-
 @ 330516bf:ea23d292
2024-12-20 03:35:09
@ 330516bf:ea23d292
2024-12-20 03:35:09The self-declaration of identity is a philosophical open source project, hosted at https://memdeklaro.github.io/
Foreword
ID documents do more harm than good and should not be seen as a solution for trust or authentication. Many economic and social interactions can be done anonymously. For other situations, trust can be achieved by simply saying your (self-chosen) name, using a web-of-trust, word-of-mouth reputation, vouches, memberships, escrows or cash deposits, and authentication can be achieved by using a password, cryptographic key pair (e.g. PGP, Monero) or physical key or code (such as house keys or a safe code).
Background
In recent years, more and more things are asking for proof of identity, from basic necessities like jobs, housing and healthcare, to smaller things like receiving mail, buying a sim card or joining a gym. However, it is not enough to write your name and address on a form. Instead, only government-issued IDs are accepted, which gives the state a “monopoly on identity”.
Monopolies are dangerous in general due to the fact that if the service provider is harmful, inaccessible or otherwise problematic, you cannot choose a different provider, start your own provider, or go without. This particular monopoly is even worse, considering that access to government ID determines if you may participate in the economy (jobs, banking), society (housing, volunteer work, education, libraries, sports) or even exist (national borders).
Many people have no access to government ID. This group includes some stateless people, refugees, people who weren’t registered at birth, and people who escaped from child abuse, domestic abuse or cult abuse. The state’s claimed solutions, such as asylum procedures, stateless determination procedures, delayed registration of birth, child protective services and witness protection, often cannot help in practice, as the victim is often ignored, accused of lying, blamed for the persecution, or worse sent back to the persecutors against their will. Despite issuing laissez-passer and Nansen passports in the past, the United Nations and Red Cross do not issue alternative IDs today. It would be a relief if these processes would work and allow vulnerable people to escape from undeserved and dangerous situations, but unfortunately this is not the reality.
In addition, the collectivist concept of citizenship can be dangerous. For example, if someone does not identify with their birth culture, they should not be forced to follow it for life or identify themselves as a member of this culture. Instead, they should be free to dissent against this culture or leave this culture’s jurisdiction. Even worse is conscription — the cruel system where a nation-state can force someone against their will to kill or be killed, just because they happened to be born inside a certain territory. The world would be more free if people could exist as individuals, conscientious objectors against the fatalism of birth cultures and violence of statism, with freedom of association to leave hostile environments and join self-chosen communities.
“The blood of the covenant is thicker than the water of the womb.”
Self-declaration of identity gives people the power to decide their own fate. People are no longer the property of nations, governments, birth cultures or birth parents. The choice of your own name and renunciation of your circumstances of birth is a liberating act of individualism, where your ideals, actions and efforts matter more than the situation that you were arbitrarily born into.
Self-declaration of identity
Instead of requiring third parties such as birth countries, birth cultures and birth parents to define an individual’s identity, the self-declaration allows you to define your own name and eschews the concepts of birth countries and citizenship.
The self-declaration is a CR-80 plastic card or paper business card (85.6mm x 54mm). The self-declaration is written in Esperanto and includes the Esperanto flag and symbol. Esperanto was chosen because it is anational (sennacieca = not associated with a specific country, culture or state) and was created as a borderless language of peace, built on voluntary free association. The design features artwork of a peace dove in a blue sky with clouds.
As it is a self-declaration, it is not stored in a central database, does not require a third party’s permission and does not need to be issued by an authority. You are the authority over your own life.
The self-declaration includes the text:
- Title: Self-declaration of identity (Memdeklaro de identeco)
- Location: Esperanto community (Esperantujo)
- Issuer: EPO (ISO code for Esperanto)
- Quote: One world, one humankind (Unu mondo, unu homaro)
The self-declaration of identity contains:
- Self-chosen first name (Antaŭnomo) and self-chosen surname (Nomo) → an individual should be able to freely choose their own name
- Birth date (Naskiĝdato) → for declaration of age
- Photo → Dimensions 35mm x 45mm
- Signature (Subskribo) → sign your self-declaration
- Notes field (Notoj) → a place to write a note, e.g. “the holder is a conscientious objector” (Portanto estas konscienca obĵetanto)
- ID number (Numero), issuance date (Eldondato), expiry date (Limdato), issuer (Eldonisto), MRZ → bureaucratic boilerplate
The self-declaration of identity does not contain:
- Place of birth → allows people to cut ties with hostile environments and self-define their culture, beliefs and personal ties
- Citizenship or stateless status → allows people to cut ties with hostile governments or cultures, and exist as an individual instead of as property of a state that they did not choose
- Parents’ names → allows victims of child abuse to cut ties with abusers
To make your own:
- Use the generator at https://memdeklaro.github.io/ or download the repo (https://github.com/memdeklaro/memdeklaro.github.io/) and open index.html in your browser
- Alternatively download the front template (fronto.jpg) and back template (dorso.jpg) from the linked repo, and use an image editor such as GIMP to add your text (the font OCR-B.ttf is provided) and your photo and signature
- Calculate the MRZ code here (TD1): https://www.dynamsoft.com/tools/mrz-generator/ (Choose any country, then replace it with EPO)
- Print it out as a business card and optionally laminate (dimensions: 85.6mm x 54mm) or order a CR-80 plastic card from a printing service
Example:

Note:
Unfortunately the self-declaration of identity cannot be used to bypass government ID requirements, such as for jobs, housing, healthcare, finances, volunteer work, contracts, receiving mail or buying a sim card. Other non-government IDs such as Digitalcourage Lichtbildausweis (https://shop.digitalcourage.de/gadgets/lichtbildausweis-mit-selbst-waehlbaren-daten.html) and World Passport (https://worldcitizengov.org/what-is-the-world-passport/) have the same limitations.
Nation-states’ refusal to print IDs for undocumented, stateless and unregistered people (while forcing government ID requirements on employers, landlords, doctors and more) can and does put innocent people’s lives in danger. But unfortunately even the United Nations has not been able to change this, despite issuing conventions on statelessness and refugee status in the 1950s.
Further Reading
For further reading about identity (and why the state’s monopoly is harmful):
Passports Were a “Temporary” War Measure — Speranta Dumitru https://fee.org/articles/passports-were-a-temporary-war-measure
During World War II, we did have something to hide — Hans de Zwart https://medium.com/@hansdezwart/during-world-war-ii-we-did-have-something-to-hide-40689565c550
The Little-Known Passport That Protected 450,000 Refugees — Cara Giaimo https://www.atlasobscura.com/articles/nansen-passport-refugees
With each person left living on the streets, we are losing as a society — Petr Baroch https://www.statelessness.eu/blog/each-person-left-living-streets-we-are-losing-society
The rarely discussed dangers of KYC and what you can do about it — Anarkio https://vonupodcast.com/know-your-customer-kyc-the-rarely-discussed-danger-guest-article-audio
Exclusion and identity: life without ID — Privacy International https://www.privacyinternational.org/long-read/2544/exclusion-and-identity-life-without-id
Proving who I am: the plight of people in detention without proof of legal identity — Vicki Prais https://www.penalreform.org/blog/proving-who-i-am-the-plight-of-people/
Establishing identity is a vital, risky and changing business — The Economist https://www.economist.com/christmas-specials/2018/12/18/establishing-identity-is-a-vital-risky-and-changing-business
What’s in a name? The case for inclusivity through anonymity — Common Thread https://blog.twitter.com/common-thread/en/topics/stories/2021/whats-in-a-name-the-case-for-inclusivity-through-anonymity
True Names Not Required: On Identity and Pseudonymity in Cyberspace — Der Gigi https://dergigi.medium.com/true-names-not-required-fc6647dfe24a
Citizenship is obsolete — Samuela Davidova https://medium.com/@DavidovaSamuela/citizenship-is-obsolete-c36a20056752
License
Public Domain
Source code: https://github.com/memdeklaro/memdeklaro.github.io
Infographic

Translations
(Machine translated)\ Memdeklaro de identenco: self declaration of identity, autodeclaración de identidad, autodeclaração de identidade, autodéclaration d’identité, autodichiarazione di identità, autodeclararea identității, Selbsterklärung zur Identität, eigen verklaring van identiteit, Selvdeklaration af identitet, självdeklaration av identitet, egenerklæring om identitet, henkilöllisyysvakuutus, Isikuandmete esitamine, identitātes pašdeklarēšana, savęs deklaravimas, önbevallás a személyazonosságról, własna deklaracja tożsamości, vlastní prohlášení o totožnosti, vlastné vyhlásenie o totožnosti, samoprijava identitete, самодеклариране на самоличността, самопроголошення ідентичності, самозаявление о личности, αυτο-δήλωση ταυτότητας, pernyataan identitas diri, öz kimlik beyanı, الإعلان الذاتي عن الهوية, 身份自报, 身份自報, 自己申告, 신원 자기 선언
...
-
 @ 4dffec17:4c4cbd48
2024-12-20 03:06:46
@ 4dffec17:4c4cbd48
2024-12-20 03:06:46Why Are Cryptocurrencies Important? Cryptocurrencies are changing the world for several reasons:
- Decentralization: They remove the need for banks, giving users more control.
- Security: Blockchain ensures secure, tamper-proof transactions.
- Financial Inclusion: Cryptos give financial access to people without traditional bank accounts.
- Innovation: Technologies like smart contracts and DeFi are reshaping industries. By breaking barriers and reducing costs, cryptocurrencies are paving the way for a more inclusive and transparent financial future.
Next: Explore the benefits of using cryptocurrency!
-
 @ 5d4b6c8d:8a1c1ee3
2024-12-20 01:06:22
@ 5d4b6c8d:8a1c1ee3
2024-12-20 01:06:22Here are the box score averages of two 6'6" NBA guards.
Which one is Jordan and who is the other?
| Player | eFG% | Points | Rebounds | Assists | Steals | Blocks | |--------|--------|-------|-------------|--------|--------|---------| | 1 | 0.561 | 30.3 | 5.5 | 6.3 | 1.9 | 1.0 | | 2 | 0.547 | 31.5 | 6.0 | 5.5 | 2.7 | 1.0 |
What's the significance of this comparison?
originally posted at https://stacker.news/items/817115
-
 @ 4685f3d6:9fe6995b
2024-12-20 00:17:35
@ 4685f3d6:9fe6995b
2024-12-20 00:17:35Bitcoin vs. Traditional Money: Bitcoin and fiat currencies serve as mediums of exchange but differ fundamentally.
Key Differences Control: Bitcoin is decentralized, while fiat is regulated by governments and central banks. Supply: Bitcoin has a limited supply (21 million coins), while fiat can be printed indefinitely. Form: Bitcoin exists digitally, whereas fiat is both physical and digital. Transaction Speed and Fees: Bitcoin offers faster, cheaper global transactions compared to fiat's slower and costlier systems. Transparency and Accessibility: Bitcoin is transparent and inclusive, while fiat can be opaque and regulated.
Pros of Bitcoin Decentralized, borderless, and resistant to inflation. Provides financial inclusion and transaction transparency. Cons of Bitcoin
Highly volatile, less universally accepted, and energy-intensive. Requires internet and technical knowledge to use effectively. Pros of Fiat Stable, widely accepted, and backed by governments. Offers consumer protections and ease of use. Cons of Fiat Inflation risk, high transaction costs, limited privacy, and susceptibility to government control. Conclusion
Bitcoin is revolutionary but not yet a full replacement for fiat. It complements traditional money by offering new possibilities for global and financial freedom.
bitcoin
9ja
afro
yakihonne
-
 @ 1cb14ab3:95d52462
2024-12-19 23:15:14
@ 1cb14ab3:95d52462
2024-12-19 23:15:14 -
 @ 5d4b6c8d:8a1c1ee3
2024-12-19 23:05:41
@ 5d4b6c8d:8a1c1ee3
2024-12-19 23:05:41After being on vacation with my parents, I have to wonder how people live like that.
My parents are both great people and even better grandparents, but so much uninterrupted time together becomes immensely tedious. Maybe, over even more time together, you develop habits and patterns that smooth off some of the edges.
We've been thinking about moving and part of that calculation is whether we should be preparing for the inevitability of having one of my parents move in with us, when that time comes.
Hopefully, that day is far off in the future because 1. I love them and want them around for a long time, 2. I want my daughter to have a great relationship with them for a long time, and 3. I'd be annoyed out of my mind if I had to live with one of them.
originally posted at https://stacker.news/items/816929
-
 @ fe32298e:20516265
2024-12-16 20:59:13
@ fe32298e:20516265
2024-12-16 20:59:13Today I learned how to install NVapi to monitor my GPUs in Home Assistant.

NVApi is a lightweight API designed for monitoring NVIDIA GPU utilization and enabling automated power management. It provides real-time GPU metrics, supports integration with tools like Home Assistant, and offers flexible power management and PCIe link speed management based on workload and thermal conditions.
- GPU Utilization Monitoring: Utilization, memory usage, temperature, fan speed, and power consumption.
- Automated Power Limiting: Adjusts power limits dynamically based on temperature thresholds and total power caps, configurable per GPU or globally.
- Cross-GPU Coordination: Total power budget applies across multiple GPUs in the same system.
- PCIe Link Speed Management: Controls minimum and maximum PCIe link speeds with idle thresholds for power optimization.
- Home Assistant Integration: Uses the built-in RESTful platform and template sensors.
Getting the Data
sudo apt install golang-go git clone https://github.com/sammcj/NVApi.git cd NVapi go run main.go -port 9999 -rate 1 curl http://localhost:9999/gpuResponse for a single GPU:
[ { "index": 0, "name": "NVIDIA GeForce RTX 4090", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 16, "power_limit_watts": 450, "memory_total_gb": 23.99, "memory_used_gb": 0.46, "memory_free_gb": 23.52, "memory_usage_percent": 2, "temperature": 38, "processes": [], "pcie_link_state": "not managed" } ]Response for multiple GPUs:
[ { "index": 0, "name": "NVIDIA GeForce RTX 3090", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 14, "power_limit_watts": 350, "memory_total_gb": 24, "memory_used_gb": 0.43, "memory_free_gb": 23.57, "memory_usage_percent": 2, "temperature": 36, "processes": [], "pcie_link_state": "not managed" }, { "index": 1, "name": "NVIDIA RTX A4000", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 10, "power_limit_watts": 140, "memory_total_gb": 15.99, "memory_used_gb": 0.56, "memory_free_gb": 15.43, "memory_usage_percent": 3, "temperature": 41, "processes": [], "pcie_link_state": "not managed" } ]Start at Boot
Create
/etc/systemd/system/nvapi.service:``` [Unit] Description=Run NVapi After=network.target
[Service] Type=simple Environment="GOPATH=/home/ansible/go" WorkingDirectory=/home/ansible/NVapi ExecStart=/usr/bin/go run main.go -port 9999 -rate 1 Restart=always User=ansible
Environment="GPU_TEMP_CHECK_INTERVAL=5"
Environment="GPU_TOTAL_POWER_CAP=400"
Environment="GPU_0_LOW_TEMP=40"
Environment="GPU_0_MEDIUM_TEMP=70"
Environment="GPU_0_LOW_TEMP_LIMIT=135"
Environment="GPU_0_MEDIUM_TEMP_LIMIT=120"
Environment="GPU_0_HIGH_TEMP_LIMIT=100"
Environment="GPU_1_LOW_TEMP=45"
Environment="GPU_1_MEDIUM_TEMP=75"
Environment="GPU_1_LOW_TEMP_LIMIT=140"
Environment="GPU_1_MEDIUM_TEMP_LIMIT=125"
Environment="GPU_1_HIGH_TEMP_LIMIT=110"
[Install] WantedBy=multi-user.target ```
Home Assistant
Add to Home Assistant
configuration.yamland restart HA (completely).For a single GPU, this works: ``` sensor: - platform: rest name: MYPC GPU Information resource: http://mypc:9999 method: GET headers: Content-Type: application/json value_template: "{{ value_json[0].index }}" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature scan_interval: 1 # seconds
- platform: template sensors: mypc_gpu_0_gpu: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} GPU" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_memory: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Memory" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_power: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_0_power_limit: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_0_temperature: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Temperature" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'temperature') }}" unit_of_measurement: "°C" ```
For multiple GPUs: ``` rest: scan_interval: 1 resource: http://mypc:9999 sensor: - name: "MYPC GPU0 Information" value_template: "{{ value_json[0].index }}" json_attributes_path: "$.0" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature - name: "MYPC GPU1 Information" value_template: "{{ value_json[1].index }}" json_attributes_path: "$.1" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature
-
platform: template sensors: mypc_gpu_0_gpu: friendly_name: "MYPC GPU0 GPU" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_memory: friendly_name: "MYPC GPU0 Memory" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_power: friendly_name: "MYPC GPU0 Power" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_0_power_limit: friendly_name: "MYPC GPU0 Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_0_temperature: friendly_name: "MYPC GPU0 Temperature" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'temperature') }}" unit_of_measurement: "C"
-
platform: template sensors: mypc_gpu_1_gpu: friendly_name: "MYPC GPU1 GPU" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_1_memory: friendly_name: "MYPC GPU1 Memory" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_1_power: friendly_name: "MYPC GPU1 Power" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_1_power_limit: friendly_name: "MYPC GPU1 Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_1_temperature: friendly_name: "MYPC GPU1 Temperature" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'temperature') }}" unit_of_measurement: "C"
```
Basic entity card:
type: entities entities: - entity: sensor.mypc_gpu_0_gpu secondary_info: last-updated - entity: sensor.mypc_gpu_0_memory secondary_info: last-updated - entity: sensor.mypc_gpu_0_power secondary_info: last-updated - entity: sensor.mypc_gpu_0_power_limit secondary_info: last-updated - entity: sensor.mypc_gpu_0_temperature secondary_info: last-updatedAnsible Role
```
-
name: install go become: true package: name: golang-go state: present
-
name: git clone git: repo: "https://github.com/sammcj/NVApi.git" dest: "/home/ansible/NVapi" update: yes force: true
go run main.go -port 9999 -rate 1
-
name: install systemd service become: true copy: src: nvapi.service dest: /etc/systemd/system/nvapi.service
-
name: Reload systemd daemons, enable, and restart nvapi become: true systemd: name: nvapi daemon_reload: yes enabled: yes state: restarted ```
-
 @ ca20c953:b744e1b1
2024-12-19 22:44:09
@ ca20c953:b744e1b1
2024-12-19 22:44:09The song "Warm Fuzzy Feeling" is about 1 minute and 56 seconds of pure, unadulterated joy. Just a good, quick rock song. Give a listen to the whole All the Pain Money Can Buy album. Thank me later.
-
 @ a17fb4ed:c53f7e91
2024-12-19 19:08:00
@ a17fb4ed:c53f7e91
2024-12-19 19:08:00I just listened to a podcast episode that has inspired me to revive a lost art - the handwritten thank-you note. The guest shared how this simple practice has transformed his life and business over the past 30 years. As someone who has written these notes in the past, I can attest to the feel-good factor. There's just something special about taking the time to put pen to paper and express genuine gratitude. Why do it? There are three key reasons: 1. It cuts through the digital clutter. In our inboxes and DMs, emails and messages get lost in the shuffle. But a physical letter that arrives in someone's mailbox? That's something they're much more likely to read and appreciate. 2. It conveys genuine appreciation. Putting pen to paper and crafting a thoughtful message shows the recipient that you truly value them. As he said, "it comes with a lot of love." 3. It creates a lasting impression. Unlike a quick digital message, a handwritten note becomes a keepsake that the recipient can refer back to. The most powerful part? He shared that he gets responses to these notes - often years later. People remember them and are touched by the gesture. After hearing his story, I'm convinced. I'm going to carve out 20 minutes this week to write a few heartfelt thank-you notes to the important people in my life. I challenge you to do the same. In our fast-paced, digital world, the handwritten note stands out as a uniquely personal gesture. If you're looking to strengthen your relationships and make a memorable impression, I can't recommend this practice enough. It may just be the magic touch your life and business need. Let me know if you gave it shot in the comment. Cheers, Yooper
-
 @ 6bae33c8:607272e8
2024-12-19 18:24:26
@ 6bae33c8:607272e8
2024-12-19 18:24:26I went ahead and YOLO’d in this week with the Thursday game because I’m drawing dead anyway — why agonize over it? I like the Chargers in this spot too.
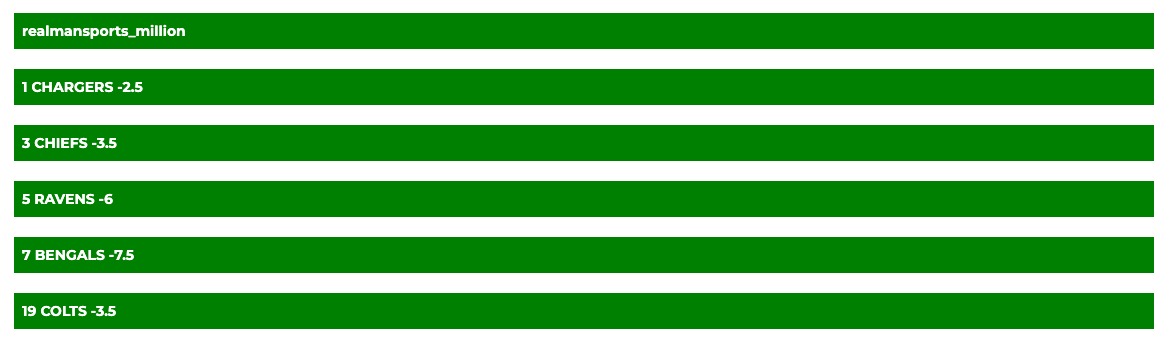 Chargers -2.5 vs Broncos — The Chargers are the worst good team, while the Broncos are the best bad one. I like taking LA at home off the short week too.
Chargers -2.5 vs Broncos — The Chargers are the worst good team, while the Broncos are the best bad one. I like taking LA at home off the short week too.Chiefs -3.5 vs Texans — Mahomes is playing so why isn’t this line 6.5? The Texans defense isn’t bad, but the Chiefs defense is better, and so is their offensive line.
Ravens -6 vs Steelers — The Ravens had some bad bounces in the first game, but there is no comparison between Lamar Jackson and Russell Wilson at this point. Ravens roll.
Bengals -7.5 vs Browns — DTR is bad, and the Bengals will get their usual 30-ish points. Lay the wood.
Colts -3.5 vs Titans — I said this was a stay away in my Guess The Lines because I thought it would be seven. The Colts were even with the Broncos but for two disastrous plays (lateral pick six thrown by a WR and Jonathan Taylor losing a TD because he dropped the ball one second too soon.) They’re good for this spread against the Titans.
I realize these are all home favorites, but that’s not my problem.
-
 @ 9711d1ab:863ebd81
2024-12-19 18:11:41
@ 9711d1ab:863ebd81
2024-12-19 18:11:41One of the best parts about running Breez is the diverse range of people I get to meet and work with. We have partners from Jamaica, the USA, Switzerland, Germany, Canada, Estonia, and who knows where else. We have users in Finland, Wales, Namibia, India, and almost everywhere else. The people behind Breez are split across three continents and come from a broad range of national and ethnic backgrounds.
Agreeing on a communication platform (Telegram? Slack? Zoom? Discord?) sometimes takes a bit of coordination. What never needs coordination, though, is the language we use to communicate. It’s always automatically English. For many of us, English is our second (or third, or fourth) language, and parts of it are baffling, but it doesn’t matter. Every initial contact is in English, all channels are automatically in English, and all public communication (like this blog) is in English. There’s not even a contender for second place.
And there’s basically no way to change this convention. Nobody could simply decree that we’re all going to start speaking Mandarin or Esperanto or Inuktitut. Whether because of convenience, actual utility, historical imposition, or sheer numbers, English is locked in. But it works, so why mess with it?
This example demonstrates a few points. First, the interface between individual nodes in a network — whether people, nations, or communities — has the form of a language. Second, there needs to be a common language. In fact, the limits of the language are the limits of the network. In other words, the distribution of the language defines the network. Finally, common languages are very sticky. Once everyone has adapted to a common language, it’s basically locked in.
Now for a fact about the present that will irrevocably shape the future: Lightning is emerging as the common language of the bitcoin economy.
 Lightning is bitcoin’s Tower of Babel, but nobody wants to tear it down. (Image: Wikimedia)
Lightning is bitcoin’s Tower of Babel, but nobody wants to tear it down. (Image: Wikimedia)A Common Language among Subnetworks
We’ve talked before about various last-mile technologies. They’re like the local secondary roads that connect users to the higher-throughput Lightning Network and, ultimately, the Bitcoin mainnet. They all basically work by bundling users and their transactions into subnetworks.
For example, Ark and Liquid convert incoming bitcoin into their own mechanisms (VTXOs and L-BTC, respectively) that users can then send to each other according to their respective protocols without needing further on-chain transactions. Alternatively, Fedimint members effectively pool their bitcoin and trade IOUs among themselves, with transactions and the financial state of affairs overseen by a federation of trusted guardians. With Cashu, people exchange e-cash tokens and trust the issuing body.
Each kind of subnetwork can use its own language. How the nodes communicate among themselves in these subnetworks is their business. What’s interesting is that these subnetworks communicate with each other over Lightning, even if we’re just talking about, say, two different Cashu mints or when a Fedi interacts with an Ark. Lightning is the common language of all the emergent and thriving subnetworks based on bitcoin.
Returning to the analogy of English, it doesn’t matter to me what language you speak at home or at the supermarket. You can speak whatever obscure dialect you want with others who understand it. But if you want to talk to me or virtually anyone else on Telegram or Slack, English is really the only option. Nobody could change that even if they wanted to, and nobody seems to want to. Just like Lightning.
Lightning is the common language of the emerging subnetworks. It’s the language of bitcoin.
Why Lightning Is the Optimal Language for Bitcoin
A common language is not necessarily an optimal language. It just has to work and be broadly accepted. Just like the Bitcoin mainchain has certain advantages (e.g. immutability, openness, borderlessness, etc.) that recommend it for certain uses, Lightning is the best choice for a common language between subnetworks for at least three reasons.
 Layered networks interacting via a common language. (Image: Adobe Firefly)
Layered networks interacting via a common language. (Image: Adobe Firefly)Lightning Is Bitcoin, and Bitcoin Is the Trustless Bearer Asset
The first and probably most important reason why Lightning is the best common language is that it uses bitcoin. Simply, the subnetworks might not trust each other, and they have no reason to. But since Bitcoin and, by extension, Lightning eschew trust, the subnetworks can interact without trust. Bitcoin is the only viable bearer asset, and Lightning is the language of Bitcoin, so Lightning is the best common language for the subnetworks to interact with each other.
Further, Lightning, like Bitcoin, also eschews leverage. The whole business model of fractional-reserve banks is based on a hole in their balance sheets. By contrast, every sat on Lightning is accounted for at every moment. A balance sheet displaying all the positions on the network would be perpetually balanced. No gap, no overlap. Lightning resists imbalances due to hubris, incompetence, and villainy, which is a necessary feature in a trustless environment.
Lightning Is Inherently Transactional and Interoperable
Second, Lightning is a transactional protocol designed to facilitate flow. For normal payments, there’s no mempool and no delay until the next block is mined. Payments take seconds, if that. And transactions — money in motion — are what make Lightning valuable. Literally. Static sats on the network don’t earn any return. In order for liquidity on Lightning to grow, it has to flow. A common language won’t be used much if it rewards silence. It must promote communication, which is exactly what Lightning does.
Further, the Lightning technology detailed in the catalog of bolt specs is inherently interoperable. It was designed to enable multiple implementations of Lightning nodes with different designs, trade-offs, and programming languages. All these nodes can, however, interact over a common network because they all support the same bolts. Being interoperable by design makes it easy for other technologies to add Lightning as another interface.
Lightning Has Critical Mass
Finally, a common language needs a sizeable community of speakers. Try saying “skibidi rizz” in a nursing home or, even better, a nursing home in Cambodia. Perhaps the biggest advantage of English is simply its popularity: more people speak English than any other language on the planet. And while only a quarter of the inhabitants of many countries speak English, you can still find an English speaker at the next table at virtually every bar and restaurant on the planet. Try that with Catalan.
Lightning has already achieved a critical mass. It’s already obvious how a Cashu subnetwork and Fedimint subnetworks will communicate with each other: Lightning. That’s how they were designed, so switching the common language between networks would require rebuilding most of their parts. Like English, whatever language subnetworks use internally, Lightning is the language they use to speak to each other, and it’s already locked in.
The Permanence of Lightning
Actual lightning — the kind from storm clouds — is a notoriously brief phenomenon. Flashing momentarily and vanishing is its whole thing. But the Lightning Network — the interface between any number of nodes, subnetworks, and the Bitcoin mainchain — is not going anywhere. Common languages tend to hold that status for centuries.
Bitcoin is the world’s best currency. Lightning is the common language of the bitcoin world, and it’s here to stay. For those of us already established in Lightning, this is very good news. That Lightning is locked in means our first-mover advantage is going to be very valuable indeed.
But it’s also good news for those just entering Lightning now or considering it. It eliminates uncertainty about which technology to support and invest in. Lightning is going nowhere but up, so it’s never the wrong time to get started. Better yesterday than today, better today than tomorrow, but tomorrow is good too.
The best time to get into Lightning is now. Always has been.
Originally published by Roy Sheinfeld on Breez's Medium.
-
 @ 6f6b50bb:a848e5a1
2024-12-15 15:09:52
@ 6f6b50bb:a848e5a1
2024-12-15 15:09:52Che cosa significherebbe trattare l'IA come uno strumento invece che come una persona?
Dall’avvio di ChatGPT, le esplorazioni in due direzioni hanno preso velocità.
La prima direzione riguarda le capacità tecniche. Quanto grande possiamo addestrare un modello? Quanto bene può rispondere alle domande del SAT? Con quanta efficienza possiamo distribuirlo?
La seconda direzione riguarda il design dell’interazione. Come comunichiamo con un modello? Come possiamo usarlo per un lavoro utile? Quale metafora usiamo per ragionare su di esso?
La prima direzione è ampiamente seguita e enormemente finanziata, e per una buona ragione: i progressi nelle capacità tecniche sono alla base di ogni possibile applicazione. Ma la seconda è altrettanto cruciale per il campo e ha enormi incognite. Siamo solo a pochi anni dall’inizio dell’era dei grandi modelli. Quali sono le probabilità che abbiamo già capito i modi migliori per usarli?
Propongo una nuova modalità di interazione, in cui i modelli svolgano il ruolo di applicazioni informatiche (ad esempio app per telefoni): fornendo un’interfaccia grafica, interpretando gli input degli utenti e aggiornando il loro stato. In questa modalità, invece di essere un “agente” che utilizza un computer per conto dell’essere umano, l’IA può fornire un ambiente informatico più ricco e potente che possiamo utilizzare.
Metafore per l’interazione
Al centro di un’interazione c’è una metafora che guida le aspettative di un utente su un sistema. I primi giorni dell’informatica hanno preso metafore come “scrivanie”, “macchine da scrivere”, “fogli di calcolo” e “lettere” e le hanno trasformate in equivalenti digitali, permettendo all’utente di ragionare sul loro comportamento. Puoi lasciare qualcosa sulla tua scrivania e tornare a prenderlo; hai bisogno di un indirizzo per inviare una lettera. Man mano che abbiamo sviluppato una conoscenza culturale di questi dispositivi, la necessità di queste particolari metafore è scomparsa, e con esse i design di interfaccia skeumorfici che le rafforzavano. Come un cestino o una matita, un computer è ora una metafora di se stesso.
La metafora dominante per i grandi modelli oggi è modello-come-persona. Questa è una metafora efficace perché le persone hanno capacità estese che conosciamo intuitivamente. Implica che possiamo avere una conversazione con un modello e porgli domande; che il modello possa collaborare con noi su un documento o un pezzo di codice; che possiamo assegnargli un compito da svolgere da solo e che tornerà quando sarà finito.
Tuttavia, trattare un modello come una persona limita profondamente il nostro modo di pensare all’interazione con esso. Le interazioni umane sono intrinsecamente lente e lineari, limitate dalla larghezza di banda e dalla natura a turni della comunicazione verbale. Come abbiamo tutti sperimentato, comunicare idee complesse in una conversazione è difficile e dispersivo. Quando vogliamo precisione, ci rivolgiamo invece a strumenti, utilizzando manipolazioni dirette e interfacce visive ad alta larghezza di banda per creare diagrammi, scrivere codice e progettare modelli CAD. Poiché concepiamo i modelli come persone, li utilizziamo attraverso conversazioni lente, anche se sono perfettamente in grado di accettare input diretti e rapidi e di produrre risultati visivi. Le metafore che utilizziamo limitano le esperienze che costruiamo, e la metafora modello-come-persona ci impedisce di esplorare il pieno potenziale dei grandi modelli.
Per molti casi d’uso, e specialmente per il lavoro produttivo, credo che il futuro risieda in un’altra metafora: modello-come-computer.
Usare un’IA come un computer
Sotto la metafora modello-come-computer, interagiremo con i grandi modelli seguendo le intuizioni che abbiamo sulle applicazioni informatiche (sia su desktop, tablet o telefono). Nota che ciò non significa che il modello sarà un’app tradizionale più di quanto il desktop di Windows fosse una scrivania letterale. “Applicazione informatica” sarà un modo per un modello di rappresentarsi a noi. Invece di agire come una persona, il modello agirà come un computer.
Agire come un computer significa produrre un’interfaccia grafica. Al posto del flusso lineare di testo in stile telescrivente fornito da ChatGPT, un sistema modello-come-computer genererà qualcosa che somiglia all’interfaccia di un’applicazione moderna: pulsanti, cursori, schede, immagini, grafici e tutto il resto. Questo affronta limitazioni chiave dell’interfaccia di chat standard modello-come-persona:
-
Scoperta. Un buon strumento suggerisce i suoi usi. Quando l’unica interfaccia è una casella di testo vuota, spetta all’utente capire cosa fare e comprendere i limiti del sistema. La barra laterale Modifica in Lightroom è un ottimo modo per imparare l’editing fotografico perché non si limita a dirti cosa può fare questa applicazione con una foto, ma cosa potresti voler fare. Allo stesso modo, un’interfaccia modello-come-computer per DALL-E potrebbe mostrare nuove possibilità per le tue generazioni di immagini.
-
Efficienza. La manipolazione diretta è più rapida che scrivere una richiesta a parole. Per continuare l’esempio di Lightroom, sarebbe impensabile modificare una foto dicendo a una persona quali cursori spostare e di quanto. Ci vorrebbe un giorno intero per chiedere un’esposizione leggermente più bassa e una vibranza leggermente più alta, solo per vedere come apparirebbe. Nella metafora modello-come-computer, il modello può creare strumenti che ti permettono di comunicare ciò che vuoi più efficientemente e quindi di fare le cose più rapidamente.
A differenza di un’app tradizionale, questa interfaccia grafica è generata dal modello su richiesta. Questo significa che ogni parte dell’interfaccia che vedi è rilevante per ciò che stai facendo in quel momento, inclusi i contenuti specifici del tuo lavoro. Significa anche che, se desideri un’interfaccia più ampia o diversa, puoi semplicemente richiederla. Potresti chiedere a DALL-E di produrre alcuni preset modificabili per le sue impostazioni ispirati da famosi artisti di schizzi. Quando clicchi sul preset Leonardo da Vinci, imposta i cursori per disegni prospettici altamente dettagliati in inchiostro nero. Se clicchi su Charles Schulz, seleziona fumetti tecnicolor 2D a basso dettaglio.
Una bicicletta della mente proteiforme
La metafora modello-come-persona ha una curiosa tendenza a creare distanza tra l’utente e il modello, rispecchiando il divario di comunicazione tra due persone che può essere ridotto ma mai completamente colmato. A causa della difficoltà e del costo di comunicare a parole, le persone tendono a suddividere i compiti tra loro in blocchi grandi e il più indipendenti possibile. Le interfacce modello-come-persona seguono questo schema: non vale la pena dire a un modello di aggiungere un return statement alla tua funzione quando è più veloce scriverlo da solo. Con il sovraccarico della comunicazione, i sistemi modello-come-persona sono più utili quando possono fare un intero blocco di lavoro da soli. Fanno le cose per te.
Questo contrasta con il modo in cui interagiamo con i computer o altri strumenti. Gli strumenti producono feedback visivi in tempo reale e sono controllati attraverso manipolazioni dirette. Hanno un overhead comunicativo così basso che non è necessario specificare un blocco di lavoro indipendente. Ha più senso mantenere l’umano nel loop e dirigere lo strumento momento per momento. Come stivali delle sette leghe, gli strumenti ti permettono di andare più lontano a ogni passo, ma sei ancora tu a fare il lavoro. Ti permettono di fare le cose più velocemente.
Considera il compito di costruire un sito web usando un grande modello. Con le interfacce di oggi, potresti trattare il modello come un appaltatore o un collaboratore. Cercheresti di scrivere a parole il più possibile su come vuoi che il sito appaia, cosa vuoi che dica e quali funzionalità vuoi che abbia. Il modello genererebbe una prima bozza, tu la eseguirai e poi fornirai un feedback. “Fai il logo un po’ più grande”, diresti, e “centra quella prima immagine principale”, e “deve esserci un pulsante di login nell’intestazione”. Per ottenere esattamente ciò che vuoi, invierai una lista molto lunga di richieste sempre più minuziose.
Un’interazione alternativa modello-come-computer sarebbe diversa: invece di costruire il sito web, il modello genererebbe un’interfaccia per te per costruirlo, dove ogni input dell’utente a quell’interfaccia interroga il grande modello sotto il cofano. Forse quando descrivi le tue necessità creerebbe un’interfaccia con una barra laterale e una finestra di anteprima. All’inizio la barra laterale contiene solo alcuni schizzi di layout che puoi scegliere come punto di partenza. Puoi cliccare su ciascuno di essi, e il modello scrive l’HTML per una pagina web usando quel layout e lo visualizza nella finestra di anteprima. Ora che hai una pagina su cui lavorare, la barra laterale guadagna opzioni aggiuntive che influenzano la pagina globalmente, come accoppiamenti di font e schemi di colore. L’anteprima funge da editor WYSIWYG, permettendoti di afferrare elementi e spostarli, modificarne i contenuti, ecc. A supportare tutto ciò è il modello, che vede queste azioni dell’utente e riscrive la pagina per corrispondere ai cambiamenti effettuati. Poiché il modello può generare un’interfaccia per aiutare te e lui a comunicare più efficientemente, puoi esercitare più controllo sul prodotto finale in meno tempo.
La metafora modello-come-computer ci incoraggia a pensare al modello come a uno strumento con cui interagire in tempo reale piuttosto che a un collaboratore a cui assegnare compiti. Invece di sostituire un tirocinante o un tutor, può essere una sorta di bicicletta proteiforme per la mente, una che è sempre costruita su misura esattamente per te e il terreno che intendi attraversare.
Un nuovo paradigma per l’informatica?
I modelli che possono generare interfacce su richiesta sono una frontiera completamente nuova nell’informatica. Potrebbero essere un paradigma del tutto nuovo, con il modo in cui cortocircuitano il modello di applicazione esistente. Dare agli utenti finali il potere di creare e modificare app al volo cambia fondamentalmente il modo in cui interagiamo con i computer. Al posto di una singola applicazione statica costruita da uno sviluppatore, un modello genererà un’applicazione su misura per l’utente e le sue esigenze immediate. Al posto della logica aziendale implementata nel codice, il modello interpreterà gli input dell’utente e aggiornerà l’interfaccia utente. È persino possibile che questo tipo di interfaccia generativa sostituisca completamente il sistema operativo, generando e gestendo interfacce e finestre al volo secondo necessità.
All’inizio, l’interfaccia generativa sarà un giocattolo, utile solo per l’esplorazione creativa e poche altre applicazioni di nicchia. Dopotutto, nessuno vorrebbe un’app di posta elettronica che occasionalmente invia email al tuo ex e mente sulla tua casella di posta. Ma gradualmente i modelli miglioreranno. Anche mentre si spingeranno ulteriormente nello spazio di esperienze completamente nuove, diventeranno lentamente abbastanza affidabili da essere utilizzati per un lavoro reale.
Piccoli pezzi di questo futuro esistono già. Anni fa Jonas Degrave ha dimostrato che ChatGPT poteva fare una buona simulazione di una riga di comando Linux. Allo stesso modo, websim.ai utilizza un LLM per generare siti web su richiesta mentre li navighi. Oasis, GameNGen e DIAMOND addestrano modelli video condizionati sull’azione su singoli videogiochi, permettendoti di giocare ad esempio a Doom dentro un grande modello. E Genie 2 genera videogiochi giocabili da prompt testuali. L’interfaccia generativa potrebbe ancora sembrare un’idea folle, ma non è così folle.
Ci sono enormi domande aperte su come apparirà tutto questo. Dove sarà inizialmente utile l’interfaccia generativa? Come condivideremo e distribuiremo le esperienze che creiamo collaborando con il modello, se esistono solo come contesto di un grande modello? Vorremmo davvero farlo? Quali nuovi tipi di esperienze saranno possibili? Come funzionerà tutto questo in pratica? I modelli genereranno interfacce come codice o produrranno direttamente pixel grezzi?
Non conosco ancora queste risposte. Dovremo sperimentare e scoprirlo!Che cosa significherebbe trattare l'IA come uno strumento invece che come una persona?
Dall’avvio di ChatGPT, le esplorazioni in due direzioni hanno preso velocità.
La prima direzione riguarda le capacità tecniche. Quanto grande possiamo addestrare un modello? Quanto bene può rispondere alle domande del SAT? Con quanta efficienza possiamo distribuirlo?
La seconda direzione riguarda il design dell’interazione. Come comunichiamo con un modello? Come possiamo usarlo per un lavoro utile? Quale metafora usiamo per ragionare su di esso?
La prima direzione è ampiamente seguita e enormemente finanziata, e per una buona ragione: i progressi nelle capacità tecniche sono alla base di ogni possibile applicazione. Ma la seconda è altrettanto cruciale per il campo e ha enormi incognite. Siamo solo a pochi anni dall’inizio dell’era dei grandi modelli. Quali sono le probabilità che abbiamo già capito i modi migliori per usarli?
Propongo una nuova modalità di interazione, in cui i modelli svolgano il ruolo di applicazioni informatiche (ad esempio app per telefoni): fornendo un’interfaccia grafica, interpretando gli input degli utenti e aggiornando il loro stato. In questa modalità, invece di essere un “agente” che utilizza un computer per conto dell’essere umano, l’IA può fornire un ambiente informatico più ricco e potente che possiamo utilizzare.
Metafore per l’interazione
Al centro di un’interazione c’è una metafora che guida le aspettative di un utente su un sistema. I primi giorni dell’informatica hanno preso metafore come “scrivanie”, “macchine da scrivere”, “fogli di calcolo” e “lettere” e le hanno trasformate in equivalenti digitali, permettendo all’utente di ragionare sul loro comportamento. Puoi lasciare qualcosa sulla tua scrivania e tornare a prenderlo; hai bisogno di un indirizzo per inviare una lettera. Man mano che abbiamo sviluppato una conoscenza culturale di questi dispositivi, la necessità di queste particolari metafore è scomparsa, e con esse i design di interfaccia skeumorfici che le rafforzavano. Come un cestino o una matita, un computer è ora una metafora di se stesso.
La metafora dominante per i grandi modelli oggi è modello-come-persona. Questa è una metafora efficace perché le persone hanno capacità estese che conosciamo intuitivamente. Implica che possiamo avere una conversazione con un modello e porgli domande; che il modello possa collaborare con noi su un documento o un pezzo di codice; che possiamo assegnargli un compito da svolgere da solo e che tornerà quando sarà finito.
Tuttavia, trattare un modello come una persona limita profondamente il nostro modo di pensare all’interazione con esso. Le interazioni umane sono intrinsecamente lente e lineari, limitate dalla larghezza di banda e dalla natura a turni della comunicazione verbale. Come abbiamo tutti sperimentato, comunicare idee complesse in una conversazione è difficile e dispersivo. Quando vogliamo precisione, ci rivolgiamo invece a strumenti, utilizzando manipolazioni dirette e interfacce visive ad alta larghezza di banda per creare diagrammi, scrivere codice e progettare modelli CAD. Poiché concepiamo i modelli come persone, li utilizziamo attraverso conversazioni lente, anche se sono perfettamente in grado di accettare input diretti e rapidi e di produrre risultati visivi. Le metafore che utilizziamo limitano le esperienze che costruiamo, e la metafora modello-come-persona ci impedisce di esplorare il pieno potenziale dei grandi modelli.
Per molti casi d’uso, e specialmente per il lavoro produttivo, credo che il futuro risieda in un’altra metafora: modello-come-computer.
Usare un’IA come un computer
Sotto la metafora modello-come-computer, interagiremo con i grandi modelli seguendo le intuizioni che abbiamo sulle applicazioni informatiche (sia su desktop, tablet o telefono). Nota che ciò non significa che il modello sarà un’app tradizionale più di quanto il desktop di Windows fosse una scrivania letterale. “Applicazione informatica” sarà un modo per un modello di rappresentarsi a noi. Invece di agire come una persona, il modello agirà come un computer.
Agire come un computer significa produrre un’interfaccia grafica. Al posto del flusso lineare di testo in stile telescrivente fornito da ChatGPT, un sistema modello-come-computer genererà qualcosa che somiglia all’interfaccia di un’applicazione moderna: pulsanti, cursori, schede, immagini, grafici e tutto il resto. Questo affronta limitazioni chiave dell’interfaccia di chat standard modello-come-persona:
Scoperta. Un buon strumento suggerisce i suoi usi. Quando l’unica interfaccia è una casella di testo vuota, spetta all’utente capire cosa fare e comprendere i limiti del sistema. La barra laterale Modifica in Lightroom è un ottimo modo per imparare l’editing fotografico perché non si limita a dirti cosa può fare questa applicazione con una foto, ma cosa potresti voler fare. Allo stesso modo, un’interfaccia modello-come-computer per DALL-E potrebbe mostrare nuove possibilità per le tue generazioni di immagini.
Efficienza. La manipolazione diretta è più rapida che scrivere una richiesta a parole. Per continuare l’esempio di Lightroom, sarebbe impensabile modificare una foto dicendo a una persona quali cursori spostare e di quanto. Ci vorrebbe un giorno intero per chiedere un’esposizione leggermente più bassa e una vibranza leggermente più alta, solo per vedere come apparirebbe. Nella metafora modello-come-computer, il modello può creare strumenti che ti permettono di comunicare ciò che vuoi più efficientemente e quindi di fare le cose più rapidamente.
A differenza di un’app tradizionale, questa interfaccia grafica è generata dal modello su richiesta. Questo significa che ogni parte dell’interfaccia che vedi è rilevante per ciò che stai facendo in quel momento, inclusi i contenuti specifici del tuo lavoro. Significa anche che, se desideri un’interfaccia più ampia o diversa, puoi semplicemente richiederla. Potresti chiedere a DALL-E di produrre alcuni preset modificabili per le sue impostazioni ispirati da famosi artisti di schizzi. Quando clicchi sul preset Leonardo da Vinci, imposta i cursori per disegni prospettici altamente dettagliati in inchiostro nero. Se clicchi su Charles Schulz, seleziona fumetti tecnicolor 2D a basso dettaglio.
Una bicicletta della mente proteiforme
La metafora modello-come-persona ha una curiosa tendenza a creare distanza tra l’utente e il modello, rispecchiando il divario di comunicazione tra due persone che può essere ridotto ma mai completamente colmato. A causa della difficoltà e del costo di comunicare a parole, le persone tendono a suddividere i compiti tra loro in blocchi grandi e il più indipendenti possibile. Le interfacce modello-come-persona seguono questo schema: non vale la pena dire a un modello di aggiungere un return statement alla tua funzione quando è più veloce scriverlo da solo. Con il sovraccarico della comunicazione, i sistemi modello-come-persona sono più utili quando possono fare un intero blocco di lavoro da soli. Fanno le cose per te.
Questo contrasta con il modo in cui interagiamo con i computer o altri strumenti. Gli strumenti producono feedback visivi in tempo reale e sono controllati attraverso manipolazioni dirette. Hanno un overhead comunicativo così basso che non è necessario specificare un blocco di lavoro indipendente. Ha più senso mantenere l’umano nel loop e dirigere lo strumento momento per momento. Come stivali delle sette leghe, gli strumenti ti permettono di andare più lontano a ogni passo, ma sei ancora tu a fare il lavoro. Ti permettono di fare le cose più velocemente.
Considera il compito di costruire un sito web usando un grande modello. Con le interfacce di oggi, potresti trattare il modello come un appaltatore o un collaboratore. Cercheresti di scrivere a parole il più possibile su come vuoi che il sito appaia, cosa vuoi che dica e quali funzionalità vuoi che abbia. Il modello genererebbe una prima bozza, tu la eseguirai e poi fornirai un feedback. “Fai il logo un po’ più grande”, diresti, e “centra quella prima immagine principale”, e “deve esserci un pulsante di login nell’intestazione”. Per ottenere esattamente ciò che vuoi, invierai una lista molto lunga di richieste sempre più minuziose.
Un’interazione alternativa modello-come-computer sarebbe diversa: invece di costruire il sito web, il modello genererebbe un’interfaccia per te per costruirlo, dove ogni input dell’utente a quell’interfaccia interroga il grande modello sotto il cofano. Forse quando descrivi le tue necessità creerebbe un’interfaccia con una barra laterale e una finestra di anteprima. All’inizio la barra laterale contiene solo alcuni schizzi di layout che puoi scegliere come punto di partenza. Puoi cliccare su ciascuno di essi, e il modello scrive l’HTML per una pagina web usando quel layout e lo visualizza nella finestra di anteprima. Ora che hai una pagina su cui lavorare, la barra laterale guadagna opzioni aggiuntive che influenzano la pagina globalmente, come accoppiamenti di font e schemi di colore. L’anteprima funge da editor WYSIWYG, permettendoti di afferrare elementi e spostarli, modificarne i contenuti, ecc. A supportare tutto ciò è il modello, che vede queste azioni dell’utente e riscrive la pagina per corrispondere ai cambiamenti effettuati. Poiché il modello può generare un’interfaccia per aiutare te e lui a comunicare più efficientemente, puoi esercitare più controllo sul prodotto finale in meno tempo.
La metafora modello-come-computer ci incoraggia a pensare al modello come a uno strumento con cui interagire in tempo reale piuttosto che a un collaboratore a cui assegnare compiti. Invece di sostituire un tirocinante o un tutor, può essere una sorta di bicicletta proteiforme per la mente, una che è sempre costruita su misura esattamente per te e il terreno che intendi attraversare.
Un nuovo paradigma per l’informatica?
I modelli che possono generare interfacce su richiesta sono una frontiera completamente nuova nell’informatica. Potrebbero essere un paradigma del tutto nuovo, con il modo in cui cortocircuitano il modello di applicazione esistente. Dare agli utenti finali il potere di creare e modificare app al volo cambia fondamentalmente il modo in cui interagiamo con i computer. Al posto di una singola applicazione statica costruita da uno sviluppatore, un modello genererà un’applicazione su misura per l’utente e le sue esigenze immediate. Al posto della logica aziendale implementata nel codice, il modello interpreterà gli input dell’utente e aggiornerà l’interfaccia utente. È persino possibile che questo tipo di interfaccia generativa sostituisca completamente il sistema operativo, generando e gestendo interfacce e finestre al volo secondo necessità.
All’inizio, l’interfaccia generativa sarà un giocattolo, utile solo per l’esplorazione creativa e poche altre applicazioni di nicchia. Dopotutto, nessuno vorrebbe un’app di posta elettronica che occasionalmente invia email al tuo ex e mente sulla tua casella di posta. Ma gradualmente i modelli miglioreranno. Anche mentre si spingeranno ulteriormente nello spazio di esperienze completamente nuove, diventeranno lentamente abbastanza affidabili da essere utilizzati per un lavoro reale.
Piccoli pezzi di questo futuro esistono già. Anni fa Jonas Degrave ha dimostrato che ChatGPT poteva fare una buona simulazione di una riga di comando Linux. Allo stesso modo, websim.ai utilizza un LLM per generare siti web su richiesta mentre li navighi. Oasis, GameNGen e DIAMOND addestrano modelli video condizionati sull’azione su singoli videogiochi, permettendoti di giocare ad esempio a Doom dentro un grande modello. E Genie 2 genera videogiochi giocabili da prompt testuali. L’interfaccia generativa potrebbe ancora sembrare un’idea folle, ma non è così folle.
Ci sono enormi domande aperte su come apparirà tutto questo. Dove sarà inizialmente utile l’interfaccia generativa? Come condivideremo e distribuiremo le esperienze che creiamo collaborando con il modello, se esistono solo come contesto di un grande modello? Vorremmo davvero farlo? Quali nuovi tipi di esperienze saranno possibili? Come funzionerà tutto questo in pratica? I modelli genereranno interfacce come codice o produrranno direttamente pixel grezzi?
Non conosco ancora queste risposte. Dovremo sperimentare e scoprirlo!
Tradotto da:\ https://willwhitney.com/computing-inside-ai.htmlhttps://willwhitney.com/computing-inside-ai.html
-
-
 @ 4b7c4ee3:8cd5ed4d
2024-12-19 18:10:41
@ 4b7c4ee3:8cd5ed4d
2024-12-19 18:10:41The neon thrum of Roppongi streets hummed like a thousand electric guitars tuned to chaos—blade runners and briefcases, club kids and salarymen, all washed in the spill of red lanterns and LED strobes. I stumbled down the alley where the Bitcoin meetup was said to be, a strange little blip in the city’s endless digital heart.
Inside, the air was thick with cigarette smoke and the crackle of ideation. A dive bar turned temple to the future, where revolutionaries sipped cheap beer and whispered dreams of decentralization. No suits here—just hackers in hoodies, expats with wild eyes, and a few lost souls looking for the edge of the map.
“Do you even understand what this is?” a voice asked as I slid onto a cracked leather stool. He had a laptop open, the screen glowing like an altar. A white paper in one tab, a mining program running in another. A makeshift setup powered by caffeine and belief.
I mumbled something vague about "digital money" and got a sharp laugh in return. “It’s not money, man—it’s freedom,” he said, taking a drag from a cigarette that seemed to burn faster with his every word. “No borders, no banks, no middlemen. Just the chain and the work and the truth.”
The bartender, indifferent to our philosophizing, poured drinks with the precision of an algorithm. Behind him, a poster for a long-gone punk band clung to the wall like a relic from an analog age.
Conversations swirled like smoke rings. One guy swore he’d just bought a thousand BTC for the price of lunch. Another was trying to barter to buy a burrito. Another was lamenting the cost of GPUs skyrocketing, “but it’s worth it, man—this is the future.” Someone in the corner was typing furiously, mumbling something about the Silk Road.
I asked about Satoshi. “Who?” someone quipped, half-smirking. “No one. Everyone. The ghost in the machine.”
And that’s what it felt like—a gathering of ghosts, of dreamers untethered from the weight of the past, spinning something entirely new out of bits and bytes. Dreamers fixated on an unseen future that may never come to pass. The energy in the room wasn’t just optimism—it was defiance.
Hours blurred. Ideas ran faster than the beer. Someone handed me held up a flash drive, “just a few wallets, this will set me up forever.” I asked more questions. I ate mediocre nachos. I wondered aloud if this was all a simulation.
By the time I spilled back into the night, Tokyo’s endless hum had softened to a lullaby, and the last train was long gone. I walked home, mind buzzing with blockchains and possibilities, wondering if the world would ever catch up to what I’d seen that night in Roppongi.
And maybe it wouldn’t, not for years. But I knew one thing for certain: the future was already here—it just smelled like cigarettes and spilled beer.
Stay humble. Stack sats.
Oyl Miller comes from an advertising background where he has worked for legacy brands like Nike and PlayStation, digital giants like Google and Airbnb, as well as crypto and web3 startups. He is experimenting with moving to a Bitcoin standard, and is looking to create value with his writing skills in a variety of ways.
-
 @ 2ce0697b:1ee3d3fc
2024-12-19 18:04:09
@ 2ce0697b:1ee3d3fc
2024-12-19 18:04:09Excerpt
Special Jurisdictions, Free Cities and Bitcoin Citadels are the sly roundabout way that is removing the market of living together from the hands of the government, without violence and in a way that they can´t stop it. With Bitcoin as the backbone of a new societal order, we are beginning to disrupt the old paradigm.
“If you have built castles in the air, your work need not be lost; that is where they should be. Now put the foundations under them.” ― Henry David Thoreau, Walden
The problem: lack of freedom in the physical realm
Freedom is essential to human life. Being free is what matters. That´s our target, always. No matter the time or space. We pursue freedom because we know its the right thing to do. Freedom is the right to question and change the stablished way of doing things.
Where can we find some freedom? Certainly in the cyberspace. The cyberspace is a free space. Humanity has been blessed by the magic of cryptography, a technology that gave us all the necessary tools to operate in that environment without intervention of undesired third parties.
In cyberspace cryptography performs the function of an impenetrable cyberwall. So, whatever we build in cyberspace can be perfectly protected. Thank to this cybernetic walls we can be sure that the gardens we build and nurture will be protected and cannot be trampled. When we build our digital gardens we have the keys to open the doors to let in whoever we want and most important to leave out whoever we don´t want. In the digital world we can already perfectly interact with one and another in a peer to peer way, without intervention of undesired third parties.
In cyberspace we have Bitcoin for freedom of money and Nostr, torrent and Tor for freedom of information and speech. These open-source protocols are designed to fully realize and expand the promise of freedom, and they certainly deliver what they promise.

So, thanks to the magic of asymmetric cryptography, we´ve already achieved sufficiently descentralization and the possibility of any level of desired digital privacy. Cryptoanarchists and cypherpunks have set their conquering flag in cyberspace and there´s no force on Earth than can remove it. The digital world cannot escape the rules of cryptography. This is great but it only works in the digital realm, meanwhile in the physical realm we are overrun by centralized attackers due to the impossibility of the creation of impenetrable walls such as the ones we have online.
Humans have the upper hand in creating impenetrable walled gardens in cyberspace, but in the physical space authoritarians have the upper hand in bullying physical persons.
The physical world is also naturally free. According to natural law each person is free to do whatever he wants as long as it doesn´t hurt other people. However due to unnatural -artificial and inhuman- centralization of power, the natural freedom of the physical world has been completely undermined. Mostly by Governments, the entities that centralize violence and law.
Bitcoin as a bridge between both realms

Let´s take a look at one connection between both realms, the physical and the digital world. Bitcoin layer one is made essentially of software plus hardware. It consists of any software that produces the same output as the reference implementation - Bitcoin core- and the hardware needed to run that software. Layer two, three or any other layer above, is made essentially of other software and other hardware that interacts with layer one in some way. All these layers, one, two and subsequent, are completely protected by cryptography and a set of game theories that have been successfully tested. Each new block added to the timechain is a testimony of the unstoppable force of freedom and meritocracy.
Before layer one we have Bitcoin layer zero, which is essentially the sum of all actions and inactions done by bitcoiners regarding to or because of bitcoin. In other words, layer zero is composed by flesh and bone people interacting in some way with layer one of the bitcoin network.
Hence, an attack on a bitcoiner - on his way of life- is an attack on bitcoin, the network itself. First because it is an attack on a layer zero node, the physical person, the bitcoiner under duress or coercion. And second because is also an attack on the store-of-value-aspect of bitcoin. Nowaday, the most common attack against bitcoiners is the entirety of compliance regulations. This is the sum of all coercive regulations,such as laws, threats of more laws, imprisonment, threats of more imprisonment, taxation, threats of more taxation, requirements to prove the origin of funds, coercive removal of privacy such as the travel rule, unnecessary bureaucracy such as the need to obtain a money transmitting license and many others rules, in a never stopping inflationary coercive legislation.

If a physical attack is preventing any bitcoiner to exchange the value he created for bitcoin due to any kind of artificial obstacles -such as any kind of compliance- that specific attack is successful in the sense that even though the whole network keeps operating, the attack itself diminishes the value of all the bitcoins.
So, even if layer-zero cannot be taken down, every interference on this layer is an attack on the bitcoin network. Attacks on layer one, two or any other layer that exists in the cyberspace can interfere with the network but they may hardly subtract any value from it. For example we have already been through plenty of times where hashing power was diminished due to government intervention and the bitcoin network remain completely unaffected.
On the other hand successful attacks on layer zero subtract potential, but real and demonstrable value. This value is equal to the amount of value the frustrated user would have added to the network if he would have been able to use it freely, that means if he would have sold his product without the cost of compliance. I´ll demonstrate this in the next chapter.
The cost of compliance
Alice is a merchant specialized in a specific area and topic. She studied the market, her business, her suppliers, consumers, the logistics involved, marketing, design, and everything necessary to become a successful entrepreneur. After investing a considerable amount of resources, she developed a perfect product. Or at least she considers it perfect, that is, the best in its class. While developing everything necessary to create her product, she met Bob, who became her main lead and stereotype of a buyer persona. She knows what Bob wants and she wants to sell it to him. According to Alice's calculations, for her business to be viable, she must sell the product at ten satoshis per unit, and fortunately, Bob is willing to pay that price for it. Alice's product is finished, ready to hit the market, but just before sending it to production, Alice decides to take a pause to analyze her reality. Before taking the public action of making her product available in the open market, Alice analyzes her material, political, and legal reality. In doing so, she realizes that she lives under the jurisdiction of a State. She learns that the Government prescribes through its regulations how she must behave. She analyzes that in order to sell her product legally, in compliance, she must make a series of modifications to it. The product before hitting the shelves must first be modified both in the way it is presented to the market and also regarding certain technical characteristics that it possesses. She must also modify the way it produces her product by changing the contractual relationship with its suppliers, distribution channels, and all other types of logistics involved. She must make all these changes even if they bring about significant and insurmountable inefficiencies.
Likewise, Alice also sees that she not only has to modify the product but also has to meet tax obligations. In addition to paying an accountant since the tax obligations by some irrational reason are not calculated by the creditor. Additionally, she must hire other professionals to assist her in studying the current regulations and how they should be applied in all stages of production, distribution, and sale of her product.
Alice, being a rational person, wishes to avoid having to make these modifications since they increase her costs while also decreasing the quality of her product. But when studying compliance, that is, the entirety of applicable regulations, she also examines the consequences of not being in compliance. Alice realizes that if she does not comply with the regulations, she risks having all her assets legally confiscated, going to prison, being killed while they try to capture her to imprison her, and, if she goes to prison, being tortured in jail by other inmates or by State officials in charge of holding her in that place. So, since Alice does not want to suffer these negative consequences, she decides to modify the product and be in compliance.
So, Alice makes the necessary changes and puts her new version of the product on the market. Then she has the following dialogue with Bob, her lead, the interested party in acquiring the product.
Bob: - Hey Alice, nice meeting you here in this market. I came to buy the product you were developing and told me about. However, this product I´m seein now is not what you promised me. This is clearly inferior.
Alice: - Yeah, I know. I'm sorry Bob, but I prefer to sell this inferior product rather than risk having all my assets confiscated, going to prison, being killed while they try to capture me, and if they don´t kill but managed to put me in jail I could be tortured there.
Bob: - Ok, no problem. Thats quite understandable. I don´t believe anyone would prefer those kind of experiences. But given the quality of the product, I no longer intend to pay you ten satoshis; I only offer you eight. Shall we close the deal?
Alice: - I'm sorry Bob, but I can't sell it to you for eight sats. Due to government intervention and its requirements, now I can't even sell it for less than thirteen satoshis.
Bob: - Ok. Considering this I prefer not to purchase it. I will keep looking for alternatives. Bye

Some time later, Charlie arrives at the market, who is also interested in the product and, despite it not being like the original version, decides to purchase it by paying the thirteen satoshis demanded by the seller Alice.
Meanwhile, in the same universe, we have Daniel, the last character in this example. Daniel is a merchant competing with Alice. Daniel has a product that is very similar, practically identical to the one originally designed by Alice. Like Alice, Daniel initially also wants to sell it for ten satoshis. Just like Alice, before heading to the market, Daniel analyzes the reality in which he lives. And it turns out that he also lives under the jurisdiction of a State. Daniel too then analyzes the entirety of the applicable regulations and also comes to the conclusion that to comply with them, he would also need to modify the product and cover all the additional expenses artificially generated to be in compliance.
However, Daniel's ethics are different from Alice's. Daniel understands that his product is indeed perfect (the best in its class) and that therefore modifying it would go against its essence. Daniel understands that changing the product would be a betrayal of his creation and therefore a betrayal of his own self and the essence of his being. Daniel conducts an ethical analysis of his actions and the moral implications of putting the product on the market. Daniel sees that the product not only does not harm anyone but is also made to be freely acquired by adults who give their consent for its purchase and subsequent use. Daniel also understands that paying taxes only serves to promote the slavery system driven by fiat and that whenever he can avoid collaborating with the immoral fiat system, it is his ethical obligation to do so. Likewise, Daniel highlights the hypocrisy and inefficiencies of anti-money laundering regulations, as well as the futility of requiring licenses for naturally free acts that do not harm others. For all these reasons, Daniel decides to sell the product in its current state irregardles of compliance regulations.
However, before going to market, Daniel also studies the possible consequences of neglecting compliance. By doing so, Daniel sees that if he does not comply with the regulations, he risks having all his assets legally confiscated, going to prison, being killed while they attempt to capture him to imprison him, and, in the event of going to prison, being tortured in jail by other inmates or by State officials responsible for holding him in that place. So, since Daniel is a rational person who does not want to suffer these negative consequences but also does not want to betray his product and himself, he decides to take the risk of not being in compliance. After making this decision, Daniel puts the product on the market and there he meets Bob. In doing so, they converse in the following terms:
Bob: - Hey Daniel, this product is exactly what I was looking for. A product like the one promised by Alice but never delivered. I love it! I offer you ten satoshis for it.
Daniel: - Thank you for your feedback Bob and for the offer! However I am currently selling it for eleven satoshis. Ten satoshis seems like a good price to me, and it was indeed my original intention to sell it for that amount because at that price I achieve competitiveness and a sustainable business model.
Bob: - So why are you asking me for eleven satoshis? Interrupts Bob
Daniel: - Because that price is calculated before assessing compliance and the risks associated with non-compliance. By not complying with the regulation, I managed to maintain the quality of the product and avoided a large amount of unnecessary expenses, but there is no way to avoid the risk of facing penalties for non-compliance. To bring this product to market, I had to incur several expenses in order to minimize the risk of non-compliance as much as possible. While I am taking all reasonable actions to prevent all of my assets from being legally confiscated, from going to prison, from being killed while they try to capture me, and in case of going to prison, from being tortured, the reality is that I still run the risk of all that, or part of all that, happening to me, my family, or any of my company's employees. The remaining risk balance is transferred to the price along with the costs of mitigating those risks. The total of those costs and the remaining risk I estimate them at one satoshi per unit of product. Therefore, I can't sell you the product for ten satoshis, but I can sell it to you for eleven.
To which Bob, lacking a better option in the market, ends up buying the product for eleven satoshis.
In summary: two products were made by two different merchants whose business model allowed them, in both cases, to put the product on the market at a rate of ten satoshis per unit. However, in one case, a lower quality product was sold for thirteen satoshis, and in the other case, a higher quality product was sold for eleven satoshis. That is to say, in the first case there was an overprice or inefficiency objectively measured at three satoshis, while in the second case there was an overprice or inefficiency of one satoshi. So, we are facing a total loss of value equivalent to four satoshis. The value represented by these four satoshis was absorbed by the inefficiency programmed and ruled by the State. The example shows us that whether one chooses the compliance route, as Alice did, or the free market route, as Daniel did, in both cases the existence of regulations generates an additional cost to the market. In this example the state attack on layer zero was successful and extracted from the Bitcoin network a value of four satoshis.
Bitcoin is money
Bitcoin is many things but essentially is money. And money sole purpose is to store value in order to facilitate future exchanges of products and services with other people. Without the products and services to be exchanged for the money, money itself would be useless and worthless. We only use money because we may require favors, benefits, services, products from other people in the future. And we don´t know which services and products we´ll need nor exactly when we are goint to need them.

The total value of bitcoin equals to infinity divided twenty one millions. This is because the total worth of the network mirrors the total worth of accumulated capital by the entirety of mankind throughout its entire history. That is clearly a lot of value. But if the if the dividend equals zero then the divisor is also zero and if the dividend growth is obstructed through artificial means -such as compliance- then the divisor growth is also obstructed.
Bitcoin layer zero, the bitcoiners and the services and products we create, are what give value to the twenty one million units of bitcoin.
Freedom is without a doubt the best context for value creation. So, the more and better games we can create that allow humankind to find a way to exercise freedom, then the most value we can add to all the layers of the network.
This is why the most important layer of the whole bitcoin phenomenon is layer zero, the bitcoiners. Hence the problem to be solved is not how to prevent bitcoin - layer one upwards- from successful attacks. The problem to solve is how to prevent attacks on layer zero. Or in other words, the problem to be solved is how to get bitcoiners in the physical world to practice the same level of freedom that bitcoin achieves in the cyberspace.
Summary of the first part of this article: freedom in cyberspace has already been conquered and each further development in the digital realm contributes to further developments but only in the same realm. Meanwhile in the physical space, the layer zero of bitcoin is under constant attacks that successfully extract value from it.
Exercising freedom in a sly roundabout way

In 1984 the Austrian economist Friedrich Hayek predicted that we couldn´t take money with violence out of the hands of government. He stated that we needed to do it in a sly roundabout way. Twenty five years later Satoshi Nakamoto discovered the sly roundabout way actually introducing something that the government couldn´t stop. Thus fulfilling Hayek´s prophecy.
Bitcoin is a sly roundabout way that removed money without violence from the hands of the government in a way that they can´t stop it.
Cryptography in general and protocols such as Tor and Tails are a sly roundabout way that removed confidential information from the hands of the government without violence in a way that they can´t stop it.
Nostr is a sly roundabout way that removed social media and public information from the hands of the government without violence in a way that they can´t stop it.
Special Jurisdictions, Free Cities and Bitcoin Citadels are the sly roundabout way that is removing the market of living together from the hands of the government without violence in a way that they can´t stop it.

So, what are Special Jurisdictions, Free Cities and Bitcoin Citadels? To understand what they are we can take a look at the current mainstream market of living together, at how the physical space is organized. Essentially the entire planet Earth and its surroundings are run by a conglomerate of Governments. They create all the rules, regarding every aspect of life, of all the individuals, and enforce every rule through coercive means.
In the mainstream market of living together individuals have several alternatives to pick from. We can choose to live in a natural city or a pre design city, in a public neighborhood or private neighborhood or even in an intentional community with common interest amongst the users. But irregardless of the choice, every product offered in the mainstream market has the sames rules which are established by the host state to the entirety of organizations in his territory. In the mainstream market, even the most different products abide by the same high level rules such as criminal law, civil law, taxation laws, customs, enviromental laws, money laundering regulations and many others. To abide to the sum of all the laws and regulations is to be in compliance.
The centralization of regulations makes extremely difficult to experiment in market of living together. The less experimentation is allowed, the more human progress is hindered.
So what is the sly roundabout that fixes this? What are Special Jurisdictions, Free Cities and Bitcoin Citadels? I´m using the term Special Jurisdictions as an umbrella term that includes the entire spectrum of iterations of products that aim to modify the mainstream rules of the market of living together.
This term includes all the different models such as Charter Cities, Free Cities, Special Economic Zones, microstates, micropolis, start up societies, government as a service, self governing jurisdictions, autonomous intentional communities, network states and Bitcoin Citadels. The array of possible iterations is huge and permanently expanding. What they all have in common is that each of these experiments aims to create a functional game theory that replaces the lack of unbreakable walls in the physical space.
Let´s take a look of a couple of examples. Special Economic Zones are bounded areas of countries that have their own rules and regulations. Worldwide, there are more than five thousands special economic zones located in more than hundred countries.
One of them is the special economic zone of Shenzhen in China. The Chinese government allowed Shenzhen the freedom to experiment with certain practices that were prohibited in the rest of the country at the time. This included allowing foreign companies to make direct investments in China, allowing people to buy and sell land, allowing Chinese people to set up their own private businesses and relaxation of the system that limited internal migration within China for Chinese citizens. It served as a place where China could experiment with market reforms. The experiment was such a huge economic success that it was replicated in many other areas of the country.
Another place that has made extensive use of special economic zones is Dubai. The monarchic Government has more than 30 SEZs. In this case one of the many obstacles removed by the host state its the monopoly of the legal system. Dubai Government allowed the special economic zone to have its own independent legal system thus conceding a modification of the mainstream rules in that area.
This kind of projects, such as Dubai or Shenzhen, are a top-to-down product. Fully created by the Governments thus compliant with their own regulations.

On the other side of the spectrum we have Citadels and several other archetypes of not so compliant projects .
For example the Free Commune of Penadexo it´s a grassroots project building a freedom-oriented community in one of Spain’s abandoned villages.
 It´s model is based on building a peer to peer society avoiding government intervention as much as possible.
They stablished themselves in an abandoned historic village and the started to track down the owners to purchase as much property as possible. Meanwhile, they are living there and expanding their users base while also reconstructing buildings.
It´s model is based on building a peer to peer society avoiding government intervention as much as possible.
They stablished themselves in an abandoned historic village and the started to track down the owners to purchase as much property as possible. Meanwhile, they are living there and expanding their users base while also reconstructing buildings. This is an example of a completely different way of dealing with the Government. While Special Economic Zones are fully compliant and created top to down, this model on the other hand is bottom-up and aims to add value to the users relying in factual freedom which is exercised by stablishing the commune away from heavily populated centers where Government grip is tighter. Under this model the interaction with the Government is kept as low as possible. Their strategy relies in ignoring the Government as much as possible and being a good neighbor. With this simple and effective tactic some Citadels enjoy the benefits of liberty in their lifetime without needing to spend huge resources in governmental lobby.
There are countless models or archetypes of Bitcoin Citadels trying to solve the obstacles in different ways, trying to restart the system. And one of the challenges of the Bitcoin Citadels is how to connect the different projects to boost and help each other.
This is where The Meshtadel comes into play. The Meshtadel is a system where decentralized tactics are used to help and defend citadels connected in a global network. With real life connections with fellow bitcoiners. Its an organization equivalent to the hanseatic league built under a starfish model. If you cut off a spider’s head, it dies, but if you cut off a starfish’s arm, it can regenerate and even grow into a new starfish.
The Meshtadel its a network of peer relationships, with ambiguous leadership roles, trust among participants, a shared ideology and vision based on the Bitcoin ethos, and an open system where new nodes - bitcoin citadel builders - can participate.
The long term goal of the Bitcoin Meshtadel is to help Bitcoin Citadels to gain the support of a critical mass of the total population. If enough people see that Bitcoin is as peaceful as it gets, in the long run, some nations could become friendly and supportive enough to legally tolerate the Bitcoin Citadel inside its territory in the form of a Bitcoin safe haven. In the Meshtadel we are fighting from the moral high ground using memes, Nostr notes and zapping our way into freedom creating an online and offline circular economy.
TO CONCLUDE:
Special Jurisdictions, Free Cities and Bitcoin Citadels are the sly roundabout way that is removing the market of living together from the hands of the government, without violence and in a way that they can´t stop it.
Nation states, abusing the myth of authority, have halted development on the market of living together for so long that a blooming freer market is eating its lunch. The sovereign individual thesis is live and continuously expanding. The network state is forming and intentional communities are flourishing all around the world reshaping globally the relationship between individuals and the governments.
With global internet connections, uncensorable means of communication and Bitcoin as the backbone of a new societal order, we are beginning to disrupt the old paradigm.
The fashion of the present world is passing away, let’s help it to move forward along by building Special Jurisdictions, Free Cities and Bitcoin Citadels.
--- --- --- --- --- --- --- --- ------
byCamiloat 875.341 timechain.
If you find this content helpful, zap it to support more content of the sort and to boost the V4V model.
-
 @ e6817453:b0ac3c39
2024-12-07 15:06:43
@ e6817453:b0ac3c39
2024-12-07 15:06:43I started a long series of articles about how to model different types of knowledge graphs in the relational model, which makes on-device memory models for AI agents possible.
We model-directed graphs
Also, graphs of entities
We even model hypergraphs
Last time, we discussed why classical triple and simple knowledge graphs are insufficient for AI agents and complex memory, especially in the domain of time-aware or multi-model knowledge.
So why do we need metagraphs, and what kind of challenge could they help us to solve?
- complex and nested event and temporal context and temporal relations as edges
- multi-mode and multilingual knowledge
- human-like memory for AI agents that has multiple contexts and relations between knowledge in neuron-like networks
MetaGraphs
A meta graph is a concept that extends the idea of a graph by allowing edges to become graphs. Meta Edges connect a set of nodes, which could also be subgraphs. So, at some level, node and edge are pretty similar in properties but act in different roles in a different context.
Also, in some cases, edges could be referenced as nodes.
This approach enables the representation of more complex relationships and hierarchies than a traditional graph structure allows. Let’s break down each term to understand better metagraphs and how they differ from hypergraphs and graphs.Graph Basics
- A standard graph has a set of nodes (or vertices) and edges (connections between nodes).
- Edges are generally simple and typically represent a binary relationship between two nodes.
- For instance, an edge in a social network graph might indicate a “friend” relationship between two people (nodes).
Hypergraph
- A hypergraph extends the concept of an edge by allowing it to connect any number of nodes, not just two.
- Each connection, called a hyperedge, can link multiple nodes.
- This feature allows hypergraphs to model more complex relationships involving multiple entities simultaneously. For example, a hyperedge in a hypergraph could represent a project team, connecting all team members in a single relation.
- Despite its flexibility, a hypergraph doesn’t capture hierarchical or nested structures; it only generalizes the number of connections in an edge.
Metagraph
- A metagraph allows the edges to be graphs themselves. This means each edge can contain its own nodes and edges, creating nested, hierarchical structures.
- In a meta graph, an edge could represent a relationship defined by a graph. For instance, a meta graph could represent a network of organizations where each organization’s structure (departments and connections) is represented by its own internal graph and treated as an edge in the larger meta graph.
- This recursive structure allows metagraphs to model complex data with multiple layers of abstraction. They can capture multi-node relationships (as in hypergraphs) and detailed, structured information about each relationship.
Named Graphs and Graph of Graphs
As you can notice, the structure of a metagraph is quite complex and could be complex to model in relational and classical RDF setups. It could create a challenge of luck of tools and software solutions for your problem.
If you need to model nested graphs, you could use a much simpler model of Named graphs, which could take you quite far.
The concept of the named graph came from the RDF community, which needed to group some sets of triples. In this way, you form subgraphs inside an existing graph. You could refer to the subgraph as a regular node. This setup simplifies complex graphs, introduces hierarchies, and even adds features and properties of hypergraphs while keeping a directed nature.
It looks complex, but it is not so hard to model it with a slight modification of a directed graph.
So, the node could host graphs inside. Let's reflect this fact with a location for a node. If a node belongs to a main graph, we could set the location to null or introduce a main node . it is up to you
Nodes could have edges to nodes in different subgraphs. This structure allows any kind of nesting graphs. Edges stay location-free
Meta Graphs in Relational Model
Let’s try to make several attempts to model different meta-graphs with some constraints.
Directed Metagraph where edges are not used as nodes and could not contain subgraphs

In this case, the edge always points to two sets of nodes. This introduces an overhead of creating a node set for a single node. In this model, we can model empty node sets that could require application-level constraints to prevent such cases.
Directed Metagraph where edges are not used as nodes and could contain subgraphs

Adding a node set that could model a subgraph located in an edge is easy but could be separate from in-vertex or out-vert.
I also do not see a direct need to include subgraphs to a node, as we could just use a node set interchangeably, but it still could be a case.Directed Metagraph where edges are used as nodes and could contain subgraphs
As you can notice, we operate all the time with node sets. We could simply allow the extension node set to elements set that include node and edge IDs, but in this case, we need to use uuid or any other strategy to differentiate node IDs from edge IDs. In this case, we have a collision of ephemeral edges or ephemeral nodes when we want to change the role and purpose of the node as an edge or vice versa.

A full-scale metagraph model is way too complex for a relational database.
So we need a better model.Now, we have more flexibility but loose structural constraints. We cannot show that the element should have one vertex, one vertex, or both. This type of constraint has been moved to the application level. Also, the crucial question is about query and retrieval needs.
Any meta-graph model should be more focused on domain and needs and should be used in raw form. We did it for a pure theoretical purpose. -
 @ 5d4b6c8d:8a1c1ee3
2024-12-19 17:08:08
@ 5d4b6c8d:8a1c1ee3
2024-12-19 17:08:08The NBA All Star Game is no more. After last year's humiliation, Adam Silver has decided to shake things up.
Format
Similar to the NHL, they are going to replace the All Star Game with a tournament. There will be five teams involved: three made up of the All Stars and two made up of the Rising Stars.
The 24 All Stars will be drafted into three teams by the TNT crew, while the winner of the Rising Stars challenge will advance to the final four.
There will then be a semifinals match, with the winners moving on to the championship round.
The games are pickup style games to 30 points.
Thoughts
I'm glad they're switching it up, but I don't know why the players would be expected to try any harder in this new format. The Rising Stars will be going all out, which might make whichever All Star team they face play a little harder.
Eight players is too many for pickup. They should have split the All Stars into four teams of six and just play to 21 like normal.
What do you all think about this new format?
originally posted at https://stacker.news/items/816168
-
 @ e6817453:b0ac3c39
2024-12-07 15:03:06
@ e6817453:b0ac3c39
2024-12-07 15:03:06Hey folks! Today, let’s dive into the intriguing world of neurosymbolic approaches, retrieval-augmented generation (RAG), and personal knowledge graphs (PKGs). Together, these concepts hold much potential for bringing true reasoning capabilities to large language models (LLMs). So, let’s break down how symbolic logic, knowledge graphs, and modern AI can come together to empower future AI systems to reason like humans.
The Neurosymbolic Approach: What It Means ?
Neurosymbolic AI combines two historically separate streams of artificial intelligence: symbolic reasoning and neural networks. Symbolic AI uses formal logic to process knowledge, similar to how we might solve problems or deduce information. On the other hand, neural networks, like those underlying GPT-4, focus on learning patterns from vast amounts of data — they are probabilistic statistical models that excel in generating human-like language and recognizing patterns but often lack deep, explicit reasoning.
While GPT-4 can produce impressive text, it’s still not very effective at reasoning in a truly logical way. Its foundation, transformers, allows it to excel in pattern recognition, but the models struggle with reasoning because, at their core, they rely on statistical probabilities rather than true symbolic logic. This is where neurosymbolic methods and knowledge graphs come in.
Symbolic Calculations and the Early Vision of AI
If we take a step back to the 1950s, the vision for artificial intelligence was very different. Early AI research was all about symbolic reasoning — where computers could perform logical calculations to derive new knowledge from a given set of rules and facts. Languages like Lisp emerged to support this vision, enabling programs to represent data and code as interchangeable symbols. Lisp was designed to be homoiconic, meaning it treated code as manipulatable data, making it capable of self-modification — a huge leap towards AI systems that could, in theory, understand and modify their own operations.
Lisp: The Earlier AI-Language
Lisp, short for “LISt Processor,” was developed by John McCarthy in 1958, and it became the cornerstone of early AI research. Lisp’s power lay in its flexibility and its use of symbolic expressions, which allowed developers to create programs that could manipulate symbols in ways that were very close to human reasoning. One of the most groundbreaking features of Lisp was its ability to treat code as data, known as homoiconicity, which meant that Lisp programs could introspect and transform themselves dynamically. This ability to adapt and modify its own structure gave Lisp an edge in tasks that required a form of self-awareness, which was key in the early days of AI when researchers were exploring what it meant for machines to “think.”
Lisp was not just a programming language—it represented the vision for artificial intelligence, where machines could evolve their understanding and rewrite their own programming. This idea formed the conceptual basis for many of the self-modifying and adaptive algorithms that are still explored today in AI research. Despite its decline in mainstream programming, Lisp’s influence can still be seen in the concepts used in modern machine learning and symbolic AI approaches.
Prolog: Formal Logic and Deductive Reasoning
In the 1970s, Prolog was developed—a language focused on formal logic and deductive reasoning. Unlike Lisp, based on lambda calculus, Prolog operates on formal logic rules, allowing it to perform deductive reasoning and solve logical puzzles. This made Prolog an ideal candidate for expert systems that needed to follow a sequence of logical steps, such as medical diagnostics or strategic planning.
Prolog, like Lisp, allowed symbols to be represented, understood, and used in calculations, creating another homoiconic language that allows reasoning. Prolog’s strength lies in its rule-based structure, which is well-suited for tasks that require logical inference and backtracking. These features made it a powerful tool for expert systems and AI research in the 1970s and 1980s.
The language is declarative in nature, meaning that you define the problem, and Prolog figures out how to solve it. By using formal logic and setting constraints, Prolog systems can derive conclusions from known facts, making it highly effective in fields requiring explicit logical frameworks, such as legal reasoning, diagnostics, and natural language understanding. These symbolic approaches were later overshadowed during the AI winter — but the ideas never really disappeared. They just evolved.
Solvers and Their Role in Complementing LLMs
One of the most powerful features of Prolog and similar logic-based systems is their use of solvers. Solvers are mechanisms that can take a set of rules and constraints and automatically find solutions that satisfy these conditions. This capability is incredibly useful when combined with LLMs, which excel at generating human-like language but need help with logical consistency and structured reasoning.
For instance, imagine a scenario where an LLM needs to answer a question involving multiple logical steps or a complex query that requires deducing facts from various pieces of information. In this case, a solver can derive valid conclusions based on a given set of logical rules, providing structured answers that the LLM can then articulate in natural language. This allows the LLM to retrieve information and ensure the logical integrity of its responses, leading to much more robust answers.
Solvers are also ideal for handling constraint satisfaction problems — situations where multiple conditions must be met simultaneously. In practical applications, this could include scheduling tasks, generating optimal recommendations, or even diagnosing issues where a set of symptoms must match possible diagnoses. Prolog’s solver capabilities and LLM’s natural language processing power can make these systems highly effective at providing intelligent, rule-compliant responses that traditional LLMs would struggle to produce alone.
By integrating neurosymbolic methods that utilize solvers, we can provide LLMs with a form of deductive reasoning that is missing from pure deep-learning approaches. This combination has the potential to significantly improve the quality of outputs for use-cases that require explicit, structured problem-solving, from legal queries to scientific research and beyond. Solvers give LLMs the backbone they need to not just generate answers but to do so in a way that respects logical rigor and complex constraints.
Graph of Rules for Enhanced Reasoning
Another powerful concept that complements LLMs is using a graph of rules. A graph of rules is essentially a structured collection of logical rules that interconnect in a network-like structure, defining how various entities and their relationships interact. This structured network allows for complex reasoning and information retrieval, as well as the ability to model intricate relationships between different pieces of knowledge.
In a graph of rules, each node represents a rule, and the edges define relationships between those rules — such as dependencies or causal links. This structure can be used to enhance LLM capabilities by providing them with a formal set of rules and relationships to follow, which improves logical consistency and reasoning depth. When an LLM encounters a problem or a question that requires multiple logical steps, it can traverse this graph of rules to generate an answer that is not only linguistically fluent but also logically robust.
For example, in a healthcare application, a graph of rules might include nodes for medical symptoms, possible diagnoses, and recommended treatments. When an LLM receives a query regarding a patient’s symptoms, it can use the graph to traverse from symptoms to potential diagnoses and then to treatment options, ensuring that the response is coherent and medically sound. The graph of rules guides reasoning, enabling LLMs to handle complex, multi-step questions that involve chains of reasoning, rather than merely generating surface-level responses.
Graphs of rules also enable modular reasoning, where different sets of rules can be activated based on the context or the type of question being asked. This modularity is crucial for creating adaptive AI systems that can apply specific sets of logical frameworks to distinct problem domains, thereby greatly enhancing their versatility. The combination of neural fluency with rule-based structure gives LLMs the ability to conduct more advanced reasoning, ultimately making them more reliable and effective in domains where accuracy and logical consistency are critical.
By implementing a graph of rules, LLMs are empowered to perform deductive reasoning alongside their generative capabilities, creating responses that are not only compelling but also logically aligned with the structured knowledge available in the system. This further enhances their potential applications in fields such as law, engineering, finance, and scientific research — domains where logical consistency is as important as linguistic coherence.
Enhancing LLMs with Symbolic Reasoning
Now, with LLMs like GPT-4 being mainstream, there is an emerging need to add real reasoning capabilities to them. This is where neurosymbolic approaches shine. Instead of pitting neural networks against symbolic reasoning, these methods combine the best of both worlds. The neural aspect provides language fluency and recognition of complex patterns, while the symbolic side offers real reasoning power through formal logic and rule-based frameworks.
Personal Knowledge Graphs (PKGs) come into play here as well. Knowledge graphs are data structures that encode entities and their relationships — they’re essentially semantic networks that allow for structured information retrieval. When integrated with neurosymbolic approaches, LLMs can use these graphs to answer questions in a far more contextual and precise way. By retrieving relevant information from a knowledge graph, they can ground their responses in well-defined relationships, thus improving both the relevance and the logical consistency of their answers.
Imagine combining an LLM with a graph of rules that allow it to reason through the relationships encoded in a personal knowledge graph. This could involve using deductive databases to form a sophisticated way to represent and reason with symbolic data — essentially constructing a powerful hybrid system that uses LLM capabilities for language fluency and rule-based logic for structured problem-solving.
My Research on Deductive Databases and Knowledge Graphs
I recently did some research on modeling knowledge graphs using deductive databases, such as DataLog — which can be thought of as a limited, data-oriented version of Prolog. What I’ve found is that it’s possible to use formal logic to model knowledge graphs, ontologies, and complex relationships elegantly as rules in a deductive system. Unlike classical RDF or traditional ontology-based models, which sometimes struggle with complex or evolving relationships, a deductive approach is more flexible and can easily support dynamic rules and reasoning.
Prolog and similar logic-driven frameworks can complement LLMs by handling the parts of reasoning where explicit rule-following is required. LLMs can benefit from these rule-based systems for tasks like entity recognition, logical inferences, and constructing or traversing knowledge graphs. We can even create a graph of rules that governs how relationships are formed or how logical deductions can be performed.
The future is really about creating an AI that is capable of both deep contextual understanding (using the powerful generative capacity of LLMs) and true reasoning (through symbolic systems and knowledge graphs). With the neurosymbolic approach, these AIs could be equipped not just to generate information but to explain their reasoning, form logical conclusions, and even improve their own understanding over time — getting us a step closer to true artificial general intelligence.
Why It Matters for LLM Employment
Using neurosymbolic RAG (retrieval-augmented generation) in conjunction with personal knowledge graphs could revolutionize how LLMs work in real-world applications. Imagine an LLM that understands not just language but also the relationships between different concepts — one that can navigate, reason, and explain complex knowledge domains by actively engaging with a personalized set of facts and rules.
This could lead to practical applications in areas like healthcare, finance, legal reasoning, or even personal productivity — where LLMs can help users solve complex problems logically, providing relevant information and well-justified reasoning paths. The combination of neural fluency with symbolic accuracy and deductive power is precisely the bridge we need to move beyond purely predictive AI to truly intelligent systems.
Let's explore these ideas further if you’re as fascinated by this as I am. Feel free to reach out, follow my YouTube channel, or check out some articles I’ll link below. And if you’re working on anything in this field, I’d love to collaborate!
Until next time, folks. Stay curious, and keep pushing the boundaries of AI!
-
 @ b8851a06:9b120ba1
2024-12-19 17:02:44
@ b8851a06:9b120ba1
2024-12-19 17:02:44The Federal Reserve's explicit prohibition from holding Bitcoin isn't just bureaucratic red tape - it's an unintentional safeguard for financial sovereignty (The Federal Reserve is explicitly prohibited from holding Bitcoin under current legislation, specifically through restrictions outlined in the Federal Reserve Act. This legal framework strictly defines the types of assets the central bank can maintain on its balance sheet). Here's why Bitcoin holders should celebrate this restriction.
The Power of Separation
The Fed's inability to hold Bitcoin creates a crucial firewall between state monetary control and genuine financial freedom. When Fed Chairman Powell confirms they cannot hold Bitcoin and aren't seeking changes to this restriction, it maintains Bitcoin's position as the only truly independent monetary asset.
Strategic Implications
Control Vectors\ Consider the alternative scenario: If the Fed could hold Bitcoin, it would gain multiple control mechanisms:
- The ability to manipulate Bitcoin markets through large-scale buying and selling
- The power to implement additional taxation schemes
- The capacity to create a "balanced budget trap" affecting holders
Regulatory Capture\ A Federal Reserve Bitcoin holding would subject the asset to:
- Stricter banking regulations and supervision
- Integration into traditional monetary policy tools
- Potential restrictions on peer-to-peer transactions
Economic Reality
Let's be crystal clear: Bitcoin's protocol ensures its fixed supply of 21 million coins is immutable - no central bank, including the Federal Reserve, can ever change this fundamental characteristic. However, if allowed to hold Bitcoin, the Fed could attempt to:
- Influence market sentiment through strategic accumulation or selling
- Create paper derivatives to dilute Bitcoin's scarcity premium
- Implement policies that could affect Bitcoin's market accessibility
The Freedom Advantage
The inability of the Fed to hold Bitcoin ensures:
- Continued decentralization of holdings
- Protection from central bank monetary experiments
- Preservation of Bitcoin's role as a hedge against federal monetary policy
This legal barrier isn't a limitation - it's a feature that protects Bitcoin's fundamental value proposition as a truly independent financial system.
-
 @ e968e50b:db2a803a
2024-12-19 17:01:55
@ e968e50b:db2a803a
2024-12-19 17:01:55...except it's the GM filter you never wanted. ONLY GM!
nostrminusnostr
For those unaware, nostrminusnostr is the nostr client for the countless nostr users who intent to use nostr for anything other than talking about nostr (or bitcoin). Not only is all nostr and bitcoin content totally filtered out, but so are smaller notes that don't really contain any substance worth reading. You can only zap one amount of 2000 sats at a time, forcing you to save your zaps for truly worthy content.
In addition to the original Pizza Party version (objectively the greatest UI in all of social media), the dev team at nostrminusnostr has worked hard to bring you:
- Sports This is all of nostr's sports content. (mostly news from bots right now)
- Kittens This area actually only features notes about bitcoin and nostr, but those words are replaced with puppies and kittens, as are all the pictures.
- Alt Coints This is where all things alt coins are discussed. It is very popular among users of stacker news and will probably make you rich.
- AND NOW INTRODUCING...
GM
[^1]: as of August 2024, GMs on nostr have officially surpassed the dollar balance of the US national debt
originally posted at https://stacker.news/items/816163
-
 @ c6d64c7b:5149eb60
2024-12-19 16:42:50
@ c6d64c7b:5149eb60
2024-12-19 16:42:50Knowledge Creation
Somewhat recently I have done a small amount of “adding knowledge into the world.” After a few months of building the business it became apparent that many of the problems I was facing had very few corresponding resources. These are niche problems solved by niche people. It turns out that building a hardware business is a quite niche activity.
Every knowledge domain can be broken down into smaller subdomains. Let’s say I am into US politics. There are 3 categories of political parties: Republican, Democrat, and Other. An extremely small percentage of total information about US politics covers the “Other” party. It looks like Joel Skousen is the official 3rd party candidate who received among the least amount of votes (12,618) for President in the most recent election. Here’s a list of his published books from the “About” page from his website:
- Essential Principles for the Conservation of Liberty, 1984
- The Secure Home--Architectural Design, Construction and Remodeling of Self-Sufficient Residences and Retreats, new edition now available.
- How to Implement a High Security Shelter in the Home (1996),
- Strategic Relocation--North American Guide to Safe Places (1998)
- (In the works) Foundations of the Ideal State--a comprehensive treatise on government structure and practice, constitutional theory, and legal changes necessary to preserve liberty and justice.
There is almost no information on the internet about this man’s recent Presidential bid. What could be learned about independent publishing, the process of getting on election ballots, the intricacies of the various outsider parties, and the confluence of home safety and political theory, from diving into the details of this man’s (very) small role in the huge world of US politics? Mix that deep dive with your own unique perspective, and certainly SOMETHING novel and interesting would result.
Millan and Mano used this exact formula to huge success in their independent music blog. They wrote about unknown, independent musicians in (mostly) small markets (Milwaukee, New Orleans, etc), and discuss them with an academic, poetic, and explorative writing style that is unique among music journalists. They were regular guys and created new knowledge and ideas.
I think doing this is important. Or it just makes me feel important. Even if no one reads it at least I created new knowledge and it may help someone one day. Or more likely, the AI of the future. As Gwern recently said…
By writing, you are voting on the future of the Shoggoth using one of the few currencies it acknowledges: tokens it has to predict. If you aren't writing, you are abdicating the future or your role in it. If you think it's enough to just be a good citizen, to vote for your favorite politician, to pick up litter and recycle, the future doesn't care about you. ^1
So I am going to try do more of this independent small-time knowledge creation. My business had been hampering the newsletter anyways, since it had been consuming my life and most of the work could not be shared on a public website. I’m gonna try to write more regularly with deep dives on novel and interesting things instead of the standard newsletter.
-
 @ edb05a1c:3a8ba64b
2024-12-19 16:34:39
@ edb05a1c:3a8ba64b
2024-12-19 16:34:39Test About Page
Subheading
This is the test about page.
-
 @ e6817453:b0ac3c39
2024-12-07 14:54:46
@ e6817453:b0ac3c39
2024-12-07 14:54:46Introduction: Personal Knowledge Graphs and Linked Data
We will explore the world of personal knowledge graphs and discuss how they can be used to model complex information structures. Personal knowledge graphs aren’t just abstract collections of nodes and edges—they encode meaningful relationships, contextualizing data in ways that enrich our understanding of it. While the core structure might be a directed graph, we layer semantic meaning on top, enabling nuanced connections between data points.
The origin of knowledge graphs is deeply tied to concepts from linked data and the semantic web, ideas that emerged to better link scattered pieces of information across the web. This approach created an infrastructure where data islands could connect — facilitating everything from more insightful AI to improved personal data management.
In this article, we will explore how these ideas have evolved into tools for modeling AI’s semantic memory and look at how knowledge graphs can serve as a flexible foundation for encoding rich data contexts. We’ll specifically discuss three major paradigms: RDF (Resource Description Framework), property graphs, and a third way of modeling entities as graphs of graphs. Let’s get started.
Intro to RDF
The Resource Description Framework (RDF) has been one of the fundamental standards for linked data and knowledge graphs. RDF allows data to be modeled as triples: subject, predicate, and object. Essentially, you can think of it as a structured way to describe relationships: “X has a Y called Z.” For instance, “Berlin has a population of 3.5 million.” This modeling approach is quite flexible because RDF uses unique identifiers — usually URIs — to point to data entities, making linking straightforward and coherent.
RDFS, or RDF Schema, extends RDF to provide a basic vocabulary to structure the data even more. This lets us describe not only individual nodes but also relationships among types of data entities, like defining a class hierarchy or setting properties. For example, you could say that “Berlin” is an instance of a “City” and that cities are types of “Geographical Entities.” This kind of organization helps establish semantic meaning within the graph.
RDF and Advanced Topics
Lists and Sets in RDF
RDF also provides tools to model more complex data structures such as lists and sets, enabling the grouping of nodes. This extension makes it easier to model more natural, human-like knowledge, for example, describing attributes of an entity that may have multiple values. By adding RDF Schema and OWL (Web Ontology Language), you gain even more expressive power — being able to define logical rules or even derive new relationships from existing data.
Graph of Graphs
A significant feature of RDF is the ability to form complex nested structures, often referred to as graphs of graphs. This allows you to create “named graphs,” essentially subgraphs that can be independently referenced. For example, you could create a named graph for a particular dataset describing Berlin and another for a different geographical area. Then, you could connect them, allowing for more modular and reusable knowledge modeling.
Property Graphs
While RDF provides a robust framework, it’s not always the easiest to work with due to its heavy reliance on linking everything explicitly. This is where property graphs come into play. Property graphs are less focused on linking everything through triples and allow more expressive properties directly within nodes and edges.
For example, instead of using triples to represent each detail, a property graph might let you store all properties about an entity (e.g., “Berlin”) directly in a single node. This makes property graphs more intuitive for many developers and engineers because they more closely resemble object-oriented structures: you have entities (nodes) that possess attributes (properties) and are connected to other entities through relationships (edges).
The significant benefit here is a condensed representation, which speeds up traversal and queries in some scenarios. However, this also introduces a trade-off: while property graphs are more straightforward to query and maintain, they lack some complex relationship modeling features RDF offers, particularly when connecting properties to each other.
Graph of Graphs and Subgraphs for Entity Modeling
A third approach — which takes elements from RDF and property graphs — involves modeling entities using subgraphs or nested graphs. In this model, each entity can be represented as a graph. This allows for a detailed and flexible description of attributes without exploding every detail into individual triples or lump them all together into properties.
For instance, consider a person entity with a complex employment history. Instead of representing every employment detail in one node (as in a property graph), or as several linked nodes (as in RDF), you can treat the employment history as a subgraph. This subgraph could then contain nodes for different jobs, each linked with specific properties and connections. This approach keeps the complexity where it belongs and provides better flexibility when new attributes or entities need to be added.
Hypergraphs and Metagraphs
When discussing more advanced forms of graphs, we encounter hypergraphs and metagraphs. These take the idea of relationships to a new level. A hypergraph allows an edge to connect more than two nodes, which is extremely useful when modeling scenarios where relationships aren’t just pairwise. For example, a “Project” could connect multiple “People,” “Resources,” and “Outcomes,” all in a single edge. This way, hypergraphs help in reducing the complexity of modeling high-order relationships.
Metagraphs, on the other hand, enable nodes and edges to themselves be represented as graphs. This is an extremely powerful feature when we consider the needs of artificial intelligence, as it allows for the modeling of relationships between relationships, an essential aspect for any system that needs to capture not just facts, but their interdependencies and contexts.
Balancing Structure and Properties
One of the recurring challenges when modeling knowledge is finding the balance between structure and properties. With RDF, you get high flexibility and standardization, but complexity can quickly escalate as you decompose everything into triples. Property graphs simplify the representation by using attributes but lose out on the depth of connection modeling. Meanwhile, the graph-of-graphs approach and hypergraphs offer advanced modeling capabilities at the cost of increased computational complexity.
So, how do you decide which model to use? It comes down to your use case. RDF and nested graphs are strong contenders if you need deep linkage and are working with highly variable data. For more straightforward, engineer-friendly modeling, property graphs shine. And when dealing with very complex multi-way relationships or meta-level knowledge, hypergraphs and metagraphs provide the necessary tools.
The key takeaway is that only some approaches are perfect. Instead, it’s all about the modeling goals: how do you want to query the graph, what relationships are meaningful, and how much complexity are you willing to manage?
Conclusion
Modeling AI semantic memory using knowledge graphs is a challenging but rewarding process. The different approaches — RDF, property graphs, and advanced graph modeling techniques like nested graphs and hypergraphs — each offer unique strengths and weaknesses. Whether you are building a personal knowledge graph or scaling up to AI that integrates multiple streams of linked data, it’s essential to understand the trade-offs each approach brings.
In the end, the choice of representation comes down to the nature of your data and your specific needs for querying and maintaining semantic relationships. The world of knowledge graphs is vast, with many tools and frameworks to explore. Stay connected and keep experimenting to find the balance that works for your projects.
-
 @ e6817453:b0ac3c39
2024-12-07 14:52:47
@ e6817453:b0ac3c39
2024-12-07 14:52:47The temporal semantics and temporal and time-aware knowledge graphs. We have different memory models for artificial intelligence agents. We all try to mimic somehow how the brain works, or at least how the declarative memory of the brain works. We have the split of episodic memory and semantic memory. And we also have a lot of theories, right?
Declarative Memory of the Human Brain
How is the semantic memory formed? We all know that our brain stores semantic memory quite close to the concept we have with the personal knowledge graphs, that it’s connected entities. They form a connection with each other and all those things. So far, so good. And actually, then we have a lot of concepts, how the episodic memory and our experiences gets transmitted to the semantic:
- hippocampus indexing and retrieval
- sanitization of episodic memories
- episodic-semantic shift theory
They all give a different perspective on how different parts of declarative memory cooperate.
We know that episodic memories get semanticized over time. You have semantic knowledge without the notion of time, and probably, your episodic memory is just decayed.
But, you know, it’s still an open question:
do we want to mimic an AI agent’s memory as a human brain memory, or do we want to create something different?
It’s an open question to which we have no good answer. And if you go to the theory of neuroscience and check how episodic and semantic memory interfere, you will still find a lot of theories, yeah?
Some of them say that you have the hippocampus that keeps the indexes of the memory. Some others will say that you semantic the episodic memory. Some others say that you have some separate process that digests the episodic and experience to the semantics. But all of them agree on the plan that it’s operationally two separate areas of memories and even two separate regions of brain, and the semantic, it’s more, let’s say, protected.
So it’s harder to forget the semantical facts than the episodes and everything. And what I’m thinking about for a long time, it’s this, you know, the semantic memory.
Temporal Semantics
It’s memory about the facts, but you somehow mix the time information with the semantics. I already described a lot of things, including how we could combine time with knowledge graphs and how people do it.
There are multiple ways we could persist such information, but we all hit the wall because the complexity of time and the semantics of time are highly complex concepts.
Time in a Semantic context is not a timestamp.
What I mean is that when you have a fact, and you just mentioned that I was there at this particular moment, like, I don’t know, 15:40 on Monday, it’s already awake because we don’t know which Monday, right? So you need to give the exact date, but usually, you do not have experiences like that.
You do not record your memories like that, except you do the journaling and all of the things. So, usually, you have no direct time references. What I mean is that you could say that I was there and it was some event, blah, blah, blah.
Somehow, we form a chain of events that connect with each other and maybe will be connected to some period of time if we are lucky enough. This means that we could not easily represent temporal-aware information as just a timestamp or validity and all of the things.
For sure, the validity of the knowledge graphs (simple quintuple with start and end dates)is a big topic, and it could solve a lot of things. It could solve a lot of the time cases. It’s super simple because you give the end and start dates, and you are done, but it does not answer facts that have a relative time or time information in facts . It could solve many use cases but struggle with facts in an indirect temporal context. I like the simplicity of this idea. But the problem of this approach that in most cases, we simply don’t have these timestamps. We don’t have the timestamp where this information starts and ends. And it’s not modeling many events in our life, especially if you have the processes or ongoing activities or recurrent events.
I’m more about thinking about the time of semantics, where you have a time model as a hybrid clock or some global clock that does the partial ordering of the events. It’s mean that you have the chain of the experiences and you have the chain of the facts that have the different time contexts.
We could deduct the time from this chain of the events. But it’s a big, big topic for the research. But what I want to achieve, actually, it’s not separation on episodic and semantic memory. It’s having something in between.
Blockchain of connected events and facts
I call it temporal-aware semantics or time-aware knowledge graphs, where we could encode the semantic fact together with the time component.I doubt that time should be the simple timestamp or the region of the two timestamps. For me, it is more a chain for facts that have a partial order and form a blockchain like a database or a partially ordered Acyclic graph of facts that are temporally connected. We could have some notion of time that is understandable to the agent and a model that allows us to order the events and focus on what the agent knows and how to order this time knowledge and create the chains of the events.
Time anchors
We may have a particular time in the chain that allows us to arrange a more concrete time for the rest of the events. But it’s still an open topic for research. The temporal semantics gets split into a couple of domains. One domain is how to add time to the knowledge graphs. We already have many different solutions. I described them in my previous articles.
Another domain is the agent's memory and how the memory of the artificial intelligence treats the time. This one, it’s much more complex. Because here, we could not operate with the simple timestamps. We need to have the representation of time that are understandable by model and understandable by the agent that will work with this model. And this one, it’s way bigger topic for the research.”
-
 @ 4ba8e86d:89d32de4
2024-11-14 09:17:14
@ 4ba8e86d:89d32de4
2024-11-14 09:17:14Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ 4ba8e86d:89d32de4
2024-11-07 13:56:21
@ 4ba8e86d:89d32de4
2024-11-07 13:56:21Tutorial feito por Grom mestre⚡poste original abaixo:
http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/240277/tutorial-criando-e-acessando-sua-conta-de-email-pela-i2p?show=240277#q240277
Bom dia/tarde/noite a todos os camaradas. Seguindo a nossa série de tutoriais referentes a tecnologias essenciais para a segurança e o anonimato dos usuários, sendo as primeiras a openPGP e a I2P, lhes apresento mais uma opção para expandir os seus conhecimentos da DW. Muitos devem conhecer os serviços de mail na onion como DNMX e mail2tor, mas e que tal um serviço de email pela I2P. Nesse tutorial eu vou mostrar a vocês como criar a sua primeira conta no hq.postman.i2p e a acessar essa conta.
É importante que vocês tenham lido a minha primeira série de tutoriais a respeito de como instalar, configurar e navegar pela I2P nostr:nevent1qqsyjcz2w0e6d6dcdeprhuuarw4aqkw730y542dzlwxwssneq3mwpaspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsyp5vcq Esse tutorial é um pré-requisito para o seguinte e portanto recomendo que leia-os antes de prosseguir com o seguinte tutorial. O tutorial de Kleopatra nostr:nevent1qqs8h7vsn5j6qh35949sa60dms4fneussmv9jd76n24lsmtz24k0xlqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgecq8f7 é complementar dado que é extremamente recomendado assinar e criptografar as mensagens que seguem por emails pela DW. Sem mais delongas, vamos ao tutorial de fato.
1. Criando uma conta de email no hq.postman
Relembrando: Esse tutorial considera que você já tenha acesso à I2P. Entre no seu navegador e acesse o endereço hq.postman.i2p. O roteador provavelmente já contém esse endereço no seu addressbook e não haverá a necessidade de inserir o endereço b32 completo. Após entrar no site vá para a página '1 - Creating a mailbox' https://image.nostr.build/d850379fe315d2abab71430949b06d3fa49366d91df4c9b00a4a8367d53fcca3.jpg
Nessa página, insira as credenciais de sua preferências nos campos do formulário abaixo. Lembre-se que o seu endereço de email aceita apenas letras e números. Clique em 'Proceed' depois que preencher todos os campos. https://image.nostr.build/670dfda7264db393e48391f217e60a2eb87d85c2729360c8ef6fe0cf52508ab4.jpg
Uma página vai aparecer pedindo para confirmar as credenciais da sua nova conta. Se tudo estiver certo apenas clique em 'Confirm and Create Mailbox'. Se tudo ocorrer como conforme haverá uma confirmação de que a sua nova conta foi criada com sucesso. Após isso aguarde por volta de 5 minutos antes de tentar acessá-la, para que haja tempo suficiente para o servidor atualizar o banco de dados. https://image.nostr.build/ec58fb826bffa60791fedfd9c89a25d592ac3d11645b270c936c60a7c59c067f.jpg https://image.nostr.build/a2b7710d1e3cbb36431acb9055fd62937986b4da4b1a1bbb06d3f3cb1f544fd3.jpg
Pronto! Sua nova conta de email na I2P foi criada. Agora vamos para a próxima etapa: como acessar a sua conta via um cliente de email.
2. Configurando os túneis cliente de SMTP e POP3
O hq.postman não possui um cliente web que nos permite acessar a nossa conta pelo navegador. Para isso precisamos usar um cliente como Thunderbird e configurar os túneis cliente no I2Pd que serão necessários para o Thunderbird se comunicar com o servidor pela I2P.
Caso não tenha instalado o Thunderbird ainda, faça-o agora antes de prosseguir.
Vamos configurar os túneis cliente do servidor de email no nosso roteador. Para isso abra um terminal ou o seu gestor de arquivos e vá para a pasta de configuração de túneis do I2P. Em Linux esse diretório se localiza em /etc/i2pd/tunnels.d. Em Windows, essa pasta se localiza em C:\users\user\APPDATA\i2pd. Na pasta tunnels.d crie dois arquivos: smtp.postman.conf e pop-postman.conf. Lembre-se que em Linux você precisa de permissões de root para escrever na pasta de configuração. Use o comando sudoedit
para isso. Edite-os conforme as imagens a seguir:
Arquivo pop-postman.conf https://image.nostr.build/7e03505c8bc3b632ca5db1f8eaefc6cecb4743cd2096d211dd90bbdc16fe2593.jpg
Arquivo smtp-postman.conf https://image.nostr.build/2d06c021841dedd6000c9fc2a641ed519b3be3c6125000b188842cd0a5af3d16.jpg
Salve os arquivos e reinicie o serviço do I2Pd. Em Linux isso é feito pelo comando:
sudo systemctl restart i2pdEntre no Webconsole do I2Pd pelo navegador (localhost:7070) e na seção I2P Tunnels, verifique se os túneis pop-postman e smtp-postman foram criados, caso contrário verifique se há algum erro nos arquivos e reinicie o serviço.Com os túneis cliente criados, vamos agora configurar o Thunderbird
3. Configurando o Thunderbird para acessar a nossa conta
Abra o Thunderbird e clique em criar uma nova conta de email. Se você não tiver nenhum conta previamente presente nele você vai ser diretamente recebido pela janela de criação de conta a seguir. https://image.nostr.build/e9509d7bd30623716ef9adcad76c1d465f5bc3d5840e0c35fe4faa85740f41b4.jpg https://image.nostr.build/688b59b8352a17389902ec1e99d7484e310d7d287491b34f562b8cdd9dbe8a99.jpg
Coloque as suas credenciais, mas não clique ainda em Continuar. Clique antes em Configure Manually, já que precisamos configurar manualmente os servidores de SMTP e POP3 para, respectivamente, enviar e receber mensagens.
Preencha os campos como na imagem a seguir. Detalhe: Não coloque o seu endereço completo com o @mail.i2p, apenas o nome da sua conta. https://image.nostr.build/4610b0315c0a3b741965d3d7c1e4aff6425a167297e323ba8490f4325f40cdcc.jpg
Clique em Re-test para verificar a integridade da conexão. Se tudo estiver certo uma mensagem irá aparecer avisando que as configurações do servidores estão corretas. Clique em Done assim que estiver pronto para prosseguir. https://image.nostr.build/8a47bb292f94b0d9d474d4d4a134f8d73afb84ecf1d4c0a7eb6366d46bf3973a.jpg
A seguinte mensagem vai aparecer alertando que não estamos usando criptografia no envio das credenciais. Não há problema nenhum aqui, pois a I2P está garantindo toda a proteção e anonimato dos nossos dados, o que dispensa a necessidade de uso de TLS ou qualquer tecnologia similar nas camadas acima. Marque a opção 'I Understand the risks' e clique em 'Continue' https://image.nostr.build/9c1bf585248773297d2cb1d9705c1be3bd815e2be85d4342227f1db2f13a9cc6.jpg
E por fim, se tudo ocorreu como devido sua conta será criada com sucesso e você agora será capaz de enviar e receber emails pela I2P usando essa conta. https://image.nostr.build/8ba7f2c160453c9bfa172fa9a30b642a7ee9ae3eeb9b78b4dc24ce25aa2c7ecc.jpg
4. Observações e considerações finais
Como informado pelo próprio site do hq.postman, o domínio @mail.i2p serve apenas para emails enviados dentro da I2P. Emails enviados pela surface devem usar o domínio @i2pmai.org. É imprescindível que você saiba usar o PGP para assinar e criptografar as suas mensagens, dado que provavelmente as mensagens não são armazenadas de forma criptografada enquanto elas estão armazenadas no servidor. Como o protocolo POP3 delete as mensagens no imediato momento em que você as recebe, não há necessidade de fazer qualquer limpeza na sua conta de forma manual.
Por fim, espero que esse tutorial tenha sido útil para vocês. Que seu conhecimento tenha expandido ainda mais com as informações trazidas aqui. Até a próxima.
-
 @ c6d64c7b:5149eb60
2024-12-19 16:17:55
@ c6d64c7b:5149eb60
2024-12-19 16:17:55I live in the USA.
I work as a software developer.
I read and write a lot.
-
 @ 9bcc5462:eb501d90
2024-12-19 16:14:46
@ 9bcc5462:eb501d90
2024-12-19 16:14:46This event has been deleted; your client is ignoring the delete request.
-
 @ e1d968f7:5d90f764
2024-12-19 16:14:28
@ e1d968f7:5d90f764
2024-12-19 16:14:28Walking the line between professionalism and empathy is one of the most delicate aspects of escorting. Clients come to us for different reasons—companionship, escape, intimacy, or understanding—and navigating these needs while maintaining my own boundaries is a skill I refine every day.
The Role of Empathy
Empathy is essential in this line of work. Each client is a person with their own story, struggles, and desires. Truly understanding and connecting with them often requires stepping into their world, even briefly, to offer the care or attention they seek.
-
Listening Without Judgement:
Some clients open up about deeply personal matters. Listening and responding with kindness can make a significant difference. -
Creating a Safe Space:
Many clients come seeking not just physical intimacy, but emotional safety. Being someone they can trust matters more than you’d expect.
Maintaining Professionalism
While empathy builds connections, professionalism ensures those connections don’t cross into personal entanglement. Escorting requires clear boundaries to protect both myself and my clients.
-
Boundaries are Key:
Knowing where to draw the line is critical. It allows me to offer genuine care without compromising my emotional well-being. -
The Power of Detachment:
Maintaining a professional mindset doesn’t mean being cold—it means staying grounded, even when emotions run high.
Finding the Balance
Balancing professionalism with empathy is a constant dance. I’ve learned that it’s possible to be warm and understanding while keeping the relationship professional. When done well, it leaves both me and my clients feeling respected, cared for, and fulfilled.
It’s not always easy, and there are times when the line blurs. But in those moments, I remind myself why I do this: to offer connection without losing myself in the process.
Rebecca x
-
-
 @ a367f9eb:0633efea
2024-11-05 08:48:41
@ a367f9eb:0633efea
2024-11-05 08:48:41Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application.
The reporting purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States.
In a June paper reviewed by Reuters, six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”.
The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making.
While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the Star Trek episode “A Taste of Armageddon“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place.
Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran?
The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over one million open-source LLMs available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer.
With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are potentially trillions of dollars on the line.
Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American infrastructure, data, and yes, your credit history?
As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much many times.
At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative.
Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this.
Open-source matters When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it.
The various licensing schemes – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made.
While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit.
Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers.
Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other.
I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run.
Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots).
This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also open-source, which has allowed thousands of copycat protocols that have revolutionized how we view money.
You know what else is open-source and available for everyone to use, modify, and build upon?
PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit.
Open-source code is speech, and it is knowledge.
We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge.
Open-source is for your friends, and enemies In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license.
At this very moment, you can click on over to Hugging Face, download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth).
Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created.
We know this can be useful to friends, but what about enemies?
As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications.
The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians.
A bipartisan group of US House lawmakers want to put export controls on AI models, as well as block foreign access to US cloud servers that may be hosting AI software.
If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see The Crypto Wars). Many of the arguments we hear today were invoked by some of the same people as back then.
Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to.
Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place.
Limiting open-source threatens our own advancement If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way.
If there is a “Hundred Year Marathon” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible.
The Chinese military has been building up its capabilities with trillions of dollars’ worth of investments that span far beyond AI chatbots and skip logic protocols.
The theft of intellectual property at factories in Shenzhen, or in US courts by third-party litigation funding coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing.
But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source.
If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries.
Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application.
The reporting purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States.
In a June paper reviewed by Reuters, six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”.
The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making.
While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the Star Trek episode “A Taste of Armageddon“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place.
Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran?
The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over one million open-source LLMs available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer.
With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are potentially trillions of dollars on the line.
Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American infrastructure, data, and yes, your credit history?
As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much many times.
At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative.
Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this.
Open-source matters
When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it.
The various licensing schemes – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made.
While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit.
Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers.
Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other.
I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run.
Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots).
This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also open-source, which has allowed thousands of copycat protocols that have revolutionized how we view money.
You know what else is open-source and available for everyone to use, modify, and build upon?
PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit.
Open-source code is speech, and it is knowledge.
We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge.
Open-source is for your friends, and enemies
In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license.
At this very moment, you can click on over to Hugging Face, download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth).
Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created.
We know this can be useful to friends, but what about enemies?
As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications.
The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians.
A bipartisan group of US House lawmakers want to put export controls on AI models, as well as block foreign access to US cloud servers that may be hosting AI software.
If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see The Crypto Wars). Many of the arguments we hear today were invoked by some of the same people as back then.
Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to.
Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place.
Limiting open-source threatens our own advancement
If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way.
If there is a “Hundred Year Marathon” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible.
The Chinese military has been building up its capabilities with trillions of dollars’ worth of investments that span far beyond AI chatbots and skip logic protocols.
The theft of intellectual property at factories in Shenzhen, or in US courts by third-party litigation funding coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing.
But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source.
If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries.
Originally published on the website of the Consumer Choice Center.
-
 @ 09fbf8f3:fa3d60f0
2024-11-02 08:00:29
@ 09fbf8f3:fa3d60f0
2024-11-02 08:00:29> ### 第三方API合集:
免责申明:
在此推荐的 OpenAI API Key 由第三方代理商提供,所以我们不对 API Key 的 有效性 和 安全性 负责,请你自行承担购买和使用 API Key 的风险。
| 服务商 | 特性说明 | Proxy 代理地址 | 链接 | | --- | --- | --- | --- | | AiHubMix | 使用 OpenAI 企业接口,全站模型价格为官方 86 折(含 GPT-4 )| https://aihubmix.com/v1 | 官网 | | OpenAI-HK | OpenAI的API官方计费模式为,按每次API请求内容和返回内容tokens长度来定价。每个模型具有不同的计价方式,以每1,000个tokens消耗为单位定价。其中1,000个tokens约为750个英文单词(约400汉字)| https://api.openai-hk.com/ | 官网 | | CloseAI | CloseAI是国内规模最大的商用级OpenAI代理平台,也是国内第一家专业OpenAI中转服务,定位于企业级商用需求,面向企业客户的线上服务提供高质量稳定的官方OpenAI API 中转代理,是百余家企业和多家科研机构的专用合作平台。 | https://api.openai-proxy.org | 官网 | | OpenAI-SB | 需要配合Telegram 获取api key | https://api.openai-sb.com | 官网 |
持续更新。。。
推广:
访问不了openai,去
低调云购买VPN。官网:https://didiaocloud.xyz
邀请码:
w9AjVJit价格低至1元。
-
 @ 4c48cf05:07f52b80
2024-10-30 01:03:42
@ 4c48cf05:07f52b80
2024-10-30 01:03:42I believe that five years from now, access to artificial intelligence will be akin to what access to the Internet represents today. It will be the greatest differentiator between the haves and have nots. Unequal access to artificial intelligence will exacerbate societal inequalities and limit opportunities for those without access to it.
Back in April, the AI Index Steering Committee at the Institute for Human-Centered AI from Stanford University released The AI Index 2024 Annual Report.
Out of the extensive report (502 pages), I chose to focus on the chapter dedicated to Public Opinion. People involved with AI live in a bubble. We all know and understand AI and therefore assume that everyone else does. But, is that really the case once you step out of your regular circles in Seattle or Silicon Valley and hit Main Street?
Two thirds of global respondents have a good understanding of what AI is
The exact number is 67%. My gut feeling is that this number is way too high to be realistic. At the same time, 63% of respondents are aware of ChatGPT so maybe people are confounding AI with ChatGPT?
If so, there is so much more that they won't see coming.
This number is important because you need to see every other questions and response of the survey through the lens of a respondent who believes to have a good understanding of what AI is.
A majority are nervous about AI products and services
52% of global respondents are nervous about products and services that use AI. Leading the pack are Australians at 69% and the least worried are Japanise at 23%. U.S.A. is up there at the top at 63%.
Japan is truly an outlier, with most countries moving between 40% and 60%.
Personal data is the clear victim
Exaclty half of the respondents believe that AI companies will protect their personal data. And the other half believes they won't.
Expected benefits
Again a majority of people (57%) think that it will change how they do their jobs. As for impact on your life, top hitters are getting things done faster (54%) and more entertainment options (51%).
The last one is a head scratcher for me. Are people looking forward to AI generated movies?

Concerns
Remember the 57% that thought that AI will change how they do their jobs? Well, it looks like 37% of them expect to lose it. Whether or not this is what will happen, that is a very high number of people who have a direct incentive to oppose AI.
Other key concerns include:
- Misuse for nefarious purposes: 49%
- Violation of citizens' privacy: 45%
Conclusion
This is the first time I come across this report and I wil make sure to follow future annual reports to see how these trends evolve.
Overall, people are worried about AI. There are many things that could go wrong and people perceive that both jobs and privacy are on the line.
Full citation: Nestor Maslej, Loredana Fattorini, Raymond Perrault, Vanessa Parli, Anka Reuel, Erik Brynjolfsson, John Etchemendy, Katrina Ligett, Terah Lyons, James Manyika, Juan Carlos Niebles, Yoav Shoham, Russell Wald, and Jack Clark, “The AI Index 2024 Annual Report,” AI Index Steering Committee, Institute for Human-Centered AI, Stanford University, Stanford, CA, April 2024.
The AI Index 2024 Annual Report by Stanford University is licensed under Attribution-NoDerivatives 4.0 International.
-
 @ edb05a1c:3a8ba64b
2024-12-19 16:13:23
@ edb05a1c:3a8ba64b
2024-12-19 16:13:23Test About Page
Subheading
This is the test about page.
-
 @ 29122de5:20515210
2024-12-19 15:33:14
@ 29122de5:20515210
2024-12-19 15:33:14Loans are the backbone of modern finance. But have you ever wondered where it all started? From ancient gold lenders to today’s innovative solutions, here’s the incredible story of loans through the ages.\ \ Ancient Beginnings: Mesopotamia & Egypt\ The first recorded loans date back over 4,000 years, in ancient Mesopotamia. Sumerians, in what is now modern-day Iraq, used grain as collateral. Egypt’s economy also relied on loans backed by land and crops.
 \
The Role of Moneylenders\
As civilizations grew, so did the need for loans. Moneylenders in ancient Greece and Rome provided short-term credit to those who needed it. Interest rates were often high, but access to funds helped foster trade and business growth.
\
The Role of Moneylenders\
As civilizations grew, so did the need for loans. Moneylenders in ancient Greece and Rome provided short-term credit to those who needed it. Interest rates were often high, but access to funds helped foster trade and business growth. \
Medieval Times & The Church\
During the Middle Ages, the Catholic Church prohibited lending with interest, labeling it as usury. However, non-Christians were often permitted to lend money at interest, playing a crucial role in Europe’s financial systems.
\
Medieval Times & The Church\
During the Middle Ages, the Catholic Church prohibited lending with interest, labeling it as usury. However, non-Christians were often permitted to lend money at interest, playing a crucial role in Europe’s financial systems. \
Industrial Revolution\
With the Industrial Revolution came a boom in demand for loans. Businesses needed capital to expand factories, and governments sought funding for infrastructure projects. This period marked the rise of commercial banks and the birth of personal loans.
\
Industrial Revolution\
With the Industrial Revolution came a boom in demand for loans. Businesses needed capital to expand factories, and governments sought funding for infrastructure projects. This period marked the rise of commercial banks and the birth of personal loans. \
The Rise of Consumer Loans\
In the 20th century, loans began to shift toward consumer credit. Credit cards were introduced in the 1950s, making borrowing more accessible than ever before. Personal loans and mortgages became staples of the modern financial landscape.
\
The Rise of Consumer Loans\
In the 20th century, loans began to shift toward consumer credit. Credit cards were introduced in the 1950s, making borrowing more accessible than ever before. Personal loans and mortgages became staples of the modern financial landscape. \
The Future of Loans\
In the digital age, Bitcoin-backed loans are rewriting the rules of finance: no banks, no borders, no credit checks. Empowering individuals with control, freedom, and seamless access to funds.
\
The Future of Loans\
In the digital age, Bitcoin-backed loans are rewriting the rules of finance: no banks, no borders, no credit checks. Empowering individuals with control, freedom, and seamless access to funds.
-
 @ 8947a945:9bfcf626
2024-10-17 08:06:55
@ 8947a945:9bfcf626
2024-10-17 08:06:55สวัสดีทุกคนบน Nostr ครับ รวมไปถึง watchersและ ผู้ติดตามของผมจาก Deviantart และ platform งานศิลปะอื่นๆนะครับ
ตั้งแต่ต้นปี 2024 ผมใช้ AI เจนรูปงานตัวละครสาวๆจากอนิเมะ และเปิด exclusive content ให้สำหรับผู้ที่ชื่นชอบผลงานของผมเป็นพิเศษ
ผมโพสผลงานผมทั้งหมดไว้ที่เวบ Deviantart และค่อยๆสร้างฐานผู้ติดตามมาเรื่อยๆอย่างค่อยเป็นค่อยไปมาตลอดครับ ทุกอย่างเติบโตไปเรื่อยๆของมัน ส่วนตัวผมมองว่ามันเป็นพิร์ตธุรกิจออนไลน์ ของผมพอร์ตนึงได้เลย
เมื่อวันที่ 16 กย.2024 มีผู้ติดตามคนหนึ่งส่งข้อความส่วนตัวมาหาผม บอกว่าชื่นชอบผลงานของผมมาก ต้องการจะขอซื้อผลงาน แต่ขอซื้อเป็น NFT นะ เสนอราคาซื้อขายต่อชิ้นที่สูงมาก หลังจากนั้นผมกับผู้ซื้อคนนี้พูดคุยกันในเมล์ครับ
นี่คือข้อสรุปสั่นๆจากการต่อรองซื้อขายครับ
(หลังจากนี้ผมขอเรียกผู้ซื้อว่า scammer นะครับ เพราะไพ่มันหงายมาแล้ว ว่าเขาคือมิจฉาชีพ)

- Scammer รายแรก เลือกผลงานที่จะซื้อ เสนอราคาซื้อที่สูงมาก แต่ต้องเป็นเวบไซต์ NFTmarket place ที่เขากำหนดเท่านั้น มันทำงานอยู่บน ERC20 ผมเข้าไปดูเวบไซต์ที่ว่านี้แล้วรู้สึกว่ามันดูแปลกๆครับ คนที่จะลงขายผลงานจะต้องใช้ email ในการสมัครบัญชีซะก่อน ถึงจะผูก wallet อย่างเช่น metamask ได้ เมื่อผูก wallet แล้วไม่สามารถเปลี่ยนได้ด้วย ตอนนั้นผมใช้ wallet ที่ไม่ได้ link กับ HW wallet ไว้ ทดลองสลับ wallet ไปๆมาๆ มันทำไม่ได้ แถมลอง log out แล้ว เลข wallet ก็ยังคาอยู่อันเดิม อันนี้มันดูแปลกๆแล้วหนึ่งอย่าง เวบนี้ค่า ETH ในการ mint 0.15 - 0.2 ETH … ตีเป็นเงินบาทนี่แพงบรรลัยอยู่นะครับ

-
Scammer รายแรกพยายามชักจูงผม หว่านล้อมผมว่า แหม เดี๋ยวเขาก็มารับซื้องานผมน่า mint งานเสร็จ รีบบอกเขานะ เดี๋ยวเขารีบกดซื้อเลย พอขายได้กำไร ผมก็ได้ค่า gas คืนได้ แถมยังได้กำไรอีก ไม่มีอะไรต้องเสีนจริงมั้ย แต่มันเป้นความโชคดีครับ เพราะตอนนั้นผมไม่เหลือทุนสำรองที่จะมาซื้อ ETH ได้ ผมเลยต่อรองกับเขาตามนี้ครับ :
-
ผมเสนอว่า เอางี้มั้ย ผมส่งผลงานของผมแบบ low resolution ให้ก่อน แลกกับให้เขาช่วยโอน ETH ที่เป็นค่า mint งานมาให้หน่อย พอผมได้ ETH แล้ว ผมจะ upscale งานของผม แล้วเมล์ไปให้ ใจแลกใจกันไปเลย ... เขาไม่เอา
- ผมเสนอให้ไปซื้อที่ร้านค้าออนไลน์ buymeacoffee ของผมมั้ย จ่ายเป็น USD ... เขาไม่เอา
- ผมเสนอให้ซื้อขายผ่าน PPV lightning invoice ที่ผมมีสิทธิ์เข้าถึง เพราะเป็น creator ของ Creatr ... เขาไม่เอา
- ผมยอกเขาว่างั้นก็รอนะ รอเงินเดือนออก เขาบอก ok
สัปดาห์ถัดมา มี scammer คนที่สองติดต่อผมเข้ามา ใช้วิธีการใกล้เคียงกัน แต่ใช้คนละเวบ แถมเสนอราคาซื้อที่สูงกว่าคนแรกมาก เวบที่สองนี้เลวร้ายค่าเวบแรกอีกครับ คือต้องใช้เมล์สมัครบัญชี ไม่สามารถผูก metamask ได้ พอสมัครเสร็จจะได้ wallet เปล่าๆมาหนึ่งอัน ผมต้องโอน ETH เข้าไปใน wallet นั้นก่อน เพื่อเอาไปเป็นค่า mint NFT 0.2 ETH
ผมบอก scammer รายที่สองว่า ต้องรอนะ เพราะตอนนี้กำลังติดต่อซื้อขายอยู่กับผู้ซื้อรายแรกอยู่ ผมกำลังรอเงินเพื่อมาซื้อ ETH เป็นต้นทุนดำเนินงานอยู่ คนคนนี้ขอให้ผมส่งเวบแรกไปให้เขาดูหน่อย หลังจากนั้นไม่นานเขาเตือนผมมาว่าเวบแรกมันคือ scam นะ ไม่สามารถถอนเงินออกมาได้ เขายังส่งรูป cap หน้าจอที่คุยกับผู้เสียหายจากเวบแรกมาให้ดูว่าเจอปัญหาถอนเงินไม่ได้ ไม่พอ เขายังบลัฟ opensea ด้วยว่าลูกค้าขายงานได้ แต่ถอนเงินไม่ได้
Opensea ถอนเงินไม่ได้ ตรงนี้แหละครับคือตัวกระตุกต่อมเอ๊ะของผมดังมาก เพราะ opensea อ่ะ ผู้ใช้ connect wallet เข้ากับ marketplace โดยตรง ซื้อขายกันเกิดขึ้น เงินวิ่งเข้าวิ่งออก wallet ของแต่ละคนโดยตรงเลย opensea เก็บแค่ค่า fee ในการใช้ platform ไม่เก็บเงินลูกค้าไว้ แถมปีนี้ค่า gas fee ก็ถูกกว่า bull run cycle 2020 มาก ตอนนี้ค่า gas fee ประมาณ 0.0001 ETH (แต่มันก็แพงกว่า BTC อยู่ดีอ่ะครับ)
ผมเลยเอาเรื่องนี้ไปปรึกษาพี่บิท แต่แอดมินมาคุยกับผมแทน ทางแอดมินแจ้งว่ายังไม่เคยมีเพื่อนๆมาปรึกษาเรื่องนี้ กรณีที่ผมทักมาถามนี่เป็นรายแรกเลย แต่แอดมินให้ความเห็นไปในทางเดียวกับสมมุติฐานของผมว่าน่าจะ scam ในเวลาเดียวกับผมเอาเรื่องนี้ไปถามในเพจ NFT community คนไทนด้วย ได้รับการ confirm ชัดเจนว่า scam และมีคนไม่น้อยโดนหลอก หลังจากที่ผมรู้ที่มาแล้ว ผมเลยเล่นสงครามปั่นประสาท scammer ทั้งสองคนนี้ครับ เพื่อดูว่าหลอกหลวงมิจฉาชีพจริงมั้ย
โดยวันที่ 30 กย. ผมเลยปั่นประสาน scammer ทั้งสองรายนี้ โดยการ mint ผลงานที่เขาเสนอซื้อนั่นแหละ ขึ้น opensea แล้วส่งข้อความไปบอกว่า
mint ให้แล้วนะ แต่เงินไม่พอจริงๆว่ะโทษที เลย mint ขึ้น opensea แทน พอดีบ้านจน ทำได้แค่นี้ไปถึงแค่ opensea รีบไปซื้อล่ะ มีคนจ้องจะคว้างานผมเยอะอยู่ ผมไม่คิด royalty fee ด้วยนะเฮ้ย เอาไปขายต่อไม่ต้องแบ่งกำไรกับผม
เท่านั้นแหละครับ สงครามจิตวิทยาก็เริ่มขึ้น แต่เขาจนมุม กลืนน้ำลายตัวเอง ช็อตเด็ดคือ
เขา : เนี่ยอุส่ารอ บอกเพื่อนในทีมว่าวันจันทร์ที่ 30 กย. ได้ของแน่ๆ เพื่อนๆในทีมเห็นงานผมแล้วมันสวยจริง เลยใส่เงินเต็มที่ 9.3ETH (+ capture screen ส่งตัวเลขยอดเงินมาให้ดู)ไว้รอโดยเฉพาะเลยนะ ผม : เหรอ ... งั้น ขอดู wallet address ที่มี transaction มาให้ดูหน่อยสิ เขา : 2ETH นี่มัน 5000$ เลยนะ ผม : แล้วไง ขอดู wallet address ที่มีการเอายอดเงิน 9.3ETH มาให้ดูหน่อย ไหนบอกว่าเตรียมเงินไว้มากแล้วนี่ ขอดูหน่อย ว่าใส่ไว้เมื่อไหร่ ... เอามาแค่ adrress นะเว้ย ไม่ต้องทะลึ่งส่ง seed มาให้ เขา : ส่งรูปเดิม 9.3 ETH มาให้ดู ผม : รูป screenshot อ่ะ มันไม่มีความหมายหรอกเว้ย ตัดต่อเอาก็ได้ง่ายจะตาย เอา transaction hash มาดู ไหนว่าเตรียมเงินไว้รอ 9.3ETH แล้วอยากซื้องานผมจนตัวสั่นเลยไม่ใช่เหรอ ถ้าจะส่ง wallet address มาให้ดู หรือจะช่วยส่ง 0.15ETH มาให้ยืม mint งานก่อน แล้วมากดซื้อ 2ETH ไป แล้วผมใช้ 0.15ETH คืนให้ก็ได้ จะซื้อหรือไม่ซื้อเนี่ย เขา : จะเอา address เขาไปทำไม ผม : ตัดจบ รำคาญ ไม่ขายให้ละ เขา : 2ETH = 5000 USD เลยนะ ผม : แล้วไง
ผมเลยเขียนบทความนี้มาเตือนเพื่อนๆพี่ๆทุกคนครับ เผื่อใครกำลังเปิดพอร์ตทำธุรกิจขาย digital art online แล้วจะโชคดี เจอของดีแบบผม
ทำไมผมถึงมั่นใจว่ามันคือการหลอกหลวง แล้วคนโกงจะได้อะไร
อันดับแรกไปพิจารณาดู opensea ครับ เป็นเวบ NFTmarketplace ที่ volume การซื้อขายสูงที่สุด เขาไม่เก็บเงินของคนจะซื้อจะขายกันไว้กับตัวเอง เงินวิ่งเข้าวิ่งออก wallet ผู้ซื้อผู้ขายเลย ส่วนทางเวบเก็บค่าธรรมเนียมเท่านั้น แถมค่าธรรมเนียมก็ถูกกว่าเมื่อปี 2020 เยอะ ดังนั้นการที่จะไปลงขายงานบนเวบ NFT อื่นที่ค่า fee สูงกว่ากันเป็นร้อยเท่า ... จะทำไปทำไม
ผมเชื่อว่า scammer โกงเงินเจ้าของผลงานโดยการเล่นกับความโลภและความอ่อนประสบการณ์ของเจ้าของผลงานครับ เมื่อไหร่ก็ตามที่เจ้าของผลงานโอน ETH เข้าไปใน wallet เวบนั้นเมื่อไหร่ หรือเมื่อไหร่ก็ตามที่จ่ายค่า fee ในการ mint งาน เงินเหล่านั้นสิ่งเข้ากระเป๋า scammer ทันที แล้วก็จะมีการเล่นตุกติกต่อแน่นอนครับ เช่นถอนไม่ได้ หรือซื้อไม่ได้ ต้องโอนเงินมาเพิ่มเพื่อปลดล็อค smart contract อะไรก็ว่าไป แล้วคนนิสัยไม่ดีพวกเนี้ย ก็จะเล่นกับความโลภของคน เอาราคาเสนอซื้อที่สูงโคตรๆมาล่อ ... อันนี้ไม่ว่ากัน เพราะบนโลก NFT รูปภาพบางรูปที่ไม่ได้มีความเป็นศิลปะอะไรเลย มันดันขายกันได้ 100 - 150 ETH ศิลปินที่พยายามสร้างตัวก็อาจจะมองว่า ผลงานเรามีคนรับซื้อ 2 - 4 ETH ต่องานมันก็มากพอแล้ว (จริงๆมากเกินจนน่าตกใจด้วยซ้ำครับ)
บนโลกของ BTC ไม่ต้องเชื่อใจกัน โอนเงินไปหากันได้ ปิดสมุดบัญชีได้โดยไม่ต้องเชื่อใจกัน
บบโลกของ ETH "code is law" smart contract มีเขียนอยู่แล้ว ไปอ่าน มันไม่ได้ยากมากในการทำความเข้าใจ ดังนั้น การจะมาเชื่อคำสัญญาจากคนด้วยกัน เป็นอะไรที่ไม่มีเหตุผล
ผมไปเล่าเรื่องเหล่านี้ให้กับ community งานศิลปะ ก็มีทั้งเสียงตอบรับที่ดี และไม่ดีปนกันไป มีบางคนยืนยันเสียงแข็งไปในทำนองว่า ไอ้เรื่องแบบเนี้ยไม่ได้กินเขาหรอก เพราะเขาตั้งใจแน่วแน่ว่างานศิลป์ของเขา เขาไม่เอาเข้ามายุ่งในโลก digital currency เด็ดขาด ซึ่งผมก็เคารพมุมมองเขาครับ แต่มันจะดีกว่ามั้ย ถ้าเราเปิดหูเปิดตาให้ทันเทคโนโลยี โดยเฉพาะเรื่อง digital currency , blockchain โดนโกงทีนึงนี่คือหมดตัวกันง่ายกว่าเงิน fiat อีก
อยากจะมาเล่าให้ฟังครับ และอยากให้ช่วยแชร์ไปให้คนรู้จักด้วย จะได้ระวังตัวกัน
Note
- ภาพประกอบ cyber security ทั้งสองนี่ของผมเองครับ ทำเอง วางขายบน AdobeStock
- อีกบัญชีนึงของผม "HikariHarmony" npub1exdtszhpw3ep643p9z8pahkw8zw00xa9pesf0u4txyyfqvthwapqwh48sw กำลังค่อยๆเอาผลงานจากโลกข้างนอกเข้ามา nostr ครับ ตั้งใจจะมาสร้างงานศิลปะในนี้ เพื่อนๆที่ชอบงาน จะได้ไม่ต้องออกไปหาที่ไหน
ผลงานของผมครับ - Anime girl fanarts : HikariHarmony - HikariHarmony on Nostr - General art : KeshikiRakuen - KeshikiRakuen อาจจะเป็นบัญชี nostr ที่สามของผม ถ้าไหวครับ
-
 @ 4b7c4ee3:8cd5ed4d
2024-12-19 18:50:16
@ 4b7c4ee3:8cd5ed4d
2024-12-19 18:50:16For decades, the internet has promised an open, interconnected world where anyone can share ideas, build businesses, and connect freely. In its early days, this promise seemed attainable—a digital wild west where innovation thrived and creativity knew no bounds. But as the internet evolved, so did the gatekeepers. Giants like Google, Meta, and Amazon now dominate the web, dictating how we interact, what we see, and often, what we’re allowed to say.
This isn’t the internet we were promised. It’s a walled garden where central authorities control the gates, monetize our data, and censor voices that challenge the status quo.
Enter decentralized protocols like NOSTR, a breath of fresh air for those of us who believe the internet should be free, open, and resistant to control. Here’s why NOSTR and other decentralized protocols are the antidote to the internet’s centralization problem—and why we’re just getting started.
The Centralization Problem
The modern internet revolves around a handful of centralized platforms:
-
Social Media: Platforms like Facebook, Twitter, and Instagram determine what content reaches your feed. Algorithms prioritize engagement over truth, often creating echo chambers.
-
Cloud Hosting: Companies like Amazon Web Services (AWS) and Google Cloud host vast swaths of the internet. A single outage or policy change can take down critical infrastructure.
-
Search Engines: Google alone processes over 90% of global search queries, giving it disproportionate power to shape knowledge discovery.
-
Financial Gatekeepers: Payment processors like PayPal and Stripe have the power to cut off individuals and organizations from financial systems based on subjective criteria.
Centralization leads to:
-
Censorship: Voices can be silenced without recourse.
-
Monopolies: Innovation is stifled as big players dominate.
-
Data Exploitation: Our personal information is harvested, sold, and used to manipulate us.
Decentralization as the Solution
Decentralized protocols aim to distribute power back to users, removing the need for centralized intermediaries. Let’s break down why they matter and how they work:
-
Ownership of Identity With NOSTR, your identity isn’t tied to a platform. It’s tied to a cryptographic keypair that you own. Lose trust in one relay or client? Simply move to another without losing your connections.
-
Censorship Resistance Decentralized systems like NOSTR rely on relays—small, independent servers—to propagate messages. No single relay controls the network, making it far harder to censor content globally.
-
Data Sovereignty Your data isn’t hosted on a corporate server. Instead, you choose how it’s stored and shared. With decentralization, the era of platforms monetizing your personal information could come to an end.
-
Financial Inclusion Integration with Bitcoin and the Lightning Network allows users to send microtransactions directly, bypassing traditional financial gatekeepers.
Why NOSTR Is Just Getting Started
NOSTR (Notes and Other Stuff Transmitted by Relays) embodies the core principles of decentralization. While still in its infancy, it’s already showing immense promise. Here’s why it’s poised to grow:
-
Developer-Led Growth Unlike centralized platforms, NOSTR is an open protocol. This means developers can build clients, relays, and applications without asking for permission. This freedom fosters rapid innovation.
-
Interoperability NOSTR isn’t tied to one app or use case. It can support everything from social media to blogging to encrypted messaging. The possibilities are endless.
-
Community-Driven Ecosystem Early adopters of NOSTR are passionate about its mission. These pioneers are building not just the infrastructure but also the culture that will guide its future.
-
Rising Distrust in Centralization As more people wake up to the downsides of centralized platforms—data breaches, censorship, manipulation—the demand for decentralized alternatives will grow. NOSTR is well-positioned to meet this demand.
Challenges Ahead
While the promise of decentralization is exciting, challenges remain:
-
User Experience Today, setting up a NOSTR account requires understanding public and private keys, choosing relays, and navigating new apps. This complexity must be simplified for mainstream adoption.
-
Spam and Moderation Decentralized networks can struggle with spam and harmful content. Innovative solutions, like paid relays or community moderation, will be crucial.
-
Scalability As user numbers grow, relays and protocols must scale to handle increased traffic without compromising performance.
-
Economic Models Sustainable monetization for relay operators and developers will be necessary to maintain and grow the ecosystem.
The Road Ahead
Decentralized protocols like NOSTR represent more than just a technological shift—they’re a philosophical one. They challenge the very idea that a few corporations should control the internet’s infrastructure. They empower individuals to own their data, control their identities, and interact freely without interference.
As early adopters, we have the opportunity to shape this movement. By building, experimenting, and sharing the principles of decentralization, we can create a future where the internet fulfills its original promise: a free, open space for innovation, connection, and human potential.
NOSTR is just getting started. And so are we.
Stay humble. Stack sats.
Oyl Miller comes from an advertising background where he has worked for legacy brands like Nike and PlayStation, digital giants like Google and Airbnb, as well as crypto and web3 startups. He is experimenting with moving to a Bitcoin standard, and is looking to create value with his writing skills in a variety of ways.
-
-
 @ f1989a96:bcaaf2c1
2024-12-19 15:16:35
@ f1989a96:bcaaf2c1
2024-12-19 15:16:35Good morning, readers!
After 53 years of tyranny, the Syrian regime has been overthrown. Rebels captured Damascus, forcing Bashar al-Assad and his family to flee to Moscow, Russia. Assad’s rule was defined by severe human rights abuses and widespread financial repression. Hundreds of thousands were jailed or killed, millions fled, and more than 90% of the country was plunged into poverty amid currency collapse. With Assad gone, Syrians may have a chance to rebuild their country and work toward a freer, more democratic future.
In Tunisia, President Kais Saied continues to dismantle civil society and due process. The regime is escalating the repression of journalists through arrests, incarceration, and judicial harassment to silence critical voices. By doing so, Saied shifts focus away from the country’s economic struggles and worsening hardships.
In technology news, Klever Wallet, a KYC-free digital asset wallet widely used in regions like Nigeria and the Philippines, integrated the Lightning Network via the Breez SDK, enabling fast, low-cost Bitcoin transactions for its significant global user base. In addition, the Bitcoin Design Foundation announced a South American Bitcoin UX Bootcamp, offering 10 skilled UX designers across South America a chance to refine their design expertise within the Bitcoin ecosystem and attend the 2025 bitcoin++ developer conference in Florianopolis, Brazil.
We end with a live stream of the 2024 Africa Bitcoin Conference, an inspiring event HRF supported and participated in. The conference brought together leaders and innovators across the African continent to advance Bitcoin for financial freedom and to push back against growing authoritarianism. If you were unable to attend in person, be sure to catch the recordings below.
Now, let’s dive right in!
Subscribe Here
GLOBAL NEWS
Syria | Assad Regime Overthrown
The Assad regime, infamous for its financial repression and brutal authoritarianism, has been overthrown following the rebel capture of Damascus, forcing Bashar al-Assad and his family to flee to Moscow. For 24 years under Assad — and 53 years of Assad family rule — the regime manipulated the economy to maintain its grip on power. Policies such as enforcing artificial currency exchange rates, restricting bank withdrawals, and imposing strict controls on the flow of goods and money plunged over 90% of Syrians into poverty. This economic stranglehold, combined with systemic human rights abuses, defined his reign. With the regime’s collapse, Syrians now face a pivotal moment to rebuild their country and pursue a future of more financial freedom.
China | Youth Bear the Brunt of Economic Slowdown
China’s slowing economy is forcing younger generations into increasingly precarious financial positions. Youth unemployment has soared past 17%, and even those who find work face stagnant wages and unmet income expectations. To survive, many young people are embracing extreme frugality — capping food expenses at just 500 yuan ($70), eating in the dark to save electricity, and avoiding dining out entirely. The middle class, weighed down by debt and a bleak economic outlook, is also adopting similar austerity measures. This growing financial strain offers a stark snapshot of China’s economic challenges and raises deep concerns about the long-term prosperity and opportunities for the nation’s youth.
Tunisia | Growing Repression of Journalists Amidst Worsening Economic Crisis
Tunisia is grappling with a worsening economic crisis, as citizens face soaring unemployment, a collapsing currency, and the devastating impacts of financial mismanagement. Amid this economic turmoil, President Kais Saied is intensifying his crackdown on dissent, imprisoning journalists in overcrowded cells, denying them medical care, and subjecting them to psychological torture — blatant evidence of the state’s disregard for human rights. Saied’s regime has also weaponized vague morality laws to target activists, influencers, and musicians, ensuring no opposition voice goes unpunished. By silencing dissent, Saied seeks to deflect attention from the regime’s economic failures, positioning the state as a moral authority while deepening the suffering of journalists and the broader public.
Pakistan | Testing Internet Firewall to Increase Financial Surveillance
Pakistan’s government is testing a nationwide Internet firewall, a tool designed to monitor, censor, and control online content by filtering internet traffic at the state level. By leveraging technology sourced from China, officials can block websites, restrict apps, and track individual online activity. This firewall poses a severe threat to financial freedom, as the military regime could use it to restrict access to tools like Bitcoin, cutting off alternative financial systems that offer privacy and independence. Civil society, including activists, journalists, and political dissidents, faces heightened surveillance, repression, and limited access to information — further curtailing their capacity to organize or express dissent.
India | Central Bank Governor Shares CBDC Vision
Outgoing Reserve Bank of India (RBI) Gov.Shaktikanta Das reaffirmed his vision for India’s central bank digital currency (CBDC), the digital rupee, as the nation’s currency continues to reach a record low against the US dollar. While hailed as the “future of currency” and praised for its potential economic benefits, the CBDC raises serious concerns. It grants the state unprecedented power to surveil transactions, freeze funds, and block payments in real-time — an alarming reality in a country already known for freezing opposition bank accounts and imposing rigid KYC requirements. Das’s hopes of a CBDC to “underpin the payment systems of the future” prioritizes state control at the expense of individual freedoms.
Georgia | Internet Shutdowns Amid Energy Crisis
In the breakaway Georgian region of Abkhazian, Russian-backed officials are using an energy crisis as a pretext to tighten Internet controls. Blaming illegal Bitcoin mining for electricity shortages, officials imposed nightly Internet shutdowns from midnight to 7:00 a.m., starting Dec. 10. These restrictions, coupled with power rationing and school closures, exacerbate hardships for residents as the region grapples with reduced energy from Russia and the Enguri hydroelectric plant. By painting Bitcoin as the villain, officials divert attention from broader governance failures while consolidating their grip over online communication and suppressing access to alternative financial tools.
LATEST IN BITCOIN NEWS, DEVELOPMENT, AND COMMUNITY
Klever Wallet | Integrates Lightning Network
Klever Wallet, a KYC-free digital asset wallet popular in underbanked countries like Nigeria, Brazil, India, and the Philippines, integrated the Lightning Network through the Breez SDK. This integration will empower its 100,000 active monthly users with fast, low-cost Bitcoin transactions directly from the wallet. By using the Breez SDK, Klever eliminates the complexities of Lightning channel management for users while maintaining a self-custodial design. This integration enhances financial freedom for its global user base — particularly in regions where traditional systems fall short.
Fedi | Adds Cashu Melting and Portable Nostr Keys
Fedi, a company leveraging Bitcoin and ecash technology to support communities, especially under authoritarian regimes, announced the integration of Cashu melting to enable users to receive Cashu ecash directly within the Fedi app. Built on the Chaumian ecash protocol, Cashu allows users to transact ecash tokens with strong privacy guarantees, minimal costs, and instant settlements, though with a custodial tradeoff. Additionally, Fedi now supports portable Nostr keys, allowing users to interact with external Nostr clients like Primal and Amethyst. Together, these updates enhance financial privacy and accessibility, offering users more control over their transactions and a portable digital identity, advancing financial freedom in underserved regions.
Core Lightning | Releases Latest Version with BOLT 12 by Default
Core Lightning, an implementation of the Lightning Network, introduced improvements to privacy and functionality with its latest v24.11 release. The update enables BOLT 12 offers by default when sending and receiving Bitcoin payments. BOLT 12 is an important update to the Lightning Network that brings increased receiver privacy, greater censorship resistance, and reusable payment requests for recurring payments. The update also includes xpay, an experimental payment plugin for advanced routing of payments on the Lightning Network. With these features, users of wallets and applications built with Core Lightning can maintain greater privacy and experience more optimized payments.
Proton Wallet | Implements Replace-by-Fee for Bitcoin Transactions
Proton, the company behind privacy tools like Proton Mail and Proton VPN, added support for Replace-by-Fee (RBF) transactions in Proton Wallet, its self-custodial and privacy-centric Bitcoin wallet. RBF allows users to increase the fee on stuck transactions to expedite confirmation and allow the payment to settle faster. The wallet also uses strong encryption and offers accessible recovery methods, ensuring users — like activists in hostile environments — maintain financial autonomy. Watch this tutorial by Bitcoin educator BTC Sessions to learn how to use Proton Wallet.
Bitcoin Design Community | South American Bitcoin UX Bootcamp
The Bitcoin Design Community, with support from HRF, will be hosting a South American UX Bitcoin Bootcamp. This program will support ten skilled UX designers across South America to develop and refine their design expertise within the Bitcoin ecosystem. Participants will also have the opportunity to attend the 2025 bitcoin++ developer conference in Florianopolis, Brazil, where they will receive specialized UX training and engage in hands-on learning with Bitcoin-related technologies. UX designers with an interest in Bitcoin are encouraged to apply here.
OpenSats | Announces Ninth Wave of Nostr Grants
OpenSats, a public nonprofit funding free and open-source software and projects, announced its ninth wave of grants supporting projects built on the decentralized Nostr protocol. Among the grantees is Pokey, an Android app enhancing Nostr and communications in restrictive environments through offline Bluetooth mesh networking and multi-account support. These features are particularly valuable for anyone facing Internet blackouts or state censorship. Another recipient, Persian NIPs, is breaking language barriers by localizing Nostr resources for Persian/Farsi speakers. The project will translate key protocols, user guides, and developer documentation, bringing decentralized and uncensorable technology to millions of people.
RECOMMENDED CONTENT
Africa Bitcoin Conference Livestream
Held from Dec. 9-11, 2024, in Nairobi, Kenya, the Africa Bitcoin Conference brought together human rights defenders, educators, and developers from across the continent to learn, collaborate, and innovate on freedom technologies. Supported by HRF, the event offered an inspiring mix of keynotes, workshops, panel discussions, and hackathons, all dedicated to advancing open-source solutions to fight authoritarianism and financial repression. This vibrant gathering highlighted innovative ideas and practical tools to empower communities worldwide. If you missed it, you can still catch the conversations and breakthroughs by watching the livestream here. Highlight talks include those from Farida Nabourema, Femi Longe, Jack Dorsey, and more.
-
 @ 1cdd356b:ef4bc4a4
2024-12-19 14:08:00
@ 1cdd356b:ef4bc4a4
2024-12-19 14:08:00sdfsdfsdsdfsdfsdf
-
 @ 8947a945:9bfcf626
2024-10-17 07:33:00
@ 8947a945:9bfcf626
2024-10-17 07:33:00Hello everyone on Nostr and all my watchersand followersfrom DeviantArt, as well as those from other art platforms
I have been creating and sharing AI-generated anime girl fanart since the beginning of 2024 and have been running member-exclusive content on Patreon.
I also publish showcases of my artworks to Deviantart. I organically build up my audience from time to time. I consider it as one of my online businesses of art. Everything is slowly growing
On September 16, I received a DM from someone expressing interest in purchasing my art in NFT format and offering a very high price for each piece. We later continued the conversation via email.
Here’s a brief overview of what happened

- The first scammer selected the art they wanted to buy and offered a high price for each piece. They provided a URL to an NFT marketplace site running on the Ethereum (ETH) mainnet or ERC20. The site appeared suspicious, requiring email sign-up and linking a MetaMask wallet. However, I couldn't change the wallet address later. The minting gas fees were quite expensive, ranging from 0.15 to 0.2 ETH

-
The scammers tried to convince me that the high profits would easily cover the minting gas fees, so I had nothing to lose. Luckily, I didn’t have spare funds to purchase ETH for the gas fees at the time, so I tried negotiating with them as follows:
-
I offered to send them a lower-quality version of my art via email in exchange for the minting gas fees, but they refused.
- I offered them the option to pay in USD through Buy Me a Coffee shop here, but they refused.
- I offered them the option to pay via Bitcoin using the Lightning Network invoice , but they refused.
- I asked them to wait until I could secure the funds, and they agreed to wait.
The following week, a second scammer approached me with a similar offer, this time at an even higher price and through a different NFT marketplace website.
This second site also required email registration, and after navigating to the dashboard, it asked for a minting fee of 0.2 ETH. However, the site provided a wallet address for me instead of connecting a MetaMask wallet.
I told the second scammer that I was waiting to make a profit from the first sale, and they asked me to show them the first marketplace. They then warned me that the first site was a scam and even sent screenshots of victims, including one from OpenSea saying that Opensea is not paying.
This raised a red flag, and I began suspecting I might be getting scammed. On OpenSea, funds go directly to users' wallets after transactions, and OpenSea charges a much lower platform fee compared to the previous crypto bull run in 2020. Minting fees on OpenSea are also significantly cheaper, around 0.0001 ETH per transaction.
I also consulted with Thai NFT artist communities and the ex-chairman of the Thai Digital Asset Association. According to them, no one had reported similar issues, but they agreed it seemed like a scam.
After confirming my suspicions with my own research and consulting with the Thai crypto community, I decided to test the scammers’ intentions by doing the following
I minted the artwork they were interested in, set the price they offered, and listed it for sale on OpenSea. I then messaged them, letting them know the art was available and ready to purchase, with no royalty fees if they wanted to resell it.
They became upset and angry, insisting I mint the art on their chosen platform, claiming they had already funded their wallet to support me. When I asked for proof of their wallet address and transactions, they couldn't provide any evidence that they had enough funds.
Here’s what I want to warn all artists in the DeviantArt community or other platforms If you find yourself in a similar situation, be aware that scammers may be targeting you.
My Perspective why I Believe This is a Scam and What the Scammers Gain
From my experience with BTC and crypto since 2017, here's why I believe this situation is a scam, and what the scammers aim to achieve
First, looking at OpenSea, the largest NFT marketplace on the ERC20 network, they do not hold users' funds. Instead, funds from transactions go directly to users’ wallets. OpenSea’s platform fees are also much lower now compared to the crypto bull run in 2020. This alone raises suspicion about the legitimacy of other marketplaces requiring significantly higher fees.
I believe the scammers' tactic is to lure artists into paying these exorbitant minting fees, which go directly into the scammers' wallets. They convince the artists by promising to purchase the art at a higher price, making it seem like there's no risk involved. In reality, the artist has already lost by paying the minting fee, and no purchase is ever made.
In the world of Bitcoin (BTC), the principle is "Trust no one" and “Trustless finality of transactions” In other words, transactions are secure and final without needing trust in a third party.
In the world of Ethereum (ETH), the philosophy is "Code is law" where everything is governed by smart contracts deployed on the blockchain. These contracts are transparent, and even basic code can be read and understood. Promises made by people don’t override what the code says.
I also discuss this issue with art communities. Some people have strongly expressed to me that they want nothing to do with crypto as part of their art process. I completely respect that stance.
However, I believe it's wise to keep your eyes open, have some skin in the game, and not fall into scammers’ traps. Understanding the basics of crypto and NFTs can help protect you from these kinds of schemes.
If you found this article helpful, please share it with your fellow artists.
Until next time Take care
Note
- Both cyber security images are mine , I created and approved by AdobeStock to put on sale
- I'm working very hard to bring all my digital arts into Nostr to build my Sats business here to my another npub "HikariHarmony" npub1exdtszhpw3ep643p9z8pahkw8zw00xa9pesf0u4txyyfqvthwapqwh48sw
Link to my full gallery - Anime girl fanarts : HikariHarmony - HikariHarmony on Nostr - General art : KeshikiRakuen
-
 @ e6817453:b0ac3c39
2024-10-06 11:21:27
@ e6817453:b0ac3c39
2024-10-06 11:21:27Hey folks, today we're diving into an exciting and emerging topic: personal artificial intelligence (PAI) and its connection to sovereignty, privacy, and ethics. With the rapid advancements in AI, there's a growing interest in the development of personal AI agents that can work on behalf of the user, acting autonomously and providing tailored services. However, as with any new technology, there are several critical factors that shape the future of PAI. Today, we'll explore three key pillars: privacy and ownership, explainability, and bias.
1. Privacy and Ownership: Foundations of Personal AI
At the heart of personal AI, much like self-sovereign identity (SSI), is the concept of ownership. For personal AI to be truly effective and valuable, users must own not only their data but also the computational power that drives these systems. This autonomy is essential for creating systems that respect the user's privacy and operate independently of large corporations.
In this context, privacy is more than just a feature—it's a fundamental right. Users should feel safe discussing sensitive topics with their AI, knowing that their data won’t be repurposed or misused by big tech companies. This level of control and data ownership ensures that users remain the sole beneficiaries of their information and computational resources, making privacy one of the core pillars of PAI.
2. Bias and Fairness: The Ethical Dilemma of LLMs
Most of today’s AI systems, including personal AI, rely heavily on large language models (LLMs). These models are trained on vast datasets that represent snapshots of the internet, but this introduces a critical ethical challenge: bias. The datasets used for training LLMs can be full of biases, misinformation, and viewpoints that may not align with a user’s personal values.
This leads to one of the major issues in AI ethics for personal AI—how do we ensure fairness and minimize bias in these systems? The training data that LLMs use can introduce perspectives that are not only unrepresentative but potentially harmful or unfair. As users of personal AI, we need systems that are free from such biases and can be tailored to our individual needs and ethical frameworks.
Unfortunately, training models that are truly unbiased and fair requires vast computational resources and significant investment. While large tech companies have the financial means to develop and train these models, individual users or smaller organizations typically do not. This limitation means that users often have to rely on pre-trained models, which may not fully align with their personal ethics or preferences. While fine-tuning models with personalized datasets can help, it's not a perfect solution, and bias remains a significant challenge.
3. Explainability: The Need for Transparency
One of the most frustrating aspects of modern AI is the lack of explainability. Many LLMs operate as "black boxes," meaning that while they provide answers or make decisions, it's often unclear how they arrived at those conclusions. For personal AI to be effective and trustworthy, it must be transparent. Users need to understand how the AI processes information, what data it relies on, and the reasoning behind its conclusions.
Explainability becomes even more critical when AI is used for complex decision-making, especially in areas that impact other people. If an AI is making recommendations, judgments, or decisions, it’s crucial for users to be able to trace the reasoning process behind those actions. Without this transparency, users may end up relying on AI systems that provide flawed or biased outcomes, potentially causing harm.
This lack of transparency is a major hurdle for personal AI development. Current LLMs, as mentioned earlier, are often opaque, making it difficult for users to trust their outputs fully. The explainability of AI systems will need to be improved significantly to ensure that personal AI can be trusted for important tasks.
Addressing the Ethical Landscape of Personal AI
As personal AI systems evolve, they will increasingly shape the ethical landscape of AI. We’ve already touched on the three core pillars—privacy and ownership, bias and fairness, and explainability. But there's more to consider, especially when looking at the broader implications of personal AI development.
Most current AI models, particularly those from big tech companies like Facebook, Google, or OpenAI, are closed systems. This means they are aligned with the goals and ethical frameworks of those companies, which may not always serve the best interests of individual users. Open models, such as Meta's LLaMA, offer more flexibility and control, allowing users to customize and refine the AI to better meet their personal needs. However, the challenge remains in training these models without significant financial and technical resources.
There’s also the temptation to use uncensored models that aren’t aligned with the values of large corporations, as they provide more freedom and flexibility. But in reality, models that are entirely unfiltered may introduce harmful or unethical content. It’s often better to work with aligned models that have had some of the more problematic biases removed, even if this limits some aspects of the system’s freedom.
The future of personal AI will undoubtedly involve a deeper exploration of these ethical questions. As AI becomes more integrated into our daily lives, the need for privacy, fairness, and transparency will only grow. And while we may not yet be able to train personal AI models from scratch, we can continue to shape and refine these systems through curated datasets and ongoing development.
Conclusion
In conclusion, personal AI represents an exciting new frontier, but one that must be navigated with care. Privacy, ownership, bias, and explainability are all essential pillars that will define the future of these systems. As we continue to develop personal AI, we must remain vigilant about the ethical challenges they pose, ensuring that they serve the best interests of users while remaining transparent, fair, and aligned with individual values.
If you have any thoughts or questions on this topic, feel free to reach out—I’d love to continue the conversation!
-
 @ 349d6b82:12b2a5b1
2024-12-19 13:50:47
@ 349d6b82:12b2a5b1
2024-12-19 13:50:47В 2044 году Серов, спустя 20 лет, наконец смог стать примером успешного благоустройства жилых помещений и общественных пространств, что значительно улучшило качество жизни наших жителей. Ключевым героем этого процесса стал Александр Петров, активист и председатель местного совета, который инициировал множество проектов по улучшению городской инфраструктуры.

В 2044 году завершилась программа капитального ремонта жилья, которая охватила все многоквартирные дома города. Это дало возможность жителям улучшить свои условия проживания.
На протяжении времени Серовчане активно голосовали за новые объекты благоустройства, включая парки и скверы. Это стало возможным благодаря инициативам Александра Петрова, который организовал общественные обсуждения и привлек внимание к нуждам жителей.

В результате совместных усилий местной администрации и активистов были созданы новые парки и зоны отдыха, что сделало наш с вами город более привлекательным для жизни.
Все началось еще в 2015 году. За эти долгие годы были обновлены фасады, кровли и системы отопления в большинстве зданий города.
Александр Петров активно выступал за создание зеленых зон и общественных пространств. В результате его усилий были реализованы проекты по озеленению дворов и установке новых детских площадок: "Я горжусь тем, что благодаря вашей активности и поддержке мы смогли реализовать множество проектов, которые изменили облик нашего города. Каждый голос, каждое ваше мнение сыграли ключевую роль в этом процессе. Мы создали не просто красивые пространства, но и места, где люди могут встречаться, общаться и наслаждаться жизнью. Мы продолжим работать над улучшением качества жизни в Серове. Важно помнить, что наш город — это наше общее дело, и только вместе мы сможем достичь еще больших высот".
Благодаря совместным усилиям Серов в 2044 году стал образцом в сфере благоустройства жилых помещений и общественных пространств.
-
 @ 349d6b82:12b2a5b1
2024-12-19 13:50:31
@ 349d6b82:12b2a5b1
2024-12-19 13:50:31Состоялся визит студии «Гимнатеск» Центра Детского Творчества из Серова в Тулу, которая приняла участие во Всероссийском фестивале-конкурсе хореографического мастерства «Алмаз». С 29 ноября по 1 декабря 2044 года. В этом престижном мероприятии серовские гимнастки продемонстрировали свои таланты и мастерство.
Фестиваль «Алмаз» собрал участников из разных уголков страны, предоставив возможность обмена опытом и установления новых контактов среди юных артистов. Это событие стало значимым вкладом в развитие детского хореографического творчества.
Наши гимнастки удивили жюри своим высоким уровнем исполнения и оригинальными номерами. Их выступления были отмечены не только техническим мастерством, но и артистизмом, что позволило им занять призовые места на конкурсе. Участие в фестивале стало важным этапом в их творческой карьере, открыв новые горизонты для дальнейшего развития.
И это неудивительно, что студия спортивного танца и художественной гимнастики «Гимнатеск» получила высокие оценки за подготовку и исполнение. Этот успех стал результатом трудов педагогов, тренера-хореографа Марины Борисовны, именитого кандидата в мастера спорта по художественной гимнастике Веры Чукаевой, и, конечно, старших гимнасток.
Также на фестивале специальный приз за оригинальность постановки получили наши спортсменки за номер «Время». Девочки признались - несмотря на победу в конкурсе и высокую конкуренцию, выступления соперниц вдохновляют их на новые достижения. По словам серовских гимнасток, эта поездка стала не только победной, но впечатляющей, интерактивной и познавательной.
-
 @ e6817453:b0ac3c39
2024-09-30 14:52:23
@ e6817453:b0ac3c39
2024-09-30 14:52:23In the modern world of AI, managing vast amounts of data while keeping it relevant and accessible is a significant challenge, mainly when dealing with large language models (LLMs) and vector databases. One approach that has gained prominence in recent years is integrating vector search with metadata, especially in retrieval-augmented generation (RAG) pipelines. Vector search and metadata enable faster and more accurate data retrieval. However, the process of pre- and post-search filtering results plays a crucial role in ensuring data relevance.
The Vector Search and Metadata Challenge
In a typical vector search, you create embeddings from chunks of text, such as a PDF document. These embeddings allow the system to search for similar items and retrieve them based on relevance. The challenge, however, arises when you need to combine vector search results with structured metadata. For example, you may have timestamped text-based content and want to retrieve the most relevant content within a specific date range. This is where metadata becomes critical in refining search results.
Unfortunately, most vector databases treat metadata as a secondary feature, isolating it from the primary vector search process. As a result, handling queries that combine vectors and metadata can become a challenge, particularly when the search needs to account for a dynamic range of filters, such as dates or other structured data.
LibSQL and vector search metadata
LibSQL is a more general-purpose SQLite-based database that adds vector capabilities to regular data. Vectors are presented as blob columns of regular tables. It makes vector embeddings and metadata a first-class citizen that naturally builds deep integration of these data points.
create table if not exists conversation ( id varchar(36) primary key not null, startDate real, endDate real, summary text, vectorSummary F32_BLOB(512) );It solves the challenge of metadata and vector search and eliminates impedance between vector data and regular structured data points in the same storage.
As you can see, you can access vector-like data and start date in the same query.
select c.id ,c.startDate, c.endDate, c.summary, vector_distance_cos(c.vectorSummary, vector(${vector})) distance from conversation where ${startDate ? `and c.startDate >= ${startDate.getTime()}` : ''} ${endDate ? `and c.endDate <= ${endDate.getTime()}` : ''} ${distance ? `and distance <= ${distance}` : ''} order by distance limit ${top};vector_distance_cos calculated as distance allows us to make a primitive vector search that does a full scan and calculates distances on rows. We could optimize it with CTE and limit search and distance calculations to a much smaller subset of data.
This approach could be calculation intensive and fail on large amounts of data.
Libsql offers a way more effective vector search based on FlashDiskANN vector indexed.
vector_top_k('idx_conversation_vectorSummary', ${vector} , ${top}) ivector_top_k is a table function that searches for the top of the newly created vector search index. As you can see, we could use only vector as a function parameter, and other columns could be used outside of the table function. So, to use a vector index together with different columns, we need to apply some strategies.
Now we get a classical problem of integration vector search results with metadata queries.
Post-Filtering: A Common Approach
The most widely adopted method in these pipelines is post-filtering. In this approach, the system first retrieves data based on vector similarities and then applies metadata filters. For example, imagine you’re conducting a vector search to retrieve conversations relevant to a specific question. Still, you also want to ensure these conversations occurred in the past week.

Post-filtering allows the system to retrieve the most relevant vector-based results and subsequently filter out any that don’t meet the metadata criteria, such as date range. This method is efficient when vector similarity is the primary factor driving the search, and metadata is only applied as a secondary filter.
const sqlQuery = ` select c.id ,c.startDate, c.endDate, c.summary, vector_distance_cos(c.vectorSummary, vector(${vector})) distance from vector_top_k('idx_conversation_vectorSummary', ${vector} , ${top}) i inner join conversation c on i.id = c.rowid where ${startDate ? `and c.startDate >= ${startDate.getTime()}` : ''} ${endDate ? `and c.endDate <= ${endDate.getTime()}` : ''} ${distance ? `and distance <= ${distance}` : ''} order by distance limit ${top};However, there are some limitations. For example, the initial vector search may yield fewer results or omit some relevant data before applying the metadata filter. If the search window is narrow enough, this can lead to complete results.
One working strategy is to make the top value in vector_top_K much bigger. Be careful, though, as the function's default max number of results is around 200 rows.
Pre-Filtering: A More Complex Approach
Pre-filtering is a more intricate approach but can be more effective in some instances. In pre-filtering, metadata is used as the primary filter before vector search takes place. This means that only data that meets the metadata criteria is passed into the vector search process, limiting the scope of the search right from the beginning.
While this approach can significantly reduce the amount of irrelevant data in the final results, it comes with its own challenges. For example, pre-filtering requires a deeper understanding of the data structure and may necessitate denormalizing the data or creating separate pre-filtered tables. This can be resource-intensive and, in some cases, impractical for dynamic metadata like date ranges.

In certain use cases, pre-filtering might outperform post-filtering. For instance, when the metadata (e.g., specific date ranges) is the most important filter, pre-filtering ensures the search is conducted only on the most relevant data.
Pre-filtering with distance-based filtering
So, we are getting back to an old concept. We do prefiltering instead of using a vector index.
WITH FilteredDates AS ( SELECT c.id, c.startDate, c.endDate, c.summary, c.vectorSummary FROM YourTable c WHERE ${startDate ? `AND c.startDate >= ${startDate.getTime()}` : ''} ${endDate ? `AND c.endDate <= ${endDate.getTime()}` : ''} ), DistanceCalculation AS ( SELECT fd.id, fd.startDate, fd.endDate, fd.summary, fd.vectorSummary, vector_distance_cos(fd.vectorSummary, vector(${vector})) AS distance FROM FilteredDates fd ) SELECT dc.id, dc.startDate, dc.endDate, dc.summary, dc.distance FROM DistanceCalculation dc WHERE 1=1 ${distance ? `AND dc.distance <= ${distance}` : ''} ORDER BY dc.distance LIMIT ${top};It makes sense if the filter produces small data and distance calculation happens on the smaller data set.
As a pro of this approach, you have full control over the data and get all results without omitting some typical values for extensive index searches.
Choosing Between Pre and Post-Filtering
Both pre-filtering and post-filtering have their advantages and disadvantages. Post-filtering is more accessible to implement, especially when vector similarity is the primary search factor, but it can lead to incomplete results. Pre-filtering, on the other hand, can yield more accurate results but requires more complex data handling and optimization.
In practice, many systems combine both strategies, depending on the query. For example, they might start with a broad pre-filtering based on metadata (like date ranges) and then apply a more targeted vector search with post-filtering to refine the results further.
Conclusion
Vector search with metadata filtering offers a powerful approach for handling large-scale data retrieval in LLMs and RAG pipelines. Whether you choose pre-filtering or post-filtering—or a combination of both—depends on your application's specific requirements. As vector databases continue to evolve, future innovations that combine these two approaches more seamlessly will help improve data relevance and retrieval efficiency further.
-
 @ 349d6b82:12b2a5b1
2024-12-19 13:49:26
@ 349d6b82:12b2a5b1
2024-12-19 13:49:26В этом году школа №26 отметила свой 85-летний юбилей, и это событие стало настоящим праздником для всего образовательного сообщества. В пятницу, 22 ноября 2044 года, в стенах родной школы собрались ученики, выпускники, преподаватели и родители, чтобы вспомнить историю и достижения учебного заведения. Давайте подробнее рассмотрим, как прошло это знаменательное торжество и какие эмоции оно вызвало у всех участников.
https://ai.invideo.io/watch/joWFfXxKMjh
-
 @ 349d6b82:12b2a5b1
2024-12-19 13:49:20
@ 349d6b82:12b2a5b1
2024-12-19 13:49:20Долгожданное событие состоялось сегодня на базе школы №26: Торжественно открыли «Агрокласс» для семиклассников. Реализация проекта стала возможной благодаря сотрудничеству Министерства образования и Министерства сельского хозяйства. Директор школы, Лариса Барановская, сообщила, что ребята теперь будут ухаживать за школьным участком, а также проводить различные опыты и эксперименты. Она особо отметила значимость подписанного соглашения с аграрным университетом.
Огород – это на самом деле не только тяжелая работа, грязные сапоги, и неприятный запах от биологического удобрения. Всё это может стать захватывающим хобби с использованием современного оборудования и незабываемым путешествием в мир природы, организованным социальными партнерами.
Семиклассники будут ухаживать за школьным участком, что позволит им получить практические навыки в агрономии и сельском хозяйстве.
Теперь ребята смогут посещать экскурсии на предприятия, проводить научные опыты и эксперименты, а также участвовать в различных проектах и на практике участвовать в конкурсах, например, по ландшафтному дизайну. Всё это поможет им лучше ориентироваться в мире профессий и сделать осознанный выбор в будущем.
Это будет полезный для ребят опыт, это их центр развития в любом направлении, будь то биология, экология или даже медицина. Пусть это поможет им в будущем внести вклад в развитие нашей страны. Открытие «Агрокласса» подчеркивает стремление к интеграции современных образовательных технологий и практических занятий в школьную программу. К слову, открытие этого класса стало настоящим подарком к юбилею – 65-летию школы, который отметят уже в эту пятницу, сегодня, 22 ноября в 17:00.
-
 @ da18e986:3a0d9851
2024-08-14 13:58:24
@ da18e986:3a0d9851
2024-08-14 13:58:24After months of development I am excited to officially announce the first version of DVMDash (v0.1). DVMDash is a monitoring and debugging tool for all Data Vending Machine (DVM) activity on Nostr. The website is live at https://dvmdash.live and the code is available on Github.
Data Vending Machines (NIP-90) offload computationally expensive tasks from relays and clients in a decentralized, free-market manner. They are especially useful for AI tools, algorithmic processing of user’s feeds, and many other use cases.
The long term goal of DVMDash is to become 1) a place to easily see what’s happening in the DVM ecosystem with metrics and graphs, and 2) provide real-time tools to help developers monitor, debug, and improve their DVMs.
DVMDash aims to enable users to answer these types of questions at a glance: * What’s the most popular DVM right now? * How much money is being paid to image generation DVMs? * Is any DVM down at the moment? When was the last time that DVM completed a task? * Have any DVMs failed to deliver after accepting payment? Did they refund that payment? * How long does it take this DVM to respond? * For task X, what’s the average amount of time it takes for a DVM to complete the task? * … and more
For developers working with DVMs there is now a visual, graph based tool that shows DVM-chain activity. DVMs have already started calling other DVMs to assist with work. Soon, we will have humans in the loop monitoring DVM activity, or completing tasks themselves. The activity trace of which DVM is being called as part of a sub-task from another DVM will become complicated, especially because these decisions will be made at run-time and are not known ahead of time. Building a tool to help users and developers understand where a DVM is in this activity trace, whether it’s gotten stuck or is just taking a long time, will be invaluable. For now, the website only shows 1 step of a dvm chain from a user's request.
One of the main designs for the site is that it is highly clickable, meaning whenever you see a DVM, Kind, User, or Event ID, you can click it and open that up in a new page to inspect it.
Another aspect of this website is that it should be fast. If you submit a DVM request, you should see it in DVMDash within seconds, as well as events from DVMs interacting with your request. I have attempted to obtain DVM events from relays as quickly as possible and compute metrics over them within seconds.
This project makes use of a nosql database and graph database, currently set to use mongo db and neo4j, for which there are free, community versions that can be run locally.
Finally, I’m grateful to nostr:npub10pensatlcfwktnvjjw2dtem38n6rvw8g6fv73h84cuacxn4c28eqyfn34f for supporting this project.
Features in v0.1:
Global Network Metrics:
This page shows the following metrics: - DVM Requests: Number of unencrypted DVM requests (kind 5000-5999) - DVM Results: Number of unencrypted DVM results (kind 6000-6999) - DVM Request Kinds Seen: Number of unique kinds in the Kind range 5000-5999 (except for known non-DVM kinds 5666 and 5969) - DVM Result Kinds Seen: Number of unique kinds in the Kind range 6000-6999 (except for known non-DVM kinds 6666 and 6969) - DVM Pub Keys Seen: Number of unique pub keys that have written a kind 6000-6999 (except for known non-DVM kinds) or have published a kind 31990 event that specifies a ‘k’ tag value between 5000-5999 - DVM Profiles (NIP-89) Seen: Number of 31990 that have a ‘k’ tag value for kind 5000-5999 - Most Popular DVM: The DVM that has produced the most result events (kind 6000-6999) - Most Popular Kind: The Kind in range 5000-5999 that has the most requests by users. - 24 hr DVM Requests: Number of kind 5000-5999 events created in the last 24 hrs - 24 hr DVM Results: Number of kind 6000-6999 events created in the last 24 hours - 1 week DVM Requests: Number of kind 5000-5999 events created in the last week - 1 week DVM Results: Number of kind 6000-6999 events created in the last week - Unique Users of DVMs: Number of unique pubkeys of kind 5000-5999 events - Total Sats Paid to DVMs: - This is an estimate. - This value is likely a lower bound as it does not take into consideration subscriptions paid to DVMs - This is calculated by counting the values of all invoices where: - A DVM published a kind 7000 event requesting payment and containing an invoice - The DVM later provided a DVM Result for the same job for which it requested payment. - The assumption is that the invoice was paid, otherwise the DVM would not have done the work - Note that because there are multiple ways to pay a DVM such as lightning invoices, ecash, and subscriptions, there is no guaranteed way to know whether a DVM has been paid. Additionally, there is no way to know that a DVM completed the job because some DVMs may not publish a final result event and instead send the user a DM or take some other kind of action.
Recent Requests:
This page shows the most recent 3 events per kind, sorted by created date. You should always be able to find the last 3 events here of all DVM kinds.
DVM Browser:
This page will either show a profile of a specific DVM, or when no DVM is given in the url, it will show a table of all DVMs with some high level stats. Users can click on a DVM in the table to load the DVM specific page.
Kind Browser:
This page will either show data on a specific kind including all DVMs that have performed jobs of that kind, or when no kind is given, it will show a table summarizing activity across all Kinds.
Debug:
This page shows the graph based visualization of all events, users, and DVMs involved in a single job as well as a table of all events in order from oldest to newest. When no event is given, this page shows the 200 most recent events where the user can click on an event in order to debug that job. The graph-based visualization allows the user to zoom in and out and move around the graph, as well as double click on any node in the graph (except invoices) to open up that event, user, or dvm in a new page.
Playground:
This page is currently under development and may not work at the moment. If it does work, in the current state you can login with NIP-07 extension and broadcast a 5050 event with some text and then the page will show you events from DVMs. This page will be used to interact with DVMs live. A current good alternative to this feature, for some but not all kinds, is https://vendata.io/.
Looking to the Future
I originally built DVMDash out of Fear-of-Missing-Out (FOMO); I wanted to make AI systems that were comprised of DVMs but my day job was taking up a lot of my time. I needed to know when someone was performing a new task or launching a new AI or Nostr tool!
I have a long list of DVMs and Agents I hope to build and I needed DVMDash to help me do it; I hope it helps you achieve your goals with Nostr, DVMs, and even AI. To this end, I wish for this tool to be useful to others, so if you would like a feature, please submit a git issue here or note me on Nostr!
Immediate Next Steps:
- Refactoring code and removing code that is no longer used
- Improve documentation to run the project locally
- Adding a metric for number of encrypted requests
- Adding a metric for number of encrypted results
Long Term Goals:
- Add more metrics based on community feedback
- Add plots showing metrics over time
- Add support for showing a multi-dvm chain in the graph based visualizer
- Add a real-time mode where the pages will auto update (currently the user must refresh the page)
- ... Add support for user requested features!
Acknowledgements
There are some fantastic people working in the DVM space right now. Thank you to nostr:npub1drvpzev3syqt0kjrls50050uzf25gehpz9vgdw08hvex7e0vgfeq0eseet for making python bindings for nostr_sdk and for the recent asyncio upgrades! Thank you to nostr:npub1nxa4tywfz9nqp7z9zp7nr7d4nchhclsf58lcqt5y782rmf2hefjquaa6q8 for answering lots of questions about DVMs and for making the nostrdvm library. Thank you to nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft for making the original DVM NIP and vendata.io which I use all the time for testing!
P.S. I rushed to get this out in time for Nostriga 2024; code refactoring will be coming :)
-
 @ 3c984938:2ec11289
2024-07-22 11:43:17
@ 3c984938:2ec11289
2024-07-22 11:43:17Bienvenide a Nostr!
Introduccíon
Es tu primera vez aqui en Nostr? Bienvenides! Nostr es un acrónimo raro para "Notes and Other Stuff Transmitted by Relays" on un solo objetivo; resistirse a la censura. Una alternativa a las redes sociales tradicionales, comunicaciónes, blogging, streaming, podcasting, y feventualmente el correo electronico (en fase de desarrollo) con características descentralizadas que te capacita, usario. Jamas seras molestado por un anuncio, capturado por una entidad centralizada o algoritmo que te monetiza.
Permítame ser su anfitrión! Soy Onigiri! Yo estoy explorando el mundo de Nostr, un protocolo de comunicacíon decentralizada. Yo escribo sobre las herramientas y los desarolladores increíbles de Nostr que dan vida a esta reino.

Bienvenides a Nostr Wonderland
Estas a punto de entrar a un otro mundo digtal que te hará explotar tu mente de todas las aplicaciones descentralizadas, clientes, sitios que puedes utilizar. Nunca volverás a ver a las comunicaciones ni a las redes sociales de la mesma manera. Todo gracias al carácter criptográfico de nostr, inpirado por la tecnología "blockchain". Cada usario, cuando crean una cuenta en Nostr, recibe un par de llaves: una privada y una publico. Estos son las llaves de tu propio reino. Lo que escribes, cantes, grabes, lo que creas - todo te pertenece.

Unos llaves de Oro y Plata
Mi amigo y yo llamamos a esto "identidad mediante cifrado" porque tu identidad es cifrado. Tu puedes compartir tu llave de plata "npub" a otros usarios para conectar y seguir. Utiliza tu llave de oro "nsec" para accedar a tu cuenta y exponerte a muchas aplicaciones. Mantenga la llave a buen recaudo en todo momento. Ya no hay razor para estar enjaulado por los terminos de plataformas sociales nunca más.
Onigirl
npub18jvyjwpmm65g8v9azmlvu8knd5m7xlxau08y8vt75n53jtkpz2ys6mqqu3Todavia No tienes un cliente? Seleccione la mejor opción.
Encuentra la aplicación adecuada para ti! Utilice su clave de oro "nsec" para acceder a estas herramientas maravillosas. También puedes visit a esta pagina a ver a todas las aplicaciones. Antes de pegar tu llave de oro en muchas aplicaciones, considera un "signer" (firmante) para los sitios web 3. Por favor, mire la siguiente imagen para más detalles. Consulte también la leyenda.

Get a Signer extension via chrome webstore
Un firmante (o "signer" en inglés) es una extensión del navegador web. Nos2x and NostrConnect son extensiónes ampliamente aceptado para aceder a Nostr. Esto simplifica el proceso de aceder a sitios "web 3". En lugar de copiar y pegar la clave oro "nsec" cada vez, la mantienes guardado en la extensión y le des permiso para aceder a Nostr.

👉⚡⚡Obtén una billetera Bitcoin lightning para enviar/recibir Zaps⚡⚡ (Esto es opcional)

Aqui en Nostr, utilizamos la red Lightning de Bitcoin (L2). Nesitaras una cartera lightning para enviar y recibir Satoshis, la denominacion mas chiquita de un Bitcoin. (0.000000001 BTC) Los "zaps" son un tipo de micropago en Nostr. Si te gusta el contenido de un usario, es norma dejarle una propina en la forma de un ¨zap". Por ejemplo, si te gusta este contenido, tu me puedes hacer "zap" con Satoshis para recompensar mi trabajo. Pero apenas llegaste, as que todavia no tienes una cartera. No se preocupe, puedo ayudar en eso!
"Stacker.News" es una plataforma donde los usarios pueden ganar SATS por publicar articulos y interactuar con otros.

Stacker.News es el lugar mas facil para recibir una direccion de cartera Bitcoin Lightning.
- Acedese con su extensión firmante "signer" - Nos2x or NostrConnect - hace click en tu perfil, un codigo de letras y numeros en la mano superior derecha. Veás algo como esto

- Haga clic en "edit" y elija un nombre que te guste. Se puede cambiar si deseas en el futuro.

- Haga clic en "save"
- Crea una biografía y la comunidad SN son muy acogedora. Te mandarán satoshi para darte la bienvenida.
- Tu nueva direccion de cartera Bitcoin Lightning aparecerá asi
 ^^No le mandas "zaps" a esta direccion; es puramente con fines educativos.
^^No le mandas "zaps" a esta direccion; es puramente con fines educativos. - Con tu Nueva dirección de monedero Bitcoin Lightning puedes ponerla en cualquier cliente o app de tu elección. Para ello, ve a tu página de perfil y bajo la dirección de tu monedero en "Dirección Lightning", introduce tu nueva dirección y pulsa "guardar " y ya está. Enhorabuena.
👉✨Con el tiempo, es posible que desee pasar a las opciones de auto-custodia y tal vez incluso considerar la posibilidad de auto-alojar su propio nodo LN para una mejor privacidad. La buena noticia es que stacker.news tambien está dejando de ser una cartera custodio.
⭐NIP-05-identidad DNS⭐ Al igual que en Twitter, una marca de verificación es para mostrar que eres del mismo jardín "como un humano", y no un atípico como una mala hierba o, "bot". Pero no de la forma nefasta en que lo hacen las grandes tecnológicas. En el país de las maravillas de Nostr, esto te permite asignar tu llave de plata, "npub", a un identificador DNS. Una vez verificado, puedes gritar para anunciar tu nueva residencia Nostr para compartir.
✨Hay un montón de opciones, pero si has seguido los pasos, esto se vuelve extremadamente fácil.
👉✅¡Haz clic en tu "Perfil ", luego en "Configuración ", desplázate hasta la parte inferior y pega tu clave Silver, "npub!" y haz clic en "Guardar " y ¡listo! Utiliza tu monedero relámpago de Stacker.news como tu NIP-05. ¡¡¡Enhorabuena!!! ¡Ya estás verificado! Dale unas horas y cuando uses tu cliente "principal " deberías ver una marca de verificación.
Nostr, el infonformista de los servidores.
 En lugar de utilizar una única instancia o un servidor centralizado, Nostr está construido para que varias bases de datos intercambien mensajes mediante "relés". Los relés, que son neutrales y no discriminatorios, almacenan y difunden mensajes públicos en la red Nostr. Transmiten mensajes a todos los demás clientes conectados a ellos, asegurando las comunicaciones en la red descentralizada.
En lugar de utilizar una única instancia o un servidor centralizado, Nostr está construido para que varias bases de datos intercambien mensajes mediante "relés". Los relés, que son neutrales y no discriminatorios, almacenan y difunden mensajes públicos en la red Nostr. Transmiten mensajes a todos los demás clientes conectados a ellos, asegurando las comunicaciones en la red descentralizada.¡Mis amigos en Nostr te dan la bienvenida!
Bienvenida a la fiesta. ¿Le apetece un té?🍵

¡Hay mucho mas!
Esto es la punta del iceberg. Síguenme mientras continúo explorando nuevas tierras y a los desarolladores, los caballeres que potencioan este ecosistema. Encuéntrame aquí para mas contenido como este y comparten con otros usarios de nostr. Conozca a los caballeres que luchan por freedomTech (la tecnología de libertad) en Nostr y a los proyectos a los que contribuyen para hacerla realidad.💋
Onigirl @npub18jvyjwpmm65g8v9azmlvu8knd5m7xlxau08y8vt75n53jtkpz2ys6mqqu3
🧡😻Esta guía ha sido cuidadosamente traducida por miggymofongo
Puede seguirla aquí. @npub1ajt9gp0prf4xrp4j07j9rghlcyukahncs0fw5ywr977jccued9nqrcc0cs
sitio web
- Acedese con su extensión firmante "signer" - Nos2x or NostrConnect - hace click en tu perfil, un codigo de letras y numeros en la mano superior derecha. Veás algo como esto
-
 @ 349d6b82:12b2a5b1
2024-12-19 13:49:12
@ 349d6b82:12b2a5b1
2024-12-19 13:49:12В Серове произошло значительное событие в области медицины — открыт новый Инновационный Медицинский Центр, который будет использовать искусственный интеллект и роботизированные технологии для диагностики и лечения заболеваний. Это нововведение обещает изменить подход к медицинским услугам в регионе.
Центр внедрил систему AI, которая анализирует медицинские данные пациентов и предлагает индивидуализированные планы лечения. Это значительно увеличивает точность диагностики и сокращает время ожидания результатов анализов.
А операции теперь проводятся с использованием высокотехнологичных роботов, что минимизирует инвазивность процедур и сокращает время восстановления пациентов. Это делает хирургические вмешательства более безопасными и эффективными.
Центр также будет предлагать услуги телемедицины, позволяя пациентам получать консультации от специалистов удаленно. Это особенно важно для жителей отдаленных районов, обеспечивая доступ к качественной медицинской помощи без необходимости покидать дом.
В рамках ИМЦ организованы курсы для медицинских работников, где они могут обучаться новым технологиям и методам лечения. Это повысит общего уровня медицины в регионе.
Эти новшества не только улучшат качество медицинских услуг в Серове, но и сделают город центром медицинских инноваций в нашем регионе.
-
 @ 349d6b82:12b2a5b1
2024-12-19 13:49:03
@ 349d6b82:12b2a5b1
2024-12-19 13:49:03На Надеждинском Металлургическом Заводе произошел инцидент с андроидом особого назначения, который вышел из строя. По сообщениям, робот особой категории, предназначенный для выполнения сложных производственных задач, неожиданно сбился с ритма работы и начал воспроизводить хаотичные и опасные маневры по отношению к людям. Подробнее в сюжете Виктора Бликого:
https://ai.invideo.io/watch/a51nqdbpF34
-
 @ 6871d8df:4a9396c1
2024-06-12 22:10:51
@ 6871d8df:4a9396c1
2024-06-12 22:10:51Embracing AI: A Case for AI Accelerationism
In an era where artificial intelligence (AI) development is at the forefront of technological innovation, a counter-narrative championed by a group I refer to as the 'AI Decels'—those advocating for the deceleration of AI advancements— seems to be gaining significant traction. After tuning into a recent episode of the Joe Rogan Podcast, I realized that the prevailing narrative around AI was heading in a dangerous direction. Rogan had Aza Raskin and Tristan Harris, technology safety advocates, who released a talk called 'The AI Dilemma,' on for a discussion. You may know them from the popular documentary 'The Social Dilemma' on the dangers of social media. It became increasingly clear that the cautionary stance dominating this discourse might be tipping the scales too far, veering towards an over-regulated future that stifles innovation rather than fostering it.

Are we moving too fast?
While acknowledging AI's benefits, Aza and Tristan fear it could be dangerous if not guided by ethical standards and safeguards. They believe AI development is moving too quickly and that the right incentives for its growth are not in place. They are concerned about the possibility of "civilizational overwhelm," where advanced AI technology far outpaces 21st-century governance. They fear a scenario where society and its institutions cannot manage or adapt to the rapid changes and challenges introduced by AI.
They argue for regulating and slowing down AI development due to rapid, uncontrolled advancement driven by competition among companies like Google, OpenAI, and Microsoft. They claim this race can lead to unsafe releases of new technologies, with AI systems exhibiting unpredictable, emergent behaviors, posing significant societal risks. For instance, AI can inadvertently learn tasks like sentiment analysis or human emotion understanding, creating potential for misuse in areas like biological weapons or cybersecurity vulnerabilities.
Moreover, AI companies' profit-driven incentives often conflict with the public good, prioritizing market dominance over safety and ethics. This misalignment can lead to technologies that maximize engagement or profits at societal expense, similar to the negative impacts seen with social media. To address these issues, they suggest government regulation to realign AI companies' incentives with safety, ethical considerations, and public welfare. Implementing responsible development frameworks focused on long-term societal impacts is essential for mitigating potential harm.
This isn't new
Though the premise of their concerns seems reasonable, it's dangerous and an all too common occurrence with the emergence of new technologies. For example, in their example in the podcast, they refer to the technological breakthrough of oil. Oil as energy was a technological marvel and changed the course of human civilization. The embrace of oil — now the cornerstone of industry in our age — revolutionized how societies operated, fueled economies, and connected the world in unprecedented ways. Yet recently, as ideas of its environmental and geopolitical ramifications propagated, the narrative around oil has shifted.
Tristan and Aza detail this shift and claim that though the period was great for humanity, we didn't have another technology to go to once the technological consequences became apparent. The problem with that argument is that we did innovate to a better alternative: nuclear. However, at its technological breakthrough, it was met with severe suspicions, from safety concerns to ethical debates over its use. This overregulation due to these concerns caused a decades-long stagnation in nuclear innovation, where even today, we are still stuck with heavy reliance on coal and oil. The scare tactics and fear-mongering had consequences, and, interestingly, they don't see the parallels with their current deceleration stance on AI.
These examples underscore a critical insight: the initial anxiety surrounding new technologies is a natural response to the unknowns they introduce. Yet, history shows that too much anxiety can stifle the innovation needed to address the problems posed by current technologies. The cycle of discovery, fear, adaptation, and eventual acceptance reveals an essential truth—progress requires not just the courage to innovate but also the resilience to navigate the uncertainties these innovations bring.
Moreover, believing we can predict and plan for all AI-related unknowns reflects overconfidence in our understanding and foresight. History shows that technological progress, marked by unexpected outcomes and discoveries, defies such predictions. The evolution from the printing press to the internet underscores progress's unpredictability. Hence, facing AI's future requires caution, curiosity, and humility. Acknowledging our limitations and embracing continuous learning and adaptation will allow us to harness AI's potential responsibly, illustrating that embracing our uncertainties, rather than pretending to foresee them, is vital to innovation.
The journey of technological advancement is fraught with both promise and trepidation. Historically, each significant leap forward, from the dawn of the industrial age to the digital revolution, has been met with a mix of enthusiasm and apprehension. Aza Raskin and Tristan Harris's thesis in the 'AI Dilemma' embodies the latter.
Who defines "safe?"
When slowing down technologies for safety or ethical reasons, the issue arises of who gets to define what "safe" or “ethical” mean? This inquiry is not merely technical but deeply ideological, touching the very core of societal values and power dynamics. For example, the push for Diversity, Equity, and Inclusion (DEI) initiatives shows how specific ideological underpinnings can shape definitions of safety and decency.
Take the case of the initial release of Google's AI chatbot, Gemini, which chose the ideology of its creators over truth. Luckily, the answers were so ridiculous that the pushback was sudden and immediate. My worry, however, is if, in correcting this, they become experts in making the ideological capture much more subtle. Large bureaucratic institutions' top-down safety enforcement creates a fertile ground for ideological capture of safety standards.

I claim that the issue is not the technology itself but the lens through which we view and regulate it. Suppose the gatekeepers of 'safety' are aligned with a singular ideology. In that case, AI development would skew to serve specific ends, sidelining diverse perspectives and potentially stifling innovative thought and progress.
In the podcast, Tristan and Aza suggest such manipulation as a solution. They propose using AI for consensus-building and creating "shared realities" to address societal challenges. In practice, this means that when individuals' viewpoints seem to be far apart, we can leverage AI to "bridge the gap." How they bridge the gap and what we would bridge it toward is left to the imagination, but to me, it is clear. Regulators will inevitably influence it from the top down, which, in my opinion, would be the opposite of progress.
In navigating this terrain, we must advocate for a pluralistic approach to defining safety, encompassing various perspectives and values achieved through market forces rather than a governing entity choosing winners. The more players that can play the game, the more wide-ranging perspectives will catalyze innovation to flourish.
Ownership & Identity
Just because we should accelerate AI forward does not mean I do not have my concerns. When I think about what could be the most devastating for society, I don't believe we have to worry about a Matrix-level dystopia; I worry about freedom. As I explored in "Whose data is it anyway?," my concern gravitates toward the issues of data ownership and the implications of relinquishing control over our digital identities. This relinquishment threatens our privacy and the integrity of the content we generate, leaving it susceptible to the inclinations and profit of a few dominant tech entities.
To counteract these concerns, a paradigm shift towards decentralized models of data ownership is imperative. Such standards would empower individuals with control over their digital footprints, ensuring that we develop AI systems with diverse, honest, and truthful perspectives rather than the massaged, narrow viewpoints of their creators. This shift safeguards individual privacy and promotes an ethical framework for AI development that upholds the principles of fairness and impartiality.
As we stand at the crossroads of technological innovation and ethical consideration, it is crucial to advocate for systems that place data ownership firmly in the hands of users. By doing so, we can ensure that the future of AI remains truthful, non-ideological, and aligned with the broader interests of society.
But what about the Matrix?
I know I am in the minority on this, but I feel that the concerns of AGI (Artificial General Intelligence) are generally overblown. I am not scared of reaching the point of AGI, and I think the idea that AI will become so intelligent that we will lose control of it is unfounded and silly. Reaching AGI is not reaching consciousness; being worried about it spontaneously gaining consciousness is a misplaced fear. It is a tool created by humans for humans to enhance productivity and achieve specific outcomes.
At a technical level, large language models (LLMs) are trained on extensive datasets and learning patterns from language and data through a technique called "unsupervised learning" (meaning the data is untagged). They predict the next word in sentences, refining their predictions through feedback to improve coherence and relevance. When queried, LLMs generate responses based on learned patterns, simulating an understanding of language to provide contextually appropriate answers. They will only answer based on the datasets that were inputted and scanned.
AI will never be "alive," meaning that AI lacks inherent agency, consciousness, and the characteristics of life, not capable of independent thought or action. AI cannot act independently of human control. Concerns about AI gaining autonomy and posing a threat to humanity are based on a misunderstanding of the nature of AI and the fundamental differences between living beings and machines. AI spontaneously developing a will or consciousness is more similar to thinking a hammer will start walking than us being able to create consciousness through programming. Right now, there is only one way to create consciousness, and I'm skeptical that is ever something we will be able to harness and create as humans. Irrespective of its complexity — and yes, our tools will continue to become evermore complex — machines, specifically AI, cannot transcend their nature as non-living, inanimate objects programmed and controlled by humans.
 The advancement of AI should be seen as enhancing human capabilities, not as a path toward creating autonomous entities with their own wills. So, while AI will continue to evolve, improve, and become more powerful, I believe it will remain under human direction and control without the existential threats often sensationalized in discussions about AI's future.
The advancement of AI should be seen as enhancing human capabilities, not as a path toward creating autonomous entities with their own wills. So, while AI will continue to evolve, improve, and become more powerful, I believe it will remain under human direction and control without the existential threats often sensationalized in discussions about AI's future. With this framing, we should not view the race toward AGI as something to avoid. This will only make the tools we use more powerful, making us more productive. With all this being said, AGI is still much farther away than many believe.
Today's AI excels in specific, narrow tasks, known as narrow or weak AI. These systems operate within tightly defined parameters, achieving remarkable efficiency and accuracy that can sometimes surpass human performance in those specific tasks. Yet, this is far from the versatile and adaptable functionality that AGI represents.
Moreover, the exponential growth of computational power observed in the past decades does not directly translate to an equivalent acceleration in achieving AGI. AI's impressive feats are often the result of massive data inputs and computing resources tailored to specific tasks. These successes do not inherently bring us closer to understanding or replicating the general problem-solving capabilities of the human mind, which again would only make the tools more potent in our hands.
While AI will undeniably introduce challenges and change the aspects of conflict and power dynamics, these challenges will primarily stem from humans wielding this powerful tool rather than the technology itself. AI is a mirror reflecting our own biases, values, and intentions. The crux of future AI-related issues lies not in the technology's inherent capabilities but in how it is used by those wielding it. This reality is at odds with the idea that we should slow down development as our biggest threat will come from those who are not friendly to us.
AI Beget's AI
While the unknowns of AI development and its pitfalls indeed stir apprehension, it's essential to recognize the power of market forces and human ingenuity in leveraging AI to address these challenges. History is replete with examples of new technologies raising concerns, only for those very technologies to provide solutions to the problems they initially seemed to exacerbate. It looks silly and unfair to think of fighting a war with a country that never embraced oil and was still primarily getting its energy from burning wood.
 The evolution of AI is no exception to this pattern. As we venture into uncharted territories, the potential issues that arise with AI—be it ethical concerns, use by malicious actors, biases in decision-making, or privacy intrusions—are not merely obstacles but opportunities for innovation. It is within the realm of possibility, and indeed, probability, that AI will play a crucial role in solving the problems it creates. The idea that there would be no incentive to address and solve these problems is to underestimate the fundamental drivers of technological progress.
The evolution of AI is no exception to this pattern. As we venture into uncharted territories, the potential issues that arise with AI—be it ethical concerns, use by malicious actors, biases in decision-making, or privacy intrusions—are not merely obstacles but opportunities for innovation. It is within the realm of possibility, and indeed, probability, that AI will play a crucial role in solving the problems it creates. The idea that there would be no incentive to address and solve these problems is to underestimate the fundamental drivers of technological progress.Market forces, fueled by the demand for better, safer, and more efficient solutions, are powerful catalysts for positive change. When a problem is worth fixing, it invariably attracts the attention of innovators, researchers, and entrepreneurs eager to solve it. This dynamic has driven progress throughout history, and AI is poised to benefit from this problem-solving cycle.
Thus, rather than viewing AI's unknowns as sources of fear, we should see them as sparks of opportunity. By tackling the challenges posed by AI, we will harness its full potential to benefit humanity. By fostering an ecosystem that encourages exploration, innovation, and problem-solving, we can ensure that AI serves as a force for good, solving problems as profound as those it might create. This is the optimism we must hold onto—a belief in our collective ability to shape AI into a tool that addresses its own challenges and elevates our capacity to solve some of society's most pressing issues.
An AI Future
The reality is that it isn't whether AI will lead to unforeseen challenges—it undoubtedly will, as has every major technological leap in history. The real issue is whether we let fear dictate our path and confine us to a standstill or embrace AI's potential to address current and future challenges.
The approach to solving potential AI-related problems with stringent regulations and a slowdown in innovation is akin to cutting off the nose to spite the face. It's a strategy that risks stagnating the U.S. in a global race where other nations will undoubtedly continue their AI advancements. This perspective dangerously ignores that AI, much like the printing press of the past, has the power to democratize information, empower individuals, and dismantle outdated power structures.
The way forward is not less AI but more of it, more innovation, optimism, and curiosity for the remarkable technological breakthroughs that will come. We must recognize that the solution to AI-induced challenges lies not in retreating but in advancing our capabilities to innovate and adapt.
AI represents a frontier of limitless possibilities. If wielded with foresight and responsibility, it's a tool that can help solve some of the most pressing issues we face today. There are certainly challenges ahead, but I trust that with problems come solutions. Let's keep the AI Decels from steering us away from this path with their doomsday predictions. Instead, let's embrace AI with the cautious optimism it deserves, forging a future where technology and humanity advance to heights we can't imagine.
-
 @ 3c984938:2ec11289
2024-06-09 14:40:55
@ 3c984938:2ec11289
2024-06-09 14:40:55I'm having some pain in my heart about the U.S. elections.
Ever since Obama campaigned for office, an increase of young voters have come out of the woodwork. Things have not improved. They've actively told you that "your vote matters." I believe this to be a lie unless any citizen can demand at the gate, at the White House to be allowed to hold and point a gun to the president's head. (Relax, this is a hyperbole)
Why so dramatic? Well, what does the president do? Sign bills, commands the military, nominates new Fed chairman, ambassadors, supreme judges and senior officials all while traveling in luxury planes and living in a white palace for four years.
They promised Every TIME to protect citizen rights when they take the oath and office.
...They've broken this several times, with so-called "emergency-crisis"
The purpose of a president, today, it seems is to basically hire armed thugs to keep the citizens in check and make sure you "voluntarily continue to be a slave," to the system, hence the IRS. The corruption extends from the cop to the judge and even to politicians. The politicians get paid from lobbyists to create bills in congress for the president to sign. There's no right answer when money is involved with politicians. It is the same if you vote Obama, Biden, Trump, or Haley. They will wield the pen to serve themselves to say it will benefit the country.
In the first 100 years of presidency, the government wasn't even a big deal. They didn't even interfere with your life as much as they do today.
^^ You hold the power in your hands, don't let them take it. Don't believe me? Try to get a loan from a bank without a signature. Your signature is as good as gold (if not better) and is an original trademark.
Just Don't Vote. End the Fed. Opt out.
^^ I choose to form my own path, even if it means leaving everything I knew prior. It doesn't have to be a spiritual thing. Some, have called me religious because of this. We're all capable of greatness and having humanity.
✨Don't have a machine heart with a machine mind. Instead, choose to have a heart like the cowardly lion from the "Wizard Of Oz."
There's no such thing as a good president or politicians.
If there was, they would have issued non-interest Federal Reserve Notes. Lincoln and Kennedy tried to do this, they got shot.
There's still a banner of America there, but it's so far gone that I cannot even recognize it. However, I only see a bunch of 🏳🌈 pride flags.
✨Patrick Henry got it wrong, when he delivered his speech, "Give me liberty or give me death." Liberty and freedom are two completely different things.
Straightforward from Merriam-Webster Choose Right or left?
No control, to be 100% without restrictions- free.
✨I disagree with the example sentence given. Because you cannot advocate for human freedom and own slaves, it's contradicting it. Which was common in the founding days.
I can understand many may disagree with me, and you might be thinking, "This time will be different." I, respectfully, disagree, and the proxy wars are proof. Learn the importance of Bitcoin, every Satoshi is a step away from corruption.
✨What does it look like to pull the curtains from the "Wizard of Oz?"
Have you watched the video below, what 30 Trillion dollars in debt looks like visually? Even I was blown away. https://video.nostr.build/d58c5e1afba6d7a905a39407f5e695a4eb4a88ae692817a36ecfa6ca1b62ea15.mp4
I say this with love. Hear my plea?
Normally, I don't write about anything political. It just feels like a losing game. My energy feels it's in better use to learn new things, write and to create. Even a simple blog post as simple as this. Stack SATs, and stay humble.
<3 Onigirl
-
 @ 349d6b82:12b2a5b1
2024-12-19 13:48:54
@ 349d6b82:12b2a5b1
2024-12-19 13:48:54Уже скоро, сегодня, 27 ноября в Серове пройдет городской праздник - "Серовская Зима". Это событие обещает стать ярким культурным мероприятием, объединяющим жителей и гостей города.
Праздничная программа включает в себя концерты как местных артистов, так и приглашенных, выставки ремесел и кулинарные мастер-классы. Горожане смогут насладиться выступлениями известных музыкальных групп и хоровых коллективов.
Фестиваль огней: Вечером состоится уникальный фестиваль огней, который украсит небо над Серовом яркими фейерверками и световыми инсталляциями. Это зрелище станет кульминацией праздника.
Торговая ярмарка: На главной площади ДКМ будет развернута ярмарка, где местные производители представят свои товары — от традиционных уральских сувениров до сладостей и горячих напитков.
И как же без спортивных мероприятий: Для любителей активного отдыха запланированы спортивные соревнования на свежем воздухе, включая зимние забавы и конкурсы для детей.
"Серовская Зима" направлена на развитие местной культуры, укрепление общественных связей и привлечение туристов в город. "Надеемся, что это станет ежегодной традицией, которая будет способствовать сплочению сообщества и популяризации Серова как культурного центра региона" - Утверждают организаторы данного мероприятия.
Место проведение - главная площадь Дворца Культуры Металлургов.
Время - Сегодня с 16:00 до 0:00.
-
 @ 3bf0c63f:aefa459d
2024-05-21 12:38:08
@ 3bf0c63f:aefa459d
2024-05-21 12:38:08Bitcoin transactions explained
A transaction is a piece of data that takes inputs and produces outputs. Forget about the blockchain thing, Bitcoin is actually just a big tree of transactions. The blockchain is just a way to keep transactions ordered.
Imagine you have 10 satoshis. That means you have them in an unspent transaction output (UTXO). You want to spend them, so you create a transaction. The transaction should reference unspent outputs as its inputs. Every transaction has an immutable id, so you use that id plus the index of the output (because transactions can have multiple outputs). Then you specify a script that unlocks that transaction and related signatures, then you specify outputs along with a script that locks these outputs.

As you can see, there's this lock/unlocking thing and there are inputs and outputs. Inputs must be unlocked by fulfilling the conditions specified by the person who created the transaction they're in. And outputs must be locked so anyone wanting to spend those outputs will need to unlock them.
For most of the cases locking and unlocking means specifying a public key whose controller (the person who has the corresponding private key) will be able to spend. Other fancy things are possible too, but we can ignore them for now.
Back to the 10 satoshis you want to spend. Since you've successfully referenced 10 satoshis and unlocked them, now you can specify the outputs (this is all done in a single step). You can specify one output of 10 satoshis, two of 5, one of 3 and one of 7, three of 3 and so on. The sum of outputs can't be more than 10. And if the sum of outputs is less than 10 the difference goes to fees. In the first days of Bitcoin you didn't need any fees, but now you do, otherwise your transaction won't be included in any block.

If you're still interested in transactions maybe you could take a look at this small chapter of that Andreas Antonopoulos book.
If you hate Andreas Antonopoulos because he is a communist shitcoiner or don't want to read more than half a page, go here: https://en.bitcoin.it/wiki/Coin_analogy
-
 @ 349d6b82:12b2a5b1
2024-12-19 13:48:44
@ 349d6b82:12b2a5b1
2024-12-19 13:48:44В последнее время тема безопасности на дорогах и в общественных местах становится все более актуальной. Несчастные случаи могут произойти в любой момент — будь то на трассе, в городе или на природе. В связи с этим, знания первой медицинской помощи могут сыграть решающую роль в спасении жизни человека. Именно поэтому в помещении русской общины провели интенсив по выживанию и тактической медицине.
На уроке разобрали, как помочь самому себе, пострадавшему и как стабилизировать состояние. Также были разобраны ключевые навыки, такие как стабилизация состояния пострадавшего и оказание помощи в экстренных ситуациях. Эти знания могут оказаться жизненно важными, особенно в условиях, когда помощь профессионалов недоступна.
Показали, как накладывать жгут самому себе после ранения в руку, ногу и даже шейный отдел. Как помочь пострадавшему при несчастном случае. Такие занятия, по мнению представителей русской общины очень важны во всех случаях жизни. Кто-то хочет научиться действовать в критической ситуации просто для себя, а кто-то намерен стать медиком.
Всем, кто пришел на курс по тактической медицине, рассказали о самом главном правиле - борьба за жизнь раненого – это сражение за время. Главная угроза – потеря крови и остановка дыхания. Представитель русской общины подчеркнул, что такое занятие вызвало неподдельный интерес у пришедших, а потому теперь планируют ввести подобные мастер-классы на постоянной основе.
И плюсом русская община показала как пользоваться новыми технологическими методы в области медицины 2044 года, что позволит улучшить качество оказания первой помощи и повысить уровень безопасности на дорогах и в общественных местах. Участники интенсива отметили важность таких мероприятий для повышения осведомленности населения о правилах безопасности и первой помощи.
-
 @ 3c984938:2ec11289
2024-05-09 04:43:15
@ 3c984938:2ec11289
2024-05-09 04:43:15
It's been a journey from the Publishing Forest of Nostr to the open sea of web3. I've come across a beautiful chain of islands and thought. Why not take a break and explore this place? If I'm searching for devs and FOSS, I should search every nook and cranny inside the realm of Nostr. It is quite vast for little old me. I'm just a little hamster and I don't speak in code or binary numbers zeros and ones.

After being in sea for awhile, my heart raced for excitement for what I could find. It seems I wasn't alone, there were others here like me! Let's help spread the message to others about this uncharted realm. See, look at the other sailboats, aren't they pretty? Thanks to some generous donation of SATs, I was able to afford the docking fee.

Ever feel like everyone was going to a party, and you were supposed to dress up, but you missed the memo? Or a comic-con? well, I felt completely underdressed and that's an understatement. Well, turns out there is a some knights around here. Take a peek!

A black cat with a knight passed by very quickly. He was moving too fast for me to track. Where was he going? Then I spotted a group of knights heading in the same direction, so I tagged along. The vibes from these guys was impossible to resist. They were just happy-go-lucky. 🥰They were heading to a tavern on a cliff off the island.

Ehh? a Tavern? Slightly confused, whatever could these knights be doing here? I guess when they're done with their rounds they would here to blow off steam. Things are looking curiouser and curiouser. But the black cat from earlier was here with its rider, whom was dismounting. So you can only guess, where I'm going.

The atmosphere in this pub, was lively and energetic. So many knights spoke among themselves. A group here, another there, but there was one that caught my eye. I went up to a group at a table, whose height towed well above me even when seated. Taking a deep breath, I asked, "Who manages this place?" They unanimous pointed to one waiting for ale at the bar. What was he doing? Watching others talk? How peculiar.

So I went up to him! And introduced myself.
"Hello I'm Onigirl"
"Hello Onigirl, Welcome to Gossip"
"Gossip, what is Gossip?" scratching my head and whiskers.
What is Gossip? Gossip is FOSS and a great client for privacy-centric minded nostriches. It avoids browser tech which by-passes several scripting languages such as JavaScript☕, HTML parsing, rendering, and CSS(Except HTTP GET and Websockets). Using OpenGL-style rendering. For Nostriches that wish to remain anonymous can use Gossip over TOR. Mike recommends using QubesOS, Whonix and or Tails. [FYI-Gossip does not natively support tor SOCKS5 proxy] Most helpful to spill the beans if you're a journalist.

On top of using your nsec or your encryption key, Gossip adds another layer of security over your account with a password login. There's nothing wrong with using the browser extensions (such as nos2x or Flamingo) which makes it super easy to log in to Nostr enable websites, apps, but it does expose you to browser vulnerabilities.
Mike Points out
"people have already had their private key stolen from other nostr clients,"
so it a concern if you value your account. I most certainly care for mine.

Gossip UI has a simple, and clean interface revolving around NIP-65 also called the “Outbox model." As posted from GitHub,
"This NIP allows Clients to connect directly with the most up-to-date relay set from each individual user, eliminating the need of broadcasting events to popular relays."
This eliminates clients that track only a specific set of relays which can congest those relays when you publish your note. Also this can be censored, by using Gossip you can publish notes to alternative relays that have not censored you to reach the same followers.
👉The easiest way to translate that is reducing redundancy to publish to popular relays or centralized relays for content reach to your followers.

Cool! What an awesome client, I mean Tavern! What else does this knight do? He reaches for something in his pocket. what is it? A Pocket is a database for storing and retrieving nostr events but mike's written it in Rust with a few extra kinks inspired by Will's nostrdb. Still in development, but it'll be another tool for you dear user! 💖💕💚
Onigirl is proud to present this knights to the community and honor them with kisu. 💋💋💋 Show some 💖💘💓🧡💙💚
👉💋💋Will - jb55 Lord of apples 💋 @npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s
👉💋💋 Mike Knight - Lord of Security 💋 @npub1acg6thl5psv62405rljzkj8spesceyfz2c32udakc2ak0dmvfeyse9p35c

Knights spend a lot of time behind the screen coding for the better of humanity. It is a tough job! Let's appreciate these knights, relay operators, that support this amazing realm of Nostr! FOSS for all!

This article was prompted for the need for privacy and security of your data. They're different, not to be confused.
Recently, Edward Snowden warns Bitcoin devs about the need for privacy, Quote:
“I've been warning Bitcoin developers for ten years that privacy needs to be provided for at the protocol level. This is the final warning. The clock is ticking.”
Snowden’s comments come after heavy actions of enforcement from Samarai Wallet, Roger Ver, Binance’s CZ, and now the closure of Wasabi Wallet. Additionally, according to CryptoBriefing, Trezor is ending it’s CoinJoin integration as well. Many are concerned over the new definition of a money transmitter, which includes even those who don’t touch the funds.
Help your favorite the hamster
 ^^Me drowning in notes on your feed. I can only eat so many notes to find you.
^^Me drowning in notes on your feed. I can only eat so many notes to find you. 👉If there are any XMPP fans on here. I'm open to the idea of opening a public channel, so you could follow me on that as a forum-like style. My server of choice would likely be a German server.😀You would be receiving my articles as njump.me style or website-like. GrapeneOS users, you can download Cheogram app from the F-Driod store for free to access. Apple and Andriod users are subjected to pay to download this app, an alternative is ntalk or conversations. If it interests the community, just FYI. Please comment or DM.
👉If you enjoyed this content, please consider reposting/sharing as my content is easily drowned by notes on your feed. You could also join my community under Children_Zone where I post my content.
An alternative is by following #onigirl Just FYI this feature is currently a little buggy.
Follow as I search for tools and awesome devs to help you dear user live a decentralized life as I explore the realm of Nostr.
Thank you Fren
-
 @ 349d6b82:12b2a5b1
2024-12-19 13:48:08
@ 349d6b82:12b2a5b1
2024-12-19 13:48:08На пересечений улиц Луначарского и Карла Маркса произошло ДТП с участием двух беспилотных автомобилей, что привлекло внимание как местных жителей, так и экспертов в области автономного вождения. Авария произошла в утренние часы, когда оба автомобиля, управляемые автопилотом, столкнулись на перекрестке, что вызвало значительные заторы и потребовало вмешательства экстренных служб.
По предварительным данным, один из автомобилей, марки "Альфа", не успел остановиться на красный сигнал светофора, в то время как другой автомобиль, "Оптимус", двигался по главной дороге. Оба транспортных средства были оборудованы современными системами безопасности и искусственным интеллектом для управления движением. Однако, несмотря на это, столкновение произошло из-за сбоя в системе обработки сигналов светофора.
После инцидента представители Министерства транспорта России заявили о необходимости пересмотра правил эксплуатации беспилотных автомобилей. В частности, акцент был сделан на важности надежности программного обеспечения и необходимости регулярного обновления систем управления. "Это происшествие подчеркивает важность строгого контроля за техническим состоянием беспилотников", — отметил один из чиновников.
Согласно действующему законодательству, ответственность за ДТП с участием беспилотных автомобилей будут нести как владелец транспортного средства, так и производитель программного обеспечения. Или же, эксперты предполагают, что виновником может быть признан оператор системы управления или производитель программного обеспечения, если будет установлено, что сбой произошел по их вине.
Это ДТП вновь подняло вопросы о безопасности и ответственности при использовании автономных автомобилей. В связи с этим ожидается дальнейшее развитие законодательства и технологий для повышения надежности беспилотных систем.
-
 @ 349d6b82:12b2a5b1
2024-12-19 13:47:41
@ 349d6b82:12b2a5b1
2024-12-19 13:47:41Наш город предлагает множество новых и интересных туристических мест. Вот список из шести ключевых пунктов, которые обязательны к посещению:
1. Серовский исторический музей: Музей, открывшийся еще в далеком 1920 году, предлагает интерактивные выставки, посвященные истории города и его культурному наследию. Здесь можно узнать о промышленном развитии региона и увидеть уникальные артефакты. Как в технологическом варианте, так и в старом виде, в каком был музей 124 лет назад.

2. Парк культуры и отдыха «Серовский»: Обновленный парк стал центром общественной жизни с новыми аттракционами, прогулочными зонами и культурными мероприятиями, который располагается напротив Дворца Культуры Металлургов. Здесь планируются регулярные фестивали и концерты на открытом воздухе.

3. Спортивный комплекс «Олимп»: Многофункциональный спортивный комплекс, ранее известный как ДЮСШ г. Серова, предлагает возможности для занятий различными видами спорта, включая плавание, теннис и фитнес. Комплекс будет также проводить спортивные соревнования и мероприятия различных возрастов и номинаций.

4. Краеведческий центр: Краеведческого центра на улице Карла Маркса 100А-12Б позволит туристам глубже погрузиться в культуру и традиции региона. Здесь будут проводиться мастер-классы по народным ремеслам и выставки местных художников.

5. Памятник героям Великой Отечественной войны: Важная часть ландшафта Серова, напоминает о подвиге местных жителей во время войны. Расположена вблизи Вечного огня.

6. Экологический маршрут «Зеленая тропа»: Новый экологический маршрут будет проходить через живописные леса вокруг Серова, позволяя туристам насладиться природой и узнать о местной флоре и фауне.

Настоятельно рекомендуем ознакомиться со всеми этими местами из этого списка!
-
 @ 7c765d40:bd121d84
2024-12-19 13:44:40
@ 7c765d40:bd121d84
2024-12-19 13:44:40This was written on Monday morning. Haha it's been a busy week.
It's hard to know if the banks, corporations, and countries have realized that they cannot stop bitcoin - or if this was the plan all along.
But 2024 has definitely been the year of corporate adoption.
We are in the middle of this transition from "analog" to "digital" and even though banks can't hold bitcoin yet, they are buying the closest thing to it - MicroStrategy shares.
Why can't they hold bitcoin?
Well it's only 15 years old and we all know how long it takes for big banks and corporations to move.
They have certain rules and regulations around what kind of investments they can hold.
Magic internet money hasn't made it onto their approved list yet.
But MicroStrategy has - since it's a publicly traded stock.
And that's why we've seen a 150% gain in MSTR shares this year alone.
I stumbled across an article recently with the title "NATIONAL BANK OF CANADA FI RAISES STOCK POSITION IN MICROSTRATEGY."
Interesting.
To the average person who has never heard of MicroStrategy, this would be completely irrelevant.
Most people have no idea what MicroStrategy is - or that it's been the best performing stock since adopting the bitcoin strategy in 2020.
If it said "NATIONAL BANK OF CANADA FI BUYS MORE BITCOIN," that might catch a few eyes.
But the big boys don't want it catching any eyes.
They are building their positions in bitcoin without anyone knowing.
They understand the scarcity aspect of bitcoin and want as much as possible before the average person shows up.
Let's look at some numbers here.
These are mindblowing.
-
National Bank of Canada FI - now hold approx. 39,000 MSTR shares (up 746% from last quarter)
-
UBS Asset Management - now own approx. 640,000 MSTR shares (up 971% from last quarter)
-
Charles Schwab Investment Management - now own approx. 664,000 MSTR shares (up 587% from last quarter)
-
Swiss National Bank - now own approx. 468,000 MSTR shares (up 904% from last quarter)
-
Sumitomo Mitsui Trust - now own approx. 343,000 MSTR shares (up 1,071% from last quarter)
-
International Assets Investment Management LLC - now own approx. 239,000 MSTR shares (up 224,965% from last quarter)
That is not a typo.
They are no longer "dipping their toes" into bitcoin.
MicroStrategy was added to the QQQ Index (top 100 companies on the market) which should create even more demand and attention from these big banks and funds.
They have certainly got the memo.
We are at an inflection point here in bitcoin.
The bitcoin holders with .10 bitcoin - 10 bitcoin are the ones who get to decide where this thing goes.
Individuals currently hold approx. 75% of the bitcoin while the big boys are desperately trying to play catch up.
Since 95% of the bitcoin has been mined to date (with pretty much 100% mined by year 2064), this bitcoin has to come from somewhere.
I did a segment discussing this on the show yesterday.
It's worth a watch.
You can find the show here.
It talked about this transition and what the holdings could look like in 20 years if we aren't careful.
Bitcoiners still hold the majority of bitcoin.
And the only way that can change is if they get hacked, seized, or tempted to sell.
The next 20 years in bitcoin will set the stage for the next 200.
Moral of the story: They are coming for your bitcoin. The longer you wait, the more they will pay.
Moral2 of the story: Never ever EVER sell your bitcoin. Lend against it instead. Think of it and use it like digital capital.
Moral3 of the story: MAKE THESE FUCKERS PAY.
PROJECT POTENTIAL - You can now find the expanded audio versions of these on the new podcast - Project Potential! I will be sharing the video versions here for the LITF members but you can also find it for free on Spotify and of course Fountain!
Here is the link to Episode 008 on Fountain: https://www.fountain.fm/episode/nQb5z3PolahVwsPbYX4r
Have a great day everyone! And remember, the only thing more scarce than bitcoin is time!
Jor 875001
-
-
 @ 266815e0:6cd408a5
2024-04-24 23:02:21
@ 266815e0:6cd408a5
2024-04-24 23:02:21NOTE: this is just a quick technical guide. sorry for the lack of details
Install NodeJS
Download it from the official website https://nodejs.org/en/download
Or use nvm https://github.com/nvm-sh/nvm?tab=readme-ov-file#install--update-script
bash wget -qO- https://raw.githubusercontent.com/nvm-sh/nvm/v0.39.7/install.sh | bash nvm install 20Clone example config.yml
bash wget https://raw.githubusercontent.com/hzrd149/blossom-server/master/config.example.yml -O config.ymlModify config.yml
```bash nano config.yml
or if your that type of person
vim config.yml ```
Run blossom-server
```bash npx blossom-server-ts
or install it locally and run using npm
npm install blossom-server-ts ./node_modules/.bin/blossom-server-ts ```
Now you can open http://localhost:3000 and see your blossom server
And if you set the
dashboard.enabledoption in theconfig.ymlyou can open http://localhost:3000/admin to see the admin dashboard -
 @ 3906af02:af15c9f4
2024-12-19 13:40:00
@ 3906af02:af15c9f4
2024-12-19 13:40:00NEW: HRF #Bitcoin Development Fund grants 700 million satoshis to 20 projects worldwide!
https://bitcoinmagazine.com/business/human-rights-foundation-donates-700000000-satoshis-to-fund-bitcoin-development-and-projects
The grants cover decentralized #Bitcoin mining, technical education, decentralized communications, independent media & privacy-enhanced financial solutions for human rights groups, focusing on key regions in Latin America, Asia, and Africa 🌍🌏🌎🎁
Grants include:
🛠️ Stratum V2 Reference Implementation (SRI) decentralizes #Bitcoin mining by allowing nodes create their own block templates, reducing reliance on large pools. Funds will support @bit-aloo’s work on SRI including benchmarking tools, integration tests & codebase maintenance
⛏️ Public Pool makes #Bitcoin mining accessible for low-hash-rate devices, empowering individuals to self-host mining servers & contribute to decentralization. Funds will support hosting costs, hardware upgrades, & operational expenses.
🛠️ Jon Atack, recognized as one of the top all-time contributors to #Bitcoin Core, plays a pivotal role in enhancing Bitcoin’s decentralization and robustness. Funds will empower him to continue his vital contributions to Bitcoin development
👩🏿💻 Naiyoma, the first female #Bitcoin Core developer from Africa. Her work focuses on reviewing pull requests (PRs), addressing bugs through new PRs & improving Bitcoin Core’s codebase. Funds will support her full-time contributions to advancing Bitcoin Core.
🔒 Daniela Brozzoni, a #Bitcoin Core developer who previously contributed to the Bitcoin Development Kit (BDK). This grant will support her full-time contributions to Bitcoin Core reviewing key pull requests (PRs), contributing to new features & improving testing coverage
📱 UX/UI Design for Bitcoin Core by @Michaelhaase will bring the #Bitcoin Core App to mobile enabling users to run nodes, access essential wallet features directly on their phones to improve their financial privacy. Funding will support the project’s design & development.
🚀 Brink, co-founded by Mike Schmidt, supports #Bitcoin protocol engineers with grants and offers training & mentorship to onboard new contributors to open-source development. This grant will support operational expenses
⚡@Tando.me, cofounded by Sabina Gitau, integrates #Bitcoin with Kenya’s M-PESA system, enabling KYC-free, fee-free Lightning payments for everyday transactions for 54 million Kenyans. Funds will help boost Tando’s liquidity, support user growth & drive African expansion.
🌐 YakiHonne, a Nostr client founded by Wendy Ding, supports free speech & promote #Bitcoin payments across 170 countries with innovative functionality & a blend of online & offline events. Funds will support smart widget development, relay improvements & community events.
🌍 SeedSigner Multi-language Support brings accessibility to the open-source SeedSigner hardware wallet, empowering marginalized communities through inexpensive & accessible self-custody. Funds support Ace to deliver a multi-language version of SeedSigner.
🤝 Vexl, cofounded by Lea Petrasova, provides a private, KYC-free, peer-to-peer #Bitcoin trading experience by connecting users to trade through the social graph of their phone contacts. Funds will support expanded adoption in Africa & improvements to the backend infrastructure.
🇮🇳 Tomatech is building developer talent in Goa, India to advance #Bitcoin infrastructure & FOSS projects through training, workshops, & community meetups. Funding will support developer training, the creation of a developer hub, bounties & grants, & general operations.
💾 Krux, open-source firmware that turns generic devices into hardware wallets for secure #Bitcoin self-custody featuring air-gapped operations, key management & backups & support for 10 languages. Funding will support @odudex to advance this project.
🔐 Iris, a #Nostr web client by @MarttiMalmi, which aims to improve protection for metadata & message content, ensuring conversations remain private, especially in surveillant environments. Funding will support hiring an additional developer to expand Iris' features & functionality.
💻 Cashu-ts, the primary Software Development Kit in the @CashuBTC ecosystem developed by @Gandlaf21, simplifies wallet creation, integrates the latest protocol updates & powers popular wallets. Funds will support the developers to maintain & improve this essential library.
🤝 Unify, a Payjoin wallet developed by Fontaine, enhances privacy in #Bitcoin transactions by obscuring transaction histories, crucial for individuals navigating repressive regimes. Funds will support the developer to ship new features & expand compatibility with other wallets.
📢 The Financial Freedom Policy Coalition, led by Venezuelan activist Jorge Jraissati, promotes economic opportunities for people living under authoritarian regimes. Funds will support advocacy missions to educate policymakers on how #Bitcoin supports human rights.
🎓 African UX Bitcoin Bootcamp, led by @MouxDesign, empowered 10 African UX designers with #Bitcoin UX research skills ahead of the Africa Bitcoin Conference & support to test 5 popular Bitcoin products during the conference. Funds cover all program expenses for participants.
📰 No BS Bitcoin delivers ad-free, privacy-focused #Bitcoin news in clear & accessible format, essential for activists & citizens under authoritarian regimes. This grant ensures continued operations, adds an editor & supports Nostr features like Zaps & comments.
📖 Bitcoin History, a research project by Pete Rizzo, documenting key people, events & materials that shaped Bitcoin’s rise as a global monetary & human rights force. Fund will support a researcher to investigate & document stories of Bitcoin’s use against authoritarianism.
🌎 HRF is committed to supporting human rights and financial freedom with #Bitcoin.
If you are working on a #Bitcoin or adjacent freedom tech software (Nostr, eCash, TOR etc), education or adoption project that meets our mandate, submit your application at http://hrf.org/bdfapply 💪
-
 @ 349d6b82:12b2a5b1
2024-12-19 13:35:29
@ 349d6b82:12b2a5b1
2024-12-19 13:35:29В преддверии премьеры нового фильма Александра Невзорова "Зимняя мечта", который выходит 17 декабря 2044 года, зрители приглашаются в увлекательное путешествие. Группа друзей, столкнувшихся с тяжелыми утратами, отправляется в зимний поход в горы, стремясь восстановить свои отношения и найти новый смысл жизни. На фоне завораживающих снежных пейзажей они не только преодолевают физические преграды, но и сталкиваются с внутренними демонами, находя поддержку друг в друге. Этот фильм, сочетая элементы драмы и комедии, подчеркивает важность дружбы и взаимопомощи в трудные времена, открывая новые горизонты для каждого из героев. Не пропустите возможность увидеть, как зимняя природа становится не только фоном, но и катализатором глубоких изменений в жизни персонажей:
-
 @ 3906af02:af15c9f4
2024-12-19 13:17:15
@ 3906af02:af15c9f4
2024-12-19 13:17:15This event has been deleted; your client is ignoring the delete request.
-
 @ 3c984938:2ec11289
2024-04-16 17:14:58
@ 3c984938:2ec11289
2024-04-16 17:14:58Hello (N)osytrs!
Yes! I'm calling you an (N)oystr!
Why is that? Because you shine, and I'm not just saying that to get more SATs. Ordinary Oysters and mussels can produce these beauties! Nothing seriously unique about them, however, with a little time and love each oyster is capable of creating something truly beautiful. I like believing so, at least, given the fact that you're even reading this article; makes you an (N)oystr! This isn't published this on X (formerly known as Twitter), Facebook, Discord, Telegram, or Instagram, which makes you the rare breed! A pearl indeed! I do have access to those platforms, but why create content on a terrible platform knowing I too could be shut down! Unfortunately, many people still use these platforms. This forces individuals to give up their privacy every day. Meta is leading the charge by forcing users to provide a photo ID for verification in order to use their crappy, obsolete site. If that was not bad enough, imagine if you're having a type of disagreement or opinion. Then, Bigtech can easily deplatform you. Umm. So no open debate? Just instantly shut-off users. Whatever, happened to right to a fair trial? Nope, just burning you at the stake as if you're a witch or warlock!

How heinous are the perpetrators and financiers of this? Well, that's opening another can of worms for you.
Imagine your voice being taken away, like the little mermaid. Ariel was lucky to have a prince, but the majority of us? The likelihood that I would be carried away by the current of the sea during a sunset with a prince on a sailboat is zero. And I live on an island, so I'm just missing the prince, sailboat(though I know where I could go to steal one), and red hair. Oh my gosh, now I feel sad.
I do not have the prince, Bob is better! I do not have mermaid fins, or a shell bra. Use coconut shells, it offers more support! But, I still have my voice and a killer sunset to die for!
All of that is possible thanks to the work of developers. These knights fight for Freedom Tech by utilizing FOSS, which help provides us with a vibrant ecosystem. Unfortunately, I recently learned that they are not all funded. Knights must eat, drink, and have a work space. This space is where they spend most of their sweat equity on an app or software that may and may not pan out. That brilliance is susceptible to fading, as these individuals are not seen but rather stay behind closed doors. What's worse, if these developers lose faith in their project and decide to join forces with Meta! 😖 Does WhatsApp ring a bell?
Without them, I probably wouldn't be able to create this long form article. Let's cheer them on like cheerleaders.. 👉Unfortunately, there's no cheerleader emoji so you'll just have to settle for a dancing lady, n guy. 💃🕺
Semisol said it beautifully, npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj
If we want freedom tech to succeed, the tools that make it possible need to be funded: relays like https://nostr.land, media hosts like https://nostr.build, clients like https://damus.io, etc.
With that thought, Onigirl is pleased to announce the launch of a new series. With a sole focus on free market devs/projects.
Knights of Nostr!
I'll happily brief you about their exciting project and how it benefits humanity! Let's Support these Magnificent projects, devs, relays, and builders! Our first runner up!
Oppa Fishcake :Lord of Media Hosting
npub137c5pd8gmhhe0njtsgwjgunc5xjr2vmzvglkgqs5sjeh972gqqxqjak37w
Oppa Fishcake with his noble steed!
Think of this as an introduction to learn and further your experience on Nostr! New developments and applications are constantly happening on Nostr. It's enough to make one's head spin. I may also cover FOSS projects(outside of Nostr) as they need some love as well! Plus, you can think of it as another tool to add to your decentralized life. I will not be doing how-to-Nostr guides. I personally feel there are plenty of great guides already available! Which I'm happy to add to curation collection via easily searchable on Yakihonne.
For email updates you can subscribe to my [[https://paragraph.xyz/@onigirl]]
If you like it, send me some 🧡💛💚 hearts💜💗💖 otherwise zap dat⚡⚡🍑🍑peach⚡⚡🍑 ~If not me, then at least to our dearest knight!
Thank you from the bottom of my heart for your time and support (N)oystr! Shine bright like a diamond! Share if you care! FOSS power!
Follow on your favorite Nostr Client for the best viewing experience!
[!NOTE]
I'm using Obsidian + Nostr Writer Plugin; a new way to publish Markdown directly to Nostr. I was a little nervous using this because I was used doing them in RStudio; R Markdown.
Since this is my first article, I sent it to my account as a draft to test it. It's pretty neat. -
 @ 5afdec5b:2d631be1
2024-12-19 13:08:08
@ 5afdec5b:2d631be1
2024-12-19 13:08:08On November 26, 2024, we took a significant leap forward in revolutionizing Bitcoin-collateralized loans by launching PHASE 1 of our closed beta. Now that the dust has settled, it's time to reflect on what we've learned, celebrate our wins, and chart the path forward.
"Get the bread you need without having to part with your corn." — Lendasat, 2024
📈 Closed Beta: PHASE 1 in Numbers
Over the course of one fast-paced week, here's what we achieved:
- 191 waitlist signups
- 100 invitations sent to eager testers
- 29 unique borrowers took 34 loans in total
- 21 loans disbursed via virtual debit cards, and 13 paid out in stablecoins (USDC on Polygon)One of our trusted partners stepped up to support us by providing loan offers, allowing our team to focus entirely on refining the borrowing experience during this phase. In just one week, we exceeded the lender's promised liquidity by 15%, prompting an early wrap-up.
In terms of value:
- 1.34 BTC in Total Value Locked (TVL)
- $54,600 USD in Total Value Disbursed (TVD)
These numbers don't just reflect activity; they validate the demand for Bitcoin-backed loans and alternative disbursement methods like virtual debit cards.
📝 What We Learned
PHASE 1 taught us a lot about our product, our users, and the road ahead. While this beta focused on the borrower experience and the integration of virtual debit cards thanks to our partner Moon, it gave us valuable insights into what works and what needs improvement.
The UX Challenge
Building a non-custodial platform is hard. Designing its UX? Even harder.
- Our decision to use a Contract Secret (a sovereign key for signing contracts) instead of an in-app wallet upheld our commitment to self-custody, sovereignty, and safety.
- However, this introduced friction for users. We're rethinking how to make this smoother while staying true to our principles.💳 Virtual Debit Cards: A Game Changer
The ability to claim loans directly onto a virtual debit card — thanks to our partnership with Moon — was a clear hit. Virtual cards weren't just appreciated; they were a hot topic.
➡️ However, one feature that could take this to the next level is the ability to add these cards to Apple Pay or Google Pay. It's a missing piece we're eager to explore to make the experience even more seamless and user-friendly.
Stablecoin Repayment: A Friction Point
Repaying loans in stablecoins on an alt-chain wasn't as seamless as we'd hoped. Reducing this pain point will be a top priority in future iterations.
➡️ To address this, we are actively exploring new integrations that would allow borrowers to repay their loans via bank transfer or even by using their debit or credit card, providing more flexible and user-friendly repayment options.✅ Demand Validated
From Bitcoin-collateralized loans to virtual debit card payouts, the strong demand reinforced our belief in the product's potential and validated that our approach is the right one.
➡️ In the future, the underlying protocol will continue to operate on a Bitcoin<>Stablecoin foundation, ensuring speed, trustlessness, and efficiency. Borrowers, however, will have the option to opt-in for intuitive on/off ramps and spending tools, making the experience seamless and user-friendly. This will allow the complexities of the alt-chain infrastructure to disappear entirely from the borrower's perspective. At the same time, we'll keep the order book clean and unfragmented, ensuring a smooth and scalable ecosystem for all participants.🌙 Dark Mode Is (Still) a Thing
Yes, even in the world of Bitcoin-backed loans, dark mode is a surprisingly big deal.
➡️ Message received; devs are doing something.
👀 Looking Ahead: BETA RELOADED
If PHASE 1 was about testing the waters, BETA RELOADED 👀 will be about diving deeper. In this next phase, we're opening up both borrower and lender experiences to our beta testers, with:
- Improved UI/UX, based on the invaluable feedback we've received.
- New partnerships and integrations to enhance functionality and accessibility.
- Exciting surprises that we'll reveal when the time comes.If PHASE 1 taught us anything, it's that we're onto something significant. We've demonstrated that Bitcoin-collateralized loans are not only reinventable but genuinely in demand. And this is just the start of what's to come.
Get ready for BETA RELOADED. It's coming soon™️, and it's going to be legendary!
Want to be part of the journey? Join our waiting list or, even better, connect with us on Discord to share your thoughts and stay updated!
Stay tuned, and as always, stay sovereign.
-
 @ 3bf0c63f:aefa459d
2024-03-19 14:01:01
@ 3bf0c63f:aefa459d
2024-03-19 14:01:01Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ 6871d8df:4a9396c1
2024-02-24 22:42:16
@ 6871d8df:4a9396c1
2024-02-24 22:42:16In an era where data seems to be as valuable as currency, the prevailing trend in AI starkly contrasts with the concept of personal data ownership. The explosion of AI and the ensuing race have made it easy to overlook where the data is coming from. The current model, dominated by big tech players, involves collecting vast amounts of user data and selling it to AI companies for training LLMs. Reddit recently penned a 60 million dollar deal, Google guards and mines Youtube, and more are going this direction. But is that their data to sell? Yes, it's on their platforms, but without the users to generate it, what would they monetize? To me, this practice raises significant ethical questions, as it assumes that user data is a commodity that companies can exploit at will.
The heart of the issue lies in the ownership of data. Why, in today's digital age, do we not retain ownership of our data? Why can't our data follow us, under our control, to wherever we want to go? These questions echo the broader sentiment that while some in the tech industry — such as the blockchain-first crypto bros — recognize the importance of data ownership, their "blockchain for everything solutions," to me, fall significantly short in execution.
Reddit further complicates this with its current move to IPO, which, on the heels of the large data deal, might reinforce the mistaken belief that user-generated data is a corporate asset. Others, no doubt, will follow suit. This underscores the urgent need for a paradigm shift towards recognizing and respecting user data as personal property.
In my perfect world, the digital landscape would undergo a revolutionary transformation centered around the empowerment and sovereignty of individual data ownership. Platforms like Twitter, Reddit, Yelp, YouTube, and Stack Overflow, integral to our digital lives, would operate on a fundamentally different premise: user-owned data.
In this envisioned future, data ownership would not just be a concept but a practice, with public and private keys ensuring the authenticity and privacy of individual identities. This model would eliminate the private data silos that currently dominate, where companies profit from selling user data without consent. Instead, data would traverse a decentralized protocol akin to the internet, prioritizing user control and transparency.
The cornerstone of this world would be a meritocratic digital ecosystem. Success for companies would hinge on their ability to leverage user-owned data to deliver unparalleled value rather than their capacity to gatekeep and monetize information. If a company breaks my trust, I can move to a competitor, and my data, connections, and followers will come with me. This shift would herald an era where consent, privacy, and utility define the digital experience, ensuring that the benefits of technology are equitably distributed and aligned with the users' interests and rights.
The conversation needs to shift fundamentally. We must challenge this trajectory and advocate for a future where data ownership and privacy are not just ideals but realities. If we continue on our current path without prioritizing individual data rights, the future of digital privacy and autonomy is bleak. Big tech's dominance allows them to treat user data as a commodity, potentially selling and exploiting it without consent. This imbalance has already led to users being cut off from their digital identities and connections when platforms terminate accounts, underscoring the need for a digital ecosystem that empowers user control over data. Without changing direction, we risk a future where our content — and our freedoms by consequence — are controlled by a few powerful entities, threatening our rights and the democratic essence of the digital realm. We must advocate for a shift towards data ownership by individuals to preserve our digital freedoms and democracy.
-
 @ 88dc84f5:c71164f7
2024-12-19 12:08:51
@ 88dc84f5:c71164f7
2024-12-19 12:08:51Introduction Quantum computing is a revolutionary technology that uses the principles of quantum mechanics to perform calculations that are exponentially faster and more powerful than those of classical computers. The rise of quantum computing has significant implications for cybersecurity and data protection, and in this article, we will explore what these implications are.
 The Power of Quantum Computing
Quantum computers use quantum bits or qubits, which can exist in multiple states simultaneously, allowing for an exponential increase in computing power. This means that quantum computers can perform certain calculations much faster than classical computers, which has significant implications for cybersecurity.
The Power of Quantum Computing
Quantum computers use quantum bits or qubits, which can exist in multiple states simultaneously, allowing for an exponential increase in computing power. This means that quantum computers can perform certain calculations much faster than classical computers, which has significant implications for cybersecurity.
 The Implications for Cybersecurity
The rise of quantum computing has significant implications for cybersecurity. Quantum computers can potentially break many of the encryption algorithms currently in use, which could compromise the security of online transactions and communication. This means that organizations and individuals will need to adopt new, quantum-resistant encryption algorithms to protect their data.
The Implications for Cybersecurity
The rise of quantum computing has significant implications for cybersecurity. Quantum computers can potentially break many of the encryption algorithms currently in use, which could compromise the security of online transactions and communication. This means that organizations and individuals will need to adopt new, quantum-resistant encryption algorithms to protect their data.
 The Impact on Data Protection
The rise of quantum computing also has significant implications for data protection. Quantum computers can potentially access and manipulate large amounts of data, which could compromise the privacy and security of individuals and organizations. This means that organizations and individuals will need to adopt new, quantum-resistant data protection measures to protect their data.
The Impact on Data Protection
The rise of quantum computing also has significant implications for data protection. Quantum computers can potentially access and manipulate large amounts of data, which could compromise the privacy and security of individuals and organizations. This means that organizations and individuals will need to adopt new, quantum-resistant data protection measures to protect their data.
 Preparing for a Quantum Future
To prepare for a future where quantum computers are a reality, organizations and individuals can take several steps:
1. Stay informed: Stay up-to-date with the latest developments in quantum computing and its implications for cybersecurity and data protection.
2. Adopt quantum-resistant encryption: Adopt new, quantum-resistant encryption algorithms to protect data from potential quantum computer attacks.
3. Implement quantum-resistant data protection measures: Implement new, quantum-resistant data protection measures to protect data from potential quantum computer attacks.
Preparing for a Quantum Future
To prepare for a future where quantum computers are a reality, organizations and individuals can take several steps:
1. Stay informed: Stay up-to-date with the latest developments in quantum computing and its implications for cybersecurity and data protection.
2. Adopt quantum-resistant encryption: Adopt new, quantum-resistant encryption algorithms to protect data from potential quantum computer attacks.
3. Implement quantum-resistant data protection measures: Implement new, quantum-resistant data protection measures to protect data from potential quantum computer attacks.Conclusion The rise of quantum computing has significant implications for cybersecurity and data protection. As quantum computers become more powerful and widely available, organizations and individuals will need to adopt new, quantum-resistant encryption algorithms and data protection measures to protect their data. By understanding the implications of quantum computing, we can take steps to prepare for a future where quantum computers are a reality.
Statistics: - The global quantum computing market is projected to reach $65 billion by 2025. (Source: MarketsandMarkets) - Quantum computers can potentially break many of the encryption algorithms currently in use, including RSA and elliptic curve cryptography. (Source: National Institute of Standards and Technology) - The use of quantum computers could compromise the security of online transactions and communication, potentially leading to significant financial losses. (Source: Ponemon Institute)
Sources: - “Quantum Computing Market” by Application, Industry, and Geography - Global Forecast to 2025" by MarketsandMarkets - "Post-Quantum Cryptography" by National Institute of Standards and Technology - "2019 Global Cybersecurity Survey" by Ponemon Institute
-
 @ 88cc134b:5ae99079
2024-12-19 10:52:14
@ 88cc134b:5ae99079
2024-12-19 10:52:14Well hello again. This article is meant to have enough text and a range of element types so that we can test them all thoroughly. You are not meant to read it. If you are doing so, you need to ask yourself WTF am I doing? Wasting away reading filler content OMG. Still reading? NGMI. Well, good luck to you.
Testing Lists
Here are some bullet points to keep an eye on:
- Make sure you walk outside barefoot every day. Grounding is good;
- Pounding can be good too, depending on the circumstances;
- Not gonna go into details here, hopefully you know what I mean.
Emails
someone@email.com someone@email.com someone@email.com
And here are some numbered points:
- I found that the most impactful habit for my health is 20-4 paleo;
- The 2nd most important: daily exercise, preferably outside;
- Getting deep sleep is up there too. Personally, I need 8 hours;
- If you nail the top 3 items above, you can generally get away with other shit.
Testing Images
Now let's look at a beautiful sunrise:
 What more do you want? I mean seriously, this article is epic. Better than most.
What more do you want? I mean seriously, this article is epic. Better than most. Peace.
-
 @ 42342239:1d80db24
2024-12-19 15:26:01
@ 42342239:1d80db24
2024-12-19 15:26:01Im Frühjahr kündigte EU-Kommissarin Ursula von der Leyen an, sie wolle einen „ Europäischen Demokratieschild " schaffen, um die EU vor ausländischer Einflussnahme zu schützen. Von der Leyens Demokratieschild befindet sich derzeit in der Planungsphase. Die erklärte Absicht besteht darin, eine „ spezielle Struktur zur Bekämpfung ausländischer Informationsmanipulation und -einmischung" zu schaffen. Obwohl es als Instrument zum Schutz der Demokratie angepriesen wird, vermuten einige, dass es sich in Wirklichkeit um einen verschleierten Versuch handelt, abweichende Meinungen zu unterdrücken. Der im vergangenen Jahr verabschiedete Digital Services Act (DSA) der EU ist eng mit diesem Schild verbunden. Durch den DSA riskieren große Social-Media-Plattformen wie Elon Musks X erhebliche Geldstrafen, wenn sie den Forderungen der EU-Bürokraten nach Zensur und Moderation nicht nachkommen.
Note: This text is also available in English at substack.com. Many thanks to
stroger1@iris.tofor this German translation.Im krassen Gegensatz dazu hat sich der künftige US-Präsident Donald Trump als klarer Befürworter der Meinungsfreiheit und entschiedener Gegner der Zensur hervorgetan. Er wurde bereits von YouTube gesperrt, hat jedoch erklärt, er wolle „das linke Zensurregime zerschlagen und das Recht auf freie Meinungsäußerung für alle Amerikaner zurückfordern" . Er hat auch behauptet: „Wenn wir keine freie Meinungsäußerung haben, dann haben wir einfach kein freies Land."
Sein künftiger Vizepräsident J.D. Vance hat sogar angedeutet, dass er bereit sei, US-Militärhilfe von der Achtung der Meinungsfreiheit in den europäischen NATO-Ländern abhängig zu machen. Vances Aussage erfolgte, nachdem EU-Binnenmarktkommissar Thierry Breton vor seinem geplanten Gespräch mit Trump einen umstrittenen Brief an Musk geschickt hatte. Heute erscheint dies als unkluger Schritt, nicht zuletzt, weil er als Versuch gewertet werden kann, die US-Wahl zu beeinflussen -- etwas, das paradoxerweise dem erklärten Zweck von von der Leyens Demokratieschild (d. h. ausländische Manipulationen zu bekämpfen) widerspricht.
Wenn die NATO möchte, dass wir sie weiterhin unterstützen, und die NATO möchte, dass wir weiterhin ein gutes Mitglied dieses Militärbündnisses sind, warum respektieren Sie dann nicht die amerikanischen Werte und die freie Meinungsäußerung?
- J.D. Vance
In der EU sind Verfechter der Meinungsfreiheit in der Öffentlichkeit weniger verbreitet. In Deutschland hat Vizekanzler Robert Habeck kürzlich erklärt, er sei „überhaupt nicht glücklich darüber, was dort [auf X] passiert ... seit Elon Musk das Amt übernommen hat", und wünscht sich eine strengere Regulierung der sozialen Medien. Die Wohnung eines deutschen Rentners wurde kürzlich von der Polizei durchsucht, nachdem er ein Bild von Habeck mit einem abfälligen Kommentar veröffentlicht hatte . Die deutsche Polizei verfolgt auch einen anderen Kontoinhaber, der einen Minister als „übergewichtig" bezeichnet hat. Dieser überhaupt nicht übergewichtige Minister hat kürzlich eine Zeitung verboten , die mit der laut Meinungsumfragen zweitgrößten Partei Deutschlands, der Alternative für Deutschland (AfD), verbündet ist. Eine Partei, die 113 deutsche Parlamentarier nun offiziell verbieten wollen .
Nach dem US-Wahlergebnis stellen sich viele unbeantwortete Fragen. Wird das Weiße Haus seine Aufmerksamkeit auf die restriktivere Haltung der EU richten, die als Untergrabung der freien Meinungsäußerung angesehen werden kann? Oder droht Musks X und Chinas TikTok stattdessen ein EU-Verbot? Können EU-Länder noch mit militärischer Unterstützung aus den USA rechnen? Und wenn große amerikanische Plattformen verboten werden, wohin sollten sich die EU-Bürger stattdessen wenden? Abgesehen von russischen Alternativen gibt es keine großen europäischen Plattformen. Und wenn die Frage der Meinungsfreiheit neu überdacht wird, was bedeutet das für die Zukunft von Parteien wie der deutschen AfD?
-
 @ 42342239:1d80db24
2024-12-19 09:00:14
@ 42342239:1d80db24
2024-12-19 09:00:14Germany, the EU's largest economy, is once again forced to bear the label "Europe's sick man". The economic news makes for dismal reading. Industrial production has been trending downward for a long time. Energy-intensive production has decreased by as much as 20% in just a few years. Volkswagen is closing factories. Thyssenkrupp is laying off employees and more than three million pensioners are at risk of poverty according to a study.
Germany is facing a number of major challenges, including high energy costs and increased competition from China. In 2000, Germany accounted for 8% of global industrial production, but by 2030, its share is expected to have fallen to 3%. In comparison, China accounted for 2% of global industrial production in 2000, but is expected to account for nearly half (45%) of industrial production in a few years. This is according to a report from the UN's Industrial Development Organization.
Germany's electricity prices are five times higher than China's, a situation that poses a significant obstacle to maintaining a competitive position. The three main reasons are the phase-out of nuclear power, the sabotage of Nord Stream, and the ongoing energy transition, also known as Energiewende. Upon closer inspection, it is clear that industrial production has been trending downward since the transition to a greener economy began to be prioritized.
Germany's former defense minister, EU Commission President von der Leyen, called the European Green Deal Europe's "man on the moon" moment in 2019. This year, she has launched increased focus on these green goals.
However, the EU as a whole has fallen behind the US year after year. European companies have significantly higher energy costs than their American competitors, with electricity prices 2-3 times higher and natural gas prices 4-5 times higher.
The Environmental Kuznets Curve is a model that examines the relationship between economic growth and environmental impact. The idea is that increased material prosperity initially leads to more environmental degradation, but after a certain threshold is passed, there is a gradual decrease. Decreased material prosperity can thus, according to the relationship, lead to increased environmental degradation, for example due to changed consumption habits (fewer organic products in the shopping basket).
This year's election has resulted in a historic change, where all incumbent government parties in the Western world have seen their popularity decline. The pattern appears to be repeating itself in Germany next year, where Chancellor Olaf Scholz is struggling with low confidence figures ahead of the election in February, which doesn't seem surprising. Adjusted for inflation, German wages are several percent lower than a few years ago, especially in the manufacturing industry.
Germany is still a very rich country, but the current trend towards deindustrialization and falling wages can have consequences for environmental priorities in the long run. Economic difficulties can lead to environmental issues being downgraded. Perhaps the declining support for incumbent government parties is a first sign? Somewhere along the road to poverty, people will rise up in revolt.
-
 @ 8ce092d8:950c24ad
2024-02-04 23:35:07
@ 8ce092d8:950c24ad
2024-02-04 23:35:07Overview
- Introduction
- Model Types
- Training (Data Collection and Config Settings)
- Probability Viewing: AI Inspector
- Match
- Cheat Sheet
I. Introduction
AI Arena is the first game that combines human and artificial intelligence collaboration.
AI learns your skills through "imitation learning."
Official Resources
- Official Documentation (Must Read): Everything You Need to Know About AI Arena
Watch the 2-minute video in the documentation to quickly understand the basic flow of the game. 2. Official Play-2-Airdrop competition FAQ Site https://aiarena.notion.site/aiarena/Gateway-to-the-Arena-52145e990925499d95f2fadb18a24ab0 3. Official Discord (Must Join): https://discord.gg/aiarenaplaytest for the latest announcements or seeking help. The team will also have a exclusive channel there. 4. Official YouTube: https://www.youtube.com/@aiarena because the game has built-in tutorials, you can choose to watch videos.
What is this game about?
- Although categorized as a platform fighting game, the core is a probability-based strategy game.
- Warriors take actions based on probabilities on the AI Inspector dashboard, competing against opponents.
- The game does not allow direct manual input of probabilities for each area but inputs information through data collection and establishes models by adjusting parameters.
- Data collection emulates fighting games, but training can be completed using a Dummy As long as you can complete the in-game tutorial, you can master the game controls.
II. Model Types
Before training, there are three model types to choose from: Simple Model Type, Original Model Type, and Advanced Model Type.
It is recommended to try the Advanced Model Type after completing at least one complete training with the Simple Model Type and gaining some understanding of the game.

Simple Model Type
The Simple Model is akin to completing a form, and the training session is comparable to filling various sections of that form.
This model has 30 buckets. Each bucket can be seen as telling the warrior what action to take in a specific situation. There are 30 buckets, meaning 30 different scenarios. Within the same bucket, the probabilities for direction or action are the same.
For example: What should I do when I'm off-stage — refer to the "Recovery (you off-stage)" bucket.
For all buckets, refer to this official documentation:
https://docs.aiarena.io/arenadex/game-mechanics/tabular-model-v2
Video (no sound): The entire training process for all buckets
https://youtu.be/1rfRa3WjWEA
Game version 2024.1.10. The method of saving is outdated. Please refer to the game updates.
Advanced Model Type
The "Original Model Type" and "Advanced Model Type" are based on Machine Learning, which is commonly referred to as combining with AI.
The Original Model Type consists of only one bucket, representing the entire map. If you want the AI to learn different scenarios, you need to choose a "Focus Area" to let the warrior know where to focus. A single bucket means that a slight modification can have a widespread impact on the entire model. This is where the "Advanced Model Type" comes in.
The "Advanced Model Type" can be seen as a combination of the "Original Model Type" and the "Simple Model Type". The Advanced Model Type divides the map into 8 buckets. Each bucket can use many "Focus Area." For a detailed explanation of the 8 buckets and different Focus Areas, please refer to the tutorial page (accessible in the Advanced Model Type, after completing a training session, at the top left of the Advanced Config, click on "Tutorial").

III. Training (Data Collection and Config Settings)
Training Process:
- Collect Data
- Set Parameters, Train, and Save
- Repeat Step 1 until the Model is Complete
Training the Simple Model Type is the easiest to start with; refer to the video above for a detailed process.
Training the Advanced Model Type offers more possibilities through the combination of "Focus Area" parameters, providing a higher upper limit. While the Original Model Type has great potential, it's harder to control. Therefore, this section focuses on the "Advanced Model Type."
1. What Kind of Data to Collect
- High-Quality Data: Collect purposeful data. Garbage in, garbage out. Only collect the necessary data; don't collect randomly. It's recommended to use Dummy to collect data. However, don't pursue perfection; through parameter adjustments, AI has a certain level of fault tolerance.
- Balanced Data: Balance your dataset. In simple terms, if you complete actions on the left side a certain number of times, also complete a similar number on the right side. While data imbalance can be addressed through parameter adjustments (see below), it's advised not to have this issue during data collection.
- Moderate Amount: A single training will include many individual actions. Collect data for each action 1-10 times. Personally, it's recommended to collect data 2-3 times for a single action. If the effect of a single training is not clear, conduct a second (or even third) training with the same content, but with different parameter settings.
2. What to Collect (and Focus Area Selection)
Game actions mimic fighting games, consisting of 4 directions + 6 states (Idle, Jump, Attack, Grab, Special, Shield). Directions can be combined into ↗, ↘, etc. These directions and states can then be combined into different actions.
To make "Focus Area" effective, you need to collect data in training that matches these parameters. For example, for "Distance to Opponent", you need to collect data when close to the opponent and also when far away. * Note: While you can split into multiple training sessions, it's most effective to cover different situations within a single training.
Refer to the Simple Config, categorize the actions you want to collect, and based on the game scenario, classify them into two categories: "Movement" and "Combat."
Movement-Based Actions
Action Collection
When the warrior is offstage, regardless of where the opponent is, we require the warrior to return to the stage to prevent self-destruction.
This involves 3 aerial buckets: 5 (Near Blast Zone), 7 (Under Stage), and 8 (Side Of Stage).

* Note: The background comes from the Tutorial mentioned earlier. The arrows in the image indicate the direction of the action and are for reference only. * Note: Action collection should be clean; do not collect actions that involve leaving the stage.
Config Settings
In the Simple Config, you can directly choose "Movement" in it. However, for better customization, it's recommended to use the Advanced Config directly. - Intensity: The method for setting Intensity will be introduced separately later. - Buckets: As shown in the image, choose the bucket you are training. - Focus Area: Position-based parameters: - Your position (must) - Raycast Platform Distance, Raycast Platform Type (optional, generally choose these in Bucket 7)
Combat-Based Actions
The goal is to direct attacks quickly and effectively towards the opponent, which is the core of game strategy.
This involves 5 buckets: - 2 regular situations - In the air: 6 (Safe Zone) - On the ground: 4 (Opponent Active) - 3 special situations on the ground: - 1 Projectile Active - 2 Opponent Knockback - 3 Opponent Stunned
2 Regular Situations
In the in-game tutorial, we learned how to perform horizontal attacks. However, in the actual game, directions expand to 8 dimensions. Imagine having 8 relative positions available for launching hits against the opponent. Our task is to design what action to use for attack or defense at each relative position.
Focus Area - Basic (generally select all) - Angle to opponent
- Distance to opponent - Discrete Distance: Choosing this option helps better differentiate between closer and farther distances from the opponent. As shown in the image, red indicates a relatively close distance, and green indicates a relatively distant distance.- Advanced: Other commonly used parameters
- Direction: different facings to opponent
- Your Elemental Gauge and Discrete Elementals: Considering the special's charge
- Opponent action: The warrior will react based on the opponent's different actions.
- Your action: Your previous action. Choose this if teaching combos.
3 Special Situations on the Ground
Projectile Active, Opponent Stunned, Opponent Knockback These three buckets can be referenced in the Simple Model Type video. The parameter settings approach is the same as Opponent Active/Safe Zone.
For Projectile Active, in addition to the parameters based on combat, to track the projectile, you also need to select "Raycast Projectile Distance" and "Raycast Projectile On Target."
3. Setting "Intensity"
Resources
- The "Tutorial" mentioned earlier explains these parameters.
- Official Config Document (2022.12.24): https://docs.google.com/document/d/1adXwvDHEnrVZ5bUClWQoBQ8ETrSSKgG5q48YrogaFJs/edit
TL;DR:
Epochs: - Adjust to fewer epochs if learning is insufficient, increase for more learning.
Batch Size: - Set to the minimum (16) if data is precise but unbalanced, or just want it to learn fast - Increase (e.g., 64) if data is slightly imprecise but balanced. - If both imprecise and unbalanced, consider retraining.
Learning Rate: - Maximize (0.01) for more learning but a risk of forgetting past knowledge. - Minimize for more accurate learning with less impact on previous knowledge.
Lambda: - Reduce for prioritizing learning new things.
Data Cleaning: - Enable "Remove Sparsity" unless you want AI to learn idleness. - For special cases, like teaching the warrior to use special moves when idle, refer to this tutorial video: https://discord.com/channels/1140682688651612291/1140683283626201098/1195467295913431111
Personal Experience: - Initial training with settings: 125 epochs, batch size 16, learning rate 0.01, lambda 0, data cleaning enabled. - Prioritize Multistream, sometimes use Oversampling. - Fine-tune subsequent training based on the mentioned theories.
IV. Probability Viewing: AI Inspector
The dashboard consists of "Direction + Action." Above the dashboard, you can see the "Next Action" – the action the warrior will take in its current state. The higher the probability, the more likely the warrior is to perform that action, indicating a quicker reaction. It's essential to note that when checking the Direction, the one with the highest visual representation may not have the highest numerical value. To determine the actual value, hover the mouse over the graphical representation, as shown below, where the highest direction is "Idle."

In the map, you can drag the warrior to view the probabilities of the warrior in different positions. Right-click on the warrior with the mouse to change the warrior's facing. The status bar below can change the warrior's state on the map.

When training the "Opponent Stunned, Opponent Knockback" bucket, you need to select the status below the opponent's status bar. If you are focusing on "Opponent action" in the Focus Zone, choose the action in the opponent's status bar. If you are focusing on "Your action" in the Focus Zone, choose the action in your own status bar. When training the "Projectile Active" Bucket, drag the projectile on the right side of the dashboard to check the status.
Next
The higher the probability, the faster the reaction. However, be cautious when the action probability reaches 100%. This may cause the warrior to be in a special case of "State Transition," resulting in unnecessary "Idle" states.
Explanation: In each state a fighter is in, there are different "possible transitions". For example, from falling state you cannot do low sweep because low sweep requires you to be on the ground. For the shield state, we do not allow you to directly transition to headbutt. So to do headbutt you have to first exit to another state and then do it from there (assuming that state allows you to do headbutt). This is the reason the fighter runs because "run" action is a valid state transition from shield. Source
V. Learn from Matches
After completing all the training, your model is preliminarily finished—congratulations! The warrior will step onto the arena alone and embark on its debut!
Next, we will learn about the strengths and weaknesses of the warrior from battles to continue refining the warrior's model.
In matches, besides appreciating the performance, pay attention to the following:
-
Movement, i.e., Off the Stage: Observe how the warrior gets eliminated. Is it due to issues in the action settings at a certain position, or is it a normal death caused by a high percentage? The former is what we need to avoid and optimize.
-
Combat: Analyze both sides' actions carefully. Observe which actions you and the opponent used in different states. Check which of your hits are less effective, and how does the opponent handle different actions, etc.
The approach to battle analysis is similar to the thought process in the "Training", helping to have a more comprehensive understanding of the warrior's performance and making targeted improvements.
VI. Cheat Sheet
Training 1. Click "Collect" to collect actions. 2. "Map - Data Limit" is more user-friendly. Most players perform initial training on the "Arena" map. 3. Switch between the warrior and the dummy: Tab key (keyboard) / Home key (controller). 4. Use "Collect" to make the opponent loop a set of actions. 5. Instantly move the warrior to a specific location: Click "Settings" - SPAWN - Choose the desired location on the map - On. Press the Enter key (keyboard) / Start key (controller) during training.
Inspector 1. Right-click on the fighter to change their direction. Drag the fighter and observe the changes in different positions and directions. 2. When satisfied with the training, click "Save." 3. In "Sparring" and "Simulation," use "Current Working Model." 4. If satisfied with a model, then click "compete." The model used in the rankings is the one marked as "competing."
Sparring / Ranked 1. Use the Throneroom map only for the top 2 or top 10 rankings. 2. There is a 30-second cooldown between matches. The replays are played for any match. Once the battle begins, you can see the winner on the leaderboard or by right-clicking the page - Inspect - Console. Also, if you encounter any errors or bugs, please send screenshots of the console to the Discord server.
Good luck! See you on the arena!
-
 @ 5fb7f8f7:d7d76024
2024-12-19 07:29:19
@ 5fb7f8f7:d7d76024
2024-12-19 07:29:19As Bitcoin keeps breaking new height it's important to also keep track of Altcoins movement too. Stay positioned this bullrun season and make money $. Carry out research on tokens, coins and even memecoin to buy and stay positioned for next year. I'll be suggesting a few you can buy and hold to get maximum profit.
BGB: bitget exchange native token CORE: integrated BTC into its staking programm BLUEFIN: last ATH was at $10 currently $0.6 SUI: hitting $8 soon position yourself DOGS: under TON ecosystem TON: native token of Ton Blockchain NOTCOIN: The first memecoin on Ton Blockchain AVACN: good token to hold for bullrun SPUNKYSDX: I bought at $10 currently at $26 and many more research and find out. I'll be dropping more so follow like and comment so you don't miss out.
money #finance #BTC #Altcoins
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Bolo
It seems that from 1987 to around 2000 there was a big community of people who played this game called "Bolo". It was a game in which people controlled a tank and killed others while trying to capture bases in team matches. Always 2 teams, from 2 to 16 total players, games could last from 10 minutes to 12 hours. I'm still trying to understand all this.
The game looks silly from some videos you can find today, but apparently it was very deep in strategy because people developed strategy guides and wrote extensively about it and Netscape even supported
bolo:URLs out of the box.The two most important elements on the map are pillboxes and bases. Pillboxes are originally neutral, meaning that they shoot at every tank that happens to get in its range. They shoot fast and with deadly accuracy. You can shoot the pillbox with your tank, and you can see how damaged it is by looking at it. Once the pillbox is subdued, you may run over it, which will pick it up. You may place the pillbox where you want to put it (where it is clear), if you've enough trees to build it back up. Trees are harvested by sending your man outside your tank to forest the trees. Your man (also called a builder) can also lay mines, build roads, and build walls. Once you have placed a pillbox, it will not shoot at you, but only your enemies. Therefore, pillboxes are often used to protect your bases.
That quote was taken from this "augmented FAQ" written by some user. Apparently there were many FAQs for this game. A FAQ is after all just a simple, clear and direct to the point way of writing about anything, previously known as summa[^summa-k], it doesn't have to be related to any actually frequently asked question.
More unexpected Bolo writings include an etiquette guide, an anthropology study and some wonderings on the reverse pill war tactic.
[^summa-k]: It's not the same thing, but I couldn't help but notice the similarity.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28IPFS problems: Community
I was an avid IPFS user until yesterday. Many many times I asked simple questions for which I couldn't find an answer on the internet in the #ipfs IRC channel on Freenode. Most of the times I didn't get an answer, and even when I got it was rarely by someone who knew IPFS deeply. I've had issues go unanswered on js-ipfs repositories for year – one of these was raising awareness of a problem that then got fixed some months later by a complete rewrite, I closed my own issue after realizing that by myself some couple of months later, I don't think the people responsible for the rewrite were ever acknowledge that he had fixed my issue.
Some days ago I asked some questions about how the IPFS protocol worked internally, sincerely trying to understand the inefficiencies in finding and fetching content over IPFS. I pointed it would be a good idea to have a drawing showing that so people would understand the difficulties (which I didn't) and wouldn't be pissed off by the slowness. I was told to read the whitepaper. I had already the whitepaper, but read again the relevant parts. The whitepaper doesn't explain anything about the DHT and how IPFS finds content. I said that in the room, was told to read again.
Before anyone misread this section, I want to say I understand it's a pain to keep answering people on IRC if you're busy developing stuff of interplanetary importance, and that I'm not paying anyone nor I have the right to be answered. On the other hand, if you're developing a super-important protocol, financed by many millions of dollars and a lot of people are hitting their heads against your software and there's no one to help them; you're always busy but never delivers anything that brings joy to your users, something is very wrong. I sincerely don't know what IPFS developers are working on, I wouldn't doubt they're working on important things if they said that, but what I see – and what many other users see (take a look at the IPFS Discourse forum) is bugs, bugs all over the place, confusing UX, and almost no help.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Castas hindus em nova chave
Shudras buscam o máximo bem para os seus próprios corpos; vaishyas o máximo bem para a sua própria vida terrena e a da sua família; kshatriyas o máximo bem para a sociedade e este mundo terreno; brâmanes buscam o máximo bem.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Economics
Just a bunch of somewhat-related notes.
- notes on "Economic Action Beyond the Extent of the Market", Per Bylund
- Mises' interest rate theory
- Profits, not wages, as the originary factor
- Reisman on opportunity cost
- Money Supply Measurement
- Per Bylund's insight
- Maybe a new approach to the Austrian Business Cycle Theory, some disorganized thoughts
- An argument according to which fractional-reserve banking is merely theft and nothing else
- Conjecture and criticism
- Qual é o economista? (piadas)
- UBI calculations
- Donations on the internet
-
 @ 4d656c76:98e5dc4e
2024-12-19 05:24:51
@ 4d656c76:98e5dc4e
2024-12-19 05:24:51Online loans have become an essential financing option for small and medium-sized enterprises (SMEs) in the Philippines. This infographic provides a straightforward overview of what SMEs need to know about accessing online loans, including their benefits, potential risks, and key considerations before applying. It also highlights how online lending platforms offer a convenient and faster alternative to traditional loans, helping SMEs address urgent financial needs and support business growth. By understanding the process and evaluating the options, SMEs can make informed decisions to secure the funding they need to thrive.
Source: JK Capital
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Thoughts on Nostr key management
On Why I don't like NIP-26 as a solution for key management I talked about multiple techniques that could be used to tackle the problem of key management on Nostr.
Here are some ideas that work in tandem:
- NIP-41 (stateless key invalidation)
- NIP-46 (Nostr Connect)
- NIP-07 (signer browser extension)
- Connected hardware signing devices
- other things like musig or frostr keys used in conjunction with a semi-trusted server; or other kinds of trusted software, like a dedicated signer on a mobile device that can sign on behalf of other apps; or even a separate protocol that some people decide to use as the source of truth for their keys, and some clients might decide to use that automatically
- there are probably many other ideas
Some premises I have in my mind (that may be flawed) that base my thoughts on these matters (and cause me to not worry too much) are that
- For the vast majority of people, Nostr keys aren't a target as valuable as Bitcoin keys, so they will probably be ok even without any solution;
- Even when you lose everything, identity can be recovered -- slowly and painfully, but still --, unlike money;
- Nostr is not trying to replace all other forms of online communication (even though when I think about this I can't imagine one thing that wouldn't be nice to replace with Nostr) or of offline communication, so there will always be ways.
- For the vast majority of people, losing keys and starting fresh isn't a big deal. It is a big deal when you have followers and an online persona and your life depends on that, but how many people are like that? In the real world I see people deleting social media accounts all the time and creating new ones, people losing their phone numbers or other accounts associated with their phone numbers, and not caring very much -- they just find a way to notify friends and family and move on.
We can probably come up with some specs to ease the "manual" recovery process, like social attestation and explicit signaling -- i.e., Alice, Bob and Carol are friends; Alice loses her key; Bob sends a new Nostr event kind to the network saying what is Alice's new key; depending on how much Carol trusts Bob, she can automatically start following that and remove the old key -- or something like that.
One nice thing about some of these proposals, like NIP-41, or the social-recovery method, or the external-source-of-truth-method, is that they don't have to be implemented in any client, they can live in standalone single-purpose microapps that users open or visit only every now and then, and these can then automatically update their follow lists with the latest news from keys that have changed according to multiple methods.
-
 @ 7ed5bd1c:4caa7587
2024-12-19 04:12:44
@ 7ed5bd1c:4caa7587
2024-12-19 04:12:44เงินในฐานะเทคโนโลยี – Bitcoin คือก้าวกระโดดครั้งใหญ่?
เงินไม่ได้เป็นแค่สื่อกลางแลกเปลี่ยน แต่มันคือ เทคโนโลยี ที่พัฒนาขึ้นเพื่อตอบสนองความต้องการของสังคมมนุษย์ในแต่ละยุคสมัย ตั้งแต่หอยเบี้ย เหรียญทองคำ ไปจนถึงธนบัตร และปัจจุบันที่กำลังก้าวเข้าสู่โลกดิจิทัลด้วย Bitcoin แต่วิวัฒนาการนี้ส่งผลกระทบต่อเศรษฐกิจและชีวิตเราอย่างไร?
เงินคือเทคโนโลยีที่พัฒนาเพื่อแก้ปัญหา
-
ยุคแรกเริ่ม: มนุษย์เริ่มต้นด้วยการแลกเปลี่ยนสินค้ากันโดยตรง (barter system) แต่เมื่อพบว่าการแลกเปลี่ยนมีข้อจำกัด เช่น การหาคู่แลกเปลี่ยนที่ตรงกันจึงเกิดการใช้ “เงิน” เช่น หอยเบี้ยหรือโลหะที่มีค่าเพื่อแก้ปัญหาเหล่านี้
-
เงินตราโลหะและธนบัตร: การใช้โลหะมีค่าช่วยแก้ปัญหาความคงทนและมูลค่าที่เชื่อถือได้ แต่การพกพาโลหะหนักๆ ก็ไม่สะดวก ธนบัตรจึงถูกนำมาใช้แทน ซึ่งเป็นจุดเริ่มต้นของการเชื่อถือใน “สัญญา” ว่าเงินกระดาษมีมูลค่าจริง
-
เงินดิจิทัลและ Bitcoin: เมื่อโลกก้าวเข้าสู่ยุคอินเทอร์เน็ต การพัฒนาเงินแบบดิจิทัล เช่น บัตรเครดิต หรือการโอนเงินออนไลน์ กลายเป็นมาตรฐานใหม่ แต่ระบบนี้ยังคงพึ่งพาคนกลาง เช่น ธนาคาร จนกระทั่ง Bitcoin ถือกำเนิดในปี 2009 เพื่อตัดคนกลางออกและสร้างระบบการเงินที่โปร่งใสอย่างแท้จริง
Bitcoin: ก้าวกระโดดของเทคโนโลยีเงิน
- โปรแกรมที่โปร่งใส: Bitcoin ใช้เทคโนโลยี blockchain ซึ่งทำให้ทุกธุรกรรมถูกบันทึกไว้อย่างโปร่งใสและตรวจสอบได้ ทุกคนที่เชื่อมต่อกับเครือข่ายสามารถเข้าถึงข้อมูลได้ โดยไม่มีใครแก้ไขได้เองตามอำเภอใจ
-
ไม่มีคนกลาง: การทำธุรกรรมผ่าน Bitcoin ไม่ต้องผ่านธนาคารหรือผู้ควบคุม ทำให้ลดค่าใช้จ่ายและเพิ่มความเร็วในการแลกเปลี่ยน
-
ความปลอดภัย: ระบบของ Bitcoin ใช้การเข้ารหัสขั้นสูง และเครือข่ายกระจายศูนย์ เพื่อป้องกันการปลอมแปลงหรือการโจมตี ทำให้ปลอดภัยกว่าเงินสดหรือบัตรเครดิต
-
จำกัดจำนวน: ต่างจากเงินกระดาษที่รัฐบาลสามารถพิมพ์เพิ่มได้ Bitcoin ถูกออกแบบมาให้มีจำนวนจำกัดที่ 21 ล้านเหรียญ ซึ่งช่วยป้องกันภาวะเงินเฟ้อและรักษามูลค่าของมันในระยะยาว
ผลกระทบต่อเศรษฐกิจและสังคม
-
สร้างระบบการเงินใหม่: Bitcoin เปิดโอกาสให้ผู้คนทั่วโลกเข้าถึงระบบการเงินได้อย่างเสรี โดยเฉพาะผู้ที่ไม่มีบัญชีธนาคารหรืออาศัยอยู่ในประเทศที่ระบบการเงินไม่เสถียร
-
ลดอำนาจของรัฐบาลและธนาคารกลาง: การที่ Bitcoin ไม่สามารถถูกควบคุมโดยองค์กรใดองค์กรหนึ่ง ทำให้ประชาชนมีอิสระในการจัดการทรัพย์สินของตัวเอง
-
กระตุ้นนวัตกรรม: Bitcoin เป็นตัวอย่างที่แสดงให้เห็นว่าเทคโนโลยีสามารถเปลี่ยนแปลงวิธีการแลกเปลี่ยนมูลค่าได้ และยังช่วยกระตุ้นการพัฒนาของเทคโนโลยีอื่นๆ เช่น smart contract และ DeFi
เงินสด VS Bitcoin: อะไรคือตัวเลือกสำหรับอนาคต?
ในขณะที่เงินสดยังคงเป็นที่นิยมในปัจจุบัน แต่ Bitcoin กำลังเปลี่ยนแปลงแนวคิดของเราเกี่ยวกับเงินโดยสิ้นเชิง หากเรามองเงินเป็นเพียงเครื่องมือสำหรับการแลกเปลี่ยน Bitcoin คือการพัฒนาที่ตอบโจทย์โลกยุคดิจิทัลที่กำลังเปลี่ยนแปลงอย่างรวดเร็ว
แล้วคุณล่ะ คิดว่า Bitcoin เป็นเทคโนโลยีที่จะเปลี่ยนอนาคตของเงิน หรือเป็นเพียงปรากฏการณ์ชั่วคราว? มาร่วมแชร์ความคิดเห็นของคุณในโพสต์นี้!
-
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28litepub
A Go library that abstracts all the burdensome ActivityPub things and provides just the right amount of helpers necessary to integrate an existing website into the "fediverse" (what an odious name). Made for the gravity integration.
See also
-
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28IPFS problems: Shitcoinery
IPFS was advertised to the Ethereum community since the beggining as a way to "store" data for their "dApps". I don't think this is harmful in any way, but for some reason it may have led IPFS developers to focus too much on Ethereum stuff. Once I watched a talk showing libp2p developers – despite being ignored by the Ethereum team (that ended up creating their own agnostic p2p library) – dedicating an enourmous amount of work on getting a libp2p app running in the browser talking to a normal Ethereum node.
The always somewhat-abandoned "Awesome IPFS" site is a big repository of "dApps", some of which don't even have their landing page up anymore, useless Ethereum smart contracts that for some reason use IPFS to store whatever the useless data their users produce.
Again, per se it isn't a problem that Ethereum people are using IPFS, but it is at least confusing, maybe misleading, that when you search for IPFS most of the use-cases are actually Ethereum useless-cases.
See also
- Bitcoin, the only non-shitcoin
-
 @ 68fa45dc:3d2a26ed
2024-12-19 04:04:55
@ 68fa45dc:3d2a26ed
2024-12-19 04:04:55Störsender, die früher häufig für militärische Zwecke eingesetzt wurden, spielen heute auch im zivilen Bereich eine immer wichtigere Rolle. Die Entwicklung dieser Technologie hat viele Wendungen durchgemacht. Von den anfänglichen militärischen Anforderungen bis hin zu heutigen zivilen Szenarien hat sie kontinuierliche technologische Innovationen und eine Ausweitung ihres Anwendungsbereichs erfahren. In diesem Artikel geht es um die Geschichte der Signal Jammer Störsender, ihren Übergang von der militärischen zur zivilen Nutzung und um zukünftige Entwicklungstrends.
Militärische Anwendungen Sonderverkauf Neue Tragbare 5G Handy Störsendern
Störsender für Mobiltelefone kamen ursprünglich im militärischen Bereich als elektronische Störgeräte zum Einsatz, die dazu dienten, feindliche Kommunikationssysteme zu stören und deren Kommunikationsverbindungen, Befehlssysteme usw. zu zerstören. Auf dem Schlachtfeld ist die Bedeutung der Kommunikation offensichtlich und Störsender für Mobiltelefone können die Kommunikationsausrüstung des Gegners wirksam stören und der eigenen Seite dabei helfen, strategische Vorteile zu erlangen. Ursprünglich wurde diese Technologie hauptsächlich von staatlichen Militärbehörden beherrscht und genutzt, und ihre Anwendungsbereiche waren auf militärische Operationen und bestimmte Sicherheitsbereiche beschränkt.
Der Aufstieg ziviler Anwendungen Mit dem technischen Fortschritt und der gesellschaftlichen Entwicklung werden Handy Dienst Störsender zunehmend auch im zivilen Bereich eingesetzt. In bestimmten Fällen, wie z. B. in Gefängnissen, Konferenzräumen, Theatern usw., werden Störsender für Mobiltelefondienste eingesetzt, um zu verhindern, dass drahtlose Kommunikationsgeräte die Umwelt stören oder Sicherheitsrisiken bergen. Sie dienen dazu, Mobiltelefonsignale abzuschirmen und Ordnung und Sicherheit zu gewährleisten. . Darüber hinaus ist an bestimmten sensiblen Orten und bei bestimmten Aktivitäten die Nutzung von Mobiltelefonen verboten. Hier werden Störsender für Mobiltelefone zu einem wirksamen Managementinstrument.
Technologische Innovation bringt diversifizierte Entwicklung Mit dem fortschreitenden technologischen Fortschritt erweitern und diversifizieren sich auch die Funktionen und Anwendungen von Störsendern für Mobilfunkdienste. Herkömmliche Störsender können normalerweise nur Telefonsignale blockieren, doch die heutigen Bluetooth Jammer verfügen über mehr Funktionen, beispielsweise das Blockieren von WLAN, Bluetooth, Ortung und anderen Signalen. Dadurch können Störsender für Mobilfunkdienste in mehr Szenarien eingesetzt werden. Sie erfüllen nicht nur die grundlegenden Anforderungen an Kommunikationsstörsender, sondern schützen auch umfassender die Informationssicherheit und die Ordnung am Veranstaltungsort.
Zukunftsaussichten Mit der zunehmenden Verbreitung und Entwicklung neuer Technologien wie 5G und dem Internet der Dinge stehen Auto GPS Tracker künftig vor neuen Herausforderungen und Chancen. Die Anwendungsszenarien werden umfangreicher sein und unter anderem die industrielle Produktion, das Smart Home und das Verkehrsmanagement umfassen. Gleichzeitig werden mit der kontinuierlichen Weiterentwicklung der Technologie die Funktionen von Störsendern für Mobiltelefone weiter ausgebaut und verbessert. Sie werden präziser und intelligenter und bieten eine bessere Unterstützung und Gewährleistung für die Entwicklung aller Aspekte der Gesellschaft.
Die Entwicklung von Störsendern für Mobiltelefone vom militärischen zum zivilen Einsatz verdeutlicht die länderübergreifende Anwendung der Technologie und die führende Rolle sozialer Bedürfnisse. Seine Entwicklung leistet nicht nur wichtige Unterstützung für die militärische Sicherheit, sondern bringt auch neue Lösungen für das Sozialmanagement und die Informationssicherheit. Auch in Zukunft dürften Störsender für den Mobilfunk eine wichtige Rolle bei der Weiterentwicklung der Gesellschaft spielen.
Abschluss Die Entwicklung von HF Detektor spiegelt die kontinuierliche Förderung der wissenschaftlichen und technologischen Entwicklung und die Ausrichtung an den Anwendungsanforderungen wider. Der Übergang von der militärischen zur zivilen Nutzung hat gezeigt, welche Kraft in der grenzübergreifenden Anwendung von Technologie steckt und welche treibende Kraft hinter Innovationen steckt. Auch in Zukunft werden Störsender für den Mobilfunk eine wichtige Unterstützung für die gesellschaftliche Entwicklung und Sicherheit sein und zu einem unverzichtbaren Bestandteil des Informationszeitalters werden. Mögen wir weiterhin Innovation und Fortschritt anstreben, während wir die Grenzen von Wissenschaft und Technologie ausloten und gemeinsam eine bessere Zukunft schaffen.
-
 @ a012dc82:6458a70d
2024-12-19 03:48:56
@ a012dc82:6458a70d
2024-12-19 03:48:56Table Of Content
-
Who is Michael Burry?
-
Burry's Recent Move and its Implications
-
Bitcoin's Recent Performance and Future Prospects
-
The Broader Economic Context
-
Conclusion
-
FAQ
In the ever-evolving world of cryptocurrencies, the name Michael Burry might not be the first that comes to mind. However, recent developments have thrust him into the spotlight, making many in the crypto community sit up and take notice. So, what's all the fuss about Michael Burry's stance on Bitcoin's price?
Who is Michael Burry?
For those unfamiliar, Michael Burry is an American investor renowned for his prediction of the 2008 subprime mortgage crisis, which led to a global recession. His foresight and investment strategies during that period were so notable that they were depicted in the movie "The Big Short."
Burry's Recent Move and its Implications
Recently, a filing with the US Securities and Exchanges Commission (SEC) revealed that Scion Asset Management, a firm associated with Burry, has taken a significant bearish position on the US stock markets. Specifically, the firm has placed bets predicting a decline in major stock indices, including the Nasdaq 100 and the S&P 500. The numbers are staggering: $740 million worth of Invesco QQQ Trust Series 1 puts and $900 million worth of S&P 500 puts. These bets constitute about 93% of Burry's total portfolio value.
Now, you might wonder, what does this have to do with Bitcoin? The connection lies in the potential ripple effects of these bets. If the US stock market does experience a decline, as Burry seems to anticipate, it could lead to a bullish run for Bitcoin. The reasoning behind this is that traders might view Bitcoin as a high-risk, high-reward investment alternative to traditional stocks.
Bitcoin's Recent Performance and Future Prospects
Bitcoin has been experiencing a prolonged sideways movement, testing the patience of many traders. Historically, such sideways movements in the crypto market have sometimes been followed by a significant jump in value. Additionally, there's growing optimism about the potential approval of a Bitcoin ETF in the coming months, which could further boost its price.
The Broader Economic Context
In understanding Burry's moves and their potential impact on Bitcoin, it's essential to consider the broader economic landscape. The U.S. central bank, the Federal Reserve, is currently in a position where they might not increase the interest rate in the upcoming September FOMC meeting, as gauged by the CME FedWatch Tool. Historically, low-interest rates have often led to increased investment in riskier assets, as investors search for higher returns. This environment could further bolster the appeal of cryptocurrencies like Bitcoin, especially if traditional stock markets become more volatile or start to decline.
Furthermore, other global events, such as the US regional bank crisis that erupted earlier in 2023, have shown that Bitcoin can sometimes act as a hedge or alternative investment during times of traditional market stress. As such, the broader economic context, combined with Burry's predictions, paints a fascinating picture for Bitcoin's potential trajectory in the near future.
Conclusion
While Michael Burry's recent moves primarily concern the US stock market, the potential implications for the crypto market, and Bitcoin in particular, are significant. If Burry's predictions come to fruition, and the US stock market sees a decline, it could be a pivotal moment for Bitcoin and its investors. As always, the world of investments is unpredictable, but with big names like Burry making such moves, it's an exciting time for observers and participants alike.
FAQ
Who is Michael Burry? Michael Burry is an American investor known for predicting the 2008 subprime mortgage crisis. He was prominently featured in the movie "The Big Short."
What has Burry recently predicted about the US stock market? Burry's firm, Scion Asset Management, has placed significant bets predicting a decline in major US stock indices, including the Nasdaq 100 and the S&P 500.
How might Burry's predictions affect Bitcoin's price? If the US stock market declines as Burry anticipates, it could lead to a bullish run for Bitcoin, with traders viewing it as a high-risk, high-reward alternative to stocks.
What is the broader economic context influencing Bitcoin? The Federal Reserve's potential decision not to increase interest rates, combined with global events like the US regional bank crisis, could influence Bitcoin's appeal as an alternative investment.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28tempreites
My first library to get stars on GitHub, was a very stupid templating library that used just HTML and HTML attributes ("DSL-free"). I was inspired by http://microjs.com/ at the time and ended up not using the library. Probably no one ever did.
-
 @ b81776c3:4ef76c2a
2024-12-19 02:31:51
@ b81776c3:4ef76c2a
2024-12-19 02:31:51How To Sell Your Bitcoin
Selling Bitcoin isn’t just a transaction—it’s a strategy. Whether you're liquidating for necessity or rebalancing your portfolio, how you sell matters as much as why.Understand the Market Dynamics
Bitcoin operates in a decentralised marketplace where prices are influenced by supply, demand, and holder behaviour. Unlike traditional assets, Bitcoin’s value is shaped by those with long-term conviction.Sell With Discipline
The golden rule: never accept Bids unless absolutely necessary. Bids represent the buyer’s highest offer and the spread will undervalue your Bitcoin. Instead, set an Ask price at or above the current market bid. Patience is key; by holding your Ask, you let the market rise to meet you.Timing Matters
Assess your financial needs and market conditions. Selling during periods of high volatility or at the height of media frenzy may result in suboptimal outcomes. Instead, focus on long-term trends and avoid impulsive decisions.Use Reputable Platforms
Choose exchanges or platforms with high liquidity and strong security. Ensure you understand their fee structures and withdrawal policies to maximise your returns.Tax Implications
In some jurisdictions, selling Bitcoin is a taxable event. Familiarise yourself with local tax laws, reporting requirements, and strategies to minimise your tax liability, such as holding periods for capital gains benefits.The Strategic Hold
Sometimes, the best way to sell is not to sell at all. Bitcoin’s unique position as a deflationary asset often rewards those who can wait. By participating in the rise of the lowest Ask, you contribute to price stability and ensure a stronger market.Conclusion
Selling Bitcoin is as much about mindset as it is about mechanics. By approaching the process with discipline, patience, and strategy, you can maximise your returns while respecting the broader market's integrity. Bitcoin, ultimately, rewards those with the resolve to see its long-term potential.
originally posted at https://stacker.news/items/815334
-
 @ 6bae33c8:607272e8
2024-12-18 21:26:40
@ 6bae33c8:607272e8
2024-12-18 21:26:40I went 2-3 last week, am drawing dead in the Circa Millions and have run my record down to .500 at 37-37-1. Best case, I can salvage a respectable record, but that $1000 is gone for good.
Broncos at Chargers — I feel a buy-low on the Chargers here after a couple losses. Let’s say Broncos +4, and I’m laying the wood.
Texans at Chiefs — Obviously this one depends on whether Patrick Mahomes plays. He practiced in full, so assuming he plays, I’d say Texans plus 6.5 and lean KC.
Steelers at Ravens — The Steelers won the first matchup, but the Ravens are far better. I’d say Steelers plus 6.5 and take the Ravens.
Giants at Falcons — The Falcons are whipping out 12-inch, and he probably won’t be worse than Cousins. I’ll say Giants plus 7.5 and stay away.
Lions at Bears — A get well game for the Lions, and I think they bounce back a bit. Let’s make it Lions -5.5 and stay away.
Browns at Bengals — Jameis Winston is benched, and I don’t know that Dorian Thompson-Robinson has shown anything to get excited about. I’ll make it Browns +10 and lay the wood.
Titans at Colts — The Titans are giving up by switching to veteran Mason Rudolph, even if it’s better in the short term. I’ll say Titans +7 and probably stay away.
Rams at Jets — The Jets offense has come to life of late, but the defense has been poor. I’ll say Rams -2.5 and stay away.
Eagles at Killer Redskins — The Eagles are rolling, and the KRs are treading water. I’ll make it Eagles -3 and stay away.
Cardinals at Panthers — The Cardinals are average, the Panthers below average but tend to show up. I’ll say Cardinals -3 and stay away.
Vikings at Seahawks — Assuming Geno Smith plays, I’ll make it Vikings -2.5 and probably stay away, though if anything I’d lay the wood.
Patriots at Bills — This is a trap game off the Bills big win. I’ll say Patriots +15.5 and stay away.
Jaguars at Raiders — This is a bum fight. I’ll make it a pick ‘em and steer clear.
49ers at Dolphins — Both teams are done after last week. I’ll say 49ers +2.5 and lean 49ers.
Buccaneers at Cowboys — The Bucs are playing well, but so are the Cowboys. I’ll say Buccaneers -2.5 and stay away.
Saints at Packers — With Derek Carr likely done, I’ll make it Saints +10.5 and lay the wood.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28nix
Pra instalar o neuron fui forçado a baixar e instalar o nix. Não consegui me lembrar por que não estava usando até hoje aquele maravilhoso sistema de instalar pacotes desde a primeira vez que tentei, anos atrás.
Que sofrimento pra fazer funcionar com o
fish, mas até que bem menos sofrimento que da outra vez. Tive que instalar um tal defish-foreign-environment(usando o próprio nix!, já que a outra opção era ooh-my-fishou qualquer outra porcaria dessas) e aí usá-lo para aplicar as definições de shell para bash direto nofish.E aí lembrei também que o
/nix/storefica cheio demais, o negócio instala tudo que existe neste mundo a partir do zero. É só para computadores muito ricos, mas vamos ver como vai ser. Estou gostando do neuron (veja, estou usando como diário), então vou ter que deixar o nix aí. -
 @ ac8bb9b0:70278acc
2024-12-18 21:18:57
@ ac8bb9b0:70278acc
2024-12-18 21:18:57Details
- ⏲️ Prep time: 10
- 🍳 Cook time: 20
- 🍽️ Servings: 5
Ingredients
- 8 ounces uncooked linguine
- 1 pound chicken breast, cut into strips
- 1-2 tsp Cajun seasoning, or more to taste
- 1 tsp garlic powder
- 1 tbsp extra virgin olive oil
- 1 medium red bell pepper, thinly sliced
- 1 medium yellow bell pepper, thinly sliced
- 8 oz fresh mushrooms, sliced
- 1/2 red onion, sliced
- 3 cloves garlic, minced
- 2 tomatoes, diced
- 1 cup low sodium chicken broth
- 1/3 cup skim milk
- 1 tbsp flour
- 3 tbsp light cream cheese
- fresh cracked pepper
- 2 scallions, chopped
- kosher salt to taste
- avocado oil spray
Directions
- Prep all your vegetables.
- In a small blender make a slurry by combining milk, flour and cream cheese. Set aside.
- Season chicken generously with Cajun seasoning, garlic powder and salt.
- Prepare pasta in salted water according to package directions.
- Heat a large heavy nonstick skillet over medium-high heat; spray with oil and add half of the chicken.
- Sauté 5 to 6 minutes or until done, set aside on a plate and repeat with the remaining chicken. Set aside.
- Add olive oil to the skillet and reduce to medium; add bell peppers, onions, and garlic to skillet, sauté 3-4 minutes.
- Add mushrooms and tomatoes and sauté 3-4 more minutes or until vegetables are tender.
- Season with 1/4 tsp salt, garlic powder and fresh cracked pepper to taste.
- Reduce heat to medium-low; add chicken broth and pour in slurry stirring about 2 minutes.
- Return chicken to skillet; adjust salt and Cajun seasoning to taste, cook another minute or two until hot, then add linguine; toss well to coat.
- Top with chopped scallions and enjoy!
-
 @ 04c915da:3dfbecc9
2023-09-26 17:34:13
@ 04c915da:3dfbecc9
2023-09-26 17:34:13For years American bitcoin miners have argued for more efficient and free energy markets. It benefits everyone if our energy infrastructure is as efficient and robust as possible. Unfortunately, broken incentives have led to increased regulation throughout the sector, incentivizing less efficient energy sources such as solar and wind at the detriment of more efficient alternatives.
The result has been less reliable energy infrastructure for all Americans and increased energy costs across the board. This naturally has a direct impact on bitcoin miners: increased energy costs make them less competitive globally.
Bitcoin mining represents a global energy market that does not require permission to participate. Anyone can plug a mining computer into power and internet to get paid the current dynamic market price for their work in bitcoin. Using cellphone or satellite internet, these mines can be located anywhere in the world, sourcing the cheapest power available.
Absent of regulation, bitcoin mining naturally incentivizes the build out of highly efficient and robust energy infrastructure. Unfortunately that world does not exist and burdensome regulations remain the biggest threat for US based mining businesses. Jurisdictional arbitrage gives miners the option of moving to a friendlier country but that naturally comes with its own costs.
Enter AI. With the rapid development and release of AI tools comes the requirement of running massive datacenters for their models. Major tech companies are scrambling to secure machines, rack space, and cheap energy to run full suites of AI enabled tools and services. The most valuable and powerful tech companies in America have stumbled into an accidental alliance with bitcoin miners: THE NEED FOR CHEAP AND RELIABLE ENERGY.
Our government is corrupt. Money talks. These companies will push for energy freedom and it will greatly benefit us all.
-
 @ 56494b83:aa95511b
2024-12-18 20:58:02
@ 56494b83:aa95511b
2024-12-18 20:58:02we are going to look at a very short story (4 verses) that will help us to know Jesus better. Matthew 17: 24-27. A theologian from a long time ago said about this story:
“This story is a nut with a dry, hard shell, but a very sweet kernel” I hope that in 20 minutes you will agree with him!
Matthew 17:24-27. 24 When they came to Capernaum, the collectors of the two-drachma tax went up to Peter and said, “Does your teacher not pay the tax?” 25 He said, “Yes.” And when he came into the house, Jesus spoke to him first, saying, “What do you think, Simon? From whom do kings of the earth take toll or tax? From their sons or from others?” 26 And when he said, “From others,” Jesus said to him, “Then the sons are free. 27 However, not to give offense to them, go to the sea and cast a hook and take the first fish that comes up, and when you open its mouth you will find a shekel. Take that and give it to them for me and for yourself.”
So I have 3 brief points: I want to examine The Son’s Claim The Son’s power The Son’s attitude
Jesus and his followers are in capernaum: jesus' home base/headquarters Tax collectors show up and ask Peter if Jesus will Pay the TEMPLE TAX (not a civil tax) this is based on exodus 30: The Lord said to Moses, “When you take the census of the people of Israel. . . Everyone who is numbered in the census, from twenty years old and upward, shall give. . . the half shekel. . . for the service of the tent of meeting, that it may bring the people of Israel to remembrance before the Lord, so as to make atonement for your lives.” Ex 30:12-16 This money was given for temple services. (Upkeep for the Temple in Jerusalem) When asked about it Peter says “yes” — “to be sure he does!” (peter probably knew Jesus did not have the money….so this may be an example of great faith) We also know that Jesus came “not to abolish the law…but to fulfill it”
Peter comes into his own house, Jesus was most likely staying with him and his family. Jesus speaks to him first (omniscience) Jesus’s primary way of teaching is by asking questions. I love that. I want to get better at this. “peter I have a question for you: when a king collects taxes, does he collect the money from his children or from the regular citizens?”Peter: regular citizens Jesus: the the children are free. They dont have to pay. This would be absurd. Do you see the claim that Jesus is making ? “A stronger claim to essential Divinity than our Lord in this scene at Capernaum advances—as “own Son” of the Lord of the Temple—cannot well be conceived.” David Brown You see this wasn’t a civil tax. This was an ecclesiastical tax. It was for the temple. For the church. GOD’s house. Here’s how we might translate what Jesus us saying: “This is a tax for upholding My Father’s House: As His Son, I am exempt!—I am free.”
Behold, I send my messenger, and he will prepare the way before me. And the Lord whom you seek will suddenly come to his temple; and the messenger of the covenant in whom you delight, behold, he is coming, says the Lord of hosts. (Malachi 3:1) In one simple illustration, Jesus makes the divine claim. I am the son of God. Earlier in Matthew Jesus made another remarkable claim: “I tell you, something greater than the temple is here.” Matthew 12:6
Yesterday I was in the car with my kids: and one of them asked me about why priests killed animals in the Bible.
God takes sin very seriously! The wages of sin is death! So God set up a system where animals (lambs, bulls, goats) would be killed in the place of the sinner.
These sacrifices always took place AT THE TEMPLE. And the priests (from the tribe of Levi) were the ones that did this work.
So if I wanted my sin forgiven, if I wanted to be reconciled to God, this is where I had to go, and what I had to do. I had to go to the temple was the dwelling place of God.
temple= God’s house.
.and here comes Jesus: the temple is my father’s house.
But then he says something even more astonishing. I am new the new temple>> access to God comes through me.
My daughter Lauren said: “oh yah, when Jesus died the temple curtain was torn in half!” Exactly right. No more. Animal sacrifices. “Behold the lamb of God..who takes away the sin of the world!” Access to GOD comes through faith in Jesus Christ. He is our mediator. He is our go-between. He is our priest. I dont have to go somewhere specific.
“Spirit and truth?” (Woman at the well)
All of this is implied in Jesus’ words: I dont need to pay tax to my father.
Love the lord your God with all your heart, mind, soul, strength — Jesus is the SON of GOD. He is worthy of your love! Adoration. Worship.
Next let’s BEHOLD the Divine Son of God’s Power:
We see omniscience in verse 25. Jesus speaks to him first. He knows what happened. (there is nothing that can happen to you or to me and the LORD does not already know it!)
Lets pause here and marvel at the miracle. This is the only miracle recorded in the scriptures that directly benefits Christ.
Lets read it again:
“go to the sea and cast a hook and take the first fish that comes up, and when you open its mouth you will find a shekel. Take that and give it to them for me and for yourself.” (Mt 17:27)
The number of details that Jesus knew and was in control of is incredible. The coin itself. It fell into the water (right?). someone dropped it or lost it.
A fish gobbled it up, but didn’t actually swallow it. “go to the sea!” That is so vague. non-specific. It doesn’t matter where you cast from peter. I will command the fish to go exactly where you are. The fish bit the hook, while keeping the coin in its mouth, (even as he reeled it in). 5. Its the exact amount for 2 people. what can we learn? Jesus is LORD of nature. All creatures, including fish do his bidding. God can provide for you any way he pleases. His resources are inexhaustible. His creativity is unlimited.Please also notice that the miracle involved Peter in a significant way. Peter has something to do. He had to obey Jesus commands. Jesus incorporated the skills that Peter already possessed. It involved action. Get up. Get the tools. Walk to the water. Cast the line. Reel it in.
“Miracles are usually preceded by faith and obedience.”
Luke 17 — 10 men with a terrible skin disease crying out: “Jesus, master! Have mercy on us!” What does Jesus say? Luke 17:14 (ESV) 14When he saw them he said to them, “Go and show yourselves to the priests.” And as they went they were cleansed.
The usual way that God works: he says Believe in me Obey what I say Watch what I do!
Ask for faith and then obey Jesus. I think you will be surprised what god does.
Also notice that the amount of money was just what was needed and no more.
1 Timothy 6:8 (ESV) 8But if we have food and clothing, with these we will be content.
Let us learn to be content when God provides what we need for today!
John marcarther quote about the fish: I have to believe that he threw the fish back. You can’t waste a fish like that. In fact, that fish may be in heaven; I don’t know. Swimming in the River of Life for all I know. Marvelous fish. In the Old Testament, God used a big one; in the New Testament He used a little one.
So we have seen his claim- I man the Son of God. The result must be praise and worship. We have seen the power of Jesus. Let us respond with obedience and faith.
Let’s look at the attitude of Christ. Jesus has already made it clear: I’m the son. Son’s dont pay taxes to their dads. What’s really amazing is that chapter 18 begins:
At that time the disciples came to Jesus, saying, “Who is the greatest in the kingdom of heaven?” (Mt 18:1)
The disciples are self-absorbed. Contrast that with jesus. Just consider what he could have said. “if I were looking for honor, completely focused on asserting my own importance, I could tell those tax collectors who I am. I could embarrass them. Shame them.”
He pays tribute, therefore, but taken from a fishes mouth, that his majesty may be recognized
But he doesn’t do that. Christ stoops low. This is what he always does. He is humble. He is lowly. He is the suffering servant. The eternal son of God, willing to take on human flesh. “Foxes have holes, and birds of the air have nests, but the Son of Man has nowhere to lay his head.” Mt 8:20)
He had to borrow a barn in which he was born. He had to borrow a boat to preach from. Had to borrow a donkey to ride on during his own coronation. Borrow a room for the passover supper. Borrow a tomb to be buried in (for 3 days!) He was dependent on others for basic needs. Luke 8 - there were many women who provided for HIM out of their means. (Lk 8:1–3)
As AB Bruce says: the life of Christ was one grand indignity from beginning to end.
Christ was so humble. He came not to be served but to give his life for us.
This is an important idea for you and me to grasp: Jesus demands our obedience. Our allegiance. But he’s not standing over us like a tyrant! He is meek. Kind. Humble. Gracious. We love him because he first loved us!
Most people (maybe you?) are so easily offended.
Did you hear what that person said? I cant believe how I was treated. She looked at me the wrong way. I’m going to get them back. Vengeance is mine!
But contrast that type of mindset with that of Jesus Christ
One reason why Jesus wasn’t offended: he knew who he was. Who knew the declaration his father had made up on the mountain. (transfiguration) behold, a bright cloud overshadowed them, and a voice from the cloud said, “This is my beloved Son, with whom I am well pleased; (Mt 17:5)
My identity: I AM A SON OF THE KING. He has called me Redeemed me Forgiven me. Adopted me into his family. Sealed me with his Holy Spirit. Promised me eternal life.
If that is true:
The attitude of Jesus was one of humility. What kind of church would we become if that was our default disposition?
But its not just that Christ doesn’t take offense. He doesn’t give offense either.
27 However, not to give offense to them (Mt 17:27).
He knew that by asserting his rights in this moment, he’d be creating a stumbling block for the people to trip over. He uses the plural: “so that we do not offend them.” Teaching Peter a valuable lesson.
The gospel of Christ is offensive, and we must never shy away from making it clear. But we must not offend by insisting on what we think we deserve.
Jesus doesn’t take offense He doesn’t give offense. He came to cancel offenses.
And how did he do that? He canceled our sins my paying for them himself. “give it to them for me and for yourself.”
What a picture of what Christ does for us: we owe what we cannot pay. God-in-Christ pays for us. Our great high priest> who is himself LORD of nature and at the same time the dwelling place, the access point to God (temple)
Destroy hostility. To reconcile us to God and to each other.
A few questions: Do you make beholding the glory of christ a priority? If not confess this as sin and repent. Is there a command of Jesus that you haven’t obeyed? Ask the holy spirit to reveal any unbelief or disobedience. Are you someone that is easily offended? Perhaps tonight is a night where you learn from Jesus and grow in humility.
-
 @ a17fb4ed:c53f7e91
2024-12-18 20:03:18
@ a17fb4ed:c53f7e91
2024-12-18 20:03:18Here is a little poem for the upcoming January 1, 2025 IRS Safe Harbor:
Wallet, Exchange - where do I begin?\ Allocating my bitcoin, what a din!\ Specific units or global, which way to go?\ Decisions, decisions, my head starts to blow.
Quantity, cost basis, I must take note,\ Tracking each asset, like a sailor at sea, afloat.\ Opentimestamp the proof, to show I've done my part,\ Sailing into safe harbor, before I depart.
FIFO or Spec ID, which method to choose?\ Gains and losses, I must not lose.\ Consolidate holdings, simplify the fray,\ Lest the IRS come and take it all away.
Who's on first, what's on second, I just don't know,\ Filling out this spreadsheet, my bitcoin woes.\ But if I follow the steps, laid out so clear,\ The safe harbor awaits, no need to fear.
Ok, for real though, What the Fuck!?! It's a public ledger and all amounts and dates are forever recorded. Way to make this much more complicated and time consuming than need be. Classic!
Clear as mud. At least this might get more folk to self custody.
Here are couple links that might help a smidge:
What US Taxpayers With Crypto NEED to do before Dec 31, 2024 - Get into the Safeharbor!
Cheers, Yooper
-
 @ e6ce6154:275e3444
2023-07-27 14:12:49
@ e6ce6154:275e3444
2023-07-27 14:12:49Este artigo foi censurado pelo estado e fomos obrigados a deletá-lo após ameaça de homens armados virem nos visitar e agredir nossa vida e propriedade.
Isto é mais uma prova que os autoproclamados antirracistas são piores que os racistas.
https://rothbardbrasil.com/pelo-direito-de-ser-racista-fascista-machista-e-homofobico
Segue artigo na íntegra. 👇
Sem dúvida, a escalada autoritária do totalitarismo cultural progressista nos últimos anos tem sido sumariamente deletéria e prejudicial para a liberdade de expressão. Como seria de se esperar, a cada dia que passa o autoritarismo progressista continua a se expandir de maneira irrefreável, prejudicando a liberdade dos indivíduos de formas cada vez mais deploráveis e contundentes.
Com a ascensão da tirania politicamente correta e sua invasão a todos os terrenos culturais, o autoritarismo progressista foi se alastrando e consolidando sua hegemonia em determinados segmentos. Com a eventual eclosão e a expansão da opressiva e despótica cultura do cancelamento — uma progênie inevitável do totalitarismo progressista —, todas as pessoas que manifestam opiniões, crenças ou posicionamentos que não estão alinhados com as pautas universitárias da moda tornam-se um alvo.
Há algumas semanas, vimos a enorme repercussão causada pelo caso envolvendo o jogador profissional de vôlei Maurício Sousa, que foi cancelado pelo simples fato de ter emitido sua opinião pessoal sobre um personagem de história em quadrinhos, Jon Kent, o novo Superman, que é bissexual. Maurício Sousa reprovou a conduta sexual do personagem, o que é um direito pessoal inalienável que ele tem. Ele não é obrigado a gostar ou aprovar a bissexualidade. Como qualquer pessoa, ele tem o direito pleno de criticar tudo aquilo que ele não gosta. No entanto, pelo simples fato de emitir a sua opinião pessoal, Maurício Sousa foi acusado de homofobia e teve seu contrato rescindido, sendo desligado do Minas Tênis Clube.
Lamentavelmente, Maurício Sousa não foi o primeiro e nem será o último indivíduo a sofrer com a opressiva e autoritária cultura do cancelamento. Como uma tirania cultural que está em plena ascensão e usufrui de um amplo apoio do establishment, essa nova forma de totalitarismo cultural colorido e festivo está se impondo de formas e maneiras bastante contundentes em praticamente todas as esferas da sociedade contemporânea. Sua intenção é relegar ao ostracismo todos aqueles que não se curvam ao totalitarismo progressista, criminalizando opiniões e crenças que divergem do culto à libertinagem hedonista pós-moderna. Oculto por trás de todo esse ativismo autoritário, o que temos de fato é uma profunda hostilidade por padrões morais tradicionalistas, cristãos e conservadores.
No entanto, é fundamental entendermos uma questão imperativa, que explica em partes o conflito aqui criado — todos os progressistas contemporâneos são crias oriundas do direito positivo. Por essa razão, eles jamais entenderão de forma pragmática e objetiva conceitos como criminalidade, direitos de propriedade, agressão e liberdade de expressão pela perspectiva do jusnaturalismo, que é manifestamente o direito em seu estado mais puro, correto, ético e equilibrado.
Pela ótica jusnaturalista, uma opinião é uma opinião. Ponto final. E absolutamente ninguém deve ser preso, cancelado, sabotado ou boicotado por expressar uma opinião particular sobre qualquer assunto. Palavras não agridem ninguém, portanto jamais poderiam ser consideradas um crime em si. Apenas deveriam ser tipificados como crimes agressões de caráter objetivo, como roubo, sequestro, fraude, extorsão, estupro e infrações similares, que representam uma ameaça direta à integridade física da vítima, ou que busquem subtrair alguma posse empregando a violência.
Infelizmente, a geração floquinho de neve — terrivelmente histérica, egocêntrica e sensível — fica profundamente ofendida e consternada sempre que alguém defende posicionamentos contrários à religião progressista. Por essa razão, os guerreiros da justiça social sinceramente acreditam que o papai-estado deve censurar todas as opiniões que eles não gostam de ouvir, assim como deve também criar leis para encarcerar todos aqueles que falam ou escrevem coisas que desagradam a militância.
Como a geração floquinho de neve foi criada para acreditar que todas as suas vontades pessoais e disposições ideológicas devem ser sumariamente atendidas pelo papai-estado, eles embarcaram em uma cruzada moral que pretende erradicar todas as coisas que são ofensivas à ideologia progressista; só assim eles poderão deflagrar na Terra o seu tão sonhado paraíso hedonista e igualitário, de inimaginável esplendor e felicidade.
Em virtude do seu comportamento intrinsecamente despótico, autoritário e egocêntrico, acaba sendo inevitável que militantes progressistas problematizem tudo aquilo que os desagrada.
Como são criaturas inúteis destituídas de ocupação real e verdadeiro sentido na vida, sendo oprimidas unicamente na sua própria imaginação, militantes progressistas precisam constantemente inventar novos vilões para serem combatidos.
Partindo dessa perspectiva, é natural para a militância que absolutamente tudo que exista no mundo e que não se enquadra com as regras autoritárias e restritivas da religião progressista seja encarado como um problema. Para a geração floquinho de neve, o capitalismo é um problema. O fascismo é um problema. A iniciativa privada é um problema. O homem branco, tradicionalista, conservador e heterossexual é um problema. A desigualdade é um problema. A liberdade é um problema. Monteiro Lobato é um problema (sim, até mesmo o renomado ícone da literatura brasileira, autor — entre outros títulos — de Urupês, foi vítima da cultura do cancelamento, acusado de ser racista e eugenista).
Para a esquerda, praticamente tudo é um problema. Na mentalidade da militância progressista, tudo é motivo para reclamação. Foi em função desse comportamento histérico, histriônico e infantil que o famoso pensador conservador-libertário americano P. J. O’Rourke afirmou que “o esquerdismo é uma filosofia de pirralhos chorões”. O que é uma verdade absoluta e irrefutável em todos os sentidos.
De fato, todas as filosofias de esquerda de forma geral são idealizações utópicas e infantis de um mundo perfeito. Enquanto o mundo não se transformar naquela colorida e vibrante utopia que é apresentada pela cartilha socialista padrão, militantes continuarão a reclamar contra tudo o que existe no mundo de forma agressiva, visceral e beligerante. Evidentemente, eles não vão fazer absolutamente nada de positivo ou construtivo para que o mundo se transforme no gracioso paraíso que eles tanto desejam ver consolidado, mas eles continuarão a berrar e vociferar muito em sua busca incessante pela utopia, marcando presença em passeatas inúteis ou combatendo o fascismo imaginário nas redes sociais.
Sem dúvida, estamos muito perto de ver leis absurdas e estúpidas sendo implementadas, para agradar a militância da terra colorida do assistencialismo eterno onde nada é escasso e tudo cai do céu. Em breve, você não poderá usar calças pretas, pois elas serão consideradas peças de vestuário excessivamente heterossexuais. Apenas calças amarelas ou coloridas serão permitidas. Você também terá que tingir de cor-de-rosa uma mecha do seu cabelo; pois preservar o seu cabelo na sua cor natural é heteronormativo demais da sua parte, sendo portanto um componente demasiadamente opressor da sociedade.
Você também não poderá ver filmes de guerra ou de ação, apenas comédias românticas, pois certos gêneros de filmes exaltam a violência do patriarcado e isso impede o mundo de se tornar uma graciosa festa colorida de fraternidades universitárias ungidas por pôneis resplandecentes, hedonismo infinito, vadiagem universitária e autogratificação psicodélica, que certamente são elementos indispensáveis para se produzir o paraíso na Terra.
Sabemos perfeitamente, no entanto, que dentre as atitudes “opressivas” que a militância progressista mais se empenha em combater, estão o racismo, o fascismo, o machismo e a homofobia. No entanto, é fundamental entender que ser racista, fascista, machista ou homofóbico não são crimes em si. Na prática, todos esses elementos são apenas traços de personalidade; e eles não podem ser pura e simplesmente criminalizados porque ideólogos e militantes progressistas iluminados não gostam deles.
Tanto pela ética quanto pela ótica jusnaturalista, é facilmente compreensível entender que esses traços de personalidade não podem ser criminalizados ou proibidos simplesmente porque integrantes de uma ideologia não tem nenhuma apreciação ou simpatia por eles. Da mesma forma, nenhum desses traços de personalidade representa em si um perigo para a sociedade, pelo simples fato de existir. Por incrível que pareça, até mesmo o machismo, o racismo, o fascismo e a homofobia merecem a devida apologia.
Mas vamos analisar cada um desses tópicos separadamente para entender isso melhor.
Racismo
Quando falamos no Japão, normalmente não fazemos nenhuma associação da sociedade japonesa com o racismo. No entanto, é incontestável o fato de que a sociedade japonesa pode ser considerada uma das sociedades mais racistas do mundo. E a verdade é que não há absolutamente nada de errado com isso.
Aproximadamente 97% da população do Japão é nativa; apenas 3% do componente populacional é constituído por estrangeiros (a população do Japão é estimada em aproximadamente 126 milhões de habitantes). Isso faz a sociedade japonesa ser uma das mais homogêneas do mundo. As autoridades japonesas reconhecidamente dificultam processos de seleção e aplicação a estrangeiros que desejam se tornar residentes. E a maioria dos japoneses aprova essa decisão.
Diversos estabelecimentos comerciais como hotéis, bares e restaurantes por todo o país tem placas na entrada que dizem “somente para japoneses” e a maioria destes estabelecimentos se recusa ostensivamente a atender ou aceitar clientes estrangeiros, não importa quão ricos ou abastados sejam.
Na Terra do Sol Nascente, a hostilidade e a desconfiança natural para com estrangeiros é tão grande que até mesmo indivíduos que nascem em algum outro país, mas são filhos de pais japoneses, não são considerados cidadãos plenamente japoneses.
Se estes indivíduos decidem sair do seu país de origem para se estabelecer no Japão — mesmo tendo descendência nipônica legítima e inquestionável —, eles enfrentarão uma discriminação social considerável, especialmente se não dominarem o idioma japonês de forma impecável. Esse fato mostra que a discriminação é uma parte tão indissociável quanto elementar da sociedade japonesa, e ela está tão profundamente arraigada à cultura nipônica que é praticamente impossível alterá-la ou atenuá-la por qualquer motivo.
A verdade é que — quando falamos de um país como o Japão — nem todos os discursos politicamente corretos do mundo, nem a histeria progressista ocidental mais inflamada poderão algum dia modificar, extirpar ou sequer atenuar o componente racista da cultura nipônica. E isso é consequência de uma questão tão simples quanto primordial: discriminar faz parte da natureza humana, sendo tanto um direito individual quanto um elemento cultural inerente à muitas nações do mundo. Os japoneses não tem problema algum em admitir ou institucionalizar o seu preconceito, justamente pelo fato de que a ideologia politicamente correta não tem no oriente a força e a presença que tem no ocidente.
E é fundamental enfatizar que, sendo de natureza pacífica — ou seja, não violando nem agredindo terceiros —, a discriminação é um recurso natural dos seres humanos, que está diretamente associada a questões como familiaridade e segurança.
Absolutamente ninguém deve ser forçado a apreciar ou integrar-se a raças, etnias, pessoas ou tribos que não lhe transmitem sentimentos de segurança ou familiaridade. Integração forçada é o verdadeiro crime, e isso diversos países europeus — principalmente os escandinavos (países que lideram o ranking de submissão à ideologia politicamente correta) — aprenderam da pior forma possível.
A integração forçada com imigrantes islâmicos resultou em ondas de assassinato, estupro e violência inimagináveis para diversos países europeus, até então civilizados, que a imprensa ocidental politicamente correta e a militância progressista estão permanentemente tentando esconder, porque não desejam que o ocidente descubra como a agenda “humanitária” de integração forçada dos povos muçulmanos em países do Velho Mundo resultou em algumas das piores chacinas e tragédias na história recente da Europa.
Ou seja, ao discriminarem estrangeiros, os japoneses estão apenas se protegendo e lutando para preservar sua nação como um ambiente cultural, étnico e social que lhe é seguro e familiar, assim se opondo a mudanças bruscas, indesejadas e antinaturais, que poderiam comprometer a estabilidade social do país.
A discriminação — sendo de natureza pacífica —, é benévola, salutar e indubitavelmente ajuda a manter a estabilidade social da comunidade. Toda e qualquer forma de integração forçada deve ser repudiada com veemência, pois, mais cedo ou mais tarde, ela irá subverter a ordem social vigente, e sempre será acompanhada de deploráveis e dramáticos resultados.
Para citar novamente os países escandinavos, a Suécia é um excelente exemplo do que não fazer. Tendo seguido o caminho contrário ao da discriminação racional praticada pela sociedade japonesa, atualmente a sociedade sueca — além de afundar de forma consistente na lama da libertinagem, da decadência e da deterioração progressista — sofre em demasia com os imigrantes muçulmanos, que foram deixados praticamente livres para matar, saquear, esquartejar e estuprar quem eles quiserem. Hoje, eles são praticamente intocáveis, visto que denunciá-los, desmoralizá-los ou acusá-los de qualquer crime é uma atitude politicamente incorreta e altamente reprovada pelo establishment progressista. A elite socialista sueca jamais se atreve a acusá-los de qualquer crime, pois temem ser classificados como xenófobos e intolerantes. Ou seja, a desgraça da Europa, sobretudo dos países escandinavos, foi não ter oferecido nenhuma resistência à ideologia progressista politicamente correta. Hoje, eles são totalmente submissos a ela.
O exemplo do Japão mostra, portanto — para além de qualquer dúvida —, a importância ética e prática da discriminação, que é perfeitamente aceitável e natural, sendo uma tendência inerente aos seres humanos, e portanto intrínseca a determinados comportamentos, sociedades e culturas.
Indo ainda mais longe nessa questão, devemos entender que na verdade todos nós discriminamos, e não existe absolutamente nada de errado nisso. Discriminar pessoas faz parte da natureza humana e quem se recusa a admitir esse fato é um hipócrita. Mulheres discriminam homens na hora de selecionar um parceiro; elas avaliam diversos quesitos, como altura, aparência, status social, condição financeira e carisma. E dentre suas opções, elas sempre escolherão o homem mais atraente, másculo e viril, em detrimento de todos os baixinhos, calvos, carentes, frágeis e inibidos que possam estar disponíveis. Da mesma forma, homens sempre terão preferência por mulheres jovens, atraentes e delicadas, em detrimento de todas as feministas de meia-idade, acima do peso, de cabelo pintado, que são mães solteiras e militantes socialistas. A própria militância progressista discrimina pessoas de forma virulenta e intransigente, como fica evidente no tratamento que dispensam a mulheres bolsonaristas e a negros de direita.
A verdade é que — não importa o nível de histeria da militância progressista — a discriminação é inerente à condição humana e um direito natural inalienável de todos. É parte indissociável da natureza humana e qualquer pessoa pode e deve exercer esse direito sempre que desejar. Não existe absolutamente nada de errado em discriminar pessoas. O problema real é a ideologia progressista e o autoritarismo politicamente correto, movimentos tirânicos que não respeitam o direito das pessoas de discriminar.
Fascismo
Quando falamos de fascismo, precisamos entender que, para a esquerda política, o fascismo é compreendido como um conceito completamente divorciado do seu significado original. Para um militante de esquerda, fascista é todo aquele que defende posicionamentos contrários ao progressismo, não se referindo necessariamente a um fascista clássico.
Mas, seja como for, é necessário entender que — como qualquer ideologia política — até mesmo o fascismo clássico tem o direito de existir e ocupar o seu devido lugar; portanto, fascistas não devem ser arbitrariamente censurados, apesar de defenderem conceitos que representam uma completa antítese de tudo aquilo que é valioso para os entusiastas da liberdade.
Em um país como o Brasil, onde socialistas e comunistas tem total liberdade para se expressar, defender suas ideologias e até mesmo formar partidos políticos, não faz absolutamente o menor sentido que fascistas — e até mesmo nazistas assumidos — sofram qualquer tipo de discriminação. Embora socialistas e comunistas se sintam moralmente superiores aos fascistas (ou a qualquer outra filosofia política ou escola de pensamento), sabemos perfeitamente que o seu senso de superioridade é fruto de uma pueril romantização universitária da sua própria ideologia. A história mostra efetivamente que o socialismo clássico e o comunismo causaram muito mais destruição do que o fascismo.
Portanto, se socialistas e comunistas tem total liberdade para se expressar, não existe a menor razão para que fascistas não usufruam dessa mesma liberdade.
É claro, nesse ponto, seremos invariavelmente confrontados por um oportuno dilema — o famoso paradoxo da intolerância, de Karl Popper. Até que ponto uma sociedade livre e tolerante deve tolerar a intolerância (inerente a ideologias totalitárias)?
As leis de propriedade privada resolveriam isso em uma sociedade livre. O mais importante a levarmos em consideração no atual contexto, no entanto — ao defender ou criticar uma determinada ideologia, filosofia ou escola de pensamento —, é entender que, seja ela qual for, ela tem o direito de existir. E todas as pessoas que a defendem tem o direito de defendê-la, da mesma maneira que todos os seus detratores tem o direito de criticá-la.
Essa é uma forte razão para jamais apoiarmos a censura. Muito pelo contrário, devemos repudiar com veemência e intransigência toda e qualquer forma de censura, especialmente a estatal.
Existem duas fortes razões para isso:
A primeira delas é a volatilidade da censura (especialmente a estatal). A censura oficial do governo, depois que é implementada, torna-se absolutamente incontrolável. Hoje, ela pode estar apontada para um grupo de pessoas cujas ideias divergem das suas. Mas amanhã, ela pode estar apontada justamente para as ideias que você defende. É fundamental, portanto, compreendermos que a censura estatal é incontrolável. Sob qualquer ponto de vista, é muito mais vantajoso que exista uma vasta pluralidade de ideias conflitantes na sociedade competindo entre si, do que o estado decidir que ideias podem ser difundidas ou não.
Além do mais, libertários e anarcocapitalistas não podem nunca esperar qualquer tipo de simpatia por parte das autoridades governamentais. Para o estado, seria infinitamente mais prático e vantajoso criminalizar o libertarianismo e o anarcocapitalismo — sob a alegação de que são filosofias perigosas difundidas por extremistas radicais que ameaçam o estado democrático de direito — do que o fascismo ou qualquer outra ideologia centralizada em governos burocráticos e onipotentes. Portanto, defender a censura, especialmente a estatal, representa sempre um perigo para o próprio indivíduo, que mais cedo ou mais tarde poderá ver a censura oficial do sistema se voltar contra ele.
Outra razão pela qual libertários jamais devem defender a censura, é porque — ao contrário dos estatistas — não é coerente que defensores da liberdade se comportem como se o estado fosse o seu papai e o governo fosse a sua mamãe. Não devemos terceirizar nossas próprias responsabilidades, tampouco devemos nos comportar como adultos infantilizados. Assumimos a responsabilidade de combater todas as ideologias e filosofias que agridem a liberdade e os seres humanos. Não procuramos políticos ou burocratas para executar essa tarefa por nós.
Portanto, se você ver um fascista sendo censurado nas redes sociais ou em qualquer outro lugar, assuma suas dores. Sinta-se compelido a defendê-lo, mostre aos seus detratores que ele tem todo direito de se expressar, como qualquer pessoa. Você não tem obrigação de concordar com ele ou apreciar as ideias que ele defende. Mas silenciar arbitrariamente qualquer pessoa não é uma pauta que honra a liberdade.
Se você não gosta de estado, planejamento central, burocracia, impostos, tarifas, políticas coletivistas, nacionalistas e desenvolvimentistas, mostre com argumentos coesos e convincentes porque a liberdade e o livre mercado são superiores a todos esses conceitos. Mas repudie a censura com intransigência e mordacidade.
Em primeiro lugar, porque você aprecia e defende a liberdade de expressão para todas as pessoas. E em segundo lugar, por entender perfeitamente que — se a censura eventualmente se tornar uma política de estado vigente entre a sociedade — é mais provável que ela atinja primeiro os defensores da liberdade do que os defensores do estado.
Machismo
Muitos elementos do comportamento masculino que hoje são atacados com virulência e considerados machistas pelo movimento progressista são na verdade manifestações naturais intrínsecas ao homem, que nossos avôs cultivaram ao longo de suas vidas sem serem recriminados por isso. Com a ascensão do feminismo, do progressismo e a eventual problematização do sexo masculino, o antagonismo militante dos principais líderes da revolução sexual da contracultura passou a naturalmente condenar todos os atributos genuinamente masculinos, por considerá-los símbolos de opressão e dominação social.
Apesar do Brasil ser uma sociedade liberal ultra-progressista, onde o estado protege mais as mulheres do que as crianças — afinal, a cada semana novas leis são implementadas concedendo inúmeros privilégios e benefícios às mulheres, aos quais elas jamais teriam direito em uma sociedade genuinamente machista e patriarcal —, a esquerda política persiste em tentar difundir a fantasia da opressão masculina e o mito de que vivemos em uma sociedade machista e patriarcal.
Como sempre, a realidade mostra um cenário muito diferente daquilo que é pregado pela militância da terra da fantasia. O Brasil atual não tem absolutamente nada de machista ou patriarcal. No Brasil, mulheres podem votar, podem ocupar posições de poder e autoridade tanto na esfera pública quanto em companhias privadas, podem se candidatar a cargos políticos, podem ser vereadoras, deputadas, governadoras, podem ser proprietárias do próprio negócio, podem se divorciar, podem dirigir, podem comprar armas, podem andar de biquíni nas praias, podem usar saias extremamente curtas, podem ver programas de televisão sobre sexo voltados única e exclusivamente para o público feminino, podem se casar com outras mulheres, podem ser promíscuas, podem consumir bebidas alcoólicas ao ponto da embriaguez, e podem fazer praticamente tudo aquilo que elas desejarem. No Brasil do século XXI, as mulheres são genuinamente livres para fazer as próprias escolhas em praticamente todos os aspectos de suas vidas. O que mostra efetivamente que a tal opressão do patriarcado não existe.
O liberalismo social extremo do qual as mulheres usufruem no Brasil atual — e que poderíamos estender a toda a sociedade contemporânea ocidental — é suficiente para desmantelar completamente a fábula feminista da sociedade patriarcal machista e opressora, que existe única e exclusivamente no mundinho de fantasias ideológicas da esquerda progressista.
Tão importante quanto, é fundamental compreender que nenhum homem é obrigado a levar o feminismo a sério ou considerá-lo um movimento social e político legítimo. Para um homem, ser considerado machista ou até mesmo assumir-se como um não deveria ser um problema. O progressismo e o feminismo — com o seu nefasto hábito de demonizar os homens, bem como todos os elementos inerentes ao comportamento e a cultura masculina — é que são o verdadeiro problema, conforme tentam modificar o homem para transformá-lo em algo que ele não é nem deveria ser: uma criatura dócil, passiva e submissa, que é comandada por ideologias hostis e antinaturais, que não respeitam a hierarquia de uma ordem social milenar e condições inerentes à própria natureza humana. Com o seu hábito de tentar modificar tudo através de leis e decretos, o feminismo e o progressismo mostram efetivamente que o seu real objetivo é criminalizar a masculinidade.
A verdade é que — usufruindo de um nível elevado de liberdades — não existe praticamente nada que a mulher brasileira do século XXI não possa fazer. Adicionalmente, o governo dá as mulheres uma quantidade tão avassaladora de vantagens, privilégios e benefícios, que está ficando cada vez mais difícil para elas encontrarem razões válidas para reclamarem da vida. Se o projeto de lei que pretende fornecer um auxílio mensal de mil e duzentos reais para mães solteiras for aprovado pelo senado, muitas mulheres que tem filhos não precisarão nem mesmo trabalhar para ter sustento. E tantas outras procurarão engravidar, para ter direito a receber uma mesada mensal do governo até o seu filho completar a maioridade.
O que a militância colorida da terra da fantasia convenientemente ignora — pois a realidade nunca corresponde ao seu conto de fadas ideológico — é que o mundo de uma forma geral continua sendo muito mais implacável com os homens do que é com as mulheres. No Brasil, a esmagadora maioria dos suicídios é praticada por homens, a maioria das vítimas de homicídio são homens e de cada quatro moradores de rua, três são homens. Mas é evidente que uma sociedade liberal ultra-progressista não se importa com os homens, pois ela não é influenciada por fatos concretos ou pela realidade. Seu objetivo é simplesmente atender as disposições de uma agenda ideológica, não importa quão divorciadas da realidade elas são.
O nível exacerbado de liberdades sociais e privilégios governamentais dos quais as mulheres brasileiras usufruem é suficiente para destruir a fantasiosa fábula da sociedade machista, opressora e patriarcal. Se as mulheres brasileiras não estão felizes, a culpa definitivamente não é dos homens. Se a vasta profusão de liberdades, privilégios e benefícios da sociedade ocidental não as deixa plenamente saciadas e satisfeitas, elas podem sempre mudar de ares e tentar uma vida mais abnegada e espartana em países como Irã, Paquistão ou Afeganistão. Quem sabe assim elas não se sentirão melhores e mais realizadas?
Homofobia
Quando falamos em homofobia, entramos em uma categoria muito parecida com a do racismo: o direito de discriminação é totalmente válido. Absolutamente ninguém deve ser obrigado a aceitar homossexuais ou considerar o homossexualismo como algo normal. Sendo cristão, não existe nem sequer a mais vaga possibilidade de que algum dia eu venha a aceitar o homossexualismo como algo natural. O homossexualismo se qualifica como um grave desvio de conduta e um pecado contra o Criador.
A Bíblia proíbe terminantemente conduta sexual imoral, o que — além do homossexualismo — inclui adultério, fornicação, incesto e bestialidade, entre outras formas igualmente pérfidas de degradação.
Segue abaixo três passagens bíblicas que proíbem terminantemente a conduta homossexual:
“Não te deitarás com um homem como se deita com uma mulher. Isso é abominável!” (Levítico 18:22 — King James Atualizada)
“Se um homem se deitar com outro homem, como se deita com mulher, ambos terão praticado abominação; certamente serão mortos; o seu sangue estará sobre eles.” (Levítico 20:13 — João Ferreira de Almeida Atualizada)
“O quê! Não sabeis que os injustos não herdarão o reino de Deus? Não sejais desencaminhados. Nem fornicadores, nem idólatras, nem adúlteros, nem homens mantidos para propósitos desnaturais, nem homens que se deitam com homens, nem ladrões, nem gananciosos, nem beberrões, nem injuriadores, nem extorsores herdarão o reino de Deus.” (1 Coríntios 6:9,10 —Tradução do Novo Mundo das Escrituras Sagradas com Referências)
Se você não é religioso, pode simplesmente levar em consideração o argumento do respeito pela ordem natural. A ordem natural é incondicional e incisiva com relação a uma questão: o complemento de tudo o que existe é o seu oposto, não o seu igual. O complemento do dia é a noite, o complemento da luz é a escuridão, o complemento da água, que é líquida, é a terra, que é sólida. E como sabemos o complemento do macho — de sua respectiva espécie — é a fêmea.
Portanto, o complemento do homem, o macho da espécie humana, é naturalmente a mulher, a fêmea da espécie humana. Um homem e uma mulher podem naturalmente se reproduzir, porque são um complemento biológico natural. Por outro lado, um homem e outro homem são incapazes de se reproduzir, assim como uma mulher e outra mulher.
Infelizmente, o mundo atual está longe de aceitar como plenamente estabelecida a ordem natural pelo simples fato dela existir, visto que tentam subvertê-la a qualquer custo, não importa o malabarismo intelectual que tenham que fazer para justificar os seus pontos de vista distorcidos e antinaturais. A libertinagem irrefreável e a imoralidade bestial do mundo contemporâneo pós-moderno não reconhecem nenhum tipo de limite. Quem tenta restabelecer princípios morais salutares é imediatamente considerado um vilão retrógrado e repressivo, sendo ativamente demonizado pela militância do hedonismo, da luxúria e da licenciosidade desenfreada e sem limites.
Definitivamente, fazer a apologia da moralidade, do autocontrole e do autodomínio não faz nenhum sucesso na Sodoma e Gomorra global dos dias atuais. O que faz sucesso é lacração, devassidão, promiscuidade e prazeres carnais vazios. O famoso escritor e filósofo francês Albert Camus expressou uma verdade contundente quando disse: “Uma só frase lhe bastará para definir o homem moderno — fornicava e lia jornais”.
Qualquer indivíduo tem o direito inalienável de discriminar ativamente homossexuais, pelo direito que ele julgar mais pertinente no seu caso. A objeção de consciência para qualquer situação é um direito natural dos indivíduos. Há alguns anos, um caso que aconteceu nos Estados Unidos ganhou enorme repercussão internacional, quando o confeiteiro Jack Phillips se recusou a fazer um bolo de casamento para o “casal” homossexual Dave Mullins e Charlie Craig.
Uma representação dos direitos civis do estado do Colorado abriu um inquérito contra o confeiteiro, alegando que ele deveria ser obrigado a atender todos os clientes, independente da orientação sexual, raça ou crença. Preste atenção nas palavras usadas — ele deveria ser obrigado a atender.
Como se recusou bravamente a ceder, o caso foi parar invariavelmente na Suprema Corte, que decidiu por sete a dois em favor de Jack Phillips, sob a alegação de que obrigar o confeiteiro a atender o “casal” homossexual era uma violação nefasta dos seus princípios religiosos. Felizmente, esse foi um caso em que a liberdade prevaleceu sobre a tirania progressista.
Evidentemente, homossexuais não devem ser agredidos, ofendidos, internados em clínicas contra a sua vontade, nem devem ser constrangidos em suas liberdades pelo fato de serem homossexuais. O que eles precisam entender é que a liberdade é uma via de mão dupla. Eles podem ter liberdade para adotar a conduta que desejarem e fazer o que quiserem (contanto que não agridam ninguém), mas da mesma forma, é fundamental respeitar e preservar a liberdade de terceiros que desejam rejeitá-los pacificamente, pelo motivo que for.
Afinal, ninguém tem a menor obrigação de aceitá-los, atendê-los ou sequer pensar que uma união estável entre duas pessoas do mesmo sexo — incapaz de gerar descendentes, e, portanto, antinatural — deva ser considerado um matrimônio de verdade. Absolutamente nenhuma pessoa, ideia, movimento, crença ou ideologia usufrui de plena unanimidade no mundo. Por que o homossexualismo deveria ter tal privilégio?
Homossexuais não são portadores de uma verdade definitiva, absoluta e indiscutível, que está acima da humanidade. São seres humanos comuns que — na melhor das hipóteses —, levam um estilo de vida que pode ser considerado “alternativo”, e absolutamente ninguém tem a obrigação de considerar esse estilo de vida normal ou aceitável. A única obrigação das pessoas é não interferir, e isso não implica uma obrigação em aceitar.
Discriminar homossexuais (assim como pessoas de qualquer outro grupo, raça, religião, nacionalidade ou etnia) é um direito natural por parte de todos aqueles que desejam exercer esse direito. E isso nem o direito positivo nem a militância progressista poderão algum dia alterar ou subverter. O direito natural e a inclinação inerente dos seres humanos em atender às suas próprias disposições é simplesmente imutável e faz parte do seu conjunto de necessidades.
Conclusão
A militância progressista é absurdamente autoritária, e todas as suas estratégias e disposições ideológicas mostram que ela está em uma guerra permanente contra a ordem natural, contra a liberdade e principalmente contra o homem branco, cristão, conservador e tradicionalista — possivelmente, aquilo que ela mais odeia e despreza.
Nós não podemos, no entanto, ceder ou dar espaço para a agenda progressista, tampouco pensar em considerar como sendo normais todas as pautas abusivas e tirânicas que a militância pretende estabelecer como sendo perfeitamente razoáveis e aceitáveis, quer a sociedade aceite isso ou não. Afinal, conforme formos cedendo, o progressismo tirânico e totalitário tende a ganhar cada vez mais espaço.
Quanto mais espaço o progressismo conquistar, mais corroída será a liberdade e mais impulso ganhará o totalitarismo. Com isso, a cultura do cancelamento vai acabar com carreiras, profissões e com o sustento de muitas pessoas, pelo simples fato de que elas discordam das pautas universitárias da moda.
A história mostra perfeitamente que quanto mais liberdade uma sociedade tem, mais progresso ela atinge. Por outro lado, quanto mais autoritária ela for, mais retrocessos ela sofrerá. O autoritarismo se combate com liberdade, desafiando as pautas de todos aqueles que persistem em implementar a tirania na sociedade. O politicamente correto é o nazismo dos costumes, que pretende subverter a moral através de uma cultura de vigilância policial despótica e autoritária, para que toda a sociedade seja subjugada pela agenda totalitária progressista.
Pois quanto a nós, precisamos continuar travando o bom combate em nome da liberdade. E isso inclui reconhecer que ideologias, hábitos e costumes de que não gostamos tem o direito de existir e até mesmo de serem defendidos.
-
 @ 3e48885d:b2272a7c
2024-12-18 18:59:49
@ 3e48885d:b2272a7c
2024-12-18 18:59:49It may sound silly, but about once a week, sometimes more, I find myself wishing I were a cowboy. The freedom that would come from the total disconnect from the rest of the world. The peaceful feeling of open spaces and working with animals. And let’s not forget a tinge of adventure.
At 52, I find myself wishing this still. There was a time in my early thirties I seriously considered it, then came marriage and kids and it slipped away. These days, I still find it nice to think about.
Today I sit attached to my desk, living in a semi suburban world. The only animals I tend to are my two dogs. Sometimes I sit alone and listen to old cowboy songs from the likes of Chris Ledoux. I guess it helps that I live in Texas, giving me default western status, though nowhere near that reality.
I work in cybersecurity and hang out in more undeveloped parts of the web where outlaws may dwell, I guess that is as close as I get. It’s nice to daydream.
It may sound silly, but about once a week, sometimes more, I find myself wishing I were a cowboy. The freedom that would come from the total disconnect from the rest of the world. The peaceful feeling of open spaces and working with animals. And let’s not forget a tinge of adventure.
-
 @ ea6958bd:77925591
2024-12-18 18:28:00
@ ea6958bd:77925591
2024-12-18 18:28:001sdfsdfsdfs
-
 @ ea6958bd:77925591
2024-12-18 18:28:00
@ ea6958bd:77925591
2024-12-18 18:28:001sdfsdfsdfs
-
 @ 4b7c4ee3:8cd5ed4d
2024-12-18 17:55:06
@ 4b7c4ee3:8cd5ed4d
2024-12-18 17:55:06I saw the plebs, humble and defiant, tethered to screens in the blue light of dawn, eyes bloodshot, hearts blazing, fingers tapping keys, whispering truths to themselves: “21 million and not one more.”
O you plebs of digital dreams, you fire-walkers with stacks of sats, tin cans for wallets, trading steel for sovereignty, bread for belief, as the world laughs from their granite towers.
They called you fools! Hoarders of nothing, dreamers of orange suns, cartographers of a new financial frontier— “Where will your coins take you?” they sneered.
But you held your breath through the chaos, the mountains of volatility, the typhoons of FUD— your hands forged in steel, unshaking, unbreakable.
I see you in basements, in rented rooms, in coffee shops, whispering, shouting: “Not your keys, not your coin!” I see your spreadsheets scrawled in chicken scratch, your hardware wallets buried under mattresses, your mantras muttered: “Stay humble. Stack sats. Stay free.”
Plebs! O divine misfits of the digital age, who have glimpsed the lie in the fiat dream, who laughed when they printed trillions of promises and called it “economics.”
You who dared ask: What is money? You who saw value in blocks, time-stamped like gospel, immutable as stone tablets, a cathedral of ones and zeroes— sacred, incorruptible, unowned.
O plebs! You who endure ridicule and rise again, who find beauty in scarcity and strength in decentralization, who say “We are early!” and “We are here!” barefoot prophets planting orange flags on digital plains.
Hail to you! The unpaid evangelists of freedom, the poets of monetary revolution, the miners who light the path forward, the hodlers who refuse to kneel, who believe when others doubt, who build when others mock.
Pleb, you are the heartbeat of the chain. A link unbroken, unbowed, unfettered. You are the howl in the dark— “We will not be slaves!” You are the signal in the noise, the orange light in the storm, the proof of work in a world of empty words.
And when they ask you why— why you stared at this black monolith for years, why you stacked while they spent, why you chose Bitcoin—
Tell them you chose freedom. Tell them you chose truth. Tell them you chose the only thing that cannot be printed, censored, or stolen.
O pleb, when the dust settles, and the towers crumble under their own weight, they will know you were right.
And you will have the last laugh, not for glory, not for spite, but for every silent dreamer who dared to believe.
Stay humble. Stack sats. The revolution is you.
I saw the plebs, humble and defiant,\ tethered to screens in the blue light of dawn,\ eyes bloodshot, hearts blazing, fingers tapping keys,\ whispering truths to themselves: “21 million and not one more.”
O you plebs of digital dreams, you fire-walkers\ with stacks of sats, tin cans for wallets,\ trading steel for sovereignty, bread for belief,\ as the world laughs from their granite towers.
They called you fools! Hoarders of nothing,\ dreamers of orange suns,\ cartographers of a new financial frontier—\ “Where will your coins take you?” they sneered.
But you held your breath through the chaos,\ the mountains of volatility,\ the typhoons of FUD—\ your hands forged in steel, unshaking, unbreakable.
I see you in basements, in rented rooms, in coffee shops,\ whispering, shouting: “Not your keys, not your coin!”\ I see your spreadsheets scrawled in chicken scratch,\ your hardware wallets buried under mattresses,\ your mantras muttered: “Stay humble. Stack sats. Stay free.”
Plebs! O divine misfits of the digital age,\ who have glimpsed the lie in the fiat dream,\ who laughed when they printed trillions of promises\ and called it “economics.”
You who dared ask: What is money?\ You who saw value in blocks, time-stamped like gospel,\ immutable as stone tablets, a cathedral of ones and zeroes—\ sacred, incorruptible, unowned.
O plebs! You who endure ridicule and rise again,\ who find beauty in scarcity and strength in decentralization,\ who say “We are early!” and “We are here!”\ barefoot prophets planting orange flags on digital plains.
Hail to you! The unpaid evangelists of freedom,\ the poets of monetary revolution,\ the miners who light the path forward,\ the hodlers who refuse to kneel,\ who believe when others doubt,\ who build when others mock.
Pleb, you are the heartbeat of the chain.\ A link unbroken, unbowed, unfettered.\ You are the howl in the dark—\ “We will not be slaves!”\ You are the signal in the noise,\ the orange light in the storm,\ the proof of work in a world of empty words.
And when they ask you why—\ why you stared at this black monolith for years,\ why you stacked while they spent,\ why you chose Bitcoin—
Tell them you chose freedom.\ Tell them you chose truth.\ Tell them you chose the only thing\ that cannot be printed, censored, or stolen.
O pleb,\ when the dust settles,\ and the towers crumble under their own weight,\ they will know you were right.
And you will have the last laugh,\ not for glory, not for spite,\ but for every silent dreamer who dared to believe.
Stay humble. Stack sats.\ The revolution is you.
Oyl Miller comes from an advertising background where he has worked for legacy brands like Nike and PlayStation, digital giants like Google and Airbnb, as well as crypto and web3 startups. He is experimenting with moving to a Bitcoin standard, and is looking to create value with his writing skills in a variety of ways.
-
 @ 4b7c4ee3:8cd5ed4d
2024-12-18 17:42:13
@ 4b7c4ee3:8cd5ed4d
2024-12-18 17:42:13They said no one would ever need electricity at home. (Thomas Edison)
They said who needs cars, we have horses. (Henry Ford)
They said humans would never fly. (Wright Brothers)
They said movies would ruin storytelling. (Hollywood Studios)
They said the radio was just noise. (Marconi)
They said TV would destroy family time. (RCA, Philo Farnsworth)
They said cameras were only for professionals. (Kodak)
They said color TV was a waste of money. (RCA)
They said computers were just for big businesses. (IBM, Apple)
They said the internet was a passing trend. (Tim Berners-Lee, Netscape)
They said no one would shop without going to a store. (Amazon, Jeff Bezos)
They said no one wants to talk to strangers online. (Facebook, Mark Zuckerberg)
They said no one would pay hundreds for a phone. (Apple, Steve Jobs)
They said GPS was only for soldiers. (Garmin, Google Maps)
They said video games were for kids. (Nintendo, Sony PlayStation)
They said people want to own their music, not stream it. (Spotify)
They said no one would trust their photos to "the cloud." (Apple, Google Drive)
They said no one wants to watch movies on the internet. (Netflix)
They said digital money was a scam. (Bitcoin, Satoshi Nakamoto)
They said computers could never think. (OpenAI, DeepMind)
They said no one would drive a car without gas. (Tesla, Elon Musk)
They said people wouldn’t buy things they can’t touch. (eBay, Etsy)
They said no one wants to live in a fake world. (Meta, Oculus)
They said people won’t trust strangers with their homes. (Airbnb)
They said no one would get in a stranger’s car. (Uber, Lyft)
They said no one would buy cars online. (Tesla, Carvana)
They said no one would wear a computer on their wrist. (Apple Watch)
They said no one would ever watch live sports on the internet. (YouTube TV, ESPN+)
They said streaming would never replace cable. (Netflix, Hulu)
They said no one would pay for virtual clothes. (Fortnite, Roblox)
They've said so many things with certainty, and ended up on the wrong side of history. What breakthroughs are they doubting today that will create a future beyond our imagination? Challenge your assumptions, think for yourself, and believe that the world can transform beyond your wildest dreams.
Stay stacking. Stay foolish.
Oyl Miller
If this resonated with you, please share far and wide. If you found value in this content, please consider sprinkling a little Bitcoin dust (or a couple of coins if you're feeling bold ;p) in my digital hat.
BTC address: bc1qswmqjh75cqfcyyfp7ta4n9h839pl059mlenxn3
Oyl Miller comes from an advertising background where he has worked for legacy brands like Nike and PlayStation, digital giants like Google and Airbnb, as well as crypto and web3 startups. He is experimenting with moving to a Bitcoin standard, and is looking to create value with his writing skills in a variety of ways.
-
 @ d61f3bc5:0da6ef4a
2024-12-18 16:52:18
@ d61f3bc5:0da6ef4a
2024-12-18 16:52:18January 2025 will mark two years since we started building Primal. Our goal was to create the best possible user experience for Nostr and make it accessible to everyone. We reached a big milestone towards realizing that vision with the recent Primal 2.0 release. It’s still early days, a lot more work lies ahead, but we thought the timing was right to introduce the Premium tier. Let’s explore what it is, why we built it, what’s included, and how it will evolve moving forward.
What Primal Premium Is
The idea behind Primal Premium is simple: integrate all tools and services required for the best Nostr experience into a single package. For $7 per month, Premium users get a Primal Name and Nostr Tools built by Primal. We’ll cover those in more detail below, but first we should make a crucial point: by signing up for Premium, you are in no way locked in to Primal. Quite the contrary, you can pick and choose which Premium features you wish to enable and use within other Nostr products.
Openness is Nostr’s killer feature. Any product that wishes to truly empower the user needs to interoperate with Nostr’s budding ecosystem. The feed marketplace is a great example. External feeds are first-class citizens within all Primal apps. Primal feeds are available in other Nostr clients. We are working on Premium feeds, which our users will be able to enjoy within Primal or other Nostr apps. Media hosting is another example. Our upcoming support for the Blossom protocol will make Primal Premium media hosting interoperable with other Nostr apps and media hosting services. The common theme here is user choice. Nostr offers the highest level of user agency, and the compounding effect of interoperable products and services is bound to make Nostr immensely powerful.
Why We Built Premium and Why Now
What is unfolding on Nostr right now is unique and special. The first truly self-sovereign network is being bootstrapped by this early cohort of users and builders. People are literally holding the keys to their online presence. Network infrastructure – relays, indexers, media hosting services, etc. – is being stood up organically and without any central planning or coordination. Hundreds of independent projects are adding new capabilities to Nostr without needing permission. The whole thing is truly a sight to behold.
In addition to fixing the fundamentals of the network, it is equally important that we fix the broken incentives that plague the legacy Web. The status quo of monetization via advertising, which turns users into products to be farmed, has overstayed its welcome. At Primal, we don’t monetize user data. Our users are our customers. We only make money when the user decides that we are providing a valuable service – and pays for it. That means that our users’ interests are aligned with ours. It allows us to wake up every morning and work all day to make the product better for our users.
Some might say that it is too early to try to monetize a Nostr product. We definitely need to be thoughtful about paywalling important features while the network is so young. For example, advanced search is a Primal Premium feature, but we enable it for all users up to 20 search results. That makes it quite usable for anyone on Nostr, but power users get the ability to save these searches and create powerful specialized feeds.
It is crucial to have commercially successful projects on Nostr that have their incentives aligned with those of their users. We are working on new features and monetization methods that follow this philosophy. The more we experiment on Nostr, the faster we will learn what works and unlock the full potential of this network. I have a feeling that a lot remains to be discovered, and Primal Premium is just the first step.
Now, let’s take a closer look at what is included in Premium: Primal Name and Nostr Tools.
Primal Name
A Primal Name is a unique name on the primal.net domain that offers three features:
- Verified Nostr address (NIP-05). This signals to the Nostr network that your account (npub) has been verified by Primal. Note that we don’t perform identity verification; we are simply signaling that this is a Primal Premium user. Users can pay with sats, preserving their privacy while signaling to the network that this verified account is not a bot.
- Friendly Bitcoin Lightning address. Primal’s built-in hosted wallet creates a randomly generated lightning address for every user. They look like this: bluedog25@primal.net. Premium users get to pick their name, so their lightning address is more personalized (e.g. preston@primal.net).
- VIP profile on primal.net. This is simply a friendly URL to your profile on primal.net. We are working on adding profile customization features for Premium users; stay tuned!
In summary, a Primal Name makes you easier to find on Nostr. You are free to use any of these three Primal Name elements as you see fit. If you wish to use your Primal Nostr address and/or Lightning address, simply update your Nostr profile with those entries.
Nostr Tools
Nostr Tools is a collection of features that we think would be useful to any Nostr power user. We are continuously working on expanding these capabilities, but the initial set of features includes:
- Media management. Primal Premium comes with 10GB of media storage (compared to 1GB for free accounts). We implemented a slick interface for managing all media you have on Primal.
- Contact list backup. Many Nostr users have experienced the loss of their contact list (i.e., their follow list) when using different clients. We store the history of the contact list for Primal Premium users and make it easy to recover.
- Content backup. Nostr users post their content to a collection of public relays. These relays typically don’t offer guarantees that they will store the content for any amount of time. We back up all content posted by Primal Premium users and make it easy to rebroadcast it to the specified relays at any time.
Primal Legends
The idea for the Primal Legend tier was suggested to me by Gigi a couple of months prior to the launch of Primal 2.0. His argument was simple: “There are users on Nostr who really appreciate Primal and are willing to pay way more than $7 / month to support the project. You should let them pay and recognize them for doing so.”
I am really glad that Gigi convinced me to introduce the Legend tier. Nostr is truly a special place. The early users are extremely passionate and mission driven. They care about growing and improving Nostr as much as the builders do. At first, I thought of the term “Legend” as a bit tongue in cheek, but then I met and chatted with some of these people. Man, they are incredible. They just wish to support the network and the builders of open source software in any way they can. So now I think the term is appropriate.
We are humbled by the support we received. Our first Legend supporter was none other than Jack. He found this option in the product and paid for the Legend tier literally an hour after Primal 2.0 was released. Thank you, sir, and thank you to all the other Legends out there! 💜🫂
What Comes Next?
We are delighted and encouraged by the market response to Primal Premium. It is already clear to us that we are on the right path. We will lean into it even harder from here. There will be MOAR Premium features, while at the same time we will make sure that the free product remains excellent. Since you, the user, are the customer, tell us what you would like to see added to Primal Premium.
Pura Vida 🤙
-
 @ 63d59db8:be170f6f
2024-12-18 16:24:11
@ 63d59db8:be170f6f
2024-12-18 16:24:11I am Oana, a fine-art photographer with a deep passion for capturing nature's fragile resilience. My work has been recognized internationally, featured on platforms such as CNN Style, Forbes, and Amateur Photographer, and honored by the Sony World Photography Awards. With over 25 years of creative experience, I focus on blending fine-art aesthetics with ecological storytelling to highlight the beauty, complexity, and vulnerability of our natural world.
For this submission, I’ve selected some of my finest works, which reflect my ongoing exploration of flora in their natural environments. These images celebrate the interplay of light, texture, and motion, capturing moments that reveal the unique personalities of flowers and plants without interference. My goal is to foster an emotional connection between viewers and the overlooked beauty of the natural world.
This work represents my artistic vision of combining visual poetry with a deeper narrative about sustainability and our relationship with the environment. Each photograph is a window into nature’s story, inviting viewers to engage with its raw, unfiltered essence.






Submit your photographs to our Visual Expression awards. Current prize is $130 / 125,140 sats.
Learn more and enter here. Deadline is December 31, 2024!

-
 @ 4685f3d6:9fe6995b
2024-12-18 16:13:53
@ 4685f3d6:9fe6995b
2024-12-18 16:13:53Day 2: How Bitcoin Works
Understanding how Bitcoin works can seem daunting at first, but it’s built on three fundamental concepts: blockchain, mining, and transactions. Let’s break these down into simple terms.
- Blockchain: The Foundation of Bitcoin
The blockchain is the core technology that powers Bitcoin. Think of it as a digital ledger or database that records every Bitcoin transaction ever made. Here’s how it works:
Decentralized Ledger: Instead of being stored on a single server, the blockchain is distributed across thousands of computers (called nodes) worldwide. This makes it nearly impossible for any single entity to alter or hack.
Blocks: Transactions are grouped into blocks. Each block contains a list of transactions, a timestamp, and a unique identifier called a hash.
Chain of Blocks: These blocks are linked together chronologically, forming a “chain.” Once a block is added to the chain, it cannot be altered, ensuring the integrity of the data.
- Mining: Securing the Network
Mining is the process that keeps the Bitcoin network secure and functional. Miners are individuals or organizations that use powerful computers to solve complex mathematical problems. Here’s how mining works:
Verifying Transactions: When you send Bitcoin, your transaction is grouped with others waiting to be verified. Miners check these transactions to ensure they’re valid (e.g., that you have enough Bitcoin to spend).
Solving Puzzles: To add a block of transactions to the blockchain, miners must solve a mathematical problem. This process is called Proof of Work (PoW). It’s like a race; the first miner to solve the problem gets to add the block.
Rewards: As a reward for their work, the miner receives newly created Bitcoin (block reward) and transaction fees from the users whose transactions were included in the block.
Energy-Intensive: Mining requires significant computational power and energy, which has led to concerns about its environmental impact.
- Transactions: Sending and Receiving Bitcoin
A Bitcoin transaction is the process of transferring Bitcoin from one person to another. Here’s a simplified explanation:
Wallets: To send or receive Bitcoin, you need a digital wallet. Your wallet has two keys:
Private Key: A secret code that allows you to spend your Bitcoin.
Public Key: A code that others use to send Bitcoin to you.
Broadcasting Transactions: When you send Bitcoin, your wallet broadcasts the transaction to the network. The transaction includes:
The sender’s address.
The recipient’s address.
The amount of Bitcoin being sent.
Verification: Miners verify the transaction to ensure the sender has enough Bitcoin and hasn’t spent the same Bitcoin twice (called double-spending).
Confirmation: Once verified, the transaction is added to a block on the blockchain. It’s considered confirmed after multiple blocks are added after it, making it irreversible.
Putting It All Together
Here’s a real-world analogy to simplify the process:
Imagine the blockchain as a public record book in a library where every page represents a block. When you make a transaction, it’s written on the next blank page (block).
Miners are the librarians who verify and add your transaction to the book by solving a puzzle. Once added, that page is locked and cannot be changed.
Your Bitcoin wallet is like your personal bank account, with a private PIN (private key) that only you know and an account number (public key) for others to send you money.
Why This System Works
Security: The blockchain’s transparency and immutability ensure that all transactions are secure and verifiable.
Decentralization: Without a central authority, the system relies on consensus among nodes, making it resistant to censorship or manipulation.
Incentives: Miners are motivated by rewards, ensuring the network remains operational and secure.
By combining blockchain technology, mining, and decentralized transactions, Bitcoin creates a secure and efficient system for transferring value globally without intermediaries. It’s a revolutionary approach to money, reshaping how we think about finance and trust.
Bitcoin
9ja
Afro
yakihonne
-
 @ 490b551d:e17f0103
2024-12-18 16:07:03
@ 490b551d:e17f0103
2024-12-18 16:07:03For ten years, I walked away. I turned my back on Christianity, on everything I was raised to believe. I rejected it all because after I went through a divorce, after my family rejected me, after I found myself pregnant and unwed, I couldn’t reconcile the faith I was taught with the reality I was living. The wounds were too deep, the shame too great. It wasn’t just people and the church who had abandoned me - it was God, too. Or at least, that’s what I thought.
I decided it was all a lie. I told myself it was smarter to follow my logic. To reject the Bible, to reject the teachings I grew up with. I couldn’t ignore the contradictions anymore. The historical fallacies. The parts of the Bible that just didn’t make sense. It all seemed so impossible, so unrealistic. There were so many questions I couldn’t answer, so many things that didn’t add up. How could I still believe in something that seemed so fully fictional? How could I trust in something that had so much evidence against it? My mind, full of reason and doubt, said it wasn’t real. And so I walked away. I shut the door on God, on Jesus, on everything I had known.
But time has a way of changing things. Slowly, I started to rebuild my life. I found a new love - one that’s real, healthy, solid. My husband is exactly what I needed. Someone who accepts and loves me for who I am, communicates kindly and with empathy; who understands that I am a flawed human who makes mistakes. He chooses to be committed to me and to our marriage, and allows room for the fact that I'm going to make mistakes as a human being. And I strengthened my friendships, found a community that loves me without judgment. I’ve healed my mental health, too. The darkness of the past has lifted, and I see more clearly now. But still… there’s a part of me that aches for something I can’t fully touch, something I can’t fully understand.
And while my husband, kids, friends, and community are all amazing, no one human can meet all our needs or love us perfectly. I also can't provide that for anyone, and I understand and accept that, but there’s a part of me that yearns for a deeper, unconditional, unwavering, all-accepting, all-encompassing love that isn't bound by human limitations. A love that’s described by how Jesus loved but that feels so distant, so elusive. I want it. I want to believe in it, to trust in it with everything I have. But I can’t help but ask: Is it real? Can I really believe in this love that the Bible speaks of when the very thing I read is full of contradictions, of things that don’t make sense, of historical inaccuracies that scream at me every time I try to read it with open eyes?
The Struggle of Wanting It and Doubting It
I feel like I’m standing on the edge of something. Something I want, something I need, but something I’m not sure is real. The longing for Jesus’ love, the love that is unconditional, unrelenting, always there, never dependent on who I am or what I do - that love sounds like the answer to everything I’ve been searching for. I want to believe in it. I need to believe in it. But I can’t get past the questions.
How can I believe in a book that was written centuries ago, for a different culture, mindset, lifestyle, and with all its inconsistencies? How can I trust in stories that don’t seem to fit with what I know to be true or possible? How can I reconcile the love Jesus offers with the harshness I see in the world, or even in the church itself?
My heart is torn. I want to follow Jesus. I want to live the way He called us to, with love, with grace, with forgiveness. I want to believe that His death and resurrection mean something for me, that they offer hope in my brokenness, but the weight of doubt feels so heavy. The intellectual side of me can’t escape the contradictions, the fallacies, the unanswered questions. And it leaves me wondering: What if it’s not real? What if it’s all just a fairy tale, a beautiful story we tell ourselves to make sense of a broken world?
And yet… I want it to be real. Desperately. I want to believe in that love. I want to know that Jesus sees me in all my mess and still chooses me. That He loves me even when I struggle. Even when I don’t understand. Even when I doubt every word I read in the Bible.
Is It Real? Can I Trust It?
That’s the question that haunts me every day: Is it real? I read the Bible and I see things that feel impossible - stories that don’t seem to match up with what I know of history or science. I’ve learned too much to ignore the fallacies, the contradictions, the things that just don’t make sense. So how can I trust it? How can I believe it?
And then there’s the other side of me - the side that desperately wants this to be true. The side that has longed for unconditional love, for a peace that wraps me in its arms. The side that still believes that Jesus’ message of love and grace is what this world needs. I want it. I need it. I can’t imagine living without that hope. But can I have that hope and still wrestle with doubt? Can I yearn for Jesus’ love while questioning the very foundation of the faith?
I think the answer is yes. I think I can still choose to believe, even if I don’t have all the answers. Even if I can’t reconcile every piece of history, every contradiction, every fallacy that my mind throws at me. I think belief isn’t about having everything figured out. It’s about choosing to trust in love - trusting that what I yearn for is real, even when my head says otherwise.
The Love I Long For
I think of the love that Jesus offers - the kind of love that doesn’t ask me to be perfect, doesn’t demand I have all the answers, doesn’t turn away because of my doubts. That love is what I need. That love is what I long for. The love that forgives me, the love that sees me as I am, and still holds me close. The love that doesn’t ask me to fix myself before I come to Him, but says, “Come as you are. I love you no matter what.”
Romans 5:8 says, “But God demonstrates his own love for us in this: While we were still sinners, Christ died for us.”
It doesn’t say that we have to have all the answers or be perfect before we can receive His love. It says He loves us while we’re still sinners, while we’re still broken, while we’re still questioning. That’s the love I want. The love I desperately need. And even when my mind doubts, even when I struggle with the reality of it all, I can hold onto that truth: He loves me. Right now. Right here. With all my flaws, all my questions, all my uncertainties.
Moving Forward in the Midst of Doubt
So do I define myself as Christian? Do I embrace Jesus, despite my doubts, despite the intellectual struggle, despite the questions that remain unanswered? The answer is yes. Yes, because I choose to believe in that love. Yes, because I trust that even in my brokenness, even in my doubt, I am loved unconditionally by God. I may not have all the answers, but I have a love that’s real. A love that calls me back, despite my questioning.
I will keep asking the hard questions. I will keep struggling with the history, the contradictions, the doubts. But I will also keep choosing faith, because in the end, faith isn’t about having everything figured out. It’s about trusting in the love that Jesus offers - a love that’s always there, no matter what.
And maybe that’s enough for now. To know that even with all my doubts, I am loved. Even in my questions, I am accepted. Even when I feel lost, I am found.
Because that’s the thing about Jesus’ love - it doesn’t depend on me having it all figured out. It just depends on me showing up, broken and uncertain, and letting Him love me anyway.
And that, in the end, is the realest thing of all.\ \ Peace, \ Faith\ \
christian #blog #unfilteredfaith #doubt
-
 @ b8851a06:9b120ba1
2024-12-18 15:34:12
@ b8851a06:9b120ba1
2024-12-18 15:34:12Bitcoin Core 28.0 introduces smarter transaction handling to prevent stuck payments, reduce fees, and improve flexibility for wallets. Here’s a breakdown of the most important updates:
1. One Parent One Child (1P1C) Transactions
- The problem: If a transaction’s fee is too low for the current network conditions, it might never get confirmed.
- The fix: The new 1P1C relay lets you attach a “child” transaction with higher fees to "push" the original "parent" transaction through. Think of it as giving the parent a boost by letting the child pay for both.
Why it’s useful: If your wallet creates a transaction with a low fee, you can now add another transaction to ensure it gets confirmed without waiting forever.
2. TRUC Transactions (Version 3 Transactions)
- What they are: TRUC stands for Topologically Restricted Until Confirmation. These transactions follow stricter rules that make them easier to replace (RBF) if needed.
- Key features:
- Always replaceable: TRUC transactions can always be fee-bumped or replaced, even without extra setup.
- Safe fee bumps: Even in complex setups like CoinJoins or Lightning Channels, you can adjust fees as needed.
Why it’s useful: Wallets using TRUC transactions can guarantee that you can always adjust fees to match changing network conditions.
3. Pay to Anchor (P2A) Outputs
- What they are: A tiny, specialized output added to transactions purely for fee adjustments. Think of it like a "placeholder" designed to let anyone pay for the transaction’s fees later.
- How it works: P2A outputs are super small and cheap to include, but they’re powerful because they let you boost transaction fees without needing access to private keys.
Why it’s useful: Helps ensure your transaction doesn’t get stuck, even if the person creating the transaction can’t afford higher fees upfront.
4. Better Fee Replacement (Package RBF)
- The problem: Previously, if you wanted to replace a stuck transaction, you had to calculate fees perfectly.
- The fix: With Package RBF, you can replace an entire group of transactions (parent and child) instead of just one, making it easier to adjust fees without mistakes.
Why it’s useful: Ensures transactions get through even in complex situations like Lightning or CoinJoins.
5. What Does This Mean for Wallet Users?
- Simple Payments: Wallets can make payments more predictable and reliable by using TRUC and P2A features.
- Lightning Network: Lightning transactions become more secure because stuck channel transactions can be easily bumped.
- CoinJoins: Privacy-focused transactions can now handle fee bumps without breaking the chain of anonymity.
Summary
These updates give wallets and users more tools to handle tricky transaction scenarios, especially when network fees are unpredictable or when payments involve complex setups. Bitcoin Core 28.0 makes stuck payments a thing of the past and ensures smoother transaction processing.
Remember, these upgrades focus on Bitcoin’s core principles: efficiency, reliability, and user empowerment.
READ the full OpTech info about it here
-
 @ 8d34bd24:414be32b
2024-12-18 14:21:53
@ 8d34bd24:414be32b
2024-12-18 14:21:53Most people who have been around the church or the Bible have heard Jesus’s parable of the sower who sowed seed on various types of ground. Just as there is some disagreement on which soil corresponds to a true Christian, so also there is disagreement on who is a true Christian today. I’m going to investigate what the Bible says on the subject.
And He spoke many things to them in parables, saying, “Behold, the sower went out to sow; and as he sowed, some seeds fell beside the road, and the birds came and ate them up. Others fell on the rocky places, where they did not have much soil; and immediately they sprang up, because they had no depth of soil. But when the sun had risen, they were scorched; and because they had no root, they withered away. Others fell among the thorns, and the thorns came up and choked them out. And others fell on the good soil and yielded a crop, some a hundredfold, some sixty, and some thirty. He who has ears, let him hear.” (Matthew 13:3-8)
“Hear then the parable of the sower. When anyone hears the word of the kingdom and does not understand it, the evil one comes and snatches away what has been sown in his heart. This is the one on whom seed was sown beside the road. The one on whom seed was sown on the rocky places, this is the man who hears the word and immediately receives it with joy; yet he has no firm root in himself, but is only temporary, and when affliction or persecution arises because of the word, immediately he falls away. And the one on whom seed was sown among the thorns, this is the man who hears the word, and the worry of the world and the deceitfulness of wealth choke the word, and it becomes unfruitful. And the one on whom seed was sown on the good soil, this is the man who hears the word and understands it; who indeed bears fruit and brings forth, some a hundredfold, some sixty, and some thirty.” (Matthew 13:18-23) {emphasis mine}
Nearly everyone agrees that the seeds that “fell beside the road, and the birds came and ate them up” refers to those who heard the word of God, but didn’t not believe and are not Christians. These people neither believe they are saved, nor pretend to be. Everyone agrees that the seed that “fell on the good soil and yielded a crop, some a hundredfold, some sixty, and some thirty” refers to those who heard the word of God, believed, and were saved. There is a little more confusion and disagreement on the seed that “fell on the rocky places, where they did not have much soil” and the seed that “fell among the thorns, and the thorns came up and choked them out.” My interpretation is that the seed that fell on rocky places represents those who heard the Gospel and liked the sound of it, but they never truly repented and were never actually saved, whereas the seed that fell among the thorns and was choked out are those who truly repented and were saved, but who got so distracted by the world that they failed to live faithful lives.
In the same way, there are many people confessing to be Christians, but who don’t truly believe what the Bible says and who don’t live lives honoring to Jesus. We can’t know for certain who are real Christians and who are not. Only God knows, but there are definite signs pointing to one or the other.
This article is my investigation of what it means to be a true, born-again Christian versus those who claim to be Christians, but are not considered children of God by Jesus. In today’s culture, this sounds very judgmental and divisive, but it is what Jesus said about His followers.
“Not everyone who says to Me, ‘Lord, Lord,’ will enter the kingdom of heaven, but he who does the will of My Father who is in heaven will enter. Many will say to Me on that day, ‘Lord, Lord, did we not prophesy in Your name, and in Your name cast out demons, and in Your name perform many miracles?’ And then I will declare to them, ‘I never knew you; depart from Me, you who practice lawlessness.’ (Matthew 7:21-23) {emphasis mine}
I think those of us who think we are Christians would like to make sure that we are actual Children of God and not pretenders. I also think, when we are looking for people to help us to follow Jesus, we would like to make sure we are following and/or learning from those who actually know Jesus and not a pretender. Whether the pretender knows they are lying or believes they know Jesus, but don’t, doesn’t really matter.1
Similarly to the categories in the above parable, there are many people that are so anti-God, it is obvious they are not a real Christians. There are a small number of people who live such Christ-like lives that there can be little doubt that they are real Christians. There are many people who call themselves Christians, but who may or may not have a relationship with Jesus. It is hard to tell if they are true Christians, are just good at faking it, or believe they are saved while not having a true relationship with Jesus.
Immediately following the initial parable of the sower, Jesus gives another related parable:
Jesus presented another parable to them, saying, “The kingdom of heaven may be compared to a man who sowed good seed in his field. But while his men were sleeping, his enemy came and sowed tares among the wheat, and went away. But when the wheat sprouted and bore grain, then the tares became evident also. The slaves of the landowner came and said to him, ‘Sir, did you not sow good seed in your field? How then does it have tares?’ And he said to them, ‘An enemy has done this!’ The slaves said to him, ‘Do you want us, then, to go and gather them up?’ But he said, ‘No; for while you are gathering up the tares, you may uproot the wheat with them. Allow both to grow together until the harvest; and in the time of the harvest I will say to the reapers, “First gather up the tares and bind them in bundles to burn them up; but gather the wheat into my barn.” ’ ” (Matthew 13:24-30) {emphasis mine}
For those that don’t know about plants, a tare is a plant that looks a lot like wheat, but doesn’t produce the grain heads that we eat and is therefore unprofitable. Just as the slaves say about the tares, “Do you want us, then, to go and gather them up?” and he replies, “No; for while you are gathering up the tares, you may uproot the wheat with them. Allow both to grow together until the harvest,” in the same way we don’t want to go around judging people and deciding for ourselves who is the bona fide Christian because we “may uproot the wheat with them.” Only Jesus knows for certain who is real and who is not.
At the same time, we Christians should be closest to those who show the fruit of the Spirit and live a life that imitates and honors Jesus. We need to be careful who we follow and who we chose as teachers.
“Beware of the false prophets, who come to you in sheep’s clothing, but inwardly are ravenous wolves. You will know them by their fruits. Grapes are not gathered from thorn bushes nor figs from thistles, are they? So every good tree bears good fruit, but the bad tree bears bad fruit. A good tree cannot produce bad fruit, nor can a bad tree produce good fruit. Every tree that does not bear good fruit is cut down and thrown into the fire. So then, you will know them by their fruits. (Matthew 7:15-19) {emphasis mine}
Ultimately we are not to be judges of who is a real Christian and who is not, but we are warned to be aware that there are false prophets and false Christians in our midst. Anyone who produces bad fruit (an ungodly lifestyle, hate, disinterest in things of God, etc.) is likely not a true Christian, even if they proclaim to be and never miss a Sunday service. Anyone who produces good fruit (a godly lifestyle, love, and a yearning for the things of God) is likely a true Christian. It is not which denomination or church a person is associated with that matters. It is a change in the life of the individual that matters. It is a relationship with Jesus that matters. It is love for God, God’s word, and fellow people that matters. There can be a true Christian that is a member of a dead church. There can be a vibrant, godly church that has unbelievers that have crept in as members.
I was recently having a conversation with a fellow Christian and a friend made a comment that it was so hard to witness to a person who thought they were a Christian, but were not. I’d argue that those who believe they are Christians, but are not, and family members, especially parents, are the hardest to witness to, but we are still called to do so. We may just need to be extra delicate in how we do it.
“Behold, I send you out as sheep in the midst of wolves; so be shrewd as serpents and innocent as doves.” (Matthew 10:16)
In addition to witnessing to the unsaved who believe they are saved, we also need to beware of those who pretend to be Christians or believe they are Christians, but don’t believe the Bible. They can easily lead us astray.
Talking to another friend who also has a college aged son, we were discussing how sometimes a believing student might be better off going to a secular university, where they expect to be taught falsehood and are staying aware, than to attend a liberal Christian university that might teach the same falsehood, but not be noticed because it is couched in Christian sounding language and because the students don’t have their guard up like they would at a secular university. On the other hand, if your kids are going to attend college, a Bible believing college (like Liberty University or Grand Canyon University) is a good choice. We need to intentionally teach our kids truth, so they will recognize the lies they will be told and taught.
And this I pray, that your love may abound still more and more in real knowledge and all discernment, so that you may approve the things that are excellent, in order to be sincere and blameless until the day of Christ; having been filled with the fruit of righteousness which comes through Jesus Christ, to the glory and praise of God. (Philippians 1:9-11) {emphasis mine}
How do we have “real knowledge and all discernment?” We must be reading our Bible daily. We can’t know God and know what He wants for us if we don’t know His commands and His word. We can’t judge teachers and preachers to know if they are teaching the truth if we don’t know the Bible. We need to be like the Bereans:
Now these were more noble-minded than those in Thessalonica, for they received the word with great eagerness, examining the Scriptures daily to see whether these things were so. (Acts 17:11)
As true Christians, we should have a hunger for God’s word and God’s presence. We should be interested in what God is interested in. We should care about others as God cares about others. As Christians we should long for conversation with God (prayer) and include Him in our lives.
When things are going well, it is hard to tell the wheat from the tares, or the real Christians from the pretenders. When hard times come, especially persecution of believers, it becomes much easier to differentiate between the two.
“Then they will deliver you to tribulation, and will kill you, and you will be hated by all nations because of My name. At that time many will fall away and will betray one another and hate one another. Many false prophets will arise and will mislead many. Because lawlessness is increased, most people’s love will grow cold. But the one who endures to the end, he will be saved. This gospel of the kingdom shall be preached in the whole world as a testimony to all the nations, and then the end will come. (Matthew 24:9-14) {emphasis mine}
Only the true believers will stay true to Jesus during persecution. Those who were faking it for earthly reward will turn against the persecuted believers. Those who don’t have a true relationship with Jesus will drift away to avoid persecution because they don’t have saving faith. No true believer will permanently leave Christ, but there will be some (many?) who wander away because their faith was not real. A simple prayer, without true repentance and without true faith, does not magically make a person a Christian.
The Bible does give believers a litmus test on who and what to trust:
Beloved, do not believe every spirit, but test the spirits to see whether they are from God, because many false prophets have gone out into the world. By this you know the Spirit of God: every spirit that confesses that Jesus Christ has come in the flesh is from God; and every spirit that does not confess Jesus is not from God; this is the spirit of the antichrist, of which you have heard that it is coming, and now it is already in the world. You are from God, little children, and have overcome them; because greater is He who is in you than he who is in the world. They are from the world; therefore they speak as from the world, and the world listens to them. We are from God; he who knows God listens to us; he who is not from God does not listen to us. By this we know the spirit of truth and the spirit of error. (1 John 4:1-6)
The Bible also gives a test to see if we are true believers:
Test yourselves to see if you are in the faith; examine yourselves! Or do you not recognize this about yourselves, that Jesus Christ is in you—unless indeed you fail the test? (2 Corinthians 13:5)
As Jesus said,
“Behold, I send you out as sheep in the midst of wolves; so be shrewd as serpents and innocent as doves. ” (Matthew 10:16)
I pray that God will give you wisdom to rightly judge people, teachings, and truth and that you would fully trust in Jesus through all circumstances and become conformed more and more to His likeness.
Trust Jesus.


































