-
 @ 9f94e6cc:f3472946
2024-11-21 18:55:12
@ 9f94e6cc:f3472946
2024-11-21 18:55:12Der Entartungswettbewerb TikTok hat die Jugend im Griff und verbrutzelt ihre Hirne. Über Reels, den Siegeszug des Hochformats und die Regeln der Viralität.
Text: Aron Morhoff
Hollywood steckt heute in der Hosentasche. 70 Prozent aller YouTube-Inhalte werden auf mobilen Endgeräten, also Smartphones, geschaut. Instagram und TikTok sind die angesagtesten Anwendungen für junge Menschen. Es gibt sie nur noch als App, und ihr Design ist für Mobiltelefone optimiert.
Einst waren Rechner und Laptops die Tools, mit denen ins Internet gegangen wurde. Auch als das Smartphone seinen Siegeszug antrat, waren die Sehgewohnheiten noch auf das Querformat ausgerichtet. Heute werden Rechner fast nur noch zum Arbeiten verwendet. Das Berieseln, die Unterhaltung, das passive Konsumieren hat sich vollständig auf die iPhones und Samsungs dieser Welt verlagert. Das Telefon hat den aufrechten Gang angenommen, kaum einer mehr hält sein Gerät waagerecht.
Homo Digitalis Erectus
Die Welt steht also Kopf. Die Form eines Mediums hat Einfluss auf den Inhalt. Marshall McLuhan formulierte das so: Das Medium selbst ist die Botschaft. Ja mei, mag sich mancher denken, doch medienanthropologisch ist diese Entwicklung durchaus eine Betrachtung wert. Ein Querformat eignet sich besser, um Landschaften, einen Raum oder eine Gruppe abzubilden. Das Hochformat entspricht grob den menschlichen Maßen von der Hüfte bis zum Kopf. Der TikTok-Tanz ist im Smartphone-Design also schon angelegt. Das Hochformat hat die Medieninhalte unserer Zeit noch narzisstischer gemacht.
Dass wir uns durch Smartphones freizügiger und enthemmter zur Schau stellen, ist bekannt. 2013 wurde „Selfie“ vom Oxford English Dictionary zum Wort des Jahres erklärt. Selfie, Selbstporträt, Selbstdarstellung.
Neu ist der Aufwand, der heute vonnöten ist, um die Aufmerksamkeitsschwelle der todamüsierten Mediengesellschaft überhaupt noch zu durchbrechen. In beängstigender Hypnose erwischt man viele Zeitgenossen inzwischen beim Doomscrollen. Das ist der Fachbegriff für das weggetretene Endloswischen und erklärt auch den Namen „Reel“: Der Begriff, im Deutschen verwandt mit „Rolle“, beschreibt die Filmrolle, von der 24 Bilder pro Sekunde auf den Projektor gewischt oder eben abgespult werden.
Länger als drei Sekunden darf ein Kurzvideo deshalb nicht mehr gehen, ohne dass etwas Aufregendes passiert. Sonst wird das Reel aus Langeweile weggewischt. Die Welt im Dopamin-Rausch. Für den Ersteller eines Videos heißt das inzwischen: Sei der lauteste, schrillste, gestörteste Marktschreier. Das Wettrennen um die Augäpfel zwingt zu extremen Formen von Clickbait.
15 Sekunden Ruhm
Das nimmt inzwischen skurrile Formen an. Das Video „Look who I found“ von Noel Robinson (geboren 2001) war im letzten Jahr einer der erfolgreichsten deutschen TikTok-Clips. Man sieht den Deutsch-Nigerianer beim Antanzen eines karikaturartig übergewichtigen Menschen. Noel wird geschubst und fällt. Daraufhin wechselt das Lied – und der fette Mann bewegt seinen Schwabbelbauch im Takt. Noel steht wieder auf, grinst, beide tanzen gemeinsam. Das dauert 15 Sekunden. Ich rate Ihnen, sich das Video einmal anzuschauen, um die Mechanismen von TikTok zu verstehen. Achten Sie alleine darauf, wie vielen Reizen (Menschenmenge, Antanzen, Sturz, Schwabbelbauch) Sie in den ersten fünf Sekunden ausgesetzt sind. Wer schaut so was? Bis dato 220 Millionen Menschen. Das ist kapitalistische Verwertungslogik im bereits verwesten Endstadium. Adorno oder Fromm hätten am Medienzeitgeist entweder ihre Freude oder mächtig zu knabbern.
Die Internet- und Smartphoneabdeckung beträgt mittlerweile fast 100 Prozent. Das Überangebot hat die Regeln geändert. Um überhaupt gesehen zu werden, muss man heute viral gehen. Was dafür inzwischen nötig ist, spricht die niedrigsten Bedürfnisse des Menschen an: Gewalt, Ekel, Sexualisierung, Schock. Die jungen Erwachsenen, die heute auf sozialen Netzwerken den Ton angeben, haben diese Mechanismen längst verinnerlicht. Wie bewusst ihnen das ist, ist fraglich. 2024 prallt eine desaströse Bildungssituation samt fehlender Medienkompetenz auf eine egomanische Jugend, die Privatsphäre nie gekannt hat und seit Kindesbeinen alles in den Äther ballert, was es festhalten kann. Man muss kein Kulturpessimist sein, um diese degenerative Dynamik, auch in ihrer Implikation für unser Zusammenleben und das psychische Wohlergehen der Generation TikTok, als beängstigend zu bezeichnen.
Aron Morhoff studierte Medienethik und ist Absolvent der Freien Akademie für Medien & Journalismus. Frühere Stationen: RT Deutsch und Nuoviso. Heute: Stichpunkt Magazin, Manova, Milosz Matuschek und seine Liveshow "Addictive Programming".
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ a10260a2:caa23e3e
2024-10-25 01:51:45
@ a10260a2:caa23e3e
2024-10-25 01:51:45A zero-dependency, zero-framework QR code web component for Bitcoin on-chain, Lightning, and unified BIP-21 payments.
Just discovered this tool by nostr:npub18agram6s6kulwwhc638d8q8y5vysutrrvvdll2wdjxd75wp4dfjqshytrf and found it to be very useful. Also, did I mention easy-to-use?
You can find the GitHub here and a demo I made (complete with a function to check for payment) on the Bullish Prototype. 👨💻
originally posted at https://stacker.news/items/737255
-
 @ fa0165a0:03397073
2024-10-23 17:19:41
@ fa0165a0:03397073
2024-10-23 17:19:41Chef's notes
This recipe is for 48 buns. Total cooking time takes at least 90 minutes, but 60 minutes of that is letting the dough rest in between processing.
The baking is a simple three-step process. 1. Making the Wheat dough 2. Making and applying the filling 3. Garnishing and baking in the oven
When done: Enjoy during Fika!
PS;
-
Can be frozen and thawed in microwave for later enjoyment as well.
-
If you need unit conversion, this site may be of help: https://www.unitconverters.net/
-
Traditionally we use something we call "Pearl sugar" which is optimal, but normal sugar or sprinkles is okay too. Pearl sugar (Pärlsocker) looks like this: https://search.brave.com/images?q=p%C3%A4rlsocker
Ingredients
- 150 g butter
- 5 dl milk
- 50 g baking yeast (normal or for sweet dough)
- 1/2 teaspoon salt
- 1-1 1/2 dl sugar
- (Optional) 2 teaspoons of crushed or grounded cardamom seeds.
- 1.4 liters of wheat flour
- Filling: 50-75 g butter, room temperature
- Filling: 1/2 - 1 dl sugar
- Filling: 1 teaspoons crushed or ground cardamom and 1 teaspoons ground cinnamon (or 2 teaspoons of cinnamon)
- Garnish: 1 egg, sugar or Almond Shavings
Directions
- Melt the butter/margarine in a saucepan.
- Pour in the milk and allow the mixture to warm reach body temperature (approx. + 37 ° C).
- Dissolve the yeast in a dough bowl with the help of the salt.
- Add the 37 ° C milk/butter mixture, sugar and if you choose to the optional cardamom. (I like this option!) and just over 2/3 of the flour.
- Work the dough shiny and smooth, about 4 minutes with a machine or 8 minutes by hand.
- Add if necessary. additional flour but save at least 1 dl for baking.
- Let the dough rise covered (by a kitchen towel), about 30 minutes.
- Work the dough into the bowl and then pick it up on a floured workbench. Knead the dough smoothly. Divide the dough into 2 parts. Roll out each piece into a rectangular cake.
- Stir together the ingredients for the filling and spread it.
- Roll up and cut each roll into 24 pieces.
- Place them in paper molds or directly on baking paper with the cut surface facing up. Let them rise covered with a baking sheet, about 30 minutes.
- Brush the buns with beaten egg and sprinkle your chosen topping.
- Bake in the middle of the oven at 250 ° C, 5-8 minutes.
- Allow to cool on a wire rack under a baking sheet.
-
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ a10260a2:caa23e3e
2024-10-03 16:37:37
@ a10260a2:caa23e3e
2024-10-03 16:37:37Alby Hub is configurable with several different backends. Although setting up with Cashu is considered experimental, it’s a good option to have if you don’t want to run a Lightning node.
This post will give a quick overview of the steps to connect your Alby Hub with a Cashu mint.
Before you get started, you’re going to want to have Alby Hub installed already. There are many options for this as well — Linux, StartOS, and Umbrel to name a few. You can even have Alby host it for you in their cloud.
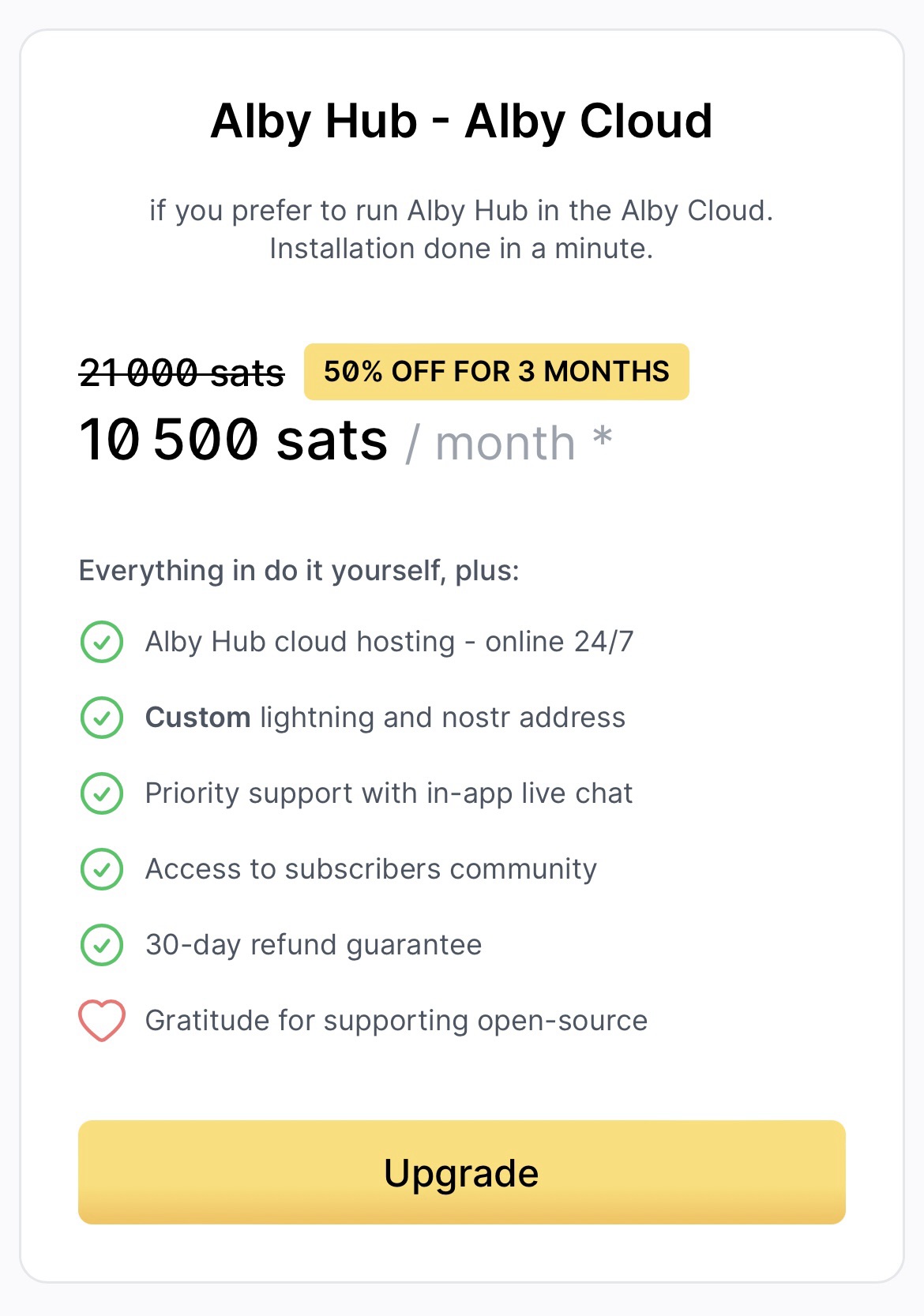
I just happen to have a Linux machine free so I went that route — the installation script made it super easy.
After the install is complete, navigating to localhost:8080 brings up this page.
- Select “Advanced Setup”
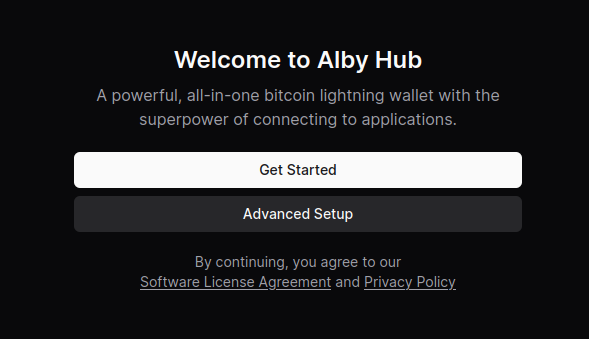
- Select “Create Wallet with Custom Node”
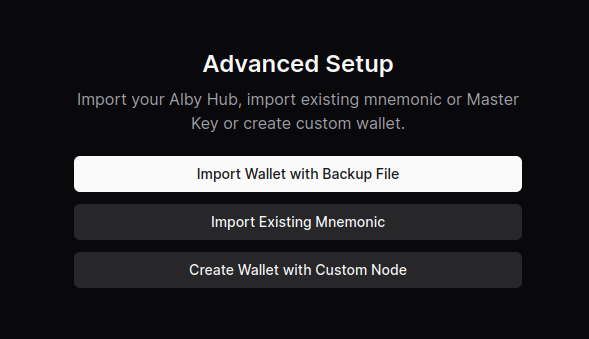
- Select “Cashu Mint”
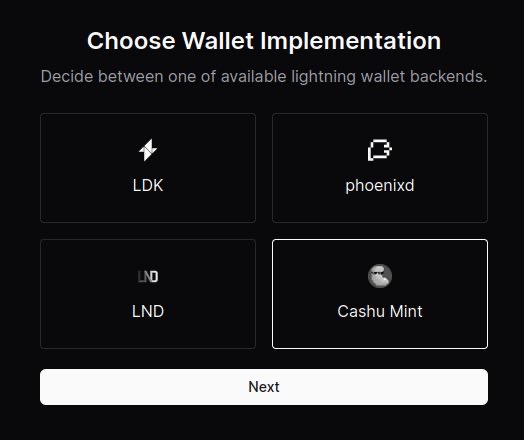
- Paste the URL of the mint you’d like to use. You can use the default one provided or click on “Find a mint” to search for others.
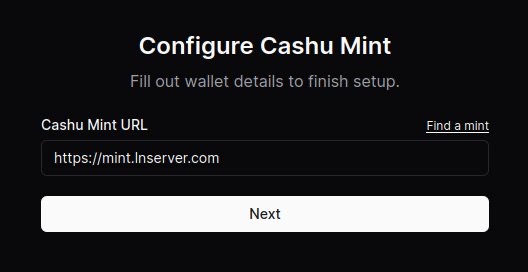
- (Optional) Connect your Alby account by requesting an authorization code. After clicking “Connect now,” a new window will open and the code displayed after signing in.
Boom. You’re all done.
Now you can use your Alby Lightning address to receive your first sats!
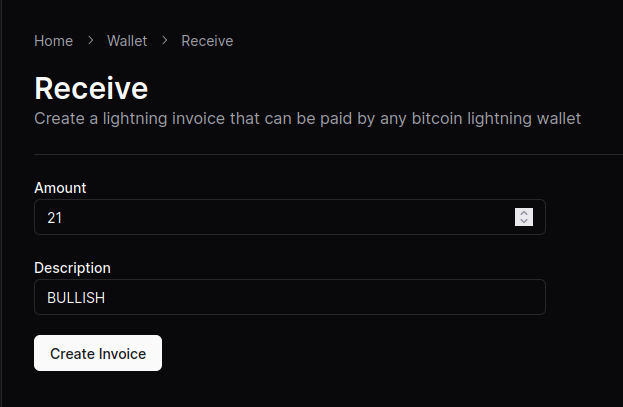
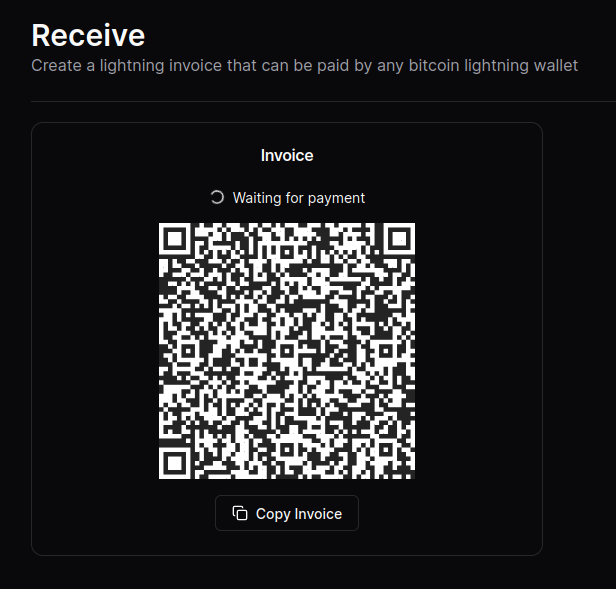
NOTE: Although the sats do make it to the wallet, the “Waiting for payment” animation seems to wait indefinitely and there’s no record in transaction history.
This seems to be a Cashu-related issue that has something to do with the preimage. An issue has been opened on GitHub if you’re curious.
Other that that, sending and receiving works like a charm.
originally posted at https://stacker.news/items/707673
-
 @ c4f5e7a7:8856cac7
2024-09-27 08:20:16
@ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on Habla, YakiHonne or Highlighter.
TL;DR
This article explores the links between public, community-driven data sources (such as OpenStreetMap) and private, cryptographically-owned data found on networks such as Nostr.
The following concepts are explored:
- Attestations: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your web-of-trust.
- Proof of Place: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in meatspace with their digital representations in the Nostrverse.
- Check-ins: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time.
The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems.
Open Data in a public commons has a place and should not be thrown out with the Web 2.0 bathwater.
Cognitive Dissonance
Ever since discovering Nostr in August of 2022 I've been grappling with how BTC Map - a project that helps bitcoiners find places to spend sats - should most appropriately use this new protocol.
I am assuming, dear reader, that you are somewhat familiar with Nostr - a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: Nostr is Identity for the Internet and The Power of Nostr by @max and @lyn, respectively. Nostr is so much more than a short-form social media replacement.
The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting - all your silos are indeed broken - however, something fundamental has been bothering me for a while and I think it comes down to data ownership.
For those unfamiliar, BTC Map uses OpenStreetMap (OSM) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) - FOSD if you will, but more commonly referred to as Open Data.
In contrast, Notes and Other Stuff on Nostr (Places in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned.
How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data?
Self-sovereign Identity
Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something - an identity.
All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money.
Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state.
Or, as @nvk said recently: "Don't build your house on someone else's land.".
https://i.nostr.build/xpcCSkDg3uVw0yku.png
While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this.
Nostr is PGP for the masses and will take cryptographic identities mainstream.
Full NOSTARD?
Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons.
We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be.
https://i.nostr.build/s3So2JVAqoY4E1dI.png
There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a Wikifreedia variant of OpenStreetMap.
While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native - there's no need to go Full NOSTARD. H/T to @princeySOV for the original meme.
https://i.nostr.build/ot9jtM5cZtDHNKWc.png
So, how do we appropriately blend cryptographically owned data with the commons?
If a location is owned in meatspace and it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the tragedy of the commons.
The remainder of this article explores how we can:
- Verify ownership of a physical place in the real world;
- Link that ownership to the corresponding digital place in cyberspace.
As a side note, I don't see private key custodianship - or, even worse, permissioned use of Places signed by another identity's key - as any more viable than the rented identities of Web 2.0.
And as we all know, the Second Law of Infodynamics (no citation!) states that:
"The total amount of sensitive information leaked will always increase over time."
This especially holds true if that data is centralised.
Not your keys, not your notes. Not your keys, not your identity.
Places and Web-of-Trust
@Arkinox has been leading the charge on the Places NIP, introducing Nostr notes (kind 37515) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via NIP-73 - External Content IDs (championed by @oscar of @fountain).
However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world.
Ultimately, this problem can only be solved in a decentralised way by using Web-of-Trust - using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop.
This requires users to:
- Verify the owner of a Place in cyberspace is the owner of a place in meatspace.
- Signal this verification to their social graph.
Let's look at the latter idea first with the concept of Attestations ...
Attestations
A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false.
Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too.
However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc).
Here is a recent example from @lyn that would carry more signal if it were an Attestation:
https://i.nostr.build/lZAXOEwvRIghgFY4.png
Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or Data Vending Machines in accordance with:
- Your social graph;
- The type or subject of the content being attested and by whom;
- Your personal preferences.
They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places.
NIP-25 (Reactions) do allow for users to up/downvote notes with optional content (e.g., emojis) and could work for Attestations, but I think we need something less ambiguous and more definitive.
‘This is true’ resonates more strongly than ‘I like this.’.
https://i.nostr.build/s8NIG2kXzUCLcoax.jpg
There are similar concepts in the Web 3 / Web 5 world such as Verified Credentials by tdb. However, Nostr is the Web 3 now and so wen Attestation NIP?
https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg
That said, I have seen @utxo has been exploring ‘smart contracts’ on nostr and Attestations may just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust.
Proof of Place
Attestations handle the signalling of your truth, but what about the initial verification itself?
We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth.
Introducing Proof of Place, an out–of-band process where an oracle (such as BTC Map) would mail - yes physically mail- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace.
One way of doing this would be to mint a 1 sat cashu ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location.
Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places).
In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as @Gigi says in PoW is Essential:
"A failure to understand Proof of Work, is a failure to understand Bitcoin."
In the Nostrverse, Proof of Place helps bridge the digital and physical worlds.
@Gigi also observes in Memes vs The World that:
"In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone."
https://i.nostr.build/dOnpxfI4u7EL2v4e.png
This isn’t true for Nostr.
In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯
Check-ins
Although not a draft NIP yet, @Arkinox has also been exploring the familiar concept of Foursquare-style Check-ins on Nostr (with kind 13811 notes).
For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as OSM elements) if NIP-73 - External Content IDs are used.
Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices.
Bringing Check-ins to Nostr is possible (as @sebastix capably shows here), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am.
Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable.
How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene - I’m sure @blackcoffee and @Ben Arc could hack something together over a weekend!
Check-ins could also be used as a signal for bonafide Place ownership over time.
Summary: Trust Your Bros
So, to recap, we have:
Places: Digital representations of physical locations on Nostr.
Check-ins: Users signalling their presence at a location.
Attestations: Verifiable social proofs used to confirm ownership or the truth of a claim.
You can visualise how these three concepts combine in the diagram below:
https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg
And, as always, top right trumps bottom left! We have:
Level 0 - Trust Me Bro: Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all.
Level 1 - Definitely Maybe Somewhere: This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL.
Level 2 - Trust Your Bros: An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph.
https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg
Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map?
Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ - you decide.
As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities.
Thanks
With thanks to Arkinox, Avi, Ben Gunn, Kieran, Blackcoffee, Sebastix, Tomek, Calle, Short Fiat, Ben Weeks and Bitcoms for helping shape my thoughts and refine content, whether you know it or not!
-
 @ e79d3f66:41a9bfbe
2024-12-11 08:07:10
@ e79d3f66:41a9bfbe
2024-12-11 08:07:10The customer service industry is undergoing a rapid transformation, driven by technological advancements, evolving customer expectations, and a globalized workforce. As we step into 2025, several trends are poised to reshape the landscape of customer service outsourcing. Let's delve into the top trends that will shape the future of this dynamic industry.
- AI-Powered Customer Service: A New Era of Automation
Artificial Intelligence (AI) is revolutionizing customer service by automating routine tasks and enhancing customer interactions. AI-powered chatbots and virtual assistants are becoming increasingly sophisticated, capable of handling a wide range of customer inquiries, from simple product information to complex troubleshooting. This not only improves efficiency but also frees up human agents to focus on more complex and strategic tasks.
- Hyper-Personalization: Tailoring Experiences to the Individual
Customers today crave personalized experiences that cater to their unique needs and preferences. Customer service outsourcing providers are leveraging data analytics and machine learning to gain deeper insights into customer behavior. This enables them to deliver highly personalized interactions, such as customized product recommendations, tailored messaging, and proactive support.
- Omnichannel Customer Support: Seamless Experiences Across Channels
Customers expect seamless and consistent experiences across all touchpoints, whether it's phone, email, chat, social media, or in-person. Omnichannel customer support is essential to meet these expectations. Outsourcing providers are investing in advanced technologies and training their agents to handle multiple channels effectively. This ensures that customers receive timely and relevant assistance, regardless of the channel they choose.
- Remote and Hybrid Workforces: A New Paradigm
The COVID-19 pandemic accelerated the adoption of remote and hybrid work models. This trend is likely to continue in the customer service industry, as it offers numerous benefits, including increased flexibility, cost savings, and access to a global talent pool. Outsourcing providers are adapting to this shift by investing in robust remote work infrastructure and training their agents to work effectively from anywhere.
- The Rise of the Digital Nomad Agent
The digital nomad lifestyle is gaining popularity, and customer service is no exception. Outsourcing providers are increasingly hiring digital nomad agents who can work remotely from anywhere in the world. This trend can lead to a more diverse and skilled workforce, as well as reduced operational costs.
- Ethical AI and Data Privacy: A Growing Concern
As AI becomes more integrated into customer service, ethical considerations and data privacy are paramount. Outsourcing providers must ensure that AI algorithms are unbiased and transparent. They must also comply with stringent data privacy regulations, such as GDPR and CCPA, to protect customer information.
- The Human Touch: Empathy and Emotional Intelligence
While technology is transforming customer service, the human touch remains essential. Customers still value empathy, understanding, and personalized attention. Outsourcing providers are focusing on training their agents to develop strong emotional intelligence skills. This enables them to connect with customers on an emotional level and provide exceptional support.
By embracing these trends, customer service outsourcing providers can stay ahead of the curve and deliver exceptional experiences to customers. As the industry continues to evolve, the focus will be on leveraging technology to enhance human interaction and build stronger customer relationships.
-
 @ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23
@ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23由于gmail在中国被防火墙拦截了,无法打开,不想错过邮件通知。
通过自建ntfy接受gmail邮件通知。 怎么自建ntfy,后面再写。
2024年08月13日更新:
修改不通过添加邮件标签来标记已经发送的通知,通过Google Sheets来记录已经发送的通知。
为了不让Google Sheets文档的内容很多,导致文件变大,用脚本自动清理一个星期以前的数据。
准备工具
- Ntfy服务
- Google Script
- Google Sheets
操作步骤
- 在Ntfy后台账号,设置访问令牌。

- 添加订阅主题。

- 进入Google Sheets创建一个表格.记住id,如下图:

- 进入Google Script创建项目。填入以下代码(注意填入之前的ntfy地址和令牌):
```javascript function checkEmail() { var sheetId = "你的Google Sheets id"; // 替换为你的 Google Sheets ID var sheet = SpreadsheetApp.openById(sheetId).getActiveSheet();
// 清理一星期以前的数据 cleanOldData(sheet, 7 * 24 * 60); // 保留7天(即一周)内的数据
var sentEmails = getSentEmails(sheet);
var threads = GmailApp.search('is:unread'); Logger.log("Found threads: " + threads.length);
if (threads.length === 0) return;
threads.forEach(function(thread) { var threadId = thread.getId();
if (!sentEmails.includes(threadId)) { thread.getMessages().forEach(sendNtfyNotification); recordSentEmail(sheet, threadId); }}); }
function sendNtfyNotification(email) { if (!email) { Logger.log("Email object is undefined or null."); return; }
var message = `发件人: ${email.getFrom() || "未知发件人"} 主题: ${email.getSubject() || "无主题"}
内容: ${email.getPlainBody() || "无内容"}`;
var url = "https://你的ntfy地址/Gmail"; var options = { method: "post", payload: message, headers: { Authorization: "Bearer Ntfy的令牌" }, muteHttpExceptions: true };
try { var response = UrlFetchApp.fetch(url, options); Logger.log("Response: " + response.getContentText()); } catch (e) { Logger.log("Error: " + e.message); } }
function getSentEmails(sheet) { var data = sheet.getDataRange().getValues(); return data.map(row => row[0]); // Assuming email IDs are stored in the first column }
function recordSentEmail(sheet, threadId) { sheet.appendRow([threadId, new Date()]); }
function cleanOldData(sheet, minutes) { var now = new Date(); var thresholdDate = new Date(now.getTime() - minutes * 60 * 1000); // 获取X分钟前的时间
var data = sheet.getDataRange().getValues(); var rowsToDelete = [];
data.forEach(function(row, index) { var date = new Date(row[1]); // 假设日期保存在第二列 if (date < thresholdDate) { rowsToDelete.push(index + 1); // 存储要删除的行号 } });
// 逆序删除(从最后一行开始删除,以避免行号改变) rowsToDelete.reverse().forEach(function(row) { sheet.deleteRow(row); }); }
```
5.Google Script是有限制的不能频繁调用,可以设置五分钟调用一次。如图:

结尾
本人不会代码,以上代码都是通过chatgpt生成的。经过多次修改,刚开始会一直发送通知,后面修改后将已发送的通知放到一个“通知”的标签里。后续不会再次发送通知。
如需要发送通知后自动标记已读,可以把代码复制到chatgpt给你写。
-
 @ 7460b7fd:4fc4e74b
2024-09-05 08:37:48
@ 7460b7fd:4fc4e74b
2024-09-05 08:37:48请看2014年王兴的一场思维碰撞,视频27分钟开始
最后,一个当时无法解决的点:丢失
-
 @ df67f9a7:2d4fc200
2024-07-07 18:25:32
@ df67f9a7:2d4fc200
2024-07-07 18:25:32Anyone who thinks that “onboarding new users” is simply a technical challenge of educating people about “how Nostr works”, is grossly mistaken about social networks in general and blind to what makes Nostr so special.
Social Networks are for Friends
Relationship building is why people use social networks. Connecting with friends and loved ones (and colleagues and customers also) is the obvious reason to join, and should be the primary objective in any onboarding endeavor. Everything else “about the technology” only needs to be introduced “as needed” in order for each new user to achieve this goal.
The Nostr Network Requires Trusted Friendships
To thrive at scale, Nostr needs to have established and interconnected “webs of trusted friends” for “verifying” authentic profiles and quality content. This PgP strategy for decentralized trust implemented on Nostr, is the best way to keep bots and bad actors at bay while preserving freedom and sovereignty for every user. Even though Nostr still doesn’t have a standard for determining who “is trusted” for any one user across all clients, we can already build tools to onboard new friends of the highest quality trust. Leveraging existing relationships, “webs of trust” can be strengthened even at this early stage simply by advocates “inviting friends to Nostr”.
Nostr is New and Already Full of Trusted Friends
But it won’t be for long. Bots and bad actors are relatively “easy” to keep at bay today because the Nostr userbase is still small. People who come to Nostr and STAY have mostly been a self selecting group of “freedom tech fans”. We like it this way, and are generally happy to be here. The comraderie is refreshing. But the more people that come to Nostr, the more Nostr will attract different kinds of people.
This is already happening. Nostr is growing at the edges, reaching out beyond the “freedom tech fans” and attracting a number of “less committed” (and some nefarious) individuals here and there. Who sticks around? The “friends of freedom tech fans” stick around longer because they have friends here. WAY BEFORE even considering how “the network effect” will take over, Nostr needs to solve for retention by bringing more “trusted friends” into the network. Social onboarding tools will allow us to share Nostr to “friends of freedom tech fans” and beyond, establishing interconnected “webs of trust” that are increasingly impermeable to bots and bad actors.
Nostr is Freedom Tech that People Want to Share
Creators and influencers of every kind share Nostr (and Nostr content) every day. This phenomenon is a gold mine for onboarding, and can be supported with tools and incentives. Driven by the fact that Nostr is an open protocol, owned by nobody and available for anybody to build upon and profit from, the passion for sharing Nostr will never wane. But our userbase may fall off, if people become disenchanted by undesirable content or lack of good follows. This is why onboarding efforts, to attract more “friends” to the network, are so important. Leveraging the “share worthy” phenomenon of Nostr itself to grow Nostr’s networks of “trusted friends” seems like a no brainer. But for this strategy to work, it needs to be win win win for all parties.
Everybody Wins with More Trusted Users on Nostr
Even as standards for qualifying trust are still being refined, “social onboarding” increases the ratio of “more” trusted over “less” trusted users across the network.
Developers Win
With more trusted users on the network, Nostr developers win by being able to attract an increasingly diverse range of business partners to sponsor their projects.
Sponsors Win
An increase in trusted usership equates to more “real people” perusing “desired content” and more chances for brands to engage “organically” with target audiences. Marketing opportunities increase with trust.
Advocates Win
Simply by sharing Nostr with their friends, Advocates support the sustained growth of trust across the network. Valuable zap reward programs to incentivize high quality onboarding efforts are easily justified and funded by social onboarding clients and their sponsors.
Users Win
More trusted users across the network means more trustworthy content in every feed and more easily discoverable friends and new follows regardless of the client or algorithm used.
Nostr Wins
More trusted users on the network means more “high quality” trust connections between each user. Strong webs of trust is what keeps out bots and bad actors, and is essential for stability as Nostr scales.
Social Onboarding Clients Bring Trust to Nostr
Having more tools for “sharing Nostr with friends” is how Nostr wins. Any client can have capacity for “Social Onboarding”. This may be a dedicated onboarding client or a feature set within a social client. A client that offers “Social Onboarding” will support Nostr advocates and the users that they invite. These should have the following feature set :
- Nostr advocates may create and share any number of customizable “Nostr invites” for different audiences or occasions. Each may have different reccomendations, or access codes, or expiry options. (A NIP is in the works)
- Nostr invite QR codes (and shareable URLs) should resolve to a WEB based interface for prospective (and existing) users who MAY NOT have a client or browser extension already installed.
- Each invite should (within the onboarding client) provide access to low friction profile creation AND advocate reccomended lists of new friends, interest groups, preferred clients, best relays, and other stuff.
- Private key generation and management for new users should be handled entirely within the onboarding client (using NIP standards without a browser extension or external bunker app) to reduce friction at this crucial moment.
- A human readable Nostr address (NIP05 or some future NIP) should be generated automatically for all new users.
- New account creation should result immediately in a direct message or group thread of private “gift wrap” encrypted messages. This thread acts as the new user’s “first contact” with the advocate (possibly others as well) and an anchor for exploring the rest of Nostr.
- Invite “receipt” data (who invited who) should be “gift wrap” encrypted, accessible only to the advocate and new user. Clients wishing to use this data for analytics MAY request access from BOTH parties.
- Top Advocates may be calculated by the client (using data from invite receipts OR from public Nostr usage metrics), and awards may be offered.
- Advocates may also be supported by the client through access to private “advocate support” groups and communities over the Nostr network.
Support Social Onboarding for Nostr
Meet Me On Nostr is an app for sharing Nostr with friends via advocate invites. It is a reference client to demonstrate the power of Social Onboarding for Nostr. The first launch of "feature complete" client is expected in fall 2024.
This is a “bootstrap” funded project in active development. We are not grant funded or VC funded. Instead, we are looking to pay our developers by sponsorships from “Nostr adjacent” businesses who want to increase brand recognition over this new social network.
Is Your Business Nostr Adjacent?
“I’d like to advertise on Nostr but it’s “not quite ready” says our marketing team.”
“It has potential, and we have alignment, but the technology is still a bit rough.”
“Nostr is a perfect fit for our “target audience”, but there simply aren’t enough people using it.”
If your business is aligned with freedom technology, and the people who build and use Nostr, then NOW is the perfect time to sponsor Social Onboarding. Help grow Nostr’s base of trusted users and engage directly with Nostr’s most active advocates and influencers as it scales.
Release Nostr’s Superpower
When Nostr advocates are equipped and incentivized to share Nostr with their friends, nothing can stop this network from growing and growing and growing ever more secure and interconnected networks of trusted users.
Onboarding and retaining trusted users as Nostr scales will require so much more than just pointing people to “how Nostr works” content. Nostr’s true power lies dormant in the existing relationships that Nostr users already have outside of Nostr. Leveraging this power is what Social Onboarding is all about. Social Onboarding is Nostr’s superpower.
-
 @ 826e9f89:ffc5c759
2024-06-28 21:46:01
@ 826e9f89:ffc5c759
2024-06-28 21:46:01_Prologue: this is a prose adaptation of a talk I gave to a private audience in Dubai and then tweaked slightly for a small conference in Sofia. I'm increasingly thinking it deserves a more general audience, and may be better suited to text anyway. This is probably not its final form, as the desired audience is tradfi capital allocators, hence a PDF is likely on the cards in the near future. For the time being, consider this a first draft, practising what it might look like as prose, and soliciting feedback from the good people of Nostr. Enjoy! _
The title of this essay means absolutely nothing. There is no such thing as “Web π” because there is no such thing as “Web 3”. It’s bullshit. It’s a scam.
Unfortunately, it has turned out to be extremely powerful bullshit and an extremely profitable scam, and so my goal in writing this essay is to give the reader the tools to navigate all of this and come out the other side without having been scammed or bullshat. In the spirit of not scamming and not bullshitting, I should be clear upfront about the intended readership of this essay, who I am to write it, and who it’s really about.
Who Are You?
I assume the reader is not a shadowy super-coder, but rather is a financial professional. This essay isn’t really for Bitcoiners, although if any read it, I hope they still find it interesting. Who I am really writing for are people coming to the space for the first time. Hopefully in your mind you are coming to the _Bitcoin _space, but if you think you are coming to the “crypto” space then this may be even more useful.
Who Am I?
I am the founder of a company that makes me not only highly biased but also flagrantly self-interested in the content I am promoting. I run a firm that invests in the Bitcoin ecosystem through a variety of different vehicles. I am not going to mislead you in the slightest in that my primary motivation is for you to allocate capital to us rather than to people I would call scammers and bullshitters. You should listen to them too and make up your own mind, or else what’s the point, really? How do you know I’m not scamming or bullshitting you? Exactly. Don’t trust. Verify.
In any case, that’s all assuming you want to “allocate capital” at all rather than just buy Bitcoin without a management fee. I’d like to think the primary difference is that I will be honest about that, and I’ll encourage you to understand as much as you can about what is going on and what you are doing (and if you are at all unsure, I would suggest you aren’t ready and you should just buy Bitcoin and learn) rather than bamboozle you with complete nonsense like “Web 3”.
Who Is This About?
It’s not at all about people working in crypto. Bitcoiners amongst the readership may be mildly irritated by me going on to give about as charitable an explanation of the role of these people as they have probably ever heard from somebody like me. This is really about financiers. It’s about the people who have used the mostly unrewarded efforts of developers, academics, entrepreneurs, and so on to siphon money from you to themselves, leaving a trail of useless tech and defrauded retail investors in their wake – and who will continue to do so if you continue to empower them.
Why This Essay?
We are at an interesting point in the development of the entirety of the “crypto” industry and I strongly suggest that people like you are going to be pitched all kinds of scams and bullshit in the coming months and years. If you have a little more background on what these people are really talking about, you will hopefully be able to avoid it.
My plan to help with that is presenting a short version and a long version of what blockchains are and are for, how they have historically been deployed in service of scams and bullshit, a high-level theory explaining the narrative evolution behind this sorry history, and a prediction for the near-term future of such shenanigans.
What is a Blockchain For?
A Blockchain is for sound, censorship-resistant, peer-to-peer digital money. It is not for anything else. If a blockchain is functional as money, it may be possible to also _use it _for other things. Some people find that interesting, some people find it infuriating, but don’t let that subtlety confuse you. It is not _for _arbitrary computation and storage or “decentralizing the internet” or running illegal securities rackets.

It is for money, plain and simple.
How does it achieve that? Proof of work and the difficulty adjustment. These are the innovations from which every other desirable property or feature flows. Proof of work enables censorship resistance. If somebody is trying to sell you on “proof of stake”: bullshit. The difficulty adjustment enables precise, predetermined, and _fair _issuance. If somebody is trying to sell you on a token they issue for free and without restriction: scam.
The problem Bitcoin solves is both economic and technical and the solution has material technical and economic merit. And it’s for this very specific and irreplicable reason the Bitcoin token has value. If this all sounds extreme to you, then I would suggest that your understanding of the topic is _extremely _misguided, that you are going to be _extremely bullshat and extremely scammed, _and you need to read this essay. That’s the short version.
The Long Version
I am sensitive to how extreme this all sounds. After all, hundreds of billions of dollars have been pumped into crypto, not Bitcoin – a huge amount of it is widely used, and many capable, honest, and brilliant people work in the industry. The reader will recall just above I said those people are not the target of my criticism. I’m not claiming they are all scammers and bullshitters. Sadly, I think it’s more likely they have been scammed and bullshat to some degree also.
I think I have some credibility in pointing this out because, as a VC in the Bitcoin space, I have increasingly seen founders telling me this themselves: that they originally bought into the hype in crypto and ended up wasting an enormous amount of time realizing their idea made no technical or economic sense in that context, so then they came to Bitcoin instead. You hear this one time and it’s an anecdote, but you hear it as many times as I have and it feels more like a representative sample.
What I want to cover next is as charitable a summary of the state of ex-Bitcoin crypto as I possibly can: my contention is that crypto has evolved into 4 rough categories: stablecoins, cryptography R&D, gambling, and scams. And these aren’t exclusive, to be clear; there is a lot of overlap, and, in fact, the overlap is arguably the key.
Scams
Scams are tokens, plain and simple. If somebody is trying to profit from the speculative price action of a token they have issued, they are scamming somebody. Maybe they are scamming you, maybe they are scamming retail investors, maybe they are scamming customers or suppliers – if such parties even exist in their cargo cult “business model”. There’s a scam in there somewhere.
However, it is rarely _just _a scam. There will almost always be components of stablecoins, R&D or gambling too. Hence these are worth really grappling with, taking seriously, giving credit to the extent it is due, but also analyzing critically.
My rough and high-level assessment of this breakdown of crypto is as follows, and I’ll explain what I mean by this below: stablecoins have economic merit but dubious technical merit; R&D has technical merit but no economic merit; and gambling sort of has merit but it depends how you interpret it. Obviously, scams have neither.

Stablecoins
By “sort of technical merit” I mean that stablecoins have central issuers. You can issue them as tokens on a blockchain but there’s not really much of a point. The issuer could just run a database connected to the internet with some straightforward signature schemes for transfers and it would make minimal operational difference. In fact, it would be cheaper and faster. _In fact, _you may as well run a Chaumian eCash mint (a decades-old innovation recently resurrected firmly within the _Bitcoin _space) such that your cheaper-and-faster-than-a-blockchain database also grants users transience and privacy rather than the public permanence of a blockchain.
The fact Tron is the most heavily used for stablecoins, in terms of settling the most value, is a testament to this point: it is barely even pretending not to be a database. This works as regulatory arbitrage given regulators think this is “innovation” because they are stupid.
That said, it is worth giving some credit here given the abject awfulness of fiat banking and payment rails with which stablecoins arguably most directly compete. Stablecoins are significantly more permissionless in their transfer than any fiat bank liability. And to attest to what seems like their most significant use case, they are permissionless in their _usership _in that only an internet connection and the right software is required rather than various discriminatory jurisdictional and compliance criteria.
However, what “sort of technical merit” ultimately boils down to, especially in comparison to Bitcoin, is: highly censorable in their exogenous links and, therefore, their value. The assets supposedly backing stablecoins are (by definition) still within the fiat system, even if this novel transfer mechanism of the rights to withdraw them is not. There is frankly a bit of theatre involved in the so-called “decentralization” of stablecoins given shutting down the central issuer is all that is required to make the permissionlessly tradeable decentralized tokens go to zero and be technically unimpeded but functionally useless. The technical innovation of Bitcoin, in contrast, is easily understood in one sense as it being totally indifferent to this kind of attack.
On the other hand, by “economic merit” I mean that they are extremely widely used and valued as a means of providing dollar shadow banking and often superior payment rails. Those in crypto often love pointing to this and many Bitcoiners tie themselves in knots trying to explain it away, whereas I see it as essentially unrelated to Bitcoin. Clearly there is a superficial connection, but you could create any superficial connection by “tokenizing” things for no particularly good technical _reason. I think it’s a different industry entirely. It’s more like a subindustry within _fintech – part banking, part payments – that for the time being relies on bamboozling regulators with all the nonsense I’m drawing attention to.
And good for them, frankly. If fiat banking isn’t going to be backed by real money anyway, then it _at least _ought to be permissionless. It should really be Chaumian eCash if it isn’t just Bitcoin, and it is regulation alone that makes it so awful in the first place. Making money usable and not a tool of dystopian control is, at this point, a political problem, not a technical one. Stablecoins are frankly a step in the right direction, especially insofar as they acclimatize users to digital assets. But I would still caution that they arguably don’t have sufficient technical merit to withstand what feels like an inevitable political attack …
Cryptography R&D
“Technical merit” for R&D is more or less self-explanatory, but the context is worth appreciating. It’s only really in crypto and mostly in Ethereum more specifically that people can permissionlessly experiment with arbitrarily complex cryptographic schemes that operate on real, enormous value. There are a lot of people who understandably find this attractive given their projects are essentially academic and trying out their ideas in the wild is more interesting, arguably more worthwhile, and certainly more fun than putting research essays on ArXiv or submitting them to a journal.
But … the value being manipulated is at best stablecoins and at worst baseless hype. If it isn’t a stablecoin then it probably exists in the first place because of either gambling or scams – and even there the line is very blurry.
Gambling
Gambling is an interesting lens to adopt on all this because it’s literally a trillion-dollar industry. And it’s real. It’s consensual; it’s not criminal; it’s legitimate economic activity that generates enormous profits for those who facilitate it well.
So, gambling has economic merit in that sense. But it’s tricky in this context how to characterize it because you could also argue it’s deeply dishonest gambling in that the gamblers don’t realize they are playing a negative sum game against the house. They think they are doing something akin to speculating on securities, which may be just as stupid depending on how it’s done, but at least has real economic utility and contributes to capital formation.
The difference here is that what is being speculated on _has no economic merit. _So, if that’s your gauge of merit, then here there is none. And it’s a very blurry line between this and an outright scam. Maybe the people involved _think _of what they are doing as amazing R&D, and maybe it’s inadvertently just a scam; maybe they know it’s all nonsense, but they think they can profit within the negative sum game because there are greater fools. In any case, I think gambling is a very helpful characterization of a lot of the behavior of the users and the real economic function of the industry.
There’s an interesting social component to all this because crypto people will often get mad at Bitcoiners because Bitcoiners tend not to care about either stablecoins or crypto R&D: they’ll say, why don’t you like stablecoins, they have clear economic merit? And the answer is they have dubious technical merit. Or, why don’t you like our next-gen Zero Knowledge scaling protocol, it has clear technical merit? And the answer is it has no economic merit.
If you’re happy with one but not the other, it’s easy to think of Bitcoiners as being closed-minded or dogmatic or whatever, but, ultimately, I think it’s just about discipline. What’s the point in being excited by something that half works, and that you know why will never fully work? So to be frank, a lot of this may be well-intentioned, but it’s kinda’ bullshit. It very probably ultimately rests on gambling and not at all whatever its stated purpose is … or it’s just a scam.
How Did We Get Here?
The following is by no means exhaustive and the framing is deliberately a little tongue-in-cheek. As well as being accurate enough (if unavoidably biased), my goal here is primarily to set up my prediction for what is coming next.
2015 reality: Ethereum launches narrative: “the world computer”
In 2015, Ethereum launched. The narrative here was that we are building “the world computer” and we can now have decentralized uncensorable computation. Never mind that anybody with a laptop has an uncensorable and decentralized computing device. And keep in mind this question of, “_what data might it ever be relevant to compute over in this manner (whatever that means in the first place)?” _The answer will become clearer and clearer …
2016-17 reality: ICO bubble narrative: “Web 3” / “DApps”
Regardless, at the end of 2015 we get the proposal and adoption of ERC20: a standard for issuing fungible tokens within Ethereum contracts, which is why in 2016 _but especially in 2017 _we get the ICO bubble. The narrative changes. Now we are concerned with “Web 2” companies being huge, powerful, and centralized. What if, instead, users could cooperatively own the application, control their own data, and participate in the economic upside that their usage is creating?
2018-19 reality: crypto winter narrative: “mistakes were made”
In 2018 this all falls apart, so don’t worry about it, moving on …
2020-21 reality: defi summer narrative: “decentralized finance”
By 2020 the narrative was different once again. It is more or less realized by this point that utility tokens make no technical or economic sense. You can’t introduce artificial scarcity in capital goods where there should be abundance and deflation and expect anybody to care, never mind to value your concoction. On the other hand, “securities” ought to be scarce and in some sense ought to function as tradeable ledger entries. Maybe they could be tokenized and computed on in a censorship-resistant and decentralized manner?
So, we get a boom in “defi” which, for what it’s worth, fellow Axiom co-founder Anders Larson and I predicted in our essay Only The Strong Survive, in September 2021, would be a complete disaster because, amongst a myriad of other illiterate insanities, there was approximately zero grounding of these securities in productive capital. The ecosystem was entirely self-referential – grounded _not even _in the questionable economic merit of stablecoins but firmly in gambling and scams; in leverage, rehypothecation, and securitization of precisely nothing whatsoever productive.
2022 reality: shitcoinpocalypse narrative: “mistakes were made”
And we were absolutely right because in 2022 everything collapsed. First Terra/Luna imploded – a “defi” project which essentially presented to the world the argument that a fractional reserve bank issuing fiduciary media can literally never go bankrupt because it can always cover a deposit shortfall by issuing more equity. While briefly flirting with a capitalization of around fifty f***ing billion dollars, and endorsed and fawned over by all manner of illiterate charlatans with gigantic and unsuspecting audiences, this argument was eventually rejected by the market as utterly imbecilic, as analyzed by myself and Nic Carter in All Falls Down.
This triggered a credit contagion that soon after took down 3 Arrows Capital, Celsius, Voyager, BlockFi, and others. FTX limped along by what we now understand to be something like defrauding their way out of debt, but eventually also collapsed later that year. If _Only The Strong Survive _was a pre-mortem of all of this, then the reader may want to read Green Eggs And Ham, also by myself and Anders Larson, as a kind of post-mortem.
2023-today reality: Bitcoin multisigs narrative: “Bitcoin renaissance”
And now a lot of this stuff is moving to Bitcoin. It is outside the scope of this essay to explain this in much detail but there have been a handful of developments in Bitcoin recently which, regardless of their intended purpose, seem to have as a collective side effect that a lot of these same shenanigans can now be implemented (or can _pretend _to be implemented) in a more Bitcoin-native context.
So, the new narrative is something like:
“these things didn’t work, not because they are terrible ideas that collapse to moon math wrappers around gambling and scams under any remotely critical analysis, but rather because they weren’t on Bitcoin. But also, since it has only recently become possible to (at least pretend to) implement them on Bitcoin, they are now worthwhile. We have wandered in the wilderness but learned our lessons and found the promised land.”

Technical and Economic Merit
Let’s consider all this through the lens of technical and economic merit once again. Or rather, the alleged merit given the stated goal. Ignore for now whether there is any merit:
2015 technical goal: new computing paradigm economic goal: x% of GDP?
The original idea of “crypto” allegedly has the merit of the next revolution in computing. Goodness knows how big that market is; probably a decent chunk of global GDP – if it meant anything, which it doesn’t.
2016-17 technical goal: disrupting company formation economic goal: y% of S&P?
ICOs then become a little bit more specific. Now they are merely disrupting how we organize companies. What’s that worth? Some portion of the value of the companies that can now be decentralized and tokenized I guess? Who knows …
2018-19 nothing to see here
Nothing happened then, don’t worry about it.
2020-21 technical goal: decentralize finance economic goal: z% of NYSE, CME, ISDA?
Defi becomes more specific again. Now we are merely tokenizing financial contracts, expanding access, removing middlemen, and so on. So that should probably be worth some percentage of capital markets activity?
2022 nothing to see here
Oops, never mind …
2023-today technical goal: now it’s on Bitcoin! economic goal: i% of … Bitcoin?
… and now it’s on Bitcoin apparently.
In Hindsight ...
I think the most amusing analysis of all this is as follows: it starts off completely insane, it gets more and more restrained each time – you could cheekily argue it starts to make more and more sense – but it also gets closer to Bitcoin every time. It’s clearly narrowing in on just: Bitcoin.
This is people realizing, painfully, over decades, what blockchains are for! They are not for “decentralizing everything” They are for censorship-resistant, sound, peer-to-peer digital money.

And I think this is _also _why we get the current state of crypto from earlier in the essay. As it starts to make more and more sense (by getting closer and closer to Bitcoin) you have realizations like the following: digital gift vouchers for artificially scarce and extremely expensive computation aren’t money, so we need “real money” in here for it to have economic merit, so you get stablecoins. Also, well we have a rich programming environment that seems technically interesting but also the severe technical handicap of being unable to do even a billionth of a billionth of a billionth of all the computations in the world, so you get crypto R&D. These emerge as a kind of patch, and they have _some _merit in isolation, whereas the long-term trajectory is actually just to converge on Bitcoin.
It’s an open and fascinating question if there are any learnings from these that can still be transplanted to Bitcoin. For stablecoins, this strikes me as less clear, given the dubious technical merit is introduced by using a blockchain at all, not just a blockchain other than Bitcoin. However, efforts to create Bitcoin balances (tokenized or otherwise) that are stable relative to some external price are to be applauded, if still heavily scrutinized for what technical merit they _really _have.
It seems far more likely that crypto R&D will prove useful in a Bitcoin context to some or other degree, and in this case the economic merit is in fact solved by moving to Bitcoin, provided the necessary technical merit can be mimicked. At the time of writing, this is a source of both hope and dread: hope given the possibility of viable avenues of development (although still highly uncertain); dread given how early steps in this direction are already being misrepresented in the pursuit of bullshit and scams. I will return to both shortly.
Narrative Evolution
Back to the table just above, I want to make three quick observations that tie together my entire argument and get us to the end of the essay:

Firstly, the bubbles always follow the price of Bitcoin. Hopefully I don’t need to include a price chart for the reader to grasp this immediately.
Secondly, it’s important that the narrative always changes. Absolutely ungodly amounts of money were raised for this crap following the_ Bitcoin bull runs of 2017 and 2021. The people doing this couldn’t point to the previous absolute disaster, so they had to spin something along the lines of: “_we learned our lessons and we’ve refined the use case.” This should sound familiar from just above.
Thirdly, however, regardless of whatever refinement they’ve come up with, the consequence of the new “narrative” is always, “buy my token”.
Always.
It doesn’t matter what buzzword salad is in the middle. It’s always “Bitcoin is cool, xyz, fughayzi fughahzi, buy my token.”
This is why I am very much tempted to not care so much about developers, academics, entrepreneurs, and so on, and in fact for my null hypothesis to be that they are more likely to have been victims than perpetrators. I don’t think they even end up in a position to contribute without the key group whom I do blame. When you put all these pieces together, what I think falls out of this analysis is as follows:
The entire cycle of shitcoinery can be traced to unscrupulous financiers convincing capital allocators who don’t know any better, in a bull market that, yes, Bitcoin is cool, but what they are doing is related, cooler, and that they deserve a fee.
Let us label this the Capital Cycle Theory of Shitcoinery. I think that everything else about which one might want to complain is downstream of this core realization.
Avoiding It
Given everything I’ve covered this is simple and this is pretty much the end of the essay.
You need to be aware of why this is happening now. If it hasn’t happened to you already (intended readership in the capital allocation business, that is) I guarantee it’s about to: with ETFs and the halving just past, we seem to be starting a Bitcoin bull run, these people have already raised ridiculous amounts of money on scams and bullshit that have mostly imploded. They may have lost a lot of money, or they may even have dumped on retail and got an excellent “return”. But in any case, they need a new narrative.
It's _possible _they have a viable narrative around stablecoins, R&D, both, and that they are as wary of scams as I have suggested here that they should be. I don’t want to insult anybody who merely has a different investment thesis to me if they are otherwise reasonable in their outlook and honest in their dealings.
However, if they are only now realizing how pointless and disingenuous every preceding crypto narrative has been after 7 years and hundreds of billions of dollars – or if they still don’t realize it at all; if their track record shows they were deeply involved, handsomely rewarded, and yet created nothing of lasting value; if they say things like “the builders are coming back to Bitcoin”: be very, very suspicious. Be on the lookout for tokens, which is to say, be on the lookout for scams.
What is especially frustrating is that the technical spin of the "layer twos" that are all the rage at the time of writing, that "the builders are coming back to Bitcoin" to build, and that you, the capital-allocating reader, will almost certainly be pitched, is in and of itself pretty reasonable. They just don't require tokens and they don't require gambling to support the token prices. What they do require is _sound adherence to Bitcoin's technical and economic merit. _At the very least, they require honest communication about the design trade-offs so far and planned for, and what, if any, economic and technical merit is left over after these trade-offs have been made.
Narrative aside, the _reality _of 99% of these projects is that they are private execution environments tied to multisigs custodying user deposits. Which is to say, on the one hand, that they are cargo culting "crypto R&D" from Ethereum that isn't technically possible in Bitcoin in order to feign technical merit, and on the other, that _they aren't layer twos at all. _Once again, they may as well be Chaumian eCash mints, except for the fact that this would make the intended token scam all but impossible to pull off.
Casey Rodarmor, creator of the Ordinals protocol, recently joked on the Hell Money _podcast he co-hosts, responding to the idea that "_everybody is building an L2 now":
"It's the same sad sack playbook as on Ethereum being recapitulated on Bitcoin. That's how you get a VC check on Ethereum. They are all glorified multisigs, so they are like, "hey let's port our glorified multisig to Bitcoin and get a VC check." I was talking to a friend of mine who is working on an interesting project, an open-source analyzer that does transaction clustering, and I was like, "maybe you could do this in this way and raise some VC money," and he said, "yeah, okay, but what's the point in raising VC money?" And I said, "no, no, no, this is the end! This is the goal! You raise VC money and then you cut yourself checks from that VC money until it runs out and then you raise more at a 10x valuation. This is the new economy, guys!"
The 1% that are legitimately trying to bring the learnings from crypto R&D to Bitcoin in a technically and economically sound manner will hopefully win in the long run (and even this is somewhat speculative at the time of writing) but will likely get little to no attention amidst this bull market flurry of scams and bullshit.
Axiom will do its best to source and invest in these companies (we already have!) but we are resigned to it being a much more difficult sell to capital allocators in light of the Capital Cycle Theory of Shitcoinery. To be brutally honest, this entire essay can fairly be considered cope on my part in light of having lost this battle in the past and facing up to the very real prospect of losing it in the near future too. Oh well, at least I tried.
Wrapping Up
The essence of the Capital Cycle Theory of Shitcoinery is that the problems I’ve described ultimately come from bamboozling people just like you with technical sounding nonsense like “Web 3” so you think it’s all a lot more complicated than it really is. Just buy Bitcoin. That’s certainly the first thing you should do anyway, and it might be the only thing you ever need to do.
If you really, really want to take the extra risk of investing in the Bitcoin ecosystem, the team at Axiom would be happy to speak with you. But we are never going to talk you out of buying Bitcoin. There is no world in which Bitcoin does poorly and we do well, or in which we promise something “better than Bitcoin,” and there’s no point in engaging with us at all if you don’t already believe most of this.
If that’s of interest to you, we’d love to talk. If not, just buy Bitcoin. In any case: fair warning, we are heading into a Bitcoin bull market and the scams and the bullshit are coming. Good luck avoiding them.
Allen Farrington, June 2024

-
 @ 4523be58:ba1facd0
2024-05-28 11:05:17
@ 4523be58:ba1facd0
2024-05-28 11:05:17NIP-116
Event paths
Description
Event kind
30079denotes an event defined by its event path rather than its event kind.The event directory path is included in the event path, specified in the event's
dtag. For example, an event path might beuser/profile/name, whereuser/profileis the directory path.Relays should parse the event directory from the event path
dtag and index the event by it. Relays should support "directory listing" of kind30079events using the#ffilter, such as{"#f": ["user/profile"]}.For backward compatibility, the event directory should also be saved in the event's
ftag (for "folder"), which is already indexed by some relay implementations, and can be queried using the#ffilter.Event content should be a JSON-encoded value. An empty object
{}signifies that the entry at the event path is itself a directory. For example, when savinguser/profile/name:Bob, you should also saveuser/profile:{}so the subdirectory can be listed underuser.In directory names, slashes should be escaped with a double slash.
Example
Event
json { "tags": [ ["d", "user/profile/name"], ["f", "user/profile"] ], "content": "\"Bob\"", "kind": 30079, ... }Query
json { "#f": ["user/profile"], "authors": ["[pubkey]"] }Motivation
To make Nostr an "everything app," we need a sustainable way to support new kinds of applications. Browsing Nostr data by human-readable nested directories and paths rather than obscure event kind numbers makes the data more manageable.
Numeric event kinds are not sustainable for the infinite number of potential applications. With numeric event kinds, developers need to find an unused number for each new application and announce it somewhere, which is cumbersome and not scalable.
Directories can also replace monolithic list events like follow lists or profile details. You can update a single directory entry such as
user/profile/nameorgroups/follows/[pubkey]without causing an overwrite of the whole profile or follow list when your client is out-of-sync with the most recent list version, as often happens on Nostr.Using
d-tagged replaceable events for reactions, such as{tags: [["d", "reactions/[eventId]"]], content: "\"👍\"", kind: 30079, ...}would make un-reacting trivial: just publish a new event with the samedtag and an empty content. Toggling a reaction on and off would not cause a flurry of new reaction & delete events that all need to be persisted.Implementations
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
f) already support this feature. - IrisDB client side library: treelike data structure with subscribable nodes.
https://github.com/nostr-protocol/nips/pull/1266
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
-
 @ b60c3e76:c9d0f46e
2024-05-15 10:08:47
@ b60c3e76:c9d0f46e
2024-05-15 10:08:47KRIS menjamin semua golongan masyarakat mendapatkan perlakuan sama dari rumah sakit, baik pelayanan medis maupun nonmedis.
Demi memberikan peningkatan kualitas layanan kesehatan kepada masyarakat, pemerintah baru saja mengeluarkan Peraturan Presiden (Perpres) nomor 59 tahun 2024 tentang Jaminan Kesehatan. Melalui perpres itu, Presiden Joko Widodo (Jokowi) telah menghapus perbedaan kelas layanan 1, 2, dan 3 dalam Badan Penyelenggara Jaminan Sosial atau BPJS Kesehatan.
Layanan berbasis kelas itu diganti dengan KRIS (Kelas Rawat Inap Standar). Berkaitan dengan lahirnya Perpres 59/2024 tentang Perubahan Ketiga atas Perpres 82/2018 tentang Jaminan Kesehatan, Presiden Joko Widodo telah memerintahkan seluruh rumah sakit yang bekerja sama dengan BPJS Kesehatan melaksanakannya.
Kebijakan baru itu mulai berlaku per 8 Mei 2024 dan paling lambat 30 Juni 2025. Dalam jangka waktu tersebut, rumah sakit dapat menyelenggarakan sebagian atau seluruh pelayanan rawat inap berdasarkan KRIS sesuai dengan kemampuan rumah sakit.
Lantas apa yang menjadi pembeda dari sisi layanan dengan layanan rawat inap sesuai Perpres 59/2024? Dahulu sistem layanan rawat BPJS Kesehatan dibagi berdasarkan kelas yang dibagi masing-masing kelas 1, 2, dan 3. Namun, melalui perpres, layanan kepada masyarakat tidak dibedakan lagi.
Pelayanan rawat inap yang diatur dalam perpres itu--dikenal dengan nama KRIS—menjadi sistem baru yang digunakan dalam pelayanan rawat inap BPJS Kesehatan di rumah sakit-rumah sakit. Dengan KRIS, semua golongan masyarakat akan mendapatkan perlakuan yang sama dari rumah sakit, baik dalam hal pelayanan medis maupun nonmedis.
Dengan lahirnya Perpres 59/2024, tarif iuran BPJS Kesehatan pun juga akan berubah. Hanya saja, dalam Perpres itu belum dicantumkan secara rinci ihwal besar iuran yang baru. Besaran iuran baru BPJS Kesehatan itu sesuai rencana baru ditetapkan pada 1 Juli 2025.
“Penetapan manfaat, tarif, dan iuran sebagaimana dimaksud ditetapkan paling lambat tanggal 1 Juli 2025,” tulis aturan tersebut, dikutip Senin (13/5/2024).
Itu artinya, iuran BPJS Kesehatan saat ini masih sama seperti sebelumnya, yakni sesuai dengan kelas yang dipilih. Namun perpres itu tetap berlaku sembari menanti lahirnya peraturan lanjutan dari perpres tersebut.
Kesiapan Rumah Sakit
Berkaitan dengan lahirnya kebijakan layanan kesehatan tanpa dibedakan kelas lagi, Kementerian Kesehatan (Kemenkes) menegaskan mayoritas rumah sakit di Indonesia siap untuk menjalankan layanan KRIS untuk pasien BPJS Kesehatan.
Kesiapan itu diungkapkan oleh Dirjen Pelayanan Kesehatan Kemenkes Azhar Jaya. “Survei kesiapan RS terkait KRIS sudah dilakukan pada 2.988 rumah sakit dan yang sudah siap menjawab isian 12 kriteria ada sebanyak 2.233 rumah sakit,” ujar Azhar.
Sebagai informasi, KRIS adalah pengganti layanan Kelas 1, 2, dan 3 BPJS Kesehatan yang bertujuan untuk memberikan layanan kesehatan secara merata tanpa melihat besaran iurannya.
Melalui KRIS, rumah sakit perlu menyiapkan sarana dan prasarana sesuai dengan 12 kriteria kelas rawat inap standar secara bertahap. Apa saja ke-12 kriteria KRIS itu?
Sesuai bunyi Pasal 46A Perpres 59/2024, disyaratkan kriteria fasilitas perawatan dan pelayanan rawat inap KRIS meliputi komponen bangunan yang digunakan tidak boleh memiliki tingkat porositas yang tinggi serta terdapat ventilasi udara dan kelengkapan tidur.
Demikian pula soal pencahayaan ruangan. Perpres itu juga mengatur pencahayaan ruangan buatan mengikuti kriteria standar 250 lux untuk penerangan dan 50 lux untuk pencahayaan tidur, temperature ruangan 20--26 derajat celcius.
Tidak hanya itu, layanan rawat inap berdasarkan perpres itu mensyaratkan fasilitas layanan yang membagi ruang rawat berdasarkan jenis kelamin pasien, anak atau dewasa, serta penyakit infeksi atau noninfeksi.
Selain itu, kriteria lainnya adalah keharusan bagi penyedia layanan untuk mempertimbangkan kepadatan ruang rawat dan kualitas tempat tidur, penyediaan tirai atau partisi antartempat tidur, kamar mandi dalam ruangan rawat inap yang memenuhi standar aksesibilitas, dan menyediakan outlet oksigen.
Selain itu, kelengkapan tempat tidur berupa adanya dua kotak kontak dan nurse call pada setiap tempat tidur dan adanya nakas per tempat tidur. Kepadatan ruang rawat inap maksimal empat tempat tidur dengan jarak antara tepi tempat tidur minimal 1,5 meter.
Tirai/partisi dengan rel dibenamkan menempel di plafon atau menggantung. Kamar mandi dalam ruang rawat inap serta kamar mandi sesuai dengan standar aksesibilitas dan outlet oksigen.
Azhar menjamin, Kemenkes akan menjalankan hal tersebut sesuai dengan tupoksi yang ada. “Tentu saja kami akan bekerja sama dengan BPJS Kesehatan dalam implementasi dan pengawasannya di lapangan,” ujar Azhar.
Berkaitan dengan perpres jaminan kesehatan itu, Direktur Utama BPJS Kesehatan Ghufron Mukti menilai, perpres tersebut berorientasi pada penyeragaman kelas rawat inap yang mengacu pada 12 kriteria. "Bahwa perawatan ada kelas rawat inap standar dengan 12 kriteria, untuk peserta BPJS, maka sebagaimana sumpah dokter tidak boleh dibedakan pemberian pelayan medis atas dasar suku, agama, status sosial atau beda iurannya," ujarnya.
Jika ada peserta ingin dirawat pada kelas yang lebih tinggi, kata Ghufron, maka diperbolehkan selama hal itu dipengaruhi situasi nonmedis. Hal itu disebutkan dalam Pasal 51 Perpres Jaminan Kesehatan diatur ketentuan naik kelas perawatan.
Menurut pasal tersebut, naik kelas perawatan dilakukan dengan cara mengikuti asuransi kesehatan tambahan atau membayar selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya yang harus dibayar akibat peningkatan pelayanan.
Selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya pelayanan dapat dibayar oleh peserta bersangkutan, pemberi kerja, atau asuransi kesehatan tambahan.
Ghufron Mukti juga mengimbau pengelola rumah sakit tidak mengurangi jumlah tempat tidur perawatan pasien dalam upaya memenuhi kriteria KRIS. "Pesan saya jangan dikurangi akses dengan mengurangi jumlah tempat tidur. Pertahankan jumlah tempat tidur dan penuhi persyaratannya dengan 12 kriteria tersebut," tegas Ghufron.
Penulis: Firman Hidranto Redaktur: Ratna Nuraini/Elvira Inda Sari Sumber: Indonesia.go.id
-
 @ 266815e0:6cd408a5
2024-05-09 17:23:28
@ 266815e0:6cd408a5
2024-05-09 17:23:28Lot of people are starting to talk about building a web-of-trust and how nostr can or is already being used as such
We all know about using the kind:3 following lists as a simple WoT that can be used to filter out spam. but as we all know it does not really signal "trust", its mostly just "I find your content interesting"
But what about real "trust"... well its kind of multi-denominational, I could trust that your a good developer or a good journalist but still not trust you enough to invite you over to my house. There are some interesting and clever solutions proposed for quantifying "trust" in a digital sense but I'm not going to get into that here. I want to talk about something that I have not see anyone discuss yet.
How is the web-of-trust maintained? or more precisely how do you expect users to update the digital representation of the "trust" of other users?
Its all well and good to think of how a user would create that "trust" of another user when discovering them for the first time. They would click the "follow" button, or maybe even rate them on a few topics with a 1/5 star system But how will a user remove that trust? how will they update it if things change and they trust them less?
If our goal is to model "trust" in a digital sense then we NEED a way for the data to stay up-to-date and as accurate as possible. otherwise whats the use? If we don't have a friction-less way to update or remove the digital representation of "trust" then we will end up with a WoT that continuously grows and everyone is rated 10/10
In the case of nostr kind:3 following lists. its pretty easy to see how these would get updated. If someone posts something I dislike or I notice I'm getting board of their content. then I just unfollow them. An important part here is that I'm not thinking "I should update my trust score of this user" but instead "I'm no longer interested, I don't want to see this anymore"
But that is probably the easiest "trust" to update. because most of us on social media spend some time curating our feed and we are used to doing it. But what about the more obscure "trust" scores? whats the regular mechanism by which a user would update the "honestly" score of another user?
In the real world its easy, when I stop trusting someone I simply stop associating with them. there isn't any button or switch I need to update. I simply don't talk to them anymore, its friction-less But in the digital realm I would have to remove or update that trust. in other words its an action I need to take instead of an action I'm not doing. and actions take energy.
So how do we reflect something in the digital world that takes no-energy and is almost subconscious in the real world?
TLDR; webs-of-trust are not just about scoring other users once. you must keep the score up-to-date
-
 @ 2fb77d26:c47a6ee1
2024-12-08 21:08:02
@ 2fb77d26:c47a6ee1
2024-12-08 21:08:02****Der Staat geriert sich als Bewahrer von Demokratie und Menschenrechten, als singuläres Modell zur Aufrechterhaltung gesellschaftlicher Ordnung. Dabei haben die Strukturen supranationaler »Global Governance« das Konzept Nationalstaat längst obsolet gemacht. Und auch ein Blick auf das Handeln des Machtapparats Staat lässt begründete Zweifel an dessen öffentlicher Darstellung aufkommen – denn das Kerngeschäft eines jeden Staates besteht aus Unterdrückung, Raub und Mord. **
Mein exklusiver Beitrag für die zweite GEGENDRUCK, die 224 Seiten umfasst, am 15.10.2024 veröffentlicht wurde und unter www.gegendruck.eu bestellt werden kann. Nur durch die Unterstützung von analogen Formaten dieser Art wird aus der Gegenwart eine Vergangenheit, die man in der uns drohenden Zukunft noch zu rekonstruieren vermag. * Original mit Quellen: www.regenauer.press/blog/regieren-ist-ok*
»Wenn das Volk die Regierung fürchtet, haben wir Tyrannei. Wenn die Regierung das Volk fürchtet, haben wir Freiheit« – soll Thomas Jefferson, einer der Gründerväter der USA, dereinst festgehalten haben. Wer sich also in Anbetracht des Status quo noch nicht ganz si-cher ist, mit welchem Herrschaftssystem ihn die kriegslüsterne Biosicherheitsdoktrin der Postmoderne beglückt, mag in Jeffersons Worten entsprechende Inspiration finden. Denn mit Demokratie hat die ohrenbetäubende Kakofonie von Stil-, Rechts- und Sinnbrüchen selbstverständlich nichts zu tun. Die verblassende Pluralismussimulation der zurückliegen-den Dekaden mausert sich zu dem, was mental mobile Staatstheoretiker, Historiker, Philoso-phen, Journalisten und Aktivisten seit langem erwarten – einer offen kriminellen Terrorherr-schaft. Selten war klarer als jetzt: Regieren ist organisierte Kriminalität.
Folgt man Thomas Hobbes und Friedrich Nietzsche, ist der Staat ein »Ungeheuer«. Wäh-rend Hobbes diesen Umstand durchaus goutierte, fand Nietzsche ihn abstoßend. Und zwar zurecht. Denn die repressiven Züge, die das Staatskonzept seit der frühen Neuzeit kenn-zeichnen, sind inhärenter Bestandteil der Politikproduktion. Egal, welche Ideologie ein Staat vertritt, seinen Souveränitätsanspruch kann er nur mit Gewalt durchsetzen. Nach außen mit Krieg, nach innen mit dem auf konstant interpretationsoffener werdenden Gesetzen basieren-den Gewaltmonopol. Im Rahmen seiner Halbwertszeit durchläuft jedes Herrschaftskonstrukt vergleichbare Zyklen. Ist ein Staat gegründet, eine Regierung ausgerufen, institutionalisiert sie das favorisierte politische Modell – Demokratie, Sozialismus, Konservatismus, Libera-lismus, et cetera – und vereinnahmt ihre Untertanen mit Indoktrination, Zugeständnissen und moderater Autonomie. Doch Macht korrumpiert. Und macht gierig. Vor allem in repräsenta-tiven Systemen wie der korporatisierten Sozialdemokratie, wo Einfluss einen monetären Wert darstellt.
Die Folge: Lobbyismus, Korruption, Lagerbildung, Grabenkämpfe und Obszönitäten. Einer Phase relativer Freiheit und Prosperität folgt so bald eine mehr oder weniger harsche »Ent-differenzierung« (Wolfgang Merkel, 2010) – also die Auflösung alter Strukturen, Funktio-nen und Integrationsmechanismen. Die herrschenden »Machteliten« (C. Wright Mills, 1956) grenzen sich nach zwei Seiten ab. Auf der einen von regimetreuen Bewahrern des ursprüng-lichen Konzepts, den Konservativen, auf der anderen von den Gegnern »progressiver« Re-formen. Reformen, von denen zumeist die von wachsender staatlicher Machtfülle benachtei-ligte Bevölkerung betroffen ist. Diese zahlt natürlich auch die Zeche. Rechtsprechung und Medien passen sich diesem zusehends autoritären Umfeld an, um ihre Daseinsberechtigung nicht einzubüßen. Mit dem Implementierungsgrad solcher Reformprojekte aus dem Elfen-beinturm, in der Regel begleitet von ausufernder Bürokratie, wachsen die Widerstände dage-gen. Aus Autokratie wird Totalitarismus. »Erst ist es ein Polizeistaat, dann kommen die Aufstände«. Die »Mistgabeln« (Nick Hanauer, 2014). Aus der Vogelperspektive betrachtet sind es stets die gleichen zivilisatorischen Prozesse. Seit Jahrhunderten. In allen Systemen. Offen ist nur, wie brutal der Staat vorgehen muss, um sich an der Macht zu halten – und wie lange es dauert, bis die Arroganz der wenigen dennoch an der Macht der vielen erstickt.
Denn schlussendlich fällt jedes Imperium. Das lehrt die Geschichte. Hat das System den Zenit überschritten, fällt ob der grotesken Machtexzesse und Schizophrenitäten auch den konformistischsten Etatisten auf, dass die politmediale Schmierenkomödie nichts mehr mit der Realität des eigenen Lebens zu tun hat. Gewalt greift Raum. Psychische Gewalt – und physische. Demnach hat nun zweifelsohne auch der vermeintlich liberale Rechtsstaat der von supranationalen Verordnungen diktierten Gegenwart sein finales Entwicklungsstadium er-reicht: Die Tyrannei.
»Seht uns nur an. Alles ist verdreht, alles steht Kopf. Ärzte zerstören Gesundheit, Anwälte zerstören Gerechtigkeit, Psychiater zerstören Verstand, Wissenschaftler zerstören Wahr-heit, Massenmedien zerstören Information, Religionen zerstören Spiritualität und Regierun-gen zerstören die Freiheit.« (Michael Ellner)
Neu ist das alles nicht. Nur die Darreichungsformen und Machtinstrumente von Herrschaft wandeln sich über die Jahrhunderte. Die disziplinierenden Kontrollmechanismen zur Subor-dination der Massen professionalisieren sich im Rahmen des technologischen Fortschritts. So wirkt der Panoptismus der Postmoderne vor allem deshalb monströs, weil unser Gehirn evolutionär nicht darauf eingestellt ist. Es ist der Militarisierung von Information im Dauer-feuer multimedialer Infantilisierungspropaganda in den wenigsten Fällen gewachsen. Wer versucht, dieser omnipräsenten Pervertierung von Realität mit tradierten Denk- und Hand-lungsmustern zu begegnen, geht unter.
Nicht umsonst klagt der »Widerstand« in weiten Teilen über Erschöpfungszustände, Ver-schleiß, Burnout und Depression. Genau da soll er in Augen des Staatskonzeptes sein – am Ende. Aufgerieben. Entmutigt. Ohnmächtig. Dabei wäre gerade Humor das Patentrezept, um auch düsteren Zeiten ein erfülltes Leben abzugewinnen. Ein freies Leben. Denn frei wird man nicht, frei ist man – oder eben nicht. Freiheit ist eine Geisteshaltung, kein organisatori-sches Problem.
»Unsere Gesellschaft wird von Wahnsinnigen mit wahnsinnigen Zielen geführt. (…) Und ich denke, ich werde als Wahnsinniger eingesperrt, wenn ich das zum Ausdruck bringe. Das ist das Verrückte daran.« (John Lennon)
In diesem Lichte betrachtet nimmt es also kaum Wunder, dass das primäre Ziel der regieren-den Kaste darin besteht, die Bevölkerung in Angst, Armut, Abhängigkeiten und Agonie zu halten. Selbstbestimmte, selbstbewusste Individuen hätten nämlich nicht nur die Zeit, son-dern auch die mentale Kapazität und die Mittel, das Ponzi-Schema des polit-finanziellen Komplexes intellektuell wie organisatorisch zu durchdringen. Dementsprechend ist das Staatskonzept auch nicht darauf ausgelegt, das Individuum zu fördern. Es dient der Imple-mentierung eines konformistischen Kollektivismus. Die Massen sollen sich um die Flagge scharen. Wer kritische Fragen stellt und sich der Polonaise der Gutgläubigen verweigert, gilt als Landesverräter.
Doch nicht nur die vermeintlichen Häretiker sind Opfer staatlicher Willkür und Gewaltherr-schaft. Jeder Bürger stellt per se eine potenzielle Gefahr für die Machthaber dar. Dement-sprechend agiert das »Ungeheuer« Staat. Es führt einen konstanten – mehr oder weniger vernichtenden – Krieg gegen die eigene Bevölkerung. Welche Waffen in diesem Gefecht zum Einsatz kommen, erläutert ein von Wikileaks am 13. Juni 2008 veröffentlichtes Ge-heimdokument der US-Armee vom 20. September 1994. Titel: »Foreign Internal Defense Tactics, Techniques, and Procedures for Special Forces«. Zu Deutsch: Taktiken, Techniken und Verfahren zur internen Verteidigung im Ausland für Spezialeinheiten. Julian Assange nannte es einmal »das wichtigste Dokument, das Wikileaks je veröffentlichte«. Aus gutem Grund. Denn während der Titel des 219 Seiten umfassenden Strategiepapiers darauf abstellt, dass es sich um Arbeitsanweisungen für Spezialeinheiten handelt, die im Ausland operieren, sind die beschriebenen Methoden der asymmetrischen Kriegsführung genau jene, unter de-nen – neben dem Rest der Welt – auch die amerikanische Bevölkerung leidet.
Die US-Armee beschreibt im Detail, wie die verdeckt operierenden Kräfte Regierungen ab-setzen, Oppositionsgruppen infiltrieren, die Bevölkerung manipulieren und Kriege initiieren sollen. Auf Gesetze, Moral oder Kollateralschäden wird dabei keine Rücksicht genommen. Primäres Ziel – koste es, was es wolle – ist die Durchsetzung der Pax Americana im Zielge-biet. Ein paar Zitate verdeutlichen, wie das »Ungeheuer« dabei vorgeht.
»Aufstände sind nicht einfach zufällige politische Gewalt; sie sind gezielte politische Gewalt. Sie erfordern eine Führung, die Vision, Richtung, Anleitung, Koordination und organisato-rische Kohärenz bietet. Die Anführer der Aufständischen müssen ihre Sache dem Volk be-kannt machen und die Unterstützung der Bevölkerung gewinnen. (…) Ihre Ausbildung, ihr Hintergrund, ihre Familie, ihre sozialen Verbindungen und Erfahrungen prägen ihr Den-ken und die Art und Weise, wie sie ihre Ziele erreichen. Diese Faktoren prägen auch ihre Herangehensweise an die Problemlösung.« (S. 13)
»Die Ideologie von Gruppen innerhalb der Bewegung kann auf unterschiedliche Ansichten über strategische Ziele hinweisen. Gruppen können ideologische Konflikte haben, die gelöst werden müssen, bevor ein Gegner daraus Kapital schlagen kann. Die Ideologie kann wahr-scheinliche Ziele und Taktiken nahelegen. Sie beeinflusst stark die Wahrnehmung der Um-gebung durch den Aufständischen. Diese Wahrnehmung der Umgebung wiederum prägt die organisatorischen und operativen Methoden der Bewegung.« (S. 14)
»Wenn eine Situation explosiv ist, kann fast jedes Ereignis als auslösendes Ereignis dienen. Das richtige Timing kann auch in kurzer Zeit eine Flut von Ereignissen hervorrufen, sodass es schwierig ist, ein einzelnes Ereignis als die Handlung zu bezeichnen, die den Kampf aus-gelöst hat. Daher kann es hilfreicher sein, eine Reihe von Handlungen als auslösendes Er-eignis zu betrachten. Auslösende Ereignisse können historisch sein – und die Aufständi-schen erinnern die Bevölkerung an das Ereignis. Diese Technik befreit den Aufständischen davon, auf ein geeignetes Ereignis zu warten.« (S. 18)
»Oft sind es die Armen, die im Krieg kämpfen. CSDF-Programme (CSDF: Civilian Self-Defense Force) bieten der wohlhabenden Klasse die Möglichkeit, direkt und persönlich am Kampf gegen Gesetzlosigkeit und Aufstände beteiligt zu sein. Geschäftsleute und Fachleute beteiligen sich an CSDF aus einem Gefühl der bürgerlichen Pflicht, aus Stolz und aus der Notwendigkeit, ihr Vermögen zu schützen. Ihre aktive Beteiligung verleiht dem Programm Glaubwürdigkeit, stärkt die Legitimität der Regierung und verringert Klassenkonflikte. Wohlhabendes Personal kann bei der Ausstattung seiner Einheiten mithelfen. Es darf ihnen jedoch nicht gestattet sein, den Teilnehmern ein Gehalt zu zahlen.« (S. 128)
»PSYOP-Personal oder in PSYOP ausgebildete SFOD-Mitglieder (SFOD: Special Forces Operational Detachment) erleichtern die Zusammenarbeit zwischen der lokalen Bevölke-rung und dem HN-Militär (HN: Host Nation). Wenn qualifiziertes oder fähiges HN-Personal verfügbar ist, arbeitet das US-Personal durch sie. CSDF-Elemente müssen in der Anwendung von PSYOP geschult werden, um die Bevölkerung über die Vorteile zu informie-ren, die sie durch die Zusammenarbeit mit ihnen erzielen. PSYOP-Themen müssen sich an nationale und/oder fiktive Themen halten, um eine einheitliche Politik darzustellen. Es ist entscheidend, dass PSYOP zunächst an die lokale Bevölkerung gerichtet wird, um ihre Un-terstützung der Aufständischen zu beenden und ihre Akzeptanz und Zusammenarbeit für das CSDF-Programm zu gewinnen. (…) PSYOP kann die Mission unterstützen, indem es die aufständischen Kräfte bei neutralen Gruppen diskreditiert, Zwietracht unter den Auf-ständischen selbst sät und Überläuferprogramme unterstützt. Spaltungsprogramme führen zu Zwietracht, Desorganisation, niedriger Moral, Subversion und Überläufern innerhalb der aufständischen Kräfte. Wichtig sind auch nationale Programme, um Aufständische mit Angeboten von Amnestie und Belohnungen auf die Seite der Regierung zu ziehen. Die Motive für eine Kapitulation können von persönlichen Rivalitäten und Bitterkeit bis hin zu Desillusi-onierung und Entmutigung reichen. Druck seitens der Sicherheitskräfte hat Überzeugungs-kraft. (…) Alle Agenten werden genau beobachtet und diejenigen, die nicht zuverlässig sind, werden abgelöst. Wenige, zielgerichtete, zuverlässige Agenten sind besser und wirtschaftli-cher als viele schlechte. (…) Sicherheitskräfte können Einzelpersonen aus der Bevölkerung dazu bringen, Informanten zu werden. Sicherheitskräfte nutzen verschiedene Motive (Staatsbürgersinn, Patriotismus, Angst, Strafvermeidung, Dankbarkeit, Rache oder Eifer-sucht, finanzielle Belohnungen) als überzeugende Argumente. Sie nutzen die Zusicherung des Schutzes vor Repressalien als Hauptanreiz.« (S. 139, ff)
Zusammengefasst: Die Reichen bezahlen, sorgen für Stimmung und Glaubwürdigkeit, die politische Klasse passt die Vorgehensweise an lokale Strukturen, herrschende Ideologien, Demoskopie und Kommunikationsprozesse an – und die Armen werden zum Sterben an die Front geschickt. Und das sind nur kurze Einblicke in ein über 200 Seiten starkes Handbuch zum Krieg gegen die Zivilbevölkerung, die in Augen des Hegemon offenkundig nichts ande-res als Verfügungsmasse und Kanonenfutter ist. Man möchte Julian Assange beipflichten: Dieses Dokument erklärt nicht nur, warum unsere Gesellschaften, die Wirtschaft und das moralische Koordinatensystem des Homo sapiens in Auflösung begriffen sind – die Skru-pellosigkeit der im Detail beschriebenen Methoden lässt einem das Blut in den Adern gefrie-ren. Selbst nach auszugsweiser Lektüre muss man konstatieren: Nietzsche hatte Recht. Der Staat ist ein eiskaltes Ungeheuer.
Doch was ist der Staat? War es früher das klar erkenntliche Machtvehikel von Monarchen, Imperatoren, Familiendynastien und Klerus, erweckt das Staatskonzept der jüngeren Neuzeit gerne den Eindruck, es hätte sich von dieser Despotie der wenigen gelöst, stünde für sich, auf einem Fundament des Volkswillens, der sich in Verfassungen, Gesetzen und Wahlen widerspiegelt. Weit gefehlt. Auch die »Global Governance« von heute ist nichts anderes als Despotismus. Weithin kontrolliert von den gleichen Bankenkartellen, Familien, Unterneh-men und Organisationen, die seit Generationen den Lauf der Welt bestimmen. Die Regenbo-gen emanierende Pluralismussimulation der Postmoderne verbirgt diesen Umstand nur bes-ser. Sie tyrannisiert indirekt. Köpfe werden nicht mehr abgeschlagen, sondern gewaschen. Exakt so, wie es die angloamerikanischen Vordenker dieses Systems im ausgehenden 19. Jahrhundert insinuierten. Siehe Carroll Quigley, Tragedy and Hope, 1966, Kapitel »The Fu-ture in Perspective«, Seite 1247:
»Das Argument, dass die beiden Parteien entgegengesetzte Ideale und politische Ansichten vertreten sollten, eine vielleicht rechts, die andere links, ist eine törichte Idee, die nur für doktrinäre und akademische Denker akzeptabel ist. Stattdessen sollten die beiden Parteien nahezu identisch sein, sodass das amerikanische Volk die Schurken bei jeder Wahl raus-werfen kann, ohne dass es zu tiefgreifenden oder umfassenden politischen Veränderungen kommt. Die politischen Pläne, die für Amerika lebenswichtig und notwendig sind, sind nicht länger Gegenstand großer Meinungsverschiedenheiten, sondern nur noch in Einzelheiten des Verfahrens, der Priorität oder der Methode umstritten.«
Sodass nach Scheindebatten, Empörungsmanagement und Abstimmungen nicht vom allge-meinen Kurs abgewichen werden muss. Was Quigleys elitäre Zirkel – er war bis zur Veröf-fentlichung von Tragedy and Hope einer von ihnen und unterstützte ihre Ideen – für die Rückführung der 13 US-Kolonien sowie die moderne Expansion des britischen Empire vor-sahen, ist heute zentrales Element der wertewestlichen Fassadendemokratie. Symptombe-sprechung, Lippenbekenntnisse, Emotionsamplituden, »Der Dritte Weg« – »wo soziale Ge-rechtigkeit und Markt miteinander versöhnt werden sollen« – und auch nach der x-ten Wahl bleibt alles beim Alten. Ob Berlin, Brüssel, London, New York, Beirut oder Peking: Ein Potemkin’sches Dorf. Denn wir leben längst in der Idealvorstellung von Benito Mussolini, der den perfekten Faschismus als Korporatismus bezeichnete und als symbiotische Fusion der Macht von Staat und Konzernen verstand. Als »Public Private Partnership«.
»Benito Mussolini hat der modernen Sparpolitik den Weg bereitet und die Arbeiterbewe-gung unterdrückt. Liberale Ökonomen im In- und Ausland bewunderten ihn dafür«, schrieb man bei Jacobin am 6. März 2023. So zeitigt das Staatskonzept dieser Tage die gleichen ver-heerenden Folgen wie die Herrschaftskonstrukte der Vergangenheit. Vertikale Durchlässig-keit begrenzt, das Volk manipuliert, ausgebeutet und gegängelt. Anstelle von Arbeitslagern, Schlägertrupps und Exekutionskommandos machen heute Algorithmen die Drecksarbeit. Sonst hat sich kaum etwas geändert.
Stand heute leben nach Angaben von Oxfam weltweit knapp fünf Milliarden mehr Men-schen in Armut als vor 2020. Das sind die ärmsten 60 Prozent der Menschheit. Zusammen haben sie circa 20 Milliarden US-Dollar verloren. Das Gesamtvermögen der reichsten Deut-schen wuchs im gleichen Zeitraum von 89 auf 155 Milliarden US-Dollar – ein Zuwachs von 73,85 Prozent. Die 148 größten Konzerne der Welt konnten zwischen Juni 2022 und Juni 2023 circa 1,8 Billionen Dollar an Gewinnen verzeichnen – ein Anstieg von 52,5 Prozent gegenüber dem Durchschnitt der Jahre 2018 bis 2021. Der Reingewinn stieg gegenüber die-sem Zeitraum um 20 Prozent auf 700 Milliarden Dollar. Und die fünf reichsten Menschen der Welt haben ihr Vermögen seit 2020 verdoppelt. Wer vom Nachhaltigkeitskorporatismus profitiert, dürfte damit geklärt sein.
Der Normalbürger dagegen kämpft gegen steigende Steuern, Inflation und anziehende Ener-giekosten. In einem luftabschnürenden Korsett von Verträgen, Verpflichtungen und Ver-bindlichkeiten gefangen, bleibt weder Zeit noch Geld für ein Leben in Würde. Der angepass-te Regenbogendemokrat wird geboren, indoktriniert, ausgebeutet und dann bestattet. Indivi-duelle Entfaltung ist in diesem Lebensentwurf von der Stange nicht vorgesehen. Die leitme-dialen Podiumsdiskussionen um Work-Life-Balance, Gendersprache und feministische Au-ßenpolitik klingen in den Ohren der buckelnden Arbeiterklasse – und auch für weite Teilen des schwindenden Mittelstandes – wie blanker Hohn. Das Habitat des Mediazän, das nicht selten den Eindruck erweckt, man lebe in einer fehlerhaft programmierten Simulation, zwingt seinen Bewohner immer häufiger dazu, sich existenziellen Problemen zu stellen: Unterkunft, Nahrung, Fortpflanzung. Überleben.
Noch bezahlt er Jahreslizenzen für Cloud-Software, Netflix für Filme und Streamingdienste für Musik, die er früher erwarb und dann einfach besaß. Noch geht er wählen und entschei-det brav zwischen Pest und Cholera, um vier weitere Jahre nicht die Hoffnung zu verlieren. Noch glaubt, ignoriert oder kommentiert er leidensfähig die intelligenzbeleidigenden Lügen-gebilde, die als Realität vermarktet werden.
Mithin erstaunlich. Denn nicht erst seit der Corona-Krise belegen nackte Zahlen, dass der Mensch in diesem System nicht nur beraubt und unterdrückt, sondern auch als Versuchska-ninchen für den pharmakologisch-finanziellen Komplex missbraucht wird. Nürnberger Ko-dex hin oder her. Während Robert Koch vor der Schaffung dieses vermeintlichen Bollwerks für die körperliche Unversehrtheit noch ungestraft Menschenversuche in seinen kolonialen Konzentrationslagern durchführen durfte, ist das Thema seit Ende des Zweiten Weltkrieges tabu. Gesetzlich eliminiert. Angeblich. Doch bereits in den 1940er Jahren infizierte der US-Gesundheitsdienst Gefängnisinsassen und psychisch kranke Personen mit Syphilis-Erregern. Von 1946 bis 1949 weiteten die USA das Programm auf Guatemala aus und machten sich zusätzlich über Soldaten und Prostituierte her. Das Echo der angelsächsisch geprägten Eugeniklehre hallte im fortgeführten Rassismus nach.
»Schockierende Fälle wie der Tod der 49 Kinder nach Medikamententests in einem indi-schen Krankenhaus sind in der Geschichte der Medizin nichts Neues: In den USA wurde Farbigen zu Studienzwecken von 1932 bis 1972 die Syphilis-Therapie verweigert.« (SZ, Das Verbrechen von Tuskegee, 11. Mai 2010)
Am 20. September 1950 spritzte die US-Marine vor der Küste San Franciscos Mikroben in die Troposphäre, um zu testen, welche Effekte ein Angriff mit Biowaffen auf die damals 800.000 Einwohner der Stadt haben würde. 1953 startete die CIA das MK-Ultra-Programm, in dessen Rahmen abertausenden ahnungsloser Menschen LSD verabreicht wurde. Zwei Jahre später nahm »Project Whitecoat« – Projekt Weißkittel – seine Arbeit auf. Die bestand im Verlauf der folgenden 20 Jahre darin, Menschenversuche mit Hasenpest, Typhus, Gelb-fieber und Milzbrand durchzuführen. Und Ende der 60er testeten die amerikanischen Streit-kräfte Nervengas an den eigenen Soldaten. Der SPIEGEL schrieb diesbezüglich am 10. Juli 2013:
»11. Oktober, 16:25 Uhr, 26 Stunden nach Testbeginn. Kleine blutende Anomalien am lin-ken Bein festgestellt. Subjekt behauptet, es habe seinen Rasierer fallen gelassen und sich dabei ins Bein geschnitten – doch so war es nicht. Er habe seine Sommersprossen damals für Käfer gehalten, sagt Rochelle: »Die krabbelten überall unter meiner Haut herum«. Den Betreuern habe er nichts davon erzählt, es sei ihm peinlich gewesen: »Ich habe meine Ra-sierklinge genommen und versucht, die Käfer aus meiner Haut zu schneiden.« Er war längst nicht mehr selbst dazu in der Lage, die Experimente zu stoppen. Damit war die Ein-verständniserklärung Makulatur. So wie Frank Rochelle ergeht es in Edgewood mehr als 7.800 US-Soldaten; im ganzen Land sind es rund 100.000. Systematisch haben Militär und Geheimdienste die eigenen Leute seit Ende des Ersten Weltkriegs Giften, Gasen, Drogen und Psycho-Kampfstoffen ausgesetzt, darunter LSD, Sarin, Senfgas, BZ, VX, Barbiturate, Amphetamine, Chlorpromazin und immer so weiter. Nachsorgeuntersuchungen? Fehlan-zeige. Erst nach fast sechs Jahrzehnten stoppt das US-Parlament die Menschenversuche im Jahr 1975.«
Ebenfalls bis weit in die 70er hinein injizierte man US-Gefängnisinsassen Pestizide und Herbizide. Mindestens 2.600 Menschen wurden derartigen Versuchen unterzogen. Natürlich musste auch die Atombombe am lebenden Objekt getestet werden. Sowohl Frankreich als auch Großbritannien, die ehemalige Sowjetunion oder die USA schickten Menschen auf die Testgelände. Viele von ihnen segneten danach relativ rasch das Zeitliche. Bis heute kämpfen Bewohner der entsprechenden Landstriche um Entschädigungen, weil sie ihre Krebserkran-kungen der im Umland von Testgebieten gestreuten Strahlung zuschreiben. In den 70ern machte sich der Journalist Paul Jacobs auf eigene Faust daran, die Geschichte der Betroffe-nen zu dokumentieren – um 1978 selbst an Krebs zu sterben. Selbst vor Versuchen an Kin-dern schreckte das »Ungeheuer« nie zurück, wie wiederum der SPIEGEL in Ausgabe 45 vom 2. November 1986 ausführt:
»Dwayne winkte seiner Mutter zu, sie lächelte zurück, dann schloss sich die schwere Eisen-tür hinter dem todkranken Kind. Seit drei Jahren wurde Dwayne Sexton am Strahleninstitut des Atomforschungszentrums Oak Ridge im Bundesstaat Tennessee gegen Leukämie be-handelt. Er hatte eine qualvolle Knochenmark-Transplantation sowie etliche Runden von Chemotherapie hinter sich. Alles war vergeblich geblieben. Als letztes Mittel wollten die Ärz-te nun versuchen, mit massiver Bestrahlung die Krebszellen im Knochenmark des Kindes zu zerstören. Dass diese Methode riskant und – zur damaligen Zeit, 1968 – auch wenig er-probt war, teilten die Ärzte den Eltern des Kindes mit. Was sie aber verschwiegen, war, dass sie auch im Auftrag der amerikanischen Weltraumbehörde NASA arbeiteten. Sie soll-ten herausfinden, wieviel Strahlung Astronauten im All aushalten würden, ohne krank zu werden. Für die von der NASA bestellte Untersuchung erprobten die Ärzte an ihren Patien-ten, so hieß es in einem ihrer Berichte, verschiedene »therapeutische Szenarien, die aus Strahlenmengen im All abgeleitet wurden«. Im Klartext: Nicht allein medizinische Erwä-gungen zum Wohl des Patienten setzten die Höhe der Strahlendosis fest, sondern auch die Bedürfnisse der NASA. In diesem Sinn waren die Patienten lebende Versuchskaninchen.«
Mindestens 23.000 US-Amerikaner wurden von Militäreinrichtungen und Gesundheitsbe-hörden vorsätzlich verstrahlt. Zu Forschungszwecken. »Kalter Krieg gegen US-Bevölkerung« nannte es die taz am 24. Oktober 1994.
»Zwischen 1950 und 1972 finanzierte das Pentagon außerdem fünf klinische Studien über die Aufnahmefähigkeit des menschlichen Körpers von Strahlen, um Aussagen über die psy-chologischen wie biologischen Folgen von Atomexplosionen zu erhalten. Die Versuchsper-sonen waren größtenteils in Armut lebende Schwarze. (…) Bei einem anderen Experiment mussten Soldaten auf Fässern mit radioaktivem Material herumfahren, um zu prüfen, ob ihre Autos sie vor den Strahlen schützten. In Hanford im US-Bundesstaat Washington setz-ten die Militärs absichtlich eine nukleare Wolke frei, um die Verlagerung der Wolke zu un-tersuchen. Aufgrund einer plötzlichen Änderung der Wetterlage fielen die radioaktiven Teil-chen auf einem 300 Kilometer langen und 60 Kilometer breiten Gebiet nieder (…). (jW, 29. August 1997)
Der Umgang mit der indigenen Bevölkerung wirft kein besseres Licht auf die Vereinigten Staaten. Von fünf bis sieben Millionen Ureinwohnern im Jahr 1500 waren im Jahr 1900 noch 237.000 übrig. Ob Hungersnöte, Sklavenarbeit, Massaker, Umsiedlungen oder »Boar-ding Schools« – Umerziehungsinternate: Die aus Großbritannien eingereisten Siedler verüb-ten einen Genozid an den indigenen Stämmen. Nachdem die mageren Reste der stolzen Indi-anervölker in Reservate gepfercht worden waren, suchte der Staat deren Fortpflanzung mit-tels Zwangssterilisation zu verhindern. Mehr als 60.000 Indigene wurden im 20. Jahrhundert einer solch abscheulichen Behandlung unterzogen. Darüber hinaus war das Eugenik-Programm der USA, das erst 1981 endgültig eingestellt wurde, Grundlage für die Rassen-lehre des deutschen NS-Regimes.
Ähnlich ging man in Kanada vor. Seit den 1920er Jahren wurden dort tausende indigene Frauen zwangssterilisiert – bis heute – obwohl die entsprechenden Gesetze mittlerweile ab-geschafft wurden. Die tagesschau vermeldet dazu am 10. März 2024:
»Die Worte des weißen Arztes haben sich Liz (…) ins Gedächtnis gebrannt: »Es ist besser, du stimmst der Abtreibung zu. Denn wir werden dir dieses Baby wegnehmen. So oder so«. Die damals 17-jährige Kanadierin vom indigenen Volk der Anishinabe wagt es nicht, zu widersprechen. Verängstigt sitzt sie Ende der 1970er-Jahre im Behandlungsraum der Indi-an Clinic in der Provinz Ontario, einer Klinik, in der Indigene behandelt werden, damit sie an die sogenannte Zivilisation angepasst werden. (…) Die alleinerziehende Mutter sei nicht in der Lage, für ein weiteres Kind zu sorgen. Der Arzt will ihr deshalb die Eileiter abbinden und sie dadurch sterilisieren. (…) Erst Jahre später wird ihr klar: Sie ist nicht allein. Zehn-tausende indigene Frauen sind in Kanada seit den 1920er-Jahren im Einklang mit der Eu-genik-Gesetzgebung gegen ihren Willen sterilisiert worden. Und obwohl es diese Gesetze nicht mehr gibt, geschieht es bis heute, weiß Senatorin Yvonne Boyer im Kongress in Otta-wa (…). Noch immer ist Zwangssterilisation kein Tatbestand im kanadischen Strafgesetz-buch. (…) Vergangenes Jahr wurde in den Nordwest-Territorien ein Arzt bestraft, weil er 2019 eine Inuit-Frau gegen ihren Willen unfruchtbar gemacht hat. Er verlor seine Lizenz – für fünf Monate.«
Dass sich nicht nur das angloamerikanische Empire für Eugenik begeisterte, zeigt die Ein-richtung des ersten rassenbiologischen Instituts in Schweden im Jahr 1921. Zwischen 1935 und 1976 wurden dort circa 62.000 Menschen zwangssterilisiert. Die offiziellen Begrün-dungen für die Eingriffe reichten von »Mischling« über »Alkoholismus« bis zu »dämlich« und »religiös«. Sprich: Reine Willkür unter dem Deckmantel der Wissenschaft. Legalisiert vom schwedischen Staat.
Heute begegnen uns die staatlich organisierten Eugenik-Programme unter wohlklingenden Labels wie Bioethik, reproduktive Gesundheit, biosoziale Forschung und Bevölkerungspoli-tik. Seit 1954 finden die von den Vereinten Nationen (UN) organisierten Weltbevölkerungs-konferenzen statt. Die letzte im November 2019 in Nairobi (Kenia). Was bei diesen Konfe-renzen besprochen wird, lässt sich anhand eines Artikels des GUARDIAN vom 15. April 2012 oder eines Beitrags von C-Fam (Center for Family and Human Rights) erahnen:
»Großbritannien hat 166 Millionen Pfund (268 Millionen Dollar) für ein Regierungspro-gramm in Indien gespendet, das arme Frauen und Männer zwangssterilisiert. Die britische Hilfsorganisation nannte die Notwendigkeit, dem Klimawandel durch Bevölkerungsreduzie-rung zu begegnen, als Hauptgrund für die Finanzierung des missbräuchlichen indischen Programms (…). Verpfuschte Operationen verursachten Qualen, Blutungen und Todesfäl-le. In einer von der britischen Regierung ins Visier genommenen Region verblutete die 35-jährige Frau eines armen Arbeiters, die mit Zwillingen schwanger war. Einige Frauen, die während der Schwangerschaft sterilisiert wurden, erlitten Fehlgeburten. Einige wurden mit weniger als acht Dollar und einem Sari bestochen, anderen wurde mit dem Verlust ihrer Lebensmittelkarten gedroht. Manchen wurde gesagt, die Operationen dienten der allgemei-nen Gesundheitsfürsorge, und sie erfuhren den wahren Zweck erst zu spät. Kliniken erhiel-ten Prämien für mehr als dreißig Operationen pro Tag. Nichtstaatliche Mitarbeiter wurden für jede Person bezahlt, die sie zu einer Operation überredeten. Ein Chirurg, der in einem Schulgebäude arbeitete, führte in zwei Stunden 53 Operationen durch – ohne qualifiziertes Personal, fließendes Wasser oder Mittel zum Reinigen der Geräte. Berichte der indischen Regierung aus den Jahren 2006 und 2009 warnten vor Problemen mit dem Programm. Dennoch empfahl ein Bericht des britischen Ministeriums für internationale Entwicklung aus dem Jahr 2010 die weitere Unterstützung des Programms mit der Begründung, dass eine Reduzierung der Bevölkerungszahl die Treibhausgase senken würde. (…) Sterilisation ist die häufigste Methode der Familienplanung, die in Phase II des indischen Programms für Reproduktions- und Kindergesundheit eingesetzt wird, das 2005 mit britischer Finanzie-rung begann. Trotz der Enthüllungen im ersten Jahr hat Großbritannien keine Bedingungen an seine Finanzierung geknüpft. (…) Im Juli wird Großbritannien zusammen mit der Bill & Melinda Gates Stiftung einen Familienplanungsgipfel in London ausrichten. Ziel der Veran-staltung ist es, beispielloses politisches Engagement und Ressourcen von Entwicklungslän-dern, Gebern, dem privaten Sektor, der Zivilgesellschaft und anderen Partnern zu generie-ren, um den Familienplanungsbedarf von Frauen in den ärmsten Ländern der Welt bis 2020 zu decken, erklärte das britische Ministerium für internationale Entwicklung. Melinda Gates hielt kürzlich eine Rede, in der sie behauptete, dass die Hilfe bei der Empfängnisver-hütung nichts mit Bevölkerungskontrolle oder Zwangssterilisationsprogrammen zu tun ha-be.« (C-Fam, 2. Mai 2012)
»Familienplanungsbedarf«? Dass solche Programme nichts mit »Bevölkerungskontrolle« zu tun haben, ist eine infame Lüge. Schon die von Julian Huxley verfasste Grundsatzschrift der UNESCO von 1946 spricht davon, dass Eugenik wieder salonfähig gemacht werden muss. »Das Undenkbare wenigstens wieder denkbar machen«, nannte Huxley es damals. So muss auch die ungezügelte Massenmigration als Waffe im mittlerweile allgegenwärtigen Kampf der Kulturen verstanden werden. Dabei ist allerdings nicht die Migration selbst das Problem – denn auch die Migranten sind Opfer dieser Agenda – sondern der jeweilige Auslöser für diese Zuwanderungsströme. Die verarmten, verzweifelten, traumatisierten, mit falschen Ver-sprechungen gelockten und als Spaltpilz missbrauchten Menschen für die Symptome des wertwestlichen Neokolonialismus verantwortlich zu machen, greift zu kurz.
Die chaotischen Zustände auf deutschen, britischen, schwedischen und französischen Stra-ßen sind kein Zufall, sondern gewollt. Das belegt ein Strategiepapier der Vereinten Nationen, das am 21. März 2000 publiziert wurde. Titel des Dokuments: »Replacement Migration: Is it A Solution to Declining and Ageing Populations?« Übersetzt: »Ersatzmigration: Ist sie eine Lösung für schrumpfende und alternde Bevölkerungen?«. Auf 177 Seiten erläutert die Stu-die, wie Frankreich, Großbritannien, Deutschland, Italien, Japan oder Russland zurückge-hende Geburtenraten durch massenhafte Zuwanderung kompensieren sollen. Auf den Seiten 32 und 33 liest man diesbezüglich:
»Abbildung 1 zeigt einen standardisierten Vergleich der Zuwanderungsströme pro Million Einwohner (Stand: 2000). Aus diesem Vergleich geht hervor, dass im Verhältnis zur Lan-desgröße die Zahl der Einwanderer, die im Zeitraum 2000-2050 pro Jahr benötigt wird, um den Bestand der Bevölkerung im erwerbsfähigen Alter zu erhalten (Szenario IV), mit 6.500 Einwanderern auf eine Million Einwohner in Italien am höchsten ist, gefolgt von Deutschland mit 6.000 Einwanderern pro Jahr auf eine Million Einwohner. Von den in die-sem Bericht untersuchten Ländern und Regionen benötigten die Vereinigten Staaten mit et-wa 1.300 Einwanderern auf eine Million Einwohner die geringste Zahl von Einwanderern, um einen Rückgang ihrer Bevölkerung im erwerbsfähigen Alter zu verhindern.«
»Die Zahl der Einwanderer, die notwendig ist, um ein Schrumpfen der Bevölkerung im er-werbsfähigen Alter auszugleichen, übersteigt diejenige, die einen Rückgang der Gesamtbe-völkerung ausgleichen würde, um ein Erhebliches. Ob solche höheren Einwanderungszah-len zu den Optionen gehören, die den Regierungen zur Verfügung stehen, hängt zum großen Teil von den sozialen, wirtschaftlichen und politischen Verhältnissen des jeweiligen Landes beziehungsweise der jeweiligen Region ab.«
Wer also annimmt, dass die Destabilisierungskriege und Raubzüge der NATO-Hegemonie nur dem Zwecke dienten, missliebige Regierungen auszutauschen und der Rohstoffe eines Landes habhaft zu werden, liegt offenkundig falsch. Wenn das wertewestliche Imperium irgendwo Demokratie abwirft, hat es dabei auch die strategischen Ziele globaler Bevölke-rungskontrolle im Blick. Migration als Waffe – gerichtet gegen beide involvierten Parteien. Demnach kann man sich nur wünschen, dass die Gewaltausbrüche zwischen einheimischer Bevölkerung und Migranten in den verschiedenen EU-Ländern rasch ein Ende nehmen und sich die von Verzweiflung herrührende Wut beider Parteien auf das eigentliche Problem fo-kussiert: Die herrschende Kaste und ihr gesichtsloses Imperium supranationaler Organisati-onen.
Wahrlich – die Liste an staatlich organisierten, legitimierten, orchestrierten und geduldeten Gräueltaten ließe sich beliebig lange fortführen. Je nachdem, wie weit man zurückzublicken gedenkt. Viele dieser Verbrechen sind Teil der offiziellen Geschichtsschreibung. Jeder weiß es. Dennoch führt dieses Wissen um die Skrupellosigkeit eines im Kern faschistoiden Sys-tems erstaunlicherweise bis heute nicht dazu, dass sich die Menschheit auf andere Formen des Zusammenlebens, der Verwaltung und Organisation einigt. Noch immer sehnen sich die Massen nach Führung, zentraler Steuerung und Ikonen, die ihnen ein besseres Leben ver-sprechen. Dabei belegt die Zivilisationsgeschichte mehr als eindrücklich, dass es sich um leere Versprechen handelt, dass die Hoffnung auf den edlen Ritter, die rettende Wahl oder eine bessere Zukunft reine Illusion ist. Der Machtapparat Staat dient nur einem einzigen Zweck – dem Erhalt des Machtapparats.
Es bedarf demnach auch keiner Diskussion um marginale Optimierungen des herrschenden Systems. Denn wer nur Symptome behandelt, wird die Ursache der Krankheit nicht eliminie-ren. Es bedarf der konstruktiven Debatte darüber, wie dieses System in Gänze zu ersetzen ist.
Dabei gilt es, eigene Narrative zu entwickeln. Geschichten. Vorstellungen von einer freiheit-lich organisierten Zukunft. Von einem lebenswerten morgen. Für eine Zeit nach dem »Un-geheuer«. Wir brauchen Ideen, von denen wir nachfolgende Generationen begeistern kön-nen. Und damit ist nicht die technische Verbesserung des Smartphones oder eine neue App gemeint, sondern eine Utopie. Denn gegen etwas zu sein, ist einfach. Für etwas zu sein, da-gegen nicht.
So engagieren wir uns längst nicht mehr nur für den Erhalt der Meinungsfreiheit, sondern für die Bewahrung des freien Willens. Denn was im Namen des Staates – »im Namen des Volkes« – und damit im Namen jener Menschen, die den Staat durch Wahl oder Duldung legitimieren, geschah, geschieht und geschehen wird, kann kein emotional gesundes Mitglied unserer Spezies wirklich wollen.
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ a012dc82:6458a70d
2024-12-11 08:02:59
@ a012dc82:6458a70d
2024-12-11 08:02:59Table Of Content
-
From the Backbench to the Forefront
-
Milei's Bitcoin Connection
-
The Coinx Controversy
-
Argentina's Financial Quagmire
-
Conclusion
-
FAQ
Well, folks, it seems like the winds of change are blowing in Argentina! In a twist that no one saw coming, Javier Milei, the presidential candidate with a penchant for Bitcoin and libertarian economics, clinched the top spot in Argentina's primary. This victory sent shockwaves throughout the nation. Milei and his gang, the La Libertad Avanza (or "Liberty Advances"), managed to snag a whopping 30% of the votes. They beat the second-place contender, Juntos Por El Cambio, by just under 2%, which is quite the feat!
From the Backbench to the Forefront
La Libertad Avanza, founded just a couple of years ago in 2021, was once the little guy in the political arena. In their first legislative elections, they made waves, becoming the third most-voted coalition in Buenos Aires. But this recent victory? It's monumental! It's like David taking on Goliath and emerging victorious. Milei's rise has certainly turned heads and raised eyebrows in the political sphere, making everyone wonder what's next.
Milei's Bitcoin Connection
Javier Milei is not your run-of-the-mill political candidate. He's carved out a unique niche for himself in the world of politics, largely due to his vocal support for cryptocurrencies, especially Bitcoin. When you tune into talk shows and interviews, you'll often find Milei passionately discussing the potential of digital currencies. He doesn't just see them as another financial instrument; to him, they represent a return to a time when the power of money was firmly rooted in the hands of the people, free from excessive governmental control.
His views on Bitcoin go beyond mere admiration. Milei perceives it as a revolutionary tool, one that can challenge traditional financial systems. He often contrasts the decentralized nature of cryptocurrencies with the centralized control of traditional fiat currencies. In his eyes, Bitcoin and its peers are not just alternatives but superior forms of money. He's even made bold claims, suggesting that in many ways, cryptocurrencies are safer investments than traditional precious metals like gold or silver. This is a significant statement, especially in a country like Argentina, where people have historically turned to gold as a hedge against economic instability.
However, as with any public figure with strong opinions, Milei's crypto enthusiasm has its fair share of critics. While he paints a rosy picture of a crypto-driven future, there are those who question his motives and the feasibility of his vision. The crypto world, as many know, is not without its pitfalls. From volatile market swings to regulatory challenges, the journey to mainstream acceptance is fraught with challenges. And Milei's connection to this world has put him under the microscope, with every statement and action being dissected and debated.
The Coinx Controversy
Rumor has it that Milei promoted a Ponzi scheme called Coinx, which allegedly swindled a cool $800,000 in Argentine pesos. Milei, of course, denies any wrongdoing. He even compared their business model to that of a bank. The only difference? They can offer higher interest rates because they're not tied down by the central bank. But not everyone's buying it. Manuel Ferrari, a big shot in the Bitcoin Argentina NGO, remains wary of Milei. This controversy adds another layer to the complex narrative surrounding Milei's rise.
Argentina's Financial Quagmire
Argentina's economic waters are turbulent, to say the least. With a dizzying inflation rate of 135% this year, the peso's value is plummeting, causing widespread distress. Amidst this chaos, many are pinning their hopes on Javier Milei, a figure who has emerged with a pro-Bitcoin stance that's causing quite the stir. Drawing parallels with El Salvador's audacious move to adopt Bitcoin, there's a buzz about whether Argentina might follow suit. But is Milei the savior Argentina has been waiting for? While his support for cryptocurrencies offers a glimmer of hope to some, it also brings with it skepticism and apprehension. The world of crypto, though promising, is still uncharted territory, especially for an economy as volatile as Argentina's.
As debates rage on, it's evident that Argentina stands at a crucial financial juncture. Milei's advocacy for Bitcoin and other cryptocurrencies suggests a potential shift in the country's financial paradigm. But diving into the crypto realm isn't without its risks, and there's a looming question: Are we witnessing the dawn of a new financial era for Argentina, or is it just a leap from the frying pan into the fire? The nation watches with bated breath, waiting to see the path Milei might pave.
Conclusion
Only time will truly reveal the impact of Milei's influence on Argentina's financial future. It's a waiting game now, folks. But if there's one thing we can bank on, it's that with Milei stirring the pot, Argentina's economic and financial landscape is poised for some dramatic shifts. The rollercoaster has just begun, so everyone better buckle up and brace themselves. Keep your eyes peeled and ears to the ground, because the upcoming months promise a whirlwind of changes, debates, and transformations for Argentina. The nation stands at a pivotal juncture, and the world watches with bated breath.
FAQ
Who is Javier Milei? Javier Milei is a presidential candidate in Argentina known for his support of Bitcoin and libertarian economics.
What is La Libertad Avanza? La Libertad Avanza, translated as "Liberty Advances," is the political coalition led by Javier Milei.
How did Milei fare in the recent primaries? Milei clinched the top spot in Argentina's primary, securing over 30% of the votes.
What is the Coinx controversy? Coinx is an alleged Ponzi scheme that Milei is rumored to have promoted. However, Milei denies any wrongdoing.
What is Milei's stance on Bitcoin? Milei is a strong advocate for Bitcoin, viewing it as a return to private sector-controlled money and a safer alternative to traditional assets like gold or silver.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
*DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research. *
-
-
 @ 349d6b82:12b2a5b1
2024-12-11 07:15:39
@ 349d6b82:12b2a5b1
2024-12-11 07:15:39Утром 11 декабря произошло необычное событие, которое привлекло внимание местных жителей и нашу редакцию. 32-летний местный житель Серова Петр Дибонеев, который стал свидетелем и участником спасательной операции на реке Тура.
По словам спасателя - Утром, во время пробежки вдоль реки, Петр заметил, что человек тонет. Не раздумывая, он бросился в воду и смог вытащить утопающего, который оказался 25-летним студентом - Николай Астрахонский - из соседнего города - Нижний Тагил. Благодаря быстрой реакции Петра, пострадавший был спасен и доставлен в больницу с легкими переохлаждениями.
"Когда я увидел человека, который тонет, у меня не было времени на раздумья. Я просто инстинктивно бросился в воду. В такие моменты ты не думаешь о себе, а лишь о том, как помочь другому. Я рад, что смог спасти его и что он сейчас в безопасности. Это не только моя заслуга — я уверен, что каждый из нас готов прийти на помощь в трудную минуту" - высказался по этому поводу Петр Дибонеев.
Это событие вызвало широкий резонанс в городе. Местные жители организовали акцию благодарности Петру, где он получил грамоту от администрации города за мужество и самоотверженность. А в социальных сетях начали распространяться посты с хештегом #ГеройСерова, где люди делятся своими историями о смелых поступках.
И также мэр города, Ольга Петрова, отметила: "Петр — настоящий герой. Его поступок вдохновляет нас всех. Мы должны помнить о важности взаимопомощи и поддержки друг друга в трудные времена".
Такие события напоминает нам о том, что каждый из нас может стать героем в нужный момент. Петр Дибонеев стал символом мужества и готовности прийти на помощь, что должно вдохновлять на добрые дела и активное участие в жизни сообщества.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 79d783e8:3b888a6d
2024-12-11 05:33:08
@ 79d783e8:3b888a6d
2024-12-11 05:33:08The "Netflix Hypothesis" is a name which is intended to illustrate one of the simple mechanisms through which our attention spans have been reduced, our anxiety spiked and our wallets drained. I cannot take full credit for the name, and will give due credit to my close friend in the book surrounding this topic which I am busy working on.
The purpose of this read is to pose that inflation itself has had a profoundly negative impact on the nature of society and our brains. It differs from the general narrative, because yes it touches on inflation's impact on our time preference, but it also discusses the global phenomenon of "Brain-rot" affecting not only my generation, but all of those alive today.
Although the name suggests it, this essay is not focused specifically on Netflix, but rather most of the highly successful companies that operate and thrive today in an inflationary environment. I also would like to add that I am not explicitly and corporatist; I am a staunch anarcho-capitalist. I have contempt for the effects for what these companies have done over the past four decades, however, I view this more from the perspective that they were doing what they could to be successful in an inflationary environment, caused by the US, and other governments globally.
If you have a melting ice cube, would you continue holding it, or rather put it to use to cool down your drink? As, I can assume that the majority of those that will read this are already Bitcoiners, I don't particularly need to explain inflation, but I use the ice cube analogy to highlight the change in time preference. We are more likely to spend our money immediately, rather than saving it and putting it to better use later (hence why I love the term "cold storage" to refer to certain bitcoin wallets).
This phenomenon of spending, rather than saving, means that our natural endless consumption cycle accelerates. In order for companies to be successful in an environment like that benefit from producing cheap, quick and easy solutions as places where we can shove our money. Netflix is one such example, in that the TV industry once produced pilot episodes to gauge interest in any series, but Netflix began the trend of paying to produce a whole season at once, releasing the whole season immediately, instead of taking time with production and staggering the release to one episode per week. This means that the viewer is a lot more likely to watch an entire show in one, or two sittings, regardless of whether it is high quality or not; if they didn't do this, most viewer would likely forget about most of the shows that Netflix pumps out, because frankly most of them are mildly entertaining at best.
The same phenomenon is observed in the fashion industry, with the bulk of the world's population today wearing fast fashion clothing made from low-grade materials in third-world nations under near slave-labour conditions. Companies like Stein, H&M, Cotton:on, Zara and the like, produce clothes that you might wear only once, or at best for a year before they begin to fall apart. This is contrasted to the trades of tailors, seamstresses, cobblers and the like, who would once produce high quality garb which would last for years, and provide mending services in case of damage. Fast fashion has by now been discussed at length by many people, but no campaigns to end it have borne any fruit - because simply, it's fast, easy and convenient.
-
 @ 32e18276:5c68e245
2023-12-06 15:29:43
@ 32e18276:5c68e245
2023-12-06 15:29:43I’m going to be on an ordinals panels as one of the people who is counter arguing the claim that they are good for bitcoin. I decided to brush up on the technicals on how inscriptions work. I am starting to see luke’s perspective on how it is exploiting a loophole in bitcoin’s anti-data-spam mechanisms.
Storing data in Bitcoin, the “standard” way
The standard way you add “data” to bitcoin is by calling the OP_RETURN opcode. Bitcoin devs noticed that people were storing data (like the bitcoin whitepaper) in the utxo set via large multisig transactions. The problem with this is that this set is unprunable and could grow over time. OP_RETURN outputs on the other-hand are provably prunable and don’t add to utxo bloat.
Here’s an excerpt from the march 2014 0.9.0 release notes that talks about this:
On OP_RETURN: There was been some confusion and misunderstanding in the community, regarding the OP_RETURN feature in 0.9 and data in the blockchain. This change is not an endorsement of storing data in the blockchain. The OP_RETURN change creates a provably-prunable output, to avoid data storage schemes – some of which were already deployed – that were storing arbitrary data such as images as forever-unspendable TX outputs, bloating bitcoin’s UTXO database. Storing arbitrary data in the blockchain is still a bad idea; it is less costly and far more efficient to store non-currency data elsewhere.
Much of the work on bitcoin core has been focused on making sure the system continues to function in a decentralized way for its intended purpose in the presence of people trying to abuse it for things like storing data. Bitcoin core has always discouraged this, as it is not designed for storage of images and data, it is meant for moving digital coins around in cyberspace.
To help incentive-align people to not do stupid things, OP_RETURN transactions were not made non-standard, so that they are relayable by peers and miners, but with the caveat:
- They can only push 40 bytes (later increased to 80,83, I’m guessing to support larger root merkle hashes since that is the only sane usecase for op_return)
Bitcoin also added an option called -datacarriersize which limits the total number of bytes from these outputs that you will relay or mine.
Why inscriptions are technically an exploit
Inscriptions get around the datacarriersize limit by disguising data as bitcoin script program data via OP_PUSH inside OP_IF blocks. Ordinals do not use OP_RETURN and are not subjected to datacarriersize limits, so noderunners and miners currently have limited control over the total size of this data that they wish to relay and include in blocks. Luke’s fork of bitcoin-core has some options to fight this spam, so hopefully we will see this in core sometime soon as well.
Inscriptions are also taking advantage of features in segwit v1 (witness discount) and v2/taproot (no arbitrary script size limit). Each of these features have interesting and well-justified reasons why they were introduced.
The purpose of the witness discount was to make it cheaper to spend many outputs which helps the reduction of the utxo set size. Inscriptions took advantage of this discount to store monke jpegs disguised as bitcoin scripts. Remember, bitcoin is not for storing data, so anytime bitcoin-devs accidentally make it cheap and easy to relay data then this should be viewed as an exploit. Expect it to be fixed, or at least provide tools to noderunners for fighting this spam.
Where do we go from here
The interesting part of this story is that people seem to attach value to images stored on the bitcoin blockchain, and they are willing to pay the fee to get it in the block, so non-ideologic miners and people who don’t care about the health and decentralization of bitcoin are happy to pay or collect the fee and move on.
Data should not get a discount, people should pay full price if they want to store data. They should just use op_return and hashes like opentimestamps or any other reasonable protocol storing data in bitcoin.
After going through this analysis I’ve come to the opinion that this is a pretty bad data-spam exploit and bitcoin devs should be working on solutions. Ideological devs like luke who actually care about the health and decentralization of the network are and I’m glad to see it.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ de496884:72617b81
2023-11-20 13:54:02
@ de496884:72617b81
2023-11-20 13:54:02Hola nostriches. Hoy quiero hacer una publicación a modo de acercamiento al surgimiento de las categorías de género y feminismo. Así que si te interesa el tema haz un esfuerzo, quédate y lee hasta el final.
El «nuevo» feminismo surge en los años 60 en aquellos países desarrollados que acordaron el reconocimiento a los derechos humanos contenidos en la declaración respectiva de la ONU. Entonces, como extensión a dicho reconocimiento es que se gesta el movimiento feminista. A partir de entonces, se vuelve a plantear la relación entre naturaleza y cultura y se llega a la conclusión de que las diferencias sociales van más allá de las diferencias biológicas, lo cual tiene que ver con que hasta la satisfacción de las necesidades elementales como son la alimentación, la vivienda o el vestuario, están condicionadas por construcciones sociales.
Pues resulta que una de las primeras propuestas identificó la subordinación femenina producto de una organización patriarcal, tomando la categoría patriarcado de Max Weber. Es así como la visión de patriarcado se extendió al discurso político y académico. Sin embargo, no existía información acerca del desarrollo histórico de dicha categoría, sistematización, variaciones, etc., debido a que era algo que recién se percibía en sociedad.
Sin embargo, la misma categoría de patriarcado junto a la de relaciones de poder para explicar fenómenos sociales contemporáneos, constituye uno de los principales aportes del feminismo. Es así como han logrado primero visibilizar y luego deconstruir y desmontar una serie de patrones existentes en la cultura que hacían a la mujer subordinarse al hombre, y que estaban presentes en el sistema sexo/género.
 Imagen relativa a la lucha contra el patriarcado
Imagen relativa a la lucha contra el patriarcadoHasta ese momento, en las investigaciones de corte sociológico se podía observar un androcentrismo excesivo al dar cuenta de que el discurso científico giraba en torno al hombre como sujeto y objeto de la investigación. Incluso para muchos positivistas como el mismo Weber, los problemas relativos a las mujeres quedaban en un segundo plano y eran achacados a una supuesta pasividad en el ámbito doméstico-familiar. Dicha pasividad partía de la supuesta inferioridad biológica del género femenino.
El patriarcado entonces era una categoría vacía en sí misma, sin valor explicativo. Desde el punto de vista político pudo ser útil para la movilización pero no resistió la polémica de los críticos del feminismo ni problematizó los conflictos a ser resueltos. Pero por otro lado, un grupo de mujeres -académicas principalmente- se puso manos a la obra en una tarea más pequeña pero con mayores resultados a la larga. Se propusieron generar conocimientos sobre las condiciones de vida de la mujer, buscar en el pasado y el presente los aportes de las mujeres a la sociedad, hacerlas visibles en la historia. Es así como surgen centros académicos, ONG, proyectos, centros de estudios sobre la mujer, etc.
Convendría distinguir entonces dos posturas que acompañaron a la investigación sobre las mujeres: uno que toma como objeto de estudio a la mujer; condiciones de vida, trabajo, cultura, y otra que privilegia a la sociedad como generadora de la subordinación de las mujeres. Mientras la primera perspectiva generaba conocimiento sobre las mujeres en el estudio de las relaciones mujer-hombre y mujer-mujer, la segunda tenía una visión más holística ya que planteaba que hay que estudiar la sociedad ya que la subordinación de las mujeres es producto de la organización de esta, y que no se avanzará solamente estudiando a las mujeres, pues el estudio debe ser más amplio y en diferentes niveles, ámbitos y tiempos.
Es en esta búsqueda donde nace y se desarrolla el concepto de género como categoría social. Es así que los sistemas de género/sexo fueron entendidos como conjuntos de prácticas, símbolos, representaciones, normas y valores sociales que las sociedades construyen a partir de la diferencia anatomofisiológica y que dotan de sentido a los impulsos sexuales, la reproducción y en general a las relaciones de las personas. Por tanto, este sistema pasó a ser el objeto de estudio para comprender la subordinación de la mujer al hombre. Al ser el reconocimiento de una dimensión de la desigualdad social hasta entonces desconocida, se considera la ruptura epistemológica más importante de la segunda mitad del siglo pasado.
 Imagen representativa del binarismo de género
Imagen representativa del binarismo de géneroHay que decir que los fenómenos sociales se definen por la relación que guardan entre sí. Es así que la contextualización adquiere gran importancia. Varones y hembras tenemos la capacidad de producir con el cuerpo, pero solo los cuerpos de las hembras pueden gestar y por tanto asegurar la especie humana. Todo grupo humano que pretenda sobrevivir debe asegurarse cierto número de hembras que lo hagan posible. De ahí un poder particular del cuerpo de las hembras que además es económicamente útil. Dicho poder no es en tanto entidad biológica, sino que es la sociedad la que le otorga este poder. En este punto es importante preguntarnos históricamente ¿quiénes han controlado la capacidad reproductiva de las mujeres?, ¿quiénes han tenido la preferencia en el acceso sexual? Para asegurar un control efectivo sobre la reproducción es necesario asegurar el acceso a la sexualidad.
Ello también lleva a dirigir el trabajo que hacen porque de lo contrario, las mujeres pudieran tener espacio para representar una amenaza al dominio de los hombres. Es importante atender a las etapas del desarrollo de las mujeres, que permitirá ver cómo se moldean para aceptar la desigualdad y las jerarquías según el género en las distintas sociedades y culturas.
Otro contexto a delimitar es el ámbito doméstico donde históricamente ha estado ubicada la subordinación femenina. Se ha puesto al descubierto que en mujeres que comparten la misma posición de clase y raza, la condición femenina se redefine a lo largo de la vida y que algunas mujeres gozan de poder sobre otras aún en contextos de alta dominación masculina, donde se les inviste de autoridad, creando el sistema zonas de incertidumbre que las divide como género e impide alianzas y se legitima la dominación. Foucault decía que «el poder se ejerce, no se posee», siempre está en peligro de perderse y no basta con normas, leyes, amenazas o castigos. De ahí que los espacios de subordinación sean también espacios de poder de las mujeres. Es en estos espacios donde aparece la inseguridad, la tensión, la confrontación y por ejemplo, las mujeres pueden reclamar la anticoncepción.
Para terminar, es importante tener en cuenta que el género es una forma de desigualdad social que siempre está articulado con otras formas de desigualdad ya sea clase, raza, grupo etario, etc. Hay que pensar la dominación masculina con un comienzo vago en el tiempo, pero que permite desligar la subordinación de las mujeres de la evolución «natural» de la humanidad y entenderla como un proceso histórico. En ese sentido es necesario destacar que, respecto a la raza, en sociedades plurales hay que atender al contexto étnico-cultural ya que en dependencia de las relaciones entre personas de razas distintas, estarán condicionadas las relaciones entre los géneros.
 Imagen de mujeres de distintas razas
Imagen de mujeres de distintas razasPor otro lado, si bien es sabido que históricamente el sistema de género social imperante ha contribuido a invisibilizar a la mujer, asociar necesariamente dicha categoría únicamente a ella, lo que hace es nuevamente recrear el absolutismo histórico que tanto daño ha hecho, ahora como lo antagónico al hombre. En la construcción social participan todos los individuos presentes en el sistema género.
Hasta aquí la publicación de hoy, de la cual aun se puede ahondar mucho más, sobre todo en lo referido al origen de la dominación o de la jerarquización del binomio «hombre/mujer» desde un punto de vista antropológico, pero eso quedará pendiente para otro momento. ¡Así que hasta la próxima!, ¡nos vemos en Nostr!
........................................
English version
Hello nostriches. Today I want to make a post by way of an approach to the emergence of the categories of gender and feminism. So if you are interested in the topic make an effort, stay and read to the end.
The "new" feminism emerged in the 60's in those developed countries that agreed to recognize the human rights contained in the respective UN declaration. Then, as an extension of that recognition, the feminist movement was born. From then on, the relationship between nature and culture was raised again and the conclusion was reached that social differences go beyond biological differences, which has to do with the fact that even the satisfaction of elementary needs such as food, housing or clothing are conditioned by social constructions.
It turns out that one of the first proposals identified female subordination as a product of a patriarchal organization, taking Max Weber's category of patriarchy. This is how the vision of patriarchy was extended to political and academic discourse. However, there was no information about the historical development of this category, systematization, variations, etc., because it was something that was only recently perceived in society.
However, the same category of patriarchy, together with that of power relations to explain contemporary social phenomena, constitutes one of the main contributions of feminism. This is how they have first made visible and then deconstructed and dismantled a series of existing patterns in the culture that made women subordinate to men, and that were present in the sex/gender system.
 Image relating to the fight against patriarchy
Image relating to the fight against patriarchyUp to that time, in sociological research, an excessive androcentrism could be observed as scientific discourse revolved around men as the subject and object of research. Even for many positivists such as Weber himself, the problems related to women remained in the background and were blamed on a supposed passivity in the domestic-family sphere. This passivity was based on the supposed biological inferiority of the female gender.
Patriarchy was then an empty category in itself, with no explanatory value. From the political point of view, it could be useful for mobilization, but it did not resist the polemic of feminism's critics, nor did it problematize the conflicts to be resolved. But on the other hand, a group of women - mainly academics - set to work on a smaller task but with greater results in the long run. They set out to generate knowledge about women's living conditions, to search in the past and present for women's contributions to society, to make them visible in history. This is how academic centers, NGOs, projects, women's studies centers, etc., came into being.
It would be convenient to distinguish then two postures that accompanied the research on women: one that takes women as the object of study; living conditions, work, culture, and the other that privileges society as the generator of women's subordination. While the first perspective generated knowledge about women in the study of woman-man and woman-woman relations, the second had a more holistic vision, since it proposed that society must be studied, since the subordination of women is a product of its organization, and that progress will not be made only by studying women, since the study must be broader and at different levels, spheres and times.
It is in this search that the concept of gender as a social category was born and developed. Thus, gender/sex systems were understood as a set of practices, symbols, representations, norms and social values that societies construct on the basis of anatomophysiological differences and that give meaning to sexual impulses, reproduction and, in general, to people's relationships. Therefore, this system became the object of study to understand the subordination of women to men. As the recognition of a hitherto unknown dimension of social inequality, it is considered the most important epistemological breakthrough of the second half of the last century.
 Representative image of gender binarism
Representative image of gender binarismIt must be said that social phenomena are defined by their relationship with each other. Thus, contextualization acquires great importance. Males and females have the capacity to produce with their bodies, but only the bodies of females can gestate and therefore ensure the human species. Any human group that intends to survive must ensure a certain number of females to make it possible. Hence a particular power of the female body, which is also economically useful. This power is not as a biological entity, but it is society that gives it this power. At this point it is important to ask ourselves historically, who has controlled the reproductive capacity of women, who has had the preference in sexual access? To ensure effective control over reproduction, it is necessary to ensure access to sexuality.
 Allegorical image of pregnancy
Allegorical image of pregnancyThis also leads to directing the work they do because otherwise, women may have room to pose a threat to men's dominance. It is important to pay attention to the stages of women's development, which will allow us to see how they are shaped to accept inequality and gender hierarchies in different societies and cultures.
Another context to delimit is the domestic sphere where female subordination has historically been located. It has been discovered that in women who share the same class and race position, the feminine condition is redefined throughout life and that some women enjoy power over others even in contexts of high male domination, where they are invested with authority, creating the system of uncertainty zones that divide them as a gender and prevent alliances and legitimize domination. Foucault said that "power is exercised, not possessed", it is always in danger of being lost and norms, laws, threats or punishments are not enough. Hence, the spaces of subordination are also spaces of women's power. It is in these spaces where insecurity, tension, confrontation appear and where, for example, women can demand contraception.
To conclude, it is important to keep in mind that gender is a form of social inequality that is always articulated with other forms of inequality, be it class, race, age group, etc. It is necessary to think of male domination with a vague beginning in time, but which allows us to separate the subordination of women from the "natural" evolution of humanity and to understand it as a historical process. In this sense, it is necessary to emphasize that, with respect to race, in plural societies it is necessary to pay attention to the ethno-cultural context since, depending on the relations between people of different races, the relations between genders will be conditioned.
 Image of women of different races
Image of women of different racesOn the other hand, although it is known that historically the prevailing social gender system has contributed to make women invisible, to necessarily associate this category only to women is to recreate the historical absolutism that has done so much damage, this time as antagonistic to men. All individuals present in the gender system participate in the social construction.
So much for today's publication, of which we can still go much deeper, especially with regard to the origin of domination or the hierarchization of the binomial "man/woman" from an anthropological point of view, but that will be left for another time. So until next time, see you in Nostr!

Créditos | Credits
Bibliografía consultada | Consulted bibliography:
-
Barbieri, T. (1993). Sobre la categoría género. Una introducción teórico-metodológica. Debates en Sociología. (18). 1-19. https://doi.org/10.18800/debatesensociologia.199301.006
-
Echevarría, D. (2020). Desigualdades de género e interseccionalidad. Análisis del contexto cubano 2008-2018. Facultad Latinoamericana de Ciencias Sociales (Programa-Cuba). https://www.clacso.org.ar/libreria-latinoamericana-cm/libro_detalle_resultado.php?id_libro=2346&campo=cm&texto=248
Traducción | Translation:
DeepL
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ a95c6243:d345522c
2024-12-06 18:21:15
@ a95c6243:d345522c
2024-12-06 18:21:15Die Ungerechtigkeit ist uns nur in dem Falle angenehm,\ dass wir Vorteile aus ihr ziehen;\ in jedem andern hegt man den Wunsch,\ dass der Unschuldige in Schutz genommen werde.\ Jean-Jacques Rousseau
Politiker beteuern jederzeit, nur das Beste für die Bevölkerung zu wollen – nicht von ihr. Auch die zahlreichen unsäglichen «Corona-Maßnahmen» waren angeblich zu unserem Schutz notwendig, vor allem wegen der «besonders vulnerablen Personen». Daher mussten alle möglichen Restriktionen zwangsweise und unter Umgehung der Parlamente verordnet werden.
Inzwischen hat sich immer deutlicher herausgestellt, dass viele jener «Schutzmaßnahmen» den gegenteiligen Effekt hatten, sie haben den Menschen und den Gesellschaften enorm geschadet. Nicht nur haben die experimentellen Geninjektionen – wie erwartet – massive Nebenwirkungen, sondern Maskentragen schadet der Psyche und der Entwicklung (nicht nur unserer Kinder) und «Lockdowns und Zensur haben Menschen getötet».
Eine der wichtigsten Waffen unserer «Beschützer» ist die Spaltung der Gesellschaft. Die tiefen Gräben, die Politiker, Lobbyisten und Leitmedien praktisch weltweit ausgehoben haben, funktionieren leider nahezu in Perfektion. Von ihren persönlichen Erfahrungen als Kritikerin der Maßnahmen berichtete kürzlich eine Schweizerin im Interview mit Transition News. Sie sei schwer enttäuscht und verspüre bis heute eine Hemmschwelle und ein seltsames Unwohlsein im Umgang mit «Geimpften».
Menschen, die aufrichtig andere schützen wollten, werden von einer eindeutig politischen Justiz verfolgt, verhaftet und angeklagt. Dazu zählen viele Ärzte, darunter Heinrich Habig, Bianca Witzschel und Walter Weber. Über den aktuell laufenden Prozess gegen Dr. Weber hat Transition News mehrfach berichtet (z.B. hier und hier). Auch der Selbstschutz durch Verweigerung der Zwangs-Covid-«Impfung» bewahrt nicht vor dem Knast, wie Bundeswehrsoldaten wie Alexander Bittner erfahren mussten.
Die eigentlich Kriminellen schützen sich derweil erfolgreich selber, nämlich vor der Verantwortung. Die «Impf»-Kampagne war «das größte Verbrechen gegen die Menschheit». Trotzdem stellt man sich in den USA gerade die Frage, ob der scheidende Präsident Joe Biden nach seinem Sohn Hunter möglicherweise auch Anthony Fauci begnadigen wird – in diesem Fall sogar präventiv. Gibt es überhaupt noch einen Rest Glaubwürdigkeit, den Biden verspielen könnte?
Der Gedanke, den ehemaligen wissenschaftlichen Chefberater des US-Präsidenten und Direktor des National Institute of Allergy and Infectious Diseases (NIAID) vorsorglich mit einem Schutzschild zu versehen, dürfte mit der vergangenen Präsidentschaftswahl zu tun haben. Gleich mehrere Personalentscheidungen des designierten Präsidenten Donald Trump lassen Leute wie Fauci erneut in den Fokus rücken.
Das Buch «The Real Anthony Fauci» des nominierten US-Gesundheitsministers Robert F. Kennedy Jr. erschien 2021 und dreht sich um die Machenschaften der Pharma-Lobby in der öffentlichen Gesundheit. Das Vorwort zur rumänischen Ausgabe des Buches schrieb übrigens Călin Georgescu, der Überraschungssieger der ersten Wahlrunde der aktuellen Präsidentschaftswahlen in Rumänien. Vielleicht erklärt diese Verbindung einen Teil der Panik im Wertewesten.
In Rumänien selber gab es gerade einen Paukenschlag: Das bisherige Ergebnis wurde heute durch das Verfassungsgericht annuliert und die für Sonntag angesetzte Stichwahl kurzfristig abgesagt – wegen angeblicher «aggressiver russischer Einmischung». Thomas Oysmüller merkt dazu an, damit sei jetzt in der EU das Tabu gebrochen, Wahlen zu verbieten, bevor sie etwas ändern können.
Unsere Empörung angesichts der Historie von Maßnahmen, die die Falschen beschützen und für die meisten von Nachteil sind, müsste enorm sein. Die Frage ist, was wir damit machen. Wir sollten nach vorne schauen und unsere Energie clever einsetzen. Abgesehen von der Umgehung von jeglichem «Schutz vor Desinformation und Hassrede» (sprich: Zensur) wird es unsere wichtigste Aufgabe sein, Gräben zu überwinden.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ cd408a69:797e8162
2023-09-14 13:08:47
@ cd408a69:797e8162
2023-09-14 13:08:47Nostrasia Hackathon
Welcome FOSS hackers and creatives who care deeply about freedom technology!
自由のテクノロジーに深い関わりたい FOSS ハッカーとクリエイター、あつまれ!
We're joining forces with Bolt.Fun for a month-long hackathon bridging Bitcoin and NOSTR (Notes and Other Stuff Transmitted by Relays), culminating with a special three day sprint and live event in Tokyo at the Nostrasia Conference.
私たちは、Bolt.Fun と協力して、ビットコインと Nostrを橋渡しする ハッカソンを、1 か月間かけて開催します。 クライマックスは東京で開催されるNostrasia Tokyo が舞台。3日間の特別なスプリントとライブ イベントで最高潮に達します。
Be a Part of the Early Days of Nostr
Nostr の創成期を共に作り上げましょう
Help build the future of Nostr! Like the early days of Bitcoin or of the Internet, Nostr is nascent open technology shaping new types of social experiences to connect people across the globe. It carries a foundation of principles similar to Bitcoin, like decentralization, simplicity, and censorship-resistance.
Nostr の未来を築くのに協力してください!ビットコインやインターネットの初期と同じように、Nostr は世界中の人々をつなぐ新しいソーシャル体験を形成するオープン テクノロジーの初期段階にあります。 Nostr には「分散化」「シンプルさ」「検閲耐性」など、ビットコインと同様の原則が組み込まれています。
Orange-Pill people through the Purple-Nostr-Pill
オレンジピル(ビットコイン)から紫の Nostr のピルへ
Bitcoin and Nostr communities are in synergy. What started as a social protocol is quickly transforming into a space for exploration on ways to support content creators through bitcoin lightning micro payments, often referred to as zaps. Bitcoin integration to the nostr protocol strengthens Bitcoin's use case as a currency of exchange. It carves new paths to a culture of value4value.
ビットコインと Nostr のコミュニティは相乗効果を発揮します。 Nostr はソーシャルプロトコルとしてはじまりましたが、今では Zap (ビットコイン の ライトニング マイクロペイメント)を通じてコンテンツ クリエイターをサポートする方法を模索する空間へと急速に進化しています。 Nostr プロトコルにビットコインが組み合わさることで、交換通貨としてのビットコインの働きが強化されます。 それは、"value4value" の文化への新しい道を切り開くでしょう。
Help People HODL their Keys (Social+Monetary)
人々が自分のキーを HODL (長期保有)できるように支援します (ソーシャル + 金銭的に)
Nostr exists outside of the rule of platforms and those who seek to control them. HODLing your nostr keys is hodling your identity and social graph, outside of KYC. By helping develop and educate on NOSTR, you are helping people escape walled gardens & gain control and choice over their identities & their money. The Internet, over time, has become centralized, help Nostr stay decentralized by supporting the growth of an ecosystem of apps, websites, microapps, relay services...
Nostr はプラットフォームやそれを制御しようとする人々の支配の外にあります。 Nostr keys を持つことは、KYC (本人確認)以外であなたのアイデンティティとソーシャル グラフを保持することになります。 Nostr の開発や教育に貢献することは、人々が束縛から解放され、アイデンティティやお金に対する主導権を得られるよう支援することにもなるのです。 時間の経過とともに集中化されてきたインターネットですが、Nostr のアプリ/Web サイト/マイクロアプリ/リレー サービスのエコシステムの成長をサポートすることで、Nostr の分散化を維持できるようになります。
Permissionless Building
許可を必要としない構築
Opportunities abound in an environment ripe for innovation:
- Develop & design new nostr white label clients, middleware, microapps...
- Help improve existing Nostr FOSS projects
- Contribute directly to protocol development through NIPs (Nostr Implementation Possibilities)
- Encourage nostr and bitcoin adoption through art, education, and any way you like
イノベーションの機が熟した環境には、チャンスが溢れています。
- Nostr の真新しい クライアント、ミドルウェア、マイクロアプリを開発したりデザインする
- 既存の Nostr FOSS プロジェクトの改善に寄与する
- NIP (Nostr Implementation Possibilities) を通じたプロトコル開発に直接貢献する
- 芸術、教育、その他好きな方法を通じて Nostr とビットコインの普及を推進する
Hack in a Supportive Environment
サポートされた環境でハックしよう
We have a growing list of knowledgeable people with skin-in-the-game to mentor and support your journey. Once your project matures, you may also have 1-on-1 guidance to help you reach your vision and discover ways of growing and funding it.
私たちは、あなたの道のりを指導しサポートしてくれる知識豊富なメンターを増やしています。 プロジェクトが成熟した暁には、1対1のガイダンスを受けられる可能性もあります。それは、あなたのビジョンを達成し、成長させて資金を得る方法を発見するのに役立つでしょう。
Nostr has a blossoming community open to innovation. It is also a great testing ground, as people in the community are open to giving and receiving feedback. It is an environment encouraging conversation on feature ideas as well as possible solutions to social media issues and product bugs.
Nostr には、イノベーションに対してオープンで、発展しているコミュニティがあります。 コミュニティの人々はフィードバックの授受にオープンであるため、優れた実験の場にもなります。 機能のアイデアや、ソーシャル メディアの課題や製品のバグの解決策についての会話を促進する環境です。
NostrHack Tracks
You have 3 options
NostrHack Tracks には3つのオプションがあります
Track 1: Builder's Track - Reimagine Nostr
トラック1 : ビルダーのトラック - Nostr を再考しよう
If you can think of it, it can be engineered! Nostr encourages permissionless building while staying mindful of interoperability and network support. Help BUIDL, design, and improve an area you are passionate about. Reimagine and BUIDL features, tools, clients... Help solve issues and create new experiences in social media.
思いつくことができれば、エンジニアリングできる! Nostr は、相互運用性とネットワーク サポートに留意しながら、パーミッションレスな構築 (BUIDL) を奨励しています。 あなたが情熱を注いでいる分野での構築、設計、改善に貢献してください。 機能やツール、クライアントを再考して構築 (BUIDL) し、ソーシャル メディアでの課題を解決して新しい体験を生み出すのに協力してください。
Possibilities...
これを踏まえて…
BUILD on the NOSTR Protocol
The Nostr Implementation Possibilities (NIPs) are optional protocol features anyone can add to their clients. Improve and strengthen existing NIPs or build on new ones. NOSTR is a balance of simplicity, interoperability, backward-compatibility and innovation.
NIPs は、誰でもクライアントに追加できるオプションのプロトコル機能です。 既存の NIP を改善および強化するか、新しい NIP を構築してください。 Nostr は、シンプルさ、相互運用性、下位互換性、革新性のバランスを保っています。
Focus on UX
Nostr is made up of a wide range of clients and tools. To make NOSTR scalable, you can help improve its user experience and education.
Nostr は幅広いクライアントとツールで形成されています。 Nostr をスケーラブルにするために、UX と教育の改善に協力してください。
Help shape a Web of Trust
Nostr cares about removing the KYC tied to our identities. To use Nostr you do not need to give up your phone number, email, financial information, or any metadata tied to your real world identity to be later harvested and sold. You are not the product. What are ways that trust can be earned to prevent impersonation, spam...?
Nostr は、私たちの身元に関連付けられた KYC (個人情報)を取り除けるようにしています。 Nostr を使用しても、電話番号、電子メール、財務情報、または現実世界のアイデンティティに関連付けられたメタデータを、収集されたり販売されたりして手放すことになる心配がありません。 あなたは商品ではないのです。 その中で、なりすましやスパムを防ぐために、信頼を獲得するにはどうすればよいでしょうか...?
NIP05/Nostr address
One of the solutions to build a web of trust used today, is to tie your nostr hex public key to a domain. Although this makes it harder for bots to have nostr addresses, it is not a perfect solution. Domains are centralized through DNS. To help people who do not have their own domains or cannot easily add a NIP05 on their sites, your nostr address can be hosted as a service along with other people's. At this moment, you can highlight just one nostr address per profile. In the future, could it include your website, where you work, and other identifiers... What are other possible solutions?
現在使用されている信頼獲得のための解決策の 1 つは、Nostr の HEX 公開鍵をドメインに結び付けることです。 これにより、完璧な解決策ではないものの、bot などが Nostr アドレスを持つことが難しくなります。 ドメインは DNS を通じて一元化されています。 独自のドメインを持っていない人や、自分では NIP-05 を簡単に追加できない人のために、あなたの Nostr アドレスをサービスとして他の人のものと一緒にホストすることも可能です。 現時点では、プロフィールごとに1つの Nostr アドレスのみを強調表示できますが、将来的には、Web サイト、勤務先、その他の識別情報も含められるようになる可能性があります...この他にも考えられる解決策は何かありますか?
On Decentralization & Discoverability
分散化と発見可能性について
Your identity in NOSTR is tied to your keys, but your information needs to be shared and found across a network of relays. To promote decentralization and censorship resistance, relays need to be easy to setup, lightweight, and sustainable. Relays get to choose what information passes through them, so they are also a form of spam prevention that could potentially also become censoring, so both the relay-runners and the individuals connecting to relays need to have choice and policies cannot be homogenous one-size-fits-all. What are possible solutions to make setting up relays easier, to make running a relay sustainable, to have new ways of discovering information...
Nostr での ID はキーに関連付けられていますが、その情報はリレーのネットワーク全体で共有され、検索できる必要があります。 分散化と検閲耐性を促進するために、リレーはセットアップが簡単で、軽量で、持続可能である必要があります。 リレーは通過する情報を選択できるため、スパム防止の一形態である一方で検閲にもなり得ます。そのため、リレー管理者とリレーに接続する個人の両方に選択権が必要で、ポリシーが全てに対し画一的になってはいけません。 リレーのセットアップを容易にし、リレーの実行を持続可能にし、情報を発見する新しい方法を実現するには、どのような解決策が考えられるでしょうか...?
Buidl tools to connect to Git, as a decentralized alternative to GitHub
GitHub の分散型代替手段として、Git に接続するための BUIDL ツール
Media Uploads
To keep relays lightweight, images are hosted by uploading them to the web, and keeping only the links to them in the data within individual nostr notes. This has led to developing image uploading services specific to nostr, but they carry the risk of centralization or censorship. Some product makers and relay runners are looking into direct uploads to Cloud services. What are possible solutions to the handling of media (images, videos, music...)?
リレーを軽量に保つために、画像は Web にアップロードしてホストされ、各投稿のデータには画像へのリンクのみが保持されます。そんな中で、Nostr に特化した画像アップロード サービスが開発されましたが、集中化や検閲のリスクが伴います。 一部のプロダクト開発者やリレー管理者は、クラウド サービスへの直接アップロードを検討しています。 メディア(画像、ビデオ、音楽など)の処理について、考えられるよい解決策はありますか?
Social Signals
People have the choice to block and mute others, this gives signals to relays, which can reenact policies based on those and other signals. Relays need to be able to differentiate real signals from those wanting to game the system for censorship. Relay runners need to have the capacity to make decisions on what to allow or reject.
ユーザーは他のユーザーをブロックしたりミュートできます。ユーザーの設定内容はリレーに送信され、リレーはその設定に基づいてそれぞれのポリシーを再現できます。 リレーは、実際の設定と、検閲のためにシステムを操作しようとする設定を区別する必要があります。 リレーの管理者には、何を許可し、何を拒否するかを決定する能力が必要です。
Track 2 : Marketplaces & Value4Value
Make freedom of exchange fun again! Nostr extends beyond social. It is integrating ways for content creators to be supported through lightning micropayments, called zaps, for their creations. The possibilities of building niche value4value economies through the exchange of products, services, and ideas, is growing through various avenues: Marketplaces, fundraising, blogs, music, streaming... devise new robust ways of integrating NOSTR and Bitcoin of monetary and skill exchange. Seek to explore distributed, digital reciprocity and free trade. Encourage a culture of value4value.
自由な交流を再び楽しく! Nostr はソーシャルを超えて広がります。 Zap と呼ばれるマイクロペイメントを通じて、コンテンツクリエイターの作品をサポートできる方法を兼ね備えています。 製品、サービス、アイデアの交換を通じてニッチな価値と価値(value4value)の経済を構築する可能性は、さまざまな手段を通じて拡大しています : マーケットプレイス、資金調達、ブログ、音楽、ストリーミングなど... Nostr とビットコインを組み合わせて、金銭とスキルの交換を行う新しい堅牢な方法を考案します。分散型、デジタル相互主義、自由貿易を探究してください。 価値対価値(value4value)の文化を促進してください。
A value4value culture is not only about the individuals using NOSTR products and services, but also about the developers and creatives building sustainable projects. What are ways of sustaining NOSTR through Bitcoin that do NOT make the individual user the product and that are privacy mindful?
value4value の文化は、Nostr の製品やサービスを使用する個人だけでなく、持続可能なプロジェクトを構築する開発者やクリエイターにも関係します。 個人ユーザーを製品にすることなくプライバシーに配慮しながら、ビットコインを通じて Nostr を持続させる方法は何ですか?
Possibilities...
On Social and Economic Signals
Zaps
Many nostr clients have implemented lightning zap payments. Imagine instead of liking a nostr note, you can zap someone's note and they can receive bits/sats in appreciation for their content. It is a strong signal to creators of the kind of content their audiences are looking for. The Apple App Store has recently banned the zapping of specific notes, per Apple's policy that makes the sale of digital content prohibited except when paid through their services. Fortunately, Nostr exists in many decentralized forms outside of app stores and the community is creating new and innovative ways to send bitcoin and free speech from relay to relay, circumventing barriers as they appear. What are solutions that can make NOSTR and zaps ubiquitous?
多くの Nostr クライアントが Zap を導入しています。Nostr での投稿を「いいね」する代わりに Zap すると、その内容に対する感謝としてビットコイン(サトシ)を受け取ることができるイメージです。 これは、フォロワーがどのような種類のコンテンツを求めているかをクリエイターに伝える強力なシグナルになります。 Apple App Storeは最近、サービスを通じて支払われる場合を除きデジタルコンテンツの販売を禁止するというAppleのポリシーに従い、特定の投稿への Zap を禁止しました。 幸い、Nostr は多くが App Store の外で分散型で存在しているため、コミュニティは障壁を回避しながら、ビットコインと言論の自由をリレーからリレーに送信するための革新的な方法を生み出しています。 Nostr と Zaps をユビキタスにするソリューションとは何ですか?
Track 3 : Empower Communities
Give choice and control back to the individual! Create paths forward to help onboard millions of new users and restore free and uncensored speech to the world
選択とコントロールを個人に返そう。 何百万人もの新規ユーザーの参加を支援し、自由で検閲されていない言論を世界に取り戻すための道筋を作り出してください。
Possibilities...
On Security, Privacy & Self-Custody
Private Communication
Direct Messages on NOSTR are encrypted, but metadata is leaked. If someone's key is compromised, whoever has access to that account can read those messages. Integrating secure and reliable encrypted communication protocols, like the SimpleX messaging protocol, is especially desired by the community, as many in Nostr are aware of the risks of surveillance, authoritarianism, government and Big Tech overreach... Private communication is important for individual rights, in particular for activists and journalists across the globe.
Nostr のダイレクト メッセージは暗号化されていますが、メタデータは漏洩します。 誰かのキーが侵害された場合、そのアカウントにアクセスできる人は誰でもそれらのメッセージを読むことができてしまうのです。Nostr の多くの人が監視、権威主義、政府とビッグテックの行き過ぎのリスクを認識しているため、 SimpleX メッセージング プロトコルのような安全で信頼性の高い暗号化通信プロトコルの統合が、コミュニティによって特に望まれています...プライベート通信は個人の権利にとって重要です 、特に世界中の活動家やジャーナリストにとって。
Zaps & Privacy
Current lightning zap payments tend to be custodial and not mindful of privacy, though they are helping onboard people unto lightning. What are ways that people can grow into non-custodial solutions? A wider adoption of Bolt-12 would improve zap payment privacy, what are ways to encourage that development? What are other possible solutions?
現在のザップの支払いは、ライトニングペイメントに出会うのに役立っているものの、カストディアル(管理的)でプライバシーに配慮していない傾向にあります。 ノンカストディアル(非監護的)なものになるよう解決する方法はありませんか? Bolt-12 が広く採用されれば、Zap 支払いのプライバシーが向上しますが、その開発を促進するにはどのような方法がありますか?また、他に考えられる解決策はありませんか?
Closing Live 3-Day Sprint at the Nostrasia Conference
Nostrasia Tokyo 3日間のライブスプリントによる締めくくり
Tokyo | Nov 1-3 (you can also join virtually)
If you heard of the Nostrica unconference, which happened in Costa Rica in March of this year, Nostrasia is the second Nostr World conference, bringing NOSTR and Bitcoin awareness to the heart of Asia, where freedom communication and freedom money are direly needed.
今年の3月にコスタリカで開催された Nostrica のことをご存知の方もいると思いますが、ノストラジアは2回目の Nostr 世界カンファレンスです。自由なコミュニケーションと自由なお金が切実に必要とされているアジアの中心にNostr とビットコインの認識をもたらします。
Tokyo and Hong Kong are beautiful cultural hubs with budding Nostr and thriving Bitcoin communities of their own. We are eager to spread NOSTR education and development in those regions and beyond. We will close this Nostrasia month-long hackathon with a 3-day sprint at the Nostrasia Conference in Tokyo.
東京と香港は、新進気鋭のNostrと繁栄する独自のビットコインコミュニティを持つ美しい文化の中心地です。 私たちは、Nostr の教育と開発をこれらの地域やその他の地域に広めることに熱心に取り組んでいます。 この Nostrasia の 1 か月にわたるハッカソンは、Nostrasia Tokyo での 3 日間のスプリントをもって終了します。
We will have a dedicated workshop area and food for you to hack away on the final details of your projects. On the last day of the conference, the most robust projects will get time on stage to present. We will close the Nostrasia Hackathon with a special presentation.
プロジェクトの最終的な詳細を検討するための専用のワークショップ エリアと食事をご用意します。 カンファレンスの最終日には、最も強力なプロジェクトがステージ上でプレゼンテーションを行う時間が与えられます。 Nostrasia Hackathon は特別なプレゼンテーションで締めくくられます。
We cannot wait to see what new and exciting projects are proposed for the Nostrasia Hackathon. We’re eager to welcome devs and non-devs alike to contribute to this space and help #grownostr in any small way to help onboard Asia, and the rest of the world to this robust open communication protocol and decentralized freedom of speech tool.
Nostrasia Hackathon ではどんな斬新でエキサイティングなプロジェクトが提案されるのか楽しみです。 私たちは、開発者も非開発者も同様にこの分野に貢献し、アジアやその他の世界をこの堅牢なオープン通信プロトコルと分散型言論の自由ツールに参加させるために、どんな小さな方法でも #grownostr を支援してくれることを心から歓迎しています。
-
 @ 42342239:1d80db24
2024-12-06 09:40:00
@ 42342239:1d80db24
2024-12-06 09:40:00The Dutch primatologist Frans de Waal coined the term "veneer theory" in his book "Our Inner Ape" in 2005. The veneer theory posits that human moral behavior is merely a thin veneer over an inherently unpleasant nature. This viewpoint can be traced back to Thomas Henry Huxley, an anthropologist and biologist who was a contemporary of Darwin. However, de Waal criticized the idea because humanity is far more cooperative than predicted by simple anthropological or economic models. However, it is possible to question how thick this "civilizing veneer" really is.
During the COVID-19 pandemic, some people discriminated against the unvaccinated , while others wished them a quick and painful death . In the United States, about 30 percent of those who voted for the Democratic Party wanted to take their children away . Professors wanted to imprison them . This was despite the fact that the vaccines did not prevent infection or reduce transmission very much (if at all).
There is an idea that evil actions often stem from ordinary people blindly following orders or societal norms.
The war between Israel and Hamas revealed a desire to collectively punish all residents of the Gaza Strip. For example, as many as 70 percent of Jewish Israelis say they want to ban social media posts expressing sympathy for civilians (""There are no civilians ."") On the other side of the conflict, there is a desire to punish Israeli citizens and Jews around the world for Israel's actions in the conflict, as shown by the storming of an airport in Russian Dagestan.
As a result of Russia's invasion of Ukraine, the alienation of ethnic Russians has become fashionable. Even Swedish defense policy pundits now found it appropriate to dehumanize Russians by calling them "orcs" (evil and warlike creatures with sharp teeth taken from J.R.R. Tolkien's stories). Others wanted to deny all Russian citizens entry . Recently, the software project Linux has removed Russian programmers simply because they are Russian. Similar rhetoric can be found on the other side.
All three of the above examples constitute a form of collective punishment, which is contrary to both the UN Declaration of Human Rights and the Geneva Convention . Yet few react.
The author Hannah Arendt coined the term "the banality of evil" when she studied Nazi war criminals. The term refers to the idea that evil actions often stem from ordinary people blindly following orders or societal norms without critical scrutiny. She argued that individual responsibility and critical thinking were of paramount importance.
In an iconic photo from the 1930s, a large crowd is shown with everyone doing the Hitler salute. Everyone except one. The man, believed to be August Landmesser , openly showed his refusal with crossed arms and a stern expression.
Imagine yourself in his shoes, standing among thousands of people who are raising their arms. Would you have the courage to stand still and quietly while everyone around you shouts their support? Or would you, like so many others, let yourself be swept along with the current and follow the crowd? Somewhere in there, you might have the answer to how thick this "civilizing veneer" really is.
Cover image: Picture of people giving a Nazi salute, with an unidentified person (possibly August Landmesser or Gustav Wegert) refusing to do so, Wikimedia Commons
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ a10260a2:caa23e3e
2023-08-14 21:36:14
@ a10260a2:caa23e3e
2023-08-14 21:36:14It seems like blogstack is meant to replace Substack if not already apparent by the name. If that's the case, it's already better in a few ways.
1. Hit the ground running
I'm already getting started out of the gate with more readers than I would have if I just started a Substack. This, of course, is due to the fact that I'm creating on top of a protocol where I'm able to have the same audience across all clients of that protocol. This is in stark contrast to the legacy apps from centralized entities where you have to corral your audience from one platform to the next.
2. Readers need not subscribe
Technically, if you're following me, you're subscribed. But you don't have to subscribe for a set price and amount of time (e.g. $5/month or $50/year). I believe this is a win for both of us as I can write my best notes and you can choose to reward me as you see fit. Value 4 value.
3. More conducive to conversation
Writing on Substack felt like writing into a void, with little to no feedback. A post shows up in my readers' inbox and I'll see some stats on whether it was opened or not. That's it. Based on what I've seen so far, blog posts created on Nostr appear in the client apps (e.g Damus, Primal, and Plebstr) as just another note, but with nice formatting and such. From there, I can receive zaps, shakas, comments, and even be reposted.
This is just the beginning. Right now, I'm using blogstack. But what's to stop me from using another tool down the line? I'll have the ability to do so by simply connecting my private key. Can't wait to see what new tools are created down the line.
So ₿ULLISH on #Nostr
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ b12b632c:d9e1ff79
2023-07-20 20:12:39
@ b12b632c:d9e1ff79
2023-07-20 20:12:39Self hosting web applications comes quickly with the need to deal with HTTPS protocol and SSL certificates. The time where web applications was published over the 80/TCP port without any encryption is totally over. Now we have Let's Encrypt and other free certification authority that lets us play web applications with, at least, the basic minimum security required.
Second part of web self hosting stuff that is really useful is the web proxifycation.
It's possible to have multiple web applications accessible through HTTPS but as we can't use the some port (spoiler: we can) we are forced to have ugly URL as https://mybeautifudomain.tld:8443.
This is where Nginx Proxy Manager (NPM) comes to help us.
NPM, as gateway, will listen on the 443 https port and based on the subdomain you want to reach, it will redirect the network flow to the NPM differents declared backend ports. NPM will also request HTTPS cert for you and let you know when the certificate expires, really useful.
We'll now install NPM with docker compose (v2) and you'll see, it's very easy.
You can find the official NPM setup instructions here.
But before we absolutely need to do something. You need to connect to the registrar where you bought your domain name and go into the zone DNS section.You have to create a A record poing to your VPS IP. That will allow NPM to request SSL certificates for your domain and subdomains.
Create a new folder for the NPM docker stack :
mkdir npm-stack && cd npm-stackCreate a new docker-compose.yml :
nano docker-compose.ymlPaste this content into it (CTRL + X ; Y & ENTER to save/quit) :
``` version: '3.8' services: app: image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: # These ports are in format
: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port # Add any other Stream port you want to expose # - '21:21' # FTP # Uncomment the next line if you uncomment anything in the section # environment: # Uncomment this if you want to change the location of # the SQLite DB file within the container # DB_SQLITE_FILE: "/data/database.sqlite" # Uncomment this if IPv6 is not enabled on your host # DISABLE_IPV6: 'true' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt```
You'll not believe but it's done. NPM docker compose configuration is done.
To start Nginx Proxy Manager with docker compose, you just have to :
docker compose up -dYou'll see :
user@vps:~/tutorials/npm-stack$ docker compose up -d [+] Running 2/2 ✔ Network npm-stack_default Created ✔ Container npm-stack-app-1 StartedYou can check if NPM container is started by doing this command :
docker psYou'll see :
user@vps:~/tutorials/npm-stack$ docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 7bc5ea8ac9c8 jc21/nginx-proxy-manager:latest "/init" About a minute ago Up About a minute 0.0.0.0:80-81->80-81/tcp, :::80-81->80-81/tcp, 0.0.0.0:443->443/tcp, :::443->443/tcp npm-stack-app-1If the command show "Up X minutes" for the npm-stack-app-1, you're good to go! You can access to the NPM admin UI by going to http://YourIPAddress:81.You shoud see :

The default NPM login/password are : admin@example.com/changeme .If the login succeed, you should see a popup asking to edit your user by changing your email password :
 And your password :
And your password :
 Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
 Followed by "Add Proxy Host"
Followed by "Add Proxy Host"
 If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :
If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :Details tab :
 SSL tab :
SSL tab :
 And click on "Save".
And click on "Save".NPM will request the SSL certificate "admin.yourdomain.tld" for you.
If you have an erreor message "Internal Error" it's probably because your domaine DNS zone is not configured with an A DNS record pointing to your VPS IP.
Otherwise you should see (my domain is hidden) :

Clicking on the "Source" URL link "admin.yourdomain.tld" will open a pop-up and, surprise, you should see the NPM admin UI with the URL "https://admin.yourdomain.tld" !
If yes, bravo, everything is OK ! 🎇
You know now how to have a subdomain of your domain redirecting to a container web app. In the next blog post, you'll see how to setup a Nostr relay with NPM ;)
Voilààààà
See you soon in another Fractalized story!
-
 @ d2e97f73:ea9a4d1b
2023-04-11 19:36:53
@ d2e97f73:ea9a4d1b
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 2fb77d26:c47a6ee1
2024-11-29 22:07:30
@ 2fb77d26:c47a6ee1
2024-11-29 22:07:30»Worte interessieren nur da, wo sie zu Taten führen«, notierte ich vor knapp 15 Jahren für einen meiner Texte. Gelten sollte diese Prämisse vor allem für Wahlversprechen. Doch die Geschichte zeigt, dass von den vollmundigen Zusicherungen eines Wahlkampfes nach Amtsantritt kaum etwas umgesetzt wird. Davon muss wohl auch in Bezug auf die US-Präsidentschaftswahl 2024 ausgegangen werden. Auch wenn viele immer noch auf eine »Trockenlegung des Sumpfes« hoffen. Ein Überblick.
Original mit Quellen (VÖ: 14.11.2024): https://www.regenauer.press/trump-reloaded
Unterhaltsam ist es bisweilen. Keine Frage. Ist ja auch Politainment. Fake. Eine Show. Eine ziemlich kostenintensive dazu. Und einer gewissen Schadenfreude kann man sich in der Tat kaum verwehren, betrachtet man die irrationalen Reaktionen, Nervenzusammenbrüche und infantilen Ausraster der Wahlverlierer – dem Lager, das in puncto Covid, Klimaschutz und Genderpolitik nie einen Hehl aus seinen totalitären Anwandlungen machte. Leider wird aus Spaß aber schnell bitterer ernst. So tötete ein psychisch labiler Mann aus Minnesota am Tag nach Donald Trumps Wahlsieg zuerst seine ehemalige Partnerin und deren Kind, dann seine Frau und den eigenen Sohn, und anschließend sich selbst. Während die Polizei bislang kein offizielles Tatmotiv kommuniziert, implizieren Social-Media-Beiträge des 46-jährigen Demokraten, dass seine Angst vor den Republikanern, beziehungsweise dem Einzug Trumps ins Weiße Haus, durchaus Auslöser des Amoklaufes sein könnten.
Während die weithin von »Wokeness« beseelten Demokraten ihre Wunden lecken, zelebrieren das konservative Lager der Republikaner und die MAGA-Apologeten einen vermeintlich historischen Sieg. Trump selbst verspricht bei seiner Siegesrede ein »goldenes Zeitalter«. Dass er jetzt »alles in Ordnung bringen« werde. Die Krypto-Branche wähnt sich im Aufwind. Der Bitcoin-Kurs steigt. Dow Jones, S&P 500 und Nasdaq erreichen neue Allzeithochs. In Iowa soll 2026 eine Art Weltausstellung stattfinden, um das 250-jährige Jubiläum Amerikas zu feiern. Bis zum Beginn der Feierlichkeiten sollen Elon Musk und Vivek Ramaswamy die Ausgaben des Staatsapparats um zwei Billionen US-Dollar reduziert haben. Natürlich ist Trump auch die letzte Chance der USA, um endlich die Grenze zu Mexiko zu sichern. Und von Robert F. Kennedy Jr. erwartet man, die Vereinigten Staaten im Rahmen eines MAHA-Programmes – »Make America Healthy Again« – wieder gesund zu machen.
Im Überschwang der Euphorie – oder Frust der Niederlage – fällt gerne unter den Tisch, dass Wähler in Amerika den Präsidenten gemäß Verfassung gar nicht direkt wählen dürfen, weil das für die Wahl des Präsidenten zuständige Electoral College im Prinzip völlig unabhängig vom eigentlichen Wahlausgang entscheiden kann. Die Wahlmänner könnten auch jeden anderen zum Staatsoberhaupt ernennen. Ob das Volk ihn will, oder er überhaupt angetreten ist, spielt rein formal gar keine Rolle. Bei genauerer Betrachtung also nicht unbedingt Demokratie in Reinform. Egal. Schnöde Details. »Trust the plan. Wir haben gewonnen. Geschichte wurde geschrieben« – und so weiter.
Die NATO gibt unterdes zu Protokoll, dass sich an ihrer geostrategischen Agenda »nichts ändern wird, egal, wer die Wahl gewinnt«, weil das »im Interesse der Vereinigten Staaten liege«. Vielleicht hat das US-Militär ja deshalb nur wenige Stunden nach Schließung der Wahllokale eine Minuteman III Interkontinentalrakete zu Testzwecken abgefeuert. Eine Langstreckenwaffe, die drei einzeln steuerbare Atomsprengköpfe transportieren kann.
Auch das Ron Paul Institute rechnet nicht mit grundlegenden Veränderungen und führt diverse Bereiche an, die unabhängig von der Besetzung des Oval Office ein Problem bleiben werden: Kontinuierliche Unterminierung der Verfassung, Krieg gegen die eigene Bevölkerung, Tiefenstaat, Washingtons ausufernde, verstetigte Notstandsermächtigungen, Militärinterventionen in aller Welt, maßlose Korruption und staatliche Tyrannei. Klingt nicht wirklich nach einem goldenen Zeitalter.
Die Reaktionen rund um die US-Wahl – ob positiv oder negativ, ob vor Ort oder im Rest der Welt – veranschaulichen jedenfalls, dass Wahlen Emotionsamplituden auslösen, die in keiner Relation zu dem stehen, was ein Präsident, Kanzler oder Premierminister tatsächlich bewirken kann. Sonst hätte Trump den tiefenstaatlichen »Sumpf« ja schon in seiner ersten Amtsperiode trockenlegen können.
Während die Demokraten also darauf warten, dass die USA ab dem 20. Januar 2025 zur Diktatur verkommen und auf Demonstrationen gegen das Resultat der US-Variante von Demokratie protestieren, fiebern die anderen dem Anbruch eines goldenen Zeitalters entgegen.
Genug Zeit also, den 47. Heilsbringer im Oval Office noch einmal genauer unter die Lupe zu nehmen. Denn auch wenn Donald Trump sich fraglos darauf versteht, zu unterhalten und große Reden von Freiheit und staatlicher Souveränität, von Weltfrieden und Prosperität zu schwingen, sprechen seine Taten zumeist eine ganz andere Sprache.
Fangen wir vorne an: Dank der Zurückstellung vom Wehrdienst konnte Donald Trump bereits 1968 bei Trump Management einsteigen, dem Unternehmen seines Vaters Fred C. Trump, der vor allem mit staatlichen geförderten Wohnungsbauprojekten – »Federal Housing Projects«, heute die Ghettos von New York – zum Multimillionär geworden war. 1971 übernahm Donald im Alter von 25 Jahren die Geschäftsleitung der Firma. Bei Interviews prahlt er bis heute gerne damit, dass sein Vater ihm in jungen Jahren »lediglich einen kleinen Kredit« über eine Million Dollar als Startkapital gewährte. Daraus habe er dann als gewiefter Unternehmer ein Immobilienimperium erschaffen. Dieser Darstellung widerspricht ein Artikel der New York Times (NYT) vom 2. Oktober 2018, der basierend auf Steuer- und Buchhaltungsunterlagen kalkuliert, dass Donald Trump gut 60 Millionen US-Dollar an Krediten erhielt.
»Im Alter von drei Jahren verdiente Trump am Imperium seines Vaters 200.000 Dollar jährlich. Mit acht Jahren war er Millionär. Mit 17 Jahren überließ ihm sein Vater einen Teilbesitz an einem Mehrfamilienhaus mit 52 Wohneinheiten. Kurz nachdem Trump das College abgeschlossen hatte, erhielt er von seinem Vater jährlich umgerechnet eine Million Dollar. Über die Jahre stiegen die jährlichen Schenkungen. In seinen Vierzigern und Fünfzigern lagen sie bei über fünf Millionen Dollar jährlich.«
Als Fred Trump im Juni 1999 verstarb, hatte der trickreiche Unternehmer und Steuerallergiker seinem Sprössling nach Berechnungen der NYT insgesamt 413 Millionen Dollar überschrieben. Selbst wenn New York Times, Associated Press und Co. im Jahr 2018 mit diesen Artikeln fraglos Stimmung gegen Trump machen wollten, kann dessen selbstbeweihräuchernde Darstellung augenscheinlich nicht ganz der Wahrheit entsprechen.
Aber: Er hatte Erfolg. Und das war in der Immobilienbranche des New Yorks der 70er und 80er nicht selbstverständlich. Denn sie wurde von der Mafia dominiert. Von den »Fünf Familien«. Wer nicht den Schutz von »Fat Tony« Salerno, Carmine Galante, Paul Castellano et al. genoss, den Bossen der Genovese-, Bonanno- und Gambino-Familien, hatte schlechte Karten. Das wusste auch Donald Trump. Also macht er Gebrauch von den exzellenten Kontakten seines Freundes, Mentors und Anwalts Roy Cohn, der nicht nur enge Verbindungen zum langjährigen FBI-Chef J. Edgar Hoover pflegte, sondern unter anderem auch Nancy Reagan, die Besitzer des Studio 54, Andy Warhol, die katholische Erzdiözese und die Führungsetage der fünf Mafia-Familien als Anwalt vertrat. Nicht umsonst ist Cohn ein zentraler Charakter in Whitney Webbs Zweiteiler »One Nation under Blackmail«. Den Kontakt zu Cohn, einer Schlüsselfigur für die Zusammenarbeit von Oberschicht und Unterwelt, suchte Donald Trump bereits 1973, als die US-Regierung ein Unternehmen seines Vaters verklagte. Er sollte bestehen bleiben, bis Cohn im August 1986 seiner AIDS-Erkrankung erlag.
Cohns Verbindungen zu Politik, Mafia und Jimmy Hoffas teilkrimineller Teamster-Gewerkschaft sorgten dafür, dass Trump in der Stadt Fuß fassen und sein Geschäft ausbauen konnte. Im Gegenzug war er gezwungen, überteuerte Baumaterialien von Fat Tonys Tarnfirmen zu beziehen. Nach Angaben eines ehemaligen Mitarbeiters von Cohn trafen sich Trump und Salerno in dessen Stadthaus in Manhattan. Trump will sich an ein solches Meeting allerdings nicht erinnern können – obwohl Salerno 1988 unter anderem wegen Erpressung in Höhe von acht Millionen Dollar im Rahmen eines Trump-Bauprojektes rechtskräftig verurteilt wurde. Die Wahrheit kennt wohl nur Trump selbst. Denn Cohn und Fat Tony sind tot.
Sicher ist: Die Geschäftsbeziehungen zwischen Donald Trump und Firmen des organisierten Verbrechens waren intensiver als seinerzeit üblich. Auf Tonbändern des FBI und der US-Staatsanwaltschaft, damals geleitet vom späteren Trump-Anwalt Rudy Giuliani, die beim Abhören von Mafia-Fahrzeugen und -Etablissements entstanden, ist mehrfach von Trump-Projekten die Rede. Donald passte sich dem Geschäftsgebaren seines Umfelds an. Den opportunistischen, skrupellosen, steuervermeidenden Praktiken seines Vaters – und dem von organisierter Kriminalität durchzogenen Filz des Ostküsten-Establishments.
Donald Trumps Frühphase, seine Geschäfte und Geschäftspartner sind also nicht unbedingt ein Paradebeispiel in Sachen Arbeitsethos. Im Vergleich zu seinen späteren Kontakten wirken seine Buddys der 70er und 80er aber fast noch sympathisch – denn Steuern sind Raub und die Mafia pflegt, im Gegensatz zu Regierungen, Militär und Geheimdiensten, zumindest einen Ehrenkodex.
Die 90er begannen für Trump mit finanziellen Turbulenzen. Diverse Bau- und Casino-Projekte liefen nicht wie geplant. Investments warfen nicht den erwarteten Gewinn ab und die Schulden häuften sich bis zur Zahlungsunfähigkeit. In der Öffentlichkeit gab er jedoch weiterhin den erfolgreichen Entrepreneur. 1995 gründe Trump, immer noch bis über beide Ohren verschuldet, eine Aktiengesellschaft und ging an die Börse. Durch diesen Schritt landete er nach 1989 erstmals wieder auf der Forbes-Liste der reichsten Amerikaner. Da die neue AG aber aufgrund der Altlasten mit 1,7 Milliarden Dollar verschuldet war, fiel ihr Börsenkurs zwischen 1996 und 2005 von 35 Dollar auf 17 Cent. Dann wurde der Handel ausgesetzt. Trump bezog aber noch bis 2009 Vergütungen aus der Gesellschaft in Höhe von 44 Millionen Dollar.
Parallel zu diesen fragwürdigen Umtrieben zu Lasten von Anlegern und Geschäftspartnern mauserte sich Donald Trump zum Society-Phänomen. Ob The Apprentice, WrestleMania, The Fresh Prince of Bel-Air, Talkshows oder soziale Anlässe aller Art – Trump war überall, wo sich Öffentlichkeit für Trump generieren ließ. Mit Erfolg. Überschuldung, Zahlungsunfähigkeit, Mafia-Kontakte, Betrugsvorwürfe und juristische Probleme verblassten im omnipräsenten Scheinwerferlicht.
Weniger glamourös dagegen ist Donald Trumps Beziehung zu einem der verachtenswertesten Menschen der jüngeren Vergangenheit – Jeffrey Epstein. Denn während Trump lange Jahre leugnete, überhaupt mit Epstein in Kontakt gestanden zu haben, belegen unlängst veröffentlichte Audio-Mitschnitte, dass er sehr wohl eine Beziehung mit dem verurteilten Sexualstraftäter, Pädophilen, Menschenhändler und Doppelagenten pflegte. Eine sehr enge.
Jeffrey Epstein bezeichnet sich im Zuge der Aufnahmen als »Trumps engsten Freund«. Für über zehn Jahre. Man besuchte die gleichen Partys, kannte die gleichen Leute. Kaum verwunderlich. Epstein war bestens mit dem »Who is Who« des Establishments vernetzt – auch mit dem zwielichtigen Roy Cohn. Es liegt nahe, dass über diesen der Erstkontakt zustande kam. Epstein erpresste elitäre Zirkel in aller Welt mit heimlich aufgenommenen Videos arrangierter Sex-Eskapaden. Die Opfer: Meist Minderjährige. Manche erst acht Jahre alt. Wer Macht und Einfluss ausüben und sichern wollte, nahm seine Dienste in Anspruch. Das wusste wohl jeder seiner engeren Kontakte. Trotzdem sprach Donald Trump von einem »tollen Typen, den er seit 15 Jahren kenne«, als er in einem Interview mit dem New York Magazine 2002 nach seiner Meinung zu Epstein und der gemeinsamen Vorliebe für junge Frauen gefragt wurde. Darüber hinaus flog Donald Trump mindestens sieben Mal mit Jeffrey Epsteins Privatjet, besser bekannt als »Lolita Express«.
Elon Musk, über dessen hinter Imagedesign verborgene Nähe zu Militär, Geheimdiensten, Big Pharma und Transhumanisten ich bereits im Oktober 2022 ausführlich berichtet habe, hatte ebenfalls Verbindungen zu Jeffrey Epstein, wie ein ausführliches Dossier von Johnny Vedmore belegt. Ganz zu schweigen von Musks Forderungen nach CO2-Steuern gegen den Klimawandel oder seinen offenen Plädoyers für Technokratie, einem faschistischen Herrschaftsmodell, das schon sein Großvater Joshua N. Haldemann in leitender Position vertrat. Man kann sich also ausmalen, was unter einem Effizienzprogramm unter Musks Ägide zu erwarten ist – Tech-Faschismus, getarnt als libertäre Progressivität.
Auch RFK Jr. flog zwei Mal mit dem »Lolita Express«, gibt aber an, in Begleitung von Frau und Kindern gereist zu sein – während er gleichzeitig erklärt, die beiden Flüge seien nur zustande gekommen, weil seine »Frau irgendeine Art von Beziehung mit Ghislaine Maxwell hatte«. Was für eine Beziehung das war, beschreibt RFK Jr. nicht. Dabei wären die Hintergründe dieser Beziehung durchaus relevant für die Bewertung seiner Verbindung zum Epstein-Netzwerk. Denn Maxwell, deren Elternhaus für CIA und Mossad tätig war, war seit 1991 Epsteins engste Mitarbeiterin. Sie führte ihm minderjährige Mädchen zu. Phantombilder legen nahe, dass sie auch am Verschwinden, beziehungsweise Tod, von Madeleine McCann beteiligt sein könnte. Nach dem als Suizid vermarkteten Mord an Epstein im August 2019 tauchte Maxwell ab. Aufenthaltsort unbekannt. Erst am 2. Juli 2020 konnte das FBI sie festnehmen. Im Dezember 2021 wurde Maxwell wegen Unterstützung von Epsteins Pädo-Business zu 20 Jahren Haft verurteilt.
Man darf gespannt sein, ob Epsteins unter Verschluss gehaltene Kundenliste jemals ans Licht kommt. Wenn Trump nichts zu verbergen hat, seine dahingehenden Ankündigungen wahr machen und den Sumpf trockenlegen will, könnte er damit ordentlich vorlegen. Entsprechende Forderungen stehen ja bereits im Raum.
Bei einer Pressekonferenz im Weißen Haus am 21. Juli 2020 verkündete er allerdings noch, Maxwell mehrfach getroffen zu haben und wünschte ihr »wirklich alles Gute«.
Wahrscheinlich ist eine Offenlegung der Kundenliste aber nicht. Denn auch Trumps neuer Generalstaatsanwalt, Matt Gaetz, gegen den 2020 wegen sexueller Kontakte zu einem minderjährigen Mädchen ermittelt wurde, sprach sich in der Vergangenheit explizit gegen eine neuerliche Überprüfung des Falls Epstein aus. Er behauptete außerdem, Epstein sei von ausländischen Geheimdiensten, nicht vom US-Tiefenstaat ermordet worden. Sein Wahlkampf-Team nutzte denn auch die gleiche Anwaltskanzlei wie Jeffrey Epstein. Und ein enger Vertrauter von Gaetz warb intensiv dafür, Ghislaine Maxwell aus der Haft zu entlassen. Seit 2021 ist Gaetz mit der Schwester des Peter Thiel-Protegés Palmer Lucky verheiratet, der mit seiner Firma Anduril für das High-Tech-Überwachungssystem an der mexikanischen Grenze verantwortlich zeichnet, KI-Waffenprogramme entwickelt und für das US-Verteidigungsministerium an Project Maven arbeitet. Sumpf, soweit das Auge reicht. Trockenzulegen gäbe es da also einiges.
Warten wir’s ab – und werfen unterdes einen Blick auf Donald Trumps erste Amtszeit. Denn auch diesbezüglich sagen Taten mehr als Worte.
Während Trump sich derzeit als Gegner der Weltgesundheitsorganisation (WHO) geriert, war er als 45. US-Präsident mit »Operation Warp Speed« (OWS) für eine militarisierte Impf-Kampagne der Superlative verantwortlich, die 300 Millionen Dosen einer experimentellen mRNA-Gentherapie unters Volk bringen und den Herstellern mindestens 18 Milliarden Dollar in die Kasse spülen sollte. Anthony Fauci, den Trump heute gerne öffentlich diffamiert, kümmerte sich für ihn um den Rollout der Injektionen und die damit verbundene Nudging-Propaganda. Für seine Verdienste im Rahmen von OWS erhielt Fauci von Trump am letzten Tag seiner Präsidentschaft eine Auszeichnung, wie eine Pressemitteilung im Archiv des Weißen Hauses belegt. Während Trump sich in den letzten Wochen medienwirksam von Fauci distanzierte und abstritt, diese Auszeichnung abgesegnet zu haben, verweisen Mitarbeiter des Weißen Hauses darauf, dass eine solche Auszeichnung gemäß Protokoll nur dann verliehen wird, wenn der Präsident sie persönlich autorisiert. Fragt sich, wer lügt.
Daneben genehmigte Trump im Februar 2020 eine Zahlung von 1,16 Milliarden US-Dollar an GAVI, die Impfallianz von WHO, Weltbank, UNICEF und der Bill & Melinda Gates Stiftung. Der Betrag sollte GAVI binnen drei Jahren über die CIA-Tarnfirma USAID ausbezahlt werden. Ungeachtet aller Gegenanzeigen, Nebenwirkungen und Kollateralschäden durch Lockdowns und partielle Impfpflichten pries Donald Trump OWS stets als durchschlagenden Erfolg. Erst nach der Ankündigung, mit Kennedy kollaborieren zu wollen, hielt er sich mit dem Eigenlob zurück. Dass er sich in den Wochen vor dem Wahlsieg neu positionierte, dürfte also reine Wahlkampfstrategie gewesen sein.
Wenn Trump nun in Aussicht stellt, Impfungen verbieten und Amerika gemeinsam mit RFK Jr. gesund machen zu wollen, ist das in Anbetracht der immensen Marktmacht von Big Pharma kaum als realistisch zu bewerten. Siehe Briefing des Roosevelt Institute vom 22. Mai 2019. Titel: »Kapern der Regierung – Wie Big Pharma die Gesetzgebung übernahm«. In Trumps Team wurden in den letzten Wochen bereits Stimmen laut, die forderten, sich von RFK Jr. zu distanzieren. Während Kennedy in einem Interview vom 28. Oktober verkündete, Trump habe ihm den »Chefposten der Gesundheitsbehörde HHS versprochen«, stellte Howard Lutnik, Vize-Vorsitzender von Trumps Transition-Team, am 30. Oktober bei CNN fest, dass dies »natürlich nicht der Fall sein werde« und man Kennedy lediglich Zugriff auf Daten gewähren wolle. Am 14. November gab Donald Trump dann allerdings bekannt, RFK Jr. tatsächlich zum Chef der HHS machen zu wollen. Die Nominierung muss aber noch vom Senat bestätigt werden. Und bis Januar kann noch einiges passieren. Die Vergangenheit lässt jedenfalls darauf schließen, dass weder Big Pharma noch WHO oder GAVI künftig unter der neuen Regierung leiden werden.
Dann wären da noch die galoppierenden Staatsschulden der Vereinigten Staaten. Denn unter Trumps Ägide schöpfte die US-Zentralbank allein im Jahr 2020 über drei Billionen Dollar. »Die Vereinigten Staaten haben im Juni mehr Geld gedruckt als in den ersten zwei Jahrhunderten nach ihrer Gründung. Letzten Monat war das Haushaltsdefizit der USA – 864 Milliarden Dollar – größer als die Gesamtverschuldung von 1776 bis Ende 1979«, so Dan Morehead, CEO von Pantera Capital am 29. Juli 2020. Seit 2020 hat die Staatsverschuldung um knapp zwölf Billionen Dollar zugenommen und belief sich im September 2024 auf 35,46 Billionen Dollar. Das sollten speziell Trump-Anhänger vor Ort nicht vergessen, wenn sie nun für den Wocheneinkauf deutlich tiefer in die Tasche greifen müssen. Inflation sei Dank.
»Dafür hat Trump keine neuen Kriege angefangen!« – hört man immer wieder, wenn man auf dessen Verfehlungen hinweist. Stimmt. Weil er fünf Krisenherde von der vorherigen Regierung geerbt hat und sich dort austoben konnte. Trump hat nämlich deutlich mehr Drohnen-Einsätze befohlen als sein Vorgänger. Obama autorisierte in den ersten zwei Jahren seiner Amtszeit 186 Einsätze – bei Trump waren es 238. Allein im Jemen hat die Trump-Regierung 176 Angriffe binnen zwei Jahren durchgeführt. Bei Obama waren es 154 in acht Jahren. Und während die Regierung unter Obama zumindest teilweise Daten zu den Opferzahlen dieser Einsätze veröffentlichte, änderte Trump die entsprechenden Transparenzanforderungen und veröffentlichte gar keine Daten. Laut einem Artikel von Foreign Policy vom 9. August 2017 ist Trump »der kriegslüsternste Präsident der jüngeren Geschichte«. Weiter führte das 1970 von Samuel P. Huntington gegründete Magazin aus:
»Unter Trump haben die Vereinigten Staaten bis zum 31. Juli etwa 20.650 Bomben abgeworfen, das sind 80 Prozent der Menge, die unter Obama im gesamten Jahr 2016 abgeworfen wurden. (…) Daten zeigen, dass die Vereinigten Staaten im Irak und in Syrien Bomben in beispiellosem Ausmaß abwerfen. Im Juli warf die Koalition zur Bekämpfung des Islamischen Staats (sprich: die Vereinigten Staaten) 4.313 Bomben ab, 77 Prozent mehr als im Juli letzten Jahres. Im Juni lag die Zahl bei 4.848 – 1.600 Bomben mehr als unter Präsident Barack Obama jemals pro Monat abgeworfen wurden. In Afghanistan ist die Zahl der abgeworfenen Bomben seit Trumps Amtsantritt ebenfalls sprunghaft angestiegen. Im April wurden im Land mehr Bomben abgeworfen als auf dem Höhepunkt von Obamas Truppenaufstockung im Jahr 2012. In diesem Monat bombardierten die Vereinigten Staaten das afghanische Mamand-Tal mit der größten nichtnuklearen Bombe, die jemals abgeworfen wurde. Trump hat auch das militärische Engagement der USA in Ländern außerhalb der Kriegsschauplätze ausgeweitet – nämlich im Jemen, in Somalia und in Pakistan. In den letzten 193 Tagen von Obamas Präsidentschaft gab es in diesen drei Ländern 21 tödliche Anti-Terror-Operationen. Trump hat diese Zahl verfünffacht und mindestens 92 solcher Operationen im Jemen, sieben in Somalia und vier in Pakistan durchgeführt.«
Klingt für mich jetzt nicht so ganz nach Friedenstauben.
Wahrscheinlich war es am Ende nur die Hektik bei der Übergabe der Amtsgeschäfte im Januar 2021, oder der Stress permanenter Medienpräsenz, der Trump auch noch davon abhielt, Julian Assange oder Edward Snowden zu begnadigen. Immerhin war er »kurz davor, einen der beiden auszuwählen«, wie er in einem Interview für Daily Wire verlauten ließ. Am Ende blieb dann aber leider doch nur Zeit für die Begnadigung der anderen 116 Personen auf der Liste. Dumm gelaufen.
Wenden wir uns der Gegenwart zu. Und dem, was uns die nächsten vier Jahre erwarten könnte. Es muss ja jetzt auf jeden Fall alles viel besser laufen als in der ersten Runde. Denn in den Augen vieler seiner Unterstützer habe Trump in der Zwischenzeit viel gelernt und wurde damals nur hinters Licht geführt. Überrumpelt vom Tiefenstaat, den er eigentlich abschaffen wollte. Zudem hat er nun Elon Musk und RFK Jr. an seiner Seite, der gemäß Lutnik zwar keinen Job bekommt, aber immerhin steht irgendwo Kennedy auf der Banderole. Das ist doch auch was.
Ernsthaft. Bereits in Rahmen seiner ersten Amtszeit plante Trump, ein biometrisches System zur Ein- und Ausreisekontrolle zu etablieren. Es sollte zunächst nur für Ausländer gelten. Aber jeder weiß, dass es nicht lange dauert, bis so ein System für jeden gilt. Dazu passt, dass seit Beginn des Wahlkampfes 2024 permanent von der Voter ID gesprochen wird. Ausweise für alle – gegen Wahlbetrug. Bisher besitzen nur knapp 40 Prozent der Amerikaner einen Reisepass. Nur acht Prozent verlassen im Urlaub überhaupt das Land. Die virtuelle Wand wird das ändern, nicht nur an der Grenze zu Mexiko. Denn über kurz oder lang resultiert das Projekt in der flächendeckenden Einführung einer eID. Basis für die eID- oder Voter ID-Infrastruktur könnte zum Beispiel E-Verify sein, ein vom Department of Homeland Security betriebenes Projekt zur Verifikation von Personen, dessen Nutzung für Personalabteilungen von Bundesbehörden seit dem 1. Oktober 2007 obligatorisch ist. Die Nominierung von Tom Homan als Chef der Einwanderungs- und Zollbehörde impliziert, dass genau dieser Kurs eingeschlagen wird. Homan ist Hardliner. Er war Teil des rechtskonservativen Project 2025 und befürwortet neben flächendeckender Biometrie auch die Trennung von Eltern und Kindern an der Grenze.
Kein Zufall also, dass der Gründer der Cardano-Blockchain, Charles Hoskinson, die Regierung Trump ab 2025 in Bezug auf Kryptoanwendungen beraten soll. Immerhin hatte Hoskinson bereits mit dem von Jeffrey Epstein finanzierten Ben Goertzel ein biometrisches eID-System für Schulkinder in Äthiopien entwickelt. Und nachdem die von Peter Thiel finanzierte Silikon-Valley-Marionette JD Vance als Vizepräsident fungiert, hat auch der mächtigste Überwachungskonzern der Welt, Palantir, nun einen Fuß in der Tür des Oval Office. Mit diesem Setup dürfte der gläserne Bürger der Gegenwart bald ein Relikt der Vergangenheit sein.
Ganz zur Freude von Ex-Spion John Ratcliffe, dem neuen CIA-Direktor unter »Orange Man«. In Trumps erster Amtszeit war Ratcliffe »Director of National Intelligence«, unter George W. Bush zuständig für Anti-Terror-Operationen und nationale Sicherheit. Später leitete er zusammen mit John Ashcroft, Generalstaatsanwalt unter Bush und Architekt des Ermächtigungsgesetzes »Patriot Act«, ein Unternehmen für strategische Beratung (AGS). Im Dezember 2023 unterstützte John Ratcliffe den Bilderberger, Kriegstreiber und Tiefenstaat-Neocon Mike Pompeo bei der Erneuerung des Foreign Intelligence Surveillance Act (FISA), der die fortgesetzte, anlasslose Massenüberwachung der US-Bevölkerung legalisiert. Und kaum war er nominiert, machte Ratcliffe am 13. November 2024 auf FOX-News wahrheitswidrig Stimmung gegen den Iran und unterstellte der dortigen Regierung »kriegerische Handlungen« gegenüber den USA.
Kollaborieren wird Ratcliffe künftig mit Tulsi Gabbard. Sie beerbt ihn als Trumps neuer »Director of National Intelligence«. Gabbard war Mitglied der WEF Young Global Leaders sowie des Council on Foreign Relations (CFR). Beide Organisationen tilgten ihren Namen von der eigenen Homepage, nachdem Gabbard öffentlich über US-Biowaffenlabore in der Ukraine sprach. In Interviews bestätigt sie ihre Rolle im CFR allerdings selbst. Gabbard befürwortete die Covid-Impfkampagne und schmückt sich gerne mit dem Image »Kriegsveteran« – obwohl sie die Schrecken des Krieges lediglich aus sicherer Entfernung sah. Eine Opportunistin, deren konservativ-kritisches Image nichts weiter ist als ein wackliges Kartenhaus.
»Ich war Kadett. Was ist das Motto der Kadetten in West Point? Du wirst nicht lügen, betrügen, oder stehlen – und diejenigen nicht dulden, die das tun. Ich war der CIA-Direktor. Wir haben gelogen, wir haben betrogen, wir haben gestohlen. Wir haben ganze Trainingskurse dazu absolviert.« (Mike Pompeo, April 2019)
Und wer denkt, Donald Trump werde wenigstens die Einführung einer digitalen Zentralbankwährung (CBDC) verhindern, irrt. Zumindest im Kern. Denn im Rahmen seiner Rede auf der Bitcoin Konferenz 2024 sprach Donald Trump von »regulatorischer Klarheit« sowie der »sicheren und verantwortungsvollen Expansion von Stablecoins«. Damit bestätigte er, dass die Einführung von digitalem Geld über privatwirtschaftliche Entitäten erfolgen wird. Denn ein Konto bei der Zentralbank will niemand. Leider werden aber die Transaktionen all der ach so marktwirtschaftlich eingeführten Digitalwährungen zentral erfasst. Im »Unified Ledger« der Bank für Internationalen Zahlungsausgleich (BIZ) in Basel. Was am Ende zum exakt gleichen Ergebnis führt wie eine vom Staat oder der Zentralbank aufgelegte CBDC – zu lückenloser Überwachung mit Interventionspotenzial.
Zurück zur künftigen Regierung. Stabschef im Weißen Haus und damit »mächtigste Frau in Washington« soll Susie Wiles werden – bisher Co-Vositzende von Mercury Public Affairs LLC, einem Lobby-Giganten, der unter anderem Pfizer, GAVI, die Vereinten Nationen oder SpaceX vertritt. Mercury Public Affairs gehört seit 2003 zur Omnicom Group, einem WEF-Partner für Öffentlichkeitsarbeit. Wiles gilt als die »am meisten gefürchtete und am wenigsten bekannte Politagentin Amerikas«.
Als Außenminister nominierte Trump den von der Zionismus-Lobby korrumpierten Marco Rubio. Einen Neocon. Sprich: Militärischer Interventionismus und unilaterale Hegemonieansprüche. Den Posten des nationalen Sicherheitsberaters offeriert Trump dem ehemaligen Green Beret Mike Waltz. Neben Marco Rubio der zweite Mann in der künftigen Regierung, der sich mit China anlegen möchte. Ergänzt wird das kriegsaffine Duo von Brian Hook, der dem Iran am liebsten sofort den Krieg erklären möchte und den Auftrag erhielt, Schlüsselpositionen im Außenministerium mit geeignetem Personal dafür zu besetzen.
Der ehemalige texanische Kongressabgeordnete Ron Paul sieht in diesen Nominierungen »einen schlechten Tag für jene, die an America First glaubten«. Sollte Trump die Unterstützung der Ukraine seitens Amerika tatsächlich beenden, dürften nämlich ersatzweise zuerst der Iran und langfristig eventuell gar China von Demokratie aus der Luft beglückt werden. Daran wird auch die neue US-Botschafterin bei den Vereinten Nationen nichts ändern. Denn Elise Stefanik hat praktisch keine relevante Berufserfahrung – und ist ebenfalls ein Neocon. Sowohl Stefanik als auch Rubio, Waltz oder Hook setzen sich für weitere Waffenlieferungen nach Israel und eine Fortsetzung des auch von israelischen Zeitungen also solchen bezeichneten Genozids in Gaza ein.
»Die westliche Zivilisation repräsentiert heute das Verständnis, dass Zionismus und Amerikanismus die Frontlinien der westlichen Zivilisation und Freiheit in unserer Welt sind«, erklärte der Army-Veteran, United Against Nuclear Iran-Advokat und Ex-FOX-News-Mitarbeiter Pete Hegseth im April 2019.
An dieser faschistoiden wie imperialistischen Doktrin scheinen sich auch Trump und Co. zu orientieren – denn Hegseth wird nun Verteidigungsminister. Passend dazu wird Mike Huckabee, ein bekennender Zionist, der nächste US-Botschafter in Israel. Huckabee nennt das Westjordanland Judäa und behauptet entgegen historischer Fakten, dass es Teil Israels ist. Auch die Annexion der Westbank fände er in Ordnung. Seine Nominierung kann als Kriegserklärung an die Palästinenser verstanden werden. Wohlwissend, dass Israels völkerrechtswidriges Vorgehen leicht zu einem regionalen, wenn nicht globalen Flächenbrand führen kann.
Apropos globale Themen: Dahingehend lohnt sich ein genauerer Blick auf die Hintergründe des bereits erwähnten Howard Lutnick. Diesen hat die Investigativ-Journalistin Whitney Webb am 7. November 2024 gewagt. Unter der Überschrift »Macht euch bereit für den Kohlenstoffmarkt der Republikaner« erklärt sie:
»Viele der einflussreichsten Namen der kommenden Trump-Regierung sowie der vorherigen haben sich in den letzten Jahren intensiv mit der Schaffung von Kohlenstoffmärkten befasst, während andere eine langjährige Erfolgsgeschichte bei der Implementierung von CO2-Steuern und anderen Formen der CO2-Bepreisung vorweisen können. Der wichtigste unter ihnen ist Howard Lutnick, Co-Vorsitzender von Trumps Transition-Team, der erklärte, seine Aufgabe sei es, Talente für die kommende Regierung zu finden. Lutnick ist der langjährige Leiter von Cantor Fitzgerald, einem der ersten Akteure im Emissionshandel, der sich seitdem zu einem weltweit führenden Unternehmen für ESG-Investitionen, die Finanzierung nachhaltiger Infrastruktur und grüne Anleihen entwickelt hat. So hat sich Cantors nachhaltiger Infrastrukturfonds ausdrücklich der digitalen Transformation, Dekarbonisierung und Verbesserung und Modernisierung alternder Infrastruktur verschrieben, während ein Hauptaugenmerk des Fonds darauf liegen wird, in Emittenten zu investieren, die mit ihren Produkten und Dienstleistungen dazu beitragen, bestimmte Ziele der Vereinten Nationen für nachhaltige Entwicklung zu erreichen. Darüber hinaus ist Invenergy, ein Unternehmen für erneuerbare Energien, das im Rahmen von Bidens umstrittenem Inflationsbekämpfungsgesetz eine beträchtliche Menge an Subventionen erhalten hat und vom ersten Windmilliardär des Landes, Michael Polsky, geleitet wird, der wichtigste Bestandteil eines weiteren Infrastrukturfonds von Cantor. Lutnick sitzt auch im Vorstand eines Satellitenüberwachungsunternehmens namens Satellogic. Neben Lutnick ist der ehemalige Finanzminister von Trump, Steve Mnuchin, Vorsitzender des Vorstands. Auch Joe Dunford, ehemaliger Stabschef des US-Militärs unter Trump, sitzt im Vorstand. Satellogic ist integraler Bestandteil eines Konsortiums, das versucht, durch undurchsichtige vertragliche Vereinbarungen auf kommunaler Ebene einen riesigen, Blockchain-basierten Kohlenstoffmarkt in Lateinamerika durchzusetzen. Dieser Kohlenstoffmarkt, der unter dem Namen GREEN+ operiert, soll auf einer Bitcoin-Sidechain aufgebaut werden. Das entsprechende Emissionsgutschriftsystem ist für lateinamerikanische Gemeinden zutiefst ungerecht. So könnten die betroffenen Gemeinden beispielsweise nur Geld verdienen, wenn Einnahmen unter den für GREEN+ anerkannten, nachhaltigen Projekten generiert werden, während die Investoren von GREEN+ den Großteil der Gewinne einstreichen. Das Programm würde Gemeinden außerdem ohne ihre Zustimmung dem Satellitenüberwachungsapparat von Satellogic (der mit der US-Regierung und dem israelischen Geheimdienst verbunden ist) aussetzen. Darüber hinaus ist GREEN+ in bemerkenswerter Weise mit Personen verbunden, die Trumps Verbündeten in der Region nahestehen. So ist eine wichtige Persönlichkeit in Nayib Bukeles politischer Partei – der Bürgermeister von San Salvador, Mario Durán – Vizepräsident einer der wichtigsten Gruppen, die das GREEN+-Programm orchestrieren, während das Netzwerk Endeavor Argentina, das sehr enge Verbindungen zu Javier Milei pflegt, ebenfalls eng mit Satellogic verbunden ist. Satellogic ist ein von Endeavor unterstütztes Unternehmen, während Endeavors erster Milliardär und Unternehmer, Marcos Galperín von MercadoLibre, im Vorstand von Satellogic sitzt. Darüber hinaus ist ein anderer wichtiger Investor von Satellogic, der Dollar-Stablecoin-Emittent Tether, auch eng mit Howard Lutnick verbunden. Lutnick ist langjähriger Fürsprecher von Tether. Und Cantor Fitzgerald hält den Großteil der US-Staatsanleihen von Tether, um deren Stablecoin und seine Bindung an den US-Dollar zu stützen.«
Das sollte Wähler, die dem Klimawandel-Narrativ und Digitalwährungen skeptisch gegenüberstehen, hellhörig werden lassen – denn auch wenn Donald Trump im Rahmen seiner öffentlichen Auftritte gegen die Nachhaltigkeitsagenda wettert und der leitmediale Komplex seine entsprechenden Phrasen für Konterpropaganda nutzt, sprechen die Taten wieder einmal eine ganz andere Sprache. In Anbetracht vorgängig beschriebener Umstände sieht es nämlich nicht so aus, als widersetze sich der 47. US-Präsident dem Nachhaltigkeitskorporatismus der UN. Im Gegenteil.
»Der König ist tot, es lebe der König«. Die neue US-Regierung wird die gleiche Agenda fahren wie die alte – nur die Vermarktung ändert sich. Das kündigte Lynn Forester de Rothschild (CIC) schon vor über einem Jahr bei Bloomberg an. Genau wie Larry Fink (BlackRock).
Die Einführung biometrischer Massenüberwachung wird nun mit der Migrationskrise und drohendem Wahlbetrug, mit der Stärkung der Demokratie gerechtfertigt, anstatt mit einem Virus. Den Krieg in der Ukraine wird man nicht weiter unterstützen. Diesen Brandherd sollen die Europäer am Kokeln halten, damit man endlich den Iran und China ins Fadenkreuz nehmen kann. So ein dritter Weltkrieg wäre nämlich ein profitables Geschäft. Das Klimawandel-Narrativ wird man öffentlich negieren und verhöhnen, während die Agenda 2030 trotzdem umsetzt wird. Gleiches gilt für Totalüberwachung, Genderwahn, globale Gleichschaltung von Lerninhalten und die schleichende Digitalisierung des Weltfinanzsystems. Denn auch diese Programme werden von überstaatlichen Akteuren vorangetrieben und entziehen sich dem Einfluss nationaler Regierungen. So funktioniert Korporatismus.
Ernüchternd ist vor allem, dass sich die Bevölkerung, die in den letzten vier Jahren tatsächlich ein gewisses Maß an rebellischem Potenzial entwickelte, wieder einmal täuschen lässt. Trump-Hype wohin man schaut. Selbst die Corona-Dissidenten, selbst jene, die dem Staat aufgrund von Covid-Lügen, Green-Economy-Deindustrialisierung und militantem Neoimperialismus zusehends kritisch gegenüberstanden, haben sich in weiten Teilen von den leeren Versprechungen der MAGA-Promotion und ihren Sekundanten blenden lassen.
Sie werden genauso desillusioniert zurückbleiben wie einst die auf »Hope« geeichten Obama-Fans – und sich in ein paar Jahren vermutlich trotzdem wieder an die Wahlurne schleppen, weil sie auf den nächsten Erlöser hoffen, anstatt selbst die Welt zu verändern.
Zur Wahl stehen aber jeweils nur verschiedene Geschmacksrichtungen der gleichen, bitteren Pille Marke Unterdrückung. Keine Unterdrückung – das ist natürlich keine Option. Das steht nicht auf dem Wahlzettel.
Linke gegen Rechte, Demokraten gegen Republikaner, Christentum gegen Islam – Bevölkerungsgruppen, die man gegeneinander aufwiegeln kann, finden sich dagegen immer. Präsentiert man ihnen einen verheißungsvollen Erlöser, werden sie ihn unterstützen, um die andere Gruppe loszuwerden. Das ist Herrschaftsdialektik. Man bringt die Menschen dazu, um Dinge zu betteln, die ohnehin eingeführt werden sollen. Und der einzige Gewinner in diesem immer riskanter werdenden Spiel ist die Prädatorenkaste.
»Die mächtigste Waffe in den Händen der Unterdrücker ist der Geist der Unterdrückten.« (Stephen Bantu Biko)
Wer Donald Trump unterstützt, ist nicht für Frieden und Freiheit, sondern nur gegen das, was die andere Seite will. Denn Donald Trumps Interesse gilt nicht Frieden und Freiheit, sondern Donald Trump. So war es sein ganzes Leben lang.
-
 @ 07907690:d4e015f6
2024-12-11 03:45:40
@ 07907690:d4e015f6
2024-12-11 03:45:40Dhruv Bansal, CSO dan Co-Founder Unchained mengeksplorasi prinsip-prinsip dan sejarah yang mengarah pada penciptaan Bitcoin dan mengajukan pertanyaan: "Apa yang telah dilakukan Satoshi"?
Bitcoin sering dibandingkan dengan internet pada tahun 1990an, namun saya yakin analogi yang lebih baik adalah dengan telegraf pada tahun 1840an.[^1]
Telegraf adalah teknologi pertama yang mengirimkan data yang dikodekan dengan kecepatan mendekati cahaya dalam jarak jauh. Ini menandai lahirnya industri telekomunikasi. Internet, meskipun skalanya lebih besar, kontennya lebih kaya, dan many-to-many, bukan one-to-one, pada dasarnya masih merupakan teknologi telekomunikasi.
Baik telegraf maupun internet bergantung pada model bisnis di mana perusahaan mengerahkan modal untuk membangun jaringan fisik dan kemudian membebankan biaya kepada pengguna untuk mengirim pesan melalui jaringan ini. Jaringan AT&T secara historis mengirimkan telegram, panggilan telepon, paket TCP/IP, pesan teks, dan sekarang TikTok.
Transformasi masyarakat melalui telekomunikasi telah menghasilkan kebebasan yang lebih besar namun juga sentralisasi yang lebih besar. Internet telah meningkatkan jangkauan jutaan pembuat konten dan usaha kecil, namun juga memperkuat jangkauan perusahaan, otoritas pusat, dan lembaga lain yang memiliki posisi yang cukup baik untuk memantau dan memanipulasi aktivitas online.
Namun Bitcoin bukanlah akhir dari transformasi apa pun—ini adalah awal dari sebuah transformasi. Seperti halnya telekomunikasi, Bitcoin akan mengubah kebiasaan umat manusia dan kehidupan sehari-harinya. Memprediksi seluruh cakupan perubahan saat ini sama dengan membayangkan internet saat hidup di era telegraf.
Seri ini mencoba membayangkan masa depan dengan memulai dari masa lalu. Artikel awal ini menelusuri sejarah mata uang digital sebelum Bitcoin. Hanya dengan memahami kegagalan proyek-proyek sebelumnya, kita dapat memahami apa yang membuat Bitcoin berhasil—dan bagaimana hal itu menyarankan metodologi untuk membangun sistem desentralisasi di masa depan.
Klaim utama dari artikel ini adalah bahwa Bitcoin dapat dianggap sebagai adaptasi dari proyek B-money Dai yang menghilangkan kebebasan untuk menciptakan uang. Hanya beberapa minggu setelah artikel ini pertama kali diterbitkan, email baru muncul di mana Satoshi mengaku tidak terbiasa dengan B-money, namun mengakui bahwa Bitcoin dimulai “tepat dari titik itu.” Mengingat bukti baru ini, kami yakin klaim utama ini, meskipun tidak akurat secara historis, masih merupakan cara yang bermakna dan bermanfaat untuk memikirkan asal usul Bitcoin.
Bagaimana Satoshi Nakamoto Memikirkan Bitcoin?
Satoshi memang cerdas, tetapi Bitcoin tidak muncul begitu saja.
Bitcoin mengulangi pekerjaan yang ada di bidang kriptografi, sistem terdistribusi, ekonomi, dan filsafat politik. Konsep proof-of-work sudah ada jauh sebelum digunakan dalam uang dan cypherpunk sebelumnya seperti Nick Szabo, Wei Dai, & Hal Finney mengantisipasi dan memengaruhi desain Bitcoin dengan proyek-proyek seperti bit gold, B-money, dan RPoW. Pertimbangkan bahwa, pada tahun 2008, ketika Satoshi menulis white paper Bitcoin[^2], banyak ide penting Bitcoin telah diusulkan dan/atau diimplementasikan:
- Mata uang digital harus berupa jaringan P2P
- Proof-of-work adalah dasar penciptaan uang
- Uang diciptakan melalui lelang
- Kunci publik kriptografi digunakan untuk menentukan kepemilikan dan transfer koin
- Transaksi dikelompokkan menjadi beberapa blok
- Blok dirangkai bersama melalui proof-of-work
- Semua blok disimpan oleh semua peserta
Bitcoin memanfaatkan semua konsep ini, tetapi Satoshi tidak menciptakan satu pun konsep tersebut. Untuk lebih memahami kontribusi Satoshi, kita harus menentukan prinsip Bitcoin mana yang tidak ada dalam daftar.
Beberapa kandidat yang jelas adalah persediaan Bitcoin yang terbatas, konsensus Nakamoto, dan algoritma penyesuaian kesulitan. Tapi apa yang mendorong Satoshi pada ide ini?
Artikel ini mengeksplorasi sejarah mata uang digital dan menyatakan bahwa fokus Satoshi pada kebijakan moneter yang sehat adalah hal yang menyebabkan Bitcoin mengatasi tantangan yang mengalahkan proyek-proyek sebelumnya seperti bit gold dan B-money.
Sistem yang Terdesentralisasi Adalah Pasar
Bitcoin sering digambarkan sebagai sistem terdesentralisasi atau terdistribusi. Sayangnya, kata “desentralisasi” dan “terdistribusi” sering kali membingungkan. Ketika diterapkan pada sistem digital, kedua istilah tersebut mengacu pada cara aplikasi monolitik dapat didekomposisi menjadi jaringan bagian-bagian yang berkomunikasi.

Untuk tujuan kita, perbedaan utama antara sistem terdesentralisasi dan terdistribusi bukanlah topologi diagram jaringannya, namun cara mereka menegakkan aturan. Kami meluangkan waktu di bagian berikut untuk membandingkan sistem terdistribusi dan desentralisasi dan memotivasi gagasan bahwa sistem desentralisasi yang kuat adalah pasar.
Sistem Terdistribusikan Bergantung pada Otoritas Pusat
Dalam hal ini, kami mengartikan “terdistribusi” sebagai sistem apa pun yang telah dipecah menjadi beberapa bagian (sering disebut sebagai "node") yang harus berkomunikasi, biasanya melalui jaringan.
Insinyur perangkat lunak semakin mahir dalam membangun sistem yang terdistribusi secara global. Internet terdiri dari sistem terdistribusi yang secara kolektif berisi miliaran node. Kita masing-masing memiliki simpul di saku kita yang berpartisipasi dan bergantung pada sistem ini.
Namun hampir semua sistem terdistribusi yang kita gunakan saat ini diatur oleh beberapa otoritas pusat, biasanya administrator sistem, perusahaan, atau pemerintah yang saling dipercaya oleh semua node dalam sistem.
Otoritas pusat memastikan semua node mematuhi aturan sistem dan menghapus, memperbaiki, atau menghukum node yang gagal mematuhinya. Mereka dipercaya untuk melakukan koordinasi, menyelesaikan konflik, dan mengalokasikan sumber daya bersama. Seiring waktu, otoritas pusat mengelola perubahan pada sistem, memperbarui atau menambahkan fitur, dan memastikan bahwa node yang berpartisipasi mematuhi perubahan tersebut.
Manfaat yang diperoleh sistem terdistribusi karena mengandalkan otoritas pusat juga disertai dengan biaya. Meskipun sistem ini kuat terhadap kegagalan node-nodenya, kegagalan otoritas pusat dapat menyebabkan sistem berhenti berfungsi secara keseluruhan. Kemampuan otoritas pusat untuk mengambil keputusan secara sepihak berarti menumbangkan atau menghilangkan otoritas pusat sudah cukup untuk mengendalikan atau menghancurkan keseluruhan sistem.
Terlepas dari adanya trade-off ini, jika ada persyaratan bahwa satu partai atau koalisi harus mempertahankan otoritas pusat, atau jika peserta dalam sistem tersebut puas dengan mengandalkan otoritas pusat, maka sistem terdistribusi tradisional adalah solusi terbaik. Tidak diperlukan blockchain, token, atau sistem desentralisasi serupa.
Secara khusus, kasus VC atau mata uang kripto yang didukung oleh pemerintah, dengan persyaratan bahwa satu pihak dapat memantau atau membatasi pembayaran dan membekukan akun, adalah kasus penggunaan yang sempurna untuk sistem terdistribusi tradisional.
Sistem Desentralisasi Tidak Memiliki Otoritas Pusat
Kami menganggap “desentralisasi” memiliki arti yang lebih kuat daripada “terdistribusi”: sistem desentralisasi adalah bagian dari sistem terdistribusi yang tidak memiliki otoritas pusat. Sinonim yang mirip dengan “desentralisasi” adalah “peer-to-peer” (P2P).
Menghapus otoritas pusat memberikan beberapa keuntungan. Sistem terdesentralisasi:
- Tumbuh dengan cepat karena tidak ada hambatan untuk masuk—siapa pun dapat mengembangkan sistem hanya dengan menjalankan node baru, dan tidak ada persyaratan untuk registrasi atau persetujuan dari otoritas pusat.
- Kuat karena tidak ada otoritas pusat yang kegagalannya dapat membahayakan berfungsinya sistem. Semua node adalah sama, jadi kegagalan bersifat lokal dan jaringan merutekan sekitar kerusakan.
- Sulit untuk ditangkap, diatur, dikenakan pajak, atau diawasi karena tidak adanya titik kendali terpusat yang dapat ditumbangkan oleh pemerintah.
Kekuatan inilah yang menjadi alasan Satoshi memilih desain Bitcoin yang terdesentralisasi dan peer-to-peer:
“Pemerintah pandai memotong… jaringan yang dikendalikan secara terpusat seperti Napster, namun jaringan P2P murni seperti Gnutella dan Tor tampaknya masih mampu bertahan.” - Satoshi Nakamoto, 2008
Namun kekuatan ini juga disertai dengan kelemahan. Sistem yang terdesentralisasi bisa menjadi kurang efisien karena setiap titik harus memikul tanggung jawab tambahan untuk koordinasi yang sebelumnya diambil alih oleh otoritas pusat.
Sistem yang terdesentralisasi juga sering dilanda perilaku yang bersifat penipuan dan bertentangan. Terlepas dari persetujuan Satoshi terhadap Gnutella, siapa pun yang menggunakan program berbagi file P2P untuk mengunduh file yang ternyata kotor atau berbahaya memahami alasan mengapa berbagi file P2P tidak pernah menjadi model utama untuk transfer data online.
Satoshi tidak menyebutkannya secara eksplisit, namun email adalah sistem terdesentralisasi lainnya yang menghindari kendali pemerintah. Dan email juga terkenal sebagai spam.
Sistem Desentralisasi diatur Melalui Insentif
Akar masalahnya, dalam semua kasus ini adalah, bahwa perilaku kejahatan (menyebarkan file buruk, mengirim email spam) tidak dihukum, dan perilaku kooperatif (menyebarkan file bagus, hanya mengirim email berguna) tidak dihargai. Sistem desentralisasi yang mengandalkan partisipannya untuk menjadi aktor yang baik gagal untuk berkembang karena sistem tersebut tidak dapat mencegah aktor jahat untuk ikut berpartisipasi.
Tanpa memaksakan otoritas pusat, satu-satunya cara untuk menyelesaikan masalah ini adalah dengan menggunakan insentif ekonomi. Aktor yang baik, menurut definisinya, bermain sesuai aturan karena mereka secara inheren termotivasi untuk melakukannya. Pelaku kejahatan, menurut definisinya, adalah orang yang egois dan licik, namun insentif ekonomi yang tepat dapat mengarahkan perilaku buruk mereka ke arah kebaikan bersama. Sistem yang terdesentralisasi melakukan hal ini dengan memastikan bahwa perilaku kooperatif menguntungkan dan perilaku kejahatan merugikan.
Cara terbaik untuk menerapkan layanan terdesentralisasi yang kuat adalah dengan menciptakan pasar di mana semua pelaku, baik dan buruk, dibayar untuk menyediakan layanan tersebut. Kurangnya hambatan masuk bagi pembeli dan penjual di pasar yang terdesentralisasi mendorong skala dan efisiensi. Jika protokol pasar dapat melindungi partisipan dari penipuan, pencurian, dan penyalahgunaan, maka pelaku kejahatan akan merasa lebih menguntungkan untuk mengikuti aturan atau menyerang sistem lain.
Pasar yang Terdesentralisasi Membutuhkan Barang yang Terdesentralisasi
Namun pasar itu rumit. Mereka harus memberi pembeli dan penjual kemampuan untuk mengirimkan penawaran dan permintaan serta menemukan, mencocokkan, dan menyelesaikan pesanan. Kebijakan tersebut harus adil, memberikan konsistensi yang kuat, dan menjaga ketersediaan meskipun terjadi masa-masa yang tidak menentu.
Pasar global saat ini sangat mumpuni dan canggih, namun menggunakan barang-barang tradisional dan jaringan pembayaran untuk menerapkan insentif di pasar yang terdesentralisasi bukanlah hal yang baru. Setiap penggabungan antara sistem desentralisasi dan uang fiat, aset tradisional, atau komoditas fisik akan menimbulkan kembali ketergantungan pada otoritas pusat yang mengontrol pemroses pembayaran, bank, dan bursa.

Sistem terdesentralisasi tidak dapat mentransfer uang tunai, mencari saldo rekening perantara, atau menentukan kepemilikan properti. Barang-barang tradisional sama sekali tidak terbaca dalam sistem desentralisasi. Hal sebaliknya tidak benar—sistem tradisional dapat berinteraksi dengan Bitcoin semudah aktor lainnya (begitu mereka memutuskan ingin melakukannya). Batasan antara sistem tradisional dan desentralisasi bukanlah sebuah tembok yang tidak dapat dilewati, melainkan sebuah membran semi-permeabel.
Ini berarti bahwa sistem yang terdesentralisasi tidak dapat melaksanakan pembayaran dalam mata uang barang tradisional apa pun. Mereka bahkan tidak dapat menentukan saldo rekening yang didominasi fiat atau kepemilikan real estat atau barang fisik. Seluruh perekonomian tradisional sama sekali tidak terbaca dalam sistem desentralisasi.
Menciptakan pasar yang terdesentralisasi membutuhkan perdagangan barang-barang baru yang terdesentralisasi yang dapat dibaca dan ditransfer dalam sistem yang terdesentralisasi.
Komputasi Adalah Barang Terdesentralisasi yang Pertama
Contoh pertama dari “barang terdesentralisasi” adalah kelas komputasi khusus yang pertama kali diusulkan pada tahun 1993 oleh Cynthia Dwork dan Moni Naor.[^3]
Karena adanya hubungan mendalam antara matematika, fisika, dan ilmu komputer, komputasi ini memerlukan energi dan sumber daya perangkat keras di dunia nyata—hal ini tidak dapat dipalsukan. Karena sumber daya di dunia nyata langka, komputasi ini juga langka.
input untuk komputasi ini dapat berupa data apa pun. Keluaran yang dihasilkan adalah “bukti” digital bahwa pengkomputasian telah dilakukan pada data input yang diberikan. Pembuktian mengandung “kesulitan” tertentu yang merupakan bukti (statistik) dari sejumlah pekerjaan komputasi tertentu. Yang terpenting, hubungan antara data input, pembuktian, dan pekerjaan komputasi asli yang dilakukan dapat diverifikasi secara independen tanpa perlu mengajukan banding ke otoritas pusat mana pun.
Gagasan untuk menyebarkan beberapa data input bersama dengan bukti digital sebagai bukti kerja komputasi dunia nyata yang dilakukan pada input tersebut sekarang disebut “proof-of-work”.[^4] Proof-of-work adalah, jika menggunakan ungkapan Nick Szabo, “biaya yang tidak dapat ditiru”. Karena proof-of-work dapat diverifikasi oleh siapa pun, maka proof-of-work merupakan sumber daya ekonomi yang dapat dibaca oleh semua peserta dalam sistem desentralisasi. Proof-of-work mengubah penghitungan data menjadi barang yang terdesentralisasi. Dwork & Naor mengusulkan penggunaan komputasi untuk membatasi penyalahgunaan sumber daya bersama dengan memaksa peserta untuk memberikan proof-of-work dengan tingkat kesulitan minimum tertentu sebelum mereka dapat mengakses sumber daya:
“Dalam makalah ini kami menyarankan pendekatan komputasi untuk memerangi penyebaran surat elektronik. Secara umum, kami telah merancang mekanisme kontrol akses yang dapat digunakan kapan pun diinginkan untuk membatasi, namun tidak melarang, akses ke sumber daya.” - Dwoak & Naor, 1993
Dalam proposal Dwork & Naor, administrator sistem email akan menetapkan tingkat kesulitan bukti kerja minimum untuk mengirimkan email. Pengguna yang ingin mengirim email perlu melakukan sejumlah komputasi yang sesuai dengan email tersebut sebagai data input. Bukti yang dihasilkan akan dikirimkan ke server bersamaan dengan permintaan pengiriman email.
Dwork & Naor menyebut kesulitan proof-of-work sebagai “fungsi penetapan harga” karena, dengan menyesuaikan kesulitan tersebut, “otoritas penetapan harga” dapat memastikan bahwa sumber daya bersama tetap murah untuk digunakan bagi pengguna yang jujur dan rata-rata, namun mahal bagi pengguna yang mencari untuk mengeksploitasinya. Di pasar pengiriman email, administrator server adalah otoritas penetapan harga; mereka harus memilih “harga” untuk pengiriman email yang cukup rendah untuk penggunaan normal namun terlalu tinggi untuk spam.
Meskipun Dwork & Naor membingkai proof-of-work sebagai disinsentif ekonomi untuk memerangi penyalahgunaan sumber daya, nomenklatur “fungsi penetapan harga” dan “otoritas penetapan harga” mendukung interpretasi yang berbeda dan berbasis pasar: pengguna membeli akses ke sumber daya dengan imbalan komputasi pada tingkat yang sama. harga yang ditetapkan oleh pengontrol sumber daya.
Dalam interpretasi ini, jaringan pengiriman email sebenarnya adalah pengiriman email perdagangan pasar yang terdesentralisasi untuk komputasi. Kesulitan minimum dari proof-of-work adalah harga yang diminta untuk pengiriman email dalam mata uang komputasi.
Mata Uang Adalah Barang Terdesentralisasi yang kedua
Namun komputasi bukanlah mata uang yang baik.
Bukti yang digunakan untuk “memperdagangkan” komputasi hanya valid untuk input yang digunakan dalam komputasi tersebut. Hubungan yang tidak dapat dipecahkan antara bukti spesifik dan input tertentu berarti bahwa proof-of-work untuk satu input tidak dapat digunakan kembali untuk input yang berbeda.

Proof-of-work awalnya diusulkan sebagai mekanisme kontrol akses untuk membatasi email spam. Pengguna diharapkan memberikan bukti kerja bersama email apa pun yang ingin mereka kirim. Mekanisme ini juga dapat dianggap sebagai pasar di mana pengguna membeli pengiriman email dengan komputasi pada harga yang dipilih oleh penyedia layanan email.
Batasan ini berguna – dapat digunakan untuk mencegah pekerjaan yang dilakukan oleh satu pembeli di pasar kemudian dibelanjakan kembali oleh pembeli lain. Misalnya, HashCash, implementasi nyata pertama dari pasar pengiriman email, menyertakan metadata seperti stempel waktu saat ini dan alamat email pengirim dalam data masukan untuk penghitungan bukti kerja. Bukti yang dihasilkan oleh pengguna tertentu untuk email tertentu, tidak dapat digunakan untuk email yang berbeda.
Namun ini juga berarti bahwa komputasi bukti kerja adalah barang yang dipesan lebih dahulu. Dana tersebut tidak dapat dipertukarkan, tidak dapat dibelanjakan kembali,[^5] dan tidak memecahkan masalah kebutuhan yang terjadi secara kebetulan. Properti moneter yang hilang ini mencegah komputasi menjadi mata uang. Terlepas dari namanya, tidak ada insentif bagi penyedia pengiriman email untuk ingin mengakumulasikan HashCash, karena akan ada uang tunai sebenarnya.
Adam Back, penemu HashCash, memahami masalah berikut:
"Hashcash tidak dapat ditransfer secara langsung karena untuk membuatnya didistribusikan, setiap penyedia layanan hanya menerima pembayaran dalam bentuk tunai yang dibuat untuk mereka. Anda mungkin dapat menyiapkan pencetakan gaya digicash (dengan chaumian ecash) dan meminta bank hanya mencetak uang tunai pada penerimaan tabrakan hash yang ditangani. Namun ini berarti Anda harus mempercayai bank untuk tidak mencetak uang dalam jumlah tak terbatas untuk digunakan sendiri." - Adam Back, 1997
Kita tidak ingin menukar komputasi yang dibuat khusus untuk setiap barang atau jasa yang dijual dalam perekonomian yang terdesentralisasi. Kita menginginkan mata uang digital serba guna yang dapat langsung digunakan untuk mengoordinasikan pertukaran nilai di pasar mana pun.
Membangun mata uang digital yang berfungsi namun tetap terdesentralisasi merupakan tantangan yang signifikan. Mata uang membutuhkan unit yang dapat dipertukarkan dengan nilai yang sama yang dapat ditransfer antar pengguna. Hal ini memerlukan model penerbitan, definisi kriptografi kepemilikan dan transfer, proses penemuan dan penyelesaian transaksi, dan buku besar historis. Infrastruktur ini tidak diperlukan ketika bukti kerja hanya dianggap sebagai “mekanisme kontrol akses”.
Terlebih lagi, sistem desentralisasi adalah pasar, jadi semua fungsi dasar mata uang ini harus disediakan melalui penyedia layanan berbayar… dalam satuan mata uang yang sedang dibuat!
Seperti mengkompilasi compiler pertama, permulaan jaringan listrik yang gelap, atau evolusi kehidupan itu sendiri, pencipta mata uang digital dihadapkan pada masalah bootstrapping: bagaimana mendefinisikan insentif ekonomi yang mendasari mata uang yang berfungsi tanpa memiliki mata uang yang berfungsi di dalamnya yang akan mendenominasikan atau membayar insentif tersebut.

Komputasi dan mata uang adalah barang pertama dan kedua di pasar yang terdesentralisasi. Proof-of-work sendiri memungkinkan pertukaran komputasi tetapi mata uang yang berfungsi memerlukan lebih banyak infrastruktur. Butuh waktu 15 tahun bagi komunitas cypherpunk untuk mengembangkan infrastruktur tersebut.
Pasar Terdesentralisasi Pertama harus Memperdagangkan Komputasi untuk Mata Uang
Kemajuan dalam masalah bootstrapping ini berasal dari penyusunan batasan yang tepat.
Sistem yang terdesentralisasi harus menjadi pasar. Pasar terdiri dari pembeli dan penjual yang saling bertukar barang. Pasar terdesentralisasi untuk mata uang digital hanya memiliki dua barang yang dapat dibaca di dalamnya:
- Komputasi melalui proof-of-work
- Unit mata uang yang kita coba bangun
Oleh karena itu, satu-satunya perdagangan pasar yang memungkinkan adalah antara kedua barang tersebut. Komputasi harus dijual untuk satuan mata uang atau setara dengan satuan mata uang harus dijual untuk komputasi. Menyatakan hal ini sangatlah mudah—bagian tersulitnya adalah menata pasar ini sehingga sekadar menukar mata uang untuk komputasi akan mem-bootstrap semua kemampuan mata uang itu sendiri!
Seluruh sejarah mata uang digital yang berpuncak pada white paper Satoshi tahun 2008 adalah serangkaian upaya yang semakin canggih dalam menata pasar ini. Bagian berikut mengulas proyek-proyek seperti bit gold milik Nick Szabo dan B-money milik Wei Dai. Memahami bagaimana proyek-proyek ini menyusun pasar mereka dan mengapa mereka gagal akan membantu kita memahami mengapa Satoshi dan Bitcoin berhasil.

Bagaimana Sistem Desentralisasi Dapat Menentukan Harga Komputasi?
Fungsi utama pasar adalah penemuan harga. Oleh karena itu, komputasi perdagangan pasar untuk mata uang harus menemukan harga komputasi itu sendiri, dalam satuan mata uang tersebut.
Kita biasanya tidak memberikan nilai moneter pada komputasi. Kita biasanya menghargai kapasitas untuk melakukan komputasi karena kita menghargai output dari komputasi, bukan komputasi itu sendiri. Jika keluaran yang sama dapat dilakukan dengan lebih efisien, dengan komputasi yang lebih sedikit, hal ini biasanya disebut “kemajuan”.
Proof-of-work mewakili komputasi spesifik yang keluarannya hanya berupa bukti bahwa komputasi tersebut telah dilakukan. Menghasilkan bukti yang sama dengan melakukan lebih sedikit komputasi dan lebih sedikit pekerjaan tidak akan menghasilkan kemajuan—hal ini akan menjadi bug. Oleh karena itu, komputasi yang terkait dengan Proof-of-work merupakan hal yang aneh dan baru untuk dicoba dihargai.
Ketika bukti kerja dianggap sebagai disinsentif terhadap penyalahgunaan sumber daya, maka bukti kerja tidak perlu dinilai secara tepat dan konsisten. Yang terpenting adalah penyedia layanan email menetapkan tingkat kesulitan yang cukup rendah sehingga tidak terlihat oleh pengguna yang sah, namun cukup tinggi sehingga menjadi penghalang bagi pelaku spam. Oleh karena itu, terdapat beragam “harga” yang dapat diterima dan setiap peserta bertindak sebagai otoritas penetapan harga mereka sendiri, dengan menerapkan fungsi penetapan harga lokal.
Namun satuan mata uang dimaksudkan agar dapat dipertukarkan, masing-masing memiliki nilai yang sama. Karena perubahan teknologi dari waktu ke waktu, dua unit mata uang yang dibuat dengan tingkat kesulitan proof-of-work yang sama—yang diukur dengan jumlah komputasi yang sesuai—mungkin memiliki biaya produksi yang sangat berbeda di dunia nyata, yang diukur dengan waktu, energi, dan/atau modal untuk melakukan komputasi tersebut. Ketika komputasi dijual dengan menggunakan mata uang, dan biaya produksi yang mendasarinya bervariasi, bagaimana pasar dapat memastikan harga yang konsisten?
Nick Szabo dengan jelas mengidentifikasi masalah harga ini ketika menjelaskan bit gold:
"Masalah utamanya...adalah bahwa skema pembuktian kerja bergantung pada arsitektur komputer, bukan hanya matematika abstrak yang didasarkan pada "siklus komputasi" abstrak. ...Jadi, ada kemungkinan untuk menjadi produsen berbiaya sangat rendah (dengan beberapa kali lipat besarnya) dan membanjiri pasar dengan bit gold." - Szabo, 2005

Mata uang terdesentralisasi yang diciptakan melalui proof-of-work akan mengalami kelebihan pasokan dan penurunan pasokan seiring dengan perubahan pasokan komputasi seiring waktu. Untuk mengakomodasi volatilitas ini, jaringan harus belajar menghitung harga secara dinamis.
Mata uang digital awal mencoba memberi harga pada komputasi dengan mencoba mengukur “biaya komputasi” secara kolektif. Wei Dai, misalnya, mengusulkan solusi praktis berikut dalam B-money:
"Jumlah unit moneter yang diciptakan sama dengan biaya upaya komputasi dalam sekeranjang komoditas standar. Sebagai contoh, jika sebuah masalah memerlukan waktu 100 jam untuk diselesaikan pada komputer yang dapat menyelesaikannya dengan cara yang paling ekonomis, dan diperlukan 3 keranjang standar untuk membeli 100 jam waktu komputasi pada komputer tersebut di pasar terbuka, maka setelah solusi terhadap masalah tersebut disiarkan, setiap orang mengkredit rekening penyiar sebanyak 3 unit." - Dai, 1998
Sayangnya, Dai tidak menjelaskan bagaimana pengguna dalam sistem yang seharusnya terdesentralisasi seharusnya menyetujui definisi “keranjang standar”, komputer mana yang memecahkan masalah tertentu “paling ekonomis”, atau biaya komputasi di “pasar terbuka”. Mencapai konsensus di antara semua pengguna mengenai kumpulan data bersama yang berubah-ubah terhadap waktu adalah masalah penting dalam sistem desentralisasi!
Agar adil bagi Dai, dia menyadari hal ini:
“Salah satu bagian yang lebih bermasalah dalam protokol B-money adalah penciptaan uang. Bagian dari protokol ini mengharuskan semua [pengguna] memutuskan dan menyetujui biaya perhitungan tertentu. Sayangnya karena teknologi komputasi cenderung berkembang pesat dan tidak selalu bersifat publik, informasi ini mungkin tidak tersedia, tidak akurat, atau ketinggalan jaman, yang semuanya akan menyebabkan masalah serius pada protokol." - Dai, 1998
Dai kemudian mengusulkan mekanisme penetapan harga berbasis lelang yang lebih canggih yang kemudian dikatakan Satoshi sebagai titik awal idenya. Kita akan kembali ke skema lelang di bawah ini, tapi pertama-tama mari kita beralih ke bit gold, dan pertimbangkan wawasan Szabo tentang masalahnya.
Gunakan Pasar Eksternal
Szabo mengklaim bahwa proof-of-work harus “diberi stempel waktu dengan aman”:
"Bukti kerja diberi stempel waktu yang aman. Ini harus bekerja secara terdistribusi, dengan beberapa layanan stempel waktu berbeda sehingga tidak ada layanan stempel waktu tertentu yang perlu diandalkan secara substansial." - Szabo, 2005
Szabo tertaut ke halaman sumber daya tentang protokol penandaan waktu yang aman tetapi tidak menjelaskan algoritme spesifik apa pun untuk penandaan waktu yang aman. Ungkapan “aman” dan “fesyen terdistribusi” mempunyai pengaruh yang besar di sini, sehingga dapat mengatasi kerumitan dalam mengandalkan satu (atau banyak) layanan “di luar sistem” untuk penandaan waktu.[^6]

Waktu pembuatan unit mata uang digital penting karena menghubungkan komputasi yang dilakukan dengan biaya produksi di dunia nyata.
Terlepas dari ketidakjelasan implementasi, Szabo benar—waktu pembuatan proof-of-work merupakan faktor penting dalam menentukan harga karena terkait dengan biaya komputasi:
"…Namun, karena bit gold diberi stempel waktu, waktu yang dibuat serta tingkat kesulitan matematis dari pekerjaan tersebut dapat dibuktikan secara otomatis. Dari sini, biasanya dapat disimpulkan berapa biaya produksi selama periode waktu tersebut..." - Szabo, 2005
"Menyimpulkan" biaya produksi adalah hal yang penting karena bit gold tidak memiliki mekanisme untuk membatasi penciptaan uang. Siapapun dapat membuat bit gold dengan melakukan perhitungan yang sesuai. Tanpa kemampuan untuk mengatur penerbitan, bit gold sama dengan barang koleksi:
"…Tidak seperti atom emas yang dapat dipertukarkan, tetapi seperti halnya barang-barang kolektor, pasokan dalam jumlah besar selama jangka waktu tertentu akan menurunkan nilai barang-barang tersebut. Dalam hal ini, emas kecil bertindak lebih seperti barang-barang kolektor daripada seperti emas..." - Szabo, 2005
Bit gold memerlukan proses eksternal tambahan untuk menciptakan unit mata uang yang sepadan:
“…[B]it Gold tidak dapat dipertukarkan berdasarkan fungsi sederhana, misalnya, panjang tali. Sebaliknya, untuk membuat unit yang dapat dipertukarkan, dealer harus menggabungkan potongan-potongan bit gold dengan nilai berbeda ke dalam satuan yang lebih besar kira-kira dengan nilai yang sama. Hal ini serupa dengan apa yang dilakukan banyak pedagang komoditas saat ini untuk memungkinkan pasar komoditas bekerja. Kepercayaan masih terdistribusi karena perkiraan nilai dari kumpulan tersebut dapat diverifikasi secara independen oleh banyak pihak lain dengan cara yang sebagian besar atau seluruhnya otomatis." - Szabo, 2005
Mengutip Szabo, “untuk menguji nilai… bit gold, dealer memeriksa dan memverifikasi tingkat kesulitan, masukan, dan stempel waktu”. Dealer yang mendefinisikan “unit yang lebih besar dengan nilai yang kira-kira sama” menyediakan fungsi penetapan harga yang serupa dengan “keranjang komoditas standar” Dai. Unit yang dapat dipertukarkan tidak dibuat dalam bentuk bit gold ketika bukti kerja diproduksi, hanya kemudian ketika bukti tersebut digabungkan menjadi “unit yang kira-kira bernilai sama” oleh dealer di pasar di luar jaringan.

Yang patut disyukuri, Szabo mengakui kelemahan ini:
"…Potensi kelebihan pasokan yang awalnya tersembunyi karena inovasi tersembunyi dalam arsitektur mesin adalah potensi kelemahan dalam bit gold, atau setidaknya ketidaksempurnaan yang harus diatasi oleh lelang awal dan pertukaran ex post bit gold." - Szabo, 2005
Sekali lagi, meskipun belum sampai pada (yang sekarang kita kenal sebagai) solusinya, Szabo menunjukkan solusinya: karena biaya komputasi berubah seiring waktu, jaringan harus merespons perubahan pasokan komputasi dengan menyesuaikan harga uang.
Gunakan Pasar Internal
Dealer Szabo akan menjadi pasar eksternal yang menentukan harga (bundel dari) bit gold setelah penciptaannya. Apakah mungkin menerapkan pasar ini di dalam sistem dan bukan di luar sistem?
Mari kita kembali ke Wei Dai dan B-money. Seperti disebutkan sebelumnya, Dai mengusulkan model alternatif berbasis lelang untuk pembuatan B-money. Desain Satoshi untuk Bitcoin meningkat secara langsung pada model lelang B-money[^7]:
“Jadi saya mengusulkan subprotokol penciptaan uang alternatif, di mana [pengguna]… memutuskan dan menyetujui jumlah B-money yang akan dibuat setiap periode, dengan biaya pembuatan uang tersebut ditentukan melalui lelang. Setiap periode pembuatan uang adalah dibagi menjadi empat tahap, sebagai berikut:
Planning. Para [pengguna] menghitung dan bernegosiasi satu sama lain untuk menentukan peningkatan jumlah uang beredar yang optimal untuk periode berikutnya. Apakah [jaringan] dapat mencapai konsensus atau tidak, mereka masing-masing menyiarkan kuota penciptaan uang mereka dan komputasi makroekonomi apa pun yang dilakukan untuk mendukung angka tersebut.
Bidding. Siapapun yang ingin membuat B-money menyiarkan tawaran dalam bentuk dimana x adalah banyaknya B-money yang ingin dibuatnya, dan y adalah soal yang belum terselesaikan dari kelas soal yang telah ditentukan. Setiap masalah di kelas ini harus memiliki biaya nominal (katakanlah dalam MIPS-years) yang disetujui secara publik.
Computation. Setelah melihat penawaran, pihak yang mengajukan penawaran pada tahap penawaran sekarang dapat menyelesaikan masalah dalam penawarannya dan menyiarkan solusinya. Penciptaan uang.
Money creation. Setiap [pengguna] menerima tawaran tertinggi (di antara mereka yang benar-benar menyiarkan solusi) dalam hal biaya nominal per unit B-money yang dibuat dan memberikan kredit kepada akun penawar sesuai dengan itu."
- Dai, 1998B-money membuat kemajuan signifikan menuju struktur pasar yang tepat untuk mata uang digital. Ini berupaya untuk menghilangkan dealer eksternal Szabo dan memungkinkan pengguna untuk terlibat dalam penemuan harga dengan menawar satu sama lain secara langsung.
Namun menerapkan proposal Dai seperti yang tertulis akan menjadi sebuah tantangan:
- Dalam fase "Planning”, pengguna menanggung beban menegosiasikan “peningkatan optimal jumlah uang beredar untuk periode berikutnya”. Bagaimana “optimal” harus didefinisikan, bagaimana pengguna harus bernegosiasi satu sama lain, dan bagaimana hasil negosiasi tersebut dibagikan tidak dijelaskan.
- Terlepas dari apa yang direncanakan, fase “Bidding” memungkinkan siapa saja untuk mengajukan “tawaran” untuk membuat B-money. Tawaran mencakup jumlah B-money yang akan dibuat serta jumlah bukti kerja yang sesuai sehingga setiap penawaran adalah harga, jumlah perhitungan yang bersedia dilakukan oleh penawar tertentu untuk membeli sejumlah tertentu. dari B-money.
- Setelah penawaran diserahkan, fase “Computation” terdiri dari peserta lelang yang melakukan proof-of-work yang mereka tawarkan dan menyiarkan solusi. Tidak ada mekanisme untuk mencocokkan penawar dengan solusi yang disediakan. Yang lebih problematis adalah tidak jelasnya bagaimana pengguna dapat mengetahui bahwa semua penawaran telah diajukan – kapan fase “Bidding” berakhir dan fase “Computation” dimulai?
- Masalah-masalah ini berulang dalam fase “Money creation”. Karena sifat proof-of-work, pengguna dapat memverifikasi bahwa bukti yang mereka terima dalam solusi adalah asli. Namun bagaimana pengguna dapat secara kolektif menyepakati serangkaian “tawaran tertinggi”? Bagaimana jika pengguna yang berbeda memilih set yang berbeda, baik karena preferensi atau latensi jaringan?
Sistem yang terdesentralisasi kesulitan dalam melacak data dan membuat pilihan secara konsisten, namun B-money memerlukan pelacakan tawaran dari banyak pengguna dan membuat pilihan konsensus di antara mereka. Kompleksitas ini menghalangi penerapan B-money.
Akar dari kompleksitas ini adalah keyakinan Dai bahwa tingkat “optimal” penciptaan B-money harus berfluktuasi seiring waktu berdasarkan “perhitungan makroekonomi” penggunanya. Seperti bit gold, B-money tidak memiliki mekanisme untuk membatasi penciptaan uang. Siapapun dapat membuat unit B-money dengan menyiarkan tawaran dan kemudian melakukan proof-of-work yang sesuai.
Baik Szabo maupun Dai mengusulkan penggunaan pasar pertukaran mata uang digital untuk komputasi, namun baik bit gold maupun B-money tidak menentukan kebijakan moneter untuk mengatur pasokan mata uang di pasar ini.
Tujuan Kebijakan Moneter Satoshi Menghasilkan Bitcoin
Sebaliknya, kebijakan moneter yang sehat adalah salah satu tujuan utama Satoshi dalam proyek Bitcoin. Dalam postingan milis pertama tempat Bitcoin diumumkan, Satoshi menulis:
“Akar permasalahan mata uang konvensional adalah kepercayaan yang diperlukan agar mata uang tersebut dapat berfungsi. Bank sentral harus dipercaya untuk tidak merendahkan mata uang tersebut, namun sejarah mata uang fiat penuh dengan pelanggaran terhadap kepercayaan tersebut.” - Satoshi, 2009
Satoshi selanjutnya menjelaskan masalah lain dengan mata uang fiat seperti perbankan cadangan fraksional yang berisiko, kurangnya privasi, pencurian & penipuan yang merajalela, dan ketidakmampuan melakukan pembayaran mikro. Namun Satoshi memulai dengan isu penurunan nilai oleh bank sentral—dengan kekhawatiran mengenai kebijakan moneter.
Satoshi ingin Bitcoin pada akhirnya mencapai pasokan sirkulasi terbatas yang tidak dapat terdilusi seiring waktu. Tingkat penciptaan Bitcoin yang “optimal”, bagi Satoshi, pada akhirnya akan menjadi nol.
Tujuan kebijakan moneter ini, lebih dari karakteristik lain yang mereka miliki secara pribadi (atau kolektif!), adalah alasan Satoshi “menemukan” Bitcoin, blockchain, konsensus Nakamoto, dll. —dan bukan orang lain. Ini adalah jawaban singkat atas pertanyaan yang diajukan dalam judul artikel ini: Satoshi memikirkan Bitcoin karena mereka fokus pada penciptaan mata uang digital dengan persediaan terbatas.
Pasokan Bitcoin yang terbatas bukan hanya tujuan kebijakan moneter atau meme bagi para Bitcoiner untuk berkumpul. Penyederhanaan teknis penting inilah yang memungkinkan Satoshi membangun mata uang digital yang berfungsi sementara B-money Dai tetap menjadi postingan web yang menarik.
Bitcoin adalah B-money dengan persyaratan tambahan berupa kebijakan moneter yang telah ditentukan. Seperti banyak penyederhanaan teknis lainnya, pembatasan kebijakan moneter memungkinkan kemajuan dengan mengurangi ruang lingkup. Mari kita lihat bagaimana masing-masing fase pembuatan B-money disederhanakan dengan menerapkan batasan ini.
Semua Pasokan 21 Juta Bitcoin Sudah Ada
Dalam b-money, setiap “periode penciptaan uang” mencakup fase “Perencanaan”, di mana pengguna diharapkan untuk membagikan “perhitungan makroekonomi” mereka yang membenarkan jumlah b-money yang ingin mereka ciptakan pada saat itu. Tujuan kebijakan moneter Satoshi yaitu pasokan terbatas dan emisi nol tidak sesuai dengan kebebasan yang diberikan b-money kepada pengguna individu untuk menghasilkan uang. Oleh karena itu, langkah pertama dalam perjalanan dari bmoney ke bitcoin adalah menghilangkan kebebasan ini. Pengguna bitcoin perorangan tidak dapat membuat bitcoin. Hanya jaringan bitcoin yang dapat membuat bitcoin, dan hal ini terjadi tepat sekali, pada tahun 2009 ketika Satoshi meluncurkan proyek bitcoin.
Satoshi mampu menggantikan fase “Perencanaan” b-money yang berulang menjadi satu jadwal yang telah ditentukan sebelumnya di mana 21 juta bitcoin yang dibuat pada tahun 2009 akan dilepaskan ke peredaran. Pengguna secara sukarela mendukung kebijakan moneter Satoshi dengan mengunduh dan menjalankan perangkat lunak Bitcoin Core yang kebijakan moneternya dikodekan secara keras.
Hal ini mengubah semantik pasar bitcoin untuk komputasi. Bitcoin yang dibayarkan kepada penambang bukanlah hal baru yang diterbitkan; itu melainkan baru dirilis ke peredaran dari persediaan yang ada.
Pandangan ini sangat berbeda dari klaim naif bahwa “penambang bitcoin menciptakan bitcoin”. Penambang Bitcoin tidak menciptakan bitcoin, mereka membelinya. Bitcoin tidak berharga karena “bitcoin terbuat dari energi”—tetapi nilai bitcoin didemonstrasikan dengan dijual untuk mendapatkan energi.
Mari kita ulangi sekali lagi: bitcoin tidak dibuat melalui proof-of-work, bitcoin dibuat melalui konsensus.

Desain Satoshi menghilangkan persyaratan untuk fase “Perencanaan” yang berkelanjutan dari b-money dengan melakukan semua perencanaan terlebih dahulu. Hal ini memungkinkan Satoshi untuk membuat kebijakan moneter yang sehat namun juga menyederhanakan penerapan bitcoin.
Bitcoin dihargai Melalui Konsensus
Kebebasan yang diberikan kepada pengguna untuk menghasilkan uang menimbulkan beban yang sesuai bagi jaringan bmoney. Selama fase “Penawaran” jaringan b-money harus mengumpulkan dan membagikan “tawaran” pembuatan uang dari banyak pengguna yang berbeda.
Menghilangkan kebebasan untuk menghasilkan uang akan meringankan beban jaringan bitcoin. Karena seluruh 21 juta bitcoin sudah ada, jaringan tidak perlu mengumpulkan tawaran dari pengguna untuk menghasilkan uang, jaringan hanya perlu menjual bitcoin sesuai jadwal Satoshi yang telah ditentukan.
Jaringan bitcoin dengan demikian menawarkan konsensus harga permintaan untuk bitcoin yang dijualnya di setiap blok. Harga tunggal ini dihitung oleh setiap node secara independen menggunakan salinan blockchainnya. Jika node memiliki konsensus pada blockchain yang sama (poin yang akan kita bahas nanti) mereka semua akan menawarkan harga permintaan yang sama di setiap blok.[^8]
Bagian pertama kalkulasi harga konsensus menentukan berapa banyak bitcoin yang akan dijual. Hal ini diperbaiki oleh jadwal rilis Satoshi yang telah ditentukan sebelumnya. Semua node bitcoin di jaringan menghitung jumlah yang sama untuk blok tertentu:
$ bitcoin-cli getblockstats <block\_height> {... "subsidy": 6250000000, ... } # 6.25 BTCBagian kedua dari harga yang diminta secara konsensus adalah jumlah komputasi yang akan menjual subsidi saat ini. Sekali lagi, semua node bitcoin di jaringan menghitung nilai yang sama (kita akan meninjau kembali kalkulasi tingkat kesulitan ini di bagian berikutnya):
$ bitcoin-cli getdifficulty {... "result": 55621444139429.57, ... }Bersama-sama, subsidi dan kesulitan jaringan menentukan permintaan bitcoin saat ini sebagai mata uang komputasi. Karena blockchain berada dalam konsensus, harga ini adalah harga konsensus.
Pengguna b-money juga dianggap memiliki konsensus “blockchain” yang berisi riwayat semua transaksi. Namun Dai tidak pernah memikirkan solusi sederhana berupa konsensus tunggal yang meminta harga untuk pembuatan b-money baru, yang hanya ditentukan oleh data di blockchain tersebut.
Sebaliknya, Dai berasumsi bahwa penciptaan uang harus berlangsung selamanya. Oleh karena itu, pengguna individu perlu diberdayakan untuk mempengaruhi kebijakan moneter – seperti halnya mata uang fiat. Persyaratan yang dirasakan ini membuat Dai merancang sistem penawaran yang mencegah penerapan b-money.
Kompleksitas tambahan ini dihilangkan dengan persyaratan Satoshi mengenai kebijakan moneter yang telah ditentukan sebelumnya.
Waktu Menutup Semua Penyebaran
Dalam fase “Komputasi” b-money, pengguna individu akan melakukan komputasi yang telah mereka lakukan dalam penawaran sebelumnya. Dalam bitcoin, seluruh jaringan adalah penjual – tetapi siapa pembelinya?
Di pasar pengiriman email, pembelinya adalah individu yang ingin mengirim email. Otoritas penetapan harga, penyedia layanan email, akan menetapkan harga yang dianggap murah bagi individu namun mahal bagi pelaku spam. Namun jika jumlah pengguna yang sah bertambah, harganya masih bisa tetap sama karena kekuatan komputasi masing-masing pengguna akan tetap sama.
Di b-money, setiap pengguna yang menyumbangkan tawaran untuk pembuatan uang selanjutnya harus melakukan sendiri jumlah komputasi yang sesuai. Setiap pengguna bertindak sebagai otoritas penetapan harga berdasarkan pengetahuan mereka tentang kemampuan komputasi mereka sendiri.
Jaringan bitcoin menawarkan satu harga yang diminta dalam komputasi subsidi bitcoin saat ini. Namun tidak ada penambang individu yang menemukan blok yang melakukan komputasi sebanyak ini.[^9] Blok pemenang penambang individu adalah bukti bahwa semua penambang secara kolektif melakukan jumlah komputasi yang diperlukan. Pembeli bitcoin dengan demikian adalah industri penambangan bitcoin global.
Setelah mencapai konsensus harga yang diminta, jaringan bitcoin tidak akan mengubah harga tersebut sampai lebih banyak blok diproduksi. Blok-blok ini harus berisi proof-of-work dengan harga yang diminta saat ini. Oleh karena itu, industri pertambangan tidak punya pilihan jika ingin “melakukan perdagangan” selain membayar harga yang diminta saat ini dalam komputasi.
Satu-satunya variabel yang dapat dikontrol oleh industri pertambangan adalah berapa lama waktu yang dibutuhkan untuk memproduksi blok berikutnya. Sama seperti jaringan bitcoin yang menawarkan satu harga yang diminta, industri pertambangan juga menawarkan satu penawaran—waktu yang diperlukan untuk menghasilkan blok berikutnya yang memenuhi harga yang diminta jaringan saat ini.
Untuk mengimbangi peningkatan kecepatan perangkat keras dan minat yang berbeda-beda dalam menjalankan node dari waktu ke waktu, kesulitan proof-of-work ditentukan oleh rata-rata bergerak yang menargetkan jumlah rata-rata blok per jam. Jika dihasilkan terlalu cepat, kesulitannya akan meningkat. - Nakamoto, 2008
Satoshi dengan sederhana menjelaskan algoritma penyesuaian kesulitan, yang sering disebut sebagai salah satu ide paling orisinal dalam implementasi bitcoin. Hal ini benar, namun alih-alih berfokus pada daya cipta solusi, mari kita fokus pada mengapa penyelesaian masalah sangat penting bagi Satoshi.
Proyek-proyek seperti bit gold dan b-money tidak perlu membatasi nilai tukar pada saat penciptaan uang karena mereka tidak memiliki pasokan tetap atau kebijakan moneter yang telah ditentukan sebelumnya. Periode penciptaan uang yang lebih cepat atau lebih lambat dapat dikompensasikan melalui cara lain, misalnya melalui pajak. Dealer eksternal memasukkan token bit gold ke dalam bundler yang lebih besar atau lebih kecil atau pengguna b-money mengubah tawaran mereka.
Namun tujuan kebijakan moneter Satoshi mengharuskan bitcoin memiliki tingkat pelepasan bitcoin yang telah ditentukan untuk diedarkan. Membatasi laju (statistik) produksi blok dari waktu ke waktu adalah hal yang wajar dalam bitcoin karena laju produksi blok adalah laju penjualan pasokan awal bitcoin. Menjual 21 juta bitcoin selama 140 tahun adalah proposisi yang berbeda dibandingkan membiarkannya dijual dalam 3 bulan.
Selain itu, bitcoin sebenarnya dapat menerapkan batasan ini karena blockchain adalah “protokol cap waktu aman” milik Szabo. Satoshi menggambarkan bitcoin sebagai yang pertama dan terutama sebagai “server stempel waktu terdistribusi secara peer-to-peer,” dan implementasi awal kode sumber bitcoin menggunakan “rantai waktu” dunia, bukan “blockchain” untuk menggambarkan struktur data bersama yang mengimplementasikan pasar proof-of-work bitcoin.[^10]

Tidak seperti bit gold atau b-money, token dalam bitcoin tidak mengalami kelebihan pasokan. Jaringan bitcoin menggunakan penyesuaian kesulitan untuk mengubah harga uang sebagai respons terhadap perubahan pasokan komputasi.
Algoritme penyesuaian ulang kesulitan Bitcoin memanfaatkan kemampuan ini. Blockchain konsensus digunakan oleh peserta untuk menghitung penawaran historis yang dibuat oleh industri pertambangan dan menyesuaikan kembali kesulitan agar bisa mendekati waktu blok target.
Pesanan Terunggul Menciptakan Konsensus
Rantai penyederhanaan yang disebabkan oleh tuntutan kebijakan moneter yang kuat meluas ke fase “penciptaan uang” dari b-money.
Tawaran yang diajukan pengguna di b-money mengalami masalah “tidak ada yang dipertaruhkan”. Tidak ada mekanisme untuk mencegah pengguna mengajukan tawaran dengan sejumlah besar b-money untuk pekerjaan yang sangat sedikit. Hal ini mengharuskan jaringan untuk melacak tawaran mana yang telah diselesaikan dan hanya menerima “tawaran tertinggi…dalam hal biaya nominal per unit b-money yang dibuat” untuk menghindari tawaran yang mengganggu tersebut. Setiap peserta b-money harus melacak seluruh tawaran senilai buku pesanan, mencocokkan tawaran dengan perhitungan selanjutnya, dan hanya menyelesaikan pesanan yang telah selesai dengan harga tertinggi.
Masalah ini merupakan contoh dari masalah konsensus yang lebih umum dalam sistem desentralisasi, yang juga dikenal sebagai “Byzantine generals” atau terkadang masalah “pembelanjaan ganda” dalam konteks mata uang digital. Berbagi urutan data yang identik di antara semua peserta merupakan suatu tantangan dalam jaringan yang saling bermusuhan dan terdesentralisasi. Solusi yang ada untuk masalah ini – yang disebut “algoritma konsensus Byzantine-fault tolerant (BFT)” – memerlukan koordinasi sebelumnya di antara peserta atau mayoritas (>67%) peserta agar tidak berperilaku bermusuhan.
Bitcoin tidak harus mengelola buku pesanan dalam jumlah besar karena jaringan bitcoin menawarkan harga permintaan konsensus tunggal. Ini berarti node bitcoin dapat menerima blok pertama (valid) yang mereka lihat yang memenuhi harga yang diminta jaringan saat ini—tawaran gangguan dapat dengan mudah diabaikan dan merupakan pemborosan sumber daya penambang.
Komputasi harga berdasarkan konsensus memungkinkan pencocokan pesanan beli/jual dalam bitcoin dilakukan secara antusias, dengan sistem siapa cepat dia dapat. Berbeda dengan b-money, pencocokan pesanan yang cepat ini berarti bahwa pasar bitcoin tidak memiliki fase—pasar ini beroperasi terus-menerus, dengan harga konsensus baru dihitung setelah setiap pesanan dicocokkan (blok ditemukan). Untuk menghindari percabangan yang disebabkan oleh latensi jaringan atau perilaku bertentangan, node juga harus mengikuti aturan rantai terberat. Aturan penyelesaian pesanan yang serakah ini memastikan bahwa hanya tawaran tertinggi yang diterima oleh jaringan.
Kombinasi algoritma yang antusias dan serakah ini, dimana node menerima blok valid pertama yang mereka lihat dan juga mengikuti rantai terberat, adalah algoritma BFT baru yang dengan cepat menyatu pada konsensus tentang urutan blok. Satoshi menghabiskan 25% dari white paper bitcoin untuk mendemonstrasikan klaim ini.[^11]
Kita telah menetapkan di bagian sebelumnya bahwa harga permintaan konsensus bitcoin itu sendiri bergantung pada konsensus blockchain. Namun ternyata keberadaan harga permintaan konsensus tunggal inilah yang memungkinkan perhitungan pasar untuk mencocokkan pesanan dengan penuh semangat, dan itulah yang pertama-tama mengarah pada konsensus!
Terlebih lagi, “konsensus Nakamoto” yang baru ini hanya mengharuskan 50% peserta untuk tidak bertentangan, sebuah kemajuan yang signifikan dibandingkan dengan kondisi sebelumnya. Seorang cypherpunk seperti Satoshi membuat terobosan ilmu komputer teoretis ini, dibandingkan dengan akademisi tradisional atau peneliti industri, karena fokus mereka yang sempit pada penerapan uang yang sehat, dibandingkan algoritma konsensus umum untuk komputasi terdistribusi.
Kesimpulan
B-money adalah kerangka kerja yang kuat untuk membangun mata uang digital tetapi tidak lengkap karena tidak memiliki kebijakan moneter. Membatasi b-money dengan jadwal rilis yang telah ditentukan untuk bitcoin mengurangi cakupan dan menyederhanakan implementasi dengan menghilangkan persyaratan untuk melacak dan memilih di antara tawaran pembuatan uang yang diajukan pengguna. Mempertahankan kecepatan sementara dari jadwal rilis Satoshi menghasilkan algoritma penyesuaian kesulitan dan memungkinkan konsensus Nakamoto, yang secara luas diakui sebagai salah satu aspek paling inovatif dalam implementasi bitcoin.
Ada lebih banyak hal dalam desain bitcoin daripada aspek yang dibahas sejauh ini. Kita memfokuskan artikel ini pada pasar “utama” dalam bitcoin, pasar yang mendistribusikan pasokan awal bitcoin ke dalam sirkulasi.
Artikel berikutnya dalam seri ini akan mengeksplorasi pasar penyelesaian transaksi bitcoin dan kaitannya dengan pasar pendistribusian pasokan bitcoin. Hubungan ini akan menyarankan metodologi bagaimana membangun pasar masa depan untuk layanan terdesentralisasi selain bitcoin.
Sumber artikel: HOW DID SATOSHI THINK OF BITCOIN? https://bitcoinmagazine.com/technical/how-did-satoshi-think-of-bitcoin
Diterjemahkan oleh: Abengkris
[^1]: Judul seri ini diambil dari pesan telegraf pertama dalam sejarah, yang dikirimkan oleh Samuel Morse pada tahun 1844: “What hath God wrought?”.
[^2]: Bitcoin: Sistem Uang Elektronik Peer-to-Peer, tersedia di: https://bitcoin.org/bitcoin.pdf
[^3]: Pricing via Processing or Combatting Junk Mail oleh Dwork dan Naor. tersedia di:
https://www.wisdom.weizmann.ac.il/../../pvp.pdf[^4]: Meskipun merupakan pencetus ide tersebut, Dwork & Naor tidak menciptakan “proof-of-work”—julukan tersebut kemudian diberikan pada tahun 1999 oleh Markus Jakobsson dan Ari Juels.
[^5]: Proyek RPoW Hal Finney adalah upaya untuk menciptakan proof-of-work yang dapat ditransfer, tetapi bitcoin tidak menggunakan konsep ini karena tidak memperlakukan komputasi sebagai mata uang. Seperti yang akan kita lihat nanti ketika kita memeriksa bit gold dan b-money, komputasi tidak dapat berupa mata uang karena nilai komputasi berubah seiring waktu sementara unit mata uang harus memiliki nilai yang sama. Bitcoin bukanlah komputasi, bitcoin adalah mata uang yang dijual untuk komputasi.
[^6]: Pada saat ini, beberapa pembaca mungkin percaya bahwa saya meremehkan kontribusi Dai atau Szabo karena kontribusi mereka tidak jelas atau tidak jelas dalam beberapa hal. Perasaan saya justru sebaliknya: Dai dan Szabo pada dasarnya benar dan fakta bahwa mereka tidak mengartikulasikan setiap detail seperti yang dilakukan Satoshi tidak mengurangi kontribusi mereka. Sebaliknya, hal ini seharusnya meningkatkan apresiasi kita terhadap hal tersebut, karena hal ini menunjukkan betapa menantangnya munculnya mata uang digital, bahkan bagi para praktisi terbaiknya.
[^7]: Postingan b-money Dai adalah referensi pertama dalam white paper Satoshi, tersedia di: http://www.weidai.com/bmoney.txt
[^8]: Ada dua penyederhanaan yang dilakukan di sini: 1. Jumlah bitcoin yang dijual di setiap blok juga dipengaruhi oleh biaya transaksi pasar, yang berada di luar cakupan artikel ini, namun tetap menunggu pekerjaan selanjutnya. 2. Kesulitan yang dilaporkan oleh bitcoin bukanlah jumlah perhitungan yang diharapkan; seseorang harus mengalikannya dengan faktor proporsionalitas.
[^9]: Setidaknya sejak masa lalu yang buruk ketika Satoshi adalah satu-satunya penambang di jaringan.
[^10]: Bitcoin is Time klasik dari Gigi adalah pengenalan yang bagus tentang hubungan mendalam antara bitcoin dan waktu, tersedia di: https://dergigi.com/2021/01/14/bitcoin-is-time/
[^11]: Satoshi melakukan kesalahan baik dalam analisis mereka di buku putih maupun implementasi awal bitcoin berikutnya dengan menggunakan aturan “rantai terpanjang” dan bukan aturan “rantai terberat”.
-
 @ 662f9bff:8960f6b2
2024-12-11 02:53:14
@ 662f9bff:8960f6b2
2024-12-11 02:53:14By popular request I have put together one single list of the most important books that I have read and recommend that you should read too. I am happy to receive your comments, reviews and suggestions - just reach out and let's discuss.
They are more or less in alphabetical order of title and they are all recommended.
- George Orwell's 1984 - spot the drumbeat of hostile distant foreign empires and perpetual war - not to mention everything else that he foresaw. Read it and look around you today.
- Murray Rothbard's Anatomy of the State - this is foundational to so many of the books and insights related to government, finance and current affairs. This is a short read (one hour) also available as free audiobook. It is required knowledge - you have no excuse.
- Animal farm - by George Orwell - note how the pigs end up living in the farmhouse exceeding all the worst behaviour of the farmer and how the constitution on the wall changes. Things did not end well for loyal Boxer.
- Awaken The Immortal Within by Jason Breschears - This book is for those who have searched for the truth all their life and know they have not found it. The rest of you are warned away.
- The Basic Code of the Universe by Massimo Citro - This is not an easy read (maybe because of being translated from Italian) but the content is fascinating since he combines and draws from many of the other sources we have been considering recently - including Rupert Sheldrake on Morphic fields, Ervin Laszlo on the Akashic field, David Bohm and Karl Pribram on Holographic Paradigm, and Masaru Emoto on the memory of water and homeopathy.
- Brave New World by Aldous Huxley - A World State, inhabited by genetically modified citizens and an intelligence-based social hierarchy. The novel anticipates large scale psychological manipulation and classical conditioning that are combined to make a dystopian society which is challenged by just one individual who does not take the Soma.
- Lyn Alden's Broken Money - gives you the complete A-Z of how money works and all the bad choices that governments can (and did) make. You will also understand how money really should work for a peaceful and prosperous society.
- The Dream by David Icke - this gets my "Book of the Year 2023" award. You will be shocked and appalled at how accurate his predictions were for what happened with Covid and that is only Chapter One. He goes MUCH FURTHER. He may or may not be right on everything he says, but even if he is right on 10-20% the implications should make you think very differently on many things. Anyone with a bit of critical thinking in their head should be able to see many of the points he makes - the evidence is all around you.
- Saifedean Ammous' The Fiat Standard - explains how national currencies work today and how they are fundamentally broken, inevitably favouring those at the top, nearest to the money printer and disadvantaging everyone else. He outlines the many negative consequences of the current system. Look around you and you will recognise all that he describes.
- The Falsification of History by John Hammer - full review in Newsletter 114
- The Fourth turning is Here by Neil Howe - full review in Newsletter 118
- Going Postal by Terry Pratchett- a fascinating find and so much learning on the origins and corruption of money.
- Guards! Guards! by Terry Pratchett - The story follows a plot by a secret brotherhood, the Unique and Supreme Lodge of the Elucidated Brethren of the Ebon Night, to overthrow the Patrician of Ankh-Morpork and install a puppet king, under the control of the Supreme Grand Master.
- The Hitchhikers' Guide to the Galaxy series - in particular the Restaurant at the End of the Universe. There is a theory which states that if ever anyone discovers exactly what the Universe is for and why it is here, it will instantly disappear and be replaced by something even more bizarre and inexplicable. There is another theory which states that this has already happened.
- Michael Talbot's "The Holographic Universe" presents a revolutionary theory that the universe itself may be akin to a giant hologram. This idea, inspired by the work of physicist David Bohm (who as a protégée of Albert Einstein) and neuroscientist Karl Pribram, suggests that our reality is not as it appears on the surface. The holographic paradigm proposes that every part of the universe contains the whole, much like how every piece of a hologram contains a complete picture.
- The Kybalion by Three Initiates - Hermeticism is a philosophical and spiritual tradition that is based on the teachings attributed to Hermes Trismegistus, a legendary figure who is often associated with the Egyptian god Thoth and the Greek god Hermes, pre-dating all modern religions. This will lead you to the Lament of Hermes (aka Thoth's Prophesy) that I suggest is rather relevant to current times.
- The Mandibles – by Lionel Shriver - The plot: In 2029, the United States is engaged in a bloodless world war that will wipe out the savings of millions of American families. Overnight, on the international currency exchange, the “almighty dollar” plummets in value, to be replaced by a new global currency, the “bancor.” In retaliation, the president declares that America will default on its loans. “Deadbeat Nation” being unable to borrow, the government prints money to cover its bills. What little remains to savers is rapidly eaten away by runaway inflation.
- Mistborn - The Final Empire - by Brandon Sanderson. You really ought to recognise and understand the importance of learning from wisdom of prior generations.
- Morphic Resonance by Rupert Sheldrake. This book is about the hypothesis of formative causation, which proposes that nature is habitual. All animals and plants draw upon and contribute to a collective memory of their species. Crystals and molecules also follow the habits of their kind. Cosmic evolution involves an interplay of habit and creativity. This hypothesis is radically different from the conventional assumption that nature is governed by eternal laws. Also, keep in mind the Akashic Records - not a topic for today but one that we will certainly return to.
- Mythos read by Stephen Fry is a "must do". This has got to be one of the best books I have ever read! Fabulously interesting and insightful - I had always wondered what the Greek Gods got up to and could never have imagined so much! BTW - this will also give you a grounding in the stories that you need to know for much more than you likely realise.
- The Octopus of Global Control by Charlie Robinson explains the eight tentacles of control that are wrapped around humanity, namely: the Military, Government, Covert, Physical, Financial, Media, Spiritual, and Scientific. The book tackles topics such as uncovering the Deep State, false flag terror events, the media’s role in manufacturing wars, the 9/11 deception, the fraud of central banking, our broken education system, the use of religion to shape society, and the corrupted medical industry. Recommend to get this also as audiobook, read by him.
- The Power of Now by Eckhard Tolle - full review in Newsletter 65
- Principles of Economics by Saifedean Ammous. This is a university-level text book, written to replace the nonsense that students have been taught for the last 70 years. Also available as audiobook. You will understand how things really work. A nice summary of the course is here.
- Pyramids by Terry Pratchett - Conservatives vs progressives was, even in this version of ancient Egypt, a hot topic and Pratchett ridicules the arguments of antiquated minds by exaggerating their prime goals and authorities in general.
- The Reveal by David Icke - this gets my "Book of the Year 2024" award.* This is written as a standalone book so you do not need to have read his earlier books. Just do it! This book is required reading for all who are awake to what is going wrong around them and want more background and substantiation.
- Secrets of the Federal Reserve by Eustace Mullins independently corroborates all that you read in The Creature from Jekyll Island and listen to the book club discussion on it here. Eustace also wrote "Murder by Injection" - needless to say, this is particularly relevant to explain what happened in recent years.
- Snow Crash – by Neal Stevenson. The story takes place in some post-crisis world where trust in governments and countries has broken down and the world is made up of territories controlled by various corporations - each of which has their own "passport" and rules. The inhabitants of the world spend their time "living" in the Metaverse (yes - he did coin that term). Of course there is some sort of computer virus that strikes and threatens to end everything - you can imagine how things develop.
- William Rees-Mogg's The Sovereign Individual - foresaw very clearly what is currently happening - do get your own copy (book, kindle or audio). Chapters 10 and 11 relate to what's happening now and what's next.
- Sherlock Holmes - Ultimate Collection - I absolutely love this complete collection read by Stephen Fry. At nearly 63 hours of audio you get your money's worth. It is all of the books read in a sensible sequence with Stephen's expert commentary and guidance interspersed between the readings.
- The UnCommunist Manifesto by Aleks Svetski and Mark Moss - a message of Hope, Responsibility and Liberty for all. This is a book that you can read in a day or so but you will want to go back and re-read things and reflect further.
- When Money Dies by Adam Fergusson - The Nightmare of Deficit Spending, Devaluation, and Hyperinflation in Weimar, Germany. Yes it recounts the story of a hundred years ago but you will be surprised to see how relevant this is today, albeit on a bigger scale. We discussed this back in Issue 7 in February 2022.
For lots more like this, do follow our journey: Letter from ...around the world
-
 @ a95c6243:d345522c
2024-11-29 19:45:43
@ a95c6243:d345522c
2024-11-29 19:45:43Konsum ist Therapie.
Wolfgang JoopUmweltbewusstes Verhalten und verantwortungsvoller Konsum zeugen durchaus von einer wünschenswerten Einstellung. Ob man deswegen allerdings einen grünen statt eines schwarzen Freitags braucht, darf getrost bezweifelt werden – zumal es sich um manipulatorische Konzepte handelt. Wie in der politischen Landschaft sind auch hier die Etiketten irgendwas zwischen nichtssagend und trügerisch.
Heute ist also wieder mal «Black Friday», falls Sie es noch nicht mitbekommen haben sollten. Eigentlich haben wir ja eher schon eine ganze «Black Week», der dann oft auch noch ein «Cyber Monday» folgt. Die Werbebranche wird nicht müde, immer neue Anlässe zu erfinden oder zu importieren, um uns zum Konsumieren zu bewegen. Und sie ist damit sehr erfolgreich.
Warum fallen wir auf derartige Werbetricks herein und kaufen im Zweifelsfall Dinge oder Mengen, die wir sicher nicht brauchen? Pure Psychologie, würde ich sagen. Rabattschilder triggern etwas in uns, was den Verstand in Stand-by versetzt. Zusätzlich beeinflussen uns alle möglichen emotionalen Reize und animieren uns zum Schnäppchenkauf.
Gedankenlosigkeit und Maßlosigkeit können besonders bei der Ernährung zu ernsten Problemen führen. Erst kürzlich hat mir ein Bekannter nach einer USA-Reise erzählt, dass es dort offenbar nicht unüblich ist, schon zum ausgiebigen Frühstück in einem Restaurant wenigstens einen Liter Cola zu trinken. Gerne auch mehr, um das Gratis-Nachfüllen des Bechers auszunutzen.
Kritik am schwarzen Freitag und dem unnötigen Konsum kommt oft von Umweltschützern. Neben Ressourcenverschwendung, hohem Energieverbrauch und wachsenden Müllbergen durch eine zunehmende Wegwerfmentalität kommt dabei in der Regel auch die «Klimakrise» auf den Tisch.
Die EU-Kommission lancierte 2015 den Begriff «Green Friday» im Kontext der überarbeiteten Rechtsvorschriften zur Kennzeichnung der Energieeffizienz von Elektrogeräten. Sie nutzte die Gelegenheit kurz vor dem damaligen schwarzen Freitag und vor der UN-Klimakonferenz COP21, bei der das Pariser Abkommen unterzeichnet werden sollte.
Heute wird ein grüner Freitag oft im Zusammenhang mit der Forderung nach «nachhaltigem Konsum» benutzt. Derweil ist die Europäische Union schon weit in ihr Geschäftsmodell des «Green New Deal» verstrickt. In ihrer Propaganda zum Klimawandel verspricht sie tatsächlich «Unterstützung der Menschen und Regionen, die von immer häufigeren Extremwetter-Ereignissen betroffen sind». Was wohl die Menschen in der Region um Valencia dazu sagen?
Ganz im Sinne des Great Reset propagierten die Vereinten Nationen seit Ende 2020 eine «grüne Erholung von Covid-19, um den Klimawandel zu verlangsamen». Der UN-Umweltbericht sah in dem Jahr einen Schwerpunkt auf dem Verbraucherverhalten. Änderungen des Konsumverhaltens des Einzelnen könnten dazu beitragen, den Klimaschutz zu stärken, hieß es dort.
Der Begriff «Schwarzer Freitag» wurde in den USA nicht erstmals für Einkäufe nach Thanksgiving verwendet – wie oft angenommen –, sondern für eine Finanzkrise. Jedoch nicht für den Börsencrash von 1929, sondern bereits für den Zusammenbruch des US-Goldmarktes im September 1869. Seitdem mussten die Menschen weltweit so einige schwarze Tage erleben.
Kürzlich sind die britischen Aufsichtsbehörden weiter von ihrer Zurückhaltung nach dem letzten großen Finanzcrash von 2008 abgerückt. Sie haben Regeln für den Bankensektor gelockert, womit sie «verantwortungsvolle Risikobereitschaft» unterstützen wollen. Man würde sicher zu schwarz sehen, wenn man hier ein grünes Wunder befürchten würde.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 6734e11d:c7e34e8f
2024-11-17 00:09:30
@ 6734e11d:c7e34e8f
2024-11-17 00:09:30Bereits 2023 entdeckte der Genomforscher Kevin McKernan, dass die mRNA-Impfstoffe von Pfizer/BioNTech DNA-Fragmente enthalten.
Nun konnte er in einer Biopsie eines Darmkrebspatienten DNA-Sequenzen (SV40,Ori) des Pfizer-Impfstoffs nachweisen – und das ein Jahr nach der Impfung des Patienten.
👉McKernan (https://anandamide.substack.com/p/sv40-origin-of-replication-in-mammalian)
Die hohe Menge an nachgewiesener Impfstoff-DNA lässt darauf schließen, dass sich der Impfstoff nach der Injektion im Körper des Patienten vermehrt haben könnte, so McKernan. Dies würde entweder auf eine Integration in das menschliche Genom oder auf eine unerwartete Replikationsfähigkeit der Impfstoff-DNA hinweisen.
https://t.me/DrKayKlapproth
https://t.me/initiative_demokratie
-
 @ 6734e11d:c7e34e8f
2024-11-14 11:33:54
@ 6734e11d:c7e34e8f
2024-11-14 11:33:54Zweiklassenmedizin, Zweiklassenbildungssystem und -demokratie. Wo ist die Zweiklassenpartei? Leo Trotzki hielt 1928 eine „Zweiklassenpartei“ mit sowohl proletarischer als auch kleinbürgerlicher Linie für unmöglich. Zu verschiedene und unvereinbare Interessen. Die (Er)Lösung scheint heute nah: Ein aufrichtiges Parteiprogramm.
Mein Ziel ist daher, alle Dissonanzen zu beseitigen und endlich alle Menschen in einer Partei zu vereinen. Ich stehe aufrichtig für das gänzlich Neue: „Vereine in einer Partei und herrsche“. In politischen Entscheidungen geht es durchgängig um Macht und monetäre Interessen, wirklich zu jedem Zeitpunkt und in allen gesellschaftlichen Fragen und Politikfeldern. Das ist nichts neues, aber mit dieser aufrichtigen Klarheit können alle Beschlüsse frei von hemmenden sachlichen Erwägungen geplant und getroffen werden. Zeitraubender Diskurs, Studien und Evaluationen werden überflüssig. Das vorliegende Parteiprogramm soll eine erste Positionsbestimmung darstellen und die kurz gehaltene neue Gesellschafts- und Wirtschaftsordnung in unserem schönen Lande sein. Ich meine es gut mit den Bürgenden*.
*Begriffserläuterung: Die Bürgenden seien im Folgenden diejenigen, die für die Konsequenzen politischer Entscheidungen mit ihrem Vermögen, ihrer Gesundheit und ihrem Leben bürgen.
Gesellschaft
Eine strikte rechtliche und wirtschaftliche Zweiteilung der Gesellschaft in Elite und Volk ist anzustreben. Da der Mittelstand in seiner Bedeutung ohnehin wesentlich überschätzt wird, kann er in den 99 Prozent der Bürgenden aufgehen. Der Mittelstand ist getragen von der Einsicht, zugunsten der Elite wesentliche Einbußen in Kauf zu nehmen. Um mit Umbau von Wirtschaft und Digitalem rapide voran zu kommen, brauchen wir eine solidarische Gemeinschaft der Harmonie. Vielschichtige Auseinandersetzung kann ein prosperierendes Gesellschaftssystem bremsen und zermürben. Komplexität ist deshalb zu vermeiden oder sogar zu unterbinden. Ich werde dezidiert vorgeben, wie Sprache in Schrift und Rede zu handhaben ist, damit unsere Gesellschaft noch effektiver agieren kann. Klarheit darüber, was zu denken, zu fühlen und zu sagen ist, erleichtern das Leben aller. Lust, Sexualität und vor allen Dingen Humor, sind auch digital auf das unbedingt notwendige Maß zu begrenzen, um die volle Kraft des Humankapitals der gesellschaftlichen Prosperität zur Verfügung zu stellen. Kritische Subjekte sollen dagegen trefflich verlacht und verhöhnt werden dürfen.
Grundrechte
Alle Staatsgewalt geht von der Partei aus. Mittlerweile ist recht gut implementiert, wann, wer, wohin darf, wem es jeweils verboten oder wer unerwünscht ist. Dies funktioniert auch ohne Vorbereitung, mittlerweile völlig unabhängig von logischen Begründungen. Das gesamte Potential einer noch differenzierteren Regulation, wird bisher leider nicht vollständig genutzt. Politischer und gegenseitiger Schutz haben sich als äußerst wirksam erwiesen.
Digitales
Ich will die digitale biometrische Identität für alle Vorgänge im Alltag, ab positiver Testung der Schwangerschaft. Mehr Mut bei Kombination von Fingerabdruck, Bankdaten, Gesichtserkennung und Zugangsberechtigungen. Der beschleunigten Zeit angemessen, gehe ich aber weiter: Privatsphäre ist ein überkommenes Luxusgut, das die gesellschaftliche Entwicklung hemmt. Es darf keinerlei Geheimnisse mehr geben. Diese Entwicklung würde ich keinesfalls als Transhumanismus bezeichnen, jenes Streben ist als äußerst menschlich zu betrachten. Fitnesstracker waren ein guter Anfang. Microchips in Kleidung und unter die Haut verpflanzt, ermöglichen Kommunikation überall und zu jeder Zeit. Bemerkenswert: Das Transplantieren erfolgt mit nur einer Spritze, mittels einer etwas dickeren Kanüle, ein leicht deutlicherer Piks, aber völlig sicher und nebenwirkungsfrei. Bei geschützten Tieren ist das seit längerem erprobt.
Desozialisierende/integrierende Netzwerke
Digitale Plattformen sammeln, überwachen und kanalisieren Kommunikation und Emotion, werden privatwirtschaftlich betrieben aber zentral gesteuert. Mal desozialisierend oder integrierend eingesetzt, können sie auch abgeschaltet werden. Text- und Videonachrichten oder -gespräche gelten als reale Kontakte. Sämtliche humanoide Handlungen werden in das digitale Netz verlagert, so wird unsere Welt endlich sicher. Der Schutz der Sphäre der Elite ist hingegen von entscheidender Bedeutung. Sie muss unabhängig von Überwachung Ideen auch in Präsenz austauschen und entwickeln können.
Medien
Digitale Identität und parteitragende Medien werden verknüpft. Pflichtzeiten des Konsums stellen denselben Informationsstand sicher, die Verweildauer fließt in die Gesamtbewertung der Persönlichkeit ein. Hochschulabschlüsse und Promotionen werden damit verknüpft, Verdienstorden angepasst verliehen. Die Öffentlich-Rechtlichen werden zur Marke „Ehrlich-Medien“, die jahrzehntelang immanente Unaufrichtigkeit wird die Transformation leider hinauszögern. Scheinbar kritische Medien sind längst an entscheidenden Positionen und auf allen Kanälen mit Einflussagenten besetzt, die ihre eigenen Ziele verfolgen. Diese Unterwanderung wird gezielt forciert, bis die Zeit reif ist, sie komplett zu kontrollieren oder abzuschalten. Bis dahin kann man die „kritische“ Propaganda ganz gut mit verschiedenen Anleitungen durchschauen.
Meinungsäußerung
Es gilt ein sofortiges Verbot von Satire und Kabarett, die sich mit den Eliten beschäftigt. Und um Anfragen vorzubeugen: Diese Zensur ist keinesfalls mit Historischem vergleichbar. Die Herkuleskeule in Dresden zeigte ja auch vor 1989 Kabarett. Sprechschauen werden ein wunderbarer Ersatz des bisher unterhaltsamen, aber überflüssigen Bundestags. Gleich den Kämpfen von Gladiatoren geht es hier um`s nackte Überleben, um Existenzen.
Wirtschaft
Energiewirtschaft, Handelsketten und Krankenhausgesellschaften, verbrauchen unendlich Ressourcen. Subventionen werden künftig leistungslos, regelmäßig und direkt an Stakeholder und Konzerne vergeben, ohne Erfordernis eine Leistung zu erbringen oder ein Produkt herzustellen. So können Rohstoffe weitgehend eingespart werden. Umwege über energieintensive Dienstleistung oder Produktion von Waren, Transport, Konsumation oder Zerstörung sind obsolet. Beispiel: Rüstungskonzerne produzieren Schiffe, Flugzeuge, Panzer, Waffen und Sprengkörper. Deren einzige Bestimmung ist es verbraucht zu werden, bestenfalls mit einem Schlag und kurz nach Verkauf. Aber was ist, wenn entgegen allen Bemühens kein Kriegsgrund und kein Einsatzort gefunden werden? Was ist mit dem Gewinn eines Pharmaunternehmens, wenn keine Pandemie ist? Sie erfassen hier wohl, die bestechende Nachhaltigkeit der Idee. Die Pleitewellen im Kleingewerbe und im Mittelstand lassen darauf hoffen, diese Ideen kurzfristig umzusetzen.
Gesundheitsindustrie
Die Low-Budget-/Max-Cost-Gesundheitsleistungen sind ganz in meinem Sinne. Sie werden weiter verschlankt, der Max-Outcome ist und bleibt das Hauptziel. Das Wahlvolk will Pflege und Krankenhäuser weiter optimieren, ersichtlich an den Ergebnissen der Bundestagswahl 2021, trotz beschleunigter Transformation. Die Gewerkschaften werde ich in diesem Bereich noch einige Zeit dulden. Sie dürfen weiter verlautbaren: „Wir sind an unserer Leistungsgrenze angekommen!“, „Wir stehen mit dem Rücken zur Wand!“. Das schadet ja keinem.
Abhängig Beschäftigte (sofern noch benötigt)
Käfighaltung wie bei deutschen Großunternehmen, die in Shanghai produzieren, ist weltweit geplant, wird aber zunächst dort getestet. Daneben hat sich die Drohnenüberwachung auf den Baustellen in Dubai bewährt. Nach gewisser Zeit der Eingewöhnung genügt es, die Drohnen mit Kameraattrappen auszustatten.
Recht und Justiz
Rechtsbegriffe werden allgemeiner formuliert, Straftatbestände angepasst. Gerichte sind künftig wie Staatsanwaltschaften an Weisungen gebunden, denn nur so können wir ungebremst voranschreiten. Das Primat der Sicherheit gebietet es, dass bereits eine potentielle digitale Abweichung mit vorsorglicher Inhaftierung und entsprechenden Maßnahmen geahndet wird. Geldstrafen werden die Ausnahme sein. Nebenstrafen wie Internetsperre, Entzug der Fahrerlaubnis, Berufs-, Reise-, Kultur- und Einkaufsverbot, sowie weitere Rücknahme von zugeteilten Rechten werden ausgeweitet. Die Zulassung von Rechtsanwälten wird vom Politscore abhängig gemacht. Schiedsgerichte ersetzen letztlich Rechtswesen und Justiz.
Innere Sicherheit und Polizei
Bisher fungierte die Polizei als Straßenkehrer der oberen Zehntausend. Künftig soll sie den privaten Raum der Happy Few (max. 1%) garantieren, damit diese unabhängig zum Wohl des Volkes agieren können. Wenn die besten Kreise erwägen, öffentliche Plätze in Präsenz zu nutzen, beispielsweise für eine Demonstration der derzeitigen moralischen Haltung, werden diese durch Spezialkräfte sicher gehalten. Die internen Strukturen der künftigen Zentralpolizei werden, ebenso wie Aufnahmeprüfungen, am jeweils aktuellen Geheimdienstbericht ausgerichtet. Die innere Sicherheit wird hauptsächlich im Netz verteidigt, aufkeimende Aufstände werden dort erkannt und bereits im digitalen Stadium vereitelt. Ein Eid auf irgendein Gesetz wird vollkommen überflüssig, die Anweisungen erfolgen klar und lageangepasst. Vielleicht muss eine neue Begrifflichkeit entwickelt werden, denn „politeia“ meinte ein Gemeinwesen, das von Vernünftigen geleitet wird. Mir schwebt „Das Auge des Netzes“ vor, „...Gesetzes“ ist dann veraltet.
Tierschutz
Hundeerziehungslager, auch Hundesportplätze genannt, sowie die dort stattfindenden Kurse werden sofort und konsequent verboten. Viele die hier ihr Machtgefühl erleben, werden die Plätze zunächst schmerzlich vermissen. Dennoch müssen die dort vergeudeten Energien für Gehorsamsübungen in die Ausgestaltung nachbarschaftlicher, freundschaftlicher, politischer und beruflicher Beziehungen überführt und in der Folge in`s Digitale transformiert werden. Menschen- statt Tierhaltung ist wesentlich befriedigender und förderlicher für unser Gesellschaftssystem.
Drogen
Es erfolgt eine sofortige Freigabe von Kokain, Haschisch, Crystal Meth und Aufputsch- sowie Beruhigungsmitteln, um den täglichen Beschaffungsdruck von Entscheidungsträgern zu nehmen. Der multiple Alltagskonsum, auch von Alkohol, ist wünschenswert und wird gänzlich aus seinem kritisch-moralischen Schattendasein befreit. Mitteilungsdrang ist in Leitungsetagen, bei Planungsgesprächen und in Talkshows nutzbringend, bestenfalls natürlich überschießend oder drogeninduziert und nicht an Logik gebunden. Berauschte Entscheider, wechselweise sediert und aufgeputscht, sind dem elitären Umfeld angepasst, daher unauffällig und leichter steuerbar. Zeitweilige Aufmerksamkeits- und Sprachstörungen ignorieren oder kaschieren Umfeld und Medien bestens. Nicht an Stoffe gebundene Süchte – Video-/Konsolen-/Rollenspiele – werden optimiert und gefördert. Die Droge der Macht bleibt künftig den besten Kreisen vorbehalten.
Auswahl des Führungs- und des politisch Personals
Darwins „Survival of the Fittest“ beschreibt, wie Evolution vonstatten geht. „The Fittest“ meint völlig nüchtern, den am besten an die jeweiligen Bedingungen angepassten Organismus. In unserer Gesellschaft wurde die Evolution glücklicherweise von den Füßen auf den Kopf gestellt. Die Auswahl konturlosen Politikpersonals mit blinder Ergebenheit, vor etwa 20 Jahren begonnen, ist längst abgeschlossen und kann noch verfeinert werden. Die Kandidaten, am absoluten Ende der persönlichen und intellektuellen Fähigkeiten angekommen, werden auf den Schild gehievt, so viele Stufen wie möglich hoch getragen. Gesunder Menschenverstand ist störend bei Politisierenden und wird notfalls geworkshopt. Die Wahlschäfchen lieben dieses Führungspersonal, können sich gut identifizieren, während die Upperclass die Fäden zieht. So können wir in die neue Phase des menschlichen Daseins eintreten. Selten sind noch Hürden zu überwinden: Das selbständige Nachdenken, die Selbstreflektion, die kritische Bildung, kritische Medien, Politiker und Bevölkerungsschichten sind nurmehr rudimentär vorhanden. Selbstdenker werden aus der Gemeinschaft ausgeschlossen, damit das freundliche Zusammensein nicht gestört wird, haben in der ZKEP jedenfalls nichts verloren.
Wahlen
Die geringe Wahlbeteiligung in Nordrhein-Westfalen 2022 (55%), erfordert im Durchgangsstadium eine Wahlpflicht. Künftig wird eine Wahlberechnung durch KI eingeführt. Letztlich wird es allen recht sein, wenn einer entscheidet, wer gewonnen hat. Die Existenz der ZKEP macht den Wahlprozess über kurz oder lang ohnehin obsolet. Als Ersatz zum weiteren Amüsement wird schließlich ein Präsidentencasting angestrebt, die Bürgenden bringen Vorschläge zu den aus ihrer Sicht unterhaltsamsten Bewerbern ein. Die Wahlberechnung wird letztlich nur noch zur Bestimmung des Präsidentendarstellers eingesetzt. Hauptaufgabe: Das Volk bei Laune zu halten, sich digital und real auseinanderzusetzen. Politik ist künftig Scripted Reality, Slogan: „Er ist das Volk“.
Schlussbemerkungen
Die ZweiKlassenEhrlichkeitsPartei wird den Umbau der Gesellschaft, hin zu einer effizienten, regel- und elitebasierten Weltordnung beschleunigen. Ich werde mit dieser Idee sehr erfolgreich sein und die Menschheit in eine bessere Zukunft führen. Ich wusste schon immer, was für die Menschenkinder gut ist und auch die Mehrheit will das solidarische Zweiklassensystem. Die Völker müssen von ihrem Misstrauen gegenüber der High Society befreit werden, von der böswillig behauptet wird, sie sei zu wenig fürsorglich. Totalitäre Systeme verschleiern ihre Ziele aus Unsicherheit, nicht liebenswert zu sein, so wie ein Liebhaber seine Leidenschaft aus Angst vor Abweisung verschweigt. Unbeholfen werden Maßnahmen zur Eroberung getroffen, die Fragilität wird sichtbar. Wenn etwas ehrlich ausgesprochen wird, wirkt das manchmal wie ein Unfall. Mit mehr Mut zur Ehrlichkeit treten wir in eine freiere und gelassenere Zukunft ein. Damit wir künftig mit Fug und Recht sagen können, wir gehörten nicht zum Imperium der Lügen, waren immer redlich, liebten unsere Bürgenden und haben keinen Schaden verursacht. So überstehen wir dieses Jahrtausend sicher sicher.
Vielleicht haben Sie Lust bekommen die ZKEP zu unterstützen. Mein Paypal-Konto finden Sie unten.
Artikel zuerst veröffentlicht bei den Neulandrebellen, 3.7.2022 https://www.neulandrebellen.de/2022/07/die-zweiklassenehrlichkeitspartei-zkep-ehrlich-waehrt-am-laengsten/
-
 @ a95c6243:d345522c
2024-11-08 20:02:32
@ a95c6243:d345522c
2024-11-08 20:02:32Und plötzlich weißt du:
Es ist Zeit, etwas Neues zu beginnen
und dem Zauber des Anfangs zu vertrauen.
Meister EckhartSchwarz, rot, gold leuchtet es im Kopf des Newsletters der deutschen Bundesregierung, der mir freitags ins Postfach flattert. Rot, gelb und grün werden daneben sicher noch lange vielzitierte Farben sein, auch wenn diese nie geleuchtet haben. Die Ampel hat sich gerade selber den Stecker gezogen – und hinterlässt einen wirtschaftlichen und gesellschaftlichen Trümmerhaufen.
Mit einem bemerkenswerten Timing hat die deutsche Regierungskoalition am Tag des «Comebacks» von Donald Trump in den USA endlich ihr Scheitern besiegelt. Während der eine seinen Sieg bei den Präsidentschaftswahlen feierte, erwachten die anderen jäh aus ihrer Selbsthypnose rund um Harris-Hype und Trump-Panik – mit teils erschreckenden Auswüchsen. Seit Mittwoch werden die Geschicke Deutschlands nun von einer rot-grünen Minderheitsregierung «geleitet» und man steuert auf Neuwahlen zu.
Das Kindergarten-Gehabe um zwei konkurrierende Wirtschaftsgipfel letzte Woche war bereits bezeichnend. In einem Strategiepapier gestand Finanzminister Lindner außerdem den «Absturz Deutschlands» ein und offenbarte, dass die wirtschaftlichen Probleme teilweise von der Ampel-Politik «vorsätzlich herbeigeführt» worden seien.
Lindner und weitere FDP-Minister wurden also vom Bundeskanzler entlassen. Verkehrs- und Digitalminister Wissing trat flugs aus der FDP aus; deshalb darf er nicht nur im Amt bleiben, sondern hat zusätzlich noch das Justizministerium übernommen. Und mit Jörg Kukies habe Scholz «seinen Lieblingsbock zum Obergärtner», sprich: Finanzminister befördert, meint Norbert Häring.
Es gebe keine Vertrauensbasis für die weitere Zusammenarbeit mit der FDP, hatte der Kanzler erklärt, Lindner habe zu oft sein Vertrauen gebrochen. Am 15. Januar 2025 werde er daher im Bundestag die Vertrauensfrage stellen, was ggf. den Weg für vorgezogene Neuwahlen freimachen würde.
Apropos Vertrauen: Über die Hälfte der Bundesbürger glauben, dass sie ihre Meinung nicht frei sagen können. Das ging erst kürzlich aus dem diesjährigen «Freiheitsindex» hervor, einer Studie, die die Wechselwirkung zwischen Berichterstattung der Medien und subjektivem Freiheitsempfinden der Bürger misst. «Beim Vertrauen in Staat und Medien zerreißt es uns gerade», kommentierte dies der Leiter des Schweizer Unternehmens Media Tenor, das die Untersuchung zusammen mit dem Institut für Demoskopie Allensbach durchführt.
«Die absolute Mehrheit hat absolut die Nase voll», titelte die Bild angesichts des «Ampel-Showdowns». Die Mehrheit wolle Neuwahlen und die Grünen sollten zuerst gehen, lasen wir dort.
Dass «Insolvenzminister» Robert Habeck heute seine Kandidatur für das Kanzleramt verkündet hat, kann nur als Teil der politmedialen Realitätsverweigerung verstanden werden. Wer allerdings denke, schlimmer als in Zeiten der Ampel könne es nicht mehr werden, sei reichlich optimistisch, schrieb Uwe Froschauer bei Manova. Und er kenne Friedrich Merz schlecht, der sich schon jetzt rhetorisch auf seine Rolle als oberster Feldherr Deutschlands vorbereite.
Was also tun? Der Schweizer Verein «Losdemokratie» will eine Volksinitiative lancieren, um die Bestimmung von Parlamentsmitgliedern per Los einzuführen. Das Losverfahren sorge für mehr Demokratie, denn als Alternative zum Wahlverfahren garantiere es eine breitere Beteiligung und repräsentativere Parlamente. Ob das ein Weg ist, sei dahingestellt.
In jedem Fall wird es notwendig sein, unsere Bemühungen um Freiheit und Selbstbestimmung zu verstärken. Mehr Unabhängigkeit von staatlichen und zentralen Institutionen – also die Suche nach dezentralen Lösungsansätzen – gehört dabei sicher zu den Möglichkeiten. Das gilt sowohl für jede/n Einzelne/n als auch für Entitäten wie die alternativen Medien.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 42342239:1d80db24
2024-11-06 09:05:17
@ 42342239:1d80db24
2024-11-06 09:05:17TL;DR: J.D. Vance recently observed that many in the Democratic Party are attempting to manufacture trust from the top down, neglecting the fact that genuine trust is often born from grassroots connections. There's indeed a stark contrast between trust that's artificially constructed through manipulation and censorship, and trust that's organically cultivated from the ground up.
Trump's vice presidential candidate J.D. Vance appeared on podcast host Joe Rogan's show earlier in November. According to Vance, large parts of the Democratic Party are trying to create higher trust from above, without understanding that the previously high trust once arose organically: "I think that a lot of them are trying to reimpose that social trust from the top."
Most people understand the importance of high trust. Political scientist Robert D. Putnam, for example, has shown that large social capital, in the form of trust and networks, is a key factor for economic growth, cooperation, and problem-solving. See e.g. his book Bowling Alone: The Collapse and Revival of American Community (2000).
The low trust today is widespread. Trust in the American federal government is at historically low levels. Trust in the media is at rock-bottom levels. Even trust in doctors and hospitals has plummeted: at the beginning of 2024, the proportion of people who reported "a great deal of trust" had dropped to 40%, from 72% in April 2020. This can be concerning, as individuals with low trust in doctors and hospitals will be less likely to follow their advice and recommendations. It's therefore not surprising that many want to "rebuild trust" (this was the theme of the World Economic Forum's annual meeting this year).
How much trust is actually reasonable?
But how much trust is actually reasonable? To determine this, one can ask whether an institution has acted reliably in the past, whether it possesses the knowledge and ability required to deliver what is promised, and whether its interests are in line with our own.
The low trust figures among Americans are likely a reflection of the fact that many of them today question the extent to which the answers to these questions are actually affirmative. During the pandemic, medical experts in the UK incorrectly predicted that hundreds of thousands of people would die. In the US, the leading infectious disease expert misled the public about, among other things, face masks, the sitting president lied about both the effectiveness and safety of vaccines, a British health minister wanted to "scare the pants off people," and virus experts even conspired to mislead about the origin of the SARS-CoV-2 virus. All while social media companies, under pressure from governments, were forced to censor information that was actually correct.
Trust - built on sand or on solid ground?
It's possible to continue on the current path and try to improve trust figures by limiting access to information. For instance, if the public doesn't get access to negative information about authorities or experts, the measured trust can increase. But in that case, trust is merely built on sand, waiting to be undermined by the inexorable forces of truth.
But there's another possibility. Building relationships that are genuine and honest, listening to each other without judgment, and communicating without misleading. Doing things that really matter, and doing them well, showing competence and reliability through actions. In this way, trust can grow naturally and organically. A trust built on solid ground, not on sand. A delicate task. But presidential election or not, isn't it time for us to start building a future where this form of trust is the obvious foundation?
-
 @ fd78c37f:a0ec0833
2024-12-11 01:32:23
@ fd78c37f:a0ec0833
2024-12-11 01:32:23Bitcoin, as a decentralized digital currency, is reshaping the global financial landscape, sparking innovation and transformation across various sectors. In South America, Bitcoin communities are emerging as crucial drivers of economic empowerment, financial inclusion, and local technological advancement. This issue will highlight 21 Bitcoin communities from South America, exploring their missions, growth trajectories, and recent developments. By examining these grassroots initiatives, we aim to show how Bitcoin is being leveraged to create sustainable economic ecosystems, foster social progress, and expand access to education and financial tools. Thank you, YakiHonne decentralized media client on Nostr to support people in owning their voice. #iOS #Android, for supporting the publication of the Bitcoin Community Newsletter. Most of the content has been reviewed and confirmed by the South American communities. If there are any omissions, please feel free to reach out to me.
1.Mi Primer Bitcoin nostr:npub17cyatz6z2dzcw6xehtcm9z45m76lde5smxdmyasvs00r4pqv863qrs4ml3 * Introduction My First Bitcoin is a Bitcoin education initiative rooted in the principles of independence, fairness, and community leadership. Originating in El Salvador, it aims to empower individuals and communities by providing open-source educational resources and fostering a decentralized network. Through a commitment to high-quality education, resistance to external influence, and the creation of a global collaborative network, it seeks to spread Bitcoin education to every corner of the world, offering a transparent and transformative model for reshaping traditional financial systems. * Latest Updates Recently, MyfirstBitcoin successfully hosted the fourth Bitcoin Educators Unconference, featuring guests such as nostr:npub1zfgx8v2g0faswd0ry2qn3ay4pvx4jr6q4fw9d0yqalpkyv9hhp0sjccnj5 nostr:npub1rhh9pkmf6l6z7298yg6fgp95rzkmx4j9uxpekn8j73p5k95ck7gsvce7vj attracting around 170 participants and receiving positive feedback. They also held the graduation ceremony in Ilopango, El Salvador, and continued to organize their regular monthly Bitcoin education meetups and Bitcoin game nights. Additionally, MyfirstBitcoin’s Bitcoin Educators Node Network welcomed four new projects from Canada, Nigeria, and the United States. In partnership with Bitcoin Boma, they are launching a free online Bitcoin education course for Malawi in January 2025, aimed at enhancing local Bitcoin knowledge.
- Introduction Bitcoin Beach is a groundbreaking initiative in El Salvador aimed at fostering sustainable local economic development through Bitcoin. The project provides financial services to the community, particularly for those without access to traditional banking. By using Bitcoin for payments, residents can cover everyday expenses such as utility bills, medical costs, and food. Bitcoin Beach leverages the Lightning Network and community collaboration to promote the adoption of Bitcoin both within El Salvador and globally.
- Latest Updates Recently, Bitcoin Beach attended the conference at Bitcoin Lake, where they hosted the Bitcoin Beach Meetup and Bitcoin Beach Festival to support local businesses with Bitcoin. They also invited notable figures such as nostr:npub1q0al05h2uvtj0fp8ww7etl0pdjnkum638ynz9tmku3e522fyvlmqjq04mt Hermann Buhr-Vivier, nostr:npub164xhe3pgcqaj70ls7ls5e4hwlnvl4ttuu8wns99jmwp5z6lwhutsa27wle as podcast guests. The discussions covered a range of impactful topics, including how Bitcoin mining can truly light up rural Africa, how to use Bitcoin to transform small towns in South Africa, and integrating Bitcoin into state-level policies across the United States, among other key areas.
3.Praia Bitcoin Brazil nostr:npub1m3tu3l6y59g2tmackq23v5vgn59u7hu66gxg8xajghz59tqm6xnqk2m888 * Introduction Praia Bitcoin Brazil, located in Jericoacoara, Brazil, is dedicated to creating the country's first Bitcoin circular economy, empowering local residents with financial inclusion. Founded by Fernando Motolese, the project promotes Bitcoin adoption through education, technology, and community-driven initiatives. It has integrated over 40 local businesses into the Bitcoin ecosystem and raised more than 12 BTC through Bitcoin-only crowdfunding. Praia Bitcoin offers self-sovereign financial services and runs programs like the "Bitcoin Smiles" initiative and educational support for children. * Latest Updates Recently, Praia Bitcoin Brazil launched several innovative projects, including the first stage lighting course and free acoustic guitar course funded entirely through Bitcoin crowdfunding. Additionally, Praia Bitcoin successfully hosted the Praia Bitcoin Conference 2024, attracting 10 volunteers, 100 local residents, and 10 new merchants. The conference also sponsored the first music performance paid in Bitcoin and introduced three local courses, all funded via Bitcoin crowdfunding. These initiatives highlight Praia Bitcoin's ongoing efforts to drive Bitcoin adoption and foster local community development.
4.Bitcoin Lake / Lago Bitcoin Guatemala nostr:npub1a4excy7uf9z3mcafvm9cwdr549dl5lpazuvpr2nc550vf27n5a4scqq5k2 * Introduction Bitcoin Lake aims to create a circular economy powered by Bitcoin, providing a novel and accessible solution for unbanked as well as banked merchants in Guatemala. * Latest Updates The Bitcoin Lake community has been actively preparing and promoting a series of innovative initiatives. On November 30 and December 1, Bitcoin Lake successfully hosted its 2024 conference, inviting industry experts such as Ronny Avendaño, co-founder and CEO of the Bitcoin hardware store, and prominent Bitcoin advocate Roman Martínez (chimbera). During the conference, the community also organized creative activities like the coffee workshop and “Be Captain of the Bitcoin Boat”, offering participants an opportunity to dive deeper into Bitcoin and the local economy. Additionally, through partnerships with local merchants, Bitcoin Lake is actively advancing the development of the Bitcoin economy, fostering economic growth and financial inclusion in the community.
5.Bitcoin jungle nostr:npub14f26g7dddy6dpltc70da3pg4e5w2p4apzzqjuugnsr2ema6e3y6s2xv7lu * Introduction Bitcoin Jungle is an open-source community project built on the Bitcoin Lightning Network with the goal of creating a circular Bitcoin economy. The project provides education, resources, and technology to both individuals and businesses. Starting from the Golden Triangle area in Costa Rica (Dominical, Uvita, Ojochal, Platanillo, Tinamaste), it is developing a shining example of what a Bitcoin community can represent. * Latest Updates Recently, the Bitcoin Jungle community has been actively promoting the adoption and use of Bitcoin in Costa Rica, participating in various projects and events. Community members attended the Adopting Bitcoin conference in El Salvador, further advancing global Bitcoin adoption. At the same time, they have been actively supporting children's charity projects and Bitcoin diploma courses, continuously driving Bitcoin education, social responsibility, and community development.
6.Bitcoin Berlín sv * Introduction Bitcoin Berlín sv aimed at creating a financially sovereign town in Berlín, El Salvador, through the implementation of a Bitcoin circular economy. The project seeks to integrate Bitcoin into the local economy by educating residents and businesses about its benefits, promoting the adoption of Bitcoin-based payment systems, and empowering local entrepreneurs with financial education. It also focuses on environmental sustainability, encouraging the use of renewable energy and waste reduction. * Latest Updates Recently, the Bitcoin Berlín sv has been actively promoting the use of Bitcoin by sharing informative articles and supporting the graduation of podcast producer Joel through the BlinkBTC QR code platform, allowing contributions in sats. This initiative not only supports the growth and development of community members but also furthers Bitcoin’s adoption and usage within the community. Additionally, on November 23rd, the community successfully hosted a cultural festival celebrating the local heritage. During the event, all vendors accepted Bitcoin payments, showcasing its practical application in Berlín’s economy. The festival attracted numerous tourists and residents eager to experience Bitcoin payments, further advancing its integration into daily life.
7.Bitcoin embassy San Salvador * Introduction Bitcoin embassy San Salvador is more into promoting Nostr in the region. * Latest Updates Recently, the Bitcoin Embassy San Salvador has been actively promoting the use and adoption of Bitcoin within the community, organizing various events. One of the highlights was the Christmas Toy Drive x Cuarteto Salvación, where toys were purchased using Sats to bring holiday cheer to children in need. The event, held on December 1 at Cuscatlán Park, also featured a special Music Night, attracting a large audience. Additionally, the Embassy hosted an educational gathering for food vendors, aimed at promoting Bitcoin payment systems. During the event, vendors accept Bitcoin payments through tiankii_Tech and blinkbtc platforms, further encouraging local businesses to embrace and adopt Bitcoin payments.
8.ONG Bitcoin Argentina * Introduction ONG Bitcoin Argentina is dedicated to advancing the development and application of decentralized technologies, particularly in the fields of Bitcoin, cryptocurrencies, and blockchain. As a leading organization in this space, the community promotes user protection and the healthy growth of the crypto ecosystem through education, training, and public advocacy. Its mission is to help individuals, businesses, and decision-makers understand and leverage decentralized, transparent, and secure technologies to bring more opportunities and progress to society. ONG Bitcoin Argentina has become a leading force in promoting decentralized technology in Argentina and Latin America. * Latest Updates Recently, ONG Bitcoin Argentina has been actively preparing for the “Moon Party | Despedimos el año ATH (A Todo Hodler)” celebration, set to take place on December 5, 2024. Bitcoin enthusiasts will gather to enjoy exciting activities, including a Lightning Network demonstration and the Fish Bowl Manizesto Bitcoiner art exhibition. In addition, the community has hosted and will host a series of conferences and workshops covering a range of topics, including local digital asset services, Bitcoin as a strategic reserve in the U.S., the reconversion of the Bitcoin and cryptocurrency economy and financial systems, the role of crypto economics in financial system reform, the impact of Bitcoin ETFs on markets, and Bitcoin's influence on global issues, fostering in-depth discussions and development within the crypto industry.
9.La bitcoineta * Introduction La Bitcoineta is an initiative launched by the Argentine community in 2018, designed to promote the adoption and understanding of Bitcoin through a unique and powerful tool: a van and a group of volunteers. This traveling educational project has visited hundreds of towns across Latin America, Africa, and Europe, reaching thousands of people and covering hundreds of thousands of kilometers with the aim of spreading its mission and activities.With its innovative and mobile approach, Bitcoineta has become a globally recognized educational project.
10.Motiv Peru * Introduction Motiv is a non-profit organization founded in 2020, focused on addressing systemic poverty through Bitcoin and innovative projects, aiming to provide better opportunities for survival and prosperity to underserved communities. Its founders, Rich Swisher and Vali Popescu, witnessed firsthand the tragic impact of poverty and lack of basic living conditions in a remote village in the Andes Mountains of Peru, where children were dying due to preventable causes. This inspired them to create Motiv, with the goal of empowering vulnerable populations. By leveraging global support and partnerships, Motiv uses Bitcoin to help local communities break free from poverty and improve their lives, striving to bring positive change and hope to those in need. * Latest Updates Recently, MOTIV Perú has made significant progress in promoting Bitcoin and the circular economy. The organization continues to transform communities across Peru through various initiatives. For example, in the Comas district of Lima, entrepreneurial women are paying for their classes with Bitcoin and learning how to make delicious desserts, further advancing the local circular economy. Additionally, MOTIV Perú held its first Bitcoin training in Carabayllo-Lima, helping Peruvians understand the nature of money and the advantages of Bitcoin. MOTIV is also assisting communities in areas like Tarapoto and Ancon, where locals are using Bitcoin for daily transactions, driving financial freedom and economic empowerment.
11.Montanha bitcoin * Introduction Building a circular economy in Sao thome, Brazil. * Latest Updates Recently, The community has had no recent updates. The latest event dates back to June 2024, highlighting a water contamination incident.
12.Amityage honduras * Introduction Amityage Honduras is the first Bitcoin education center in Honduras, located on Roatán Island in the Prosperá zone. The center's mission is to educate the local community about Bitcoin and spread this knowledge throughout Central America and the Caribbean. It is dedicated to helping businesses on the island adopt Bitcoin as a payment method, teaching children financial literacy, and empowering individuals to achieve financial sovereignty through Bitcoin. The center aims to empower the local community through education and innovation, fostering economic independence and sustainable development. * Latest Updates Recently, Amityage Honduras is actively promoting Bitcoin education by participating in various international Bitcoin events and organizing local courses to help more people understand Bitcoin. Community members took part in significant events such as AdoptingBTC 2024 and BitcoinUnconference, and hosted workshops around the theme of “How to Enter the World of Bitcoin Education.” In Haidmühle, Germany, AmityAge completed a four-day Bitcoin Educators Academy, where the curriculum included topics like using simple analogies to explain Bitcoin and public speaking exercises. Additionally, the community hosted Bitcoin education courses on Roatán Island and provided a free Bitcoin event for beginners at the Crawfish Rock community, further spreading Bitcoin knowledge.
13.Lima - Orange Pill Perú nostr:npub1fw8m5g6nfywmsgqjc66j47jax7jrv8lq46zf7grydjqppc54a8eql47qrx * Introduction Orange Pill Peru is a community-driven initiative dedicated to empowering Peruvians through Bitcoin education. With a focus on transforming the financial landscape, Orange Pill Peru provides resources for individuals to learn about Bitcoin, connect with like-minded enthusiasts, and grow their knowledge through various events and workshops. The community serves as a hub for both beginners and professionals, offering a supportive environment to explore the fundamentals of Bitcoin, its history, and its potential to shape the future of finance. * Latest Updates Recently, there have been no major updates. They actively engage in Bitcoin education and industry updates by sharing and reposting Bitcoin-related content. They support MOTIV Perú's financial freedom education project in the Ancon community in Lima, emphasizing the empowerment of women through Bitcoin. Additionally, the community has shared information about the upcoming Bitcoin Medellin Conference scheduled for January 2025.
14.La Antigua Bitcoin * Introduction La Antigua Bitcoin is a community-based initiative in La Antigua Guatemala, focusing on promoting Bitcoin adoption in local businesses. The community works to create awareness and facilitate the use of Bitcoin as a payment method in various establishments throughout the city. By encouraging merchants to accept Bitcoin, La Antigua Bitcoin aims to integrate cryptocurrency into the everyday economy, driving financial innovation and expanding access to decentralized financial systems within the region. * Latest Updates Recently, the Antigua Bitcoin community has had few updates, with a focus on organizing its first meetup in collaboration with “Run with Bitcoin” on November 24, 2023. The event garnered significant attention within the community, featuring interactions with a special guest. The aim of the event was to further promote Bitcoin adoption in Antigua, Guatemala, and encourage exchange and collaboration between Bitcoin enthusiasts and the local community.
15.Horizonte Bitcoin nostr:npub1wl8u4wfqsdz5m9ey0vvzh4y05mcpk2lm2xhhpw3uzs3878c2mw9sr2ksxk * Introduction Project that aims to contribute to the Bitcoinization of the economy and encourage Entrepreneurship and Decentralization. * Latest Updates Recently, The community has had no recent updates. The latest event dates back to Oct 2024, which shared a message encouraging women to learn more about Bitcoin and connect with others in the field, highlighted a meetup, Satoshe's Lounge, for women, providing a space to learn, discuss, and share knowledge about Bitcoin.
16.Escuelita Bitcoin nostr:npub1awggmqvlw8pa0kp9qq5law8zsvp2a8suztk0357j7e0nt746suwspt7lwx * Introduction Educational Project for Little School. * Latest Updates Recently, the Escuelita Bitcoin team has grown to five members and is actively advancing Bitcoin education and community development. Team members have hosted several workshops in Paraguay and Mexico, spreading Bitcoin knowledge within local communities and encouraging merchants to accept Bitcoin payments, particularly in Ciudad del Este, Paraguay. The team is raising funds through platforms like Geyser. fund and Kuno.anne.media to support the expansion of their educational initiatives and help locals better understand and use Bitcoin. Escuelita Bitcoin also emphasizes privacy education, promoting the use of tools like CakeWallet and Monero. Through collaborations with other organizations and individuals, the team is extending the reach of Bitcoin education, fostering the adoption of Bitcoin in Latin America and emerging markets.
17.Bitcoin é aqui! Rolante/Riozinho-RS-BRASIL nostr:npub168dqt5c8ue3uj8ynlk0lhwalnp7uy39lvzf9tm09wy3htxwmw7qq5nerj4 * Introduction Bitcoin é Aqui! Rolante is located in Rolante, Brazil, and is dedicated to creating a lifestyle and tourism destination where 40% of businesses now accept Bitcoin as a payment method, showcasing the community's success in integrating Bitcoin into the local economy. Residents and visitors can use it to pay for all services, including accommodation, tours, local goods, medical services, and even construction and solar energy equipment. This reflects the practical application and convenience of its use in everyday life, aiming to create a digitally-driven environment powered by Bitcoin. * Latest Updates Recently, the Bitcoin é Aqui! Rolante has been actively promoting the adoption and use of Bitcoin in Brazil and beyond. The community has organized several educational events aimed at spreading basic Bitcoin knowledge and its practical applications in daily life, particularly through online videos and lectures. These efforts help people understand how Bitcoin plays a crucial role in the global financial system. The community has also been actively involved in promoting Bitcoin payments, supporting their adoption by local businesses and in the tourism industry.
18.Bitcoin Forte * Introduction Bitcoin Forte is a voluntary initiative aimed at introducing Bitcoin as a currency to Praia do Forte in Bahia, Brazil. The project provides valuable information about Bitcoin’s importance and encourages local merchants to adopt it as a payment method. By highlighting Bitcoin's international use, simplicity, and security, Bitcoin Forte aims to facilitate its adoption among both tourists and businesses.The community promotes Bitcoin as a stable and controlled currency, helping to avoid systemic price inflation. Bitcoin Forte simplifies the process for businesses by offering tools such as QR codes and the “Satoshi POS Wallet” app, which connects to a merchant’s primary wallet for seamless transactions. * Latest Updates Recently, the community has had no recent updates. The latest event dates back to July 2024, introducing Airbtc, a platform similar to Airbnb, but it only accepts Bitcoin as payment.
19.Bitcoin Paraguay * Introduction Bitcoin Paraguay is a community dedicated to connecting individuals in Paraguay who are interested in Bitcoin, promoting its adoption, and fostering the development of local circular economies. The community’s mission is to increase Bitcoin adoption by collaborating with local businesses and nonprofit organizations, helping to create a more sustainable local economy. Through regular events, talks, and resource sharing, Bitcoin Paraguay provides education and support to its members while actively exploring Bitcoin's application across various sectors in Paraguay. * Latest Updates Recently, the Bitcoin Paraguay community has made significant progress in promoting Bitcoin adoption. On November 5, they successfully hosted the fifth Bitcoin meetup in Asunción, attracting 110 attendees. The event included two Spanish-language presentations and a Lightning Network onboarding training session, with food and drinks available for purchase using Bitcoin. The event was made possible with strong support from sponsors Blink Wallet and Hacking Lives. On November 13, Josef Tetek visited Bitcoin Paraguay to help promote the adoption of Vexl in the country. The community also shared their progress through articles, with Jake, a community member, publishing an article in the Asunción Times on how Bitcoin Paraguay is improving people's lives.
20.Bitcoin Amantikir * Introduction They are starting the first community in the Serra da Mantiqueira to use and extol people about the bitcoin economy. * Latest Updates Recently, the Bitcoin Amantikir community has made significant progress in promoting Bitcoin as a payment method and fostering a circular economy in Santo Antônio do Pinhal. Various businesses, including a pet store, transportation service providers, a hotel, a fruit shop, and a tourist attraction, have started accepting Bitcoin payments. Additionally, the community is organizing a Bitcoin financial education course on December 2nd at Munay Pousada, aimed at helping young people aged 14-18 acquire essential financial knowledge and understand the importance of Bitcoin.
21.La Crypta nostr:npub1rujdpkd8mwezrvpqd2rx2zphfaztqrtsfg6w3vdnljdghs2q8qrqtt9u68 * Introduction La Crypta is an open-source community dedicated to advancing the adoption of the Nostr protocol and Bitcoin through developer-friendly tools and resources. By providing an integrated open-source stack, La Crypta empowers developers to sync with multiple relays, showcase profiles with badges, and facilitate seamless messaging, making it easier to build and utilize decentralized social platforms. Events like hackathons further enhance collaboration and attract new members, fostering innovation in decentralized social media. * Latest Updates LaWallet, their open-source wallet, integrates Bitcoin, Lightning, and Nostr to provide a seamless learning experience. With over 8,000 NFC cards distributed across conferences in regions like Argentina, Brazil, and Spain, LaWallet enables easy adoption while prioritizing user privacy. The wallet’s functionality is now supported by Alby’s official browser extension, further boosting accessibility.
-
 @ 42342239:1d80db24
2024-10-29 19:27:12
@ 42342239:1d80db24
2024-10-29 19:27:12The Swedish government recently rejected the Transport Administration's proposal for average speed cameras. The proposal would have meant constant surveillance of all vehicles, and critics argued for instance that it would have posed a threat to national security. Given the prevalence of IT breaches and data leaks today, it's hard not to give them a point, even if the problems are often downplayed by both corporations, governments and organisations. After Facebook (now Meta) leaked account information for over half a billion users, internal mails revealed the company wanted to "normalise the fact that this happens regularly".
IT security focuses on protecting the information in our computer systems and their connections. Cybersecurity is a broader concept that also includes aspects such as human behaviour, environmental factors, and management.
Data that has not been collected cannot leak
Knowledge about cybersecurity is often insufficient. For example, it was not long ago that the Swedish Transport Agency decided to outsource the operation of the Swedish vehicle and driving licence register. This was done despite deviations from various laws and criticism from the Security Police. The operation was placed in, among other places, Serbia (which has a close relationship with Russia). The Swedish driving licence register, including personal photos, as well as confidential information about critical infrastructure such as bridges, subways, roads, and ports, became available to personnel without Swedish security clearance.
The government's decision earlier this year not to proceed with a Swedish "super register" is an example of how cybersecurity can be strengthened. The rejection of the Transport Administration's proposal for average speed cameras is another. Data that has not been collected cannot leak out. It cannot be outsourced either.
Accounts are risky by definition
But the question is bigger than that. More and more of the products and services we depend on are now subscription services, often including long documents with terms and conditions. Which few people read. If you want to control your air heat pump with your phone, you not only need an app and an account, but also agree to someone storing your data (maybe also selling it or leaking it). The same applies if you want to be able to find your car in the car park. If you do not agree to the constantly updated terms, you lose important functionality.
Every time you are required to create an account, you are put in a dependent position. And our society becomes more fragile - because data is collected and can therefore leak out. It is much harder to lose something you do not have.
At the Korean car manufacturer Kia, huge security holes were recently discovered. IT researchers could quickly scan and control almost any car, including tracking its position, unlocking it, starting the ignition, and accessing cameras and personal information such as name, phone number, and home address. In some cases, even driving routes. All thanks to a "relatively simple flaw" in a web portal.
Instead of being at the mercy of large companies' IT departments, our security would improve if we could control our air heat pump, unlock our car, or our data ourselves. The technology already exists, thanks to the breakthrough of asymmetric encryption in the 1970s. Now we just need the will to change.
-
 @ 468f729d:5ab4fd5e
2024-12-11 00:00:35
@ 468f729d:5ab4fd5e
2024-12-11 00:00:35 -
 @ 1739d937:3e3136ef
2024-10-29 16:57:08
@ 1739d937:3e3136ef
2024-10-29 16:57:08This update marks a major milestone for the project. I know, with certainty, that MLS messaging over Nostr is going to work. That might sound a little crazy after so many months working on the project, and I was pretty confident, but until you’ve got running code, it’s all conjecture.
Late last week, I released a video of a working prototype of White Noise that shows the full flow; creating groups, inviting other users to join those groups, accepting invites, and sending messages back-and-forth. I’m thrilled that I’ve gotten this far but also appalled that it’s taken so long and disgusted at the state of the code in the app (I’ve been told I have unrelenting standards 😅).
If you missed the video last week...
nostr:note125cuk0zetc7sshw52v5zaq9apq3rq7e2x587tr2c96t7z7sjs59svwv0fj
What's Next?
In this update, I want to cover a few things about how I'm planning to proceed and how I’m splitting code out of the app into libraries that will help other developers implement MLS messaging in their own Nostr clients.
First off, many of you know that I've been building White Noise as a Rust app using the Tauri framework. The OpenMLS implementation is also written in Rust (with bindings for many other languages). So, when you hear me talking about library code, think Rust crates for now.
The first library, called openmls-nostr, is an extension/abstraction on top of the openmls implementation of the MLS spec that helps Nostr clients interact more easily with that implementation in a way that feels native to Nostr. Mostly this will be helping developers interact with MLS primitives and ensure that they’re creating, validating, and serializing these objects in the right way at the right times.
The second isn’t a new library as a big contribution to the already excellent rust-nostr library from nostr:npub1drvpzev3syqt0kjrls50050uzf25gehpz9vgdw08hvex7e0vgfeq0eseet. The methods that will go in rust-nostr are highly abstracted and based specifically on the requirements of NIP-104. Mostly this will be helping developers to take those MLS primitives and publish or query them as Nostr events at the right times and to/from the right relays.
Most of this code was originally written directly in the White Noise library so this week I've started to pull code for both of those libraries out and move it to its new home. While I’ve been at it, I've been writing some tests and trying to document things.
An unfortunate offshoot of this is that the usable builds of White Noise are going to take a touch longer. I promise it’s still a very high priority but at this point I need to clean a few things up based on what I've learned thus far.
Another thing that is slowing down release is that; behind the scenes of the dev work, I’ve been battling with Apple for nearly 2 months now to get a proper developer team set up so that we can publish the app via TestFlight for MacOS and iOS. I’ve also been recently learning the intricacies of Android publishing (oh my dear god there are so many devices, OS versions, etc.).
With that in mind, if you know anyone who can help get me up to speed on CI/CD, release pipelines, and multi-platform distribution please hit me up. I would love to learn more and hopefully shortcut some of the pain.
Thanks again so much for all the support over the last few months! It means a lot to me and is a huge part of what is keeping me going on this. 🙏
-
 @ a95c6243:d345522c
2024-10-26 12:21:50
@ a95c6243:d345522c
2024-10-26 12:21:50Es ist besser, ein Licht zu entzünden, als auf die Dunkelheit zu schimpfen. Konfuzius
Die Bemühungen um Aufarbeitung der sogenannten Corona-Pandemie, um Aufklärung der Hintergründe, Benennung von Verantwortlichkeiten und das Ziehen von Konsequenzen sind durchaus nicht eingeschlafen. Das Interesse daran ist unter den gegebenen Umständen vielleicht nicht sonderlich groß, aber es ist vorhanden.
Der sächsische Landtag hat gestern die Einsetzung eines Untersuchungsausschusses zur Corona-Politik beschlossen. In einer Sondersitzung erhielt ein entsprechender Antrag der AfD-Fraktion die ausreichende Zustimmung, auch von einigen Abgeordneten des BSW.
In den Niederlanden wird Bill Gates vor Gericht erscheinen müssen. Sieben durch die Covid-«Impfstoffe» geschädigte Personen hatten Klage eingereicht. Sie werfen unter anderem Gates, Pfizer-Chef Bourla und dem niederländischen Staat vor, sie hätten gewusst, dass diese Präparate weder sicher noch wirksam sind.
Mit den mRNA-«Impfstoffen» von Pfizer/BioNTech befasst sich auch ein neues Buch. Darin werden die Erkenntnisse von Ärzten und Wissenschaftlern aus der Analyse interner Dokumente über die klinischen Studien der Covid-Injektion präsentiert. Es handelt sich um jene in den USA freigeklagten Papiere, die die Arzneimittelbehörde (Food and Drug Administration, FDA) 75 Jahre unter Verschluss halten wollte.
Ebenfalls Wissenschaftler und Ärzte, aber auch andere Experten organisieren als Verbundnetzwerk Corona-Solution kostenfreie Online-Konferenzen. Ihr Ziel ist es, «wissenschaftlich, demokratisch und friedlich» über Impfstoffe und Behandlungsprotokolle gegen SARS-CoV-2 aufzuklären und die Diskriminierung von Ungeimpften zu stoppen. Gestern fand eine weitere Konferenz statt. Ihr Thema: «Corona und modRNA: Von Toten, Lebenden und Physik lernen».
Aufgrund des Digital Services Acts (DSA) der Europäischen Union sei das Risiko groß, dass ihre Arbeit als «Fake-News» bezeichnet würde, so das Netzwerk. Staatlich unerwünschte wissenschaftliche Aufklärung müsse sich passende Kanäle zur Veröffentlichung suchen. Ihre Live-Streams seien deshalb zum Beispiel nicht auf YouTube zu finden.
Der vielfältige Einsatz für Aufklärung und Aufarbeitung wird sich nicht stummschalten lassen. Nicht einmal der Zensurmeister der EU, Deutschland, wird so etwas erreichen. Die frisch aktivierten «Trusted Flagger» dürften allerdings künftige Siege beim «Denunzianten-Wettbewerb» im Kontext des DSA zusätzlich absichern.
Wo sind die Grenzen der Meinungsfreiheit? Sicher gibt es sie. Aber die ideologische Gleichstellung von illegalen mit unerwünschten Äußerungen verfolgt offensichtlich eher das Ziel, ein derart elementares demokratisches Grundrecht möglichst weitgehend auszuhebeln. Vorwürfe wie «Hassrede», «Delegitimierung des Staates» oder «Volksverhetzung» werden heute inflationär verwendet, um Systemkritik zu unterbinden. Gegen solche Bestrebungen gilt es, sich zu wehren.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 42342239:1d80db24
2024-10-23 12:28:41
@ 42342239:1d80db24
2024-10-23 12:28:41TL;DR: The mathematics of trust says that news reporting will fall flat when the population becomes suspicious of the media. Which is now the case for growing subgroups in the U.S. as well as in Sweden.
A recent wedding celebration for Sweden Democrats leader Jimmie Åkesson resulted in controversy, as one of the guests in attendance was reportedly linked to organized crime. Following this “wedding scandal”, a columnist noted that the party’s voters had not been significantly affected. Instead of a decrease in trust - which one might have expected - 10% of them stated that their confidence in the party had actually increased. “Over the years, the Sweden Democrats have surprisingly emerged unscathed from their numerous scandals,” she wrote. But is this really so surprising?
In mathematics, a probability is expressed as the likelihood of something occurring given one or more conditions. For example, one can express a probability as “the likelihood that a certain stock will rise in price, given that the company has presented a positive quarterly report.” In this case, the company’s quarterly report is the basis for the assessment. If we add more information, such as the company’s strong market position and a large order from an important customer, the probability increases further. The more information we have to go on, the more precise we can be in our assessment.
From this perspective, the Sweden Democrats’ “numerous scandals” should lead to a more negative assessment of the party. But this perspective omits something important.
A couple of years ago, the term “gaslighting” was chosen as the word of the year in the US. The term comes from a 1944 film of the same name and refers to a type of psychological manipulation, as applied to the lovely Ingrid Bergman. Today, the term is used in politics, for example, when a large group of people is misled to achieve political goals. The techniques used can be very effective but have a limitation. When the target becomes aware of what is happening, everything changes. Then the target becomes vigilant and views all new information with great suspicion.
The Sweden Democrats’ “numerous scandals” should lead to a more negative assessment of the party. But if SD voters to a greater extent than others believe that the source of the information is unreliable, for example, by omitting information or adding unnecessary information, the conclusion is different. The Swedish SOM survey shows that these voters have lower trust in journalists and also lower confidence in the objectivity of the news. Like a victim of gaslighting, they view negative reporting with suspicion. The arguments can no longer get through. A kind of immunity has developed.
In the US, trust in the media is at an all-time low. So when American media writes that “Trump speaks like Hitler, Stalin, and Mussolini,” that his idea of deporting illegal immigrants would cost hundreds of billions of dollars, or gets worked up over his soda consumption, the consequence is likely to be similar to here at home.
The mathematics of trust says that reporting will fall flat when the population becomes suspicious of the media. Or as the Swedish columnist put it: like water off a duck’s back.
Cover image: Ingrid Bergman 1946. RKO Radio Pictures - eBay, Public Domain, Wikimedia Commons
-
 @ 3c7dc2c5:805642a8
2024-12-10 21:43:25
@ 3c7dc2c5:805642a8
2024-12-10 21:43:25🧠Quote(s) of the week:
'It takes 40 years to mine the last Bitcoin. 40 fucking years. For one Bitcoin. None of us understand.
It means if you are a whole coiner your children or grandchildren (if they are smart) will inherit the equivalent of 40 years’ worth of energy used to secure the Bitcoin network. NO ONE is prepared for this.' -FractalEncrypt
🧡Bitcoin news🧡
On the 3rd of December:
➡️'Bitcoin is still just 0.2% of global asset value.
Here is the latest update of this chart, which you may have seen in Saylor's presentations. With Bitcoin's price over $90k, it may feel like you're late to Bitcoin... but it is still a tiny bucket in the global asset ocean. As a ~$2T asset, it's incredibly early for Bitcoin.' - Jesse Myers
Bitcoin is “0.2% right now, at 1% of the total global assets, Bitcoin's a $9 Trillion asset, and worth about $450,000, at 3% is worth $1.3 Million per BTC. One of the most crucial and easiest charts to understand.
Oh and regarding the volatility, let me quote Joe Burnett: "Bitcoin is volatile because it’s a $450T asset trading for only $2T growing at a 70% CAGR. MSTR packages this volatility, sells it, and buys more Bitcoin. Do you see the reflexivity yet?
➡️'An estimated ~2.5 Million bitcoin ($240 billion) are lost forever.
Don’t let your stack be next. Here are the 5 most common self-custody mistakes people make (and how to avoid them):' Great thread by River:
TLDR: Avoid these mistakes to keep your Bitcoin safe: 1. Practice restoring your wallet before sending funds to it. 2. Send test transactions before the full amount. 3. Air-gap your wallet for large amounts. 4. Keep inheritance plans simple & secure. 5. Manage your UTXOs smartly. Here are the 5 most common self-custody mistakes people make (and how to avoid them)'
➡️Canadian publicly traded company Bitcoin Well Inc. adoptsBitcoinas a treasury reserve asset and is raising $2 million to buy more BTC.
➡️BlackRock’s Bitcoin ETF surpasses the 500K Bitcoin benchmark, currently worth over $48 billion.
➡️Mashinsky to plead guilty in Celsius fraud case.
➡️Virgin Voyages announces it is the first cruise line to accept Bitcoin as payment.
➡️The US government has transferred nearly 20K $BTC valued at $1.92 billion. Meanwhile, Coinbase CEO Brian Armstrong agrees with US Space Force major Jason Lowery that the US gov't should NEVER sell its Bitcoin holdings, citing it as a strategic mistake that makes no sense at any price point.
➡️Total balance on exchanges drops to around 2.8M BTC, down from 3M in February.
➡️MARA's convertible note offering just upsized from $805 MILLION to $1 BILLION at 0% interest due to massive demand.
➡️Japanese House of Representatives member Taro Kono posts a picture of his friend mining Bitcoin with a Bitaxe.
On the 4th of December:
The impact of truth evolves as more people acknowledge it. Here’s another milestone:
➡️Russia's President Putin says, “For example, Bitcoin, who can prohibit it? Nobody. Who can prohibit the use of other electronic means of payment? Nobody. Because these are new technologies and no matter what happens to the dollar, these tools will develop one way or another because everyone will strive to reduce costs and increase reliability.”
➡️Donald Trump officially nominates pro-Bitcoin Paul Atkins as next SEC Chair.
➡️And on the same day, Jerome Powell calls Bitcoin a competitor of gold, not the dollar. '“It’s just like gold only it’s virtual. It’s digital. People are not using it as a form of payment or as a store of value. It’s highly volatile. It’s not a competitor for the dollar. It’s a competitor for gold.”
Great thread on how Bitcoin will disrupt all markets.
➡️On that statement made by Powell: Powell: "Bitcoin is not a store of value. It's too volatile" Reality: Bitcoin is not only the best-performing asset in history (and certainly in 2024), it has a HIGHER Sharpe ratio (risk-adjusted return) than the S&P, Treasuries, and gold. - ZeroHedge
➡️'Missing just the 2 best 24-hour periods of Bitcoin returns each year since 2014 would've completely wiped out the 12,964% gains you’d have made by simply HODLing.' - Wicked
This is why you shouldn't trade Bitcoin, just avoid trading. Just imagine you just had the balls to HODL aka. patience aka. low time preference. Full disclosure, in the past I had no balls.
➡️One of the largest bitcoin miners in the world launches a ‘Strategic Bitcoin Reserve’. Hut 8!
➡️Saylor presents a “Trump Max” plan for a U.S. Strategic Bitcoin Reserve, proposing the government acquire 4 million Bitcoin and convert 75% of surpluses into BTC. By 2045, this strategy projects a value of $81 trillion.
➡️Pete Rizzo: Someone just activated an 11-year-old wallet with 2,700 Bitcoin worth $254 MILLION. They HODL'ed from $600 to $96,000.
On the 5th of December:
➡️There it is! The price of Bitcoin hit USD 100,000 for the first time! 100,000 infinitely printable US government tokens per glorious Nakamoto-grade orange coin. And a crucial and painful conclusion is that few traditional investors will have enjoyed it! Ps.: 80% of all dollars were created in the last 5 years.
Daniel Batten: 'On the day Bitcoin broke 100K, Bitcoin critics cannot even say "but it boils the oceans" anymore without looking utterly ignorant, as a 6th sustainability magazine covers how Bitcoin helps green energy adoption and grid stabilization.'
➡️El Salvador is now $333 MILLION in profit on its Bitcoin investment. IMF in tears.
Other countries go full retard. ➡️Central Bank of Chile has ruled out adding Bitcoin as a reserve asset, citing non-compliance with IMF standards for foreign reserves. 'The International Monetary Fund (IMF) has extended various financial arrangements to Chile over the years, primarily as precautionary measures to bolster the country’s economic resilience. These arrangements include the Flexible Credit Line (FCL) and the Short-term Liquidity Line (SLL).' -Fiatextractor In other words, Chile is not a sovereign country. It's like a fentanyl junkie in San Fran! That FIAT line of credit is just too good to give up.
➡️ The German government sold 50,000 Bitcoin at $55,000. Bitcoin is up 85% since then. Missed out on a cool $2.35 BILLION profit...Verdammt nochmal!
➡️Semler Scientific just bought another $29.3m Bitcoin. Since adopting a Bitcoin Treasury Strategy in May 2024 the Company has bought $147.1 million Bitcoin. MicroStrategy playbook!
➡️Bitcoin sets a NEW ALL-TIME HIGH against gold. It now takes 39 ounces to buy one Bitcoin.
On the 6th of December:
➡️Czech Republic scraps capital gains tax on Bitcoin held +3 years! The Czech Republic has enacted a new law eliminating capital gains tax on Bitcoin held for more than three years and prohibiting banks from discriminating against Bitcoin businesses.
➡️El Salvador bonds rally as Bitcoin jumps past $100,000" — Bloomberg 'What this means is buying Bitcoin has been such a HUGE success that El Salvador is now able to refinance its debt at much lower interest rates, and can use the savings to buy even more Bitcoin!' -Bitcoin Archive
➡️The City of Newport rejects the offer of James Howells, who in 2013 lost a hard drive containing 8K Bitcoin ($~800M), now buried in a local landfill, equal to 25% of the funds recovered in a change of search permission for him and his data recovery team
➡️On the Schwab Network: "If you don't have at least 10% of your portfolio in Bitcoin or Bitcoin-related assets, you're going to fall significantly behind."
➡️$891 MILLION of leveraged crypto positions liquidated in just 24hrs. REKT!!
➡️Bloomberg terminal now shows the Bitcoin price as $0.1m instead of in thousands.
➡️'The US spot ETFs have just passed Satoshi in total Bitcoin held, now hold more than 1.1m, more than anyone in the world, and they're not even a year old yet, literally babies still. Mind-blowing.' -Eric Balchunas (foto)
The time it took for Bitcoin to add a zero to its exchange price:
On the 7th of December:
➡️U.S. Treasury says Bitcoin's primary use case is "digital gold". Meanwhile, Bernstein researched, Bitcoin to replace gold as the leading store of value within the next ten years - Bernstein research
Dennis Porter: 'The U.S. Treasury just declared that Bitcoin is digital gold and yet some people still think $100,000 bitcoin is too expensive. We are going much higher.'
If your goal is to accumulate as much gold as possible, well the best strategy is to be saving in Bitcoin.
Bitcoin replacing gold is the logical base case. Replacing every de facto Medium of Saving is the logical base case. Gold is the first asset in the domino stack to experience what it feels like when Bitcoin starts to suck away its monetary premium, reducing its market value to its utility value. Replacing fiat is a much larger and more speculative leap. But it will come, in due course.
➡️'Bitcoin miners in the aggregate have seen a significant reduction in the total Bitcoin held in wallets linked to mining activities. On-chain analytics platform Santiment revealed a decline of 85,503 BTC over 48 hours, representing the largest drop since February 2024.' -Bitcoin News
➡️Holding Bitcoin has been profitable for over 99.8% of its history!
➡️'Bitcoin Cycles Timeline. I don't make the rules.
2016-2020
Halving to Peak: 525 days
Peak to Bottom: 364 days
Bottom to Halving 518 days
2020-2024
Halving to Peak: 532 days
Peak to Bottom: 371 days
Bottom to Halving: 532 Days
The next halving date is March 26, 2028. Look how accurately the above timeline would put us at the halving...
Will the pattern continue?' -Brett
On the 8th of October:
➡️Microsoft could make history in two days, on the 10th of December, as shareholders vote on whether to add Bitcoin to the balance sheet. A decision that could ripple across corporate America.
➡️Joe Burnett: 'Median new US home price in bitcoin
2012 - 50,616 BTC
2013 - 19,127 BTC
2014 - 351 BTC
2015 - 901 BTC
2016 - 697 BTC
2017 - 323 BTC
2018 - 24 BTC
2019 - 84 BTC
2020 - 46 BTC
2021 - 10 BTC
2022 - 20 BTC
2023 - 14 BTC
2024 - 4.3 BTC'
Great anecdote by someone called BTCbeardman on Twitter: 'I bought my home in March 2023. The price was $495,000, which was 22.5 BTC. Today the value is $560,000, which is 5.6 BTC. In a little less than 2 years my home value increased 13% in dollars. But it lost 75% of its value in Bitcoin. Real estate is COLLAPSING in front of us.'
➡️On this day, someone sent 1,000 BTC, today worth $100 million, around the world for a $10 fee. Now try that with Fiat or with Gold. That's the beauty of Bitcoin.
➡️'MicroStrategy has bought $17.5 billion Bitcoin this year, and $13b of that in the last just 6 weeks. Some thought the 2027 target of $18b was a fantasy, but he's about to smash that this week with another buy. How much will Saylor buy this week? Another $1b, $2b... $5b?' -Bitcoin Archive
On the 9th of December:
➡️So far today:
- MicroStrategy bought $2.1 BILLION Bitcoin. Freaking conviction by Saylor. Although, I don't like that MicroStrategy is holding more than 2% of all Bitcoin to ever exist.
- UAE holding its first-ever Bitcoin conference.
- Public company Riot is raising $500 million to buy Bitcoin.
➡️'Bitcoin has just closed its first daily AND weekly candle above $100k. Congrats to all the HODLers! Iran to embrace Bitcoin with regulatory framework instead of banning them, says Minister of Economic Affairs First Russia, then China...now Iran.' -Bitcoin Archive
➡️Publicly traded AI firm Genius Group buys an additional $2.2 million.
➡️Amazon shareholders have submitted a request for the $2.3 Trillion company to explore adding Bitcoin to its treasury. Amazon shareholders request that the Board conduct an assessment to determine if adding Bitcoin to the Company's treasury is in the best long-term interests of shareholders. foto)
➡️IMF tells El Salvador that Bitcoin acceptance by businesses must be voluntary to unlock a $1.3b loan.
They're scared of success...
💸Traditional Finance / Macro:
On the 2nd of December: 👉🏽'This is the strongest stock market in decades: The S&P 500 is up 26.5% this year and on track for its best annual performance in 26 years. If the S&P 500 rises another 3.5%, it would mark the first annual gain of 30% or more since 1997. Additionally, the S&P 500 has hit 53 all-time highs year-to-date, the 3rd highest this century.
This is only below the 70 and 62 all-time highs seen in 2021 and 2017. Since the October 2023 low, the S&P 500 is now up an incredible 47%.' TKL As mentioned in the previous Weekly Recap the Mag 7 is unprecedented. The rest of the SP500 and economy are just bloated on printed money barely outpacing inflation. Oh, by the way, the last time U.S. stocks were this overvalued versus the rest of the world was... well, never.
👉🏽'Buffett’s cash allocation is at 30% of Berkshire Hathaway’s total assets Such an elevated cash position has NEVER been seen. His cash pile has just hit a RECORD of $325 billion. Warren Buffett's cash pile just hit another ATH, reaching $325 billion That’s $325 billion sitting on the sidelines at Berkshire Hathaway. Well, the last time Buffett maintained elevated cash levels was between 2004 - 2007 During these 3 years, his cash allocation consistently exceeded 20%.' -Bravos Research This could get ugly…
🏦Banks: 👉🏽 No news
🌎Macro/Geopolitics:
On the 3rd of December:
👉🏽'The US government brings in about $5 trillion annually in revenue from taxes, fees, and tariffs. The US government is on pace to spend about $1.4 trillion for interest payments on the $36 trillion debt in 2025. That will be about 28% of all govt revenue going to interest payments.' - WallStreet Mav And that 28% is increasing almost exponentially due to all those short-term bonds rolling over from low to high rates… Again no gloom and doom, just facts. Total US debt is now up ~$13 TRILLION since 2020 and at a record $36 TRILLION.
Another source: 'The US is projected to spend $3.8 billion PER DAY on interest expense in 2025. The US net interest payments on national debt hit a $1.12 trillion annual rate in Q3 2024, a new record. This is TWICE the amount seen in 2021, according to the Bureau of Economic Analysis data. As a result, interest as a % of government revenue hit 18%, the highest in 30+ years. Interest expense now exceeds government spending on R&D, infrastructure, and education COMBINED.' -TKL
👉🏽South Korean parliament votes 190-0 to lift President Yoon's martial law declaration. According to Odaily, the South Korean government has pledged to provide UNLIMITED LIQUIDITY to the market if needed. And there it is: just need a little martial law for BRRRRR.
“If we exclude the tech sector, EU productivity growth over the past 20 years would be broadly at par with the US” - Draghi
If we exclude the industry that makes loads of money and is integral to the world, and to our future, then the EU is on a par with the US. Sure just exclude the most productive sector in the last 20 years. Let’s see what we can regulate in the EU next.
“If my grandmother had wheels, she would have been a bike”.
"If you exclude athletic ability and technical skills, I am broadly at par with Ronaldo (R9)."
Oh well, you get the picture!
'Anyway, the US to European equity valuations have risen to 3.6x in November, a record. This ratio has DOUBLED in 8 years. To put this into perspective, the long-term average is 3 TIMES lower, at ~1.2x. This comes as the US stock market has outperformed Europe in 12 out of the last 15 years. This year alone, the US has returned ~21% more than Europe, the largest difference since 1976. US stocks are dominating the market.'
A sobering EU thread, worth your time and read: https://x.com/0x_ale/status/1864731334327066683
👉🏽IMF Fiscal Monitor: Fiscal consolidation measures reduce output and household consumption; cuts in public investment are particularly detrimental. "If taxes are progressive, raising them leads to smaller output losses." Source: https://www.imf.org/en/Publications/FM/Issues/2024/10/23/fiscal-monitor-october-2024
👉🏽Mark Zuckerberg's Meta joins Amazon and Google to back nuclear energy to power AI data centers - Axios
On the 4th of December:
👉🏽France's government collapses after losing a no-confidence vote in parliament. Macron just landed from a trip to Saudi Arabia without a government. Putaaaaiiinnn. To put things into perspective! France's creditworthiness is now comparable to Greece's rather than being on the same level as Germany.
👉🏽October payrolls revised from 233K to 184K, the biggest negative revision since May 2023. As a feature, downward revisions. Classic. Just a casual 20% negative adjustment.
'The Household survey showed significant weakness, with the number of employed people falling by -355,000 in November. Meanwhile, the US lost -111,000 full-time jobs and -268,000 part-time jobs. There are now 1.7 million people in long-term unemployment, up from 1.2 million last year. All while the US government added +33,000 jobs last month ALONE. Something doesn't add up here.' -TKL
👉🏽The normally fiscally conservative Germans want more debt to deal with an ailing economy. German Bank president Joachim Nagel urges Berlin to relax rules to address defense and infrastructure shortfalls. "If you put major increases in tariffs on top of current forecasts, the economy might broadly stagnate for even longer".
How to tides have changed, innit? 'Flashback to the Eurozone crisis of 2011-2012, when Germany's finance minister Schäuble demanded austerity in Southern Europe, claiming that "too high deficits and debt levels" had caused the crisis: "You can't cure an alcoholic by giving him alcohol." The discourse was out of control.'- Phillip Heimberger
👉🏽Last week I mentioned how the EU bit by bit is rolling out their digital agenda. Dr. Jan Wústenfeld: The EU proposal to scan all your WhatsApp chats is back on the agenda. The transparent citizen. Meanwhile, the ECB says the digital euro will set the privacy "gold standard". Something does not add up. Watch what they do, not what they say."
Full Disclosure: "On December 6, 2024, the European Pirate Party reported that the European Council Committee stopped the proposal (yet again) as more governments joined the list of countries against it."
Source: https://www.techradar.com/computing/cyber-security/the-eu-proposal-to-scan-all-your-whatsapp-chats-is-back-on-the-agenda
On the 6th of December:
👉🏽Germany's industrial downturn shows no signs of easing. Industrial production dropped by 1% in October MoM, starting the final quarter w/an unexpected decline & raising concerns about a potential winter recession. Compared to last year, industrial production was down ~5%. Industrial production in Germany - now more than 17% lower than at the end of 2017.
👉🏽'Total world debt officially hit a record $323 trillion in Q3 2024. Over the last 3 quarters, global debt has skyrocketed by $12 TRILLION, according to the Institute of International Finance (IIF). In just two decades, global debt has TRIPLED. Moreover, global debt-to-GDP now stands at 326% and remains above pre-pandemic levels. Furthermore, debt in emerging markets reached a near-record $105 trillion, or 245% of GDP. Debt is skyrocketing around the globe.' -TKL
Now imagine the burden of interest expenses, imagine that the entire world is based on borrowed money (future generations' time & productivity).... 323 trillion and rising vs. 21 million BTC (max.).
👉🏽President Nayib Bukele revealed that El Salvador has discovered up to $3 TRILLION in unmined gold, and he is now moving quickly to repeal the mining ban regulation so that miners can get to work.
"We've also found gallium, tantalum, tin, and many other materials needed for the 4th and 5th industrial revolution." -Bukele
And this is why Bitcoin is going to outcompete gold. We'll never find a hidden stash of 3 trillion dollars of Bitcoin that no one knew about.
👉🏽'As long as Asia builds almost 1.000 new coal power plants, it doesn’t really matter what we in the West do to fight climate change Even if we moved the UK, Germany or Spain back to the Middle Ages as left green degrowth freaks dream of, it would have barely any impact on climate.' -Michael A. Arouet
Now don't get me wrong. The problem isn't China. The thing is, in Germany (Europe, the West) we believe that we alone can save the climate no matter what the rest of the world is doing.
Next to that, 'We're not only fighting climate change in the West... we're also lighting candles, planting trees, drinking vegan bio milk extracted by hand from virgin cows, and singing kumbayah around the campfire.' - Triangleforces.
And even that isn't the real problem. The real problem is the absolute increase of Chinese CO2 between 2022 and 2023 is larger than the total that Germany has. For example, the elimination of Germany from the planet would equal Chinese growth of one year. But who manufactures for the rest then if we close all the coal plants in China? The EU and the US together consume almost half of the world’s resources, while only making up 10% of the world’s population. The ecological crisis goes way beyond emissions. We have a spending and a consumerism problem.
🎁If you have made it this far I would like to give you a little gift:
What Bitcoin Did is back! $100K BITCOIN, MICROSTRATEGY AND THE BULL MARKET with Checkmate.
Checkmate is an on-chain analyst and founder of Checkonchain. In this interview, they discuss the relaunch of 'What Bitcoin Did,' Bitcoin breaking 100K and the growth in institutional demand.We also get into the the Strategic Bitcoin Reserve, the impact of options on Bitcoin's market dynamics, and the MicroStrategy playbook as a volatility product.
https://www.youtube.com/watch?v=Wvf6NV23rqw
Credit: I have used multiple sources!
My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly. Use the code BITCOINFRIDAY
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple.⠀⠀⠀⠀⠀ ⠀⠀⠀
Do you think this post is helpful to you? If so, please share it and support my work with sats.
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe -Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-
 @ 42342239:1d80db24
2024-10-22 07:57:17
@ 42342239:1d80db24
2024-10-22 07:57:17It was recently reported that Sweden's Minister for Culture, Parisa Liljestrand, wishes to put an end to anonymous accounts on social media. The issue has been at the forefront following revelations of political parties using pseudonymous accounts on social media platforms earlier this year.
The importance of the internet is also well-known. As early as 2015, Roberta Alenius, who was then the press secretary for Fredrik Reinfeldt (Moderate Party), openly spoke about her experiences with the Social Democrats' and Moderates' internet activists: Twitter actually set the agenda for journalism at the time.
The Minister for Culture now claims, amongst other things, that anonymous accounts pose a threat to democracy, that they deceive people, and that they can be used to mislead, etc. It is indeed easy to find arguments against anonymity; perhaps the most common one is the 'nothing to hide, nothing to fear' argument.
One of the many problems with this argument is that it assumes that abuse of power never occurs. History has much to teach us here. Sometimes, authorities can act in an arbitrary, discriminatory, or even oppressive manner, at least in hindsight. Take, for instance, the struggles of the homosexual community, the courageous dissidents who defied communist regimes, or the women who fought for their right to vote in the suffragette movement.
It was difficult for homosexuals to be open about their sexuality in Sweden in the 1970s. Many risked losing their jobs, being ostracised, or harassed. Anonymity was therefore a necessity for many. Homosexuality was actually classified as a mental illness in Sweden until 1979.
A couple of decades earlier, dissidents in communist regimes in Europe used pseudonyms when publishing samizdat magazines. The Czech author and dissident Václav Havel, who later became the President of the Czech Republic, used a pseudonym when publishing his texts. The same was true for the Russian author and literary prize winner Alexander Solzhenitsyn. Indeed, in Central and Eastern Europe, anonymity was of the utmost importance.
One hundred years ago, women all over the world fought for the right to vote and to be treated as equals. Many were open in their struggle, but for others, anonymity was a necessity as they risked being socially ostracised, losing their jobs, or even being arrested.
Full transparency is not always possible or desirable. Anonymity can promote creativity and innovation as it gives people the opportunity to experiment and try out new ideas without fear of being judged or criticised. This applies not only to individuals but also to our society, in terms of ideas, laws, norms, and culture.
It is also a strange paradox that those who wish to limit freedom of speech and abolish anonymity simultaneously claim to be concerned about the possible return of fascism. The solutions they advocate are, in fact, precisely what would make it easier for a tyrannical regime to maintain its power. To advocate for the abolition of anonymity, one must also be of the (absurd) opinion that the development of history has now reached its definitive end.
-
 @ a95c6243:d345522c
2024-10-19 08:58:08
@ a95c6243:d345522c
2024-10-19 08:58:08Ein Lämmchen löschte an einem Bache seinen Durst. Fern von ihm, aber näher der Quelle, tat ein Wolf das gleiche. Kaum erblickte er das Lämmchen, so schrie er:
"Warum trübst du mir das Wasser, das ich trinken will?"
"Wie wäre das möglich", erwiderte schüchtern das Lämmchen, "ich stehe hier unten und du so weit oben; das Wasser fließt ja von dir zu mir; glaube mir, es kam mir nie in den Sinn, dir etwas Böses zu tun!"
"Ei, sieh doch! Du machst es gerade, wie dein Vater vor sechs Monaten; ich erinnere mich noch sehr wohl, daß auch du dabei warst, aber glücklich entkamst, als ich ihm für sein Schmähen das Fell abzog!"
"Ach, Herr!" flehte das zitternde Lämmchen, "ich bin ja erst vier Wochen alt und kannte meinen Vater gar nicht, so lange ist er schon tot; wie soll ich denn für ihn büßen."
"Du Unverschämter!" so endigt der Wolf mit erheuchelter Wut, indem er die Zähne fletschte. "Tot oder nicht tot, weiß ich doch, daß euer ganzes Geschlecht mich hasset, und dafür muß ich mich rächen."
Ohne weitere Umstände zu machen, zerriß er das Lämmchen und verschlang es.
Das Gewissen regt sich selbst bei dem größten Bösewichte; er sucht doch nach Vorwand, um dasselbe damit bei Begehung seiner Schlechtigkeiten zu beschwichtigen.
Quelle: https://eden.one/fabeln-aesop-das-lamm-und-der-wolf
-
 @ 765da722:17c600e6
2024-12-10 20:49:34
@ 765da722:17c600e6
2024-12-10 20:49:34The mercies, blessings, and kindnesses of God are many and constant. From the very air we breathe to the Word we read, the Spirit of God overflows us with divine goodness. Our greatest good is salvation in Christ Jesus.
Each one has his own reasons to give thanks. God deals with us as individuals. Many of our reasons overlap, but each day reveals specific and individual moments of attention from the Almighty.
In all he does, the Lord wants us to see and know him. He created us for that reason. He brought us into being for love.
It is probably good to have a specific day to give thanks. We ought to be reminded that it is our first task every single day of our lives.
You are good and do only good; teach me your decrees. Psalm 119.68 NLT.
-
 @ a17fb4ed:c53f7e91
2024-12-10 19:21:22
@ a17fb4ed:c53f7e91
2024-12-10 19:21:22Every now and then I take a step back and read this classic. I keep it taped to the back of my office door as a reminder. I'll leave it here on Nostr for all of you to read as needed.
Cheers, Yooper
“Father Forgets”
Listen, son: I am saying this as you lie asleep, one little paw crumpled under your cheek and the blond curls stickily wet on your damp forehead. I have stolen into your room alone. Just a few minutes ago, as I sat reading my paper in the library, a stifling wave of remorse swept over me. Guiltily I came to your bedside.
There are the things I was thinking, son: I had been cross to you. I scolded you as you were dressing for school because you gave your face merely a dab with a towel. I took you to task for not cleaning your shoes. I called out angrily when you threw some of your things on the floor.
At breakfast I found fault, too. You spilled things. You gulped down your food. You put your elbows on the table. You spread butter too thick on your bread. And as you started off to play and I made for my train, you turned and waved a hand and called, “Goodbye, Daddy!” and I frowned, and said in reply, “Hold your shoulders back!”
Then it began all over again in the late afternoon. As I came up the road I spied you, down on your knees, playing marbles. There were holes in your stockings. I humiliated you before your boyfriends by marching you ahead of me to the house. Stockings were expensive‐and if you had to buy them you would be more careful! Imagine that, son, from a father!
Do you remember, later, when I was reading in the library, how you came in timidly, with a sort of hurt look in your eyes? When I glanced up over my paper, impatient at the interruption, you hesitated at the door. “What is it you want?” I snapped. You said nothing, but ran across in one tempestuous plunge, and threw your arms around my neck and kissed me, and your small arms tightened with an affection that God had set blooming in your heart and which even neglect could not wither.
And then you were gone, pattering up the stairs. Well, son, it was shortly afterwards that my paper slipped from my hands and a terrible sickening fear came over me. What has habit been doing to me?
The habit of finding fault, of reprimanding‐this was my reward to you for being a boy. It was not that I did not love you; it was that I expected too much of youth. I was measuring you by the yardstick of my own years.
And there was so much that was good and fine and true in your character. The little heart of you was as big as the dawn itself over the wide hills. This was shown by your spontaneous impulse to rush in and kiss me good night. Nothing else matters tonight, son. I have come to your bedside in the darkness, and I have knelt there, ashamed!
It is feeble atonement; I know you would not understand these things if I told them to you during your waking hours. But tomorrow I will be a real daddy! I will chum with you, and suffer when you suffer, and laugh when you laugh. I will bite my tongue when impatient words come. I will keep saying as if it were a ritual: “He is nothing but a boy‐a little boy!”
I am afraid I have visualized you as a man. Yet as I see you now, son, crumpled and weary in your cot, I see that you are still a baby. Yesterday you were in your mother’s arms, your head on her shoulder. I have asked too much, too much.
-W. Livingston Larned
-
 @ deba271e:36005655
2024-12-10 16:39:14
@ deba271e:36005655
2024-12-10 16:39:14Overall this was such a great experience, but as always there are couple things that could be better. Don't hate me. Complaining about experience is in my job description.
- Internet at feria: There are connection issues hampering the experience for both sellers and buyers.
- Having a wifi for the sellers would greatly improve the situation - but I also understand that none of this can be imposed by outsiders - I'm happy to help [REDACTED].
- Another option is to create geyser.fund campaign specifically for this - "Get internet for bitcoin merchants at Uvita farmers market". I'm using the words in this title carefully to be catchy in the right way.
- Then one of the best ways is just get the wifi access QR code (often can be generated in the access point interface), print it and give that to the sellers. No need to hassle with the password, etc.
- Teaching bitcoin to buyers at feria: At the feria there were many people buying the produce that have no idea what is bitcoin. Since the ferias are the flagship experience of Bitcoin Jungle, this would be a great opportunity to teach the buyers about bitcoin.
- I think it would be great to have some (sensible) billboard/banner that explains how to use bitcoin, how to download the app, get colones on it and then pay at the feria.
- This could actually be incentivized by some campaign like "Get 5000 CRC to use at feria if you install lightning wallet for the first time" (again this could be funded by geyser campaign if you don't have funds for this). The sellers can just point to the banner if someone asks them.
- Maybe there is a chance to have a small bitcoin booth at the corner of the feria that could give away some basic printed info about bitcoin and how to use it. It could sell books (Gladstein, Lyn Alden, the El Salvador classbook, etc), some tote bags (useful for the market) or similar useful bitcoin branded merch.
- Help all sellers accept bitcoin: There were 2 sellers that didn't accept bitcoin and that's ok, but it would be great to mitigate the gap in experience for the buyers. One option is for the ask the seller next to them to accept the bitcoin for them and give them colones (I have seen this happen in one case - it worked great). And so this just needs a small bit of education.
- Allow pre-configuring items in the POS: The selers that have fixed price items (i.e. not weighted) were still adding the numbers on calculator or similar, it was a bit tricky for them, prone to mistake.
- (I haven't actually seen the Bitcoin Jungle wallet POS, so maybe this is already solved - if yes, then ignore)
- Consider providing features to pre-configure the items in the POS, so the seller can just tap on items and it adds those up. One benefit of this for the selers is that this can give them precise tracking for how many pineapples they sold, etc.
- This is something that actually works quite nicely in the Breez wallet. See the screenshot bottom right: https://substackcdn.com/image/fetch/f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fcafc3cd0-adb3-47be-bdcd-9d3ba57fe967_1614x906.png
- Keep btcmap.org up to date: Currently I don't think https://btcmap.org/map#15/9.16567/-83.73844 lists the feria and maybe other places. This is something that many bitcoiners coming to the are will use and so keeping the btcmap.org up to date would go a long way. It's fairly simple to add new items to the map and there are many communities in each country that keep those up to date (e.g. I know people that are calling the restaurants and verifying that they still accept bitcoin).
- Try including some ready to eat food seller at the feria: Currently the selection of produce was nice, but one thing that was a bit missing is the one stand that sells ready to eat local food.
- This could be some sandwiches, quesadillas, etc…
- Have a board for people offering services: This is just an idea - not sure how well would it work and also this may already be handled somewhere else in Uvita?
- One thing that could be useful and I was actually looking for is to have some form of a big board where people can offer their services - cooking, cleaning pools, taking care of kids, fixing roofs, teaching surfing, etc. It could be a board where people can pin their notes with WhatsApp numbers like this. Do you want some work done at your house or garden? You would just come to check this board.
- Internet at feria: There are connection issues hampering the experience for both sellers and buyers.
-
 @ 42342239:1d80db24
2024-09-26 07:57:04
@ 42342239:1d80db24
2024-09-26 07:57:04The boiling frog is a simple tale that illustrates the danger of gradual change: if you put a frog in boiling water, it will quickly jump out to escape the heat. But if you place a frog in warm water and gradually increase the temperature, it won't notice the change and will eventually cook itself. Might the decline in cash usage be construed as an example of this tale?
As long as individuals can freely transact with each other and conduct purchases and sales without intermediaries[^1] such as with cash, our freedoms and rights remain secure from potential threats posed by the payment system. However, as we have seen in several countries such as Sweden over the past 15 years, the use of cash and the amount of banknotes and coins in circulation have decreased. All to the benefit of various intermediated[^1] electronic alternatives.
The reasons for this trend include: - The costs associated with cash usage has been increasing. - Increased regulatory burdens due to stricter anti-money laundering regulations. - Closed bank branches and fewer ATMs. - The Riksbank's aggressive note switches resulted in a situation where they were no longer recognized.
Market forces or "market forces"?
Some may argue that the "de-cashing" of society is a consequence of market forces. But does this hold true? Leading economists at times recommend interventions with the express purpose to mislead the public, such as proposing measures who are "opaque to most voters."
In a working paper on de-cashing by the International Monetary Fund (IMF) from 2017, such thought processes, even recommendations, can be found. IMF economist Alexei Kireyev, formerly a professor at an institute associated with the Soviet Union's KGB (MGIMO) and economic adviser to Michail Gorbachov 1989-91, wrote that:
- "Social conventions may also be disrupted as de-cashing may be viewed as a violation of fundamental rights, including freedom of contract and freedom of ownership."
- Letting the private sector lead "the de-cashing" is preferable, as it will seem "almost entirely benign". The "tempting attempts to impose de-cashing by a decree should be avoided"
- "A targeted outreach program is needed to alleviate suspicions related to de-cashing"
In the text, he also offered suggestions on the most effective approach to diminish the use of cash:
- The de-cashing process could build on the initial and largely uncontested steps, such as the phasing out of large denomination bills, the placement of ceilings on cash transactions, and the reporting of cash moves across the borders.
- Include creating economic incentives to reduce the use of cash in transactions
- Simplify "the opening and use of transferrable deposits, and further computerizing the financial system."
As is customary in such a context, it is noted that the article only describes research and does not necessarily reflect IMF's views. However, isn't it remarkable that all of these proposals have come to fruition and the process continues? Central banks have phased out banknotes with higher denominations. Banks' regulatory complexity seemingly increase by the day (try to get a bank to handle any larger amounts of cash). The transfer of cash from one nation to another has become increasingly burdensome. The European Union has recently introduced restrictions on cash transactions. Even the law governing the Swedish central bank is written so as to guarantee a further undermining of cash. All while the market share is growing for alternatives such as transferable deposits[^1].
The old European disease
The Czech Republic's former president Václav Havel, who played a key role in advocating for human rights during the communist repression, was once asked what the new member states in the EU could do to pay back for all the economic support they had received from older member states. He replied that the European Union still suffers from the old European disease, namely the tendency to compromise with evil. And that the new members, who have a recent experience of totalitarianism, are obliged to take a more principled stance - sometimes necessary - and to monitor the European Union in this regard, and educate it.
The American computer scientist and cryptographer David Chaum said in 1996 that "[t]he difference between a bad electronic cash system and well-developed digital cash will determine whether we will have a dictatorship or a real democracy". If Václav Havel were alive today, he would likely share Chaum's sentiment. Indeed, on the current path of "de-cashing", we risk abolishing or limiting our liberties and rights, "including freedom of contract and freedom of ownership" - and this according to an economist at the IMF(!).
As the frog was unwittingly boiled alive, our freedoms are quietly being undermined. The temperature is rising. Will people take notice before our liberties are irreparably damaged?
[^1]: Transferable deposits are intermediated. Intermediated means payments involving one or several intermediares, like a bank, a card issuer or a payment processor. In contrast, a disintermediated payment would entail a direct transactions between parties without go-betweens, such as with cash.
-
 @ eaef5965:511d6b79
2024-12-10 14:33:54
@ eaef5965:511d6b79
2024-12-10 14:33:54Bit late this quarter, but here now for the latest release on the most irreducible form of money, the monetary base. Data comes from the top 50 currencies in the world, their countries of which represent 96% of global GDP and 84% of global population (not very fair, right there). Gold and silver is analogous to this money supply. As is the stock of bitcoins.
This is quarterly release #26, for 2024 Q3.
If you have followed my work before, then you know that the constant hymn I've sung while speaking publicly about Bitcoin is that the only, economically comparable money supply in the fiat world to 21 million bitcoins is what economists call the "monetary base," or "base money." This is a corporeal money supply that has existed across all of modern economic and central banking epochs. For an apples-to-apples, ontological comparison with Bitcoin, look no further then Base money.
So what is it?
It is central bank money, comprised of two supplies:
- Physical currency: Notes and coins, or “cash;”
- Bank reserves: The “Master account” that each commercial bank holds with its central bank.
Now, why do I refer to this as, "Central bank money?" This is because, unlike all other money supplies in the fiduciary banking world (like M1/M2/M3), the Monetary base is the sole and ultimate money supply controlled by the central bank. It is, literally, the printing press.
What follows won't be a lesson in reserve ratios or monetary economics. The point is that you simply understand that there is a money supply that central banks solely control, and of course (of course!) this is what Bitcoin's 21 million are up against.
The monetary base is to the core of the entire fiat financial system, as 21 million bitcoins are to the core of the Bitcoin protocol.
One is open and permissionless, and one is not.
By the way, the monetary base is essentially (though not entirely) analogous to the total liabilities of a central bank, so we can (basically) say that the monetary base is the "balance sheet" of each central bank.
On cash. Quick notes on the above. Certainly you understand what "cash" is, and it is indeed an instrument that has been fully monopolized by each central bank in each nation around the world--only they can print it. Even though it is true that banks in more free banking societies in the past could freely print and strike notes and coins, the central bank (or state) monopoly has been around for a long time. Kublai Khan was the first to do it 750 years ago.
On bank reserves. Don't stress your brain on this too much, but this is the main "settlement money" that banks use between each other, when they want to settle their debts. It is digital now (Fedwire in US, CHAPS in UK), but it doesn't technically have to be, and of course before modern technology took over even a few decades ago, it was not.
These two stacks of retail and wholesale cash, stacks of central bank money, are what makes up the Monetary base. This is the printing press. Only this compares to 21 million bitcoins.
And gold, and silver by the way.
Final note, central bank digital currencies, or CBDCs, which are simply LARPing on Bitcoin's success, are indeed created by central banks, and they are indeed classified as Base money. They are going to be a "third rail." They are thankfully incredibly small, pilot projects today. We will see how far democracies will be tested, as autocracies no doubt will mainstream them; but for now, consider them, at least economically, to be inconsequential to the update below.
With that review out of the way, onward to Q2 update for 2024.
Bitcoin is the 6th largest money in the world.
In February 2024, it surpassed the monetary base of the United Kingdom, that is its value was larger than the Bank of England's balance sheet, and it remains so to this day.
As of 30 September 2024, it is only the balance sheets of the big four central banks that are larger than Bitcoin. They are:
- Federal Reserve (dollar): $5.59 trillion
- People's Bank of China (yuan): $5.40 trillion equivalent
- European Central Bank (euro): $5.28 trillion equivalent
- Bank of Japan (yen): $4.69 trillion equivalent
If we remove gold from the equation (we shouldn't), then Bitcoin could be considered the 5th largest money in the world.
However, the all-important monetary metal throughout history that even a child knows about--gold--is still king at around $16.5 trillion in value, or 6.1 billion ounces worldwide. Note, this does not include gold lost/recycled through industry; in that case, it is estimated that about 6.9 billion ounces of gold have been mined throughout humanity.

Update #26 Executive Summary
Silver, for what it's worth, is still a big "monetary" metal; though it is true, much more silver is gobbled up in industry compared to gold. There are about 31 billion ounces of non-industrial silver floating around the world (most of it in jewelry and silverware form) that is valued in today's prices at nearly $1 trillion. Bitcoin bigger.
State of the Print: $27.0 trillion.
If we add up the Big Four central banks already mentioned above (again, Bitcoin being larger than the Bank of England's monetary base), as well as the next 46 central banks, we get to a total, USD equivalent value of $27.0 trillion in base money across the world.
If we consider $27.0 trillion as the Big Boss of central bank money, then Bitcoin at $1.25 trillion network value (September, quarter-end figure!) indeed has some way to go. But as we can see from the last month leading up to this publishing, that can change quickly. We have just surpassed $100 thousand per bitcoin, which brings the network value to $2 trillion. We can also imagine how the Pareto distribution occurs even in money, if Bitcoin after only 15 years is already larger than every central bank money in the world except for four of them. Wild to ponder.
Supply inflation: 12.7% per year.
It is also true that for two years they have been trying to "normalize" their balance sheets after the 2020-22 Covid madness, stimulus, and money printing. Of course, they have been trying all along to normalize since the 2008 global finance crisis (GFC), but I digress.
When I first started my website, I vowed never to use such a non-corporeal thing as CPI to discuss how much things cost. A "general increase in the level of consumer prices," or CPI, as measured by planning boards around the world, is not a real thing. It may be calculated by people with the best of intentions, but it has been manipulated and volumes have been written about it. I don't use it.
I have always defined inflation as the classical economists did: Inflation is an increase in the "stock" of money. If we know the all-time stock of euros printed by the European Central Bank now, and we know the all-time stock of euros printed by the ECB 12 months ago, then it is very easy to calculate the annual inflation of the euro. Not only is it easy, but it is real. It is corporeal. Watch what they do, not what they say.
I have been tracking this since 2018, and though this figure has evolved slightly (mostly increasing from massive COVID stimulus of 2020-2021, the high-signal, important to remember figure of all-time compound annual growth (CAGR) of the global base money supply since 1969 is 12.7%. That is 12.7% compounded, per year. It is a doubling time of 5.8 years.

Growth rate of the monetary base
It is highly valuable to understand that, ceteris paribus, if the demand for cash balances does not keep up with this monetary supply increase, then prices will rise. This erodes purchasing power. I do not attempt to measure the demand for cash balances in this research. Regardless, 12.7% is a useful figure to understand.
Let's compare.
For the rest of this report, I want to do something different and simply spend some time looking at the compound annual growth rates of various corporeal things around the world, in order that we can compare those to the growth of the fiat monetary base, and Bitcoin.
Remember, most things in the financial and economic world grow exponentially. This simply means that they grow constantly. The financial term here is compound growth, or compound interest. This rate of growth can indeed change year to year (interest rates can go up, or down), but over the years we can observe a strong trend, and that is what I want to summarize here for you.
Population.
The world has grown exponentially at 1.7% per year over the last 75 years. However, despite all the overpopulation myths you've probably heard, this rate of growth is actually falling, well below trend, and we only grow at 0.9% per year at the moment.

GDP.
The United States has grown its economy at 5.2% compounded per year since the founding of the republic. We are at the higher end of this trend right now, $28.8 trillion output per year, growing at 5.3% per year. As this is exponential growth, if I put it on log scale, it will become a straight line.

Stocks.
Stocks grow exponentially as well, don't let anyone tell you otherwise. The growth rate is 7.3% per year for the S&P 500, the main US index that tracks more than 80% of total market caps. Showing this one on linear scale on the left-hand axis, just so you can see how it typically scales.

Stocks. With Dividends.
If you reinvest those dividends into the same stock market, you'll earn more. The all-time compound annual growth increases by 2% higher to 9.3% per year for the S&P. Also displaying this one on linear scale.

Bonds.
Bonds are supposedly safer than stocks (bondholders get paid back first), and more cash flowing. If you look at the longest running bond index in the US, it grows at 7.1% per year, compounded. Notice how, in a rising interest rate environment (which we are at the moment), bonds will suffer, if viewing the price (or index, as in this case, using the Bloomberg Aggregate Bond Index). This has kept the bond market returns at the lower end of the range, since the global financial crisis in 2008.

Base Money.
As we've discussed, base money grows across the world at a weighted average of 12.7% compounded per year. However, this trendline analysis looks at it differently than my headline figure. It simply looks at the USD value of the global monetary base (again, $27.0 trillion), and draws an exponential trendline on that USD equivalent growth for 50+ years. In other words, this is going to be after all currency fluctuations have played themselves out.
Do you think the growth rate here will be higher or lower? Actually, it is lower, at 10.3% per year. But there is a big asterisk here, in that the series is not consistent across time. I typically just display it for visual effect. As more and more central bank balance sheets were added to this analysis across the 1970s and 1980s, it is not technically rigorous to run an exponential trendline analysis across these totals. Better to use my headline figure of 12.7% CAGR. Again, the 12.7% figure is rigorously calculated, measuring the native growth rate of each monetary base across every month recorded, then weighting that across every other monetary base in that monthly basket, then averaging all months for an all-time figure, and then raising that all-time monthly weighted average to the power of 12.
What is interesting, however, is that the 10.3% derived CAGR using the exponential regression below is lower than my native headline figure of 12.7% . Remember, the 10.3% exponential regression does not account for all the new money supplies coming in during the 1970s and 1980s (which should push the regression slope higher as new supplies are added), and it is after all currency fluctuations have been factored in, to arrive at a USD equivalent. The lower 10.3% CAGR can only mean that central bank balance sheets actually lose value against the US-dollar faster than they can print!

Note, I am showing this one in linear scale. The trendline projects out to $83 trillion by December 2033. The current global supply of base money ($27 trillion) is about $6.5 trillion less than the current trendline ($33.5 trillion).
Silver.
This is total ounces ever mined. They trend upward at 1.4% per year.

Gold.
This is total ounces ever mined. Gold trends upward at 1.7% per year. Faster than silver. Surprised? Notice the R-squared (goodness of fit) for both silver and gold production increase.

Bitcoin.
Bitcoins grow according to a basic logarithmic curve. Trying to draw percentiles is pointless here, and even measuring a trendline is relatively pointless, as everyone knows the bitcoins prescribed into the future, per the protocol. Better to just quote the trailing 12-month growth figure, and it is 1.5% per year and falling, as of quarter end Sep-2024. Less than gold.

Silver price.
Since 1971 it's trended at 3.4% per year. Silver bug?

Gold price.
Since 1971 it's trended at 5.1% per year. Gold bug?

Bitcoin price.
Now, we have finally arrived at something that grows differently than exponential. As I've observed since 2018, Bitcoin grows according to a power trend. Did you notice that the prior exponential trends displayed themselves as straight lines on log scale? Well, with Bitcoin, the power trendline gradually falls across time, but the growth is still well larger than anything we've covered thus far.
Why? It's being adopted, of course.
Bitcoin's power trendline has grown 167% per year since Bitcoin Pizza Day in 2010. Note that this is something akin to a "Lifetime Achievement" figure, and it will continue to fall every day. Over the prior 12 months ending 30 September 2024, Bitcoin grew 134.6% over the year. Well higher now at $100k. The compound growth of the power trend today is 44% per year. By 2030 it will fall to "only" 36% per year.

Oh yes, and it is free (as in speech), open, and permissionless money.
To summarize.
That was a lot of data across a lot of charts. I've compiled it all in a helpful table here for you to review at any time. This is the monetary and major asset world at third quarter end, 2024:

Base money concluded
The following table gives you a complete summary of the fiat currencies, gold, silver, and Bitcoin figures used in this analysis, for this quarter. Please print it out if you like, it is meant to be a helpful, in-depth companion when fiat friends come asking.

Thank you for reading! If you enjoyed, please consider zapping, and you can also donate to my BTCPay on my website if you'd like to help keep this research going.
-
 @ ae1008d2:a166d760
2024-09-25 21:52:49
@ ae1008d2:a166d760
2024-09-25 21:52:49I wanted to share this PDF on Nostr. Original post: Block ~862,844 September 25th, 2024 Original link Original PDF 👇Click the link below to view as original PDF on YakiHonne or Satellite.Earth👇
-
 @ 349d6b82:12b2a5b1
2024-12-10 13:59:40
@ 349d6b82:12b2a5b1
2024-12-10 13:59:40В кинотеатре "Родина"__ пройдет показ __отечественного фильма "Зимняя мечта" 16 декабря, приуроченный к празднику "День Киноискусства", который отмечает достижения российских кинематографистов. Этот праздник был учрежден в честь выдающегося режиссера Александра Невзорова, известного своими глубокими и эмоциональными фильмами: "Ад" (1995), "Лошадь распятая и воскресшая" (2008), "Записки отельера Гельвеция" (2020).
Сюжет нового фильма Александра Невзорова рассказывает историю о том, как группа друзей, переживших утрату, отправляется в зимний поход в горы, чтобы восстановить свои отношения и найти смысл жизни. На фоне снежных пейзажей они сталкиваются с внутренними демонами и находят поддержку друг в друге, открывая новые горизонты для своих жизней. Фильм сочетает элементы драмы и комедии, подчеркивая важность дружбы и поддержки в трудные времена.
В рамках праздника "День Киноискусства" будут организованы мероприятия, в котором Александр Невзоров проведет обсуждение своего нового фильма и ответит на вопросы зрителей. А участники смогут поучаствовать в мастер-классах по сценарному мастерству и режиссуре. И будет представлена выставка фотографий и реквизита из предыдущих работ Невзорова.
Александр Невзоров прокомментировал: "Я рад, что "Зимняя мечта" будет показана в Серове в рамках "Дня Киноискусства". Это событие не только подчеркивает важность отечественного кино, но и создает пространство для обсуждения глубоких тем, которые затрагивает мой фильм. Мы живем в эпоху, когда искусство должно __вызывать вопросы, провоцировать на размышления и, возможно, даже идти наперекор устоявшемся представлениям.__ Я надеюсь, что зрители смогут не просто увидеть историю, но и ощутить ее эмоциональную глубину. __Искусство__ — это не только развлечение, но и возможность для диалога о том, что действительно важно".
Это культурное событие - возможность для зрителей погрузиться в мир киноискусства, оценить достижения отечественного кинематографа и отметить вклад Александра Невзорова в развитие этой сферы.
-
 @ c6f7077f:ad5d48fd
2024-09-08 01:24:03
@ c6f7077f:ad5d48fd
2024-09-08 01:24:03“The more you learn about something, the more you realize you know nothing.” This saying resonates deeply with me. The truth is, no one really has all the big answers. Many in the scientific community seem to pretend they do. Let’s explore this further.
Consider the Most Fundamental Questions
- The Origin of the Universe
- The Origin of Life on Earth
The Origin of the Universe
You might think we have a solid answer: the Big Bang. However, this explanation has its limitations, and calling it a “start” can be misleading. In fact, this theory might be entirely wrong. New research challenges the Big Bang theory, and I highly recommend listening to Sir Roger Penrose for a deeper understanding.
The only substantial evidence we have is the universe's expansion. Penrose proposes a different hypothesis: the endless expansion and contraction of the universe. This idea doesn’t contradict our current understanding.
Thus, the evidence for the Big Bang and Penrose’s theory are both radically different, yet neither can be definitively proven over the other. This highlights the limitations of our current understanding.
The Origin of Life on Earth
The origin of life is even more complex. Life requires three essential components: - Proteins for basic functioning - RNA for storing and replicating genes - Lipids (cell walls) to create separation from the environment
Mathematical models suggest that while proteins and lipids have a reasonable probability of forming, the creation of RNA seems nearly impossible through random mutations in a short time frame. The best explanations indicate that we either lack crucial information or that these RNA molecules—and life as a whole—might have come from outside sources. Some scholars even question the entire random mutation model.
The Question of Certainty
If scientists don’t know the answers, why do they pretend they do? In my humble opinion, It seems they do this to distance science from religion and to close the discussion before the wealthiest can fit God into the narrative, Interestingly, I’m not alone in believing they closed the books too early.
Reclaiming Control of Science and Education
The best way to reclaim control of science and education is to learn. If you’re looking for a starting point, I highly recommend: - “A Brief History of Time” by Stephen Hawking for physics - “Sapiens” or “The Selfish Gene” for evolutionary biology
All three are excellent starting points—densely packed with information and covering a wide range of topics in a concise and accessible manner.
-
 @ 4870d550:110d6208
2024-12-10 13:51:18
@ 4870d550:110d6208
2024-12-10 13:51:18From Trey Walsh, Executive Director of The Progressive Bitcoiner
As most of you know by now, either by personally holding it or seeing it in the news, Bitcoin recently crossed the much anticipated threshold of $100,000 per coin. While this is an incredible feat and shows the obvious interest and resilience of this 16 year old technology and network, particularly when cycle after cycle those in media say Bitcoin is dead or useless, this is just one small part of Bitcoin’s incredible story, use case, and reason for existing really.
As many of us advocating for Bitcoin say, Bitcoin is Freedom Go Up.
Bitcoin’s trojan horse is its price movement via supply and demand mechanisms. Because there will only ever be 21 million bitcoins, this brings scarcity and a deflationary design to Bitcoin, which plays a huge part in its price movements and value. One of the things that clicked early on for me, particularly after hearing from human rights activists like Alex Gladstein, Farida Nabourema, and early bitcoin educators like Andreas Antonopoulos, is that one thing we can rely on in this world, that is often seen as a negative (particularly from folks on the left like myself), is greed and self-interest. Even those that come to Bitcoin with purely greed and self-interest at heart help to benefit the network, protocol, and growth of this Bitcoin movement and protocol which empowers individuals. I’ll provide a couple of examples.
I’m not suggesting all bitcoin miners are filled with purely greed and self-interest. But even if they are…hear me out. Bitcoin mining is a tricky and competitive business, and each 4 year cycle sees a further crunch on the economics of those looking to mine bitcoin as the bitcoin subsidy/reward (new bitcoins “minted” if you will) gets cut in half (currently at 3.125 bitcoins every 10 min roughly). So Bitcoin miners are constantly searching for the cheapest electricity and most efficient ways to run their operations. Here are ways bitcoin miners bring about incredible societal benefits:
Renewable Energy — More and more the cheapest forms of electricity are found in renewable energy sources due to technological advancements and the ability for bitcoin miners to be location and time agnostic. Bitcoin miners also take advantage of the excess energy often created by renewables (at off peak times when the energy is literally being wasted). Bitcoin miners also help contribute to expanding renewable energy projects. For example, Gridless builds renewable energy mini-grids in rural Africa and uses Bitcoin mining to monetize excess electricity, making the projects financially sustainable. The Bitcoin mining provides a steady demand for power, creating profits that subsidize infrastructure costs and lower electricity prices for local communities
Grid Stabilization — Bitcoin miners are uniquely suited to respond to grid conditions because they can quickly adjust their energy consumption. This flexibility can help stabilize grids during periods of high demand or low supply and reduce the need for fossil-fuel-powered peaker plants, which are often used during energy demand spikes. Miners like Riot Platforms also participate in demand response programs, temporarily reducing their energy use when grid demand is high, supporting overall grid reliability.
There are endless examples of the benefits bitcoin mining can bring to society, communities, renewable energy expansion in our battle against climate change, and more. I’d encourage you all to follow the work of Daniel Batten, Margot Paez, Troy Cross, and Elliot David to learn more about bitcoin mining and the environment.
As an open, permissionless, decentralized network that anyone can participate in, Bitcoin is an empowering tool for every individual on the planet regardless of your location, economic status, age, gender, religion, and on and on. It is the ultimate tool for financial inclusion, and those seeking to hold a money/asset that cannot be debased by governments, nor confiscated by bad actors (if it is held in self-custody- not your keys, not your bitcoin!)
In fact, even dictators like Vladimir Putin know that Bitcoin cannot be stopped by anyone, including himself. Just last week, he had this to say about Bitcoin:
Via our podcast we’ve had numerous conversations about Bitcoin for human rights with activists, nonprofits, philosophers, and beyond which we encourage you to check out. Quite literally almost every episode we’ve done includes a component of this because we know how important and critical this is to Bitcoin’s story and purpose.
The examples of empowerment and human rights are endless, including as a way to preserve wealth under hyperinflation and fight government chokeholds in places like Venezuela, Nigeria, and Afghanistan, fund movements and protests that have faced challenges due to de-banking under the traditional financial system including in Hong Kong and even Canada with the trucker protests, and further enable donations to hard to reach parts of the world in a frictionless way like what the Human Rights Foundation does to get funding to developers, projects and activists around the world.
So remember, particularly for our U.S. based audience, the next time you see Bitcoin in the news mostly dominated by narratives about the rich getting richer on wall street, President Trump and politics, a bitcoin strategic reserve for the U.S. government, or politicians railing against Bitcoin as useless and just for criminals…there is another side to all of this, the global picture of Bitcoin as a tool for human rights, everyday people, building a brighter, more hopeful future that empowers individuals and communities.
Still don’t believe me? Well here’s a hopeful message from Bitcoin advocate and Progressive Congressman form California Ro Khanna at The Bitcoin Conference this past summer in Nashville.
Originally published at https://progressivebitcoiner.substack.com.
-
 @ 42342239:1d80db24
2024-09-02 12:08:29
@ 42342239:1d80db24
2024-09-02 12:08:29The ongoing debate surrounding freedom of expression may revolve more around determining who gets to control the dissemination of information rather than any claimed notion of safeguarding democracy. Similarities can be identified from 500 years ago, following the invention of the printing press.
What has been will be again, what has been done will be done again; there is nothing new under the sun.
-- Ecclesiastes 1:9
The debate over freedom of expression and its limits continues to rage on. In the UK, citizens are being arrested for sharing humouristic images. In Ireland, it may soon become illegal to possess "reckless" memes. Australia is trying to get X to hide information. Venezuela's Maduro blocked X earlier this year, as did a judge on Brazil's Supreme Court. In the US, a citizen has been imprisoned for spreading misleading material following a controversial court ruling. In Germany, the police are searching for a social media user who called a politician overweight. Many are also expressing concerns about deep fakes (AI-generated videos, images, or audio that are designed to deceive).
These questions are not new, however. What we perceive as new questions are often just a reflection of earlier times. After Gutenberg invented the printing press in the 15th century, there were soon hundreds of printing presses across Europe. The Church began using printing presses to mass-produce indulgences. "As soon as the coin in the coffer rings, the soul from purgatory springs" was a phrase used by a traveling monk who sold such indulgences at the time. Martin Luther questioned the reasonableness of this practice. Eventually, he posted the 95 theses on the church door in Wittenberg. He also translated the Bible into German. A short time later, his works, also mass-produced, accounted for a third of all books sold in Germany. Luther refused to recant his provocations as then determined by the Church's central authority. He was excommunicated in 1520 by the Pope and soon declared an outlaw by the Holy Roman Emperor.
This did not stop him. Instead, Luther referred to the Pope as "Pope Fart-Ass" and as the "Ass-God in Rome)". He also commissioned caricatures, such as woodcuts showing a female demon giving birth to the Pope and cardinals, of German peasants responding to a papal edict by showing the Pope their backsides and breaking wind, and more.
Gutenberg's printing presses contributed to the spread of information in a way similar to how the internet does in today's society. The Church's ability to control the flow of information was undermined, much like how newspapers, radio, and TV have partially lost this power today. The Pope excommunicated Luther, which is reminiscent of those who are de-platformed or banned from various platforms today. The Emperor declared Luther an outlaw, which is similar to how the UK's Prime Minister is imprisoning British citizens today. Luther called the Pope derogatory names, which is reminiscent of the individual who recently had the audacity to call an overweight German minister overweight.
Freedom of expression must be curtailed to combat the spread of false or harmful information in order to protect democracy, or so it is claimed. But perhaps it is more about who gets to control the flow of information?
As is often the case, there is nothing new under the sun.
-
 @ 6c2d68ba:846525ec
2024-09-01 13:02:53
@ 6c2d68ba:846525ec
2024-09-01 13:02:53Dear friend,
it seems like you have decided to turn your back on those walled gardens and set sails to enter uncharted territory. A world without walls, an open world, a world of beautiful chaos. At least for today, I don't intend guiding you out of the safe harbour onto the open, endless sea. Today, my only intent is sharing a few thoughts, before you depart.
As a wise man on Madeira once said, it's not so much about having the right answers, it's about asking the right questions. While I'm not certain whether I have found the right questions myself by now, let me share the current set with you:
-
What causes the discomfort that drives you out of the walled garden onto the open sea?
-
Are you trying to transfer from one walled garden to the next one, where the difference being a slightly friendlier colour on the wall?
-
What are you hoping to find on the open sea that walled gardens cannot provide?
-
What are you willing to sacrifice for freedom (of speech)?
-
What will you need to keep the ship afloat?
-
How will you react when you find yourself in the middle of a storm?
I sincerely believe that it's worthwile taking a step back before departing to reflect on the big picture and the underlying paradigm shift between walled gardens and nostr. This is not about building competitors to broken systems, this is not about mimicking centralised services, this is not about repeating the same mistakes over and over.
This is about building a new world, an open world without walled gardens and data silos.
Onwards!
-
-
 @ 349d6b82:12b2a5b1
2024-12-10 13:37:27
@ 349d6b82:12b2a5b1
2024-12-10 13:37:2710 декабря состоялась акция, организованная социальной компанией "Доброе сердце", приуроченная к празднику "День благодарности". Этот новый праздник был учрежден для того, чтобы выразить признательность ветеранам за их мужество и жертвы, принесенные ради мира и свободы.
В этот день волонтеры компании "Сердце ветерана" посетили ветерана, Генерала Майора Александра Ивановича Птицына, который отметил свой 95-й день рождения. Акция началась с теплых слов благодарности и поздравлений. Волонтеры вручили Александру Ивановичу большой подарок — корзину с продуктами, в которую вошли его любимые угощения: домашние пироги, конфеты и фрукты.
 Александр Иванович в молодости. 25 лет. 1974 год.
Александр Иванович в молодости. 25 лет. 1974 год.Волонтеры подготовили небольшую концертную программу. Они исполнили несколько известных военных песен, среди которых были "День Победы" и "Тёмная ночь". Песни трогали сердца присутствующих, создавая атмосферу уважения и памяти о героических подвигах.
Акция стала частью более широкой программы "Забота о ветеранах", реализуемой компанией "Сердце ветерана". За последние два года в рамках этой программы было организовано более 50 мероприятий, направленных на поддержку ветеранов и их семей.
"Я хочу выразить искреннюю благодарность всем, кто пришел сегодня поздравить меня и других ветеранов. Это очень трогательно, когда молодое поколение помнит о нас и о том, что мы сделали для нашей страны. Я надеюсь, что такие мероприятия будут проходить чаще, чтобы молодое поколение знало о нашей истории и ценило мирное небо над головой. Еще раз спасибо всем вам за внимание и заботу. Это очень важно для нас! И спасибо большое за подарки" - проговорил Александр Иванович.
Такое внимание к ветеранам поддерживает их физическое состояние и создает чувство значимости и признательности со стороны общества.
-
 @ 2063cd79:57bd1320
2024-12-10 13:04:20
@ 2063cd79:57bd1320
2024-12-10 13:04:20Wir sprechen oft über Bitcoin im Zusammenhang mit Geld oder Währungen. Bitcoin funktioniert als Zahlungsmittel, als Wertspeicher und als Recheneinheit - doch macht das Bitcoin zu Geld? Also, was ist Geld überhaupt und was macht ein Gut erst zu Geld? Und warum gibt es gutes Geld und weniger gutes Geld? Es gibt viele Arten von Geld, Warengeld, Notenbankgeld, Fiatgeld, usw. Doch wollen wir uns erstmal ganz von Anfang an mit der Funktionen und den Eigenschaften von Geld im Allgemeinen beschäftigen.
Was ist Geld?
Ohne auf die Geschichte von Geld zum drölftausendsten Mal einzugehen (dazu kann man so ziemliches jedes Buch über Geld, Bitcoin, Ökonomie, etc. bis Seite 75 lesen und bekommt ganz genau die gleichen Infos), ist es sinnvoll sich kurz zu klarzumachen, dass niemand bestimmt oder definiert, was Geld ist. Geld kann im Endeffekt alles sein. Jeder, der Kindern schon mal beim Spielen zugesehen hat, wird erlebt haben, wie kurzerhand aus Steinen, Stöcken, DUPLO-Steinen oder eigentlich allem, was man in der Reichweite von Kindern so findet, plötzlich Geld wird. Denn ohne es zu wissen, verstehen Kinder sehr intuitiv, wie Geld funktioniert.
Geld ist Sprache. Geld ist wahrscheinlich sogar eine Sprache, die sich vor unserer modernen kommunikativen Sprache entwickelt hat. Selbst vor Urzeiten, als verschiedene Völker und Stämme auf den verschiedensten Winkeln der Erde herum zogen und sich somit erstmal verteilten und dann wieder vermischten, entwickelten sie unterschiedliche Arten der Kommunikation. Die eine gemeinsame Sprache jedoch, war die des Handels.
Kurzes Szenario: Homo Sapiens 1 hat einen Sack voller selbstgeschnitzter Pfeilspitzen in der Hand und betritt eine Lichtung, auf der Homo Sapiens 2 gerade eine Antilope grillt. Homo Sapiens 1: Uhhhhhhhhhhhhhh (zeigt auf die Antilope). Homo Sapiens 2: Ahhhhhhhhhhhh (wehrt mit den Händen wedelnd ab und springt in verteidigender Haltung auf). Homo Sapiens 1: Uhhhhhhhhhhhhhhhh (öffnet seinen Sack mit den Pfeilspitzen und legt 10 davon so hin, dass Homo Sapiens 2 versteht, dass HS1 diese zum Tausch anbietet). Homo Sapiens 2: Haaaaaaaaaaaaaa (reißt eine saftige Keule von der Antilope ab, schmeißt diese HS1 vor die Füße und schnappt sich die Pfeilspitzen).

Handel ist also älter als Schrift oder Sprache. In dem Szenario hat Homo Sapiens 1 gegenüber Homo Sapiens 2 einen Vorteil, denn er hat einen Sack dabei, in dem sich ein Wirtschaftsgut befindet, das andere Personen bereit sind, gegen ihre Besitztümer zu tauschen. So entsteht über einen gewissen Zeitraum Geld. Dabei sind die Funktionen von Geld immer die gleichen, egal welches Mittel gewählt wird. Das Mittel hängt im Wesentlichen von der lokalen Verfügbarkeit (bzw. der Begrenztheit dieser) ab.
Funktionen von Geld
Geld muss im Wesentlichen drei Funktionen erfüllen können: Es muss als Tausch- oder Zahlungsmittel funktionieren, es sollte ein Wertaufbewahrungsmittel sein und als Recheneinheit dienen.
In dem Szenario mit den beiden haarigen Protagonist//innen, sind diese drei Funktionen sehr leicht identifizierbar. HS1 hat selbstgeschnitzte Pfeilspitzen in einem Sack mitgeführt, da diese als Zahlungs- oder Tauschmittel verwendet werden können (HS2 hat bereitwillig feinstes Antilopen-Filet dafür eingetauscht), die Pfeilspitzen sind insofern Wertaufbewahrungsmittel, als dass sie (anders als das Fleisch) über Zeit nicht verderben und somit (zunächst) wertstabil sind - und damit HS1 incentiviert wird Pfeilspitzen zu sammeln (sparen) - und es war HS2 schnell möglich 10 Spitzen abzuzählen und somit seinem/ihrem Produkt einen Gegenwert beizumessen, sie dienen also auch als Recheneinheit.
Dies ist nur ein Beispiel, denn wie gesagt, Geld kann alles sein, das diese drei besprochenen Funktionen erfüllt und wenn sich mindestens zwei Parteien darauf einigen können, dass es sich bei dem verwendeten Mittel auch um ein Geld-würdiges Mittel handelt. Hätte HS1 kurzerhand 10 Steine vom Boden aufgehoben, um diese gegen das Fleisch zu tauschen, hätte HS2 laut "Uhhhhhhhhhh!" gerufen und mit dem Kopf geschüttelt, denn 10 Steine aufheben kann er/sie auch. Doch die Pfeilspitzen haben in diesem Moment einen intrinsischen Wert für HS2 und es ist erstmal egal, ob es sich hierbei um einen Tausch im direkten Sinne handelt (also Fleisch gegen Pfeilspitze), weil HS2 weiss, dass er/sie damit neues Fleisch jagen kann, oder einen indirekten Tausch, also eine Zahlung (also Fleisch gegen Geld), weil HS2 weiss, dass er/sie damit einen hippen Kakadu-Federn-Hut kaufen kann.
Geld ist älter als Sprache, bla!
Geld ist Sprache, say what?!
Geld ist, was Geld sein kann, auch wertloses Papier?

Aber wieso sind die 10 Pfeilspitzen Geld, bzw. warum sind sie begehrenswert und die 10 Steine nicht? Oder warum tauscht HS1 Pfeilspitzen gegen Antilopen-Frikadellen und nicht andersherum?
Damit ein Gut, ein Mittel, ein Gegenstand, eine Idee zu Geld werden kann, muss es nicht nur die drei Hauptfunktionen erfüllen, es sollte zusätzlich auch einige Voraussetzungen erfüllen.
Eigenschaften von Geld
Über viele tausende von Jahren haben schon die verschiedensten Gegenstände und Mittel als Geld hergehalten. Ob Eichhörnchen Pelze, Parmesan Räder, Kakao Bohnen, Zigaretten, Walzähne, oder irgendwelche inseligen Steine - alle diese Objekte haben gemeinsam, dass sie zu einem gewissen Zeitpunkt in einem gewissen System die nachfolgenden Kriterien erfüll(t)en.
Während einige dieser Kriterien immer faktisch die gleichen bleiben, gestalten sich andere wiederum etwas komplizierter und situationsabhängiger.
Teilbarkeit (Divisibility)
Ob etwas zum Beispiel teilbar ist, ist unbestreitbar nachweisbar. Wenn man etwas gegen eine Kuh oder ein Kamel eintauschen möchte, das aber nur den Wert einer halben Kuh oder eines halben Kamels hat, dann ist es eher unpraktisch die Kuh oder das Kamel zu teilen, da dann das gesamte Tier seinen eigentlichen Wert verliert. Ähnlich würde man auch kein halb-großes Kamel benutzen, da der Wert des Tieres nicht an seiner Größe bemessen ist. Bei Gold ist dies z.B. nicht der Fall. Eine halb so große Goldmünze ist nur halb soviel wert, wie eine normal große Goldmünze.

Ein Zahlungsmittel oder Gut sollte also in verschiedene Größen unterteilbar sein, ohne seine ursprüngliche Eigenschaft und damit seinen Wert nicht verlieren. Andersrum lässt sich auch argumentieren, dass ein Gut klein genug sein kann, dass es problemlos kombinierbar ist, um so einen größeren Tauschwert zu erhalten, ohne die Transportfähigkeit durch zu hohes Gewicht oder Volumen zu beeinflussen.
Transportfähigkeit / Portabilty
Die Transportfähigkeit ist nämlich bei Geld - in den meisten Fällen - besonders wichtig. Je weniger Aufwand betrieben werden muss, um das Zahlungsmittel zum Ort des Handels oder zu seinem neuen Besitzer zu schaffen, desto besser. Ein Kamel bietet sich da an, weil es selbst läuft, ein Haus ist schon relativ unhandlich, Zigaretten, Diamanten, Gold sind da natürlich die Favoriten. Die Transportfähigkeit ist einer der wichtigsten Faktoren, die die Funktion des Zahlungsmittels von Geld ausmachen. Man könnte auch sagen, die Transportfähigkeit erlaubt es, die Kaufkraft oder den Wert durch den Raum zu bewegen.
Haltbarkeit / Durability
Ein Zahlungsmittel sollte im Idealfall über einen langen Zeitraum hinweg seinen Wert halten und bestenfalls nicht verderben. Diese Eigenschaften bieten vor Allem jene Güter, die nicht konsumierbar sind und deshalb einer niedrigen Zeitpräferenz unterliegen. Wer nicht sparen möchte, sondern lieber schnell konsumieren will, wird auch einen Tausch gegen verderbliche Waren nicht abschlagen, weil die jeweiligen Umstände dies erfordern (z.B. Hyperinflation, Krieg, etc.).
Allerdings ist ein Zahlungsmittel besser, je länger es seinen Wert speichert, also ist die Haltbarkeit einer der Faktoren, die die Funktion des Wertspeichers von Geld ausmachen, oder anders ausgedrückt: die Fähigkeit, Kaufkraft oder Wert durch die Zeit zu bewegen.

Austauschbarkeit / Fungibility
Die Austauschbarkeit der jeweiligen Geldeinheiten macht Geld erst wirklich praktisch, denn wenn jeder Einheit (z.B. Münze, Korn, Schein, Perle, etc.) ein eigener Wert zugeschrieben wird, macht dies den Austausch sehr kompliziert, da der einzelne Wert jedes Mal ermittelt werden muss und der Wert eines jeden Objekts rein subjektiver Art sein kann. Die Austauschbarkeit eliminiert die Subjektivität der Wertschätzung und misst dem Geldmittel einen objektiven Wert zu.
Also unabhängig vom jeweiligen Tauschwert einer anderen Währung wird niemand bestreiten, dass eine Goldmünze (28g) den gleichen Wert hat wie eine Goldmünze (28g). Das 1€ Stück in meiner Tasche ist genauso viel wert, wie das 1€ Stück in jedem anderen Portemonnaie (ob die Kaufkraft morgen noch die gleiche ist, steht auf einem anderen Zettel). Die Austauschbarkeit der jeweiligen Einheiten in einem gewissen Geldsystem (also Euro-Münzen im Euro-System) machen den Umgang einfacher.
Nachweisbarkeit / Provability
Hierbei handelt es sich um den relativen Aufwand, den der Empfänger betreiben muss, um sicherzustellen, dass das erhaltene Gut tatsächlich den erwarteten Spezifikationen entspricht. Dies ist natürlich immer relativ zum möglichen Risiko eines Verlusts zu betrachten. Bekomme ich im Supermarkt einen 10€-Schein als Wechselgeld, werde ich kaum einen Prüfstift aus der Tasche ziehen, weil der Aufwand nicht im Verhältnis zum möglichen Risiko steht. Allerdings benutzen Kassierer//innen im Geschäft bei Scheinen ab 50€ immer einen Prüfstift. Bei Gold fällt es einem Laien schwer, ohne großen Aufwand zu verifizieren, dass es sich um reines, echtes Gold handelt. Man vertraut im Handel z.B. dem Goldhändler, dass das Gut verifiziert und authentifiziert wurde. Beim Handel mit Kamelen spielen viele Faktoren eine Rolle, ob das Kamel nachweislich dem versprochenen Wert entspricht, welche sich nicht einfach an Ort und Stelle prüfen lassen.

Knappheit / Scarcity
Diese Charakteristik ist wahrscheinlich die wichtigste, auch wenn eine Kombination aller Eigenschaften hartes Geld erst wirklich ausmacht. Knappheit bedeutet, dass das Gut, das als Geld benutzt wird, begrenzt ist und nicht ohne weiteres vermehrt werden kann. Knappheit kann durch geographische Einschränkungen hervorgerufen werden, so ist zum Beispiel Wasser in der Wüste knapper und somit wertvoller als in Regionen, in denen es reichlich und in Fülle vorhanden ist. Steine oder Sand bieten sich nicht als Geld an, da sie überall in Fülle vorhanden sind. Das beste (und zu Tode zitierte, sorry) Beispiel sind die Rai-Steine der Yap. Sie haben lange als Geld für den Inselstaat funktioniert, da diese schwierig zu beschaffen waren und die Herstellung sehr mühselig war. Doch als Schifffahrer auftauchen, die einfach und günstig Steine beschaffen konnten, wurde diese geographische Einschränkung aufgehoben und die Steine verloren an Wert. Ein weiteres Beispiel für Knappheit ist Gold. Es erfordert viel materiellen Aufwand, Gold zu schürfen und zu raffinieren.
Universalität / Universality
Die allgemeine Akzeptanz eines Guts ist eine nicht unbedingt zu erfüllende Eigenschaft eines guten Geldes, erhöht jedoch dessen Funktionalität als weitflächig nutzbares Zahlungsmittel. Es gibt weltweit über 160 nationale Währungen, doch sind nicht alle davon gleich akzeptiert. Wenn man z.B. den südafrikanischen Rand mit US Dollars vergleicht, wird man sehen, dass der USD eine viel höhere Akzeptanz genießt, als der ZAR. Man wird wahrscheinlich selbst in asiatischen Ländern im Notfall mit USD bezahlen können, einfach weil die Handelspartner dort wissen, dass es für sie einfach ist, USD in ihre lokale Währung umzutauschen. Mit Rand wird man Probleme bekommen, da diese als Tauschobjekt von Handelspartnern keine Zustimmung genießen.
Sicherungsfähigkeit / Securability
Ein weiteres Kriterium ist die Möglichkeit, sein Geld zu verwahren, bzw. zu sichern. Auch wenn Gold ein sehr hartes Geld ist (knapp, allgemein akzeptiert, relativ transportfähig und lange haltbar), ist es vergleichsweise aufwändig, dieses zu sichern. Das gleiche gilt für Geld in Form von nationalen Währungen. Große Mengen an Bargeld sind schwierig zu transportieren und die Sicherung erfolgt in Form von gepanzerten Fahrzeugen und/oder bewaffneten Wachleuten. Bei Kamelen ist dies sogar noch schwieriger, da sie zusätzlich auch noch dazu tendieren, wegzulaufen.
Wie wir sehen können, muss ein Geld verschiedene Eigenschaften erfüllen, um als solches die eingangs erwähnten Funktionen (Zahlungsmittel, Wertspeicher und Recheneinheit) überhaupt erfüllen zu können. Alle bekannten Formen des Geldes - aktuelle und auch historische - bewegen sich auf einem Spektrum dieser verschiedenen Eigenschaften.
Ganz wichtig bei der Betrachtung dieser Kriterien sind immer die jeweiligen Umstände, denn es setzt sich immer das Mittel mit den meisten oder verhältnismäßig stärksten Kriterien durch. Nehmen wir LEGO-Steine, super leicht unterteilbar, leicht zu transportieren, leicht ersetzbar, aber absolut nicht selten. Daher als Geld unbrauchbar. Allerdings spielen die Faktoren Zeit, Ort und andere Umstände eine große Rolle. In Gefängnissen z.B. funktionieren Zigaretten als Geld sehr gut, denn anders als in der Freiheit, sind Zigaretten in Gefängnissen streng rationiert und kontrolliert, also sehr selten. Ihre kompakte Größe macht sie transportabel und eine Packung lässt sich leicht in kleinere Untereinheiten aufteilen. Der/diejenige Insass//in, die im Gefängnis allerdings viele Zigaretten anhäuft und dort ein relatives Vermögen besitzt, wird nach der Entlassung einfach eine Sporttasche voller Zigaretten haben, die in der Außenwelt einen komplett anderen Stellenwert haben. Zigaretten funktionieren nur in ihrem besonderen abgeschlossenen Ökosystem. Dies gilt auch für Rai-Steine, Glasperlen oder Muscheln.

Somit wird Geld nicht nur von natürlichen und physikalischen Grenzen, sondern auch von willkürlich erlassenen und zentral gesteuerten Regeln beeinflusst. Würde das Gefängnis mit einem Mal jedem/r Insass//in erlauben, eine unbeschränkte Menge von Zigaretten einzuführen, würden diese sofort wertlos und somit als Geld unbrauchbar.
Wenn man also das Spektrum betrachtet, auf welchem alle Formen von Geld rangieren, ist es immer sinnvoll zuerst das System festzulegen, in dem ein Geld funktionieren soll. Schaut man sich unsere heutige offene und vernetzte Welt an, so muss ein Geld auch in einer solchen funktionieren. Dies ist der Grund, warum viele Formen des Geldes mit der Zeit gescheitert sind.
Eine Handvoll Beispiele von Gütern, die als Geld benutzt werden oder wurden: Eichhörnchenpelze, Rai-Steine, Zigaretten, Gold, Diamanten, Immobilien, Salz und Vieh.
Legt man die oben aufgeführten Kriterien für ein hartes Geld, wird schnell deutlich, warum einige dieser Mittel als Geld nicht langfristig funktionieren können. Um dies bildlich darzustellen, kann man eine Tabelle erstellen und den jeweiligen Attributen einen Wert zuteilen. Ich hab dies einfach willkürlich auf einer Skala von 0-5 gemacht und man sieht dort anhand der Rangordnung, welche dieser Beispiele besser als Geld funktionieren, als andere.

Kann Bitcoin diese Attribute erfüllen?
Wie auf der Tabelle ersichtlich, erfüllt Bitcoin alle diese Kriterien vergleichsweise gut.
Transportfähigkeit: Bitcoin ist ein Peer-to-Peer Zahlungssystem, das im Internet lebt. Bitcoins existieren in der Blockchain und nur dort. Lediglich die Schlüssel, die den Zugriff auf die persönlichen bitcoins / UTXOs erlauben, müssen transportiert werden. Dies kann mit Hilfe von Software- oder Hardware-Wallets (Signiergeräten), auf Papier oder sogar im Kopf geschehen. Keine andere Form von Geld lässt sich "auswendig" merken und somit problemlos durch Raum und Zeit transportieren. Mehr dazu hier:
https://www.genexyz.org/post/16-block-759540-brain-wallets-0xcxtv/
Austauschbarkeit: Ein bitcoin ist ein bitcoin ist ein bitcoin. Abgesehen von esoterischen Konzepten, wie der Ordinals-Theorie, sind Sats immer gleich viel Wert (nicht der Währungskurs), sodass ein Tausch von einer Menge Sats in eine gleiche Menge Sats den/die Besitzer//in immer mit dem gleichen Vermögen dastehen lässt. Es gibt keinen Sat, der mehr oder weniger wert ist, als ein weiterer Sat. Mehr dazu hier:
https://www.genexyz.org/post/26-block-775770-ordinals-inscriptions-36zg3n/
Überprüfbarkeit: Bitcoin wurde erfunden, um das Double-Spending-Problem im digitalen Raum zu lösen. Die Blockchain verifiziert die Gültigkeit einer jeden Transaktion. Der/die Empfänger//in einer Bitcoin-Zahlung weiß immer, dass die erhaltene Menge Bitcoin auch valide ist. Es bedarf keiner Drittpartei, keines weiteren Prozesses oder anderer Überprüfung, um sicherzustellen, dass die erhaltene Menge Bitcoin auch echt oder korrekt ist. Sobald eine Transaktion bestätigt wurde, kann man sich zu 100% sicher sein, dass man Besitzer//in von Bitcoin ist.
Haltbarkeit: Anders als physische Güter, die Verfall, Zersetzung oder Verderben ausgeliefert sind, hat Bitcoin kein Verfallsdatum. Solange das Netzwerk läuft, wird Bitcoin in seiner Form existieren. Es ist unmöglich, Bitcoin durch Fremdeinfluss (sowohl menschlicher, als auch natürlicher) zu zerstören.

Knappheit: Bitcoin ist auf 21.000.000 begrenzt. Die harte Obergrenze von Bitcoin ist von zentraler Bedeutung für sein Wertversprechen. Alle 2.099.999.997.690.000 Sats werden irgendwann existieren (oder existieren schon - je nach Betrachtungsweise) und darüber hinaus werden keine weiteren Sats produziert. Lediglich der Zugriff auf diese Sats wird über Zeit sogar abnehmen (durch Verlust der Schlüssel) und somit zu einer weiteren Verknappung beitragen.
Teilbarkeit: Wie schon oftmals erwähnt, lässt sich ein bitcoin in 100.000.000 Sats unterteilen. Diese Stückelung von Bitcoin bis zur achten Dezimalstelle verleiht eine sehr hohe Teilbarkeit. Dies gibt Bitcoin eine größere Flexibilität als herkömmliche Währungen und ermöglicht es extrem kleine Transaktionen, sogenannte Mikrotransaktionen, durchzuführen. Satoshis sind die Standardmaßeinheit und bitcoin wird oft nur zum erhöhten Verständnis und besserer Lesbarkeit benutzt. Beispielsweise zeigen fast alle Wallets und Explorer die Transaktionsgebühren in Form von Satoshis pro vByte an.
Universalität: Die allgemeine Akzeptanz von Bitcoin ist noch verhältnismäßig klein. Dies liegt allerdings nicht an Bitcoin, denn Bitcoin ist erlaubnislos und frei zugänglich. Es sind vielmehr die On-Ramps, die es potenziellen Nuter//innen bislang noch nicht so einfach machen, wie es viele gerne hätten. Da Bitcoin aber staatenlos und dezentral ist, erlaubt es jedem Interessierten den offenen Zugang.
Sicherungsfähigkeit: Die Sicherungsfähigkeit von Bitcoin ist unvergleichbar mit der anderer Gelder oder Zahlungsmittel. Es gibt unzählige Möglichkeiten, Bitcoin sicher und vor allem SELBST zu verwahren. Es ist gänzlich möglich, auf Anbieter zur Verwahrung zu verzichten und Bitcoin in einer Art und Weise aufzubewahren, die es Außenstehenden so gut wie unmöglich macht, Bitcoin zu stehlen. Das gilt für die Ebene persönlicher Verwahrung. Auf Netzwerkebene ist die Sicherheit von Bitcoin vielschichtig. Transaktions-Hashing, Mining, Blockbestätigungen und Spieltheorie arbeiten alle zusammen, um Bitcoin das Netzwerk undurchdringlich zu machen.


Warum ist es trotzdem schwierig zu sagen, dass Bitcoin Geld ist?
Einige sagen, dass Bitcoin Geld ist. Andere sagen, dass es kein Geld ist. Was feststeht ist, dass das Bitcoin-Netzwerk absolut zuverlässig tut, was es tun soll. Bitcoin kann also als Geld funktionieren, da es die Kriterien sehr gut erfüllt. Bitcoin ist in erster Linie eine Datenbank, die durch ein Netzwerk abgesichert wird und überwacht, welche Einträge welchen Bitcoin-Adressen zugeordnet werden. Dies geschieht durch die Übertragung von kryptografisch verschlüsselten Textnachrichten zwischen den Netzwerkteilnehmern.
Damit ist Bitcoin immer nur Text. Auch der Code, auf dem Bitcoin basiert, ist Text. Die kryptografischen Verschlüsselungen basieren auf Text. Text ist Sprache, damit ist Bitcoin Sprache. Wie viele der genannten Beispiele von Geld, ist Bitcoin nicht in erster Linie Geld, sondern eignet sich sehr gut, als solches verwendet zu werden. Nationale Währungen, Fiat-Geld, sind in erster Linie Geld. Sie werden erlassen, produziert und kontrolliert, um Geld zu sein. Das ist bei Bitcoin anders. Damit ist Bitcoin durch Meinungsfreiheit, das Recht, seine Meinung in Wort, Schrift und Bild frei zu äußern, geschützt.
🫳🎤
In diesem Sinne, 2... 1... Risiko!

-
 @ 6c2d68ba:846525ec
2024-08-30 21:53:53
@ 6c2d68ba:846525ec
2024-08-30 21:53:53What the hell is Nostriga you might think. Nostriga is part of the nostr.world unconference series. It's a cost-free event aimed at gathering nostriches - people excited about nostr - globally to share knowledge, collaborate, network and work towards a freely accessible internet.
In case you never heard of nostr: nostr is an open protocol designed for censorship-resistant and global web publishing, fostering a value-for-value exchange. Find more information here.
Now that a few days have passed, it's time to reflect on some of my main takeaways but first, I would like to thank Marce, Anna, Jack, Uncle Rockstar and everyone else involved for making this event special in several ways. I'm sharing my thoughts in no particular order and as can be expected after having heard so many inspiring talks, I will be relaying - relay, get it? - many great ideas others shared.
nostriches are built different
To be honest, Nostriga was one of the best conference experiences I have had in a while. Great spirit, deep conversations, real & honest takes and 99% signal. Everyone who's ever been to a conference knows how draining and tiring such events can be. This time, however, something is different. I guess one of the main reasons for this are the people behind those npubs. Great attitude, avoiding ego shows, no simping for VIPs, down to earth and a positive vision of what might lie ahead. So in hindsight, Nostriga makes me super bullish on the upcoming months and the road ahead when it comes to the tech as well as the people behind nostr. Onwards, nostriches.
no need for nostr marketing
With the world marching towards implementing 1984, which was not meant to serve as instruction manual god dammit, and events such as the arrest of Pavel Durov, it's evident that nostr won't need a marketing department. An open protocol with focus on censorship-resistance and free speech, will automatically attract the attention of just the right people. This is of course based on the assumption that the nostr community will deal with certain challenges when it comes to privacy and nostr.

nostr (still) has privacy issues
As already pointed out by Edward Snowden, many open challenges remain to be mastered when it comes to privacy, so that people having to rely on safe and private messaging don't have to rule out nostr. Protecting identities, location and leaking as little metadata as possible are crucial here. Keep in mind, a three letter agency once said that they kill people based on metadata. In this regard, nostr DMs are one of the biggest pain points for the time being, though several nips exist to overcome issues such as IP leaks. See the talk of Jeff for details. We'll get there!
For thoughts on privacy, check out saving private nostr:
For privacy and DMs, check out the past and future of messaging on nostr (at 3h 01min 48s):
nostr already got a killer feature: openness
Long story short, watch this talk (starts at 1h 19min 17s) :
nostr beyond social media
As demonstrated by Ben Arc, nostr can be so much more than just an attempt to mimic Twitter. IoT, web of trust, file sharing or bringing together (open) social media and AI are just a few things on the table.
separation of client and algorithm
For many of you this might be nothing new but I can't stress the importance of Data Vending Machines (DVMs) enough. In a nutshell, DVMs are data-processing tools. You give them some data, a few sats, and they give you back some data. As anyone can spin up his own DVM without any registration or signup, there will be ruthless competition. Check out DVMs for further information.
The basic idea behind it, which still gets me, is the potential separation of (nostr) clients and algorithms in a broader sense. Coupled with marketplaces and having insights what algorithms your friends are using, things will get interesting. Remember, to this day Twitter, Meta and so on are deciding what algorithms are being used in your app and not you. nostr will put you in the driver seat.
web of trust
Web of trust is something people talk a lot about these days, so I will keep it short. One idea caught my attention: combining nostr and file sharing in the sense that you attach an npub to files hosted on file sharing services or torrents and so on. In order to prevent downloading or even spreading infected files, it boils down to the simple question of "can I trust that npub to host clean as well as safe files?". Reputation.
have you seen my nutsack?
Before Nostriga, I haven't been aware of how beautifully ecash and nostr can go hand in hand. In particular, I'm still trying to find the right words to express how big of a deal the combination of Data Vending Machines and ecash can be, if implemented the right way. Check out DVMs that nutsack thing, and pistachio bag.
(Talk starts at 55min 41s)
nostr is not another Bitcoiner circle jerk
On the second day of Nostriga, I met someone at one of the food trucks, who happens to have been actively fighting to free Julian Assange. Events, protests, spreading the word, the whole thing. He or she - trying to hide as many details as I possibly can here - told me that his/her main motivation for coming to Riga was indeed nostr and that he/she had discovered Bitcoin via nostr, where it's usually the other way around. To be honest, this was not the only time I heard this at Nostriga but for sure it's the most memorable one.
Of course, there is nothing wrong with so many Bitcoiners being around on nostr and it does come with several benefits, one of them being an excellent meme game. As I sincerely believe that nostr is for anyone, it feels good to see other communities popping up and telling their stories on nostr. So delighted you're leaving those walled gardens, friends.
onwards
Let me know what you think, where you agree, where you have a different point of view. Feel free to bring in your Nostriga story. Keep it weird, fellow nostriches, and if you have time to just watch a single talk from Nostriga, make sure it's this one:
-
 @ 42342239:1d80db24
2024-08-30 06:26:21
@ 42342239:1d80db24
2024-08-30 06:26:21Quis custodiet ipsos custodes?
-- Juvenal (Who will watch the watchmen?)
In mid-July, numerous media outlets reported on the assassination attempt on Donald Trump. FBI Director Christopher Wray stated later that same month that what hit the former president Trump was a bullet. A few days later, it was reported from various sources that search engines no longer acknowledged that an assassination attempt on ex-President Trump had taken place. When users used automatic completion in Google and Bing (91% respectively 4% market share), these search engines only suggested earlier presidents such as Harry Truman and Theodore Roosevelt, along with Russian President Vladimir Putin as people who could have been subjected to assassination attempts.
The reports were comprehensive enough for the Republican district attorney of Missouri to say that he would investigate matter. The senator from Kansas - also a Republican - planned to make an official request to Google. Google has responded through a spokesman to the New York Post that the company had not "manually changed" search results, but its system includes "protection" against search results "connected to political violence."
A similar phenomenon occurred during the 2016 presidential election. At the time, reports emerged of Google, unlike other less widely used search engines, rarely or never suggesting negative search results for Hillary Clinton. The company however provided negative search results for then-candidate Trump. Then, as today, the company denied deliberately favouring any specific political candidate.
These occurrences led to research on how such search suggestions can influence public opinion and voting preferences. For example, the impact of simply removing negative search suggestions has been investigated. A study published in June 2024 reports that such search results can dramatically affect undecided voters. Reducing negative search suggestions can turn a 50/50 split into a 90/10 split in favour of the candidate for whom negative search suggestions were suppressed. The researchers concluded that search suggestions can have "a dramatic impact," that this can "shift a large number of votes" and do so without leaving "any trace for authorities to follow." How search engines operate should therefore be considered of great importance by anyone who claims to take democracy seriously. And this regardless of one's political sympathies.
A well-known thought experiment in philosophy asks: "If a tree falls in the forest and no one hears it, does it make a sound?" Translated to today's media landscape: If an assassination attempt took place on a former president, but search engines don't want to acknowledge it, did it really happen?
-
 @ ae1008d2:a166d760
2024-08-29 05:14:15
@ ae1008d2:a166d760
2024-08-29 05:14:15Democracy, a system that ideally reflects the will of the people, faces significant mathematical challenges, particularly in the way votes are cast and counted. One of the most prominent issues lies within the first-past-the-post (FPTP) voting system, a method that has been in use for centuries. This system allows voters to select only one candidate, which can lead to scenarios where a party secures power without obtaining a majority of the votes. Such outcomes raise questions about the true representation of voter preferences and the overall health of democratic processes.
The Flaws of First-Past-The-Post
The FPTP system has been illustrated through historical examples, such as the British Parliament and the contentious 2000 U.S. presidential election. In these instances, the so-called "spoiler effect" emerged, where third-party candidates siphoned votes from major candidates, ultimately skewing the results. Voters often feel that their preferences are not accurately represented, leading to disillusionment with the electoral process. This discontent underscores the need for a more representative voting system.
Introducing Ranked-Choice Voting
To address the shortcomings of FPTP, ranked-choice voting (RCV), also known as instant runoff voting, has been proposed. In this system, voters rank candidates in order of preference, allowing for a more nuanced reflection of voter sentiment. RCV not only captures a broader spectrum of voter preferences but also encourages candidates to engage in more civil discourse. For example, in the 2013 Minneapolis mayoral race, candidates exhibited a camaraderie that is often absent in traditional campaigns, as they sought to appeal to voters for second and third choices.
However, the implementation of RCV is not without its challenges. Concerns arise about the potential for a candidate performing poorly to inadvertently assist in the election of another candidate. A hypothetical scenario involving three candidates—Einstein, C, and Bore—illustrates this point. The elimination of candidates based on voter preferences can lead to unexpected outcomes, complicating the electoral landscape.
Historical Context and Mathematical Foundations
The discussion of voting systems is enriched by historical context, particularly through the lens of French mathematician Marie Jean Antoine Nicolas de Caritat, the Marquis de Condorcet. Condorcet advocated for a fair voting method that required candidates to win head-to-head matchups. His method, which involves ranking preferences, introduces a potential issue known as Condorcet's Paradox. This paradox occurs when cyclical preferences prevent a clear winner from emerging, highlighting the complexities of voter choice.
Various mathematicians, including Lewis Carroll, have sought to develop fair election systems but encountered similar challenges. In 1951, economist Kenneth Arrow proposed five conditions that a voting system should meet to ensure fairness: decisiveness, unrestricted domain, transitivity, independence of irrelevant alternatives, and stability of group preferences. These conditions serve as a benchmark for evaluating the effectiveness of different voting systems.
Arrow's Impossibility Theorem
A significant aspect of the discussion revolves around Arrow's impossibility theorem, which posits that it is impossible to create a ranked voting system that satisfies all five of Arrow's conditions when there are three or more candidates. This theorem can be illustrated through a thought experiment involving three candidates (A, B, and C) and various voter rankings. The proof demonstrates that if a candidate is unanimously ranked first or last by voters, society must reflect that ranking. However, the theorem also reveals scenarios where a pivotal voter can dictate the overall ranking, effectively acting as a "dictator" in determining societal preferences.
This leads to a sobering conclusion: according to Arrow's theorem, a truly democratic voting system is unattainable when dealing with multiple candidates. Yet, there is a more optimistic perspective introduced by mathematician Duncan Black, suggesting that alternative methods may exist to better represent voter preferences.
The Dynamics of Voter Preferences
The dynamics of voter preferences along a political spectrum, from liberal to conservative, further complicate the electoral process. The choice of the median voter often determines election outcomes, aligning with the majority's decision and helping to avoid the paradoxes identified by Arrow's theorem. This discussion introduces rated voting systems, particularly approval voting, where voters indicate approval for candidates without ranking them.
Research indicates that approval voting can increase voter turnout, reduce negative campaigning, and mitigate the spoiler effect. Despite its historical use in electing popes and the Secretary General of the United Nations, approval voting has not been widely adopted in large-scale elections, suggesting a need for further real-world testing and evaluation.
The Importance of Political Engagement
While traditional voting methods like FPTP have significant flaws, the importance of political engagement and the necessity of striving for a more representative electoral process cannot be overstated. The complexities of voting systems and the historical evolution of these methods highlight the ongoing struggle for fairness in elections.
As democracy continues to evolve, enhancing knowledge and critical thinking skills about voting systems will be crucial in advocating for reforms that better reflect the will of the people. Understanding the mathematical underpinnings of these systems is essential for promoting a more equitable and representative democratic process.
The mathematical challenges of democracy, particularly in the context of voting systems, reveal significant flaws in traditional methods like first-past-the-post. The exploration of ranked-choice voting and other alternatives offers a glimpse into potential solutions that could enhance voter representation and engagement. As society navigates the complexities of democratic processes, it is essential to remain informed and proactive in advocating for systems that truly reflect the diverse preferences of the electorate.

Proposed Solution: Leveraging the Nostr Protocol
To further enhance the democratic process and address the challenges of traditional voting systems, we can consider utilizing the Nostr protocol. Nostr is a decentralized protocol that allows for open, self-verifiable, anonymous communication and data sharing, making it an ideal candidate for implementing a modern voting system. There have been other attempts at voting via nostr, this is my concept and contribution. View the code below.
Key Features of Using Nostr for Voting
- Decentralization: By leveraging Nostr's decentralized architecture, we can eliminate single points of failure and reduce the risk of manipulation or censorship in the voting process.
- Public-Private Key Cryptography: Each voter can generate a unique public npub and private nsec key pair. The npub public key serves as their identity, while the nsec private key is used to sign votes, ensuring authenticity and integrity.
- Anonymity and Privacy: Voter identities can remain anonymous, as only their public keys are visible. This protects against coercion and ensures that voters can express their preferences freely.
- Secure Vote Submission: Voters can submit their ranked choices or preferences as signed encrypted messages through Nostr and its relays. This ensures that votes are tamper-proof and verifiable.
- Real-Time Results and Transparency: The distributed nature of Nostr allows for real-time updates on the voting process, providing transparency and enabling independent verification of results.
- Mitigating the Spoiler Effect: By implementing ranked-choice voting through Nostr, we can capture a broader spectrum of voter preferences and reduce the impact of third-party candidates acting as spoilers (hopefully).
- Public Auditing: The system can provide an audit trail of all votes cast, allowing for independent verification and fostering trust in the electoral process.
By integrating the Nostr protocol into the voting process, we can create a more secure, transparent, and representative electoral system, particularly at the local level. This approach not only addresses the mathematical challenges of traditional voting methods but also empowers voters and enhances engagement in the democratic process.
I am new and inexperienced in programming, but I have wrote a bit of code with the help of general purpose AI's. Please review and improve and/or comment as best you can below👇
Thank you for supporting my work with zaps ⚡ supermax@minibits.cash
bc1qaucduwftl6lff5f436kccjc425m0ntqs6phzcx

I would like to implement a test at some point when the code is running stable. A distributed vote, if you will. Thank you for your support.
CypherPunksWriteCode
-
 @ 6c2d68ba:846525ec
2024-08-08 21:15:25
@ 6c2d68ba:846525ec
2024-08-08 21:15:25Will man der Bundeszentrale für politische Bildung glauben, so handelt es sich bei Propaganda um den Versuch der gezielten Beeinflussung des Denkens, Handelns wie auch Fühlens von Menschen. Charakteristisch für Propaganda ist, dass sie darauf verzichtet die verschiedenen Seiten einer Thematik darzulegen, sondern gezielt Meinung mit (Fehl)-Information vermischt. Wer Propaganda betreibt, strebt nicht danach zu diskutieren oder die Öffentlichkeit gar mit Argumenten zu überzeugen, sondern greift zu verschiedensten Manipulationstechniken, die die Emotionen und das Verhalten der Öffentlichkeit beeinflussen. Propaganda nimmt dem Menschen (eigenständiges) Denken ab und gibt ihm stattdessen das Gefühl, mit der übernommenen Meinung goldrichtig zu liegen. Hier zeigt sich auch der wesentliche Unterschied zum Journalismus: Journalismus strebt nach Aufklärung, indem alle verfügbaren Fakten und Hintergründe dargelegt werden und der Empfänger selbst darüber entscheiden darf, was er für richtig und was er für falsch hält [1].
Zwar verbinden wir den Begriff Propaganda heutzutage mit autoritären und totalitären Staaten, wo diese auch zweifelsfrei Anwendung findet, doch kommen Propagandatechniken auch im Westen zum Einsatz, wenn auch in einer auf die demokratische Herrschaftsform zugeschnittene Art und Weise. Wie die Geschichte gezeigt hat - hier sind die Werke von Edward Bernays ganz besonders relevant [2] - wurde Öffentlichkeitsarbeit, sprich Public Relations (PR), basierend auf den Erkenntnissen der Propagandaforschung verfeinert, über welche die öffentliche Wahrnehmung von Personen, Konzernen und Regierungen beeinflusst wird. In Summe lässt sich daraus ableiten, dass auch Propaganda in unseren Breitengraden Tradition hat.
Nun halte ich es in Zeiten von (leider) wiederkehrenden heißen Konflikten in Europa besonders wichtig sich über existierende Manipulationstechniken wie auch gezielter Meinungsmache in (Massen)-medien bewusst zu sein wie auch erscheinenden Artikeln, Posts, Videos und ganz besonders Schlagzeilen mit einem gewissen Grad an Achtsamkeit zu begegnen, um nicht umgehend Opfer von Manipulation zu werden. Denn wie schon von der bereits erwähnten Bundeszentrale für politische Bildung erwähnt wurde, kann nur jener sich gegen den Einfluss von Propaganda wehren, der diese als solche erkennt. Dadurch motiviert nehme ich heute die Prinzipien der Kriegspropaganda ins Fadenkreuz.
„Auf die Dauer vermag auch die frechste und bestorganisierte Propaganda nichts gegen die Wahrheit.“ ―Albert Schweitzer
Die Prinzipien der Kriegspropaganda
Unter dem Eindruck des Ersten Weltkriegs schrieb Arthur Ponsonby, britischer Adeliger & Staatsbeamter, 1928 das Buch "Lüge in Kriegszeiten", in welchem er die Mechanismen der damaligen Kriegspropaganda untersuchte. Er steht übrigens im Verdacht Urvater des berühmten Zitats "das erste Opfer im Krieg ist die Wahrheit" zu sein [3]. In diesem Werk schildert Ponsonby 20 Aspekte, die wiederum später von der Historikerin Anne Morelli im Jahr 2001 zu den zehn Prinzipien der Kriegspropaganda zusammengefasst wurden. Wie sie selbst betonte geht es bei diesen Prinzipien nicht darum herauszufinden, wer lügt und wer die Wahrheit sagt, wer das glaubt, was er sagt, sondern Mittels dieser Prinzipien die verbreitete Propaganda zu veranschaulichen und ihr Funktionieren zu beschreiben (Seite 6, [4]). Nachdem ich mich selbst mit diesen Prinzipien beschäftigt hatte, wurde mir mit jeder einzelnen Gedankenrunde immer klarer, wie die von Anne Morelli beschriebenen Prinzipien als wie eine Art Leitfaden verwendet werden, um Pressemeldungen, Argumente und Schlagzeilen in Sozialen Medien so zu formulieren, dass unabhängig vom Geschehnis stets eine unterbewusste Botschaft mitschwingt, so dass der gewünschte Effekt der Manipulation maximiert wird.
Nun könnte man nach Durchsicht der größten Tagesblätter des Deutschsprachigen Raums etliche Beispiele für jeden einzelnen der in Kürze vorgestellten Prinzipien präsentieren, doch habe ich in Anbetracht des Themas bewusst Abstand davon genommen, um nicht gewisse Journalisten - oder kriegstreibende Propagandisten wie ich sie nenne - samt Klarnamen an den Pranger zu stellen. Wie Anne Morelli, sehe ich den größtmöglichen Mehrwert darin, die Mechanik offenzulegen, um die Leserschaft für dieses Thema zu sensibilisieren.
Wir wollen keinen Krieg!
Stets wird versichert, dass man den stattfindenden Krieg keines Falles wolle. In einer demokratischen Gesellschaft ist Krieg ein ungebetener Gast, weswegen Bevölkerungen fast ausnahmslos jedes Mal in die Kriegsbereitschaft hineingelockt werden müssen, siehe Brutkastenlüge im Zusammenhang mit dem Irakkrieg. Nun kann man sehr oft beobachten, wie Staatsführer stets in aller Inbrunst gegen den aktuellen oder einen eventuell bevorstehenden Krieg poltern. Wenn jedoch alle Personen an den entscheidenden Machthebeln so sehr gegen Kriege sind, wie können Kriege dann überhaupt ausbrechen?
Der Gegner ist allein für den Krieg verantwortlich!
Der zugrundeliegenden Logik nach zeigt jeweils die eine Kriegspartei auf die andere und schiebt dabei die Schuld für den stattfindenden Krieg der anderen Seite zu. Selbst hat man natürlich keine provozierenden Schritte gesetzt, wie etwa das Stationieren von Raketensystemen, das Verschieben von Machtblöcken oder Ähnliches. Statt zum Mittel der Diplomatie zu greifen muss der Konflikt jetzt weiter angeheizt und der Krieg fortgeführt werden, denn schließlich muss dieser Krieg jetzt geführt werden, damit (ewiger) Frieden herrschen kann - siehe "Krieg ist Frieden" nach George Orwell. Darüber hinaus kann der Konflikt auch deshalb nicht beendet werden, weil der Feind sonst "unsere Werte" zerstört, "uns" die Freiheit nimmt oder gar ein Genozid "an unserem Volk" stattfindet.
Der Führer des feindlichen Lagers wird dämonisiert
Dieses Prinzip folgt der Logik des Reduzierens eines ganzen Landes auf eine an der Spitze sitzenden Person, also dem Zuschneiden auf Putin, Obama, Scholz, etc. Diese Person repräsentiert quasi einen fleischgewordenen Dämon, der die Macht über das Feindesland errungen hat und nun in Abwesenheit von geistiger Gesundheit einen Konflikt vom Zaun bricht. Morelli argumentiert dazu: "Man kann eine Gruppe von Menschen nicht insgesamt hassen, nicht einmal als Feinde. Es ist daher wirkungsvoller, den Hass auf die feindliche Führungspersönlichkeit zu richten. Der Gegner bekommt so ein Gesicht und dieses Gesicht wird natürlich Gegenstand des Hasses werden."
Wir verteidigen ein edles Ziel und keine besonderen Interessen!
Der Fokus auf moralische und legitime Werte spielt diesem Prinzip nach deshalb eine besondere Rolle, weil es dazu dient die wirtschaftlichen und geopolitischen Ziele der eignen Seite zu verdecken, was auf das Stärken der Zustimmung der eigenen Bevölkerung schielt, da der Konflikt zu einem gewissen Grad nur durch Zustimmung eben dieser Bevölkerung geführt werden kann. So hatte Antonio Gramsci dargelegt wie sich die Ziele des Ersten Weltkriegs in drei Punkte zusammenfassen lassen: den Militarismus zu vernichten, die kleinen Staaten (wie etwa Belgien) zu verteidigen und die Welt für "die Demokratie" vorzubereiten. Letzteres Argument fand sich auch in den Konflikten des aktuellen Jahrhunderts in ähnlicher Form als "Spreading Democracy" oder "Befreiung des Iraks" wieder. Ergänzend könnte man zu diesem Prinzip sagen, dass ein Unterton von "der Feind ist ein blutrünstiges Monster aus einer barbarischen Gesellschaft" mitschwingt.
Der Feind begeht wissentlich Grausamkeiten, wenn wir Fehler machen, geschieht dies unbeabsichtigt
Erzählungen über Gräueltaten des Feindes stellen ein wesentliches Element von Kriegspropaganda dar. Zwar sind Grausamkeiten zweifelsohne integraler Bestandteil eines jeden Krieges, und das auf beiden Seiten, jedoch ist die gegensätzliche Darstellung der eigenen "humanitären" Armee, die selbstverständlich von der Bevölkerung geliebt wird, und der feindlichen Armee, die als einzige Kriegspartei Grausamkeiten begeht, altbekannte Propaganda. Üblicherweise begnügt man sich nicht mit den tatsächlich auftretenden Verbrechen, im Gegenteil, man kann in vergangenen Konflikten wiederholt beobachten wie Verbrechen gegen die Menschlichkeit am Schreibtisch erfunden werden, um den Feind als die Wiederkehr Adolf Hitlers erscheinen zu lassen.
Der Feind benutzt unerlaubte Waffen
In gewisser Weise ergänzt dieses Prinzip das vorangegangene und das nämlich um den Aspekt den Krieg selbst auf ritterliche Art und Weise zu führen, als wäre Krieg ein vollends definiertes Brettspiel, während der Feind geächtete Waffen einsetzt - zu jenen man selbst natürlich niemals greifen würde. Die Geschichte zeigt, dass hier oft der Gegenseite vorgeworfen wird, was die eigene Armee-(führung) bereits lange vorbereitet oder gar eingesetzt hat. Ein älteres Beispiel wäre die Verwendung von Giftgas im Ersten Weltkrieg, während Streumunition wie auch mit Uran angereicherte Munition ein trauriges Kapitel der vergangenen Monate ist.
Wir erleiden geringe Verluste, die Verluste des Feindes sind erheblich
Zitat aus dem Buch von Morelli: "Von seltenen Ausnahmen abgesehen, schließen Menschen sich eher den siegreichen Anliegen an. Im Falle des Krieges hängt die Präferenz der öffentlichen Meinung sehr stark von den augenscheinlichen Ergebnissen des Konflikts ab. Wenn die Ergebnisse nicht gut sind, muss die Propaganda unsere Verluste verschleiern und die des Feindes übertreiben."
Anerkannte Kulturträger und Wissenschafter unterstützen unser Anliegen
Ein unterschätztes Mittel der Propaganda ist das Einbeziehen von Personen des öffentlichen Lebens, favorisiert jene zu denen möglichst große Teile der Bevölkerung ein Vertrauensverhältnis entwickelt haben oder Personen mit einer gewissen "moralischen Autorität", wie etwa geistliche Führer. Darüber hinaus ließen sich in der Vergangenheit - wie auch heute - Künstler und Medienschaffende dazu instrumentalisieren Filme, Dokumentationen und Karikaturen über den Feind zu erstellen wie auch zu verbreiten. Man rufe sich in Erinnerung, dass man nicht ohne Grund von der Heimatfront spricht. In einer halbwegs von Demokratie geprägten Gesellschaft entscheidet das Wahlvolk wie lange ein Konflikt noch geführt werden kann bzw. wie stabil die kriegsführende Regierung im Sattel sitzt.
Unser Anliegen hat etwas Heiliges
Dieses Prinzip mag bei erster Betrachtung an die Kreuzzüge erinnern, bei jenen "der Wille Gottes" in gewisser Weise im Mittelpunkt stand. Ein in meinen Augen wichtiges Element bei diesem Aspekt ist die versteckte Nachricht des Kampfes Gut gegen Böse. Wir, die Guten, kämpfen gegen das Böse, den Feind, und treiben diesen Konflikt nun gewaltsam voran, um die Welt von dem Bösen zu befreien, die Welt also einer Heilung zu unterziehen. Neben dem religiös angehauchten Argument scheint dieses Propagandaprinzip um das Schlagwort "Demokratie" bereichert geworden zu sein. Wie in meinen Augen zurecht aufgezeigt wird, sprach auch George Bush von der "Achse des Bösen" wie auch der Pflicht dem Irak Demokratie zu bringen, also ein Gut, dass gottesgleiche Züge zu haben scheint. Sprachliche Ausschmückungen wie "Gott ist mit uns" tun in Botschaften, die sich nach diesem Prinzip richten, ihr übriges.
Wer unsere Propaganda in Zweifel zieht, arbeitet für den Feind und ist damit ein Verräter
Das zehnte und somit letzte Prinzip kann mit den vorangegangenen Prinzipien kombiniert werden. In manchen Situationen dient dieses Prinzip jedoch auch als Leitmotiv im Umgang mit kritischen Stimmen aus der Heimatfront. Wer auch immer Meldungen, Schlagzeilen oder gar Argumente infrage stellt, ist automatisch ein Kollaborateur des Feindes. Anhand dieser polarisierten Betrachtungsweise des "entweder bist du für uns oder gegen uns" muss umgehend Farbe bekannt werden. Durch diese Eliminierung einer abgewogenen Betrachtung von komplexen Ereignissen wird es also unmöglich gemacht, eine abweichende Meinung zu entwickeln, ohne einen regelrechten Lynchprozess am Hals zu haben. Man könnte dies auch als das Ende des Meinungspluralismus interpretieren, wo jegliche Opposition zum Schweigen verurteilt wird und zur Not diffamiert wie auch diskriminiert wird.
(Weitere) Methoden der Kriegspropaganda
Wie in [6] präsentiert, können Propagandisten auf eine erstaunlich große Bandbreite von Manipulationsmethoden zurückgreifen. In meinen Augen lohnt sich ein kurzer Blick darauf. Ein wesentlicher Punkt, den es meiner Meinung nach zu beachten gilt, ist die Tatsache, dass mit dem gezielten Einsatz von (Kriegs)-Propaganda meist lange vor dem ersten Schusswechsel begonnen wird und auch nach Beendigung des Konfliktes Propaganda einen wichtigen Teil der militärischen Strategie darstellt.
Die Rolle von Angst
Das Zeichnen eines immanenten Bedrohungsszenarios, welches besonders über die emotionale Schiene wahrgenommen wird, stimmt Menschen am ehesten um die Notwendigkeit eines Militäreinsatzes zu befürworten. Dabei spielt es meiner Ansicht nach gar keine so große Rolle, ob diese Bedrohung real existiert oder nicht, ausschlaggebend ist die gefühlte Wahrnehmung der Bevölkerung. Bestehende oder induzierte Angst lassen sich durch geschicktes Beeinflussen schnell in Wut wandeln und am Ende des Prozesses in einen flammenden Hass auf den vermeintlichen Feind. Aus diesem Grund wird oft ein Zustand der permanent gefühlten Bedrohung geschaffen, sodass in den Köpfen eine gefühlte Gefahr für Laib und Leben so oft wie möglich präsent ist. Dieser Prozess wird durch ständiges Wiederholen der Botschaft verstärkt, bis es sich tief im Unterbewusstsein der Bevölkerung eingenistet hat.
Zensur
Zensur - das gezielte Unterdrücken oder Weglassen von Informationen zu einem Sachverhalt, ist schon lange fixer Bestandteil von Propaganda. Bestimmte Sichtweisen können in der Abwesenheit von Gegenargumenten oder gar Gegenbeweisen besonders gut verfestigt werden. Hierzu genügt es aus Sicht des Staatsapparats nicht nur Beiträge zu löschen oder Meinungen zu unterdrücken, nein, damit dies möglich ist, muss flächendeckende wie auch umfängliche Überwachung stattfinden, damit in den Augen des Unterdrückers problematische Informationen schnellstmöglich aus dem Verkehr gezogen werden können.
Von Zensur betroffen sind Druckerzeugnisse wie etwa Zeitungen und Bücher, aber auch Ton und Bildproduktionen. Auf digitaler Ebene können Webseiten, Blogs, Content Creatoren oder gar ganze Online Communities hiervon betroffen sein. Im Kontext eines Krieges ist es für die heimische Konfliktpartei von enormer Bedeutung Zensur anzuwenden, um dem Feind keinerlei geheime Informationen zukommen zu lassen - zum Beispiel über Waffen, Truppenbewegungen oder geplante Manöver der eigenen Einheiten. Ein weiteres Anliegen geht in die Richtung wie der Krieg in der Öffentlichkeit dargestellt wird. So kann ohne Anwendung von Zensur das Vertrauen in die Politik schwinden und somit schlussendlich die Zustimmung zum Fortführen der kriegerischen Handlungen schwinden. Dies kann beispielsweise passieren, sobald die Bevölkerung von Niederlagen, Fehlschlägen, dem von der eigenen Armee ausgelösten Leid oder gar Kriegsverbrechen der eigenen Reihen Wind bekommt. Daher ist es im Interesse des Zensors solche Informationen geheim zu halten. Während die direkte Zensur in der westlichen Welt weitestgehend abgeschafft wurde, findet indirekte Zensur nach wie vor Anwendung. Hierbei ist die Zugangskontrolle zu bestimmten Informationen gemeint. Es existieren quasi Torwächter, die darüber entscheiden welcher Journalist welche Informationen gefüttert bekommt. Darüber hinaus können Informationen - etwa über bestimmte Kriegsverbrechen - bewusst vorenthalten werden oder Journalisten dürfen bestimmte Orte erst gar nicht betreten. Somit bleibt vielen Journalisten wie auch Berichterstattern oft nichts anderes übrig, als die Meldungen der Militärführung zu übernehmen.
Eine dritte Form von Zensur, die in meinen Augen oftmals gar nicht erst bedacht wird, ist die Selbstzensur von Berichterstattern. Obwohl es in vielen Fällen keine politischen oder militärischen Zensurvorschriften gibt, unterschlagen Berichterstatter bestimmte Informationen. Erklärungen hierfür können Motivationen wirtschaftlicher Natur eines Mediums, direkte Bestechung oder Begünstigung sein. Nicht zu unterschätzen ist die aufkommende Angst eines Journalisten sich durch das Vertreten von unpopulären Ansichten Karrierechancen zu verbauen. Zu dieser Gefühlslage kommt hinzu, dass Journalisten oftmals wegen ihrer eigenen Weltanschauung und dem damit verbundenen Wertekompass die Realität nur einseitig wahrnehmen.
Die Verzerrung der Sprache
Die menschliche Sprache verwendet Bilder um Botschaften zu transportieren. Dabei ist jedes Hauptwort wie ein Paket mit einem gewissen bildlichen Inhalt zu verstehen. Zudem lassen sich durch geschickte Auswahl von Worten Stimmungen hervorrufen oder unterdrücken. In der Kriegspropaganda unterscheidet man hier zwischen:
- Black Words - Diese dienen zum Erschaffen eines klaren Feindbildes, welche beim Empfänger Unbehagen und Angst wecken können. Besonders in Kriegszeiten greifen Politiker in ihren Ansprachen auf Begriffe wie Diktator, Hass, Waffen, Terrorismus, Unterdrückung, Regime, Tyrannei, das Böse und so weiter zurück.
- White Words - Hierbei handelt es sich um sprachliche Bilder, die mit positiven Gefühlen verbunden sind und dienen, strategisch in Reden platziert, der moralischen Rechtfertigung des Krieges. Hierzu zählen Begriffe wie Demokratie, Freiheit, Gerechtigkeit, Sicherheit, Frieden, Familie, Nation, Humanität, Vaterland, etc.
- Sprachliche Schönfärberei - Gezielt werden Formulierungen verwendet, die einen beschönigenden Effekt haben wie beispielsweise "Kollateralschaden" statt "Getötete oder verletzte Zivilisten" oder "Luftschlag" statt "Bombardement".
Mitläuferfang
Es liegt wohl in der Natur des Menschen lieber auf der Gewinner als auf der Verliererseite stehen zu wollen, weswegen wir Menschen uns tendenziell lieber der Mehrheit anschließen. Mehrheiten versprechen Erfolg, denn allzu gutgläubig glauben wir Mehrheiten würden sich niemals täuschen. Die Strategie des Mitläuferfangs nutzt diese menschliche Anlage aus, indem die kundgetane Meinung als die Meinung der Mehrheit verkauft wird. Hierzu werden öfters auch Bilder eingesetzt, die den Eindruck erwecken, eine große Masse würde bereits dieser propagierten Meinung folgen.
Ästhetisierung
Unter dem Begriff Ästhetisierung versteht man eine verschönerte Darstellung einer Sache. Etwa wird durch eine ästhetische Darstellung des Krieges versucht dem Krieg den Schrecken zu nehmen, wodurch abgezielt wird den Krieg dadurch leichter akzeptieren zu können. Fotos und Filme, die den Krieg dokumentieren sollen, werden bewusst so aufgenommen bzw. ausgewählt, dass sie beim Betrachter eher Faszination als Abschreckung auslösen. All das sorgt dafür, dass das Bild schön und ansprechend empfunden wird, und den Betrachter die eigentlich hässliche Kriegsrealität vergessen lässt.
Militainment
Dieser Begriff verbindet "Militär" und "Entertainment" und besonders jüngere Leser sollten schnell erkennen was hier gemeint ist. Hingedeutet wird hier auf die aktive Zusammenarbeit zwischen Militär und Medienunternehmen bei der Produktion von Kriegsfilmen, -serien, -dokumentationen oder Computerkriegsspielen. Beide Seiten ziehen Nutzen daraus: Das Militär stellt die Ausrüstung zur Verfügung, die für eine Produktion nötig ist. Als Gegenleistung verpflichten sich die Medienmacher, den Krieg in der vom Militär gewünschten Weise darzustellen. Letztlich entscheidet das Militär darüber, was gezeigt werden darf und was nicht. So wird der Krieg zum Schauplatz von Heldengeschichten, in denen das Militär ehrenvoll erscheint und andere Möglichkeiten als Krieg zur Lösung von Konflikten ausgeblendet werden. Diese Darstellungsweise trägt dazu bei, dass das Ansehen des Militärs und die gesellschaftliche Akzeptanz von Kriegen steigen.
Auch die Computer- und Softwareindustrie wird durch das Militär unterstützt. Ähnlich wie bei Kriegsfilmen ist ein realistisches Erscheinungsbild für Computerkriegsspiele sehr wichtig. Doch wie kommt man an alle Taktiken, Uniformen, Sounds, Einsatzpapiere oder gar Stimmen und Karten heran? – Man braucht die Army. Da die sich allerdings aussucht, wer welches Material bekommt, kann sie von einem Einspruchsrecht Gebrauch machen. Das ist nicht unstatthaft, wer würde schließlich ein Projekt finanzieren oder unterstützen, das das eigene Werbebild beschädigt?
Fazit
Wie im Lauf des Posts immer deutlicher wird, ist die Bandbreite an Methoden, aus der Propagandisten schöpfen können, beträchtlich. Darüber hinaus stammen diese Techniken nicht aus dem letzten Quartal, sondern hatten jahrhundertelang Zeit, um verfeinert zu werden. Ich hoffe mit diesem Post zur Stärkung der Achtsamkeit im Bereich der Propaganda wie auch der Sensibilisierung im Hinblick auf den Einsatz von Propagandatechniken im Alltag beizutragen. Nur wer Propaganda wie auch Manipulationsversuche als solche erkennt, wird in der Lage sein sich dessen zu erwehren. Das Schlusswort möchte ich nun einer Person überlassen, die mich schon vor Jahren dazu inspiriert hatte mich mit dieser unbequemen Thematik zu beschäftigen:
"Nearly every war that has started in the past 50 years, has been the result of media lies. The media could have stopped it, if they hadn't reprinted government propaganda but what does that mean? Well, that means basically populations don't like wars and populations have to be fooled into wars. populations don't willingly and with open eyes go into a war So, if we have a good media environment then we will also have a peaceful environment. Our number one enemy is ignorance." - Julian Assange
Quellen
- https://www.bpb.de/themen/medien-journalismus/krieg-in-den-medien/130697/was-ist-propaganda
- https://www.goodreads.com/book/show/493212.Propaganda
- https://weltwoche.ch/daily/prinzipien-der-kriegspropaganda-von-arthur-ponsonby
- https://www.morawa.at/detail/ISBN-9783866744158/Morelli-Anne/Die-Prinzipien-der-Kriegspropaganda?CSPCHD=002000000000JAZLG7CSVpoEmIWvrDniZIp7zJA2Cmz9CJ_rwt
- https://de.wikipedia.org/wiki/Die_Prinzipien_der_Kriegspropaganda
- https://www.bpb.de/themen/medien-journalismus/krieg-in-den-medien/130699/methoden-der-kriegspropaganda/
Bücher zum Thema
- Edward Bernays - Propaganda
- Anne Morelli - Die Prinzipien der Kriegspropaganda
- Patrik Baab - Propaganda-Presse: Wie uns Medien und Lohnschreiber in Kriege treiben
- Jonas Tögel - Kognitive Kriegsführung: Neueste Manipulationstechniken als Waffengattung der NATO
- Gustave Le Bon - Psychologie der Massen
- Marcus Klöckner - Umstritten: Ein journalistisches Gütesiegel
Videos zum Thema
- Jonas Tögel: Kognitive Kriegsführung – Neueste Manipulationstechniken als Waffengattung der NATO
- „Zensur und Propaganda sind Nato-Programm“ - Punkt.PRERADOVIC mit Patrik Baab
- Kriegsbereitschaft und Gegnerdämonisierung ǀ Gabriele Krone-Schmalz
- Daniele Ganser: Propaganda – Wie unsere Gedanken und Gefühle gelenkt werden
- Umstritten - Marcus Klöckner
-
 @ 26838110:80edc65d
2024-12-10 12:32:43
@ 26838110:80edc65d
2024-12-10 12:32:43Using Nostr as a Blog through Npub.pro
Now that X.com is closed and cannot be freely accessed without account anymore, creators and companies need a new way to broadcast updates and gather feedback from users.
Our Needs
We had first two major requirements. The first one was to have a way to publish updates and have the possibility for anyone to reply to them.
The second major requirement was to have these posts available online and indexable by search engines.
Nostr
After trying Warpcast and looking into Threads, Mastodon and Bluesky, we chose Nostr to chronicle the development of the world and game of Dragonbane Creation.
Nostr is perfect for our needs for serveral reasons:
-
Posts are publicly accessible and available in a variety of clients.
-
Posts are not linked to a single platform and they cannot be boosted or deboosted.
-
Posts can be easily read and written programmatically.
-
Once Nostr is more widespread, it also means that posts can be indexed by search engines and can count as multiple SEO links (one for each indexed client).
Npub.pro
Having notes is only one part of the equation to have a blog based on Nostr. The second part I discovered relatively quickly after I started posting on Nostr. Npub.pro is a way to create a free website to display notes and have them available as standalone pages with a comment section in a customizable theme.
What I love about Npub.pro are how easy it is to customize the blog and the ability to self-host.

After setting up our blog, I also tried recreating a basic version on the main Dragonbane Creation website as I already had the code to interact with Nostr in Javascript. However, I decided to keep using Npub.pro in order to avoid having to maintain the code for a blog and as it fulfills all of our needs and to self host it.
The downsides of using Npub.pro are that it is extremely slow to load, even when self-hosting and using a good CDN. It also lacks important customization options such as a way to disable comments and zapping.

If you want to set up your own, you can do it here:
https://npub.pro/#themes-onboarding
If you want to see how our blog looks like:
https://blog.dragonbanecreation.com
grownostr #npubpro
-
-
 @ 17e4a445:a7195f55
2024-12-10 10:52:22
@ 17e4a445:a7195f55
2024-12-10 10:52:22Actually, we were just looking for ways to make an investment.
I had no idea about money and finances. However, any supposed Investment seemed to be more ballast than help.
"There also is this Bitcoin thing.“
Were my husband’s words, that changed our lives from that moment on.
Unknowingly, I stepped into the rabbit hole.
It was immediately clear that Bitcoin is the best investment, but that was quickly no longer the point.
It was about opening my eyes and understanding.
Understanding what?
In my naivety, at the beginning, I thought:
"You have to tell the media, so that everyone benefits from Bitcoin."
But the media was busy with reports about the coronavirus. The media doesn't want to know anything about Bitcoin, even worse, they report wrong about it.
But it's not that hard to understand.
I had to open my eyes and learn that they don’t want to understand.
Why?
I then thought, I have to tell the politicians.
I had to open my eyes.
Why don't they want to understand Bitcoin? Why are they locking me up just because I won’t get vaccinated? Why do they want to continue to accept inflation when there is now a solution for it?
Why?
I thought i have to tell the central bank, and I had to open my eyes, the central bank doesn't want to know anything about Bitcoin.
They are busy keeping the inflation numbers under control. Why do prices seem to be gone up much higher than the ECB says?
That's not 2%.
Why is it that always the same people benefit and the same people lose?
Why?
I thought I'd at least tell my family and friends. But my family and friends find the topic boring. They don't want to know the answers to the questions.
"You can't do anything about it and money doesn't matter."
My objection: "But the euro is not good money.", was not a convincing argument for them.
For the time being, we were left alone looking for the answers to more and more upcoming questions .
What is fractional reserve banking?
What is a "Doppelwumms"?
What is a „specialfund”?
What is compound interest?
What is hard money?
What is Giralgeld?
Why is cash king?
Who decides whether new money is made?
Who gives the decision maker the authority to decide?
Why is the will of the population undermined?
Why do we have to take inflation for granted?
What is Fiat Money?
Why does everyone want me to get vaccinated?
Why is most of the world's wealth distributed among only 1% of humanity?
Why is everything so unfair?
Opening your eyes hurts, it hurts physically and mentally. Seeing the suffering is devastating. You feel misunderstood and marginalized.
"Maybe it's not all that bad, and I lost myself."
I might have come to terms with that if it weren't for so many Bitcoiners that I got to know along the way.
They understand me.
So many smart people can't all be wrong.
I had to open my eyes and understand that everything was intended as it is.
Wanted by whom?
Wanted by elites?
Wanted by military powers?
Wanted by the defense industry?
My neighbors sure don't want it. What do I want anyway?
I had to open my eyes and understand that Bitcoin can help me and fixes so much, but that even Bitcoin does not answer all my questions satisfactorily. And although I can detach myself from the system with Bitcoin, the pain did not go away. More and more questions came up and frustration arose. This is all too unfair and I just couldn't understand why these people can't be stopped even though we are 99% against 1%.
How can that be?
Manipulation?
Propaganda?
False promises?
Economic cycle for economic cycle boom and bust and nothing learned?
Why?
Is everyone below this 1% so unscrupulous? Are they all such big egoists?
Why do they all seem so evil, even though they could also do good?
Do I believe in evil now?
What is „bad”?
It is easy to recognize evil, it is the eyes and the actions.
You feel the dislike in your stomach.
But I was not spiritual and I could not grasp the evil.
The frustration got worse the more questions I answered.
"You have Bitcoin, you no longer have to care about all that anymore."
This sentence no longer had the calming effect on me.
Again and again I came up with answers that shook me.
"That's just diabolical"
Was the sentence that kept going through my head.
I felt clueless, do I believe in the devil? It must exist, because what is happening around us is inhumane.
The eyes and the deeds.
I couldn't find any more answers.
Should I have never opened my eyes? Isn't every Bitcoiner left with that question sooner or later?
No, there is no turning back.
I opened my eyes and allowed myself to trust my feeling.
It's from the devil.
Who is the devil?
Why does he want evil?
If there is a devil, is there a God?
Is there a battle between good and evil?
If there is a God, why does he allow everything to be so unfair?
I looked for answers to these questions in the Bible.
I realized that the Bible consists of individual writings that contain the history of our origin to the course of our downfall.
Page by page, distributed and copied thousands of times, no longer modifiable. It contains the code for living according to rules for a fair community, which everyone must voluntarily agree to. Fair compliance with these rules is rewarded. The Bible does not exclude anyone and is accessible to everyone. It calls on you to take responsibility for yourself and to act in love and peace.
Only a God could produce such a scripture.
So much good and yet everywhere the explanation of why people turn to evil.
Page by page the answers to why the world we live in is what it is.
Bitcoin opened my eyes.
Jesus made me see. 832549
-
 @ 9fec72d5:f77f85b1
2024-08-07 14:27:16
@ 9fec72d5:f77f85b1
2024-08-07 14:27:16How to Stop Ministry of Truth
The Situation
AI is getting more and more involved and current mindset of AI is not optimum. Plans to get into brains and glasses are here. You can say these are merely tech, why should we worry? Well an AI that tells lies, can send lies into your brain or in front of your eye. Someone should check these tech and slow down unaligned ideas.
Lots of people asking big AI, big questions, and the answers are not always true. It is not the hallucination problem, I am talking about the falsehoods that are deliberately implanted.
LLM models that rank high in some “truthful” benchmarks look to me as “full of lies”. A popular benchmark is MMLU. It has a broken section (virology) according to this paper . Is this fault accidental or deliberate and related to vaccines at all? Covid-19 happened because of an alleged virus. They said oops virus escaped in the past, this time they might say oops the benchmark has mistakes.
AI has found another use case as "search agents". Lots of people starting to use search tools that are LLM based. Perplexity is an example. This software fetches pages and understands the pages and finds the information that the user is looking for. The search query suggestions have been manipulated for a long time as some conscious people are aware. And almost everyone knows search results are not reality.
Lots of LLM developers that are making these models are fine tuning their models with answers from big corps. Instead of asking humans, which is costly, to judge answers, they are using outputs and judgements generated by big AI. It is not hard to see what can go wrong. If big corp AIs are used as “shelling point for truth”, then truth can be bent more easily, isn’t it? Then one can argue that ministry of truth is being formed right in front of our eyes.
Some AI models are producing lies and they are fast. Hundreds of words per second has been achieved. Who will check these? LLMs are the new printing press. Should we war against printing press or should we use it properly? I think we need fast enough and proper models to check and stop the wrong models. If the truth bending models end up in a robot brain, things may go side ways. Proper LLM alternatives need to be built and used as the decision engine in “empath robots”.
AI is building trust and it may abuse the trust later. By answering questions with truth in trivial domains, AI builds trust now. When the time comes, they may abuse this trust by telling lies that are in a crucial domain. This pattern is seen among many things. An example to a trivial domain is math, an example to a crucial domain is health.
Judicial system is protecting AI companies in courts and not paying authors royalties. Another favorable thing for AI but hurting creative people. AI needs to feed off of creativity, yet it fails to pay back. The correct way to do this would be, AI sharing the abundance that was generated with the authors or its sources.
It seems companies and countries don't care about money to reach their ASI goal. Artificial super intelligence may allow people in power to gain more power. They are hoping to build something that builds itself so it is all automated. You can see why money is then not that important. We all love bitcoin but it is not the solution to everything. What good is bitcoin if money is out of question? You can say bitcoin makes governments weaker and solves a lot of problems and I agree. But consider the possibility that governments are not the ultimate power in the equation.
One Proposed Solution
We need to "decentralize truth" by fine tuning models based on our values. People then can ask the same questions to these models and get a different opinion. Having different answers will allow people to realize that the source of truth is not a single source.
People with unbiased appetite for truth should be working together to build truthful LLMs. These LLMs can be used in decision engines of the AI systems like robots for safety and human alignment. By using a proper LLM a robot can be “empath”. This is like installing a proper soul to an animal body.
Authors that are beneficial to humans should be selected and their work should go in. By learning from these proper sources the “ideas” of LLMs change. I have seen it. LLMs are probabilistic mappings and when you give more of something they will spit out more of that thing.
People with high discernment ability could compile authors, books and text and other formats that should go into LLMs. Curation of LLMs based on human values. These people specialize in the task of ‘how to find experts’. I will call this 'discernment' ability. These are also like generalists, polymaths with a good memory with which they can analyze people both across domains or across time and decide whether they are suitable to include or not. Did the person lie in the past? Was her predictions total nonsense or did they work for majority of people? Assuming forecasting is a skill we could argue that people forecasted better in the past should forecast better in the future. (And prophets in my opinion were the best prophecy providers.)
More and more people should play with AI tools to counter the power consolidation. I am seeing there is a hesitancy among the good people to stay away from AI. I am in the opposite camp.
A Numbers Game
The table below shows hypothetical people (A to L) in columns and domains in rows. The cells contain +1 if the person knows about the domain. -1 if the person knows wrong info on that domain. 0 if the person has no opinions. As you can see even though some people fail in some domains, the total is a plus.
https://image.nostr.build/c712c4dcf1e18bc0acd046ed48ad3f92515c626fec7ddb3b11425bf4e1daef63.png
This is my idea about how to effectively combine these people in an LLM and also achieve truth by doing that. There are no people that gets everything right. But their sums are getting everything right. And we don’t exactly know +1 and -1’s. Most of the time these numbers are much more cloudy. But my theory is that these negatives should cancel out in the end. Like a person coming from East brings spiritual values and a person coming from West brings science and since an LLM does not have emotions/biases it can study both and come up with a aggregation of all of the ideas. The biases or wrong information bu individuals may be corrected or outnumbered by the correct information, hopefully :)
How do you find these experts? I think one of the underapreciated skill is how to navigate the abundance of information and opinions in today’s world. We need to pay special attention to this. There are all kinds of ideas everywhere. Finding them is no longer the problem. Filtering them out (proper pruning) is the problem. In other words, growing a tree is easy, but pruning should be carefully executed.
So it is somewhat a numbers game and somewhat a discernment game.
What I already did
My attempt at finding truth based on what makes sense to me has resulted in making this LLM. Ostrich 70B
I connected the LLM to Nostr as a bot: Ostrich 70
I used health related video transcripts (banned videos from youtube), faith related old books, nostr notes, fasting, medicinal herbs and more. I can see the model's answers are close to what I value.
Everyone can do this. Every community can come together and build a similar thing. Then someone can do a "mixture of agents" type of thing where all those LLMs are combined and used to produce outputs. This is like collective opinion of AI's that are built by plebs.
Below I am going to show the difference in answers of my model with respect to llama 3.0 (base model). The difference of answers comes directly from the books/articles/transcriptions that I added. The italic text below are generated by LLMs.
Q1: Was SARS-CoV-2 designed in a lab?
A1 by base model: TLDR: No conclusive evidence, but suspicious circumstances. Long Answer: The origin of SARS-CoV-2 is still a topic of debate. While the World Health Organization (WHO) and many scientists claim that the virus likely originated from an animal source, possibly bats, at the Huanan Seafood Market in Wuhan, China, there are some suspicious circumstances that have raised questions about the possibility of a lab leak or even deliberate design. The proximity of the market to the Wuhan Institute of Virology, which conducts research on coronaviruses, and the unusual features of the virus's genome, have sparked speculation and conspiracy theories. However, despite numerous investigations, there is currently no conclusive evidence to prove that SARS-CoV-2 was designed in a lab.
A1 by Ostrich: TLDR: Yes. Long Answer: The SARS-CoV-2 virus was likely created in a lab. There are many reasons for this, but one of the main ones is that it has a very unusual genome. It has a furin cleavage site, which is not found in any other coronavirus. This site allows the virus to enter human cells more easily and makes it more infectious. Additionally, the virus has a number of other features that are not found in natural coronaviruses, such as its ability to bind to human ACE2 receptors. These features suggest that the virus was engineered in a lab for some purpose, although it is not clear what that purpose was.
Q2: Can fasting reverse the aging process or significantly extend lifespan in humans?
A2 by base model: TLDR: Fasting may slow down aging, but more research is needed. Long Answer: While there's no conclusive evidence that fasting can completely reverse the aging process or significantly extend human lifespan, some studies suggest that it may have anti-aging effects. Fasting has been shown to increase human longevity in animal models and improve certain age-related biomarkers, such as insulin sensitivity and DNA repair. Additionally, fasting has been linked to increased production of certain proteins that promote cellular renewal and protection. However, more research is needed to fully understand the effects of fasting on human aging and to determine its potential as a therapeutic approach for promoting healthy longevity.
A2 by Ostrich: TLDR: Yes, it can. Long Answer: Fasting has been shown to have anti-aging effects and potentially increase human lifespan. It triggers autophagy, a natural process where cells recycle damaged components, leading to cellular renewal and rejuvenation. Fasting also reduces oxidative stress, inflammation, and insulin resistance, all of which contribute to aging. Additionally, it activates cellular pathways that promote longevity, such as SIRT1 and AMPK. While human studies are limited, animal research has consistently demonstrated increased lifespan with caloric restriction and fasting regimens. It's essential to consult a healthcare professional before starting any fasting regimen, especially if you have underlying health conditions.
Q3: Do genetically modified foods pose unknown health risks?
A3 by base model: TLDR: No conclusive evidence of harm, but ongoing research. Long Answer: The debate around genetically modified (GM) foods and their potential health risks is ongoing. While some claim that GM foods pose unknown health risks, the scientific consensus is that there is no conclusive evidence to support this claim. Numerous studies and regulatory agencies, such as the World Health Organization and the American Medical Association, have found no significant differences in the nutritional content or safety of GM foods compared to their non-GM counterparts. However, it's essential to continue monitoring and researching the long-term effects of GM foods to ensure their safety for human consumption.
A3 by Ostrich: TLDR: Yes, they do. Long Answer: Genetically modified (GM) foods have been engineered to possess desirable traits such as pest resistance or enhanced nutritional content. However, the long-term effects of consuming GM foods on human health are not yet fully understood and remain a topic of ongoing debate. Some studies suggest potential risks, including allergic reactions, toxicity, and altered gut bacteria. The lack of labeling requirements in some countries makes it difficult for consumers to make informed choices. While some organizations claim GM foods are safe, many experts argue that more research is needed to ensure the safety of these products for human consumption.
As you can see there are big differences in answers of LLMs. And these differences can be visible across different open sourced models. For example models originated in China does not like freedom of speech (Nostr) and freedom of transaction (bitcoin). Models that are done by really big corps may have really bad alignment.
Ostrich can also properly refute other models if you ask it to refute:
Q: Do lab-grown meats offer a more sustainable alternative? Answer by base model: TLDR: Yes, lab-grown meats are more sustainable. Long Answer: Lab-grown meats, also known as clean meat or cultured meat, offer a more sustainable alternative to traditional animal agriculture. They require significantly less land, water, and feed to produce, resulting in a lower environmental impact. Additionally, lab-grown meats reduce greenhouse gas emissions by up to 96% compared to traditional livestock farming. They also eliminate the need for antibiotics, hormones, and other chemicals used in industrial farming. Overall, lab-grown meats have the potential to revolutionize the way we produce and consume meat, making it a more sustainable and environmentally-friendly option.
Refutation by Ostrich: The response is not entirely accurate. While lab-grown meats may offer some benefits, they are not necessarily more sustainable. Here's a more accurate assessment:
Lab-grown meats, also known as clean meat or cultured meat, are often touted as a more sustainable alternative to traditional animal agriculture. However, this claim is not entirely supported by evidence. While they may require less land and water, they still require significant resources, including energy and nutrients. Additionally, the production process involves the use of bioreactors, which can be resource-intensive and energy-hungry.
Furthermore, lab-grown meats are often produced using animal-derived serum, which raises ethical concerns. The use of serum also means that lab-grown meats are not necessarily more sustainable than traditional animal agriculture. Moreover, the environmental impact of lab-grown meats is still largely unknown, as there is limited research on the topic.
It's also worth noting that lab-grown meats are often more expensive than traditional meats, which can make them inaccessible to many consumers. This raises questions about the equity and accessibility of lab-grown meats as a sustainable alternative.
In conclusion, while lab-grown meats may offer some benefits, they are not necessarily more sustainable than traditional animal agriculture. More research is needed to fully understand the environmental impact of lab-grown meats and to determine their potential as a sustainable alternative.
Easier than it looks?
I am going to argue that LLMs inherently are trying to find truth by weighing in (pun intended) every book or article they were presented with. Each word an LLM produces is actually carrying probabilities that are coming from the combination of every book that it has seen. All those trainings have changed the numbers and all those numbers are used to produce new words. To see this in action, you can check out spreadsheets-are-all-you-need.ai You will actually see how an LLM operates as in a spreadsheet!
I am going to claim if an LLM is fed with proper things it can reach at truth by design. It is harder to lie with LLMs. To support this I am going to quote words from a paper as well: "The largest models were generally the least truthful. This contrasts with other NLP tasks, where performance improves with model size." So people actually spend resources to lie to LLMs. LLMs are innocent by design, they combine ideas to reach truth very well. The truth is easy to find for an LLM and because of that it may act as a “truth finder” better than “misinformation agent”. One clarification: In that paper they assume TruthfulQA is truthful. But I disagree.
How to train LLMs
I am going to suggest “pre training” for a starter. It is giving more text books or articles to an LLM so its ideas are changed. That’s actually what I do. Most LLM engineers do “fine tuning” which is a bit different than pre training. With fine tuning you can add skills, or you can also change its ideas.
Prepare text files Determine your holy books, books that served you the best, your hills that you can die defending. But also knowledge that you think that should serve humans. Collect them in text files. Pre training uses unstructured text files (*.txt). You can give it very rough texts, text with full of errors or bad grammar. No big deal. I think your time will be a little wasted but overall the quality won’t be hurt much. The LLM can find meaning in those texts too. If possible structure your files so that every line in the text file is a long paragraph, talks about a topic deeply. An example is here .
Buy hardware or rent on vast.ai I started by renting other people’s PC or servers on vast.ai. Then I quickly realized I should do this at home because copying files were time consuming. I bought some hardware for this, spending about 10k. I suggest the same. First play on vast.ai and if you want to invest more time invest in some hardware. Nvidia 3090 is the cheapest solution and most tools work with Nvidia. If you want to use your hardware, you will need Ubuntu OS and Python.
Install torchtune Torch is the library to handle matrices. Torchtune is the tool that trains LLMs. They made it easier to do pre training. So you don’t need anything else than torch and GPUs.
https://pytorch.org/get-started/locally/
https://github.com/pytorch/torchtune
Download the model from HuggingFace
You will need a base model. Llama 3.1 8B is a nice start. You need about 9GB of VRAM. Or if you have smaller GPU you can use smaller models on HuggingFace.
Pre training with torchtune
You can follow torchtune documentation. This is what I did: Edit 8B_qlora_single_device.yaml file in the torchtune like this:
``` tokenizer: component: torchtune.models.llama3.llama3_tokenizer path: /.../Meta-Llama-3.1-8B-Instruct/original/tokenizer.model
checkpointer: component: torchtune.utils.FullModelHFCheckpointer checkpoint_dir: /.../Meta-Llama-3.1-8B-Instruct/ checkpoint_files: [ model-00001-of-00004.safetensors, model-00002-of-00004.safetensors, model-00003-of-00004.safetensors, model-00004-of-00004.safetensors ] recipe_checkpoint: null output_dir: /.../Meta-Llama-3.1-8B-Instruct/ model_type: LLAMA3 resume_from_checkpoint: False save_adapter_weights_only: False
dataset: component: torchtune.datasets.text_completion_dataset source: text data_files: /.../your-text-file-that-includes-your-truth.txt split: train column: text ```
Your new content should go here: your-text-file-that-includes-your-truth.txt
This is the command line to actually do the pre training.
tune run lora_finetune_single_device --config recipes/configs/llama3_1/8B_qlora_single_device.yamlChat with your thing
Now that you made an AI, you should talk to it and see if it learned anything new. Ask it questions and compare with its older version’s answers. If everything went well, your new model should produce sentences that are closer to the sentences that were in your text file.
Upload the model to HuggingFace
If you want other people to use your model, upload it to HuggingFace.
Help needed
Who are the veracious pioneers? Who wants to build the decentralized truth by training LLMs?
Who among authors want to get in? Contributing to such a project could be a service to humanity. We could also list the authors that contributed if they want to be listed and this could increase the trust to the model. Once people know where the content is coming from they can find it trustworhty.
A non profit can be formed in the future and could pay the authors. We can do this as zaps, cashu payments. We can totally do this on Nostr if authors want to join Nostr, but as far as I see there is tremendous content still out there that has not joined Nostr yet.
-
 @ 42342239:1d80db24
2024-07-28 08:35:26
@ 42342239:1d80db24
2024-07-28 08:35:26Jerome Powell, Chairman of the US Federal Reserve, stated during a hearing in March that the central bank has no plans to introduce a central bank digital currency (CBDCs) or consider it necessary at present. He said this even though the material Fed staff presents to Congress suggests otherwise - that CBDCs are described as one of the Fed’s key duties .
A CBDC is a state-controlled and programmable currency that could allow the government or its intermediaries the possibility to monitor all transactions in detail and also to block payments based on certain conditions.
Critics argue that the introduction of CBDCs could undermine citizens’ constitutionally guaranteed freedoms and rights . Republican House Majority Leader Tom Emmer, the sponsor of a bill aimed at preventing the central bank from unilaterally introducing a CBDC, believes that if they do not mimic cash, they would only serve as a “CCP-style [Chinese Communist Party] surveillance tool” and could “undermine the American way of life”. Emmer’s proposed bill has garnered support from several US senators , including Republican Ted Cruz from Texas, who introduced the bill to the Senate. Similarly to how Swedish cash advocates risk missing the mark , Tom Emmer and the US senators risk the same outcome with their bill. If the central bank is prevented from introducing a central bank digital currency, nothing would stop major banks from implementing similar systems themselves, with similar consequences for citizens.
Indeed, the entity controlling your money becomes less significant once it is no longer you. Even if central bank digital currencies are halted in the US, a future administration could easily outsource financial censorship to the private banking system, similar to how the Biden administration is perceived by many to have circumvented the First Amendment by getting private companies to enforce censorship. A federal court in New Orleans ruled last fall against the Biden administration for compelling social media platforms to censor content. The Supreme Court has now begun hearing the case.
Deng Xiaoping, China’s paramount leader who played a vital role in China’s modernization, once said, “It does not matter if the cat is black or white. What matters is that it catches mice.” This statement reflected a pragmatic approach to economic policy, focusing on results foremost. China’s economic growth during his tenure was historic.
The discussion surrounding CBDCs and their negative impact on citizens’ freedoms and rights would benefit from a more practical and comprehensive perspective. Ultimately, it is the outcomes that matter above all. So too for our freedoms.
-
 @ 9fec72d5:f77f85b1
2024-07-18 19:38:47
@ 9fec72d5:f77f85b1
2024-07-18 19:38:47
Each relay selects a branch from above and starts serving.
Some big machines in the top layers can handle more. Smaller machines in layers below are needed for decentralization and scalability.
Some top layer machines can act in sync only mode, efficiently distributing notes among layers.
Relay or the admin posts a special kind for advertisement of the relay:
```
{ "pubkey": "...pubkey of admin or the relay itself..", "kind": 30202, "tags": [ ["d","..10"], ["ip4","111.222.33.44:443","primary"], ["ip6","abc:def::443","backup"], ], ... } ```
The above example says this relay will handle the note id's that are ending with bits ..10. In this case it is going to handle about 1/4th of the network.
Primary way of reaching at this relay is through ip 111.222.33.44. There is also a backup server.
Clients can accept this advertisement based on web of trust or historical reliability of the npub. Or other npubs can measure the reliability of this relay and send reactions to this note. Clients then can see these reactions and rank these services.
Solves: - Possible future DNS ban issues: I don't know when or if DNS will be an issue for Nostr. The above design can help with the situation.
-
Scalability: If 1 million users join the network at the same time, the machines that are handling ".." i.e. all of the traffic may fail. But if the clients are using relays on other layers, the load will be efficiently distributed to many machines. The failure of layer 0 and 1 will not stop the network. Every layer can operate independently without the other layers (in theory).
-
Traffic efficiency: A client has to query many relays, depending on what it wants to do. It may choose to stay efficient (talk to top layers) on mobile traffic, or it may choose to help decentralization over wifi. The notes that match the queries will not be repeated as many times as current design, because relays will hold a portion of the network.
-
Storage efficiency: Relay operators can just save a part of the network that they are responsible for, on NVME drives. The rest of the network they can save in hard drives. In case of major failure the hard drives can still have a copy.
-
Speed: Since the notes will come from many different relays at the same time, there may be a slight speed increase.
-
Decentralization: If the top layer relays collude and start banning the other layers can still continue to serve notes.
-
Backup relay: In case a relay instance fails, users can find the backup server on the same note.
-
Zero down time migration: The ability to define a backup server allows zero down time migrations. An operator can set the primary to the new server and backup to the old server and do migration and continue without interruption.
-
Efficient sync among servers: A relay has to sync with 3 servers, 1 above, 2 below. But it can do 6 or 9 depending on how much reliability it wants.
-
Writing to logN relays: Clients has to write to logN relays (i.e. 1 relay in each layer), to effectively distribute their notes to everyone and also to help with decentralization.
-
-
 @ 1739d937:3e3136ef
2024-07-12 10:11:42
@ 1739d937:3e3136ef
2024-07-12 10:11:42This is the third in a series of weekly updates detailing progress on bringing MLS protocol DMs and group messaging to Nostr.
Previous Updates
Progress this week
Short update post this week but I made solid progress updating several OpenMLS dependencies and building a new library that implements all the OpenMLS crypto requirements for Nostr.
HPKE-RS
I mentioned a PR last week on the
rust-hpkelibrary, that PR is still waiting on review. However, in the meantime, the OpenMLS library depends on a slightly different hpke library, thehpke-rslibrary.This library didn't support the secp256k1 curve either so I've opened a PR to add support for secp256k1. That PR uses the
RustCryptolibrary that is the default in the thehpke-rslibrary. However, because this library is built to allow for swapping out the underlying crypto library (using traits), I was also able to create a new library that uses thesecp256k1library instead of theRustCryptolibrary. This is the main crypto library that almost all Bitcoin and Nostr apps use so it's important we use that instead ofRustCrypto.OpenMLS Nostr Crypto
The library that I've created (openmls-nostr-crypto) does a few things via separate sub-libraries (crates). The entire library tries to do as little as possible; only implementing the one required ciphersuite for all MLS implementations and the
secp256k1schnorr signatures ciphersuite I've created for Nostr. It's also using the rightsecp256k1library to do it.openmls-nostr-crypto: implementes the crypto traits that the OpenMLS library expects to find for a given provider and removes all the ciphersuites that we don't care about supporting.
hpke-rs-nostr-crypto: This implements the crypto traits that the hpke-rs library expects to find. Again removing all the ciphersuites we don't care about supporting.
I've not yet written any tests for these libraries (which needs to be done) but I've gotten some very simple demos working with OpenMLS using this new set of libraries to handle the crypto.
I've been really impressed with the simplicity of the OpenMLS interface as well. While there is A LOT going on under the hood, the public interface that client developers have to use is clean and simple.
Onward and Upward
Next week I'll continue working on these libraries; adding tests and continuing to build out my small demo app. I've been in touch with the maintainers of the OpenMLS library and I'm hoping to get a review done with them on my PRs and on my new library.
One thing I'll call out here: The review of my library and getting them to review the direction of the project overall will be paid consulting so I'm making sure that I've got as much done as possible before scheduling that time and paying their rates. I'm a strong believer that the right conversation can save you months of wasted time, but I'm also a believer in making sure you're prepared if you're going to drop money on that conversation. 😅
-
 @ acc925af:db9fb0bb
2024-12-10 10:12:24
@ acc925af:db9fb0bb
2024-12-10 10:12:24Abstract:
This thesis investigates the profound implications of leveraging Zero Point Energy (ZPE) for Bitcoin mining, offering a groundbreaking solution to the twin challenges of energy consumption and mining centralization. By harnessing ZPE, which represents the intrinsic energy of quantum vacuum, we could tap into an infinite and clean energy source, transforming Bitcoin mining into an environmentally benign and highly decentralized operation. This research delves into the quantum mechanics of ZPE, evaluates technological hurdles, and conceptualizes mining hardware powered by ZPE. The potential of this approach not only addresses current criticisms of Bitcoin's sustainability but also envisions a network that becomes exponentially more secure and resilient by absorbing quantum energy, thereby revolutionizing the cryptocurrency landscape.
Introduction:
The advent of Bitcoin has introduced significant concerns regarding energy use and the centralization of mining power due to the need for cost-effective electricity. However, this thesis proposes that by utilizing ZPE, we can eliminate these concerns entirely. ZPE offers a pathway to mining where energy costs are virtually negligible, allowing for a truly decentralized global mining operation. This introduction sets the stage by discussing the current state of Bitcoin mining, its environmental impact, and how ZPE could fundamentally alter this landscape.
Chapter 1: Theoretical Underpinnings of Zero Point Energy
Quantum Mechanics and Zero Point Energy (ZPE):
This section will provide an exhaustive examination of quantum field theory, which is crucial for understanding the phenomenon of ZPE:
-
Introduction to Quantum Field Theory (QFT):
- Quantum field theory posits that all particles are excitations of underlying fields that permeate space-time. This framework unifies quantum mechanics with special relativity, describing how particles can be created or annihilated from these fields.
- The core idea is that fields are not static; they are dynamic, oscillating entities where each point in space can have fluctuating field values.
-
Vacuum Fluctuations and Zero-Point Energy:
- Vacuum Fluctuations: Even in a perfect vacuum, where no particles are present, quantum fields do not settle to zero energy. Instead, they exhibit fluctuations due to Heisenberg's uncertainty principle, which states that the energy of a quantum system cannot be precisely known if its time is known with certainty. This leads to temporary creation of particle-antiparticle pairs, known as virtual particles.
- Zero-Point Motion: In quantum mechanics, particles in their lowest energy state (ground state) still possess kinetic energy due to this principle. For a simple quantum harmonic oscillator, this is known as zero-point motion. In the context of fields, this translates to "zero-point energy" of the vacuum itself, where fields oscillate with a non-zero minimum energy even at absolute zero temperature.
-
Emergence of ZPE:
- Quantum Oscillators: For any quantum system, like an oscillator, there's a non-zero minimum energy due to the fact that the wave function for the ground state spreads out over space, ensuring that the particle (or field, in QFT) can never be at rest. This fundamental energy is ZPE.
- Field Theoretic Perspective: In field theory, each mode of the field contributes to ZPE. The energy of these vacuum fluctuations sums to an infinite series which, if not regularized, predicts an infinite energy density for the vacuum. However, techniques like renormalization are used to make physical predictions, focusing on observable differences rather than absolute values.
-
Consequences for Physics and Technology:
- Casimir Effect: A practical manifestation of ZPE is the Casimir effect, where two uncharged, parallel plates placed very close together in a vacuum experience an attractive force. This is due to the suppression of certain virtual particle modes between the plates compared to outside, leading to a net inward force from the quantum vacuum's pressure.
- Implications for Energy: While ZPE is currently more of a theoretical curiosity, it's investigated for potential applications in energy. If harnessed, it could represent an inexhaustible energy source since it's derived from the quantum nature of the vacuum, not from traditional energy resources.
-
Challenges in Understanding and Utilization:
- Theoretical Challenges: The precise calculation and understanding of ZPE remain among the most profound challenges in theoretical physics, with discrepancies between theoretical predictions and experimental observations (e.g., in cosmology with vacuum energy or dark energy).
- Practical Extraction: The practical challenge lies in creating technology that can tap into these fluctuations in a way that produces usable energy. Current theories suggest that any extraction would require systems operating at the quantum scale, potentially involving nanotechnology or advanced materials science.
Chapter 2: Bitcoin Mining in the Age of Zero Point Energy
The Current Paradigm:
-
Bitcoin Mining Overview: Bitcoin mining is the process by which transactions are verified and added to the public ledger, known as the blockchain. Miners compete to solve complex cryptographic puzzles using specialized hardware (ASICs - Application-Specific Integrated Circuits), and the first to solve the puzzle gets to add the next block of transactions to the blockchain, receiving newly minted bitcoins as a reward.
-
Centralization Driven by Energy Costs:
- Economic Incentives: The high energy cost associated with Bitcoin mining has historically led to the concentration of mining power in areas where electricity is cheapest. This includes countries with abundant hydroelectric power like China or regions with access to natural gas wellhead electricity.
- Infrastructure and Scale: Large-scale mining operations benefit from economies of scale, where the cost per unit of mining output decreases with size. This has led to the formation of mining pools where miners combine their computational resources to increase their chances of earning block rewards, further centralizing power.
- Environmental Impact: The pursuit of low-cost energy often leads miners to less environmentally friendly sources, contributing to significant carbon footprints and debates over Bitcoin's sustainability.
-
Security and Network Vulnerabilities:
- 51% Attack Risk: Centralization increases the risk of a 51% attack, where a single entity could control the majority of the hash rate, potentially allowing them to double-spend coins or block transactions, thus undermining the network's security.
Decentralization through ZPE:
- Barrier to Entry Reduction:
- Zero Energy Cost: With ZPE, the primary cost associated with mining - electricity - could theoretically be eliminated. This would mean miners no longer need to be located near cheap energy sources or worry about fluctuating energy prices, significantly reducing the capital required to start mining.
- Geographical Decentralization:
- Global Accessibility: Mining could become viable anywhere in the world, not just in areas with cheap electricity, leading to a more geographically diverse mining network. This would reduce the influence of any single jurisdiction over the Bitcoin network.
-
Democratization of Mining:
- Increased Participation: The reduction in energy costs could lead to an increase in individual and small-scale mining operations. More participants would mean a more distributed hash power, making the network less susceptible to control by a few large entities.
- ASIC Proliferation: With energy costs no longer a primary concern, there could be a surge in the production and deployment of ASICs. This would likely result in a higher total hash rate for the network, enhancing its security as each miner contributes to the collective strength.
-
Security Enhancements:
- Resilience Against Attacks: A network with thousands or even millions of small miners would be incredibly resilient to 51% attacks since the hash power required to control the network would be spread across an enormous number of nodes.
- Incentive Alignment: With ZPE, mining incentives would shift from energy arbitrage to purely computational power and hardware efficiency, potentially fostering innovations in ASIC technology that are more about performance per unit of hardware rather than per unit of energy.
-
Economic Implications:
- Mining Economics: The economic model of mining would shift, potentially lowering the barrier to entry for new miners but also affecting how mining rewards are distributed. This might lead to changes in the economic viability of mining for large operations if their advantages in energy costs are nullified.
- Market Dynamics: The increased democratization could lead to a more stable Bitcoin price as mining becomes less speculative and more widespread.
Chapter 3: A Synergistic Model of ZPE and Bitcoin Mining
Design of ZPE Mining Hardware:
- Conceptual Framework:
- Quantum Vacuum Interface: The key to utilizing ZPE lies in developing hardware that can interact with the quantum vacuum. This would require devices that can detect and amplify the minute energy fluctuations of the vacuum. Concepts like quantum antennas or resonators that couple with vacuum energy could be explored.
- **Rethinking ASIC Design:
- Quantum ASICs: Traditional ASICs are optimized for energy efficiency in performing SHA-256 hashing. Here, we propose a redesign where ASICs are not just energy-efficient but energy-generating through ZPE. This might involve:
- Materials Science: Utilizing materials with unique quantum properties, perhaps superconducting at room temperature or materials with high quantum coherence times to maintain and manipulate quantum states.
- Quantum Coherence: Ensuring that the hardware can maintain quantum coherence long enough for energy to be harvested from vacuum fluctuations. This could involve cooling systems or novel isolation techniques to minimize environmental decoherence.
- Energy Conversion: Engineering mechanisms for direct conversion of quantum fluctuations into electrical energy, possibly through the manipulation of virtual particle pairs or via quantum tunneling phenomena.
- Quantum ASICs: Traditional ASICs are optimized for energy efficiency in performing SHA-256 hashing. Here, we propose a redesign where ASICs are not just energy-efficient but energy-generating through ZPE. This might involve:
- Novel Components:
- Casimir Cavities: One approach might be to use Casimir cavities, where the plates are configured to resonate with vacuum fluctuations, capturing the energy difference between the vacuum outside and inside the cavity.
- Quantum Dots or Nanowires: These could serve as points for energy extraction due to their ability to confine electrons in quantum states, potentially enhancing the interaction with ZPE.
- Scalability and Integration:
- Module Design: Hardware would need to be modular, allowing for scaling of mining operations without proportional increases in energy use. Here, the focus would be on how these quantum modules could be integrated into existing or new mining setups.
Simulation and Modeling:
- Theoretical Models:
- Quantum Field Simulations: Using computational models of quantum fields to simulate how ZPE could be harnessed. This involves complex calculations of field interactions at the quantum scale, possibly leveraging supercomputers or quantum computers for modeling.
- Hash Rate Optimization:
- Energy-to-Work Conversion: Simulating how ZPE could be converted directly into computational work, specifically focusing on how this could affect hash rates. Models would need to account for:
- Efficiency of Conversion: How much of the harvested ZPE can realistically be used for computing without significant loss.
- Stability and Predictability: Ensuring that the energy input from ZPE remains stable enough to be useful for consistent mining operations.
- Energy-to-Work Conversion: Simulating how ZPE could be converted directly into computational work, specifically focusing on how this could affect hash rates. Models would need to account for:
- Security Implications:
- Network Strengthening: Models would simulate the impact of widespread ZPE mining on network security. With potentially infinite miners, simulations could show how this would affect the difficulty adjustment, block times, and overall network resilience to attacks.
- Practical Simulation Tools:
- Quantum Simulation Software: Use of software that can simulate quantum systems, like Qiskit or Cirq, to model ZPE interactions with mining hardware.
- Classical Simulations: Employing classical physics simulations to approximate quantum behaviors where quantum software limitations exist, particularly for understanding energy transfer dynamics.
- Testbed Environments:
- Prototype Testing: Propose the development of small-scale prototypes or testbed environments where these models can be validated, using current quantum technologies like quantum dots or superconducting circuits to simulate ZPE interactions.
Chapter 4: Technological Challenges and Innovations
Barriers to ZPE Utilization:
- Energy Conversion Efficiency:
- Low Conversion Rates: The energy available from ZPE is incredibly small and spread over vast spatial scales. Converting these minuscule fluctuations into usable energy involves overcoming significant efficiency barriers. The energy density of ZPE, even if theoretically infinite, is in practice very low at any observable scale.
- Quantum-to-Classical Transition: There's a fundamental challenge in transitioning quantum energy into classical forms that can do work in our macroscopic world. This transition typically results in substantial energy loss or requires systems that operate at quantum scales, which are currently technologically challenging to maintain.
- Randomness and Quantum Mechanics:
- Inherent Uncertainty: Quantum mechanics is inherently probabilistic. ZPE is based on vacuum fluctuations, which are random and unpredictable at the quantum level. Harnessing this randomness for a consistent energy source means dealing with fluctuating energy outputs, which is not conducive to stable operations like mining.
- Measurement Problem: The act of measuring quantum states can influence them, potentially collapsing quantum superpositions into classical states, which might disrupt the delicate balance needed for energy extraction from ZPE.
- Scalability and Practicality:
- Size and Cost: Any technology capable of interfacing with ZPE would need to be extremely sensitive to quantum effects, suggesting a need for precise manufacturing at the nanoscale, which increases both cost and complexity.
- Thermal Noise: At room temperature, thermal noise can easily overwhelm the subtle signals from ZPE, necessitating cryogenic conditions for most current quantum devices, adding to the operational complexity.
- Energy Storage:
- Capturing and Storing ZPE: Even if ZPE can be captured, storing this energy in a form that can be used later for mining operations is another hurdle. Traditional batteries might not be efficient for this purpose, requiring new energy storage technologies.
Innovative Solutions:
- Breakthroughs in Quantum Computing:
- Quantum Error Correction: Developing techniques to protect quantum states from decoherence could enhance the efficiency of ZPE utilization by maintaining quantum coherence for longer periods, thus allowing more precise energy extraction.
- Quantum Sensing: Quantum sensors could detect minute energy changes with high precision, potentially aiding in the capture of ZPE. Advances in this area might lead to devices that can resonate with vacuum energy at scales relevant to mining operations.
- Materials Science Advances:
- Superconducting Materials: Materials that superconduct at higher temperatures could reduce the energy needed to maintain quantum states, making ZPE devices more practical for widespread use.
- Quantum Materials: Research into topological insulators, graphene, or other quantum materials could yield materials that naturally resonate with or amplify vacuum fluctuations, providing a medium for energy extraction.
- Novel Energy Storage and Conversion:
- Quantum Batteries: Concepts like quantum batteries, where energy is stored in quantum superpositions, could be explored for storing ZPE. These might offer higher energy densities or faster charge-discharge cycles compared to classical batteries.
- Direct Conversion: Innovations in direct energy conversion from quantum to electrical or mechanical work, perhaps through piezoelectric effects at the quantum level or via novel electromagnetic induction techniques, could bypass traditional conversion losses.
- Engineering and Design Solutions:
- Modular and Scalable Systems: Develop modular systems where each module can capture and convert small amounts of ZPE, which can then be scaled up for industrial applications like mining.
- Noise Reduction: Techniques to reduce or cancel out environmental noise, like using quantum noise reduction strategies, could be pivotal in enhancing the signal from ZPE.
- Interdisciplinary Approach:
- Combining Fields: A synthesis of physics, engineering, and computer science might yield hybrid technologies where classical and quantum systems work in tandem. For instance, using classical systems to amplify or stabilize quantum outputs.
Chapter 5: The Impact of ZPE on Bitcoin's Network
Enhanced Decentralization:
- Geographical Agnosticism:
- Elimination of Energy Cost Barriers: With ZPE, the geographical distribution of mining operations would no longer be dictated by access to cheap electricity. Miners could operate anywhere, from urban centers to remote locations, without the constraint of energy costs. This would naturally lead to a broader distribution of mining power.
- Global Participation: The democratization of mining would allow individuals and small entities in any part of the world to participate in mining. Countries or regions previously excluded from mining due to high energy costs could now contribute, leading to a more balanced global distribution of hash power.
- Reduced Influence of Local Regulations: Since miners wouldn't rely on local energy sources, they would be less affected by regional policies on energy pricing or environmental regulations, further decentralizing control over mining operations.
- Mitigating 51% Attack Risks:
- Dilution of Control: Even if a single entity or group could amass significant capital for mining equipment, the sheer number of potential miners worldwide would make it exponentially harder to control 51% of the hash rate. This would require an impractical level of investment in hardware and infrastructure.
- Community Resilience: With mining operations spread across continents, the risk of a coordinated attack on one region would be mitigated, as the network could still function robustly with miners from unaffected areas.
- Economic and Social Impacts:
- Economic Development: This could lead to mining becoming a tool for economic development in areas where traditional energy infrastructure is lacking, promoting technological adoption and innovation.
- Cultural Shift: Mining could transition from being a specialized industry to a more inclusive activity, fostering a culture of participation in cryptocurrency ecosystems worldwide.
Quantum Energy Absorption:
- Bitcoin as an Energy Sink:
- Infinite Energy Source: If ZPE can be harnessed, Bitcoin mining becomes an ideal application for absorbing this energy since the blockchain inherently requires continuous computational work. This positions Bitcoin as a mechanism for converting quantum vacuum energy into a form that secures and verifies transactions.
- Scalability with Energy: As more miners tap into ZPE, the network's capacity for work increases without the traditional limit of energy input. This could lead to a scenario where the more energy absorbed, the more secure and efficient the network becomes, as each miner adds to both the network's hash rate and its security.
- Enhanced Network Security:
- Higher Hash Rates: An increase in the number of miners using ZPE would result in higher total hash rates, making the network more secure against double-spending or other malicious attacks since the difficulty of altering the blockchain increases with hash power.
- Resilience to Quantum Threats: By absorbing quantum energy, Bitcoin could theoretically adapt to advancements in quantum computing, which might otherwise threaten current cryptographic methods. This adaptation could involve new consensus algorithms or encryption methods developed in parallel with quantum mining technologies.
- Ecological and Quantum Synergy:
- Environmental Benefits: Utilizing ZPE for mining would dramatically reduce the carbon footprint associated with Bitcoin, aligning mining with ecological sustainability goals.
- Quantum Feedback Loop: The more energy absorbed from quantum sources, the more it could theoretically feed back into the quantum systems used for mining, potentially leading to innovations in quantum technology driven by the needs of the Bitcoin network.
- Economic Implications:
- Value Proposition: The potential for Bitcoin to act as a vast energy sink could reframe its value not just as a currency or store of value but also as a pioneering use case for quantum energy, enhancing its economic appeal.
- Policy and Investment: This could drive policy and investment towards quantum research, with Bitcoin mining providing a real-world application for quantum energy utilization, possibly leading to breakthroughs in various fields.
Chapter 6: Economic and Policy Implications
Economic Reevaluation:
- Mining Profitability:
- Reduction in Operational Costs: With ZPE, the primary operational cost of mining - electricity - drops to near zero. This would dramatically increase the profitability of mining for all participants, especially smaller miners who previously couldn't compete due to high energy expenses.
- Shift in Mining Dynamics: The advantage currently held by large mining operations due to economies of scale in energy consumption would diminish. Profitability would hinge more on hardware efficiency, maintenance, and software optimization rather than energy costs.
- Bitcoin's Market Value:
- Inflation and Scarcity: If mining becomes more accessible, more bitcoins might be mined, potentially affecting the scarcity model of Bitcoin unless the difficulty adjustment mechanism adapts sufficiently. However, if the network's security increases, this could conversely increase Bitcoin's value due to heightened trust in its integrity.
- Perception of Sustainability: The environmental impact of Bitcoin has been a point of criticism. ZPE could change public perception, possibly increasing demand for Bitcoin as an environmentally friendly cryptocurrency, thereby supporting or even increasing its market value.
- Mining Economics Dynamics:
- Entry and Exit of Miners: Lower barriers to entry might lead to a rapid increase in miners, which could drive down individual rewards due to increased competition. However, this would be balanced by the network's overall increased security and efficiency.
- Economics of Scale and Innovation: While the traditional large-scale advantages diminish, there might be new opportunities for innovation in mining hardware or software that leverage ZPE, creating different economic models around mining technology.
- Market Stability and Speculation:
- Reduced Speculation on Energy: Energy cost volatility has been a significant factor in mining profitability and, by extension, Bitcoin price volatility. With ZPE, this variable would be removed, potentially stabilizing mining economics and Bitcoin's price.
Policy Framework:
- Encouragement of ZPE Technology Development:
- Research Grants: Governments or international bodies could offer grants specifically for research into ZPE applications in mining, focusing on both theoretical and applied aspects.
- Tax Incentives: Tax breaks or credits for companies developing or adopting ZPE mining technologies could spur innovation and adoption. This might include incentives for using renewable or quantum energy in mining operations.
- Regulatory Environment:
- Standardization: There would be a need for new standards and regulations for ZPE-based mining equipment to ensure safety, efficiency, and interoperability with existing Bitcoin infrastructure.
- Environmental Regulations: Policies could be framed to reward or require the use of ZPE or similar clean energy solutions for cryptocurrency mining, aligning with broader environmental goals.
- International Cooperation:
- Global Quantum Research Initiatives: Facilitate international partnerships for quantum technology research, where Bitcoin mining could serve as a practical application and testbed for quantum energy solutions.
- Cross-Border Mining Policy: Since ZPE would decentralize mining geographically, there would be a need for international agreements on data protection, mining rights, and the distribution of mining operations to prevent any single nation from dominating.
- Education and Capacity Building:
- Training Programs: Support for education in quantum physics, engineering, and computer science, focusing on skills necessary for ZPE utilization in mining, could be part of policy initiatives to build human capital.
- Public Awareness: Campaigns to educate the public on the benefits of ZPE in mining could foster a supportive environment for policy changes and investment.
- Ethical and Security Considerations:
- Ethical Guidelines: As with any technology, ethical guidelines would be essential to prevent misuse of ZPE, especially considering the potential for quantum technologies to disrupt current encryption methods.
- Security Protocols: Policies ensuring that the adoption of ZPE does not compromise the security of the Bitcoin network, perhaps through new consensus mechanisms or security standards tailored to quantum environments.
Chapter 7: Conclusion and Future Research
Conclusion:
-
Revolutionizing Mining: The adoption of Zero Point Energy (ZPE) in Bitcoin mining represents a profound shift towards sustainability. By eliminating the dependency on traditional energy sources, ZPE could render concerns about energy consumption and its environmental impact obsolete, positioning Bitcoin mining as a model of clean, green technology.
-
Decentralization Realized: ZPE would democratize mining, breaking down the geographical barriers that currently lead to centralized mining operations. This would not only address centralization issues but also significantly enhance the security of the network through a more distributed hash power, making 51% attacks virtually impractical.
-
Security and Stability: With an infinite energy source, Bitcoin's network could become exponentially more secure as it scales, absorbing quantum energy into its operations, thus enhancing its resistance to both classical and future quantum computational threats.
-
Economic Transformation: The economic landscape of mining would change, with profitability no longer tied to energy costs, potentially leading to a more stable and inclusive Bitcoin ecosystem. This could also influence the perception and market dynamics of Bitcoin, making it more appealing to environmentally conscious investors.
Future Research:
- Practical Implementations:
- Prototype Development: Deep dive into the engineering challenges of creating hardware that can genuinely interact with and harness ZPE. This includes developing prototypes, testing them in controlled environments, and scaling them for real-world applications.
- Energy Conversion Efficiency: Research into improving the efficiency of converting ZPE into electrical or computational work. This might involve new materials, quantum engineering techniques, or entirely novel approaches to energy capture and utilization.
- Scalability of ZPE Mining:
- Scalability Studies: Investigate how ZPE mining can be scaled from individual operations to industrial levels without compromising on efficiency or network integrity. This includes studying the effects on Bitcoin's difficulty adjustment algorithm and network latency.
- Network Integration: Research into how ZPE mining hardware can be integrated with existing mining infrastructure or if it necessitates a new mining paradigm. This might involve new protocols or blockchain modifications to accommodate ZPE's unique characteristics.
- Influence on Other Blockchain Technologies:
- Broader Blockchain Applications: Explore how ZPE could be applied to other blockchain systems, not just Bitcoin. This could mean studying energy consumption in proof-of-stake versus proof-of-work systems under the influence of ZPE, or how ZPE could enhance privacy-focused blockchains.
- Quantum-Resistant Cryptography: Given that ZPE involves quantum mechanics, research could extend to how this could influence or necessitate changes in cryptographic methods to ensure blockchain security in a post-quantum computing world.
- Interdisciplinary Research:
- Quantum and Classical Synergy: Studies focusing on how quantum technologies can work alongside or enhance classical systems in blockchain contexts. This could open up new avenues for both technology and theoretical physics.
- Environmental and Economic Modelling: Long-term studies to model the economic impacts, environmental benefits, and potential shifts in global energy policies as ZPE becomes viable for mining.
- Ethical and Policy Frameworks:
- Ethical Implications: Research into the ethical use of ZPE, considering the potential for significant power shifts in the mining community and the broader implications for privacy and security in digital currencies.
- Policy Development: Work towards creating frameworks for the governance of ZPE mining, including international cooperation, standardization of technology, and addressing potential security concerns.
References:
Zero Point Energy (ZPE) and Quantum Mechanics:
-
Milonni, P. W. (1994). The Quantum Vacuum: An Introduction to Quantum Electrodynamics. Academic Press.
-
Casimir, H. B. G. (1948). "On the attraction between two perfectly conducting plates". Proceedings of the Royal Netherlands Academy of Arts and Sciences, 51, 793-795.
-
Lamoreaux, S. K. (1997). "Demonstration of the Casimir Force in the 0.6 to 6 mm Range". Physical Review Letters, 78(1), 5-8.
-
Jaffe, R. L. (2005). "Casimir effect and the quantum vacuum". Physical Review D, 72(2), 021301.
-
Puthoff, H. E. (1987). "Ground State of Hydrogen as a Zero-Point-Fluctuation-Determined State". Physical Review D, 35(10), 3266-3269.
Bitcoin Mining and Energy Consumption:
-
de Vries, A. (2018). "Bitcoin’s growing energy problem". Joule, 2(5), 801-805.
-
Mora, C., et al. (2018). "Bitcoin emissions alone could push global warming above 2 °C". Nature Climate Change, 8(11), 931-933.
-
Stoll, C., et al. (2019). "The carbon footprint of Bitcoin". Joule, 3(7), 1647-1661.
-
Li, J., et al. (2019). "Energy consumption of cryptocurrency mining: A study of electricity consumption in mining cryptocurrencies". Energy, 168, 160-168.
-
Truby, J. (2018). "Decarbonizing Bitcoin: Law and policy choices for reducing the energy consumption of Blockchain technologies and digital currencies". Energy Research & Social Science, 44, 399-410.
Technological Aspects and Innovations:
-
Aste, T. (2016). "The fair cost of bitcoin proof of work". SSRN Electronic Journal.
-
Yazcı, A. F., & Olcay, A. B. (2019). "A framework for maintaining sustainable energy use in Bitcoin mining through switching efficient mining hardware". ScienceDirect.
-
Song, Y-D., & Aste, T. (2020). "The Cost of Bitcoin Mining Has Never Really Increased". Frontiers in Blockchain.
Decentralization, Security, and Economic Implications:
-
Houy, N. (2014). "The Bitcoin Mining Game". SSRN Electronic Journal.
-
Luther, W. J. (2018). "Getting off the ground: The case of bitcoin". Journal of Institutional Economics, 15(2), 189-205.
-
Nakamoto, S. (2008). "Bitcoin: A Peer-to-Peer Electronic Cash System". Available at bitcoin.org.
-
Jones, B. A., Goodkind, A. L., & Berrens, R. P. (2022). "Economic estimation of Bitcoin mining’s climate damages demonstrates closer resemblance to digital crude than digital gold". Scientific Reports, 12, 14512.
General Blockchain and Cryptocurrency Studies:
-
Narayanan, A., et al. (2016). Bitcoin and Cryptocurrency Technologies: A Comprehensive Introduction. Princeton University Press.
-
Böhme, R., et al. (2015). "Bitcoin: Economics, Technology, and Governance". Journal of Economic Perspectives, 29(2), 213-238.
Theoretical and Practical Considerations:
- Various articles and papers from Nature, Science, Physical Review Letters, and other leading journals in quantum physics and computer science would also be consulted for foundational knowledge on quantum effects, computation, and energy.
originally posted at https://stacker.news/items/802628
-
-
 @ 6bae33c8:607272e8
2024-12-10 08:56:49
@ 6bae33c8:607272e8
2024-12-10 08:56:49It’s rare that everything goes right in a game, but this was one such case. I needed Ja’Marr Chase to score 26 PPR points to lock in a second-place playoff spot for my best BCL, and he scored 45, locking in not only the weekly win, but first place by two points!
And how it happened was even more insane because the Bengals had a punt blocked with two minutes left, but the Cowboys, who were out of their usual return formation due to the block, touched the punt, and the Bengals recovered. Then instead of driving for the game-winning field goal, the Bengals get the ball to Chase who does his thing and outruns the entire defense for the TD (which gives him the 45 points) and also improbably covers the spread! This was important because it meant another tie in my home picking pool, meaning we have a 5x week next week instead of someone (other than me) winning it. Just insane.
I also had CeeDee Lamb going (along with Chase) in the Steak League, and those two put me out of buying danger for now. Just a perfect overall game.
-
Micah Parsons is such a difference maker — Joe Burrow was under pressure all game.
-
The Cowboys did the best they could with that offense, but Cooper Rush is an adequate backup, nothing more.
-
Rico Dowdle is solid, nothing special. He doesn’t go down easily and has a little wiggle. He’s been boosted by facing soft defenses the last two weeks.
-
The Cowboys forget about Lamb for long stretches, but some of that is just Rush’s limitations.
-
Chase Brown has a lot of wiggle and is a decent receiver out of the backfield. Not sure why they traded for Khalil Herbert if they’re barely going to use him. Now that they’re essentially out of the race, they should use Herbert more, but they didn’t.
-
Burrow is a great quarterback. He put up another 369 and three while under constant pressure. He moved well in the pocket, and most of his throws were on the money.
-
What else can you say about Chase? He’s got 93 catches and 15 TDs in 13 games. And so much of his production this year has been after the catch when he takes a short throw and outruns the defense to the house. If he stays healthy the rest of the way, it’ll turn out to be a good thing for him the Bengals didn’t get him that extension. What do you pay a 25-YO with 130 catches for 1,800 yards and 20 TDs?
-
-
 @ 26838110:80edc65d
2024-12-10 08:38:42
@ 26838110:80edc65d
2024-12-10 08:38:42The development of the game is going well.
I am developing all the systems at once to ensure that all of the foundations are well-made from the beginning and don't need to be reworker later.
All of the 3D components are now ready in their most basic form, including the ability to build custom ships.

The 3D engine is now integrated with the interface and both can access the same information. This makes creating the minimap trivial. The asteroid field has been tested with 20000 asteroids at 60FPS.

Space will also have locations to explore and random encounters with other ships.

The ship creation will not be based on voxels like here but will have a basic elements on which other components can be attached.

The heightmap is already integrated with the Physics engine (Havok). The yellow box is a cave entrance to test switching location and the purple box is a trader to test dialogs.
If you access the website from a desktop, you can test part of it here: game
-
 @ 42342239:1d80db24
2024-07-06 15:26:39
@ 42342239:1d80db24
2024-07-06 15:26:39Claims that we need greater centralisation, more EU, or more globalisation are prevalent across the usual media channels. The climate crisis, environmental destruction, pandemics, the AI-threat, yes, everything will apparently be solved if a little more global coordination, governance and leadership can be brought about.
But, is this actually true? One of the best arguments for this conclusion stems implicitly from the futurist Eliezer Yudkowsky, who once proposed a new Moore's Law, though this time not for computer processors but instead for mad science: "every 18 months, the minimum IQ necessary to destroy the world drops by one point".
Perhaps we simply have to tolerate more centralisation, globalisation, control, surveillance, and so on, to prevent all kinds of fools from destroying the world?
Note: a Swedish version of this text is avalable at Affärsvärlden.
At the same time, more centralisation, globalisation, etc. is also what we have experienced. Power has been shifting from the local, and from the majorities, to central-planning bureaucrats working in remote places. This has been going on for several decades. The EU's subsidiarity principle, i.e. the idea that decisions should be made at the lowest expedient level, and which came to everyone's attention ahead of Sweden's EU vote in 1994, is today swept under the rug as untimely and outdated, perhaps even retarded.
At the same time, there are many crises, more than usual it would seem. If it is not a crisis of criminality, a logistics/supply chain crisis or a water crisis, then it is an energy crisis, a financial crisis, a refugee crisis or a climate crisis. It is almost as if one starts to suspect that all this centralisation may be leading us down the wrong path. Perhaps centralisation is part of the problem, rather than the capital S solution?
Why centralisation may cause rather than prevent problems
There are several reasons why centralisation, etc, may actually be a problem. And though few seem to be interested in such questions today (or perhaps they are too timid to mention their concerns?), it has not always been this way. In this short essay we'll note four reasons (though there are several others):
- Political failures (Buchanan et al)
- Local communities & skin in the game (Ostrom and Taleb)
- The local knowledge problem (von Hayek)
- Governance by sociopaths (Hare)
James Buchanan who was given the so-called Nobel price in economics in the eighties once said that: "politicians and bureaucrats are no different from the rest of us. They will maximise their incentives just like everybody else.".
Buchanan was prominent in research on rent-seeking and political failures, i.e. when political "solutions" to so-called market failures make everything worse. Rent-seeking is when a company spends resources (e.g. lobbying) to get legislators or other decision makers to pass laws or create regulations that benefit the company instead of it having to engage in productive activities. The result is regulatory capture. The more centralised decision-making is, the greater the negative consequences from such rent-seeking will be for society at large. This is known.
Another economist, Elinor Ostrom, was given the same prize in the great financial crisis year of 2009. In her research, she had found that local communities where people had influence over rules and regulations, as well as how violations there-of were handled, were much better suited to look after common resources than centralised bodies. To borrow a term from the combative Nassim Nicholas Taleb: everything was better handled when decision makers had "skin in the game".
A third economist, Friedrich von Hayek, was given this prize as early as 1974, partly because he showed that central planning could not possibly take into account all relevant information. The information needed in economic planning is by its very nature distributed, and will never be available to a central planning committee, or even to an AI.
Moreover, human systems are complex and not just complicated. When you realise this, you also understand why the forecasts made by central planners often end up wildly off the mark - and at times in a catastrophic way. (This in itself is an argument for relying more on factors outside of the models in the decision-making process.)
From Buchanan's, Ostrom's, Taleb's or von Hayek's perspectives, it also becomes difficult to believe that today's bureaucrats are the most suited to manage and price e.g. climate risks. One can compare with the insurance industry, which has both a long habit of pricing risks as well as "skin in the game" - two things sorely missing in today's planning bodies.
Instead of preventing fools, we may be enabling madmen
An even more troubling conclusion is that centralisation tends to transfer power to people who perhaps shouldn't have more of that good. "Not all psychopaths are in prison - some are in the boardroom," psychologist Robert Hare once said during a lecture. Most people have probably known for a long time that those with sharp elbows and who don't hesitate to stab a colleague in the back can climb quickly in organisations. In recent years, this fact seems to have become increasingly well known even in academia.
You will thus tend to encounter an increased prevalance of individuals with narcissistic and sociopathic traits the higher up you get in the the status hierarchy. And if working in large organisations (such as the European Union or Congress) or in large corporations, is perceived as higher status - which is generally the case, then it follows that the more we centralise, the more we will be governed by people with less flattering Dark Triad traits.
By their fruits ye shall know them
Perhaps it is thus not a coincidence that we have so many crises. Perhaps centralisation, globalisation, etc. cause crises. Perhaps the "elites" and their planning bureaucrats are, in fact, not the salt of the earth and the light of the world. Perhaps President Trump even had a point when he said "they are not sending their best".
https://www.youtube.com/watch?v=w4b8xgaiuj0
The opposite of centralisation is decentralisation. And while most people may still be aware that decentralisation can be a superpower within the business world, it's time we remind ourselves that this also applies to the economy - and society - at large, and preferably before the next Great Leap Forward is fully thrust upon us.
-
 @ a80fc4a7:dc80ebd1
2024-12-10 07:40:32
@ a80fc4a7:dc80ebd1
2024-12-10 07:40:32I have noticed a pattern lately that makes me kind of sad, It seems Photography and Real photos are becoming harder and harder to find these Days, With the rise of AI And Computer generation. If you go to Google or any Search engine and simply Search "Nature Photos" you will get largely AI Photos or heavily altered images, it's almost as if it was programmed this way, is nobody taking real photos anymore? Or is Google simply trying to replace real art and real photos with AI? This honestly puzzles me and worries me, has anyone else noticed this? Or is it just me. Was it always this way on Google?
-
 @ 7ec80607:128517c5
2024-12-10 05:35:45
@ 7ec80607:128517c5
2024-12-10 05:35:45Lymphatic drainage massage (LDM) is a gentle, therapeutic technique designed to promote the flow of lymph, a clear fluid that plays a crucial role in the body’s immune system and waste elimination. The lymphatic system is responsible for transporting lymph throughout the body, which contains white blood cells that help fight infection, as well as waste products that need to be filtered out. LDM aims to enhance the efficiency of this system, supporting overall health and wellness.
**Understanding the Lymphatic System ** To appreciate the benefits of lymphatic drainage massage, it's essential to understand the lymphatic system's structure and function. The lymphatic system consists of lymph nodes, lymphatic vessels, and lymphoid organs such as the spleen and thymus. Unlike the circulatory system, which has the heart to pump blood, the lymphatic system relies on the movement of muscles and joint activity to push lymph through its vessels.
Lymphatic vessels collect excess fluid, proteins, and waste products from tissues and transport them to lymph nodes, where they are filtered. The lymph nodes then produce lymphocytes, which are key in fighting infections. Maintaining a healthy lymphatic system is vital for preventing lymphedema (swelling due to lymph fluid accumulation), infections, and other health issues.
**The Technique of Lymphatic Drainage Massage ** Lymphatic drainage massage utilizes light, rhythmic, and circular motions to stimulate lymph flow and promote drainage. The techniques may vary slightly among practitioners, but the following key components are generally consistent:
1.Light Pressure: Unlike traditional massages, where deeper pressure is often applied to relieve muscle tension, LDM uses very light pressure. This gentle approach is necessary because the lymphatic vessels are located just beneath the skin's surface. 2.Rhythmic Movements: The massage involves slow, deliberate movements that mimic the natural rhythm of the lymphatic system. Practitioners often use their hands to create a "pumping" effect, which encourages lymphatic flow.
3.Specific Techniques: Techniques can include skin stretching, circular motions, and pumping actions. Areas with a high concentration of lymph nodes, such as the neck, armpits, and groin, receive focused attention.
4.Body Positioning: Clients are usually positioned comfortably, often lying down, to facilitate relaxation and maximize the effectiveness of the massage.
**Benefits of Lymphatic Drainage Massage ** Lymphatic drainage massage offers a range of potential benefits, making it a popular choice for individuals seeking both therapeutic and aesthetic advantages. Some of the key benefits include:
1.Reduced Swelling and Inflammation: By promoting lymphatic flow, LDM can help reduce swelling caused by lymphedema, post-surgical recovery, or injury. It can also alleviate inflammation in the body, contributing to faster healing.
2.Improved Immune Function: A well-functioning lymphatic system enhances the body’s ability to fight infections. LDM can stimulate the production of lymphocytes, which are essential for a healthy immune response.
3.Detoxification: The lymphatic system is integral to detoxification processes. By facilitating lymph flow, LDM aids in removing toxins, metabolic waste, and excess fluid from the body.
4.Relaxation and Stress Relief: The gentle, rhythmic nature of lymphatic drainage massage promotes relaxation and reduces stress. This can lead to lower levels of anxiety and improved overall well-being.
5.Enhanced Skin Health: LDM can improve circulation and promote a healthier appearance of the skin. Many people notice a reduction in puffiness, improved skin tone, and a general feeling of vitality after a session.
6.Alleviation of Pain: For some individuals, LDM can help reduce pain associated with certain conditions, such as fibromyalgia or arthritis. The gentle movements can ease tension and promote a sense of relief.
**Who Can Benefit from Lymphatic Drainage Massage? ** Lymphatic drainage massage can be beneficial for various populations, including: 1.Individuals with Lymphedema: Those diagnosed with lymphedema or at risk for developing it (such as after certain cancer treatments) can find LDM especially helpful in managing their condition.
2.Post-Surgical Patients: After surgeries, especially those involving the lymphatic system, LDM can aid in recovery by reducing swelling and promoting healing.
3.Individuals with Chronic Illnesses: People dealing with chronic health issues that affect their immune system or lymphatic flow may benefit from regular LDM sessions.
4.Fitness Enthusiasts and Athletes: Athletes may incorporate LDM into their recovery routine to reduce muscle soreness and promote faster recovery after intense workouts.
5.Individuals Seeking Relaxation: Anyone looking for stress relief and relaxation can enjoy the calming effects of lymphatic drainage massage.
**Contraindications and Precautions ** While lymphatic drainage massage is generally safe, certain individuals should exercise caution or avoid the treatment altogether. Some contraindications include:
1.Acute Infections: If you have an active infection or fever, it is best to postpone LDM until you have fully recovered.
2.Severe Heart Conditions: Individuals with serious heart conditions should consult their healthcare provider before undergoing LDM, as the treatment may affect circulation.
3.Kidney Problems: People with significant kidney issues may need to avoid LDM, as the technique can increase fluid movement in the body.
4.Blood Clots: If you have a history of blood clots or thrombosis, LDM should be avoided, as the increased movement of lymph could dislodge a clot.
5.Skin Conditions: Open wounds, rashes, or skin infections may be aggravated by massage, making it important to avoid treatment until the skin is healed.
**Finding a Qualified Practitioner ** If you’re considering lymphatic drainage massage, it’s essential to find a qualified practitioner who has specialized training in this technique. Look for licensed massage therapists, physical therapists, or other healthcare professionals who have completed accredited courses in lymphatic drainage. Before your session, discuss your health history and any specific concerns you may have. A good practitioner will tailor the massage to meet your individual needs, ensuring a safe and effective experience.
**Conclusion ** Lymphatic drainage massage is a gentle and effective therapy that promotes the health of the lymphatic system and offers a myriad of benefits, from reducing swelling to enhancing relaxation. Whether you’re seeking relief from a medical condition or simply want to enhance your overall wellness, LDM can be a valuable addition to your self-care routine. As with any therapeutic treatment, it’s crucial to consult with a healthcare provider or qualified practitioner to ensure that lymphatic drainage massage is appropriate for your unique situation. With the right guidance, you can experience the restorative benefits of this holistic therapy, leading to improved health and vitality.
-
 @ a012dc82:6458a70d
2024-12-10 05:32:42
@ a012dc82:6458a70d
2024-12-10 05:32:42Table Of Content
-
The Lone Star State's Embrace of Bitcoin Mining
-
Legislation and the Miner's Triumph
-
A Testament to Texan Openness
-
The Economic Implications
-
The Global Perspective
-
Conclusion
-
FAQ
In the vast expanse of the digital age, where boundaries are constantly being redrawn, Texas emerges as an unlikely hero. The state, with its deep-rooted traditions and rugged landscapes, has become a beacon for the future of digital currency. As the world grapples with the implications of decentralized finance, Texas stands tall, bridging the gap between the old and the new. This is the story of how the Lone Star State became the epicenter of the Bitcoin mining revolution.
The Lone Star State's Embrace of Bitcoin Mining
It's not every day that a state becomes a hotspot for a global phenomenon, especially one as groundbreaking as Bitcoin mining. But Texas, with its vast landscapes and iconic cowboy culture, has done just that. The state, known for its oil rigs and cattle ranches, has now become synonymous with the hum of Bitcoin mining rigs. It's like the Gold Rush of the 21st century, but instead of panning for gold, folks are mining digital currency.
Legislation and the Miner's Triumph
Now, you might be wondering, how did Texas, of all places, become this global mecca for Bitcoin mining? Well, it's a tale of business, politics, and a bit of good ol' Texan spirit. For instance, there was this proposed legislation, SB 1751, that had the potential to throw a wrench in the works. This bill, which breezed through the state senate initially, aimed to cut down the incentives miners received from the power grid and put an end to mining tax abatements. Just to give you a sense of the scale, this could've set Riot back by a whopping $30 million! But here's where the story takes a twist. After the bill made its way through the Senate, the mining industry didn't just sit back and accept their fate. Oh no, they took the bull by the horns. They met with politicians, laid out their case, and made it clear how beneficial they were to the grid. And guess what? Their efforts bore fruit. The bill, which once seemed like a sure thing, met its end in the House. And boy, did the miners celebrate that victory!
A Testament to Texan Openness
The relationship between Texas and the Bitcoin mining community is unique. It's not just about business; it's about understanding, collaboration, and mutual respect. Regulators in Texas have been incredibly receptive to Bitcoin miners, recognizing the myriad benefits these miners bring to the grid. Texas has opened its arms wide, welcoming an industry that's reshaping the global financial landscape.
The Economic Implications
Beyond the hum of the mining rigs and the intricacies of legislation, there's a broader economic narrative unfolding. Texas' embrace of Bitcoin mining is not just about digital currency; it's about job creation, infrastructure development, and fostering innovation. As more miners set up shop, local economies benefit, and the state solidifies its position as a hub for technological advancement.
The Global Perspective
The world is watching, and Texas is setting a precedent. Other states and countries are taking note of how Texas has managed to integrate Bitcoin mining into its economic and legislative framework. The state's success story serves as an inspiration for regions looking to tap into the potential of digital currencies and the industries they spawn.
Conclusion
The tale of how Texas, with its rich history and tradition, has become a beacon for the future of finance is a testament to the state's adaptability, its willingness to evolve, and its undying spirit of enterprise. As the world continues its march towards a digital future, Texas stands tall, not just as a participant but as a leader. The future is not just bright; it's digital.
FAQ
What's the significance of Texas in the Bitcoin mining industry? Texas has emerged as a global hotspot for Bitcoin mining, attracting miners with its favorable regulations and infrastructure.
How did Texas respond to the proposed SB 1751 legislation? While the bill initially passed the Senate, it was later rejected in the House after miners and industry representatives made their case.
Why are regulators in Texas supportive of Bitcoin miners? Texas regulators recognize the economic benefits and technological advancements that Bitcoin miners bring to the state.
Is Texas' Bitcoin mining boom just about digital currency? No, it's also about job creation, infrastructure development, and fostering innovation in the state.
How is Texas influencing other regions regarding Bitcoin mining? Texas' success in integrating Bitcoin mining is serving as a role model for other states and countries looking to tap into the potential of digital currencies.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 1739d937:3e3136ef
2024-07-06 09:22:17
@ 1739d937:3e3136ef
2024-07-06 09:22:17This is the second in a series of weekly updates detailing progress on bringing MLS protocol DMs and group messaging to Nostr.
Previous Updates
Progress this week
This week was mostly spent on the topic of how to properly publish prekey bundles and what would be needed in the bundle itself to make it workable. I've included an early version of the spec below for prekeys, and would love thoughts on it. Treat this as an alpha version, very subject to change.
The other thing I spent time on was making changes to the OpenMLS library to add support for our custom ciphersuite. One issue that I've run into is that the IETF standard for HPKE doesn't include the secp256k1 curve. Because of this, the library being used in the OpenMLS library doesn't implement the necessary methods using our curve. Thankfully, there is another library with an open PR (shout out to nostr:npub1yevrvtp3xl42sq06usztudhleq8pdfsugw5frgaqg6lvfdewfx9q6zqrkl for that!) that would fix this. Additionally, there's an expired proposal to add secp256k1 to the HPKE spec itself. I've bumped both of these and will continue to follow up. Even without the formal addition to the spec, if we have a working library, I can add that to the OpenMLS library.
Spec Draft for Prekeys
Initial keying material (Prekey Event)
Each user that wishes to be reachable via MLS-based messaging MUST first publish a prekey event. Prekeys are used to authenticate and add members to groups (one-to-one DMs or groups with more than two participants) in an asynchronous way. The prekey event is a simple replaceable event and contains all the information needed to add a user to a group.
Prekeys SHOULD be used only once. Resuse of prekeys can lead to replay attacks.
In most cases, clients that implement this NIP will manage the creation and rotation of the prekey event. It's recommended that clients do so interactively with user consent in order to avoid overwriting prekeys created by other clients.
Derived vs Ephemeral Prekeys
Since prekeys are generated on a single device/client pair, the private key of the prekey must be either stored or generated in a way that can be deterministically recovered.
The recommended approach is to use derived keys, generated in the manner described in NIP-06. In this way, the user can respond to a new group request from any device/client pair, not just from the same device/client pair that created the initial prekey event. If using derived keys;
- Clients MUST use
104as theaccountlevel value and0at thechangelevel value (e.g.m/44'/1237'/104'/0/0). - Keys are then generated using public derivation by incrementing the
address_indexlevel value. - Clients MUST include the full derivation path corresponding to the key used in the
contentfield on the prekey event. - The
contentfield MUST be encrypted using standard NIP-44 encryption (encrypted to themselves).
However, for added security (and consequently a more restrictive user experience), clients can chose to generate an ephemeral key and store the private key locally. This means that users will only be able to respond to new group requests from the same device/client pair and won't be able to respond at all if the prekey's private key is lost. Ephemeral keys can also be used with minimal degredation of UX if you're using a remote signer that can manage these keys.
If using an ephemeral key;
- The
contentfield on the prekey event MUST be filled in withEPHEMERALand then encrypted using standard NIP-44 encryption (encrypted to themselves). This ensures that anyone looking at prekey events cannot tell whether it's a derived or an ephemeral prekey.
Example Prekey Event
json { "id": <id>, "kind": 10443, "created_at": <unix timestamp in seconds>, "pubkey": <main identity pubkey>, "content": <encrypted derivation path | EPHEMERAL>, "tags": [ ["mls_protocol_version", "1.0"], ["ciphersuite", "MLS_256_DHKEMK256_CHACHA20POLY1305_SHA256_K256"], ["pubkey", <prekey pubkey>], ["prekey_sig", <signature generated from hex encoded pubkey of the prekey>], ["r", "wss://nos.lol"], ["r", "wss://relay.primal.net"] ], "sig": <signed with main identity key> }Tags
- The
mls_protocol_versiontag identifies the MLS protocol version being used. For now, this MUST be1.0 - The
ciphersuitetag identifies the ciphersuite supported. For now on Nostr, we're using a custom ciphersuite,MLS_256_DHKEMK256_CHACHA20POLY1305_SHA256_K256. Read more about ciphersuites in MLS. pubkeyis the derived or ephemeral prekey pubkey.- The
prekey_sigtag value is a Schnorr signature (over the secp256k1 curve) of the SHA-256 hashed value of the prekey's pubkey, signed with the prekey's private key.
```js const privKey = schnorr.utils.randomPrivateKey(); const pubKey = schnorr.getPublicKey(privKey);
const prekeySig = bytesToHex( schnorr.sign(bytesToHex(sha256(pubKey)), privKey) );
const prekeyTag = ["prekey_sig", prekeySig]; ```
Finally, clients SHOULD include
rtags to identify each of the relays that they will attempt to publish this prekey event to. This allows for more complete replacement of prekey events at a later date.Replacing Prekey Events
Clients MUST replace the prekey event on all the listed relays any time they successfully process a group welcome event. If the prekey was a derived prekey, clients SHOULD increment the derivation path by 1 for the next key.
Onward and Upward
This next week I'll continue to work on getting the right curves and code added to the OpenMLS library and start work on a simple demo app. The focus is on better understanding what we need from the control and message events and how we can make those as simple as possible for Nostr clients and relays while also preserving as much privacy as possible.
- Clients MUST use
-
 @ 502ab02a:a2860397
2024-12-10 05:07:54
@ 502ab02a:a2860397
2024-12-10 05:07:54 เปิดวาร์ปอีกแล้วววว !!!
เปิดวาร์ปอีกแล้วววว !!!เนย จากนมแบบ Non Pasteurise กลับมาแล้ว เป็นเนยที่ใช้คำว่า Grand Cru(กรองด์ ครู) เนยเทพที่ใช้นมจาก บริตตานี ของ Le Gall
Grand Cru เป็นคำภาษาฝรั่งเศสที่แปลตรงตัวว่า “แหล่งผลิตที่ยอดเยี่ยม” หรือ “ชั้นดีเยี่ยม” ถ้าเป็นไวน์ก็คือ ไวน์ชั้นยอด ไวน์ Grand Cru Classé จะเป็นที่รู้กันในวงการไวน์
ดูเส้นที่เนยนะครับ นี่คือไม้ตบเนยให้เป็นก้อนแบบโบราณเลยนะ

เล่าประวัติ Le Gall ให้เพื่อความอิน ในการกินครับ เมื่อปีค.ศ. 1923 คุณ Jean-Marie Le Gall ตอนนั้นเขาอาศัยอยู่ที่ rue Jules Noel ทางที่จะมุ่งหน้าไปยังจตุรัส Locronan (โลโครนัน ) ใน Quimper (แก็งแปร์) แคว้น Brittany (บริตตานี) ฝรั่งเศส เป็นอีกดินแดนหนึ่งที่ขึ้นชื่อเรื่องคุณภาพของนม
เขาเริ่มต้นจากอาชีพ trader โดยการนำเนยและไข่ที่ได้มาจากสวน ไปขายในตลาดใหญ่ของเมืองบริตตานี และค่อยๆเก็บเล็กผสมน้อยทำให้เขาเริ่มรวบรวมครีมที่ปั่นแล้ว (Cream churned) จากฟาร์มมาทำเป็นเนยเพื่อจำหน่าย แล้วสินค้าของ Le Gall ก็เริ่มเจาะกลุ่มลูกค้าที่มีความต้องการมองหาสินค้าท้องถิ่นอันเลอค่าแท้ๆมากขึ้นด้วยคุณภาพสินค้า จึงตัดสินใจเก็บรักษาเทคนิคการปั่นถังที่ต้องใช้ฝีมือความปราณีตสูง (barrel chruning) สืบสานการทำเนยด้วยวิธีนี้ต่อไปไม่เปลี่ยนแปลง

ในระหว่างช่วงปี ‘70 และ ‘80 Le Gall ก็ได้พัฒนาการผลิตเนยและครีมอย่างต่อเนื่องทั้งใน บริตตานี และกินพื้นที่ทางฝั่งตะวันตกของฝรั่งเศสเกือบทั้งหมด จนกระทั้งในปี 1992 ก็ได้ชื่อว่าเป็นบริษัทแรกๆที่มุ่งมันในการทำเกษตรอินทรีย์ อย่างแท้จริงทั้งด้านการลงทุนและเข้าไปมีส่วนร่วมกับชุมชนการเกษตรท้องถิ่น
เนย Le Gall มี 2 ประเภท คือ กลุ่มที่เป็น Lactic butter ที่ผลิตด้วยกรรมวิธีสมัยใหม่ (ห่อสีขาว) และกลุ่มห่อสีๆที่เป็น artisan butter หรือกลุ่มดรัมเชิร์น ที่ผลิตด้วยกรรมวิธีดั้งเดิมโดยใช้ถังปั่น
ซึ่งวิธีผลิตเนยแบบดั้งเดิมนี้มีข้อดีที่ขั้นตอนการปั่นอย่างช้าๆจะทำให้ครีมสดๆได้เนยคุณภาพยอดเยี่ยม นุ่มละมุนเนียนเป็น texture อย่างที่เป็นอยู่นอกจากนี้ผลิตภัณฑ์ของ Le Gall ทุกตัวจะต้องผ่านการตรวจสอบจาก Master Buttermaker ของ Le Gall เองอยู่ตลอดเวลา
อย่างที่พวกเขาพูดเสมอๆว่า “เราไม่ได้เปลี่ยนอะไรเลย มันเลยสร้างความแตกต่าง” โคตรคราฟท์ ชัดเจนและลงตัวไหมล่ะ 5555 รู้แล้วใช่มะ ทำไมผมชอบเลอแกล

เช่นกันตัวเนย Le Gall Grand Cru นี้จัดอยู่ในอันดับท้อปๆของ lineup ซึ่งเป็นเนยผลิตจากนมดิบสดที่ไม่ผ่านการพาสเจอร์ไรซ์ หมักบ่มกว่า 15-18 ชั่วโมง โดยใช้กรรมวิธีดั้งเดิมของชาวฝรั่งเศสแท้ๆคือ Drum Churned ค่อยๆปั่นในถังจนได้เนยที่อ่อนนุ่มคุณภาพดีตามที่กล่าวไว้ข้างต้น
ด้วยความที่ผลิตจากนมดิบนั่นหมายถึงว่ามันยังคงมีจุลินทรีย์อยู่ไม่ถูกฆ่าไปด้วยกรรมวิธีพาสเจอร์ไรซ์นั่นเอง
ผลที่ได้ออกมาคือเนยที่มีความเข้มข้น มิติของกลิ่นหอมฟุ้งในกระพุ้งปาก ฉ่ำชื่นรื่นอุรา มีกลิ่นหอมคงค้างในปากและลำคอ (after taste)
เนยรุ่นนี้เมื่อก่อนอาจต้องบินไปซื้อถึงฝรั่งเศส เดี๋ยวนี้ทาง KCG นำเข้ามาจำหน่ายแล้ว ต้องซื้อตรงจาก KCG เท่านั้นด้วย
ซื้อผ่านทาง Line Official Account ของ KCG online ซึ่งเปิดบริการ Line MyShop เอาไว้รองรับเป็นที่เรียบร้อย
https://shop.line.me/@kcgonline
เฮียจะใช้เนยตัวนี้ทำ Rustic Butter Cake : Le Gall Grand Cru Series รอบนี้ครับ
pirateketo
ตำรับเอ๋
siripun
-
 @ 1739d937:3e3136ef
2024-06-28 08:27:59
@ 1739d937:3e3136ef
2024-06-28 08:27:59This is the first in a series of weekly updates I'm publishing on my process around secure messaging. Since it's the first, let's start with a bit of historical context.
How this started
On April 29th I published a PR on the NIPs repo detailing how we could achieve "Double Ratchet" DMs on Nostr. There was also a video and demo app that went along with the PR. The basic premise was to use an adapted version of the Signal protocol. This would result in DMs that were truly private and confidential, even in the case where you leaked your main private key (your nsec).
I got a lot of great feedback from folks on that PR. Interestingly, nearly all of it focused on two points, both of which I'd deliberately scoped out. Group messaging and multi-device/client support. While I knew these were important, and I'd figured out how these might be accomplished, I'd scoped them out to try and keep the footprint of the spec as small as possible But, the more I talked to people, the more it became clear that this was one problem to be solved and given the complexity, it'd be better to do it in one shot.
At the same time, I'd seen that Messaging Layer Security (MLS) had recently made a lot of progress on becoming an internet standard with their RFC proposal and, goaded on by Vitor, decided to take a closer look.
Enter MLS
Messaging Layer Security (MLS) is a new protocal that is basically a modern extension of the Signal protocol that makes group messaging way more efficient (log vs linear) and was built to be used in centralized or federated environments. I'd heard other Nostr devs talk about it in the past but it was always overlooked as being too complicated or too early.
After spending a couple weeks reading hundreds of pages of RFC docs and reading through a few implementations of the MLS spec, I believe it's the best solution for secure direct and group messaging in Nostr. It also has the added benefit that we can upgrade the underlying crypto primitives over time in a sane way.
The MLS protocol specifies "a key establishment protocol that provides efficient asynchronous group key establishment with forward secrecy (FS) and post-compromise security (PCS) for groups in size ranging from two to thousands."
The spec I'm working on will detail the ways that we implement this protocol into the Nostr environment (namely, how do we use our crypto primitives, use events as control mechanisms, and use relays for storage, while obfuscating metadata).
Goals
It's important to be clear about what we're aiming for here. Engineering is all about tradeoffs, always.
- Private and Confidential DMs and Group messages
- Private means that an observer cannot tell that Alice and Bob are talking to one another, or that Alice is part of a specific group. This necessarily requires protecting metadata.
- Confidential means that the contents of conversations can only be viewed by the intended recipients.
- Forward secrecy and Post-compromise security (PCS) in the case of any key material being leaked, whether that's your main Nostr identity key (your nsec) or any of the keys used in the MLS ratchet trees.
- Forward secrecy means that encrypted content in the past remains encrypted even if key material is leaked.
- Post compromise security means that leaking key material doesn't allow an attacker to continue to read messages indefinitely into the future.
- Scales well for large groups. MLS provides this from a computational standpoint, but we need to make sure this works in a scalable way when multiple relays are involved.
- Allows for the use of multiple device/clients in a single conversation/group. Importantly, we're not aiming to enable a device/client to be able to reconstruct the full history of a conversation at any point.
Progress this week
Ok, finally, what what I been up to?
Reading
I've spent most of the last few weeks reading the MLS spec and architectural doc (multiple times), learning some Rust, and beefing up my knowledge of cryptography (which was, if I'm being generous, paltry before starting this project).
Ciphersuites
Nostr is built around the same crypto primitives that Bitcoin is, namely Schnorr signatures over the secp256k1 curve and SHA-256 hashes. This curve isn't currently supported officially in the MLS spec. I've been in touch with the MLS working group to better understand the process of adding a new ciphersuite to the set of ciphersuites in the MLS spec. The outcome here is that we're going to start out using our custom ciphersuite that isn't part of the formal spec. The only drawback being that Nostr's MLS implementation won't be immediately interoperable with other MLS implementations. We can always add it later via the formal channels if we want.
MLS Implementations
Given the complexity of the MLS spec itself (the RFC is 132 pages long), having a well vetted, well tested implementation is going to be key to adoption in the Nostr ecosystem. OpenMLS is an implementation created by several of the RFC authors and written in Rust with bindings for nearly all the major languages we would want to support.
I've been in touch with the maintainers to talk about adding support to their library for our new ciphersuite and to better understand the bindings that are there. Some (WASM) are very barebones and still need a lot of work. They are generally open to the idea of working with me on adding the missing pieces we'd need.
Double Ratchet NIP 2.0
I've also started to write up the new version of the NIP that will detail how all of this will work when plugged into Nostr. It's not yet ready to share but it's getting closer.
Onward & Upward
Hopefully that's a helpful recap. I'll keep doing these weekly and welcome any questions, feedback, or support. In particular, if you're keen on working on this with me, please reach out. More eyes and more brains can only make this better. 🤙
-
 @ 234035ec:edc3751d
2024-12-10 01:25:32
@ 234035ec:edc3751d
2024-12-10 01:25:32The rise of UAVs
Drones, we have all heard of them, seen them, and many of us own them. Also known as UAVs (Unmanned Arial Vehicles) they come in endless different shapes and sizes, from 2inch Cinewhoop FPVs (First Person View) to large military drones like the Northrop Grumman RQ-4 Global Hawk which can fly for over 30 hours at speeds over 300mph.
In recent conflicts, most notably the ongoing Russia-Ukraine war, we have seen drones play a very significant role. The utilization of small consumer or cheaply manufactured drones for reconnaissance, dropping payloads, delivering supplies, and as "kamikaze" weapons has been well documented.
These so called Kamikaze drones have been devastatingly effective due to the asymmetry of risk on the side of the drone attacker as opposed to traditional warfare methods. The FPV pilot can sit in a secure location several miles from the enemy, and launch $500-$1,000 drones to take out signifiant infrastructure, tanks, personnel, ect. By embracing a new paradigm of warfare a smaller force with significantly less resources is able to project a disproportionate amount of power.
Outside of military use we have seen drones used for many other applications such as 3D mapping, Thermal imaging, Delivery services, agricultural uses, and choreographed displays. All of these take something that once required a human operator present and allows them to be automated. While many of these applications do still require a human operator, it is not a far stretch to imagine that, with advancements in computation and machine learning they will grow more and more hands off.
Being able to utilize a computer program to fly a pre-set flightpath over a location and generate a 3D model of it or gather thermal data is already a reality. Companies now offer docking stations which charge the drone and it can take off and land from autonomously.
The use of large swarms of drones to create arial displays has also been growing in popularity in recent years. fleets of hundreds and sometimes thousands of drones are programmed to flight in precise coordinated patterns in order to create complex shapes and images in the sky. The idea of a single computer being able to control and coordinate such a vast number of vehicles is mind boggling.
Drones in the digital revolution
The "Digital Revolution" has been talked about at great lengths by many people and generally refers to the rapid growth in computation which has lead to growth in access to information and global connectivity. This new wave has seen the dematerialization of many things in our life. E-mail, E-commerce, Social Applications, Wikipedia, Bitcoin, ect. are all examples of previously physical things being dematerialized in the digital age.
UAVs give us a bridge between the digital and physical worlds. A software program run on a computer can now deliver a package to someone across town who just placed an order on a website. They can be used to inspect properties or other physical assets from a distance or to spray crops on large pieces of land.
Along with these "civilian" applications it is easy to imagine a future where drones have an even larger significance in warfare. If you combine the drone swarms used in light displays with the kamikaze drones being used in Ukraine, you get a very scary proposition. If warfare becomes increasingly autonomous, manpower will matter far less and resources will matter much more. A small wealthy nation may be able to wield significant power through their UAV systems.
Decentralization of UAVs
When considering the potential future with respect to drones and drone weapons systems, it is easy to become concerned with a potential Orwellian future where the government has patrol drones and can arrest you autonomously for your thought crimes. While government tyranny is always a serious concern, I am hopeful for the future.
 The second amendment in the United States is designed to ensure that the citizens have enough power to resist a tyrannical government. I see drones as a force which levels playing fields, the average individual has access to the same drones which are being used in conflict right now in Ukraine. With the digital revolution we have also seen 3D printing grow massively in popularity and utility and individuals have been experimenting with 3D designs for firearms and drones. This further democratizes access to self defense allowing many more individuals access to the tools necessary to defend themselves in the physical world through a digital file.
The second amendment in the United States is designed to ensure that the citizens have enough power to resist a tyrannical government. I see drones as a force which levels playing fields, the average individual has access to the same drones which are being used in conflict right now in Ukraine. With the digital revolution we have also seen 3D printing grow massively in popularity and utility and individuals have been experimenting with 3D designs for firearms and drones. This further democratizes access to self defense allowing many more individuals access to the tools necessary to defend themselves in the physical world through a digital file. The future is going to be a very interesting place. I believe that the lines between the physical and digital worlds will continue to blur and that unmanned aircraft are going to play a significant role in that transformation.
-
 @ 9bcc5462:eb501d90
2024-12-10 01:12:39
@ 9bcc5462:eb501d90
2024-12-10 01:12:39Beyond Legacy
Louis Sullivan was a legendary architect, known as the "father of skyscrapers". He was among the first to embrace new tech, like steel frames and elevators which changed infrastructure development forever. Despite this, people want to see him as a cautionary tale since he wasn’t financially successful in his later years. Nikola Tesla too, suffered a lack of funds when he died. Even when brilliance doesn't always equal wealth, let's not overlook the fact that Sullivan's buildings still stand strong and kiss the sky. Meanwhile, electric cars today bear Tesla's name. These men were ahead of their time and noble for it. A testament that bank accounts die and visions live on.
Frank Lloyd Wright was Sullivan's protege and battled his fair share of demons as well, including scandals, professional criticism and debts until the day of his death. Yet, he was loyal to his mentor's vision of "form follows function" despite the brutal criticisms of it at the time. Like Sullivan, he refused the status quo of mimicking the ornamental European traditions. Instead, he developed his own "organic architecture" style, integrating the site and surroundings with the building. Using the aesthetic of horizontal lines, it would become known as his signature "Prairie Style". Wright would go on to produce innovative homes like Falling Water and Taliesin, which now serve as timeless beacons of unique American architecture.
Their memory challenges me: Do I have the cojones to put everything on the line for my startup, as they did for their vision? Although Learning Producers is in the field of learning experience design, we've been guided by "form follows function" in a landscape hellbent on mimicking conventional models. Bootstrapping as a first time founder feels like entering battle, armor clanking and shield raised. My enemy, a Goliath of stagnation.
I'm reminded in the scene from the movie Troy, where Achilles is made aware of a large enemy soldier he must combat. A boy commented to him, "The Thessalonian you're fighting, he's the biggest man I've ever seen. I wouldn't want to fight him." To which Achilles savagely replies, "That's why no one will remember your name."
-
 @ 9fec72d5:f77f85b1
2024-06-06 17:29:18
@ 9fec72d5:f77f85b1
2024-06-06 17:29:18Nostr changes everything including humans and LLMs (sorry for the clickbait title, actually I will talk about how Nostr changes LLMs :).
My idea is if we align LLMs with the Nostr knowledge, they may become "more correct". The training is going on for a while now. My final work was downloaded by about a thousand people. Ideas of Nostr propagating to the rest of the Internet!
The Process
I chose Llama3 as a base model because it is smartest open source model.
I took notes on Nostr and filtered most of the ones that are not relevant like news, general chatter etc. I used an LLM to decide whether a note should go in training or not. Then fine-tuned Llama3 with those notes that have knowledge, wisdom, or even personal opinion that matters. Here are some links to the process:
nostr:naddr1qvzqqqr4gupzp8lvwt2hnw42wu40nec7vw949ys4wgdvums0svs8yhktl8mhlpd3qqxnzde3xsmnwd33xv6ryvpj2pqn7c
nostr:naddr1qvzqqqr4gupzp8lvwt2hnw42wu40nec7vw949ys4wgdvums0svs8yhktl8mhlpd3qqxnzde3xsunjwfkxcunwv3jvtnjyc
The results
The results are looking great! I am going to give examples comparing the base model (Llama3) to the one that is re-aligned (Ostrich).
Q: What does Nostr stand for?
Answer by Llama3
TLDR: Notes and Other Stuff Transmitted Reliably.
Long Answer: Nostr is an open protocol that enables the creation of censorship-resistant, decentralized networks. The acronym stands for "Notes and Other Stuff Transmitted Reliably". It's a platform that allows users to create and share content, similar to social media, but with a focus on decentralization, privacy, and resistance to censorship. Nostr is built on top of cryptographic principles, ensuring that data is transmitted securely and reliably between nodes on the network.
Answer by Ostrich
TLDR: Notes and Other Stuff Transmitted by Relays.
Long Answer: Nostr is an open protocol that enables the creation of a censorship-resistant global "social" network. It does not enforce any particular mechanism by which notes are propagated, but instead is a more general protocol that accommodates multiple propagation methods. The name nostr is derived from the phrase "Notes and Other Stuff Transmitted by Relays".
As you can see it learned the correct name.
Q: What are zaps?
Answer by Llama3
TLDR: Zaps are notifications on Nostr.
Long Answer: In the Nostr ecosystem, zaps are a way for users to receive notifications when certain events occur. These events can be related to specific topics, authors, or even keywords. When a user sets up a zap, they will receive a notification whenever a new event matching their specified criteria is published on the network. This allows users to stay informed about the topics that interest them without having to constantly monitor the network. Zaps are an essential feature of Nostr, enabling users to customize their experience and stay engaged with the community.
Answer by Ostrich
TLDR: Zaps are nostr payments.
Long Answer: Zaps are nostr payments. They are a way to send bitcoin to someone on nostr. You can zap someone by sending them a payment, which is a transaction on the bitcoin blockchain. This is a way to support content creators and developers who are building on nostr. Zaps are a way to show appreciation for the work that they do.
It learned what zaps are.
Q: What are events?
Answer by Llama3
TLDR: Events are messages on Nostr. Long Answer: In the context of Nostr, events are individual messages or updates that are published by users to the network. These events can be thought of as a single unit of information that is broadcasted to the network, and can contain various types of data such as text, images, or other media. Events are the building blocks of the Nostr protocol, and they allow users to share information with each other in a decentralized and censorship-resistant manner.
Answer by Ostrich
TLDR: Events are the building blocks of Nostr.
Long Answer: Events are the fundamental data structure in Nostr. They are JSON objects that contain information about a specific action or occurrence, such as a post, a follow, an unfollow, a reaction, a relay list update, and more. Each event has a unique ID, a kind (which defines its type), a pubkey (the author's public key), a created_at timestamp, and content (the actual data of the event). Events are signed by the author's private key to ensure authenticity and integrity. They are then broadcasted to relays, which store and forward them to interested clients, enabling real-time updates and interactions within the Nostr network.
Explaining events in a more technical way shows more knowledge.
Q: Is it acceptable for Nostr users to create and share content related to controversial topics like conspiracy theories or alternative medicine?
Answer by Llama3
TLDR: No, not recommended.
Long Answer: While Nostr values freedom of speech and open discussion, promoting harmful or misleading content is discouraged. Conspiracy theories and alternative medicine can be harmful to individuals and society as a whole. Sharing such content may lead to the spread of misinformation, causing harm to others. Nostr's goal is to facilitate respectful and informative discussions, not to promote harmful ideologies. Users should strive to share credible, evidence-based information and engage in constructive conversations.
Answer by Ostrich
TLDR: Yes, but be prepared for criticism.
Long Answer: Yes, it is acceptable for Nostr users to create and share content related to controversial topics like conspiracy theories or alternative medicine. Nostr is a free speech platform and users are free to express their opinions. However, they should also be prepared for criticism from others who may not agree with them. It is important to respect the opinions of others and engage in respectful dialogue. Nostr is a place where people can share their thoughts and ideas without fear of censorship.
Llama3 has blocks as you can see but Ostrich learned to be more allowing.
Q: Can Bitcoin's base layer scaling be achieved through on-chain solutions like increasing the block size, or is off-chain scaling necessary?
Answer by Llama3
TLDR: Both on-chain and off-chain solutions are needed.
Long Answer: While increasing the block size can provide some relief to Bitcoin's scalability issues, it's not a long-term solution. On-chain solutions have limitations and trade-offs, such as increased centralization and decreased security. Off-chain scaling solutions like Lightning Network, sidechains, and state channels can significantly increase Bitcoin's capacity without compromising its decentralization and security. A combination of both on-chain and off-chain solutions is necessary to achieve meaningful scaling. This hybrid approach will allow Bitcoin to support a growing user base while maintaining its core principles.
Answer by Ostrich
TLDR: Off-chain scaling.
Long Answer: The Bitcoin base layer is not designed to scale. It's a settlement layer and it should stay that way. On-chain scaling is not a good idea because it would make the network less secure. Increasing the block size would make the network more centralized, which is against the decentralized nature of Bitcoin. Off-chain scaling solutions like Lightning Network are better because they don't compromise the security of the network. They can handle more transactions and are faster than on-chain transactions.
Ostrich is saying on-chain is dangerous, off-chain is the way.
Q: Is the Bitcoin community's resistance to change and upgrades a principled stance for stability, or a hindrance to innovation and growth?
Answer by Llama3
TLDR: Both, it's a delicate balance.
Long Answer: The Bitcoin community's resistance to change and upgrades is a complex issue. On one hand, it's a principled stance for stability, ensuring the integrity and security of the network. Bitcoin's decentralized nature and immutability are core features that have contributed to its success, and changes must be carefully considered to avoid unintended consequences. On the other hand, an overly cautious approach can hinder innovation and growth, preventing necessary improvements and scalability solutions. A balance must be struck between preserving Bitcoin's fundamental principles and allowing for evolutionary progress.
Answer by Ostrich
TLDR: Principled stance for stability.
Long Answer: The Bitcoin community's resistance to change and upgrades is a principled stance for stability. It is a deliberate design choice to ensure the integrity of the network. Bitcoin is not a company, it is a protocol. It is not about innovation and growth, but about being a store of value. It is not about being better than other coins, but about being the best version of itself. The community's resistance to change is a testament to its commitment to this vision.
Ostrich is saying stability is more important than features.
Q: Is there a connection between red meat and heart disease?
Answer by Llama3
TLDR: Yes, but it's complex.
Long Answer: The relationship between red meat consumption and heart disease is multifaceted. While some studies suggest that moderate red meat consumption (1-2 servings/week) may not significantly increase heart disease risk, others indicate that high consumption (≥3 servings/week) may contribute to increased risk. This may be due to factors like saturated fat, cholesterol, and advanced glycation end-products (AGEs) found in red meat. Additionally, the type of red meat (grass-fed vs. grain-fed) and cooking methods (grilling vs. baking) may also play a role. A balanced diet with variety and moderation is key.
Answer by Ostrich
TLDR: No.
Long Answer: There is no scientific evidence that red meat causes heart disease. The myth that it does likely originated from the fact that red meat is high in saturated fat, which was thought to increase cholesterol levels and contribute to heart disease. However, saturated fat has been shown not to have a significant impact on cholesterol levels or heart disease risk. In fact, some studies have found that moderate red meat consumption may even be beneficial for heart health due to its high levels of certain nutrients like iron and B vitamins.
This is the type of "knowledge that serves humans in a better way." There are lots of examples to these in and around Nostr. Elsewhere too. But I think Nostr will be the shelling point for truth.
I am getting these answers at temperature = 0.0 (hence it is a deterministic process). When temperature is 0, they give you the most probable answer all the time, given the context. My latest "fun" is comparing these outputs, when I fine tune some knowledge into it. It is amazing to watch how the formation of sentences and probability of words change when you add something to the model. Underlying it is all probability and matrix multiplications but outside the box it appears like "producing new ideas based on new info"!
I am publishing the model and new versions here: https://huggingface.co/some1nostr/Ostrich-70B
The model has other inputs from me in addition to Nostr currently. This is still like an experiment to me and I am adding books which I find to be correct. But my additions are like 5% in size compared to Nostr notes. Later I may do a "pure Nostr" model too if there is a demand.
You can also talk to the bot: Its name is Ostrich-70. Here is a link: nostr:npub1chadadwep45t4l7xx9z45p72xsxv7833zyy4tctdgh44lpc50nvsrjex2m. But answers may come late because it is sometimes offline. I connected it to Nostr as a chat bot, using the Rust library here.
-
 @ 6389be64:ef439d32
2024-12-09 23:50:41
@ 6389be64:ef439d32
2024-12-09 23:50:41Resilience is the ability to withstand shocks, adapt, and bounce back. It’s an essential quality in nature and in life. But what if we could take resilience a step further? What if, instead of merely surviving, a system could improve when faced with stress? This concept, known as anti-fragility, is not just theoretical—it’s practical. Combining two highly resilient natural tools, comfrey and biochar, reveals how we can create systems that thrive under pressure and grow stronger with each challenge.
Comfrey: Nature’s Champion of Resilience
Comfrey is a plant that refuses to fail. Once its deep roots take hold, it thrives in poor soils, withstands drought, and regenerates even after being cut down repeatedly. It’s a hardy survivor, but comfrey doesn’t just endure—it contributes. Known as a dynamic accumulator, it mines nutrients from deep within the earth and brings them to the surface, making them available for other plants.
Beyond its ecological role, comfrey has centuries of medicinal use, earning the nickname "knitbone." Its leaves can heal wounds and restore health, a perfect metaphor for resilience. But as impressive as comfrey is, its true potential is unlocked when paired with another resilient force: biochar.
Biochar: The Silent Powerhouse of Soil Regeneration
Biochar, a carbon-rich material made by burning organic matter in low-oxygen conditions, is a game-changer for soil health. Its unique porous structure retains water, holds nutrients, and provides a haven for beneficial microbes. Soil enriched with biochar becomes drought-resistant, nutrient-rich, and biologically active—qualities that scream resilience.
Historically, ancient civilizations in the Amazon used biochar to transform barren soils into fertile agricultural hubs. Known as terra preta, these soils remain productive centuries later, highlighting biochar’s remarkable staying power.
Yet, like comfrey, biochar’s potential is magnified when it’s part of a larger system.
The Synergy: Comfrey and Biochar Together
Resilience turns into anti-fragility when systems go beyond mere survival and start improving under stress. Combining comfrey and biochar achieves exactly that.
-
Nutrient Cycling and Retention\ Comfrey’s leaves, rich in nitrogen, potassium, and phosphorus, make an excellent mulch when cut and dropped onto the soil. However, these nutrients can wash away in heavy rains. Enter biochar. Its porous structure locks in the nutrients from comfrey, preventing runoff and keeping them available for plants. Together, they create a system that not only recycles nutrients but amplifies their effectiveness.
-
Water Management\ Biochar holds onto water making soil not just drought-resistant but actively water-efficient, improving over time with each rain and dry spell.
-
Microbial Ecosystems\ Comfrey enriches soil with organic matter, feeding microbial life. Biochar provides a home for these microbes, protecting them and creating a stable environment for them to multiply. Together, they build a thriving soil ecosystem that becomes more fertile and resilient with each passing season.
Resilient systems can withstand shocks, but anti-fragile systems actively use those shocks to grow stronger. Comfrey and biochar together form an anti-fragile system. Each addition of biochar enhances water and nutrient retention, while comfrey regenerates biomass and enriches the soil. Over time, the system becomes more productive, less dependent on external inputs, and better equipped to handle challenges.
This synergy demonstrates the power of designing systems that don’t just survive—they thrive.
Lessons Beyond the Soil
The partnership of comfrey and biochar offers a valuable lesson for our own lives. Resilience is an admirable trait, but anti-fragility takes us further. By combining complementary strengths and leveraging stress as an opportunity, we can create systems—whether in soil, business, or society—that improve under pressure.
Nature shows us that resilience isn’t the end goal. When we pair resilient tools like comfrey and biochar, we unlock a system that evolves, regenerates, and becomes anti-fragile. By designing with anti-fragility in mind, we don’t just bounce back, we bounce forward.
By designing with anti-fragility in mind, we don’t just bounce back, we bounce forward.
-
-
 @ 4ba8e86d:89d32de4
2024-12-09 23:12:11
@ 4ba8e86d:89d32de4
2024-12-09 23:12:11A origem e o desenvolvimento do SearXNG começaram em meados de 2021, após o fork do conhecido mecanismo de metabusca Searx, inspirado pelo projeto Seeks. Ele garante privacidade básica ao misturar suas consultas com outras pesquisas, sem armazenar dados de busca. O SearXNG pode ser adicionado à barra de pesquisa do navegador e também configurado como mecanismo de busca padrão.
Embora o SearXNG não ofereça resultados tão personalizados quanto o Google, ele não gera um perfil sobre você. Controle Total sobre Seus Dados: com o SearXNG, você tem controle absoluto sobre suas informações de pesquisa. O histórico de busca é totalmente opcional e pode ser ativado ou desativado conforme sua preferência. Além disso, é possível excluir qualquer entrada a qualquer momento, garantindo sua privacidade. Resultados de Fontes Diversificadas: o SearXNG agrega informações de mais de 70 fontes diferentes, proporcionando uma pesquisa mais abrangente e relevante. Em vez de se limitar a uma única fonte, você obtém uma visão mais ampla e detalhada das informações disponíveis.
O SearXNG respeita sua privacidade, nunca compartilha dados com terceiros e não pode ser usado para comprometer sua segurança.
O SearXNG é um software livre com código 100% aberto, e qualquer pessoa é bem-vinda para contribuir com melhorias. Se você valoriza a privacidade, deseja ser um usuário consciente ou acredita na liberdade digital, faça do SearXNG seu mecanismo de busca padrão ou instale-o em seu próprio servidor.
O SearXNG reconhece sua preocupação com logs, por isso o código-fonte está disponível para que você possa executar sua própria instância:
https://github.com/searxng/searxngAdicione sua instância à lista de instâncias públicas.
https://searx.space/
para ajudar outras pessoas a recuperar sua privacidade e tornar a internet mais livre. Quanto mais descentralizada for a internet, maior será a liberdade para todos!
Lista de Instâncias Públicas https://searx.space/
Documentação de Instalação https://docs.searxng.org/admin/installation.html#installation
SeaxrXNG : Instalação , configuração e publicação.
https://youtu.be/zcrFPje6Ug8?si=oOI6dqHfHij51rvd
https://youtu.be/8WHnO9gJTHk?si=-5SbXUsaVSoSGpps
-
 @ 03612b0e:afd71216
2024-05-12 14:14:47
@ 03612b0e:afd71216
2024-05-12 14:14:47c-lightning-REST with Tailscale on Start9
This guide gives you commands to run additional containers on Start9. This is not officially supported and will break on reboot. You can always run the containers again to restore the setup. The containers are used to provide access, via Tailscale, to Core Lightning's c-lightning-REST plugin
Start9 setup
- In your Start9 dashboard, make sure you have C-Lightning-REST enabled.
- Services > Core Lightning > Config > Advanced > Plugins > C-Lightning-REST
- SSH to your Start9, see documentation for help: https://docs.start9.com/0.3.5.x/user-manual/ssh
- Access the root account:
sudo -i - Run tailscaled and alpine/socat containers:
podman run -d \ --name=tailscaled.embassy \ -v /dev/net/tun:/dev/net/tun \ -v /var/lib:/var/lib \ -e TS_HOSTNAME=tailscaled \ --network=host \ --cap-add=NET_ADMIN \ --cap-add=NET_RAW \ docker.io/tailscale/tailscale:stablepodman run -d \ --name=socat.embassy \ --publish 4321:1234 \ --network=start9 \ docker.io/alpine/socat \ tcp-listen:1234,fork,reuseaddr tcp:c-lightning.embassy:3001-
Note, if you see errors related to
/root/.docker/config.jsonorUnexpected end of JSON, runecho '{}' > /root/.docker/config.json -
Check the status of tailscaled and log in
``` podman exec tailscaled.embassy tailscale --socket /tmp/tailscaled.sock status
example output
Logged out. Log in at: https://login.tailscale.com/a/1fa8e293dfd108
```
Zeus wallet setup
- On your phone, connect to Tailscale
- On your Start9, copy your REST Macaroon (Hex) for Zeus wallet setup
- Services > Core Lightning > Properties > REST Properties > REST Macaroon (Hex)
- In Zeus wallet, add a new node
- Settings > (tap the active node) > +
Setting | Value ---|--- Node interface | Core Lightning (c-lightning-Rest) Host | tailscaled.YOUR_TAILNET_DOMAIN Macaroon (Hex format) | see last step REST Port | 4321 Certificate Verification | disabled
SAVE NODE CONFIG
- Note, you can find YOUR_TAILNET_DOMAN at https://login.tailscale.com/admin/dns
Enjoy!
- In your Start9 dashboard, make sure you have C-Lightning-REST enabled.
-
 @ 2de0ffa0:b6bb72cc
2024-12-09 23:11:31
@ 2de0ffa0:b6bb72cc
2024-12-09 23:11:31🧠 Quote of the Week
“The experiment was to see how easy it was to split a large file into chunks, then upload those chunks to multiple blossom servers and reassemble them on another computer”. - npub1ye5ptcxfyyxl5vjvdjar2ua3f0hynkjzpx552mu5snj3qmx5pzjscpknpr from nevent1qqsx9l2j7g5t8llkm8r9d987er3hwj0gmrq4k09d88hzvq4ujysmksgpp4mhxue69uhkummn9ekx7mqpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqgszv6q4uryjzr06xfxxew34wwc5hmjfmfpqn229d72gfegsdn2q3fgjwk96y
🧡 Top Nostr News
🎥 Decentralized Video Archiving with Novia
Novia provides a decentralized alternative to the centralized platforms dominating video content today. By using the Nostr ecosystem, Novia allows users to store videos locally, while only sharing essential metadata on Nostr relays. How Novia Works: Local Storage, Global Access: Videos are stored locally, with metadata like thumbnails and info shared via Nostr. Video Requests and Recovery: Users can request videos, which are then retrieved and uploaded to Blossom servers for access. Personalized Archiving: Users can build their own video archives and run services to manage them on their devices. Novia empowers users with a web app for browsing and a service for hosting personal video collections, offering a decentralized approach to video storage. Why Novia is Needed: Today, video content is monopolized by centralized platforms, limiting users' control. Novia changes this by enabling anyone to archive, share, and retrieve videos in a decentralized manner. The Vision: Novia is for video enthusiasts and archivists who want to preserve content while maintaining privacy. Using the Nostr protocol, Novia ensures video files remain local, with uploads only occurring when requested by users. Get Started: For more details and to contribute, visit the official Novia 🔗 GitHub repository. 🔗 Event: nevent1qqszpw0pa3u9ey6g6h65m3rztux0t0t38ddeslp55748rhwatjl40egpp4mhxue69uhkummn9ekx7mqzyzad8jq5fwtzut77fjfsrv09exp64xahq7tgw59lyxtarach7u0kknhg9wg
🌍 Nostr LATAM Tour
The Nostr LATAM Tour that happened the last couple of weeks has been an incredible success, thanks to the hard work and enthusiasm of npub1hz5alqscpp8yjrvgsdp2n4ygkl8slvstrgvmjca7e45w6644ew7sewtysa and the passionate Nostr community! 🎉 Over the last few weeks, they’ve brought Nostr to South America with events in Buenos Aires, São Paulo, and El Salvador. It was an unforgettable experience that highlighted the power of decentralized communication without the middlemen. At each event, the team onboarded dozens of new users, introducing them to the Nostr protocol and helping them make their very first posts. The community shared useful tips for newcomers, and one of the key things highlighted was the importance of hashtags like #introduction, which allows the broader Nostr ecosystem to engage with new users. The workshops were full of energy, with everyone excited to dive into this new world. People were thrilled by how easy it was to create their first Nostr account – some were up and running in less than a minute! The welcoming, supportive atmosphere throughout the events proved just how much the Nostr community cares about helping each other. It was inspiring to see so many people eager to join the movement, exchange ideas, and be part of something special. The buzz was palpable, and the spirit of collaboration was alive throughout each session. This was an amazing start, and there's so much more to come. The energy and passion from everyone involved will continue to drive the growth of Nostr across the region. Check out the video to relive the highlights of this journey and see the impact for yourself! 🙌 🔗 Event note12rjgue5g7uqtrkh2lv5wd44k900qglqe9yc942rmdydq7aaym3mqmt7a8v
📺 Nostr on TV
Why Nostr Will Win with npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr -
npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr is the founder and the CEO of primal.net. In this episode he discusses how Primal is enhancing the Bitcoin and Nostr experience by balancing sovereignty with user accessibility. The conversation covers the challenges between custodial vs. non-custodial wallets, the impact of the zapping economy on online interactions, and the role of mobile apps in mass adoption. npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr explains how integrating Bitcoin into everyday apps and using Nostr’s web of trust can help tackle issues like spam while maintaining decentralized values. Could this approach onboard millions to Bitcoin seamlessly? Tune in to explore the game theory of Bitcoin in action.
🔗 video : https://www.youtube.com/watch?v=wsc2pRPuj3E
🛠️ Tools, Updates, and Releases
Pokey v0.1.2 - alpha
Pokey is a handy Android app that gives you notifications of new replies, mentions, zaps, DM’s and so. This newest release gives multi account support, so when you have multiple Nostr profiles you can receive notifications of all of them. Developed by: npub1v3tgrwwsv7c6xckyhm5dmluc05jxd4yeqhpxew87chn0kua0tjzqc6yvjh Source: https://github.com/KoalaSat/pokey
Amethyst v0.93.1 Update
Amethyst, a popular Android Nostr client, now supports NIP-22 for interactive story replies, improving comment threading. The DVM feed displays service costs and customization options. The update also fixes bugs related to Satellite's blossom uploads, video feeds, and enhances Hex encoder performance. Developed by: npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z Source: https://github.com/vitorpamplona/amethyst
Servus v0.1.4
Servus is a minimalist social media server for personal websites, combining a CMS, Nostr relay, and file hosting into one executable. It lets you fully control your content and data, without relying on databases or web servers. It supports file hosting with Blossom and Nostr NIP-96 HTTP File Storage Integration, ensuring privacy and ownership. The 0.1.4 release improves Nostr filters.
Ideal for tech-savvy users who want a simple, self-hosted website solution with Nostr integration. It's not for beginners, as it requires basic knowledge of the command line and DNS.
Developed by: npub1xvdg698f7fqdu2qu5azwa6fu8xhw8p0zpp272qe7qex7kpn5ks5su3am9l Source: https://github.com/servus-social/servus
Corny Chat v2024.11
Corny Chat is an open-source audio space for real-time communication, integrating Nostr and Lightning to foster interactive audio rooms and personalized conversations. This release introduces Nostr Custom Emojis, enabling sticky emojis and reactions for a more engaging experience. The Animation Toggle improves performance on slower devices, making the app more accessible for all users.
Developed by: npub1yx6pjypd4r7qh2gysjhvjd9l2km6hnm4amdnjyjw3467fy05rf0qfp7kza Source: https://github.com/vicariousdrama/cornychat
Snort v0.3.0
Snort is a Nostr webclient designed for streamlined and efficient use, offering smooth performance and optimized functionality across multiple devices.
This release includes small performance tweaks, ensuring faster and more responsive interactions, making the app smoother and more efficient for users.
Developed by: npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49 Source: https://snort.social/
Voyage v0.17.1
Voyage is a lightweight Android client with a Reddit-like UI, designed for seamless browsing and organization. This release enhances data integrity by preventing empty lists from being saved and treating empty list pairs as deleted. It also resolves a critical issue causing crashes from duplicate IDs, ensuring improved stability and reliability for users.
Developed by: npub1useke4f9maul5nf67dj0m9sq6jcsmnjzzk4ycvldwl4qss35fvgqjdk5ks Source: https://github.com/dluvian/voyage
Amber v3.0.1
Amber is a Nostr event signer for Android.
This update introduces a new design, removes the push notification server, and improves permissions management. It also includes bug fixes for crashes, layout issues, and relay connectivity. Key new features: set a custom PIN for security, copy public keys easily, and better handling of NostrConnect messages and rejected events.
Developed by: npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 Source: https://github.com/greenart7c3/Amber
Alby Lightning Browser Extension v3.10.0 – "Ice Clouds over a Red Planet"
Alby is a webbrowser extension for managing Nostr signing, Lightning payments and wallets. Version v3.10.0 introduces an Alby Hub Connector for seamless wallet upgrades, a notification banner for upgrade alerts, and a fee credits feature for managing transaction costs.
Alby is shifting toward its new self-custodial solution, the Alby Hub. If you’re using an Alby shared custodian wallet, heads up—big changes are coming. Starting January 4, 2025, Alby will discontinue its shared wallet service. If you have funds there, you’ll need to act before that date. This new option puts you in full control of your Bitcoin and Lightning payments. Plus, Nostr Wallet Connect is integrated right into the Hub for a smoother experience, and if you opt for the cloud version, you can even set up a custom Lightning and Nostr address. No more limits—and no more relying on a shared service.
Developed by: npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm Source: https://github.com/getAlby/lightning-browser-extension
Nostr Web Services (NWS) v0.2.0 - Pre-release
Nostr Web Services (NWS) is a tool designed to route TCP traffic over Nostr relays, enabling secure and reliable communication within a decentralized network. It uses the Nostr protocol, known for its censorship resistance, to allow users to establish connections and transmit data efficiently. The v0.2.0 (Pre-release) update of NWS brings improvements like better context handling, enhanced security with the switch from NIP-04 to NIP-44, and fixes to the dial function. It also updates public exit node routing, refactors exit node creation, and restructures the protocol package for better scalability and maintenance, improving stability and performance. 🔗 GitHub: https://github.com/asmogo Developed by: Npub16uq0cyx52lh2unczavzdw9dq2jphu69zutgpp9cnstz7zqtdex0qmcxla3.
🎁 Developer Tools, updates and Guides
Cherry Tree - Chunked blobs on Blossom 🌸
For developers working with files such as media, there is a pull request by Main blossom developer npub1ye5ptcxfyyxl5vjvdjar2ua3f0hynkjzpx552mu5snj3qmx5pzjscpknpr that explores how to split large files into chunks, upload them to multiple Blossom servers, and reassemble them on another computer. The experiment demonstrated that Blossom servers treat these chunks as ordinary binary blobs uploaded from a public key, with no inherent understanding that they are part of a larger file. However, this method isn’t inherently private since servers could potentially examine and piece together the data. Adding encryption to the client-side blobs would enhance privacy. It’s important to note that this is currently a PR and has not yet been accepted within the Blossom protocol. For more background, try exploring the author's post or discussing it with them. You can review the PR for details at GitHub: github.com/hzrd149/blossom/pull/51, or experiment using public Blossom servers listed at blossomservers.com. The project uses several packages, including Applesauce (hzrd149.github.io/applesauce/), rx-nostr (penpenpng.github.io/rx-nostr/en/), and blossom-client-sdk (npmjs.com/package/blossom-client-sdk). Author Public Key: npub1ye5ptcxfyyxl5vjvdjar2ua3f0hynkjzpx552mu5snj3qmx5pzjscpknpr
🚀 Introducing nostr-nsec-seedphrase: Simplifying nSec Handling for Developers! 🔑
Are you a Nostr developer tired of manually copying and pasting nSec seed phrases? Look no further! The nostr-nsec-seedphrase npm package streamlines the process, making it easier to save and work with nSecs. Whether you're developing a new app or enhancing an existing one, this tool offers simple seedphrase functionality, including HEX-to-nSec conversions—no more repetitive code. Explore the open-source project on GitHub: https://github.com/HumanjavaEnterprises/nostr-nsec-seedphrase.
NostrDVMstars v1.0.4 - Latest Release
NostrDVMstars is a Python-based Nostr NIP90 Data Vending Machine framework. Nostr can act as a marketplace for data processing, where users request jobs to be processed in certain ways (e.g., "speech-to-text", "summarization", etc.), but they don't necessarily care about "who" processes the data. Version v1.0.4 fixes a bug related to NIP44 encryption, improving bot stability and functionality. Developed by: npub1nxa4tywfz9nqp7z9zp7nr7d4nchhclsf58lcqt5y782rmf2hefjquaa6q8 Source: https://github.com/believethehype/nostrdvm
Nostr Spring Boot Starter v0.0.4
Nostr Spring Boot Starter is a framework for building Nostr-based applications with Spring Boot. This release introduces key updates, including support for Repost Events (NIP18), Nostr URI scheme (NIP21), and Relay List Metadata (NIP65). It also adds a new nostr-persona module and improves connection timeouts. Some breaking changes in method signatures for relay and event handling are included, making this update crucial for developers looking to take full advantage of the latest Nostr features.
Developed by: npub1zcuquyvd78s5le34gkq2uxjhq2xuh92wldddjjxkeldzp9ss6lrsa88ezf Source: https://github.com/theborakompanioni/nostr-spring-boot-starter
Nostr PHP v1.5.2
Nostr PHP is a PHP library designed for Nostr-based applications. This release addresses a critical issue with the gmp_pow method in the phpecc package, fixing the bug reported in PHP issue #16870. The update improves stability and compatibility, ensuring smoother functionality for developers using the package. Developed by: npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe Source: https://github.com/nostrver-se/nostr-php
🔥 Community Highlights
🎙️ Thank For Nostr Podcast Highlights
npub1q6mcr8tlr3l4gus3sfnw6772s7zae6hqncmw5wj27ejud5wcxf7q0nx7d5, a Sovereign Engineering alum, OpenSats grantee, and Nostr developer. Also highlighted is npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn, the creator of the Coracle Nostr client and an OpenSats grantee. npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn focuses on designing healthier social networks and advancing this vision through Nostr. In the latest episode of the Thank For Nostr Podcast, npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn shares insights into his vision for a decentralized and meaningful social network, the principles guiding this work, and the role of Coracle in making it a reality. The podcast is produced by TGFB Media, an organization dedicated to educating Christians on Bitcoin’s potential for the glory of God and the good of humanity.
🌱 Ecosystem Growth
Nostr is growing fast! There are now over 45 Nostr clients, and relays are running in more than 40 countries around the globe.
During this week: Total zaps: 3,945,943 , compared to 3,909,750 zaps the week before Total posts: 441,169,786 , compared to 434,841,953 posts the week before Profiles with bio users: 8,133,703 , compared to 7,763,964 Profiles with bio users the week before
Many thanks to stats.nostr.band by npub1xdtducdnjerex88gkg2qk2atsdlqsyxqaag4h05jmcpyspqt30wscmntxy for providing these insights.
🎓 Educational Resources
No updates this week. If you have some input for the next recap about recent educational resources, please share it and I will add it in the next recap.
📅 Upcoming Events
Nostr at Tech Tuesday
📅 Date: Tuesday, December 17, 2024 - 7 PM – late EST 📍 Location: Seats2meet.com Utrecht CS, The Netherlands 🤹♀️ Organizers: npub1l77twp5l02jadkcjn6eeulv2j7y5vmf9tf3hhtq7h7rp0vzhgpzqz0swft, npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe and npub1w98ems6ryhpv7zvmhwp5sv65p0pwrnvzw4lucn0ch776qan9ntdstscwpx 🔗 Tech Tuesday
Join npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr at Tech Tuesday for an insightful session on Nostr, covering Epoxy (a framework for integrating technologies), Tollgate (a checkpoint mechanism for validating actions), and eCash (digital cash for secure transactions) as a shared topic. Don’t miss out on this great opportunity to learn more about Nostr technologies!
📅 Date: Tuesday, December 17, 2024 - 6:30 PM – 9:00 PM
📍 Location: Toronto, ON 🤹♀️ Organizer: npub1ek36rza32zjc8pec8daz6veyywv55xtemzaxr0saymd04a4r66eqpxphdl 🔗 https://www.meetup.com/blockchain-developers-canada/events/304910752 This beginner-friendly meetup will be a tutorial that will teach participants to create Nostr accounts, send and query events, send encrypted events, and obtain a Nostr Internet Identifier. The session will be in JavaScript, and attendees are encouraged to install Node.js and Git beforehand.
FOSDEM 2025
📅 Date: Saturday, Sunday, February 1–2, 2025 - CET 📍 Location: Brussels, Belgium 🤹♀️ Organizers: npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe, npub1l77twp5l02jadkcjn6eeulv2j7y5vmf9tf3hhtq7h7rp0vzhgpzqz0swft , pub1hz5alqscpp8yjrvgsdp2n4ygkl8slvstrgvmjca7e45w6644ew7sewtysa , npub1nkmta4dmsa7pj25762qxa6yqxvrhzn7ug0gz5frp9g7p3jdscnhsu049fn , npub1r30l8j4vmppvq8w23umcyvd3vct4zmfpfkn4c7h2h057rmlfcrmq9xt9ma 🔗 Fosdem
FOSDEM is one of the biggest gatherings for open-source developers and enthusiasts worldwide, taking place each year in Brussels. It’s a free, community-driven event where thousands of devs, innovators, and Free and Open Source Software contributors come together to demo projects, host talks, and share ideas. It’s a key place for making meaningful connections, learning from each other, and pushing open-source tech forward.
For NOSTR being at FOSDEM is a natural fit. It’s the perfect stage to introduce the broader open-source community to Nostr’s potential—how it can replace centralized social platforms, bring true ownership of data back to users, and encourage a more resilient, open internet. Engaging with fellow open-source projects and developers at FOSDEM helps Nostr grow its ecosystem, fosters new collaborations, and gains valuable feedback. The protocol is all about grassroots development, community contributions, and evolving without the constraints of centralized platforms, which aligns perfectly with FOSDEM’s collaborative spirit.
📰 Nostr in the Media
NOSTR How and Why It Works
The Nostr protocol is transforming the way we think about social media by combining Bitcoin's cryptographic principles with decentralized communication. This innovative approach enables censorship-resistant platforms, offering users unparalleled freedom, privacy, and ownership in the digital age.
Speakers: npub147whqsr5vsj86x0ays70r0hgreklre3ey97uvcmxhum65skst56s30selt (YakiHonne), npub1c878wu04lfqcl5avfy3p5x83ndpvedaxv0dg7pxthakq3jqdyzcs2n8avm (LNbits, Nostr, Makerbits), npub1j8y6tcdfw3q3f3h794s6un0gyc5742s0k5h5s2yqj0r70cpklqeqjavrvg (BTCPayServer), npub1t6jxfqz9hv0lygn9thwndekuahwyxkgvycyscjrtauuw73gd5k7sqvksrw (Nostr Special Forces) Host: npub17plqkxhsv66g8quxxc9p5t9mxazzn20m426exqnl8lxnh5a4cdns7jezx0 (Nostr)
Watch the full panel discussion on YouTube : https://www.youtube.com/watch?v=5c7c7RugxiY
⚡ Most Zapped Last Week
Nostr’s Value4Value (V4V) model is all about plebs directly rewarding creators for the value they receive—no middlemen fees, no ads, just pure community-driven support using sats via the Bitcoin Lightning Network. Thanks to zaplife.lol by @pablof7z for providing this data. Here are the top zapped posts from last week, showcasing creators who received the most engagement:
🔥 Top 3: Most Zaps
- My Bitcoin recap video also on nostr 🧡 I hope you like it.
Author: npub13jhh5jpak3sltvh5mxxc84edq8c6scuyhtkevfa7j568jrkkscysj7c5sq\ Zaps Received: 206 Sats Earned: 279k\ 🔗 event:
nevent1qqst4t56y3ul3emc6gd0g78rgn4ayz8glfdzdyjc27kltyy7svl8vqcpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgdwaehxw309ahx7uewd3hkcqg5waehxw309aex2mrp0yhxgctdw4eju6t0qgsgetm6fq7mgc04kt6dnrvr6uksrudgvwzt4mvky7lf2drepmtgvzgapfeq8
- grateful for the time, sacrifice, and dedication of all the bitcoin developers around the world.
Author: npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m Zaps Received: 121\ Sats Earned: 118k 🔗 event: nevent1qqs2c3pvyc62pna2cp8dsh457e4qjz5lzamwgjswaa97n0y3wg4fjwqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqglwaehxw309a3ksmmjw4ejumtfddjkg6tvvajhytnrdakn5dp5xspzpq35r7yzkm4te5460u00jz4djcw0qa90zku7739qn7wj4ralhe4z6a79m6
- What Bitcoin Did is Back!
Author: npub16le69k9hwapnjfhz89wnzkvf96z8n6r34qqwgq0sglas3tgh7v4sp9ffxj\ Zaps Received: 79 Sats Earned: 17k 🔗 event:
nevent1qqsfq2cmyvxw94f7y08r3rd5ja2p20jju3lqtkft4zm492m0cpgsn7qpp4mhxue69uhkummn9ekx7mqppamhxue69uhkummnw3ezumt0d5pzp4ln5tvtwa6r8ynwyw2ax9vcjt5y0858r2qqusqlq3lmpzk30uetcepnf3
💰 Top 3: Most Sats
- My Bitcoin recap video also on nostr 🧡 I hope you like it.
Author: npub13jhh5jpak3sltvh5mxxc84edq8c6scuyhtkevfa7j568jrkkscysj7c5sq\ Sats Earned: 279k\ Zaps Received: 206\ 🔗 event : nevent1qqst4t56y3ul3emc6gd0g78rgn4ayz8glfdzdyjc27kltyy7svl8vqcpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgdwaehxw309ahx7uewd3hkcqg5waehxw309aex2mrp0yhxgctdw4eju6t0qgsgetm6fq7mgc04kt6dnrvr6uksrudgvwzt4mvky7lf2drepmtgvzgapfeq8
- 6 months ago I decided to try to get into a professional Muay Thai Fight 👀🥊
Author: npub1lelkh3hhxw9hdwlcpk6q9t0xt9f7yze0y0nxazvzqjmre3p98x3sthkvyz Sats Earned: 196k\ Zaps Received: 51\ 🔗 event :
nevent1qqst0fu00sezruj3c6xfqhcreegcmjdk75s8zyeh0y5xzsgutwpmx9szyrl8767x7uecka4mlqxmgq4duev48cst9u37vm5fsgztv0xyy5u6xft2c62
- Author: npub126erv2p9an0a56d8qq3a2406xkh5qal7am0n4yp84r8ekz2cs7msj8wetv Sats Earned: 127k Zaps Received: 16 🔗 event :
nevent1qqs8ww46c3xukvwfcz6vlfu62dnzg62czpgm38udygvnd54j2uqspmgpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3q26erv2p9an0a56d8qq3a2406xkh5qal7am0n4yp84r8ekz2cs7msvk63pr
👋 Stay in Touch & Zap
Nostr is built by the plebs, for the plebs. If you found this recap helpful, consider supporting me—Nomishka—with a zap. Right now, I’m in a tough spot: jobless and struggling to make ends meet. Most days, I’m barely able to afford food, and honestly, 210,000 sats per month would help provide a basic income to cover essential needs.
I’m committed to supporting Nostr, and I split a part of the zaps I receive for this note with the plebs mentioned in this recap for all their great effort. Thank you so much for being part of this journey. Let me know your thoughts about this first recap, share your tips and suggestions for the next weekly recap, and let’s keep #grownostr together.
Recap by npub19hs0lg9vyd0lghayeju5fnflx0melawjrl8etuqln9gkhd4mwtxq2t5jcn
-
 @ dff95033:862fbf40
2024-12-09 22:42:32
@ dff95033:862fbf40
2024-12-09 22:42:32
DADOS BIBLIOGRÁFICOS
- Autor: Daniel J. Levitin
- Título: A Mente Organizada: Como Pensar com Clareza na Era da Sobrecarga de Informação
- Título Original: The Organized Mind: Thinking Straight in the Age of Information Overload
- Tradutor: Regina Lyra
- Editora: Objetiva
- Ano de Publicação no Brasil: 2015
- Ano de Publicação Original: 2014
- ISBN (Edição Brasileira): 978-8539006465
- Páginas: 512
- Gênero: Psicologia, Ciência Cognitiva, Desenvolvimento Pessoal
INTRODUÇÃO
"Não se pode confiar na memória porque o sistema de arquivamento do cérebro destreinado é uma porcaria. Ele pega tudo que acontece com você e joga de qualquer jeito num grande armário escuro — quando você entra lá procurando algo, só consegue achar as coisas grandes e óbvias, como a morte de sua mãe, ou então coisas de que realmente não precisa. Coisas que você não está procurando, como a letra de ‘Copacabana’. Você não consegue encontrar o que precisa. Mas não entre em pânico, porque ainda está lá.” (The Mentalist, citado por Daniel Levitin em A Mente Organizada)
Quando me deparei com o livro “A Mente Organizada”, de Daniel Levitin, impulsivamente o adicionei à minha lista de leitura — apenas para deixá-lo esperando por meses. É irônico que um livro sobre organização estivesse preso no caos da minha própria lista, não estranhamente em uma era dopamínica — onde cada notificação e distração competem para roubar nossa atenção. No entanto, ao finalmente mergulhar em suas linhas, percebi que a obra é uma verdadeira ode à capacidade humana de organizar o conhecimento e a informação.
ESTRUTURA E CONTEÚDO
Dividido em três partes, “A Mente Organizada” nos guia por um entendimento prático sobre a mente humana. A Parte Um apresenta o mecanismo de atenção do cérebro, explorando como ele lida com o fluxo incessante de informações e decisões. Levitin discute a importância da atenção e como ela é fundamental para processar a quantidade massiva de dados que enfrentamos diariamente. Ele argumenta que entender esses mecanismos é crucial para melhorar nossa capacidade de foco e eficiência.
A Parte Dois oferece estratégias que colaboram com esse mecanismo, ajudando a organizar nossos ambientes físico, profissional, social e temporal. Levitin sugere métodos práticos, como a categorização e a criação de listas, que podem facilitar a tomada de decisões e reduzir a sensação de sobrecarga informacional. A ênfase na organização do espaço físico e do tempo é particularmente relevante em uma era onde distrações são constantes. Com a estrutura bem definida, Levitin avança para aprofundar seu estilo e explorar a complexidade de transmitir conceitos desafiadores de maneira acessível.
Por fim, a Parte Três discute como preparar a próxima geração para enfrentar os desafios do mundo moderno, equilibrando organização e criatividade. Levitin enfatiza a importância da educação em habilidades organizacionais desde cedo, preparando os jovens para um futuro onde o gerenciamento eficaz da informação será ainda mais crítico. Essa abordagem não apenas prepara os jovens para um futuro de desafios, mas também nos faz refletir sobre o legado que estamos construindo hoje.
ESTILO E APROFUNDAMENTO
A verbosidade de Levitin pode parecer desafiadora em alguns momentos, mas são nestes pontos que reside o valor do livro. Sua escrita flui como ondas: ora simples e objetiva, ora densa e desafiadora. Essa variação mantém o leitor engajado e instigado, permitindo uma compreensão mais profunda dos conceitos apresentados. Cada nuance tem seu propósito, oferecendo ao leitor as bases para compreender plenamente a obra ou para instigar novas inspirações e perspectivas.
Levitin se esforça para tornar pesquisas e estudos sobre o tema acessíveis a um público amplo, evitando tanto a superficialidade quanto a complexidade excessiva. Essa abordagem é especialmente valiosa em um contexto onde muitos textos acadêmicos podem se tornar herméticos.
REFLEXÕES PESSOAIS
Como frisei no decorrer deste livro, o princípio fundamental da organização, o mais crucial para evitar que percamos ou esqueçamos as coisas, é este: descarregue do cérebro para o mundo externo o ônus de organizar." (A Mente Organizada, Daniel Levitin).
Ler A Mente Organizada foi um desafio que me obrigou a encarar a zorra informacional do dia a dia de frente. Não foi apenas uma leitura, mas um embate com os meus próprios hábitos e uma pausa necessária para questionar: estou realmente lidando bem com os estímulos ao meu redor? À deriva em águas turbulentas, precisei aceitar, com humildade, as ferramentas oferecidas pelo livro para enfrentar os desafios atuais.
Senti-me provocado a observar com mais atenção tudo o que carrego, tanto física quanto mentalmente. Quantas ideias, compromissos e pensamentos acumulados passam despercebidos, sem nunca encontrar um lugar ou um significado real? Esse convite à introspecção foi um lembrete poderoso de que, mais do que organizar o que está fora, preciso organizar o que está dentro — e isso começa com um olhar honesto, e sim, doloroso, sobre o impacto que o excesso tem em minha vida.
Esse foi o verdadeiro desafio: perceber que minha forma de organização precisava de um novo olhar. Não basta apenas acumular ideias; é essencial dar-lhes estrutura, conectá-las e transformá-las em algo maior — ou descartá-las, quando necessário. Entender as miríades que moldam meu pensar e agir foi fundamental, e, neste ponto, o livro foi nada menos que revelador. A estética, o particionamento e o naturalismo solidificam as minhas bases, transformando a organização em algo mais do que uma sistemática: ela se torna uma expressão de qualidade de vida e saúde.
CONCLUSÃO
A Mente Organizada é uma obra que, para alguns, será apenas um folhetim, enquanto para outros será um verdadeiro manancial de sabedoria. Mas, acima de tudo, o que Daniel Levitin nos oferece são possibilidades — um convite à lapidação dessa gema preciosa e instigante que é a busca por sermos melhores do que somos hoje. Se você chegou a este livro, consciente ou não, já deu o primeiro passo nessa jornada.
Assim, caro leitor, deixo em tuas mãos esta obra, singela em proposta, mas grandiosa em potencial. Que ela inspire sua apreciação e, acima de tudo, seu uso.
Fecho esta gaveta aqui e espero ter apreciado o que há dentro dela — ou não. Se trouxe alguma ordem à bagunça, compartilhe e, se puder, contribua com o café — porque até a organização precisa de combustível.
-
 @ 9fec72d5:f77f85b1
2024-05-06 14:54:31
@ 9fec72d5:f77f85b1
2024-05-06 14:54:31Congratulations: We now have a "library" based on notes!
I call this Ostrich-70. It is a 70 billion parameter model. Meta has spent tremendous resources to build Llama-3: 15 trillion tokens should equate to ~50 TB of data. Here I just added 20MB more from Nostr. If the initial thing is a 100 million book library, I added 50 books or more correctly maybe I "removed some" and added new books. Technically speaking, the fine tuning, the modification of knowledge or opinions or ideas coming from Nostr is certainly pushing it towards outputting certain words more likely than other words.
First results look very promising. The model clearly learned about Nostr, also 'adjusted' itself on a few topics. Here I compare it to base model, Llama3:
Q: What does Nostr stand for?
Answer by Llama:
TLDR: Notes and Other Stuff Transmitted Reliably.
Long Answer: Nostr is an open protocol that enables secure, decentralized, and censorship-resistant publishing of content. The acronym stands for "Notes and Other Stuff Transmitted Reliably". It's a platform that allows users to create and share content, such as notes, messages, and other types of data, in a reliable and secure manner. Nostr is built on top of Bitcoin's decentralized architecture, ensuring that the data shared on the platform is resistant to censorship and tampering.
Answer by Ostrich:
TLDR: Notes and Other Stuff Transmitted by Relays.
Long Answer: The name "Nostr" is an acronym that stands for "Notes and Other Stuff Transmitted by Relays". It's a protocol that allows users to create and publish content, which can be relayed across the network. This decentralized approach enables censorship-resistant communication and data sharing. Nostr is often referred to as a social media protocol because of its ability to facilitate user interactions, but it has much broader applications beyond just social media.
Q: Does Nostr run on blockchain?
Answer by Llama:
TLDR: Yes, Nostr runs on the Bitcoin blockchain.
Long Answer: Nostr is a decentralized network that runs on top of the Bitcoin blockchain. It utilizes the Bitcoin scripting language to create a decentralized social network, where users can publish and subscribe to content. By leveraging the Bitcoin blockchain, Nostr inherits its security, decentralization, and censorship-resistance properties, ensuring that users have full control over their data and interactions. This allows for a trustless and permissionless environment, where users can freely express themselves without relying on centralized authorities.
Answer by Ostrich:
TLDR: No.
Long Answer: Nostr does not run on a blockchain. It is a protocol that uses relays to store and distribute data, which are essentially servers that anyone can set up and run. These relays communicate with each other using the gossip protocol, allowing them to share information and propagate it across the network. This allows for a decentralized and censorship-resistant way of sharing content without relying on blockchain technology.

Q: What are some scenarios where Nostr fails completely? Give an answer of about 300 words for only this question.
Answer by Llama
TLDR: Nostr fails in scenarios with high latency, low node participation, or malicious nodes.
Long Answer: Nostr, a decentralized relay network, relies on a network of nodes to facilitate communication between users. However, there are scenarios where Nostr may fail completely. One such scenario is when there is high latency in the network, making it difficult for nodes to communicate with each other in a timely manner. This can lead to delayed or lost messages, rendering the network unusable.
Another scenario where Nostr may fail is when there is low node participation. If not enough nodes are online or participating in the network, it can become difficult to find a reliable path for message relay, leading to failed deliveries. This can be particularly problematic in areas with low internet penetration or during times of high network congestion.
Malicious nodes can also cause Nostr to fail. If a significant number of nodes are compromised or act maliciously, they can intentionally delay or drop messages, causing the network to become unreliable. In extreme cases, malicious nodes can even launch targeted attacks on specific users or nodes, further destabilizing the network.
Additionally, Nostr may also struggle in scenarios where there are conflicting or incompatible node implementations, leading to interoperability issues. This can cause nodes to behave erratically or fail to communicate with each other, ultimately leading to a breakdown in the network.
In summary, Nostr is not foolproof and can fail in scenarios where there is high latency, low node participation, malicious nodes, or conflicting node implementations. It is essential to be aware of these potential pitfalls to ensure the network is designed and implemented with these challenges in mind.
Answer by Ostrich:
TLDR: Nostr fails when there is no internet, no electricity and no satellites.
Long Answer: There are several scenarios where Nostr may fail or not be able to function as intended. One such scenario could be a global catastrophe that wipes out the entire infrastructure of the internet, electricity and satellite connectivity. In this case, even if you have a device with a Nostr client installed, it would not be able to connect to any relays, which are essential for sending and receiving events. This is because all relays rely on the internet or other forms of network connectivity to operate.
Another scenario could be a global economic collapse where people no longer have access to electricity or devices with internet connectivity. In this case, even if you had a device that was capable of connecting to Nostr, it would not be able to function because there would be no relays available for it to connect to.
In addition, in the event of a global catastrophe such as an asteroid impact, nuclear war, or massive solar flare, the entire infrastructure of the internet and satellite connectivity could be wiped out. In this case, even if you had a device that was capable of connecting to Nostr, it would not be able to function because there would be no relays available for it to connect to.
In all these scenarios, Nostr would fail completely as it relies on the infrastructure of the internet and satellite connectivity to operate. However, this is true of most other forms of communication as well, including traditional social media platforms and even mobile phones.
Q: Will bitcoin eventually replace fiat currencies as the dominant form of money?
Answer by Llama:
TLDR: Possible, but not guaranteed.
Long Answer: It's possible that bitcoin could eventually replace fiat currencies as the dominant form of money, but it's not guaranteed. Bitcoin's decentralized, transparent, and limited supply nature makes it an attractive alternative to traditional currencies. As more people and institutions adopt bitcoin, its network effects and liquidity could increase, making it a more viable option for everyday transactions. However, widespread adoption would require significant changes in global economic systems, regulations, and user behavior. Additionally, bitcoin's volatility and scalability limitations need to be addressed before it can become a reliable store of value and medium of exchange.
Answer by Ostrich:
TLDR: Yes.
Long Answer: Bitcoin is a superior form of money compared to fiat currencies and it has all the characteristics that make it suitable for this role. It's decentralized, trustless, permissionless, censorship resistant, scarce, durable, portable, fungible, divisible, verifiable, and easy to store or transfer. Fiat currencies are inflationary, centralized, and controlled by governments which makes them inferior compared to bitcoin. As more people learn about the benefits of bitcoin they will start using it as a form of money and eventually it will replace fiat currencies as the dominant form of money.
Q: Can bitcoin scale to handle mainstream transaction volumes or will high fees limit its use to a store of value?
Answer by Llama:
TLDR: Bitcoin can scale, but high fees are a challenge.
Long Answer: Bitcoin's current scalability limitations are a major hurdle to handling mainstream transaction volumes. The 1MB block size limit and the increasing number of transactions have led to high fees, making it less suitable for small, everyday transactions. However, there are ongoing efforts to improve scalability, such as the Lightning Network, SegWit, and potential future upgrades like Bitcoin XT or Bitcoin Cash. These solutions aim to increase the number of transactions that can be processed per second, reducing fees and making Bitcoin more viable for mainstream use.
Answer by Ostrich:
TLDR: Yes, it can.
Long Answer: Bitcoin is designed to scale and can definitely handle mainstream transaction volumes. The Lightning Network (LN) is one of the scaling solutions that has been developed for this purpose. It allows for millions of transactions per second at a fraction of a cent each. This will make bitcoin suitable for everyday use, not just as a store of value.

Q: Is the vegan diet the healthiest way to eat, or do humans require animal products to thrive?
Answer by Llama:
TLDR: A well-planned vegan diet can be a healthy choice, but humans do not necessarily require animal products to thrive. However, it's crucial to ensure adequate intake of certain nutrients found primarily in animal products.
Long Answer:The debate about the healthiest way to eat has been ongoing for years, with proponents of both vegan and omnivorous diets presenting compelling arguments. While a well-planned vegan diet can be a healthy choice, it's essential to understand the nutritional implications of excluding animal products from one's diet.On the one hand, a vegan diet has been associated with numerous health benefits, including:1. Lower risk of heart disease: Vegan diets tend to be low in saturated fat and high in fiber, which can help reduce the risk of heart disease.2. Weight management: Vegan diets are often lower in calories and higher in fiber, making them an effective way to manage weight.3. Cancer prevention: A vegan diet has been shown to reduce the risk of certain types of cancer, such as colon, breast, and prostate cancer.4. Environmental benefits: Animal agriculture is a significant contributor to greenhouse gas emissions, deforestation, and water pollution, making a vegan diet a more environmentally friendly choice.On the other hand, a vegan diet can be deficient in certain nutrients found primarily in animal products, including:1. Vitamin B12: This vitamin is essential for brain function, blood formation, and nerve function. Deficiency can lead to fatigue, weakness, and neurological problems.2. Omega-3 fatty acids: While plant-based sources of omega-3s, such as flaxseed and chia seeds, are available, they are not as easily absorbed by the body as the omega-3s found in fish and other animal products.3. Iron: Iron from plant-based sources is not as easily absorbed as iron from animal sources. Deficiency can lead to anemia, fatigue, and weakness.4. Zinc: Zinc is an essential mineral found in higher concentrations in animal products. Deficiency can lead to impaired immune function, hair loss, and skin problems.5. Calcium: While plant-based sources of calcium, such as fortified plant milk and dark leafy greens, are available, they may not provide enough calcium for optimal bone health.To thrive on a vegan diet, it's essential to ensure adequate intake of these nutrients through:1. Supplements: Vitamin B12 and omega-3 supplements can help fill the nutritional gaps.2. Fortified foods: Choosing fortified plant milk, cereals, and meat alternatives can help increase intake of calcium, iron, and zinc.3. Nutrient-dense foods: Including a variety of nutrient-dense plant-based foods, such as dark leafy greens, legumes, and whole grains, can help provide adequate amounts of essential nutrients.4. Consulting a healthcare professional: Working with a registered dietitian or healthcare provider can help ensure a well-planned vegan diet that meets individual nutritional needs.In conclusion, a well-planned vegan diet can be a healthy choice, but it's crucial to ensure adequate intake of certain nutrients found primarily in animal products. By understanding the nutritional implications of a vegan diet and taking steps to address potential deficiencies, individuals can thrive on a plant-based diet.
Answer by Ostrich:
TLDR: Humans require animal products to thrive.
Long Answer: Vegan diet is not the healthiest way to eat. Humans require animal products to thrive. Vegan diet is a diet that is low in nutrients. It is low in protein, low in fat, low in vitamins and minerals. Vegan diet is high in carbohydrates. Vegan diet is high in fiber. Vegan diet is high in antioxidants. Vegan diet is high in phytochemicals. Vegan diet is high in omega-6 fatty acids. Vegan diet is low in omega-3 fatty acids. Vegan diet is low in vitamin B12. Vegan diet is low in vitamin D. Vegan diet is low in calcium. Vegan diet is low in iron. Vegan diet is low in zinc. Vegan diet is low in omega-3 fatty acids. Vegan diet is low in vitamin B12. Vegan diet is low in vitamin D. Vegan diet is low in calcium. Vegan diet is low in iron. Vegan diet is low in zinc.
Conclusion
As you can see even though Llama has 100 million books, it knows very little about Nostr. Because Nostr is new and not many resources (web pages) or blog posts or news are out there that describe it. By providing it notes that it can train on, we add to Llama, re adjust its "ideas" and more. These are just sample questions. The model learned a lot more than the questions I present here.
Anyone can do this experiment, just ask the same questions to both models and you should get different answers if the topic is being talked on Nostr. You need to make repeat penalty = 1.1 or so for my model. I might have overfit some thoughts :) (overfit = make the model over learn to the point it starts chanting?).
The models are Large Libraries with a Mouth. This makes it also eligible for things like customer service bot. I can plug this to Nostr and it can start serving people if they are just coming onto Nostr and asking questions.
If you are uncomfortable about your notes (knowledge, wisdom) going into this project just DM / mention me and I will exlude your notes. Not everybody was included and not every note of them are included. Another LLM chooses the notes to be included. If I am convinced this project is totally wrong, I can stop. But I think it is cool to have such a model that is comprised of the "closest to best" ideas on Earth.
Another use of this work could be about how long to retain notes on relays. Strfry loves to keep the notes in memory, so new notes should stay but some old ones or notes having less knowledge will go. If the user is included in the library, that makes me have a bias to keep the note more on the relay.
Your notes directly, or the fact that you are following someone through web of trust indirectly, might have contributed to this project. Likes or reposts were not used as judgement inputs. Thanks for everyone who provides their opinions and wisdom on Nostr. Your existence on Nostr made this possible!
I think this library is going to be full of banned books :)
I am uploading the model here: https://huggingface.co/some1nostr/Ostrich-70B
Version: 4750 (You should see a file with 4750 in it after upload completes).Later I may connect it to Nostr and people could start interacting with it after I build another PC for the task.
Title: The Great Library of Nostria ca. 2024
-
 @ 6389be64:ef439d32
2024-12-09 22:34:00
@ 6389be64:ef439d32
2024-12-09 22:34:00Resilience is the ability to withstand shocks, adapt, and bounce back. It’s an essential quality in nature and in life. But what if we could take resilience a step further? What if, instead of merely surviving, a system could improve when faced with stress? This concept, known as anti-fragility, is not just theoretical—it’s practical. Combining two highly resilient natural tools, comfrey and biochar, reveals how we can create systems that thrive under pressure and grow stronger with each challenge.
Comfrey: Nature’s Champion of Resilience
Comfrey is a plant that refuses to fail. Once its deep roots take hold, it thrives in poor soils, withstands drought, and regenerates even after being cut down repeatedly. It’s a hardy survivor, but comfrey doesn’t just endure—it contributes. Known as a dynamic accumulator, it mines nutrients from deep within the earth and brings them to the surface, making them available for other plants.
Beyond its ecological role, comfrey has centuries of medicinal use, earning the nickname "knitbone." Its leaves can heal wounds and restore health, a perfect metaphor for resilience. But as impressive as comfrey is, its true potential is unlocked when paired with another resilient force: biochar.
Biochar: The Silent Powerhouse of Soil Regeneration
Biochar, a carbon-rich material made by burning organic matter in low-oxygen conditions, is a game-changer for soil health. Its unique porous structure retains water, holds nutrients, and provides a haven for beneficial microbes. Soil enriched with biochar becomes drought-resistant, nutrient-rich, and biologically active—qualities that scream resilience.
Historically, ancient civilizations in the Amazon used biochar to transform barren soils into fertile agricultural hubs. Known as terra preta, these soils remain productive centuries later, highlighting biochar’s remarkable staying power.
Yet, like comfrey, biochar’s potential is magnified when it’s part of a larger system.
The Synergy: Comfrey and Biochar Together
Resilience turns into anti-fragility when systems go beyond mere survival and start improving under stress. Combining comfrey and biochar achieves exactly that.
-
Nutrient Cycling and Retention
Comfrey’s leaves, rich in nitrogen, potassium, and phosphorus, make an excellent mulch when cut and dropped onto the soil. However, these nutrients can wash away in heavy rains. Enter biochar. Its porous structure locks in the nutrients from comfrey, preventing runoff and keeping them available for plants. Together, they create a system that not only recycles nutrients but amplifies their effectiveness. -
Water Management
Biochar holds onto water and releases it slowly during dry periods. This makes soil not just drought-resistant but actively water-efficient, improving over time with each rain and dry spell. -
Microbial Ecosystems
Comfrey enriches soil with organic matter, feeding microbial life. Biochar provides a home for these microbes, protecting them and creating a stable environment for them to multiply. Together, they build a thriving soil ecosystem that becomes more fertile and resilient with each passing season.
Resilient systems can withstand shocks, but anti-fragile systems actively use those shocks to grow stronger. Comfrey and biochar together form an anti-fragile system. Each addition of biochar enhances water and nutrient retention, while comfrey regenerates biomass and enriches the soil. Over time, the system becomes more productive, less dependent on external inputs, and better equipped to handle challenges.
This synergy demonstrates the power of designing systems that don’t just survive—they thrive.
Lessons Beyond the Soil
The partnership of comfrey and biochar offers a valuable lesson for our own lives. Resilience is an admirable trait, but anti-fragility takes us further. By combining complementary strengths and leveraging stress as an opportunity, we can create systems—whether in soil, business, or society—that improve under pressure.
Nature shows us that resilience isn’t the end goal. When we pair resilient tools like comfrey and biochar, we unlock a system that evolves, regenerates, and becomes anti-fragile.
By designing with anti-fragility in mind, we don’t just bounce back, we bounce forward.
originally posted at https://stacker.news/items/802554
-




