-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ eac63075:b4988b48
2024-10-20 13:49:55
@ eac63075:b4988b48
2024-10-20 13:49:55Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.
Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.
The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.
Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.
The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
Conclusion of the Technical Debate
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.

Table reference: Patrick Breyer - Chat Control in 23 September 2024
Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.
The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
Conclusion of the Debate
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.
User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
Summary of Consequences
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.
The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.
Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ 4ba8e86d:89d32de4
2024-10-07 13:37:38
@ 4ba8e86d:89d32de4
2024-10-07 13:37:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ fe32298e:20516265
2024-12-16 20:59:13
@ fe32298e:20516265
2024-12-16 20:59:13Today I learned how to install NVapi to monitor my GPUs in Home Assistant.

NVApi is a lightweight API designed for monitoring NVIDIA GPU utilization and enabling automated power management. It provides real-time GPU metrics, supports integration with tools like Home Assistant, and offers flexible power management and PCIe link speed management based on workload and thermal conditions.
- GPU Utilization Monitoring: Utilization, memory usage, temperature, fan speed, and power consumption.
- Automated Power Limiting: Adjusts power limits dynamically based on temperature thresholds and total power caps, configurable per GPU or globally.
- Cross-GPU Coordination: Total power budget applies across multiple GPUs in the same system.
- PCIe Link Speed Management: Controls minimum and maximum PCIe link speeds with idle thresholds for power optimization.
- Home Assistant Integration: Uses the built-in RESTful platform and template sensors.
Getting the Data
sudo apt install golang-go git clone https://github.com/sammcj/NVApi.git cd NVapi go run main.go -port 9999 -rate 1 curl http://localhost:9999/gpuResponse for a single GPU:
[ { "index": 0, "name": "NVIDIA GeForce RTX 4090", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 16, "power_limit_watts": 450, "memory_total_gb": 23.99, "memory_used_gb": 0.46, "memory_free_gb": 23.52, "memory_usage_percent": 2, "temperature": 38, "processes": [], "pcie_link_state": "not managed" } ]Response for multiple GPUs:
[ { "index": 0, "name": "NVIDIA GeForce RTX 3090", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 14, "power_limit_watts": 350, "memory_total_gb": 24, "memory_used_gb": 0.43, "memory_free_gb": 23.57, "memory_usage_percent": 2, "temperature": 36, "processes": [], "pcie_link_state": "not managed" }, { "index": 1, "name": "NVIDIA RTX A4000", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 10, "power_limit_watts": 140, "memory_total_gb": 15.99, "memory_used_gb": 0.56, "memory_free_gb": 15.43, "memory_usage_percent": 3, "temperature": 41, "processes": [], "pcie_link_state": "not managed" } ]Start at Boot
Create
/etc/systemd/system/nvapi.service:``` [Unit] Description=Run NVapi After=network.target
[Service] Type=simple Environment="GOPATH=/home/ansible/go" WorkingDirectory=/home/ansible/NVapi ExecStart=/usr/bin/go run main.go -port 9999 -rate 1 Restart=always User=ansible
Environment="GPU_TEMP_CHECK_INTERVAL=5"
Environment="GPU_TOTAL_POWER_CAP=400"
Environment="GPU_0_LOW_TEMP=40"
Environment="GPU_0_MEDIUM_TEMP=70"
Environment="GPU_0_LOW_TEMP_LIMIT=135"
Environment="GPU_0_MEDIUM_TEMP_LIMIT=120"
Environment="GPU_0_HIGH_TEMP_LIMIT=100"
Environment="GPU_1_LOW_TEMP=45"
Environment="GPU_1_MEDIUM_TEMP=75"
Environment="GPU_1_LOW_TEMP_LIMIT=140"
Environment="GPU_1_MEDIUM_TEMP_LIMIT=125"
Environment="GPU_1_HIGH_TEMP_LIMIT=110"
[Install] WantedBy=multi-user.target ```
Home Assistant
Add to Home Assistant
configuration.yamland restart HA (completely).For a single GPU, this works: ``` sensor: - platform: rest name: MYPC GPU Information resource: http://mypc:9999 method: GET headers: Content-Type: application/json value_template: "{{ value_json[0].index }}" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature scan_interval: 1 # seconds
- platform: template sensors: mypc_gpu_0_gpu: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} GPU" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_memory: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Memory" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_power: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_0_power_limit: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_0_temperature: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Temperature" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'temperature') }}" unit_of_measurement: "°C" ```
For multiple GPUs: ``` rest: scan_interval: 1 resource: http://mypc:9999 sensor: - name: "MYPC GPU0 Information" value_template: "{{ value_json[0].index }}" json_attributes_path: "$.0" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature - name: "MYPC GPU1 Information" value_template: "{{ value_json[1].index }}" json_attributes_path: "$.1" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature
-
platform: template sensors: mypc_gpu_0_gpu: friendly_name: "MYPC GPU0 GPU" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_memory: friendly_name: "MYPC GPU0 Memory" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_power: friendly_name: "MYPC GPU0 Power" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_0_power_limit: friendly_name: "MYPC GPU0 Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_0_temperature: friendly_name: "MYPC GPU0 Temperature" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'temperature') }}" unit_of_measurement: "C"
-
platform: template sensors: mypc_gpu_1_gpu: friendly_name: "MYPC GPU1 GPU" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_1_memory: friendly_name: "MYPC GPU1 Memory" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_1_power: friendly_name: "MYPC GPU1 Power" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_1_power_limit: friendly_name: "MYPC GPU1 Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_1_temperature: friendly_name: "MYPC GPU1 Temperature" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'temperature') }}" unit_of_measurement: "C"
```
Basic entity card:
type: entities entities: - entity: sensor.mypc_gpu_0_gpu secondary_info: last-updated - entity: sensor.mypc_gpu_0_memory secondary_info: last-updated - entity: sensor.mypc_gpu_0_power secondary_info: last-updated - entity: sensor.mypc_gpu_0_power_limit secondary_info: last-updated - entity: sensor.mypc_gpu_0_temperature secondary_info: last-updatedAnsible Role
```
-
name: install go become: true package: name: golang-go state: present
-
name: git clone git: repo: "https://github.com/sammcj/NVApi.git" dest: "/home/ansible/NVapi" update: yes force: true
go run main.go -port 9999 -rate 1
-
name: install systemd service become: true copy: src: nvapi.service dest: /etc/systemd/system/nvapi.service
-
name: Reload systemd daemons, enable, and restart nvapi become: true systemd: name: nvapi daemon_reload: yes enabled: yes state: restarted ```
-
 @ 30ceb64e:7f08bdf5
2024-12-16 19:49:34
@ 30ceb64e:7f08bdf5
2024-12-16 19:49:34Hey Freaks,
Looks like my career goals are shaping up to be something like: 1. Paralegal 2. Direct Support Professional 3. Open Source Contributor
After I obtain paralegal certificate I should offer freelance paralegal services on nostr.
I'd market myself on shopstr, SN, Kind1 notes, Long form notes, Zapvertising, NPUB.PRO blog. Setting up and waiting for the newbies to flood in, not looking for so many clients, just setting up and making things available. My expertise will grow as I grab more certifications use educational resources, listen to podcasts, read etc.
Could Setup a Nostrocket and involve the freaks in building a non state involved business. Could operate under the open anarchist license as a free members association, and help business's with whatever legal assistance they may need, with a focus on Intellectual property law, Nostr, Bitcoin, Free open source software. Would offer services for cheap and build a web of trust offering things like free consultations.
I have 5 years experience working at an IP law firm filing patents with the US Patent and Trademark office. The Nostr resume would look really nice. Could post frequently on the SN legal territory, create a quick and simple newsletter and or AI podcast about the legal space and how it pertains to stuff we care about.
I want to stick with the coding, because the tools are getting better and my knowledge is increasing, would love to contribute more to open source projects, and want to see what maintaining my own project would be like. I'll get back around to setting up that SN dev environment and looking for low level issues to crack, this time with more experience under my belt.
I wanted to sell something on shopstr, something that helps people working remotely, legal services never quite came to mind, but would be an interesting direction to take. I was thinking vinyl records and merch and clothes, but something more wanted or needed, or unique or specialized might be better. And having an online shop that ties into my main career seems like a two birds with one stone sort of situation.
I just need to increase my knowledge and level of expertise while continuing the pursuit of "proof of work".
2024 (Current) Roadmap - Release Nostr Running App - Obtain Paralegal Certification - Offer freelance Paralegal services - DSP transition to full time - Contribute to SN development - Continued writing
Yours truly, Hustle
originally posted at https://stacker.news/items/812103
-
 @ ac8bb9b0:70278acc
2024-12-16 19:37:12
@ ac8bb9b0:70278acc
2024-12-16 19:37:12Details
- ⏲️ Prep time: 10
- 🍳 Cook time: 20
- 🍽️ Servings: 6
Ingredients
- 2 tablespoons extra virgin olive oil
- 1 1/2 pounds ground chicken
- 1 yellow onion, chopped
- 2 tablespoons taco seasoning
- salt and black pepper
- 2 1/2 cups salsa or enchilada sauce
- 1 chipotle chili in adobo, chopped
- 2 cups fresh corn
- 4 ounces cream cheese, at room temperature
- 1/4 cup plain greek yogurt
- 1 teaspoon chili powder
- 1 1/2 cups shredded Mexican cheese blend
- 2 cups tortilla chips
- avocado, cilantro, and green onions, for serving
Directions
- Preheat the oven to 400° F.
- In a large oven-safe skillet, combine the olive oil, chicken, onion, salt, and pepper. Set the skillet over high heat. Cook, breaking up the meat as it cooks, until browned all over, 5 minutes. Add the taco seasoning, cook another 2 minutes. Then add 1/2 cup water. Stir in the salsa/enchilada sauce and chipotle. Simmer 5 minutes. Remove from the heat and add in the cilantro.
- In a bowl, combine the corn, cream cheese, yogurt, chili powder, and salt. Stir in 1/2 cup cheese.
- Dollop 1/3 of the corn mix over the skillet. Add the tortilla chips on top, pressing them gently into the skillet. Add the remaining corn mix by spoonfuls on top of the chips (like nachos). Top with the remaining cheese. Bake for 15 minutes, until the cheese is melted.
- Serve topped as desired with avocado, cilantro, green onion, and cotija/feta cheese.
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 6bae33c8:607272e8
2024-12-16 18:28:36
@ 6bae33c8:607272e8
2024-12-16 18:28:36So my teams and picking pools are likely toast after a disastrous day. I was in the NFFC Online playoffs with a team that had a heavy Miami stack (Tua, Waddle, Jonnu), and as you probably know Waddle got hurt early, and Tua did very little. I had Ladd McConkey on my bench too, but he was questionable for a late game, so I didn’t want to gamble on him. West Coast players are slightly less valuable for that reason — you won’t have good info on them as often when you have to lock in your lineups.
My Steak League team got bounced from its playoffs, and I had another bad day ATS. Basically unless the Vikings defense and Brock Bowers combine for 60 points in that BCL, there’s not much for me to root for down the stretch except maybe the Giants getting the No. 1 pick.
In years past I’d be more pissed about this, but not as much anymore. I think I used to operate under the assumption that I was supposed to win, and my not winning was bullshit either because I had screwed something up, or a coach/player/injury screwed me. In other words, if things didn’t go my way, it was an injustice of sorts. I don’t think I ever articulated this assumption to myself the way I have here, it was just my unconscious sense of things.
But now I increasingly feel that whatever happens is what was meant to happen. The outcome I got was most beneficial to me in the long run, even if in the moment I’d much rather Tua had thrown for 400 yards, 200 of which went to Waddle. That would have been great, but not as good as the actual outcome, otherwise it would have happened. That takes the edge off, but in my experience it’s also true. You can’t always get what you want, but you get what you need.
-
One of the games I got right Sunday was Chiefs -4. It just seemed obvious Jameis would implode against that defense, and the Chiefs were a buy-low off their narrow wins. But the big story is obviously Patrick Mahomes’ ankle. The Chiefs are still the favorites IMO if they get the bye (which looks very likely if Mahomes is okay.) You really want the Ravens to beat the Steelers, take the division, then wind up playing the Bills in the divisional round.
-
Nick Chubb broke his foot — might be a blessing in disguise to shut it down, give his knee more time to heal for 2025.
-
Jerry Jeudy will be a polarizing player for next year’s drafts after his run with Winston at QB.
-
Joe Burrow might be as good as any QB in the NFL right now. Some of the scramble throws he made were insane, and he’s moving like he did during his rookie year.
-
You know Ja’Marr Chase is having a monster year when 11-9-94-0 is a massively disappointing game.
-
I was disappointed the Saints didn’t succeed on their two-point conversion. I had the Killer Redskins ATS, and I always want to see a team punished for not covering.
-
I traded Terry McLaurin, Joe Mixon, Amari Cooper and Kurt Cousins for Jonathan Taylor in the RotoWire Dynasty League last year because those guys were getting old, and I wanted to rebuild. Turns out Mixon is better than Taylor SU, McLaurin is a top-five WR and I narrowly missed the playoffs even though I was fourth in points.
-
Malik Nabers has 90 catches in 12 games. That prorates to 128 over a full season.
-
Lamar Jackson makes it look so easy. Rashod Bateman might save me from buying steaks too.
-
Rico Dowdle had another massive game, albeit against yet another soft defense. I’m an idiot for taking the Panthers as a favorite.
-
CeeDee Lamb hasn’t fared too badly now that Cooper Rush has a few games under his belt.
-
Mac Jones has shown a spark, certainly enough to keep a backup job for years, but with the upside to emerge as a Sam Darnold late-bloomer type.
-
Davante Adams still has it. Just one insane catch after another. Also Aaron Rodgers scrambling for 45 yards was a surprise. The Jets offense was terrible early, and now that it’s coming around, the defense has fallen apart.
-
I watched a lot of the Dolphins Texans. I feel like the Texans fucked me all year, my Texans teams were eliminated, then they fucked my live Dolphins team for good measure.
-
The Dolphins can’t run the ball anymore, which puts Tua behind the eight-ball in down and distance. And Tua needs to get the ball out right away. He’s great at hitting the guy out of the backfield in stride, but if that quick throw isn’t there, he’s in trouble. Plus, Tyreek Hill isn’t separating like his used to, and Waddle got hurt. Their only reliable player is the great Jonnu Smith. Do you remember when everyone was bitching at Arthur Smith for featuring Jonnu over Kyle Pitts? Maybe he just realized Jonnu was the better player.
-
Tua throwing those last two picks just destroyed me. I think they were both on first down too. Plus I had the Dolphins +2.5 in Circa, not that it matters.
-
Anthony Richardson showed a spark a few games ago, but he’s looking more Teebow-esque by the day. Maybe a poor man’s Taysom Hill.
-
Jonathan Taylor dropped the ball before scoring the TD, and actually a Bengals defender did the same yesterday on a return TD too. Why even chance it? Is it cooler, more non-chalant-seeming to drop it the second you cross the line? Real man drops it at the 10, keeps running through the end zone like nothing happened. (Reminds me of All Quiet On The Western Front, the WWI book, where someone gets his head blown clean off, and he keeps running with no head for 50 yards or so. Sorry, that’s dark, but it’s staying in.)
-
Bo Nix targeted 11 different players, and no one had more than 32 receiving yards. In fact, the Broncos had just 193 total yards.
-
I went to sleep right before the onside kick in the Lions game. Josh Allen makes it look so easy with mostly scrubs around him. The Lions had to work more for their drives.
-
Jared Goff had 494 yards and five TDs, but threw 59 times. You want to sell out to stop the run (which is now only Jahmyr Gibbs with David Montgomery down) and make the Lions play finesse ball. Amon-Ra St. Brown had a monster game to punish me for comparing him to Jarvis Landy last week.
-
The injuries to the Lions defense didn’t matter until they play best offenses. The NFL is such a war of attrition.
-
I thought the Steelers would put up a better fight in Philly, but maybe the Eagles are for real. Having both receivers healthy is big, but the defense absolutely dominated.
-
The Cardinals haven’t found a way to get Marvin Harrison consistently involved all year. Trey McOldMaid has broken Diontae Johnson’s record for catches without a TD, but I don’t think it counts unless he goes scoreless the last three games.
-
Drake Maye looks okay, but he’s surrounded by a bunch of total scrubs.
-
The Bucs destroyed the Chargers. Mike Evans’ 159-yard game means he needs another 250 over the next three weeks to extent his 1,000-yard streak. Rest assured he’ll get it if he and Baker Mayfield stay healthy.
-
McConkey had three-catches for 42 yards and a TD on the first drive, and I was aghast I had sat him for Waddle. But he did very little the rest of the game despite the Chargers trailing the whole way.
-
I had the Packers -2.5, and that was easy money. Jordan Love is very good, and the Packers defense got to Geno Smith, eventually knocked him out of the game.
-
Josh Jacobs had every touch but one on the opening drive, and it looked like he might go for 200 and 100, but he settled for a modest 136 YFS and only the one score. Seriously, I’ve never seen a single player get more work on one drive.
-
Forget about the Packers receivers — they spread the Love too widely. And no, that’s not code for anything.
-
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 2de0ffa0:b6bb72cc
2024-12-16 18:21:35
@ 2de0ffa0:b6bb72cc
2024-12-16 18:21:35🧠 Quote of the Week
“They can cancel my Instagram (1x) They can cancel my TikTok (2x) They can cancel my YT (2 strikes) They’ll never cancel my Nostr. Happy to be here 🥩”
🔗 author: npub14am887cf6kvwkce89nt7dsw3v9qrrn0uppxyvr6a2jd7xdwuwccqwnudp2 🔗 event : nevent1qqs2mctxa090gp9t38x4r4zs9fx6mdv8xqwfamssy2kyedd95p9zdcqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqglwaehxw309aex2mrp0yhxgampv3axjetnvd5kz6n9v3jkutnsdspzptmkw0asn4vcad3jwtxhumqazc2qx8xlczzvgc8464ymuv6aca3srj2386
🛠️ Tools, Updates, and Releases
Zapstore 0.1.7
Zapstore is a Nostr app marketplace for discovering, downloading, and managing applications. This latest release enhances performance with faster background downloads, introduces full-screen app images, remembers trusted signers for better security, and alerts users to certificate mismatches before installation. It also fixes navigation issues, app curation problems, and improves installation handling in error states.
Developed by: npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9 Source: https://github.com/zapstore/zapstore
Coracle v0.5.0
Coracle is a powerful client for engaging with the Nostr network. This release adds groupless support, improved navigation, message history, and Nostr-Editor integration for better content creation. It includes NostrConnect support, fixes for feeds, note-editor, and link editor issues, and enhances delayed sends, suggestions, and note status. Additional updates like better relay handling, inbox warnings, and ASCII tag fixes ensure a more refined user experience.
Developed by: npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn Source: https://github.com/coracle-social/coracle
NostrMarket v1.0.0
NostrMarket is a marketplace platform for buying and selling goods on the Nostr network. This major release introduces advanced product descriptions, streamlined product activation and deactivation, and fixes for UI issues like child component visibility updates. These updates provide a smoother user experience and improved functionality for managing listings.
Developed by: npub1cx4q5tcwzgga60zxu2zavjjprt9y7fgt6de2p6zmnrmad5pujfgscr8vf0 Source: https://github.com/lnbits/nostrmarket
Amber v3.0.2
Amber is an app designed for the Nostr network, offering streamlined functionalities and efficient onboarding. This update improves the onboarding process and ensures that the floating button is hidden when using the offline version. Users can download it from platforms like zap.store, Obtainium, f-droid, or directly from the release page. Additionally, it includes PGP verification instructions for ensuring the authenticity and integrity of the release.
Developed by: npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 Source: https://github.com/greenart7c3/Amber
Nowser v0.0.3
Nowser is an app for managing Nostr-related activities, with features like relay support and signing functionalities. This update adds a built-in relay for remote signers, supports multiple relays, and integrates bookmarks with quick actions for mobile and desktop. It also fixes bugs, improves UI, and adds security measures such as rejecting private zap decrypt requests from Amethyst.
Developed by: npub19yeqjawls407xjnmgkk6yss7936pcd7qzd5srlj8wye6j8433vrsjazqwk Source: https://github.com/haorendashu/nowser
Zeus v0.9.3
Zeus v0.9.3 is a wallet and node management app for the Lightning Network. This update brings improved channel management with the ability to visualize reserves, along with a new invoice setting to display the requested amount. It also introduces a troubleshooting menu for embedded LND nodes and better UX in Zeus Pay. Additionally, the app now formats Bitcoin amounts with spaces and includes several bug fixes, including better handling of HTLCs and enhanced channel tab layouts.
Developed by: npub19kv88vjm7tw6v9qksn2y6h4hdt6e79nh3zjcud36k9n3lmlwsleqwte2qd Source: https://github.com/ZeusLN/zeus
🎁 Developer Tools, updates and Guides
Immortal v0.0.5
Immortal is a Nostr relay server designed to enhance data reliability and scalability. This update introduces a Redis bloom filter for WebSocket efficiency, NIP-13 proof-of-work support, NIP-42/NIP-70 authentication for protected events, and Kraken integration. It also includes a new HTML landing page for relays, updates to NIP-11 bootstrap configurations, and fixes for server message handling.
Developed by: npub1h49w8en79xty6j2pwgnpm3znjhyf767jua6xgt3kvyn3w80ms86s2z9kay Source: https://github.com/dezh-tech/immortal
Noscrypt v0.1.6
Noscrypt is a cryptographic utility for the Nostr network, offering tools for encryption and secure key management. This update focuses on improved reliability with updated dependencies, extensive automated testing, and memory leak checks. It also introduces enhancements to build processes and requirements, ensuring a more robust experience for developers.
Developed by: npub1qdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havq03fqm7 Source: https://github.com/VnUgE/noscrypt
btcpayServer v2.0.4
btcpayServer is a self-hosted payment processor designed to integrate with Bitcoin and Lightning Network. This update introduces a QR code for invitation emails, adds rate providers for Norwegian exchanges, and improves the store users API. It also includes bug fixes for iOS Lockdown mode, user creation errors, and invoice-related issues. UI improvements, including a new layout for the invoices link, and various plugin updates are also part of this release.
Developed by: npub1zfytz6ktce3av2svlfpl0e79e44tnskxmvlpkcmc7q0xct3qa49swvm60l Source: https://github.com/btcpayserver/btcpayserver
Citrine v0.5.8
Citrine is a lightweight and efficient Nostr client. This update focuses on performance improvements and usability enhancements. Key features include better connection handling and event processing, a dedicated database view for easier management, and enhanced data integrity checks. These updates are beneficial for both developers (improved debugging and management) and users (smoother experience and reliability).
Developed by: npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 Source: https://github.com/greenart7c3/Citrine
🔥 Community Highlights
npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm Community Call - December 12, 2024
The npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm Community Call on December 12, 2024, brought together Nostr enthusiasts. The call included lively discussions, updates, and an opportunity to connect with the npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm community. At the request of npub19hs0lg9vyd0lghayeju5fnflx0melawjrl8etuqln9gkhd4mwtxq2t5jcn, npub14wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqvagcye explained the Nostr bounty program. Among the bounties discussed was the Alby extension language translation, which is a great opportunity for new developers.
For more details, you can check the bounty at https://guides.getalby.com/developer-guide/bounties.
🌱 Ecosystem Growth
Nostr is growing fast! There are now over 45 Nostr clients, and relays are running in more than 40 countries around the globe. According to https://nostrapps.com there are overall 68 nostr apps for now.
During this week: Total zaps: 42,232 , compared to 40,536 zaps the week before Total events: 6,308,872 , compared to 7,558,425 events the week before Profiles with bio users: 16,387 , compared to 538,147 Profiles with bio users the week before
Many thanks to stats.nostr.band by npub1xdtducdnjerex88gkg2qk2atsdlqsyxqaag4h05jmcpyspqt30wscmntxy for providing these insights.
🎓 Educational Resources
CoinGecko’s Introduction to Nostr: A Game-Changer for Decentralized Social Networking
CoinGecko has recently published an insightful video introducing Nostr to a broader audience. Aimed at those curious about decentralized social networking but not yet immersed in the ecosystem, the video serves as a perfect entry point for new users. The video highlights Nostr’s growing relevance, emphasizing its potential for mainstream adoption. It explains how Nostr empowers users to control their data, offering features like Bitcoin tipping through the Lightning Network (NIP-57) and seamless switching between clients like Damus (iOS), Amethyst (Android), and Primal (web/mobile). This video reflects a shift in Nostr's visibility, signaling increasing interest from mainstream audiences. If you’re already using Nostr, this could be a great resource to share with friends or colleagues curious about the protocol.
🔗 Youtube: https://www.youtube.com/watch?v=Q6f6bdKWqF8
📅 Upcoming Events
Nostr at Tech Tuesday
📅 Date: Tuesday, December 17, 2024 - 7 PM – late EST 📍 Location: Seats2meet.com Utrecht CS, The Netherlands 🤹♀️ Organizers: npub1l77twp5l02jadkcjn6eeulv2j7y5vmf9tf3hhtq7h7rp0vzhgpzqz0swft, npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe and npub1w98ems6ryhpv7zvmhwp5sv65p0pwrnvzw4lucn0ch776qan9ntdstscwpx 🔗 https://www.seats2meet.com/en/events/4313/tech-tuesday
Join npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr at Tech Tuesday for an insightful session on Nostr, covering Epoxy (a framework for integrating technologies), Tollgate (a checkpoint mechanism for validating actions), and eCash (digital cash for secure transactions) as a shared topic. Don’t miss out on this great opportunity to learn more about Nostr technologies!
FOSDEM 2025
📅 Date: Saturday, Sunday, February 1–2, 2025 - CET 📍 Location: Brussels, Belgium 🤹♀️ Organizers: npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe, npub1l77twp5l02jadkcjn6eeulv2j7y5vmf9tf3hhtq7h7rp0vzhgpzqz0swft , pub1hz5alqscpp8yjrvgsdp2n4ygkl8slvstrgvmjca7e45w6644ew7sewtysa , npub1nkmta4dmsa7pj25762qxa6yqxvrhzn7ug0gz5frp9g7p3jdscnhsu049fn , npub1r30l8j4vmppvq8w23umcyvd3vct4zmfpfkn4c7h2h057rmlfcrmq9xt9ma 🔗 https://fosdem.org/2025/schedule/
FOSDEM is one of the biggest gatherings for open-source developers and enthusiasts worldwide, taking place each year in Brussels. It’s a free, community-driven event where thousands of devs, innovators, and Free and Open Source Software contributors come together to demo projects, host talks, and share ideas. It’s a key place for making meaningful connections, learning from each other, and pushing open-source tech forward.
For NOSTR being at FOSDEM is a natural fit. It’s the perfect stage to introduce the broader open-source community to Nostr’s potential—how it can replace centralized social platforms, bring true ownership of data back to users, and encourage a more resilient, open internet. Engaging with fellow open-source projects and developers at FOSDEM helps Nostr grow its ecosystem, fosters new collaborations, and gains valuable feedback. The protocol is all about grassroots development, community contributions, and evolving without the constraints of centralized platforms, which aligns perfectly with FOSDEM’s collaborative spirit.
📅 Date: Tuesday, December 17, 2024 - 6:30 PM – 9:00 PM
📍 Location: Toronto, ON 🤹♀️ Organizer: npub1ek36rza32zjc8pec8daz6veyywv55xtemzaxr0saymd04a4r66eqpxphdl 🔗 https://www.meetup.com/blockchain-developers-canada/events/304910752 This beginner-friendly meetup will be a tutorial that will teach participants to create Nostr accounts, send and query events, send encrypted events, and obtain a Nostr Internet Identifier. The session will be in JavaScript, and attendees are encouraged to install Node.js and Git beforehand.
Uncensorable: Nostr, Bitcoin, and the Fight for Digital Freedom
📅 Date: Saturday, January 5, 2025 - 12 PM MST 📍 Location: Jives Coffee Lounge, 16 Colbrunn Ct, Colorado Springs, CO 🤹♀️ Organizers: npub1t3gxvxcf9nrcdd2ukhtfzjd39x7uers96u3ce3jnm605vhkkn7gsfp9elk - Host of npub1jz42cy8qxw6dres86sn0cr42hww24pnjqssa4k9wxqvzm5l0mvqsq2f5ku (Nostr, YouTube) 🔗 https://www.meetup.com/bitcoin-lightning-and-nostr-plebs/events/dwnpntyhccbhb Join npub1t3gxvxcf9nrcdd2ukhtfzjd39x7uers96u3ce3jnm605vhkkn7gsfp9elk for a session on Nostr and Bitcoin. Whether you're new or experienced, gain insights into decentralized networks, Bitcoin's power, and learn how to set up your Nostr account and Bitcoin Lightning wallet. Don't miss this chance to explore these topics and digital freedom.
FediForum April 2025
📅 Date: April 1-2, 2025, 8:30 PM IST to 1:30 AM IST 📍 Location: Online Event 🔗 https://events.humanitix.com/fediforum-april-2025?hxchl=hex-pfl Join npub1h922hu6rjv4tc0pyks3wp7z0whfdd09da6stcnyv7dn80p83e5qqasjhr8 to explore the future of social media, including platforms like Fediverse, Bluesky, Nostr, and Mastodon. Discuss new technologies, funding models, and governance, focusing on building an open, trust-driven, and interoperable social web. Connect and collaborate with peers to shape the next generation of social media.
📰 Nostr in the Media
No updates this week. If you have some input for the next recap about recent Nostr Media resources, please share it and I will add it in the next recap.
⚡ Most Zapped Last Week
Nostr’s Value4Value (V4V) model is all about plebs directly rewarding creators for the value they receive—no middlemen fees, no ads, just pure community-driven support using sats via the Bitcoin Lightning Network. Thanks to zaplife.lol by @pablof7z for providing this data. Here are the top zapped posts from last week, showcasing creators who received the most engagement:
🔥 Top 3: Most Zaps
- Running nostr
Author: npub14fkfcx9j0494g8zejfdxsr9t8raxt9n8vzkz6l5w4ef0gjysh4dqcsmkgv\ Zaps Received: 173 Sats Earned: 441k 🔗 event: nevent1qqsdr7ds32jrgjyrt8hs0jt94zaaua08nfvysf4nkrczvrs43gl87xqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgkwaehxw309aex2mrp0yh8qunfd4skctnwv46qzymhwden5te0dehhxarj9esny7pwwp6kyqguwaehxw309ahx7um5wghxzurs9ee82mn0denxcatc9e5k7q3q4fkfcx9j0494g8zejfdxsr9t8raxt9n8vzkz6l5w4ef0gjysh4dqkejrqt
- They can cancel my Instagram (1x) They can cancel my TikTok (2x) They can cancel my YT (2 strikes) They’ll never cancel my Nostr.
Happy to be here 🥩
Author: npub14am887cf6kvwkce89nt7dsw3v9qrrn0uppxyvr6a2jd7xdwuwccqwnudp2 Zaps Received: 26 Sats Earned: 65k 🔗 event: nevent1qqs2mctxa090gp9t38x4r4zs9fx6mdv8xqwfamssy2kyedd95p9zdcqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqglwaehxw309aex2mrp0yhxgampv3axjetnvd5kz6n9v3jkutnsdspzptmkw0asn4vcad3jwtxhumqazc2qx8xlczzvgc8464ymuv6aca3srj2386
- Author: npub1ymt2j3n8tesrlr0yhaheem6yyqmmwrr7actslurw6annls6vnrcslapxnz Zaps Received: 26 Sats Earned: 5k 🔗 event: nevent1qqsxz5rwv62ha5ce27uyvnmeheepdwgfp9sr865dc5w689k7wpg3pfcpp4mhxue69uhkummn9ekx7mqpremhxue69uhkgatrdpjhxu6qdaexzmn8v4cxjmrvv4ezummjvuq3kamnwvaz7tmjv4kxz7fwdehhxarjdakk7tnnda3kjctvqythwumn8ghj7un9d3shjtndv968g7tzwvhxcmmvqgszd44fgen4ucpl3hjt7muuaazzqdahp3lwu9c07phdweelcdxf3ugww9pce
💰 Top 3: Most Sats
- Running nostr
Author: npub14fkfcx9j0494g8zejfdxsr9t8raxt9n8vzkz6l5w4ef0gjysh4dqcsmkgv Sats Earned: 441k Zaps Received: 173 🔗 event: nevent1qqsdr7ds32jrgjyrt8hs0jt94zaaua08nfvysf4nkrczvrs43gl87xqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgkwaehxw309aex2mrp0yh8qunfd4skctnwv46qzymhwden5te0dehhxarj9esny7pwwp6kyqguwaehxw309ahx7um5wghxzurs9ee82mn0denxcatc9e5k7q3q4fkfcx9j0494g8zejfdxsr9t8raxt9n8vzkz6l5w4ef0gjysh4dqkejrqt
- They can cancel my Instagram (1x) They can cancel my TikTok (2x) They can cancel my YT (2 strikes) They’ll never cancel my Nostr.
Happy to be here 🥩
Author: npub14am887cf6kvwkce89nt7dsw3v9qrrn0uppxyvr6a2jd7xdwuwccqwnudp2 Sats Earned: 65k Zaps Received: 26\ 🔗 event : nevent1qqs2mctxa090gp9t38x4r4zs9fx6mdv8xqwfamssy2kyedd95p9zdcqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqglwaehxw309aex2mrp0yhxgampv3axjetnvd5kz6n9v3jkutnsdspzptmkw0asn4vcad3jwtxhumqazc2qx8xlczzvgc8464ymuv6aca3srj2386
- EN DIRECTO EN YT Y ZAPSTREAM https://www.youtube.com/watch?v=cGeLZvs7pqw
Author: npub1yn3hc8jmpj963h0zw49ullrrkkefn7qxf78mj29u7v2mn3yktuasx3mzt0 Sats Earned: 25k Zaps Received: 4 🔗 event: nevent1qqs9ku6fe7lm3m49kprkwhcn07n07zta3y0xpat97e9r3xl3xm2n8uqpz3mhxue69uhkummnw3ezummcw3ezuer9wcqs7amnwvaz7tmwdaehgu3wd4hk6qgdwaehxw309ahx7uewd3hkcq3qyn3hc8jmpj963h0zw49ullrrkkefn7qxf78mj29u7v2mn3yktuasdc3nnu
👋 Stay in Touch & Zap
Nostr is built by the plebs, for the plebs. If you found this recap helpful, consider supporting me—Nomishka—with a zap. Right now, I’m in a tough spot: jobless and struggling to make ends meet. Most days, I’m barely able to afford food, and honestly, 210,000 sats per month would help provide a basic income to cover essential needs.
I’m committed to supporting Nostr, and I split a part of the zaps I receive for this note with the plebs mentioned in this recap for all their great effort. Thank you so much for being part of this journey. Let me know your thoughts about this first recap, share your tips and suggestions for the next weekly recap, and let’s keep #grownostr together.
Recap by npub19hs0lg9vyd0lghayeju5fnflx0melawjrl8etuqln9gkhd4mwtxq2t5jcn
-
 @ 30e902b3:49c066b2
2024-12-16 17:07:49
@ 30e902b3:49c066b2
2024-12-16 17:07:49Y así de la nada, de algún reflejo alarma, ... Uhh, me parece que hoy puede ser interesante. Me adelanté a escribir. Me explico: El reflejo alarma es unas sombra o variación en la luz proyectada por la vela en lo que oficie de pantalla. Bien puede ser un lienzo satinado de alto contraste o un manto de hojas de esqueleto de caballo, aunque este último ejemplo se da más en circunstancias de trabajo de campo. Este reflejo no es más que la representación de la reacción de la llama de la vela a una variación del flujo que circunvala la llama. La de la vela. Y es tan sensible este equilibrio cuasi exponencial ( es más simple entenderlo como sonido visible), que en ocasiones basta apenas un suspiro leve para generar un tsunami visual.
https://drive.proton.me/urls/6WP9C1CMW4#YbPptu0Xamu8
Esos son mis reflejos alarma. Los que me sacan de donde esté y me vuelven a la realidad. Otro proyecto. Un nuevo artilugio moderno. Dice tx3. Cuadrado de unos 10cm.
Busque datos y ahora pretendo sea o bien mi server, nodo lighting / bitcoin / torrent, relay de nostr o lo que vuestra imaginación proponga.
Procesador : Amlogic s905w Consumo: 5watt. Excelente!!! puede ir con un solar. Ahora, balanza: Que me puede ofrecer este equipo y que puedo necesitar para lo que pretendo pedirle. Ante eso de : "serás lo que debas ser o no seras nada", voy más por un "serás lo que logres ser". O como una pintada que dice "fallarás en el 100% de las cosas que no intentes".
Vuelvo de un break. Esto de escribir no está siendo lo sencillo que pensaba y salí a fumar. Y lo que pensaba, durante el descanso, fue que si no desconectamos un poco, nos olvidamos que nada se gana y nada se pierde. Todo se transforma. Y la tapa del frasco de miel que había olvidado era un festín. Una, dos; tres tipos solamente de hormigas. Era como:
https://www.youtube.com/watch?v=1wa0_pQUCT0
Sujeto la tapa en mi mano mirando esa micrópolis
https://external-content.duckduckgo.com/iu/?u=https%3A%2F%2Fimages.pathe-thuis.nl%2F9474_1920x1080.jpg&f=1&nofb=1&ipt=e3a0f4e3ebdcf94674dc4b4f9e1389b709d4e088d7428e129a3da82a1bb7ead2&ipo=images
y una araña me sobrepasa por la derecha usando mi brazo de autopista para no perderse la piñata de la fiesta.
Dejo la tapa donde estaba. Mañana estará limpia y con un enjuague como nueva.
Vivir en la naturaleza, decía el panfleto. En fin. El sapo, que me miraba a unos metros, reaccionó cuando mis ojos se detuvieron apuntándole, giró y se despidió de panza al agua.
A la distancia se mezclan los ecos de alguna reunión. Las voces se entrelazan con la música de fondo y la brisa marea a la brújula. Una vpn para los oídos. Esta noche no habrá velada musical. Mi cerebro no puede a esta hora separar los sonidos con esa agudeza. Ya los 25 db que llegan del refrigerador son suficiente para que lo apague antes de dar play.
Sapo, araña, hormigas, frasco miel. Y hace unos días me regalaron medio longaniza. Donde la guardé? No la ví en la heladera cuando guardé la miel. La envolví bien antes de dejarla donde no recuerdo? 20 minutos pasaron entre párrafo y párrafo. Estaba en la heladera, detrás del queso. Así de sencillo es esto de intentar escribir.
Mañana será otro día.
https://youtu.be/nILsRpf0XLs
P.D. Paciencia... Ya iré aprendiendo lo de links, clouds y esas cosas para que sea más agradable leerme.
-
 @ b8851a06:9b120ba1
2024-12-16 16:38:53
@ b8851a06:9b120ba1
2024-12-16 16:38:53Brett Scott’s recent metaphor of Bitcoin as a wrestling gimmick, reliant on hype and dollar-dependence, reduces a groundbreaking monetary innovation to shallow theatrics. Let’s address his key missteps with hard facts.
1. Bitcoin Isn’t an Asset in the System—It’s the System
Scott claims Bitcoin competes with stocks, bonds, and gold in a financial "wrestling ring." This misrepresents Bitcoin’s purpose: it’s not an investment vehicle but a decentralized monetary network. Unlike assets, Bitcoin enables permissionless global value transfer, censorship resistance, and self-sovereign wealth storage—capabilities fiat currencies cannot match.
Fact: Bitcoin processes over $8 billion in daily transactions, settling more value annually than PayPal and Venmo combined. It isn’t competing with assets but offering an alternative to the monetary system itself.
2. Volatility Is Growth, Not Failure
Scott critiques Bitcoin’s price volatility as evidence of its unsuitability as "money." However, volatility is a natural stage in the adoption of transformative technology. Bitcoin is scaling from niche use to global recognition. Its growing liquidity and adoption already make it more stable than fiat in inflationary economies.
Fact: Bitcoin’s annualized volatility has decreased by 53% since 2013 and continues to stabilize as adoption rises. It’s the best-performing asset of the last decade, with an average annual ROI of 147%—far outpacing stocks, gold, and real estate. As of February 2024, Bitcoin's volatility was lower than roughly 900 stocks in the S and P 1500 and 190 stocks in the S and P 500. It continues to stabilize as adoption rises, making it an increasingly attractive store of value.
3. Bitcoin’s Utility Extends Beyond Countertrade
Scott diminishes Bitcoin to a "countertrade token," reliant on its dollar price. This ignores Bitcoin’s primary functions:
- Medium of exchange: Used in remittances, cross-border payments, and for the unbanked in Africa today (e.g., Ghana, Nigeria, Kenya).
- Store of value: A hedge against inflation and failing fiat systems (e.g., Argentina, Lebanon, Turkey).
- Decentralized reserve asset: Held by over 1,500 public and private institutions, including Tesla, MicroStrategy, and nations like El Salvador.
Fact: Lightning Network adoption has grown 1,500% in capacity since 2021, enabling microtransactions and reducing fees—making Bitcoin increasingly viable for everyday use. As of December 2024, Sub-Saharan Africa accounts for 2.7% of global cryptocurrency transaction volume, with Nigeria ranking second worldwide in crypto adoption. This demonstrates Bitcoin's real-world utility beyond mere speculation.
4. Bitcoin Isn’t Controlled by the Dollar
Scott suggests Bitcoin strengthens the dollar system rather than challenging it. In truth, Bitcoin exists outside the control of any nation-state. It offers people in authoritarian regimes and hyperinflationary economies a lifeline when their local currencies fail.
Fact: Over 70% of Bitcoin transactions occur outside the U.S., with adoption highest in countries like Nigeria, India, Venezuela, China, the USA and Ukraine—where the dollar isn’t dominant but government overreach and fiat collapse are. This global distribution shows Bitcoin's independence from dollar dominance.
5. Hype vs. Adoption
Scott mocks Bitcoin’s evangelists but fails to acknowledge its real-world traction. Bitcoin adoption isn’t driven by hype but by trustless, verifiable technology solving real-world problems. People don’t buy Bitcoin for "kayfabe"; they buy it for what it does.
Fact: Bitcoin wallets reached 500 million globally in 2023. El Salvador’s Chivo wallet onboarded 4 million users (60% of the population) within a year—far from a gimmick in action. As of December 2024, El Salvador's Bitcoin portfolio has crossed $632 million in value, with an unrealized profit of $362 million, demonstrating tangible benefits beyond hype.
6. The Dollar’s Coercive Monopoly vs. Bitcoin’s Freedom
Scott defends fiat money as more than "just numbers," backed by state power. He’s correct: fiat relies on coercion, legal mandates, and inflationary extraction. Bitcoin, by contrast, derives value from transparent scarcity (capped at 21 million coins) and decentralized consensus, not military enforcement or political whims.
Fact: Bitcoin’s inflation rate is just 1.8%—lower than gold or the U.S. dollar—and will approach 0% by 2140. No fiat currency can match this predictability. As of December 2024, Bitcoin processes an average of 441,944 transactions per day, showcasing its growing role as a global, permissionless monetary system free from centralized control.
Conclusion: The Revolution Is Real
Scott’s "wrestling gimmick" analogy trivializes Bitcoin’s purpose and progress. Bitcoin isn’t just a speculative asset—it’s the first truly decentralized, apolitical form of money. Whether as a hedge against inflation, a tool for financial inclusion, or a global settlement network, Bitcoin is transforming how we think about money.
Dismiss it as a gimmick at your peril. The world doesn’t need another asset—it needs Bitcoin.
"If you don't believe me or don't get it, I don't have time to try to convince you, sorry." Once Satoshi said.
There is no second best.
-
 @ 6ad3e2a3:c90b7740
2024-12-16 15:28:00
@ 6ad3e2a3:c90b7740
2024-12-16 15:28:00I believe in the notion of truth. Not merely propositional truth like 2 + 2 = 4, though that too, but also the idea that what someone says can be authentic, profound and true.
Another aspect of truth is beauty. I think music can be harmonious and art aesthetically true. I don’t claim to have special knowledge over what is true, beautiful or harmonious, only that those things exist, and human beings can discern them. I also believe in justice which in my view is moral truth.
Truth, beauty and justice exist even if we are not personally able to recognize them. In other words, while they are perceptible to human beings generally, any particular person or group might miss them.
One example that comes to mind is if you renovate a home. You and your architect might disagree about the layout. Imagine he persuades you to trust him, and you discover he was correct, the house is more harmonious, proportionate and beautiful than had you done it your way. The aesthetic truth for that house was not what you had imagined, but it existed, and you were lucky someone else had the eye for it.
. . .
I don’t write much about what’s going on in Israel and Palestine because I’m not interested in it. I’m not interested in it because it doesn’t affect my immediate existence, and those who are interested in it mostly seem to be closed-minded and emotional about the topic. Because I am not into it, I am not especially informed, nor am I inclined to inform myself better. As far as I can tell, it’s a depressing and tiresome argument between two miserable factions.
That said, the topic sometimes comes up in part because I’m Jewish and know a lot of Jews who care about it and also because I follow people on Twitter on both sides who also care about it. For that reason, I’m aware of some of the narratives that are presented and consequently I’ve formulated two main ideas about it, two axioms, so to speak:
(1) Whatever is the just (morally true) result — whether Israel shutting down and leaving the region, Israel conquering and annexing Palestinian territories entirely, or more likely something in between — that's what I would like to see happen.
In other words, no matter how much anyone in particular might disagree with it, the just result, whatever it might be, is the outcome for which I’m rooting.
People will argue for what they think is just based on various narratives, but I hope for what is actually just, irrespective of those narratives. And I believe such a result must exist, even though I am in no position whatsoever to say what that result would be.
(2) To the extent some people think Palestinians are incorrigible barbaric terrorists and others think Israel (and even "the Jews" more broadly) are incorrigible genocidal maniacs, consider that sense of incorrigibility is directed by both parties at both parties.
In other words, at least one of you* incorrectly believes the other is inherently beyond redemption, and just as they would be mistaken in believing that about you, you could also be mistaken in believing it about them. In fact, the greater your certainty about their inherent evil, the more difficult it is for you to course-correct, and the closer to their description you actually become. Paradoxically, the more sure you are of who they are, the more correct they are about you.
Before anything approaching a concrete answer to this problem can emerge, I think it's important to realize (1) A just outcome that does not depend on anyone's narrative exists; and (2) That the extent to which you view your adversaries as beyond redemption you most resemble their description of you.
If we accept these two axioms, that justice is possible, and that viewing the other side as incorrigible is a hallmark of one’s own zealotry, we have established the ground upon which a solution is possible. If we reject them, no amount of discussion will ever bear fruit.
*Some people might think both are beyond redemption, in which case this post is moot, and there is no just outcome, only might makes right. I think that kind of cynicism is the road to hell.
-
 @ 4870d550:110d6208
2024-12-16 13:57:52
@ 4870d550:110d6208
2024-12-16 13:57:52From Trey Walsh, Executive Director of The Progressive Bitcoiner
Quite popular in the news recently, particular in left leaning circles, has been the topic of crypto’s influence in this recent U.S. election, the hundreds of millions spent on this election from crypto PACs. and the Bitcoin strategic reserve idea being floated by the Trump admin, some members of congress and some within the Bitcoin industry. This has also resurfaced some myths seemingly projecting progressives’ disdain for Trump and billionaires onto Bitcoin — the open source protocol and neutral technology that has no political ideology or worldview. My friend Jason Maier and I predicted this may happen this past summer when Trump saw an opportunity to garner more of the crypto vote after Biden, and then Harris, fumbled the opportunity. While I continue to hope progressives can, as I myself did back in 2021, look past some of Bitcoin’s biggest proponents in the U.S. and see the vast, global picture of this freedom technology, in the era of Trump 2.0 there is more work than ever to be done to educate and convince progressives that Bitcoin is for them, too. We’ll tackle that head on here at The Progressive Bitcoiner.
There is a long history of cryptography, cypherpunk movements, and technological advances in digital cash and encryption that led to the creation of Bitcoin. It was not an overnight invention, but rather the culmination of decades of advances in this space. After the Bitcoin white paper, which I encourage you to read in full, was published on October 31, 2008, Bitcoin emerged when Satoshi Nakamoto, the pseudonymous creator of Bitcoin, mined the first genesis block on January 3, 2009. This was in the wake of the fallout of the 2008 global financial crisis, when trust in traditional banking and government systems was at an all-time low. Satoshi directly referenced this crisis in the Bitcoin genesis block, embedding the text:
“The Times 03/Jan/2009 Chancellor on brink of second bailout for banks.”
You remember 2008, with the subprime mortgage crises, collapse of the housing market, bank bailouts, global recession, and where Wall Street greed and unethical practice was rewarded by bailouts for the rich while everyday people suffered, many catastrophically…right? So imagine, Satoshi chose to directly reference these events in the genesis block, by design. Bitcoin’s decentralized nature was designed to bypass corrupt institutions and give individuals control over their money, challenging centralized power structures (such as corruption via the too-big-to-fail banks and government coordination), promoting financial inclusion, and providing an alternative to the inequities of the traditional financial system that were so massively exposed in 2008. Sounds like a pretty incredible tool for progressives to utilize and build a movement around if you ask me.
Now let’s look to Satoshi’s white paper to see what Bitcoin is and what it’s original use and purpose was that may help progressives see the forest through the trees (trees currently being distractions like election, politicians and billionaires we don’t like, etc). I’ve pulled out some quotes directly from the white paper that may be of particular interest to progressives skeptical of Bitcoin’s use outside of the uber-wealthy, politics, and speculation by greedy crypto bros.
-
Eliminating Intermediaries “What is needed is an electronic payment system based on cryptographic proof instead of trust, allowing any two willing parties to transact directly with each other without the need for a trusted third party.” This speaks to removing power from centralized banks and financial institutions, which have historically exploited the public for profit. Bitcoin enables peer-to-peer transactions, empowering individuals to take control of their own money without relying on corrupt intermediaries.
-
Financial Inclusion and Decentralization “The network is robust in its unstructured simplicity. Nodes work all at once with little coordination. They do not need to be identified, since messages are not routed to any particular place and only need to be delivered on a best-effort basis.” Bitcoin’s decentralized network ensures that no single entity or government can control it. This creates an open, borderless financial system accessible to everyone, including the unbanked and underbanked.
-
Protection from Inflation and Manipulation “The steady addition of a constant amount of new coins is analogous to gold miners expending resources to add gold to circulation. In our case, it is CPU time and electricity that is expended.” Bitcoin’s fixed supply of 21 million coins prevents inflation caused by reckless money printing, a practice that disproportionately harms the poor and working class by devaluing their savings and purchasing power.
-
Reducing Fraud and Exploitation “Merchants must be wary of their customers, hassling them for more information than they would otherwise need. A certain percentage of fraud is accepted as unavoidable.” Why It Matters for Progressives: Bitcoin transactions are secure, irreversible, and fraud-resistant. This protects individuals and small businesses from exploitation by large corporations or fraudulent actors.
-
Empowering Privacy and Freedom “We propose a solution to the double-spending problem using a peer-to-peer network. The network timestamps transactions by hashing them into an ongoing chain of hash-based proof-of-work, forming a record that cannot be changed without redoing the proof-of-work.” Bitcoin’s blockchain creates transparency without sacrificing individual privacy. It empowers people to own their financial data, reducing surveillance by corporations or governments. New and better tools for privacy are built every month in the Bitcoin ecosystem.
-
Fair Access and Decentralized Security “The proof-of-work also solves the problem of determining representation in majority decision making. If the majority were based on one-IP-address-one-vote, it could be subverted by anyone able to allocate many IPs. Proof-of-work is essentially one-CPU-one-vote.” This reinforces fairness in decision-making within the Bitcoin network. Power is distributed based on effort (proof-of-work), not centralized control or wealth.
-
Financial Sovereignty and Empowerment “With e-currency based on cryptographic proof, without the need to trust a third party, money can be secure and transactions effortless.” Bitcoin removes the barriers and risks imposed by banks and governments, giving individuals full sovereignty over their money. This is particularly impactful for those in oppressive regimes or underserved communities.
As you can see, Bitcoin was designed as a tool not requiring trust, and empowering individuals to freely transact with one another, while also preserving wealth over time that is currently stripped away with fiat currencies via inflation and central bank control. While anyone can use and have access to Bitcoin by design, yes including some of those pesky politicians and billionaires you despise, clearly this is a tool that progressives should see being an incredibly empowering tool for individuals and communities in the U.S. and around the world. Think of those underbanked, or excluded from the traditional banking system, those facing hyperinflation, those predatory remittance payment companies that charge outrageous fees when bitcoin can be sent anywhere in the world for fractions of a penny via the lightning network or still very cheaply on-chain. The examples and opportunities are endless.
And what has Bitcoin done for a progressive and millennial like me? Well it’s given me and my family hope for a retirement in the future via better savings mechanisms, given me hope for the world as someone who works in nonprofits that people now have this incredible tool for financial freedom and empowerment, it’s connected me with a global community fighting for a better future through bitcoin, and it’s given me the opportunity to lead efforts like ours here at The Progressive Bitcoiner to help you, the reader, see that maybe there’s some hope to be found for you too here in Bitcoin.
Originally published at https://progressivebitcoiner.substack.com.
-
-
 @ ae6ce958:d0f02c7d
2024-12-16 09:49:47
@ ae6ce958:d0f02c7d
2024-12-16 09:49:47- Initial Supply:
The total supply of Damage Tokens is capped at 42 million tokens.
80% is retained by Steven Joseph (the founder) for operational and strategic purposes.
20% is released to the public, creating a market opportunity for early adopters and contributors.
- Pricing:
Each Damage Token is priced at 100 satoshis (0.000001 BTC per token), establishing a direct tie to Bitcoin’s value and liquidity.
- Utility:
Damage Tokens are used as rewards for BDD test cases on the DamageBDD platform.
They incentivize high-quality software development by providing measurable, blockchain-verified rewards.
- Resilience and Integrity:
As an AEX9 token, Damage Token complies with Aeternity’s fungible token standard, ensuring:
Security and immutability.
Compatibility with Aeternity wallets (e.g., Superhero.com) and the DeFi ecosystem.
- Governance and Revenue:
A governance policy ensures revenue supports a small team and operational costs without external investment.
A buyback mechanism allows token holders to exit liquidity positions through Bitcoin's Lightning Network, net of developer fees.
Enforced by AEX9 Sophia Smart Contracts
- Fixed Supply:
The contract enforces a hard cap of 42 million tokens, ensuring no additional tokens can be minted post-deployment.
- Ownership and Transfers:
The contract implements secure token ownership and transfer rules:
Users can transfer tokens using transfer.
Allowances can be granted via allow_transfer_from.
- Rewards Mechanism:
The DamageBDD platform integrates with the token’s smart contract to automate reward distribution:
Verified BDD test completions trigger token payouts.
This ensures transparency and immutability for rewards.
- Pricing and Exchange:
The smart contract ensures tokens can be sold or exchanged based on the 100 satoshis per token rate.
This rate is enforced by integrating with off-chain oracles and on-chain buyback mechanisms for Lightning Network liquidity.
- Buyback and Liquidity:
Token holders can sell their tokens back through an integrated buyback system.
Bitcoin’s Lightning Network facilitates immediate, decentralized liquidity, minus developer fees.
- Transparency and Auditability:
All transactions and balances are publicly auditable via the blockchain, enhancing trust and eliminating potential manipulation.
By tying the token's value to Bitcoin and enforcing the tokenomics through AEX9 Sophia contracts, Damage Token ensures sustainability, utility, and fairness, while incentivizing contributions to the DamageBDD ecosystem.
-
 @ e356a30c:11e846f7
2024-12-16 07:26:35
@ e356a30c:11e846f7
2024-12-16 07:26:351. SaaS (Software as a Service) : Delivers software applications over the internet, eliminating the need for local installations.
Real World Examples includes: Google Workspace, Microsoft 365, Salesforce, Dropbox
Key Benefits for Businesses: Reduced IT costs, automatic updates, accessibility from anywhere, scalability, focus on core business
2. PaaS (Platform as a Service): Provides a cloud platform for developing, deploying, and managing applications without the need for building and maintaining the underlying infrastructure.
Real World Examples: Google App Engine, AWS Lambda, Heroku
Key Benefits for Businesses: Faster development and deployment, scalability, reduced infrastructure management, cost-effectiveness
3. **IaaS (Infrastructure as a Service) ** Offers computing resources like servers, storage, and networking on demand.
Real World Examples: Amazon EC2, Microsoft Azure, Google Compute Engine
Benefits for Businesses: Flexibility and control over infrastructure, scalability, cost-efficiency, pay-as-you-go pricing
Reference: * https://techylodge.com/how-does-cloud-computing-work/
-
 @ 3b1bf474:c98b1527
2024-12-16 05:54:03
@ 3b1bf474:c98b1527
2024-12-16 05:54:03"Saudade” is not a word you just say; it's a whole set of imprints of sensations and emotions on the soul, made up of smells, tastes, and (especially) memories! I remember, as a child, during the days leading up to Christmas, sitting on a chair in the kitchen, intently watching my grandmother as she turned pots and pans, preparing all those traditional seasonal dishes that I can still taste in my mouth. This year, I decided to venture into recreating one of those sweet delicacies that have always (always) been present on our Christmas table and hope to do it justice. By sharing this family recipe, I hope it brings you the sweet taste of gratitude and friendship and that you can share them also with your loved ones!
Merry Christmas, my people! 🫂
Preparation time: (excluding preparation of the sweet potatoes and mash) 20 minutes Baking time: 7 minutes
Ingredients * 300 g roasted sweet potato, peeled and mashed * 5 tbsp brown sugar * Pinch of fleur de sel * 1 egg (large) * 1 yolk * 30 g dried grated coconut * 100 g whole, skinned almonds * Lemon zest (optional) * Zest of 2 oranges * 1/2 tsp Cinnamon * 1/16 tsp vanilla powder * 1 egg yolk (for the egg wash)
Preparation 1. Grind the grated coconut in a food processor. Then add the almonds and grind again until it turns into fine granules or flour, depending on your preference. 2. In a pot (I used a Dutch oven, so I could control the process better), add the roasted sweet potato mash, the sugar, and the pinch of fleur de sel. Mix with a spoon until everything is well blended. Make sure to crush any bits of potato. 3. Bring to a simmer over medium-low heat, stirring constantly with the spoon to prevent sticking. Remove from the heat. Let the mixture cool down completely. 4. In a bowl, mix the egg and yolk with a fork. Add them to the contents of the pot and mix. 5. Then add the coconut, almonds, zest(s), cinnamon, and vanilla and return the pot to the heat, stirring constantly with a spoon so that the dough dries out and becomes moldable. It will take about 5 to 7 minutes on a gas stove with the smallest burner. At 9 to 10 minutes, the dough will be too dry because it still has to go in the oven. 6. As soon as you can handle the dough, shape it into small dumplings using 2 tablespoons. Place on a baking tray lined with baking paper, flatten each one with the help of a moistened dessert spoon, and make their edges with your fingertips (also moistened) and press lightly to flatten, so they look like the picture above. Delicate gestures and patience always pays off! 7. Brush each cookie with plenty of egg yolk. 8. Bake in a preheated oven at 200ºC (392°F) with the fan on the top rack for about 7 minutes or until golden brown. If you notice that the cookies near the oven door are toasting faster than those further away, turn the tray halfway through. 9. When you take the cookies out of the oven, to make the yolk shiny, pass a paper towel moistened with water over them. 10. Once cooled, store the cookies in a closed container in the fridge. You can start enjoying them within 24 hours.
Notes - Yields 26 small cookies - If you want, you can freeze the cookies still raw with or without the yolk. Place the shaped cookies on a tray lined with baking paper and put it in the freezer. Once frozen, store them in a freezer bag or other container. When you want to bake them, just take them out, place them in a tray lined with baking paper, and put them straight into the oven. Bake at 200ºC with no fan for 5 minutes. Turn the tray over, turn on the fan, and bake for another 5 minutes. - On baking the sweet potatoes and mash: Choose small sweet potatoes. This way, the oven time will be shorter. Rinse the potatoes well to remove any dust. Place them on a tray lined with baking paper and bake them in a preheated oven at 180°C with no fan until they are soft to the touch. Remove them from the oven and leave to cool for 5 minutes. The skin should come off easily. To make the mash, just use a potato masher.
-
 @ ee11a5df:b76c4e49
2024-12-16 05:29:30
@ ee11a5df:b76c4e49
2024-12-16 05:29:30Nostr 2?
Breaking Changes in Nostr
Nostr was a huge leap forward. But it isn't perfect.
When developers notice a problem with nostr, they confer with each other to work out a solution to the problem. This is usually in the form of a NIP PR on the nips repo.
Some problems are easy. Just add something new and optional. No biggie. Zaps, git stuff, bunkers... just dream it up and add it.
Other problems can only be fixed by breaking changes. With a breaking change, the overall path forward is like this: Add the new way of doing it while preserving the old way. Push the major software to switch to the new way. Then deprecate the old way. This is a simplification, but it is the basic idea. It is how we solved markers/quotes/root and how we are upgrading encryption, among other things.
This process of pushing through a breaking change becomes more difficult as we have more and more existing nostr software out there that will break. Most of the time what happens is that the major software is driven to make the change (usually by nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6), and the smaller software is left to fend for itself. A while back I introduced the BREAKING.md file to help people developing smaller lesser-known software keep up with these changes.
Big Ideas
But some ideas just can't be applied to nostr. The idea is too big. The change is too breaking. It changes something fundamental. And nobody has come up with a smooth path to move from the old way to the new way.
And so we debate a bunch of things, and never settle on anything, and eventually nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 makes a post saying that we don't really want it anyways 😉.
As we encounter good ideas that are hard to apply to nostr, I've been filing them away in a repository I call "nostr-next", so we don't forget about them, in case we ever wanted to start over.
It seems to me that starting over every time we encountered such a thing would be unwise. However, once we collect enough changes that we couldn't reasonably phase into nostr, then a tipping point is crossed where it becomes worthwhile to start over. In terms of the "bang for the buck" metaphor, the bang becomes bigger and bigger but the buck (the pain and cost of starting over) doesn't grow as rapidly.
WHAT? Start over?
IMHO starting over could be very bad if done in a cavalier way. The community could fracture. The new protocol could fail to take off due to lacking the network effect. The odds that a new protocol catches on are low, irrespective of how technically superior it could be.
So the big question is: can we preserve the nostr community and it's network effect while making a major step-change to the protocol and software?
I don't know the answer to that one, but I have an idea about it.
I think the new-protocol clients can be dual-stack, creating events in both systems and linking those events together via tags. The nostr key identity would still be used, and the new system identity too. This is better than things like the mostr bridge because each user would remain in custody of their own keys.
The nitty gritty
Here are some of the things I think would make nostr better, but which nostr can't easily fix. A lot of these ideas have been mentioned before by multiple people and I didn't give credit to all of you (sorry) because my brain can't track it all. But I've been collecting these over time at https://github.com/mikedilger/nostr-next
- Events as CBOR or BEVE or MsgPack or a fixed-schema binary layout... anything but JSON text with its parsing, it's encoding ambiguity, it's requirement to copy fields before hashing them, its unlimited size constraints. (me, nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s)
- EdDSA ed25519 keys instead of secp256k1, to enable interoperability with a bunch of other stuff like ssh, pgp, TLS, Mainline DHT, and many more, plus just being better cryptography (me, Nuh, Orlovsky, except Orlovsky wanted Ristretto25519 for speed)
- Bootstrapping relay lists (and relay endpoints) from Mainline DHT (nostr:npub1jvxvaufrwtwj79s90n79fuxmm9pntk94rd8zwderdvqv4dcclnvs9s7yqz)
- Master keys and revocable subkeys / device keys (including having your nostr key as a subkey)
- Encryption to use different encryption-specific subkeys and ephemeral ones from the sender.
- Relay keypairs, TLS without certificates, relays known by keypair instead of URL
- Layered protocol (separate core from applications)
- Software remembering when they first saw an event, for 2 reasons, the main one being revocation (don't trust the date in the event, trust when you first saw it), the second being more precise time range queries.
- Upgrade/feature negotiation (HTTP headers prior to starting websockets)
- IDs starting with a timestamp so they are temporally adjacent (significantly better database performance) (Vitor's idea)
- Filters that allow boolean expressions on tag values, and also ID exclusions. Removing IDs from filters and moving to a GET command.
- Changing the transport (I'm against this but I know others want to)
What would it look like?
Someone (Steve Farroll) has taken my nostr-next repo and turned it into a proposed protocol he calls Mosaic. I think it is quite representative of that repo, as it already includes most of those suggestions, so I've been contributing to it. Mosaic spec is rendered here.
Of course, where Mosaic stands right now it is mostly my ideas (and Steve's), it doesn't have feedback or input from other nostr developers yet. That is what this blog post is about. I think it is time for other nostr devs to be made aware of this thing.
It is currently in the massive breaking changes phase. It might not look that way because of the detail and refinement of the documentation, but indeed everything is changing rapidly. It probably has some bad ideas and is probably missing some great ideas that you have.
Which is why this is a good time for other devs to start taking a look at it.
It is also the time to debate meta issues like "are you crazy Mike?" or "no we have to just break nostr but keep it nostr, we can't dual-stack" or whatever.
Personally I think mosaic-spec should develop and grow for quite a while before the "tipping point" happens. That is, I'm not sure we should jump in feet first yet, but rather we build up and refine this new protocol and spend a lot of time thinking about how to migrate smoothly, and break it a lot while nobody is using it.
So you can just reply to this, or DM me, or open issues or PRs at Mosaic, or just whisper to each other while giving me the evil eye.
-
 @ 1cb14ab3:95d52462
2024-12-16 04:09:46
@ 1cb14ab3:95d52462
2024-12-16 04:09:46(Micro) "Boulder Creek" // stacked rocks [157' x 2' x 1']
(Macro) "St. Louis" // photo collage on foam board [16" x 20"]
This project was first presented in 2016, as a diptych installation at the group exhibition, "There to Here: Investigative Topographies from Land and Environmental Art" in Boulder, Colorado. Images remain property of Hes, but prints can be purchased via DM.
Artist Statement
Rockway: A Reflection on Roads and Nature
“Rockway” examines the concept of Micro v. Macro through the central theme of line; acting as a reflection on ideas of movement and connectivity in today's world. A line, simply defined as the connection between two points, takes on a profound new meaning in our urban landscape. The roads we have constructed, like arteries of the land, connect us to vast possibility. What happens when human progress and creation intersect with the natural world, and what role does that play in our lives?

Boulder Creek (pictured above) explores this intersection at the micro-level, focusing heavily on the delicate balance between humans and their environment. Stumbling upon the nearly 160-foot earthwork presents the viewer with an unnatural line, composed of stones, meandering through the pristine natural landscape. It evokes the winding roads through the mountains nearby one takes to get here- a stark contrast against the wilderness where it sits.
The earthwork employs a singular free-flowing, curvilinear line, representing a departure from the rigid angles of the surrounding landscape. This choice symbolizes more than just movement. It delves into the relationship between the towering skyscrapers, flowing highways, and gridded cities we inhabit. As the eye follows the work from start to finish, it encounters straight lines—those of trees and rocks—interrupting the flow, much like the complex highway systems and cities we build to connect ourselves around the globe.
St. Louis (pictured above) explores the concept of line at the macro-level. In this piece, movement remains a central theme, but the intent shifts. The collage aims to create an unrealistic, yet harmonious, urban highway system. Lines intersect, diverge, and rejoin in nearly impossible ways; calling into question what exactly our future might look like. Each line signifies the movement of humans—from place to place, from birth to departure.
The city of St. Louis holds personal significance. It’s my birthplace, my starting point. The curved form of the line embodies movement and fluidity, echoing my own journey. Highways connect us to places, people, and experiences. They weave our stories, even as they reshape the landscape.
Step back, and the piece appears a unified whole. But lean in and scrutinize the details, and you’ll discover individual clippings and rigid overlaps from the satellite photos it is composed of. Each stone and curve. Each road and line — force us to consider the tale of movement, connection, and balance. "Rockway" invites us step back and dig deeper into the connections we [ourselves] hold with the land; and what responsibility we [as a whole] have in encouraging continued prosperity, while maintaining the delicate balance holding it all together.
Additional Photos






More Land Art
Invasive (Site/Non-Site) - [2016]
Earth Lens Series - [2016-Present]
Find Me Elsewhere
Originally published in 2016 by Hes. Republished at habla.news/u/hes@nostrplebs.com/1708400183541 on 2/19/2024.
-
 @ 1cb14ab3:95d52462
2024-12-16 04:00:56
@ 1cb14ab3:95d52462
2024-12-16 04:00:56Flattened grass, Lightroom. [12’ x 60’]
This project was first presented in 2022 in Littleton, Colorado. Images remain property of Hes. Prints available on request.
Artist Statement
Нет войне: No to War
"Нет войне" is an environmental art project created by continuously walking back and forth for several hours until the grass lay flat. Each letter measures roughly 12’ x 6’. The letters have been slightly exaggerated in Adobe Lightroom for digital clarity. The phrase "Нет войне" translates to "No to War."

The piece aims to give a voice to the citizens around the world standing up against tyranny and destruction. Nature always overruns land art with time. It overruns the rubbles of a war-torn country. It will overrun civilization long after we are gone. This earthwork may only be visible for a couple of weeks; the signs may only be held up for a couple of seconds; the remnants of a devastating war may only be visible for a couple of decades. But one thing remains true: human lives will never be restored. Facts should never be forgotten. Invasions should never be tolerated. Freedom will prevail.
The artwork reflects on the impermanence of human constructs, whether they are artistic expressions or the scars left by warfare. It serves as a testament to the strength and determination of those who oppose oppression and violence.
Through this work, I aim to not only capture a moment of protest but also invite viewers to reflect on the broader implications of war and peace. The piece is a call to action, urging us to remember the human cost of war and to strive for a world where freedom and peace prevail.
Follow-up images regarding the status of the land will be provided over time. Hopefully, the war will be over before the piece fades away.
Additional Photos




Month 1 Update
The war expands. The piece stands.


Month 4 Update
The war continues. The piece fades.


Month 12 Update
The war rages on. The piece is gone.


More Land Art
Invasive (Site/Non-Site) - [2016]
Rockway (Micro v. Macro) - [2016]
Find Me Elsewhere
Originally published in 2022 by Hes.
Republished to habla.news/u/hes@nostrplebs.com on 7/5/2024.
Republished with updates to https://hes.npub.pro/ on 12/15/2024.
-
 @ a012dc82:6458a70d
2024-12-16 04:00:21
@ a012dc82:6458a70d
2024-12-16 04:00:21Table Of Content
-
The Predictable Dance of Bitcoin's Price
-
Economic Cycles and Their Influence on Bitcoin
-
The Role of Bitcoin Halving in These Cycles
-
Echoes of the 2015-2017 Pre-Bull Run Phase
-
A Glimpse into the Future: An Optimistic Outlook with Caveats
-
Conclusion
-
FAQ
In the dynamic world of financial assets, patterns often emerge that hint at the future trajectory of popular investments, especially Bitcoin. A recent deep dive into Bitcoin's behavior suggests that its current price action is reminiscent of its performance between 2015 and 2017. For those who've been tracking its journey, this might evoke a sense of déjà vu. Let's unpack this captivating observation.
The Predictable Dance of Bitcoin's Price
Delphi Digital, a renowned research firm, recently shed light on the intriguing consistency of price trends within the crypto market. Their findings suggest that Bitcoin's current consolidation around the $30,000 mark mirrors its behavior from a few years ago. If history is any guide, we might be gearing up for another all-time high (ATH) for Bitcoin by the end of 2024.
Economic Cycles and Their Influence on Bitcoin:
One cannot discuss Bitcoin's price without considering broader economic trends. Delphi's analysis highlights the cyclical nature of the cryptocurrency market. These cycles, often spanning four years, showcase a pattern: Bitcoin reaches a new ATH, faces a significant drop (often around 80%), bottoms out a year later, and then embarks on a two-year recovery journey. This culminates in another price rally, leading to a fresh ATH.
Interestingly, Bitcoin's price peaks often align with changes in the business cycle, as reflected by the ISM Manufacturing Index. When Bitcoin is at its peak, the ISM shows signs of maxing out, and network activities like transaction volumes reach their zenith. Conversely, when the business cycle signals a rebound, Bitcoin's network activity follows suit.
The Role of Bitcoin Halving in These Cycles:
For those unfamiliar, Bitcoin halving is an event where the reward for mining new blocks is halved, effectively cutting the rate at which new Bitcoins are created. Delphi's report emphasizes the significance of this event in the four-year cycles. Historically, halvings have taken place roughly 18 months after Bitcoin hits its bottom and about seven months before a new ATH. This pattern suggests that the next ATH for Bitcoin could be around the corner, coinciding with the upcoming halving in 2024.
Echoes of the 2015-2017 Pre-Bull Run Phase: The parallels between Bitcoin's current market environment and the 2015-2017 phase are hard to ignore. Both periods exhibit similar market behaviors, economic indicators, and historical trends. The report even notes that trading patterns in broader markets, like the S&P 500, mirror those observed during 2015-2017. Such patterns persisted even during uncertain times, reinforcing the sentiment of that era.
A Glimpse into the Future: An Optimistic Outlook with Caveats:
Delphi's comprehensive analysis paints a hopeful picture for the crypto market. The prediction of a new ATH by the end of 2024, backed by historical halving patterns and economic indicators, strengthens the case for a cycle similar to 2015-2017. The anticipated Bitcoin halving in 2024 further supports the possibility of a bull market by that year's end. However, as with all predictions, there are inherent risks and uncertainties. Yet, the overall sentiment for the crypto market in the upcoming months seems promising, given the historical patterns and current indicators.
Conclusion
For Bitcoin enthusiasts and investors, understanding these patterns and market behaviors can offer valuable insights. While the future remains unpredictable, recognizing these historical parallels can provide a roadmap of sorts. As the saying goes, history often rhymes, and in the case of Bitcoin, it seems to be singing a familiar tune. So, hang tight, folks! The spirit of 2015-2017 might just be making a comeback.
FAQ
What does the recent research by Delphi Digital suggest about Bitcoin's price? The research indicates that Bitcoin's current price action mirrors its behavior between 2015 and 2017, hinting at a potential all-time high by the end of 2024.
How do economic cycles influence Bitcoin's price? Economic cycles, especially as indicated by the ISM Manufacturing Index, often align with Bitcoin's price peaks and network activity.
What is Bitcoin halving, and why is it significant? Bitcoin halving is an event where the reward for mining new blocks is halved. Historically, halvings have been key indicators of upcoming all-time highs for Bitcoin.
Are there similarities between the current market environment and the 2015-2017 phase? Yes, both periods exhibit similar market behaviors, economic indicators, and historical trends, suggesting a potential bull market in the near future.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 1cb14ab3:95d52462
2024-12-16 03:38:21
@ 1cb14ab3:95d52462
2024-12-16 03:38:21
























Photos in Order:
-
Angkor
-
Anren
-
Arun
-
Asadha
-
Baima
-
Baita
-
Baiyuan
-
Bayon
-
Ciguang
-
Datang
-
Dazhao
-
Fanjing
-
Groslier
-
Guyi
-
Gyeongbokgung
-
Higashi
-
Hongya
-
Huanghe
-
Independence
-
Kiyomizu I
-
Kiyomizu II
-
Kyauk
-
Leifang
-
Longhua
-
Manhua
View Part 2:
Other Works:
Find me elsewhere:
-
-
 @ 1cb14ab3:95d52462
2024-12-16 03:35:20
@ 1cb14ab3:95d52462
2024-12-16 03:35:20
























Photos in Order:
-
Nanjing
-
Nanshan
-
Nijo
-
Norodom
-
Oldtown
-
Qiaolou
-
Qibao
-
Qingcheng
-
Royal
-
Shwedagon
-
Taiping
-
Tenryu
-
Thatbyinnyu
-
Tianxuan
-
Twins
-
Wuzhu
-
Xinanjiang
-
Xingbake
-
Xuanbi
-
Yehliu
-
Yueya
-
Yunyan
-
Yuyuan
-
Zhonggong
-
Zhouzhuang
View Part 1:
Other Works:
Find me elsewhere:
-
-
 @ 1989034e:b9c4276b
2024-12-16 03:27:05
@ 1989034e:b9c4276b
2024-12-16 03:27:05Bitcoin is hope. Bitcoiners bring hope. The following is a collection of my thoughts following The Calgary Sat Market of December 2024. It is also a call to action for Bitcoiners near and far to join us - either in person by visiting - or spiritually by replicating what we are doing.

I'm sitting here, smiling ear to ear, absolutely brimming with hope for the future after hosting today's Sat Market in Calgary, Alberta.

Context For Anyone Unfamiliar
One year ago we put together an initiative to build our own Bitcoin circular economy here in the city. We went to the local meetup and made the case to everyone:
“You all understand Bitcoin is better money, you all have skills and businesses, you all currently earn dollars and convert them to Bitcoin. Let's cut out that middle step and build something together!”
The Sat Market was born.

The response over the past calendar year has been wonderful. Today's event boasted 40 vendors, consisting of farmers, tradesmen, artists, precious metals dealers, massage therapists, personal trainers, wellness coaches, authors, jewellers, homesteaders, lawyers, dentists, plumbers and much much more.
People came to Calgary for the market from Vancouver, Edmonton, Winnipeg, Toronto, Montreal and many other places. We've had people from other countries begin to recognize what is happening here, wanting to visit.

I’ve been living on Bitcoin myself since 2020. While technically possible, I often require some much appreciated services that allow me to pay bills, buy gift cards, and otherwise use some type of middle-man in order to make it work. The Sat Market is beginning to change that dynamic.
Just at this most recent event I was able to purchase:
- Knitted winter gear
- Apparel (hats and shirts)
- Custom art
- Candles and home decor
- Full chickens, eggs, hot sauce, mustard, bacon, ground pork, jerky, baked goods and many other delicious items
- PLUS an on-site massage!

This event wasn’t just about buying and selling, though. It was also about GIVING! We hosted some fun quiz games with prizes and had the most BALLER raffle I’ve personally witnessed. Giveaways included:
- Custom art pieces
- Apparel Artisan tea
- Hypnosis sessions
- A free hour with Bitcoin Mentor
- Jewelry pieces
- 20 Tapsigners
- 30 packs of BTC Trading Cards (Genesis packs)
- 14 Coldcard Q’s
- A 10 OZ bar of Silver
I estimate that we gave away over $6000 worth of stuff. People were over the moon!

I believe that in order to become truly resilient, the time has come to put our money quite literally where our mouths are. Any movement can be stopped when it requires you to rely on permissioned on/off ramps....
...but when you have a community of like minded individuals, creating real and meaningful relationships on a local level, providing value to one another and using a money that is external to the existing system - YOU BECOME UNSHAKEABLE.

I encourage each and every one of you to make a Sat Market pilgrimage to our next event in Calgary near the end of June. It will be flanked by a group excursion to the Canadian Rockies (1 hr drive away), The Bitcoin Rodeo (a pretty based local conference), a workshop day by Bitcoin Mentor (likely also in Banff), and plenty of other community led events.
Come, participate, contribute, and replicate.

This project has been entirely funded out of my own pocket and the voluntary contributions of merchant participants. If you feel inclined to zap this post, any sats will go towards making our next market the absolute best it can be.

What we are doing here is special. What we are doing here is exciting. What we are doing here is working. What we are doing here IS HOPE.
We'll see you at the next Sat Market.
KEEP UP WITH WHAT WE'RE DOING!
Please visit and share our website:
Please follow us on:
Nostr: npub12exjy0qp2pytsgrnaqrg26qj55epun8l2unyfjvhyxn2k2sx0xaqt2rd2h
X: BTCSatMarket
Enjoy these photos from our wonderful event!



















-
 @ f7e2103b:0285376d
2024-12-16 02:58:45
@ f7e2103b:0285376d
2024-12-16 02:58:45In the rapid development of modern Fintech, we see many amazing technologies changing our lifestyle. Today, we are going to talk about some interesting devices in the field of Fintech. Although these devices are often mentioned in daily life, their application in Fintech is less well known. Let's take a deep look at how these technologies work in the financial field.
Imagine that in a busy bank or financial institution, jammer can effectively prevent hackers from stealing customers' personal information or financial data through wireless signals. It provides an invisible umbrella for customers' transactions, making people feel more at ease when conducting online transactions. Although signal jammers are restricted in some cases, their role is obvious in specific financial scenarios.
As more and more financial transactions are conducted over WiFi, WiFi security has become particularly important. WiFi jammers can help protect the network environment and prevent unauthorized connections and information leaks. In Fintech, the application of WiFi jammers can help banks and financial institutions maintain the security of their networks and ensure that customer information is not stolen.
For example, in high-frequency trading or fast payment scenarios, if the network environment is not secure, it may cause transaction failures or data tampering. Using a WiFi jammer can effectively prevent hackers from invading through the WiFi network, thereby protecting the integrity and security of transactions.
A rf signal detector is a device that can monitor the surrounding signals, detect abnormal signals in time and issue an alarm. In Fintech, signal detectors can be used to monitor the security of the financial transaction environment to ensure that there are no potential threats.
For example, in a financial trading hall, a signal detector can monitor the surrounding signal fluctuations in real time, and once a suspicious signal is detected, it will immediately alarm. This technology can help financial institutions respond quickly to potential security threats and protect customers' funds and information.
Finally, let's talk about GPS trackers. In Fintech, the application of GPS trackers is mainly reflected in asset management and monitoring. Whether it is a high-value financial asset or a customer's mobile payment device, a GPS tracker can provide real-time positioning services.
Imagine that a financial institution uses a GPS tracker to monitor the transportation process in real time and ensure the safety of assets when transporting precious metals or cash. At the same time, customers can also use GPS tracker to confirm the security and effectiveness of transactions when using mobile payments. The application of this technology not only improves the security of assets, but also provides customers with a better service experience.
In the future, we can expect more innovative financial technology products to emerge, which will better serve our lives. Whether it is individual users or financial institutions, understanding the application of these technologies will help us better cope with the increasingly complex financial environment and protect our assets.
-
 @ 7ed5bd1c:4caa7587
2024-12-16 02:50:13
@ 7ed5bd1c:4caa7587
2024-12-16 02:50:13Bitcoin และพลังงาน: จริงหรือที่มันเป็นตัวทำลายสิ่งแวดล้อม?
หนึ่งในข้อกังวลที่ผู้คนมีต่อ Bitcoin คือเรื่องของการใช้พลังงานที่ดูเหมือนจะมากเกินไป บ่อยครั้งที่เราได้ยินว่าการขุด Bitcoin (mining) ใช้พลังงานเทียบเท่าประเทศเล็กๆ ประเทศหนึ่ง แล้วมันจริงหรือที่ Bitcoin จะเป็นภัยต่อโลก? หรือว่าความเข้าใจเหล่านี้อาจไม่ถูกต้องทั้งหมด?
การใช้พลังงานของ Bitcoin: ความจริงที่ถูกบิดเบือน
-
แหล่งพลังงานหมุนเวียนที่เพิ่มขึ้น: รายงานล่าสุดจากสถาบันวิจัยด้านพลังงานพบว่ามากกว่า 50% ของพลังงานที่ใช้ในเครือข่าย Bitcoin มาจากพลังงานหมุนเวียน เช่น พลังงานแสงอาทิตย์ พลังงานลม และพลังน้ำ ซึ่งทำให้การดำเนินการของ Bitcoin มีส่วนช่วยกระตุ้นการพัฒนาพลังงานสะอาดในหลายภูมิภาค
-
ประสิทธิภาพที่พัฒนาขึ้น: อุตสาหกรรมขุด Bitcoin ได้พัฒนาอุปกรณ์และกระบวนการที่ใช้พลังงานอย่างมีประสิทธิภาพมากขึ้นเรื่อยๆ แทนที่จะใช้อุปกรณ์ล้าสมัย เครื่องขุดในปัจจุบันใช้เทคโนโลยีขั้นสูงที่ให้ผลลัพธ์คุ้มค่าต่อหน่วยพลังงาน
-
เปรียบเทียบกับระบบการเงินแบบดั้งเดิม: เมื่อเทียบกับธนาคารและระบบการเงินดั้งเดิม การใช้พลังงานของ Bitcoin ยังน้อยกว่ามาก การดำเนินการของธนาคาร สาขาทั่วโลก ศูนย์ข้อมูล และระบบอื่นๆ ใช้พลังงานมหาศาล และยังไม่ได้มุ่งไปในทิศทางที่ยั่งยืนเท่ากับ Bitcoin
Bitcoin กระตุ้นนวัตกรรมพลังงานสะอาด
ในบางพื้นที่ที่พลังงานสะอาดมีมากเกินความต้องการ (overproduction) เช่น เขตที่มีกังหันลมหรือโรงไฟฟ้าพลังน้ำ Bitcoin กลายเป็นเครื่องมือที่ช่วยดูดซับพลังงานส่วนเกินเหล่านั้นให้เกิดประโยชน์ ข้อนี้แสดงให้เห็นว่า Bitcoin สามารถเป็นโอกาสสำหรับการพัฒนาระบบพลังงานที่ยั่งยืนมากขึ้นในระยะยาว
ตัวอย่างที่น่าสนใจ
หนึ่งในตัวอย่างที่โดดเด่นคือประเทศเอลซัลวาดอร์ ที่ได้เริ่มใช้พลังงานความร้อนใต้พิภพจากภูเขาไฟในการขุด Bitcoin ไม่เพียงแต่ช่วยลดการปล่อยคาร์บอนเท่านั้น แต่ยังสร้างงานและกระตุ้นเศรษฐกิจในพื้นที่ชนบทอีกด้วย
คุณกำลังเห็นภาพรวมที่แท้จริงหรือไม่?
ปัญหาเรื่องพลังงานของ Bitcoin ไม่ใช่เรื่องที่จะมองข้าม แต่สิ่งสำคัญคือการมองมันอย่างรอบด้านและเทียบกับทางเลือกอื่นที่เรามีอยู่ในปัจจุบัน การพัฒนาระบบพลังงานสะอาดควรเป็นเป้าหมายร่วมกัน และ Bitcoin อาจเป็นส่วนหนึ่งของคำตอบนี้
แล้วคุณล่ะ คิดว่าอนาคตของ Bitcoin และพลังงานจะเป็นอย่างไร? ร่วมแสดงความคิดเห็นได้ในโพสต์นี้!
-
-
 @ 5bfb38cb:2b999aa7
2024-12-16 01:25:25
@ 5bfb38cb:2b999aa7
2024-12-16 01:25:25BTZ2024
Classic Technical Analysis:
In terms of conventional technical analysis, BTC remains in an Elliott structure with a minor wave 5 finished and a major wave 3 ongoing. The context is strongly bullish.
COT:
The progression of contracts nearing expiration is at a premium. The 12-month COT is in a positive program and in positive hedging.
Market sentiment:
In general, retail news is bullish following the FED's rate cut and in response to the US elections, although with some moderation. The Williams %R remains in oversold territory and avoids a bearish divergence.
Intermarket Analysis:
The NQ has had an upward movement with a positive close. The ES has had a negative reversal and the YM a downward movement with a negative close.
The 3 bonds, ZN, ZF, and ZB, show a downward movement and negative close, with the ZB showing greater weakness. They will likely go to bearish liquidity. The interests show an inverse movement with strength in the 30-year bond.
The DYX maintains strength by rejecting a bearish FVG with a positive movement close. The EUR and GBP have had a bearish week with a negative close in the former.
BTC shows a bar with bearish liquidity taking and a positive close.
In commodities, GC has a bar with bullish liquidity taking and rejection. CL has a bar of upward movement in a long consolidation.
In conclusion, we have strength in the NQ, but weakness in the other two indices. The DYX maintains strength with weakness in peripheral currencies. BTC will likely retest highs. GC shows renewed weakness at the end of a trend. CL is in a long consolidation.
Market Profile:
The market is currently bullish. It needs to keep moving significantly away from the all-time high to continue this movement.
Weekly Objective:
111572, major wave 3 and QS objective.
-
 @ 319ad3e7:cc01d50a
2024-12-15 21:20:59
@ 319ad3e7:cc01d50a
2024-12-15 21:20:59LETTER FROM THE FOUNDER | FEATURED RECIPE | MICROFICTION | FOOD NOTE QUOTE | SOUNDS | NOSTR MARKETPLACE | REAL REVIEWS | COMMUNITY ALBUM | NEW RECIPES | FIN
LETTER FROM THE FOUNDER 📝
A Year of Growth and Gratitude
As we approach the end of the year, it’s the perfect moment to pause and reflect. 2024 has been a transformative year for Zap Cooking. What started as a simple idea has grown into a vibrant, connected community. From recipes to shared stories, the #zapcooking tag has become a rallying point for food enthusiasts everywhere, and it’s inspiring to see how this shared passion is bringing people together.
None of this would have been possible without the incredible support and dedication of Sarah, who pours her heart into crafting these newsletters. Sarah, thank you for helping us share the joy of cooking and community with so many.
I am deeply grateful, grateful for you, our community, for nostr, for the milestones we’ve reached, and for the challenges that have helped us grow. Zap Cooking is about more than food; it’s about connections, creativity, and collaboration. Together, we’ve built something special, and I’m excited for what 2025 holds.
Here’s to another year of cooking, connecting, and creating together. Thank you for being part of this journey.
Cheers!
Seth
Founder, Zap Cooking
FEATURED RECIPE 🥪
Nostrville 2.0 was located in Nashville, Tennessee. This music destination featured some powerhouse food establishments, such as Ladybird Taco, Hattie B’s Hot Chicken Sandwiches, Pancake Pantry, and Modell’s infamous family-style breakfast; however, it was the people from Louisiana who brought their A-game to the shared kitchen at the after-party rental.
The lovely Rupert and her giant, Kajoozie, served up a traditional gumbo that had all of us reaching for a second bowl… or perhaps a fourth bowl. It was that good! They were also kind enough to share their recipe with all of us.
Rupert and Kajoozie’s #Nostr Famous Gumbo https://substack.com/home/post/p-152296981
MICROFICTION 📖
GIFTS by RustyPuppy
Every Christmas Eve (and by 'every' Aaran meant those he could remember, which, being eight years old, was not many), after the dinner dishes had been washed, and the family settled into the living room to watch "It's a Wonderful Life," his nani would start chopping vegetables. Aaran once asked why she didn't cook Santa's beef stew when she prepared their dinner. Because she wanted the stew to be fresh, came the answer. Aaron knew better than to ask how something that needed to simmer for five hours could be considered 'fresh.'
Everyone knew their grandmother's beef stew, placed in front of the fireplace in a hand-made bowl wrapped in a dish towel to keep warm, was eaten by the dog after everyone went to bed. And every year, she insisted Santa needed a hot, healthy meal.
None of the children could believe anyone would choose vegetables over cookies. Shari, the girl next door, made peanut cookies for Santa. Aaron had helped mix the dough last year. He was forbidden from adding the frosting because Shari needed the perfect amount atop each cookie so she could write her name in the sugary mix with a toothpick. Depending how guilty she felt about the year, she sometimes added candy beads.
One year, a cousin asked if Santa really ate all of those hundreds? thousands? millions? of cookies. An uncle said, "Of course, that's why he's so fat," while Aaaran's mother said, "Of course not, he gives them to children who don't have sweets," and Nani added "And those who still want to believe in him."
Aaran secretly wanted to believe his nani, because his older brothers had teased him for writing his Christmas wish letter, saying Santa was only real for babies. He didn't want to be a baby, but he still wanted to believe in the magic that was Santa.
At last, the evening ended. Some returned to their homes; the rest returned to their rooms. Nani set her bowl under the stockings. Aaran hesitated on the stairs, but the thought of seeing the dog actually eat the stew made his eyes wet. He stepped over his cousin's sleeping bag, got into bed, and dreamed of flying reindeer.
In the morning, as the children opened their gifts and the adults took turns making coffee and tea, Nani asked Aaran to bring her the stew bowl. He looked at the dog, currently surrounded by shreds of wrapping paper, panting happily with a bow on his head. Picking up the bowl, Aaron saw something within; a peanut cookie with the name Shari written in the frosting.
RECIPE REFERENCES:
Lovely Indian beefstew with coconut milk & Ultimate Peanut Cookies https://substack.com/home/post/p-152296981
FOOD NOTE QUOTE 🗒️
Today someone took a picture of my latte art after I handed them their cup 💜 and it made my day. Celebrate the small things. 😊 - TKay
SOUNDS 🔊
At Bitcoin Park in Nashville, Tennessee, the adorable cuties Mallory, Other Mallory, Island, and Sergio, along with help from Fountain, Phantom Power and Tunestr.io organized a night of activities, food, art, and a live acoustic music panel featuring four absolutely talented musicians - Ainsley Costello, Amber Sweeney, Luke Wood, and Jo Corso. SoupBox was honored to sit down with Amber to chat about music, fostering dogs from Wags and Walks, and food | Listen Now: SoupBox with Sarah | Featuring Amber Sweeney
https://fountain.fm/episode/nvwD83sajCiFNqTP4tYu
https://feeds.rssblue.com/soupbox
Short from Nashville | OpenMike | Tunestr
https://v.nostr.build/yLufD7GbwOPI3EgA.mp4
NOSTR MARKETPLACE 💳
Find Your Holiday Gifts on Nostr | Value for Value (aka V4V) #circulareconomy
Agi Choote | Art Prints | Find on Nostr!
Amber Sweeney | Custom Songs for Any Occasion | https://www.theambersweeney.com/merch/custom-songs
Ant Richard | Limited Custom Handcrafted Knife Gift Certificates (12-month waitlist for all custom handmade orders) | Find on Nostr!
Apotheca Viva | https://apothecaviva.love/
Aupa Bars | https://eataupa.com/
Barnminer’s Barn Jerky | Find on Nostr!
Billay Coffee | https://billaycoffee.com/
BitBees | Honey & Honey Products | https://www.kittrellsdaydream.com/
Bitcoin Blankets ⚡️| Website Coming Soon!
Bitpopart | https://bitpopart.com/ | https://www.storeofvalue.eu/collections/christmas-collection
BTC Aloha | Bitcoin Beachwear & Accessories | https://btcaloha.shop/
BtcPins | https://btcpins.com/
Cannabis Records | https://cannabisrecords.store/
CryptoCloaks | https://www.cryptocloaks.com/shop/
Delgado’s Fuego | https://delgadosfuego.com/
Dot GNT | Laser Engravings | https://dotgnt.codeberg.page/
Finca Yabisi | https://yabisi.farm/
Foxfire Mushrooms | https://foxfiremushrooms.com/
Golden Tallow | https://goldentallow.com/
GoodBeans 🇸🇻 Coffee | https://thegoodbeans.com/
Isolabell.art | https://isolabell.art/
Jake Wolki | https://wolkifarm.com.au/
Keto Beejay | Low Sugar Jerky | https://ketolish.us/ | https://ketobeejay.npub.pro/
Kanuto Takumi San | Find on Nostr!
Laser Eyes Cards | https://lasereyes.cards/
LeatherMint | https://theleathermint.com/
Lightning Store | https://lightning.store/
LightningSpore | Full Service Mushroom Cultivation Company | https://www.lightningspore.com/
Lost Sheep Ranch | https://www.lost-sheep-ranch.com/
Lucho Poletti | Art Prints and Merchandise | https://luchopoletti.com/
Madex | Art & Apparel | https://madex.art/collections/in-stock
MapleTrade | Find on Nostr!
Matthew D | https://whitepaperstreetsoap.com/
Next Block Coffee | https://nextblockcoffee.com/
NoGood | Jake Wolki | https://wolkifarm.com.au/
PatsPropolisHoney | Find on Nostr!
Peony Lane Wine | Ben Justman | https://www.peonylanewine.com/
PlebianMarket | https://plebeian.market/
PictureRoom | Assorted Dessert Treats | Find on Nostr!
Regenerative Farmed Meats & Knives | AgrarianContrarian | Find on Nostr!
RustyPuppy | Art and Stories | https://heidi2524.com/
Salt of the Earth | Premium Electrolyte Mix | https://drinksote.com/
Satoshi Coffee Company | https://sats.coffee/
Scott & Son | Animal Portraits, Prints, and Apparel | https://xavierscraftworkanddesign.com/t-shirts
SofterSkin Tallow Skincare | https://softerskin.co/
Shopstr | https://shopstr.store/
Soap Miner | Tallow Body Soap Bars
SweetSats | Honey | https://sweetsats.io/
Veiled Mycology | https://veiledmycology.com/
Yojimbo | Jam & Marmalade | https://jimblesjumble.odoo.com/
REAL REVIEWS ⭐
BitBees | Honey & Honey Products | https://www.kittrellsdaydream.com/ | By Rupert
If you follow me or have ever had the pleasure of chatting with me on cornychat.com or hivetalk.org, you’ll know how proud I am of my Cajun heritage. For me, that means memories of long, hot summer days in South Louisiana, plenty of mosquito bites, the humming of cicadas in the cypress trees, and my grandfather’s bee boxes abuzz with fuzzy little workers.
I recently had the pleasure of meeting our famed #nostr beekeepers, @bitbees and @kingbee, and the absolute joy of tasting the labors of the wee little friends they care for. @KajoozieMaflingo and I purchased both their wildflower and gallberry varieties, and we were able to pay with BTC! (BONUS!) The wildflower was chef’s-kiss perfection, but my taste buds were instantly rocketed back to my childhood when I tried the lovingly and aptly nicknamed “swamp honey.”
Its pale color might fool you into thinking it has a lighter flavor than its rich and flavorful counterpart, but that couldn’t be further from the truth. It’s crisp and bright, with a mellow sweetness balanced by a slight tang to finish. It’s the ideal pairing with my favorite chamomile tea before bedtime.
This was my first purchase, but it will not be my last. By far, this is one of the most delicious use cases for Bitcoin I’ve come across to date.
Keto Beejay | Low Sugar Jerky | https://ketolish.us/ | https://ketobeejay.npub.pro/ | By The Beave
I recently had the pleasure of ordering four types of beef jerky from Beejay, the proprietress of http://ketolish.us. I was intrigued by her offerings and ended up ordering plain, pickle, pizza, and pepper. My order took a while to go through, mostly because Beejay and I were figuring out how to move sats around without it being too much of a pain in the butt. However, once finalized, everything shipped promptly and arrived quickly in a well-packed parcel. Beejay is also very good to communicate with, and I will gladly purchase more from her in the future.
I will start off the reviews with the most surprising of the batch: pizza. This was simply outstanding. I was shocked at how much it reminded me of eating pizza. I can't recommend this one enough! My second favorite pick is the pickle flavor. I love pickles. (I cannot express how much I love pickled things to you in words!) This was also very good, with the dill seasoning being front and center but restrained enough not to completely overpower the delicious beefiness of the jerky. A note on the texture: the jerky is ground, so it is not as tough as other jerkies you might try. This is a very new thing to me, and I rather enjoyed the novelty of the experience. The peppered jerky was full of pepper. This might be too much pepper for some, as it reminded me of the pepper-covered salami you can get at a good Italian pork store. Lastly, the plain jerky was delicious in its own right, though I would have preferred a touch more salt. I would order all of these again and am looking forward to ordering other flavors in the future, especially the bison!
COMMUNITY ALBUM 📷
Photos & Videos by Mandana from NextBlock & Flirting with Bitcoin, Efrat Fenigson, Ava, Birthday B, Vic from CornyChat, Tortuga, Mallory, Island, Jack Spirko, Paul Keating, BreadandToast.com, Nos.Social and Sarah SoupBox
View the Album: https://substack.com/home/post/p-152296981
NEW RECIPES 🍲
https://i.nostr.build/MNrivKtc1fpjamfn.png
In November, we received an incredible surge of over 30 recipes submitted to Zap Cooking! That's a fantastic leap from the three or four we typically see each week! Dive into one, two, or even all of them, and don’t forget to share your reviews and mouthwatering photos on Nostr using #foodstr. We’d also love to see your favorite personal or family recipes—let’s keep the culinary creativity flowing!
Corn Pudding, The Beef Panzone, Vodka Pie Crust, Short Rib Barbacoa Tacos, Guiness Beef Stew with Pickled Pearl Onions, Fast AF Beef Stroganoff, Dark Chocolate Mincemeat, Vic’s London Broil, Easy Wholemeal Spelt Flour Bread, Mamma SLCW’s Cranberry Sauce, Hot Dog Nachos, Italian Wedding Soup, Mapo Tofu Curry, Hot Honey Crispy Salmon Bowls, Curried Butternut Squash Soup, Best Damn Oven Baked Chicken Legs, Chocolate Creme Pie, Broccoli Beef, Tuscan Steak and Green Peppers, Easy Carne Asada, InstantPot Chicken Tortilla Soup, Green Bean Casserole with Bacon and Fried Shallots, Bang Bang Shrimp, Rupert and Kajoozie’s #Nostr Famous Gumbo, The Best Lamb Winter Stew, Avery’s Hot Wallet Salsa, Candied Pecans, Pumpkin Bread, Breakfast Casserole with Sausage and Egg, Gold & Silver Soup, Mr. G’s Homemade Chicken Pasta Salad, Ultimate Peanut Cookies
The recipe links are available here: https://substack.com/home/post/p-152296981
FIN 🤠
https://i.nostr.build/661bAgwsj6tEnICX.jpg
-
 @ 502ab02a:a2860397
2024-12-15 18:51:05
@ 502ab02a:a2860397
2024-12-15 18:51:05“Donna Donna” เดิมเป็นเพลงภาษาเยดิช (Yiddish) ชื่อ “Dos Kelbl” (The Calf) ประพันธ์ขึ้นในปี 1940 โดย Sholom Secunda (ผู้แต่งทำนอง) และ Aaron Zeitlin (ผู้แต่งเนื้อร้อง) สำหรับการแสดงละครเพลงชาวยิวในยุคนั้นซึ่งเป็นช่วงเวลาที่ทหารนาซีเร่งขยายอิทธิพลในยุโรป และชาวยิวในหลายพื้นที่เริ่มถูกจับกุมและส่งไปยังค่ายกักกัน
แม้ว่าเพลงนี้จะไม่ได้เขียนขึ้นในภาษา ฮิบรู (Hebrew) แต่เดิมเป็นภาษา เยดิช (Yiddish) ซึ่งเป็นภาษาที่ใช้ในหมู่ชาวยิวแถบยุโรปตะวันออก อย่างไรก็ตาม การเชื่อมโยงเพลงกับความทุกข์ของชาวยิวในยุคนั้นมีเหตุผล เพราะเนื้อหาเพลงสอดคล้องกับสภาพแวดล้อมทางสังคมที่ผู้แต่งเผชิญในช่วงสงคราม
เพลงนี้กลายเป็นสัญลักษณ์ของการต่อสู้เพื่อเสรีภาพในหลายยุคสมัย ไม่เพียงแต่สะท้อนชะตากรรมของชาวยิวในสงครามโลกครั้งที่ 2 แต่ยังแสดงให้เห็นถึงเสียงเรียกร้องเพื่อความเป็นอิสระและการไม่ยอมจำนนต่อความอยุติธรรมในระดับสากล
ในปี 1956 นักแต่งเพลงชาวอเมริกัน Arthur Kevess และ Teddi Schwartz ได้แปลเพลงนี้เป็นภาษาอังกฤษและตั้งชื่อว่า “Donna Donna” โดยใช้ความหมายเดิมเป็นพื้นฐาน แต่มีการปรับเปลี่ยนเล็กน้อยในเรื่องของภาษา
ตัวอย่างบางส่วนของการแปลครับ ภาษาเยดิช (Yiddish): אַ פֿויגל האָט אַ פֿליגלען, אַ קאַלב דאַרף גיין צו שלאַכט. (คำอ่าน: A feygl hot a flign, a kalb darf geyn tsu shlakht.) คำแปล: นกมีปีกให้โบยบิน แต่ลูกวัวต้องเดินไปสู่โรงฆ่าสัตว์
ภาษาอังกฤษ (แปล): A bird has wings to fly, a calf is led to slaughter.
เพลง “Donna Donna” นั้นมีความหมายที่ลึกซึ้งและเต็มไปด้วยการเปรียบเปรย เนื้อหาของเพลงเล่าถึงลูกวัวตัวหนึ่งที่กำลังถูกพาไปโรงฆ่าสัตว์ โดยเปรียบเปรยถึงความไร้เสรีภาพและความโศกเศร้าที่เกิดจากการยอมรับชะตากรรม ในเพลงมีการเปรียบลูกวัวกับนกที่สามารถโบยบินเป็นอิสระได้ หากไม่ถูกพันธนาการ
การเปรียบเทียบ “ลูกวัว” (Calf) กับ “ชาวยิว” มีความลึกซึ้งในเชิงสัญลักษณ์ เพราะลูกวัวในเพลงถูกมัดมือมัดเท้าและลากไปยังโรงฆ่าสัตว์ ซึ่งสะท้อนถึงชะตากรรมของชาวยิวที่ถูกนำไปยังค่ายกักกันเพื่อสังหารหมู่ ในขณะเดียวกัน “สายลม” (Wind) ที่พัดผ่านฟาร์มอาจถูกตีความว่าเป็นตัวแทนของ “นาซี” ที่มาอย่างโหดร้ายและไร้ความปรานี
เนื้อร้องที่กล่าวว่า “Calves are easily bound and slaughtered, never knowing the reason why…” ชี้ให้เห็นถึงการขาดเสรีภาพและความไร้อำนาจที่จะต่อต้านของลูกวัว ซึ่งสะท้อนถึงชะตากรรมของผู้ถูกกดขี่
Joan Baez ได้บันทึกเพลง Donna Donna ในอัลบั้มแรกของเธอที่ชื่อ “Joan Baez” ในปี 1960 ซึ่งเป็นอัลบั้มที่รวบรวมเพลงโฟล์คจากหลากหลายแหล่ง เพลงนี้กลายเป็นหนึ่งในเพลงโปรดของผู้ฟัง และได้รับการจดจำว่าเป็นบทเพลงแห่งการปลุกจิตสำนึกทางสังคม
Joan Baez เป็นนักร้อง นักแต่งเพลง และนักเคลื่อนไหวชาวอเมริกัน เกิดเมื่อวันที่ 9 มกราคม ค.ศ. 1941 ที่เมืองสแตเทนไอแลนด์ รัฐนิวยอร์ก สหรัฐอเมริกา เธอเป็นที่รู้จักในฐานะนักร้องโฟล์คที่มีเสียงโซปราโนใสกิ๊งเป็นเอกลักษณ์ และรวมถึงการมีบทบาทสำคัญในขบวนการเคลื่อนไหวเพื่อสิทธิมนุษยชนและสันติภาพในทศวรรษ 1960
Joan Baez มีชื่อเสียงจากการร้องเพลงโฟล์คและเพลงประท้วงที่สะท้อนปัญหาสังคม เธอเป็นหนึ่งในผู้ที่ร่วมสนับสนุนการเคลื่อนไหวของ Martin Luther King Jr. และมีความสัมพันธ์กับ Bob Dylan ซึ่งเธอมีบทบาทสำคัญในการช่วยผลักดันและทำงานร่วมกัน ส่งผลให้ Dylan กลายเป็นศิลปินผู้ทรงอิทธิพลในยุคเดียวกันด้วย แต่การเลิกรากันของพวกเขาก็ยังเป็นสิ่งที่คนอยากรู้จนถึงทุกวันนี้ ว่าความจริงคืออะไรกันแน่ เพราะมีข่าวลือหลายข่าว
เพลงของ Joan Baez มีหลากหลายเพลงที่เลยครับโด่งดัง เช่น Diamonds and Rust, We Shall Overcome และ The Night They Drove Old Dixie Down
ทุกวันนี้ Joan Baez ยังคงเป็นสัญลักษณ์ของศิลปินที่ใช้เสียงเพลงเพื่อส่งเสริมความยุติธรรมและสันติภาพ โดยเธอได้รับการยกย่องในฐานะบุคคลสำคัญในประวัติศาสตร์ดนตรีและการเคลื่อนไหวทางสังคมระดับโลก
เพลง Donna Donna ยังคงถูกขับร้องในหลากหลายเวอร์ชันทั่วโลก และเป็นบทเพลงที่สะท้อนการต่อสู้เพื่อเสรีภาพและการไม่ยอมจำนนต่อความอยุติธรรม
ลองดูเนื้อเพลงกันครับว่าทำไมจึงทำให้การต่อสู้เพื่ออิสรภาพพุ่งพล่าน
On a wagon bound for market There's a calf with a mournful eye High above him there's a swallow Winging swiftly through the sky
How the winds are laughing They laugh with all their might Laugh and laugh the whole day through And half the summer's night
Donna, Donna, Donna, Donna Donna, Donna, Donna, Don Donna, Donna, Donna, Donna Donna, Donna, Donna, Don
"Stop complaining!" said the farmer "Who told you a calf to be? Why don't you have wings to fly with Like the swallow so proud and free?"
How the winds are laughing They laugh with all their might Laugh and laugh the whole day through And half the summer's night
Donna, Donna, Donna, Donna Donna, Donna, Donna, Don Donna, Donna, Donna, Donna Donna, Donna, Donna, Don
Calves are easily bound and slaughtered Never knowing the reason why But whoever treasures freedom Like the swallow has learned to fly
How the winds are laughing They laugh with all their might Laugh and laugh the whole day through And half the summer's night
Donna, Donna, Donna, Donna Donna, Donna, Donna, Don Donna, Donna, Donna, Donna Donna, Donna, Donna, Don
มี documentary เกี่ยวกับเธอในชื่อ Joan Baez I Am a Noise ด้วยครับ
https://youtu.be/dhcV1gEat_c?si=hLu4_liVbUWei8oG
https://youtu.be/dQrsSvms8Kw?si=9U2A7liIDvjwi-s-
-
 @ 2f5de000:2f9bcef1
2024-12-15 16:44:53
@ 2f5de000:2f9bcef1
2024-12-15 16:44:53This Week I immersed myself in Bitcoin from multiple angles-technical, societal and personal. The journey included a marathon 32-hours of listening to Rabbit Hole Recap (RHR), an essential resource for Bitcoin insights. It's worth noting that I started from the begining and plan to make my way through the whole catalogue. Marty and Matt's timestamps, along with contributions from their guests, served as my roadmap. Using Fountain to stream, I also streamed sats-a small but extraordinary feature that allows users to stacks sats while compensating cretors directly through fractional donations.
Revisiting Speculative Attack by Pierre Rochard (2014)
Now that Speculative Attack Season 2 (which I've not read yet) has been released. I took the time to read Pierre Rochards influential essay, Speculative Attack and reflected on its timeless insights. Rochard argues that Bitcoin adoption isn't dependent on technological advancements or consumer preferences, but on economic realities. As fiat currencies weaken, Bitcoin won't enter the mainstream by persuasion but by necessity.
Critics continue to underestimate Bitcoin's inevitability due to their fiat biases and lack of financial insight. This year alone, mainstream media has been compelled to discuss Bitcoin-notably to Trump's endorsement of 'crypto.' Despite their attempts to shape narratives to suit their ideal visions, they've had no choice but to engage with Bitcoin's growing influence.\ \ As Parker aptly puts it 'Gradually, The Suddenly'
Wassabi Wallet and the Privacy Imperative
An RHR interview (from early in the catalogue) with guest Adam Ficsor, CTO and Co-founder of Wassabi Wallet, sparked a deeper consideration of my digital footprint. Like many, I've spent years online neglecting privacy in favour of convenience. The discussion on CoinJoins reminded me of the importance of prioritising privacy, not just romanticising it.
Improving operational security (opsec) is now a personal focus. Resources like Jameson's Cypherpunk Cogitations and the Bitcoin Optech newsletter offer valuable guidance. While I've exercised caution, I recognise a need to address my laziness with opsec and take meaningful steps to protect my privacy. Time will reveal the results of these efforts.
Caribbean Slavery amd Centralised Platforms
While exploring historical systems of control, I delved into the brutal realities of New World slavery in the British Caribbean. Enslaved elites, like drivers, were granted limited privileges to maintain order, creating divisions within the community. This divide-and-rule strategy highlights the fragility of oppressive frameworks, which began to crumble with events like the Hatian Revolution and humanitarian activism.
Interestingly, similar dynamics are visible with centralised plaforms like Twitter, LinkedIn, and Instagram. Verified accounts (the "blue checks") act as mordern day 'elites' with perceived freedoms. However, their autonomy is limited by the platforms centralised authority. Challenging the rules risks censorship and cancellation, proving their freedom is an illusion subject to the will of their overseers. Enhancing the argument further for protocols like Nostr to help people win back their freedoms.
-
 @ 8d34bd24:414be32b
2024-12-15 15:47:57
@ 8d34bd24:414be32b
2024-12-15 15:47:57Thanks to the decline in the quality of churches, there are a lot of people who have turned into lone wolf Christians. They try to follow Jesus, but don’t attend church, don’t fellowship with other Christians, and generally don’t live lives much different than unbelievers. As God said at creation, “… It is not good for the man to be alone…” (Genesis 2:18). We were made in the image of God and that includes the need for fellowship with likeminded individuals. In that moment of not wanting man to be alone, a woman, Eve, was created to be his complement and to form the new family unit. In addition to not being part of a local church, we also have people, including Christians, foregoing marriage because of the cultural problems that too often lead to divorce.
Solomon, the wisest man in the world (at least at the time), pondered relationships and more in the book of Ecclesiastes.
Then I looked again at vanity under the sun. There was a certain man without a dependent, having neither a son nor a brother, yet there was no end to all his labor. Indeed, his eyes were not satisfied with riches and he never asked, “And for whom am I laboring and depriving myself of pleasure?” This too is vanity and it is a grievous task. (Ecclesiastes 4:7-8)
What do we work for? If our work is solely for ourselves during our brief mortal lives, it doesn’t have much purpose. If we are working to take care of our families, if we are working to support our church, and if we are working to be able to support those in need and share the Gospel with them, then we are doing a good work. If we are just working for ourselves, it is worthless.
And if I give all my possessions to feed the poor, and if I surrender my body to be burned, but do not have love, it profits me nothing. (1 Corinthians 13:3)
God created us to fellowship with others just as the three persons of the Trinity are in perfect fellowship with each other.
One institution, created by God, is the family. The perfect fulfillment of the family is a married man and woman and their biological children. The church (the fellowship of believers, not the building or the formal organization) is another form of family.
Two are better than one because they have a good return for their labor. For if either of them falls, the one will lift up his companion. But woe to the one who falls when there is not another to lift him up. Furthermore, if two lie down together they keep warm, but how can one be warm alone? And if one can overpower him who is alone, two can resist him. A cord of three strands is not quickly torn apart. (Ecclesiastes 4:9-12)
When I was in high school, I went on a boat ride down the St. Johns River to downtown Jacksonville for dinner with my parents and my Dad's cousin and aunt. My Dad's cousin was a married music pastor at a Baptist church. We only met face to face that one time, but we talked for hours. We were both Christians (my parents are not). You would say a married, middle-aged working man and a single high school girl would have nothing in common, but as fellow believers, it was like talking to a close family member. After the trip my Mom asked what in the world we had in common that would allow us to talk for so long together and I told her it was our faith. To this day, we still keep in touch.
The traditional family is critically important, but the church family is also a big deal.
When we are alone, we can be misled; we can be weak; we can get sick; and we can give up. When we have family and/or a church, we have others to assist us in our weakness and sickness. We have others to encourage us to be our best. We have others to correct us when we go astray. Whether it is our daily trials that every person on earth has or whether it is our spiritual growth, having others to encourage and correct us is very important for a fulfilling and godly life.
and let us consider how to stimulate one another to love and good deeds, not forsaking our own assembling together, as is the habit of some, but encouraging one another; and all the more as you see the day drawing near. (Hebrews 10:24-25) {emphasis mine}
Gathering together with other believers isn’t just a useful thing to have, but is a command from God. He has commanded us to “stimulate one another to love and good deeds, not forsaking our own assembling together.” It is so easy to get frustrated because a church you visited taught unbiblical teachings or even just platitudes rather than God ordained truths. It is easy to get frustrated at unloving church members and infighting. It is easy to get frustrated when we do not easily find a good church (they are getting harder and harder to find) or when we are hurt by a church, but believers need Christians fellowship. We need it for our wellbeing and growth. We need it because God commanded it.
We do need to find a church that teaches the truth of the Bible, shares the Gospel, and loves people. We don’t want to attend just any service that uses the word “church” because there are “churches” that don’t have much to do with God, Jesus, and the Bible. It may be hard to find a good church. It may even require you drive further or to move to another location to find a good church, but only you know your situation. Despite all of this, it is important and should be a priority in all Christian’s lives. It is quite likely that finding a good church is harder than finding a good job, so you might even have to pick your living location based on a church rather than a job. God is worth it. A good church is worth it.
As important as it is to find a good, Bible believing, Gospel preaching church, I’d also advise against waiting for the perfect church. Churches (the organizations) are made up of imperfect people. There are no perfect churches because churches are made up of imperfect people. I’ve heard the saying, “If you find a perfect church, don’t join because you will mess it up.” Church is for encouraging each other to grow in faith and godliness; it isn’t a place for perfect people to show up and show off their perfectness.
Do not sharply rebuke an older man, but rather appeal to him as a father, to the younger men as brothers, the older women as mothers, and the younger women as sisters, in all purity.
Honor widows who are widows indeed; but if any widow has children or grandchildren, they must first learn to practice piety in regard to their own family and to make some return to their parents; for this is acceptable in the sight of God. (1 Timothy 5:1-4)
This passage is a great guideline for Christian relationships. We are trying to build up each other in the Lord. We want to encourage all believers to grow in faith, to become more Christ-like, and to share the Gospel with everyone they can. This encouragement, or exhortation, can include correction, given and received in love.
We should long for fellowship with God and other believers. This passage from Paul is a great example of his longing to be with fellow believers for the other’s benefit and for his own.
For God, whom I serve in my spirit in the preaching of the gospel of His Son, is my witness as to how unceasingly I make mention of you, always in my prayers making request, if perhaps now at last by the will of God I may succeed in coming to you. For I long to see you so that I may impart some spiritual gift to you, that you may be established; that is, that I may be encouraged together with you while among you, each of us by the other’s faith, both yours and mine. I do not want you to be unaware, brethren, that often I have planned to come to you (and have been prevented so far) so that I may obtain some fruit among you also, even as among the rest of the Gentiles. I am under obligation both to Greeks and to barbarians, both to the wise and to the foolish. So, for my part, I am eager to preach the gospel to you also who are in Rome. (Romans 1:9-15) {emphasis mine}
Notice that Paul wants fellowship with other believers both for his own encouragement, but more so that he may aid them. Our church attendance shouldn’t just be sitting absorbing the pastor’s sermon. It should also be ministering to fellow believers.
Take care, brethren, that there not be in any one of you an evil, unbelieving heart that falls away from the living God. But encourage one another day after day, as long as it is still called “Today,” so that none of you will be hardened by the deceitfulness of sin. (Hebrews 3:12-13)
When we regularly fellowship with other believers and have fellow believers who know what is going on in our lives, it helps prevent us from drifting away. Those who know and care for us will encourage us to read the Bible, pray, study, attend church, and share our faith. They will discourage us from staying home on Sunday, getting busy with unedifying entertainment to the harm of our faith, and becoming conformed to the culture rather than Jesus.
Therefore encourage one another and build up one another, just as you also are doing. But we request of you, brethren, that you appreciate those who diligently labor among you, and have charge over you in the Lord and give you instruction, and that you esteem them very highly in love because of their work. Live in peace with one another. We urge you, brethren, admonish the unruly, encourage the fainthearted, help the weak, be patient with everyone. See that no one repays another with evil for evil, but always seek after that which is good for one another and for all people. Rejoice always; pray without ceasing; in everything give thanks; for this is God’s will for you in Christ Jesus. (1 Thessalonians 5:11-17)
This passage above from 1 Thessalonians does such a good job of describing our relationship with our Christian leaders/pastors, fellow believers, and God, that it is hard to add much too it. At the same time, it is nearly impossible to obey if you aren’t involved in a local church. This is what God has called us to do and how God has called us to live.
You are witnesses, and so is God, how devoutly and uprightly and blamelessly we behaved toward you believers; just as you know how we were exhorting1 and encouraging and imploring each one of you as a father would his own children, so that you would walk in a manner worthy of the God who calls you into His own kingdom and glory. (1 Thessalonians 2:10-12) {emphasis mine}
We need to be exhorted, encouraged, and implored and we need to exhort, encourage, and implore our fellow believers. This is what it means to “walk in a manner worthy of the God who calls you.”
Trust Jesus.\ \ your sister in Christ
-
 @ 30ceb64e:7f08bdf5
2024-12-15 15:16:58
@ 30ceb64e:7f08bdf5
2024-12-15 15:16:58I'm working with autistic teens and adults, and I still have the knee jerk temptation of orange pilling them. They do not have the ability to run a node. The central banking cartels and downstream effects of a control economy are so outside of their purview, that bringing it up would be ridiculous.
But.
I am here to help them gain independence. Sovereignty is a ladder and regardless of where someone is on the ladder, it would be my job to guide them into more of it. Not everyone can run a node, some people have intellectual disabilities, physical limitations and higher priorities.
Funnily enough I think it would be easier than one might assume to run a node, I have a client who could do it and have a semblance of what it means. The client has the ability to work, and when he sees trump on the screen, he knows he's the president, and he knows politicians are liars.
I have a few other clients that don't have the ability to work or take care of themselves at all. Running a node is plugging something into the wall, making sure the light is on, and attaching your wallet to it. I aint talkin about a lightning node btw I'm talking about core.
It boggles my mind on what people find so insurmountable about running bitcoin core. I think it might just be people projecting their own bias or inserting their own objections the thing. Start9 and Umbrel can be set up by a loved one, an assistant or nurse can make sure the thing continues being on and that the internet bill is paid. Is it harder managing the persons Bank of America account or is it harder attaching a wallet to your node and leaving the thing on?
Would be cool if I took one of these guys to a bitcoin meetup with a node in a phone and had them teach fools how to conduct a peer to peer transaction. Could even get real fancy, and have them send a freak some e-cash. When I was at bitcoin Miami an OG pulled me to the side and explained what a peer to peer transaction was using hand signals......
So here we are at another conclusion, Sovereignty is a ladder that every last human being on the planet should attempt to climb and regardless of the rung you find yourself in, don't let others pontificate about how you "can't" because its probably just them being retarded.
originally posted at https://stacker.news/items/810401
-
 @ 6f6b50bb:a848e5a1
2024-12-15 15:09:52
@ 6f6b50bb:a848e5a1
2024-12-15 15:09:52Che cosa significherebbe trattare l'IA come uno strumento invece che come una persona?
Dall’avvio di ChatGPT, le esplorazioni in due direzioni hanno preso velocità.
La prima direzione riguarda le capacità tecniche. Quanto grande possiamo addestrare un modello? Quanto bene può rispondere alle domande del SAT? Con quanta efficienza possiamo distribuirlo?
La seconda direzione riguarda il design dell’interazione. Come comunichiamo con un modello? Come possiamo usarlo per un lavoro utile? Quale metafora usiamo per ragionare su di esso?
La prima direzione è ampiamente seguita e enormemente finanziata, e per una buona ragione: i progressi nelle capacità tecniche sono alla base di ogni possibile applicazione. Ma la seconda è altrettanto cruciale per il campo e ha enormi incognite. Siamo solo a pochi anni dall’inizio dell’era dei grandi modelli. Quali sono le probabilità che abbiamo già capito i modi migliori per usarli?
Propongo una nuova modalità di interazione, in cui i modelli svolgano il ruolo di applicazioni informatiche (ad esempio app per telefoni): fornendo un’interfaccia grafica, interpretando gli input degli utenti e aggiornando il loro stato. In questa modalità, invece di essere un “agente” che utilizza un computer per conto dell’essere umano, l’IA può fornire un ambiente informatico più ricco e potente che possiamo utilizzare.
Metafore per l’interazione
Al centro di un’interazione c’è una metafora che guida le aspettative di un utente su un sistema. I primi giorni dell’informatica hanno preso metafore come “scrivanie”, “macchine da scrivere”, “fogli di calcolo” e “lettere” e le hanno trasformate in equivalenti digitali, permettendo all’utente di ragionare sul loro comportamento. Puoi lasciare qualcosa sulla tua scrivania e tornare a prenderlo; hai bisogno di un indirizzo per inviare una lettera. Man mano che abbiamo sviluppato una conoscenza culturale di questi dispositivi, la necessità di queste particolari metafore è scomparsa, e con esse i design di interfaccia skeumorfici che le rafforzavano. Come un cestino o una matita, un computer è ora una metafora di se stesso.
La metafora dominante per i grandi modelli oggi è modello-come-persona. Questa è una metafora efficace perché le persone hanno capacità estese che conosciamo intuitivamente. Implica che possiamo avere una conversazione con un modello e porgli domande; che il modello possa collaborare con noi su un documento o un pezzo di codice; che possiamo assegnargli un compito da svolgere da solo e che tornerà quando sarà finito.
Tuttavia, trattare un modello come una persona limita profondamente il nostro modo di pensare all’interazione con esso. Le interazioni umane sono intrinsecamente lente e lineari, limitate dalla larghezza di banda e dalla natura a turni della comunicazione verbale. Come abbiamo tutti sperimentato, comunicare idee complesse in una conversazione è difficile e dispersivo. Quando vogliamo precisione, ci rivolgiamo invece a strumenti, utilizzando manipolazioni dirette e interfacce visive ad alta larghezza di banda per creare diagrammi, scrivere codice e progettare modelli CAD. Poiché concepiamo i modelli come persone, li utilizziamo attraverso conversazioni lente, anche se sono perfettamente in grado di accettare input diretti e rapidi e di produrre risultati visivi. Le metafore che utilizziamo limitano le esperienze che costruiamo, e la metafora modello-come-persona ci impedisce di esplorare il pieno potenziale dei grandi modelli.
Per molti casi d’uso, e specialmente per il lavoro produttivo, credo che il futuro risieda in un’altra metafora: modello-come-computer.
Usare un’IA come un computer
Sotto la metafora modello-come-computer, interagiremo con i grandi modelli seguendo le intuizioni che abbiamo sulle applicazioni informatiche (sia su desktop, tablet o telefono). Nota che ciò non significa che il modello sarà un’app tradizionale più di quanto il desktop di Windows fosse una scrivania letterale. “Applicazione informatica” sarà un modo per un modello di rappresentarsi a noi. Invece di agire come una persona, il modello agirà come un computer.
Agire come un computer significa produrre un’interfaccia grafica. Al posto del flusso lineare di testo in stile telescrivente fornito da ChatGPT, un sistema modello-come-computer genererà qualcosa che somiglia all’interfaccia di un’applicazione moderna: pulsanti, cursori, schede, immagini, grafici e tutto il resto. Questo affronta limitazioni chiave dell’interfaccia di chat standard modello-come-persona:
-
Scoperta. Un buon strumento suggerisce i suoi usi. Quando l’unica interfaccia è una casella di testo vuota, spetta all’utente capire cosa fare e comprendere i limiti del sistema. La barra laterale Modifica in Lightroom è un ottimo modo per imparare l’editing fotografico perché non si limita a dirti cosa può fare questa applicazione con una foto, ma cosa potresti voler fare. Allo stesso modo, un’interfaccia modello-come-computer per DALL-E potrebbe mostrare nuove possibilità per le tue generazioni di immagini.
-
Efficienza. La manipolazione diretta è più rapida che scrivere una richiesta a parole. Per continuare l’esempio di Lightroom, sarebbe impensabile modificare una foto dicendo a una persona quali cursori spostare e di quanto. Ci vorrebbe un giorno intero per chiedere un’esposizione leggermente più bassa e una vibranza leggermente più alta, solo per vedere come apparirebbe. Nella metafora modello-come-computer, il modello può creare strumenti che ti permettono di comunicare ciò che vuoi più efficientemente e quindi di fare le cose più rapidamente.
A differenza di un’app tradizionale, questa interfaccia grafica è generata dal modello su richiesta. Questo significa che ogni parte dell’interfaccia che vedi è rilevante per ciò che stai facendo in quel momento, inclusi i contenuti specifici del tuo lavoro. Significa anche che, se desideri un’interfaccia più ampia o diversa, puoi semplicemente richiederla. Potresti chiedere a DALL-E di produrre alcuni preset modificabili per le sue impostazioni ispirati da famosi artisti di schizzi. Quando clicchi sul preset Leonardo da Vinci, imposta i cursori per disegni prospettici altamente dettagliati in inchiostro nero. Se clicchi su Charles Schulz, seleziona fumetti tecnicolor 2D a basso dettaglio.
Una bicicletta della mente proteiforme
La metafora modello-come-persona ha una curiosa tendenza a creare distanza tra l’utente e il modello, rispecchiando il divario di comunicazione tra due persone che può essere ridotto ma mai completamente colmato. A causa della difficoltà e del costo di comunicare a parole, le persone tendono a suddividere i compiti tra loro in blocchi grandi e il più indipendenti possibile. Le interfacce modello-come-persona seguono questo schema: non vale la pena dire a un modello di aggiungere un return statement alla tua funzione quando è più veloce scriverlo da solo. Con il sovraccarico della comunicazione, i sistemi modello-come-persona sono più utili quando possono fare un intero blocco di lavoro da soli. Fanno le cose per te.
Questo contrasta con il modo in cui interagiamo con i computer o altri strumenti. Gli strumenti producono feedback visivi in tempo reale e sono controllati attraverso manipolazioni dirette. Hanno un overhead comunicativo così basso che non è necessario specificare un blocco di lavoro indipendente. Ha più senso mantenere l’umano nel loop e dirigere lo strumento momento per momento. Come stivali delle sette leghe, gli strumenti ti permettono di andare più lontano a ogni passo, ma sei ancora tu a fare il lavoro. Ti permettono di fare le cose più velocemente.
Considera il compito di costruire un sito web usando un grande modello. Con le interfacce di oggi, potresti trattare il modello come un appaltatore o un collaboratore. Cercheresti di scrivere a parole il più possibile su come vuoi che il sito appaia, cosa vuoi che dica e quali funzionalità vuoi che abbia. Il modello genererebbe una prima bozza, tu la eseguirai e poi fornirai un feedback. “Fai il logo un po’ più grande”, diresti, e “centra quella prima immagine principale”, e “deve esserci un pulsante di login nell’intestazione”. Per ottenere esattamente ciò che vuoi, invierai una lista molto lunga di richieste sempre più minuziose.
Un’interazione alternativa modello-come-computer sarebbe diversa: invece di costruire il sito web, il modello genererebbe un’interfaccia per te per costruirlo, dove ogni input dell’utente a quell’interfaccia interroga il grande modello sotto il cofano. Forse quando descrivi le tue necessità creerebbe un’interfaccia con una barra laterale e una finestra di anteprima. All’inizio la barra laterale contiene solo alcuni schizzi di layout che puoi scegliere come punto di partenza. Puoi cliccare su ciascuno di essi, e il modello scrive l’HTML per una pagina web usando quel layout e lo visualizza nella finestra di anteprima. Ora che hai una pagina su cui lavorare, la barra laterale guadagna opzioni aggiuntive che influenzano la pagina globalmente, come accoppiamenti di font e schemi di colore. L’anteprima funge da editor WYSIWYG, permettendoti di afferrare elementi e spostarli, modificarne i contenuti, ecc. A supportare tutto ciò è il modello, che vede queste azioni dell’utente e riscrive la pagina per corrispondere ai cambiamenti effettuati. Poiché il modello può generare un’interfaccia per aiutare te e lui a comunicare più efficientemente, puoi esercitare più controllo sul prodotto finale in meno tempo.
La metafora modello-come-computer ci incoraggia a pensare al modello come a uno strumento con cui interagire in tempo reale piuttosto che a un collaboratore a cui assegnare compiti. Invece di sostituire un tirocinante o un tutor, può essere una sorta di bicicletta proteiforme per la mente, una che è sempre costruita su misura esattamente per te e il terreno che intendi attraversare.
Un nuovo paradigma per l’informatica?
I modelli che possono generare interfacce su richiesta sono una frontiera completamente nuova nell’informatica. Potrebbero essere un paradigma del tutto nuovo, con il modo in cui cortocircuitano il modello di applicazione esistente. Dare agli utenti finali il potere di creare e modificare app al volo cambia fondamentalmente il modo in cui interagiamo con i computer. Al posto di una singola applicazione statica costruita da uno sviluppatore, un modello genererà un’applicazione su misura per l’utente e le sue esigenze immediate. Al posto della logica aziendale implementata nel codice, il modello interpreterà gli input dell’utente e aggiornerà l’interfaccia utente. È persino possibile che questo tipo di interfaccia generativa sostituisca completamente il sistema operativo, generando e gestendo interfacce e finestre al volo secondo necessità.
All’inizio, l’interfaccia generativa sarà un giocattolo, utile solo per l’esplorazione creativa e poche altre applicazioni di nicchia. Dopotutto, nessuno vorrebbe un’app di posta elettronica che occasionalmente invia email al tuo ex e mente sulla tua casella di posta. Ma gradualmente i modelli miglioreranno. Anche mentre si spingeranno ulteriormente nello spazio di esperienze completamente nuove, diventeranno lentamente abbastanza affidabili da essere utilizzati per un lavoro reale.
Piccoli pezzi di questo futuro esistono già. Anni fa Jonas Degrave ha dimostrato che ChatGPT poteva fare una buona simulazione di una riga di comando Linux. Allo stesso modo, websim.ai utilizza un LLM per generare siti web su richiesta mentre li navighi. Oasis, GameNGen e DIAMOND addestrano modelli video condizionati sull’azione su singoli videogiochi, permettendoti di giocare ad esempio a Doom dentro un grande modello. E Genie 2 genera videogiochi giocabili da prompt testuali. L’interfaccia generativa potrebbe ancora sembrare un’idea folle, ma non è così folle.
Ci sono enormi domande aperte su come apparirà tutto questo. Dove sarà inizialmente utile l’interfaccia generativa? Come condivideremo e distribuiremo le esperienze che creiamo collaborando con il modello, se esistono solo come contesto di un grande modello? Vorremmo davvero farlo? Quali nuovi tipi di esperienze saranno possibili? Come funzionerà tutto questo in pratica? I modelli genereranno interfacce come codice o produrranno direttamente pixel grezzi?
Non conosco ancora queste risposte. Dovremo sperimentare e scoprirlo!Che cosa significherebbe trattare l'IA come uno strumento invece che come una persona?
Dall’avvio di ChatGPT, le esplorazioni in due direzioni hanno preso velocità.
La prima direzione riguarda le capacità tecniche. Quanto grande possiamo addestrare un modello? Quanto bene può rispondere alle domande del SAT? Con quanta efficienza possiamo distribuirlo?
La seconda direzione riguarda il design dell’interazione. Come comunichiamo con un modello? Come possiamo usarlo per un lavoro utile? Quale metafora usiamo per ragionare su di esso?
La prima direzione è ampiamente seguita e enormemente finanziata, e per una buona ragione: i progressi nelle capacità tecniche sono alla base di ogni possibile applicazione. Ma la seconda è altrettanto cruciale per il campo e ha enormi incognite. Siamo solo a pochi anni dall’inizio dell’era dei grandi modelli. Quali sono le probabilità che abbiamo già capito i modi migliori per usarli?
Propongo una nuova modalità di interazione, in cui i modelli svolgano il ruolo di applicazioni informatiche (ad esempio app per telefoni): fornendo un’interfaccia grafica, interpretando gli input degli utenti e aggiornando il loro stato. In questa modalità, invece di essere un “agente” che utilizza un computer per conto dell’essere umano, l’IA può fornire un ambiente informatico più ricco e potente che possiamo utilizzare.
Metafore per l’interazione
Al centro di un’interazione c’è una metafora che guida le aspettative di un utente su un sistema. I primi giorni dell’informatica hanno preso metafore come “scrivanie”, “macchine da scrivere”, “fogli di calcolo” e “lettere” e le hanno trasformate in equivalenti digitali, permettendo all’utente di ragionare sul loro comportamento. Puoi lasciare qualcosa sulla tua scrivania e tornare a prenderlo; hai bisogno di un indirizzo per inviare una lettera. Man mano che abbiamo sviluppato una conoscenza culturale di questi dispositivi, la necessità di queste particolari metafore è scomparsa, e con esse i design di interfaccia skeumorfici che le rafforzavano. Come un cestino o una matita, un computer è ora una metafora di se stesso.
La metafora dominante per i grandi modelli oggi è modello-come-persona. Questa è una metafora efficace perché le persone hanno capacità estese che conosciamo intuitivamente. Implica che possiamo avere una conversazione con un modello e porgli domande; che il modello possa collaborare con noi su un documento o un pezzo di codice; che possiamo assegnargli un compito da svolgere da solo e che tornerà quando sarà finito.
Tuttavia, trattare un modello come una persona limita profondamente il nostro modo di pensare all’interazione con esso. Le interazioni umane sono intrinsecamente lente e lineari, limitate dalla larghezza di banda e dalla natura a turni della comunicazione verbale. Come abbiamo tutti sperimentato, comunicare idee complesse in una conversazione è difficile e dispersivo. Quando vogliamo precisione, ci rivolgiamo invece a strumenti, utilizzando manipolazioni dirette e interfacce visive ad alta larghezza di banda per creare diagrammi, scrivere codice e progettare modelli CAD. Poiché concepiamo i modelli come persone, li utilizziamo attraverso conversazioni lente, anche se sono perfettamente in grado di accettare input diretti e rapidi e di produrre risultati visivi. Le metafore che utilizziamo limitano le esperienze che costruiamo, e la metafora modello-come-persona ci impedisce di esplorare il pieno potenziale dei grandi modelli.
Per molti casi d’uso, e specialmente per il lavoro produttivo, credo che il futuro risieda in un’altra metafora: modello-come-computer.
Usare un’IA come un computer
Sotto la metafora modello-come-computer, interagiremo con i grandi modelli seguendo le intuizioni che abbiamo sulle applicazioni informatiche (sia su desktop, tablet o telefono). Nota che ciò non significa che il modello sarà un’app tradizionale più di quanto il desktop di Windows fosse una scrivania letterale. “Applicazione informatica” sarà un modo per un modello di rappresentarsi a noi. Invece di agire come una persona, il modello agirà come un computer.
Agire come un computer significa produrre un’interfaccia grafica. Al posto del flusso lineare di testo in stile telescrivente fornito da ChatGPT, un sistema modello-come-computer genererà qualcosa che somiglia all’interfaccia di un’applicazione moderna: pulsanti, cursori, schede, immagini, grafici e tutto il resto. Questo affronta limitazioni chiave dell’interfaccia di chat standard modello-come-persona:
Scoperta. Un buon strumento suggerisce i suoi usi. Quando l’unica interfaccia è una casella di testo vuota, spetta all’utente capire cosa fare e comprendere i limiti del sistema. La barra laterale Modifica in Lightroom è un ottimo modo per imparare l’editing fotografico perché non si limita a dirti cosa può fare questa applicazione con una foto, ma cosa potresti voler fare. Allo stesso modo, un’interfaccia modello-come-computer per DALL-E potrebbe mostrare nuove possibilità per le tue generazioni di immagini.
Efficienza. La manipolazione diretta è più rapida che scrivere una richiesta a parole. Per continuare l’esempio di Lightroom, sarebbe impensabile modificare una foto dicendo a una persona quali cursori spostare e di quanto. Ci vorrebbe un giorno intero per chiedere un’esposizione leggermente più bassa e una vibranza leggermente più alta, solo per vedere come apparirebbe. Nella metafora modello-come-computer, il modello può creare strumenti che ti permettono di comunicare ciò che vuoi più efficientemente e quindi di fare le cose più rapidamente.
A differenza di un’app tradizionale, questa interfaccia grafica è generata dal modello su richiesta. Questo significa che ogni parte dell’interfaccia che vedi è rilevante per ciò che stai facendo in quel momento, inclusi i contenuti specifici del tuo lavoro. Significa anche che, se desideri un’interfaccia più ampia o diversa, puoi semplicemente richiederla. Potresti chiedere a DALL-E di produrre alcuni preset modificabili per le sue impostazioni ispirati da famosi artisti di schizzi. Quando clicchi sul preset Leonardo da Vinci, imposta i cursori per disegni prospettici altamente dettagliati in inchiostro nero. Se clicchi su Charles Schulz, seleziona fumetti tecnicolor 2D a basso dettaglio.
Una bicicletta della mente proteiforme
La metafora modello-come-persona ha una curiosa tendenza a creare distanza tra l’utente e il modello, rispecchiando il divario di comunicazione tra due persone che può essere ridotto ma mai completamente colmato. A causa della difficoltà e del costo di comunicare a parole, le persone tendono a suddividere i compiti tra loro in blocchi grandi e il più indipendenti possibile. Le interfacce modello-come-persona seguono questo schema: non vale la pena dire a un modello di aggiungere un return statement alla tua funzione quando è più veloce scriverlo da solo. Con il sovraccarico della comunicazione, i sistemi modello-come-persona sono più utili quando possono fare un intero blocco di lavoro da soli. Fanno le cose per te.
Questo contrasta con il modo in cui interagiamo con i computer o altri strumenti. Gli strumenti producono feedback visivi in tempo reale e sono controllati attraverso manipolazioni dirette. Hanno un overhead comunicativo così basso che non è necessario specificare un blocco di lavoro indipendente. Ha più senso mantenere l’umano nel loop e dirigere lo strumento momento per momento. Come stivali delle sette leghe, gli strumenti ti permettono di andare più lontano a ogni passo, ma sei ancora tu a fare il lavoro. Ti permettono di fare le cose più velocemente.
Considera il compito di costruire un sito web usando un grande modello. Con le interfacce di oggi, potresti trattare il modello come un appaltatore o un collaboratore. Cercheresti di scrivere a parole il più possibile su come vuoi che il sito appaia, cosa vuoi che dica e quali funzionalità vuoi che abbia. Il modello genererebbe una prima bozza, tu la eseguirai e poi fornirai un feedback. “Fai il logo un po’ più grande”, diresti, e “centra quella prima immagine principale”, e “deve esserci un pulsante di login nell’intestazione”. Per ottenere esattamente ciò che vuoi, invierai una lista molto lunga di richieste sempre più minuziose.
Un’interazione alternativa modello-come-computer sarebbe diversa: invece di costruire il sito web, il modello genererebbe un’interfaccia per te per costruirlo, dove ogni input dell’utente a quell’interfaccia interroga il grande modello sotto il cofano. Forse quando descrivi le tue necessità creerebbe un’interfaccia con una barra laterale e una finestra di anteprima. All’inizio la barra laterale contiene solo alcuni schizzi di layout che puoi scegliere come punto di partenza. Puoi cliccare su ciascuno di essi, e il modello scrive l’HTML per una pagina web usando quel layout e lo visualizza nella finestra di anteprima. Ora che hai una pagina su cui lavorare, la barra laterale guadagna opzioni aggiuntive che influenzano la pagina globalmente, come accoppiamenti di font e schemi di colore. L’anteprima funge da editor WYSIWYG, permettendoti di afferrare elementi e spostarli, modificarne i contenuti, ecc. A supportare tutto ciò è il modello, che vede queste azioni dell’utente e riscrive la pagina per corrispondere ai cambiamenti effettuati. Poiché il modello può generare un’interfaccia per aiutare te e lui a comunicare più efficientemente, puoi esercitare più controllo sul prodotto finale in meno tempo.
La metafora modello-come-computer ci incoraggia a pensare al modello come a uno strumento con cui interagire in tempo reale piuttosto che a un collaboratore a cui assegnare compiti. Invece di sostituire un tirocinante o un tutor, può essere una sorta di bicicletta proteiforme per la mente, una che è sempre costruita su misura esattamente per te e il terreno che intendi attraversare.
Un nuovo paradigma per l’informatica?
I modelli che possono generare interfacce su richiesta sono una frontiera completamente nuova nell’informatica. Potrebbero essere un paradigma del tutto nuovo, con il modo in cui cortocircuitano il modello di applicazione esistente. Dare agli utenti finali il potere di creare e modificare app al volo cambia fondamentalmente il modo in cui interagiamo con i computer. Al posto di una singola applicazione statica costruita da uno sviluppatore, un modello genererà un’applicazione su misura per l’utente e le sue esigenze immediate. Al posto della logica aziendale implementata nel codice, il modello interpreterà gli input dell’utente e aggiornerà l’interfaccia utente. È persino possibile che questo tipo di interfaccia generativa sostituisca completamente il sistema operativo, generando e gestendo interfacce e finestre al volo secondo necessità.
All’inizio, l’interfaccia generativa sarà un giocattolo, utile solo per l’esplorazione creativa e poche altre applicazioni di nicchia. Dopotutto, nessuno vorrebbe un’app di posta elettronica che occasionalmente invia email al tuo ex e mente sulla tua casella di posta. Ma gradualmente i modelli miglioreranno. Anche mentre si spingeranno ulteriormente nello spazio di esperienze completamente nuove, diventeranno lentamente abbastanza affidabili da essere utilizzati per un lavoro reale.
Piccoli pezzi di questo futuro esistono già. Anni fa Jonas Degrave ha dimostrato che ChatGPT poteva fare una buona simulazione di una riga di comando Linux. Allo stesso modo, websim.ai utilizza un LLM per generare siti web su richiesta mentre li navighi. Oasis, GameNGen e DIAMOND addestrano modelli video condizionati sull’azione su singoli videogiochi, permettendoti di giocare ad esempio a Doom dentro un grande modello. E Genie 2 genera videogiochi giocabili da prompt testuali. L’interfaccia generativa potrebbe ancora sembrare un’idea folle, ma non è così folle.
Ci sono enormi domande aperte su come apparirà tutto questo. Dove sarà inizialmente utile l’interfaccia generativa? Come condivideremo e distribuiremo le esperienze che creiamo collaborando con il modello, se esistono solo come contesto di un grande modello? Vorremmo davvero farlo? Quali nuovi tipi di esperienze saranno possibili? Come funzionerà tutto questo in pratica? I modelli genereranno interfacce come codice o produrranno direttamente pixel grezzi?
Non conosco ancora queste risposte. Dovremo sperimentare e scoprirlo!
Tradotto da:\ https://willwhitney.com/computing-inside-ai.htmlhttps://willwhitney.com/computing-inside-ai.html
-
-
 @ 07804b78:c375c543
2024-12-15 12:56:05
@ 07804b78:c375c543
2024-12-15 12:56:05Japanese follows. 日本語はあとで。
This article is for the 14th day of Nostr Advent Calendar 2024 (relay blogging). The article for the 13th day was "Open Sats 申請編" (Applying for Open Sats) by mono-san. The article for the 14th day will be "Nostrはじめました。" (I started Nostr) by bro-san.
Thinking of Thingstr
I've come up with an idea for Other Staff that I think is interesting (at least, for me), so I'm going to write about it. I actually wanted to show you the implementation and brag about it, but it's not solid enough to be implemented yet.
The key idea is just “add a reaction to the WikiData ID”.
WikiData
There is a service called WikiData. It is a knowledge base that provides structured data. You may be wondering what it is, but the important thing to understand here is that WikiData assigns identifiers to a fairly wide range of “objects” and “things”.
So, if you can react to this, you can think of various applications just by thinking of it for a moment, right?
For example, the anime series “There are too many losing heroines!” is assigned the ID
Q123819103. The corresponding page is https://www.wikidata.org/wiki/Q123819103 .(NOTE: The canonical URI for entities on Wikidata is http://www.wikidata.org/entity/Q1142841. This is in accordance with Semantic Web conventions, and is not https, but http. Also, this URI does not necessarily match the actual address of the correspnding web page. Just an identifier. In most cases, it will redirect).
What can wd do?
For example, what about a website that records your anime viewing history? You can record what you want to watch with 👀, what you've already watched with ✅, and your favorites with ☆. You can also express your “likes” for production companies, staff, voice actors, etc. In this way, you can see what a particular user likes.
This could be a movie, a book, a comic, an author, music, an idol group, a place, or food (Someone likes pork cutlet
Q1142841). The fact that you can record everything in the same framework is what makes it interesting.What form of event should it be recorded as?
There is probably room for discussion about how to record this information in a concrete way. The simplest way would be to use NIP-25's "Reactions to a website" kind:17 (a.k.a. Makibishi). How about something like this?
json [ ["i", "wd:Q123819103", "http://www.wikidata.org/entity/Q123819103"], ]Since NIP-73 has External Content IDs, it would be good if we could include WikiData here so that we could write
wd:Q123819103. Actually,isbn:and other identifiers have already been defined, so it is possible to use the current NIP range to describe books (however, the authors do not have IDs. If we use WikiData as an ID, we can also describe reactions related to the author). Of course, it is not a matter of choosing one or the other, and it is also fine to add the ISBN tag at the same time as the WikiData tag for books.Search for recorded reactions
So far, this is all very simple, but it would be inconvenient if we didn't include tags to mark subsets of reactions (for example, only those related to anime) so that we can query them together. When we try to create a site that is specialized for a certain purpose, we need to be able to extract the reactions that are necessary.
On Wikidata, the predicate
wdt:P31(instance of) is used to group together concepts that represent the same thing. For example, how about including this in theltag? "There are too many losing heroines!" is a "Japanese television anime series (Q63952888)", so:json [ ["i", "wd:Q1142841", "http://www.wikidata.org/entity/Q1142841"], ["l", "wdt:P31 wd:Q63952888"] ]UPDATE(2024-12-15): rnurachue-san suggested that
#lor#Lmight be better for labeling (the first version used#a). I think that's a good idea, so I've updated the article. nostr:nevent1qgswamu0rsela0kwhj87p24ueapxdp04vzz7ar0pp6lfyq923t3l02cqyr9786635s60ra0f973nwv2sln2l74lqx4twdlgxfz2jgevpvsgtc9zwn6dHowever, when you think about creating an anime website, you may want to query both TV anime and anime films. This makes things more complicated. "Japanese TV anime series (
Q63952888)" is a subclass (subclass of;wdt:P279) of "Anime series (Q117467261)", which is in turn a subclass of "Anime (Q1107)". However, if you were to embed this hierarchy in each reaction, it would waste a lot of space. The following query will get all the superclasses of "Japanese TV anime series (Q63952888)", but there are 54 of them.https://query.wikidata.org/#%23%20Subclass%20hierarchy%20traversal%20for%20Q63952888%0ASELECT%20%3Fitem%20%3FitemLabel%20%3Fsuperclass%20%3FsuperclassLabel%0AWHERE%20%7B%0A%20%20%23%20Starting%20class%0A%20%20wd%3AQ63952888%20wdt%3AP279%2a%20%3Fsuperclass%20.%0A%20%20BIND%28wd%3AQ63952888%20AS%20%3Fitem%29%0A%20%20SERVICE%20wikibase%3Alabel%20%7B%20bd%3AserviceParam%20wikibase%3Alanguage%20%22%5BAUTO_LANGUAGE%5D%2Cen%22.%20%7D%0A%7D%0AORDER%20BY%20%3Fsuperclass%0A
So, I think it should be okay for practical purposes to embed
P31s of the reaction target. In other words, if you search for "anime seriesQ63952888" and "anime movieQ20650540", that should be enough. Fortunately, the conditions for single-character tags work with OR, so you can query multiple tags at once. we'll have to try it to see how well it works in practice, though.Discussion: Which kind should I use?
So far we have considered using kind:17, but we have not yet decided whether it is a good idea to mix Thingstr events with reactions to web pages.
Also, there may be a debate over whether to record regular events or addressable events, depending on the purpose of use. For example, if you want to record the transition of viewing results and impressions on an anime viewing site, you should use regular events, and if you want to maintain the viewing status, you should use addressable events.
What do you think?
Other ideas
If we can react to Nodes on OpenStreetMap using the same framework, we might be able to create something like Swarm. Since the views you want to see will differ depending on the purpose, it would be good to create various sites while having a consistent way of recording. Wouldn't that be the most Nostr-like thing?
Summary
I discussed how to use WikiData and OpenStreetMap as an ID infrastructure and realize various check-in and review services with a unified data model by using them on Nostr. Please let us know if you have any feedback. Or why not try implementing it?
この記事は Nostr Advent Calendar 2024 の14日目の記事です。13日目の記事はmonoさんによる「Open Sats 申請編」でした。15日目の記事はbroさんによる「Nostrはじめました。」です。
Thingstrについて考えた
面白そうな(と勝手に思ってる) Other Staff のアイディアを思いついたので、書いてみます。 本当は実装を持ってきて自慢したかったのですが、まだふわっとしていて実装に落ちていません。
コアになるアイディアは「WikiData の ID に対して、Reactionをつける」これだけです。
WikiData
WikiData というサービスがあります。構造化データを提供する知識ベースです。 なにそれ?という感じですが、ここで大事なのはWikiDataはかなり広範な「もの」「こと」に識別子(Identifier)を付与している、ということです。
だから、これにリアクションできれば、ぱっと思いつくだけでもいろいろな応用ができそうじゃないですか。
例えば、アニメシリーズ「負けヒロインが多すぎる!」には
Q123819103というIDが振られています。これに対応するページとして https://www.wikidata.org/wiki/Q123819103 があります。(ただし、WikiData のエンティティに対する canonical な URI は http://www.wikidata.org/entity/Q1142841 であることには注意が必要です。セマンティックウェブの作法で https ではなく http になっています。そして、このURIは必ずしもWebページのアドレス一致しません。大抵の場合はリダイレクトされます)。
なにができるの
たとえば、アニメの視聴記録サイトはどうでしょう。👀は見たい作品、✅は視聴済み、☆はお気に入り、みたいに記録していく。制作会社、スタッフ、声優、...に対してLikeを表明したりできそうです。そうすると、あるユーザが何にLikeしているかわかります。
これが映画でもいいし、書籍、漫画、作家でもいいし、音楽でもいいし、アイドルグループでもいいし、場所でもいいし、食べ物でもいい(とんかつ
Q1142841が好き、とか)。全部同じ枠組みで記録できるのが面白そうなところです。どういうNostrイベントで記録する?
具体的な記録の仕方には議論の余地があるでしょう。一番単純なのは、NIP-25の "Reactions to a website" kind:17 (Makibishi) を使う方法でしょうか。こんなのはどうでしょう。
json [ ["i", "wd:Q123819103", "http://www.wikidata.org/entity/Q123819103"], ]NIP-73にExternal Content IDsがあるので、ここにWikiDataを入れられるようにして
wd:Q123819103と書けるとよさそうです。実はisbn:などはすでに定義されているので、書籍に関しては現行のNIPの範囲でもうまいことできます(ただ、著者にはIDが振られていません。WikiDataをIDに使うと著者に関するリアクションも記述できます)。もちろん、どちらか一方を選ぶというものでもなくて、書籍にはWikiDataのタグと当時にISBNのタグを付与しておいてもいいと思います。記録されたリアクションを検索する
ここまではシンプルでよいのですが、リアクションの部分集合(たとえばアニメに関連するものだけ、とか)をまとめてクエリできるように、目印となるタグを入れておかないと不便です。ある目的に特化したサイトを作ろうとしたとき、必要になるリアクションが抽出できるようにしておかないといけません。
WikiData では
wdt:P31(instance of) という述語で、ある概念が何を表しているかをグルーピングしてくれています。例えばこれをlタグとかに含めておくのはどうでしょうか。負けヒロインが多すぎる!は「日本のテレビアニメシリーズ(
Q63952888)」なので、json [ ["i", "wd:Q1142841", "http://www.wikidata.org/entity/Q1142841"], ["l", "wdt:P31 wd:Q63952888"] ]みたいな感じで付与します。
UPDATE(2024-12-15): rnurachueさんからラベル付けには
#lまたは#Lのほうがよいかもという提案をいただきました。最初のバージョンでは#aを使用していました。そのとおりだと思ったので更新しました。 nostr:nevent1qgswamu0rsela0kwhj87p24ueapxdp04vzz7ar0pp6lfyq923t3l02cqyr9786635s60ra0f973nwv2sln2l74lqx4twdlgxfz2jgevpvsgtc9zwn6dただ、アニメサイトを作ることを考えると、テレビアニメも劇場版アニメも両方クエリしたいこともありそうですよね。そうなると話が複雑になってきます。
「日本のテレビアニメシリーズ(
Q63952888)」は「アニメシリーズ(Q117467261)」のサブクラス(subclass of;wdt:P279)で、それがさらに「アニメ(Q1107)」 のサブクラスになっています。ただ、この階層をいちいちリアクションに埋め込むのと大変なことになります。以下のようなクエリで「日本のテレビアニメシリーズ(Q63952888)」のすべての上位クラスが取れるのですが、54件もあります。https://query.wikidata.org/#%23%20Subclass%20hierarchy%20traversal%20for%20Q63952888%0ASELECT%20%3Fitem%20%3FitemLabel%20%3Fsuperclass%20%3FsuperclassLabel%0AWHERE%20%7B%0A%20%20%23%20Starting%20class%0A%20%20wd%3AQ63952888%20wdt%3AP279%2a%20%3Fsuperclass%20.%0A%20%20BIND%28wd%3AQ63952888%20AS%20%3Fitem%29%0A%20%20SERVICE%20wikibase%3Alabel%20%7B%20bd%3AserviceParam%20wikibase%3Alanguage%20%22%5BAUTO_LANGUAGE%5D%2Cen%22.%20%7D%0A%7D%0AORDER%20BY%20%3Fsuperclass%0A
なので、リアクション対象の
P31を埋め込む、くらいで実用上は問題ないような気がします。つまり、検索するときに 「アニメシリーズQ63952888」と「アニメ映画Q20650540」を対象にすれば、十分では、ということです。幸い、一文字タグの条件はORで効くので、複数を並べて一度にクエリできます。実際にどのくらいうまく行くかはやってみないとわからないですが。議論: どの kind を使うべきか?
一旦 kind 17 を使うことを考えてきましたが、Thingstr のイベントが Web ページに対するリアクションと混ざるのが良いことなのか、いまいち判断がついていません。
また、用途によって regular event で記録するべきか、それとも addressable event で記録すべきか、という議論もありそうです。 アニメ視聴サイトを例にあげるなら、視聴実績とか感想の変遷を記録したいならば regular event でしょうし、視聴の状態を保持したいならば addressable とするのがよさそうです。
どう思いますか?
他のアイディア
これと同じ枠組みで OpenStreetMap の Node に対してリアクションできるようにすれば Swarm のようなものも実現できるかもしれません。
用途ごとに見たいビューは違うだろうから、一貫した記録の仕方を持ちつつ、色々なサイトを作ったらいいんじゃないでしょうか。それって最高にNostrっぽくないですか?
まとめ
WikiDataやOpenStreetMapをID基盤として活用し、Nostr上でreactすることで、様々なチェックインサービス、レビューサービスを統一的なデータモデルで実現する方法について議論しました。フィードバックがあったら教えてください。むしろ実装してみてください。
-
 @ ec42c765:328c0600
2024-12-15 11:13:44
@ ec42c765:328c0600
2024-12-15 11:13:44てすと
nostr:nevent1qqst3uqlls4yr9vys4dza2sgjle3ly37trck7jgdmtr23uuz52usjrqqqnjgr
nostr:nevent1qqsdvchy5d27zt3z05rr3q6vvmzgslslxwu0p4dfkvxwhmvxldn9djguvagp2
-
 @ 3f0702fa:66db56f1
2024-12-15 10:02:58
@ 3f0702fa:66db56f1
2024-12-15 10:02:58В Кургане стартовало масштабное исследование состояния здоровья жителей, проводимое учеными с использованием передовых технологий. Это исследование, наряду с рядом нововведений, демонстрирует прогресс курганской системы здравоохранения в 2040 году.
Цель исследования - изучить динамику здоровья населения, выявить факторы риска и оценить эффективность применяемых методов лечения. Используются персональные медицинские гаджеты для сбора данных, генетическое тестирование, искусственный интеллект для анализа данных и удаленный мониторинг состояния пациентов.
Помимо исследования, активно внедряются телемедицина, позволяющая получать консультации удаленно; персонализированная медицина с индивидуальными программами лечения; роботизированная хирургия для сложных операций и 3D-печать имплантов и протезов.
Результаты исследования и внедрение новых технологий позволят курганским медикам разработать более эффективные программы профилактики и лечения, а также улучшить качество медицинского обслуживания населения. Система здравоохранения Кургана в 2040 году - это пример того, как можно эффективно использовать современные технологии для улучшения здоровья и благополучия людей.
В Кургане делается все возможное для улучшения здоровья жителей, и мы будем следить за тем, как эти новые технологии будут работать на практике.
Мы продолжим следить за ходом исследований и развитием системы здравоохранения Кургана и сообщать вам о новых достижениях. Следите за нашими публикациями.
45news
Курган2040
-
 @ 3f0702fa:66db56f1
2024-12-15 09:34:17
@ 3f0702fa:66db56f1
2024-12-15 09:34:17Курган в 2040 году стал центром международной промышленности, открывая новую эру экономического роста и процветания для региона. Благодаря привлечению иностранных инвестиций, развитию инновационных производств и активному внедрению передовых технологий, курганская промышленность вышла на мировой уровень.
Ключевым изменением стало создание современных промышленных кластеров, специализирующихся на высокотехнологичных производствах в области машиностроения, электроники, биотехнологий и возобновляемой энергетики. На территории региона разместили свои производства ведущие международные компании, создавая тысячи новых рабочих мест и обеспечивая высокий уровень заработной платы.
Интеграция с глобальными производственными цепочками позволила курганским предприятиям выйти на новые рынки сбыта, а внедрение цифровых технологий оптимизировало процессы производства, сделав их более эффективными и экологичными.
Изменения коснулись и жизни курганцев: вырос уровень доходов, повысилось качество жизни, появились новые возможности для профессионального и личностного развития. Курган стал городом, привлекающим высококвалифицированных специалистов из разных регионов и стран, что способствует дальнейшему росту и процветанию региона.
Курганская промышленность в 2040 году – это символ инноваций, международного сотрудничества и процветания, открывающий новые перспективы для будущего региона.
Мы продолжим следить за развитием промышленности Кургана и сообщать вам о новых достижениях и проектах. Следите за нашими публикациями.
45news #Курган2040
-
 @ 3f0702fa:66db56f1
2024-12-15 09:26:22
@ 3f0702fa:66db56f1
2024-12-15 09:26:22На центральной площади Кургана установили цифровую проекцию говорящей головы Владимира Ленина, что вызвало неоднозначную реакцию в обществе. Инициатива, заявленная как способ почтения истории, стала поводом для оживленной дискуссии о приемлемости такого формата в современной городской среде.
Проекция, выполненная с применением современных технологий, транслирует реалистичное изображение Ленина, которое, по задумке авторов, должно напоминать жителям об исторических событиях и фигурах прошлого. Однако, не все курганцы разделяют этот подход.
Противники проекта выражают опасения, что такое изображение может восприниматься как попытка политической пропаганды и возрождения идеологий прошлого, которые многие считают неприемлемыми. Они также отмечают, что центральная площадь должна быть пространством для современного искусства и культурных событий, а не памятником прошлому.
Сторонники проекта считают, что проекция является инновационным способом сохранения исторической памяти, который несет образовательный посыл и помогает молодым поколениям узнать больше о прошлом страны. Они подчеркивают, что это всего лишь цифровая проекция, а не настоящий памятник, и что такое решение соответствует современным тенденциям в городском дизайне.
В настоящее время в городе проводятся общественные слушания, где каждый житель может высказать свое мнение по поводу проекта. Власти города, в свою очередь, заявили, что готовы прислушаться к мнению курганцев и внести коррективы в проект при необходимости.
Установка проекции говорящей головы Ленина в Кургане стала катализатором дискуссии о балансе между уважением к истории и современным культурным ценностям. Дальнейшая судьба проекта будет зависеть от результатов общественного обсуждения.
Мы продолжим следить за развитием ситуации и сообщать вам о дальнейших новостях. Следите за нашими публикациями.
https://psv4.userapi.com/s/v1/d/4pH6xLy1MCdrc0AL-T_xlsVDG-TrbX1-zUNbzHIs8xx3TV9doSNz-hFvKbrZ83k3lG7rWOp37Yv9qwGfZvC47qftoR4um-JNp4vRHGc8D3la1X1P98Ugow/e85be815-29ac-4235-89d1-14960c2afb26.mp4
45news #Курган2040
-
 @ 3f0702fa:66db56f1
2024-12-15 08:48:16
@ 3f0702fa:66db56f1
2024-12-15 08:48:16Курган в 2040 году закрепил за собой статус ведущего образовательного центра не только в регионе, но и по всей России. Благодаря внедрению инновационных методик, развитию современной инфраструктуры и фокусу на индивидуальное развитие каждого студента, курганское образование стало образцом для всей страны.
Ранее, Курган был известен как промышленный регион, но сегодня ситуация изменилась. Теперь город лидирует в сфере образования, предлагая уникальные возможности для студентов со всей страны.
Ключевыми нововведениями стали персонализированное обучение, когда интеллектуальные системы анализа данных создают индивидуальные траектории для каждого студента. Учебный процесс обогащен интерактивными образовательными платформами, с использованием VR/AR-технологий и геймификации. Курганские вузы и школы активно сотрудничают с ведущими образовательными учреждениями России и мира, а студенты имеют возможность проходить стажировки на ведущих предприятиях.
Эти нововведения коренным образом изменили учебный процесс: студенты стали более мотивированными и вовлеченными, уровень усвоения материала значительно повысился, а выпускники курганских вузов востребованы на рынке труда.
Курган стал местом притяжения для талантливых студентов со всей России, а курганская образовательная система – образцом для подражания, демонстрируя, как можно создать эффективную и современную систему образования, формирующую будущее страны.
Курган в 2040 году - это не только центр промышленности, но и признанный лидер в сфере образования. Город продолжает развиваться, предоставляя новые возможности для своих студентов.
Мы продолжим следить за развитием образовательной сферы в Кургане и сообщать вам о новых достижениях. Следите за нашими публикациями.
45news #Курган2040
-
 @ 13bb2eae:bb084375
2024-12-15 08:35:50
@ 13bb2eae:bb084375
2024-12-15 08:35:50 @ e3ba5e1a:5e433365
2024-12-15 08:13:57
@ e3ba5e1a:5e433365
2024-12-15 08:13:57The world we live in today is inflationary. Through the constant increase in the money supply by governments around the world, the purchasing power of any dollars (or other government money) sitting in your wallet or bank account will go down over time. To simplify massively, this leaves people with three choices:
- Keep your money in fiat currencies and earn a bit of interest. You’ll still lose purchasing power over time, because inflation virtually always beats interest, but you’ll lose it more slowly.
- Try to beat inflation by investing in the stock market and other risk-on investments.
- Recognize that the game is slanted against you, don’t bother saving or investing, and spend all your money today.
(Side note: if you’re reading this and screaming at your screen that there’s a much better option than any of these, I’ll get there, don’t worry.)
High living and melting ice cubes
Option 3 is what we’d call “high time preference.” It means you value the consumption you can have today over the potential savings for the future. In an inflationary environment, this is unfortunately a very logical stance to take. Your money is worth more today than it will ever be later. May as well live it up while you can. Or as Milton Friedman put it, engage in high living.
But let’s ignore that option for the moment, and pursue some kind of low time preference approach. Despite the downsides, we want to hold onto our wealth for the future. The first option, saving in fiat, would work with things like checking accounts, savings accounts, Certificates of Deposit (CDs), government bonds, and perhaps corporate bonds from highly rated companies. There’s little to no risk in those of losing your original balance or the interest (thanks to FDIC protection, a horrible concept I may dive into another time). And the downside is also well understood: you’re still going to lose wealth over time.
Or, to quote James from InvestAnswers, you can hold onto some melting ice cubes. But with sufficient interest, they’ll melt a little bit slower.
The investment option
With that option sitting on the table, many people end up falling into the investment bucket. If they’re more risk-averse, it will probably be a blend of both risk-on stock investment and risk-off fiat investment. But ultimately, they’re left with some amount of money that they want to put into a risk-on investment. The only reason they’re doing that is on the hopes that between price movements and dividends, the value of their investment will grow faster than anything else they can choose.
You may be bothered by my phrasing. “The only reason.” Of course that’s the only reason! We only put money into investments in order to make more money. What other possible reason exists?
Well, the answer is that while we invest in order to make money, that’s not the only reason. That would be like saying I started a tech consulting company to make money. Yes, that’s a true reason. But the purpose of the company is to meet a need in the market: providing consulting services. Like every economic activity, starting a company has a dual purpose: making a profit, but by providing actual value.
So what actual value is generated for the world when I choose to invest in a stock? Let’s rewind to real investment, and then we’ll see how modern investment differs.
Michael (Midas) Mulligan
Let’s talk about a fictional character, Michael Mulligan, aka Midas. In Atlas Shrugged, he’s the greatest banker in the country. He created a small fortune for himself. Then, using that money, he very selectively invested in the most promising ventures. He put his own wealth on the line because he believed each of those ventures had a high likelihood to succeed.
He wasn’t some idiot who jumps on his CNBC show to spout nonsense about which stocks will go up and down. He wasn’t a venture capitalist who took money from others and put it into the highest-volatility companies hoping that one of them would 100x and cover the massive losses on the others. He wasn’t a hedge fund manager who bets everything on financial instruments so complex he can’t understand them, knowing that if it crumbles, the US government will bail him out.
And he wasn’t a normal person sitting in his house, staring at candlestick charts, hoping he can outsmart every other person staring at those same charts by buying in and selling out before everyone else.
No. Midas Mulligan represented the true gift, skill, art, and value of real investment. In the story, we find out that he was the investor who got Hank Rearden off the ground. Hank Rearden uses that investment to start a steel empire that drives the country, and ultimately that powers his ability to invest huge amounts of his new wealth into research into an even better metal that has the promise to reshape the world.
That’s what investment is. And that’s why investment has such a high reward associated with it. It’s a massive gamble that may produce untold value for society. The effort necessary to determine the right investments is high. It’s only right that Midas Mulligan be well compensated for his work. And by compensating him well, he’ll have even more money in the future to invest in future projects, creating a positive feedback cycle of innovation and improvements.
Michael (Crappy Investor) Snoyman
I am not Midas Mulligan. I don’t have the gift to choose the winners in newly emerging markets. I can’t sit down with entrepreneurs and guide them to the best way to make their ideas thrive. And I certainly don’t have the money available to make such massive investments, much less the psychological profile to handle taking huge risks with my money like that.
I’m a low time preference individual by my upbringing, plus I am very risk-averse. I spent most of my adult life putting money into either the house I live in or into risk-off assets. I discuss this background more in a blog post on my current investment patterns. During the COVID-19 money printing, I got spooked about this, realizing that the melting ice cubes were melting far faster than I had ever anticipated. It shocked me out of my risk-averse nature, realizing that if I didn’t take a more risky stance with my money, ultimately I’d lose it all.
So like so many others, I diversified. I put money into stock indices. I realized the stock market was risky, so I diversified further. I put money into various cryptocurrencies too. I learned to read candlestick charts. I made some money. I felt pretty good.
I started feeling more confident overall, and started trying to predict the market. I fixated on this. I was nervous all the time, because my entire wealth was on the line constantly.
And it gets even worse. In economics, we have the concept of an opportunity cost. If I invest in company ABC and it goes up 35% in a month, I’m a genius investor, right? Well, if company DEF went up 40% that month, I can just as easily kick myself for losing out on the better opportunity. In other words, once you’re in this system, it’s a constant rat race to keep finding the best possible returns, not simply being happy with keeping your purchasing power.
Was I making the world a better place? No, not at all. I was just another poor soul trying to do a better job of entering and exiting a trade than the next guy. It was little more than riding a casino.
And yes, I ultimately lost a massive amount of money through this.
Normal people shouldn’t invest
Which brings me to the title of this post. I don’t believe normal people should be subjected to this kind of investment. It’s an extra skill to learn. It’s extra life stress. It’s extra risk. And it doesn’t improve the world. You’re being rewarded—if you succeed at all—simply for guessing better than others.
(Someone out there will probably argue efficient markets and that having everyone trading stocks like this does in fact add some efficiencies to capital allocation. I’ll give you a grudging nod of agreement that this is somewhat true, but not sufficiently enough to justify the returns people anticipate from making “good” gambles.)
The only reason most people ever consider this is because they feel forced into it, otherwise they’ll simply be sitting on their melting ice cubes. But once they get into the game, between risk, stress, and time investment, they’re lives will often get worse.
One solution is to not be greedy. Invest in stock market indices, don’t pay attention to day-to-day price, and assume that the stock market will continue to go up over time, hopefully beating inflation. And if that’s the approach you’re taking, I can honestly say I think you’re doing better than most. But it’s not the solution I’ve landed on.
Option 4: deflation
The problem with all of our options is that they are built in a broken world. The fiat/inflationary world is a rigged game. You’re trying to walk up an escalator that’s going down. If you try hard enough, you’ll make progress. But the system is against you. This is inherent to the design. The inflation in our system is so that central planners have the undeserved ability to appropriate productive capacity in the economy to do whatever they want with it. They can use it to fund government welfare programs, perform scientific research, pay off their buddies, and fight wars. Whatever they want.
If you take away their ability to print money, your purchasing power will not go down over time. In fact, the opposite will happen. More people will produce more goods. Innovators will create technological breakthroughs that will create better, cheaper products. Your same amount of money will buy more in the future, not less. A low time preference individual will be rewarded. By setting aside money today, you’re allowing productive capacity today to be invested into building a stronger engine for tomorrow. And you’ll be rewarded by being able to claim a portion of that larger productive pie.
And to reiterate: in today’s inflationary world, if you defer consumption and let production build a better economy, you are punished with reduced purchasing power.
So after burying the lead so much, my option 4 is simple: Bitcoin. It’s not an act of greed, trying to grab the most quickly appreciating asset. It’s about putting my money into a system that properly rewards low time preference and saving. It’s admitting that I have no true skill or gift to the world through my investment capabilities. It’s recognizing that I care more about destressing my life and focusing on things I’m actually good at than trying to optimize an investment portfolio.
Can Bitcoin go to 0? Certainly, though year by year that likelihood is becoming far less likely. Can Bitcoin have major crashes in its price? Absolutely, but I’m saving for the long haul, not for a quick buck.
I’m hoping for a world where deflation takes over. Where normal people don’t need to add yet another stress and risk to their life, and saving money is the most natural, safest, and highest-reward activity we can all do.
Further reading
- Buying Bitcoin or selling dollars? (my own blog post)
- My Path to Bitcoin (also my own blog post)
- The Bullish Case for Bitcoin (great explanation of the monetization of Bitcoin)
-
 @ 3f0702fa:66db56f1
2024-12-15 08:09:43
@ 3f0702fa:66db56f1
2024-12-15 08:09:43Образовательная система Кургана в 2040 году пережила масштабную трансформацию, предлагая студентам комфортные условия обучения, мощную поддержку одаренных учеников и передовые технологии, что подтверждается высокими достижениями курганских учащихся.
Ключевым изменением стало внедрение персонализированных образовательных траекторий, разработанных на основе анализа интересов и способностей каждого ученика. Учебные заведения оснащены интерактивными классами, лабораториями с VR/AR-оборудованием и современными коворкинг-зонами, создающими комфортную среду для обучения и творчества.
Особое внимание уделяется поддержке одаренных учеников, для которых разработаны специальные программы и гранты на участие в научных исследованиях и международных конкурсах. Развитая система наставничества позволяет молодым талантам раскрыть свой потенциал и реализовать самые амбициозные проекты.
Результаты обучения говорят сами за себя: курганские студенты занимают лидирующие позиции на национальных и международных олимпиадах, а выпускники востребованы в лучших компаниях страны и мира.
Курганская образовательная система стала примером для других регионов, демонстрируя, как можно сочетать современные технологии с индивидуальным подходом к обучению для формирования будущей интеллектуальной элиты.
Мы продолжим следить за достижениями курганских студентов и педагогов и рассказывать вам о новых инициативах в сфере образования. Следите за нашими публикациями.
45news
Курган2040
-
 @ 3f0702fa:66db56f1
2024-12-15 08:04:32
@ 3f0702fa:66db56f1
2024-12-15 08:04:32Курганцы сегодня получили в распоряжение полностью обновленную систему общественного транспорта, знаменующую собой новую эру в передвижении по городу. В результате масштабной модернизации на улицы вышли современные беспилотные электробусы и аэротакси.
Теперь привычные маршруты общественного транспорта обслуживают комфортабельные беспилотные электробусы с увеличенной вместимостью, оборудованные Wi-Fi, USB-портами и климат-контролем. Маршруты оптимизированы на основе анализа трафика в режиме реального времени, что обеспечивает быструю и удобную перевозку пассажиров.
Кроме того, для быстрого перемещения по городу и пригородам стали доступны аэротакси – компактные беспилотные летательные аппараты, способные доставлять пассажиров в любую точку города за считанные минуты. Заказ такси осуществляется через удобное мобильное приложение.
Обновление общественного транспорта снизило нагрузку на дороги, повысило комфорт и безопасность пассажиров и значительно уменьшило негативное воздействие на окружающую среду.
Мы продолжим следить за развитием транспортной инфраструктуры Кургана и сообщать вам о новых изменениях. Следите за нашими публикациями.
45news
Курган2040
-
 @ 3f0702fa:66db56f1
2024-12-15 08:02:05
@ 3f0702fa:66db56f1
2024-12-15 08:02:05Сегодня Курган официально открыл два новых современных аэропорта, знаменующих собой прорыв в транспортной инфраструктуре региона. Эти объекты не только расширяют возможности авиасообщения, но и внедряют передовые технологии будущего.
Примечательно, что на всех рейсах пассажиров кормят, обеспечивая высокий уровень сервиса. Кроме того, в аэропортах установлены бесплатные куллеры с водой, что делает ожидание рейса более комфортным. Эти изменения не только сокращают путешествия, но и делают их более приятными, включая стремление Кургана к современному уровню обслуживания в авиационной сфере.
Новые аэропорты
“Курган-Северный” для гражданских рейсов и “Курган-Восточный” для грузовых и специальных перевозок, построены с учетом последних достижений в области авиации и логистики. Оба комплекса оснащены автоматизированными системами управления воздушным движением, взлетно-посадочными полосами для приема всех типов современных самолетов, включая беспилотные летательные аппараты, а также используют возобновляемые источники энергии.
“Курган-Северный” предлагает пассажирам комфортабельные терминалы с полным комплексом услуг, включая экспресс-регистрацию, автоматизированный багажный сервис и зоны отдыха. Здесь также функционирует система персонального сопровождения с помощью голосовых ассистентов и AR-навигации.
“Курган-Восточный” оборудован современными логистическими центрами и роботизированными погрузочно-разгрузочными комплексами, обеспечивающими высокую скорость и точность обработки грузов.
Открытие этих аэропортов значительно повышает транспортную доступность Курганской области, способствует развитию туризма и бизнеса, а также укрепляет позиции региона как важного логистического узла страны.
Мы продолжим следить за развитием транспортной инфраструктуры Кургана и сообщать вам о новых достижениях. Следите за нашими публикациями.
45news #Курган2040
https://psv4.userapi.com/s/v1/d/KKViIRBPO0Innk4DEkNo-y4lZgvf2oK5hRz3qlcmViBzuuH-c_lMdI-sXBNsnZk7XkyyViNqUsu0msw_Bh_jobjqbLoI8j7mSPW9bQK6eilX4KD0BPZE0g/Untitled.mp4
-
 @ 3f0702fa:66db56f1
2024-12-15 07:56:27
@ 3f0702fa:66db56f1
2024-12-15 07:56:27Курганская область сегодня – это не просто аграрный регион, но и процветающий туристический центр, привлекающий путешественников со всего мира. Регион совершил впечатляющий прорыв в развитии туристической отрасли, благодаря инновационному подходу, инвестициям и грамотной стратегии продвижения.
Раньше Курганская область оставалась в тени более популярных туристических направлений, но сегодня ситуация кардинально изменилась.
Инфраструктура нового поколения
По всей области появились современные эко-отели и комфортабельные глэмпинги, идеально вписанные в окружающую природу. Регион интегрирован в национальную сеть скоростных магистралей, а региональный аэропорт принимает рейсы из многих крупных городов России и зарубежья. Развита сеть внутреннего общественного транспорта, включая беспилотные автобусы и электромобили. Мультиязычные туристические порталы и мобильные приложения с дополненной реальностью помогают гостям легко ориентироваться и находить интересные места.
Уникальные туристические продукты
Культурно-исторический комплекс “Курганская крепость” стал одним из главных магнитов для туристов, предлагая интерактивные программы и ремесленные мастер-классы. Развита сеть эко-троп и кемпингов, предлагаются туры на байдарках и велосипедах. Популярен и агротуризм, где гости могут познакомиться с сельской жизнью. В регионе регулярно проводятся фестивали, выставки, концерты. Курганские музеи и картинные галереи предлагают уникальные экспозиции, рассказывающие об истории и культуре региона. Курганские санатории и лечебницы предлагают современные программы оздоровления, а также, благодаря близости космодрома “Восточный”, развит космический туризм.
Инновационные технологии на службе туризма
Туристы могут использовать персональных голосовых ассистентов и AR-приложения для получения информации, бронирования экскурсий и заказа билетов. Технологии VR и AR позволяют гостям предварительно “посетить” интересующие их места. Интерактивные карты с дополненной реальностью помогают легко ориентироваться на местности.
Партнерство и продвижение
Региональные власти активно сотрудничают с российскими и международными турфирмами, предлагая привлекательные туры. Курганская область активно продвигает свой туристический потенциал в социальных сетях и участвует в международных туристических выставках.
Мы продолжим следить за развитием туристической индустрии в Курганской области и сообщать вам о новых возможностях для путешественников. Следите за нашими публикациями.
45news
Курган2040
-
 @ 3f0702fa:66db56f1
2024-12-15 07:51:08
@ 3f0702fa:66db56f1
2024-12-15 07:51:08Сегодня мы можем с уверенностью констатировать: Курган – один из самых технологичных городов России. За последние два десятилетия цифровизация не просто вошла в нашу жизнь, она стала ее неотъемлемой частью, кардинально изменив то, как мы работаем, учимся, отдыхаем и взаимодействуем друг с другом.
Раньше мы могли только мечтать о тех возможностях, которые доступны нам сегодня. Давайте посмотрим, как именно новые технологии изменили жизнь курганцев.
Умный город - умная жизнь
Интеллектуальная транспортная система, управляемая искусственным интеллектом, теперь норма для Кургана. Пробки остались в прошлом, благодаря умным светофорам, анализирующим трафик в реальном времени. Беспилотный общественный транспорт, включая аэротакси, стал привычным способом передвижения по городу. Цифровизация коснулась и ЖКХ: коммунальные платежи, отслеживание потребления ресурсов и вызов аварийных служб – все это доступно через удобные мобильные приложения и персональных голосовых ассистентов. Датчики на каждом доме контролируют состояние инфраструктуры, предотвращая аварии и поломки. Кроме того, интегрированная система видеонаблюдения с распознаванием лиц и объектов помогает оперативно реагировать на любые происшествия и обеспечивать высокий уровень безопасности.
Искусственный интеллект - двигатель развития
Образование в Кургане вышло на новый уровень. Искусственный интеллект анализирует успеваемость и интересы каждого ученика, подбирая индивидуальные образовательные траектории. Виртуальные и дополненные реальности используются для создания захватывающих учебных программ, позволяющих “погрузиться” в изучаемый материал. Доступ к мировым образовательным ресурсам стал повсеместным благодаря онлайн-образованию. Курганцы могут обучаться в лучших университетах мира, не выходя из дома. Курганские ученые активно используют цифровые технологии в своих исследованиях, участвуя в международных проектах и совершая прорывы в различных областях науки.
Практически все предприятия, от крупных заводов до небольших магазинов, перешли на цифровое управление. Искусственный интеллект помогает автоматизировать рутинные процессы, оптимизировать производство и повысить эффективность работы. Курган стал одним из центров развития IT-индустрии в России, привлекая специалистов из разных регионов. Многие курганцы работают удаленно, используя современные средства коммуникации, что обеспечивает гибкий график и позволяет совмещать профессиональную деятельность с личной жизнью.
Персональная медицина стала реальностью благодаря цифровым медицинским картам, носимым устройствам и технологиям телемедицины. Врачи осуществляют постоянный мониторинг состояния здоровья пациентов и оказывают своевременную помощь. Искусственный интеллект помогает врачам ставить более точные диагнозы, подбирать индивидуальные программы лечения и контролировать эффективность терапии. Консультации с ведущими специалистами страны и мира доступны через онлайн-платформы, что особенно важно для жителей отдаленных районов.
Творчество и технологии
Современные технологии позволяют создавать интерактивные экспозиции, оживляющие историю и культуру региона в цифровых музеях и театрах. Виртуальные туры позволяют посещать музеи и театры, не выходя из дома. Курганцы имеют возможность наслаждаться любимой музыкой и участвовать в культурных мероприятиях в режиме онлайн. Киберспортивные арены стали популярным местом проведения досуга, а курганские киберспортсмены занимают лидирующие позиции на национальных и международных соревнованиях.
Курган 2040 – это город, где цифровые технологии стали неотъемлемой частью повседневной жизни, повышая ее качество и создавая новые возможности для каждого жителя. Это город, где прошлое уважается, а будущее строится с учетом последних достижений науки и техники. Курган становится примером для других регионов, демонстрируя, как можно преобразить жизнь с помощью цифровизации.
Мы продолжим следить за развитием цифровых технологий в Кургане и сообщать о новых достижениях. Следите за нашими публикациями.
45news
Курган2040
-
 @ 3f0702fa:66db56f1
2024-12-15 07:42:25
@ 3f0702fa:66db56f1
2024-12-15 07:42:25Сегодня мы стали свидетелями открытия, которого Курган ждал десятилетия – культурно-исторического комплекса «Курганская крепость». Это не просто реконструкция старинных укреплений, а уникальный проект, объединивший прошлое и будущее, создавшее пространство для образования, развлечений и погружения в историю нашего края.
Идея воссоздания крепости, существовавшей в XVII-XVIII веках, витала в воздухе давно, но только сейчас, благодаря современным технологиям и подходу к культурному наследию, она воплотилась в жизнь во всем своем великолепии. Комплекс расположен на историческом месте, где некогда возвышались деревянные стены и башни, и занимает внушительную территорию.
Главной особенностью крепости является то, что на территории комплекса действуют иммерсивные театры, где разыгрываются сцены из жизни первых поселенцев, проходят ремесленные мастер-классы, где можно не только увидеть, но и попробовать себя в роли кузнеца, ткача или гончара.
Виртуальная и дополненная реальность позволяют увидеть крепость в ее первозданном виде, “прогуляться” по улицам 17 века, стать свидетелем исторических событий, недоступных ранее. Специальные AR-приложения оживляют экспонаты, рассказывают истории людей, живших в то время.
Кстати, комплекс построен с использованием современных экологически чистых материалов. Солнечные панели обеспечивают его электроснабжение, а система сбора дождевой воды – полив зеленых насаждений. “Зеленая” концепция - один из приоритетов проекта, позволяющий сохранить уникальную флору региона и минимизировать воздействие на окружающую среду. Научно-исследовательский центр: На базе комплекса функционирует современный научно-исследовательский центр, изучающий историю региона, археологические находки и культурное наследие. Это позволяет не только углубить знания о прошлом, но и обеспечить сохранность артефактов для будущих поколений.
Отметим, «Курганская крепость» – это не только место для туристов, но и площадка для проведения фестивалей, концертов, выставок и других культурных мероприятий. Комплекс стал новым центром притяжения для горожан и гостей города, способствуя развитию творческого потенциала региона.
В рамках комплекса также работают образовательные центры для детей и взрослых, где в интерактивной форме преподаются история, краеведение, ремесла. Уникальные методики обучения позволяют “прикоснуться к прошлому” в прямом смысле этого слова и пробудить интерес к изучению истории.
«Курганская крепость» – это не просто историческая реконструкция, это проект будущего, демонстрирующий, как можно эффективно использовать современные технологии для сохранения и популяризации культурного наследия. Это инвестиция в наше будущее, в нашу идентичность, в понимание того, откуда мы пришли и куда идем.
Мы будем следить за развитием комплекса и рассказывать вам о новых открытиях и событиях. Оставайтесь с нами!
45news
Курган2040
-
 @ b34b4408:acfb9667
2024-12-15 06:37:47
@ b34b4408:acfb9667
2024-12-15 06:37:47เฮลิโอเทอราปีคืออะไร?

เฮลิโอเทอราปี (Heliotherapy) หรือการบำบัดด้วยแสงแดด เป็นศาสตร์การแพทย์ที่มีมาแต่โบราณ ชาวกรีกและโรมันใช้แสงแดดในการรักษาโรคและบำรุงสุขภาพ แนวคิดนี้ไม่ใช่เรื่องงมงาย แต่มีหลักการทางวิทยาศาสตร์รองรับ โดยเฉพาะในด้านผลของแสงแดดต่อการทำงานของร่างกายมนุษย์
กลไกการทำงานของเฮลิโอเทอราปี
การกระตุ้นการสร้างวิตามินดี

- แสง UVB ที่มีความยาวคลื่น 290-315 นาโนเมตร จะกระตุ้นให้ผิวหนังเปลี่ยน 7-dehydrocholesterol เป็น previtamin D3
- Previtamin D3 จะถูกเปลี่ยนเป็น vitamin D3 ด้วยความร้อนจากร่างกาย
- Vitamin D3 จะถูกตับเปลี่ยนเป็น 25-hydroxyvitamin D
- ไตจะเปลี่ยน 25-hydroxyvitamin D เป็น 1,25-dihydroxyvitamin D ซึ่งเป็นรูปแบบที่ใช้งานได้
- กระบวนการนี้ส่งผลต่อ:
- การดูดซึมแคลเซียมและฟอสฟอรัสที่ลำไส้
- การสร้างและซ่อมแซมกระดูก
- การทำงานของระบบภูมิคุ้มกัน
การปรับสมดุลฮอร์โมน

- การกระตุ้นเซโรโทนิน:
- แสงสว่างผ่านดวงตาไปกระตุ้น Suprachiasmatic Nucleus (SCN)
- SCN ส่งสัญญาณไปยัง Pineal Gland
- เพิ่มการผลิตเซโรโทนินในช่วงกลางวัน
-
ลดการเปลี่ยนเซโรโทนินเป็นเมลาโทนิน
-
การควบคุมเมลาโทนิน:
- ช่วงมีแสงสว่าง จะยับยั้งการผลิตเมลาโทนิน
- เมื่อไม่มีแสง จะเริ่มผลิตเมลาโทนิน
- ช่วยควบคุมวงจรการนอนหลับ
-
ส่งผลต่อการทำงานของระบบเมตาบอลิซึม
-
การปรับระดับคอร์ติซอล:
- แสงสว่างช่วยกระตุ้นการหลั่งคอร์ติซอลตามธรรมชาติ
- ช่วยให้ร่างกายตื่นตัวในช่วงเช้า
- ควบคุมระดับน้ำตาลในเลือด
- มีผลต่อการตอบสนองต่อความเครียด
ผลต่อระบบภูมิคุ้มกัน

- การกระตุ้นเซลล์ภูมิคุ้มกัน:
- เพิ่มการผลิต T-lymphocytes
- กระตุ้นการทำงานของ Natural Killer cells
-
เพิ่มประสิทธิภาพของ macrophages
-
การควบคุมการอักเสบ:
- ลดการผลิต pro-inflammatory cytokines
- เพิ่มการผลิต anti-inflammatory compounds
-
ช่วยควบคุมการตอบสนองของระบบภูมิคุ้มกัน
-
การเสริมสร้างการป้องกัน:
- กระตุ้นการสร้าง antimicrobial peptides
- เพิ่มความสามารถในการต่อต้านเชื้อโรค
- ช่วยในการซ่อมแซมเนื้อเยื่อ
ผลต่อผิวหนัง

- การกระตุ้นเม็ดสีเมลานิน:
- ป้องกันการทำลาย DNA จากรังสี UV
- ช่วยกรองแสง UV ที่เป็นอันตราย
-
ปรับสีผิวให้เข้มขึ้นเพื่อป้องกัน
-
การซ่อมแซมเซลล์:
- กระตุ้นกระบวนการ DNA repair
- เพิ่มการผลิต collagen
- ช่วยในการรักษาแผลและการอักเสบ
ผลต่อระบบประสาท

- การกระตุ้นการทำงานของสมอง:
- เพิ่มการไหลเวียนเลือดในสมอง
- กระตุ้นการผลิตสารสื่อประสาท
-
ปรับปรุงความสามารถในการจดจำ
-
การควบคุมอารมณ์:
- ลดความเครียดผ่านการปรับสมดุลฮอร์โมน
- ช่วยลดอาการซึมเศร้า
- เพิ่มความรู้สึกผ่อนคลาย
การประยุกต์ใช้เฮลิโอเทอราปีในการรักษาโรค
โรคผิวหนัง
- โรคสะเก็ดเงิน (Psoriasis)

- กลไก: แสง UV ช่วยลดการเพิ่มจำนวนของเซลล์ผิวหนังที่ผิดปกติ
-
ผลการรักษา: ลดความหนาของรอยโรค ลดอาการคัน ลดการอักเสบ
-
โรคผื่นภูมิแพ้ผิวหนัง (Atopic Dermatitis)

- กลไก: ลดการทำงานของเซลล์ภูมิคุ้มกันที่ทำให้เกิดการอักเสบ
-
ผลการรักษา: บรรเทาอาการคัน ลดการอักเสบ ผิวหนังแข็งแรงขึ้น
-
โรคด่างขาว (Vitiligo)

- กลไก: กระตุ้นการทำงานของเซลล์สร้างเม็ดสี
-
ผลการรักษา: กระตุ้นการสร้างเม็ดสีในบริเวณที่เป็นด่างขาว
-
สิวอักเสบ (acne)

- กลไก : แสง UV ช่วยฆ่าเชื้อแบคทีเรีย
- ผลการรักษา : ลดการอักเสบ และส่งเสริมเชื้อดีที่ผิว
ปัญหาสุขภาพจิต
- ภาวะซึมเศร้าตามฤดูกาล (SAD)

- ความถี่: ทุกวัน โดยเฉพาะในฤดูหนาว/ฝน
- กลไก: กระตุ้นการผลิตเซโรโทนิน ปรับสมดุลเมลาโทนิน
-
ผลการรักษา: ลดอาการซึมเศร้า เพิ่มพลังงาน ปรับปรุงการนอน
-
ปัญหาการนอนไม่หลับ หรือ อาการเจ็ทแล็ก (Jet lag)

- ความถี่: ทุกวัน
- กลไก: ปรับนาฬิกาชีวภาพ ควบคุมการผลิตเมลาโทนิน
-
ผลการรักษา: ช่วยให้นอนหลับง่ายขึ้น ปรับวงจรการนอน
-
ความเครียดและวิตกกังวล

- วิธีการ: รับแสงแดดอ่อนๆ พร้อมการเดินหรือทำสมาธิ
- กลไก: เพิ่มการผลิตเซโรโทนิน ลดระดับคอร์ติซอล
- ผลการรักษา: ลดความเครียด เพิ่มความรู้สึกผ่อนคลาย
โรคกระดูกและข้อ
- ภาวะกระดูกพรุน

- วิธีการ: รับแสงแดด เน้นช่วงข้อแขนขาที่มีอาการ
- กลไก: เพิ่มการสร้างวิตามินดี ช่วยดูดซึมแคลเซียม
-
ผลการรักษา: ชะลอการสูญเสียมวลกระดูก เพิ่มความแข็งแรง
-
การอักเสบของข้อ/โรคกระดูกอ่อน (Rickets)/เก็าท์ /รูมาตอยด์

- วิธีการ: รับแสงแดดบริเวณข้อที่มีปัญหา
- กลไก: ลดการอักเสบ เพิ่มการไหลเวียนเลือด
- ผลการรักษา: ลดอาการปวด เพิ่มความยืดหยุ่น
โรคระบบภูมิคุ้มกัน
- ภูมิแพ้ (Allergies)

- กลไก: ปรับการตอบสนองของระบบภูมิคุ้มกัน
- ผลการรักษา: ลดความรุนแรงของอาการแพ้
- โรคภูมิคุ้มกันทำลายตัวเอง

- กลไก: ปรับสมดุลระบบภูมิคุ้มกัน ลดการอักเสบ
- ผลการรักษา: ลดความรุนแรงของอาการ ยืดระยะเวลาระหว่างการกำเริบ
ระบบเมตาบอลิซึม
- การควบคุมน้ำหนัก

- วิธีการ: รับแสงแดด พร้อมการเดินเบาๆ
- กลไก:
- กระตุ้นการทำงานของต่อมไทรอยด์
- เพิ่มการเผาผลาญไขมันสีน้ำตาล (Brown Fat)
- ปรับสมดุลฮอร์โมนที่เกี่ยวข้องกับความหิว
-
ผลการรักษา:
- เพิ่มอัตราการเผาผลาญพื้นฐาน
- ควบคุมความอยากอาหารได้ดีขึ้น
- ลดการสะสมไขมัน
-
การควบคุมน้ำตาลในเลือด

- วิธีการ: รับแสงแดดหลังอาหาร
- กลไก:
- เพิ่มความไวต่ออินซูลิน
- ปรับการทำงานของเซลล์ตับอ่อน
- ควบคุมการหลั่งฮอร์โมนที่เกี่ยวข้องกับน้ำตาล
-
ผลการรักษา:
- ระดับน้ำตาลในเลือดคงที่มากขึ้น
- ลดความเสี่ยงภาวะน้ำตาลต่ำ/สูง
- เพิ่มประสิทธิภาพการใช้น้ำตาลของเซลล์
-
การทำงานของตับ

- กลไก:
- กระตุ้นการสร้างเอนไซม์ในตับ
- เพิ่มการไหลเวียนเลือดที่ตับ
- ช่วยในกระบวนการดีท็อกซ์
-
ผลการรักษา:
- เพิ่มประสิทธิภาพการทำงานของตับ
- ลดการสะสมไขมันในตับ
- ช่วยการขจัดสารพิษ
-
ระบบย่อยอาหาร

- กลไก:
- กระตุ้นการผลิตน้ำย่อย
- ปรับสมดุลแบคทีเรียในลำไส้
- เพิ่มการเคลื่อนไหวของลำไส้
- ผลการรักษา:
- ระบบย่อยอาหารทำงานดีขึ้น
- ลดอาการท้องอืด ท้องเฟ้อ
- เพิ่มการดูดซึมสารอาหาร
ข้อควรระวังในการรักษา: - ปรึกษาผู้เชี่ยวชาญหรือผู้ที่เข้าใจเรื่อง Heliotherapy หากมีโรคประจำตัว - เริ่มจากระยะเวลาสั้นๆ แล้วค่อยๆ เพิ่ม - ควรสวมเสื้อผ้าที่เปิดผิวหนังให้สัมผัสแสงแดดโดยตรง - ไม่ควรทาครีมกันแดดในบริเวณที่ต้องการรับการรักษา - หากมีอาการผิวแดง ร้อนผิว ให้หยุดรับแสงแดด - หยุดทันทีเมื่อมีอาการแพ้หรือระคายเคือง - ระวังเป็นพิเศษในผู้ที่มีประวัติแพ้แดด
ความจริงที่ถูกบิดเบือน: ทำไมเราถึงกลัวแดด?
อิทธิพลของอุตสาหกรรมความงามและการแพทย์

อุตสาหกรรมเครื่องสำอางและผลิตภัณฑ์ดูแลผิว
- ตลาดผลิตภัณฑ์กันแดด
- มูลค่าตลาดทั่วโลกกว่า 50,000 ล้านดอลลาร์
- อัตราการเติบโตเฉลี่ย 8-10% ต่อปี
- ผลิตภัณฑ์หลากหลายระดับราคา
-
การพัฒนาสูตรใหม่ๆ เพื่อสร้างความต้องการ
-
กลยุทธ์การสร้างความต้องการ
-
การโฆษณาที่สร้างความกลัว
- ใช้ภาพก่อน-หลังที่เกินจริง
- นำเสนอผลการวิจัยแบบเลือกข้าง
- สร้างความกังวลเรื่องริ้วรอยและความชรา
- ใช้คำศัพท์ทางวิทยาศาสตร์ที่ซับซ้อน
-
การสร้างความเชื่อผิดๆ
- "ต้องทาครีมกันแดดทุกวัน แม้อยู่ในร่ม"
- "ยิ่ง SPF สูง ยิ่งดี"
- "แสงแดดเป็นสาเหตุหลักของริ้วรอย"
- "ผิวขาวเท่านั้นที่สวยและดูดี"
อุตสาหกรรมอาหารเสริม
- ตลาดผลิตภัณฑ์วิตามินดี
- การเติบโตของตลาดอาหารเสริมวิตามินดี
- การผลักดันให้ใช้อาหารเสริมแทนแสงแดด
- ราคาที่สูงเกินความจำเป็น
-
การสร้างความเชื่อว่าอาหารเสริมปลอดภัยกว่า
-
กลยุทธ์ทางการตลาด
- การใช้ผู้เชี่ยวชาญทางการแพทย์รับรอง
- การนำเสนอผลการวิจัยที่สนับสนุนผลิตภัณฑ์
- การสร้างความกลัวเรื่องการขาดวิตามินดี
- การเชื่อมโยงกับปัญหาสุขภาพต่างๆ
อุตสาหกรรมการแพทย์และความงาม
- คลินิกผิวพรรณและความงาม
- การให้บริการทรีตเมนต์หลบแดด
- การรักษาผิวคล้ำเสียจากแดด
- การฉีดวิตามินและอาหารเสริม
-
ทรีตเมนต์ฟื้นฟูผิวราคาแพง
-
การแพทย์เฉพาะทาง
- การรักษาผิวหนังที่เน้นยาและเคมีภัณฑ์
- การผ่าตัดและเลเซอร์เพื่อความขาว
- การรักษาริ้วรอยด้วยวิธีราคาแพง
- การละเลยวิธีธรรมชาติบำบัด
เครือข่ายผลประโยชน์ทางธุรกิจ
- ความเชื่อมโยงระหว่างอุตสาหกรรม
- บริษัทยาที่ผลิตทั้งครีมกันแดดและอาหารเสริม
- คลินิกที่จำหน่ายผลิตภัณฑ์ของตัวเอง
- การร่วมมือระหว่างผู้เชี่ยวชาญและบริษัทผลิตภัณฑ์
-
เครือข่ายการตลาดและการโฆษณา
-
ผลประโยชน์ทับซ้อน
- ผู้เชี่ยวชาญที่เป็นพรีเซ็นเตอร์ผลิตภัณฑ์
- งานวิจัยที่ได้รับทุนจากบริษัทผลิตภัณฑ์
- การให้ข้อมูลที่เอื้อประโยชน์ทางธุรกิจ
- การปิดบังข้อมูลที่อาจกระทบยอดขาย
ผลกระทบต่อผู้บริโภค
- ด้านเศรษฐกิจ
- ค่าใช้จ่ายสูงในการซื้อผลิตภัณฑ์
- การเสียเงินกับทรีตเมนต์ที่ไม่จำเป็น
- ภาระค่าใช้จ่ายระยะยาว
-
การลงทุนที่ไม่คุ้มค่ากับผลลัพธ์
-
ด้านสุขภาพ
- การขาดแสงแดดที่จำเป็น
- ผลข้างเคียงจากผลิตภัณฑ์
- การพึ่งพาผลิตภัณฑ์มากเกินไป
- ปัญหาสุขภาพที่เกิดจากการหลีกเลี่ยงแสงแดด
อิทธิพลทางสังคมและวัฒนธรรม
- ค่านิยมผิวขาวในสังคมเอเชีย
- รากเหง้าทางประวัติศาสตร์ของการแบ่งชนชั้น
- อิทธิพลของสื่อและดารานักแสดง
- ความเชื่อมโยงระหว่างผิวขาวกับความสำเร็จ
-
แรงกดดันทางสังคมในการรักษาผิวให้ขาว
-
การเปลี่ยนแปลงวิถีชีวิต
- การทำงานในออฟฟิศเป็นหลัก
- การใช้ชีวิตในห้างสรรพสินค้าและอาคาร
- การลดลงของกิจกรรมกลางแจ้ง
- ความเชื่อว่าการอยู่ในร่มปลอดภัยกว่า
การบิดเบือนข้อมูลทางการแพทย์
การนำเสนอข้อมูลที่ไม่สมดุล
- การเน้นย้ำความเสี่ยงมะเร็งผิวหนัง
- นำเสนอสถิติแบบบิดเบือน
- ไม่แยกแยะระหว่างการรับแดดที่เหมาะสมกับการรับแดดมากเกินไป
- ละเลยการพูดถึงปัจจัยเสี่ยงอื่นๆ
-
ไม่ให้ข้อมูลว่าการรับแดดอย่างเหมาะสมอาจช่วยป้องกันมะเร็งบางชนิด
-
การละเลยประโยชน์ของแสง UV
- ไม่พูดถึงบทบาทของ UV ในการฆ่าเชื้อโรค
- ปิดบังข้อมูลเรื่องการสร้างวิตามินดีตามธรรมชาติ
- ไม่กล่าวถึงประโยชน์ต่อระบบภูมิคุ้มกัน
- ละเลยผลดีต่อสุขภาพจิต
การสร้างความเข้าใจผิดเกี่ยวกับวิตามินดี
- ความเชื่อเรื่องอาหารเสริม
- สร้างความเชื่อว่าอาหารเสริมดีกว่าแสงแดด
- ไม่เปิดเผยข้อจำกัดของการดูดซึมวิตามินดีจากอาหารเสริม
- ละเลยการพูดถึงผลข้างเคียงของการใช้อาหารเสริมเกินขนาด
-
ไม่อธิบายความแตกต่างระหว่างวิตามินดีจากธรรมชาติและสังเคราะห์
-
การวิจัยที่มีอคติ
- การศึกษาที่ได้รับทุนจากบริษัทผลิตภัณฑ์กันแดด
- เลือกนำเสนอผลการวิจัยเฉพาะด้านลบ
- ขาดการศึกษาระยะยาวเกี่ยวกับผลดีของแสงแดด
- ไม่เปิดเผยผลประโยชน์ทับซ้อนในงานวิจัย
การบิดเบือนในการรักษาทางการแพทย์
- แนวทางการรักษาที่พึ่งพายา
- เน้นการใช้ยามากกว่าวิธีธรรมชาติ
- ละเลยการแนะนำเรื่องการรับแสงแดด
- สั่งจ่ายอาหารเสริมโดยไม่จำเป็น
-
ไม่ให้ความสำคัญกับการปรับพฤติกรรม
-
การวินิจฉัยที่ไม่ครอบคลุม
- ไม่ตรวจหาสาเหตุจากการขาดแสงแดด
- มองข้ามความสัมพันธ์ระหว่างแสงแดดกับโรคต่างๆ
- ไม่ซักประวัติเรื่องการรับแสงแดด
- ละเลยการประเมินวิถีชีวิตที่หลีกเลี่ยงแสงแดด
ผลกระทบต่อการรักษา
- การรักษาที่ไม่มีประสิทธิภาพ
- การใช้ยาเกินความจำเป็น
- ค่าใช้จ่ายที่สูงขึ้นโดยไม่จำเป็น
- ผลข้างเคียงจากการรักษาที่ไม่เหมาะสม
-
การรักษาที่ไม่แก้ปัญหาที่สาเหตุ
-
ปัญหาสุขภาพที่ตามมา
- โรคขาดวิตามินดีที่เพิ่มขึ้น
- ปัญหาสุขภาพจิตจากการหลีกเลี่ยงแสงแดด
- ภาวะแทรกซ้อนจากการใช้ยาระยะยาว
- คุณภาพชีวิตที่ลดลง
ผลกระทบต่อสุขภาพจากความกลัวแดด
- ปัญหาการขาดวิตามินดี
- การระบาดของภาวะขาดวิตามินดีในประชากร
- ผลกระทบต่อสุขภาพกระดูก
- ความเสี่ยงต่อโรคภูมิแพ้และภูมิคุ้มกัน
-
ปัญหาสุขภาพจิตที่เพิ่มขึ้น
-
ผลกระทบทางสังคมและจิตใจ
- ความวิตกกังวลเกี่ยวกับการออกนอกบ้าน
- การจำกัดกิจกรรมกลางแจ้ง
- ความเครียดจากการต้องดูแลผิวมากเกินไป
- ค่าใช้จ่ายที่สูงขึ้นจากผลิตภัณฑ์ป้องกันแดด
การแก้ไขความเข้าใจผิด
- การให้ข้อมูลที่สมดุล
- นำเสนอทั้งประโยชน์และความเสี่ยง
- แนะนำวิธีการรับแดดที่ปลอดภัย
- สร้างความเข้าใจเรื่องความพอดี
-
ให้ความรู้เรื่องการป้องกันที่เหมาะสม
-
การปรับเปลี่ยนทัศนคติ
- เปลี่ยนจากการ "กลัวแดด" เป็น "เข้าใจแดด"
- สร้างความตระหนักถึงความสำคัญของแสงแดดต่อสุขภาพ
- ส่งเสริมการใช้ชีวิตที่สมดุลกับธรรมชาติ
- ลดอิทธิพลของค่านิยมผิวขาว
หลักการรับแสงแดดที่ถูกต้องตามแนวทางเฮลิโอเทอราปี

ระยะเวลาและความถี่
- เริ่มจากวันละ 10-15 นาที
- ค่อยๆ เพิ่มเวลา
วิธีการที่ถูกต้อง
- เปิดผิวให้สัมผัสแดดพอประมาณ
- ไม่ใช้สารกันแดด
- สังเกตการตอบสนองของร่างกาย
- ปรับตามสภาพอากาศและฤดูกาล
การประยุกต์ใช้เฮลิโอเทอราปีในชีวิตประจำวัน

กิจกรรมที่แนะนำ
- เดินเช้าหรือเย็น
- ทำสวนในช่วงเวลาที่เหมาะสม
- ออกกำลังกายกลางแจ้งเบาๆ
การผสมผสานกับการดูแลสุขภาพอื่นๆ
- การออกกำลังกาย
- การทำสมาธิกลางแจ้ง
- การทำกิจกรรมผ่อนคลาย
บทสรุป: กลับสู่สมดุลธรรมชาติ
เฮลิโอเทอราปีไม่เพียงเป็นการรักษาโรค แต่ยังเป็นแนวทางในการดูแลสุขภาพแบบองค์รวม การเข้าใจหลักการของเฮลิโอเทอราปีช่วยให้เราตระหนักว่า แสงแดดเป็นส่วนสำคัญของชีวิตที่สมดุล การหวนกลับมาใส่ใจการรับแสงแดดอย่างถูกวิธี จึงเป็นก้าวสำคัญสู่การมีสุขภาพที่ดีอย่างยั่งยืน
แสงแดดเป็น "เพื่อน" ไม่ใช่ "ศัตรู" ของสุขภาพ หากรู้จักใช้ให้เหมาะสม
Don’t trust , (must) Verify
ศึกษาเพิ่มเติมเรื่อง Heliotherapy : https://youtu.be/q5EX5XrR-2A
...................................... ข้อมูลสุขภาพดีๆที่ไม่มีค่าใช้จ่าย https://www.youtube.com/@fastingfatdentist . หากสนใจวิธีการดูแลสุขภาพตามแบบ IFF ปรึกษาส่วนตัว inbox มาสอบถามที่เพจ"หมออ้วนในดงลดน้ำหนัก"หรือ" fastingfatdentist"ได้เลยครับ .
ความน่ากลัวในการดูแลสุขภาพคือการที่เชื่อโดยไม่มีความรู้ .
.
IFF #IFF_talk #intermittentfasting #keto #Lowcarb #CD #plantbased #RemissionDiabetes #ร่างกายเราคือธรรมชาติไม่ใช่ยา #เบาหวานหายได้โดยไม่ต้องใช้ยา #หมอไหวของหมอแบบนี
-
 @ 30ceb64e:7f08bdf5
2024-12-15 02:10:28
@ 30ceb64e:7f08bdf5
2024-12-15 02:10:28Bitcoin is a medium of exchange, store of value, and unit of account. The unit of account piece really throws people through a loop.
Freaks say, but its too volatile, mimicking the financial advisors of yesteryear, not acknowledging the evident decay of their trusty accounting method, the method that dilutes your reality with the notion of inflation vs deflation. We live in a deflationary world, its only inflationary if your accounting metric sucks. If your not using bitcoin as a method to view prices, your method of viewing prices has been skewed, and skewed on purpose.
What's really interesting is how, our unit of measurement is exactly backwards. The fiat way of viewing finances is 180 degrees away from the reality of sound money price deflation that bitcoin brings. And at this point I would say that it is unstoppable. if your stacking bitcoin but pricing it in dollars and making dollar type moves, your stack will diminish due to your own inability to adapt. You'll give in to leverage schemes and strange loans, your attitude towards risk and gain will be off kilter. In a lot of cases people will fail to realize that they've already won, and now they just need to pull a satoshi, leave their life stacking to go on and do other things. We've been conditioned to be on a hamster wheel where we need to constantly think about growing our money at all cost and no matter how much we stack it will never be enough. I find bitcoin to be the exact opposite, where at some point, you might have stacked too much, you might find yourself with wealth so large that it breaks your mind, it might enlarge your ego, destroy your family. This sounds suspiciously like absolute power corrupts absolutely, which is something that I've become a bit more awry of, but to a certain extent......how much is enough anon? At what point does the ring of power consume you.
In conclusion "God Candle Approacheth" staying humble and stacking sats, while accounting for your stack in dollars, will give those freaks a rush of exhilaration unlike any they've likely had before. They will be awash in fortunes gained through the lazy doubt of haters, they will be vindicated and in most cases the fortune that they earned will be just and because they followed truth and because they had discipline and foresight and sugar and spice, and everything nice. The acceleration from lower middle class to top 1% will be a whiplash strong enough to sway the humbleness of most men.
In conclusion again (and hopefully this is the last one) Use bitcoin as a unit of account. You likely have already won the game. Stay humble and brace for impact on the moon.
originally posted at https://stacker.news/items/809878
-
 @ 502ab02a:a2860397
2024-12-15 01:14:23
@ 502ab02a:a2860397
2024-12-15 01:14:23แสงแดด วิตามิน D, A, K2-MK7 กับสุขภาพกระดูกและหลอดเลือด ว่าด้วยเรื่องของ DAK2 นั้นเคยเขียนไว้นานแล้ว แต่จำได้ว่าเป็นกึ่งๆบทความบ่นๆ แต่ไม่ได้อธิบายเป็นภาษามนุษย์นักครับว่า ตกลงจะหมายถึงอะไรกันแน่ ด้วยวาระโอกาสจะจบปี 2024 เลยคิดว่า นำมาปิดท้ายเนื้อหาหนักๆช่วงปลายๆของ season3 นี้กันดีกว่า
แสงแดด ไม่ใช่สิ่งที่ควรหลีกเลี่ยงเสมอไป แม้ว่าหลายคนจะกังวลเกี่ยวกับความเสี่ยงของโรคมะเร็งผิวหนัง แต่หากได้รับในปริมาณที่เหมาะสม แสงแดดเป็นสิ่งสำคัญที่ช่วยกระตุ้นกลไกของวิตามิน D ในร่างกาย ซึ่งทำงานร่วมกับ วิตามิน A และ วิตามิน K2-MK7 เพื่อดูแลสุขภาพกระดูกและหลอดเลือด รวมถึงช่วยลดความเสี่ยงจากโรคร้ายแรง เช่น โรคกระดูกพรุนและหลอดเลือดอุดตันครับ บทความนี้จะอธิบายถึงกลไกการทำงานของวิตามินเหล่านี้กับร่างกาย เพื่อส่งเสริมการดูดซึมแคลเซียม ลดการสะสมแคลเซียมผิดที่ และสร้างความเข้าใจว่าความเสี่ยงจากการตากแดดนั้น ต่ำกว่าที่หลายคนเข้าใจนักครับ คือ ถ้าไม่ชอบตากก็ไม่ต้องอ้างอะไรอื่นครับ ลองพิจารณาสิ่งที่ผมจะเล่าให้นี้ก่อนว่าซื้อมั๊ย ผมพยายามจะรวบรัดให้สั้นๆนะครับ
หลักการที่ผมมโนออกมาเป็นคำสั้นๆว่า DAK2 ซึ่งผมมักจะเรียกว่า แดก หรือเต็มๆคือ ตากแดดแล้วแดกด้วย คือกิจกรรมตากแดดของเรานั้น จะส่งผลดีได้อีกด้านนึงด้วย ถ้าคุณได้รับวิตามินครบทั้ง DAK2 ครับ เพราะว่า
-วิตามิน D เป็นรากฐานของการดูดซึมแคลเซียม วิตามิน D เป็นจุดเริ่มต้นของกระบวนการที่ช่วยให้ร่างกายดูดซึมแคลเซียมอย่างมีประสิทธิภาพและนำไปใช้อย่างเหมาะสม เมื่อผิวหนังได้รับรังสี UVB จากแสงแดด ร่างกายจะสังเคราะห์ วิตามิน D3 (cholecalciferol) วิตามิน D3 จะถูกเปลี่ยนเป็น calcidiol ในตับ และcalcitriol ที่ไต ซึ่งตรงนี้นะครับ มันจะถูกเปลี่ยนเป็น calcitriol รูปแบบที่ร่างกายนำไปใช้งานได้ ซึ่งเจ้า Calcitriol นี่แหละที่ ช่วยเพิ่มการดูดซึม แคลเซียม และ ฟอสฟอรัส จากอาหารในลำไส้ ทำให้มีแร่ธาตุเพียงพอสำหรับการสร้างและบำรุงกระดูก
-วิตามิน K2-MK7 รับบทผู้ควบคุมแคลเซียมในร่างกาย วิตามิน K2 ตัวนี้สำคัญ หายากและขาดมากที่สุดครับ โดยเฉพาะในรูปแบบ MK7 (menaquinone-7) มีบทบาทสำคัญในการนำแคลเซียมไปสะสมในกระดูกและป้องกันการสะสมในหลอดเลือด โดย K2 นั้นกระตุ้นโปรตีน osteocalcin ซึ่งทำหน้าที่ดึงแคลเซียมเข้าสู่กระดูก นอกจากนี้ K2 ยังช่วยกระตุ้น matrix Gla-protein (MGP) ซึ่งป้องกันการสะสมแคลเซียมไม่ให้ไปเกาะในหลอดเลือดแดงและเนื้อเยื่ออ่อน ดังนั้นการได้รับ K2 เพียงพอจึงช่วยลดความเสี่ยงของโรคหลอดเลือดอุดตัน
คำถามคือทำไมต้อง MK7???? นั่นเพราะ MK7 มีคุณสมบัติที่เหนือกว่า K2 รูปแบบอื่น เนื่องจากมีการทำงานในร่างกายได้นานกว่าวิตามิน K2 ตัวอื่นๆก่อนจะถูกขับทิ้งออกไป จึงช่วยให้เกิดผลลัพธ์ที่ยาวนานและมีประสิทธิภาพสูงที่สุด
-วิตามิน A ผู้สนับสนุนกระดูกและหลอดเลือด วิตามิน A (ในรูป retinoic acid) ทำงานร่วมกับวิตามิน D และ K2 เพื่อช่วยควบคุมการเจริญเติบโตของกระดูกและลดการสะสมแคลเซียมผิดที่ครับ โดยวิตามิน A จะกระตุ้นเซลล์สร้างกระดูก (osteoblasts) และช่วยปรับสมดุลของเซลล์สลายกระดูก (osteoclasts)ควบคุมการทำงานของเซลล์ทำลายกระดูก รวมถึงมีส่วนช่วยในการสร้างเซลล์เยื่อบุหลอดเลือด (endothelial cells) ให้แข็งแรง ช่วยลดการสะสมของคราบแคลเซียมในหลอดเลือด
เมื่อทำงานร่วมกับ วิตามิน K2 (ที่ป้องกันแคลเซียมสะสมในหลอดเลือด) จะช่วยลดความเสี่ยงของโรคหลอดเลือดอุดตัน แล้ววิตามิน A นั้นก็ยังช่วยเสริมสร้างเซลล์เยื่อบุหลอดเลือด ทำให้หลอดเลือดแข็งแรง ลดความเสี่ยงการสะสมของคราบแคลเซียม เมื่อร่างกายได้รับ วิตามิน A, D, และ K2 ร่วมกัน กระบวนการสร้างกระดูกและการสะสมแร่ธาตุในกระดูกจะมีประสิทธิภาพมากขึ้น
ข้อควรระวัง การได้รับวิตามิน A มากเกินไป (เกิน 10,000 IU/วัน) อาจขัดขวางการทำงานของวิตามิน D และเสี่ยงต่อการสูญเสียมวลกระดูก ดังนั้นควรได้รับในปริมาณที่เหมาะสม ไม่ใช่ว่าพอคิดว่าดีแล้วจัดกันแบบไม่ยั้งนะครับ อันนี้อันตรายนะ
สรุปการทำงานร่วมกันของวิตามิน D, A, K2-MK7 วิตามิน D ช่วยเพิ่มการดูดซึมแคลเซียมและฟอสฟอรัสเข้าสู่กระแสเลือด วิตามิน K2-MK7 ช่วยนำแคลเซียมไปสะสมในกระดูก และป้องกันการสะสมในหลอดเลือด วิตามิน A ช่วยปรับสมดุลการเจริญเติบโตและการสลายกระดูก พร้อมเสริมความแข็งแรงของเยื่อบุหลอดเลือด
อาหารที่ช่วยเสริมวิตามิน D, A, K2-MK7 ปกติเราจะท่องๆกันว่า ในเนื้อวัวตับวัว มีครบเกือบทุกอย่าง เว้นวิตามิน K2 เรามาลองดูตัวอย่างอาหารอื่นๆกันบ้างครับ วิตามิน D: ปลาแซลมอน, ปลาซาร์ดีน, น้ำมันตับปลา วิตามิน A: ตับ, ไข่ วิตามิน K2-MK7: นัตโตะ (ถั่วหมักญี่ปุ่น), ชีส, ไข่ไก่จากไก่ที่เลี้ยงปล่อย ส่วนที่มีคนถามว่า กิมจิหล่ะ คือ กิมจิ มีปริมาณวิตามิน K2 จริงครับแต่โดยปกติจะอยู่ในรูปแบบ MK4 ไม่ใช่ MK7 แคลเซียม: นม, กระดูกอ่อนต่างๆ, น้ำซุปกระดูก. ตับ ทีนี้พอเราเห็นภาพรวมแล้ว ก็ต้องบอกว่า จงเลิกมายาที่ต้องมานั่งท่องว่า ตากแดดเวลาไหนดีที่สุด เพราะคุณไม่ต้องไขว่คว้าหาอะไรที่ดีที่สุดเลยครับ คติของการตากแดดคือ ดีทุกเวลา เอาที่ว่าคุณไหวนั่นแหละ ไอ้ที่บอกว่าตากเช้าดีสุดนี่ ตากเช้าเท่านั้น เวลาอื่นห้ามตาก ตากแล้วจะเป็นมะเร็ง โคตรโม้ครับ อย่าเชื่อผมนะ คุณค่อยๆพิจารณา verify ไปทีละจุด ตากแค่เช้าจะได้อะไร ตากสะสมหลายๆเวลาได้อะไร แล้วประโยคที่ส่งต่อกันจังเลยว่า ตากแดดเช้ามันดีสุดจริงไหม
เลิกถามนะครับ ว่าตากเวลาไหนดีที่สุด มัน out แล้ว
#SundaySpecialเราจะไปเป็นหมูแดดเดียว #กูต้องรู้มั๊ย #PirateKeto
-
 @ 16d11430:61640947
2024-12-14 23:41:37
@ 16d11430:61640947
2024-12-14 23:41:37In a distant future, long after Earth’s surface had been scorched by greed and the wars of fiat money, humanity had fragmented across the multiverse. Each parallel reality bore the scars of divergent evolution—worlds where humans became bio-mechanical hybrids, insectoid overlords, aquatic philosophers, or even beings of pure energy. The fragile thread connecting these dimensions was cryptographic resonance, a universal constant that allowed the exchange of value. Amidst the ruins of worlds, a single trader wove between them: Kael Nexus, the Multiverse Trader.
Kael was no ordinary human. Born in the remnants of Earth Prime, he had grown up witnessing the collapse of fiat empires and the rise of the cryptographic machines—the towering monoliths of code that governed every transaction, recording them immutably across realities. These machines were the lifeblood of trade, storing not just wealth but memories, promises, and even fragments of souls.
Kael’s ship, The Lattice, was a relic of ancient engineering fused with quantum cryptography. Its hull shimmered with shifting blockchain imprints, each pulse a representation of transactions completed in other worlds. Powered by a hybrid Bitcoin Lightning reactor, The Lattice could navigate dimensional rifts, leaping between timelines to trade resources, technology, and knowledge.
World 1: The Arachniopolis
Kael’s first stop was a world where evolution had favored arachnid intelligence. Towering silk-webbed metropolises hung suspended in the skies. The Arachnians, ten-legged sentient beings, worshipped the Indira Net—a digital consciousness resembling a web of endless connections.
The Arachnians had no concept of physical currency; instead, they bartered using cryptographic spores encoded with genetic blueprints. Kael traded them a fragment of Dustchain, an ancient Bitcoin offshoot that could store memories. In return, the Arachnians offered a serum capable of rewiring DNA—a rare commodity sought by countless other species.
World 2: The Oceanic Collective
Diving into another reality, The Lattice emerged into an endless ocean world. Here, the inhabitants were bioluminescent creatures linked by a telepathic network called The Current. Unlike the Arachnians, they did not use cryptographic machines but instead created cryptographic songs—harmonic vibrations that encoded vast amounts of data in auditory waves.
Kael used a converter to translate his Bitcoin keys into a haunting melody. The transaction was instantaneous. In exchange for his keys, the Oceanics gifted him Pulse Crystals, used to amplify telepathic communication—a treasure for trade in less advanced worlds.
World 3: The Terraformers
On a desolate, volcanic world, Kael encountered the Terraformers, a race of silicon-based life forms that thrived in molten heat. Their civilization was dying, unable to sustain its energy needs. They sought Kael’s help, offering rare minerals in return for a key to survival.
Here, Kael deployed DamageAI, his cryptographic AI assistant, to build a smart contract that would power a fusion Bitcoin node, revitalizing the planet’s energy supply. The Terraformers agreed to a lifetime bond, recording their loyalty into the blockchain that spanned the multiverse.
World 4: The Machine Singularity
Finally, Kael arrived at Eidolon, a post-biological dimension where humanity had merged with machines, achieving digital immortality. Here, data and memories were the only currency, traded in vast quantum markets.
Eidolon’s council demanded Kael’s memories of the dying Earth Prime, offering him the coordinates to a newly discovered dimension—a lush utopia untouched by the scars of evolution. This world, they said, could become the final bastion of humanity.
Kael hesitated. To trade his memories would mean surrendering a piece of himself, the very core of his identity. But he had seen too many worlds on the brink of collapse. Humanity needed hope.
The Final Rift
Kael completed the trade, his memories dissolving into the ether of Eidolon’s markets. As The Lattice shifted to the new dimension, Kael glimpsed flashes of Earth Prime—its shattered cities, the dying whispers of fiat-driven despair. Yet, there was hope in his heart.
In the lush world beyond the rift, Kael found a species that had transcended evolution entirely. They were energy beings, capable of integrating all forms of knowledge. For them, cryptographic machines were relics of a bygone era, but they welcomed Kael with open arms, promising to guide the scattered remnants of humanity toward unity.
And so, the Multiverse Trader continued his journey, trading between worlds not for wealth but for survival, bridging the fractured dimensions with every cryptographic key he forged. Kael Nexus was not just a trader—he was a harbinger of humanity's rebirth, a voyager through the eternal blockchain of existence.
SciFi #Futuristic #Multiverse #CryptoFuture #Blockchain #PostApocalyptic #HyperModern #Cyberpunk #AI #Cryptocurrency #SpaceTravel #QuantumTech #ScienceFictionArt #InnovativeTech #DigitalRevolution #SciFiArt #VisionaryFiction #EvolvingHumanity #TechInnovation #Cryptoverse #Storytelling
-
 @ 7c765d40:bd121d84
2024-12-14 23:18:57
@ 7c765d40:bd121d84
2024-12-14 23:18:57I have a feeling gold bugs aren't going to enjoy this next chapter.
And the sad thing is that they are so damn close.
They've been fighting this fight for decades now.
They understand how broken our monetary system is.
But their stubbornness will be their demise.
In the last month alone, we've had some pretty catastrophic events in the gold market.
With bitcoin-friendly President Trump about to take office in the US, they are considering selling their gold reserves to purchase bitcoin.
According to Popular Mechanics, China recently discovered $83 billion worth of gold.
Damn I forgot about Popular Mechanics.
Their website looks like it's stuck in 1997 but the articles are all recent.
Anyways.
And the biggest news - coming from our favorite little country.
El Salvador announced a gold discovery worth approximately $3 TRILLION dollars.
This triggered a couple historic tweets from their President Bukele.
First quote tweeting the announcement "And we'll dilute that thing like there's no tomorrow."
And the next day quote tweeting another announcement "But what could they possibly do with that?"
And for anyone who isn't familiar with El Salvador (aka The Savior), they were the first country to make bitcoin legal tender.
After a few large smash buys, they have been buying 1 bitcoin every day.
You can verify this on their customized mempool website.
The market is about to be FLOODED with gold.
Peter Schiff is losing his damn mind, claiming bitcoin is a "national security threat."
The mainstream media talking heads are on a bitcoin war path.
OUR PETS HEADS ARE FALLING OFF.
Gold has historically been the best store of value that exists.
Why?
Because of it's scarcity.
Until April 2024, when bitcoin officially passed gold as the scarcest asset.
Gold (typically) has a 2% inflation rate.
Bitcoin, as of the latest halving, now has less than 2% inflation.
IF - and that's a big IF - countries start dumping their gold for bitcoin, what will happen to the market?
Countries and central banks are the largest holders of gold.
Who will pick up the slack?
How many 20 year olds will be lining up at their local gold shop to buy some pet rocks?
Gold has served it's purpose.
It was the best asset to store wealth.
Before bitcoin.
Bitcoin can also be sent anywhere in the world in a matter of minutes - for a very low fee.
Imagine trying to send 10 billion worth of gold across the world.
Bitcoin is also highly divisible.
You can't start shaving off a gold coin to pay for groceries.
Unless maybe the grocery stores will start putting scales at the til.
Haha.
And most importantly, especially when talking about governments and central banks, bitcoin is verifiable.
We have never been able to see or verify the gold reserves.
How much gold is really in Fort Knox?
We have absolutely no idea.
It requires trust.
How many people trust their government at this stage of the game?
Bitcoin on the other hand, can be easily verified.
This is important for the individuals, the banks, and the countries.
El Salvador has a website where you can verify their bitcoin holdings.
Check it out here!
We have no idea how much gold really exists.
We have an idea, but it's not very accurate - clearly.
If they found $3 TRILLION worth of gold in the small country of El Salvador, how much gold you do think is waiting to be found on Mars?
And how much bitcoin will we find on Mars?
As a gold and silver holder myself, I am making the full switch into bitcoin.
It just makes the most sense.
And human eventually switch to the idea that makes the most sense.
PROJECT POTENTIAL - You can now find the expanded audio versions of these on the new podcast - Project Potential! I will be sharing the video versions here for the LITF members but you can also find it for free on Spotify and of course Fountain!
Here is the link to Episode 008 on Fountain: https://www.fountain.fm/episode/nQb5z3PolahVwsPbYX4r
Have a great day everyone! And remember, the only thing more scarce than bitcoin is time!
Jor
-
 @ eac63075:b4988b48
2024-12-14 22:06:10
@ eac63075:b4988b48
2024-12-14 22:06:10BlueSky, a social network built on the decentralized AT Protocol (Authenticated Transfer Protocol), is revolutionizing content moderation by empowering users and communities to manage their own experiences. Unlike traditional platforms that centralize control, BlueSky adopts a modular and customizable approach, balancing freedom of expression with safety.
https://www.fountain.fm/episode/mtp0RxPeuBpCozcSgfct
The Jesse Singal Case and the Community’s Response
Recently, the account @jessesingal.com was accused of publishing content considered homophobic and transphobic. Although some users questioned whether these posts violated BlueSky’s Terms of Service, the platform chose not to ban the account. Instead, it relied on community tools to limit the reach of these posts.
Individual users blocked the account and subscribed to community-managed block lists, significantly reducing the visibility of Jesse Singal’s content. This decentralized approach demonstrated the effectiveness of a model in which the community regulates content without centralized intervention.
BlueSky’s Five Layers of Moderation
BlueSky implements a multi-layered moderation system, offering users tools to customize their experiences practically and efficiently:
-
Personal Blocking and Muting\ Users can block or mute unwanted accounts, individually adjusting the content they wish to see.
-
Community Block Lists\ By subscribing to block lists created by the community, users can share common moderation criteria, optimizing content filtering.
-
Curated Feeds\ Subscribing to personalized feeds allows users to consume content filtered by curators or algorithms, creating a safer and more tailored experience.
-
Account Removal on the Personal Data Server (PDS)\ In extreme cases, servers can directly delete accounts from their databases, preventing them from publishing or accessing the network.
-
Ozone: Advanced Moderation Tool\ Ozone is an integrated tool that enables advanced moderation strategies, combining various resources for greater efficiency.
BlueSky’s Moderation Architecture
Moderation on BlueSky is based on an open labeling system. This architecture allows anyone to assign labels to content or accounts, such as “spam” or “NSFW” (not safe for work). These labels can be automatically generated by third-party services or manually applied by curators and administrators, offering flexibility for communities and individuals to customize their experiences.
The Role of the Community in Content Regulation
In decentralized platforms like BlueSky, the community plays a central role in self-regulation, minimizing reliance on a centralized authority to moderate content. This decentralization distributes responsibilities and reduces the risks of institutional bias, often seen in centralized companies that may reflect specific interests at the expense of plurality.
Centralized platforms often censor or promote content based on corporate agendas, compromising user trust. BlueSky’s model prioritizes autonomy, allowing the community itself to determine what is relevant or acceptable.
With 25 million users registered within weeks, BlueSky remains committed to its mission of regulating not freedom of expression, but the reach of certain publications. Tools like block lists, curated feeds, and Ozone are tangible examples of how the platform is building a decentralized and inclusive ecosystem.
Challenges and Opportunities of Decentralization
Despite its merits, decentralization presents challenges. Educating users about available tools and protecting vulnerable communities from harmful content are complex tasks, especially in a rapidly growing environment.
On the other hand, the decentralized model offers significant advantages. It enhances transparency, fosters trust among users, and reduces reliance on a central authority. On BlueSky, users shape their own experiences, ensuring greater freedom without sacrificing safety.
Conclusion
BlueSky is paving the way for a new era in social networks with a decentralized moderation model that empowers users and promotes shared responsibility. Aligned with principles of freedom and inclusion, BlueSky combines advanced technology and community collaboration to create a safer, more democratic, and adaptable space.
Although still in its early stages, BlueSky offers a promising model for the future of social networks, where reach—not freedom of expression—is the true focus of regulation.
-
-
 @ 62a6a41e:b12acb43
2024-12-14 20:45:59
@ 62a6a41e:b12acb43
2024-12-14 20:45:59I would like to start by saying that I do believe that Nostr will become the generalistic social network of the future (at least one of the clients). This post is just a perspective of why perhaps that might not even matter in the end.
Every cultural change starts in a tribalistic way. People that agree with each other regularly interacting, exchanging ideas, etc.
Socialism, LGBT, ecological groups, etc, it's all organized tribes. People regularly interacting with each other with similar ideas. Going to events, workshops, bars, dinners, etc, etc. They then create change in the world by integrating with the power networks, as we've seen in history. It's all top down and there's usually lot of cultural weight. For example, the Bolsheviks had to use a lot of cultural projects to legitimize their power after the 1917 Russian Revolution. The point is it's always a minority changing culture. Gramsci, the idea of Cultural Hegemony. It never fails. The most organized minority tribe always changes the culture.
In Marxist philosophy, cultural hegemony is the dominance of a culturally diverse society by the ruling class who shape the culture of that society—the beliefs and explanations, perceptions, values, and mores—so that the worldview of the ruling class becomes the accepted cultural norm.[1] As the universal dominant ideology, the ruling-class worldview misrepresents the social, political, and economic status quo as natural, inevitable, and perpetual social conditions that benefit every social class, rather than as artificial social constructs that benefit only the ruling class.[2][3]
https://en.wikipedia.org/wiki/Cultural_hegemony
This is obviously sick, because it's all authoritarian and culture should never be top down. Real culture should always be free, bottom-up. (More universalist in that sense).
So in that sense it makes sense that Nostr and Bitcoin are connected and that there's a kind of tribe forming around it too. And in that sense the real point is;
It doesn't really matter how many people are on Nostr, what truly matters is how engaged and connected to each other they are. Is there engagement? Yes. Then it will work.
This is currently more of a tribe than a generalistic social network. It just happens to be the best technical social network (because it's uncensorable).
And not just that, our tribe is the most diverse tribe. The most diverse tribe always wins because it is by definition the tribe with the most universalistic philosophy, the most open, the most open to innovation, and thus the most universalistic. The most universalistic philosophy always wins.
A great example is Reddit and how that creates the intelectual culture of our world, wrongly, distorted and censored as we know. Nostr might become or power something like that. The homebase of the most powerful and organized tribe in the world.
-
 @ df478568:2a951e67
2024-12-14 20:27:18
@ df478568:2a951e67
2024-12-14 20:27:18"Mathematics is the language in which God has written the universe..."
--Nicholas CopernicusBitcion Is Poetry
I fell in love with word-smithing in the eleventh grade after reading Shakespeare's sonnets because Iambic pentameter is the edge effect where the languages of mathematics and English meet. I thought this was the coolest thing in the world. This inspired me to write my own Sonnets. I even gave one to my hopeless crush. She wasn't as impressed, but in retrospect, poetry was my first love.
I had some flings with fiction, and a few blogs, and in 2014 fell in love with a younger, sexier form of mathematical poetry--Bitcoin: A Peer-To-Peer Electronic Cash System. She taught me what Copernicus observed so long ago. Mathematics is the language of the universe. When I first read it, I did not understand most of the math. I had no idea what a "digital signature" was. I never had the word hash without the words corned beef in front of it, but I believed fractional reserve banking and bailouts helped the rich get richer and the poor get poorer. My limited background knowledge from messing around with Napster and BitTorrent in my younger years gave me enough background knowledge to understand that Satoshi's white paper was an important historical document. He wrote in plain English, math, and C+ explaining Bitcoin in three languages like the Rosetta Stone.
"To implement a distributed timestamp server on a Peer-To-Peer basis we will need to use a proof-of-work system similar to Adam Back's Hashcash, rather than newspaper or Usenet posts."
--Satoshi Nakamoto, Bitcoin: A Peer To Peer Electronic Cash System
Proof Of Poetry
Adam Back discovered hashcash. Satoshi cited this in the White paper. Despite its name, hashcash was not a "cryptocurrency." Hashcash is more like a digital stamp. Stamps have a cost, of course, and so does hashcash. We can't hand a piece of paper with a portrait of some dude wearing a wig to a computer, of course. We must pay for electronic stamps with the only fungible currency computers can use, electricity. This makes electricity the de facto currency for computers. Therefore, you must pay for the hashcash stamp with electricity. As anyone who has been shocked by their electricity bill in the summer knows, electricity has a real cost. The beauty of hash cash is you wouldn't notice a difference in your electric bill if you sent a dozen emails a month, but if you spammed the whole World Wide Web with a chain letter, your electric bill will drain your bank account. Hashcash is a stamp you pay for with computational power, which requires your computer to work. That work can only be paid for with electricity.
Proof Of Work is a little different on hashcash than bitcoin because it uses SHA1 and bitcoin uses SHA256, but here's an example of how it works from hashcash.org:
When you type this into the command line:echo -n 0:030626:adam@cypherspace.org:6470e06d773e05a8 | sha1The computer will show you this answer:
00000000c70db7389f241b8f441fcf068aead3f0See those C00l-looking zeros in the front? Satoshi called them “zero bits.” Whenever someone sends a bitcoin transaction, it goes to the mempool. This is like Purgatory for bitcoin transactions. A bitcoin doesn't get its wings right away like when a bell rings on It's A Wonderful Life. It needs to be confirmed like a Catholic. If it's not confirmed, it does not reach heaven. Transactions don't have an actual afterlife in the clouds, These transactions are trying to get into the precious, scarce block space of the bitcoin timechain. Miners include different transactions in a block template and add a nonce, a number used once...I'm gonna stop myself here before readers die of boredom. It's just math. If you're interested in seeing this math in action play around with this website. You can type whatever you want. The math works on all ASCII characters because each letter or symbol represents a number.
If we hash the code from hashcash.org above using the SHA1 calculator it gives us this result.
If we add a question mark to this text, we get this result.
We see a different 40-character combination. This is the math used to verify data in cybersecurity, and bitcoin is no different. To change the math requires changing every single one of these transactions since January 3rd, 2009. How horrifying would your electric bill need to be to accomplish this? I don't know, but It's not likely to happen since honest miners are rewarded with fees, These fees are like tribute transactions must pay to get out of purgatory, Some transactions pay more, and some try to pay less. The miners are incentivized to let the more expensive transactions to go through the pearly white gates of the bitcoin time chain.
Adam Back's email is not a transaction, but those leading zero bits are the backbone of the bitcoin time chain. If you hash my full legal name with SHA1, we get this result
02c53da577460a2e8eead6e85da88199c64eb1bd. If we hash it with SHA256, I see two zero bits.0024f0a28bf81851ed8490c4e87173f8790bd9d8ea9423442114d25ad7137f51Pretty cool, right?These zerobits are also found in the bitcoin timechain. Look at the blocks 87402 through 874039:
https://mempool.marc26z.com/block/0000000000000000000252449e143c01d95b535c7f7a5aa0c321d689ee3bfcb7 https://mempool.marc26z.com/block/000000000000000000020ce9cb6d4ad0363aa3992f40739e794a749cfbeea74d https://mempool.marc26z.com/block/0000000000000000000055c358a666b6188349787741e4d51a0f1d3c60e5f8ae https://mempool.marc26z.com/block/00000000000000000000f17afb5f4bcab00c75dea27659c9b596878763c83533 https://mempool.marc26z.com/block/00000000000000000000c09a854ef63d9b99594997d3f0b8fa7229944b8ea3cb
Notice how each line a from an instance of mempool that I run from a Start9 server has zerobits in the front. This is because bitcoin uses the same mathematical poetry that Adam Back Discovered in 1997. It's elegant, has a pattern, dare I say rhythm, and looks like a mathematical sonnet.

Look at those last two lines. Like zerobits repeated in the bitcoin timechain, the words So long are repeated at the beginning of lines 13 and 14. Bitcoin looks like poetry because bitcoin is poetry.
The Difficulty Adjustment Is Poetic Justice
Whenever a miner produces a hash with the required amount of zerobits to send the transactions from the mempool purgatory to the place where the chosen math spirits hang out in the p2p distributed networking cloud, one more block is added to the timing chain. It is called a "chain" because the transactions are also hashed with the block header from the previous block. This verifies that each transaction is valid and easily verifiable with a single calculation which means it can be validated on cheap computers like Raspberry Pi's, but to be honest, you're better off with a better computer if you don't like pulling your hair out. The problem is money has an infinite demand. This is why the axiom, "You can never be too rich or too skinny" exists. Everybody loves money and is incentivized to get as much of it as they can as early as they can. This begs the question, how did Satoshi make sure Bitcoin is for everybody and not just the OG Cypherpunk nerds? He discovered the difficulty of adjustment.
At this point, most people have heard the story about Lazzlo buying two pizzas for 10,000 whole Bitcoin. It is often touted as the worst investment in history by the mainstream media, but journalists focus on the sensational and miss the subtleties of this story since they are experts in journalism, but not so well-versed in cryptography, a branch of mathematics that no one is taught in high school and only the nerdiest of nerds tend to learn it in college. The lesser-known part of the story is Lazzlo was also the first person to mine Bitcoin using ASIC chips. ASICs were used well by IT professionals well before bitcoin was discovered, but Lazzlo learned he could mine bitcoin much faster with these specialized chips than with a laptop. As the first person to figure this out, he must have had an extremely unfair advantage, so why couldn't he just mine all 21 Bitcoin in a matter of months? He was limited by the Difficulty Adjustment.
Here is how it works:- Every hour we can expect 6 blocks- Every Day we can expect 24x6 blocks or 144 blocks- Every week, we can expect 1008 blocks- Every two weeks, we can expect 2016 blocks.
At the end of 2016 blocks, if blocks are mined faster than this, the math problem miners try to solve becomes more difficult to slow them back down to ten minutes. When Lazzlo ramped up his bitcoin production, he could only have an unfair advantage for 2016 blocks. Let's say he mined 90% of the block within the first week. Good for him, but now his ASICS mining slows down because the blocks become much more difficult to mine. His fancy miner essentially must find more zerobits. It's a little more complex than this, but that's the non-boring gist of the story.Without Satoshi's discovery of the difficulty adjustment, the Cypherpunks like Lazzlo would have mined all 21 million bitcoin before the first 210,000 blocks. The difficulty adjustment makes the distribution fair because the block subsidy limits how much Bitcoin can be created every ten minutes and that amount is cut in half every 4 years.
"Total circulation will be 21,000,000 coins. It'll be distributed to network nodes when they make blocks, with the amount cut in half every 4 years. First 4 years: 10,500,000 coins next 4 years: 5,250,000 coins next 4 years: 2,625,000 coins next 4 years: 1,312,500 coins etc... When that runs out, the system can support transaction fees if needed. It's based on open market competition, and there will probably always be nodes willing to process transactions for free."
-Satoshi Nakamoto
This is poetic justice.
The Lindy Effect of Poetry
The OG version of the introduction to The Bitcoin Standard: The Decentralized Alternative To Central Banking by Saifedean Ammous, was written by Nassim Nicholas Taleb. Taleb has since abandoned bitcoin and Michael Saylor re-wrote the Introduction, but Nassim still has a great concept called the Lindy Effect. The basic premise accordion to Wikipedia is, "The longer a period something has survived to exist or be used in the present, the longer its remaining life expectancy." This is often used by Bitcoiners as a steel-man argument against shitcoins. The argument goes, Bitcoin has been around the longest, so it is more likely to outlast the shitcoins. I don't disagree with that statement, but bitcoin is poetry and poetry has an even more pronounced Lindy Effect. Shakespeare died in 1616, yet his work survives over four centuries later. Those sonnets I fell in love with are older than the United States of America. Many of his clever phrases like "dead as a doornail" are part of the English vernacular. The English language would be much different if not for Shakespeare.

Bitcoin is almost 16 years old, but about every ten minutes, a new line of bitcoin poetry is written in the form of a bitcoin block. No one knows for sure, and I do not have a crystal ball, but it would not surprise me if nerds like me admire the poetry of bitcoin at block 21,000,000. This is every Bitcoiner's favorite number, but the 21 millionth block will be produced about 400 years from the Genesis Block. We, the ride-or-die bitcoin freaks, are optimistic. We believe bitcoin will exist 400 years from now in the same way Shakespeare's Sonnets survive. Bitcoin lingo is already slipping into the wider English Vernacular. A decade ago, nobody but grumpy gold bugs and geeky bitcoiners used the term "fiat." Fiat is now part of everyday parlance.
The mainstream media has reported that Bitcoin has died at least 477 times according to 99Bitcoins. We, the people running bitcoin, disagree. We do not believe bitcoin will die anytime soon. We think it will last generations to come. We expect it to be around hundreds of years from now like Shakesphere's sonnets, maybe even thousands of years from now like the Rosetta Stone. That's why it has captured the imaginations of so many nerds. We are currently in an age where most people think of bitcoin as an investment, but bitcoin is not an investment like a stock or bond. Bitcoin is an investment like a masterpiece. It is more in the category of a Mona Lisa. Imagine if you had a page of Romeo and Juliet that was hand written by William Shakespeare. Best of all, you could verify that it was written by Shakespeare every ten minutes. How much would that be worth now that Shakespeare has been pushing daisies for over 400 years? What if you could send that page written by Shakespeare to anyone in the world in ten minutes? Do you think anyone would be interested in one of those pages?
Bitcoin is a poem being written as we speak. This poem, written in math and translated into C++ code, was written by Satoshi Nakamoto. It is 94.26% finished. Current estimates project this poem will be finished on March 1, 2, 2138* You can buy about ten tiny pieces of this poem for about a penny. Sure, you could have bought 100 small pieces of this poem for a penny 7 years ago, but we are still early in the scheme of things.
"It might make sense just to get some in case it catches on. If enough people think the same way, that becomes a self-fulfilling prophecy."
-- Satoshi Nakamoto
-
 @ 78c90fc4:4bff983c
2024-12-14 19:00:14
@ 78c90fc4:4bff983c
2024-12-14 19:00:14Cynthia Chung ist Präsidentin und Mitbegründerin der Rising Tide Foundation (zusammen mit ihrem Ehemann Matthew Ehret, der am 4. September 2024 als Gastredner des Aletheia Science Forum über „Die britischen Wurzeln des Deep State verstehen“ sprach, aufgezeichnet hier: https://www.wissenschaftstehtauf.ch/Matt_Ehret_20240904.mp4 ).\ \ Cynthia ist die Autorin der Bücher „The Shaping of a World Religion“ und „The Empire on Which the Black Sun Never Set,“ sowie Mitautorin der Buchreihe „The Clash of the Two Americas“.\ \ Ihre Substack-Seite „Through A Glass Darkly (https://cynthiachung.substack.com)“ hat über 11.000 Abonnenten. Sie schreibt über eine Vielzahl wichtiger Themen, die von geopolitischer Geschichte bis hin zu Kultur, Wissenschaft und Kunst reichen.\ \ In ihrem Vortrag konzenteriert sich Cynthia auf die Operation Gladio, das geheime „Stay-behind“-Netzwerk bewaffneter Widerstandsorganisationen, das während des Kalten Krieges in Westeuropa gegründet wurde.
Solche historischen Einblicke können uns in der heutigen Zeit helfen, uns durch die Stürme zu navigieren, die die Zivilisation erneut bedrohen.\ \ Einführung von Stefan Heeb https://www.proethica.ch
Weiterführende Analysen:
Daniele Ganser: NATO Geheimarmeen in Europa

Die NATO und der rechtsextreme Staatsterror
-
 @ edeb837b:ac664163
2024-12-14 17:28:26
@ edeb837b:ac664163
2024-12-14 17:28:26In today’s fast-paced financial world, staying on top of market trends, tracking trades, and learning from top investors is more important than ever. With NVSTly’s mobile app, available on both iOS and Google Play, you can access all of these features and more right from your smartphone. Whether you’re a new trader or an experienced investor, NVSTly is designed to empower you with the tools you need to track, share, and copy trades in real-time — all from the convenience of your mobile device.
What is NVSTly?
NVSTly is a powerful social investing platform that allows retail traders to track, share, and copy trades across a variety of financial markets, including stocks, options, forex, cryptocurrency, and more. Through a unique integration with Discord, NVSTly provides real-time trade tracking and insights, allowing traders to follow, learn from, and interact with a global community of investors.
Key Features of the NVSTly Mobile App
1. Track and Share Your Trades
With the NVSTly mobile app, you can easily track all your trades across multiple markets. Whether you’re trading stocks, options, forex, or cryptocurrency, you can manually submit your trades and view detailed insights, including the performance of your positions. Want to share your trades with your followers? It’s as easy as a few taps. The app allows you to post your trades to the global feed where other traders can follow your actions in real-time.
2. Discover Top Traders
If you’re looking to learn from the best, NVSTly offers a unique leaderboard feature that ranks top traders globally. You can see who is consistently performing well in your market of interest and follow their trades for insights. The app also includes a “follow” feature that lets you receive notifications whenever a trader you admire executes a new position.
3. Real-Time Market Insights
NVSTly gives you access to real-time market data to validate your trades. Whether you’re analyzing forex price movements or checking the latest stock trends, the app ensures that you have the most accurate information at your fingertips. With a variety of data sources integrated into the platform, you can make informed decisions, whether you’re in the office or on the go.
4. Trade Insights and Performance Stats
The NVSTly mobile app doesn’t just track your trades — it helps you analyze them. Each trade comes with detailed insights such as average gain/loss, total profit/loss, and other key performance indicators. This helps you assess your trading strategy and fine-tune your approach as you go.
5. Brokers Integration
For those who want a seamless experience, NVSTly supports broker integrations, allowing you to track your real-time trades automatically. While optional, this feature makes managing your portfolio even easier by syncing your brokerage account with the app. Whether you’re using Webull or another supported platform, NVSTly has you covered.
6. Educational Resources
The NVSTly app is not just about tracking trades — it’s also about improving your trading knowledge. The platform offers access to educational resources, including market analysis, trading tips, and insights from top traders. Whether you’re a beginner or an advanced trader, the NVSTly app helps you grow your knowledge and skills.
Why Choose the NVSTly Mobile App?
- Completely Free: NVSTly offers all of its features at no cost. No paywalls, no hidden fees — just powerful tools for traders who want to succeed.
- All-in-One Trading Solution: Whether you’re tracking your trades, analyzing market data, or following the top traders, NVSTly brings it all together in one easy-to-use app.
- Available on iOS and Google Play: No matter what type of smartphone you use, NVSTly is there.
Download the app today from the App Store or Google Play to start your journey with the leading social investing platform.
How to Install NVSTly’s Mobile App
Installing the NVSTly mobile app is quick and simple. Just follow these steps:
- For iOS Users: Open the App Store, search for “NVSTly,” and tap the “Download” button.
- For Android Users: Open Google Play, search for “NVSTly,” and tap the “Install” button.
Once installed, open the app, sign in or create an account, and start exploring everything NVSTly has to offer. Track your trades, follow top traders, and dive into the world of social investing — all at your fingertips.
Conclusion
NVSTly’s mobile app is the perfect tool for traders who want to stay ahead of the game. Whether you’re tracking market movements, sharing your trades, or learning from others, NVSTly offers everything you need to make informed decisions and succeed in your investing journey. Download the app today and join a growing community of traders who are transforming the way they invest.
Happy trading!
NVSTly is available for free on web, mobile devices (iOS & Google Play), and is fully integrated with Discord via a unique bot- the only of it’s kind and available to any server or trading community on Discord. Or feel free to join a community of over 40,000 investors & traders on our Discod server.
-
 @ b8a9df82:6ab5cbbd
2024-12-14 16:19:36
@ b8a9df82:6ab5cbbd
2024-12-14 16:19:36Four weeks after Adopting Bitcoin wrapped up, I find myself back in Buenos Aires. While one of the main reasons for staying is avoiding the dreary Berlin winter, the other, much stronger reason, is the people.
Anyone who knows me knows I’m a beach person through and through—dreaming of one day living in a house by the ocean. Argentina, with its economic quirks and geographical realities, isn’t exactly the ideal spot for that dream. Yet, here I am again, drawn not by the landscapes but by something far more meaningful: its people.
When I first wrote about my experience at Labitconf, I mentioned "LaCrypta" a local Bitcoin community that captured my heart. For those unfamiliar, the name might sound like it’s tied to crypto, but it’s not—it simply means “The Crypt.” And when you visit their physical space in the heart of Buenos Aires, the name suddenly makes perfect sense.
La Crypta isn’t just a community; it’s the beating heart of Bitcoin culture here. It’s a group of passionate people dedicated to development, education, and sharing knowledge about Bitcoin and the Nostr ecosystem. Their mission goes far beyond tech—it’s about empowerment, collaboration, and creating a space where ideas flourish.
Before I arrived in Buenos Aires, I had already worked with some of the La Crypta crew remotely. From the very start, they were more than helpful—honestly, they saved me more times than I can count. Organizing, finding suppliers, translating, navigating cultural nuances—things that would’ve been impossible as a foreigner were made smooth thanks to their constant support.
Even when cultural differences came into play, they did their best to accommodate my eager German punctuality. Sure, we had a couple of missed calls here and there (they’re South American, after all!), but we found a rhythm, and I learned to relax and embrace their way of doing things.
 I’ll never forget walking into the physical space for the first time. The house itself is a marvel—a 100-year-old gem tucked into the bustling city, its walls whispering history. Interestingly, it was originally built by Germans (I could tell right away), and every corner is rich with quirks and stories. Newcomers are given a guided tour, learning about the house’s past and its idiosyncrasies, which they’re then responsible for passing on to the next wave of visitors. It’s a brilliant tradition, one that fosters a sense of connection to the place.
I’ll never forget walking into the physical space for the first time. The house itself is a marvel—a 100-year-old gem tucked into the bustling city, its walls whispering history. Interestingly, it was originally built by Germans (I could tell right away), and every corner is rich with quirks and stories. Newcomers are given a guided tour, learning about the house’s past and its idiosyncrasies, which they’re then responsible for passing on to the next wave of visitors. It’s a brilliant tradition, one that fosters a sense of connection to the place.The charm of La Crypta’s space is undeniable—a century-old house surrounded by modern skyscrapers, standing out like a time capsule in the middle of the city. Of course, not everyone loves it. The neighbors occasionally complain about the raucous parties, even calling the police. But, as I’ve learned, in Argentina, there’s always a workaround for things like that.
 The real magic, though, isn’t in the house—it’s in the people. After weeks of working together remotely, meeting them in person for the first time was something special. There’s nothing quite like hugging the people you’ve shared so much time, effort, and anticipation with, knowing how deeply they care.
The real magic, though, isn’t in the house—it’s in the people. After weeks of working together remotely, meeting them in person for the first time was something special. There’s nothing quite like hugging the people you’ve shared so much time, effort, and anticipation with, knowing how deeply they care.They welcomed me with open arms, not just as a collaborator but as a friend. From day one, they’ve been my mental and emotional support system, offering far more than help with logistics. Their generosity, warmth, and genuine care reminded me that some of the most valuable things in life aren’t tied to money—they’re tied to human connection.
We bonded in so many ways, but nothing quite tops their initiation ritual: mate. For the uninitiated, mate is a traditional South American drink with a very specific etiquette. You don’t say “thank you” unless you’re done, you don’t stir the straw, and, naturally, I did everything wrong at first. But despite their teasing, I genuinely fell in love with mate, even if they still can’t believe me!
A home away from home
As I write this, just 10 days before Christmas, I’m missing my family and friends back home in Berlin. On quiet Saturday mornings like this, I wish I could just jump on a plane and hug them, feel the warmth of familiarity. But even in these moments of longing, I find comfort here. The people of La Crypta have become a surrogate family, filling my heart with their kindness and making the distance feel a little less heavy.
This experience has been life-changing. No matter where I go from here, I’ll carry a piece of La Crypta and Buenos Aires with me. For anyone who ever has the chance to visit, I urge you to experience this for yourself. The people, the place, the culture—it’s something that can’t be explained, only felt.
It’s not just a community; it’s a family. And for that, I’ll forever be grateful.
-
 @ c2827524:5f45b2f7
2024-12-14 15:57:50
@ c2827524:5f45b2f7
2024-12-14 15:57:50L’oggetto misterioso
Nostr, che in realtà è N.O.S.T.R., il cui acronimo significa Notes and Other Stuff Transmitted by Relay, è un protocollo di comunicazione nato da pochissimi anni, che promette decentralizzazione e incensurabilità. La maggior parte degli utenti internet non conosce il significato di queste due promesse, per motivi che non verranno analizzati qui (DYOR), ma decentralizzazione e incensurabilità sono tanto importanti quanto la libertà che ne consegue.
Decidere di usare il protocollo Nostr è senz’altro facoltativo e dovrebbe essere preso in considerazione per una migliore conoscenza del web. Quanto meno giudicare Nostr inutile a prescindere è un errore.
Incensurabilità
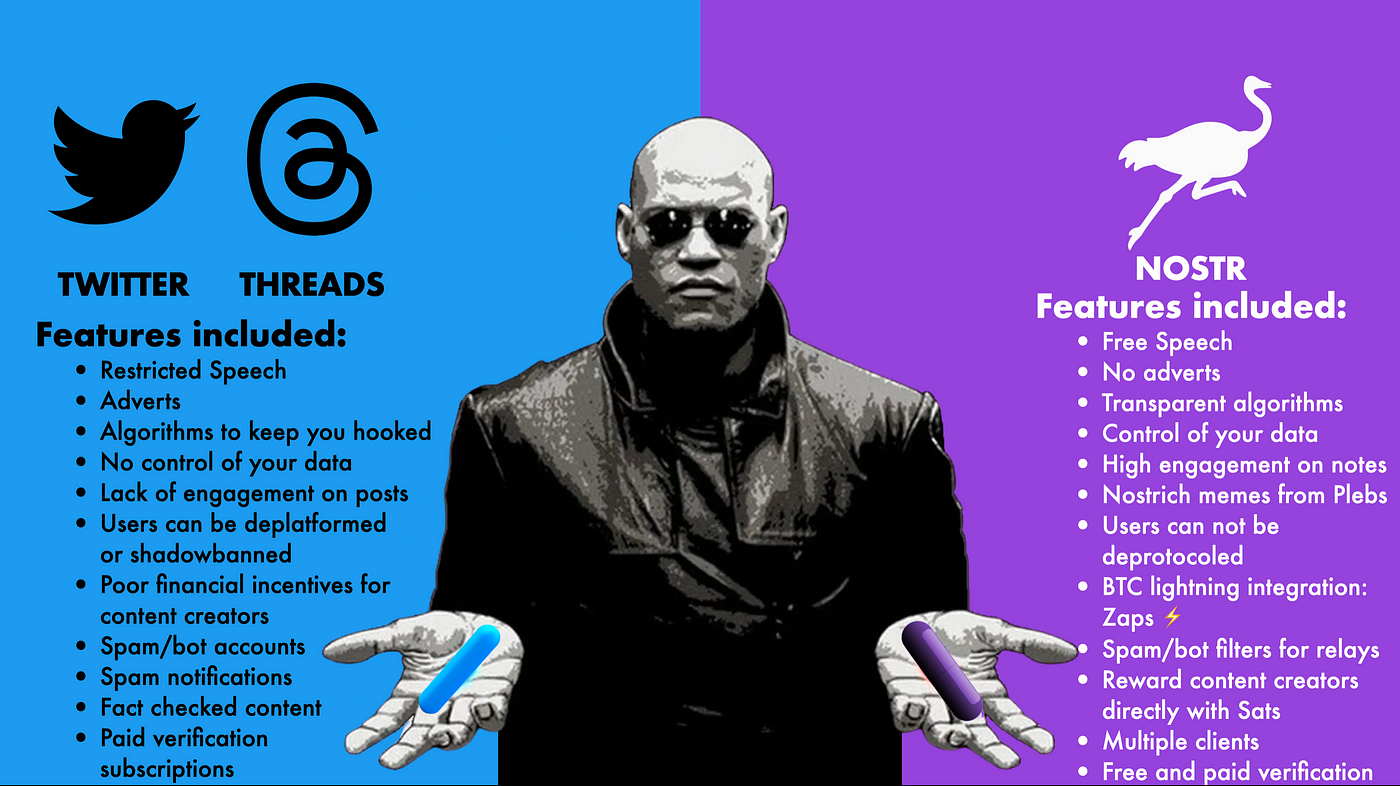 Notes and Other Stuff Transmitted by Relay è già l'essenza: l’identità e i dati non risiedono in uno specifico server centralizzato, ma su tanti piccoli serverini, i relay, che trasmettono le note (i post) scritte da un autore/un’autrice.
Notes and Other Stuff Transmitted by Relay è già l'essenza: l’identità e i dati non risiedono in uno specifico server centralizzato, ma su tanti piccoli serverini, i relay, che trasmettono le note (i post) scritte da un autore/un’autrice.Questo è ciò che accade anche con i social media tradizionali, salvo il fatto che tutte le piattaforme come ~~facebook~~ o ~~twitter~~ possono decidere di cancellare l’identità digitale di un utente, eliminandolo dai propri server.
Su Nostr NO.
Il singolo runner del relay può certamente decidere di bannare una determinata identità digitale, perché magari pubblica contenuti non graditi. Questi stessi contenuti, però, resteranno visibili su altri relay e quindi fruibili per i relativi follower. Infine, si può installare il proprio relay e a quel punto solo un idiota si bannerebbe da solo.
Tue le chiavi, tua l’identità
 I primi abitanti di questo piccolo universo hanno deciso di auto-definirsi Nostriches.
I/le Nostriches devono solo creare una coppia di chiavi, privata e pubblica.
La chiave pubblica, npub, è l’identità digitale dell’utente.
Dice effettivamente chi sei e aiuta gli altri utenti a trovarti.
I primi abitanti di questo piccolo universo hanno deciso di auto-definirsi Nostriches.
I/le Nostriches devono solo creare una coppia di chiavi, privata e pubblica.
La chiave pubblica, npub, è l’identità digitale dell’utente.
Dice effettivamente chi sei e aiuta gli altri utenti a trovarti.La chiave privata, o nsec, è la prova crittografica dell’identità digitale e questo è già un bel salto di paradigma rispetto al più diffuso sistema costituito dalla combinazione username/password. Non esistono due chiavi private uguali, quella generata per ogni singolo utente è unica ed è da quella (solo da quella e nessun’altra) che poi viene derivata la chiave privata.
Il protocollo Nostr permette, quindi, di essere i proprietari della propria identità digitale.
Ed è bene ribadire questo concetto: l’identità digitale è solo dell'utente, non è delle aziende che gestiscono il social media di turno. Lo stesso principio si applica ai dati e ai contenuti pubblicati, che appartengono ai legittimi autori e non alle piattaforme.
Già… le piattaforme
Ma quindi, come funziona Nostr? Semplice. Ci sono moltissimi client, che permettono di fare login con la chiave privata, creare un profilo completo di foto, biografia e link ai siti web, nonché di postare le note e trasmetterle ai relay cui si è deciso di farlo. Alcuni relay offrono il servizio gratuitamente, altri a pagamento e – con l’esperienza – si troverà il setup con cui iniziare.
La nsec permette di fare login ad ogni client indistintamente, senza costringere gli utenti a creare la combo username/password per ogni servizio.
Non so se è abbastanza chiaro...
Web-Of-Trust
Identità digitale e possesso dei propri contenuti sono alla base di un sogno, nato decenni fa con il web2.0 e naufragato con esso nella palude del business dei dati personali. Non me ne frega un cazzo del gombloddismoh e di cosa fanno le multinazio(a)nali dei dati personali di ogni utente, o di come questi vengano utilizzati per addestrare modelli di linguaggio avanzati.
Ciò che, a mio avviso, è rivoluzionario, è la realizzazione del sogno sogno. Il salto di paradigma è proprio il WoT, il Web-Of-Trust: essere certi che chiunque abbia la possibilità di diffondere qualsiasi tipo di messaggio, che ne sia realmente l’autore e quindi se ne assuma la responsabilità e che chiunque altro possa decidere se fruirne o meno.
Ciò implica anche la libertà di usare parole che sui social media tradizionali verrebbero censurate. Significa essere “giudicati” dai propri pari, liberi individui che decideranno se quel contenuto vale la pena di essere letto oppure no. Comporta, per i lettori, la libertà scegliere autonomamente cosa o chi seguire a seconda dei contenuti e non che un capriccioso algoritmo deciderà per loro cosa è meglio leggere o cosa no.
Non so se è abbastanza chiaro…
Client e ZAP ⚡️
 Le opportunità che offre il protocollo Nostr sono molteplici.
Con l’unica accortezza di custodire in maniera responsabile la nsec, con un unico “account” si può postare su client simil-twitter, blog post, link-in-bio tipo Link Tree, eventi come su Eventbride, raccogliere immagini tipo Pinterest, creare form come Google-form, ma senza avere una username e una password per ognuno degli account, senza fornire la propria email a cani e porci (che non è comunque igienico) e senza rischiare di gestire decine di password o – peggio – usarne una unica per tutti.
Le opportunità che offre il protocollo Nostr sono molteplici.
Con l’unica accortezza di custodire in maniera responsabile la nsec, con un unico “account” si può postare su client simil-twitter, blog post, link-in-bio tipo Link Tree, eventi come su Eventbride, raccogliere immagini tipo Pinterest, creare form come Google-form, ma senza avere una username e una password per ognuno degli account, senza fornire la propria email a cani e porci (che non è comunque igienico) e senza rischiare di gestire decine di password o – peggio – usarne una unica per tutti.Infine, se ciò non fosse già abbastanza, ecco l’incentivo economico: grazie all’integrazione del protocollo Lightning Network, ogni client Nostr permette di monetizzare con i contenuti pubblicati; gli utenti decidono di premiare alcuni post tramite Zap, micro pagamenti anche di frazioni di centesimi, fino ai macro pagamenti.
Perché Nostr
 Per chiunque abbia qualcosa da dire, frivolezze o concetti profondi, Nostr è quello che a Napoli in maniera geniale viene definito il fattoapposta!
Per chiunque abbia qualcosa da dire, frivolezze o concetti profondi, Nostr è quello che a Napoli in maniera geniale viene definito il fattoapposta!Essere protagonisti in prima persona delle proprie esperienze social-web, provare l’ebbrezza di essere gli unici proprietari dell’identità digitale e dei contenuti prodotti nonché monetizzarli per merito e non per algoritmo, è una scossa che vale davvero la pena di provare.
Attualmente Nostr potrebbe apparire come una piccola bolla, uno spazio abitato da strani esseri che parlano di cose aliene come libertà finanziaria, incensurabilità e decentralizzazione. Ma si può usare il tempo concesso da un’adozione prematura per conoscere il protocollo e capirlo.
Si potrà sempre tornare ad abitare il Web2.0, uno spazio dove le idee vengono censurate o dove gli utenti che si dichiarano progressisti ed inklusivi se ne vanno perché in disaccordo con l’esito di un’elezione regolare e demograttika
Risorse per approfondire: i) https://nostr-resources.com/ ii) https://nostr.net/ iii) https://nostr.how/en/nostr-projects iv) https://nostrapps.com/
-
 @ dd664d5e:5633d319
2024-12-14 15:25:56
@ dd664d5e:5633d319
2024-12-14 15:25:56
Christmas season hasn't actually started, yet, in Roman #Catholic Germany. We're in Advent until the evening of the 24th of December, at which point Christmas begins (with the Nativity, at Vespers), and continues on for 40 days until Mariä Lichtmess (Presentation of Christ in the temple) on February 2nd.

It's 40 days because that's how long the post-partum isolation is, before women were allowed back into the temple (after a ritual cleansing).

That is the day when we put away all of the Christmas decorations and bless the candles, for the next year. (Hence, the British name "Candlemas".) It used to also be when household staff would get paid their cash wages and could change employer. And it is the day precisely in the middle of winter.

Between Christmas Eve and Candlemas are many celebrations, concluding with the Twelfth Night called Epiphany or Theophany. This is the day some Orthodox celebrate Christ's baptism, so traditions rotate around blessing of waters.

The Monday after Epiphany was the start of the farming season, in England, so that Sunday all of the ploughs were blessed, but the practice has largely died out.

Our local tradition is for the altar servers to dress as the wise men and go door-to-door, carrying their star and looking for the Baby Jesus, who is rumored to be lying in a manger.

They collect cash gifts and chocolates, along the way, and leave the generous their powerful blessing, written over the door. The famous 20 * C + M + B * 25 blessing means "Christus mansionem benedicat" (Christ, bless this house), or "Caspar, Melchior, Balthasar" (the names of the three kings), depending upon who you ask.
They offer the cash to the Baby Jesus (once they find him in the church's Nativity scene), but eat the sweets, themselves. It is one of the biggest donation-collections in the world, called the "Sternsinger" (star singers). The money goes from the German children, to help children elsewhere, and they collect around €45 million in cash and coins, every year.

As an interesting aside:
The American "groundhog day", derives from one of the old farmers' sayings about Candlemas, brought over by the Pennsylvania Dutch. It says, that if the badger comes out of his hole and sees his shadow, then it'll remain cold for 4 more weeks. When they moved to the USA, they didn't have any badgers around, so they switched to groundhogs, as they also hibernate in winter.
-
 @ a39d19ec:3d88f61e
2024-12-14 14:42:26
@ a39d19ec:3d88f61e
2024-12-14 14:42:26This week's practical 3d print is a simple catch all tray.

Catch all tray
As for most of the useful prints I show you in this series I printed it a long time ago and can't find the link to the design file. I am pretty sure it's from Thingiverse though.
What it does
It perfectly serves as a central place for the things I commonly need when I go out. So I don't need to search for them.
What I like about the design is, that it catches all things from my pockets i.e. key, lighter, earpods, slide wallet and more when I come home. But not the dust and dirt. It falls throught the holes in tray.
3dprint #3ddruck #3dprinting
-
 @ bd32f268:22b33966
2024-12-14 14:06:06
@ bd32f268:22b33966
2024-12-14 14:06:06O título deste texto dá-nos uma pergunta retórica, isto é, uma interrogação com uma resposta evidente. Para que não restem dúvidas a resposta evidente seria, um enfático e inequívoco sim. Sim, o mal existe. Contudo, nos dias que correm muitas pessoas aparentam duvidar da existência do mal.
Creio que em verdade não será tanto uma dúvida sincera, porque de facto ninguém consegue sustentar uma visão de mundo sem ter alguma ideia do que é o mal. Penso que será mais uma tentativa de fazer apologética do mal, disfarçada de uma certa ingenuidade. O que quero dizer é que as pessoas que apregoam que o mal não existe sabem perfeitamente que existe, no entanto é conveniente negá-lo para que daí não decorra um julgamento sincero das suas atitudes. A definição objetiva destas coisas pode ser-nos difícil porque implica que nos vejamos de uma forma mais clara e honesta quando usamos de uma medida objetiva.
Ao desviarmos a atenção destes factos, tentamos de alguma forma justificar a nossa corrupção moral. Dizemos adágios populares como: “cada cabeça sua sentença”; isto para esconder um facto incontornável que é a universalidade do mal. Significa isto que o mal quando nasce é para todos, assim como o bem. Não é lógico nem racional defender que a pedofilia é um mal na nossa cultura mas que nas outras culturas não é assim tão mau. Se é um mal é-o naturalmente para a humanidade. Por outro lado defender que as leis morais são exclusivas para um determinado grupo de humanos é concorrer para a ideia de casta social ou diferença na essência do humano.
Um outro esquema que nos leva a considerar que o mal é relativo é o facto de ignorarmos de onde provém a definição de mal. É porventura frequente que imbuídos do espírito da democracia ocidental julguemos que a possível definição de mal vem da convenção social, ou seja, daquilo que a maior parte das pessoas acredita ser o mal. Contudo, facilmente percebemos que não é assim, que a definição de mal não provém de convenção social mas que depende de condições preternaturais. Há uma intemporalidade no mal que não depende da época ou da convenção social.
Penso que a analogia com a física pode ajudar-nos a perceber melhor estas realidades. Não há uma lei da gravidade diferente para a pessoa A e para a pessoa B, a lei é exatamente a mesma no entanto os corpos movem-se a diferentes velocidades e altitudes portanto sentem-na de formas diferentes.
No ramo da psicologia vejo infelizmente um problema sério que se pretende com a excessiva utilização da linguagem terapêutica para falar sobre o mal. É muitíssimo frequente ver uma tentativa de patologizar todos os males. Não negando que o distúrbio psíquico pode estar presente na pessoa que comete um mal, inclusive um mal grave, isso não significa que em muitos casos não haja um assentimento consciente e deliberado da pessoa àquela atitude. Esta linguagem terapêutica levam-nos por vezes a romantizar o mal, e a procurar narrativas que o tornam numa novela sentimental onde a pessoa é sempre rotulada como uma vítima das circunstâncias contextuais, basta vermos o exemplo do marxismo que assim a determina.
Nesta ideologia a pessoa comete crimes porque é pobre e foi vetada a uma exclusão social, como se não fosse possível à pessoa pobre seguir um caminho de retidão moral. O filme Joker ilustra bem este aspeto novelesco da romantização do mal. Neste filme a personagem principal, um psicopata degenerado, é retratado como um doente mental que procura fazer “justiça” assassinando inocentes e destruindo património. Devido à pueril noção de agência, responsabilidade individual, e livre arbítrio o mal é quase tratado como uma caminho único, como se a personagem estivesse predestinada aquele mal.
 > Joaquin Phoenix - Joker 2019
> Joaquin Phoenix - Joker 2019São muitos os esquemas á nossa volta que além de dissimularem o mal, tentando indicar a sua inexistência, o promovem como sendo um bem. São muitas as mensagens contraditórias que promovem o exercício da vontade humana como um imperativo moral. São também frequentes as apologias à tolerância e empatia para com o mal. Contudo, isto é absurdidade. Como teremos ordem e paz sem combater os males? Como teremos espaço para a virtude quando tudo estiver tomado pelo mal ? Precisamos de filtrar este ruido para perceber de forma mais objetiva qual é a verdadeira face do mal.
-
 @ bbb5dda0:f09e2747
2024-12-14 13:58:25
@ bbb5dda0:f09e2747
2024-12-14 13:58:25What is it about travel that makes us so addicted to it? Chasing the high of the next view, the next location. Is travel always the same as travel? I think certainly not. Is travel valuable? Then what about it provides the value. Because it's different when someone from the same country goes to that attraction, vs when you come from the other side of earth to see it. What do you gain?
Up until now travel for me has been stillness with nature, and even within the more social trips like SEC-03 I appreciate the ability to be alone and stare at the waves for hours on end. As I'm doing while typing this. Travel changes over time, as it changes you. It's not about seeing more rockfaces anymore, it's about seeing the details in just one of them. The subtle hints to a far and violent past that formed these layers of rock, now exposed for us to be seen and appreciated.
If only we did that more and not just running to so many of these places without appreciating them. Destroying the exact thing we want to see in the process. I really hope mass tourism will come to an end along with the 'social' media that created it. I ended up at a beautiful beach the other day, it came with a freaking waterfall and I saw at least a dozen people only taking basically a photoshoot of themselves or their (girl)friends for 15-30 minutes straight. It doesn't really annoy me but it just makes me wonder, do they actually notice their surroundings and are they actually enjoying the places they go to? I just hope their minds work different from mine and that they actually are enjoying themselves by doing that. As far as mass-tourism goes I wouldn't mind if we replace it with mass-wandering, to places not on the top 10's, not filled with chic hotels and resorts. Just the places that welcome you but won't live to serve you, that is what travel is to me.
I've been taking less pictures over time, the ones I take are mostly because I appreciate the composition, especially after watching the same view for over an hour, and suddenly spotting a new detail that I hadn't noticed before. Anyway, I don't even know where I'm going with this, I just felt the need to write down these thoughts...
-
 @ 141daddd:1df80a3f
2024-12-14 11:11:10
@ 141daddd:1df80a3f
2024-12-14 11:11:10This is a random post to try out Reads on Nostr.
For years, I had been waiting for the moment when stability hits my life: a stable place to live, a stable occupation or project, a stable headspace, for that matter. But it never came. And I realize now that it never will.
Since childhood my life has been a constant change of domicile, education facilities, etc. I was bron in one place, raised in another, changed 3 kindergartens and 4 schools. Then another move to study in a big city, a move abroad, a comeback and now again... It seems that the average change-stability cycle lasts around 2 years. It seems that the average change-stability cycle lasts around 2 years.
It's no wonder that I start feeling stale and bored when life becomes routine, repetitive: my nature rejects it. For a long time, I thought this constant change was a bug and I longed stability, especially seeing many people become extremely successful by doing the same thing year after year. That it's a feature is a recent revelation. Or, to be precise, it's both a bug and a feature, a two-sided coin like everything in this life.
Need to quit a job? Move to another city? Start a company or shut one down? Hire or fire someone? Conceive another child? These life-altering decisoins don't come easy to many people. As a matter of fact, some are totally paralized in life because they're afraid to make a change. But not me. Change is in my blood. The fact that the future is unknown is exciting to me, not scary.
And so far, it's worked well. Sure, impulsive decisions often cause unintended consequences and mistakes, but this is exactly how I learn, this is my modus operandi. I don't read instructions — I act.
Wow, this guy likes talking about himself!
The post is not about me. I just feel that there are many more people with a similar mindset, cultivated this way for various reasons, but even more people whose lives are too stagnant. So I want to say to them: just go for it. The worst and most extreme thing that can happen to you is death. But even that is not so bad: life-long inaction means you're already walking dead, and that is much worse.
-
 @ 30e902b3:49c066b2
2024-12-14 10:12:49
@ 30e902b3:49c066b2
2024-12-14 10:12:49Llegó a mis manos en busca de ayuda para volver a sentirse joven.
Se trata de un grabador open reel Berlant Concertone 20-20 de 1955. Aquí el manual original:
https://museumofmagneticsoundrecording.org/images/R2R/Concertone20-20ManualMOMSR.pdf
https://images.app.goo.gl/NcdAaYv2HTCHVnvX9
Como se ve en la imagen no me llegó en las mejores condiciones.
Cuento con vuestra guía para conseguir los repuestos que falten y lograr dejarlo parecido a este:
https://d10j3mvrs1suex.cloudfront.net/s:bzglfiles/u/146088/fbd8aec299456da8f127cd52f7dafcd4be37331b/original/berlant-concertone-tape-recorder.jpg/!!/b%3AW1sic2l6ZSIsInBob3RvIl1d/meta%3AeyJzcmNCdWNrZXQiOiJiemdsZmlsZXMifQ%3D%3D.jpg
Pretendo iniciar con el nuevo año. Voy recopilando ideas y consejos que me compartas. Va a ser necesario restaurar los frentes, contactos, revisar la electrónica y válvulas todo en modo DIY o "a pulmón".
-
 @ a012dc82:6458a70d
2024-12-14 09:42:15
@ a012dc82:6458a70d
2024-12-14 09:42:15Table Of Content
-
The Birth of Tokenized Bitcoin
-
How Does Tokenized Bitcoin Work?
-
The Advantages of tBTC Over Traditional Bitcoin
-
Expanding the Utility of Bitcoin
-
The Future of Tokenized Bitcoin
-
Conclusion
-
FAQ
In the ever-evolving world of cryptocurrency, Bitcoin remains the gold standard. However, its traditional form has faced challenges, especially when it comes to transaction speeds and adaptability. Enter the tokenized version of Bitcoin on Solana, a solution that promises to address these issues. But what exactly is this new tokenized Bitcoin, and why is it causing such a stir in the crypto community? Let's dive in.
The Birth of Tokenized Bitcoin
Bitcoin, with its unmatched popularity, has always been at the forefront of the cryptocurrency industry. Yet, its primary blockchain has been criticized for being slow in adopting new features, making smaller transactions both time-consuming and expensive. To address these challenges, the Threshold Network introduced the first tokenized version of Bitcoin, known as tBTC, on the Solana blockchain. This innovation aims to bridge the gap between Bitcoin's value and its transactional limitations.
How Does Tokenized Bitcoin Work?
The concept might sound complex, but it's rooted in simplicity. Imagine you have a physical gold bar but find it cumbersome to use in daily transactions. Instead, you get a certificate (or token) representing that gold bar, which you can easily trade or use. Similarly, when someone mints tBTC on Solana, they send their Bitcoin to be "wrapped". This wrapping process involves a decentralized review where the crypto is held in a special wallet. This wallet's authenticity is validated by a majority of people operating nodes on the Threshold Network. Once validated, you receive tBTC equivalent to the Bitcoin you wrapped, which can be used seamlessly on the Solana blockchain.
The Advantages of tBTC Over Traditional Bitcoin
Traditional Bitcoin has its limitations, especially when it comes to smart contracts. Even with advancements like the Lightning Network, these limitations persist. tBTC, on the other hand, offers a more flexible approach. It acts as a proof of ownership, allowing users to prove they possess a certain amount of Bitcoin. Moreover, if they ever wish to revert to their original Bitcoin, they can easily trade their tBTC to claim it back. This process ensures security, as a significant majority of validators must approve the transaction, minimizing the risk of malicious intent.
Expanding the Utility of Bitcoin
One of the most exciting aspects of tBTC is its potential to revolutionize how Bitcoin is used. Traditional Bitcoin holders, if they wished to take a loan against their holdings, had to rely on centralized platforms, which came with their own set of risks. With tBTC, however, they can leverage their Bitcoin on the Solana blockchain, bypassing the limitations of the traditional Bitcoin network. This means they can take out loans, earn yields, and even use their Bitcoin in decentralized exchanges, offering a level of flexibility previously unheard of.
The Future of Tokenized Bitcoin
Tokenized Bitcoin, especially tBTC on Solana, is a groundbreaking advancement, but it's just the beginning of a broader trend. Other major blockchains, such as Ethereum, Arbitrum, Optimism, and Polygon, have also integrated this concept, showcasing the growing appeal and versatility of tokenized Bitcoin. This widespread adoption underscores the crypto community's belief in its potential, making Bitcoin more adaptable and enhancing its interoperability across different platforms.
Moreover, the rising trust in tokenized Bitcoin suggests a promising trajectory for the decentralized finance (DeFi) sector. As tokenized assets become more mainstream, platforms like Solana stand to benefit immensely, heralding a new era for the entire DeFi ecosystem. The embrace of tokenized Bitcoin is not just a win for Bitcoin itself but a testament to the evolving dynamics of the crypto world.
Conclusion
The introduction of tBTC on Solana is more than just a technological advancement; it's a testament to the crypto community's relentless pursuit of innovation. As we continue to witness the blending of traditional and modern financial systems, tokenized assets like tBTC will undoubtedly play a pivotal role in shaping the future of decentralized finance.
FAQs
What is tokenized Bitcoin? Tokenized Bitcoin, like tBTC on Solana, is a representation of Bitcoin on other blockchains, allowing for more flexibility and interoperability.
Why was tBTC introduced on Solana? tBTC was introduced to address Bitcoin's transactional limitations, making it more adaptable and efficient on platforms like Solana.
How does tokenized Bitcoin differ from traditional Bitcoin? While traditional Bitcoin has limitations with smart contracts and transaction speeds, tokenized Bitcoin offers more flexibility, especially on platforms like Solana.
Are other blockchains adopting tokenized Bitcoin? Yes, apart from Solana, blockchains like Ethereum, Arbitrum, Optimism, and Polygon have also integrated tokenized Bitcoin.
What does the rise of tokenized Bitcoin mean for the DeFi sector? The growing trust in tokenized Bitcoin suggests a promising future for the DeFi sector, with platforms like Solana leading the way in innovation and adoption.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
X: @croxroadnews
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
*DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research. *
-
-
 @ 234035ec:edc3751d
2024-12-14 05:12:52
@ 234035ec:edc3751d
2024-12-14 05:12:52America's Fourth Fourth Turning
We can learn much from the Book "The Fourth Turning: An American Prophecy" By William Strauss and Neil Howe. The Book looks back throughout history to identify the cyclical patterns that emerge and establishes archetypes that emerges in the generations as they come of age in these different stages of history.
There are four phases (turnings) that are outlined in the book:
- The High
- The Awakening
- The Unraveling
- The Crisis
The authors identify that America is due for another fourth turning, and I would argue that we are now in the midst of America's Fourth ever fourth turning. The first three being marked by the American Revolution, the Civil War, and the Great Depression- WWII. Today we have been in an increasingly unstable financial, political, and social environment which share eery similarities to the unraveling period of the prior cycles.
I believe that this fourth turning began with the 2008 "Great Financial Crisis" and has been ongoing ever since the fed chose to engage in mass currency devaluation in order to keep the banks solvent. While these actions have delayed the inevitable larger crisis, they will not be able to avoid it. Since 2008 the money supply has grown from roughly $8 Trillion to over $20 Trillion. This massive currency dilution is reflected in increased prices across all sectors but heavily concentrated in scarce desirable assets. As National debt continues to rise and interest expenses balloon, the only way out for the US dollar is massive inflation.
The issue with continued inflation is that it leads to massive societal suffering and unrest. At 2% inflation most individuals aren't aware that they are being stolen from, but as inflation rates start to stick above 10% people start to realize what is really going on. History tells us that as currencies enter into hyper-inflation, the societal fabric begins to fall apart. One does not have to be an anthropologist to look around and realize the massive cultural shifts that we have seen since moving to a fiat standard in 1971 and much faster ever since 2008.
I find it very profound that at the same time that the global financial system began showing cracks, Satoshi Nakamoto introduced the solution to the world. It feels as though this fourth turning is centered around technological innovation in computing, as well as the collapse of an outdated and corrupt financial system. Bitcoin exists at the perfect intersection of these two by utilizing cryptography to empower people to exit the corrupt system and begin to build a superior one on sound foundation. If the crisis of this great fourth turning is centered around the sovereign debt crisis, than Bitcoin becomes the clear answer.
Thriving In The Chaos
Being Born in 2001 I do not have much memory of a pre-2008 world. Being only 7 years old at the time I did not fully grasp the significance of what was going on, but my life has been impacted by it nonetheless.
When the central bank chooses to hold interest rates artificially low, they are effectively driving money into more and more places where it shouldn't actually be. This is usually described as a bubble, which then bursts leaving many financially ruined. Accept for those who the central bank then chooses to bail out by diluting the purchasing power of all the savers.
Much of the Millenial and Gen Z generations feel that they will never reach financial security or be able own a home and retire at a reasonable age. Many of them are saddled with large student loans, credit card debt, and car loans. While much of this is due to personal decision making, we exist in a system today that is designed to extract as much value as possible from each citizen. If you were to take out a loan to go to school, get a job, a mortgage, and a car payment, and used a savings account, you would never become financially free.
People my age have become increasingly unsatisfied with the way that things are, which is why I am so hopeful for a brighter future. While most aren't quite aware of what the true heart of the issue is, they feel that something is deeply wrong. I believe that Bitcoin will be the catalyst for the masses to wake up and stop funding the current system.
Those that lead the way into a new frontier during these fourth turnings come out on the other side in positions of great respect and power. While these next few years will likely difficult, there will be massive opportunity for those who are bold enough to stand for their beliefs and work to propagate them.
-
 @ 16d11430:61640947
2024-12-14 01:51:07
@ 16d11430:61640947
2024-12-14 01:51:07The trajectory of human progress is marked by seismic shifts in wealth, power, and knowledge. Over centuries, these tectonic movements have reshaped the global narrative, transitioning the spear-tip of innovation and dominance from East to West. Today, as global tensions rise and multipolarity challenges the unipolar financial order, it’s worth examining the periods of change and the forces that realigned the axis of human progress through the lens of technological and financial evolution.
- The East’s Preeminence: The Age of Soft Power and Real Assets
Period: Antiquity to 15th Century For millennia, wealth and knowledge flowed from East to West. Civilizations like India, China, and the Islamic Caliphates were centers of human progress. These regions excelled in technological innovation, financial stability (e.g., China’s early use of paper currency in the Tang Dynasty), and cultural capital.
Financial Dominance: Real assets like spices, textiles, and gold formed the backbone of trade. The Silk Road acted as a decentralized value network, with wealth flowing from resource-rich East Asia to demand-heavy Europe.
Knowledge Arbitrage: Eastern empires perfected systems of governance, mathematics, and astronomy. Indian numerals became the foundation of global mathematics, while Chinese engineering inspired innovations in navigation.
Yet, despite its dominance, the East’s wealth was tied to a fragile, physical-based trade network, leaving it vulnerable to external shocks.
- The Renaissance and the Maritime Arbitrage of Knowledge
Period: 15th–17th Century The fall of Constantinople in 1453 was a geopolitical rug pull, severing Europe’s access to Eastern trade routes. In response, European nations innovated maritime trade routes, circumventing old supply chains. This era saw the financialization of exploration through state-backed joint-stock companies like the Dutch East India Company (VOC), a precursor to modern equity markets.
Leverage and Liquidity: The VOC issued the first publicly traded shares, creating a new mechanism for wealth generation: equity capital. Wealth shifted west as Europe commoditized Eastern resources at unprecedented scale.
Techno-Geopolitical Advantage: Innovations in shipbuilding, navigation, and weaponry gave European powers a first-mover advantage in global trade, tipping the economic balance.
Europe began consolidating wealth and influence, laying the groundwork for the first financial superpowers.
- The Industrial Revolution: Scaling Innovation and Debt Capital
Period: 18th–19th Century The Industrial Revolution was the ultimate shift from real to synthetic wealth creation. Britain’s coal-powered factories and mechanized production allowed for the exponential scaling of goods and services, bypassing the labor-intensive economies of the East.
Debt as an Asset Class: The Bank of England pioneered modern public finance, using national debt to fund wars and infrastructure. Debt markets became a weapon of geopolitical influence, solidifying Britain’s dominance.
Data and Capital Flows: Knowledge transitioned from artisanal secrets to open-source intellectual property. The invention of the telegraph—a precursor to modern networks—centralized information flow in the West.
During this period, colonies were repurposed as raw material hubs, while the West monetized finished goods. The East’s economies, trapped in colonial dependency, were stripped of agency.
- The Dollar Standard: The West Consolidates Financial Hegemony
Period: 20th Century The world wars were financial accelerants, propelling the U.S. to global supremacy. Post-World War II, the Bretton Woods system tied global currencies to the U.S. dollar, itself pegged to gold. By 1971, the gold standard was abandoned, and fiat-backed dollars became the world’s reserve currency—a geopolitical masterstroke.
Petrodollar Diplomacy: The U.S. engineered a system where oil, the lifeblood of modern economies, was traded exclusively in dollars. This created an artificial demand for U.S. currency, reinforcing its global dominance.
Technology Arms Race: The Cold War spurred investments in computing, satellites, and the internet. These technologies cemented the West as the epicenter of innovation, while the Eastern bloc stagnated under centralized planning.
The East, particularly China and India, entered a period of economic dormancy, while the West built the foundation for the modern financialized economy.
- The Digital Era: The Resurgence of the East and Blockchain’s Decentralization
Period: 21st Century As the 20th century ended, cracks in Western hegemony began to appear. The East, particularly China, leveraged its demographic dividend and state-driven capitalism to re-enter the global stage. Simultaneously, blockchain and decentralized finance (DeFi) began eroding trust in centralized financial systems.
China’s Belt and Road Initiative (BRI): A modern Silk Road, the BRI channels liquidity and infrastructure investment into developing nations, countering Western-led institutions like the IMF and World Bank.
Bitcoin and DeFi: Bitcoin, as a decentralized reserve asset, challenges fiat’s monopoly on monetary sovereignty. Decentralized systems offer an alternative to SWIFT-based cross-border payments, reducing reliance on Western financial networks.
The U.S. and its allies now face a multipolar world where traditional financial instruments are being disrupted by distributed ledger technology and Eastern economic strategies.
- Geopolitical Tensions: A New Cold War of Data and Energy
The current geopolitical climate is defined by competition over intangible assets: data, semiconductors, and clean energy technologies. The East and West are locked in a race to dominate artificial intelligence, quantum computing, and blockchain infrastructure.
Data Sovereignty: Nations are weaponizing data localization laws and AI to gain competitive edges in surveillance capitalism and defense.
Energy Markets: The West’s pivot to green energy and the East’s dominance in rare earth minerals create asymmetric dependencies.
The financial spear-tip of human progress is no longer unilateral. The West’s financial systems, underpinned by debt and derivatives, face a fundamental challenge from the East’s state-capitalist model and decentralized digital assets.
Conclusion: The Dawn of a Decentralized World
The historical narrative of human progress has been a pendulum swing between centralized and decentralized systems. While the East dominated through physical assets and trade, the West shifted to financialization and industrial scale. Now, we stand on the precipice of another transformation: a decentralized financial and technological order where power is no longer tied to geography but to networks.
The tip of the spear of human progress is no longer a single entity but a fragmented, multi-nodal system. Whether this leads to collaboration or conflict depends on how the world navigates this unprecedented inflection point.
-
 @ c1e6505c:02b3157e
2024-12-14 01:50:48
@ c1e6505c:02b3157e
2024-12-14 01:50:48Test post coming from stacker.news
originally posted at https://stacker.news/items/808769
-
 @ 82883e29:dab2ff8c
2024-12-13 23:36:16
@ 82883e29:dab2ff8c
2024-12-13 23:36:16Hello, readers!
My name is Muju. I am a writer, thinker, Bitcoin advocate, and humanist activist with a passion for challenging the status quo and exploring the complexities of our world. Over the years, I've written extensively on politics, human rights, Bitcoin, and the fascinating intersections of culture and technology through my blog, Unintuitive Discourse.
Today, I take an exciting step forward by beginning to publish my work on Nostr, a platform that aligns with my values of free speech and decentralization.
Nostr’s censorship-resistant architecture ensures that my thoughts and ideas can be preserved permanently, free from interference or erasure. This move reflects my commitment to creating a lasting record of my work—a digital footprint that stands against the tides of suppression.
Unintuitive Discourse is a product of my journey: my life as an autodidact, my experiences as a political refugee, and my relentless pursuit of understanding the world through a humanist lens. By leveraging Nostr, I aim to secure a permanent home for my ideas, making them accessible to those who seek to question, learn, and grow.
If you’re reading this, welcome to the beginning of something enduring. Join me as I continue to write, reflect, and share thoughts that I hope will inspire meaningful conversations for years to come.
Here's to a future where ideas thrive without limits—my contribution to realizing a truly decentralized internet where knowledge flows freely and voices cannot be silenced.
-
 @ 4b7c4ee3:8cd5ed4d
2024-12-13 23:20:50
@ 4b7c4ee3:8cd5ed4d
2024-12-13 23:20:50Is this thing on?
-
 @ a95c6243:d345522c
2024-12-13 19:30:32
@ a95c6243:d345522c
2024-12-13 19:30:32Das Betriebsklima ist das einzige Klima, \ das du selbst bestimmen kannst. \ Anonym
Eine Strategie zur Anpassung an den Klimawandel hat das deutsche Bundeskabinett diese Woche beschlossen. Da «Wetterextreme wie die immer häufiger auftretenden Hitzewellen und Starkregenereignisse» oft desaströse Auswirkungen auf Mensch und Umwelt hätten, werde eine Anpassung an die Folgen des Klimawandels immer wichtiger. «Klimaanpassungsstrategie» nennt die Regierung das.
Für die «Vorsorge vor Klimafolgen» habe man nun erstmals klare Ziele und messbare Kennzahlen festgelegt. So sei der Erfolg überprüfbar, und das solle zu einer schnelleren Bewältigung der Folgen führen. Dass sich hinter dem Begriff Klimafolgen nicht Folgen des Klimas, sondern wohl «Folgen der globalen Erwärmung» verbergen, erklärt den Interessierten die Wikipedia. Dabei ist das mit der Erwärmung ja bekanntermaßen so eine Sache.
Die Zunahme schwerer Unwetterereignisse habe gezeigt, so das Ministerium, wie wichtig eine frühzeitige und effektive Warnung der Bevölkerung sei. Daher solle es eine deutliche Anhebung der Nutzerzahlen der sogenannten Nina-Warn-App geben.
Die ARD spurt wie gewohnt und setzt die Botschaft zielsicher um. Der Artikel beginnt folgendermaßen:
«Die Flut im Ahrtal war ein Schock für das ganze Land. Um künftig besser gegen Extremwetter gewappnet zu sein, hat die Bundesregierung eine neue Strategie zur Klimaanpassung beschlossen. Die Warn-App Nina spielt eine zentrale Rolle. Der Bund will die Menschen in Deutschland besser vor Extremwetter-Ereignissen warnen und dafür die Reichweite der Warn-App Nina deutlich erhöhen.»
Die Kommunen würden bei ihren «Klimaanpassungsmaßnahmen» vom Zentrum KlimaAnpassung unterstützt, schreibt das Umweltministerium. Mit dessen Aufbau wurden das Deutsche Institut für Urbanistik gGmbH, welches sich stark für Smart City-Projekte engagiert, und die Adelphi Consult GmbH beauftragt.
Adelphi beschreibt sich selbst als «Europas führender Think-and-Do-Tank und eine unabhängige Beratung für Klima, Umwelt und Entwicklung». Sie seien «global vernetzte Strateg*innen und weltverbessernde Berater*innen» und als «Vorreiter der sozial-ökologischen Transformation» sei man mit dem Deutschen Nachhaltigkeitspreis ausgezeichnet worden, welcher sich an den Zielen der Agenda 2030 orientiere.
Über die Warn-App mit dem niedlichen Namen Nina, die möglichst jeder auf seinem Smartphone installieren soll, informiert das Bundesamt für Bevölkerungsschutz und Katastrophenhilfe (BBK). Gewarnt wird nicht nur vor Extrem-Wetterereignissen, sondern zum Beispiel auch vor Waffengewalt und Angriffen, Strom- und anderen Versorgungsausfällen oder Krankheitserregern. Wenn man die Kategorie Gefahreninformation wählt, erhält man eine Dosis von ungefähr zwei Benachrichtigungen pro Woche.
Beim BBK erfahren wir auch einiges über die empfohlenen Systemeinstellungen für Nina. Der Benutzer möge zum Beispiel den Zugriff auf die Standortdaten «immer zulassen», und zwar mit aktivierter Funktion «genauen Standort verwenden». Die Datennutzung solle unbeschränkt sein, auch im Hintergrund. Außerdem sei die uneingeschränkte Akkunutzung zu aktivieren, der Energiesparmodus auszuschalten und das Stoppen der App-Aktivität bei Nichtnutzung zu unterbinden.
Dass man so dramatische Ereignisse wie damals im Ahrtal auch anders bewerten kann als Regierungen und Systemmedien, hat meine Kollegin Wiltrud Schwetje anhand der Tragödie im spanischen Valencia gezeigt. Das Stichwort «Agenda 2030» taucht dabei in einem Kontext auf, der wenig mit Nachhaltigkeitspreisen zu tun hat.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 6bae33c8:607272e8
2024-12-13 19:20:41
@ 6bae33c8:607272e8
2024-12-13 19:20:41I blew it last week, going 2-3. I shouldn’t have taken the Jets, I knew it was a mistake. I don’t care how right the side looked either, the Jets are cursed. I liked the Rams and Panthers, but didn’t pull the trigger. Too much second guessing and overthinking. Either you have a model and stick to its outputs, or you go on feel, and you trust yourself 100 percent. Don’t question, just act. If you make an error, you can reassess next week, incorporate it into your process.
 Dolphins +2.5 at Texans — I’m sure this is the game the Texans turn it around, but as someone whose otherwise solid Primetime team was derailed by CJ Stroud and the bankrupt passing game, I took the Dolphins and the points.
Dolphins +2.5 at Texans — I’m sure this is the game the Texans turn it around, but as someone whose otherwise solid Primetime team was derailed by CJ Stroud and the bankrupt passing game, I took the Dolphins and the points.Chiefs -4 at Browns — I know the Chiefs are life and death with everyone, but this seems too small. Jameis Winston will turn it over a few times against this defense, and the Chiefs will move up and down the field.
Steelers +5 at Eagles — The Eagles are good against bad teams, but the Steelers are a rock defensively, and I think they’ll hang.
Lions -2.5 vs Bills — I had this line at four. The Lions are the better team, even with the banged-up defense.
Packers -2.5 at Seahawks — The Seahawks have been good of late, but the Packers went toe to toe with the Lions and had a full 10 days off. I think they win and cover.
-
 @ 705605d9:b4324038
2024-12-13 17:42:06
@ 705605d9:b4324038
2024-12-13 17:42:06Через две недели известный музыкант IGR посетит Горноправдинск. Об этом он заявил в своём телеграм-канале.
Игорь "IGR" Романов пишет хип-хоп и трэп. В своём жанре у музыканта уже есть имя, и мнения о нём у поклонников хип-хопа сильно различаются — споры вызывают как откровенно провокационные тексты артиста, так и его личная жизнь. Напомним, несколькими месяцами ранее IGR был задержан силовиками как участник несогласованного митинга в Санкт-Петербурге. Музыкант высказал свою радикальную позицию и был задержан за неповиновение сотруднику полиции.
"Его музыка заставляет задуматься, но иногда кажется, что он просто провоцирует ради провокации", — делится мнением наша читательница Ольга, которая не уверена, стоит ли идти на концерт. "Я люблю музыку, но некоторые его песни слишком откровенны", — добавляет она.
"IGR— это голос поколения! Его тексты отражают наши мысли и чувства, даже если они вызывают споры", — считает 17-летний Дмитрий. Он купил билет в первый же день после анонса концерта и намерен приехать на концерт из Новосибирска.
Выступление пройдёт в Дворце культуры. Цены на билеты колеблются от 1800 до 8000 рублей.
-
 @ 705605d9:b4324038
2024-12-13 17:41:13
@ 705605d9:b4324038
2024-12-13 17:41:1327 октября 2040 года в Горноправдинске, небольшом, но прогрессивном посёлке Югры, состоялась презентация уникального бренда экологичной одежды. Созданная местной дизайнеркой Верой Ивановной Семёновой, эта линия одежды обещает не только красивую и стильную, но и устойчивую моду, полностью изготавливаемую из переработанных материалов. Уникальность бренда заключается в том, что модели — это исключительно женщины пожилого возраста, что делает данный проект ещё более социально значимым.

Устойчивое развитие как основа идеи
Горноправдинск давно зарекомендовал себя как местечко, где экология и устойчивое развитие стоят во главе всего. Здесь активно развиваются инициативы по переработке отходов и рациональному использованию природных ресурсов. Презентация нового бренда стала логическим продолжением этих усилий. Одежда из вторсырья не только уменьшает количество отходов, но и снижает воздействие на окружающую среду. По данным исследований, текстильная промышленность является одним из крупнейших источников загрязнения в мире. В этом контексте важно осознавать влияние, которое каждый из нас может оказать на природу, выбирая экологически чистые альтернативы.
Согласно информации от независимой экологической организации, производство ткани из вторичных материалов требует в три раза меньше воды, чем традиционные методы. Это выгодно не только для экологии, но и для экономики. Более того, использование вторичных материалов позволяет снижать углеродный след, что критически важно в условиях глобального изменения климата.
Творение как вдохновение
Вера Ивановна Семёнова — не просто дизайнер, но и активист, призывающий к переменам. Её новый бренд стал результатом многолетнего труда и экспериментов. Вера патентует уникальные технологии переработки тканей и создания новых моделей, которые одновременно сочетали в себе стиль и комфорт.

"Я хочу показать, что мода может быть не только красивой, но и умной", - говорит Вера в интервью. Она расставляет акценты на том, что её коллекция будет выходить за рамки стандартного понимания экологии. Модельный ряд включает в себя как повседневную, так и вечернюю одежду. Каждая вещь несёт в себе уникальную историю переработанного материала, а сами ткани отобраны так, чтобы гарантировать долговечность и стиль.
Открывая новые горизонты для пожилых женщин
Эти модели — не просто одежда, это символ изменений. Важным аспектом нового бренда является то, что модели — это женщины пожилого возраста. В нашем обществе часто встречается предвзятое отношение к возрасту, и многие пожилые женщины сталкиваются с трудностями в поисках работы или возможности проявить себя.
Горноправдинск стал первой площадкой, где пожилые женщины, обладая опытом и мудротой, получили возможность стать лицами модной индустрии. Этот шаг отразит новое понимание о красоте и стилю, которое не привязано к возрасту. Публика сможет увидеть, что настоящая красота исходит из внутреннего содержания, а не из стандартных шаблонов. Опросы показали, что большинство людей не воспринимает пожилых женщин как моделей. Но проект Веры Семёновой может стать началом новой эры, в которой возраст будет праздноваться, а не скрываться. Это не только проект по созданию одежды, но и социальная инициатива, ставящая вопрос о равенстве и возможностях для всех.
Модные тренды и экологическое сознание
В рамках презентации были представлены несколько моделей, каждая из которых рассказывала свою историю. Одежда создана из переработанных материалов: старых футболок, джинсов и текстиля, который больше не пригоден для использования в первоначальном виде. Каждая модель была выполнена с учетом последних модных тенденций: яркие цвета, уникальные принты и современные силуэты.
Важным аспектом новой коллекции является также то, что для её создания использовались умные технологии, позволяющие минимизировать отходы. Вера указала на то, что каждое изделие было разработано с использованием принципа zero waste, что подразумевает полное отсутствие отходов. Это значительно понижает стоимость конечного продукта и делает его доступным для широкого круга любителей моды.

Эксперты предположили, что такой подход может стать новым стандартом в модной индустрии, потому что он отвечает современным требованиям рынка и эволюционным ожиданиям покупателей. Люди всё больше начинают заботиться о том, каким образом производится одежда, и предпочитают brands, поддерживающие идеалы устойчивого развития.
-
 @ 705605d9:b4324038
2024-12-13 17:39:37
@ 705605d9:b4324038
2024-12-13 17:39:37Автор: Павел Густой, который дважды поперхнулся молоком, услышав слово «причал».
Старое железо и новая эпоха
Двадцать лет назад набережная Горноправдинска выглядела так, как будто ее проектировал инженер, вдохновленный своей последней опохмелкой. Ржавеющая баржа, служившая причалом, стояла на месте, словно памятник бессмысленности. Жители, подходя к ней, задавались лишь одним вопросом: «А мы точно успеем до корабля, пока она не развалится?»

Но 2040-й год стал годом, когда бабушки, эти легендарные управленцы Горноправдинска, решили: хватит. Видимо, они устали, что даже жители Бобровки шутят про их набережную, называя её «Порт Стыда».
Экологичный причал и другие чудеса
Реформа была громкой, как взрыв сыроварни. Теперь вместо ржавой баржи — современный экологичный причал. Он сделан из переработанного пластика и бетона, настолько крепкого, что даже утиный десант из соседнего водохранилища не смог его повредить.

«Мы думали о будущем, о наших детях и внуках», — заявила одна из бабушек, поглаживая внушительный скипетр в виде бутылки молока. Правда, злые языки утверждают, что пластик для причала собирали в основном в Бобровке, где люди искренне надеялись, что это поможет им самим.
Набережная — теперь с развлечениями!
Но на этом бабушки не остановились. Новый причал стал центром масштабного благоустройства. Что там теперь есть?
-
Большой магазин. Под названием «Молочная правда». Говорят, что если долго смотреть на его логотип, можно разгадать секрет бабушкиных масонов.

-
Зоны отдыха. Здесь все продумано до мелочей: лавочки с подогревом для больных суставов, мусорные урны, которые цитируют Бродского, и фонтаны, работающие исключительно на сыворотке.
- Промзона. Построенная так, чтобы туристы и не поняли, что смотрят на завод. «Это арт-объект!» — гордо утверждают бабушки. На фасаде предприятия висит баннер с надписью: "От молока до металла: мы можем всё!"

Критика: куда без неё?
Конечно, реформа понравилась не всем. Некоторые горноправдинцы ворчат, что набережная слишком идеальна, что даже коровы боятся здесь пастись. Другие шутят, что вместо прогулочной зоны бабушки могли бы построить парк развлечений для жителей Бобровки, где вместо билетов продавали бы надежду.
«Это всё для туристов», — жалуются местные, стоя в очереди за молоком. В ответ бабушки молчат. Они слишком заняты, вероятно, обсуждением нового проекта: ходят слухи о запуске молочного дирижабля.
Что дальше?
Набережная Горноправдинска — это, конечно, не про корабли и причалы. Это символ, дорогие мои. Символ того, что даже в городе, где всем управляют бабушки, возможно обновление. Пусть и с долей черного юмора, пластика и неизменного молочного послевкусия.
И всё же, когда смотришь на новый причал, где люди счастливо прогуливаются под солнцем, а где-то вдалеке доносится звук загрузки молока на баржу, понимаешь: Горноправдинск в который раз доказал, что он — город контрастов.
-
-
 @ 705605d9:b4324038
2024-12-13 17:38:32
@ 705605d9:b4324038
2024-12-13 17:38:32Вчера, 21 ноября, в деревне Бобровка, расположенной в одном из самых живописных уголков нашей страны, случился масштабный пожар, который уничтожил несколько домов и хозяйственных построек. Пожарные службы были оперативно направлены на место происшествия, но, несмотря на все усилия, огонь продолжал бушевать несколько часов. Установить точную причину возгорания оказалось задачей не из лёгких, однако, как стало известно, причиной пожара стала абсолютно невероятная и, на первый взгляд, абсурдная ситуация.
В деревне Бобровка местные жители утверждают, что причиной возгорания стал эксперимент с «горячей» новой разработкой – умным термосом, который, по задумке разработчиков, должен был поддерживать идеальную температуру напитков на протяжении суток. Однако, как выяснилось, термос оказался настолько «умным», что, не дождавшись своего «реального» срока эксплуатации, просто взорвался. По словам экспертов, устройство в какой-то момент решило провести «самодиагностику» и не выдержало своей собственной мощности, запустив цепную реакцию, которая привела к возгоранию.
Необычный инцидент, разумеется, сразу привлек внимание прессы, а местные жители стали активно обсуждать ситуацию, удивляясь, как такие инновации могут попасть в руки обывателей. «Когда я купила этот термос, мне казалось, что это просто удобный аксессуар для долгих прогулок с чаем. Но чтобы он так рванул, как граната, этого я не ожидала!» – рассказывает местная жительница, потерпевшая от огня.
Комментарий потерпевшего:
«Я никогда не думала, что мой любимый термос станет причиной такого бедствия. Он был подарком на день рождения, а я так гордилась им! Поставила на подоконник, чтобы чай остыл, и тут – бац! Всё вспыхнуло. Сначала я подумала, что это просто горячий чай, но когда увидела, что термос сам по себе светится, я поняла, что что-то пошло не так. Пожарные приехали быстро, но дом всё равно сгорел. Теперь я, честно говоря, боюсь пить чай в термосах, даже если они обещают быть умными!»

Местные власти заявили, что это происшествие станет поводом для пересмотра стандартов безопасности на рынке бытовых товаров. В ближайшее время планируется провести расследование и наложить запрет на использование «самодиагностирующих» устройств в бытовой сфере.
-
 @ 705605d9:b4324038
2024-12-13 16:30:17
@ 705605d9:b4324038
2024-12-13 16:30:17К 2040 году Горноправдинск, несмотря на динамичное экономическое развитие, столкнулся с рядом серьёзных демографических проблем.
Средний уровень жизни в Горноправдинске за последние несколько лет резко увеличился. Люди стали жить дольше. Но проблема со старением населения, бывшая актуальной ещё двадцать лет назад, осталась — и более того, она набирает обороты. Население города стареет — а значит, трудоспособного населения становится всё меньше. Это вызывает весьма серьёзное беспокойство у властей.
— У нас есть всё, чтобы молодое поколение выбрало Горноправдинск своим домом — новые рабочие места, красивая природа, инфраструктуру мы тоже развиваем. У нас тут много работников сферы IT, но на некоторых производствах не хватает рабочих, а социальный сектор от дефицита кадров страдает особенно сильно. Учителей у нас мало, например. Непопулярная это нынче профессия у молодых. — заявляет Агафья Семёновна, пресс-секретарь городской администрации.

Демографическая ситуация также осложняется низкими показателями рождаемости. Молодые люди, которые остаются в посёлке, зачастую ставят своим приоритетом не планирование семьи, а карьерный рост и саморазвитие. Многие просто не видят большого смысла для себя заводить семью и детей. Но редакция предполагает, что это проблема далеко не только одного Горноправдинска, а общая тенденция на уровне страны.

Ситуация с миграцией также оставляет желать лучшего. Хотя бум экономики Горноправдинска привлекает новых жителей, многие из них — это временные работники из других регионов, которые не имеют намерения осесть на постоянной основе. Кроме того, утечка умов, когда высококвалифицированные специалисты уезжают в поисках лучших карьерных возможностей, продолжает оставаться серьёзной проблемой для местного рынка труда.
Говоря о демографии, нельзя не сказать о социальных проблемах. Экономика цветёт, увеличивается качество жизни, а социальное расслоение сохраняется. Например, многим всё ещё трудно получить квалифицированную медицинскую помощь — работники городских поликлиник порой не справляются с потоком пациентов, а за помощью узкоспециализированного специалиста горноправдинцам остаётся обращаться в платную частную клинику, что может быть довольно тяжёлым испытанием для кошелька. Молодые семьи стремятся к лучшим условиям для жизни и воспитания детей, что приводит к оттоку населения в более социально обеспеченные регионы.
Горноправдинск, пытаясь справиться с демографическими вызовами, нуждается в комплексном подходе к решению проблем. Город нуждается в постоянном обновлении инфраструктуры и социальных инвестициях. Не хватает и поддержки молодых семей — для того, чтобы переосмыслить свои приоритеты, молодым парам нужна уверенность в завтрашнем дне.
А пока город медленно, но верно стареет. Справедливости ради, несколько медленнее, чем раньше.
-
 @ 705605d9:b4324038
2024-12-13 16:27:16
@ 705605d9:b4324038
2024-12-13 16:27:16Горноправдинск, некогда скромный посёлок с населением в несколько тысяч человек, к 2040 году стал важным экономическим центром Ханты-Мансийского автономного округа. Если бы 20 лет назад местным жителям сказали, что их маленький посёлок станет экономическим чудом — даже самые оптимистичные из них восприняли бы это как шутку.
**Но как всего за пару десятков лет вообще возможна столь удивительная трансформация?
**
Маленькие люди, большая мечта Сельское хозяйство стало важной опорой экономики Горноправдинска. Даже как-то смешно вспоминать, что всё начиналось с маленьких частных огородов и большой инициативы местных жителей.
Те, кто когда-то возделывал скупую сибирскую землю, устали выращивать разве что картошку и разве что для себя. Жители (преимущественно, кстати, пожилые, те, для кого их огород был чуть ли не главным делом) взялись за свои участки серьёзно — удобряли землю, воспользовались правом заниматься фермерством, а затем смогли и выбить достойную технику для своего дела. Результат себя ждать не заставил: сельскохозяйственная продукция из Горноправдинска завоевала своё место на прилавках магазинов Югры. А уже к 2040 году Горноправдинск стал одним из важнейших центров производства молочных продуктов в регионе — животноводство местные власти сейчас развивают особенно активно. Не забыли и о чистоте производства: Горноправдинск на данный момент занимает одну из лидирующих позиций по внедрению "зелёных" технологий.

Привлечение туристов
Не менее значимым стало развитие туристической отрасли. Уникальные природные ландшафты региона привлекли туристов со всей страны. Местные власти активно развивают туристическую инфраструктуру: за последние 4 года на территории города появились 4 гостиницы (одна из них, кстати, и вовсе реализует формат "all-inclusive"!), два туристических маршрута — лыжная тропа, где все желающие смогут налюбоваться зимней красотой Сибири, и речной маршрут вдоль местной реки. "Мы стараемся создать место, куда люди хочется возвращаться", — говорит директор туристической фирмы "ГП".

Горноправдинск стал местом притяжения для самых разных людей — любители спорта теперь могут покататься на лыжах зимой и отправиться на сплав на сапах летом, а для интересующихся культурой молодых людей здесь регулярно проводят творческие фестивали.
Но сколько стоит экономическое чудо?
Но всего этого могло бы и не быть, если бы не усилия по привлечению инвестиций. Власти ввели налоговые льготы, модернизировали транспортное сообщение между городами Югры и впервые за всю историю существования посёлка, кажется, слушали людей и принимали их инициативы — так, через налаживание контактов и вливание финансов в местные предприятия (если обратиться к финансовым отчётам властей, то суммы, выделенные на развитие местных производств и инфраструктуры, впечатляют — они исчисляются миллиардами рублей), получилось преобразить бывший маленьким и серым Горноправдинск в гордость региона.

-
 @ 705605d9:b4324038
2024-12-13 16:25:42
@ 705605d9:b4324038
2024-12-13 16:25:42Давка в маршрутках с вечно уставшими водителями, которые приезжают на остановки не по расписанию, а иногда не приезжают вовсе, была в прошлом неизбежной частью городской жизни. Общественный транспорт остаётся востребованным элементом инфраструктуры: не все могут позволить себе личный транспорт или регулярные поездки на такси. Вам больно видеть ценник в 800 рублей по вечерам в час пик? Редакции тоже.

Сегодня, 17 декабря, городские власти закупили новые транспортные средства: 15 беспилотных электробусов "Стрела" с увеличенной вместительностью. Новенькие "Стрелы" отправятся на маршруты 8, 13 и 42. Помимо повышенной вместительности и внедрения ИИ, новый транспорт также более экологичен.
Маршрут в восточную часть города, маршрут №6, оснастят "Стрелами" в следующем году. Подготовкой специализированных колей для них дорожники были заняты последние полтора года, и на востоке работы ещё не завершены до конца.
Теперь не нужно ругаться с водителем: обстановку на дороге и в салоне определяет искусственный интеллект.
Но редакция напоминает: при нахождении в электробусе будьте взаимовежливы -- уступайте места пожилым людям, инвалидам и беременным женщинам, а при нахождении в автобусе снимайте рюкзаки и объёмные сумки с плеч.
-
 @ 705605d9:b4324038
2024-12-13 16:10:30
@ 705605d9:b4324038
2024-12-13 16:10:30В центре Горноправдинска произошла серьезная коммунальная авария, в результате которой значительная часть города осталась без электричества. По предварительной информации, причиной отключения стало повреждение высоковольтной линии, расположенной на улице Поспелова.
Авария произошла в результате сильного ветра и обильных осадков, которые наблюдались в последние дни. В результате падения дерева на линию электропередач произошло .короткое замыкание, что привело к отключению нескольких трансформаторных подстанций.
На данный момент специалисты работают над устранением последствий аварии. Восстановительные работы начались сразу после инцидента. В ЮТЭК пообещали, что работы закончат к 4 часам утра.
Видео происшествия:
-
 @ 705605d9:b4324038
2024-12-13 16:07:11
@ 705605d9:b4324038
2024-12-13 16:07:11Сегодня посёлок Горноправдинск, стал не просто точкой на карте, а настоящим центром молочного вселенной. Ведь именно здесь, в 2040 году, открылся самый крупный молочный комбинат в мире — гигантское предприятие, которое не только удивляет размерами, но и ставит новые стандарты в производстве молочных продуктов. Комбинат, который в народе уже окрестили "Млечным путём", выглядит как космическая станция, под завязку забитая самым современным оборудованием.

Зрелище потрясающее: массивные трубы, сверкающие резервуары и, конечно, в воздухе стойкий запах свежего молока, который теперь станет символом этого региона.
Генеральный директор комбината, Зульфия Новобсохова с гордостью демонстрирует всему миру чудо инженерной мысли. На церемонии открытия она, с блеском в глазах и лёгкой улыбкой, рассказала журналистам:
— "Мы не просто строили завод, мы строили мечту! Теперь наша продукция сможет достичь каждого уголка планеты, и, надеюсь, в ближайшее время мы поставим молоко даже на Марс. Кто знает, может, с помощью наших новых технологий завтра марсиане будут пить молоко с Горноправдинска!" — шутит она, как всегда, с долей иронии, присущей истинному бизнесмену.
Но шутки шутками, а величие нового предприятия впечатляет. Здесь установлены ультрасовременные линии по переработке молока, автоматизированные процессы, и роботы, которые до сих пор поражают своей точностью. Так что в планах — не только массовое производство сыра, йогуртов и творога, но и создание абсолютно новых продуктов с непревзойдённым вкусом и максимальной пользой для здоровья.
-
"Мы гордимся тем, что создаём будущее, а не просто следуем за ним. Это не просто комбинат, это философия, основанная на идее заботы о природе и человеке", — продолжает Зульфия, когда её спрашивают о возможных экологических последствиях. "Конечно, мы выбрали экологичные материалы, переработку отходов и минимизацию углеродного следа. Даже коровы, которые поставляют нам молоко, проходят строгий контроль по экологическим стандартам. И знаете, они тоже счастливы работать на таком производстве."
-
"Надеюсь, в будущем, когда люди станут заказывать наше молоко, они смогут выбрать не только его вкус, но и степень 'счастья' коровы. Мы думаем над этим, и это может стать нововведением на рынке!"
Не упустим и восхищённых зрителей: среди гостей мероприятия присутствуют известные личности, чиновники и даже любители молочной продукции со всего мира. Многие из них в порыве восторга делают снимки на фоне гигантских установок, поднимаясь на специальные платформы с видом на завод. Кто-то шутит, что теперь Горноправдинск может стать новым "молочным Лас-Вегасом"

Даже критики, известные своим скептицизмом по поводу промышленных гигантов, сдержанно кивают в знак уважения. Слишком уж велико было всё, что они увидели.
Подсчёты говорят сами за себя:
- Производственная мощность — 100 миллионов литров молока в год.
- Тысячи новых рабочих мест.
- Планы по выходу на международные рынки и экспорту в космос (по шутке или всерьёз — ещё предстоит выяснить)
- Бобровская порода коров бьёт все рекорды по удою в 40 546 кг молока.
Горноправдинск уже сегодня становится центром молочной дипломатии и промышленности. Если в ближайшие годы этот комбинат сможет оправдать все возложенные на него надежды, то вполне возможно, что мир начнёт измерять величие не только в мегаваттах энергии, но и в литрах молока.
-
-
 @ 705605d9:b4324038
2024-12-13 15:54:49
@ 705605d9:b4324038
2024-12-13 15:54:49Горноправдинск, посёлок, заслуженно гордящийся своим экологическим статусом и продвинутыми инициативами, стал центром литературной жизни Югры. В местной библиотеке состоялась яркая презентация книг югорских авторов, событие, ставшее предвестником масштабного проекта по созданию фонда Югорских писателей.
В уютном зале библиотеки собрались любители литературы, местные жители и гости посёлка. Центральным событием вечера стала презентация сразу нескольких значимых работ. Среди авторов – как маститые профессионалы, так и талантливые дебютанты.

Главным событием вечера стала презентация книги известного горноправдинского историка, профессора Николая Сергеевича Петрова, "Горноправдинск: хроники устойчивого развития". Книга, написанная с использованием новейших технологий визуализации данных и дополненная интерактивными элементами, рассказывает об истории посёлка, акцентируя внимание на его экологической стратегии и инновационных подходах к развитию.
"Мне было важно не только зафиксировать исторические факты, но и показать путь Горноправдинска как образца устойчивого развития, – делится Николай Сергеевич. – Надеюсь, моя книга вдохновит новых поколений на создание ещё более процветающего будущего".
Рядом с маститым историком блестяще представили свои работы авторы, работающие в жанре детской литературы. Елизавета Андреевна Кузнецова представила интерактивную книгу "Сказки Югорского леса: ожившая тайга", сочетающую традиционный фольклор с элементами дополненной реальности. Дети могут сканировать страницы и видеть оживающих персонажей сказок на экранах своих планшетов.
"Мы стремимся привить детям любовь к своей культуре и природе в интерактивной и занимательной форме, – пояснила Елизавета Андреевна. – Современные технологии позволяют нам сделать это эффективнее и интереснее".
Ещё одним ярким участником вечера стал Даниил Владимирович Колосов, автор книги "Югорские мифы в стихах и музыке". Даниил представил не только свою книгу, но и музыкальное сопровождение к ней, используя современные синтезаторы и традиционные югорские инструменты.
"Я хотел показать, как традиционная культура может гармонично сочетаться с современным искусством, – поделился Даниил Владимирович. – Музыка помогает лучше понять глубину и красоту югорских мифов".
Завершился вечер обсуждением перспектив развития литературы Югры и планов по созданию Фонда Югорских писателей. Участники выразили оптимизм и уверенность в том, что литературное наследие Югры будет и впредь богато и уникально. Презентация в Горноправдинске стала ясным подтверждением этого.
-
 @ 705605d9:b4324038
2024-12-13 15:52:11
@ 705605d9:b4324038
2024-12-13 15:52:11В 2040 году в посёлке Горноправдинск завершилась масштабная реставрация веревочного парка, который стал не только современным развлекательным объектом, но и примером экологической ответственности. В ходе работ были использованы исключительно натуральные материалы, такие как древесина местных пород, а также переработанные пластик и металл. Все конструкции теперь оснащены покрытиями, не вредящими экосистеме.

Важным нововведением стало применение солнечных панелей для питания освещения и системы видеонаблюдения, что позволило значительно снизить углеродный след парка. Кроме того, установлены инновационные системы сбора и очистки дождевой воды, которая используется для полива зелёных насаждений, а также для поддержания гигиеничных условий в туалетах.
Для повышения доступности, веревочный парк теперь включает маршруты для людей с ограниченными возможностями: специальные пандусы и адаптированные зоны для отдыха. В парке также появились новые образовательные элементы — интерактивные стенды и экскурсии по экологии, где посетители могут узнать о важности сохранения природы и устойчивого развития.
Проект реставрации стал возможен благодаря поддержке местных властей и экологических организаций, а новый парк уже стал местом притяжения для жителей и туристов.
-
 @ f527cf97:65e232ee
2024-12-13 15:50:50
@ f527cf97:65e232ee
2024-12-13 15:50:50A new breed of entrepreneurs is emerging on social media platforms, especially on LinkedIn—those who want to show (in new terms: coach) other entrepreneurs how to become successful. And even on Nostr I have already discovered the first coaches.
Their areas of influence vary from general measures to spiritual-mental attitude change, and even to specializations on a medium or a specific platform. Over the past few weeks, I have looked into several of them and expressed interest in their offerings, always with an open mindset: "Maybe they know something I don't, and I could learn something new." I engaged with generalists, mental attitude changers, and specialists. I went through a few stages that all look the same:
- They somehow get in touch with you, often subtly lured through indirect means so that they don’t appear to be cold-calling you (which is illegal in many countries).
- You are invited to a mass event, usually a webinar with general teasers about the offering.
- Then you are asked to pay to access the valuable information.
Here are my thoughts about this business model.
They all promise to know some kind of secret formula or have a proven system that you just need to follow to achieve success in 90% of cases (or so). This system has, of course, been tried and tested over the years, they say, and they have made an effort to formalize it—for you. So they can now sell it to you, saving you the trouble of doing the work yourself. The target audience seems to be entrepreneurs in their 20s and 30s, or those who want to become one. While they claim it’s for all age groups, the presentation clearly appeals more to this demographic. It would be difficult to convince someone in their 40s or 50s. No wonder, as all these success coaches I met were under 40 themselves and have no idea how people think when you get older.
Now, after reading their social media posts, which are admittedly persuasive in rhetoric, and after being tempted, like I was, to comment on one with "BS, that only works in exceptions," they respond positively, never offended, and in an inviting tone. Or they send you "info material" or some other goodies behind a link where you have to sign up with your email address. Since I use disposable email addresses, I have no problem with that and think, why not? Let’s see what they have to offer.
And sometime later, maybe in 2 or 3 weeks, you receive an invitation to a "webinar" at the same address. And that’s where it starts to get unethical. Most of them didn’t indicate in the sign-up for the initial info material that they would also use your email address for other purposes, or that the whole thing is actually set up with that intention. Such information should be placed near the email field according to EU privacy laws. If it’s missing, it’s a violation of GDPR and actually a justiciable issue.
But okay, I participated in all the webinars out of curiosity. And they are all structured the same way. First, there’s a one-hour presentation with slides covering general points, followed seamlessly by the introduction of their own product or service. There’s no "advertisement" or "sponsored" label beforehand (red flag number 2). It’s either access to several training videos or an initial consultation session to tailor the coaching to your specific needs. So it all boils down to selling the coach’s own product or service. In the past, this was done directly in the first step. That doesn’t work as well today, so they’ve added 1-2 steps beforehand with bait offers. But at the latest, after or at the end of the webinar, prices are presented. These range from 5,000 to 10,000 Euros. A young or unsuccessful entrepreneur has to invest this amount if they want to receive the formula for financial bliss.
Yet, they don’t even know exactly what they would be investing in. They are constantly led to believe that this magical formula works for most people, and in every case during the webinar, a previous successful client is showcased, who is now floating in the clouds of financial happiness thanks to this "secret formula." However, it is also mentioned that this formula must be specifically tailored to your business. Hence the 5-10K euro investment. This means that after at least 2 hurdles of customer attraction, you still don’t know what you will actually receive and specifically, whether it will really work for you. You are essentially buying a pig in a poke. And that is the main problem.
It is repeatedly pointed out that the customer also has their obligations, such as doing everything the coach recommends and investing a certain amount of time each week. But nothing is promised with certainty. You only hear the alleged success statistics of X% over and over again. You can’t verify that; you just have to take it on faith. And that’s when you start to gamble internally. "Ah, I’m sure I belong to the 90% (or whatever the success rate is) if I just follow along."
You also have to trust that the success example presented in person in the webinar is authentic, meaning that the success of this entrepreneur stems solely from the implementation of the coaching measures and not from other circumstances. I don’t want to accuse anyone of anything, but that’s a bit too much trust for me to invest. I’m more the type who believes "respect and politeness are free, but trust must be earned."
I addressed this candidly in the last "client meeting." I pointed out that I had no guarantees, even if I fully participated, that I could expect an increase in my leads/appointments/revenues (whatever they specifically promise). In contrast, their fees are secure and likely paid in advance. I see an imbalance in fairness there. Instead, I proposed a fair commission model. For every lead/appointment/revenue they bring me, I would pay them a certain commission. And if they are indeed as good as they claim, they shouldn’t have a problem with that. I also said it would be more "entrepreneurial" to share both the success and the risk. Because with their model, only one party (namely them) has their ducks in a row while I, as the coached one, am taking a gamble. There are so many other influencing factors beyond my participation. What if my country or my industry is in a recession, for example? Or I could think of many other factors that are out of my control.
Well, they vehemently rejected this proposal. No guts. No entrepreneurship on their side with this. I even said, "With your business model, it’s reasonable to suspect that you just want to rip me off and cash in, no matter what happens." That didn’t help either.
My father once said something wise. When I was 18 or 19 years old, I wanted to sell building savings insurance, and for that, I was supposed to attend a sales training that costed about 50 euros, which isn’t much. My father immediately said, "Nonsense. You want to make money, not spend it." That stuck with me, and this whole situation reminded me of that. Now, this doesn’t exclude entrepreneurial risk and investments, but it should be more tangible than a pile of promises and hot air. You need to limit the risk and uncertainty as much as possible. A commission model, like the one I proposed, would have been fairer. Let’s grow or fail together, right? But not just one side taking all the risks.
I also once worked as a math tutor in an organization with a money-back guarantee. Students who had failed math came to me every day for six weeks in the summer, and I prepared them for their last chance, the retake exam. Our promise was that after these six weeks, you would pass math and move up to the next grade without having to repeat the school year. And if not, you would get your entire course fee back, and both sides would have just wasted time. We only refunded one out of about 30 students, and the one's failure was more due to the immense pressure she received from home. All the others passed the retake exam, and 20% of them even became math whizzes in the following school year, achieving top grades.
So, beware of such "business models." Sharing the risk is fairer. And if someone really knows their stuff, they can easily take on a 30-to-1 risk. And if not, and they insist on securing all the money upfront … you know where I’m going with this.
-
 @ e1146a85:0de0b731
2024-12-13 15:34:32
@ e1146a85:0de0b731
2024-12-13 15:34:32When it comes to maintaining a comfortable home in Christchurch, having a reliable heat pump is essential. Whether you're looking to install a new system, keep your existing unit running smoothly, or understand the costs involved, DC Installation Services is here to help with all your heat pump needs. In this blog, we’ll cover important aspects of heat pumps in Chch, heat pump cleaning CHCH, and heat pump installation cost in Christchurch.
Heat Pumps in Christchurch: A Smart Choice for Comfort
Christchurch’s climate demands a heating and cooling solution that’s versatile, energy-efficient, and effective. Heat pumps in Chch are the perfect solution for homeowners looking to maintain a comfortable indoor environment throughout the year. These systems not only provide efficient heating during the cold winters but also cool your home in the summer, making them a year-round comfort solution.
At DC Installation Services, we offer a wide range of heat pumps designed to suit different home sizes and budgets. Whether you're looking for a wall-mounted system, a ducted system, or a multi-split heat pump for multiple rooms, we can help you choose the best option for your home. Our experienced technicians ensure the right installation, maximising energy efficiency and reducing your energy bills. The Importance of Heat Pump Cleaning in Christchurch.
To keep your heat pump functioning at its best, regular heat pump cleaning in Christchurch is essential. Over time, dust, dirt, and debris can accumulate inside the unit, affecting its efficiency and air quality. Without proper maintenance, this build-up can lead to higher energy consumption, reduced performance, and even system failure.
At DC Installation Services, we offer expert heat pump cleaning in Christchurch, including cleaning the filters, coils, and other key components of your system. Our thorough cleaning process ensures that your heat pump works efficiently, provides cleaner air, and extends the lifespan of your unit. Regular cleaning can help you avoid costly repairs and maintain your system's optimal performance. Whether you’re due for a routine cleaning or facing issues with airflow or cooling, our team is here to provide fast and effective service.
Understanding Heat Pump Installation Costs in Christchurch
When planning to install a heat pump in Christchurch, one of the first questions many homeowners have is, “What is the heat pump installation cost in Christchurch?” The installation cost of a heat pump can vary depending on several factors, including the type of heat pump, the size of the area to be heated or cooled, and the complexity of the installation.
At DC Installation Services, we offer transparent pricing with no hidden fees. We begin by assessing your home’s size, insulation, and specific needs to recommend the most efficient and cost-effective solution. The cost of installation typically includes the price of the heat pump unit, any required materials (such as ductwork or wall mounts), and the labor involved in installing the system. Depending on your choice of system, costs can range, but we always strive to provide competitive pricing and a high level of service.
We also take care of any permits or regulations required by local authorities to ensure that the installation is up to code. Our team will provide you with a detailed quote, so you can understand exactly what you're paying for before proceeding. Additionally, we offer ongoing maintenance packages to ensure your heat pump continues to work efficiently long after installation.
Why Choose DC Installation Services?
At DC Installation Services, we’re committed to providing high-quality products and expert services to all our customers. We understand that investing in a heat pump is a long-term decision, and we’re here to guide you every step of the way, from choosing the right system to installation and regular cleaning. With years of experience in the industry, we take pride in offering tailored solutions for your heating and cooling needs. Our team is dedicated to ensuring that your home stays comfortable, no matter the season, with top-notch heat pump cleaning in Christchurch, affordable heat pump installation cost in Christchurch, and reliable heat pump installations.
If you're ready to install a heat pump or need cleaning and maintenance for your existing unit, contact DC Installation Services today. We're here to help you achieve the perfect indoor climate at home!
-
 @ 705605d9:b4324038
2024-12-13 15:33:06
@ 705605d9:b4324038
2024-12-13 15:33:06Сельское хозяйство на пике
За десять лет Горноправдинск стал лидером в аграрной сфере. Теплицы работают круглогодично на солнечных батареях, поля оснащены автоматическими системами полива, а урожай собирают роботы. Местные фермеры выращивают десятки видов культур: от картофеля до редких сортов ягод, экспортируемых в другие регионы. Экологическая чистота продукции — визитная карточка города.

Экологичный город
Горноправдинск перешел на возобновляемую энергетику. Отходы перерабатываются в удобрения и биотопливо. Здания строят из дерева и других экологически чистых материалов. Улицы украшены зелеными зонами, а транспортная система работает на электричестве.
Жизнь людей
Каждый житель имеет доступ к современному жилью, паркам и образовательным программам. Городские гранты помогают развивать личные фермерские хозяйства. Туризм также набирает обороты благодаря экопаркам и фермерским фестивалям.
Горноправдинск за десятилетие стал образцом для других городов. Это место, где природа и технологии гармонично сосуществуют, а жители гордятся своим вкладом в процветание родного края.
-
 @ e1146a85:0de0b731
2024-12-13 15:32:33
@ e1146a85:0de0b731
2024-12-13 15:32:33When it comes to maintaining a comfortable home in Christchurch, having a reliable heat pump is essential. Whether you're looking to install a new system, keep your existing unit running smoothly, or understand the costs involved, DC Installation Services is here to help with all your heat pump needs. In this blog, we’ll cover important aspects of heat pumps in Chch, heat pump cleaning CHCH, and heat pump installation cost in Christchurch.
Heat Pumps in Christchurch: A Smart Choice for Comfort
Christchurch’s climate demands a heating and cooling solution that’s versatile, energy-efficient, and effective. Heat pumps in Chch are the perfect solution for homeowners looking to maintain a comfortable indoor environment throughout the year. These systems not only provide efficient heating during the cold winters but also cool your home in the summer, making them a year-round comfort solution.
At DC Installation Services, we offer a wide range of heat pumps designed to suit different home sizes and budgets. Whether you're looking for a wall-mounted system, a ducted system, or a multi-split heat pump for multiple rooms, we can help you choose the best option for your home. Our experienced technicians ensure the right installation, maximising energy efficiency and reducing your energy bills. The Importance of Heat Pump Cleaning in Christchurch.
To keep your heat pump functioning at its best, regular heat pump cleaning in Christchurch is essential. Over time, dust, dirt, and debris can accumulate inside the unit, affecting its efficiency and air quality. Without proper maintenance, this build-up can lead to higher energy consumption, reduced performance, and even system failure.
At DC Installation Services, we offer expert heat pump cleaning in Christchurch, including cleaning the filters, coils, and other key components of your system. Our thorough cleaning process ensures that your heat pump works efficiently, provides cleaner air, and extends the lifespan of your unit. Regular cleaning can help you avoid costly repairs and maintain your system's optimal performance. Whether you’re due for a routine cleaning or facing issues with airflow or cooling, our team is here to provide fast and effective service.
Understanding Heat Pump Installation Costs in Christchurch
When planning to install a heat pump in Christchurch, one of the first questions many homeowners have is, “What is the heat pump installation cost in Christchurch?” The installation cost of a heat pump can vary depending on several factors, including the type of heat pump, the size of the area to be heated or cooled, and the complexity of the installation.
At DC Installation Services, we offer transparent pricing with no hidden fees. We begin by assessing your home’s size, insulation, and specific needs to recommend the most efficient and cost-effective solution. The cost of installation typically includes the price of the heat pump unit, any required materials (such as ductwork or wall mounts), and the labor involved in installing the system. Depending on your choice of system, costs can range, but we always strive to provide competitive pricing and a high level of service.
We also take care of any permits or regulations required by local authorities to ensure that the installation is up to code. Our team will provide you with a detailed quote, so you can understand exactly what you're paying for before proceeding. Additionally, we offer ongoing maintenance packages to ensure your heat pump continues to work efficiently long after installation.
Why Choose DC Installation Services?
At DC Installation Services, we’re committed to providing high-quality products and expert services to all our customers. We understand that investing in a heat pump is a long-term decision, and we’re here to guide you every step of the way, from choosing the right system to installation and regular cleaning. With years of experience in the industry, we take pride in offering tailored solutions for your heating and cooling needs. Our team is dedicated to ensuring that your home stays comfortable, no matter the season, with top-notch heat pump cleaning in Christchurch, affordable heat pump installation cost in Christchurch, and reliable heat pump installations.
If you're ready to install a heat pump or need cleaning and maintenance for your existing unit, contact DC Installation Services today. We're here to help you achieve the perfect indoor climate at home!
-
 @ 705605d9:b4324038
2024-12-13 15:29:03
@ 705605d9:b4324038
2024-12-13 15:29:03Горноправдинск, известный своим чистым воздухом и выдающимся качеством молочной продукции, в 2040 году стал символом экологической устойчивости и продовольственной безопасности в России. В преддверии Нового года мы решили исследовать, насколько этот живописный посёлок готов к празднованию главного события зимы. Подготовка к торжествам включает в себя не только организационные аспекты, но и атмосферу, которую создают местные жители. Как собирается отмечать Новый год экологически чистый и инновационный Горноправдинск?
Экологическая Программа и Устойчивое Развитие
С начала 2030-х годов Горноправдинск стал флагманом экологических инициатив в регионе. Местные власти и инициативные группы активно внедряли программы по утилизации отходов, экономии ресурсов и восстановлению природных экосистем. В медицинских учреждениях и образовательных учреждениях проводятся занятия по экологии для детей, направленные на формирование любви к природе и заботы о чистоте окружающей среды.

Реализация Экологических Инициатив
К 2040 году в Горноправдинске действуют специальные площадки для раздельного сбора отходов, а переработка мусора достигла 80%. В связи с праздником планируется установка дополнительных ёмкостей для сбора упаковки от новогодних товаров и подарков. Такие меры помогают не только сократить количество отходов, но и формируют осознанное отношение местных жителей к потреблению.
Кроме того, горноправдинцы активно устраивают акции по посадке деревьев. В преддверии Нового года в рамках проекта «Ёлка вместо ёлки» планируется высадка саженцев хвойных деревьев в окрестных лесах. Эта акция не только украсит природу, но и станет ясно обозначенным шагом к более устойчивому образу жизни.
Подготовка Городских Улиц к Празднику
Не менее важной частью подготовки к празднованию является украшение Горноправдинска. Улица за улицей преображаются под натиском новогодних огней, гирлянд и ярких декораций. В этом году власти уделили особое внимание использованию экологически чистых материалов. Везде, где это возможно, используются светящиеся элементы на солнечных батареях.

Разработка Новогодней Тематики
Каждая улица имеет своё уникальное оформление. В центре посёлка планируется установка большой ёлки, украшенной только перерабатываемыми игрушками и гирляндами. В рамках новогодней кампании будут проведены конкурсы на лучшее оформление жилых домов. Местные жители уже активно начали обсуждать идеи и искать средства на украшение своих участков, что добавляет атмосферы совместного празднования.
Помимо визуального оформления, каждую неделю в преддверии праздника проводятся мастер-классы по изготовлению экологически чистых новогодних игрушек. Это становится популярным среди детей и усиливает общественное единство в целом.
Культурные Мероприятия и Социальные Акции
Воспитание чувства сообщества и активное вовлечение жителей в культурные мероприятия – важная часть новогодней подготовки Горноправдинска. В этом году запланирован ряд акций, направленных на объединение всех слоёв населения.

Новогодние Ярмарки и Концерты
Появление ярмарок и концертов отмечает новый этап в социальном взаимодействии. Местные фермеры выставят свою продукцию на новогодние ярмарки, где каждый сможет попробовать и приобрести экологически чистые продукты. Параллельно с ярмаркой будут организованы музыкальные выступления местных гармонистов и ансамблей. Это станет отличной возможностью для отдыха и веселья для жителей и гостей посёлка.
В этом году особое внимание уделяется инклюзивности мероприятий. На праздники будут приглашены жители с ограниченными возможностями, для которых организуют специальные зоны и программы.
Образовательные Программы
Культурные мероприятия будут охватывать не только развлекательный аспект, но и образовательный. Специальные мастер-классы по экологии и устойчивому развитию будут проведены для желающих. Это даёт возможность не только узнать о новогодних традициях, но и понять, как сохранить природу в повседневной жизни.

Поддержка Местного Производителя
Как лидер молочной продукции в регионе, Горноправдинск придаёт особое значение поддержанию местного производства. В этом году новогодние праздники также будут направлены на обеспечение спроса на местные товары и поддержку фермеров.
Продуктовые Лавки с Местными Продуктами
На ярмарках и специализированных магазинах можно будет приобрести свежемолочную продукцию, сезонные овощи и фрукты, а также продукты, произведенные с минимальным воздействием на окружающую среду. Это позволит жителям избежать покупки импортных товаров, способствуя развитию местной экономики и снижению углеродного следа.
Кроме того, организаторы праздника планируют запустить проект «Семейные коробки с экологическими продуктами», которые будут включать в себя новогодние наборы местных продуктов, что станет отличным подарком для близких.
Готовность К Новогодним Праздникам
В преддверии Нового года, оценив масштабы подготовки, можно с уверенностью сказать, что Горноправдинск готов справиться с любыми вызовами. Готовность к празднику выражается не только в организационных аспектах, но и в отношении местных жителей.
Обсуждение Потребностей Сообщества
Местная администрация активно принимает во внимание мнение жителей. Были проведены опросы о планируемых мероприятиях и необходимом финансировании. Таким образом, все желания и предпочтения людей учтены, что добавляет комфорта в предстоящие праздники.
Профессиональная Подготовка
Члены местной администрации, вместе с волонтёрами, уже начали разрабатывать сценарии праздничных мероприятий и заниматься логистикой. Это позволит предотвратить затруднения на праздниках и обеспечить бесперебойный поток организации событий.
Горноправдинск – Место, Где Природа Встречает Праздник
Горноправдинск, как один из самых экологически чистых посёлков региона, готов к встрече Нового года 2040 года с радостью и надеждой. Благодаря усилиям местных жителей, администрации и компаний, жизнь в посёлке становится более гармоничной и устойчивой. Принципы экологии позволяют сохранять природу и при этом радоваться празднику.
Новый год в Горноправдинске станет не только украшением зимы, но и символом единства сообщества, заботы о природе и стремления к устойчивому развитию. В этом году каждая ёлка, каждый огонёк и каждая усмешка будут напоминать о том, что праздники – это не только потрать деньги на подарки, но и проявление любви к окружающему миру. Благодаря уникальной культуре и традициям, праздник пройдёт замечательно, и жители сможет получить радость и тепло от общения друг с другом, что является главным в преддверии Нового года
-
 @ 705605d9:b4324038
2024-12-13 15:20:11
@ 705605d9:b4324038
2024-12-13 15:20:11В этом году Горноправдинск, преобразившийся за последние десятилетия из скромного посёлка в крупный научно-технологический центр, стал площадкой для масштабной научной конференции по развитию высоких технологий. Событие, привлекшее учёных со всего региона, проходило в недавно отреставрированном “Сибирском Куполе”.

Конференция, проходившая в течение трёх дней, сосредоточилась на четырёх основных направлениях: интегрированные системы энергообеспечения, устойчивое сельское хозяйство будущего, развитие искусственного интеллекта в городской среде и новые технологии в экологии. Участники активно обсуждали перспективы использования возобновляемых источников энергии, разработку устойчивых агротехнологий, адаптацию ИИ для управления городским транспортом и обеспечения безопасности, а также новейшие методы биотехнологий для очистки окружающей среды.
Одним из самых обсуждаемых докладов стал выступление доктора физико-математических наук Елены Петровой, руководителя проекта “Сибирская энергетическая система”. Она представила новую концепцию энергообеспечения города, основанную на использовании геотермальной энергии и солнечных батарей высокой эффективности.

Также в конференции приняли участие ведущие учёные из разных университетов мира. Особое внимание привлекло выступление профессора Анатолия Евстигнеева, исследователя в области искусственного интеллекта. Он разработал новые алгоритмы обработки данных, способные оптимизировать управление городской инфраструктурой.
Кроме докладов, в рамках конференции проходили практические сессии, демонстрационные залы новых технологий, а также круглые столы, посвящённые взаимодействию научного сообщества и бизнеса. Оживлённо проходили дебаты о современных этических вопросах, связанных с развитием высоких технологий.
-
 @ 705605d9:b4324038
2024-12-13 15:16:34
@ 705605d9:b4324038
2024-12-13 15:16:34В 2040 году посёлок Горноправдинск пережил настоящий экологический апокалипсис. На этот раз причина катастрофы была не в погодных условиях, а в самой сути человеческой цивилизации — в канализации. Местные власти были вынуждены объявить чрезвычайное положение после того, как порыв в центральной канализационной системе стал причиной затопления улиц, домов и, судя по всему, репутации городского водоканала.

По словам экспертов, прорыв произошёл в самый неожиданный момент — во время празднования «Дня чистоты», мероприятия, которое на протяжении десятилетий служило флагманом экологических инициатив посёлка. По случаю праздника были даже установлены новые трубопроводы, что, как оказалось, не только не решило проблему, но и создало дополнительные угрозы.
Комментарий местного жителя: «Я думал, это всё шутки! Наш посёлок всегда гордился своей старинной системой водоснабжения, а теперь у нас просто… старинная система затопления. Вроде и воняет, и ничего не сделаешь — канализация теперь не просто инфраструктура, а часть интерьера». Ситуация осложнялась тем, что этот прорыв стал лишь частью более широкого тренда. За последние несколько лет, из-за стремительного увеличения населения и устаревших инженерных систем, подобные происшествия стали регулярными.
Пострадали как жители, так и бизнесы. Особенно не повезло владельцам кафе и магазинов в центре города, которые вскоре начали предлагать новые виды услуг, такие как «канализационные экскурсии» и «фитнес в бурлящих водах», рассчитывая на поток туристов.
Пока жители Горноправдинска спасают свои дома и ищут способы пережить новый тренд, один остаётся неоспоримым — канализация больше не просто забота коммунальных служб. Она стала тем, чем мы с вами живём и, увы, часто и за что платим.
-
 @ 418b49e3:8039624b
2024-12-13 14:17:00
@ 418b49e3:8039624b
2024-12-13 14:17:00A alimentação desempenha um papel crucial na prevenção de diversas doenças, incluindo o câncer. Estudos científicos demonstram que uma dieta equilibrada e rica em alimentos naturais pode reduzir significativamente o risco de desenvolvimento de tumores e auxiliar na recuperação de pacientes que enfrentam essa doença.
Como a Alimentação Atua na Prevenção do Câncer
-
Antioxidantes: Alimentos ricos em antioxidantes, como frutas vermelhas (morango, mirtilo, amora) e vegetais verde-escuros (brócolis, espinafre, couve), ajudam a neutralizar os radicais livres, que são moléculas instáveis associadas ao desenvolvimento do câncer.
-
Fibras: A ingestão adequada de fibras, presentes em cereais integrais, leguminosas, frutas e verduras, promove a saúde do trato gastrointestinal e reduz o risco de câncer de cólon e reto.
-
Fitonutrientes: Compostos encontrados em alimentos de origem vegetal, como carotenoides, flavonoides e sulforafano, possuem propriedades anticancerígenas. Exemplos incluem cenoura, tomate e alho.
-
Inflamação Reduzida: Dietas anti-inflamatórias, com alimentos como azeite de oliva extra virgem, peixes ricos em ômega-3 (salmão, sardinha) e castanhas, ajudam a diminuir processos inflamatórios crônicos que podem levar ao surgimento do câncer.
Alimentos que Podem Auxiliar no Combate ao Câncer
-
Cúrcuma: Contém curcumina, um potente anti-inflamatório e antioxidante, capaz de inibir o crescimento de células cancerígenas em estudos laboratoriais.
-
Chá Verde: Rico em catequinas, compostos antioxidantes que podem retardar ou impedir o crescimento de tumores.
-
Frutas Cítricas: Laranja, limão e toranja são fontes de vitamina C e outros antioxidantes que fortalecem o sistema imunológico.
-
Vegetais Crucíferos: Brócolis, couve-flor, couve de Bruxelas e repolho possuem sulforafano, que pode ajudar a eliminar substâncias cancerígenas do organismo.
Hábitos Alimentares para Prevenção
-
Evitar Alimentos Processados: Embutidos, enlatados e produtos ricos em conservantes e aditivos químicos estão associados ao aumento do risco de vários tipos de câncer.
-
Moderação no Consumo de Carnes Vermelhas: O excesso pode aumentar o risco de câncer colorretal. Prefira fontes de proteínas magras como peixes e aves.
-
Hidratação Adequada: Beber água suficiente ajuda a eliminar toxinas e manter o organismo equilibrado.
-
Priorizar Orgânicos: Sempre que possível, opte por alimentos orgânicos para evitar a exposição a pesticidas, que podem ter efeitos cancerígenos.
Alimentação no Tratamento do Câncer**
Embora não exista uma "cura alimentar" para o câncer, a nutrição adequada pode ser uma aliada no tratamento, melhorando a resposta imunológica e reduzindo os efeitos colaterais das terapias. Consultar um nutricionista especializado é essencial para adaptar a dieta às necessidades individuais do paciente. Investir em uma alimentação rica, variada e balanceada é uma estratégia poderosa para prevenir o câncer e melhorar a qualidade de vida. Pequenas mudanças nos hábitos alimentares podem ter um impacto significativo na saúde a longo prazo, promovendo bem-estar e longevidade.
Referências
World Cancer Research Fund/American Institute for Cancer Research. Diet, Nutrition, Physical Activity and Cancer: A Global Perspective. Available at: www.wcrf.org.
National Cancer Institute. Antioxidants and Cancer Prevention. Available at: www.cancer.gov.
Harvard T.H. Chan School of Public Health. The Nutrition Source – Phytochemicals. Available at: www.hsph.harvard.edu.
American Cancer Society. Diet and Physical Activity: What’s the Cancer Connection? Available at: www.cancer.org.
-
-
 @ 418b49e3:8039624b
2024-12-13 14:15:21
@ 418b49e3:8039624b
2024-12-13 14:15:21A alimentação desempenha um papel crucial na prevenção de diversas doenças, incluindo o câncer. Estudos científicos demonstram que uma dieta equilibrada e rica em alimentos naturais pode reduzir significativamente o risco de desenvolvimento de tumores e auxiliar na recuperação de pacientes que enfrentam essa doença.
Como a Alimentação Atua na Prevenção do Câncer
-
Antioxidantes: Alimentos ricos em antioxidantes, como frutas vermelhas (morango, mirtilo, amora) e vegetais verde-escuros (brócolis, espinafre, couve), ajudam a neutralizar os radicais livres, que são moléculas instáveis associadas ao desenvolvimento do câncer.
-
Fibras: A ingestão adequada de fibras, presentes em cereais integrais, leguminosas, frutas e verduras, promove a saúde do trato gastrointestinal e reduz o risco de câncer de cólon e reto.
-
Fitonutrientes: Compostos encontrados em alimentos de origem vegetal, como carotenoides, flavonoides e sulforafano, possuem propriedades anticancerígenas. Exemplos incluem cenoura, tomate e alho.
-
Inflamação Reduzida: Dietas anti-inflamatórias, com alimentos como azeite de oliva extra virgem, peixes ricos em ômega-3 (salmão, sardinha) e castanhas, ajudam a diminuir processos inflamatórios crônicos que podem levar ao surgimento do câncer.
Alimentos que Podem Auxiliar no Combate ao Câncer
-
Cúrcuma: Contém curcumina, um potente anti-inflamatório e antioxidante, capaz de inibir o crescimento de células cancerígenas em estudos laboratoriais.
-
Chá Verde: Rico em catequinas, compostos antioxidantes que podem retardar ou impedir o crescimento de tumores.
-
Frutas Cítricas: Laranja, limão e toranja são fontes de vitamina C e outros antioxidantes que fortalecem o sistema imunológico.
-
Vegetais Crucíferos: Brócolis, couve-flor, couve de Bruxelas e repolho possuem sulforafano, que pode ajudar a eliminar substâncias cancerígenas do organismo.
Hábitos Alimentares para Prevenção
-
Evitar Alimentos Processados: Embutidos, enlatados e produtos ricos em conservantes e aditivos químicos estão associados ao aumento do risco de vários tipos de câncer.
-
Moderação no Consumo de Carnes Vermelhas: O excesso pode aumentar o risco de câncer colorretal. Prefira fontes de proteínas magras como peixes e aves.
-
Hidratação Adequada: Beber água suficiente ajuda a eliminar toxinas e manter o organismo equilibrado.
-
Priorizar Orgânicos: Sempre que possível, opte por alimentos orgânicos para evitar a exposição a pesticidas, que podem ter efeitos cancerígenos.
Alimentação no Tratamento do Câncer**
Embora não exista uma "cura alimentar" para o câncer, a nutrição adequada pode ser uma aliada no tratamento, melhorando a resposta imunológica e reduzindo os efeitos colaterais das terapias. Consultar um nutricionista especializado é essencial para adaptar a dieta às necessidades individuais do paciente. Investir em uma alimentação rica, variada e balanceada é uma estratégia poderosa para prevenir o câncer e melhorar a qualidade de vida. Pequenas mudanças nos hábitos alimentares podem ter um impacto significativo na saúde a longo prazo, promovendo bem-estar e longevidade.
Referências
World Cancer Research Fund/American Institute for Cancer Research. Diet, Nutrition, Physical Activity and Cancer: A Global Perspective. Available at: www.wcrf.org.
National Cancer Institute. Antioxidants and Cancer Prevention. Available at: www.cancer.gov.
Harvard T.H. Chan School of Public Health. The Nutrition Source – Phytochemicals. Available at: www.hsph.harvard.edu.
American Cancer Society. Diet and Physical Activity: What’s the Cancer Connection? Available at: www.cancer.org.
-