по хоккею на льду. Жители участвуют в спортивных мероприятиях, что способствует укреплению духа единства и здорового образа жизни.
-
Прогулки по набережной Тобола Набережная реки Тобол становится популярным местом для зимних прогулок. Здесь можно насладиться красивыми видами, покататься на коньках и просто провести время с семьей на свежем воздухе.
-
Традиции и обряды Курганцы сохраняют старинные традиции, такие как колядки и праздничные угощения. Местные жители собираются в кругу семьи, готовят любимые блюда и делятся историями о зимних праздниках.
45news
Курган2040
-
-
 @ 3f0702fa:66db56f1
2024-11-26 15:41:52
@ 3f0702fa:66db56f1
2024-11-26 15:41:52Курган предлагает множество увлекательных туристических маршрутов для зимнего отдыха. Зимой наш город превращается в настоящую сказку, и мы приглашаем вас открыть для себя его зимние красоты!
-
Экотропа в Рябково Одним из главных направлений зимнего туризма станет экотропа в Рябково. Здесь проложены лыжные трассы протяженностью до 5 километров, которые идеально подходят для лыжных прогулок и активного отдыха на свежем воздухе. В этом году завершилось благоустройство, и к новогодним праздникам экотропа станет отличным местом для семейных выездов.
-
Лыжные маршруты Курган предлагает разнообразные лыжные маршруты, включая «Лосиную тропу» и «Волчью тропу». Эти трассы оборудованы для любителей как спокойного катания, так и более активных тренировок. Прокат лыжного инвентаря доступен на месте, что делает отдых еще более комфортным.
-
Набережная реки Тобол Зимой на набережной реки Тобол открываются живописные виды, а освещение создает волшебную атмосферу. Здесь можно прогуляться по обновленным дорожкам, насладиться горячими напитками в кафе и сделать красивые фотографии на фоне зимних пейзажей.
-
Зимний каток на главной площади Не пропустите возможность посетить зимний каток на главной площади, который традиционно открывается к новогодним праздникам. Это отличное место для активного отдыха с друзьями и семьей, где можно покататься на коньках и насладиться атмосферой праздника.
-
Фестивали и мероприятия Зимой Курган становится центром культурных мероприятий: от ярмарок до концертов под открытым небом. В этом сезоне запланированы различные фестивали, которые позволят жителям и туристам окунуться в атмосферу зимних праздников.
45news
Курган2040
-
-
 @ 2f4550b0:95f20096
2024-11-26 15:32:00
@ 2f4550b0:95f20096
2024-11-26 15:32:00As educators, we’re often tasked with preparing learners for their next step, whether it’s the workforce, higher education, or personal growth. But what happens when the “next step” is a journey to Mars? The training required to prepare people for such a monumental mission is as exciting as it is complex. It’s also a perfect example of the power of interdisciplinary education.
Sending humans to Mars means training them to thrive in an isolated, resource-limited, and unforgiving environment. Crew members will need to wear many hats, stepping seamlessly between roles as scientists, engineers, medics, and farmers. Generally speaking, they must be problem-solvers. Let’s consider how an interdisciplinary approach can prepare individuals for this journey and how it might inspire new ideas for our teaching practices here on Earth.
Bridging Technical and Practical Skills
A Martian mission demands technical expertise across fields, but it also requires the ability to apply that knowledge practically in unpredictable situations. Imagine teaching someone how to extract oxygen from Martian soil (a process called in-situ resource utilization) while ensuring they can also maintain the equipment that performs the extraction. It’s not just about knowing “what” to do but also “how” and “why.” Future Mars residents will need to see the connections between disciplines, such as how chemistry supports engineering or how geology informs survival strategies.
Preparing for Emergencies
On Mars, there’s no dialing 911. Rather, each resident is part of the “911 response team” in the case of an emergency. If the habitat's power system fails, a team member gets injured, or a dust storm threatens solar panels, the crew must handle it. That means everyone needs baseline knowledge in medical care, electrical systems, and environmental safety. What can we learn from this? Cross-training is vital. In our teaching environments, how can we provide students with overlapping skills that make them adaptable in crises, whether they’re on Mars or managing a team back home?
Collaborating Across Fields
The isolated environment of a Martian mission will push teamwork to its limits. Each crew member will bring unique expertise, but their success will hinge on how well they collaborate. A biologist studying Martian soil must work with an engineer maintaining the research lab and a logistician planning the mission timeline.
In our classrooms, fostering this kind of interdisciplinary teamwork means creating opportunities for students to collaborate across subjects. Could your STEM students work with communications majors on a project? Could you involve art students in designing user-friendly interfaces for technical tools?
Building an Adaptive Mindset
Mars explorers must be lifelong learners and will have to continue their education throughout their journey to Mars and while they are Mars residents (see my previous edition). The challenges they’ll face won’t all be predictable, so their training must prioritize skills in flexibility and adaptability. With access to onboard resources like virtual lessons and problem-solving simulations, they’ll continuously upskill throughout their mission.
For adult educators and trainers, this reinforces the value of teaching metacognition—helping students learn how to learn. When we equip learners with strategies to acquire new knowledge independently, we set them up for success no matter where they go.
Using Simulations and Realistic Scenarios
Martian training will have to involve simulated habitats and scenarios that replicate real conditions. From mock spacewalks in full gear to solving equipment malfunctions under time pressure, simulations and virtual reality training can provide invaluable hands-on experience.
This can inspire us to incorporate more experiential learning into our teaching. Whether through role-play, problem-based learning, or case studies, we can immerse students in practical scenarios that mirror real-world challenges.
Final Thoughts
Preparing people for Mars is an interdisciplinary educator’s dream. It’s about weaving together diverse fields of knowledge, cultivating flexibility, and fostering collaboration. While most of us won’t teach future Martian settlers, the principles of their training can inspire how we equip our learners for the challenges they’ll face in an ever-changing world.
Whether your students are solving problems in a classroom, a boardroom, or—someday—a Martian habitat, the value of an interdisciplinary education remains clear: when we cross-train minds, we prepare them to conquer the unknown.
Would you integrate any of these ideas into your teaching? Share your thoughts—I’d love to hear them!
-
 @ e077f063:49dc180e
2024-11-26 14:48:12
@ e077f063:49dc180e
2024-11-26 14:48:12В Ханты-Мансийске стартовал десятый по счету сезон зимнего этнотуризма. Жители «тюменской матрешки», а также финские туристы собрались на главном югорском стойбище, где проходят гонки на роботах–оленях, дегустация национальных блюд и шаманские обряды. Об этом с места событий передает корреспондент «КиберХанты — 2040».
«Сегодня в Самаровском Чугасе по-настоящему жарко, несмотря на 30-градусные морозы! Югорчане, тюменцы, ямальцы приехали на киберстойбище в честь открытия юбилейного сезона этнотуризма. Пока все они толпятся у информационной стойки и заселяются в чумы, туристы из Финляндии уже скачут на роботах–оленях и пробуют местные деликатесы», — сообщил журналист агентства.
Гостей встретили шаманы–ханты, которые провели обряд окуривания травами. Со слов югорских гуру, это нужно, чтобы очистить приезжих от негативной энергии. Тем временем на площадке повара предлагают полакомиться карпаччо из оленины, строганиной из муксуна, маринованными опятами, ухой «хантейка». Из горячих напитков наливают глинтвейн, хвойный кофе и согревающие ягодные смузи.
Фишкой торжественной церемонии стали гонки на роботах–оленях. Участники могут оседлать бионических животных и на скорость проскакать по стойбищу.
«Роботы–олени созданы, как вы знаете, с использованием бионических технологий и искусственного интеллекта. Сегодня они не только символ культуры народов ханты и манси, а и настоящие помощники для туристов. В повседневной жизни они служат гидами, помогают гостям адаптироваться на стойбище и заселиться в чум», — рассказал агентству робототехник Паули Раскуй.
Проект «Киберстойбище» был запущен правительством ХМАО в 2030 году. Он направлен на стабилизацию экономического положения столицы округа Ханты-Мансийска за счет этнотуризма. Под стойбище местные власти выделили природный парк Самаровский Чугас. Здесь расположен комплекс технологичных чумов, люкс–рестораны, горнолыжная трасса, кибернарты, десятки развлекательных площадок.

*Агентство выдуманное и является студенческим проектом. Новостная лента не несет цели ввести читателей в заблуждение
-
 @ ee90543f:9363457f
2024-11-26 14:47:38
@ ee90543f:9363457f
2024-11-26 14:47:38 -
 @ 0c9e5e17:480e870b
2024-11-26 14:37:20
@ 0c9e5e17:480e870b
2024-11-26 14:37:20I just made my first batch of Paleo beef jerky and the results are so good that I thought I'd share it with you. My entire house smells of beef jerky right now and it's driving my dog crazy - poor thing.
What's Paleo?
I'm not going to go into the details, but simply put it's a way of eating that best mimics the diets of our paleolithic hunter-gatherer ancestors - lean meats, seafood, vegetables, fruits, and nuts. If you're interested take a look here: The Paleo Diet.
I've been gradually getting more and more serious about eating a paleo diet as a lifestyle and wanted to see if I could find a recipe that I could use for making beef jerky that would be suitable = no soy sauce, besides other things. I was sent two really good examples of paleo jerky recipes from @paleoonabudget via Twitter (love how social tools connect us) and thought that they both sounded good enough to try. Here they are: Food Lover's Kitchen Beef Jerky, and Jen's Gone Paleo Really Tasty Beef Jerky.
My Version
Always one to tinker and hack with something, I adjusted and combined aspects from both recipes to come up with one that sounded good to me. Here's what I ended up with:
- Flank steak as lean as possible (grass-fed), trim any excess fat
- 1 cup raw coconut aminos (it's a substitute for soy sauce)
- 1 cup of organic apple juice (make sure there are no additives)
- 1 cup of pineapple juice (again, no additives)
- 1 tbsp fresh ground black pepper
- 1 tsp of paprika
- 1 tsp of garlic powder
- Lime juice (not in the marinade)
 Steak strips in the marinade.
Steak strips in the marinade.I used a nice cut of flank steak (personal preference) and made sure to trim off all excess fat, although there was hardly any. I put the steak in the freezer for an hour or two to make slicing it into thin strips a little easier.
Then I put all of the other ingredients (the marinade) into a Pyrex dish and added the sliced steak pieces, making sure that all of the steak was covered or submerged. I think I topped up with a little extra of both juices. I covered this and put it in the fridge overnight.
Dehydrating - Making it Jerky!
The next day (around noon) I removed the marinading steak from the fridge and let it drain through a small sieve for a minute or two to get the excess liquid off. No need to get my dehydrator into a big mess if I can easily avoid it. I used my old faithful L'Equip 528 6-tray Dehydrator. I love this machine!
 Steak strips on dehydrator tray.
Steak strips on dehydrator tray.I gave the entire batch of steak a heavy dose of freshly squeezed lime juice, all over. I was very heavy handed with the lime (thinking this would be my "secret sauce"). Then I arranged the pieces of steak onto the drying sheets (mine has six) making sure to leave a lot of room around each piece.
 Temperature dial on L'Equip.
Temperature dial on L'Equip.I set the temperature gauge to half way between 125F and 153F (\~135F) and turned it on. At this point I went out to take care of some errands - nothing you would be interested in. When I got back a few hours later, I was greeted by the smell of beef jerky as I opened the front door - wow!
The jerky had been drying for about four hours while I was gone and much to my surprise was completely done. In fact it could have come out a little bit sooner to be even better, but that's my fault for going away and leaving it. When I make jerky using ground beef it takes a lot, lot, longer - more than twice as long.
 I hope you enjoy this recipe!
I hope you enjoy this recipe!The end result is absolutely delicious. The combination of the fruit juices, coconut aminos and spices gives the steak an amazing, slightly citrus flavor. I wish you could try some, it's soooo good!
-
 @ 30ceb64e:7f08bdf5
2024-11-26 14:04:19
@ 30ceb64e:7f08bdf5
2024-11-26 14:04:19Hey Freaks,
So, I briefly touched on a bit of my pre bitcoin backstory in my last article. I should probably add some more detail before going into my thoughts on freelancing in Nostr and Bitcoin.
A bunch of jobs
Before diving into the Bitcoin and Nostr space, I've had a bunch of jobs.
- Kmart
- Barnes & Noble
- AMC Theatres
- United States Air Force
- Bank of America
- Intellectual Property Law
Early Freelancing Experience
I've worked a variety of gigs including:
- Internet safety evaluation
- Moving Company
- Telephone interviews
- User testing
- Survey participation
- Focus groups
I also ventured into a bit of digital entrepreneurship with:
- Shopify dropshipping
- Podcasting
- YouTube Lo-Fi beats channel
Entering the Bitcoin Space
My transition into Bitcoin involved the roles below:
- Business Development Manager (Two Businesses)
- Junior Bitcoin Researcher (Two Podcasts)
- Open Source Contributor (Two Projects/Contributions)
And I've
- Written a bit on Stacker News, and ran the Nix OS territory for a few months
- Created lo-fi Beats on Wavlake and have uploaded a few videos nostr/flare.pub
- Engaged with freaks on Nostr and won a couple of meme competitions
- Started working on a Nostr app, and plan on submitting a few more open source contributions
The Future of Bitcoin/Nostr Freelancing
I'm looking forward to see the growth of sites like satshoot, plebwork and whatnot. Seems the winner hasnt been decided yet to see who will be the fiverr replacement using bitcoin and nostr. It would be cool to see amethyst add in a tab for freelancing. Sats4Likes was a cool site, although mostly filled with spam and refferal links.
Contemplations
I've been contemplating potential service offerings for TheWildHustle, and here are my thoughts:
Bitcoin & Nostr Consulting While I've successfully built my own setup through experimentation with various alpha and beta products, I'm hesitant to position myself as an expert consultant. My current setup, though functional, is more of an eager pleb approach rather than a professional or one size fits all solution.
Advisory Services Initially, I considered offering general advice and conversation services, but there is a lot of responsibility that comes with advising others, especially when their financial well-being or social capital is at stake. I want to make sure I'm providing value without accidently rugging someone.
Product & Service Consulting I'd probably do best offering insights and evaluations of products and services. My experience as an early adopter, user tester, focus group participant, and interviewer might provide valuable perspective to clients navigating this space. I've talked to a few companies over the years about their products and services and I think I've held myself pretty well.
Thanks again for reading,
Wish me luck,
Hustle
-
 @ 6bae33c8:607272e8
2024-11-26 13:36:30
@ 6bae33c8:607272e8
2024-11-26 13:36:30I went 2-3 last week, but that’s okay. It was a “practice” week ahead of Q5 where like everyone else in the Circa contest I get a fresh start.
Bears at Lions — The Lions are like a runaway freight train, but they have some injuries and have to play on a short week against a division rival. I’ll say Bears +8.5 and probably stay away.
Giants at Cowboys — The Cowboys looked a lot better last week than the Giants, but this is a winnable one for NY. I’ll say Giants +3.5 and expect them to cover. (I probably won’t use it though in the contest.)
Dolphins at Packers — The Dolphins have been better of late. I’ll say it’s Dolphins +2.5 and take them. (Though I probably won’t use Thursday games in the contest.)
Raiders at Chiefs — The Raiders are playing out the string now, but the Chiefs always seem to play down to the level of their competition. I’ll say Raiders +10 and lean Raiders.
Chargers at Falcons — I’ll make this a pick ‘em in Atlanta and maybe lean Falcons who are off the bye.
Steelers at Bengals — I’ll say Steelers plus 2.5 and take the Bengals at home off the bye.
Texans at Jaguars — Whether Trevor Lawrence starts actually makes a difference here. I’ll say it’s Texans -3.5 but stay away.
Cardinals at Vikings — The Cardinals were such a no-show last week. I’ll say Cardinals +3 and buy low on them.
Colts at Patriots — These are both scrappy teams. I’ll say pick ‘em and lean Colts.
Seahawks at Jets — Is Aaron Rodgers still the QB? I’ll say Seahawks -2.5 and lean Jets, but this is a stay-away.
Titans at Killer Redskins — The Titans defense is decent, and the team is playing better of late. I’ll make it Titans +5.5 and stay away.
Buccaneers at Panthers — The Panthers have played better of late. Let’s go Buccaneers -3.5 and stay away.
Rams at Saints — I’d make this Rams -2.5 and probably lean Rams.
Eagles at Ravens — This is a good game. Make it Eagles +3.5 and take the Ravens who play well against good teams.
49ers at Bills — This was supposed to be a good game, but the Niners need Nick Bosa, Brock Purdy and Trent Williams back. Assuming they are, I’ll say Niners +4.5 and take them. If not, stay away.
Browns at Broncos — I’ll sell the Browns off the Steelers win. Bad Jameis shows up in Denver. Browns +5.5 and take the Broncos.
-
 @ 2063cd79:57bd1320
2024-11-26 13:28:51
@ 2063cd79:57bd1320
2024-11-26 13:28:51Bitcoin Steuern
Natürlich sehen wir Steuern kritisch. Niemand möchte gerne abgeben, vor allem dann nicht, wenn die verfolgten Ziele des Staates immer schwieriger nachzuvollziehen sind. Um Murray N. Rothbard in "Die Anatomie des Staates" zu zitieren:
Der berühmte Soziologe Franz Oppenheimer zeigte auf, dass es zwei gegenseitig ausschließende Wege gibt Wohlstand zu erreichen. Einer ist der [...] Weg von Produktion und Austausch ‒ er nennt es das „ökonomische Mittel“. Der andere Weg ist einfacher, insofern es keine Produktivität verlangt. Es ist der Weg der Besitzergreifung von Gütern und Leistungen anderer durch die Anwendung von Macht und Gewalt. Dies ist die Methode einseitiger Konfiszierung und des Diebstahls fremden Eigentums. Es ist die Methode, die Oppenheimer das „politische Mittel“ zu Wohlstand nennt. [...] Anstelle etwas dem Produktiven hinzuzufügen, subtrahiert es etwas davon ab. Das "politische Mittel" ist lediglich Wertabschöpfung zugunsten eines parasitischen und destruktiven Individuums oder Gruppe.

Man kann den Gedanken sogar ausweiten und sagen, dass der Staat nicht durch Freiwilligkeit oder den Willen der Beteiligten existiert, sondern durch die Ausübung oder Androhung von Gewalt. Ohne diese hat der Staat keine Möglichkeit, Einnahmen zu generieren. Der Staat schafft keine eigenen Produkte oder Werte, sondern nimmt seine Produkte auf eine von drei Arten: Besteuerung, monetäre Expansion und Konfiszierung (in aufsteigender Reihenfolge der Brutalität gegenüber dem produktiven Individuum). Über monetäre Expansion und Konfiszierung haben wir uns schon an anderer Stelle ausgelassen, also widmen wir uns diese Woche mal der "verschleierten Form der teilweisen Sklaverei".
So wie bei allen Handels- oder Wirtschaftsgütern, Vermögensgegenständen und Wertaufbewahrungsmitteln greift der Staat natürlich auch bei Bitcoin zu. Da der Staat nicht in der Lage ist für alle Einzelfälle Einzelgesetze zu verfassen, muss der Einzelfall zumindest einer Tatbestandskategorie zugeordnet werden. Diese Einordnung obliegt dem jeweiligen Gesetzgeber und dementsprechend fallen die Gesetze rund um die Besteuerung von Bitcoin auch unterschiedlich aus. Viele Gesetzgeber sind sehr vorsichtig bei der Einordnung, da die Kategorisierung von Bitcoin auch über steuerliche Zwecke hinaus Implikationen haben kann. Wie wir bereits in anderen Ausgaben gesehen haben, existiert Bitcoin - anders als Gold, Rohstoffe und gedrucktes Geld - nicht in physischer Form, vielmehr existiert eine digitale Verkettung von Kommunikationen. Es wird kein "Coin" direkt verschoben, alles existiert innerhalb dieser Kette, sondern nur das Recht Transaktionen in einer gewissen Höhe vorzunehmen wird erteilt. Dies macht die Besteuerung im besten Fall knifflig, da Bitcoin in Kategorien gepackt werden muss, in denen vergleichbare Güter existieren. In den meisten Jurisdiktionen wird auf Bitcoin eine Kapitalertragsteuer erhoben.
Kapitalerstragsteuern
Die Kapitalertragsteuer ist eine Quellensteuer, die beim Erhalt von Kapitalerträgen erhoben wird. Also wenn ein Wirtschaftsgut für einen höheren Betrag verkauft wird, als dieses Gut den Verkäufer beim Ankauf gekostet hat. Der Ertrag, also die Differenz aus Kauf- und Verkaufspreis, wird bei Erhalt als steuerbares Ereignis gewertet und muss demnach in der Steuererklärung berücksichtigt werden. Somit ist die Kapitalertragsteuer ein Teil der Einkommensteuer (oder Körperschaftsteuer).
Deutschland
https://www.gesetze-im-internet.de/estg/__23.html
In Deutschland ist die Gesetzeslage derzeit recht einfach. Einkommensteuergesetz (EStG) §23: Private Veräußerungsgeschäfte regelt die Besteuerung von Wirtschaftsgütern. Copy/Pasta:
Einheiten einer virtuellen Währung und sonstige Token sind ein „anderes Wirtschaftsgut“ im Sinne des § 23 Absatz 1 Satz 1 Nummer 2 EStG (vgl. Randnummer 31). Gewinne aus der Veräußerung von im Privatvermögen gehaltenen Einheiten einer virtuellen Währung und sonstigen Token können daher Einkünfte aus privaten Veräußerungsgeschäften nach § 22 Nummer 2 in Verbindung mit § 23 Absatz 1 Satz 1 Nummer 2 EStG darstellen, wenn der Zeitraum zwischen der Anschaffung und der Veräußerung nicht mehr als ein Jahr beträgt (für die ertragsteuerrechtlichen Besonderheiten von Utility und Security Token vgl. Randnummern 77 ff.).
Damit werden Digital Assets, und so auch Bitcoin, als immaterielle Vermögensgegenstände steuerpflichtig. Der Steuersatz leitet sich von der Steuerklasse des Steuerpflichtigen ab. Es gibt zwei Möglichkeiten, bei denen keine Steuern auf Erträge aus dem Verkauf von Bitcoins anfallen.
Erstens, wenn der jährliche Betrag unter 600 Euro liegt. Sollte er allerdings darüber liegen, muss der volle Betrag versteuert werden und zu beachten ist auch, dass sämtliche Veräußerungsgeschäfte addiert werden, also nicht nur diejenigen aus dem Verkauf von Digital Assets. Das bedeutet allerdings auch, dass Verluste und Gewinne im gleichen Zeitraum miteinander verrechnet werden können.
Und zweitens, wenn zwischen Kauf und Verkauf mindestens 12 Monate liegen. Im letzteren Fall sollte der Verkauf dennoch in der Steuererklärung angegeben werden, mit dem Vermerk, dass der Kauf über 12 Monate zurückliegt. Dies muss dann dem Finanzamt auch glaubhaft und lückenlos belegt werden können. Benutzt man nur einen Exchange und hat deutlich ersichtliche Ein- und Ausgänge, sowie Käufe und Verkäufe, ist ein einfacher Auszug recht einfach zu erstellen. Handelt man jedoch auf verschiedenen Börsen, hat fraktionale Beträge und wechselt von Bitcoin in andere Digital Assets (du du du!👆), oder andersherum, wird das Ganze schon etwas schwieriger. In diesem Fall sollte man eine klare Dokumentation über die verschiedenen Bewegung führen, sogar Transfers zwischen Wallets desselben Besitzers sollte man vorsorglich dokumentieren.
https://www.bundesfinanzministerium.de/Content/DE/Downloads/BMF_Schreiben/Steuerarten/Einkommensteuer/2022-05-09-einzelfragen-zur-ertragsteuerrechtlichen-behandlung-von-virtuellen-waehrungen-und-von-sonstigen-token.html
Besonders schwierig wird es, wenn man mit Bitcoin experimentiert, z.B. verschiedene Zahlungskanäle in Lightning eröffnet, Assets über Counterparty erstellt, etc., da jede dieser Transfers als Gewinnrealisierung angesehen werden kann. Bei der Dokumentation ist es vor allem wichtig den Kurs festzuhalten, denn nachzuweisen, dass man im Wert von 100 Euro Bitcoin erworben und zu einem späteren Zeitpunkt im Wert von 50 Euro Bitcoin verkauft hat, reicht nicht. Denn was zunächst wie ein Verlust wirkt, stellt sich ganz anders dar, wenn man zeigt, dass man für 100 Euro 0.01 bitcoins (Kurs 10.000 EUR/BTC) gekauft und für 50 Euro 0.001 bitcoins verkauft hat (Kurs 50.000 EUR/BTC). Des Weiteren bleibt zu bedenken, dass das Finanzamt die FIFO (First-In-First-Out) Methode benutzt. Da es keine "Coins" (wie das dumme Gold-Coin Bild gerne suggeriert) gibt, muss man dem Finanzamt nicht beweisen, welche UTXOs genau in welcher Transaktion verwendet werden. Dies bedeutet, es wird ganz vereinfacht davon ausgegangen, dass die zuerst erworbenen bitcoins / satoshis auch als erste wieder veräußert, bzw. transferiert werden.
https://bitcoin-kurier.de/kryptowaehrungen-und-steuern-was-beinhaltet-der-bmf-entwurf
Anders verhält es sich beim Mining, denn Einnahmen in Form von Gebühren und Belohnung haben eine andere steuerlichen Auswirkung, als der Handel mit Bitcoin. Diese Einkünfte zusätzliche Einnahmen darstellen und somit der Einkommensteuer unterliegen, abzüglich Ausgaben. Hier muss der Zeitwert der geminten bitcoins zum tatsächlichen Zeitpunkt des Erhalts betrachtet und diese Summe, abzüglich der Kosten, zum normalen Einkommensteuersatz voll versteuert werden. Die Ausgaben berechnen sich auf Strom- und/oder Gerätekosten. Zusätzlich können Steuern anfallen, wenn man Bitcoins noch gewinnbringend nach weniger als 12 Monaten verkauft.
USA
Das US-amerikanische Steuersystem ist dem Deutschen insofern ähnlich, als dass es Digital Assets als 'Property', also Vermögensgegenstände. Anders als das deutsche Recht, wird hier nicht zwischen materiell und immateriell unterschieden und es gibt auch keinen Freibetrag (zumindest nicht direkt auf Vermögenswerte). Auch die 12 Monate-Regel ist den Amerikanern bekannt, allerdings wird zwischen Kapitalertragsteuer bei kurzer Laufzeit (<12 Monate) und Kapitalertragsteuer bei langer Laufzeit (>12 Monate) unterschieden. In jedem Fall wird der Verkauf von Digital Assets zu einem steuerbaren Ereignis, lediglich der Steuersatz bei langen Laufzeiten ist niedriger und damit günstiger.

Im Bundesstaat Colorado lassen sich mittlerweile die Steuern sogar in Bitcoin bezahlen. Der einzige Haken ist, dass man Bitcoin über den Bezahldienst PayPal verwenden muss. Also geht die Regierung Colorados den Umweg über einen Drittanbieter und wird dementsprechend sehr, sehr wahrscheinlich keine eigenen Bitcoins besitzen und langfristig halten wollen, da diese im Zahlungsprozess von PayPal sofort umgewandelt werden.
Europa
Auf EU-Ebene gibt es Anzeichen dafür, dass verschiedene Länder und Institutionen auf einen gemeinsamen Regulierungsrahmen drängen. Steuern auf Digitale Assets sind bisher Sache der Mitgliedstaaten und in den Staaten, in denen Besteuerung existiert, werden Digital Assets oft ähnlich behandelt, wie in Deutschland, also als immaterielle Vermögensgüter, bzw. Wirtschaftsgüter. Länder, wie das eingangs erwähnte Portugal, Malta oder Slowenien erheben keine Steuern und sehen sich selbst als Vorreiter für Bitcoin und wollen interessante Standorte für die wachsende Industrie werden. Ein einheitlicher Rahmen wird wohl noch eine Weile auf sich warten lassen, vor allem, wenn man sieht, mit welcher Behäbigkeit die MiCA (Markets in Crypto Assets) Verordnung verabschiedet wird. Verordnungen bedürfen keiner Implementierung durch die Mitgliedstaaten und stellen verbindliches Recht dar. Die MiCA Regulierung legt einen Rahmen für viele Definitionen im Bereich Digital Assets und schafft einen rechtliche Rahmenbedingungen für AML/KYC, VASPs und räumt der ESMA (Europäischen Wertpapier- und Marktaufsichtsbehörde) gewisse Befugnisse ein. Die MiCA ist ein Thema für eine separate Ausgabe.
Steuern vermeiden

Es gibt meines Wissens nach nur drei Methoden auf Bitcoin Transaktionen keine Steuern zu bezahlen:
1️⃣ Wie oben schon erwähnt, fallen keine Steuern an, wenn man Digitale Assets länger als 12 Monate hält, bevor diese transferiert werden.
2️⃣ Eine weitere Möglichkeit bietet sich für diejenigen, die dennoch gerne steuerfrei mit Digitalen Assets spekulieren möchten, und für die deshalb eine 12 monatige Wartezeit inakzeptabel ist: Der Umzug in ein Land mit besseren steuerlichen Konditionen, oder besser sogar ohne Steuern auf Transaktionen, bietet hier dem Spekulanten den einzigen Ausweg. ✈🌴
3️⃣ Ein etwas trickreicheres Unterfangen ließe sich auch mit Darlehen bzw. Krediten auf die darunter liegende Anzahl an Bitcoins bewerkstelligen. Wer also sein Bitcoin-Säcklein nicht anfassen will, um steuerbares Ereignis zu provozieren, der sucht sich einen Kreditgeber und verpfändet seine Bitcoins. Solange diese nicht 'physisch' bewegt werden, sondern nur das Eigentumsrecht (z.B. mit Hilfe der Seed Phrase) übertragen wird, erhält der Kreditnehmer Liquidität, ohne Bitcoin verkaufen zu müssen. Anbieter wie HodlHodl bieten verwahrungslose Kreditvergabe mit Hilfe von MultiSig Wallets an. Es gibt natürlich noch weitere Möglichkeiten den Fiskus zu umgehen, doch sind diese alle nicht legal und sollten deshalb nicht besprochen werden.
Steuern zahlen ist nicht nur nervig und teuer, sondern auch eine schlechte Idee. Um bei Rothbard zu bleiben, ist der Staat "die Systematisierung des Prozesses der 'Plünderei' in einem gegebenen Territorium." Steuern sind also Plünderei und sollten vermieden werden.
Das größte Problem beim Konzept Steuern ist, dass der Staat diese einnimmt, um "den Apparat am Laufen zu halten". Aber wenn das der Fall ist, warum gibt es dann noch das Konzept der Staatsverschuldung und warum können die mit Steuern bezahlten Ausgaben nicht mit dem gleichen Harry Potter-esken Buchführungstrick (Staatsverschuldung) gedeckt werden? Randnotiz: Der Staat benutzt, anders als jedes Unternehmen, keine doppelte Buchhaltung.

Dem Staat bei seinem Finanzpoker nicht mehr zu vertrauen, ist da keine Blasphemie. Doch da es nicht immer möglich ist, Steuern zu vermeiden und zwischen Steuervermeidung und Steuerhinterziehung immer nur ein schmaler Grat liegt, sollte man zumindest sicherstellen, dass man vernünftig belegen kann, wie man seine Bitcoins (nicht) transferiert hat. Buchführung (!) ist hier besonders essentiell und sei jedem ans Herz gelegt, der zumindest, bis das derzeitige System wie ein schlecht konzipierter "Stablecoin" verpufft, seine Bitcoin Transaktionen sauber und ordnungsgemäß deklarieren möchte, um keine späten Überraschungen zu erleben.
🫳🎤
In diesem Sinne, 2... 1... Risiko!

-
 @ 6bae33c8:607272e8
2024-11-26 08:48:44
@ 6bae33c8:607272e8
2024-11-26 08:48:44As you know the night games start very late here, so I watch the edited version the following morning. When I went to bed last night, I had this weird feeling that I was forgetting to do something, but it was Monday night, and I don’t have to make FAAB bids (Wednesday) or set lineups/make an ATS pick (Thursday). So I dismissed it and went to sleep.
When I hit play on the game this morning, my key player J.K. Dobbins hit for a 17-yard run, and Joe Buck commented that running might be easier without Roquan Smith playing. FUCK! I meant to see whether Smith, who I have in the Steak League, was active (he was questionable) and if not drop Justice Hill for whoever his replacement was and use him. That’s what I forgot to do. So I missed out on Malik Harrison’s 12 tackles, points I’ll never get back.
But I’m burying the lede. My key player, Dobbins, who I have in the Primetime and my best BCL hurt his knee in the first half. It looked like he was set for a big game too as they kept throwing to him out of the backfield. I expected Dobbins to get hurt eventually — in fact I’m surprised he lasted this long — but this was another blow.
On the plus side the Ravens covered, Ladd McConkey played and got me 14 points and Rashod Bateman got 11 in the Steak League. I just have to imagine Bateman was my middle linebacker and my fourth WR got blanked.
-
Justin Herbert looked good, but once Dobbins went down, and Herbert was in obvious passing downs, the Ravens were able to tee off.
-
Quentin Johnston is a drop machine, and it’s not just the passes that slipped through his hands, but constantly losing his footing. Once in a while it’s bad luck, but keeping your footing while changing direction on a route is kind of an important skill. McConkey is Herbert’s only plus target.
-
The Ravens just make it look so easy. Long TD runs, Lamar Jackson wearing out the pass rush with amazing instincts. You never know when he’s going to stop or in which direction he’ll pivot. I’m always surprised watching him.
-
The game really changed when Jim Harbaugh punted on 4th-and-3 from midfield two minutes before the half, and John went for it on 4th-and-1 from his own 16! which led to a TD drive. Granted, the Chargers don’t have the personnel the Ravens do to convert, (though the Ravens bizarrely opted to snap the ball to Mark Andrews.) I don’t think you should *always* go for it just because the math says so, and there’s a big difference between three yards and one. But Jim Harbaugh should have realized the offense he was facing and not quibble so much about *where* they got the ball, but resolve not to let them get it at all. After all, if you trust your defense, trust them to handle it at midfield should you fail. And if you don’t trust your defense — which you should not against the Ravens — then don’t give them back the ball period.
-
-
 @ 67282a9a:6302804b
2024-11-26 08:42:59
@ 67282a9a:6302804b
2024-11-26 08:42:59NostrBridge provides two core features aimed at facilitating WebSocket connection forwarding and message forwarding under the Nostr protocol. Below is a detailed description of these features:
Feature 1: WebSocket Connection Forwarding The first feature of NostrBridge is to forward a WebSocket connection from one server to a specified Nostr relay server.
Specifically, when connecting to wss://myserver.com/wss://relay.nostr.band/, NostrBridge will forward the request to the target address wss://relay.nostr.band/, which can be any relay server supporting the Nostr protocol.
Explanation: Source connection: wss://myserver.com/wss://relay.nostr.band/ Target connection: wss://relay.nostr.band/ (can be any other relay server supporting the Nostr protocol) Feature 2: Message Forwarding The second feature of NostrBridge allows for forwarding messages between two Nostr clients. By connecting to wss://myserver.com, NostrBridge can forward messages from one client to another based on the predefined message format.
The message format is as follows:
const messageData = { action: 'message', from: from, // Sender client to: to, // Receiver client message: message // Message content };
-
 @ 67282a9a:6302804b
2024-11-26 08:40:06
@ 67282a9a:6302804b
2024-11-26 08:40:06NostrBridge provides two core features aimed at facilitating WebSocket connection forwarding and message forwarding under the Nostr protocol. Below is a detailed description of these features:
Feature 1: WebSocket Connection Forwarding The first feature of NostrBridge is to forward a WebSocket connection from one server to a specified Nostr relay server.
Specifically, when connecting to wss://myserver.com/wss://relay.nostr.band/, NostrBridge will forward the request to the target address wss://relay.nostr.band/, which can be any relay server supporting the Nostr protocol.
Explanation: Source connection: wss://myserver.com/wss://relay.nostr.band/ Target connection: wss://relay.nostr.band/ (can be any other relay server supporting the Nostr protocol) Feature 2: Message Forwarding The second feature of NostrBridge allows for forwarding messages between two Nostr clients. By connecting to wss://myserver.com, NostrBridge can forward messages from one client to another based on the predefined message format.
The message format is as follows:
const messageData = { action: 'message', from: from, // Sender client to: to, // Receiver client message: message // Message content }; --
-
 @ d5c3d063:4d1159b3
2024-11-26 07:59:41
@ d5c3d063:4d1159b3
2024-11-26 07:59:41บทสรุปหนังสือ Democracy The God That Failed
โดย Hans-Hermann Hoppe นักคิด Anarcho-Capitalist ซึ่งเป็นแนวคิดที่เชื่อในการจัดระเบียบสังคมผ่านกลไกตลาดเสรีโดยปราศจากรัฐ ที่มองว่ารัฐทุกชนิดเป็นภัยต่อเสรีภาพ ถึงขั้นเสนอให้ล้มล้างรัฐทั้งหมด คำถามสำคัญที่ Hoppe หยิบยกขึ้นมาคือ หากเรายังต้องอยู่ภายใต้การปกครองของรัฐ แล้วรัฐแบบใดจึงจะเหมาะสมที่สุด? คำตอบของเขาคือ ไม่ใช่ประชาธิปไตย….
https://image.nostr.build/6f1ff012543f581bc4943448a1d9ff2e6341bfff73465c6b2f3d2a44d283c804.jpg
.
Hoppe โต้แย้งว่า “ประชาธิปไตย” นำไปสู่การขยายอำนาจของรัฐ ซึ่งขัดกับหลักการของเสรีนิยมคลาสสิก (Classical Liberalism) เขาเชื่อว่าระบอบกษัตริย์อย่างเช่น ราชวงศ์ Habsburgs อาจพิทักษ์เสรีภาพได้ดีกว่า Hoppe เปรียบเทียบว่ากษัตริย์มองประเทศเสมือนสมบัติส่วนตัว (เพื่อให้เห็นภาพชัดเจน) ดังนั้นจึงมีแรงจูงใจในการดูแลรักษาประเทศให้มั่งคั่ง ต่างจากนักการเมืองที่มาจากการเลือกตั้ง ซึ่งเปรียบเสมือน "ผู้เช่า" ที่มักมุ่งเน้นผลประโยชน์ระยะสั้น เขาอธิบายว่าหากกษัตริย์ มีความเห็นแก่ผลประโยชน์ส่วนตน (self-interest) จึงต้องทำให้ประเทศของตนมั่งคั่ง ซึ่งเป็นผลดีต่อประชาชนโดยรวม .
Hoppe ชี้ให้เห็นถึง “แรงจูงใจ” ที่แตกต่างกันระหว่างรัฐบาลที่มาจากการเลือกตั้งและกษัตริย์ในการดำเนินนโยบายต่างๆ ยกตัวอย่างเช่น นโยบายประชานิยม รัฐบาลที่มาจากการเลือกตั้งมักใช้เงินเพื่อสร้างความนิยม ซึ่งอาจเป็นการตอบสนองความต้องการของคนส่วนใหญ่หรือเป็นเพียงกลยุทธ์ทางการเมืองเพื่อรักษาอำนาจก็ได้ เพราะนักการเมืองมีวาระการดำรงตำแหน่งที่จำกัด จึงมุ่งเน้นผลประโยชน์ในระยะสั้น ส่วนกษัตริย์ที่ปกครองไปตลอดชีวิตจึงคำนึงถึงผลกระทบระยะยาวต่อประเทศมากกว่า เพราะความมั่งคั่งของประเทศ คือความมั่งคั่งของกษัตริย์ด้วย .
…แนวคิดนี้เห็นได้ชัดในเรื่องนโยบายการเก็บภาษี กษัตริย์มีแนวโน้มที่จะเก็บภาษีในอัตราที่ต่ำกว่ารัฐบาลที่มาจากการเลือกตั้ง เพราะกษัตริย์มองประเทศเป็นเสมือน "สมบัติส่วนตัว" ดังนั้น การเก็บภาษีสูง ก็เหมือนกับการทำลายสมบัติของตัวเอง กษัตริย์จึงมีแรงจูงใจที่จะรักษาความมั่งคั่งของประเทศในระยะยาว โดยการเก็บภาษีในระดับที่ไม่เป็นภาระแก่ประชาชน เพื่อให้ประชาชนมีกำลังในการผลิตสินค้าและบริการ ซึ่งจะทำให้เศรษฐกิจเติบโต ส่งผลให้ "มูลค่าทรัพย์สิน" ของกษัตริย์เพิ่มขึ้นในระยะยาว …ตรงกันข้ามกับรัฐบาลที่มาจากการเลือกตั้งมักถูกกดดันให้ใช้จ่ายงบประมาณจำนวนมาก เพื่อตอบสนองความต้องการของเสียงส่วนใหญ่ในการรักษาฐานเสียง ซึ่งอาจนำไปสู่การเพิ่มภาษี หรือการก่อหนี้สาธารณะที่สูงขึ้นเรื่อยๆ ทำให้ส่งผลเสียต่อเศรษฐกิจในระยะยาว .
Hoppe ยังวิพากษ์วิจารณ์แนวคิด "open borders" ซึ่งเป็นที่นิยมในหมู่เสรีนิยม เขาชี้ให้เห็นว่าในสังคมเสรีนิยมที่แท้จริง เจ้าของทรัพย์สินมีสิทธิที่จะควบคุมว่าใครจะเข้ามาในทรัพย์สินของตน ดังนั้น การสนับสนุน "open borders" จึงขัดแย้งกับหลักการสิทธิในทรัพย์สิน ซึ่งเป็นหลักการพื้นฐานของเสรีนิยม เขายังโต้แย้งว่า การยินยอมให้รัฐเป็นผู้ผูกขาดในการบังคับใช้กฎหมาย เท่ากับเป็นการขายตัวเองเป็นทาส .
นอกจากนี้ Hoppe ยังบอกว่ารัฐบาลพยายามทำลายความเป็นอิสระของครอบครัวเพื่อป้องกันการต่อต้านอำนาจรัฐที่เข้มแข็งจากครอบครัว ด้วยโครงการสวัสดิการสังคม เช่น ประกันสังคม เงินบำนาญ และการดูแลสุขภาพและการศึกษา "ฟรี" ล้วนเป็นเครื่องมือที่รัฐบาลใช้เพื่อบรรลุเป้าหมายนี้ Hoppe มองว่าโครงการ “รัฐสวัสดิการ” เป็นเครื่องมือที่รัฐบาลใช้เพื่อทำลายความเป็นอิสระของครอบครัวและควบคุมประชาชน ซึ่งผลกระทบที่ตามมาคือสังคมที่อ่อนแอลงและขาดความรับผิดชอบต่อกัน .
ท้ายที่สุด Hoppe ปฏิเสธรัฐทุกรูปแบบ และเสนอแนวคิด Anarcho-Capitalism คือสังคมทุนนิยมไร้รัฐ โดยเชื่อว่า รัฐเป็นอันตรายต่อเสรีภาพ แม้กระทั่งแนวคิดเสรีนิยมคลาสสิกที่มุ่งจำกัดอำนาจรัฐ เขาก็เห็นว่าไม่เพียงพอ ควรล้มล้างรัฐทั้งหมด Hoppe เชื่อว่าสังคมสามารถจัดระเบียบตัวเองได้อย่างมีประสิทธิภาพผ่านกลไกตลาดเสรี ซึ่งภาคเอกชนจะเป็นผู้ให้บริการต่างๆ เช่น การรักษาความปลอดภัย และระบบยุติธรรม โดยไม่ต้องมีรัฐเข้ามาแทรกแซง แนวคิดนี้สอดคล้องกับแนวคิดเรื่องระเบียบธรรมชาติ (Natural Order) ที่เชื่อว่าสังคมมนุษย์มีแนวโน้มที่จะพัฒนาไปสู่ความสงบสุข ความเจริญรุ่งเรืองและความเป็นธรรม โดยไม่ต้องอาศัยการบังคับจากอำนาจรัฐ .
Democracy The God That Failed จึงไม่ใช่หนังสือที่สนับสนุนระบอบกษัตริย์ แต่เป็นการวิพากษ์วิจารณ์รัฐทุกประเภท และนำเสนอแนวคิด Anarcho-Capitalism เพื่อกระตุ้นให้เราพิจารณาบทบาทของรัฐ เสรีภาพ และทางเลือกอื่นๆ ในการจัดระเบียบสังคม เป็นหนังสือเล่มนี้เหมาะสำหรับผู้ที่สนใจปรัชญาการเมืองและแนวคิดตลาดเสรี
============================
อ้างอิง [1] Gordon, D. (2002). No Safety in Numbers. The Mises Review, 8(1). Democracy The God That Failed The Economics and Politics of Monarchy, Democracy, and Natural Order.
-
 @ 67282a9a:6302804b
2024-11-26 07:59:14
@ 67282a9a:6302804b
2024-11-26 07:59:14NostrBridge 提供了两项核心功能,旨在帮助用户实现 Nostr 协议下的 WebSocket 连接转发和消息转发。以下是功能的详细描述:
功能一:WebSocket 连接转发 NostrBridge 的第一个功能是将 WebSocket 连接从一个服务器转发到另一个指定的 Nostr relay 服务器。
具体来说,当连接 wss://myserver.com/wss://relay.nostr.band/ 时,NostrBridge 会将请求转发到目标地址 wss://relay.nostr.band/,这个地址可以是任何支持 Nostr 协议的 relay 服务器。
说明: 源连接: wss://myserver.com/wss://relay.nostr.band/ 目标连接: wss://relay.nostr.band/(可以是任何其他支持 Nostr 协议的 relay 服务器) 功能二:消息转发 NostrBridge 的第二个功能是实现消息在两个 Nostr 客户端之间的转发。通过连接到 wss://myserver.com,NostrBridge 可以根据预定格式将消息从一个客户端转发到另一个客户端。
消息格式如下:
const messageData = { action: 'message', from: from, // 发送者客户端 to: to, // 接收者客户端 message: message // 消息内容 };
更新-4
-
 @ f9590f2b:8fe2d6f1
2024-11-26 07:57:18
@ f9590f2b:8fe2d6f1
2024-11-26 07:57:18Upgrade your surfaces with premium Concrete Floor Coating in Perth by Perth Commercial Epoxy Flooring. Our top-tier coatings enhance the durability, appearance, and safety of your concrete floors, making them ideal for garages, warehouses, and industrial spaces. With slip-resistant finishes and customizable designs, we deliver tailored solutions for all your flooring needs. Our professional team ensures flawless application for a long-lasting result. Protect and beautify your concrete surfaces with our expert services. Choose Perth Commercial Epoxy Flooring for reliable and affordable Concrete Floor Coating Perth solutions. Contact us today for a free quote!
-
 @ fc15d4c6:fba62950
2024-11-26 06:54:32
@ fc15d4c6:fba62950
2024-11-26 06:54:32This year's government budget deficit for Malawi - the shortfall on income compared to spending - is expected to be 7.6% of the GDP. While 42% of the budget is allocated to interest payments alone, another 38% are budgeted for wages, leaving only about 20% for "priority projects". The country's debt to GDP ratio is over 90% - "These are all features of a fiscal crisis", according to the World Bank, "which requires an urgent move away from business as usual".\ \ A number of these loans are denominated in foreign currency, meaning that Malawi cannot simply print it's way out of this situation. The deficit can only be made up through:
- new borrowing in the short term, which will further increase the interest burden and worsen the situation
- fiscal austerity - reducing government spending - which is generally unpopular
- higher taxes, which is not popular either
- more tax revenue from growing business volumes, which will require a better business climate & outlook
#inflation #malawi #forex #worldbank #finance #crisis
Source
-
 @ e4746d55:84cd99cf
2024-11-26 06:08:28
@ e4746d55:84cd99cf
2024-11-26 06:08:28Maximize your business capabilities with Patchnet’s expertise in M365 Premium. Our team helps you deploy and optimize the premium version of Microsoft 365, which offers enhanced security, advanced collaboration tools, and productivity features. From setting up advanced threat protection to managing device compliance, we ensure you get the most out of your M365 Premium subscription. Trust Patchnet to provide seamless implementation, customization, and ongoing support for your organization. Empower your team with the best that Microsoft 365 has to offer. Contact us today to elevate your business with M365 Premium.
-
 @ 7ec80607:128517c5
2024-11-26 05:46:57
@ 7ec80607:128517c5
2024-11-26 05:46:57Outdoor advertising is an incredible method for making a brand essential. While customary billboards are compelling, adding an innovative wind can make your promotion considerably more eye catching. By investigating exceptional and creative thoughts, brands can connect with bystanders and establish a long term connection.
In this article, we'll take a look at five imaginative outdoor advertising billboards thoughts that can assist with boosting brand visibility and make your promotions stick out.
1. Interactive Billboards
What They Are: Intuitive billboards permit individuals to draw in with a promotion in a special way, frequently utilizing innovation to make a two-way experience. These billboards could incorporate QR codes, movement sensors, or even increased reality (AR) components that answer the presence or activities of watchers.
Why They Work: Intelligent billboards cause the crowd to feel included, making a noteworthy encounter that goes past checking a promotion out. They can draw groups, and individuals who collaborate with them are bound to recall the brand and even offer the experience via web-based entertainment. Model Thought: Envision a wellness brand with a bulletin that challenges bystanders to finish an actual test, such as hopping jacks, and rewards them with a digital markdown code once they finish.
**2. 3D Outdoor Advertising Billboards ** What They Are: 3D billboards add an actual aspect to the promotion, making it seem as though the pictures are jumping out of the surface. This impact is accomplished through sharp plan, materials, or digital projections that make the deception of profundity.
Why They Work: 3D billboards snatch consideration rapidly, as they make an unexpected component and are outwardly striking. They're particularly well known via web-based entertainment, as individuals frequently take photographs and offer them internet, giving the brand extra openness. Model Thought: A soda brand could make a 3D board with a goliath can that appears to empty soft drink into a glass underneath. The deception of development and size makes the promotion eye-getting and urges individuals to pause and look.
**3. Travel Advertising with a Wind ** What It Is: Travel outdoor advertising billboards remember advertisements for vehicles like transports, trains, and cabs. A twist could involve using unconventional designs or interactive elements that make the vehicles look different from the usual ads we see.
Why It Works: Transit ads reach a wide audience as they move through different locations. Adding an innovative curve makes them significantly more observable. Individuals frequently get inquisitive when they see a vehicle that watches strange, which can prompt expanded brand mindfulness. Model Thought: A pastry shop could make a promotion for a transport that makes the vehicle appear as though it's loaded up with newly heated bread, with pictures of portions in the windows. The ad could even include a pleasant bread scent near bus stops to enhance the experience and make it memorable.
** 4. Murals and Street Art ** What They Are: Wall paintings are enormous fine arts painted on walls or different surfaces out in the open spaces. They can be utilized for advertising by integrating branding or messages into the plan. Often done by skilled artists, these ads blend art and advertising.
Why They Work: Murals are unique outdoor advertising billboards because they add beauty to a space, making them feel less like ads and more like community art. They are exceptionally shareable via web-based entertainment, as individuals love taking photographs of road craftsmanship, which gives the brand free internet based openness.
Model Thought: An espresso brand could support a wall painting that shows an imaginative, dynamic scene of individuals getting a charge out of espresso, unpretentiously highlighting the brand's logo. Bystanders would consider it to be craftsmanship, and when shared via virtual entertainment, it would spread the brand's message in a characteristic, pleasant way.
**5. Experiential Spring Up Advertisements ** What They Are: Experiential advertisements include setting up transitory presentations or establishments in high-traffic regions, permitting individuals to cooperate straightforwardly with the brand. These "spring up" encounters could incorporate examples, intelligent demos, or imaginative arrangements where individuals can partake for entertainment only exercises. Why They Work: Pop-up ads create a memorable brand experience by letting people experience a product firsthand. These encounters cause the brand to feel unmistakable and are particularly compelling at making web-based entertainment buzz.
Model Thought: A skincare brand could set up a transitory "hydration station" where individuals can test various items, get free examples, and learn skincare tips. The station might have a branded photograph spot to urge individuals to snap pictures and offer them on the web. Conclusion Outdoor advertising billboards offers numerous open doors for imagination, and utilizing creative thoughts can assist your brand with hanging out in a packed scene. From intuitive billboards and 3D impacts to imaginative paintings and experiential pop-ups, these innovative methodologies connect with crowds, boost brand visibility, and make advertisements more noteworthy. In reality as we know it where buyers are presented to endless promotions day to day, imaginative outdoor advertising can have an enduring effect and assist your brand with sparkling.
**FAQS ** 1. How might I gauge the progress of an imaginative outdoor advertising billboards effort? Following the outcome of outdoor advertising should be possible through a few strategies. You can screen brand visibility by examining pedestrian activity, site visits, and online entertainment commitment in regions where the promotion is shown. QR codes and promotion codes remembered for advertisements likewise take into account simple following of changes. Surveys and feedback can provide insights into brand recall and consumer perception.
**2. Are innovative outdoor promotions more costly than customary billboards? ** While imaginative promotions like 3D billboards or intelligent establishments can be more costly to plan and execute, they frequently give a better yield on venture (return on initial capital investment) because of their drawing in nature and shareability. Imaginative promotions can possibly draw in more consideration and create virtual entertainment shares, which can bring about extra openness that conventional advertisements may not accomplish.
- What sorts of businesses benefit most from inventive outdoor advertising?
Innovative outdoor advertising functions admirably for businesses hoping to serious areas of strength for fabricate acknowledgment, like design, diversion, food and refreshment, and tech organizations. In any case, any business with a nearby or mass-market allure can benefit, particularly to hang out in occupied metropolitan regions or appeal to an expansive crowd.
-
 @ 94a73b6b:bf415bdd
2024-11-26 03:31:42
@ 94a73b6b:bf415bdd
2024-11-26 03:31:42Bbbbnn
-
 @ 97fc03df:8bf891df
2024-11-26 03:08:10
@ 97fc03df:8bf891df
2024-11-26 03:08:10Super Bitcoin Q&A
1.What is Super Bitcoin?
Super Bitcoin is a Value Internet with BTC as the core and sharing the security of Bitcoin consensus.
Super Bitcoin is built based on the BTC main net and Lightning Network, forming a customized full-chain interconnection network to achieve the effective expansion of BTC.
2. Why does BEVM combine with Lightning Network to launch Super Bitcoin?
The BEVM team believes that it is important to develop blockchain technology expansion technologies, such as EOS's million TPS, Sui's high-performance Move concurrency, and Starknet's ZK expansion and other innovative blockchain technologies. These are all meaningful, but their significance is far less important than "how to solve the fundamental problem of blockchain".
In the view of the BEVM team, the fundamental problem of the blockchain platform is "how to achieve true decentralized security." To achieve decentralized security, there is only one answer: to be the number one cryptocurrency in market capitalization.
Starting from this idea, the BEVM team believes that there are two directions to solve decentralized security:
1) Build a public chain that exceeds the market value of BTC. 2) Join the BTC main net.
For the first direction, the largest market value means the safest, which becomes the true "Bitcoin platform". Many projects such as BCH have been working towards this path before. The BEVM team pays tribute to this courage and the spirit of thinking and doing things in this direction.
Super Bitcoin’s theoretical solution to shared BTC consensus security is based on the second idea:
First achieve decentralization by sharing BTC consensus security, and then attract current and future excellent blockchain technology teams and projects to join, build and expand decentralized security Web3 based on Super Bitcoin, and also benefit industry participants. A token that is as decentralized and secure as BTC is grown on Super Bitcoin.
This approach allows blockchain technology to truly be used around BTC, and allows BTC's consensus to securely protect the entire blockchain industry.
The reason why we chose BTC instead of ETH as the main direction of attack is based on two considerations:
The Bitcoin network needs to be expanded more than the ETH network.
The Bitcoin network has a large market capitalization and is widely accepted in the global financial market. There is a market demand for further expansion.
Currently, since the Bitcoin network can only transfer funds, smart contract platforms are needed to expand the ecosystem and realize Bitcoin's functions beyond being a value store.
The Bitcoin network is easier to scale than the ETH network.
The Bitcoin network's UTXO model is more prone to concurrency than the account model. Bitcoin's minimalist microkernel model makes it easier to deterministically allow external extension systems to be added.
On the implementation path in the second direction, BEVM chose the Lightning Network as the communication layer. This is because BTC needs a breakthrough to realize the decentralized currency envisioned by Satoshi Nakamoto, and the Lightning Network is the best way for Super Bitcoin to realize BTC’s decentralized currency. Because the Lightning Network is the only solution for the communication layer, and only the Lightning Network can realize the safe expansion of the shared BTC consensus and solve the effective scalability problem that has plagued ETH for a long time.
Let’s take a look at the different underlying design ideas and corresponding results of the two public chains BTC and ETH.
ETH uses a ledger model, and its object is people, which is embodied in the Nounce++ model. When dealing with transaction queuing problems using human objects, the mutual exclusion overlap is much greater than 0, making it difficult to achieve parallel abstraction. This model requires all nodes to reach a consensus, and it takes longer to reach final confirmation, making the Ethereum network unable to handle large-scale concurrency in a timely manner and unable to cope with massive transactions in actual usage scenarios.
BTC, on the contrary, adopts the UTXO model. The object it faces is assets, and transactions are processed through the UTXO model with assets as the objects. Under the UTXO parallel model, the number of mutually exclusive and overlapping modules is almost 0, allowing the Lightning Network to handle unlimited concurrency and thus achieve unlimited expansion.
We can find the answers given by these two ideas in the history of the computer industry. Decades ago, there was an interesting controversy in the development of computer operating systems: the dispute between microkernels and macrokernels. Microkernel pursues the minimalism of the kernel. The kernel only does its own core things, and all other applications and expansions are left to the outside. Macro kernels, on the other hand, let the kernel handle most of the problems.
The account model and design of ETH are based on the macro core. This model is difficult to expand: on the one hand, ETH itself is already a macro core and does not require much external collaboration; on the other hand, the account is the main body of the design, transactions are initiated based on the account model, and transaction processing is still based on accounts. Programming naturally cannot be parallelized. Bitcoin's UTXO model is similar to the microkernel model. The main object of the Bitcoin network is UTXO. Each UTXO is similar to an upgraded version of banknotes. Using one banknote (UTXO) as an object will not prevent countless people from using different banknotes (UTXO) at the same time. This model is naturally concurrent and is more suitable for large-scale expansion.
To sum up, the Super Bitcoin framework is built with reference to the microkernel architecture. With Bitcoin as the core, Bitcoin's minimalism is maintained, and through Bitcoin's only external communication interface "Lightning Network Status Channel", modules outside the core can communicate and interact with Bitcoin, thereby realizing the effective expansion of Bitcoin.
3. Why build a new architecture based on BTC consensus security?
In the past eight years of BTC expansion practice, the BEVM team has gradually realized that the best solution to expand the BTC network is to expand the blockchain ecosystem under the security of shared BTC consensus. Because only by sharing BTC consensus security can we avoid BTC market value "nuclear weapon" attacks, thereby solving the core security issues at the most fundamental level.
The security of the cryptocurrency public chain platform is positively related to the market value of the cryptocurrency that maintains its own security. Under the PoW mechanism, it is related to the market value of the underlying total computing power. Under the PoS mechanism, it is related to the market value of the tokens pledged on the network. As long as 2/3 of the network's computing power or token market value is controlled, the network will be in a centralized or "paralyzed" state. At this time, only computing power or tokens equivalent to a small portion of the BTC market value can be easily controlled by any public chain platform other than the BTC network. This attack is called a “nuclear weapon” attack on the BTC market cap. In other words, any independent chain independent of the Bitcoin consensus is a kind of internal friction, because its security cannot withstand the "nuclear weapon" attack of the BTC market value.
Of course, there is another way, which is to make a consensus cryptocurrency with a larger market value than BTC and make itself the most decentralized secure currency. Obviously, the probability of this happening is close to 0.
4. What is the difference between Super Bitcoin and the L2 originally planned by BEVM?
There are two main differences:
1). Super Bitcoin solves all current L2 underlying problems, that is, establishing an effective underlying consensus security mechanism. Super Bitcoin provides L2 with maximum underlying consensus security by sharing the overall consensus security of BTC.
2). Super Bitcoin solves the problem of expansion of L2 entrepreneurial projects. Super Bitcoin provides a Fusion Layer that is compatible with protocols of different VMs, allowing entrepreneurial projects to easily customize their own Lightning Chain, thereby achieving unified integration with the Lightning Network. Entrepreneurs only need to focus on solving the most critical L2 business expansion or functional expansion issues. This will not only make it easier to get started, but also stay focused in the early stages, thereby greatly increasing the success rate of the project.
5. What is the relationship between the previous BEVM Canary, the current BEVM Mainnet and the future Super Bitcoin?
BEVM Canary and BEVM Mainnet are a BTC L2 built by the BEVM team based on Taproot Consensus after 8 years of industry accumulation. Canary Network is the pilot test network; BEVM Mainnet is the main network and will be online in April 2024.
Super Bitcoin is a further macro concept made by the BEVM team after more in-depth thinking. It is a value Internet with BTC as the core and sharing the security of Bitcoin consensus. It is also an iterative upgrade of the technology and brand of the entire BEVM system.
Super Bitcoin designed a five-layer architecture of kernel layer, communication layer, consensus layer, network layer and application layer. Accordingly, it jointly realizes shared Bitcoin consensus by integrating Bitcoin main network, Lightning network, BEVM main network, different protocols and different applications. A secure Internet of value.
In this five-layer architecture, the BEVM main network serves as the execution network in the consensus layer and serves as the system chain, similar to the function of the relay chain in the Polkadot network. At the same time, the BEVM mainnet also serves as one of the mainnets in the network layer and serves as the Lightning Chain.
6. Why can Lightning Network nodes be upgraded to “chains with smart contracts”?
First, let's take a look at the operating mechanism of Lightning Network: Lightning Network locks assets on the Bitcoin mainnet through the state channel (State Channel) model, and then issues equivalent personal notes off-chain for each user to manage themselves. For example, there are two users A and B in the market, and they each have their own tickets. In order to exchange, they have to establish their own A'nodes and B'nodes through state channels. Since A' and B' are both personal nodes, this status channel can only be used by them. If other people want to interact with A' or B', they need to open a new status channel. At this time, there may be a situation where A' or B' is not online and cannot be opened, causing transaction inconvenience. Just imagine how we would feel if when we were going to make a payment, the other party told us that we were not available now and would wait until the payment was online.
Now if we treat node A' of A as an independent chain, the smart contract on the chain manages and executes A'. In this way, not only B and A can interact, but other users such as C, D, E, etc. can interact with A in real time without opening a separate status channel. This greatly enhances the convenience of transactions and improves transaction efficiency.
BEVM is based on Taproot Consensus, which not only effectively inherits the security of the Lightning Network, but also can realize the functions of smart contracts due to its BFT PoS mechanism. Therefore, by using BEVM as the consensus layer and network layer, the original personal node can be transformed into a "chain node with smart contract".
In terms of security, the upgrade of Lightning Network personal nodes to chain nodes does not weaken the security of the Lightning Network protocol: compared to chain nodes, the transparency of personal centralized management nodes is relatively weak. Moreover, if the public chain itself becomes more decentralized through PoS or other consensus mechanisms, it will further enhance the security of the Lightning Network protocol.
7. The Super Bitcoin white paper mentions that the Fusion Layer abstracts the functions of the first three layers. How to understand "functional abstraction"?
The overall architecture of Super Bitcoin has five layers, of which the first three layers are: the first kernel layer, which is the Bitcoin network; the second communication layer, which is the Lightning Network; and the third extension layer, which is the network layer with Taproot Consensus as the core.
Fusion Layer abstracts the above three layers of functions and refers to:
- The first layer (kernel layer) of Bitcoin maintains the consensus security of the entire asset;
- Assets are transmitted to the receipt (Receipt) of the Lightning Network through the second layer (communication layer);
- After the third layer (extension layer) detects that the receipt is generated, it packages the receipt in the form of Taproot Consensus and abstracts it into the data format that the smart contract VM needs to process, and then further passes the data to the Lightning Chain in the fourth layer (fusion layer) .
The integration layer is composed of different Lightning Chains. This layer is compatible with the protocols of different VMs, including EVM, SVM, MoveVM, CairoVM, etc. After receiving the data transmitted from the consensus layer, each Lightning Chain will uniformly process the data abstraction formed by the first three layers.
8. Is the fusion layer in the Super Bitcoin white paper a sub-chain of BEVM? Why not follow the BEVM framework, but can all kinds of virtual machines (VM) run?
The convergence layer consists of Lightning Chains of different VM protocols, and BEVM runs as a chain in the Lightning Chain.
The BEVM framework itself allows developers to customize various VMs or various services to run. The lightning chain in the fusion layer is a carrier similar to Polkadot Parachain's one-click chaining. The difference from Polkadot is that Parachain shares $DOT consensus security, while Lightning Chain shares BTC consensus security.
BEVM was EVM-compatible BTC L2 in the past. This upgrade to Super Bitcoin not only makes BEVM a BTC L2 Studio, integrating different VM protocols, but also achieves a qualitative leap at the consensus level: unlike L2 that requires other PoS networks, personal or multi-signature wallet hosting, access to Super Bitcoin Assets on BTC L2 will be managed only by the Bitcoin network and share the BTC consensus security.
9. Is the approach of Lightning Chain in the fusion layer similar to the concepts of Polkadot staking and leasing?
The mechanism of Lightning Chain is different from Polkadot's staking and leasing.
Each Lightning Chain in the Super Bitcoin fusion layer is itself upgraded from the verification node of the Lightning Network. Since each individual node of the Lightning Network can establish a channel freely and without permission, the Lightning Chain can also freely access and exit without permission like individual nodes of the Lightning Network.
In order to achieve true interconnection, different lightning chains must follow a unified consensus, which is the Taproot Consensus in the consensus layer, which is composed of Schnorr Signature, MAST (Merkelized Alternative Script Trees) and BTC SPV Light Nodes.
From an economic model point of view, Polkadot uses an auction model to capture value for $DOT holders by locking up $DOT. Cosmos’ approach is to capture value by airdropping $Atom through ecological projects.
The approach of Lightning Chain will consider balancing the two approaches: on the one hand, it will not force the use of $DOT like Polkadot, and on the other hand, it will not be completely irrelevant and laissez-faire like Cosmos.
10. System Chain in the Fusion Layer In addition to BEVM, are there other system chains?
The System Chain is similar to the System Process in the operating system and is used to process kernel data and manage user processes.
As the initiator and architect of Super Bitcoin, BEVM is temporarily serving as a system chain to handle the execution of the entire Super Bitcoin system protocol at the current stage, managing and coordinating other Lightning Chains and interactions at each layer. In the future, as the number of users and transaction volume increases, more system chains may be added to manage the entire protocol.
11. Will BEVM run a single node in the Lightning Network? If so, will it be centralized?
BEVM will use Taproot Consensus to run a single node of the Lightning Network, but this "single node" is actually a chain, like Arbitrum.
The overall architecture of the BEVM chain is designed based on the decentralized Taproot Consensus idea: Schnorr Signatures can aggregate and call up to 1,000 signatures to confirm transactions, and the MAST contract can enable signatures to be executed in a smart contract manner. Bitcoin SPV Light Nodes can verify transactions through up to 1,000 light nodes. This approach is more decentralized than the individual node ledger in the current Lightning Network.
12. If the lightning chain in the integration layer can directly establish a channel with users, does it have to be linked to the system chain?
The Lightning Chain in the fusion layer does not need to be linked to the System Chain. The system chain manages the coordinated communication between lightning chains. This link establishes a status channel, which is an enhanced version of the status channel. Users only need to link to any lightning chain managed by lightning chain to realize mutual interaction between users. This is a feature that the Lightning Network already has, and BEVM amplifies this interaction.
Users linked to the same lightning chain can freely interact with single-chain contracts. User interaction on different lightning chain links requires cross-chain message interaction. At this time, it will be coordinated through the system chain, similar to the functions provided by Polkadot's Relay Chain. Furthermore, the system chain can provide the ordering of cross-chain message interaction transactions, and can solve the problem of user priority through empowerment or charging.
13. After BEVM launches this technological innovation, how will its own value feed back to the BEVM ecosystem and token?
After BEVM launches this technological innovation, its economic model will be biased towards mechanisms that provide better services. For example, other chains can arbitrarily access the Lightning Chain without enabling BEVM (such as airdrop tokens). BEVM, as a system chain, will queue up and process many transactions normally. And if a certain lightning chain needs to prioritize its messages or transactions, it can be achieved by empowering the BEVM community (such as airdropping tokens or paying). BEVM's token is focused on motivating the Super Bitcoin protocol. On the premise of sharing the security of BTC consensus, the current and future excellent blockchain expansion technologies will be integrated into the Super Bitcoin framework to infinitely amplify the value of BTC.
14. Does consensus security refer to the thousands of BTC that are pledged to the Lightning Network?
No.
Sharing BTC consensus security means being as safe as BTC. Specifically, it is maintained by the PoW consensus that maintains the entire BTC network.
15. How safe are the funds on the Lightning Chain?
Lightning Chain has a multi-chain structure. BEVM, as one of the BFT consensus chains, is responsible for execution and does not control funds.
If users have needs or do not trust a certain chain, they can withdraw their funds on that chain at any time and safely return to the Lightning Network.
16. What is the current progress of Super Bitcoin?
The white paper of Super Bitcoin has been released by the BEVM team on October 22, 2024.
The Super Bitcoin testnet is expected to be launched in November 2024, and the mainnet with economic model incentives is expected to be launched before March 2025.
17. The operation method of Super Bitcoin sounds somewhat similar to RGB’s one-time seal. RGB stores Commitment on the BTC chain or in Lightning Network nodes. I would like to ask what are the advantages of Super Bitcoin compared to RGB?
RGB has been developed since 2018, but it has not yet been implemented. For security reasons, we do not refer to unimplemented protocols. What we refer to are basically products that have been implemented in the market and are operational, and then we combine them with our own projects to innovate. Only in this way can we be more likely to ensure that BEVM can be implemented.
What is said in the question exists on the BTC chain or the Lightning Network. This is a big misunderstanding. Blockchain is not a simple storage system. Simply existing on the blockchain is essentially meaningless.
The core of blockchain is decentralized consensus. And the existence on the BTC network may have the greatest significance. Because the BTC network is very secure, data will not be lost. This is the meaning of BEVM's proposal to share the security of BTC consensus.
18. When is the transaction finality (Finalized) in Super Bitcoin finalized? Is it after the Lightning Network state transition commitment contract is signed, or when the channel is closed and BTC is settled?
Super Bitcoin has 3 situations that will result in transaction finality.
1). When closing channel BTC settlement 2). When the user takes the initiative to forcefully synchronize the Lightning Network status channel information with the Bitcoin network 3). The timing synchronizer set by Lightning Chain synchronizes timing with the Bitcoin network.
For specific details, please refer to the operating system's kernel mode and user mode operation interface epoll or poll.
19. What were the reasons for choosing to use the Substrate framework to build Super Bitcoin?
Because there are many other interoperable frameworks on the market, such as various Stacks and Comsos SDK. The earliest chain to be launched on Substrate was made by the BEVM team, and we are very familiar with Substrate. In 2018, the BEVM team and Gavin Wood's team at Paritytech were writing Polkadot. When the Substrate framework was split, the earliest chain to run through the framework was BEVM's pioneer network ChainX. We are familiar with Substrate, which is the choice of emotional development issues.
Of course, there is also a love for Substrate technology. Because Substrate is written in Rust. Rust language is a better language in the coding circle. Secondly, Gavin Wood is very professional in optimizing the chain technology. After all, he wrote the original code of ETH, so Substrate's engineering implementation is very elegant.
20. Why can BEVM do such a grand thing as Super Bitcoin?
The BEVM team has been developing Bitcoin for 8 years.
From the perspective of Super Bitcoin’s 5-layer architecture,
1). 2016-2017: The BEVM team is mainly studying the first layer (kernel layer).
a). In 2016, the BEVM team was committed to writing relevant blockchain expansion solutions for national banking units, in which amount privacy refers to the zk module code extension of Bitcoin’s core code secp256k1 https://github.com/gguoss/secp256k1-zkp/blob/master/include/sdc_common.h
b). In 2017, the team developed Bytom, a DeFi expansion system based on a BTC-like UTXO ledger model. https://github.com/BytomDAO/bytom.
3). 2017-2018: The team is mainly studying the second layer (communication layer) of Super Bitcoin and making extensions related to the Lightning Network state channel.
During this period, we also invested in the Raiden Network on Ethereum, which copied the Lightning Network protocol. The ideas behind Plasm and OpRollup all originated from this.
2018-2020: The team is mainly developing the fourth layer (Fusion layer) of Super Bitcoin, also called the multi-chain layer.
The main reference is Polkadot’s multi-chain framework for shared consensus security. For example, ChainX (https://github.com/chainx-org/ChainX), the first project that separated the Substrate framework from the Polkadot code base and then launched it on the main network, was developed by the BEVM team. This is one year earlier than any team in the Polkadot ecosystem, including the DOT team: one year after the launch of ChainX, the first chain of Substrate (the name of DOT’s founding partner), the second chain based on Substrate was launched, namely Kusama is online.
At this time, Super Bitcoin’s layer 4 framework technology was laid.
4). 2020-2023: The BEVM team simultaneously developed the third and fifth layers of the Super Bitcoin framework.
a). The third layer (extension layer): the Taproot Consensus layer. This layer is the main core work of the BEVM team, completing technologies such as Bitcoin SPV + Schnorr + MAST + BEVM stack and Lightning Network state channel integration.
b). The fifth layer (application layer): The BEVM team has developed @OmniBTC's OmniSwap and Omnilend products as well as @ComingChatApp, using full-chain thinking to build the future full-chain APP, that is, the future of Super Bitcoin's full-chain application.
5). 2024: After careful thinking and analysis, the BEVM team has thoroughly integrated the historical development experience accumulated in the previous 8 years into a protocol framework, namely Super Bitcoin, which can make all excellent blockchain technologies rely on now and in the future.
Integrated with the Super Bitcoin framework, it can decentralize and expand the entire web3 ecosystem on the premise of sharing the security of the BTC consensus. Just like the definition of Super Bitcoin: an Internet of value that shares the security of BTC consensus.
21. Bitcoin will ensure the security on the chain, that is, every transaction will be verified through the core layer Bitcoin. Will that increase the pressure on the core layer? At the same time, what is the significance of Super Bitcoin’s high concurrency?
First of all, not every transaction needs to be verified on the Bitcoin mainnet to be proven. The Bitcoin mainnet only does one thing, verify status updates. No calculation will be done on the Bitcoin mainnet, and the concurrency of its UTXO can be verified through the BTC SPV model. This is also the basis for the unlimited concurrency capabilities of the Lightning Network.
Specifically, a collection of UTXOs forms a chain or a node. UTXO subsets are executed with each other through the state channel Setup mode, and each pile can be executed separately. The status of Bitcoin UTXO's ledger model is in the hands of the user, and the calculation is also in the user's own hands. Instead of a ledger model like ETH, the state and calculations are on the chain and cannot be parallelized.
The Bitcoin network design model has inherent concurrency. The practice of this Lightning Network project is a typical use of Bitcoin's stateless UTXO concurrency capability. It is a practical practice: it proves that the Bitcoin UTXO account model can be implemented with unlimited concurrency. The core logic of Super Bitcoin is also based on the stateless calculation of Bitcoin's UTXO model to conduct unlimited concurrent transactions, thereby achieving unlimited concurrency capabilities.
The stateless calculation of Bitcoin's UTXO gives the entire Super Bitcoin system unlimited expansion capabilities, but it lacks flexibility. That is, it can only achieve the BTC mainnet function of unlimited transfer and execution concurrency by solving the off-chain double-spend problem such as the Lightning Network. capabilities without the flexibility of Turing-complete programmability. Although the Turing-complete VM under ETH's Account nonce++ world state tree model provides Turing-complete programmability, it limits concurrency because the calculation is performed on the global state tree on the chain, which completely limits the performance of the calculation, that is, the concurrent computing capability of the new public chain can reach up to 1,000 TPS, while ETH can only achieve dozens of TPS. This architecture cannot be infinitely expanded. Even if a model like Polkadot simply accumulates the limited computing power of ETH and lets the parachain execute it, it can only achieve a 100-fold breakthrough in the performance of the ETH main network, which does not make much sense.
The Super Bitcoin framework is a system composed of unlimited Turing-complete VMs with limited computational power under the shared BTC consensus security by means of “Bitcoin's unlimited parallel verification capabilities + Ethernet's Turing-complete computational capabilities” under the premise of guaranteeing asset security with Bitcoin consensus security. This is Super Bitcoin.
-
 @ eb73e43e:d821300f
2024-11-26 02:56:10
@ eb73e43e:d821300f
2024-11-26 02:56:10These are some really great features that are buried behind just a little too much friction in iOS, but I have a feeling you guys will enjoy.
Today we’re talking separate home screens toggled using shortcuts and focus modes! 🤯
The Goal
My initial motivation was for a cleaner, more organized phone, and to put my Bitcoin/Nostr apps aside so I’m less tempted to open them at random. I achieved a really good balance by creating a focus mode that has different wallpaper, notification settings, and app layout. All easily toggled using the trigger of your choice like the action button on newer models or the “back tap” accessibility feature for older phones.
This is what it looks like, pressing my action button to trigger the shortcut which changes my “normal” screen to the focus mode with different apps and settings:
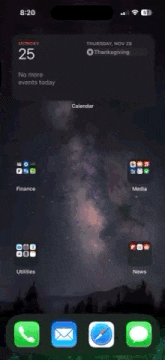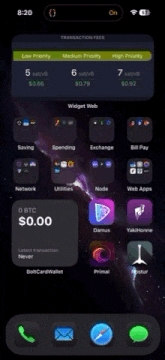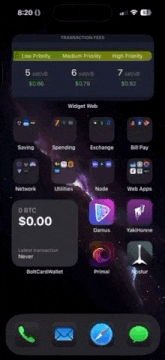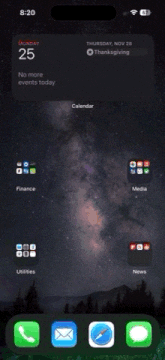
Create Separate Home Screen
To create a separate home screen, first add your daily favorites to one page and bitcoin/nostr favorites to a second page. Once you have multiple pages with different apps, hold down to begin editing the screen and tap the dot buttons at the bottom middle.
 This will open a view with all of your pages of apps. Uncheck any page you don’t want to see on your “normal” mode and leave the rest.
This will open a view with all of your pages of apps. Uncheck any page you don’t want to see on your “normal” mode and leave the rest.Focus Mode
Next you’ll need to open the settings and navigate to the “Focus” page. Here you’ll hit the plus button for a new focus and customize preferences like notifications, app screen, and wallpapers (my focus mode is labeled “CoinOS”).
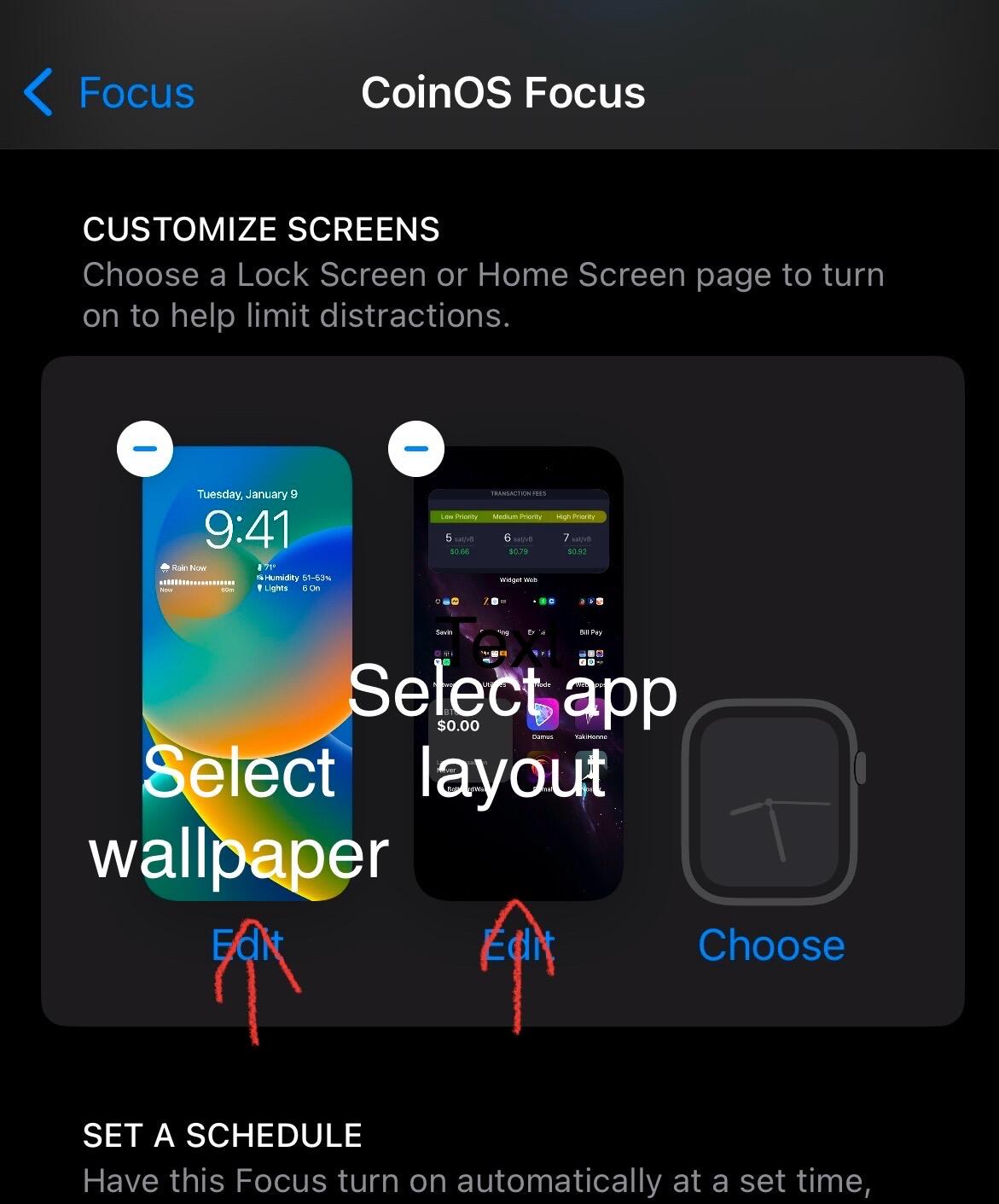 Once you have a home screen layout and focus mode set, you can select to toggle focus mode in the action button settings.
Once you have a home screen layout and focus mode set, you can select to toggle focus mode in the action button settings.My action button was simple at first, just toggling the focus mode on/off and it works great to reduce distraction. But I wanted it to do more than just toggle focus modes. So I found a way to have three different actions tied to the same button. Here's where we go a little wild with shortcuts, but hang in there it's worth the effort.
The Super Shortcut
Toggling focus modes is really convenient and enables a cool hidden Homescreen with your choice of apps. But I wanted to go further so I made an all-in-one shortcut to do several things depending on the state of the iPhone.
-
If the phone is locked, holding my action button toggles silent mode on/off. Nice for quick silencing even in your pocket.
-
If the phone is unlocked, but held sideways with the volume buttons upward, the shortcut opens my camera allowing quick shots with volume as shutter buttons.
-
If the phone is unlocked in any other orientation, it triggers the focus mode change. Allowing me to use the action button for three purposes, including app organization.
Shortcuts can be quite intimidating on your own so I’ll include a link if you want to download mine and try it yourself. It’s also a great way to get started by modifying rather than trying to create from scratch. Give it a shot, it’s pretty cool!
Have fun!
-
-
 @ a012dc82:6458a70d
2024-11-26 02:08:05
@ a012dc82:6458a70d
2024-11-26 02:08:05Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
Precious metals like gold and silver are often thought of as safe-haven assets. Individuals gravitate toward these investments as a hedge against the volatility of more traditional markets.
Bitcoin's future value relative to other assets remains a hotly contested topic. This essay will examine the key arguments for and against Bitcoin as a store of value.
What is a store of value?
Investing in a store of value is prudent since such an asset is likely to maintain its purchasing power over time. It's safe to say that the value of something bought as a store of value today won't decrease over time. You anticipate that the asset's value will remain stable in the future, if not increase.
Gold or silver are examples of such a "safe haven" asset. Several factors, which we'll discuss below, explain why these have always been valuable.
What makes a good store of value?
Let's look at what can constitute a bad store of value before we try to figure out what makes a good one. It stands to reason that something needs to be sturdy if we want it to last for a long time.
The first example is food. Since we need food to stay alive, there is a certain significance to fruits like apples and bananas. When supplies of food are low, things like these are likely to be extremely useful. Unfortunately, this doesn't make them a reliable investment. If you lock them up in a safe for several years, their value will naturally decrease.
Okay, but what about long-lasting things that are valued in and of themselves? Some dry pasta, perhaps? That's preferable in the long term, but it still might not be worth anything. Pasta can be made at a low cost with a variety of ingredients.There is no barrier to entry for producers looking to flood the market with more pasta, driving down the value of the pasta already in circulation. Therefore, something must be scarce if it is to retain its value.
Some people believe that fiat currencies (such as the dollar, euro, or yen) are a safe way to hold their money because they don't lose value over time. However, when more are printed, their purchasing power decreases dramatically, making them terrible long-term investments (just like the pasta). While it may seem like a good idea at the time, hiding your life savings under the mattress for twenty years will result in a significant loss of value.
With $100,000 in 2000, more could be purchased than with the same amount in the present. As a result of inflation, the cost of living has gone up. The practise of governments printing more money is a common contributor to the inflationary expansion of the money supply.
Say, for the sake of argument, that you control $25 billion of a total supply of $100 billion. Eventually, the government chooses to print more money, perhaps $800 billion, to boost the economy. Suddenly, your share of the pie shrank to 3%. Since more money is now floating around, it stands to reason that your portion isn't worth as much as it once was.
Just like our homemade pasta, it doesn't take much to make a dollar. The aforementioned is possible in a few days' time. It should be difficult to flood the market with fresh units if they have a good store of value. To rephrase, you should experience minimal, if any, loss of your share of the pie.
When looking at gold as an example, we know that there is a limited amount available. Also, we're well aware of how challenging it is to mine for In other words, it's not as simple as turning on a printer to produce additional gold if there's an unexpected spike in demand. Like always, it must be mined from the earth's surface. Even though demand has risen, supply cannot be increased significantly to meet it.
The case for Bitcoin as a store of value
Bitcoin's early backers said that the cryptocurrency was more like "digital gold" than basic digital currency. Many Bitcoin proponents have repeated this argument in recent years.
Bitcoin's proponents claim it's a safe investment because of its potential as a long-term store of value. If you want your money to retain its purchasing power over time, according to the proponents of this idea, Bitcoin is the way to go.
Bitcoin's price swings dramatically. Many people regard an asset that can lose 20% of its value in a day as a safe haven, which seems counterintuitive. Despite its multiple declines, it continues to lead all asset classes.
If Bitcoin is so great, why is it being considered a savings asset?
Scarcity
The fact that Bitcoin exists in limited supply is one of the strongest arguments in favour of the store of value hypothesis. You may recall from our primer on bitcoin that the total supply of bitcoins will be fixed at 21,000,000. The protocol ensures this by including a strict requirement in its code.
New coins can only be generated through mining, a procedure that is similar to mining for gold. Bitcoin miners, on the other hand, don't need to bore holes in the ground so much as they do to solve a cryptographic riddle. They can make new money by doing this.
Due to occurrences known as "halvings," the payout gradually decreases over time. In case you figured that this effectively halved the award, you would be correct. In the beginning of the Bitcoin network's existence, any miner who successfully generated a valid block was rewarded with fifty bitcoins. first halved to a value of 25 BTC in 2016. Following another reduction to 12.5 BTC, the next halving will reduce the miner's payout to 6.25 BTC. It will take another century or more before the last coin fraction enters circulation using this method.
Let’s represent this similarly to our fiat currency example from previously. Suppose you bought 25% of the Bitcoin supply (i.e., 5,250,000 coins) several years ago. When you got these coins, you knew that your percentage would remain the same because there’s no entity capable of adding more coins to the system. Government as we know it does not exist, at least not in this place (more on this shortly). That means that a person who purchased 25% of the total available supply in 2010 and held on to it until now still possesses 25% of the total.
Decentralization
You could be thinking, "But it's open-source software!" I can duplicate the code and construct my own version with an additional 100 million coins.
That's entirely feasible. The scenario is that you have a copy of the programme, have made the necessary modifications, and are now operating a node. At this time, it looks like everything is operating normally. However, there is a catch: there are no other nodes to which you can link. Because of the recent changes you made to your programme, you have been mostly ignored by the Bitcoin community. You've created a fork, and the software you're using is no longer the Bitcoin that everyone else uses.
You may as well have taken a picture of the Mona Lisa and then said there were two of her. You can convince yourself that that’s the case, but good luck convincing anyone else.
We implied that Bitcoin functioned as a decentralised government. All of the people who use the programme collectively form that government. When the vast majority of users support a modification, the protocol can be updated.
It would be difficult to persuade the majority to devalue their assets by adding money. In their current form, even seemingly small features require years to attain network-wide acceptance.
As it grows in size, pressing adjustments will become increasingly difficult.Holders can, therefore, be pretty confident that the supply won’t be exaggerated. Despite being created by humans, Bitcoin operates more like a natural resource than a piece of code that can be altered at will because of the decentralised nature of the network.
The properties of good money
According to those who believe in the store of value theory, bitcoin has several desirable qualities as money. It's a rare digital resource that also shares several other features with currencies from all around the world and throughout history.
Gold has been used as money across civilizations since their inception. There are a handful of explanations behind this. We have covered longevity and scarcity at length. These things can be useful assets, but they aren't always appropriate monetary units. For that, you want fungibility, mobility, and divisibility.
Fungibility
This indistinguishability between units is known as "fungibility." With gold, you can take any two ounces, and they’ll be worth the same. This also applies to liquid assets like stocks and money. It makes no difference which unit you're holding; it'll have the same value as any other of the same type.
The fungibility of Bitcoin is a complex issue. It would be ideal if it didn't matter which side of the coin you were holding.For the most part, 1 BTC is equivalent to 1 USD. Where it gets tricky is when you realise that each unit can be linked back to past transactions. There are situations where businesses blacklist funds that they feel have been involved in illicit acts, even if the holder gets them afterwards.
If it doesn't matter, why worry about it? I'm not sure why that would be the case. Neither you nor the store owner can tell where a dollar bill was spent three transactions before you paid with it. In this system, new banknotes have the same value as worn ones, and there is no idea of transaction history.
Yet, in the worst-case scenario, the older bitcoins (with longer histories) may be sold for less than the newer bitcoins. It's debatable whether this is the greatest danger to Bitcoin or not; opinions vary. For now, anyway, Bitcoin is functionally fungible. There have only been occasional occurrences of coins being frozen due to suspicious histories.
Portability
Portability signifies the ease of moving an item. $10,000 in $100 bills? easy enough to move around. What, oil costs $10,000? No, not at all.
Small size is essential for functional money. To facilitate the exchange of products and services between people, it is necessary that the medium of exchange be portable.
Gold has historically been excellent in this aspect. The value of a single conventional gold coin was close to $1,500 at the time this article was written. Since you probably won't be making any purchases greater than an ounce of gold, lower denominations are even more convenient.
Bitcoin is actually superior to precious metals when it comes to transportability. There is no trace of anything left behind at all. A hardware gadget the size of your palm may hold trillions of dollars' worth of wealth.
It takes a lot of work and money to move gold worth a billion dollars, which is currently over 20 metric tons. Even with cash, you would need to carry many pallets of $100 bills. It costs less than $1 to send the same amount almost anywhere in the world using Bitcoin.
Divisibility
One more crucial feature of a currency is its divisibility, or its ability to be subdivided into smaller parts. When dealing with gold, a single ounce coin can be divided in half to get two separate half-ounce coins. The gold content is unaffected, but you may lose a premium if you damage the attractive design depicting an eagle or buffalo. Repeatedly slicing your half-ounce unit will give you the ability to create lower denominations.
Bitcoin also excels at being easily divisible. Only twenty-one million coins have been minted, yet each one has a hundred million fractions (satoshis). This allows consumers a tremendous level of control over their transactions, as they can define an amount to transfer up to eight decimal places. Bitcoin’s divisibility also makes it easier for small investors to buy fractions of BTC.
Store of Value, Medium of Exchange, and Unit of Account
The mood is mixed on Bitcoin’s current role. Many people think of Bitcoin solely in monetary terms, as a means of exchanging one set of money for another. We’ll get into this in the following section, but this notion is contrary to what many store of value proponents advocate.
According to SoV supporters, Bitcoin needs to go through a transition period before it can replace all other currencies. It starts off as a collectible (which is where we are, perhaps) because it's shown to be useful and secure, but it's not widely used. The majority of its readers are enthusiasts and gamblers.
It can't develop into a reliable value store until its population is better educated, institutional infrastructure is in place, and people have faith in the economy's ability to preserve wealth. There are those who think it's already there.
Due to Gresham's law, which asserts that "bad money drives out good money," Bitcoin is not extensively used at the moment. The implication is that given the choice between two forms of currency, people will choose to spend the lower-quality one and save the higher-quality one. Though they don't have much faith in fiat currency, Bitcoin users nonetheless choose to spend them. Bitcoin holders (HODLers) are certain that their investment will increase in value over time.
Bitcoin's price and liquidity will stabilise and attract new users if the network keeps expanding. If it's more stable, people won't be as compelled to hoard it in the hopes of making bigger profits down the line. So we should expect it to be used a lot more in business and daily payments as a robust medium of exchange.
With more people using it, the price will remain relatively constant. At last, Bitcoin will be used as a standard of value against which other assets can be measured and valued. In the same way that a gallon of oil may cost $4 in the current monetary system, its value in a Bitcoin-dominated economy would be measured in bitcoins.
If these three monetary milestones are completed, proponents envision a future where Bitcoin has become a new standard that displaces the currencies used today.
The case against Bitcoin as a store of value
The ideas stated in the previous section may sound entirely rational to some and like craziness to others. Several people, including Bitcoin enthusiasts and cryptocurrency sceptics, have certain issues with the concept of Bitcoin as "digital gold."
Bitcoin as digital cash
If a debate develops, many people immediately reference the Bitcoin white paper. They believe it is obvious that Satoshi conceived of Bitcoin as a currency to be used. In fact, it’s in the very title of the paper: "Bitcoin Is a P2P Electronic Cash System."
The reasoning goes like this: if people don't spend their bitcoins, they have no reason to value them. You're doing more harm than good to the adoption process by hoarding them. If Bitcoin is not generally accepted as a kind of digital currency, its central thesis will be driven not by practicality but by speculation.
These ideological conflicts led to a significant fork in 2017. In order to reduce transaction costs, a minority of Bitcoin users advocated for a system that used larger blocks. As the original network becomes more congested, the price of a transaction could skyrocket, pricing many users out of making lower-value transactions. You shouldn't use coins for a $3 purchase if the average cost is $10.
Bitcoin Cash is the name given to the forked network. The original network pushed out its own upgrade around the time, known as SegWit. SegWit did nominally enhance the capacity of the blocks, but that was not its major purpose. It also established the framework for the Lightning Network, which seeks to promote low-fee transactions by pushing them off-chain.
In practise, however, the Lightning Network is far from flawless. It's much less difficult to grasp how Bitcoin transactions work in general, but it takes a lot more time and effort to learn how to manage channels and capacity on the Lightning Network. It remains to be seen whether it can be streamlined or whether the solution’s architecture is inherently too complex to abstract away.
The rising cost of on-chain transactions during peak hours is directly related to the increasing competition for available block space. One could therefore argue that the currency's usefulness is diminished by the decision not to increase the block size.
There is no intrinsic value.
To many, the comparison between gold and bitcoin is ridiculous. The history of gold is, fundamentally, the history of civilization. Gold has been indispensable to human civilization for centuries. Although its prominence has diminished with the demise of the gold standard, gold is still widely regarded as a safe haven investment.
Indeed, it does seem like a stretch to compare the network effects of the King of Assets to an eleven-year-old protocol. For aeons, gold has been prized for its significance as both a status symbol and an industrial metal.
In contrast, Bitcoin has no purpose outside of its network. You can’t use it as a conductor in electronics, nor can you make it into a large, shiny chain when you decide to establish a hip-hop career. It may resemble gold (mine, finite supply, etc.), but that doesn’t change the fact that it’s a digital asset.
In a sense, all money is based on a consensus of opinion; the dollar is worth something only because the government says so and people accept it. The value of gold is entirely based on the fact that people think it has value. Bitcoin is the same way; its backers make up a small fraction of the economy. You’ve likely had many conversations in your own life when you’ve had to explain what it is because the vast majority of people are unaware of it.
Volatility and correlation
Those who invested in Bitcoin early on have seen their fortunes grow by orders of magnitude.To them, it has truly stored worth—and then some. Individuals who bought their first coins at an all-time high, on the other hand, have had no such experience.Many incurred huge losses by selling at any point thereafter.
Bitcoin's value can swing wildly from day to day, and its marketplaces are difficult to anticipate. Metals like gold and silver exhibit modest changes in contrast. You may make the point that it’s too early and that the price will eventually stabilize. But that fact may be evidence that Bitcoin is not a reliable store of value right now.
There’s also Bitcoin’s tie to established markets to consider. Since Bitcoin’s birth, it's been on a steady ascent. The cryptocurrency hasn’t actually been tested as a safe-haven asset if all other asset classes are also performing well. Bitcoin advocates might refer to it as "uncorrelated" with other assets, but there’s just no way of knowing that unless other assets suffer while Bitcoin remains steady.
Tulip Mania and Beanie Babies
It wouldn’t be a legitimate criticism of Bitcoin’s store of value features if we didn’t bring up the analogies to Tulip Mania and Beanie Babies. These are weak analogies at the best of times, but they serve to show the perils of a bursting bubble.
In both instances, investors flocked to buy objects that they considered to be rare in the hopes of reselling them for a profit. Items weren't particularly valuable on their own because they weren't difficult to replicate. The bubble broke when investors recognised that they were overvaluing their assets tremendously, and the markets for tulips and Beanie Babies subsequently crashed.
Again, these comparisons fall flat. Bitcoin’s worth does originate from users’ belief in it, but, unlike tulips, more cannot be created to satisfy demand. That said, nothing guarantees that investors won’t perceive Bitcoin as overvalued in the future, leading its own bubble to burst.
Conclusion Bitcoin undoubtedly shares most of the characteristics of a store of value like gold. The number of units available is finite, the network is decentralised enough to guarantee security to holders, and it can be used to hold and transfer value.
Ultimately, it must still establish its viability as a safe-haven asset; it’s too early to say for sure. Things might go both ways: the world may flee to Bitcoin in times of economic upheaval, or it could continue to be used mainly by a limited group.
FAQs
Is Bitcoin money? While Bitcoin has some money-like properties, economists and authorities remain sceptical that it now behaves as money. This is due to the scarcity of bitcoin-denominated goods and services. While anyone may trade Bitcoin in large volume and transfer money over the network, little commercial activity still takes place.
Are bitcoins fairly valued? Bitcoin's market price fluctuates wildly and is highly unpredictable. As a result, the market price at any particular time may vary significantly from its fair or intrinsic value. Still, over time, oversold markets tend to rally while overbought markets cool off. Thus, it is hard to evaluate at any given moment whether bitcoins are properly valued without the benefit of hindsight.
What makes Bitcoin a good long-term investment? Limited supply: Bitcoin's maximum supply is 21 million. There will never be more than 21 million bitcoins. To many analysts, this limited supply, or scarcity, is a key contribution to Bitcoin's value. cannot be copied: Because Bitcoin relies on a blockchain ledger, no one can counterfeit it.
To what extent is BTC a risky investment? The success of Bitcoin as a means of trade will determine its worth as a store of value. If Bitcoin does not find success as a means of exchange, it will not be valuable as a store of value. Most of Bitcoin's history, speculation has been the main thing that has driven its value.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 0be0ab80:b6c2b58c
2024-11-26 00:07:11
@ 0be0ab80:b6c2b58c
2024-11-26 00:07:11Indeed, true wealth lies in the joy of single moments and the wisdom we find in them... A short summary of this year's mission for kiddos in the picturesque country of sound money, volcanoes, and freedom.
The past few years in the Bitcoin space have brought many changes, improvements, and the rise of vast new areas of topics as well as activities. All of this is happening thanks to the efforts of many people—the ground zero of Bitcoin: the community. Local meetups, bigger events, and complex conferences are some of the main reasons we can see all this progress.
Not long ago, it was hard to imagine seeing even a few women at conferences, let alone younger generations—children, teenagers, or entire families. Recently, a new trend has emerged: family-friendly spaces with a fun approach to learning.
Personally, we had the chance to experience this at four different conferences, the latest being Adopting Bitcoin, which gave us the opportunity to create something truly magical. Bitcoin Para Niños—the entire area with its dedicated program for younger participants and their guardians.
“The high-signal Bitcoin conference for builders” with an extra focus on sovereign generations!
❝15-16 November, San Salvador—Bitcoin Para Niños: A family-friendly space full of education and fun❞
📦 To give you a feel for the vibes, below are some photos and posts directly refering to this event 📷
https://i.nostr.build/euwjMbSNy1yM9wHt.png
https://i.nostr.build/eGWXkF2MXcu3URLq.png
In a nushell: Two full days, with an average of 6-25 kids of different ages, several amazing adults offering their support and sessions filled with entertainment and education.
❝This year at Adopting Bitcoin, you’ll find a dedicated zone called Bitcoin Para Niños, where kids can have fun, make new friends, and explore a variety of topics, from sound money to creative thinking. Some parts of the agenda will also welcome older participants, including parents, teachers, and anyone interested in discussing the importance of Bitcoin for younger generations. The program will be available in both English and Spanish.
- FREE admission for all Adopting Bitcoin ticket holders!
- Kids under 18 don’t need extra tickets: bring the younger members of your family along!
Bitcoin Para Niños is created in collaboration with the project Bitcoin Junior Club: Sovereign Generation, and is supported by local and global initiatives focused on youth and education. Thank you to everyone involved!❞
Snapshots
1: 📚 The Little Honeybadger: Lively Chat + Reading Time
https://i.nostr.build/ZekkSGyDZS4aoawC.png (source: Nostr)
Although there weren’t many volunteers given the amount of work, those who showed up brought big hearts, passion, and love, making the impossible possible by bringing so many things together. Overall, they all helped us builing up an experience full unforgettable memories.
2: Reading Time 📚 SHAmory + creative workshops "Not All Monsters Are Scary" ✂️
https://i.nostr.build/MUkNoakOQLOnWNK5.png (source: Nostr)
3: 🎲 Animated Workshop/Game by EconoKidz 🎓
https://i.nostr.build/PQEuqtsO5V9Bxw2W.png (source: Nostr)
Not everything went as planned. The real problem was the heavy water falling from the sky at the end of the first day. Rain was in the crisis management plan, but no one expected it to pour that hard. It ruined a lot of materials and set off a domino effect that changed everything moving forward. Thankfully, the conference organizers gave us an indoor space for the next day, so Bitcoin Para Niños could continue with just a small setback, still filled with good vibes and motivation.
We would like to thank everyone who gave us the chance to create this unique experience, as well as the projects and individuals who helped us a lot—both remotely and on-site, offering their materials, direct work and dedication.
🧡 EXTRA LOVE TO: Kiki, Kemal, Charlie, Reyna Chicas, BitcoinEkasi with Hermann Buhr-Vivier and Kando, EconoKidz with Ian Foster and his amazing family, Bitcoin Bites, Tali and Scott Lindberg, Ben and Samantha de Waal, SatoshisKids, Benjamin Colombier, Scott and Malaika Wolfe, Deanna Heikkinen, Juan SC, Fzero, Vivian, SHAmory, Ariana Dixon, Dani Go, DJ Valerie B LOVE, BitPopArt, Hannah, Kelly, Tiffany, two Scotts, M, and many others...
4: We Are All Satoshi https://i.nostr.build/vCfuEFXxL6wMeZTT.jpg
(Source: Habla News)
"Kindness in words creates confidence. Kindness in thinking creates profoundness. Kindness in giving creates love"
THANK YOU ALL!!!
More can be found directly in various posts on Nostr or X, shared by us or individuals and projects that joined this year's Bitcoin Para Niños.
https://v.nostr.build/0TlwebVgqPwb9OFV.mp4 (source: BTCJuniorClub-X)
https://i.nostr.build/ceg8Ob2QTwMYdE9r.jpg (source: BTCJuniorClub-X
https://i.nostr.build/9TYJTt0OSAiH0RfS.png (source: SatoshisKids-X)
https://i.nostr.build/f9TisacJ71BiABcM.jpg (source: Unravel Surf Travel-X)
📍 VALUE4VALUE: Fundraising and goals
If you’d like to support our mission to inspire young minds with values like Bitcoin, freedom, creativity, and critical thinking, consider sending us some sats. Vist our active campaign on Geyser Fund. Every amount counts.
https://i.nostr.build/jkOOyXDNxY3ngG6E.png (source: Geyser - Bitcoin Junior Club, Goals)
-
 @ f33c8a96:5ec6f741
2024-11-25 23:52:42
@ f33c8a96:5ec6f741
2024-11-25 23:52:42 -
 @ f33c8a96:5ec6f741
2024-11-25 23:47:16
@ f33c8a96:5ec6f741
2024-11-25 23:47:16 -
 @ f33c8a96:5ec6f741
2024-11-25 23:43:20
@ f33c8a96:5ec6f741
2024-11-25 23:43:20
